Patents
Literature
172 results about "Unified Extensible Firmware Interface" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
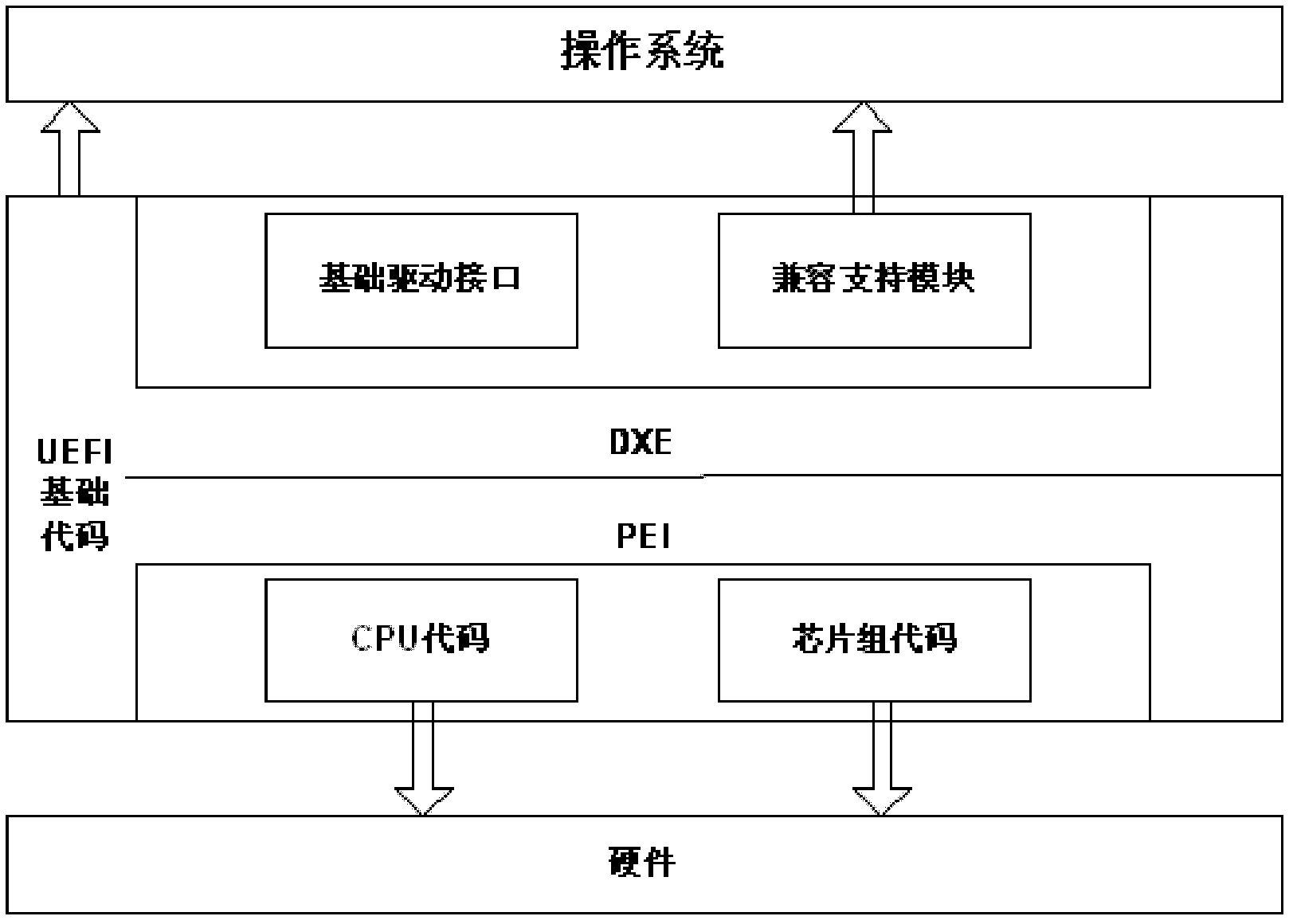
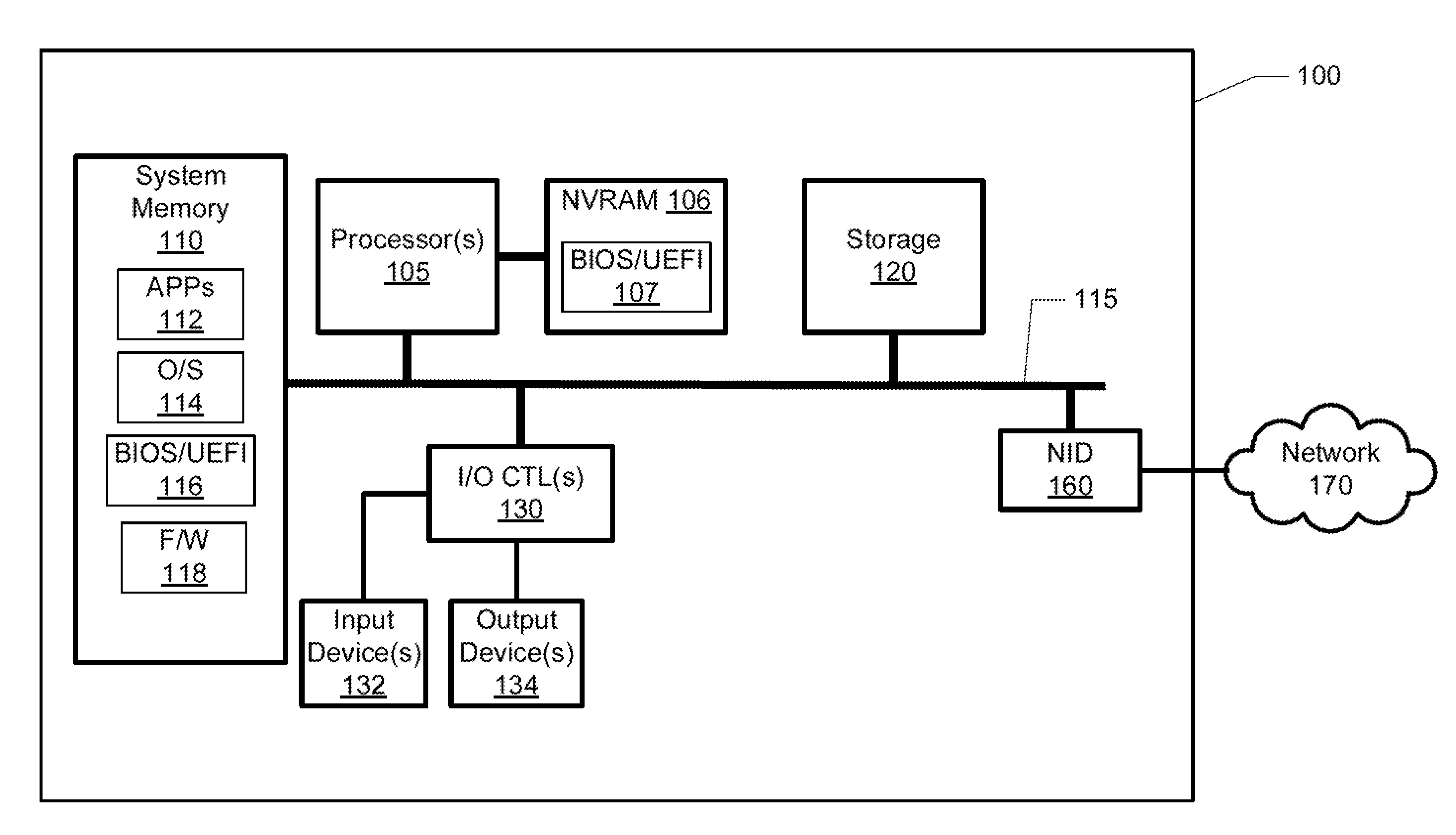
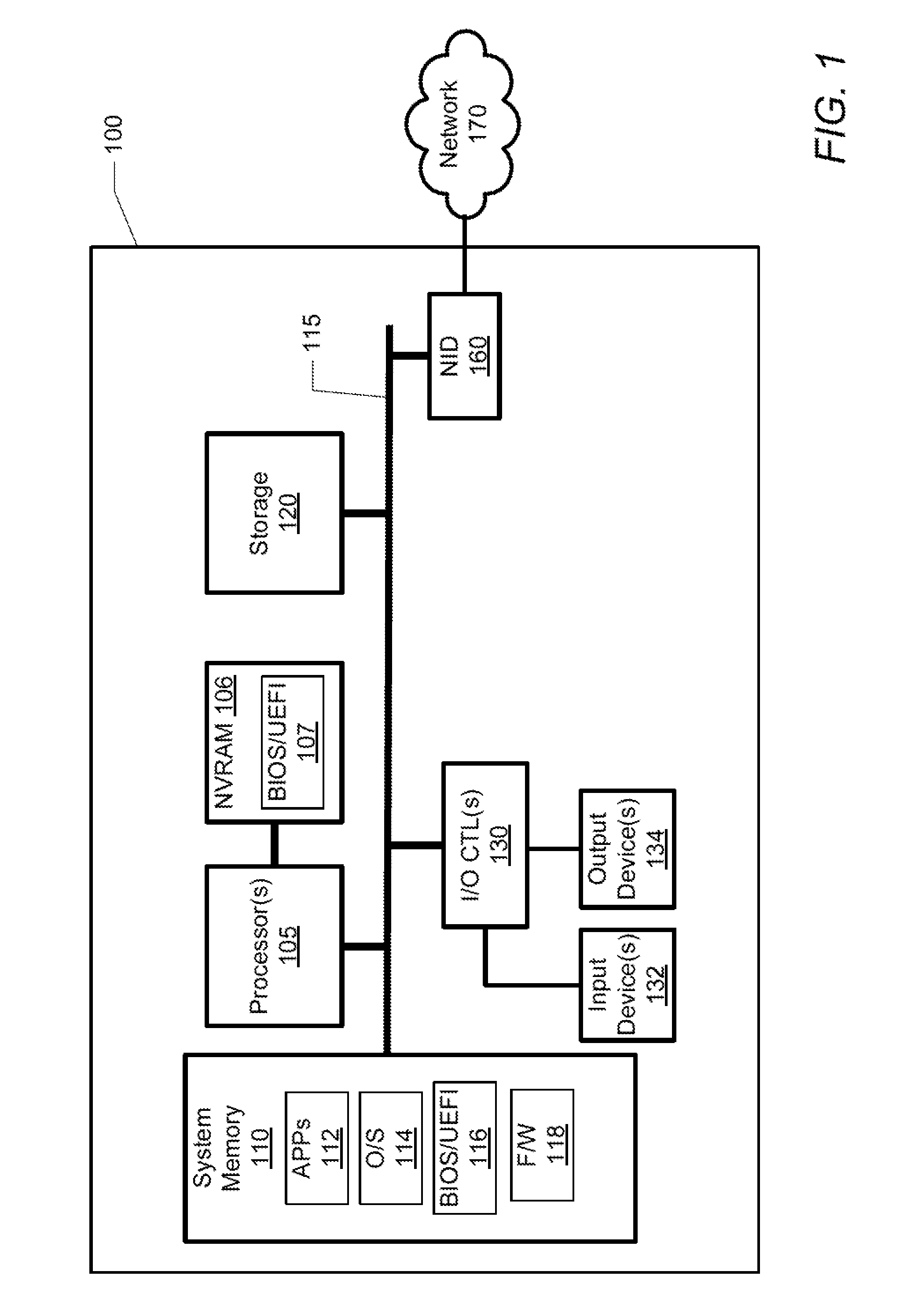
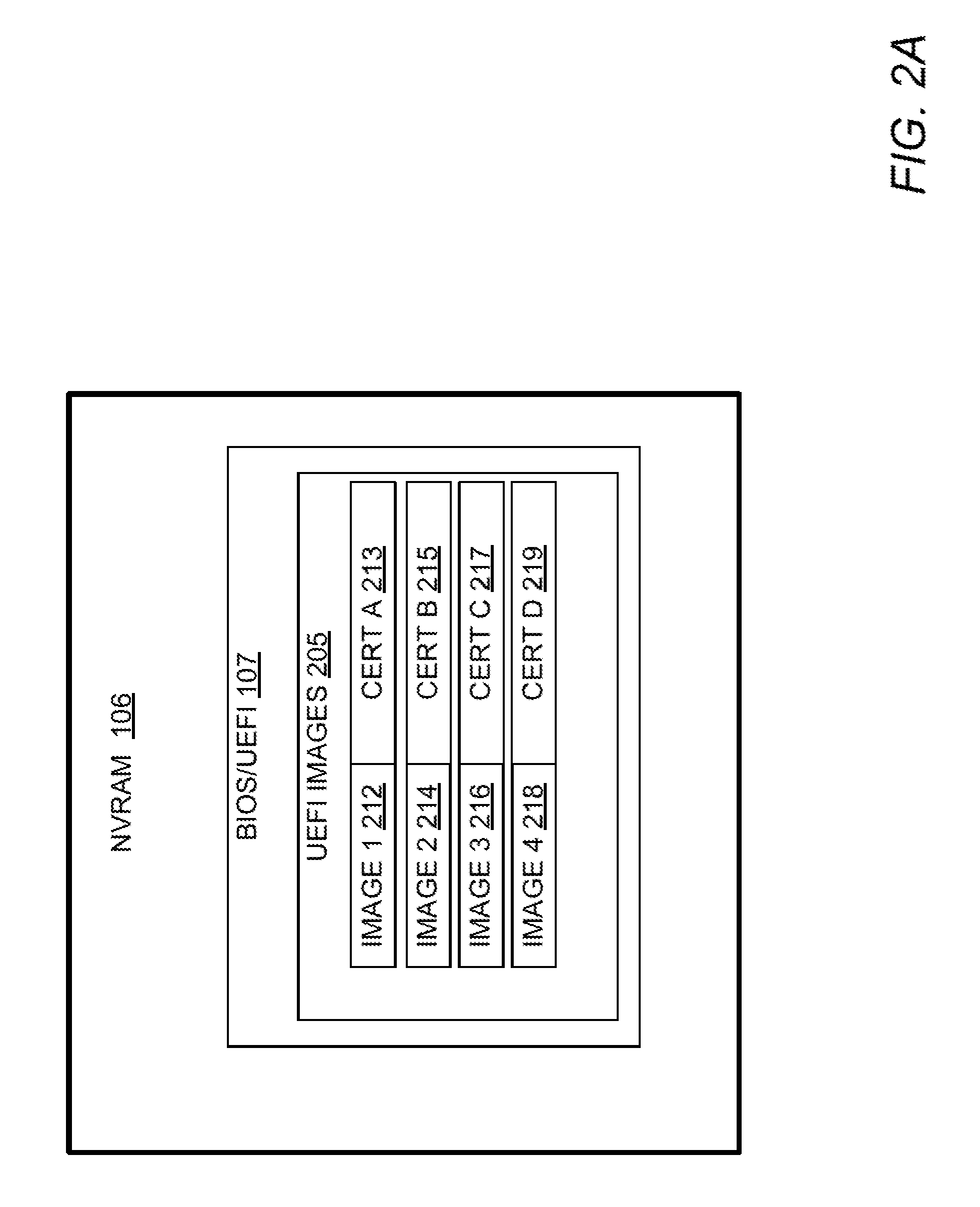
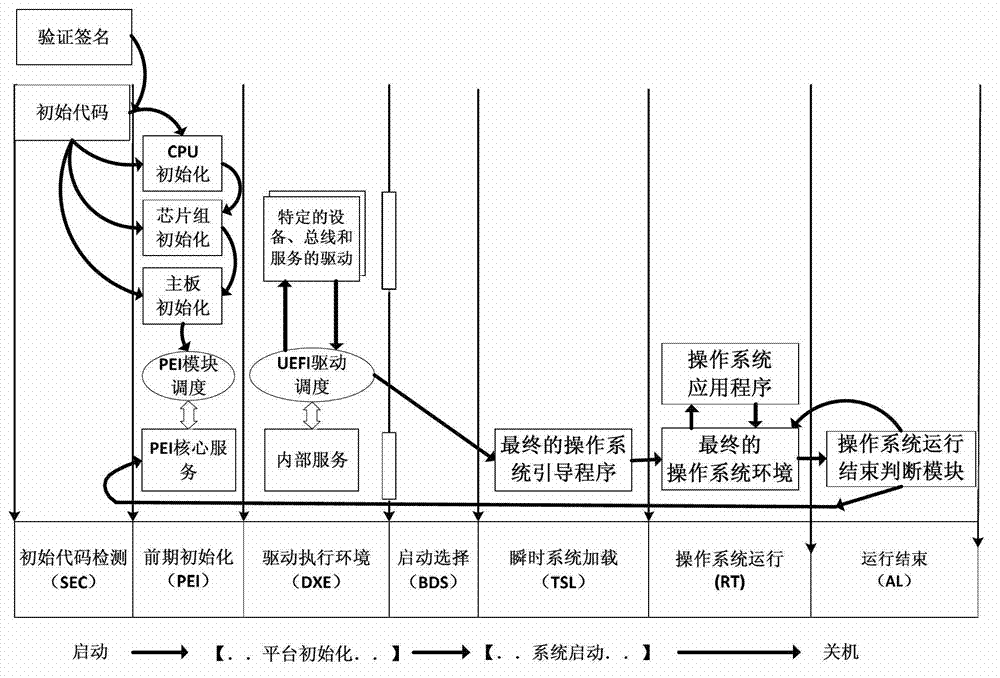
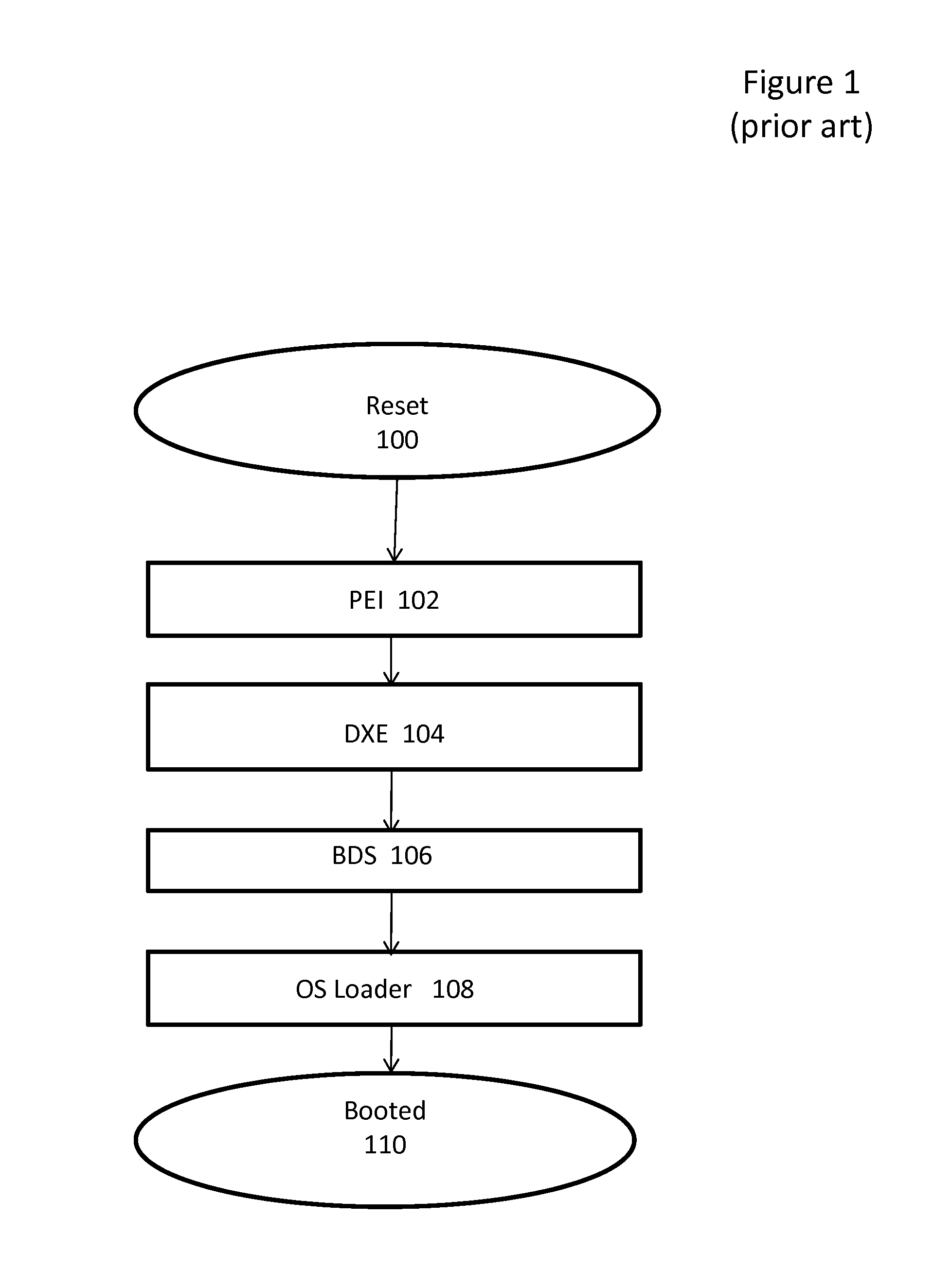
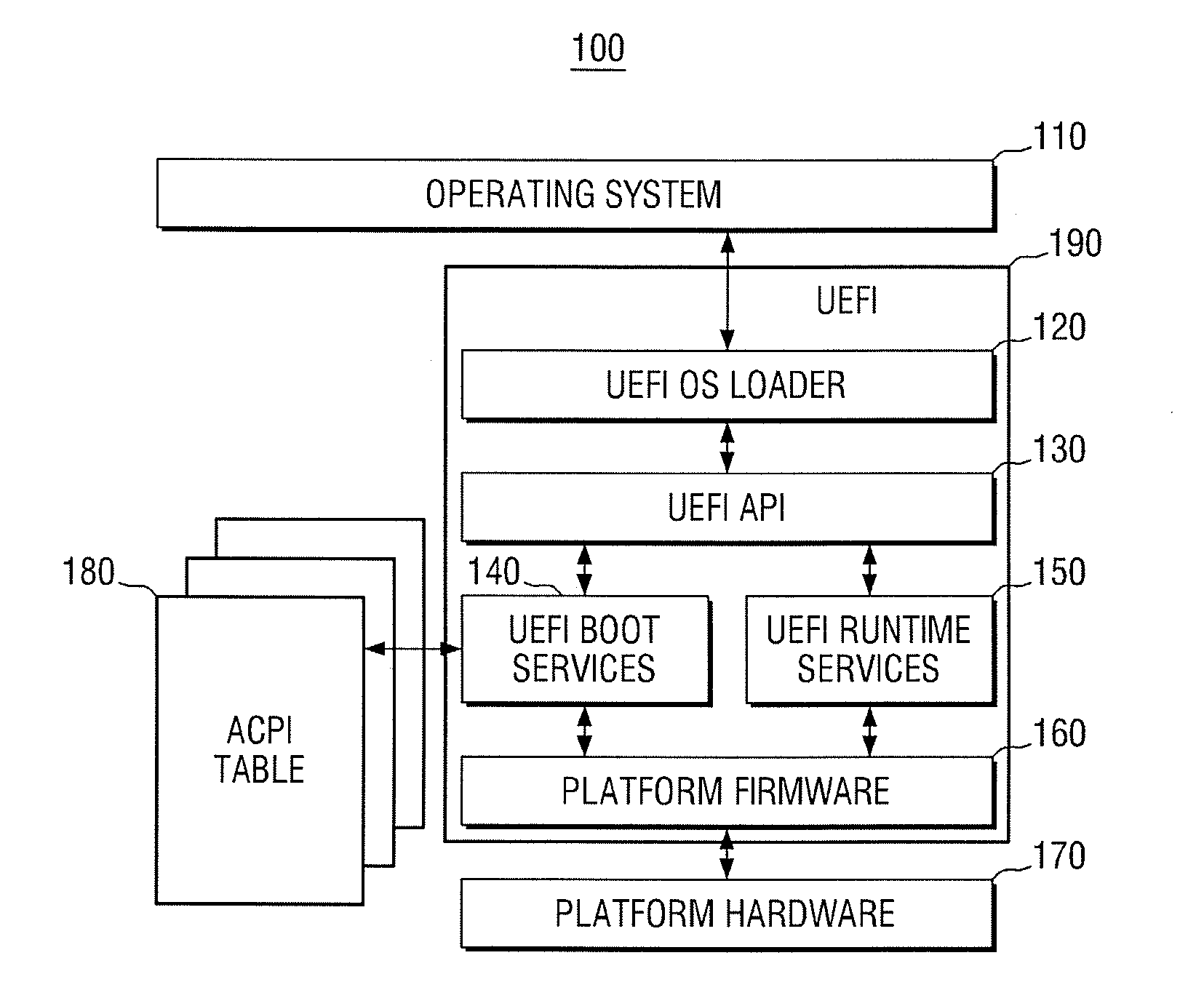
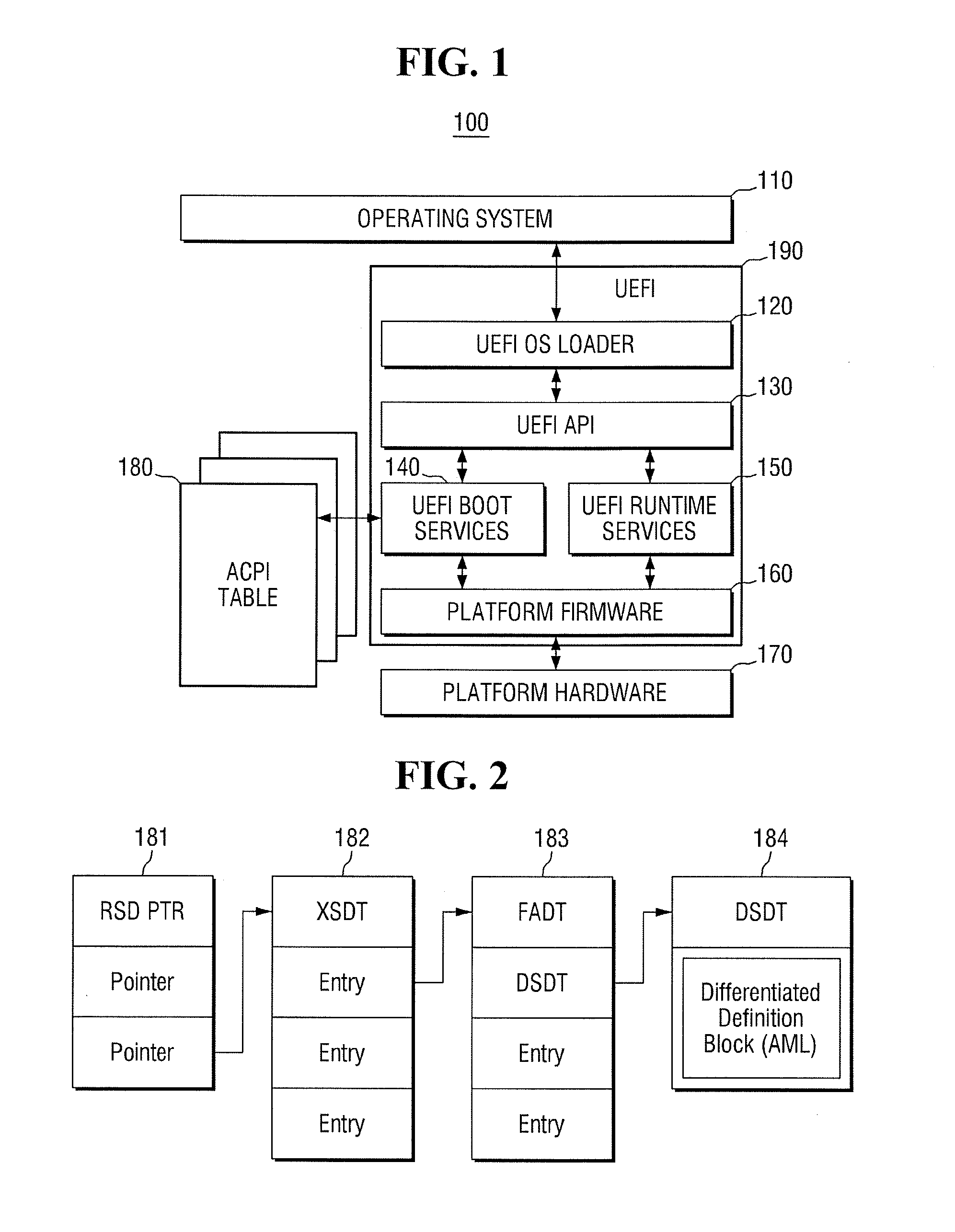
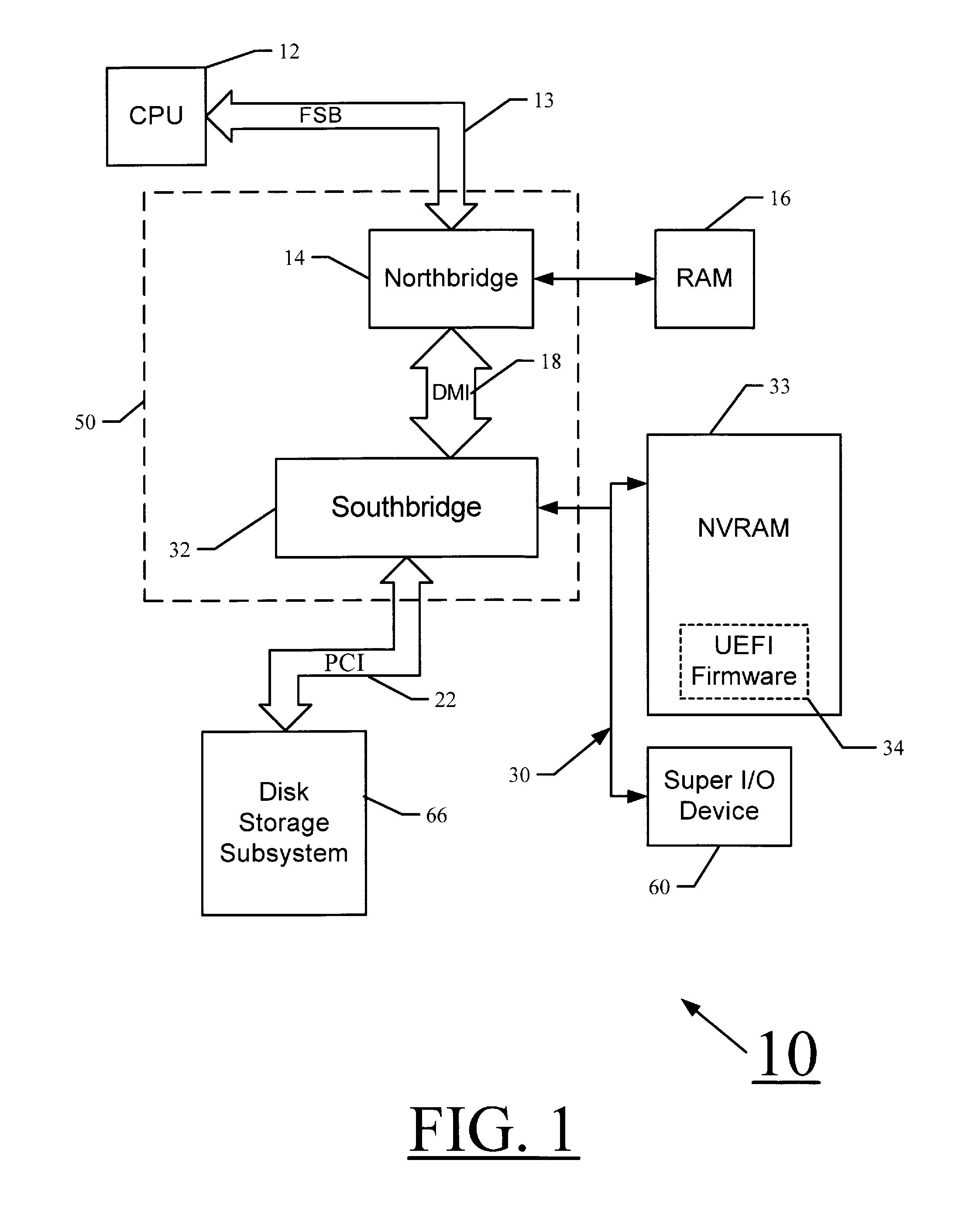
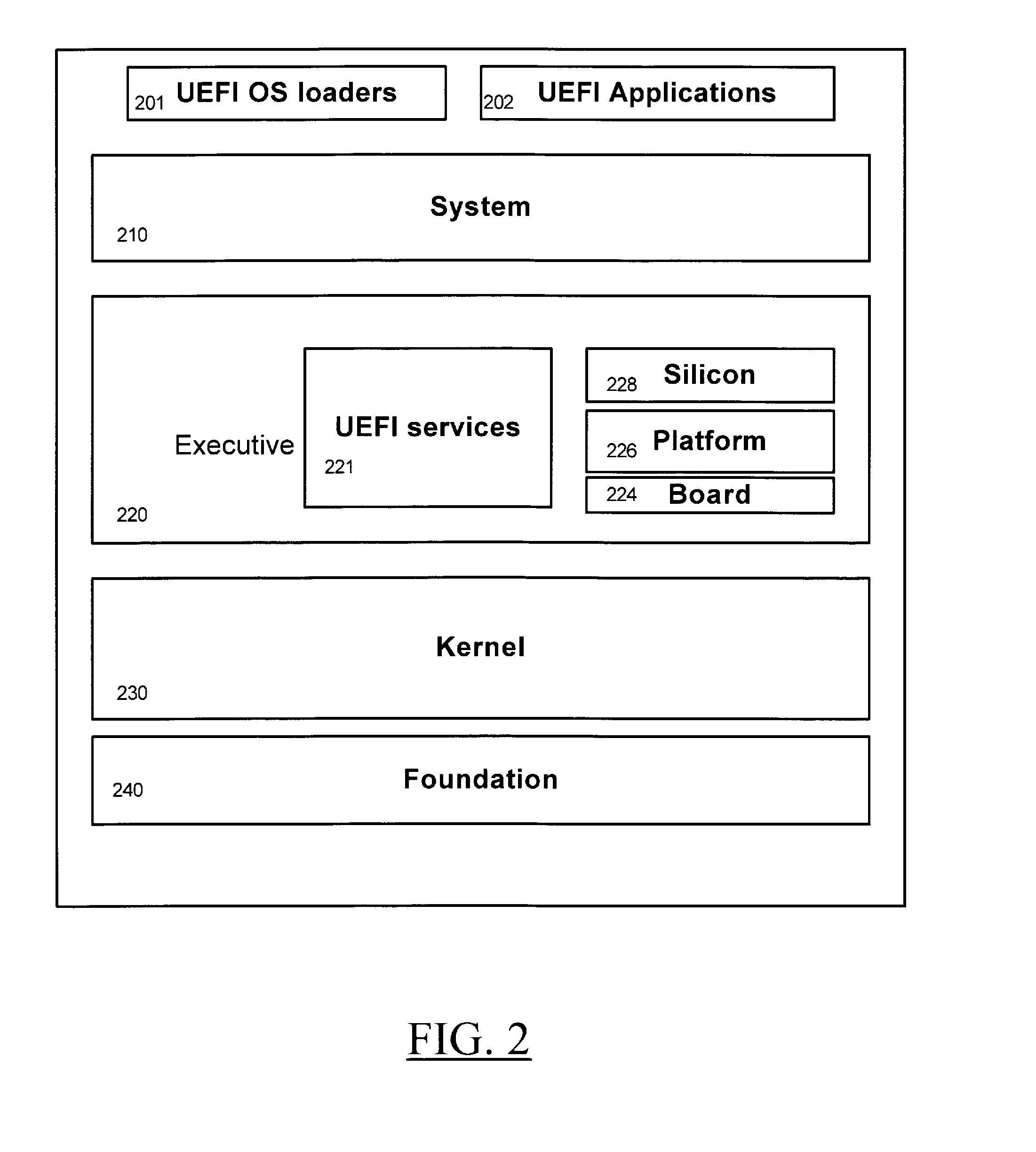
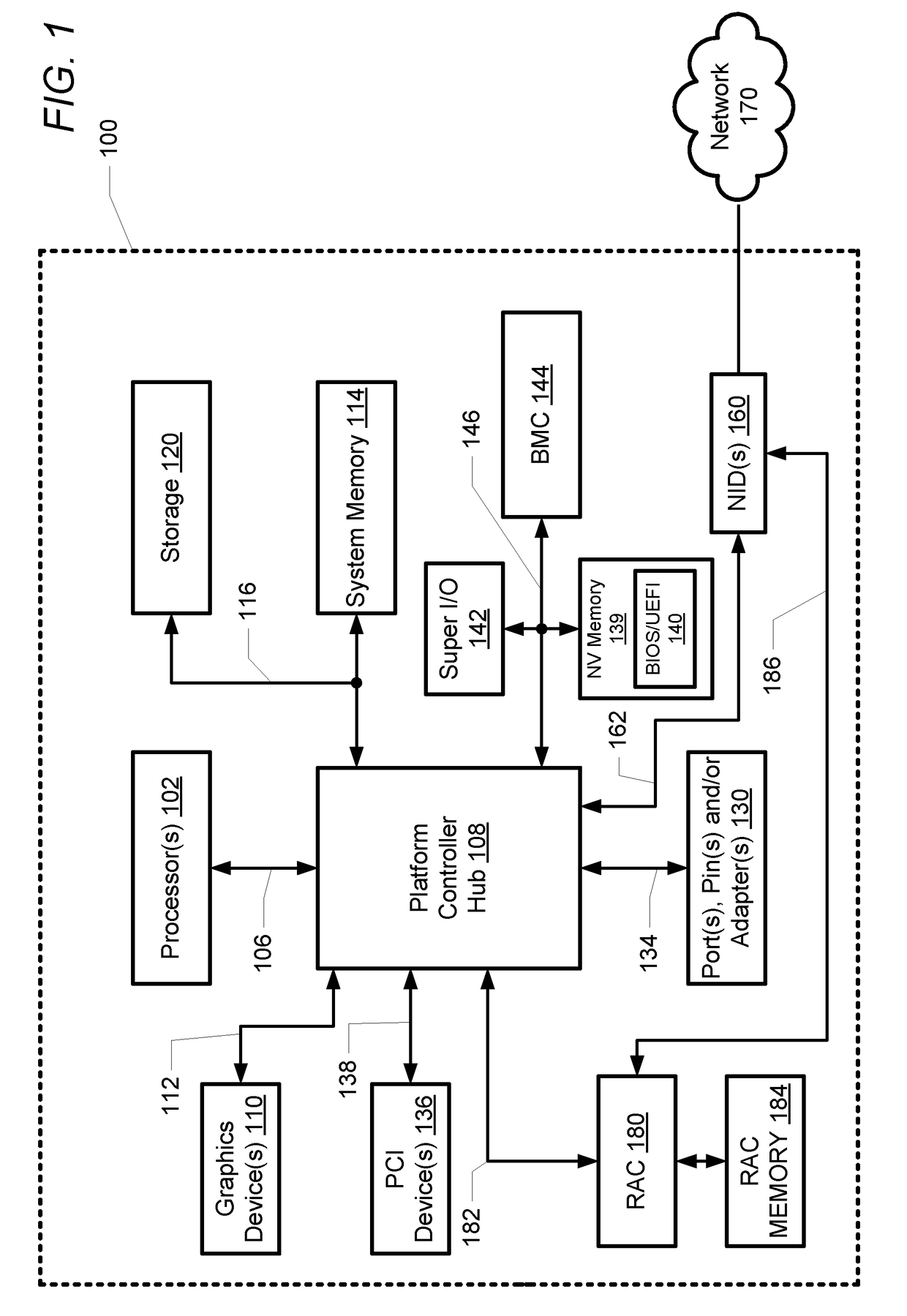
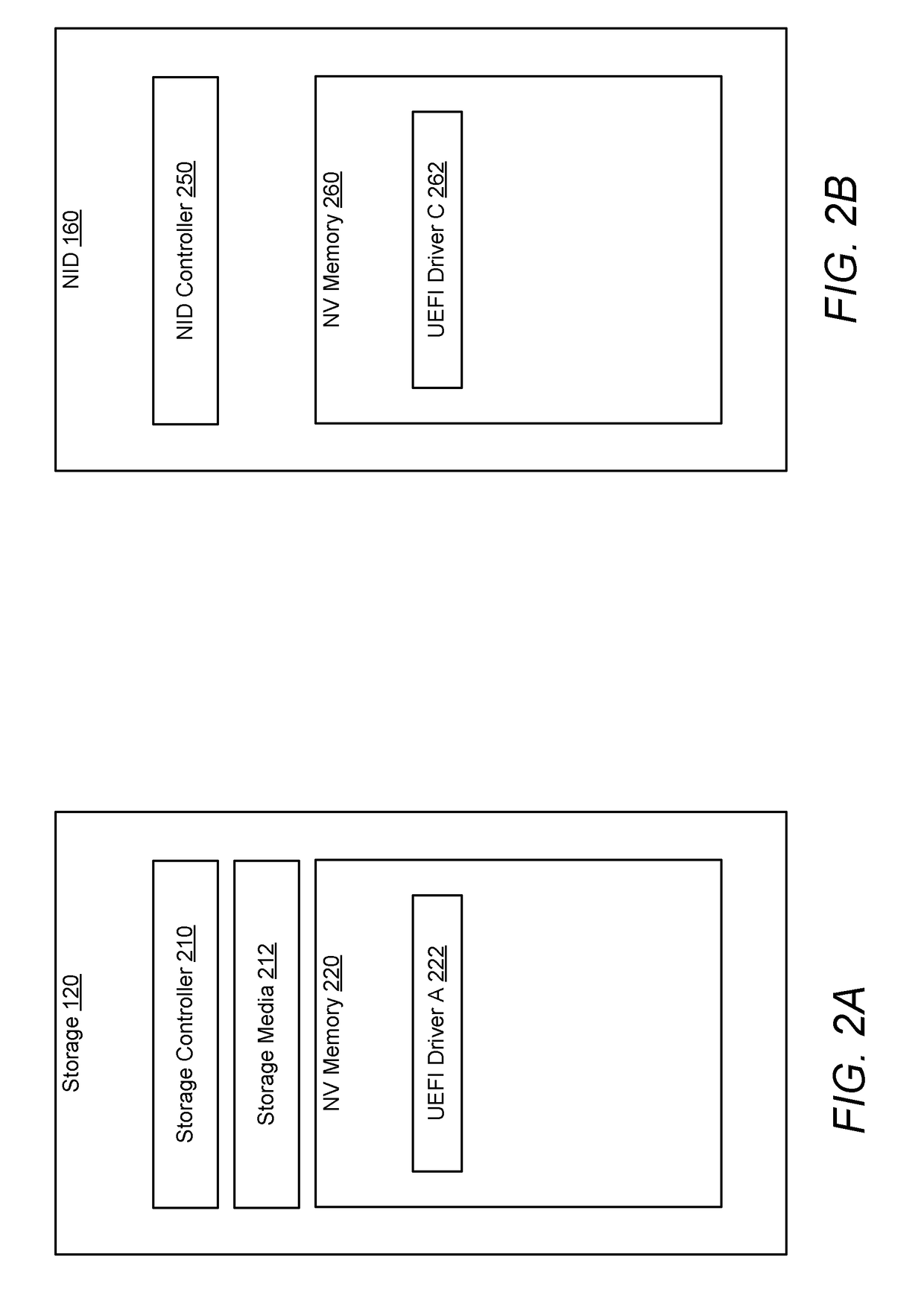
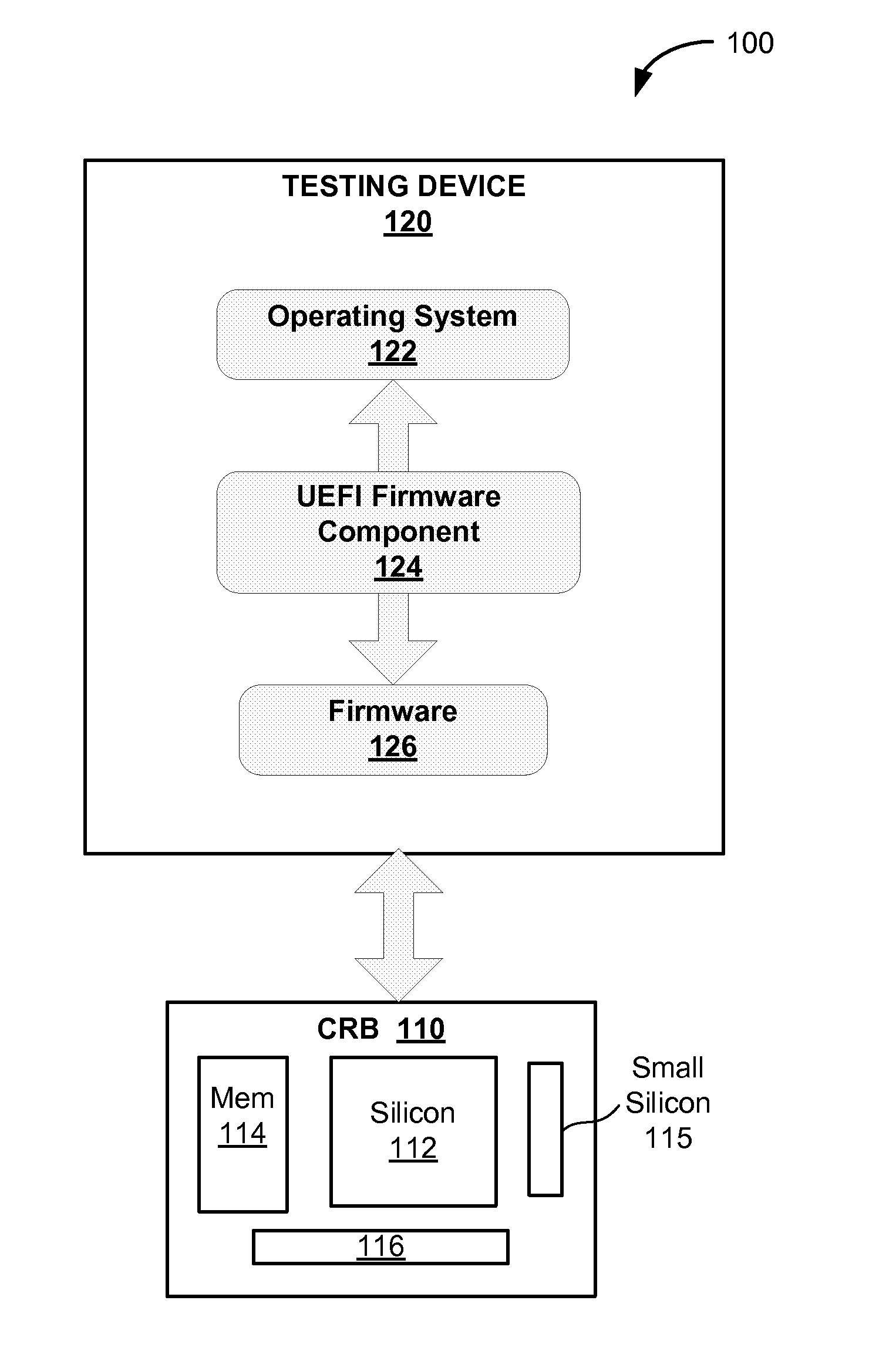
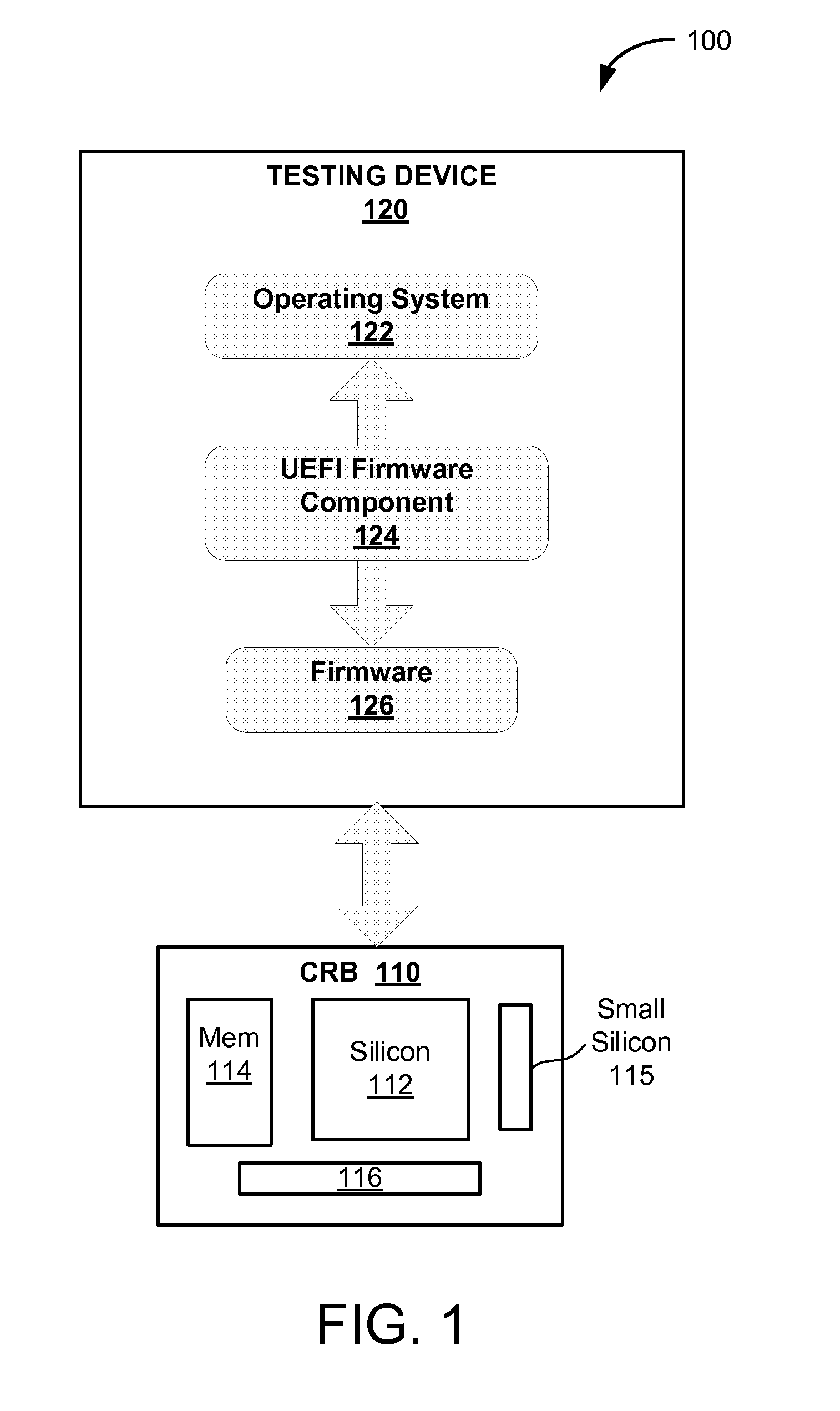
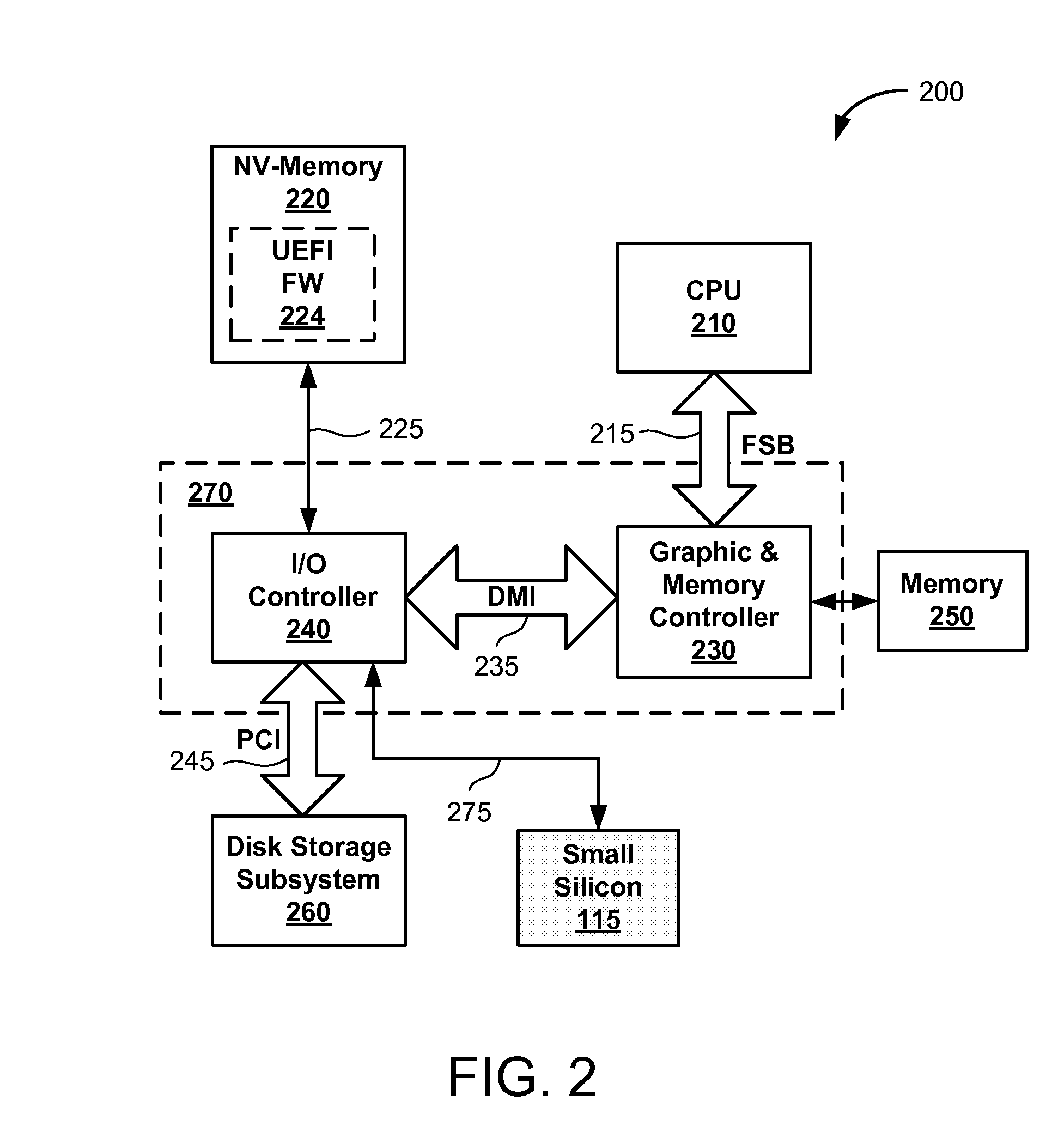
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
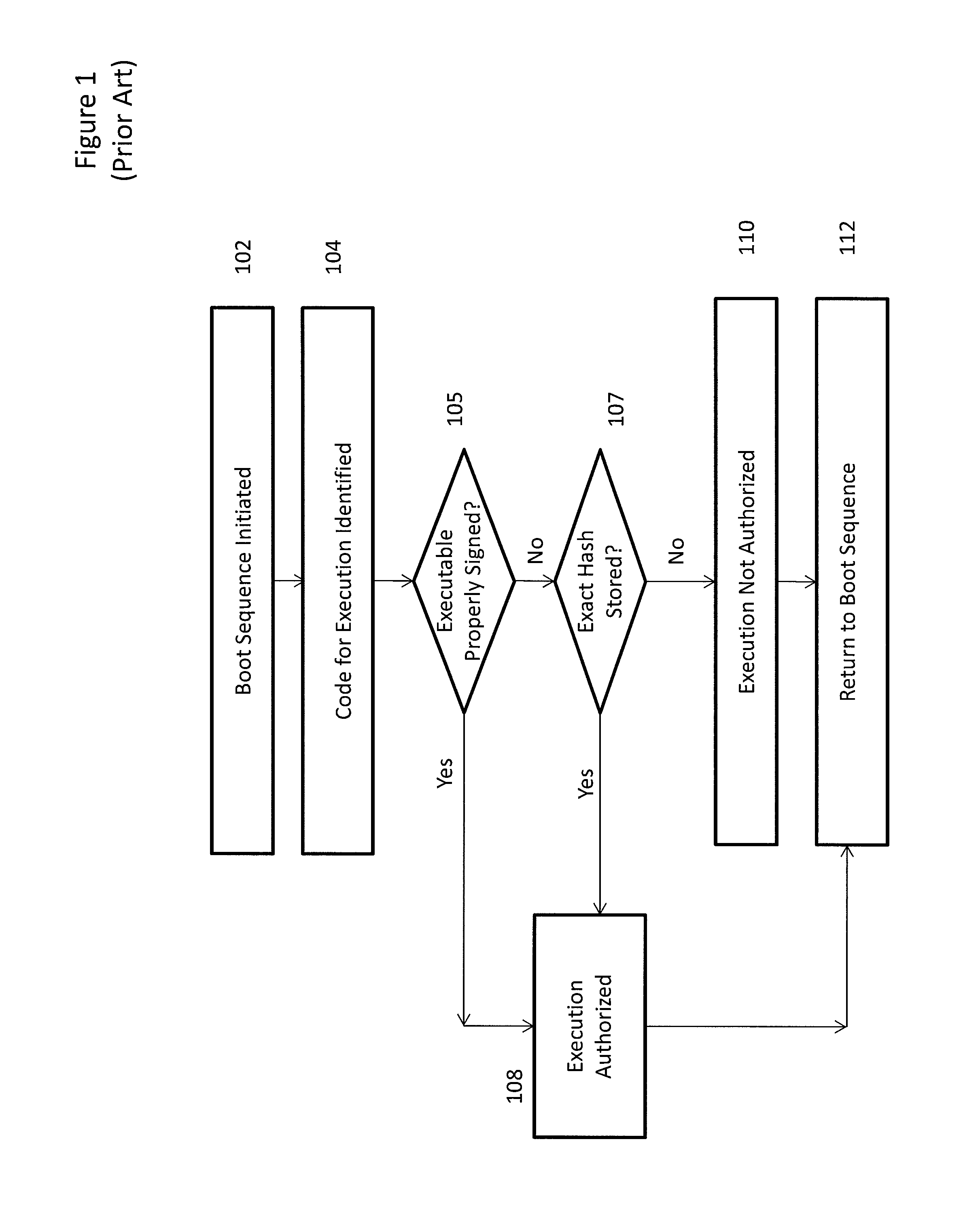
System and method to secure boot uefi firmware and uefi-aware operating systems on a mobile internet device (MID)
InactiveUS20090327741A1Digital computer detailsComputer security arrangementsTTEthernetOperational system
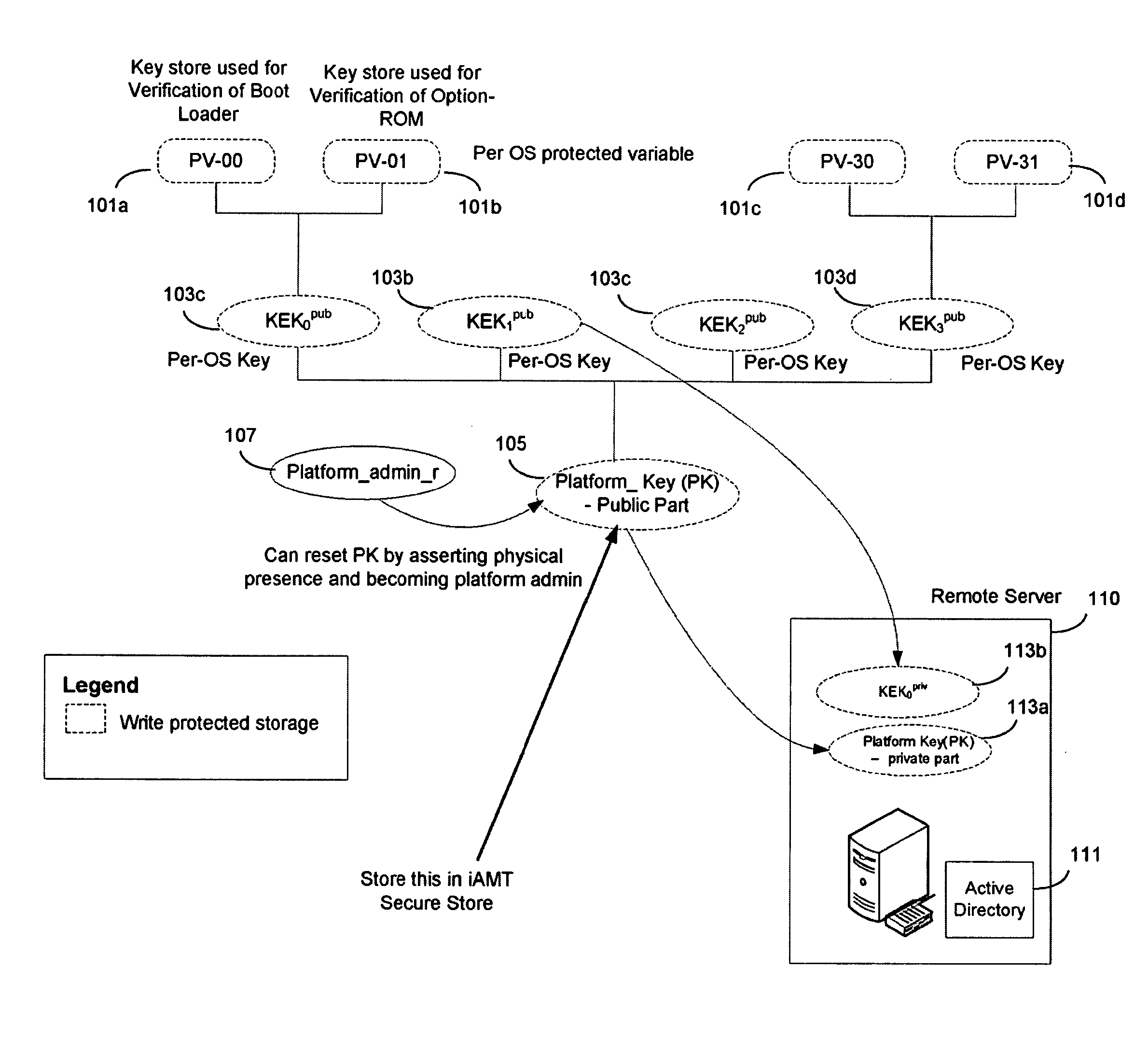
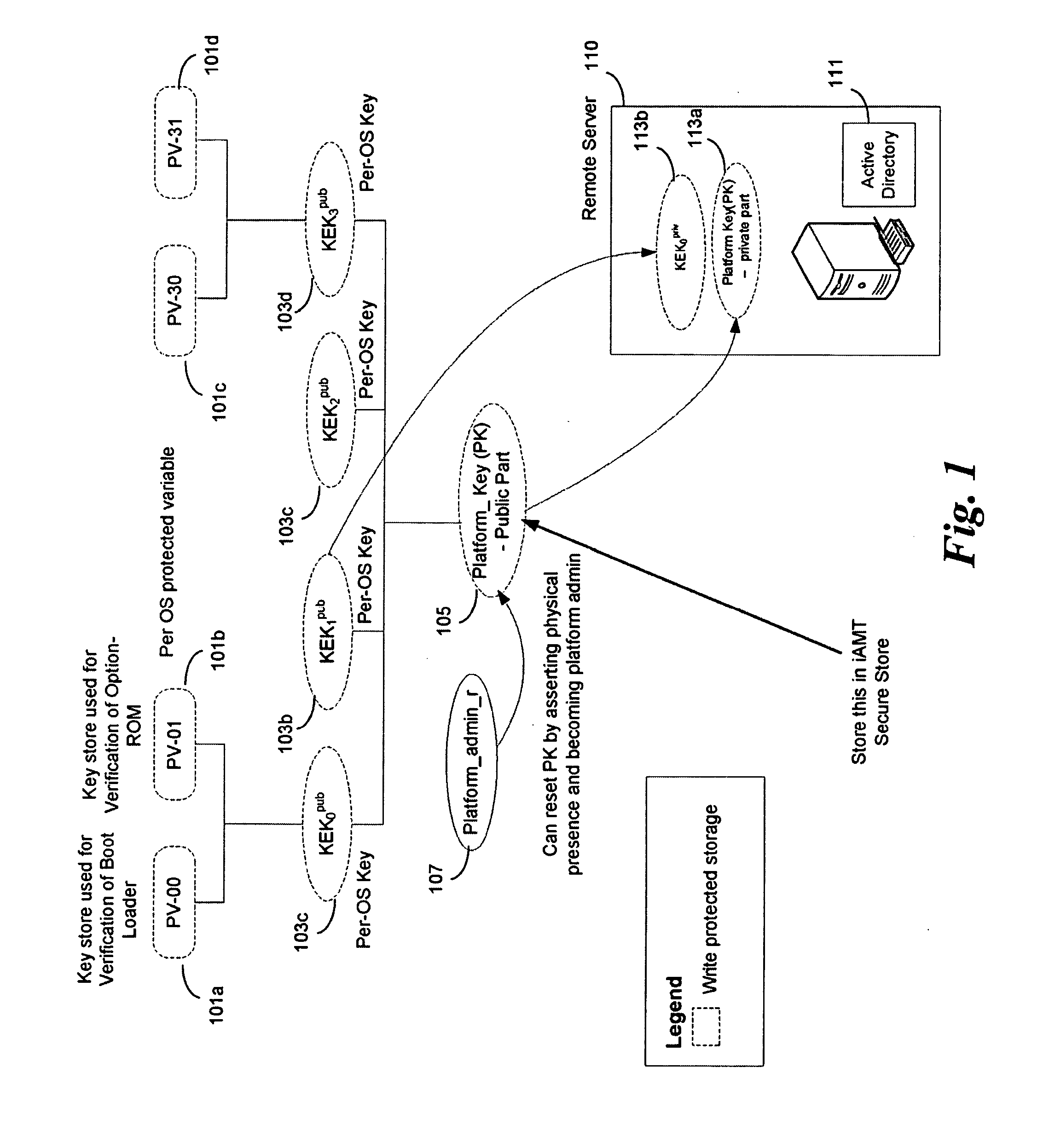
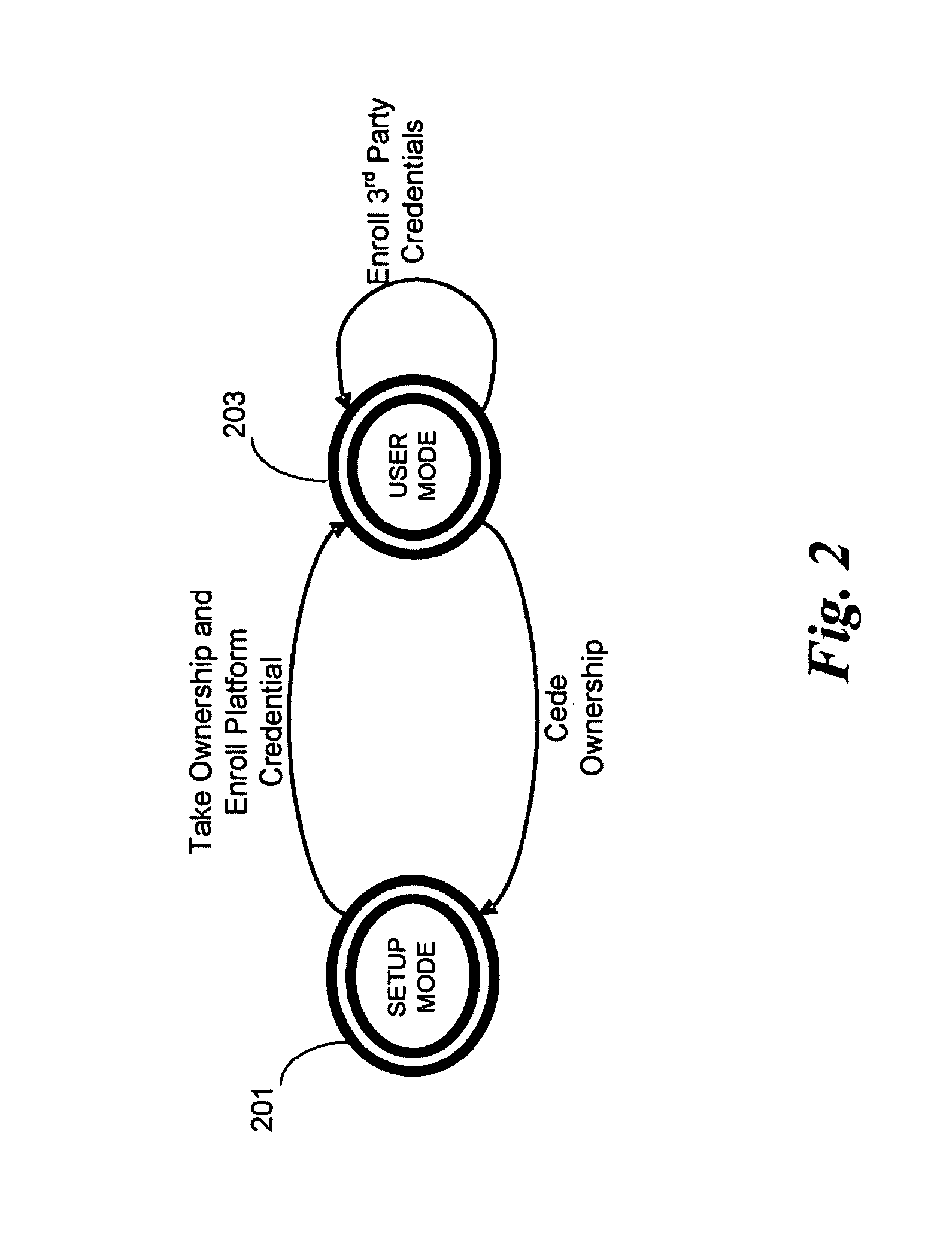
In some embodiments, the invention involves adding a capability for a platform owner or administrator to ensure that the firmware is only executed in an owner-authorized fashion, such as with signed components managed by a security processor. Embodiments may extend the Core Root of Trust for Measurement (CRTM), via use of a cryptographic unit coupled to the security processor in a mobile Internet device (MID) as a Root-of-Trust for Storage (RTS) Storage Root Key (SRK), into a unified extensible firmware interface (UEFI) Platform Initialization (PI) image authorization and boot manager. Other embodiments are described and claimed.
