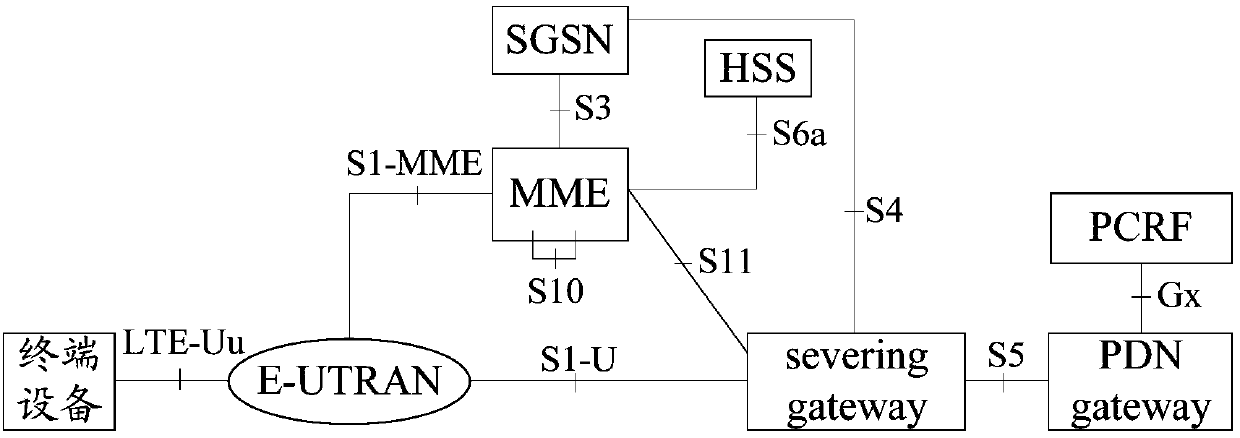
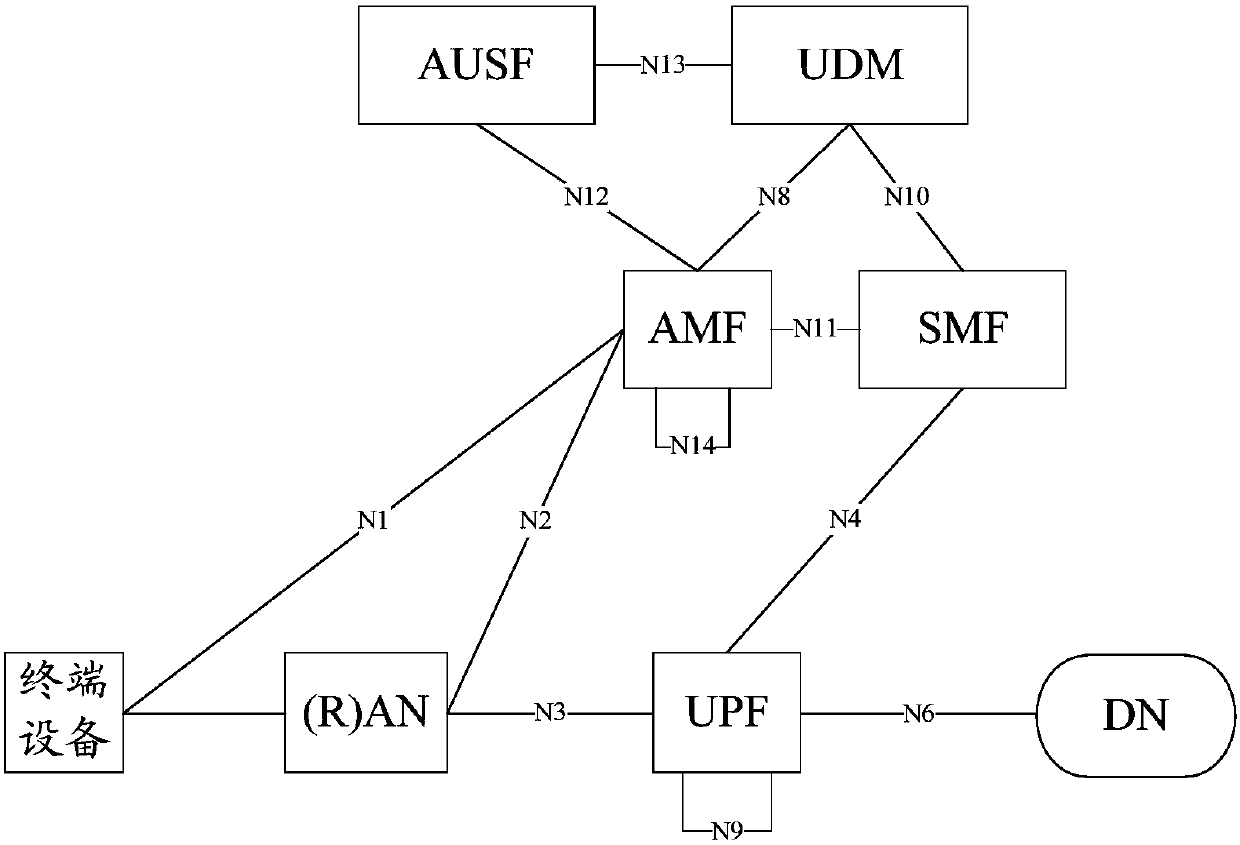
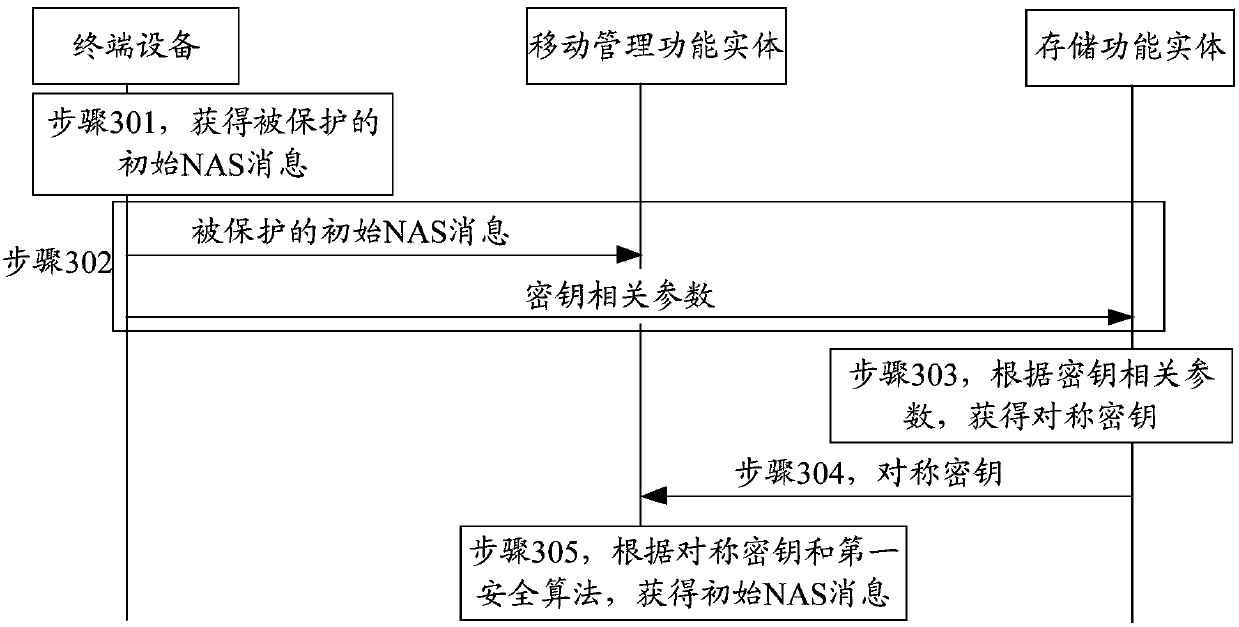
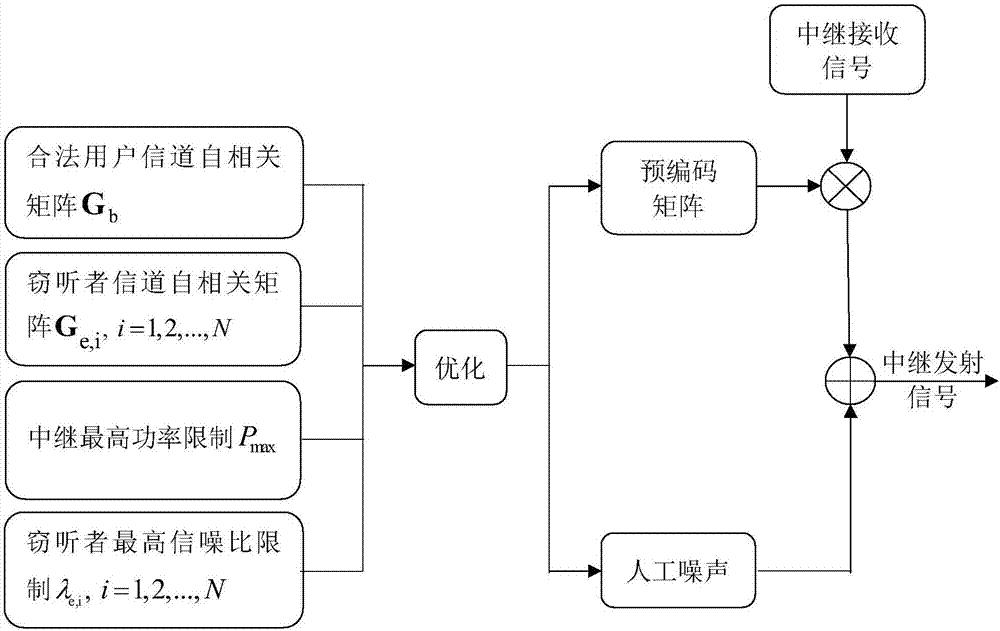
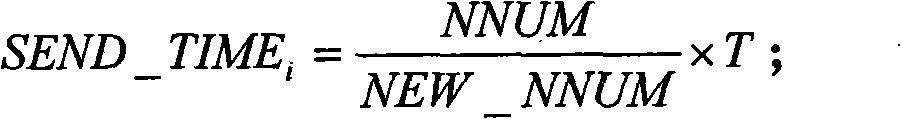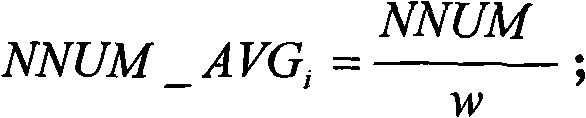Patents
Literature
219results about How to "Improve transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
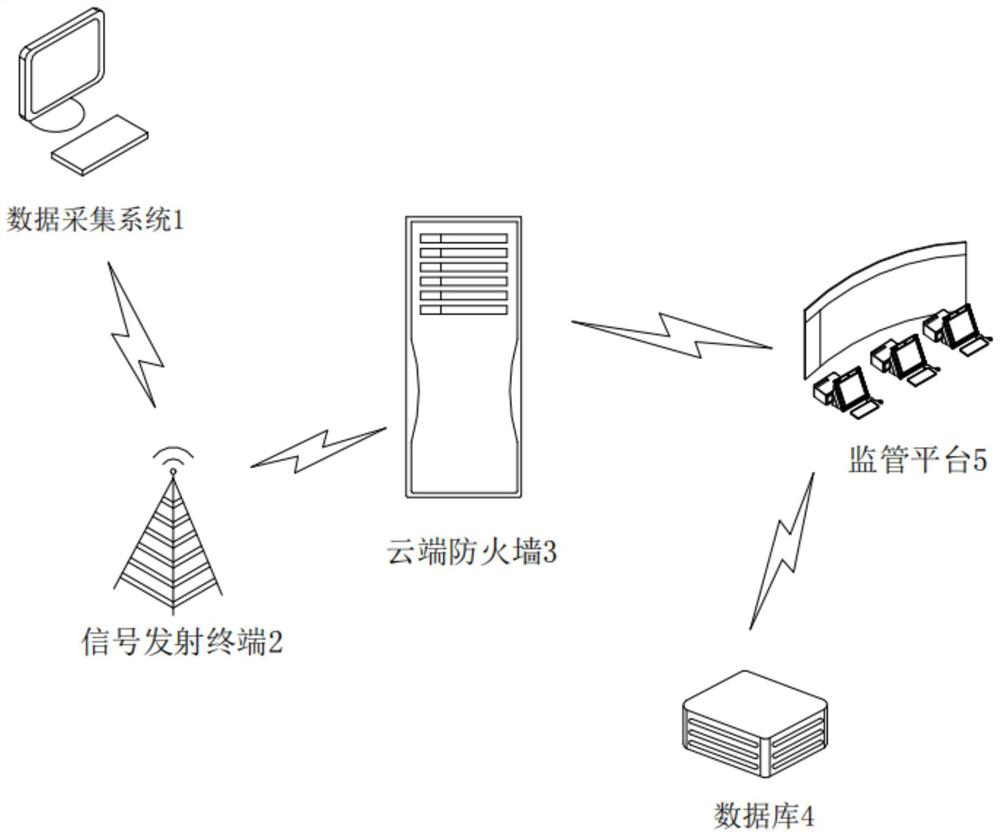
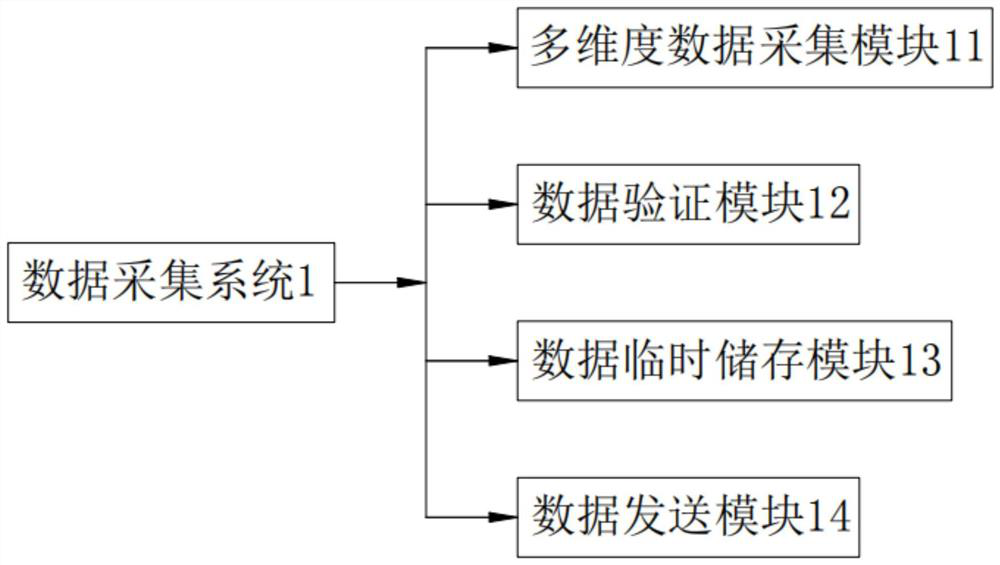
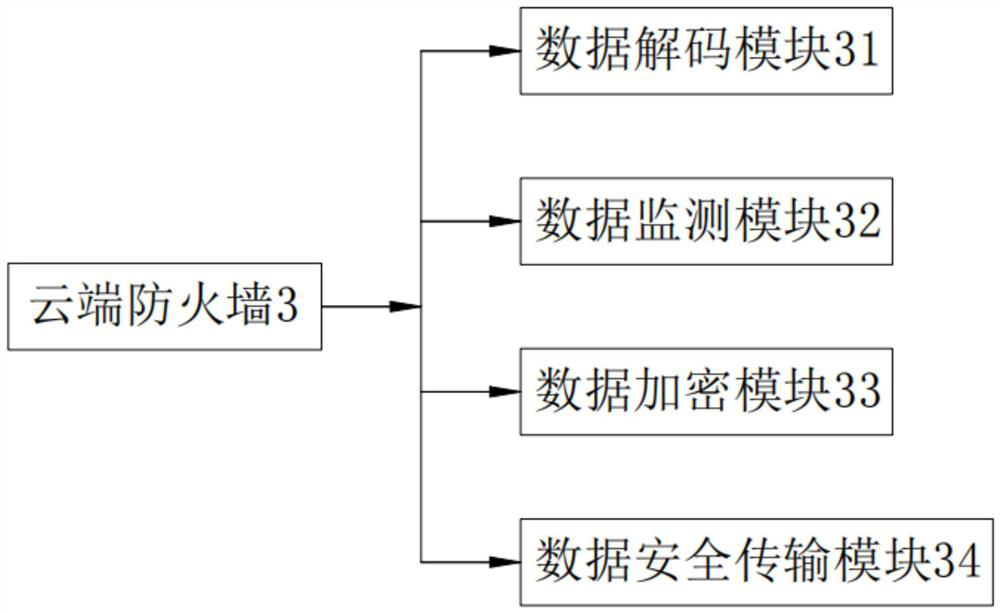
Equipment, firmware upgrading device thereof and firmware upgrading method thereof
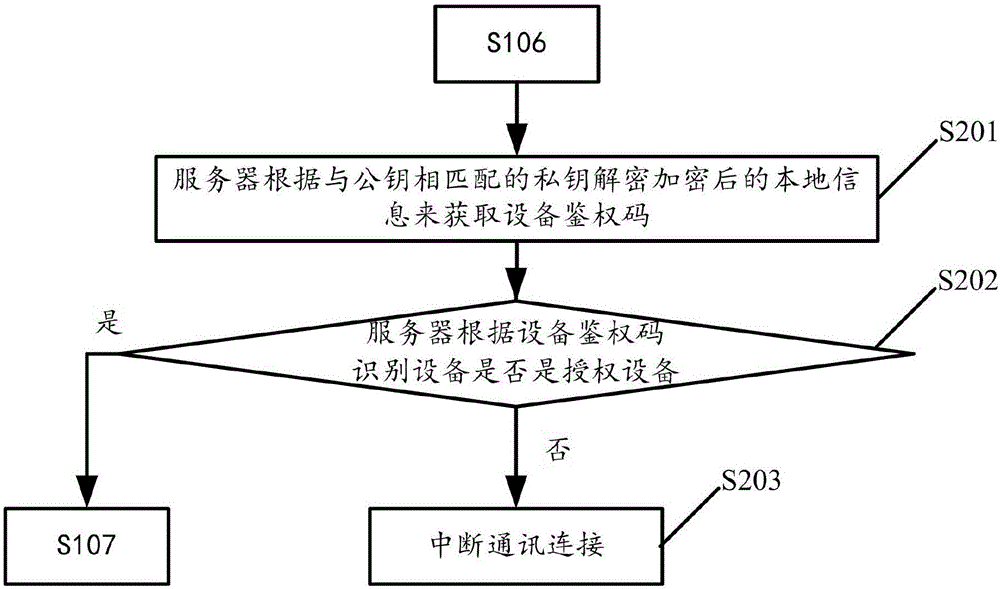
InactiveCN108196867AImprove transmission securityImprove securityUser identity/authority verificationSoftware deploymentTransmission securityFirmware
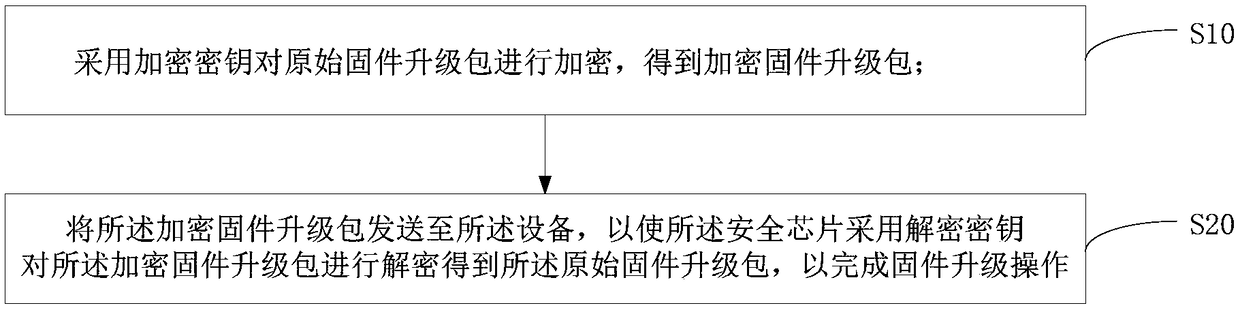
The invention discloses a firmware upgrading method of equipment. The equipment comprises a security chip which stores a decryption secret key. The firmware upgrading method includes following steps:adopting an encryption secret key to encrypt an original firmware upgrading packet to acquire an encrypted firmware upgrading packet; sending the encrypted firmware upgrading packet to the equipment to enable the security chip to adopt the decryption secret key to decrypt the encrypted firmware upgrading packet to acquire the original firmware upgrading packet to complete firmware upgrading operation. The invention further discloses the equipment and a firmware upgrading device thereof. Transmission safety of the firmware upgrading packet of the equipment is improved, so that safety in remotefirmware upgrading of the equipment is improved.
Owner:SHENZHEN EXCELSECU DATA TECH
Key management method and system
InactiveCN106535184AImprove securityImprove transmission securityTransmissionSecurity arrangementSecure transmissionTerminal equipment
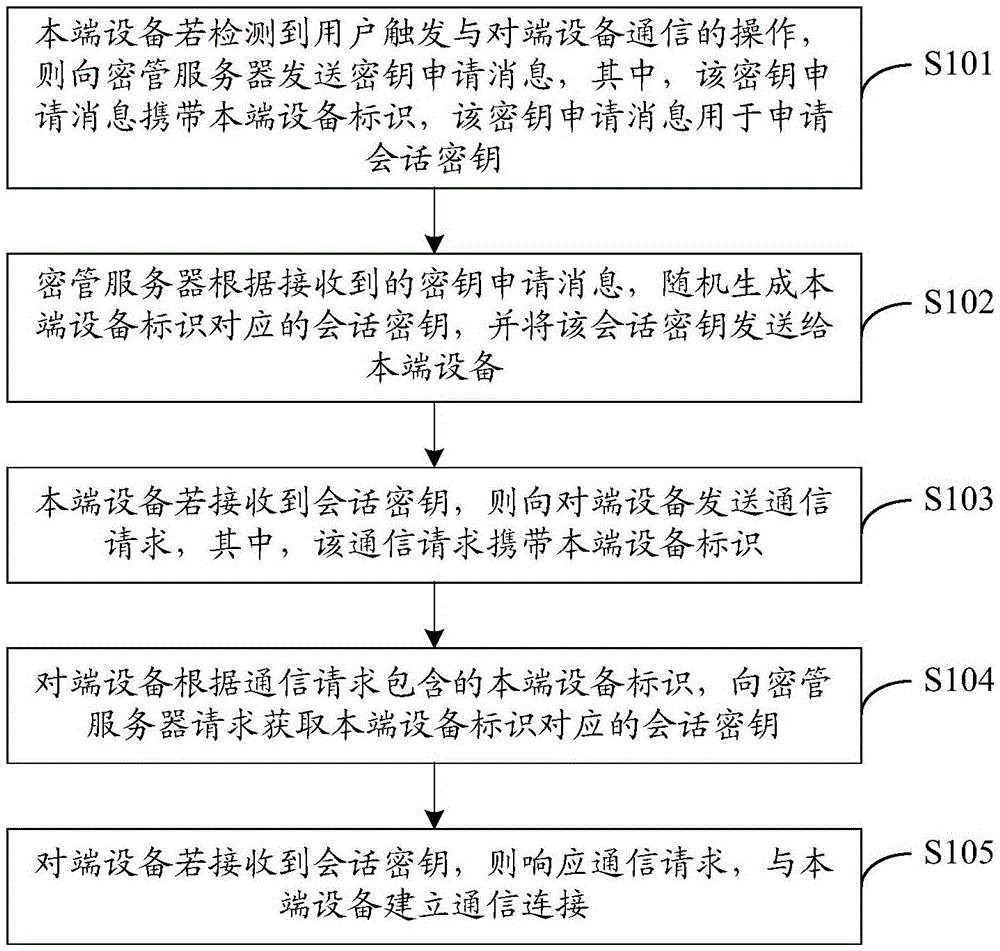
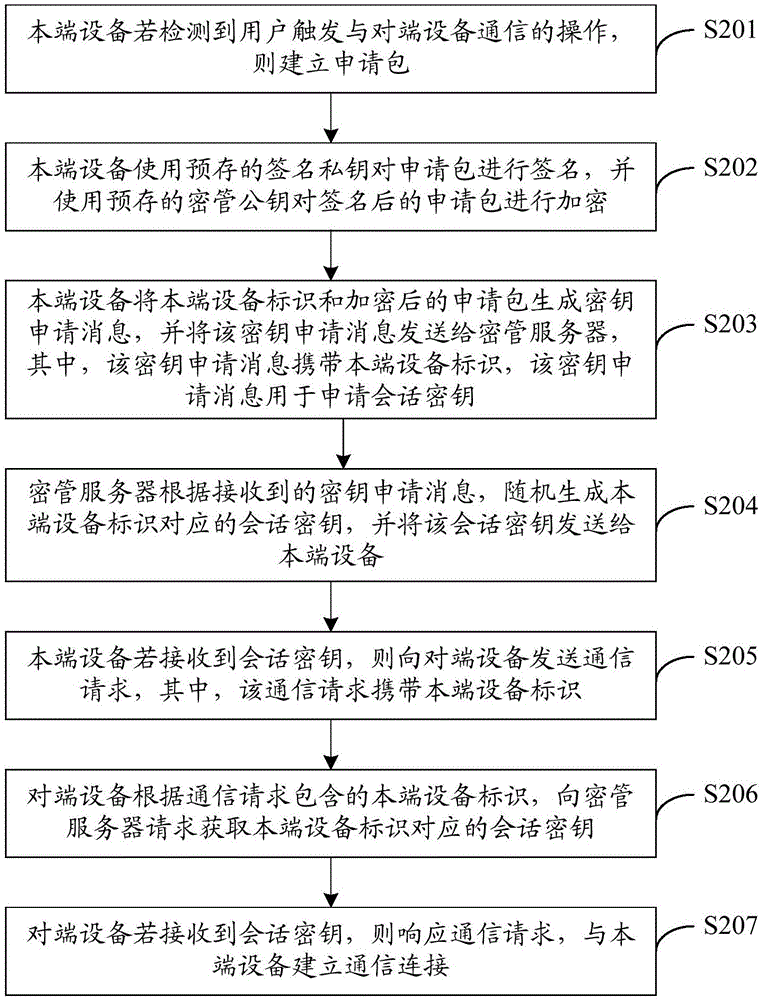
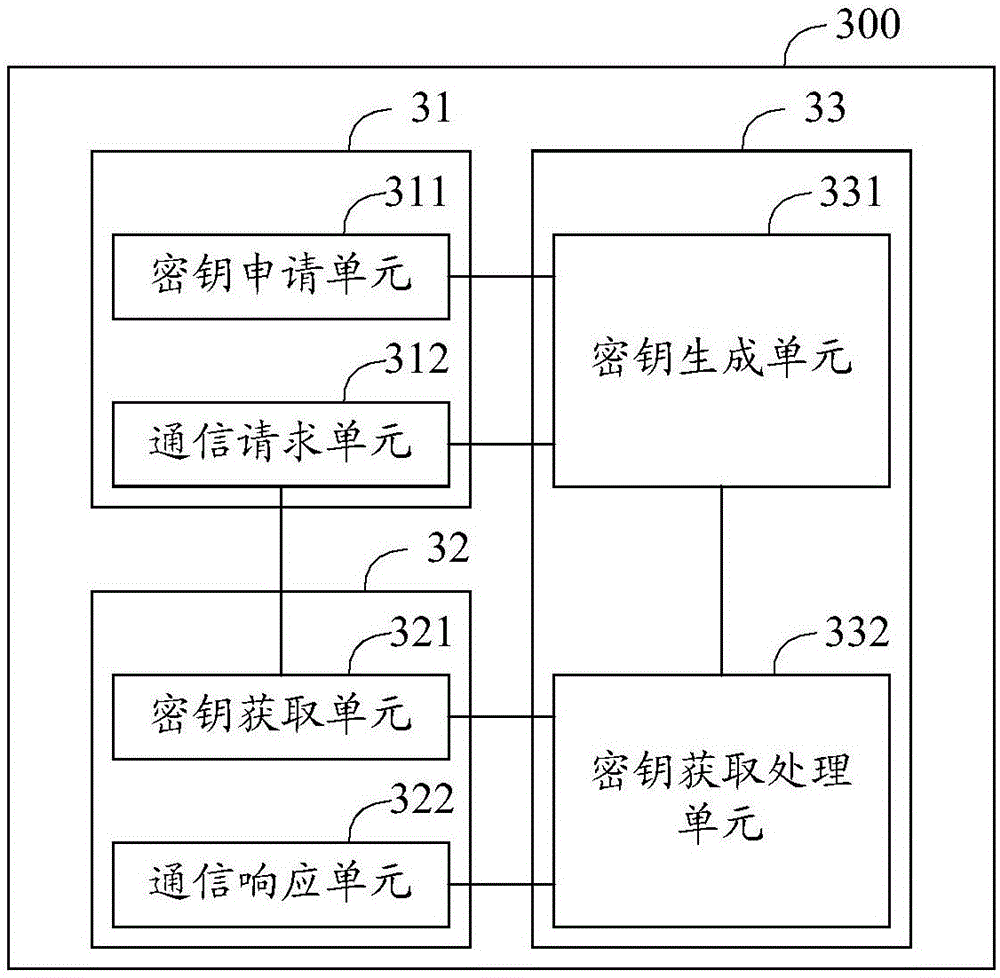
The embodiment of the invention discloses a key management method and system. The key management method includes the steps: if home terminal equipment detects that a user triggers the operation on opposite terminal equipment, the home terminal equipment sends a key application message to a key management server; according to the received key application message, the key management server generates a session key corresponding to an identifier of the home terminal equipment randomly, and sends the session key to the home terminal equipment; if the home terminal equipment receives the session key, the home terminal equipment sends a communication request to the opposite terminal equipment; according to the identifier of the home terminal equipment included in the communication request, the opposite terminal equipment requests the key management server to acquire the session key corresponding to the home terminal equipment; and if the opposite terminal equipment receives the session key, the opposite terminal equipment gives a response to the communication request and establishes communication connection with the home terminal equipment. The technical scheme of the key management method and system enables both the home terminal equipment and the opposite terminal equipment to safely acquire the session key of the communication of this time, thus improving generation safety and transmission safety for the session key, and guaranteeing safe transmission of the communication content.
