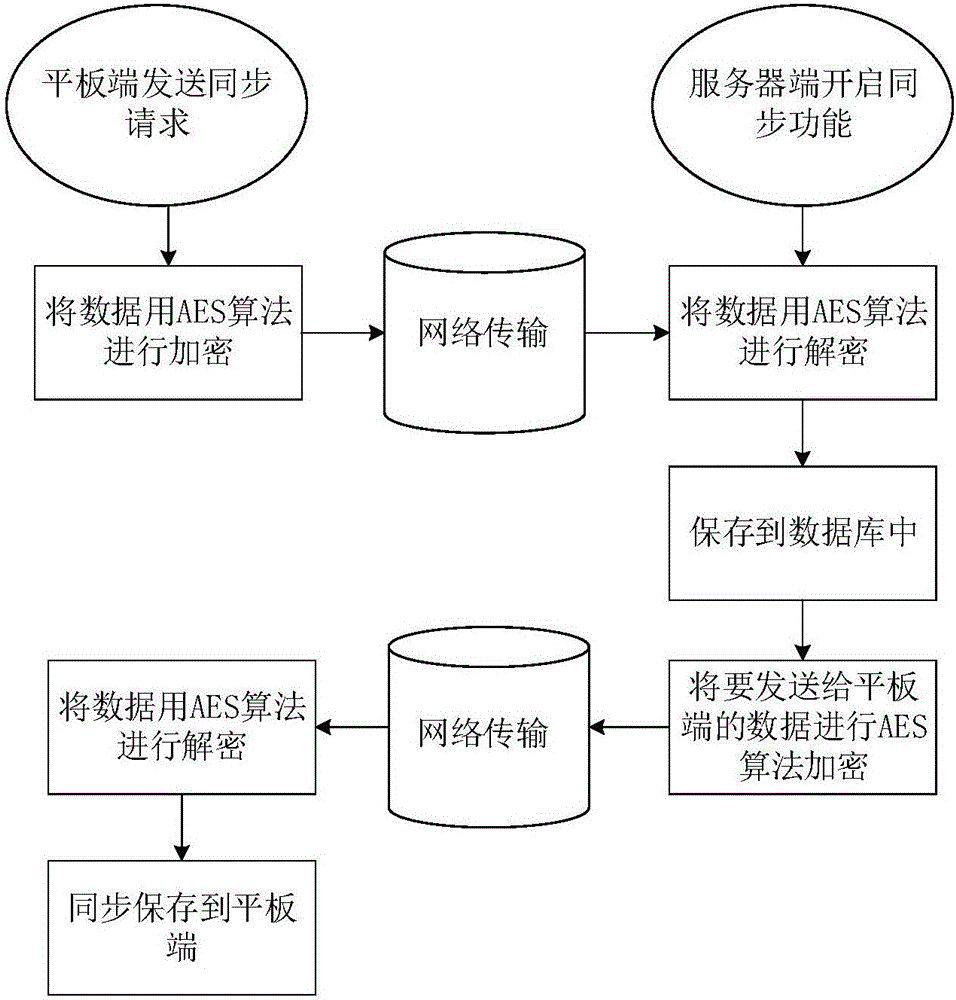
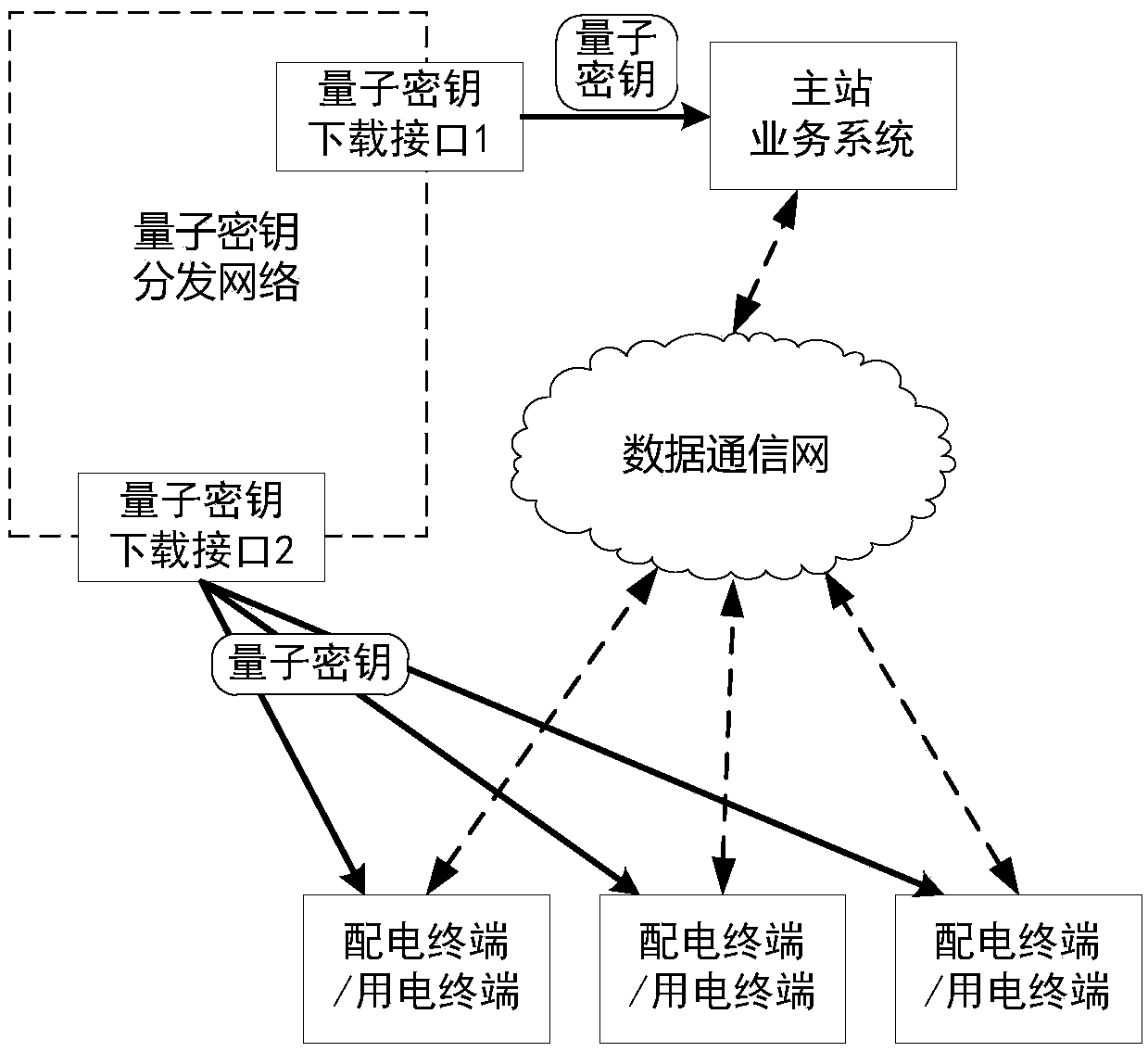
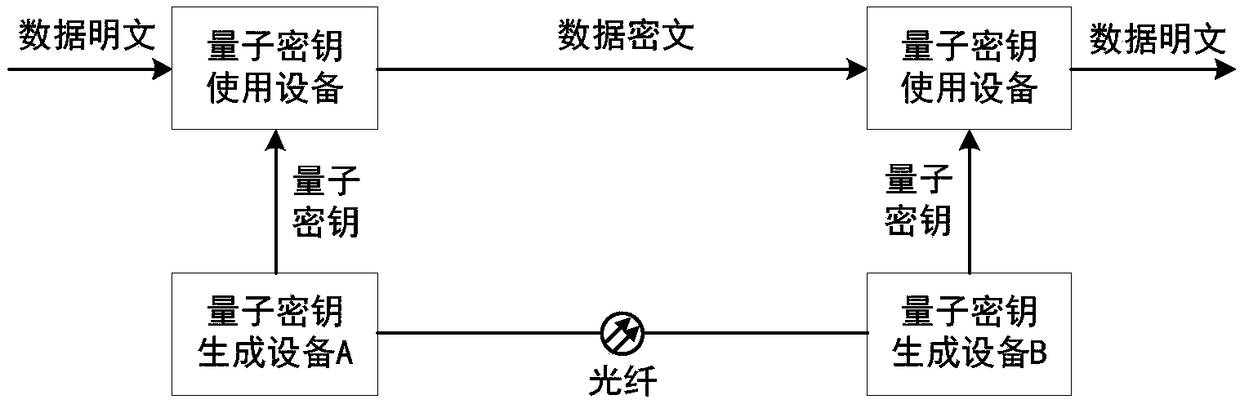
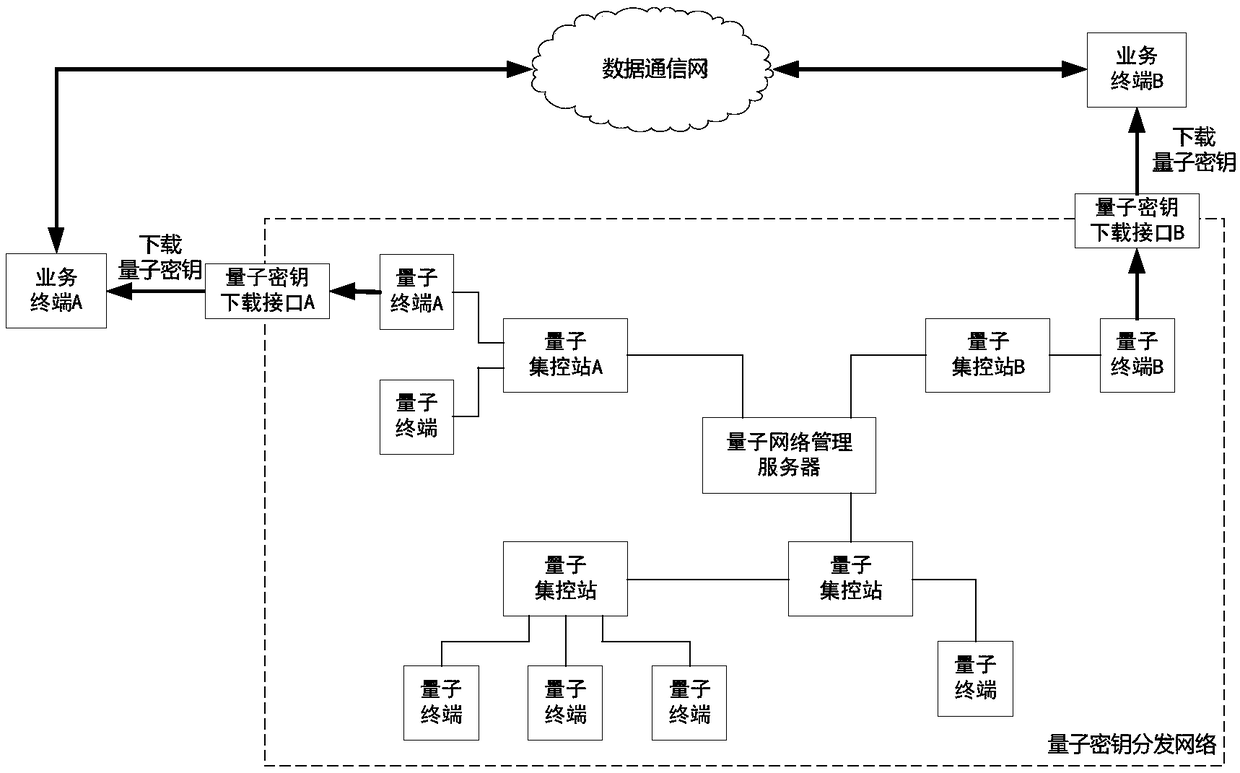
Patents
Literature
112results about How to "Ensure transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
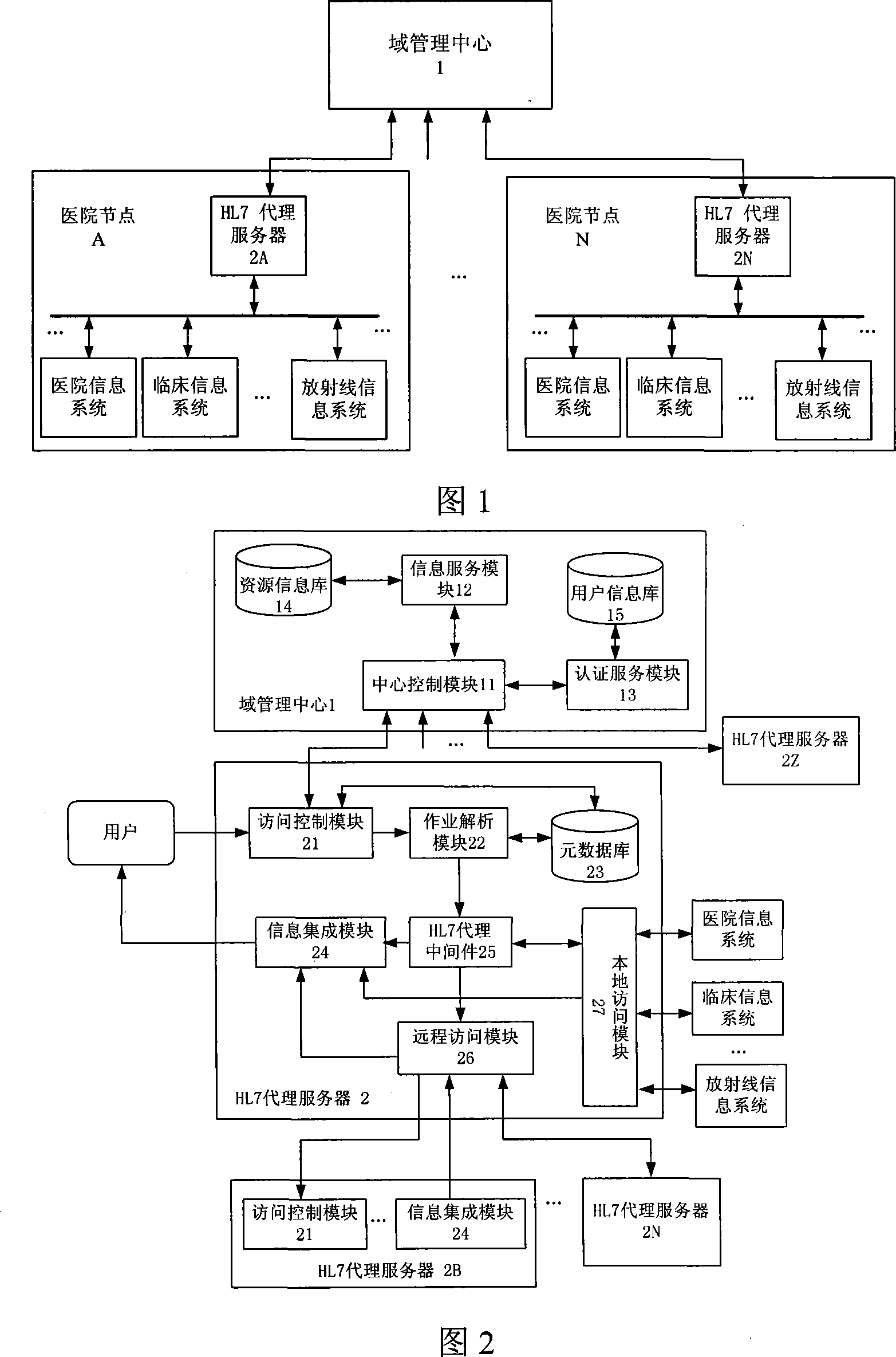
Heterogeneous medical information integrated system based on HL7 agent server
InactiveCN101083582AWill not affect the working modeSupport Information Integration RequestUser identity/authority verificationData switching by path configurationLocal information systemsProxy server
The invention discloses isomery medical information integrating system based on HL7 proxy server. It includes the following steps: receiving available resource enrollment from self area HL7 proxy server; managing it as resource metadata; responding any accessing request; setting HL7 proxy server at each hospital knot to manage medical information system; downloading available resource view in time to selecting remote integrating target for user; receiving self area medical information integrating request; accessing local or remote information system; integrating each returning knot. The invention combines centralized control with knot self rule to increase stability for whole platform, has high compatibility, interactive speed, safety etc.
Owner:HUAZHONG UNIV OF SCI & TECH
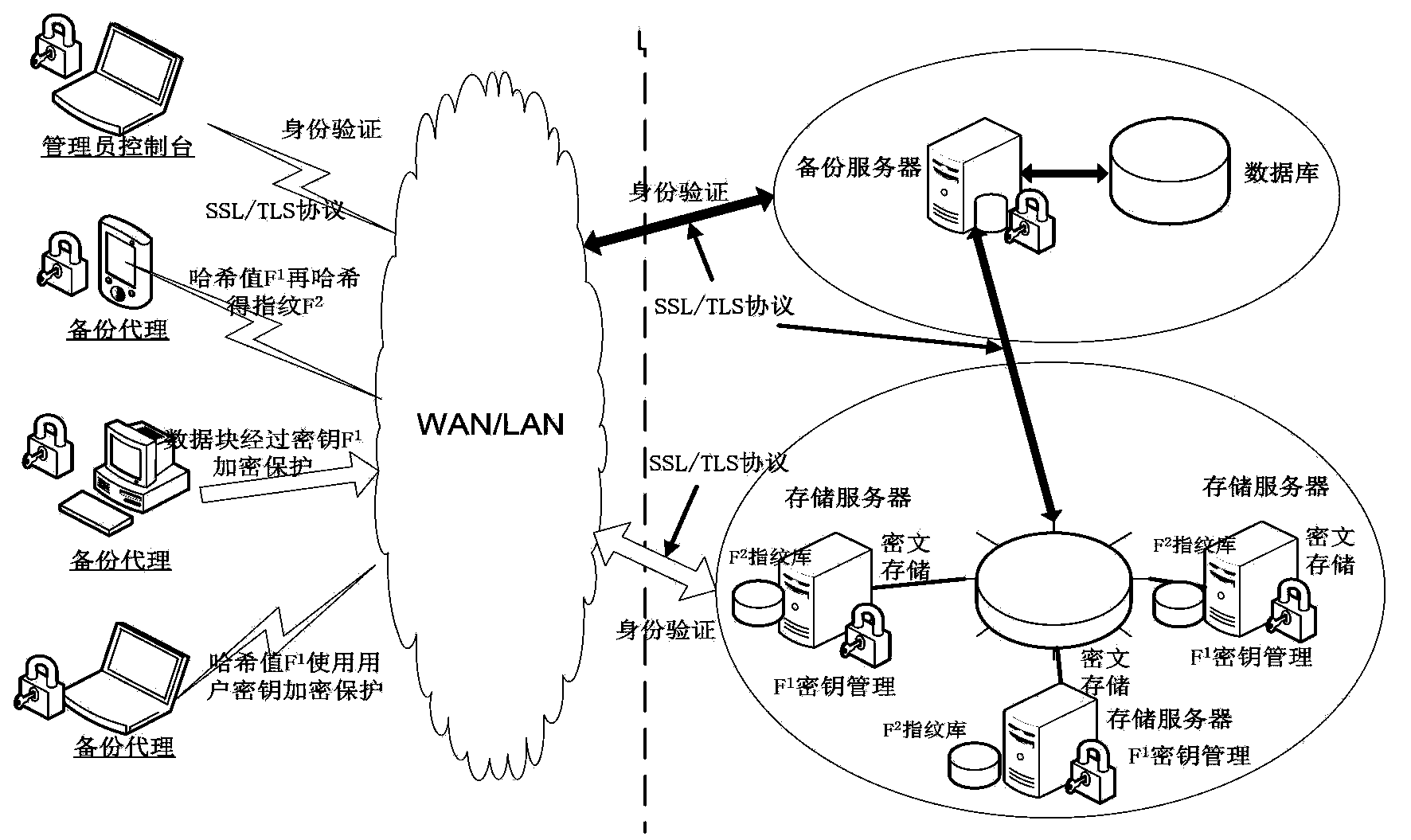
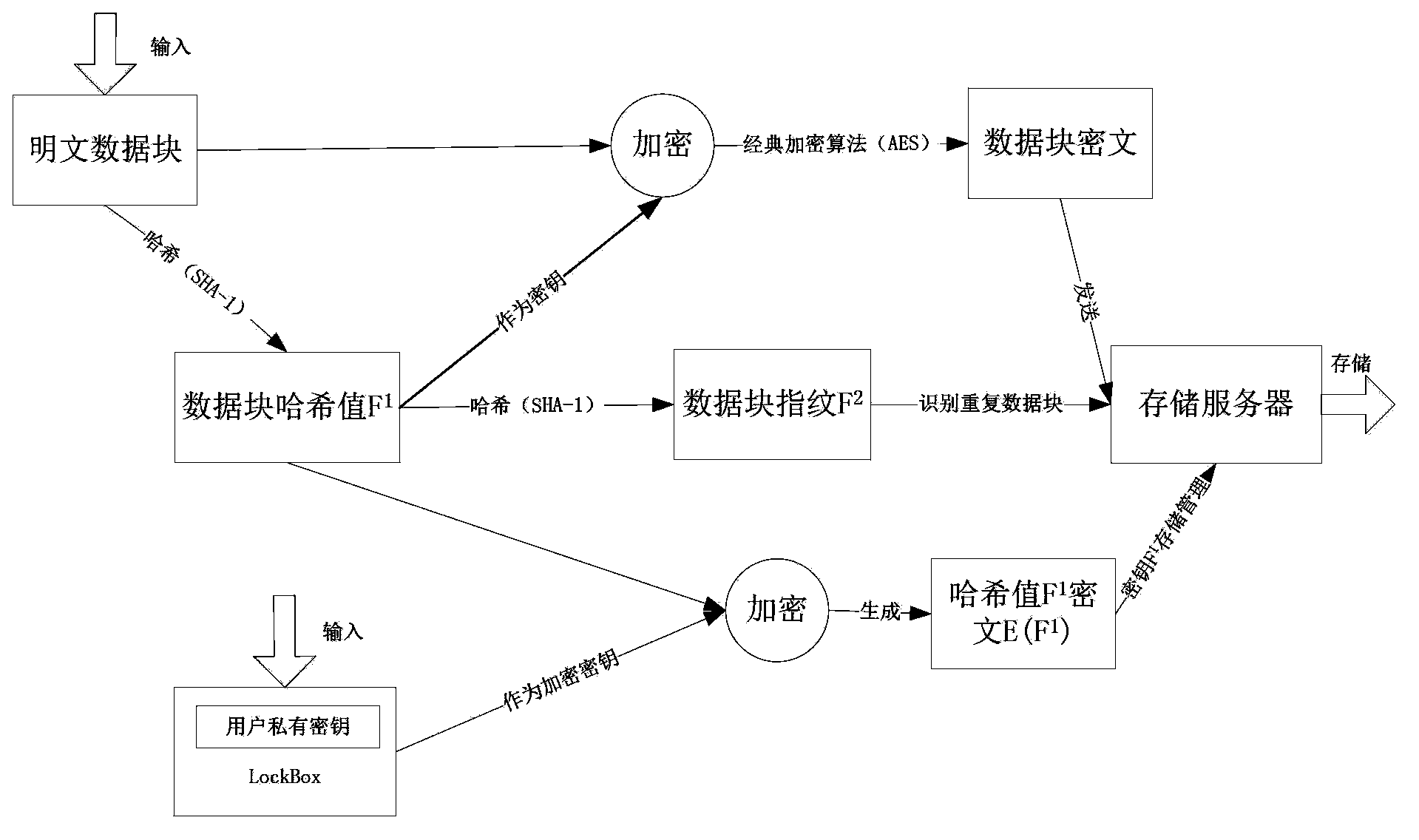
Safety data repetition removing method and system applicable to backup system
ActiveCN103530201AReduce the burden onImprove performanceUser identity/authority verificationInternal/peripheral component protectionComputer hardwareData loss
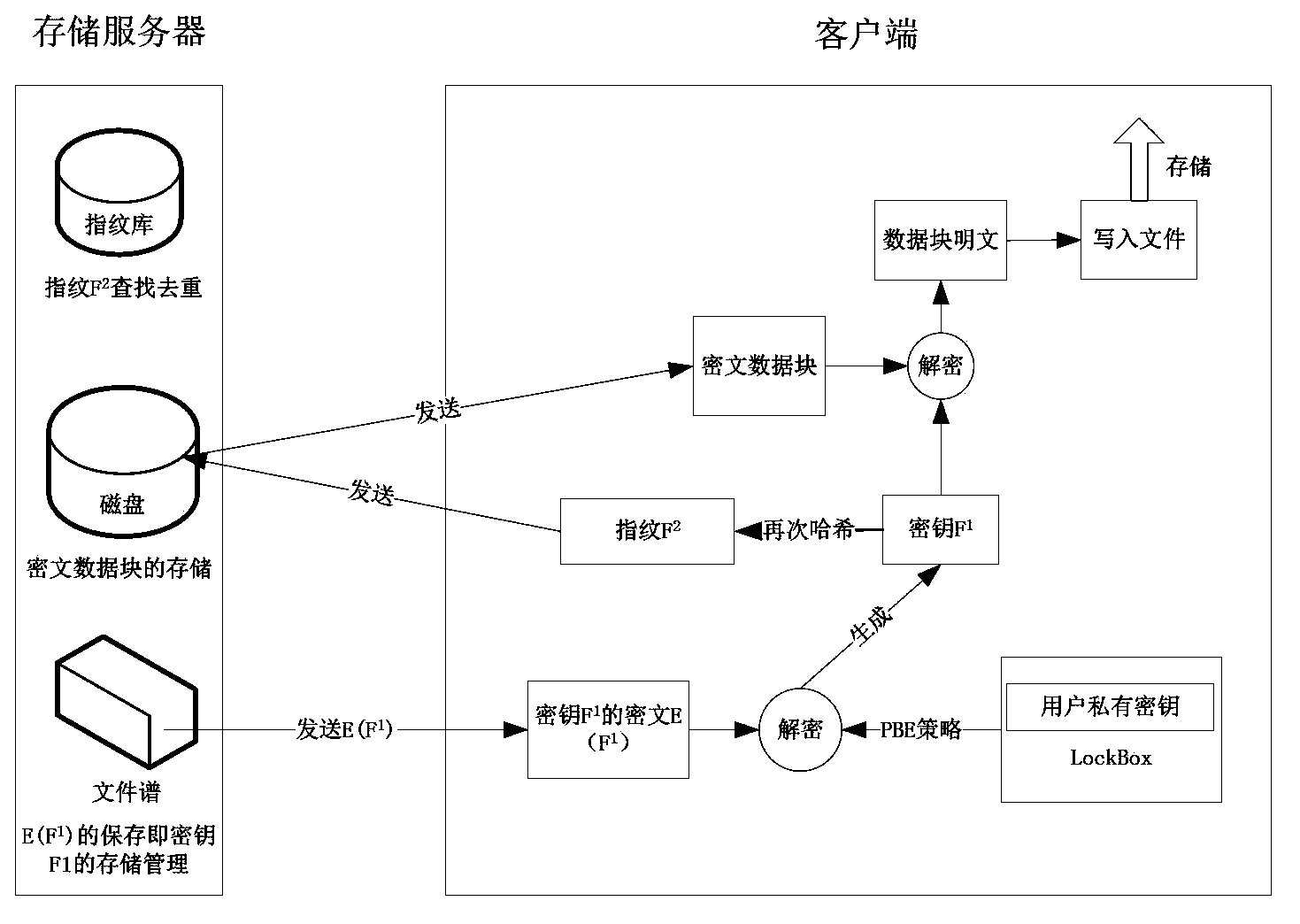
The invention discloses a safety data repetition removing method applicable to a backup system. The method includes the following steps that a backup request submitted by a user is received; all files needing backup are partitioned and multiple data blocks of different sizes are obtained; the Hash algorithm is used for calculating the Hash value F1 of each data block, wherein the Hash values F1 serve as encrypting keys of the data blocks; the Hash algorithm is used again for calculating the Hash value F2 of the Hash value F1 of each data block, wherein the Hash values F2 serve as fingerprints of the data blocks to identify repeated data blocks and the classic encryption algorithm and a private key of the user are used for encrypting the Hash values F1 of the data blocks to obtain ciphertexts E (F1) of the Hash values F1 of the data in order to protect the encrypting keys of the data blocks. All the data block fingerprints F2 and the like are packaged in sequence into fingerprint segments which are transmitted to a storage server. The SSL protocol is adopted in all communication processes. According to the safety data repetition removing method applicable to the backup system, the safety data repetition removing method is adopted to ensure that storage safety problem that data are lost or tampered is solved under the condition that the data repetition removing rate is not changed.
