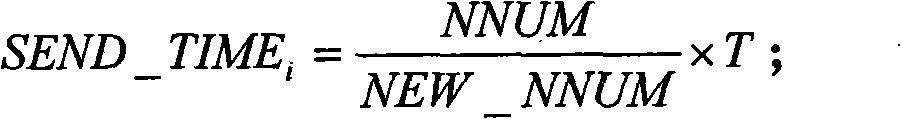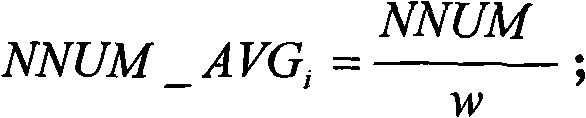Patents
Literature
65 results about "Identity protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
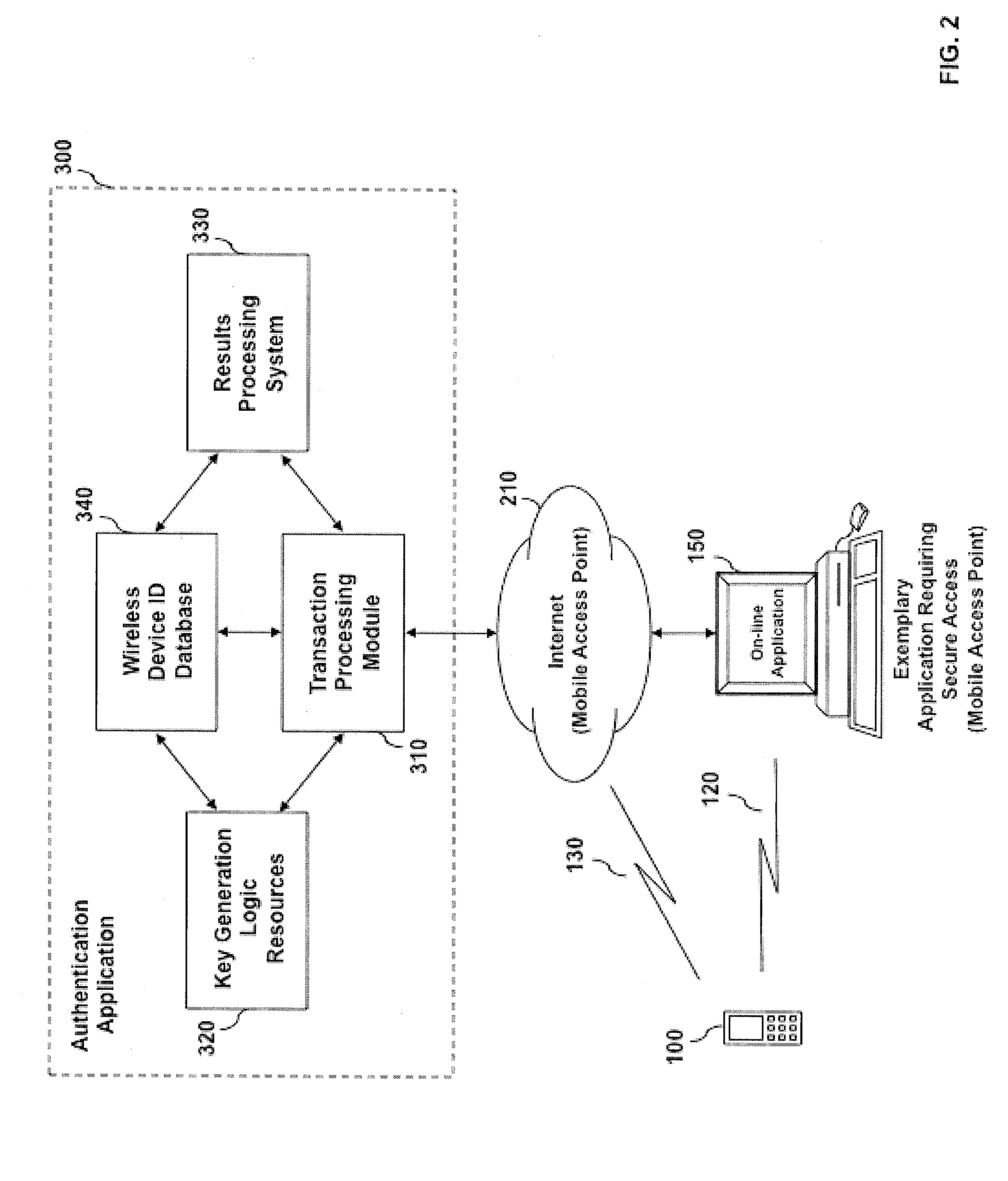
System and method for mobile identity protection of a user of multiple computer applications, networks or devices
ActiveUS8116731B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsIdentity theftFinancial transaction
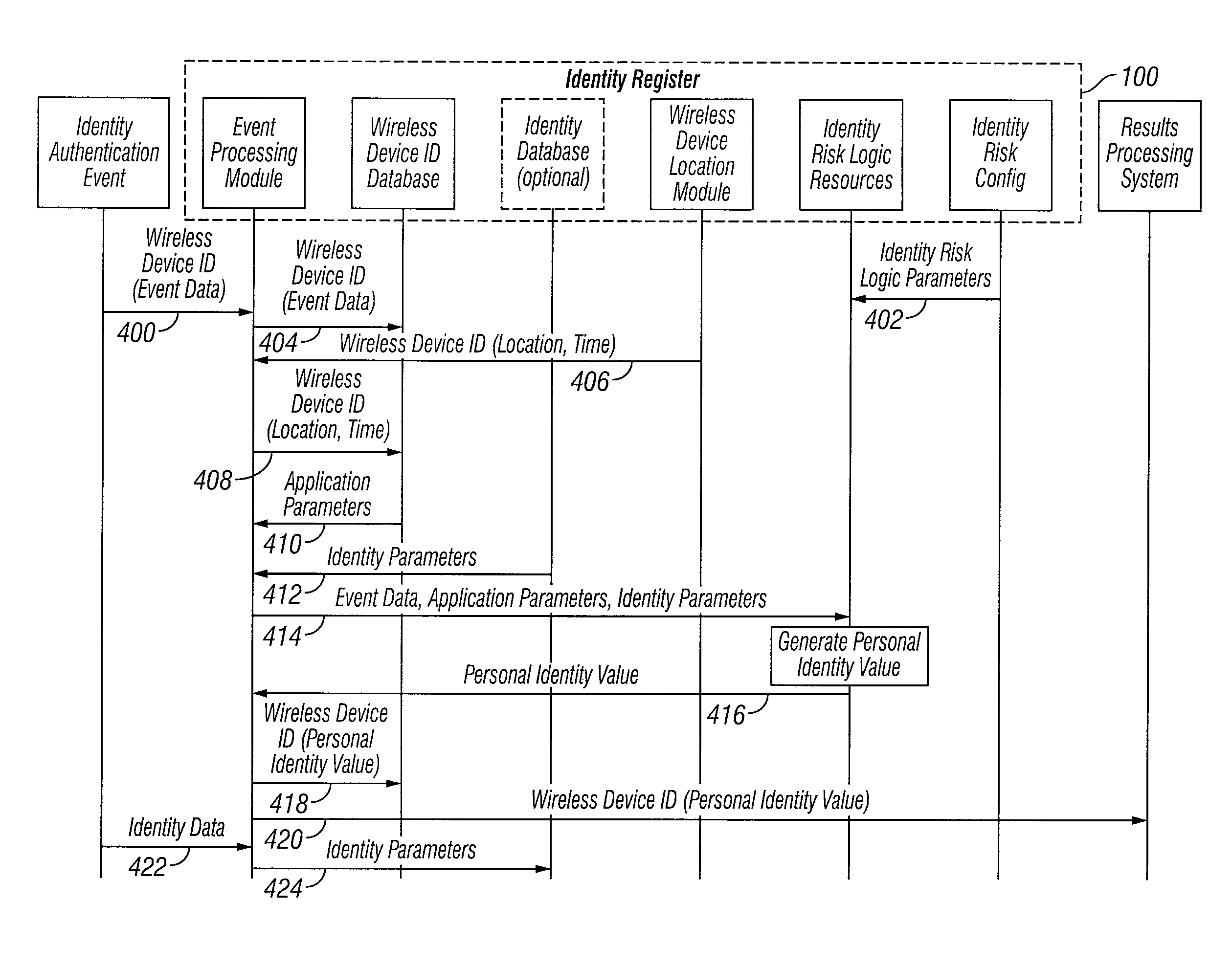
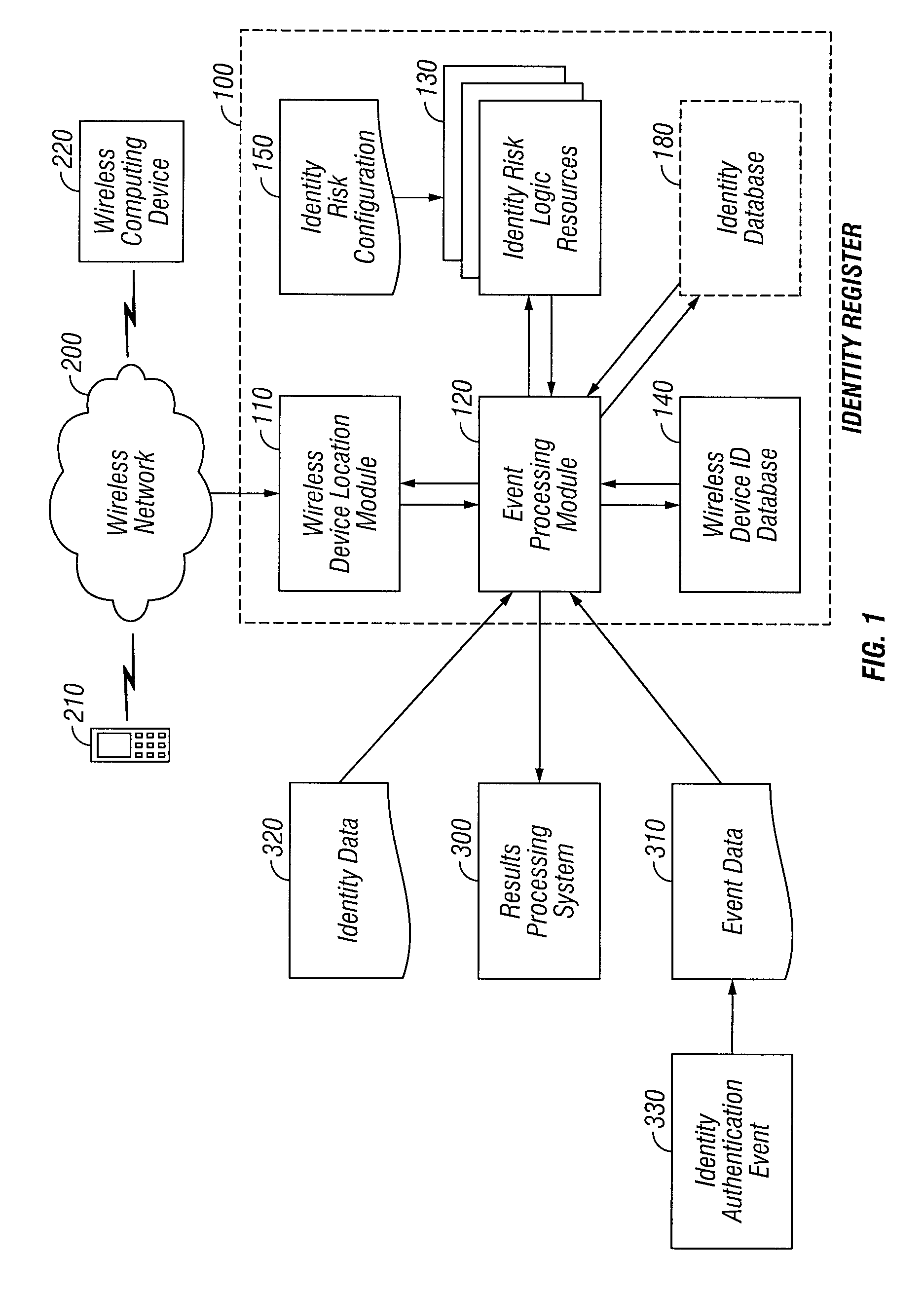
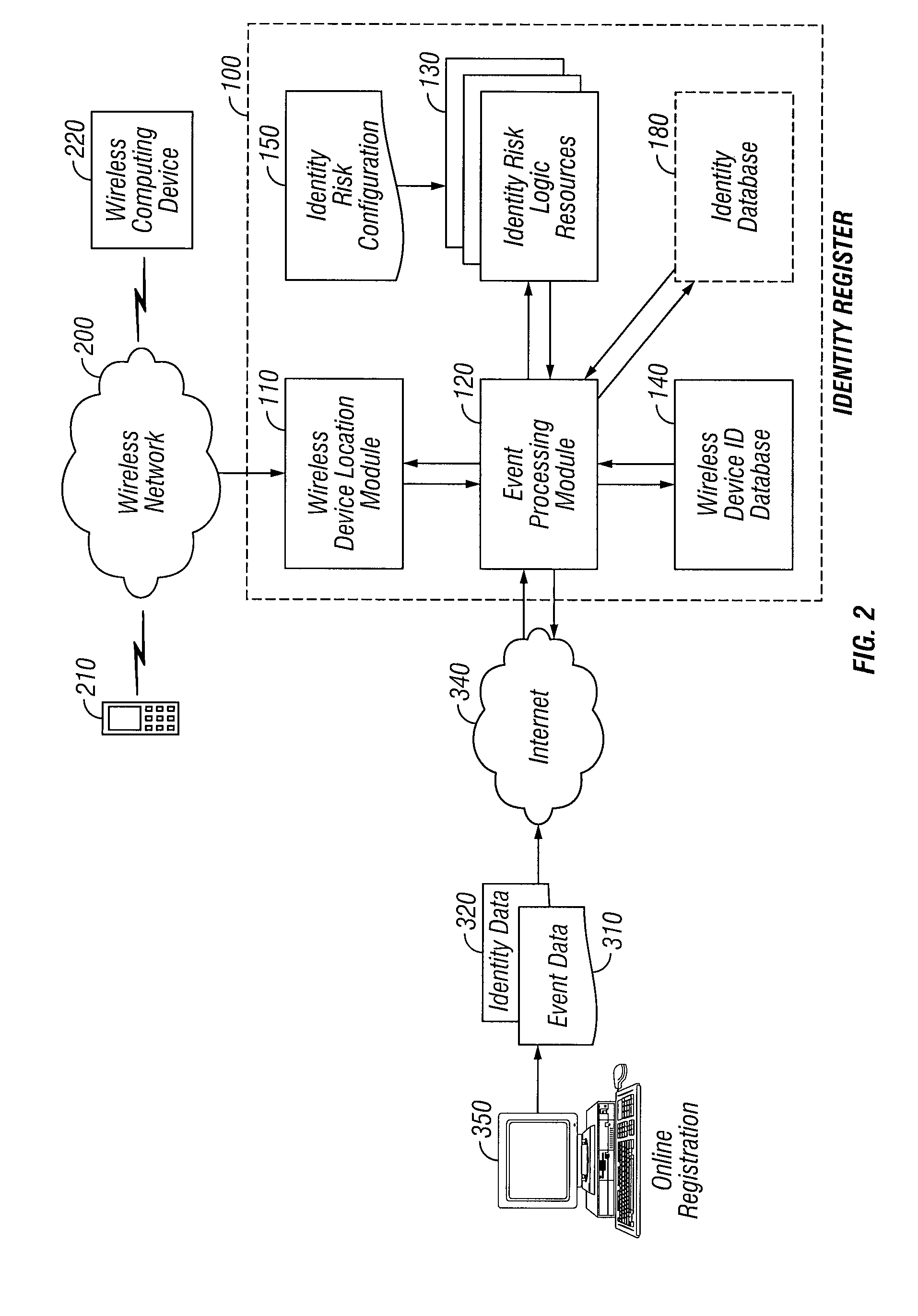
An automated system and method for authenticating entities or individuals engaging in automated or electronic transactions or activities such as financial transactions, accessing computer applications, computer software, data networks or other automated or electronic devices requiring identity verification is provided. A unique Personal Identity Value is computed and stored in an Identity Register for the entity or individual and may be used for a variety of applications including recognizing incidents of identity theft. This Personal Identity Value is based on one or more computer logic resources that incorporate the relationship among a variety of identification information elements and parameters associated with the entity or individual, such as the entity's or individual's wireless device location, the entity's or individual's home location, other associated locations, automated activities engaged in and applications accessed.
Owner:VISA INT SERVICE ASSOC
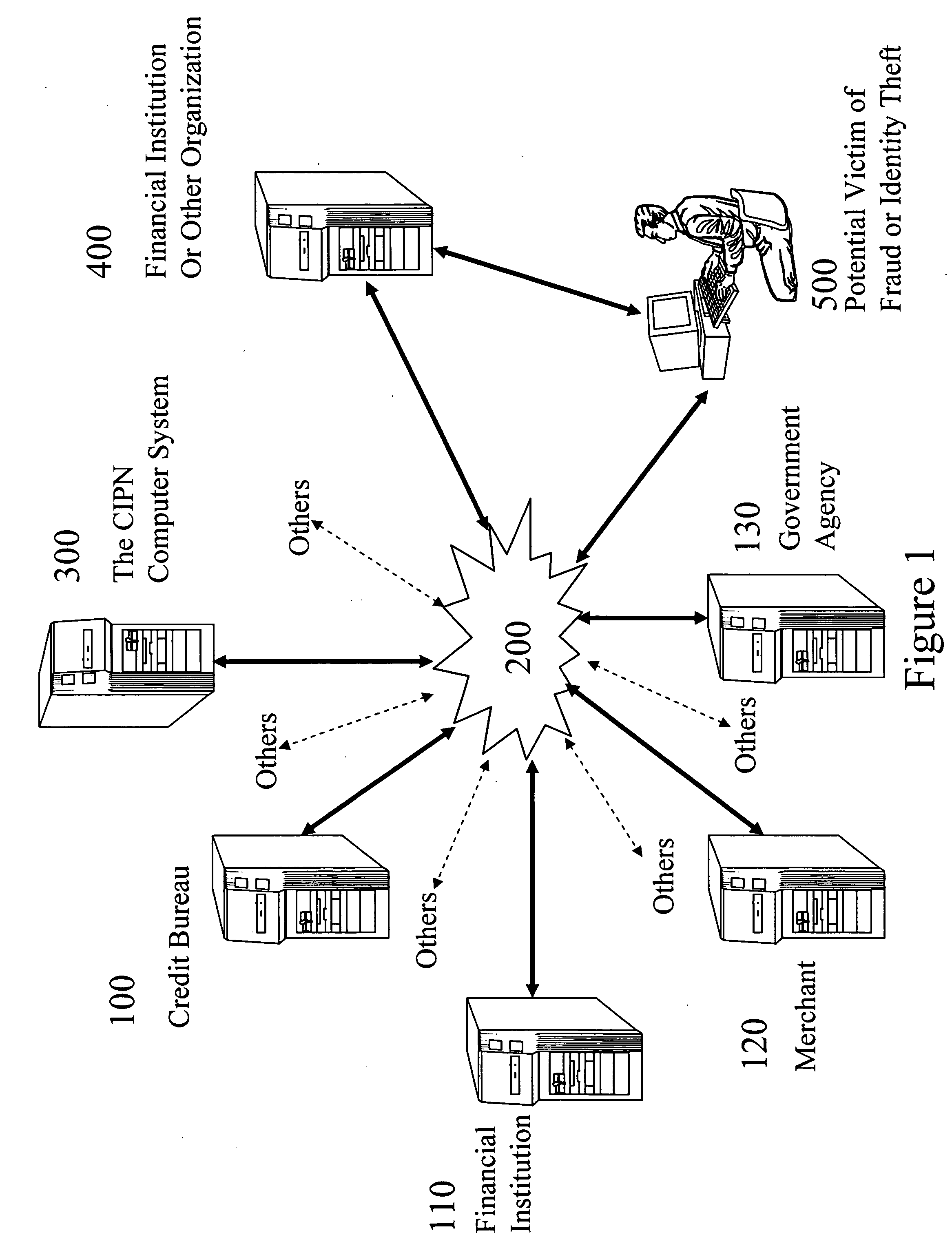
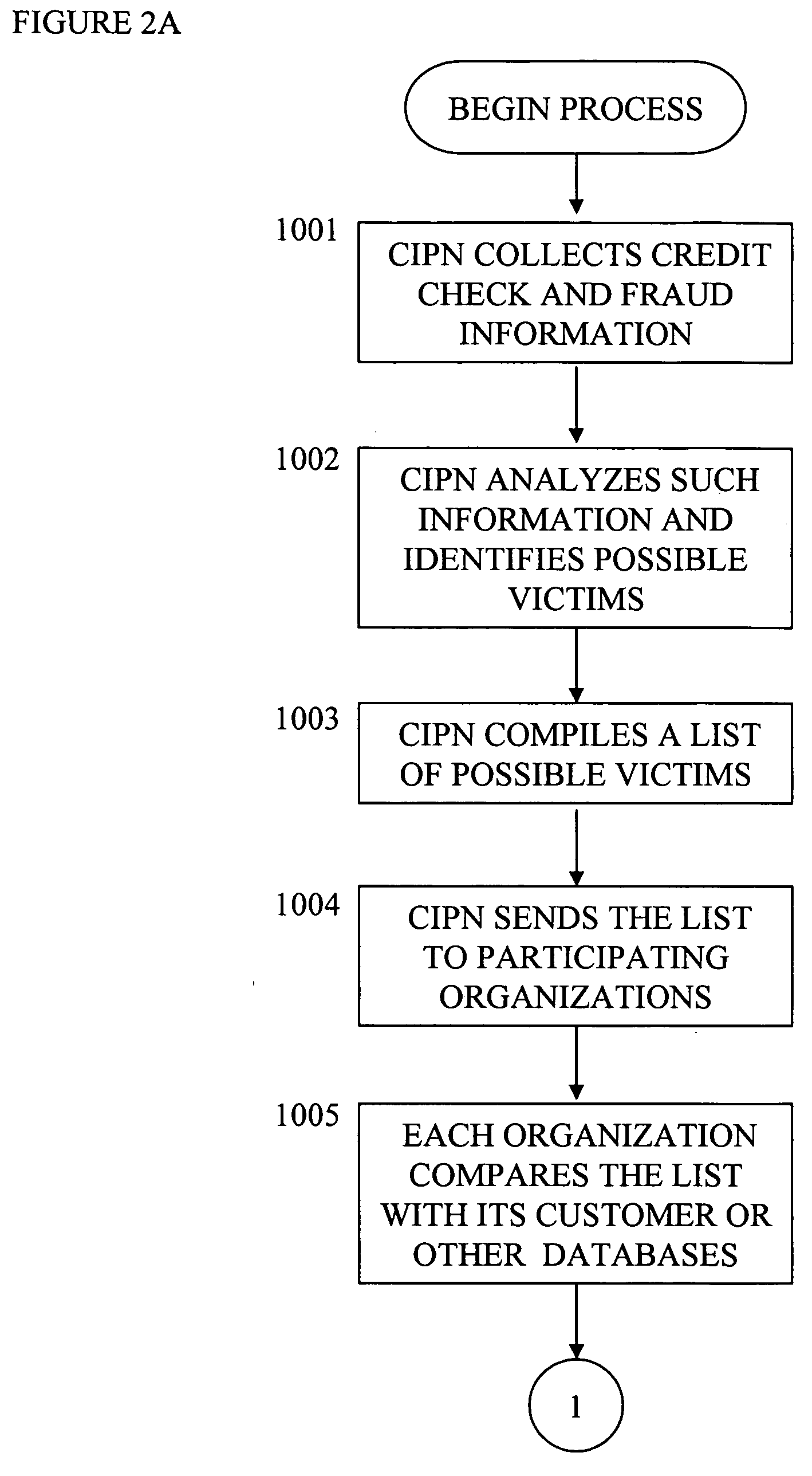
Credit and identity protection network
InactiveUS20060089905A1Prevent further lossAvoid damageFinancePayment architectureIdentity theftIdentity protection
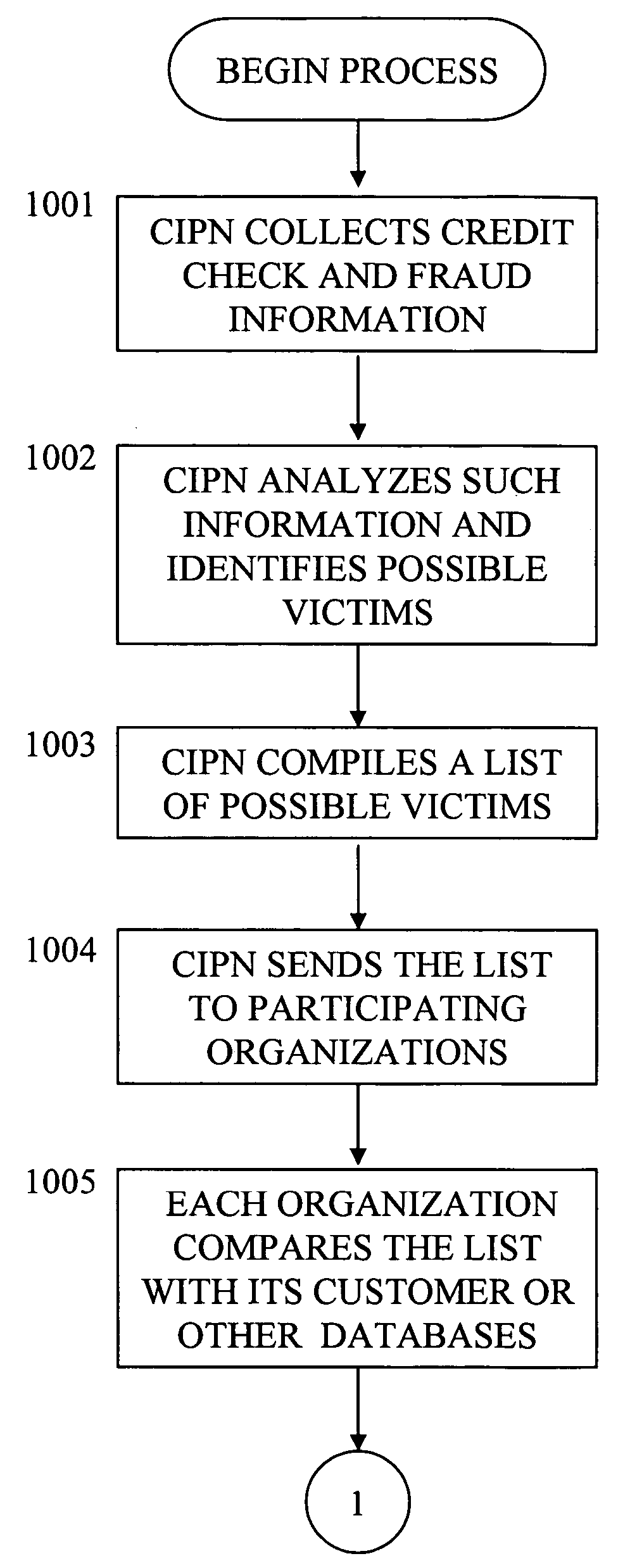
A computer network, Credit and Identity Protection Network (“CIPN”), is established to detect credit damage and identity theft occurring to individuals, organizations, and other entities. It automatically advises the potential victims to verify the possible fraudulent activities and helps them to take proper actions to protect their credit and identity. In addition, this computer network provides the potential victim with assistance in notifying financial institutions, credit bureaus, merchants, and government agencies of suspicious activities and / or of confirmed fraudulent cases so that these organizations can take proper actions to protect themselves and the victims.
Owner:SONG YUH SHEN +3
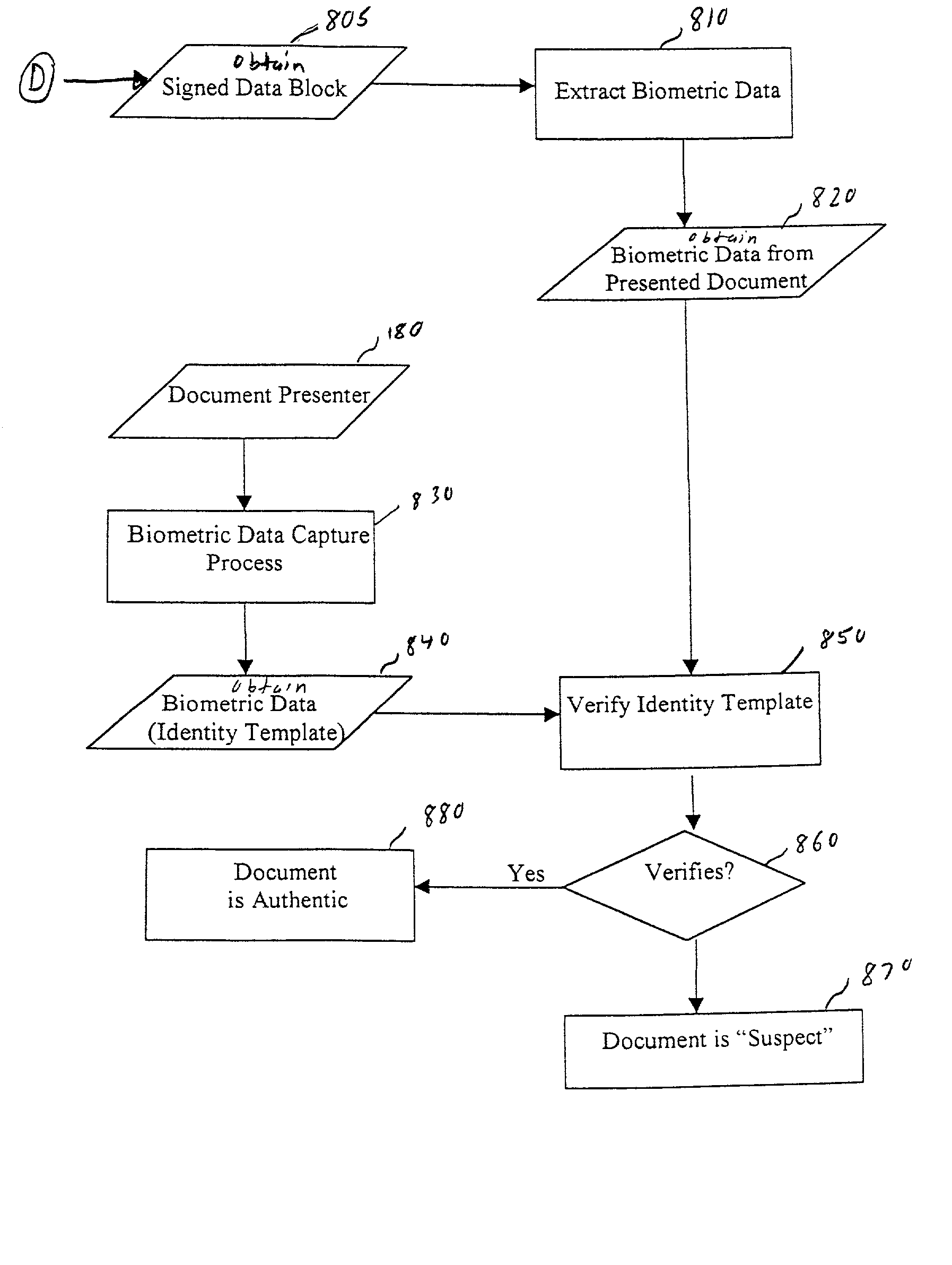
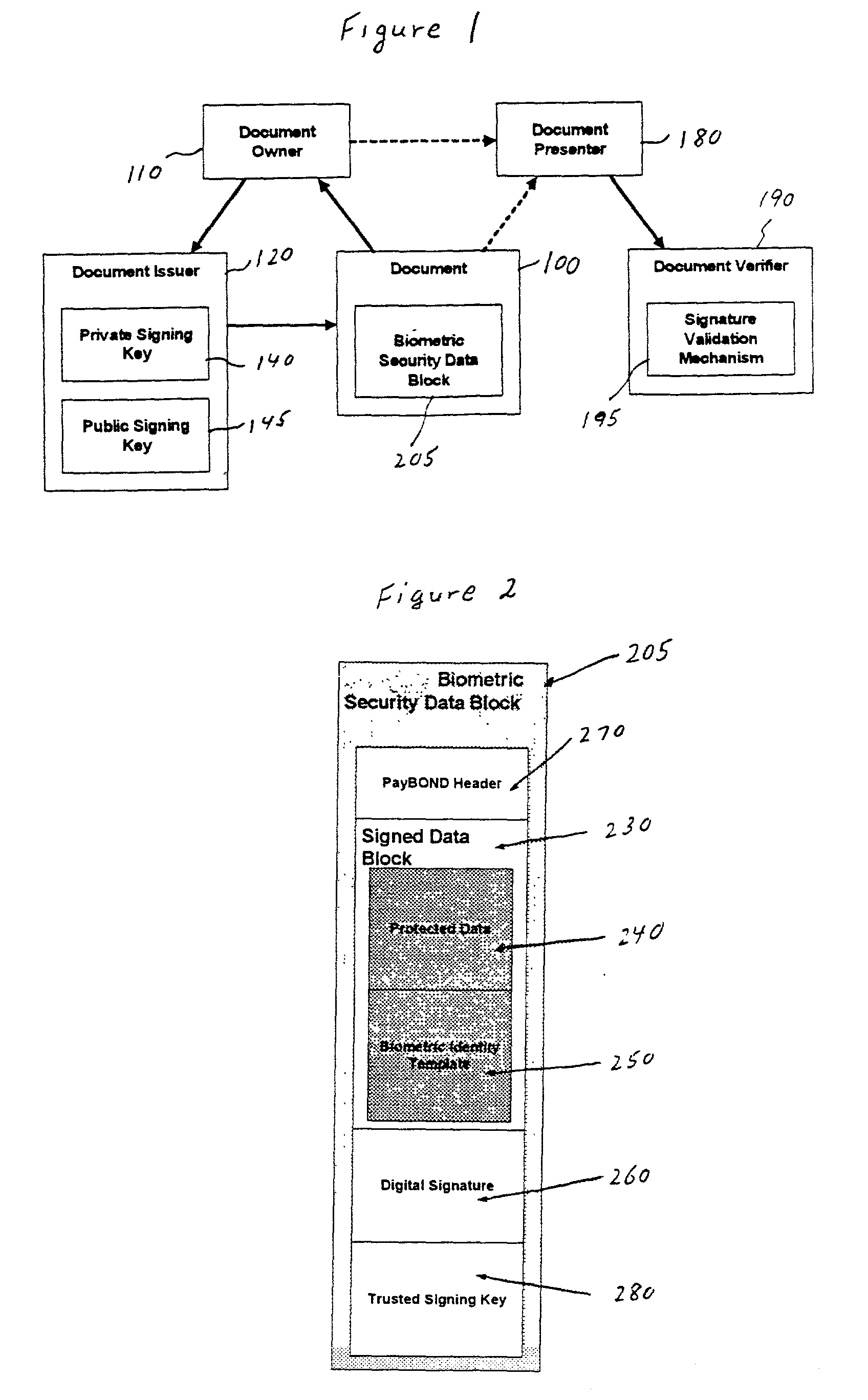
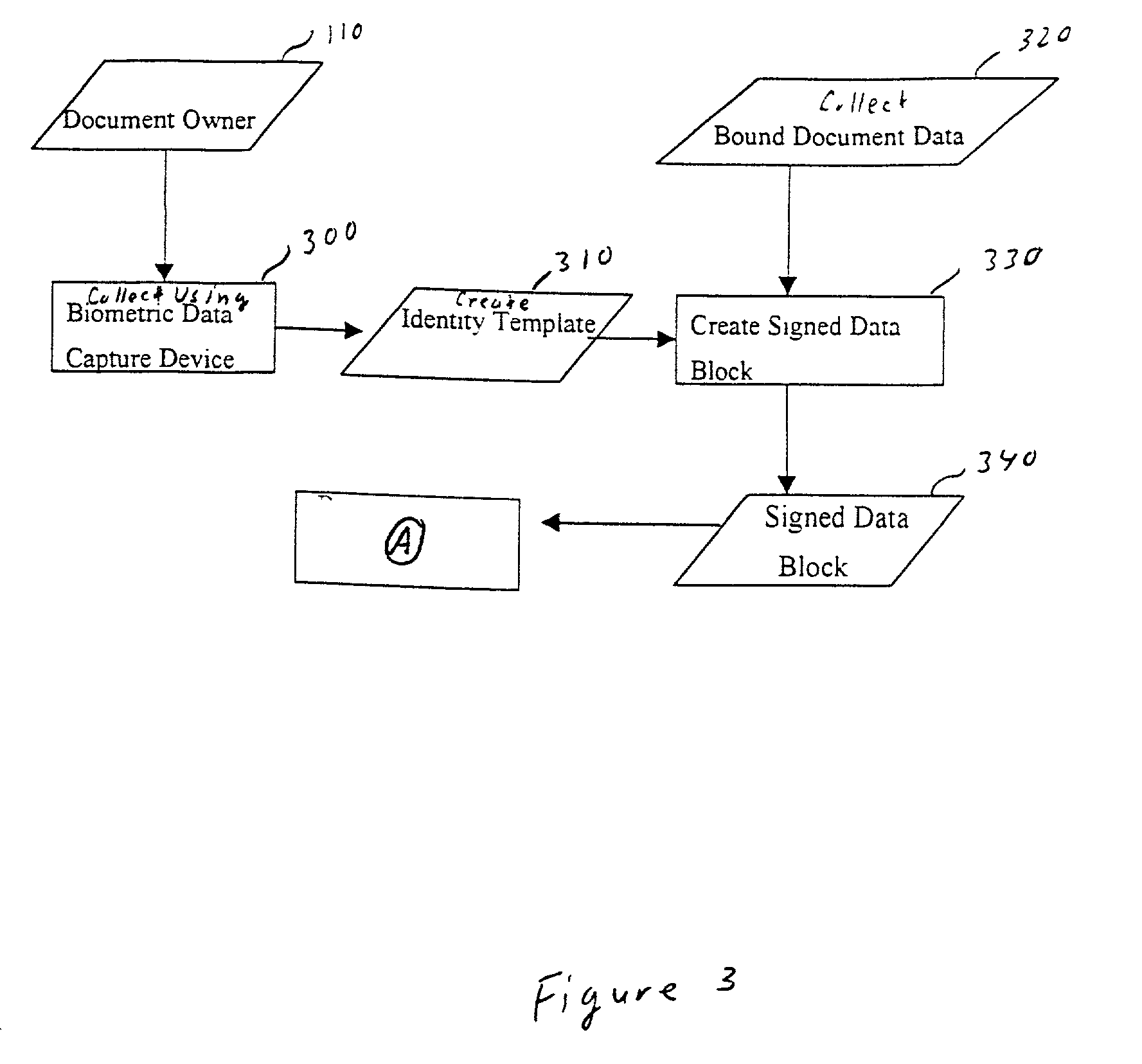
Creating counterfeit-resistant self-authenticating documents using cryptographic and biometric techniques
InactiveUS20030089764A1Easy to operatePayment architectureSpecial data processing applicationsData setBiometric data
A system and method for creating and verifying physical documents and / or smart cards based upon positively identifying the owner, holder, or presenter of the document by relating to the measurement of biometric data of the individual at the time of document and / or smart card creation and verification. The biometric data that can be included in the creation of the document include retinal scan, face print, fingerprint, voiceprint and DNA profiles, or other viable biometric data set. Also, protected data that includes important information of the document itself that is written on the document, is combined with the biometric data to provide a security data block that is printed on the document. This security data block is decoded by a document verifier when presented by a document presenter, to provide for an enhanced level of document protection and identity protection.