Owner:INTEL CORP
A UEFI trusted support system and control method thereof
InactiveCN102279914AReduce data volumeSimplify complexityPlatform integrity maintainanceSoftwareBackup
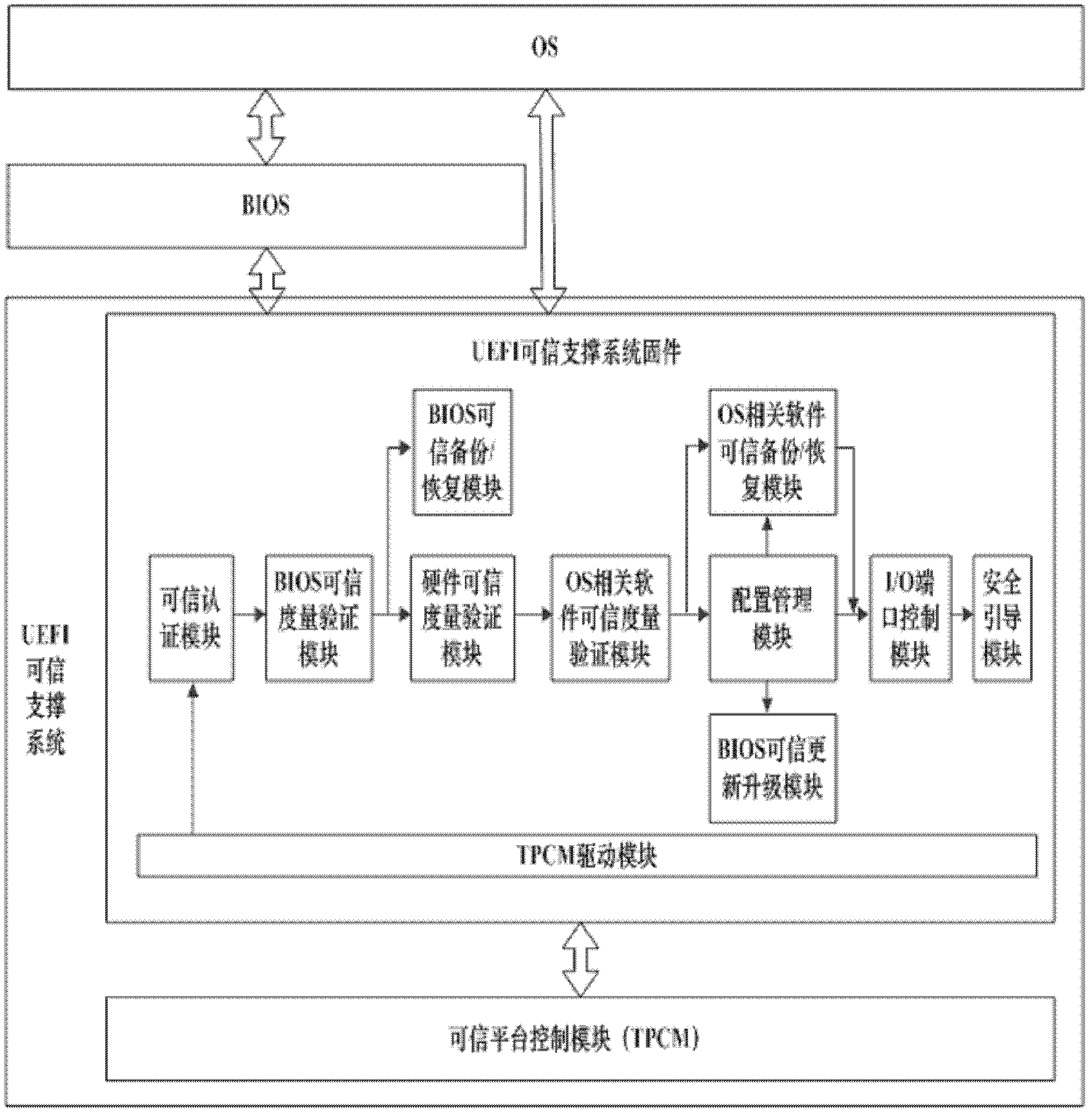
The invention discloses a unified extensible firmware interface (UEFI) trusted supporting system and a method for controlling the same. The UEFI trusted supporting system comprises UEFI trusted supporting system firmware and a trusted platform control module (TPCM), wherein the UEFI trusted supporting system firmware is stored on a nonvolatile memory and connected with the TPCM by a system bus; and the TPCM is connected with a trusted computation platform by the system bus. The method for controlling the UEFI trusted supporting system comprises the following steps of: firstly, loading a driver for the TPCM; secondly, sequentially authenticating the identity of users, performing measurement validation on a basis input / output system (BIOS), the characteristic data of hardware and a master boot record (MBR) / operating system (OS) Loader / OS Kernel, controlling different hardware peripheral interfaces according to an I / O strategy of the users, and performing safety guide setting on the system by a safety guide module; and finally, controlling by the BIOS or the OS. By the system and the method, trusted computation, the configuration management of the TPCM, the backup / recovery of the BIOS / MBR / OS Loader / OS Kernel and the physical protection of key data are realized on a firmware layer. The invention can be simultaneously applied to a Linux system which opens source codes and a Windows system which does not open the source codes, so that a fault does not occur in a trust chain between BIOS firmware and OS software, and the safety of a computer and the friendliness of human-computer interaction are improved.
