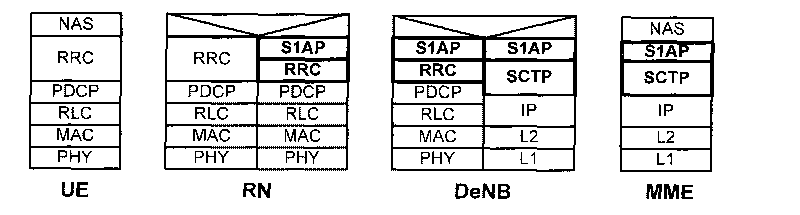
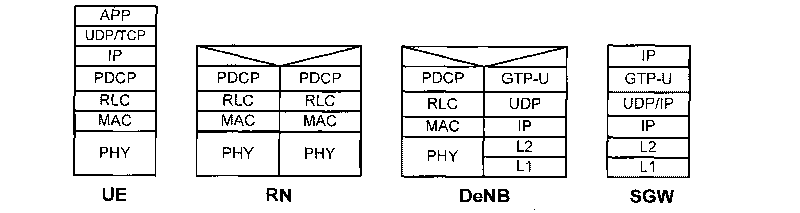
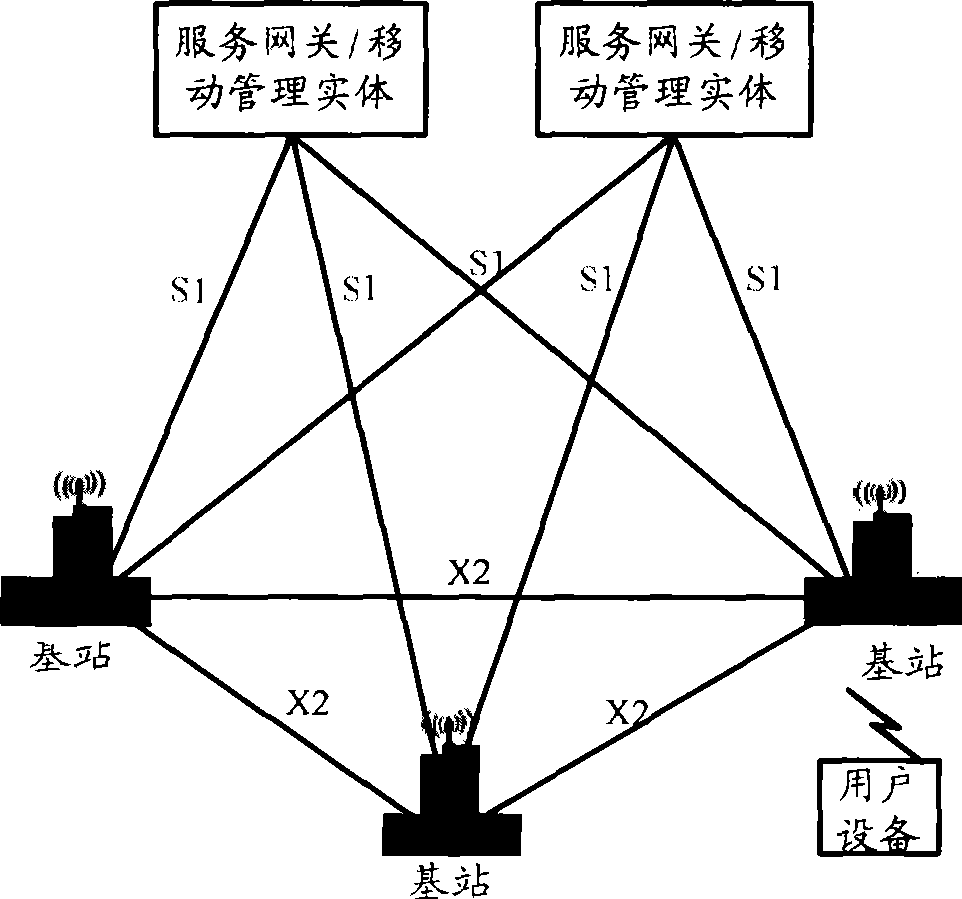
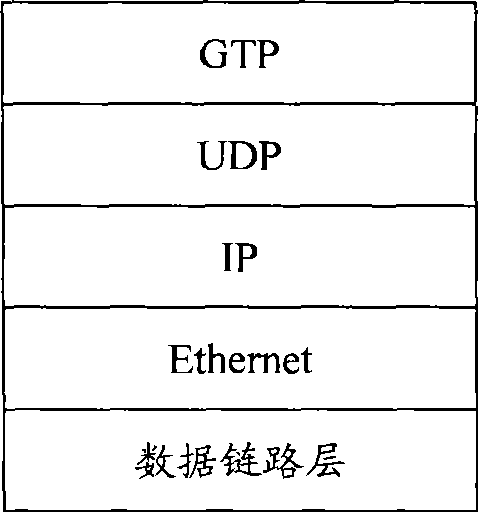
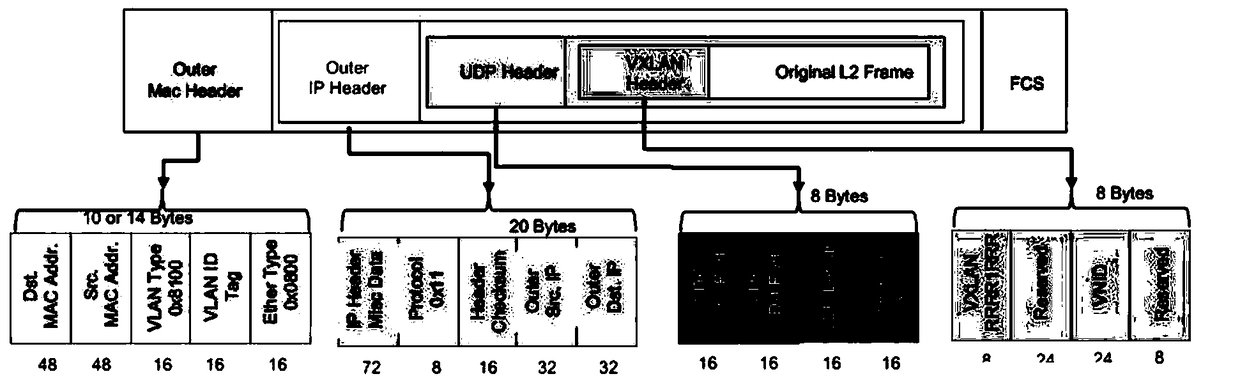
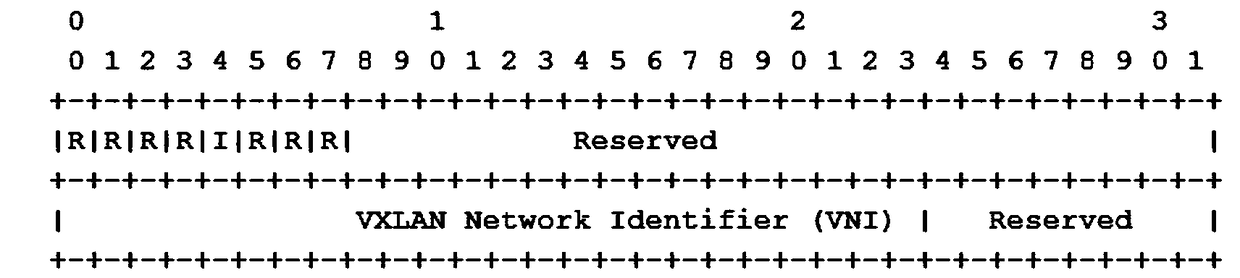
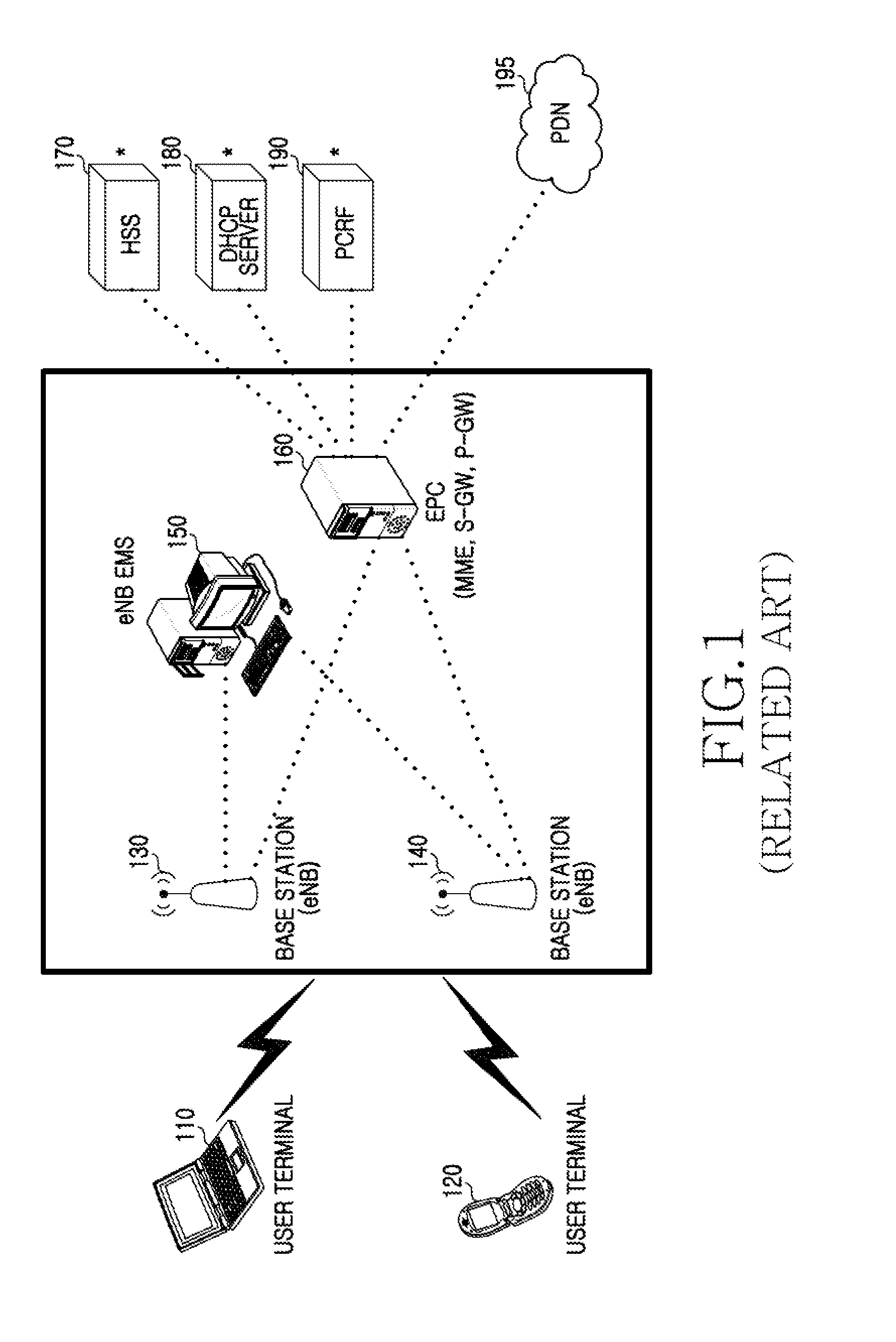
Patents
Literature
342 results about "Tunneling protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networks, a tunneling protocol is a communications protocol that allows for the movement of data from one network to another. It involves allowing private network communications to be sent across a public network (such as the Internet) through a process called encapsulation.
Method and apparatus for lightweight secure communication tunneling over the internet
InactiveUS6104716AData switching by path configurationMultiple digital computer combinationsSOCKSSecure communication
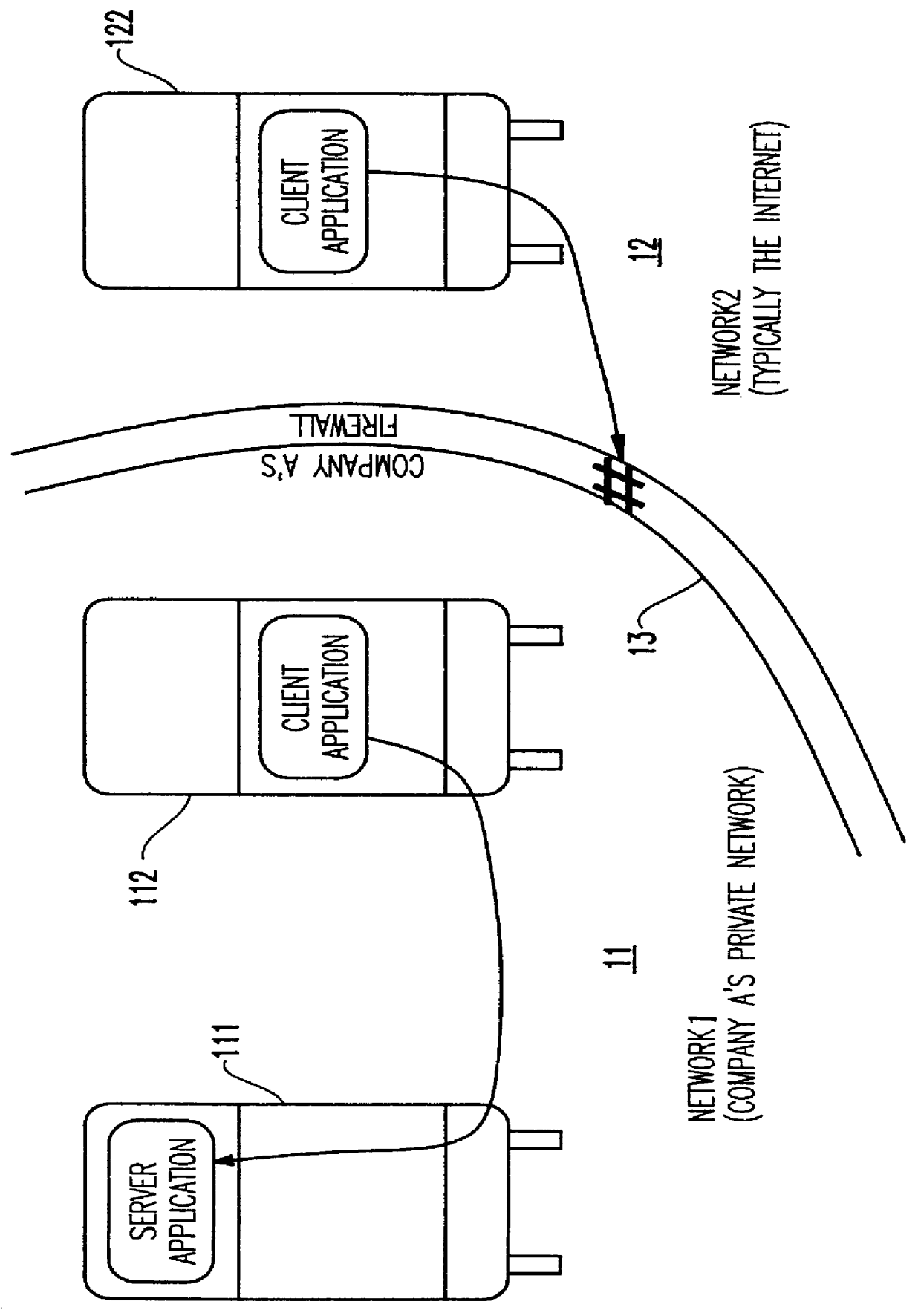
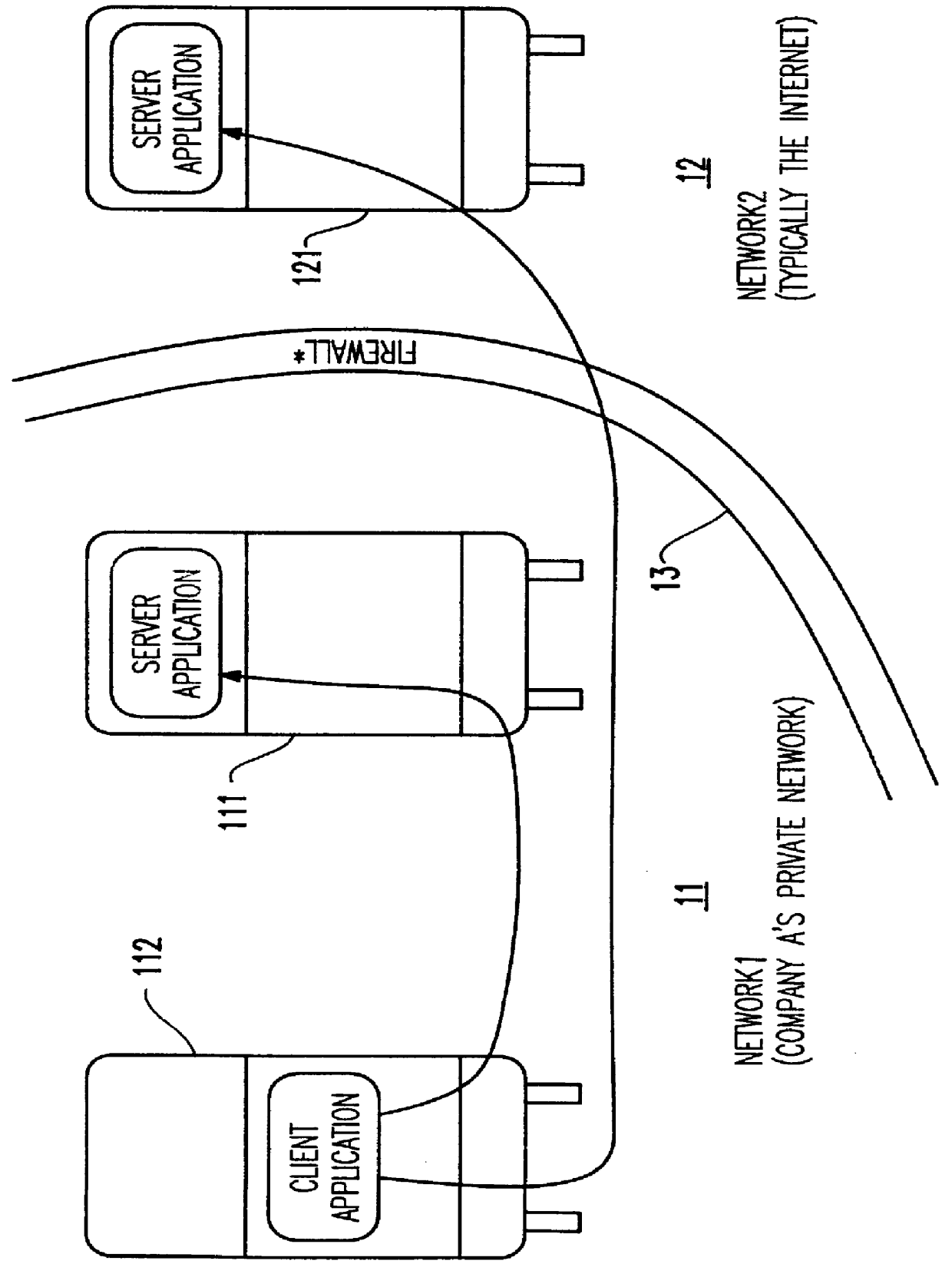
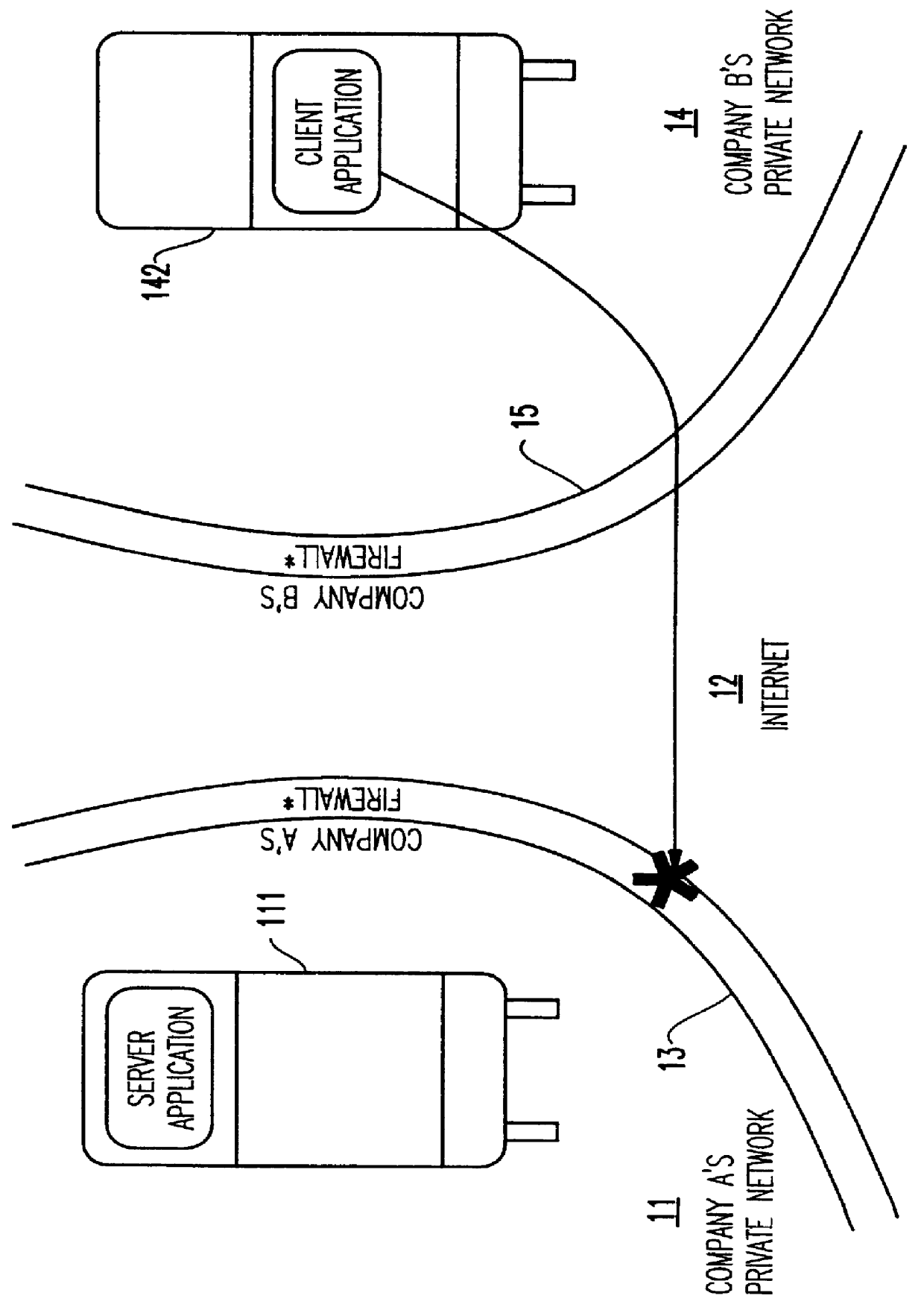
A lightweight secure tunneling protocol or LSTP permits communicating across one or more firewalls by using a middle server or proxy. Three proxies are used to establish an end-to-end connection that navigates through the firewalls. In a typical configuration, a server is behind a first firewall and a client behind a second firewall are interconnected by an untrusted network (e.g., the Internet) between the firewalls. A first inside firewall SOCKS-aware server-side end proxy connects to the server inside the first firewall. A second inside firewall SOCKS-aware client-side end proxy is connected to by the client inside the second firewall. Both server-side and client-side end proxies can address a third proxy (called a middle proxy) outside the two firewalls. The middle proxy is usually started first, as the other two end proxies (server and client) will initiate the connection to the middle proxy some time after they are started. Since the middle proxy is mutually addressable by both inside proxies, a complete end-to-end connection between the server and client is established. It is the use of one or more middle proxies together with the LSTP that establishes the secure communications link or tunnel across multiple firewalls.
Owner:IBM CORP
End-to-end virtualization
InactiveUS20120099602A1Facilitates end-to-end virtualizationData switching by path configurationData virtualizationNetwork virtualization
One embodiment of the present invention provides a system that facilitates end-to-end virtualization. During operation, a network interface residing on an end host sets up a tunnel. The network interface then encapsulates a packet destined to a virtual machine based on a tunneling protocol. By establishing a tunnel that allows a source host to address a remote virtual machine, embodiments of the present invention facilitate end-to-end virtualization.