Owner:SHENZHEN GIONEE COMM EQUIP
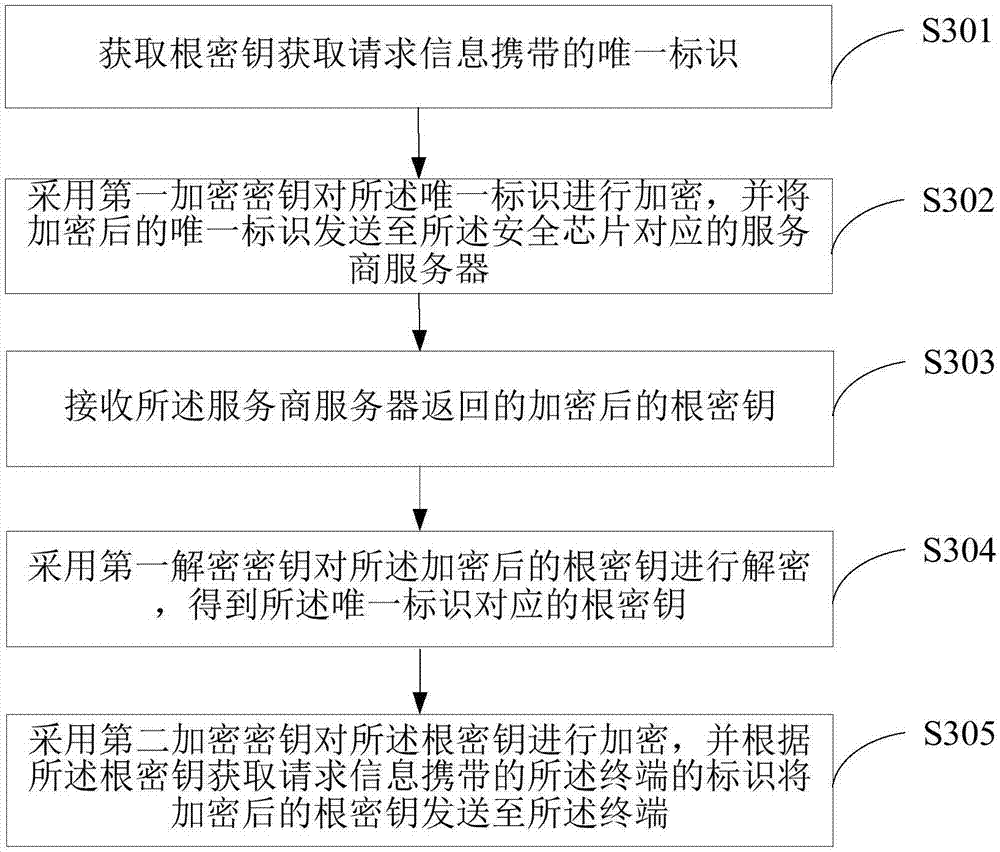
Method for obtaining root key and server
InactiveCN107276756AReduce risk of leakageImprove transmission securityKey distribution for secure communicationSecurity arrangementTransfer procedureUnique identifier
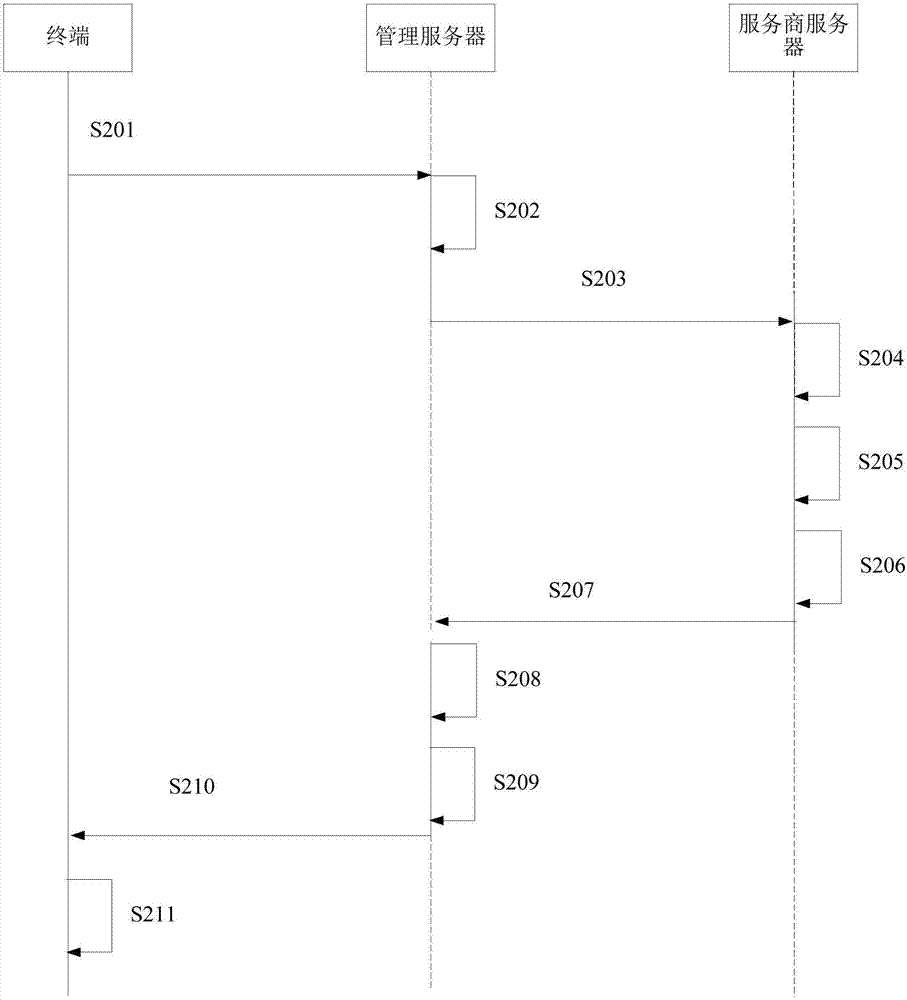
The embodiment of the invention discloses a method for obtaining a root key and a server. The method comprises the steps of obtaining a unique identifier of a security chip carried by root key obtaining request information, wherein the root key obtaining request information is sent by a terminal; encrypting the unique identifier through adoption of a first encryption key and sending the encrypted unique identifier to a service provider server corresponding to the security chip; receiving the encrypted root key returned by the service provider server; decrypting the encrypted root key through adoption of a first decryption key, thereby obtaining the root key corresponding to the unique identifier; encrypting the root key through adoption of a second encryption key and sending the encrypted root key to the terminal according to an identifier of the terminal carried by the root key obtaining request information; and decrypting the encrypted root key by the terminal through adoption of a second decryption key, thereby obtaining the root key. According to the embodiment of the invention, the risk of leaking the root key in a transmission process can be effectively reduced, the transmission security of the root key is improved, and the security of the information in the terminal is improved.
Owner:SHENZHEN GIONEE COMM EQUIP
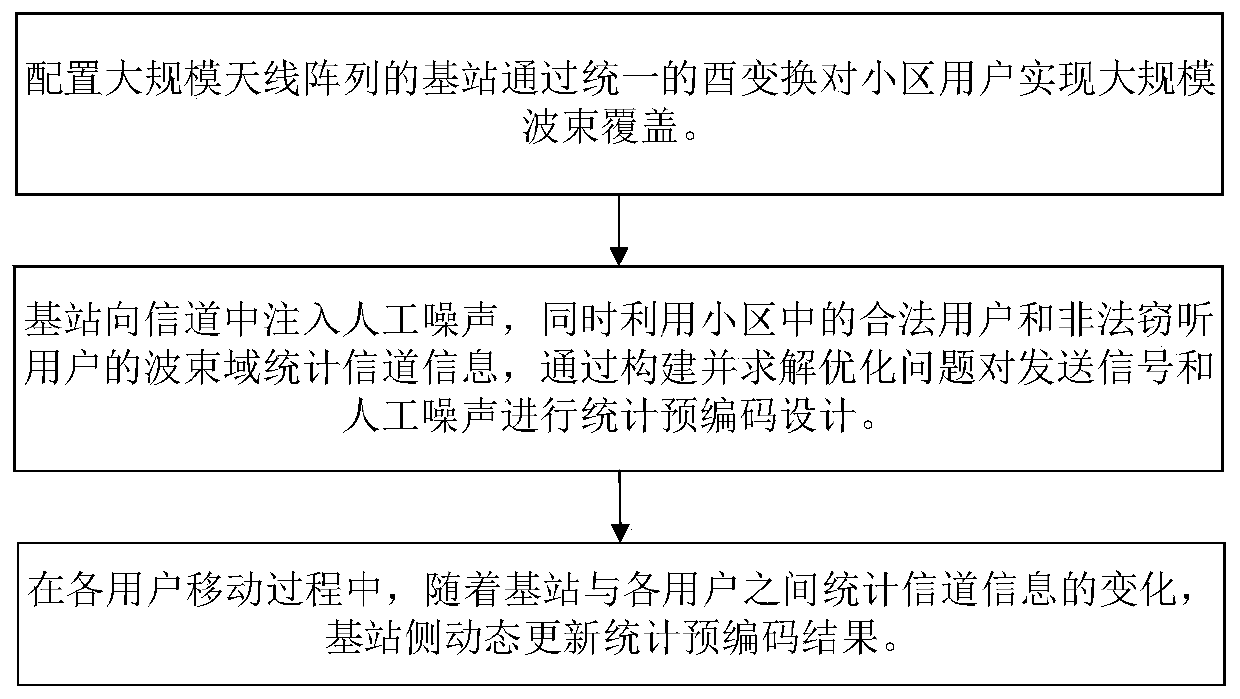
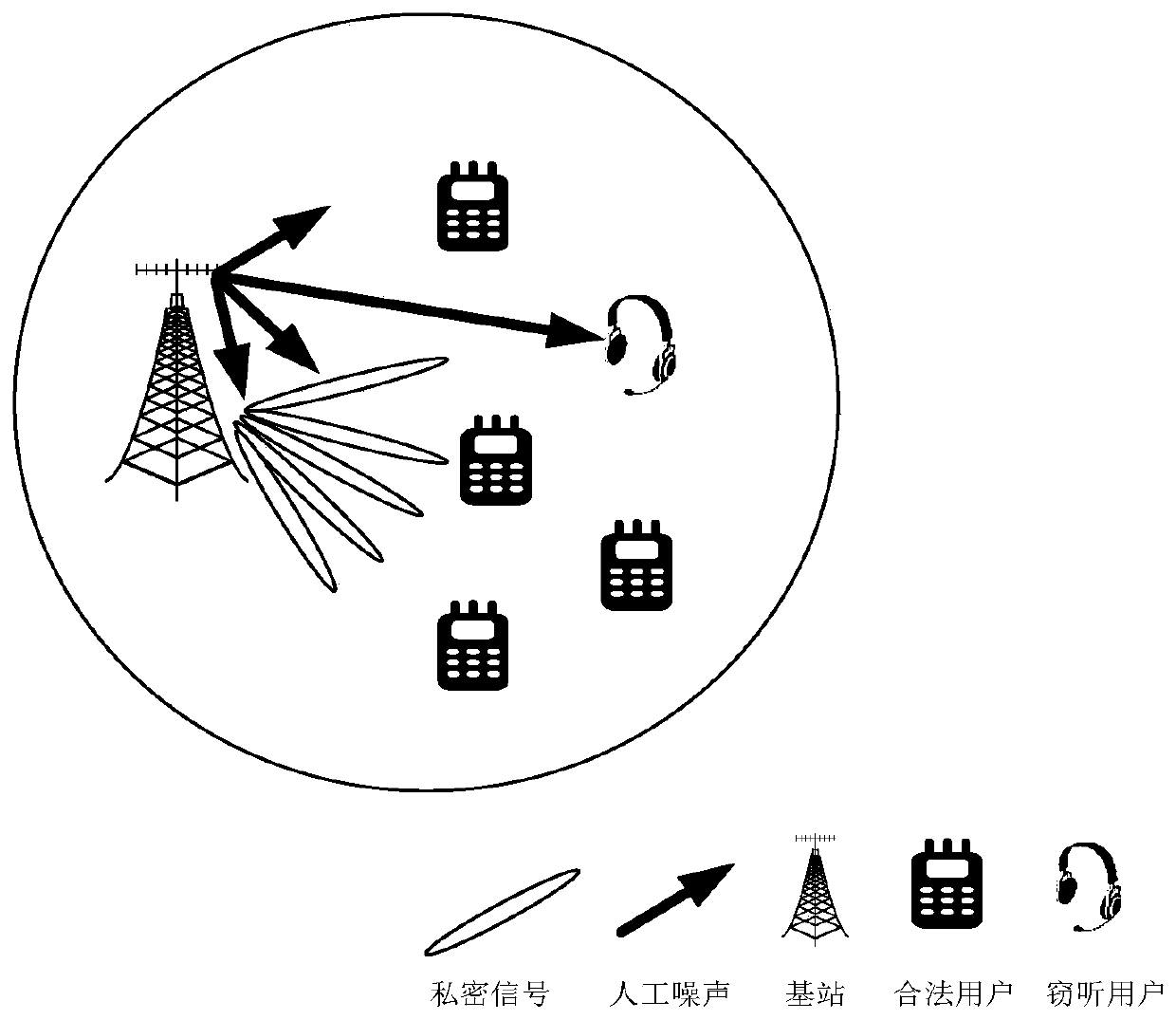
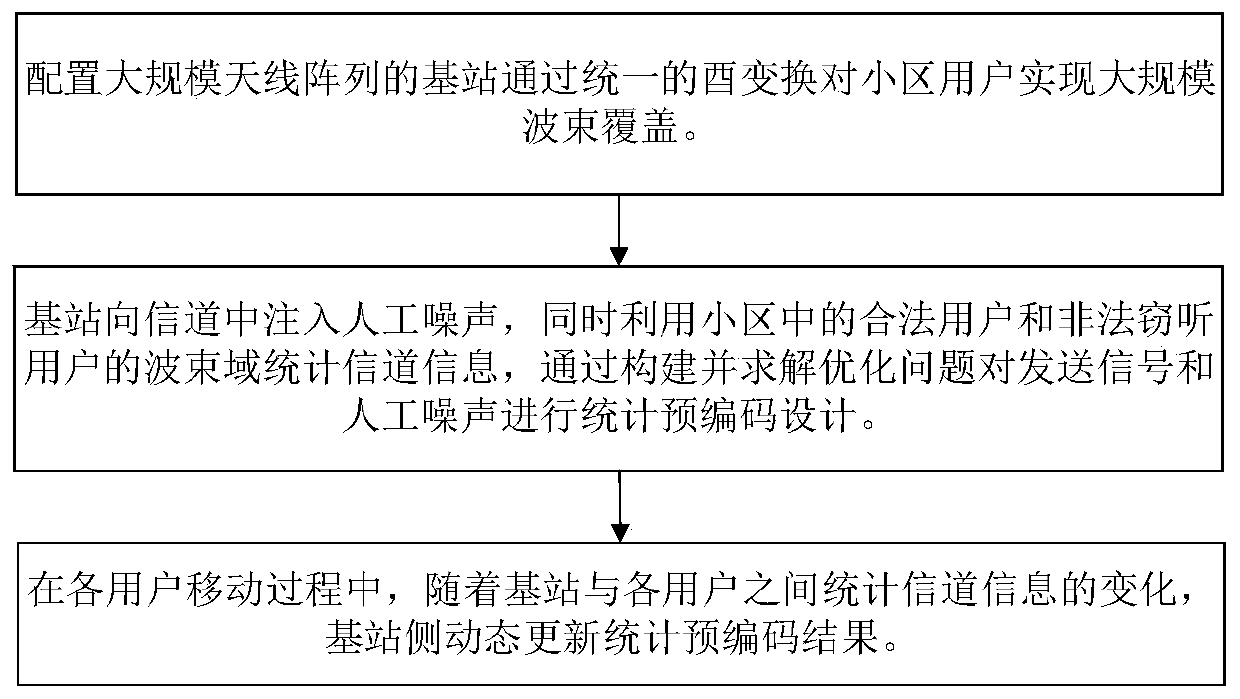
Artificial noise assisted large-scale MIMO security statistical precoding method
ActiveCN109981153AImprove efficiencyImprove spectral efficiencyRadio transmissionSecure transmissionEngineering
The invention provides an artificial noise assisted large-scale MIMO security statistical precoding method. In the method, a cell base station is configured with a large-scale antenna array, and large-scale beam coverage is realized on the whole cell by utilizing a unified unitary transformation matrix. The base station uses beam domains of legal users and eavesdropping users in a cell to count channel information and injects artificial noise into the channel to reduce the decoding capability of the eavesdropping users, and performs statistical precoding design on the signals sent to each legal user and the artificial noise sent to the eavesdropping users according to the criterion of maximizing the system reachable traversal security and rate lower bound. In the moving process of each legal user and each eavesdropping user, the base station intermittently acquires statistical channel information and dynamically updates a statistical precoding result. According to the invention, the problem that the base station side only knows the design of the beam domain secure transmission signal of the statistical channel information is solved, the realization complexity is reduced, and meanwhile, the introduction of artificial noise improves the security of system transmission.
Owner:SOUTHEAST UNIV
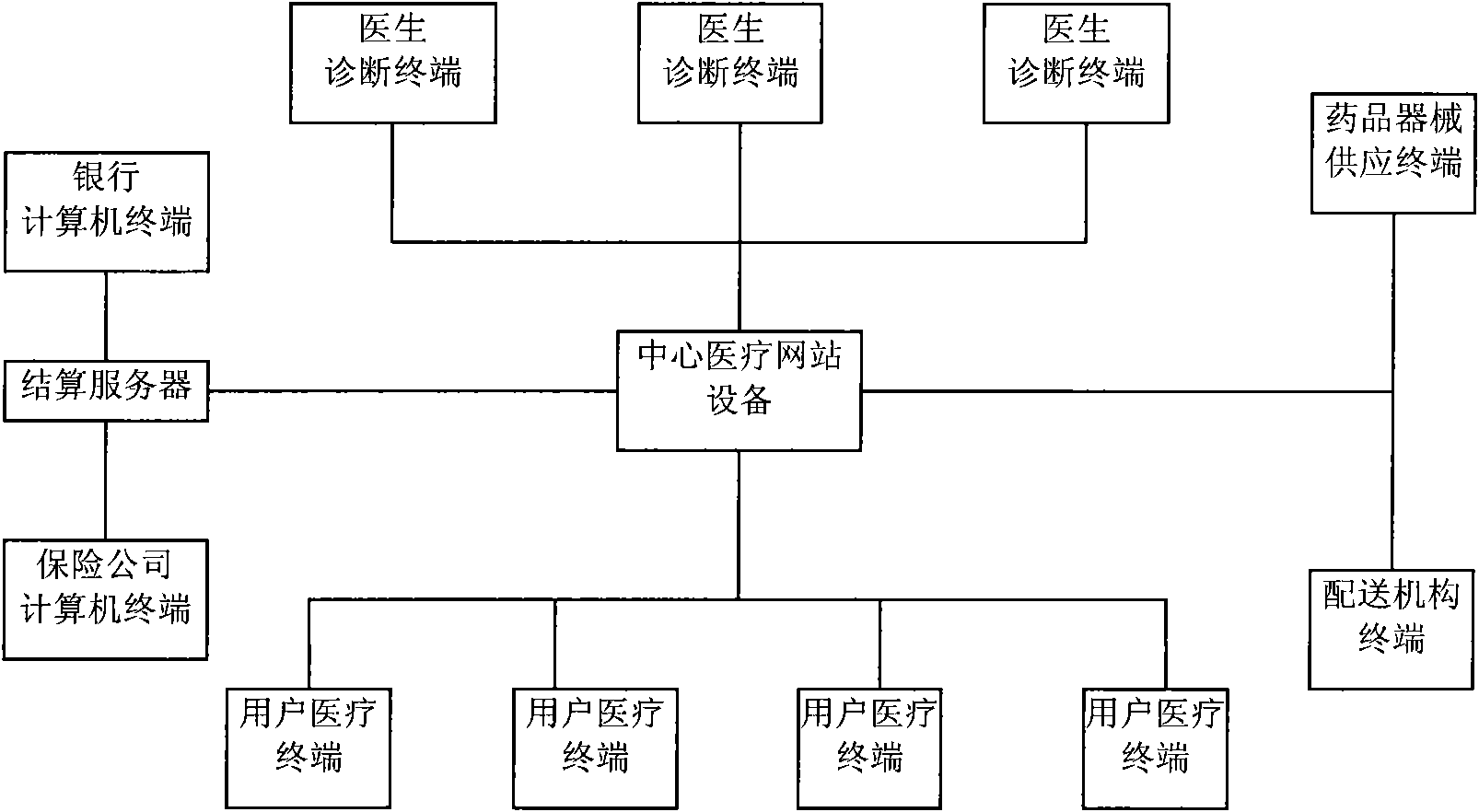
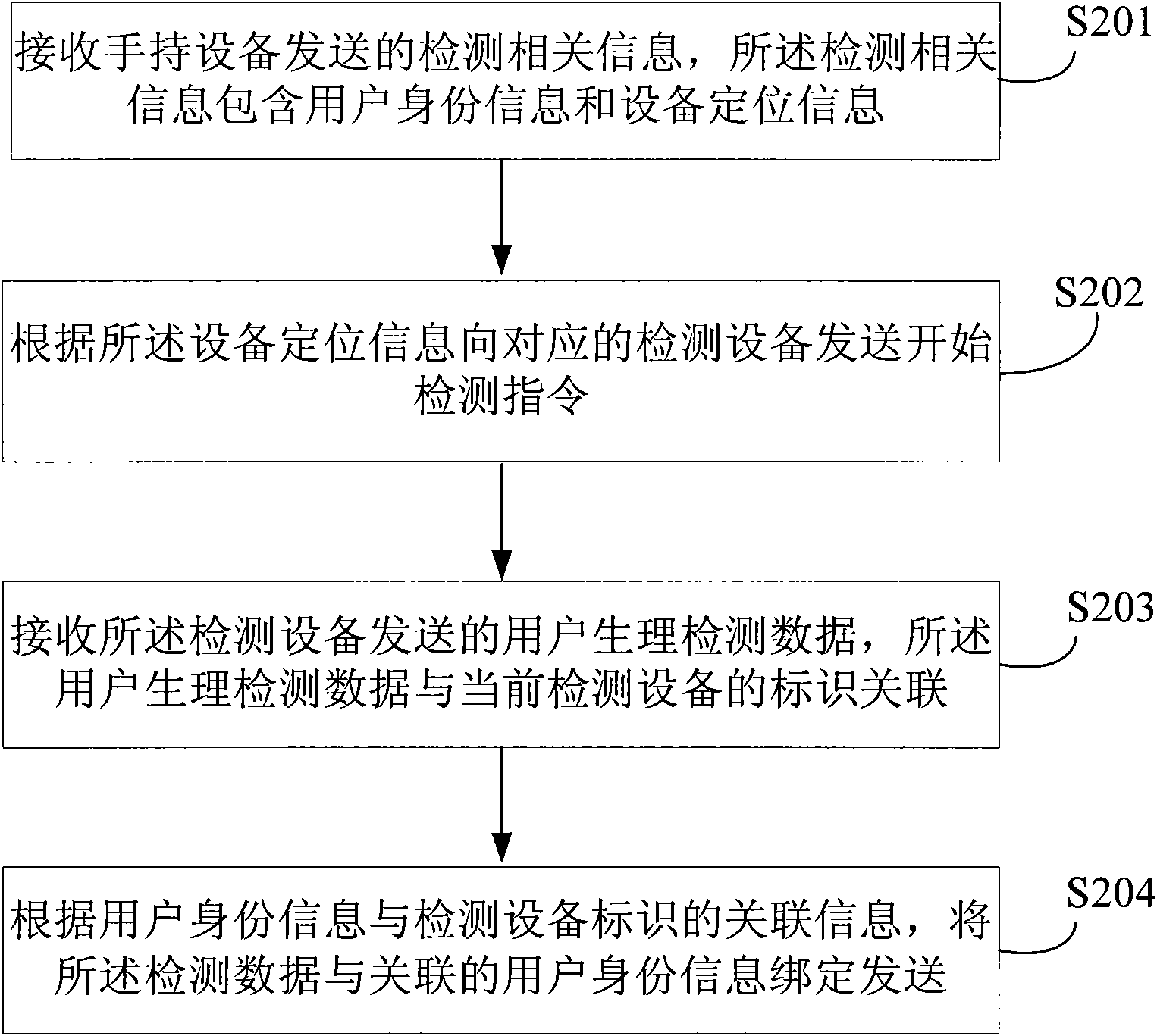
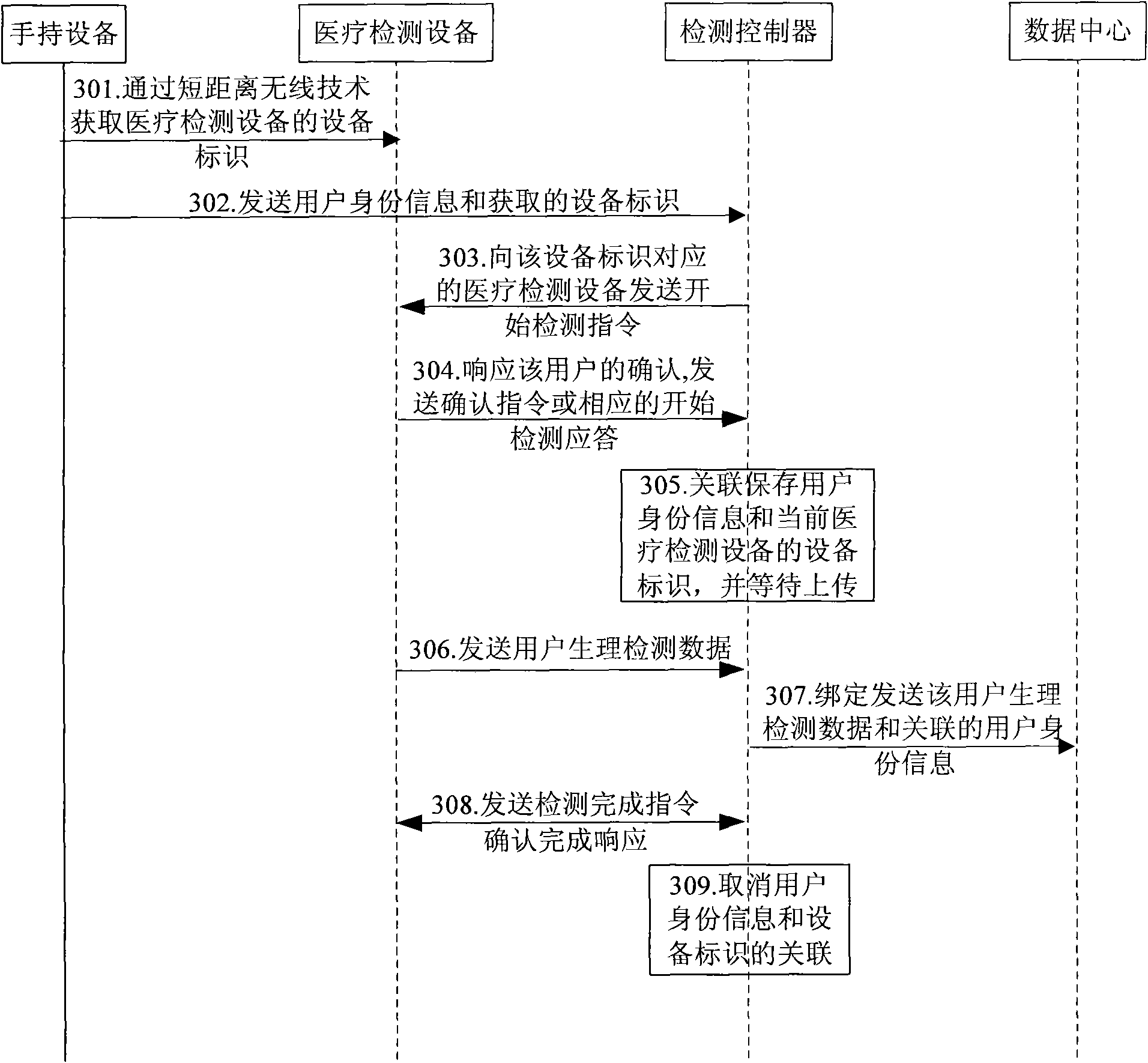
Method, device and system for remotely acquiring physical detection data of user
ActiveCN101926675AImprove transmission securityAvoid malicious eavesdroppingSurgeryTelemedicineInternet privacyHandheld equipment
The embodiment of the invention discloses a method, a device and a system for remotely acquiring physical detection data of a user. The method comprises the following steps of: receiving detection-related information transmitted by handheld equipment, wherein the detection-related information comprises user identity information and equipment positioning information; sending a detection start command to corresponding medical detection equipment according to the equipment positioning information; receiving the physical detection data of the user transmitted by the medical detection equipment, wherein the physical detection data of the user is associated with an equipment identifier of the current medical detection equipment; and binding the physical detection data of the user with the associated user identity information according to the associated information between the user identity information and the equipment identifier of the medical detection equipment for transmitting. The medical detection equipment is used for detecting a certain user, so that the physical detection data of the user is not wiretapped maliciously.
