Patents
Literature
538 results about "Transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Transmission security (TRANSEC) is the component of communications security (COMSEC) that results from the application of measures designed to protect transmissions from interception and exploitation by means other than cryptanalysis.
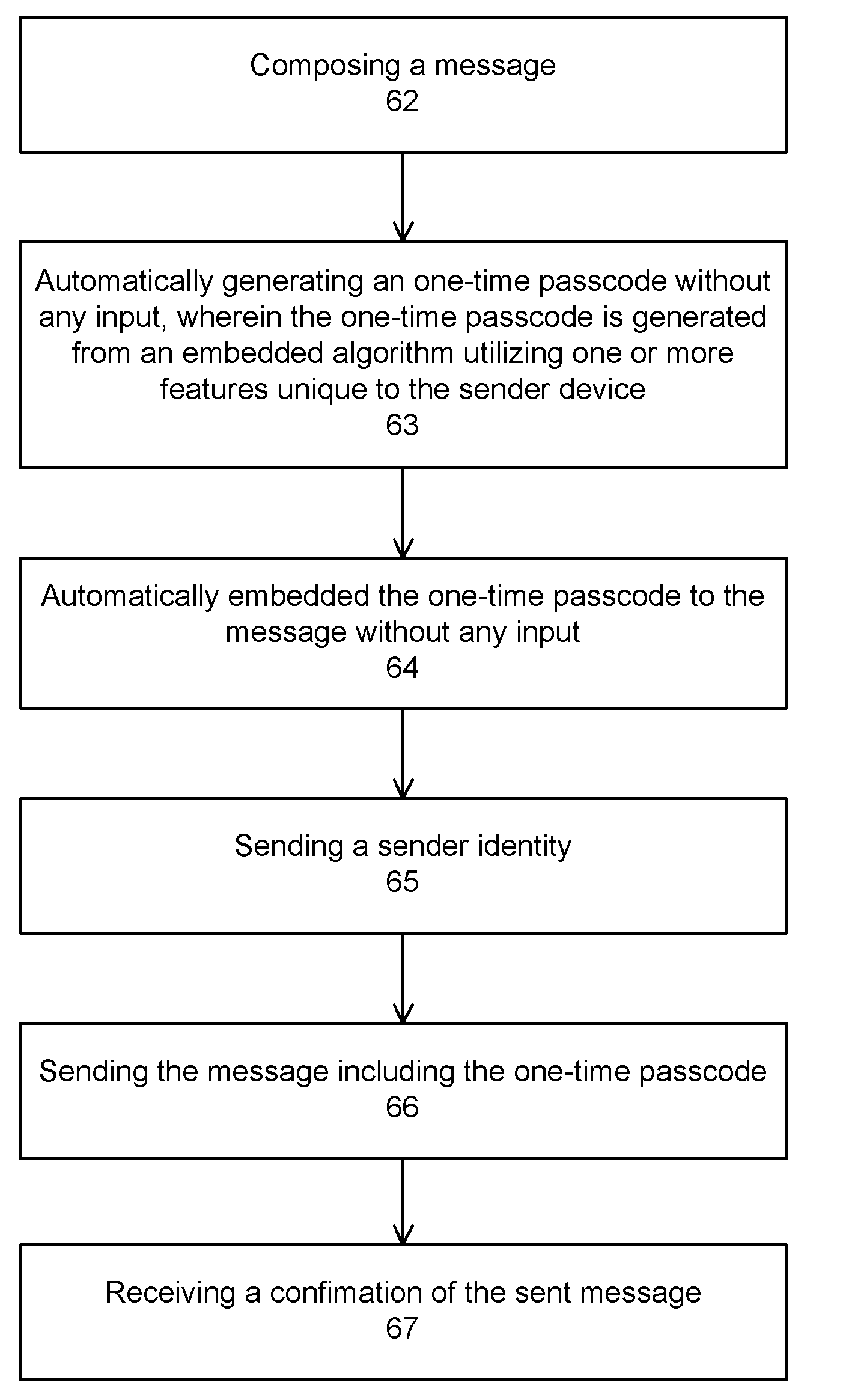
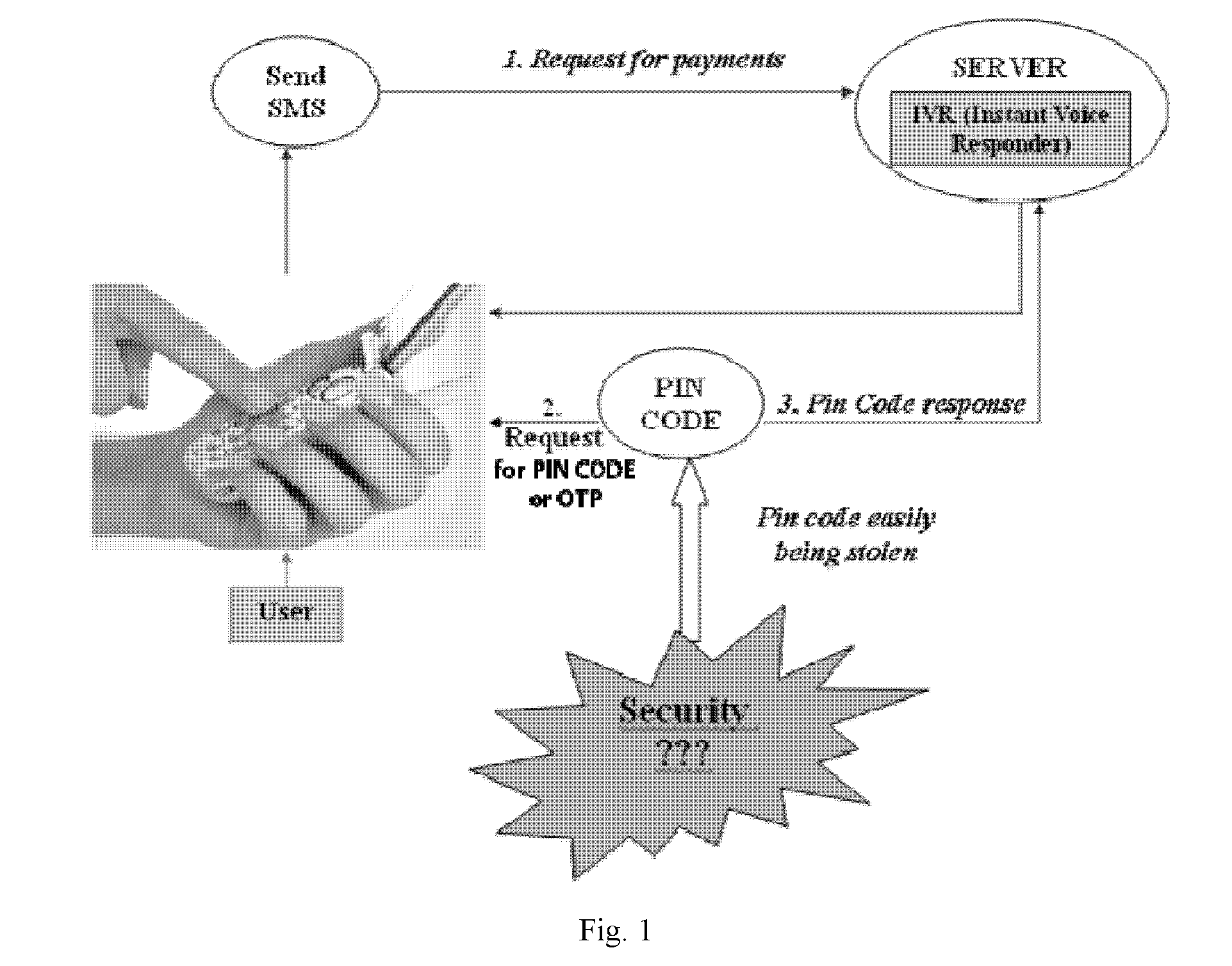
Multi-factor authentication and certification system for electronic transactions
InactiveUS20090172402A1Environment safetyImprove securityFinanceUser identity/authority verificationE-commerceOne-time password
The present invention provides computer-enable certification and authentication in, for example, e-commerce with wireless and mobile devices. The present authentication method offers ease of operation by automatically embedding a one-time passcode to the message without the sender input. A one-time key can also be used to encrypt the message, further providing transmission security. In addition, sensitive information and one-time passcode generator are pre-arranged and stored at both sender and receiver devices, avoiding information comprising in wireless environment transmission.
Owner:TRAN NGUYEN THO
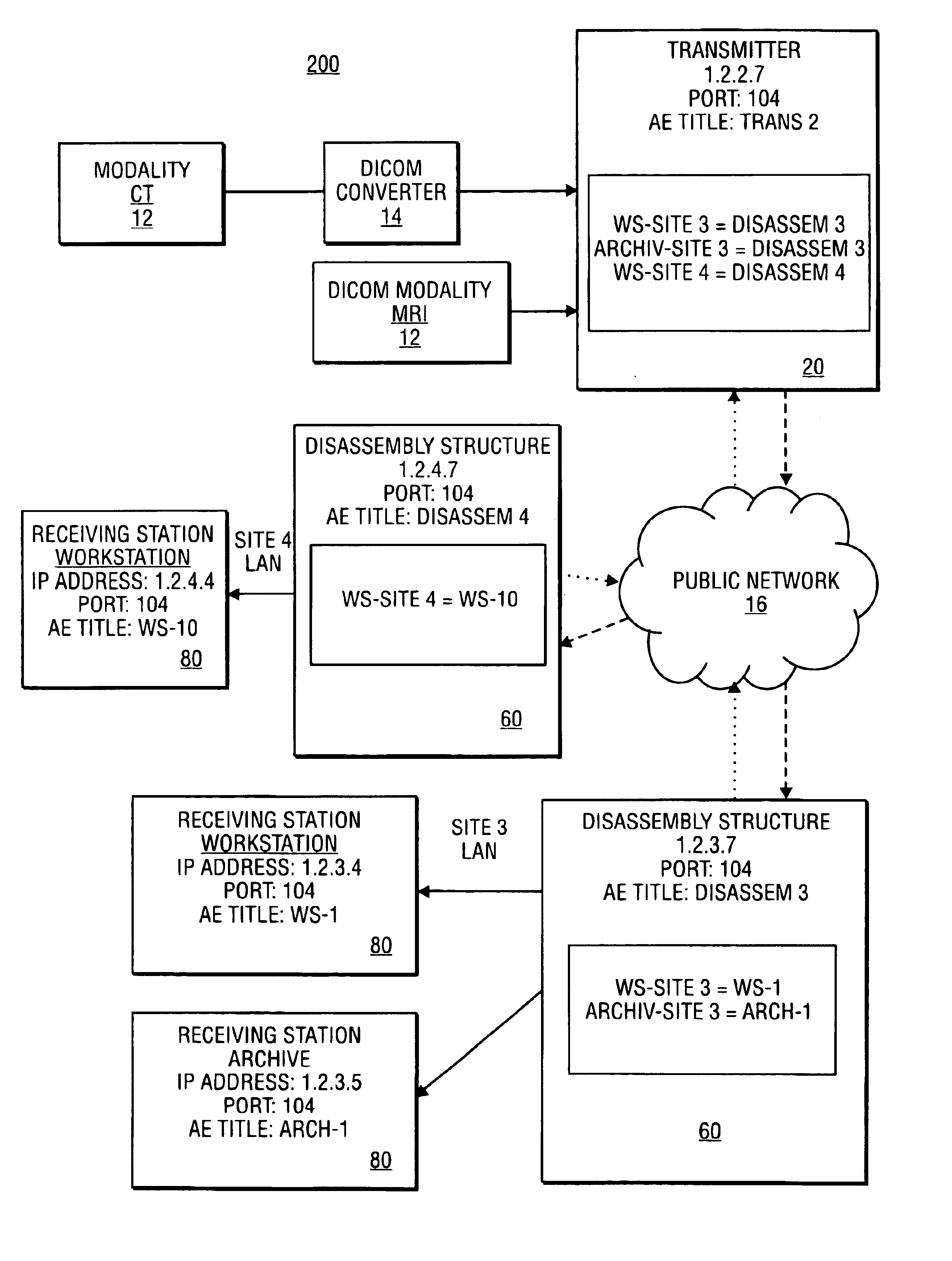
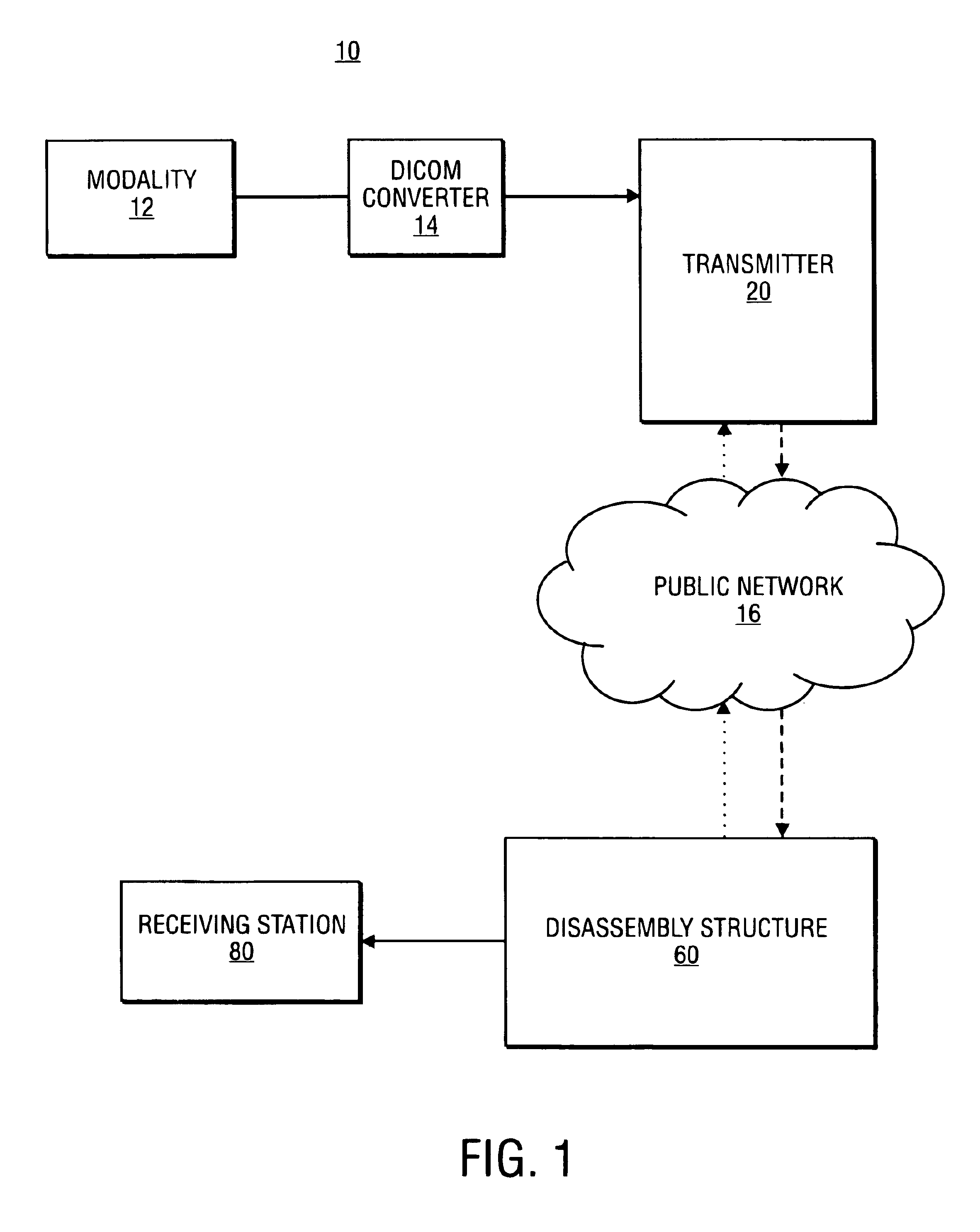
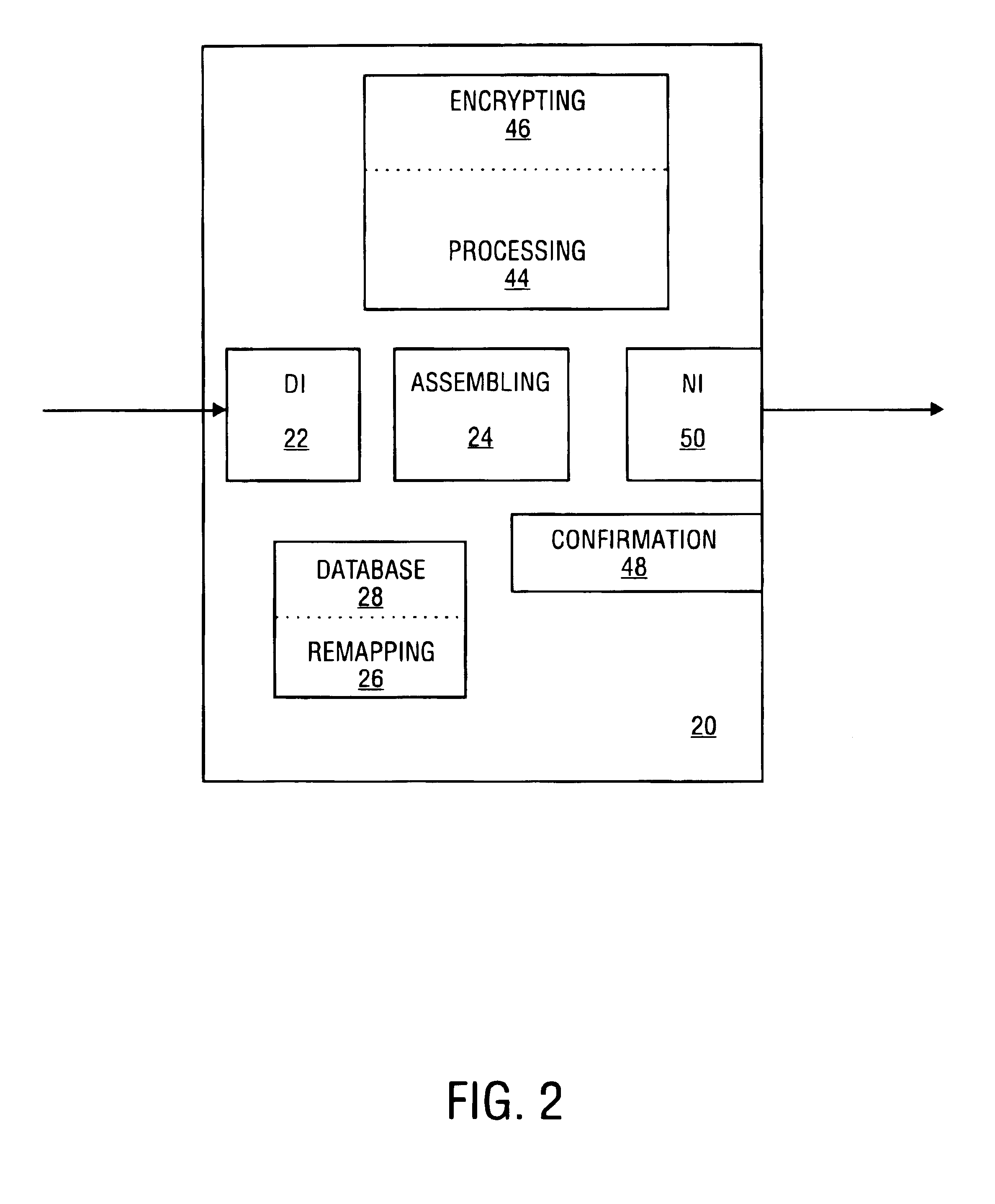
Secure network system and method for transfer of medical information
InactiveUS7028182B1Data processing applicationsComputer security arrangementsCombined usePublic network
The assembly and communication of medical information from a variety of modalities to remote stations through a public network is provided for by the combined use of a transmitter and disassembly structure. The transmitter includes an assembly unit for gathering data into packets and a processing unit to provide security for transfer. The disassembly structure reconfigures the data for relay to a receiving station. Mechanisms are provided for conserving the transfer time from transmitter to disassembly structure.
Owner:NEXSYS ELECTRONICS
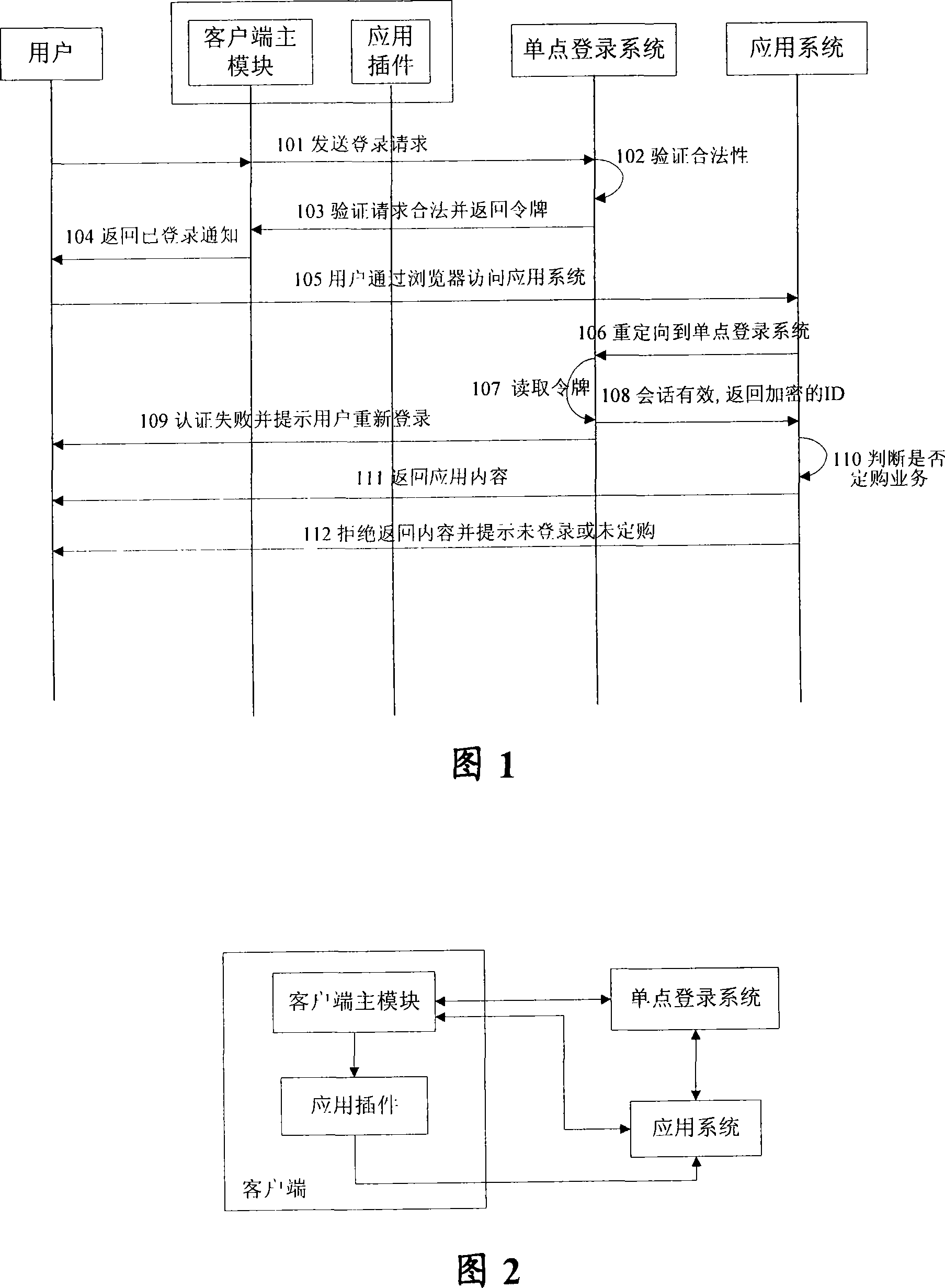
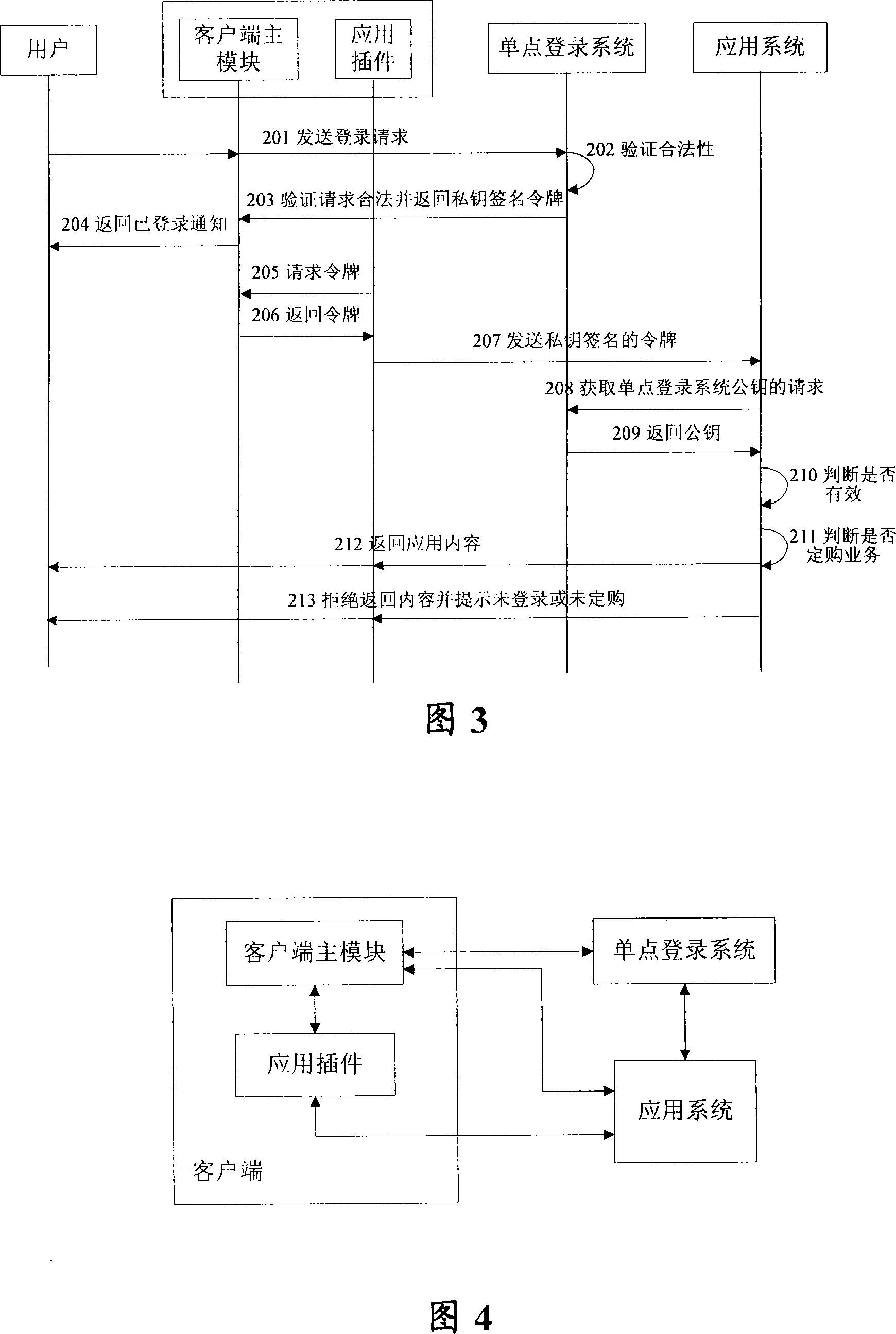
Method and device for accessing plug-in connector applied system by client terminal
ActiveCN101202753AEnsure data transmission securityPublic key for secure communicationUser identity/authority verificationTimestampPassword
The invention provides a method and a device for accessing a plug-in application system of a client, the method includes (1) a user transmits a logging-on request to a single point logging-on system and the request includes a single point logging-on account and a password; (2) when the single point logging-on system confirms the request to be legal according to the single point logging-on account and the password, a token including a user ID and a timestamp is returned to the single point logging on system; (3) the user accesses the client with a plug-in integration and the token is transmitted to the application system by the client; (4) the application system transmits a request of analyzing the token to the single point logging-on system, so as to analyze the user ID according to the returned information and the searched service contents corresponding to the user ID is returned to the client. In the invention, the user can access all authentication services by only logging on for once, thus realizing the centralized authentication and effectively ensuring the security for the system to transmit data.
