Patents
Literature
130 results about "Full virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
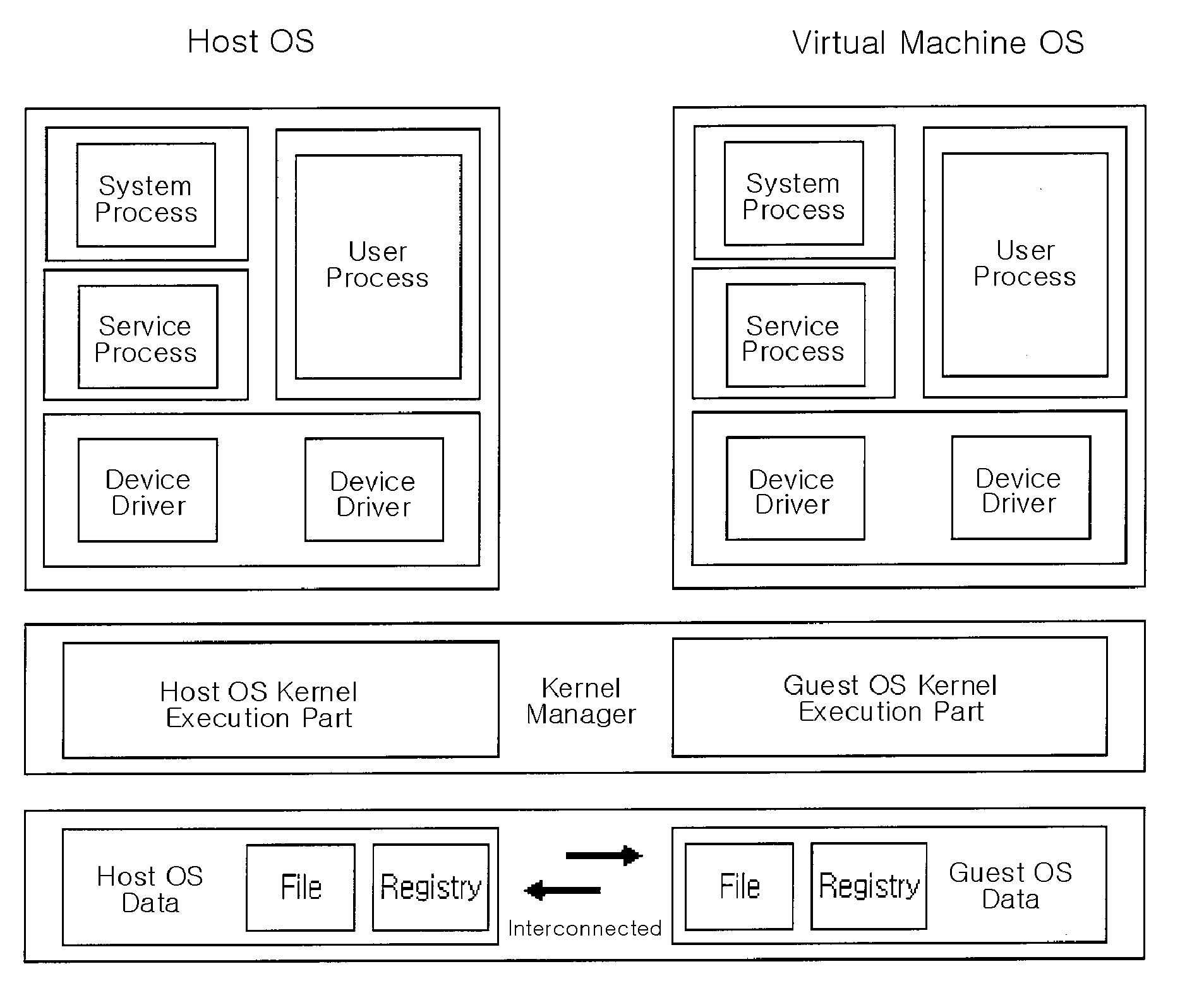
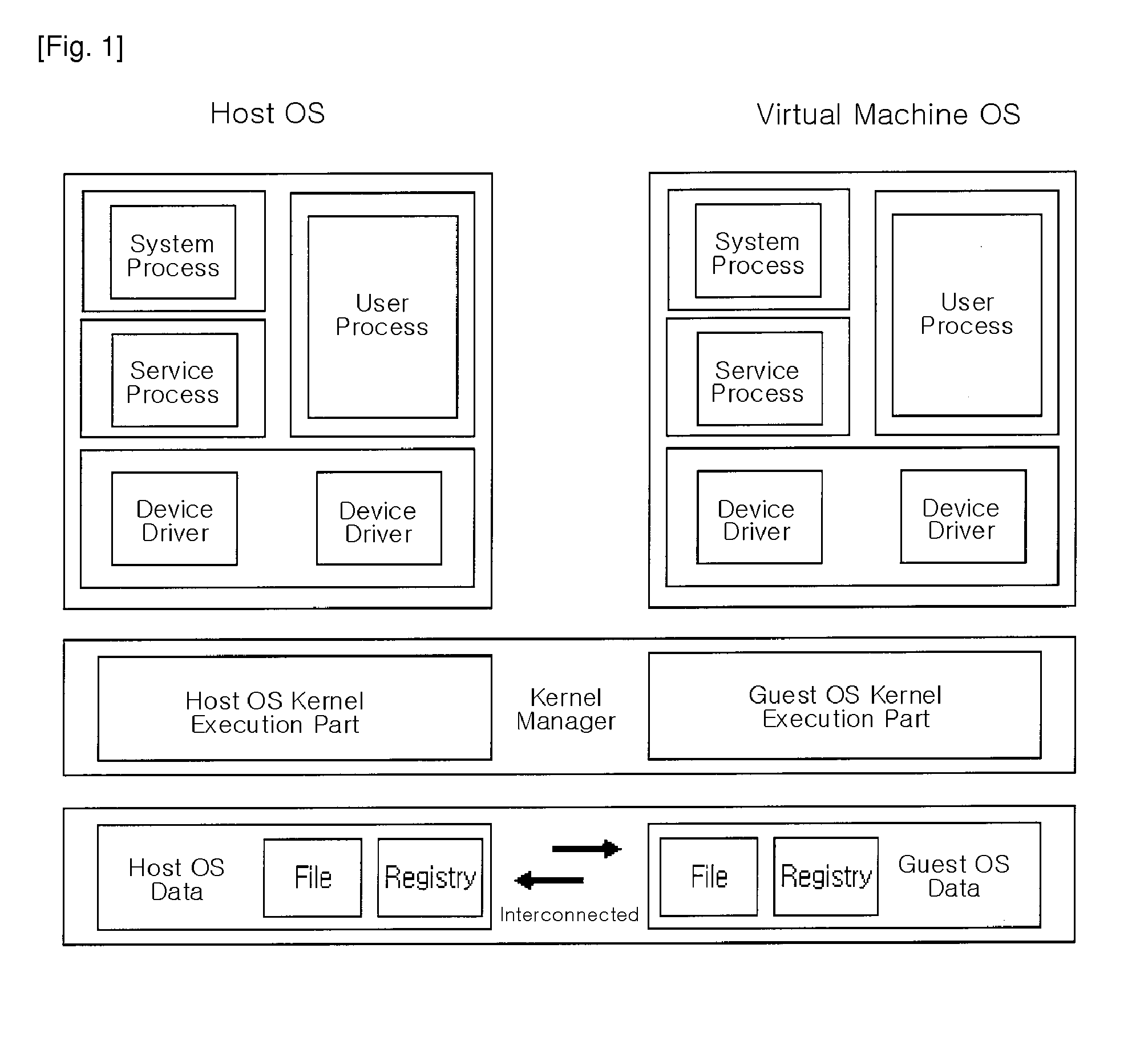
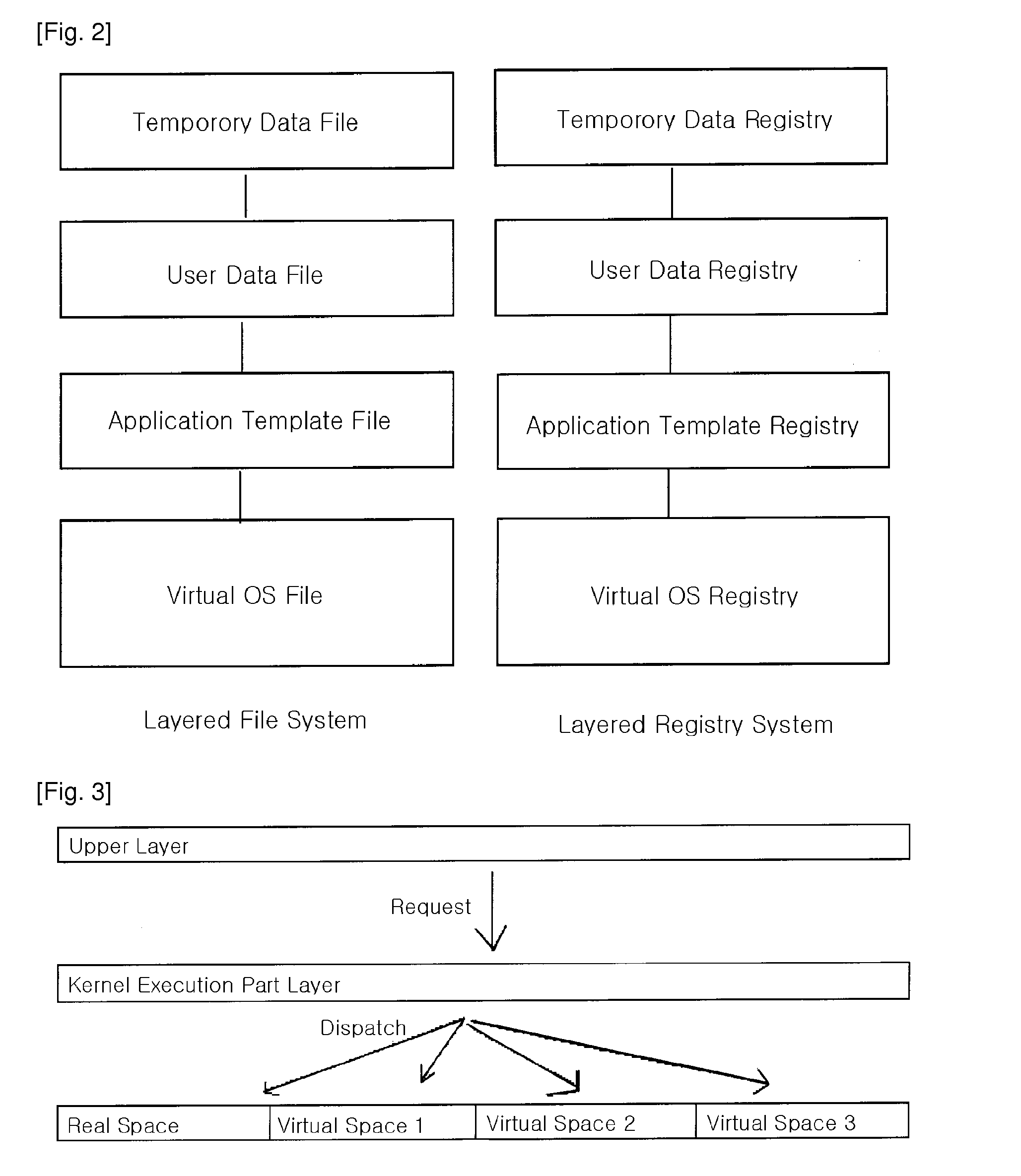
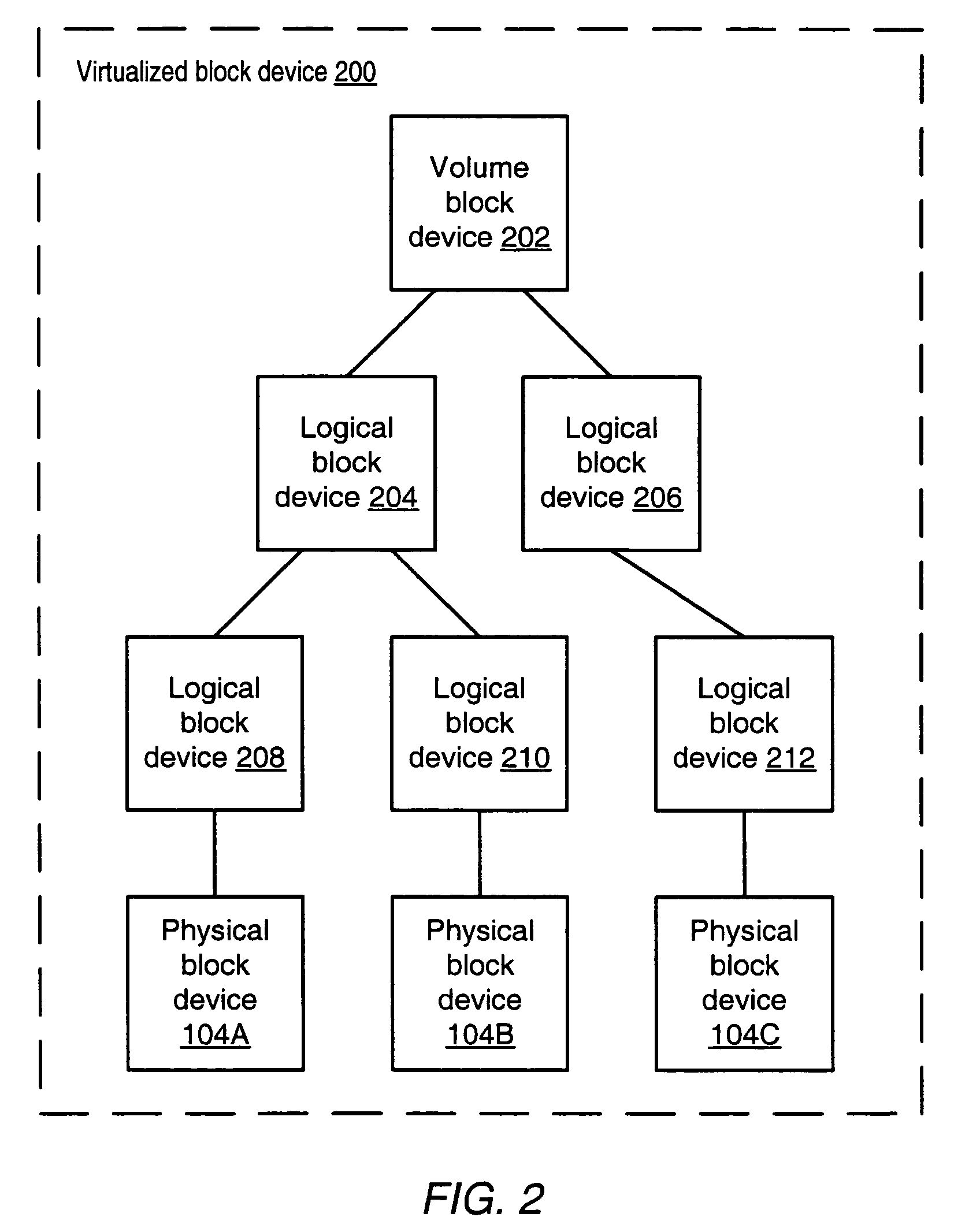
In computer science, virtualization is a modern technique developed in late 1990s and is different from simulation and emulation. Virtualization employs techniques used to create instances of an environment, as opposed to simulation, which models the environment; or emulation, which replicates the target environment such as certain kind of virtual machine environment. Full virtualization requires that every salient feature of the hardware be reflected into one of several virtual machines – including the full instruction set, input/output operations, interrupts, memory access, and whatever other elements are used by the software that runs on the bare machine, and that is intended to run in a virtual machine. In such an environment, any software capable of execution on the raw hardware can be run in the virtual machine and, in particular, any operating systems. The obvious test of full virtualization is whether an operating system intended for stand-alone use can successfully run inside a virtual machine.
End-to-end virtualization
InactiveUS20120099602A1Facilitates end-to-end virtualizationData switching by path configurationData virtualizationNetwork virtualization
One embodiment of the present invention provides a system that facilitates end-to-end virtualization. During operation, a network interface residing on an end host sets up a tunnel. The network interface then encapsulates a packet destined to a virtual machine based on a tunneling protocol. By establishing a tunnel that allows a source host to address a remote virtual machine, embodiments of the present invention facilitate end-to-end virtualization.
Owner:AVAGO TECH INT SALES PTE LTD
Data virtualization across heterogeneous formats
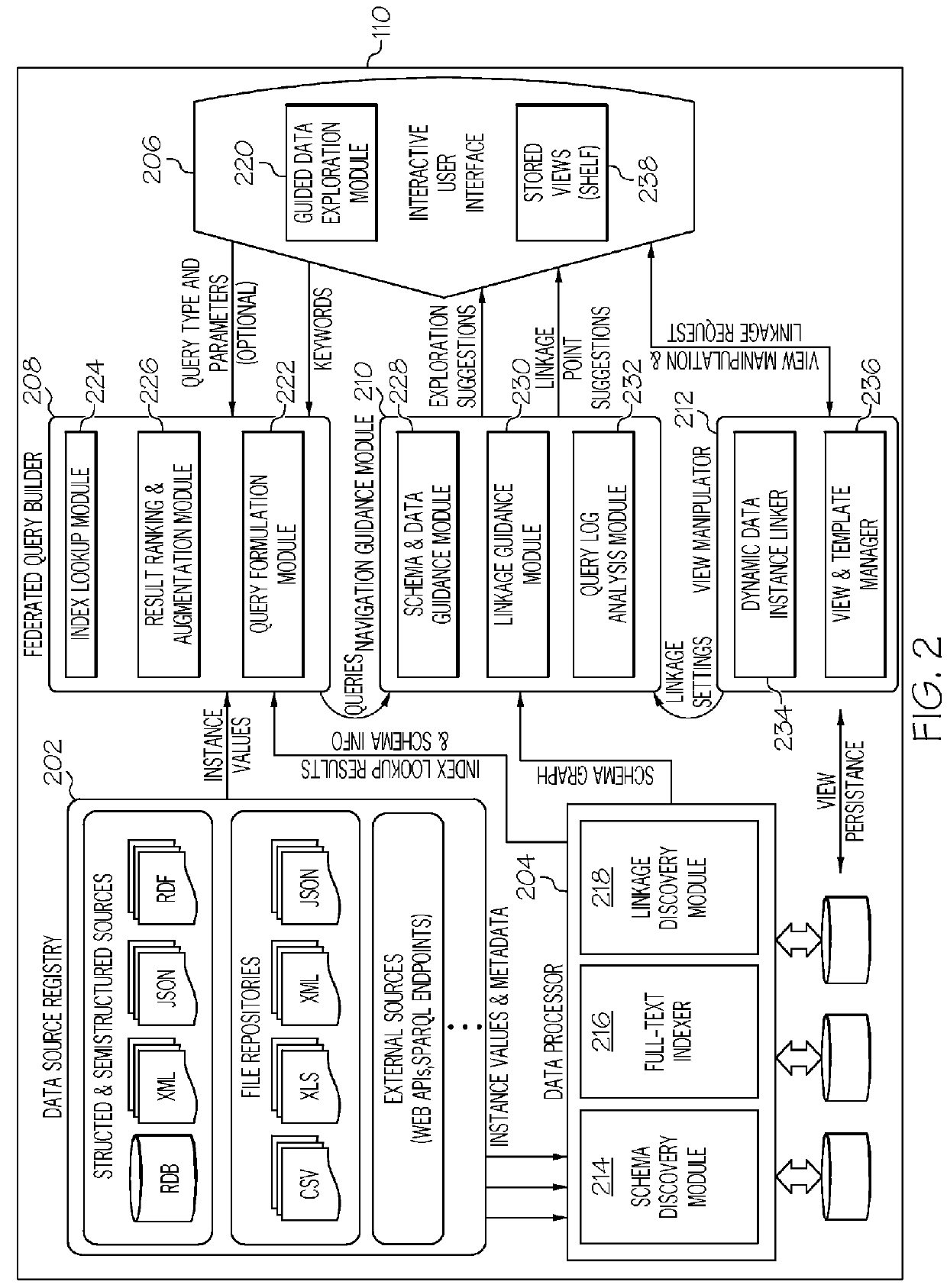
ActiveUS20160055184A1Digital data information retrievalDigital data processing detailsData sourceData virtualization
Various embodiments virtualize data across heterogeneous formats. In one embodiment, a plurality of heterogeneous data sources is received as input. A local schema graph including a set of attribute nodes and a set of type nodes is generated for each of the plurality of heterogeneous data sources. A global schema graph is generated based on each local schema graph that has been generated. The global schema graph comprises each of the local schema graphs and at least one edge between at least one of two or more attributes nodes and two or more type nodes from different local schema graphs. The edge indicates a relationship between the data sources represented by the different local schema graphs comprising the two or more attributes nodes based on a computed similarity between at least one value associated with each of the two or more attributes nodes.
Owner:IBM CORP
Movable virtual machine image
InactiveUS20100107163A1Mobility is attainableThe process is convenient and fastDigital data processing detailsError detection/correctionComputer scienceVirtual machine
The present invention provides the movable virtual machine image using the OS level virtualization and the method for creating and utilizing the movable virtual machine image. The movable virtual machine image is independent of the hardware of PCs and easy to attach or detach from the OS, thereby presents easy and quick moving, distributing, sharing and initializing.
Owner:LEE SANGGYU
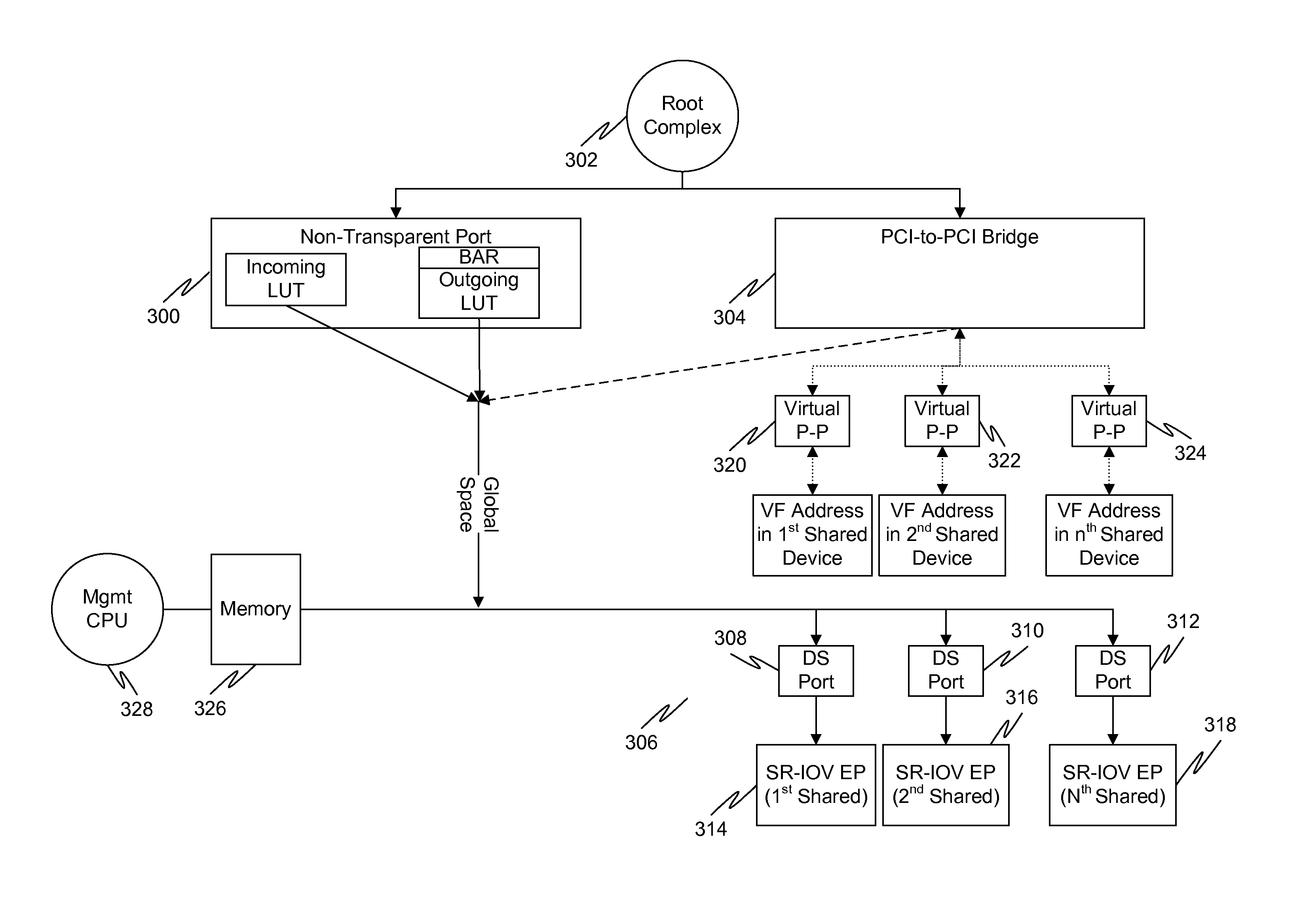
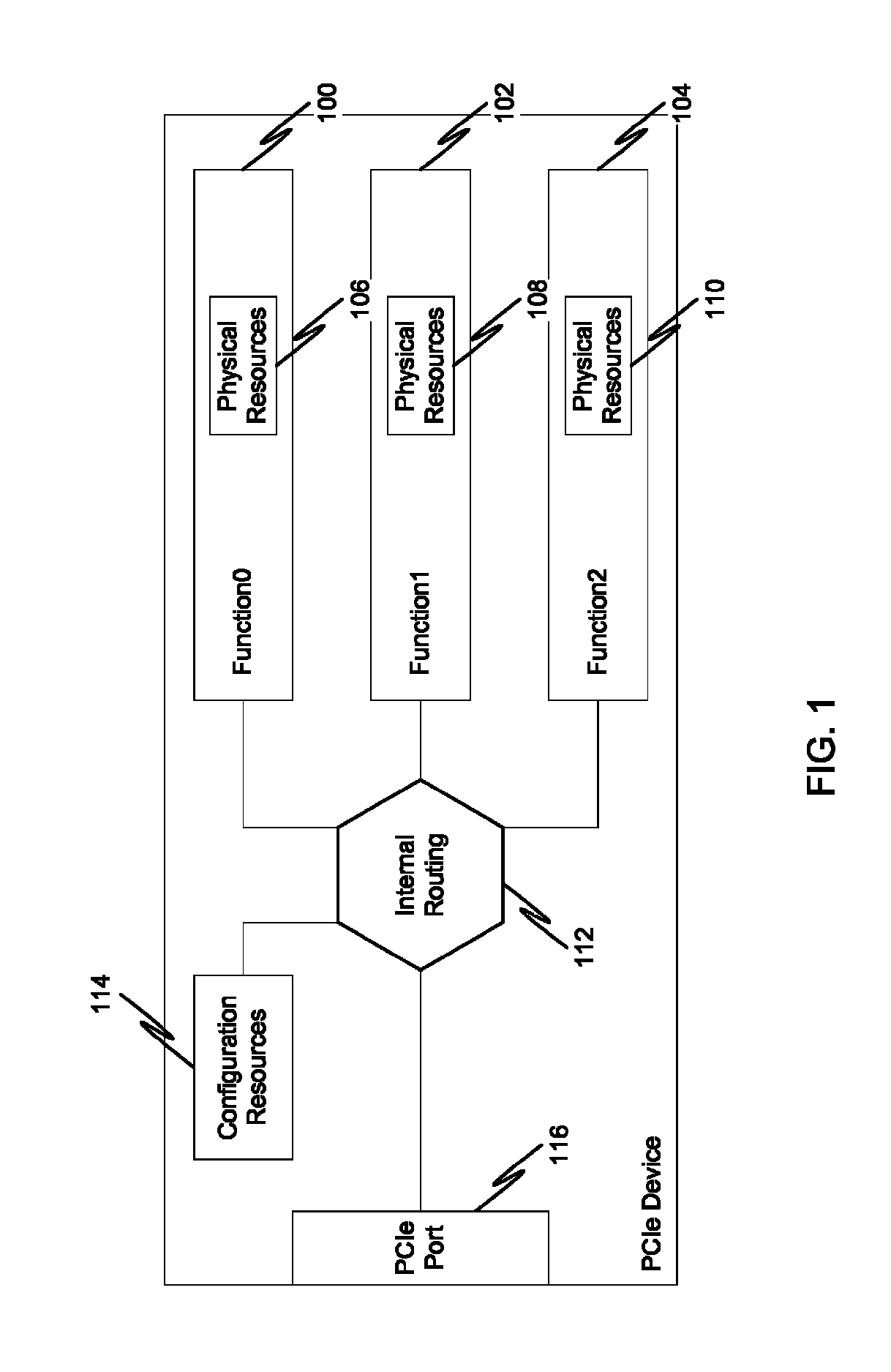
Multi-root sharing of single-root input/output virtualization
In a first embodiment of the present invention, a method for multi-root sharing of a plurality of single root input / output virtualization (SR-IOV) endpoints is provided, the method comprising: CSR redirection to a management processor which either acts as a proxy to execute the CSR request on behalf of the host or filters it and performs an alternate action, downstream routing of memory mapped I / O request packets through the switch in the host's address space and address translation with VF BAR granularity, upstream routing of requests originated by I / O devices by table lookup indexed by Requester ID, and requester ID translation using a fixed local-global RID offset.
