Patents
Literature
485 results about "Network access server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
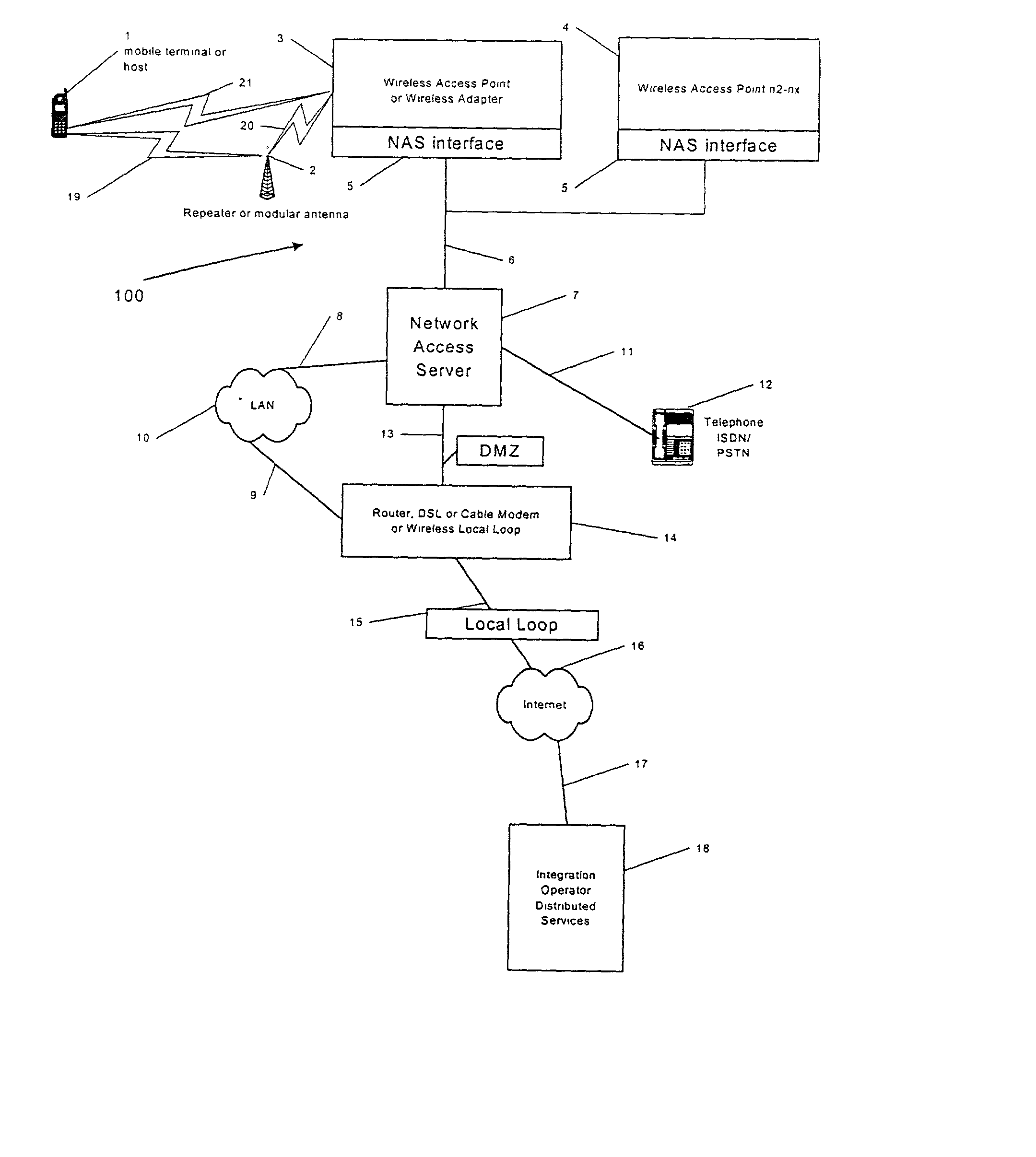
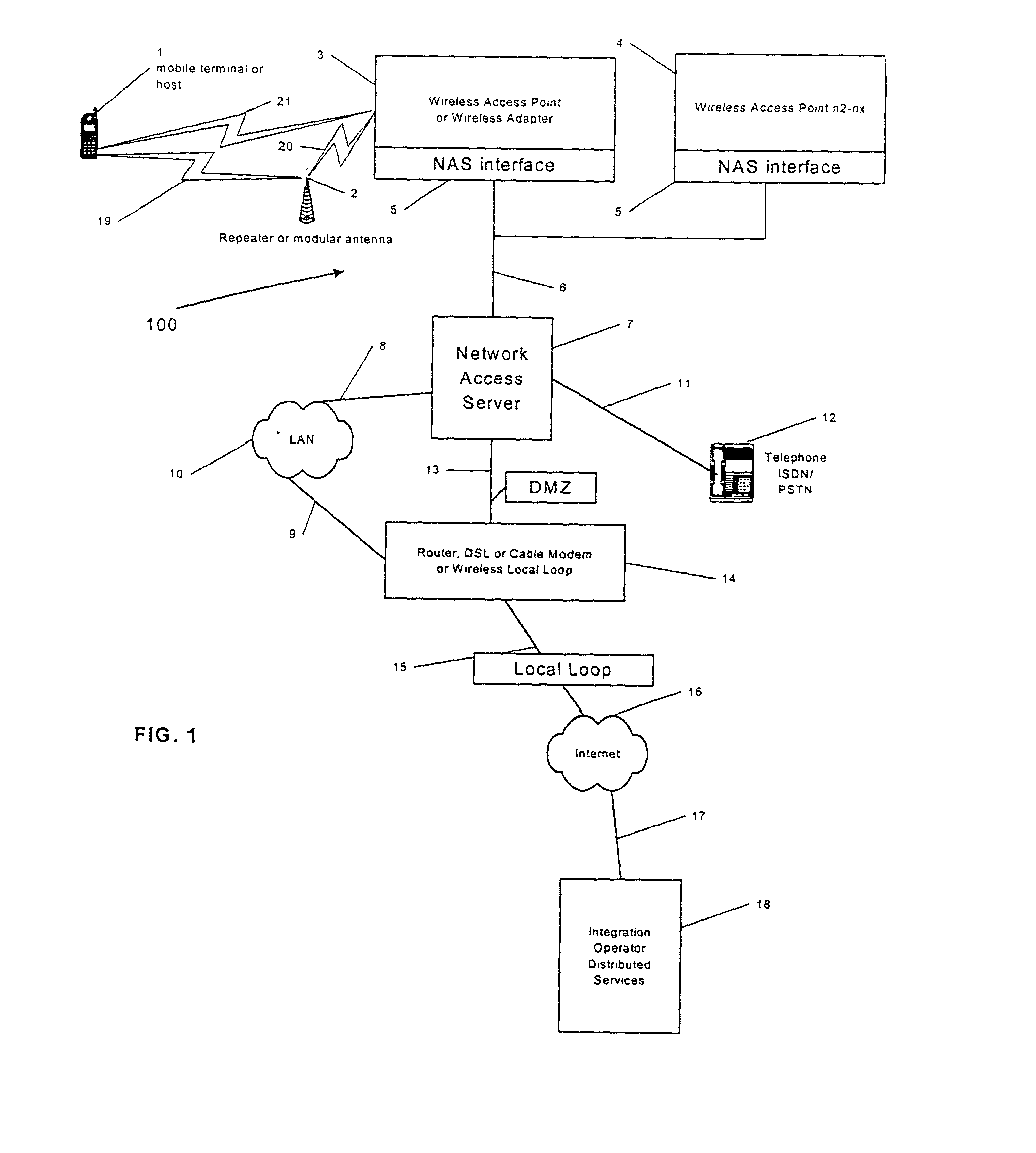
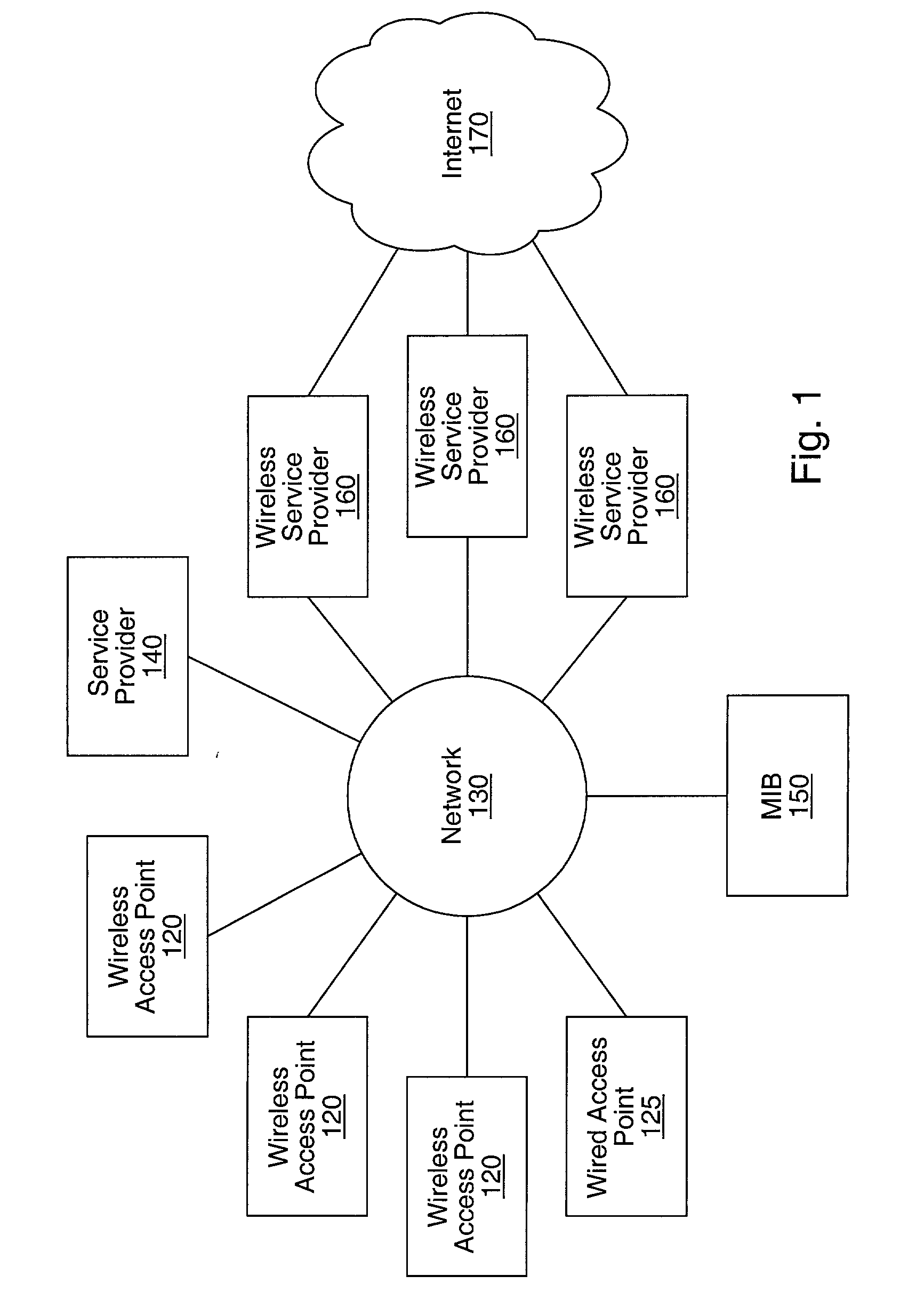
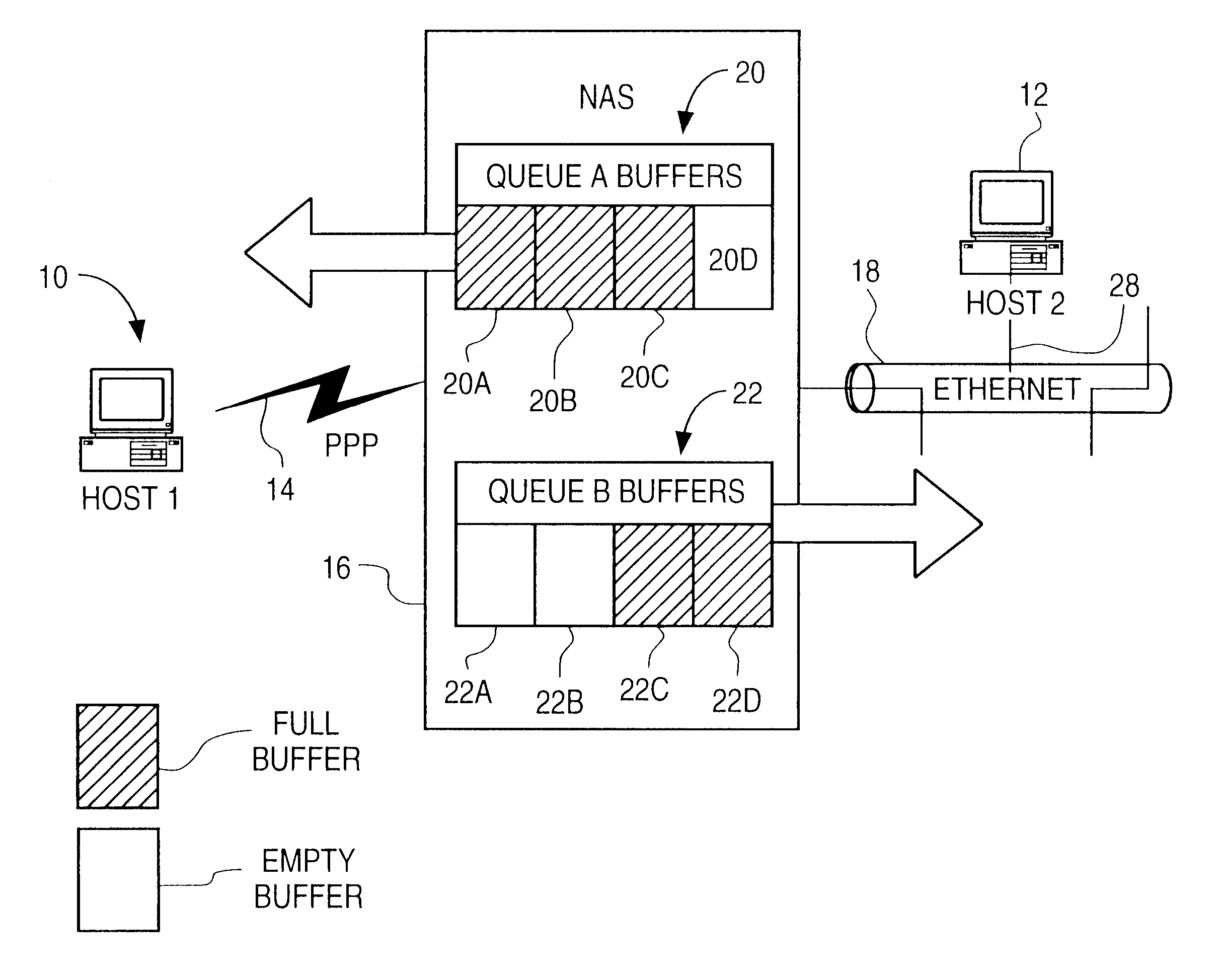
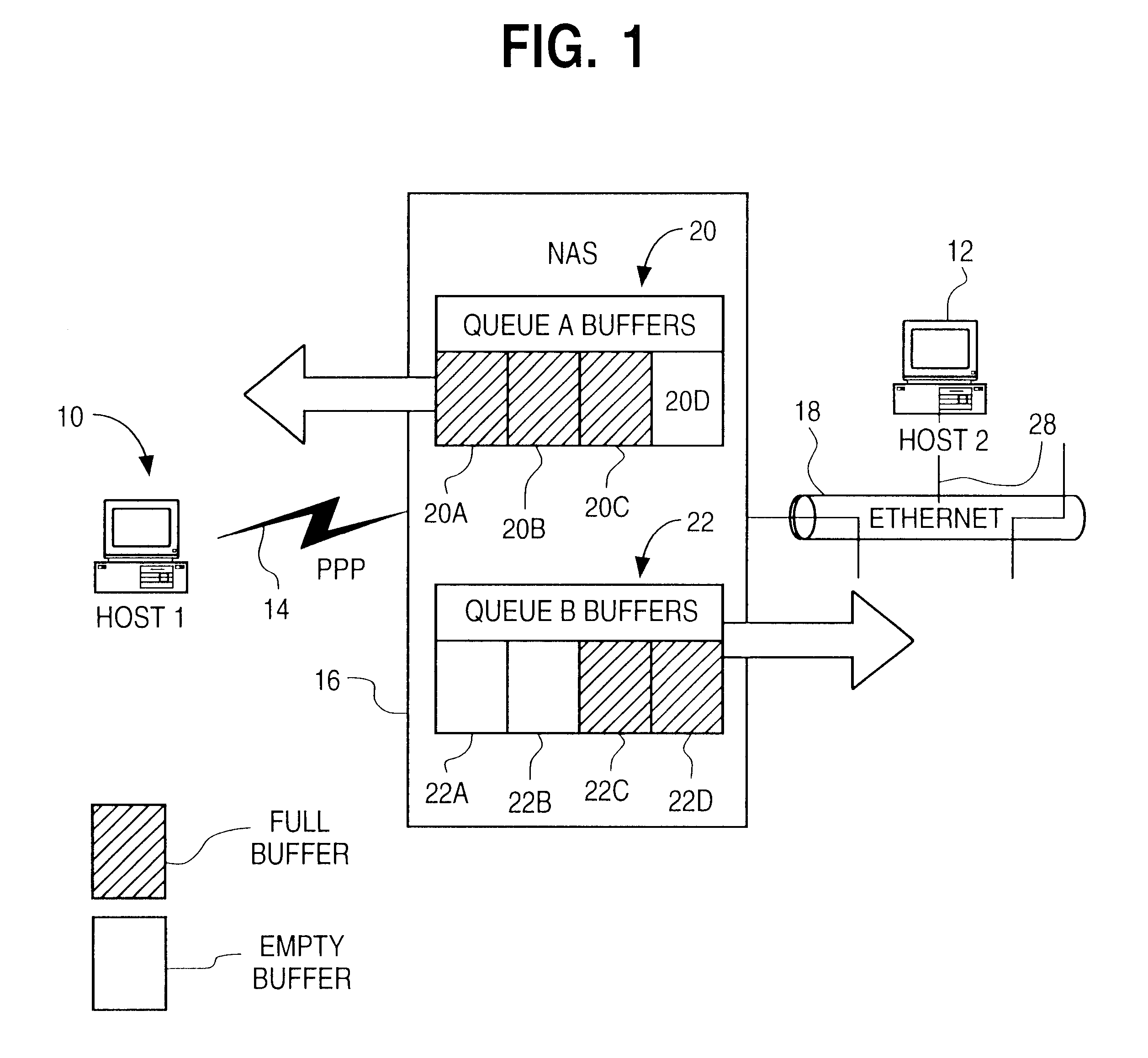
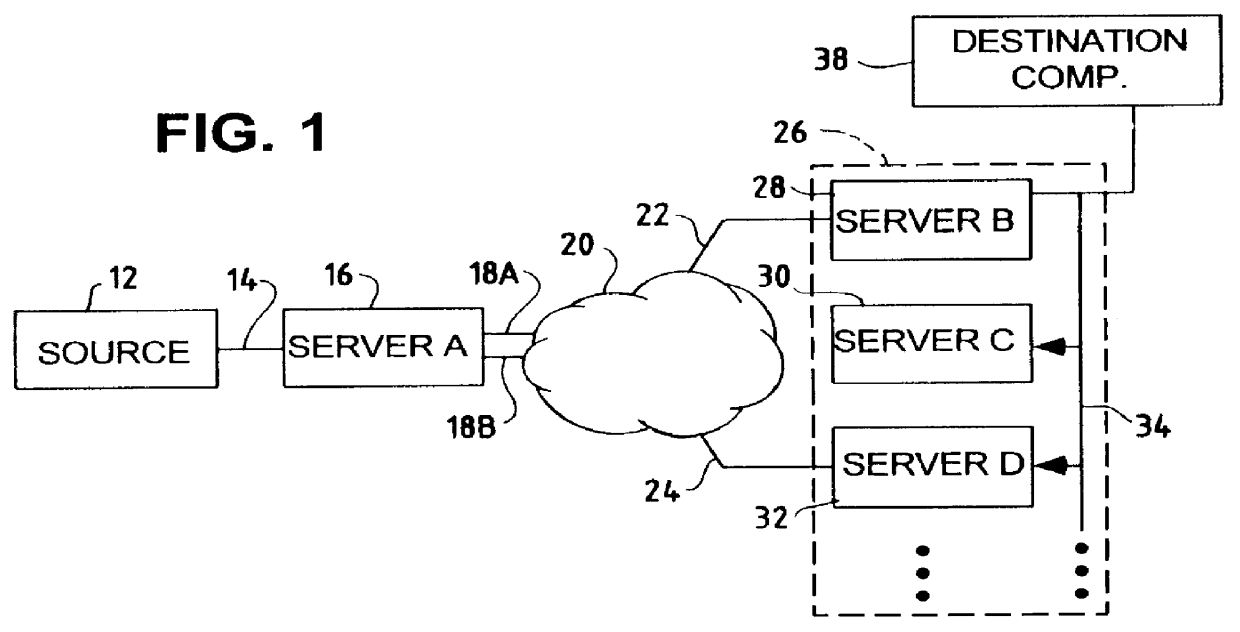
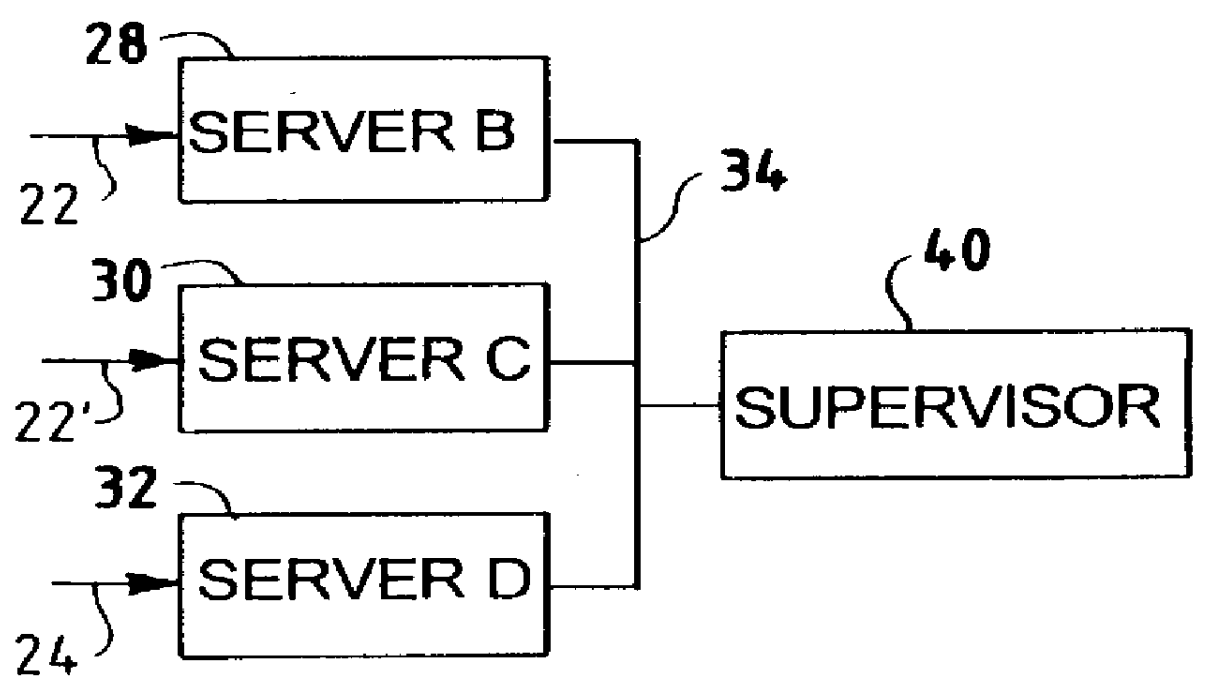
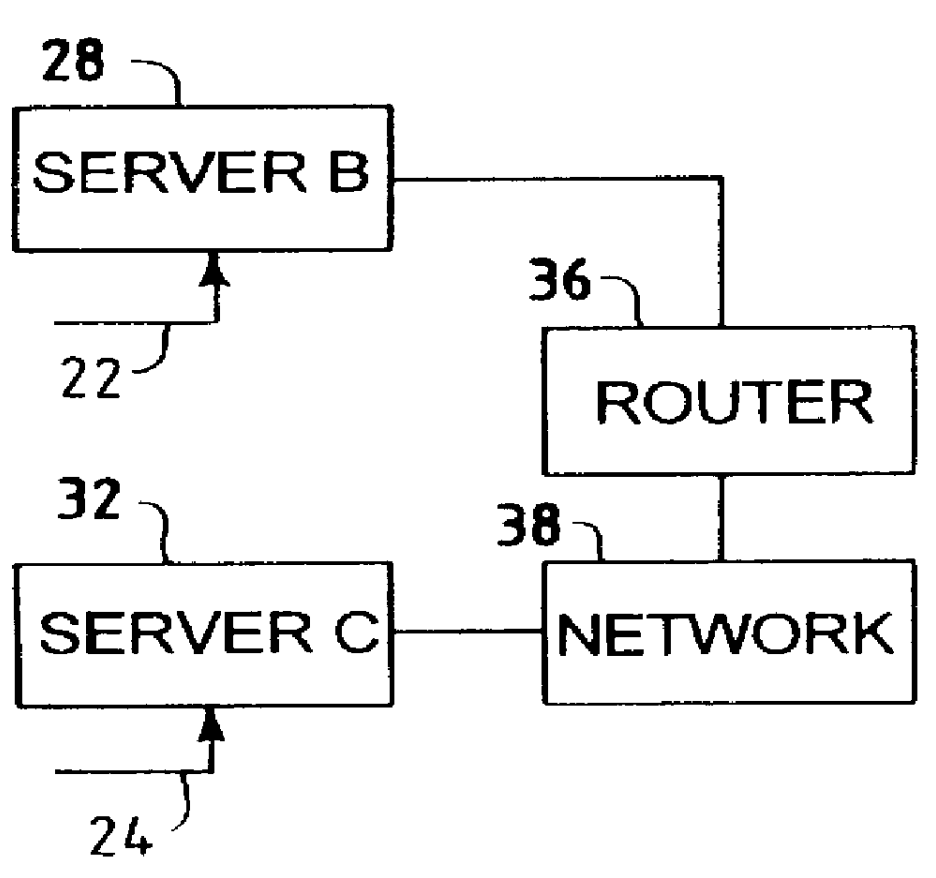
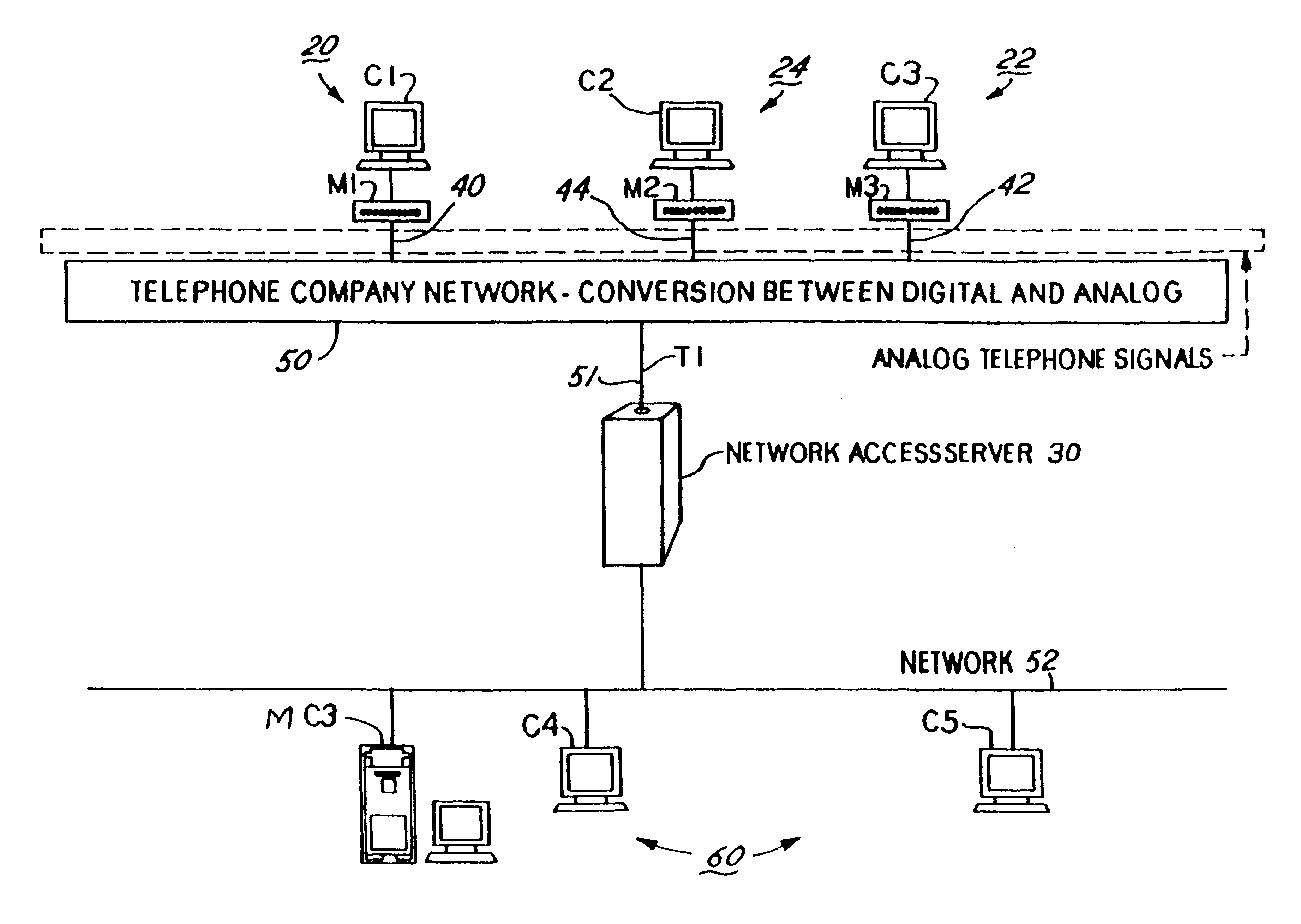
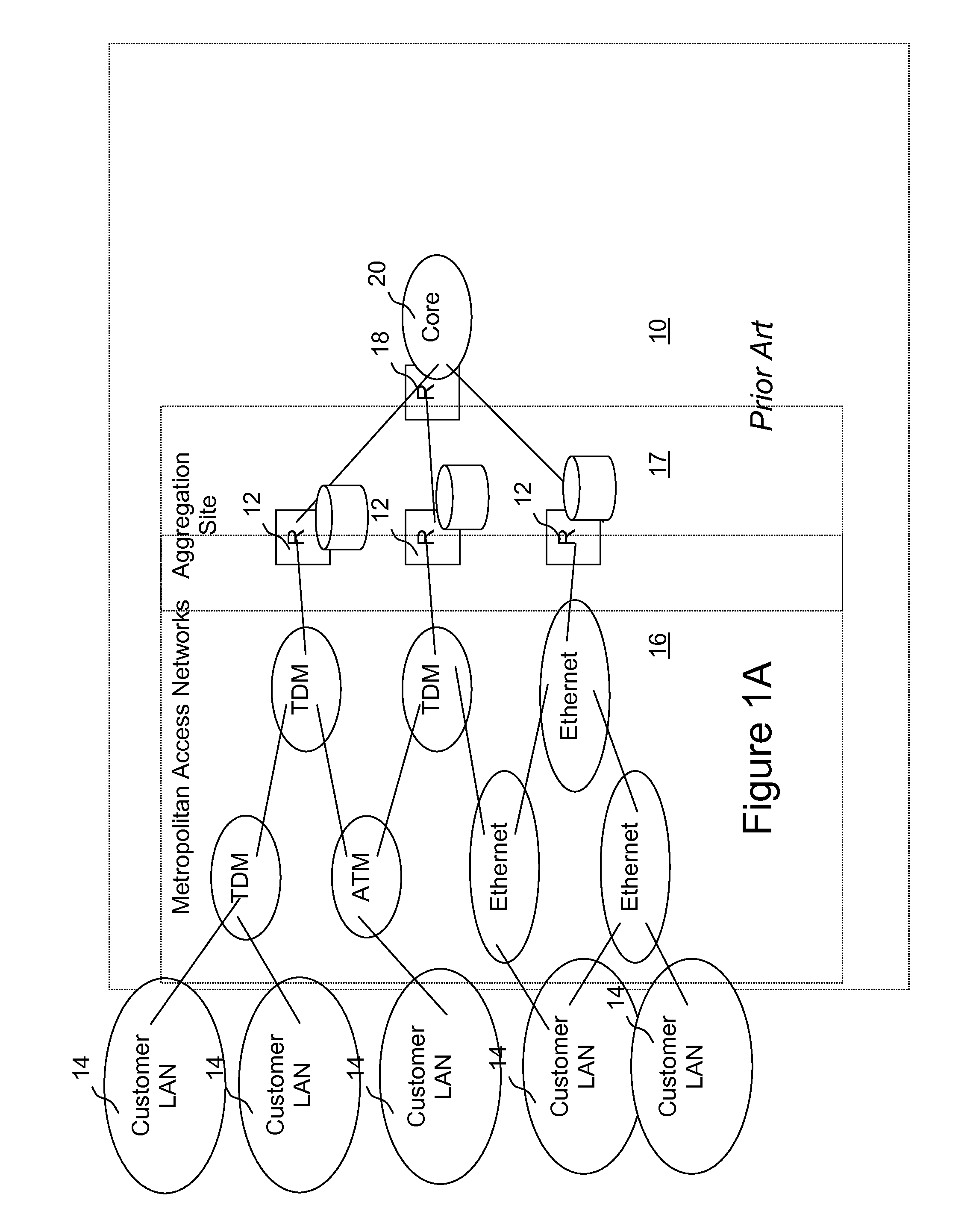
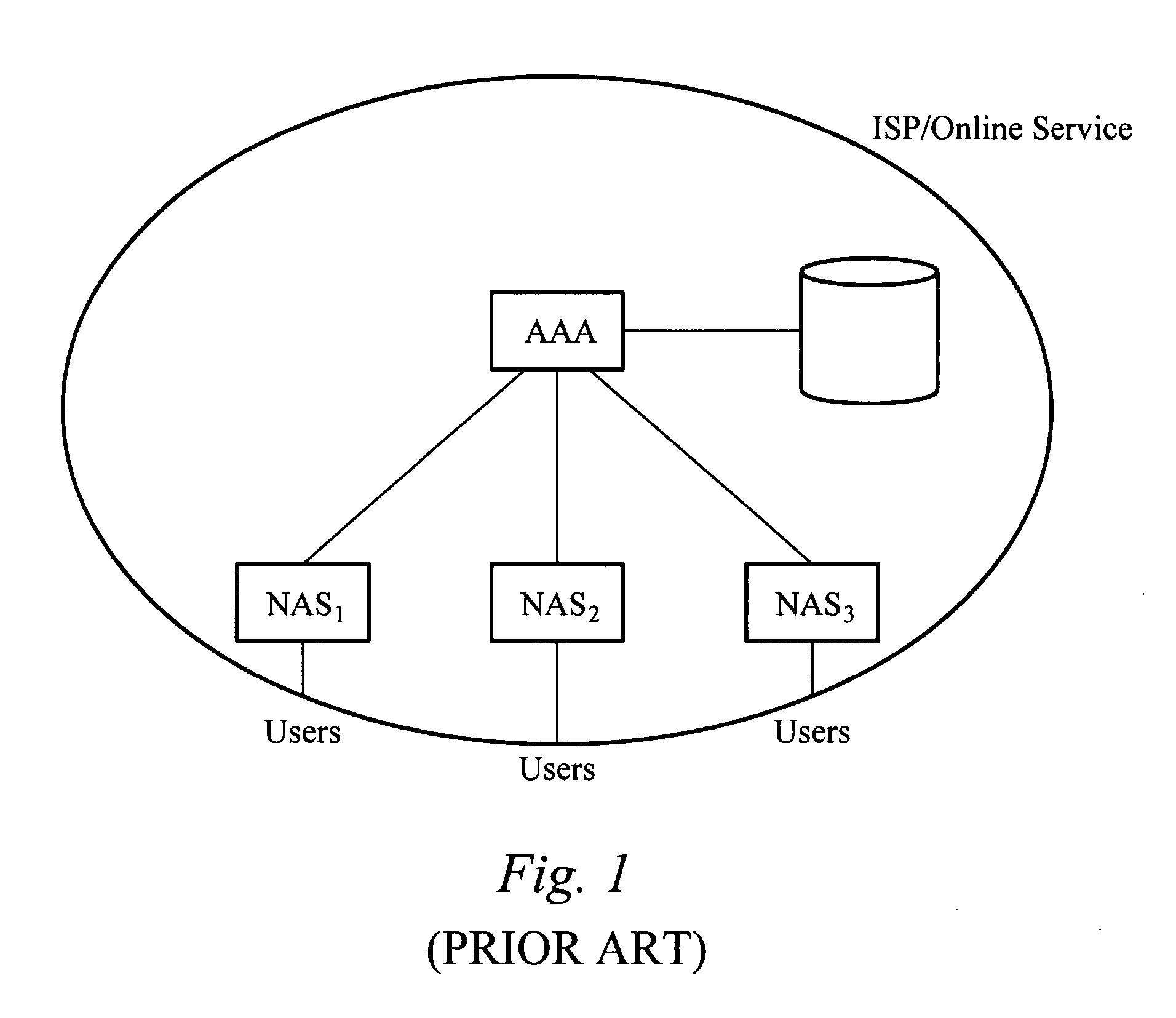
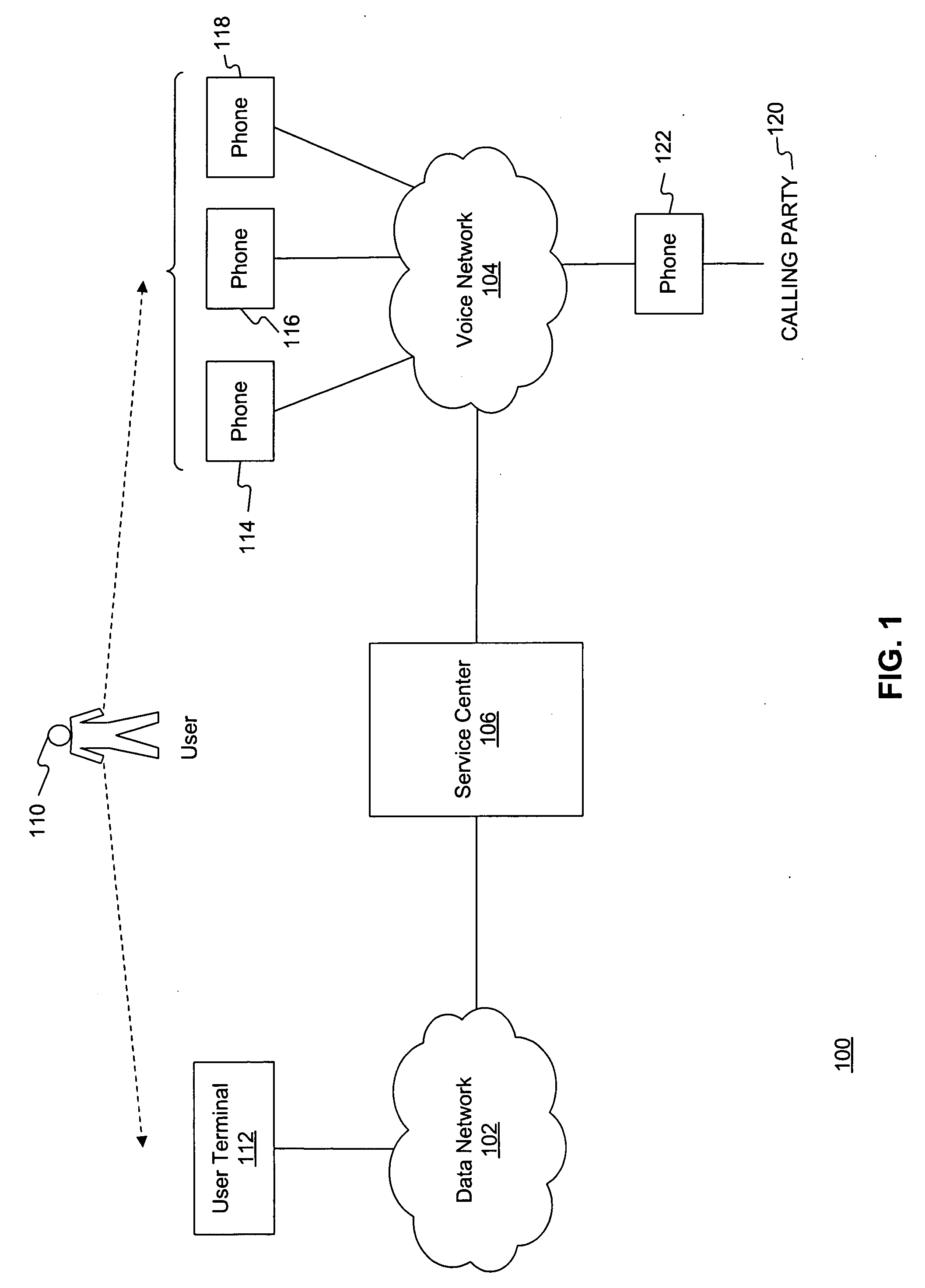
A network access server (NAS) is a single point of access to a remote resource.