Owner:AVAGO TECH INT SALES PTE LTD
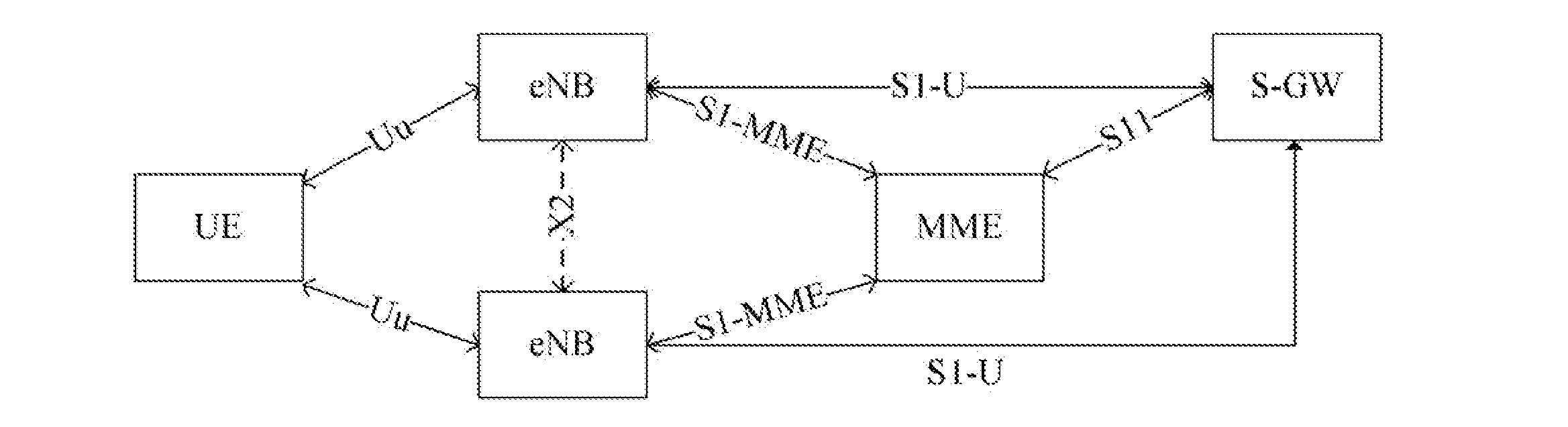
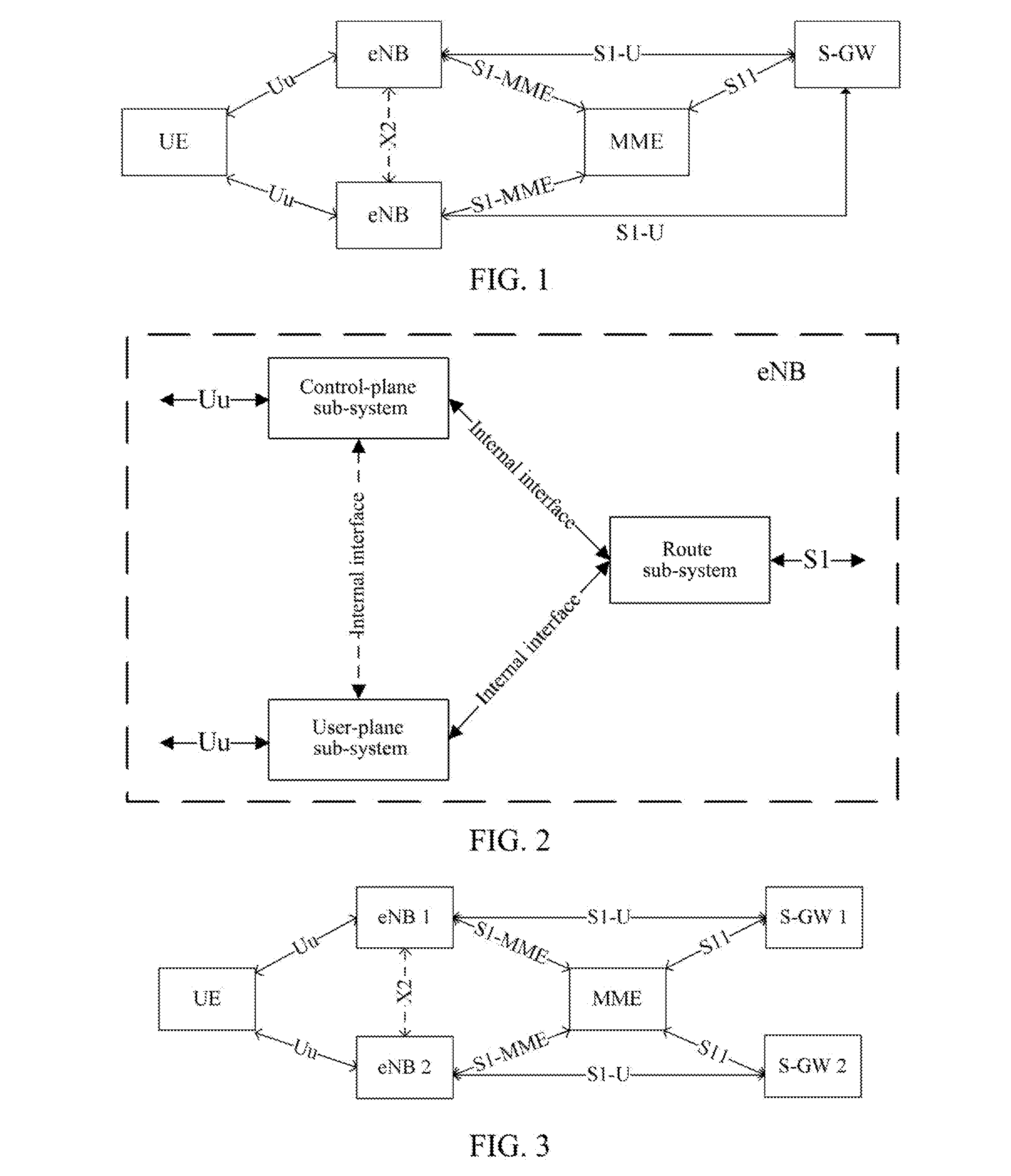
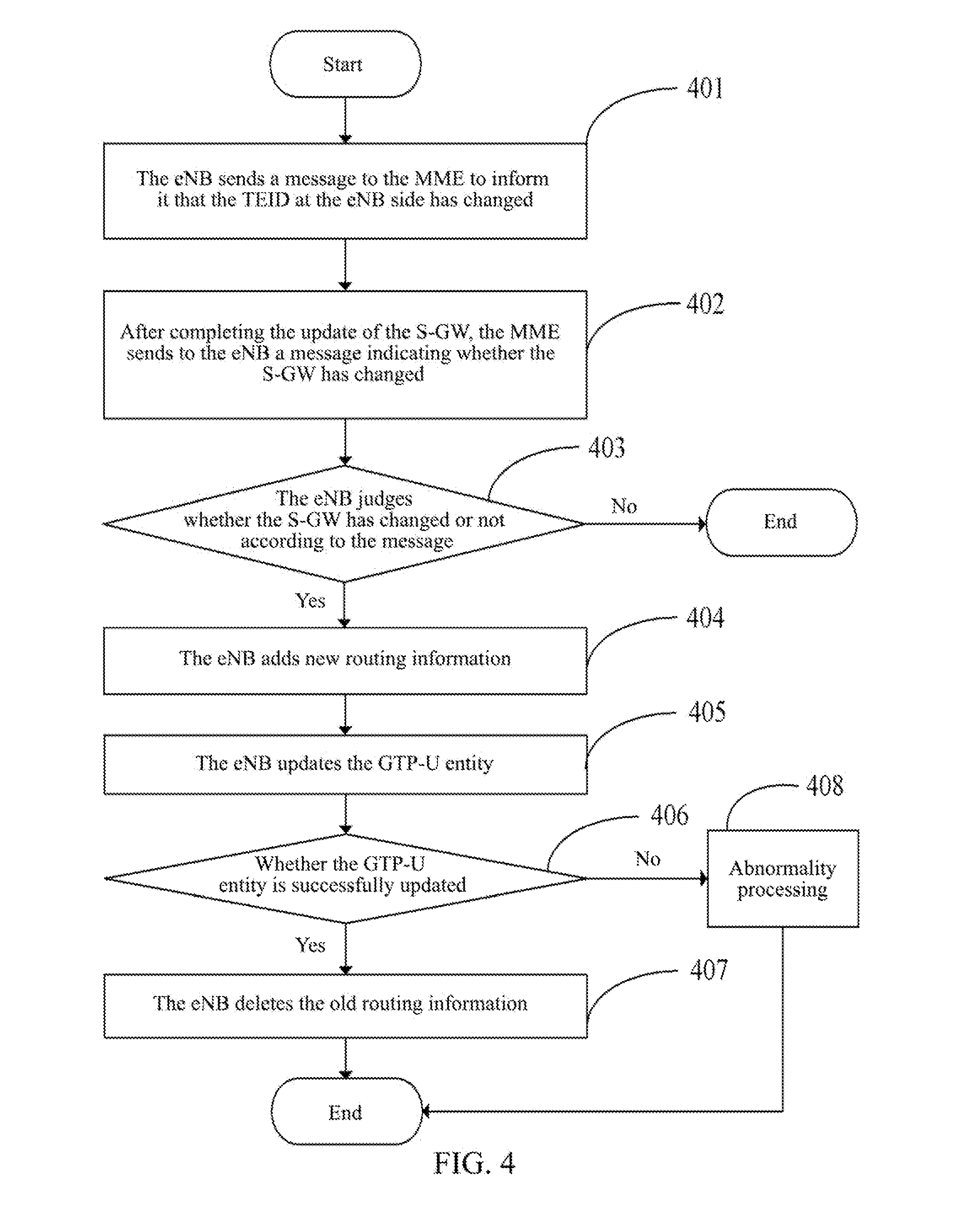
Method, system and evolved NodeB apparatus for implementing inter-evolved NodeB handover
ActiveUS8804667B2Avoid it happening againConnection managementData switching by path configurationGeneral Packet Radio ServiceRouting table
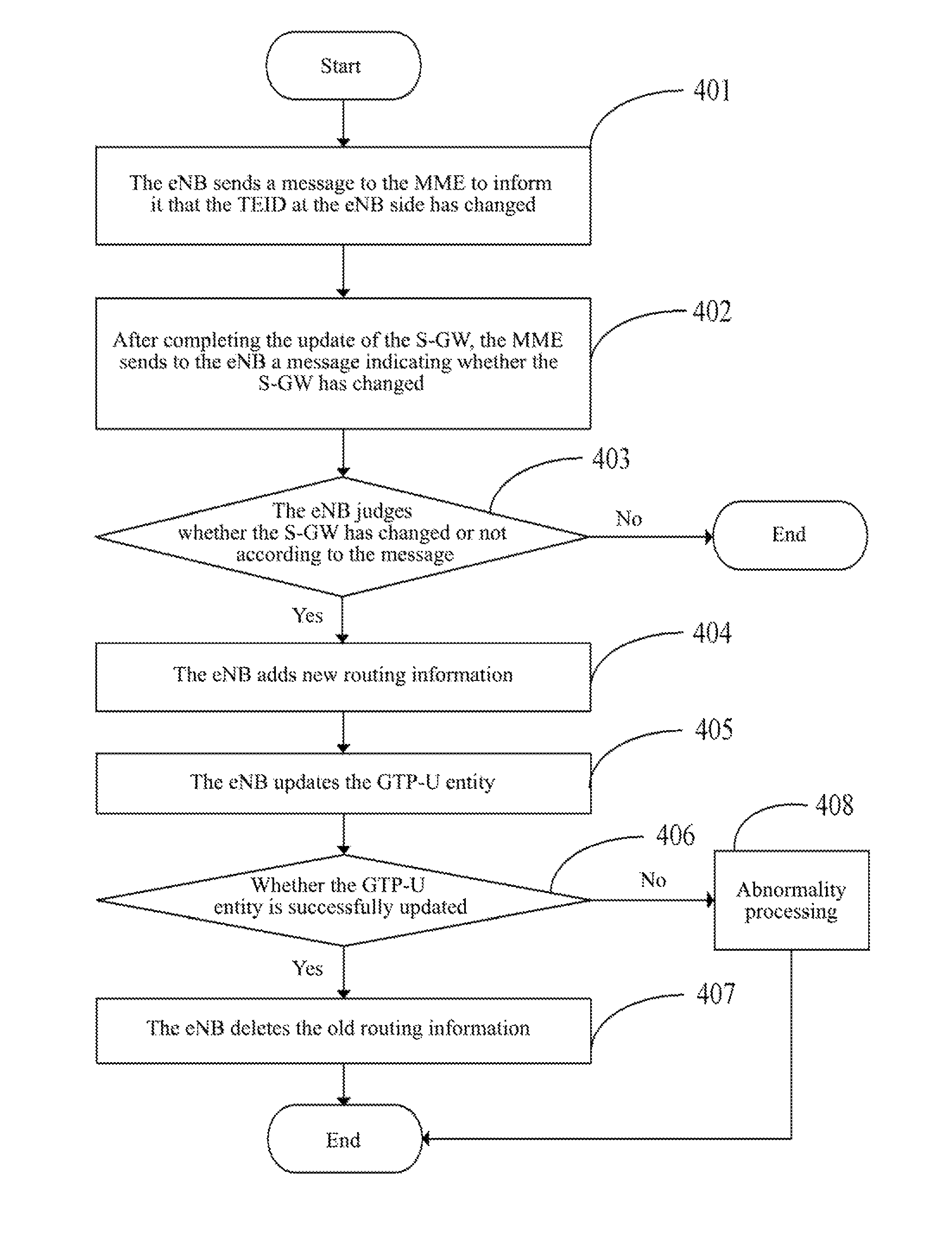
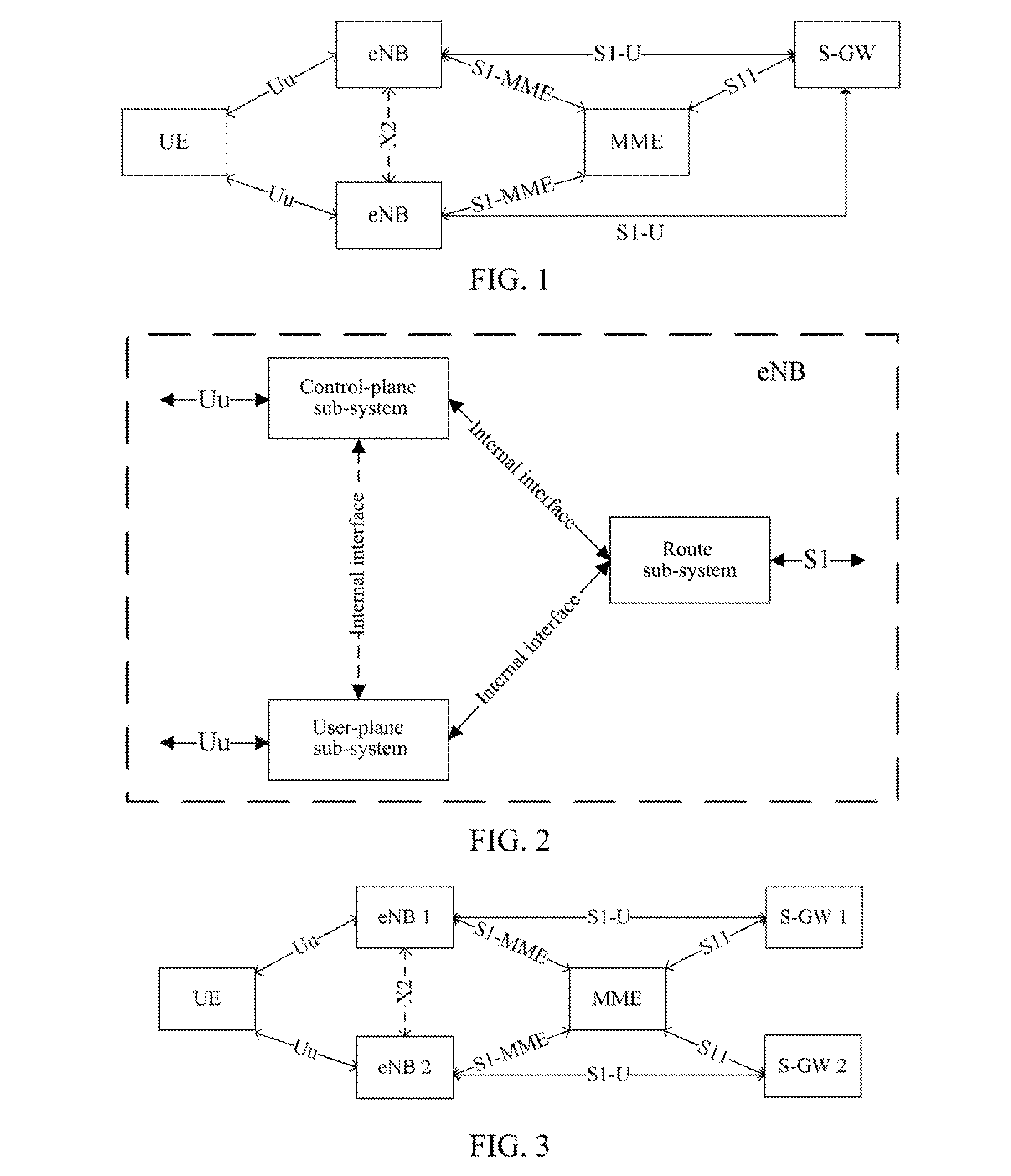
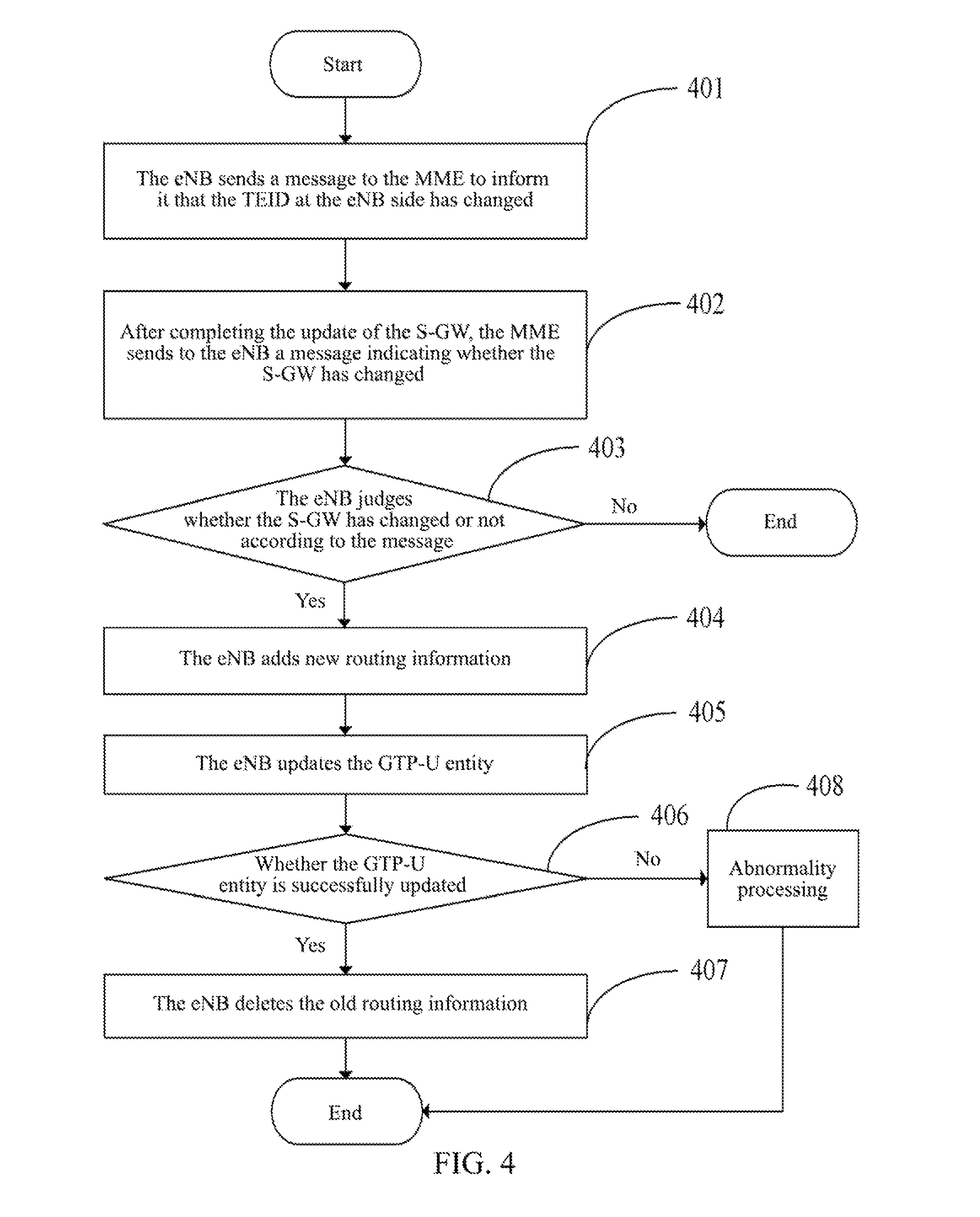
A method, a system and an evolved NodeB (eNB) apparatus for implementing inter-eNB switch are disclosed in the present invention. The method includes: when a user equipment switches from a source-side eNB to a target-side eNB, if the target-side eNB acquires via the Mobility Management Entity (MME) that the Serving Gateway (S-GW) has changed, the target-side eNB adds the new route relation of the S-GW and then updates the General Packet Radio Service (GPRS) Tunnelling Protocol User Plane (GTP-U) entity. The present invention can effectively solve the problem of the uplink data packet loss due to the time difference existing between the update to the Tunnel Endpoint Identifier (TEID) and the routing table by the eNB when inter-eNB switch is performed via X2 and the S-GW has changed, thus enhancing the user experience during the switch.
Owner:ZTE CORP
User-plane congestion management
Methods, apparatuses and systems for user-plane congestion management are provided. Among these method, apparatuses and systems is a method, implementable by a base station (and / or a serving gateway), for mitigating user plane congestion. The method may include sending a congestion indication to a core network; receiving a general packet radio system (GPRS) tunneling protocol (GTP) packet including an first internet protocol (IP) packet associated with a first flow within a bearer; obtaining, from a header of the GTP packet, an indicator indicative of a priority of the IP packet, wherein the indicator was inserted into the header of the GTP packet by the core network responsive to the congestion indication; and dropping any of the GTP packet and the first IP packet on condition that a priority of a second IP packet associated with second flow within the bearer takes precedence over the priority of the first IP packet.
Owner:INTERDIGITAL PATENT HLDG INC
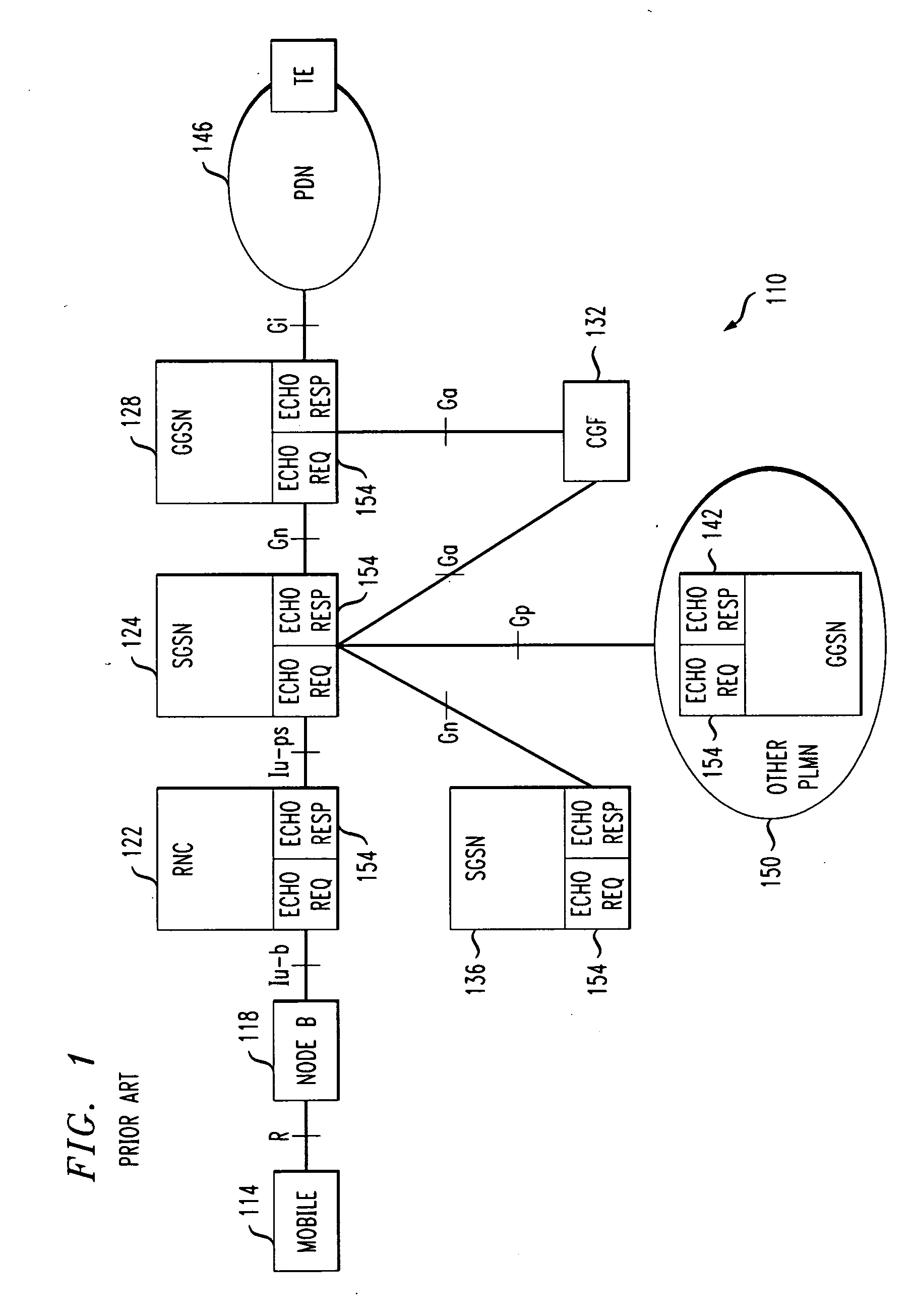
General packet radio service tunneling protocol (GTP) packet filter
InactiveUS20030081607A1Time-division multiplexData switching by path configurationGeneral Packet Radio ServiceAnalysis data
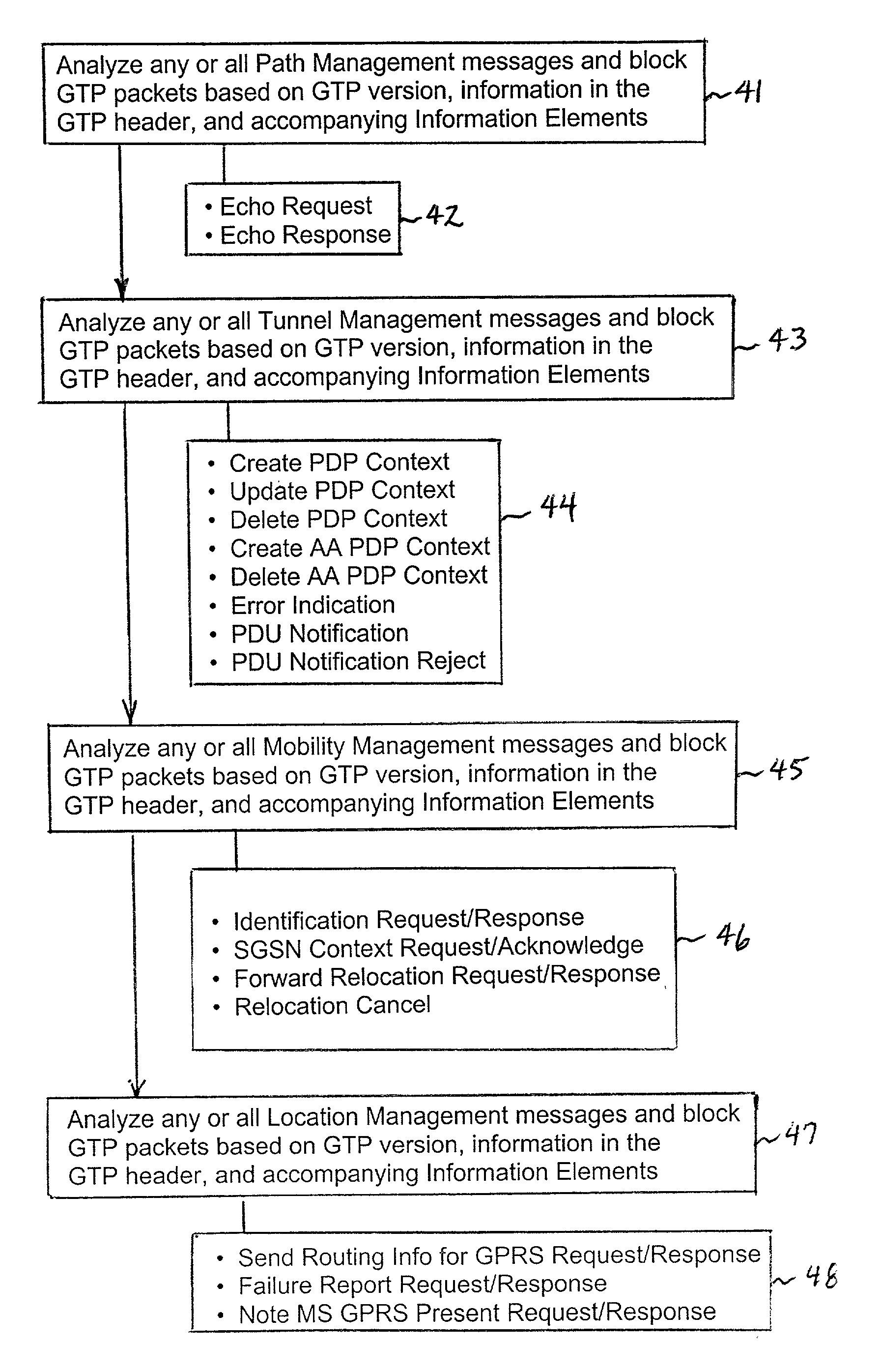
A method of filtering data packets in General Packet Radio Service (GPRS) Tunneling Protocol (GTP) signaling messages. Selected messages from GTP Path Management, GTP Tunnel Management, GTP Mobility Management, and GTP Location Management messages are analyzed against a plurality of filtering criteria, and data packets that do not meet the filtering criteria are dropped while data packets that meet the criteria are passed. The data packets may be analyzed to verify that they contain correct source, destination, and mask addresses, and that they contain UDP / TCP port numbers that are consistent with the GTP version number. The packets are also inspected at the GTP level, layer-5, and based on the GTP version, information in the GTP header, and accompanying Information Elements (IEs), selected data packets are dropped.
Owner:TELEFON AB LM ERICSSON (PUBL)
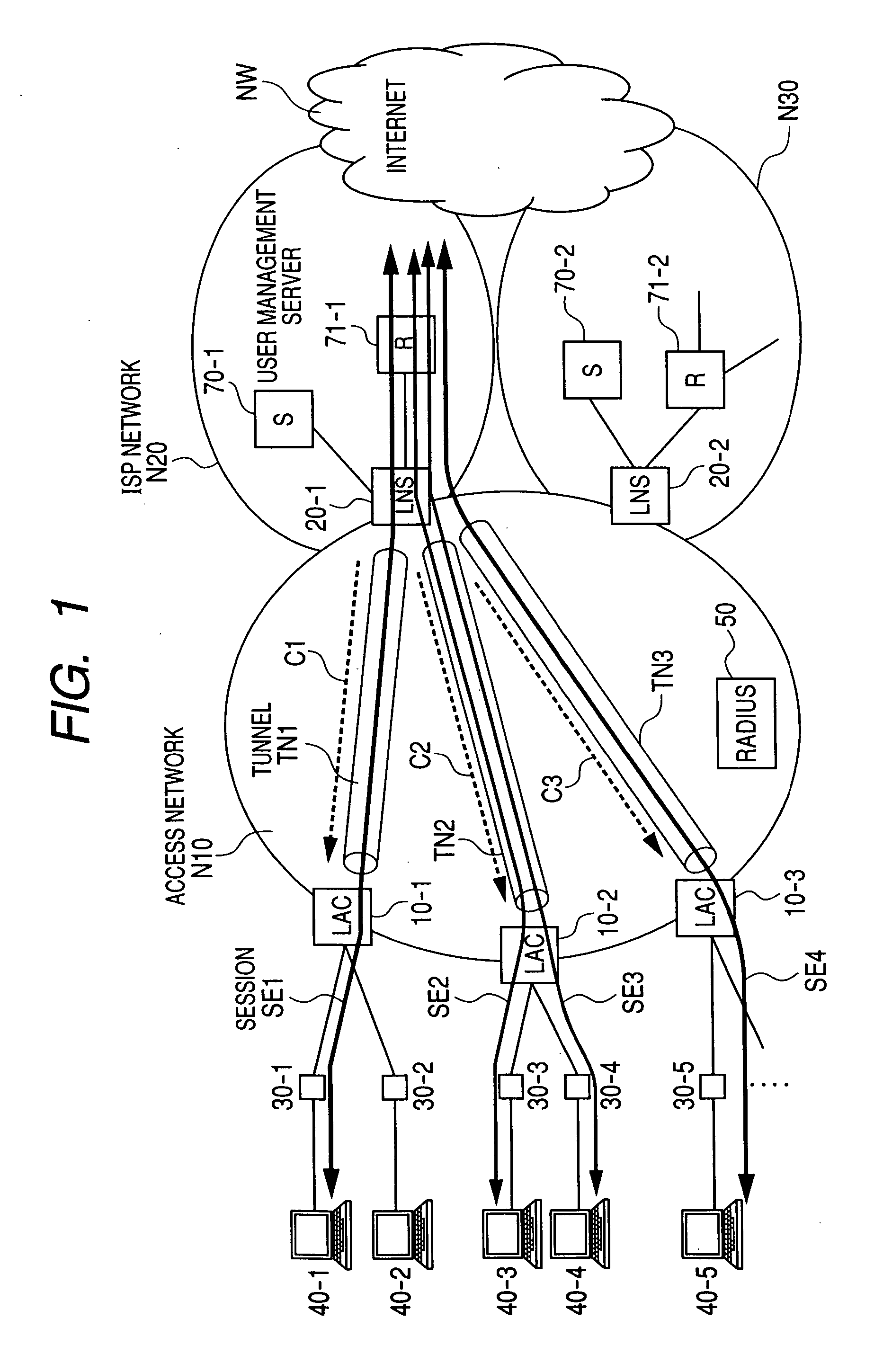
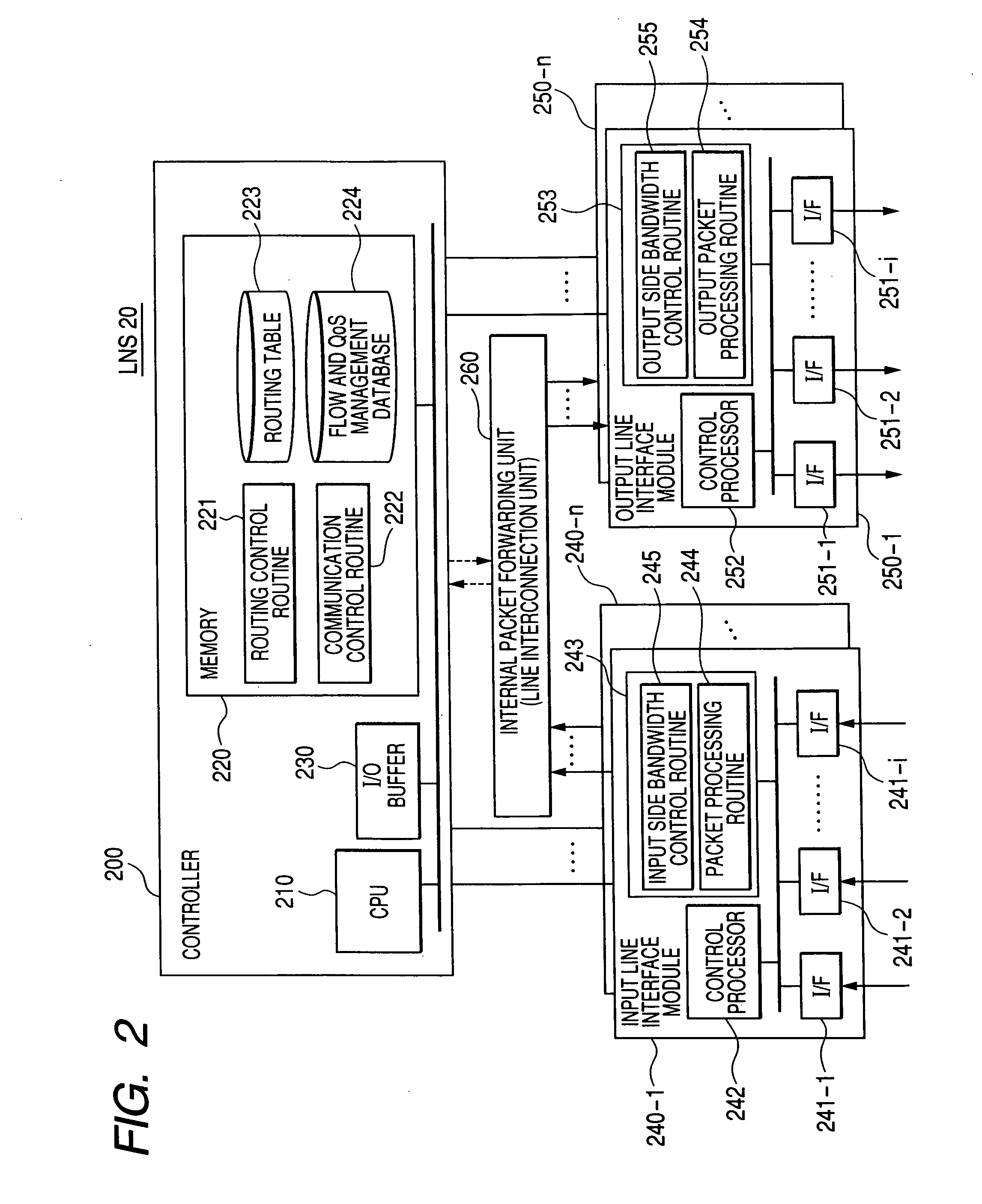
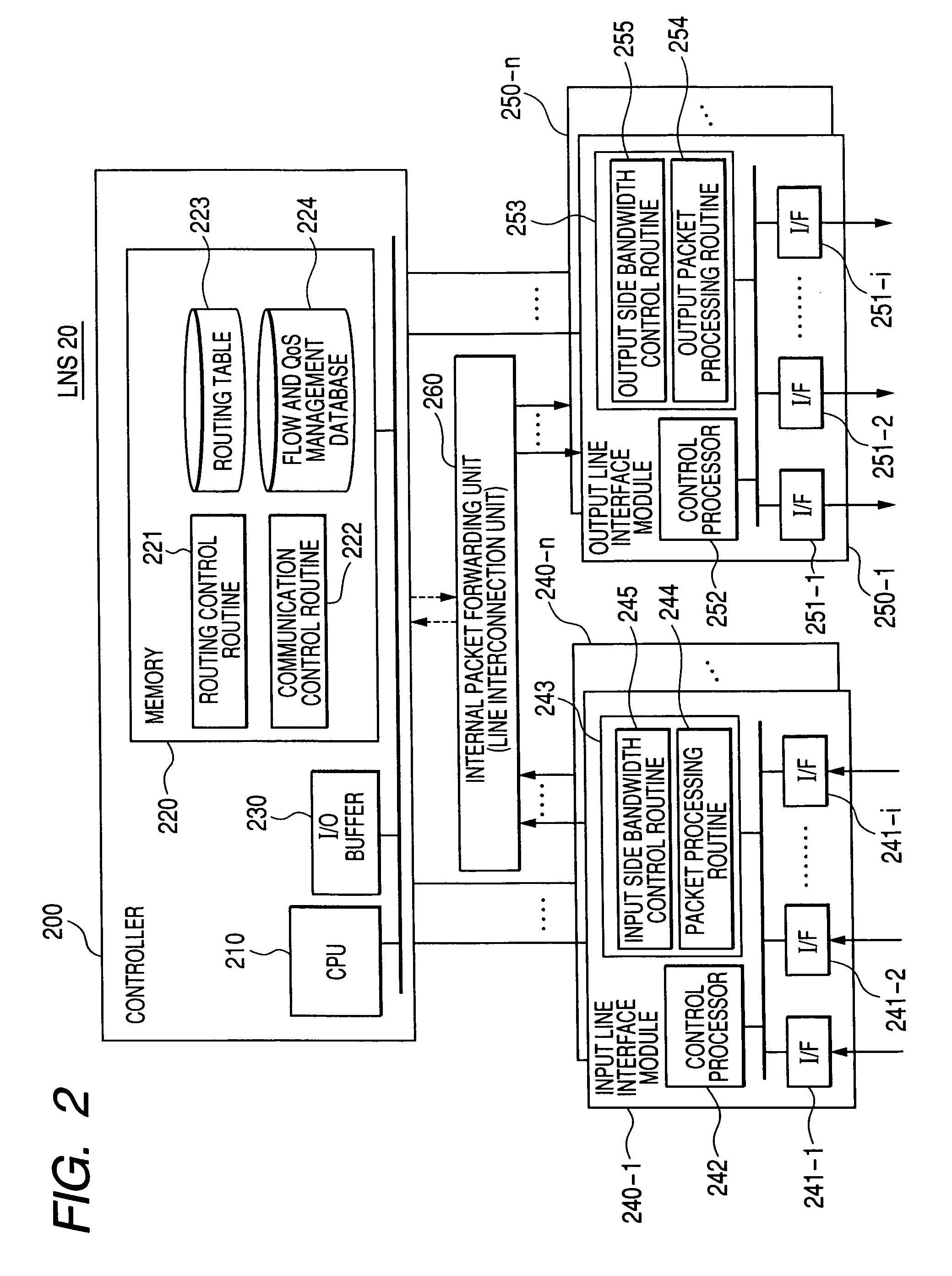
Packet forwarding apparatus and communication bandwidth control method
InactiveUS20060187942A1Data switching by path configurationStore-and-forward switching systemsTerminal equipmentEdge node
In a network for forwarding user packets by a tunneling protocol, an egress edge node to which tunnels concentrate from a plurality of ingress edge nodes allocates a bandwidth to each of sessions multiplexed through each of the tunnels and notifies each of the ingress edge nodes of the allocated bandwidth, and the ingress node notifies private routers or terminal devices of the allocated bandwidth.