Owner:中国人民解放军海军计算技术研究所 +1
Computer security access control system and method
InactiveCN101986325AImplement secure storage protectionLow costDigital data authenticationOperational systemControl system
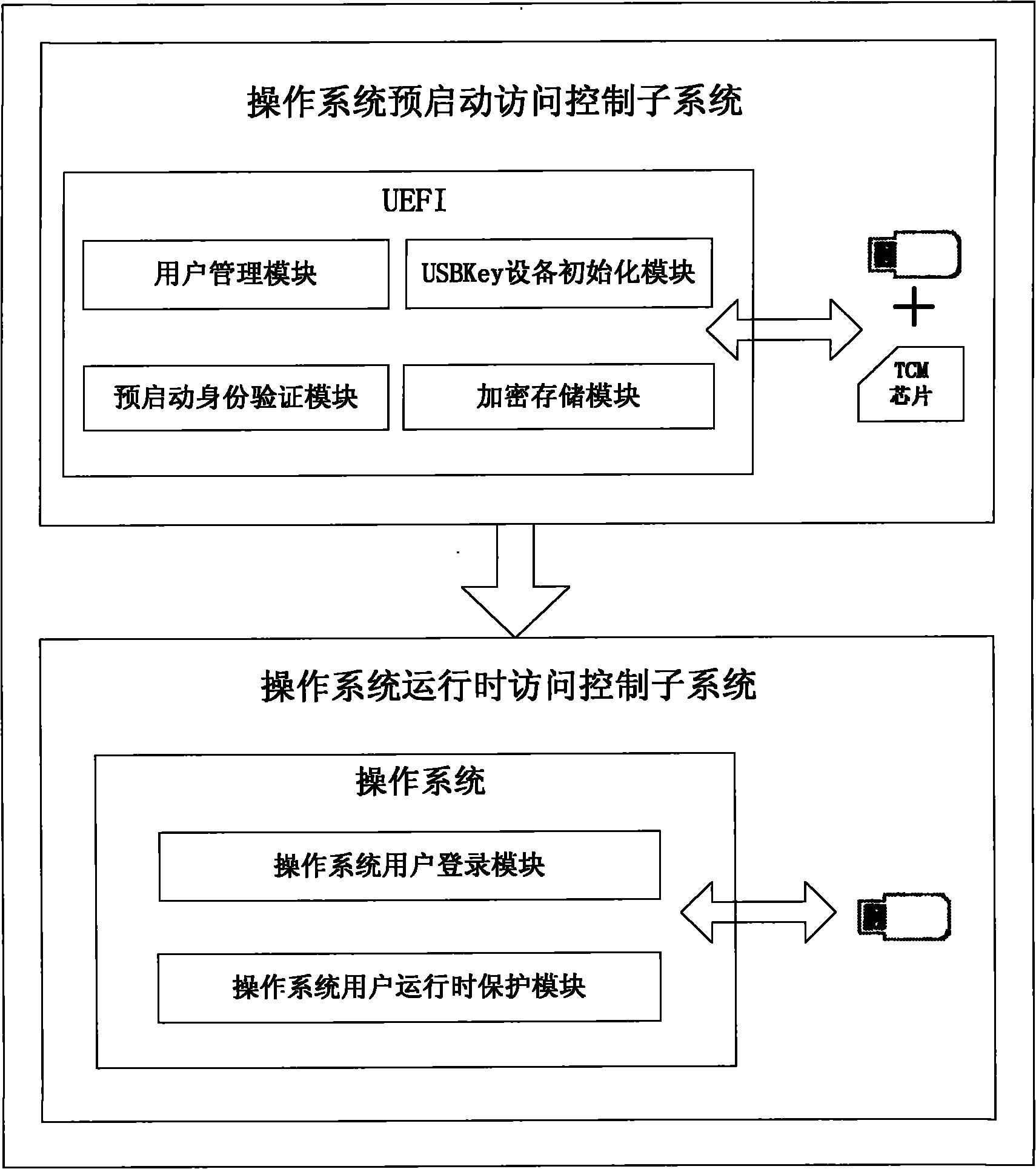
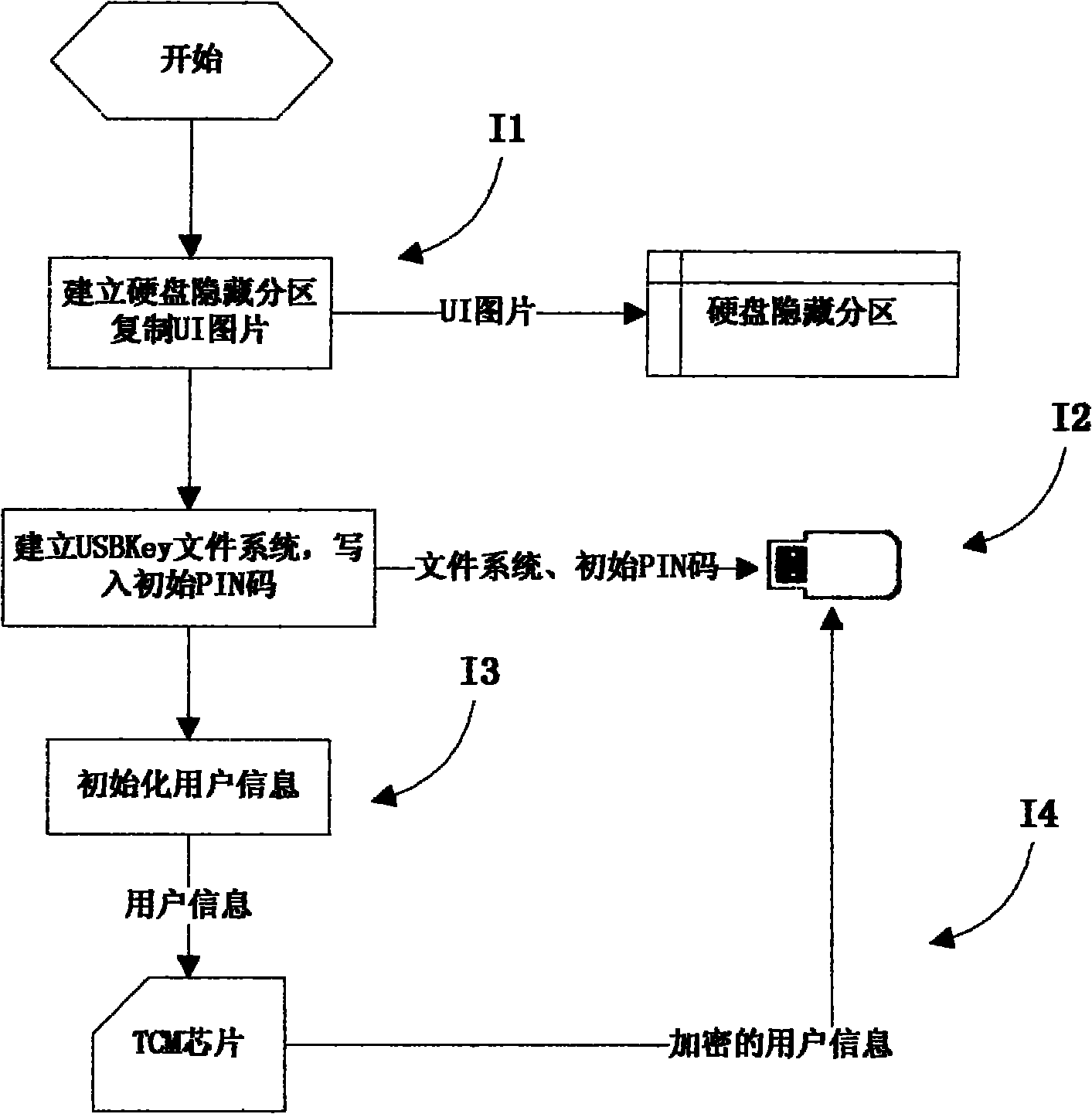
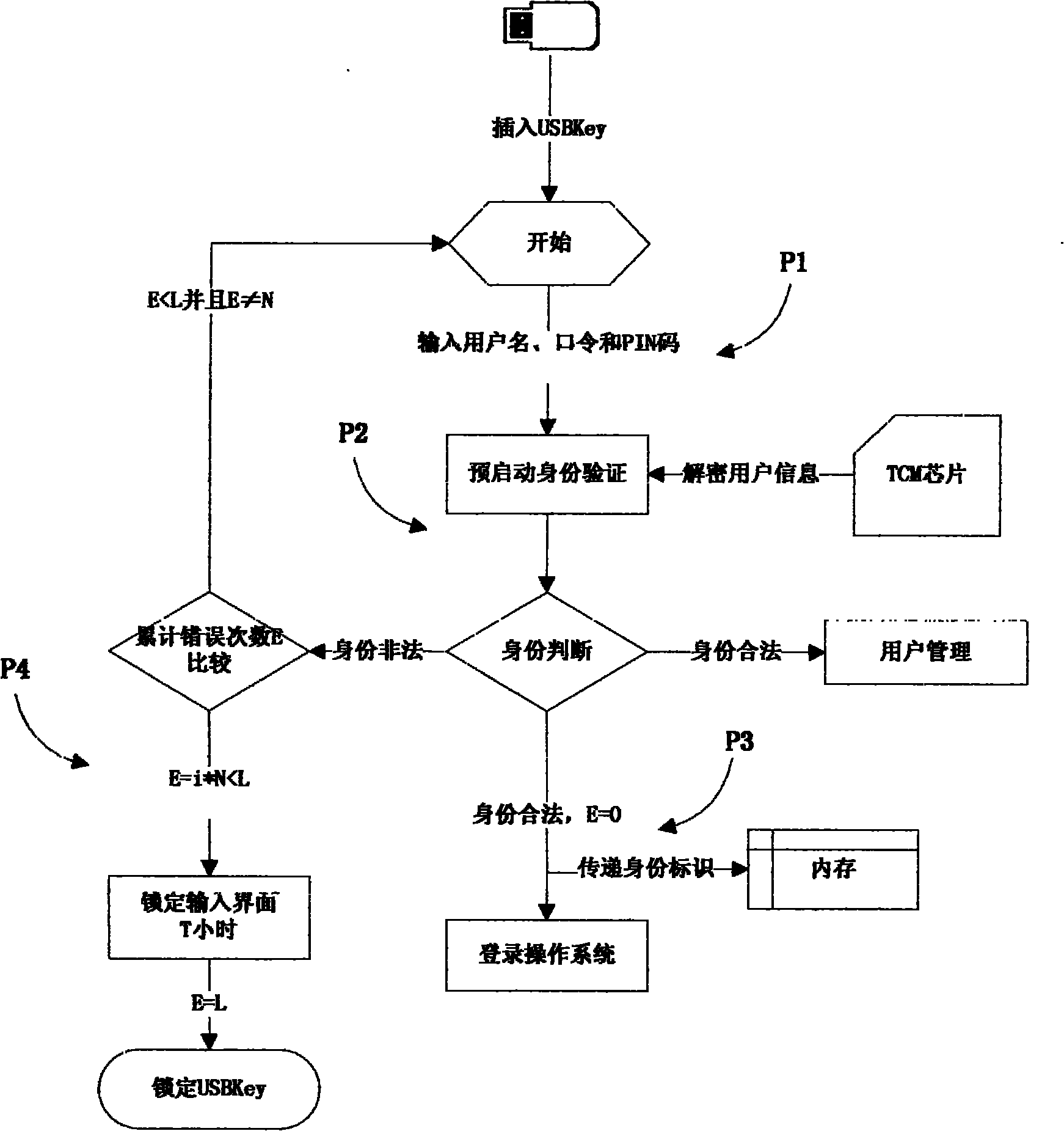
The invention discloses a computer security access control system and a computer security access control method, and belongs to the technical field of information security. A unified extensible firmware interface (UEFI) chip and a transmission control module (TCM) chip are included; a control system comprises an operating system pre-booting access control subsystem and an operating system running access control subsystem, wherein the operating system pre-booting access control subsystem comprises USBKey equipment, a USBkey equipment initialization module, a user management module, an operating system pre-booting identity authentication module and an encryption storage module; and the operating system running access control subsystem comprises USBKey equipment, an operating system user logon module, and an operating system user running protection module. The control method comprises an initialization method, an operating system pre-booting access control method and an operating system running access control method. The invention solves the problems that in the operating system, the reliability of access control is low, user identity information storage is insecure, and identity protection is insufficient in the running process after a user with legal identity logs on.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