Owner:CHINA TELECOM CORP LTD
Equipment, firmware upgrading device thereof and firmware upgrading method thereof
InactiveCN108196867AImprove transmission securityImprove securityUser identity/authority verificationSoftware deploymentTransmission securityFirmware
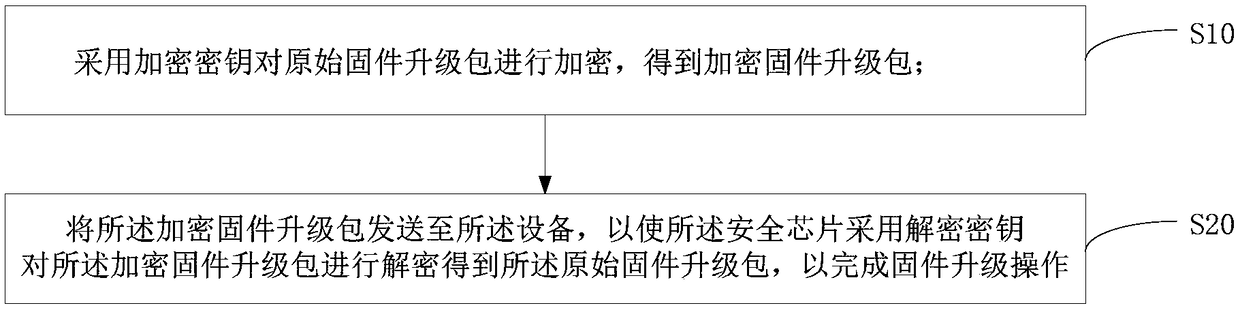
The invention discloses a firmware upgrading method of equipment. The equipment comprises a security chip which stores a decryption secret key. The firmware upgrading method includes following steps:adopting an encryption secret key to encrypt an original firmware upgrading packet to acquire an encrypted firmware upgrading packet; sending the encrypted firmware upgrading packet to the equipment to enable the security chip to adopt the decryption secret key to decrypt the encrypted firmware upgrading packet to acquire the original firmware upgrading packet to complete firmware upgrading operation. The invention further discloses the equipment and a firmware upgrading device thereof. Transmission safety of the firmware upgrading packet of the equipment is improved, so that safety in remotefirmware upgrading of the equipment is improved.
Owner:SHENZHEN EXCELSECU DATA TECH
Content-based transport security
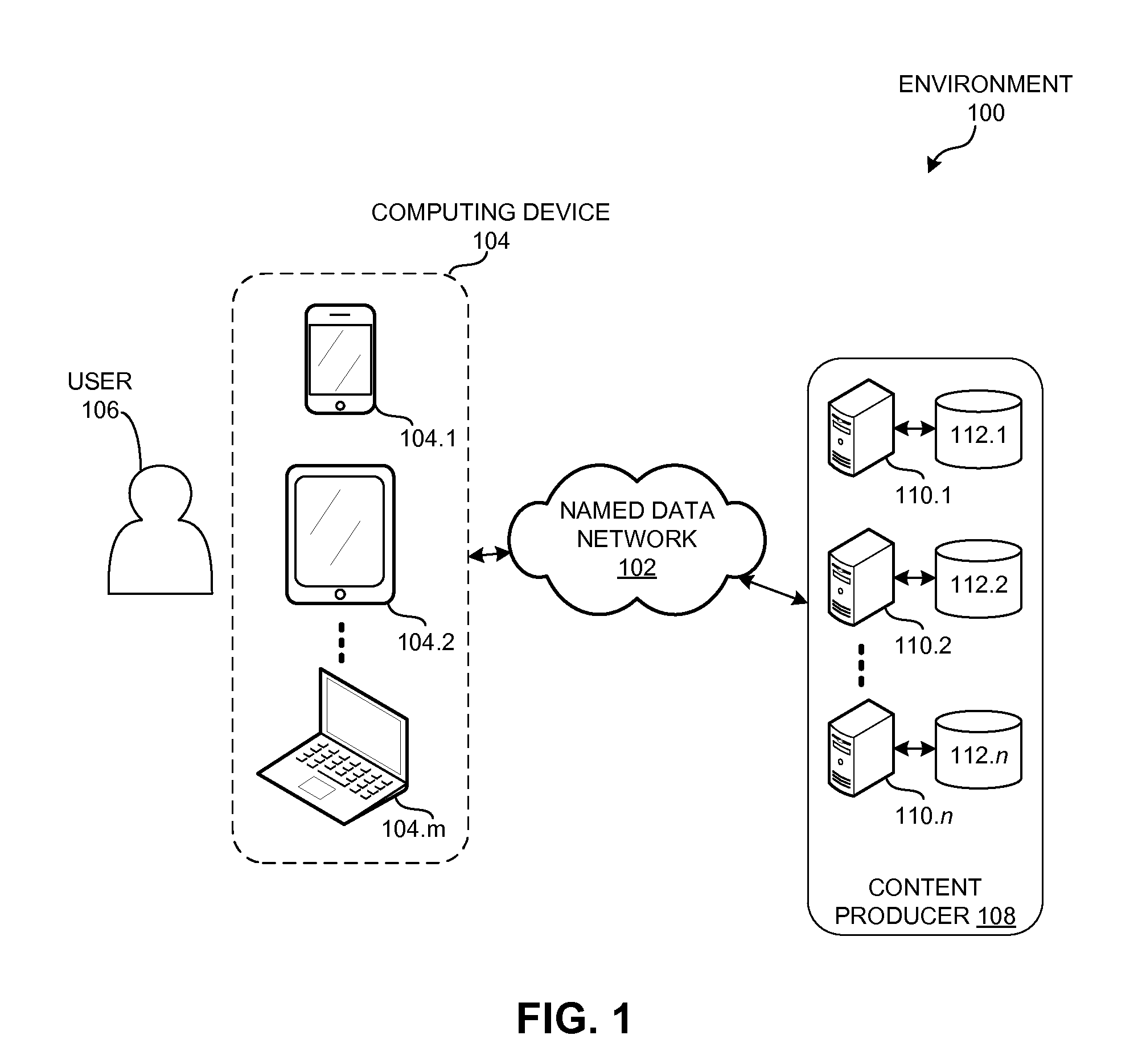
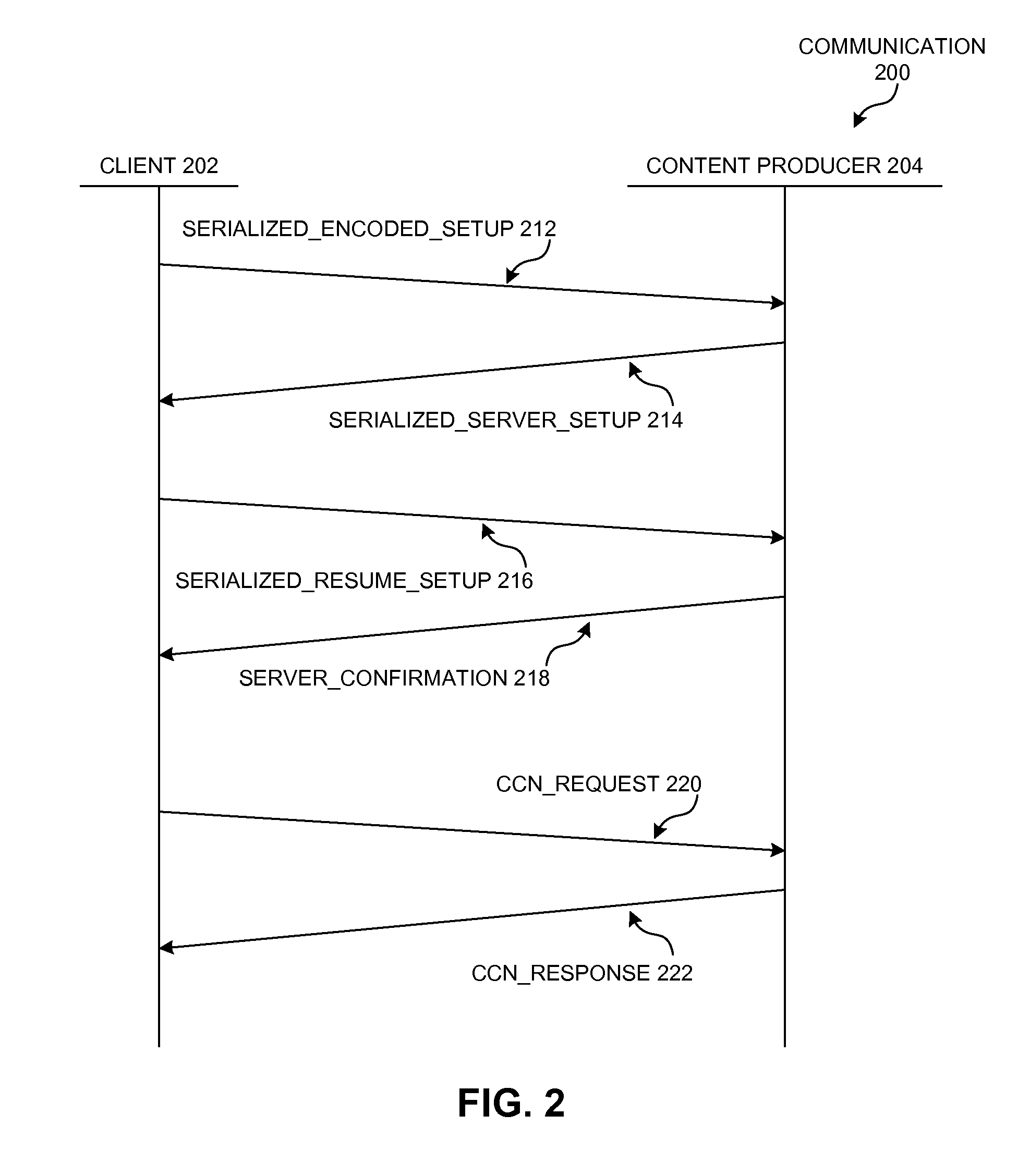
InactiveUS20150222424A1Key distribution for secure communicationPublic key for secure communicationComputerized systemRemote computer
A computer system can send a secure request over a named-data network to a remote device by generating an Interest with encrypted name components. During operation, the computer system can receive or obtain a request for data, such as from a local user or from a local application. If the system cannot satisfy the request locally, the system can determine at least a routable prefix and a name suffix associated with the request. The system can generate the secure Interest for the request by determining an encryption key that corresponds to a session with the remote computer system, and encrypts the name suffix using the session encryption key. The system then generates an Interest whose name includes the routable prefix and the encrypted name suffix, and disseminates the Interest over a named-data network to send the request to the remote computer system.
Owner:CISCO TECH INC
Security control method of event-driven network control system under multi-network attack
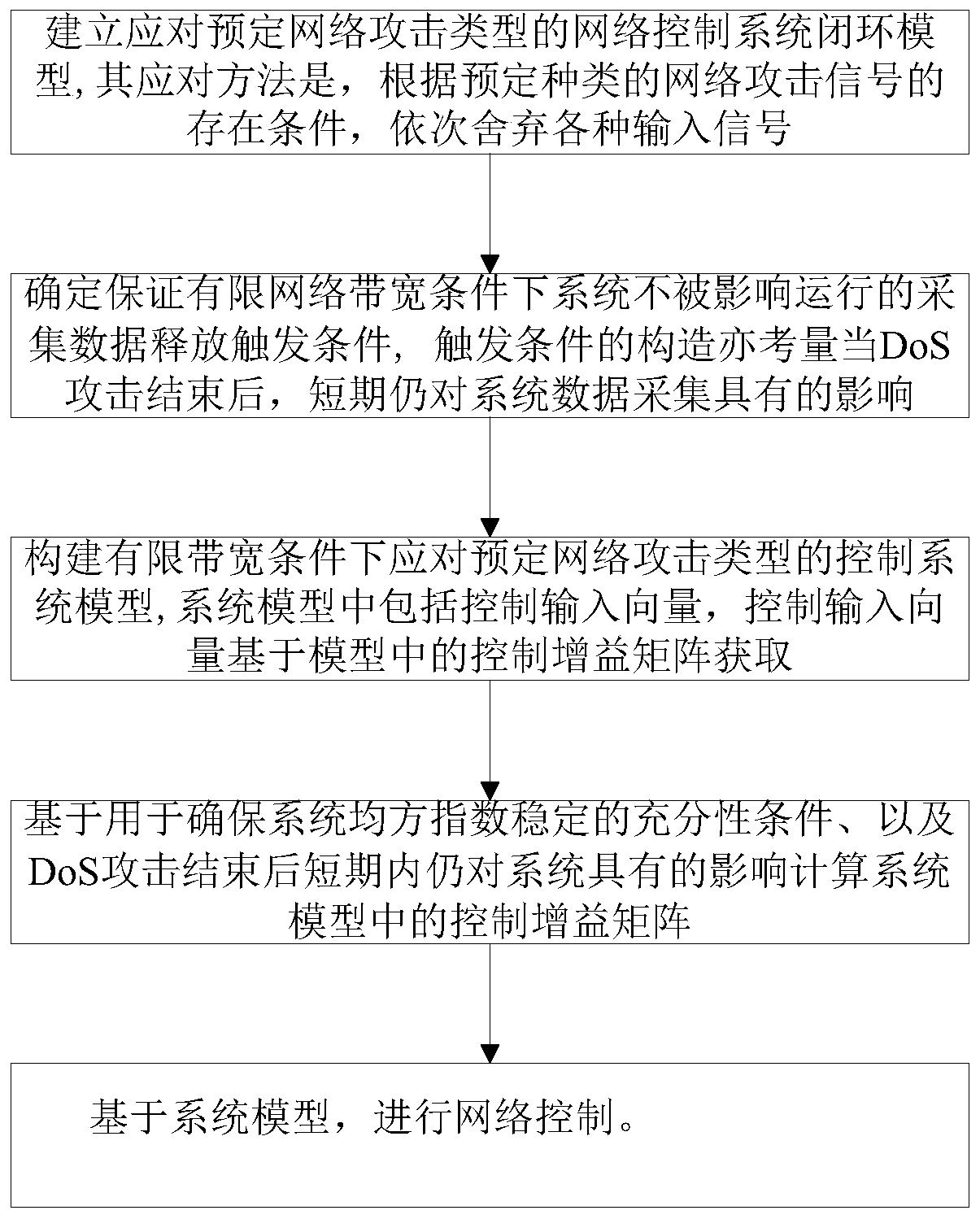
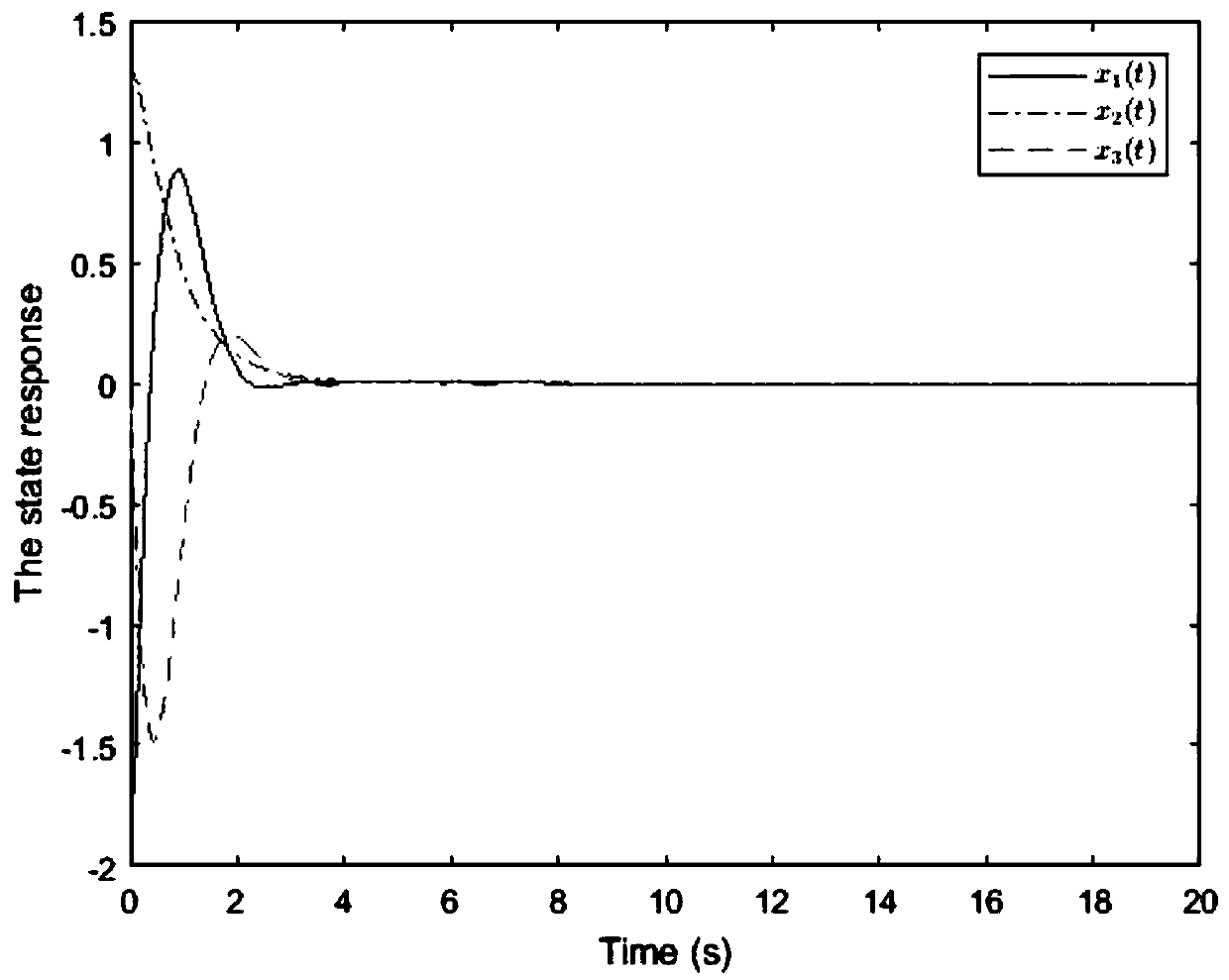
ActiveCN110213115AImprove stabilityReduce the number of transfersData switching networksLyapunov stabilityEvent trigger
The invention provides a security control method of an event-driven network control system under a multi-network attack. Considering the network transmission security problem, a random network spoofing attack, a replay attack and a DoS attack are sequentially introduced, and a system closed-loop model under the multi-network attack is established. Further considering the constraint of the limitednetwork bandwidth, an event trigger mechanism is introduced to screen and release sampling data meeting a preset event trigger condition to the network for transmission, thereby establishing a new switching system model on the basis of the system closed-loop model. Based on a switching system model, a Lyapunov stability theory is utilized to obtain a sufficiency condition for enabling the system to meet the stability of a mean square index, and a group of linear matrix inequalities is solved to obtain the gain of the state feedback controller. Compared with an existing controller design method, safe and stable operation of the network control system under the influence of multi-network attacks is guaranteed, meanwhile, the data transmission frequency is reduced, and limited network bandwidth resources are saved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
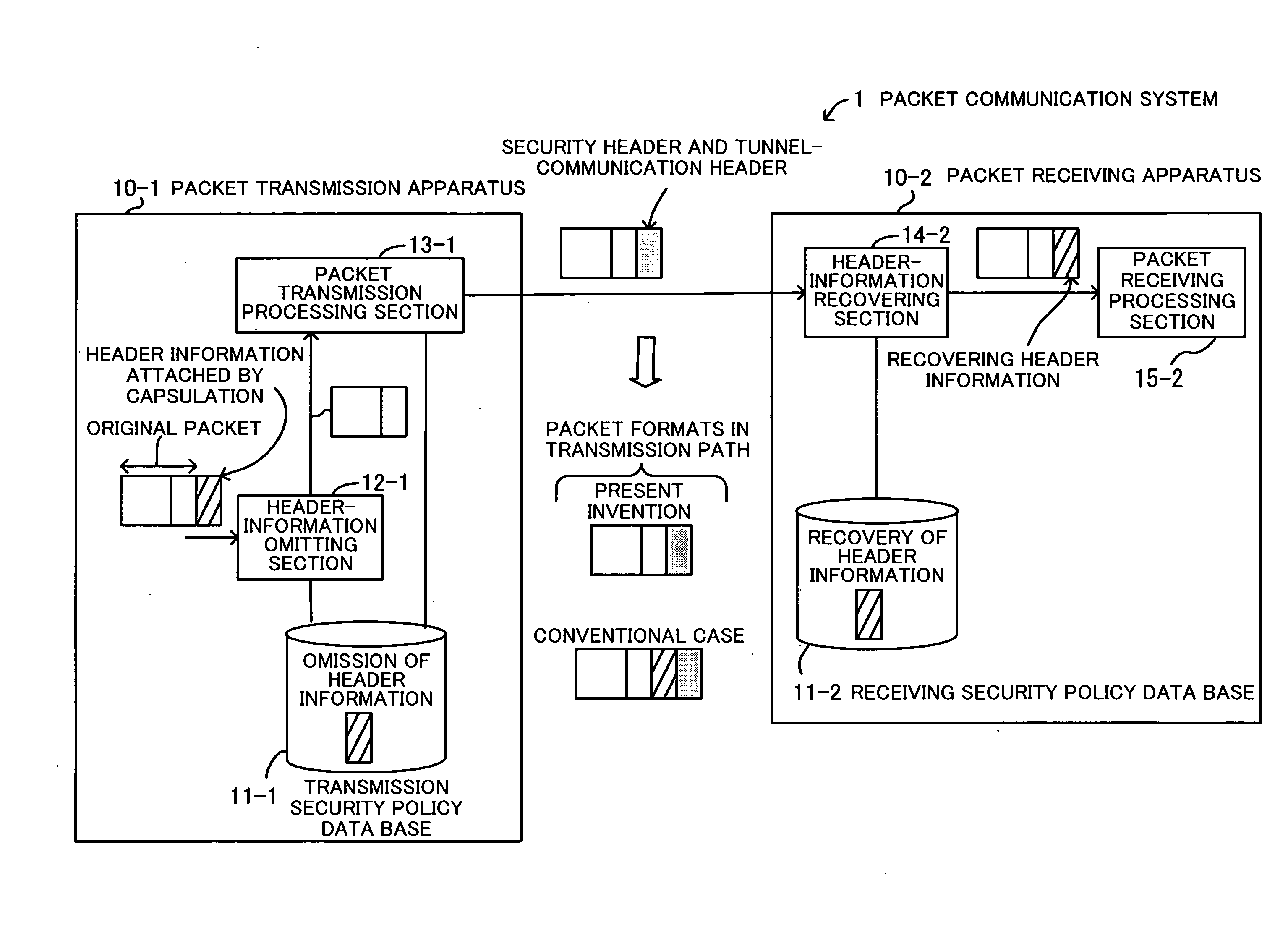
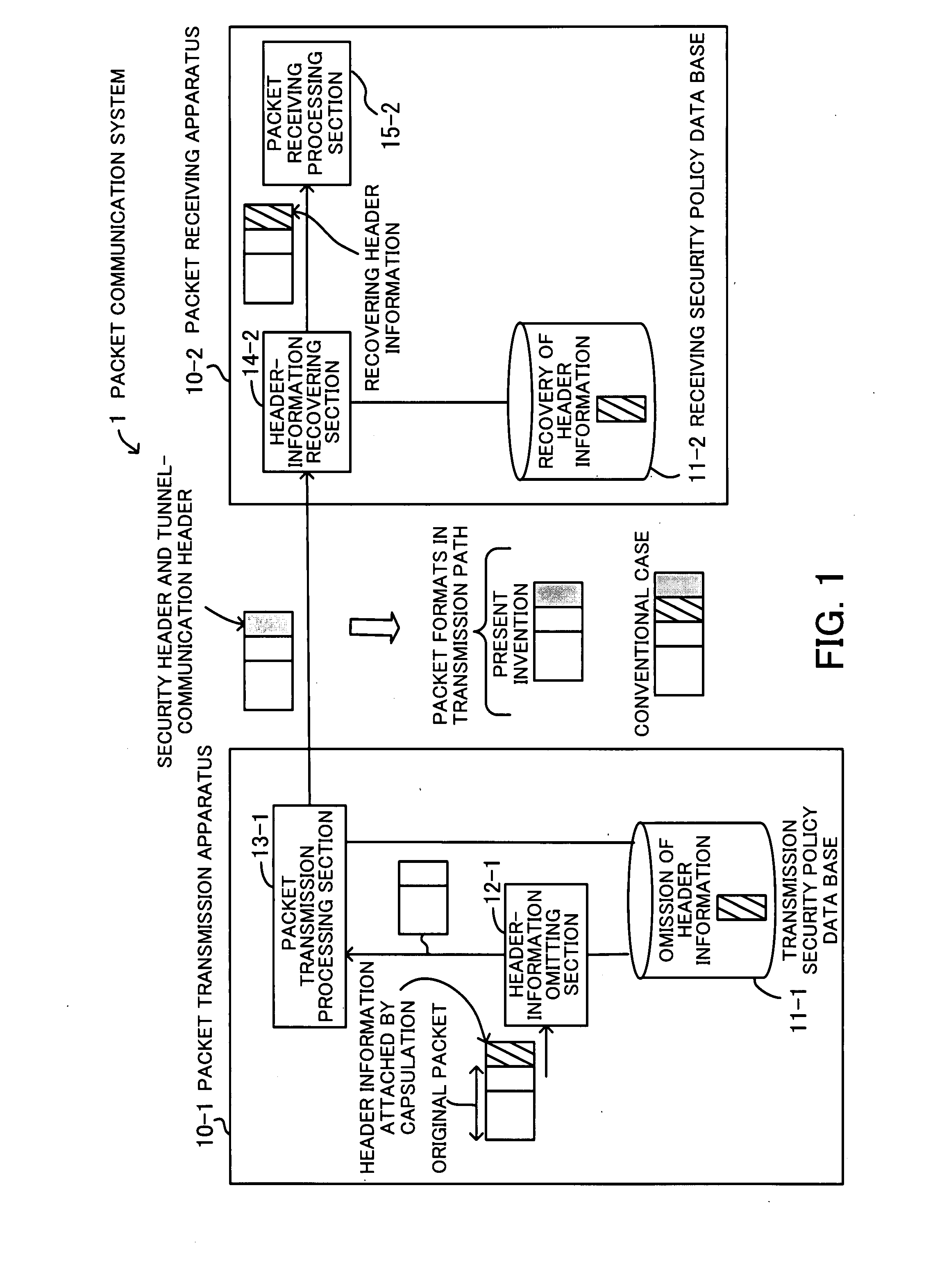
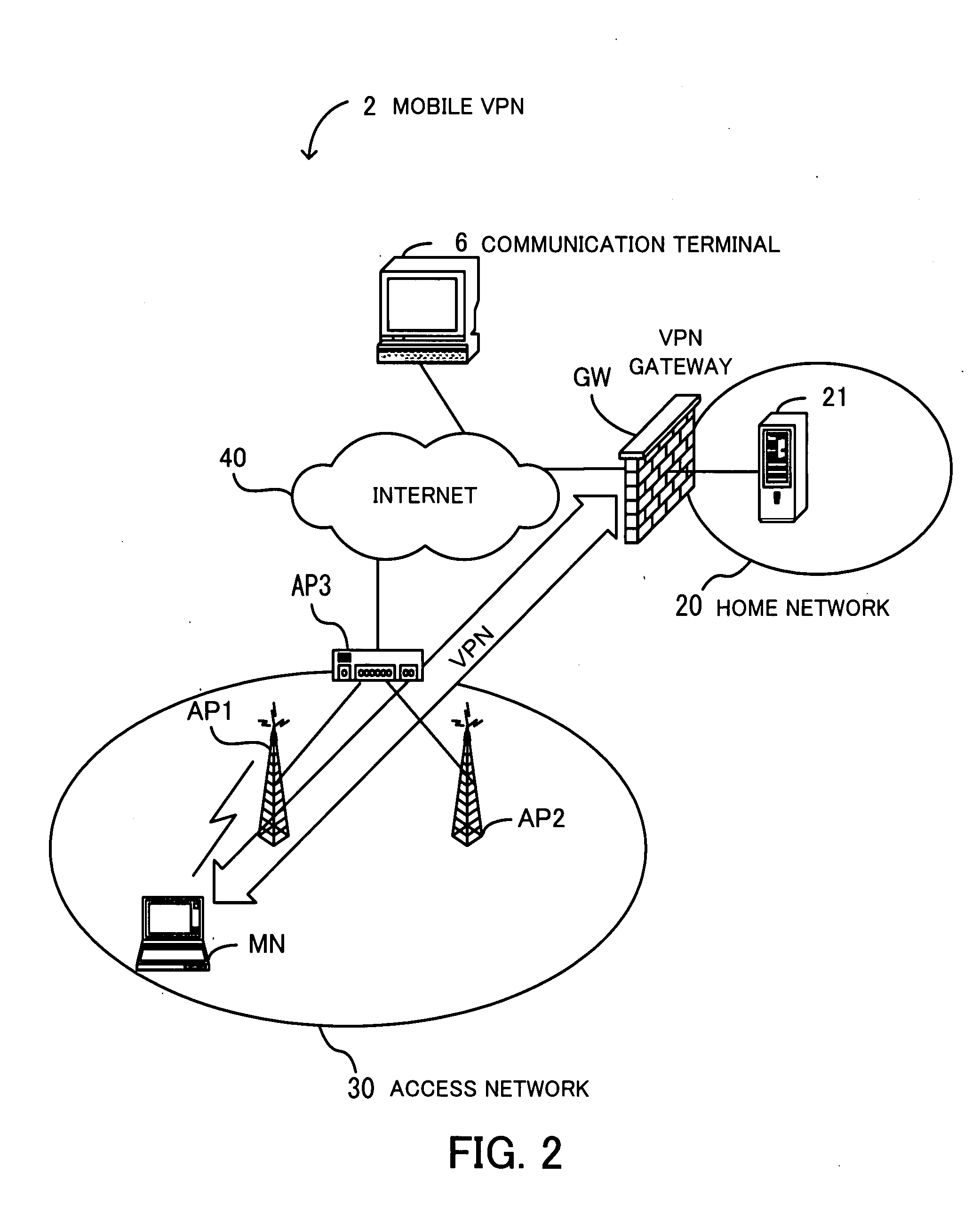
Packet communication system
InactiveUS20070186100A1Easy to useImprove security levelNetwork traffic/resource managementDigital computer detailsPacket communicationGroup communication systems
A packet communication system for effectively using network resources and for improving network operability. A transmission security policy database specifies the omission of header information attached when a transmission packet is capsulated, as a transmission security policy. A header-information omitting section omits the header information of the capsulated transmission packet. A packet transmission processing section adds a security header and a header for tunnel communication to the packet from which the header information has been omitted and transmits the packet. A receiving security policy database specifies that the header information has been omitted, as a receiving security policy. A header-information recovering section searches the receiving security policy database for a security policy for a received packet, and when recognizing that the received packet is a target packet from which the header information has been omitted, recovers the header information.