Owner:HUAZHONG UNIV OF SCI & TECH
Lightweight authentication method based on equipment identity label and gateway
ActiveCN111835752AEnsure transmission securityImprove securityKey distribution for secure communicationUser identity/authority verificationInternet privacyEngineering
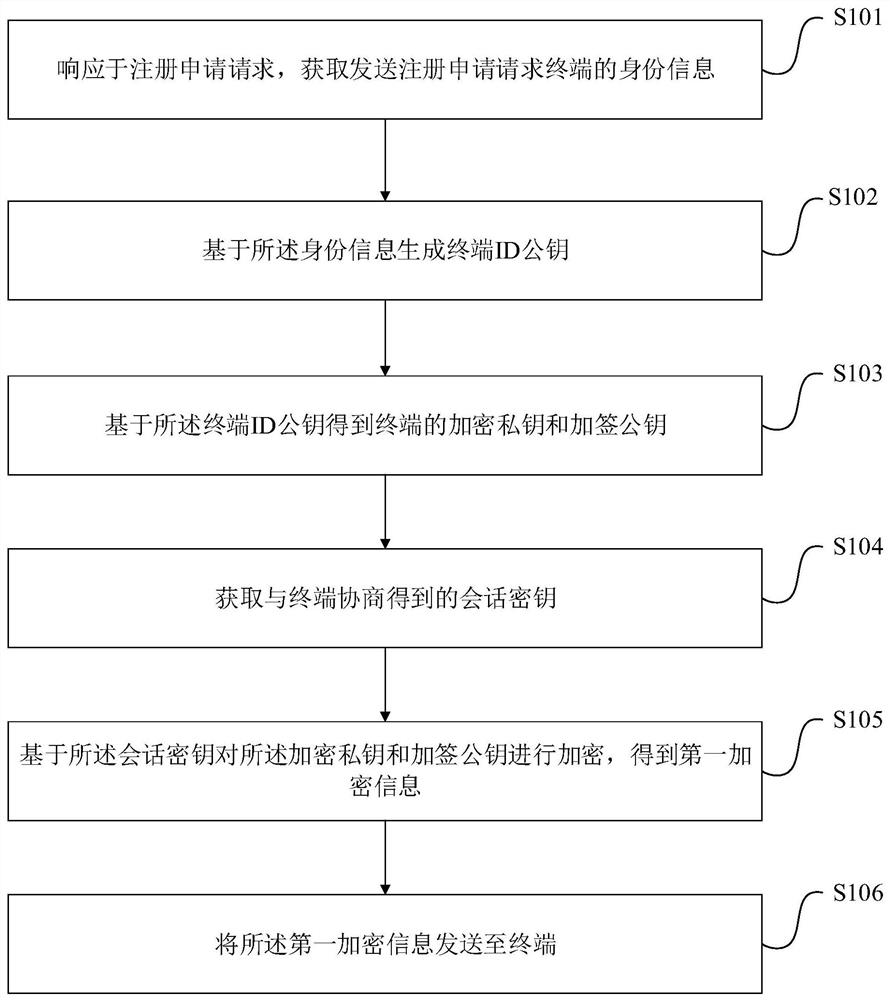
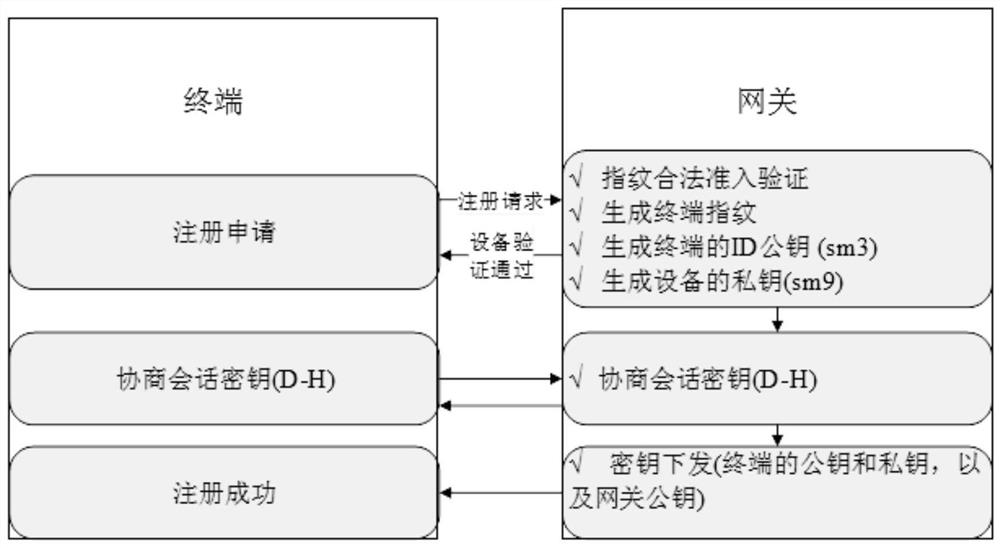
The embodiment of the invention discloses a lightweight authentication method based on an equipment identity label and a gateway. The lightweight authentication method based on the equipment identitylabel comprises a registration method and an authentication method, the registration method comprises the following steps: in response to a registration application request, obtaining the identity information of a terminal sending the registration application request; generating a terminal ID public key based on the identity information; obtaining an encrypted private key and a signed public key of the terminal based on the terminal ID public key; obtaining a session key obtained by negotiation with the terminal; encrypting the encrypted private key and the signed public key based on the session key to obtain first encrypted information; and sending the first encrypted information to the terminal. In the transmission communication of the encrypted private key and the signed public key, thesession key obtained by negotiation with the terminal is used to encrypt the communication, so that the transmission security of the encrypted private key and the signed public key is ensured, and the purpose of improving the security in lightweight registration authentication is achieved.
Owner:STATE GRID SHANXI ELECTRIC POWER +1
Method and system for the quick-speed and safe distribution of file based on P2P
InactiveCN101515947AFast transferDistribute quicklyEncryption apparatus with shift registers/memoriesPlaintextCiphertext
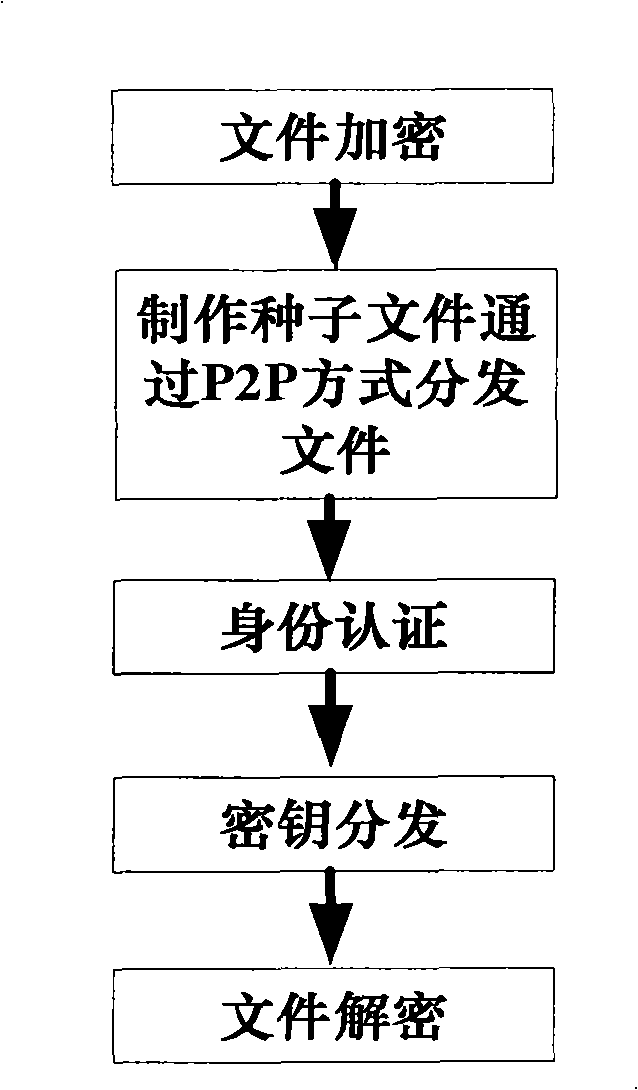
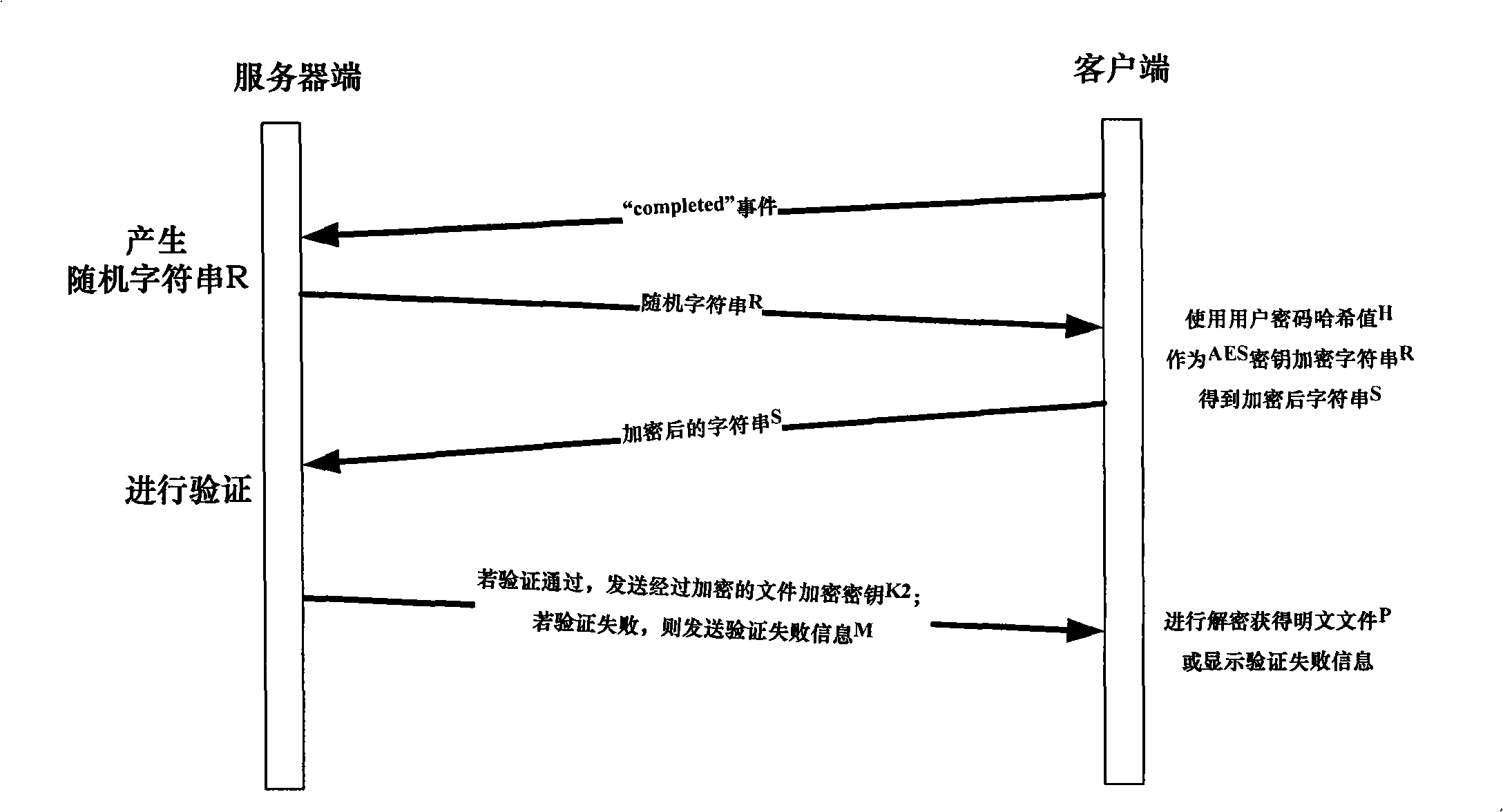
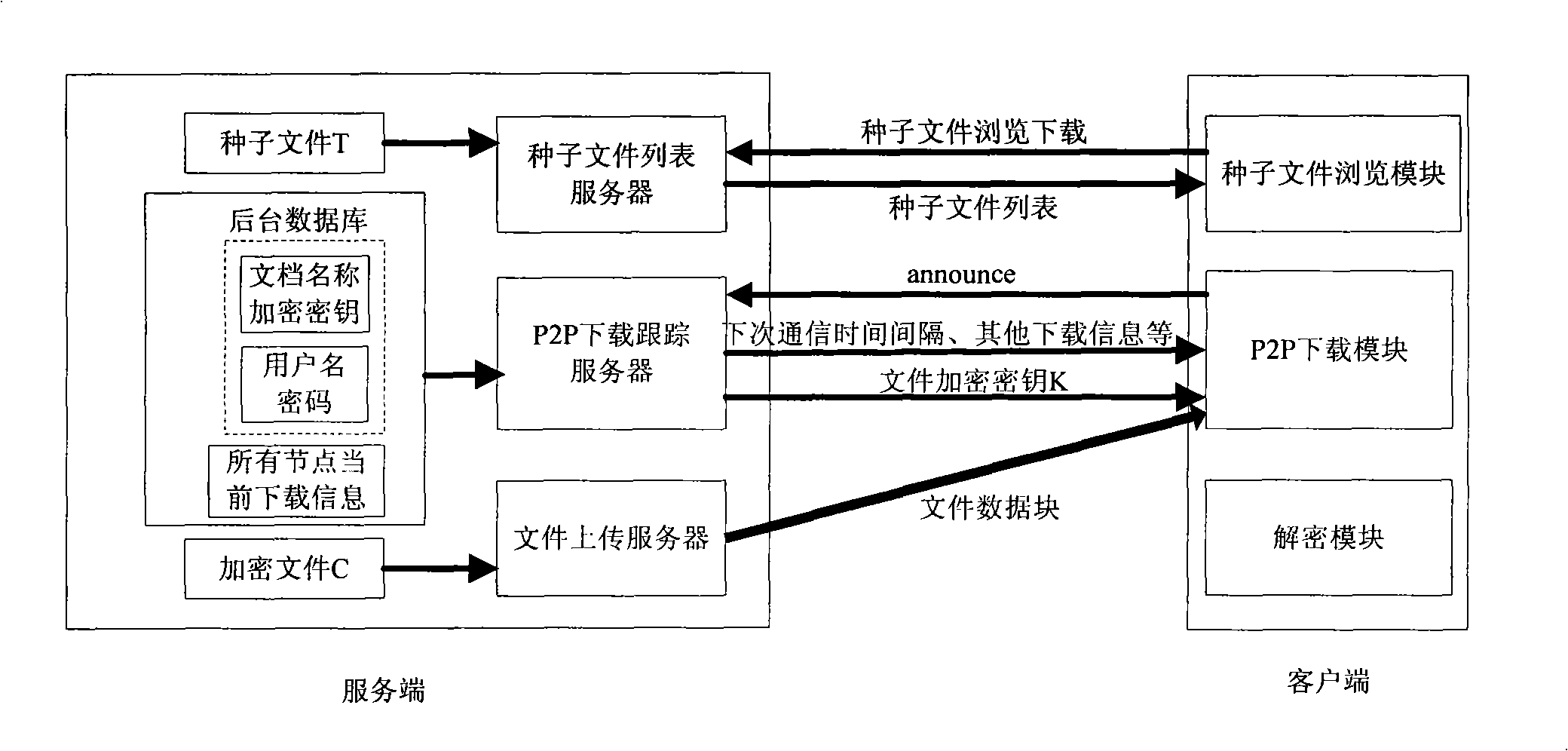
The invention discloses a method for the quick-speed and safe distribution of the file based on the P2P,including that: a, a proclaimed file is in the symmetric encrypting to form an encrypted file before being distributed and transferred, and the encrypted file is made into a seed file, which is placed in the service end and distributed in the P2P way; b, the customer end logins according to the user information, the seed file is selected and downloaded in the P2P way, then the customer is in the identity verification; c, the service end distributes the encryption key of the encrypted file for the certificated customer; d, the customer end obtains the proclaimed file through the symmetric deciphering of the encryption key and the encrypted file. The invention also discloses a system for the quick-speed and safe distribution of the file based on the P2P, comprising a service end and a customer end, wherein the service end comprises a data-base, a seed file list server, a P2P download tracking server and a file uploading server, the customer end comprises a seed file reading module, a P2P downloading module and a deciphering module. The method can satisfy the requirement for safely and quickly distributing and transferring the file under the certain condition.
Owner:ZHEJIANG UNIV
Cloud data security protection method adopting fully homomorphic encryption technology and multiple digital watermarking technology
InactiveCN105323209AEnsure transmission securityEnsure storage securityTransmissionThird partyStorage security
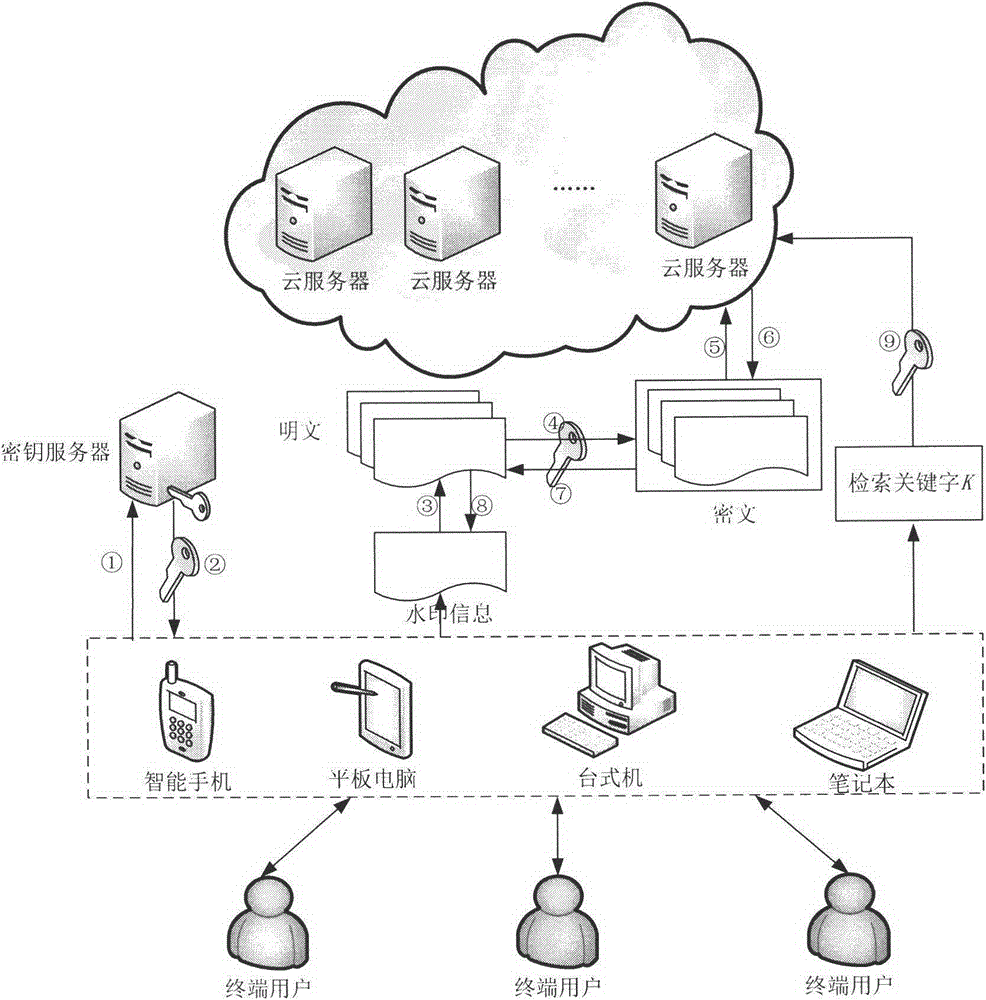
The present invention discloses a cloud data security protection method adopting a fully homomorphic encryption technology and a multiple digital watermarking technology. The cloud data security protection method is characterized in that in a cloud computing environment, a trusted third-party organization distributes a key to a user, after the user stores the key, a fully homomorphic encryption scheme is adopted to encrypt to-be-uploaded data at a user side, then the encrypted data is uploaded to a cloud side, thereby ensuring transmission security and storage security of data; in addition, when the user searches for data, direct search for ciphertext can be performed after a search keyword is encrypted, thereby improving search efficiency; and moreover, before the data is uploaded to the cloud side, a fragile watermarking and a robust watermarking are respectively embedded into the to-be-uploaded data, the purpose of embedding of the fragile watermarking is to prevent illegal modification of the data, so as to achieve authentication for integrity of the data, and the purpose of embedding of the robust watermarking is to protect copyright of the data, so as to achieve authentication for copyright of the data.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Safety dynamic migration method of Xen virtual machine
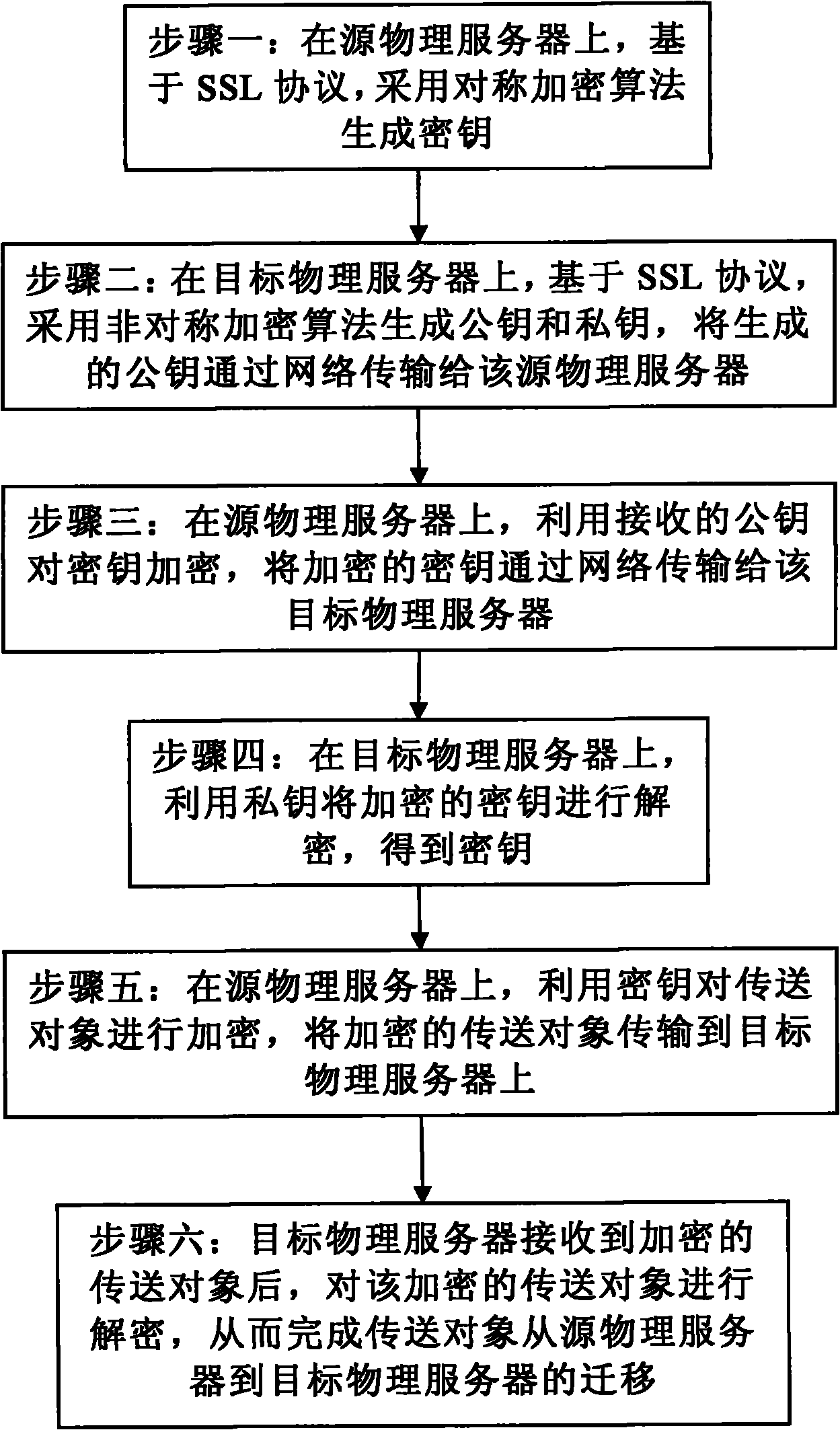
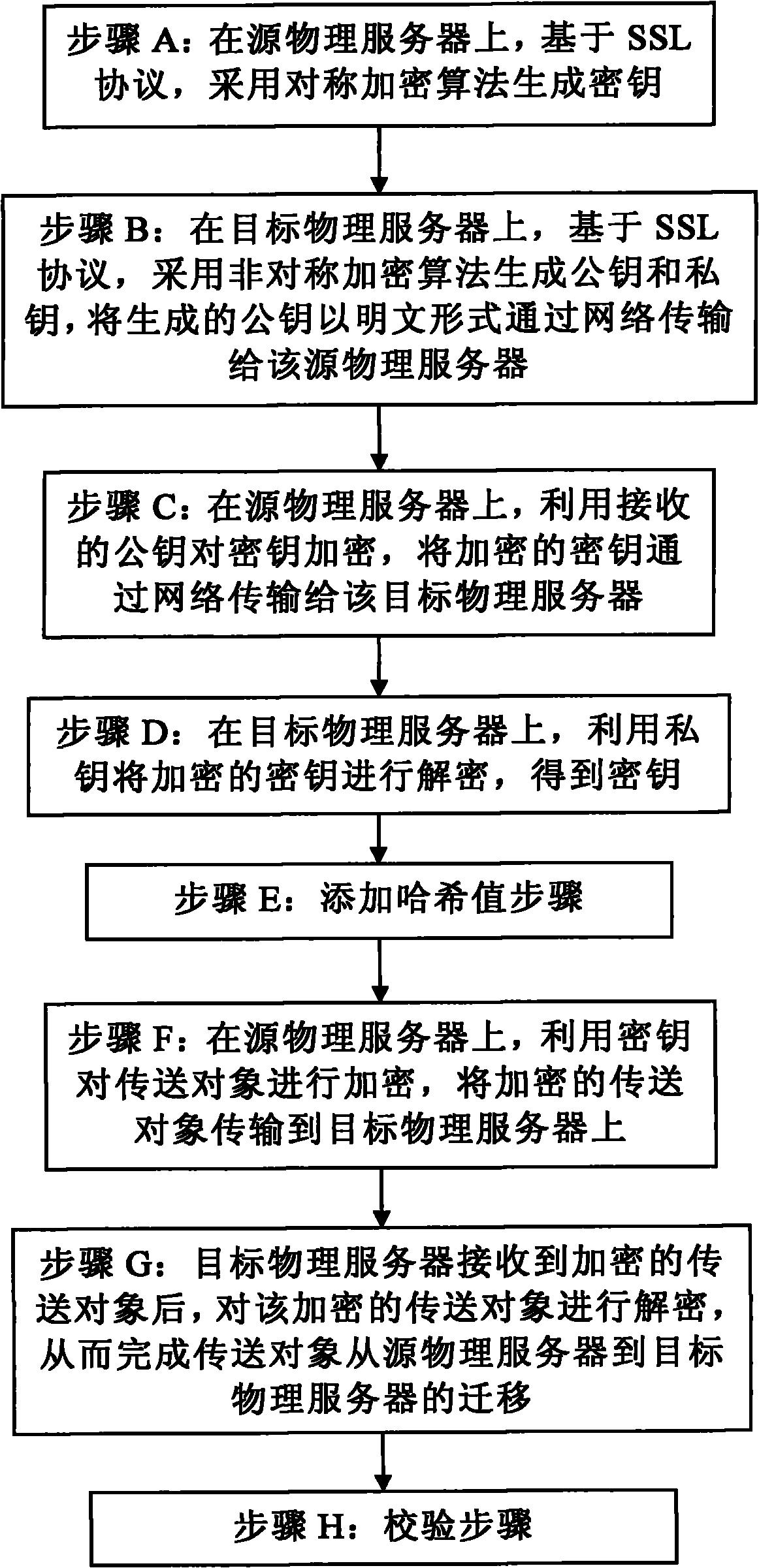
InactiveCN101984631APrevent theftPrevent tamperingEncryption apparatus with shift registers/memoriesPublic key for secure communicationVirtual machineTransmission security
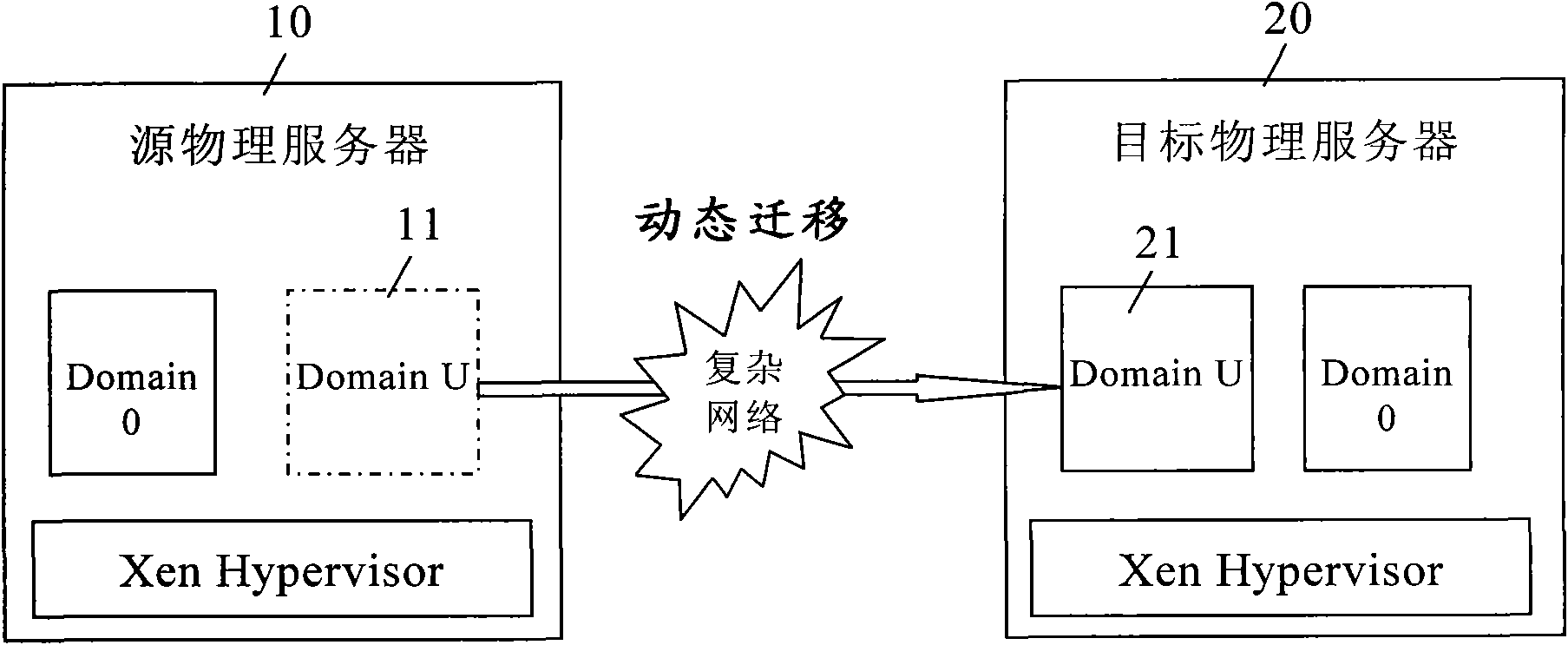
The invention discloses a safety dynamic migration method of an Xen virtual machine, which comprises the following steps: generating a key on a source physical server based on an SSL protocol by a symmetric cryptographic algorithm; generating a public key and a private key on a target physical server based on an SSL protocol by an asymmetric cryptographic algorithm, and transmitting the public key to the source physical server; encrypting the key by the public key on the source physical server, and transmitting the encrypted key to the target physical server; decrypting the encrypted key by the private key on the target physical server to obtain the key; encrypting a transfer object by the key on the source physical server, and transmitting the encrypted transfer object to the target physical server; and after the target physical server receives the encrypted transfer object, decrypting the encrypted transfer object so as to complete migration of the transfer object from the source physical server to the target physical server. The safety dynamic migration method effectively prevents a listener from stealing the transmitted data so as to ensure transmission security of the migrated data.