Owner:AVAGO TECH INT SALES PTE LTD
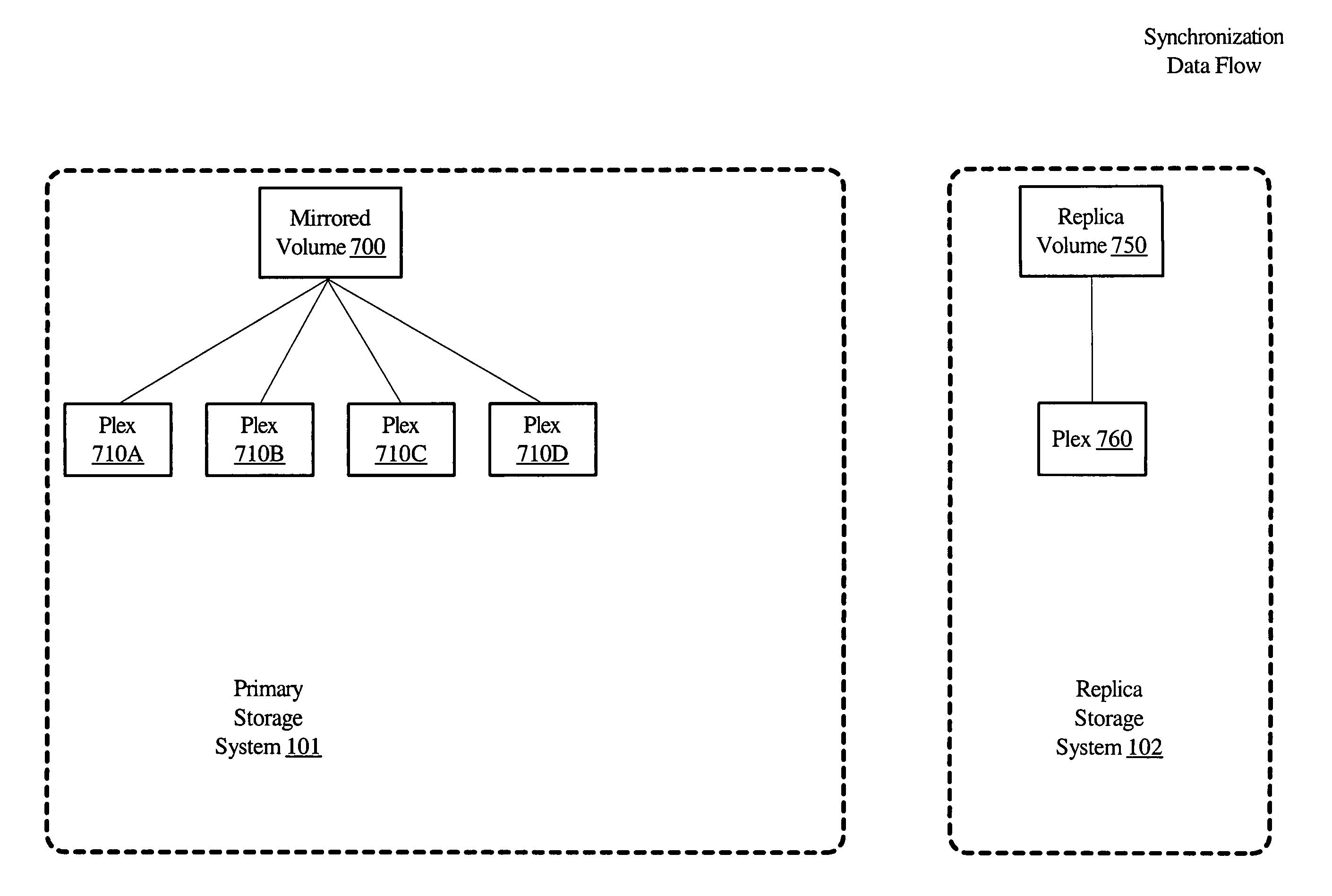
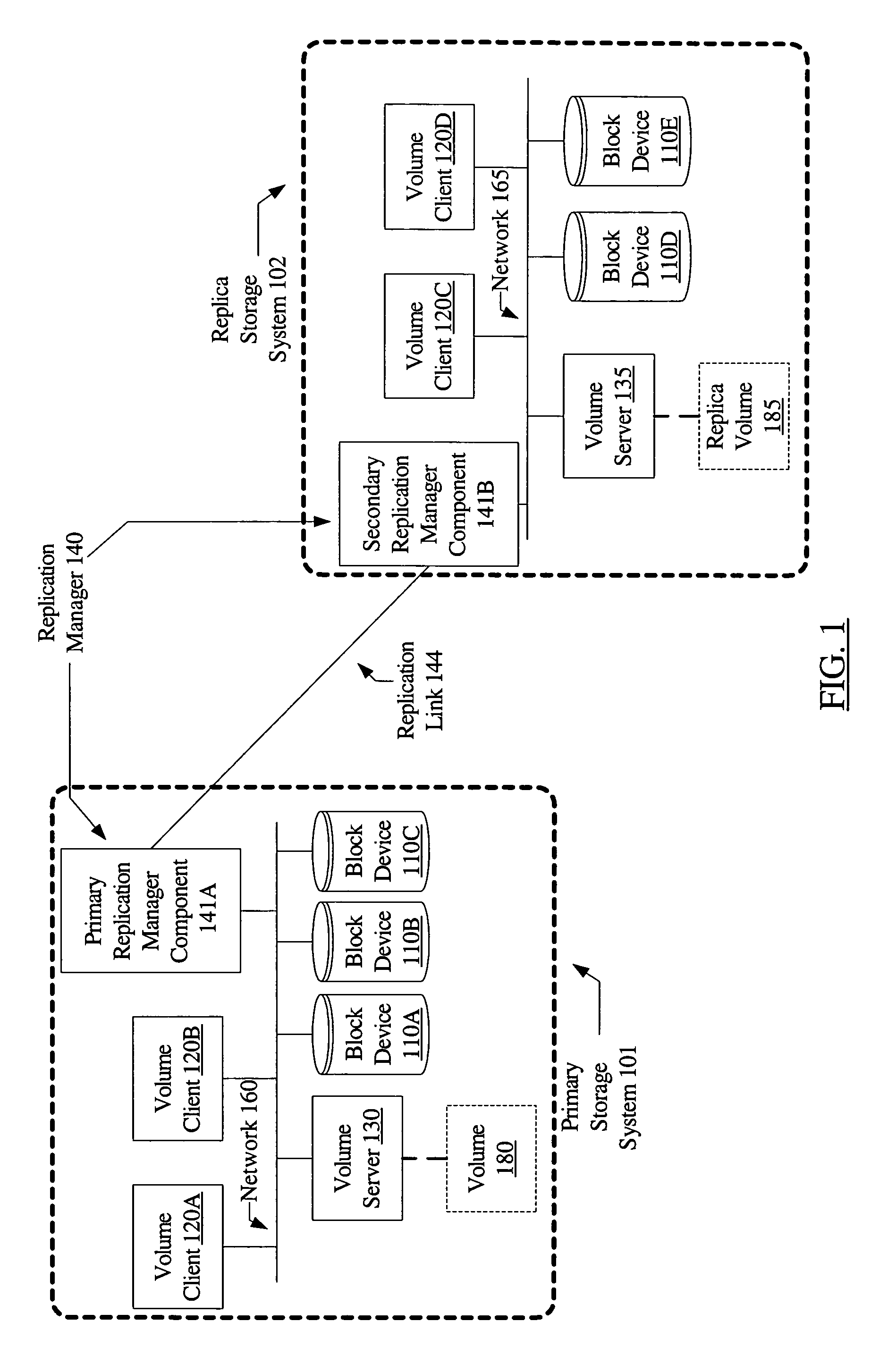
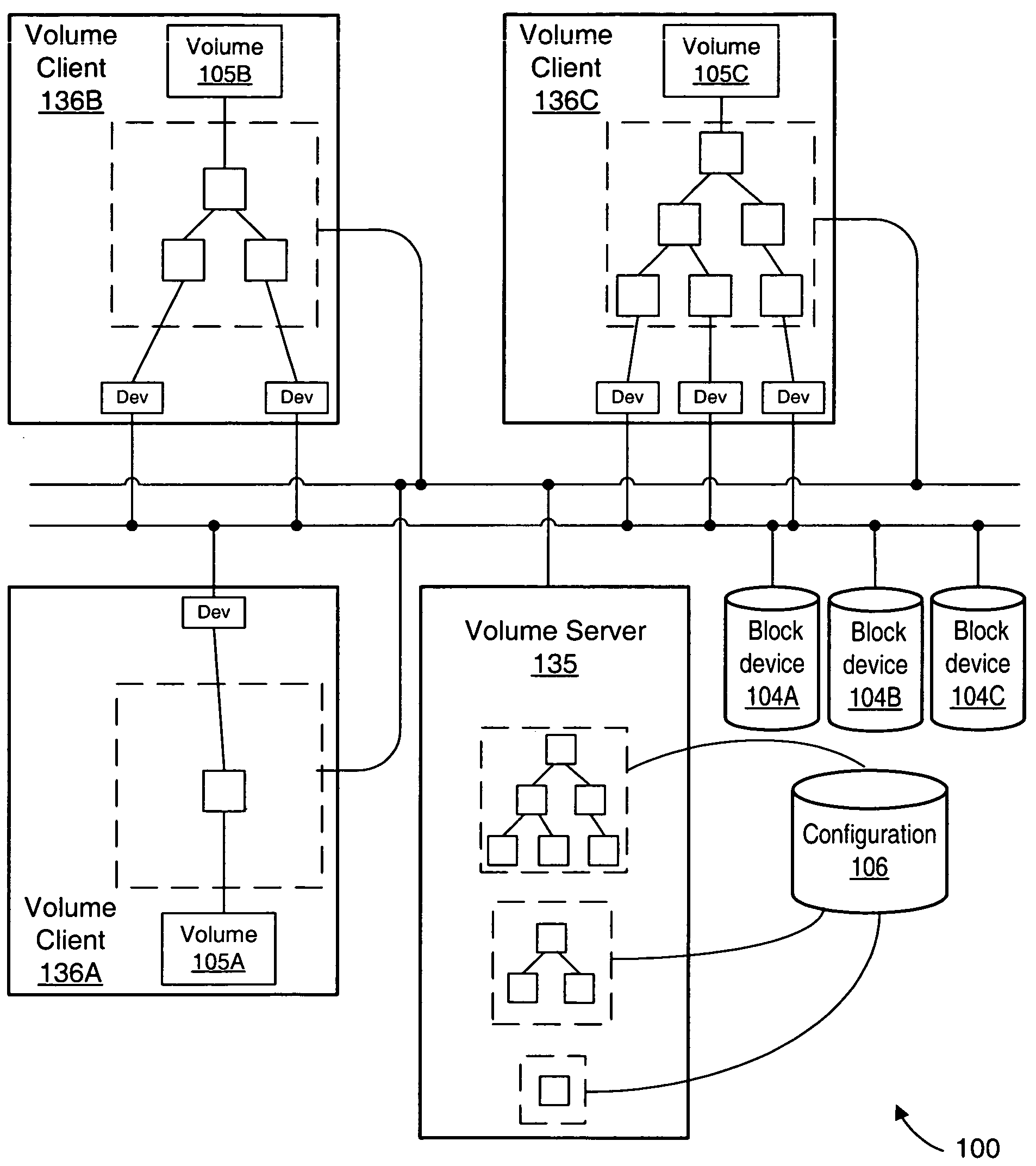
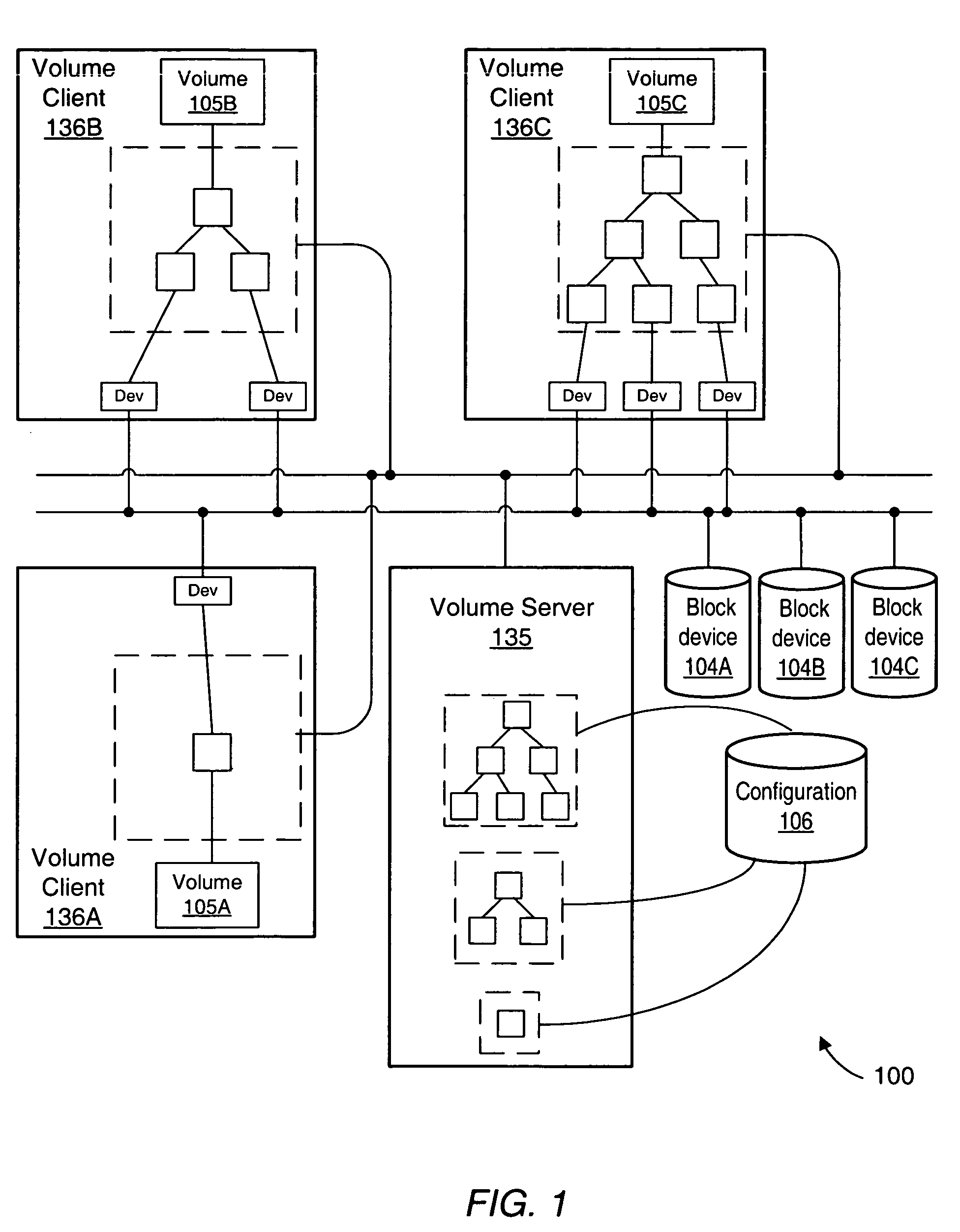
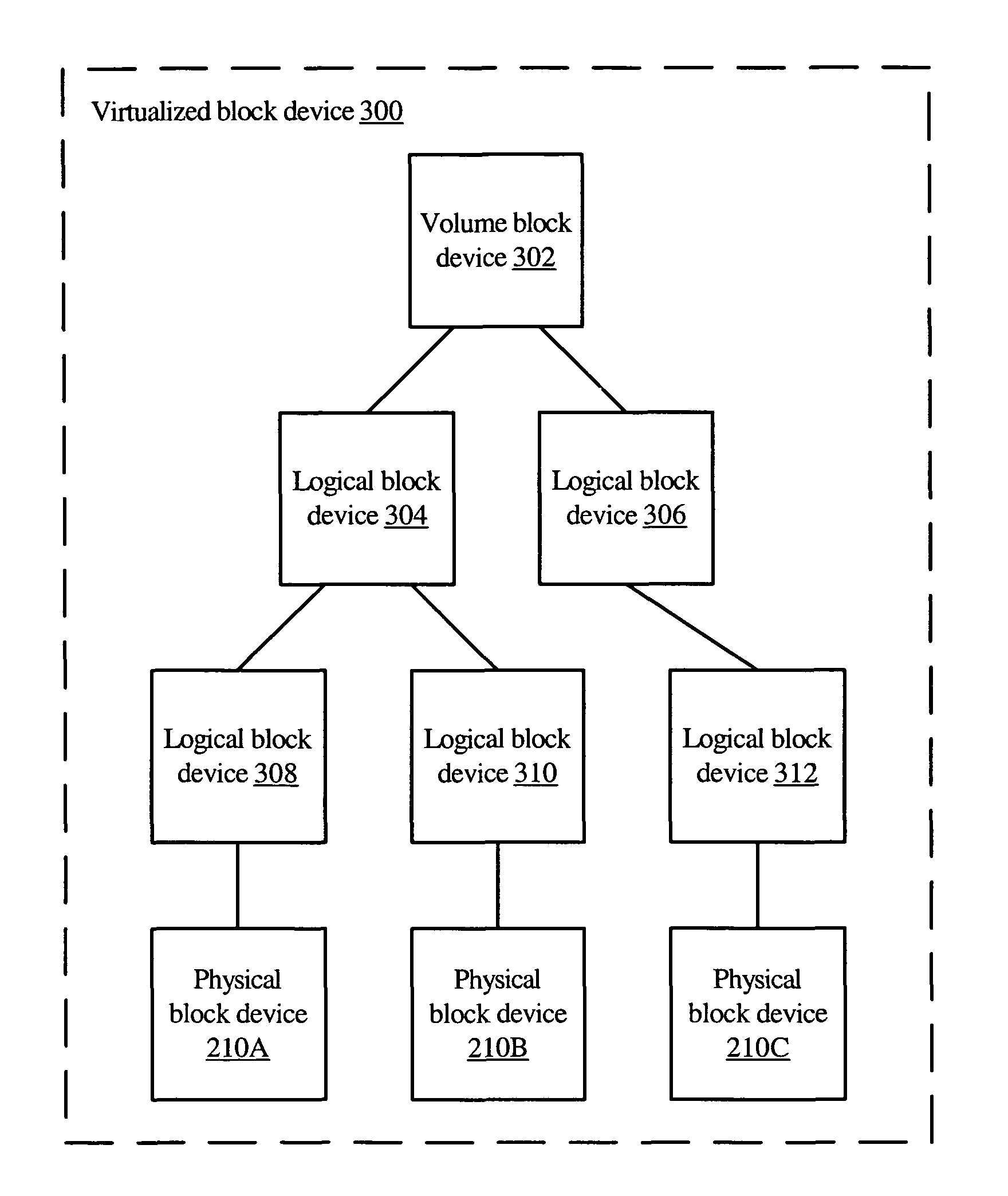
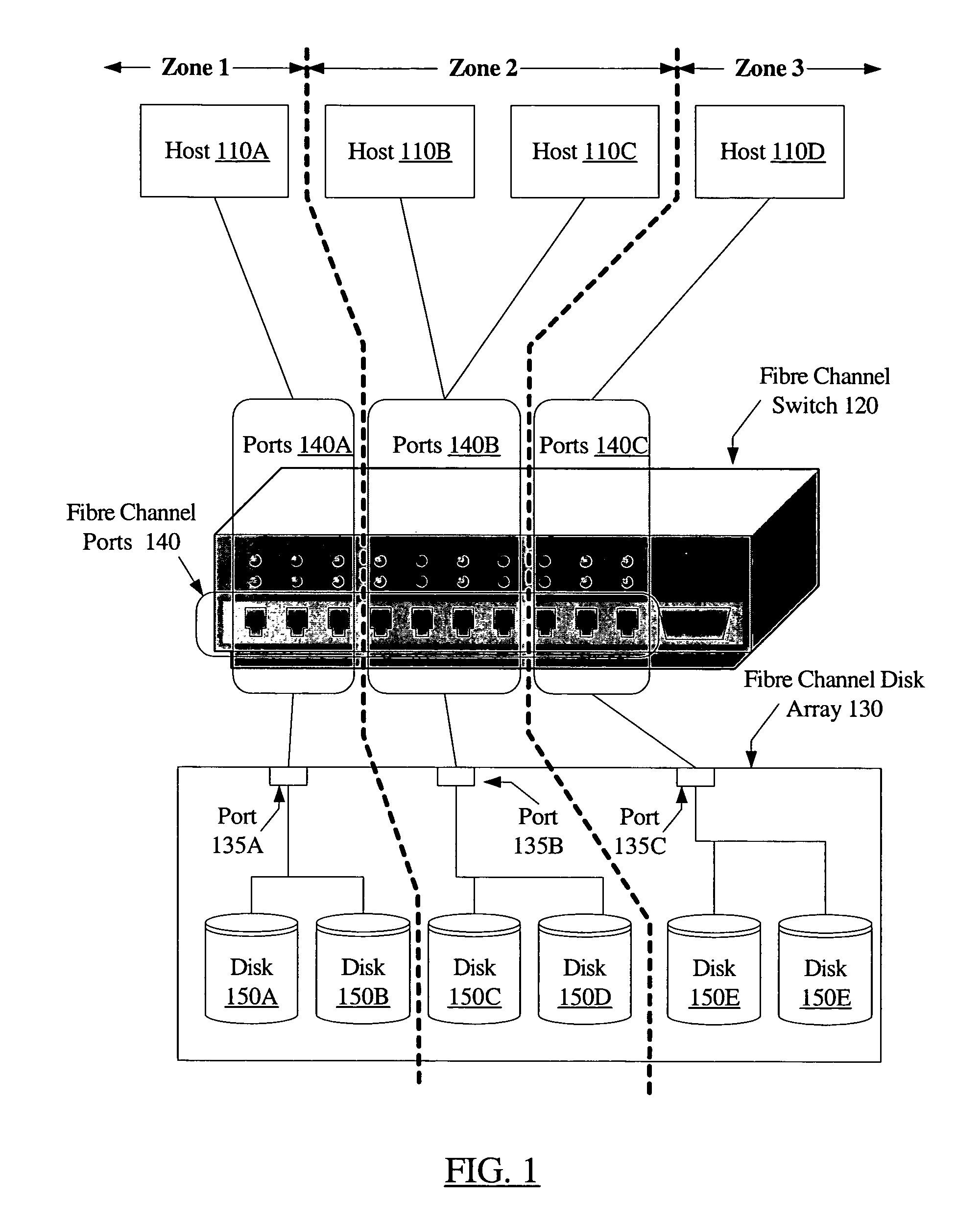
System and method for volume replication in a storage environment employing distributed block virtualization
InactiveUS7657578B1Reduce the impactReduce impactDigital data processing detailsError detection/correctionClient-sideDistributed computing
A system for volume replication in a distributed block virtualization environment includes a first and a second set of one or more physical block devices, a first and a second volume server, one or more volume clients, and a replication manager. The first volume server may be configured to aggregate storage in the first set of one or more physical block devices into one or more logical volumes, and to make the one or more logical volumes accessible to the one or more volume clients. The replication manager may be configured to operate in cooperation with the first and second volume servers and the one or more volume clients to maintain a replica of at least a subset of the one or more logical volumes at the second set of one or more physical block devices.
Owner:SYMANTEC OPERATING CORP
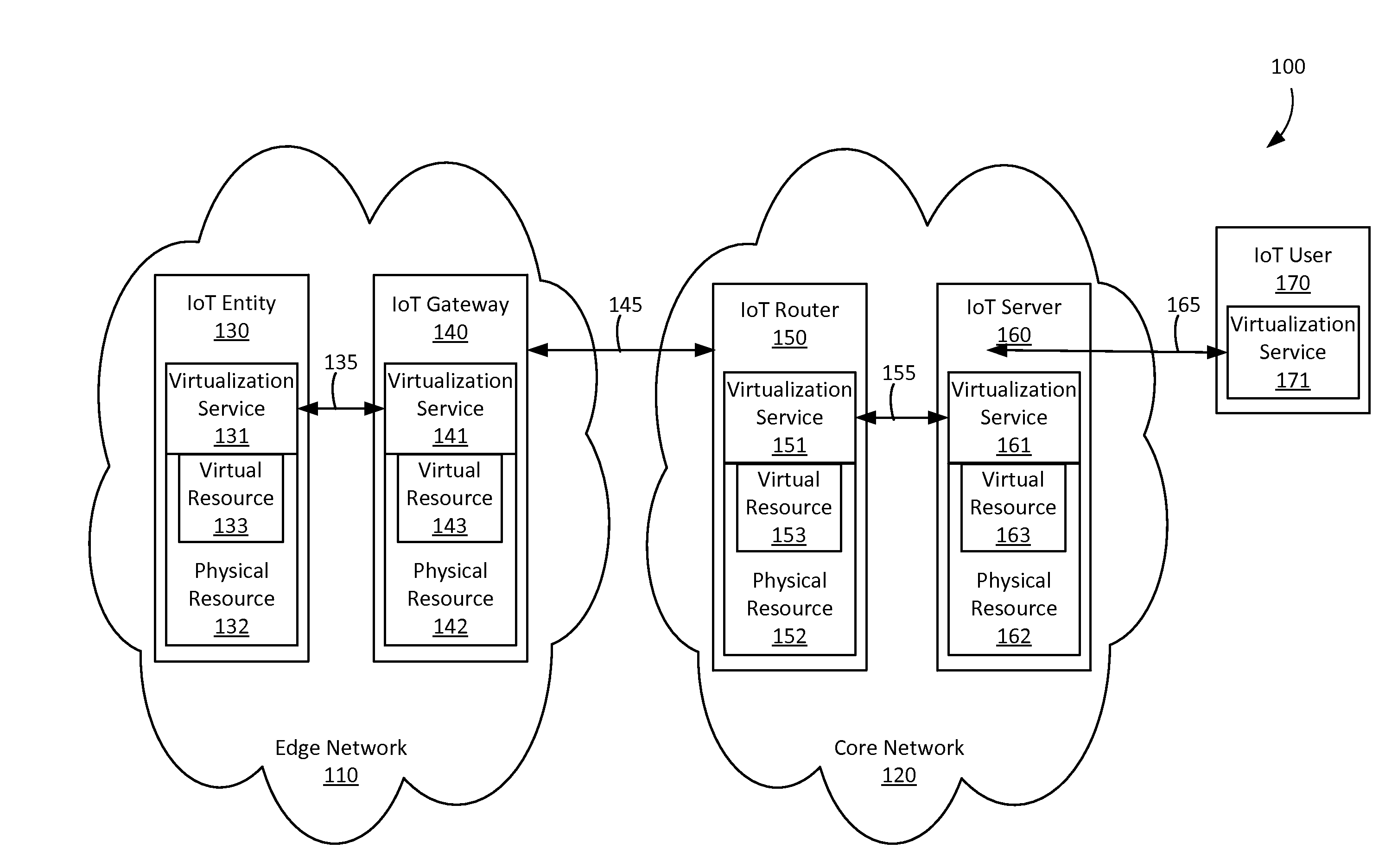
Method and apparatus for the virtualization of resources using a virtualization broker and context information
InactiveUS20160085594A1Well formedResource allocationDigital computer detailsThe InternetData virtualization
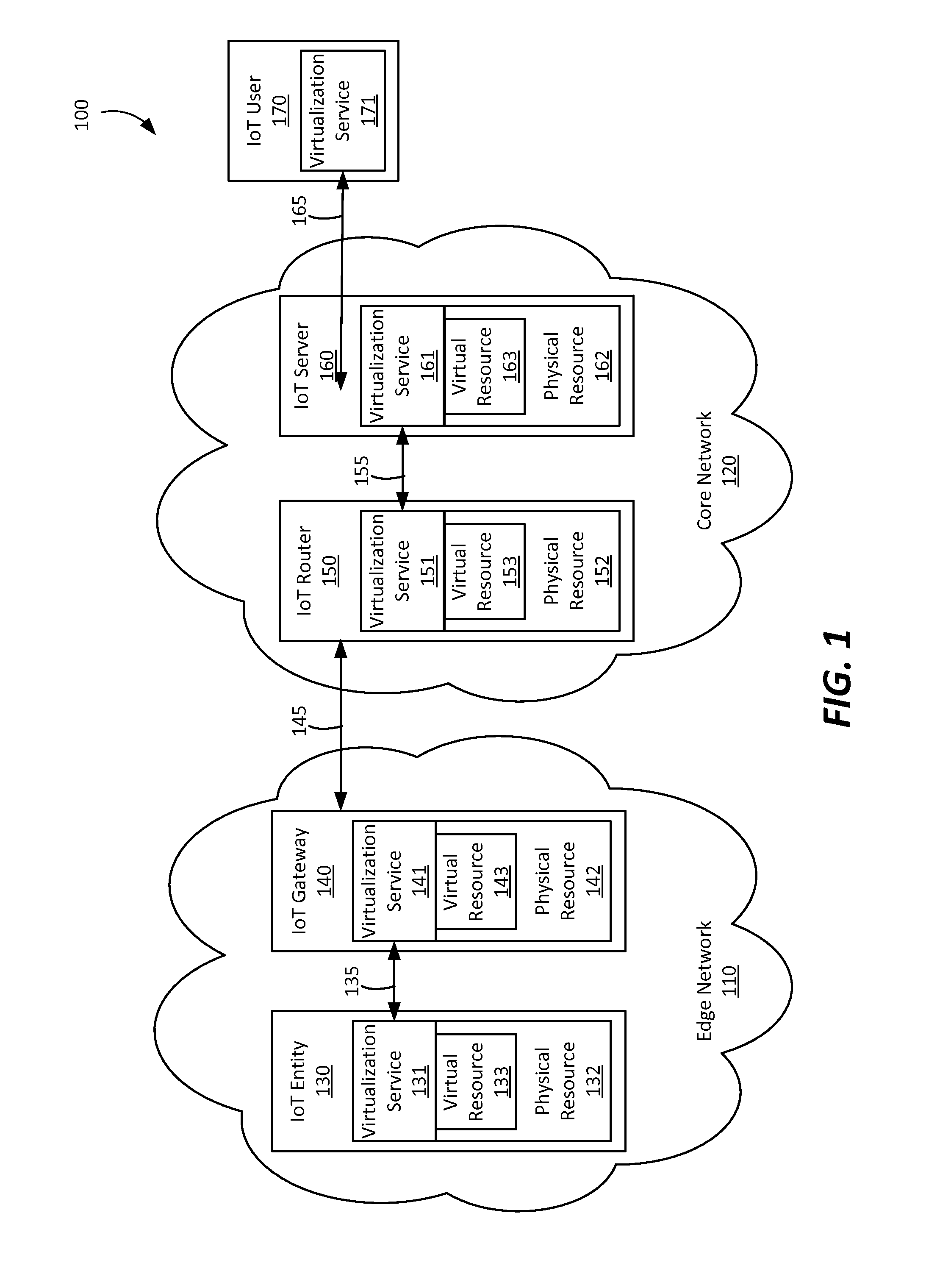
A method and entities for virtualizing resources by receiving a first virtualization request from a first entity at a virtualization broker in a network of connected entities, wherein the first virtualization request comprises context information associated with the first entity, transmitting a request from the virtualization broker to a virtualization manager for a virtualization server identifier, and receiving a virtualization server identifier from the virtualization manager. A second virtualization request may be transmitted to a virtualization server associated with the virtualization server identifier, and a first response may be received from the virtualization server comprising an indication that a resource has been virtualized. A second response comprising the indication from the virtualization broker may be transmitted to the first entity. The method is applied in the context of the Internet of Things (IoT).