Owner:HUAWEI TECH CO LTD
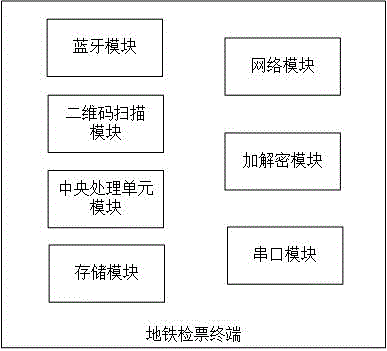
Subway ticket checking terminal based on low-power-consumption bluetooth and two-dimensional code scanning
InactiveCN105405170AFast check-inImprove transmission securityTicket-issuing apparatusWireless commuication servicesBroadcast packetInformation transmission
The invention provides a subway ticket checking terminal based on a low-power-consumption bluetooth and two-dimensional code scanning. The terminal is composed of a bluetooth module, a two-dimensional code scanning module, a central processing unit module, a storage module, a network module, an encryption and decryption module, and a serial port module. The bluetooth module is used for broadcasting a data packet with a low-power-consumption bluetooth 4.0 or above version; the two-dimensional code scanning module is used for scanning a two-dimensional code, wherein the code system of the two-dimensional code is PDF417; the encryption and decryption module is a PSAM card; and the serial port module is used for invoking an industrial personal computer device of external equipment to open a turnstile of the subway. According to the invention, on the basis of combination of the low-power-consumption bluetooth technology and two-dimensional code scanning, rapid ticket checking by the subway ticket checking terminal is realized; information transmission safety and stability are improved; the user experience degree is high; and the market prospect of popularization and application is broad.
Owner:GUANGXI MIFU NETWORK TECH
Method and device for cross-network safe transmission
InactiveCN103067405AAchieving a diffusion-proof connectionImprove securityTransmissionSecurity arrangementInternet communicationGraphics
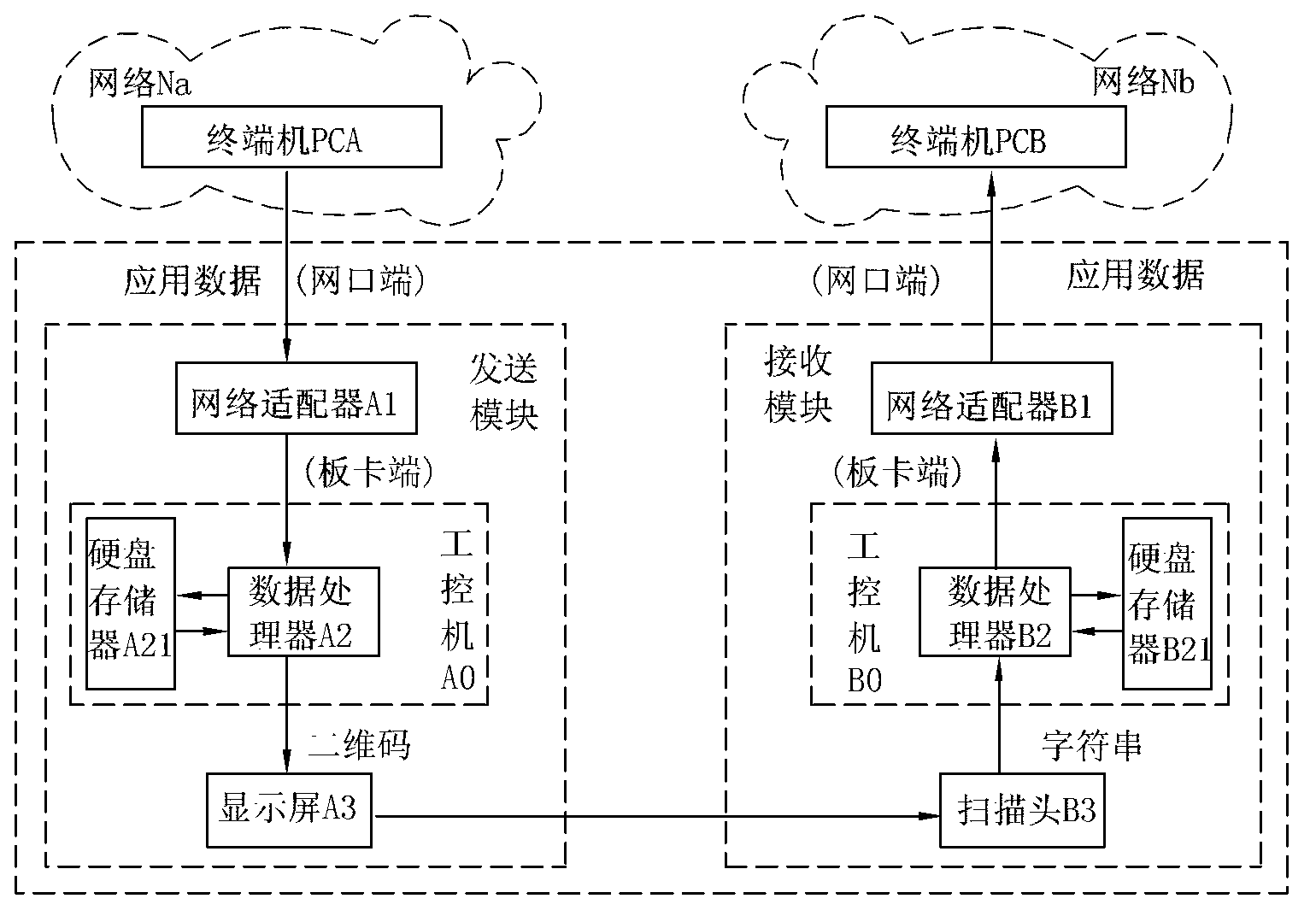
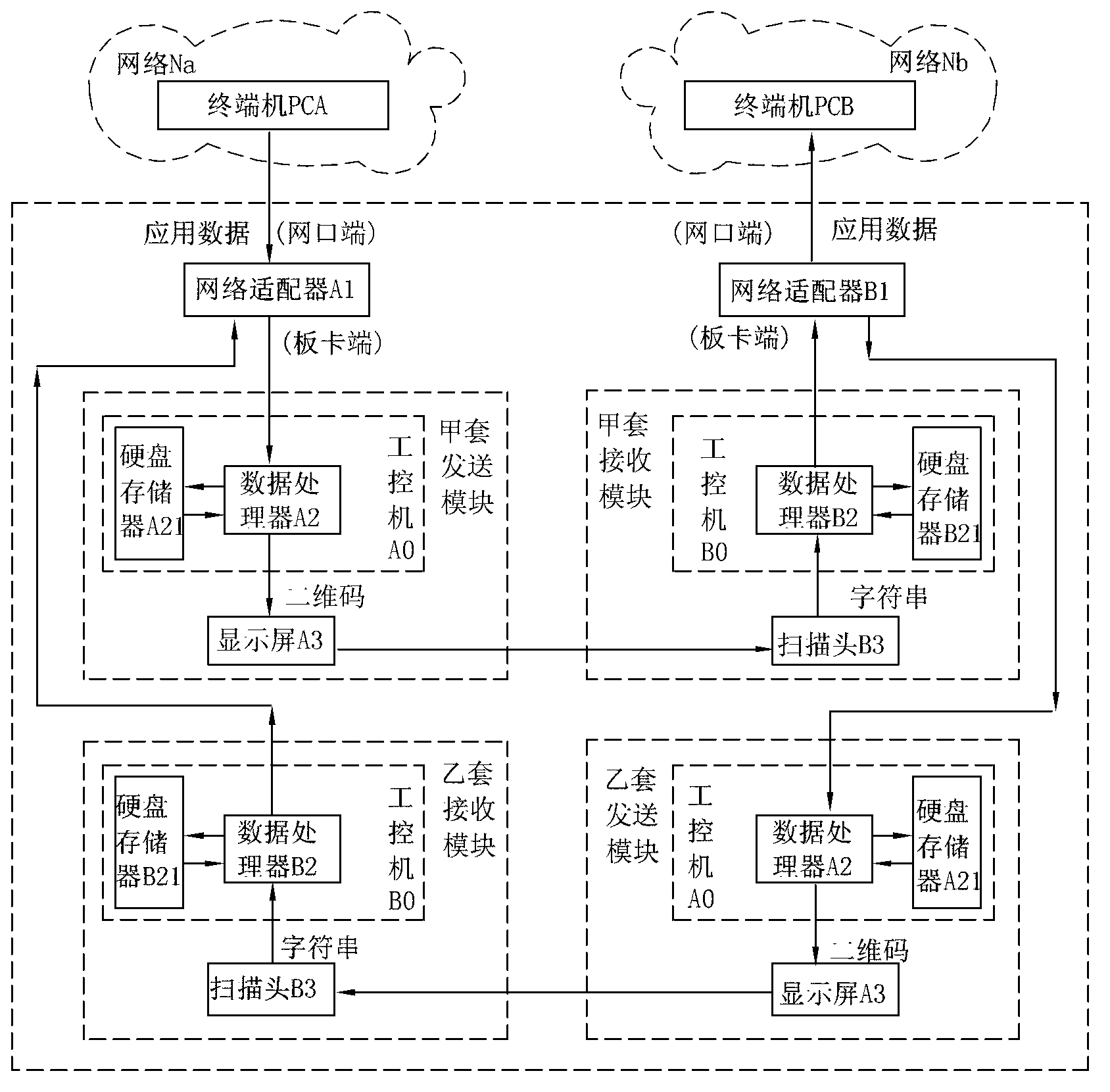
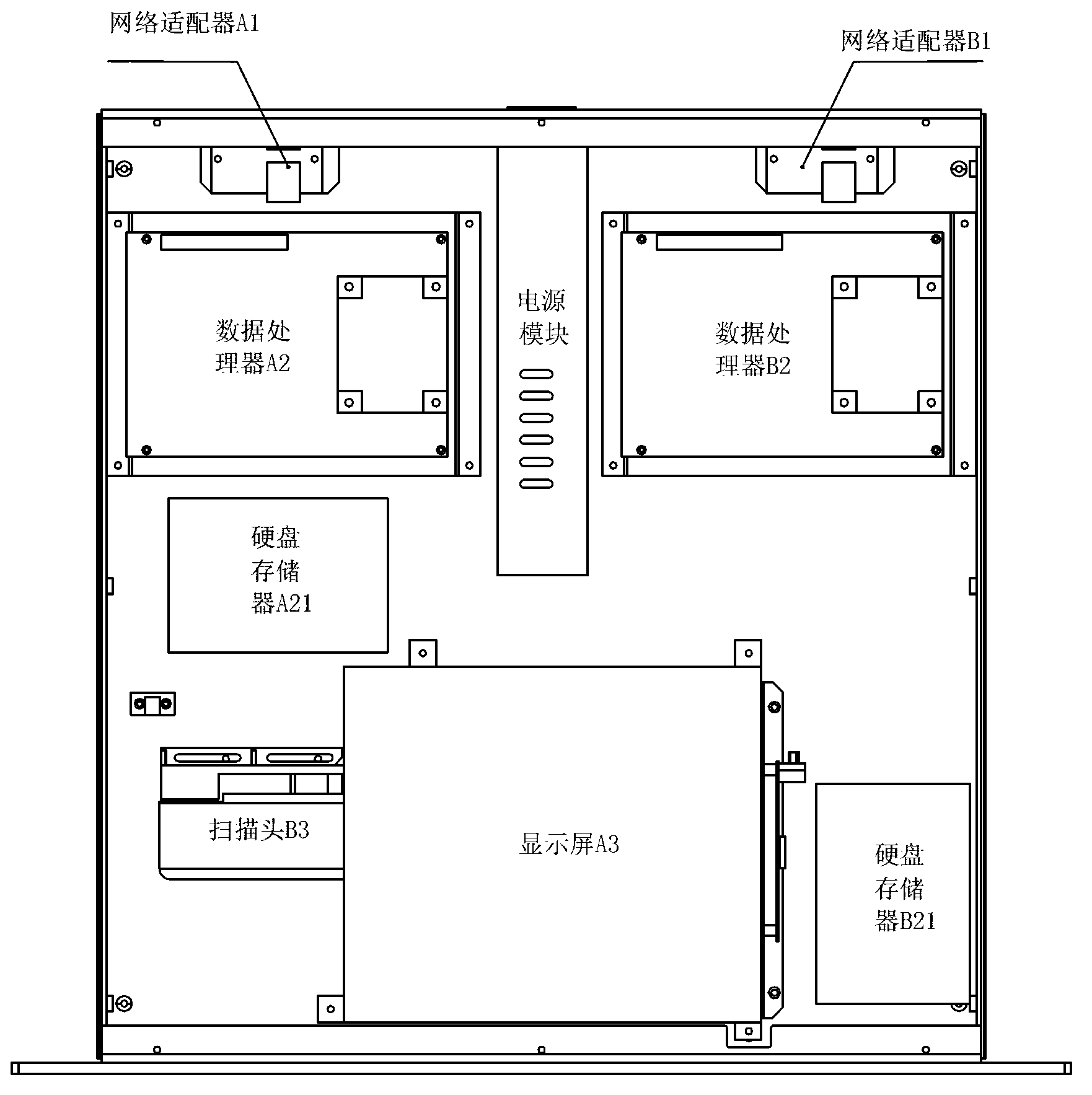
The invention relates to a method and a device for cross-network safe transmission. The method comprises receiving data flow from a network Na and selecting a data packet with an expanded-name appointed; partitioning and organizing data according to content identification and order identification of the data packet; converting the data to a corresponding character string; converting the character string to a two-dimension code pattern and displaying the two-dimension code pattern on a display screen; scanning and receiving the two-dimension code by a scan head, analyzing the two-dimension code to be the corresponding character string, converting the character string into the data packet with the expanded-name, the content identification and the order identification and sending the data packet to a network Nb. According to the method and the device for the cross-network safe transmission, two sides offering communication adopt an anti-diffusion wireless-connected communicating method and adopt a self-defined communicating protocol to achieve interconnection and intercommunication of two independent networks instead of adopting a traditional public wireless network communication protocol, and therefore independence of the two communicating networks can be guaranteed completely , the shortage that the traditional network communication protocol is lack of safety is overcome and safety factors of internet communication are greatly increased.
Owner:SHENZHEN MAXVISION TECH
Quantum secret communication network system based on quantum key distribution technology, and application thereof
PendingCN109302288AAvoid attackImprove transmission securityKey distribution for secure communicationService provisionSingle point
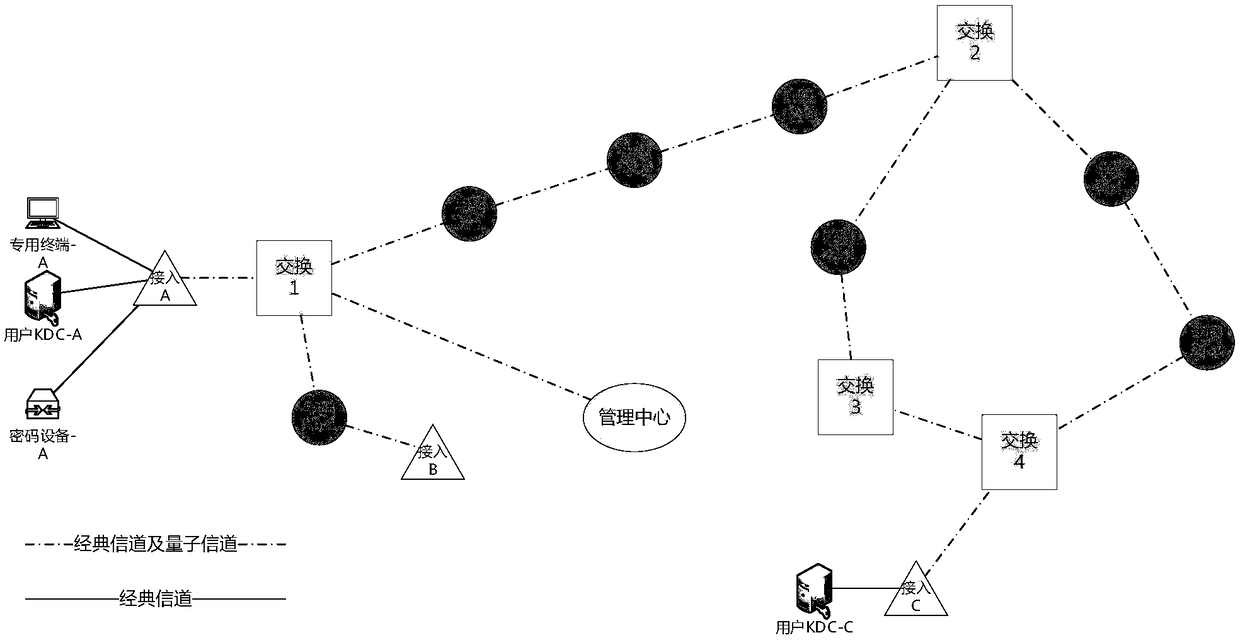
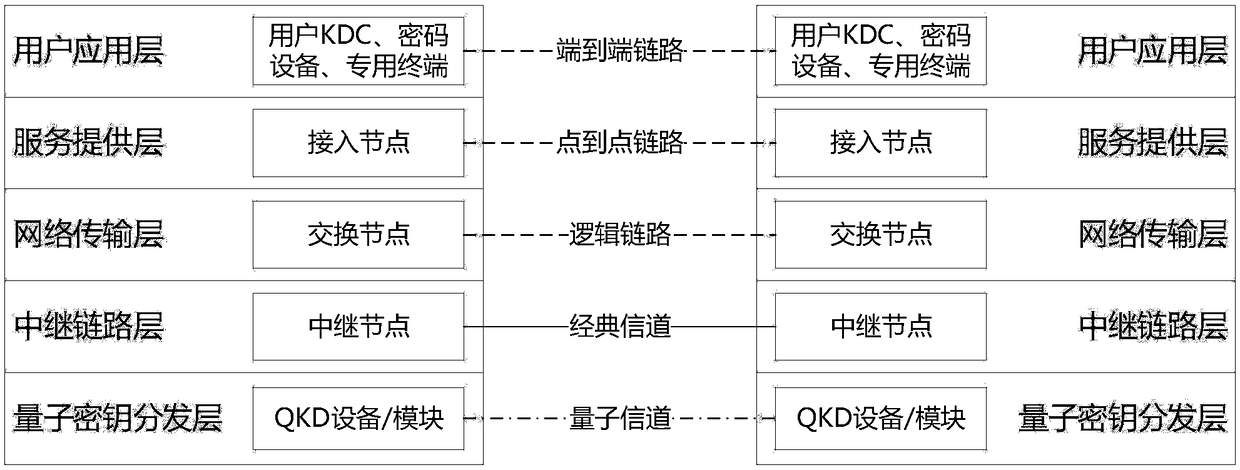
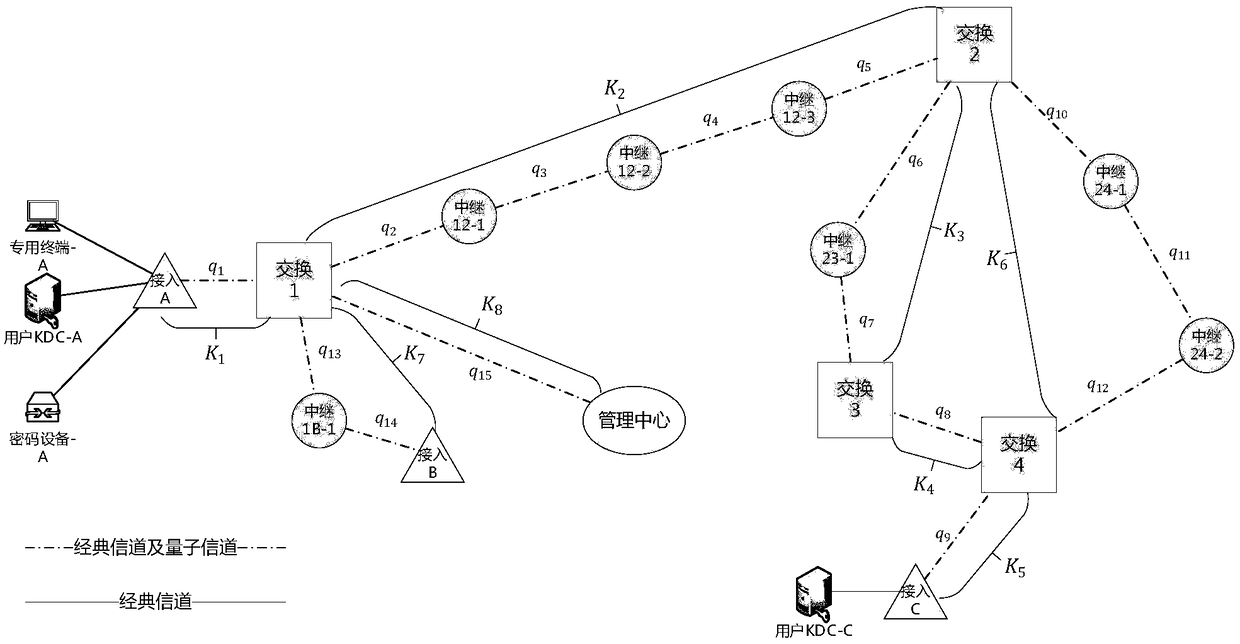
The invention discloses a quantum secret communication network system based on quantum key distribution technology, and an application thereof. The quantum secret communication network system physically comprises an access node, a switching node and a relay node, the nodes are respectively connected by using classic channels and quantum channels, wherein the classic channel for quantum key distribution performs communication in a non-IP mode; and the network system is logically divided into a quantum key distribution layer, a relay link layer, a network transmission layer, a service provisionlayer and a user application layer from bottom to top. The quantum secret communication network system disclosed by the invention overcomes the single point failure problem caused by a centralized routing server in the existing network; and the quantum secret communication network system disclosed by the invention communicates the classic channel for quantum key distribution in the non-IP mode, thereby effectively avoiding the network attacks for the TCP / IP technology, and the communication protection based on a quantum key is used as a basic function to further enhance the transmission security of the classic channel.