Owner:BEIJING 21VIANET DATA CENT
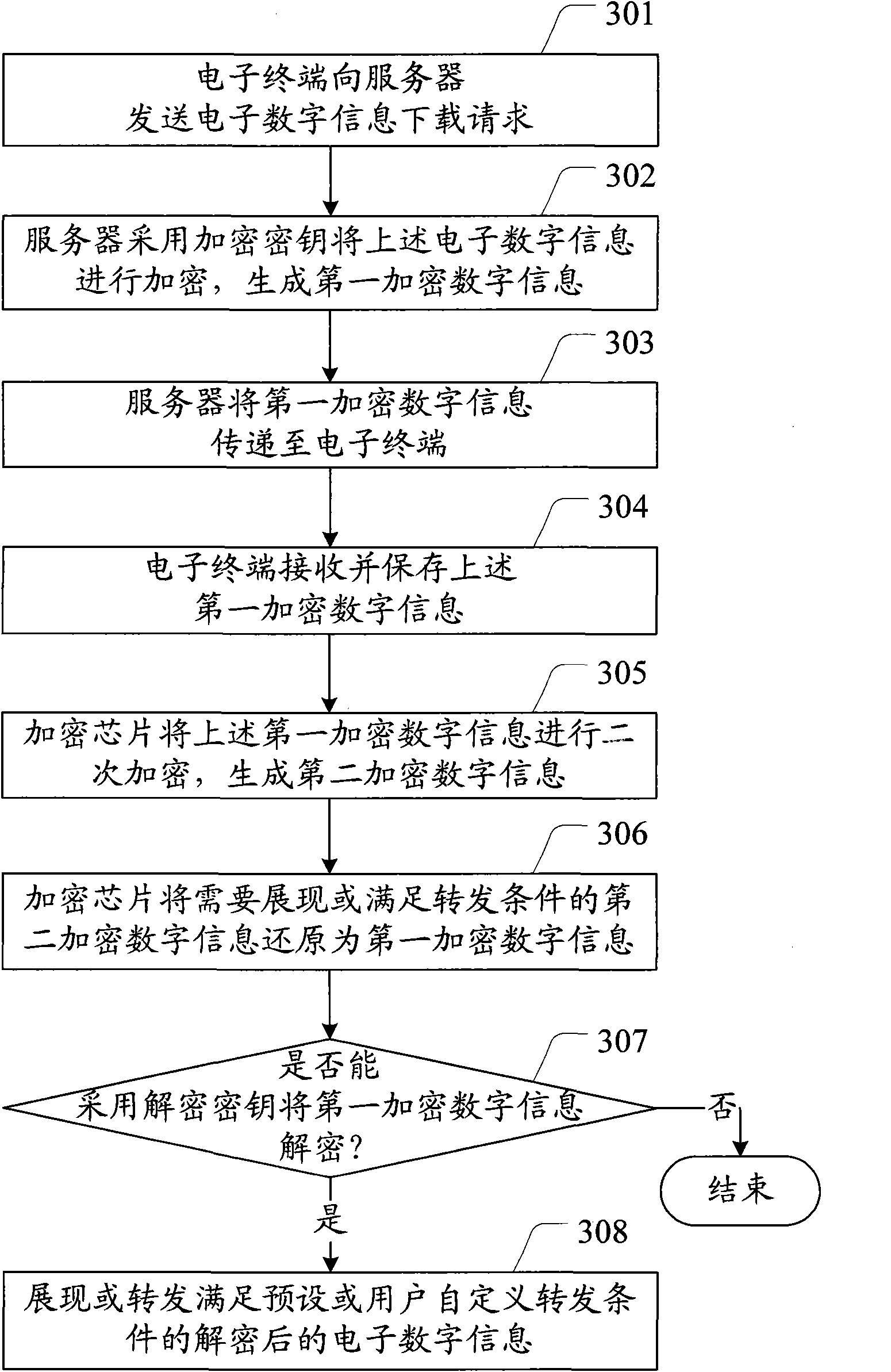
Electronic digital information copyright protection method and system as well as electronic terminal
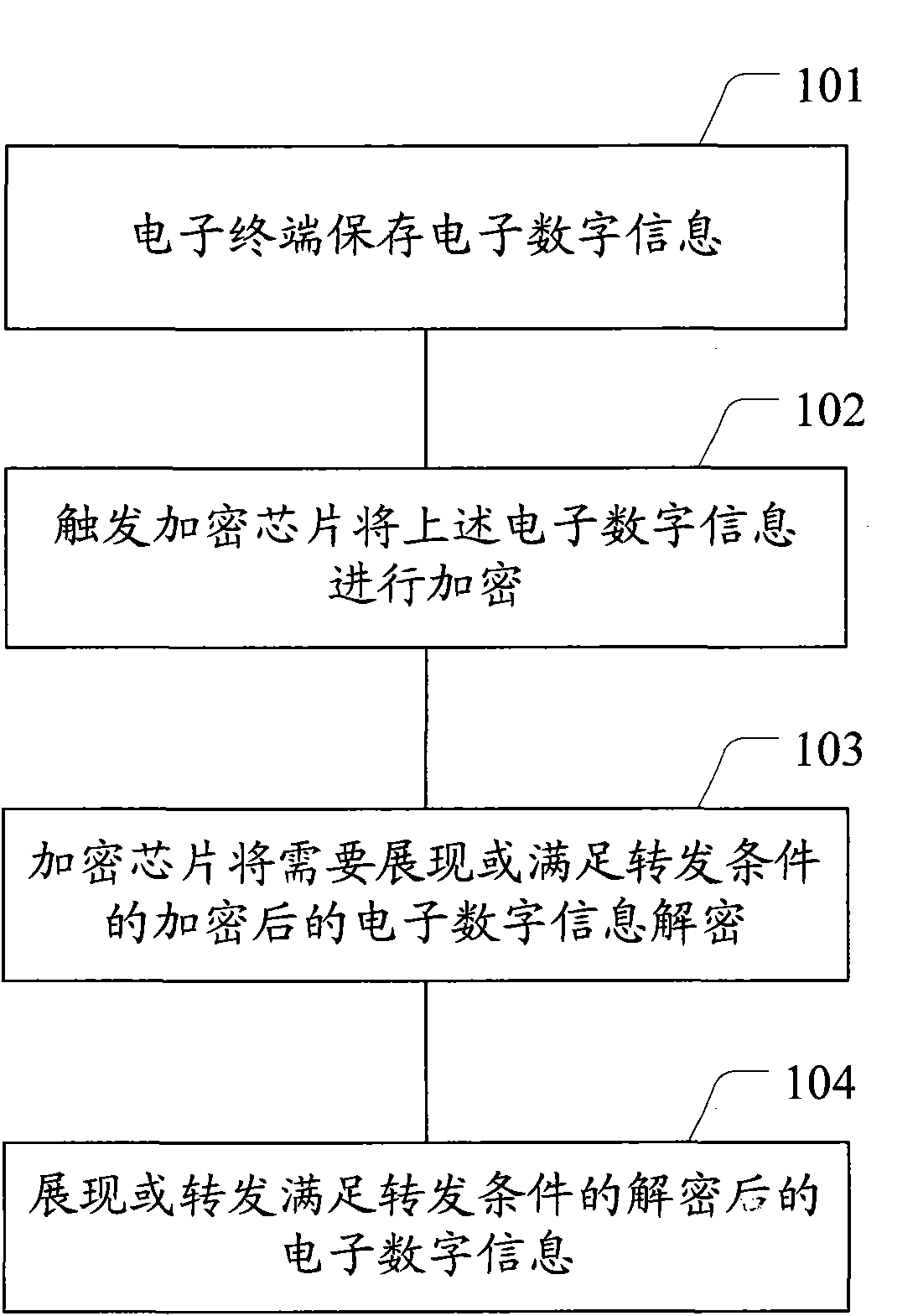
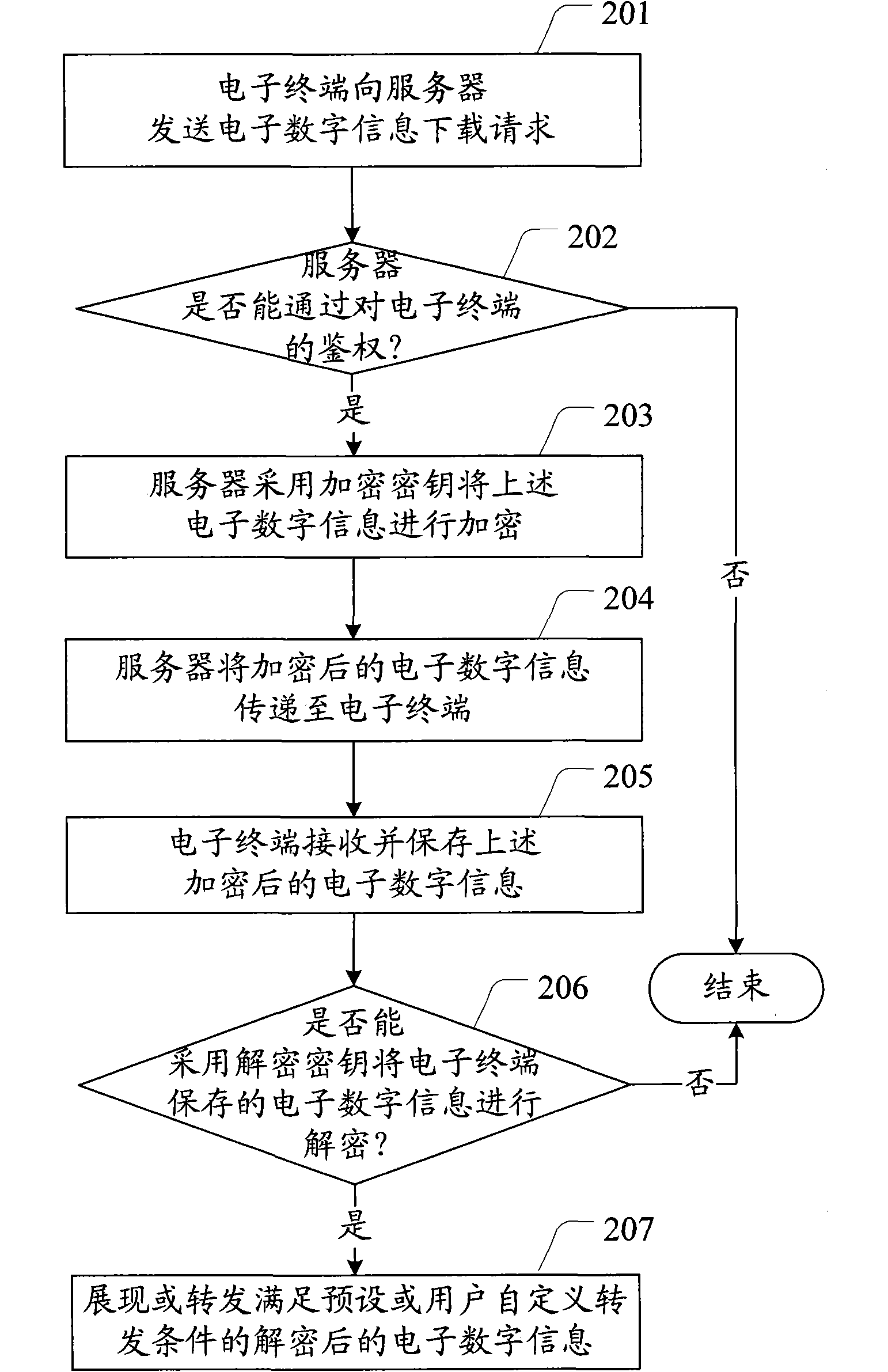
InactiveCN102117395ACopyright protectionEnsure transmission securityDigital data protectionStore-and-forward switching systemsInformation transmissionForward conditioning
The invention provides an electronic digital information copyright protection method and system as well as an electronic terminal. The method comprises: the electronic terminal transmits an electronic digital information downloading request to a server; the server encrypts the electronic digital information by use of an encryption key to obtain encrypted digital information; the server transmits the encrypted digital information to the electronic terminal; the electronic terminal receives and stores the encrypted digital information; and the electronic terminal determines whether to decrypt the encrypted digital information by use of a decryption key, and if yes, displaying the decrypted electronic digital information or forwarding the decrypted electronic digital information meeting a preset forwarding condition or a user-defined forwarding condition. Because the electronic digital information to be distributed or stored is encrypted by the encryption key, the encrypted electronic digital information has to be decrypted before being displayed for forwarded by a user, so that only the authorized user can process the electronic digital information, thereby protecting the copyright of the electronic digital information occupier.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
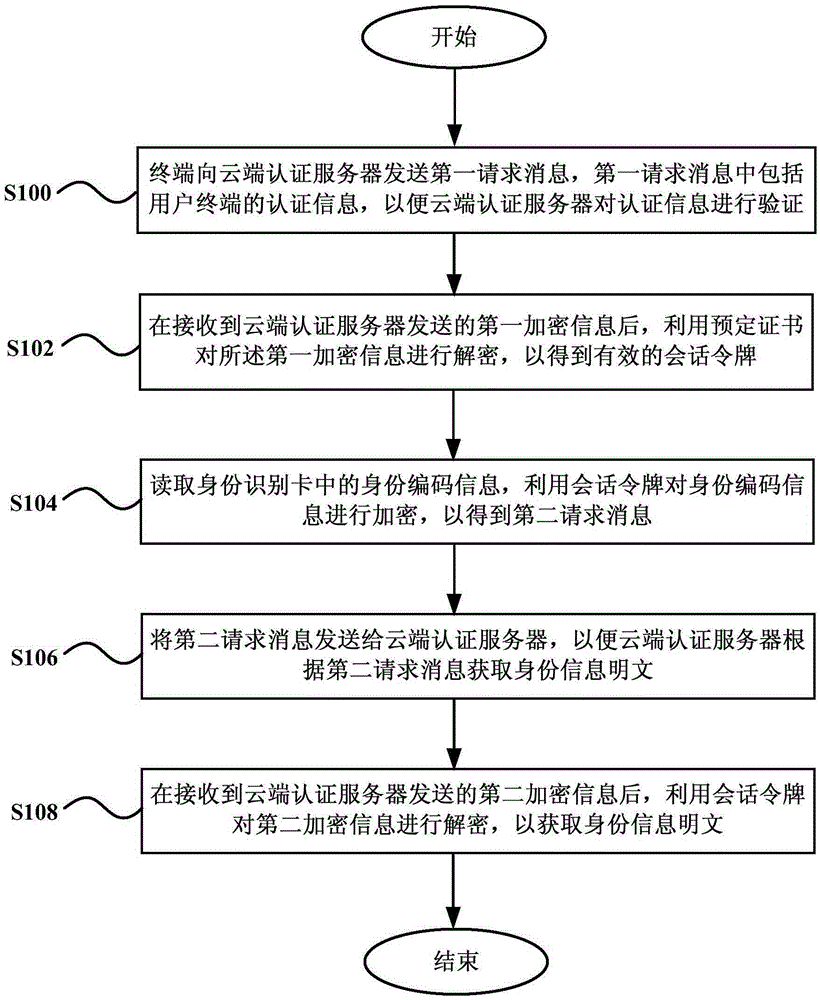
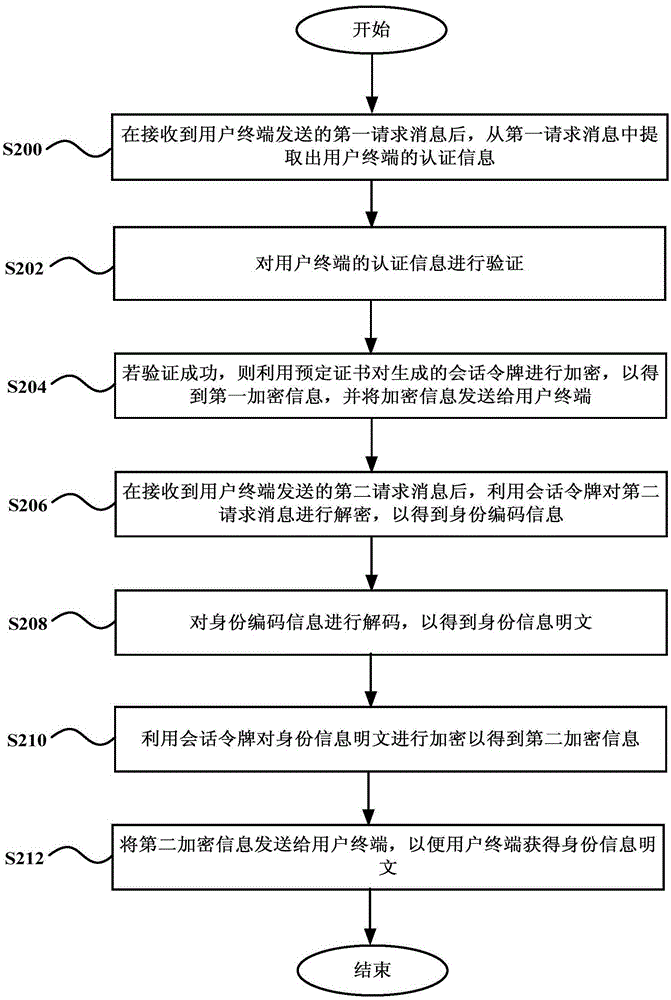
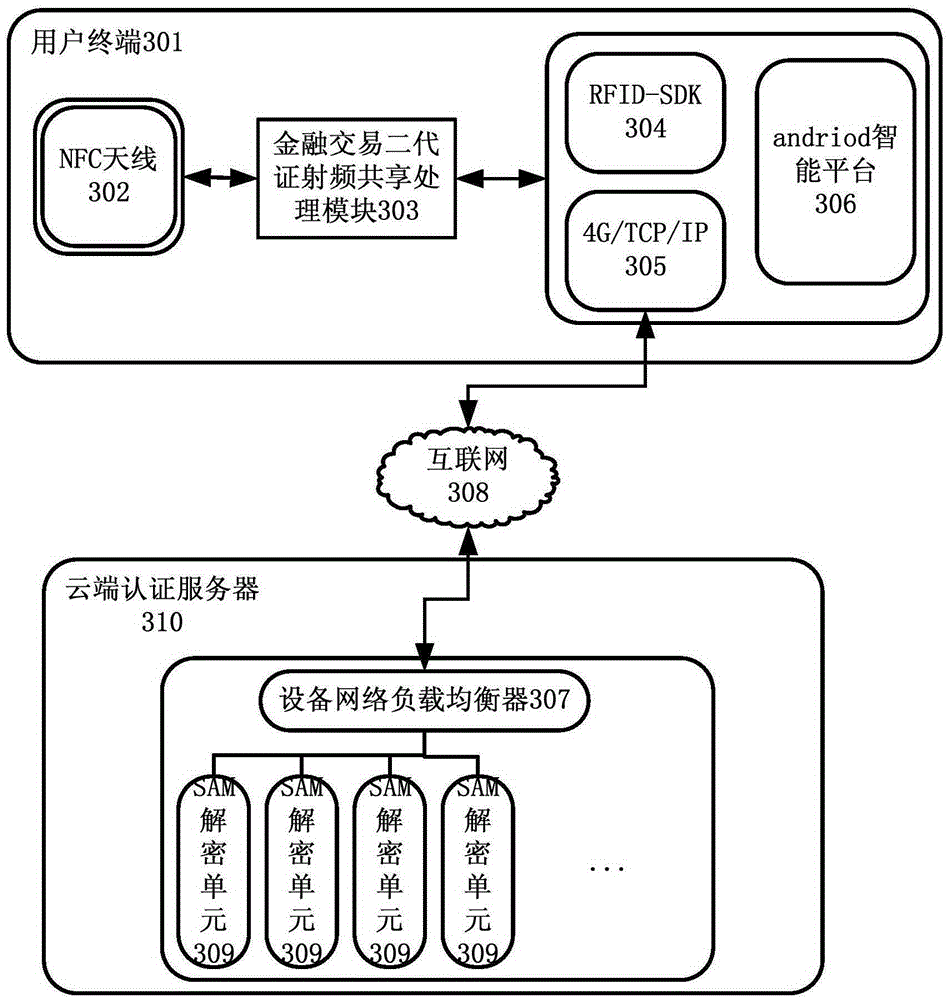
Service processing method, terminal, server and system
ActiveCN106789841AEnsure transmission securityLow costTransmissionComputer terminalAuthentication server
The invention discloses a service processing method, terminal, server and system. The method comprises that after success of handshake authentication based on a certificate encryption key between a cloud-end authentication server and a terminal, a session token of a present cloud-end service request is generated, and sent to the terminal on the basis of the a certificate encryption key; the terminal reads identity card coding information, encrypts the identity card information via the session token and sends the encrypted information to the cloud-end authentication server, so that the cloud-end authentication server obtains the identity card coding information by decryption via the session token, decrypts identity information according to an SAM decryption module, encrypts the identity information via the session token, and sends the encrypted information to the terminal, and the terminal decrypts the information via the session token and displays the decrypted information to a user; and service processing is carried out on the basis of the session token. The method, terminal, server and system are compatible with different using scenes, the hardware cost of the terminal is reduced, and the transmission safety of the identity information is ensured.
Owner:CHINA TELECOM CORP LTD
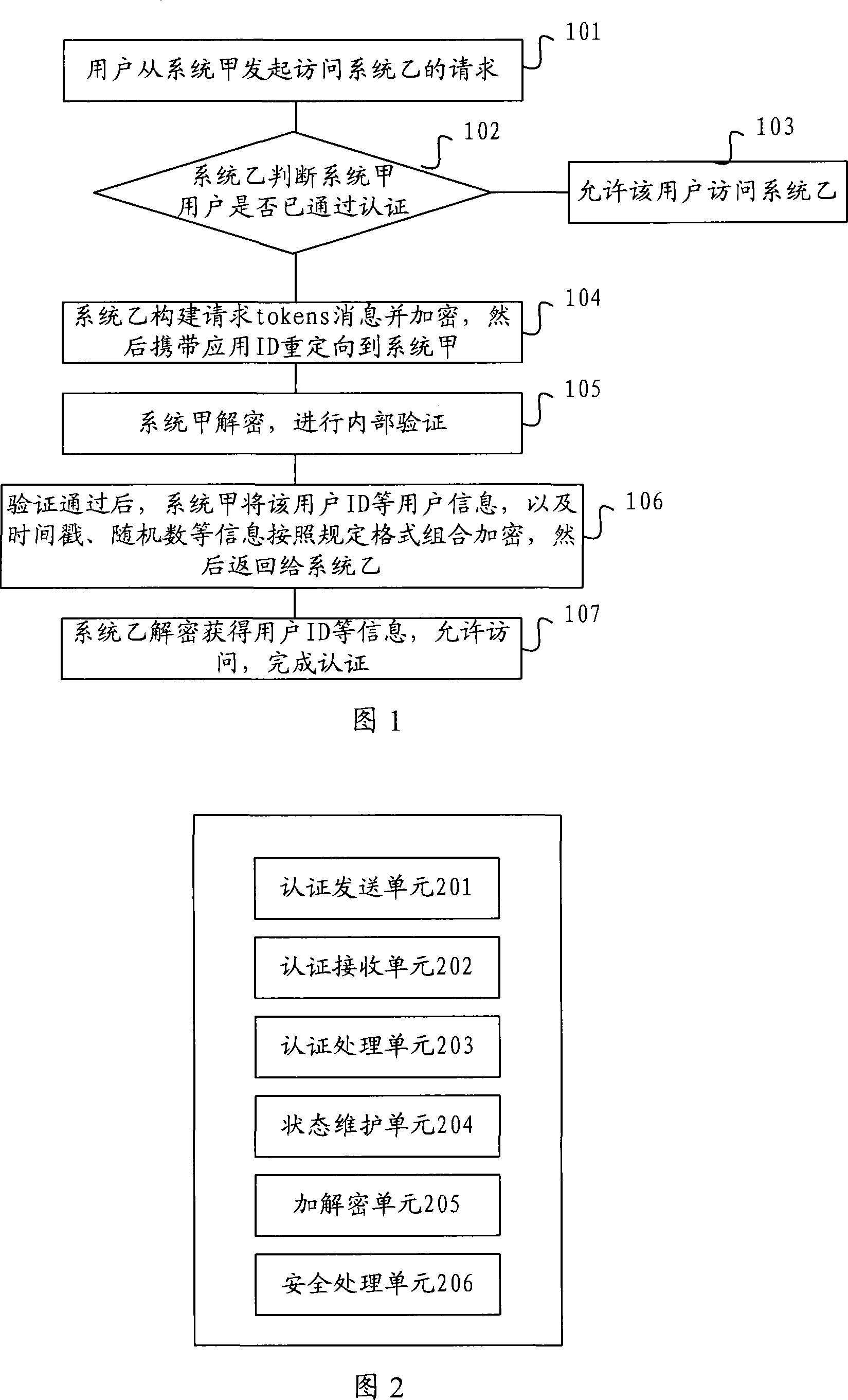
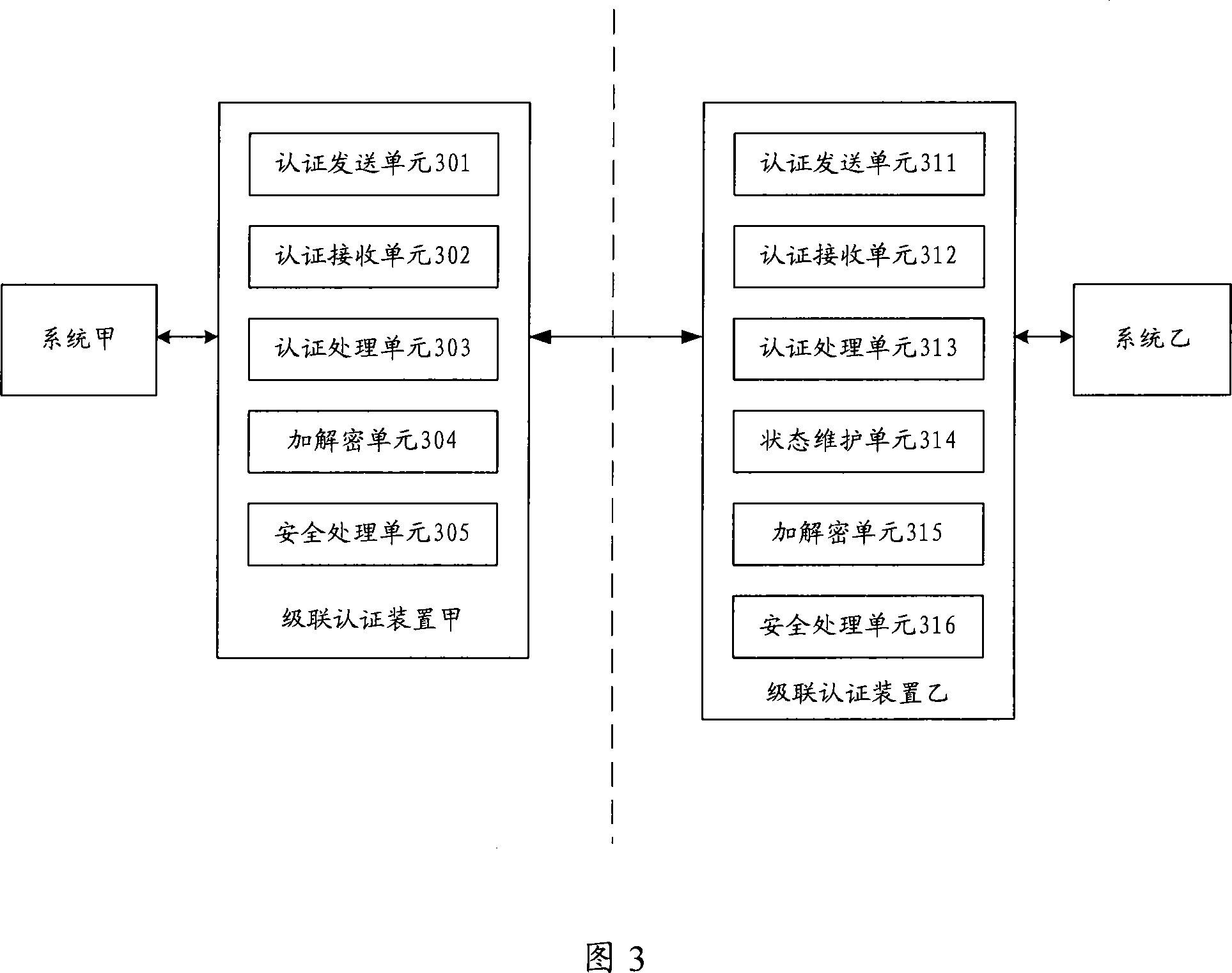
Cascade connection authentication method and device between application systems
InactiveCN101222335AImplement identity authenticationResolve incompatibilitiesKey distribution for secure communicationUser identity/authority verificationExtensibilityEncryption decryption
The invention discloses an application system cascade certification method and a device thereof; the invention can realizes user identity certification of application systems between two or more than two different or identical platforms; the certification method includes that: when a user of the system A initiates a request of visiting a system B from a system A, the system B firstly judges whether the user passes the certification, if the user of the system A does not pass the certification, the system B is directly redirected to the system A which completes the certification; if the user of the system A passes the certification, the information of the successful certification is fed back to the system B, the system B believes that the user is a valid user and allows the user to visit the system B; on the contrary, if a user of the system B visits the system A, the same process is adopted. In the mutual certification process, the data interaction can use a plurality of encryption algorithms, the user can choose the encryption-decryption algorithms by himself, thereby improving the flexibility and the expandability of the system.