Owner:HITACHI LTD
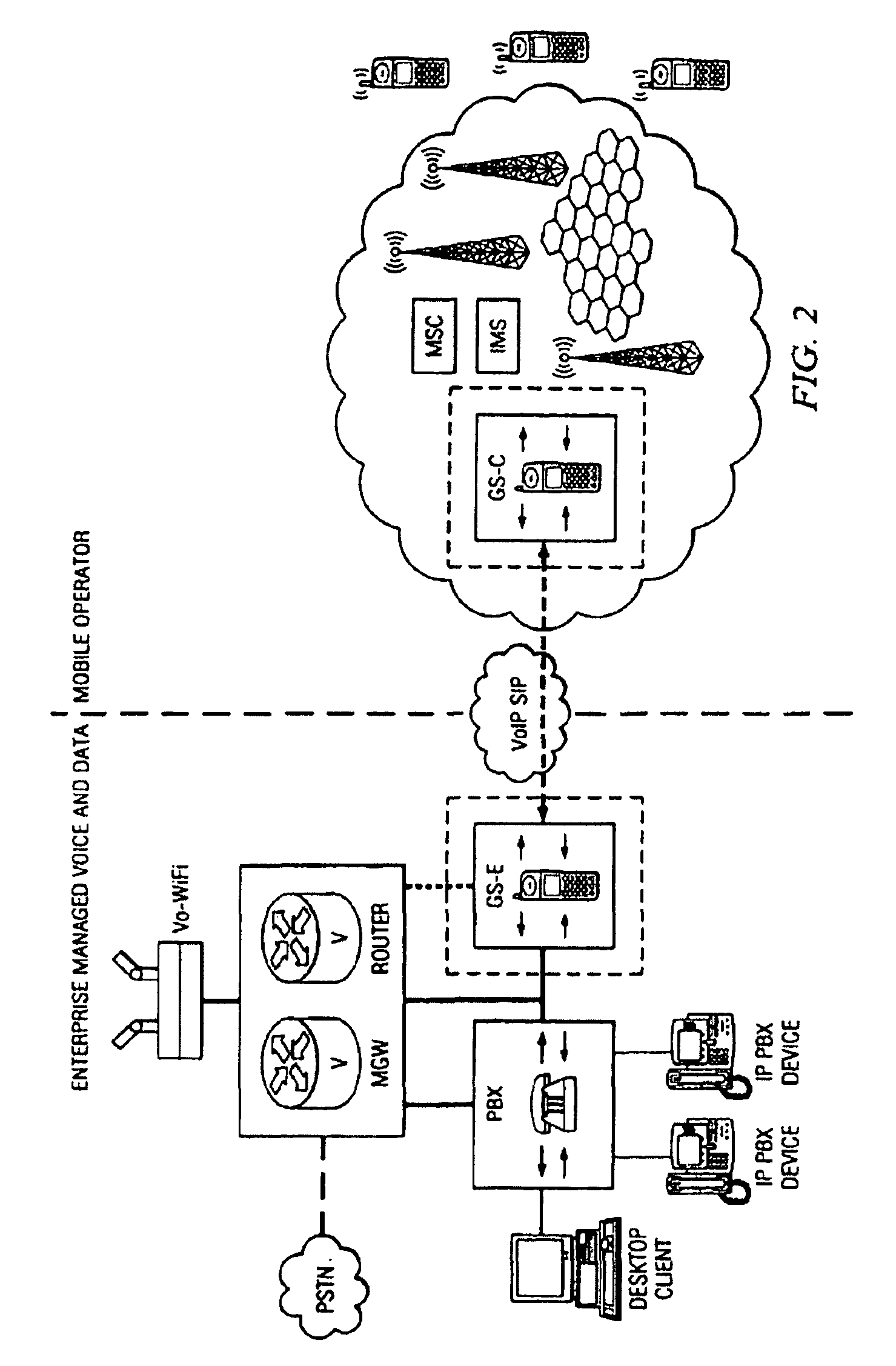
System and method for enabling VPN-less session setup for connecting mobile data devices to an enterprise data network
ActiveUS7873001B2Multiplex system selection arrangementsAccounting/billing servicesGPRS Tunnelling ProtocolMobile device
A mobile application gateway configured to interconnect mobile communication devices on a cellular network with an enterprise network is provided. The mobile application gateway includes a voice and data signaling gateway configured to provide routing functionalities, service functionalities and admission control. A gateway GPRS support node (GGSN) is configured to establish a secure data session between one or more of the mobile communication devices and the enterprise network by establishing a GPRS tunneling protocol (GTP) tunnel between a carrier-hosted serving GPRS support node (SGSN) and the GGSN.
Owner:TANGO NETWORKS
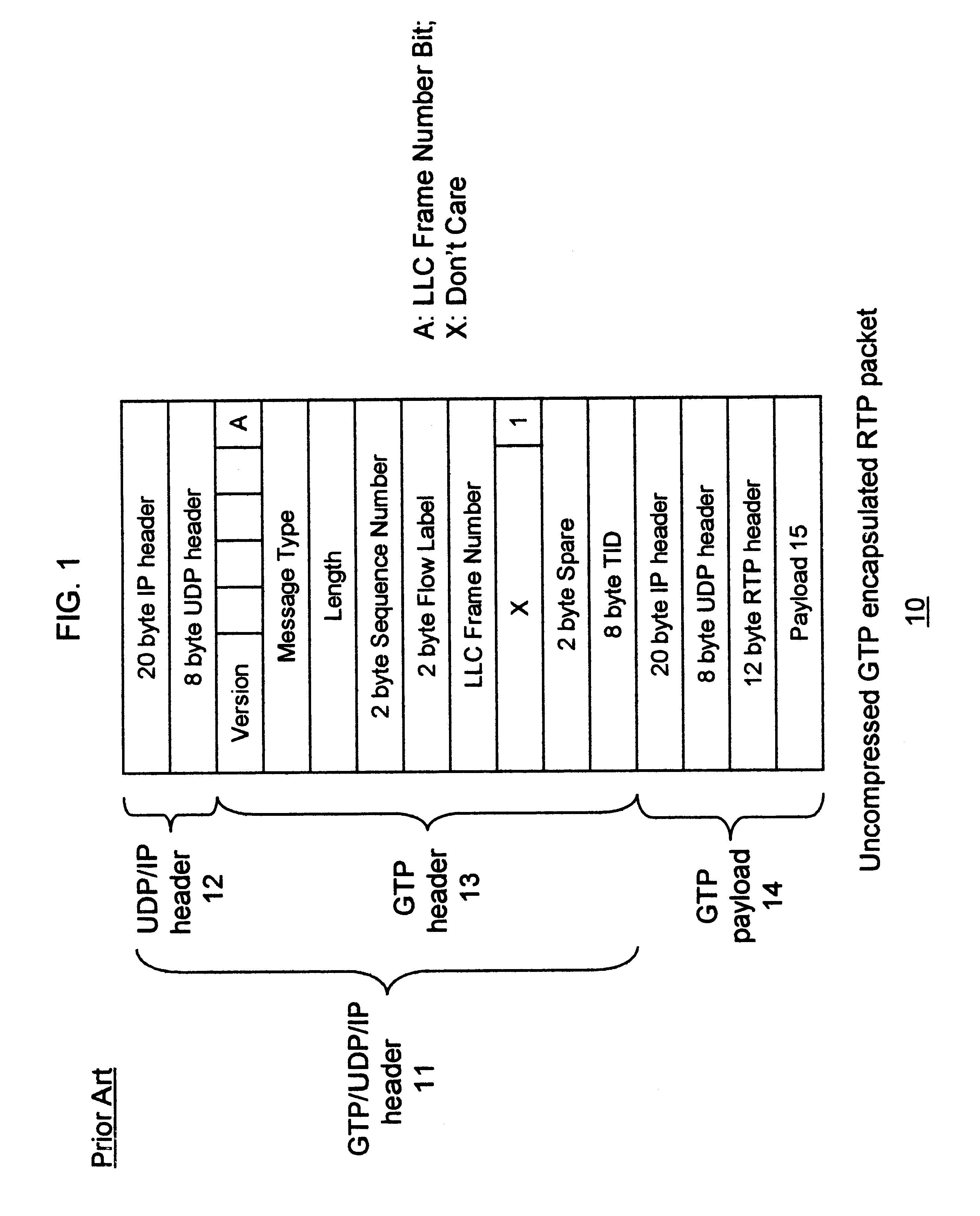
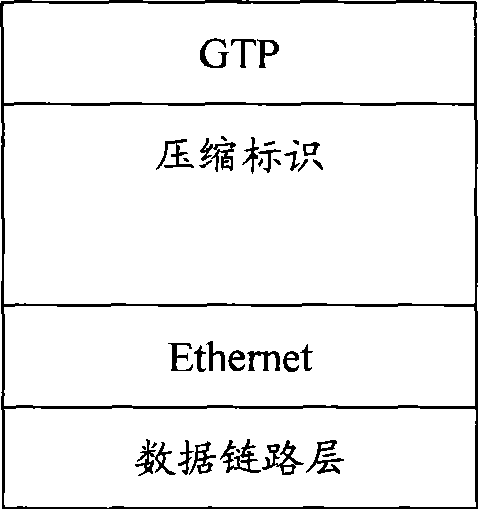
Header compression for general packet radio service tunneling protocol (GTP)-encapsulated packets
InactiveUS6839339B1Efficient transportNetwork traffic/resource managementNetwork topologiesGeneral Packet Radio ServiceTime Protocol
A UMTS (Universal Mobile Telecommunications System) core network supports a compression framework that provides for header compression of General Packet Radio Service Tunneling Protocol (GTP)-Encapsulated Packets. In particular; the GTP / UDP(User Datagram Protocol) / IP(Internet Protocol) header is compressed. In addition, the UMTS core network also supports RTP(Real Time Protocol) / UDP / IP header compression independent of the GTP / UDP / IP header compression.
Owner:LUCENT TECH INC
Distributed protocol processing and packet forwarding using tunneling protocols
InactiveUS6763018B1Time-division multiplexData switching by path configurationNetwork access serverHigh density
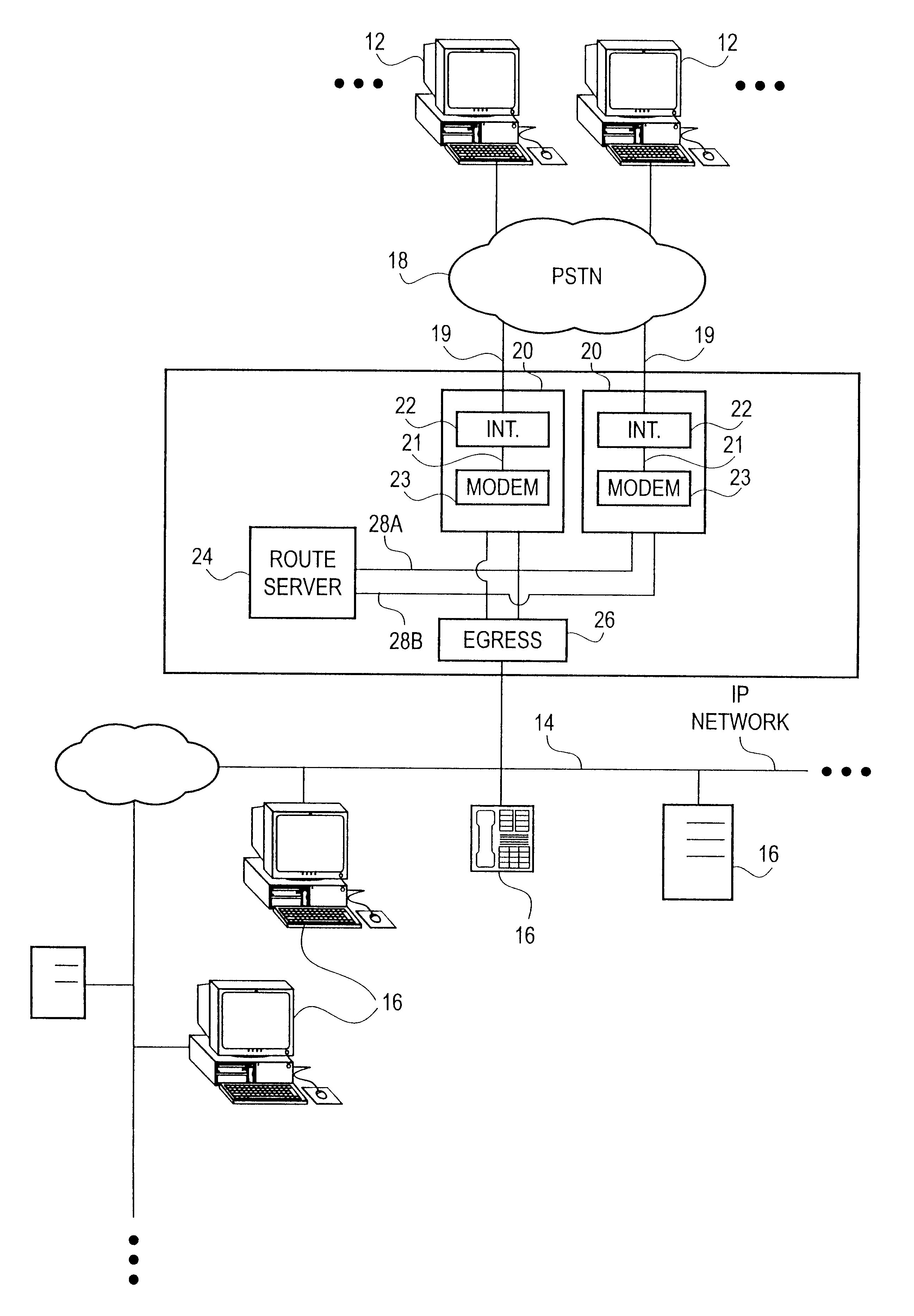
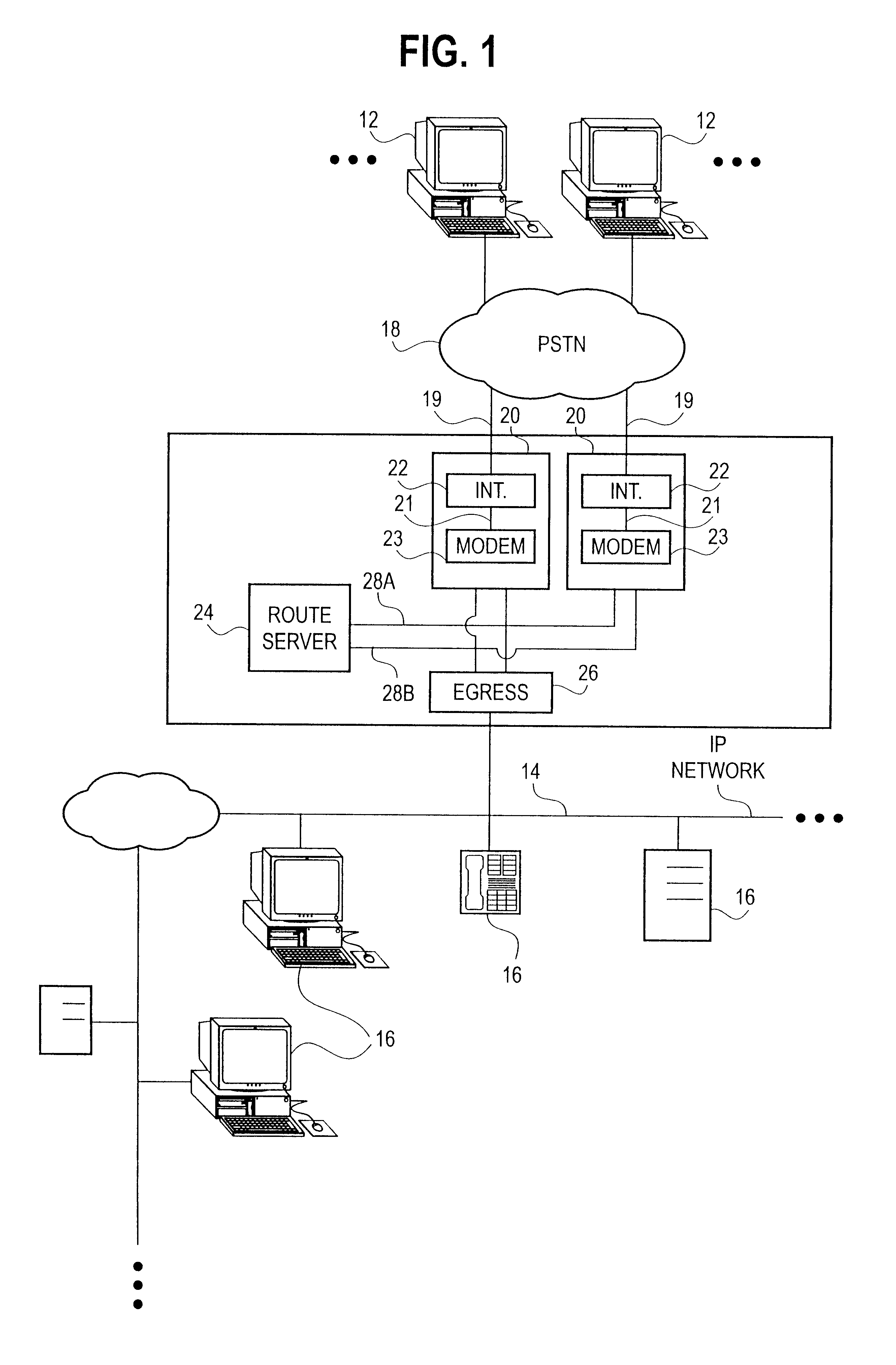
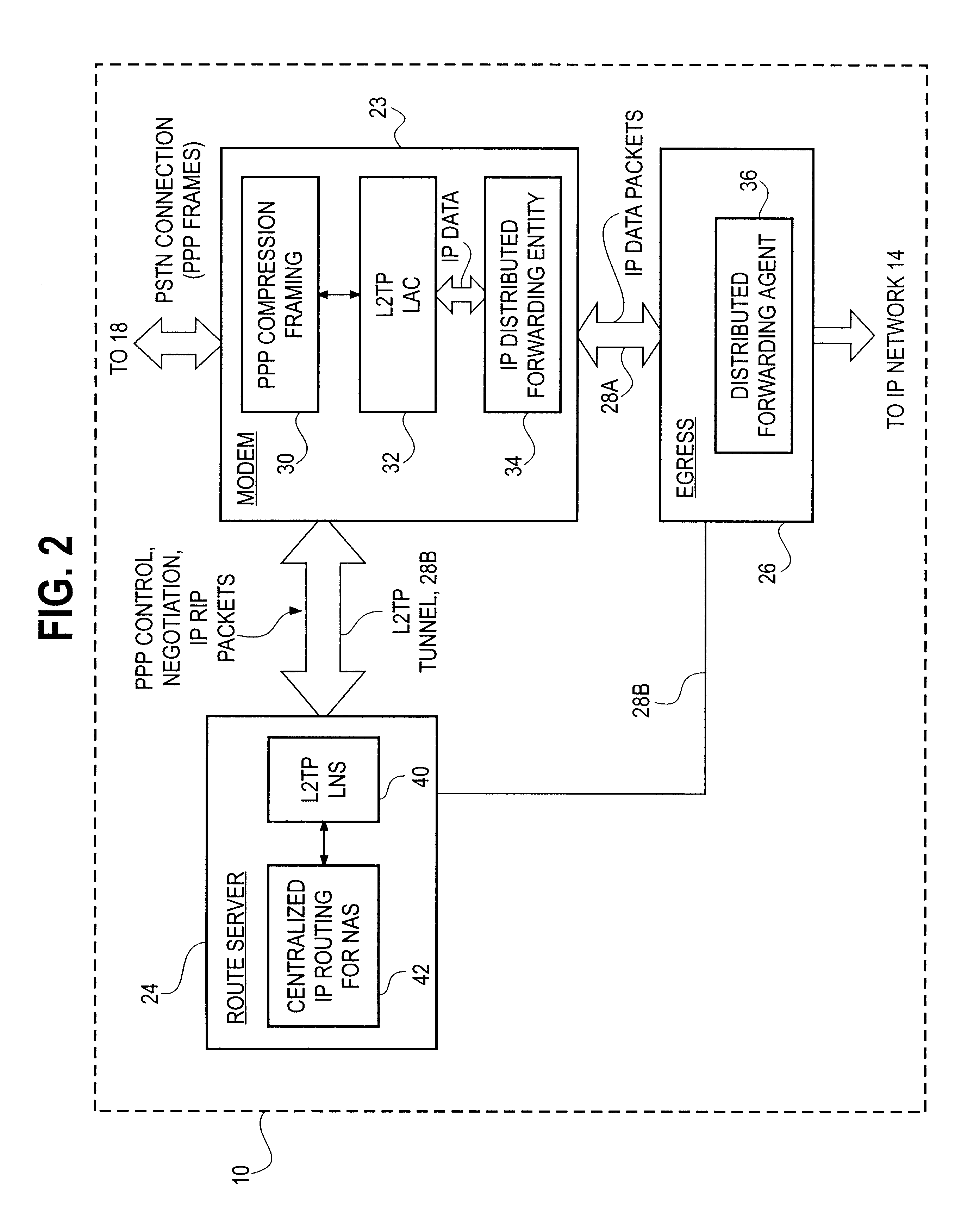
A high density network access server implements a tunneling protocol between a modem module and a route server module. PPP and routing control packets received from the PPP link are tunneled to the route server for processing. The IP data packet forwarding function for the network access server is distributed directly to the modem modules. The combination of distributed PPP processing and distributed IP data packet forwarding enables the capacity of the network access server to be scaled to orders of magnitude greater than previously known, to handle thousands or even tens of thousands of simultaneous data sessions.
Owner:VALTRUS INNOVATIONS LTD
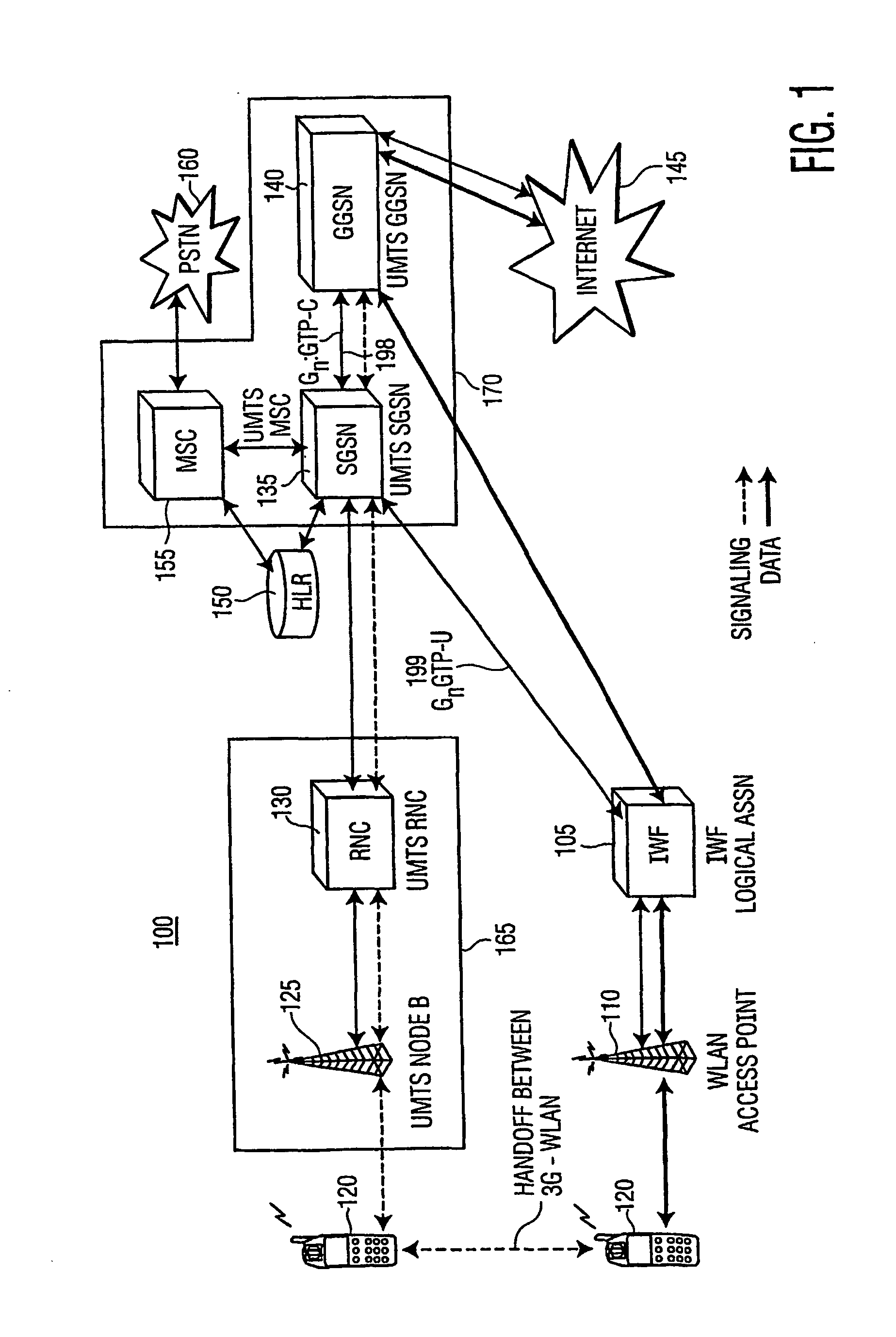
Wlan as a logical support node for hybrid coupling in an interworking between wlan and a mobile communication system
ActiveUS20060050667A1Enhanced diversionNetwork topologiesConnection managementCouplingControl signal
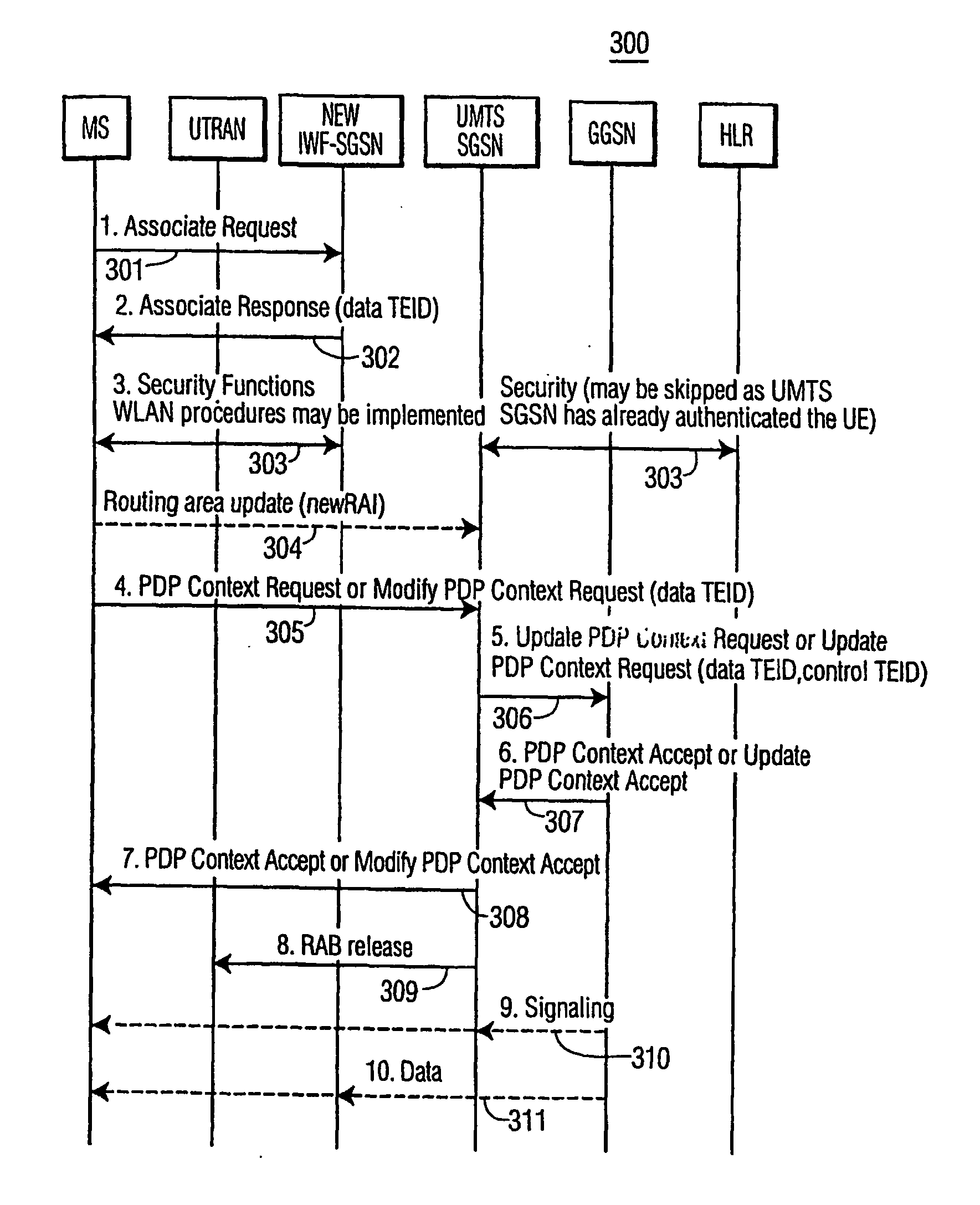
There is provided a method for supporting an internetworking between a WLAN and a mobile communications network. The mobile communications network, for example UMTS network, has a GPRS support node and a serving GPRS support node. The internetworking is facilitated by an IWF. The method comprises the steps of establishing at least one GPRS tunneling protocol tunnel between the IWF and the GGSN for transferring data signals, and establishing at least one GPRS (tunneling protocol tunnel between the GGSN and the SGSN for transferring control signals.
Owner:THOMSON LICENSING SA
Packet forwarding apparatus and communication bandwidth control method
InactiveUS7649890B2Time-division multiplexData switching by path configurationTerminal equipmentEdge node
In a network for forwarding user packets by a tunneling protocol, an egress edge node to which tunnels concentrate from a plurality of ingress edge nodes allocates a bandwidth to each of sessions multiplexed through each of the tunnels and notifies each of the ingress edge nodes of the allocated bandwidth, and the ingress node notifies private routers or terminal devices of the allocated bandwidth.