Owner:FUJITSU LTD
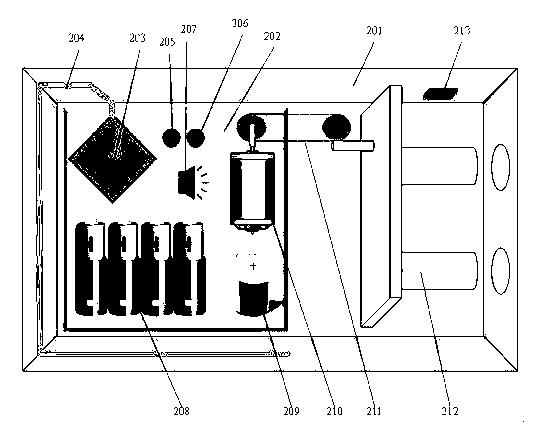
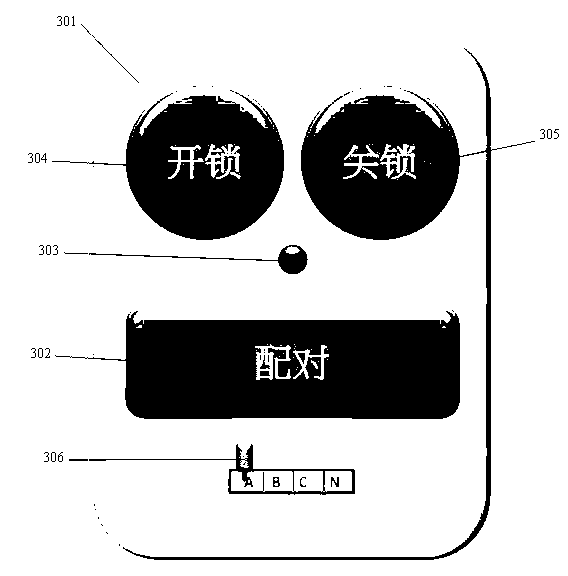
Bluetooth Low Energy (BLE) invisible intelligent lock system controlled by BLE equipment
InactiveCN103174337AMeet the priceFulfil requirementsElectric permutation locksEngineeringData transmission
The invention discloses a Bluetooth Low Energy (BLE) invisible intelligent lock system controlled by BLE equipment. The BLE invisible intelligent lock system controlled by the BLE equipment is based on the BLE wireless communication technology. The BLE invisible intelligent lock system comprises a BLE invisible intelligent lock, the BLE equipment, an application program (APP) capable of running on the BLE equipment, a BLE gateway, and the like. According to the BLE invisible intelligent lock system controlled by the BLE equipment, a key is replaced with the BLE equipment like a daily used smart phone to control the BLE intelligent lock, the BLE technology is adopted to guarantee safety of data transmission and enable the BLE intelligent lock to work over a year normally only by being powered by a battery, requirements of users for safety, convenience and price and the like of a lockset system are met, usage of the key, a lock cylinder and other parts is eliminated by adding only one BLE module, and the lock industry is promoted to step into an energy-saving and environment-friendly lower-carbon time.
Owner:鲁亚诗 +1
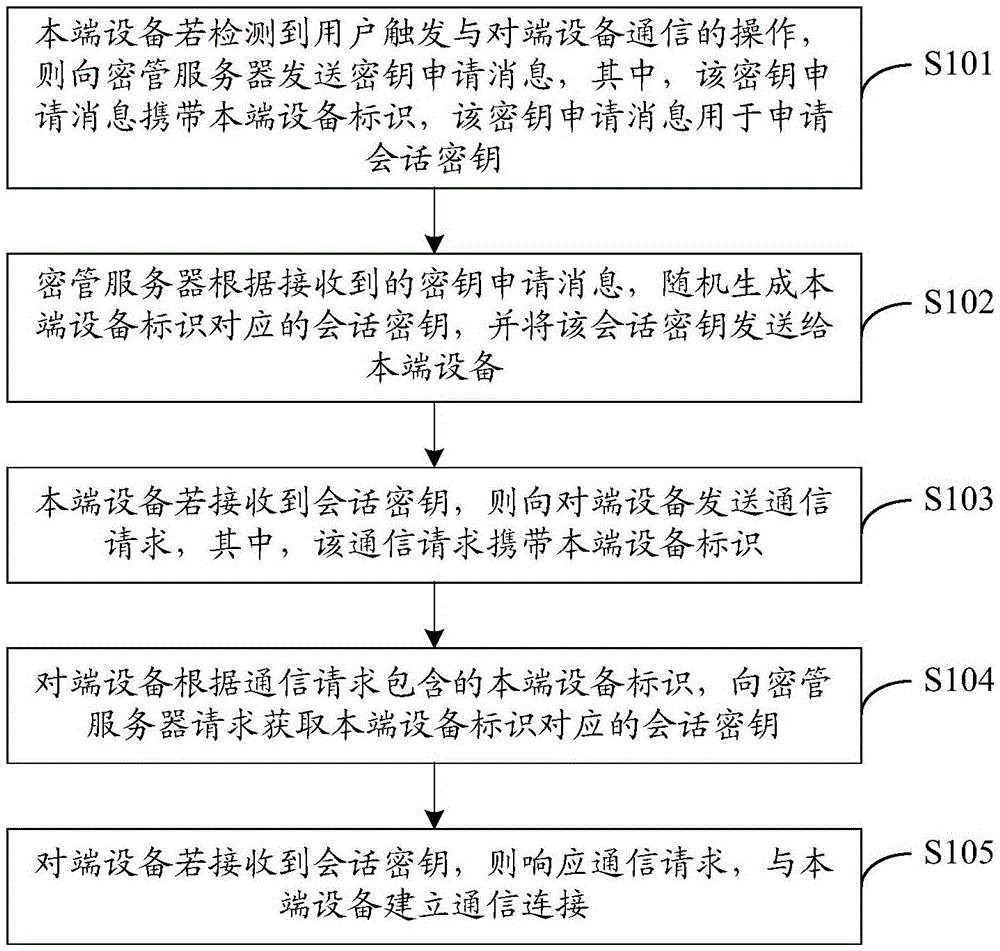
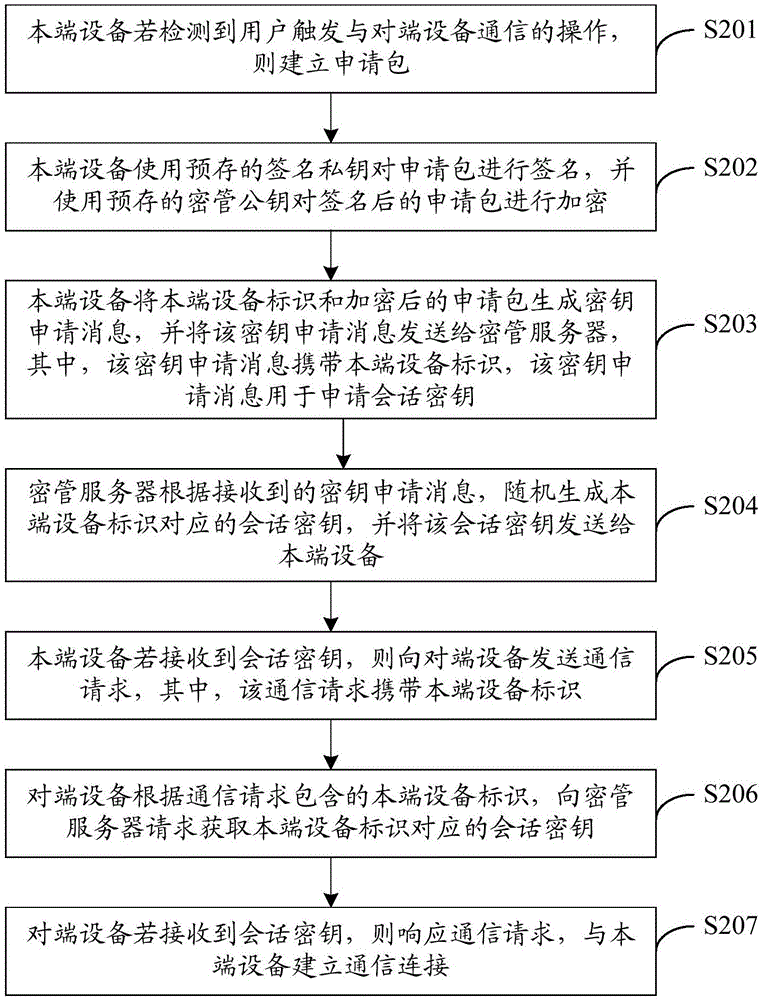
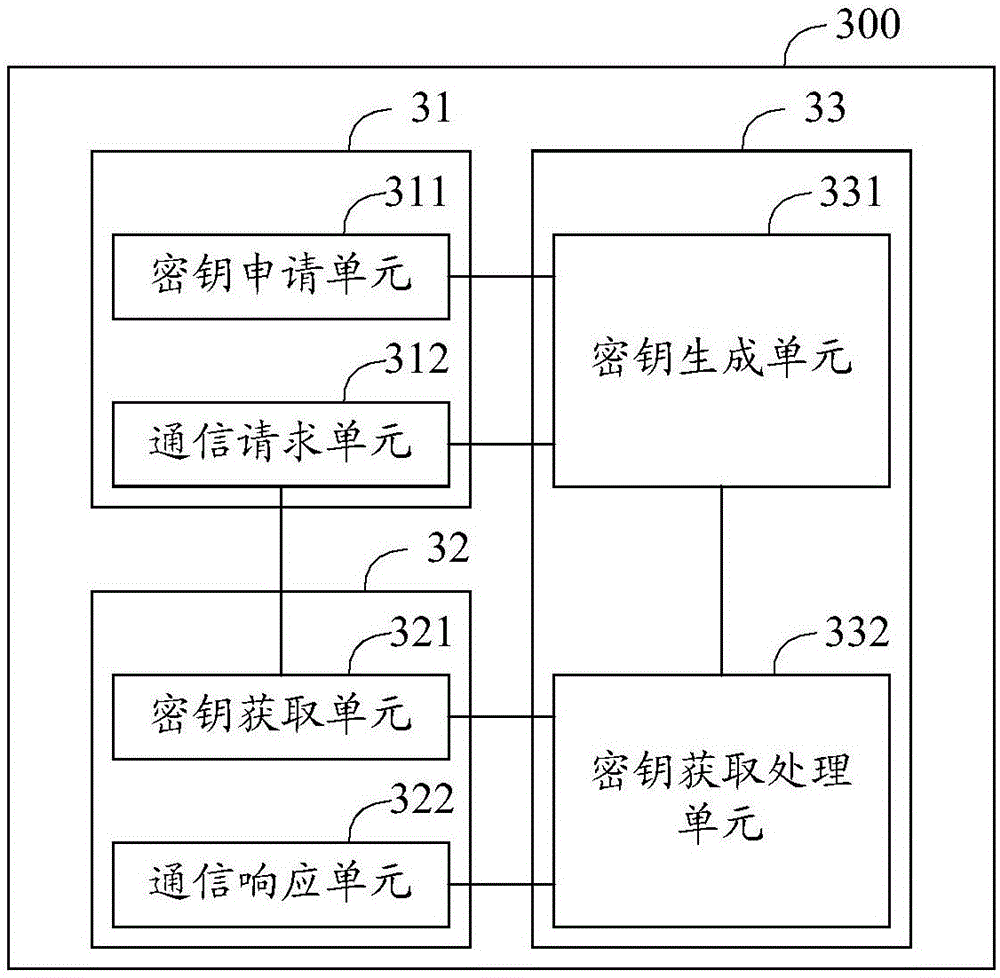
Key management method and system
InactiveCN106535184AImprove securityImprove transmission securityTransmissionSecurity arrangementSecure transmissionTerminal equipment
The embodiment of the invention discloses a key management method and system. The key management method includes the steps: if home terminal equipment detects that a user triggers the operation on opposite terminal equipment, the home terminal equipment sends a key application message to a key management server; according to the received key application message, the key management server generates a session key corresponding to an identifier of the home terminal equipment randomly, and sends the session key to the home terminal equipment; if the home terminal equipment receives the session key, the home terminal equipment sends a communication request to the opposite terminal equipment; according to the identifier of the home terminal equipment included in the communication request, the opposite terminal equipment requests the key management server to acquire the session key corresponding to the home terminal equipment; and if the opposite terminal equipment receives the session key, the opposite terminal equipment gives a response to the communication request and establishes communication connection with the home terminal equipment. The technical scheme of the key management method and system enables both the home terminal equipment and the opposite terminal equipment to safely acquire the session key of the communication of this time, thus improving generation safety and transmission safety for the session key, and guaranteeing safe transmission of the communication content.
Owner:SHENZHEN GIONEE COMM EQUIP
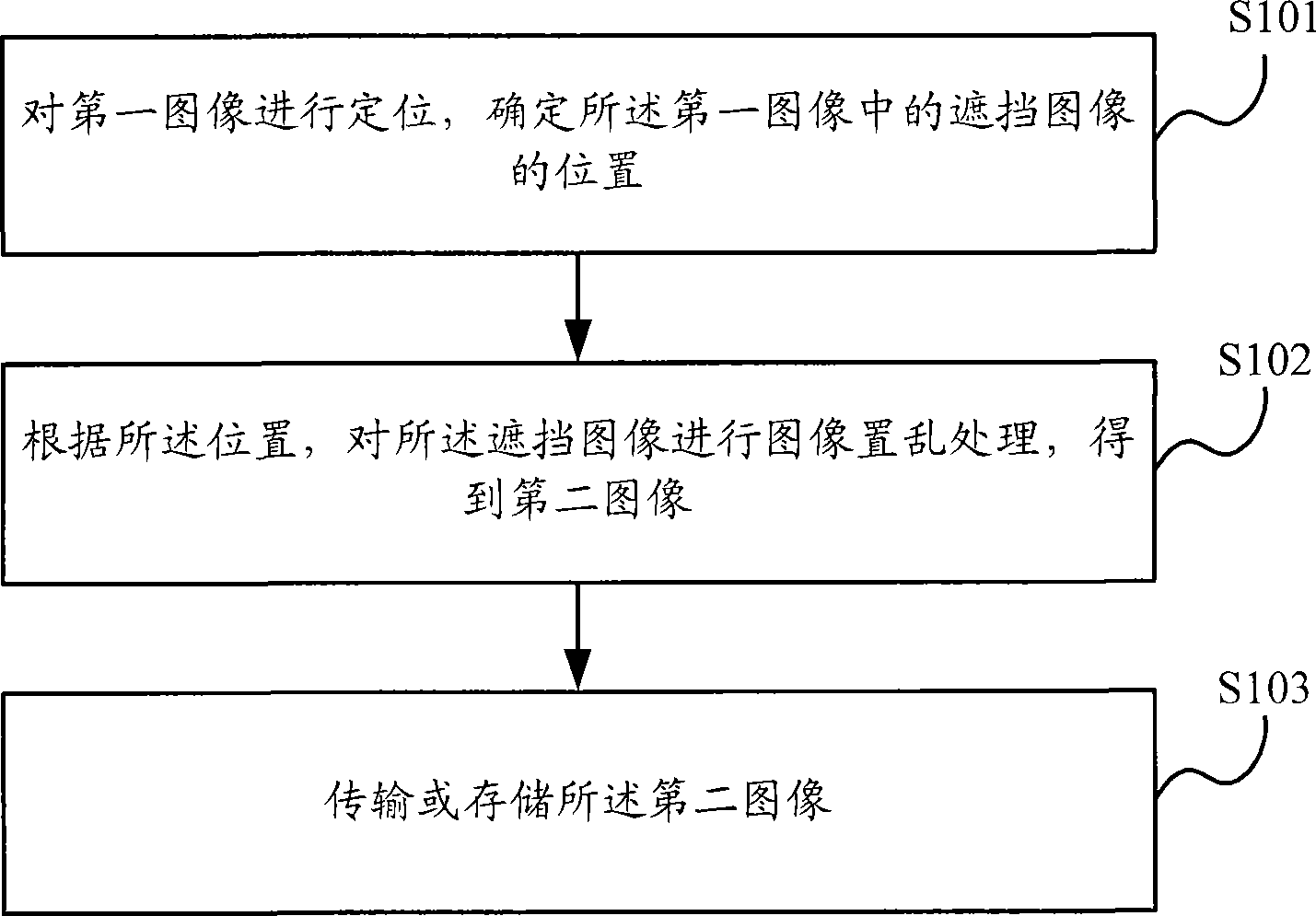
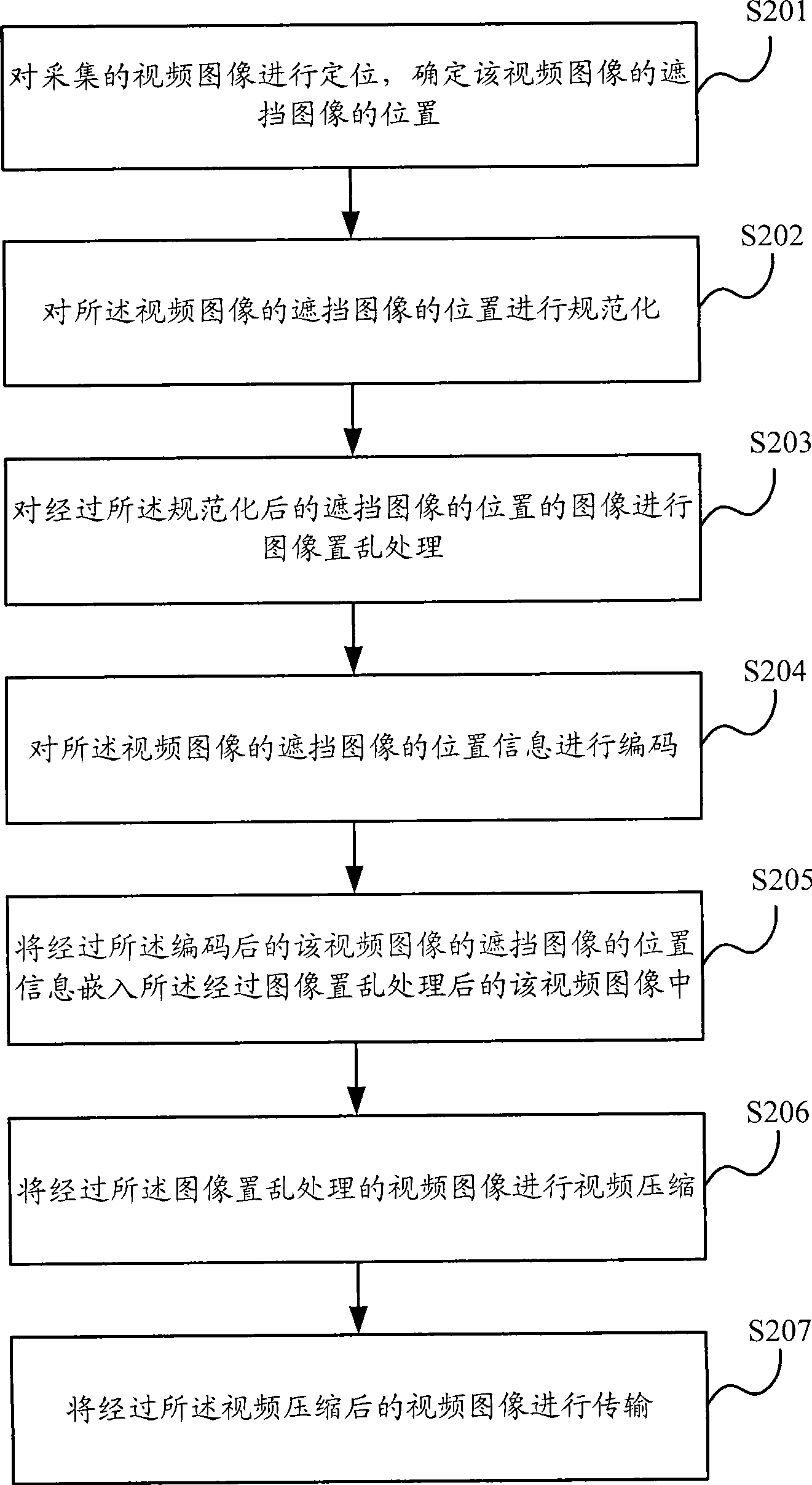
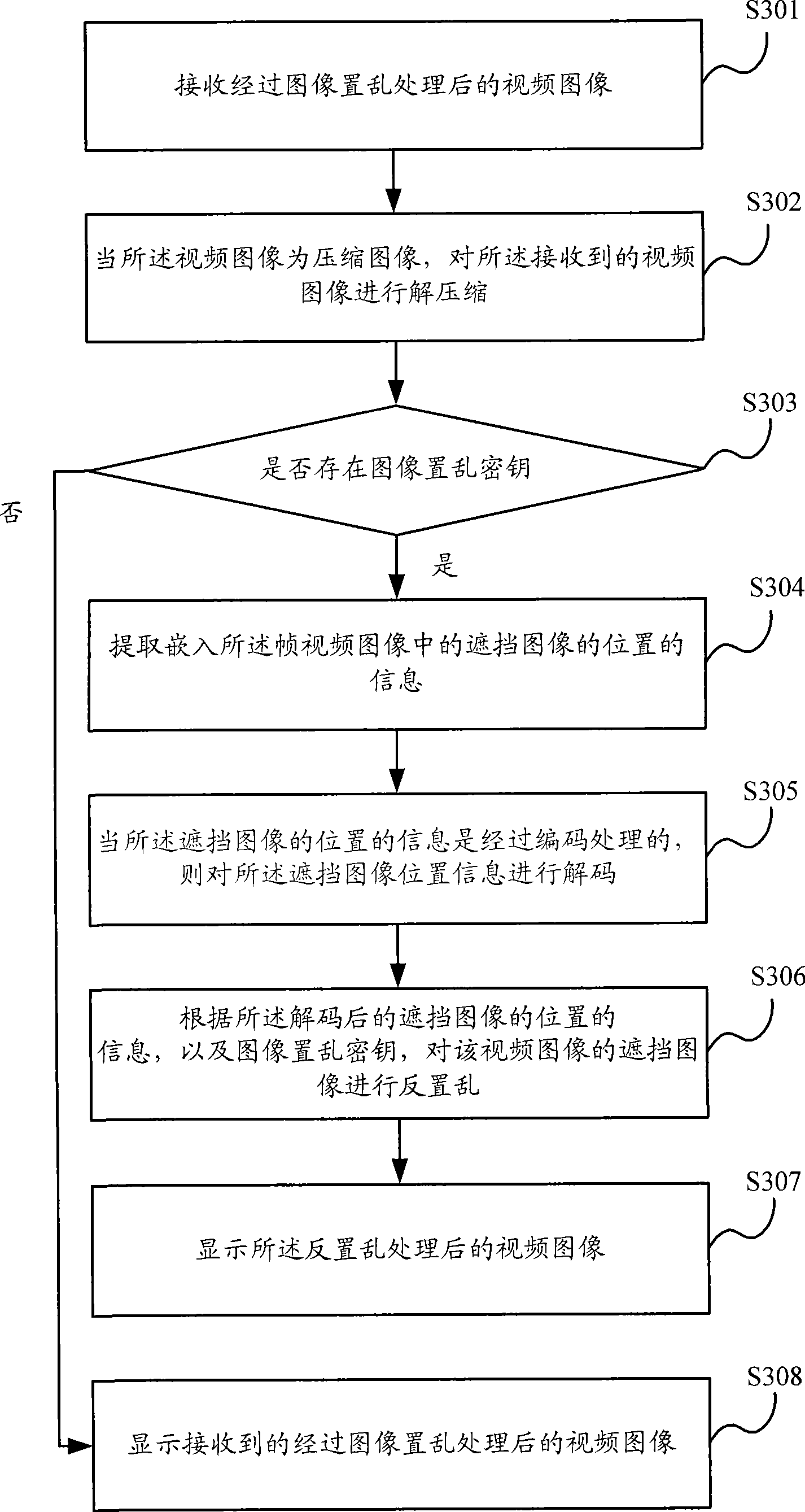
Method and apparatus blocking special position of image
InactiveCN101389005AConvenient queryAvoid Malicious SpreadClosed circuit television systemsDigital video signal modificationImaging processingComputer graphics (images)
The invention discloses a method and a device for sheltering an image particular position, which are used for solving the problem that the prior art has no proposal for sheltering video images, and can not only display original images after sheltering particular locations of the video images, but also guarantee security of image transmission. The inventive method comprises the steps of: determining the location of a sheltered image in a first image, and storing the location information of the sheltered image; performing an image scrambling to the sheltered image in accordance with the location information of the sheltered image to obtain a second image. The invention also discloses an image display method, device and an image processing method, system.