Owner:STATE GRID INFORMATION&TELECOMM
Secure transmission method based on relay strategy selection and resource allocation in relay OFDM (Orthogonal Frequency Division Multiplexing) network
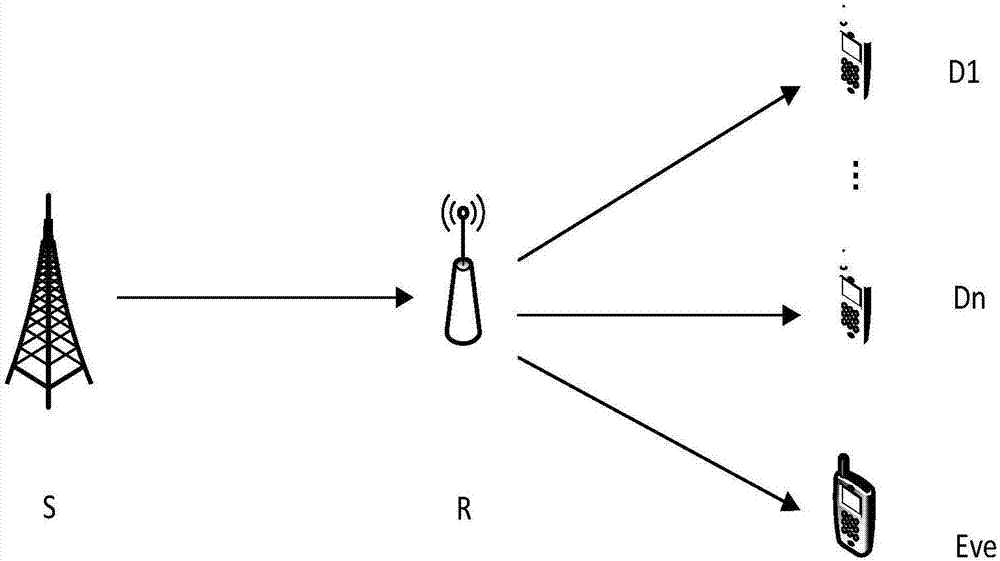
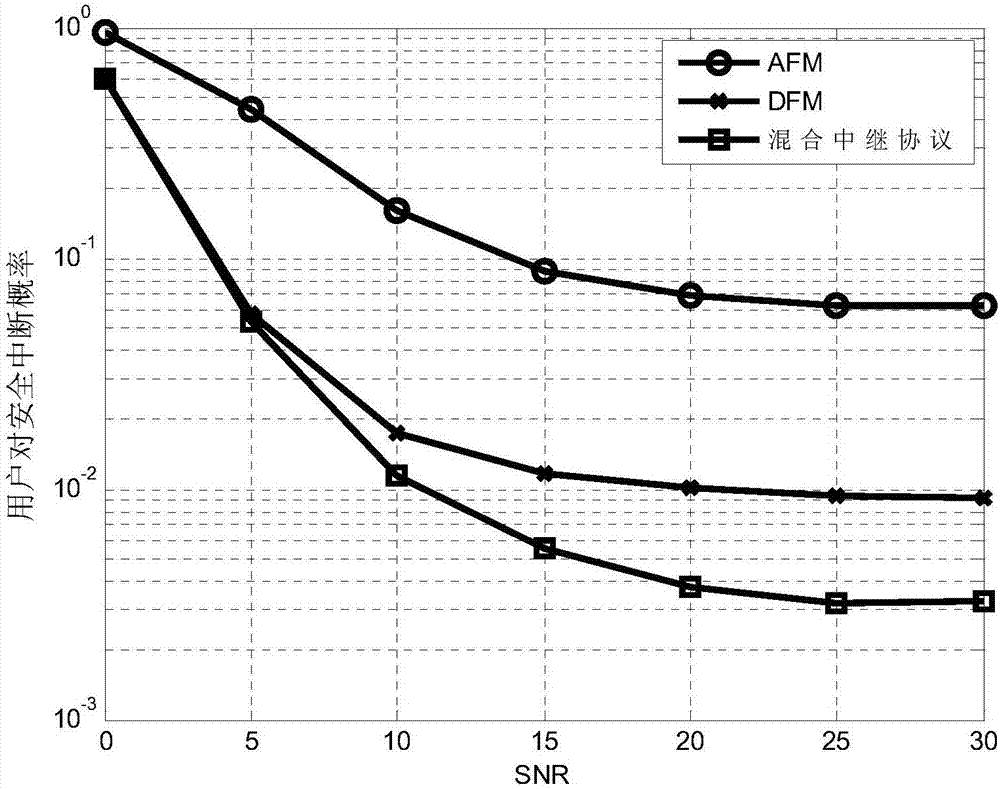
InactiveCN106900030AReduce the probability of security outagesEnsure transmission securityCommunication jammingHigh level techniquesSignal-to-quantization-noise ratioDecode and forward
The invention discloses a secure transmission method based on relay strategy selection and resource allocation in a relay OFDM (Orthogonal Frequency Division Multiplexing) network. A communication system model employed by the method comprises a sending node S, N destination receiving nodes (D <1>...D <N >), an eavesdropping node Eve and K relay nodes. The method comprises the steps of for data transmission of each time, in a second time slot, after relay strategy selection and resource allocation, sending data to the relay nodes by the sending node S; and in a second time slot, selecting one of the K relay nodes as a forwarding node to forward the data received in the first time slot to the destination node D, and moreover, eavesdropping information sent to N users by the eavesdropping node Eve. Compared with traditional modes of merely employing AF (Amplify-and-Forward) or DF (Decode-and-Forward), the method has the advantages that a lower private interruption probability is obtained in a relay strategy selection mode, and the performance difference between the method and the two traditional modes is more remarkable under a high signal to noise ratio.
Owner:XI AN JIAOTONG UNIV
Method, apparatus and storage medium for providing intelligent contract in block chain network
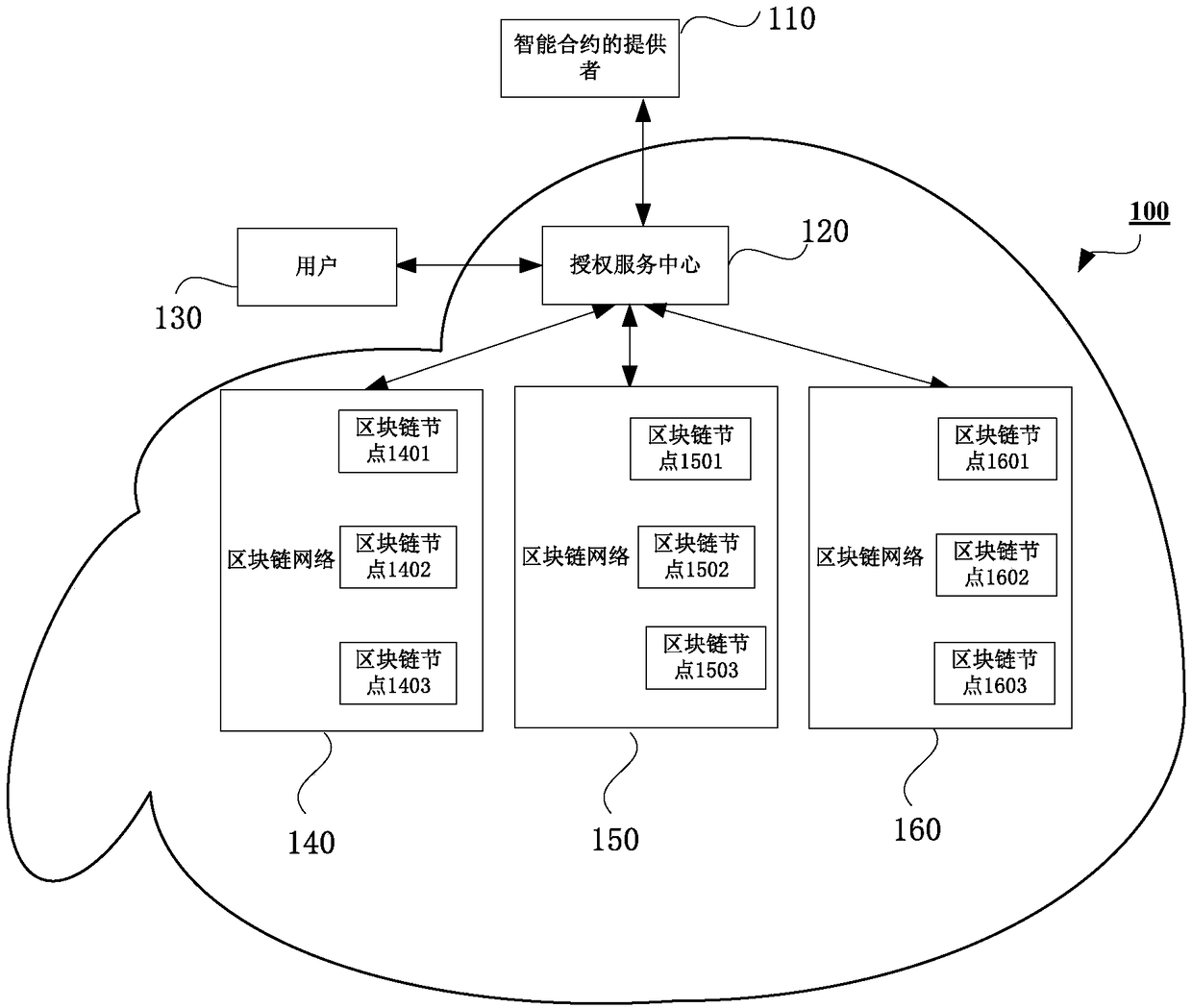
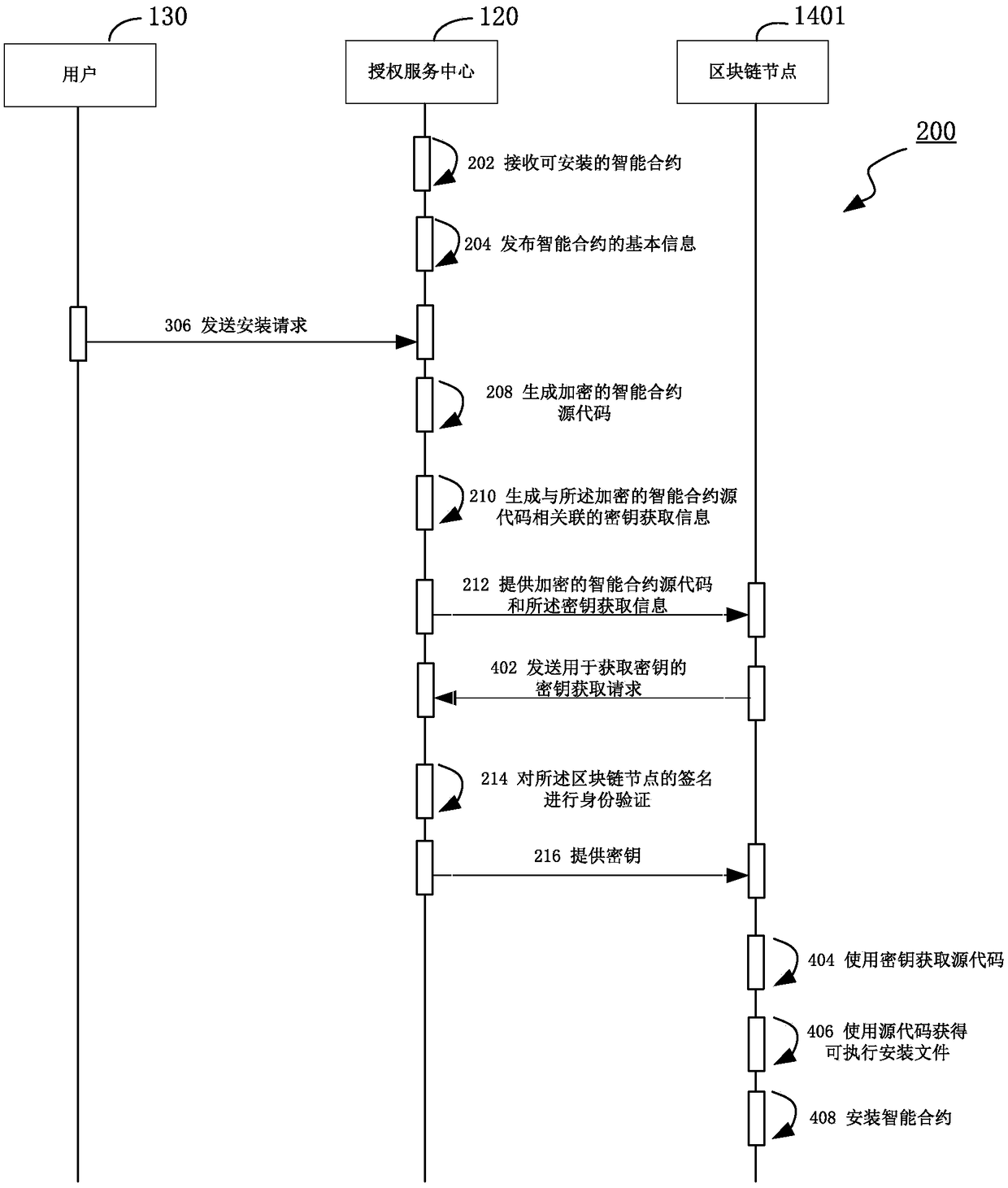
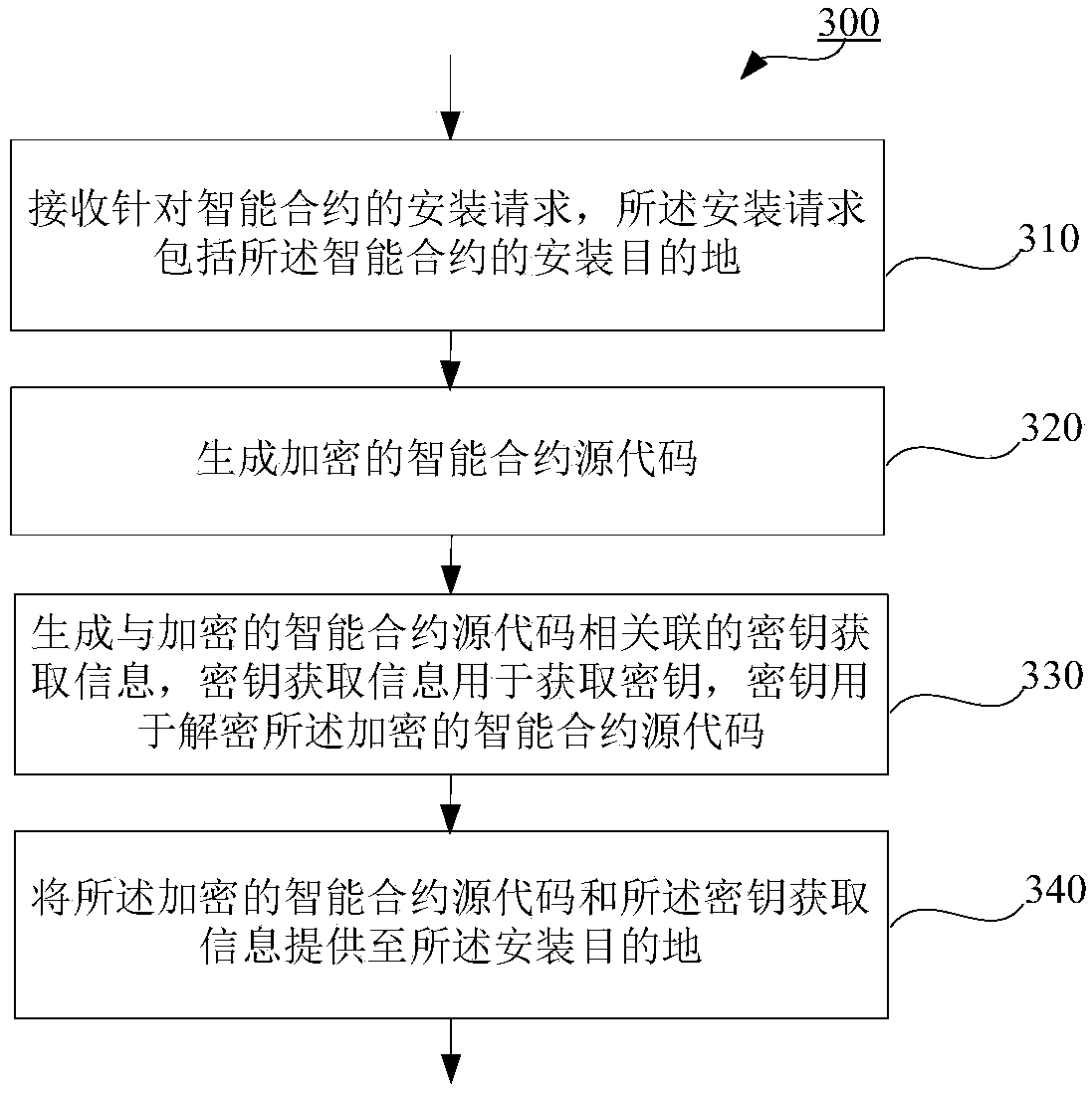
InactiveCN109255210AEnsure transmission securityPrivacy protectionDigital data protectionProgram/content distribution protectionChain networkSmart contract
Embodiments of the present invention provide a method for providing an intelligent contract in a block chain network, comprising receiving an installation request for the intelligent contract, the installation request including an installation destination of the intelligent contract; generating encrypted smart contract source code; generating key acquisition information associated with the encrypted smart contract source code, the key acquisition information being used to acquire a key, and the key being used to decrypt the encrypted smart contract source code; and providing the encrypted smart contract source code and the key acquisition information to the installation destination. The method for providing the intelligent contract in the block chain network according to the embodiment ofthe present invention can effectively guarantee the transmission security of the source code of the intelligent contract on the block chain and ensure that the source code is not obtained by an unauthorized party, thereby protecting the privacy of the source code of the intelligent contract on the block chain.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
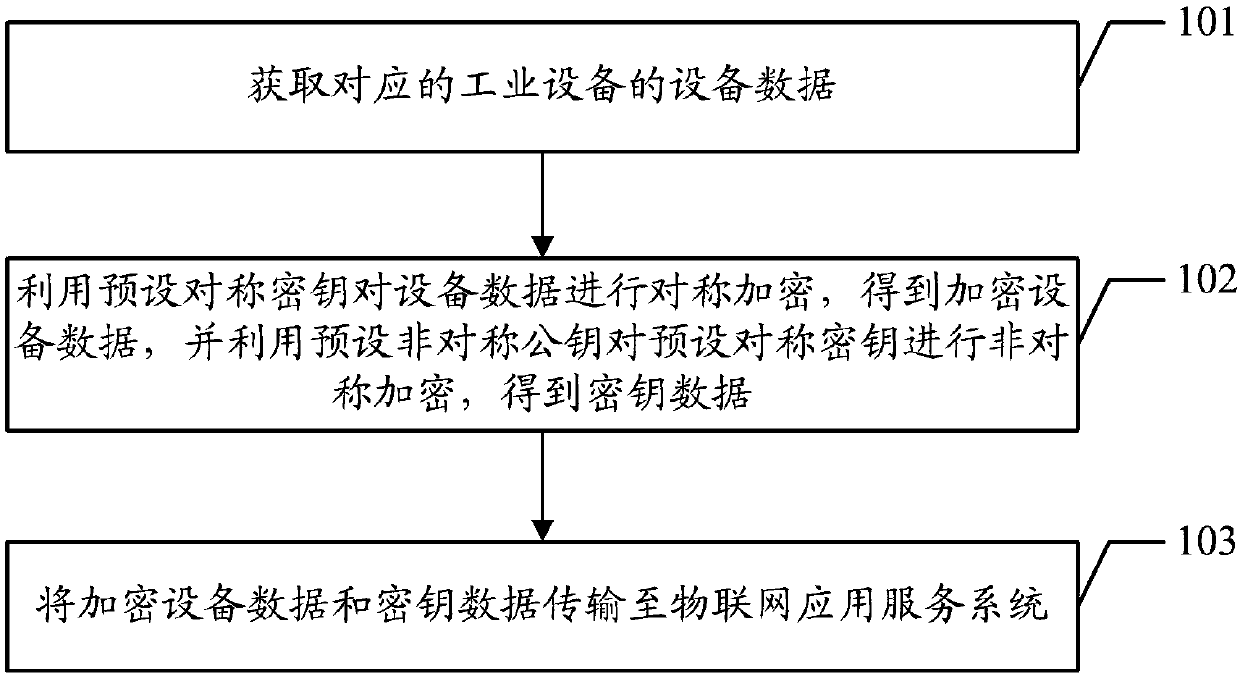
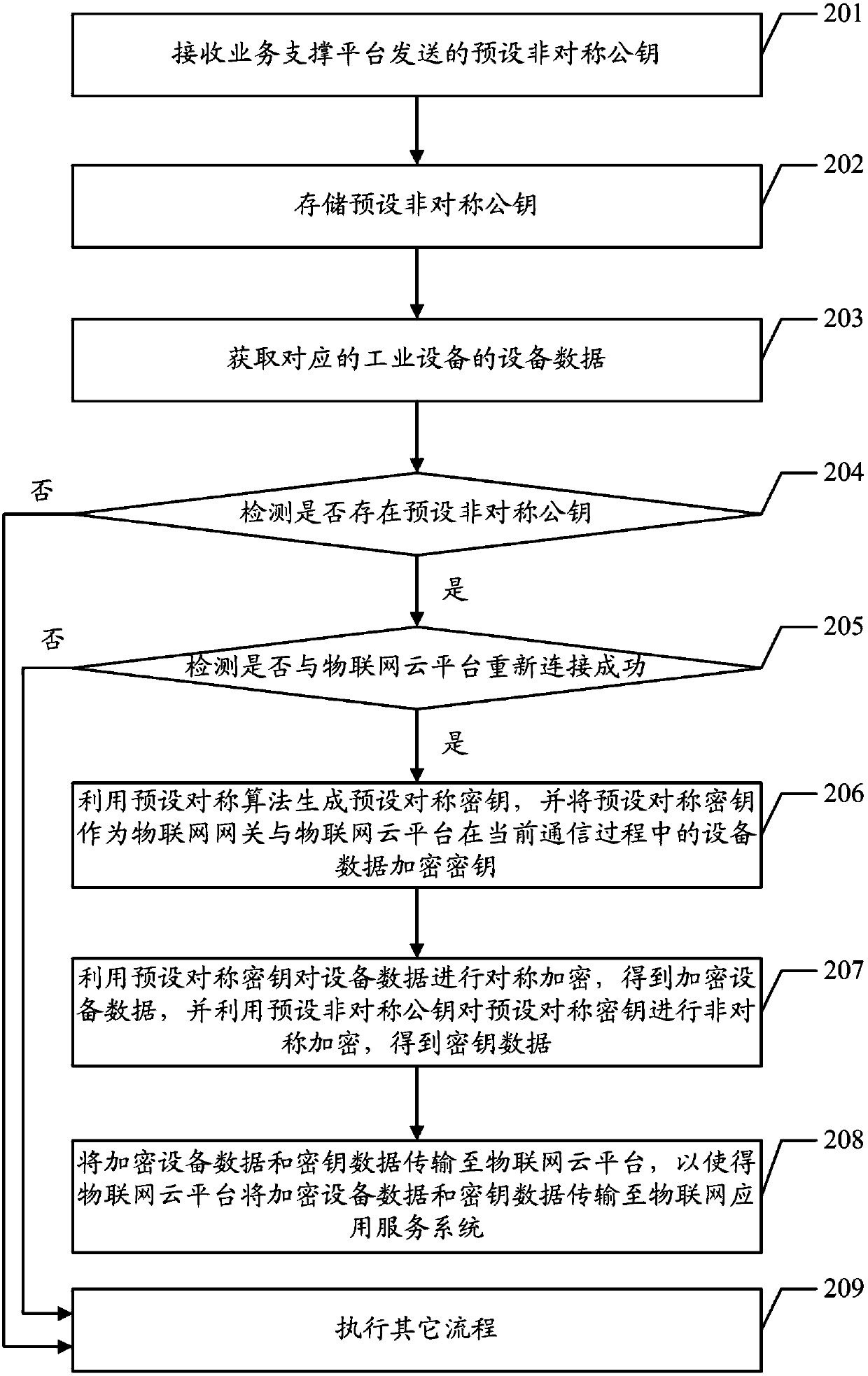
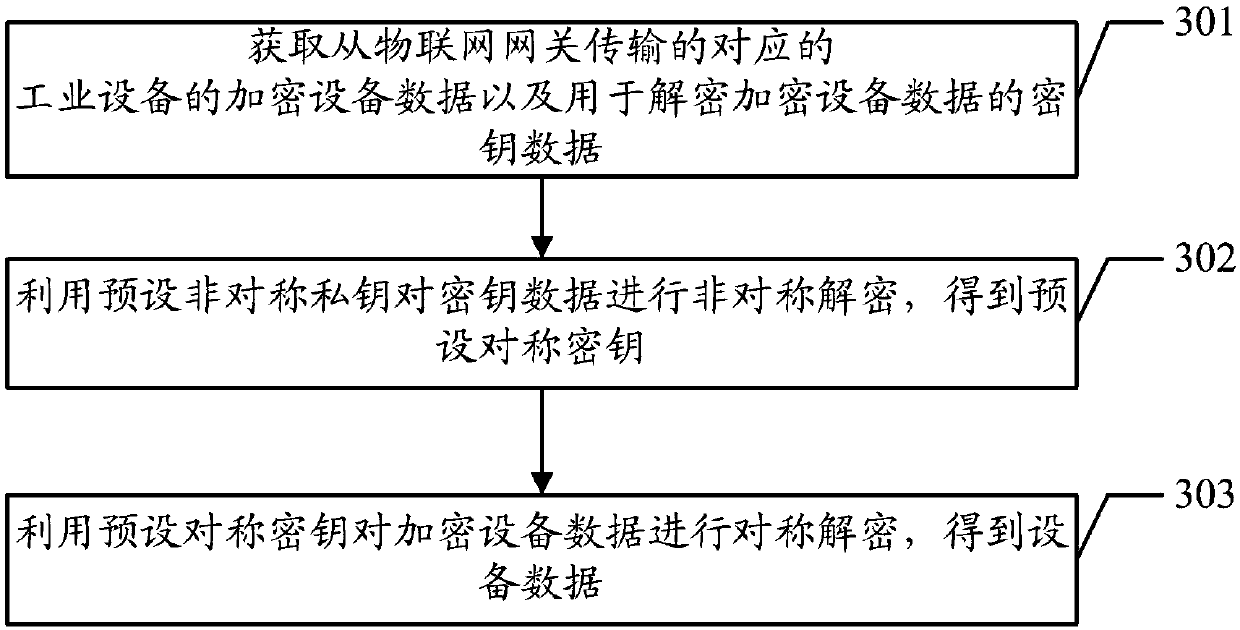
Data encryption method and device as well as data decryption method and device
InactiveCN107911370AImplement encryptionEnsure transmission securityKey distribution for secure communicationIndustrial equipmentData decryption
The embodiment of the invention discloses a data encryption method and device, a data decryption method and device, a computer device and a readable storage medium, aiming at guaranteeing the transmission security of equipment data. The data encryption method includes the following steps: acquiring equipment data of corresponding industrial equipment; performing symmetric encryption on the equipment data by using a preset symmetric key to obtain encrypted equipment data, and performing asymmetric encryption on a preset symmetric key by using a preset asymmetric public key to obtain key data; and transmitting the encrypted equipment data and the key data to an Internet of things application service system.
Owner:MIXLINKER NETWORKS INC
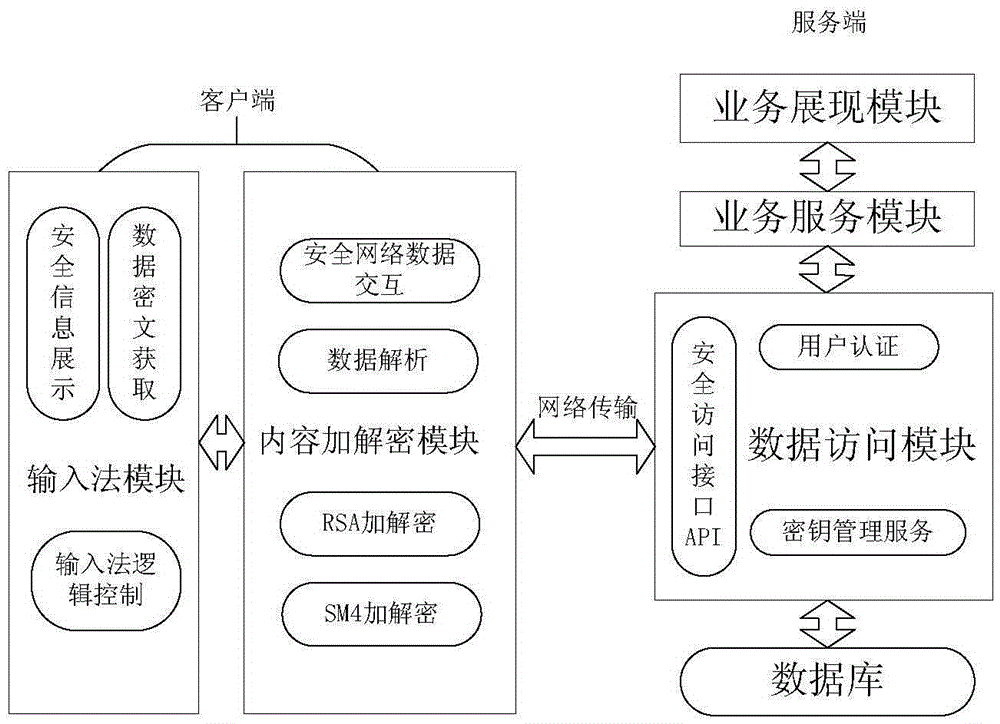
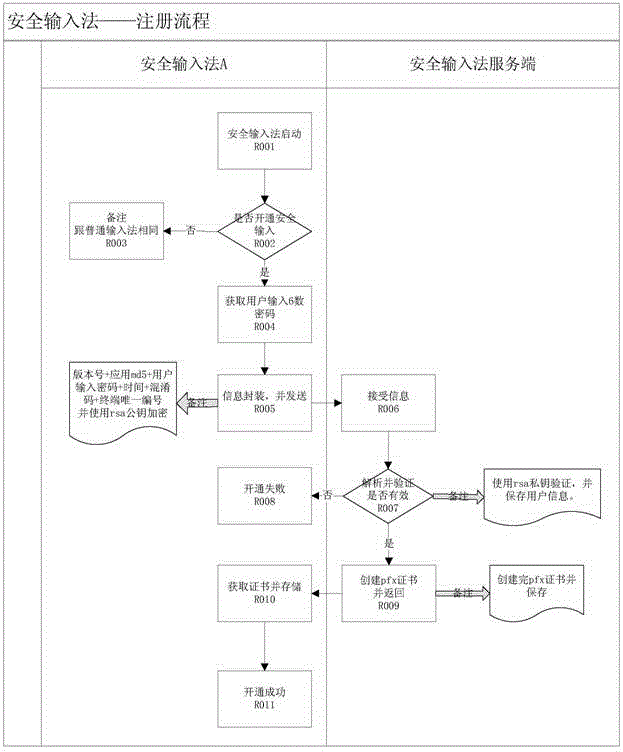
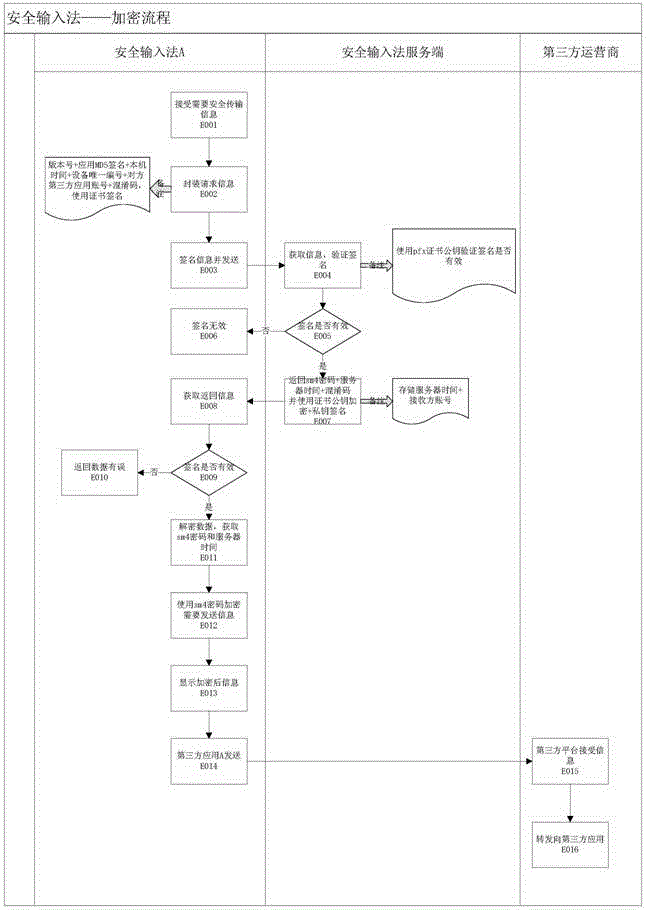
Independent encryption based network information safe input system and method
ActiveCN105516157AEasy encryption and decryptionEnsure transmission securityUser identity/authority verificationThird partyUser needs
The invention relates to an independent encryption based network information safe input system. The system comprises a safe input method client end and a safe input method server end. The safe input method client end comprises an input method module and a content encryption and decryption module. The safe input method server end comprises a business show module, a business service module and a data access module, and a safe input method. The input method is not bound with a third-party application, so that the input method and the third-party application are separated but cooperate with each other. Information that the user needs to encrypt can be encrypted flexibly, namely, a certain passage of dialogue or key content can be encrypted; the user can encrypt and decrypt the information conveniently without through complicated operation; and information and a secret key are managed and transmitted through independent channels, thereby guaranteeing safe transmission of the information.