Owner:HITACHI LTD
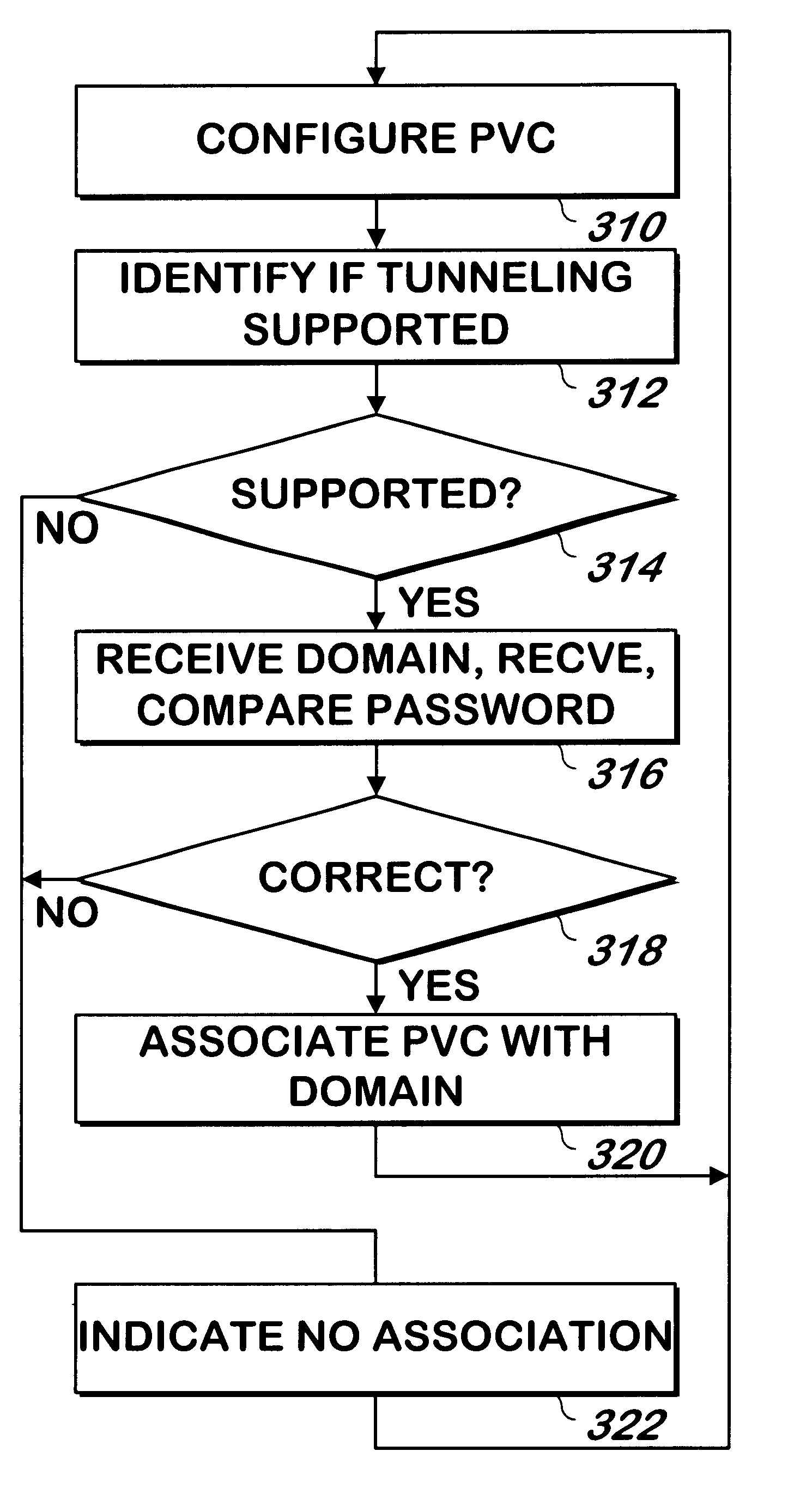
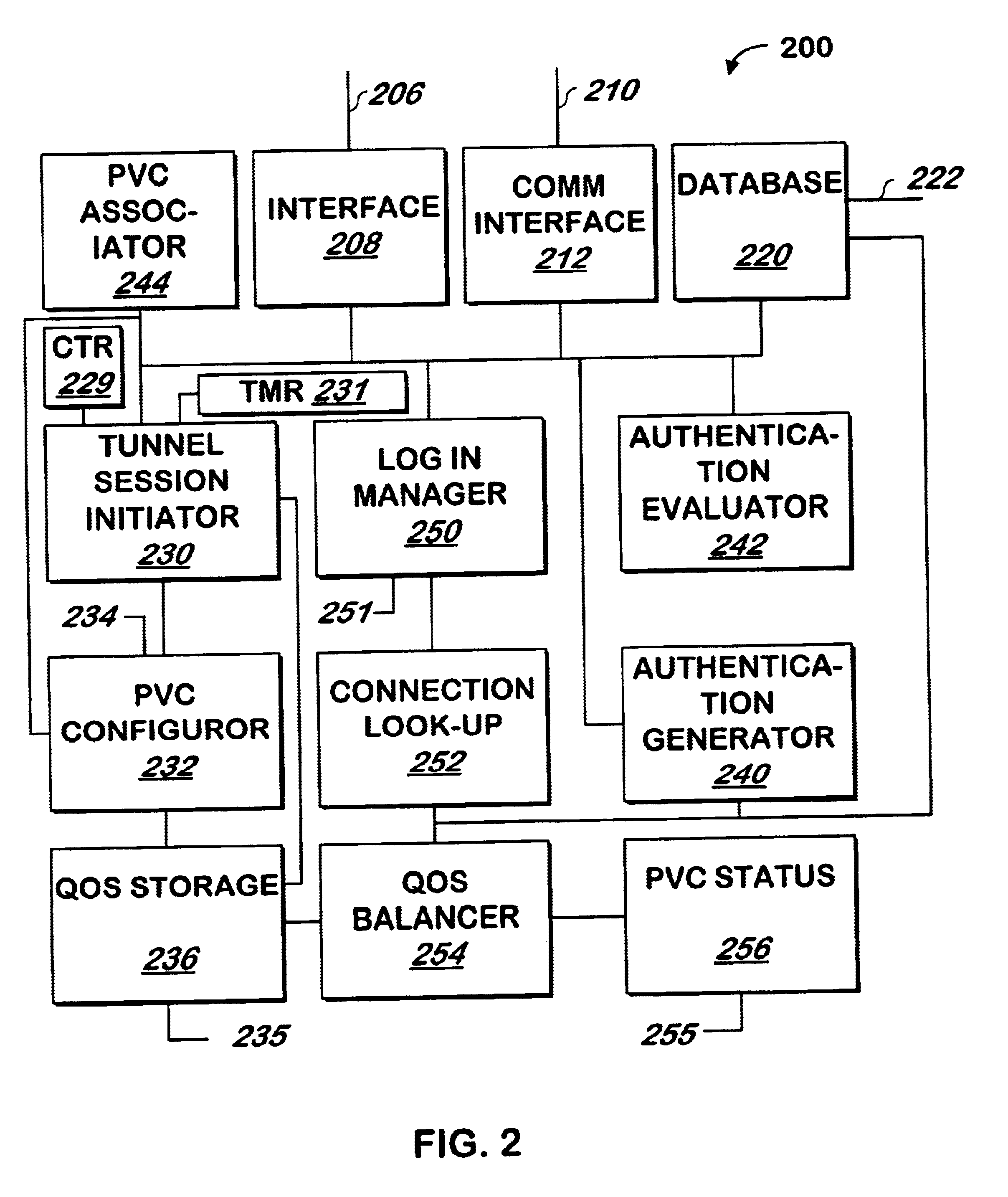
Method and apparatus for associating PVC identifiers with domain names of home gateways
InactiveUS6829242B2Load balancingEasy to manageTime-division multiplexMultiple digital computer combinationsDomain nameCommunication device
A method and apparatus associates a domain name of a home gateway with one or more PVCs. After the PVC is established, a tunneling protocol is used to request the domain name of the home gateway, and the domain name is associated with the PVC. When a user logs on via an access communication device, the user will provide a domain name of a home gateway with which the user desires to communicate. A PVC associated with the home gateway is then used to allow the user to communicate with the home gateway. The domain name of the home gateway may be periodically verified to detect any changes.
Owner:CISCO TECH INC
System and method for offloading a computational service on a point-to-point communication link
InactiveUS6950862B1Overcome problemsMultiple digital computer combinationsRadio transmissionNetwork packetCommunication link
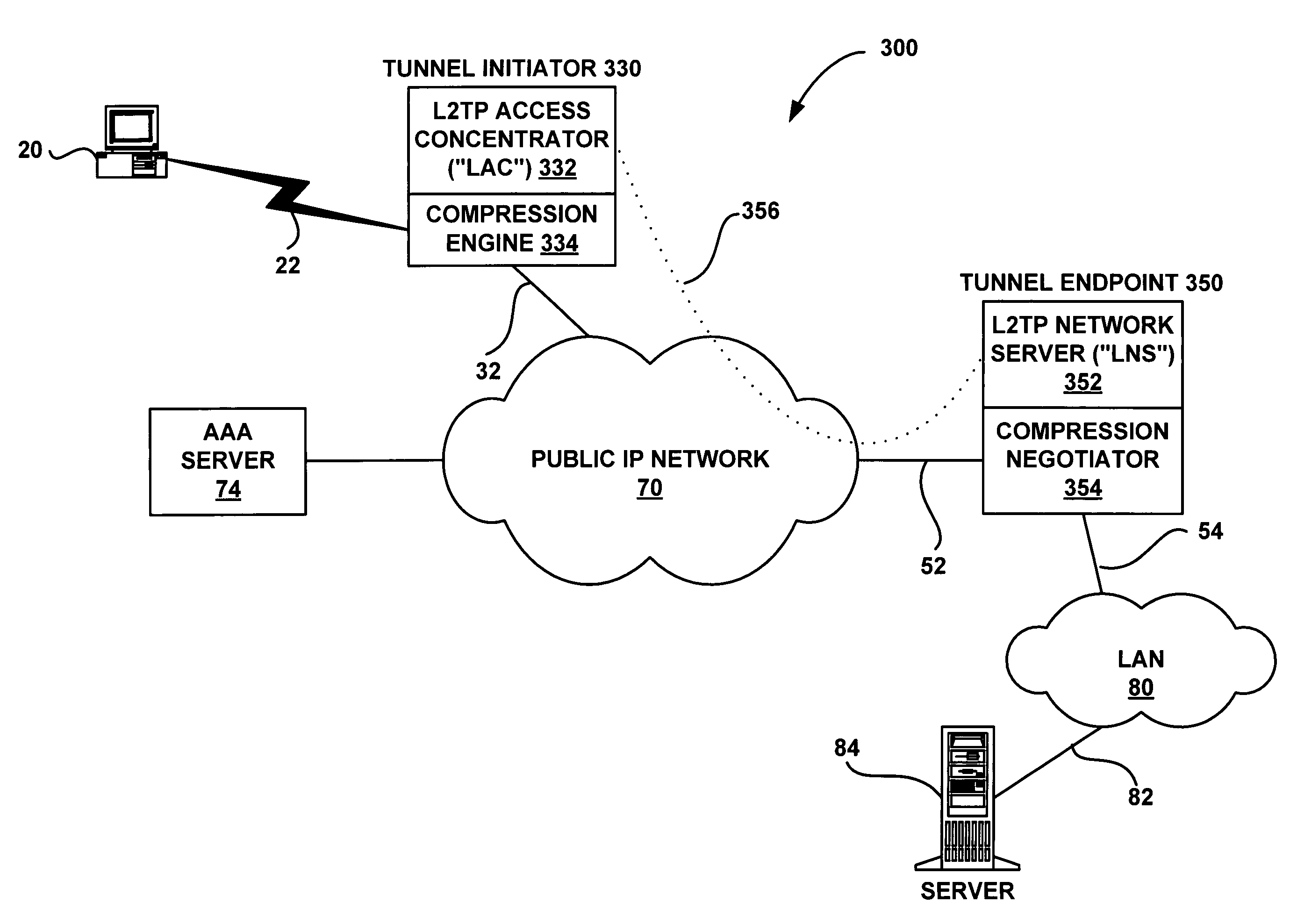
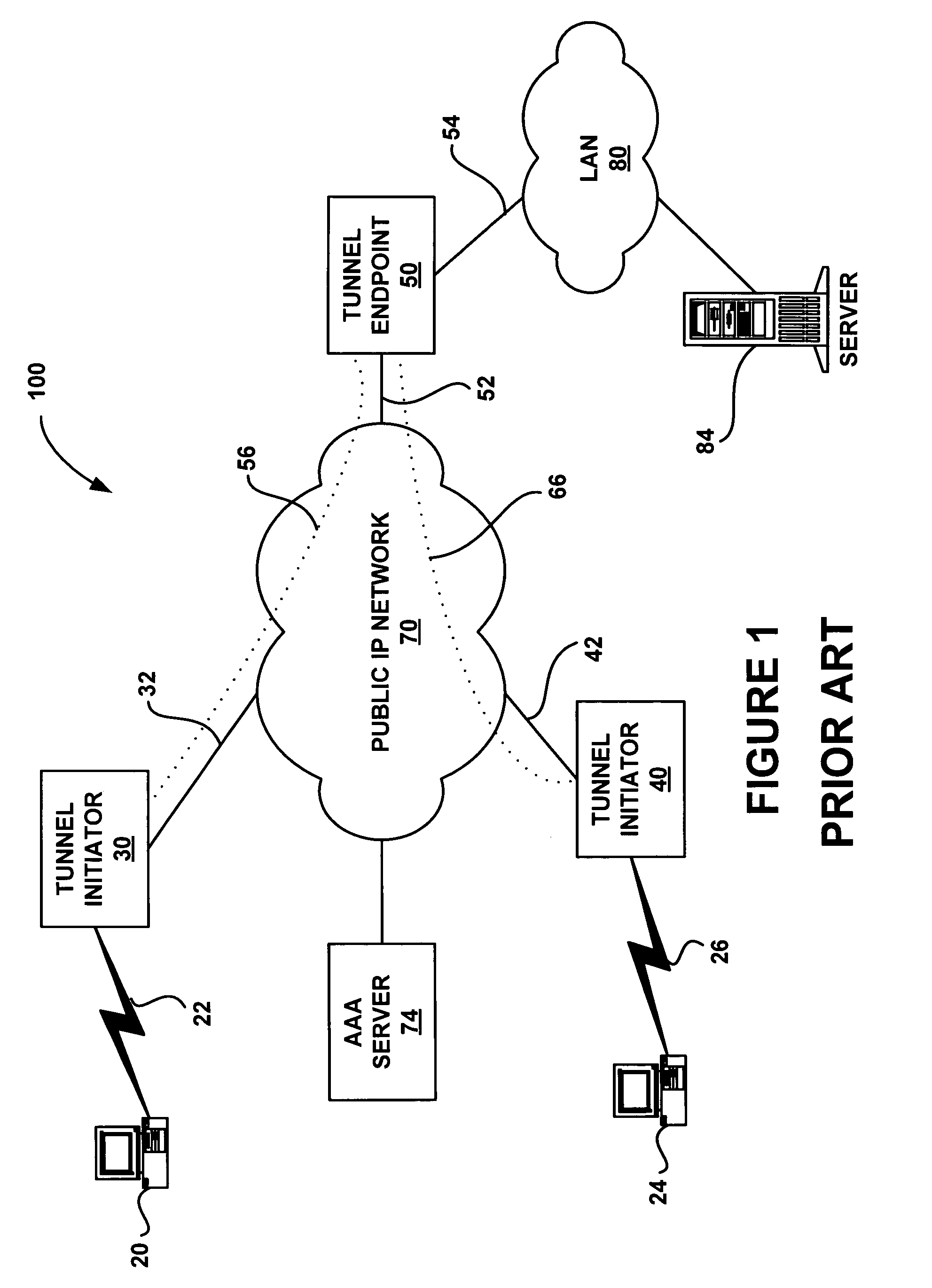
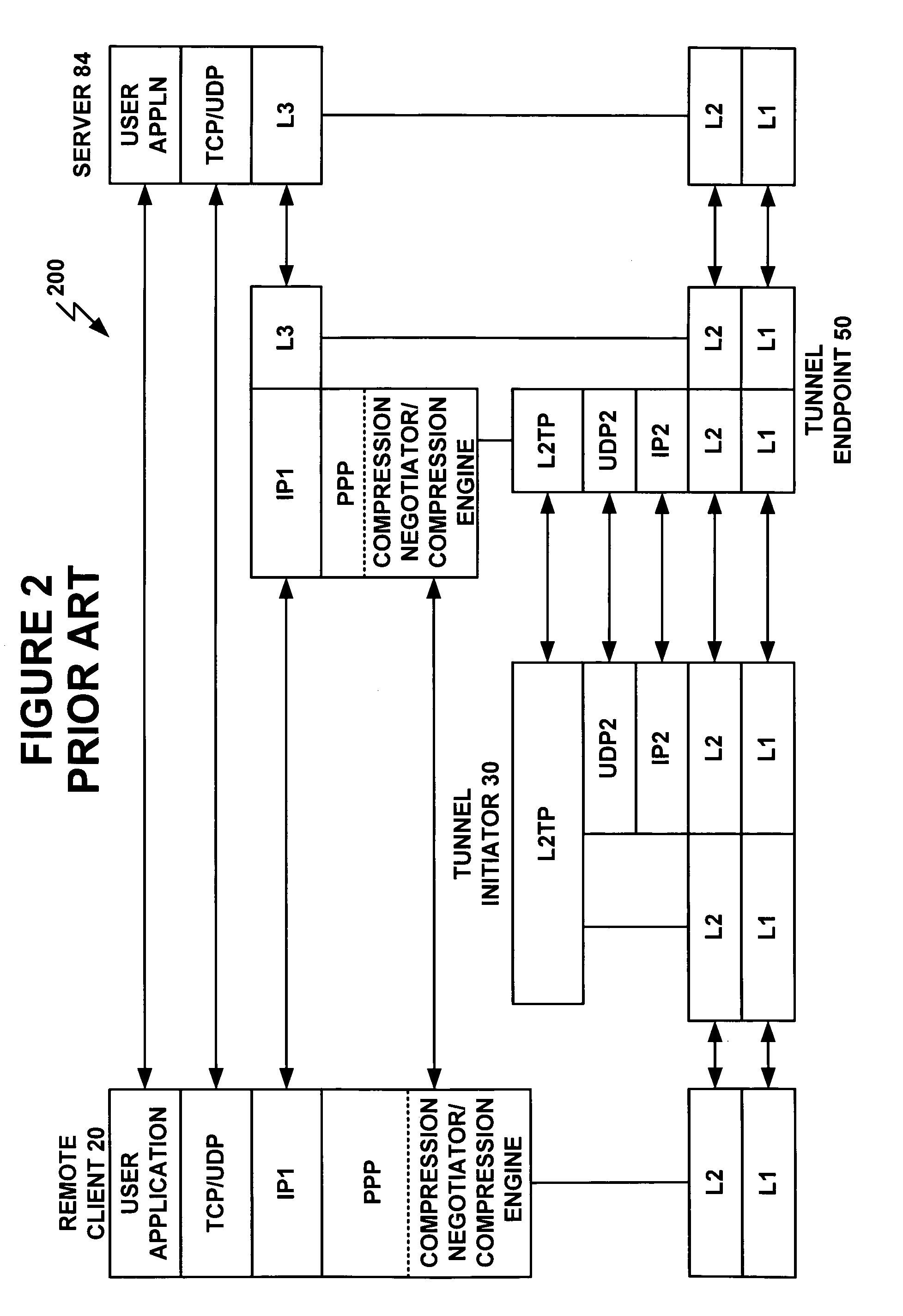
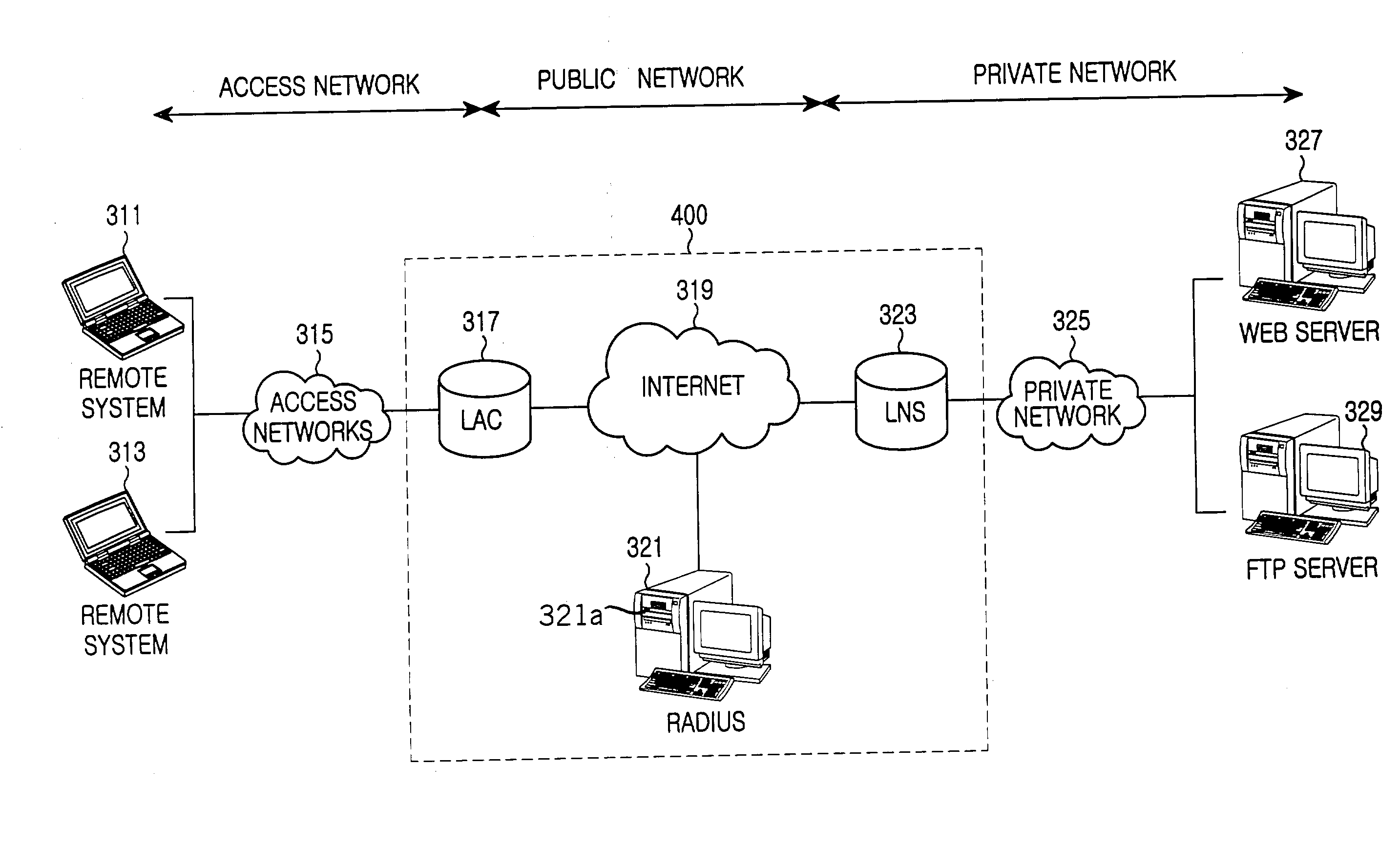
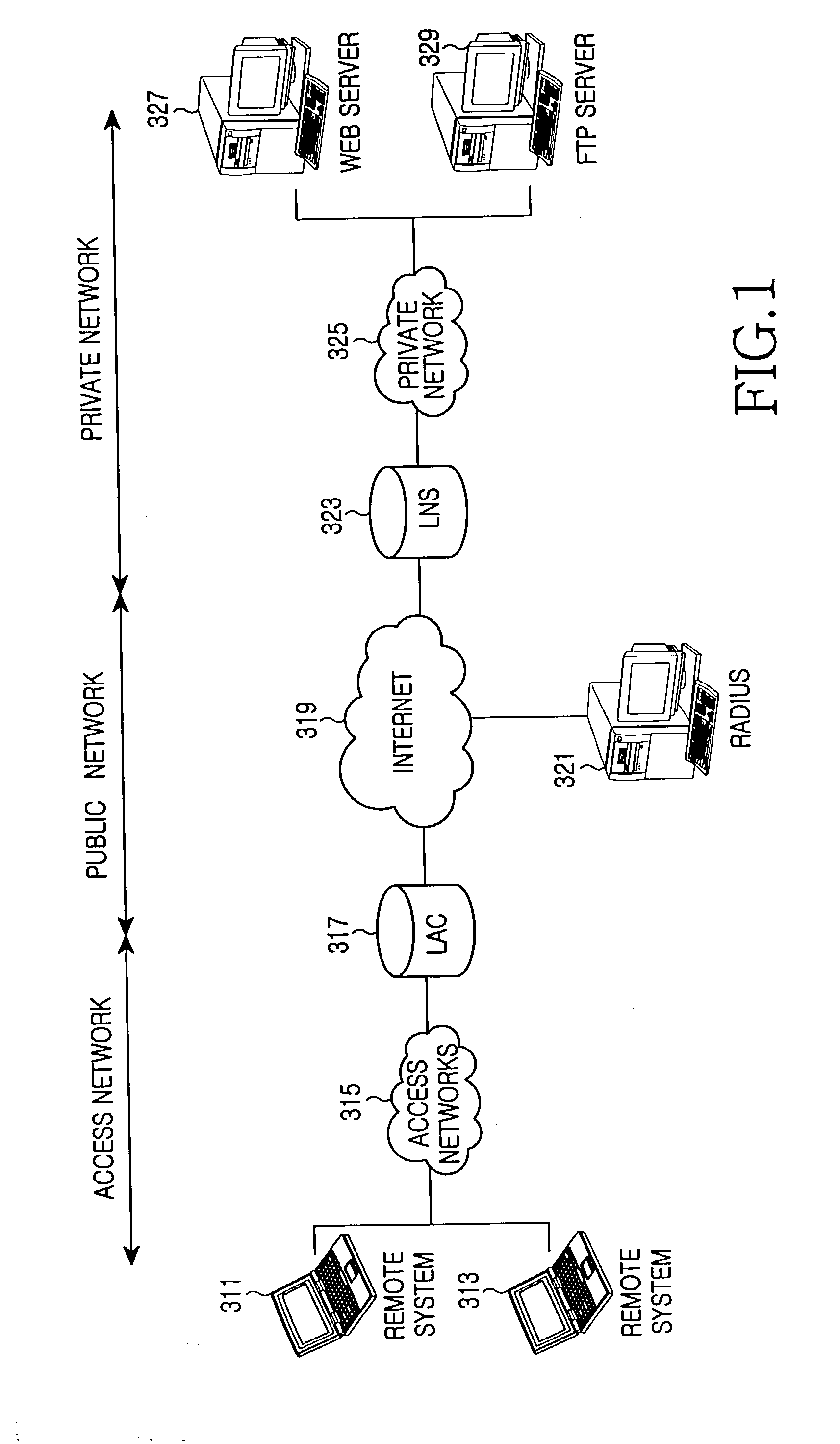
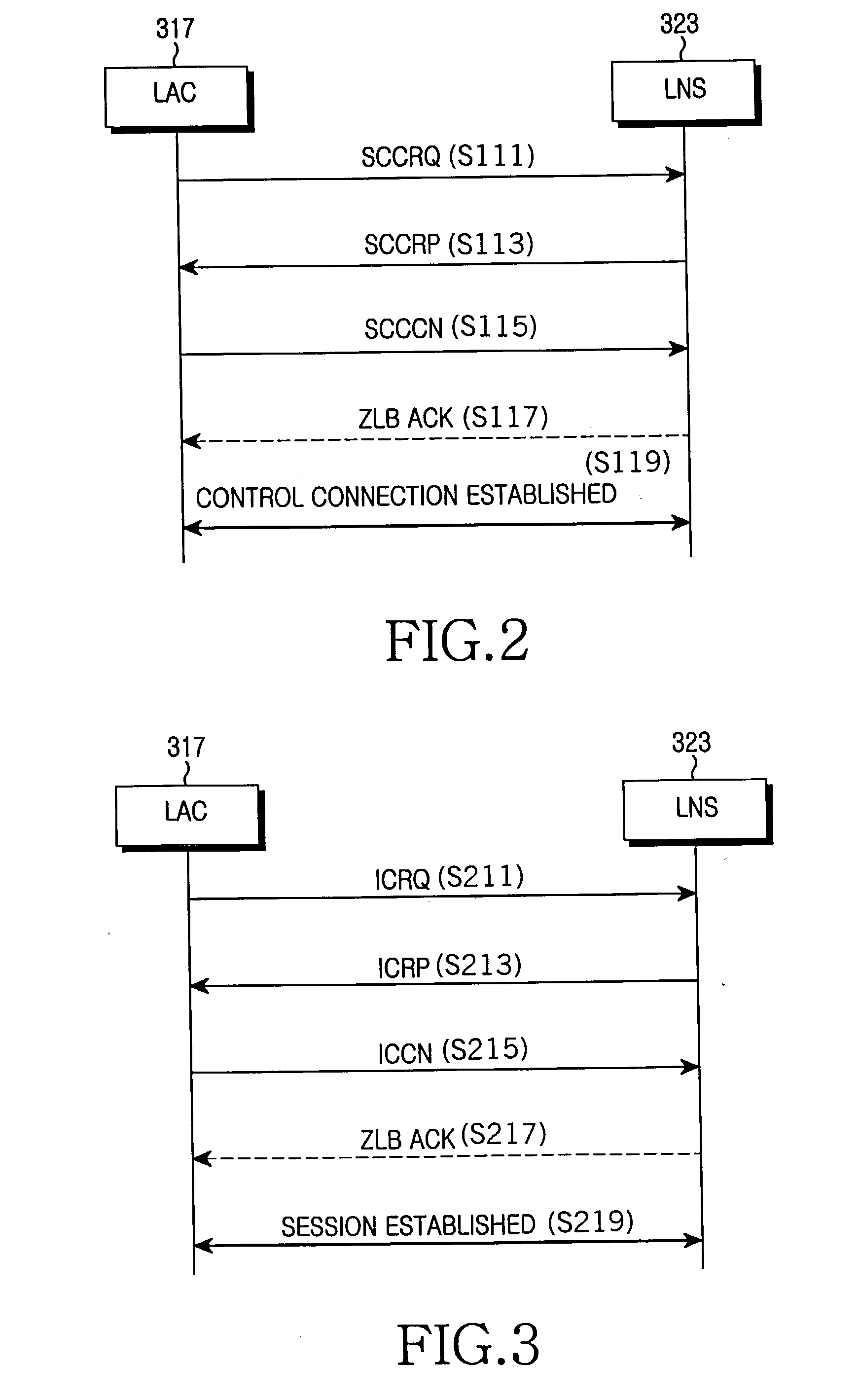
A system and method are shown for offloading a computational service on a point-to-point connection. When a tunnel initiator network device, such as a Level 2 Tunneling Protocol Access Concentrator (LAC), detects a tunnel client network device, the LAC sets up a tunnel connection with a tunnel endpoint network device, such a Level 2 Tunneling Protocol Network Server (LNS). During a process of establishing a call session on the tunnel connection, the LAC sends its compression capabilities to the LNS. When the LNS detects that the LAC is capable of compressing tunnel packets, the LNS negotiates compression parameters with the tunnel client network device. Subsequently, the LNS transmits the negotiated compression parameters to the LAC that configures a compression engine based on the received compression parameters. Hereinafter, the tunnel client network device will send compressed tunnel packets to the LAC that will decompress the received tunnel packets prior to transmitting the tunnel packets to the LNS on the tunnel connections. Similarly, the LNS will send uncompressed tunnel packets on the tunnel connection to the LAC that will compress the received tunnel packets prior to transmitting the tunnel packets to the tunnel client network device.