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
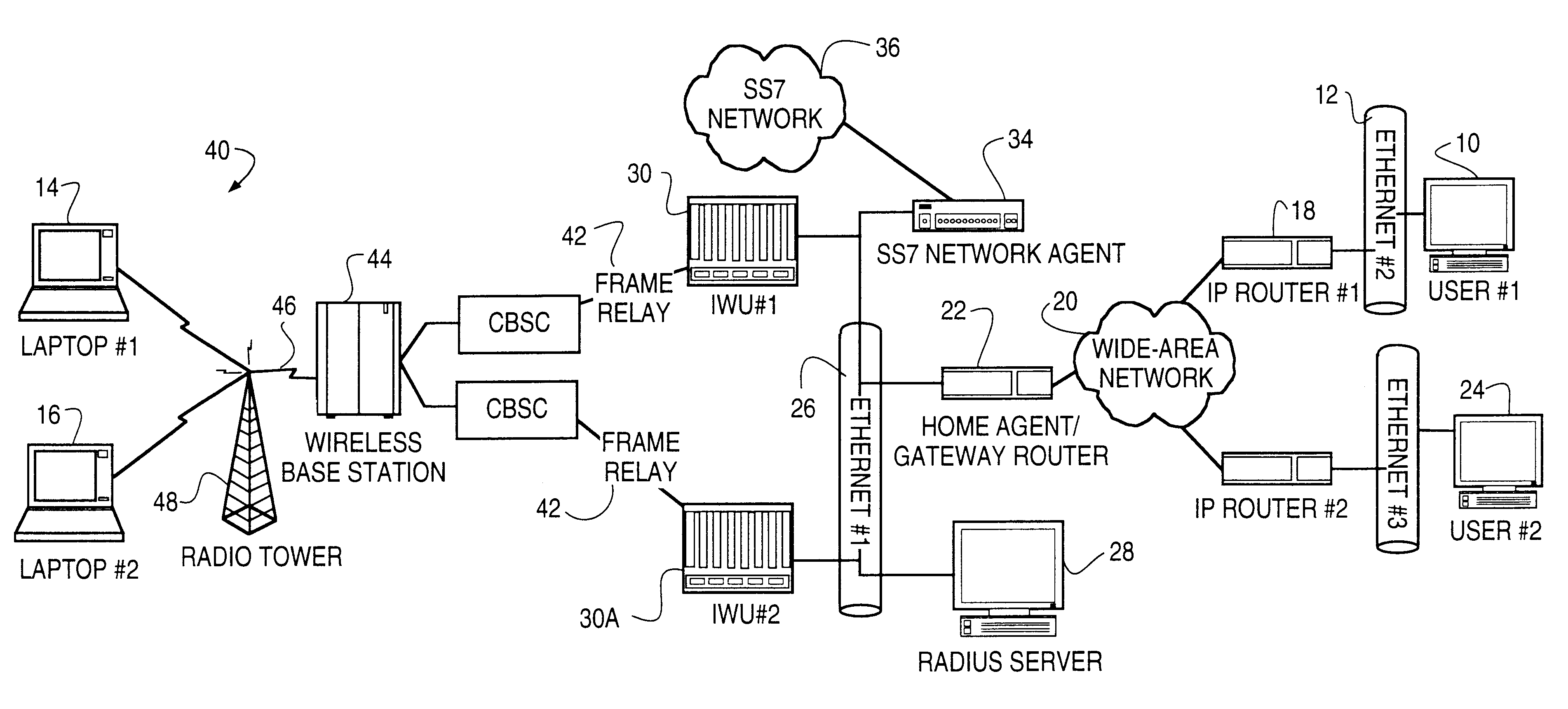
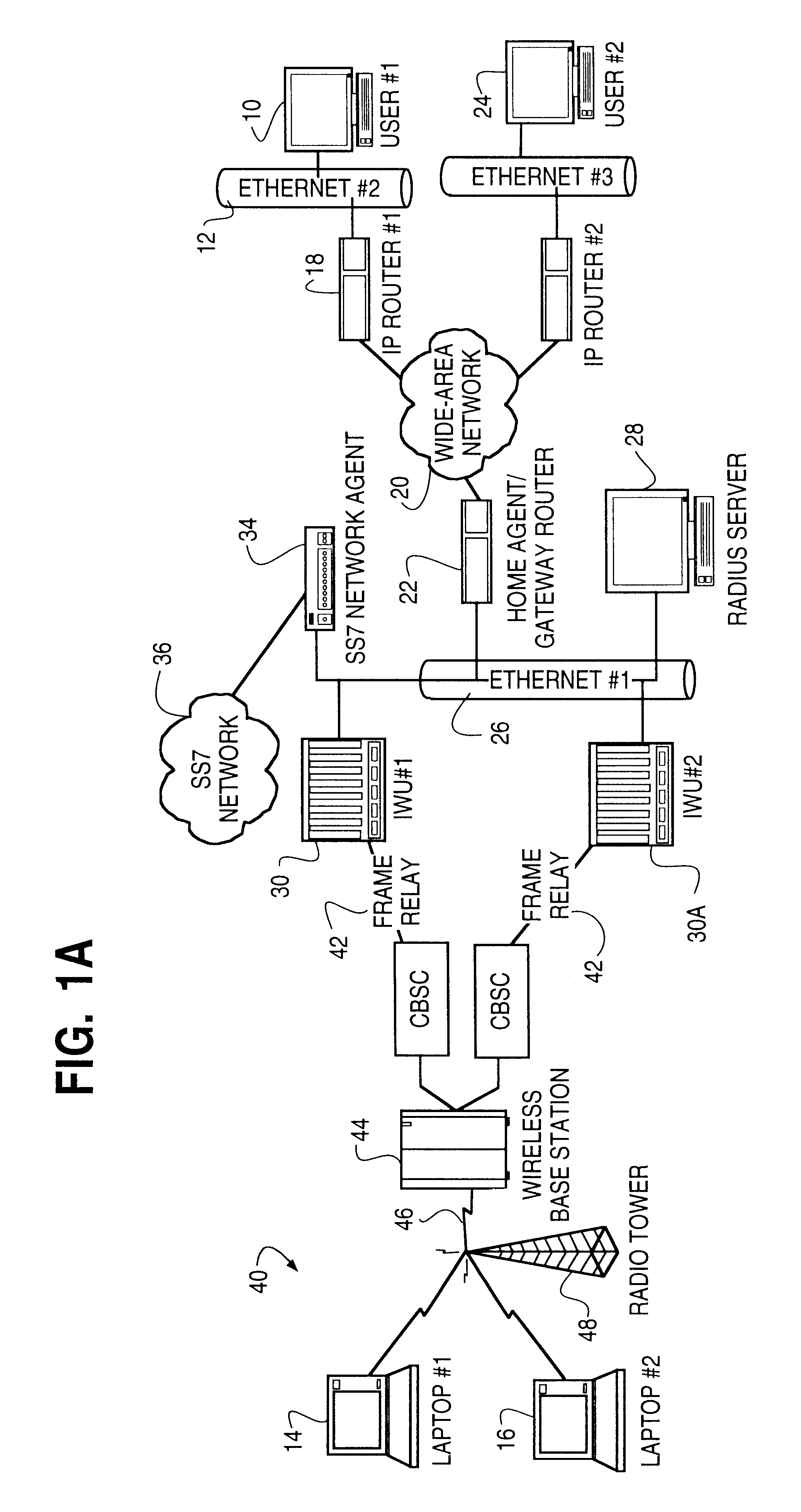
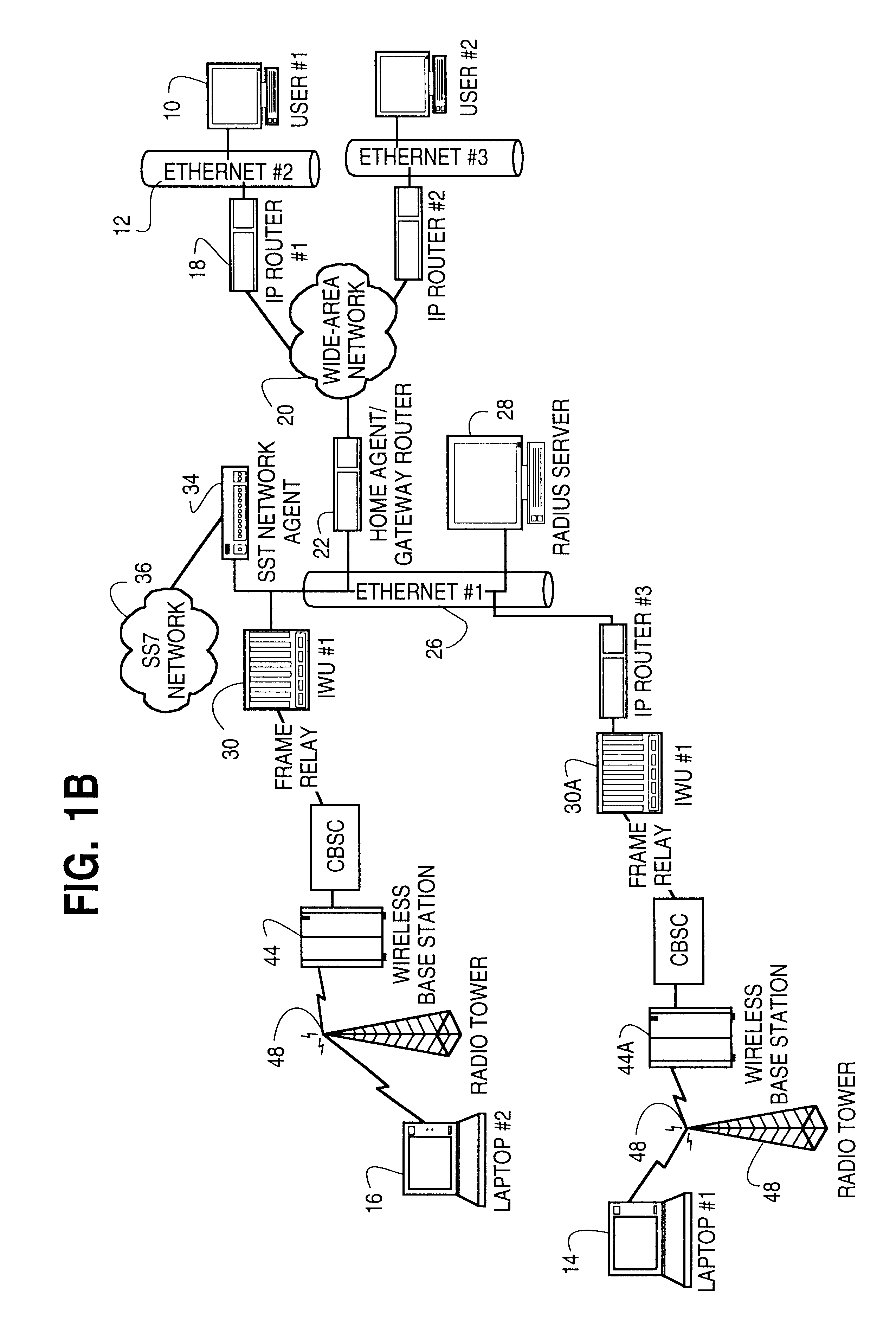
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
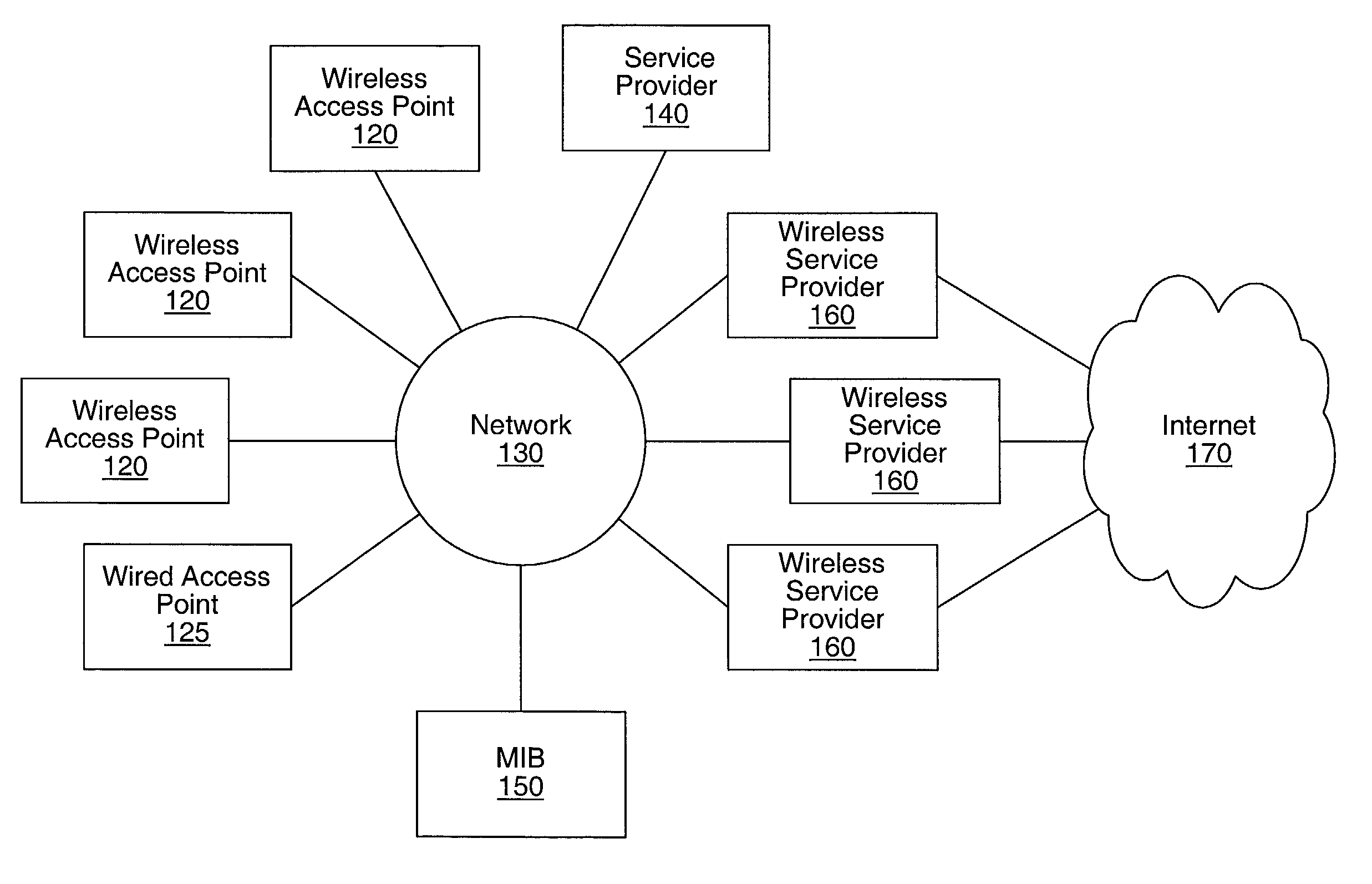
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
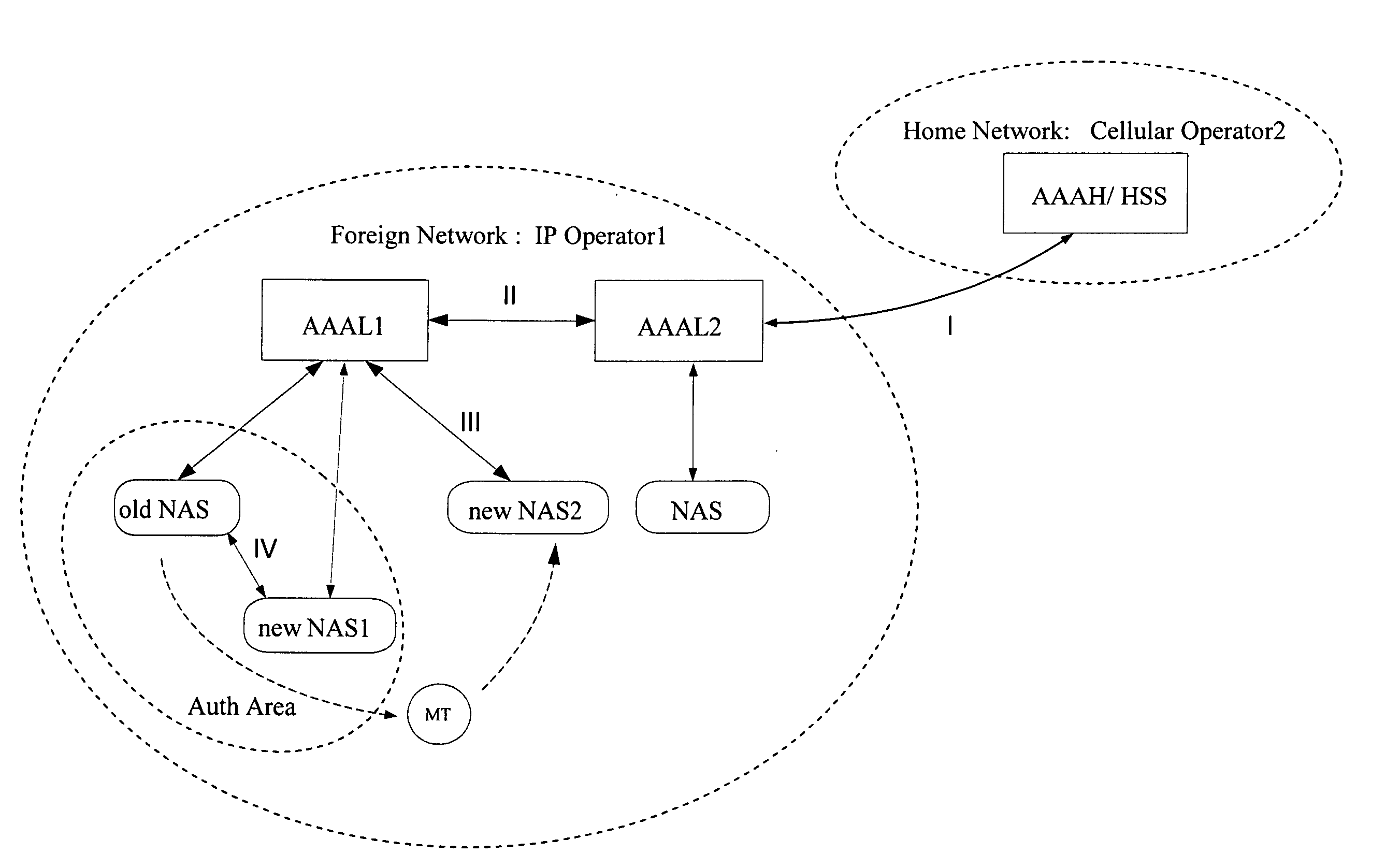
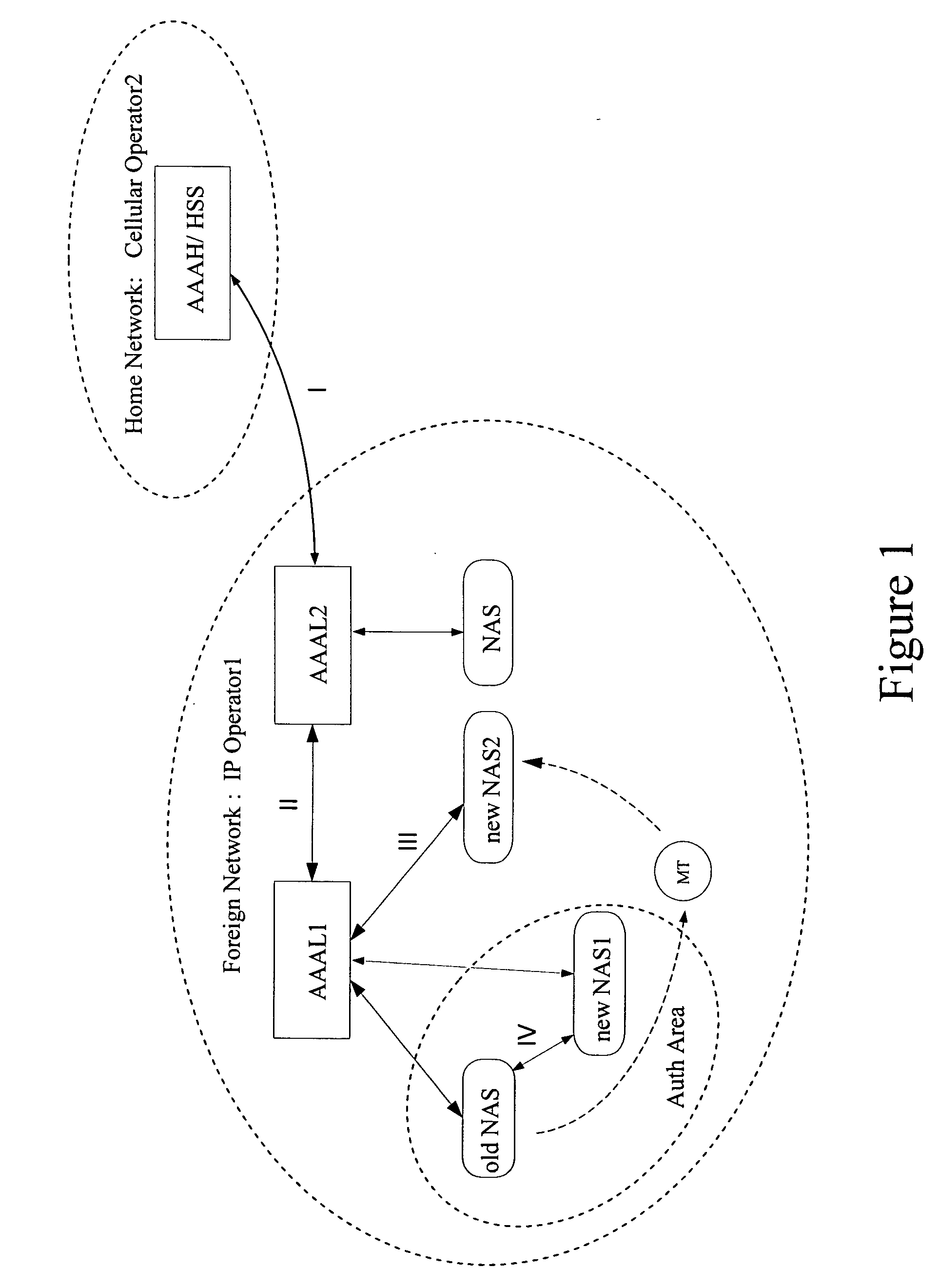
Authentication and authorization in heterogeneous networks
ActiveUS20050166043A1Optimized network access performanceImproved AAA performanceMultiplex system selection arrangementsData switching networksNetwork access serverHeterogeneous network
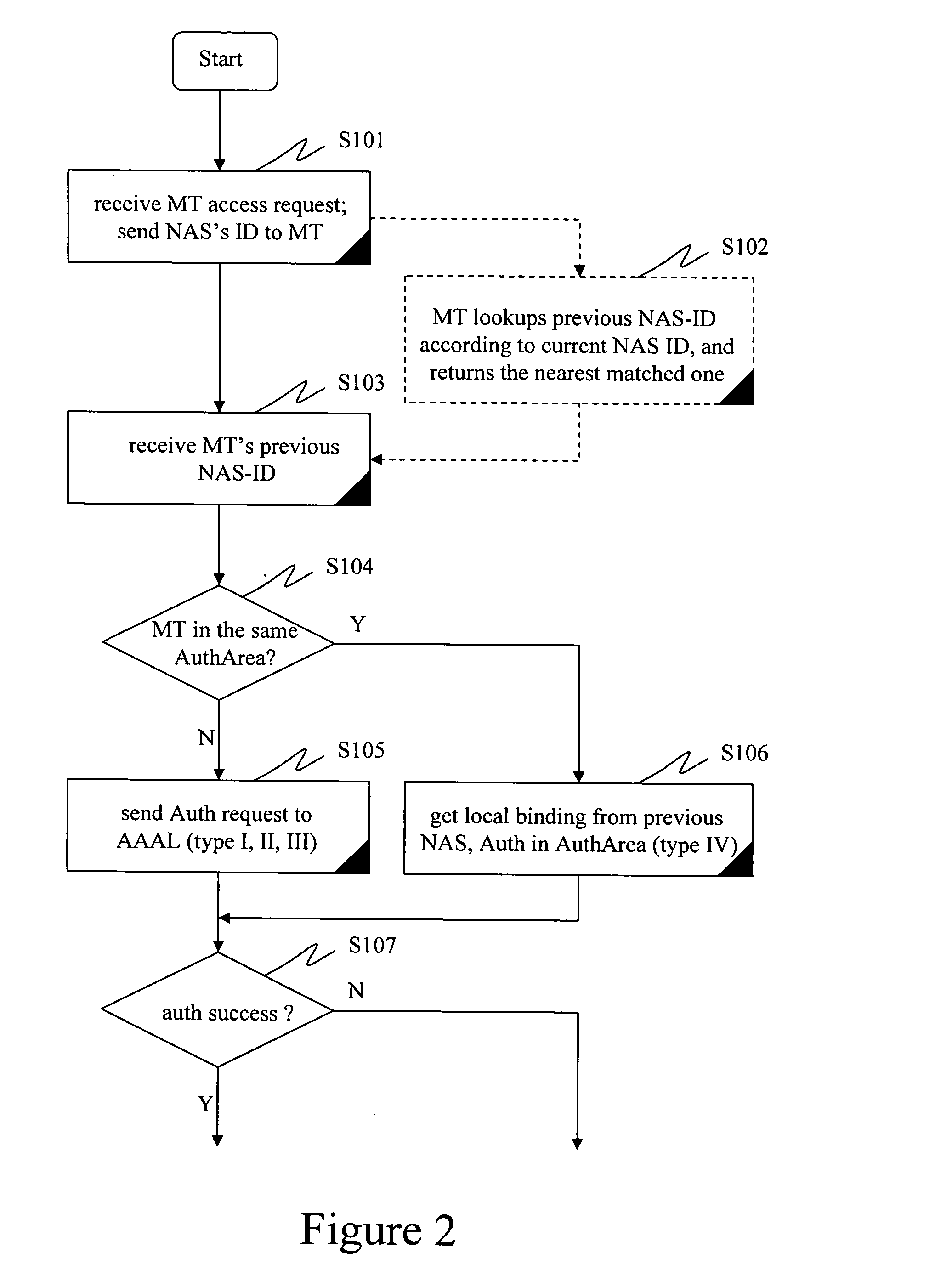
A method, system, and network elements for authentication and authorization of a mobile terminal (MT) roaming to or in a foreign network different from its home network is provided, the home network having an authentication and authorization home server (AAAH), and the foreign network having a plurality of domains each of which comprises at least one local server (AAAL1, AAAL2) for authentication, authorization and accounting, each of which local servers being connected to at least one network access server (NAS) for handling access for mobile terminals roaming to or in the foreign network, wherein an authentication and authorization of the mobile terminal is performed whenever the mobile terminal performs a roaming, wherein the authentication and authorization is performed according to a procedure pursuant to one of a plurality of hierarchy levels, whereby a combination of network elements involved in the roaming determines the hierarchy level to be used.
