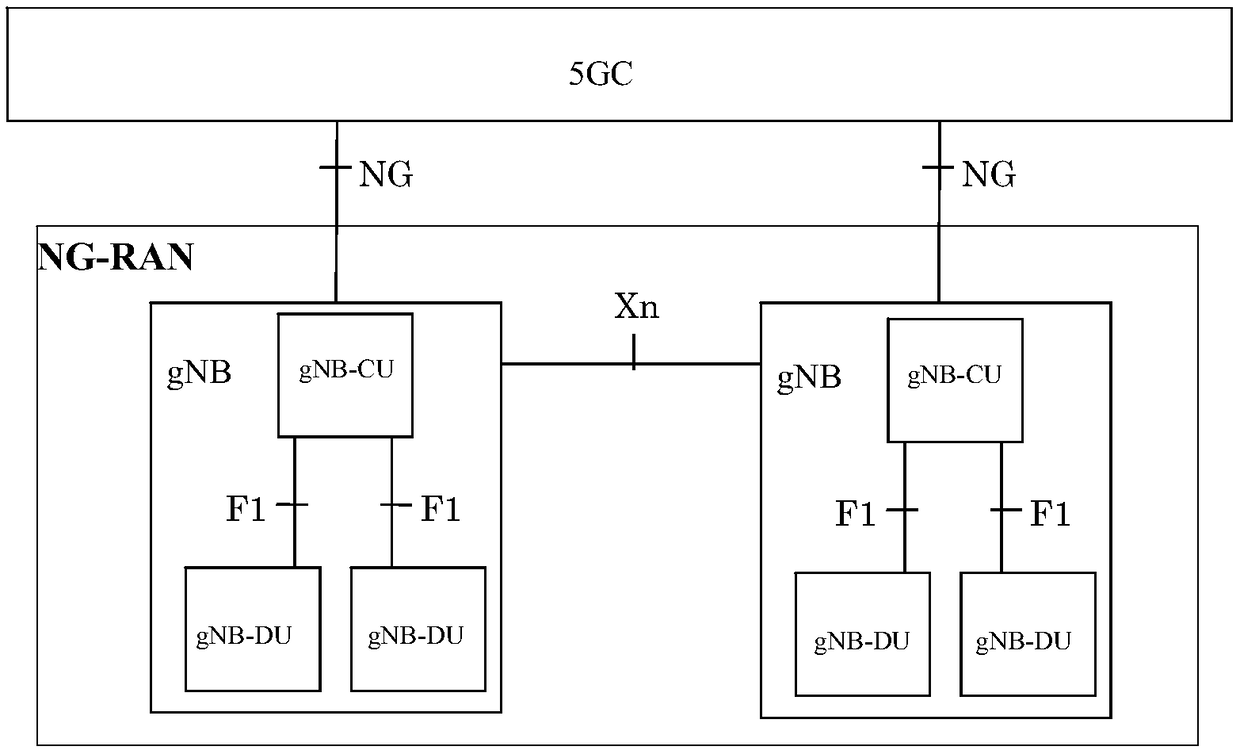
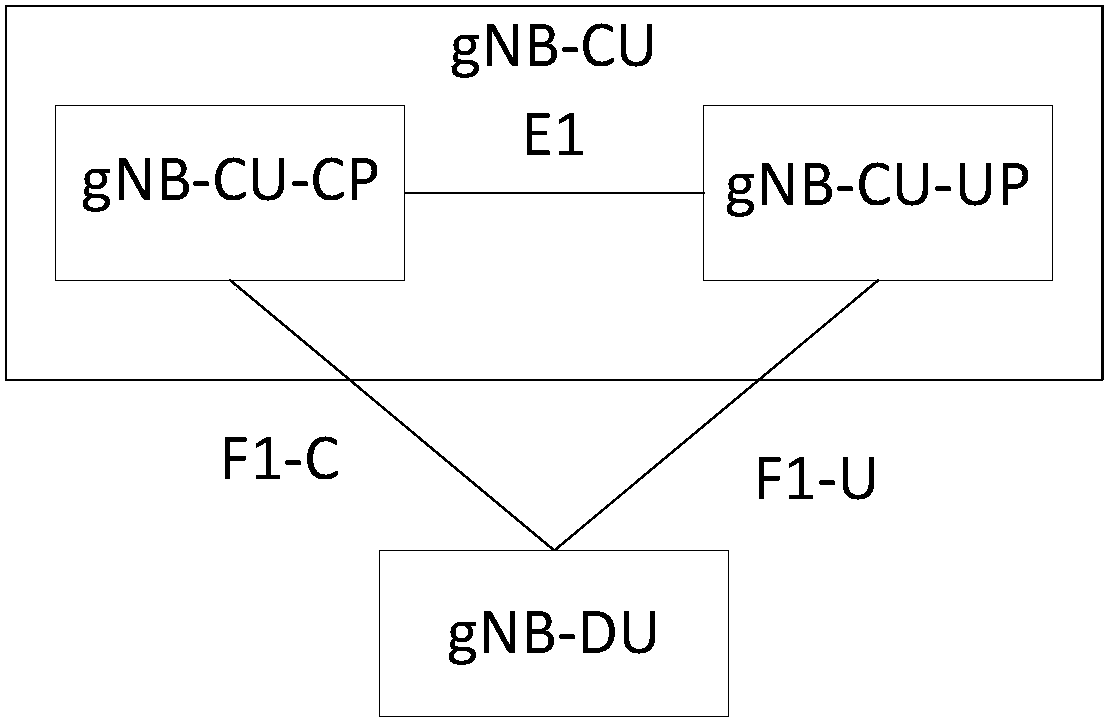
Patents
Literature
98results about How to "Achieve security isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
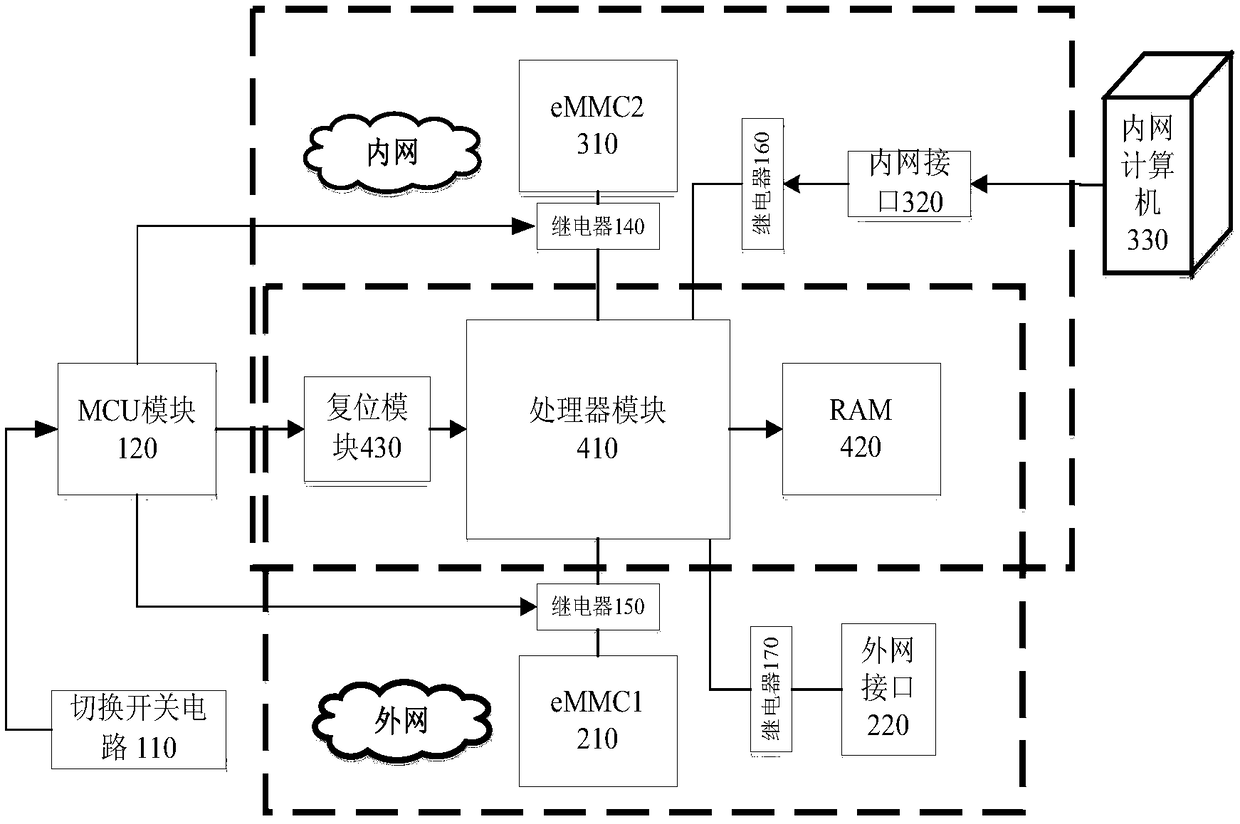
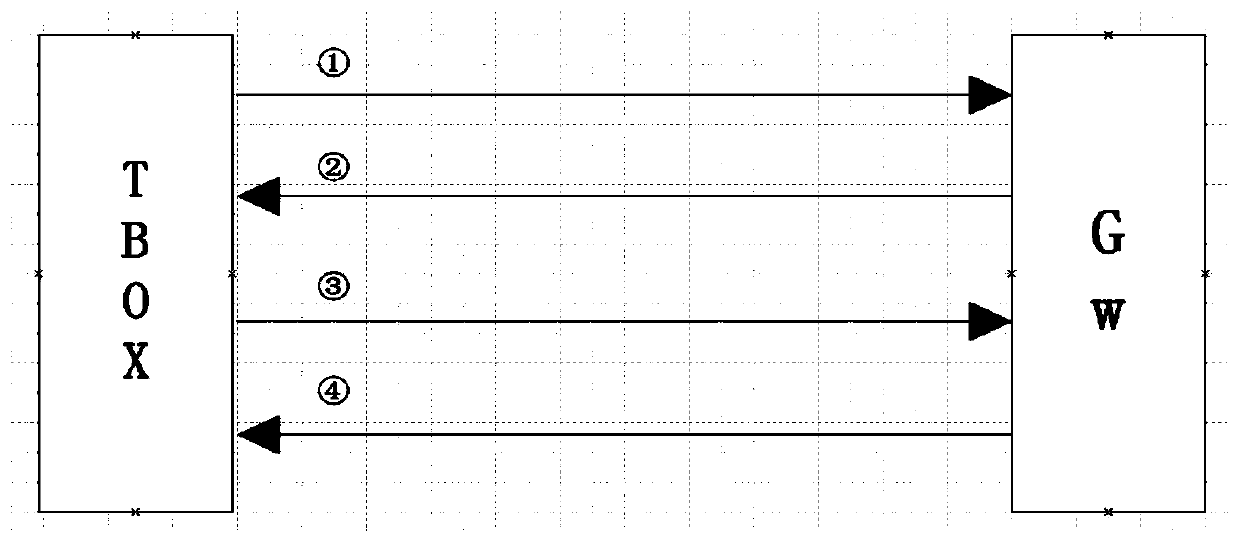
Intelligent terminal isolation system and intelligent terminal isolation method both based on processor safety extension
InactiveCN104318182AAchieve security isolationEnsure safetyInternal/peripheral component protectionSubstation equipmentAbstraction layerOperational system
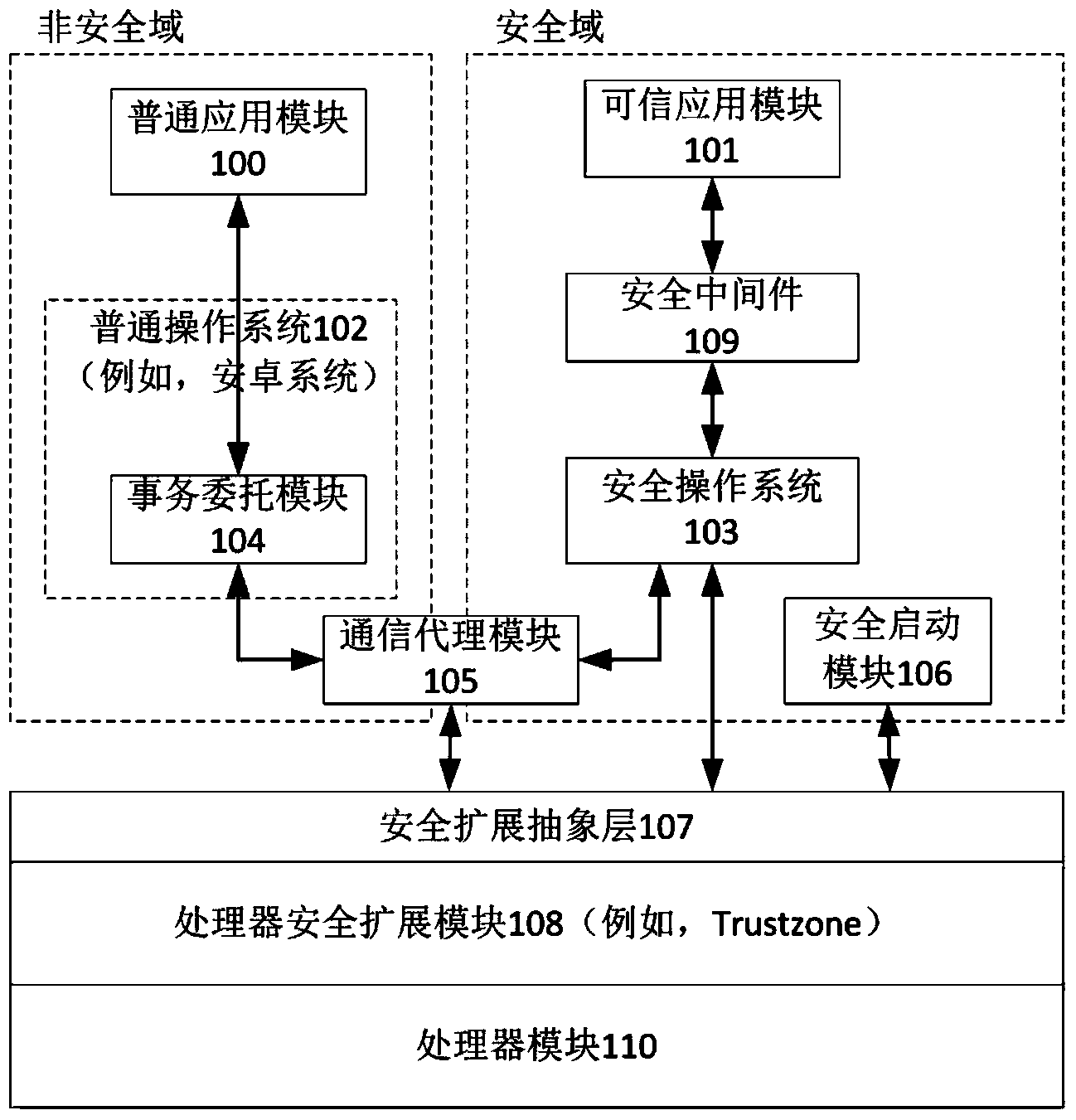
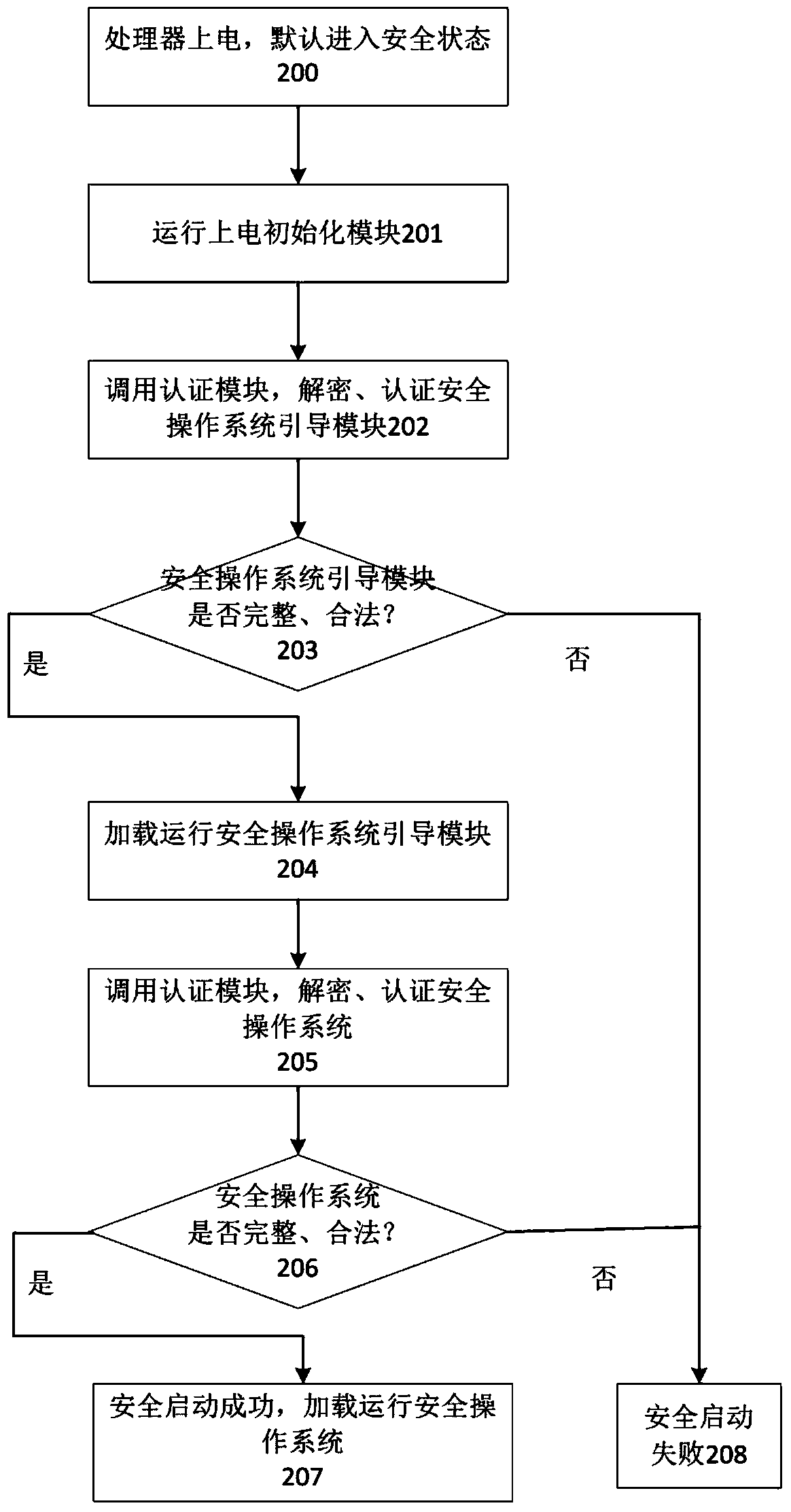
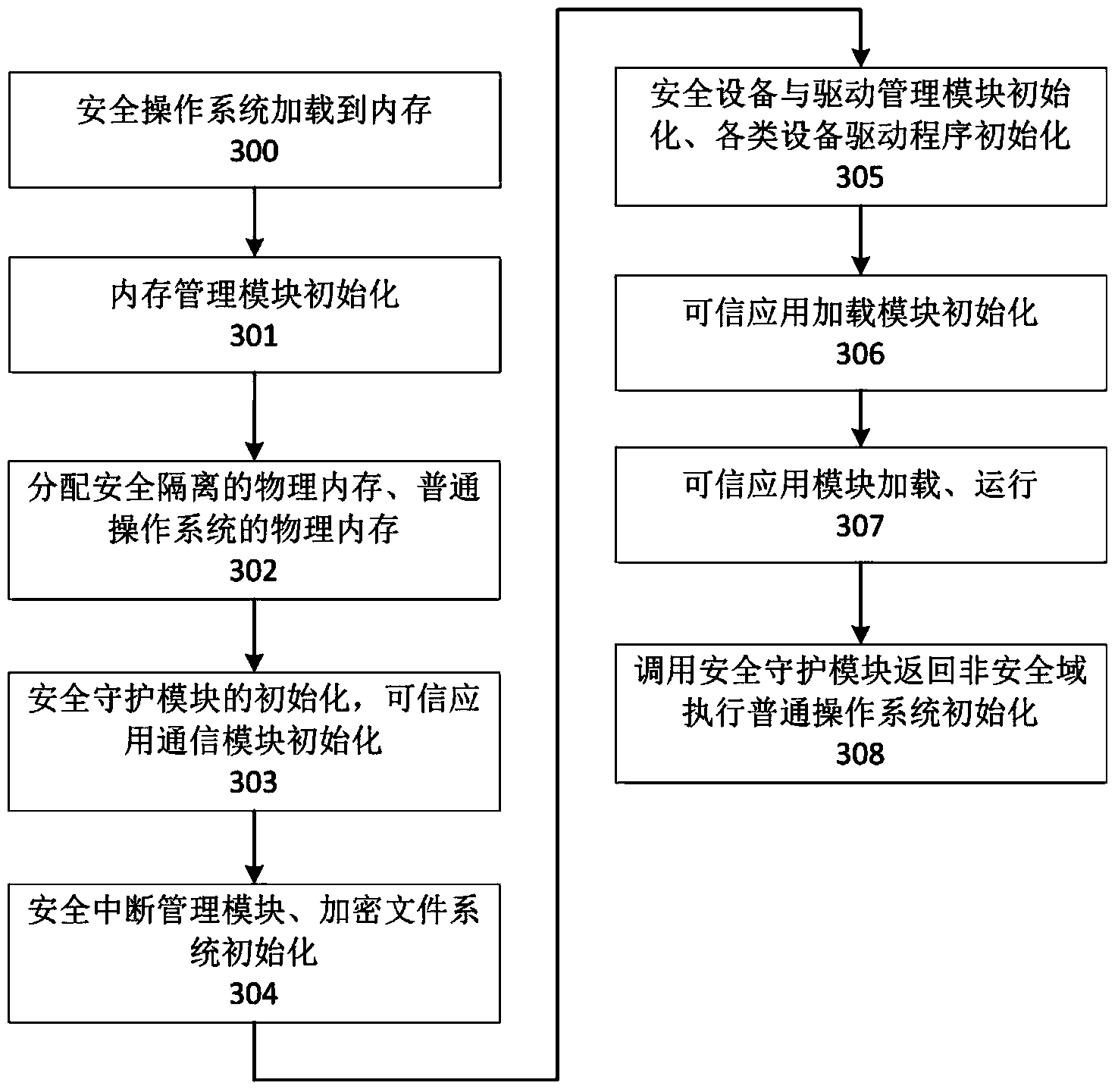
Disclosed are an intelligent terminal isolation system and an intelligent terminal isolation method both based on processor safety extension. The intelligent terminal isolation system comprises a safety starting module, a transaction commission module, a communication agent module, a safety extension abstraction layer, a safety operating system, safety middleware, credible application modules and a common application module. The safety starting module simply initializes hardware environment of an intelligent terminal, and authenticates and guides the safety operating system. The communication agent module is responsible for encapsulation and communication of bottom layer data of the credible application modules and the common application module. The safety extension abstraction layer provides a uniform calling interface to the safety operating system. The safety operating system provides mutually independent operation space for the credible application modules in a whole safety domain and manages all software and hardware resources in the safety domain. The safety middleware is a core library related to implementation of safety functions and transaction commissions and provides related functional interfaces to credible applications. The intelligent terminal isolation system and the intelligent terminal isolation method aim to provide a complete safety isolation mechanism to the intelligent terminal and improve safety of software operation environment.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Isolation device and isolation method suitable for power Internet of Things client side
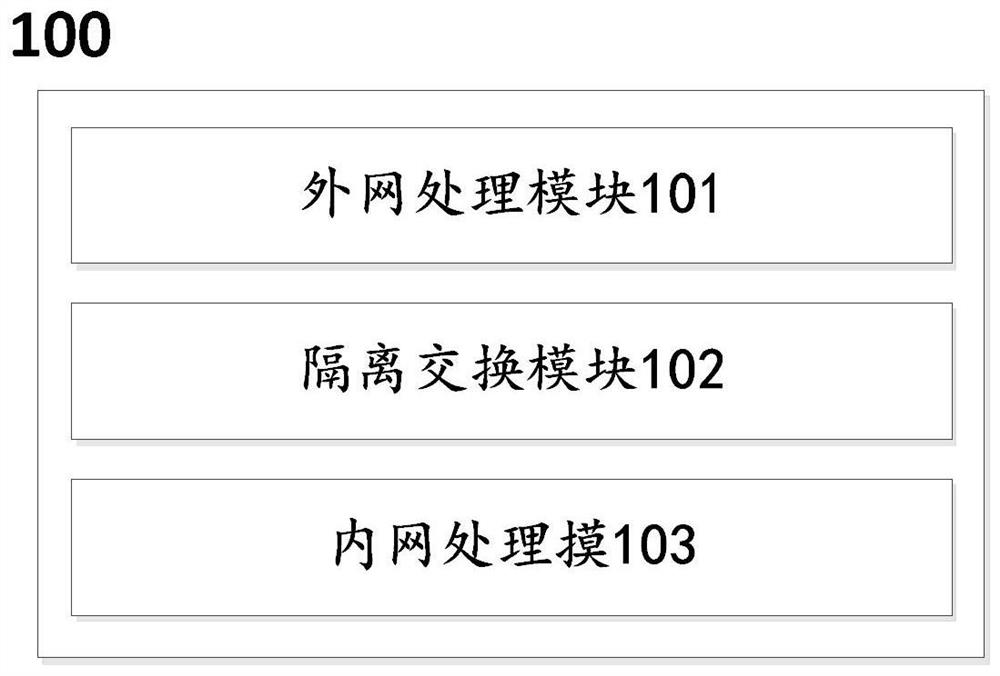
The invention relates to an isolation device and isolation method suitable for a power Internet of Things client side. The method comprises the steps: carrying out analysis of a received first data message transmitted by external network equipment through an external network processing module to obtain key information, and carrying out protocol format conversion of the key information according toa data ferry protocol to obtain a second data message; controlling the external network processing module and an internal network processing module to be in a physical isolation state by utilizing anisolation switching module, and performing format verification on the second data message; after the format of the second data message is verified, decrypting the second data message by using the internal network processing module, and conducting protocol format conversion processing on the decrypted second data message according to a special communication protocol of the power Internet of Things, so that a third data message can be obtained and sent to internal network equipment. Security isolation between an open client side access network and an electric power Internet of Things core network is realized, and a core service system can be effectively prevented from being illegally invaded.