Owner:HEWLETT PACKARD DEV CO LP
Method for realizing data forwarding and donor base station
InactiveCN101730032AForward to normal implementationConnection managementCommmunication supplementary servicesGeneral Packet Radio ServiceData radio bearer
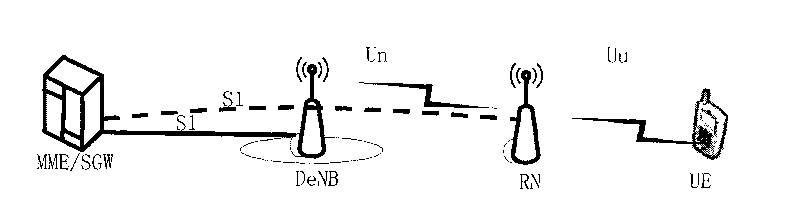
The invention discloses a method for realizing data forwarding, and a donor base station. The method comprises the following steps of: in a handover process of user equipment (UE), when a forwarding path of a bearer which needs to perform the data forwarding relates a Un interface between the donor base station and a relay node, establishing one or more data radio bearers on the Un interface; establishing a one-to-one corresponding relation between the established data radio bearer and a general packet radio service tunneling protocol (GTP) tunnel on the forwarding path of the bearer which needs to perform the data forwarding; and performing forwarding on the bearer which needs to perform the data forwarding through the established data radio bearer and a corresponding GTP tunnel. The technical scheme of the invention can realize the data forwarding in the handover process of the UE when the forwarding path of the bearer which needs to perform the data forwarding relates to the Un interface.
Owner:NEW POSTCOM EQUIP
Method, apparatus and system for transmitting data
InactiveCN101369977AReduce the ratioImprove transmission efficiencyData switching networksNetwork packetData source
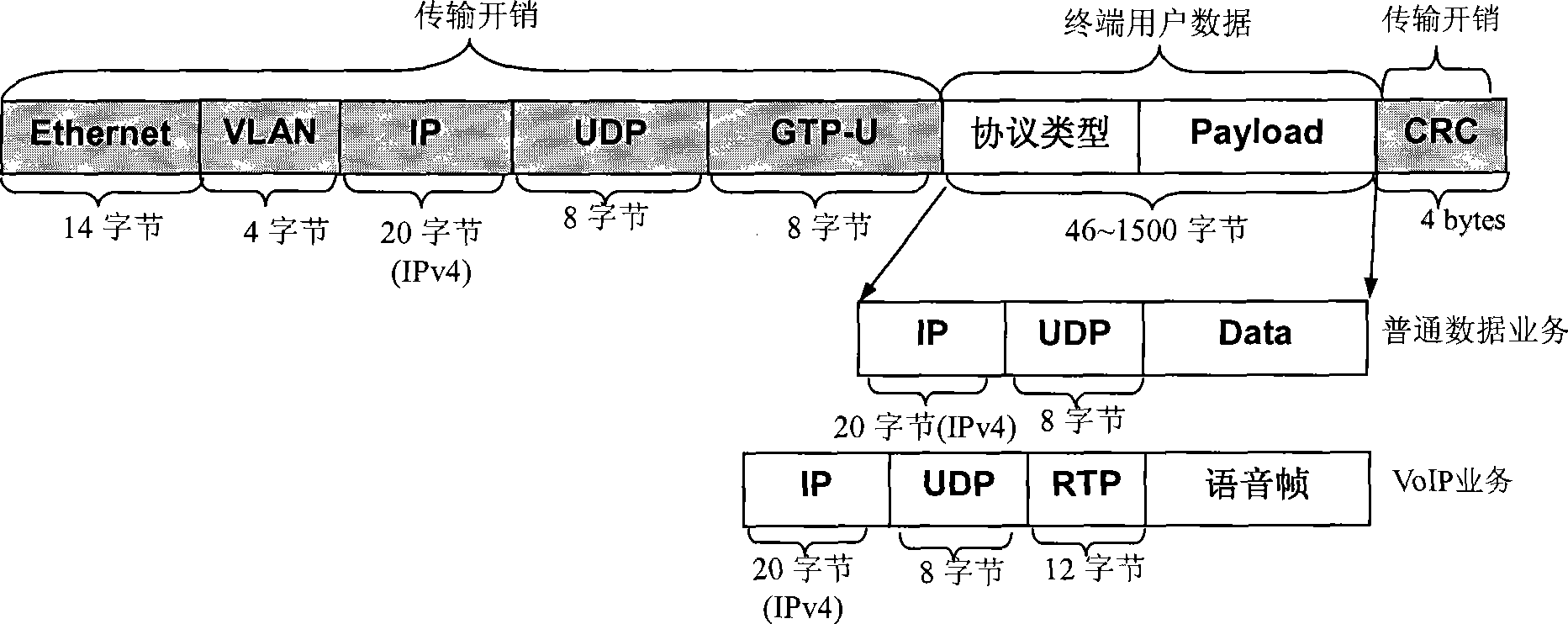
The inventive example discloses a data transmission method, device and system. Taking data transmission method as example, the inventive example comprises: receiving data packet transmitted by data source, the data packet is packaged based on GPRS tunneling protocol, resolving received data packet to obtain protocol header and user data, compressing the protocol header, then packaging user data and protocol header and transmitting to termination sink. The inventive example can reduces proportion of protocol header in data packet by compressing protocol header, so promotes transmission efficiency of data packet especially short data packet.
Owner:HUAWEI TECH CO LTD
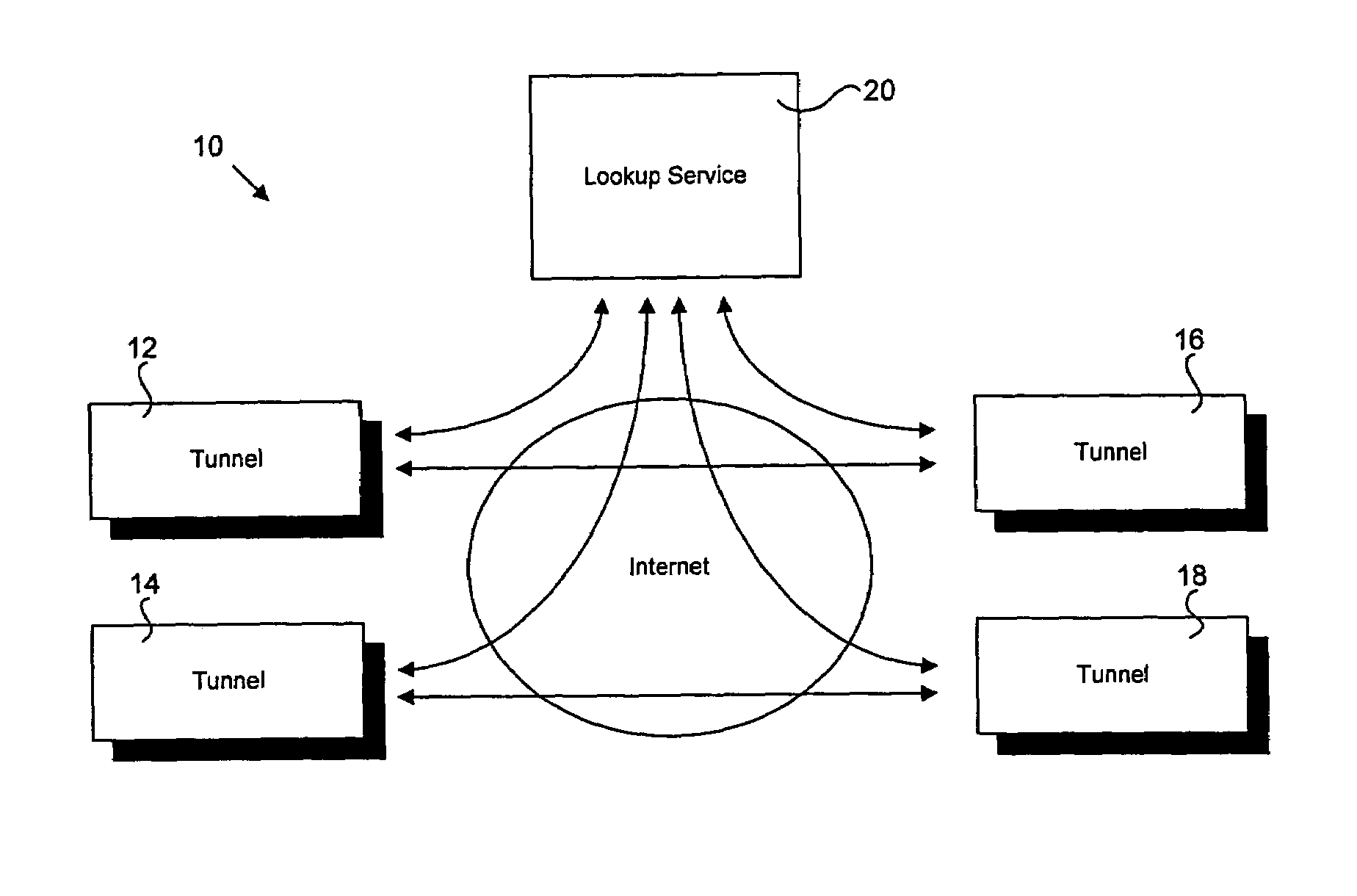
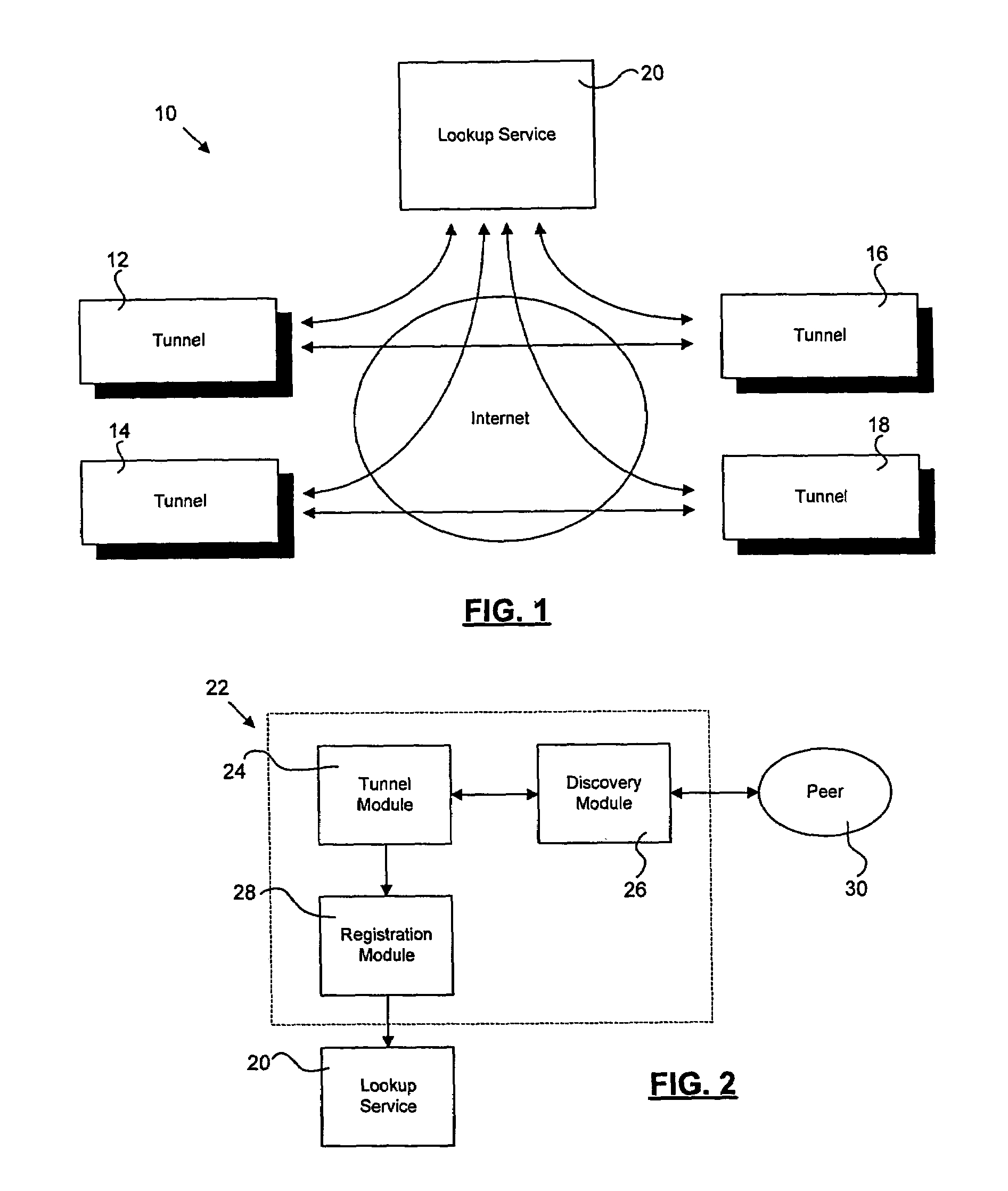
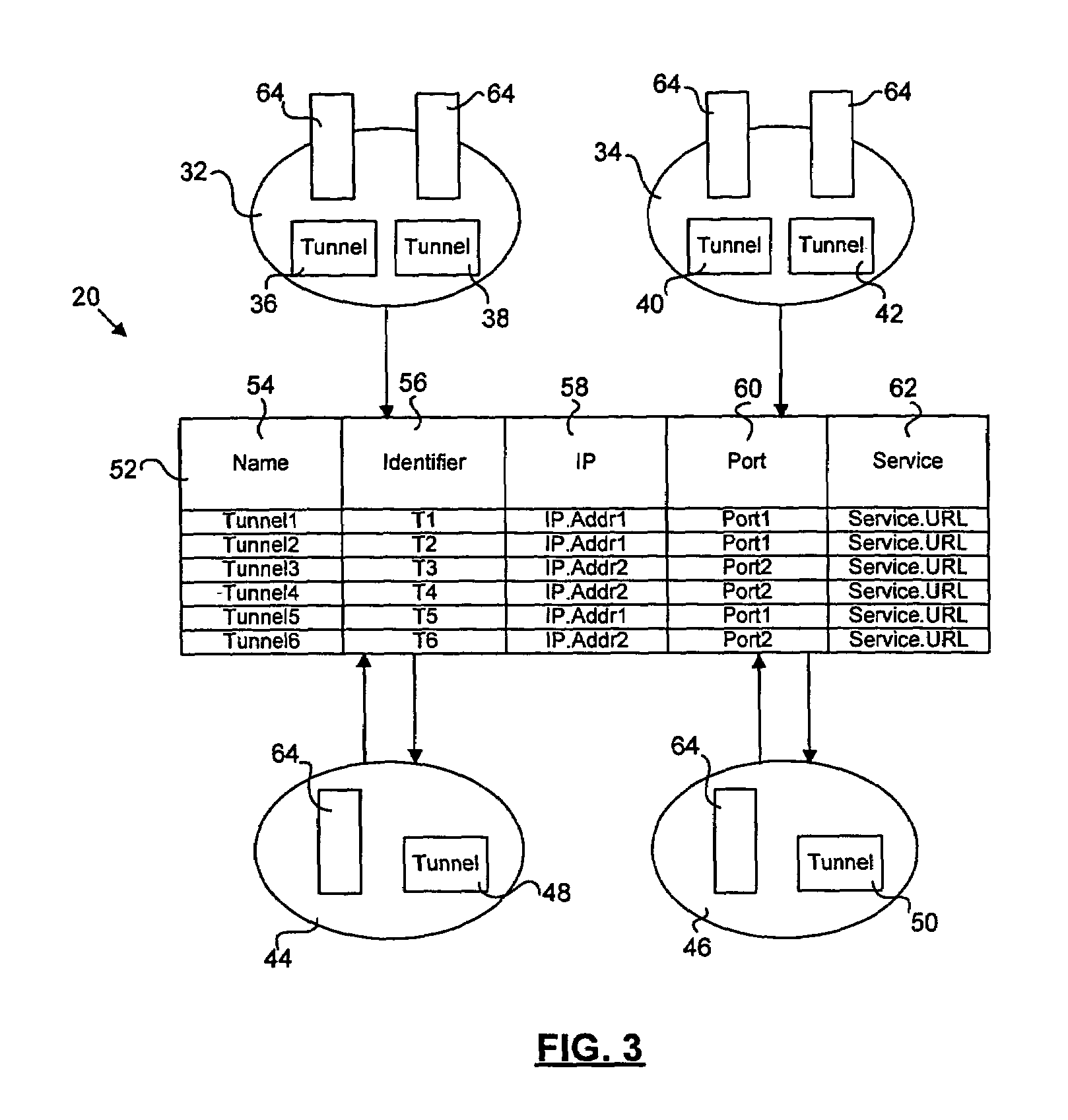
Method for dynamic selection for secure and firewall friendly communication protocols between multiple distributed modules
InactiveUS7237260B2Digital data processing detailsData switching by path configurationIp addressComputer module
Distributed modules in a network dynamically select communication protocols to communicate in a secure or firewall-protected network. Applications register with a lookup service. The lookup service maintains a lookup table including registration information for multiple applications. Registration information may include, but is not limited to, IP address, firewall restrictions, tunnel protocol, port information, and proxy queue capabilities. An application seeking to communicate acquires the registration information for a desired recipient from the lookup table. The application uses the registration information to select communication protocols necessary to communicate with the recipient.
Owner:CARL ZEISS AG +2
Maintaining a common AAA session id for a call over a network
InactiveUS7293096B1Multiple digital computer combinationsTransmissionProtocol for Carrying Authentication for Network AccessOperating system
A method, system, and apparatus are provided for maintaining a common session identifier for a call over a network. In at least one embodiment, the session identifier is provided as a non-required parameter in accordance with a tunnel protocol.
Owner:CISCO TECH INC
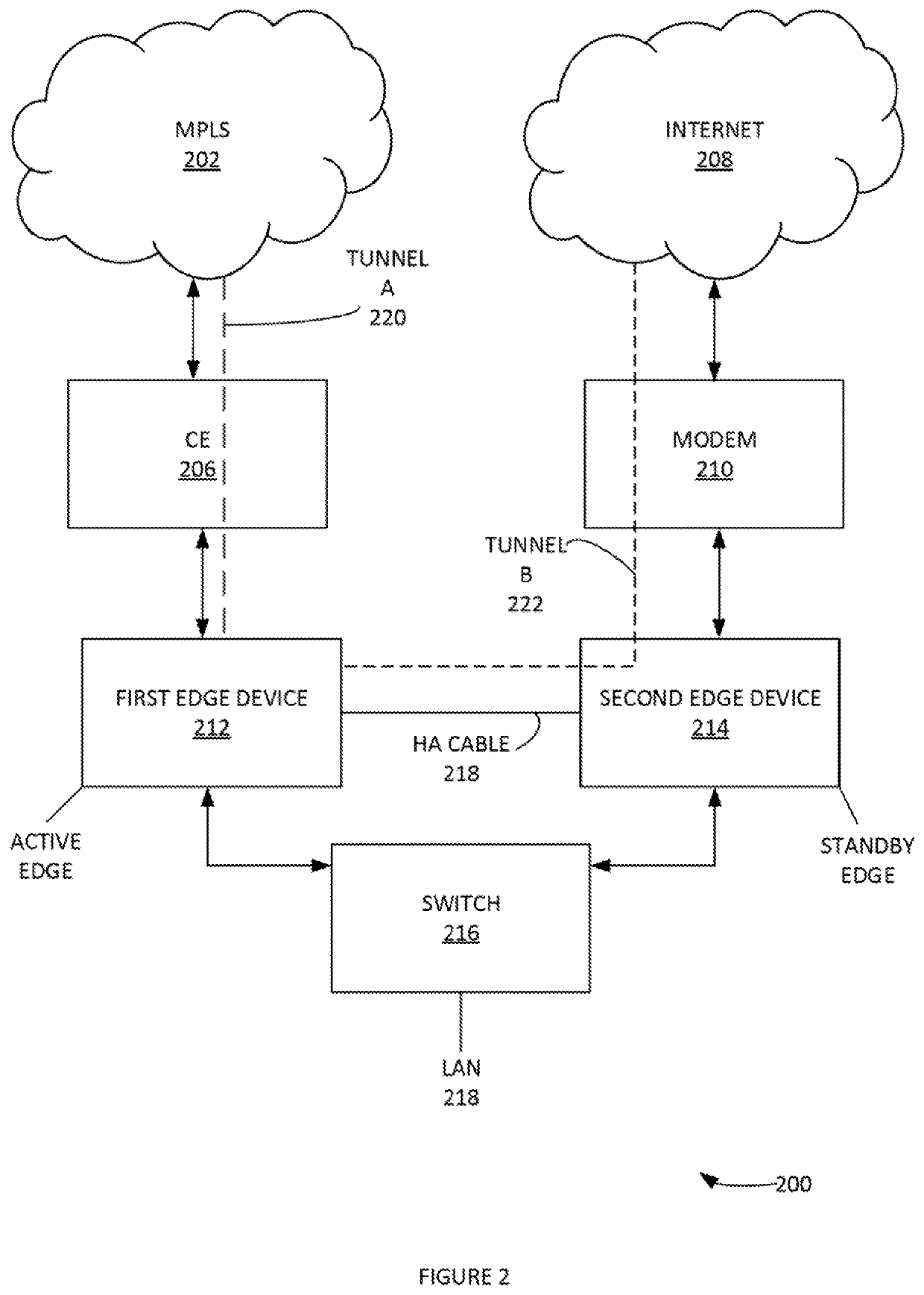
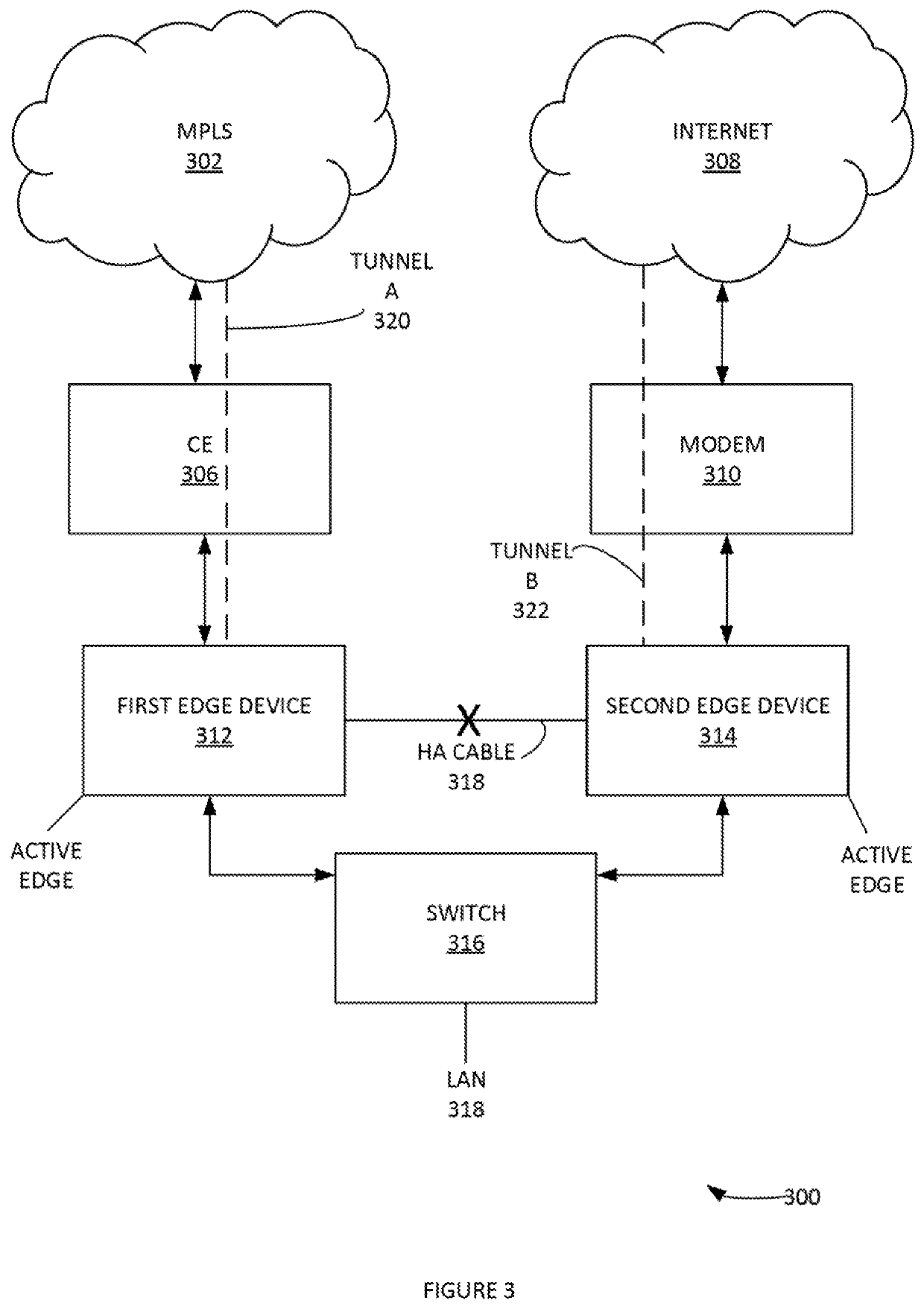
Method and system of a dynamic high-availability mode based on current wide area network connectivity
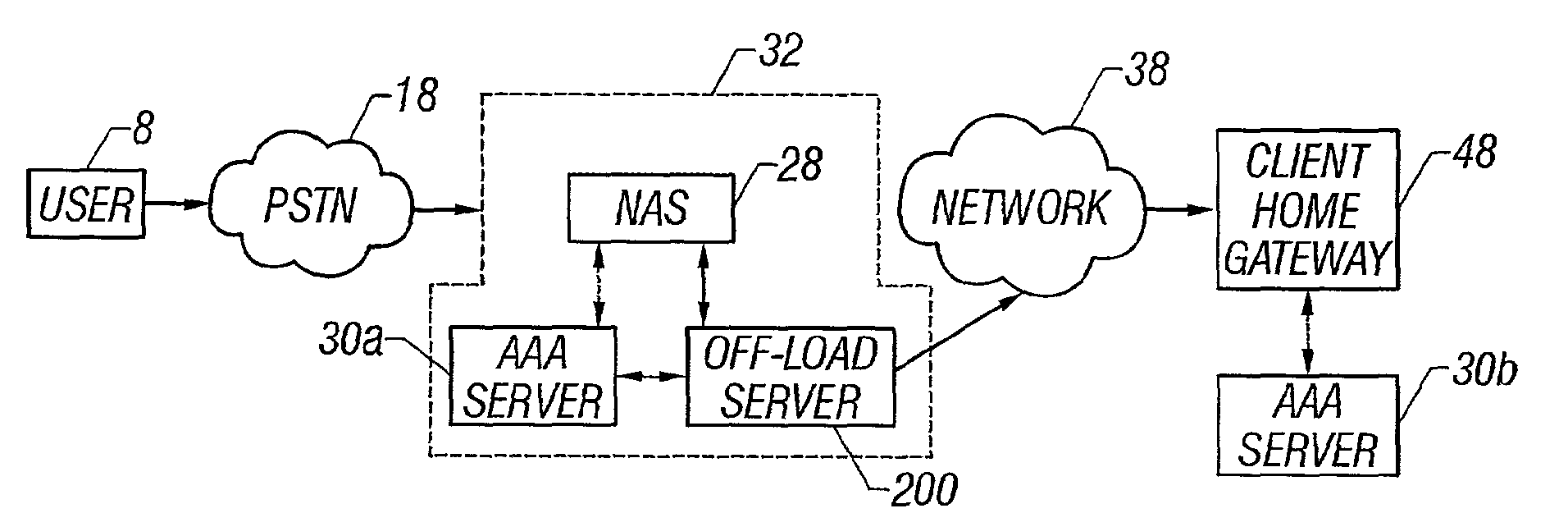
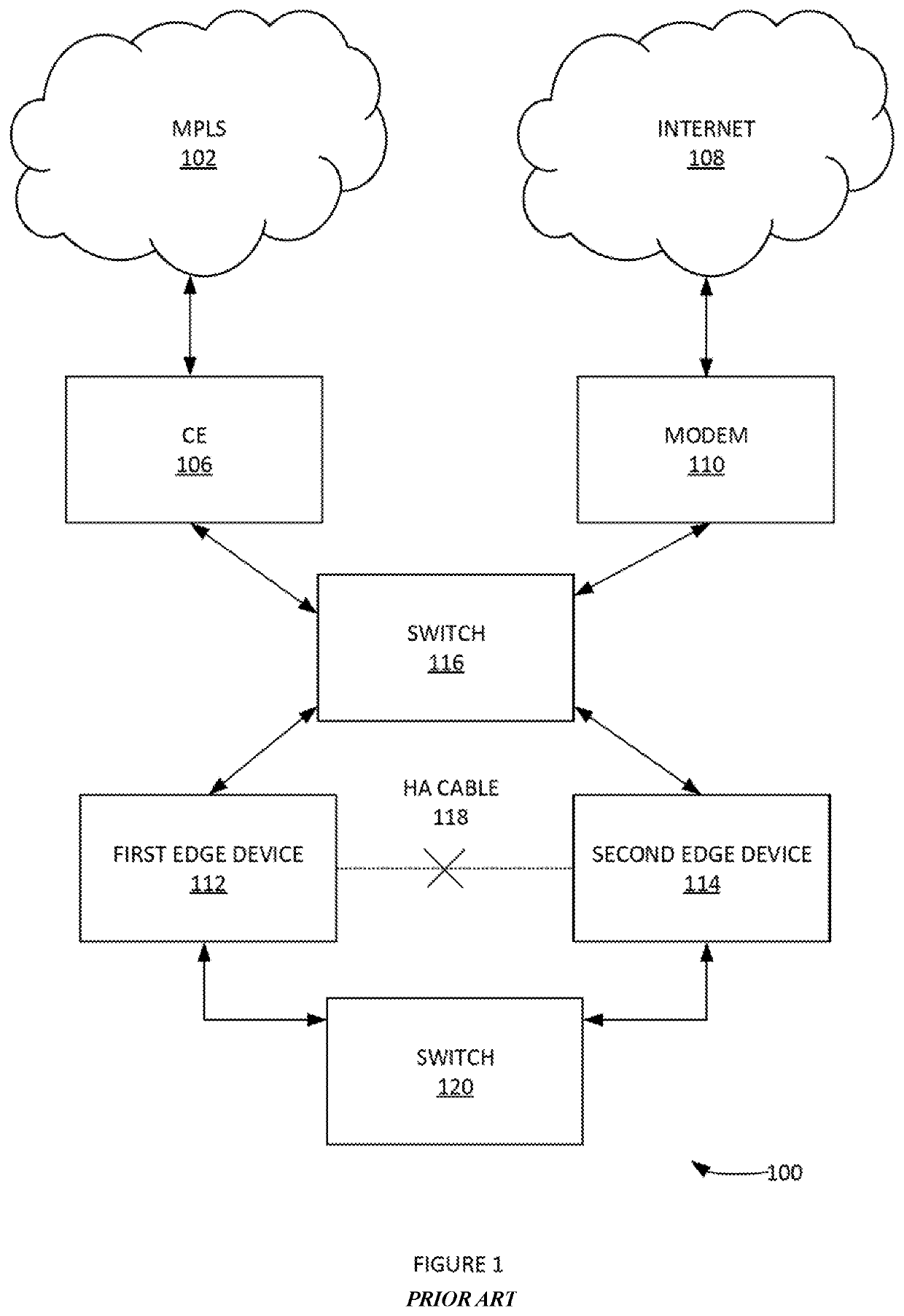
In one aspect, a method useful for implementing high availability (HA) enhancements to a computer network, comprising the steps of: providing a first edge device of a local area network (LAN); providing a second edge device of the LAN; providing a gateway system to the LAN from a wide area network; detecting that an HA cable between the first edge device and the second edge device is disconnected; establishing a network connection between the gateway system and the second edge device; with the gateway system: determining that the first edge device is active and passing network traffic, implementing a network tunneling protocol with second edge device.