Owner:中共中央办公厅电子科技学院 +1
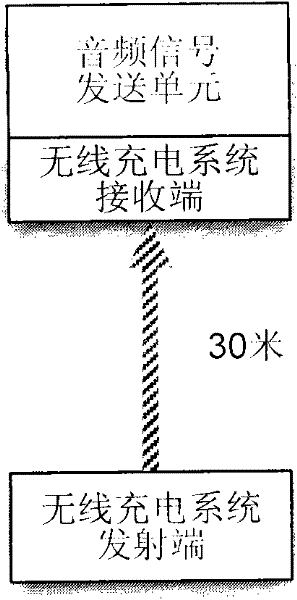
System for audio transmission via wireless network
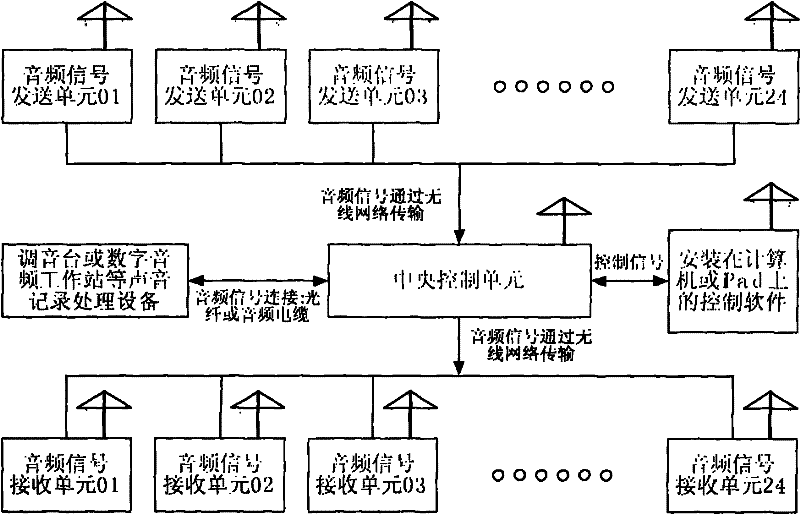
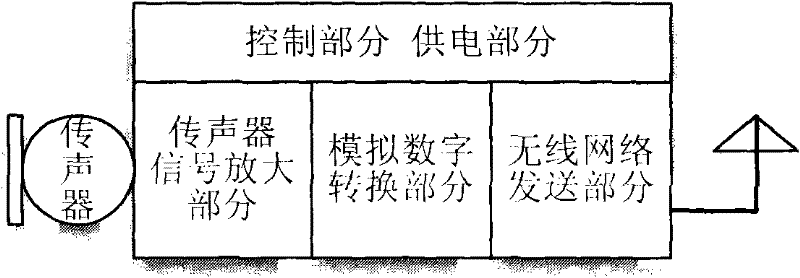
The invention relates to a system for audio transmission via a wireless network, which transmits digital audio signals via a wireless network. The system includes an audio signal transmission unit and a central control unit, wherein the audio signal transmission unit receives audio signals from a piece of upper-level audio equipment, and analog audio signals are converted to digital audio signals and network data packages transmitted to the central control unit via a wireless network. The audio data is received by the central control unit and reverted to audio signals. The system further includes a piece of audio processing equipment for storing, processing or mixing audio signals.
Owner:冯汉英
Method and device for improving reliability of communication between vehicles
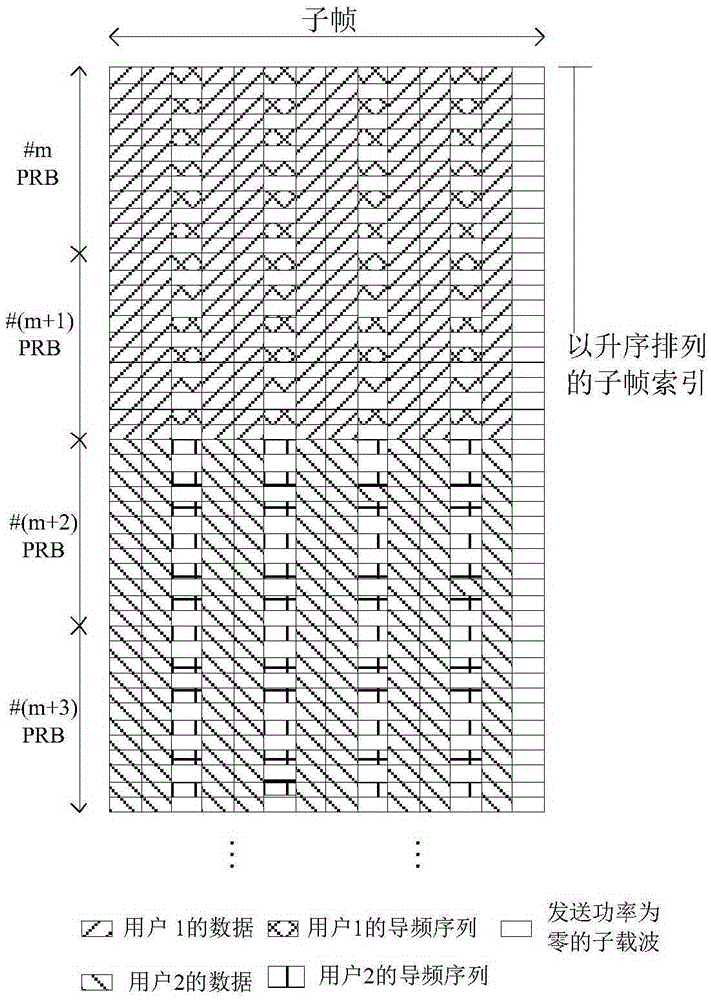
ActiveCN106656441ASolve frequency offsetSolving the Channel Estimation ProblemCarrier regulationChannel estimationTime domainResource block
The embodiment of the invention provides a method and device for improving the reliability of communication between vehicles. In one embodiment of the invention, the method comprises the steps: selecting c OFDM symbols on a physical resource block, wherein c is not less than three; transmitting pilot frequency sequences on an even number of subcarriers in the selected c OFDM symbols, and transmitting the pilot frequency sequences at zero power on an odd number of subcarriers in the selected c OFDM symbols, so as to enable each OFDM symbol for transmitting the pilot frequency sequences to be divided into a front half OFDM symbol and a rear half OFDM symbol in the time domain, wherein the front half OFDM symbol and the rear half OFDM symbol are the same. Through the configuration of the receiving and transmitting of the pilot frequency sequences, the method not only can achieve the precise channel estimation under the condition of quick channel fading during the vehicle-to-vehicle transmission, but also can achieve the precise frequency offset evaluation and compensation in the frequency domain at the same time.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
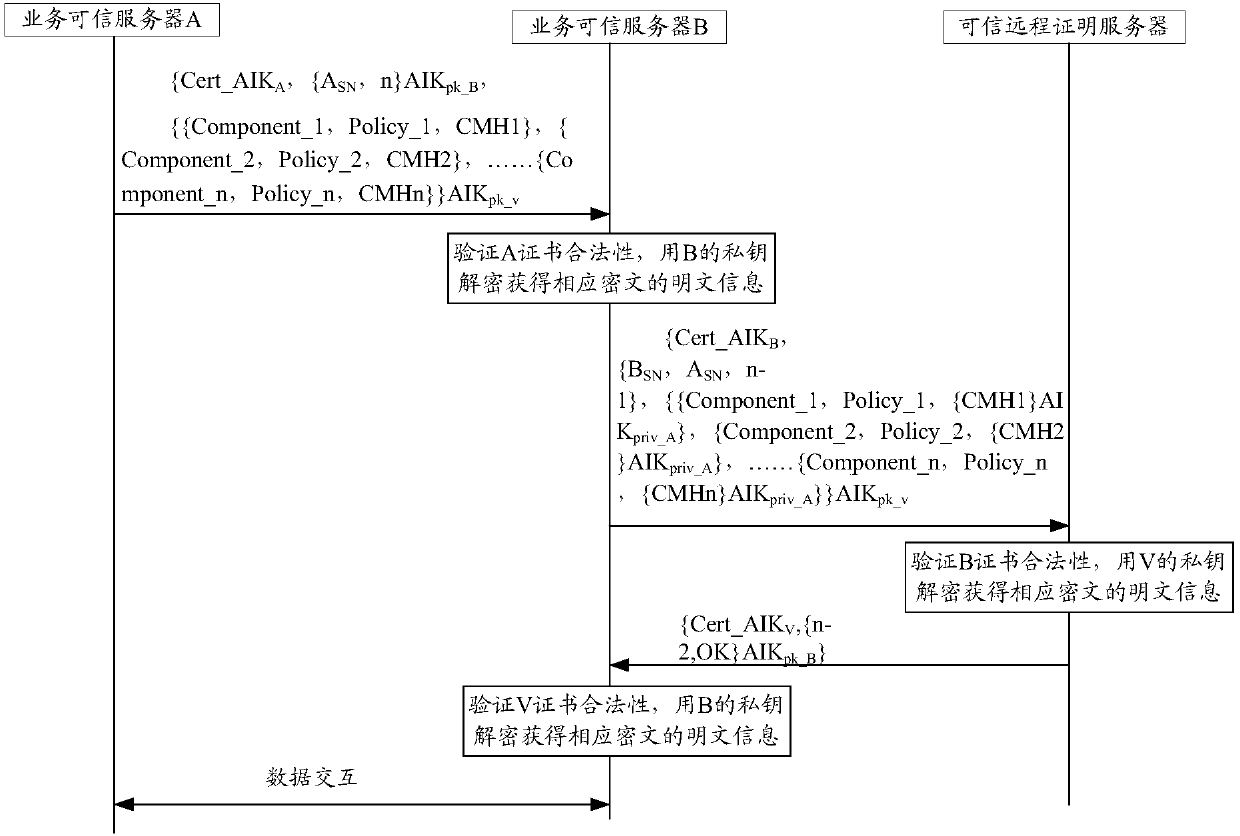
Trusted remote certification method, device and system
ActiveCN109714168AEnsure safetyGuarantee the security of private informationPublic key for secure communicationUser identity/authority verificationComputer terminalInformation security
The invention discloses a trusted remote certification method, device and system. The method comprises the following steps: receiving a challenge request sent by a first service trusted server, and obtaining to-be-verified information of the first service trusted server in the challenge request; And sending a verification request to the trusted remote attestation server, the verification request comprising to-be-verified information of the first service server; and obtaining a verification response returned by the trusted remote attestation server. The technical problems that operation of theserver terminal is affected in the strategy deployment process and plaintext transmission is adopted to cause information security in a remote proving mechanism in the related technology are solved.
Owner:ALIBABA GRP HLDG LTD
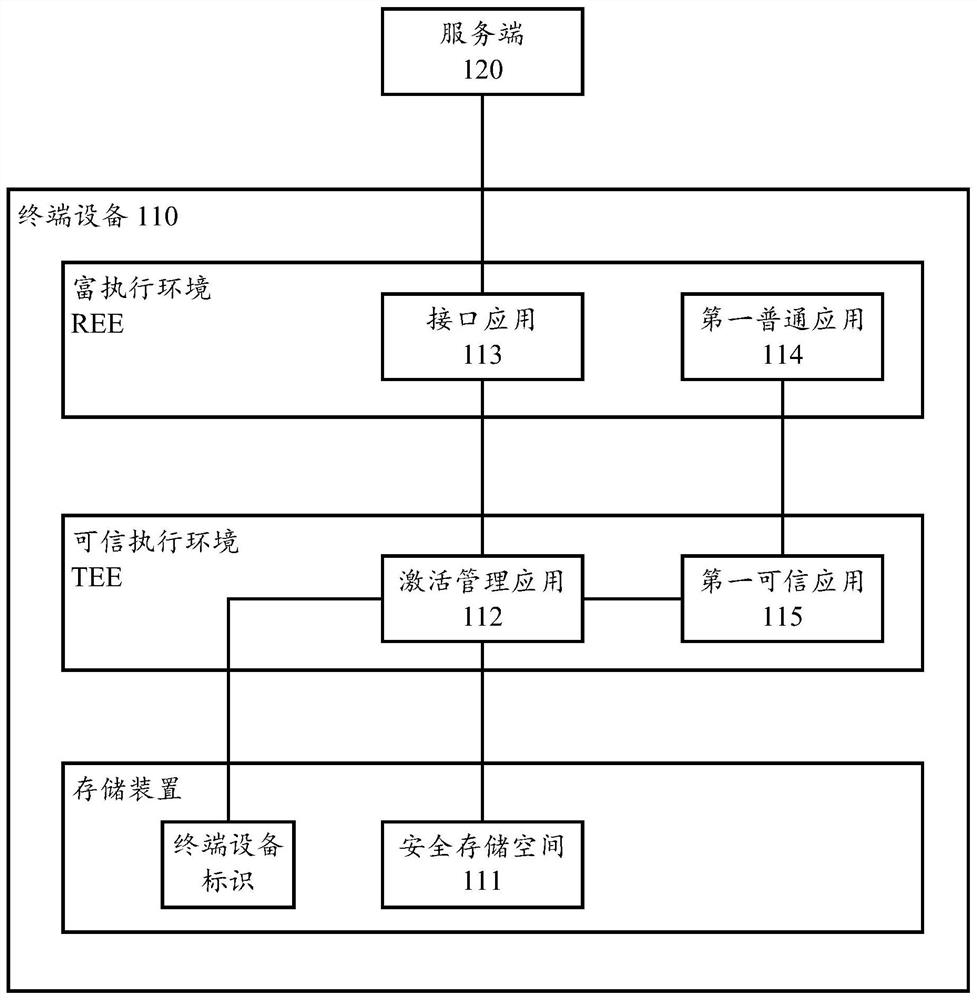
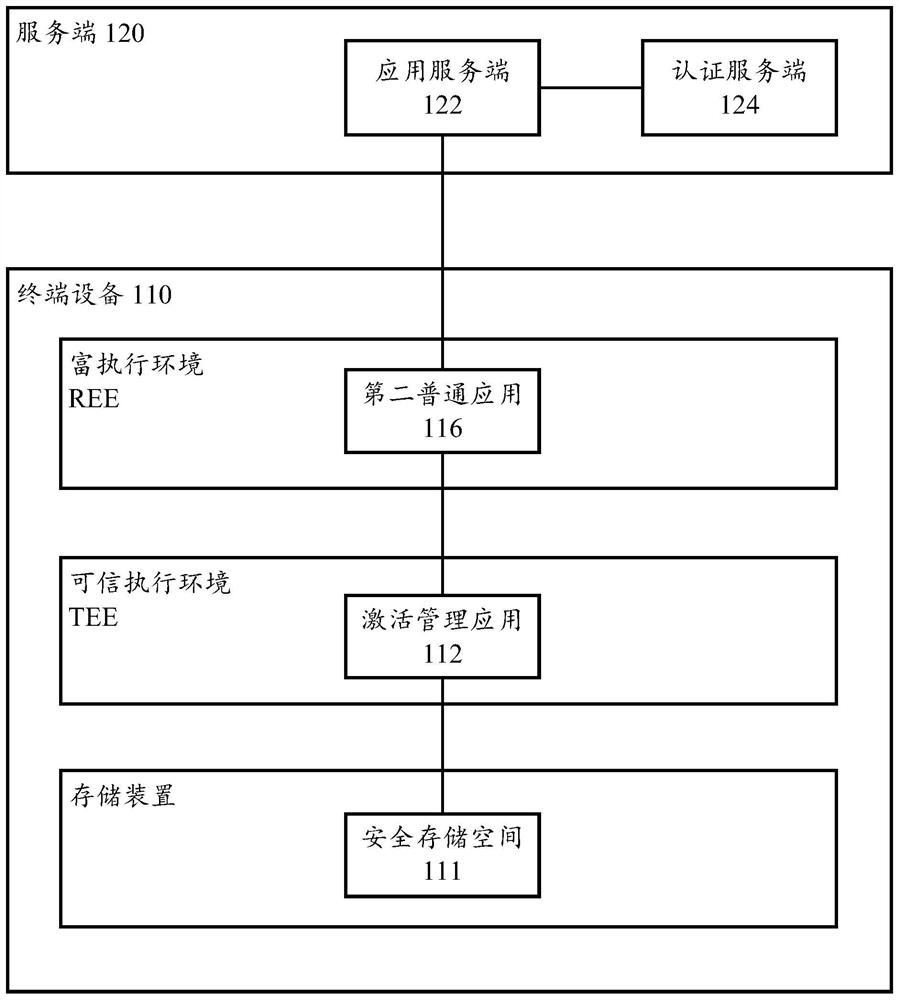
Application activation method and device based on trusted execution environment
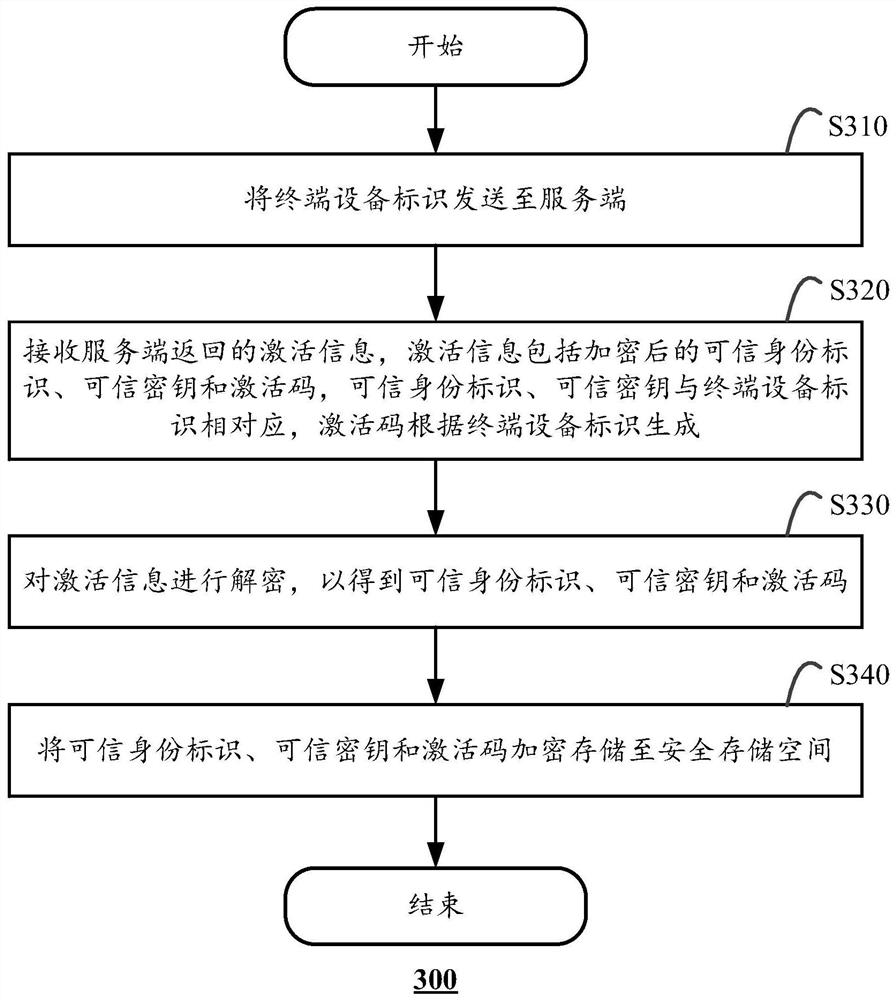
PendingCN111625829AEnsure safetyImprove transmission securityDigital data protectionPlatform integrity maintainanceTerminal equipmentEngineering
The invention discloses an activation method of a trusted execution environment, the trusted execution environment is deployed in a terminal device, and the method comprises the following steps: sending a terminal device identifier to a server; receiving activation information returned by the server, the activation information comprising an encrypted trusted identity identifier, a trusted key andan activation code, the trusted identity identifier and the trusted key corresponding to the terminal device identifier, and the activation code being generated according to the terminal device identifier; decrypting the activation information to obtain a trusted identity, a trusted key and an activation code; and encrypting and storing the trusted identity, the trusted key and the activation codeinto a secure storage space. The invention also discloses an activation verification method of the trusted execution environment, an application activation and activation verification method based onthe trusted execution environment, and a corresponding device.
Owner:ALIBABA GRP HLDG LTD
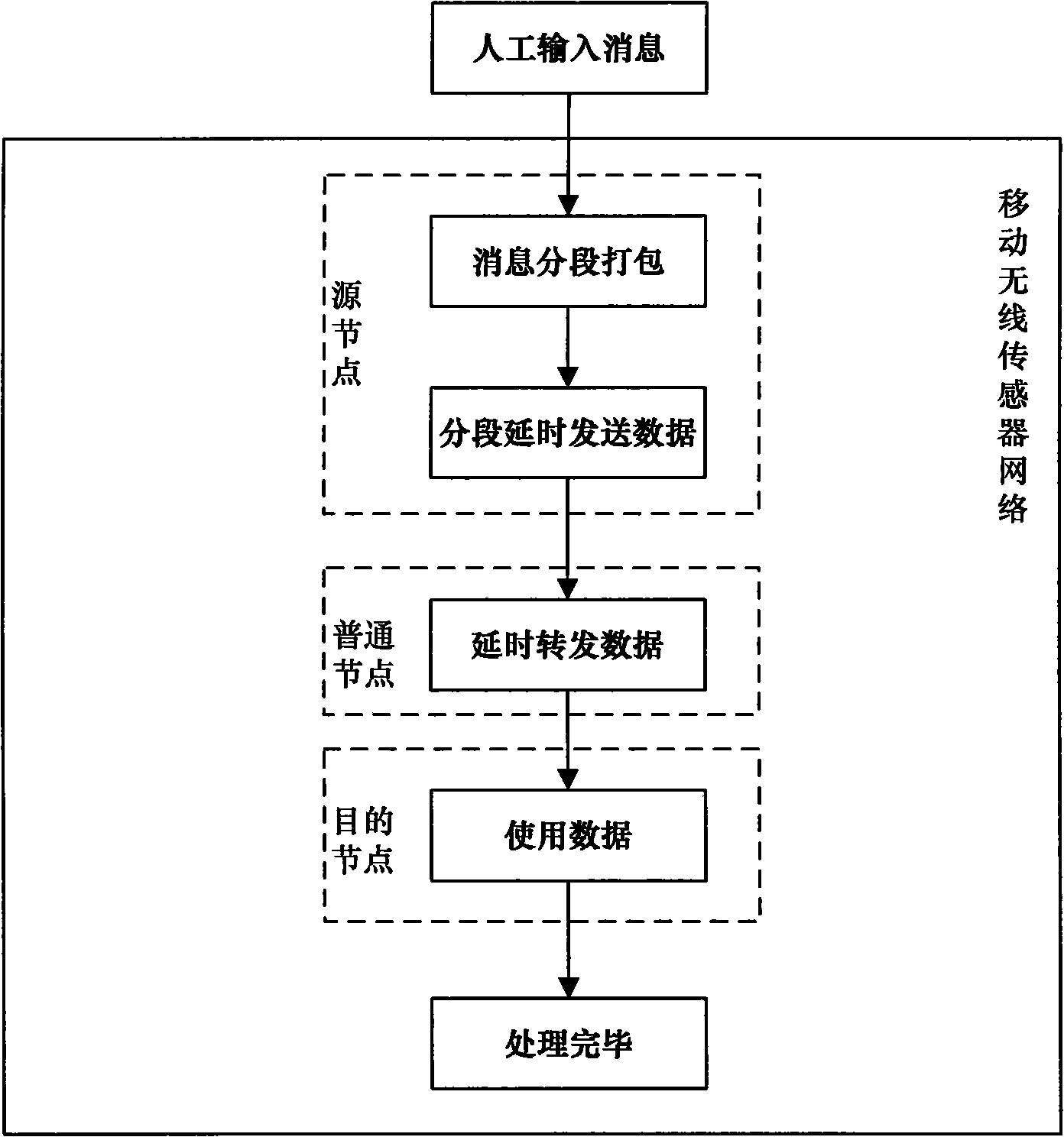
Node identity protection method of mobile wireless sensor network on basis of message time delay condition
InactiveCN101557608AEffective protectionSolve the danger of non-fragmented transmission to the sending nodeNetwork traffic/resource managementNetwork topologiesMobile wireless sensor networkTime delays
The invention discloses a node identity protection method of a mobile wireless sensor network on the basis of message time delay condition. The node identity protection method realizes segmental package, time delay transmission and time delay forwarding of a message Mi=(MDATAi, MTIMEi) by a source node Ni in a mobile wireless sensor. By the method, in the transmission process of the message Mi=(MDATAi, MTIMEi), common node Nj receiving the message Mi=(MDATAi, MTIMEi) can not position the sending place and the receiving place of the message Mi=(MDATAi, MTIMEi) and also can not obtain the transmission path of the message Mi=(MDATAi, MTIMEi); therefore, the method effectively carries out identity protection to the node for receiving and sending messages in the mobile wireless sensor.