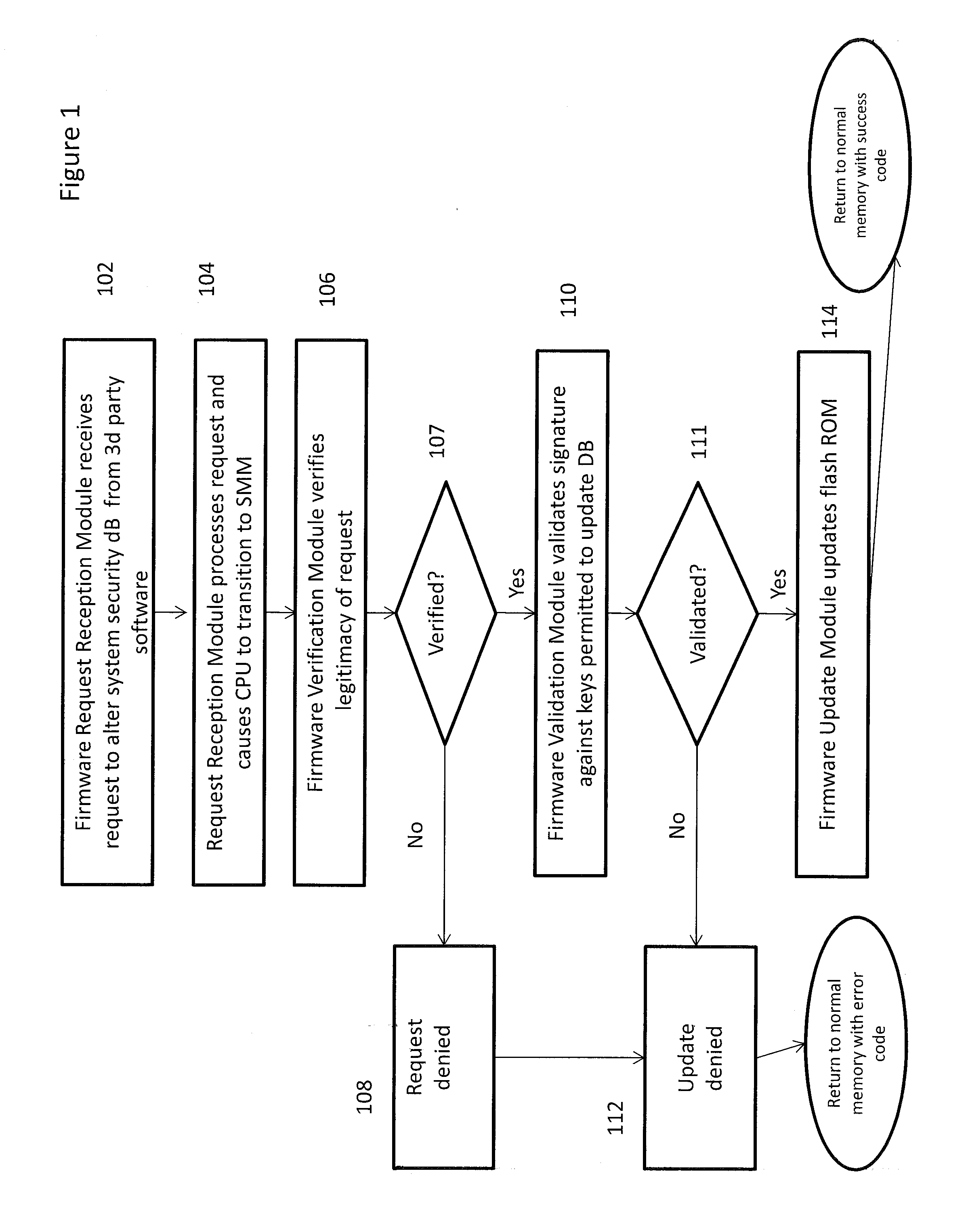
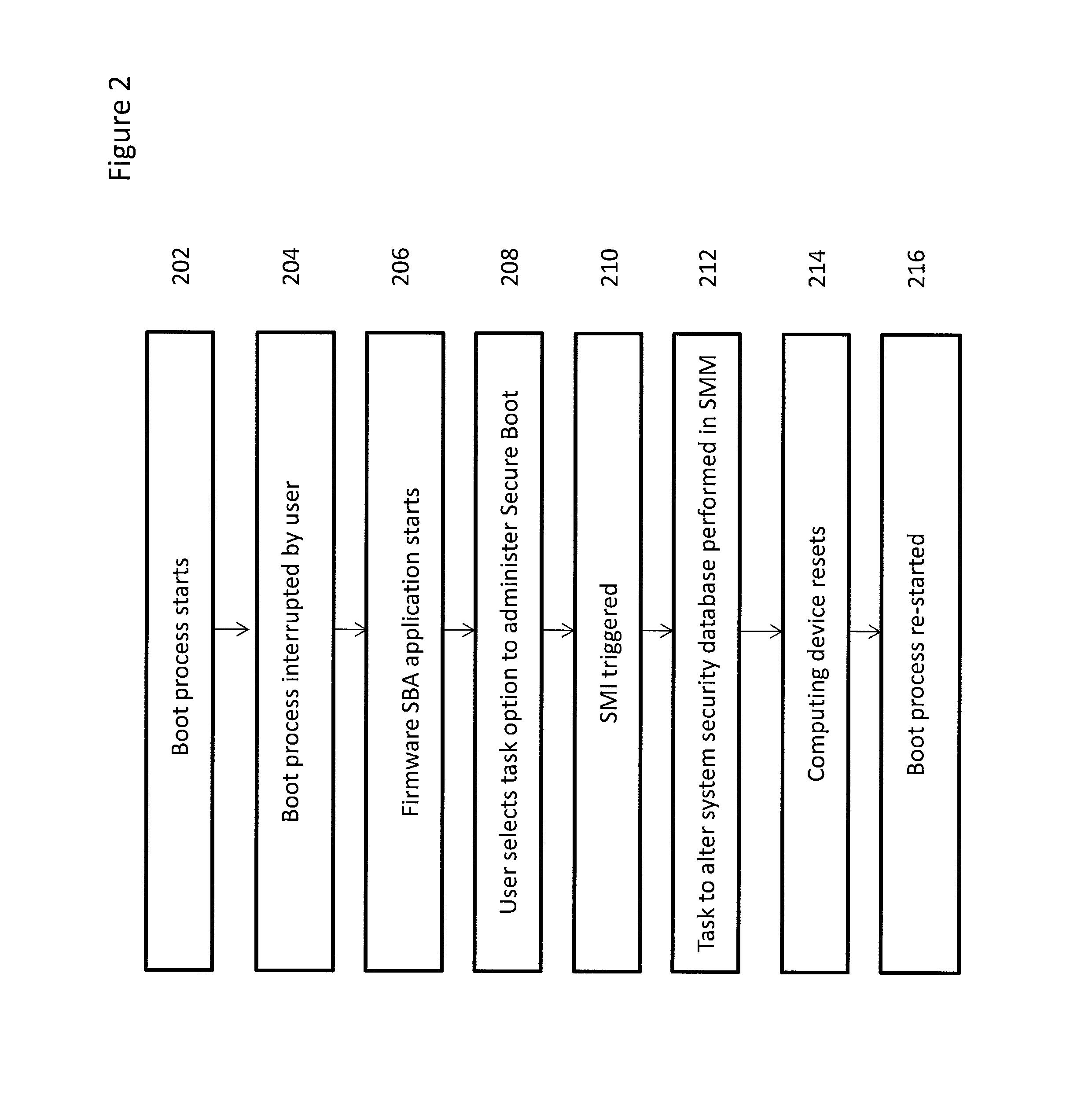
System and method for processing requests to alter system security databases and firmware stores in a unified extensible firmware interface-compliant computing device
ActiveUS20120260082A1Prevent unauthorized modificationDifficult to performData resettingComputer security arrangementsProtection systemDatabase preservation
A mechanism for allowing firmware in a UEFI-compliant device to implement the UEFI specification driver signing and Authenticated Variable elements while at the same time protecting the system security database holding the library of approved keys and lists of allowed and forbidden programs from unauthorized modifications is discussed.
Owner:INSYDE SOFTWARE
Method for optimizing boot time of an information handling system
ActiveUS20160180094A1BootstrappingPlatform integrity maintainanceHandling systemInformation handling system
A method and information handling system (IHS) that optimizes boot time. The method includes a basic input output system (BIOS) performing an authentication check of drivers during an initial boot process. The results of the authentication check are stored along with an unified extensible firmware interface (UEFI) image for each driver in an authentication results data structure (ARDS). In response to receipt of a subsequent request to enable a secure boot of the IHS, when the initial boot process was performed with the secure boot disabled, the ARDS is accessed to determine if any of the drivers failed the authentication check. When none of the drivers have failed the authentication check, the boot process is continued using the UEFI images of the drivers. When at least one of the drivers has failed its authentication check, a notification is output indicating a failure of the authentication check.