Owner:HUAWEI TECH CO LTD
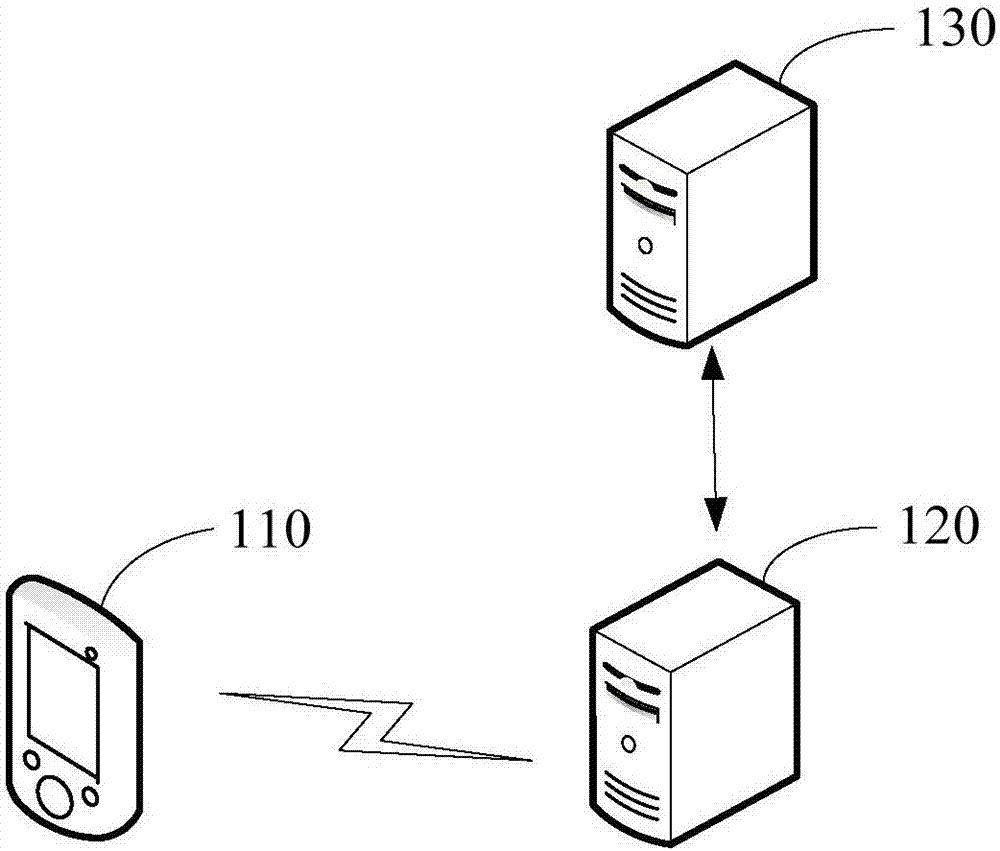
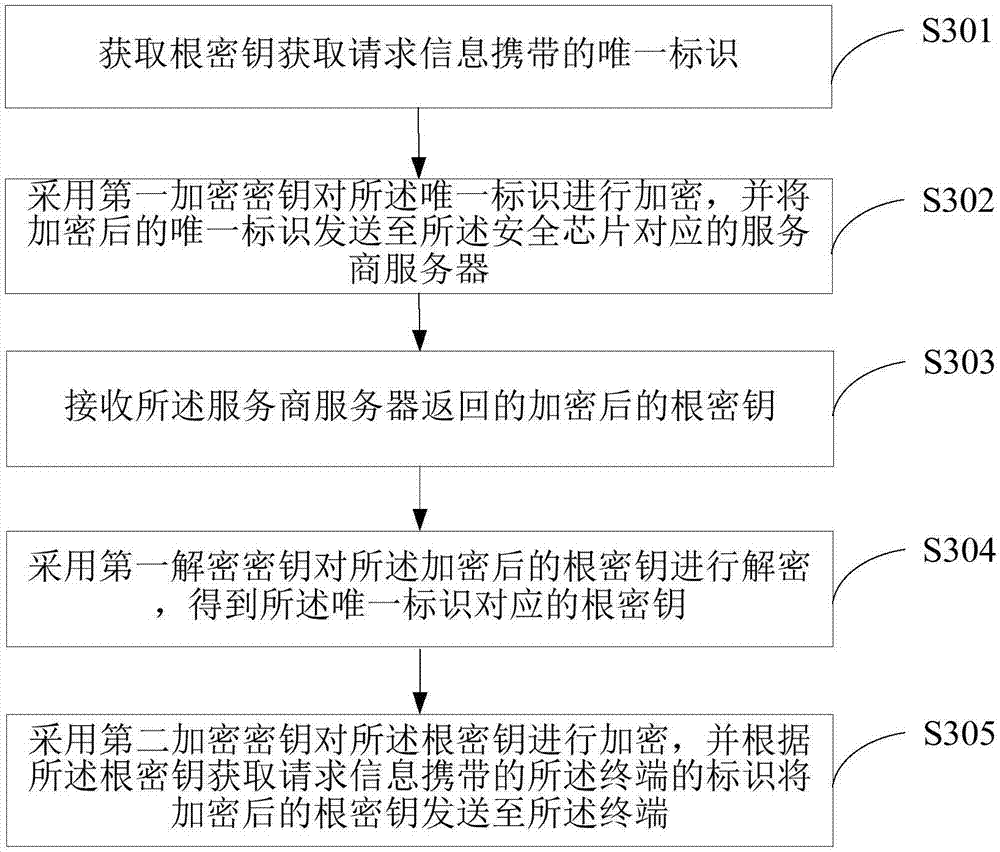
Method for obtaining root key and server
InactiveCN107276756AReduce risk of leakageImprove transmission securityKey distribution for secure communicationSecurity arrangementTransfer procedureUnique identifier
The embodiment of the invention discloses a method for obtaining a root key and a server. The method comprises the steps of obtaining a unique identifier of a security chip carried by root key obtaining request information, wherein the root key obtaining request information is sent by a terminal; encrypting the unique identifier through adoption of a first encryption key and sending the encrypted unique identifier to a service provider server corresponding to the security chip; receiving the encrypted root key returned by the service provider server; decrypting the encrypted root key through adoption of a first decryption key, thereby obtaining the root key corresponding to the unique identifier; encrypting the root key through adoption of a second encryption key and sending the encrypted root key to the terminal according to an identifier of the terminal carried by the root key obtaining request information; and decrypting the encrypted root key by the terminal through adoption of a second decryption key, thereby obtaining the root key. According to the embodiment of the invention, the risk of leaking the root key in a transmission process can be effectively reduced, the transmission security of the root key is improved, and the security of the information in the terminal is improved.
Owner:SHENZHEN GIONEE COMM EQUIP
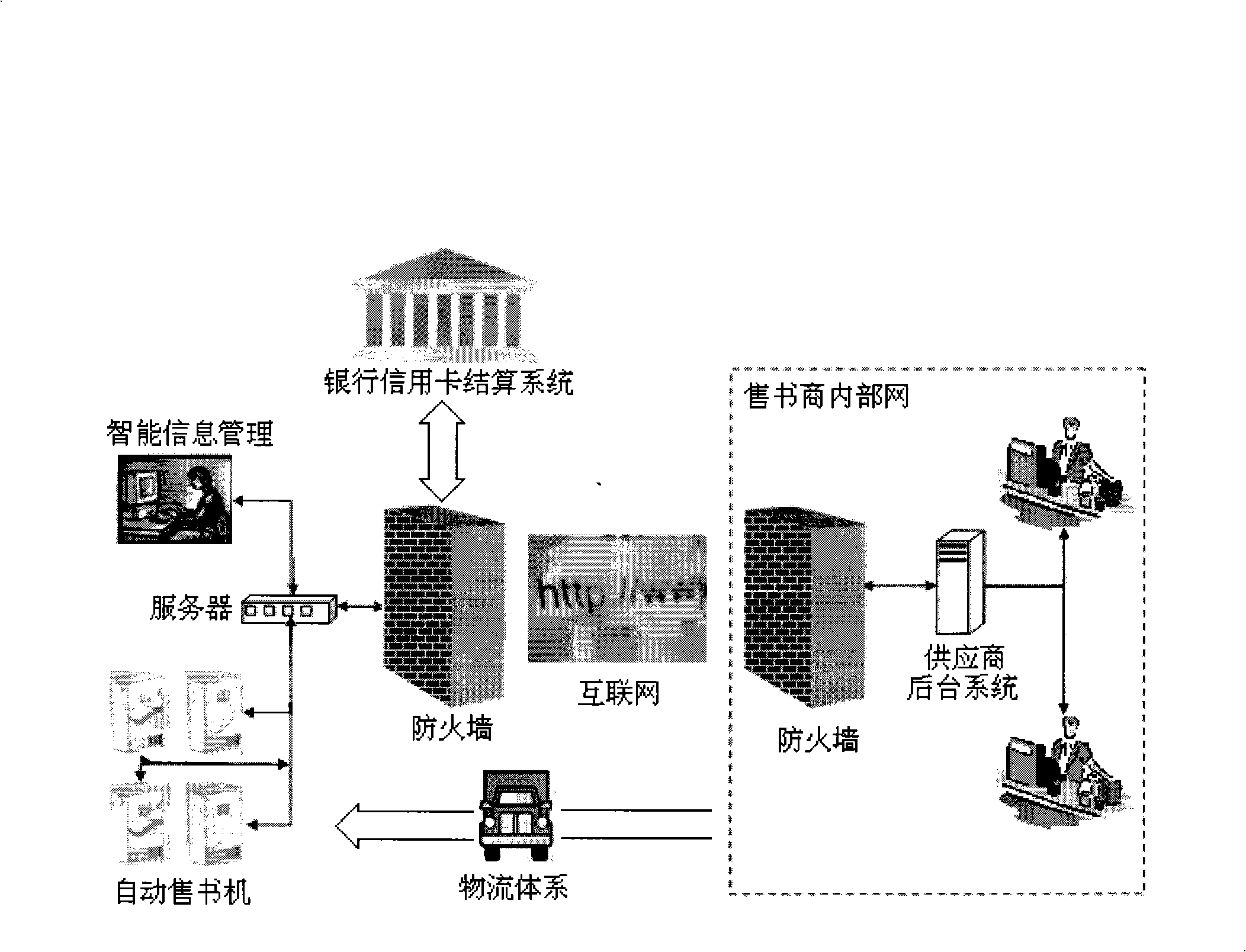
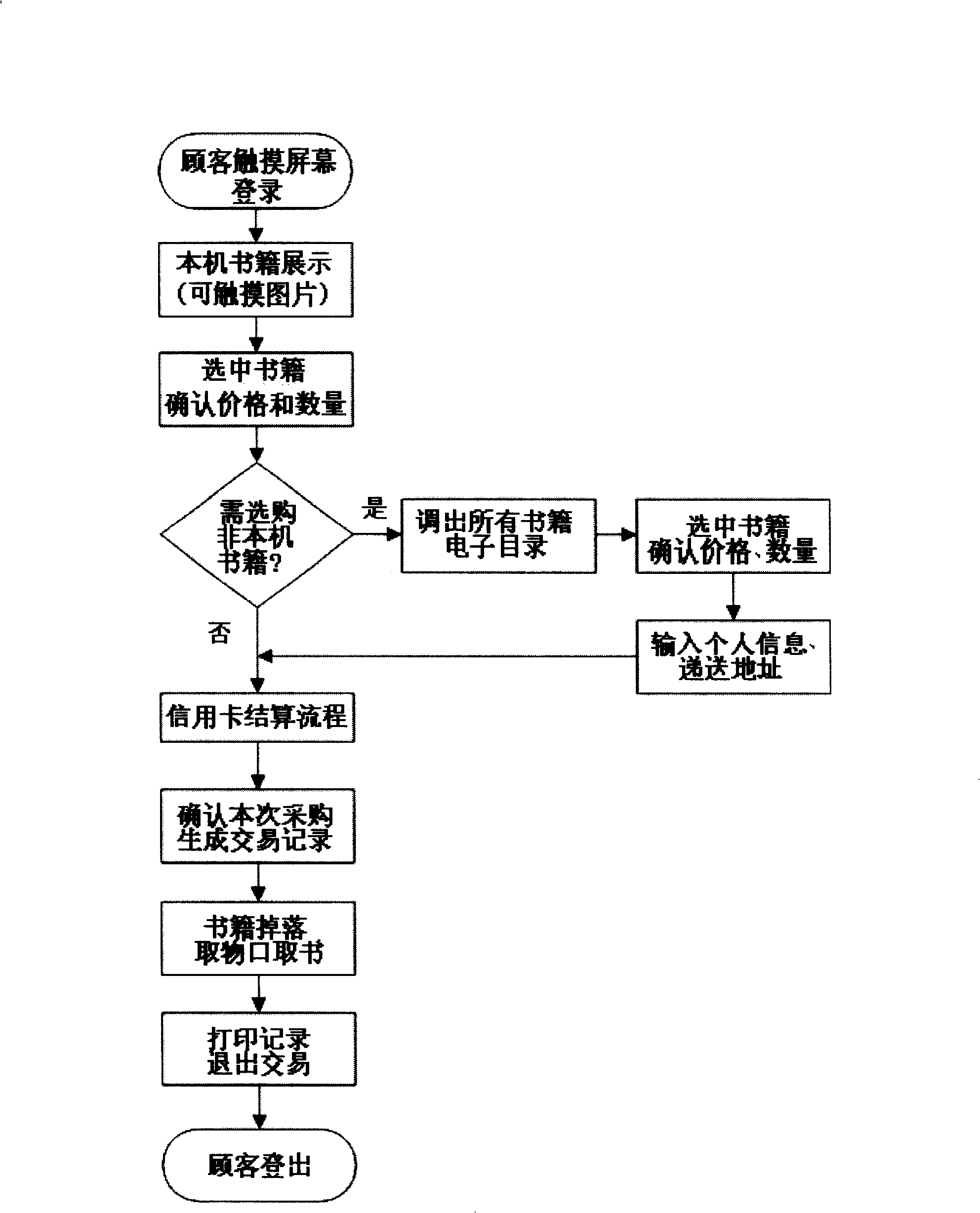
Intelligent automatic book selling system based on network technology
InactiveCN101308590ALow failure rateIncrease profitCoin-freed apparatus detailsCash registersSafety management systemsEngineering
The invention relates to a book purchase mode and a network-technology-based smart automatic book selling system through organic and integral combination of the working modes of traditional fixed-point sales, network bookstores, vending machines, advertising media launching and logistics management; the book purchase mode is provided for consumers and enables the consumers to select books easily, make payment rapidly and get the book timely; the smart automatic book selling system enables the book providers to easily publish the information and reduce the logistics links in book sales and can reduce the sales cost of books and periodicals and enable capital flow optimized utilization; a book vending machine is arranged at the networks of public places with large crowd flow and comprises an automatic book selling management system, a banking settlement management system, a multi-media advertising management and broadcast system, an intelligent information management system and a network data transmission security management system; the consumers can easily select and purchase books through a display / touch screen; in the case of no consumer register, the book vending machine automatically turns the work state to become a multi-media advertising broadcast carrier; the machine can work for the whole year and has great practicability.
Owner:洪涛
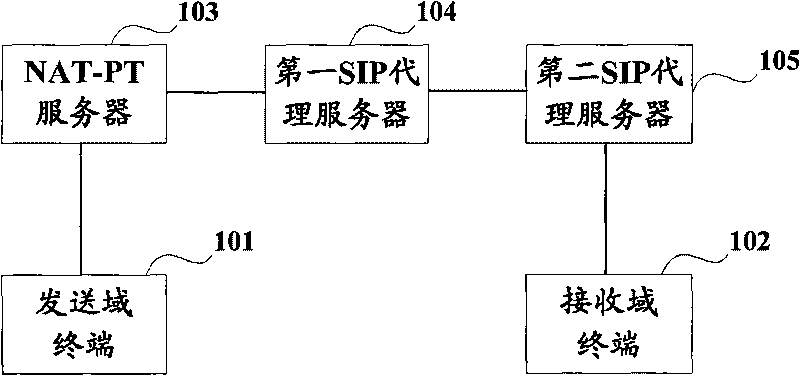
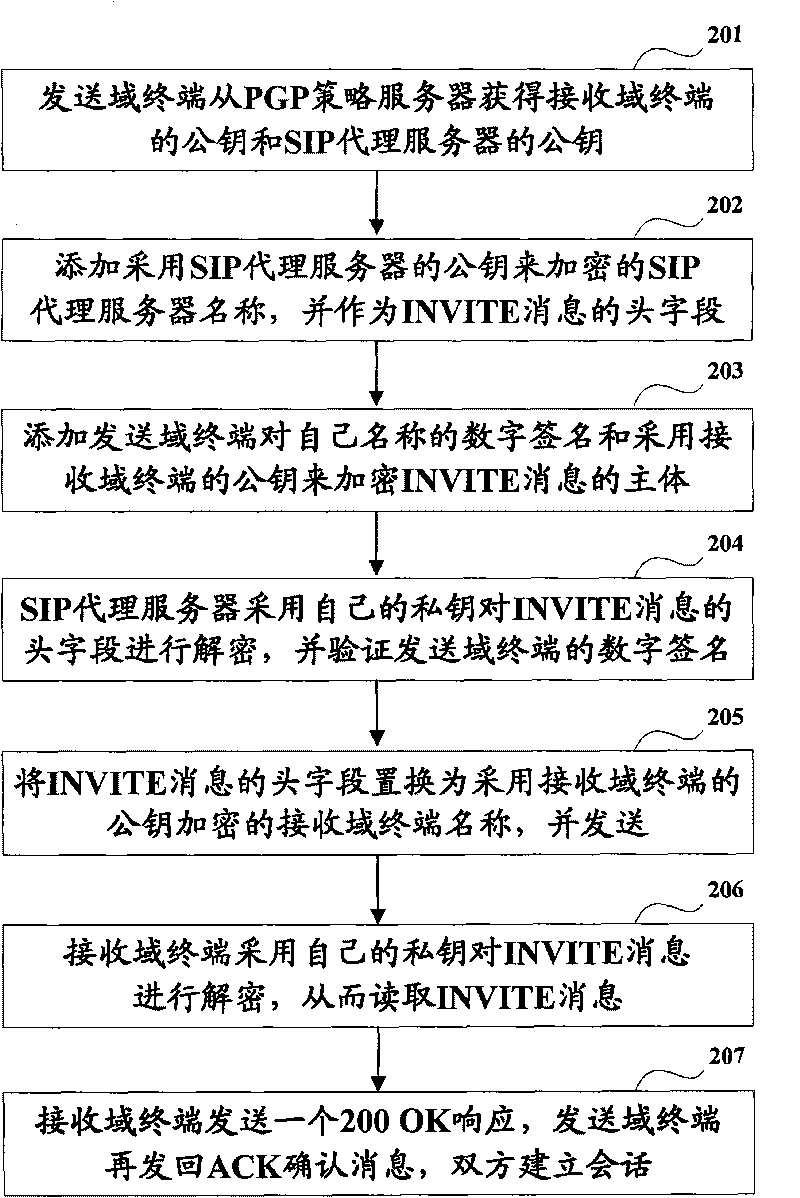
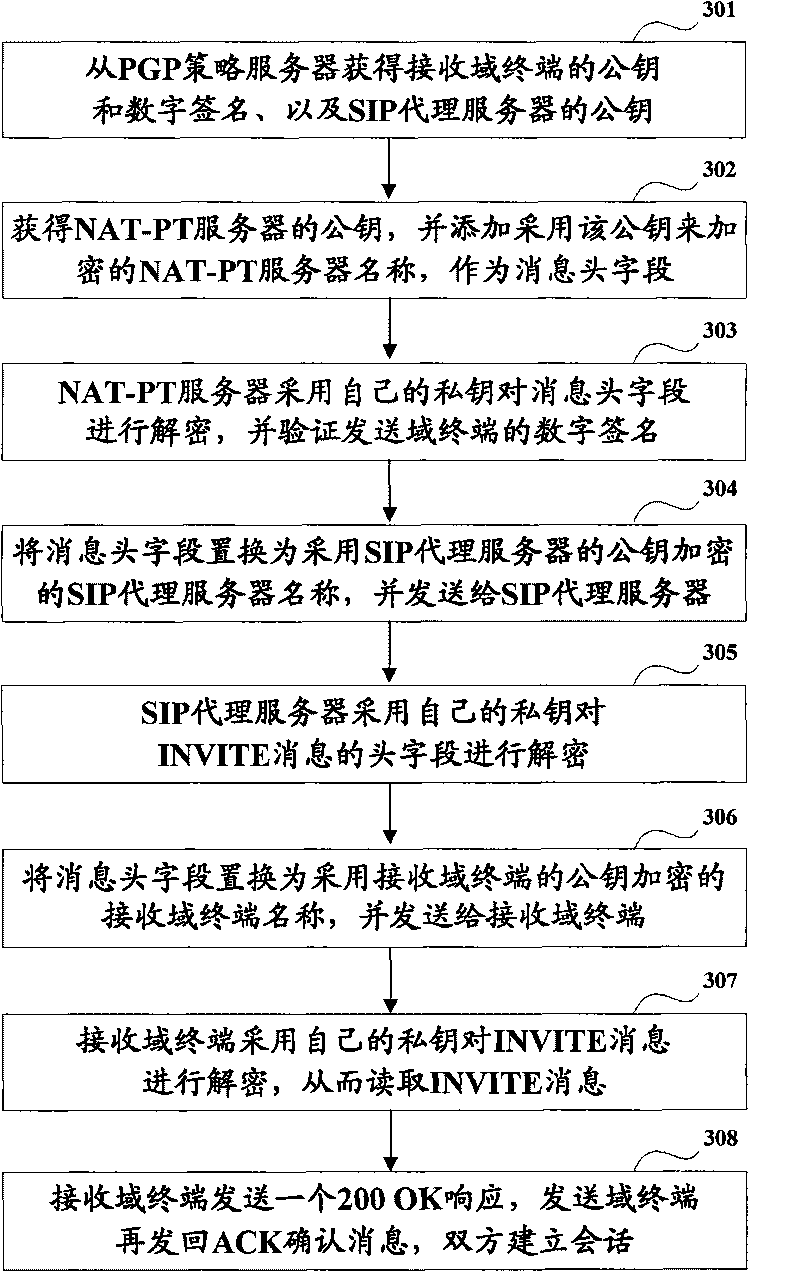
Method and system for guaranteeing SIP communication security
ActiveCN101753302AAvoid attackReduce the burden onPublic key for secure communicationUser identity/authority verificationCommunications securityDigital signature
The invention discloses a method and a system for guaranteeing SIP communication security so as to solve the problem of transmission security of SIP messages. The main technical scheme comprises the following steps of: using a PGP policy server supporting a dual stack protocol to distribute public keys to each SIP proxy server and terminal of IPv6 and IPv4; acquiring public keys uploaded to servers from other apparatuses by each proxy server and terminal through the PGP policy server; identifying terminals are either the IPv6 type or the IPv4 type through a digital signature; and replacing corresponding encryption message heads by decrypting the sent SIP messages hop-by-hop by a method of segmentation encryption of different public keys. Through the technical scheme, the method and the system can effectively reduce transmission delay, lighten intermediate-network burden, avoid ways of attacking the SIP messages such as registration, alteration of a message body and the like, and ensure the SIP communication security.