Owner:重庆交慧发掘科技有限公司
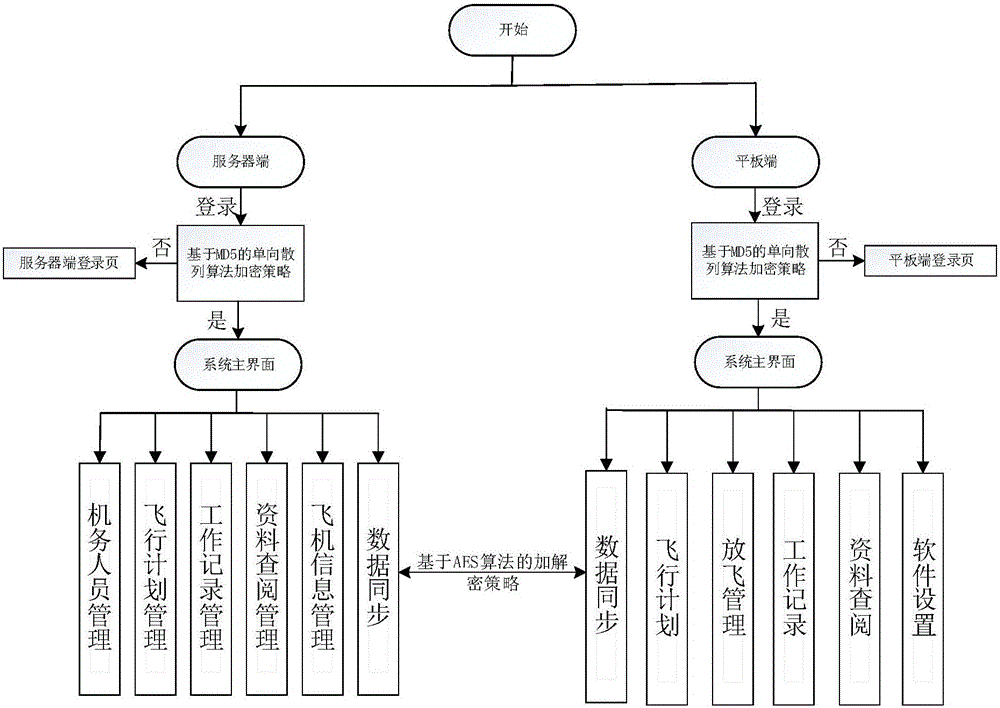
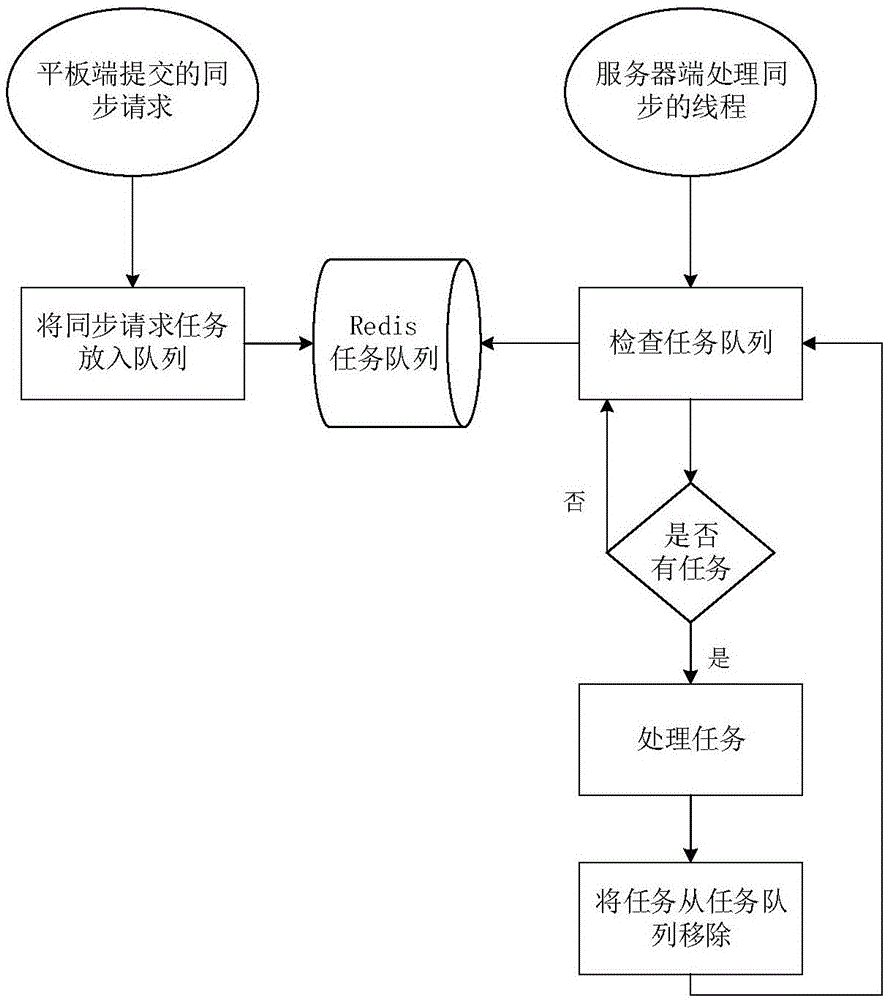
Maintenance flight service management system
InactiveCN107180108AEnsure transmission securityRelational databasesDigital data protectionData synchronizationData management
The invention discloses a maintenance flight service management system. The system comprises a maintenance flight service terminal and a maintenance flight service server. The maintenance flight service terminal has the functions of flight planning, flying management, work recording, data lookup, software setting and data synchronization. The server has the functions of maintenance personnel management, flight plan management, work record management, data lookup management, airplane information management and data synchronization. By the adoption of the technical scheme, a manual entry mode at present is avoided, informationization processing of troop maintenance flight service work is realized, and maintenance flight work is completed smoothly.
Owner:BEIJING UNIV OF TECH
Quantum secret key synchronization method for distribution terminal
PendingCN108667607AEnsure safetyFix missing issueKey distribution for secure communicationSynchronising transmission/receiving encryption devicesThird partyQuantum
The invention discloses a quantum secret key synchronization method for a distribution terminal. Sharing quantum secret keys are separately stored in quantum secret key downloading interfaces A and Bthrough distributing a unique ID for each quantum secret key, the quantum secret keys are transmitted via a method that uses a third-party safe storage medium as a medium, the quantum secret keys needed by the distribution terminal are acquired from the quantum secret key downloading interfaces via the third-party safe storage medium, and then the third-party safe storage medium is connected withthe physical interfaces of the distribution terminal one by one for transmitting the quantum secret keys to the distribution terminal. The quantum secret key synchronization method for the distribution terminal provided by the invention is the method that distributes the secret key pools formed at each distribution terminal based on the quantum secret keys in an off-line manner and negotiates ID based on the quantum secret keys; aiming at the service security protection level requirement, the two quantum secret key synchronization methods are combined, and thus the channel utilization rate isimproved, and the transmission security of the quantum secret key ID during a negotiation synchronization process is ensured.
Owner:STATE GRID INFORMATION & TELECOMM GRP +4
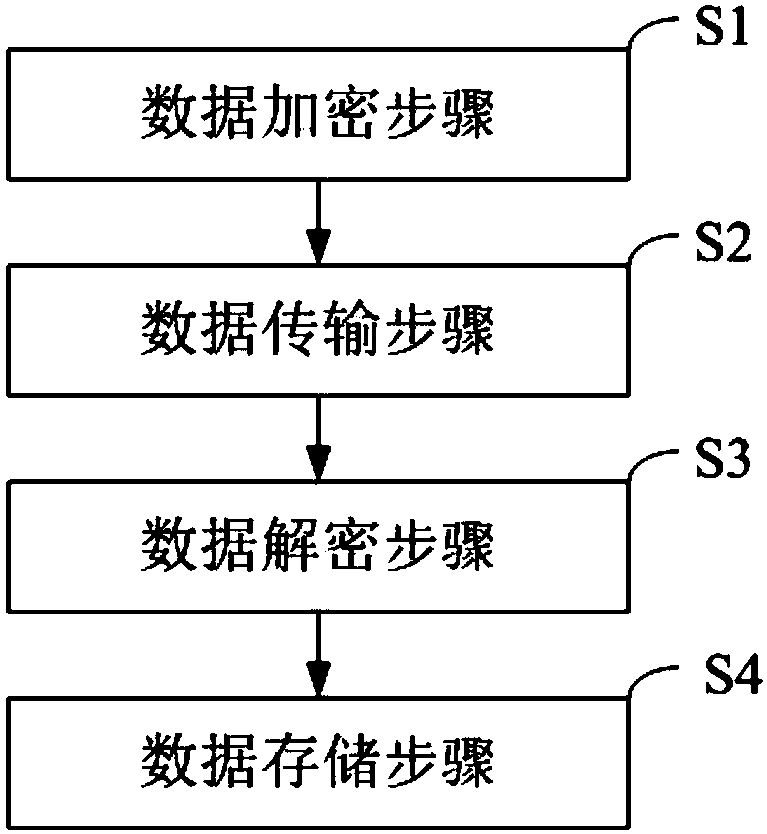
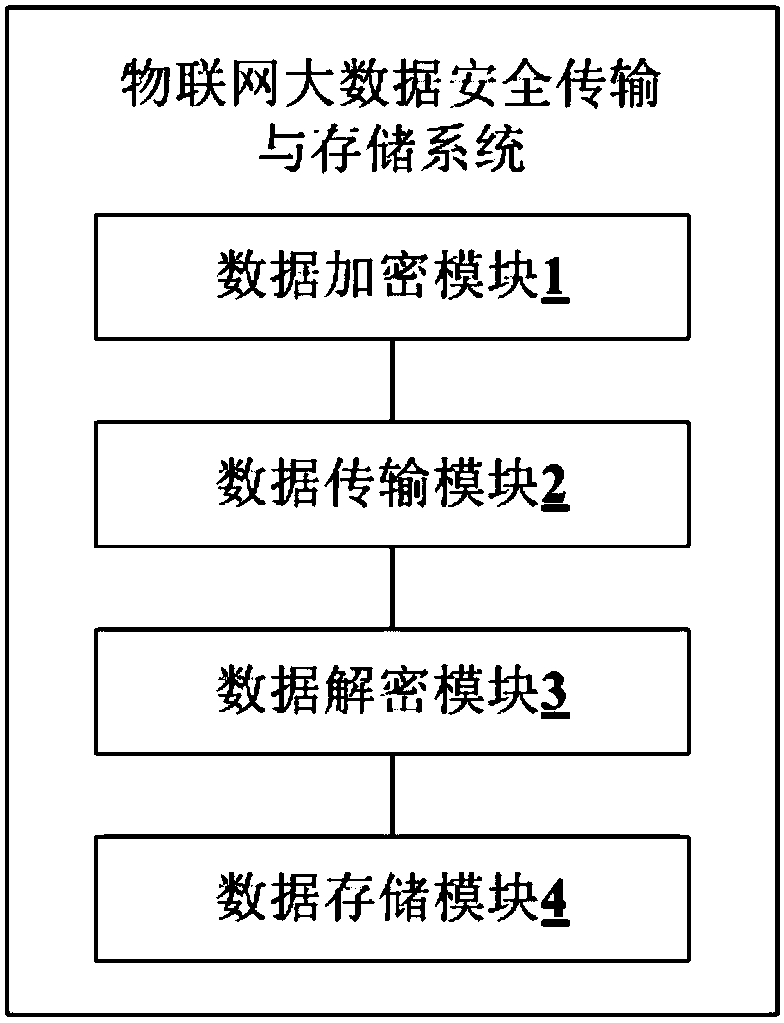
Internet-of-Things big data security transmission and storage method and system
InactiveCN107612898AEfficient storageGuaranteed timelinessKey distribution for secure communicationOriginal dataSecure transmission
The invention belongs to the technical field of the Internet of Things, and provides an Internet-of-Things big data security transmission and storage method and system. The method comprises the stepsthat target data is encrypted by adopting a key of a symmetric algorithm to generate encrypted data, and the key of the symmetric algorithm is encrypted by adopting a public key pair of an asymmetricalgorithm to generate an encrypted key; the encrypted data and the encrypted key are transmitted; the encrypted key is decrypted by adopting a private key pair of the asymmetric algorithm to obtain the key of the symmetric algorithm, and the encrypted data is decrypted according to the key obtained through decryption of the symmetric algorithm to obtain the original data; and the trigger mode of astorage is detected, and the original data obtained after decryption is stored in the storage. According to the Internet-of-Things big data security transmission and storage method and system, data security transmission and storage can be guaranteed, data tampering is prevented, and effective data storage is guaranteed.
Owner:SICHUAN MIANYANG TAIKOO SOFTWARE
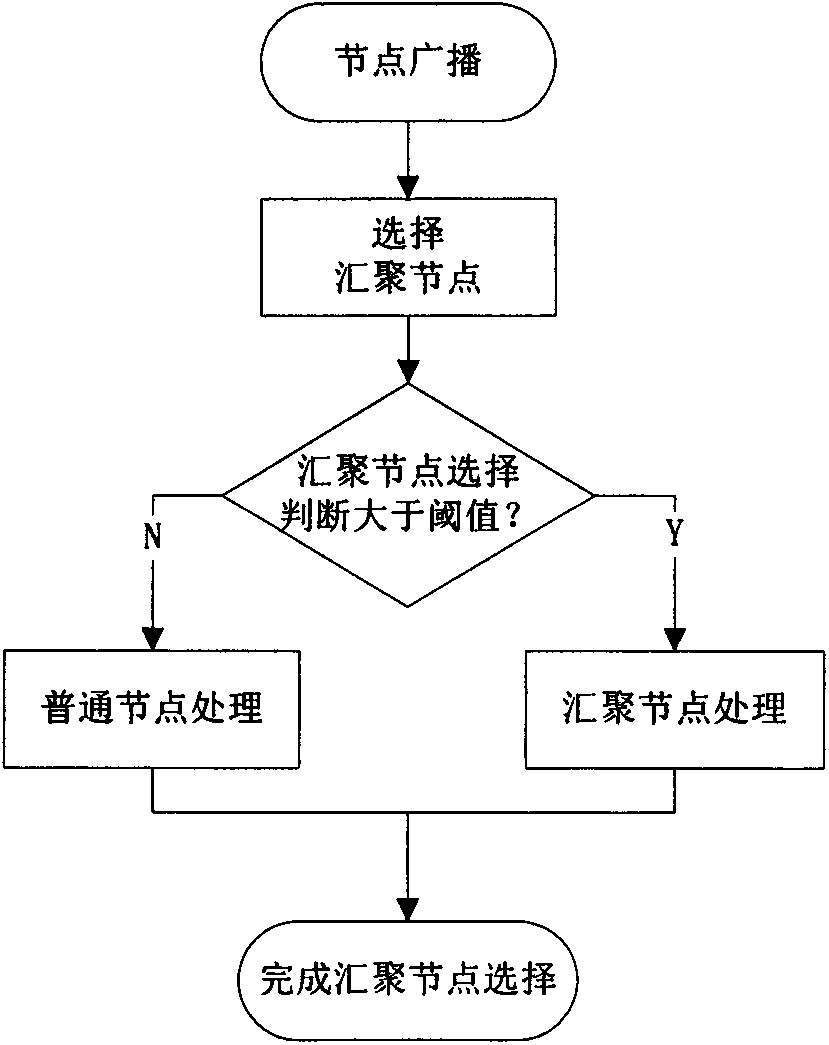
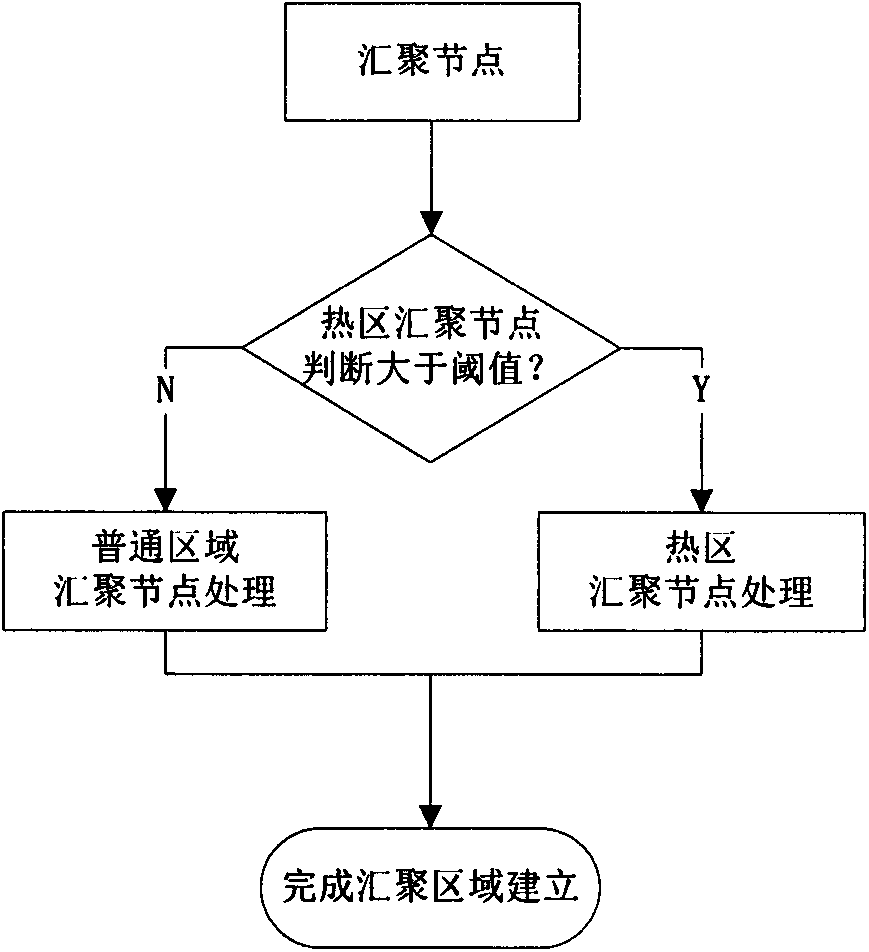
Security protocol based on received signal intensity in wireless sensor network
The present invention relates to a security protocol based on received signal intensity in a wireless sensor network, specifically to secure routing and key management. According to the number of adjacent nodes, the intensity of received signals and the energy value thereof, a convergent node is selected by a convergent node selection equation. According to the number of the adjacent nodes and the throughput of the convergent node, a hot zone is determined by a hot zone selection equation. By comparing the feature similarity between collected data and pre-stored abnormal data, abnormal data is detected. An inter-node session key is generated dynamically, and according to whether a hot zone is determined, different keys are selected to generate a function. The key and data are encrypted in a manner of combining a public key cipher mechanism and a symmetric cipher mechanism. The security protocol improves flexibility of a key, enhances the rationality for selecting a convergent node and well ensures safe transmission of inter-node data.
Owner:XIANGTAN UNIV
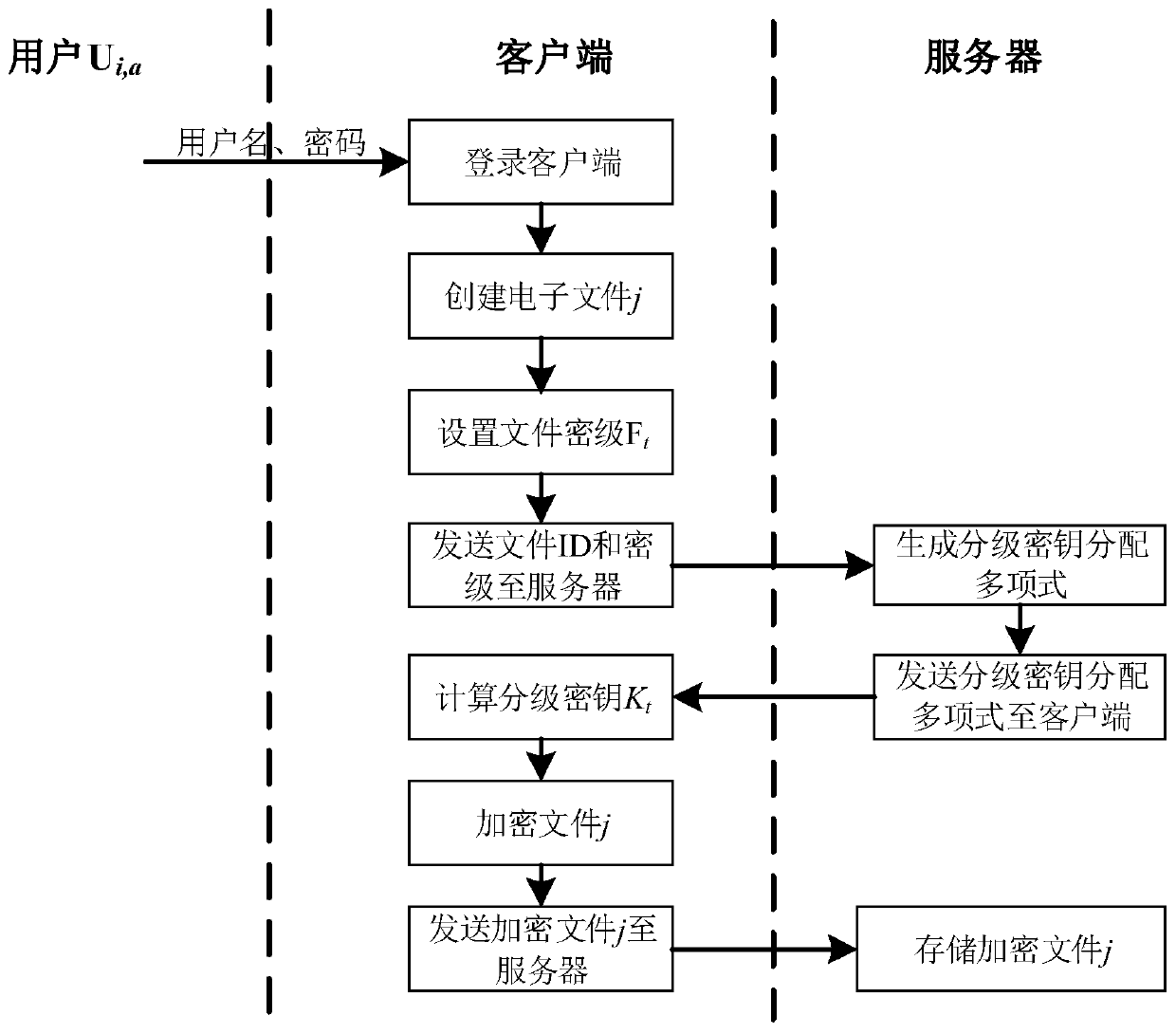
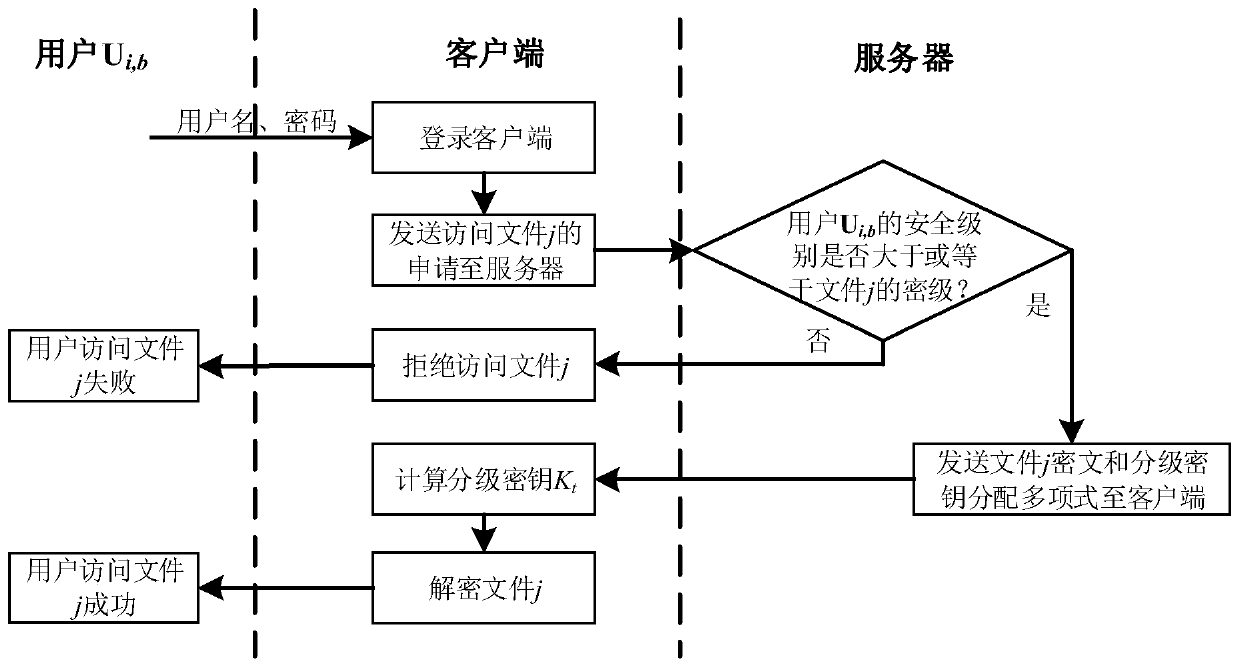
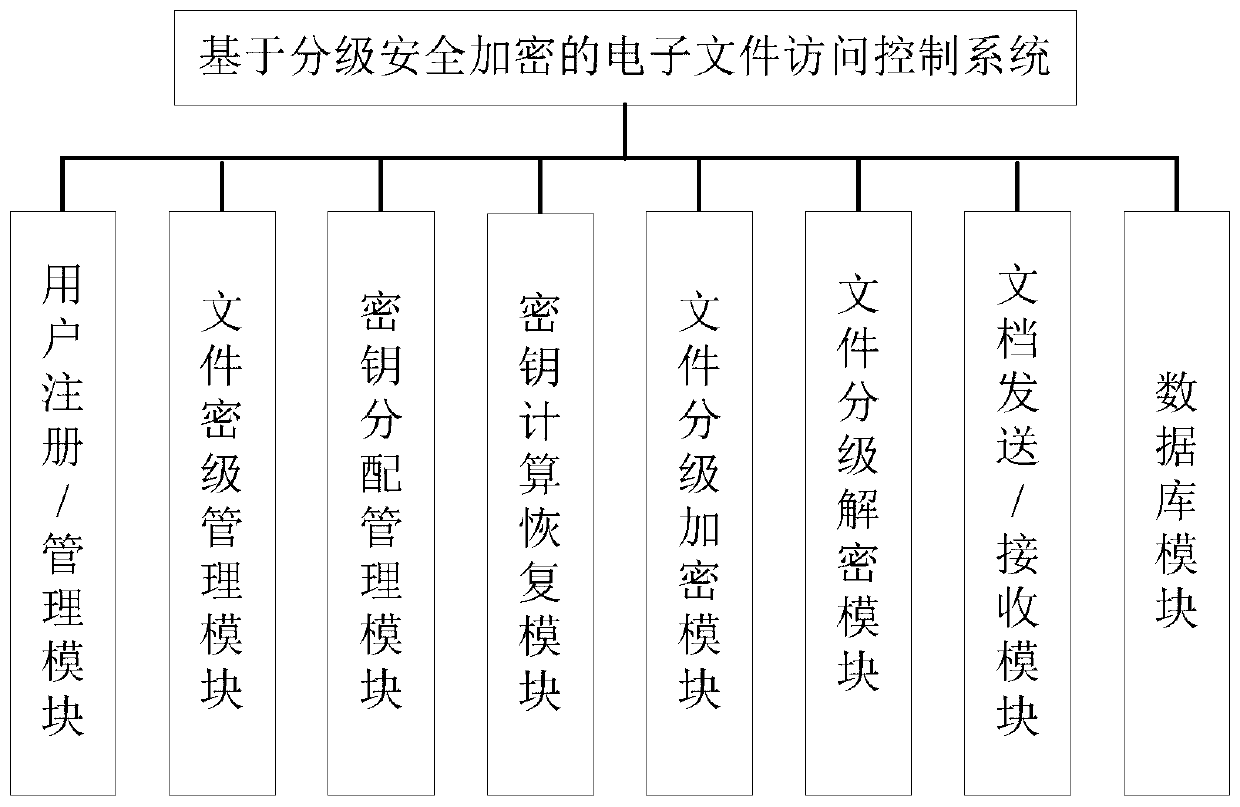
Electronic file access control method and system based on hierarchical security encryption
InactiveCN110502918AProtection securityImplement multi-level securityDigital data protectionKey distributionSecurity level
The invention discloses an electronic file access control method and system based on hierarchical security encryption. The electronic file access control method includes the steps: firstly, setting the security level of an electronic file, then distributing a grading key to an electronic file sender, carrying out grading encryption on the electronic file, carrying out grading access control, and finally updating the key. The electronic file access control system comprises a user registration / management module, an electronic file security classification management module, an electronic file classification encryption module, an electronic file classification decryption module, a key distribution management module, a key calculation recovery module, an electronic file sending / receiving moduleand a database module. According to the invention, the electronic file is encrypted in a graded manner according to the security level of the electronic file, and graded decryption and access controlare performed on the electronic file according to the security level of the user, so that the multi-level security of the electronic file is realized, and the security of the electronic file is effectively protected. Through hierarchical encryption and hierarchical decryption, hierarchical access control of the electronic file is realized.