Owner:NICIRA INC
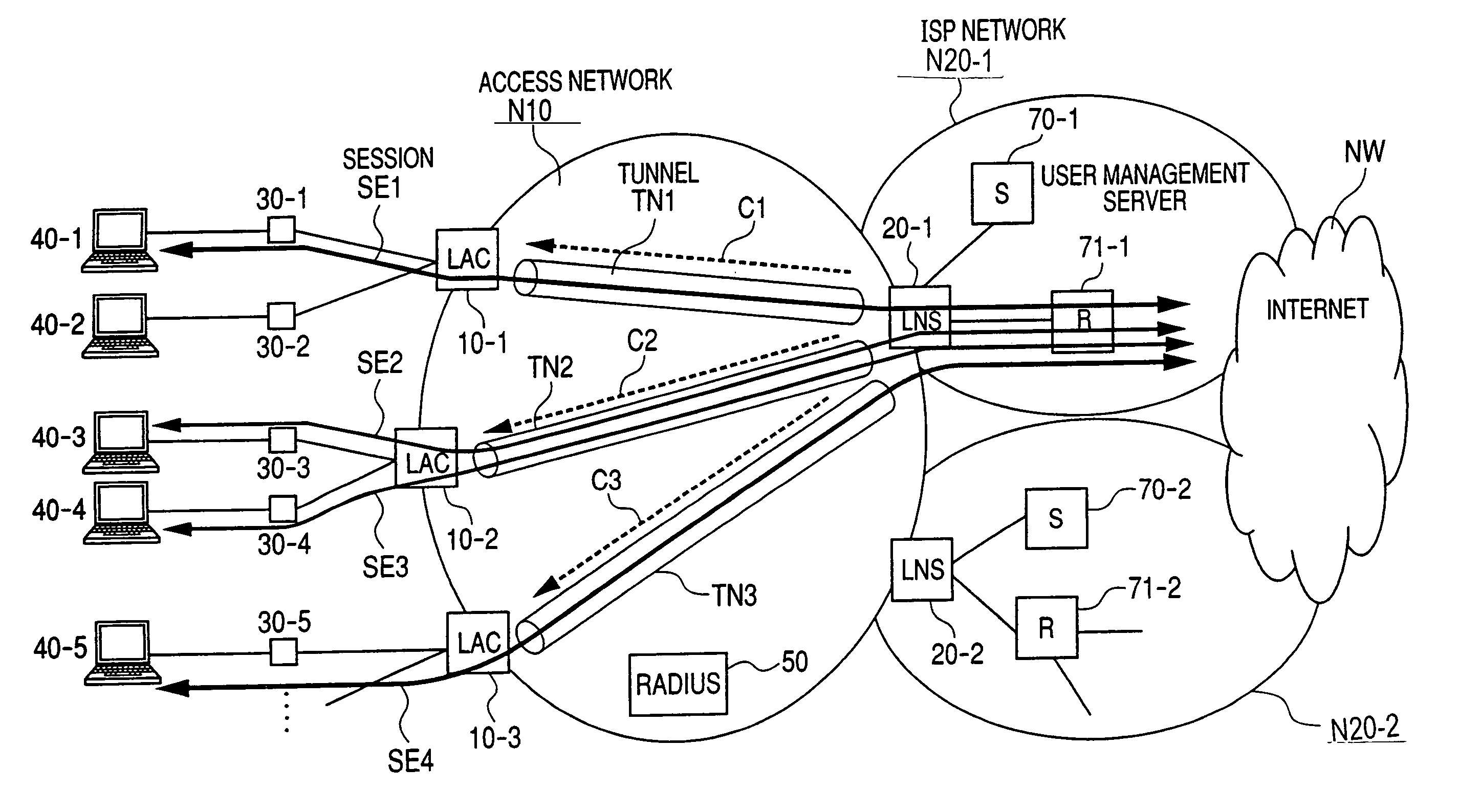
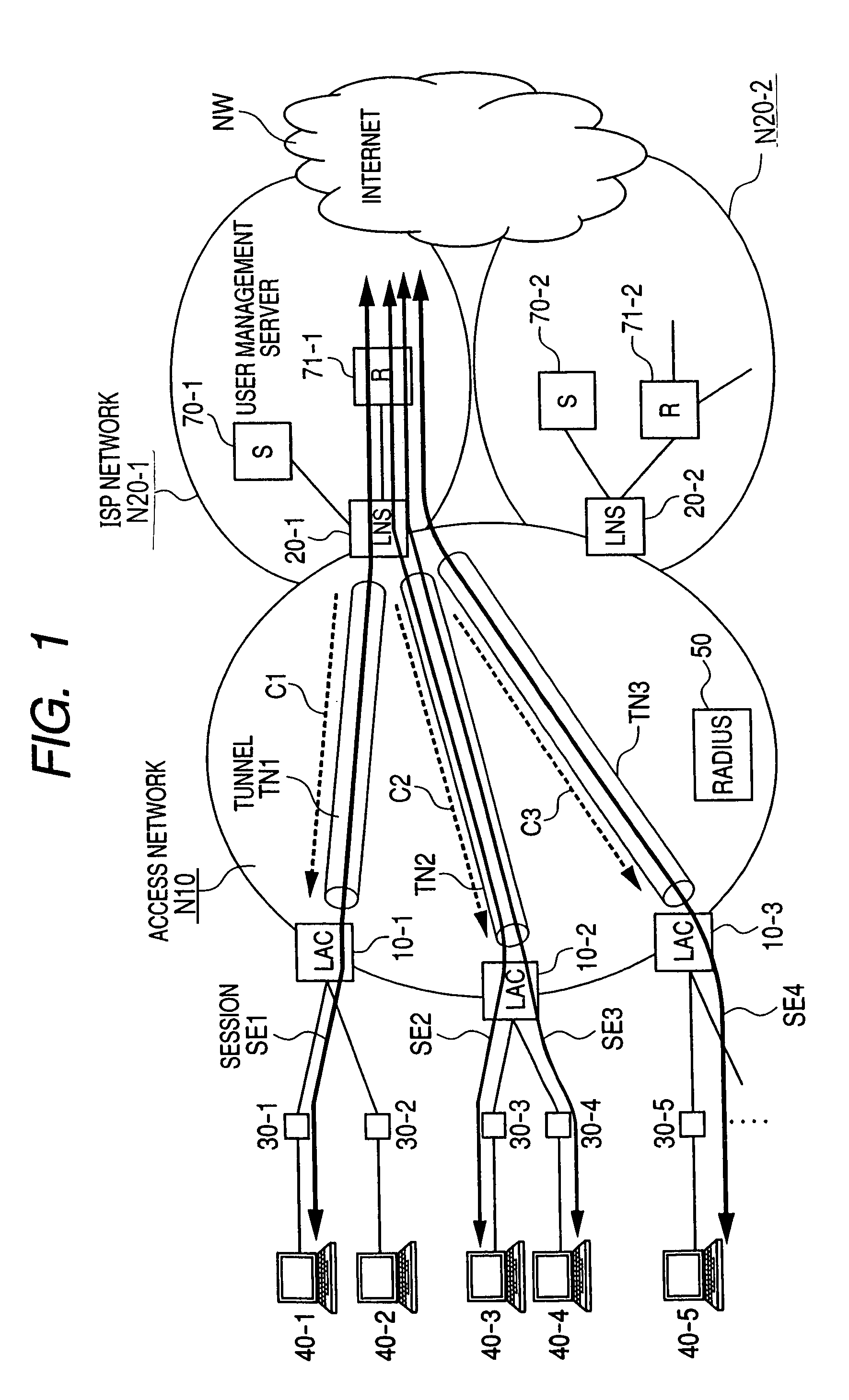
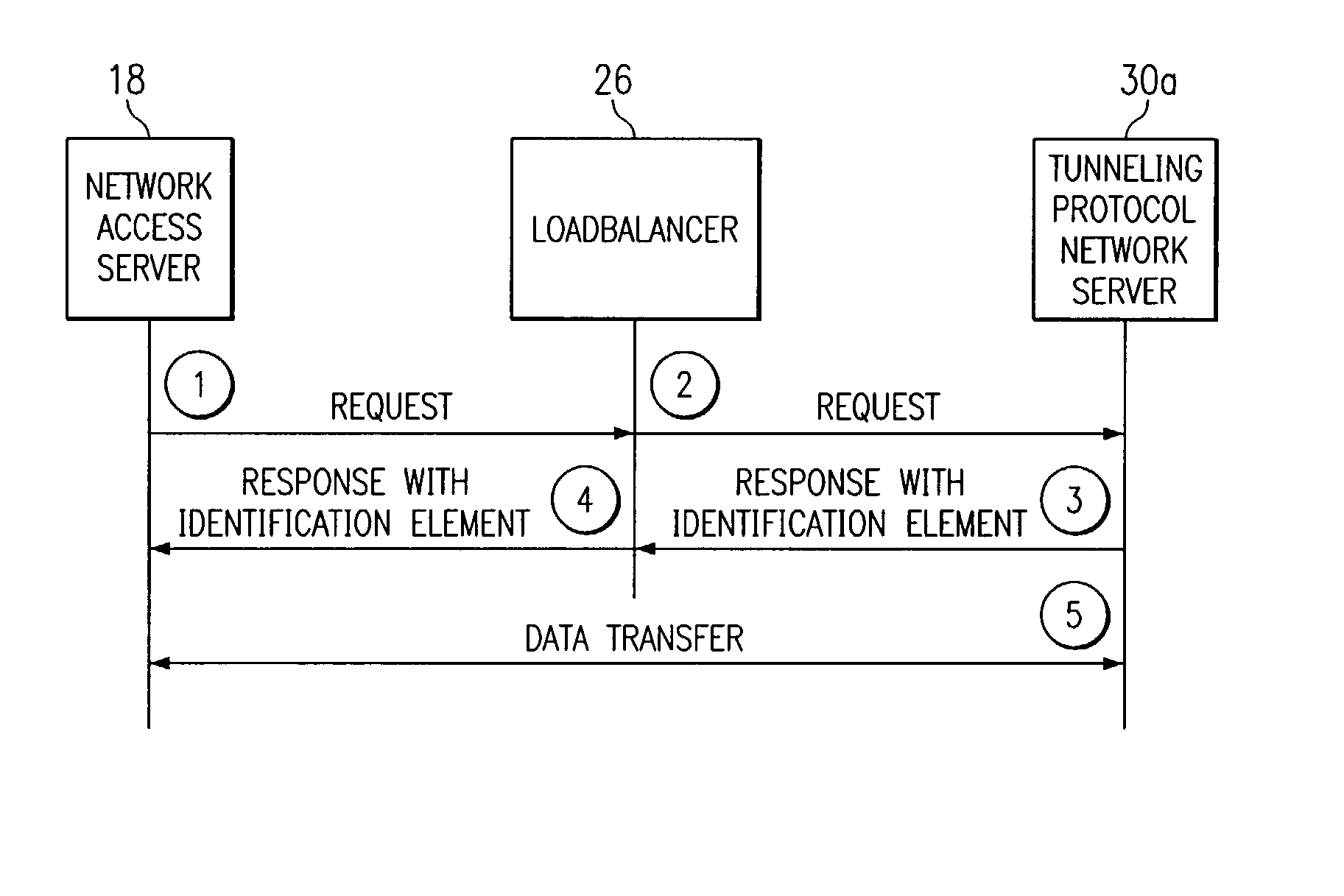
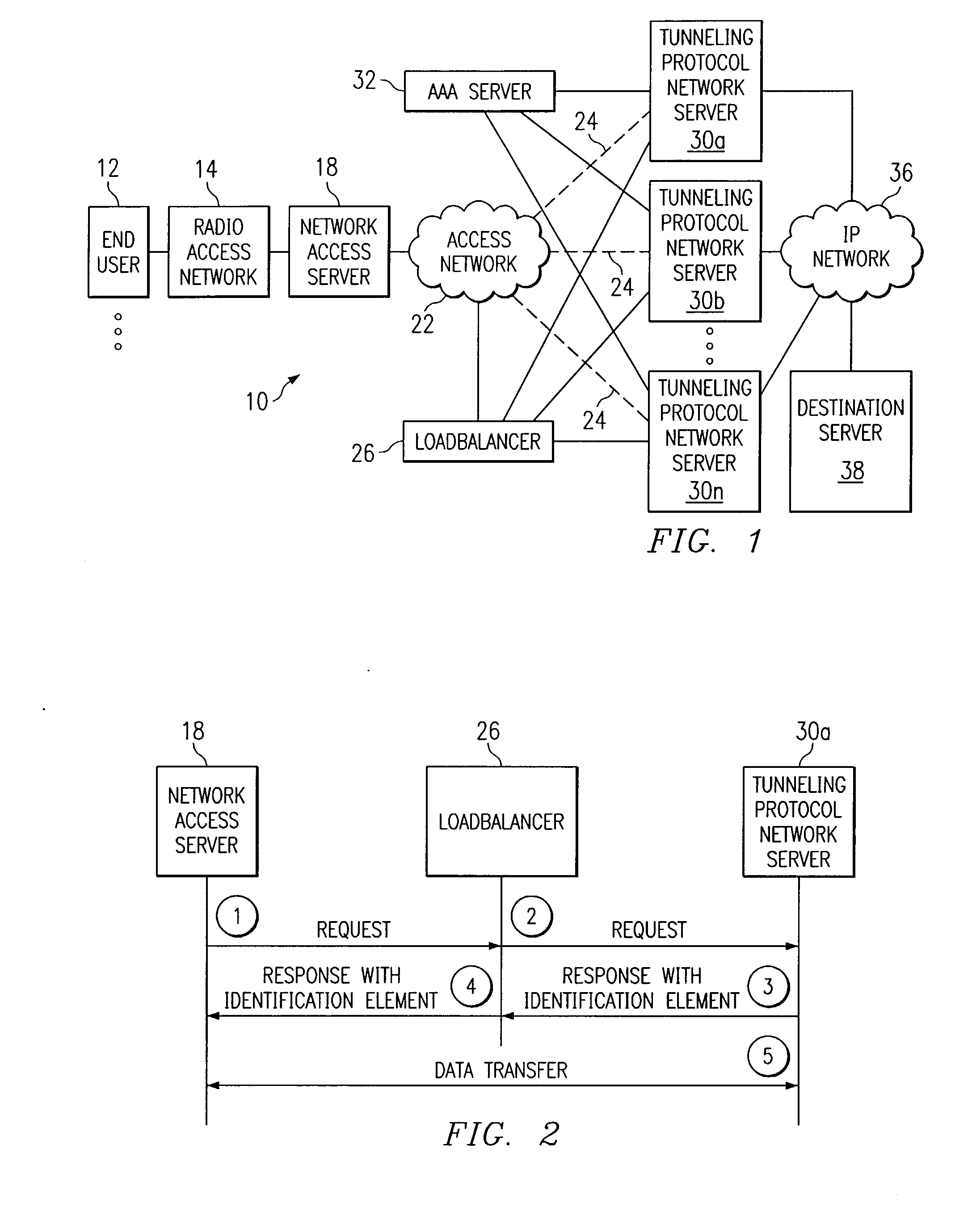
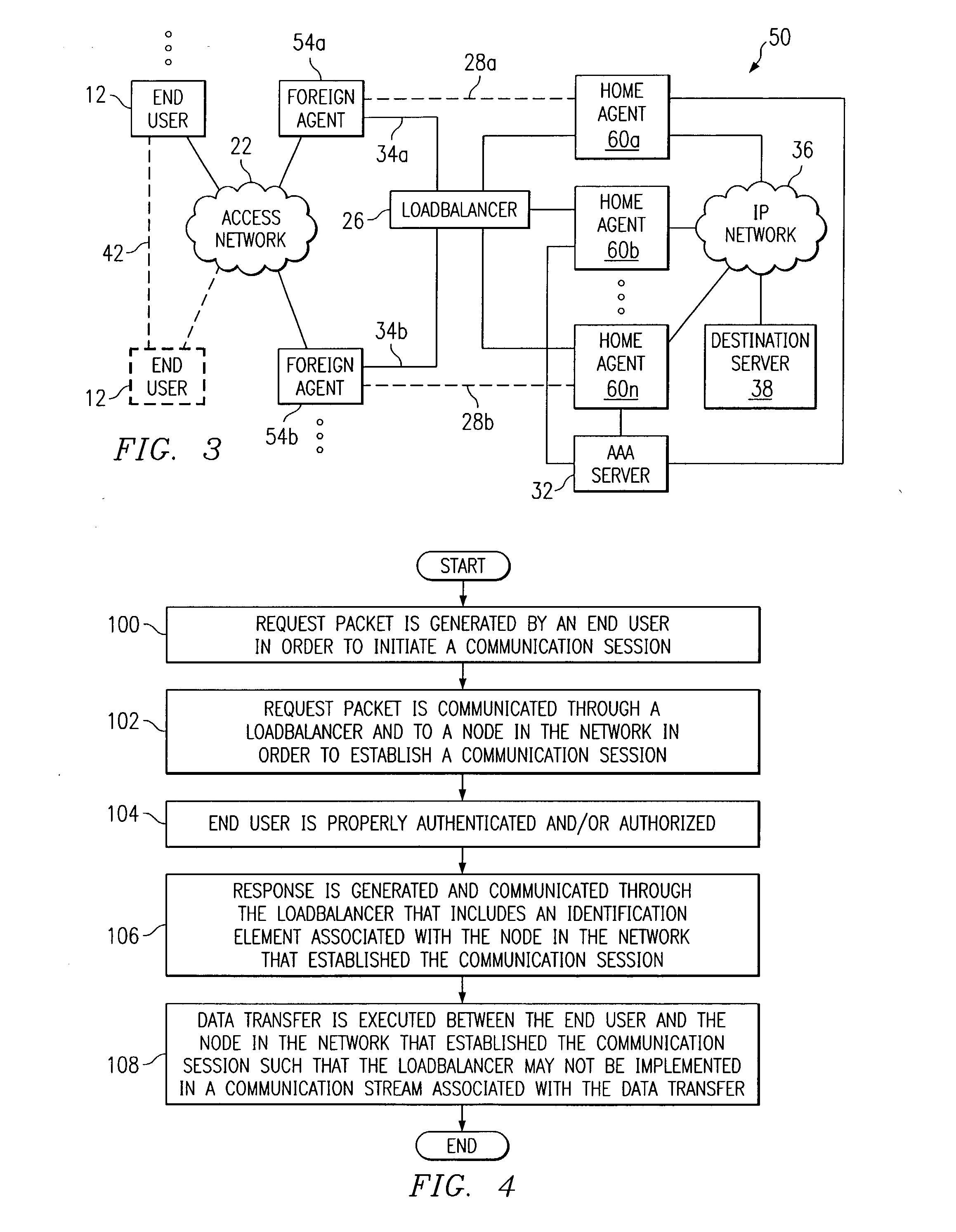
System and method for communicating in a loadbalancing environment
ActiveUS20050188065A1Reduce the burden onEliminate and greatly reduce disadvantageDigital computer detailsNetworks interconnectionNetwork access serverComputer network
A method for communicating in a loadbalancing environment is provided that in a particular embodiment includes receiving a request packet from a network access server (NAS) to initiate a communication session. The request packet is then communicated to a tunneling protocol network server (TPNS) and a response packet is received in response to the request packet. The response packet establishes a tunnel that facilitates the communication session and that includes an identification element associated with the TPNS such that a data transfer associated with the communication session is executed between the NAS and the TPNS.
Owner:CISCO TECH INC
Method, System and Evolved NodeB Apparatus for Implementing Inter-Evolved NodeB Handover
ActiveUS20120314689A1Improve user experienceAvoid it happening againConnection managementWireless commuication servicesGeneral Packet Radio ServiceRouting table
A method, a system and an evolved NodeB (eNB) apparatus for implementing inter-eNB switch are disclosed in the present invention. The method includes: when a user equipment switches from a source-side eNB to a target-side eNB, if the target-side eNB acquires via the Mobility Management Entity (MME) that the Serving Gateway (S-GW) has changed, the target-side eNB adds the new route relation of the S-GW and then updates the General Packet Radio Service (GPRS) Tunnelling Protocol User Plane (GTP-U) entity. The present invention can effectively solve the problem of the uplink data packet loss due to the time difference existing between the update to the Tunnel Endpoint Identifier (TEID) and the routing table by the eNB when inter-eNB switch is performed via X2 and the S-GW has changed, thus enhancing the user experience during the switch.
Owner:ZTE CORP
Security system for accessing virtual private network service in communication network and method thereof
InactiveUS20030163577A1Maintain securityImprove data securityCircuit switching systemsMultiple digital computer combinationsPrivate networkNetwork connection
The present invention relates to a security system for accessing a private network service in a communication network and a method thereof, in which if a request of a subscriber for accessing a private network service is sensed, layer 2 tunnel protocol (L2TP) requests the virtual private network service access to a remote authentication dial-in user service server, and according to the request for accessing the private network service, the remote authentication dial-in user service server transfers layer 2 tunnel protocol (L2TP) information on layer 2 tunnel protocol (L2TP) network connected to the virtual private network, and pre-designated secret information in the layer 2 tunnel protocol (L2TP) network server to the layer 2 tunnel protocol (L2TP) access concentrator, and finally, after receiving the information on layer 2 tunnel protocol (L2TP) network and the secret information, the layer 2 tunnel protocol (L2TP) access concentrator performs encryption on the data generated by the subscriber by using the secret information, and transferring the encoded data to the layer 2 tunnel protocol (L2TP) network server.
Owner:SAMSUNG ELECTRONICS CO LTD
Message processing method and network device
The present application relates to the field of communication, and in particular to a message processing method and a network device. The method comprises that a third network device is connected to the first interface of a first network device via a first link; the third network device is connected to the second interface of a second network device via a second link, wherein the first link and the second link have the same link identifier, the first network device receives a first message sent by the third network device, and the first message is a control protocol message; the first networkdevice packages the first message into a second message according to a tunnel protocol, wherein the second message includes a link identifier and the first message; and the first network device sendsthe second message to the second network device through a tunnel. The method processes the control protocol message by using the network processor of a forwarding plane, makes a backup of a control plane protocol table entry, and effectively improves the processing efficiency.
Owner:HUAWEI TECH CO LTD
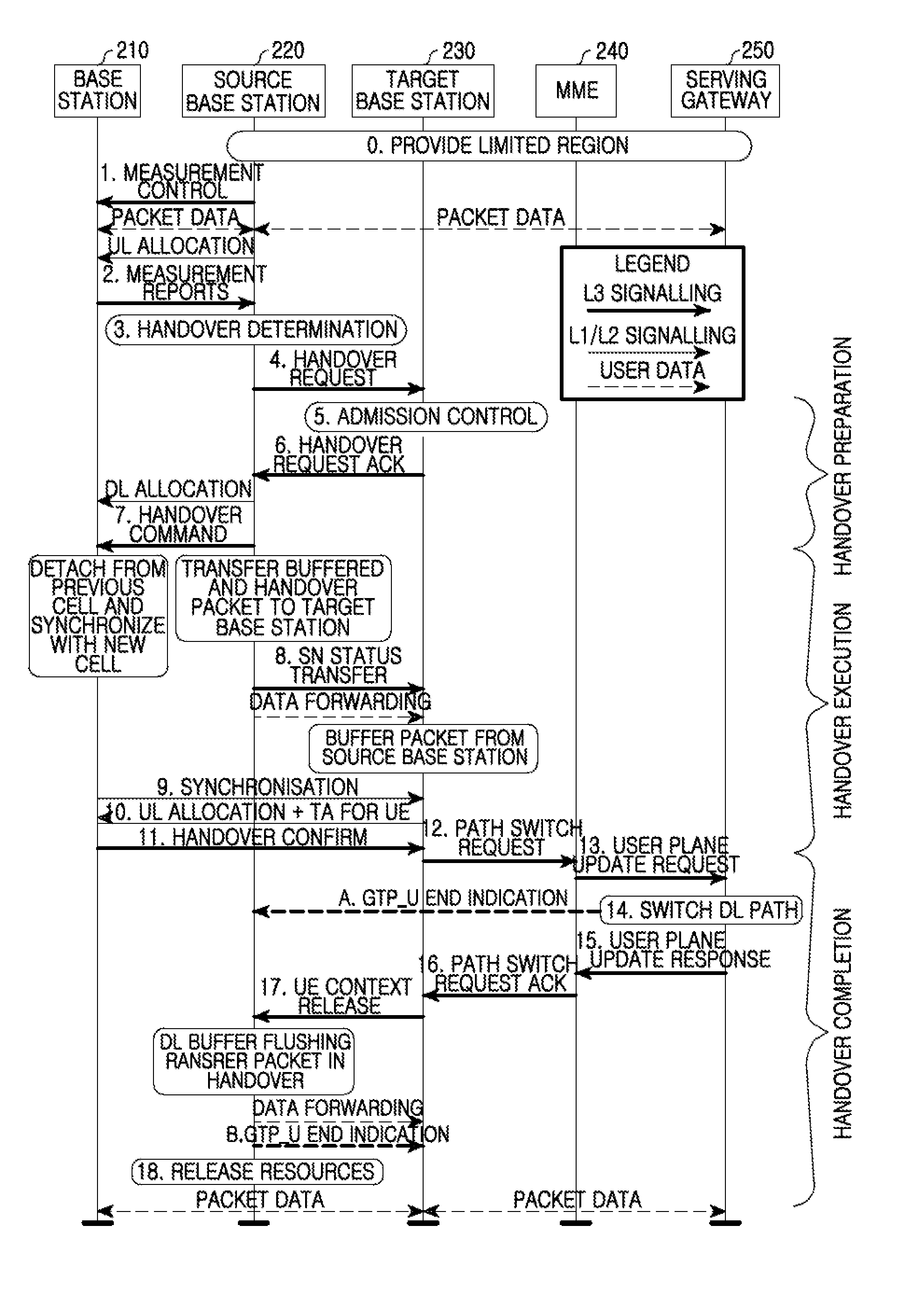
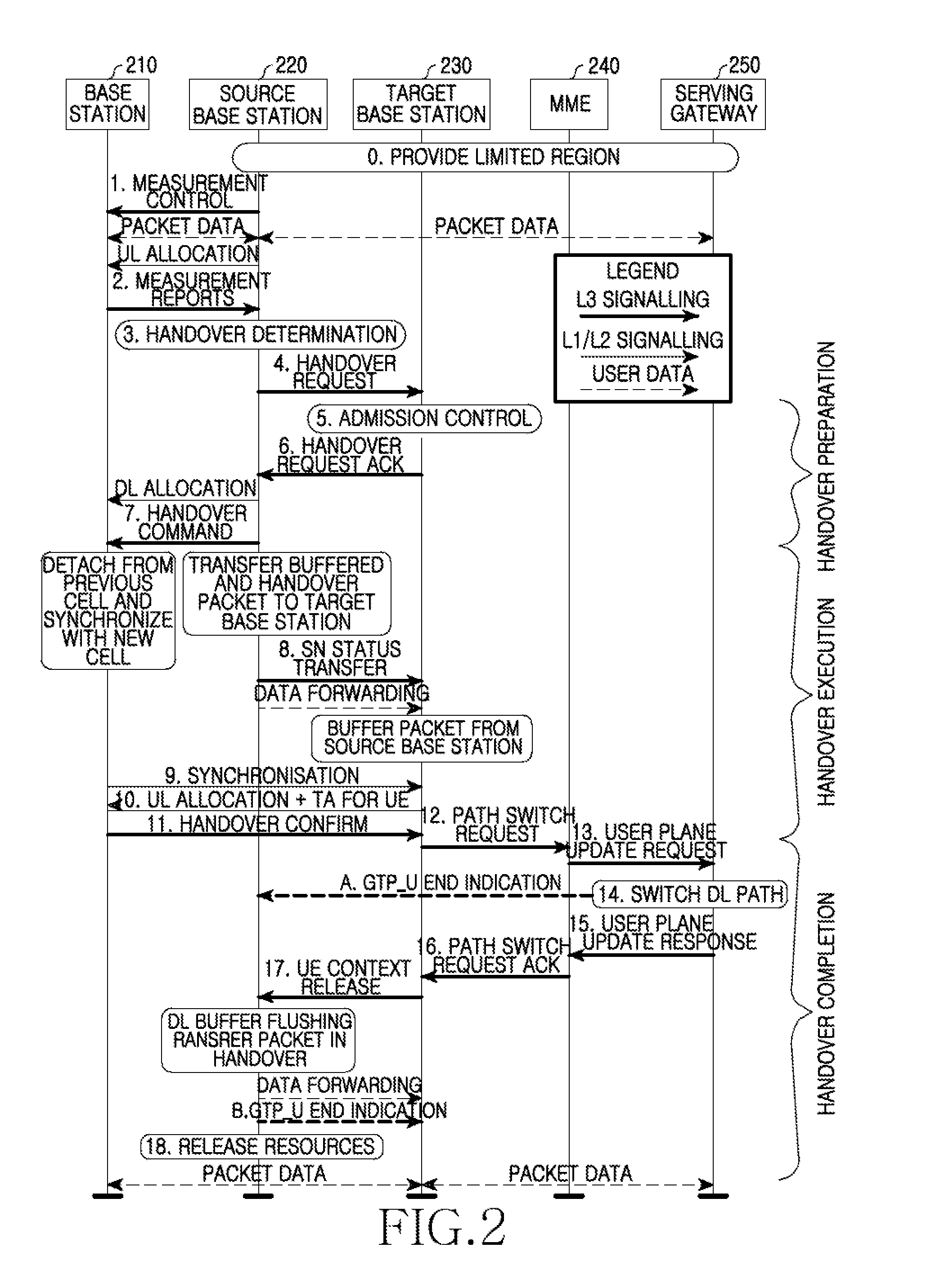
Apparatus and method for processing gtp in mobile communication system
ActiveUS20100189076A1Guaranteed normal transmissionWireless commuication servicesGeneral Packet Radio ServiceMobile communication systems