Owner:PAYFORMANCE CORP
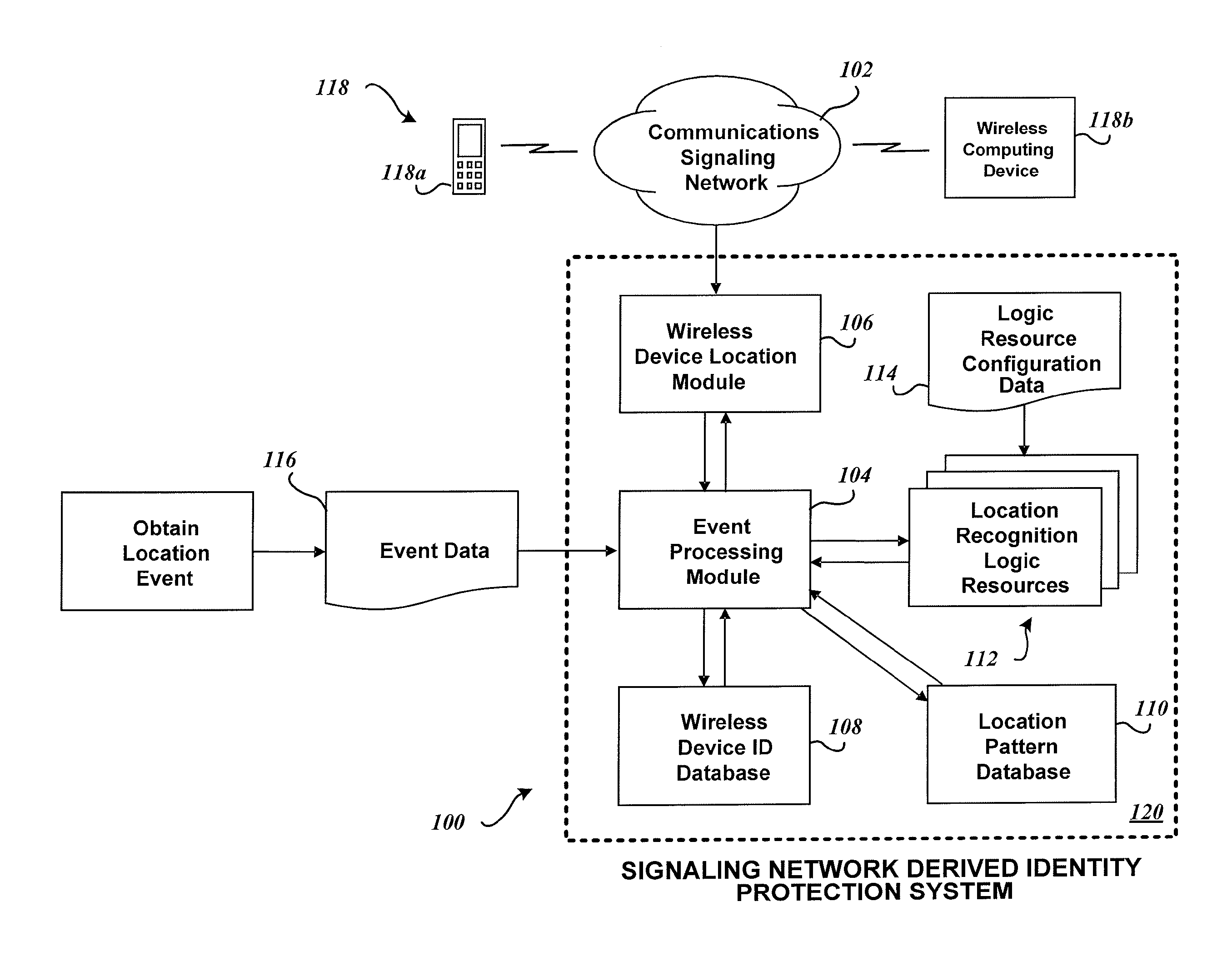
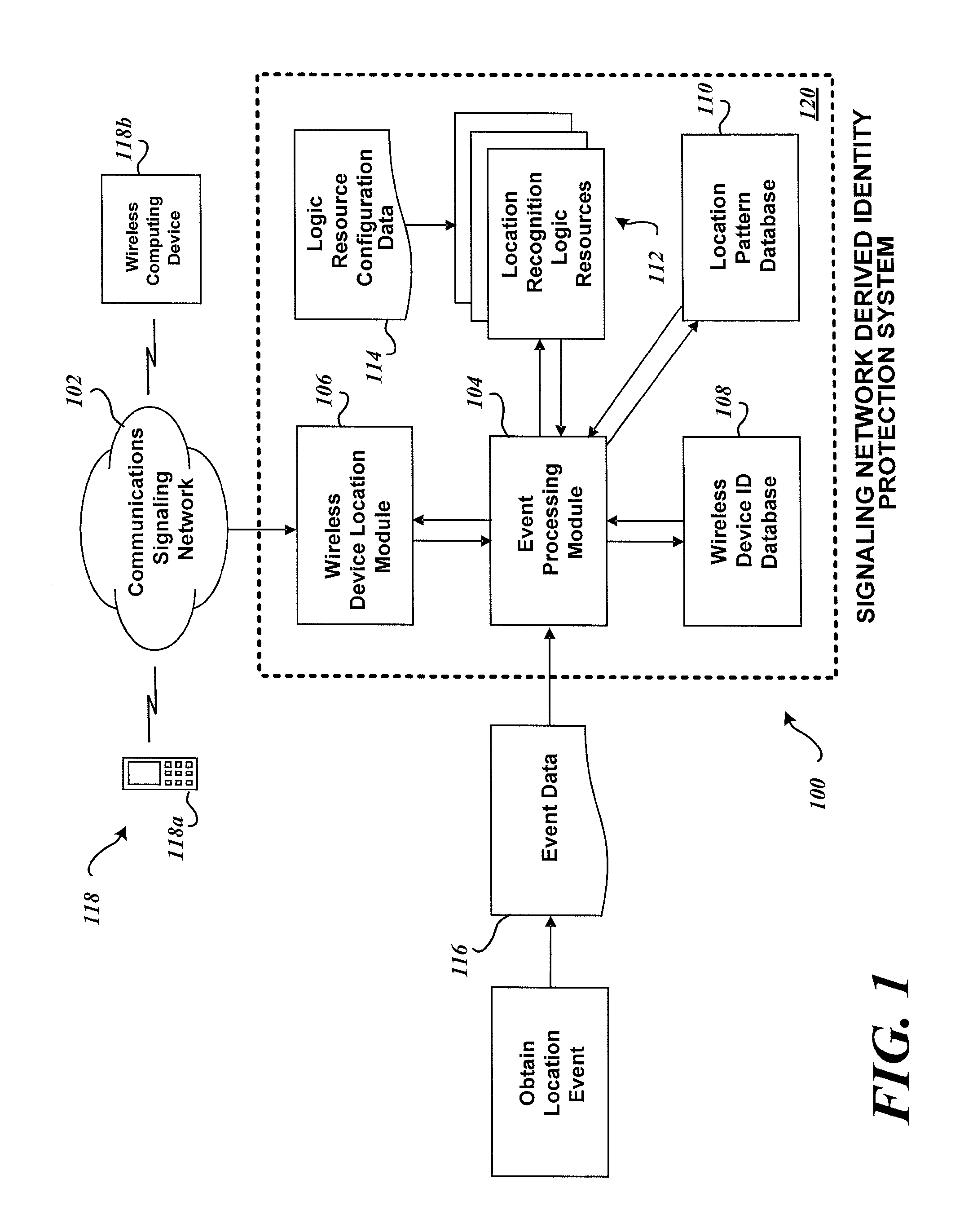
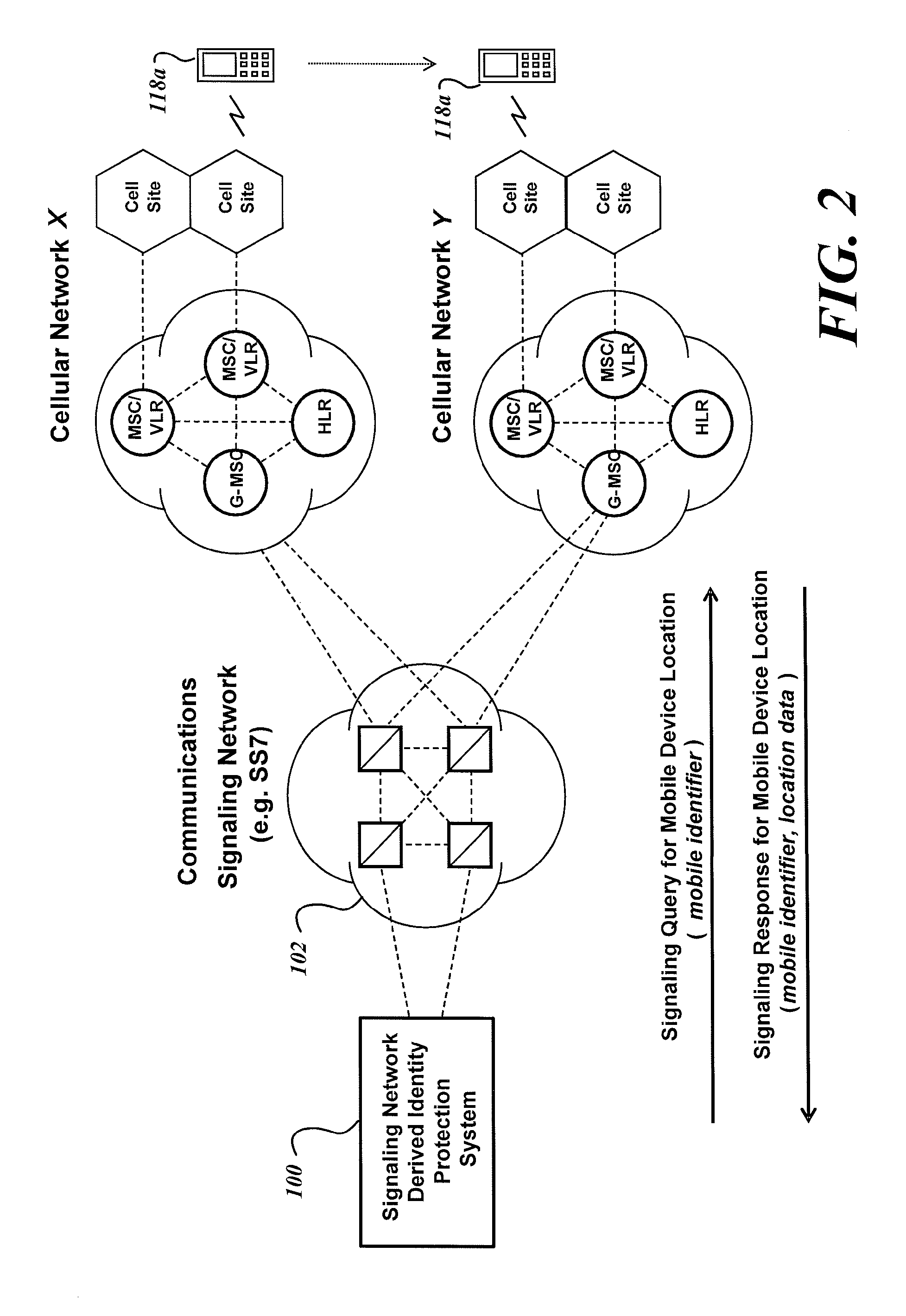
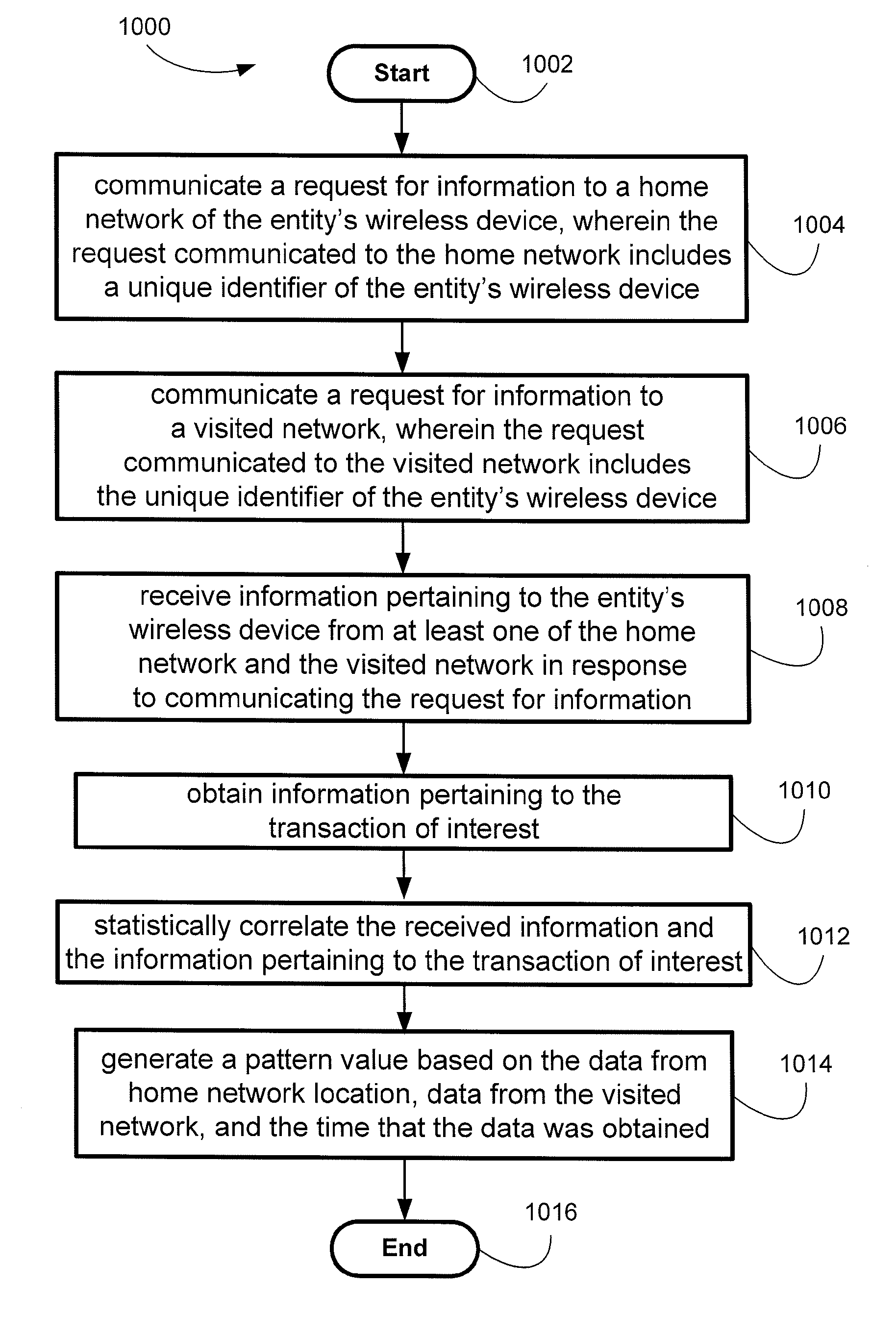
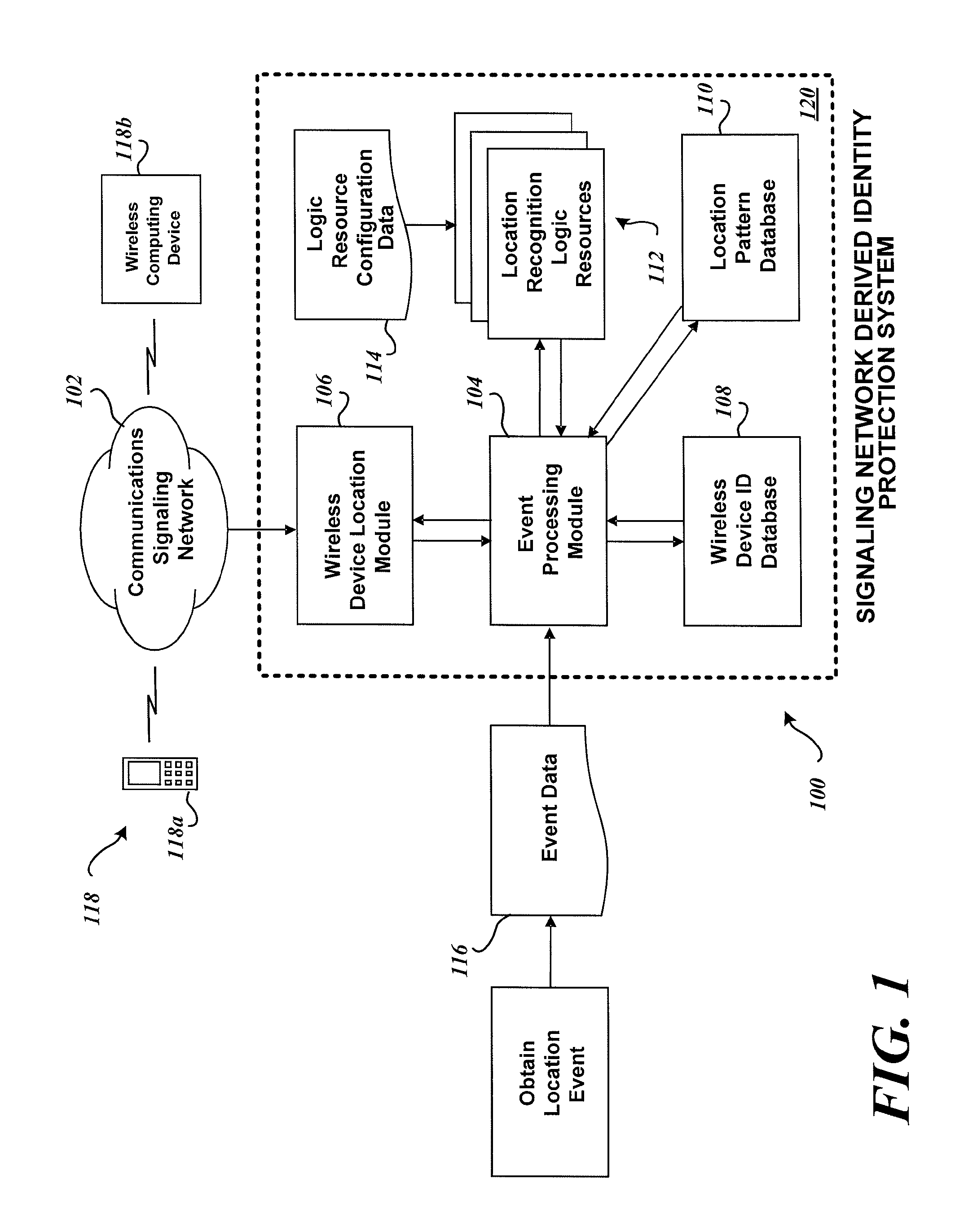
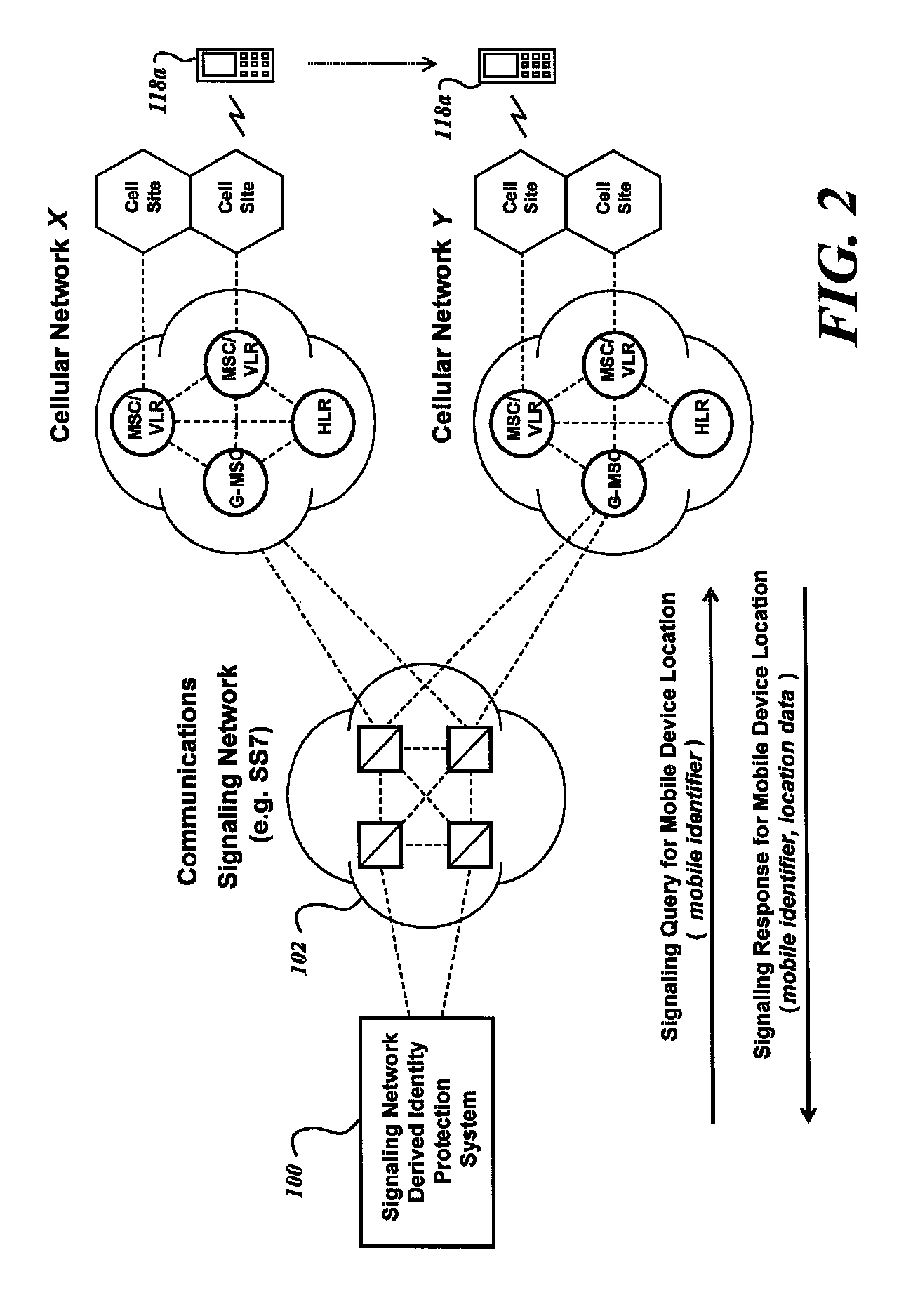
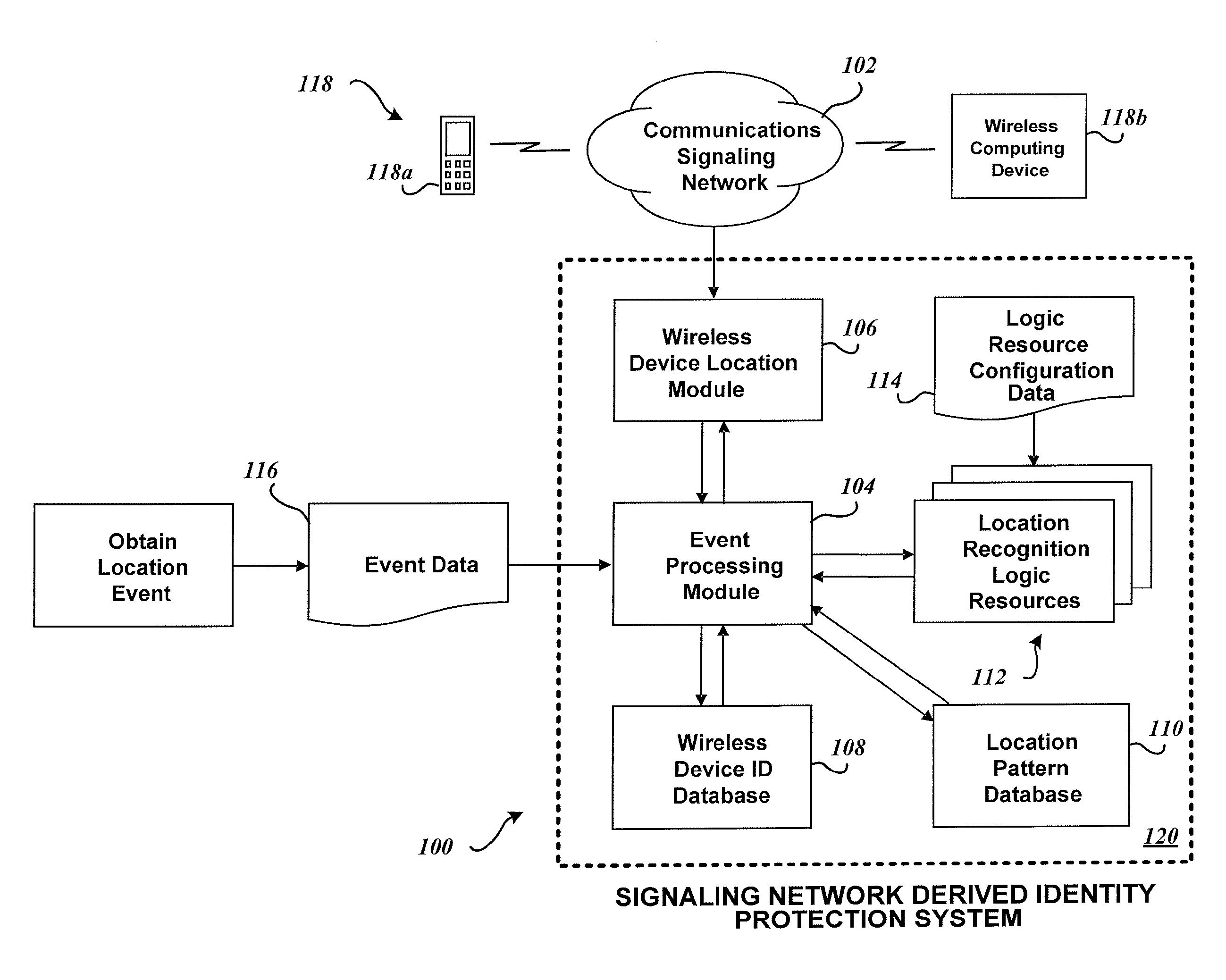
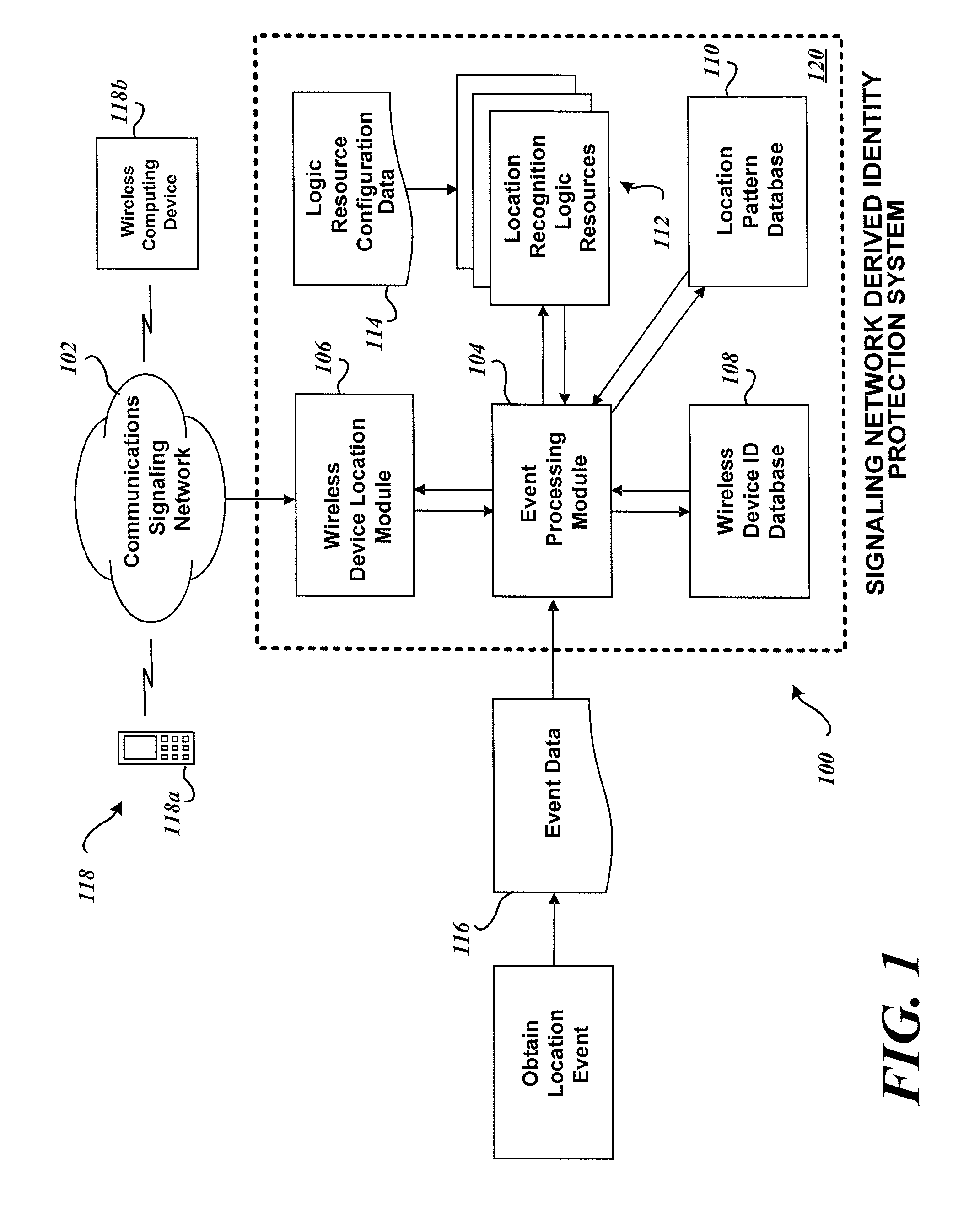
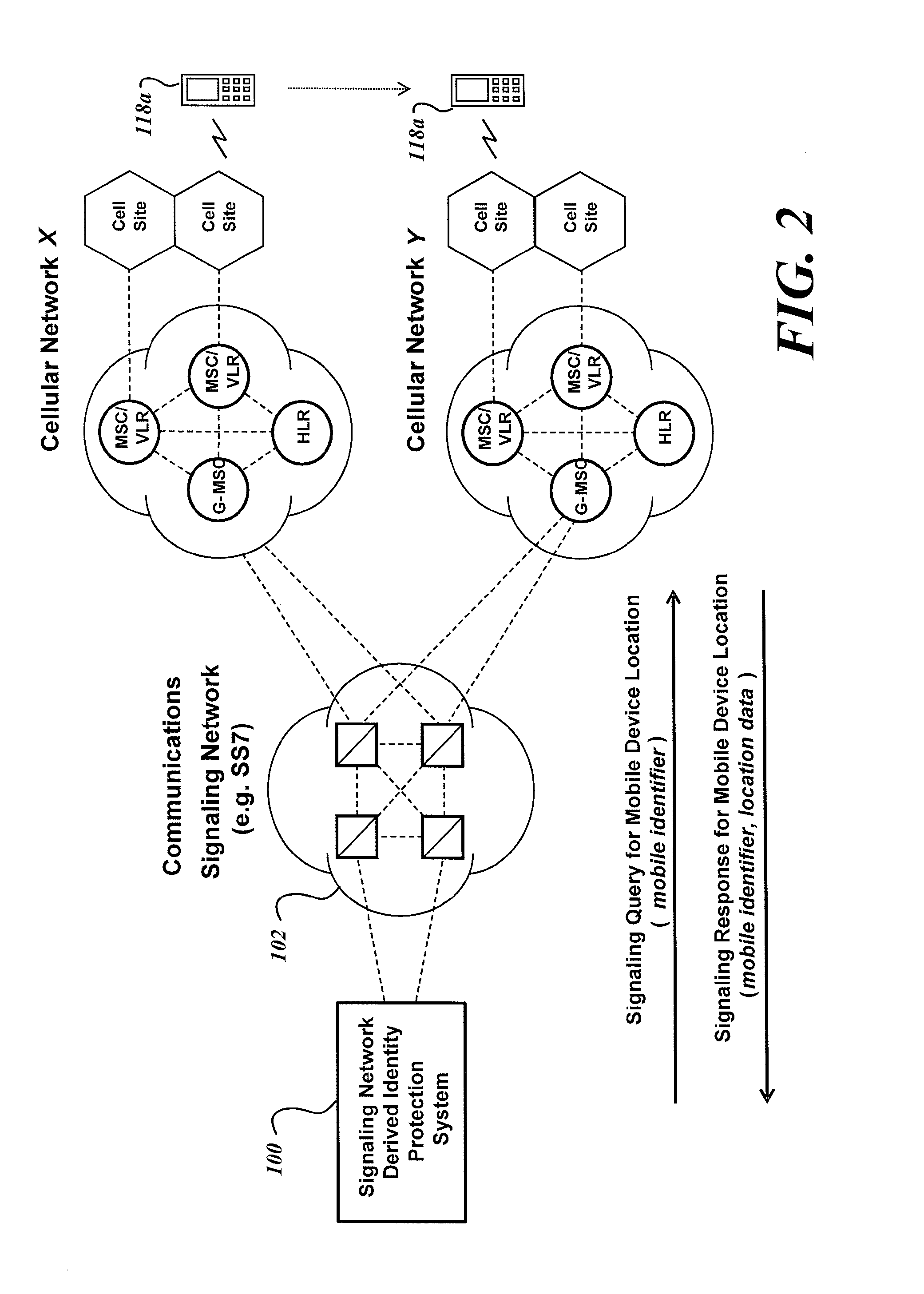
System and method for identity protection using mobile device signaling network derived location pattern recognition
ActiveUS20100130165A1Improve identityFinanceUnauthorised/fraudulent call preventionSignaling networkIdentity protection
A system and method for recognizing patterns in wireless device locations using wireless device location data derived from a communications signaling network is provided. By using wireless network supported signaling operations and messages, location data concerning the whereabouts of wireless devices, and hence wireless device users, may be obtained. The location data derived from the communications signaling network may be statistically analyzed to reveal potential geographic patterns that may indicate meaningful behaviors of the purported users of the wireless devices.