Owner:CHINA ELECTRIC POWER RES INST +2
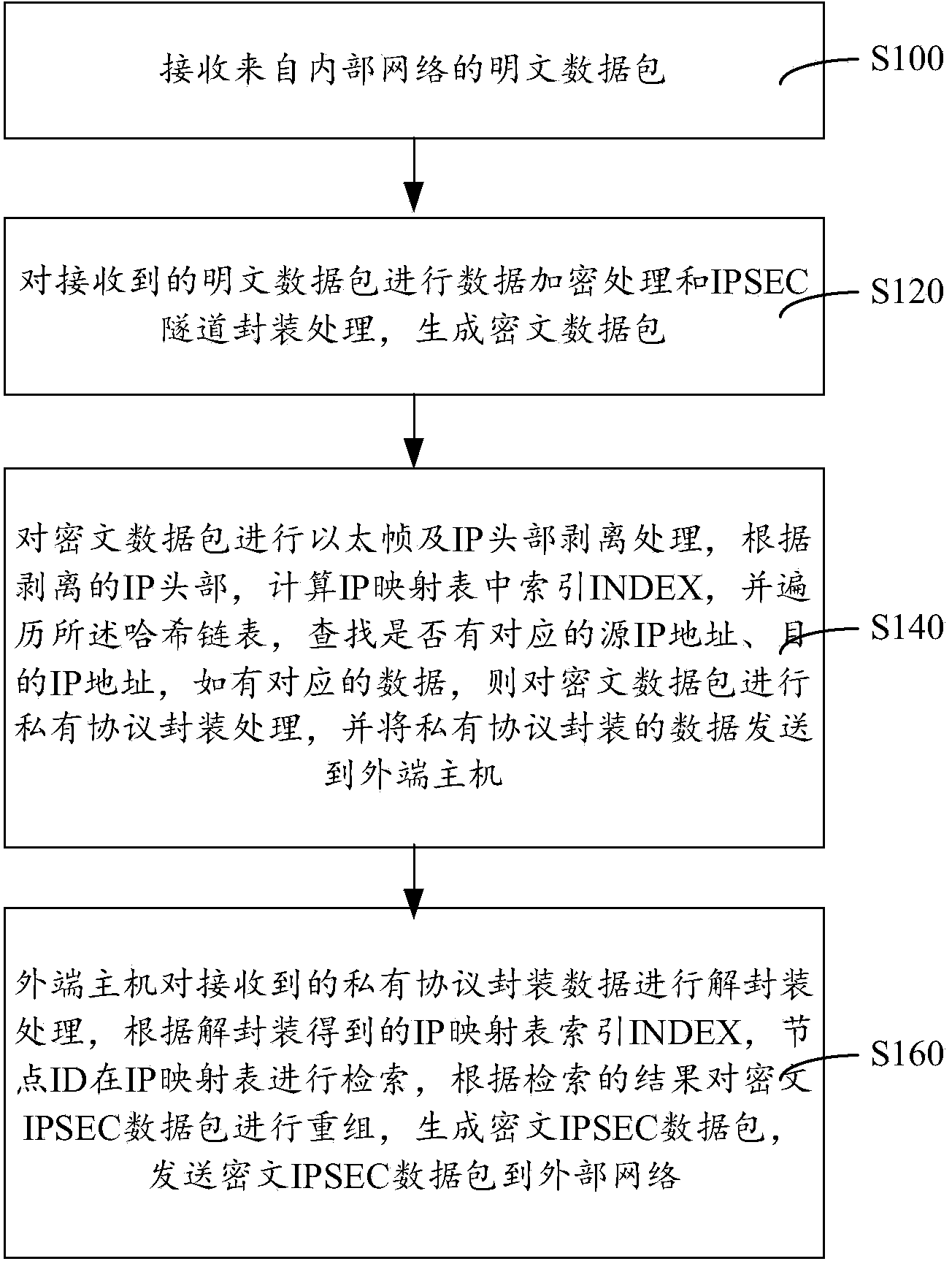
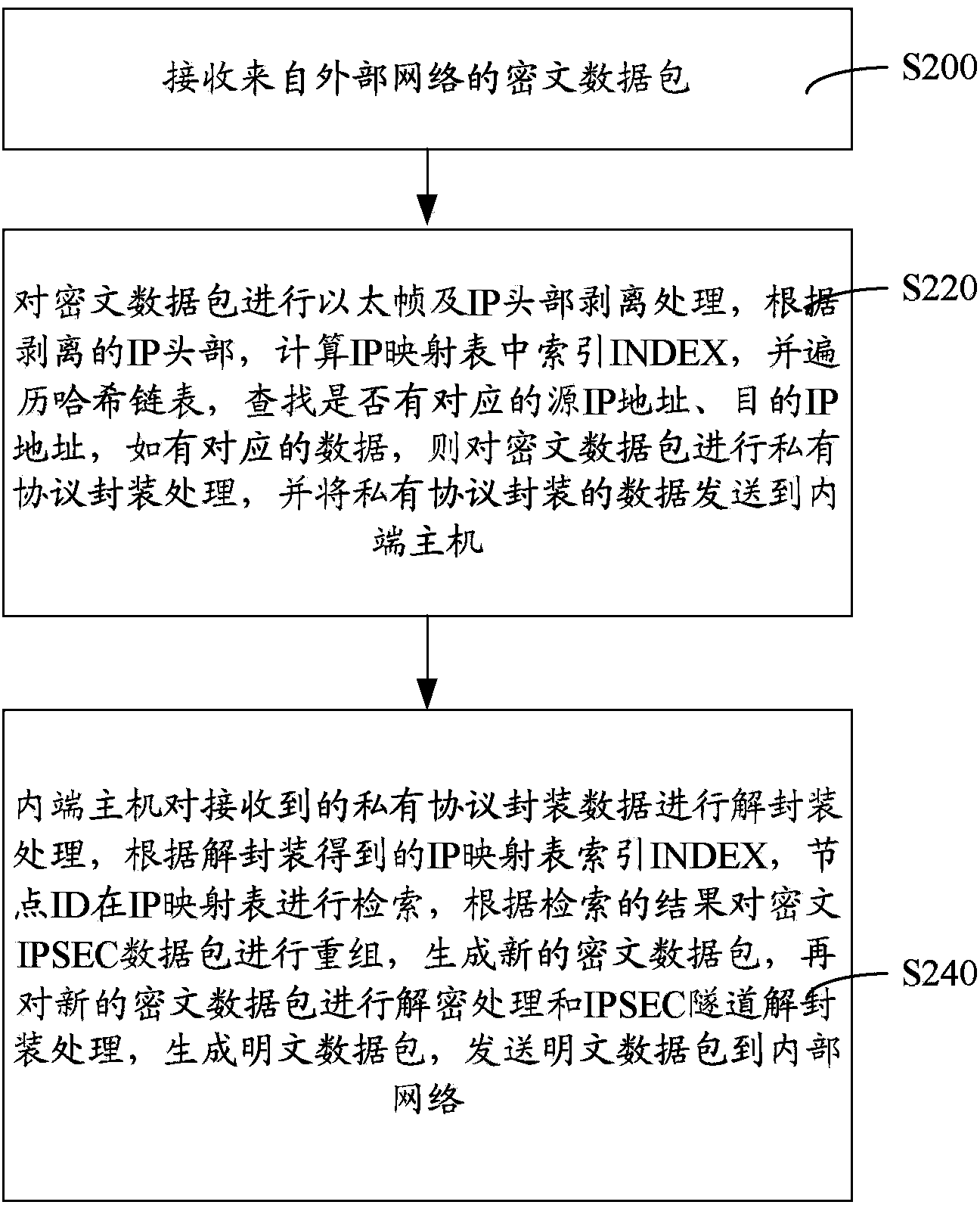
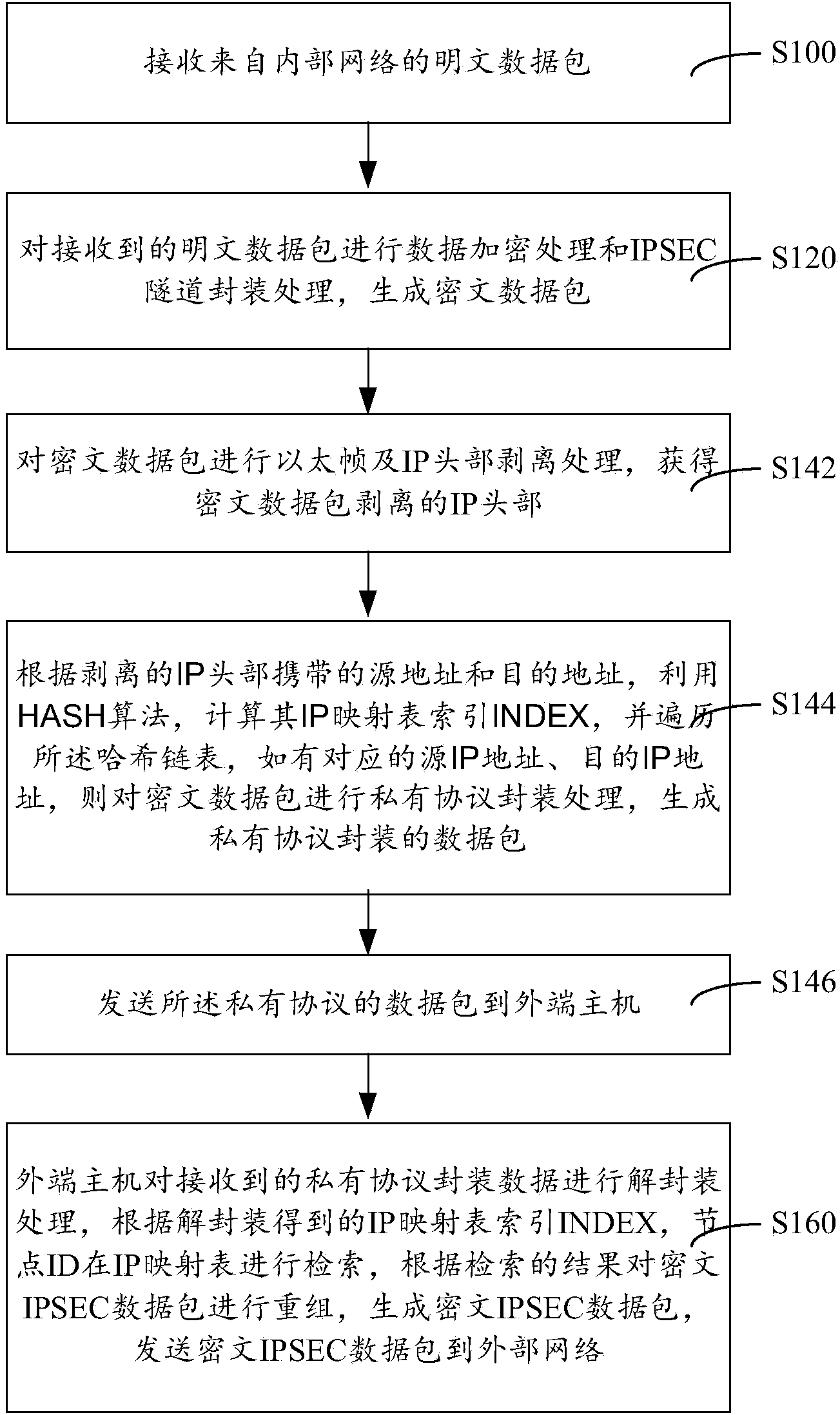
IPSEC (internet protocol security) VPN (virtual private network) device, isolation method thereof and isolation system thereof
ActiveCN103812861AAchieve security isolationPrevent intrusionTransmissionInternet protocol suiteNetwork packet
The invention provides an IPSEC (internet protocol security) VPN (virtual private network) device, an isolation method thereof and an isolation system thereof. The device comprises an inner end host, an outer end host and a non-network isolation card, the inner end host and the outer end host respectively maintain the same IP (internet protocol) mapping table, each table entry defines information such as a primary address, a destination address and IP mapping ID (identity), a data packet realizes network isolation by modes such as IP head stripping and recombination, IP mapping table search and filtering, private protocol capsulation and decapsulation and non-network isolation card transmission, an IPSEC VPN network data packet is encrypted and decrypted on an internal network host by the data packet, the device can resist malicious attack behaviors and transmission of viruses, Trojans and malicious plug-ins, security isolation in connection of an internal network and an external network is really achieved, higher-strength security protection for the internal network, the IPSEC VPN device and the network service data packet is realized, and the IPSEC VPN isolation device is high in security degree.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
MMC-HVDC system, DC side isolation device and isolation method
InactiveCN104993472AAchieve isolationAchieve security isolationDc source parallel operationEmergency protective arrangements for automatic disconnectionCapacitanceDc circuit breaker
The invention discloses an MMC-HVDC system, a DC side isolation device and an isolation method. The DC side isolation device comprises first isolation switches, current transferring switches, input / output terminals and a DC breaker. One terminal of the DC breaker is connected to the ground, and the other terminal is connected to all first isolation switches; each of the first isolation switches is connected to one input / output terminal through the current transferring switch; the current transferring switch comprises a first lightening arrester and a first IGBT group or an H bridge group, wherein either the IGBT group or the H bridge group is connected to the lightening arrester in parallel; the first IGBT group consists of N first IGBTs and N second IGBT groups; the H bridge comprises N H bridge circuits which are connected in parallel; and each of the H bridge circuit comprises a first capacitor and four third IGBTs, wherein N>=kU0 / U1, E[element of]Z. The invention realizes the isolation between the MMC and the plurality of DC circuits and the MMC-HVDC system, and saves the investment cost of the power grid.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
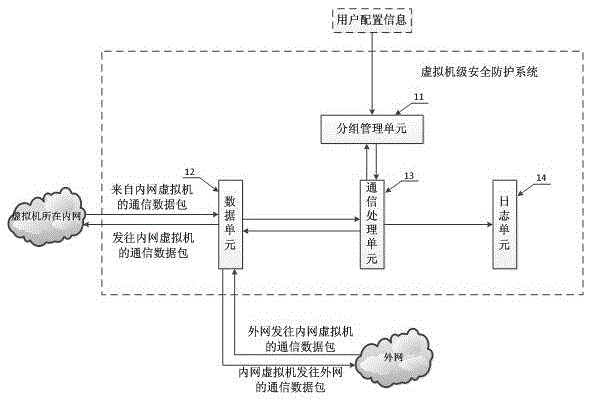
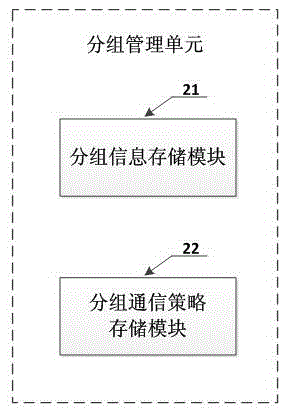
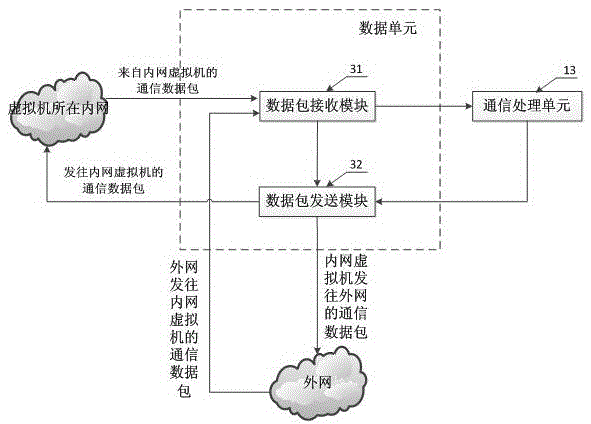
Virtual machine level security protection system and method
InactiveCN105577702ARealize group managementComprehensive monitoring of communication trafficTransmissionPacket communicationData pack
The invention provides a virtual machine level security protection system and method. The system comprises a packet management unit, a data unit, a communication processing unit and a log unit, wherein the communication processing unit is connected to the packet management unit, the data unit and the log unit; a packet management strategy of virtual machines is stored in the packet management unit, the data unit is used for receiving and sending a communication data packet and sending the communication data packet between the virtual machines to the communication processing unit, and the communication processing unit controls the communication process between the virtual machines according to the packet management strategy in the packet management unit and generates log information for the log unit. By adopting the virtual machine level security protection system and method provided by the scheme of the invention, comprehensive and precise convergence management and monitoring of the flow generated by the communication between the virtual machines can be realized, the packet communication management between the virtual machines can be realized, the security protection of a virtual machine level network system is finally realized by the flow convergence management and the packet communication management, and the virtual machine level security protection system and method have broad promotion and application prospects.
Owner:北京卫达信息技术有限公司
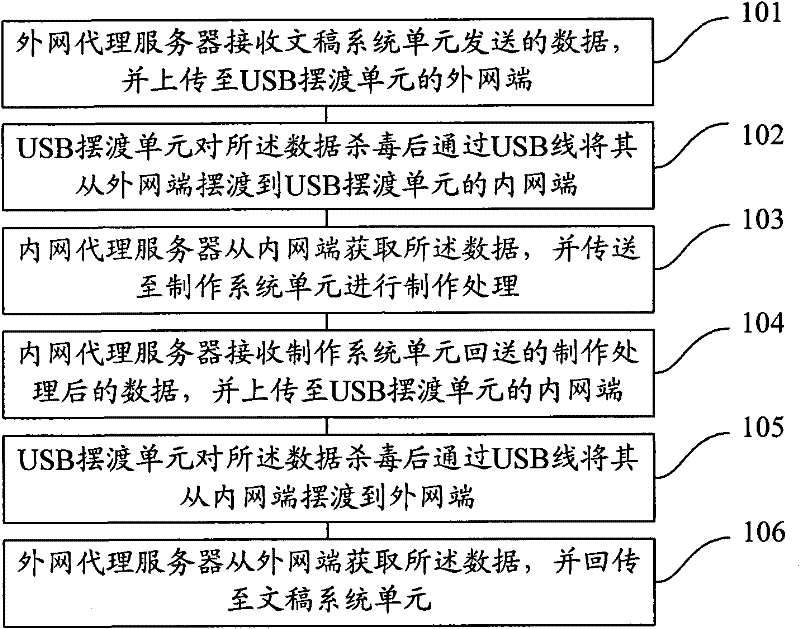
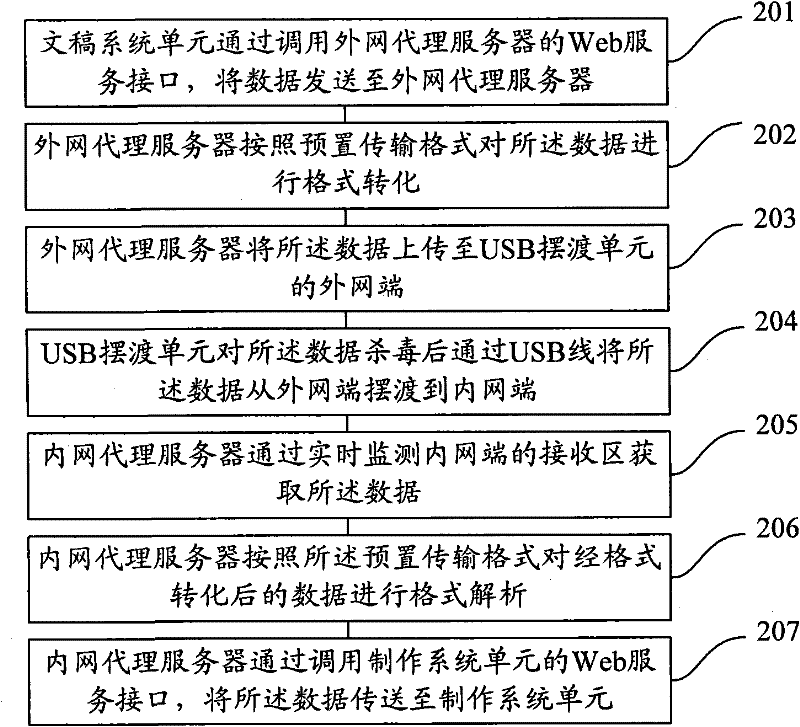
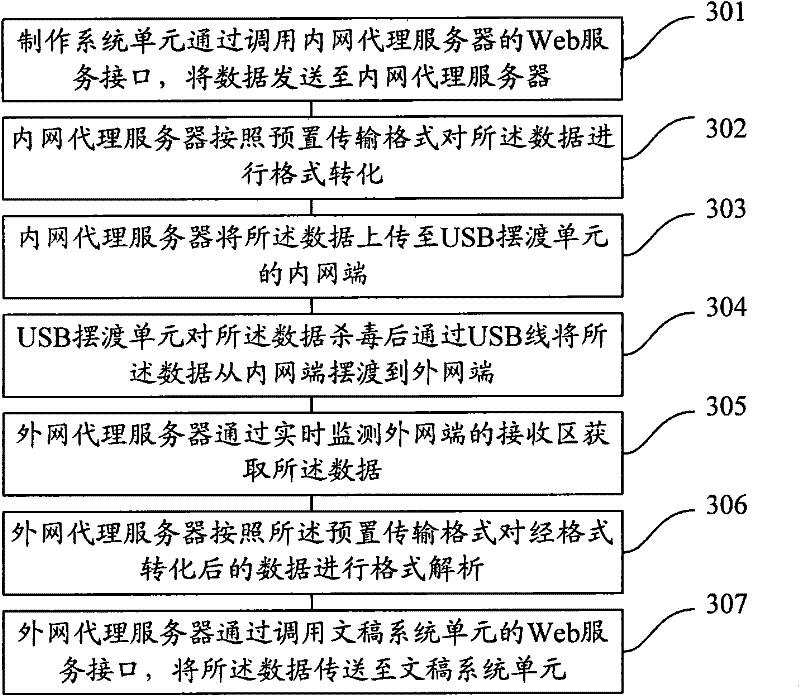
Manuscript system-based internal and external network data transmission method and system
The invention provides a manuscript system-based internal and external network data transmission method and system. The method comprises the following steps: an external network proxy server receives data sent by a manuscript system unit, and uploads the data to an external network of a universal serial bus (USB) ferrying unit; the USB ferrying unit kills viruses of the data, and ferries the data to an internal network of the USB ferrying unit from the external network through a USB wire; an internal network proxy server acquires the data from the internal network, and transmits the data to a making system unit for making and processing; the internal network proxy server receives the processed data returned by the making system unit, and uploads the data to the internal network of the USB ferrying unit; the USB ferrying unit kills viruses of the data, and ferries the data to the external network from the internal network; and the external network proxy server acquires the data from the external network, and retransmits the data to the manuscript system unit. According to the method and the system disclosed by the invention, the security in the data transmission process is ensured.