Owner:NOKIA TECHNOLOGLES OY
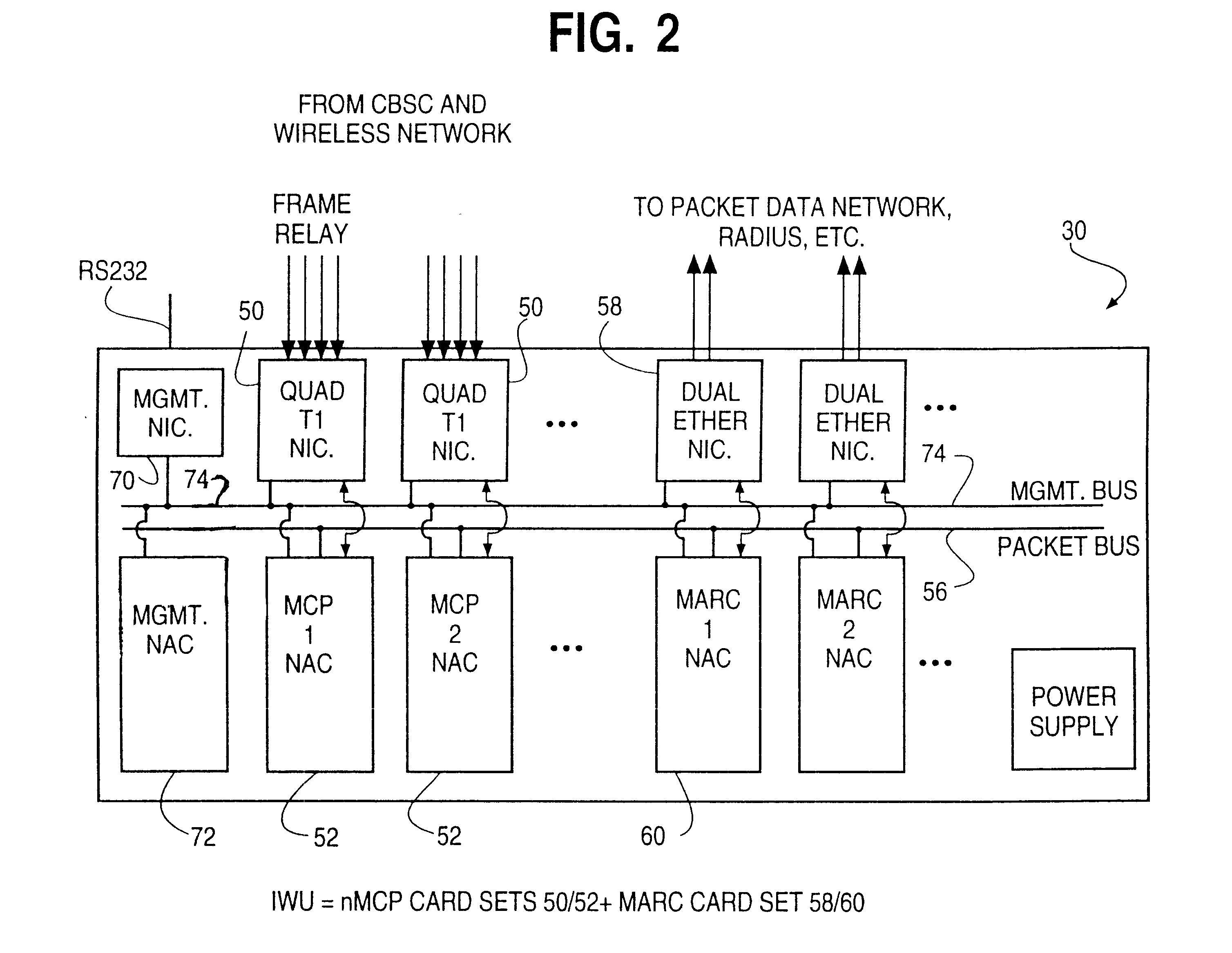
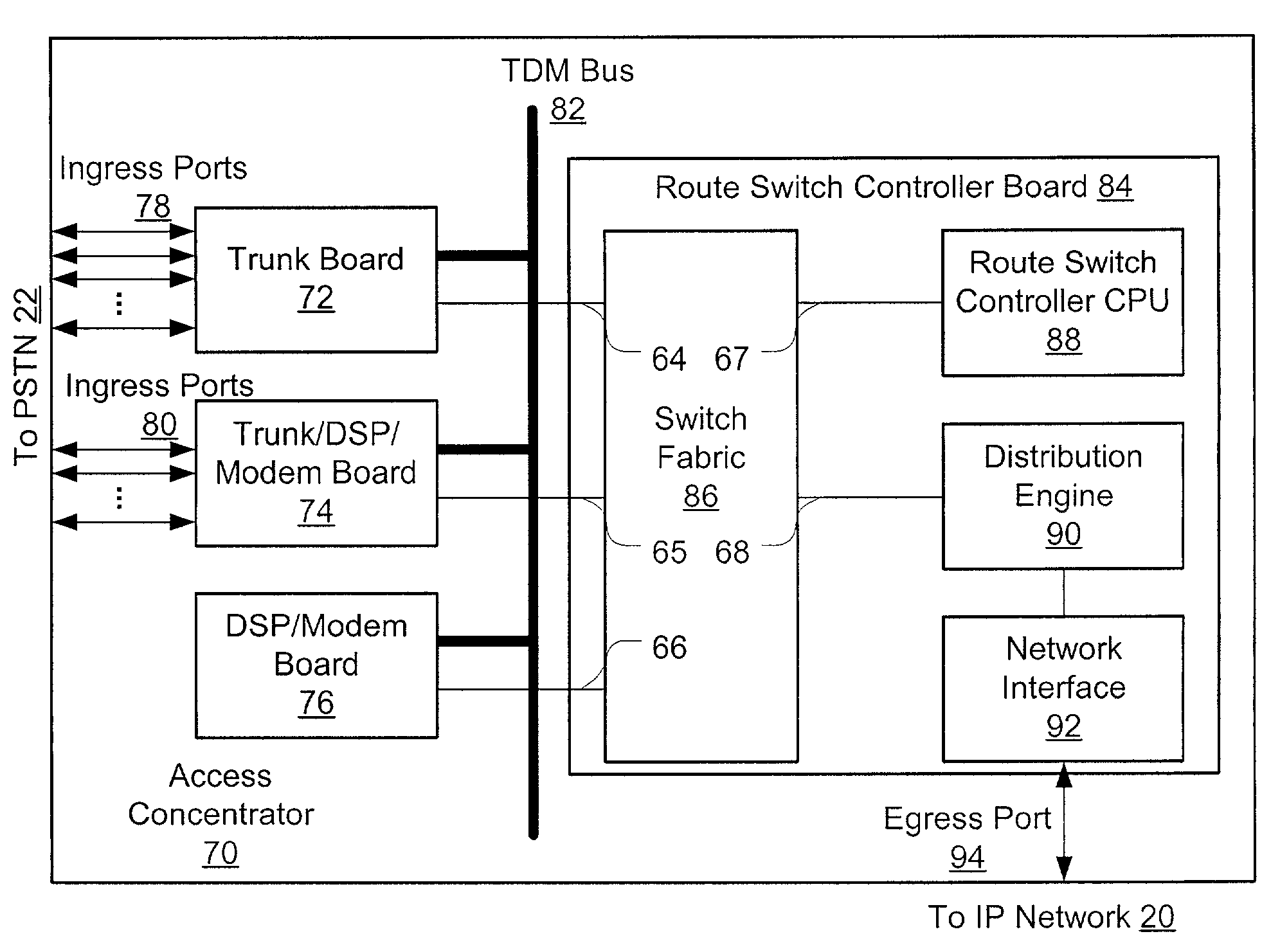
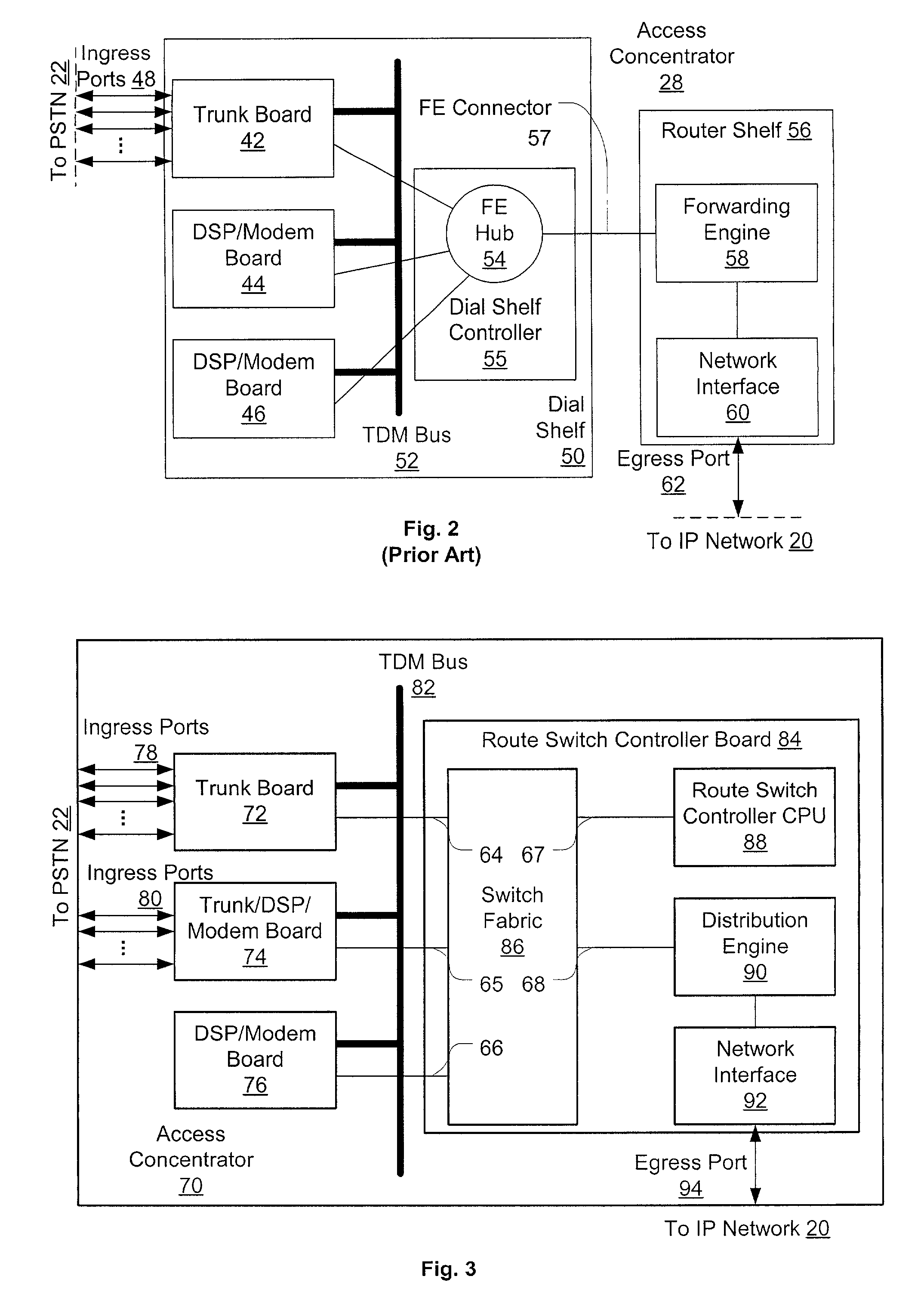
Distributed packet processing architecture for network access servers
InactiveUS6954463B1Increase the number ofRaise countData switching by path configurationNetwork access serverComputer hardware
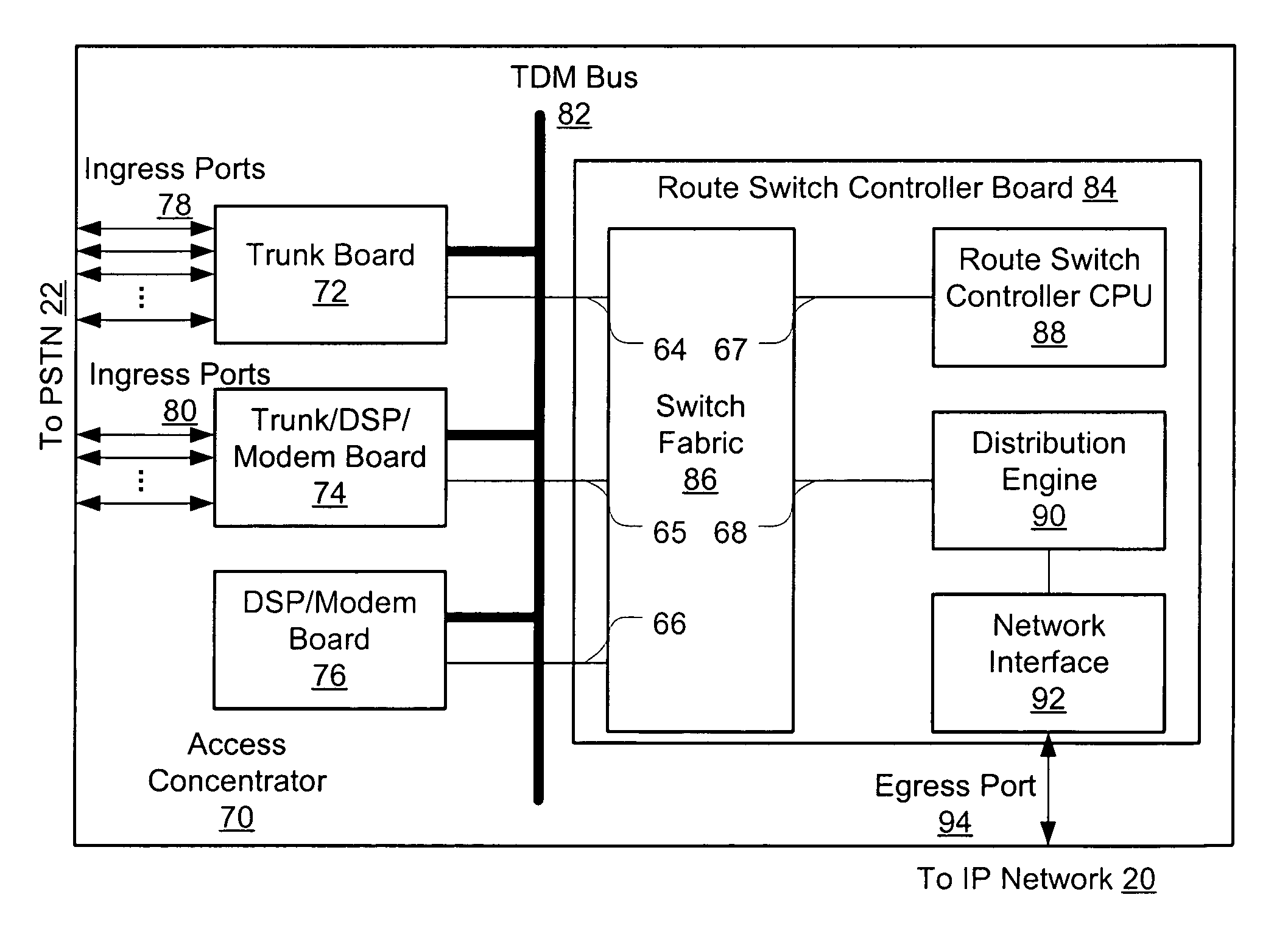
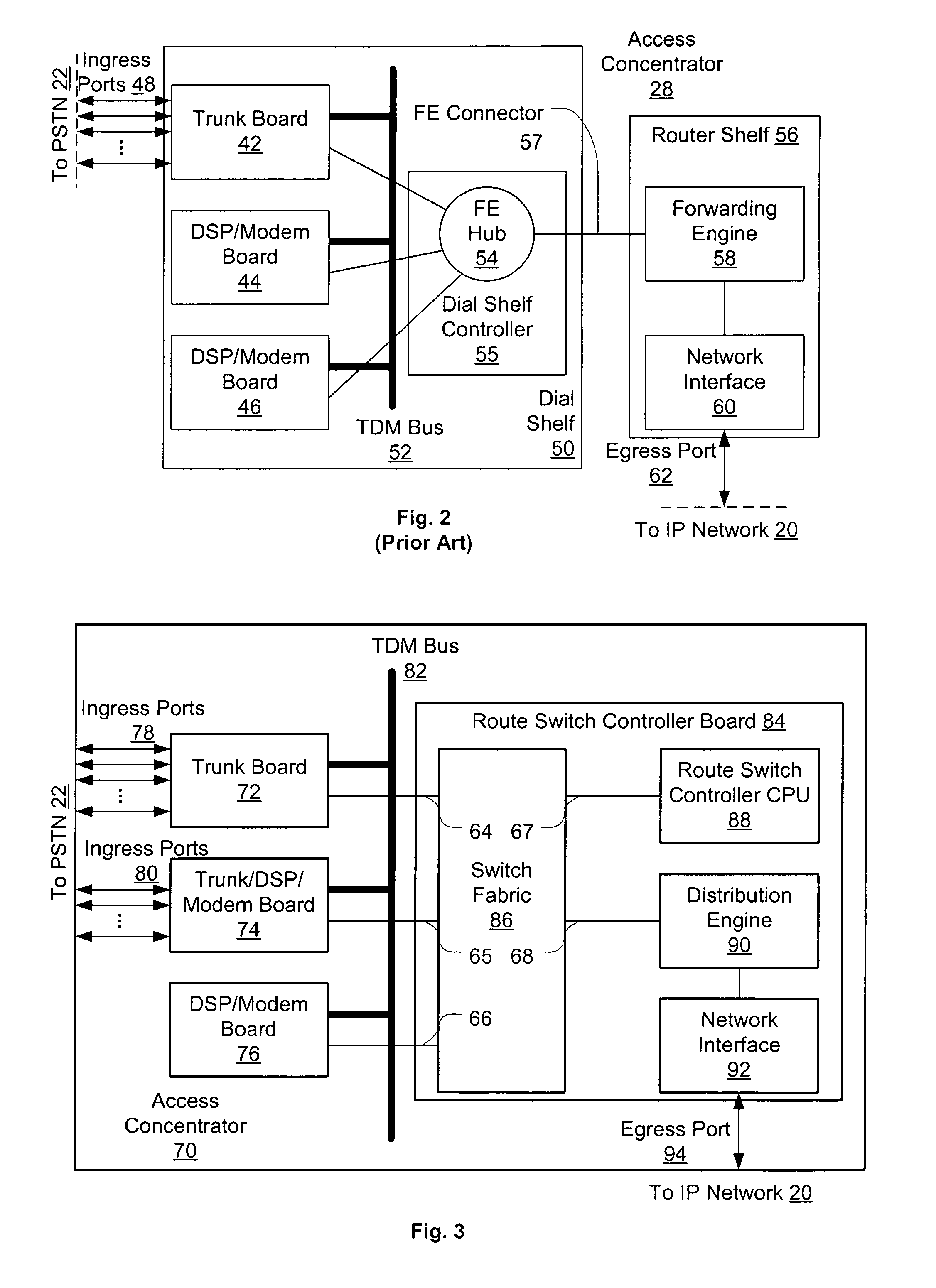
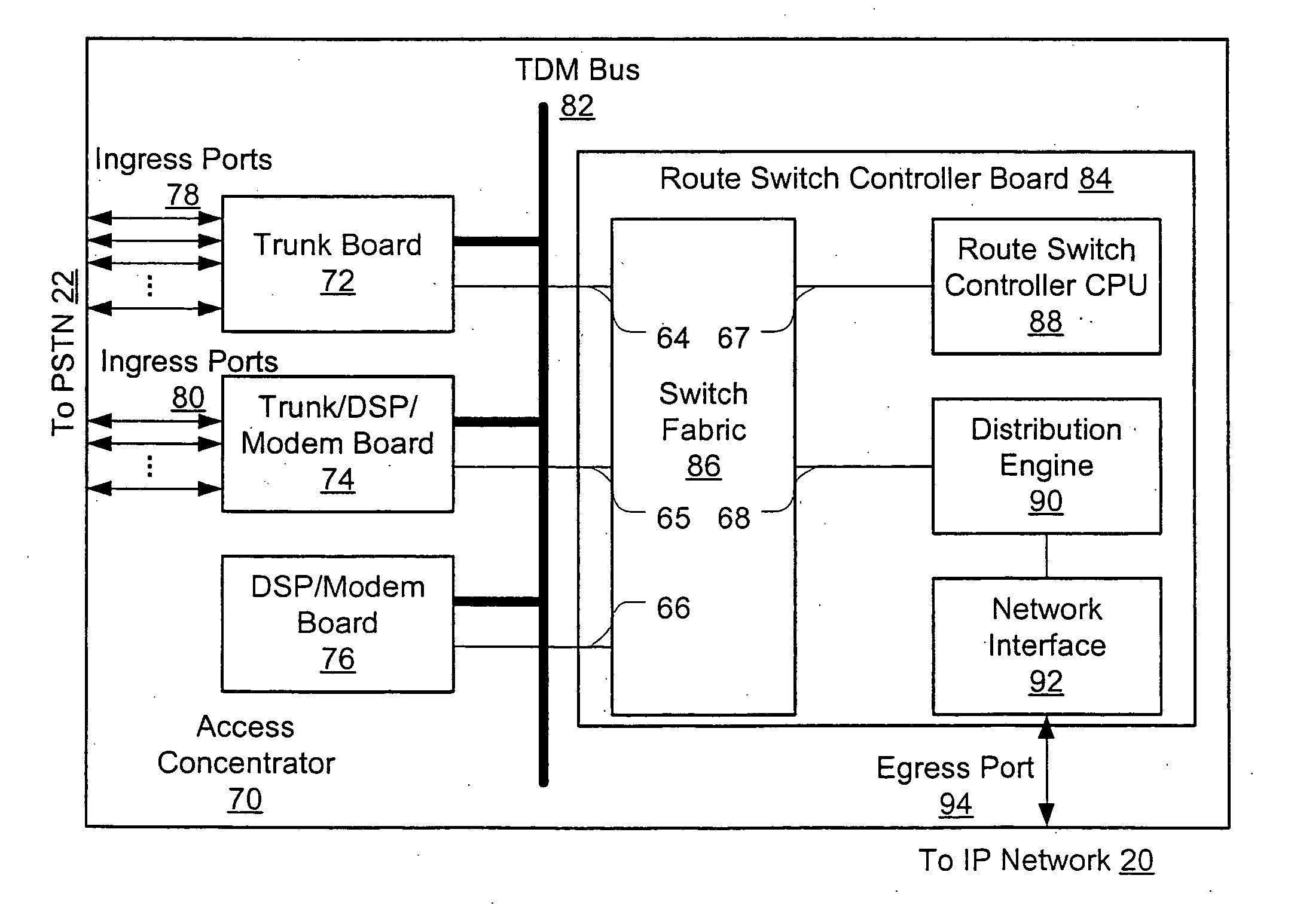
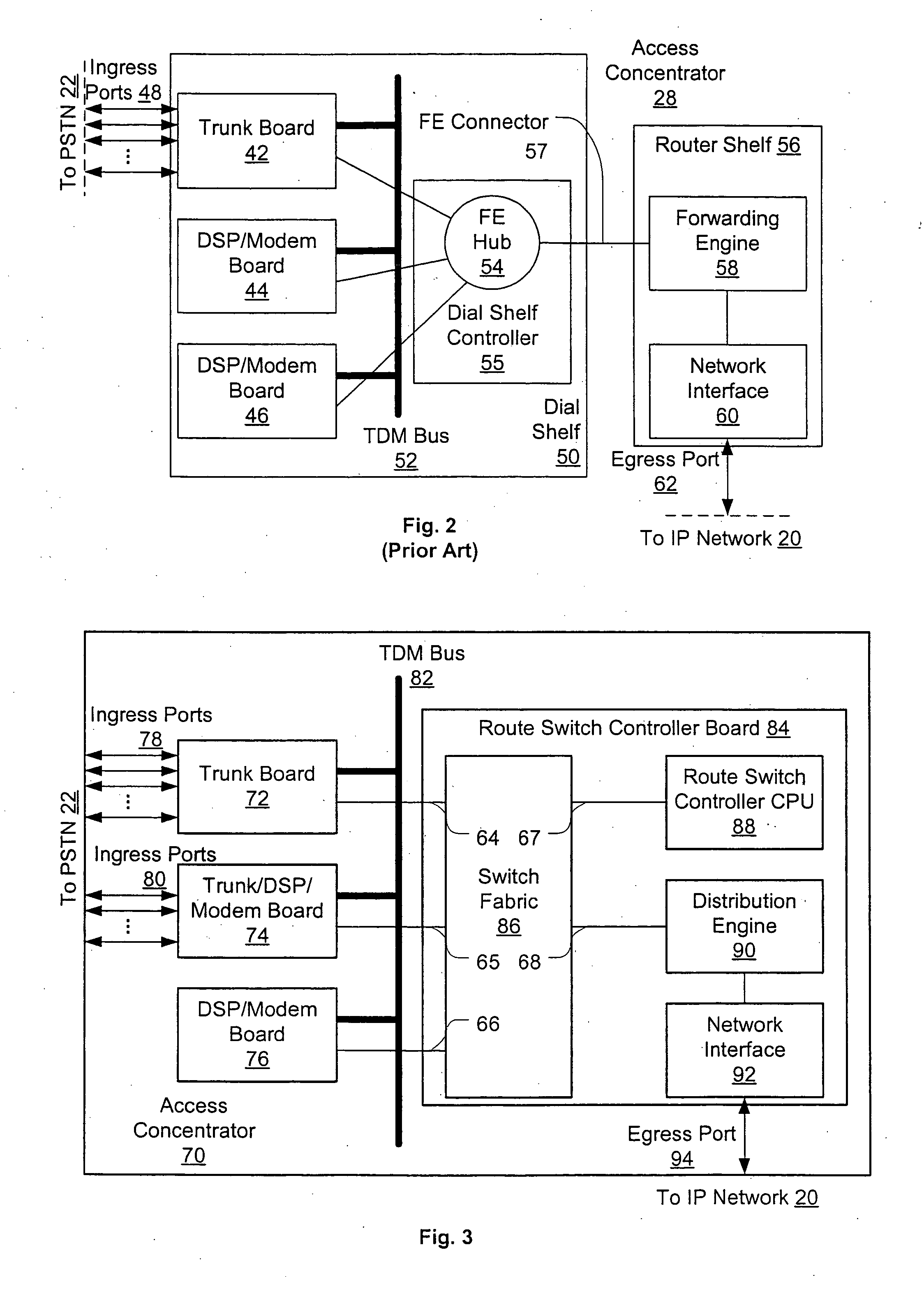
An access server architecture, and methods for use of the architecture, are disclosed. The architecture and methods are designed to increase the scalability of and balance processor load for a network access server. In this architecture, packet forwarding and packet processing are distributed amongst the cards serving the low-speed access lines, such that each line card is responsible for performing forwarding and packet processing for packets associated with the low-speed ports that line card serves. As the number of line cards expands, forwarding resources are expanded in at least rough proportion. The NAS route switch controller, and the high-speed ports, are largely relieved of packet processing tasks because the egress port uses a distribution engine that performs a cursory examination on one or more header fields on packets received—comprehending only enough information to allow each packet to be distributed to the appropriate line card for full processing.
Owner:CISCO TECH INC
Radius-based mobile internet protocol (IP) address-to-mobile identification number mapping for wireless communication
InactiveUS6466571B1Data switching by path configurationWireless network protocolsIp addressCommunication device
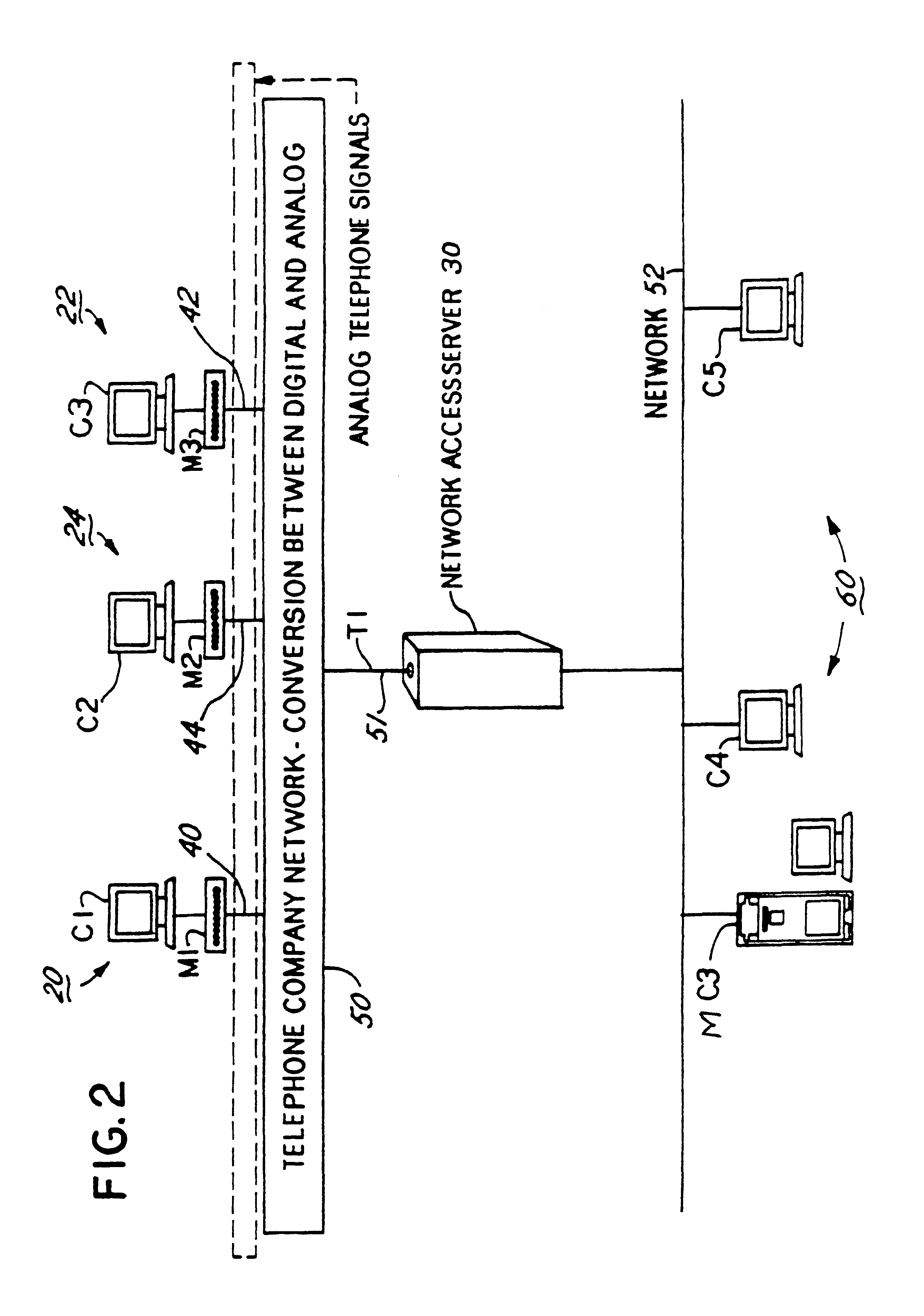
A method of finding a mobile wireless communications device when an Internet Protocol (IP) packet from a remote user is sent to the device over an IP network. The mobile device does not have to register with the IP network in order to receive the IP. The method comprises the steps of receiving the IP packet at a home agent associated with a wireless communications network. The IP packet includes an IP address assigned to the device. If there is no current mobility binding record for the mobile device, instead of dropping the packet the home agent sends an access-request packet, containing the IP address, to an authentication server. The authentication server, e.g., a RADIUS server, maintains a table mapping the IP address for the device to an identification number uniquely associated with the device, such as the device's International Mobile Subscriber Identity number. The authentication server sends an access-accept packet to the home agent in the event that the device is authorized to receive the IP packet, in which case the access-accept packet includes the identification information. The home agent uses the identification number to locate, page and automatically connect the wireless device to the IP network via an InterWorking Unit (IWU) configured as a IP network access server.
Owner:UTSTARCOM INC
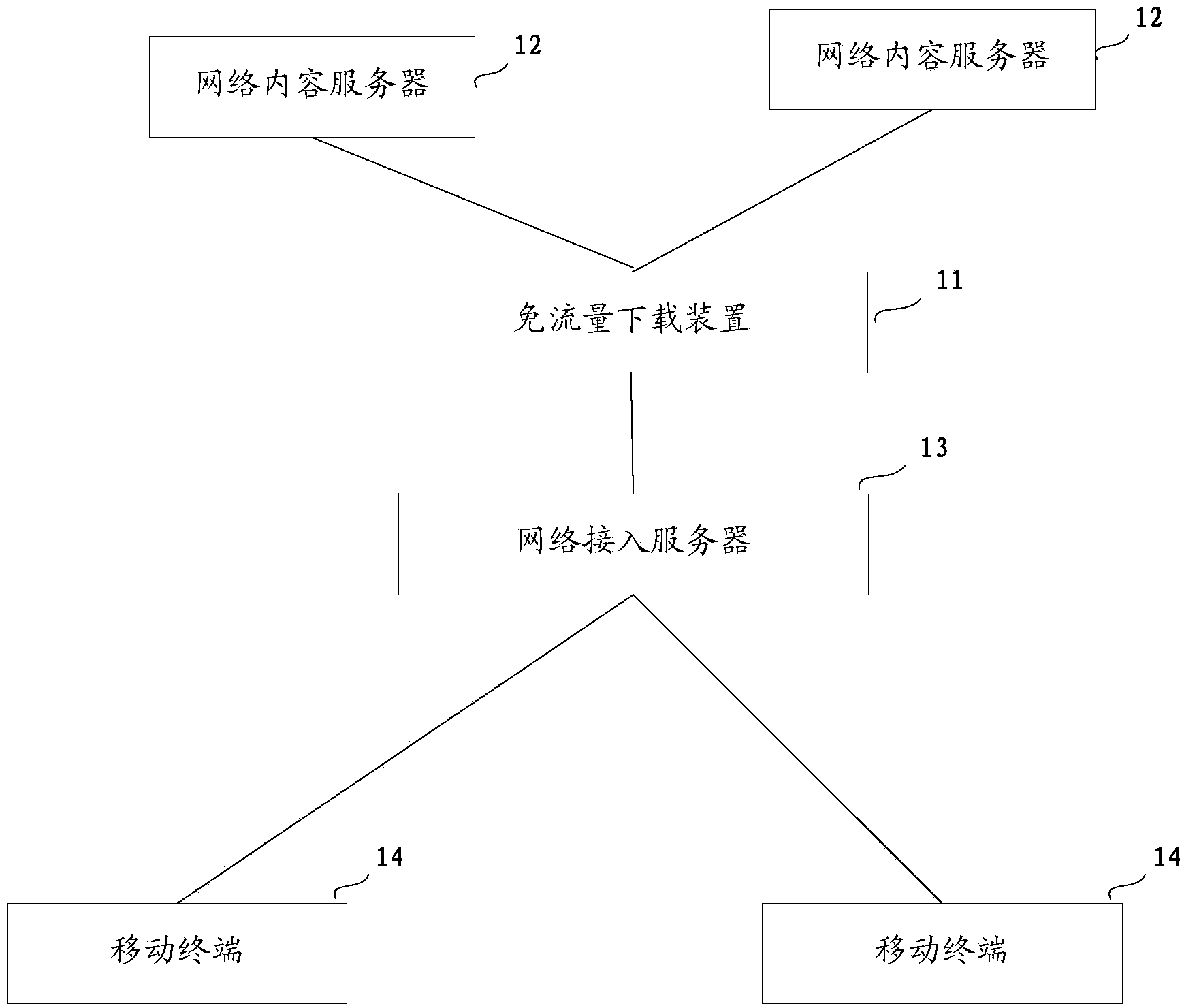
Traffic-free downloading method, device and system based on mobile terminal
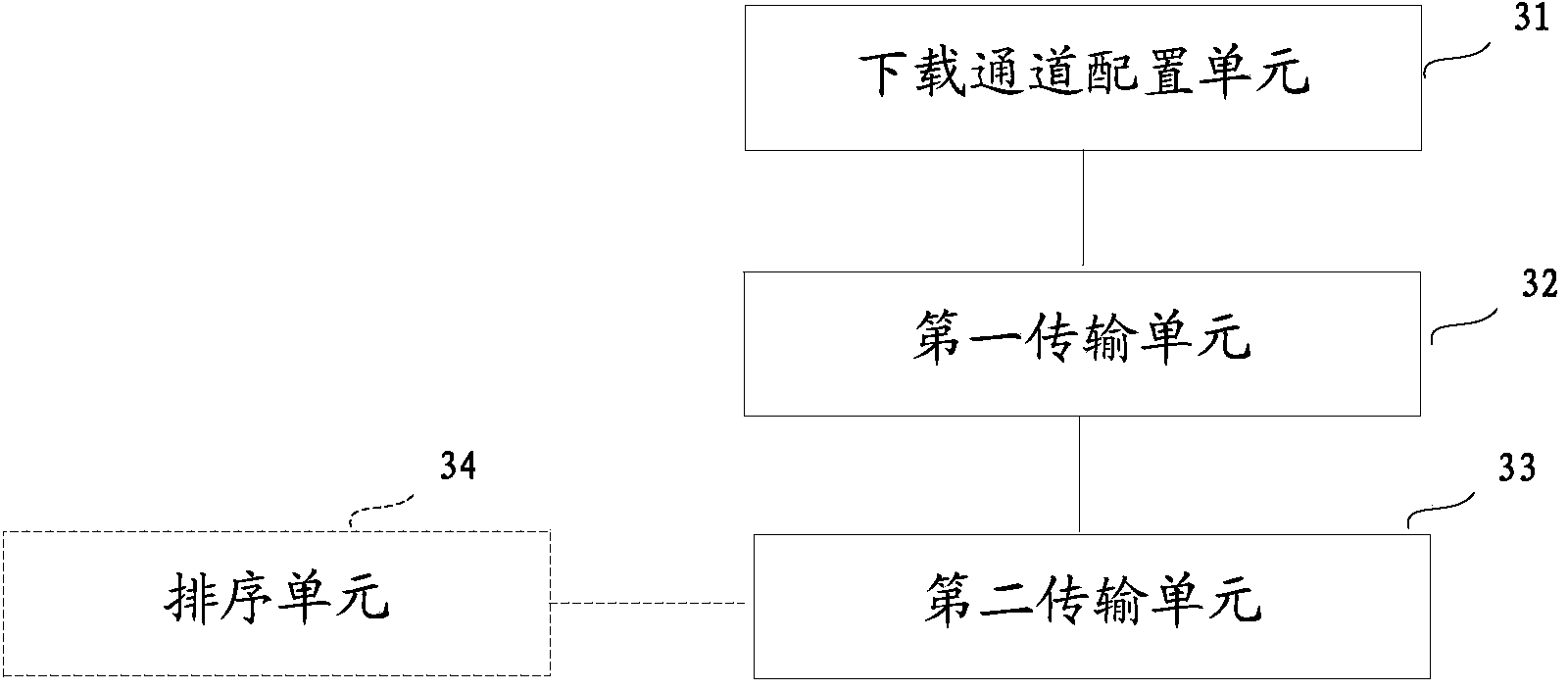
ActiveCN103841204AIncrease motivationAccounting/billing servicesTransmissionNetwork access serverTraffic capacity
The invention relates to a traffic-free downloading method, device and system based on a mobile terminal. The traffic-free downloading method, device and system are used for solving the problems that when network content is downloaded by a mobile terminal in the prior art, a user of the mobile terminal needs to pay lots of traffic fees, and accordingly user downloading enthusiasm is obviously lowered. The traffic-free downloading method comprises the steps that downloading channels with traffic-free identifications are configured for multiple terms of network content provided by a network content server, and the downloading channels and the traffic-free identifications of the downloading channels are supplied to a network access server; a special traffic-free downloading region where the multiple terms of network content can be downloaded according to a traffic-free mode is supplied to the mobile terminal through the network access server, wherein a plurality of downloading ports corresponding to all the terms of network content are formed in the special traffic-free downloading region, and each downloading port is used for being connected into one downloading channel so that the network content corresponding to the downloading port can be downloaded.