Owner:VISA INT SERVICE ASSOC
System and method for identity protection using mobile device signaling network derived location pattern recognition
ActiveUS8280348B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSignaling networkIdentity protection
A system and method for recognizing patterns in wireless device locations using wireless device location data derived from a communications signaling network is provided. By using wireless network supported signaling operations and messages, location data concerning the whereabouts of wireless devices, and hence wireless device users, may be obtained. The location data derived from the communications signaling network may be statistically analyzed to reveal potential geographic patterns that may indicate meaningful behaviors of the purported users of the wireless devices.
Owner:VISA INT SERVICE ASSOC
Methods and systems for protection of identity
InactiveUS20070078786A1Reduce harmImprove identityFinanceCharacter and pattern recognitionCredit cardEmail address
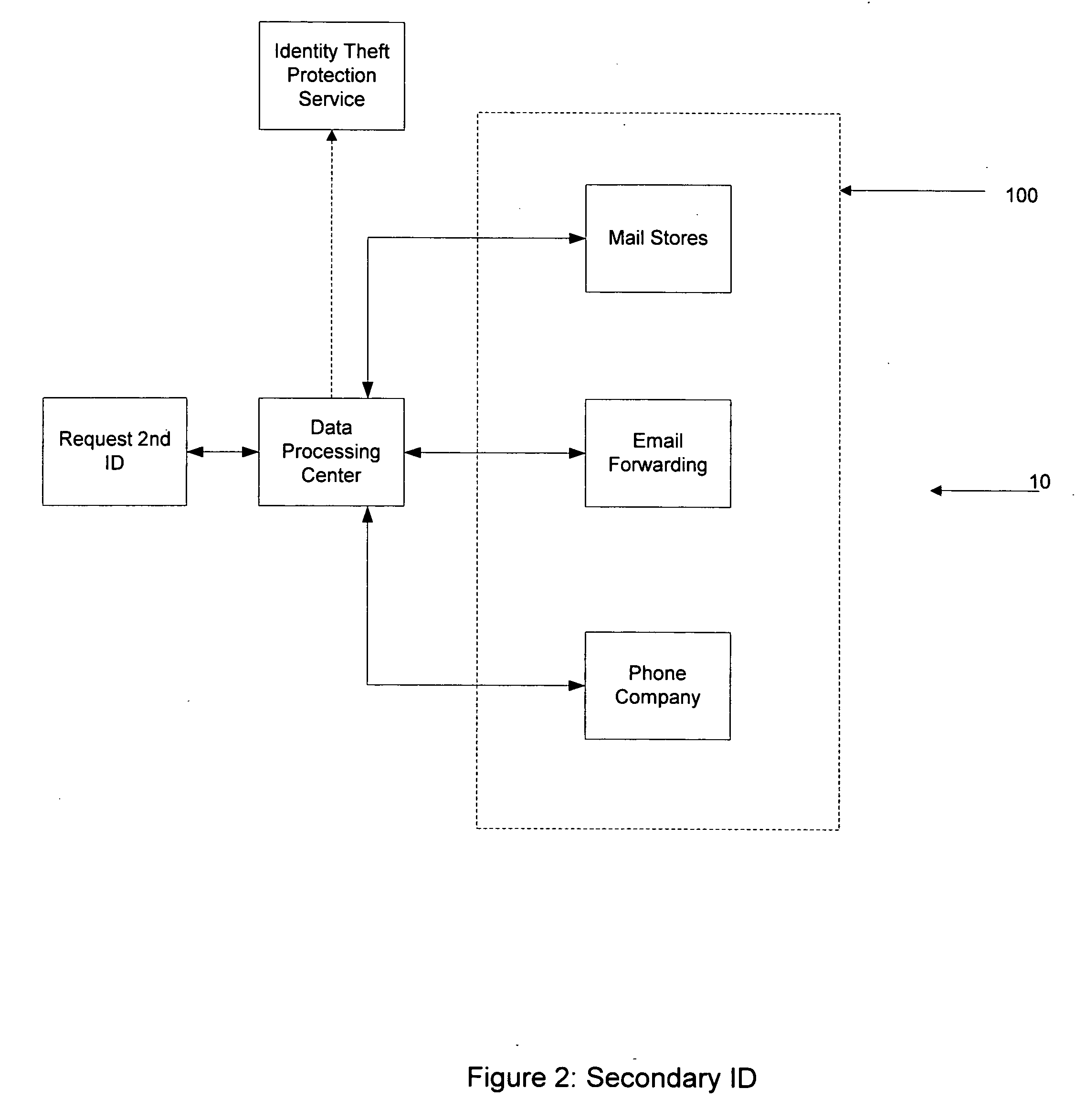
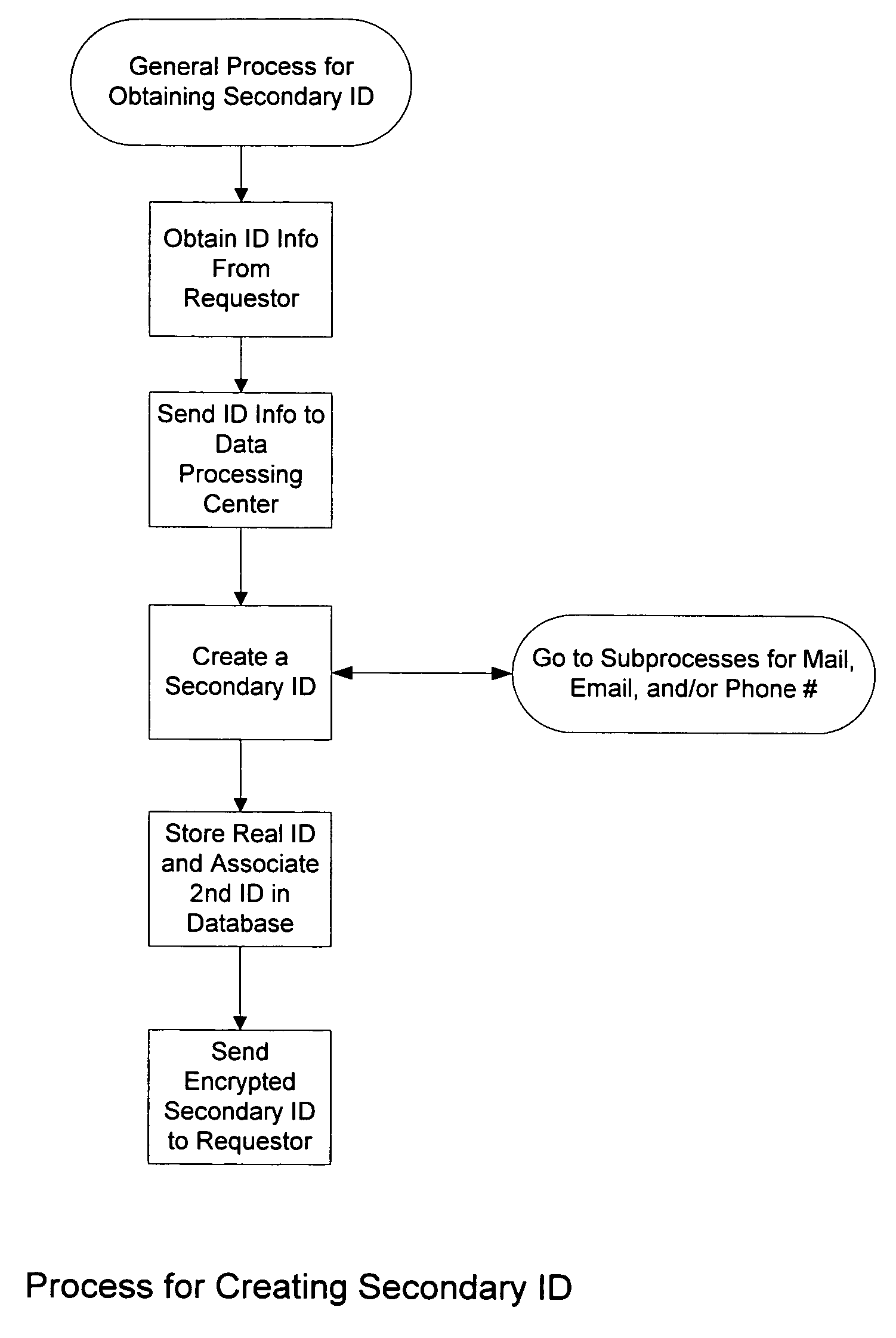
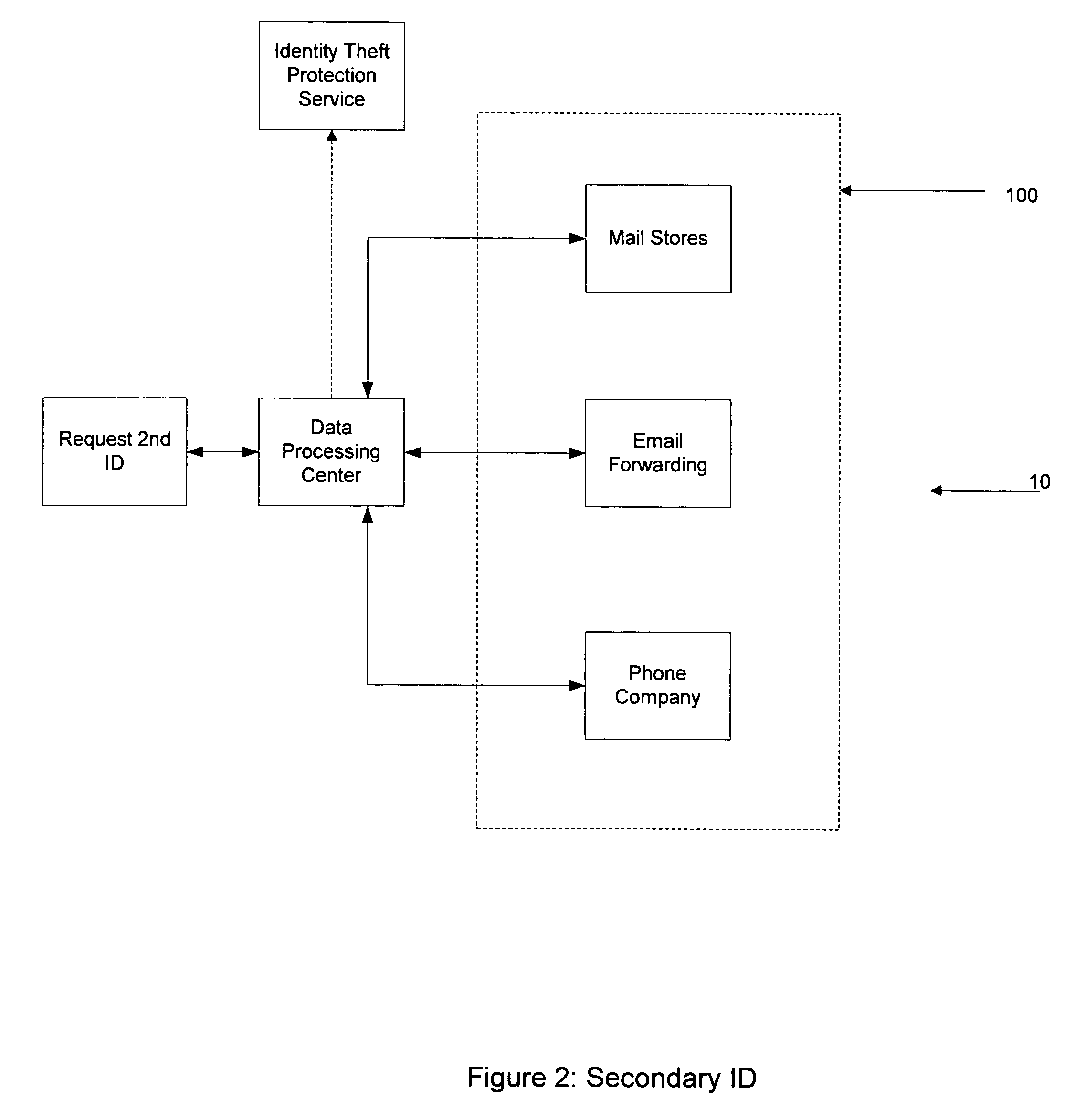
The present invention relates to a method to the creation and management of a secondary identification to avoid identify theft. Identity theft may occur over the internet, the purchase of goods and services by credit, and many other forms not yet known. The present invention creates a secondary identification for a person by creating one or more of the following secondary identifications which include a secondary email address, a secondary postal address, a secondary phone number, and any other identifying secondary information. The present invention describes methods and systems to create a secondary identification. Further, the present invention may be used to create a credit card containing the requestor's secondary identification.
Owner:SEAGATE TECH LLC
Computer security access control system and method
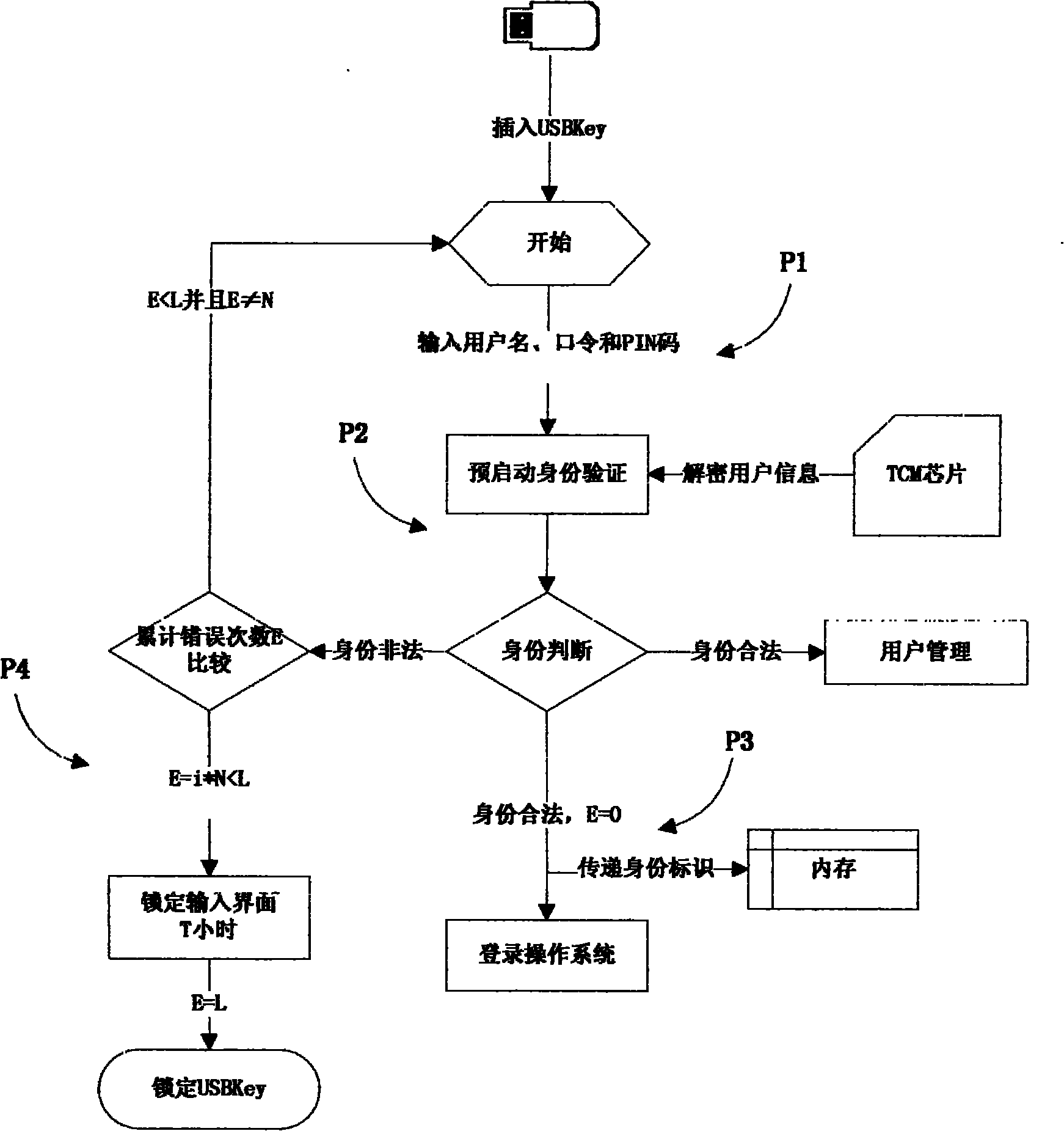
InactiveCN101986325AImplement secure storage protectionLow costDigital data authenticationOperational systemControl system
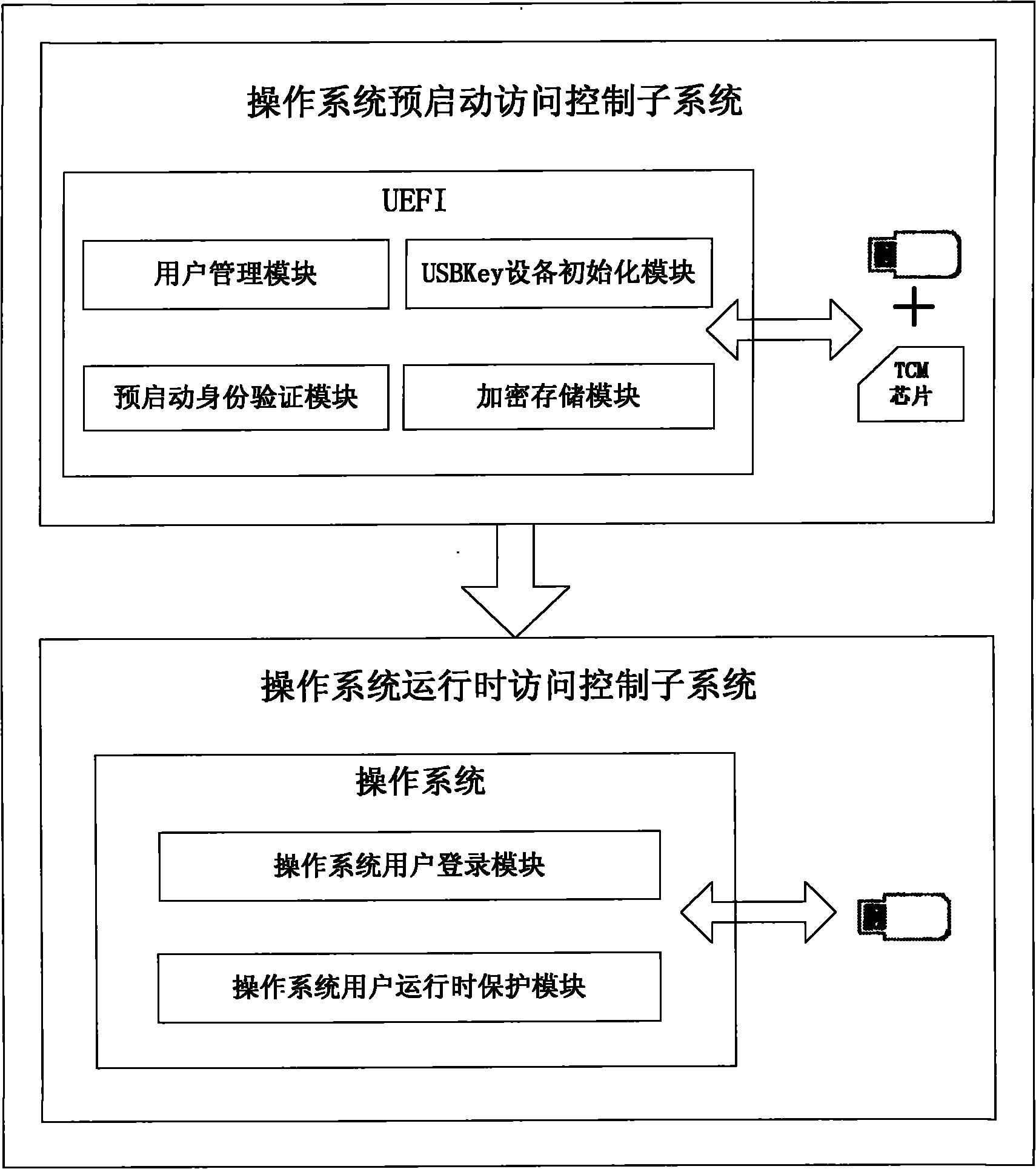
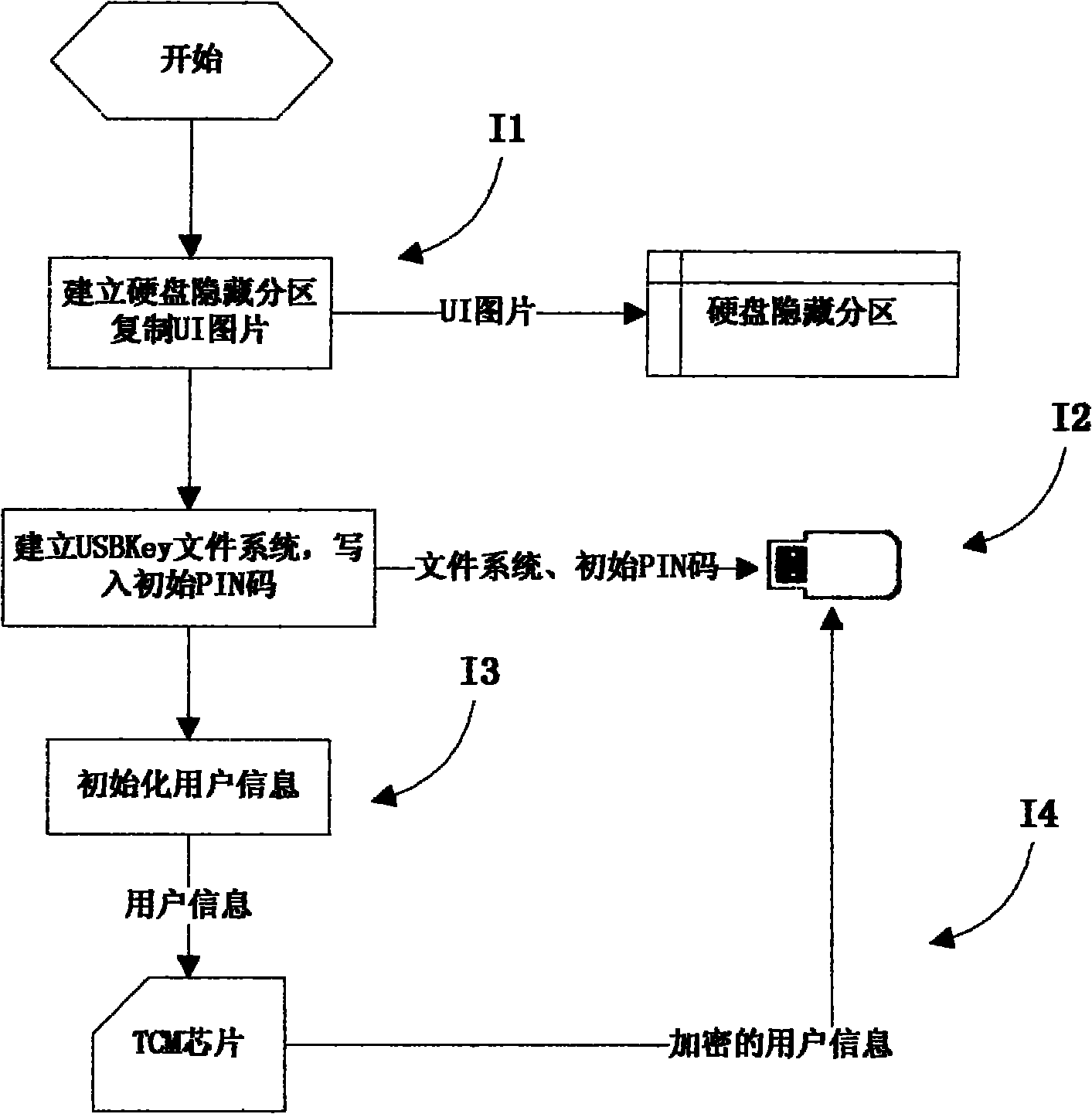
The invention discloses a computer security access control system and a computer security access control method, and belongs to the technical field of information security. A unified extensible firmware interface (UEFI) chip and a transmission control module (TCM) chip are included; a control system comprises an operating system pre-booting access control subsystem and an operating system running access control subsystem, wherein the operating system pre-booting access control subsystem comprises USBKey equipment, a USBkey equipment initialization module, a user management module, an operating system pre-booting identity authentication module and an encryption storage module; and the operating system running access control subsystem comprises USBKey equipment, an operating system user logon module, and an operating system user running protection module. The control method comprises an initialization method, an operating system pre-booting access control method and an operating system running access control method. The invention solves the problems that in the operating system, the reliability of access control is low, user identity information storage is insecure, and identity protection is insufficient in the running process after a user with legal identity logs on.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Methods and systems for protection of identity
InactiveUS7689007B2Reduce harmImprove identityFinanceCharacter and pattern recognitionCredit cardEmail address
The present invention relates to a method to the creation and management of a secondary identification to avoid identify theft. Identity theft may occur over the internet, the purchase of goods and services by credit, and many other forms not yet known. The present invention creates a secondary identification for a person by creating one or more of the following secondary identifications which include a secondary email address, a secondary postal address, a secondary phone number, and any other identifying secondary information. The present invention describes methods and systems to create a secondary identification. Further, the present invention may be used to create a credit card containing the requestor's secondary identification.
Owner:SEAGATE TECH LLC
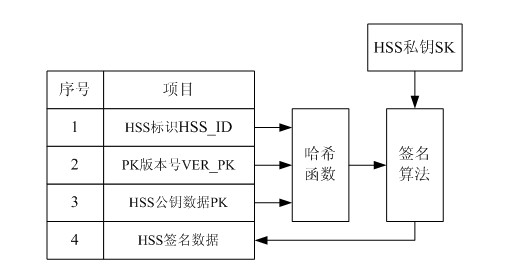
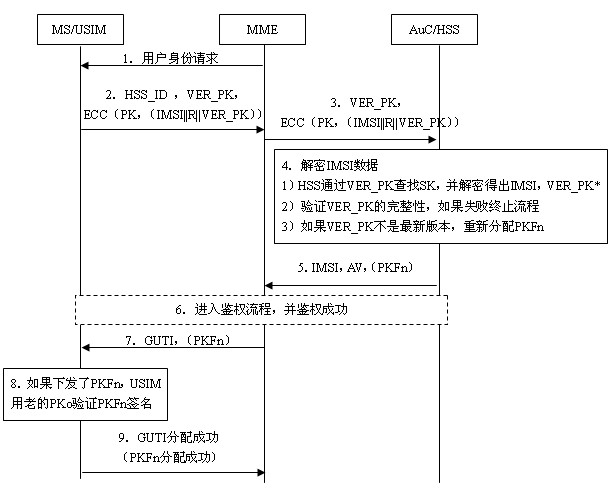
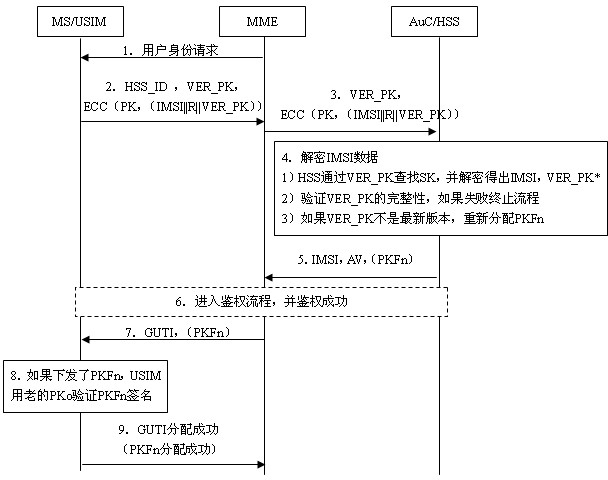
User identity protection method based on public-key mechanism
ActiveCN102026178AIncrease the difficulty of decipheringIntegrity guaranteedSecurity arrangementInternet privacyEngineering
The invention relates to the secret communication field of mobile communication technologies, and discloses a user identity protection method based on a public-key mechanism. The method comprises the following steps: an HSS (hierarchical service system) produces a pair of keys, namely, a public key PK and a secret key SK, then the public key PK is preset to a USIM (universal subscriber identity module) card of UE (user equipment) belonging to the public key PK in the form of a public key file PKF, and the secret key SK is stored in the HSS; a mobile phone sends the following information to anMME (mobility management entity), including HSS identification: HSS_ID, public-key PK version number: VER_PK; and data (IMSI || R|| VER_PK) encrypted by using an asymmetric encryption algorithm; after receiving the information, the MME sends the VER_PK and the (IMSI || R|| VER_PK) to the HSS according to the HSS_ID; and the HSS decrypts the VER_PK and the (IMSI || R|| VER_PK) by using the secret key SK. Because attackers do not know the secret key SK of the HSS, the attackers can not decrypt the (IMSI || R|| VER_PK).