Owner:CHINA DIGITAL VIDEO BEIJING
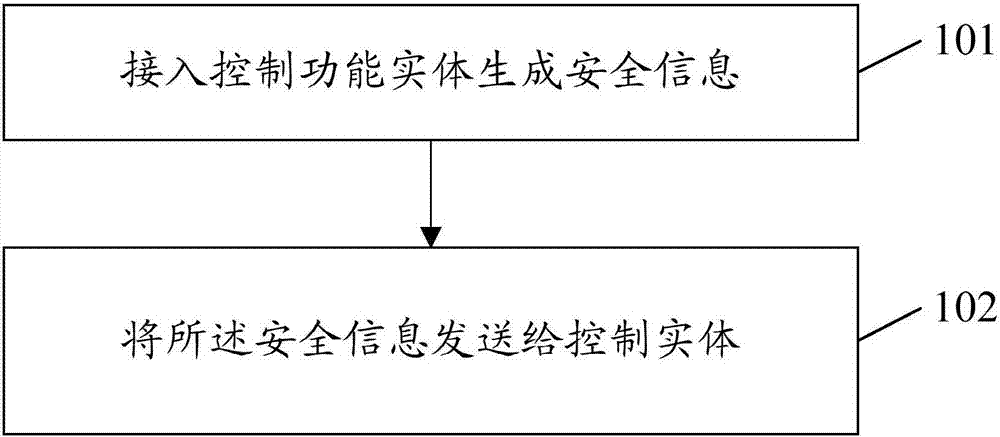
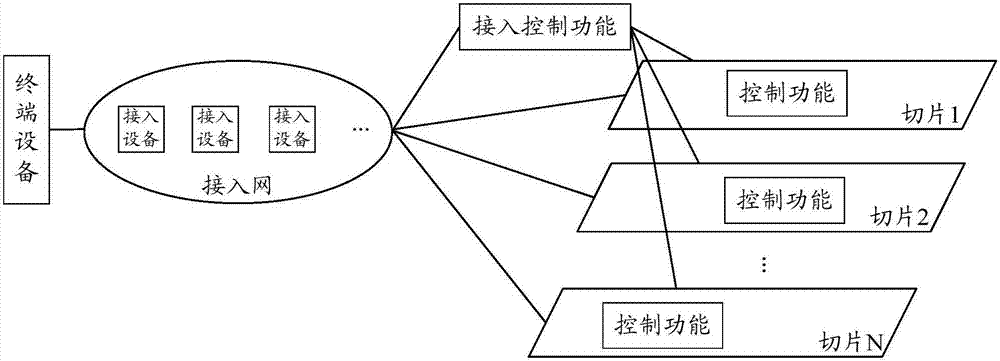
Processing method and device as well as acquisition method and device for security information
ActiveCN107094127AAchieve security isolationImprove access securityTransmissionSecurity arrangementControl functionSecurity information
The invention provides a processing method and device as well as acquisition method and device for security information. The processing method for the security information comprises the following steps: enabling an access control functional entity to generate security information; and sending the security information to a control entity. According to the embodiment of the invention, the access control functional entity authenticates and authorizes the terminal and is responsible for generating different security information for different network slices signed with the terminal, the network slices process high layer information sent by the terminal by using the generated security information to ensure that the terminal is accessed to the network slices, and thus the security isolation among the different network slices can be achieved, the access security can be improved, and the security isolation among the different network slices can be achieved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
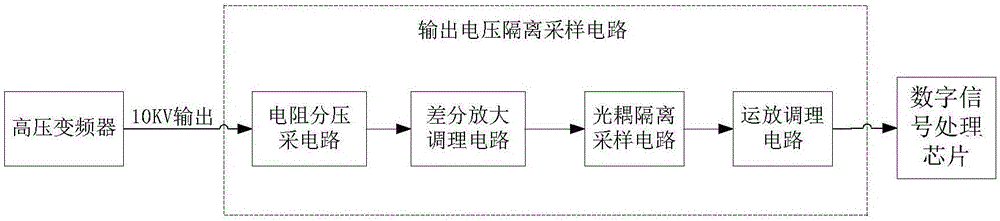
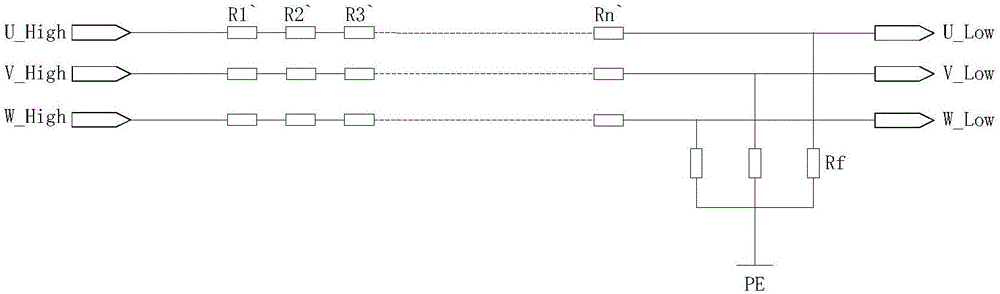
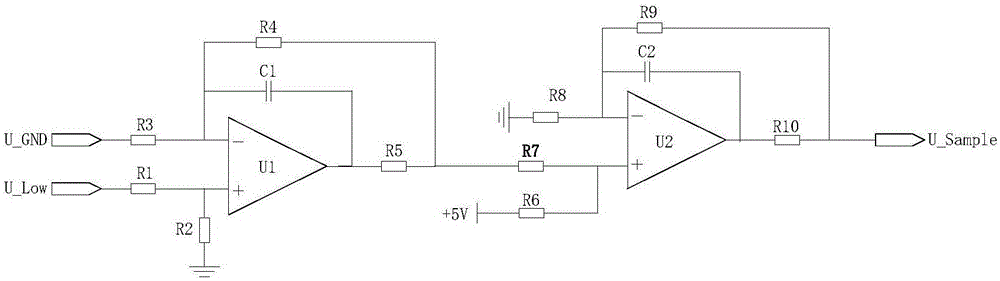
Output voltage isolation sampling circuit of high-voltage inverter
ActiveCN106645905AConvenience to workAchieve security isolationEfficient power electronics conversionMeasurement using digital techniquesOvervoltageDigital signal processing
The invention discloses an output voltage isolation sampling circuit of a high-voltage inverter. The isolation sampling circuit is composed of a resistor and divider sampling circuit, a differential amplifier conditioning circuit, an optocoupler isolation sampling circuit, and an operational amplifier conditioning circuit. The input terminal of the resistor and divider sampling circuit is connected with a voltage output terminal of a high-voltage inverter; the differential amplifier conditioning circuit is connected with the resistor and divider sampling circuit electrically; and the operational amplifier conditioning circuit is connected with the optocoupler isolation sampling circuit electrically. The voltage after processing is a voltage meeting a digital-analog signal converter sampling pin of a digital signal processing chip and is sent into a digital-analog signal converter sampling pin of a digital signal processing chip; and the digital signal processing chip carries out sampling and computing processing, so that the system is controlled to monitor the output voltage of the high-voltage inverter in real time and overvoltage protection, undervoltage protection, phase-locked bypass and other functions can be realized.
Owner:DAYU ELECTRIC
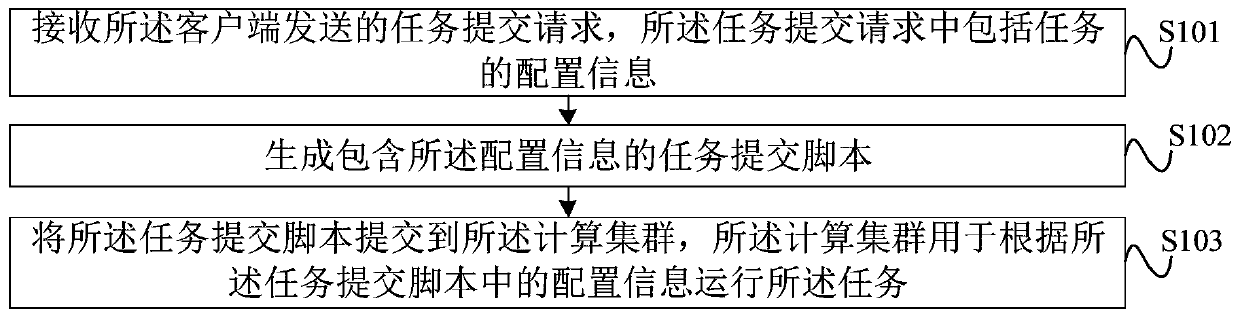
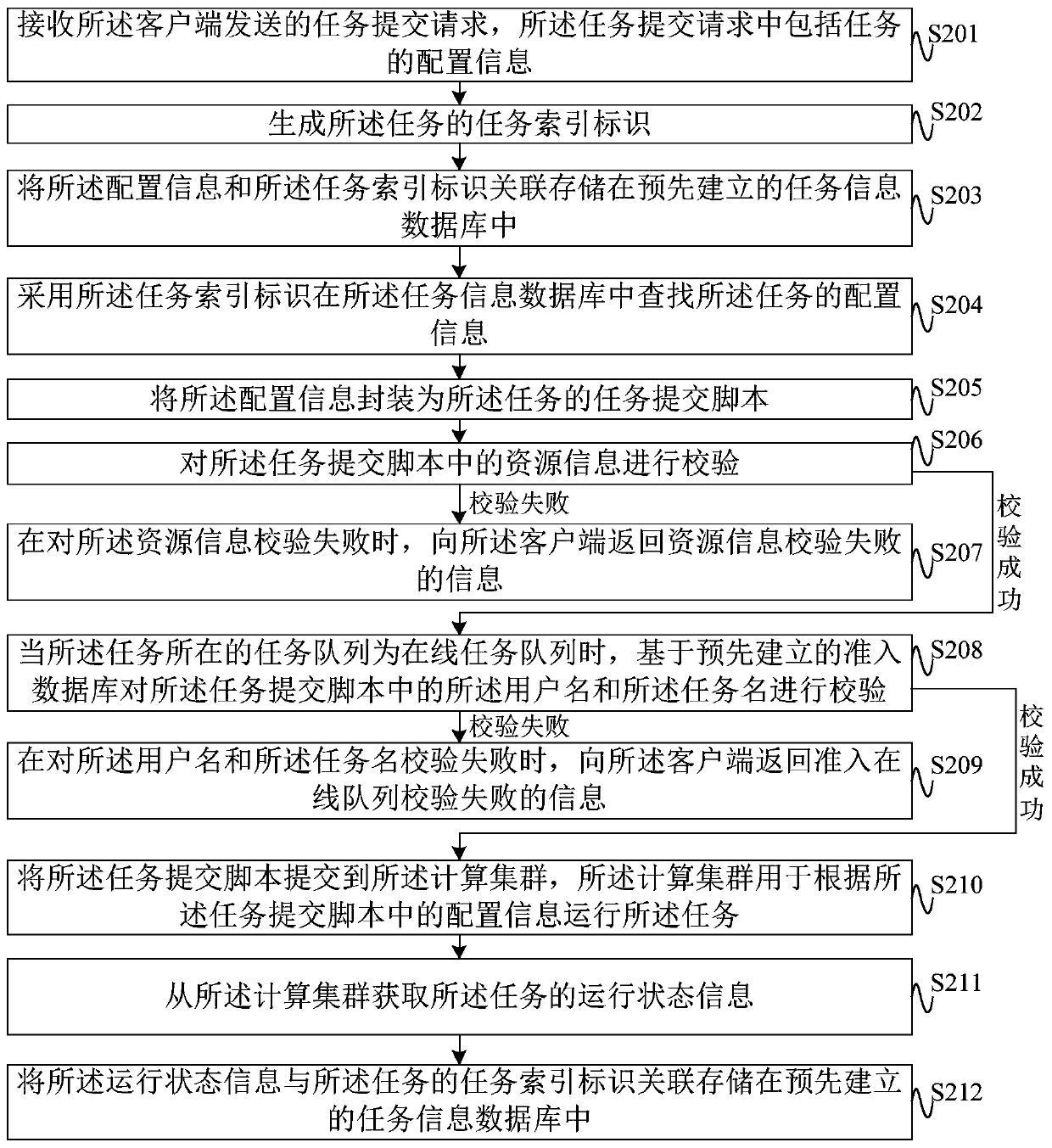
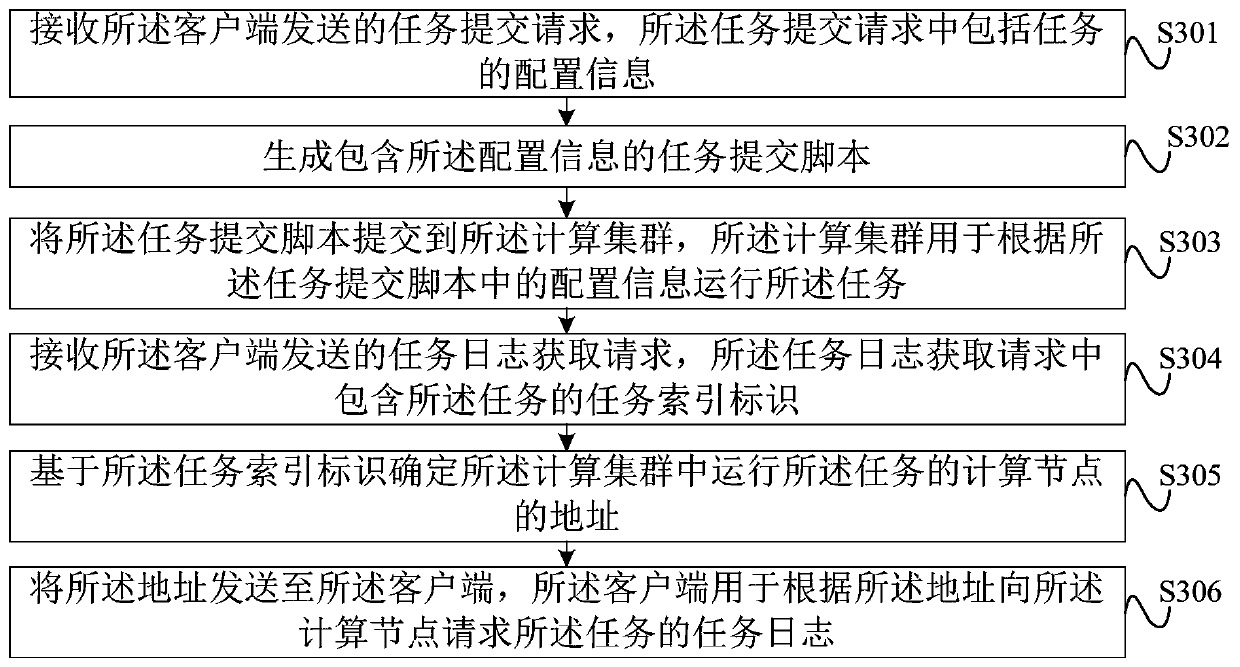
Task processing method and device, server, client, system and storage medium
PendingCN110781007AEnsure safetyAchieve security isolationResource allocationSoftware engineeringProcessing
The embodiment of the invention discloses a task processing method and a device, a server, a client, a system and a storage medium, and the task processing method comprises the steps: receiving a tasksubmission request sent by the client, and the task submission request comprises the configuration information of a task; generating a task submission script containing configuration information; andsubmitting the task submission script to a computing cluster, wherein the computing cluster is used for running the task according to the configuration information in the task submission script. According to the method of the invention, task submission is divided into a client and a server; a user only needs to configure configuration information during task running at a client; a user does not need to deeply learn meanings of various parameters of the computing cluster; therefore, on one hand, the learning cost of the user and the threshold that the user uses the computing cluster are reduced, and on the other hand, the user realizes safe isolation between the computing cluster and the user side through indirect reaction between the computing cluster and the server, and a guarantee is provided for the security of the computing cluster.
Owner:GUANGZHOU NETSTAR INFORMATION TECH CO LTD
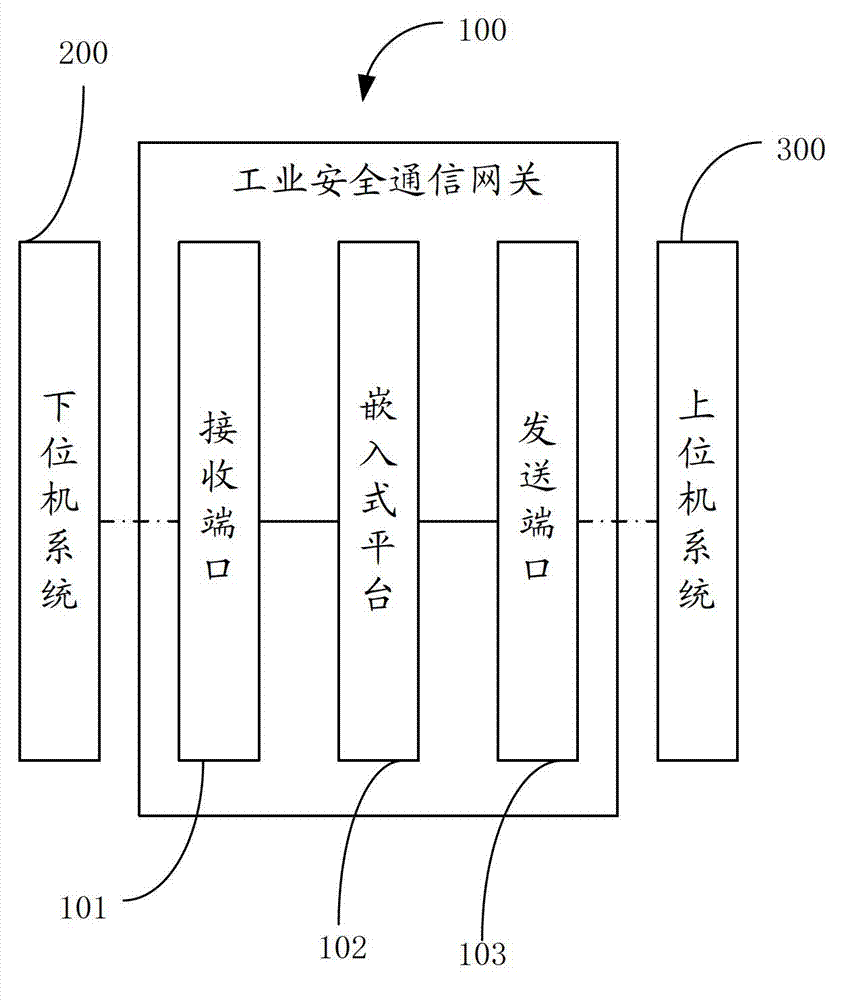
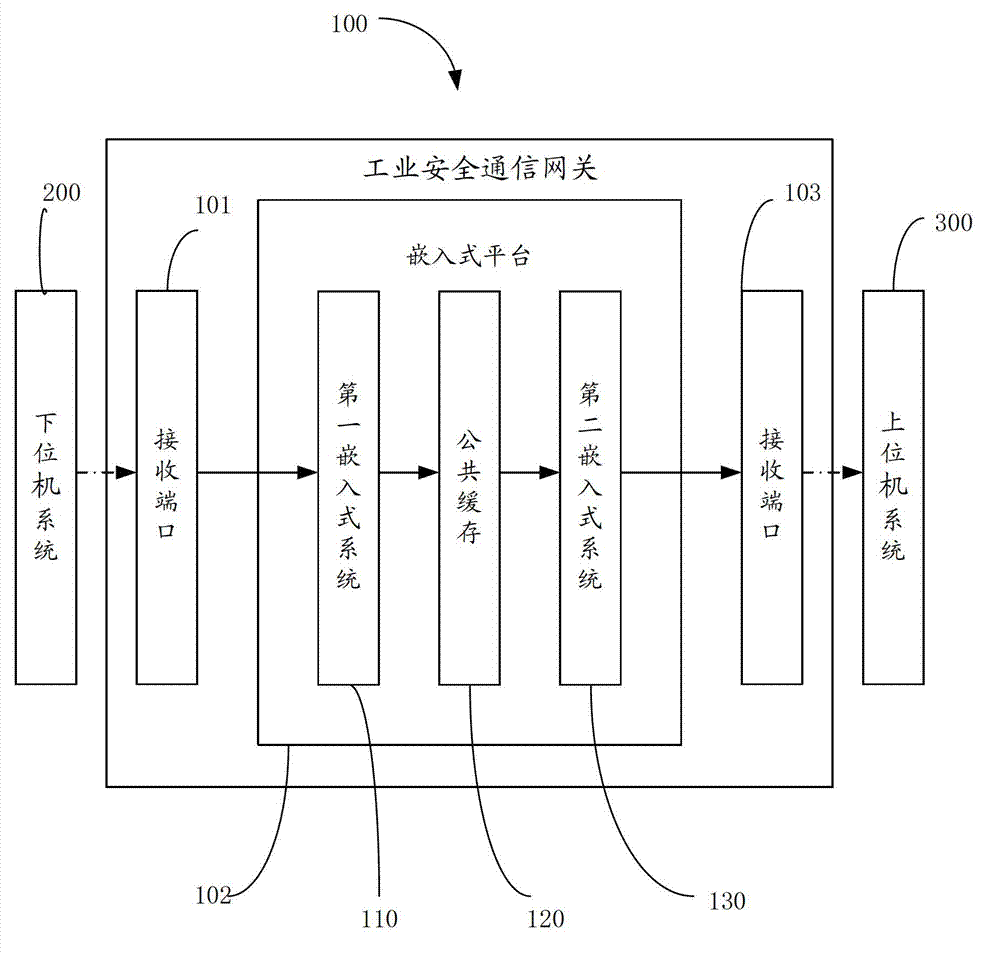
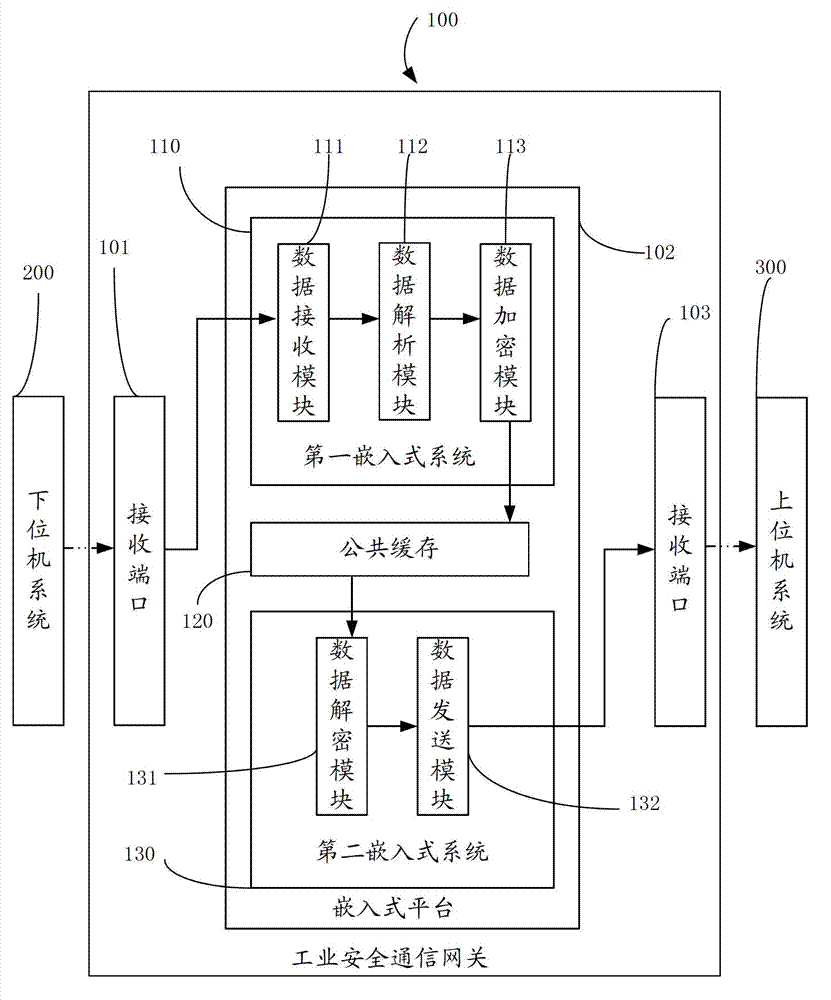
Industrial security communication gateway
The invention discloses an industrial security communication gateway, which comprises a data receiving port connected with a lower computer system, a data sending port connected with an upper computer system, and an embedded platform connected between the two ports. The industrial security communication gateway comprises two embedded systems and a public cache, wherein the two embedded systems have different functions; the first embedded system comprises a data receiving module, a data resolving module and a data encrypting module; and the second embedded system comprises a data decrypting module and a data sending module. By the industrial security communication gateway, the security of the industrial security communication gateway can be improved.