Owner:BEIHANG UNIV
IMS system based session key negotiating method
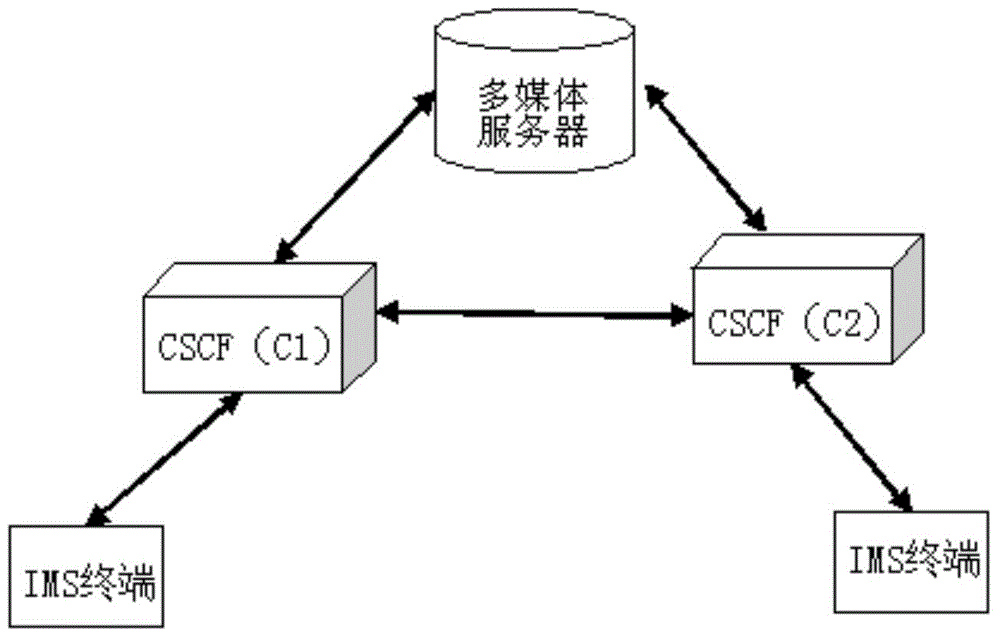
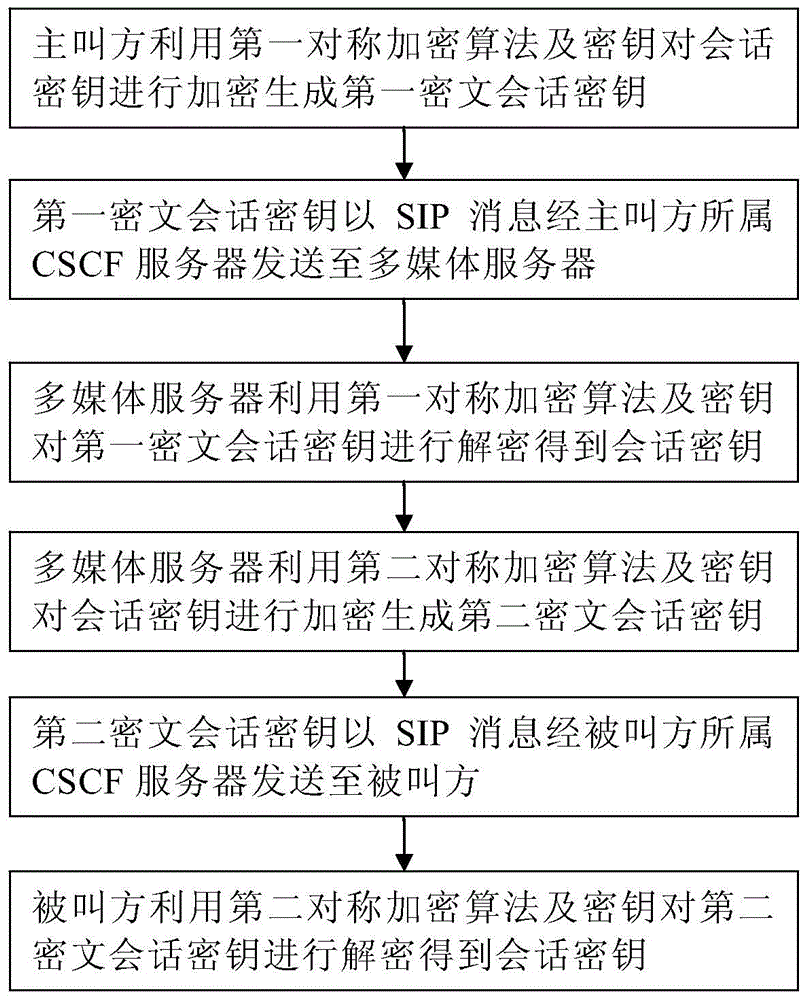
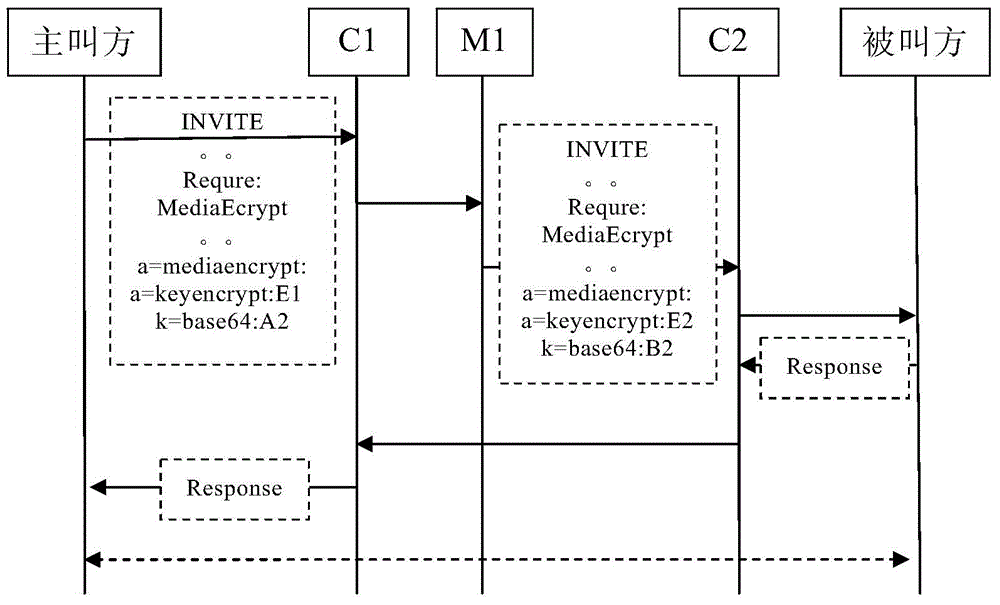
ActiveCN104683291AImprove transmission securityFast operationTransmissionMultimedia serversCiphertext
The present invention discloses an IMS system based session key negotiating method. A symmetric encryption algorithm and a secret key are configured in a multi-media server at a terminal; a calling party uses a first symmetric encryption algorithm and the secret key to encrypt the session key to generate a first ciphertext session key, and the first ciphertext session key is transmitted to the multi-media server as an SIP message via a CSCF server; and the multi-media server receives the SIP message, uses the first symmetric encryption algorithm and the secret key to decode the first ciphertext session key to obtain the session key, the multi-media server uses a second symmetric encryption algorithm and a secret key configured by a called party to encrypt the session key to generate a second ciphertext session key, the second ciphertext session key is transmitted to the called party as the SIP message via the CSCF server, and the called party receives the SIP message, and uses the second symmetric encryption algorithm and the secret key to decode the second ciphertext session key to obtain the session key. The method of the present invention can increase security for transmitting the session key.
Owner:BEIJING DATANG GOHIGH DATA NETWORKS TECH CO LTD
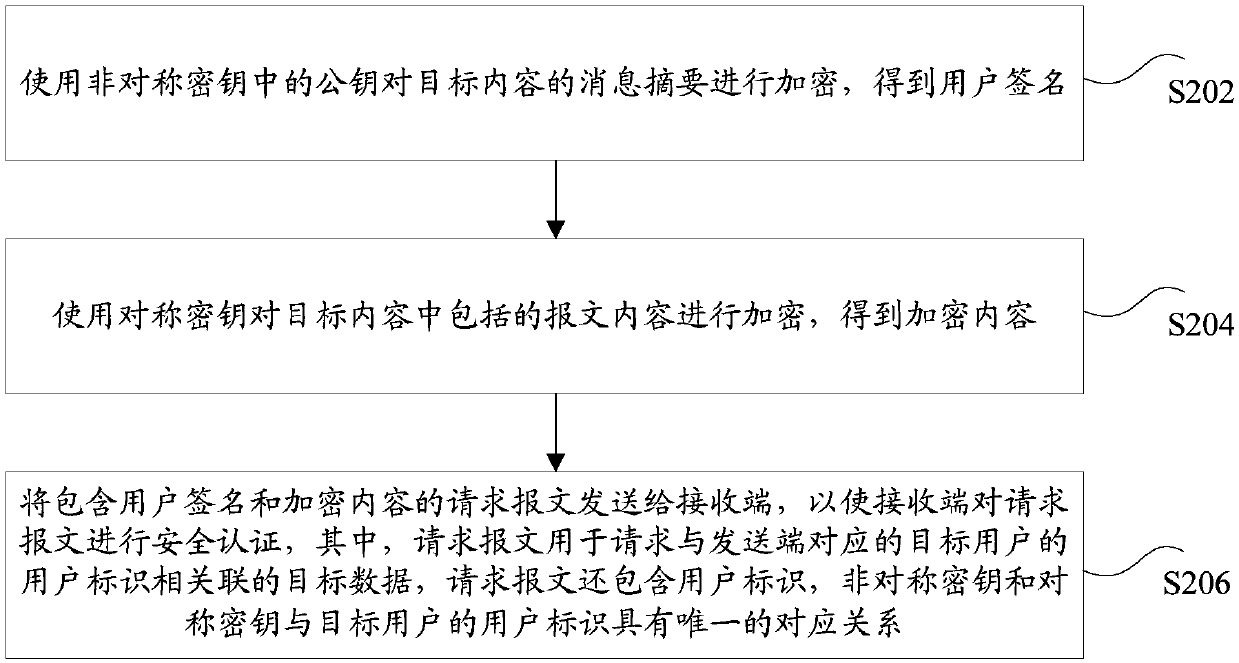
Security authentication method and device and storage medium
InactiveCN110198295AFast encryptionImprove transmission securityMultiple keys/algorithms usageUser identity/authority verificationUser identifierSecure authentication
The invention discloses a security authentication method and device and a storage medium. The method comprises the following steps: encrypting a message abstract of target content by using a public key in an asymmetric key to obtain a user signature; encrypting the message content included in the target content by using a symmetric key to obtain encrypted content; and sending a request message containing the user signature and the encrypted content to a receiving end, and sending the request message to a receiving end, thereby enabling the receiving end to carry out security authentication onthe request message. The request message is used for requesting target data associated with a user identifier of a target user corresponding to a sending end, the request message further comprises theuser identifier, and the asymmetric secret key and the symmetric secret key have a unique corresponding relation with the user identifier of the target user. According to the method and the device, the technical problem that the message transmission security is poor due to the fact that the symmetric key is intercepted in the transmission process is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
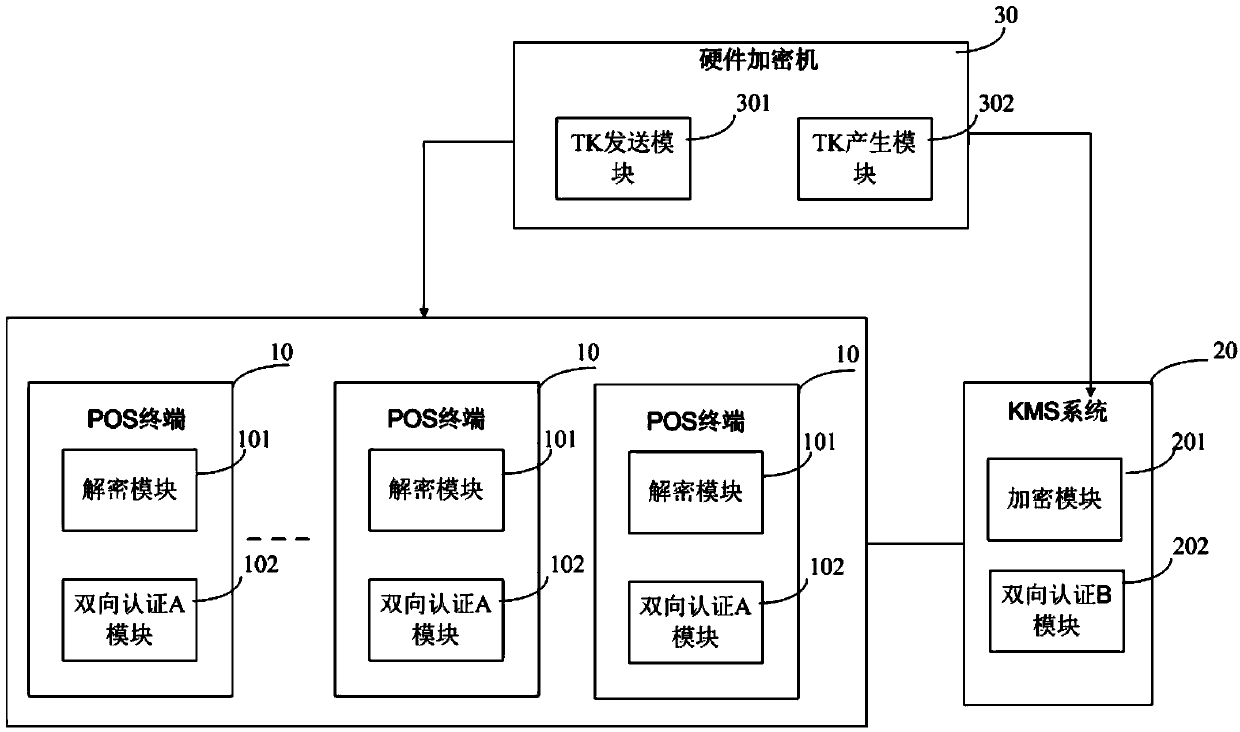
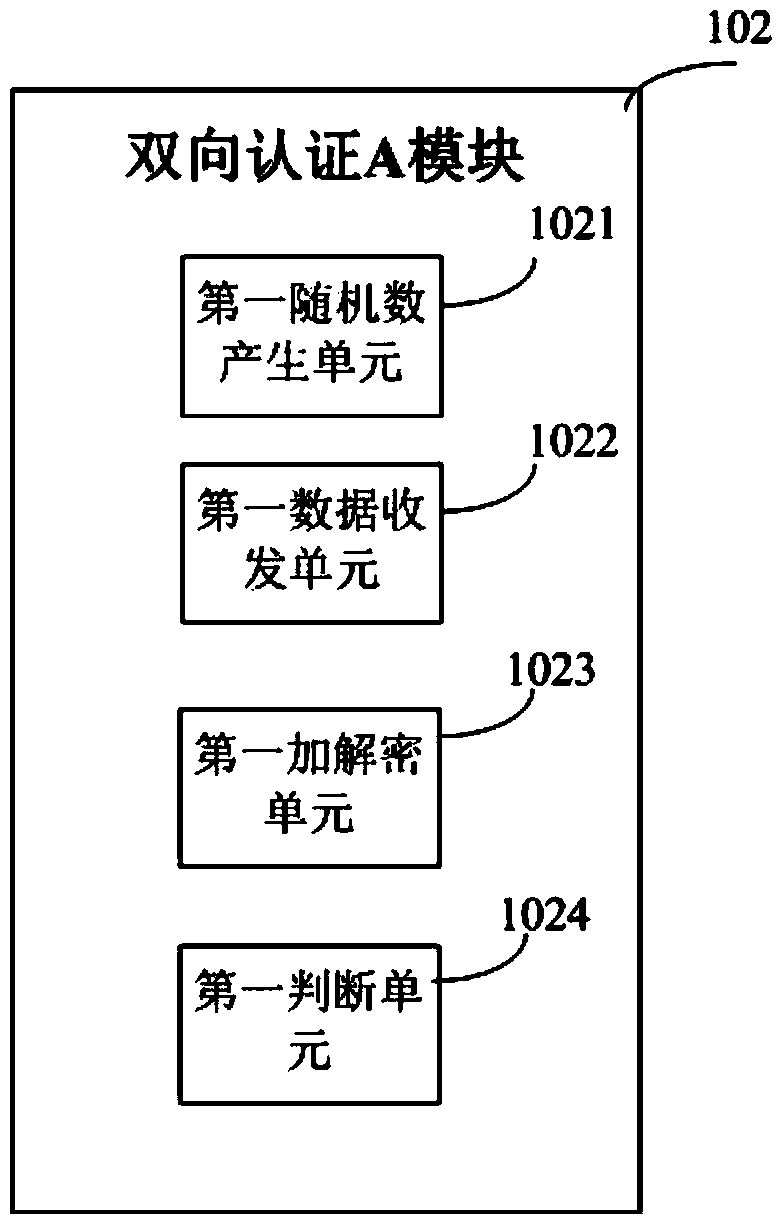
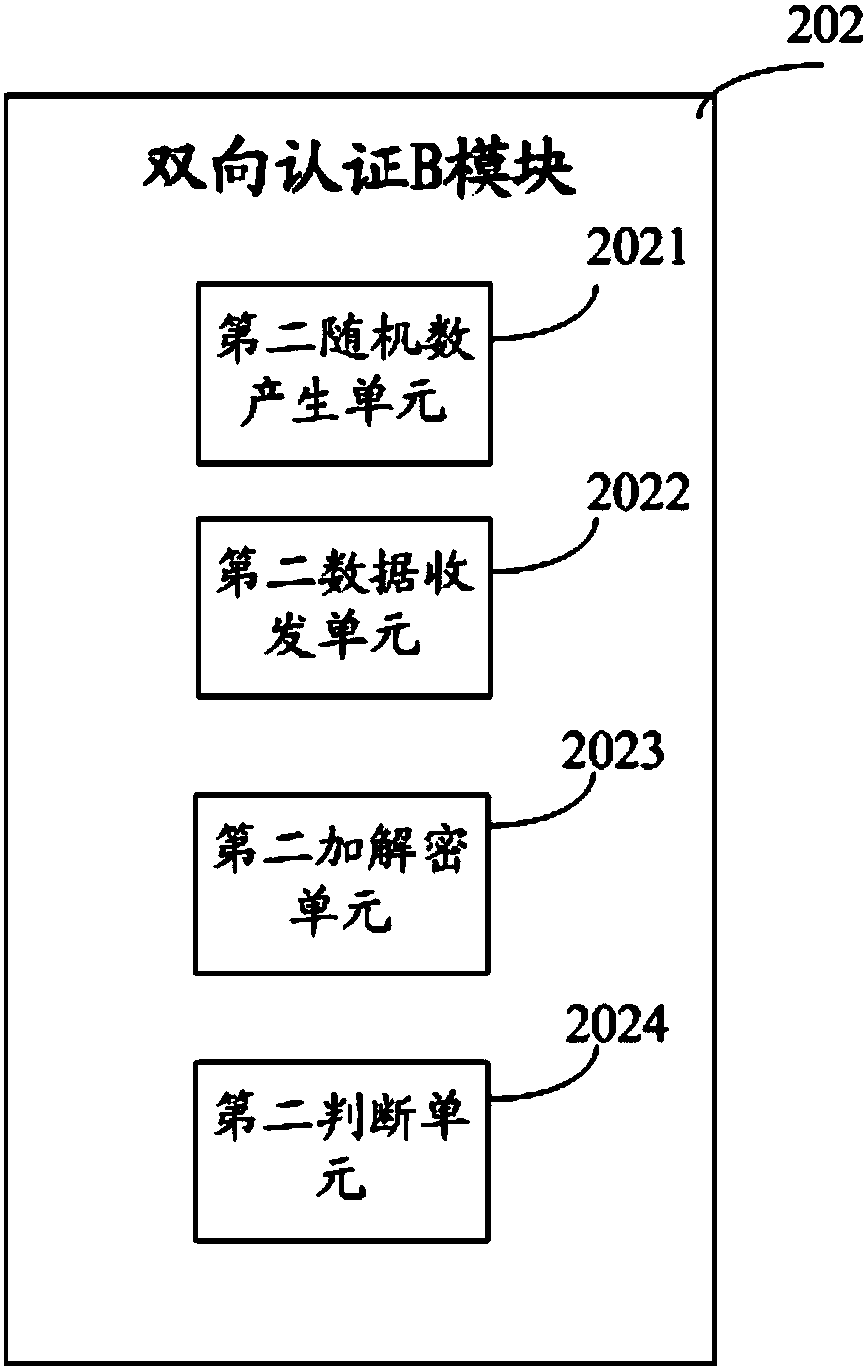
TMK (Terminal Master Key) secure downloading method and system
ActiveCN103701812ASolve the problem of low time efficiencyReduce occupancyKey distribution for secure communicationUser identity/authority verificationCiphertextComputer terminal
The invention discloses a TMK (Terminal Master Key) secure downloading method, which comprises the steps that 1) a hardware and security module generates a TK (Transmission Key), wherein the TK comprises an asymmetrical TEK (Transmission Encryption Key) and an asymmetric transmission AUK (Authentication Key), a public key Pu_tek of the TEK and a public key Pu_auk of the AUK are transmitted to a KMS (Key Management Service) system and a private key Pr_tek of the TEK and the private key Pr_auk of the AUK are injected into a POS (Point Of Sale) terminal through a secure method; 2) the POS terminal and the KMS system use the asymmetrical transmission AUK for bidirectional authentication; 3) if the AUK passes the authentication, the KMS system uses the Pu_tek to encrypt the TMK and transmits a master key ciphertext to the POS terminal; 4) the POS terminal uses the Pr_tek to decrypt the master key ciphertext Ctmk_tk to obtain a TMK. The TMK secure downloading method has the beneficial effects that the effect of remotely downloading the TMK by the POS terminal can be realized through the TK; since the TK comprises the asymmetric transmission AUK and the TEK, the transmission security of the TMK is effectively guaranteed.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
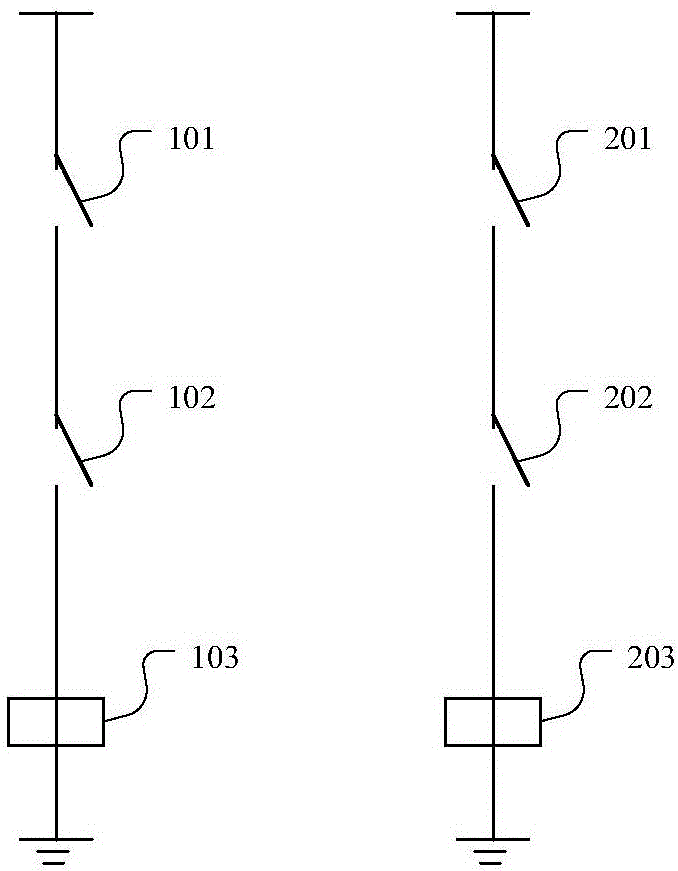
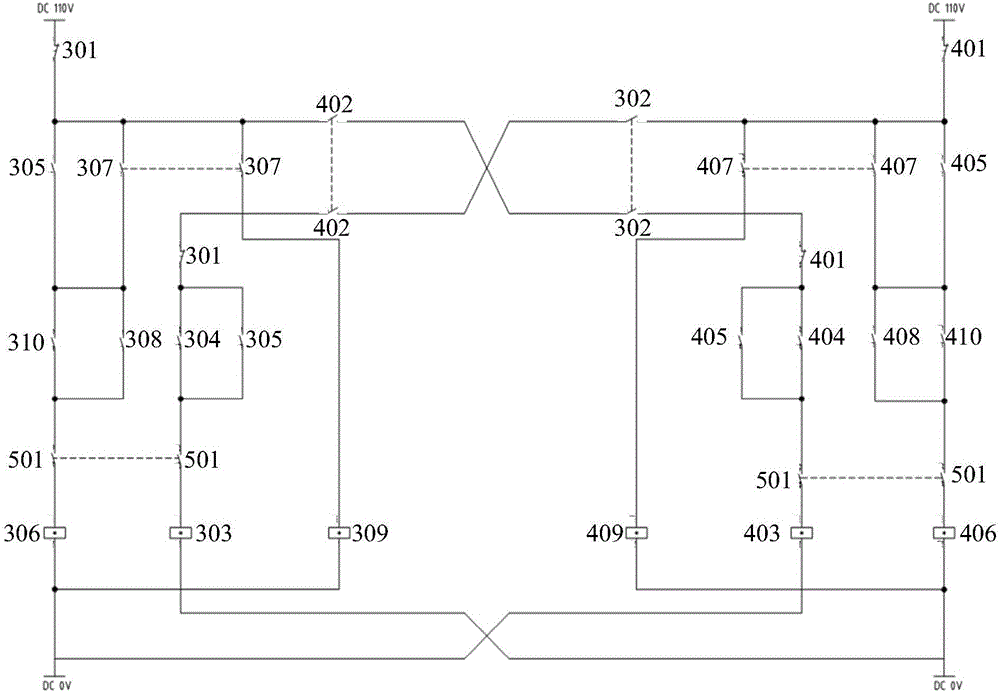
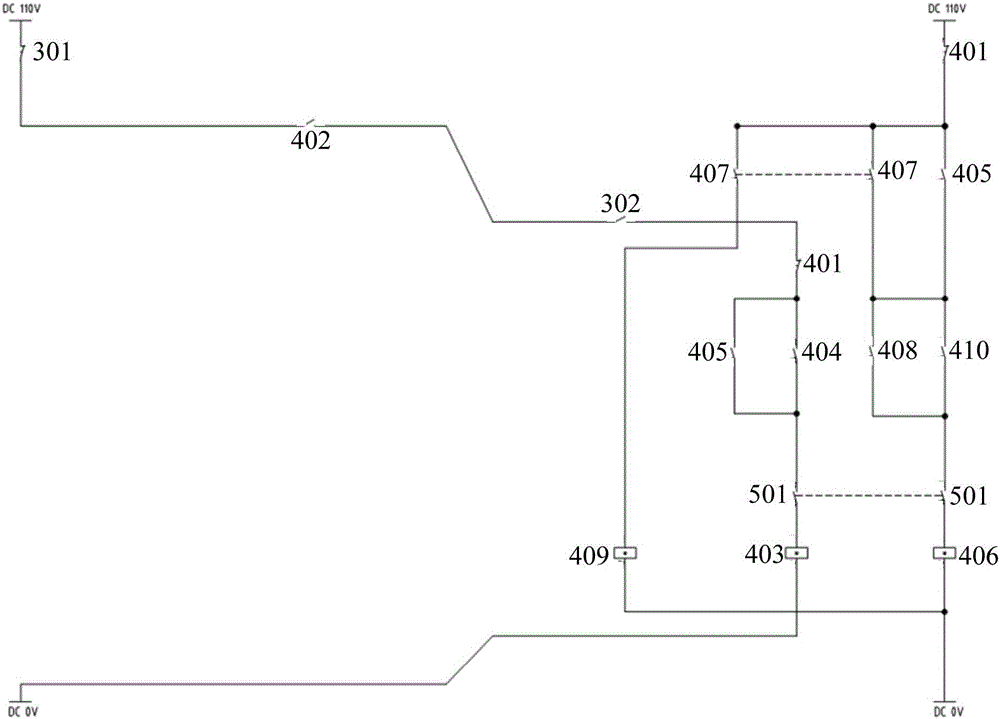
Pantograph control device and railway vehicle
The invention provides a pantograph control device and a railway vehicle. The pantograph control device comprises two pantograph control circuits which are respectively used for controlling the pantograph descending on the two sides, wherein each of the pantograph control circuits comprises a control switch, a primary relay and an opposite-side primary relay switch which are serially arranged; when the control switch or the opposite-side primary relay switch is switched off, the primary relay is powered off; the control switch is switched on or off under the operation of a user; the primary relay is used for controlling the pantograph descending under a powered off state; the opposite-side primary relay switch is controlled by an opposite-side primary relay and is switched off when the opposite-side primary relay is powered off. The pantograph control device and the railway vehicle provided by the invention have the advantages that the structure is simple, the complex network device is not required, the transmission efficiency and the safety are promoted, the simultaneous descending of the pantographs on the two sides can be realized and the service life of the pantographs can be prolonged.