Owner:BEIJING QIHOO TECH CO LTD
Increased throughput across data network interface by dropping redundant packets
InactiveUS6700871B1Improve data throughputImprove throughputError prevention/detection by using return channelTransmission systemsNetwork access serverLow speed
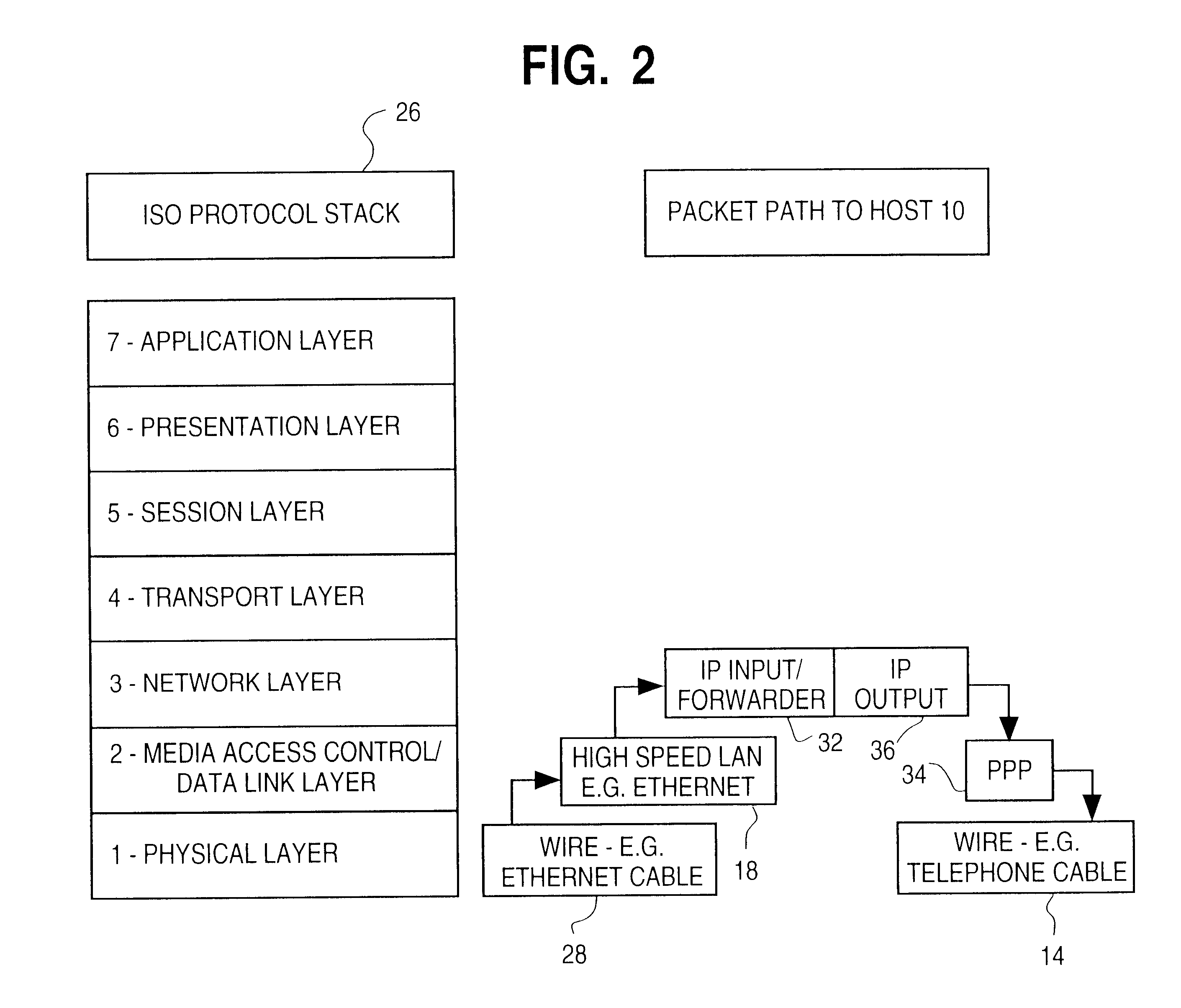
In a typical remote access application, such as access from the home to a packet-switched high speed network such as the Internet, the low-speed dial up connection to a network access is the main bottleneck in terms of the bandwidth and efficiency of transfer of data across the network access server. The present invention increases throughput through the network access server by identifying and dropping redundant, e.g., retransmitted, packets en route from the LAN or WAN to the remote terminal, thereby preserving precious bandwidth.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and system for coordination and control of data streams that terminate at different termination units using virtual tunneling
InactiveUS6157649ATime-division multiplexData switching by path configurationNetwork access serverData stream
A method for coordinating and controlling multiple data streams representing a data transmission session that terminate in different termination units (such as network access servers) using a virtual data stream tunnel is presented. The data streams are transmitted over two or more links, collectively forming a "bundle. One of the termination units that receives a data stream is designated as the termination unit to receive and reconstruct a call. The designated termination unit is the "owner" of the bundle. A termination unit that is a not a bundle owner creates a virtual tunnel to the termination unit that is the bundle owner, and sends data streams through the virtual tunnel to the bundle owner to reconstruct the call. The designated termination unit reconstructs the data streams for the bundle and directs the bundle to a destination.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Distributed processing of high level protocols, in a network access server
InactiveUS6304574B1Introduces latency and delayHeavy loadTelephone data network interconnectionsTime-division multiplexNetwork access serverModem device
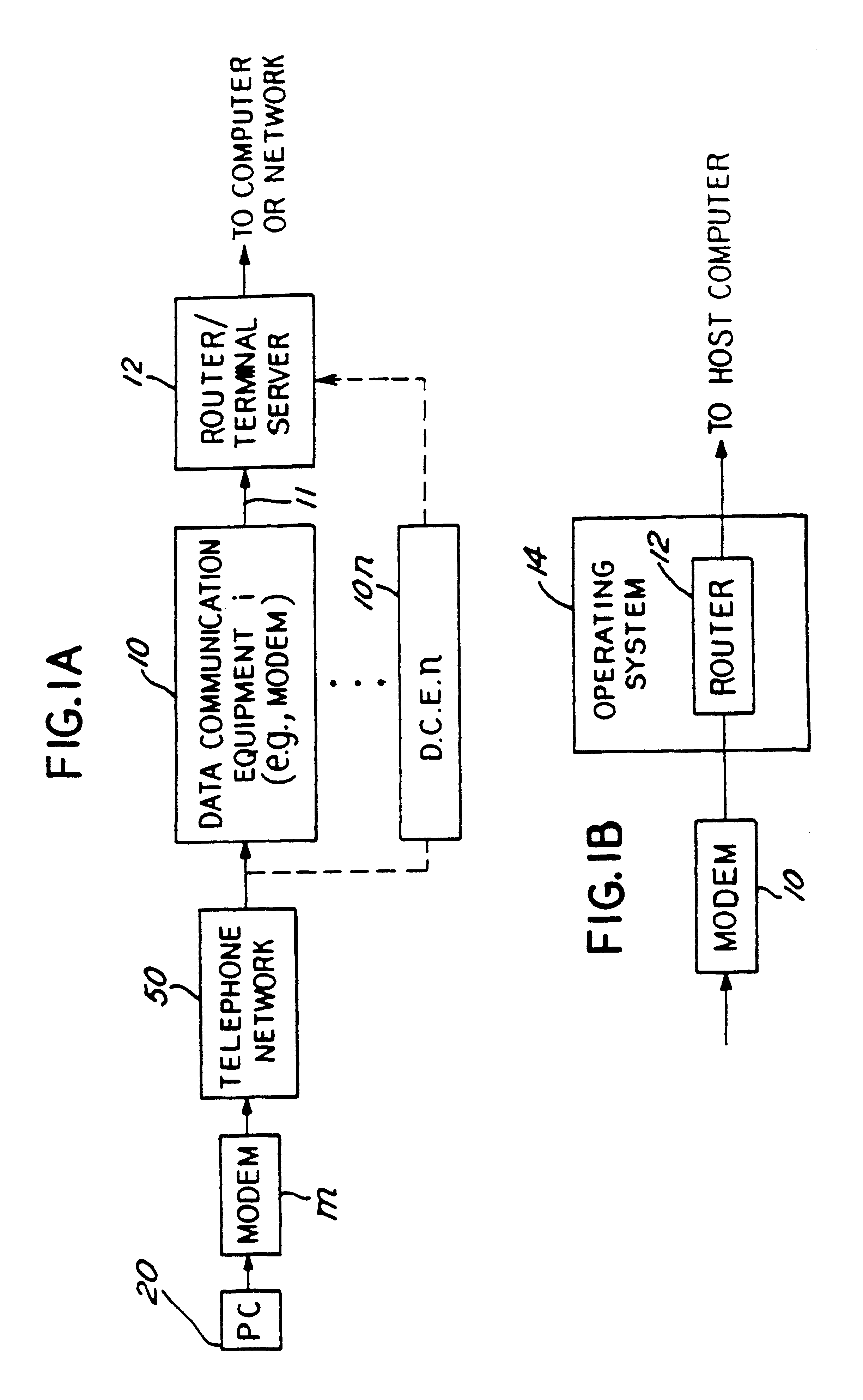
A method and apparatus for distributing protocol processing among a plurality of computing platforms. Data communications equipment such as Remote Access Devices, Communication Servers, Terminal Servers, and Dial-up Routers provide single user or large-scale multiple user communication access to various computing environments. The equipment costs and performance of such access equipment is related to the amount of CPU processing capability and memory required to support the desired number of serial communication links. It is common to use protocols that terminate in their entirely in the same processing machine. This invention encompasses methods developed to increase the cost / performance capabilities of the communication equipment that supports these serial links, primarily by means of distributing the protocol processing for higher level protocols across multiple computing platforms, including devices such as modems. Examples of such higher level protocols include PPP, SLIP and RTP.
Owner:UTSTARCOM INC
Instant activation of point-to point protocol (PPP) connection using existing PPP state
InactiveUS6628671B1Time-division multiplexWide area networksNetwork access serverPoint-to-Point Protocol
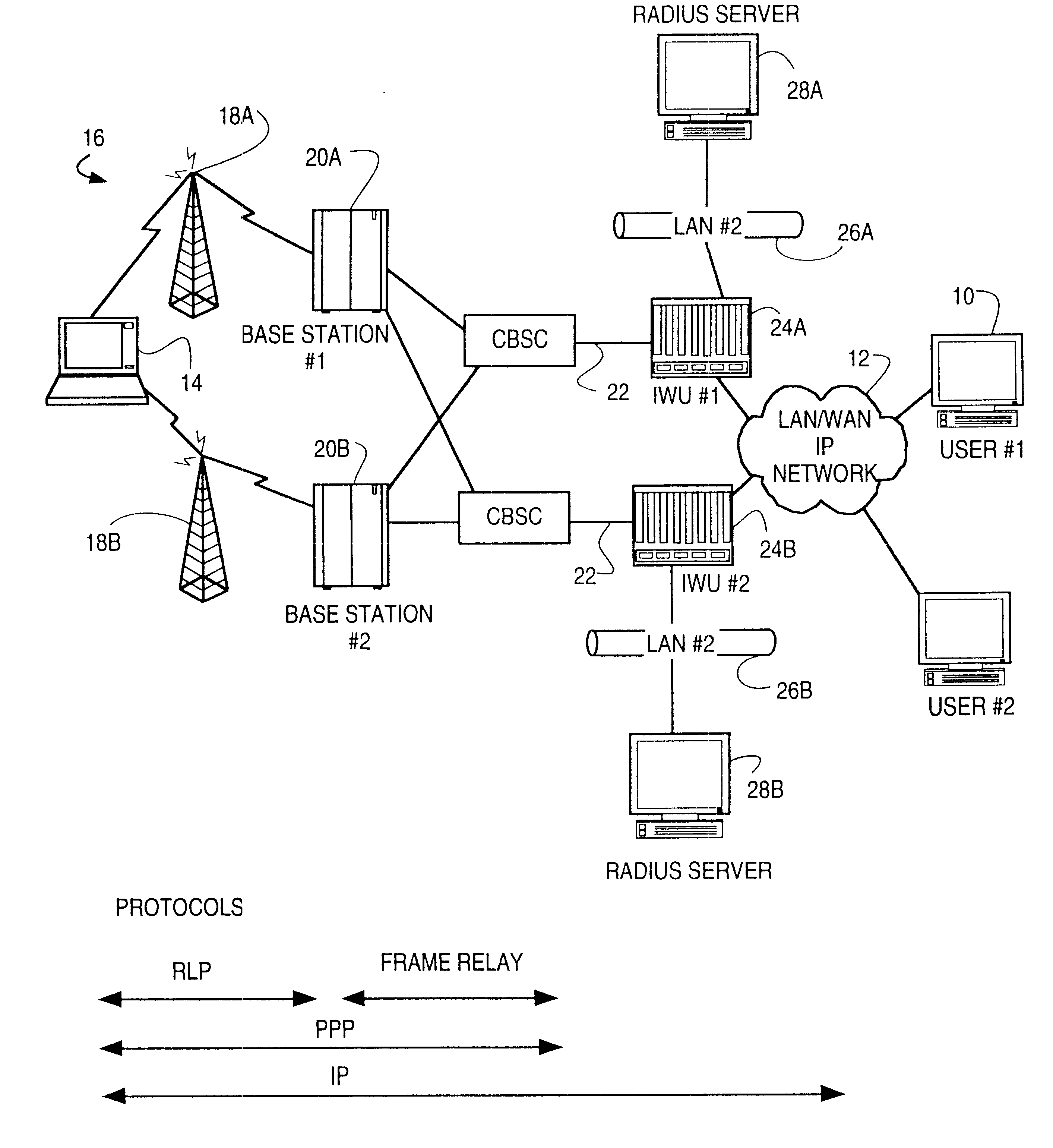
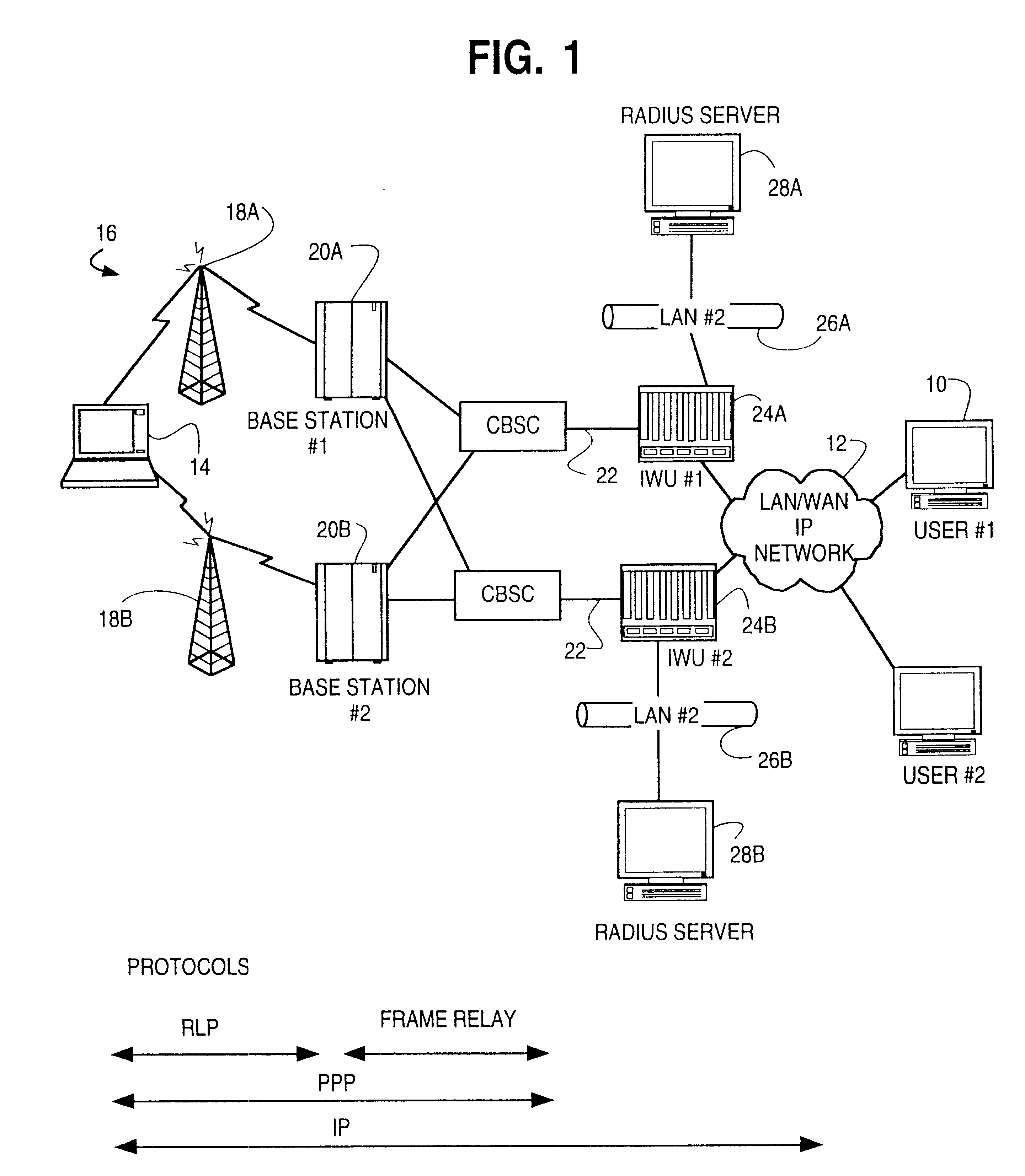
A network access server providing remote access to an IP network for a remote client initiates a PPP connection for a remote client quickly, and without requiring re-negotiation of Link Control Protocols and Network Control Protocols. The network access server has a PPP session with the remote client go dormant, for example when the user is a wireless user and goes out of range of a radio tower and associated base station. The network access server does not get rid of the PPP state for the dormant session, but rather switches that PPP state to a new session, such as when the client moves into range of a different radio tower and associated base station and initiates a new active session on the interface to the wireless network. The switching of PPP states may be within a single network access server, or from one network access server to another. This "context switching" of the active PPP session allows the mobile user to seamlessly move about the wireless network without having to re-negotiate Link Control Protocols and Network Control Protocols every time they move out of range of one radio tower and into range of another radio tower.
Owner:UTSTARCOM INC
Dynamic IP address allocation system and method
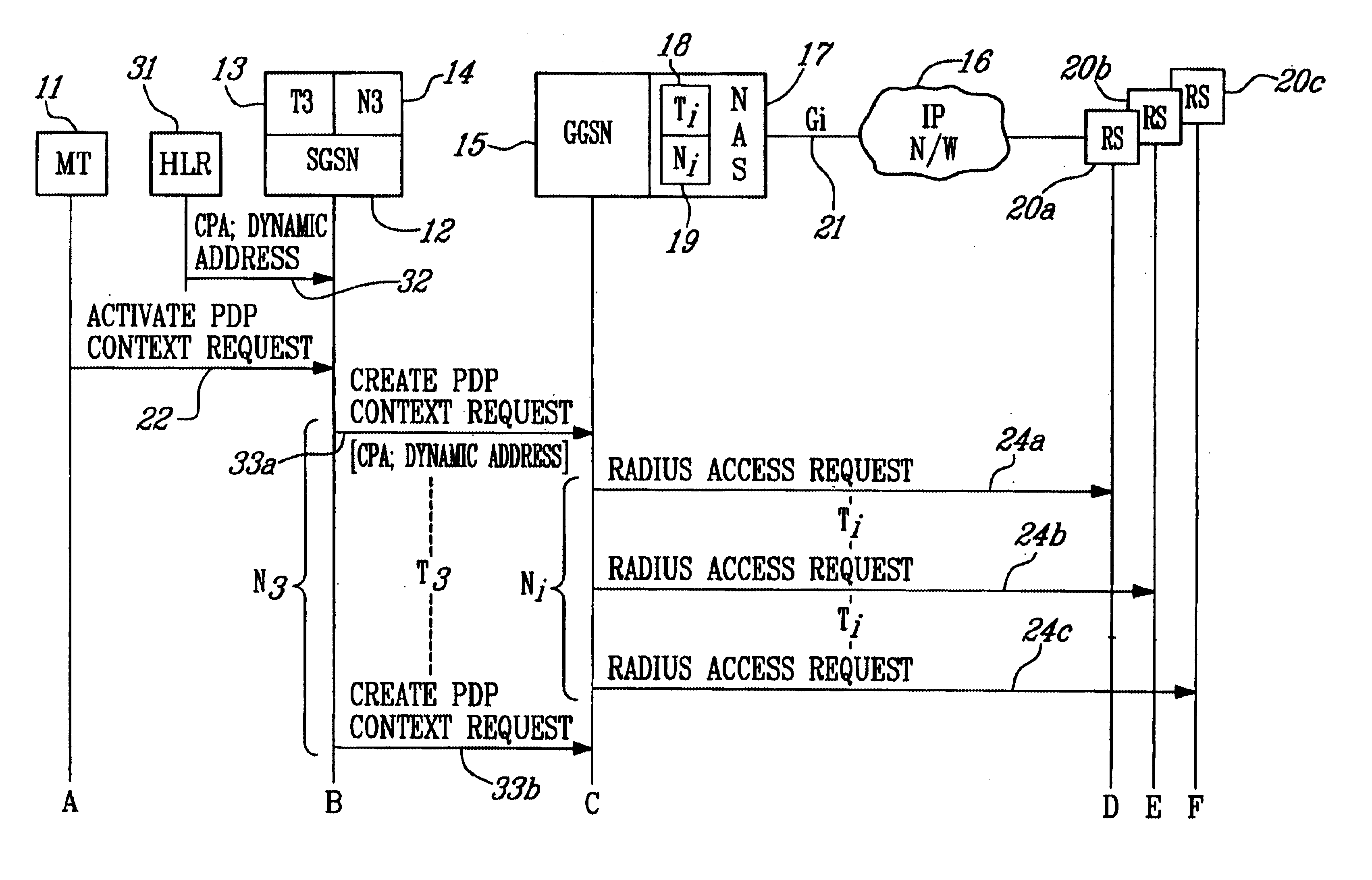
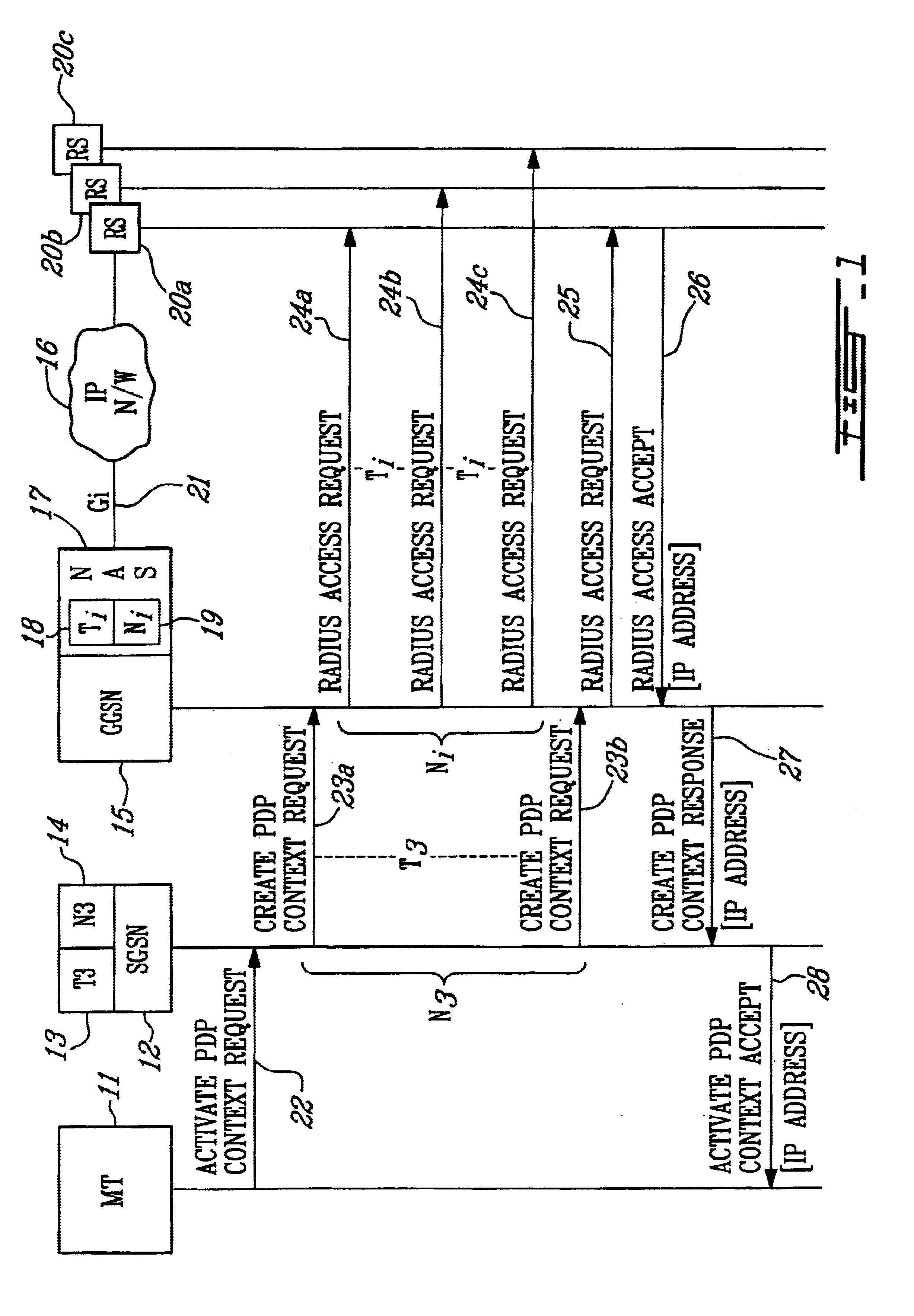
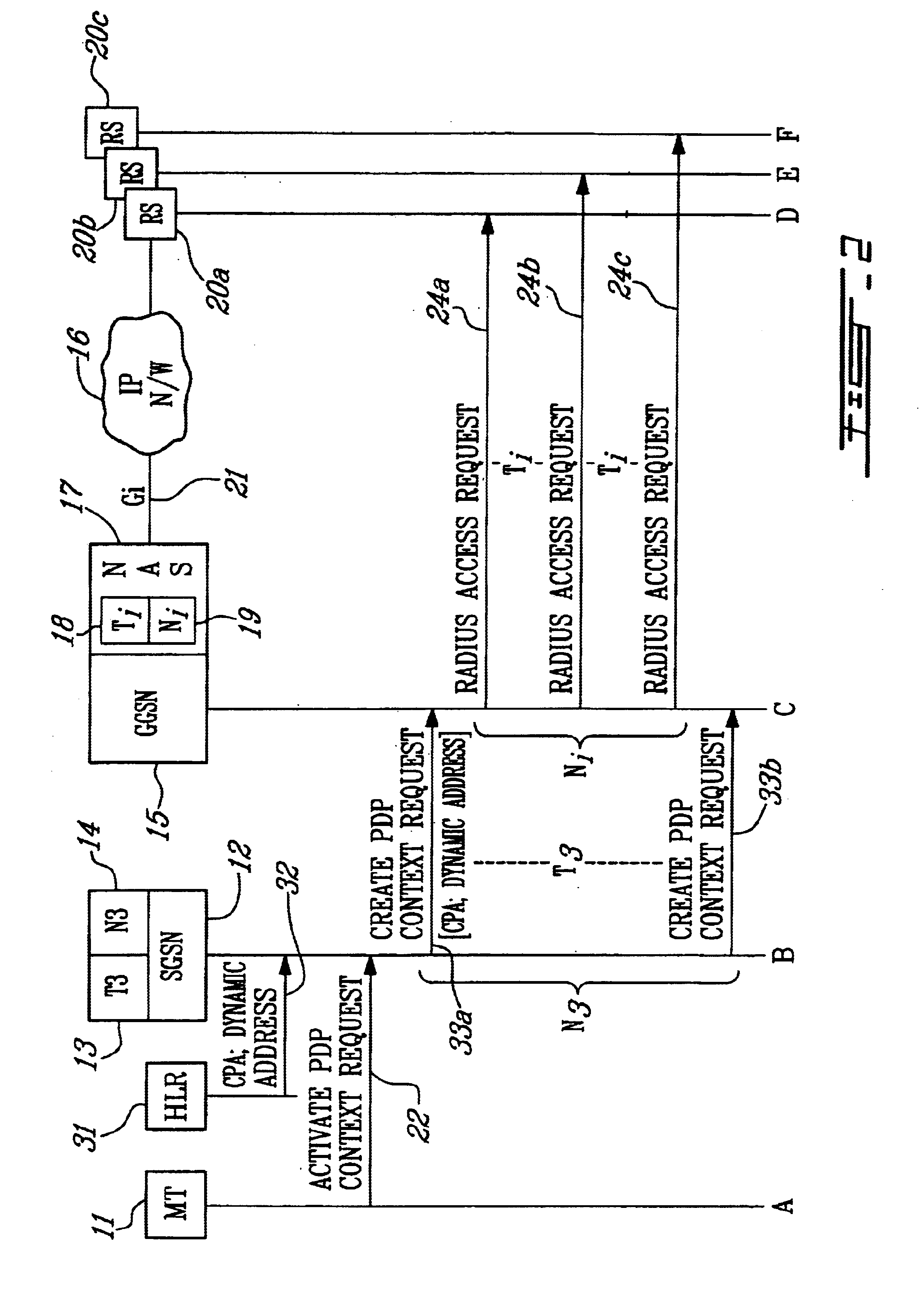
InactiveUS6687252B1Network traffic/resource managementConnection managementNetwork access serverPrivate IP
In a General Packet Radio Service (GPRS) network, a system and method of dynamically allocating an Internet Protocol (IP) address to a mobile terminal (MT) operating in the network. A Gateway GPRS Service Node (GGSN) requests IP addresses over the Gi interface from a Radius server in an IP-based network. A Conditional PDP Address (CPA) parameter is stored in the MT's Home Location Register (HLR) as part of the user subscriber data, and is passed to the GGSN during the GPRS Attach procedure. The CPA parameter indicates whether the subscriber is entitled to a backup IP address in case of failure to obtain one over the Gi interface, and whether the MT is a user of a real-time application. A timer in the GGSN sets a maximum time period (Ti) that the GGSN will wait for a response from the server, and a counter (Ni) sets the maximum number of requests that are sent. A Network Access Server (NAS) in the GGSN sends a request for an IP address from the GGSN to the server, and determines whether Ti expires without receiving a response from the server. If no response is received, the GGSN allocates an IP address. A public IP address is allocated only if the MT is a user of a real-time application. Otherwise, a private IP address is allocated.