Owner:上海金自天正信息技术有限公司
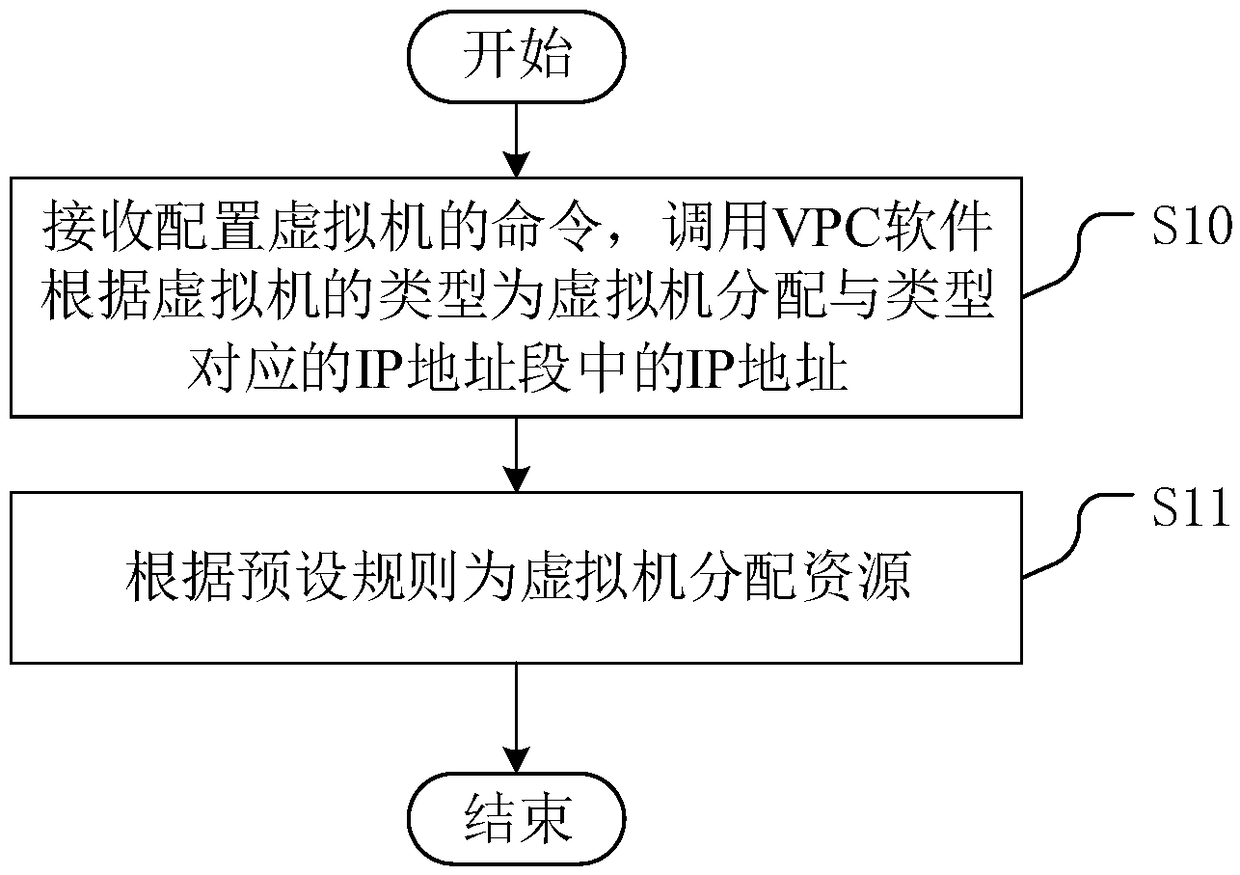
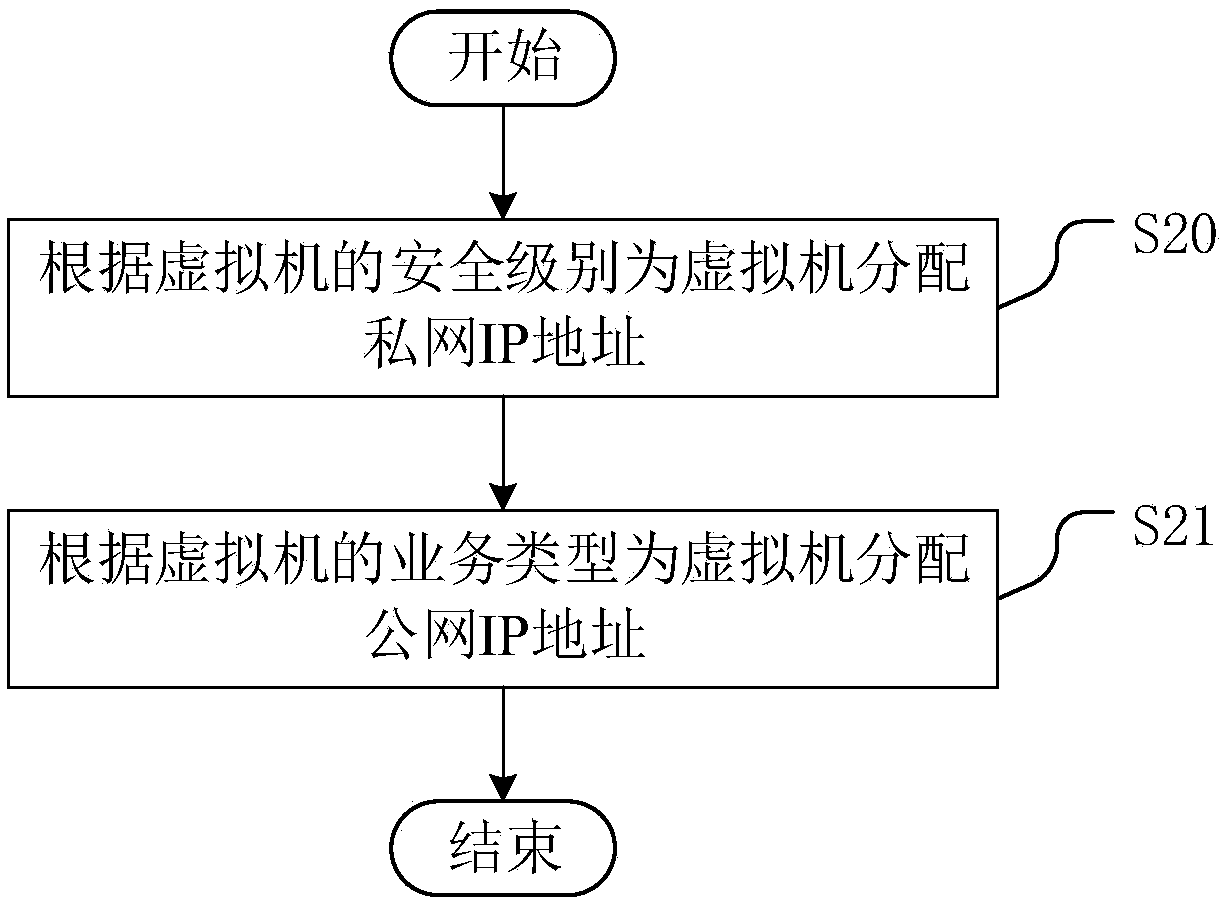
Configuration method and configuration system of virtual machine and SDN controller
InactiveCN109445912ARealize self-configurationAchieve security isolationNetworks interconnectionSoftware simulation/interpretation/emulationDisk controllerVideo transmission
The invention discloses a configuration method of a virtual machine. A mobile video transmission system is improved by an SDN technology, so that a controller and a switch are separated, and an algorithm is compiled and realized based on an SDN controller. The method comprises the following steps of receiving a command for configuring a virtual machine; and then calling VPC software, allocating anIP address in the IP address field corresponding to the type to the virtual machine according to the type of the virtual machine, wherein the IP address fields corresponding to the types are not overlapped; and allocating the resources to the virtual machines according to the preset rules, so that the virtual machines with different services or different security levels are allocated in differentIP address fields, the autonomous configuration of the virtual machines is realized, the security isolation among the virtual machines is realized, and the access security among the virtual machinesis improved. The invention also discloses a virtual machine configuration system and an SDN controller, which have the above beneficial effects.
Owner:国网新疆电力有限公司信息通信公司 +1
Program running method and device, equipment and medium
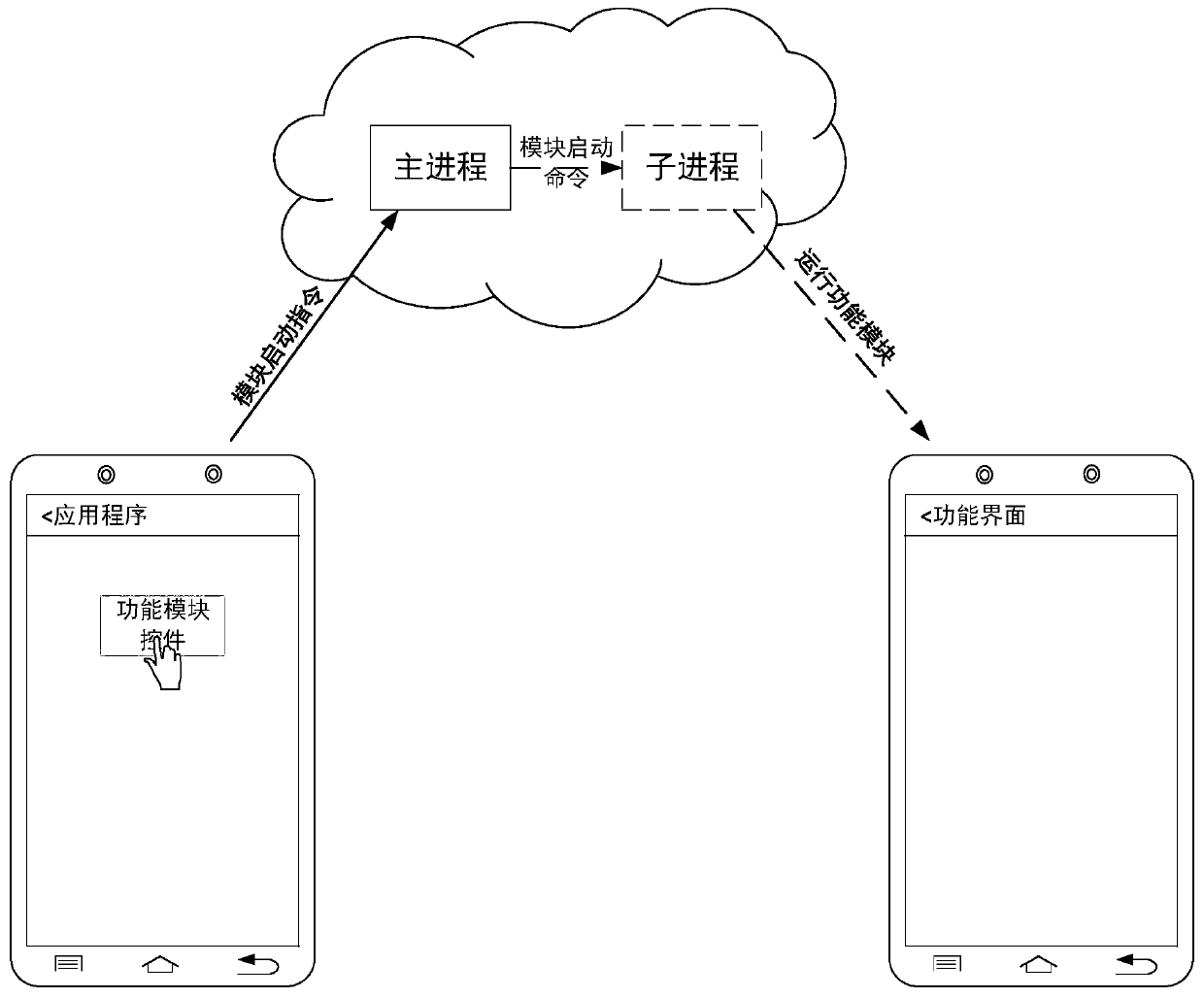
ActiveCN111381903AAchieve security isolationImprove securityPlatform integrity maintainanceProgram loading/initiatingSoftware engineeringSecure channel
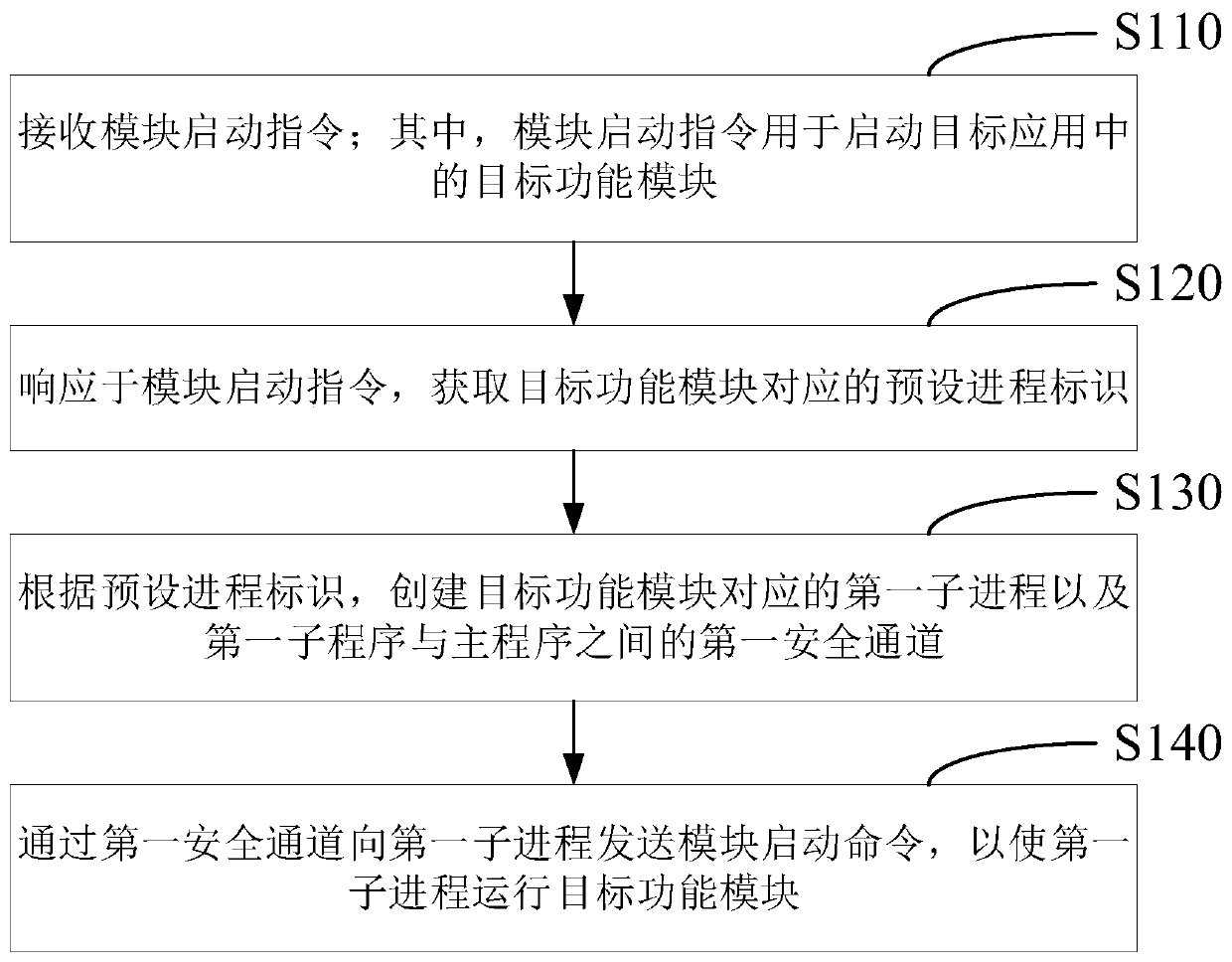
One or more embodiments of the present specification provide a program running method and device, equipment and a medium. In one embodiment, the program running method comprises the steps that a mainprocess used for running a target application receives a module starting instruction; wherein the module starting instruction is used for starting a target function module in the target application; the main process responds to the module starting instruction and obtains a preset process identifier corresponding to the target function module; the main process creates a first sub-process corresponding to the target function module and a first secure channel between the first sub-program and the main program according to a preset process identifier; and the main process sends a module starting command to the first sub-process through the first secure channel, so that the first sub-process runs the target function module.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
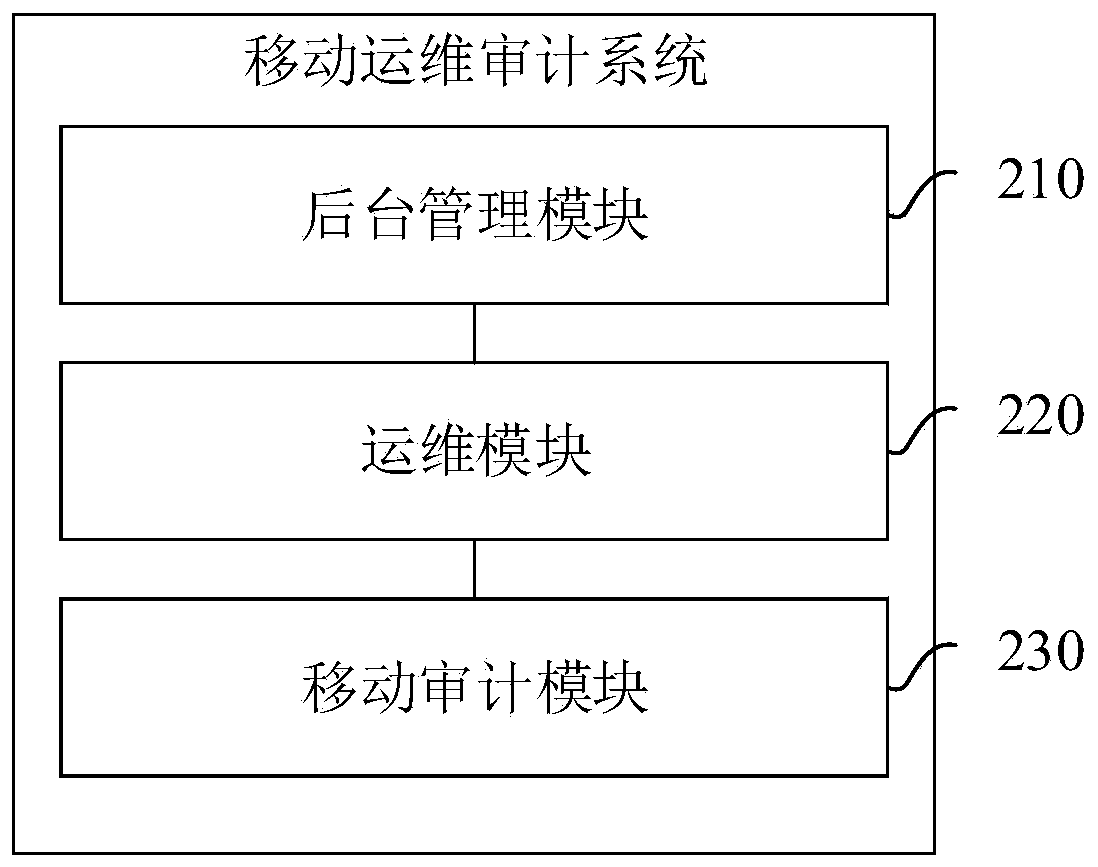
Mobile operation and maintenance auditing system
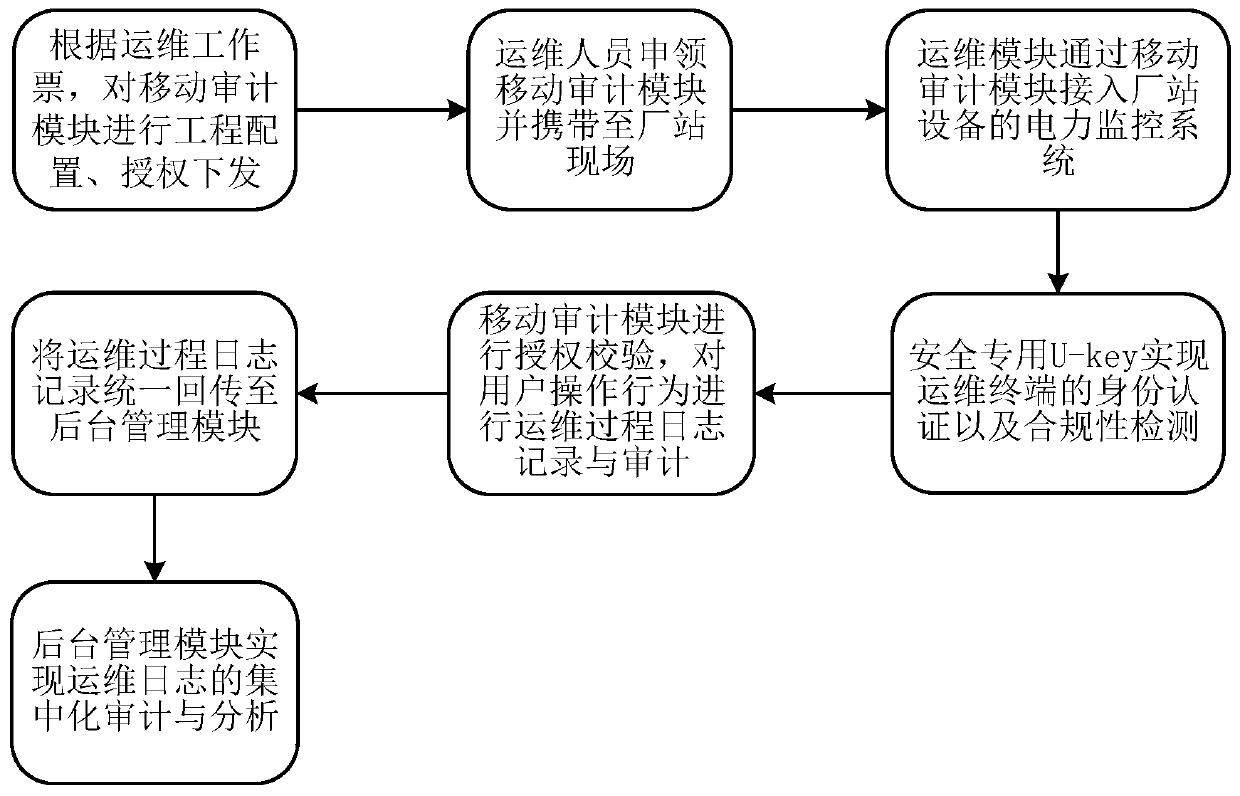
ActiveCN110011848AAchieve security isolationImprove securityData switching networksMonitoring systemMobile station
The invention relates to a mobile operation and maintenance auditing system. The system comprises a mobile auditing module, an operation and maintenance module and a background management module, thebackground management module is used for receiving the operation and maintenance work ticket, generating operation permission information according to the operation and maintenance work ticket, and sending the operation permission information to the mobile operation and maintenance auditing module; the operation and maintenance module is used for receiving an operation and maintenance operation ofa user, generating an operation and maintenance instruction according to the operation and maintenance operation, and sending the operation and maintenance instruction to the mobile auditing module;the mobile auditing module is used for judging whether the operation and maintenance authorization of the background management module is obtained or not according to the operation permission information when the operation and maintenance instruction is received; and if yes, executing the operation and maintenance instruction, and carrying out operation and maintenance on the plant station equipment according to the operation and maintenance instruction. By adopting the method, the problem that the operation and maintenance work of an existing power monitoring system is low in safety can be solved.
Owner:SHENZHEN COMTOP INFORMATION TECH
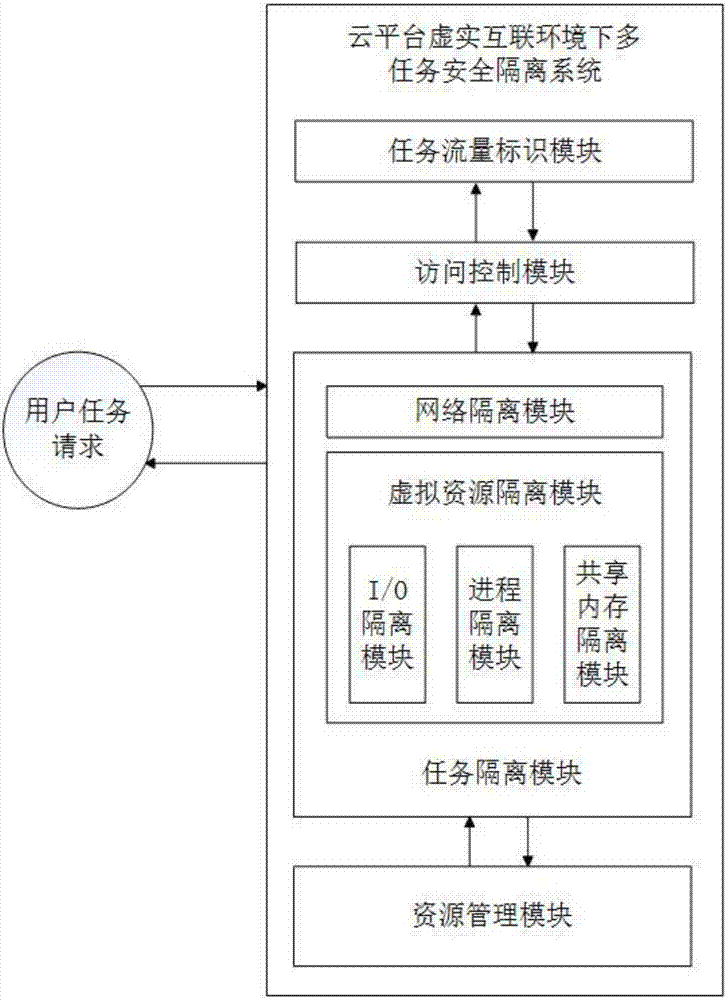
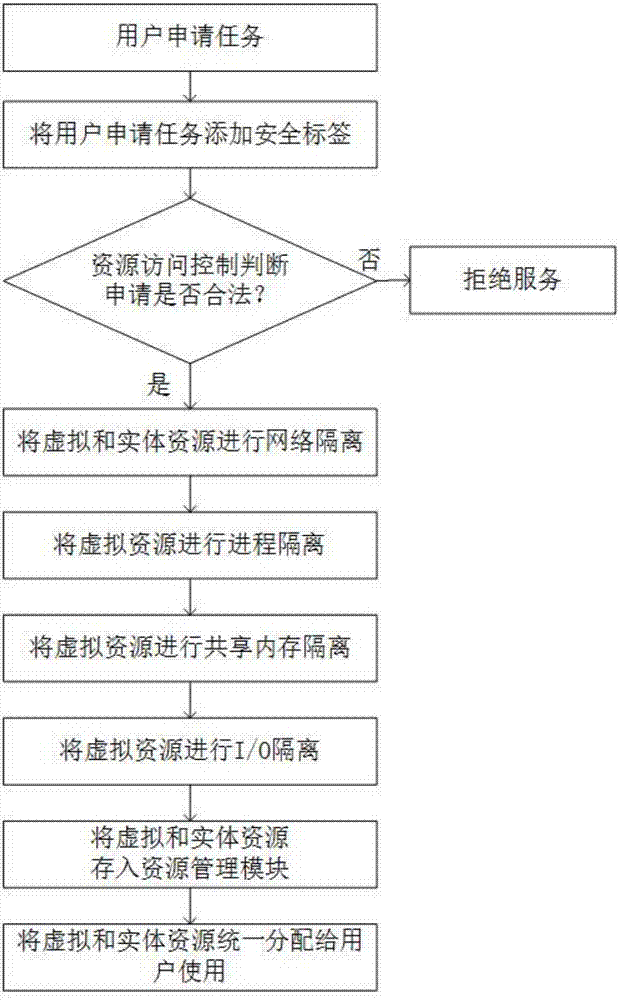
Multitask security isolation system and method under virtual-real interconnected environment of cloud platform
The invention provides a multitask security isolation system and method under a virtual-real interconnected environment of a cloud platform to solve the technical problem existing in the prior art that the unified management of multiple virtual and physical resources and the task security isolation cannot be implemented at the same time. The system comprises a task flow identification module for identifying different tasks, an access control module creating task resources according to the task identification, a task isolation module for security isolation between the tasks and between the resources, and a resource management module for unified management of the securely isolated resources. The implementing steps are as follows: the task flow label module adds a security label to a task and required resources thereof; the access control module verifies user identity and authority information and applies for the virtual and physical resources required by the task; the access control module performs network isolation and virtual resource isolation on the resources applied for the task; and the resource management module performs unified management on the securely isolated virtual and physical resources in the cloud platform and assigns the resources required by the task to the task.