Owner:成都三零瑞通移动通信有限公司
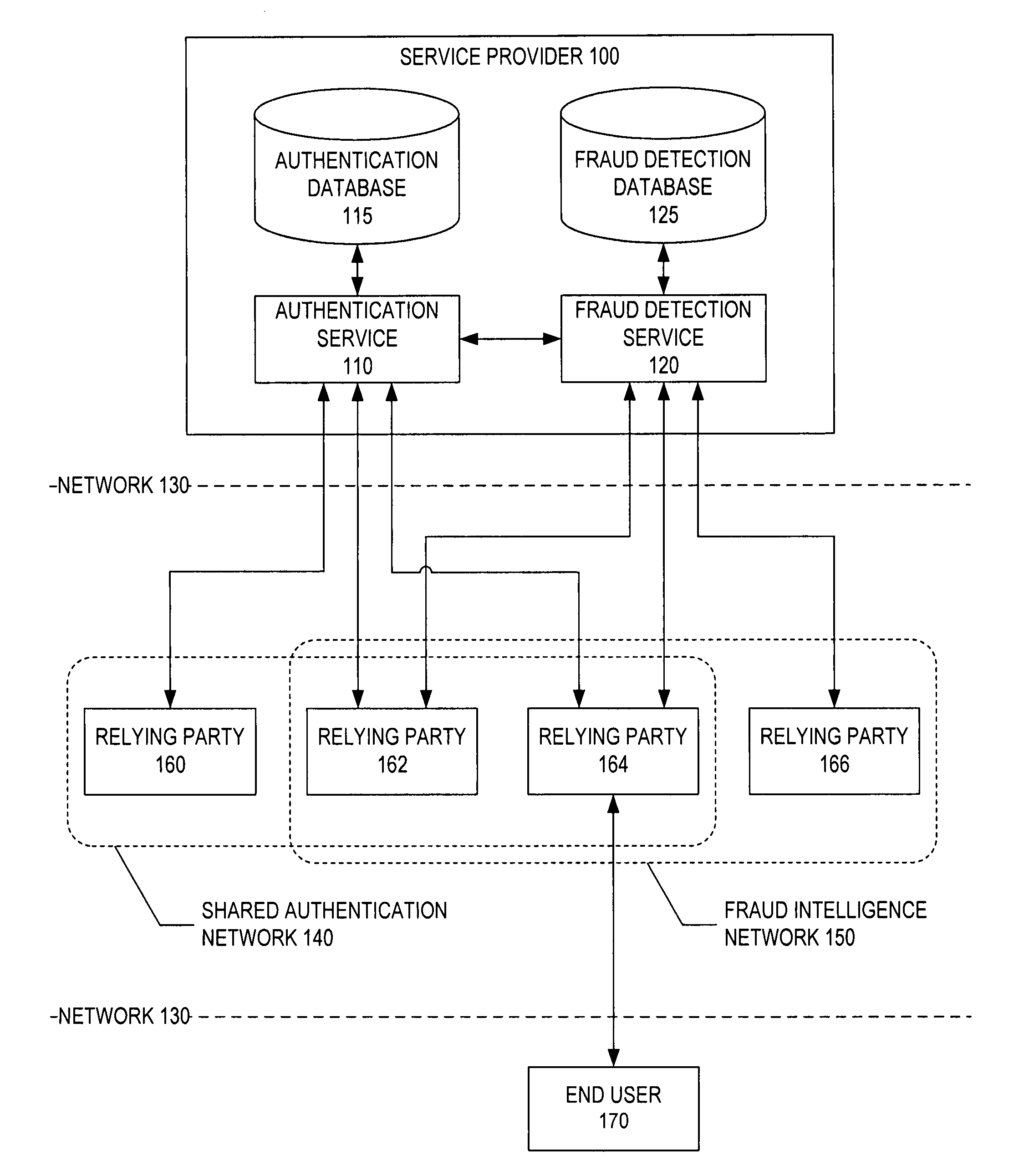
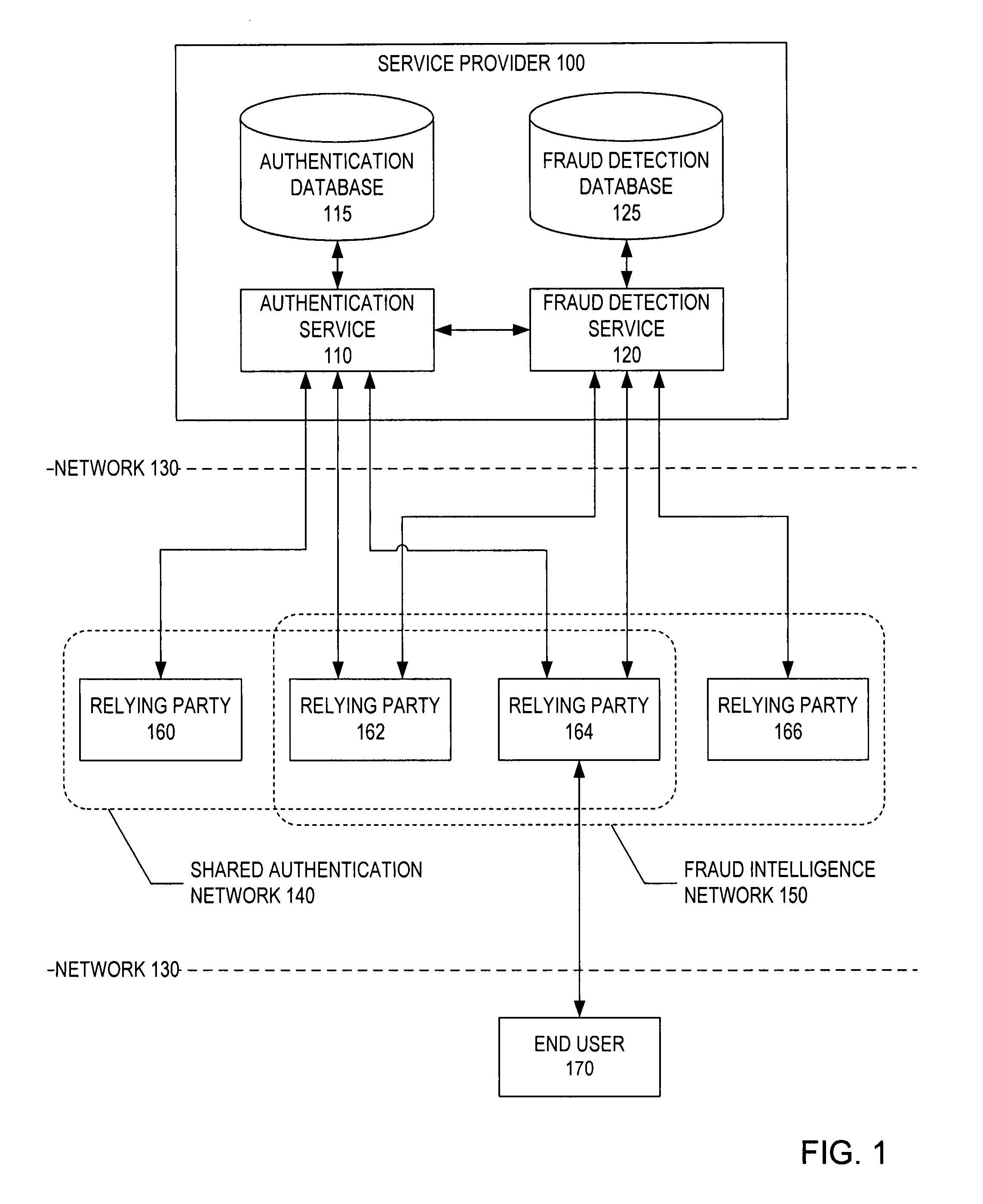
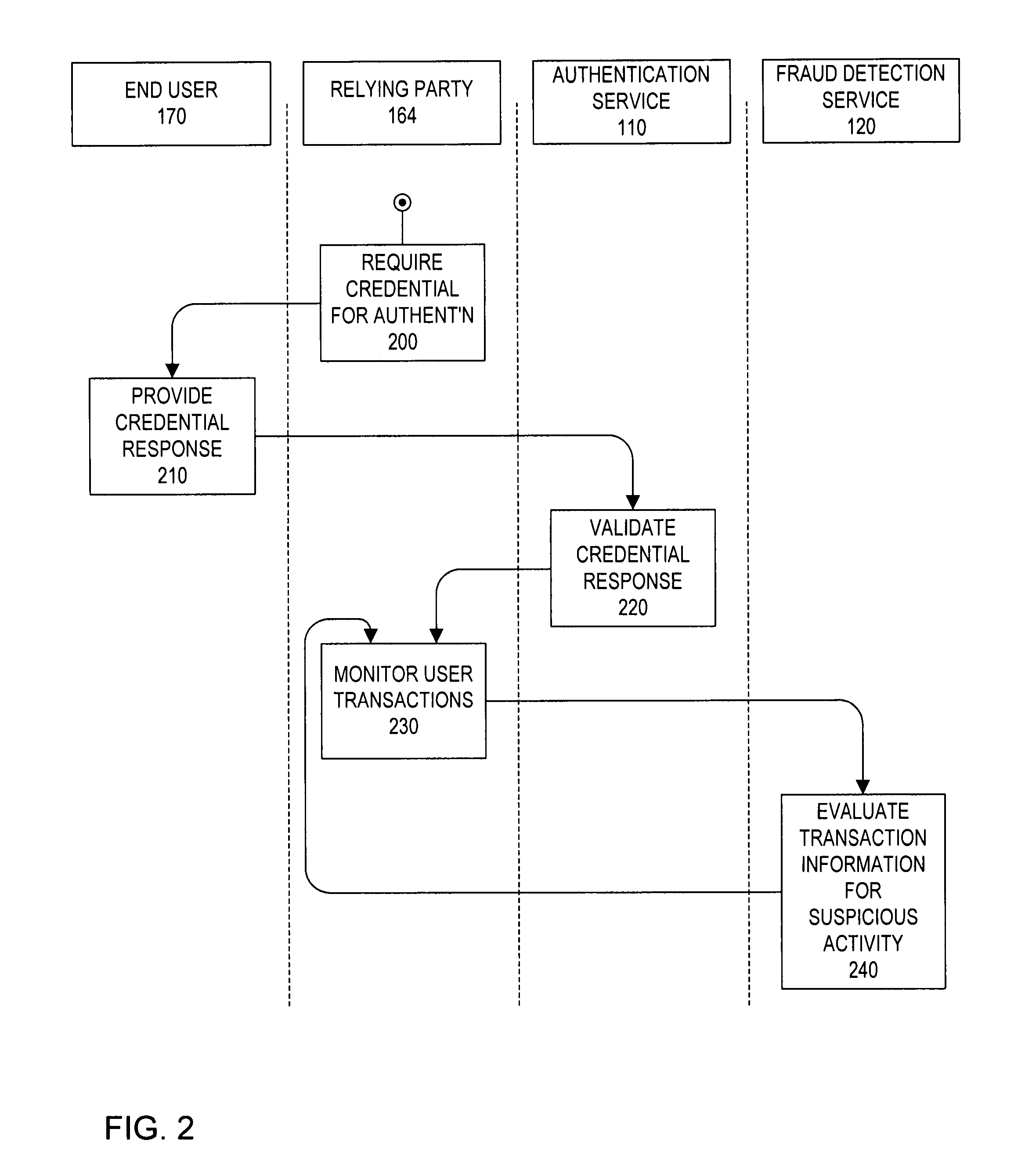
System and method for network-based fraud and authentication services
ActiveUS7861286B2Digital data processing detailsMultiple digital computer combinationsInternet Authentication ServiceIdentity protection
A system and method for providing identity protection services. According to an embodiment, a validation server receives over a network a response from a credential associated with a user, the credential response provided by the user in order to authenticate the user to one of a plurality of sites on the network that accepts the credential as a factor for authentication, the validation server verifies the credential response on behalf of the one network site, a fraud detection server receives over the network information in connection with a transaction associated with the user at the one network site, and the fraud detection server evaluates the transaction information for suspicious activity based at least in part on information provided to the fraud detection server in connection with one or more transactions at one or more sites on the network other than the one network site.
Owner:SYMANTEC CORP
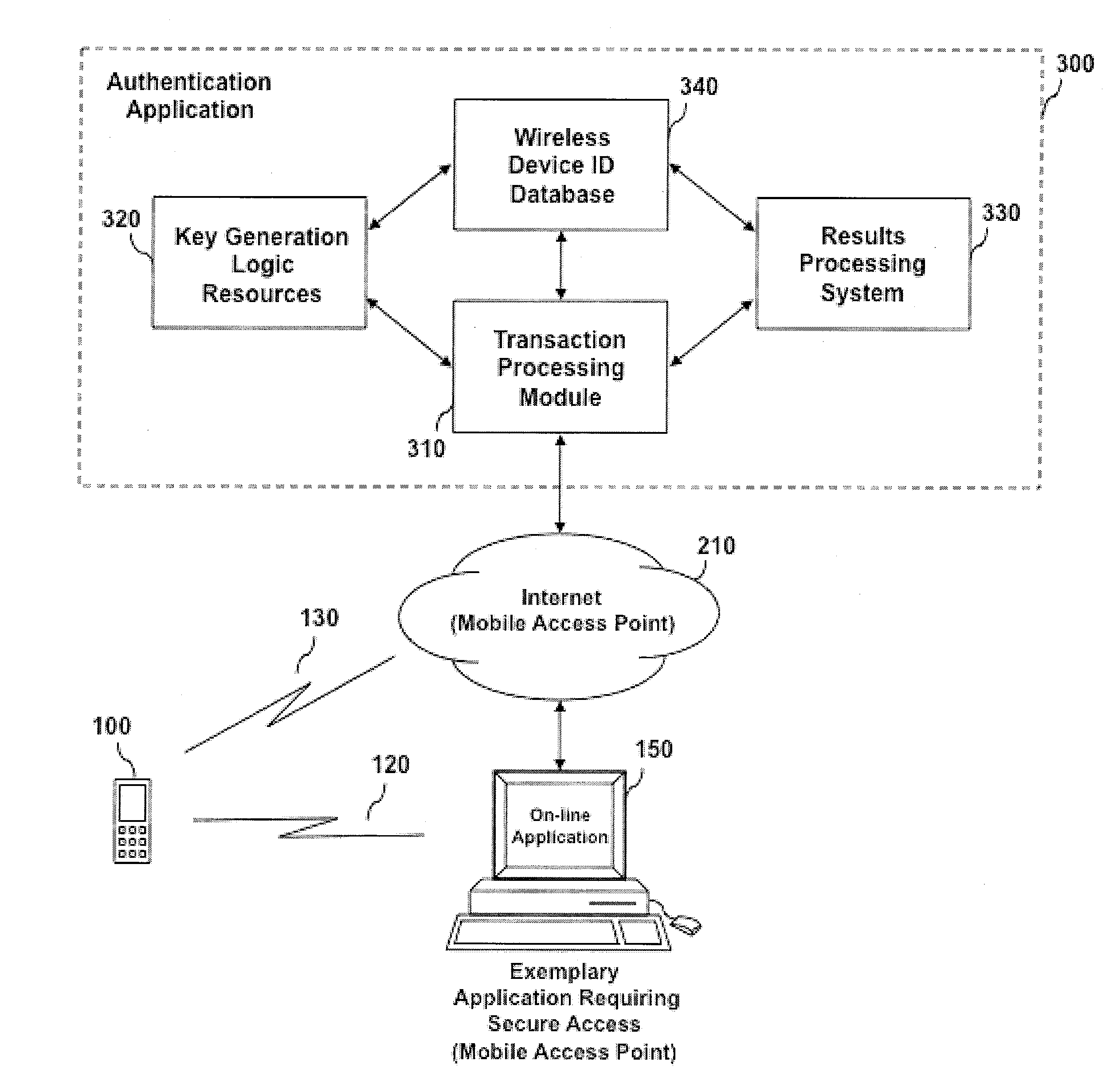
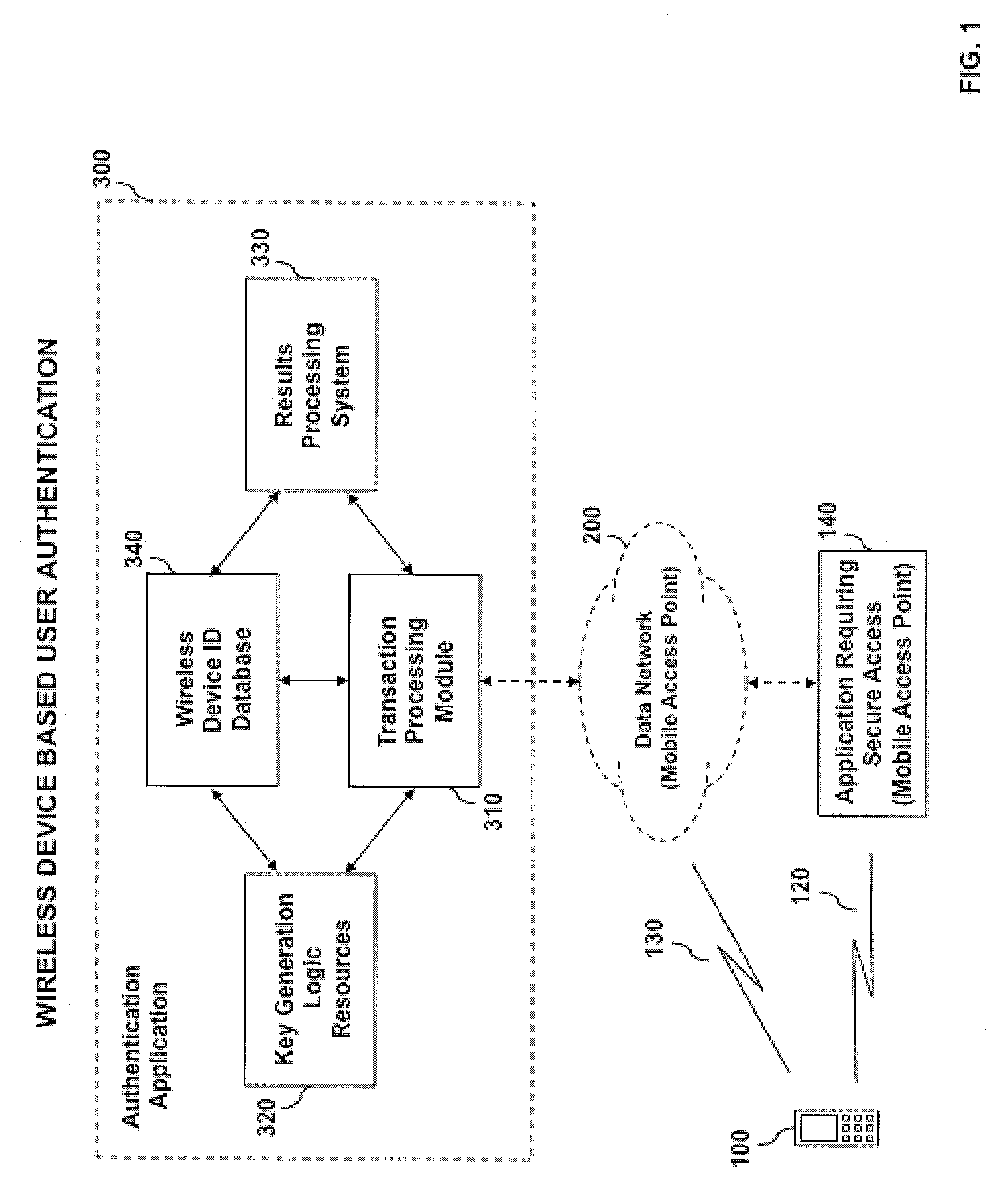
System and method for mobile identity protection for online user authentication
ActiveUS9185123B2Prevent theftUser identity/authority verificationNetwork topologiesWi-FiUnique identifier
An automated system and method for authenticating entities or individuals attempting to access a computer application, network, system or device using a wireless device is provided. The system employs one or more short-range wireless interfaces (e.g. BLUETOOTH or Wi-Fi) or long-range wireless interfaces (e.g. cellular or WiMAX) to detect the presence or location of the wireless device and it's proximity to the secure system to be accessed. The wireless device incorporates a unique identifier and secure authentication key information associated with the user of the wireless device. An authentication result is generated and may be used for a variety of applications. The application may process the result and determine the degree of access for which the entity or individual is allowed.
Owner:VISA INT SERVICE ASSOC
System and method for identity protection using mobile device signaling network derived location pattern recognition
InactiveUS20150142623A1Improve identityComplete banking machinesFinanceSignaling networkIdentity protection
A system and method for recognizing patterns in wireless device locations using wireless device location data derived from a communications signaling network is provided. By using wireless network supported signaling operations and messages, location data concerning the whereabouts of wireless devices, and hence wireless device users, may be obtained. The location data derived from the communications signaling network may be statistically analyzed to reveal potential geographic patterns that may indicate meaningful behaviors of the purported users of the wireless devices.
Owner:VISA INT SERVICE ASSOC
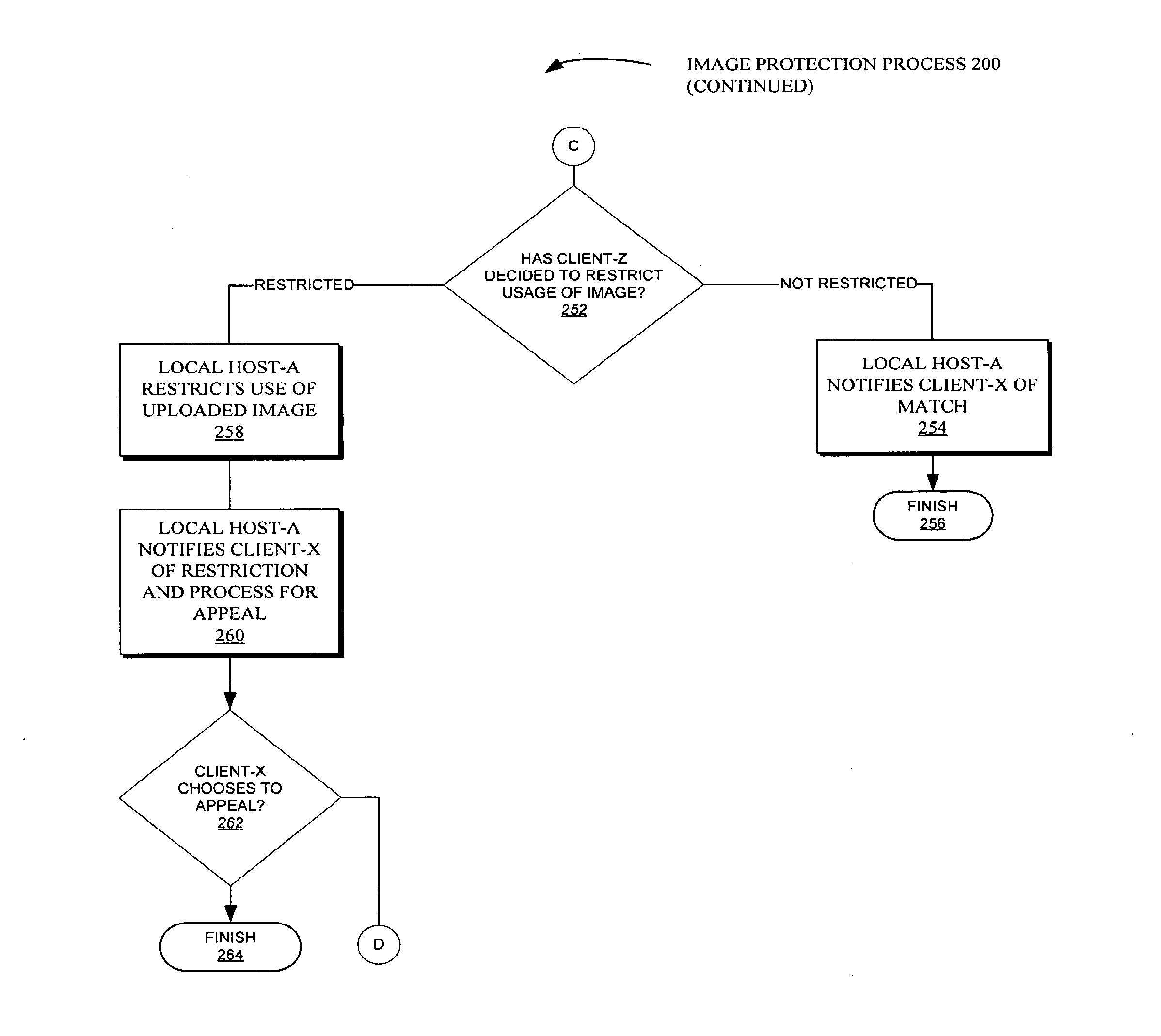
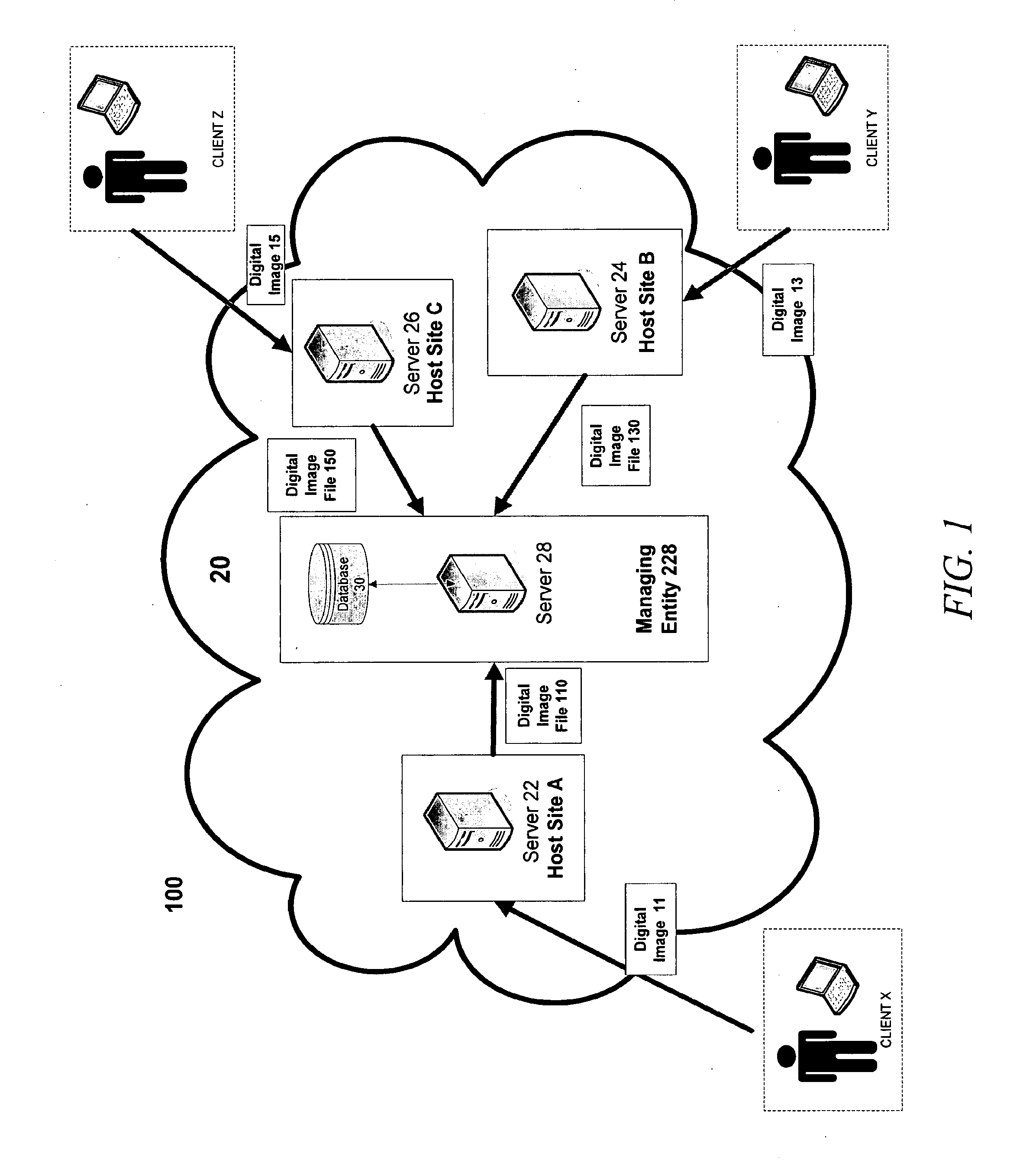
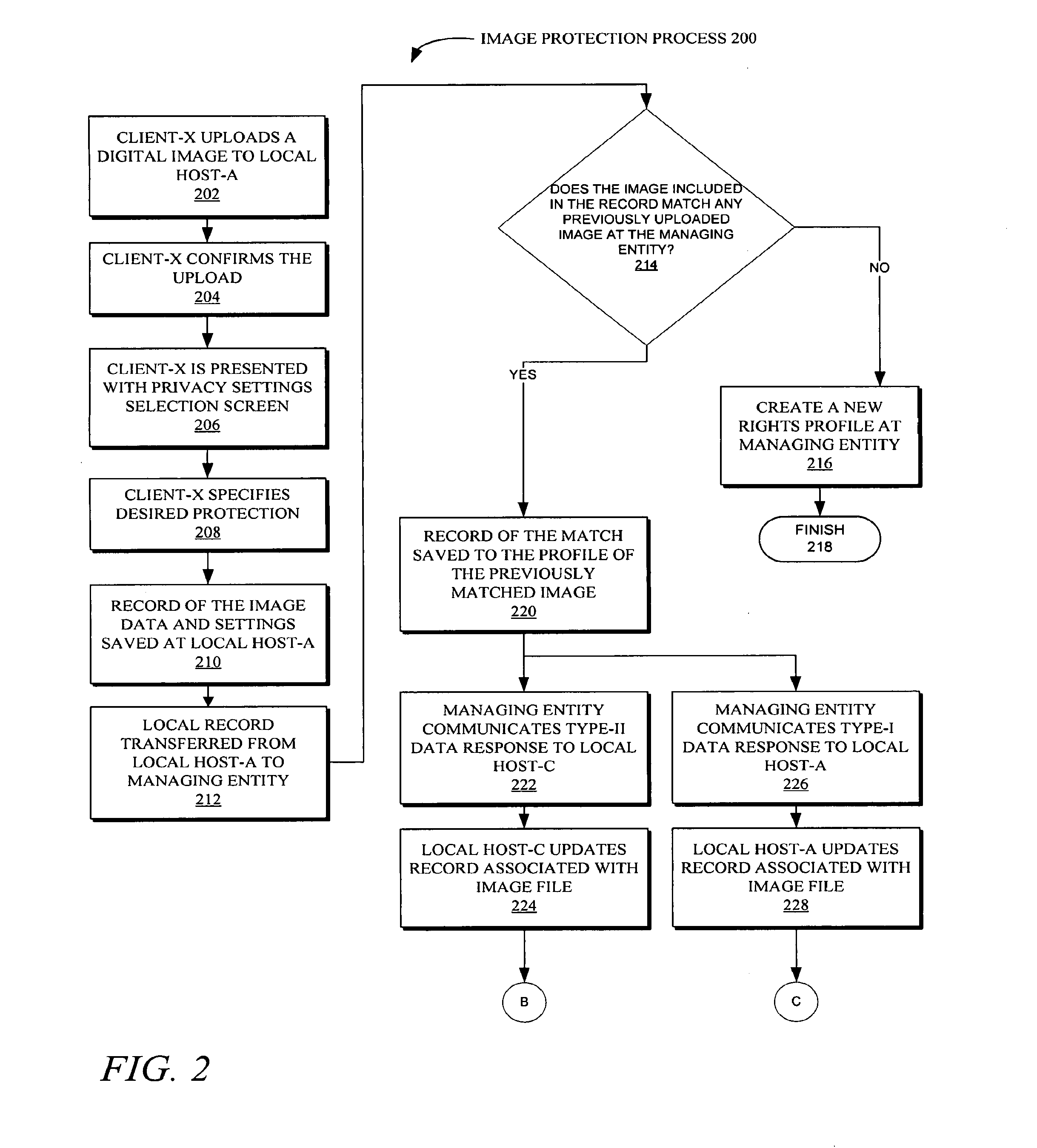
Methods and systems for providing online digital image rights management and identity protection in a digital environment
InactiveUS20160232375A1Keep full controlStill image data indexingCharacter and pattern recognitionRights managementDigital image
Owner:LOEB MICHAEL R +1
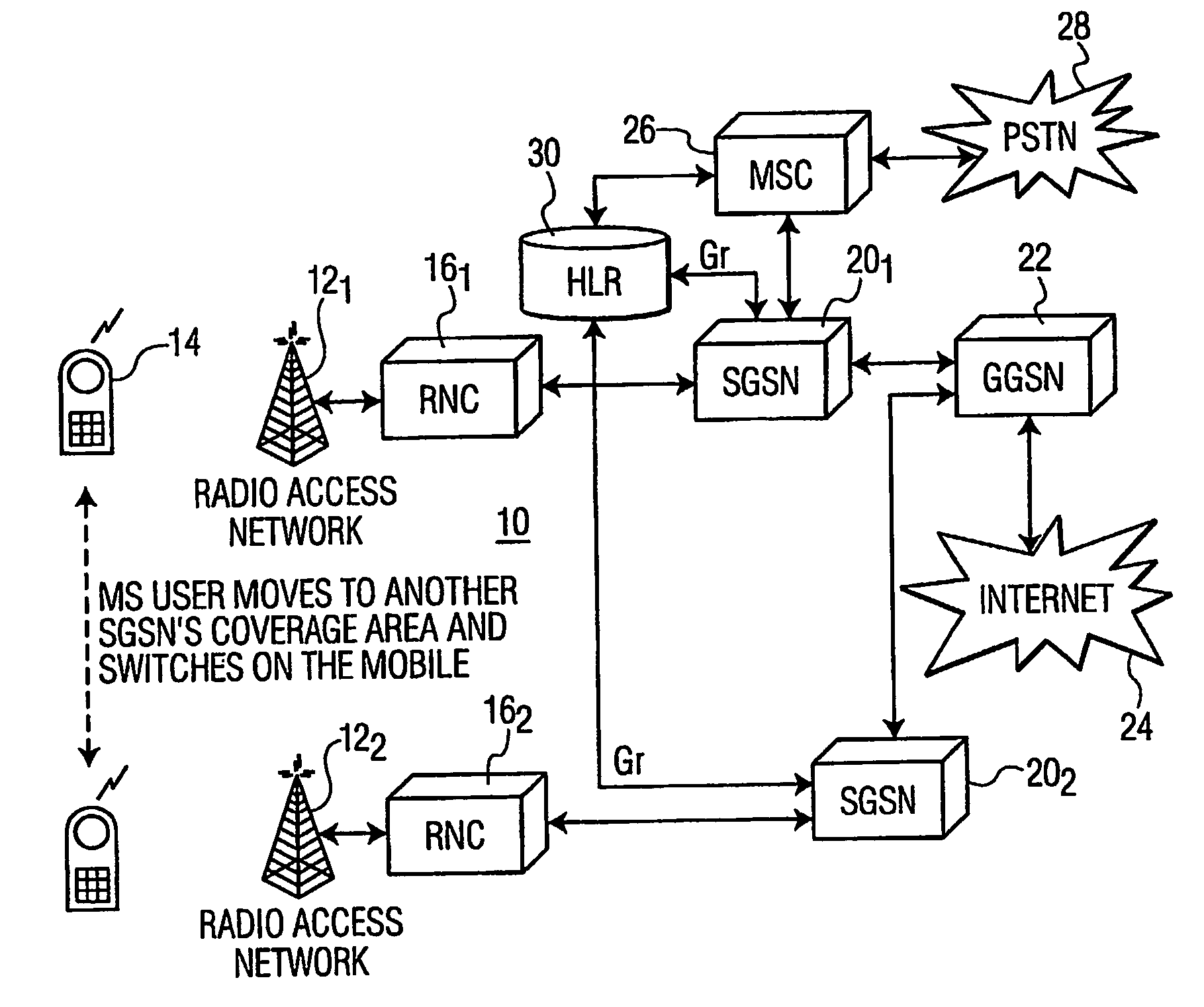
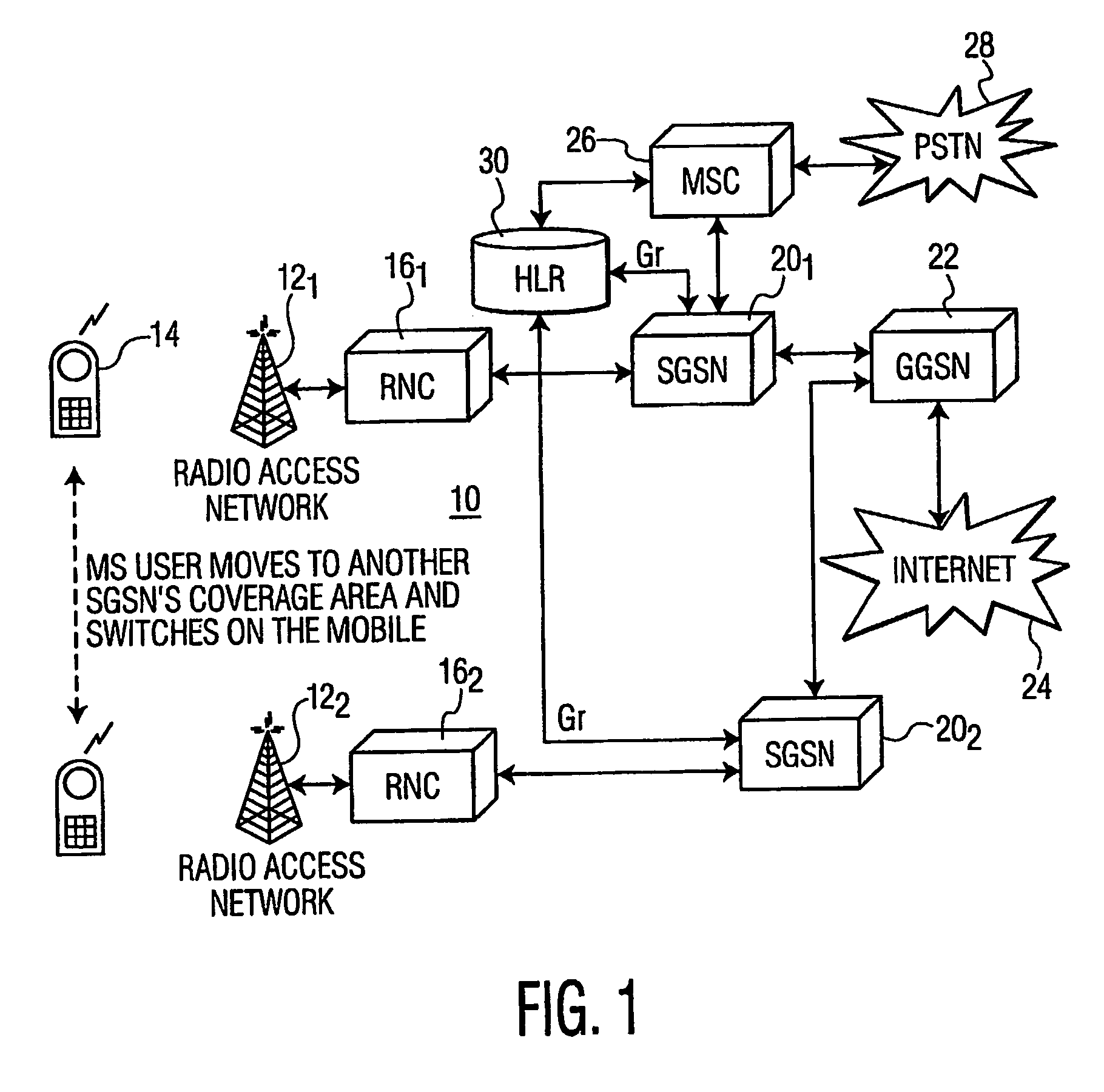
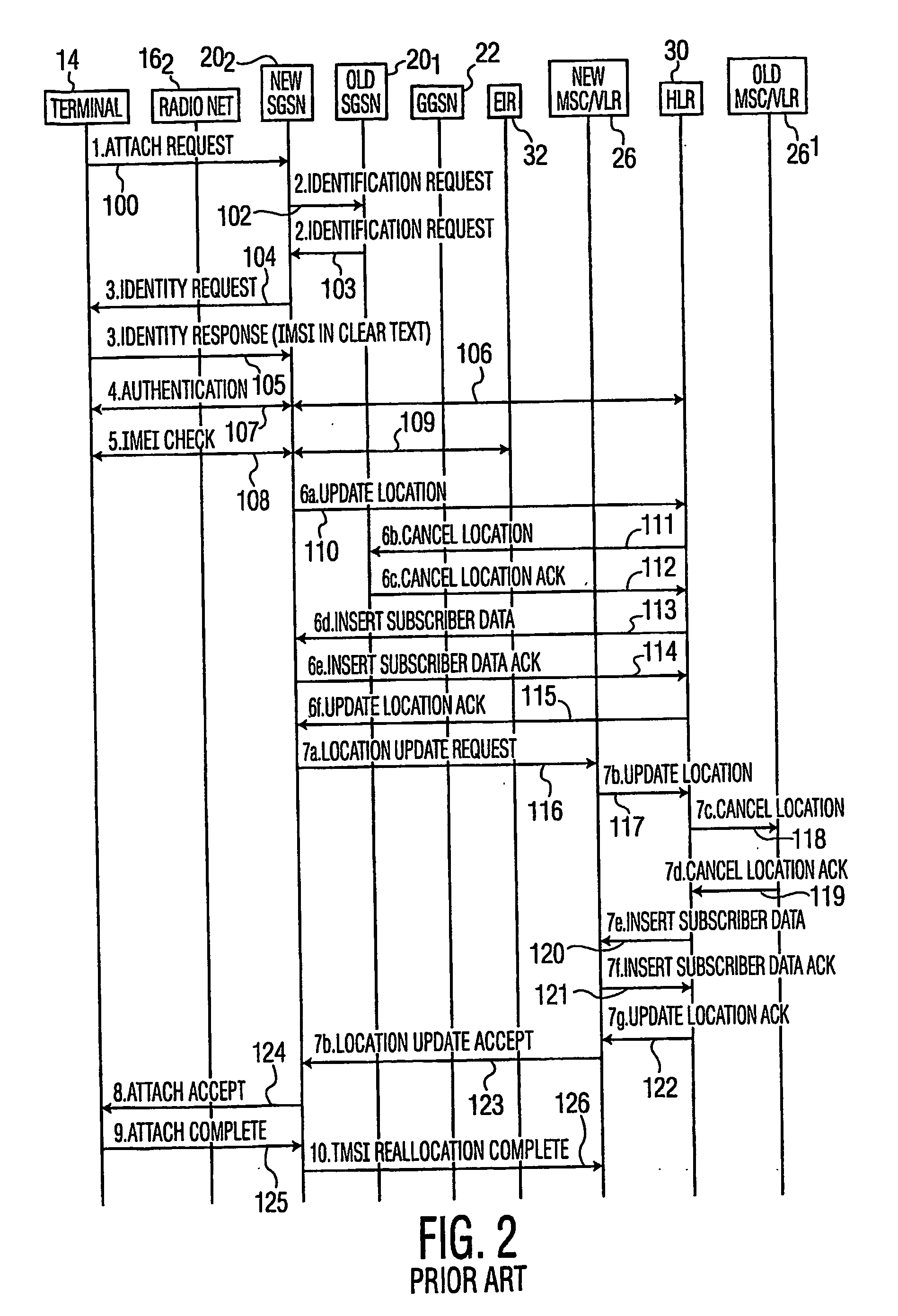
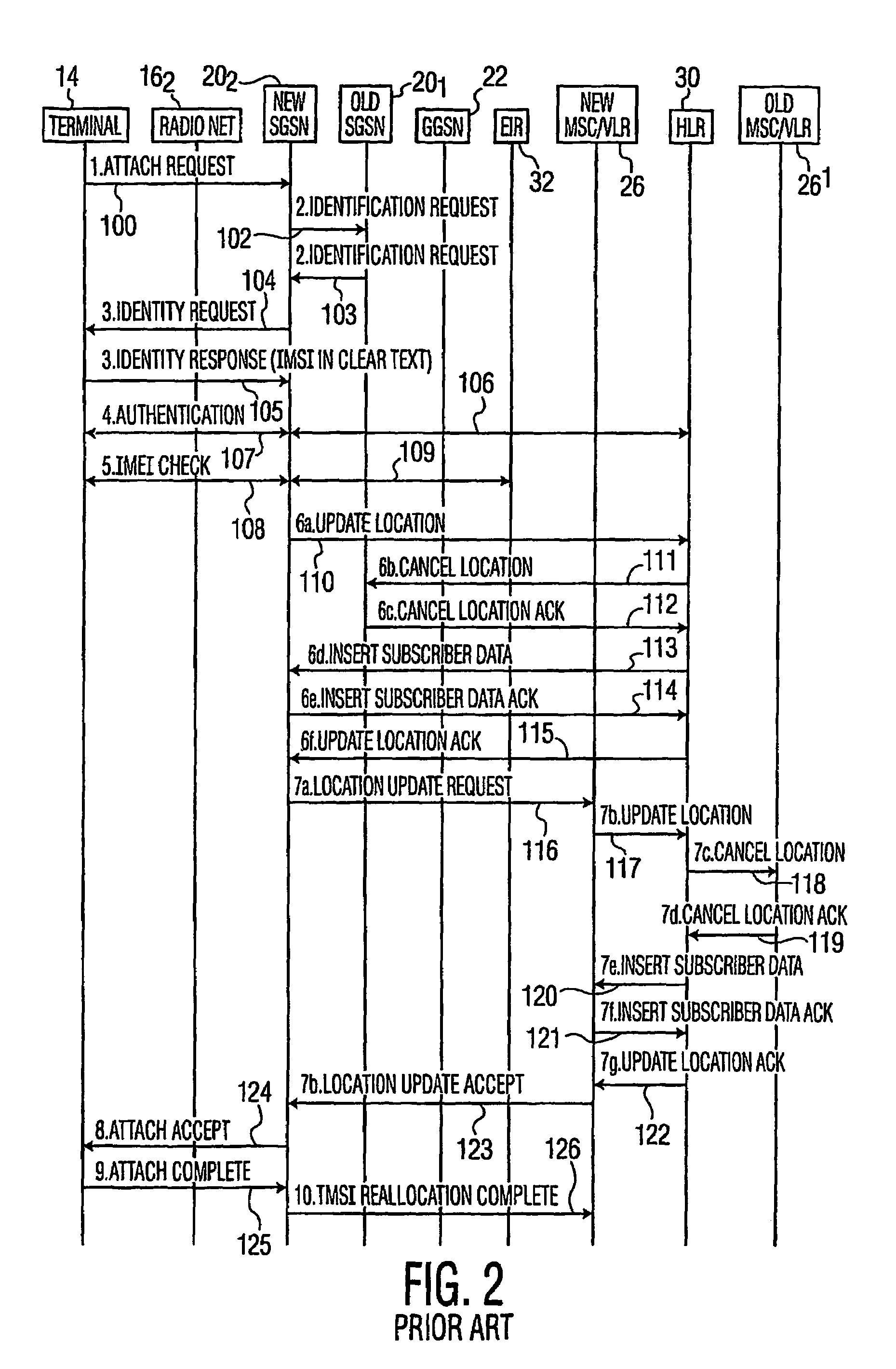
Mobile terminal identity protection through home location register modification