Owner:CRRC TANGSHAN CO LTD
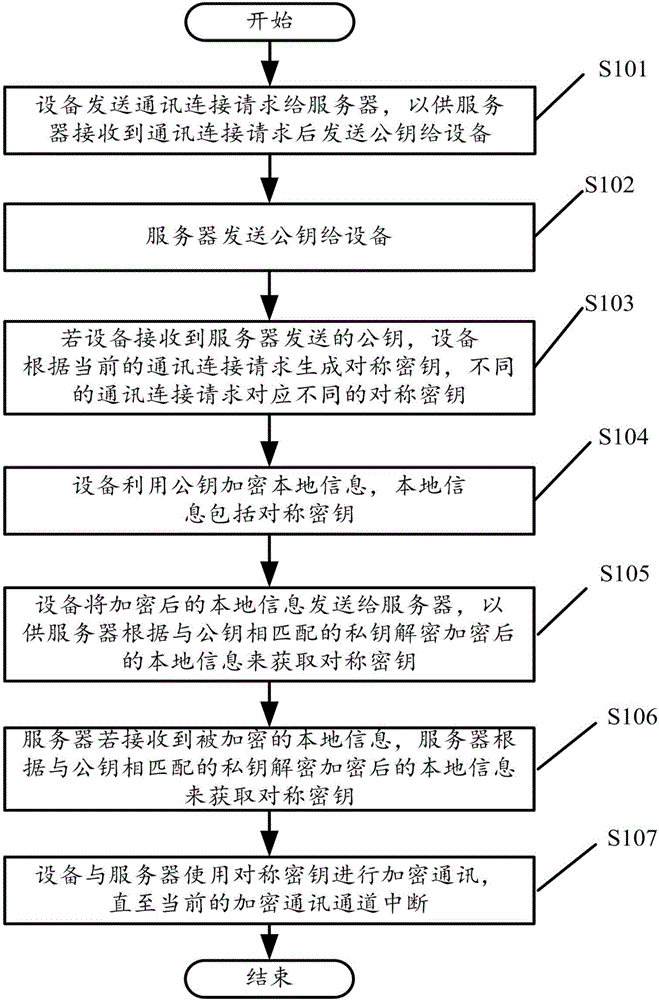
Data transmission method, device and system
ActiveCN106790223AImprove securityImprove transmission securityTransmissionInformation transmissionData transmission
The embodiment of the invention discloses a data transmission method, device and system. The system comprises the steps that the device sends a communication connection request to a server so that the server can send a public key to the device after receiving the communication connection request, and the server stores at least one set of public key and secret key; if the device receives the public key sent by the server, the device generates symmetric secret keys according to the current communication connection request, and the symmetric secret keys are different when the communication connection requests are different; the device utilizes the public key for encrypting local information, and the local information includes the symmetric secret keys; the device sends the encrypted local information to the server so that the server can obtain the symmetric secret keys according to the local information matched with the public keys and obtained after the secret keys are decrypted and encrypted; the device uses the symmetric secret keys and the server for performing encryption communication till a current encryption communication channel is interrupted. According to the data transmission method, the dynamically-changing symmetric secret keys are provided, and the information transmission security is improved.
Owner:INVT ELEVATOR CONTROL TECH WUXI
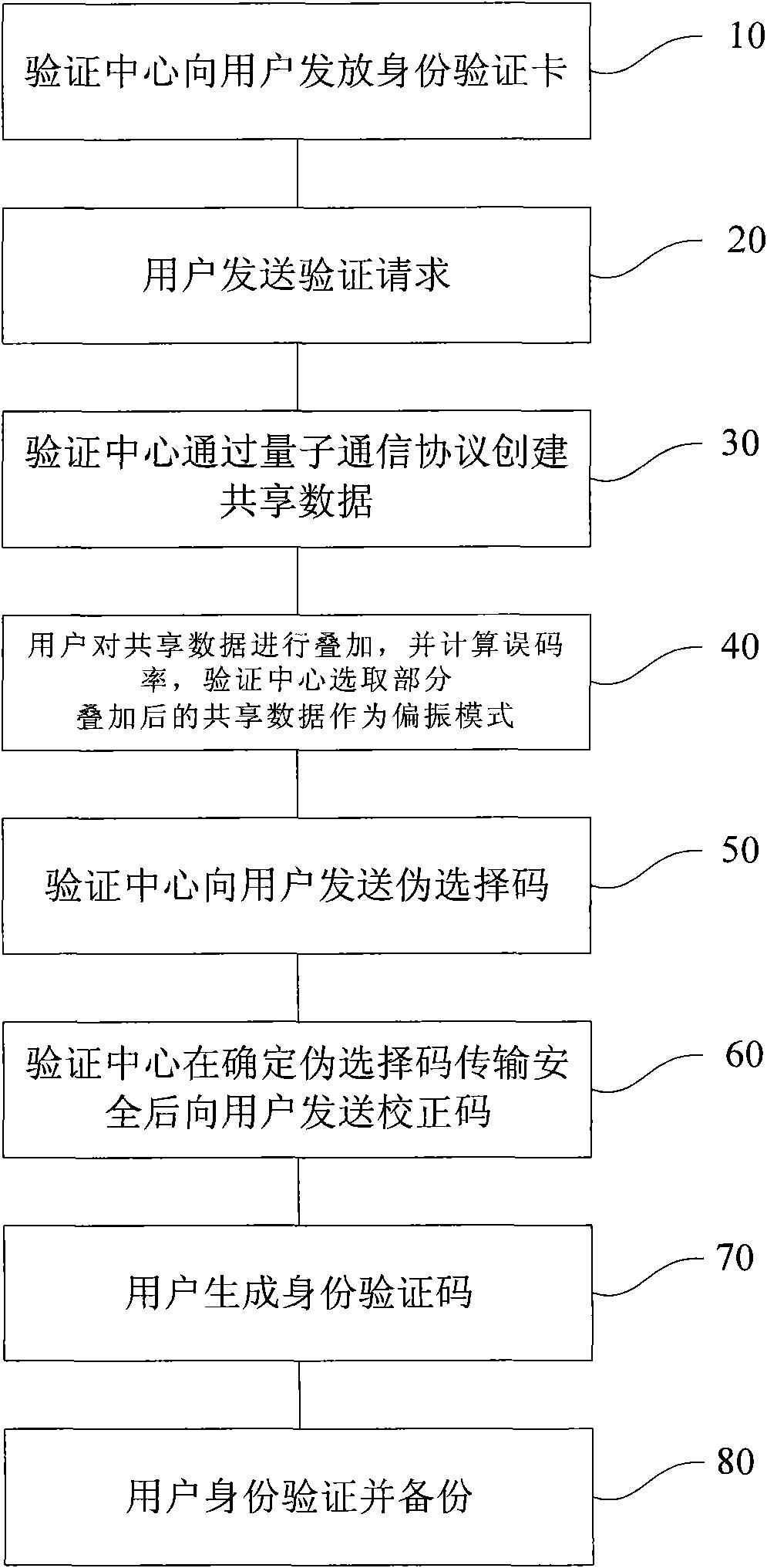
User ID authentication method and system based on quantum network
InactiveCN101854347AProtect information securityImprove transmission efficiency and transmission securityUser identity/authority verificationAuthentication systemUser authentication
The invention provides a user ID authentication method and system based on a quantum network, which comprises the following steps that: an authentication center issues an ID authentication card; a user sends an authentication request; a quantum communication protocol creates shared data; the user summates the shared data and calculates the bit error rate, and the authentication center selects part of the summated shared data as a polarization mode after determining that the bit error rate belongs to a preset threshold range; the authentication center sends a pseudo selection code and a correction code; the user calculates a selection code according to the pseudo selection code and the correction code so as to obtain an ID authentication code; the users mutually authenticate or the user authenticates with the authentication center; and the authentication center backups the authentication result. The user ID authentication method can effectively protect the private information of the user, and has the advantages of safety and reliability. The invention also provides a user ID authentication system based on the quantum network, which similarly can effectively protect the private information of the user, and has the advantages of safety and reliability.
Owner:朱律波
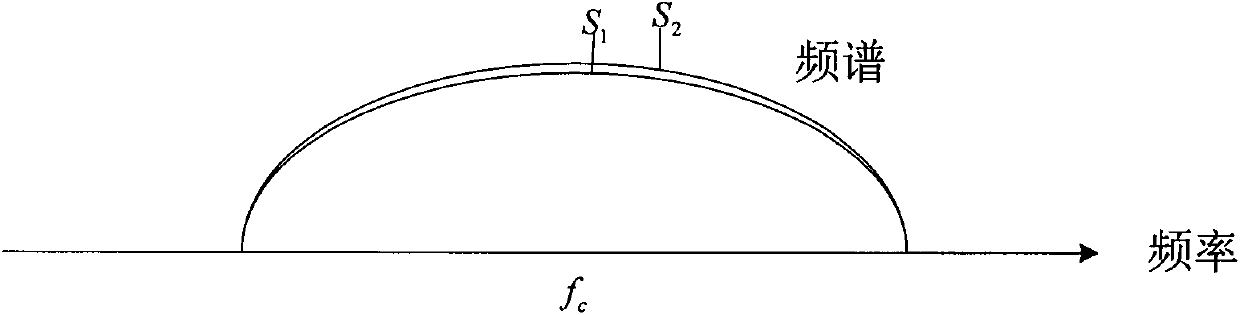
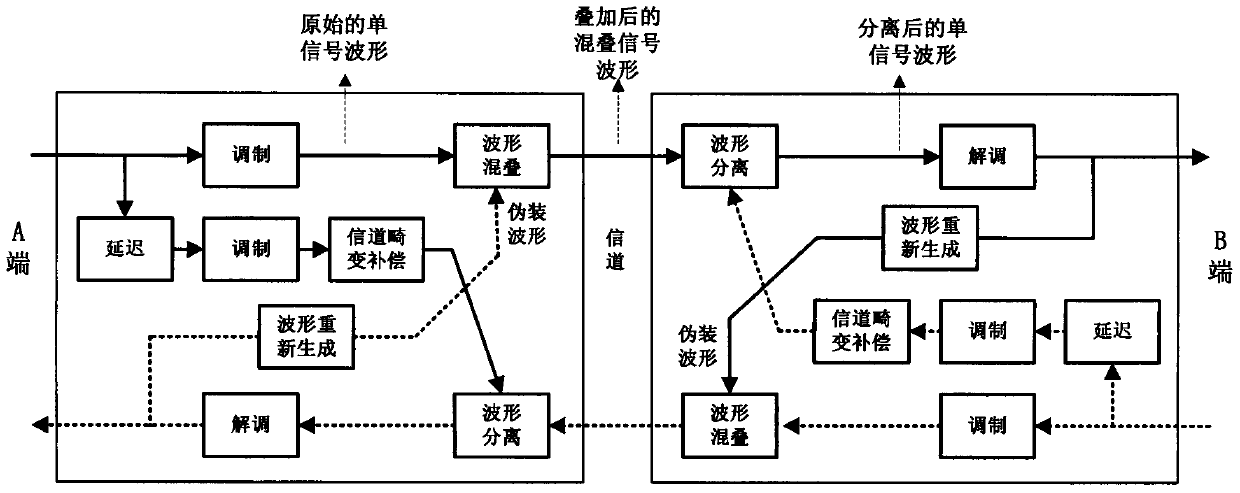
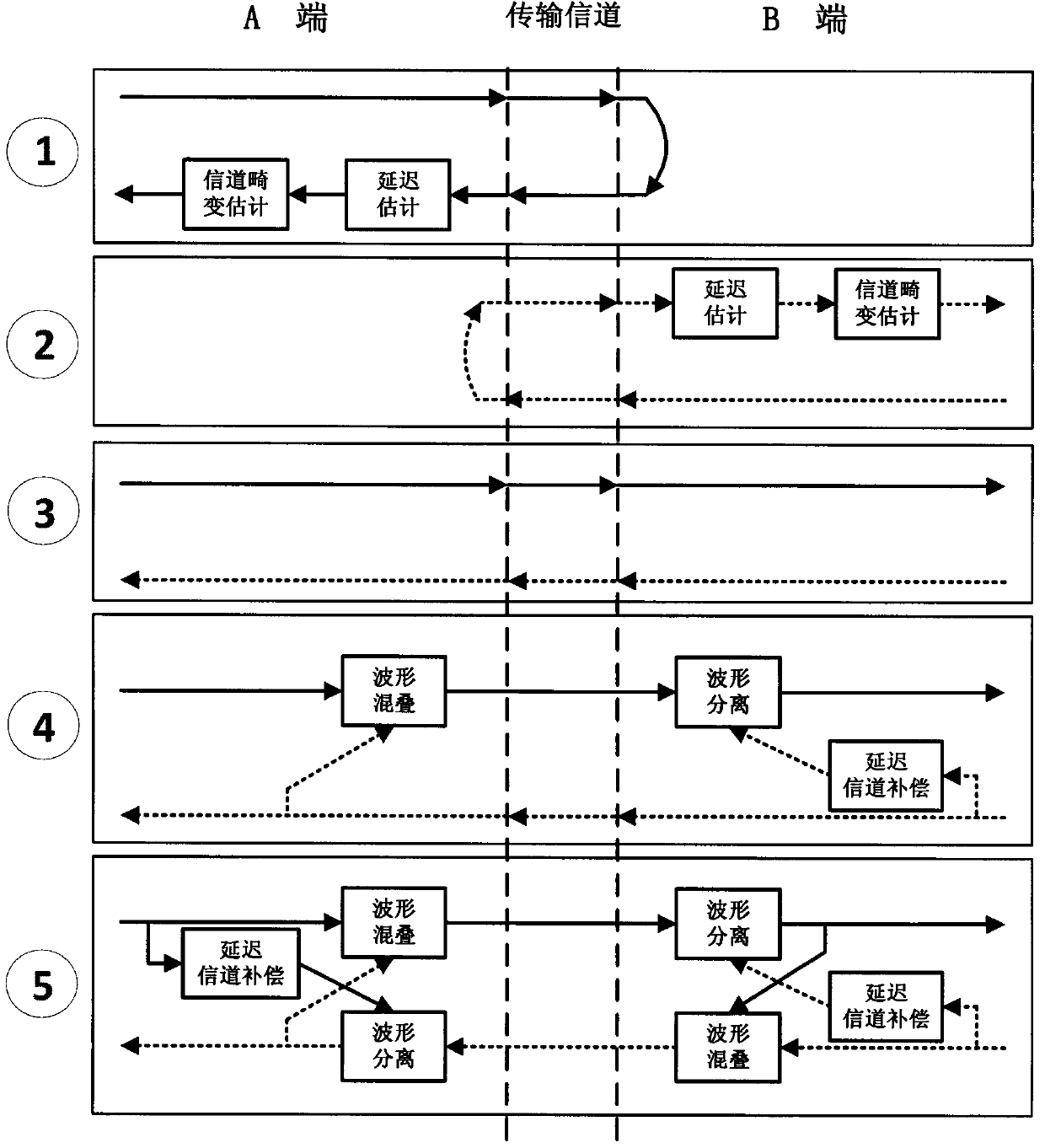
High safety communication technology based on two-way time domain waveform aliasing
InactiveCN103428124AImprove transmission securityEnsure transmission securityTransmitter/receiver shaping networksSecure communicationInformation transmission
The invention discloses a high safety communication technology based on two-way time domain waveform aliasing and belongs to the technical field of communication. The existing local signals of two communication parties are fully utilized to perform aliasing and covering on each other's signals. The two communication parties transmit and receive mixed signals. Each communication party receives and separates the signals of the other party and allows the same to be mixed with local signals for transmission. The cooperating parties can separate the signals by using local signals and waveform reconstruction offset to complete normal communication. Non-cooperating parties do not know signal samples of the cooperating parties, the mixed signals cannot be separated, and information transmission safety is guaranteed. The method aiming at the situation that communication information safety faces increasingly large threats has the advantages that the signals transmitted in channels are mixed by two signals, safety communication of the whole communication process can be achieved, and no extra communication bandwidth is needed.
Owner:中国人民解放军总参谋部第五十七研究所
Network information security intelligent analysis early warning management system based on multi-dimensional analysis
PendingCN114826691AImprove operational efficiencyImprove data transmission securityPlatform integrity maintainanceSecuring communicationDetailed dataNetwork management
The invention discloses a network information security intelligent analysis early warning management system based on multi-dimensional analysis, and relates to the technical field of network information security. The problems that when a traditional network information security management system uses network transmission and data sharing as information storage and communication means, the system is lack of security protection, dangerous signals carried in transmission cannot be tracked in real time, and information updating is slow are solved. According to the network information security intelligent analysis and early warning management system based on multi-dimensional analysis, cross correlation and multi-angle combined analysis are performed on data in different dimensions through the supervision platform, high-level summarized data are refined and deepened into low-level detailed data, the accuracy of network information security analysis is greatly improved, and the network information security analysis efficiency is improved. Through a bottom layer driving filtering technology, various behavior operation requests are intercepted in real time, bad behaviors in data information operation are dynamically tracked, processed and detected, and a decision basis is provided for network management and optimization.
Owner:深圳市博博信息咨询有限公司
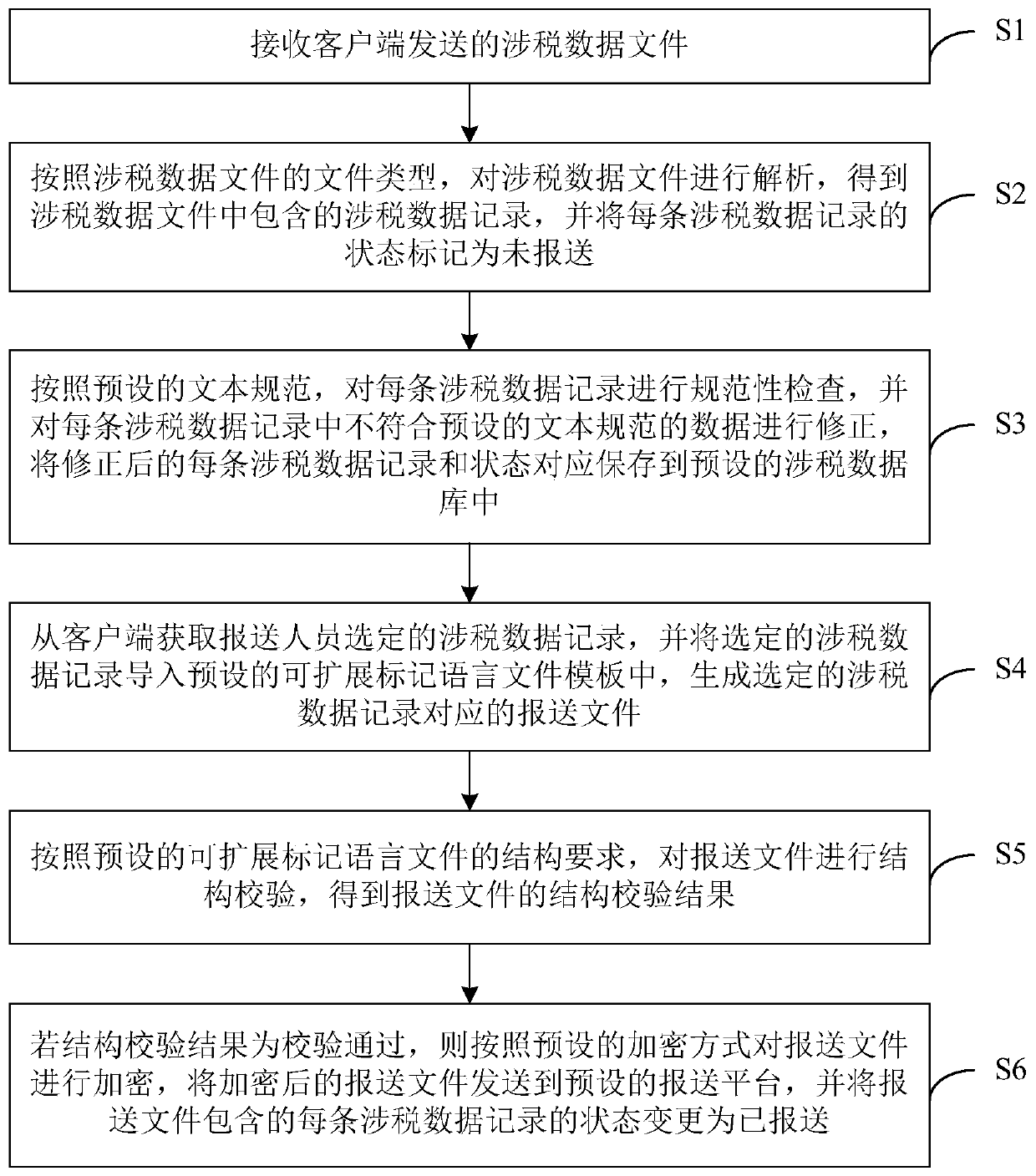
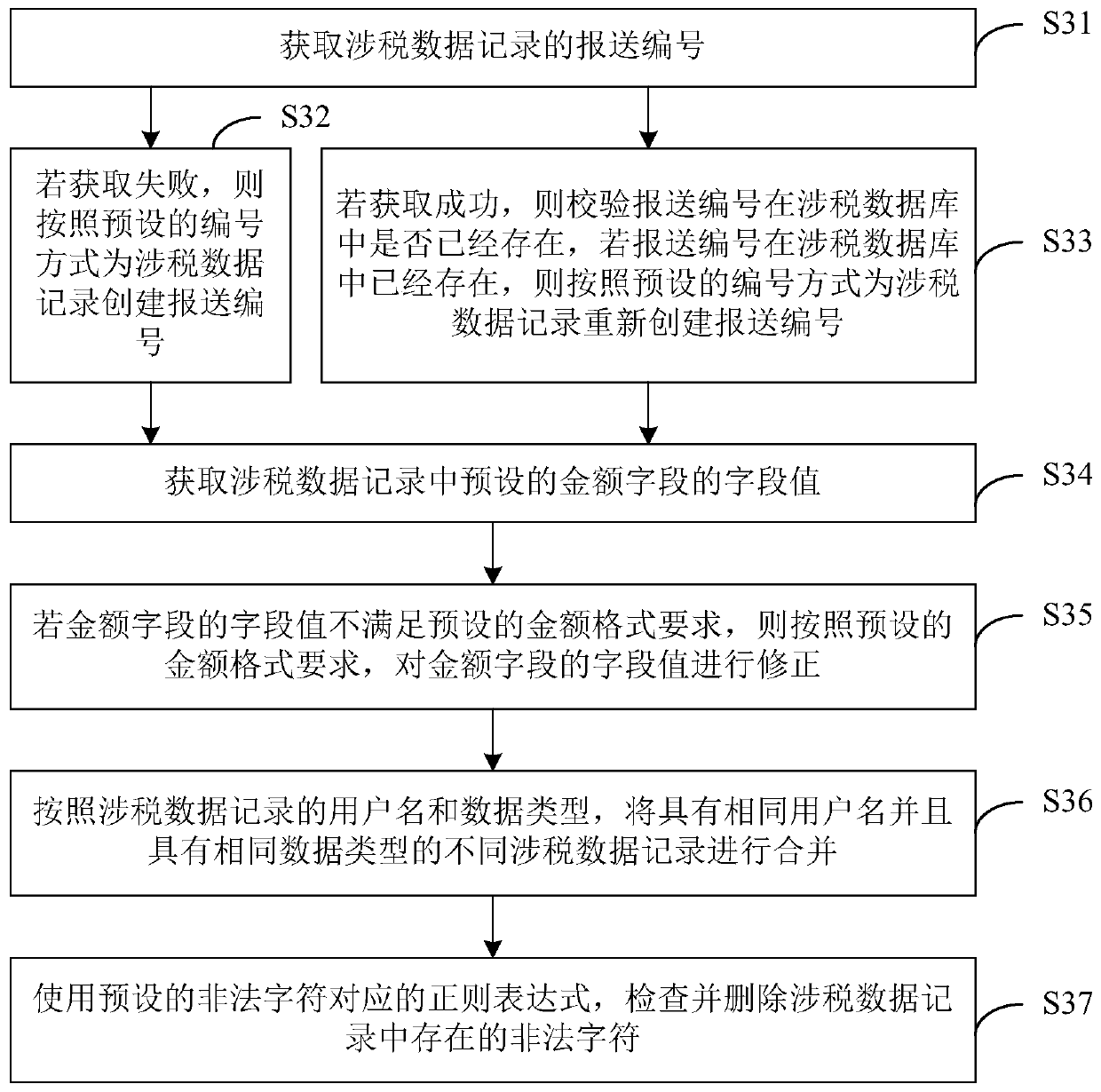
Tax-related data processing method and device, computer equipment and storage medium
ActiveCN110163735AImplement automated compliance checksEnable automatic compliance correctionsFinanceEnergy efficient computingData fileExtensible markup
The invention discloses a tax-related data processing method and device, computer equipment and a storage medium. The method comprises the following steps: receiving a tax-related data file sent by aclient; analyzing the tax-related data file to obtain a tax-related data record contained in the tax-related data file; carrying out normative checking on each tax-related data record, and correctingdata which do not conform to a preset text specification in each tax-related data record; acquiring a tax-related data record selected by a submitter from a client, and importing the selected tax-related data record into a preset extensible markup language file template to generate a submission file corresponding to the selected tax-related data record; performing structure verification on the reported file; and if the verification is passed, encrypting the submission file and sending the encrypted submission file to a preset submission platform. According to the technical scheme of the invention, automatic generation of the submission file and file structure verification are realized, and the submission processing efficiency and accuracy of the tax-related information and the transmissionsecurity are improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
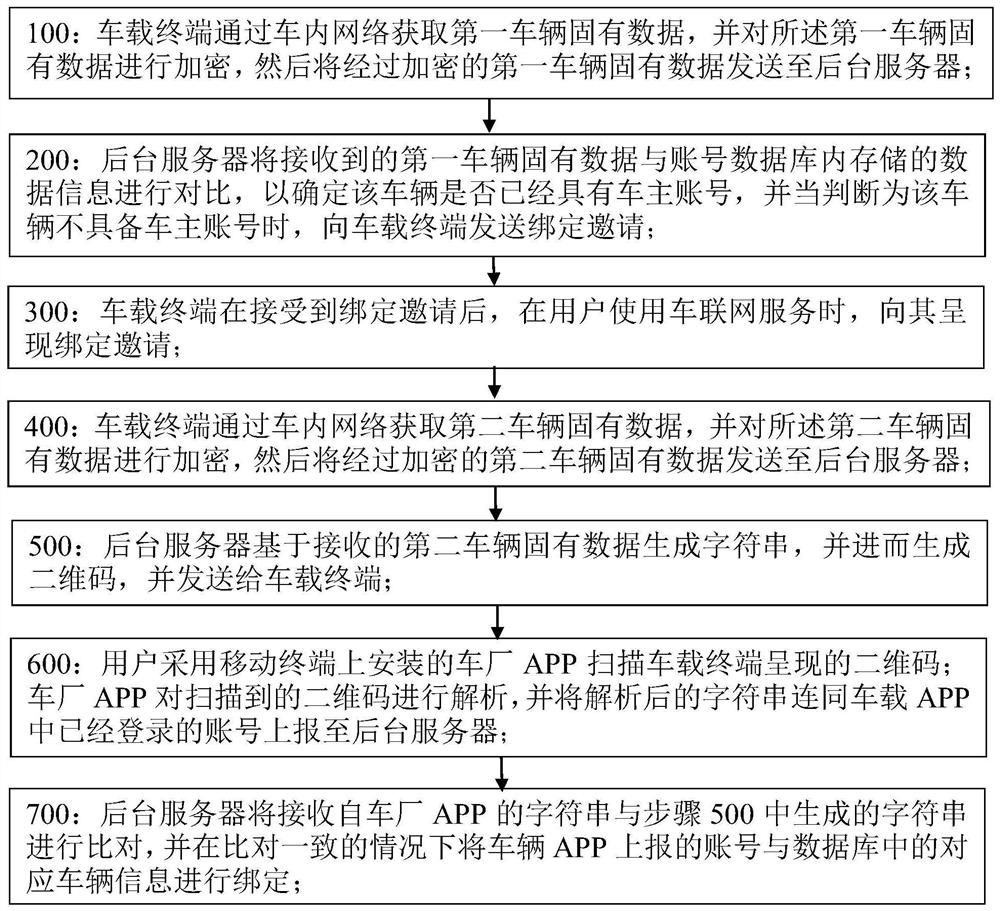
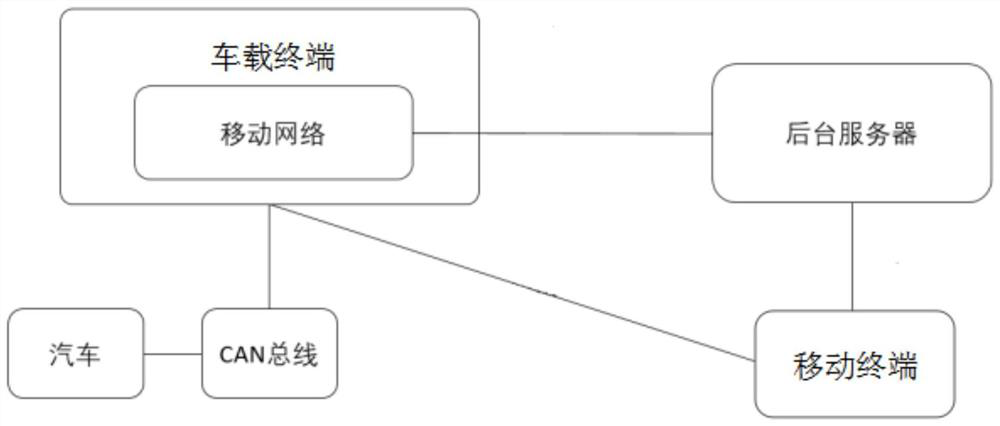
Method and system for binding vehicle to Internet of Vehicles account
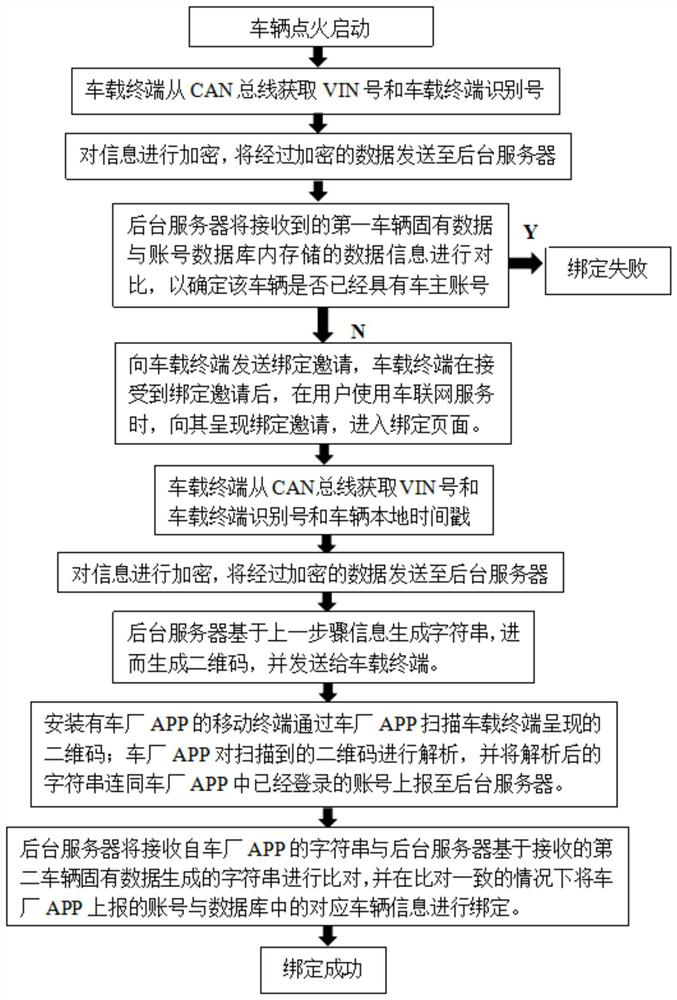
PendingCN111882008ASatisfy the demands of fast binding human-vehicle relationshipImprove transmission efficiencyRegistering/indicating working of vehiclesParticular environment based servicesIn vehicleThe Internet
The invention discloses a method for binding a vehicle to an Internet of Vehicles account, and the method comprises the steps that 100, a vehicle-mounted terminal obtains first vehicle inherent data through an in-vehicle network and sends the first vehicle inherent data to a background server in an encrypted mode; 200, the background server compares the data with data stored in an account databaseto determine whether a vehicle has a vehicle owner account or not: if the vehicle does not have the vehicle owner account, the background server sends the invitation to the vehicle-mounted terminal;300, after the vehicle-mounted terminal receives the invitation, the invitation is presented when the user uses the Internet of Vehicles service; 400, the vehicle-mounted terminal acquires second vehicle inherent data through an in-vehicle network and encrypts and sends the second vehicle inherent data to the background server; 500, the background server generates a character string based on the second vehicle inherent data, generates a QR code and sends the QR code to the vehicle-mounted terminal; 600, a mobile terminal vehicle factory APP is used for scanning the QR code, the APP analyzes the QR code to obtain a character string, and reports the character string and a logged-in account in the APP to the background server; 700, the background server compares the received character stringwith the character string in the step 500, and if the received character string is consistent with the character string in the step 500, the APP reported account is bound with corresponding vehicle information in a database.