Owner:CONVIDA WIRELESS LLC
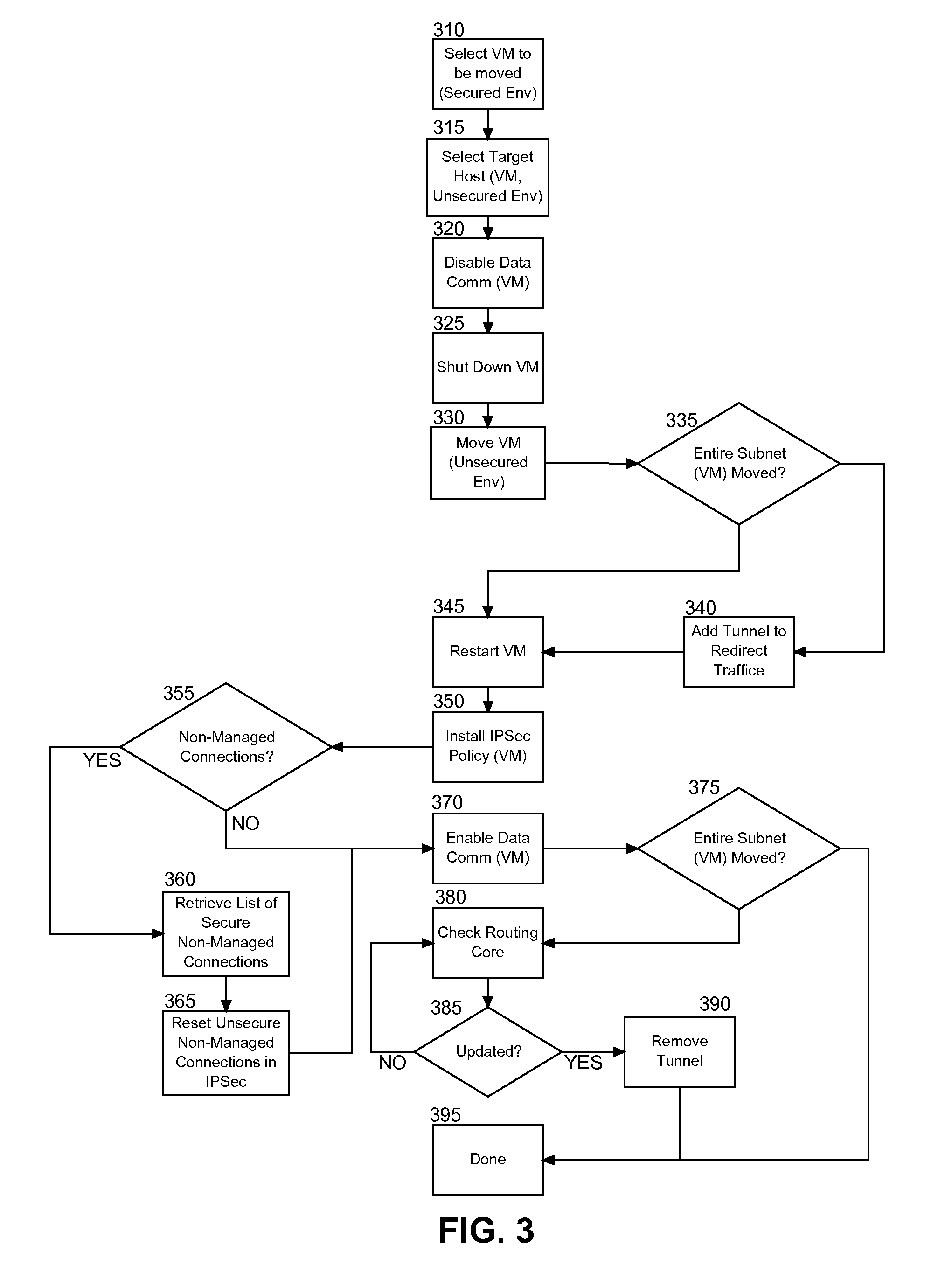
Securing live migration of a virtual machine within a service landscape
ActiveUS20100071025A1Digital data processing detailsMultiple digital computer combinationsVirtual machineLive migration
In an embodiment of the invention, a method for secure live migration of a virtual machine (VM) in a virtualized computing environment can include selecting a VM in a secure virtualized computing environment for live migration to a different virtualized computing environment and blocking data communications with the selected VM and other VMs in the secure virtualized computing environment. The selected VM can be live migrated to the different virtualized computing environment and the VM cna be restarted in the different virtualized computing environment. Notably, a secure communicative link can be established between the restarted VM and at least one other of the VMs in the secure virtualized computing environment. Finally, data communications between the restarted VM and the at least one other of the VMs can be enabled over the secure communicative link.
Owner:IBM CORP
System and method for recoverable mirroring in a storage environment employing asymmetric distributed block virtualization
ActiveUS7340640B1Error detection/correctionMemory systemsTheoretical computer scienceComputerized system
Systems and methods for performing recoverable mirroring in a storage environment employing asymmetrically distributed block virtualization. In one embodiment, the system may include a volume server, a first and a second host computer system, and a plurality of physical block devices. The volume server may be configured to aggregate storage in the plurality of physical block devices into a plurality of logical volumes, where a particular logical volume includes storage from at least two physical block devices, to make a first subset of the logical volumes available to the first host computer system for input / output, and to make a second subset of the logical volumes available to the second host computer system for input / output. The first subset and the second subset may be at least partially nonoverlapping, a given logical volume may be configured as a mirrored logical volume including a plurality of copies of a given data block.
Owner:SYMANTEC OPERATING CORP
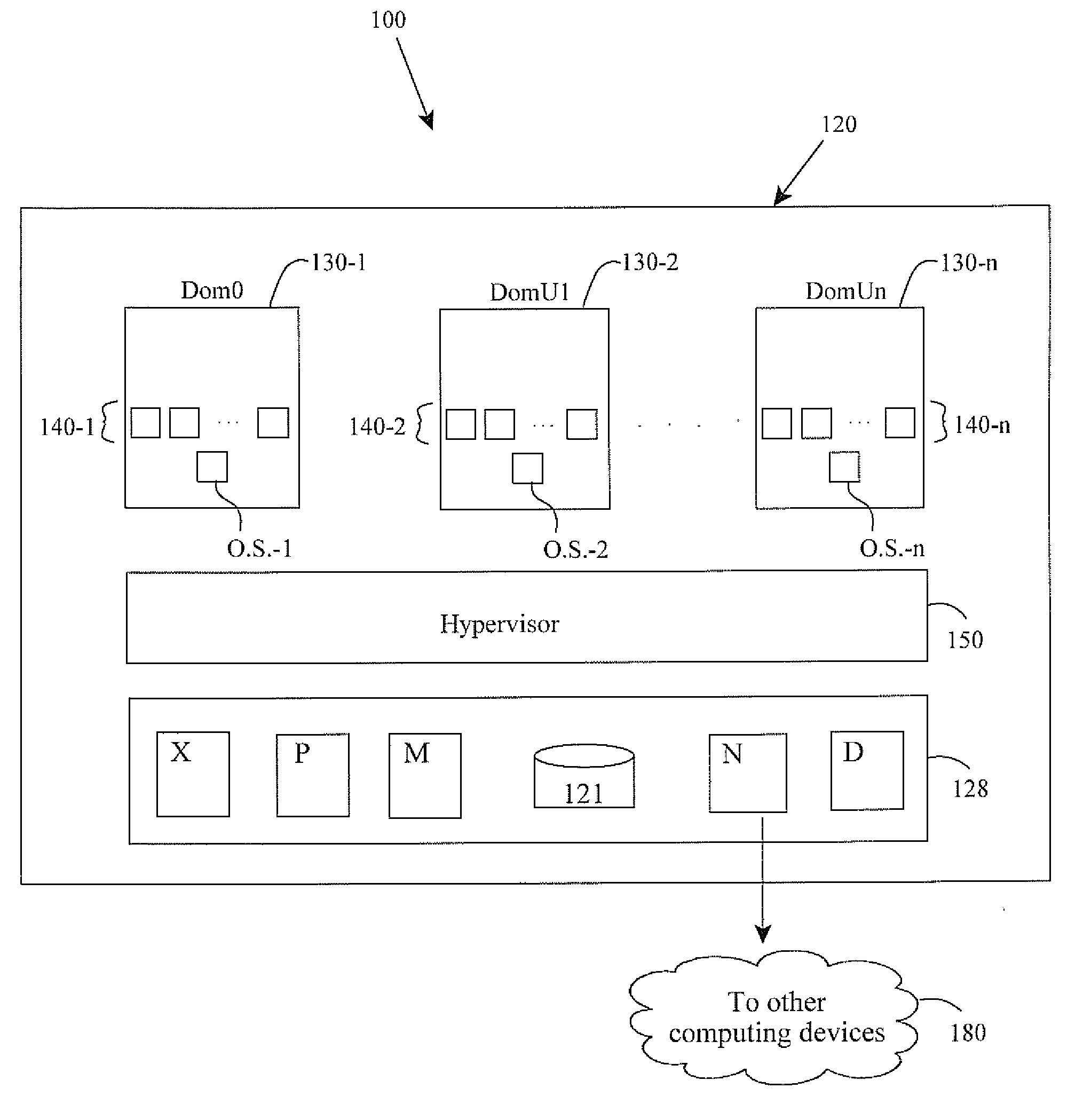
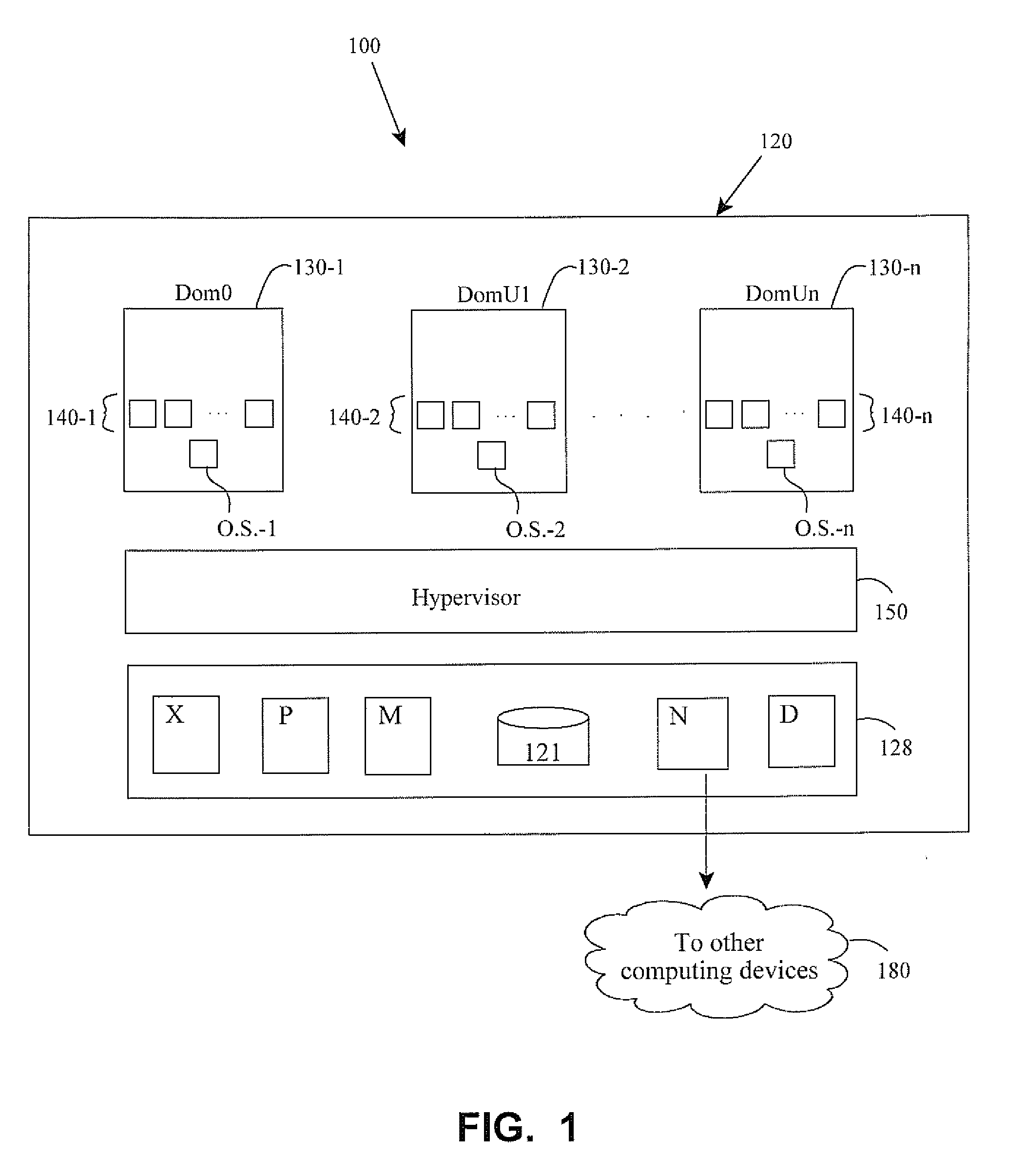
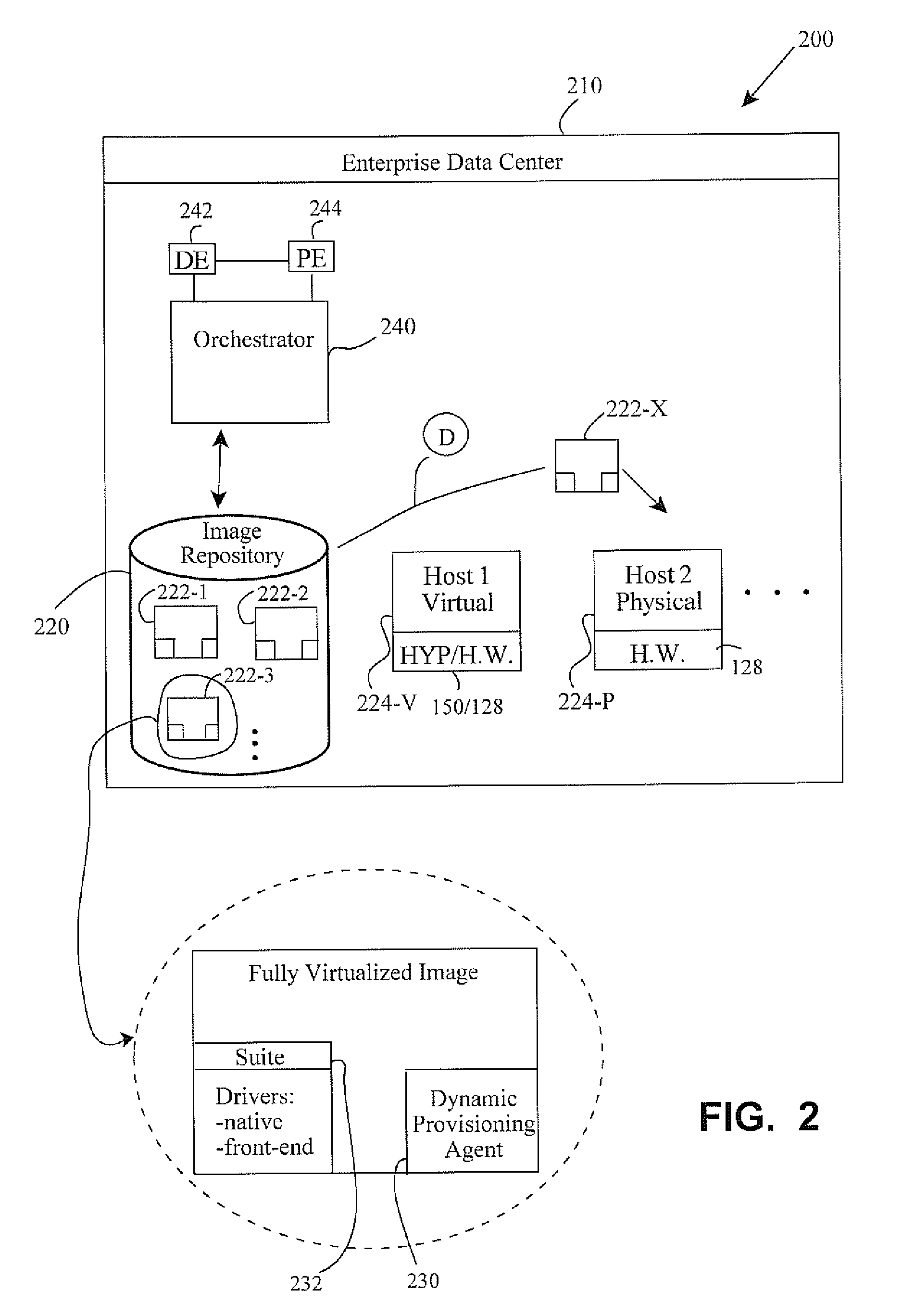
Workload management for heterogeneous hosts in a computing system environment
ActiveUS20110035754A1Improve performanceImprove resource utilizationMultiprogramming arrangementsMemory systemsData centerComputing systems
Methods and apparatus involve managing workload migration to host devices in a data center having heterogeneously arranged computing platforms. Fully virtualized images include drivers compatible with varieties of host devices. The images also include an agent that detects a platform type of a specific host device upon deployment. If the specific host is a physical platform type, the agent provisions native drivers. If the specific host is a virtual platform type, the agent also detects a hypervisor. The agent then provisions front-end drivers that are most compatible with the detected hypervisor. Upon decommissioning of the image, the image is returned to its pristine state and saved for later re-use. In other embodiments, detection methods of the agent are disclosed as are computing systems, data centers, and computer program products, to name a few.
Owner:SUSE LLC
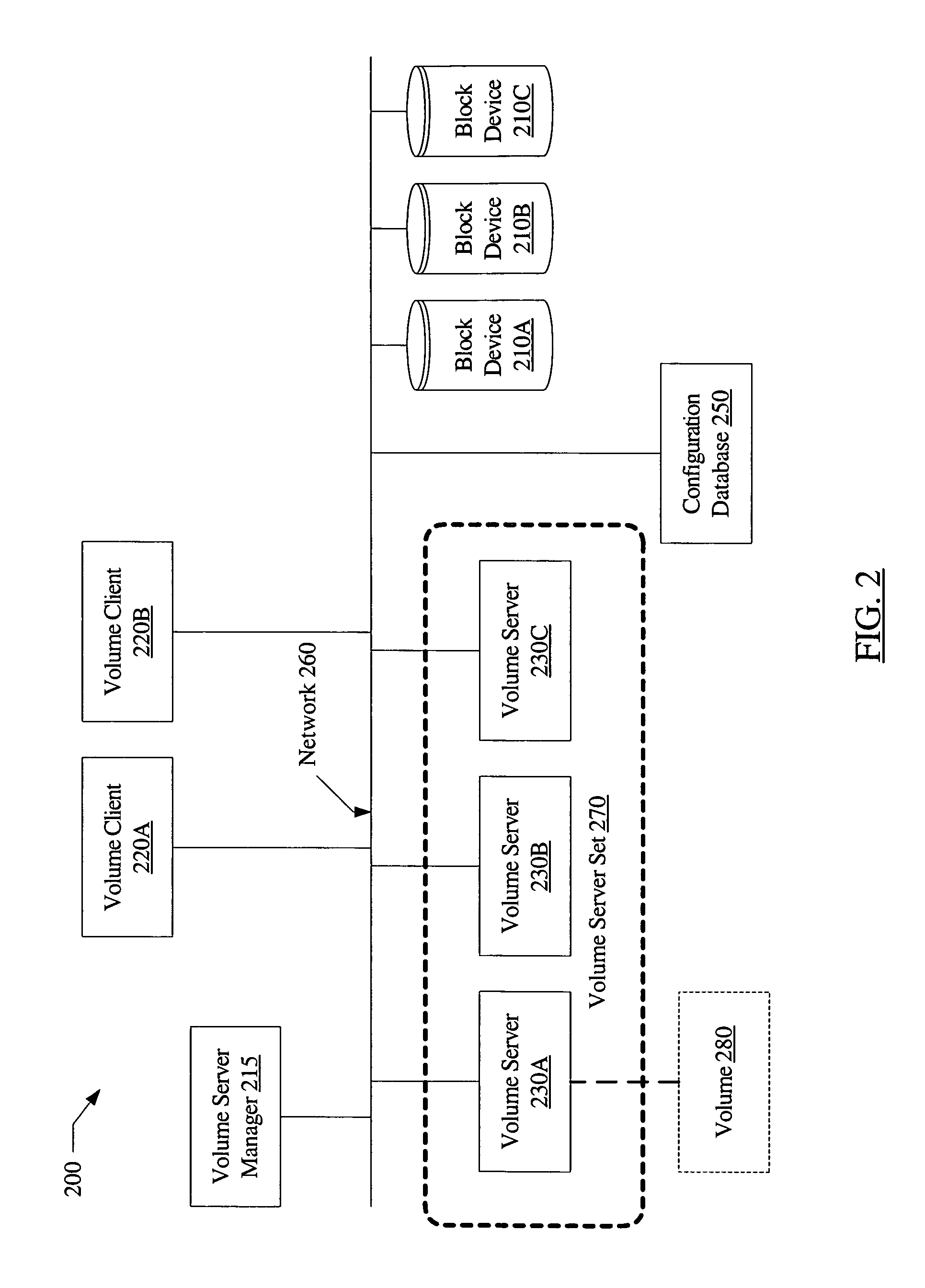
System and method for providing availability using volume server sets in a storage environment employing distributed block virtualization
A system for ensuring availability using volume server sets in a storage environment employing distributed block virtualization includes a plurality of volume servers, one or more volume clients, one or more physical block devices and a volume server manager. The volume server manager may be configured to designate the plurality of volume servers as a volume server set with an associated volume server set management policy, and to verify each volume server in the volume server set has access to storage within each block device. In addition, the volume server manager may be configured to designate a first volume server of the volume server set to aggregate storage within the block devices into a logical volume, to make the logical volume accessible to the volume clients, and to share configuration information about the volume with the other volume servers of the volume server set.
Owner:SYMANTEC OPERATING CORP
System and method for performing snapshots in a storage environment employing distributed block virtualization
Systems and methods for performing snapshots in a storage environment employing distributed block virtualization. In one embodiment, the system may include a volume server, a first and a second host computer system, and a plurality of physical block devices. The volume server may be configured to aggregate storage in the plurality of physical block devices into a plurality of logical volumes, where a particular logical volume includes storage from at least two physical block devices. The volume server may further be configured to make a first and a second subset of the logical volumes available to the first and second host computer systems for input / output, respectively. The first subset and the second subset may be at least partially nonoverlapping, and a second logical volume may be configured to store a snapshot of data stored in a first logical volume logical volume.
Owner:SYMANTEC OPERATING CORP
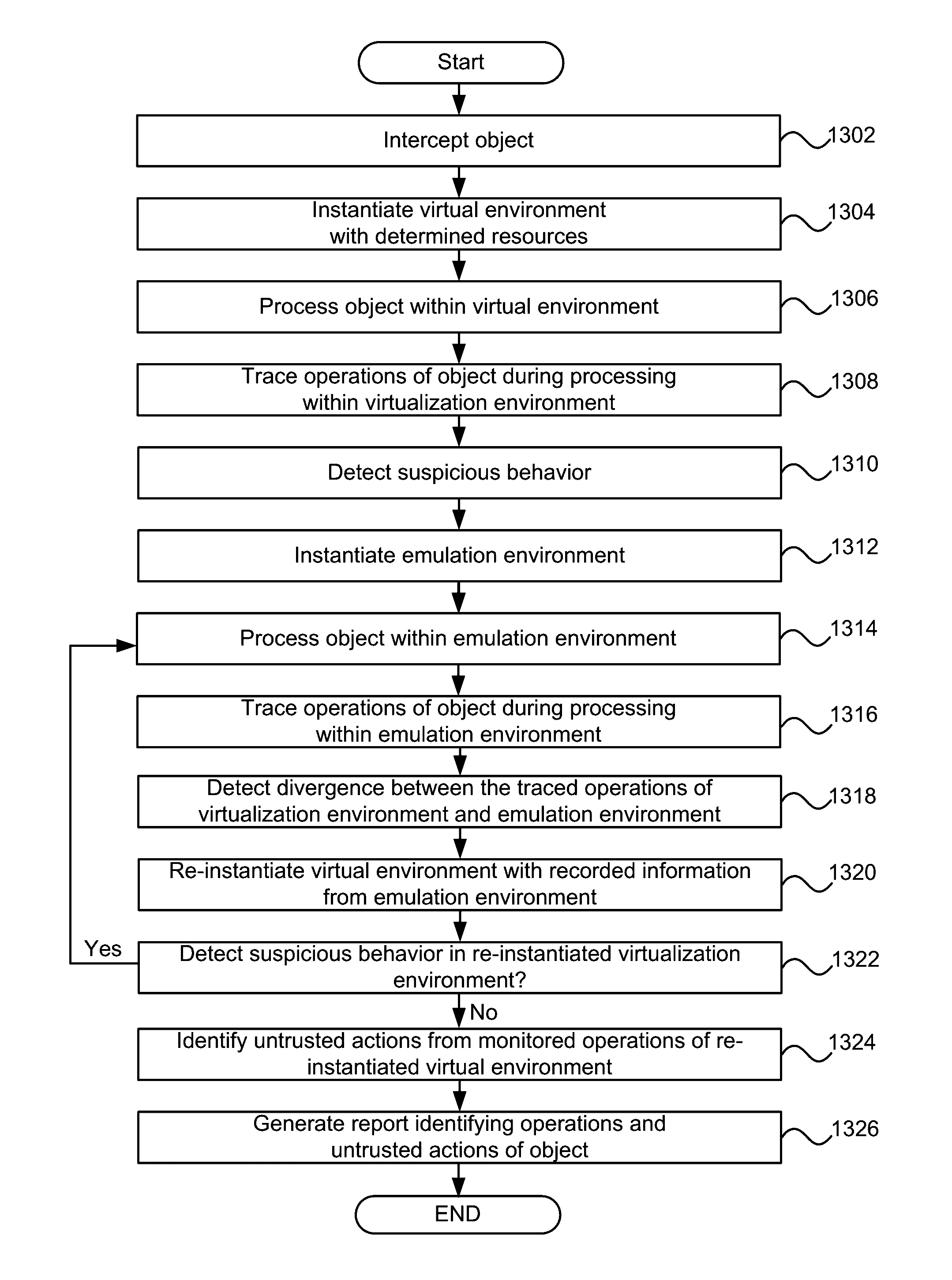
Systems and methods for virtualization and emulation assisted malware detection
Systems and methods for virtualization and emulation assisted malware detection are described. In some embodiments, a method comprises intercepting an object; instantiating and processing the object in a virtualization environment; tracing operations of the object while processing within the virtualization environment; detecting suspicious behavior associated with the object; instantiating an emulation environment in response to the detected suspicious behavior; processing, recording responses to, and tracing operations of the object within the emulation environment; detecting a divergence between the traced operations of the object within the virtualization environment to the traced operations of the object within the emulation environment; re-instantiating the virtualization environment; providing the recorded response from the emulation environment to the object in the virtualization environment; monitoring the operations of the object within the re-instantiation of the virtualization environment; identifying untrusted actions from the monitored operations; and generating a report regarding the identified untrusted actions of the object.