Owner:NEW FOUNDER HLDG DEV LLC +1
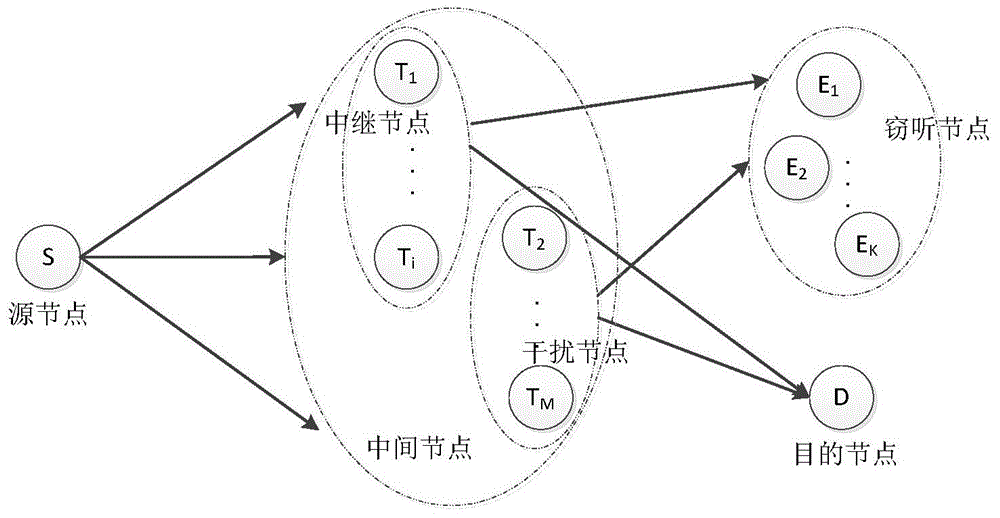
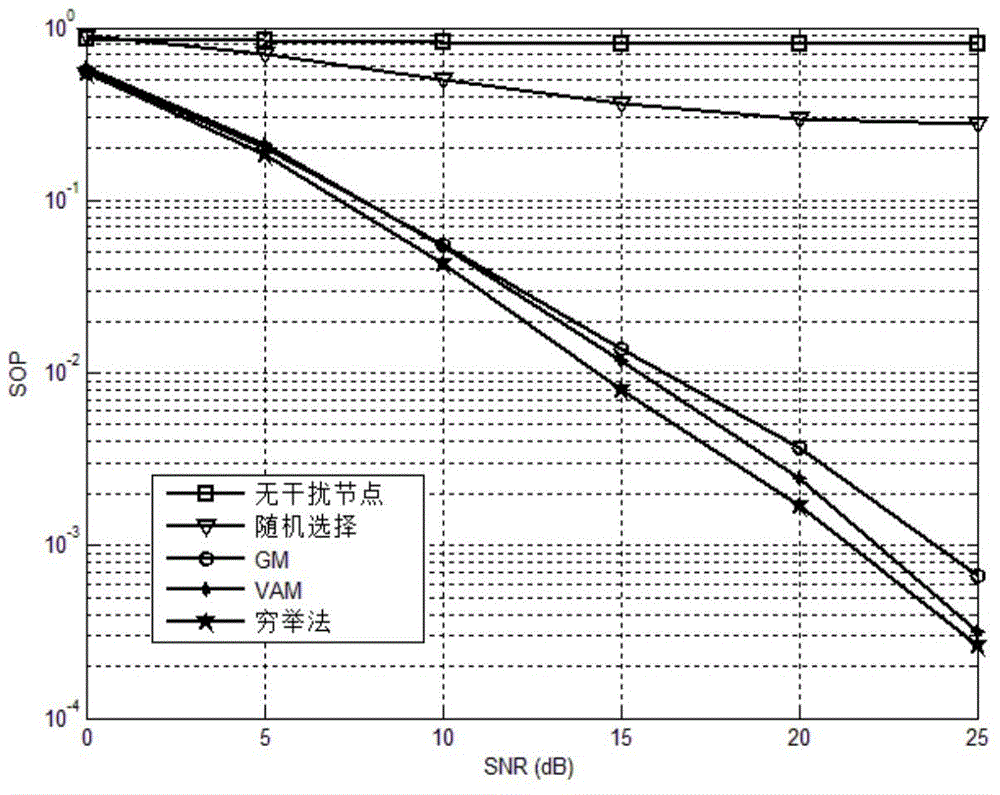
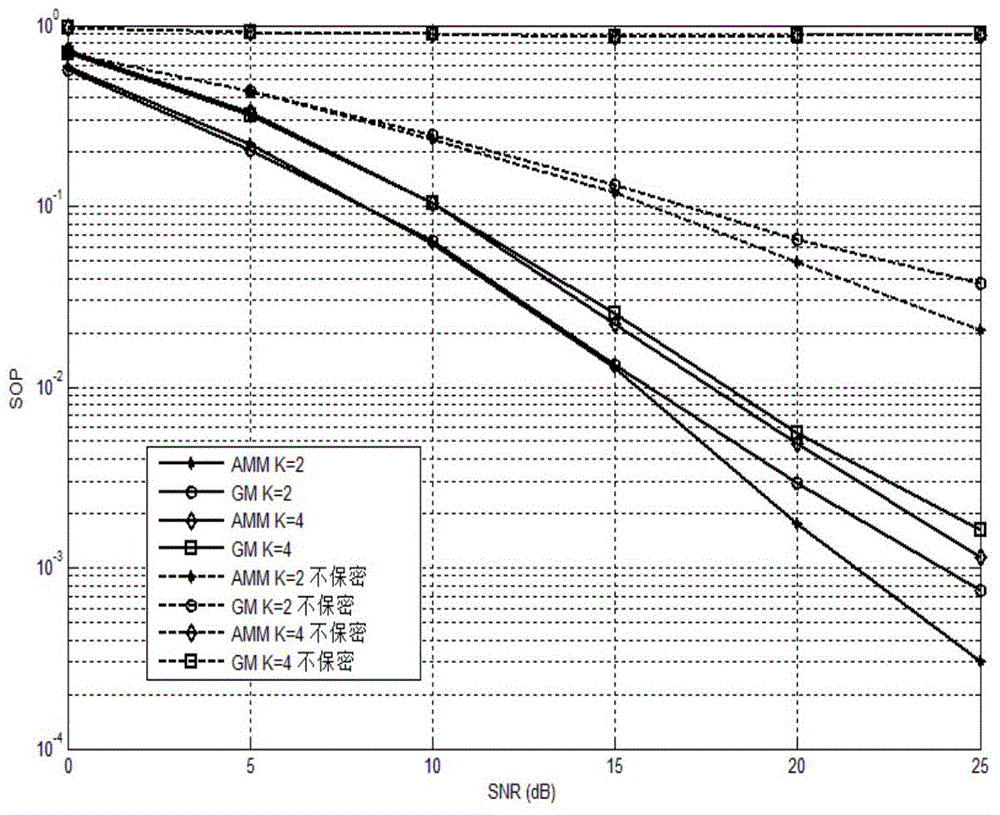
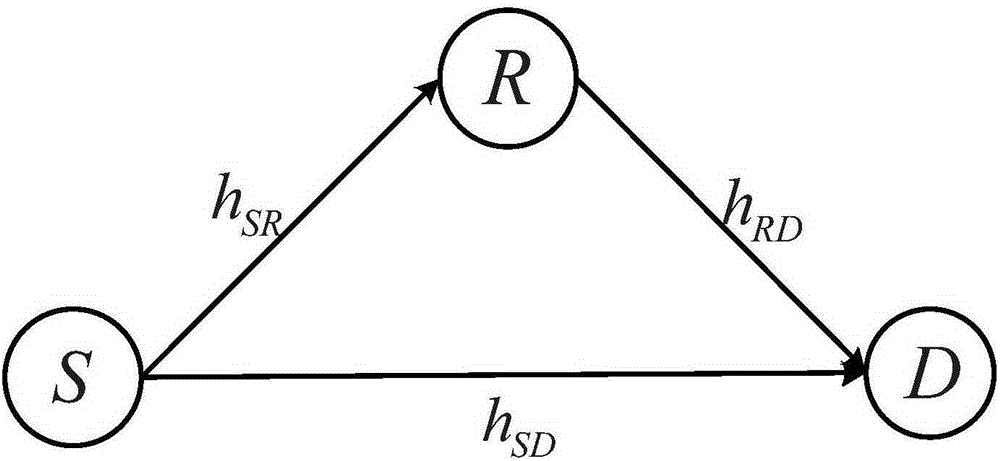
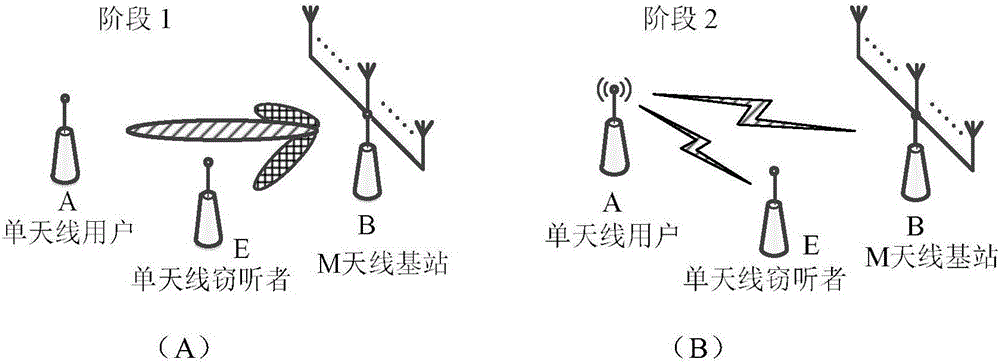
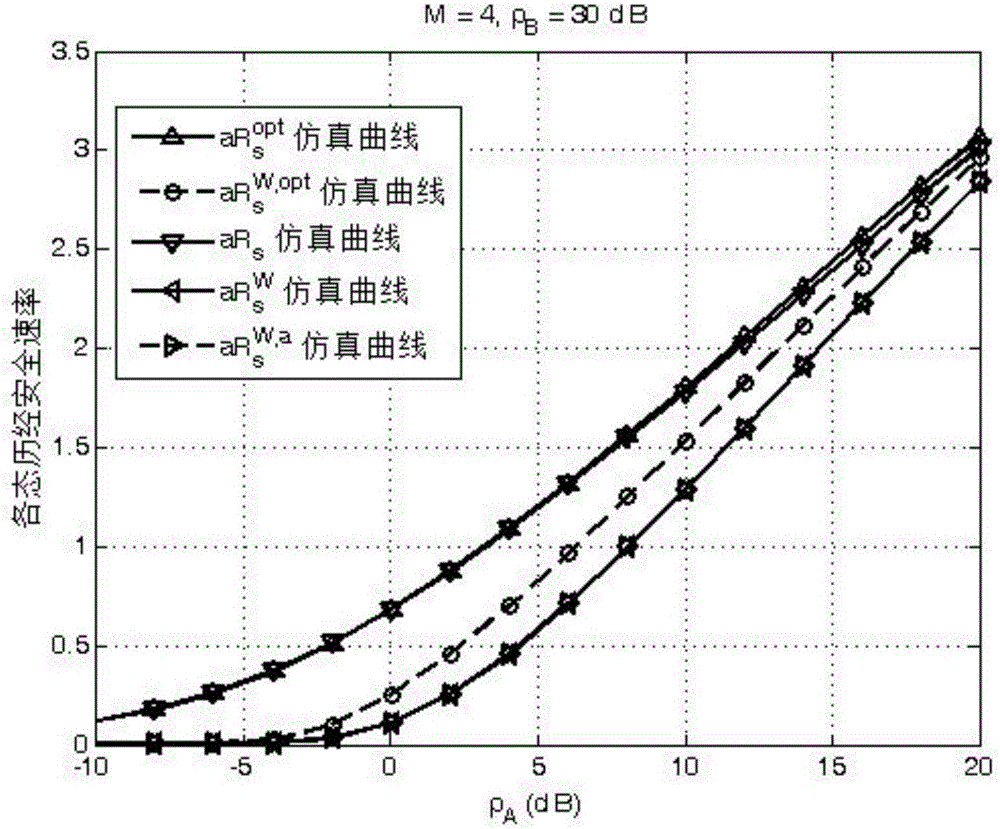
Physical layer security transmission method for keeping relay and jamming node selection result secret
InactiveCN104469755AHigh probability of safety interruptionImprove practicalityCommunication jammingSecurity arrangementUser needsChannel state information
The invention provides a physical layer security transmission method for keeping a relay and jamming node selection result secret. A wireless transmission network in which hacking nodes exist is established and comprises a source node S, a destination node D, M intermediate nodes T<1>, T<2>, ..., T<M>, and the K hacking nodes E<1>, E<2>, ..., E<K>, the whole transmission process includes two stages, wherein in the first stage, the source node broadcasts information s and considers that the information s can be successfully decoded in all the intermediate nodes in the stage; in the second stage, the selected intermediate nodes forward information to the destination node through a decoding forwarding protocol, and jamming nodes transmit jamming information to the hacking nodes. The security outage probability performance of the relay and jamming node selection result is similar to that of an optimal selection result acquired through a method of exhaustion, and the relay and jamming node selection result has high security outage probability performance; only statistical channel state information of a hacking user needs to be acquired in the relay and jamming node selection process, and high practicability is achieved; the relay and jamming node selection result is kept secret to the hacking nodes, and the transmission security of confidential signals is guaranteed.
Owner:XIAN UNIV OF TECH
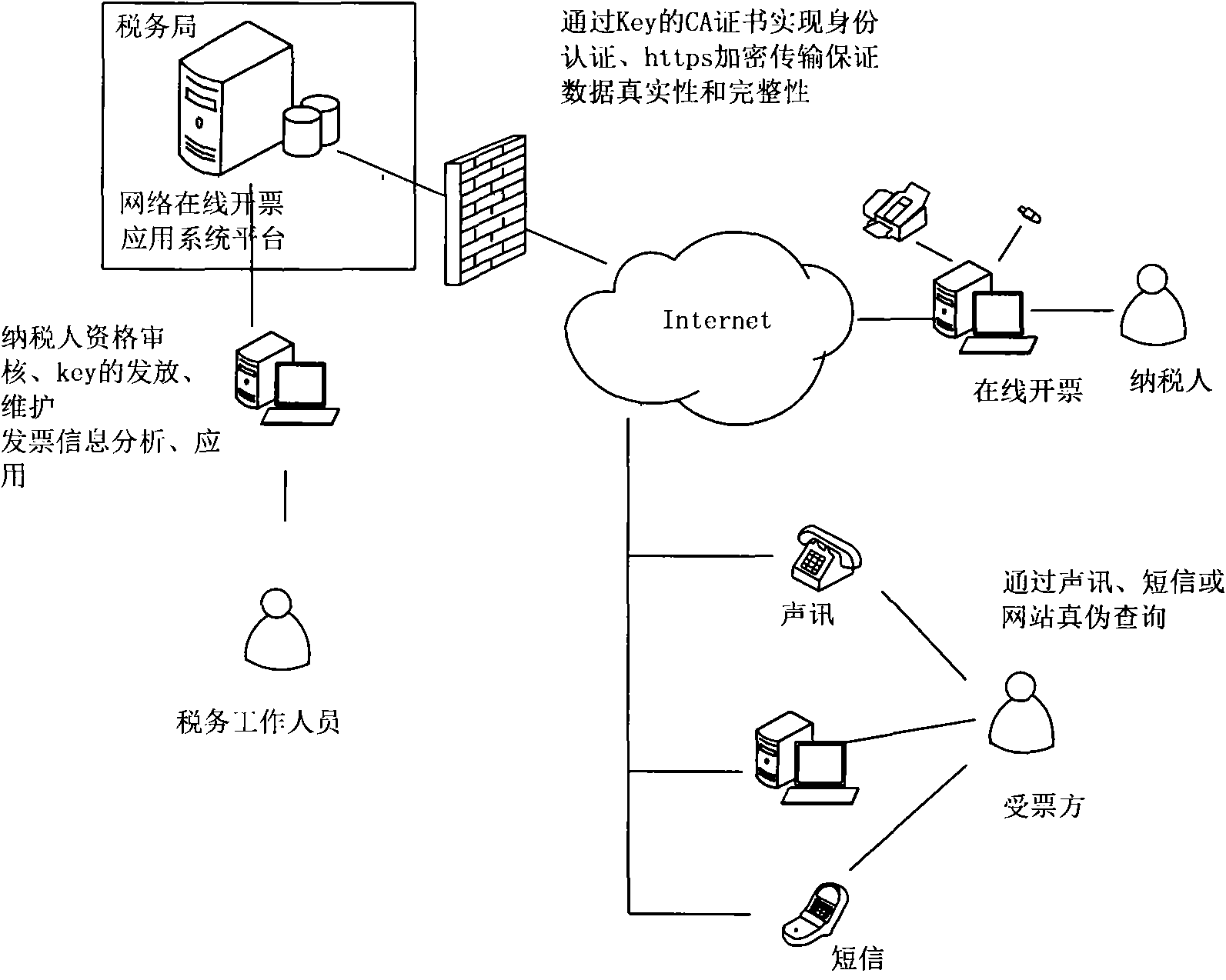
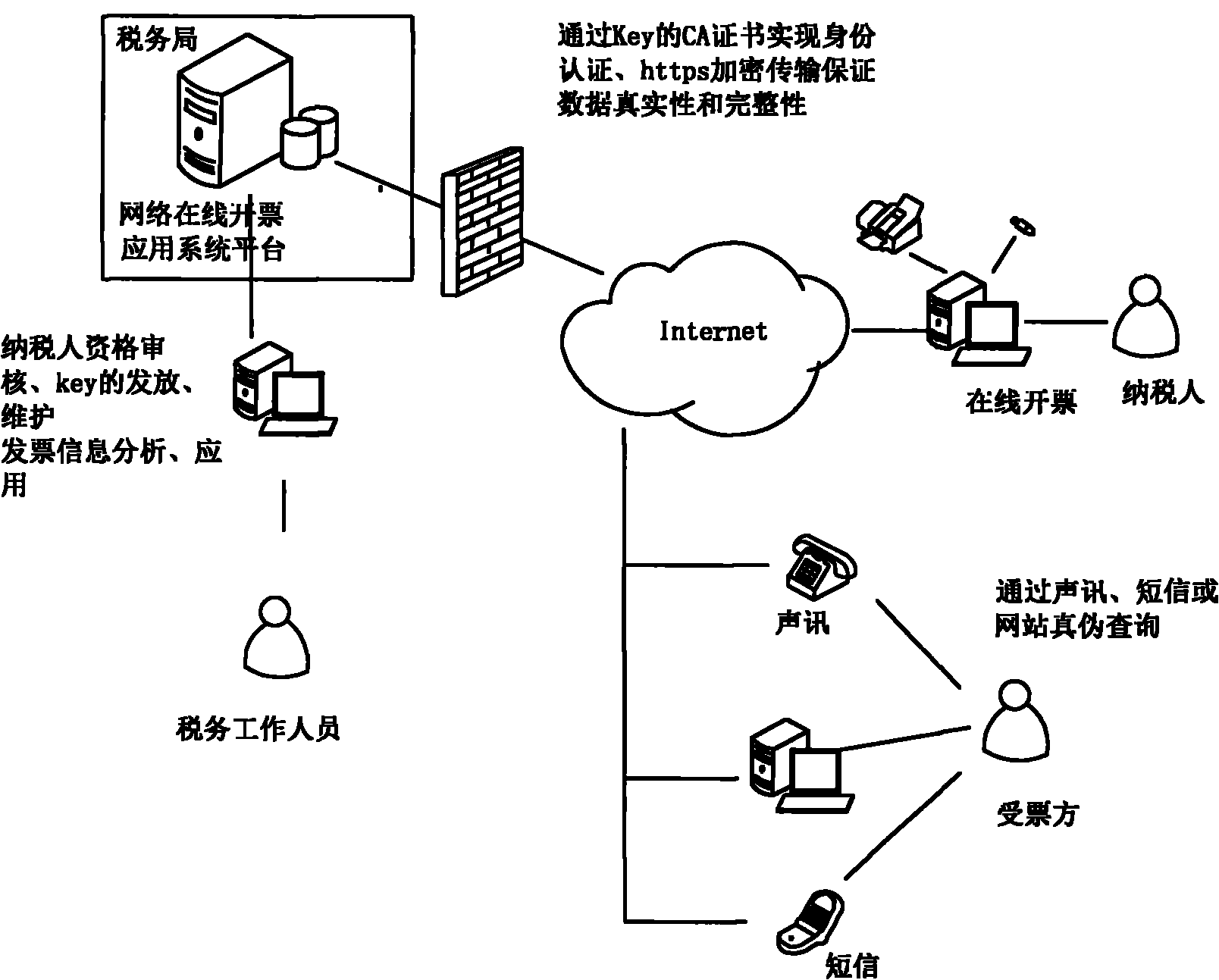
Network online invoice making method
InactiveCN101894435ASupport online updateSupport offline reportingUser identity/authority verificationCash registersData validationSource Data Verification
The invention provides a network online invoice making method. Based on internet and computer technology, the method provides comprehensive real-time management services for the links of purchase, making, use, inquiry, data application and the like of an invoice of a taxpayer. The method comprises the following steps of: realizing the authentication of a taxpayer identity by using a digital certificate; ensuring the transmission security of invoice data on the internet by using an HTTPS encryption protocol; establishing a security channel between a user and a backstage server; realizing bidirectional data security transmission by encryption technology; generating an invoice security code used for verifying the authenticity and the completeness of invoice face value information by invoice anti-counterfeiting technology. An online invoice making key is a medium for the digital certificate, a face value anti-counterfeiting algorithm and secure storage, and finishes data encryption, data decryption, digital signature, data verification and the like. Therefore, the problems of false invoice, writing false invoice, making an invoice excluding income, filling and making non-standard invoice, declaration data distortion and the like are solved fundamentally.