A system for processing General Packet Radio Service (GPRS) Tunneling Protocol (GTP) for a handover in a mobile communication system is provided. The system includes an Evolved Packet Core (EPC), a source base station, and a target base station. The EPC transmits an end data indication message to a source base station of a user terminal to inform of an update for a user plane when receiving an update request message for the user plane of the user terminal from the target base station. The source base station forwards the remaining data destined for the user terminal to the target base station when receiving the end data indication message from the EPC, and transmits the end data indication message to the target base station upon completion of the forwarding. The target base station transmits data destined for the user terminal and stored in a buffer to the user terminal when receiving the end data indication message from the source base station, and releases resources set for the forwarding with the source base station upon completion of the data transmission to the user terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
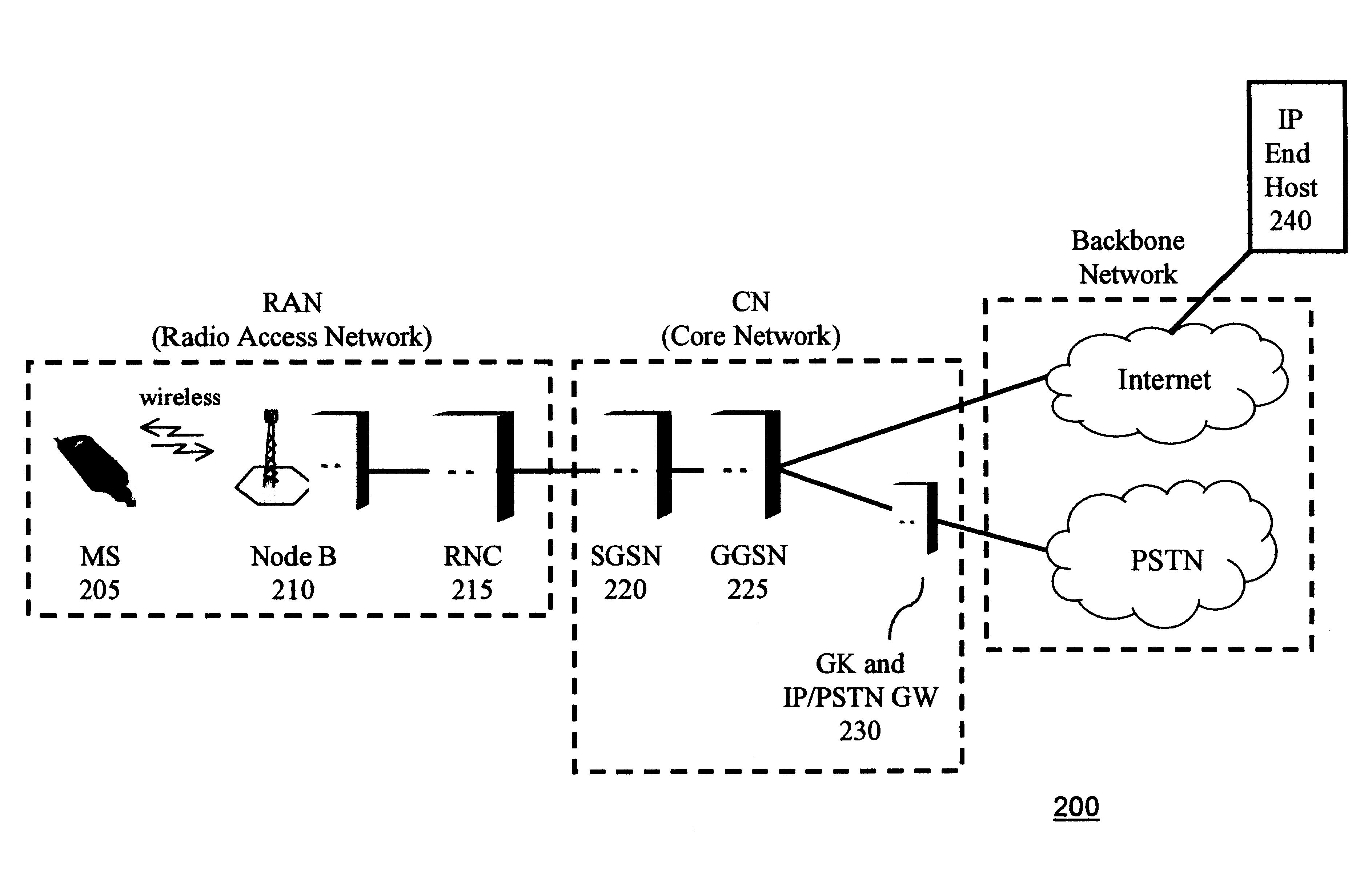
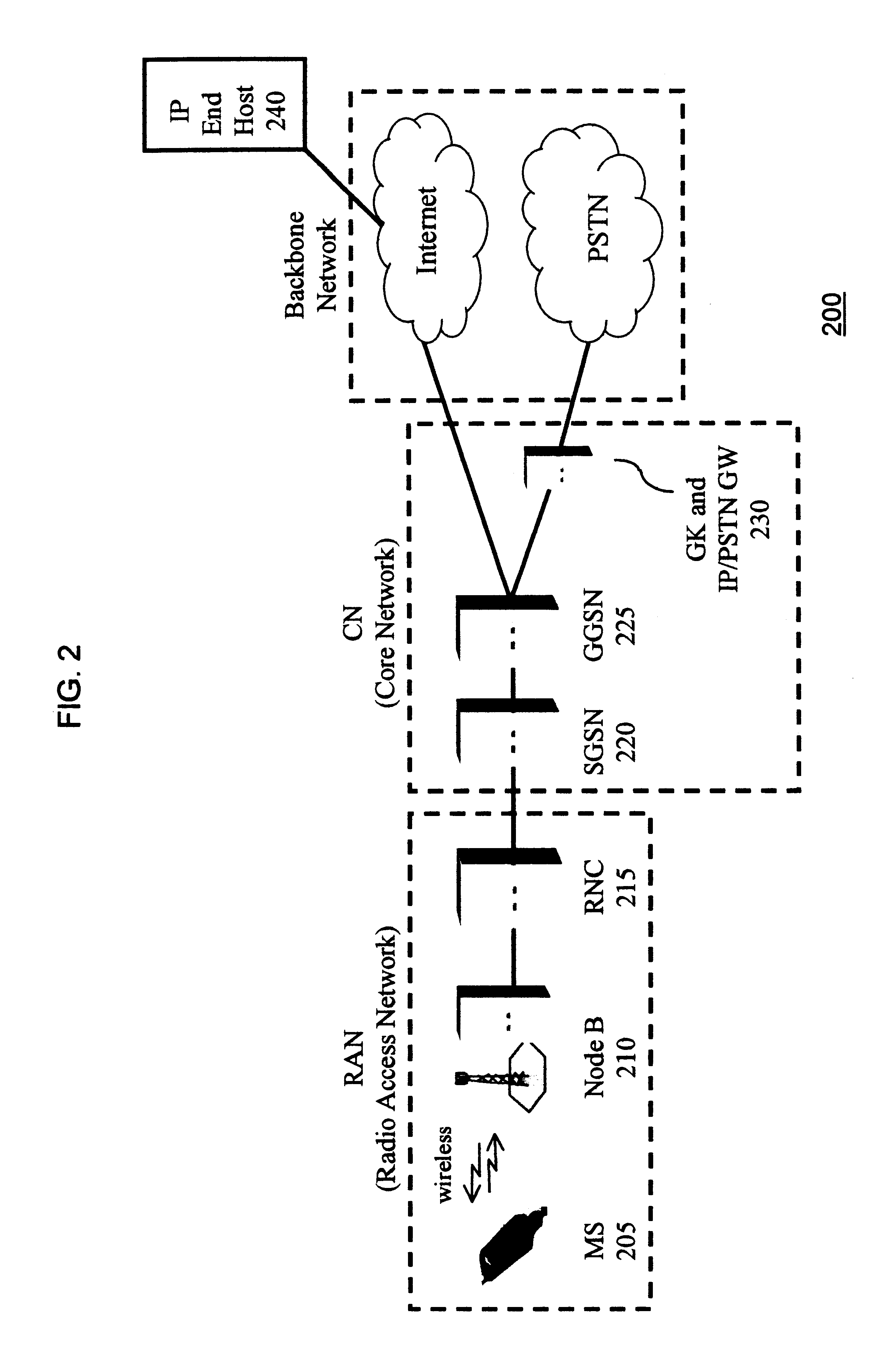
Packet radio network and method
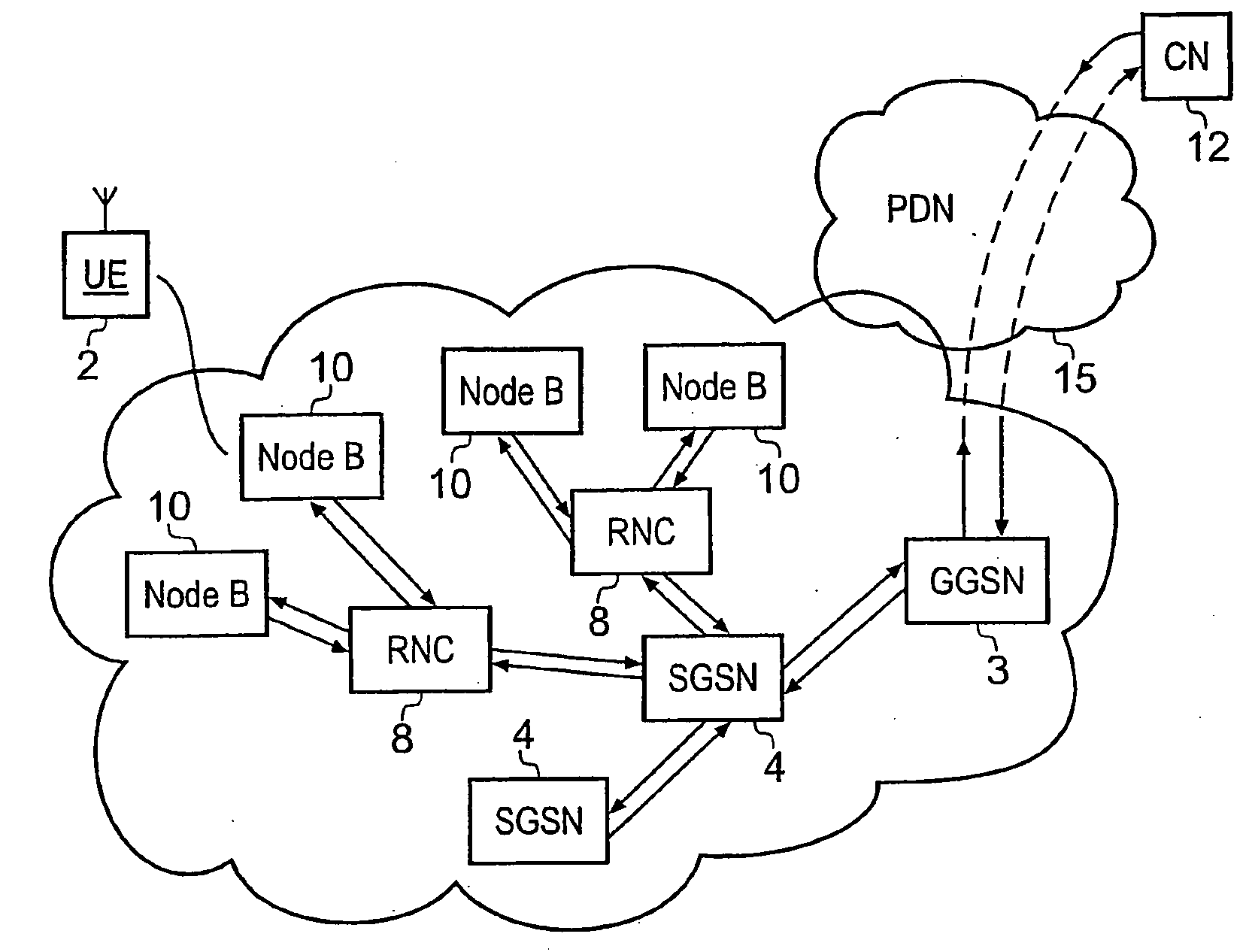
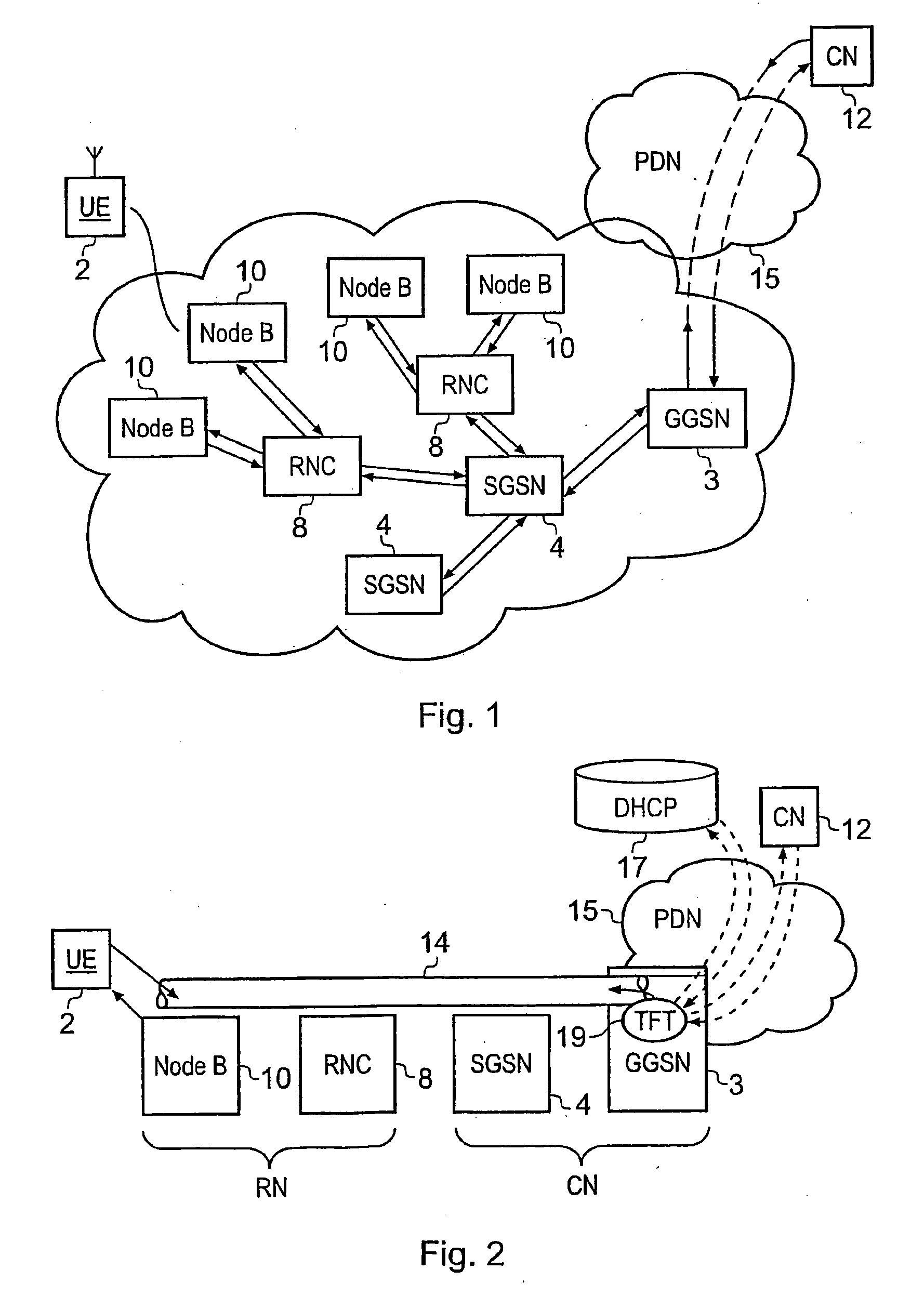
ActiveUS20090175215A1Improve efficiencyEffective resourcesConnection managementWireless network protocolsComputer networkRadio networks
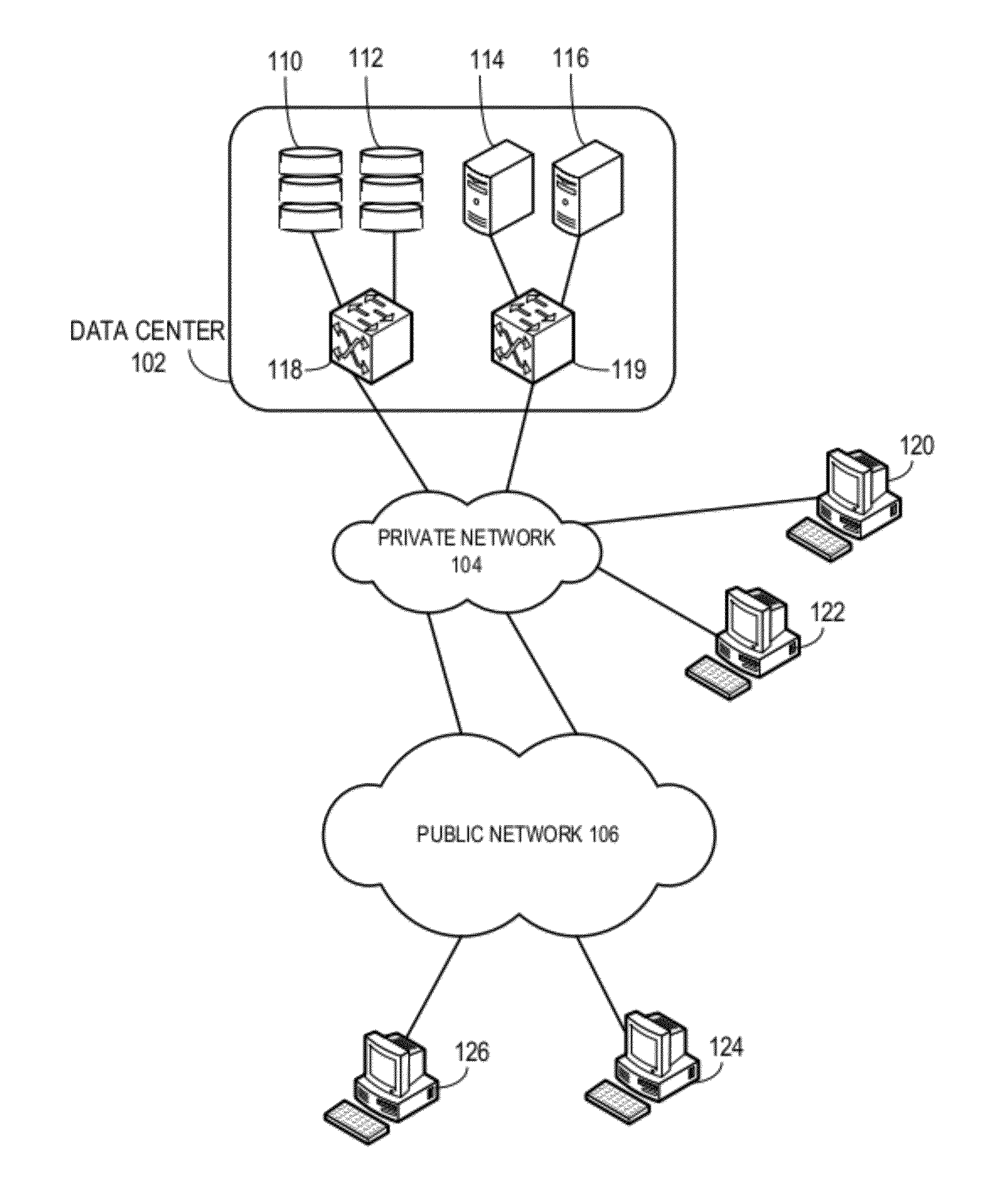
A packet radio network provides a facility for communicating internet packets to and / or from a mobile user equipment. The packet radio network comprises a gateway support node, a serving support node and a radio network controller. The gateway support node is operable to provide a packet data protocol context for controlling the communication of the internet packets to and / or from the packet radio network from and / or to the mobile user equipment via a packet communications bearer. The serving support node is connected to the gateway support node and is operable to control communications of the internet packets to and from the gateway support node to and / or from mobile user equipment to form the packet communications bearer. The radio network controller is operable to provide a radio access bearer for communicating the internet packets via a radio access interface to and / or from the mobile user equipment. In response to a packet data protocol activation request message requesting a common packet data protocol context, the serving support node is operable in combination with the gateway support node to establish a common packet data protocol context in association with a common packet communications bearer. The common packet data protocol context is established to communicate internet protocol packets via the common packet communications bearer. The common packet communications bearer is shared with at least one other communications session and is formed by the gateway support node and the serving support node using a common tunnelling protocol bearer. Therefore a packet radio network is provided which can provide a common communications bearer which can be shared between different communications sessions. As a result high-speed broadband communications, such as HSDPA can be supported efficiently, because more than one communications session shares common communications resources.
Owner:3G LICENSING SA
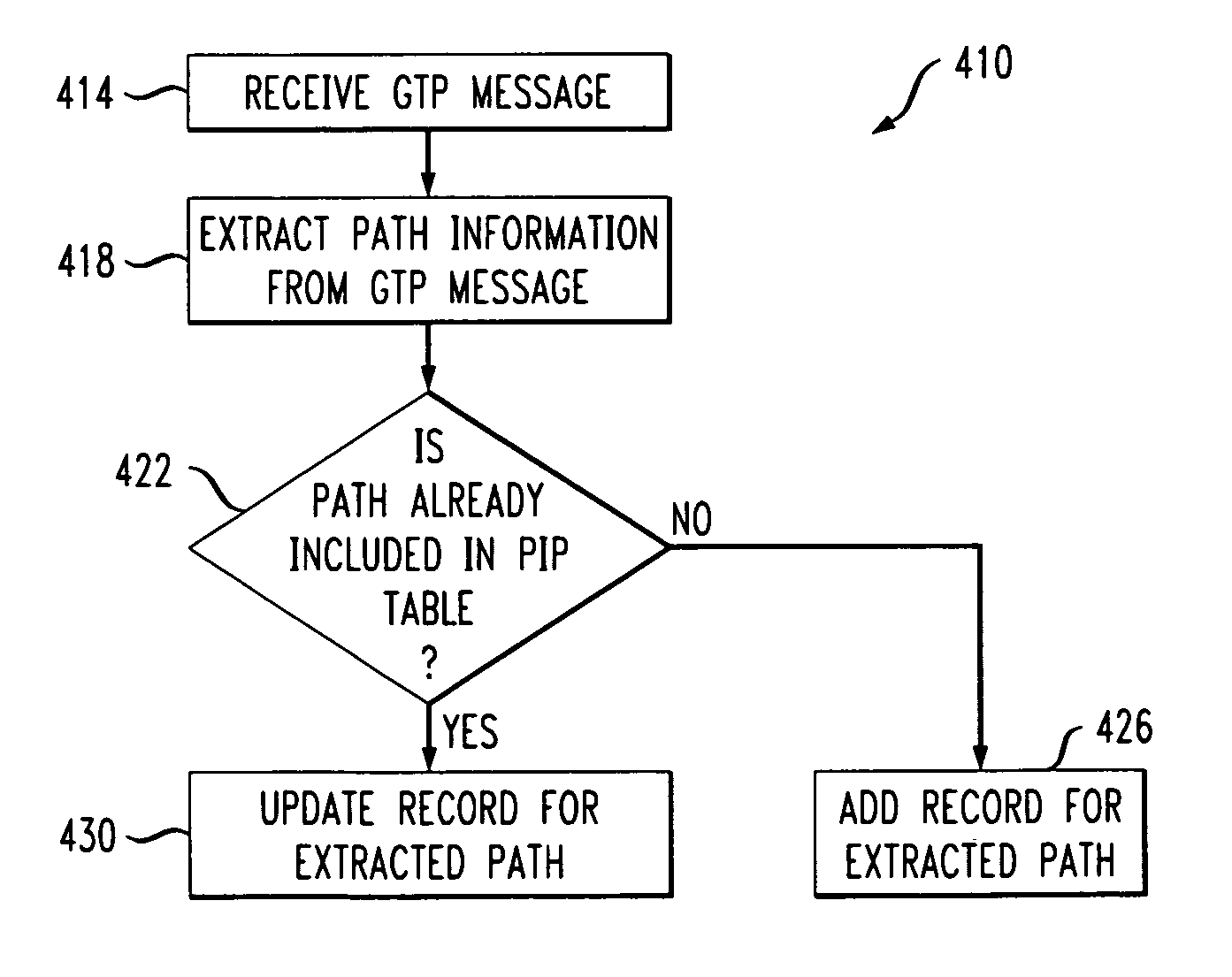
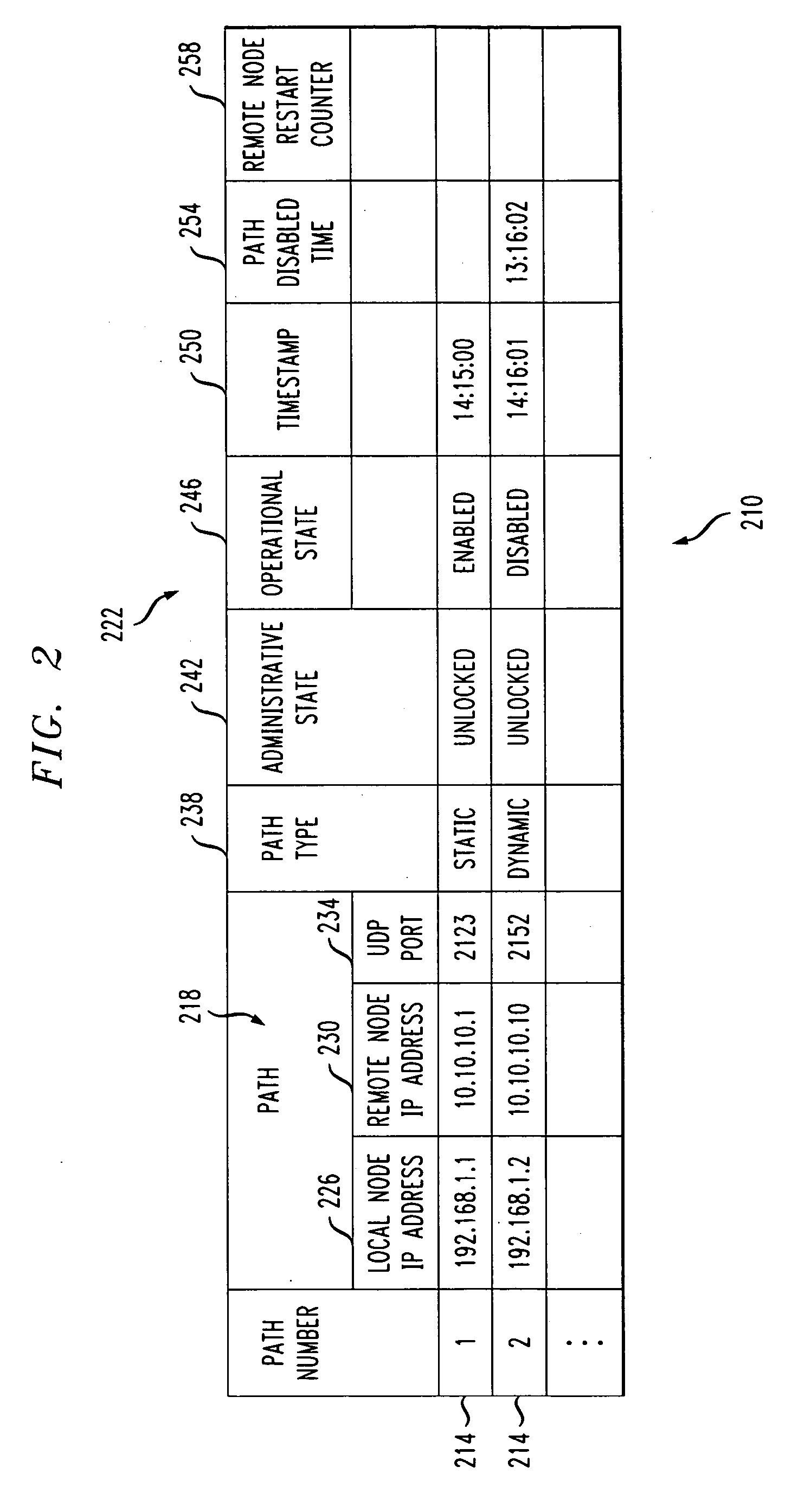
GPRS tunneling protocol path integrity protocol
ActiveUS20050201371A1Improved GTP path integrity assuranceImprove network efficiencyError preventionFrequency-division multiplex detailsPathPingProcess information
Network efficiency is improved by building and maintaining path integrity tables in nodes of a network. The tables include path integrity information for paths associated with the nodes. A path is defined by a source address, a destination address and a port or version number. Once a node is made aware of a path, either by handling network message traffic associated with the path or through manual entry, the node maintains path status information with information provided by normal network message traffic, or absent the normal network message traffic, by transmitting Echo Request messages and processing information related to Echo Response messages or the lack thereof. Information related to paths that are disabled for longer than a disabled path duration limit is deleted from the tables. A Gratuitous GTP Echo Response message can notify other nodes of an administrative state change in a node.
Owner:LUCENT TECH INC +1
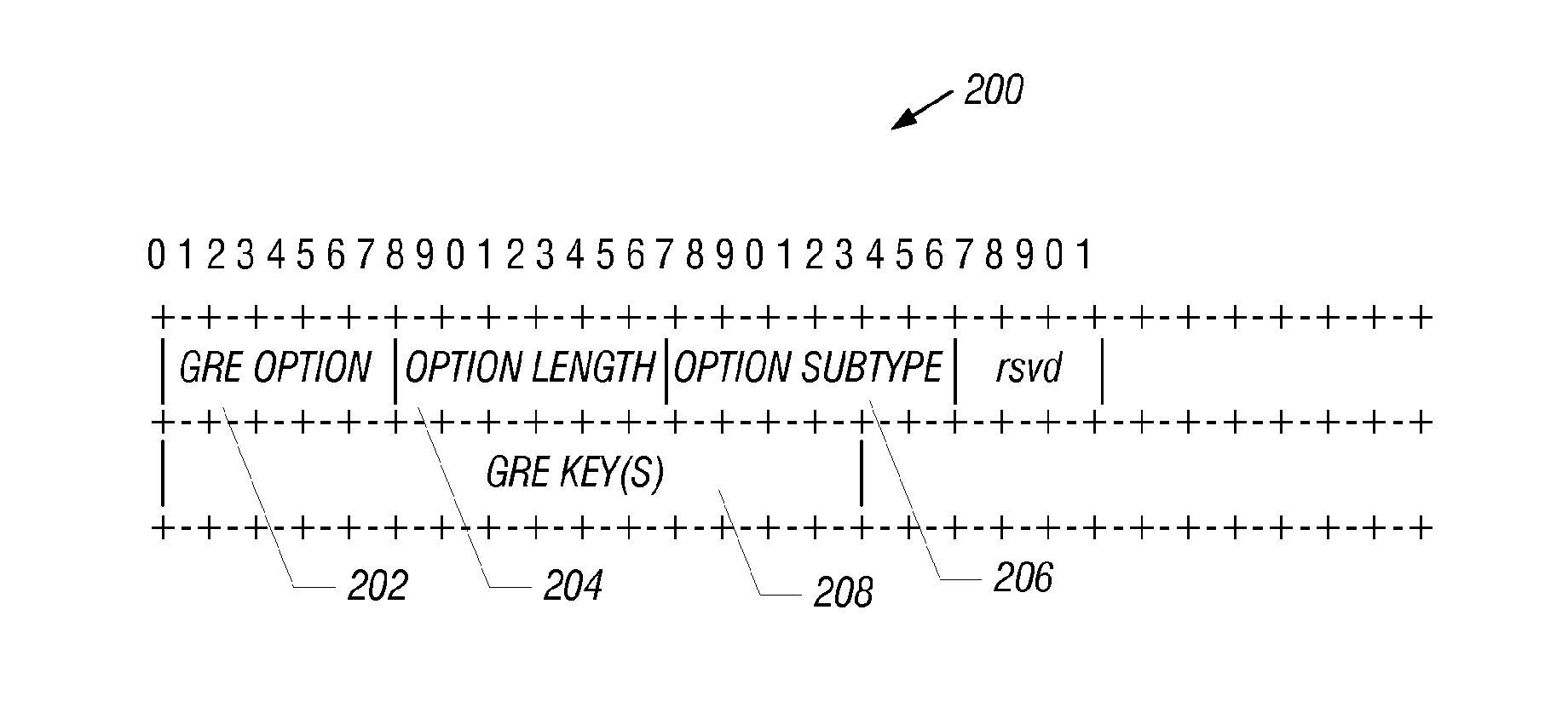
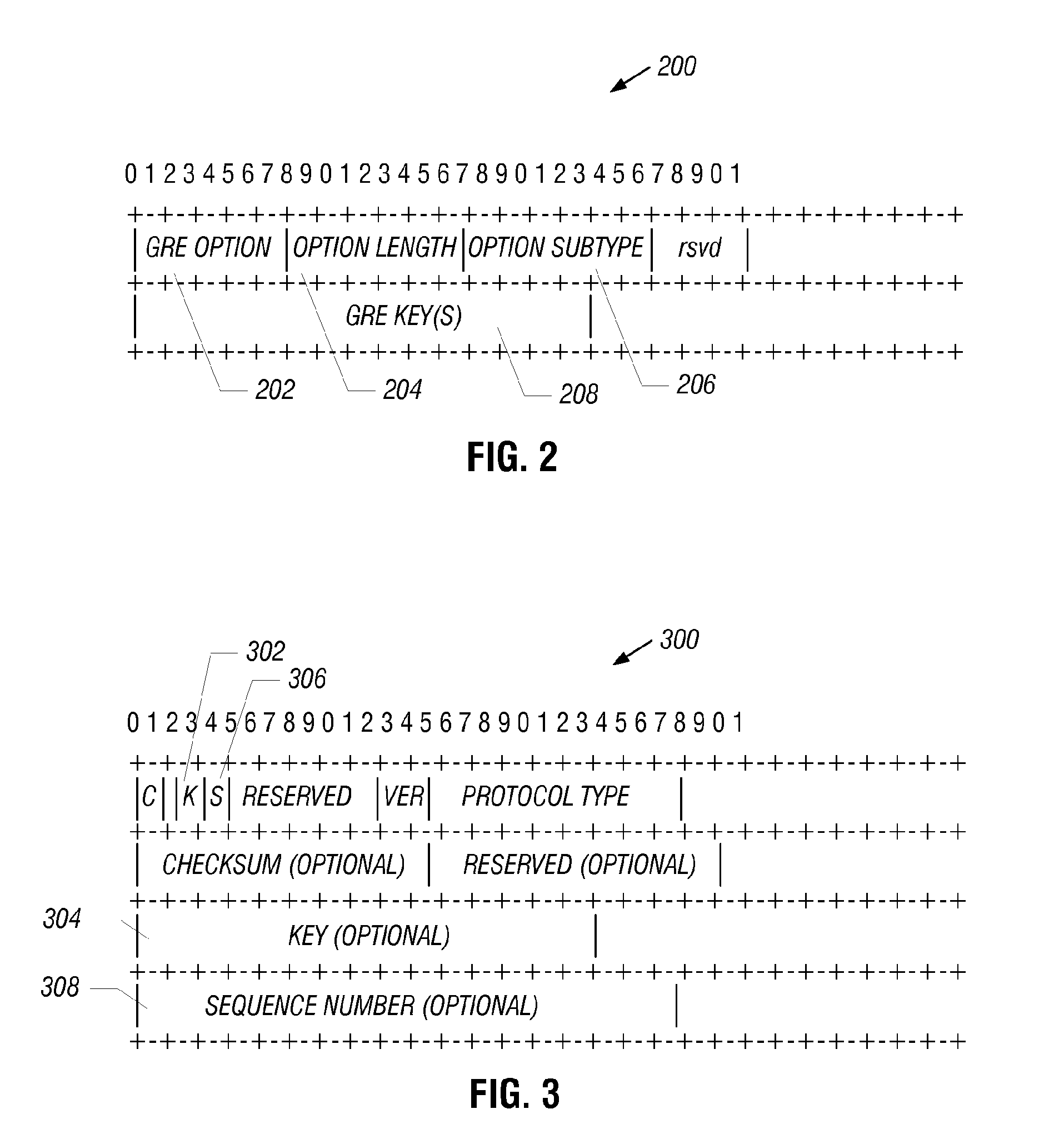
Tunneling support for mobile IP using a key for flow identification
InactiveUS20100290621A1Connection managementWireless network protocolsTraffic capacityComputer network
In a network that supports mobility of a mobile node, a tunnel between a first mobility node and a second mobility node is established in the network. The established tunnel is according to a tunneling protocol (e.g., Generic Routing Encapsulation tunneling protocol) that uses at least one key (208) for encapsulating data communicated through the tunnel. The symmetric or asymmetric key may be used for identifying a particular traffic flow in either the forward or the reverse direction between mobility nodes, e.g., when supporting mobility nodes that are using overlapping private IPv4 addressing. Signaling is communicated to provide mobility support of the mobile node according to a mobility protocol, where the mobility protocol is selected from among a Proxy Mobile Internet Protocol and Mobile IP version 6.