InactiveUS20060116122A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless mesh networkTelecommunications
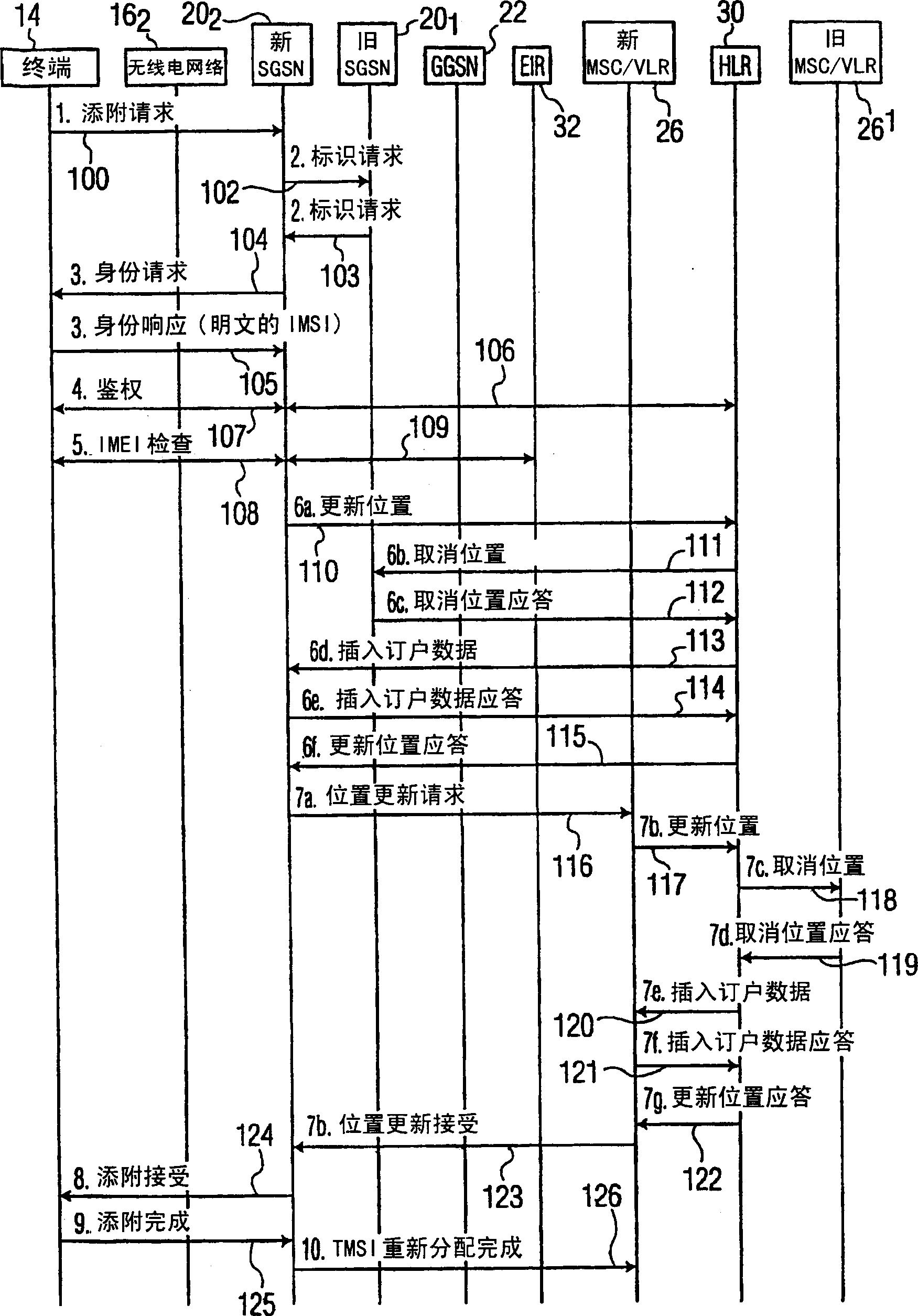
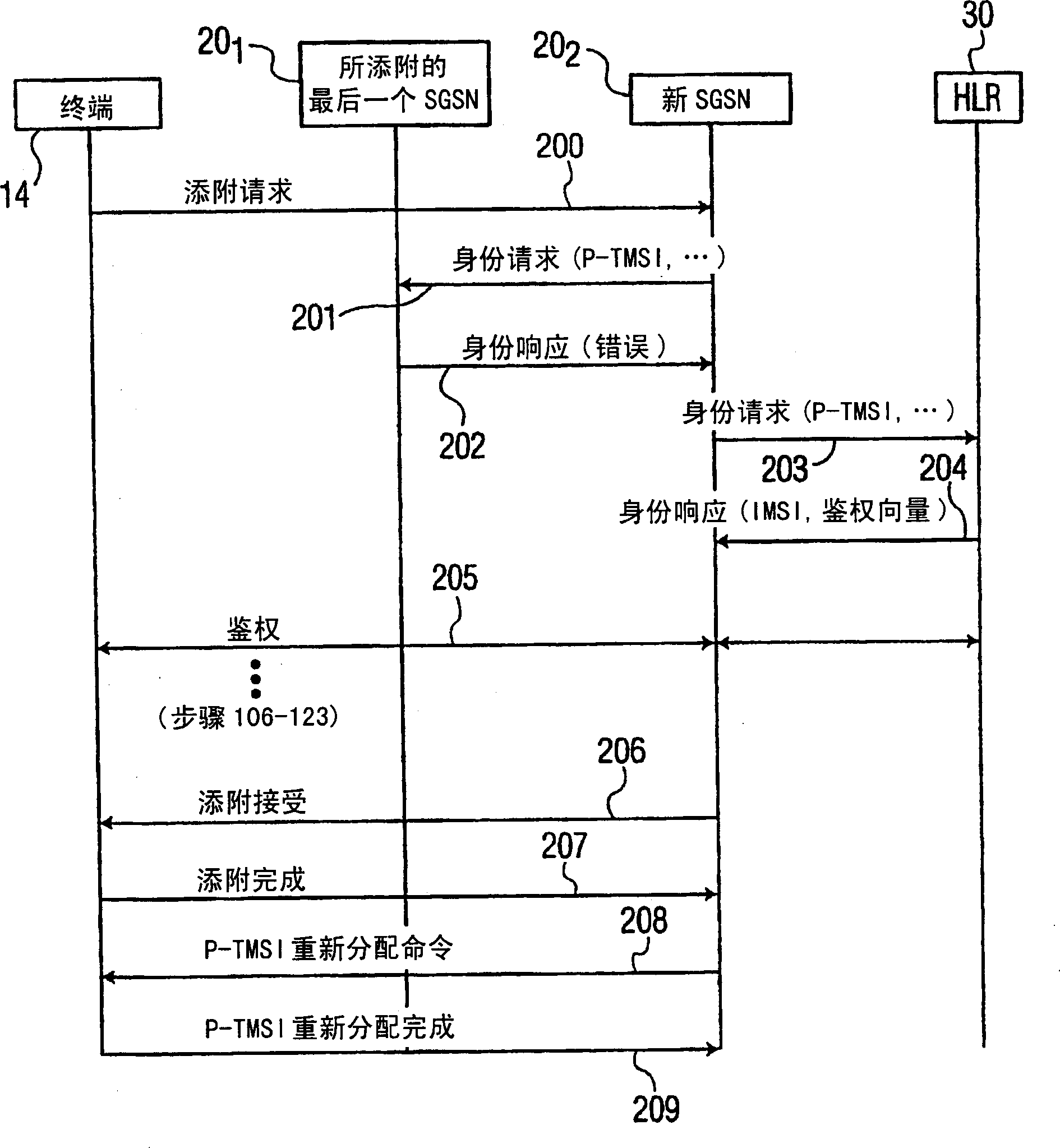
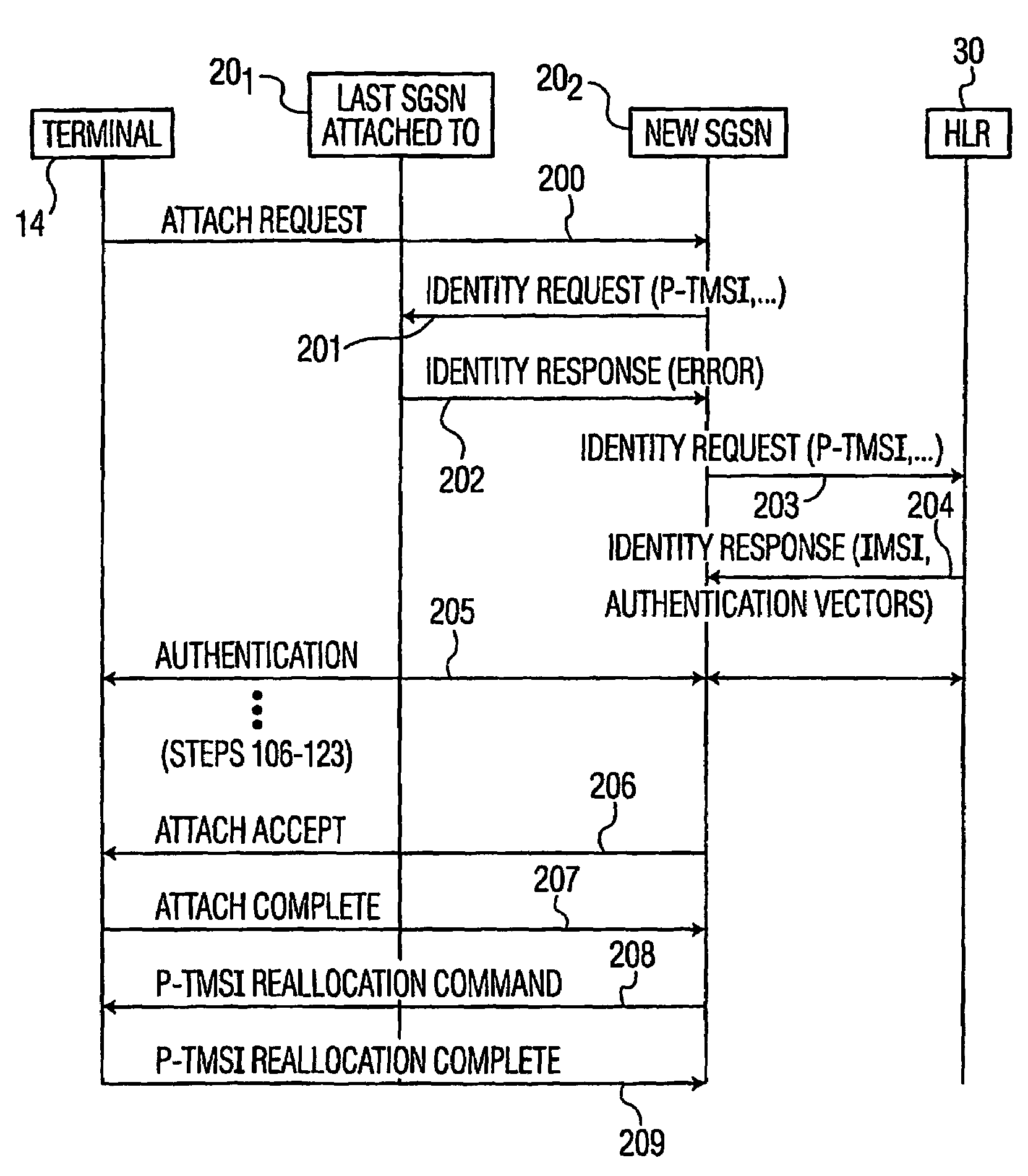
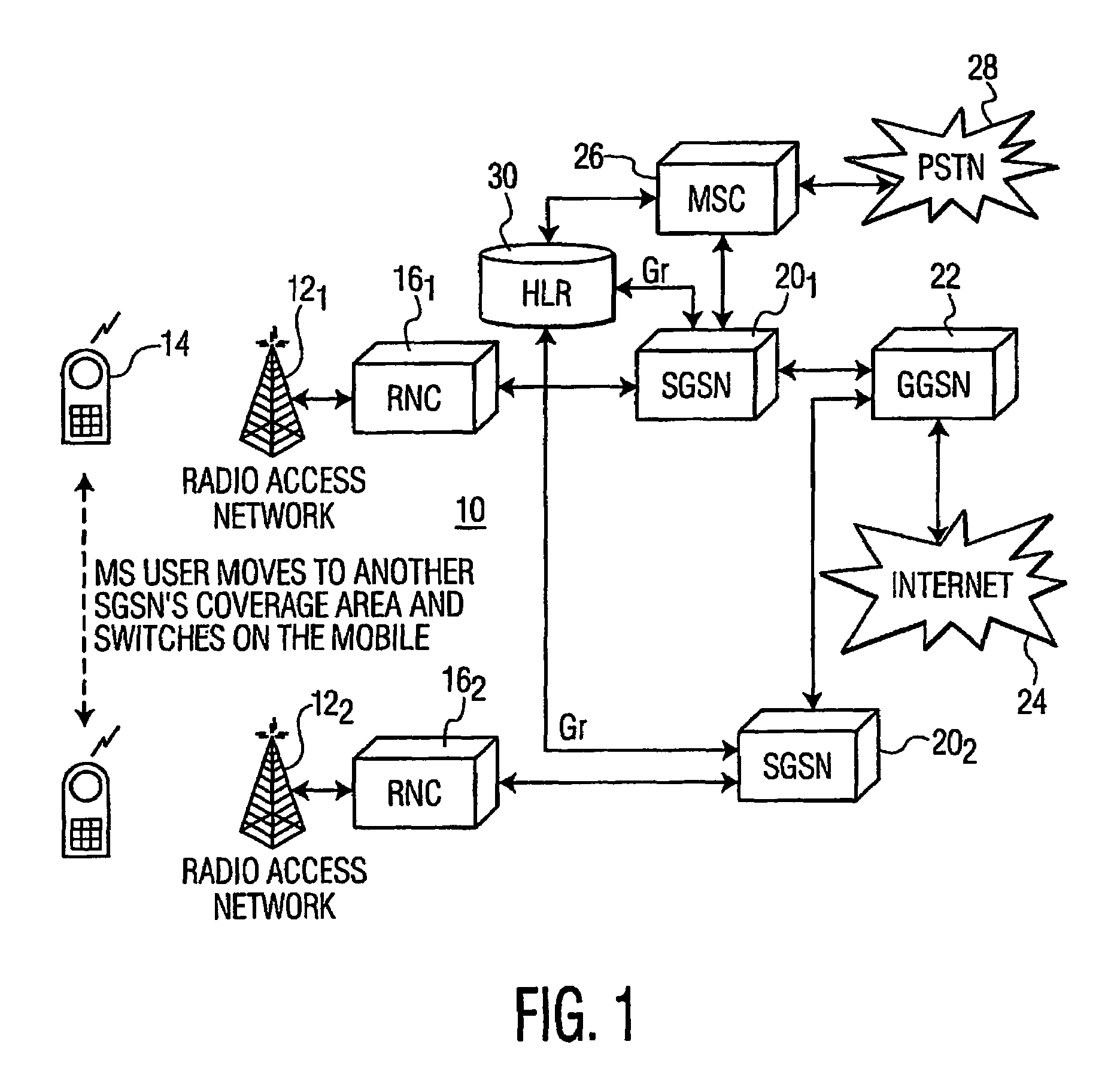
Secure access by a mobile wireless terminal of a wireless telephony network is achieved by having a Home Location Register store the terminal's temporary and permanent identities. Upon accessing the network following initial registration, the terminal sends a temporary identity to a Serving GPRS Support Node (SGSN). If no serving node in the network knows the terminal, the terminal need not sent its permanent identity in clear as was previously required. Rather, the serving node need only query the HLR since the HLR can map the terminal's temporary identity to its permanent identity. In this way, the permanent identity of the mobile wireless terminal remains secure.
Owner:THOMSON LICENSING SA
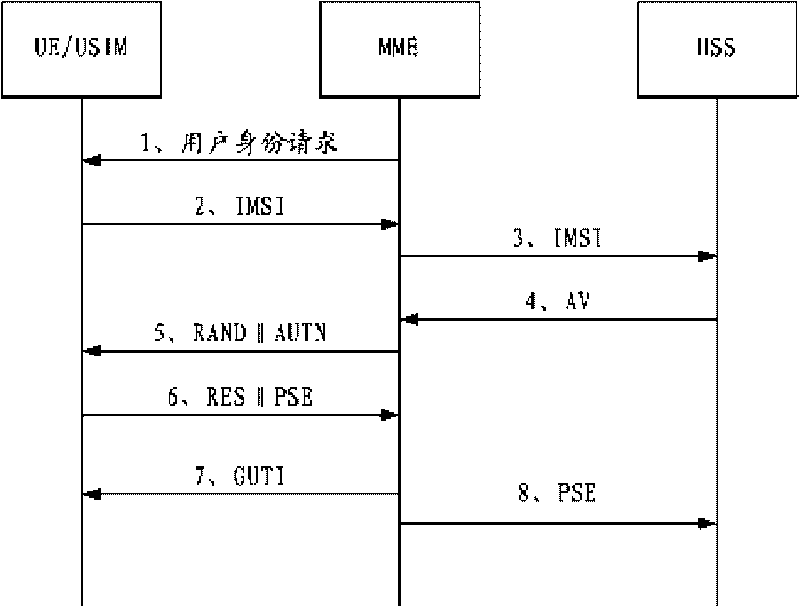
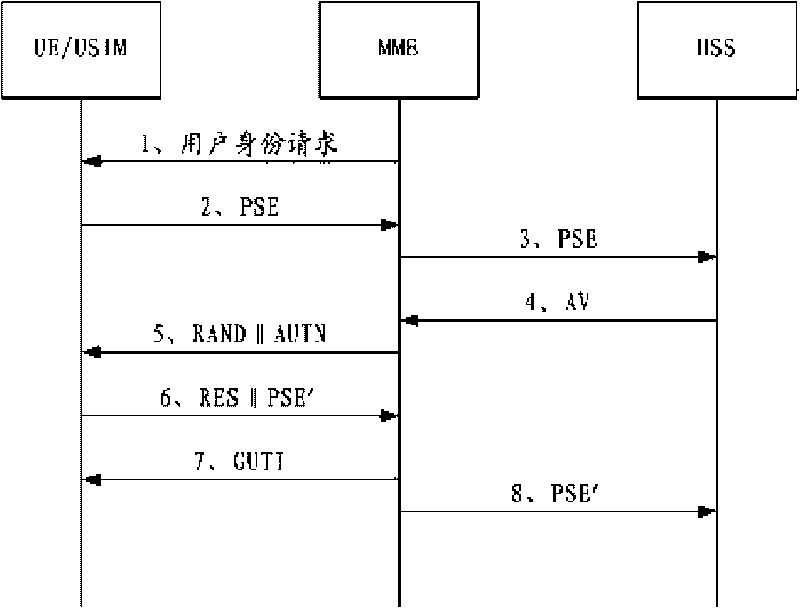
Identity protection method for mobile communication user
ActiveCN101720086AAchieve protectionIncreased tracking difficultySecurity arrangementNetwork data managementIdentity protectionComputer science
The invention is suitable for the field of mobile communication and provides an identity protection method for a mobile communication user. In the method, the identity is expressed still by an IMSI when a UE / USIM card is accessed into an LTE / SAE network for the first time by setting a pseudonym for each user, and then the user is accessed into the network by the pseudonym; the IMSI is not used, and the pseudonym can be autonomously updated by a USIM, thereby effectively protecting the identity safety of the user.
Owner:成都三零瑞通移动通信有限公司
Patient identification and information protection system and method
InactiveUS20060218626A1Easy accessDiagnosticsDigital data processing detailsProtection systemIdentity protection
A personnel identity protection mechanism and method is provided which utilizes a pseudo-name that is used in conjunction with RFID or RFID-like tags. By correlating the location of the tag wearer to equipment or professionals attending to the tag wear, identity and / or private information relating to the tag wearer can be controlled on a need-to-know basis. Concomitantly, access to the tag wearer's identity and / or private information by attending professionals, wearing a non-pseudo-name RFID or RFID-like tag, can be automatically enabled or filtered by correlating the non-pseudo-name bearing tags' proximity to the accessing system. By use of such a pseudo-name having restricted access capabilities with a RFID or RFID-like tag system, patients or institutionalized persons can be assured of a higher degree of security with respect to their private or medical information.
Owner:EDWARDS SYST TECH
Method of identity protection, corresponding devices and computer softwares
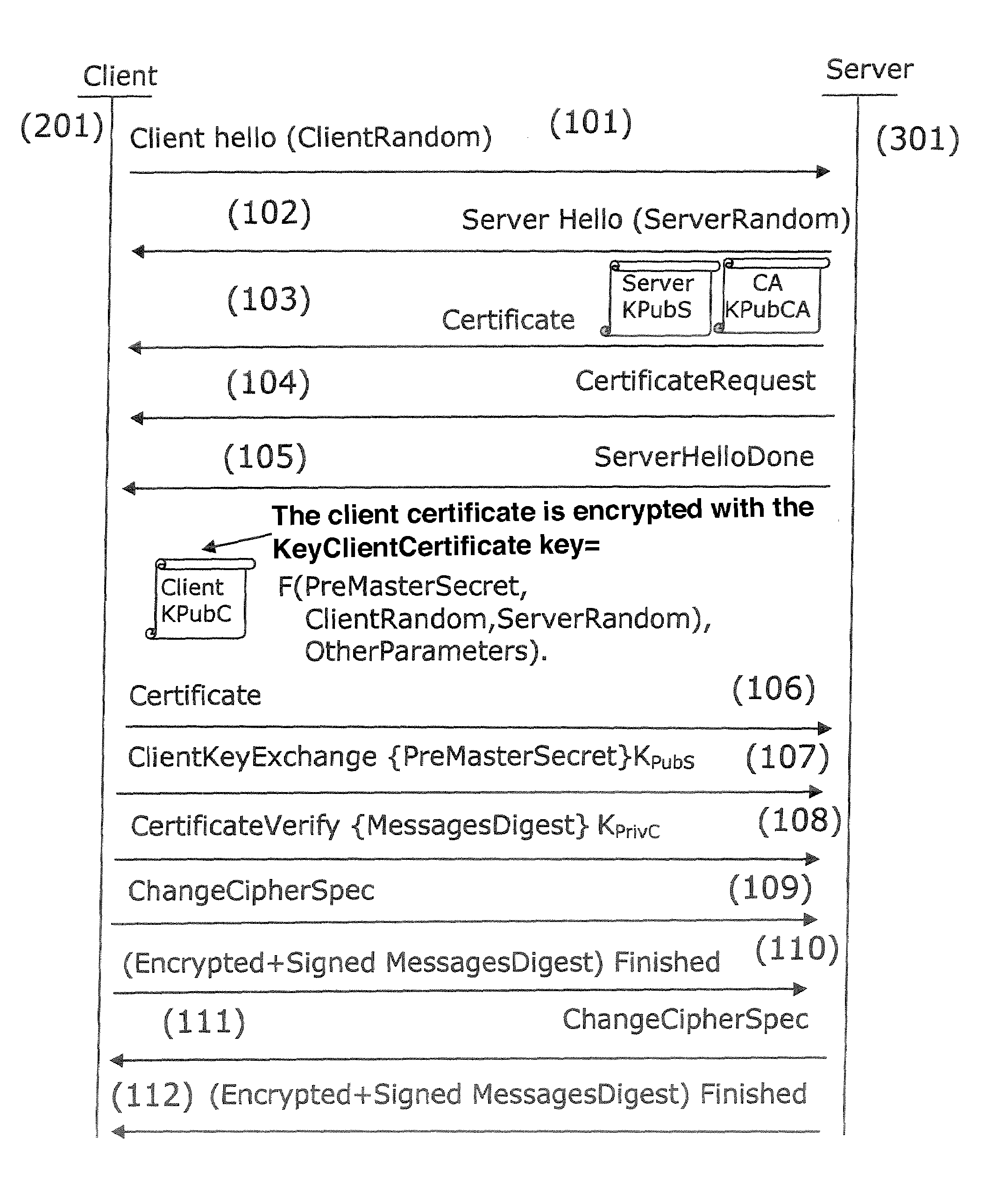
A method is provided for authenticating a client terminal with an authentication server. The client terminal holds an authentication certificate. The method includes the following phases: obtaining at least once encryption parameter by the client terminal; encrypting the authentication certificate by the client terminal, based on the at least one encryption parameter, delivering an encrypted authentication certificate; transmitting the encrypted authentication certificate to the server, obtaining the at least one encryption parameter by the server; obtaining the at east one encryption parameter by the server; decrypting the encrypted authentication certificate, based on the at least one encrypting parameter, authenticating and delivering an authentication assertion if the authentication is positive.