Owner:CYPHORT
Malware protection using file input/output virtualization
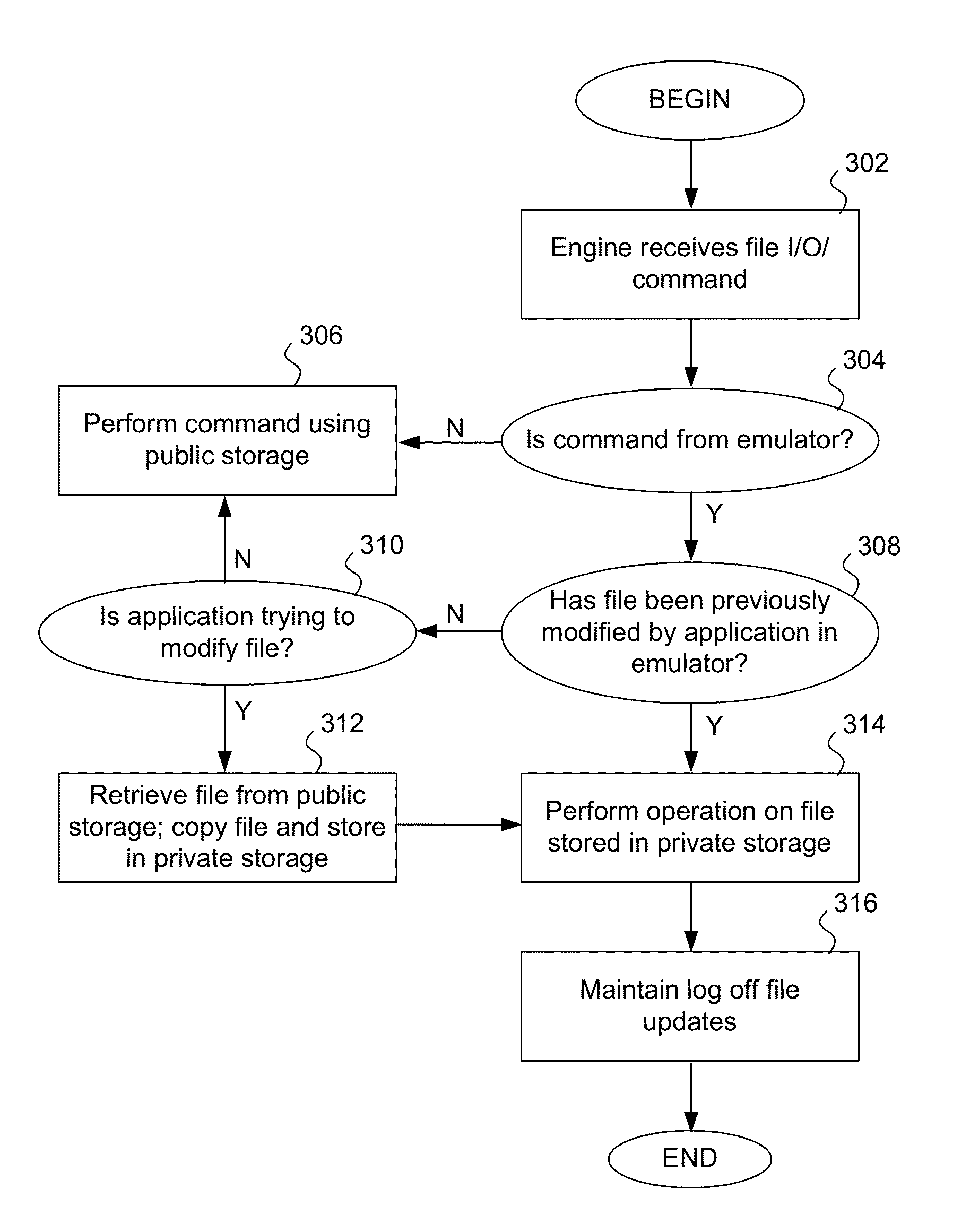
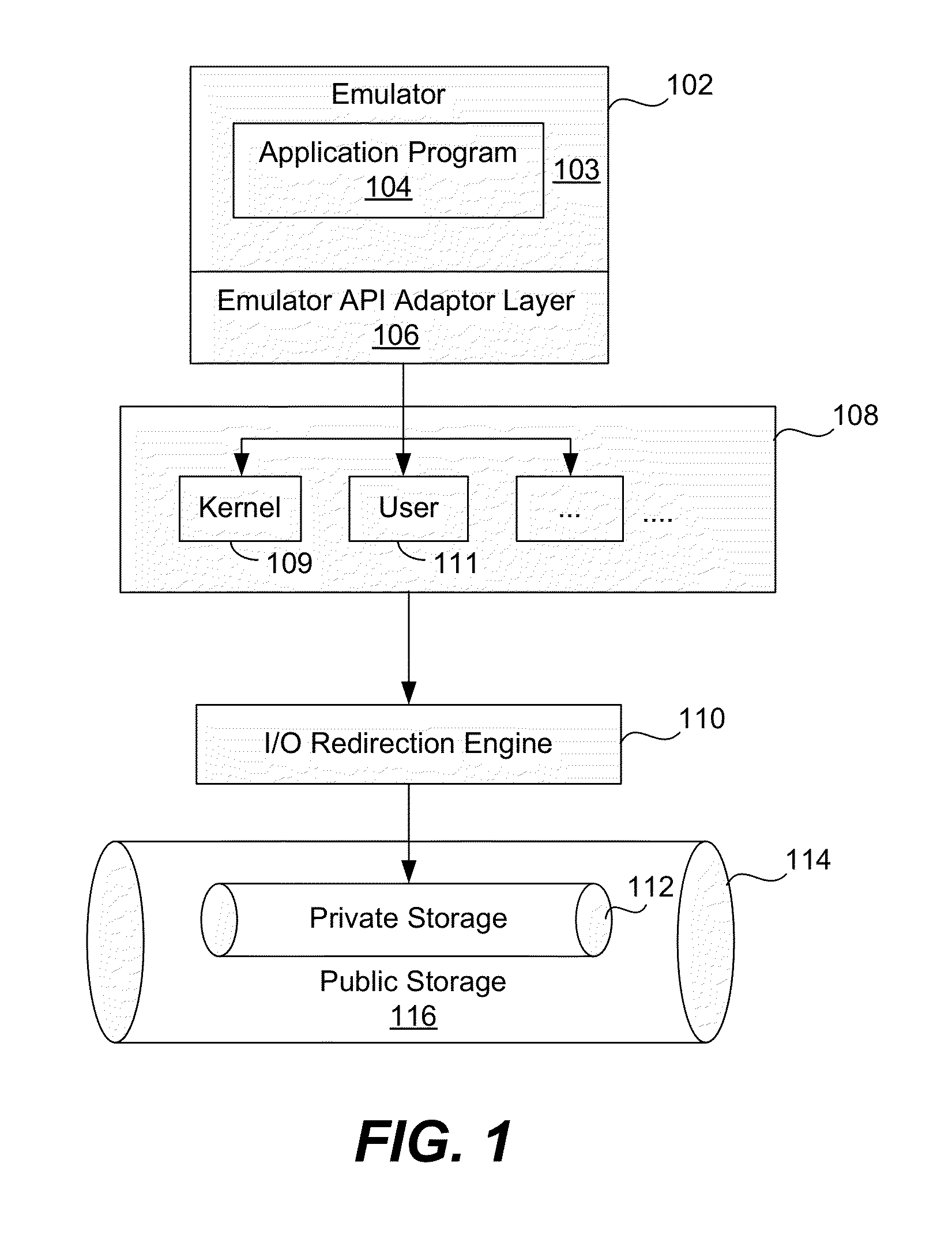
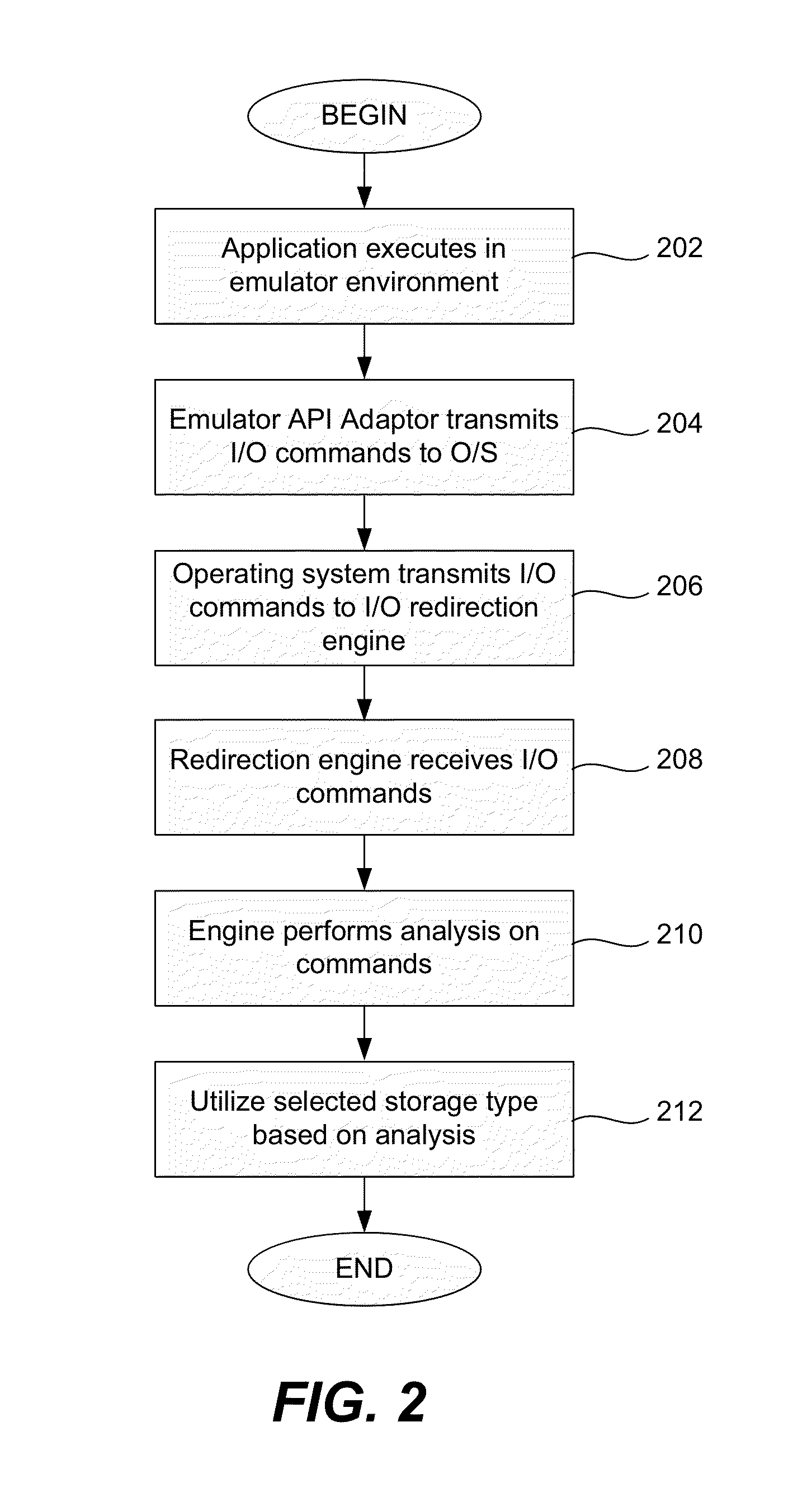
Applications running in an API-proxy-based emulator are prevented from infecting a PC's hard disk when executing file I / O commands. Such commands are redirected to an I / O redirection engine instead of going directly to the PC's normal operating system where it can potentially harm files in on the hard disk. The redirection engine executes the file I / O command using a private storage area in the hard disk that is not accessible by the PC's normal operating system. If a file that is the subject of a file I / O command from an emulated application is not in the private storage area, a copy is made from the original that is presumed to exist in the public storage area. This copy is then acted on by the command and is stored in the private storage area, which can be described as a controlled, quarantined storage space on the hard disk. In this manner the PC's (or any computing device's) hard disk is defended from potential malware that may originate from applications running in emulated environments.
Owner:TREND MICRO INC
Multi-root sharing of single-root input/output virtualization
In a first embodiment of the present invention, a method for multi-root sharing of a plurality of single root input / output virtualization (SR-IOV) endpoints is provided, the method comprising: CSR redirection to a management processor which either acts as a proxy to execute the CSR request on behalf of the host or filters it and performs an alternate action, downstream routing of memory mapped I / O request packets through the switch in the host's address space and address translation with VF BAR granularity, upstream routing of requests originated by I / O devices by table lookup indexed by Requester ID, and requester ID translation using a fixed local-global RID offset.
Owner:AVAGO TECH INT SALES PTE LTD
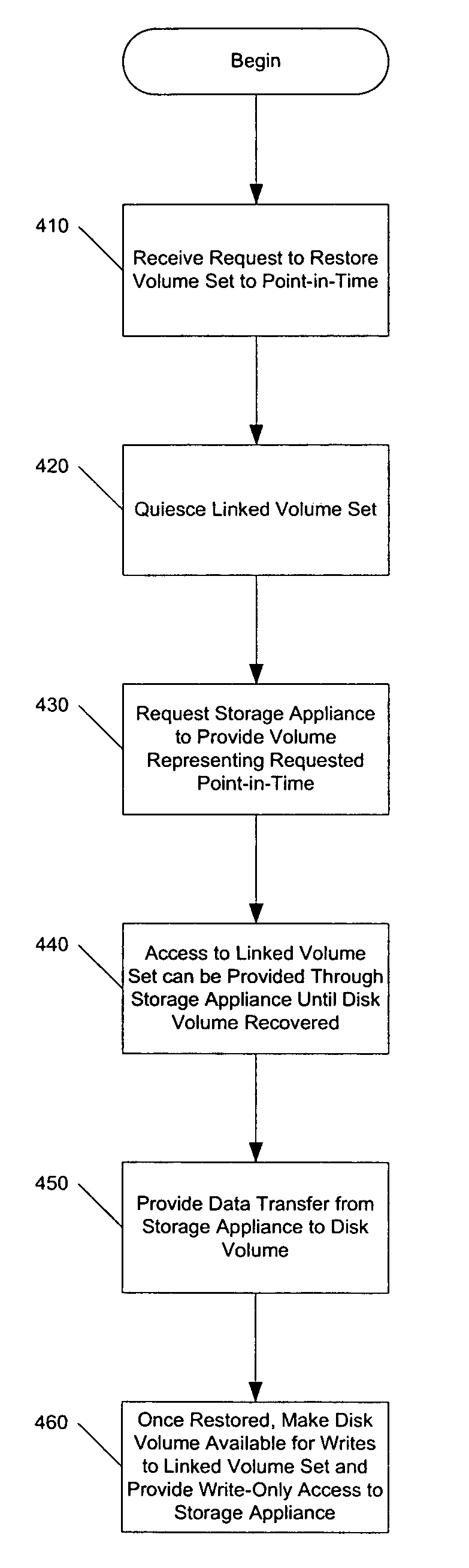
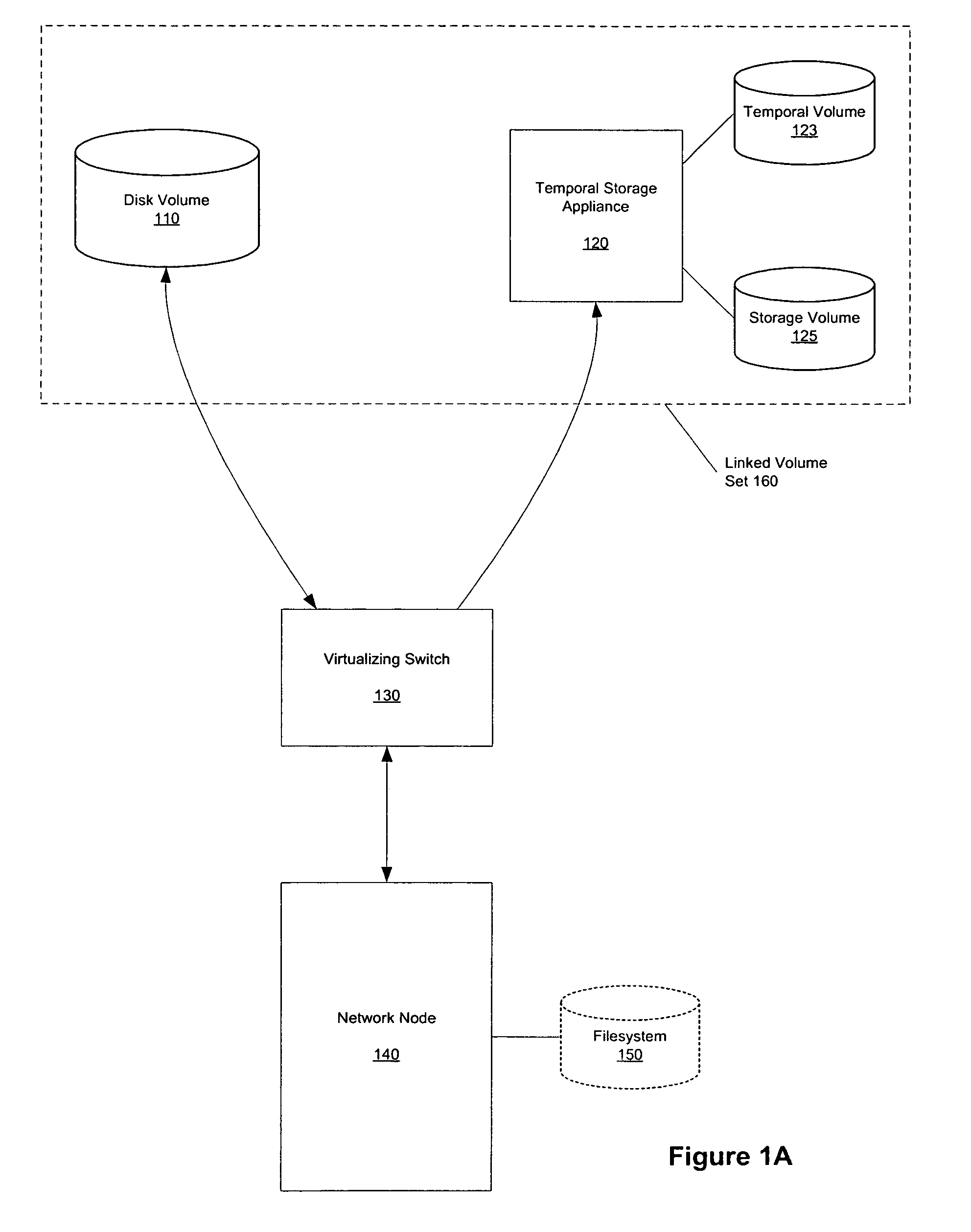
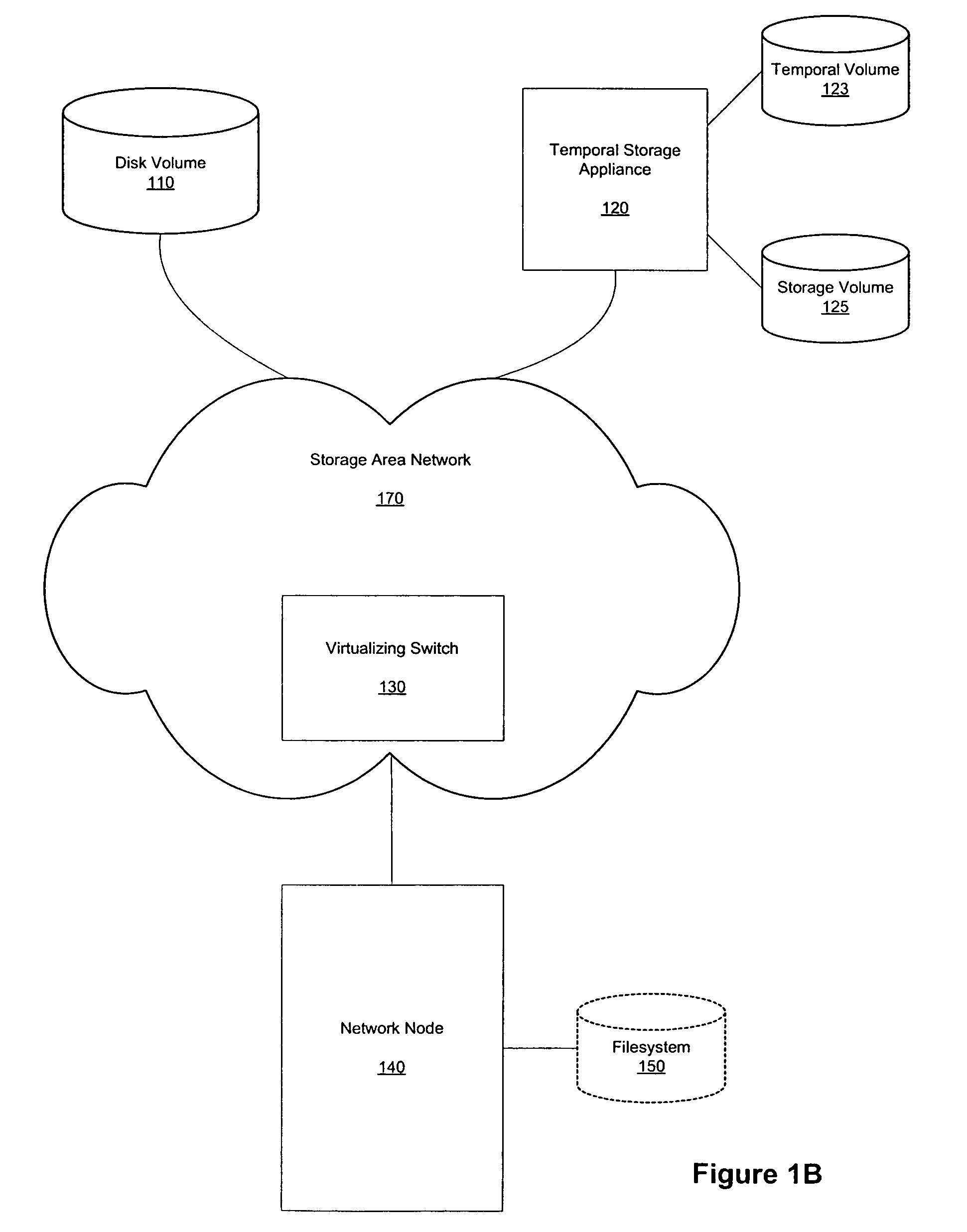
Method and apparatus for providing a temporal storage appliance with block virtualization in storage networks
ActiveUS7409495B1Data processing applicationsMemory loss protectionStorage area networkStructure based
Methods, systems, and computer program products to provide temporal storage in a fabric-based virtualization environment are presented. Such capacity is provided through the association of a temporal storage appliance, which is configured as a member of a linked VLUN with a non-temporal disk volume. The linked VLUN is provided by a virtualizing fabric switch to a network node such as a network node.
Owner:SYMANTEC OPERATING CORP
College experiment teaching platform system based on cloud desktop and constructing method thereof
InactiveCN103841207AResolutionFix security issuesTransmissionElectrical appliancesOpen sourceResource management
The invention provides a college experiment teaching platform system based on a cloud desktop and a constructing method of the college experiment teaching platform system. A physical server subsystem is constructed through a physical server supporting the Intel VT-x, VT-d, and EPT technology or the AMD-v and IOMMU technology; a virtual machine set subsystem is constructed through a KVM and the like in the expanded full virtualization technology; an MVC framework is used for developing a Web management interface and a virtual resource management subsystem and an experiment teaching management subsystem are constructed; a cloud desktop experiment teaching subsystem is constructed through an open source remote desktop protocol. According to the college experiment teaching platform system based on the cloud desktop, the difficult problems that college experiment teaching platform resources are short currently and management is disorderly are solved, the college experiment teaching cost is reduced, and the experiment teaching level and the experiment teaching efficiency are improved.
Owner:SHANGHAI DIANJI UNIV
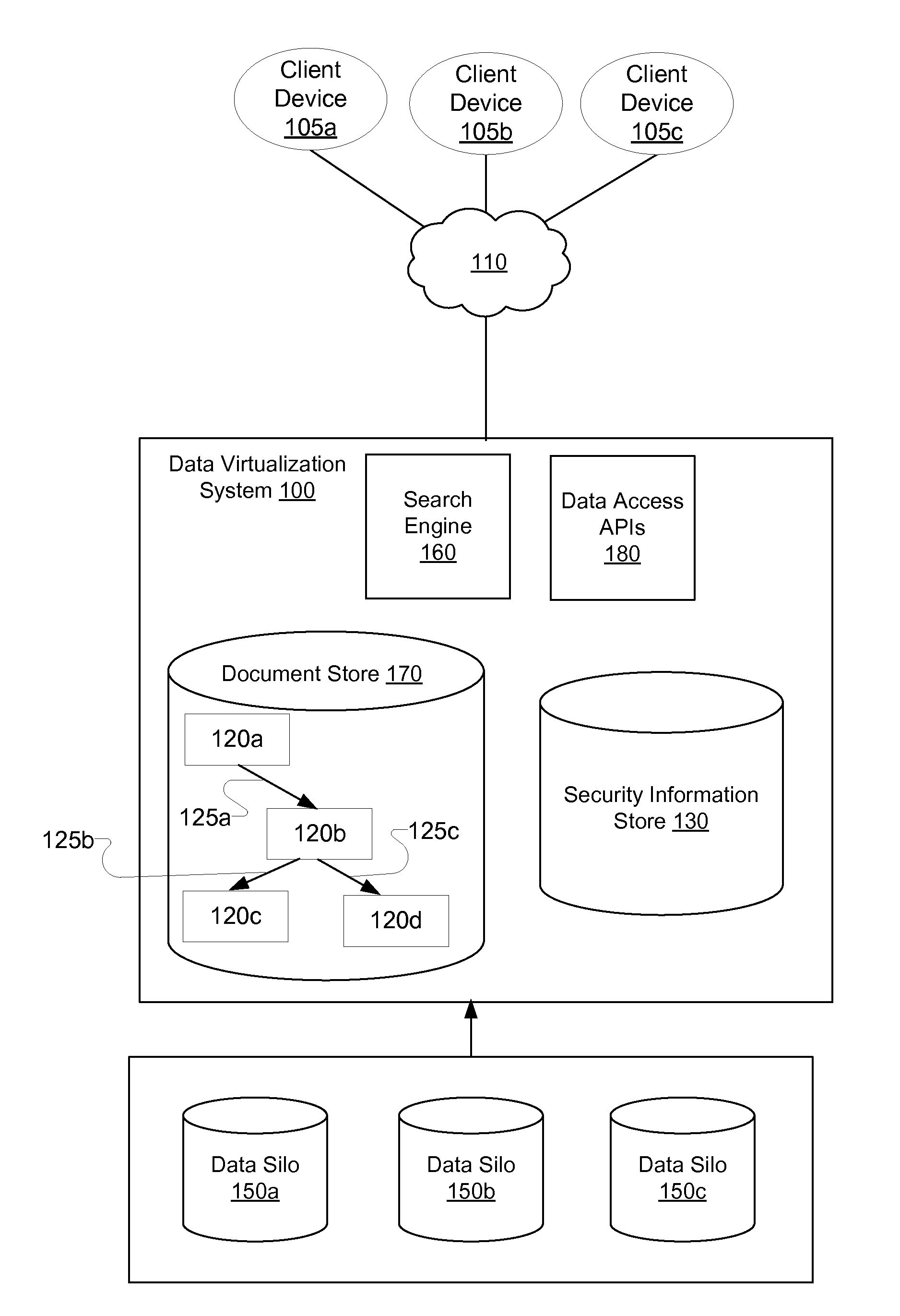
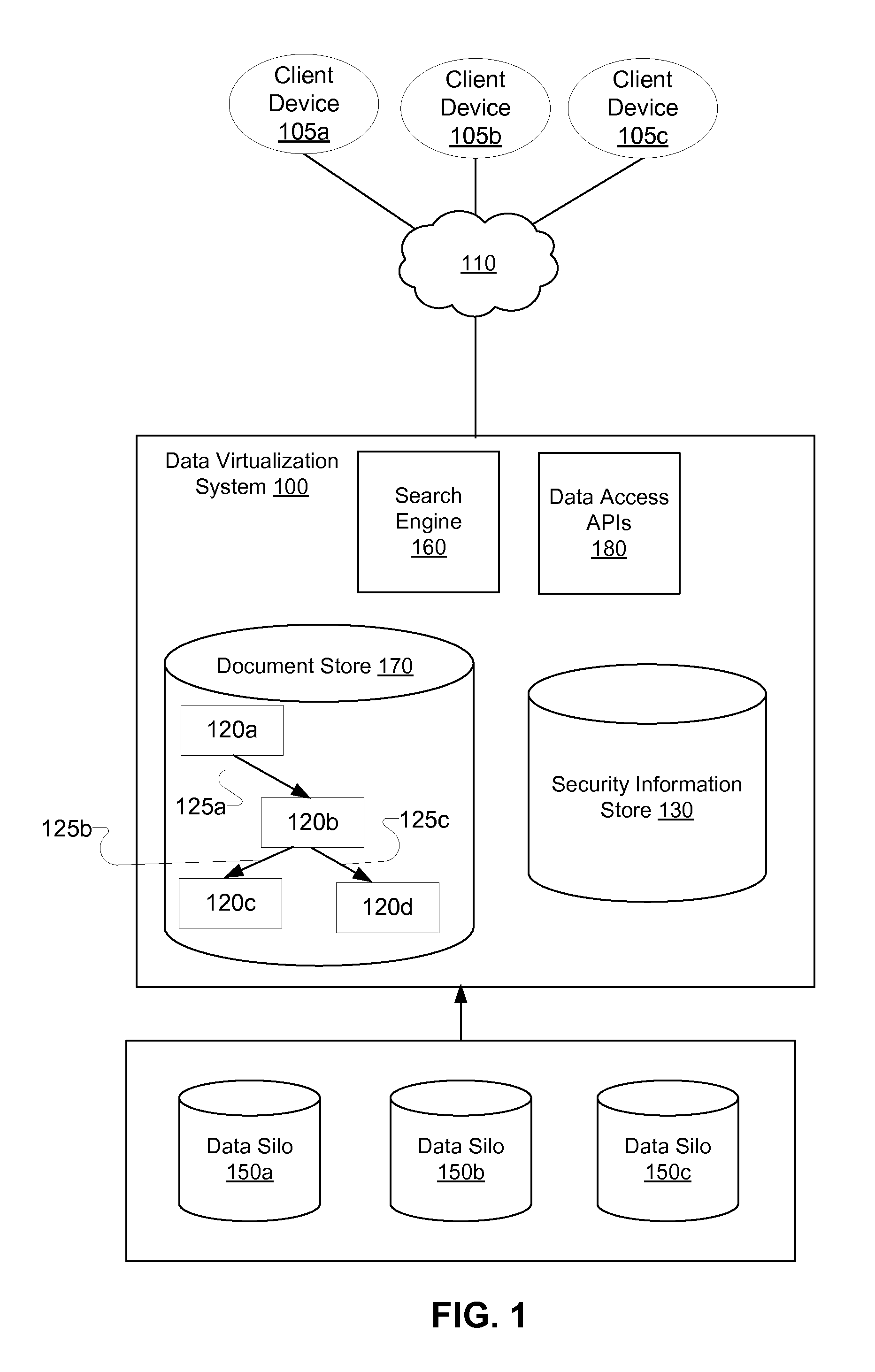
Security management for data virtualization system
InactiveUS20100198804A1Digital data processing detailsComputer security arrangementsEntity typeIslanding
Methods and systems allow access to information in an enterprise environment that stores information in data silos. Entity type metadata, relations between entity types and access control information is extracted from the data silos and represented in a data virtualization system. Metadata information representing security information extracted from multiple data silos is combined to construct global security information for the enterprise. Security roles are combined to generate global security roles and access control lists are combined to generate globalized access control lists. The global security information can be modified by system administrators. Security information is refreshed from the data silos for each session created by the user and is applied to all data access requests created using the session.