Owner:SAIC VOLKSWAGEN AUTOMOTIVE CO LTD
Composite dynamic password authentication method and authentication system applicable to plug-and-play terminal
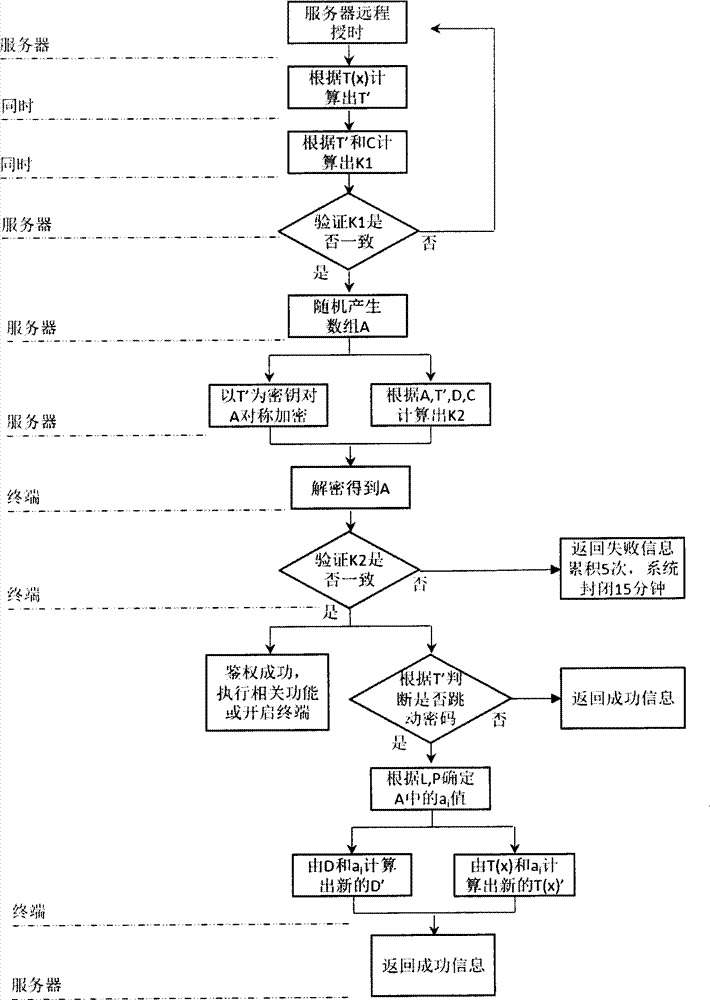
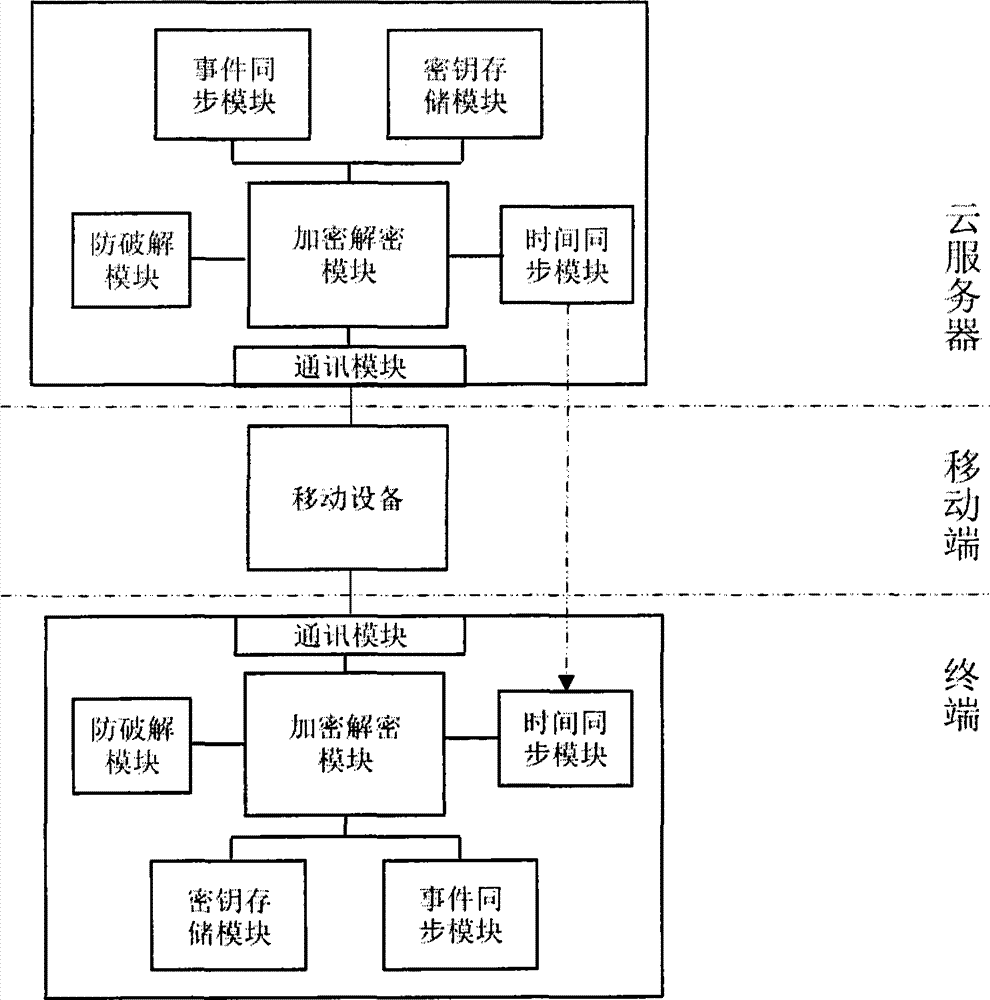
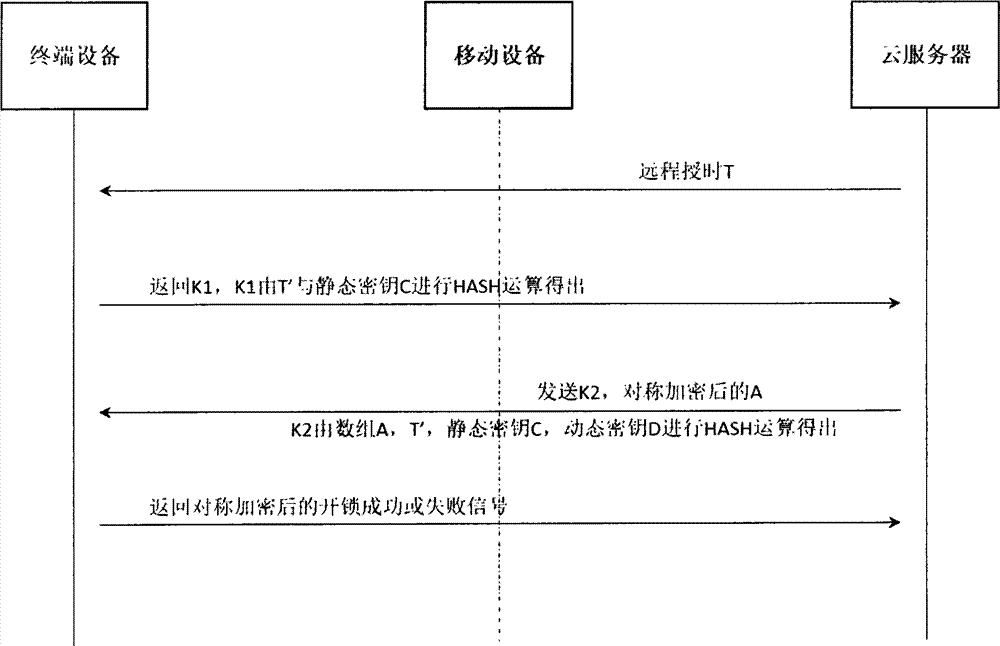
InactiveCN104717230AIncrease uncertaintyGood exposure protectionUser identity/authority verificationArray data structurePassword
The invention discloses a composite dynamic password authentication method and an authentication system applicable to a plug-and-play terminal. The method and the system comprise the following steps: providing remote time service to an embedded terminal through a server, and calculating a first key K1 and feeding back the first key K1 to the server according to time factor change T' and a built-in static key C through the terminal; generating a random number group A according to the situation that terminal right is authenticated by using K1 through the server, and calculating second keys K2, wherein the random number group A comprises a change factor ai, and K2 are HASH values of A, T', C and a built-in dynamic key D; receiving K2 through the terminal, comparing K2 with K2' calculated by the terminal, if the result shows that K2 is accordant with K2', determining whether a password is jumped or not according to characteristic values calculated according to T', if the password is jumped, obtaining ai in the random number group A according to a sequence L and a pointer P, calculating a new key D' according to D so as to replace the key, and loading the new key D' into a non-volatile memory. Two time / event synchronous dynamic password modes are adopted simultaneously, the change characteristics of the password are increased, and the method and the system are particularly applicable to bidirectional authentication of plug-and-play terminals and servers.
Owner:赵姗姗
A message protection method and device
InactiveCN109788474AImprove access efficiencyImprove transmission securityKey distribution for secure communicationSecurity arrangementTerminal equipmentTransmission security
Owner:HUAWEI TECH CO LTD
Multi-antenna relay system physical layer safety design method based on signal to noise ratios
ActiveCN107248875AImprove transmission securityReduce computational complexitySpatial transmit diversitySignal-to-noise ratio (imaging)Safety design
The invention discloses a multi-antenna relay system physical layer safety design method based on signal to noise ratios. Through combined optimization of a precoding matrix of a relay end and an artificial noise autocorrelation matrix, the signal to noise ratio of a legal reception end is maximized on the condition that a signal to noise ratio of a wiretapper is made to satisfy secret communication restriction conditions and relay end emission power restriction conditions. The method is advantaged in that a condition that only the statistics channel state information can be acquired is fully considered, and better practicality is realized.
Owner:SOUTHEAST UNIV
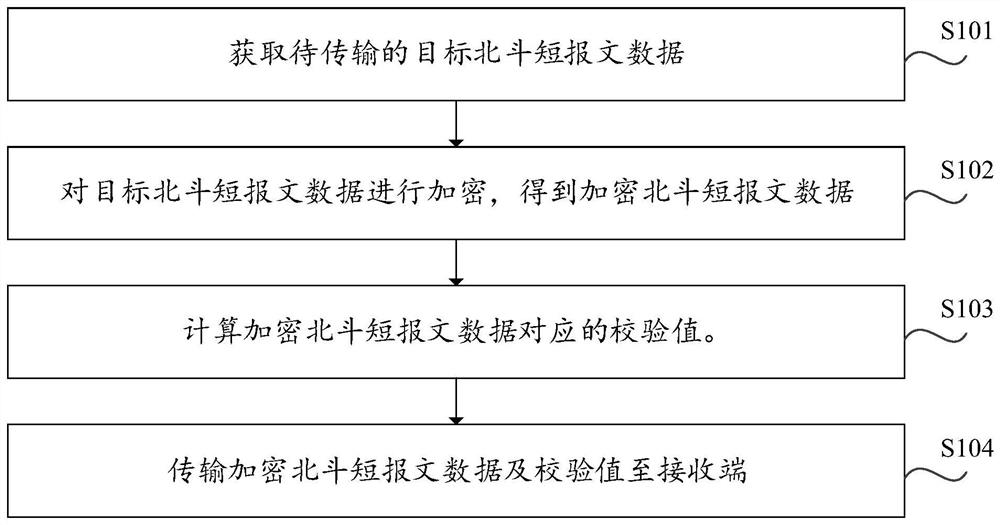
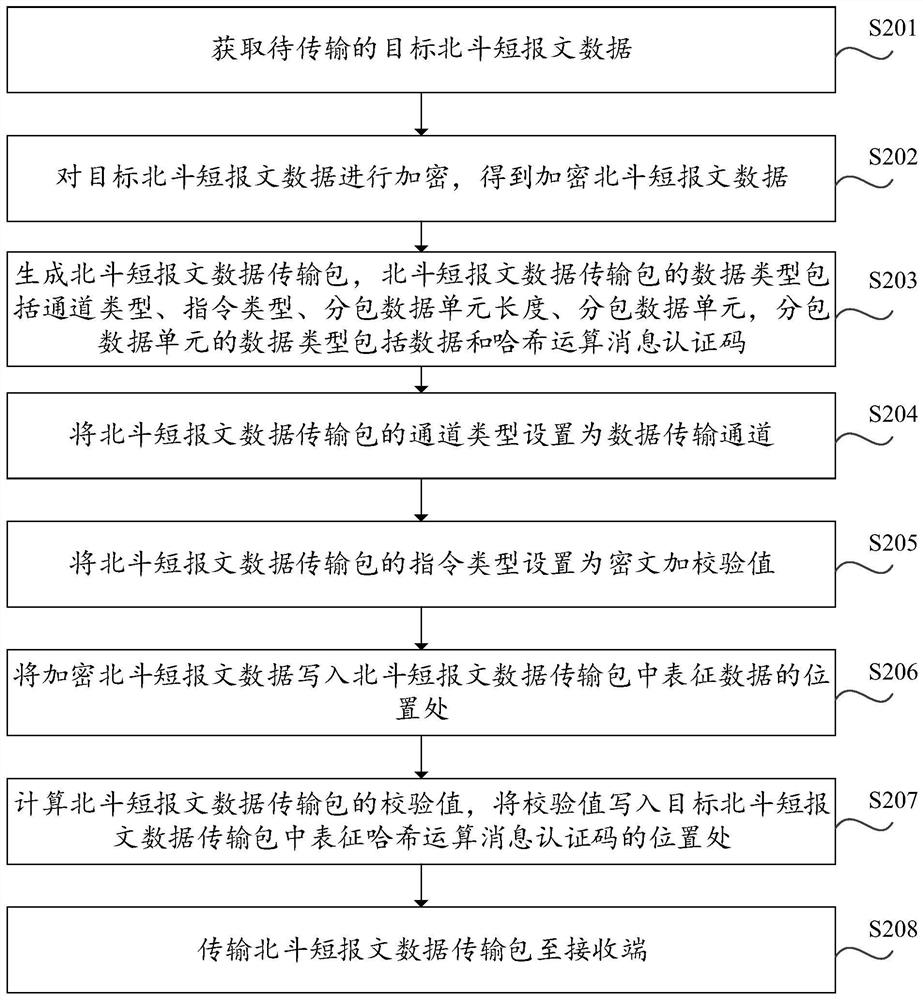
Beidou short message data transmission method and device, electronic equipment and computer medium
ActiveCN111669219AImprove transmission securityAvoid exposureRadio transmissionData transmissionTransmission security
The invention discloses a Beidou short message data transmission method and device, electronic equipment and a computer medium, which are applied to a sending end. The method includes: obtaining target Beidou short message data to be transmitted; encrypting the target Beidou short message data to obtain encrypted Beidou short message data; calculating a check value corresponding to the encrypted Beidou short message data; and transmitting the encrypted Beidou short message data and the verification value to a receiving end. In the present application, the sending end encrypts the target Beidoushort message data,; encrypted Beidou short message data is obtained, a check value corresponding to the encrypted Beidou short message data is calculated; and finally, transmitting the encrypted Beidou short message data and the check value to a receiving end. Therefore, exposure of the target Beidou short message data in the transmission process is avoided, a receiving end can determine whetherthe encrypted Beidou short message data is modified by an attacker or not based on the check value, a receiver can receive the accurate target Beidou short message data, and the transmission securityof the Beidou short message data is improved.
Owner:中电科网络安全科技股份有限公司
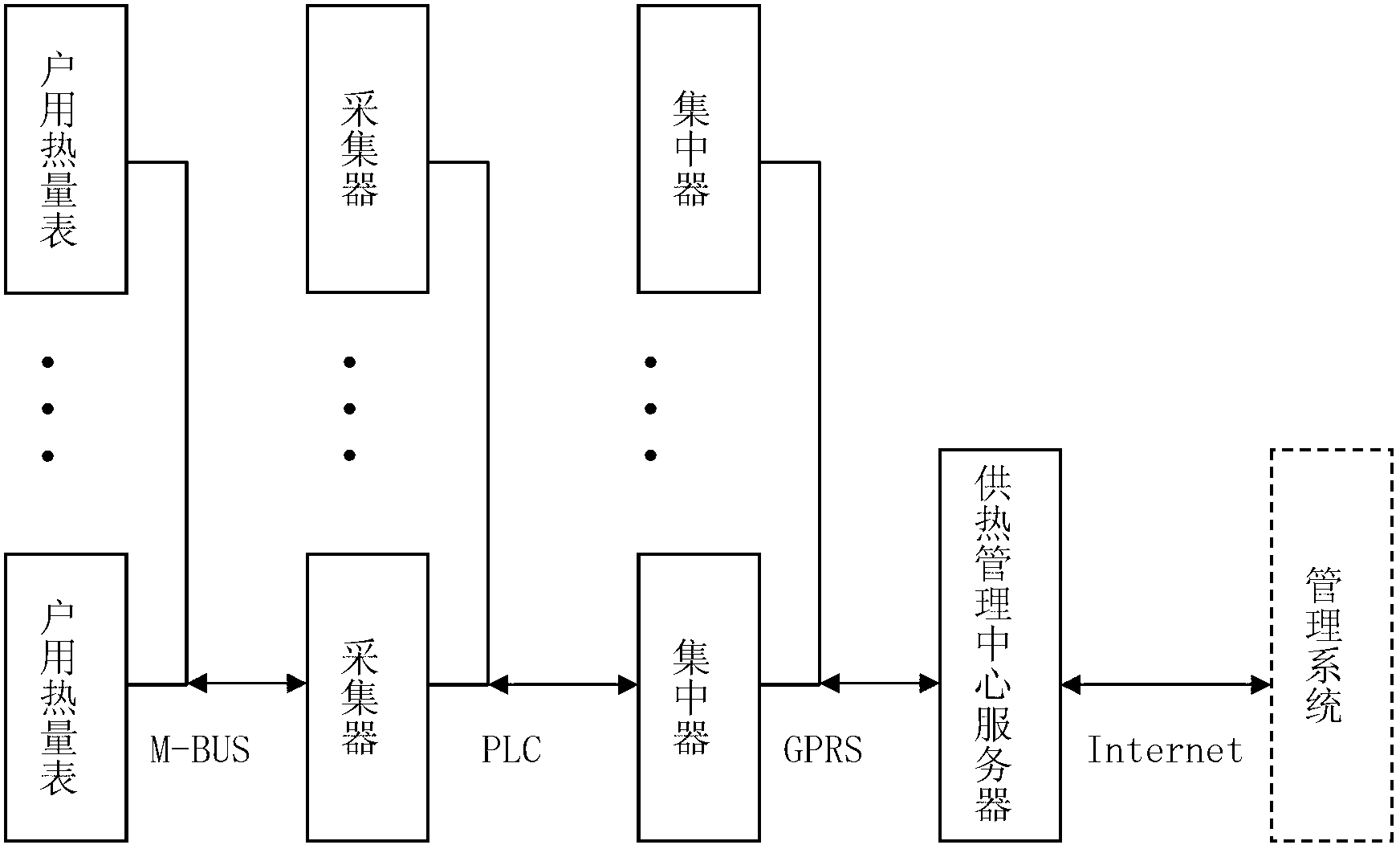
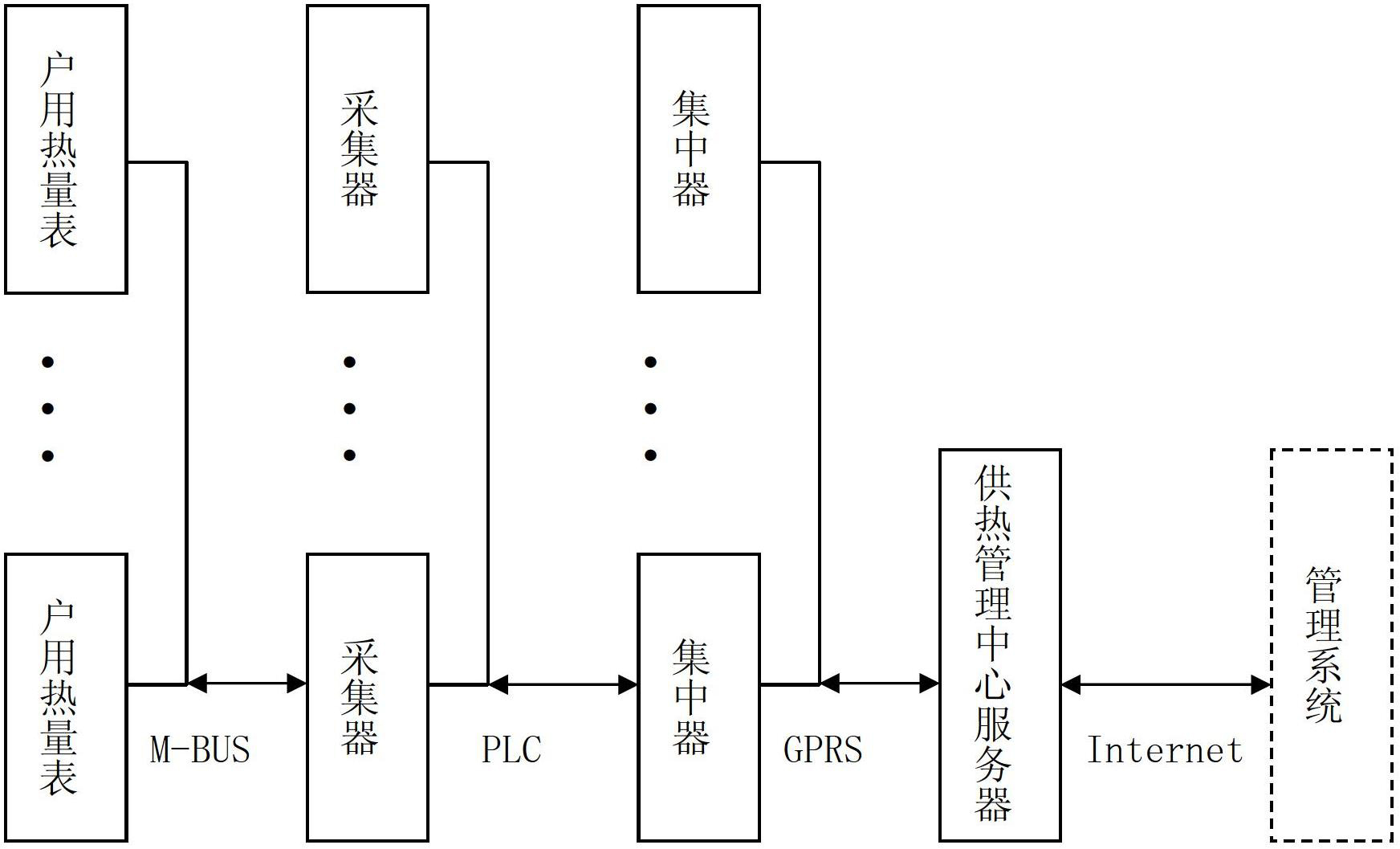
Heat metering information remote transmission system based on composite communication mode
ActiveCN102708668AHigh reliability of remote meter readingImprove reliabilityElectric signal transmission systemsTransport systemCarrier signal
The invention discloses a heat metering information remote transmission system based on a composite communication mode. The heat metering information remote transmission system comprises a plurality of household calorimeters, collectors, concentrators and a heat supply management central server, wherein M-BUS communication modules of the household calorimeters are connected with M-BUS communication modules of the collectors and transmit data through M-BUS buses; power line carrier communication modules of the collectors are connected with power line carrier communication modules of the concentrators and transmit data through power lines; and wireless communication modules of the concentrators are in wireless connection with a wireless communication module of the heat supply management central server and transmit data through a wireless network. The heat metering information remote transmission system provided by the invention can promptly, accurately and safely realize heat metering information remote transmission at comprehensive low cost, and is suitable for centralized meter reading and charge management of calorimeters.