Owner:XIDIAN UNIV
Storage battery monitoring activation device and system
InactiveCN108802622ARealize timely activationRealize real-time monitoringElectrical testingElectricityData acquisition
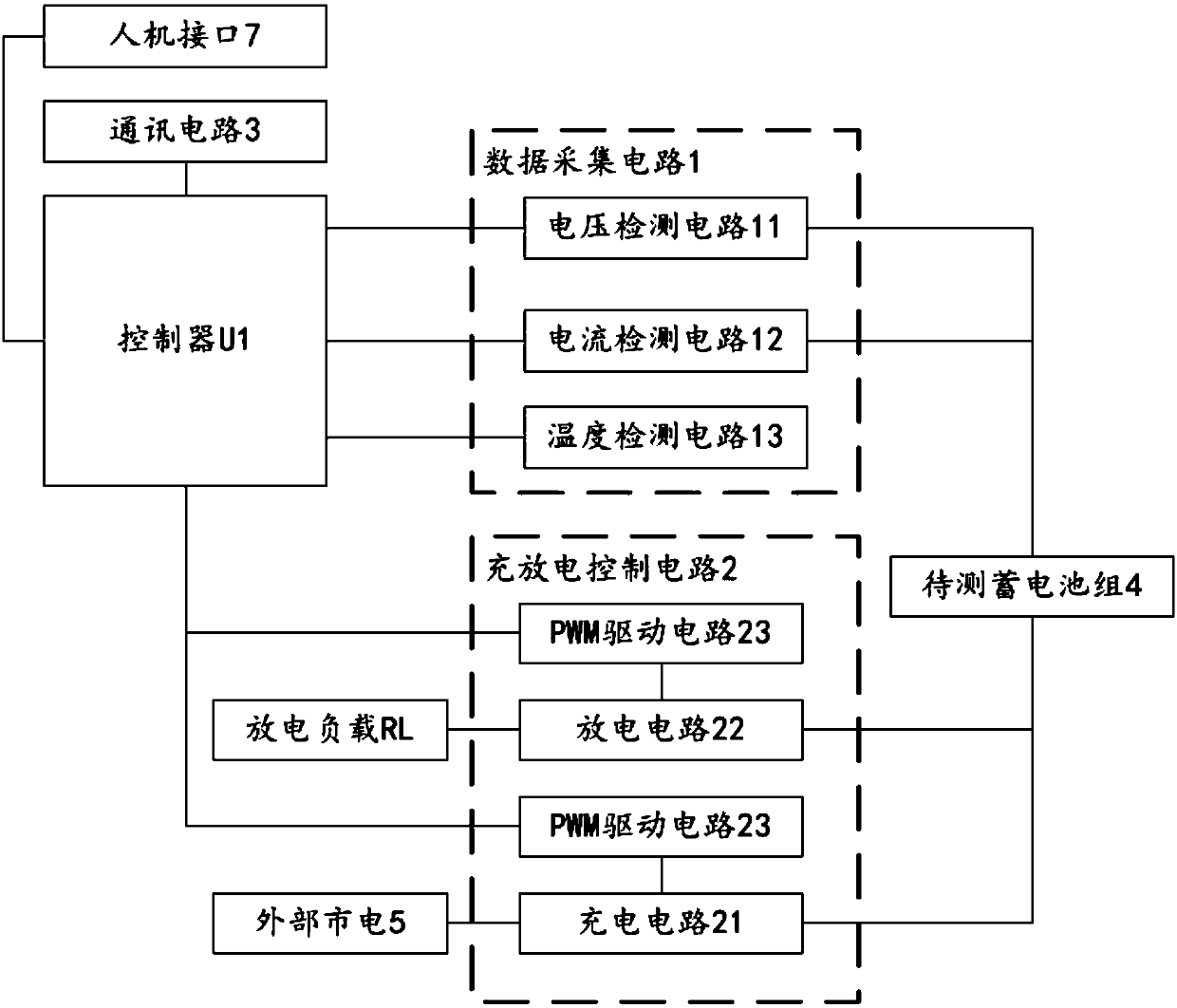
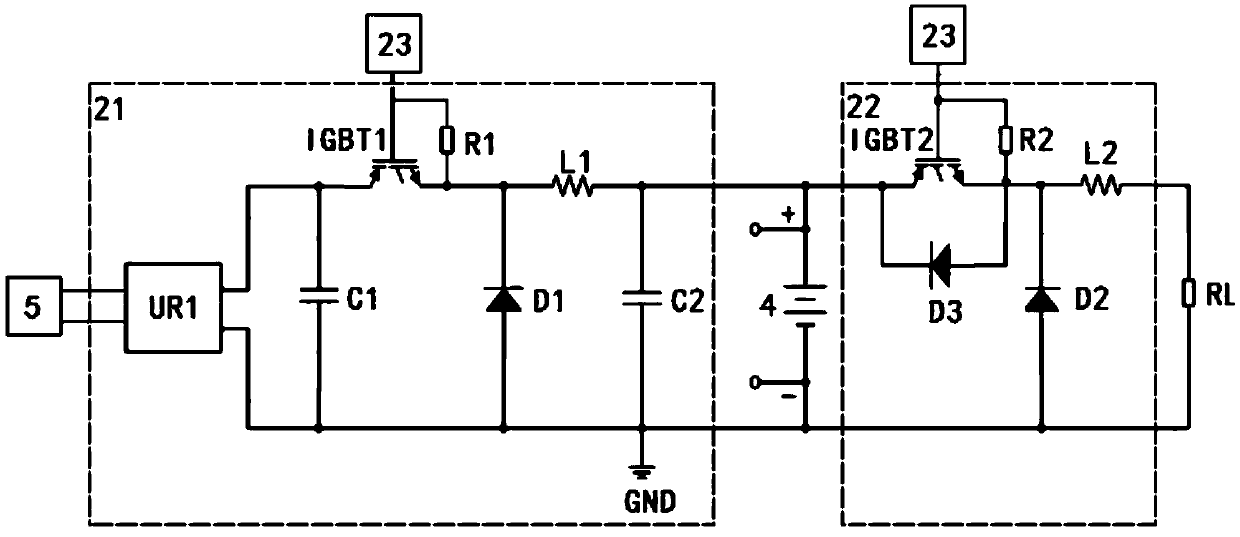
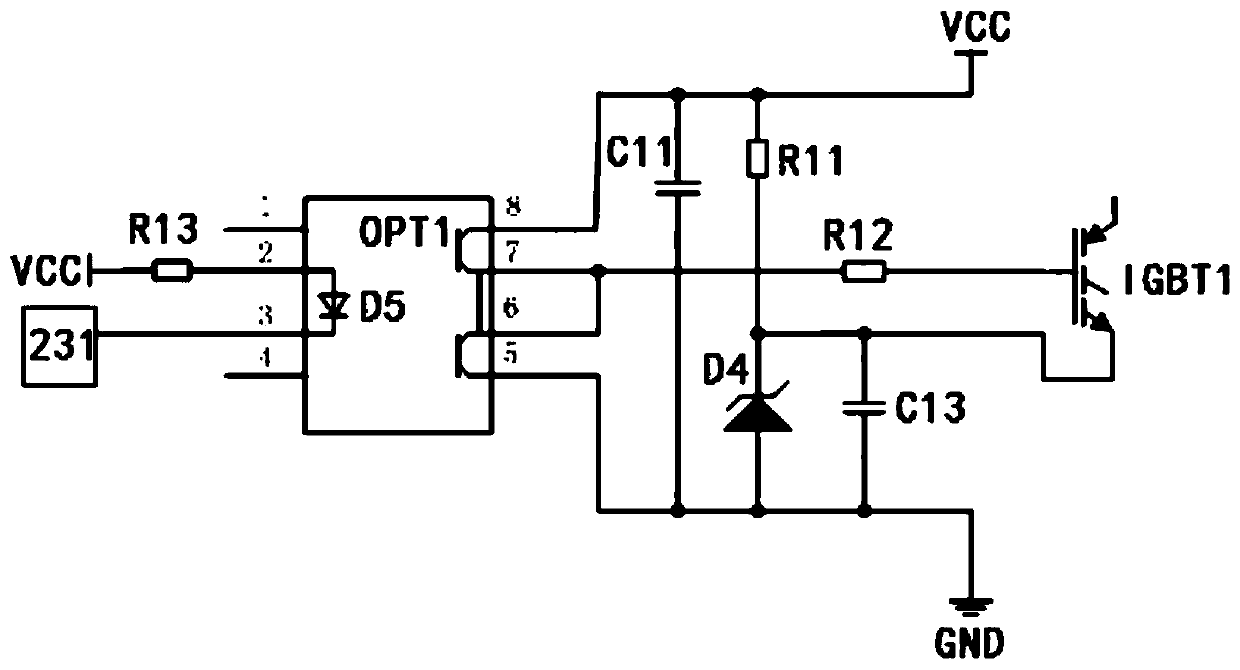
The invention relates to a storage battery monitoring activation device. The device comprises a controller U1, a data acquisition circuit, a charging and discharging control circuit, a discharging load RL and a communication circuit; the controller U1 is electrically connected with a storage battery pack to be tested through the data acquisition circuit; the controller U1 is electrically connectedwith the charging and discharging control circuit; the discharging load RL and an external mains supply are electrically connected with the battery pack to be tested through the charging and discharging control circuit; and the controller U1 is electrically connected with the communication circuit and is wirelessly connected with an external monitoring terminal through the communication circuit.With the storage battery monitoring activation device provided by the invention adopted, the performance of the battery pack can be monitored online, the remaining capacity of the battery pack can beestimated, and the performance data and the remaining capacity data can be transmitted the monitoring terminal.
Owner:WUHAN INSTITUTE OF TECHNOLOGY
Protocol security isolation system oriented to railway signal control network
InactiveCN103888446AAchieve security isolationStop transmissionTransmissionCommunication interfaceData information
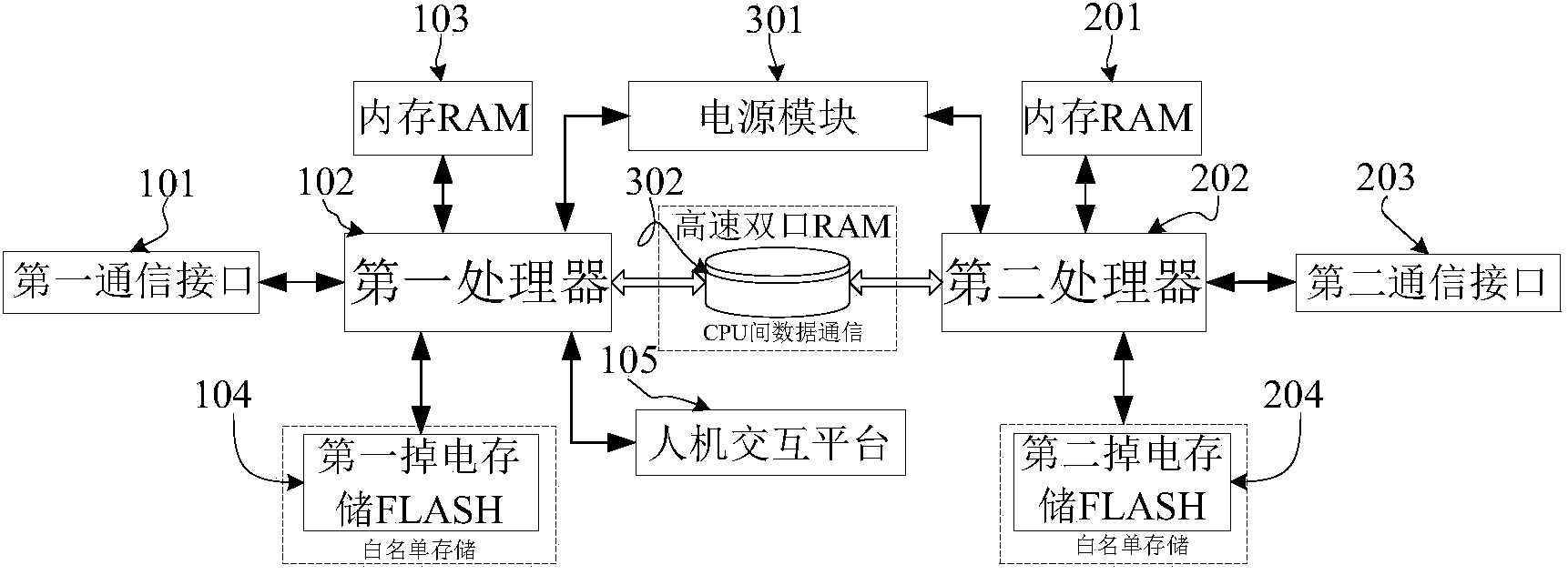
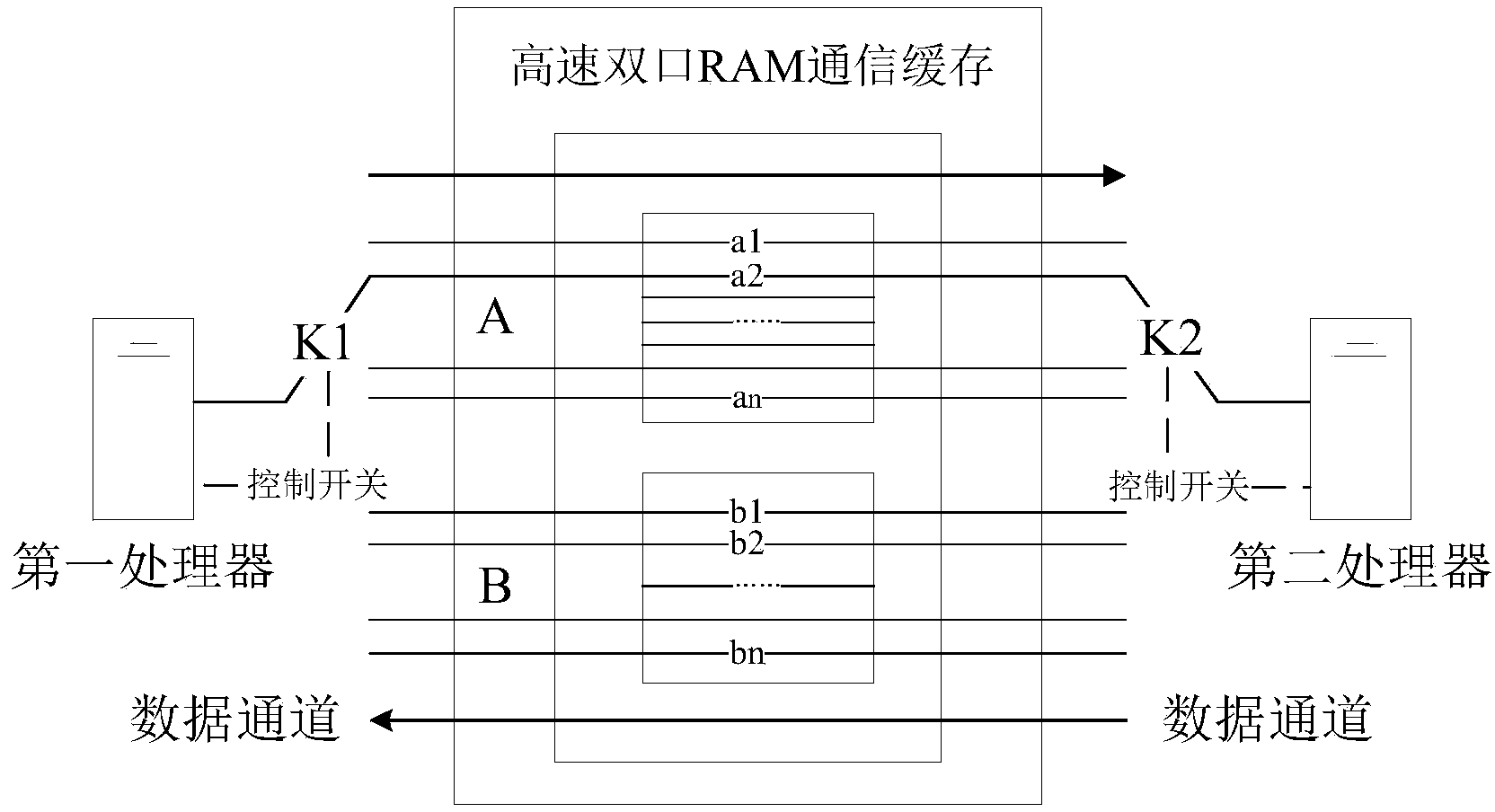
The invention discloses a protocol security isolation system oriented to a railway signal control network. The protocol security isolation system is composed of a first communication interface 101, a second communication interface 203, a first processor 102, a second processor 202, a high-speed dual-port RAM communication buffer memory 302, a memory RAM, a power-failure memory FLASH, a human-computer interaction platform 105 and a power module 301. The first communication interface and the second communication interface intercept and capture data, corresponding the network, from a link layer, the data are sent to the first processer to be analyzed, an analysis result and communication content are sent to the human-computer interaction platform 105 to be displayed and are written into a data base, safe network data information is sent to the second processor through the high-speed dual-port RAM communication buffer memory 302 in a ferry mode at the same time, and the safe network information is sent to a target terminal or a target network through the second communication interface 203 driven by the second processor. According to the protocol security isolation system oriented to the railway signal control network, multiple network technologies are combined and real-time monitoring and security isolation are carried out on the existing railway signal control network.
Owner:SOUTHWEST JIAOTONG UNIV
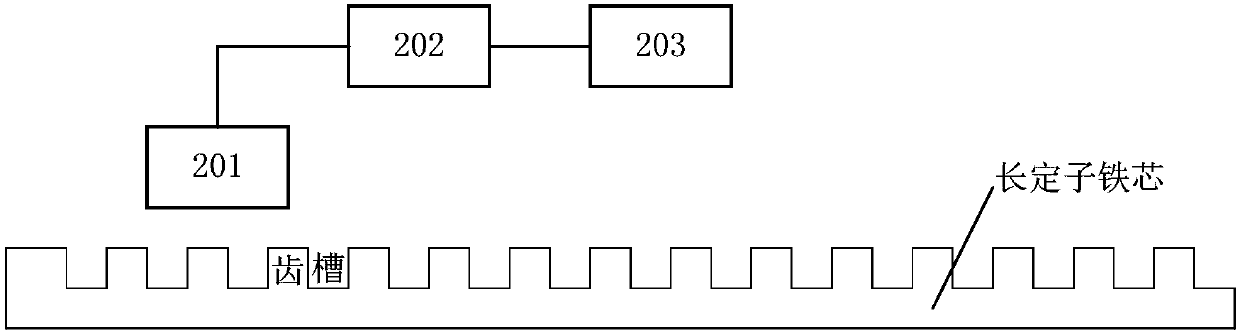
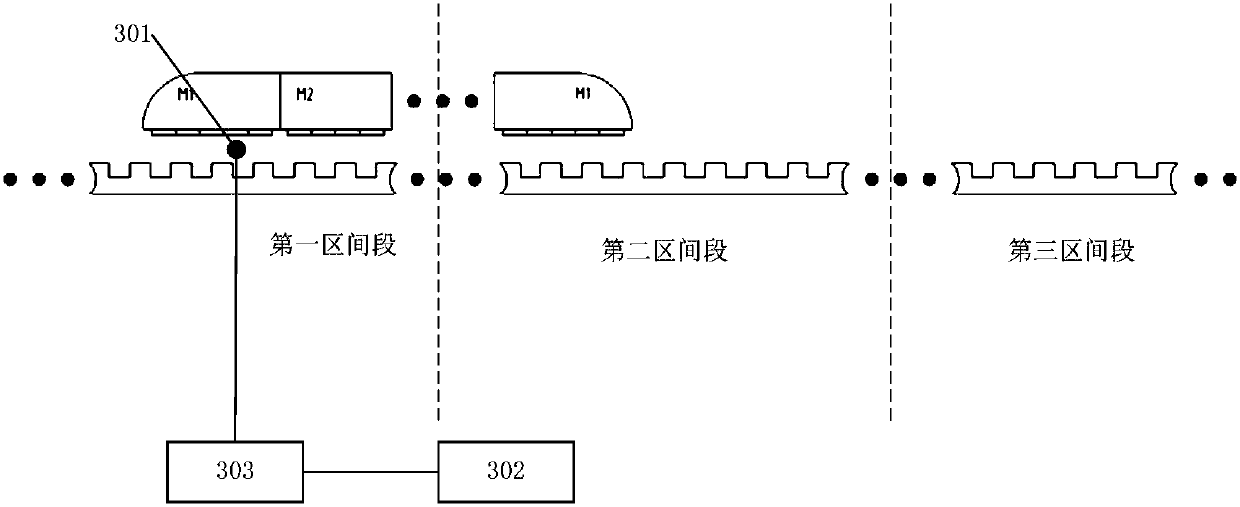
A maglev train passive speed measuring device and a maglev train speed measuring system
ActiveCN109849975AImprove stabilityImprove real-time performanceRailway traffic control systemsTraction systemPhysical security
A maglev train passive speed measuring device comprises the following parts: a passive train beacon arranged on the maglev train; a beacon reading circuit arranged in a long stator power supply interval and mounted on the track, and used for reading a beacon of the passive train and generating a corresponding train beacon signal when the maglev train passes through. According to the device, the key control parameters of a traction system do not need to be transmitted by adopting a wireless communication mode; therefore, not only can physical security isolation be realized, but also potential safety hazards caused by the fact that illegal invasion is easily caused through wireless network access can be prevented; in addition, the device can greatly improve the stability, the real-time performance and the security of data transmission.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
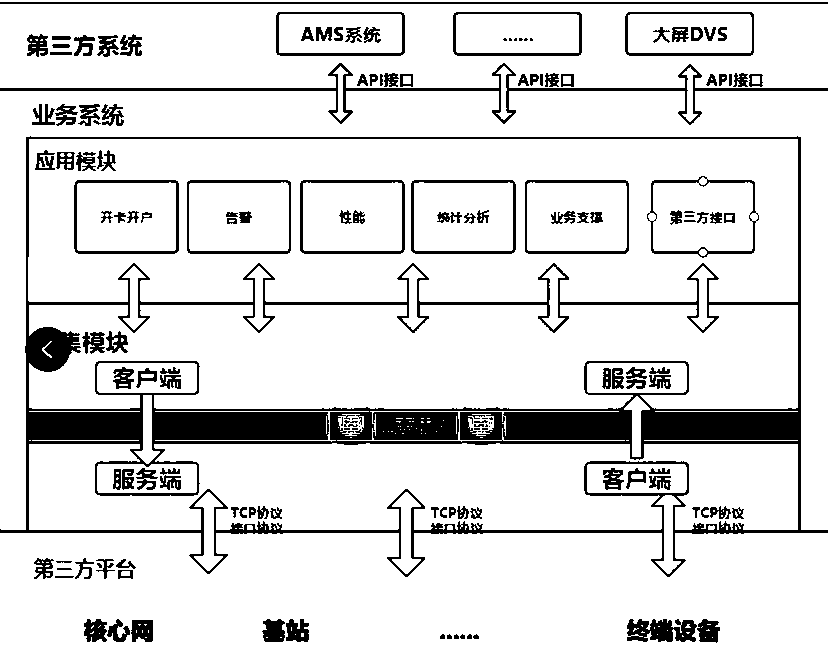
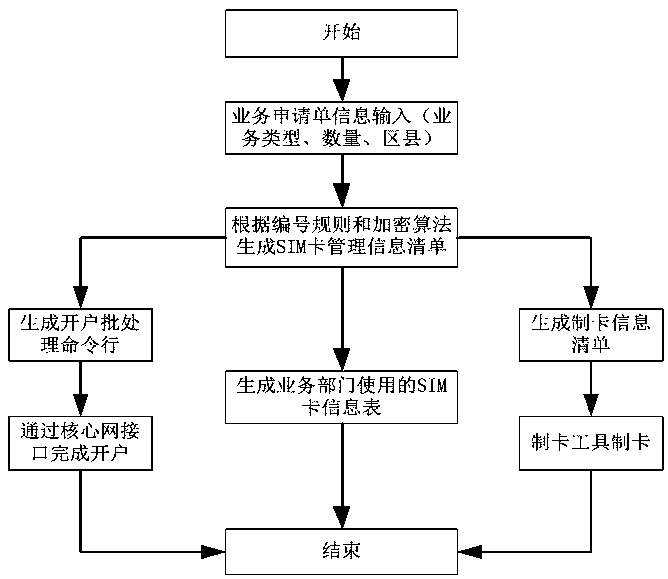
Electric power communication wireless private network operation and maintenance support platform
PendingCN111586678AAchieve security isolationGuaranteed safe transmissionDigital data information retrievalOffice automationPrivate networkStatistical analysis
An electric power communication wireless private network operation and maintenance support platform comprises a service system, a third-party platform and a third-party system. The service system is divided into an acquisition module and an application module from the aspect of functional targets. The acquisition module can support multi-protocol data acquisition; the alarm and performance data ofall core network managers and base station network managers are pulled or received in multiple modes; in order to guarantee data safety, the acquisition module is provided with an independent database storage service and supports file form storage, the data is pushed to the application module in real time through the forward and reverse isolation device, and the application module is also supported to actively pull the data. The application module covers all service function modules, and comprises core modules such as a card opening and account opening module, an alarm management module, a performance monitoring module, a service support module, a statistical analysis module and a system support module. According to the invention, the standard unified management can be formed for provinces and manufacturers, and the safe transmission of data on the Internet can be ensured.