Owner:GRP DES ECOLES DE TELECOMMGET ECOLE NAT SUPERIEURE DES TELECOMM
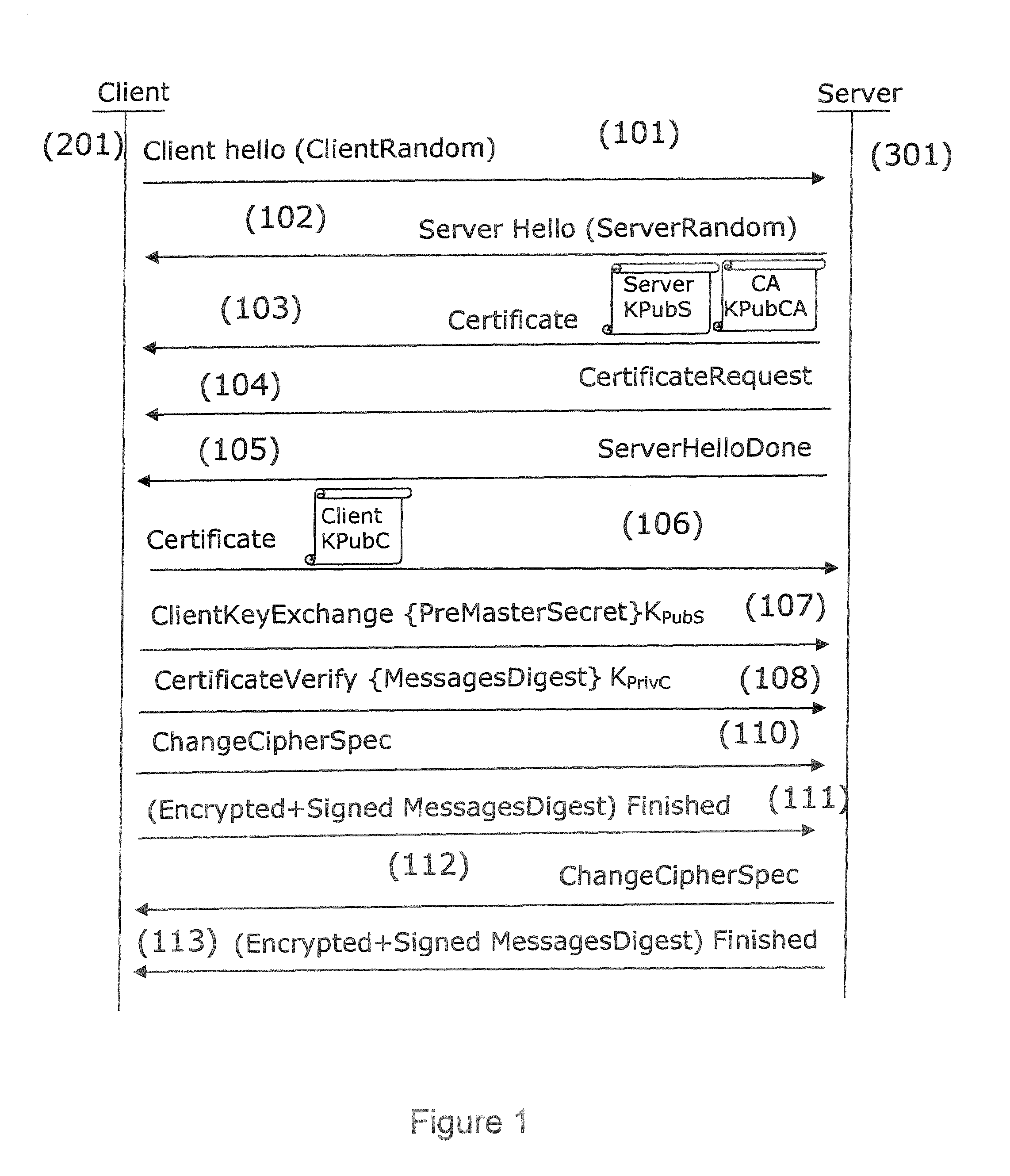
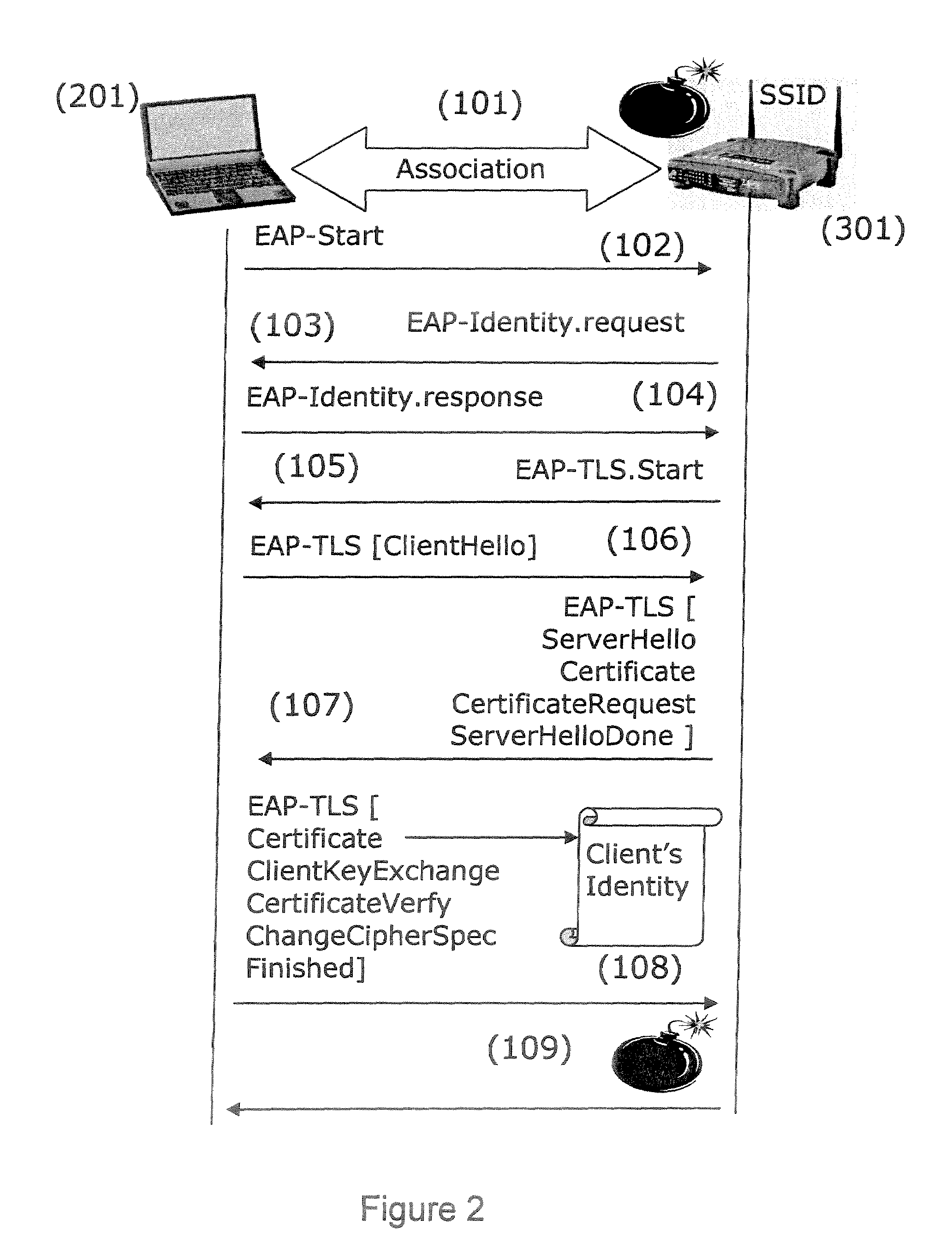
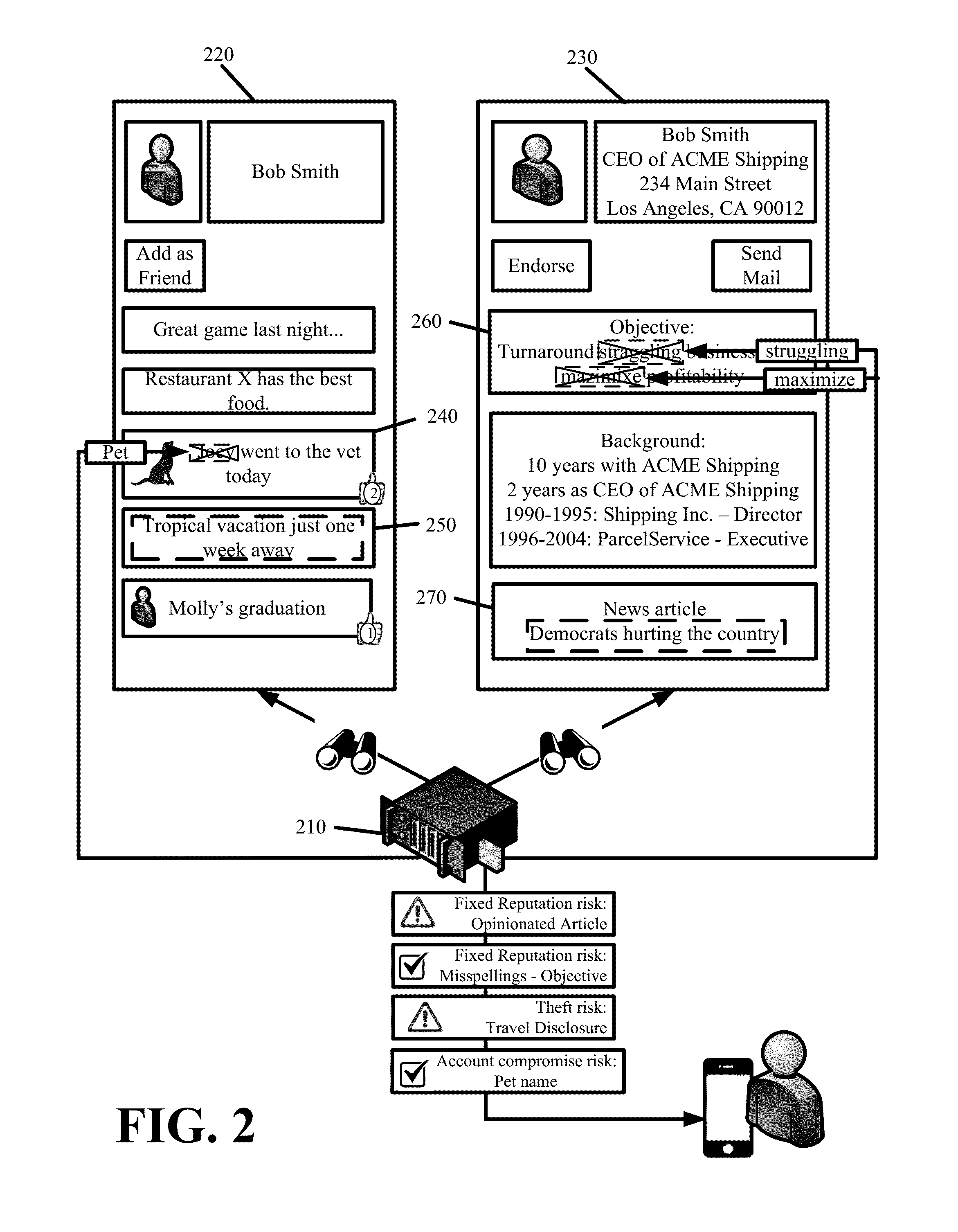
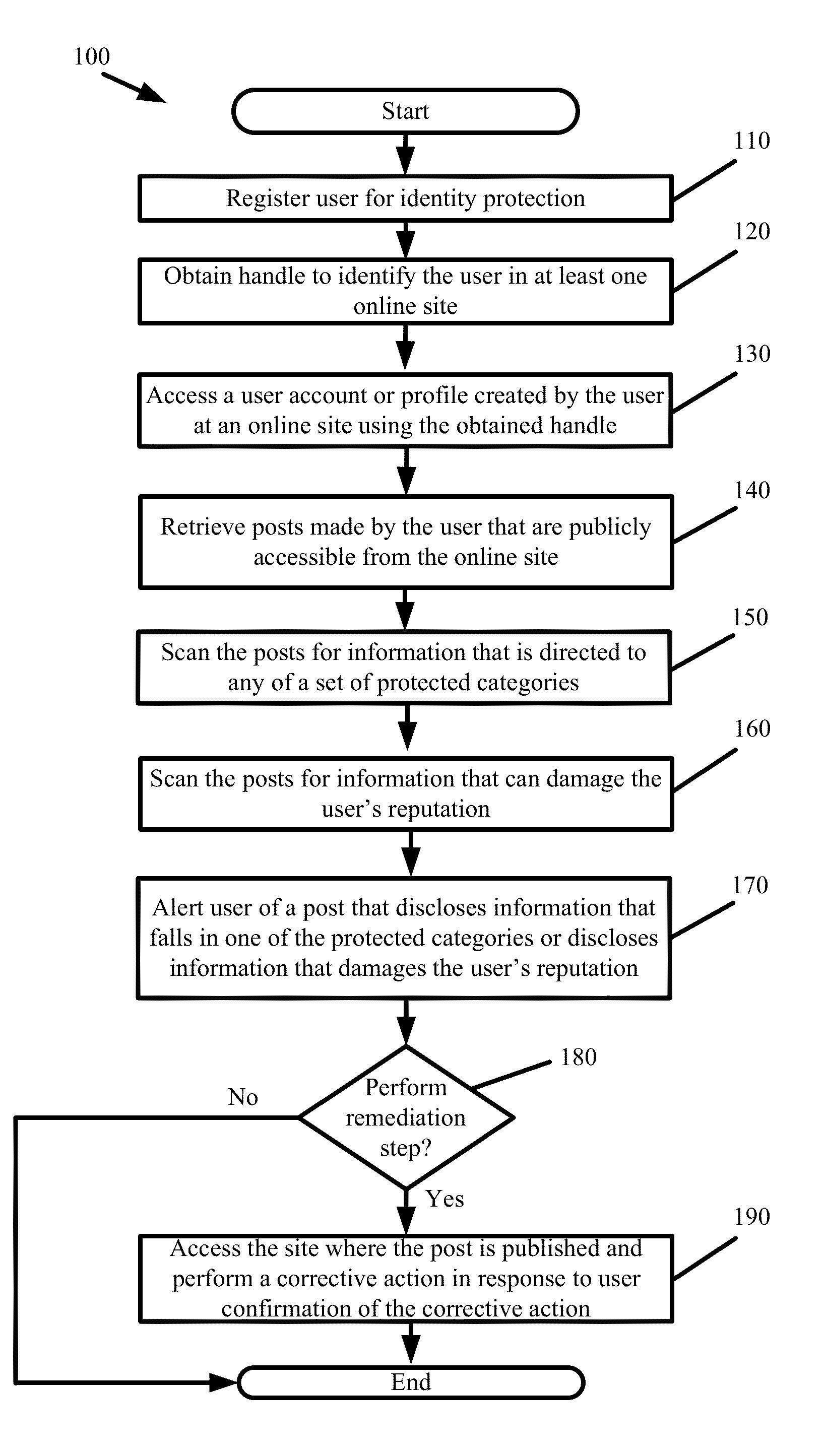
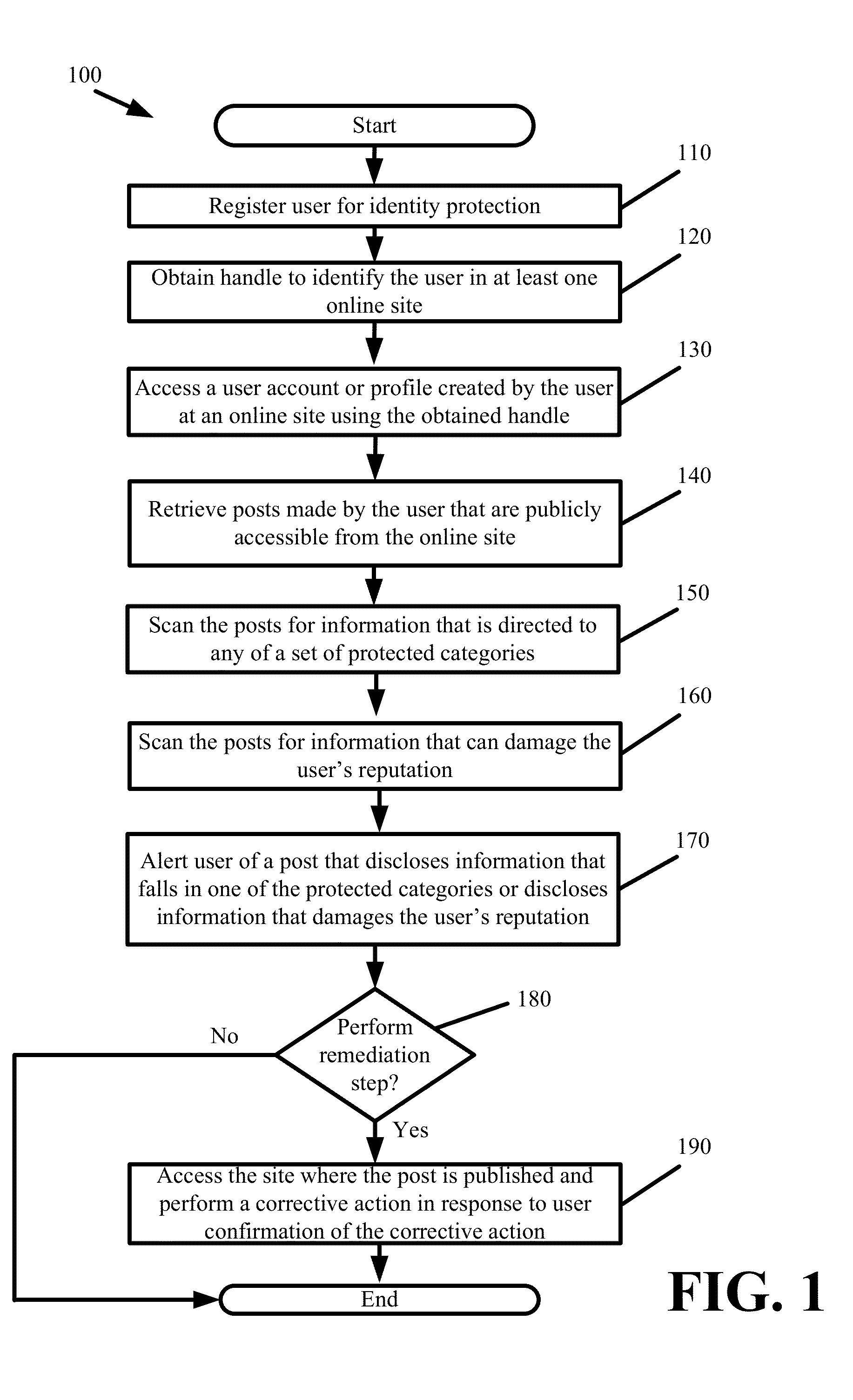
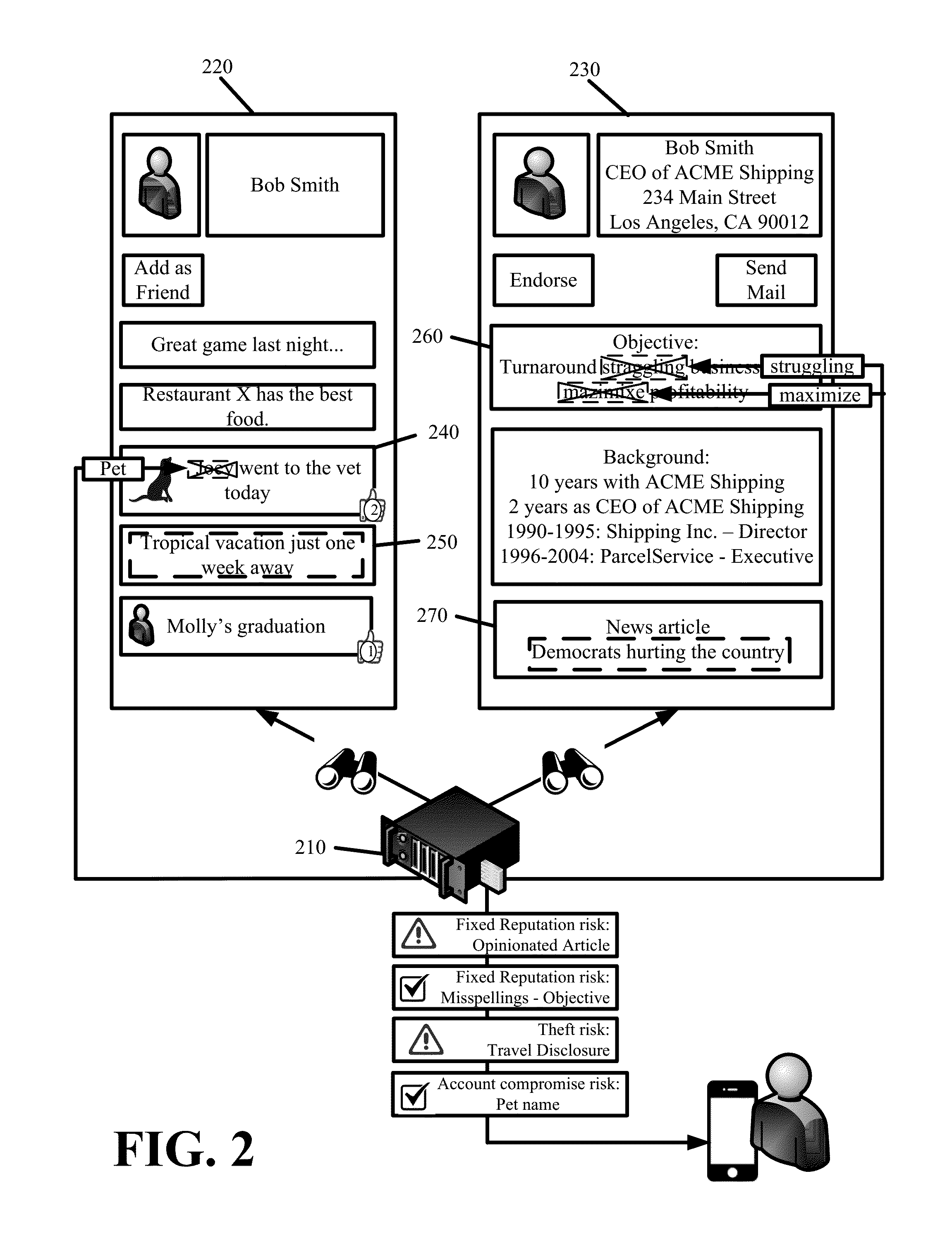
Identity Protection
Some embodiments provide holistic and comprehensive identity protection solutions. The solutions protect user identity by screening the information trail that a user leaves behind online in order to suppress or neutralize information crumbs that can subsequently be used to harm the user. The solutions audit user privacy settings, established online friends and contacts, and friend and contact activity online to limit the exposure and disclosure of user information online. The solutions perform white-hat penetration tests. The solutions report on user risk based on available online information. The solutions validate completed transactions based on monitored user movements and site visits. The solutions provide a crowd-sourced approach to identify risk based on common transactions and visits of others. The solutions prevent identity theft by verifying that disbursements are made to the correct entity.
Owner:BLUE SUN TECH
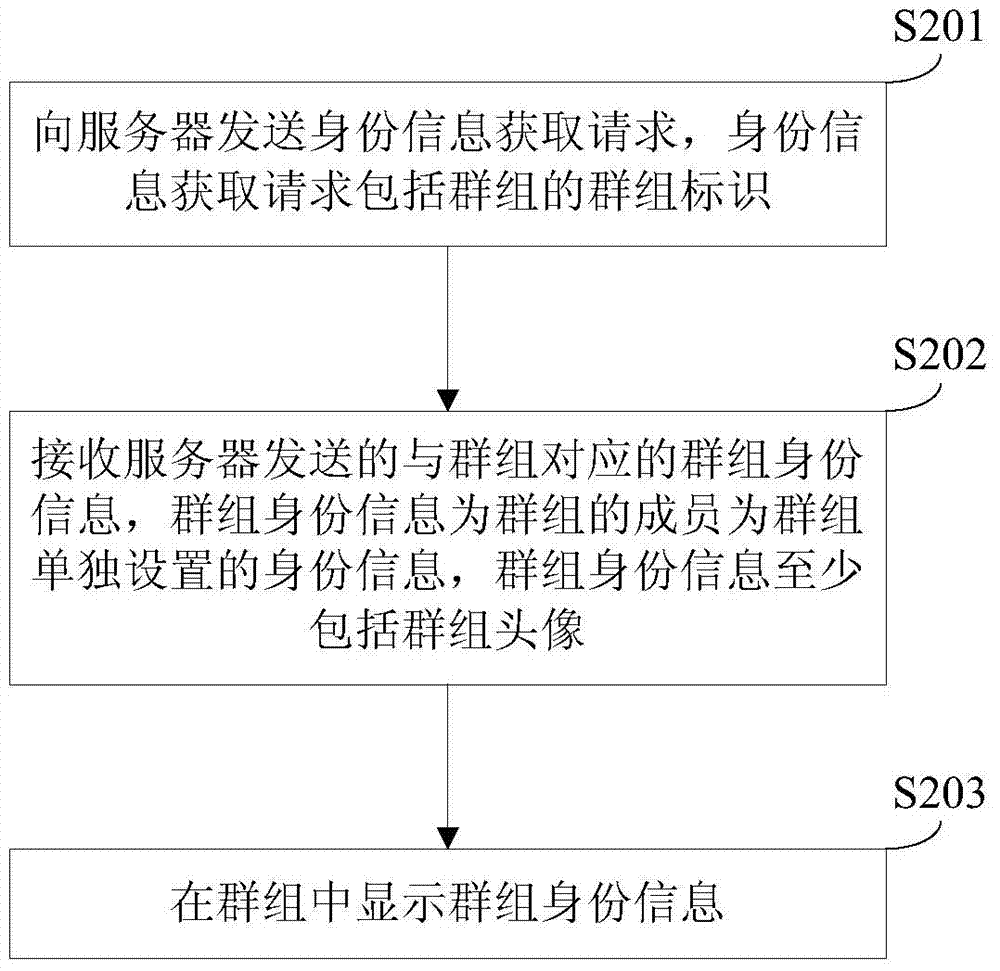
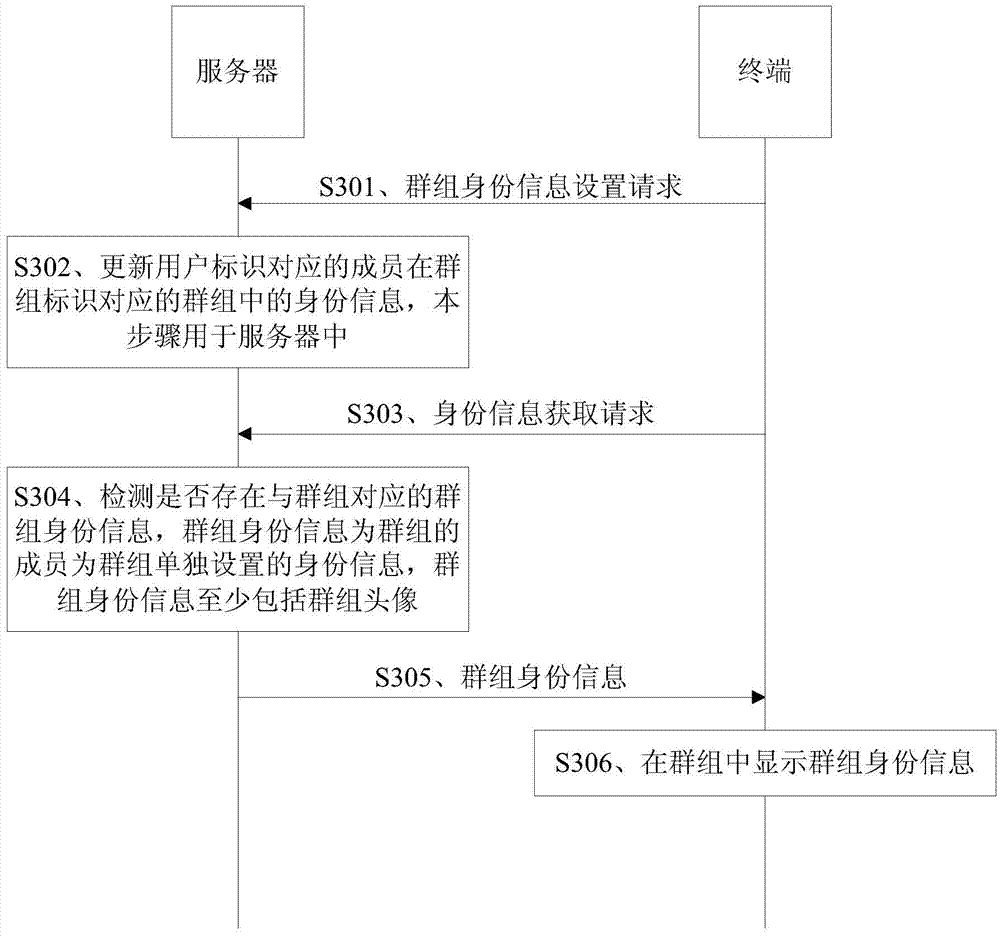
User identity protection method and apparatus
ActiveCN103763112AImprove experiencePrevent leakageSpecial service provision for substationInternet privacyThe Internet
The invention, which belongs to the internet field, discloses a user identity protection method and apparatus. The method comprises the following steps that: an identity information obtaining request sent by a terminal is received, wherein the identity information obtaining request includes a group identifier of a group; whether group identity information corresponding to the group exists is detected, wherein the group identity information is identity information that is set individually by members for the group and at least include group head pictures; and when the group identity information corresponding to the group exists, the group identity information is sent to the terminal. According to the disclosure, whether group identity information corresponding to the group exists is detected; and if so, the group identity information is sent to the terminal, so that the terminal displays group identity information in the group. For one user, different identity information like group head pictures can be used for identifying the identity in different groups, thereby effectively preventing privacy disclosure of the user. Therefore, the user experience is good.
Owner:XIAOMI INC
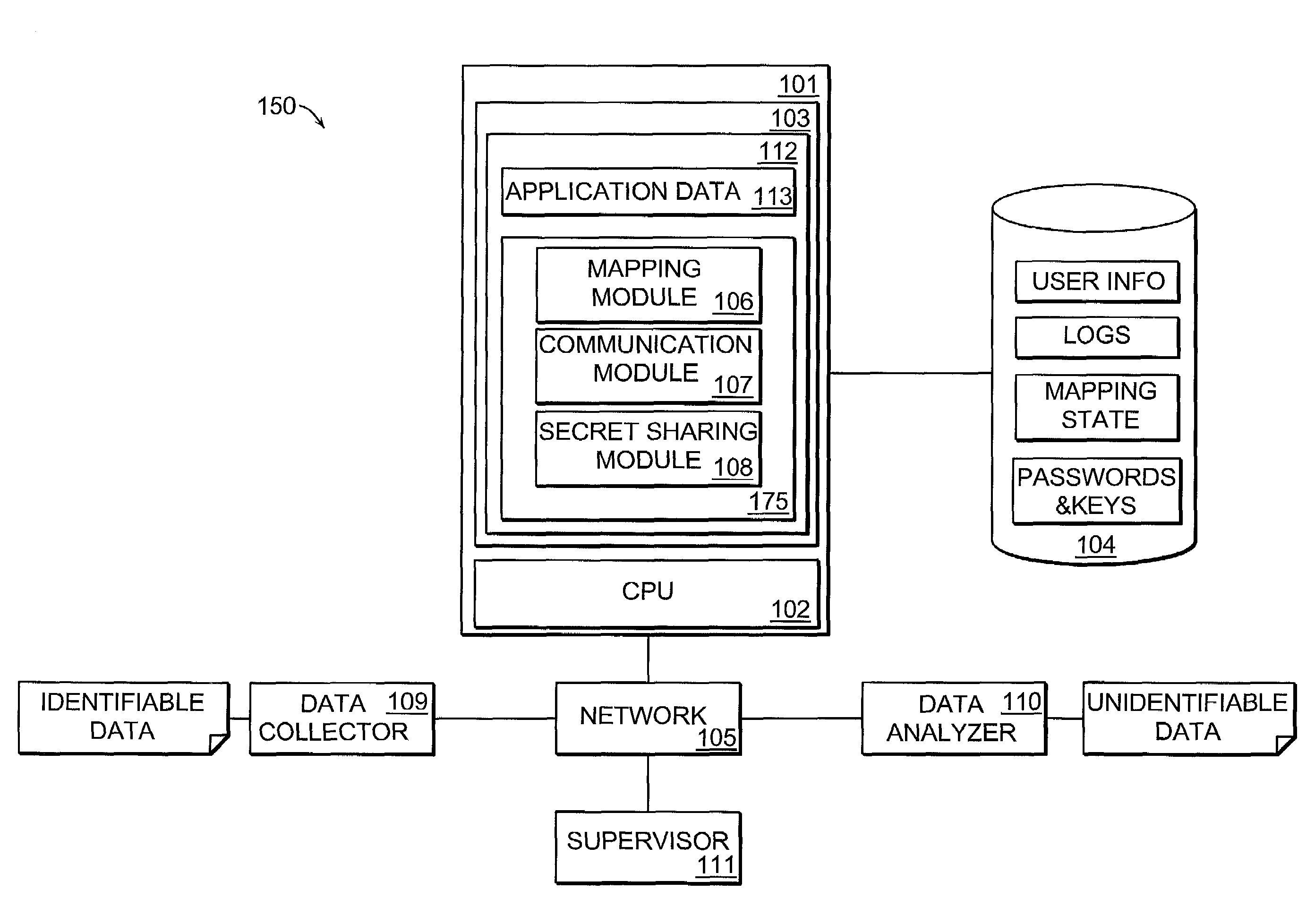
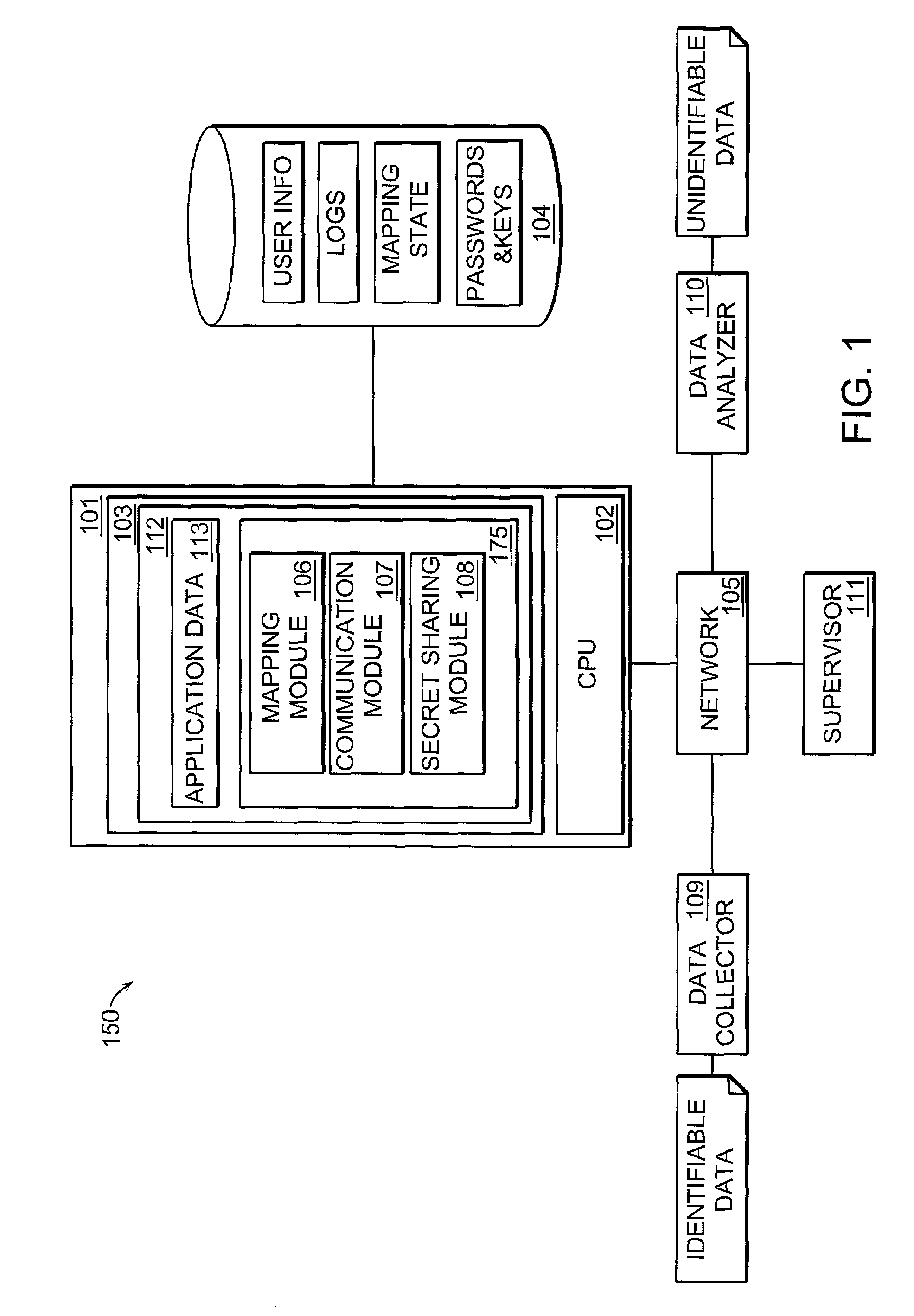
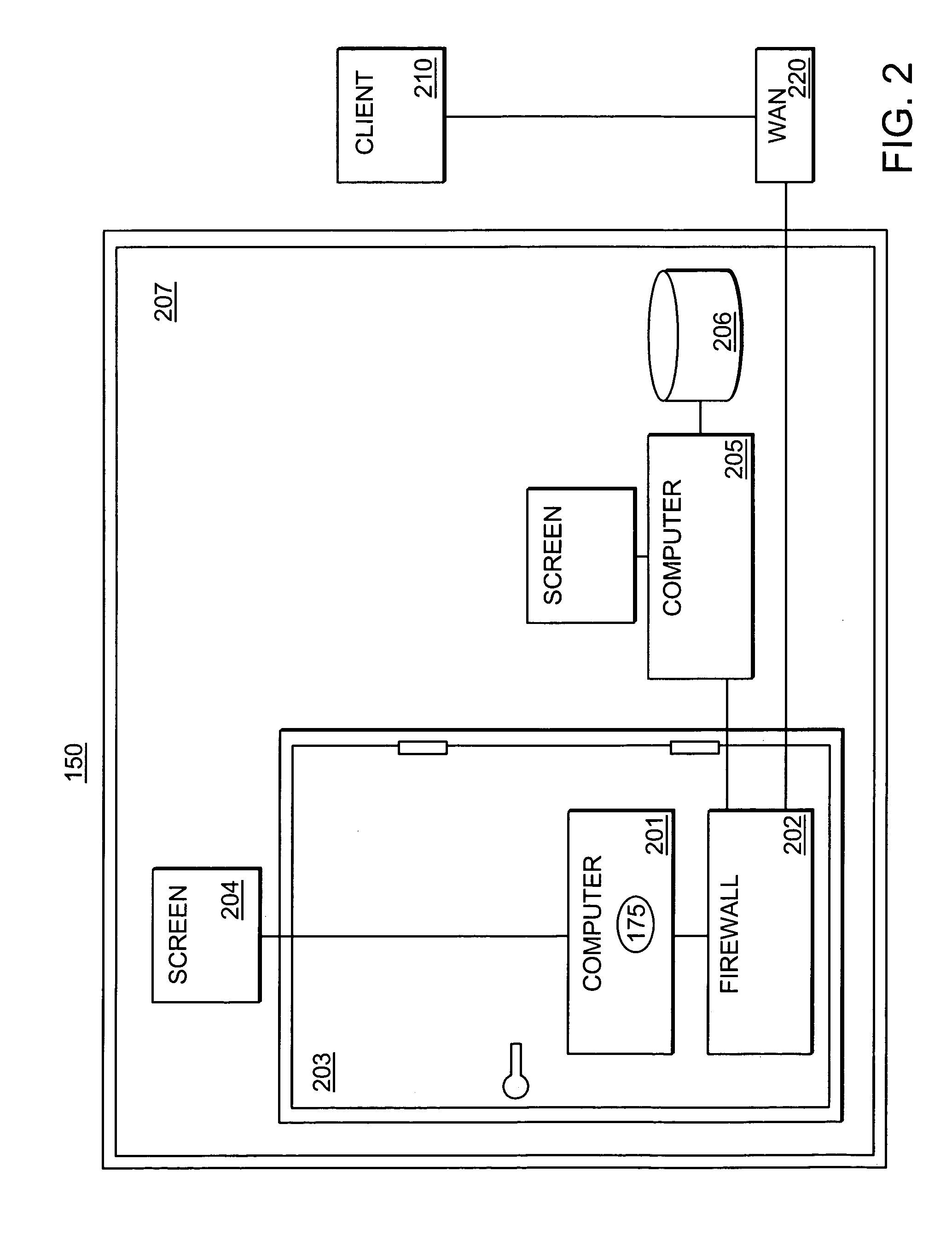
Automatic identity protection system with remote third party monitoring
ActiveUS7404079B2Key distribution for secure communicationUser identity/authority verificationThird partyNetwork packet
This invention provides an automated system for the processing of data packets, composed of personal identifiers and personal data, such that the personally identifiable data sent by one party may be considered anonymous once received by a second party. The invention uses secret sharing techniques to facilitate distributed key management of the mapping functions and strong authentication to allow the system to be operated remotely.