Owner:HANGZHOU DIANZI UNIV
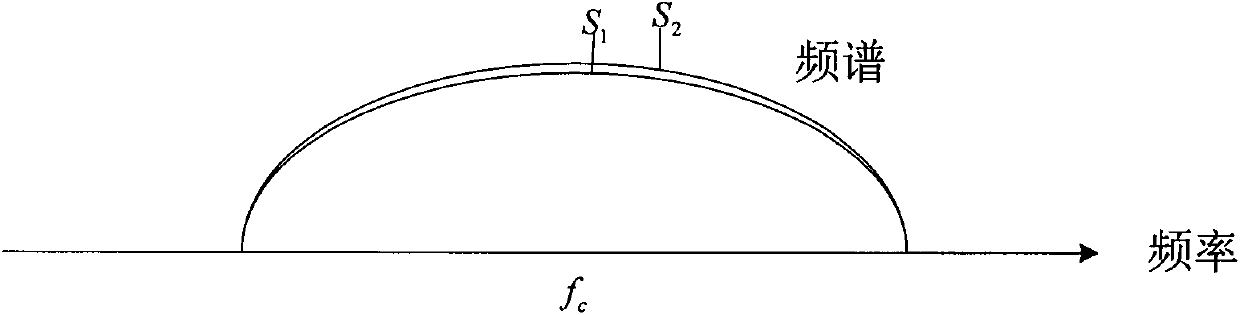
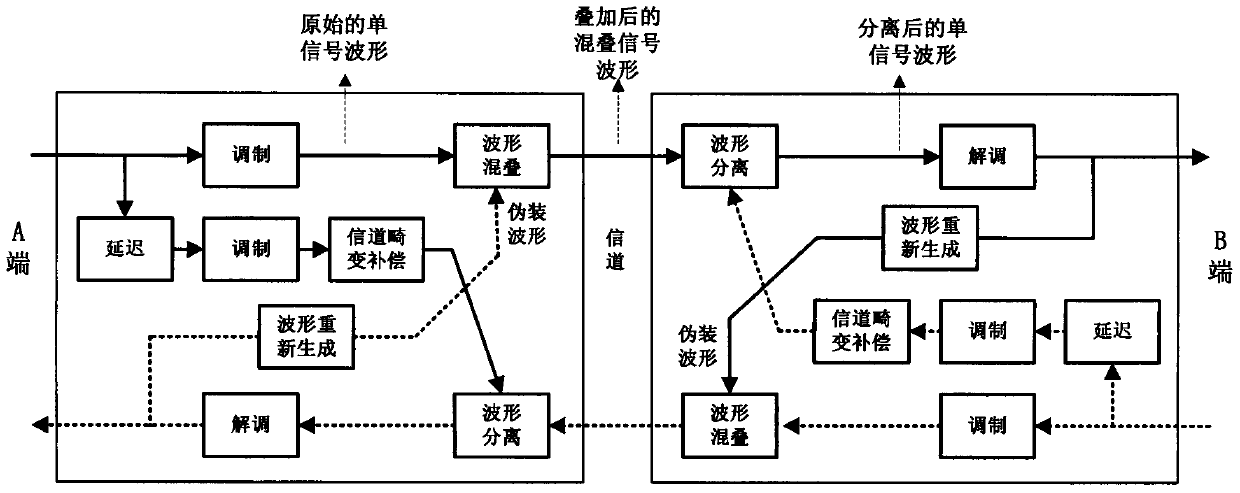
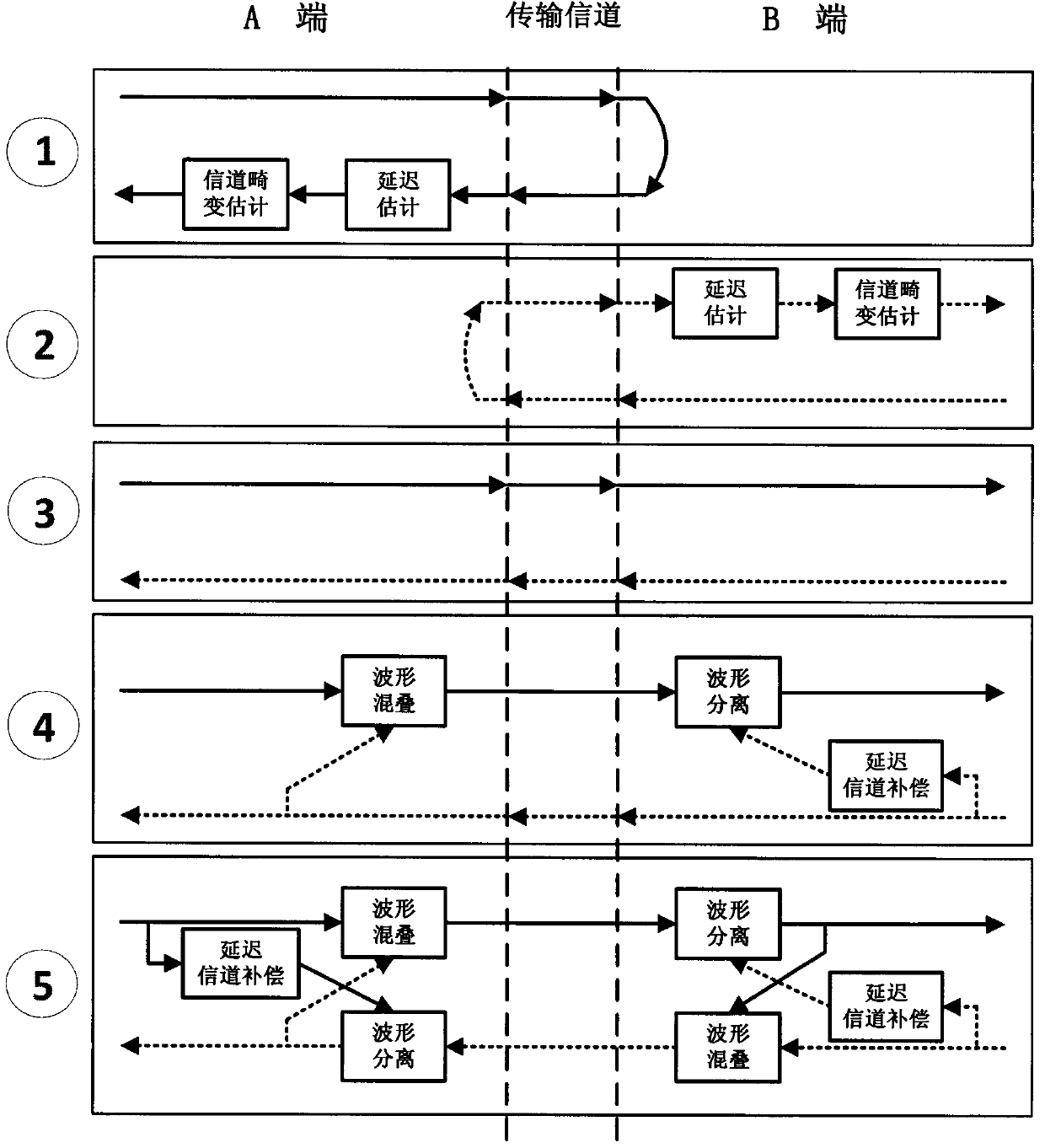
High safety communication technology based on two-way time domain waveform aliasing
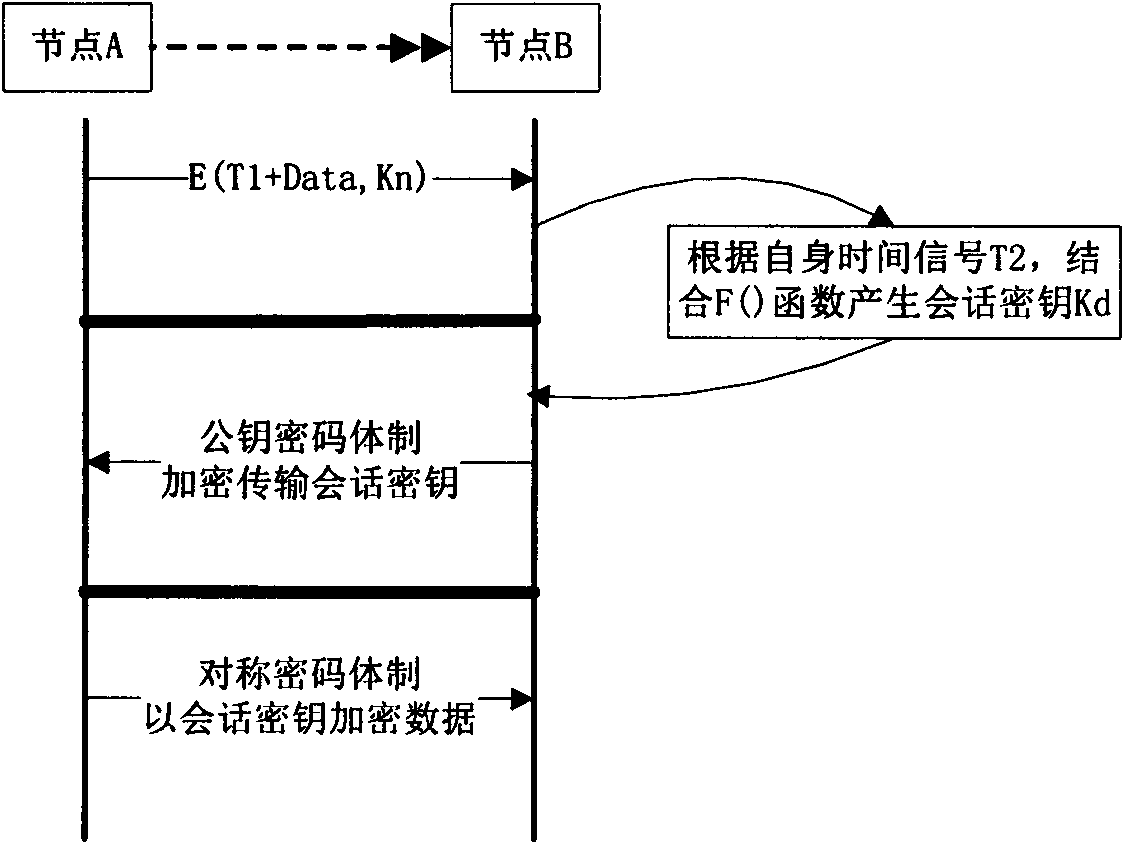
InactiveCN103428124AImprove transmission securityEnsure transmission securityTransmitter/receiver shaping networksSecure communicationInformation transmission
The invention discloses a high safety communication technology based on two-way time domain waveform aliasing and belongs to the technical field of communication. The existing local signals of two communication parties are fully utilized to perform aliasing and covering on each other's signals. The two communication parties transmit and receive mixed signals. Each communication party receives and separates the signals of the other party and allows the same to be mixed with local signals for transmission. The cooperating parties can separate the signals by using local signals and waveform reconstruction offset to complete normal communication. Non-cooperating parties do not know signal samples of the cooperating parties, the mixed signals cannot be separated, and information transmission safety is guaranteed. The method aiming at the situation that communication information safety faces increasingly large threats has the advantages that the signals transmitted in channels are mixed by two signals, safety communication of the whole communication process can be achieved, and no extra communication bandwidth is needed.
Owner:中国人民解放军总参谋部第五十七研究所
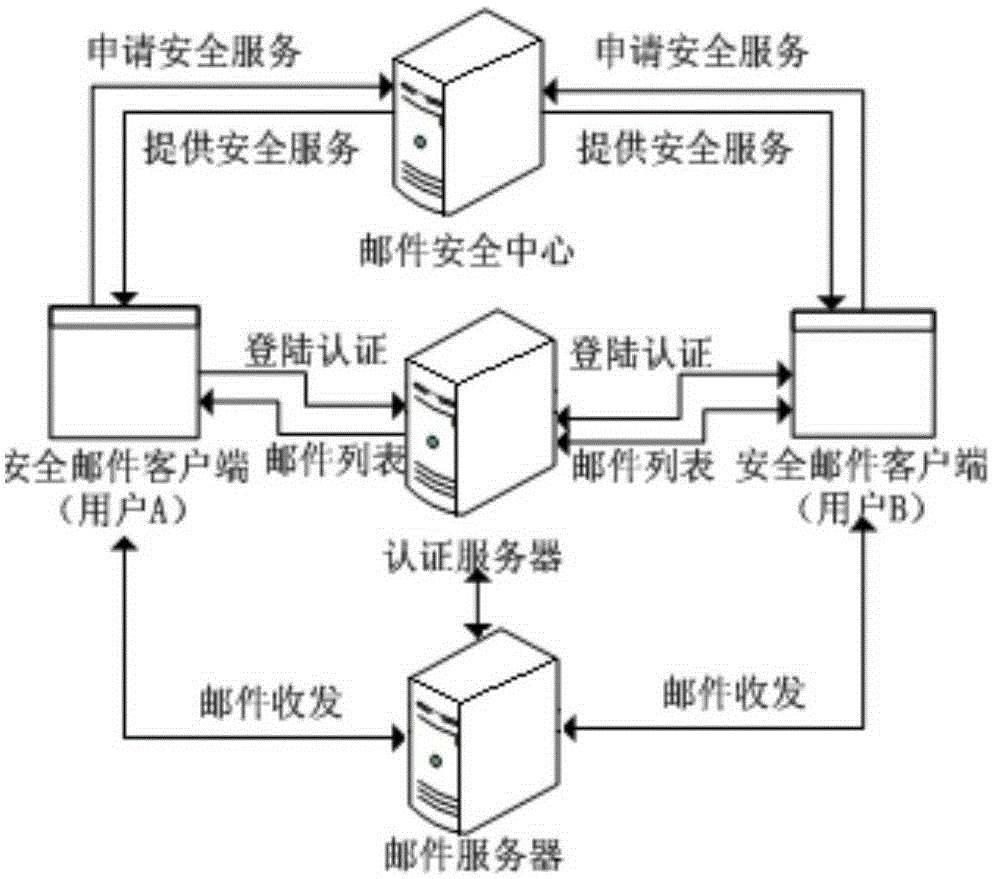
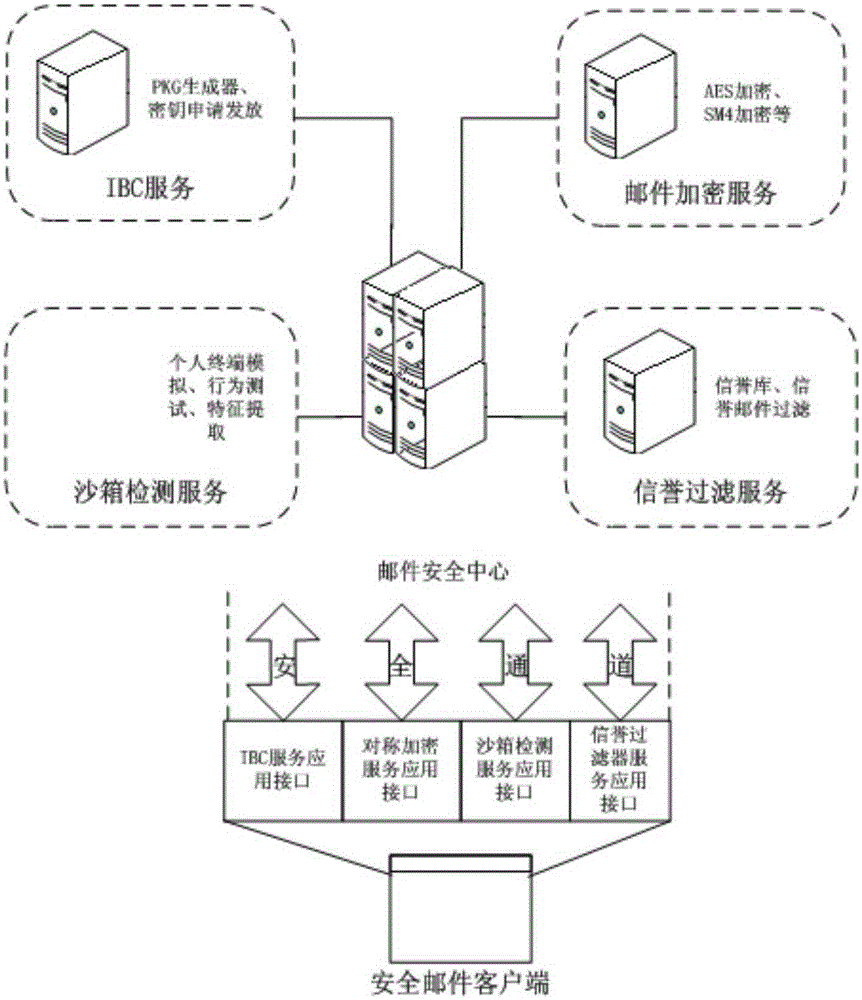
Comprehensive defense secure e-mail system
ActiveCN105227570AImprove securityEnsure transmission securityData switching networksSecurity authenticationClient-side
The invention provides a comprehensive defense secure e-mail system. The system comprises a secure e-mail sending client used for generating an encryption key; an e-mail security center used for scheduling an encryption algorithm to encrypt a sent e-mail and meanwhile scheduling an IBC encryption algorithm to encrypt the encryption key through a receiver e-mail address; and a secure e-mail receiving client used for scheduling an IBC decryption algorithm to decrypt the encryption key and scheduling a corresponding decryption algorithm to decrypt the e-mail. The comprehensive defense secure e-mail system provided by the invention adopts the IBC technology, the sand box technology and the reputation technology to form a joint e-mail box security defense system, which can effectively resist junk mails, Trojans, viruses, ATP attacks and the like and achieve multi-protection of login security authentication, transmission encryption and secure storage and the like of the e-mail system.
Owner:中电科网络安全科技股份有限公司
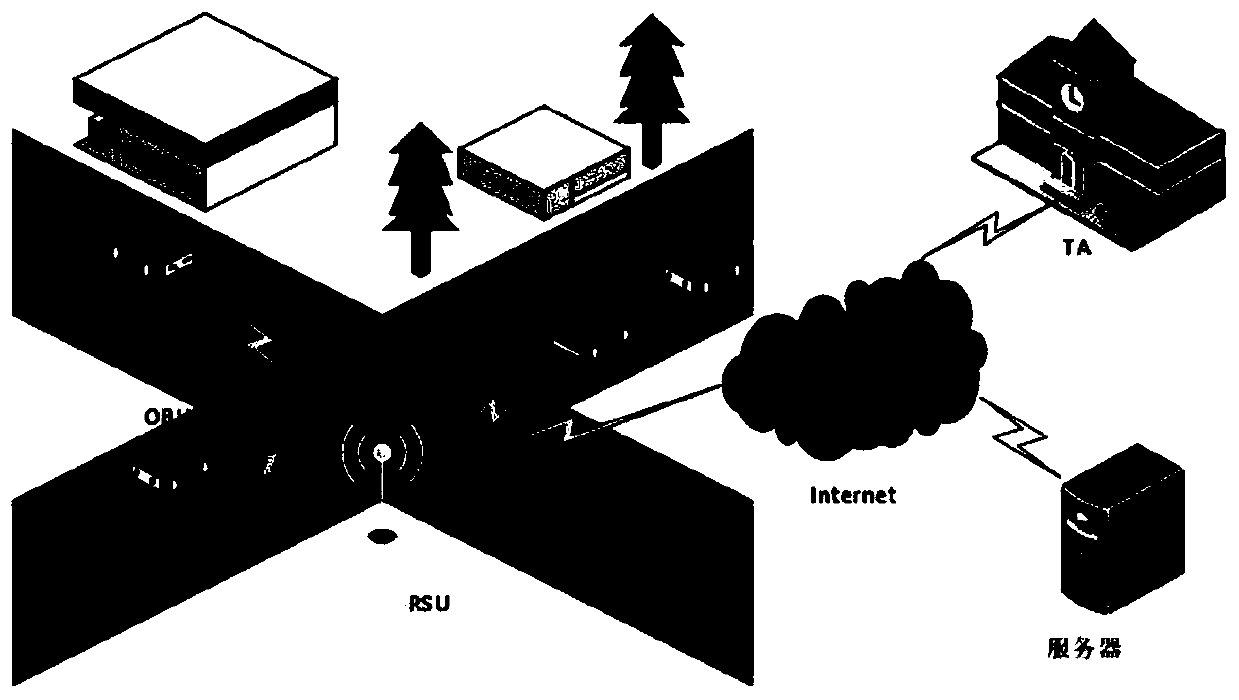
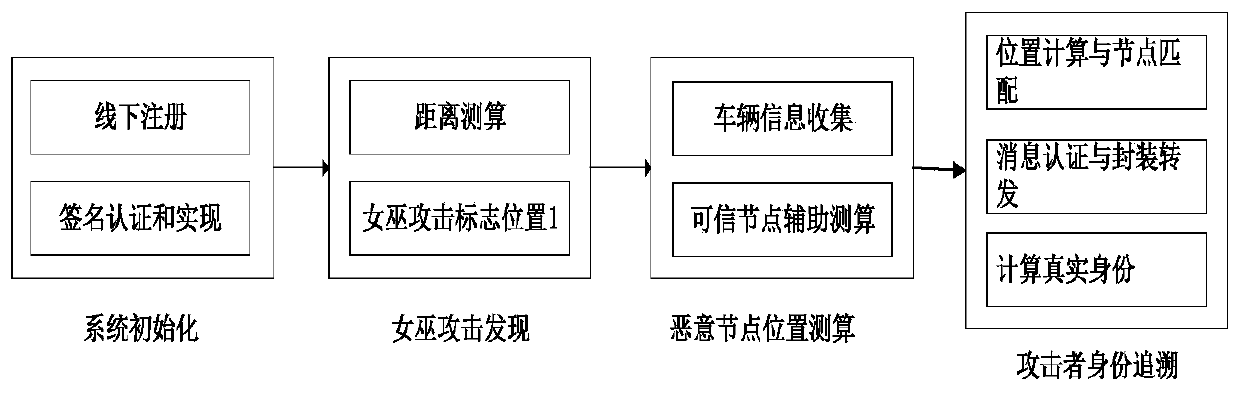
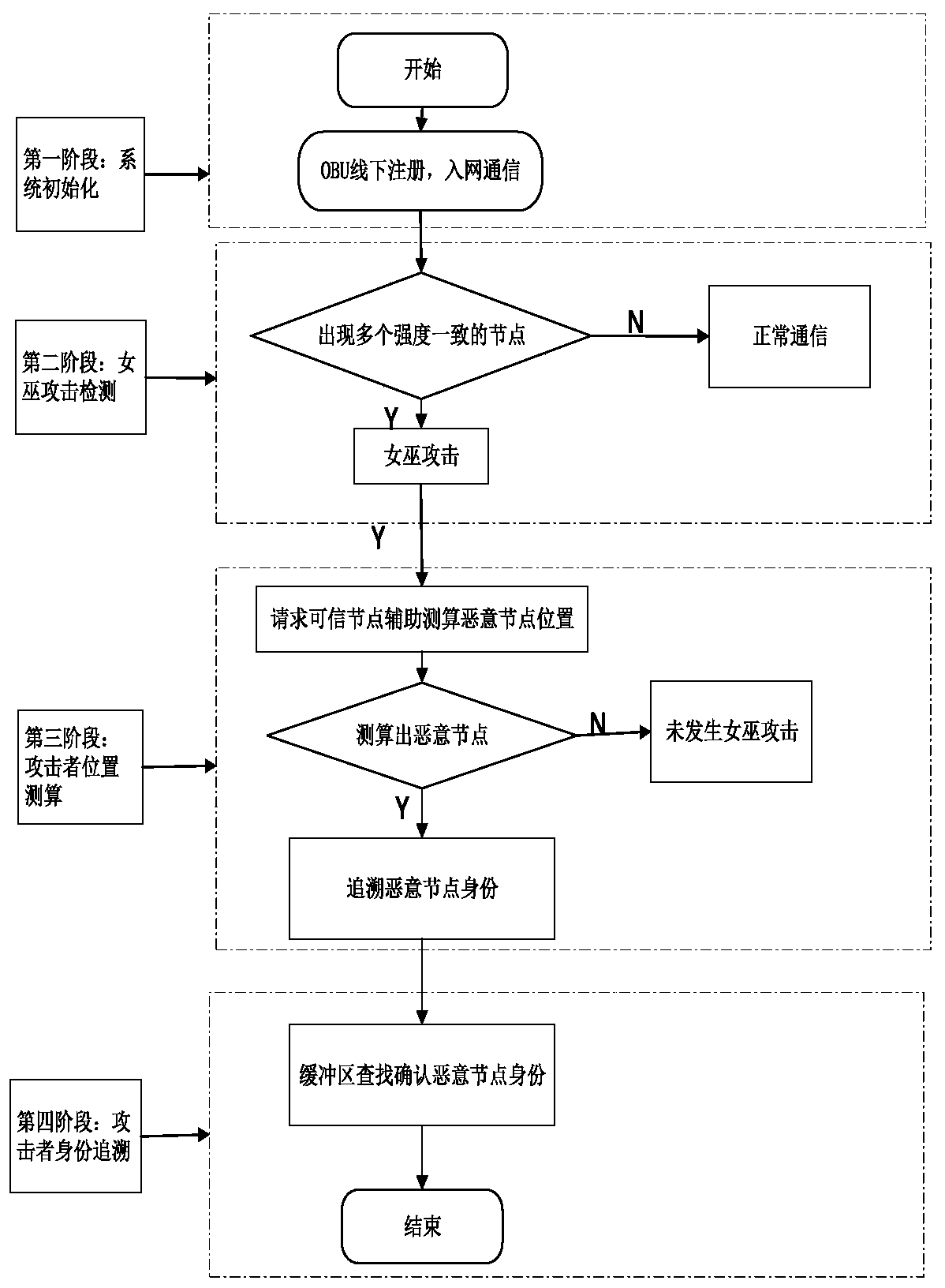
Identity traceable Sybil attack detection method in Internet of Vehicles environment
ActiveCN110536265AEnable anonymous communicationPrivacy protectionParticular environment based servicesVehicle wireless communication serviceThe InternetComputer security
The invention provides an identity traceable Sybil attack detection method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to thetechnical scheme, the Sybil attack detection method with the traceable identity in the Internet of Vehicles environment comprises the following steps of system initialization, Sybil attack discovery,malicious node positioning and attacker identity tracing. The method has the advantages that under the condition that the Sybil attack is detected, a concise method is designed to achieve positioningof the position of the attacker, and the real identity of the attacker is traced according to the positioning information.
Owner:NANTONG UNIVERSITY
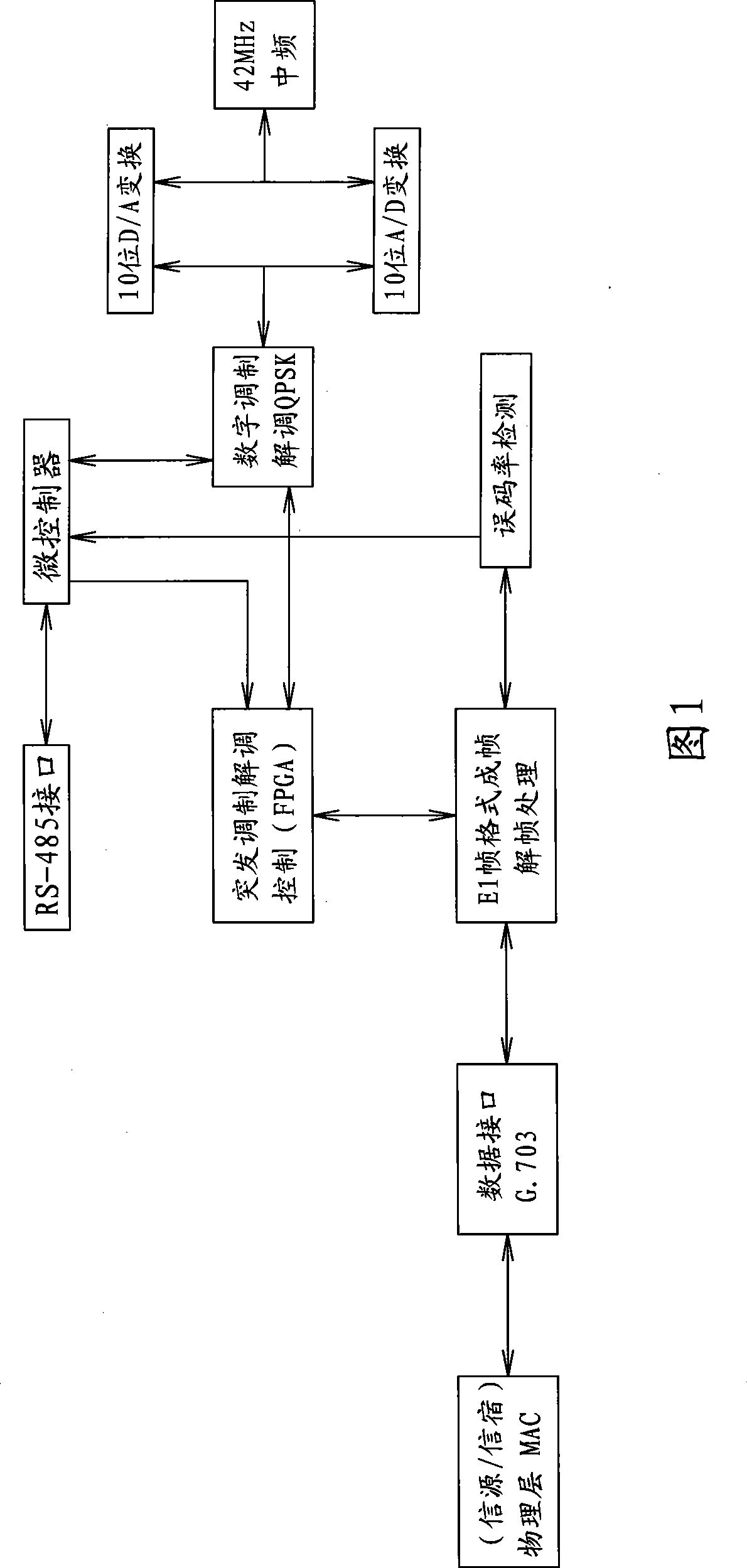
Remote distance wireless transmission method
InactiveCN101459968AIncrease profitMeet the transmission capacityError preventionActive radio relay systemsCommunication qualityWireless transmission
The invention provides a remote wireless transmitting method for self-adaptively adjusting optimum modulation modes under the precondition that the communication quality is guaranteed. The modulation mode comprises: sending a series of test data to an information sink by an information source, determining to adopt one of QPSK, 16QAM, 64QAM or 126QAM as a transmission system according to the bit error rate and the transmission speed of the test data by the information sink, feeding back to the information source, modulating to a corresponding transmission system according to feedback information of the information sink by the information source, then, sending data to the information sink, selecting a suitable transmission system according to the bit error rate and the transmission speed of received data by the information sink, feeding back to the information source, adjusting a corresponding transmission system and the speed in real time according to the feedback information of the information sink by the information source, sending the data to the information sink, and thereby self-adaptively realizing the optimization of the data transmission efficiency according to the transmission environment and the speed demands. The method is applied in wireless data digital transmission with long distance and high speed.