Owner:DELL PROD LP
UEFI and BIOS (unified extensible firmware interface and basic input output system) rapidly and safely starting method capable of being dynamically adjusted as requirements
ActiveCN103034510AOptimize timingImprove driving abilityComputer security arrangementsProgram loading/initiatingOperational systemApplication software
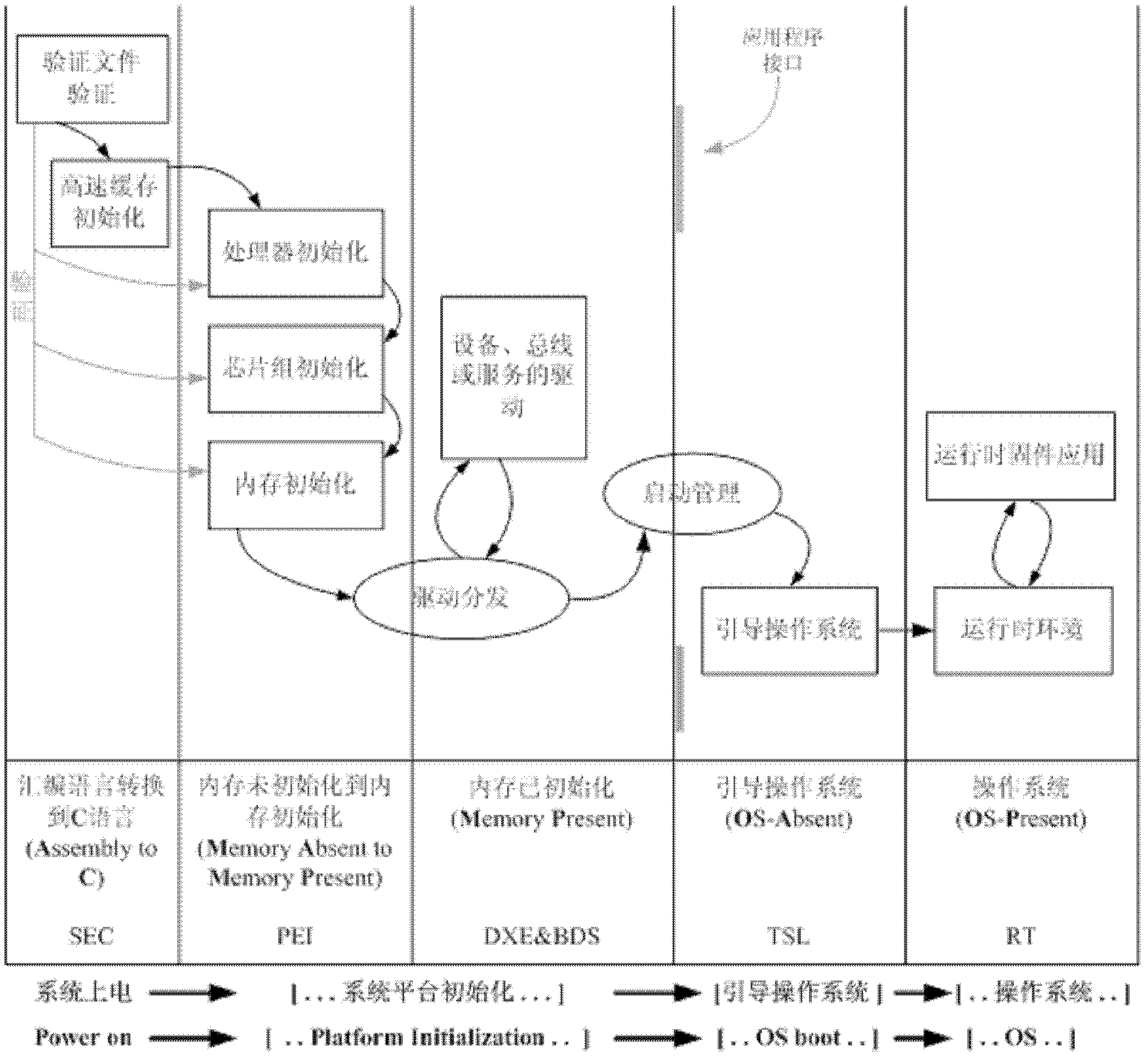
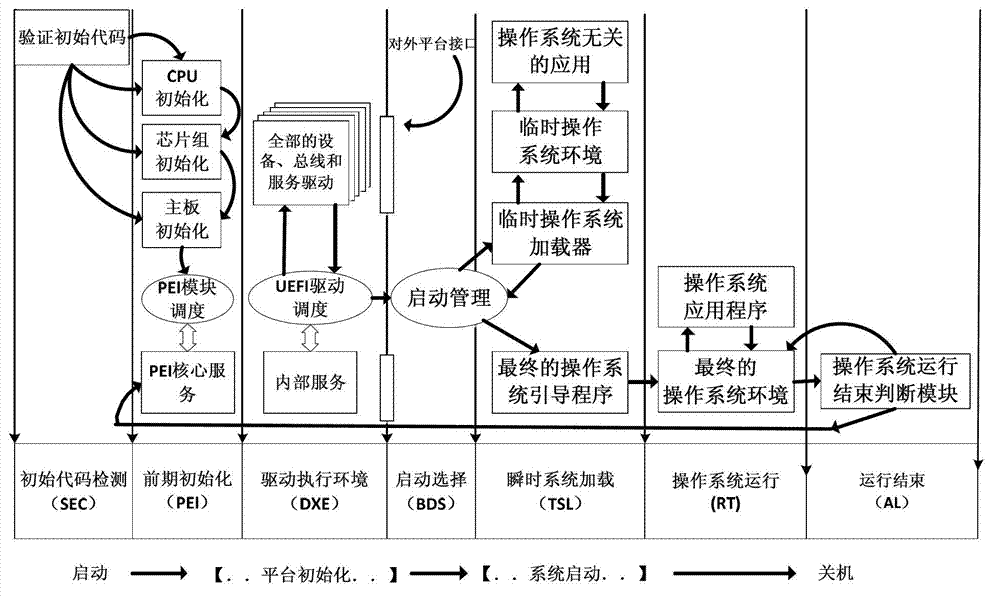
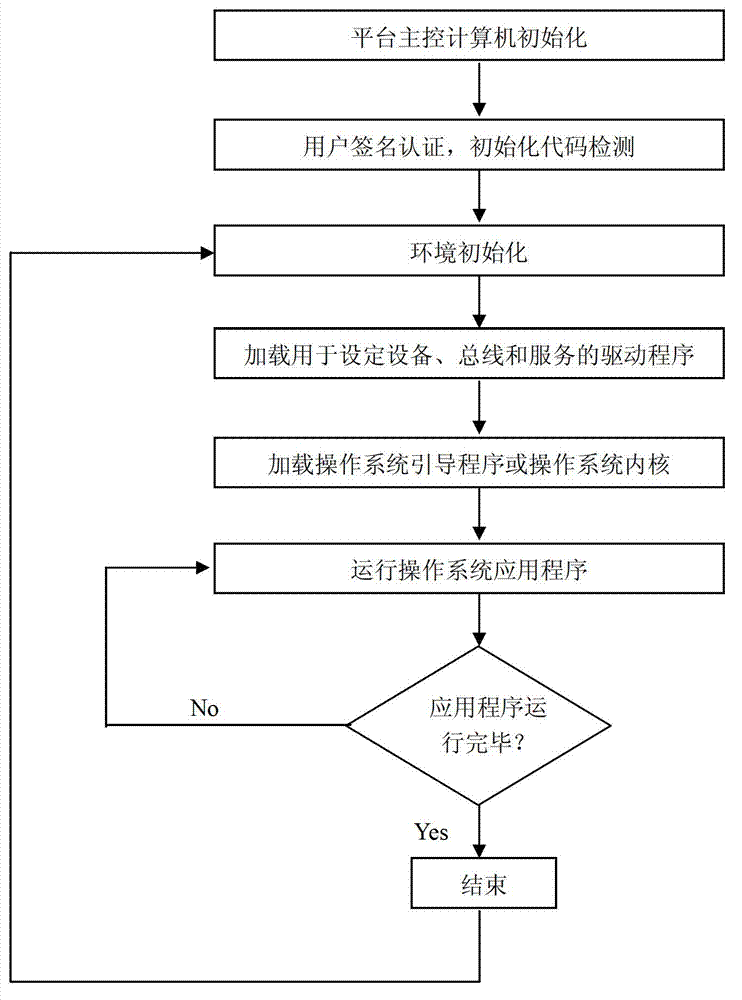
The invention discloses a UEFI and BIOS (unified extensible firmware interface and basic input output system) rapidly and safely starting method capable of being dynamically adjusted as requirements, belonging to the technical field of rapid starting of the UEFI and BIOS. The rapidly and safely starting method is characterized by being an existing rapid and safe method suitable for a system platform comprising a portable terminal or embedded equipment. The rapidly and safely starting method comprises the following stages: platform main control computer initialization, user signature authentication, initial code detection, environment initialization, drive program loading for setting equipment, buses and services, operation system guide program or operating system inner core loading, operation system application program running and judgment that whether the application program completely operates or not. With the adoption of the rapidly and safely starting method, not only is the efficiency of the system platform improved, but also the safety of an executive program of a CPU (central processing unit) is guaranteed.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