Owner:INSPUR QILU SOFTWARE IND
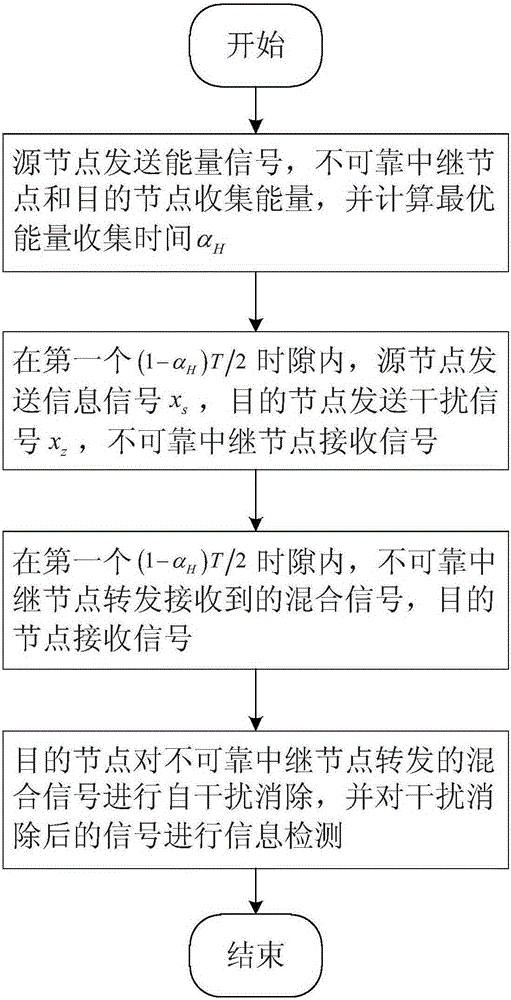
Signal energy synchronous transmission relay transmission method in physical layer safety communication
ActiveCN105245269ALower energy billsExtend network lifePower managementRadio transmissionNetwork serviceVIT signals
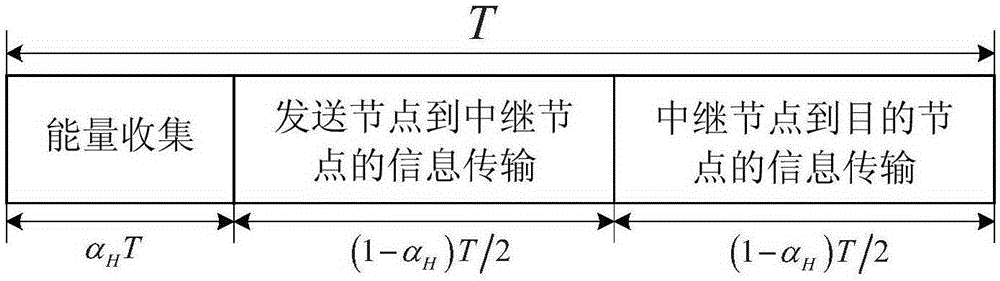
The invention discloses a signal energy synchronous transmission relay transmission method in physical layer safety communication. The method comprises the following implementation steps that: 1) a source node transmits an energy signal and calculates an optimal energy collection time scale alpha<H>, and an unreliable relay node and a destination node collect energy; 2) in a first (1-alpha<H>)T / 2 time slot, the source node transmits an information signal x<s>, the destination node transits an interference signal x<z>, and the unreliable relay node receives the signals; 3) in a second (1-alpha<H>)T / 2 time slot, the unreliable relay node forwards the received mixed signals, and the destination node receives the signals; 4) the destination node performs adaptive interference cancellation for the mixed signals forwarded by the unreliable relay node, and performs information detection on the signals of which interference is cancelled. The method provided by the invention can effectively prolong network service life of a relay network, and has low implementation complexity and high transmission safety, thus, the method can be used for a physical layer safety relay collaborative communication system.
Owner:XIDIAN UNIV
Cloud data security protection method adopting fully homomorphic encryption technology and multiple digital watermarking technology
InactiveCN105323209AEnsure transmission securityEnsure storage securityTransmissionThird partyStorage security
The present invention discloses a cloud data security protection method adopting a fully homomorphic encryption technology and a multiple digital watermarking technology. The cloud data security protection method is characterized in that in a cloud computing environment, a trusted third-party organization distributes a key to a user, after the user stores the key, a fully homomorphic encryption scheme is adopted to encrypt to-be-uploaded data at a user side, then the encrypted data is uploaded to a cloud side, thereby ensuring transmission security and storage security of data; in addition, when the user searches for data, direct search for ciphertext can be performed after a search keyword is encrypted, thereby improving search efficiency; and moreover, before the data is uploaded to the cloud side, a fragile watermarking and a robust watermarking are respectively embedded into the to-be-uploaded data, the purpose of embedding of the fragile watermarking is to prevent illegal modification of the data, so as to achieve authentication for integrity of the data, and the purpose of embedding of the robust watermarking is to protect copyright of the data, so as to achieve authentication for copyright of the data.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
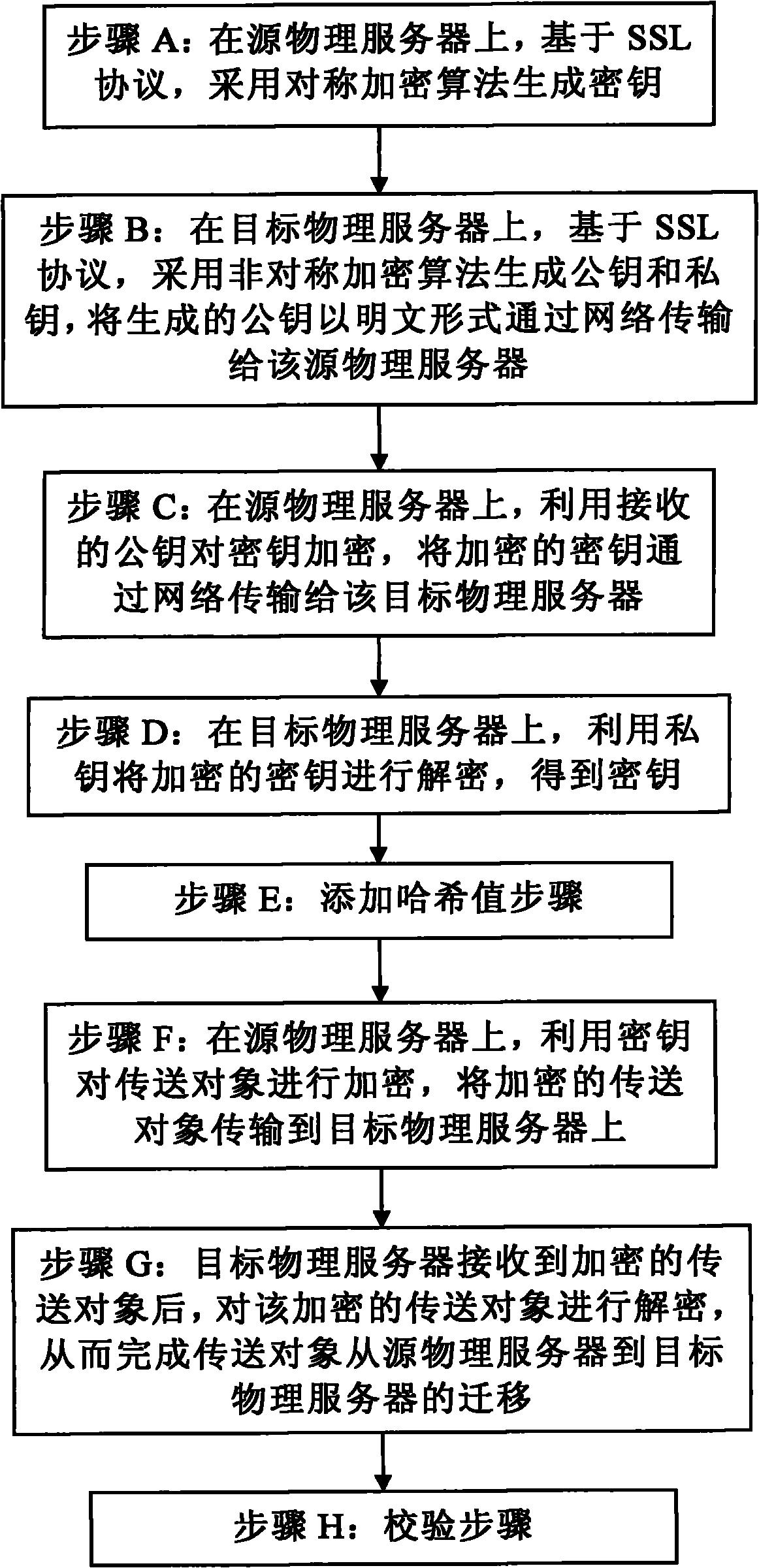
Safety dynamic migration method of Xen virtual machine
InactiveCN101984631APrevent theftPrevent tamperingEncryption apparatus with shift registers/memoriesPublic key for secure communicationVirtual machineTransmission security
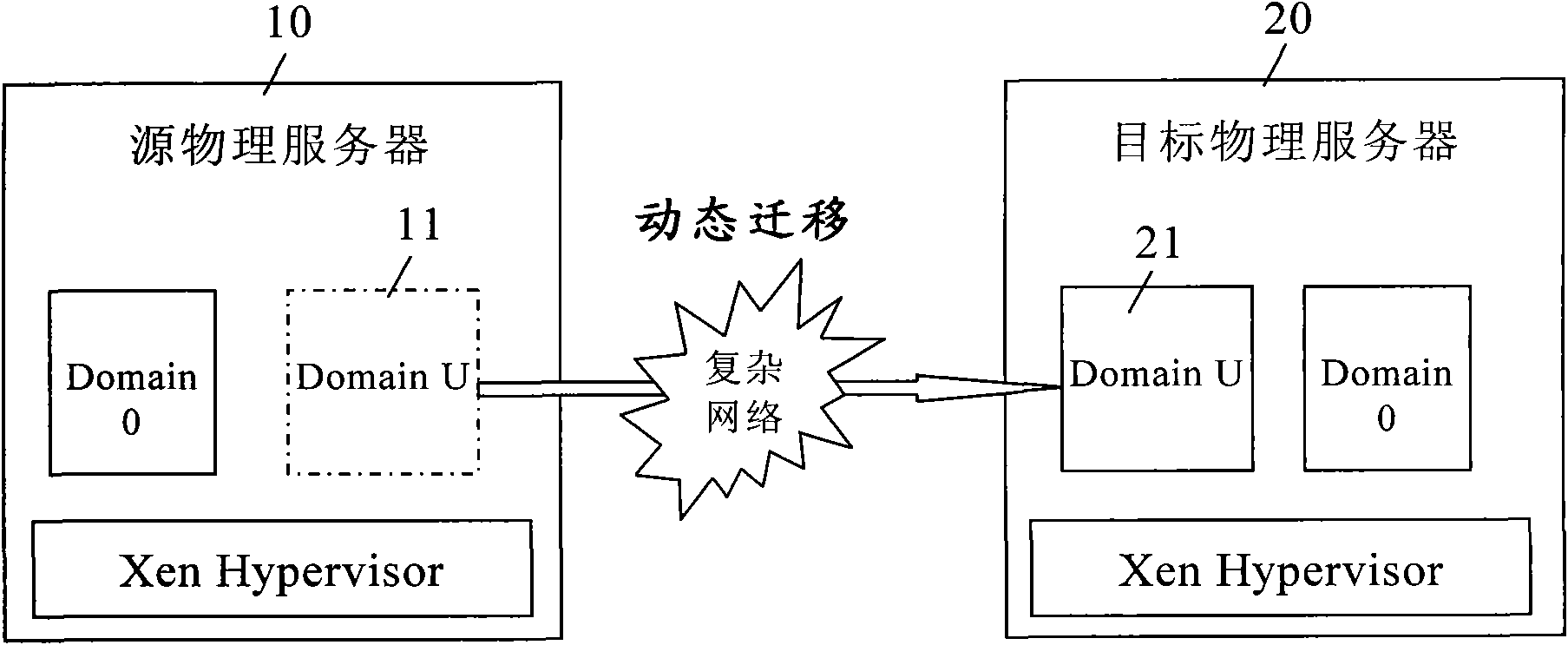
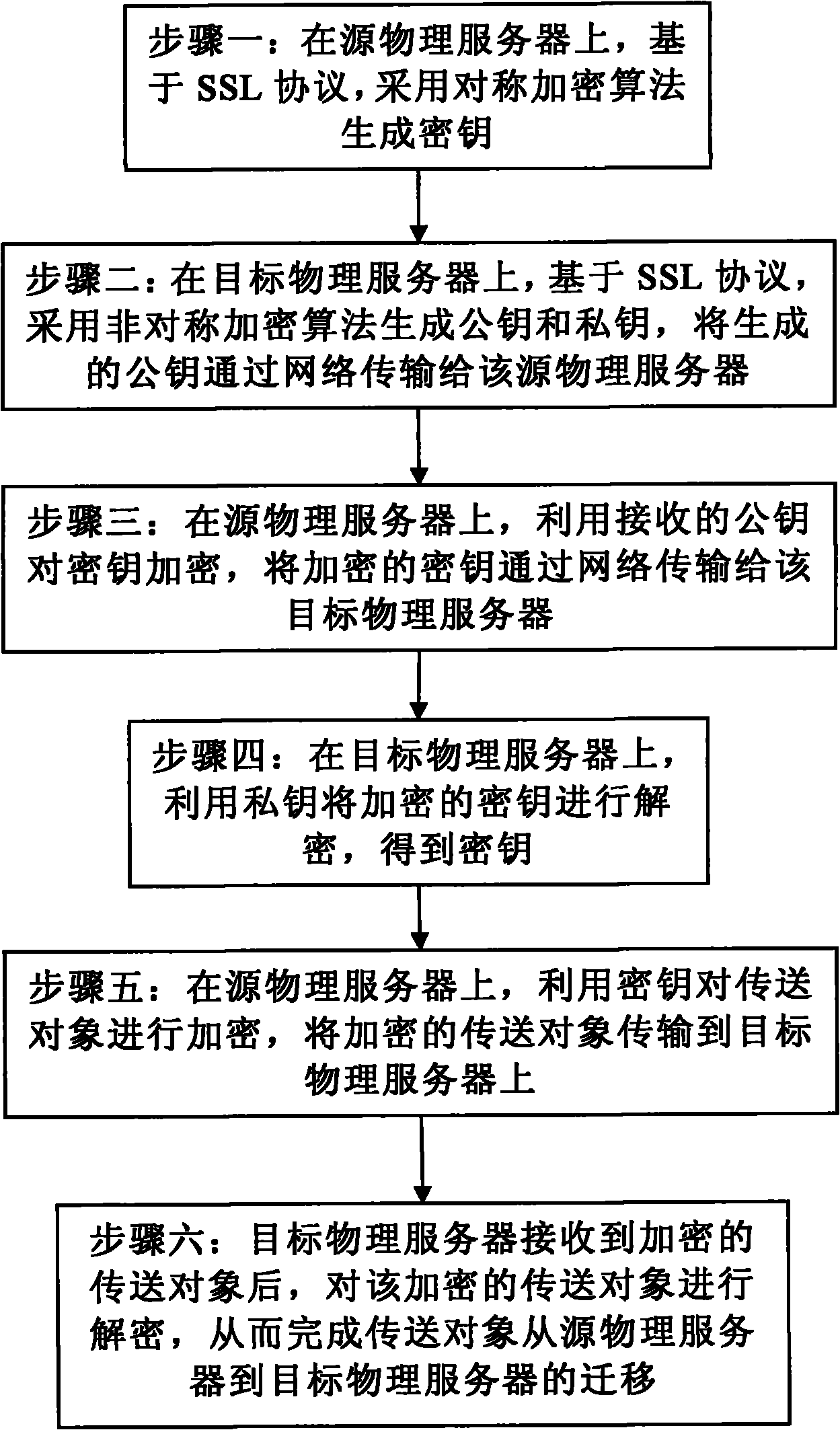
The invention discloses a safety dynamic migration method of an Xen virtual machine, which comprises the following steps: generating a key on a source physical server based on an SSL protocol by a symmetric cryptographic algorithm; generating a public key and a private key on a target physical server based on an SSL protocol by an asymmetric cryptographic algorithm, and transmitting the public key to the source physical server; encrypting the key by the public key on the source physical server, and transmitting the encrypted key to the target physical server; decrypting the encrypted key by the private key on the target physical server to obtain the key; encrypting a transfer object by the key on the source physical server, and transmitting the encrypted transfer object to the target physical server; and after the target physical server receives the encrypted transfer object, decrypting the encrypted transfer object so as to complete migration of the transfer object from the source physical server to the target physical server. The safety dynamic migration method effectively prevents a listener from stealing the transmitted data so as to ensure transmission security of the migrated data.
Owner:BEIJING 21VIANET DATA CENT
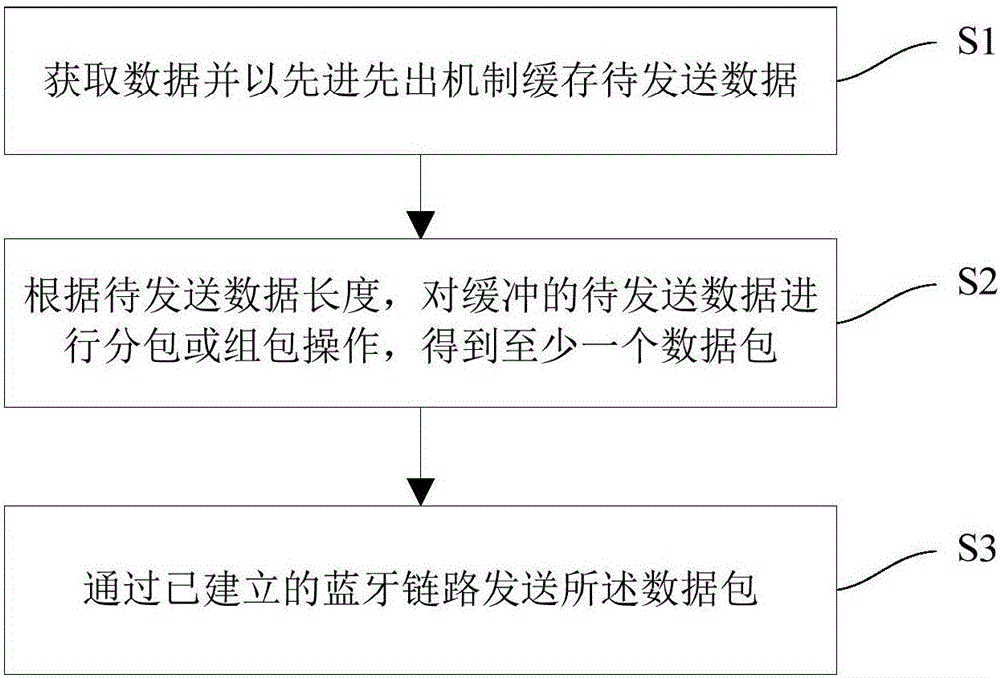
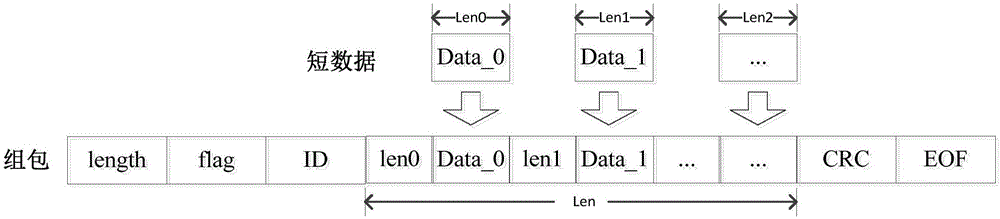
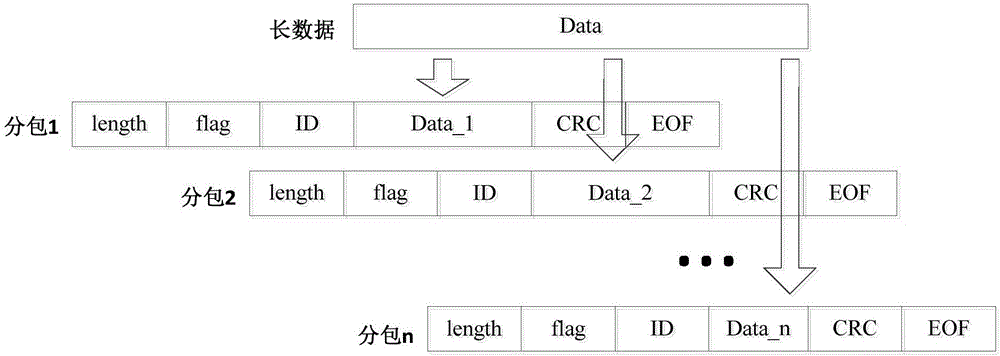
Bluetooth information sending and receiving methods
InactiveCN106571894AIntegrity guaranteedPrevent overflowSignal allocationNear-field systems using receiversData packData transmission
The invention relates to Bluetooth information sending and receiving methods in order to solve the problem that the security of Bluetooth data transmission cannot be guaranteed and the efficiency is low in the prior art. The Bluetooth information sending method of the invention, which is applied to a Bluetooth master computer carrying out communication based on SPP, comprises the following steps: S1, acquiring data, and caching to-be-sent data based on a first-in-first-out mechanism; S2, sub-packaging or packaging the cached to-be-sent data according to the length of the to-be-sent data to get at least one data packet; S3, sending the data packet through an established Bluetooth link. The Bluetooth information receiving method, which is applied to a Bluetooth slave computer carrying out communication based on SPP, comprises the following steps: S4, receiving the data packet through the established Bluetooth link; S5, reading the data in the data packet, and caching the data based on the first-in-first-out mechanism; and S6, sending the cached data to a memory in a segmented way.
Owner:SHENZHEN MINDE ELECTRONICS TECH
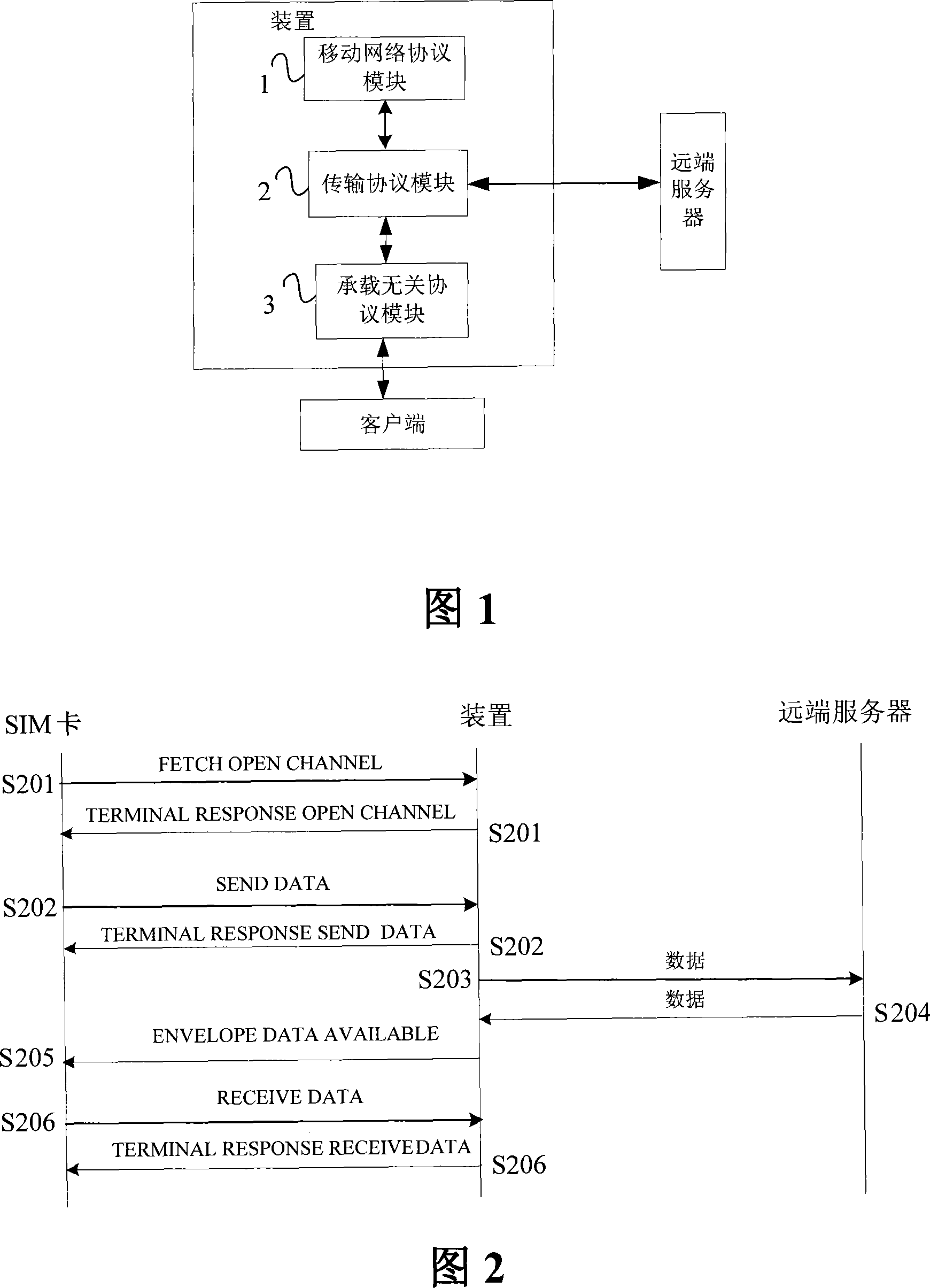
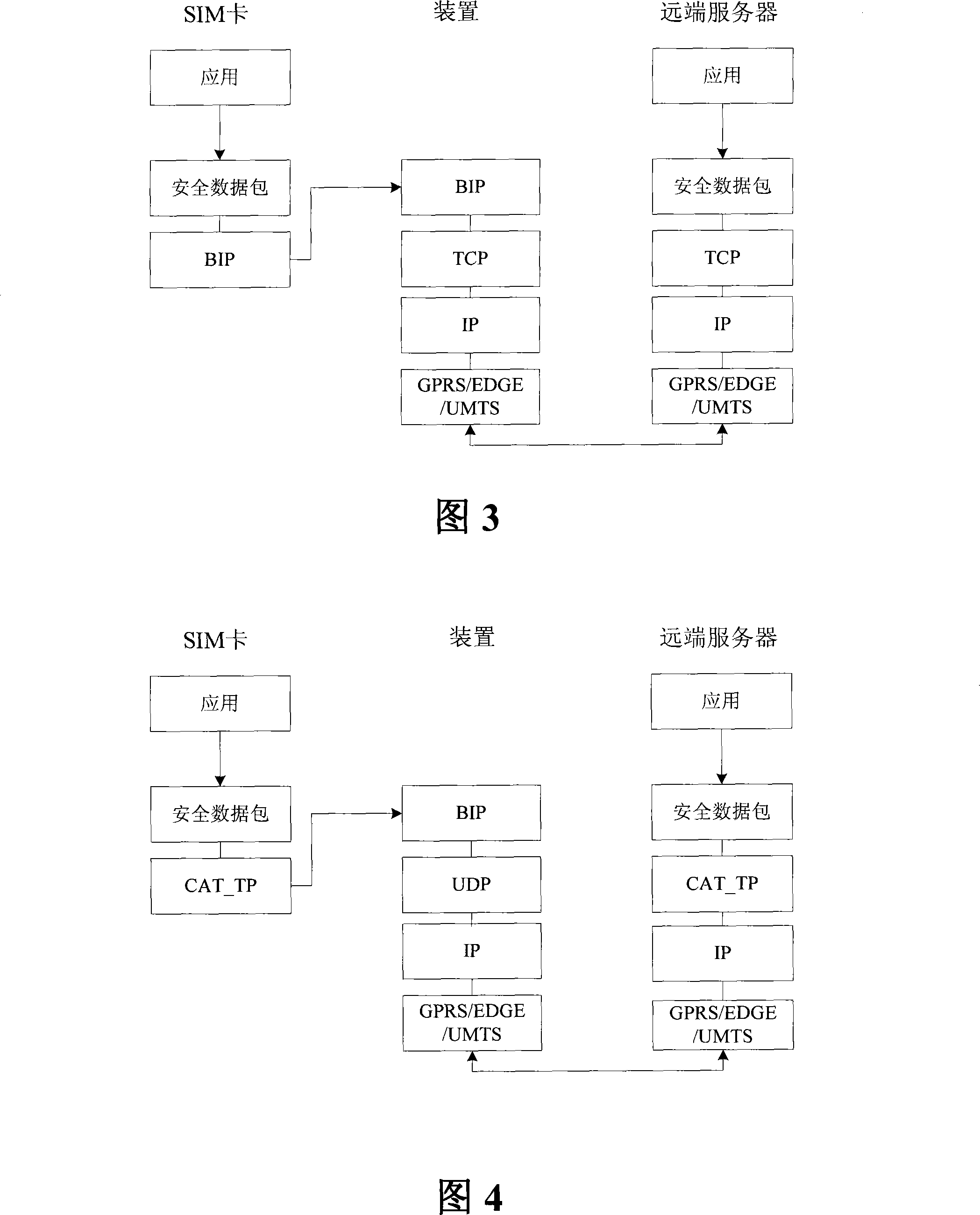
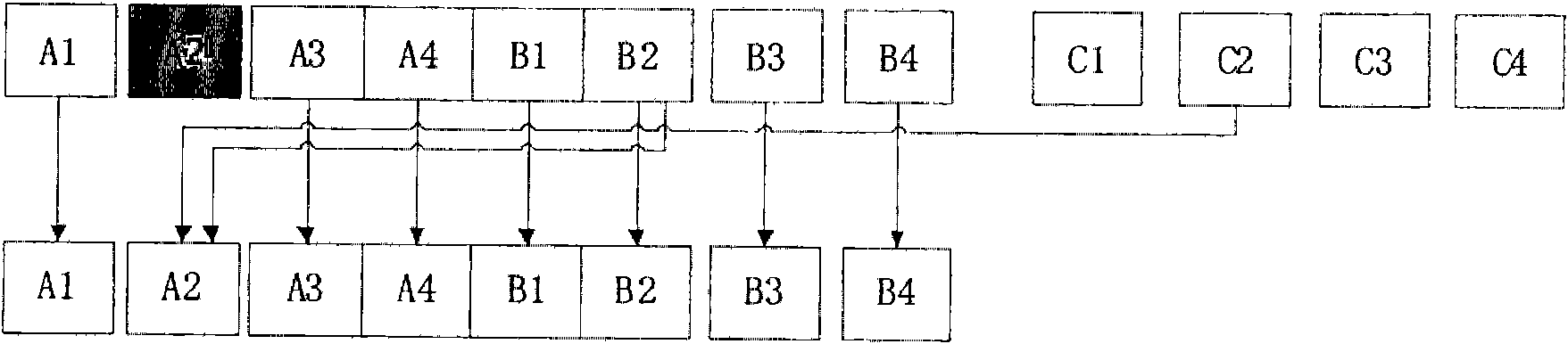
Apparatus and method for implementing OTA based on bearer independent protocol
ActiveCN101222514AIncrease transfer rateReduce overheadRadio/inductive link selection arrangementsTransmissionComputer hardwareTransmission protocol
The invention discloses a device for carrying unrelated protocol-based realization of over the air download, comprising a movable network protocol module, a transmission protocol module and a carrying unrelated protocol module, wherein the movable network protocol module is used to store and realize the movable network protocol stack which is used as a data transmission channel; the transmission protocol module is used to store and realize the transmission protocol stack and builds up a transmission layer connection with a far end server end by adopting the transmission protocol; the carrying unrelated protocol module is used to receive the data sent by a client end by the carrying unrelated protocol, send the data of the client end to the far end server by the transmission protocol stack, the transmission layer connection and the movable network protocol stack, receive the data which are sent to the client end by the far end server by the movable network protocol stack, the transmission protocol stack and the transmission layer connection and send the data to the client end by the carrying unrelated protocol, thereby improving the transmission rate and the transmission safety and reliability of the data in the over the air download.