Owner:林志华
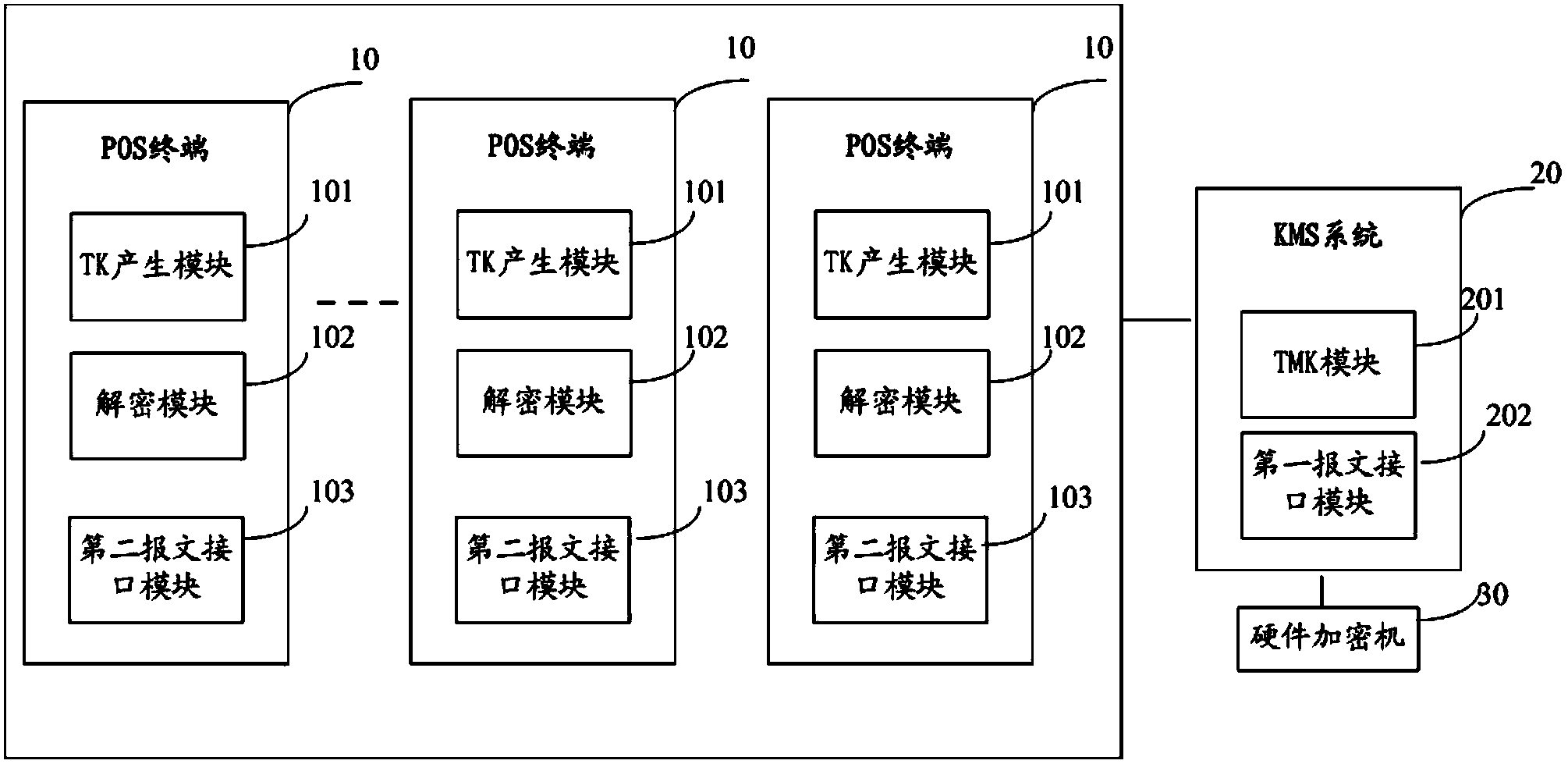
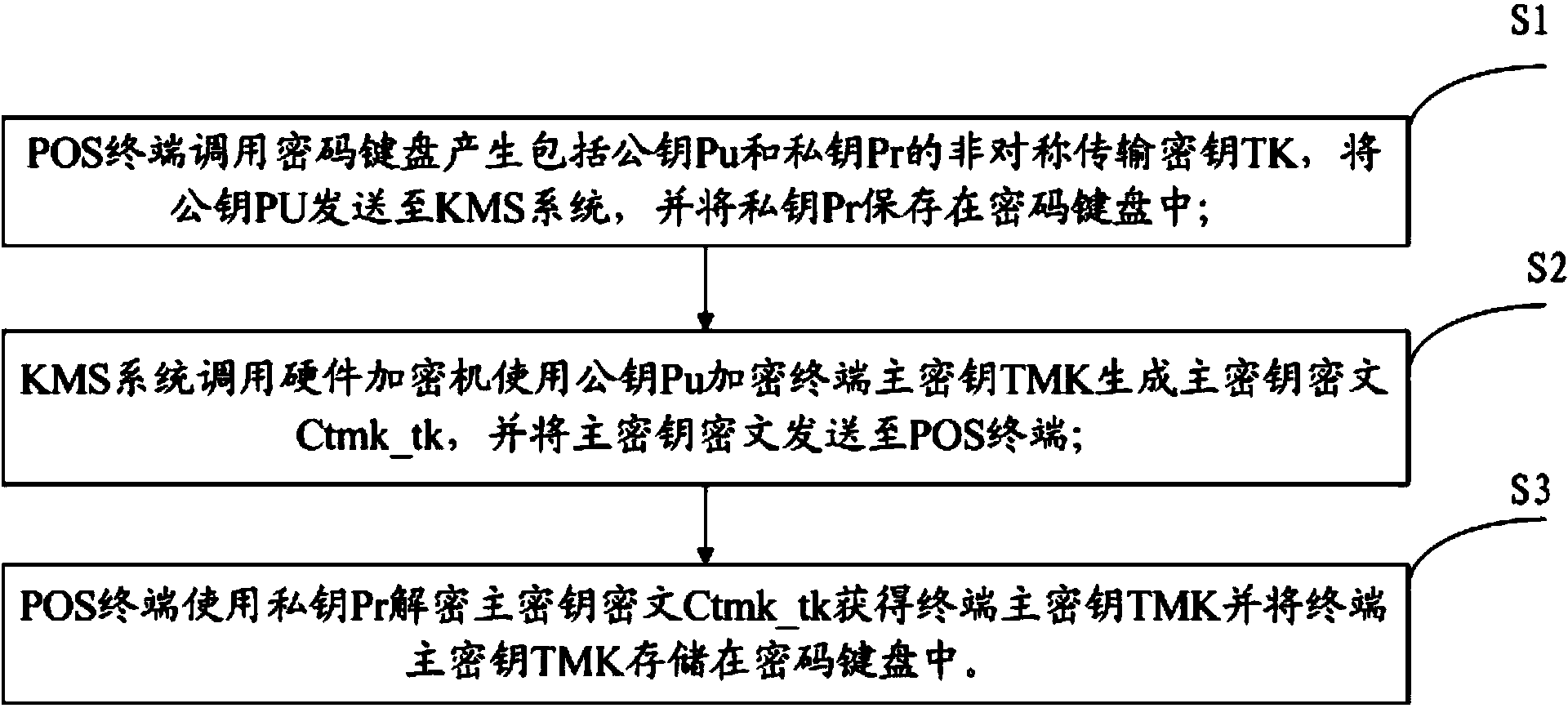
Security downloading method and system of TMK
ActiveCN103716321AEasy to downloadEnsure transmission securityKey distribution for secure communicationUser identity/authority verificationCiphertextMaster key
The invention discloses a security downloading method of a TMK. The security downloading method comprises the steps that a POS terminal produces an asymmetric TK by calling a PIN pad, the asymmetric TK comprises a public key Pu and a private key Pr, the public key Pu is sent to a KMS, and the private key Pr is stored in the PIN pad; the KMS calls a hardware and security module, the public key is used for encrypting the TMK to produce master key ciphertext Ctmk_tk, and the master key ciphertext is sent to the POS terminal; the POS terminal uses the private key Pr for decrypting the master key ciphertext Ctmk_tk to obtain the TMK and stores the TMK in the PIN pad. The invention further provides a security downloading system of the TMK. The security downloading method and system of the TMK have the advantages that the TMK is encrypted by adopting the TK, the TMK is downloaded remotely by the POS terminal, great convenience is brought to downloading of the TMK, the TK is produced randomly, a transmission process is also closed, and therefore transmission security of the TMK is guaranteed effectively.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Train coupling method and device and train uncoupling method
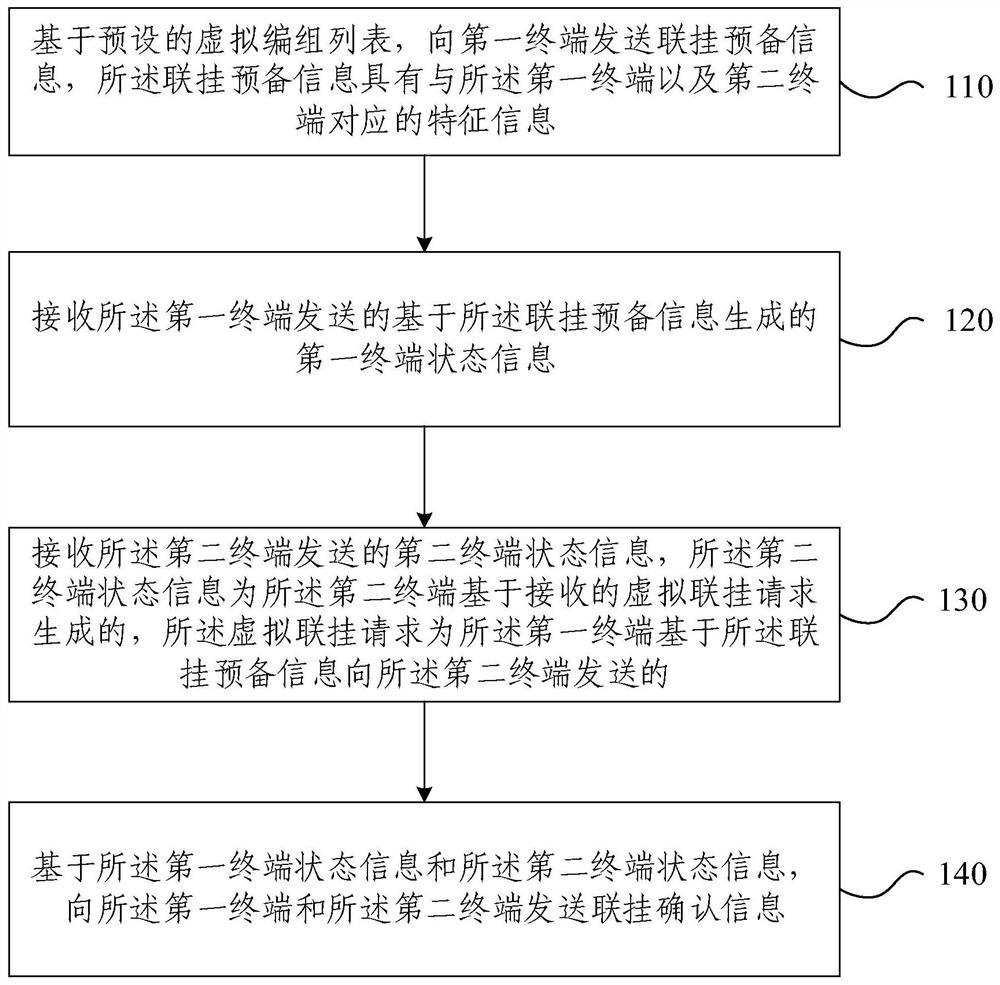
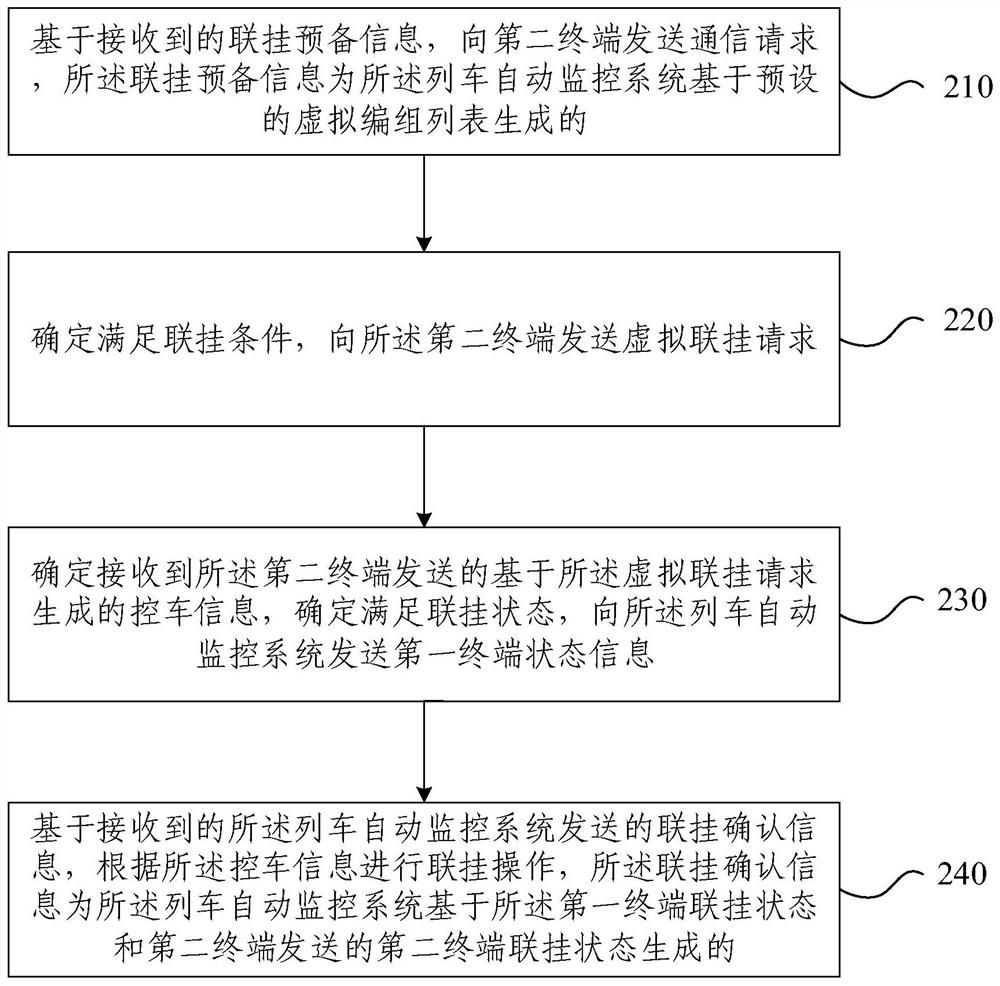
ActiveCN112319507AFlexible groupingEnsure transmission securityRailway componentsRailway stationInformation transmissionInformation transfer
The embodiment of the invention provides a train coupling method and device and a train uncoupling method. The train coupling method comprises the steps: transmitting coupling preparation informationto a first terminal based on a preset virtual marshalling list, wherein the coupling preparation information has feature information corresponding to a first terminal and a second terminal; receivingfirst terminal state information generated based on the coupling preparation information and sent by the first terminal; receiving second terminal state information sent by the second terminal, wherein the virtual coupling request is sent by the first terminal to the second terminal based on the coupling preparation information; and sending coupling confirmation information to the first terminal and the second terminal based on the first terminal state information and the second terminal state information. According to the train coupling method provided by the embodiment of the invention, theinformation confirmation is ensured in a secondary confirmation mode, the information transmission safety can be ensured, the risk of accidents is reduced, and the grouping of trains can be more flexible.
Owner:通号城市轨道交通技术有限公司
Quality management system for finished automobile production and manufacturing
InactiveCN108090675AEnsure transmission securityEncryption apparatus with shift registers/memoriesResourcesObject basedTotal quality management
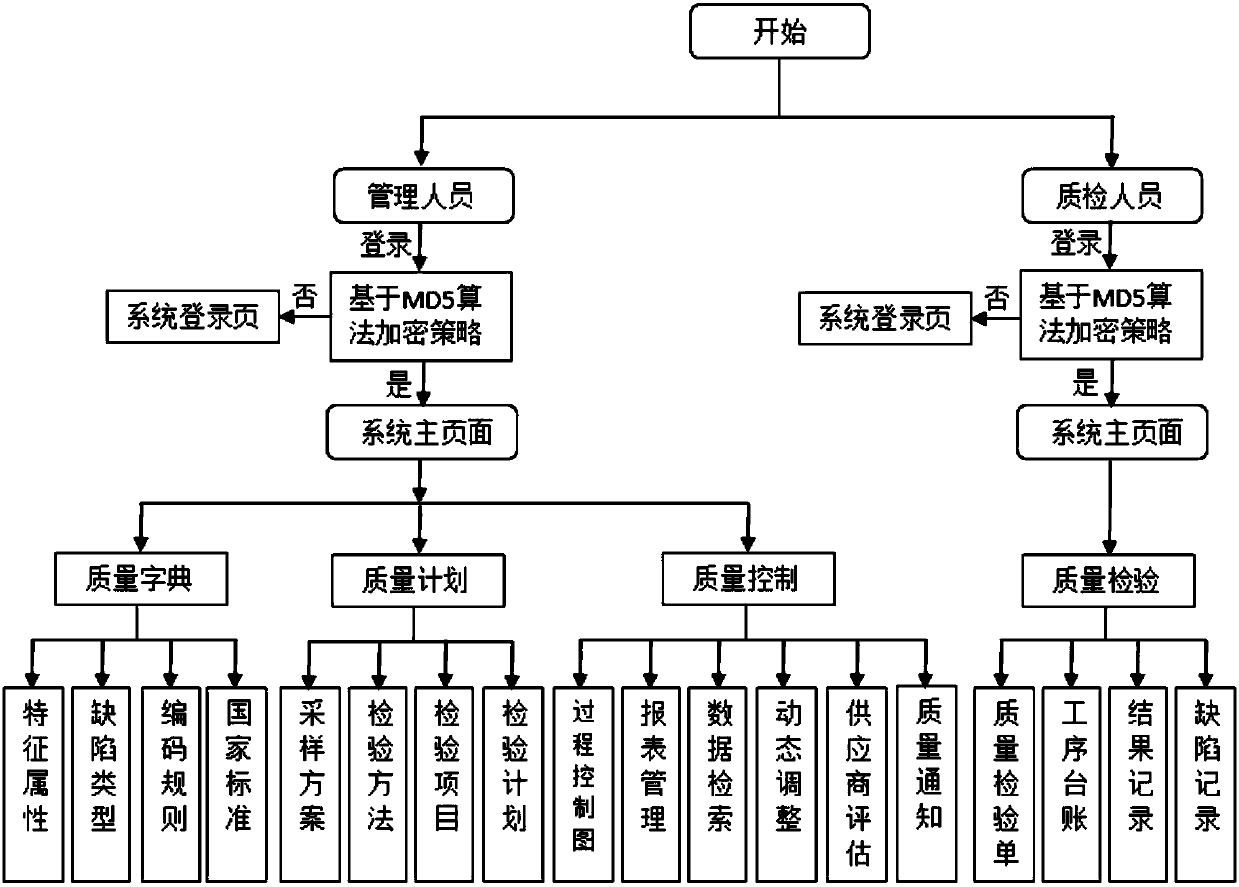
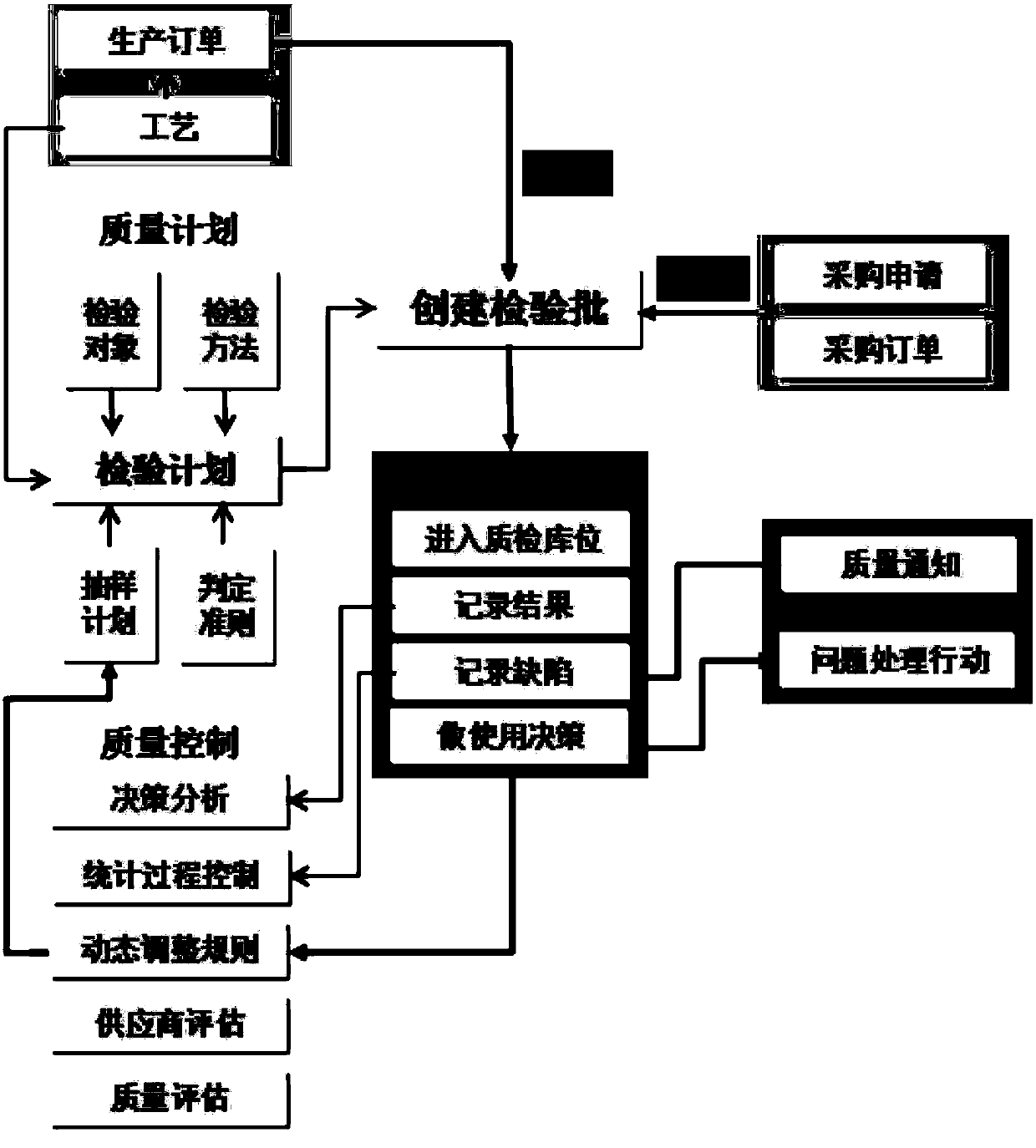
The invention discloses a quality management system for finished automobile production and manufacturing. The system is composed of a quality dictionary module, a quality planning module, a quality inspection module, and a quality control module. The quality dictionary module is used for carrying out quantification processing on characteristic attributes, defect types, coding rules of different batches, and national standards of inspection items during a production and manufacturing process and constructing essential data by using an integrated and standardized description as criteria for later-period inspection. The quality planning module is used for creating targeted inspection plans based on business demands and inspection objects. The quality inspection module is used for applying designated inspection plans to specific inspection objects based on inspection plans created in the quality planning, collecting quality data and synchronizing the data to a server side to complete product quality inspection. The quality control module is used for completing inspection on the specific inspection objects in quality inspection and realizing quality control on the same batches of inspection objects with the same batch number prefix positions.
Owner:BEIJING UNIV OF TECH
Internal and external network document interaction method
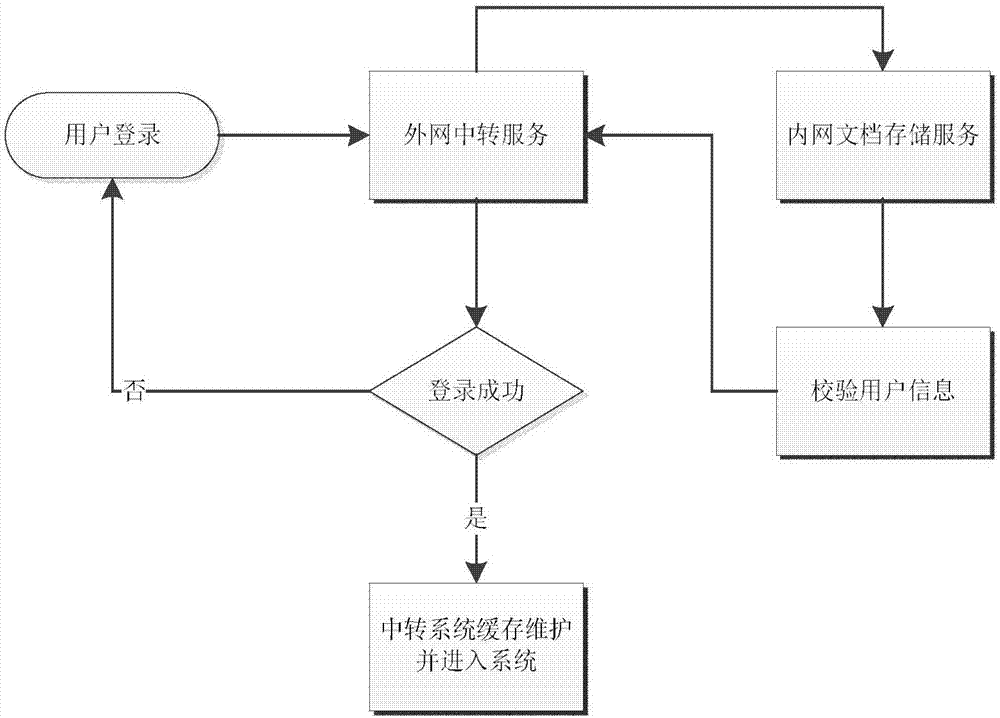
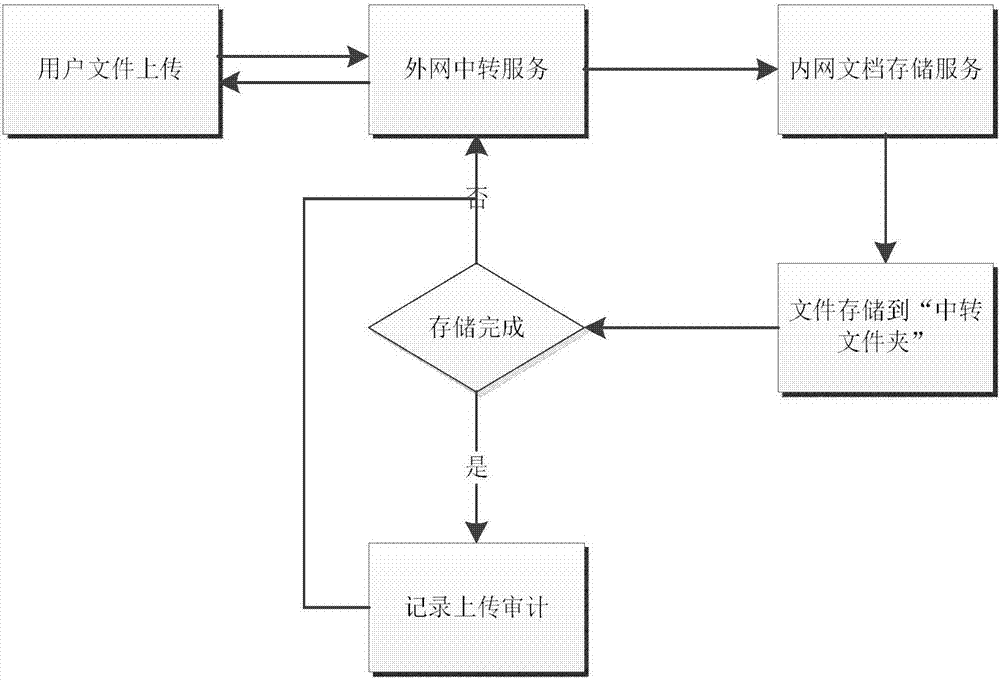
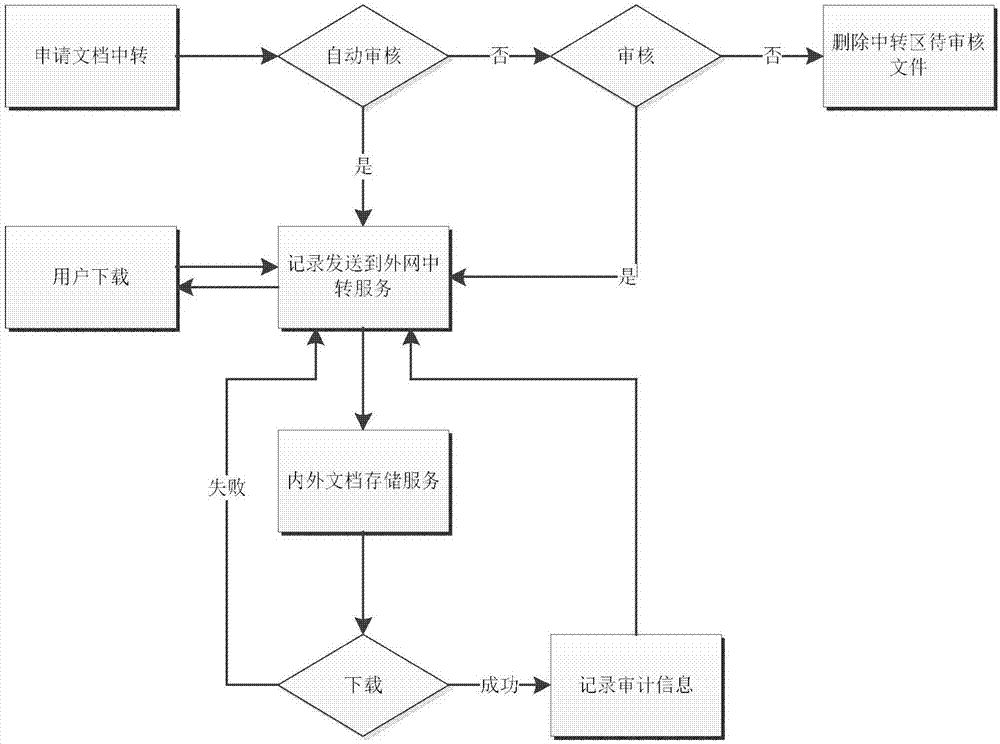
ActiveCN107026850AEnsure transmission securityWon't leakTransmissionFile system functionsService systemSystem safety
The invention discloses an internal and external network document interaction method. A document storage service system is deployed in an internal network and a document transfer service system is deployed in an external network, wherein the document storage service system is used for storing user documents, the document transfer service system is used for uploading the documents to the internal network or downloading the documents from the internal network, and a document flow is transmitted through a http request between servers. The internal and external network document interaction method disclosed by the invention has the following advantages: a more comprehensive consideration of the system security is provided; firstly, user accounts are independent, the external network cannot fully access the data of the internal network, and thus the security of each user document can be ensured; the documents that require to transfer from the internal network must be reviewed by document auditors before transfer, and thus a layer of protection is also added to the document security; secondly, an audit function is added, and if the documents are leaked, the leakage personnel can be determined through the function; and the document flow is transmitted through the http request between the servers, the data can be hardly intercepted from outside, and thus the transmission security of the data can be guaranteed.