Owner:TELEFON AB LM ERICSSON (PUBL)
Distributed protocol processing and packet forwarding using tunneling protocols
InactiveUS6763018B1Time-division multiplexData switching by path configurationNetwork access serverHigh density
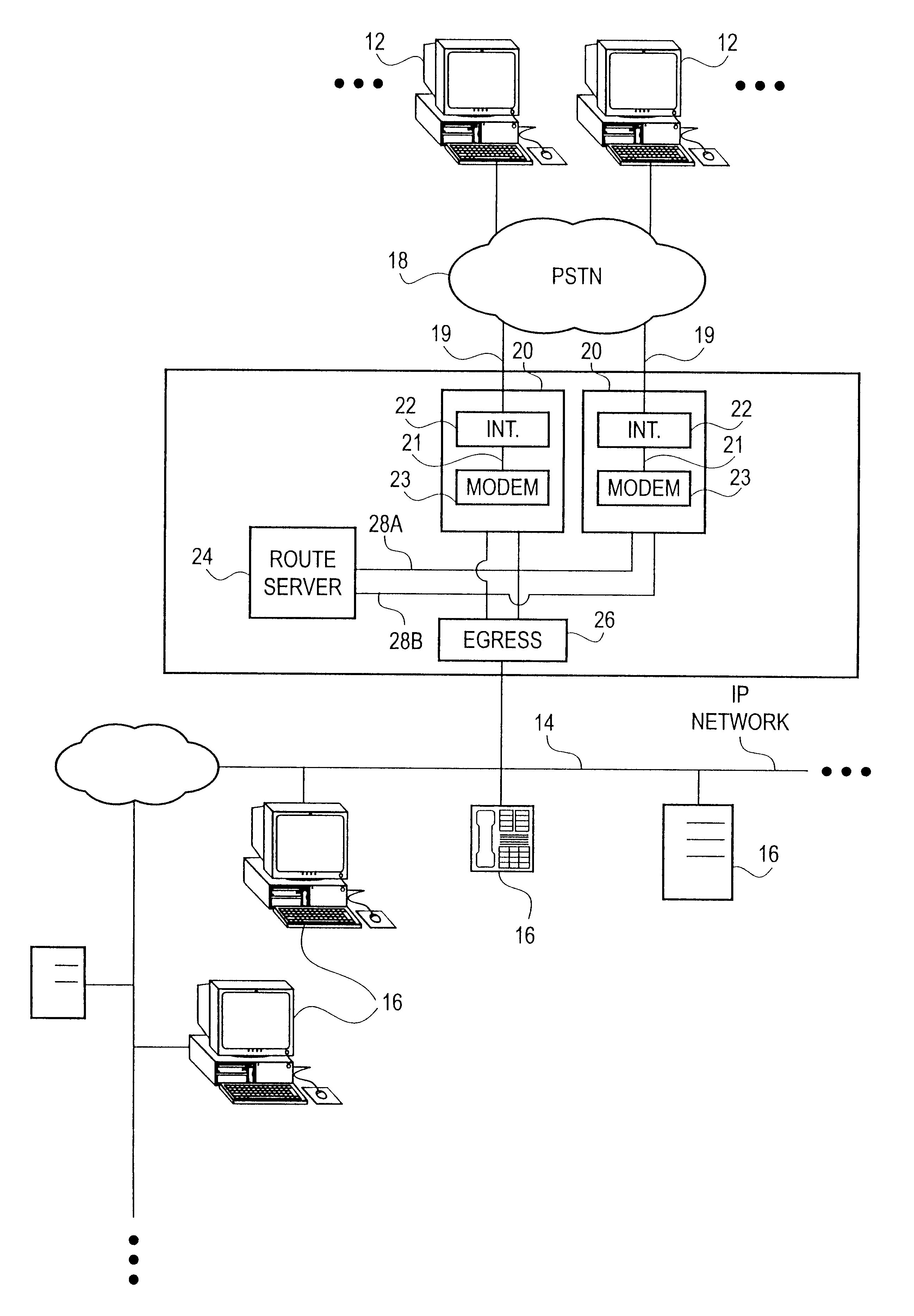
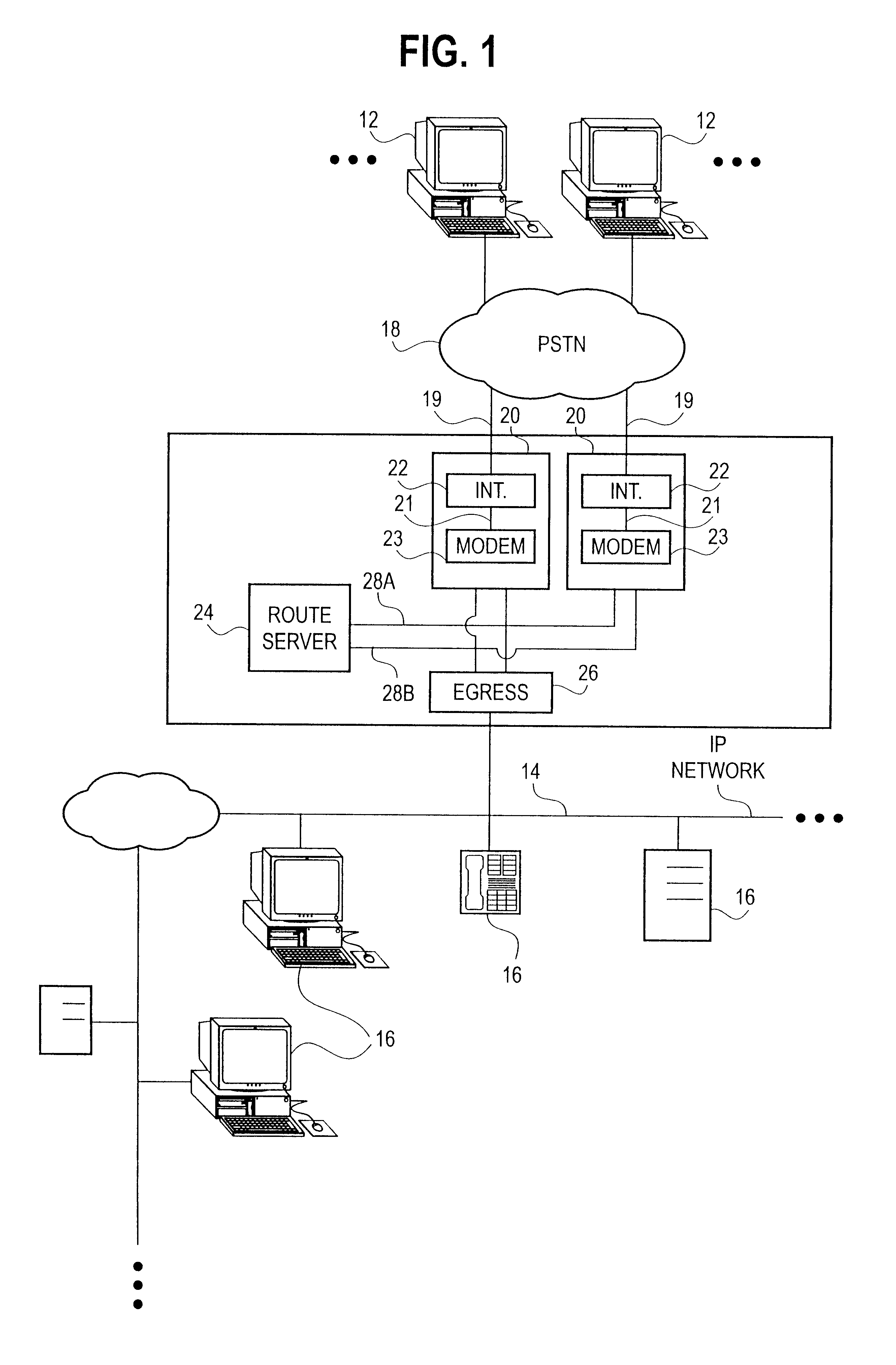
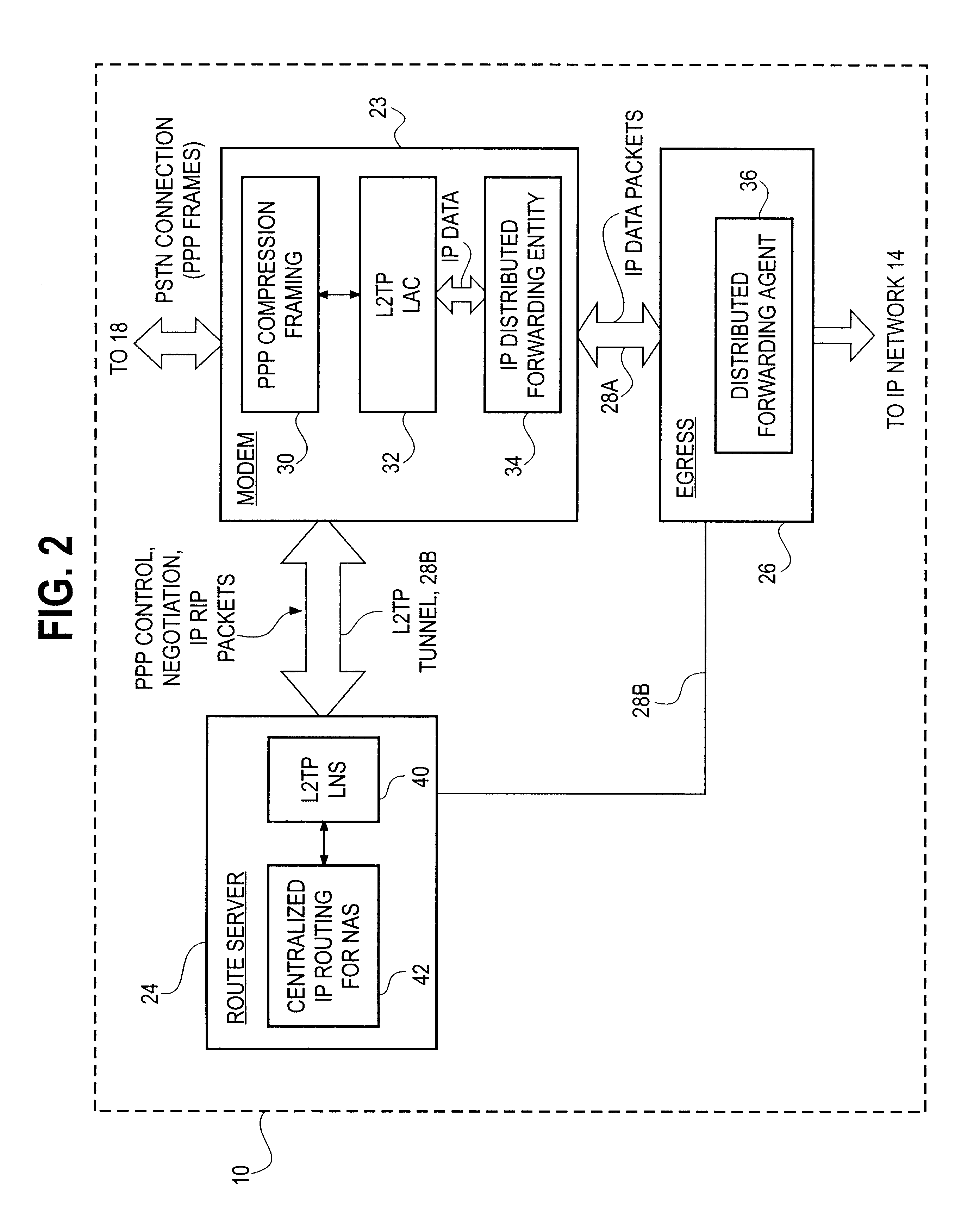
A high density network access server implements a tunneling protocol between a modem module and a route server module. PPP and routing control packets received from the PPP link are tunneled to the route server for processing. The IP data packet forwarding function for the network access server is distributed directly to the modem modules. The combination of distributed PPP processing and distributed IP data packet forwarding enables the capacity of the network access server to be scaled to orders of magnitude greater than previously known, to handle thousands or even tens of thousands of simultaneous data sessions.
Owner:VALTRUS INNOVATIONS LTD
Method for accessing a network and network access device
ActiveUS20130188634A1Inhibit functioningOptimizationEnergy efficient ICTData switching by path configurationNetwork access serverPrivate network
The invention provides for a method for accessing a virtual private network over a packet switched network, the method comprising sending, by a provider edge router, network labelling information about data packet labels to a network access device using a layer 2 network protocol. The method may be performed for accessing a hierarchical Virtual Private LAN Service network using a link layer distribution protocol as signalling protocol for Multi-Protocol Label Switching labels attached to data packets of the packet switched network.
Owner:ADVA OPTICAL NETWORKING SE
Intraserver tag-switched distributed packet processing for network access servers
Owner:CISCO TECH INC
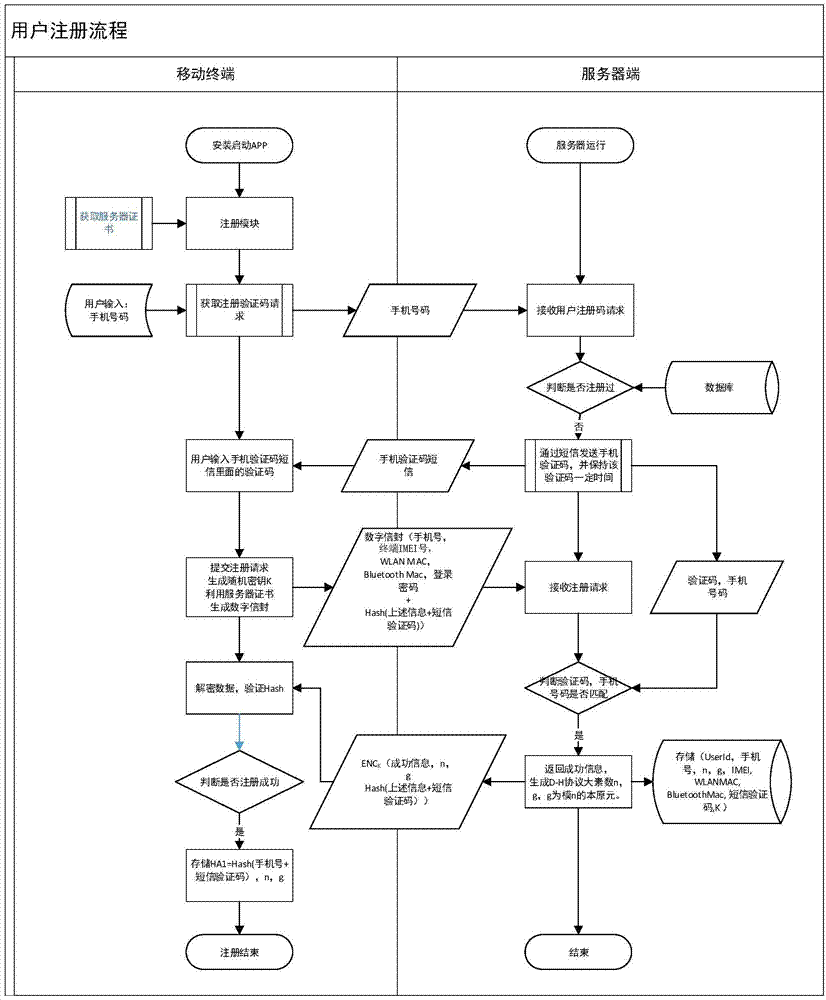
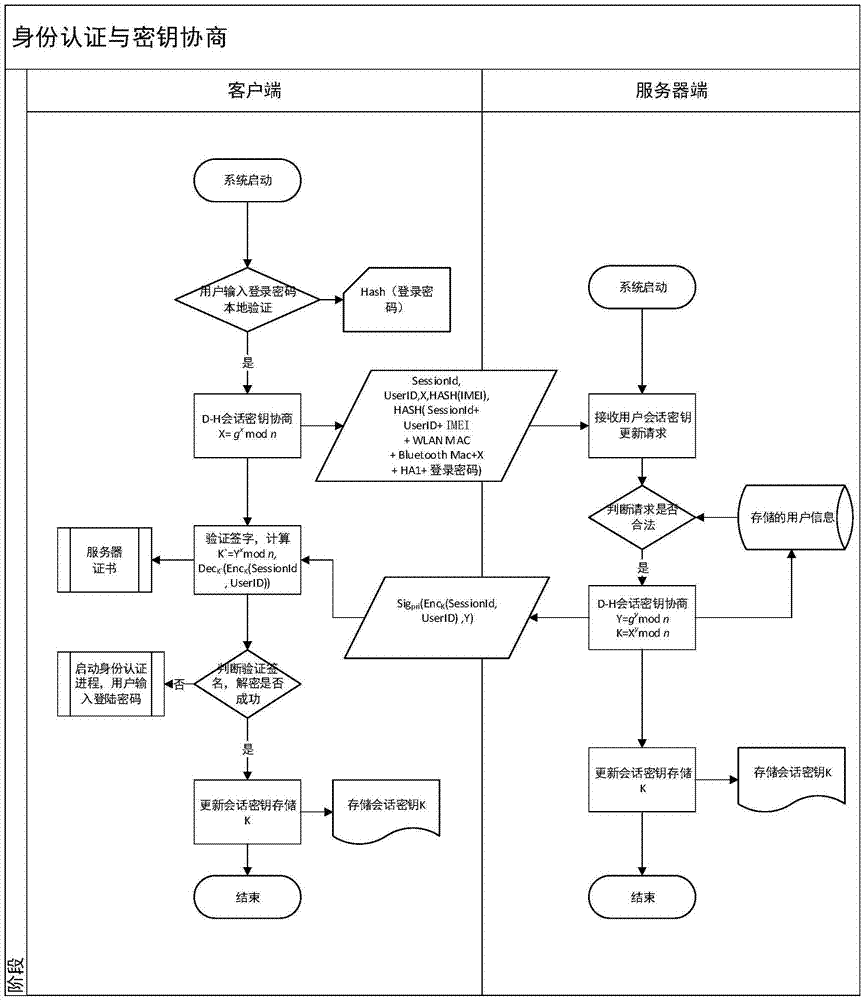
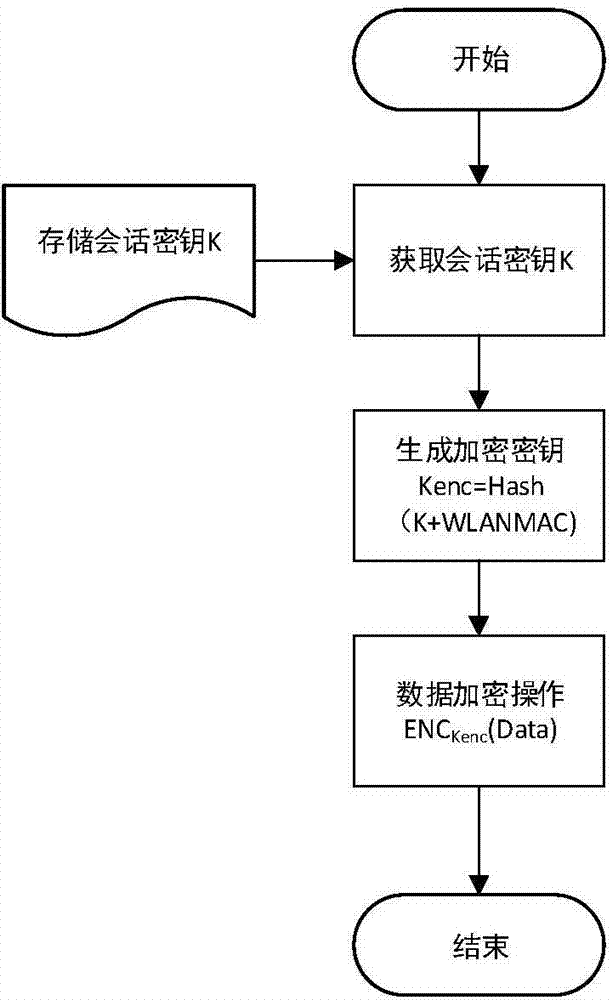
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
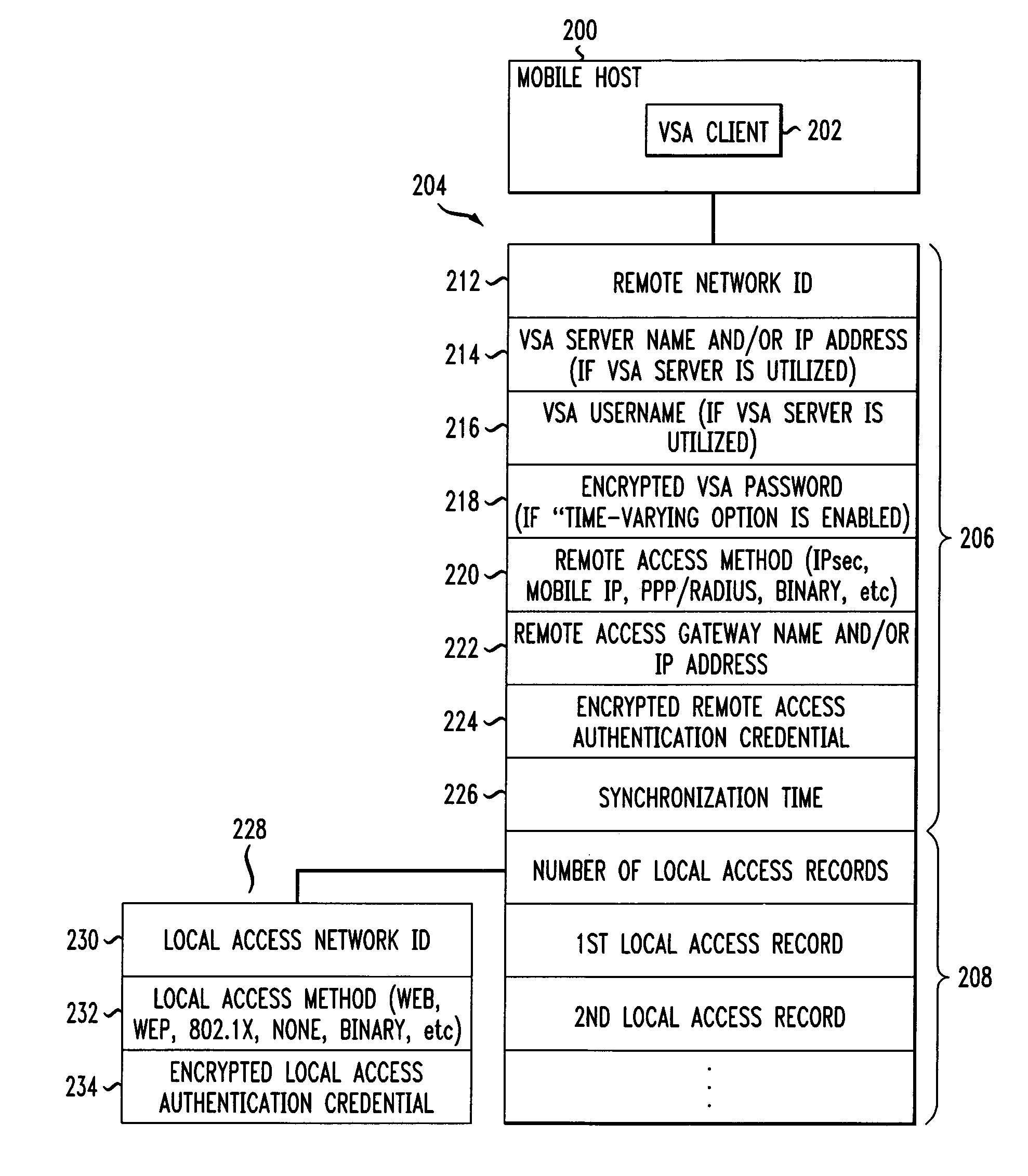
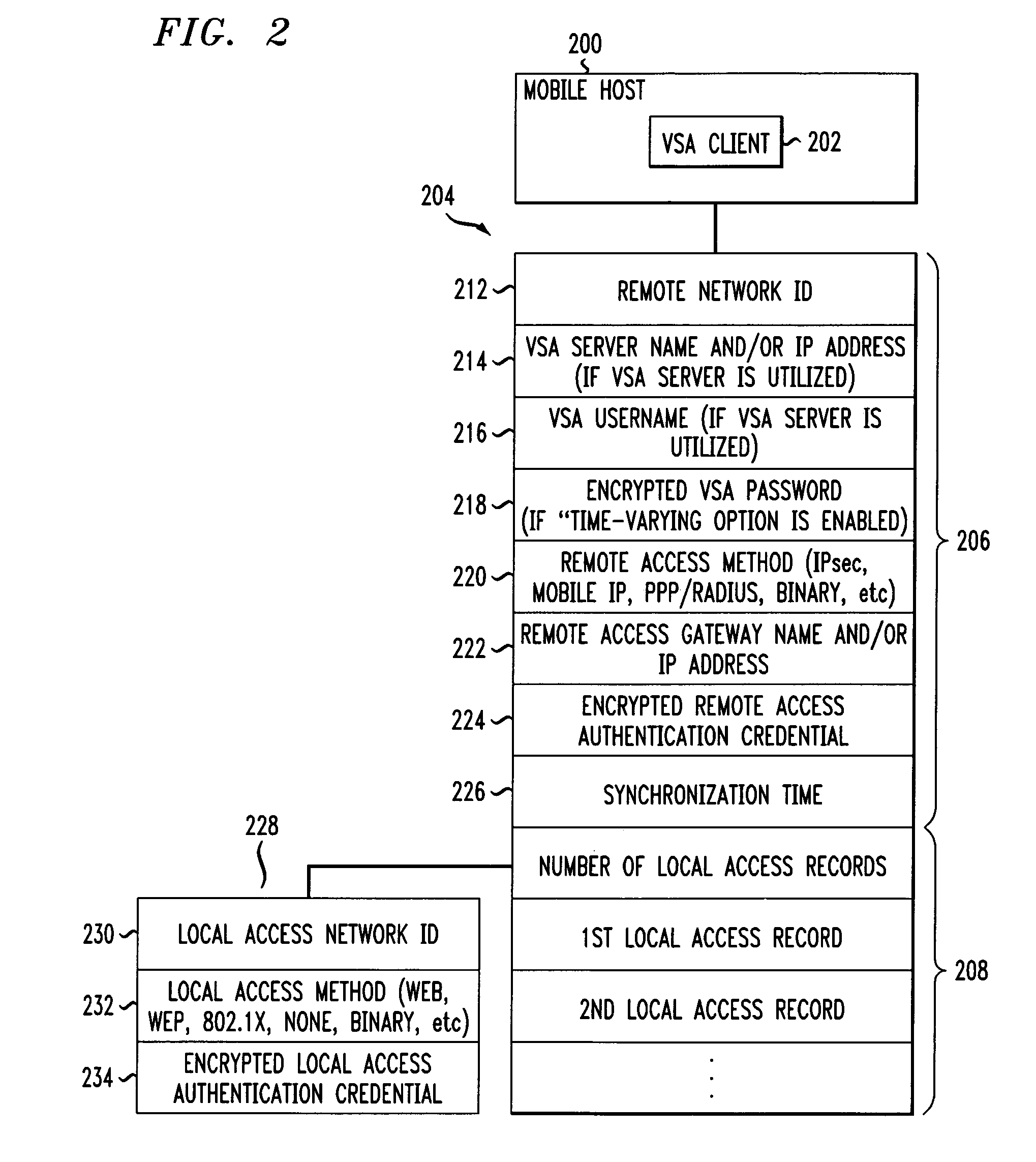
Mobile host using a virtual single account client and server system for network access and management
InactiveUS6971005B1Improve convenience performanceImprove security performanceDigital data processing detailsMultiple digital computer combinationsNetwork access serverNetwork connection
A Virtual Single Account (VSA) system that provides a mobile user with automatic authentication and connection to a remote network via local access networks with a single password, where the local access networks may be independent of the remote network. A mobile user has a single authentication credential for one VSA that is utilized by a VSA client installed on a mobile computing device. The VSA client provides for automatically authenticating and connecting the user's mobile device to a current local access network, and the target remote network such as the user's office network. All authentication credentials are encrypted using a key generated from the user's VSA password that is generated from the user's single password. The VSA client derives the key from the submitted VSA password and decrypts all authentication credentials that are required in order to connect the mobile device to the current local access network and thereafter to the office network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
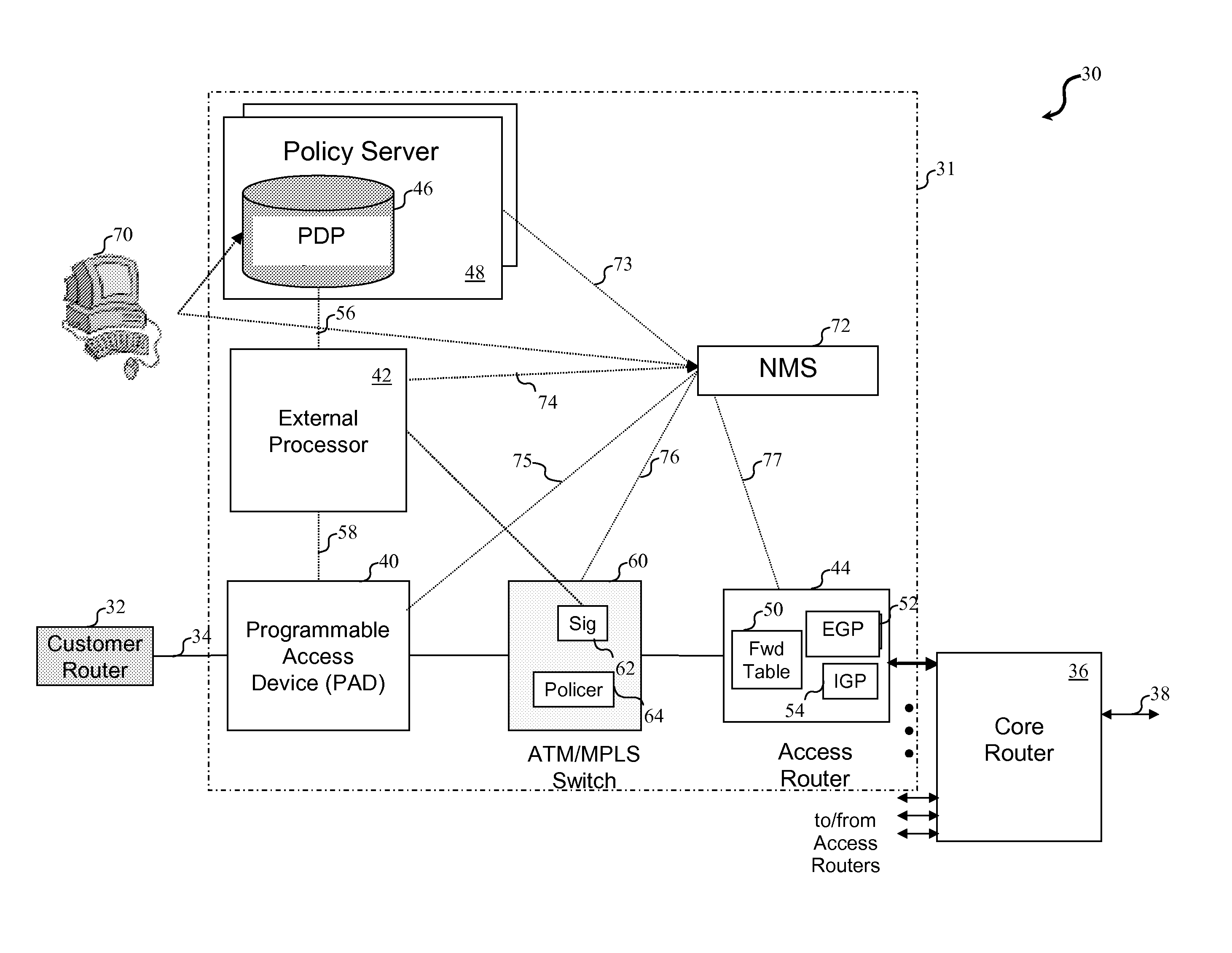
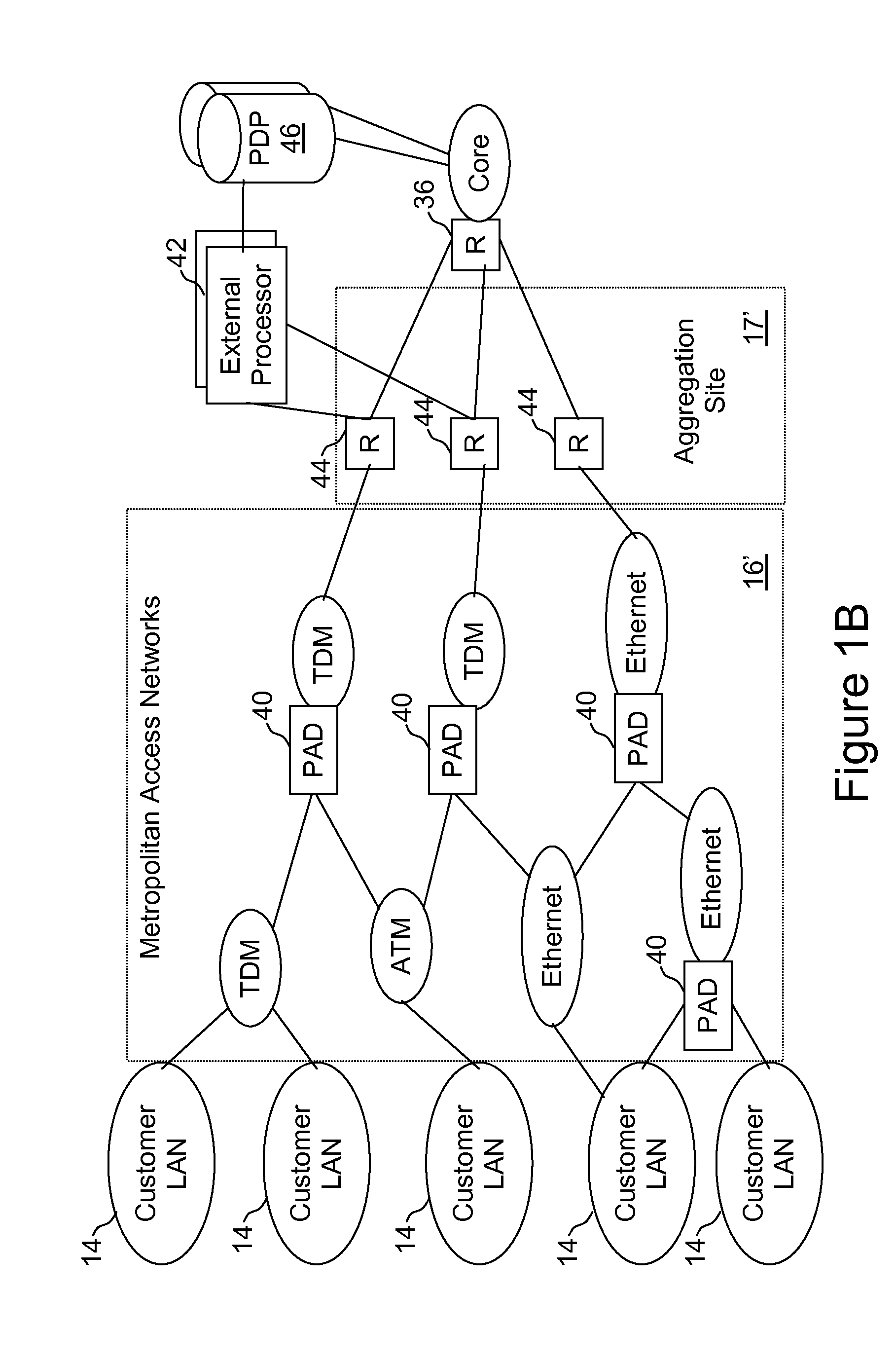
External processor for a distributed network access system
InactiveUS20110270956A1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationPolicy decisionTraffic capacity
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
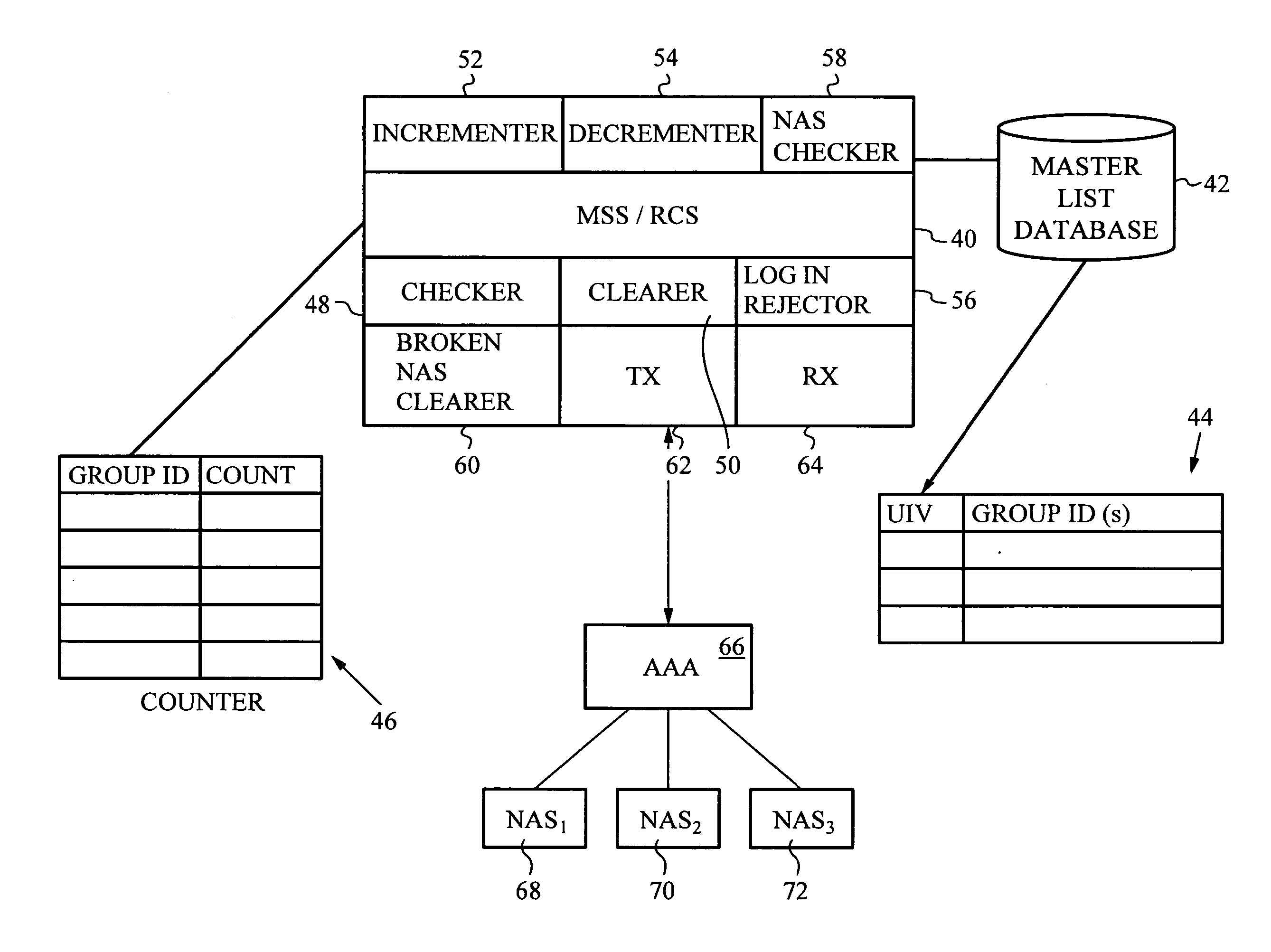
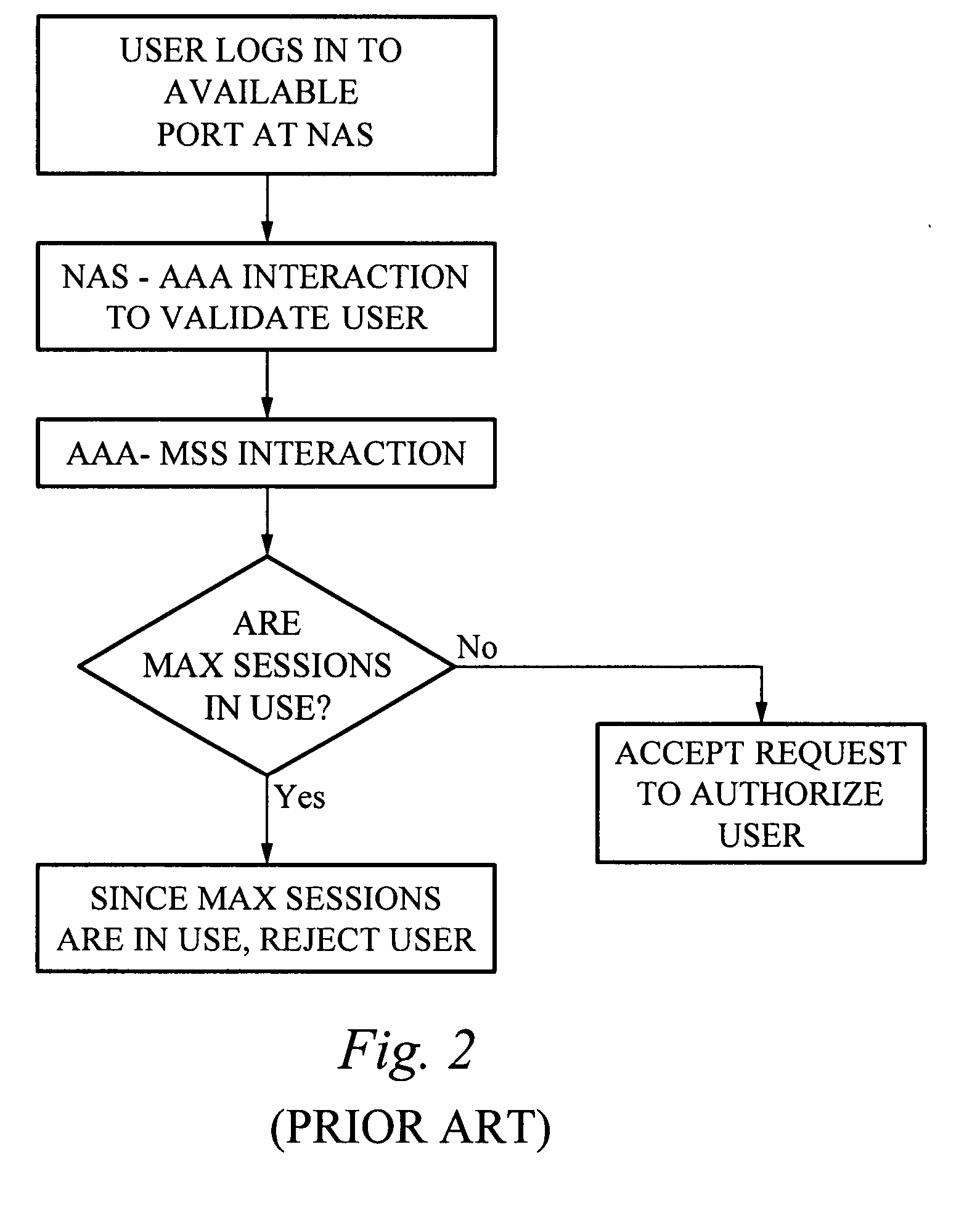
Automatic hardware failure detection and recovery for distributed max sessions server
InactiveUS20080005328A1Digital computer detailsNon-redundant fault processingNetwork access serverUnique identifier
A Max Sessions Server (MSS) automatically detects hardware and communications failures. Upon detection, counters are adjusted accordingly to maintain an accurate count of users or groups of users on a system. A database of unique identifiers for each connection is maintained, where the unique identifier is a concatenation of a Network Access Server (NAS) and the connection's incoming NAS node number. If a user requests permission to log into the system, the MSS first checks the database to determine if the unique identifier is already logged in. If so, then a hardware or communications failure has occurred and the MSS must make the appropriate adjustments to the database and counter.