Owner:INFORMATION & COMM BRANCH OF STATE GRID JIANGSU ELECTRIC POWER +2
Network isolation system
InactiveCN102752286AAchieve security isolationPrevent infiltrationTransmissionData processing systemNetwork isolation
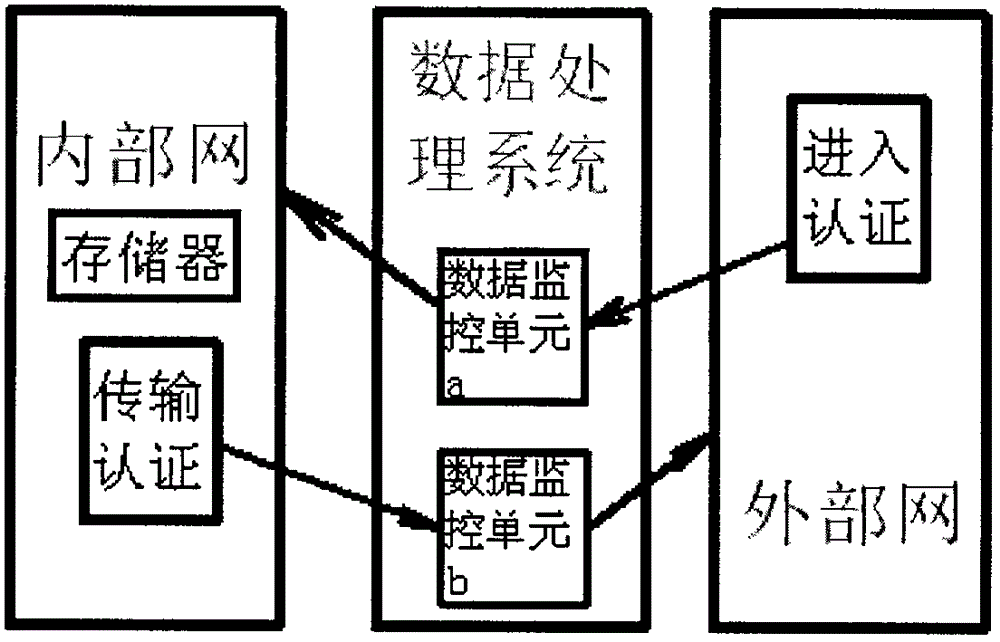
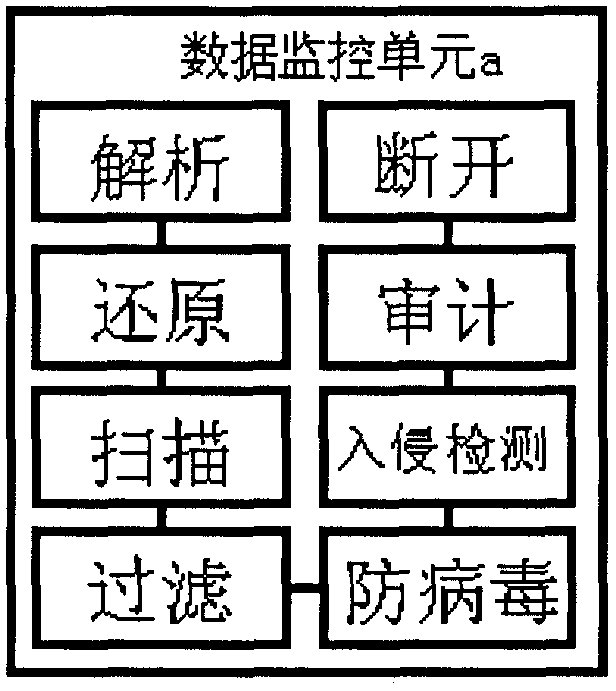
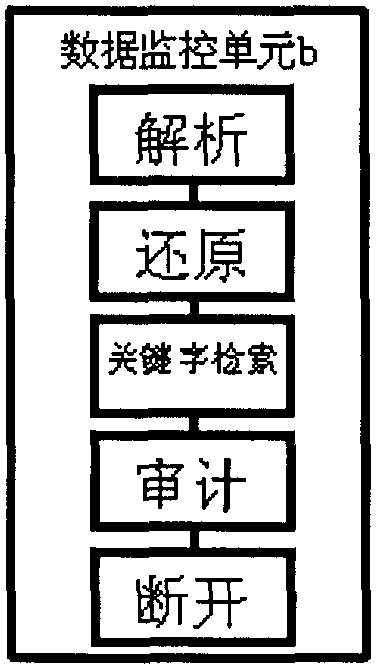
The invention discloses a network isolation system. The network isolation system comprises a data processing system used for transmitting data between an internal network and an external network, wherein the internal network is provided with a memory and transmission certificate; the external network is provided with access certificate; the data processing system consists of a data monitoring unit a and a data monitoring unit b; the transmission certificate performs one-way data transmission with the data monitoring unit b and the external network in sequence; the access certificate performs one-way data transmission with the data monitoring unit a and the internal network in sequence; the information of an internal network user is certificated by utilizing the transmission certificate; the information of an external network user is certificated by utilizing the access certificate; the memory of the internal network automatically records the information such as transmission data and user; a series of safe processing is performed by utilizing the data monitoring unit a and the data monitoring unit b; the potential safety hazard such as hacker attack, infiltration of malice code and virus and information leakage can be prevented effectively; and the safe isolation and the safe information exchange of the internal network and the external network are realized.
Owner:DONGGUAN BOSHENG ELECTRONICS TECH
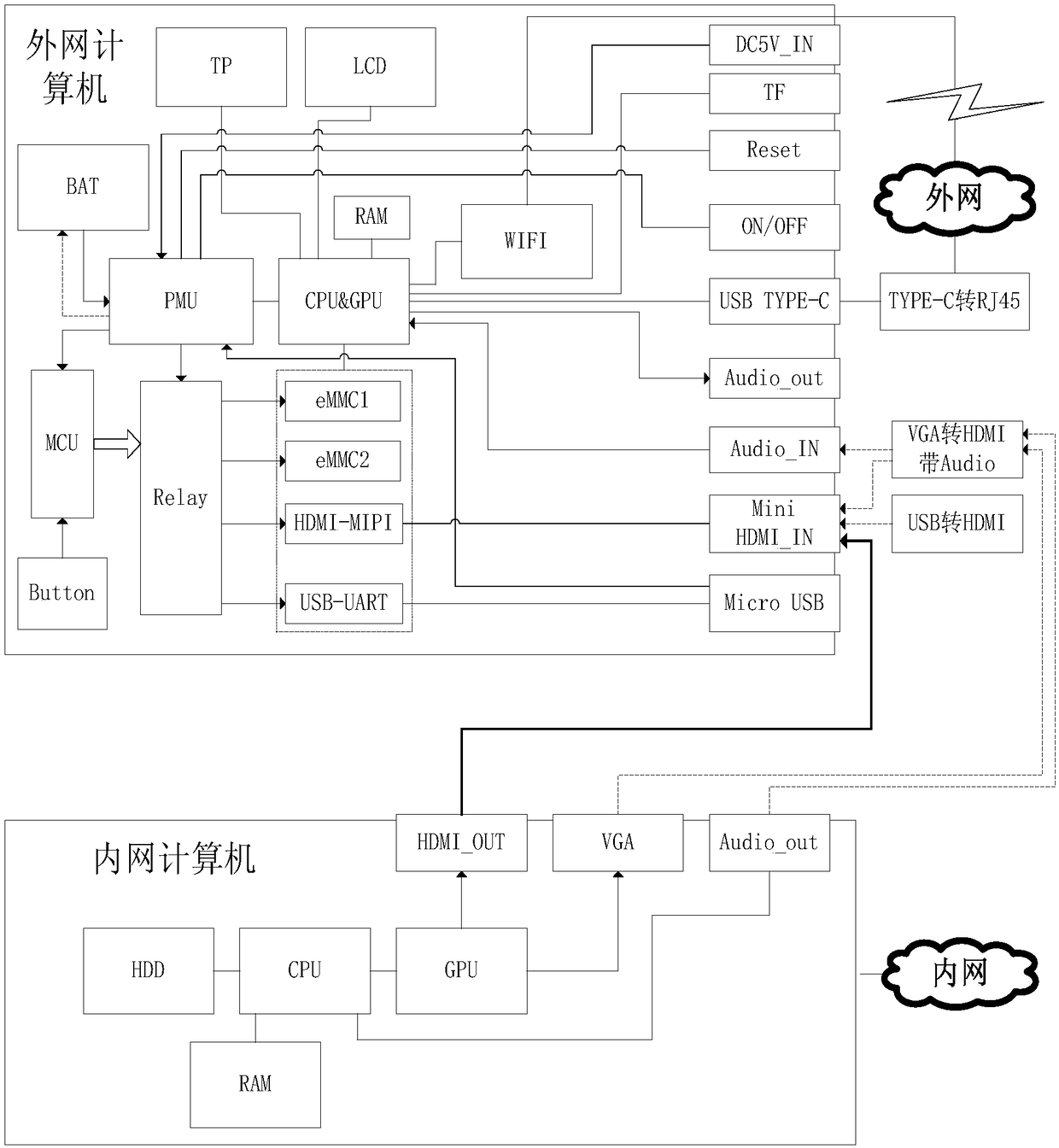
Safety isolation control computer system
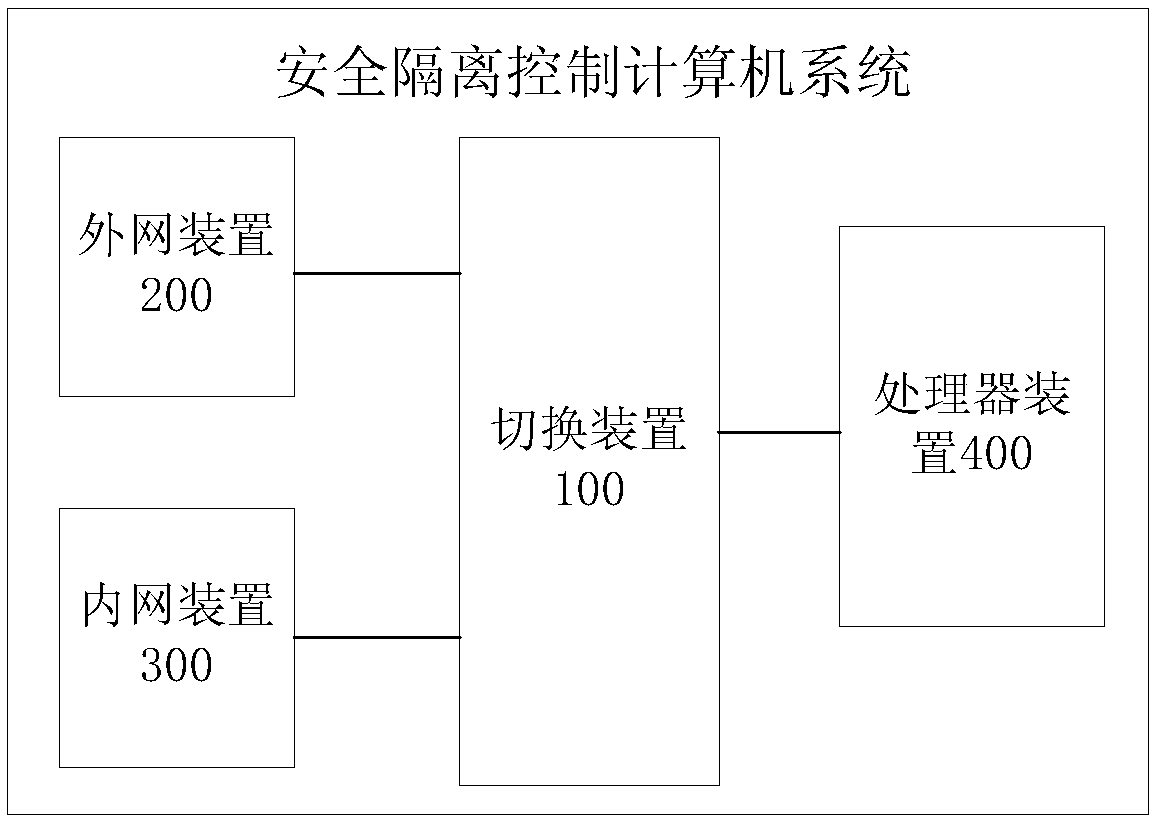
InactiveCN108540462AAchieve physical isolationAchieve security isolationTransmissionElectricityComputerized system
The invention discloses a safety isolation control computer system. The system comprises an external network device used for being in communication connection with an external network, an internal network device used for being in communication connection with an internal network, a processor device used for being electrically connected to the external network device or the internal network deviceto form an external network computer or an internal network computer, and a switching device used for switching an electric connection between the external network device and the processor device andan electric connection between the internal network device and the processor device, wherein the switching device is electrically connected to the external network device, the internal network deviceand the processor device respectively. According to the safety isolation control computer system, the electric connection between the external network device and the processor device and the electricconnection between the internal network device and the processor device are switched through the switching device, the physical isolation of the internal network and the external network can be achieved, and the safe isolation of working modes of the internal network and the external network is achieved.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
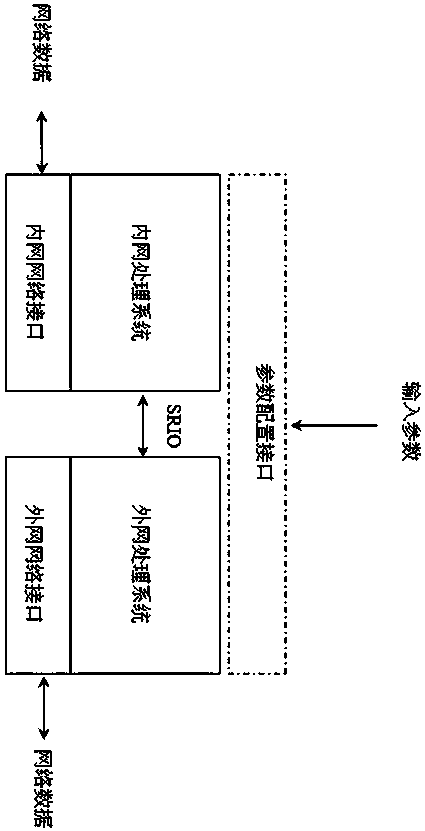
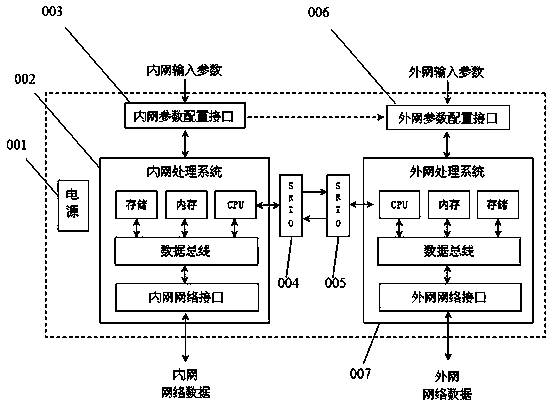
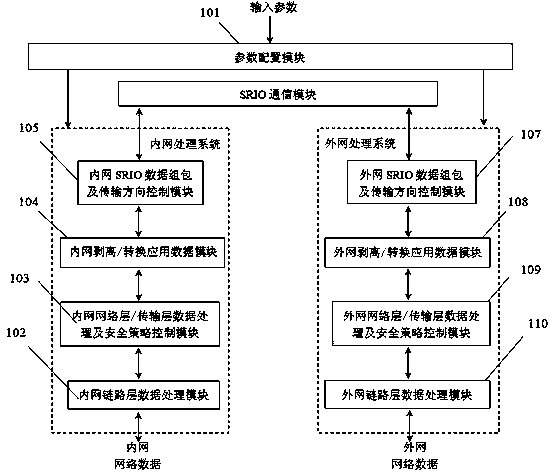
Dual-processing system network safety isolation method based on SRIO interface technology
ActiveCN108055244AAchieve security isolationAvoid Penetrating LinksTransmissionTraffic capacityHigh bandwidth
The invention aims at providing a dual-processing system network safety isolation method which is simple in structure, safe and reliable, high in transmission efficiency, enough in bandwidth and capable of realizing one-way or two-way safety isolation and based on the SRIO interface technology. The method comprises the following steps: unloading a network protocol stack to completely eradicate thepenetrability link of a network protocol, thereby realizing the one-way data safety isolation transmission or controllable two-way data safety isolation transmission of the network regions in different safety levels; since the SRIO technology supports the chip direct interconnection way, the logic layer supports the direct IO / DMA and message transfer, thereby obviously lightening the CPU load, and greatly improving the network data transmission efficiency , and the data safety isolation communication with 10G bandwidth can be realized. The method is suitable for the network boundary of the one-way or two-way safety isolation with high bandwidth traffic requirement, and is applied to the technical field of the computer network safety isolation.
Owner:珠海市鸿瑞信息技术股份有限公司
Cloud platform data access safety isolation method
InactiveCN104182503AAchieve security isolationTransmissionSpecial data processing applicationsData accessTree structure
The invention discloses a cloud platform data access safety isolation method. The method includes the following steps: 1, creating an access-right tree of all users according to different user levels, wherein the access-right tree is of a one-way pointer multilayer tree structure, users with high access rights are positioned on root nodes on low layers, and users with low access rights are positioned on leaf nodes on upper layers; 2, creating different inquiry sentences for the nodes on different layers, wherein the inquiry sentences of the root nodes can downwards inquire data of the leaf nodes at the same time, and the inquiry sentences of the leaf nodes cannot upwards inquire data of the root nodes and cannot inquire data of the nodes on same layers. By adopting the technical scheme, access-right management can be customized for graded administrative departments, so that safety isolation under different access rights during data access is realized better.
Owner:SHANGHAI TRIMAN INFORMATION & TECH
Big data stream processing method and device based on cloud native architecture
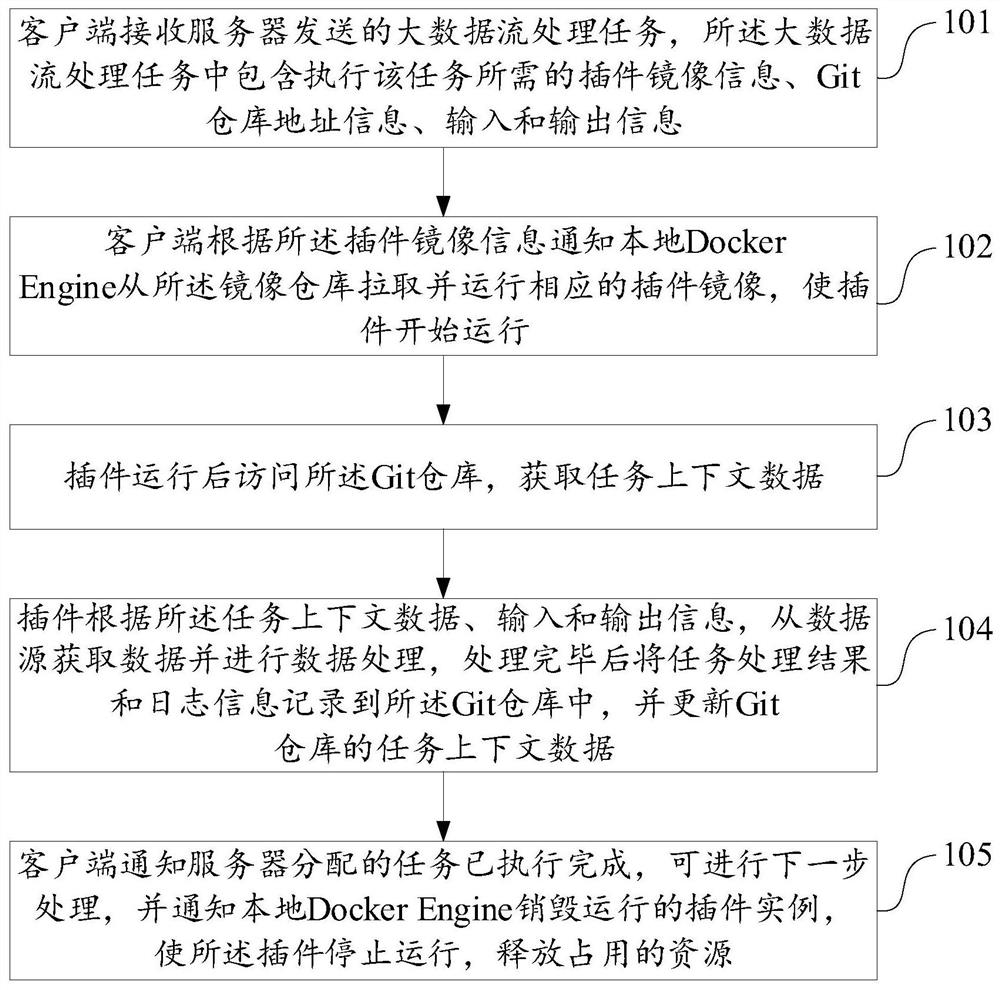
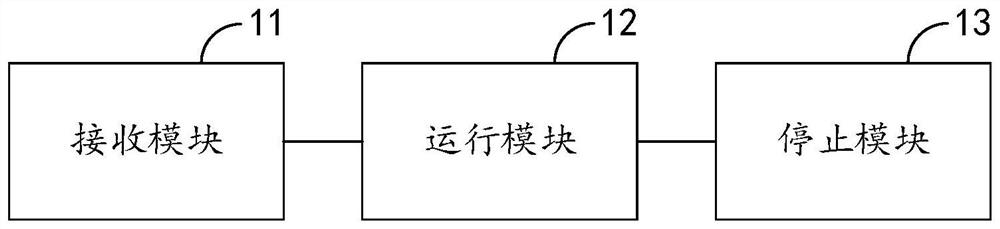
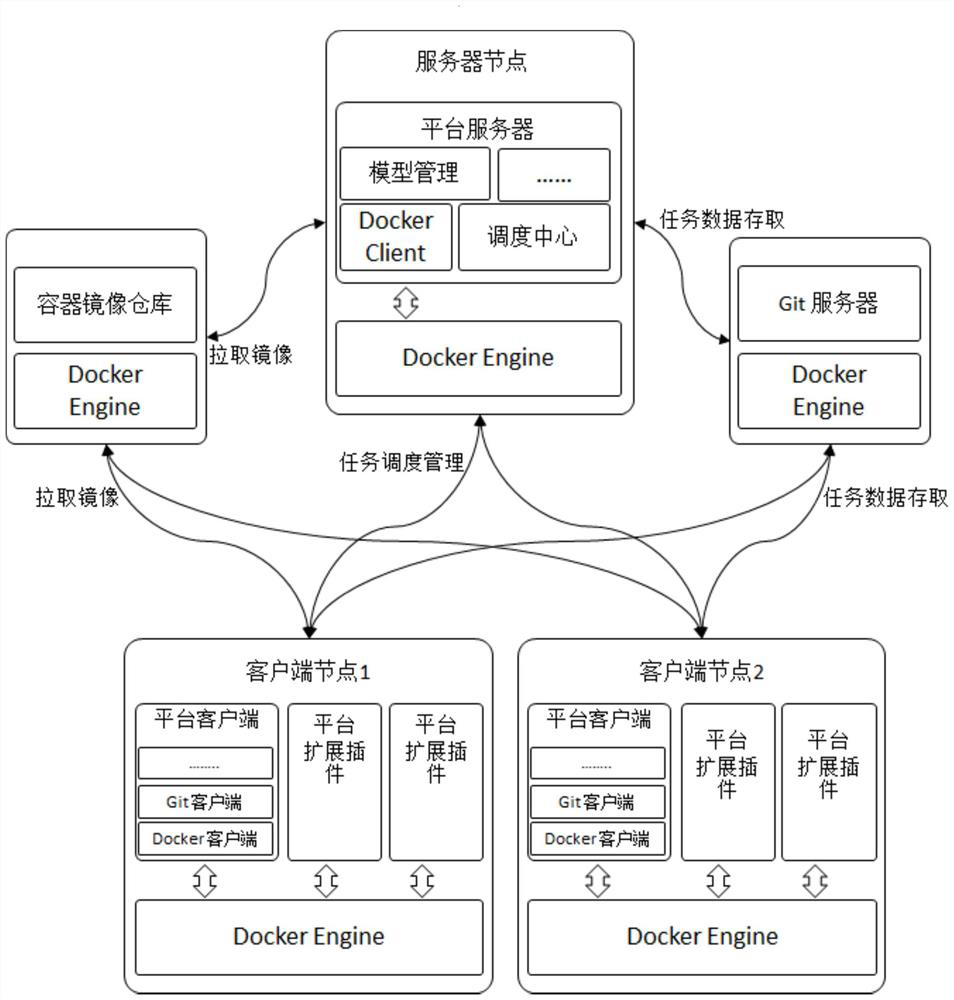
ActiveCN111880899AAchieve security isolationSolve consumptionEnergy efficient computingSoftware simulation/interpretation/emulationContext dataMirror image
The embodiment of the invention discloses a big data stream processing method and device based on a cloud native architecture, electronic equipment and a storage medium, relates to the technical fieldof big data stream processing, and is used for avoiding resource occupation and plug-in conflict of big data stream processing task execution and improving platform operation safety and stability. The method comprises the following steps: receiving a big data stream processing task sent by a server, wherein the task comprises required plug-in mirror image information, Git warehouse address information and input and output information; informing the Docker Engine to pull and run the corresponding plug-in mirror image from the mirror image warehouse, so as to enable the plug-in to start to run;enabling the plug-in to access a Git warehouse after running to obtain task context data; enabling the plug-in to acquire data from the data source and perform data processing, and record a task processing result and log information into a Git warehouse and update task context data after processing is completed; and informing the server that the task is executed completely, informing the Docker Engine to destroy the running plug-in instance, and releasing occupied resources.