Owner:DECODE GENETICS EHF
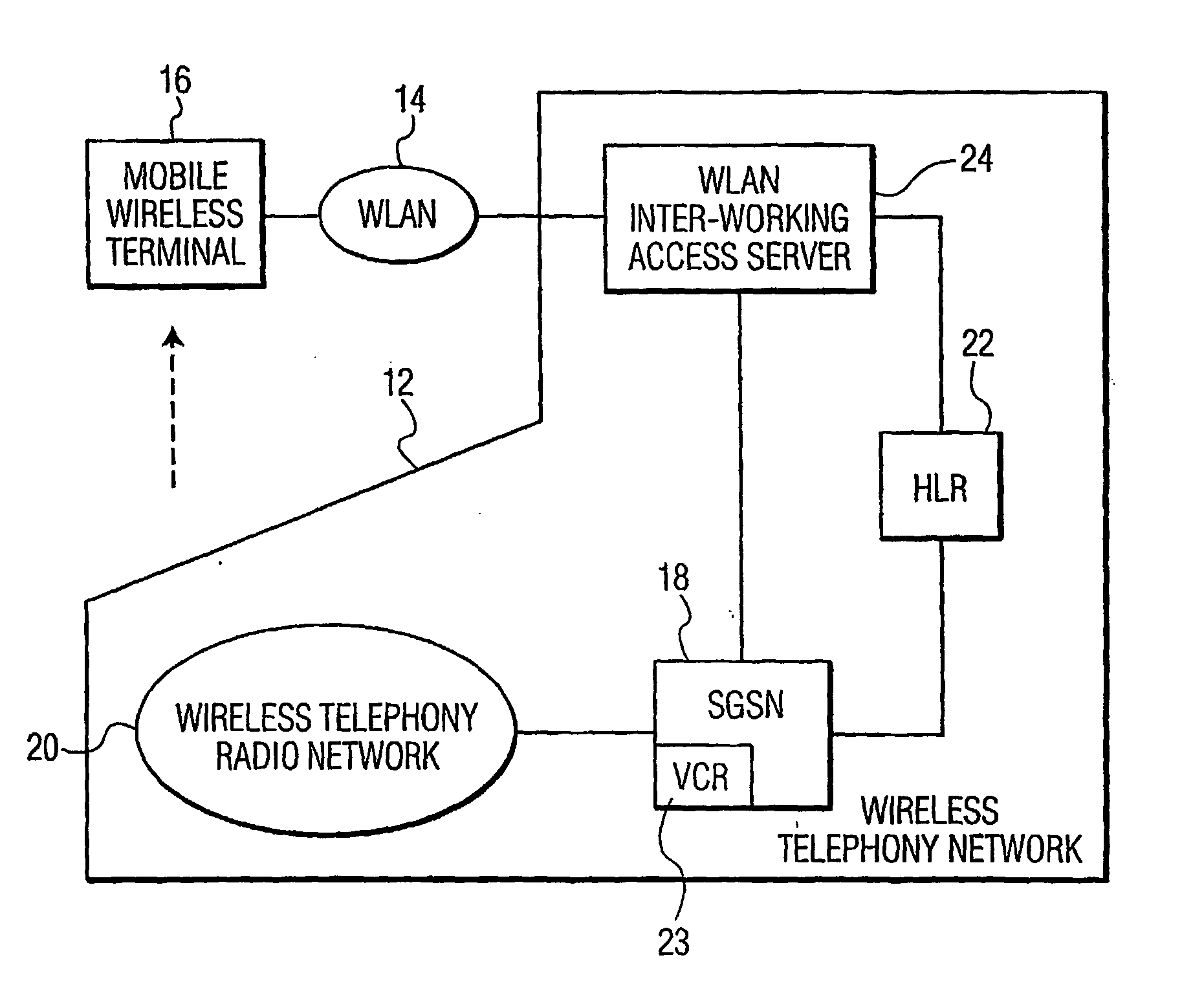
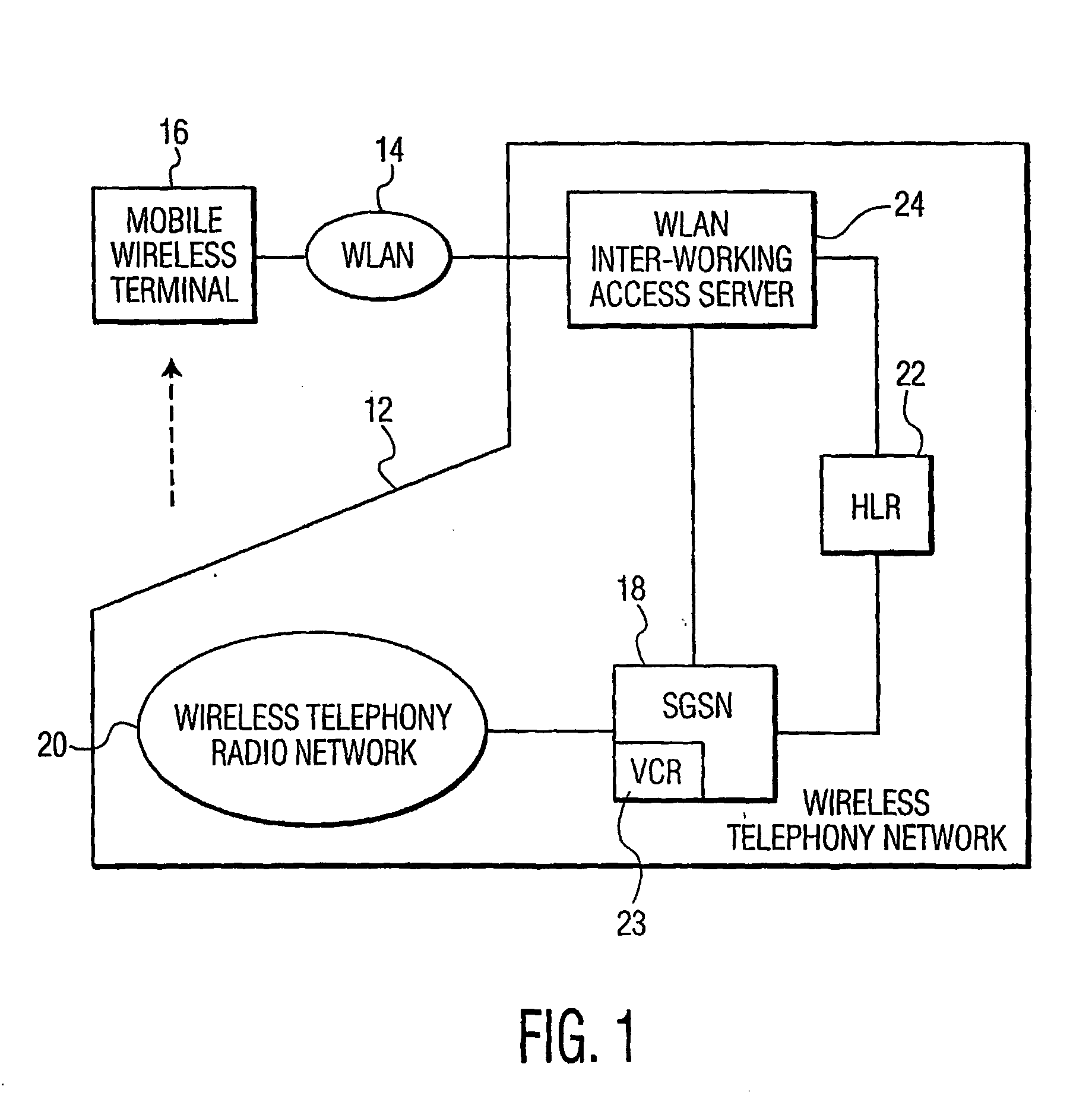
Identity protection in a lan-universal radiotelephone system
InactiveUS20050202815A1Avoid the needNetwork topologiesRadio/inductive link selection arrangementsGeneral Packet Radio ServiceWireless lan
A mobile wireless terminal, upon transitioning from a wireless telephony network to a wireless Local Area Network (LAN), seeks identification by sending the same identity information used for identification in the wireless telephony network. Upon receipt of the identity information, a wireless LAN Access Server in the wireless telephony network identifies a Serving General Packet Radio Service Serving Node (SGSN) that had last served the wireless terminal in the wireless telephony network prior to transition. The wireless LAN Access Server forwards the identity information to the SGSN, which, in turn, provides an identification response for validating the terminal.
Owner:INTERDIGITAL CE PATENT HLDG
Node identity protection method of mobile wireless sensor network on basis of message time delay condition
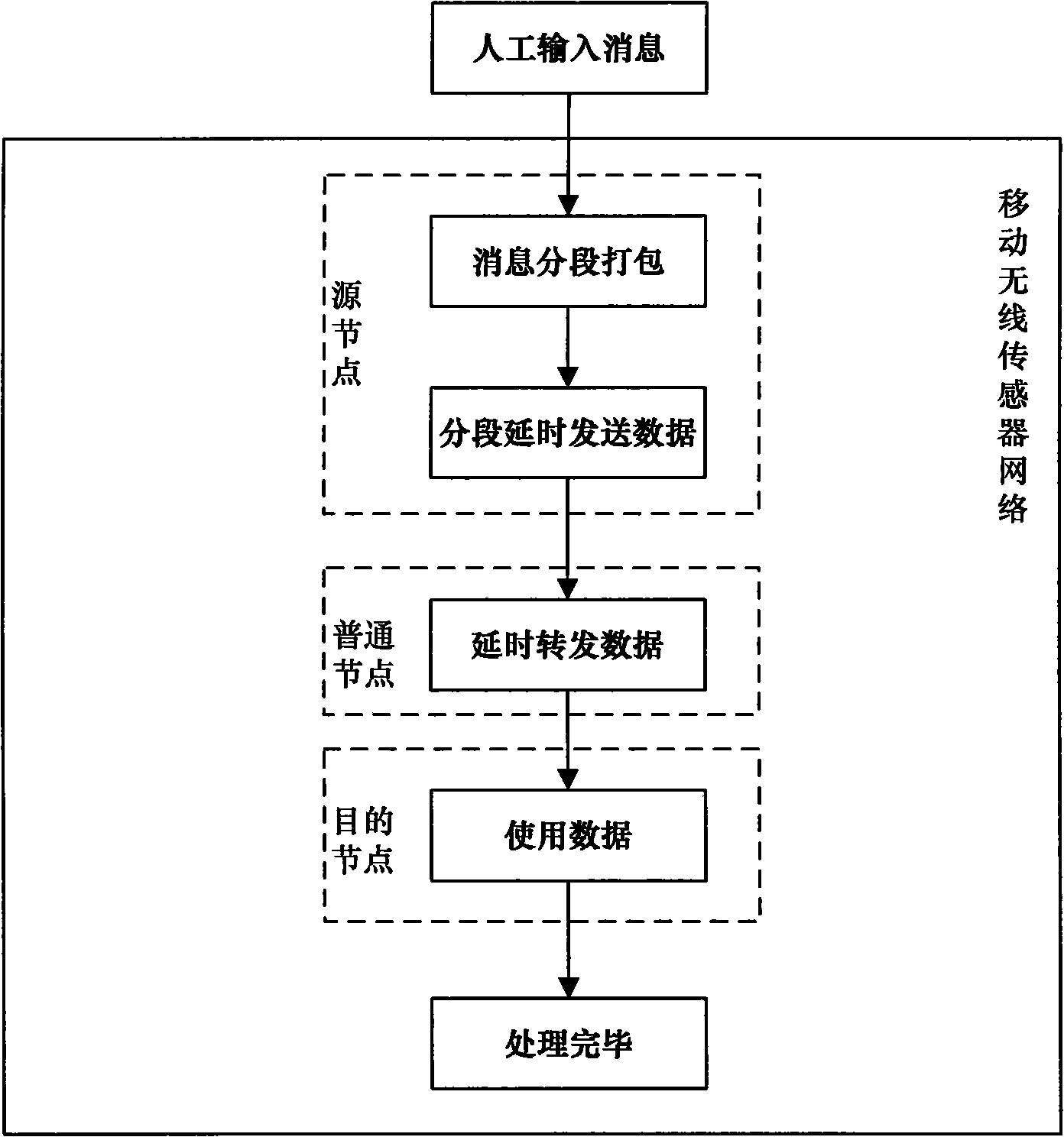
InactiveCN101557608AEffective protectionSolve the danger of non-fragmented transmission to the sending nodeNetwork traffic/resource managementNetwork topologiesMobile wireless sensor networkTime delays
The invention discloses a node identity protection method of a mobile wireless sensor network on the basis of message time delay condition. The node identity protection method realizes segmental package, time delay transmission and time delay forwarding of a message Mi=(MDATAi, MTIMEi) by a source node Ni in a mobile wireless sensor. By the method, in the transmission process of the message Mi=(MDATAi, MTIMEi), common node Nj receiving the message Mi=(MDATAi, MTIMEi) can not position the sending place and the receiving place of the message Mi=(MDATAi, MTIMEi) and also can not obtain the transmission path of the message Mi=(MDATAi, MTIMEi); therefore, the method effectively carries out identity protection to the node for receiving and sending messages in the mobile wireless sensor.
Owner:BEIHANG UNIV
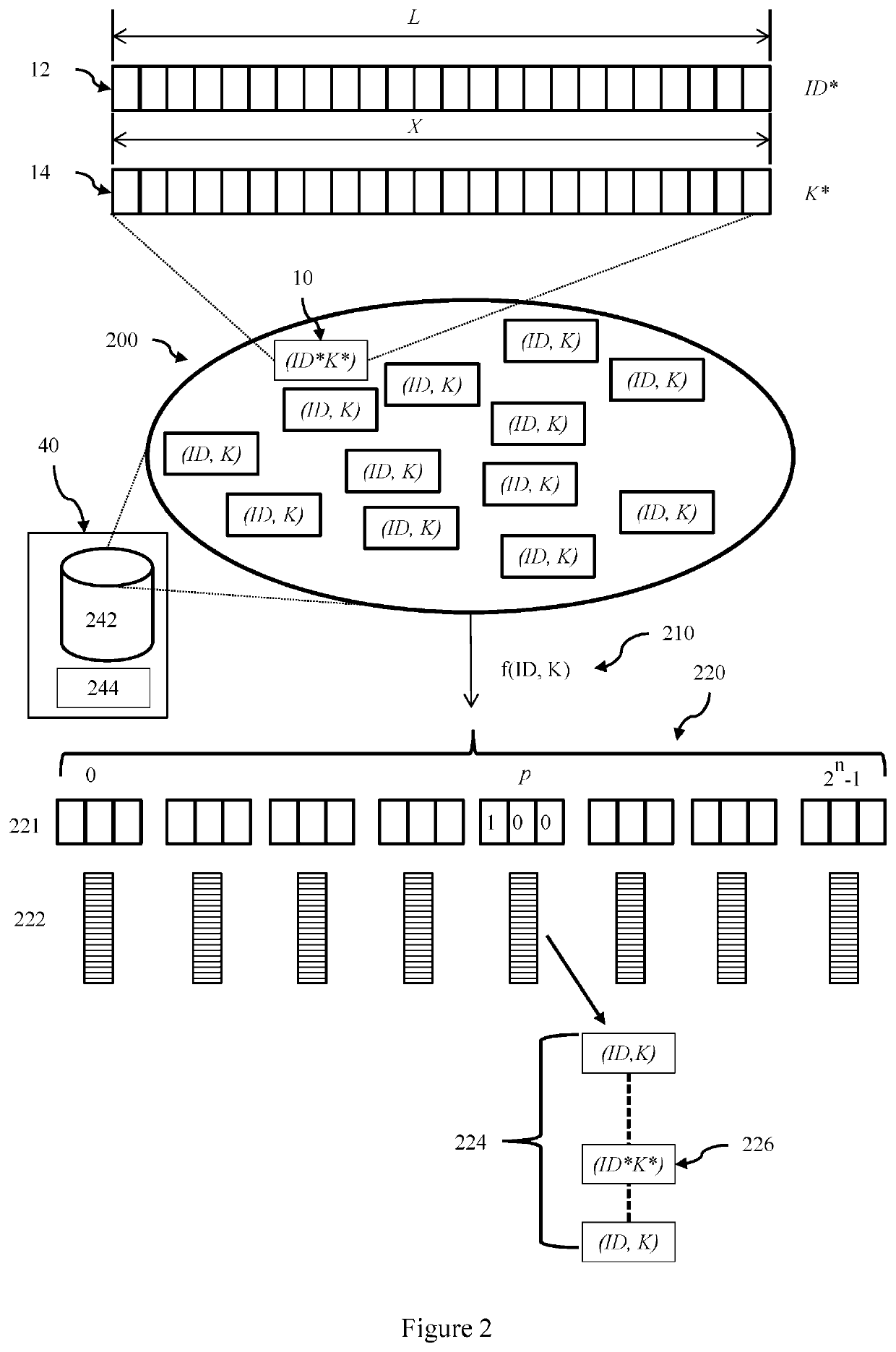
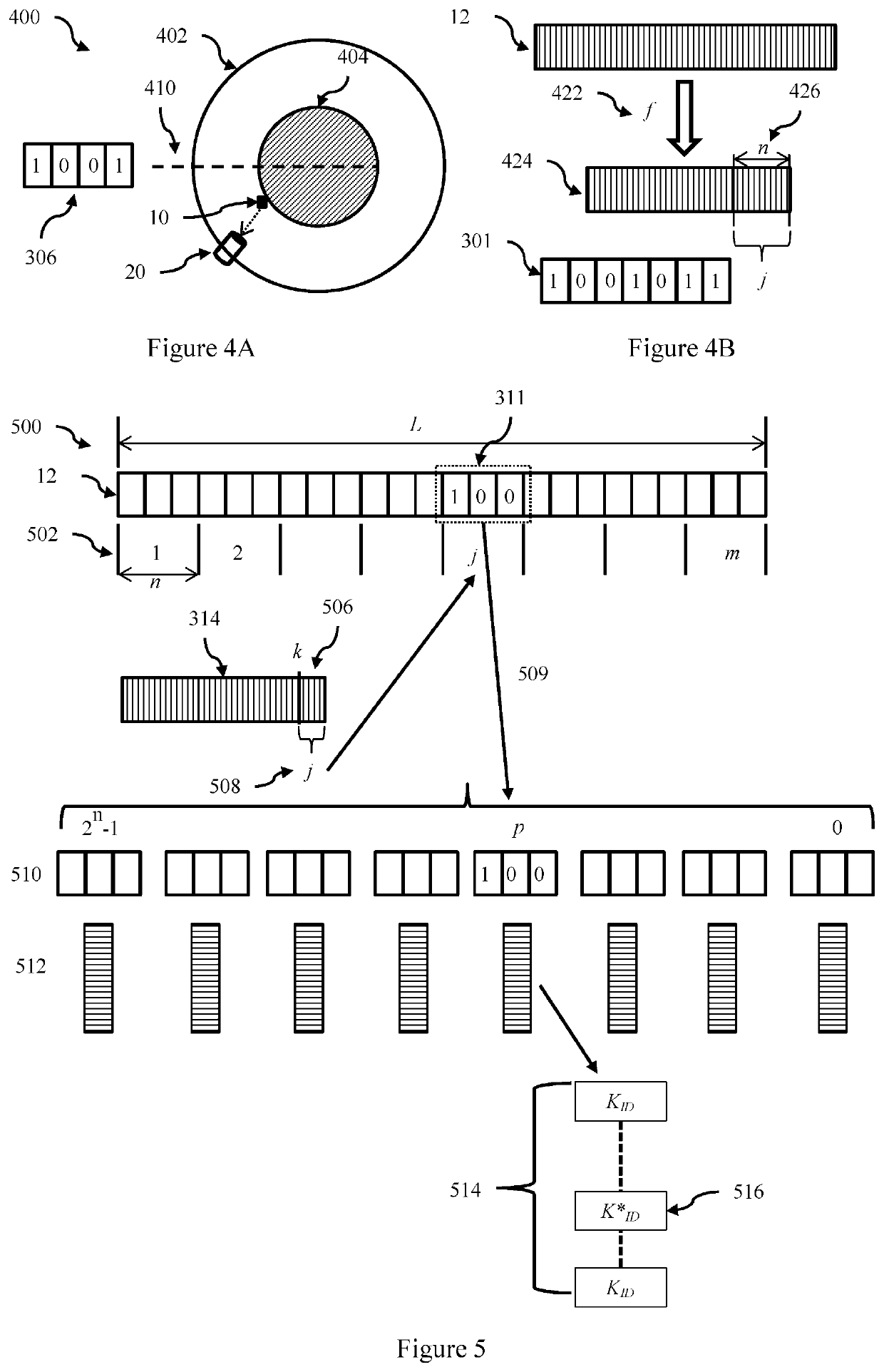
Terminal identity protection method in a communication system
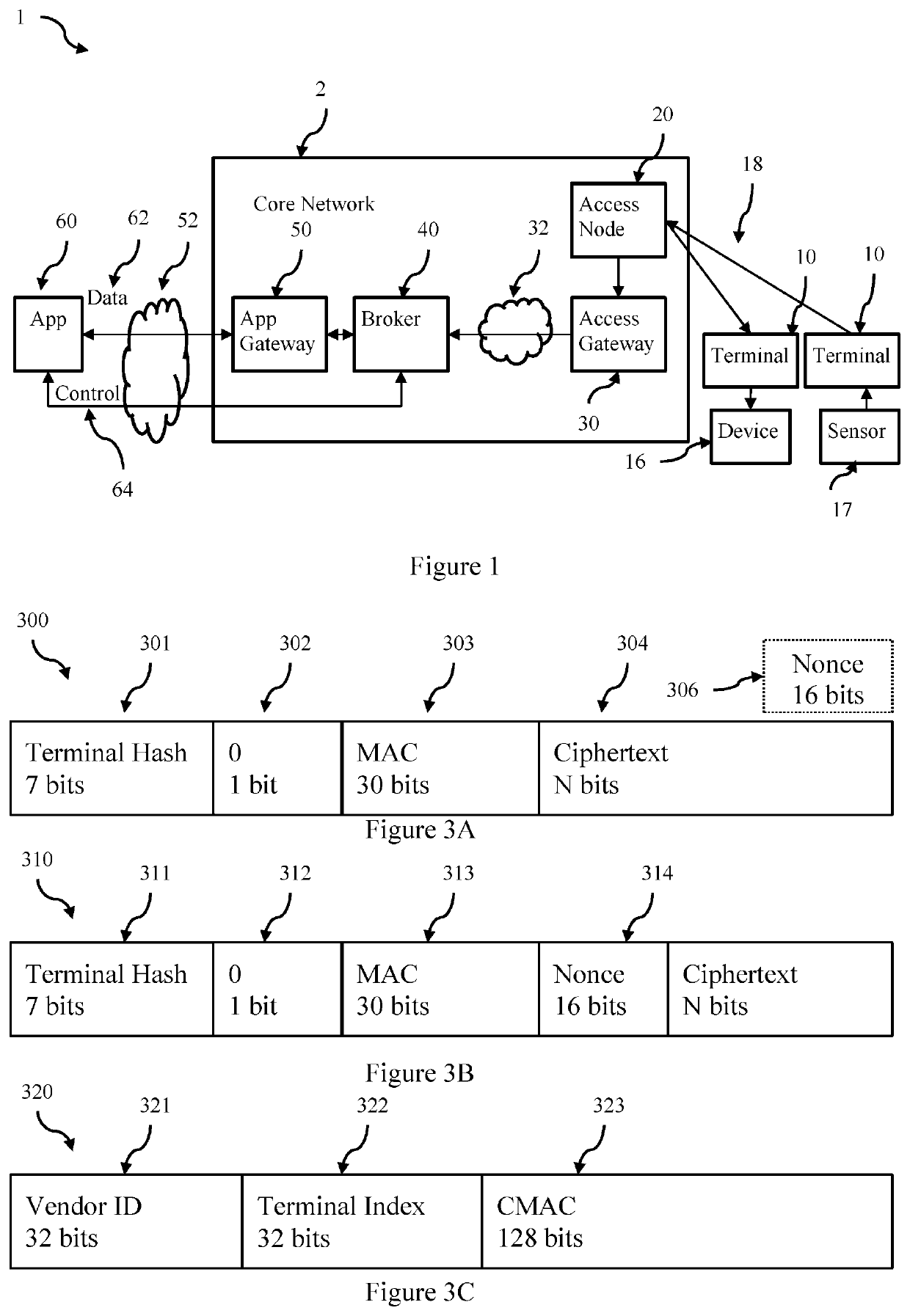
ActiveUS20200195427A1Key distribution for secure communicationUser identity/authority verificationCommunications systemEngineering
A method for determining a terminal ID from a message received from a terminal in a communication system avoids sending the terminal ID in the clear. In this system each terminal ID has an associated encryption key. A transmitted message comprises at least a Message Authentication Code (MAC), a n-bit hash, and encrypted message text. At least the terminal key and a nonce is used to generate the MAC, and neither the terminal ID or the terminal key are included in the transmitted message. An authentication broker stores the set of all (terminal ID, terminal key) pairs for the plurality of terminals in the communication system. The set of all terminal keys is grouped into at least two partitions, and on receipt of a message the authentication broker identifies the partition that includes the terminal key of the terminal that transmitted the received message using the n-bit hash (the search partition). The authentication broker then searches the search partition for the terminal key that authenticates the MAC to identify the terminal ID. In some embodiments the nonce is not included in the message but is known or obtainable by the terminal and the authentication broker. A partitioning function generates the «-bit hash from at least the nonce and a terminal key. In some embodiments the nonce is included in the received message and a partitioning function generates the n-bit hash by using the nonce to select n bits from the terminal ID. In some embodiments the partitions are arranged into hierarchical groups such as tree, and each node has a partition key, and the n-bit has is formed as the ordered set of MACs for the partition keys on the path from the root node to the leaf node partition that includes the terminal key.