Owner:QUEPLIX CORP
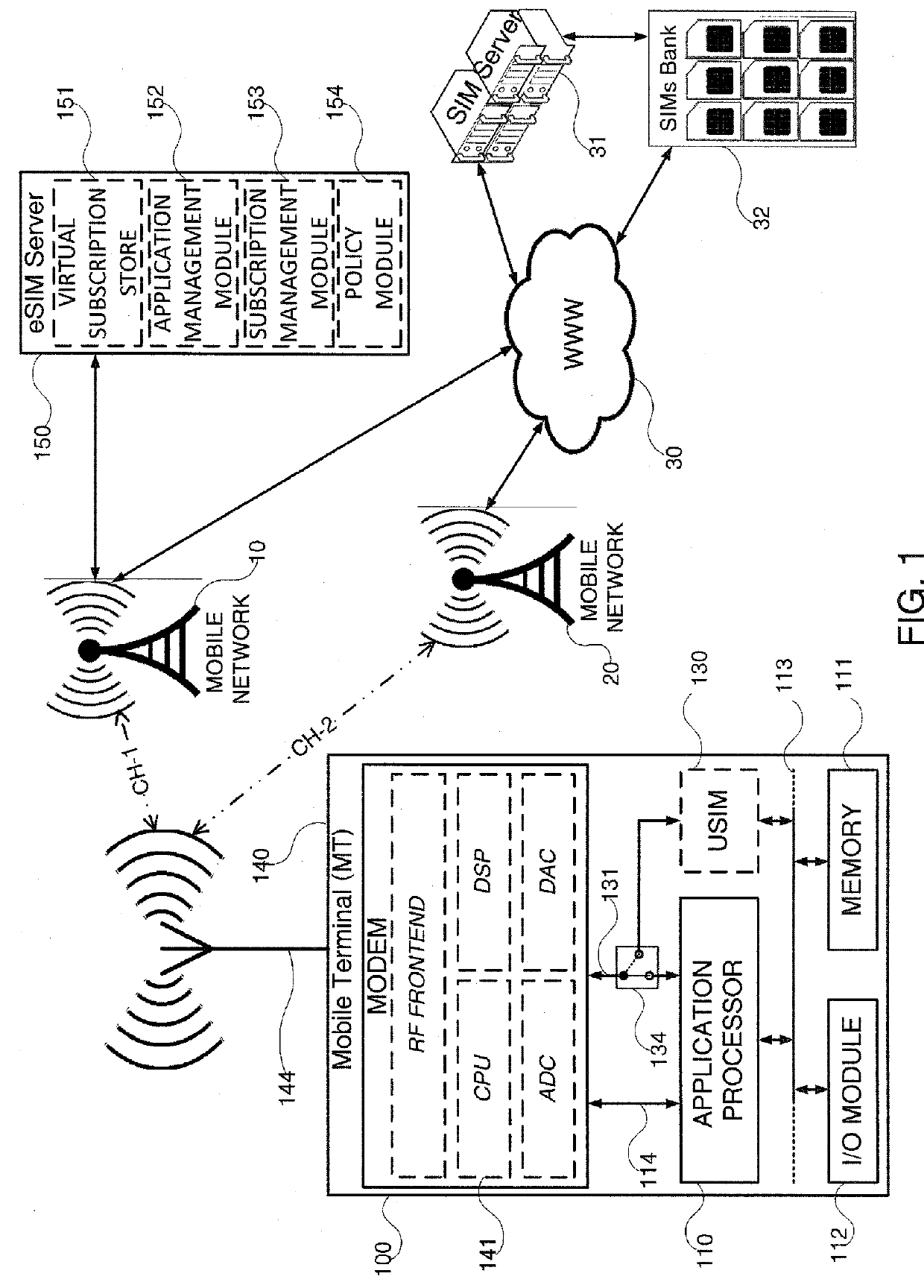
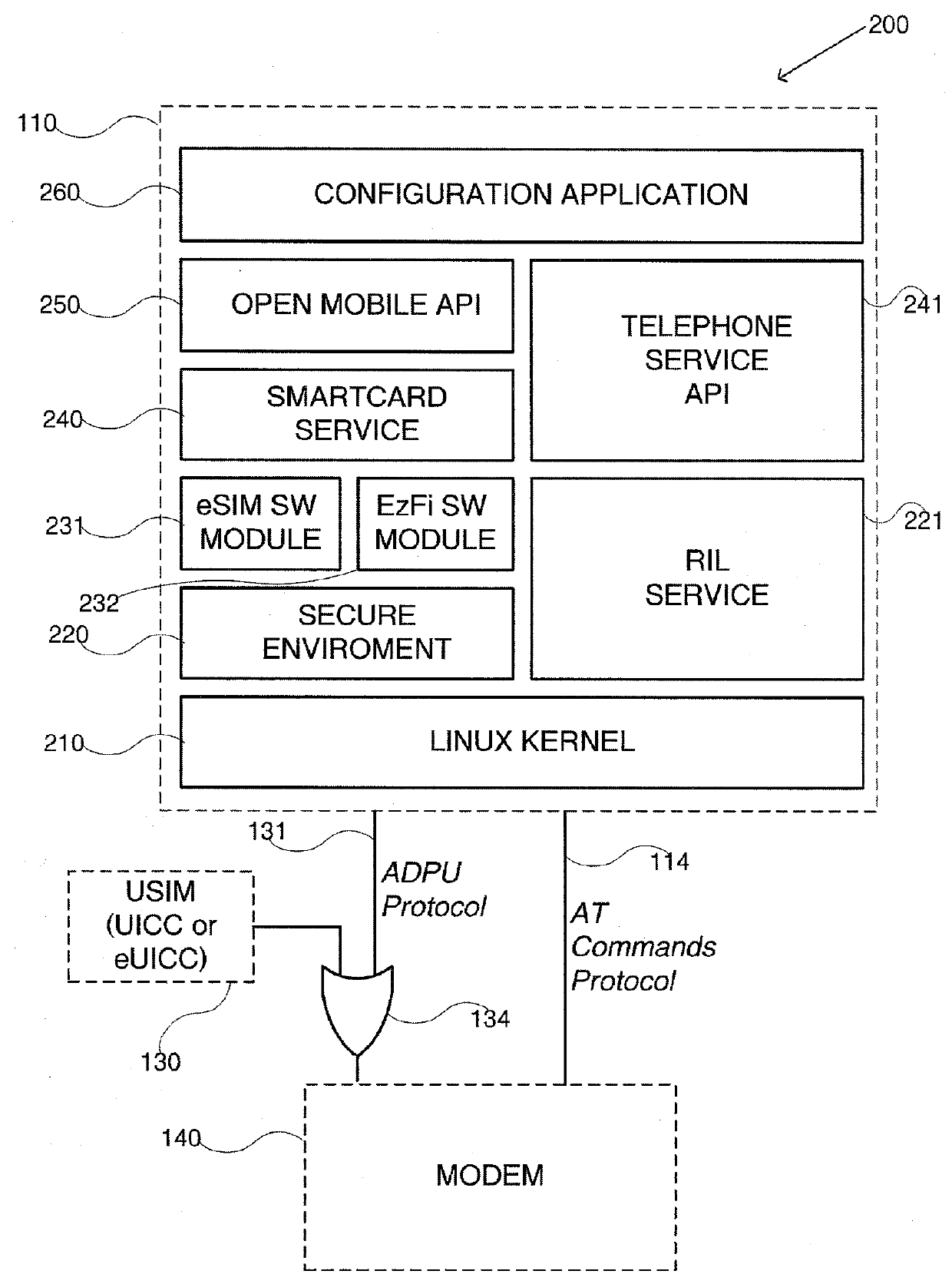
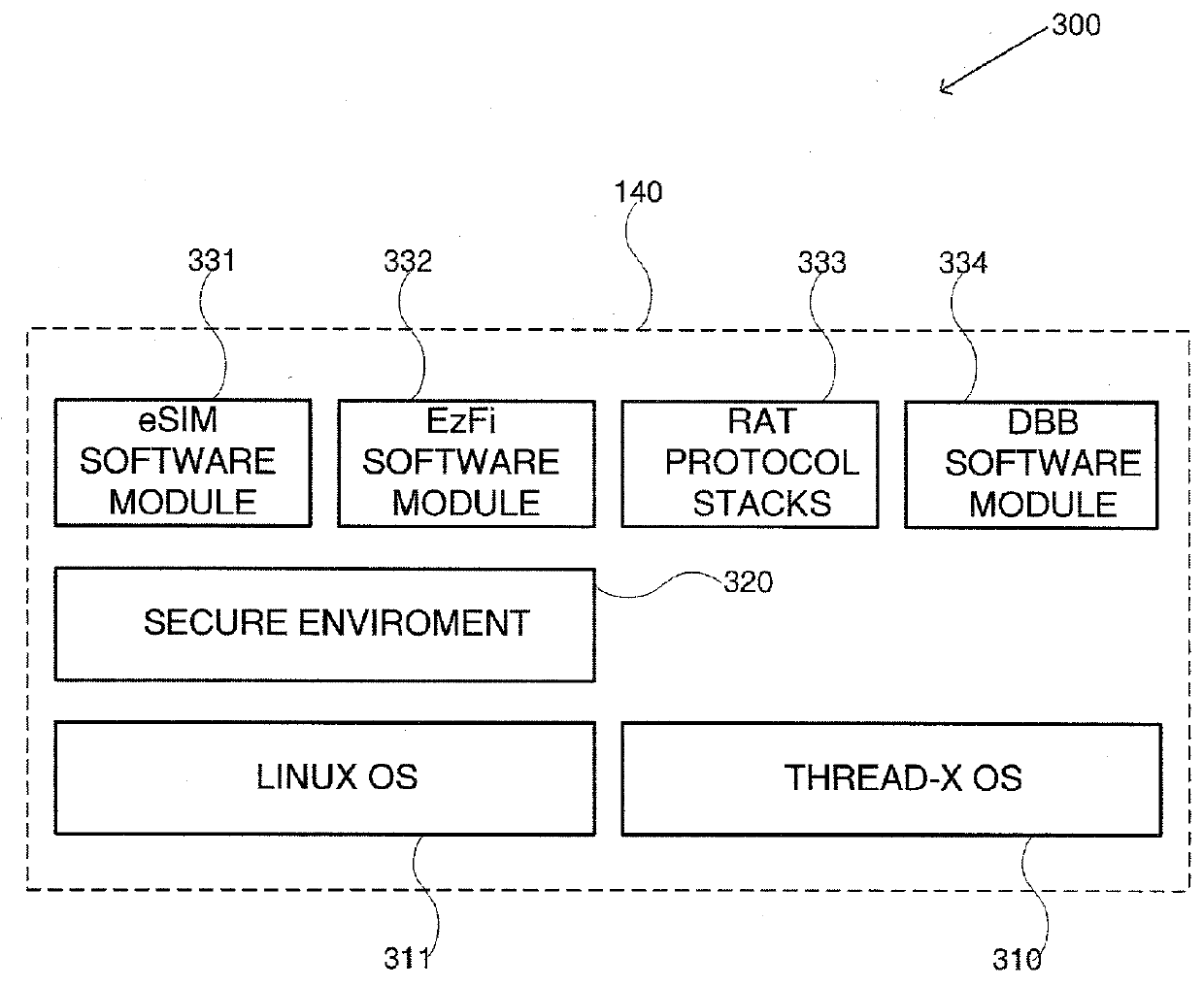
System and method for sim virtualization of sim and sim-less mobile terminals
According to a first aspect of the present disclosed subject matter, a SIM virtualization system, having servers selected from a group comprising of: eSIM server; SIM server; SIMs bank; and any combination thereof, the system comprising: a SIM-Less mobile terminal having hardware configuration selected from a group comprising of: first configuration; second configuration; and a combination thereof, the SIM-Less mobile terminal comprising: a processor configured to execute SIM virtualization functionalities; a single cellular modem capable of communicating over CH-1 and CH-2 with at least one cellular network; and a non-transitory memory capable of retaining: at least one native SIM profile used by the mobile terminal for emulating a SIM selected from a group comprising of: a universal integrated circuit card (UICC); embedded UICC (eUICC); and a combination thereof; at least one virtual SIM profile; and software stack operative to cause the mobile terminal to obtain and authenticate the at least one virtual SIM profile; and wherein the virtual SIM profile is obtained from servers selected from a group comprising of: a SIM server coupled with a SIM bank; eSIM server; and a combination thereof.
Owner:LIPOVKOV DAVID
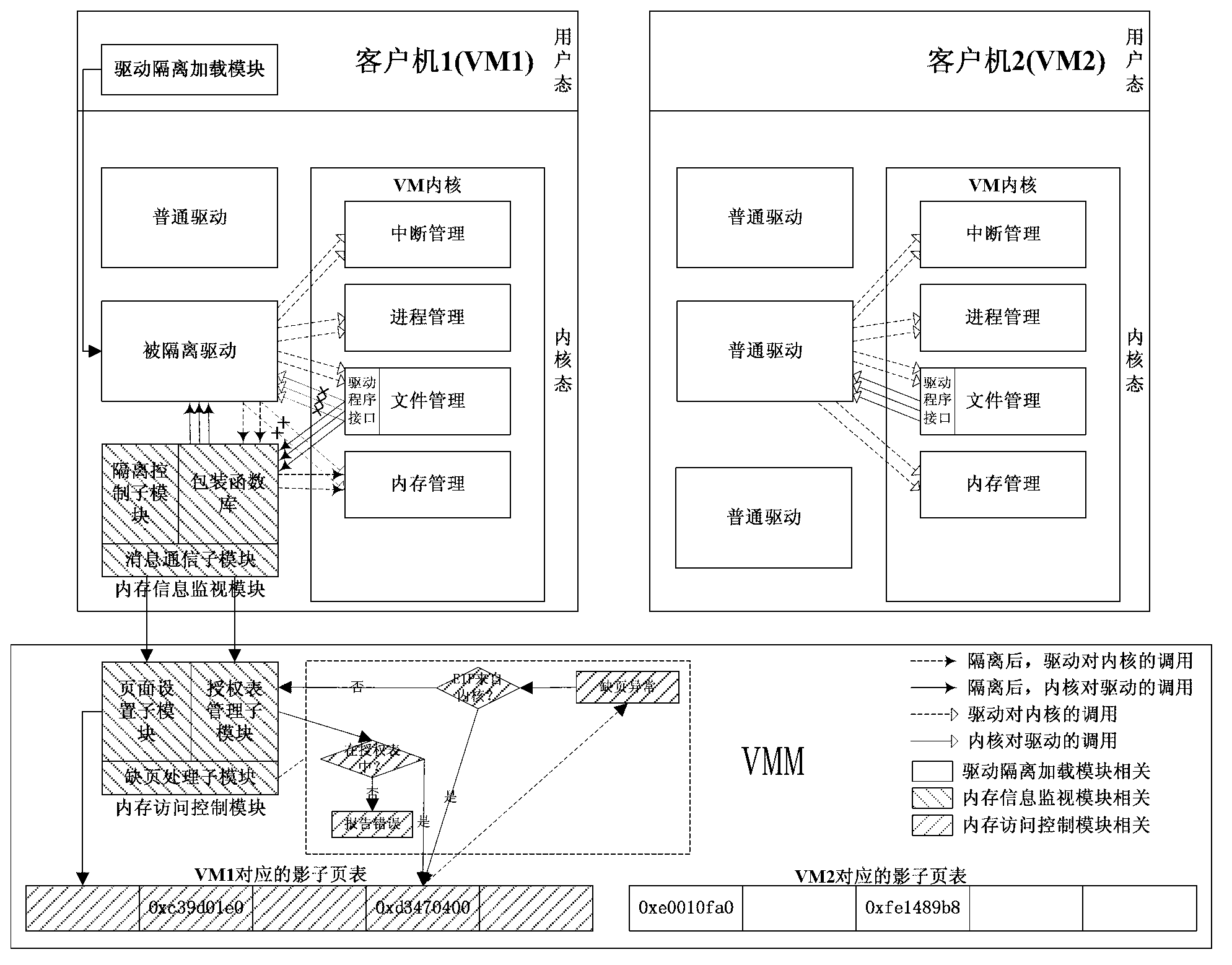
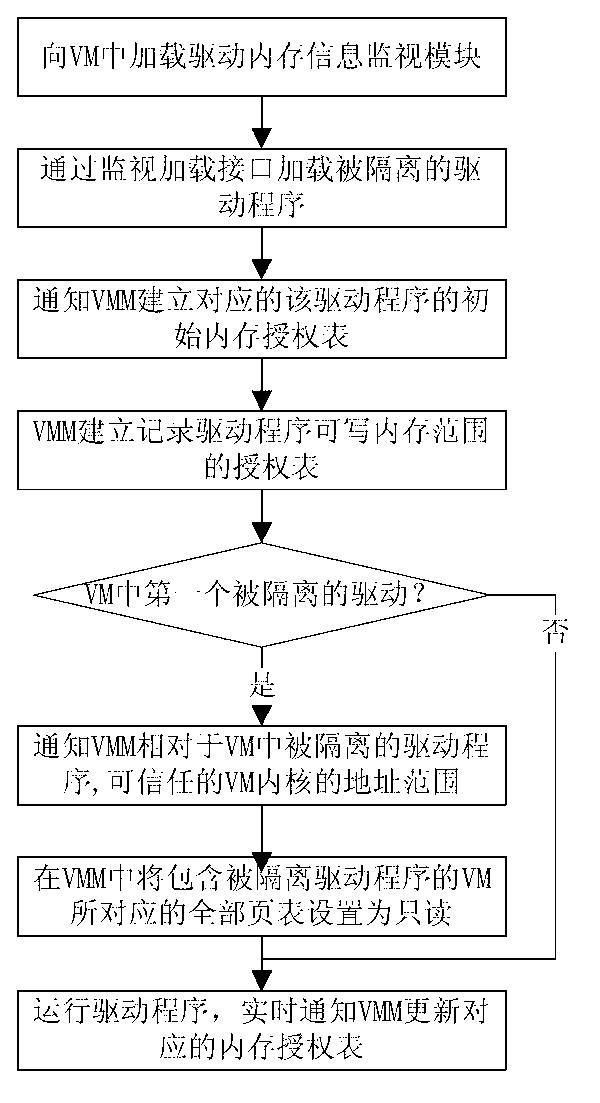
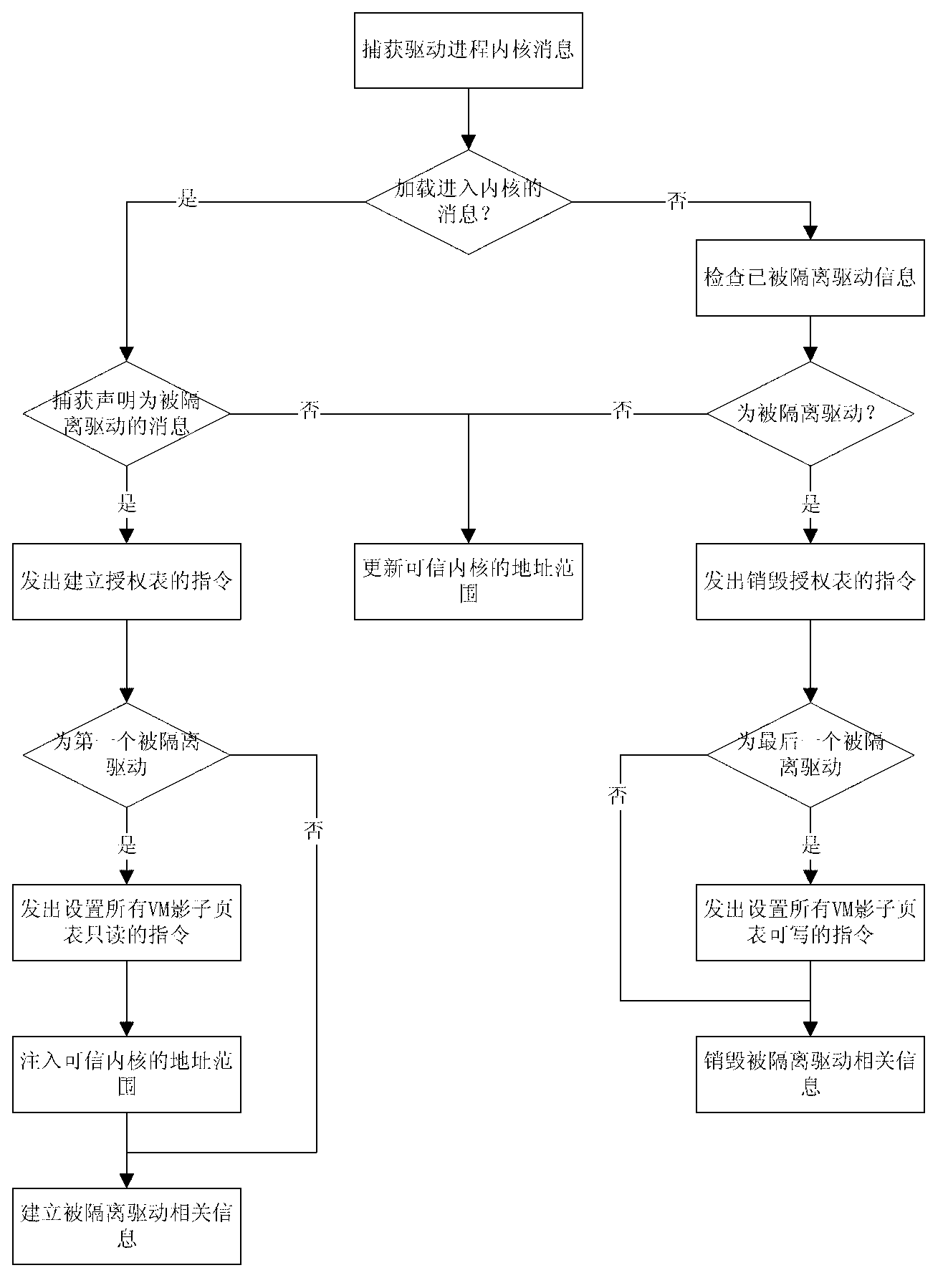
Driving separation system inside virtual machine and method
InactiveCN102938035AGuaranteed CompatibilityReal-time acquisition of memory usagePlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer moduleEngineering
The invention discloses a driving separation system inside a virtual machine and a method and relates to a computer fault tolerant technology. The system, which is simple, effective and capable of being compatible with existing operation systems and a driving program framework and isolating a driving program inside the virtual machine based on a full virtualization technology, is achieved, the driving program isolating system inside the virtual machine comprises a driving isolation uploading module which runs in a user mode of the virtual machine, a memory information monitoring module in a kernel mode of the virtual machine and a memory access control module inside a manger of the virtual machine, and memory information monitoring module in the kernel mode of the virtual machine comprises a packaging function library, a isolation control submodule and an information communication submodule.
Owner:XI AN JIAOTONG UNIV +1
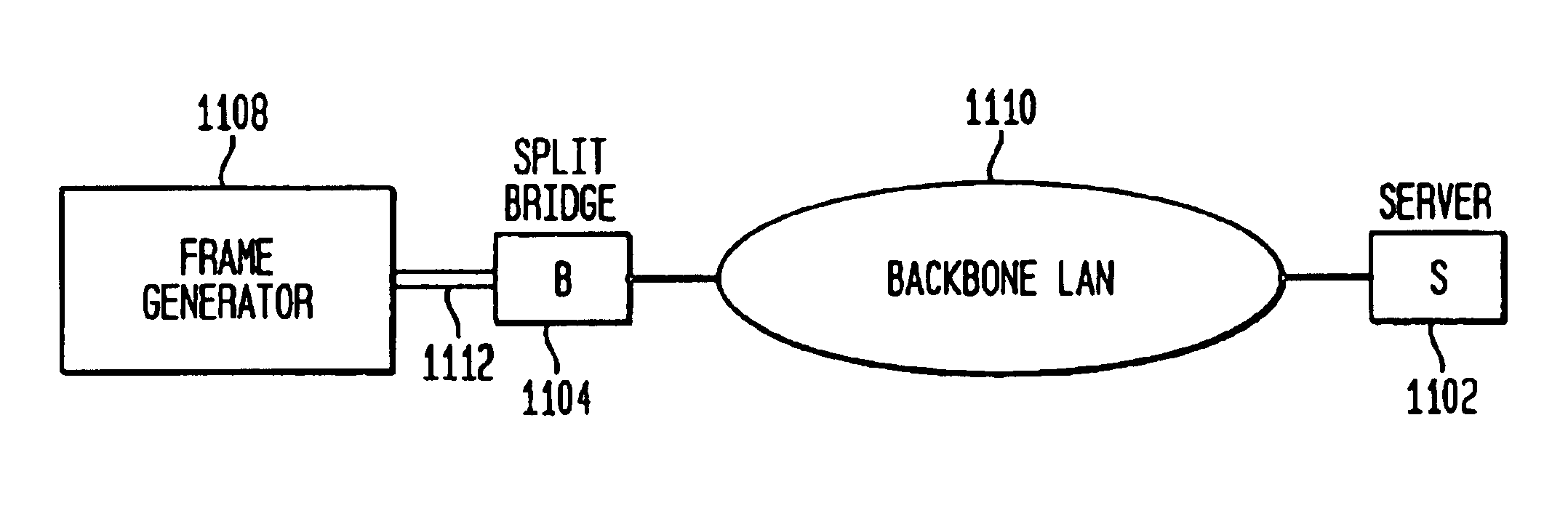
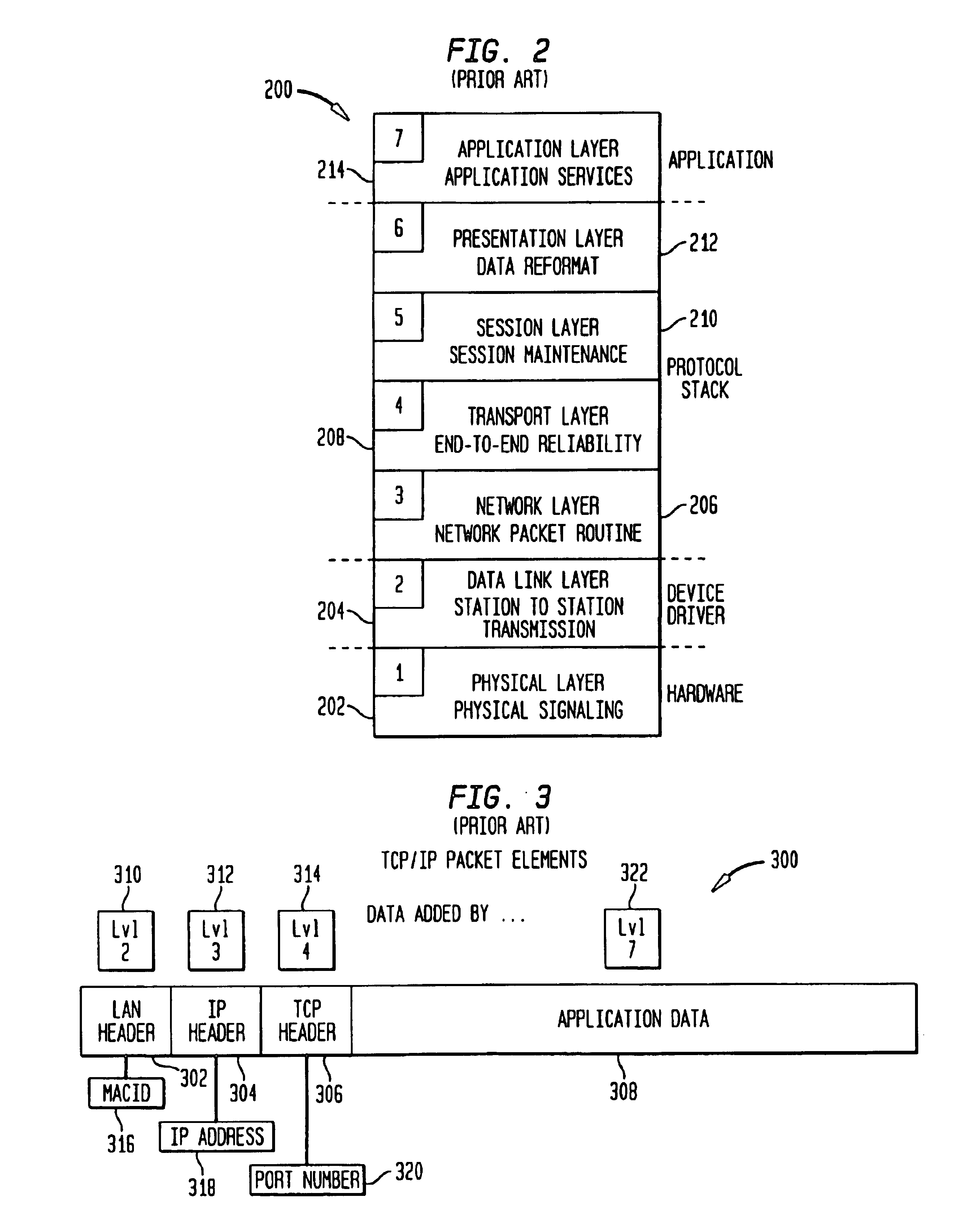
Intelligent workstation simulation-client virtualization
InactiveUS6922663B1Analogue computers for electric apparatusMultiple digital computer combinationsTraffic capacityData virtualization
A network client simulation tool that virtualizes multiple clients from a single network entity. The simulation tool builds LAN frames of protocol stack level 2, which represent data originating from multiple clients to simulate traffic from multiple clients. It also provides a method for inserting the level 2 LAN frames built onto a physical LAN for actual delivery to a system being tested for simulating real client LAN traffic environment. LAN frames in the present invention are inserted at level 2, data link layer of a protocol stack by employing a novel split bridge which receives client requests and adds bridge routing information to emulate incoming multiple client requests having different client addresses.