Owner:山东迪特智联信息科技有限责任公司
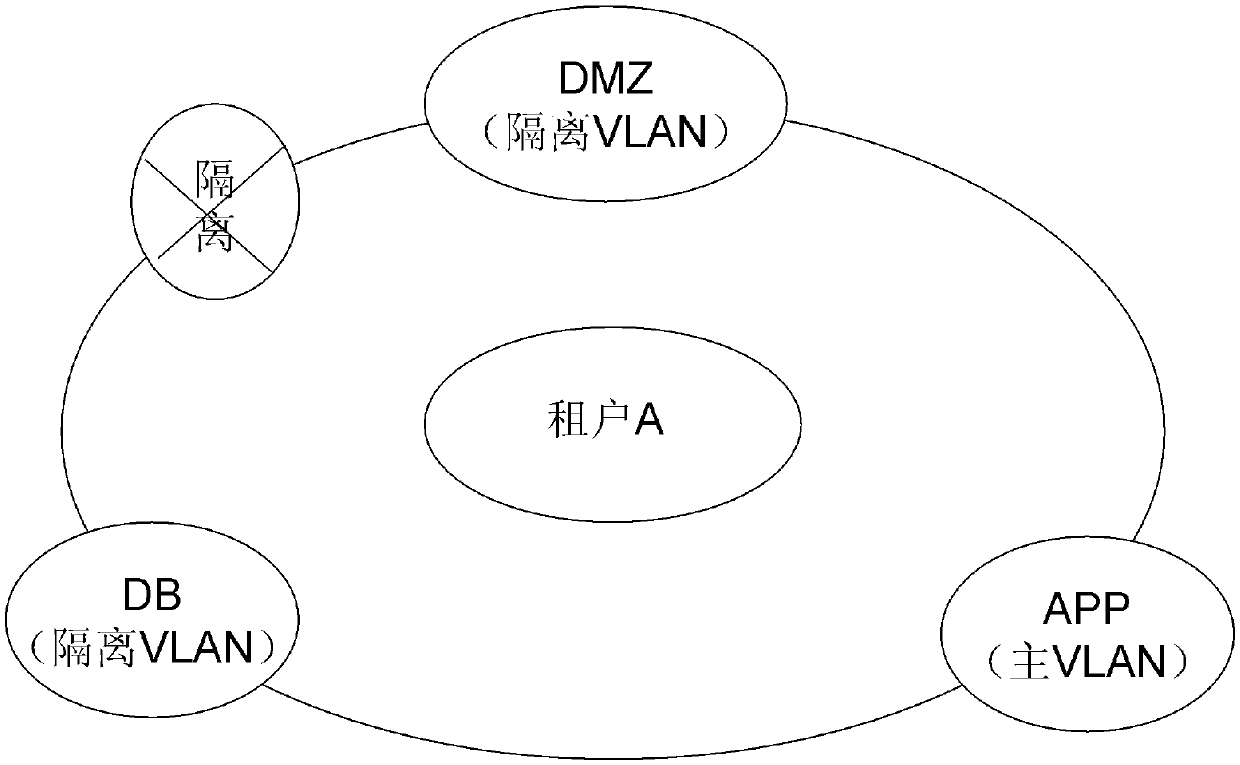
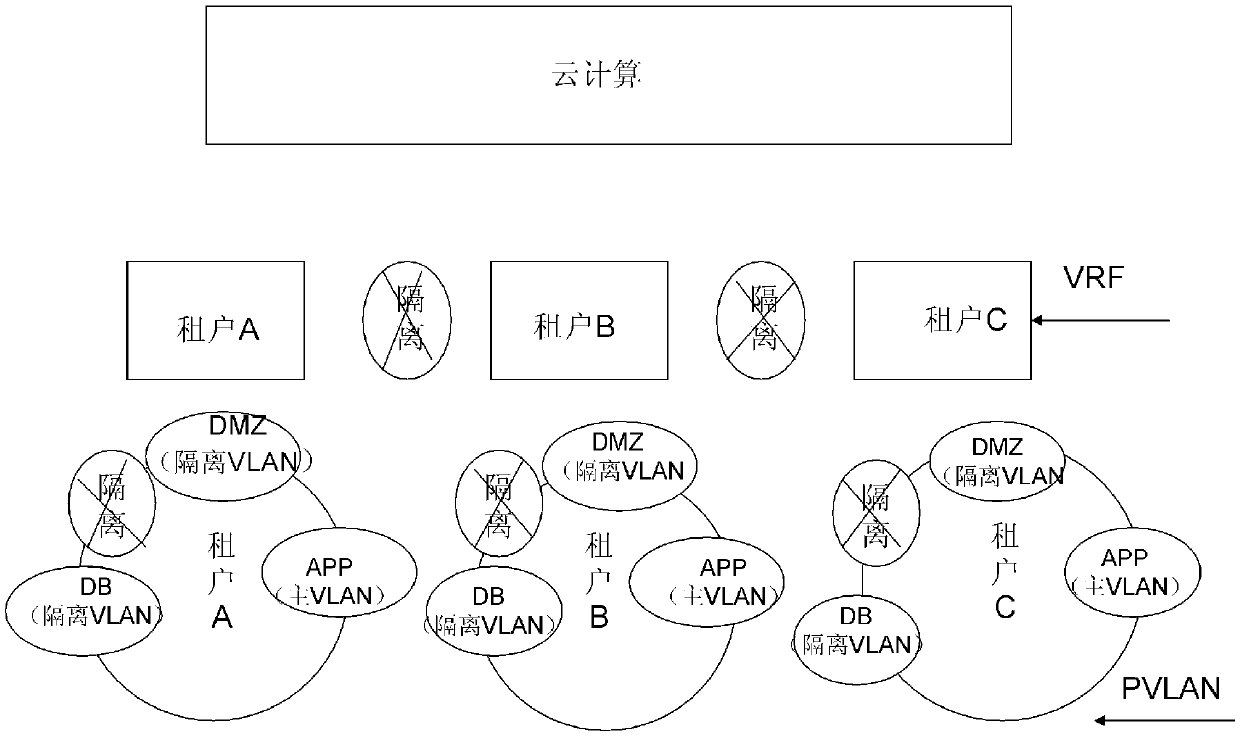
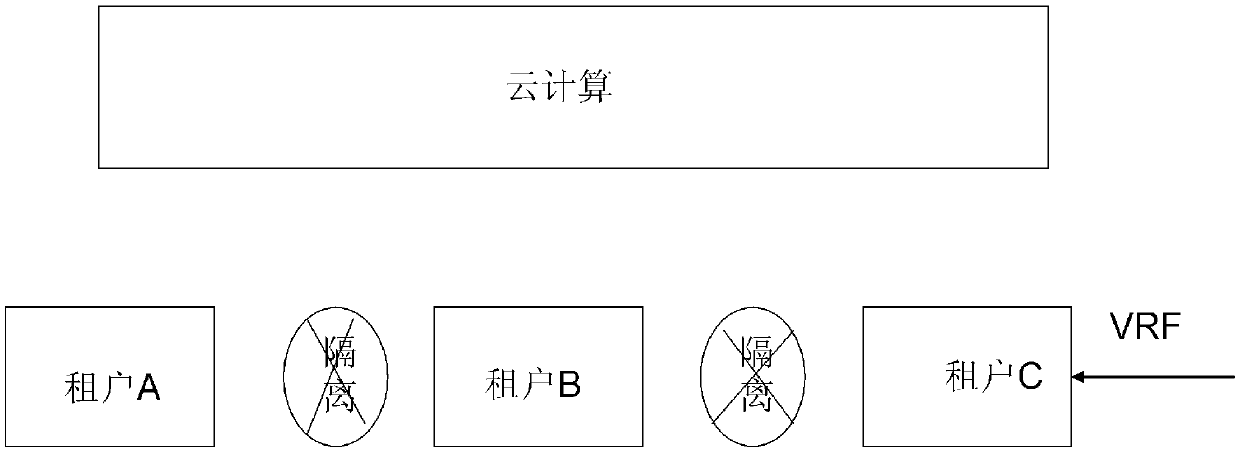
Tenant security isolation method under cloud computing
The invention relates to a tenant security isolation method under cloud computing, comprising a tenant isolation step: distinguishing different tenants based on a VRF (Virtual Routing & Forwarding Instance) so as to isolate tenants; and a tenant inner isolation step: for each tenant, utilizing the PVLAN (Private VLAN) technology to realize tenant inner security isolation. Accordingly, the tenant security isolation method under cloud computing can meanwhile realize external isolation and internal isolation, is applicable to cloud computing multi-tenant conditions, and can reasonably program and manage tenants, and improve data security.
Owner:CHINA UNIONPAY
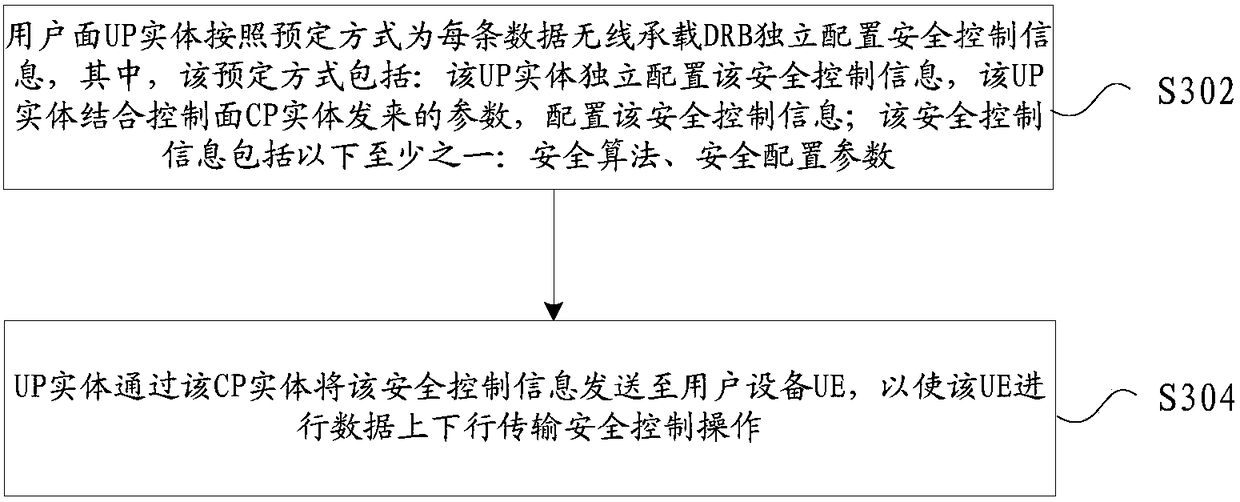
Data flow transmission security control method and device
InactiveCN109413005ASolve the problem of security management and controlWill not affect business data transmissionSecurity arrangementSecuring communicationData radio bearerData stream
The invention provides a data flow transmission security control method and device. The method comprises the steps that: a UP (User Plane) entity independently configures security control informationto each DRB (Data Radio Bearer in a preset mode, wherein the preset mode comprises that: the UP entity independently configures the security control information, and the UP entity combines parameterssent by a CP (Control Plane) entity to configure the security control information, and the security control information comprises at least one of the follows: a security algorithm and a security configuration parameter; and the UP entity sends the security control information to UE (User Equipment) by the CP entity, so that the UE carries out a data uplink and downlink transmission security control operation. By the data flow transmission security control method and device provided by the invention, a problem how to carry out security management control processing of user service data flow transmission between a CP and a UP in a scene in which network-side CP and UP network element entities are physically separated in the related art is solved, and the technical effect of effectively carrying out security management control of user service data flow transmission is achieved.
Owner:ZTE CORP
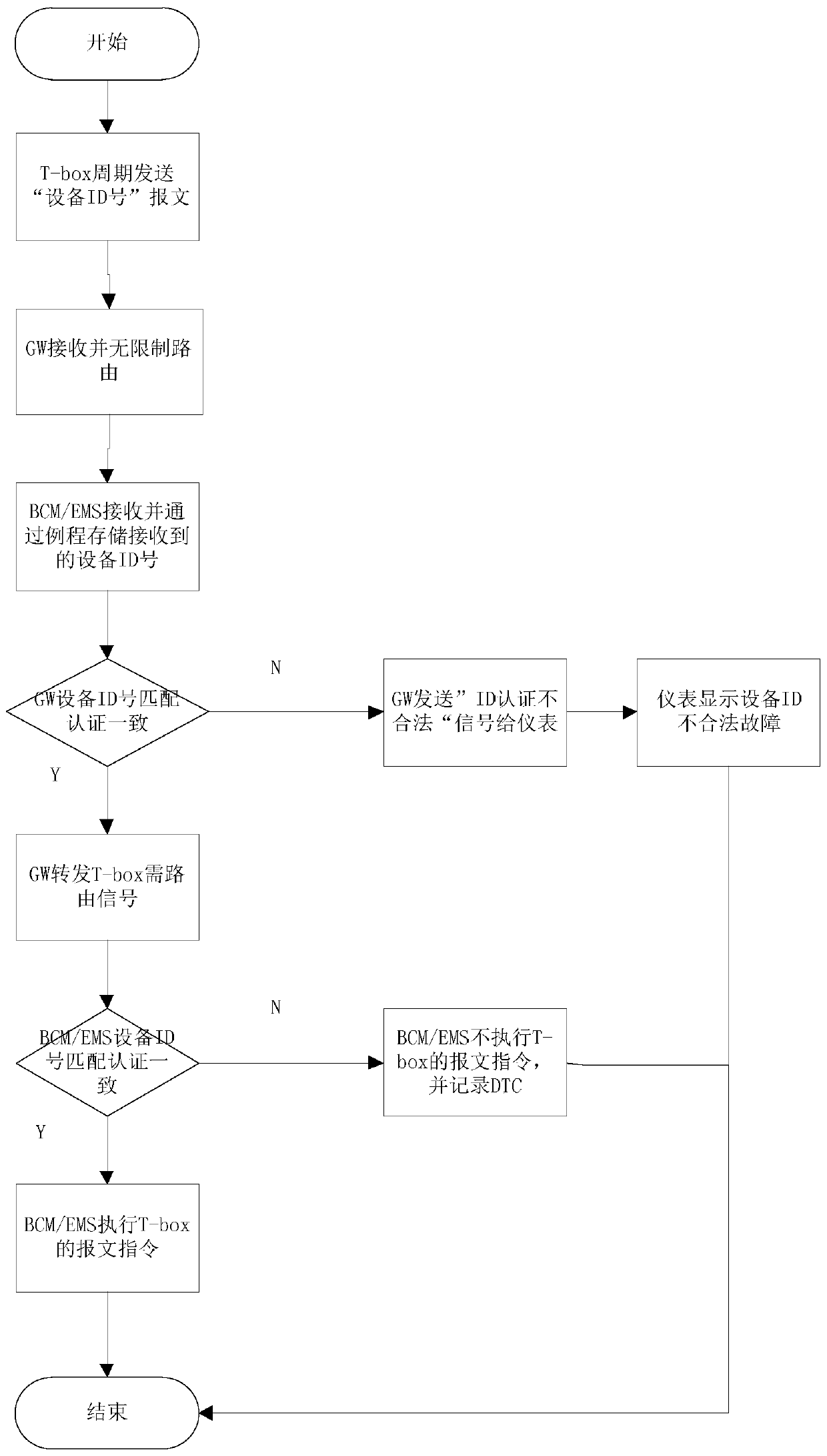
Electronic appliance architecture of a commercial vehicle and a safe communication method of the architecture
ActiveCN109905488AAchieve security isolationImprove automationTransmissionRemote controlMulti protocol
The invention discloses an electronic appliance architecture of a commercial vehicle and a safe communication method of the architecture, and designs a CAN network system for six-way commercial vehicles, which can flexibly configure advanced systems such as ADAS to realize intelligent driving of commercial vehicles with the level of L3 / L4, and performs network isolation on a remote terminal to ensure remote safety from the aspect of architecture connection. According to the method and the device, the ID configuration and verification of the remote terminal are realized, a reliable solution forensuring the legality of the terminal is provided through the storage and verification of the ID number of the remote terminal, and a feasible solution is provided for replacing the remote terminal in production and after-sales processes. Through ID gateway verification, electronic control unit ID confirmation and control information encryption, three-layer encryption of remote control is realized, and remote control security configuration is guaranteed. Through the double-rate and double-channel diagnosis and development, a reliable diagnosis scheme is provided for a multi-protocol and multi-configuration commercial vehicle, the problems that single diagnosis has high requirements on manual skills, diagnosis selection is prone to errors and the like are solved, and the automation and efficiency of diagnosis are improved.
Owner:NANJING AUTOMOBILE GROUP CORP +1
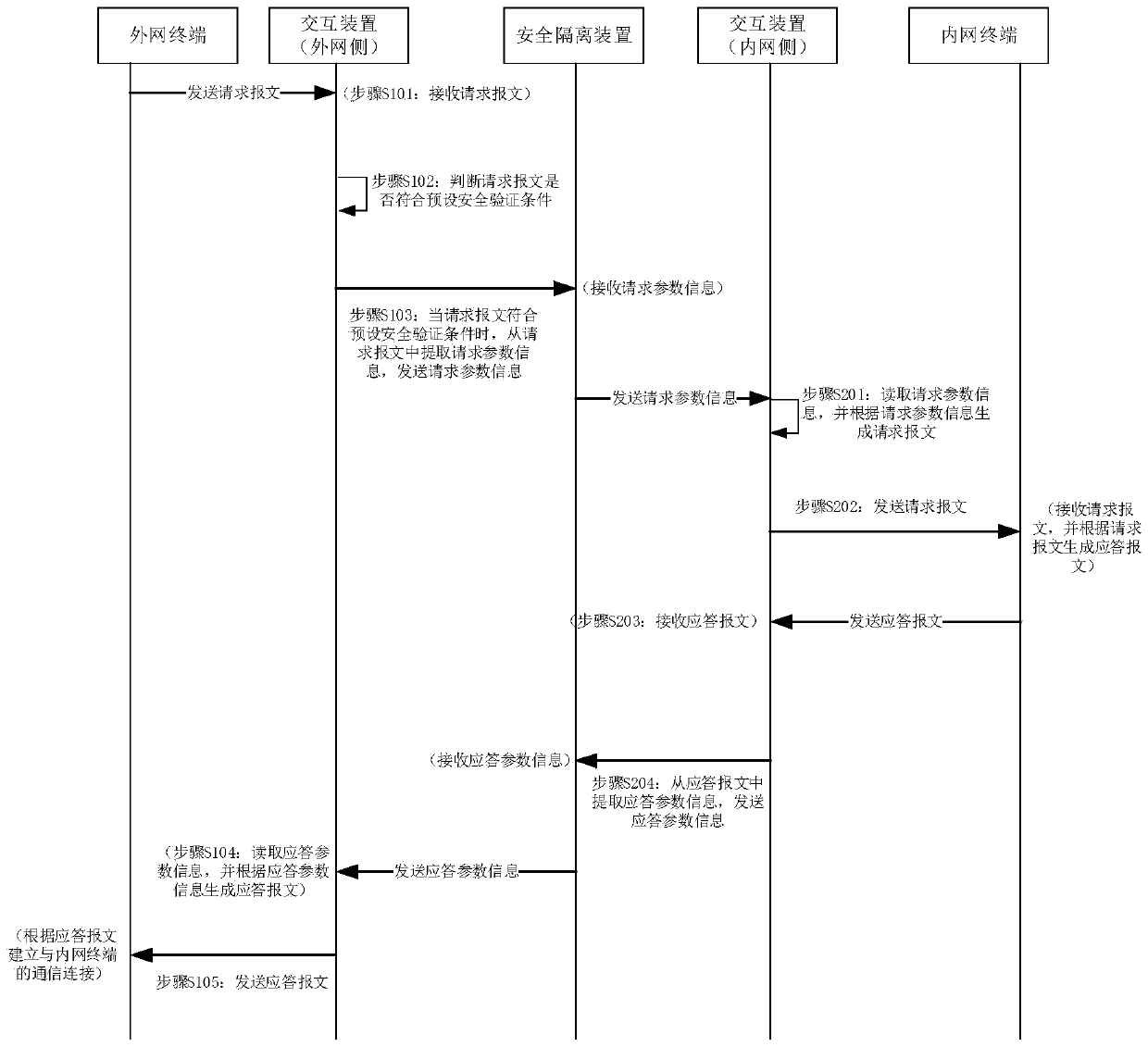
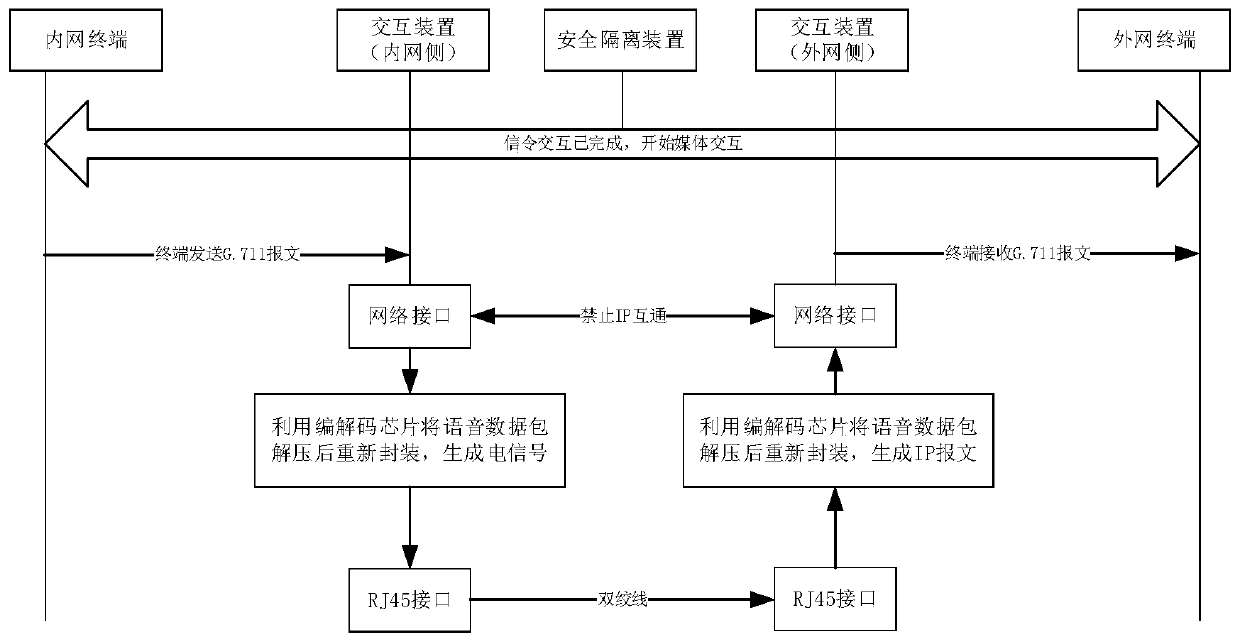
Intranet and extranet interaction method and system of power terminal and data transmission method
The invention provides an internal and external network interaction method and system of a power terminal and a data transmission method, the interaction method is applied to an interaction device ata request terminal side, and comprises the following steps: receiving a request message sent by a request terminal; judging whether the request message meets a preset security verification condition or not; when the request message meets a preset security verification condition, extracting request parameter information from the request message, and writing the request parameter information into asecurity isolation device database; reading response parameter information from the security isolation device database, and generating a response message according to the response parameter information; and sending the response message to the request terminal to establish a communication connection between the request terminal and the response terminal. Therefore, transmission of the malformed message and carried virus data between the intranet and the extranet possibly caused by transmission of the whole message is avoided, safe isolation between the intranet and the extranet is achieved, andsafe communication between the request terminal and the response terminal is guaranteed.