System and method for updating unified extensible firmware interface setting information
InactiveUS20110271268A1Specific program execution arrangementsMemory systemsData storingComputer science
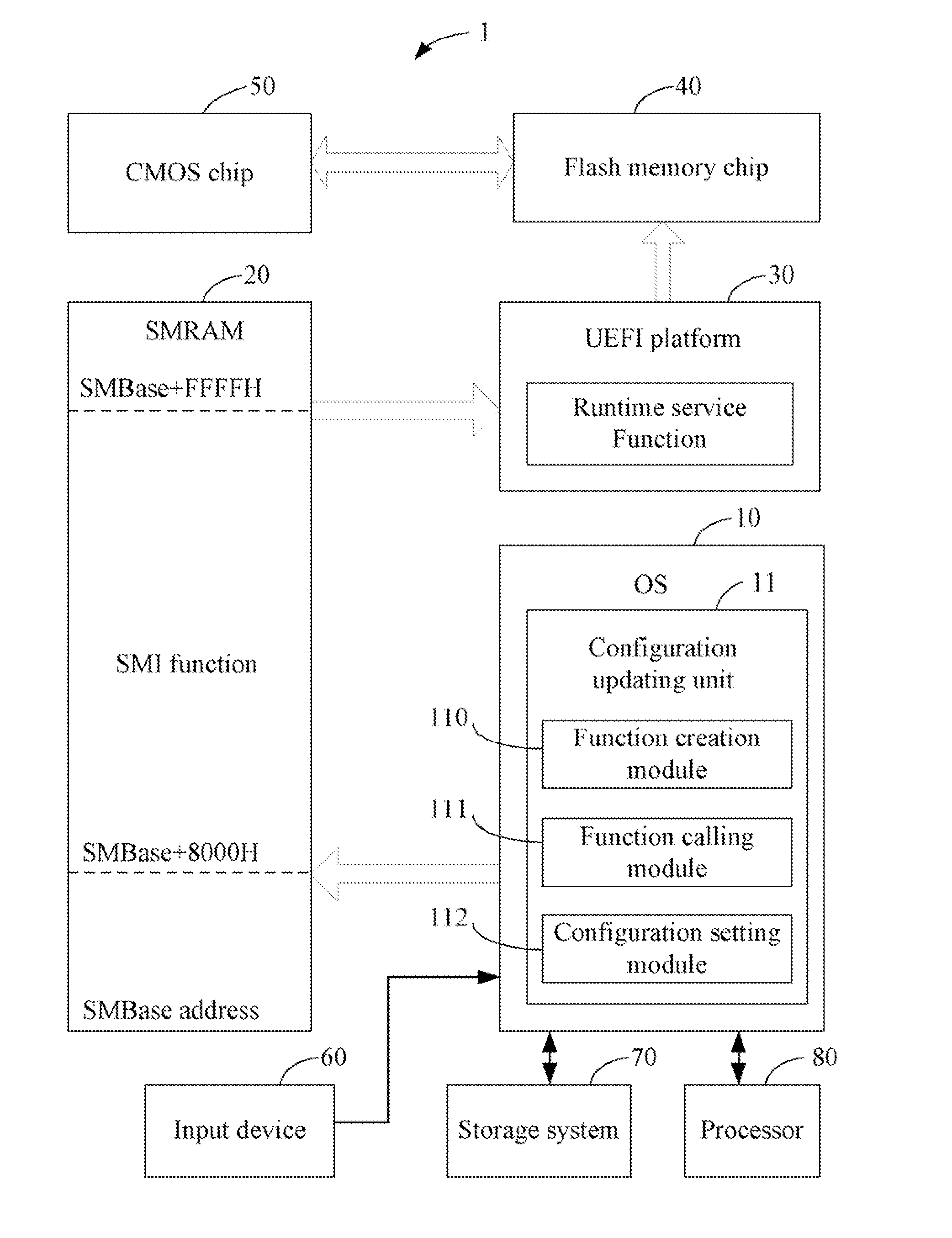
A system and method can update unified extensible firmware interface (UEFI) setting information of a computer. The method creates a system management interrupt (SMI) function based on a UEFI platform of the computer, and stores the SMI function in a SMRAM of the computer. The method further generates an access address of the SMI function when a configuration command is input from an input device, and generate a SMI handler according to the access address. Additionally, the method calls a runtime service function of the UEFI platform by executing the SMI function through the SMI handler, and executes the runtime service function to configure UEFI setting information stored in a flash memory chip and to update BIOS data stored in a CMOS chip related to the UEFI setting information.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
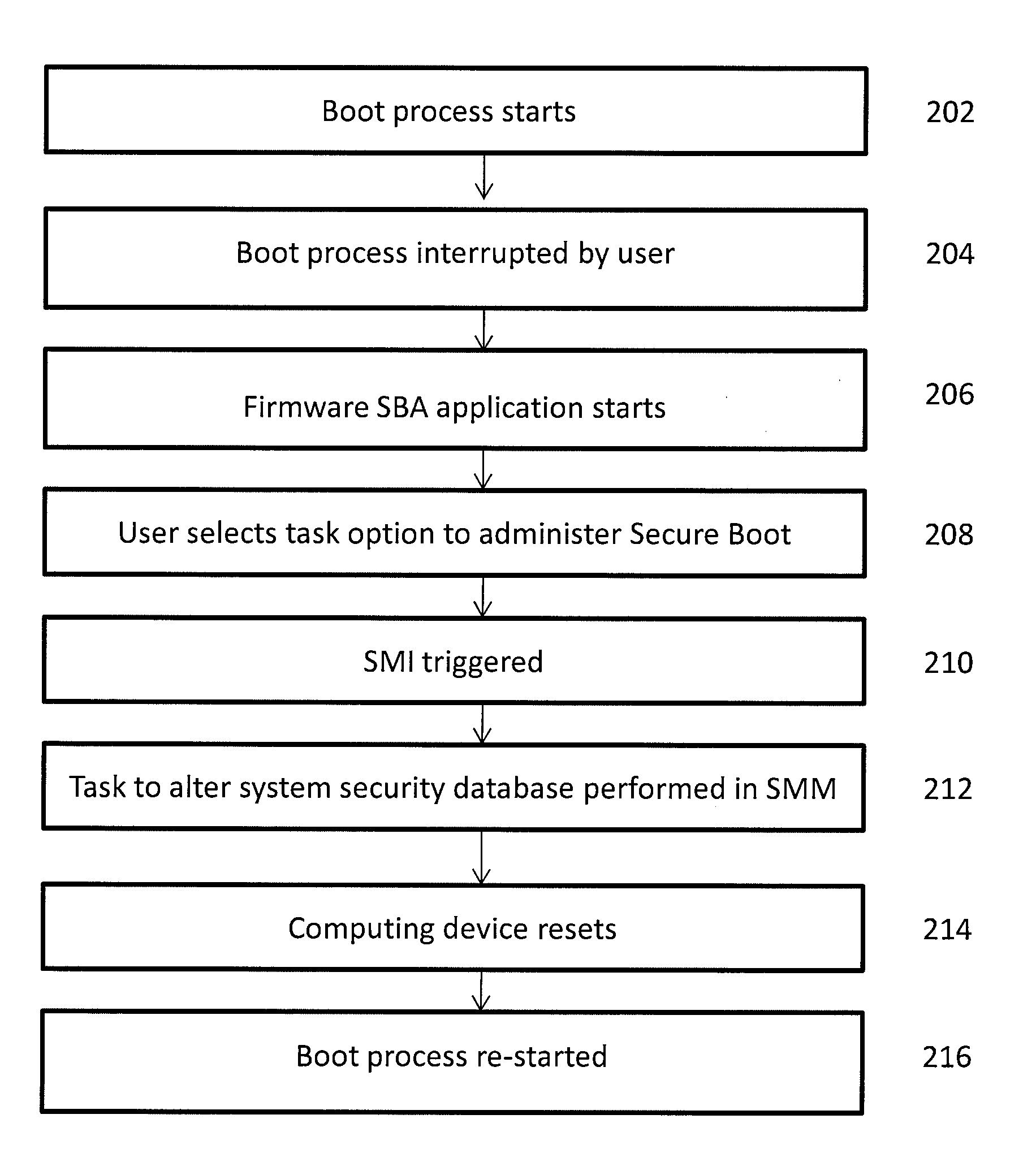
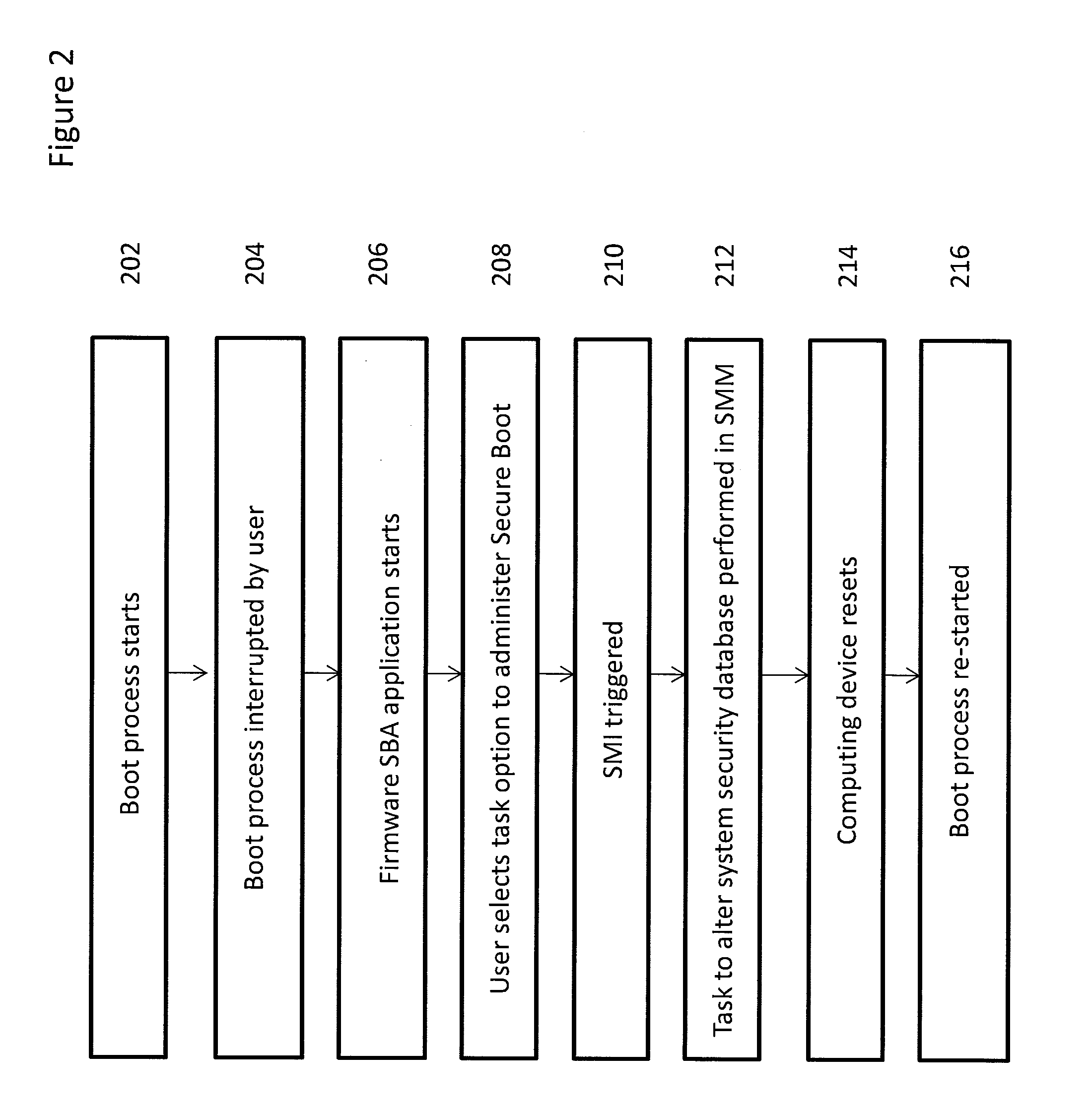
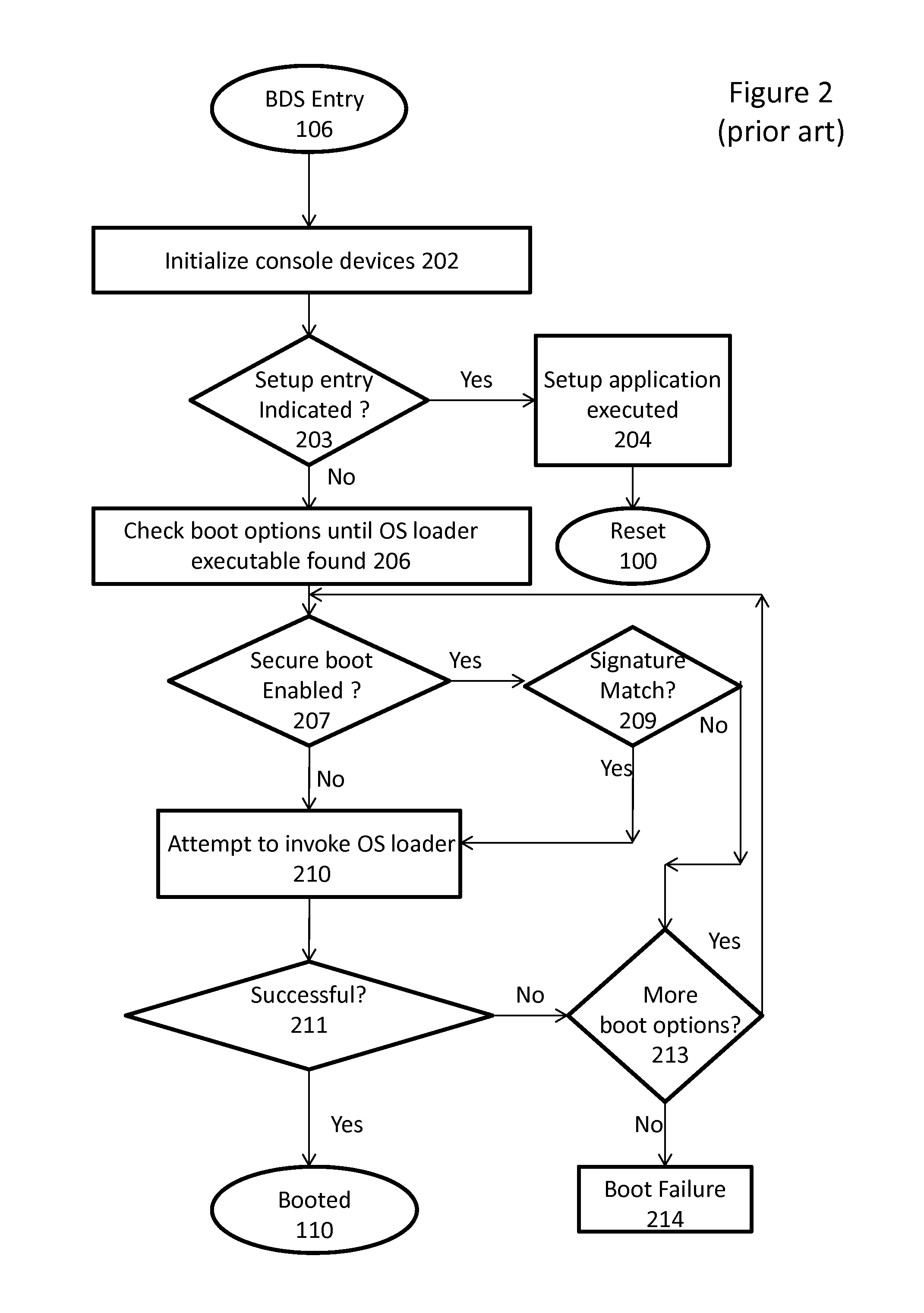
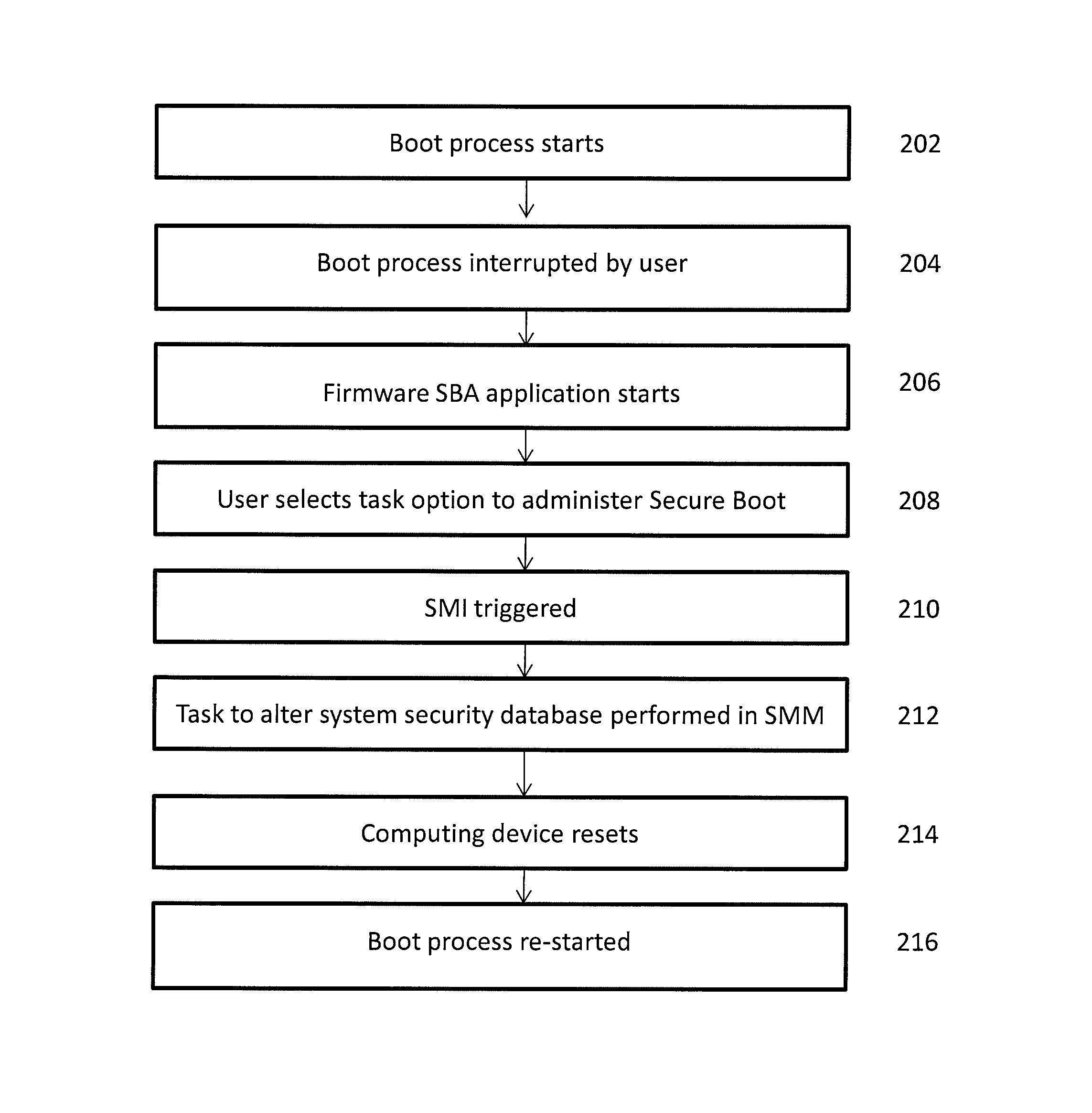
Secure boot administration in a unified extensible firmware interface (UEFI)-compliant computing device
ActiveUS20130124843A1Difficult to performDigital computer detailsBootstrappingThird partyUnified Extensible Firmware Interface
Firmware in a UEFI-compliant computing device is used to administer and alter a Secure Boot process for the computing device while continuing to provide protection from unauthorized third-party code.