Owner:INTELLECTUAL DISCOVERY INC
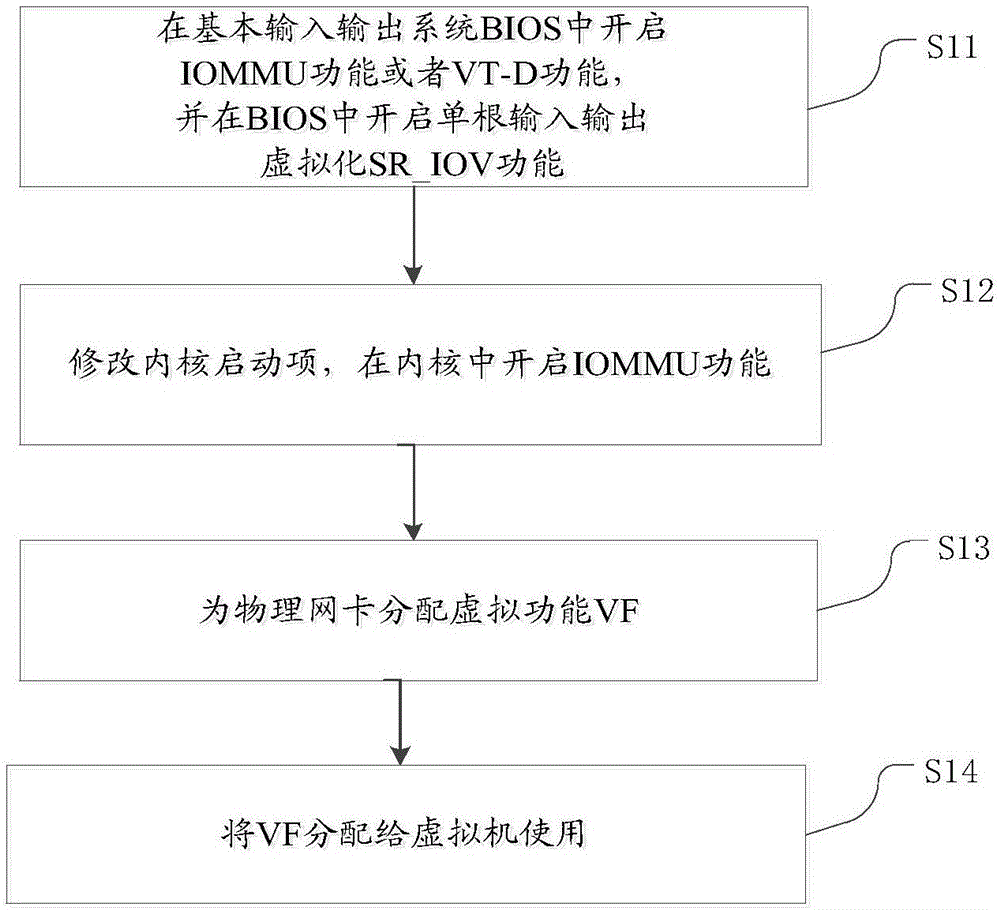
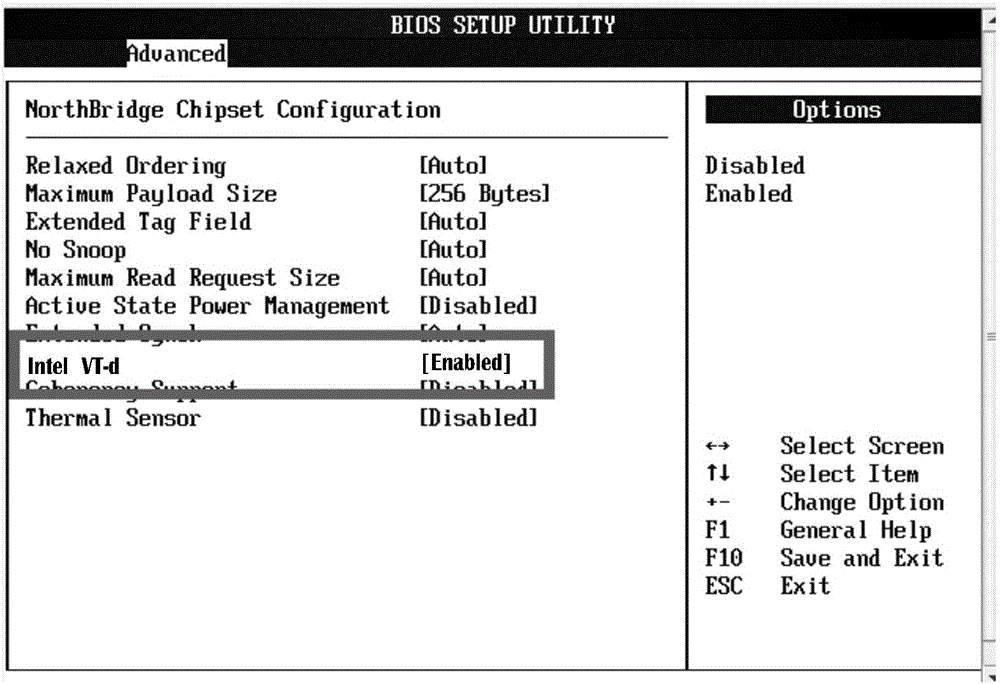
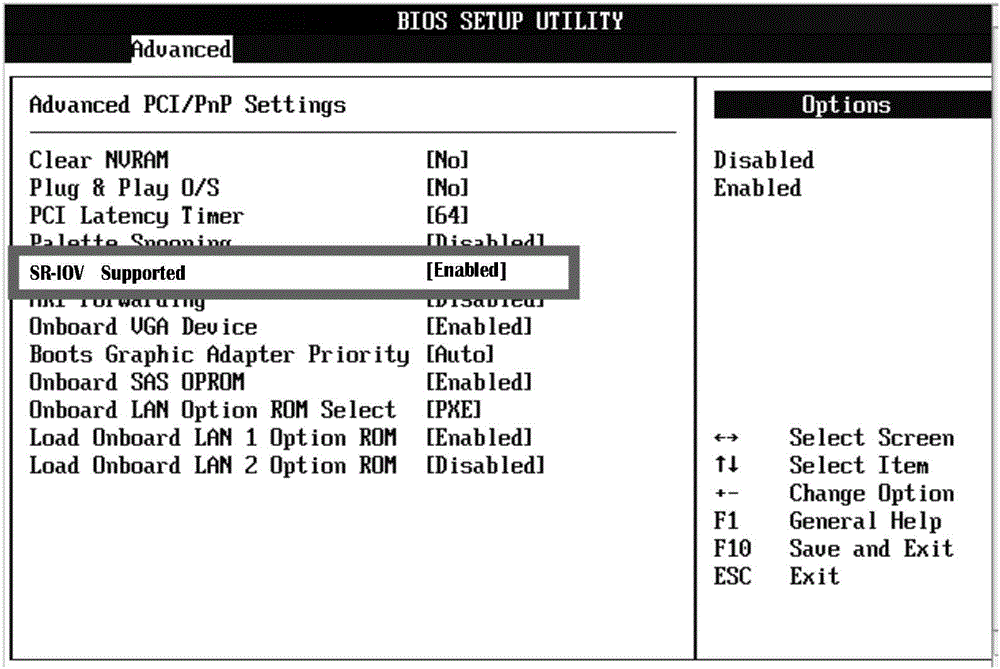
Single root_I/O virtualization (SR_IOV)-based virtualization implementation method
The present invention discloses a single root_I / O virtualization (SR_IOV)-based virtualization implementation method. The method comprises the steps of enabling an IOMMU function or a TV-D function in a basic input output system (BIOS), and enabling an SR_IOV function in the BIOS; modifying startup items of a kernel, and enabling the IOMMU function in the kernel; allocating a virtualization function (VF) for a physical network adapter; and allocating the VF to a virtual machine to use. Through adoption of the method, the virtual machine can better use the I / O.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
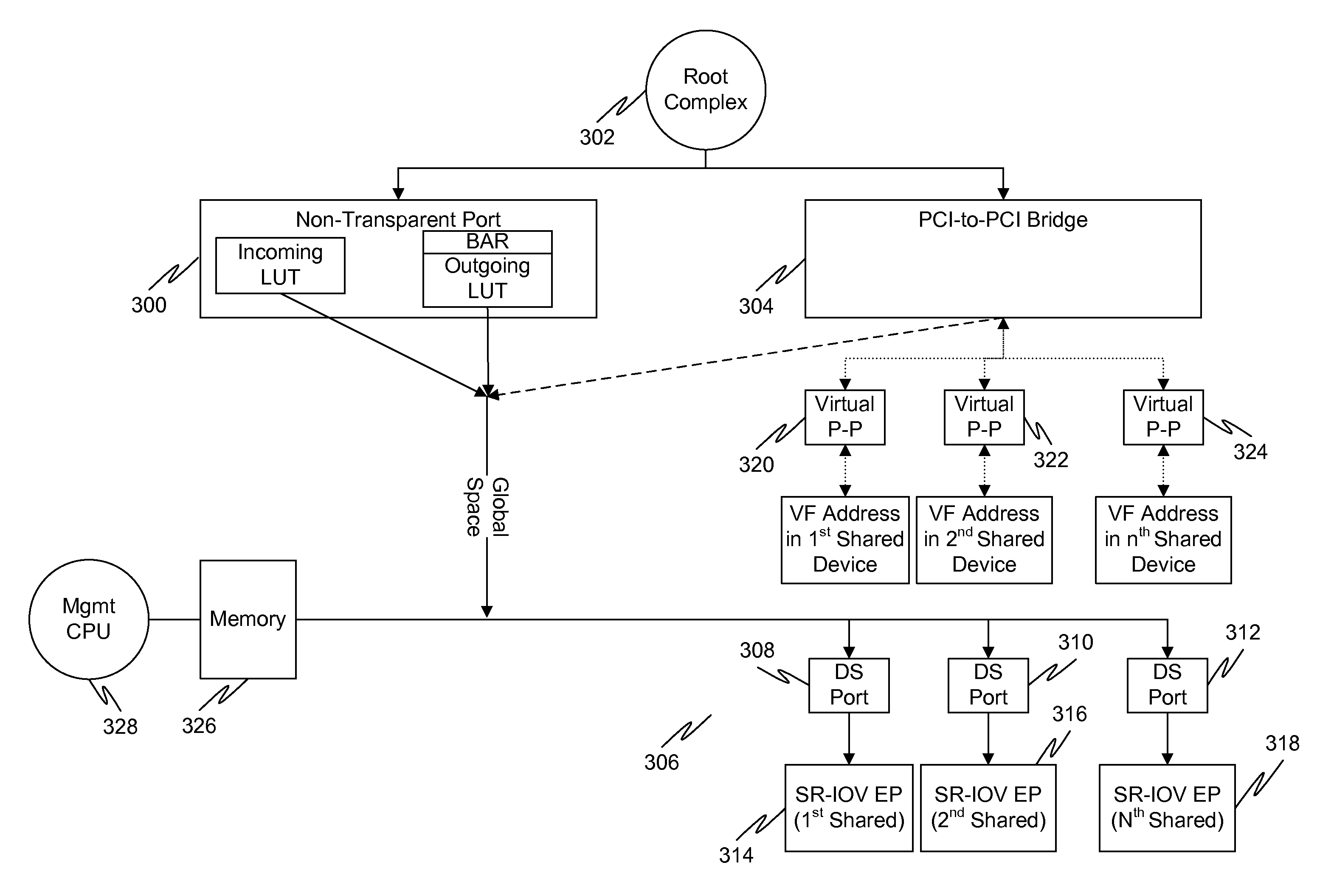
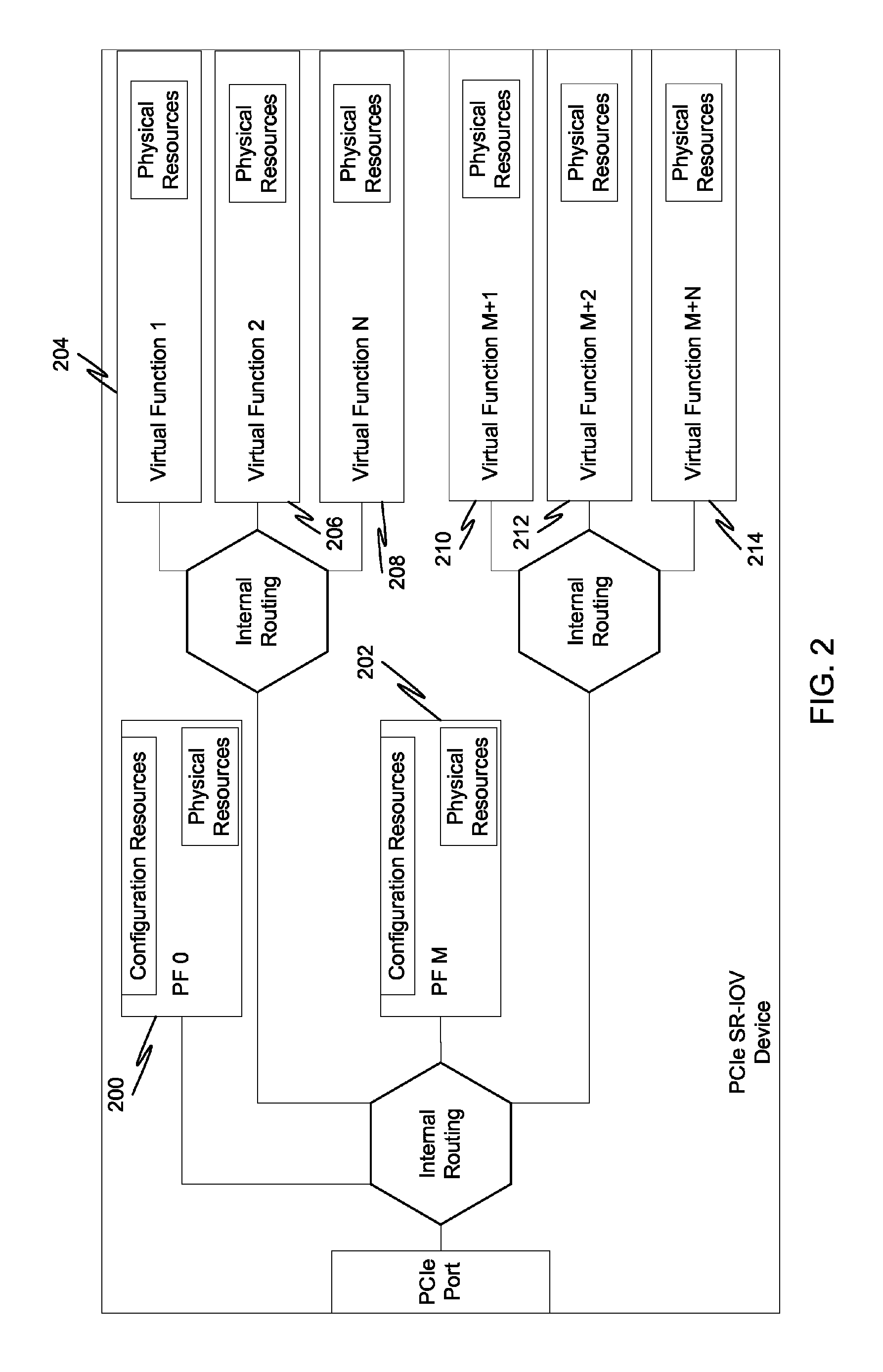
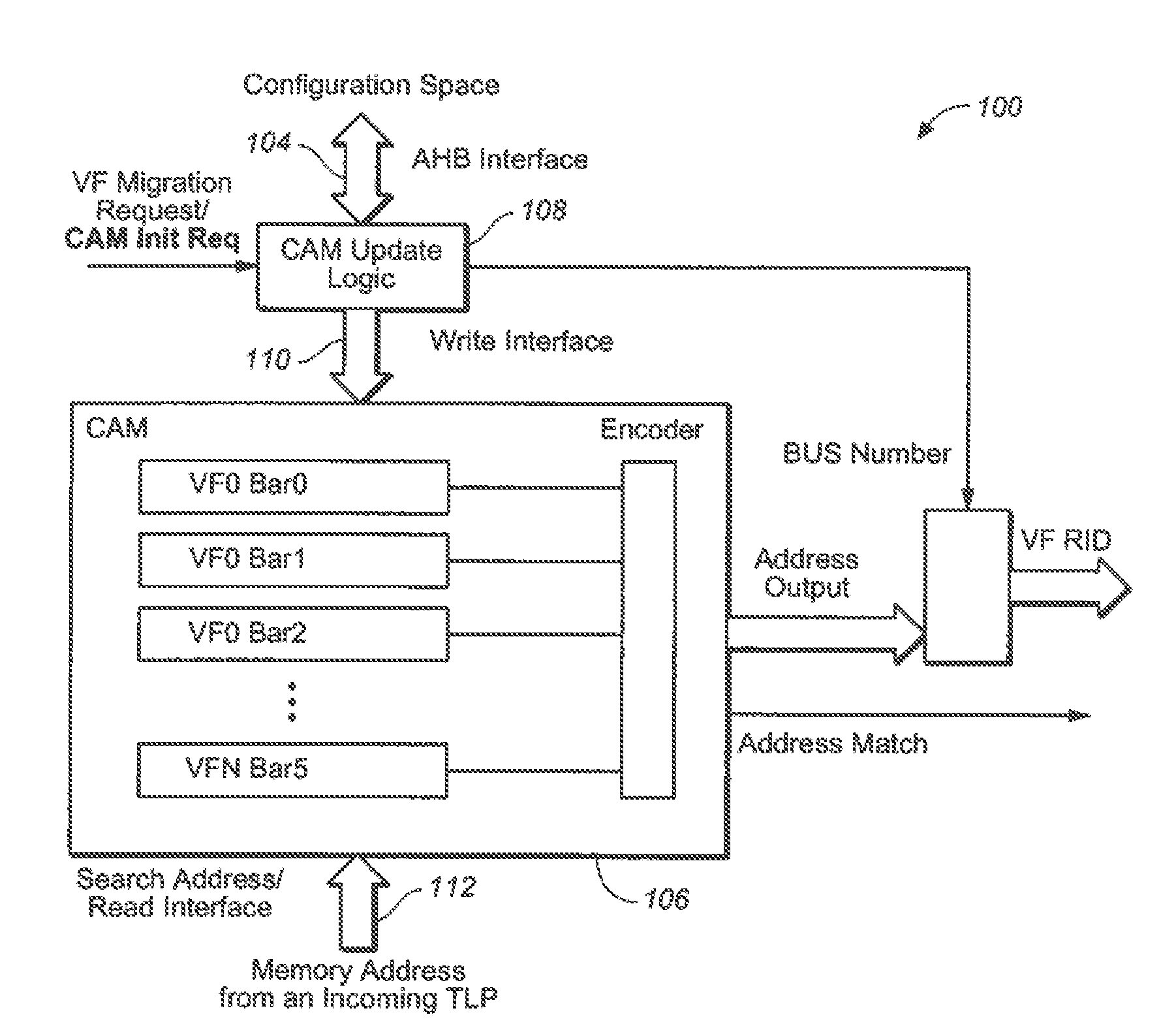
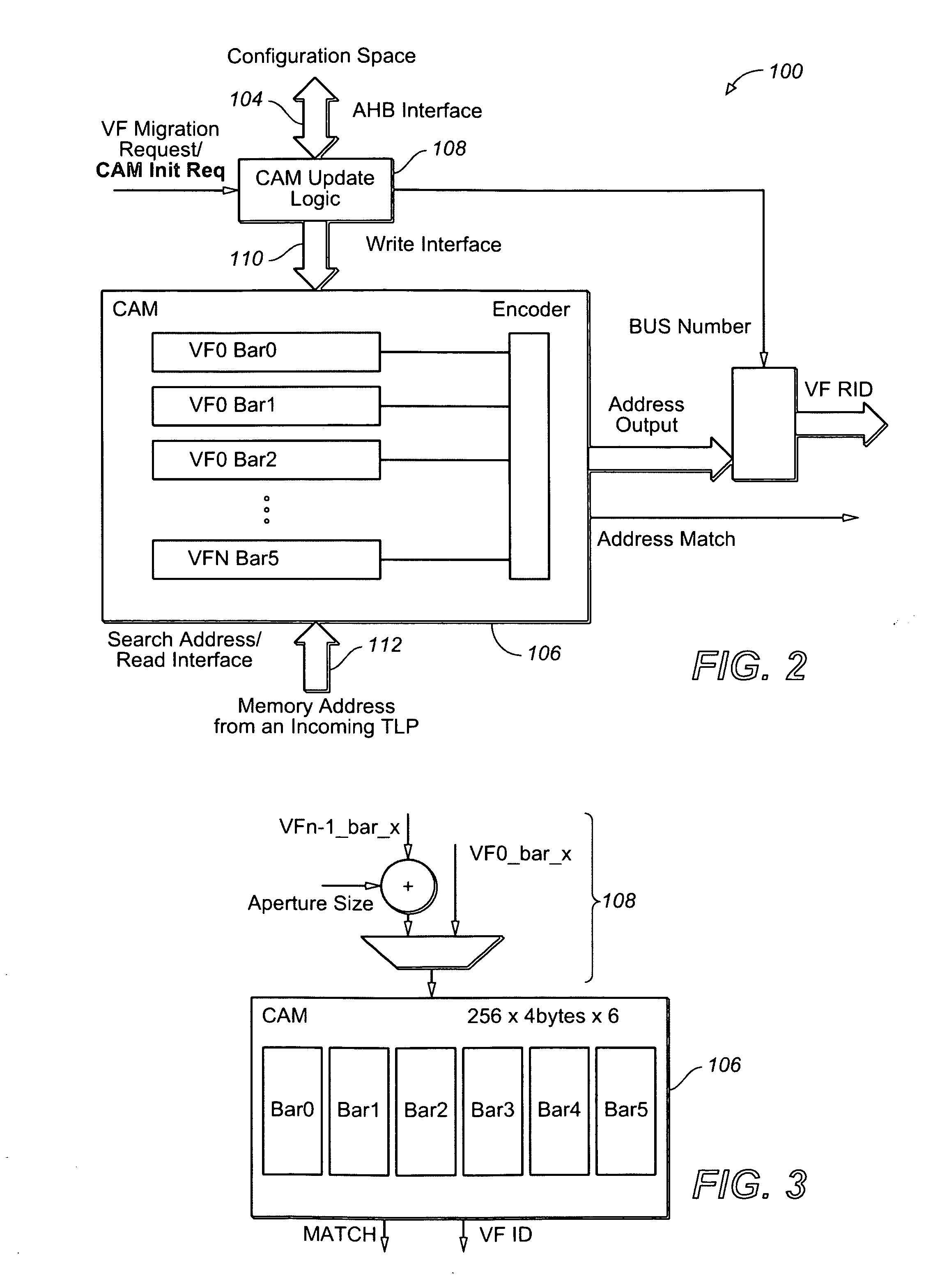
System and method for providing address decode and virtual function (VF) migration support in a peripheral component interconnect express (PCIE) multi-root input/output virtualization (IOV) environment
InactiveUS20110219161A1Memory systemsInput/output processes for data processingData virtualizationTransaction layer packet
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and method for providing address decode and virtual function (VF) migration support in a peripheral component interconnect express (PCIE) multi-root input/output virtualization (IOV) environment
ActiveUS20090248973A1Memory systemsInput/output processes for data processingData virtualizationTransaction layer packet
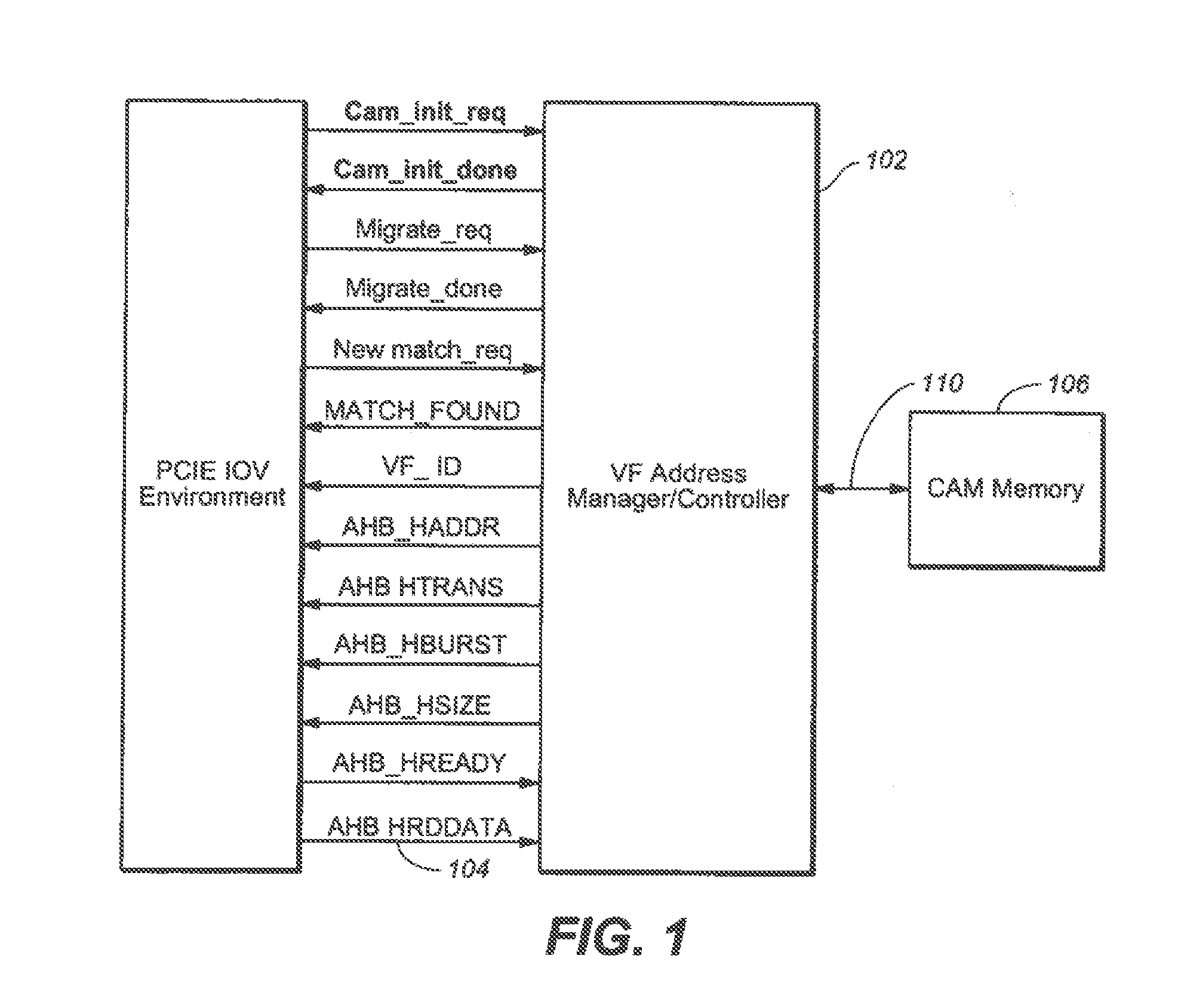
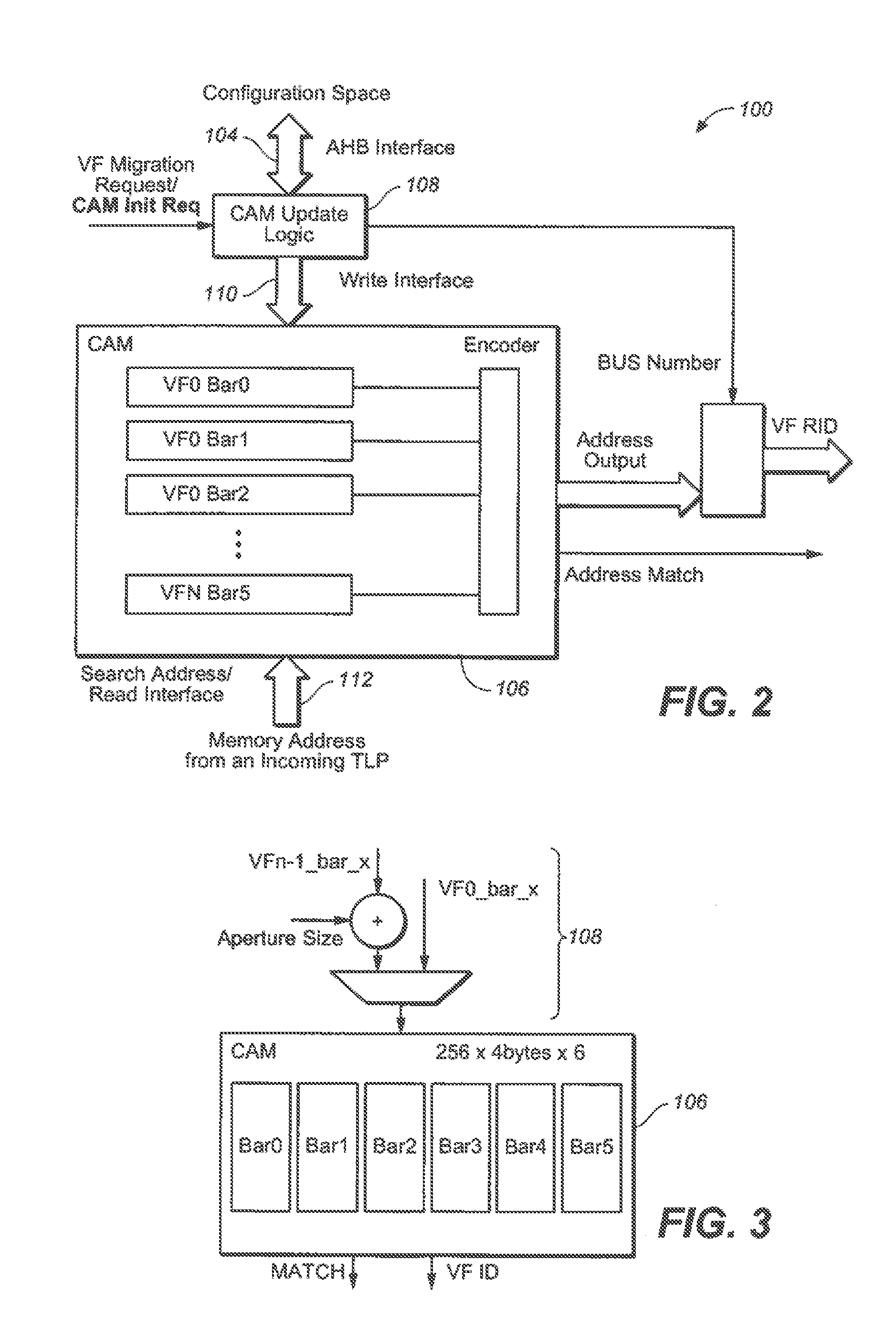
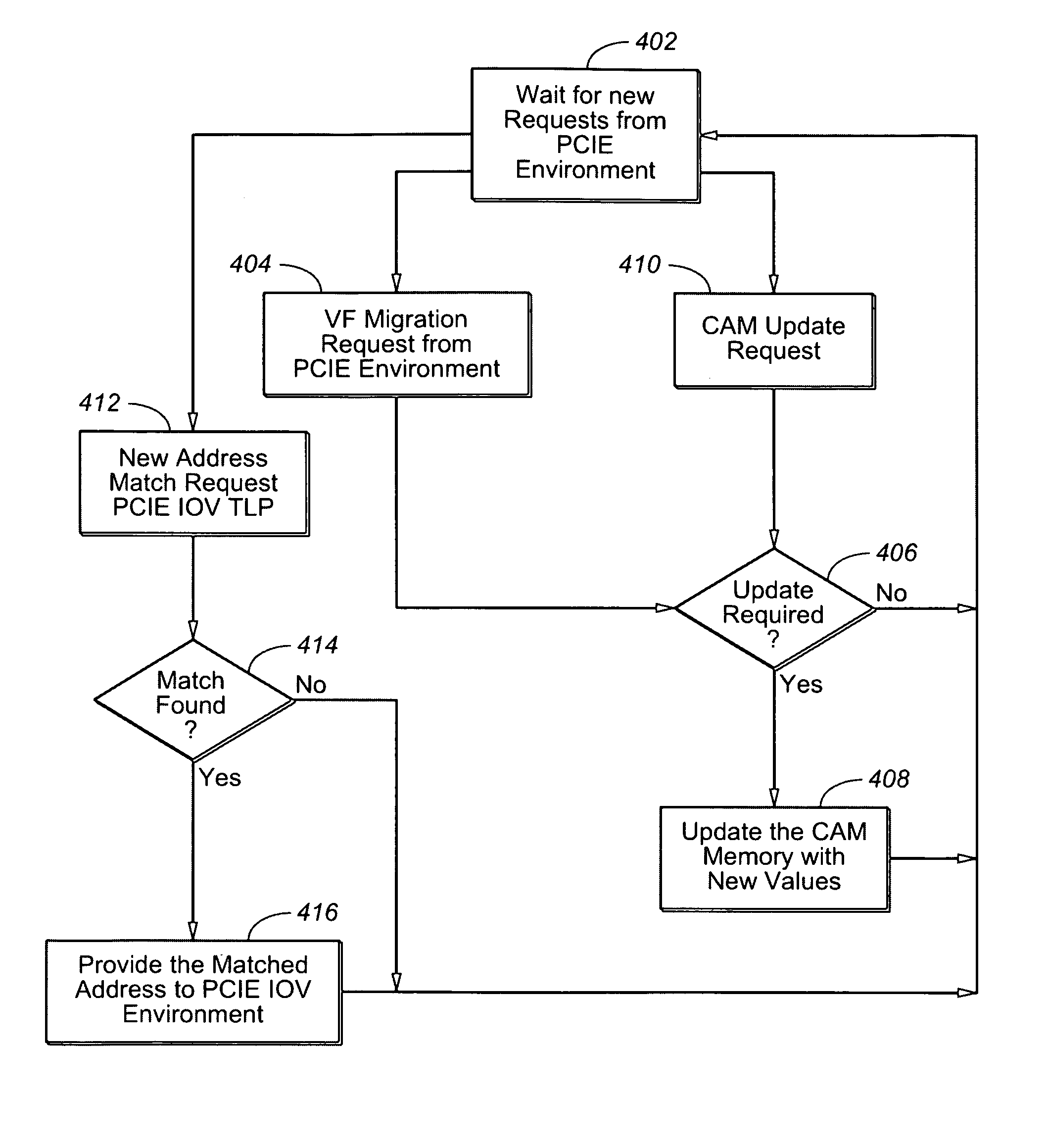
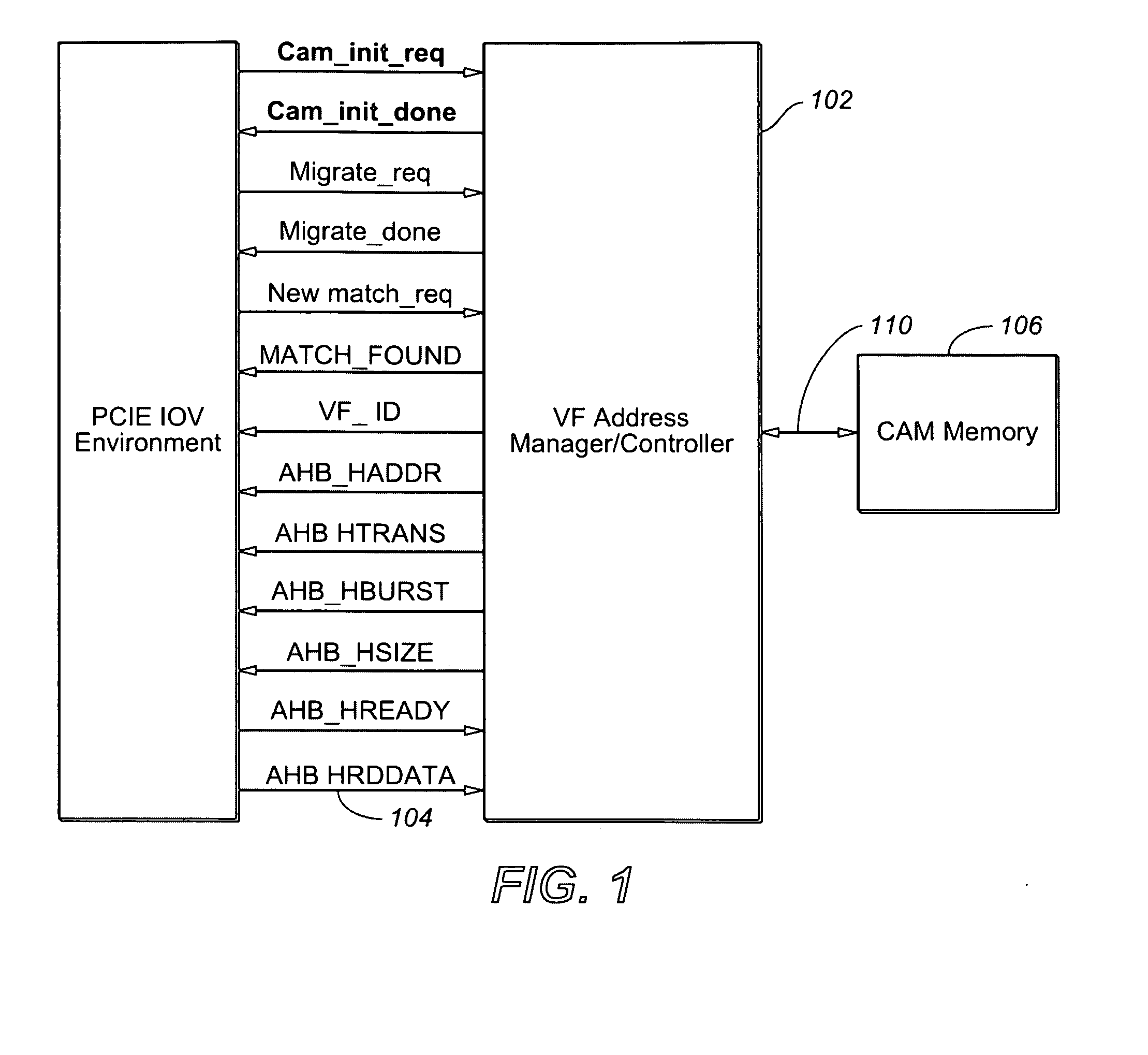
The present invention is a method for providing address decode and Virtual Function (VF) migration support in a Peripheral Component Interconnect Express (PCIE) multi-root Input / Output Virtualization (IOV) environment. The method may include receiving a Transaction Layer Packet (TLP) from the PCIE multi-root IOV environment. The method may further include comparing a destination address of the TLP with a plurality of base address values stored in a Content Addressable Memory (CAM), each base address value being associated with a Virtual Function (VF), each VF being associated with a Physical Function (PF). The method may further include when a base address value included in the plurality of base address values matches the destination address of the TLP, providing the matching base address value to the PCIE multi-root IOV environment by outputting from the CAM the matching base address value. The method may further include constructing a requestor ID for the VF associated with the matching base address value, the requestor ID being based upon the output matching base address value and a bus number for a PF which owns the CAM.