Owner:ZTE CORP
No-feedback one-way data transmission method based on single fiber structure
The invention discloses a no-feedback one-way data transmission method based on a single fiber structure; equipment comprises two one-way fiber data transmission cards which belong to a transmitting end and a receiving end respectively, and the two one-way fiber data transmission cards are connected by a single fiber through a fiber receiver, data communication between the transmitting end and the receiving end adopts a proprietary protocol to carry out data encapsulation, and the reliability of the one-way data transmission is ensued by correcting and deleting codes; as the connection between the transmitting end and the receiving end does not adopt an Ethernet protocol, a data packet is not treated by a TCP / IP protocol stack, so as to eliminate the possibility that a malicious user or a hacker uses the data packet sniffing tool to detect the proprietary protocol format and greatly enhance the transmission safety.
Owner:INST OF NAT SECURITY SCI & TECH +1
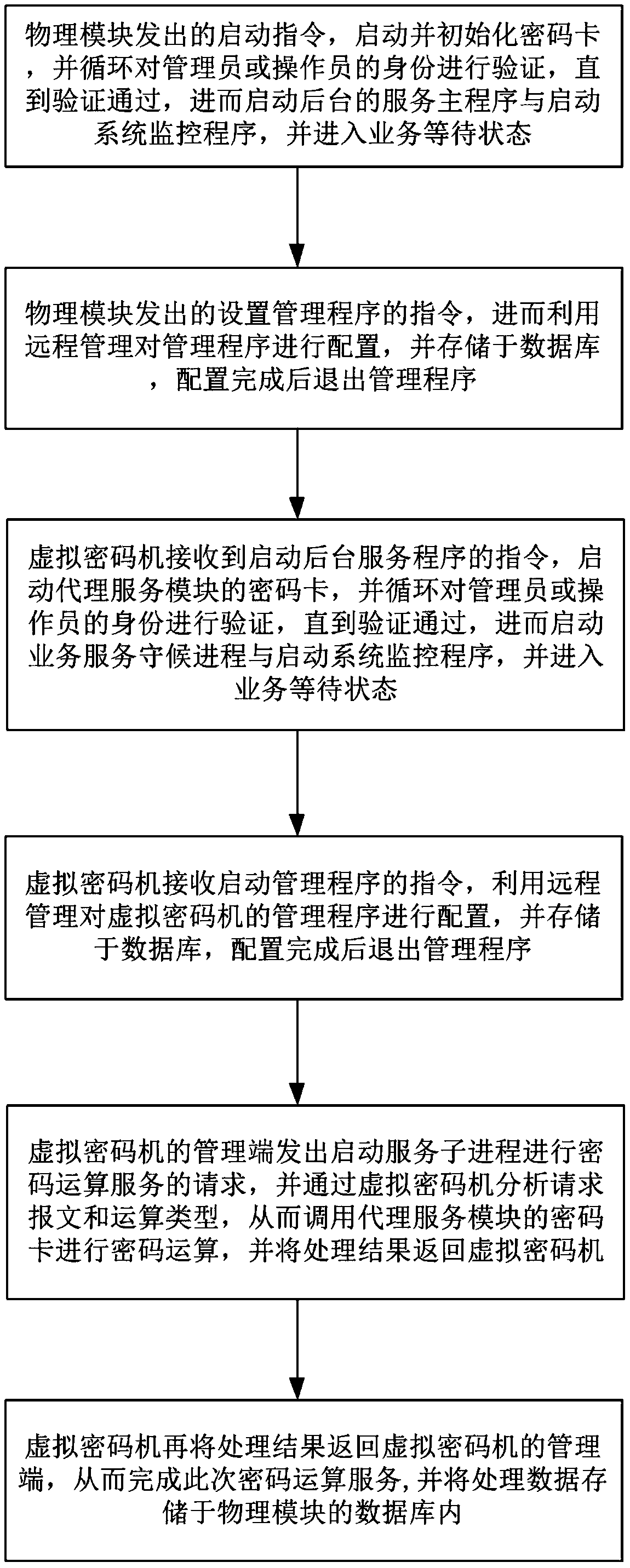
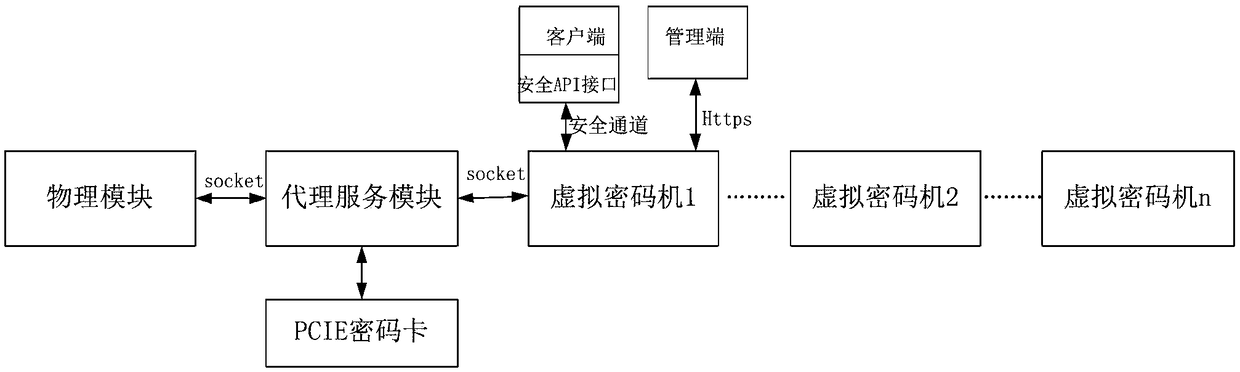
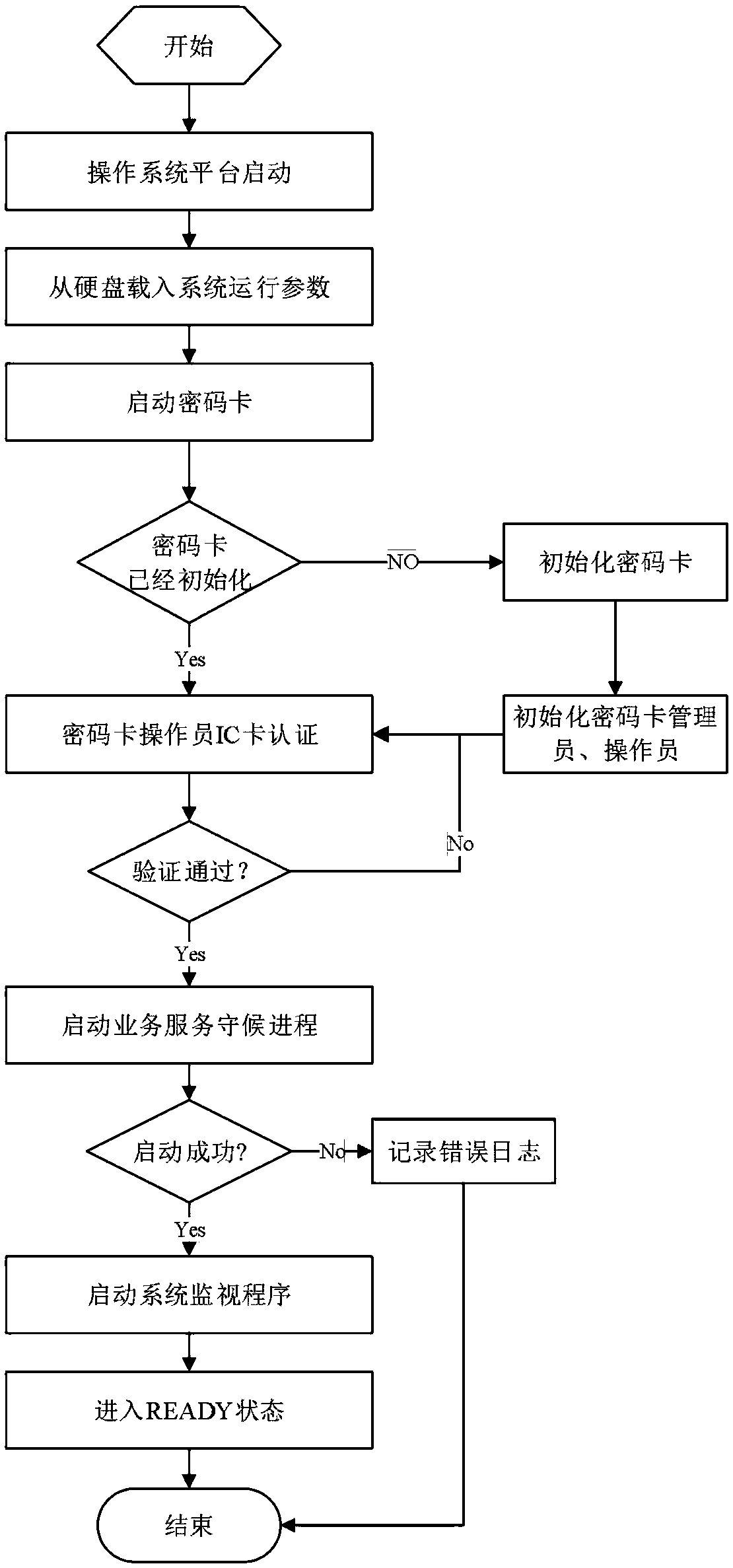
Virtualized cloud cipher machine system based on cloud computing, and implementing method thereof
ActiveCN109361517AAutomate deploymentEnableKey distribution for secure communicationMultiple keys/algorithms usageVirtualizationPassword
The invention discloses a virtualized cloud cipher machine system based on cloud computing, comprising a physical module, a proxy service module, a virtual cipher machine and a secure API interface, wherein one end of the proxy service module establishes a two-way communication connection with the physical module, and the other end establishes a two-way communication connection with a plurality ofmutually independent virtual cipher machines isolated by the virtualization technology; and the secure API interface is used for encapsulating cryptographic operations and internal key management, thereby providing a channel for the cryptographic operation of the client of the virtual cipher machine. The virtualized cloud cipher machine system based on cloud computing realizes the combination ofthe cryptographic algorithm operation, resource management and key management mechanism, so that the use of the cryptographic technology is more centralized, standardized, and easier to manage, and atthe same time, the cryptographic machine resources are allocated to the user remotely through the network, and the encryption technology is utilized to guarantee the transmission security by one password at one time, thereby ensuring the highest security of the customer data and ensuring the security of the key.
Owner:西安得安信息技术有限公司
Method and system for improving transmission security of file
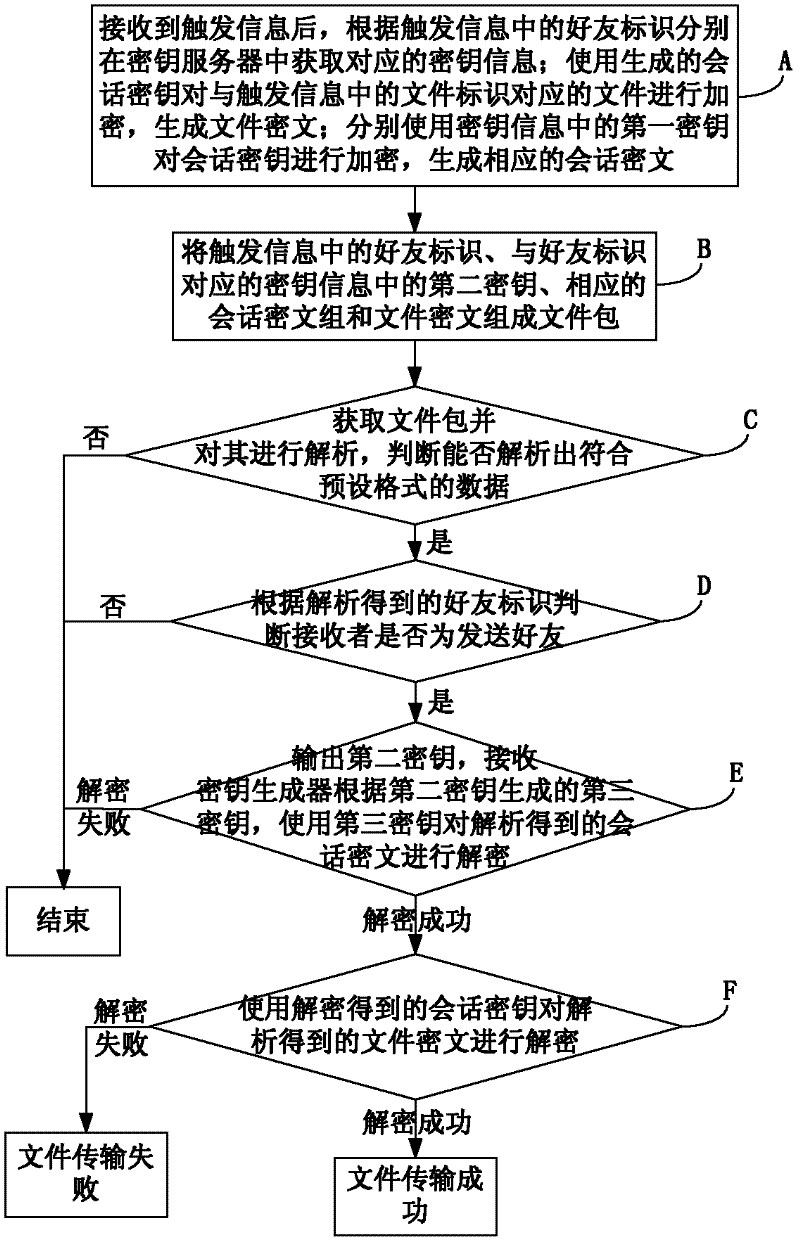
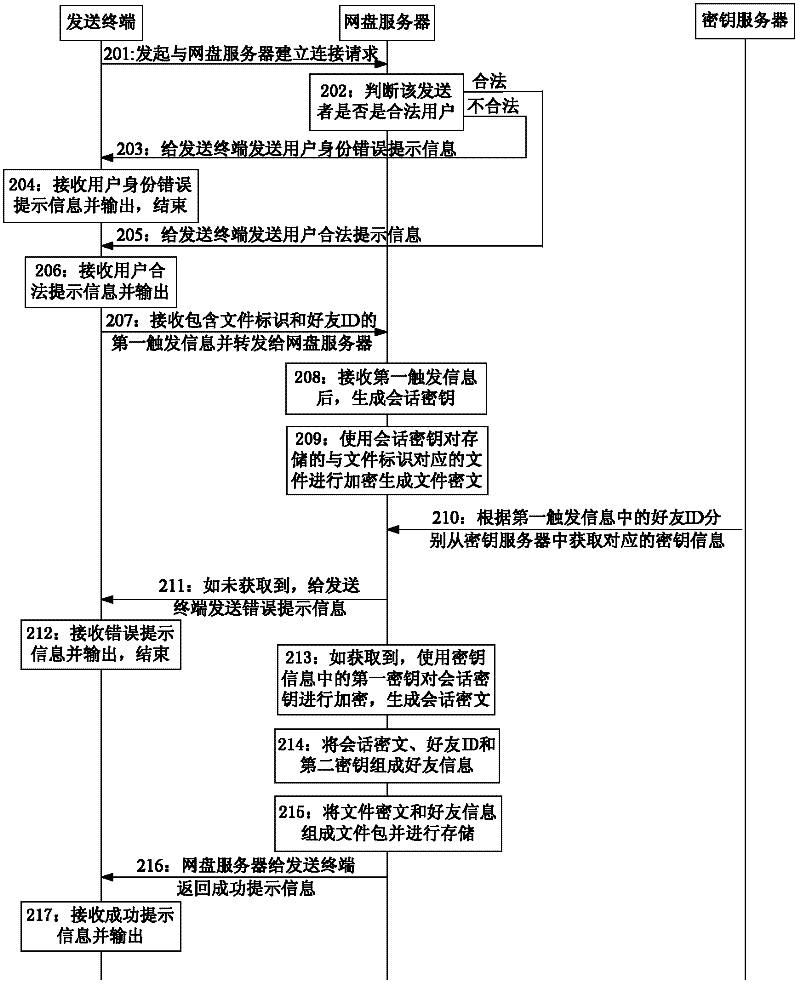
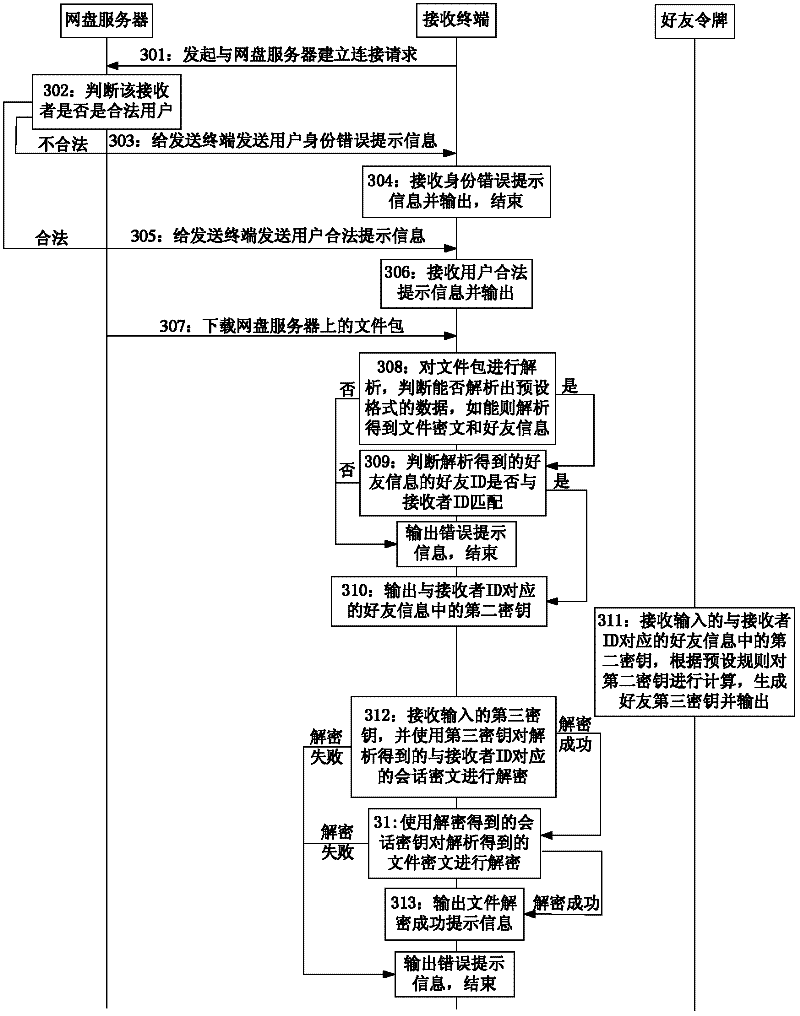
ActiveCN102420821AImprove securityPrivacy protectionUser identity/authority verificationCiphertextKey generator
The invention discloses a method and a system for improving the transmission security of a file. The method comprises the following steps of: respectively obtaining a first secret key and a second secret key, which are corresponding to each other, in a secret key server according to a friend identifier in triggering information; encrypting the file by a generated session key to generate a file ciphertext; respectively encrypting the session key by the first secret key to generate a corresponding session ciphertext; forming the friend identifier, the corresponding second secret key, the session ciphertext and the file ciphertext into a file packet; and obtaining and analyzing the file packet, outputting the second secret key which is obtained in an analysis way and is corresponding to a receiver when data which accords with a preset format is analyzed and the receiver is a transmitting friend, receiving a third secret key which is generated by a secret key generator according to the second secret key, deciphering the session ciphertext by the third secret key, and deciphering the file ciphertext by the session ciphertext which is obtained in a deciphering way. Therefore, the operation for transmitting the file to a plurality of users can be simplified, and the transmission security of the file can be further improved.