Owner:INSYDE SOFTWARE
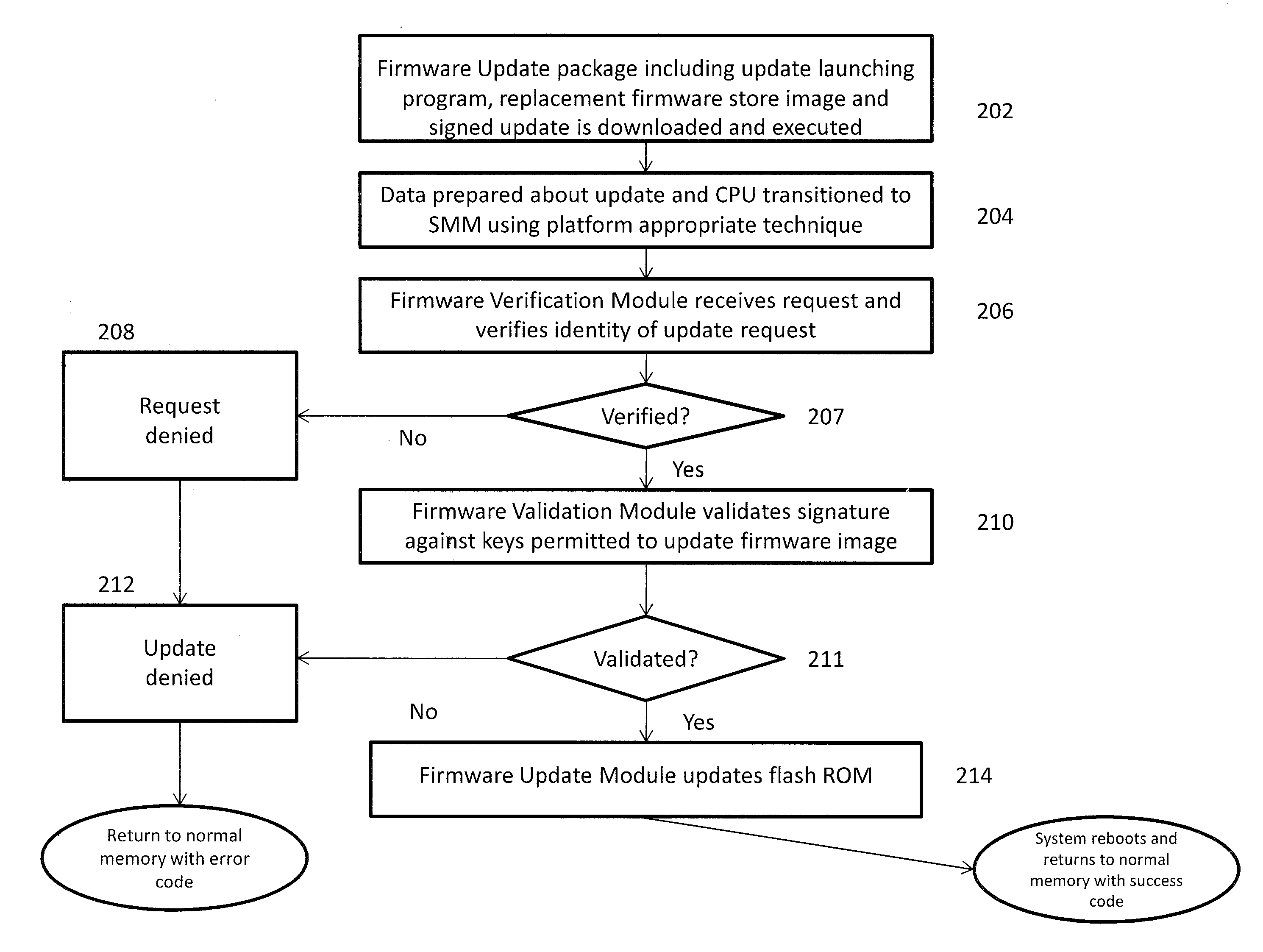
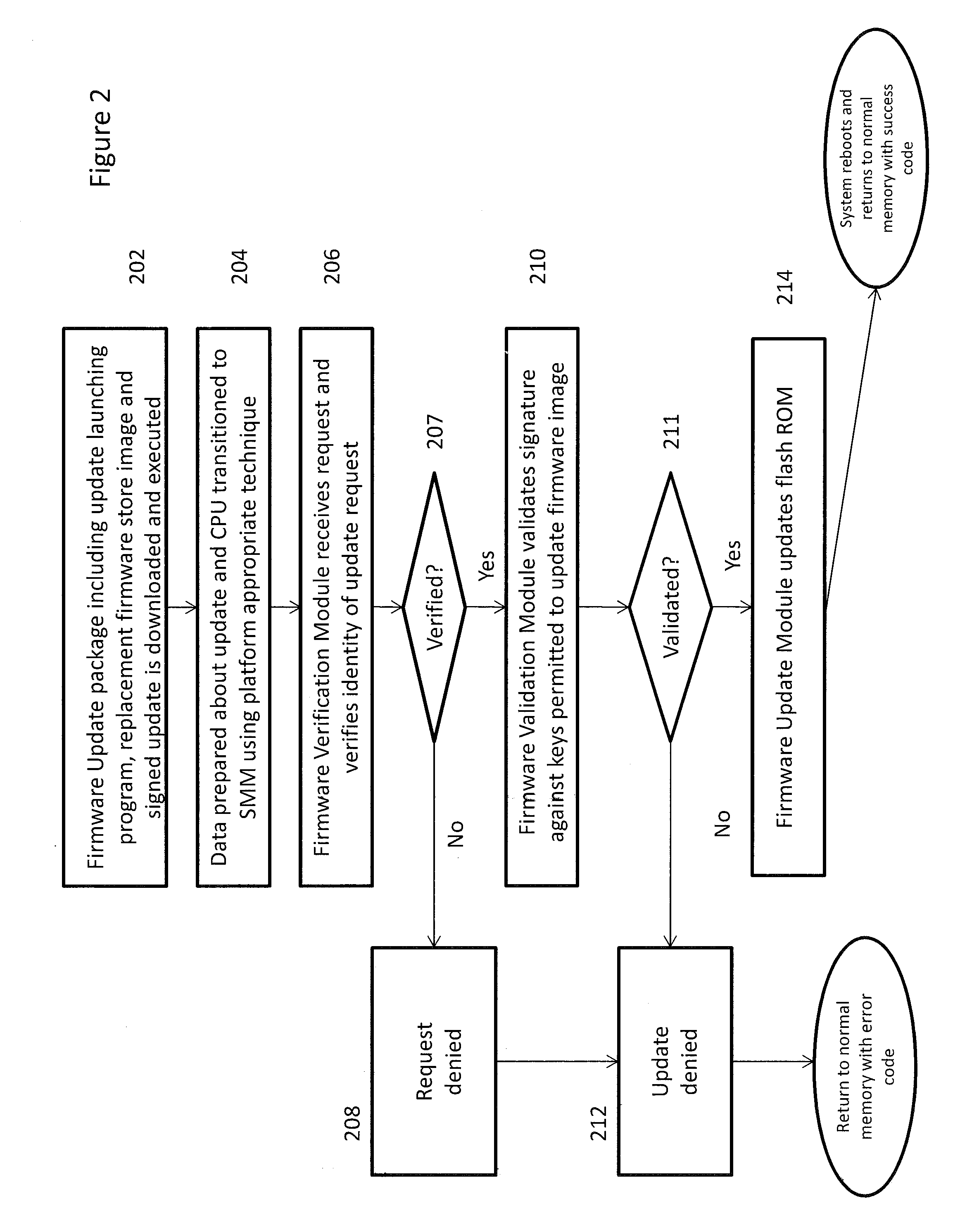
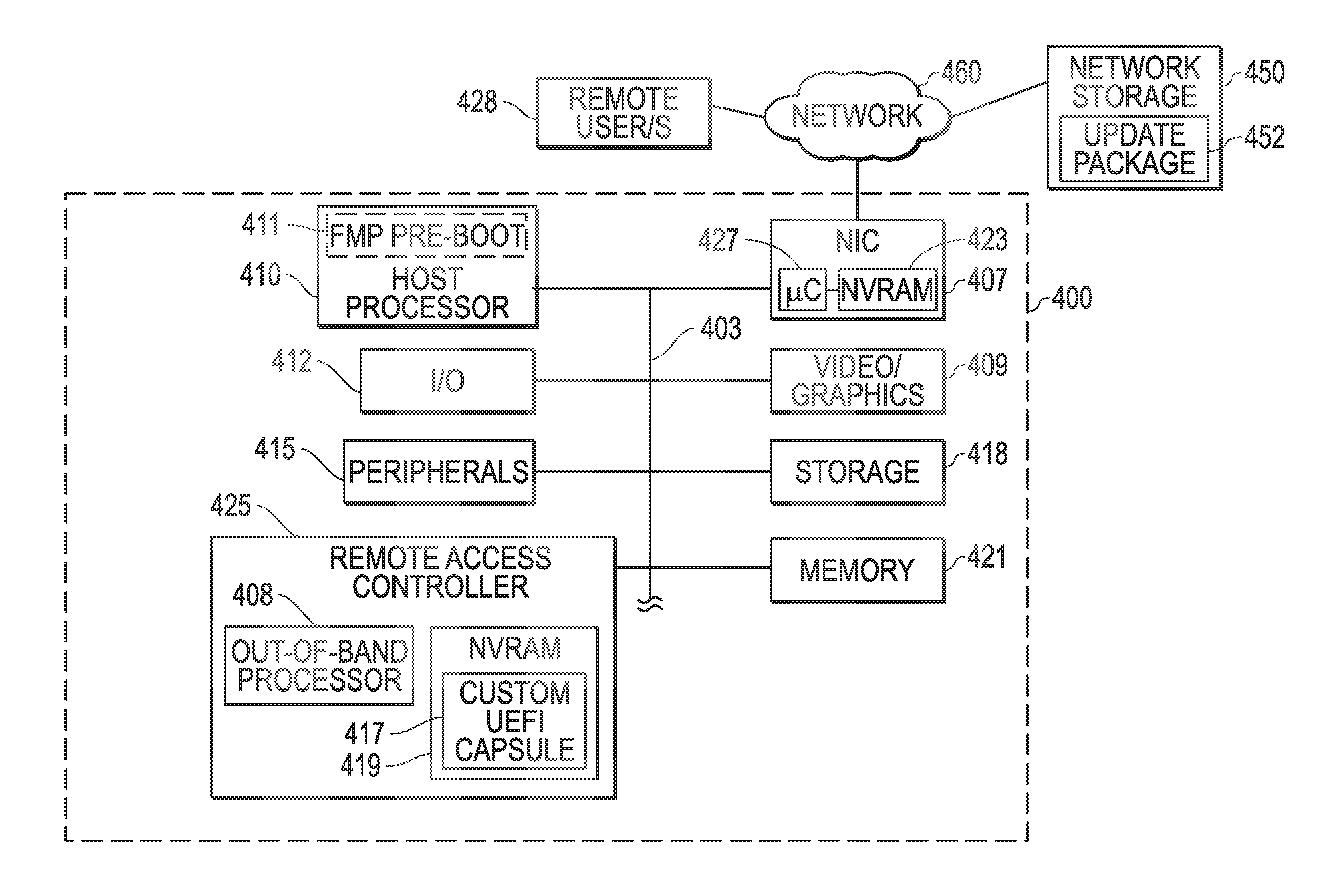
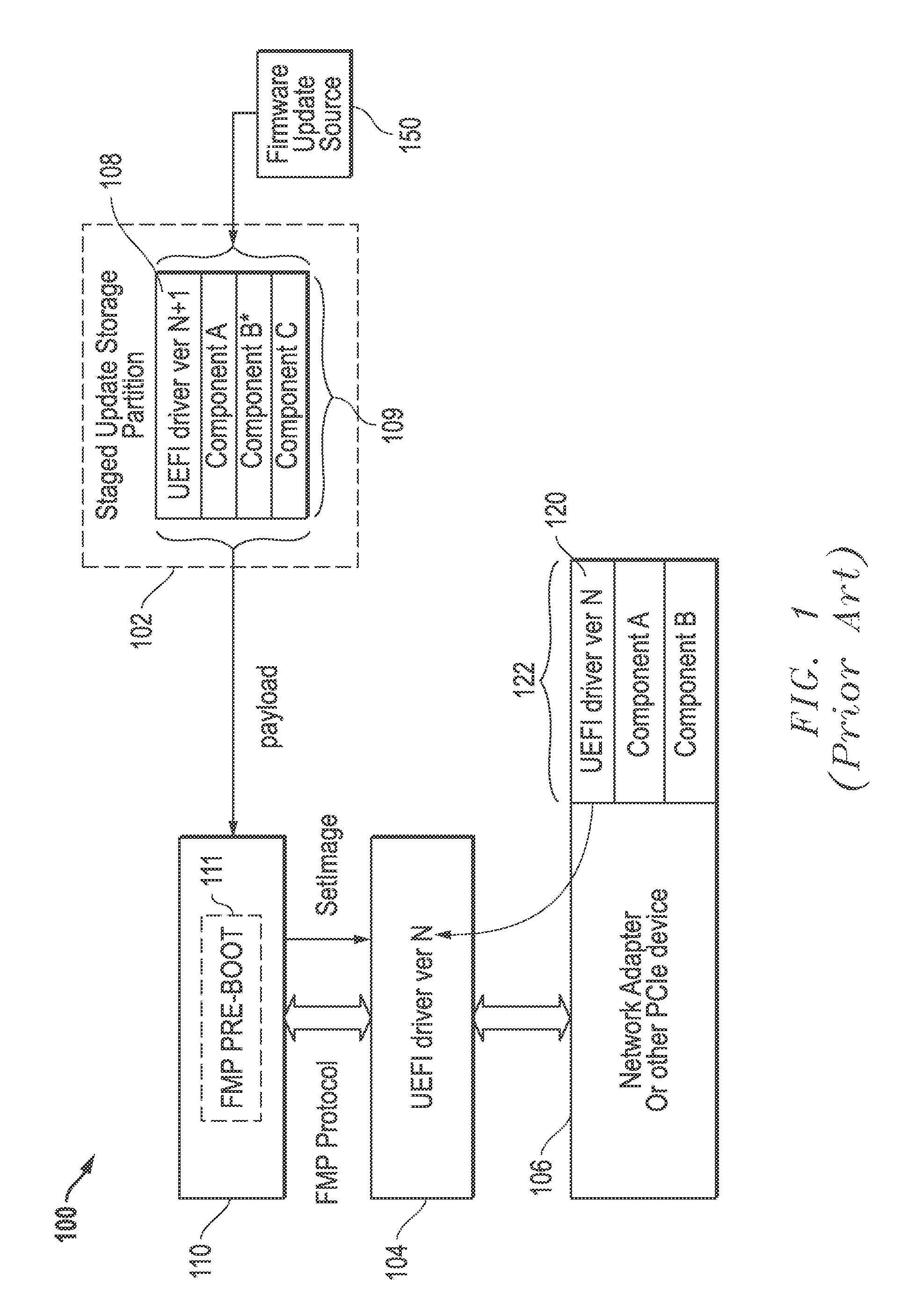
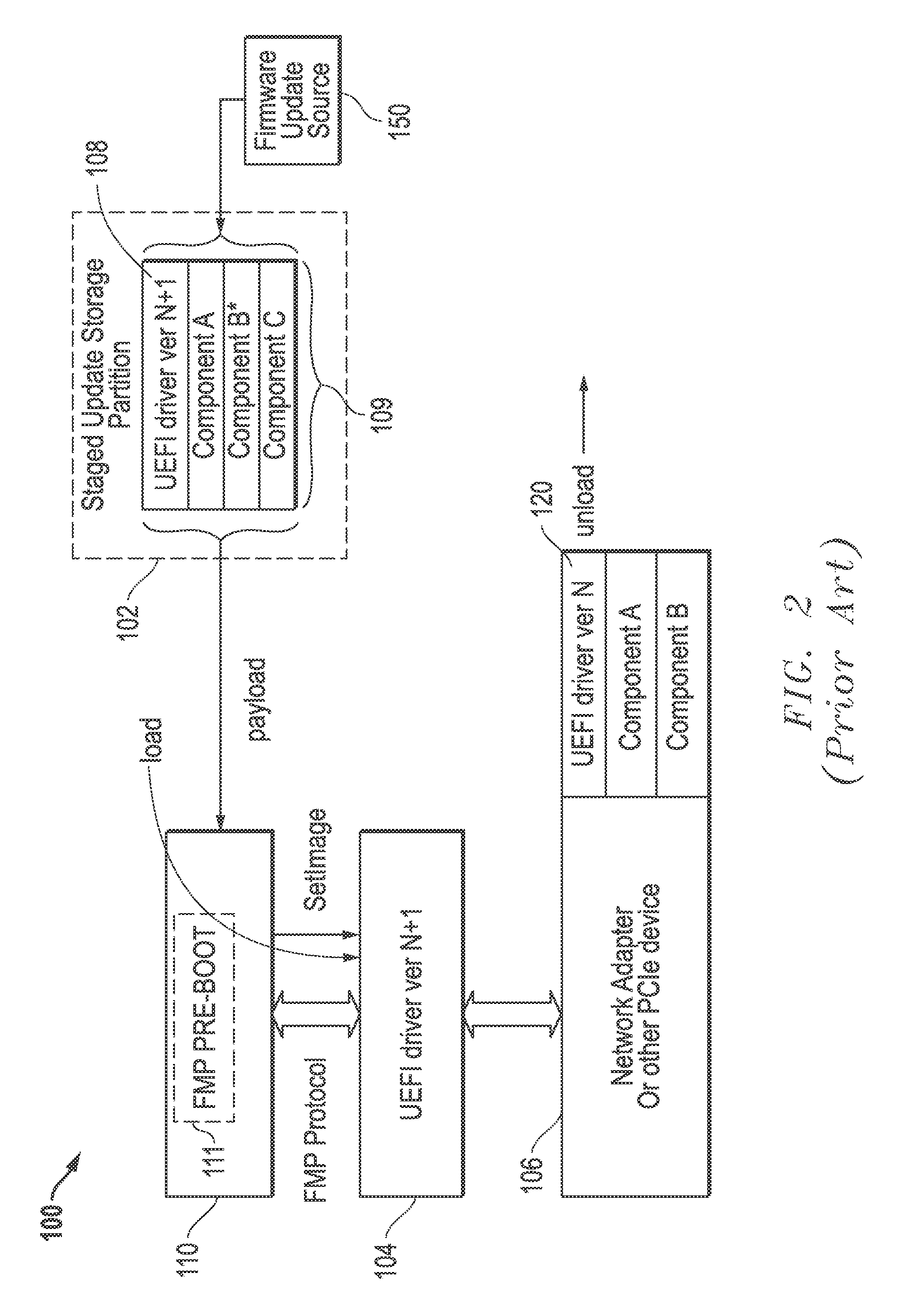
Systems and methods of device firmware delivery for pre-boot updates
ActiveUS9507581B2Minimizing useMinimize storage spaceProgram loading/initiatingTransmissionComputer moduleHandling system
Systems and methods are provided that may be implemented to deliver firmware for pre-boot updates of targeted information handling system device / devices using custom update capsules (e.g., such as custom unified extensible firmware interface capsules) and a separately-stored firmware update package that is remotely or locally stored. The custom update capsules may contain instruction payload information that may be used to determine location and desired components of the separately-stored firmware update package, and that also may be used to determine whether existing driver / drivers are to be retained in a firmware module in system memory or to be unloaded and replaced with a new (e.g., upgraded or downgraded) driver version in a firmware module in system memory as part of the firmware update.