Owner:CISCO TECH INC
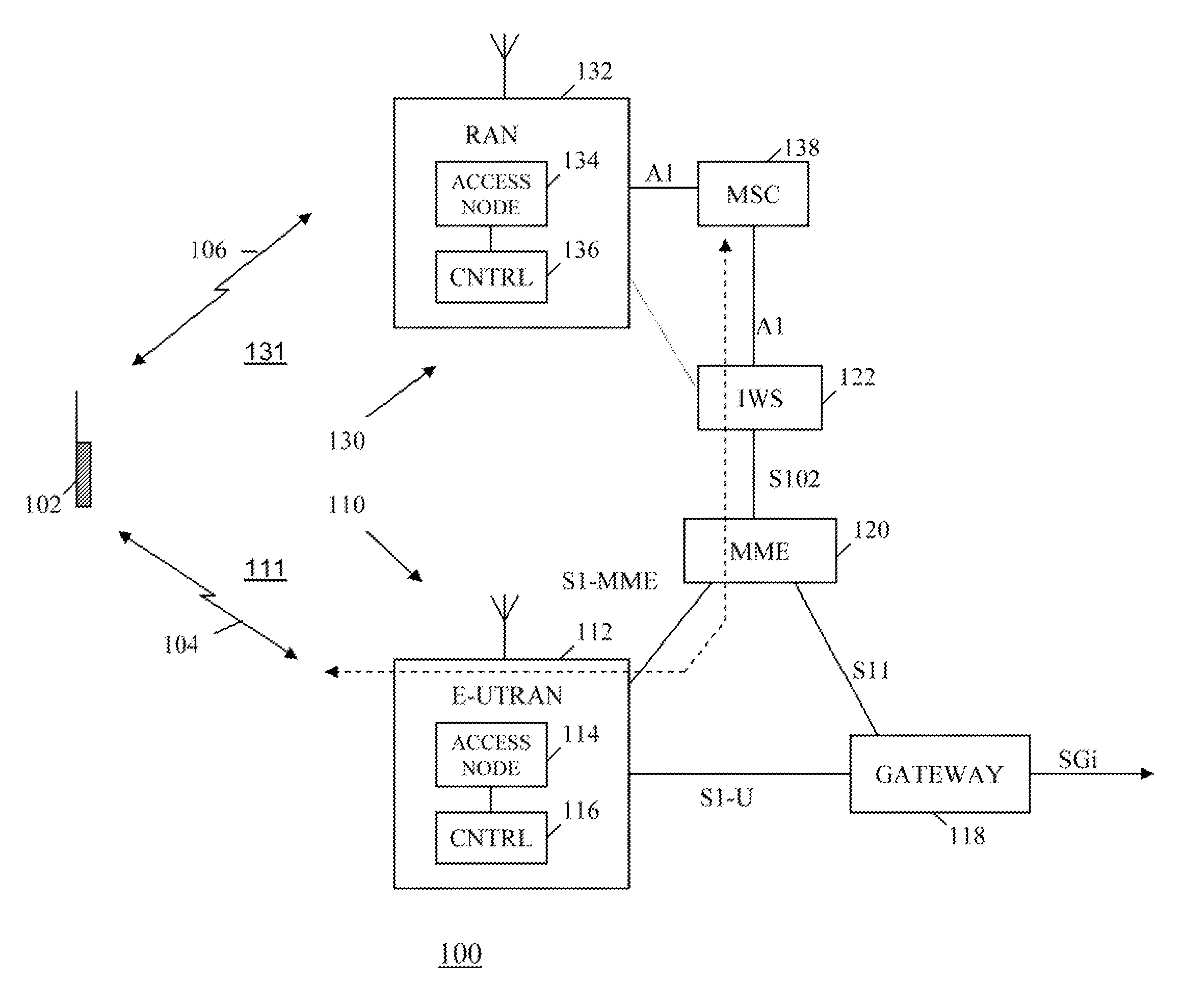
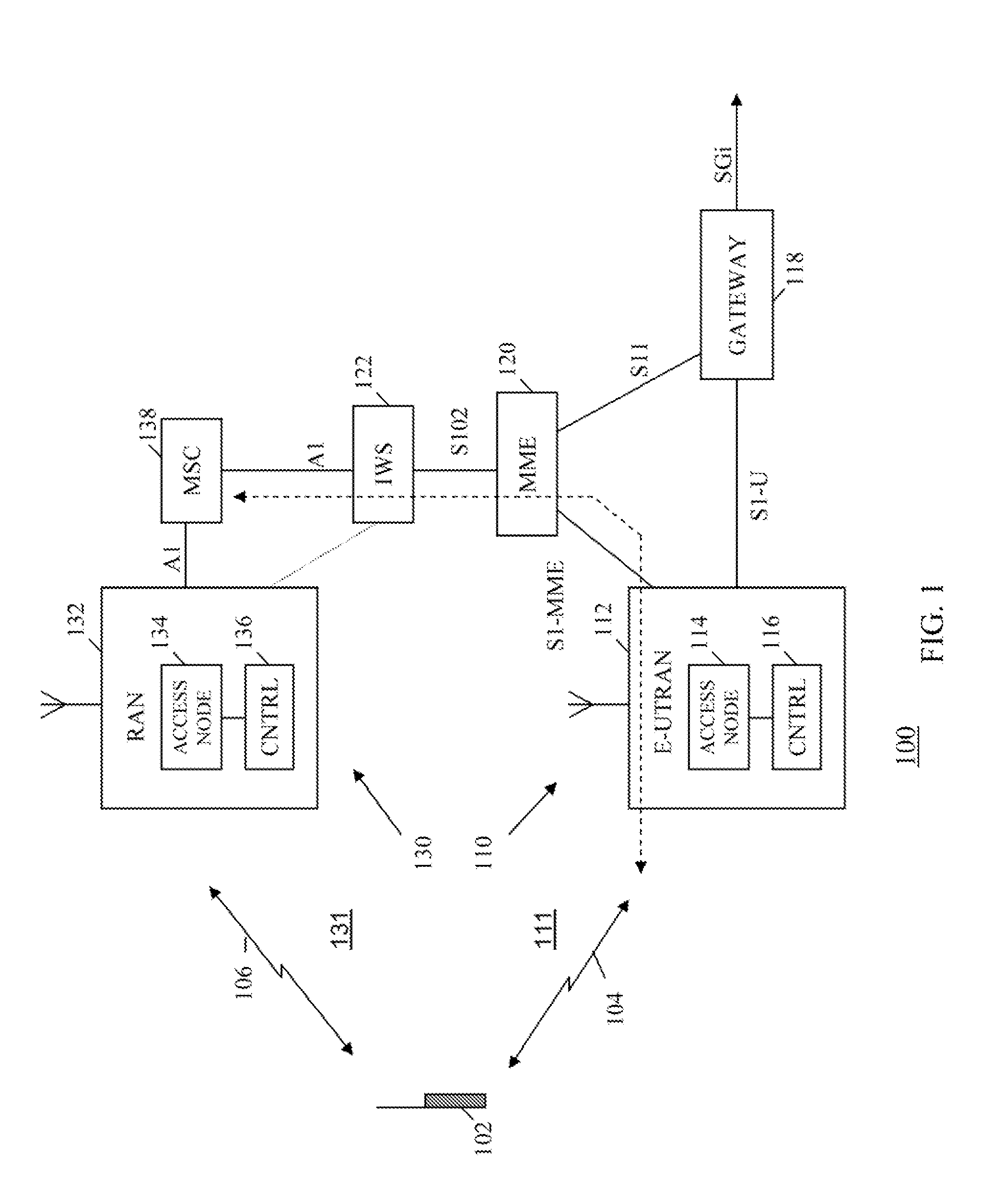
Method and apparatus for controlling network access in a multi-technology wireless communication system
InactiveUS20120170503A1Assess restrictionBroadcast transmission systemsNetwork access serverLimited access
A method and apparatus is provided for controlling network access in a communication system comprising a packet data network and a circuit switched network. The packet data network receives, from the circuit switched network, a message indicating that the circuit switched network is congested. In response to receiving the indication, the packet data network broadcasts a message informing that access to one or more services of the circuit switched network is restricted. In various embodiments, the message received from the circuit switched network may include access class barring parameters identifying one or more classes of user equipment or service classes that are one or more of being barred from accessing the circuit switched network or whose access to the circuit switched network is being reduced and / or may identify one or more coverage areas or access nodes of the circuit switched network where access is being restricted.
Owner:GOOGLE TECH HLDG LLC
Method for populating a location information database used in the delivery of emergency and other location-based services in a VoIP environment
ActiveUS20070220038A1Digital data processing detailsTelephonic communicationNetwork access serverEmergency situations
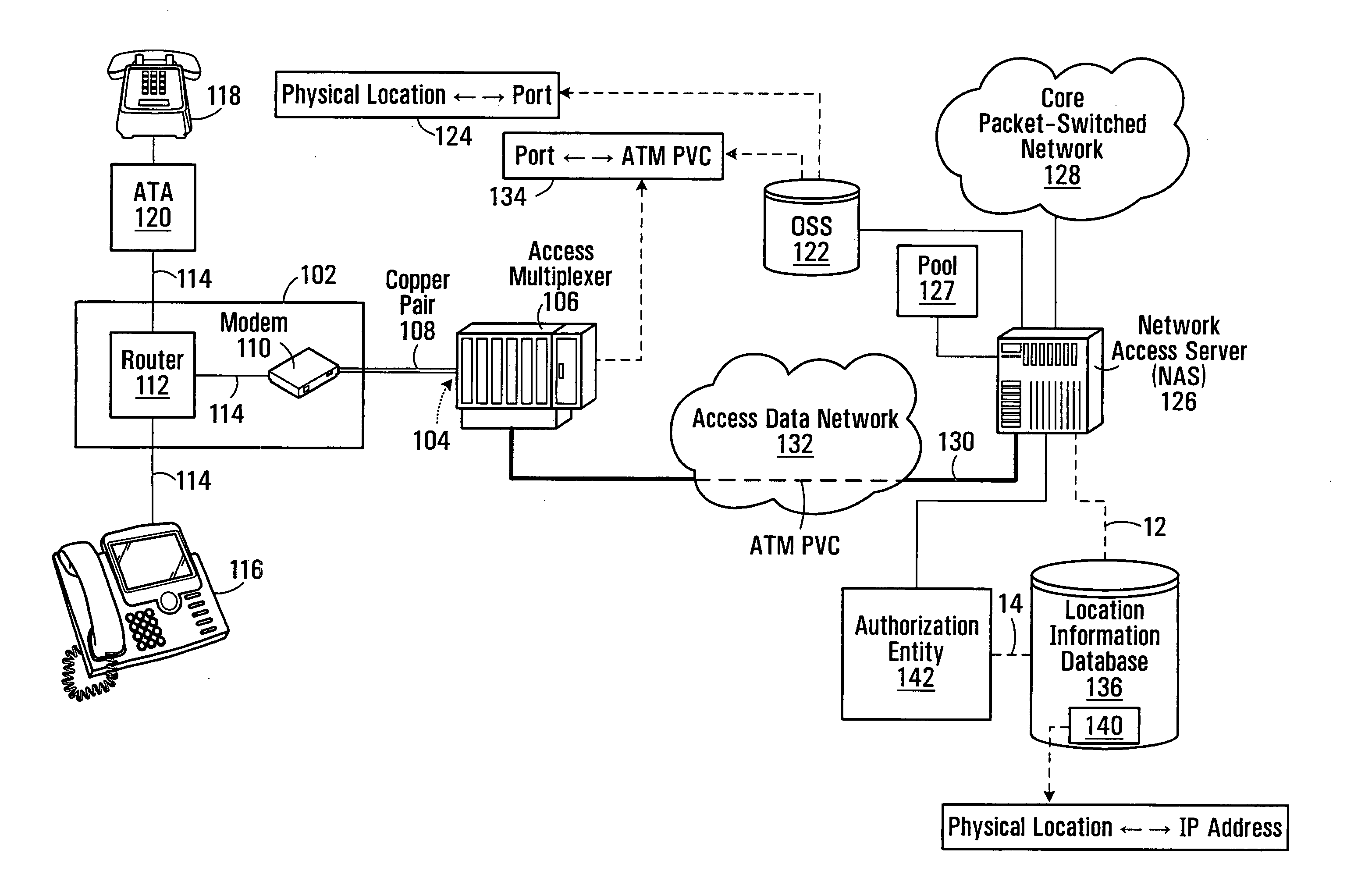
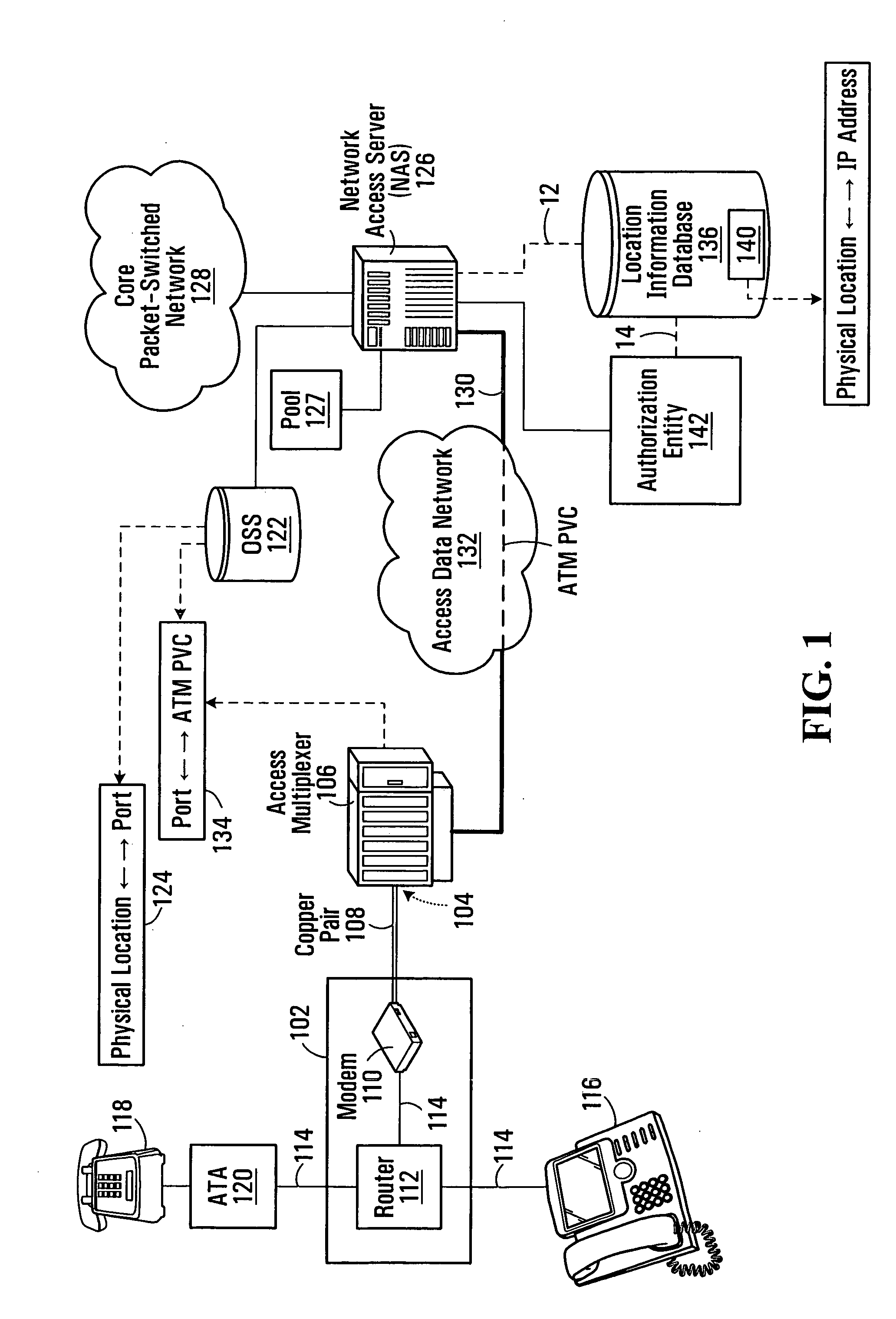
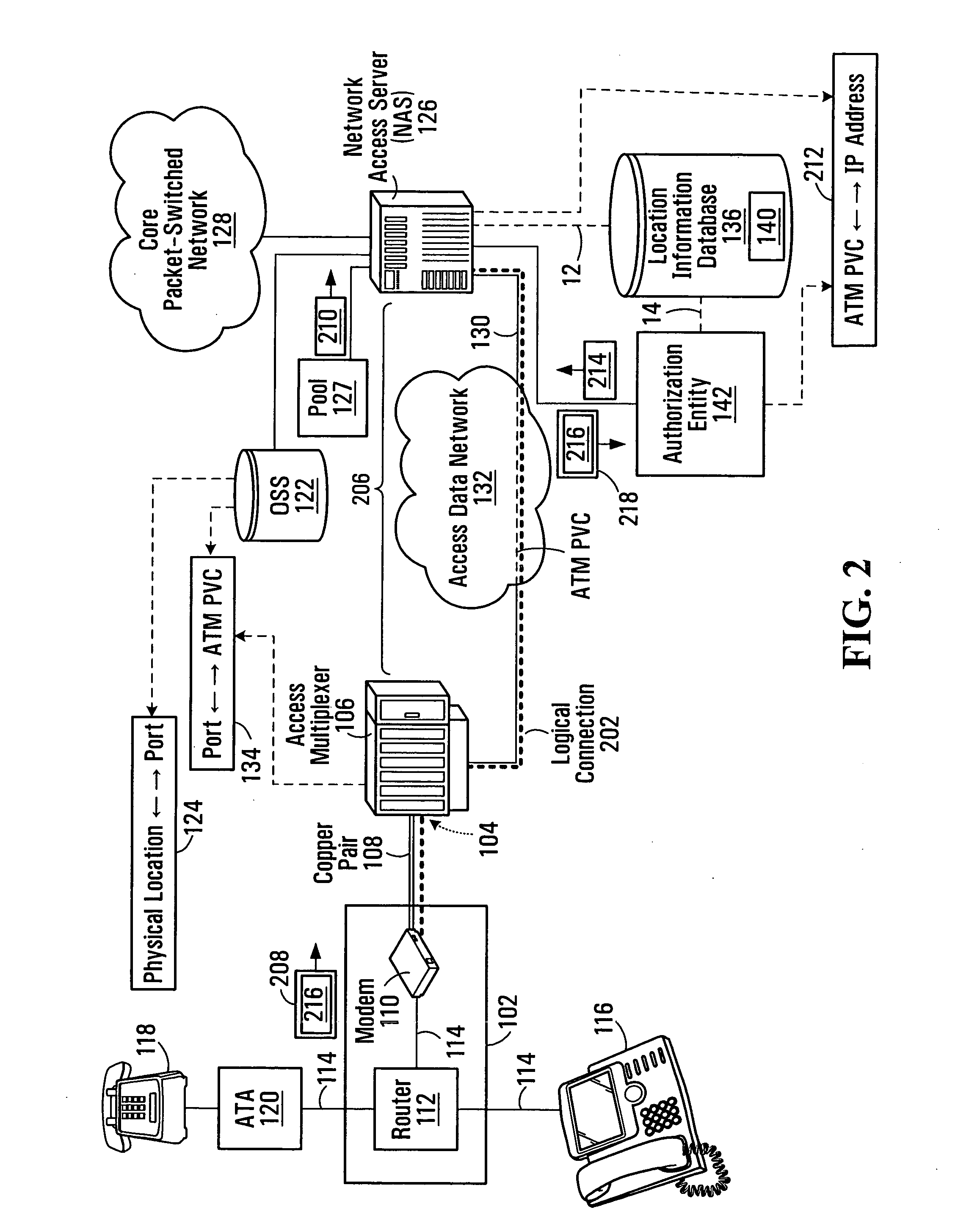
A method of populating a location information database for use in providing a location-based service to a host device that is an endpoint of a logical connection between the host device and a network access server. The method comprises receiving from the host device over the logical connection a request for network access; assigning a logical identifier to the host device in response to the receiving; determining a physical location associated with the endpoint of the logical connection; creating an association between the logical identifier and the physical location; and storing the association in the location information database.
Owner:BCE
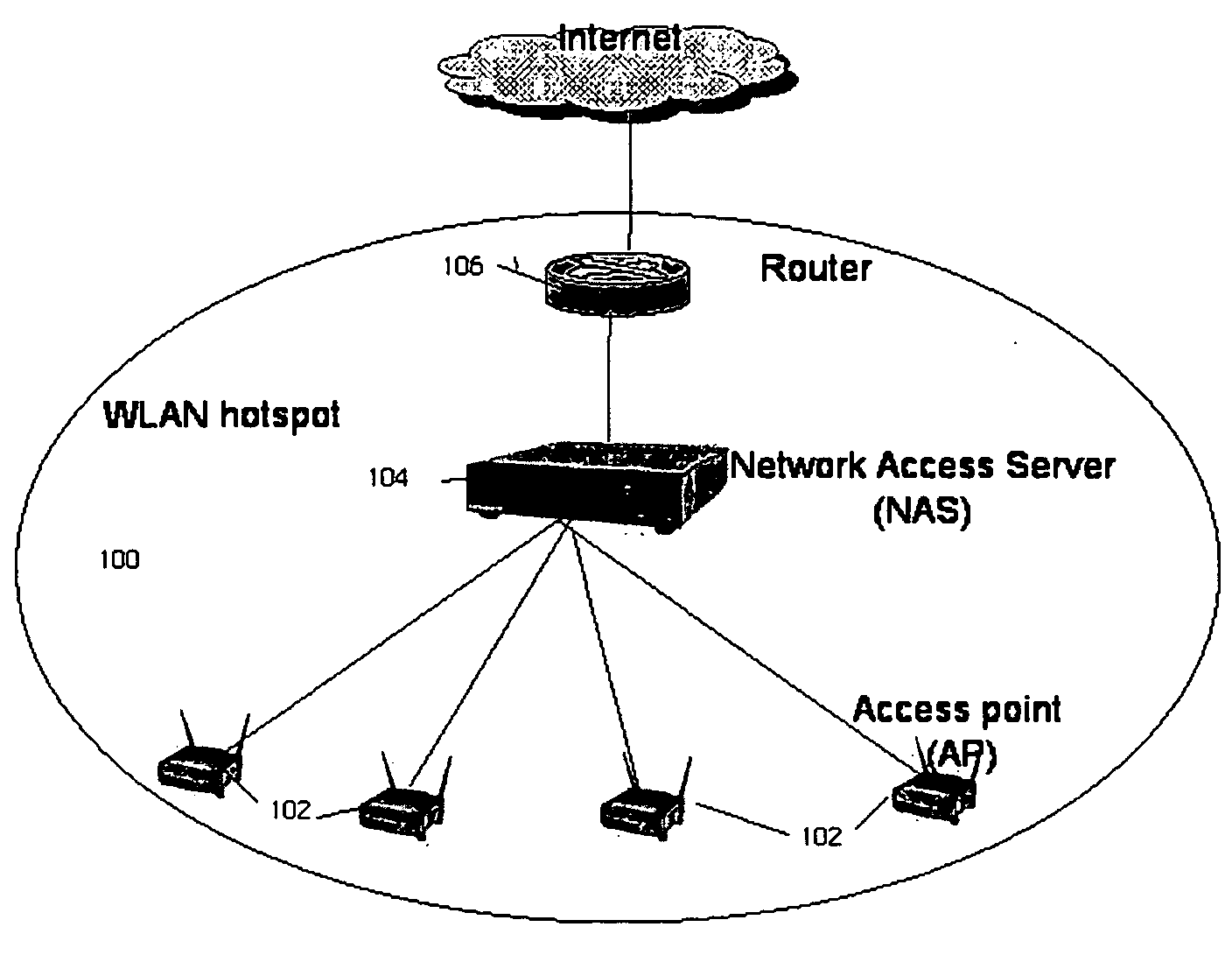
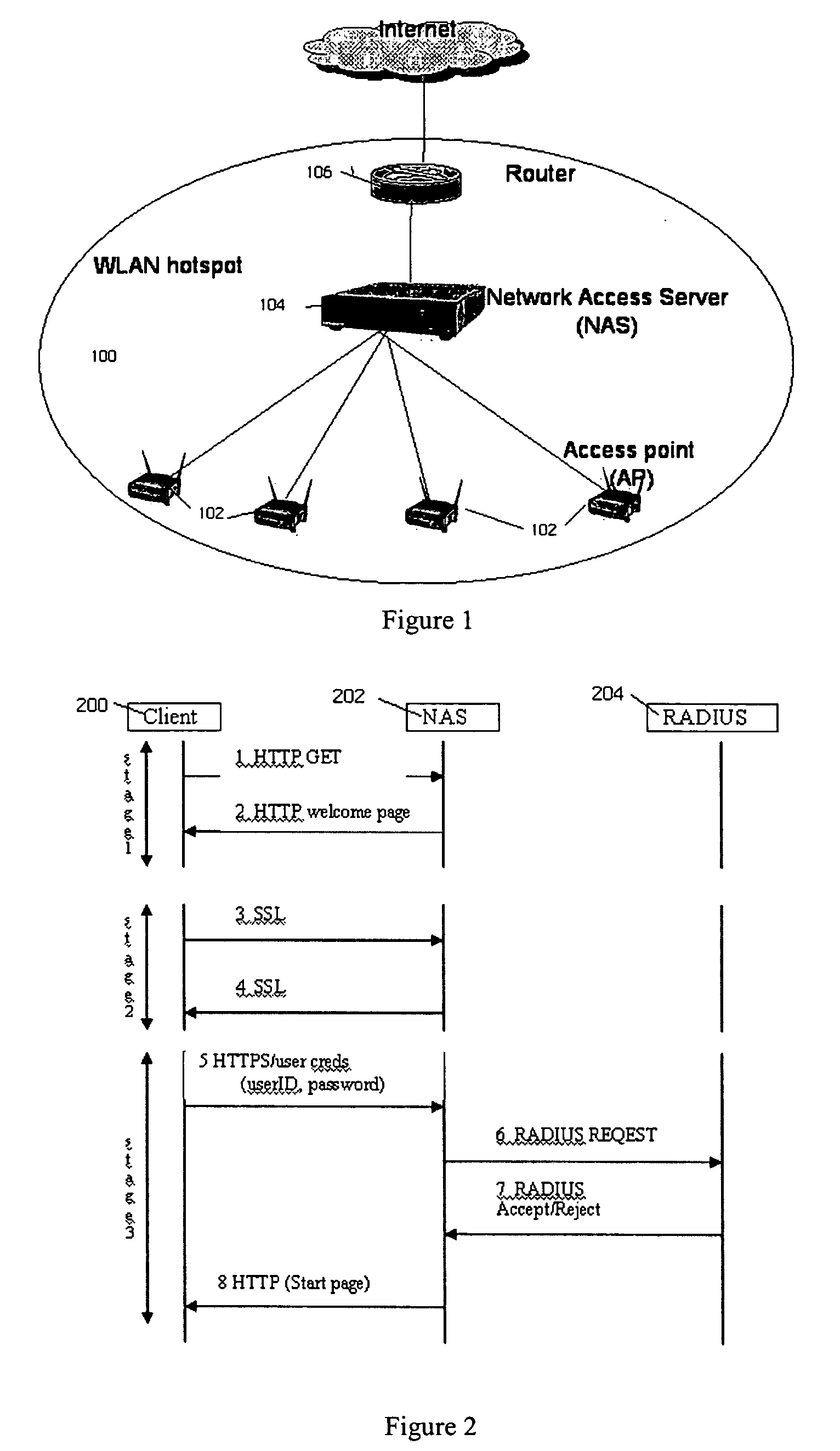
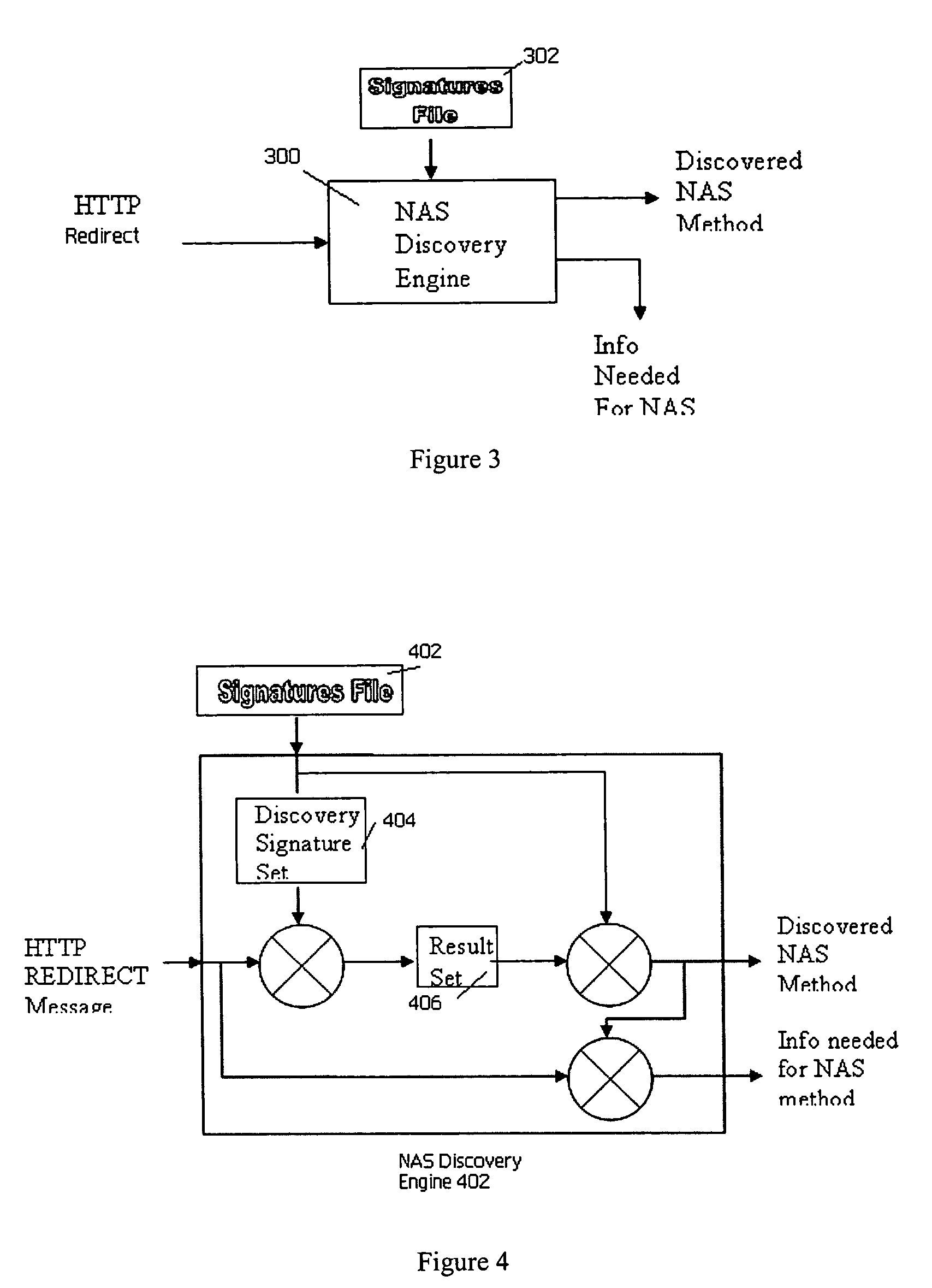
Network access server (NAS) discovery and associated automated authentication in heterogenous public hotspot networks
InactiveUS20060174127A1User identity/authority verificationNetwork topologiesPublic environmentNetwork access server
Automated HTTP-based user authentication in a public WLAN environment is facilitated across heterogeneous network access servers (NASs). Each of a set of network access servers has a given authentication protocol, and these protocols typically differ from one another. According to the invention, each authentication protocol has a unique “signature.” According to the invention, a “smart” client that is executable on a given wireless device seeking access to the public WLAN environment is provided with a set of signatures. These signatures are used by the client to determine the appropriate access protocol to use with respect to a given NAS that is controlling access to the WLAN. The client may also have the capability of discovering an unknown authentication protocol “on-the-fly” as it attempts to obtain wireless access. The set of signatures is updated in the client from time-to-time without requiring the client software to be recompiled. The present invention thus provides a generic mechanism by which a client can work with any NAS.