Owner:FEITIAN TECHNOLOGIES
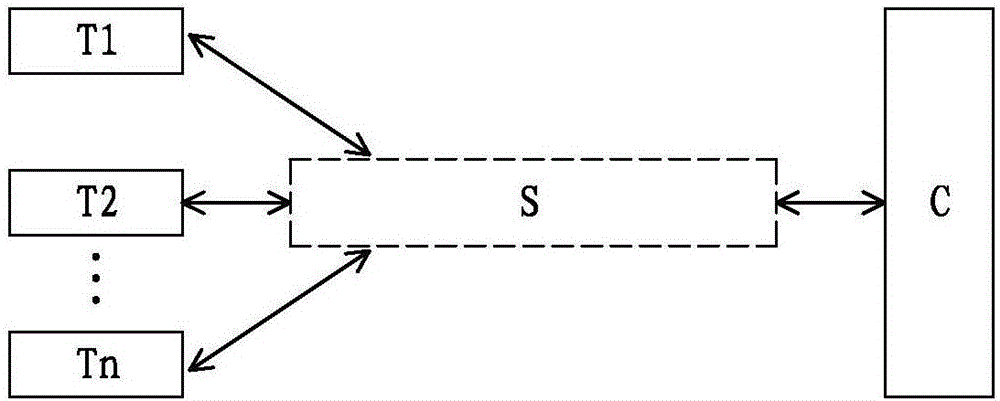
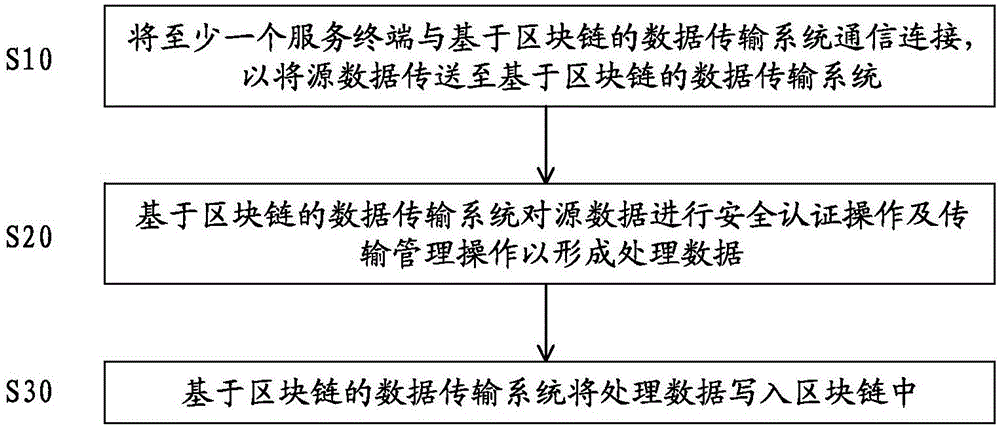
Block chain-based data transmission system and method
ActiveCN106549933AAvoid accessLow costUser identity/authority verificationTransfer procedureComputer terminal
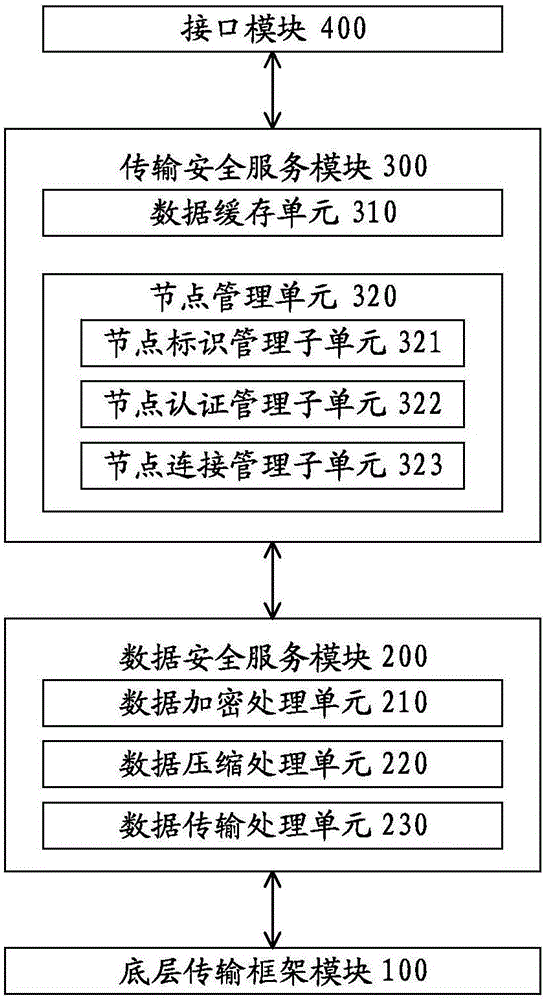
The present invention discloses a block chain-based data transmission system and method. The system comprises a bottom transmission framework module, a data security service module, a transmission security service module, and an interface module. The bottom transmission framework module is used for forwarding data between a block chain and multiple service terminals. The data security service module is in communicated connection with the bottom transmission framework module, and is used for performing security authentication on data transmitted with the bottom transmission framework module in a communicated manner. The transmission security service module is in communicated connection with the data security service module and is used for transmitting and managing data transmitted with the data security service module in a communicated manner. The interface module is in communicated connection with the transmission security service module and at least one service terminal, and is used for being invoked by at least one service terminal so as to start the data transmission system of the block chain. The data in transmission is not tampered, private data can be encrypted and transmitted safely, and block chain-based massive data transmission is safe and efficient.
Owner:中金数据(武汉)超算技术有限公司
Uplink secure transmission method based on downlink auxiliary feedback in 5G communication system
ActiveCN105007578AReduce resource consumptionEnsure safetySecurity arrangementSignal onEavesdropping
The invention discloses an uplink secure transmission method based on downlink auxiliary feedback in a 5G communication system. In the first stage, a multi-antenna base station end sends both artificial interference and artificial noise signals on a downlink by means of a wave beam formation technology; and a single-antenna user end receives an emission signal from the base station end, and scrambles the received signal to a to-be-sent secret signal so that a mixed emission signal is formed. In the second stage, the user terminal broadcasts the mixed emission signal; and the base station end receives the mixed emission signal. Since the base station end already knows an artificial interference signal emitted by the base station itself, an expected secret signal can be separated from the received signal. A single-antenna passive eavesdropping end receives mixed signals during both transmission stages, and cannot know any prior information about the artificial interference and artificial noise signals, so the possibility of stealing secret information is low. Therefore, the transmission security of a 5G uplink single-input and multi-output system is effectively guaranteed.
Owner:XI AN JIAOTONG UNIV
Lightweight Internet of Things security key negotiation method based on edge computing
ActiveCN112073379AEase the huge burdenReduce latencyKey distribution for secure communicationInternet privacyEdge computing
A lightweight Internet of Things security key negotiation method based on edge computing comprises the following steps that 1, a cloud server performs bidirectional authentication on an edge gateway and authorizes the edge gateway, and the edge gateway obtains an authentication key negotiation permission for terminal equipment; 2, the edge gateway is responsible for security authentication and management of the Internet of Things equipment in the edge gateway local area network; 3, the terminal equipment and the edge gateway carry out bidirectional authentication and key negotiation, constructa secure channel to carry out encryption protection on subsequent transmission data, and transmit the subsequent transmission data to the edge gateway in a unified manner; 4, the edge gateway carriesout preliminary processing on the data transmitted by the terminal equipment; and 5, in the subsequent process, the cloud server and the edge gateway server transmit and process the equipment data together. According to the invention, lightweight and secure Internet of Things authentication key negotiation is realized, and the Internet of Things network data transmission security is ensured.
Owner:JIANGSU ELECTRIC POWER CO +2
Communication system incorporating physical layer waveform structure
ActiveUS20100265999A1Increase speedImprove usabilityModulated-carrier systemsForward error control useCommunications systemTime division multiple access
A wireless radio transceiver system configured to transmit and receive a communications signal waveform having a time division multiple access physical layer structure and which includes a sequence of orthogonal frequency division multiple access symbols. The transceiver provides transmit diversity through space-time coding and the use of orthogonal channel probes from each transmitter. The waveform is packet based and contains a packet header definition that supports local receiver synchronization. Examples of the waveform also incorporate transmission security features.
Owner:RAYTHEON CO
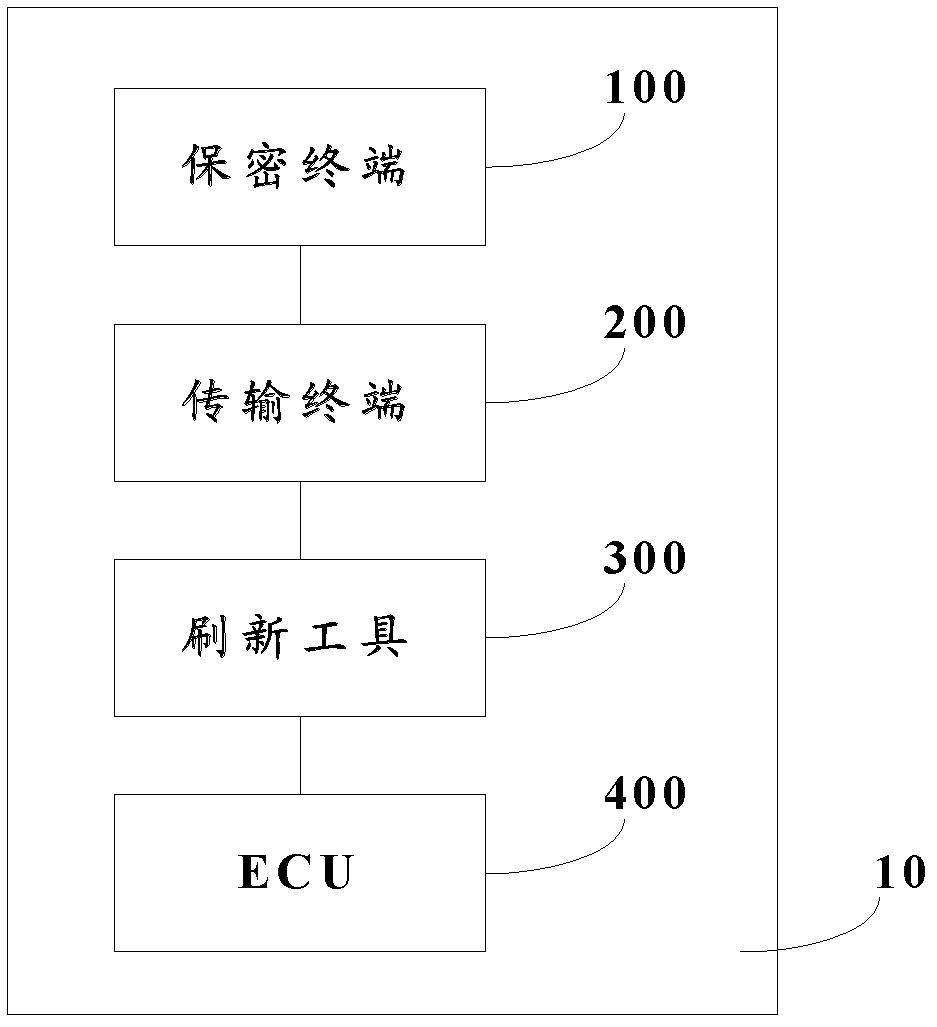
Method and system for encryption transmission electronic control unit (ECU) objective file
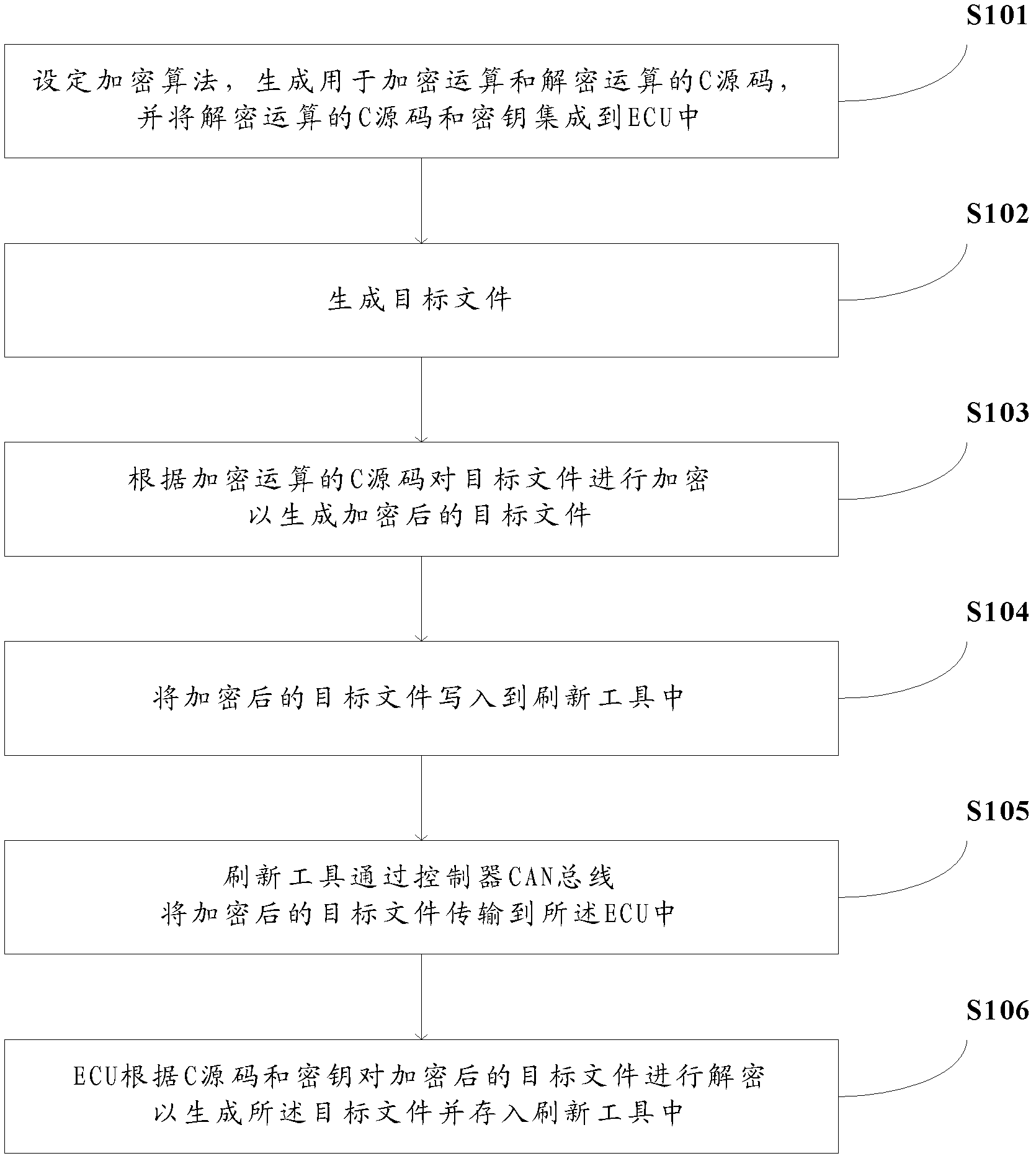
InactiveCN103166943AImprove confidentialitySimple structureEncryption apparatus with shift registers/memoriesArea networkCiphertext
The invention provides a method and a system for encryption transmission an electronic control unit (ECU) objective file. The method for encryption transmission the ECU objective file comprises the following steps: setting an encryption algorithm, generating a C source code which is used for encryption operation and decryption operation, and integrating the C source code of the decryption algorithm and a secret key to the ECU; when the objective file is generated, adopting an advanced encryption standard (AES) encryption algorithm which is achieved by C language to encrypt the objective file and to generate the ciphertext of the objective file; using a refreshing tool the objective file which is in a ciphertext form pass through a controller local area network controller area network (CAN) bus, transmitting the ciphertext of the objective file to the ECU; the ECU decrypts the objective file after encryption based on a deciphering algorithm and a secret key to generate the objective file, and storing the objective file into the refreshing tool. The method for encryption transmission the ECU objective file guarantees the objective file to exist in the ciphertext form in a transmission link by encrypting on the generated objective file and deciphering until the objective file is received by the ECU end, and therefore the transmission security of the objective file is greatly improved.
Owner:BEIQI FOTON MOTOR CO LTD
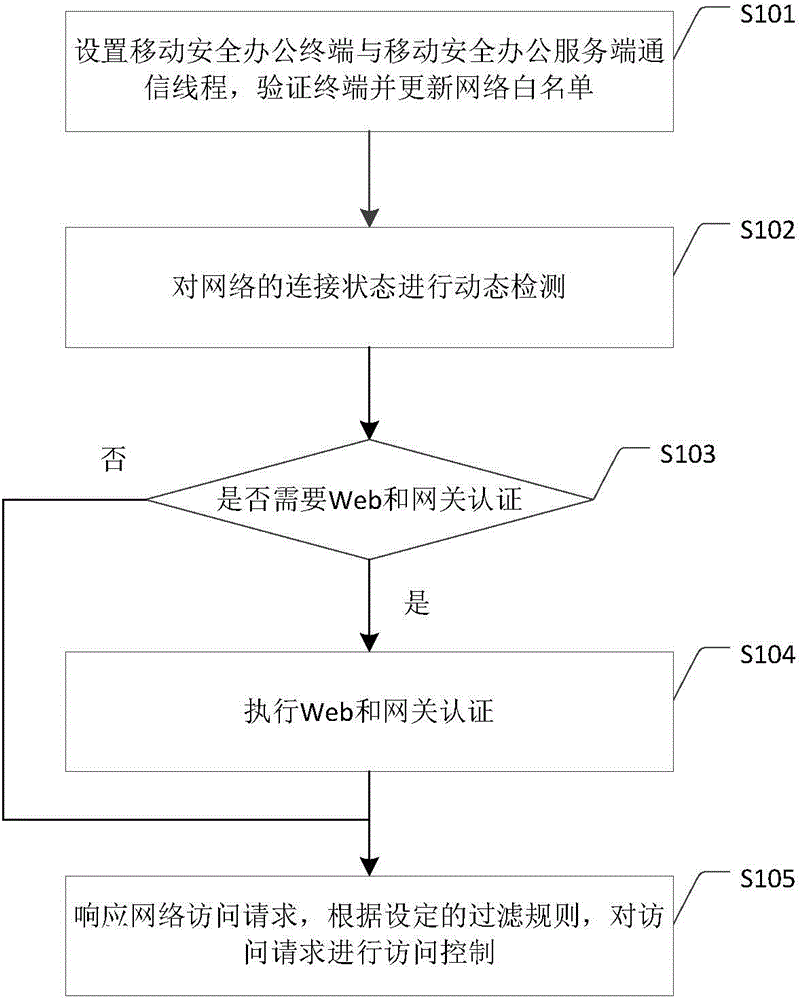
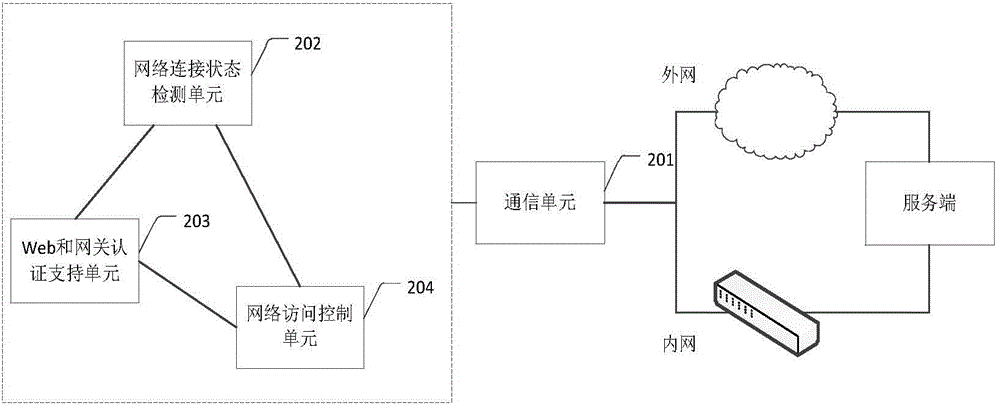
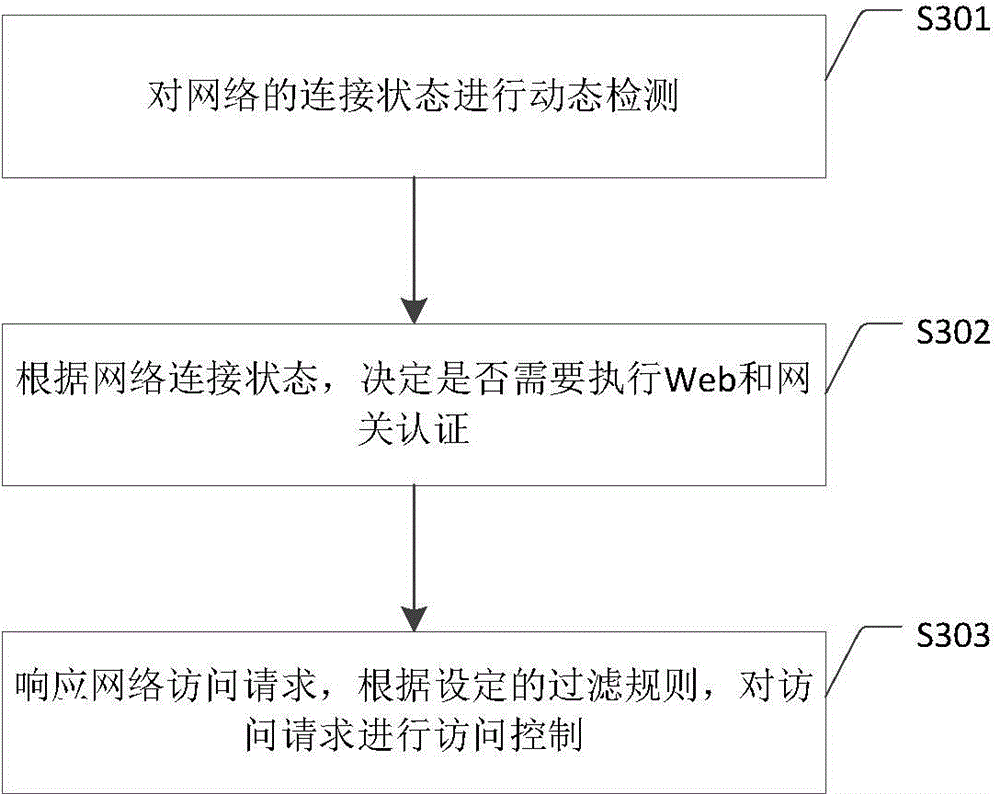
Method and system for network access control
The invention discloses a method and system for network access control, and relates to the technical field of network transmission security. When the mobile office terminal is under strict network access control, the network connection status of a terminal is dynamically detected, and the terminal can successfully pass the Web and gateway authentication according to the corresponding detection status. According to the method for network access control, the equipment is more compatible in complex changeful network environments, while the network security of the equipment is ensured, the effectiveness of network access control can be improved, the maintenance work of the security administrator can be reduced, and the support and guarantee can further be provided for the accessible network resources of the equipment.
Owner:BEIJING UNIV OF TECH
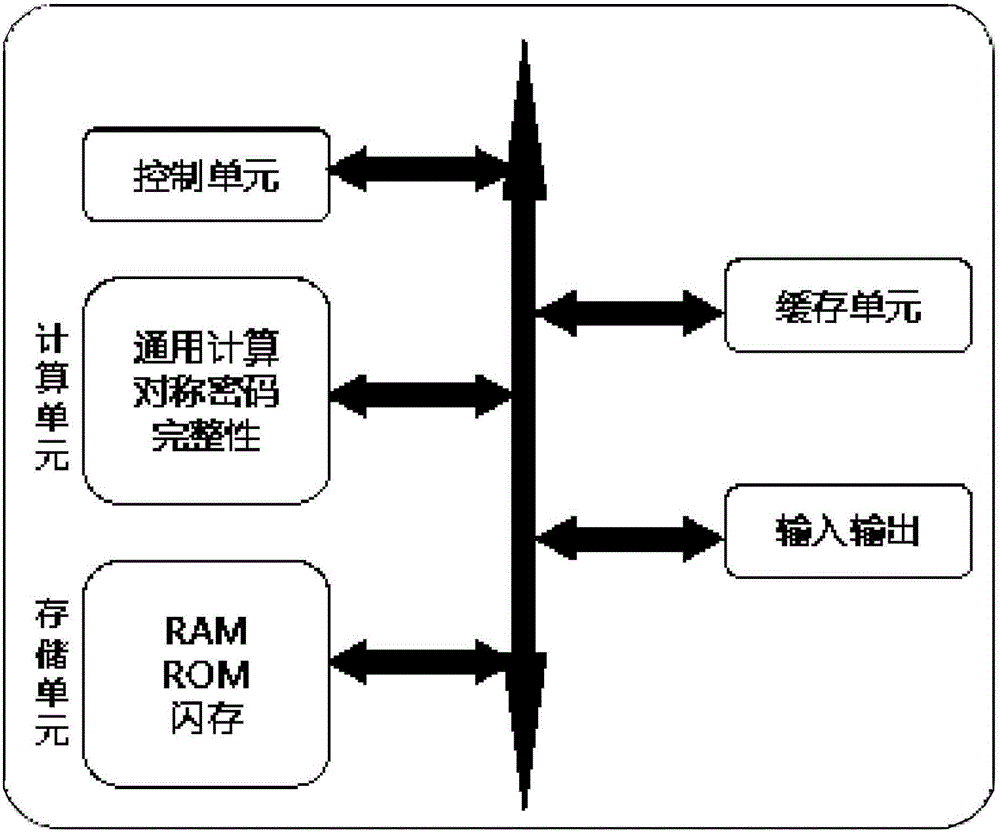
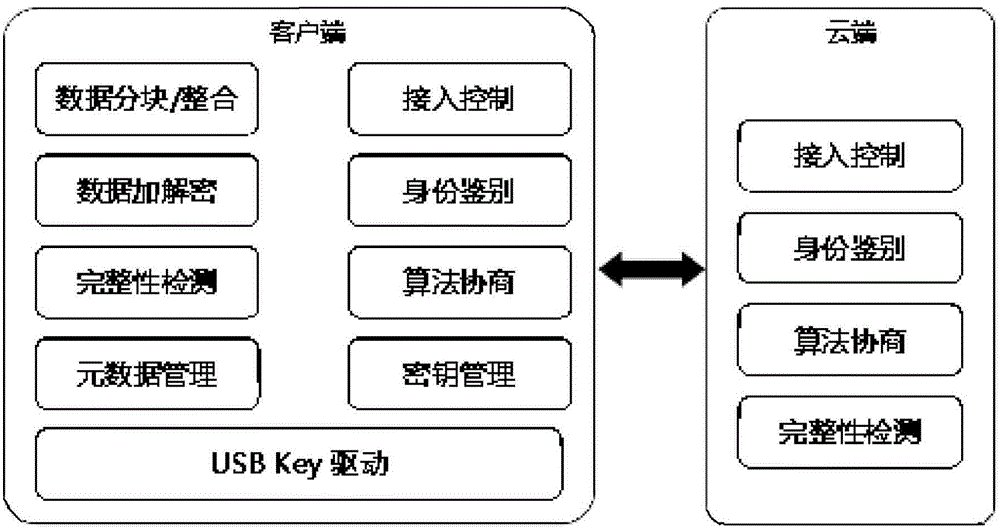
Cloud data security system based on USB Key
The invention discloses a cloud data security system based on a USB Key. The cloud data security system comprises a client and a cloud, the client is connected with the USB Key, the USB Key structurally comprises a control unit, a calculating unit, a storage unit, a cache unit and an input and output I / O logic module, and a digital certificate and a plurality of encryption algorithms and integrity detection algorithms are built in the USB Key; according to different security requirements of cloud data, different encryption algorithms are selected to finish encryption calculation of the cloud data, so as to satisfy the security demands and transmission security of different users; and the integrity detection algorithms are used for detecting the integrity of the cloud data with a block as a unit. Compared with the prior art, the cloud data security system based on USB Key can select different encryption algorithms according to the importance of the data and guarantee the integrity of the data at the same time, so as to satisfy the security demands of the users in a cloud calculation environment, and the cloud data security system is strong in practicability and is easy to promote.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com