Owner:MYRIOTA PTY LTD
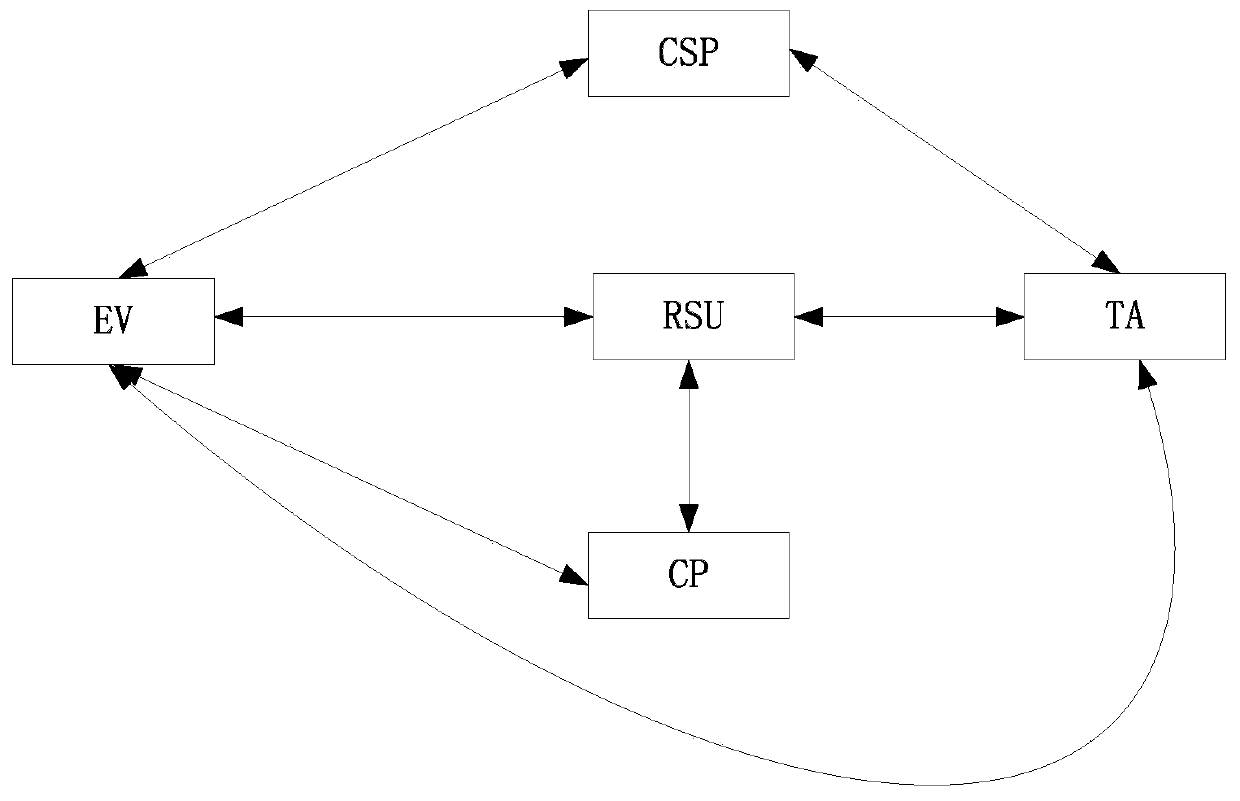
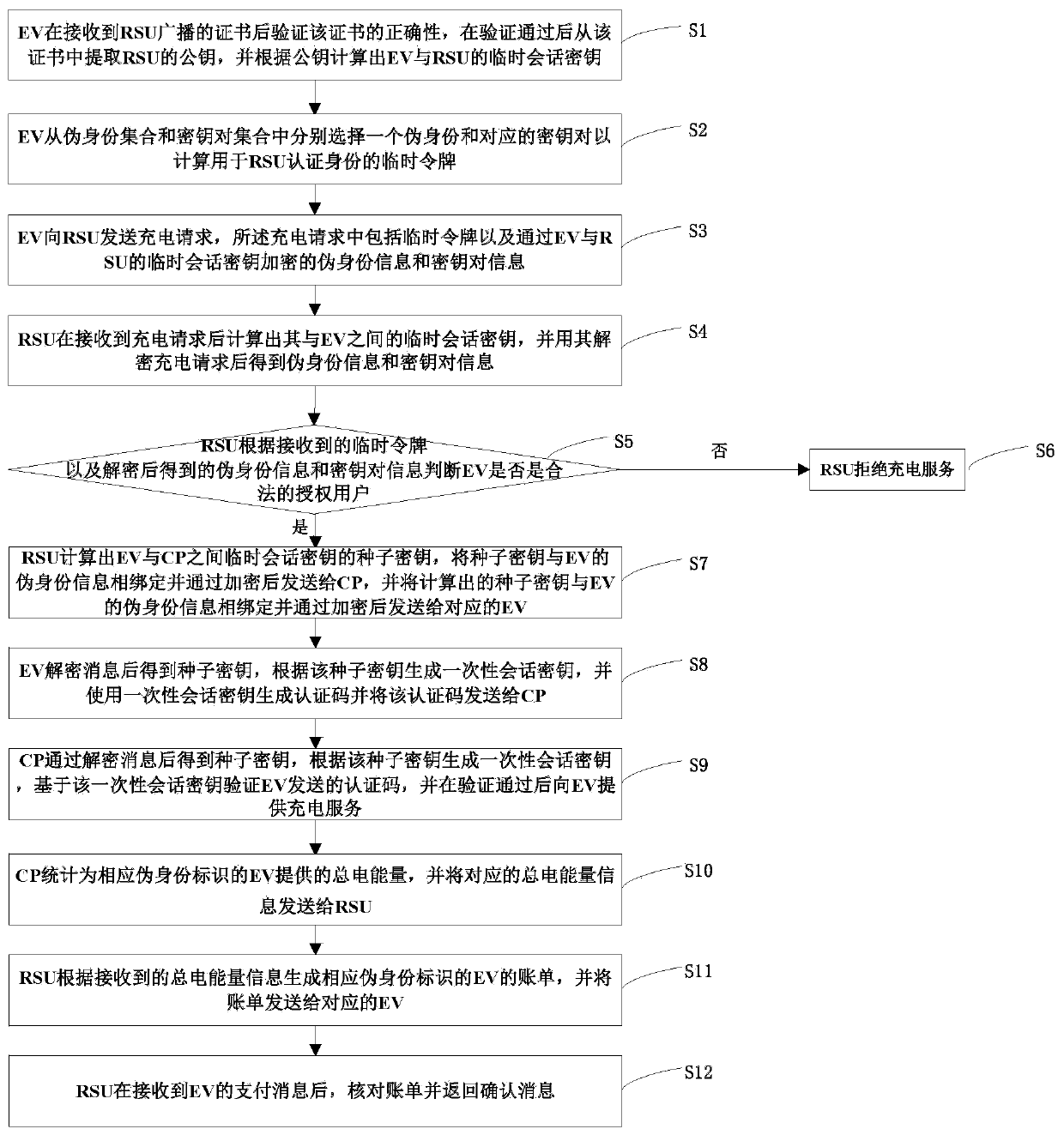
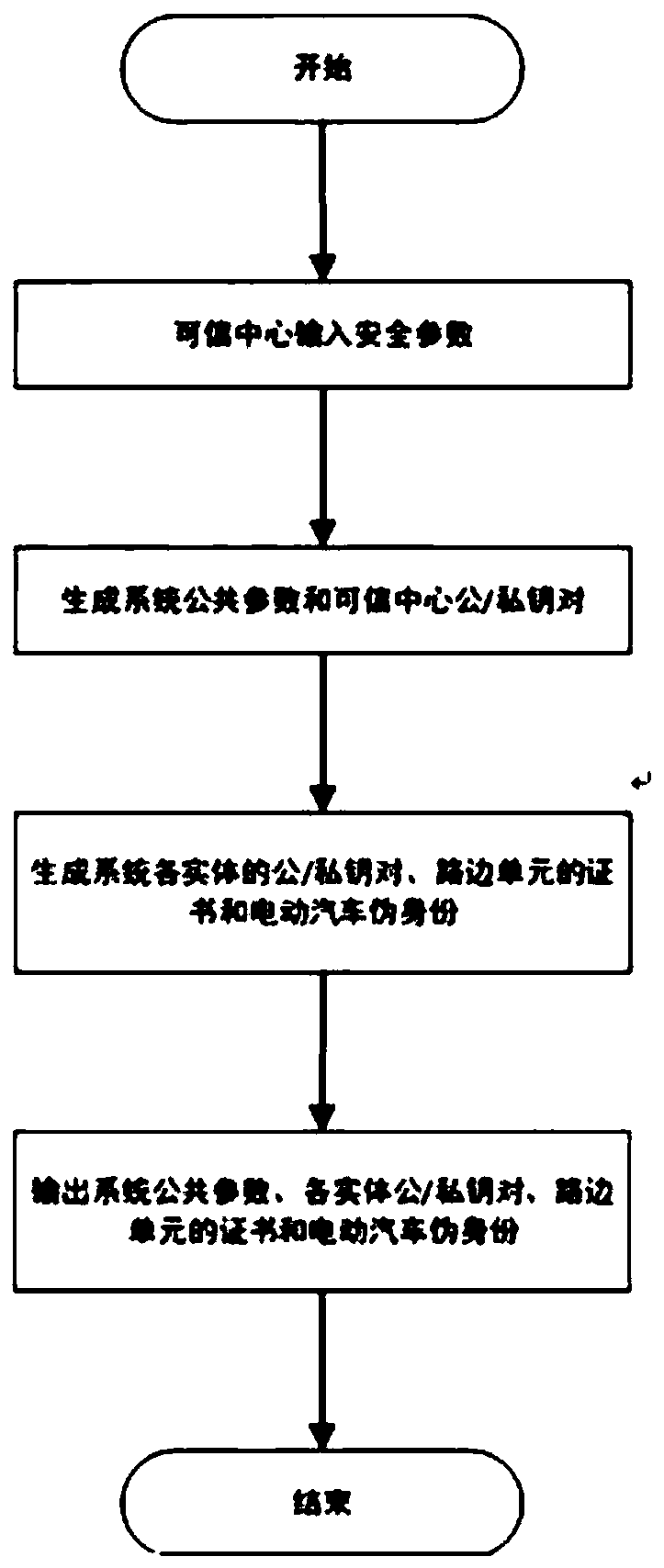
Electric vehicle charging service method capable of protecting privacy
ActiveCN111107071AImprove securityPrevention of Invasion of PrivacyKey distribution for secure communicationCharging stationsEngineeringElectric vehicle
The invention discloses an electric vehicle charging service method capable of protecting privacy. Method, the electric vehicle generates a temporary token by using the key pair allocated by the charging service provider and the pseudo identity allocated by the trusted center; authenticating to a roadside unit by using the temporary token; after the authentication is passed, the roadside unit sends a seed key required by the authentication of the charging panel to the electric vehicle; challenge response is carried out by using a disposable session key generated by the seed key to complete authentication; after the authentication is passed, the charging panel provides charging service for the electric vehicle. According to the invention, identity protection of the electric vehicle is realized by adopting the pseudo identity information; the malicious entity is prevented from obtaining the real identity of the vehicle in the charging service process; according to the method, the drivingtrack of the vehicle is exposed, so that the privacy of a vehicle owner is invaded, when the electric vehicle has any improper behavior, the trusted center can reveal the real identity of the electric vehicle, and through the method disclosed by the invention, the behaviors of the electric vehicle can be better managed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
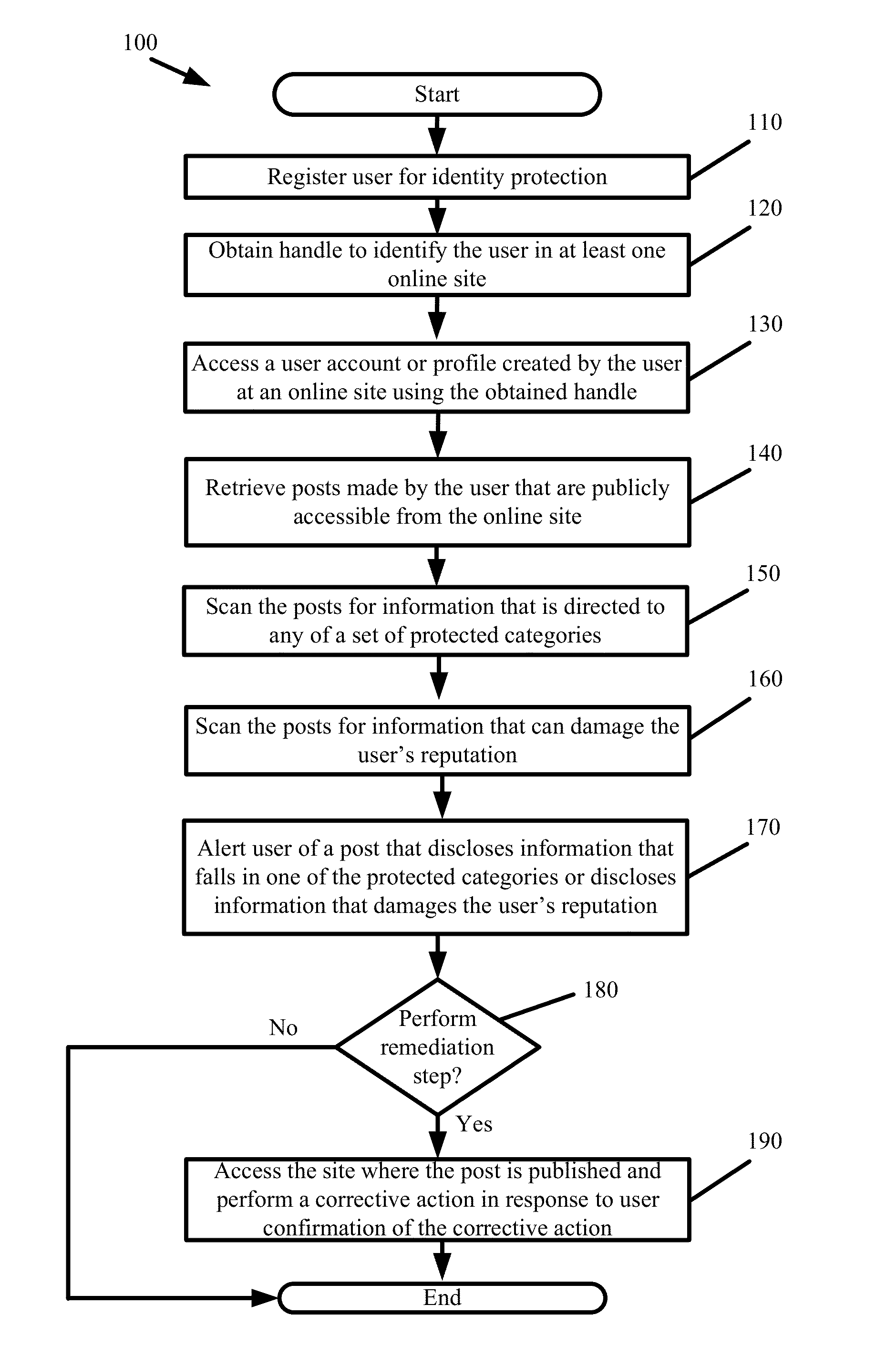
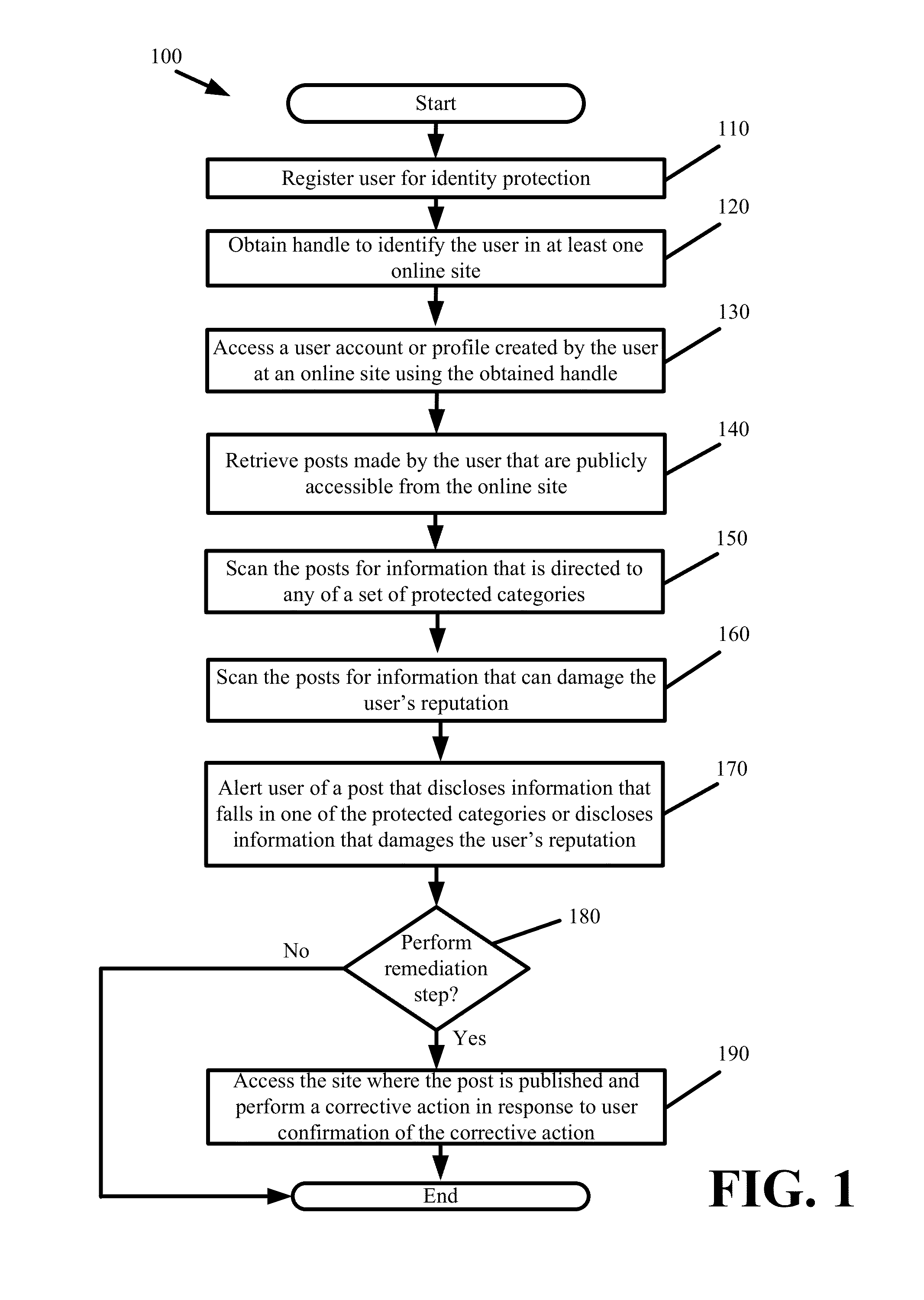
Identity Protection
InactiveUS20160148211A1Improve identityAccurate contactDigital data processing detailsMultiple digital computer combinationsCrowd sourcingSite Visit
Some embodiments provide holistic and comprehensive identity protection solutions. The solutions protect user identity by screening the information trail that a user leaves behind online in order to suppress or neutralize information crumbs that can subsequently be used to harm the user. The solutions audit user privacy settings, established online friends and contacts, and friend and contact activity online to limit the exposure and disclosure of user information online. The solutions perform white-hat penetration tests. The solutions report on user risk based on available online information. The solutions validate completed transactions based on monitored user movements and site visits. The solutions provide a crowd-sourced approach to identify risk based on common transactions and visits of others. The solutions prevent identity theft by verifying that disbursements are made to the correct entity.
Owner:BLUE SUN TECH
Efficient, secure, cloud-based identity services
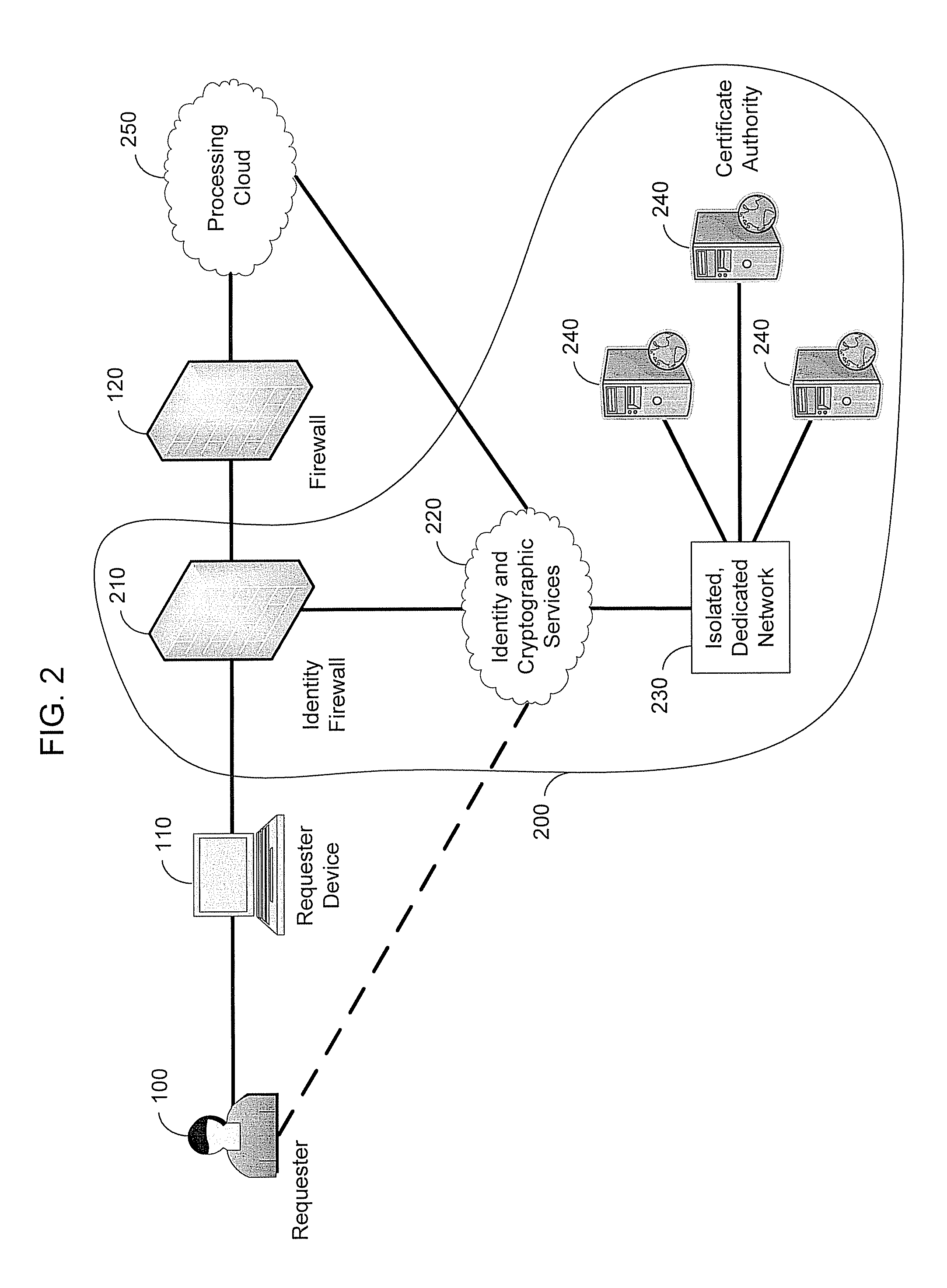
InactiveUS8667269B2Improve securityDigital data processing detailsMultiple digital computer combinationsWeb serviceSecurity Measure
An Identity Ecosystem Cloud (IEC) provides global, scalable, cloud-based, cryptographic identity services as an identity assurance mechanism for other services, such as data storage, web services, and electronic commerce engines. The IEC complements these other services by providing enhanced identity protection and authentication. An IEC performs identity services using surrogate digital certificates having encryption keys that are never exposed to the public. An individual requesting other services must meet an identity challenge before access to these other services is granted. Service requests to the IEC, and responses from the IEC, are securely encrypted. An IEC integrates smoothly into existing services by layering on top of, or being used in conjunction with, existing security measures. Identity transactions may be logged in a manner that complies with strict medical and financial privacy laws.
Owner:SURIDX
Mobile terminal identity protection through home location register modification
InactiveCN1672393AUser identity/authority verificationData switching by path configurationPlaintextTelecommunications
Secure access by a mobile wireless terminal of a wireless telephony network is achieved by having a Home Location Register store the terminal's temporary and permanent identities. Upon accessing the network following initial registration, the terminal sends a temporary identity to a Serving GPRS Support Node (SGSN). If no serving node in the network knows the terminal, the terminal need not sent its permanent identity in clear as was previously required. Rather, the serving node need only query the HLR since the HLR can map the terminal's temporary identity to its permanent identity. In this way, the permanent identity of the mobile wireless terminal remains secure.
Owner:THOMSON LICENSING SA
Mobile terminal identity protection through home location register modification
InactiveUS7215943B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless mesh networkTelecommunications
Secure access by a mobile wireless terminal of a wireless telephony network is achieved by having a Home Location Register store the terminal's temporary and permanent identities. Upon accessing the network following initial registration, the terminal sends a temporary identity to a Serving GPRS Support Node (SGSN). If no serving node in the network knows the terminal, the terminal need not sent its permanent identity in clear as was previously required. Rather, the serving node need only query the HLR since the HLR can map the terminal's temporary identity to its permanent identity. In this way, the permanent identity of the mobile wireless terminal remains secure.
Owner:THOMSON LICENSING SA
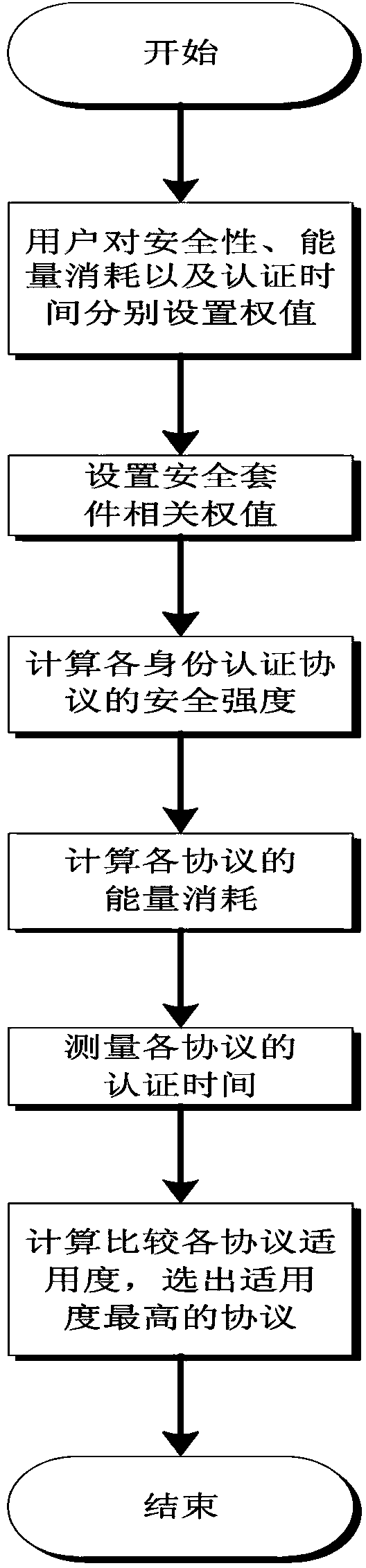
Identity authentication protocol selection method in wireless network
InactiveCN103826225AMeet individual needsSecurity arrangementHigh level techniquesPersonalizationWireless mesh network
The invention discloses an identity authentication protocol selection method in a wireless network. The identity authentication protocol selection method in the wireless network comprises the steps that the weight of importance of security, the weight of importance of energy consumption and the weight of importance of authentication time are set by a user, the applicability of each identity authentication protocol in the wireless network is calculated according the weights of importance, and an identity authentication protocol with high applicability is selected. According to the identity authentication protocol selection method in the wireless network, the characteristics, such as authentication delay and identity protection, of the identity authentication protocols in the wireless network are fully considered, a targeted authentication protocol selection method is designed. From the point of view of users, several elements, mostly concerned by the users, such as the security of the protocols, the energy consumption, the authentication time and the user preference are considered comprehensively, and a solution capable of meeting the individual requirements of the users is provided.
Owner:中电福富信息科技有限公司
Network identity protection method and device, electronic equipment and storage medium
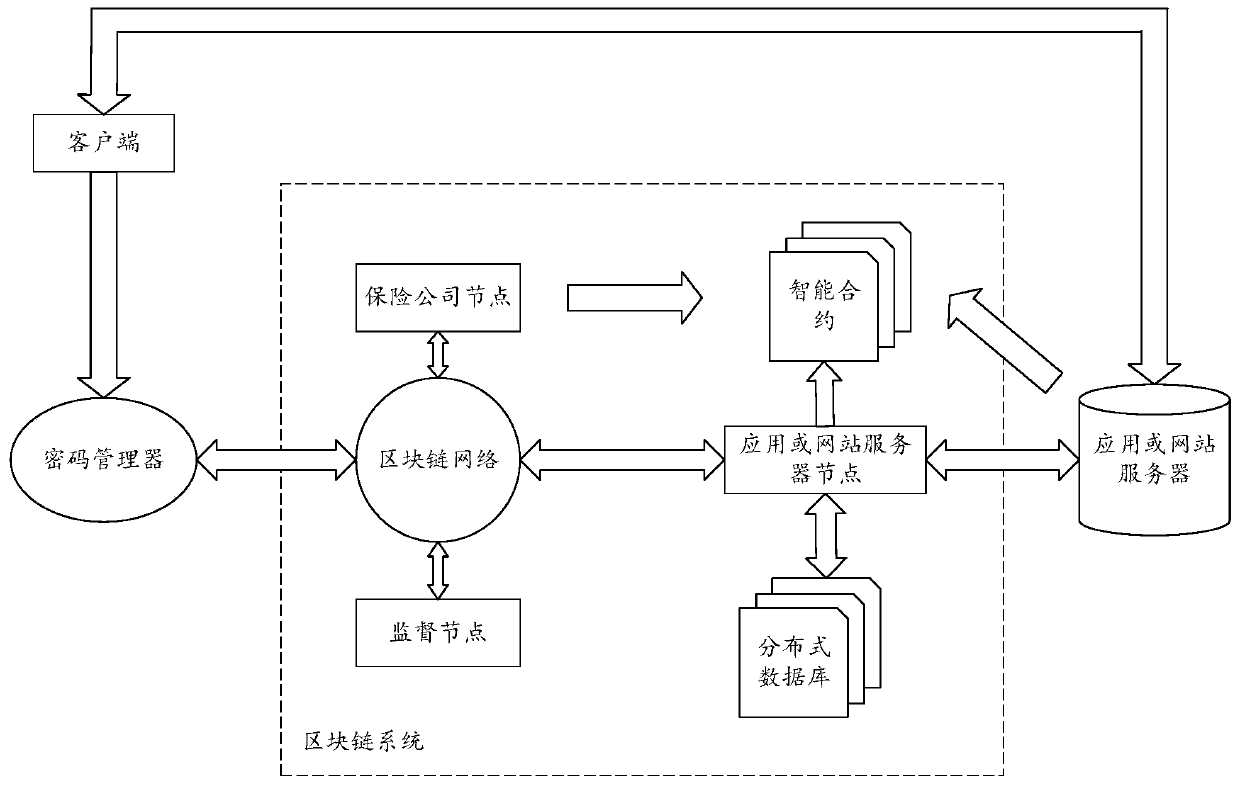
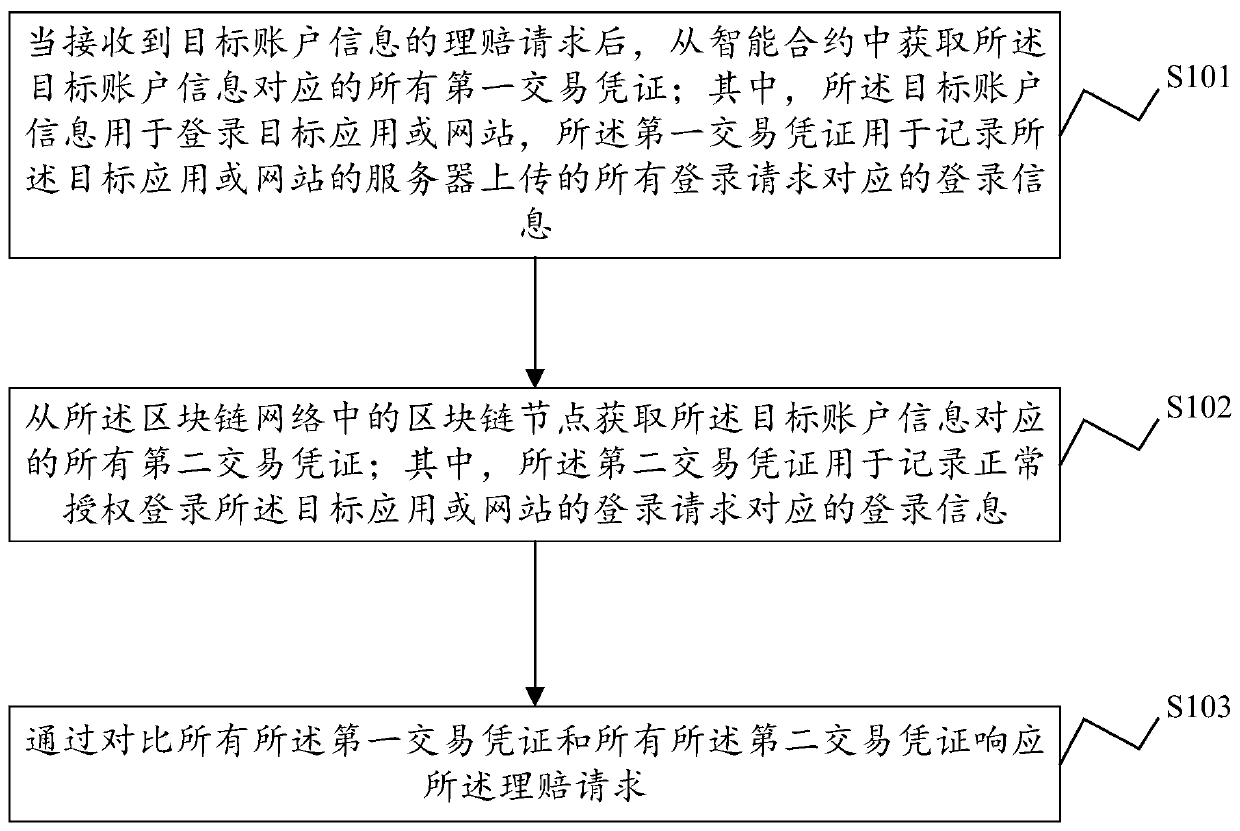
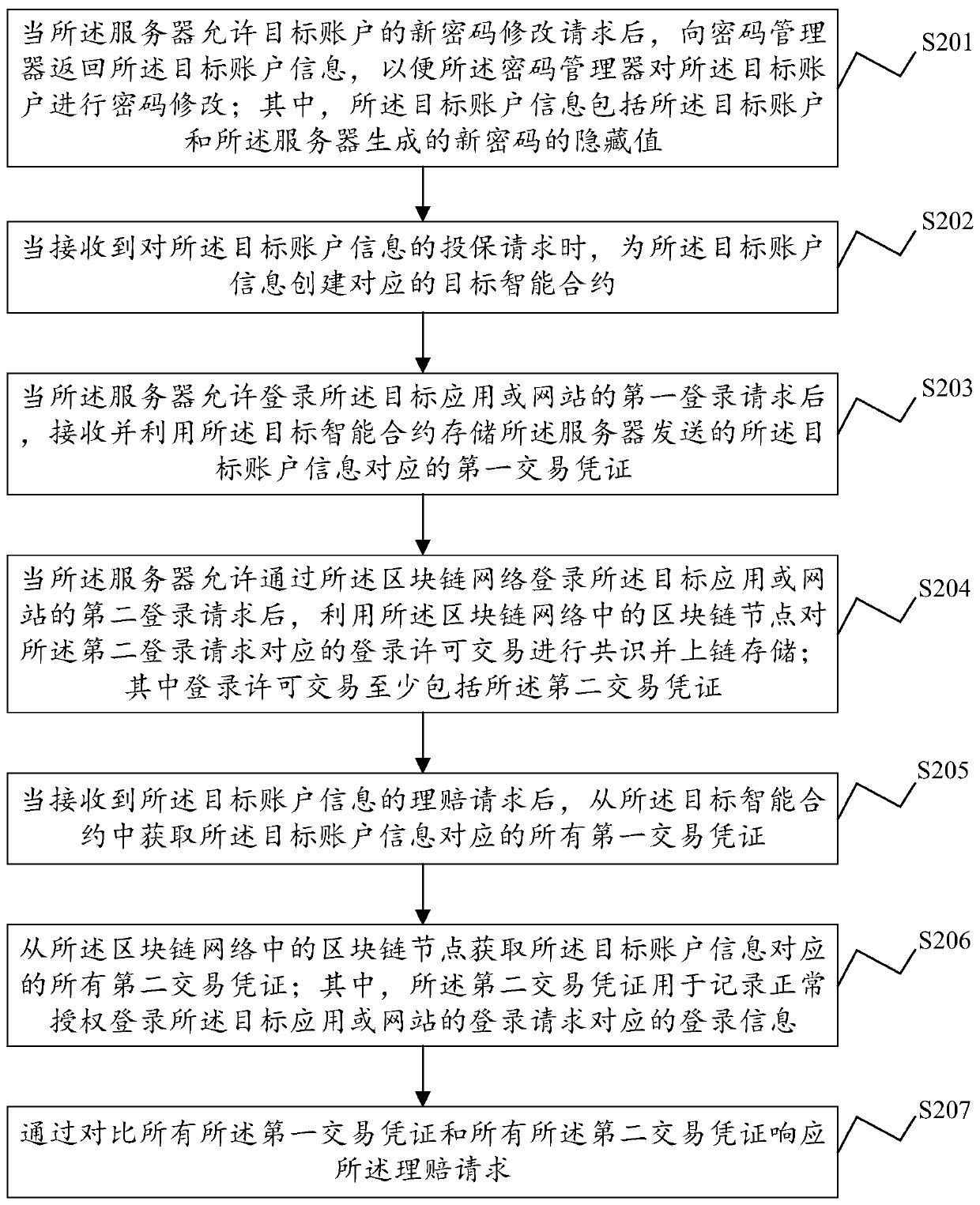
ActiveCN111353903ARealize automatic claim settlementFinanceElectronic credentialsWeb siteEngineering
The invention discloses a network identity protection method and device, electronic equipment and a computer readable storage medium, and the method comprises the steps: obtaining all first transaction certificates corresponding to target account information from an intelligent contract after a claim settlement request of the target account information is received, wherein the target account information is used for logging in a target application or website, and the first transaction certificate is used for recording login information corresponding to all login requests uploaded by a server ofthe target application or website; obtaining all second transaction certificates corresponding to the target account information from a blockchain node in the blockchain network, wherein the second transaction voucher is used for recording login information corresponding to a login request of normally authorizing to log in the target application or the website; and responding to the claim settlement request by comparing all the first transaction certificates with all the second transaction certificates. Therefore, according to the network identity protection method provided by the invention,insurance buying and automatic claim settlement are carried out on the network identity of the user.
Owner:GUANGDONG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com