Owner:STATE GRID CORP OF CHINA +8
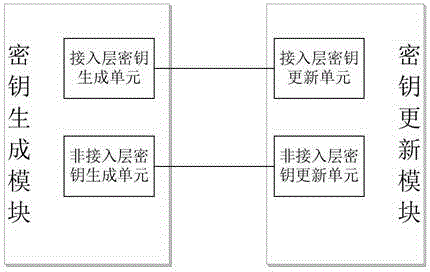
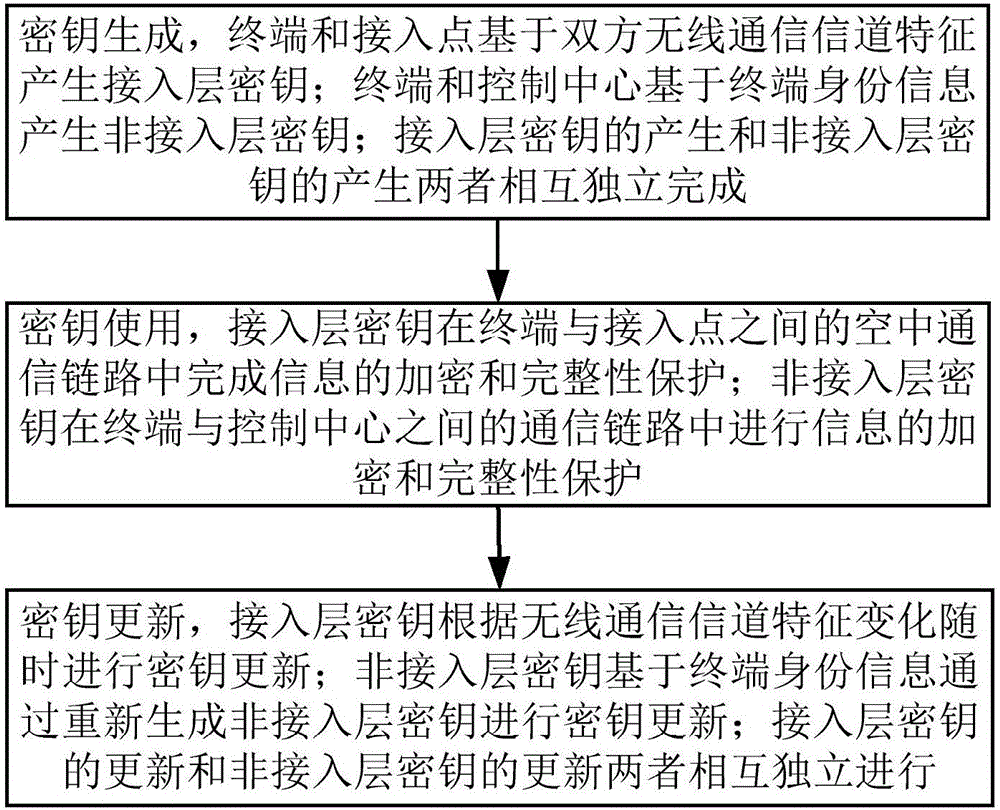
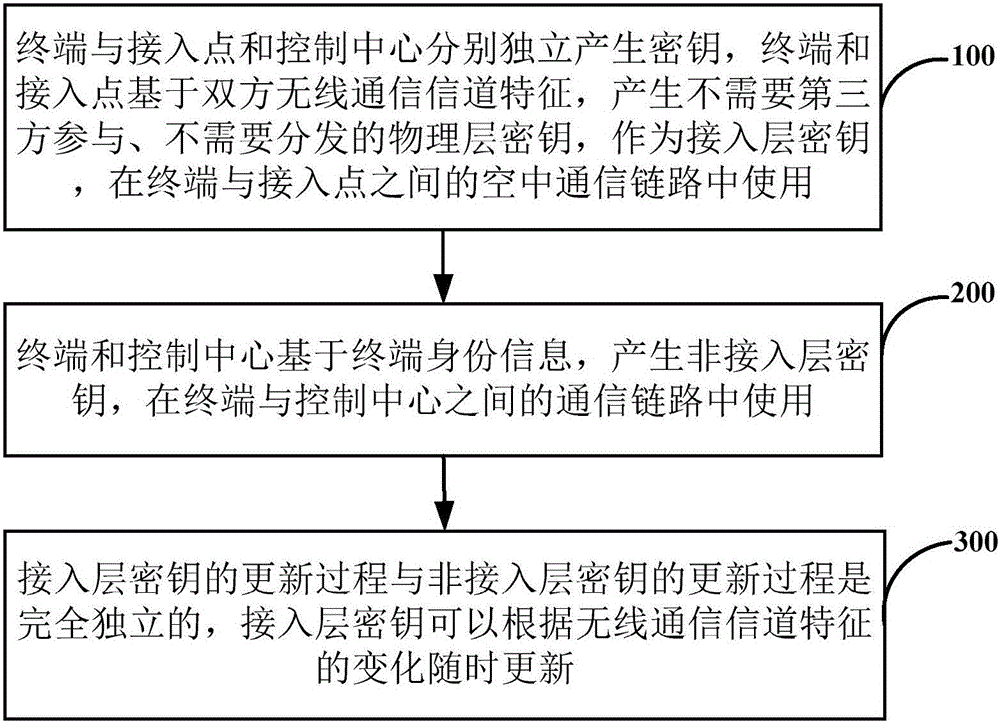
Access layer and non-access layer secret key safety isolation device and method thereof
ActiveCN106535178AEnsure safetyAchieve security isolationSecurity arrangementKey distributionComputer hardware
The invention relates to an access layer and non-access layer secret key safety isolation device and a method thereof. The method comprises steps that an access layer secret key is generated by a terminal and an access point on the basis of both-way radio communication channel characteristics; a non-access layer secret key is generated by a terminal and a control center on the basis of the terminal identity information; an update process of the access layer secret key and an update process of the non-access layer secret key are completely independent, the access layer secret key can be randomly updated according to change of the radio communication channel characteristics. According to the method, uniqueness, reciprocity and time-dependent nature of a radio channel are utilized, the physical secret key for access layer encryption and integrity protection is generated, updated and managed by the access point and the terminal, the secret key for non-access layer encryption and integrity protection is generated, updated and managed by the safety control center and the terminal on the basis of identity identification, so not only can safety isolation of the access layer secret key and the non-access layer secret key be realized, radio communication safety is improved, but also access layer secret key distribution can be avoided, and system transmission efficiency is improved.
Owner:THE PLA INFORMATION ENG UNIV
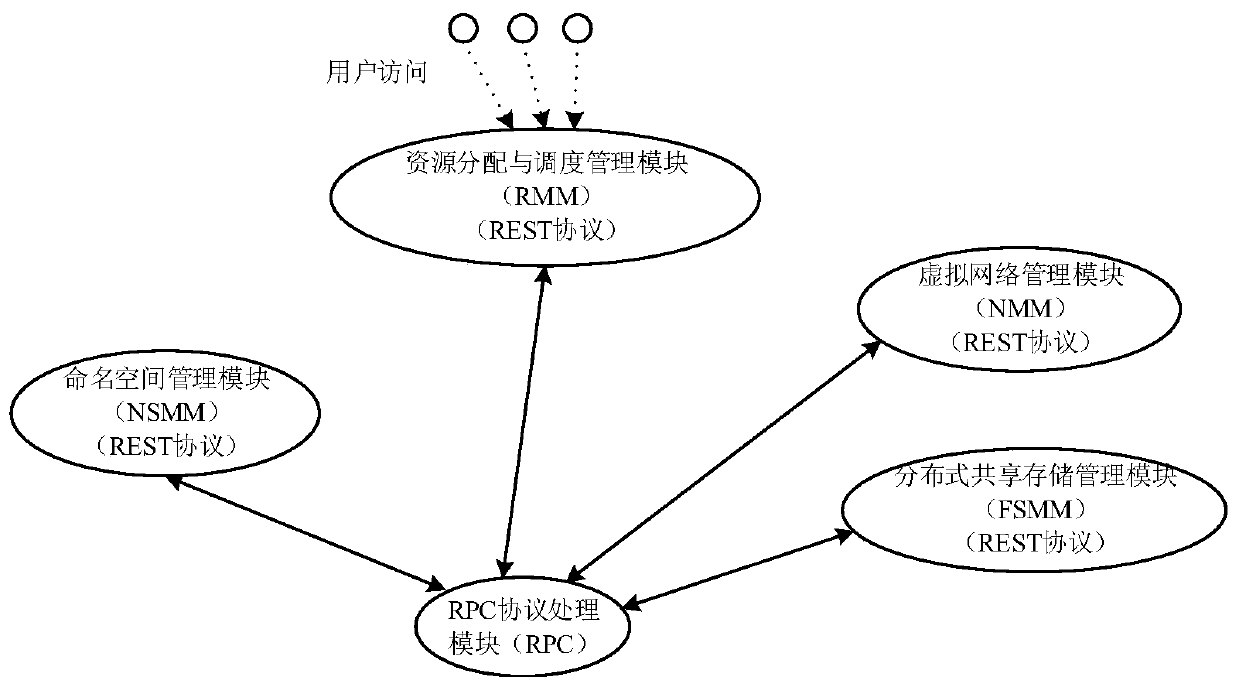
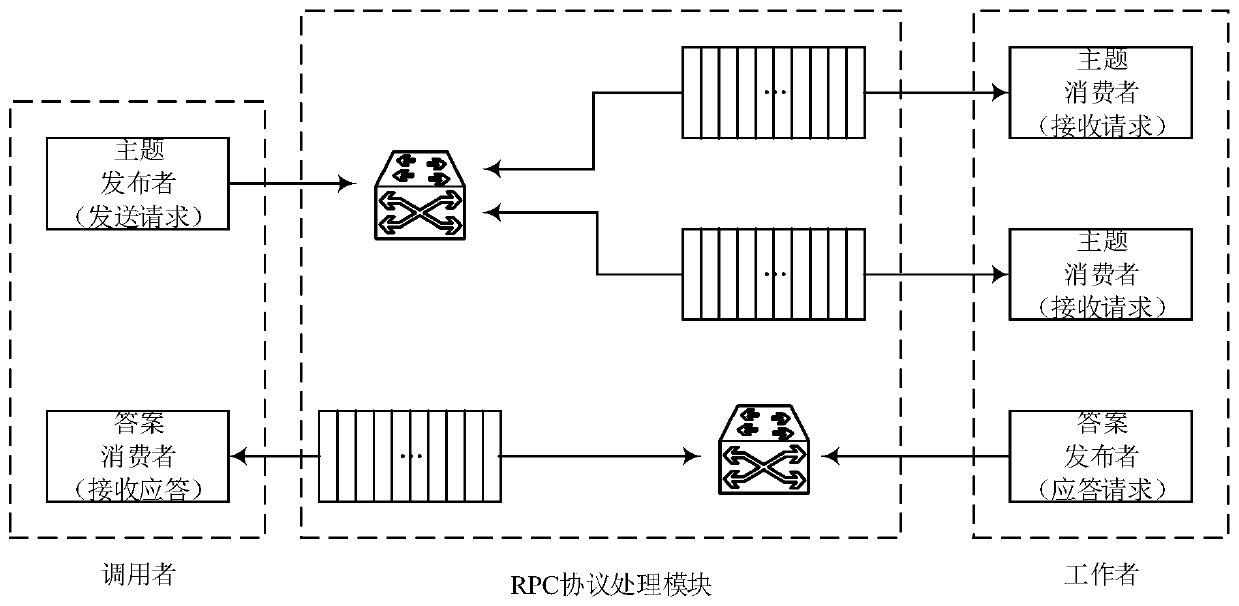
Distributed cluster system and method based on REST and RPC
ActiveCN110011984AIncrease independenceImprove scalabilityTransmissionVirtualizationDistributed File System
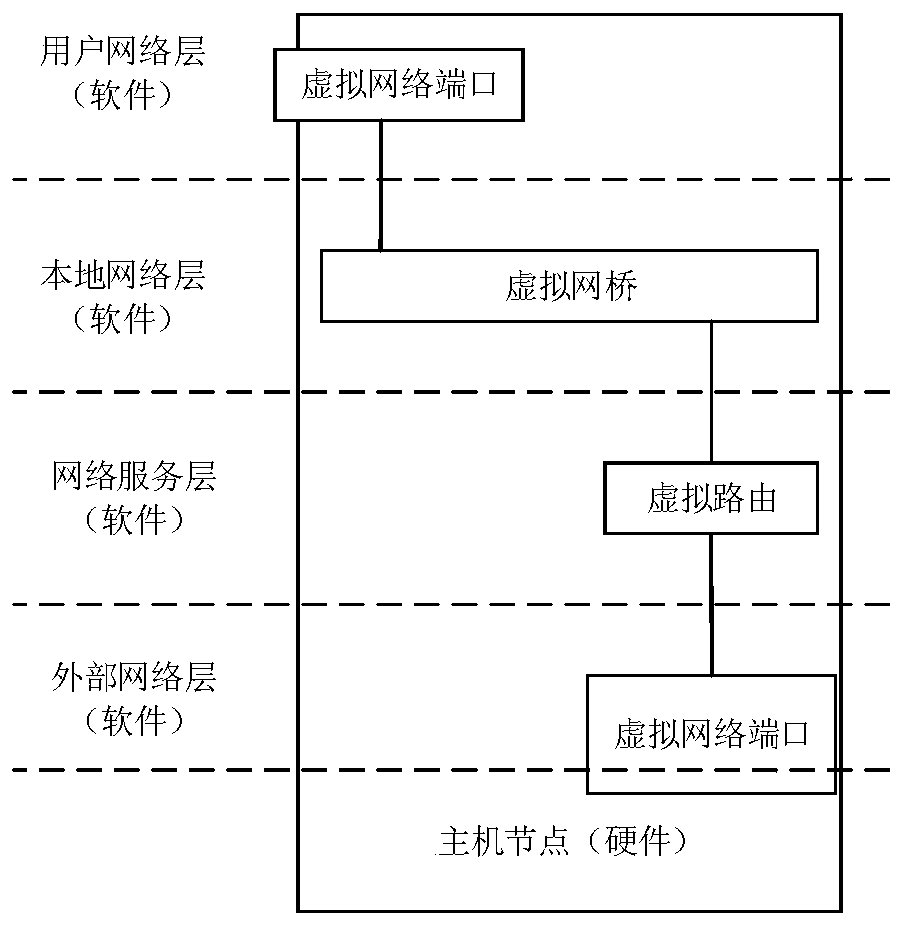
The invention discloses a distributed cluster system and method based on REST and RPC. The system is erected between a user side and a server, the user side and the server are based on Linux namespacearchitecture, and management of namespace and resources of the namespace is achieved through REST architecture; the REST aims to improve independence and loose coupling of a client server, enhance scalability of the server and simplify development of the server, and is used for processing various service requests of a user by a service front end. By adopting the RPC architecture, the defects thatthe REST communication architecture can only synchronously communicate and the communication data is only limited to texts can be overcome, and the RPC architecture is used for serving a back-end solution function business process. The user network is constructed by adopting a virtual network, and the data storage adopts a distributed file system. The reliability of user service is improved, andthe management cost and the operation and maintenance complexity are reduced.
Owner:XIAN MICROELECTRONICS TECH INST
Method and system for establishing security system based on domain mechanism
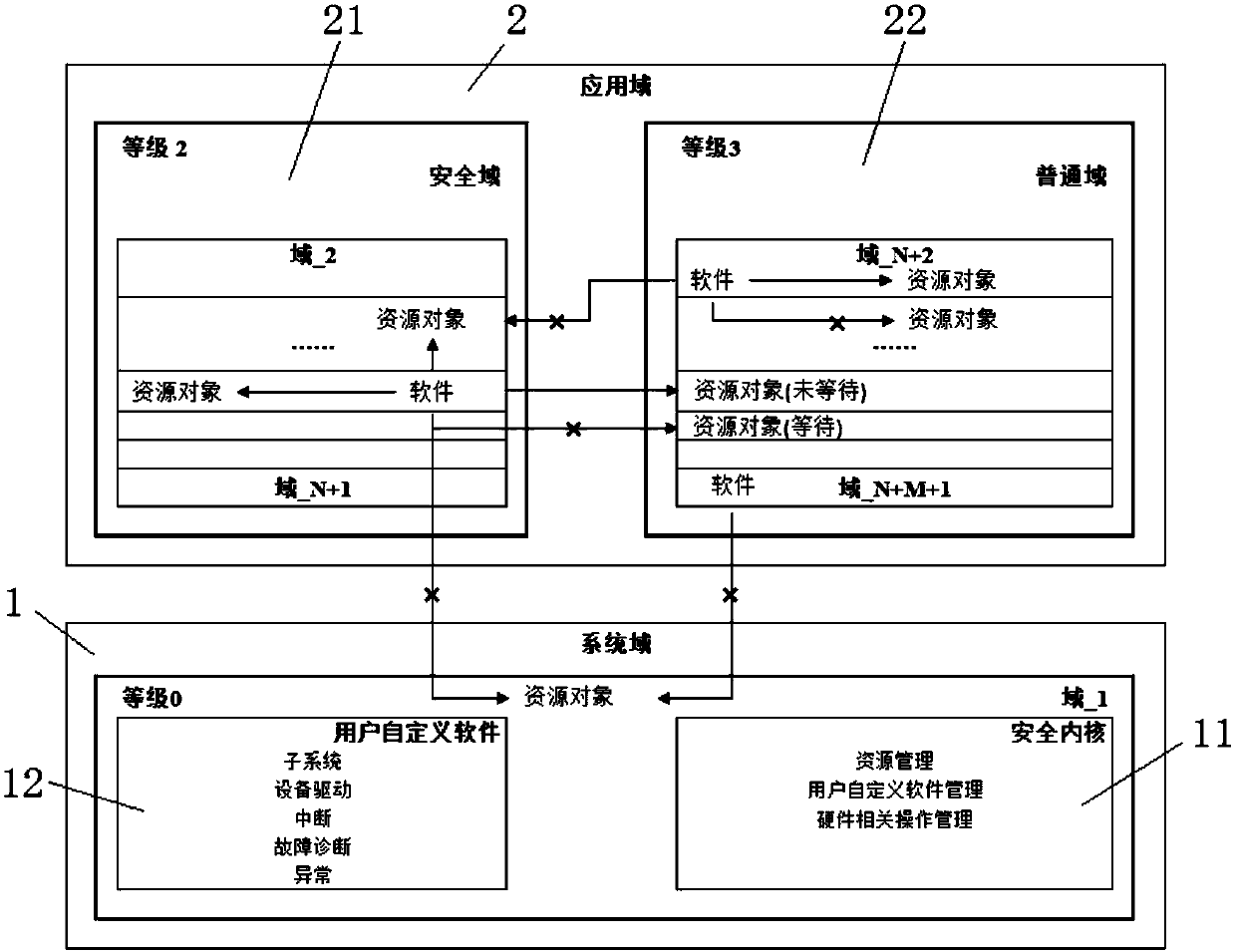
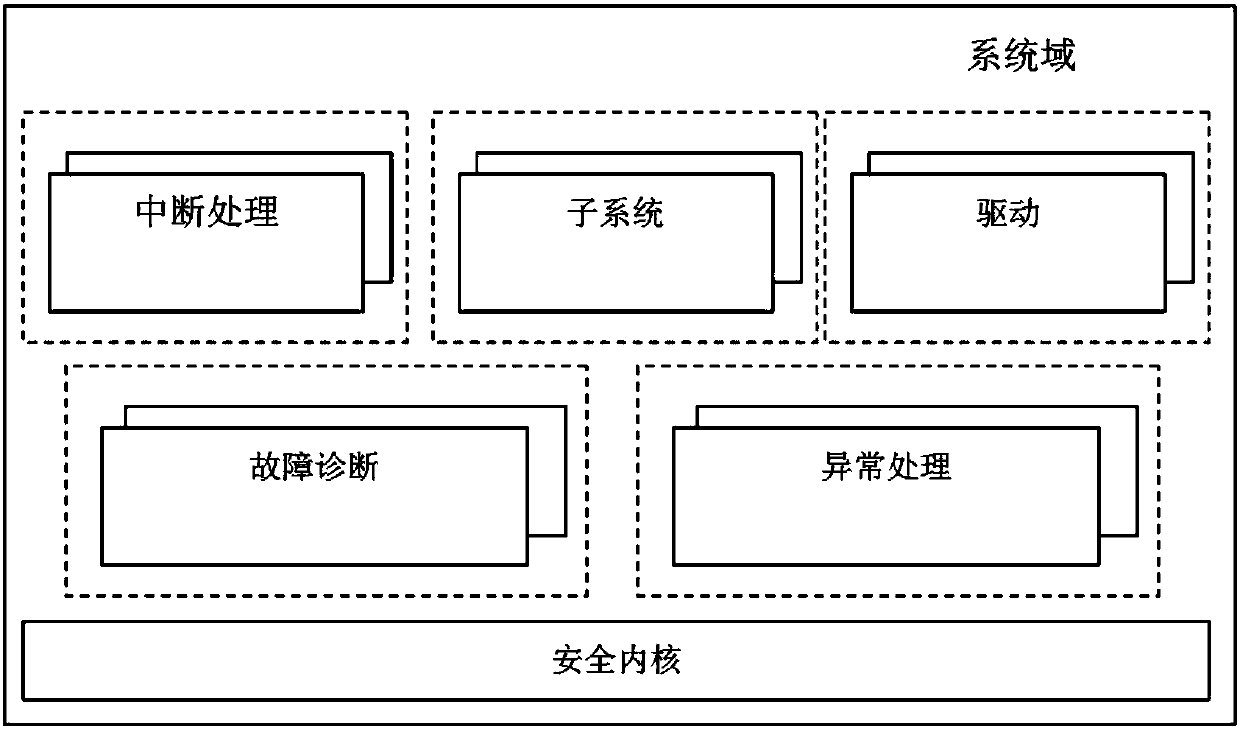
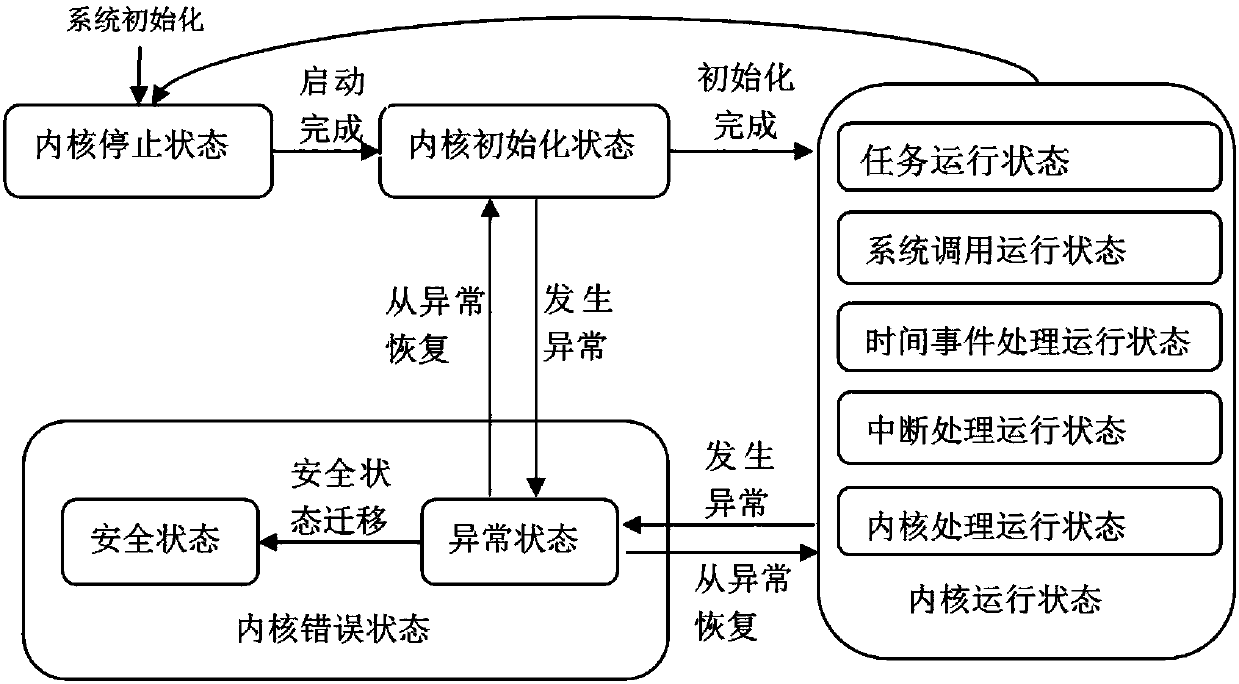
InactiveCN108021827AFlexible controlReasonable strengthInternal/peripheral component protectionPersonalizationRelevant information
The invention discloses a method and system for establishing a security system based on a domain mechanism. The method includes the following steps of configuring domain management information, setting related information of a resource object, configuring and registering a failure diagnosis routine, starting the failure diagnosis routine, establishing a domain environment, initializing a securitycore, executing scheduling and running software, intersecting a software calling security API of a security domain with the security core, intersecting a software calling ordinary API of an ordinary domain with the security core, and regularly detecting the current system state through the security core. The system comprises system domains and application domains. The application domains include the security domain and the ordinary domain. The smaller the domain value of software is, the higher the authority is; software with high authority can have access to the software itself and resourceswith lower authorities, and software with the same authority can have access to one another. The domain mechanism is sufficiently used, and security isolation is achieved; the individualized securitysystem of different grades can be established; control is flexible, and strength is reasonable; hardware characteristics are not depended on, and portability is high.
Owner:中科开元信息技术(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com