Owner:ROCKSTAR BIDCO +1
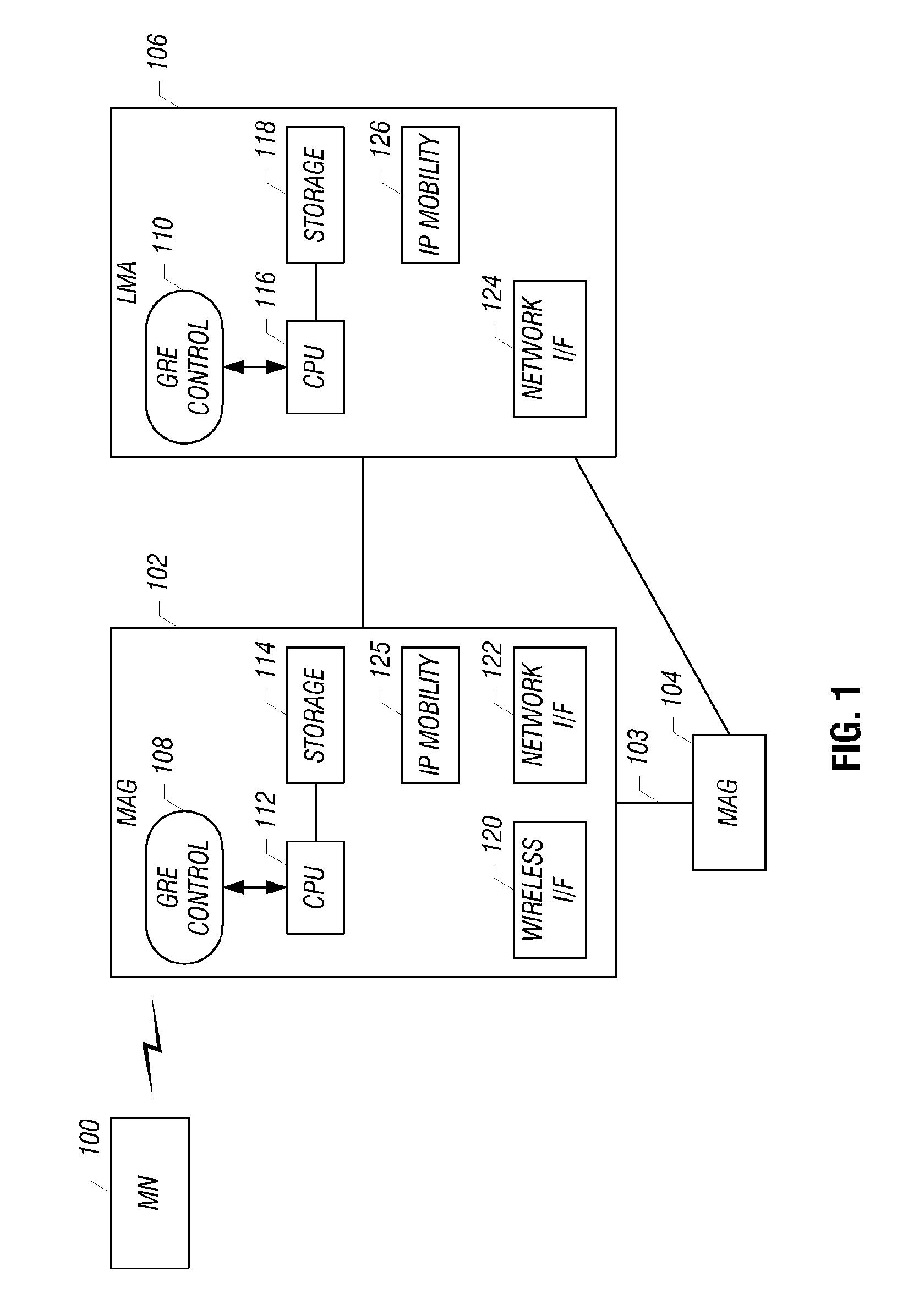
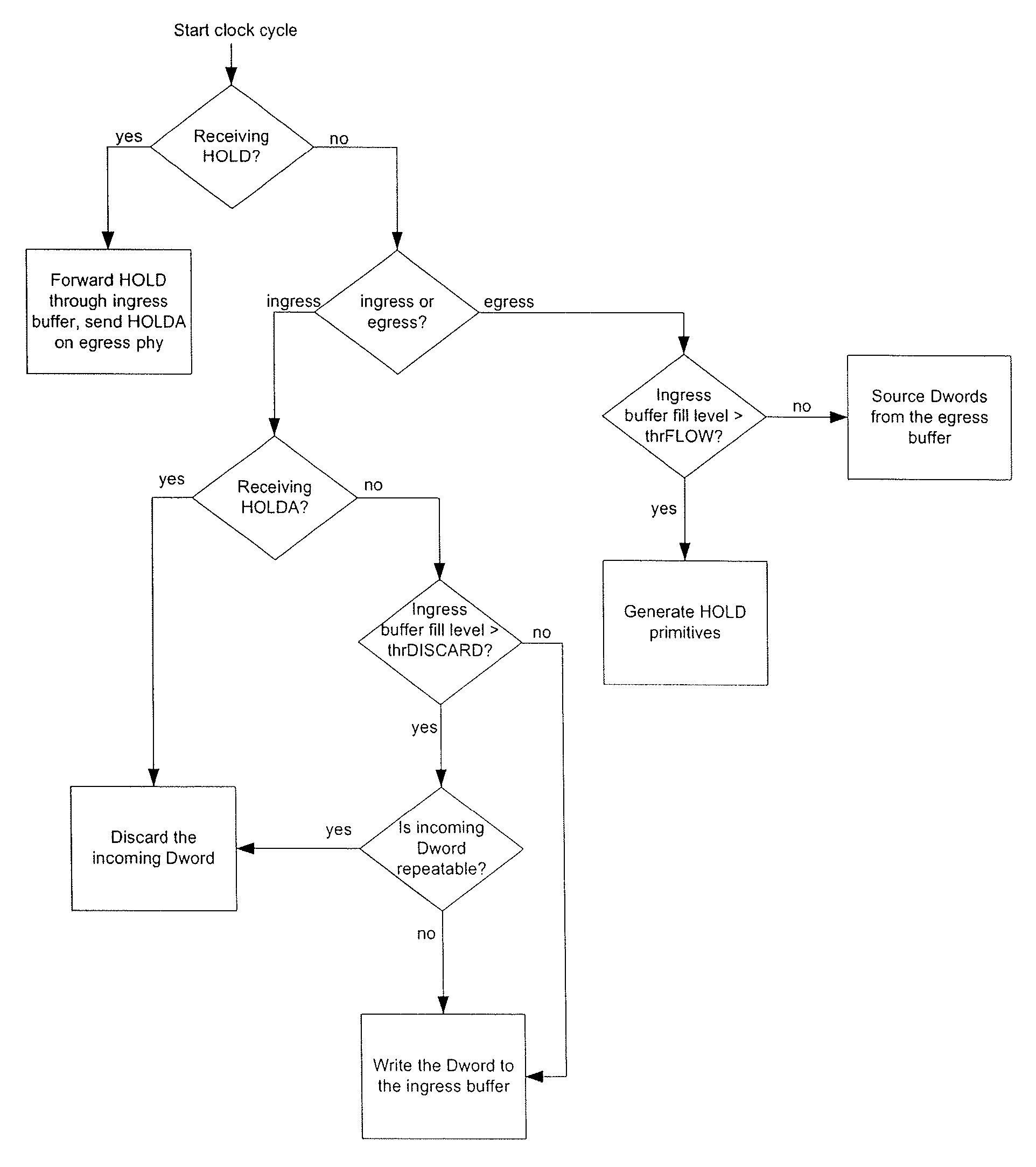
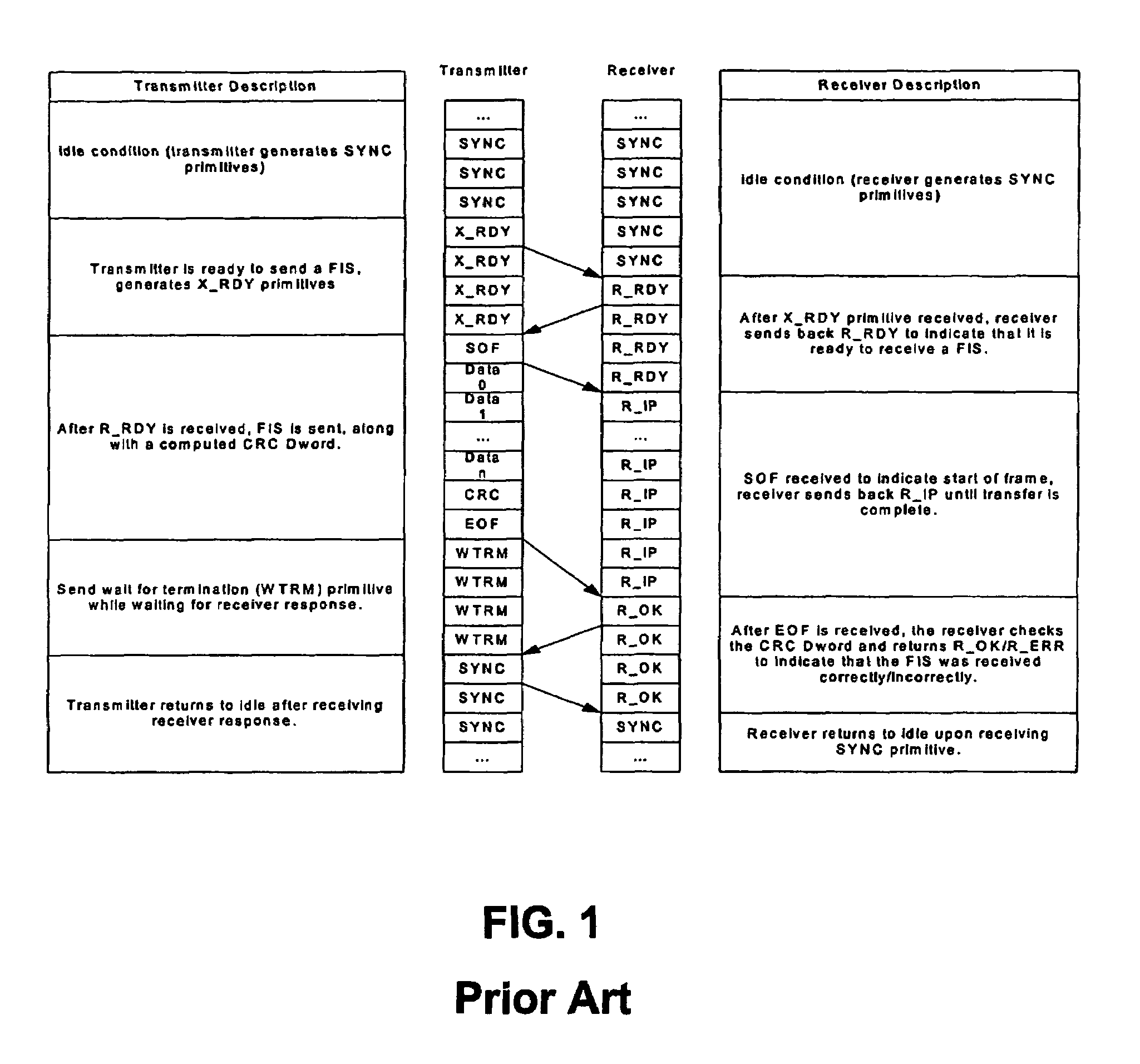
Serial tunneling protocol (STP) flow control in SAS expanders without SATA link state machine
ActiveUS7496700B1Improved STP flow control strategyMaintain integrityMultiple digital computer combinationsTransmissionTraffic capacityComputer science
A method and apparatus are disclosed for implementing STP flow control in SAS expander devices. SAS expanders are commonly used within a SAS network topology to allow multiple disk drives to connect to multiple host devices. Connections to a SATA HDD are supported using SATA Tunnelling Protocol (STP), which allows SATA traffic to be carried over a SAS network topology. Flow control in a STP connection is applied through a set of special SATA primitives, both for forward and backward flow control. A method is described herein in which STP flow control is supported without the use of a SATA link layer state machine. This allows STP flow control to be terminated on a hop-by-hop basis without knowing the data channel direction or maintaining a SATA link state machine, and while minimizing gate count.
Owner:MICROSEMI STORAGE SOLUTIONS
Method and device for transmitting data between GTP-U (GPRS Tunneling Protocol for the User plane) entities in radio connection
InactiveCN101998668ASave wireless resourcesConnection managementWireless network protocolsTelecommunicationsData transmission
The invention discloses a method and a device for transmitting data between GTP-U (GPRS Tunneling Protocol for the User plane) entities in radio connection for saving wireless resources. The method comprises the following steps: a first GTP-U entity and a second GTP-U entity establish radio bearer connection at a radio interference, and the first GTP-U entity and the second GTP-U entity save mapping relationship between GTP-U connection and radio bearer connection in the establishment of the radio bearer connection; and the first GTP-U entity and the second GTP-U entity perform user plane data upstream and downstream transmission according to respectively saved mapping relationship between GTP-U connection and radio bearer connection.
Owner:ZTE CORP
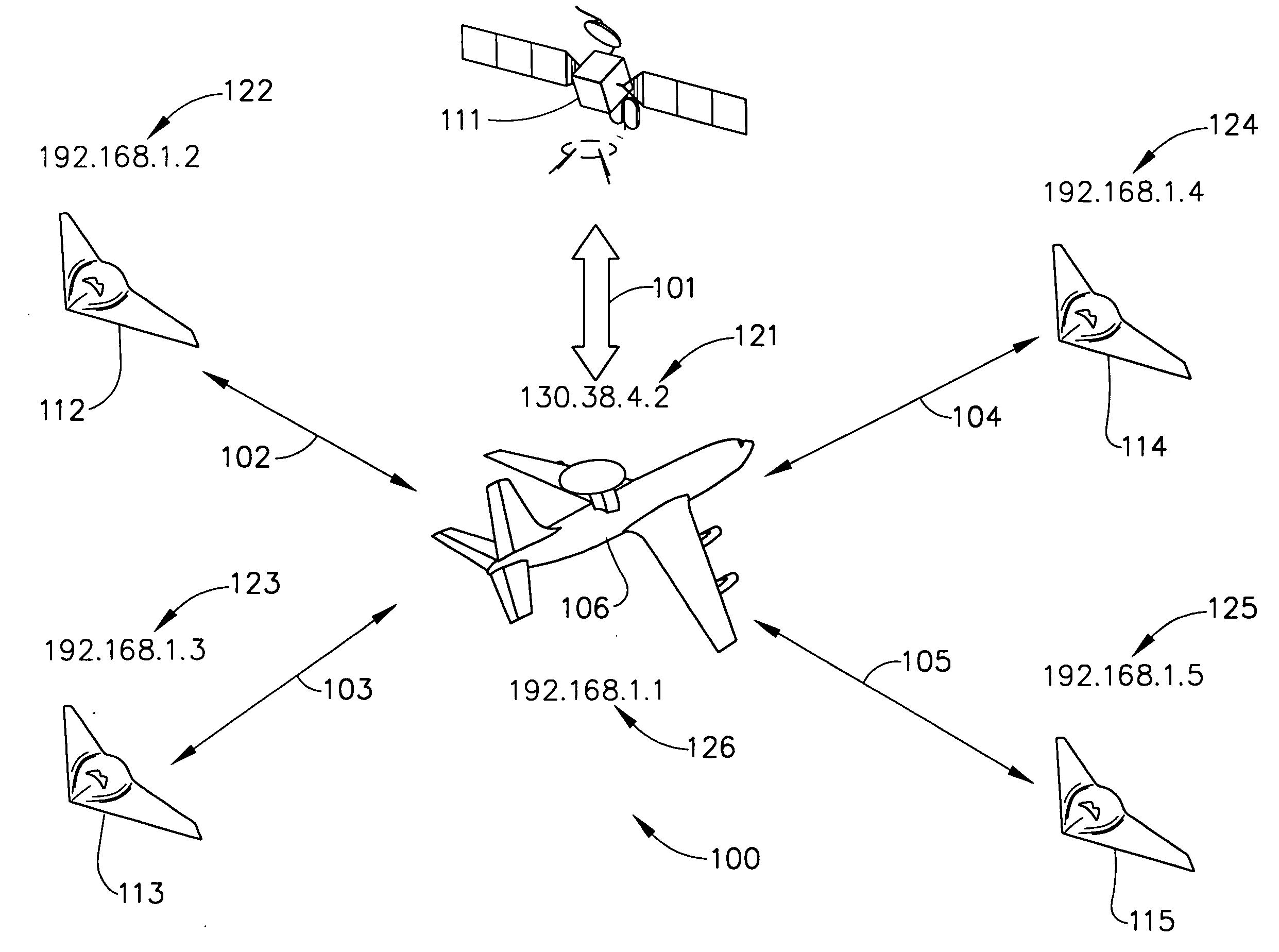
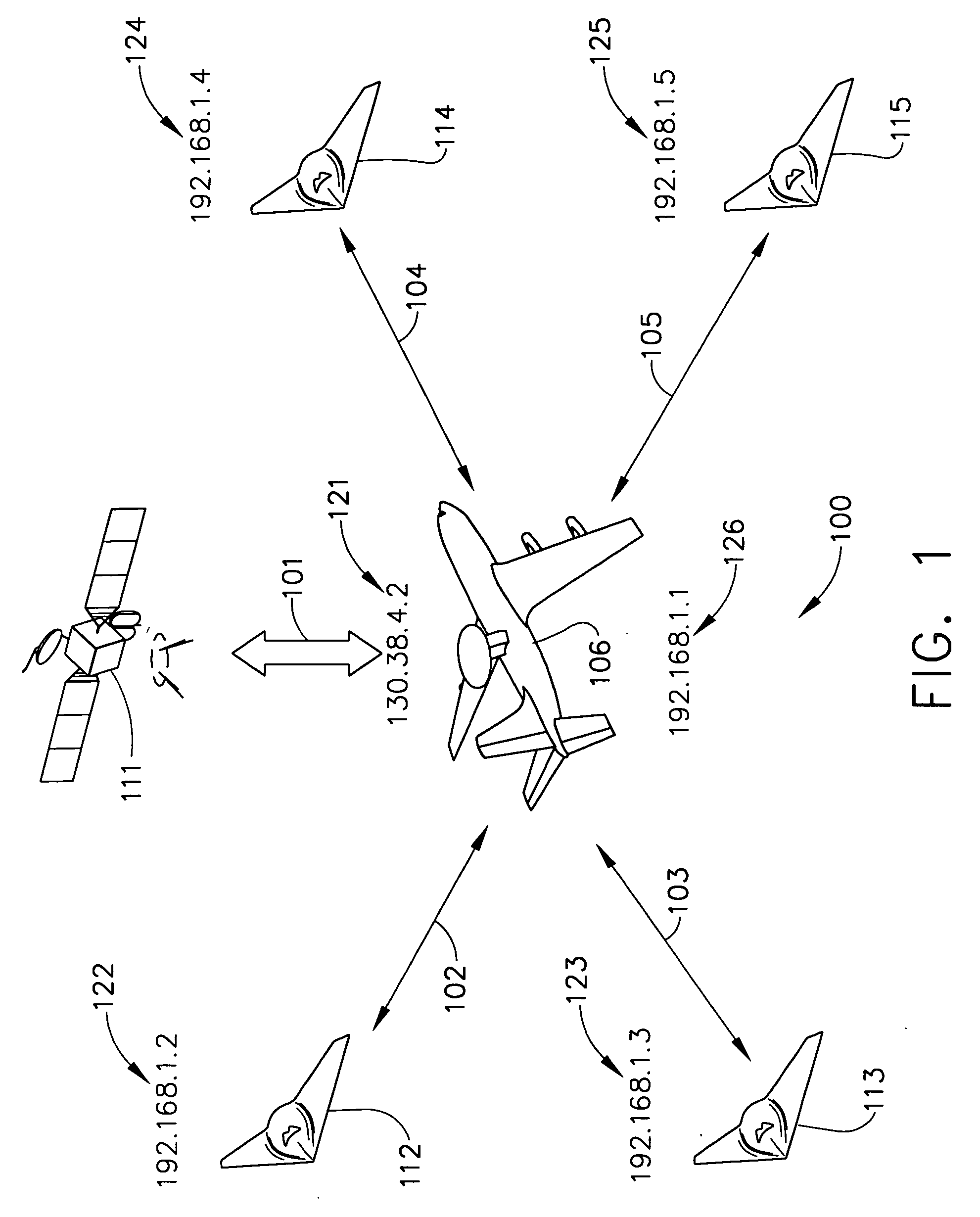
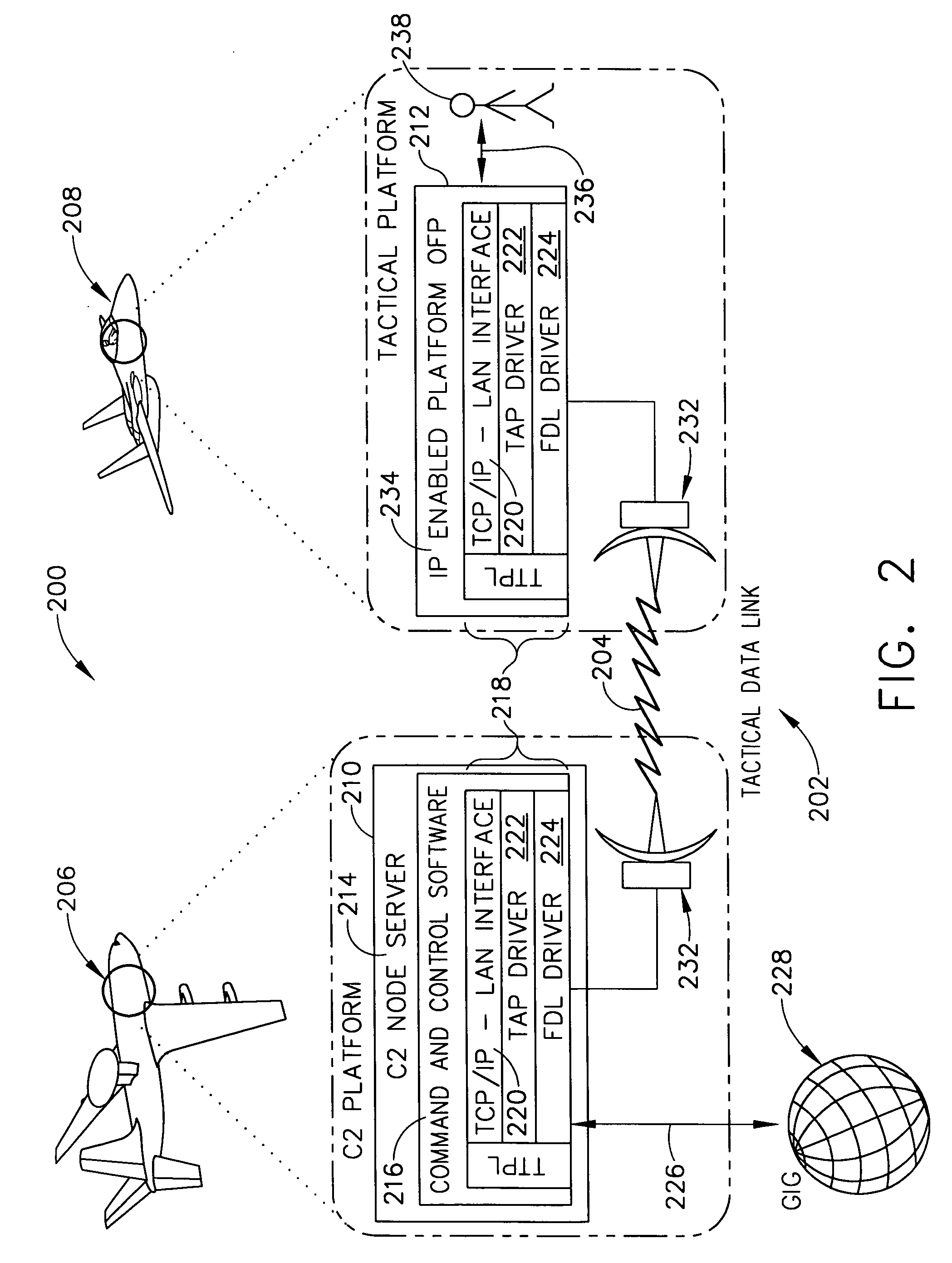
TCP/IP tunneling protocol for link 16
A method and system are provided for executing a protocol for tunneling of transmission control protocol / internet protocol (TCP / IP) packets over a tactical link. The tunneling protocol includes interfacing to a host software on a node of a tactical network using a TAP interface; breaking up ethernet packets from the TAP interface into J16.0 messages that include payload data from the ethernet packet and header information that uniquely identifies the J16.0 message for deterministic reassembly of the ethernet packet from the stream of J16.0 messages in which it is included. The J16.0 messages may be transmitted using a fighter data link over a tactical network link. At the destination node of the link, the J16.0 messages may be reassembled into ethernet packets, allowing the tactical network to be implemented as virtual private network having (internet protocol) IP addresses for each node.
Owner:THE BOEING CO
Method and apparatus for transmitting data package of GPRS tunnel protocol
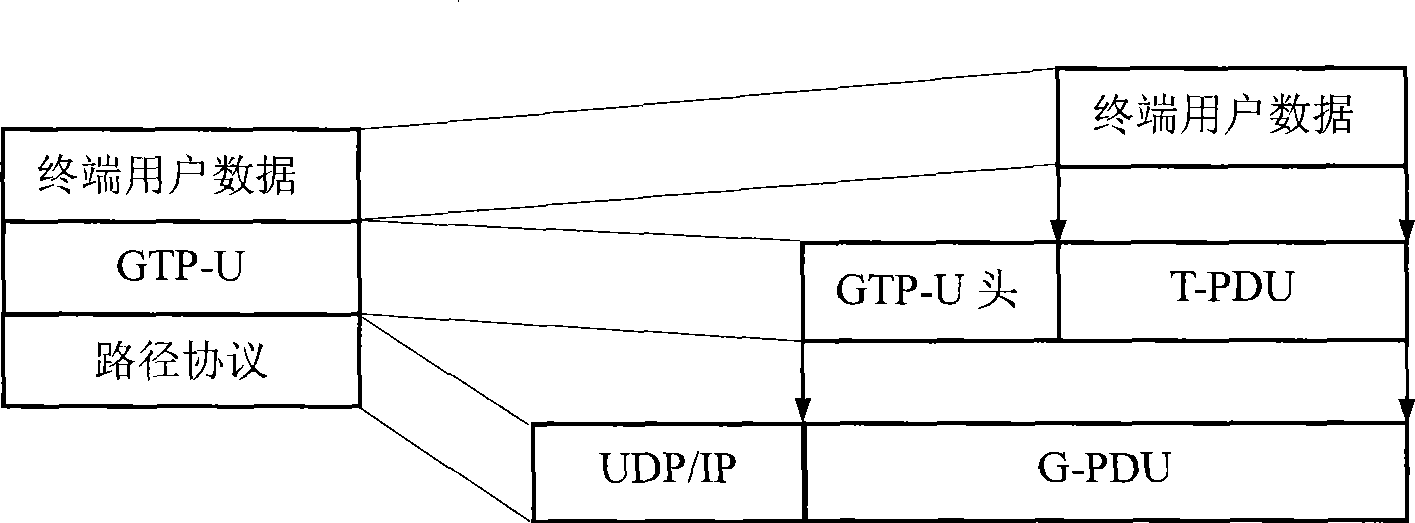
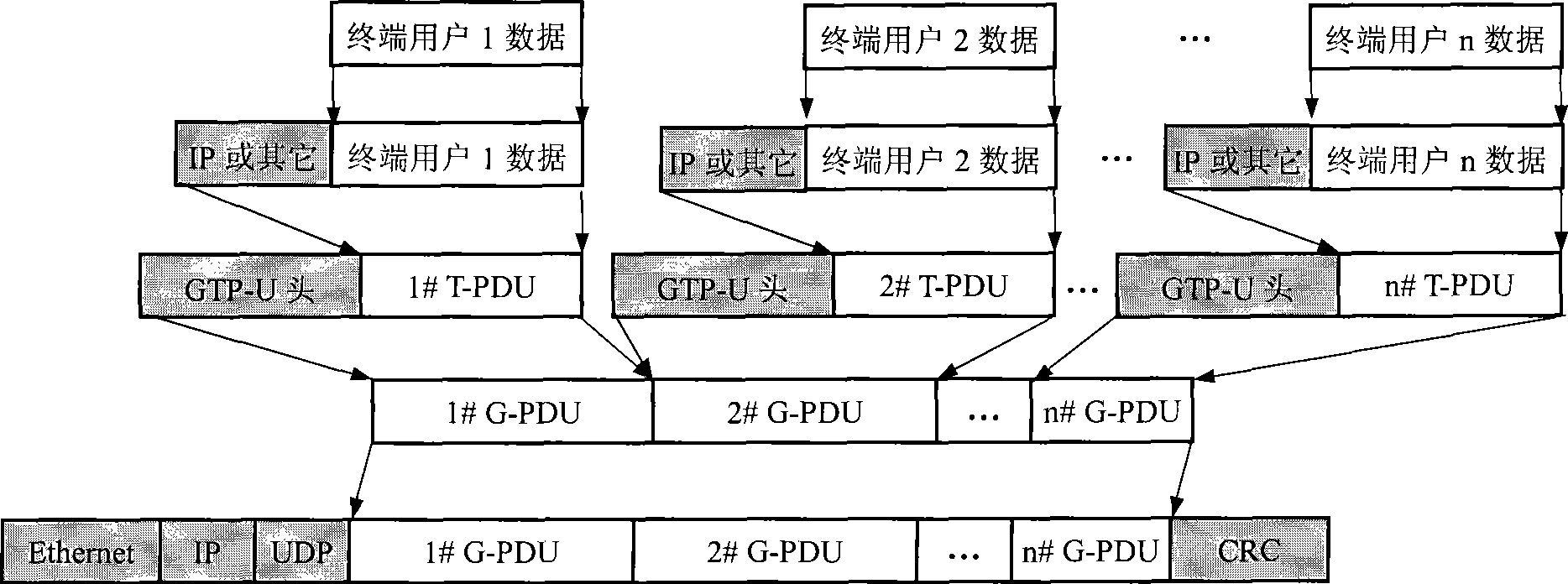
ActiveCN101388825AReduce the numberReduce loadError preventionNetworks interconnectionTelecommunicationsNetwork packet
The invention discloses a method for transmitting GTP data packets of a GPRS tunneling protocol, which comprises the following steps: multiplexing a plurality of the G-PDU packets together on a sending endpoint of a GTP tunnel, and sending the G-PDU packets to a receiving endpoint of the GTP tunnel after packing the together multiplexed G-PDU packets through the transmission path protocol. With the technical proposal of the invention, the transmission efficiency can be improved, and the transmission bandwidth can be saved, simultaneously, the number of the transferred data packets in the transmission network further can be reduced, and the load of the transmission network can be reduced, and simultaneously, the invention further discloses a GTP tunnel endpoint device.
Owner:XFUSION DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com