Owner:JIANGSU DAWN INFORMATION TECH CO LTD
Intelligent household equipment and system, and visitor password acquisition method
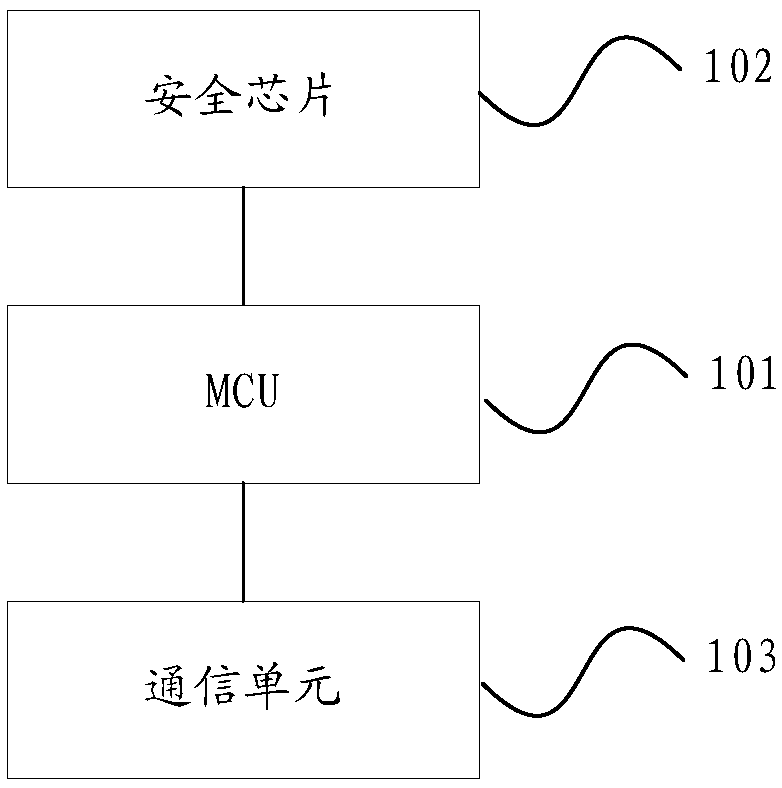
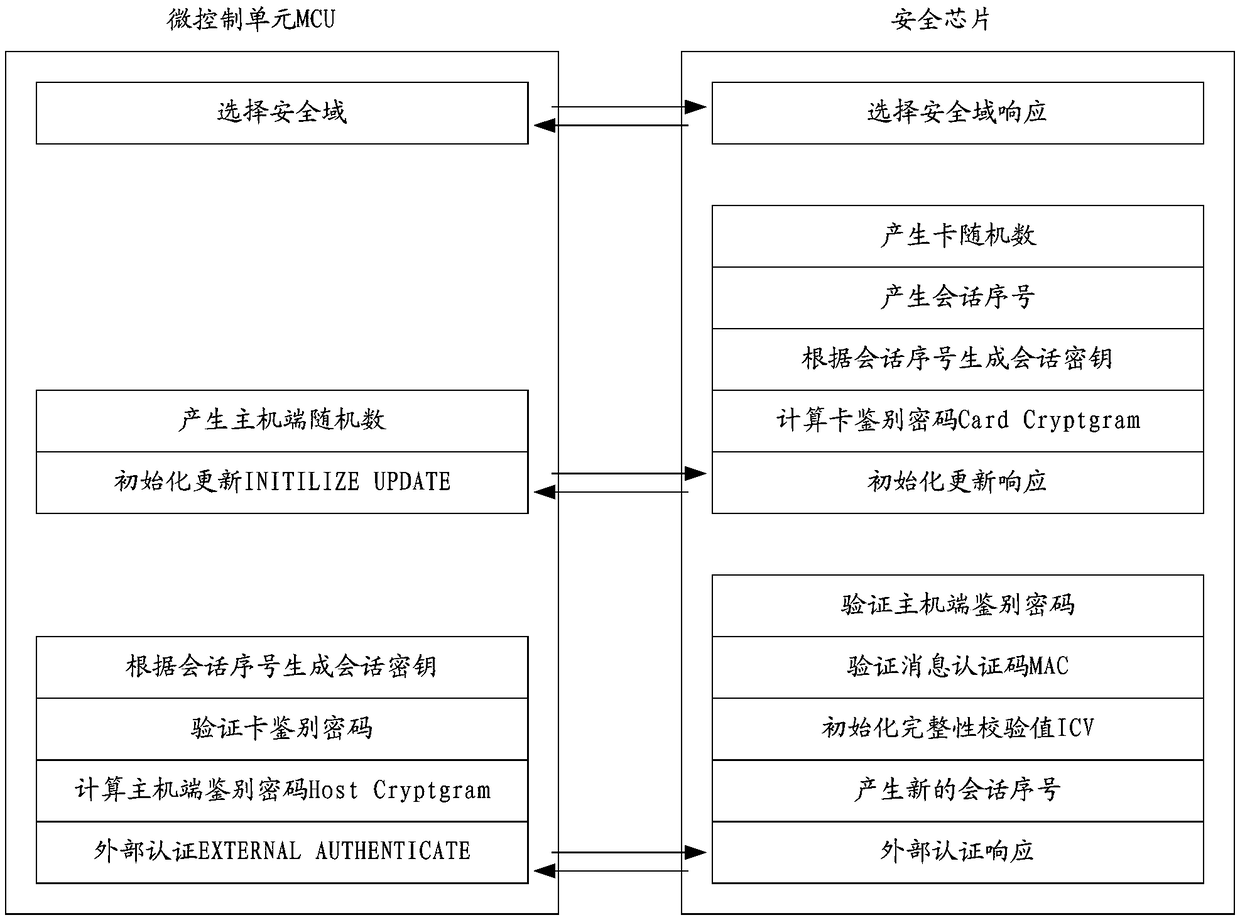
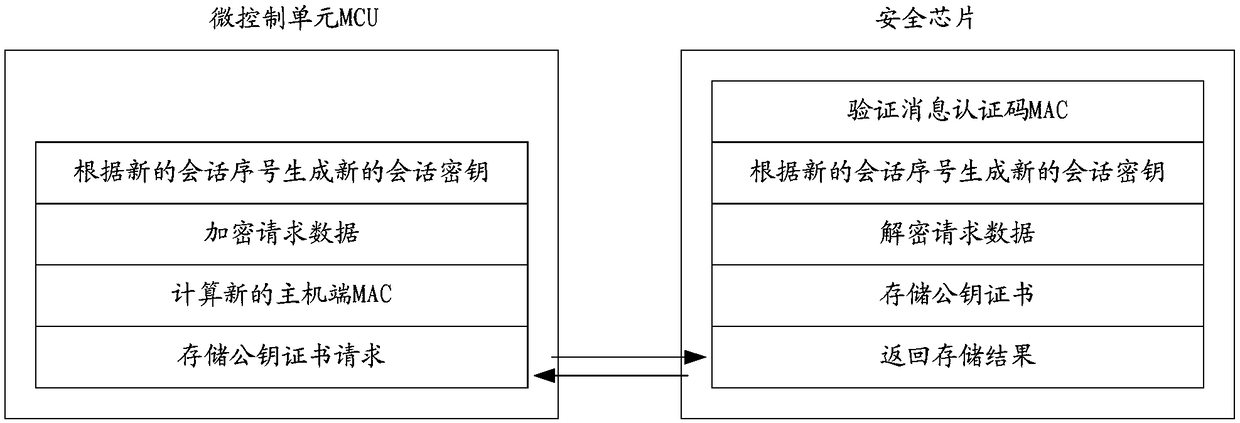
ActiveCN108712246AEnsure transmission securityPrevent Lost Guest PasswordKey distribution for secure communicationHome automation networksEquipment SafetyEncryption
The invention discloses an intelligent household equipment. The equipment includes a micro control unit (MCU) and a safety chip; the MCU is connected to the safety chip; the safety chip is used for receiving a generation visitor password management instruction sent by a remote server, and verifying the management instruction through a prestored public key certificate; and the safety chip is also used for generating a visitor password and storing after successfully verifying the management instruction, performing encryption on the visitor password through the prestored public key certificate and uploading the visitor password to the remote server. The problems in the prior art, that intelligent household equipment is easy to suffer external attacks so that passwords can be stolen and equipment safety is in danger, can be solved. A visitor password acquisition method, related equipment and a system are also disclosed.
Owner:王晓华
Health record information management service system
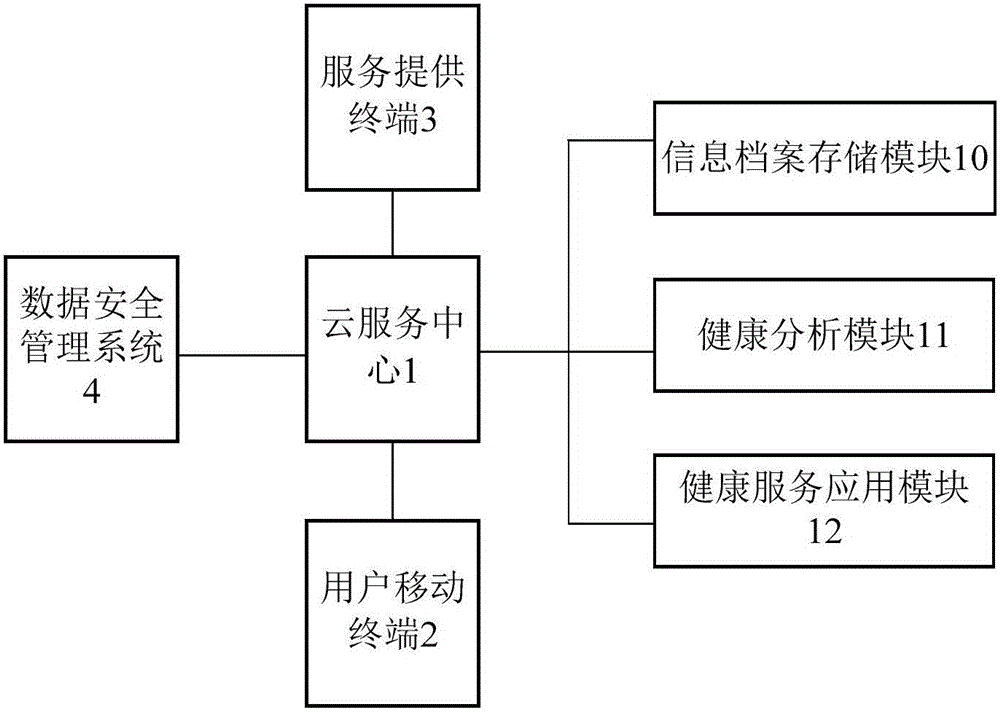
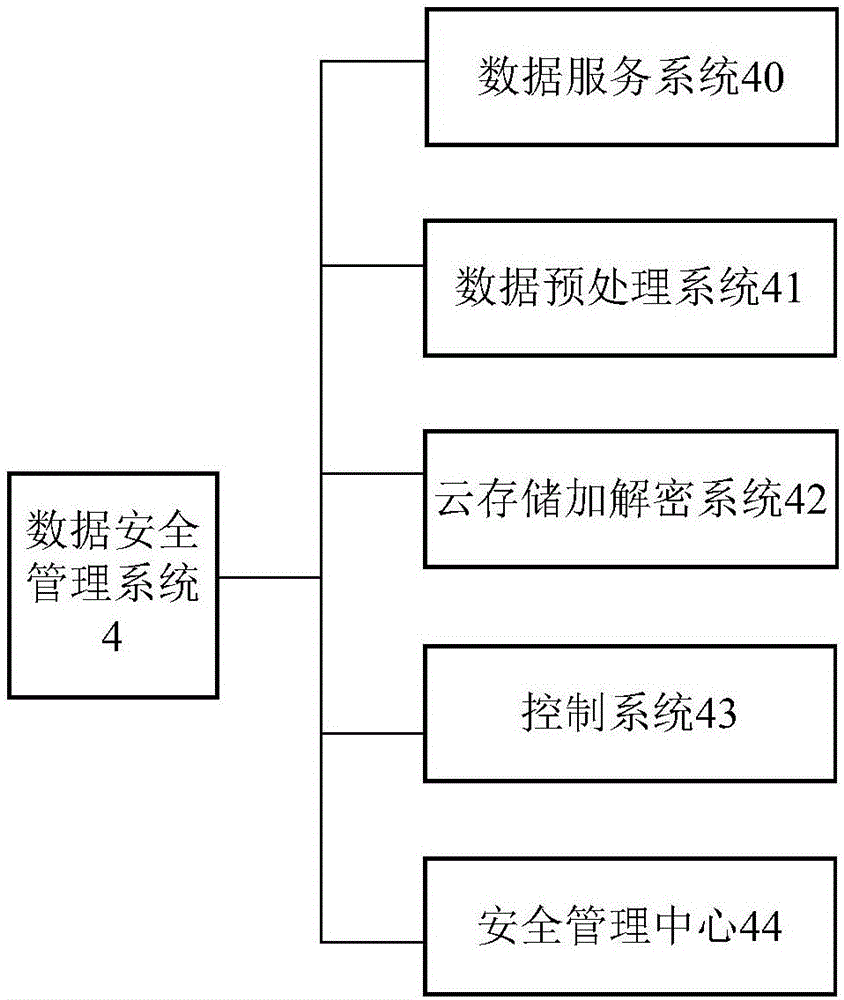
InactiveCN106326666AEnsure storage securityEnsure transmission securitySpecial data processing applicationsService provisionSafety management systems
The invention provides a health record information management service system which comprises a cloud service center, a user mobile terminal, a service providing terminal and a data safety management system. The cloud service center comprises an information file storage module, a health analysis module and a health service application module, wherein the information file storage module is used for storing health file information and generating or updating a health file under a user account according to the stored health file information, the health analysis module is used for conducting data analysis on the health file information to obtain a health analysis result and determining a matched service item from the service items provided by the service providing terminal according to the health analysis result, the health service application module is used for pushing the matched service item to the corresponding user mobile terminal according to a service request sent by the user mobile terminal, and the data safety management system is used for guaranteeing storage and transmission safety of the health file information. The health record information management service system is practical, quick, convenient and high in safety.
Owner:孟玲
Information safety transmission device and method based on homomorphic encryption and storage method
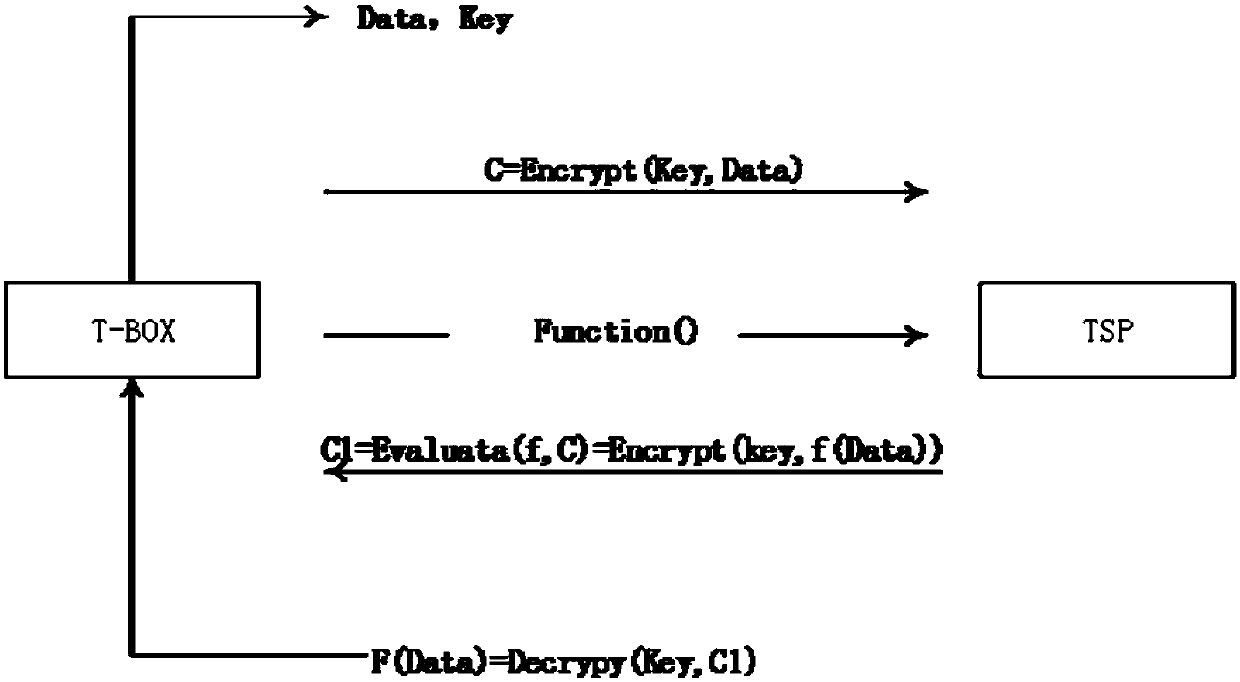
InactiveCN107682379AEnsure transmission securityEnsure storage securityCommunication with homomorphic encryptionService provisionCiphertext
The invention relates to an information safety transmission method based on homomorphic encryption, and the method comprises the following steps: 1, enabling a service enjoying side to encrypt to-be-processed data, and transmitting an obtained ciphertext to a service provider; 2, enabling the service enjoying side to provide a data processing method for the service provider, wherein the method isexpressed through a function f(); 3, enabling the service provider to process the encrypted data through the function f(), and transmitting a processing result to the service enjoying side; 4, enabling the service enjoying side to carry out the decryption calculation after receiving the data returned by the service provider, and finally obtaining an expected result. The method does not leak any privacy content of original data of a user during the processing of the encrypted data, and guarantees the transmission safety and storage safety of data. The method prevents external attacks, and avoids the sending of wrong instructions.
Owner:NANJING AUTOMOBILE GROUP CORP
Implementation method and device for securely accessing network
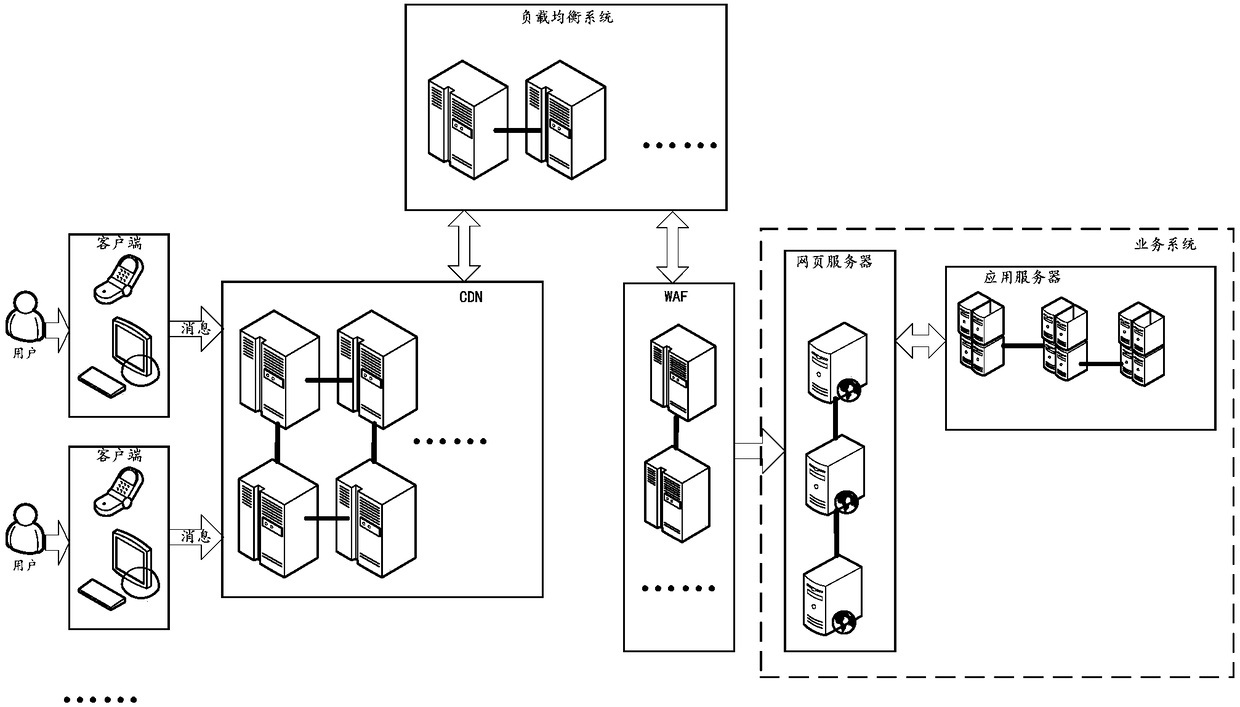
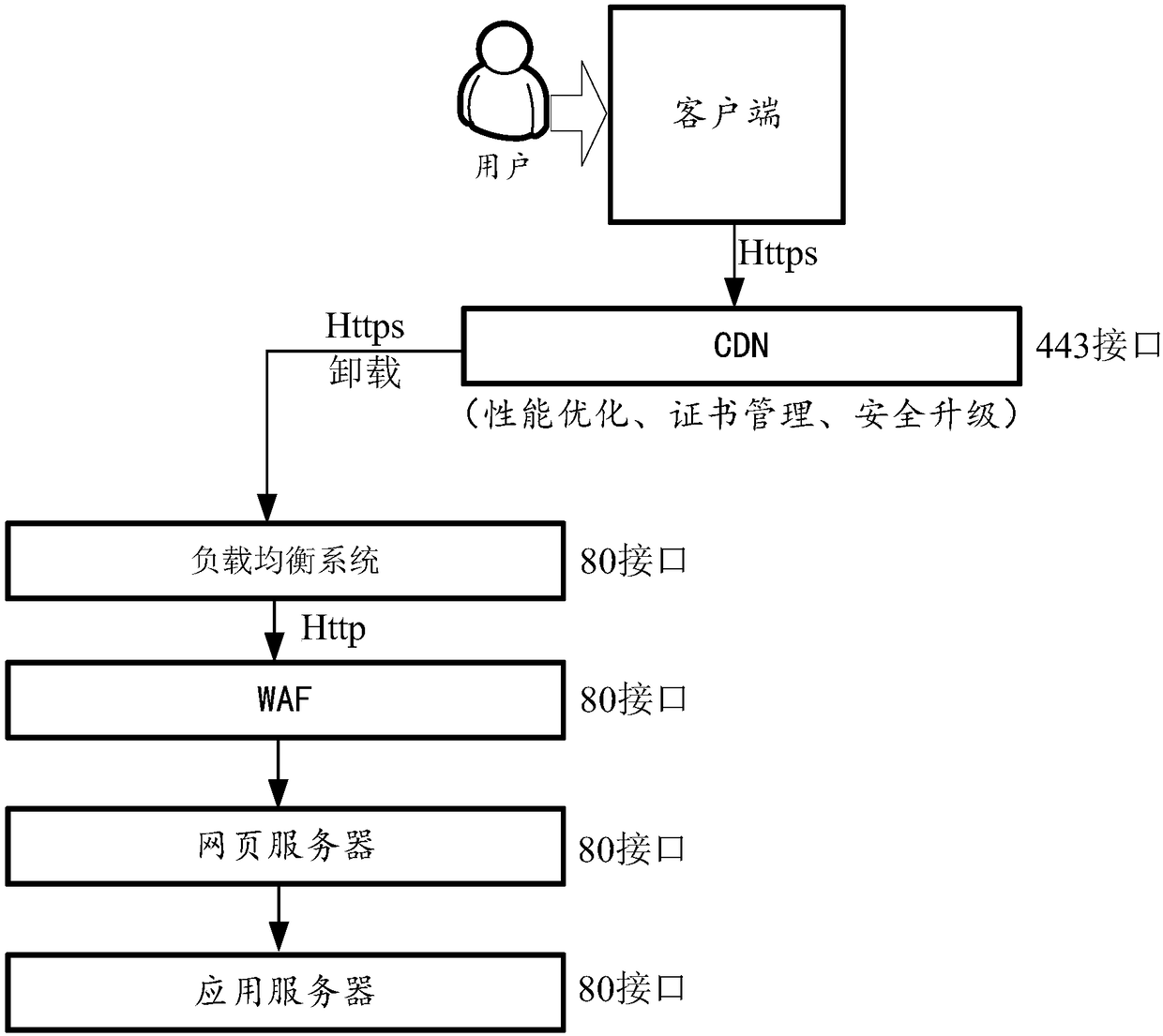
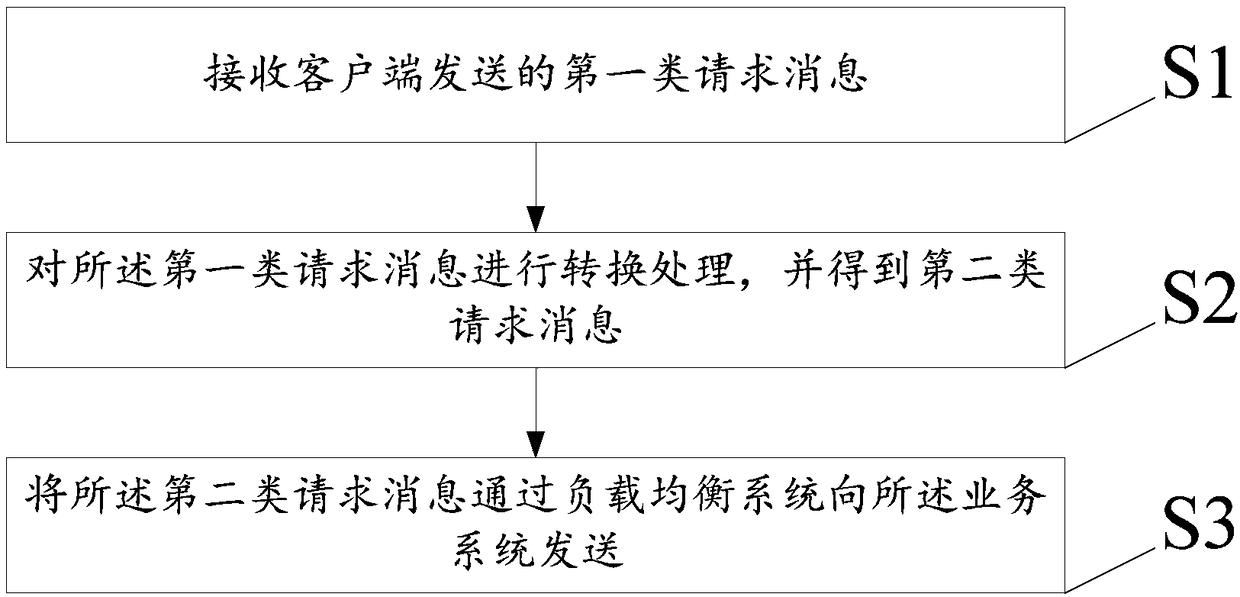
ActiveCN108737343AReduce workloadReduce coverageData switching networksAccess networkContent distribution
The embodiment of the invention discloses an implementation method and an implementation device for securely accessing a network, relates to the technical field of the Internet, and solves the problemthat how to improve the security of a website without influencing normal operation of the website. The method comprises the steps of receiving a first-class request message sent by a client, whereinthe first-class request message accords with a communication protocol between the client and a content distribution network (CDN); converting the first-class request message, and acquiring a second-class request message, wherein the second-class request message accords with the communication protocol between the CDN and a service system; and sending the second-class request message to the servicesystem via a load balancing system. The method and device provided by the invention are applicable to HTTPS modification of the total station system.
Owner:SUNING COM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com