Owner:AVAGO TECH INT SALES PTE LTD
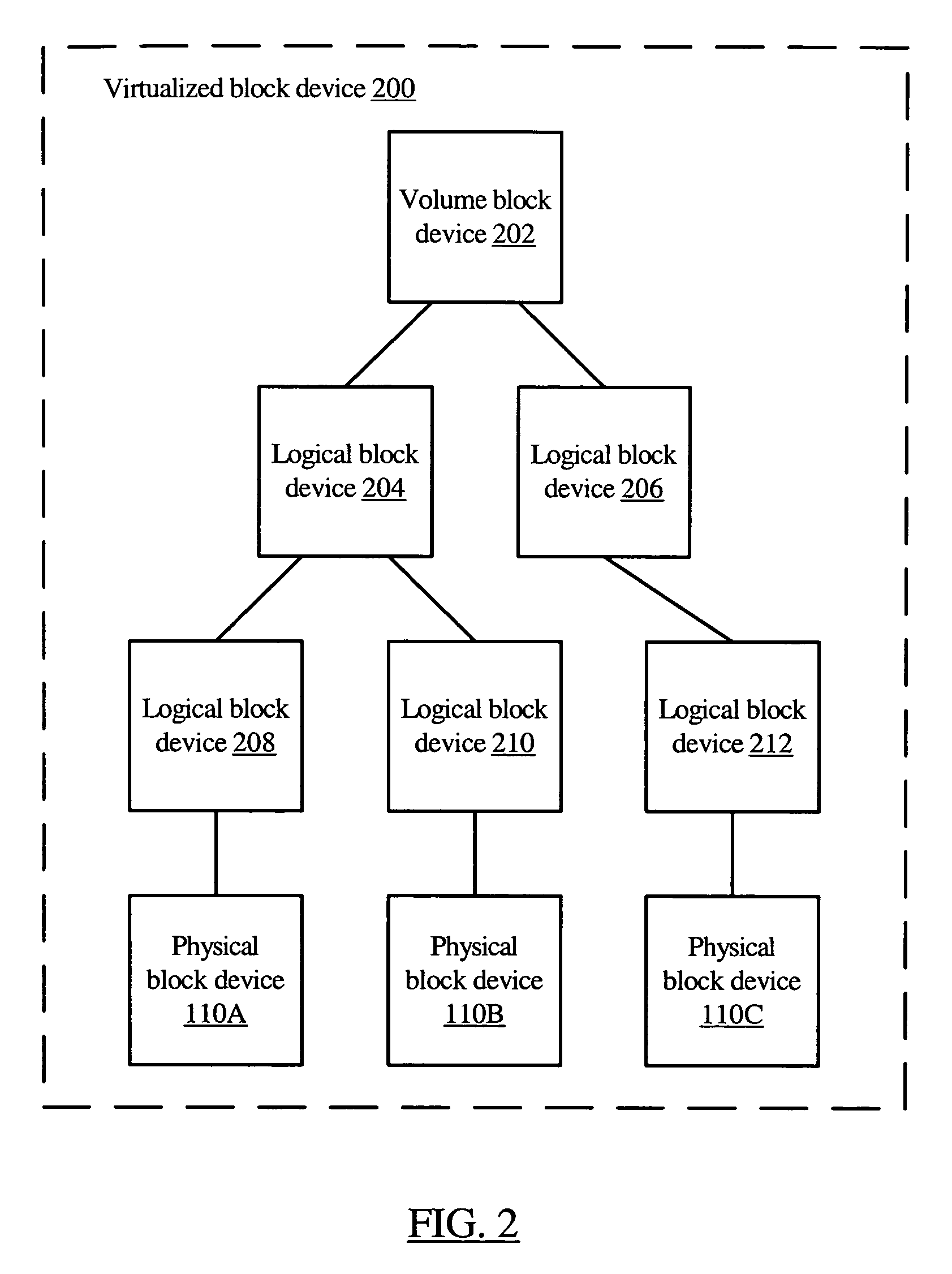
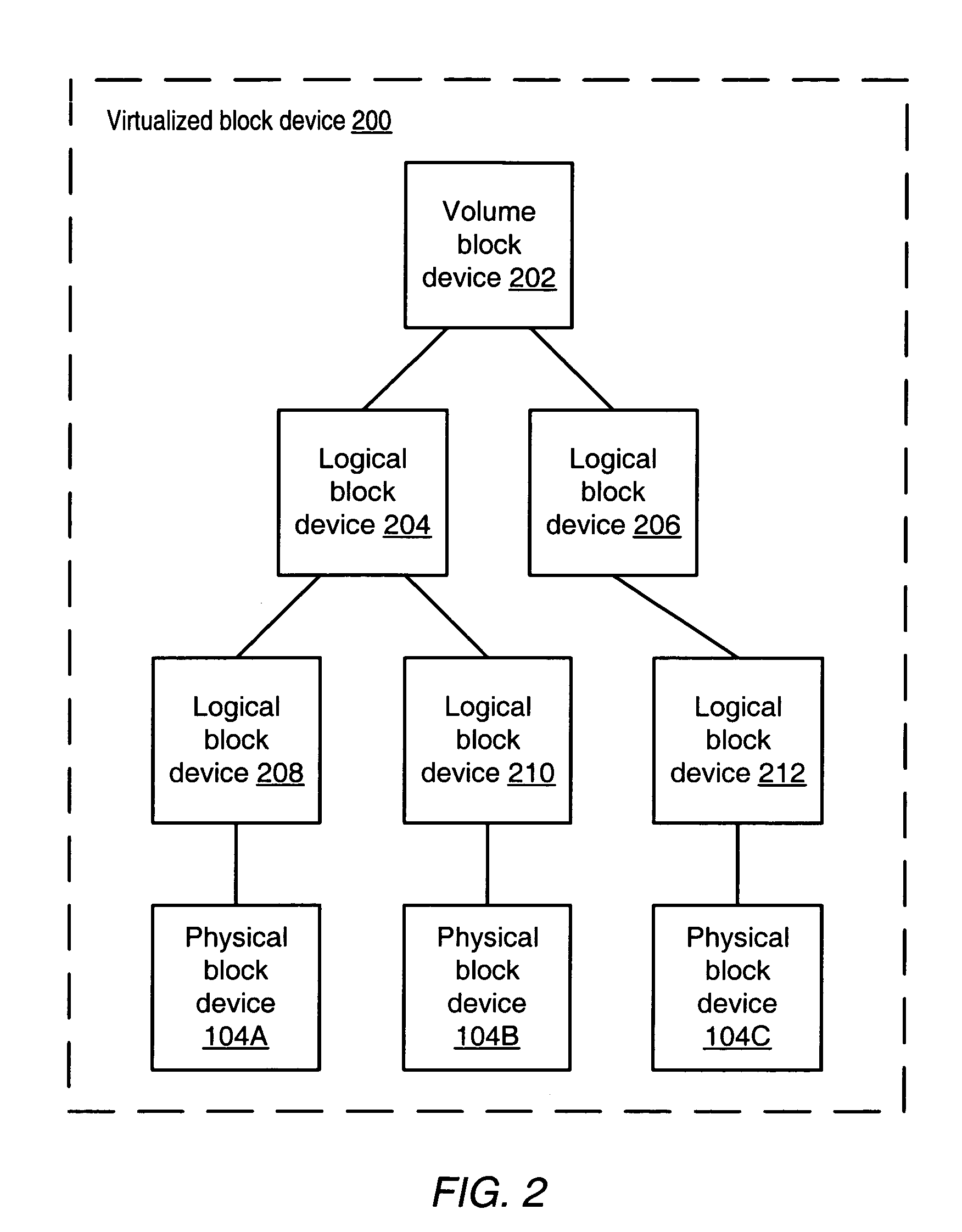
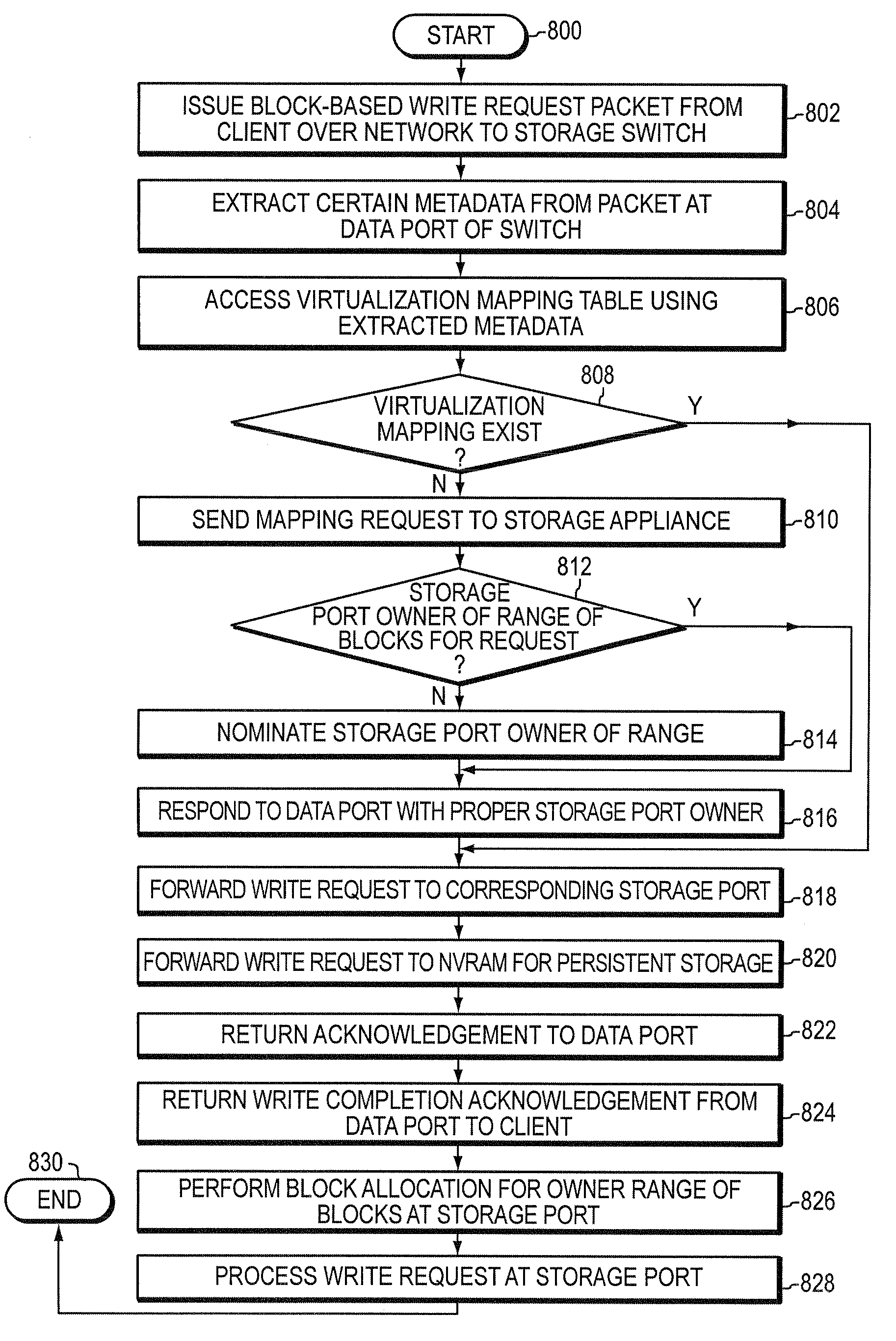
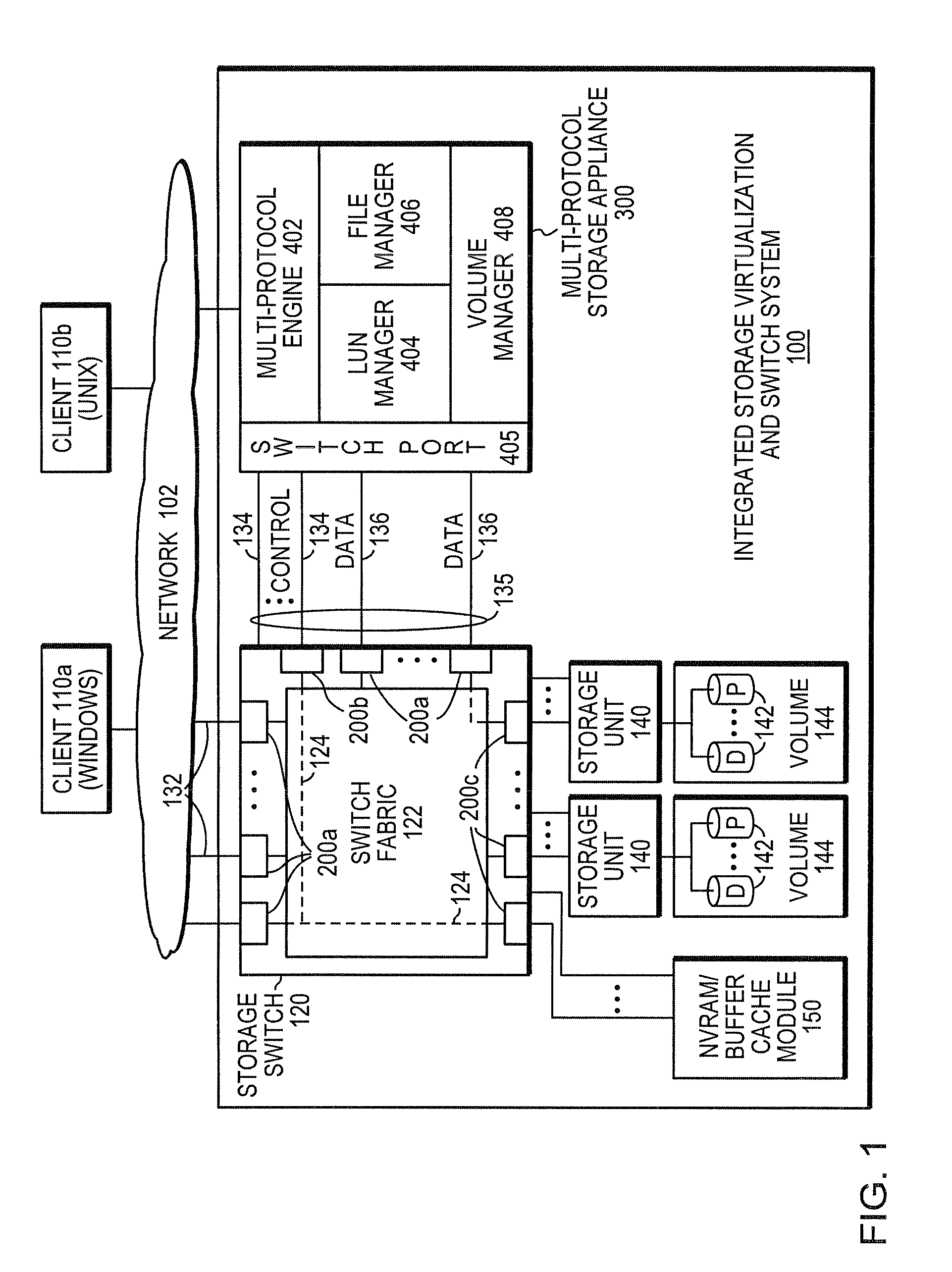
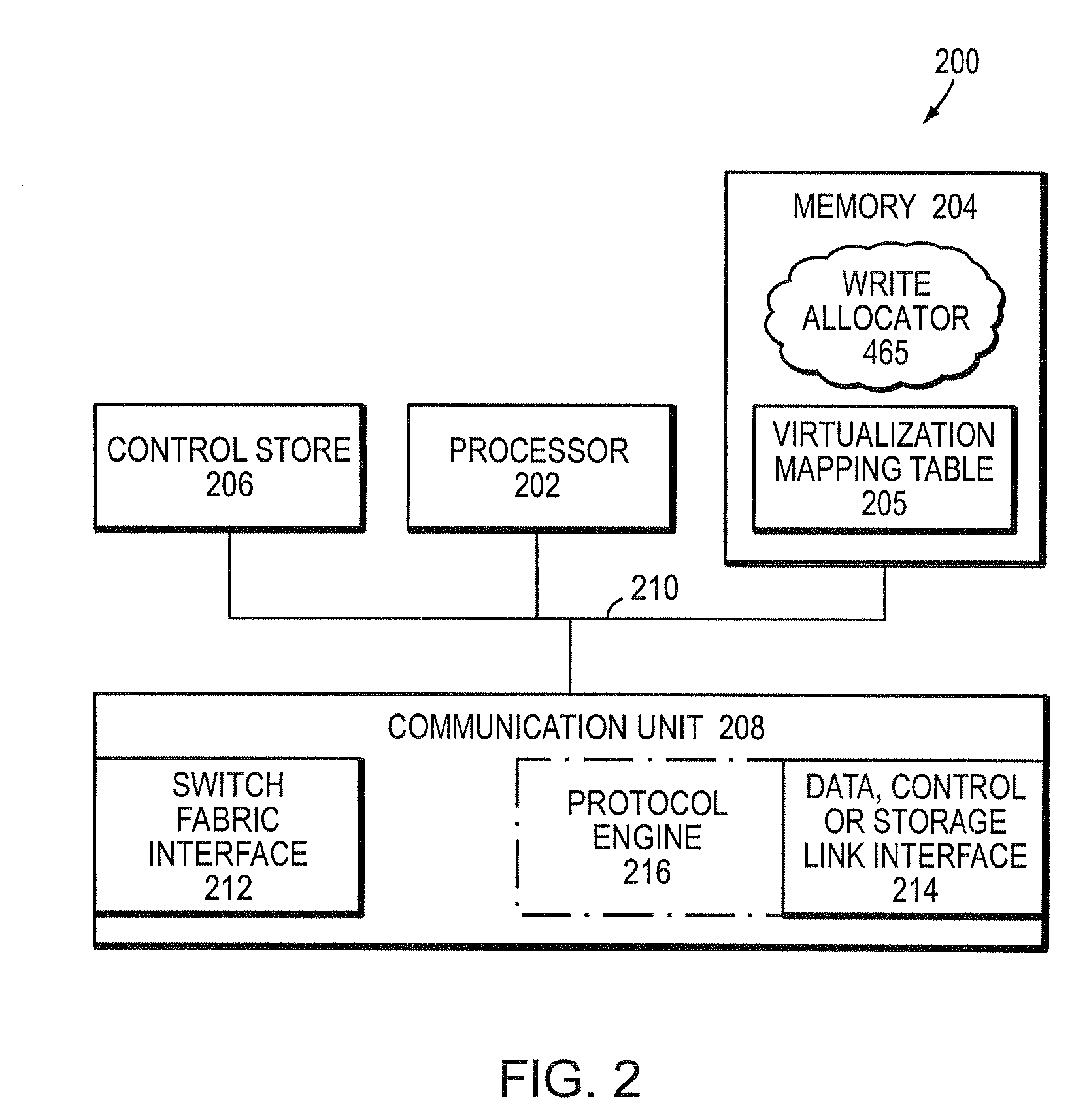
Integrated storage virtualization and switch system
ActiveUS7747836B2Improve writing efficiencyElimination of storage “hot spots”TransmissionMemory systemsOperational systemData access
A system integrates an intelligent storage switch with a flexible virtualization system to enable efficient service of file and block protocol data access requests for information stored on the system. A storage operating system executing on a storage system coupled to the switch implements the virtualization system to provide a unified view of storage to clients by logically organizing the information as named files, directories and logical unit numbers. The virtualization system is illustratively embodied as a file system having a write allocator configured to provide a flexible block numbering policy that addresses volume management capabilities, such as storage virtualization, at a finer granularity (e.g., a single block) than that of previous non-flexible storage virtualization schemes. The flexible block numbering policy also yields substantial benefits in terms of increased write efficiency and elimination of storage “hot spots”, as well as a compelling point-in-time read-only data image (snapshot) mechanism.
Owner:NETWORK APPLIANCE INC
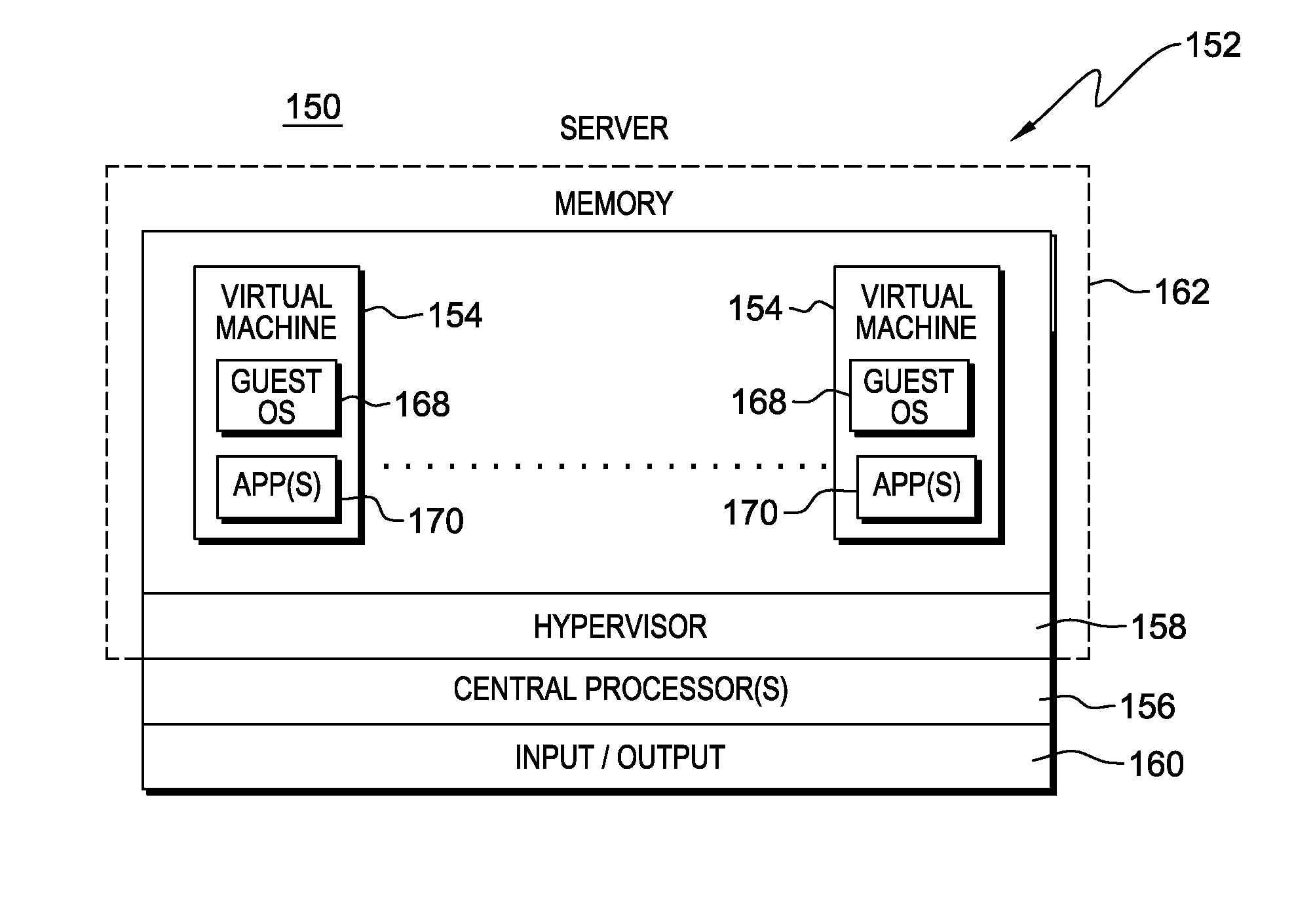
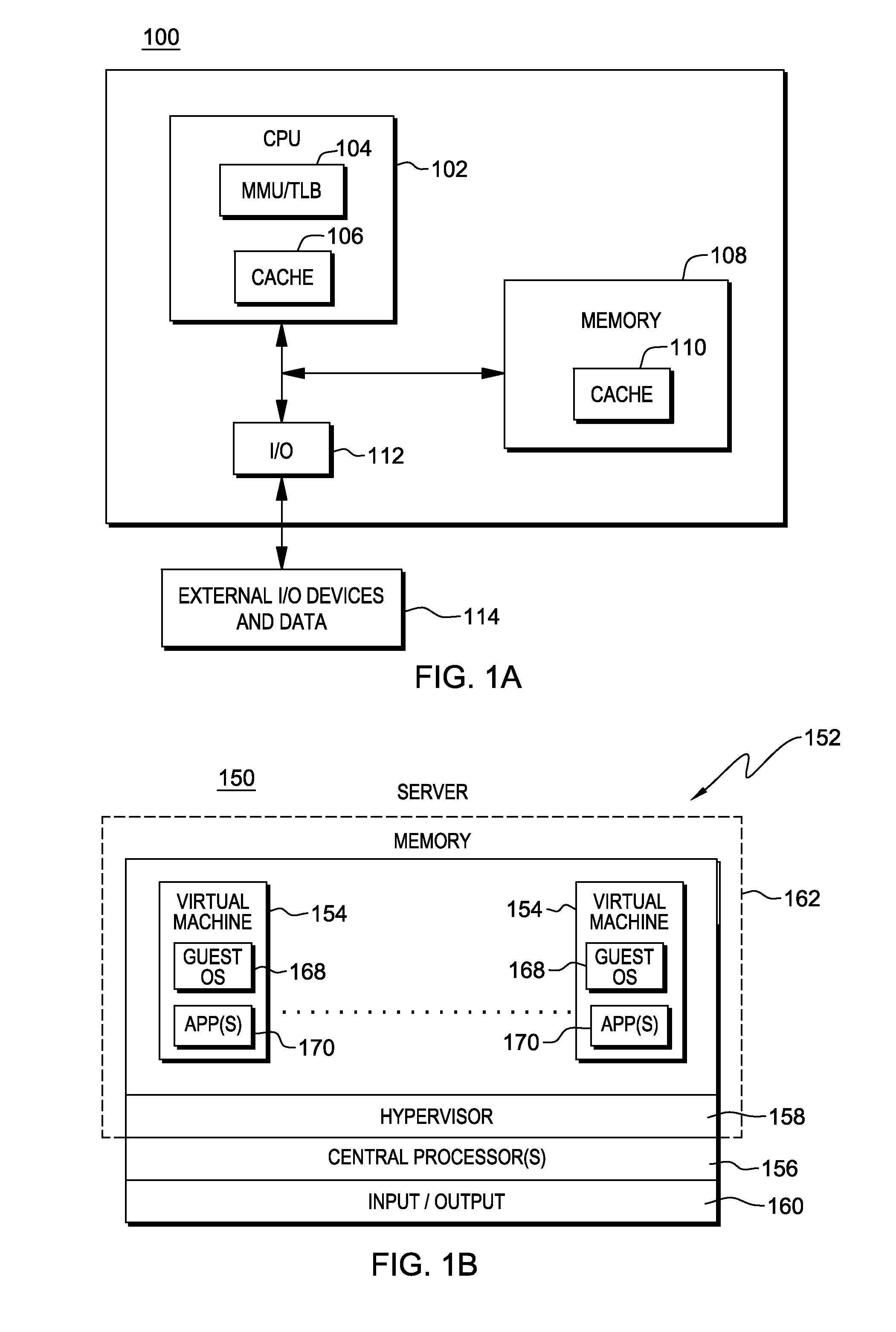
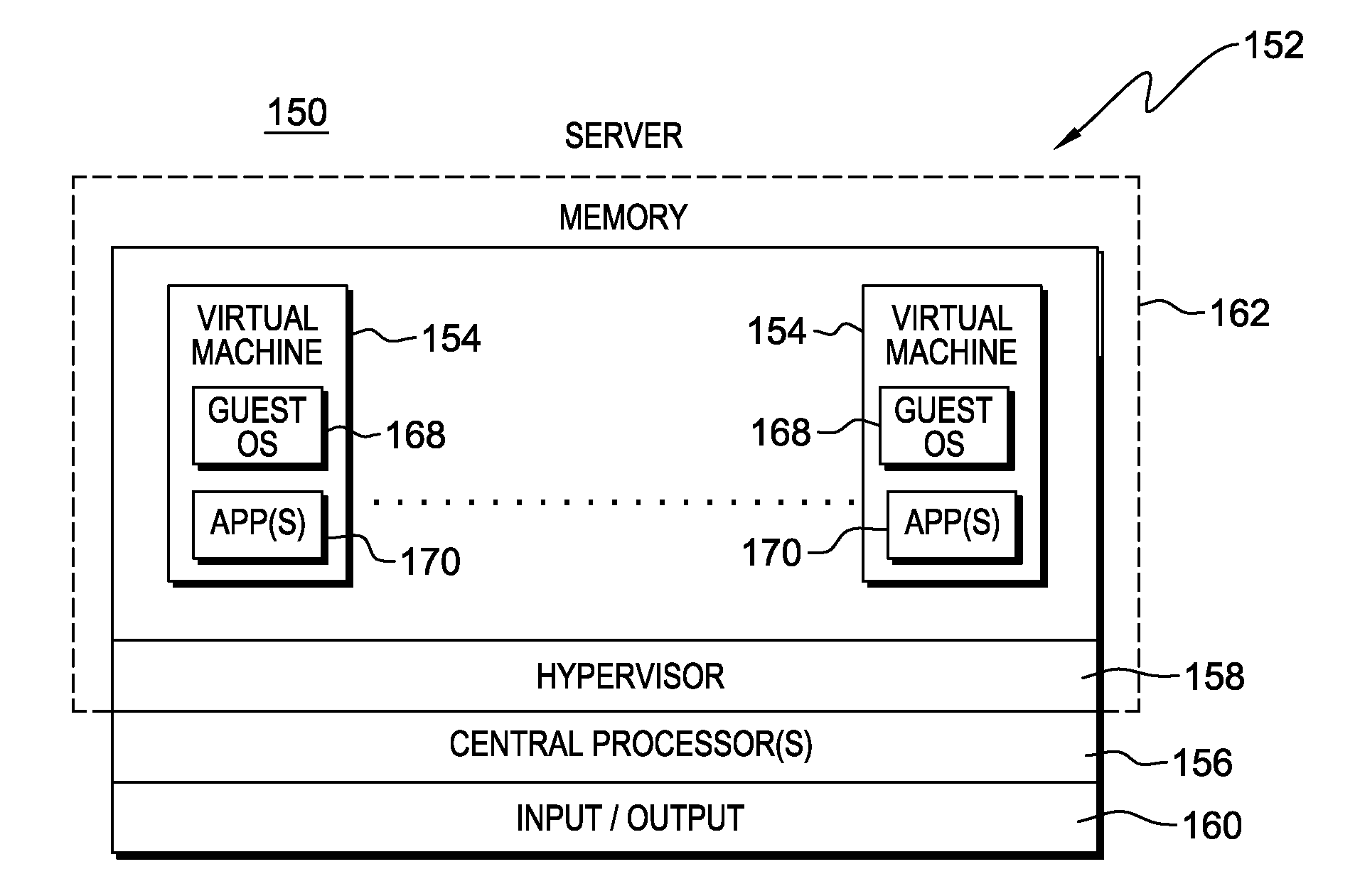
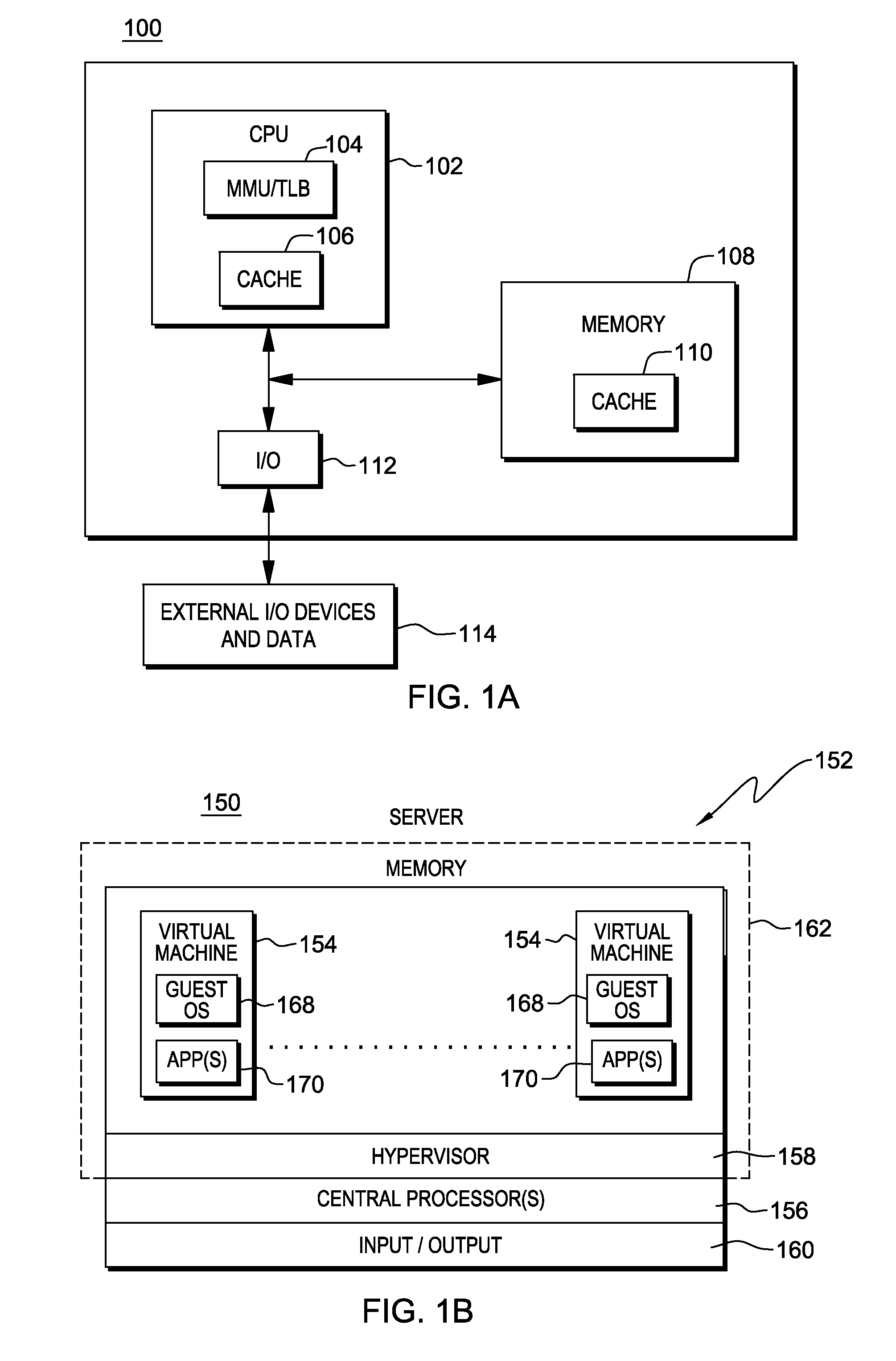
Supporting multiple types of guests by a hypervisor
ActiveUS20140101362A1Improve translationEnhanced advantageMemory architecture accessing/allocationMemory adressing/allocation/relocationTheoretical computer sciencePhysical address
A system configuration is provided that includes multiple partitions that have differing translation mechanisms associated therewith. For instance, one partition has associated therewith a single level translation mechanism for translating guest virtual addresses to host physical addresses, and another partition has a nested level translation mechanism for translating guest virtual addresses to host physical addresses. The different translation mechanisms and partitions are supported by a single hypervisor. Although the hypervisor is a paravirtualized hypervisor, it provides full virtualization for those partitions using nested level translations.
