Cloud data security system based on USB Key
A security system and cloud data technology, applied in the field of information security, can solve the problems of inability to effectively control centralized management, data out of controllable scope, insecure factors and leaks, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
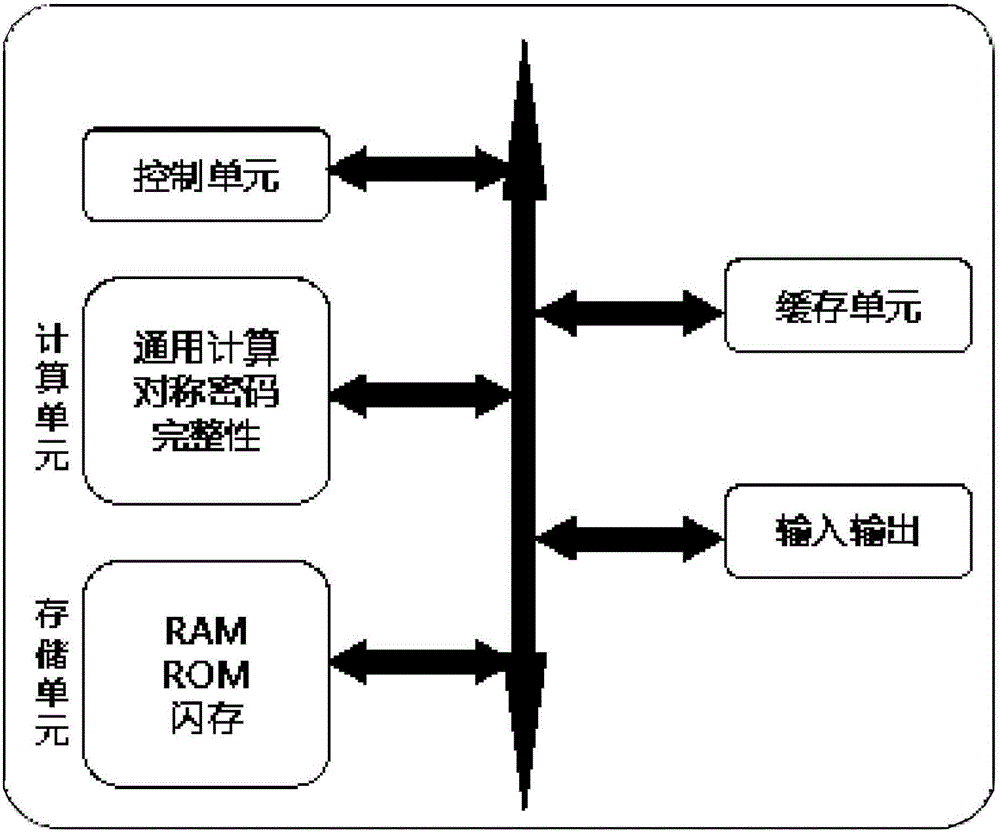
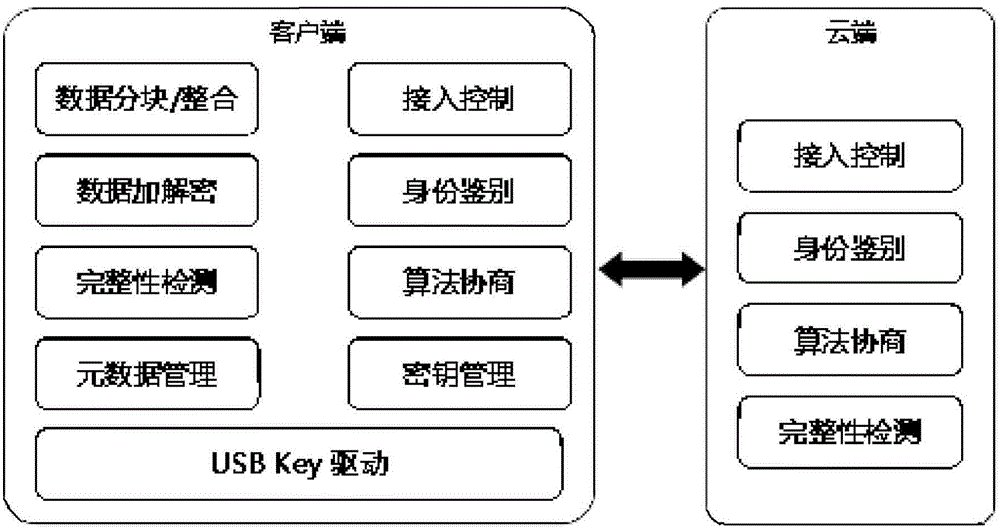
[0077] Now take the process of the user uploading the 2G data file report.dat to the cloud as an example, the hardware structure involved is as follows figure 1 , figure 2 As shown, when using this system for data transmission and downloading, the access control in step 1) and the identification in step 2) are as described above, and the specific implementation process of the data processing and transmission steps in step 3) is as follows:
[0078] a) Algorithm negotiation: According to the importance of cloud data, the client and the cloud negotiate data encryption algorithm AES (256 bits, CFB mode) and integrity detection algorithm SHA-2, and generate cloud data encryption key K (256 bits), the key ciphertext after the encryption key is encrypted with its private key, the data file to be encrypted report.dat, the file length 2G, the encryption algorithm AES and parameters (256 bits, CFB mode), the integrity detection algorithm Metadata information such as SHA-2 and time (2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com