Owner:SMITH MICRO SOFTWARE INC
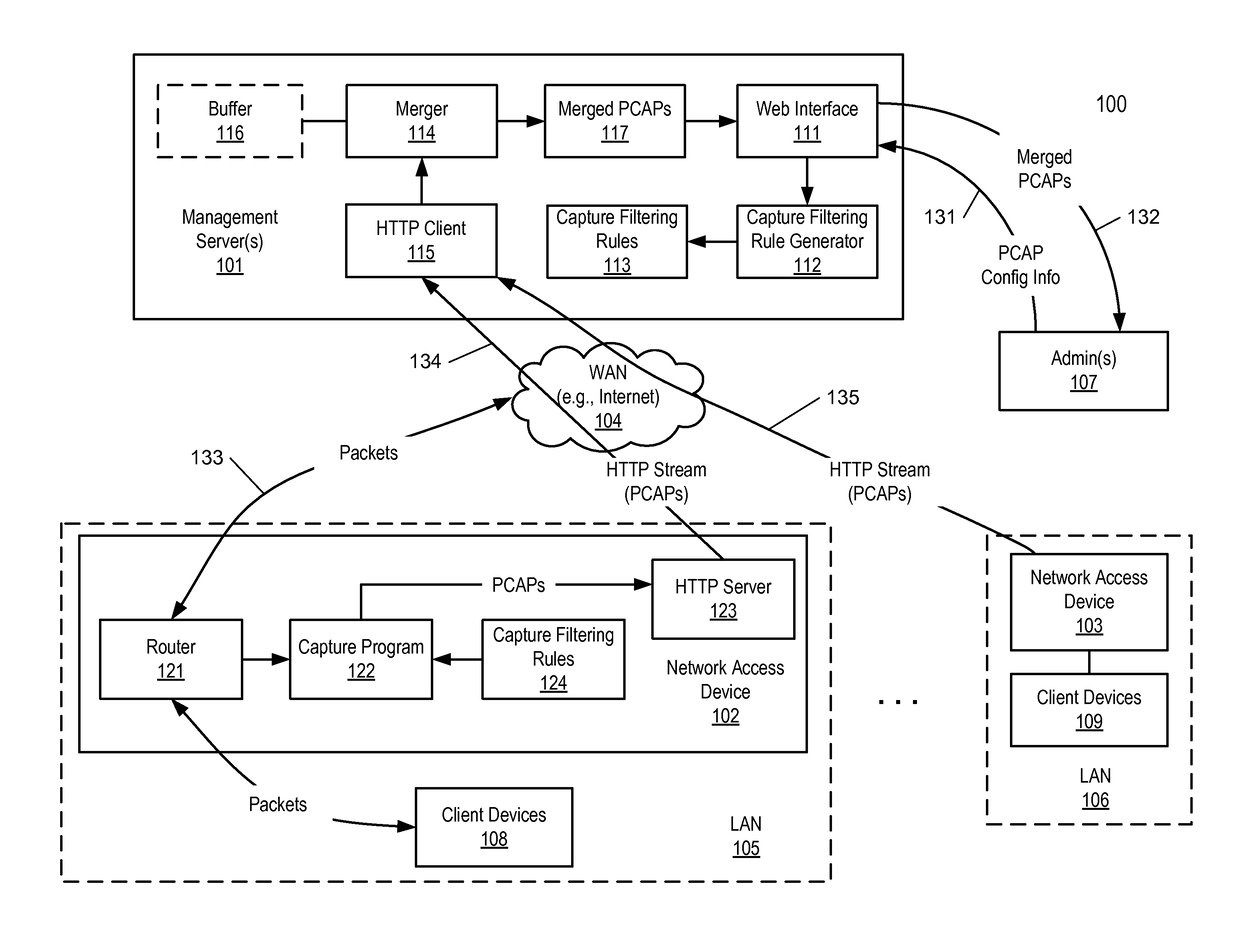
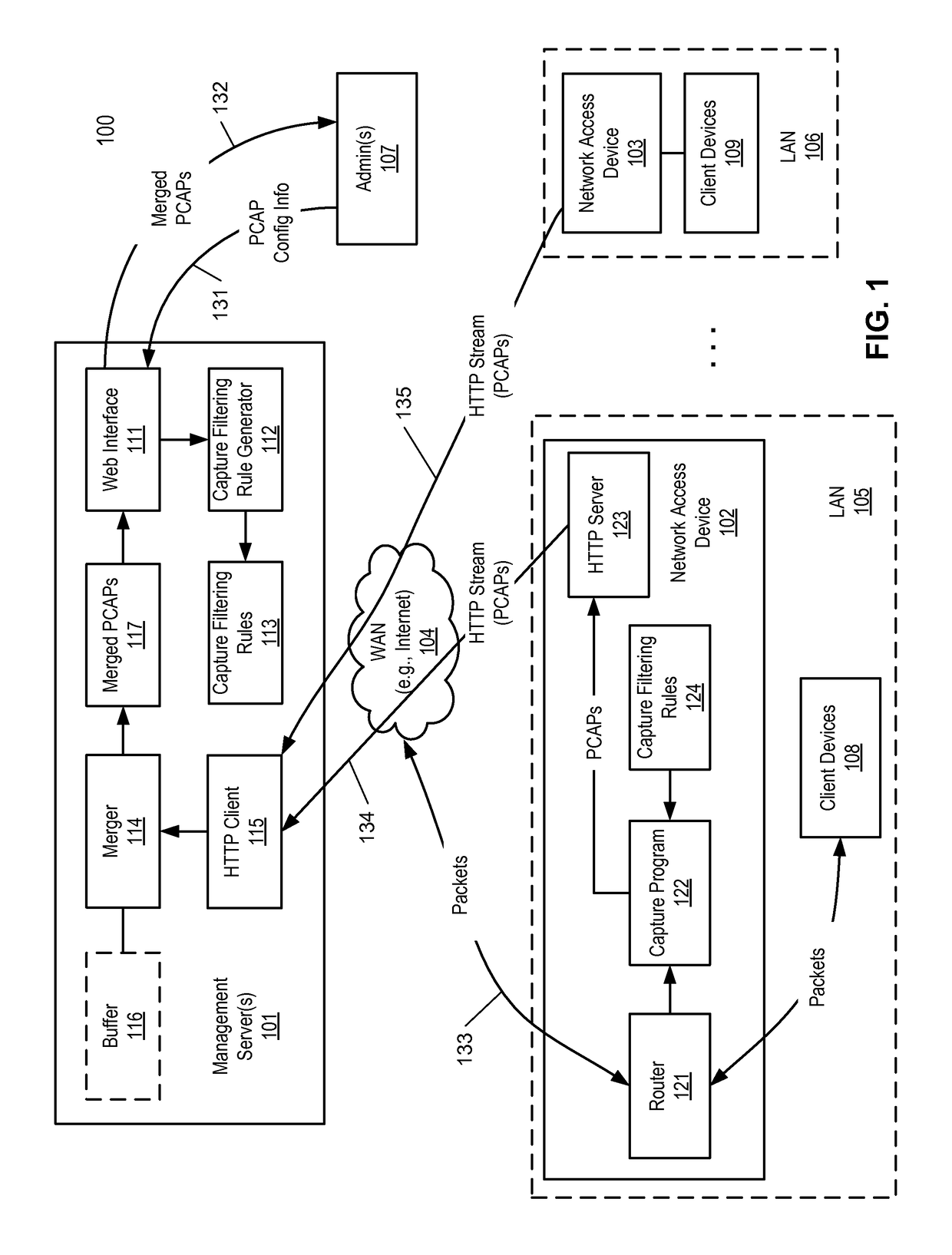
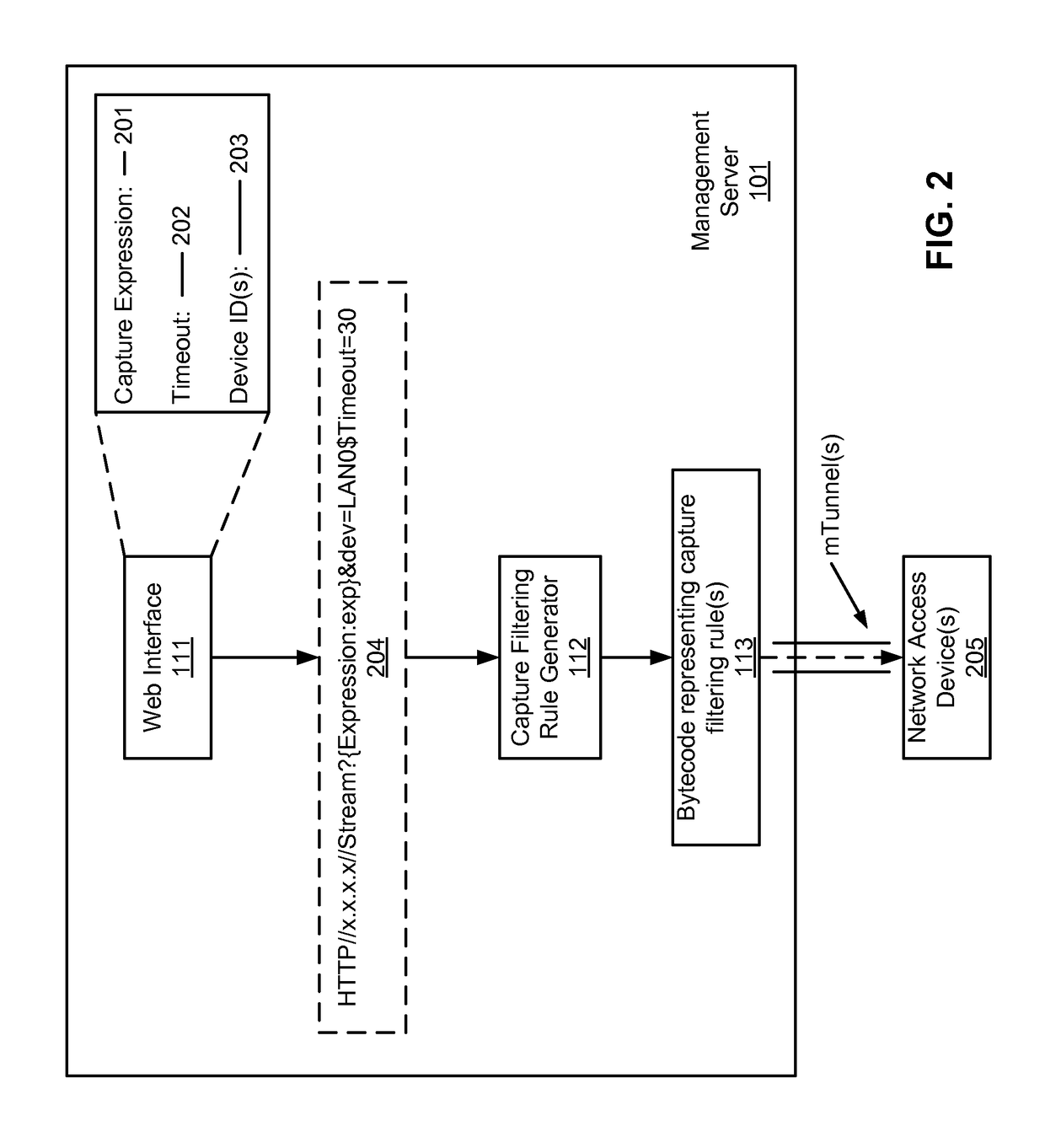
Method for streaming packet captures from network access devices to a cloud server over HTTP
ActiveUS9692802B2Multiple digital computer combinationsData switching networksNetwork access serverNetwork packet
A system for streaming packet captures over the Internet includes multiple network access devices, each operating as one of a gateway device, a wireless access point, and a network switch, and a management server communicatively coupled to the network access devices over the Internet for managing the network access devices. The management server maintains a persistent hypertext transport protocol (HTTP) connection with each of the network access devices over the Internet. The management server is to generate a bytecode based on a filtering expression for packet captures (PCAPs) representing one or more PCAPs filtering rules, transmit the bytecode to the network access devices without requiring the network access devices to compile the PCAPs filtering rules, receive PCAPs from the network access devices captured by the network access devices based on the PCAPs filtering rules, and merge the PCAPs received from the network access devices into merged PCAPs.
Owner:CISCO TECH INC
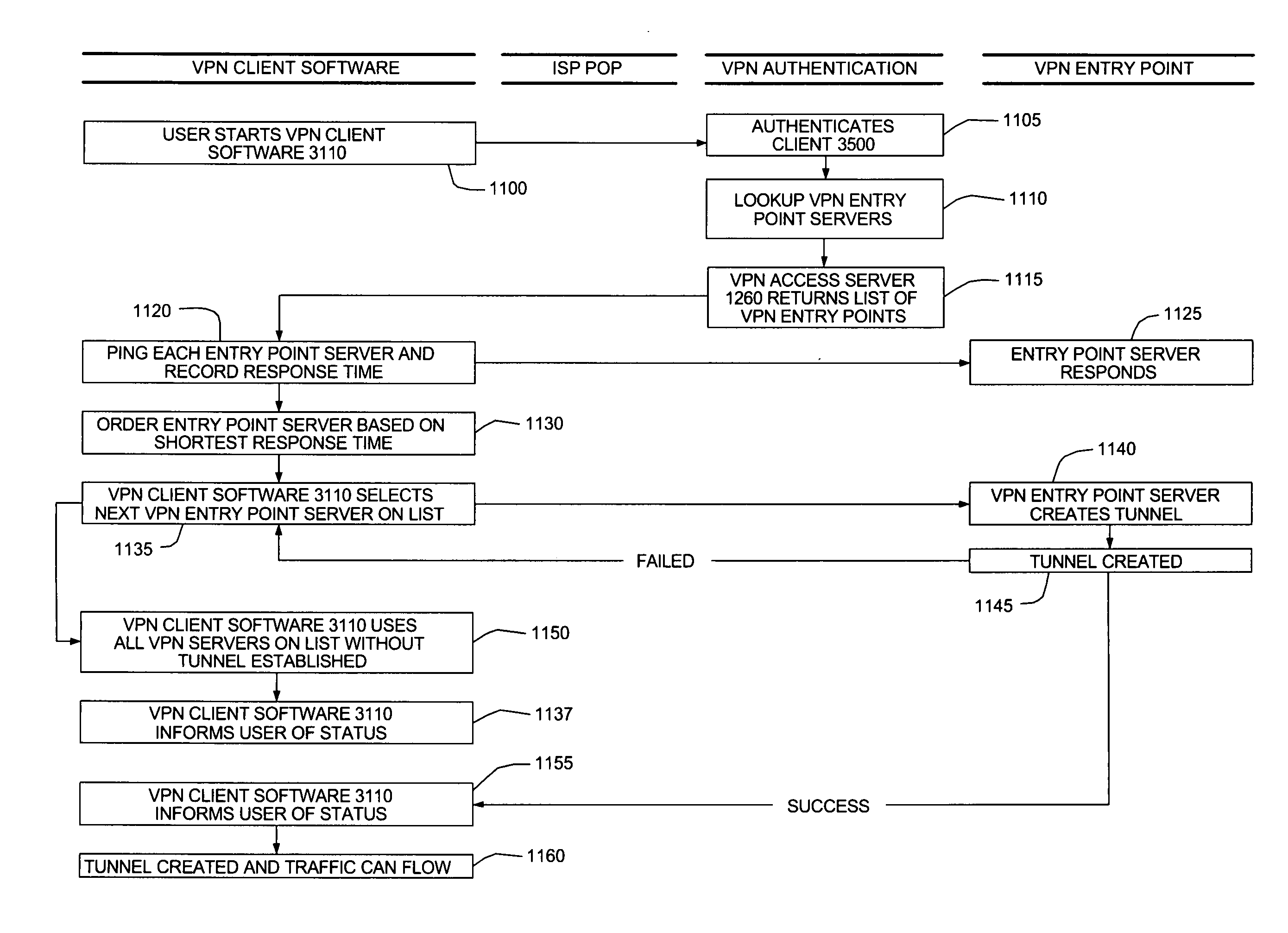
System, method and program for determining a network path by which to send a message
InactiveUS20070299954A1Multiple digital computer combinationsData switching networksNetwork access serverPrivate network
System, method and program determining a network path by which a workstation can send a message to a target network. The workstation accesses a first part of the network path via a network access server. A plurality of other servers by which the workstation can access a second part of the network path leading to the target network are identified. Respective response times to communicate between the workstation or the network access server and each of the other servers are measured. A determination is made which one of the other servers has a shortest response time. The workstation attempts to connect to the one server, before attempting to connect to other of the other servers, to access the second part of the network. The second part of the network can be a virtual private network, and the other servers are entry point servers for respective virtual private networks.
Owner:IBM CORP
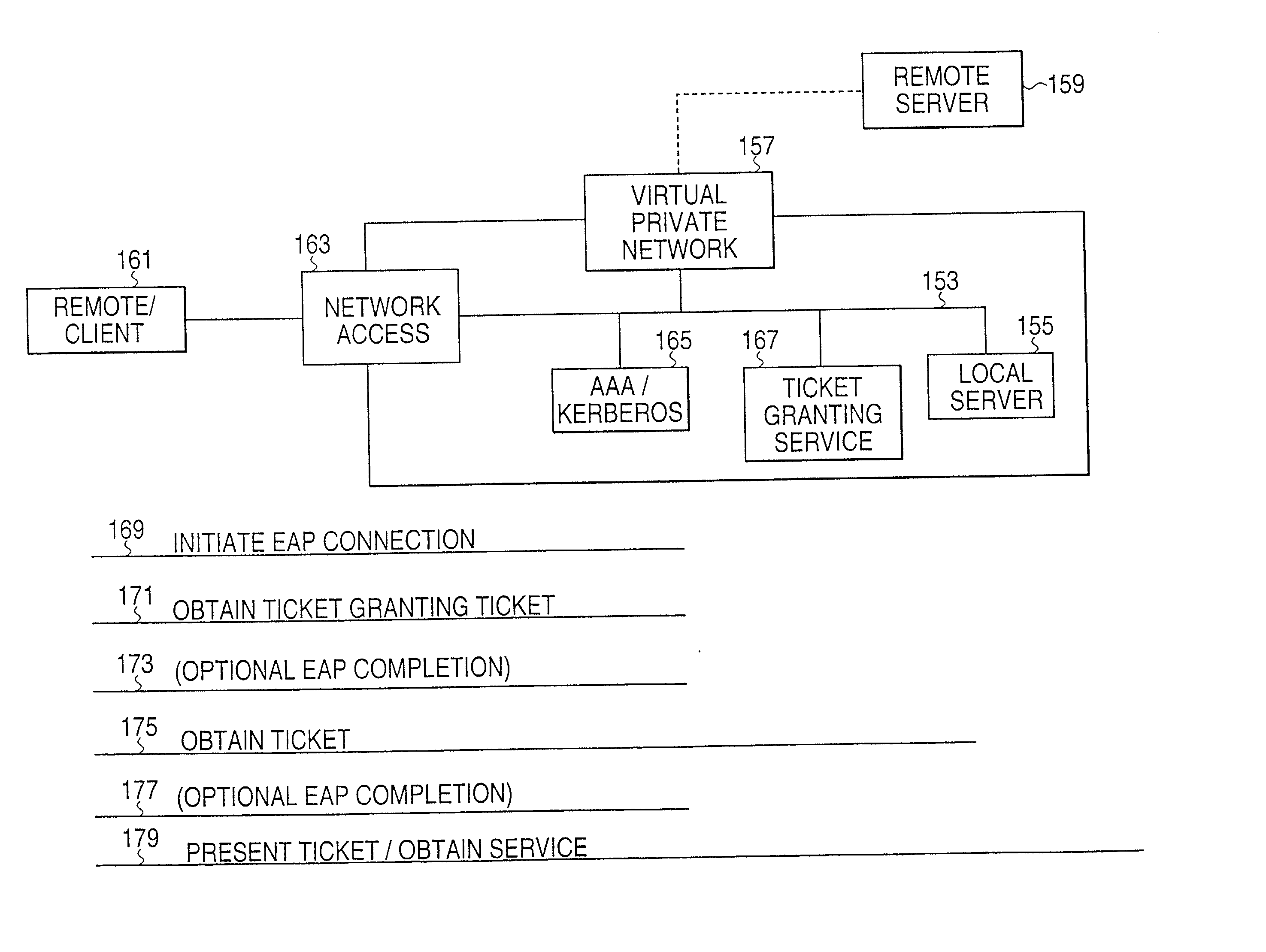
EAP telecommunication protocol extension
InactiveUS20040010713A1Digital data processing detailsMultiple digital computer combinationsNetwork access serverNetwork connection
A method for providing a network connection includes a step of initiating an EAP connection between a device seeking network access and a network by way of a network access server. The network access server is configured to selectively permit-or deny-network access. Using EAP formatted messages, the device seeking network access negotiates for an additional credential that grants an authorization for a service other than network access. The network preferably provides the credential prior to completing the EAP process for granting network access.
Owner:INTERLINK NETWORKS
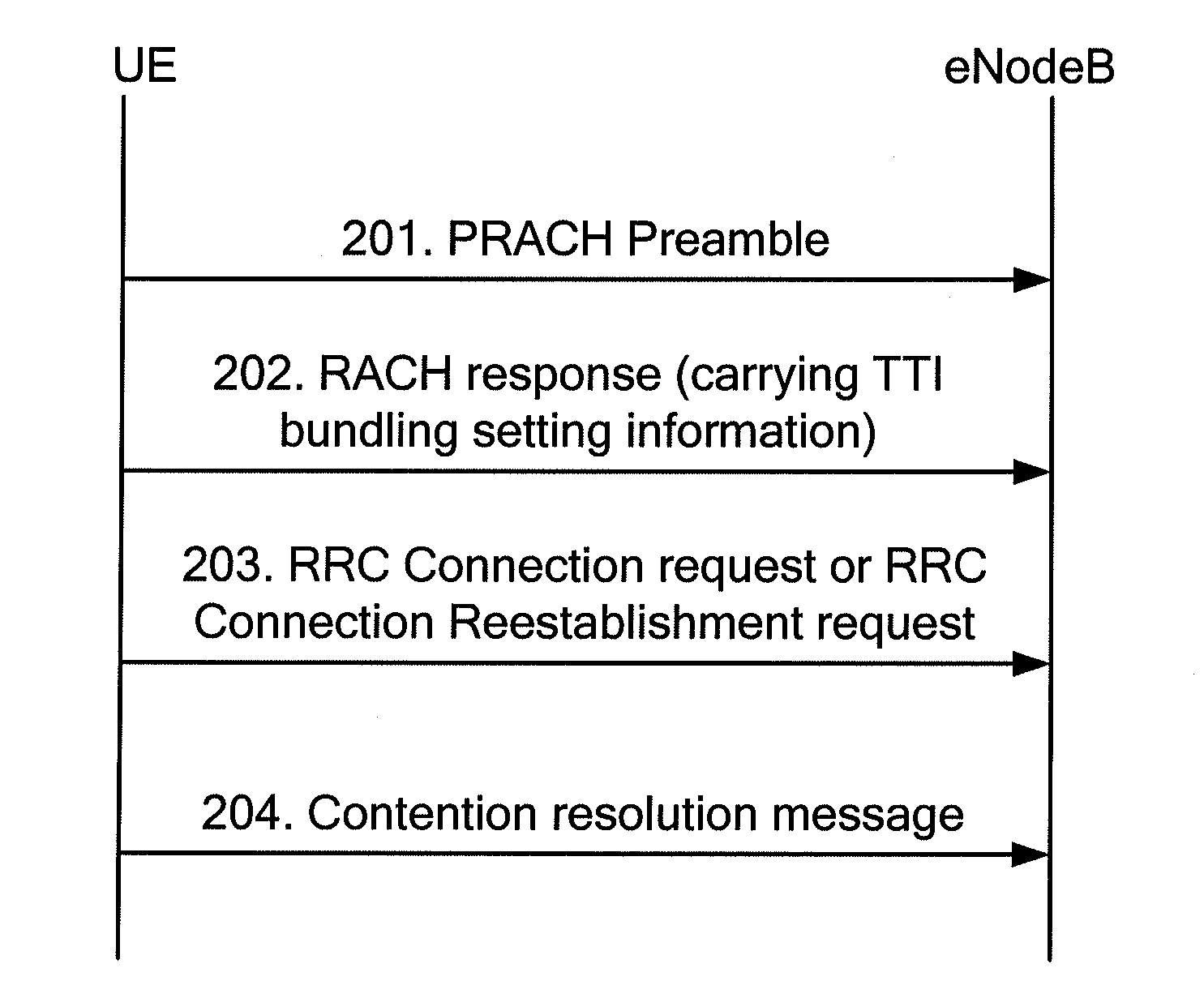
Method and system for user equipment access, and network access device
InactiveUS20110280212A1Time of random access is savedImprovement in random accessWireless commuication servicesHigh level techniquesTelecommunicationsNetwork access server
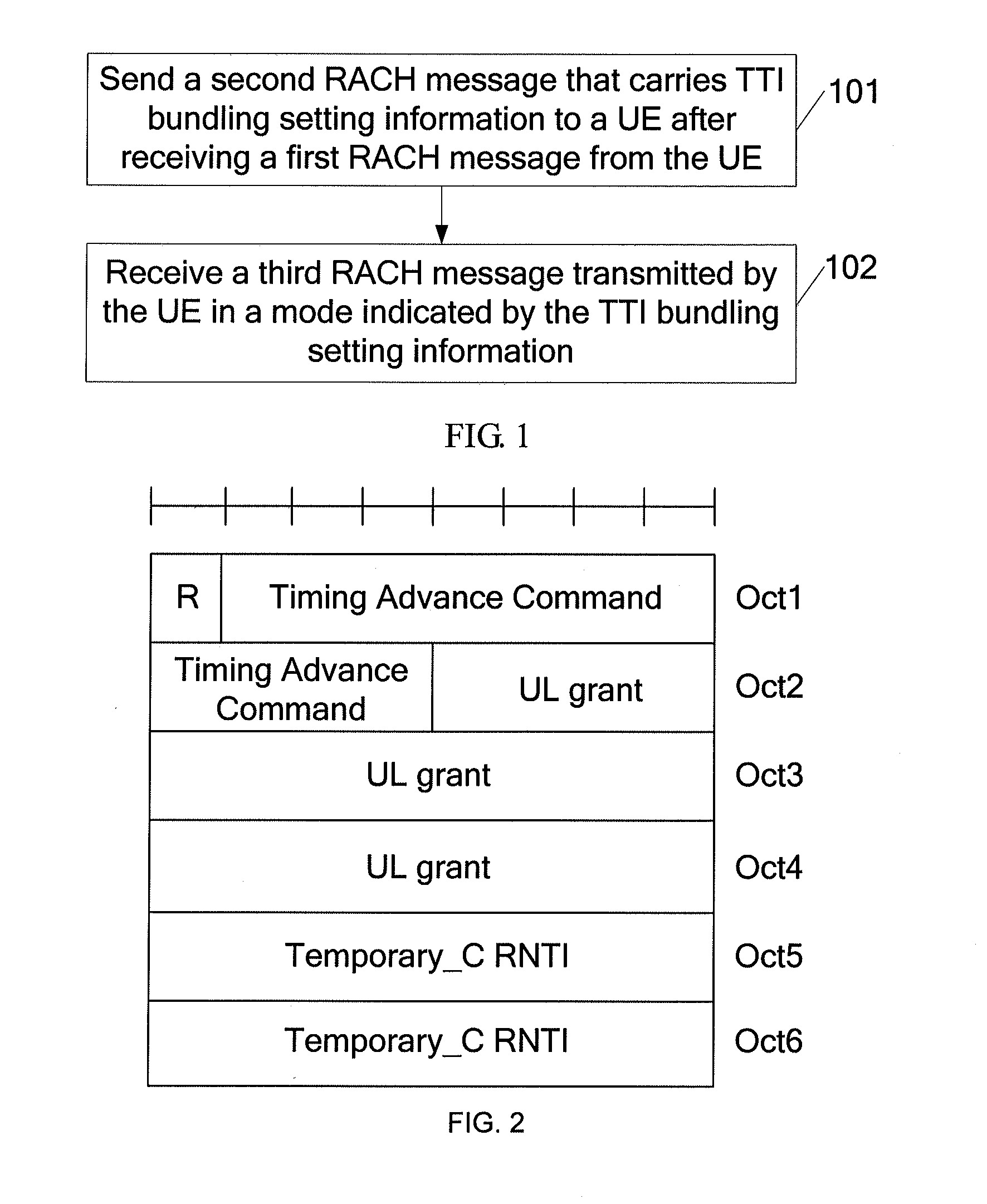
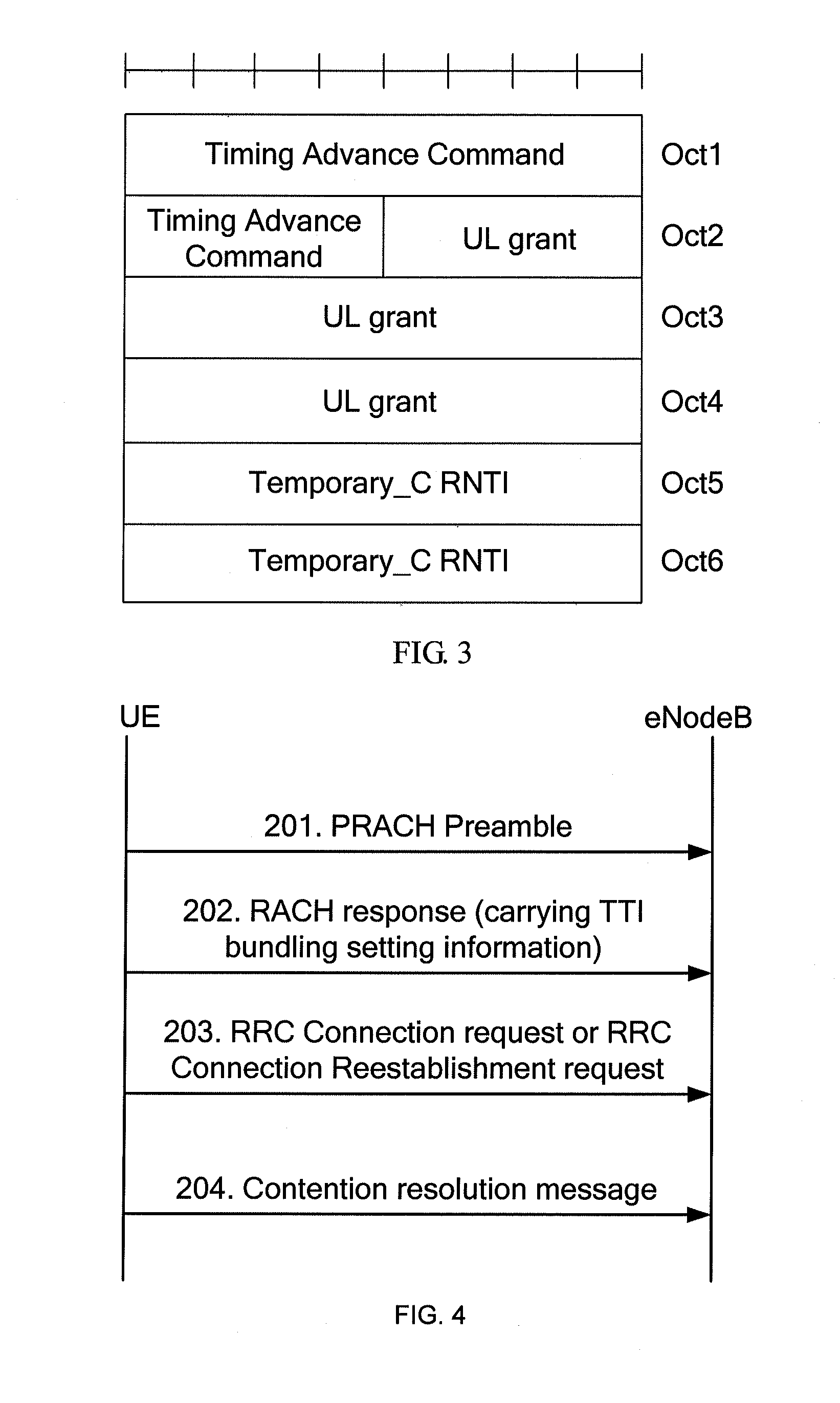
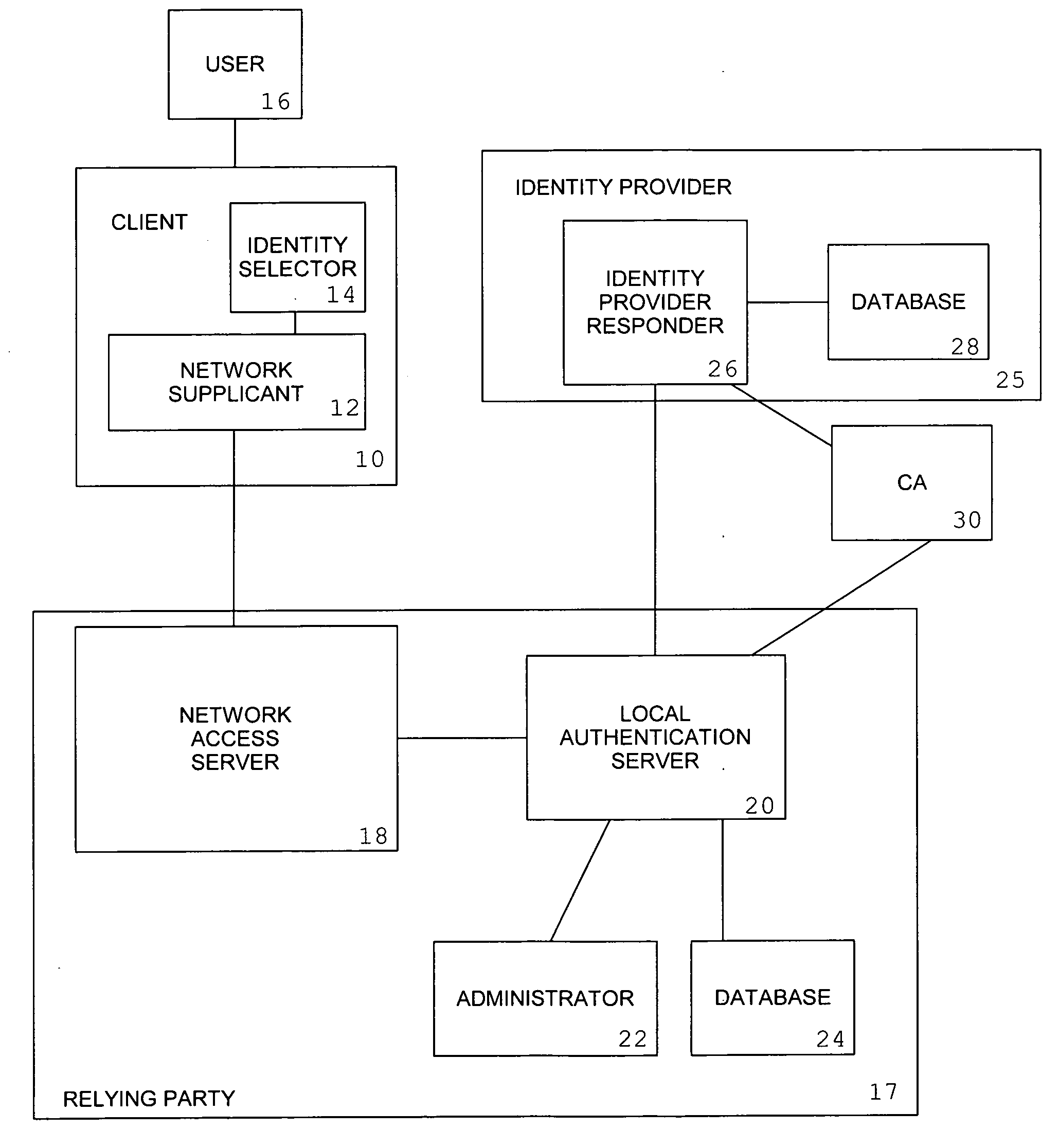
An access method and a system for User Equipment (UE), and a network access device are disclosed. The access method for UE includes: sending a second Random Access Channel (RACH) message that carries Transmission Time Interval (TTI) bundling setting information to a UE after receiving a first RACH message from the UE; and receiving a third RACH message transmitted by the UE in a mode indicated by the TTI bundling setting information. With the access method and system for UE and the network access device, the second RACH message carries TTI bundling setting information so that the UE may send the third RACH message in a TTI bundling mode. Therefore, the time of random access is effectively saved. Moreover, when a UE is power-limited, the UE may send the third RACH message in a TTI bundling mode, so that the random access rate of the UE is improved.