Owner:IBM CORP
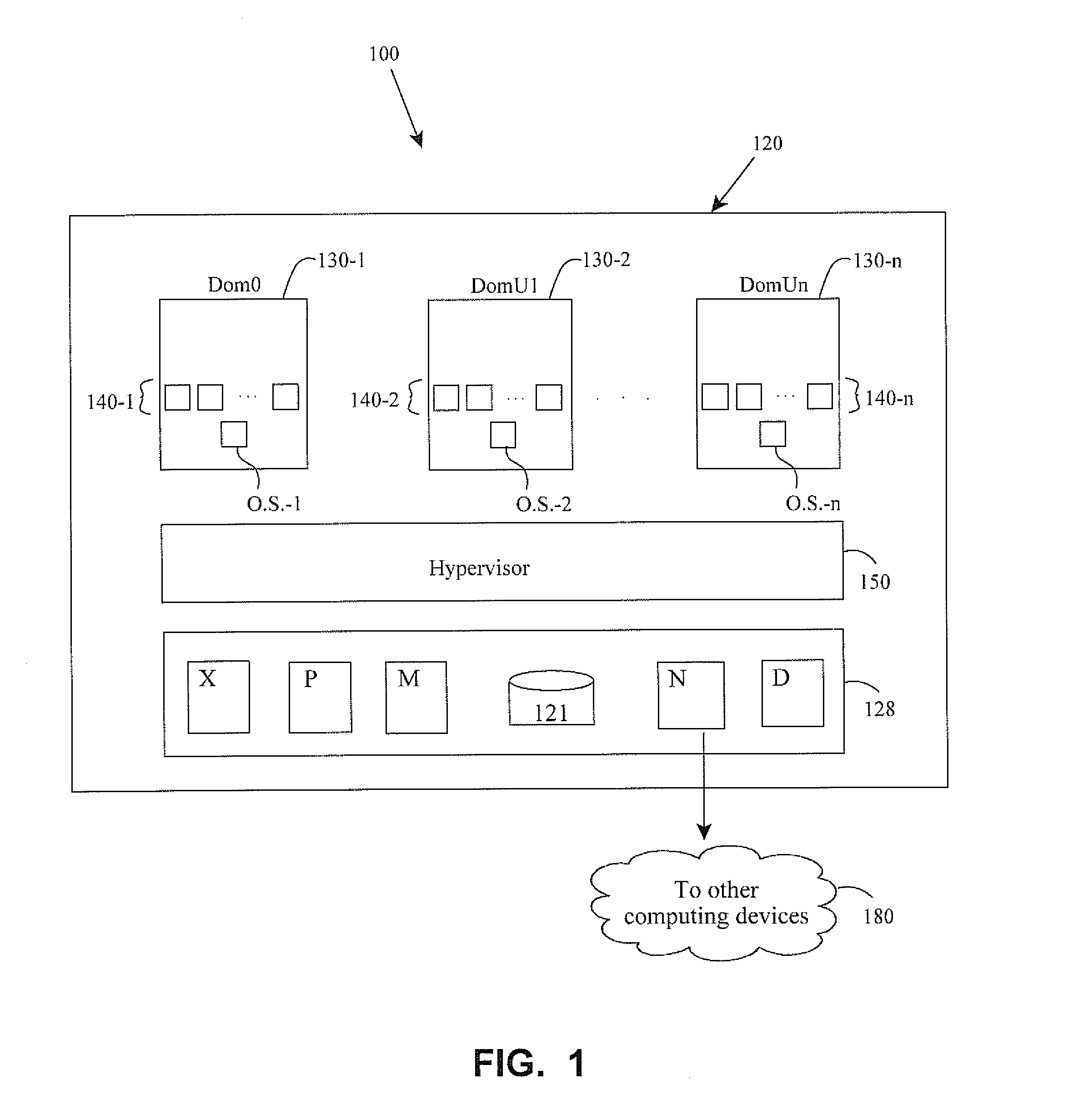
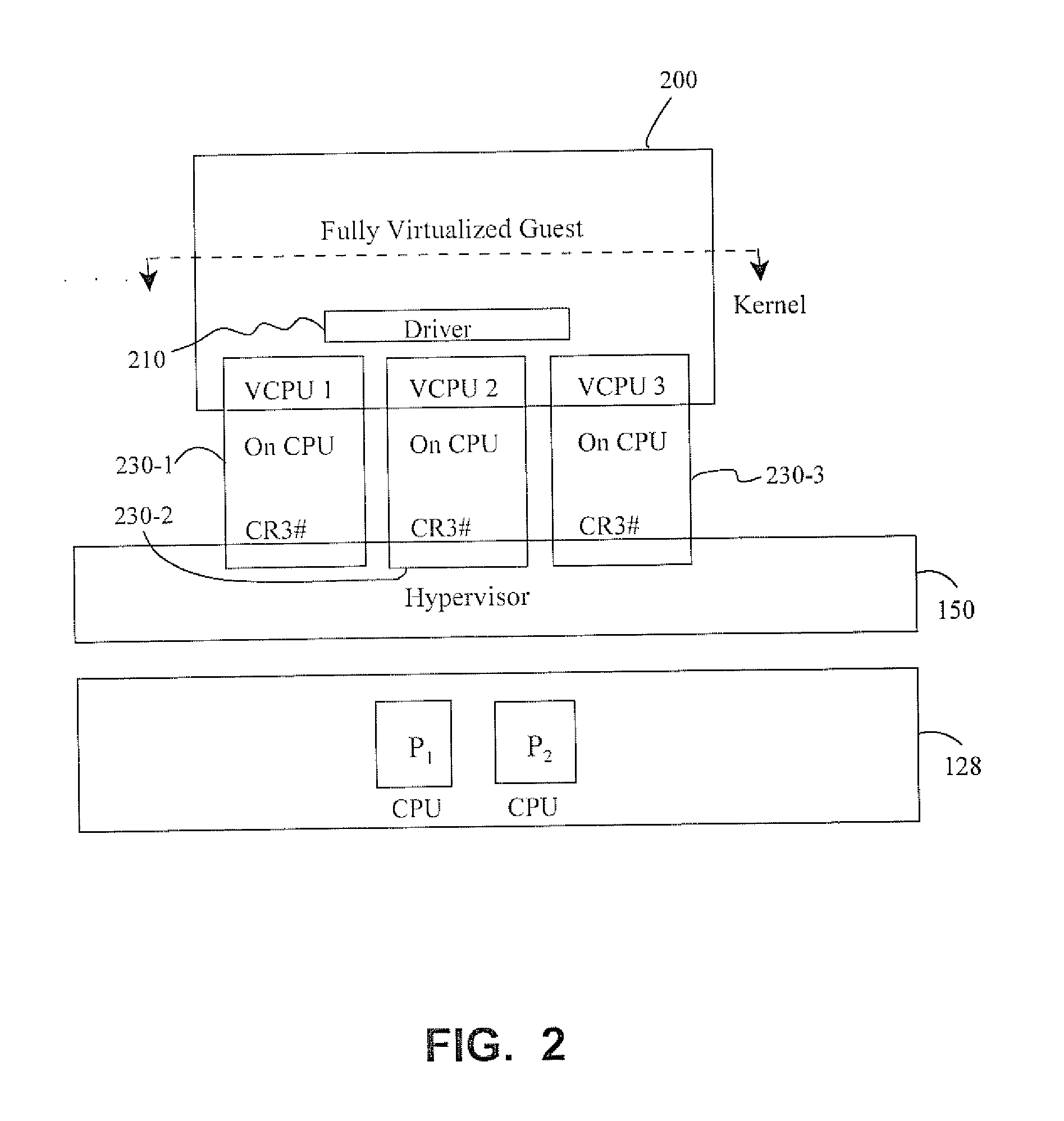
Monitoring spin locks in virtual machines in a computing system environment
ActiveUS20110119667A1Minimize overheadPerformance issueError detection/correctionMultiprogramming arrangementsOperational systemDevice Monitor
Methods and apparatus involve monitoring spin locks for guest devices. Fully virtualized guests have multiple virtual processors configured under the scheduling control of a hypervisor on a physical hardware platform. The hypervisor posts On CPU and CR3 load information to shared communications pages for each of the processors. A monitoring module in the guest device monitors the pages to ascertain forward progress of the processors. If forward progress is being made, the virtual processors continue to spin. If not, the CPU's control is variously relinquished. The monitoring module typifies a kernel driver so that the guest can maintain an unmodified operating system. Ticket spin locks, and their ordering, are also considered as are computations for lock owners. Other features contemplate computing systems and computer program products, to name a few.
Owner:SUSE LLC
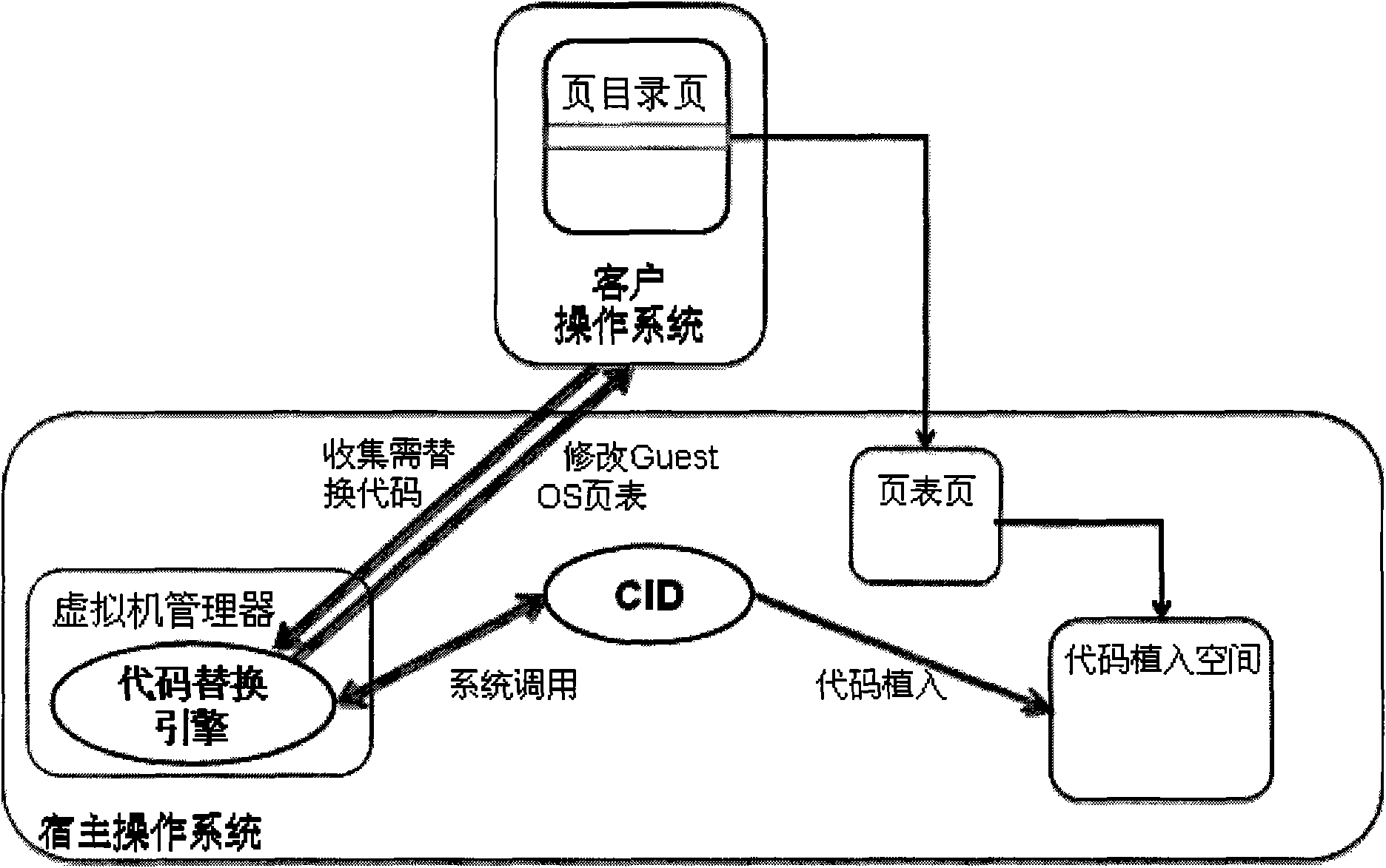
Client operating system nucleus code dynamic replacement method of virtual machine manager
InactiveCN101539868AOvercome limitationsDynamic replacement automaticMultiprogramming arrangementsSoftware simulation/interpretation/emulationCall stackOperational system
The invention discloses a client operating system nucleus code dynamic replacement method of a virtual machine manager, belonging to the software technical field. The method is as follows: (1) a host operating system is internally added with a CID process, assigned with an implantation space so as to contain implanted alternate codes, and then VMM maps the implantation space to a kernel process space of Guest OS; (2) the VMM counts codesnippet needed to be replaced; (3) the CID appoints a section of replacing codes according to the statistical results; (4) the appointed replacing codes are read into the implantation space, and a call stack in which the replacing codes locate is obtained; (5) the CID finds out calling points of the replacing codes in the Guest OS; the VMM changes skip addresses of the call points into the offset address of the appointed replacing address. The invention makes the advantages of the half virtualization method being blended into the full virtualization technology possible and does dynamic replacement for Guest OS kernel in a binary system bedding surface.
Owner:PEKING UNIV
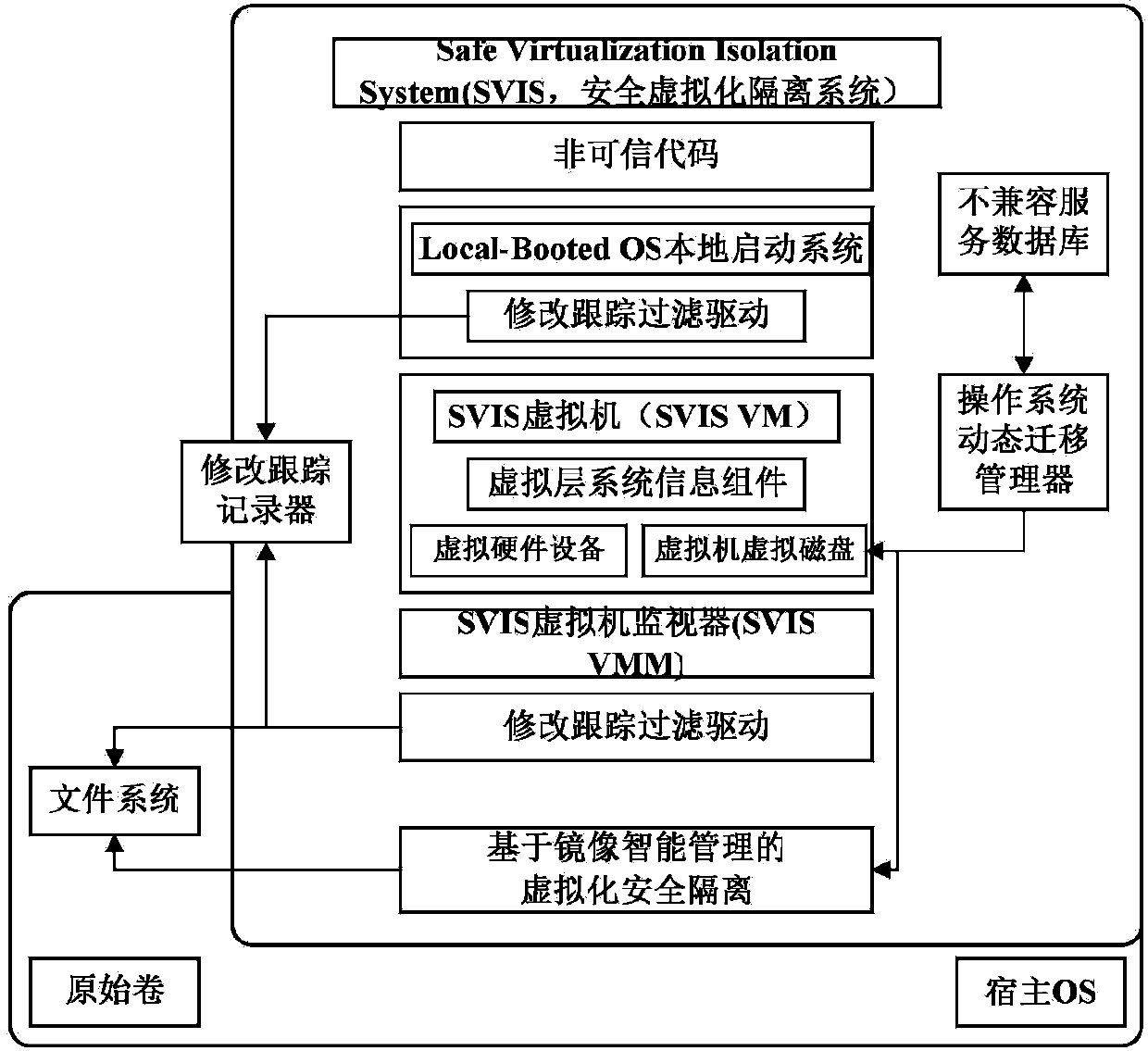
Safety virtualization isolation method based on mirror image intelligent management
InactiveCN103810422AAchieve security isolationAvoid confictPlatform integrity maintainanceIntelligent managementFunctional integrity
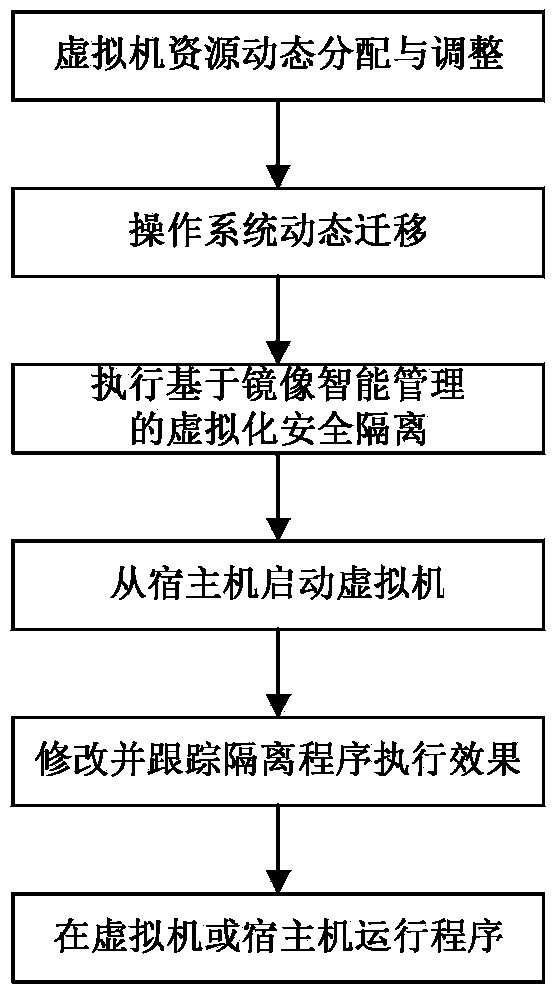
The invention relates to the technical field of cloud computing virtualization safety, in particular to a safety virtualization isolation method based on mirror image intelligent management. The method includes the following steps of dynamically distributing and adjusting virtual machine resources, dynamically moving an operating system, executing virtualization safety isolation based on mirror image intelligent management, starting virtual machines from a host machine, modifying and tracking the execution effect of isolation programs and operating programs on the virtual machines or the host machine. Through the safety virtualization isolation method, safety isolation, functional completeness, performance adaptability, behavior monitorability and the like of a virtual system can be balanced, and the safety virtualization isolation method can be used for cloud computing virtualization safety.
Owner:CLOUD COMPUTING CENT CHINESE ACADEMY OF SCI +1
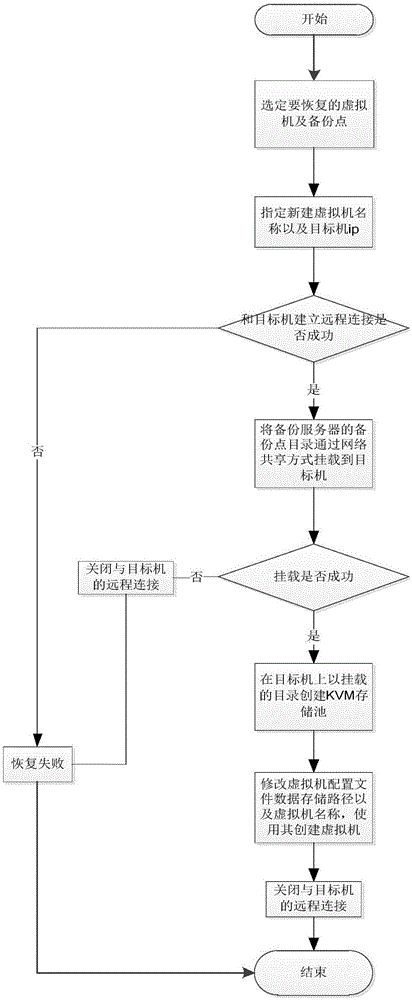
KVM virtualization-based agency mode-free backup method and system
ActiveCN106445733AReduce maintenance costsShorten the timeRedundant operation error correctionDatabase backupStop time
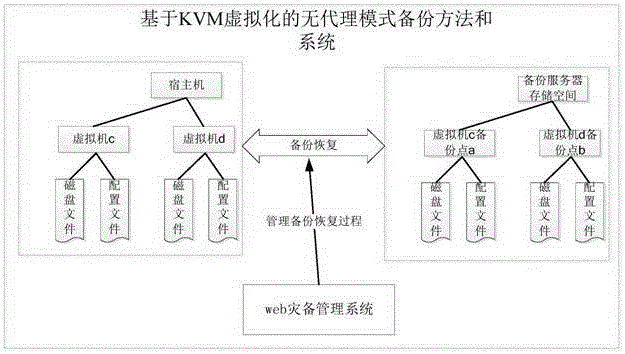
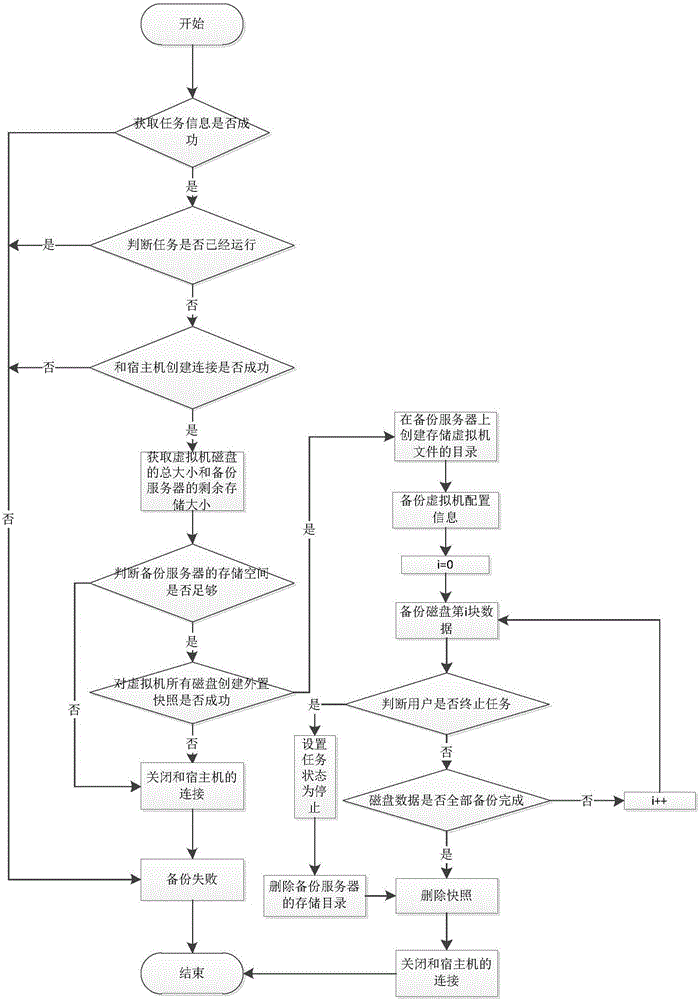
The invention relates to the technical field of database backup and recovery, in particular to a KVM virtualization-based agency mode-free backup method. The method comprises the steps of registering a host, in which a virtual machine needed to be backed up is located, in a web disaster recovery backup management system; creating a backup task; starting the backup task; creating a quick recovery task; and starting the quick recovery task, thereby realizing data backup and quick recovery. The invention furthermore provides a KVM virtualization-based agency mode-free backup system. The system comprises the web disaster recovery management system for managing the whole backup recovery process, the host comprising two or more virtual machines, and a backup server for backing up disk files and configuration files of the virtual machines. According to the method and the system, agency mode-free backup is adopted, so that system deployment and personnel maintenance costs are greatly reduced; and second-level quick recovery of the virtual machines is supported, so that enterprise application stop time is shortened and enterprise loss is reduced.
Owner:广州鼎甲计算机科技有限公司
Supporting multiple types of guests by a hypervisor
ActiveUS20140101365A1Enhanced advantageMemory architecture accessing/allocationMemory adressing/allocation/relocationTheoretical computer sciencePhysical address
A system configuration is provided that includes multiple partitions that have differing translation mechanisms associated therewith. For instance, one partition has associated therewith a single level translation mechanism for translating guest virtual addresses to host physical addresses, and another partition has a nested level translation mechanism for translating guest virtual addresses to host physical addresses. The different translation mechanisms and partitions are supported by a single hypervisor. Although the hypervisor is a paravirtualized hypervisor, it provides full virtualization for those partitions using nested level translations.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com