Owner:TIANJIN WANHUA CO LTD
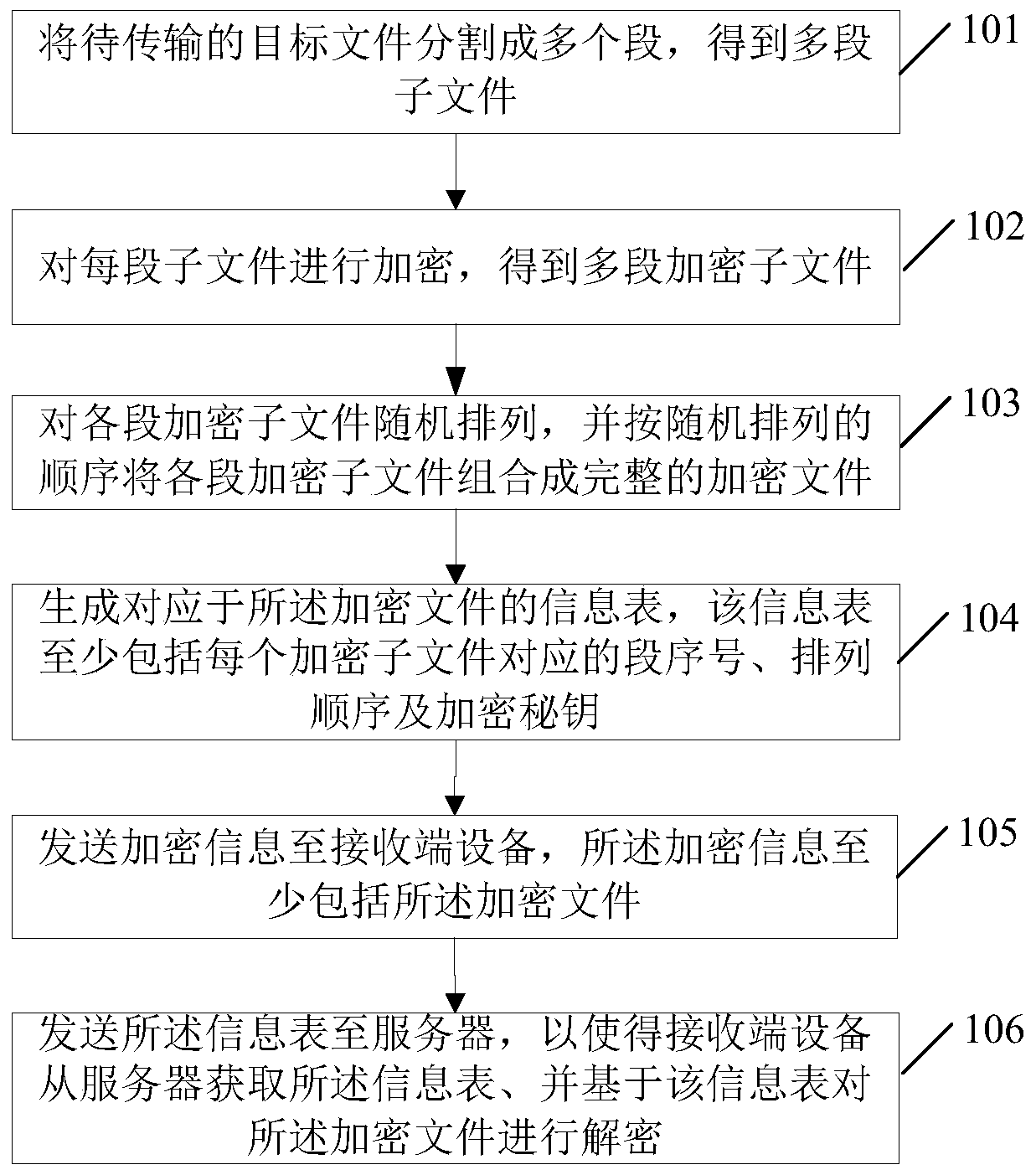
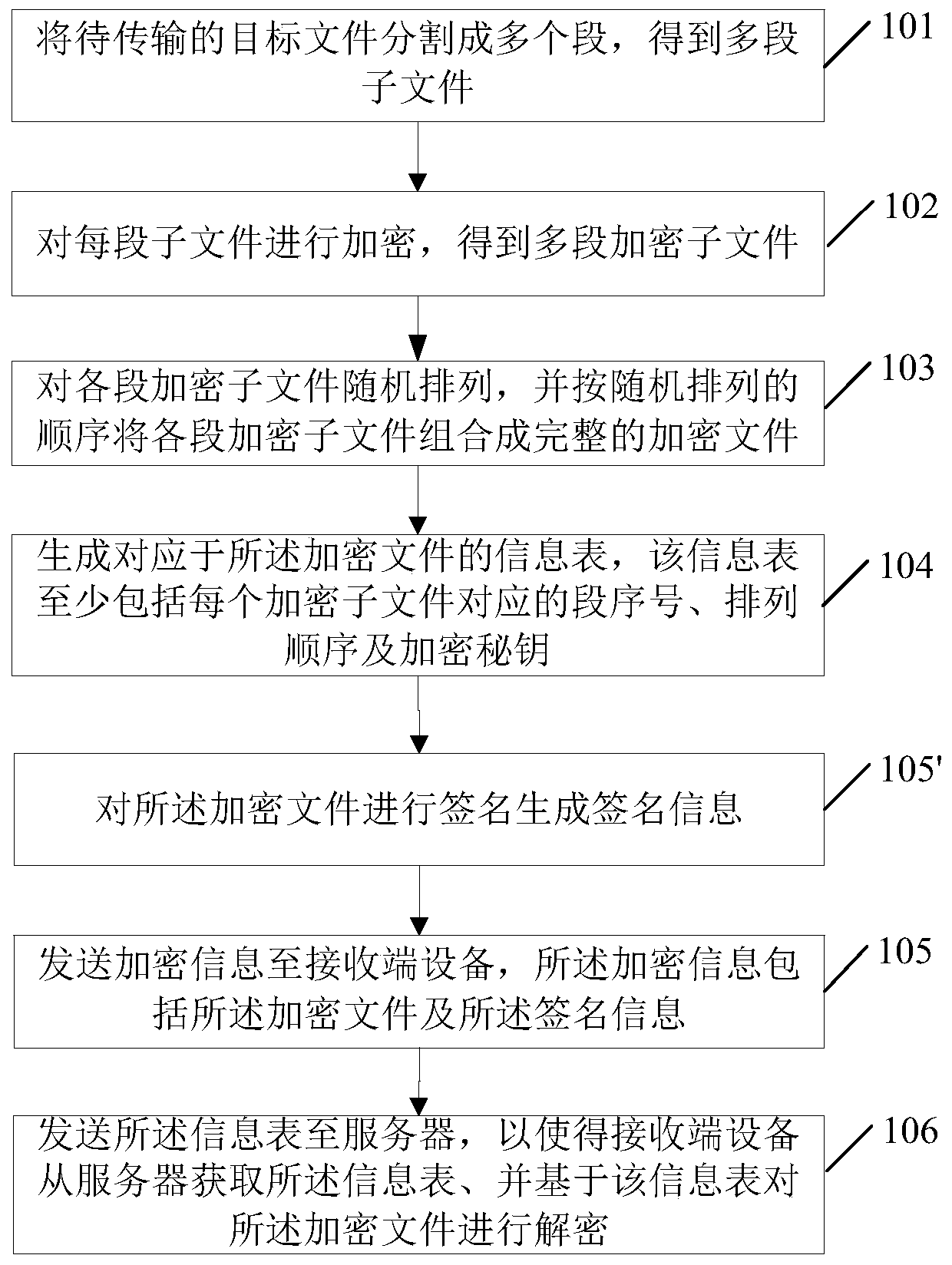
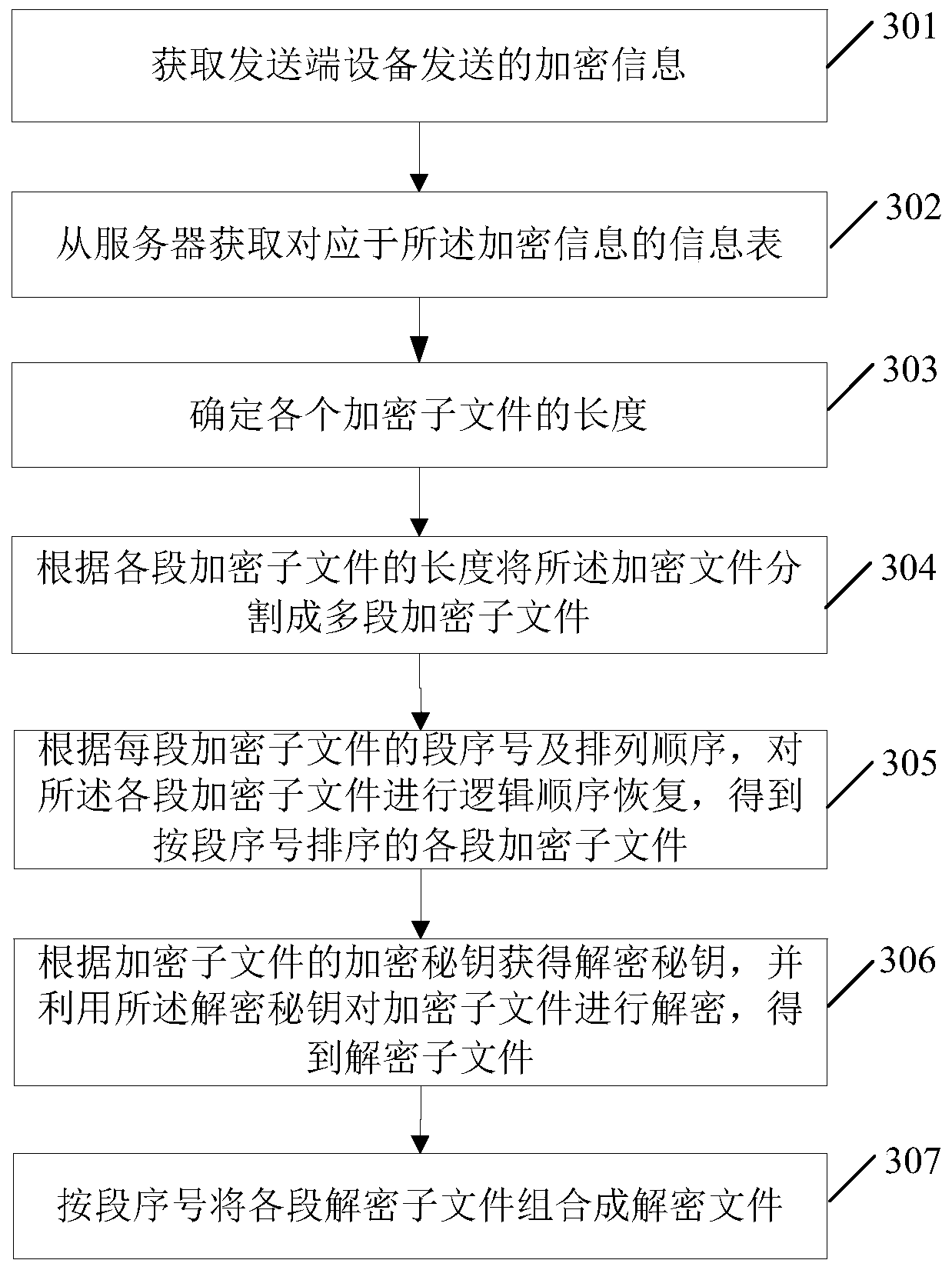
File transmitting method and system, sending end equipment and receiving end equipment
PendingCN111245818AImprove transmission securityIncrease the difficultyTransmissionEngineeringInformation security
The invention relates to a file transmitting method and system, sending end equipment and receiving end equipment, and the method comprises the steps: carrying out the random arrangement of all encryption sub-files corresponding to a to-be-transmitted target file, wherein the sequence of all encryption sub-files can be disturbed so as to improve the difficulty for an illegal person to decrypt an original file, and improve the transmission safety of file information; furthermore, the encrypted file and the information table thereof are respectively transmitted according to different lines, wherein even if an illegal person monitors the transmission line of the encrypted file, the information table cannot be obtained from the line at the same time; therefore, on the one hand, the illegal person cannot recover the original logic sequence of each encrypted sub-file according to the segment serial number and the arrangement sequence in the information table; on the other hand, the illegal person cannot obtain the encryption key and cannot crack the decryption key according to the encryption key, that is, the illegal person cannot decrypt each encrypted sub-file, so that the difficulty is provided for the illegal person to obtain the target file, and the information security of the transmitted target file is improved.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
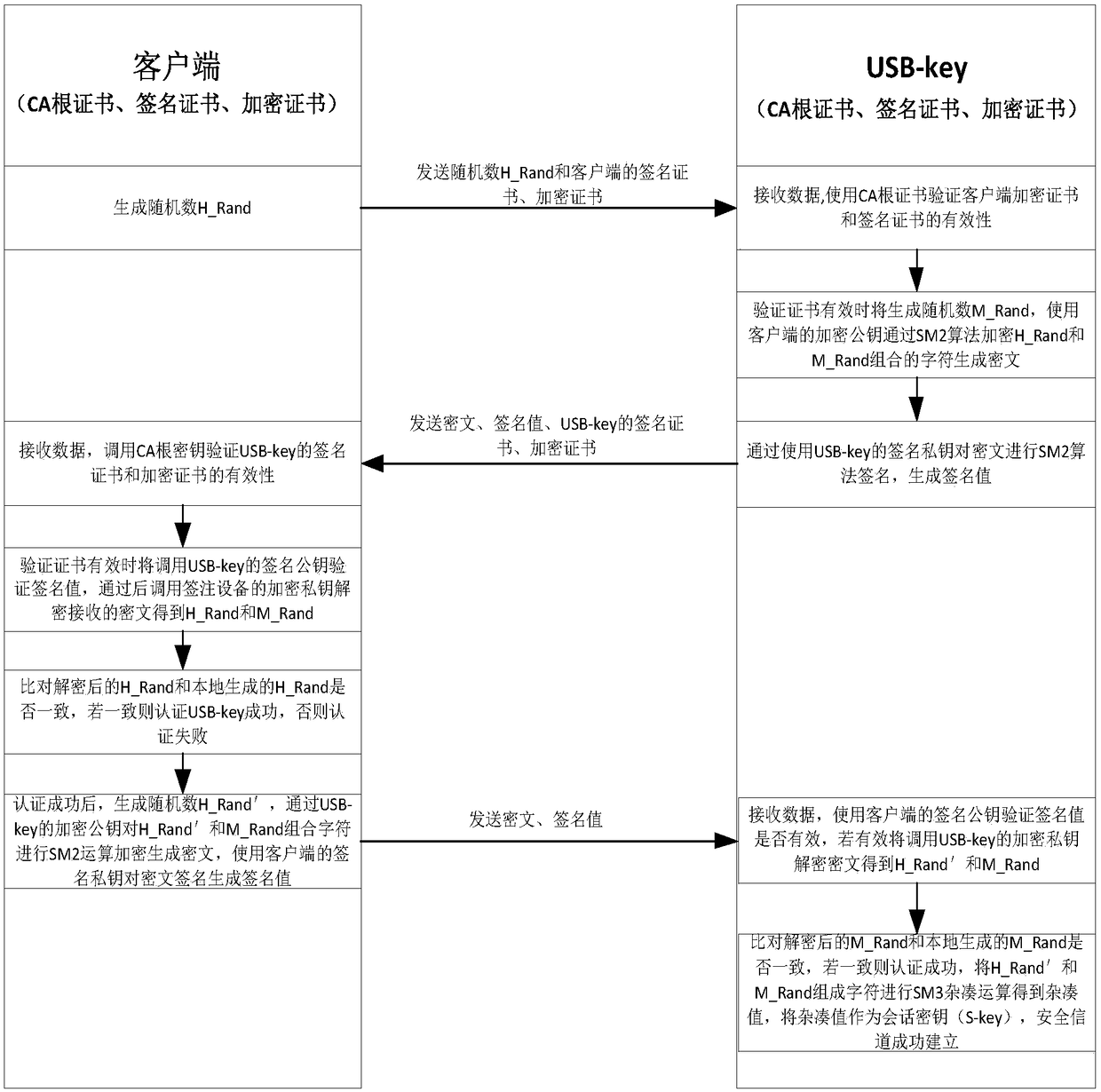
Authentication method based on USB-key
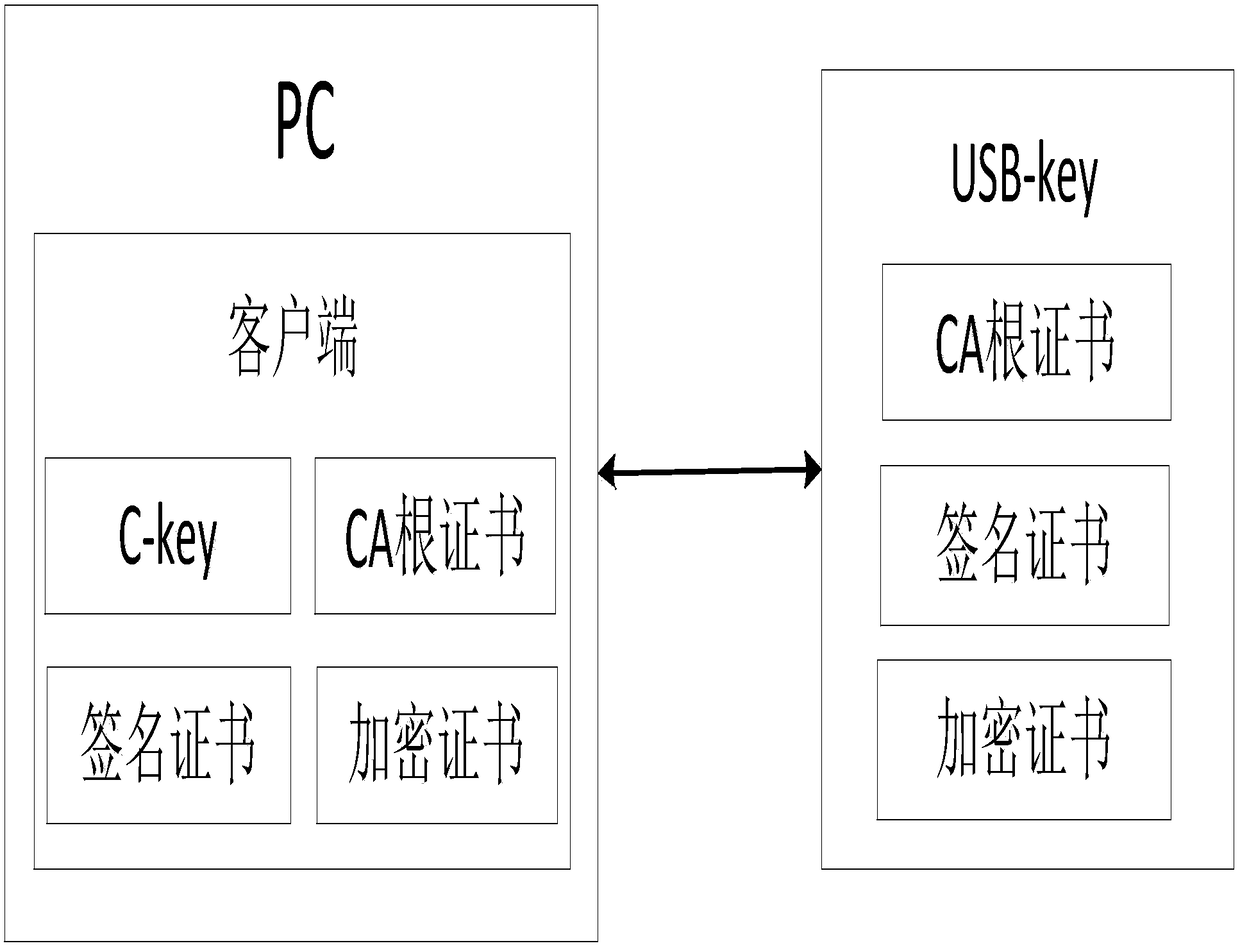
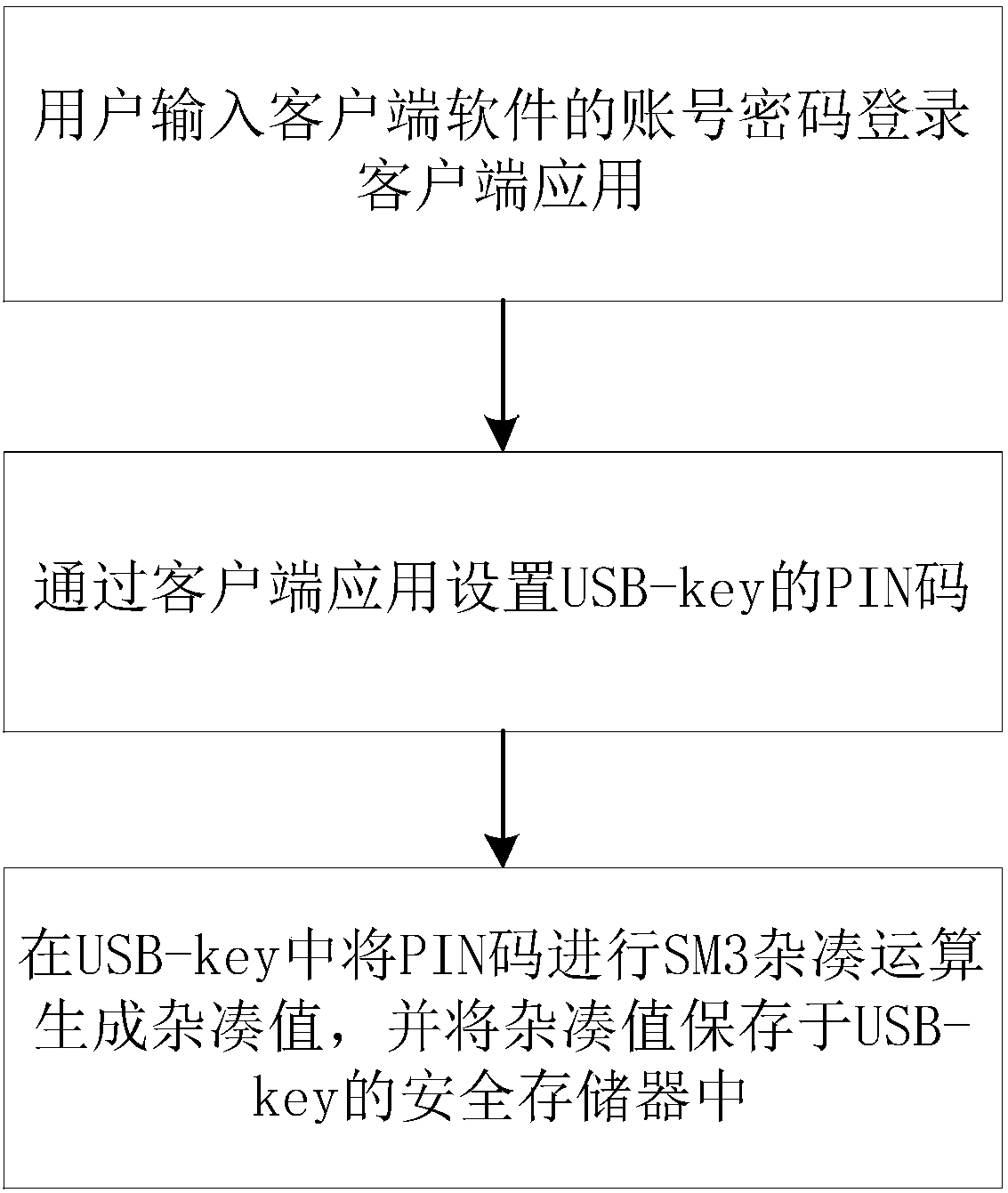
ActiveCN108551391AImprove transmission securityAvoid eavesdroppingMultiple keys/algorithms usageUser identity/authority verificationEavesdroppingUSB
The invention discloses an authentication method based on a USB-key. The method comprises the following steps: presetting a PIN code and computing a hash value; verifying the PIN code and generating averification instruction by a client, and encrypting the verification instruction to acquire a first encrypted code; analyzing the first encrypted code to acquire a verification instruction to generate a first random code, and encrypting the first random code to acquire a second encrypted code; analyzing the second encrypted code to acquire the first random code, encrypting the first random codeto acquire the third encrypted code, and encrypting the third encrypted code to acquire the fourth encrypted code; analyzing the fourth encrypted code to acquire the third encrypted code, encrypting the first random code to acquire a fifth encrypted code, and passing the verification if the fifth encrypted code is consistent with the third encrypted code. The system is used for executing the method. The data transmission security is improved by establishing a basic verification system based on PKI / CA, the later authentication procedure is processed based on a session key authenticated at earlystage, the eavesdropping on the data can be effectively avoided, thereby preventing the PIN code from leaking.
Owner:中易通科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com