Owner:HUAWEI TECH CO LTD
System and method for authentication upon network attachment
InactiveUS20080222714A1Digital data processing detailsUser identity/authority verificationNetwork access serverInformation processing
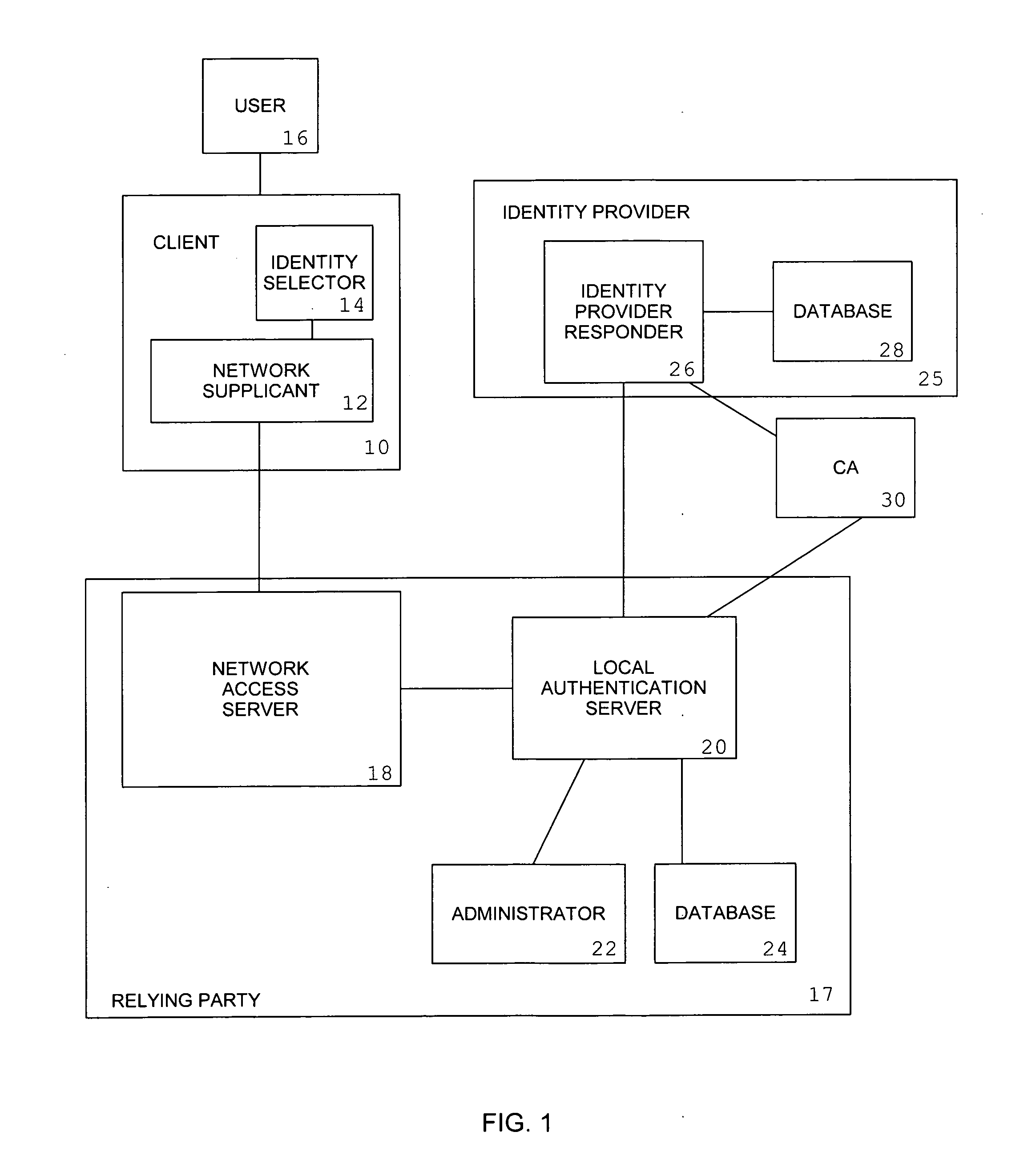
An information processing system for remote access computing comprising a network access server and a local authentication server is augmented with the capability for forwarding authentication requests by tunneling interactions between the requesting client and an identity provider.
Owner:WAHL MARK FREDERICK
Distributed packet processing architecture for network access servers
InactiveUS20060013240A1Increase the number ofRaise countData switching by path configurationExtensibilityLow speed
An access server architecture, and methods for use of the architecture, are disclosed. The architecture and methods are designed to increase the scalability of and balance processor load for a network access server device. In this architecture, packet forwarding and packet processing are distributed amongst the cards serving the low-speed access lines (i.e., line cards), such that each line card is responsible for performing forwarding and packet processing for packets associated with the low-speed ports that line card serves. Thus, as the number of line cards expands, forwarding resources are expanded in at least rough proportion. The NAS route switch controller, as well as the high-speed ports used to access the network, are largely relieved of packet processing tasks for traffic passing through the server. The egress port uses a distribution engine that performs a cursory examination on one or more header fields on packets received at the high-speed interface-comprehending only enough information to allow each packet to be distributed to the appropriate line card for full packet processing. The route switch controller updates the routing information needed by each distribution or forwarding engine, and is largely uninvolved in the processing of individual packets.
Owner:CISCO TECH INC
Method and system for network presence notification
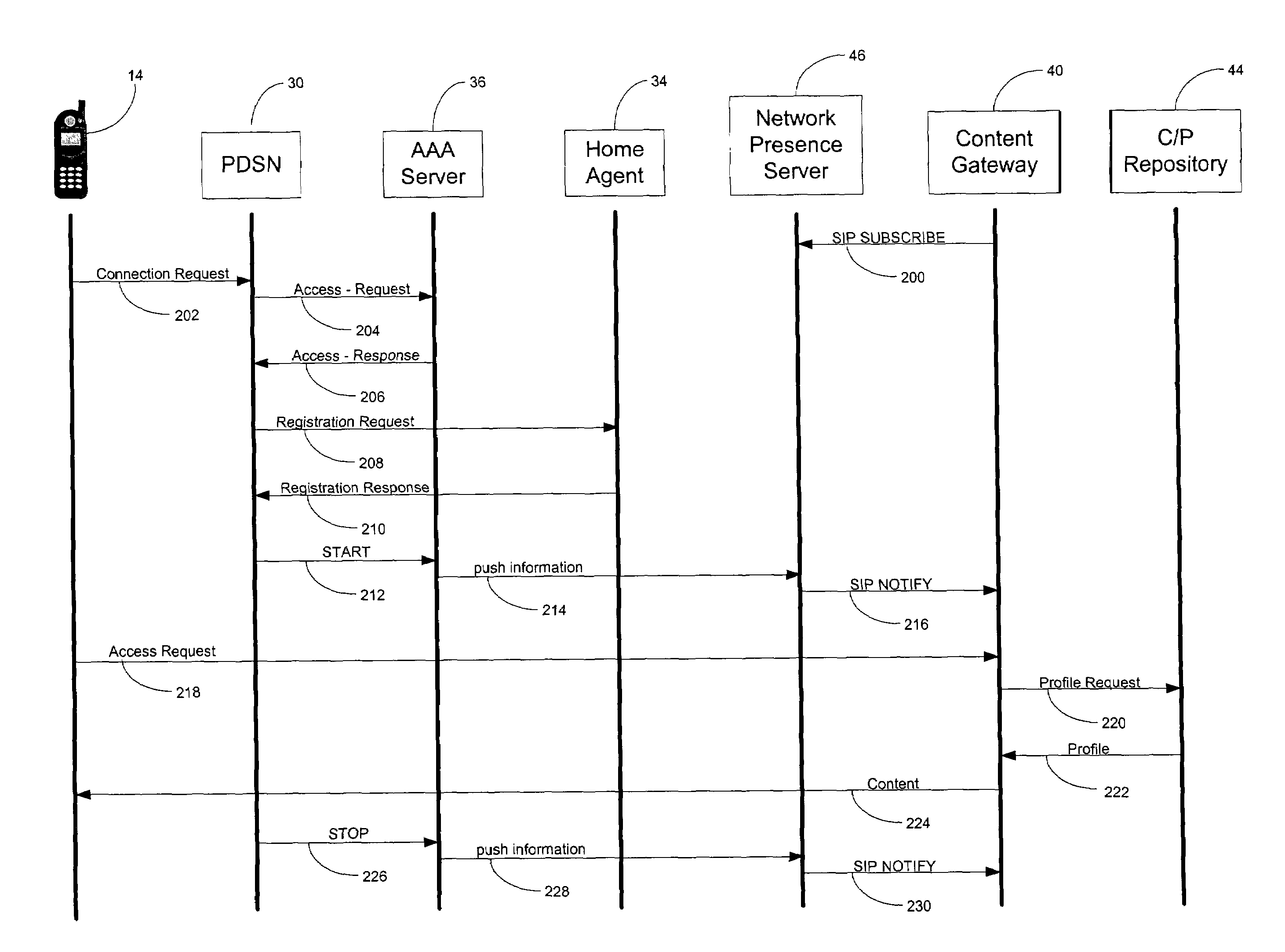
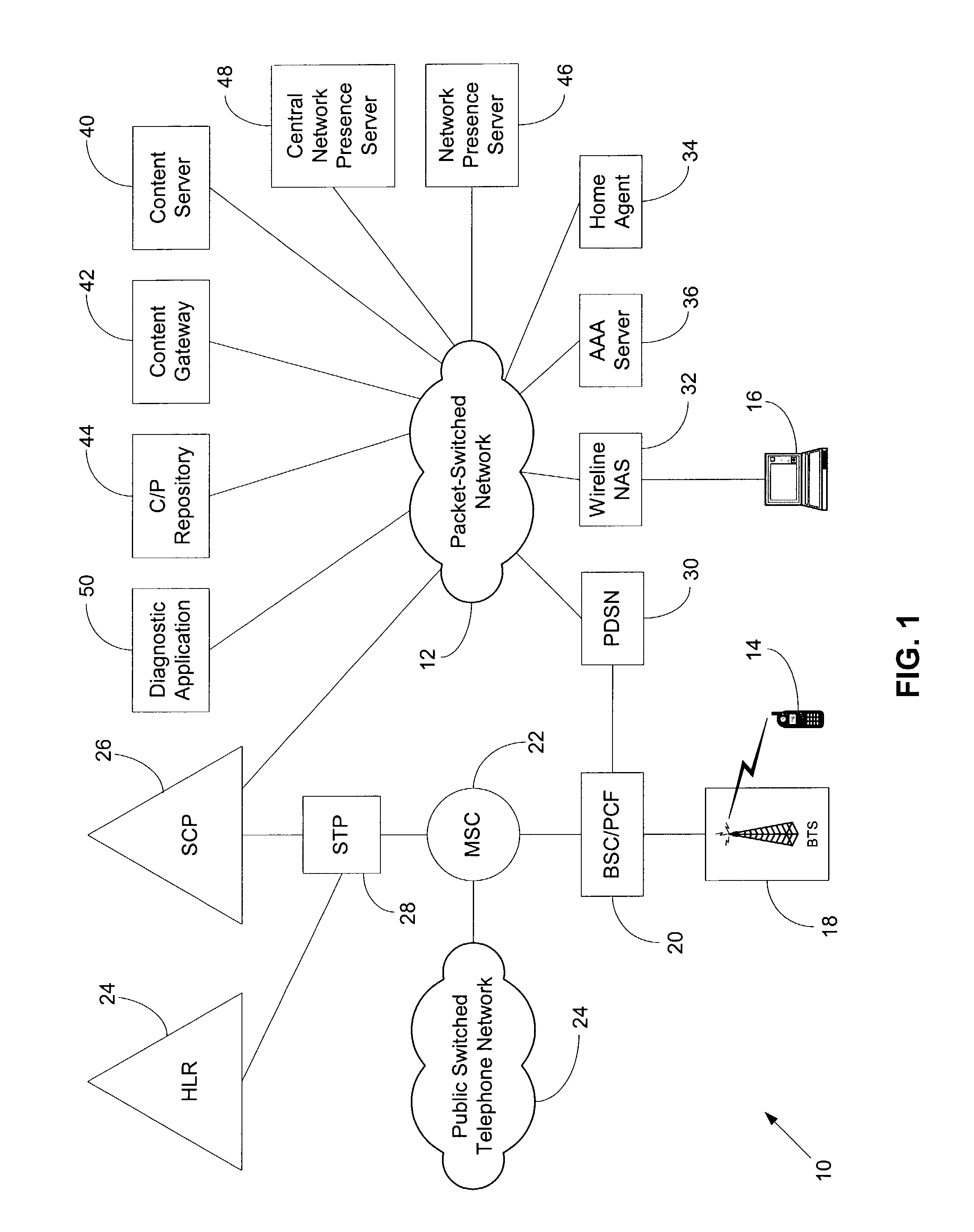
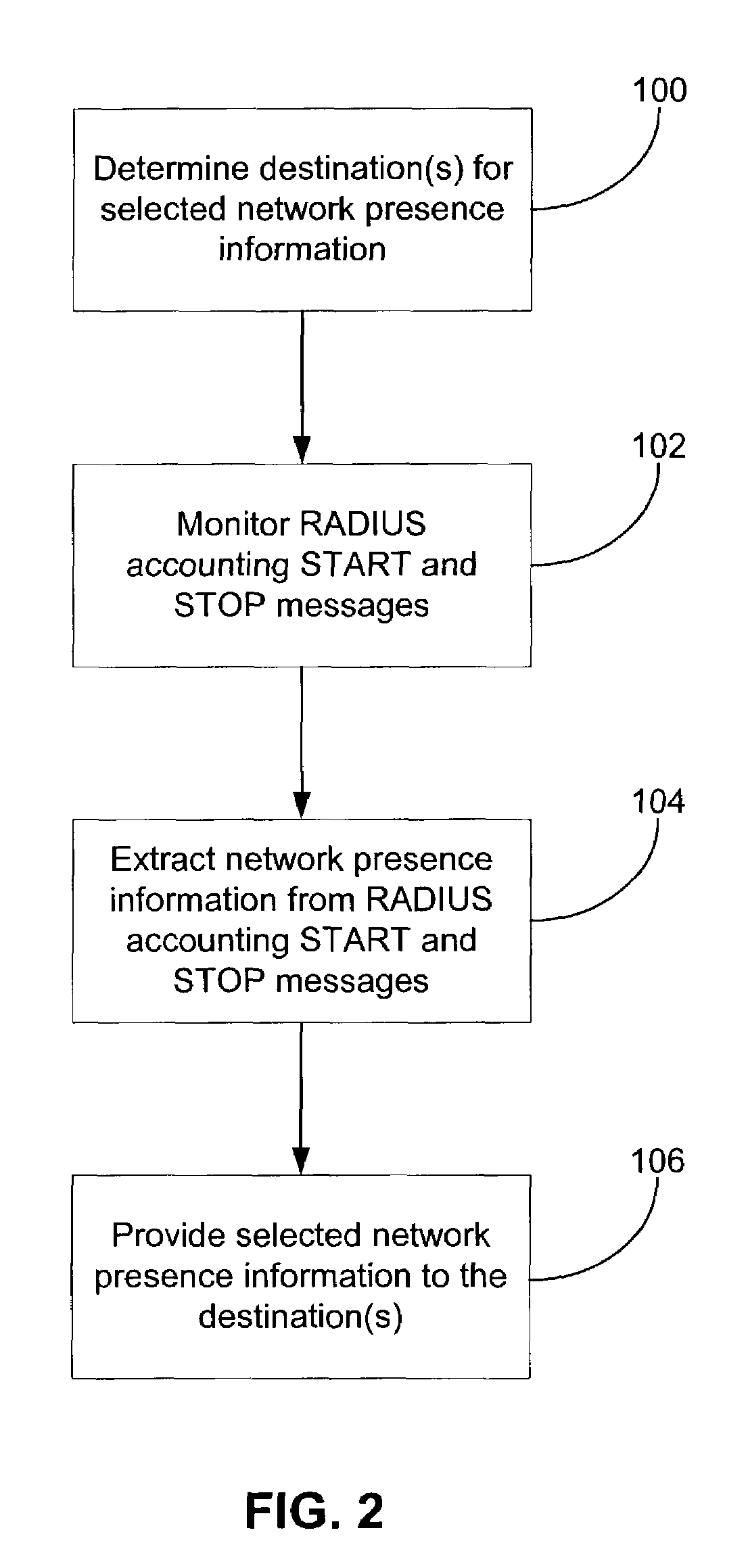
ActiveUS7545762B1Assess restrictionData switching by path configurationNetwork access serverPacket data serving node
In a packet-switched network, a subscribing application subscribes to a network presence server to receive selected network presence information. The network presence server obtains the selected network presence information, at least in part, from status messages that a network access server, such as a packet data serving node (PDSN), sends, for example, to an accounting server. The network presence server then provides the selected network presence information to the subscribing application. The selected network presence information may include an identification of a particular customer that has just initiated or terminated a data session and the network address the particular customer is or was using.
Owner:SPRINT SPECTRUM LLC
Methods and systems for CPN triggered collaboration
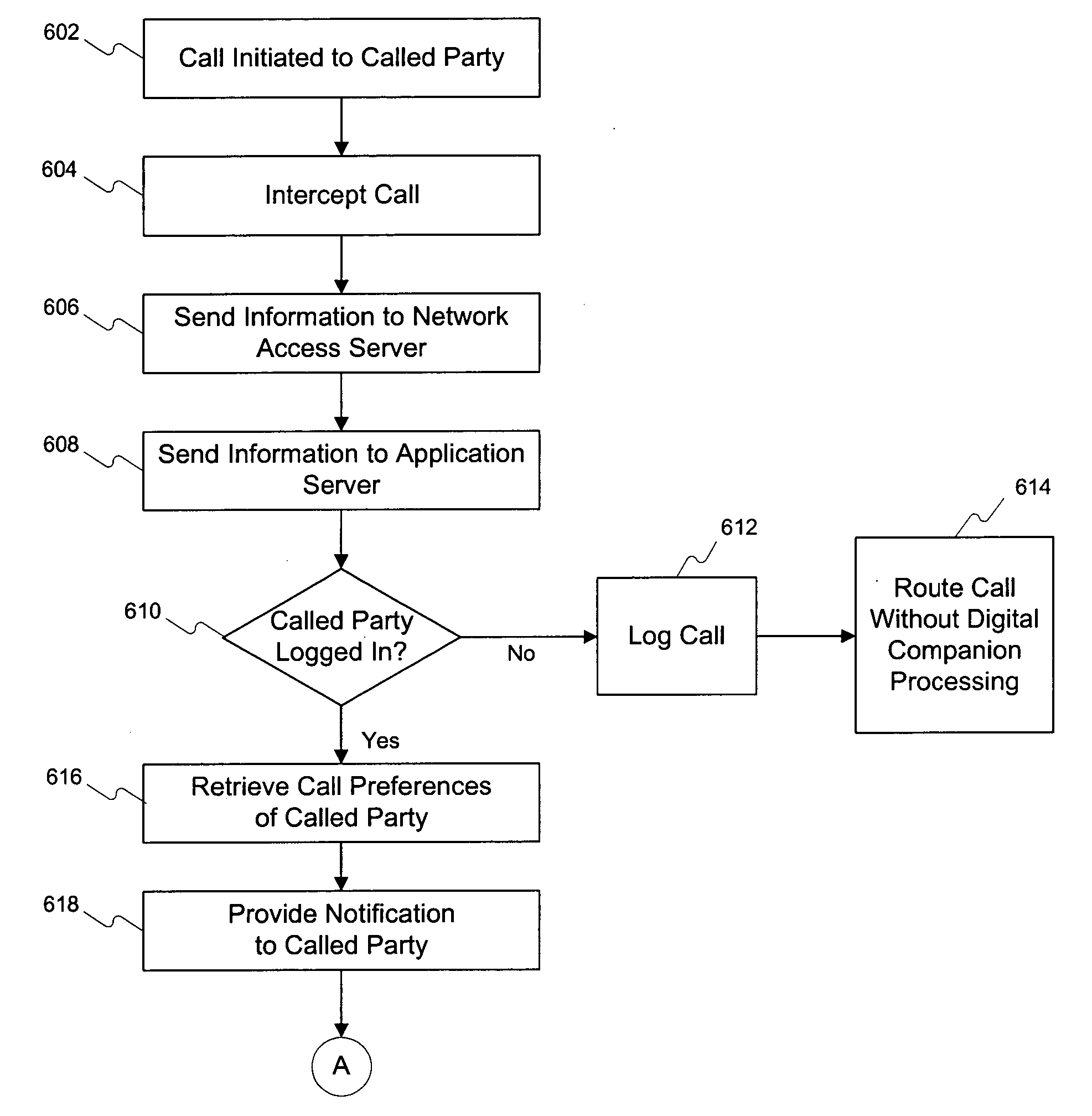
ActiveUS20050084087A1Special service for subscribersMultiple digital computer combinationsNetwork access serverApplication server
Methods and systems for initiating a collaboration between users are disclosed. An application server receives information pertaining to a call to a first user placed by a second user. A notification server sends notification of the call to a device associated with the first user. A network access server may then receive a response to the notification. Thereafter, the notification server sends a notification of a collaboration request to a device associated with the second user based on the response, and the application server initiates a collaboration between the first user and the second user based on a determination that the second user accepts the collaboration request.
Owner:VERIZON PATENT & LICENSING INC
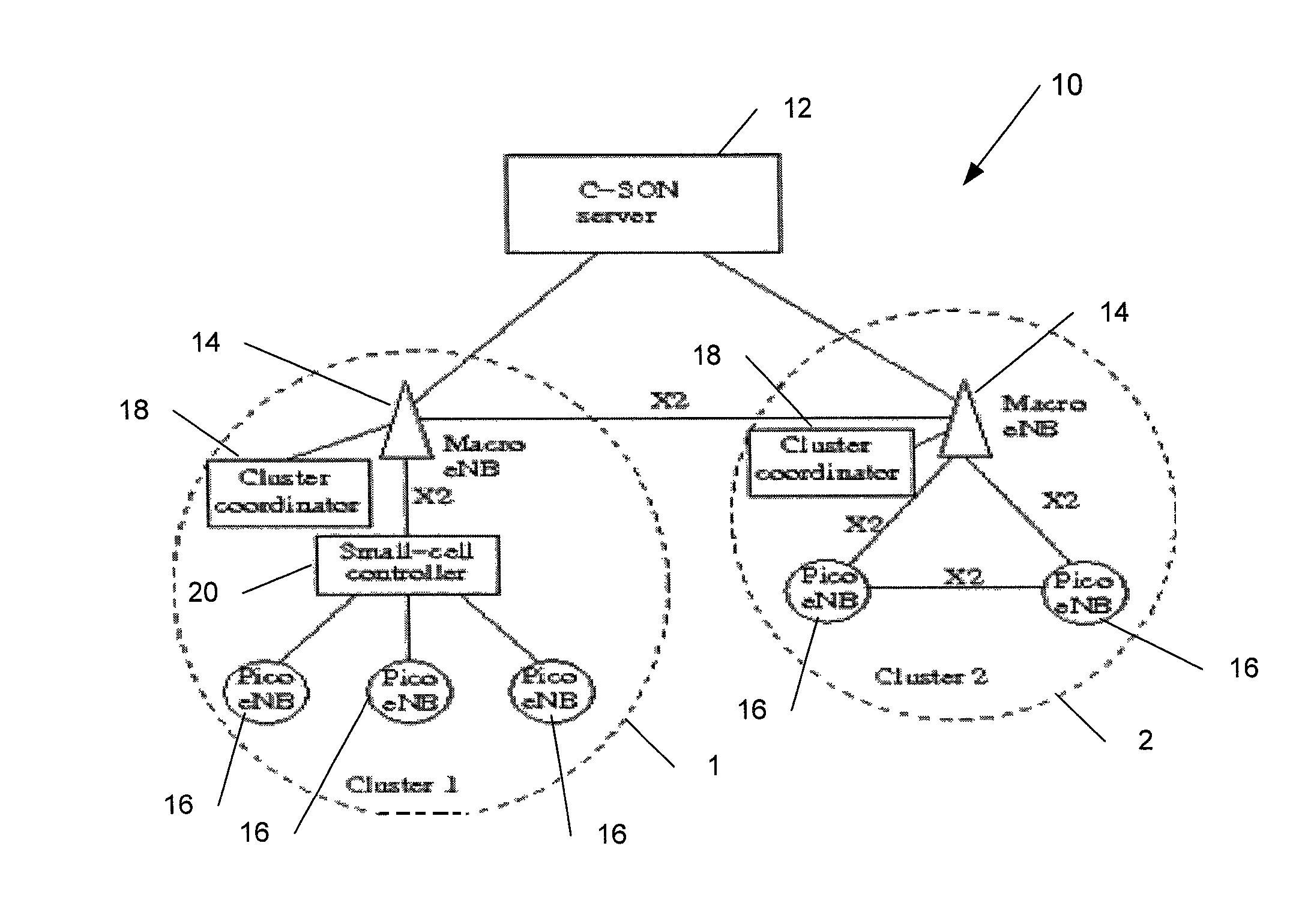
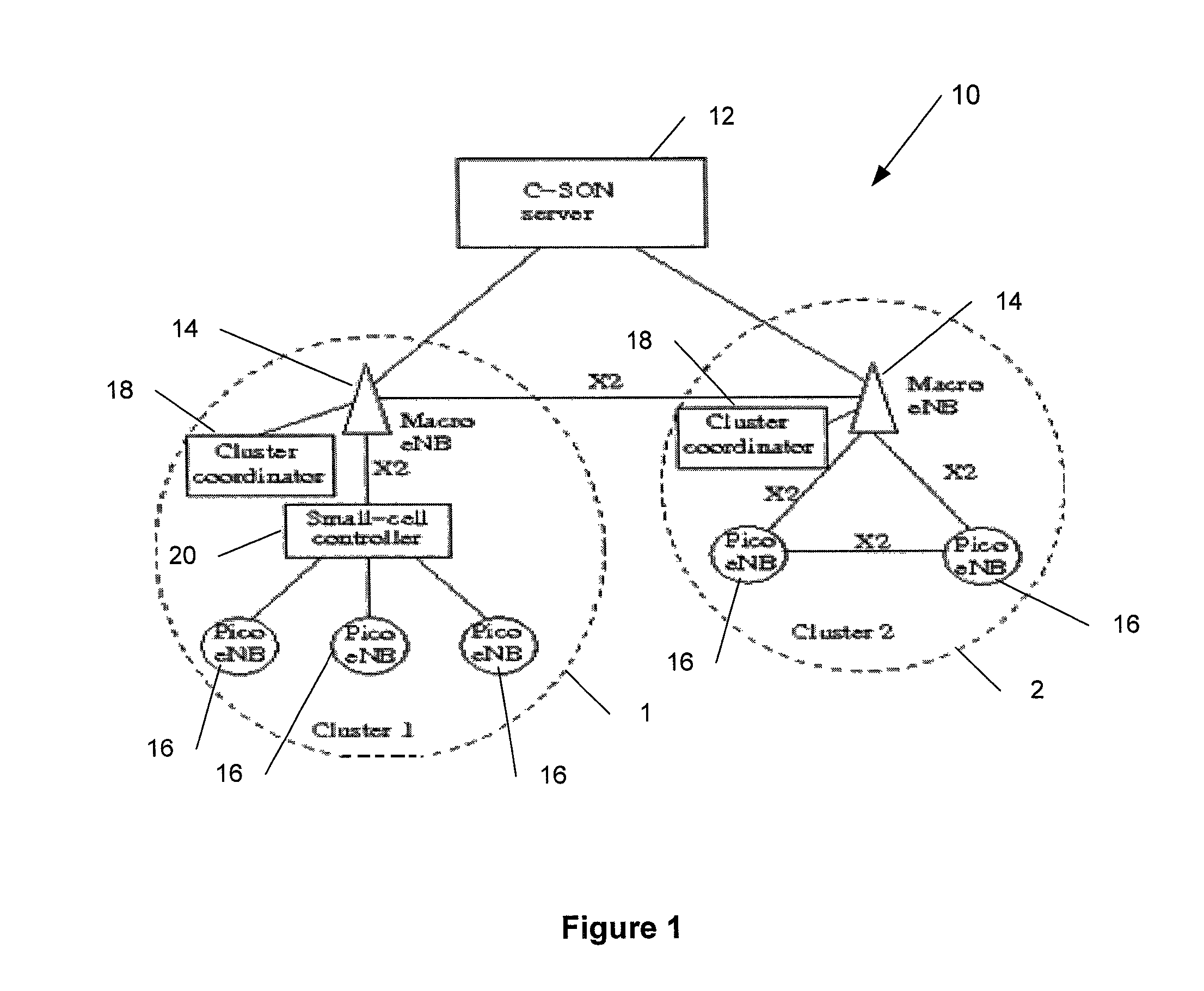
Hierarchical network and interference management
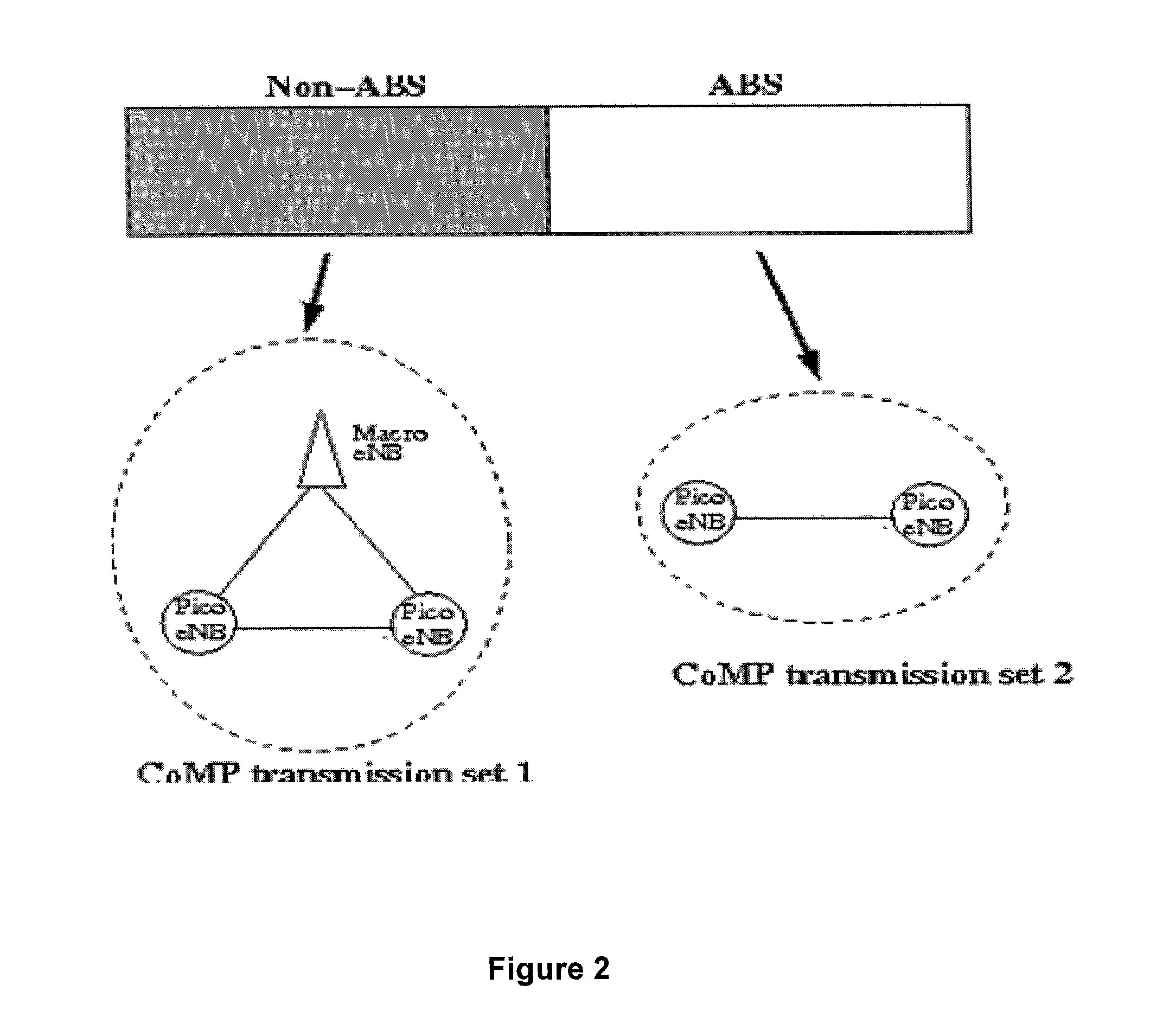
The specification and drawings present a new method, apparatus and software related product (e.g., a computer readable memory) for network management through a hierarchical architecture with a control functionality of a network server (e.g., C-SON) in relationship to clusters comprising eNBs (access points), and for implementing coordinated multi-point (CoMP) transmission and reception in conjunction with inter-cell interference coordination (ICIC) in wireless networks such as LTE wireless networks. In particular, embodiments of the invention describe control and coordination mechanisms among the network elements for different network architectures and use-case scenarios. Such mechanisms may be managed by a centralized self-organizing network controller such as C-SON and hierarchically via localized controllers (such as cluster coordinators) residing in macro eNBs depending on system architectural constraints and network state. A fault-tolerant mechanism then may be defined to recover from failure of controlling sub-elements so that the network remains stable at all times.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com