Owner:DELL PROD LP
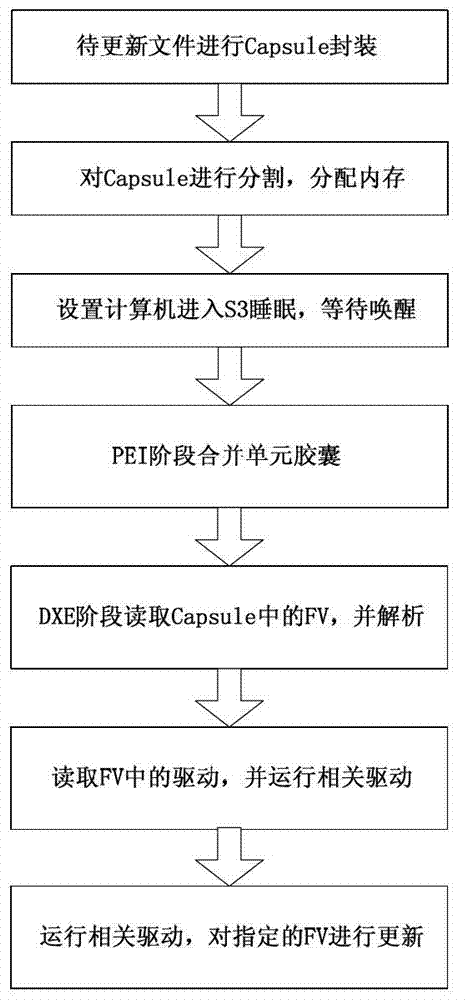
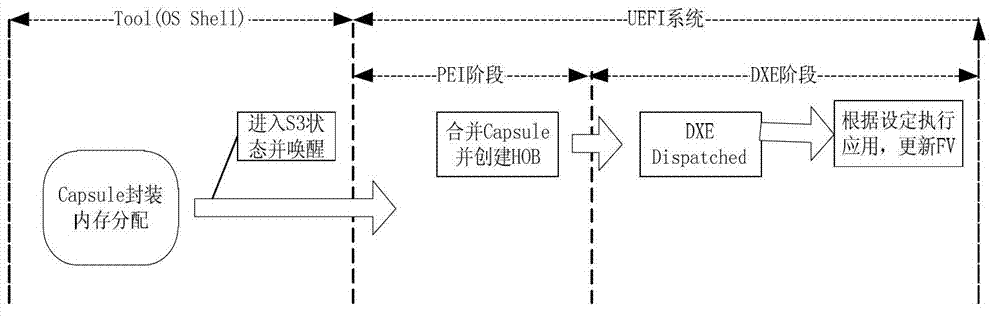
Capsule type custom-made updating method based on unified extensible firmware interface firmware system
ActiveCN103207797AThe solution cannot be unifiedProgram loading/initiatingOperational systemFile system
The invention provides a capsule type custom-made updating method based on a universal and extensible firmware interface firmware system. The method is based on a capsule mechanism of a unified extensible firmware interface (UEFI) firmware system and gets rid of that the current mainstream firmware updating technology depends on system management interrupt (SMI) drive. Through analysis of a capsule, a firmware volume (FV) module to be updated is obtained, the FV module is identified, and obtained data are wrote in firmware file system target addresses, therefore updating of the selected FV module is achieved, and a method which needs to update a whole basic input / output system (BIOS) is got rid of. The capsule mechanism solves the problem that updating tools on different hardware platforms and operation systems cannot be unified. The firmware updating method is flexile, high in application value and capable of being applied to the aspects of firmware remote refreshing, automatic firmware recovery and the like.
Owner:NANJING UNIV OF TECH
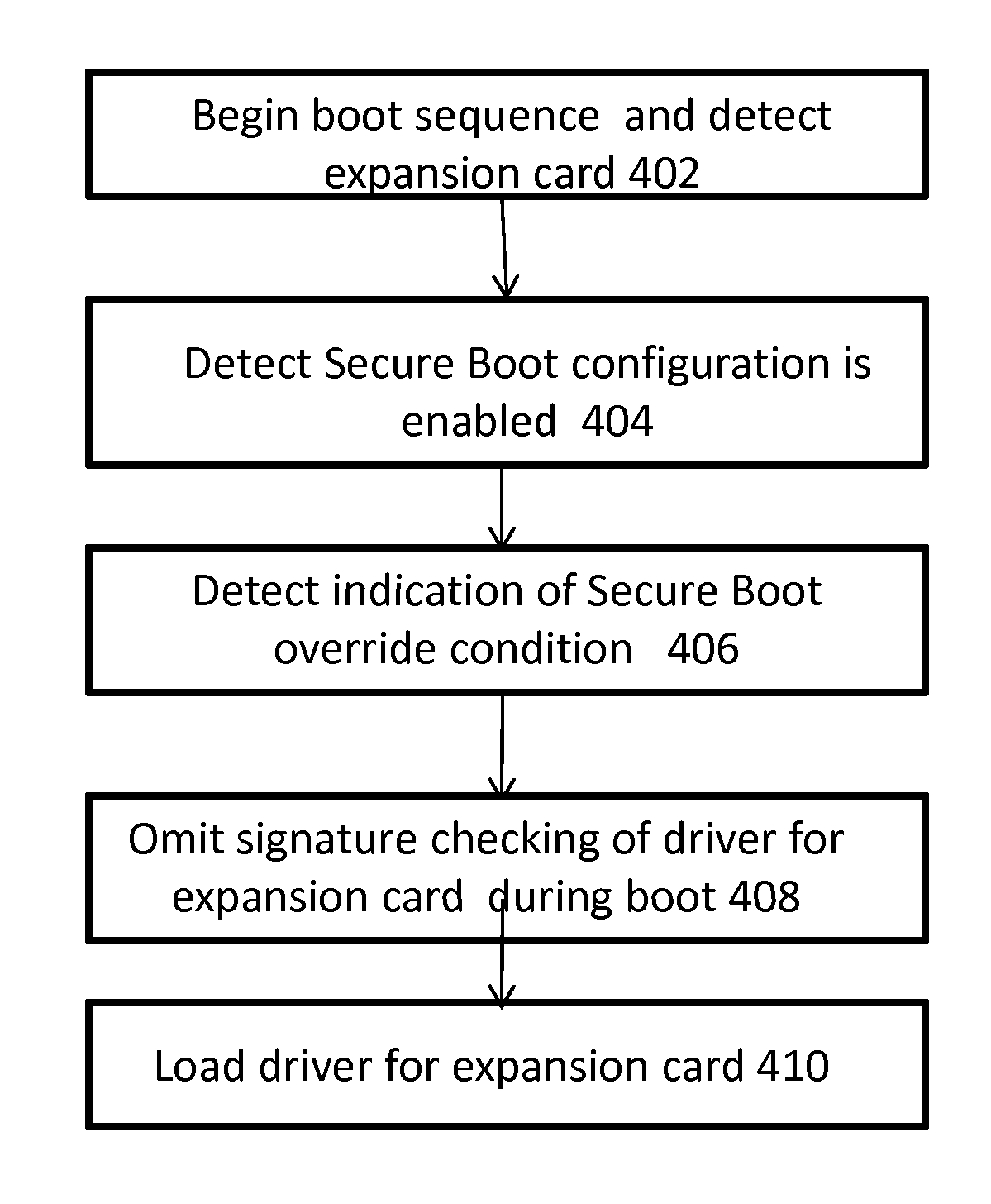
Secure boot override in a computing device equipped with unified-extensible firmware interface (UEFI)-compliant firmware
ActiveUS20140331037A1Digital computer detailsComputer security arrangementsComputerized systemApplication software
A firmware-based system and method for detecting an indicator of an override condition during a Unified Extensible Firmware Interface (UEFI) Secure Boot sequence. The indicator of the override condition may be detected based upon the pressing of a specialized button, designated key or keys or other received input that indicates both physical presence of the user and the desire, on the current boot, to bypass UEFI Secure Boot. An embodiment may work for only a single boot, not require access into a setup application, and may be accessed by externally accessible features of the computer system.
Owner:INSYDE SOFTWARE
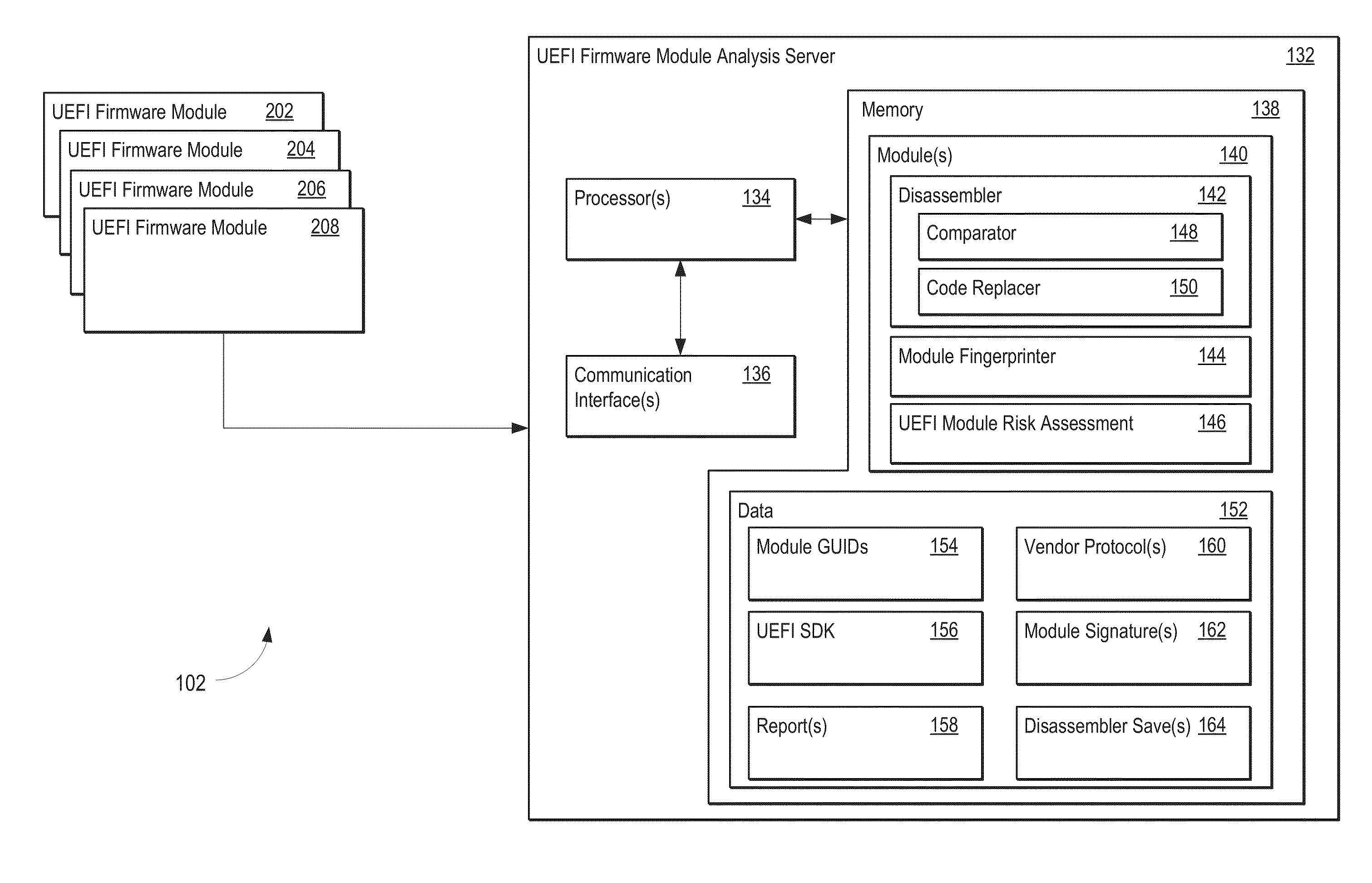
Universal extensible firmware interface module identification and analysis
ActiveUS20150199517A1Memory loss protectionError detection/correctionComputer moduleUnique identifier
The present disclosure provides a network architecture and verification platform for analyzing the various modules of a Unified Extensible Firmware Interface (UEFI) firmware image. In one embodiment, the disclosed network architecture and verification platform obtains various UEFI firmware images, such as UEFI firmware image residing on a client device or a UEFI firmware image hosted by a hardware manufacturer. The network architecture and verification platform may then segregate the various UEFI firmware modules that make up the UEFI firmware image, and subject the modules to different types of analysis. By analyzing the UEFI firmware modules individually, the network architecture and verification platform builds a repository of Globally Unique Identifiers (GUIDs) referenced by a given UEFI firmware module, which may then be referenced in future analyses to determine whether any changes, and the extent of such changes, have been made to an updated version of the given UEFI firmware module.
Owner:RAYTHEON CO
Computer system and method for controlling acpi information
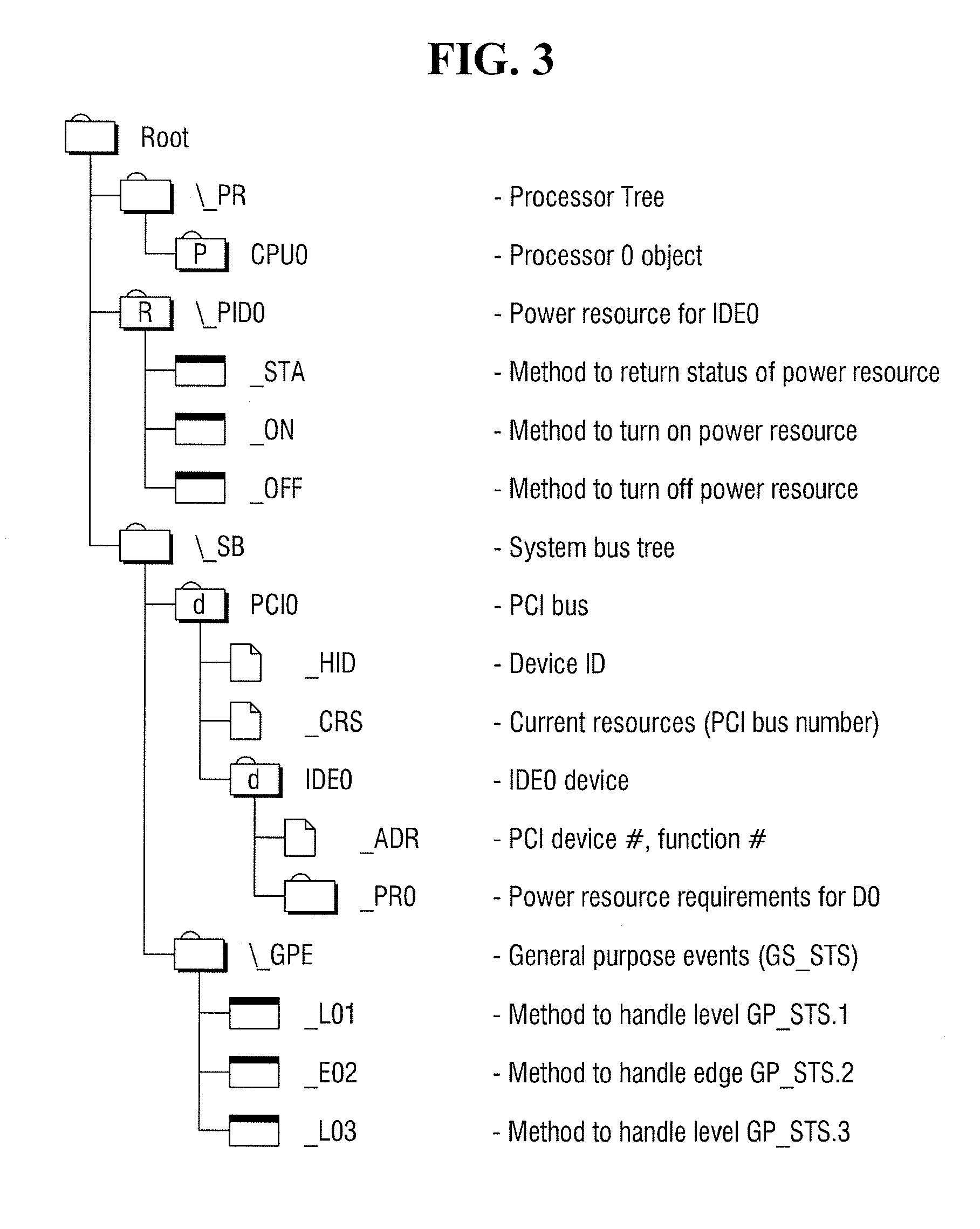
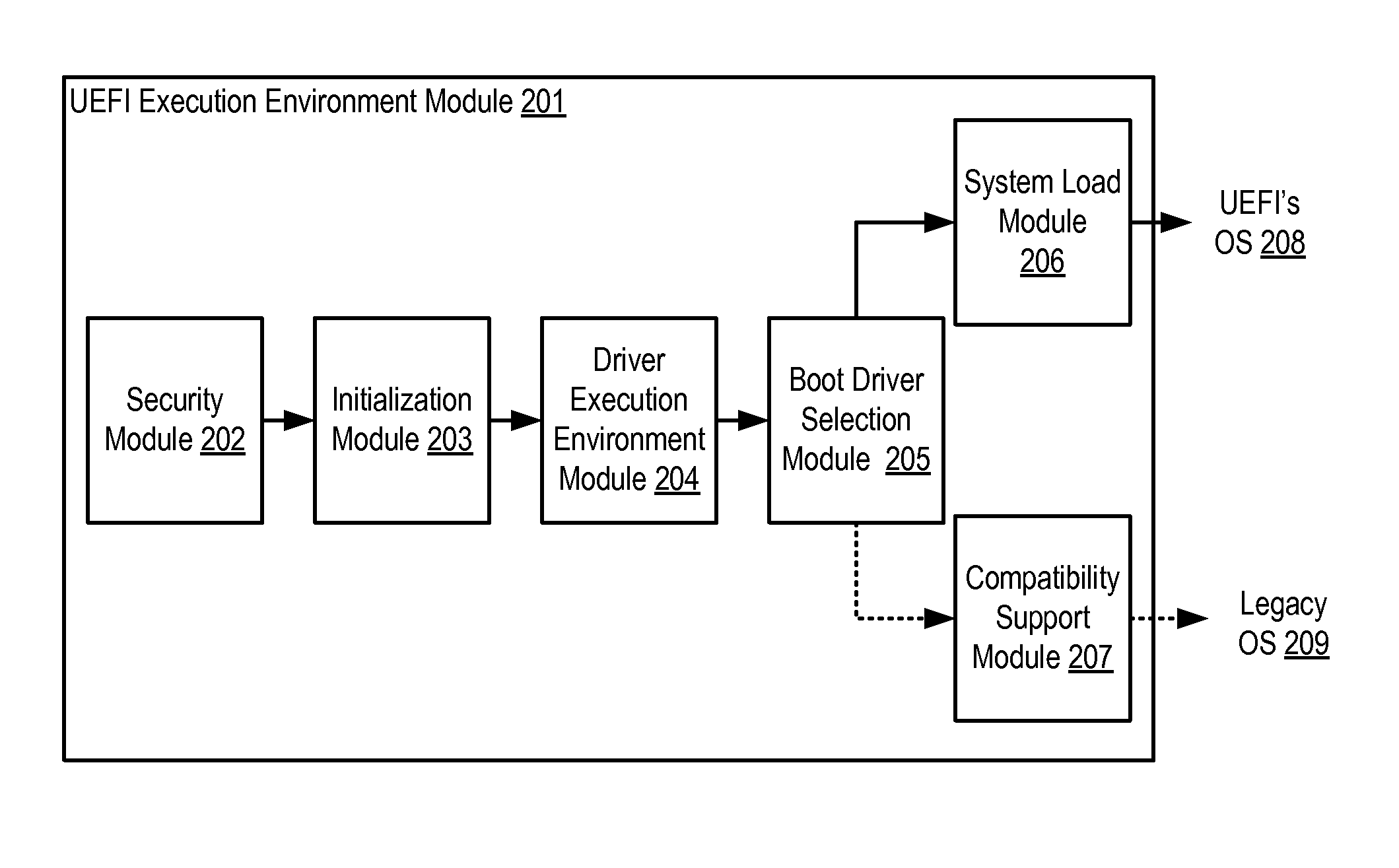
InactiveUS20140297999A1Digital computer detailsBootstrappingAdvanced Configuration and Power InterfaceUnified Extensible Firmware Interface
A computer system configured to control advanced configuration and power interface ACPI information is provided. The computer system includes a non-volatile memory configured to store an ACPI table, and a processor configured to execute a unified extensible firmware interface (UEFI), wherein a boot service of the UEFI provides a shell application, and the shell application includes an extended command to control information of the ACPI table.
Owner:SAMSUNG ELECTRONICS CO LTD
Restoring from a legacy os environment to a UEFI pre-boot environment
ActiveUS20130290778A1BootstrappingRedundant operation error correctionSystem Management ModeUnified Extensible Firmware Interface
Owner:IBM CORP
Trusted platform module support on reduced instruction set computing architectures
InactiveUS20180060077A1BootstrappingPlatform integrity maintainanceAdvanced Configuration and Power InterfaceTrusted Platform Module
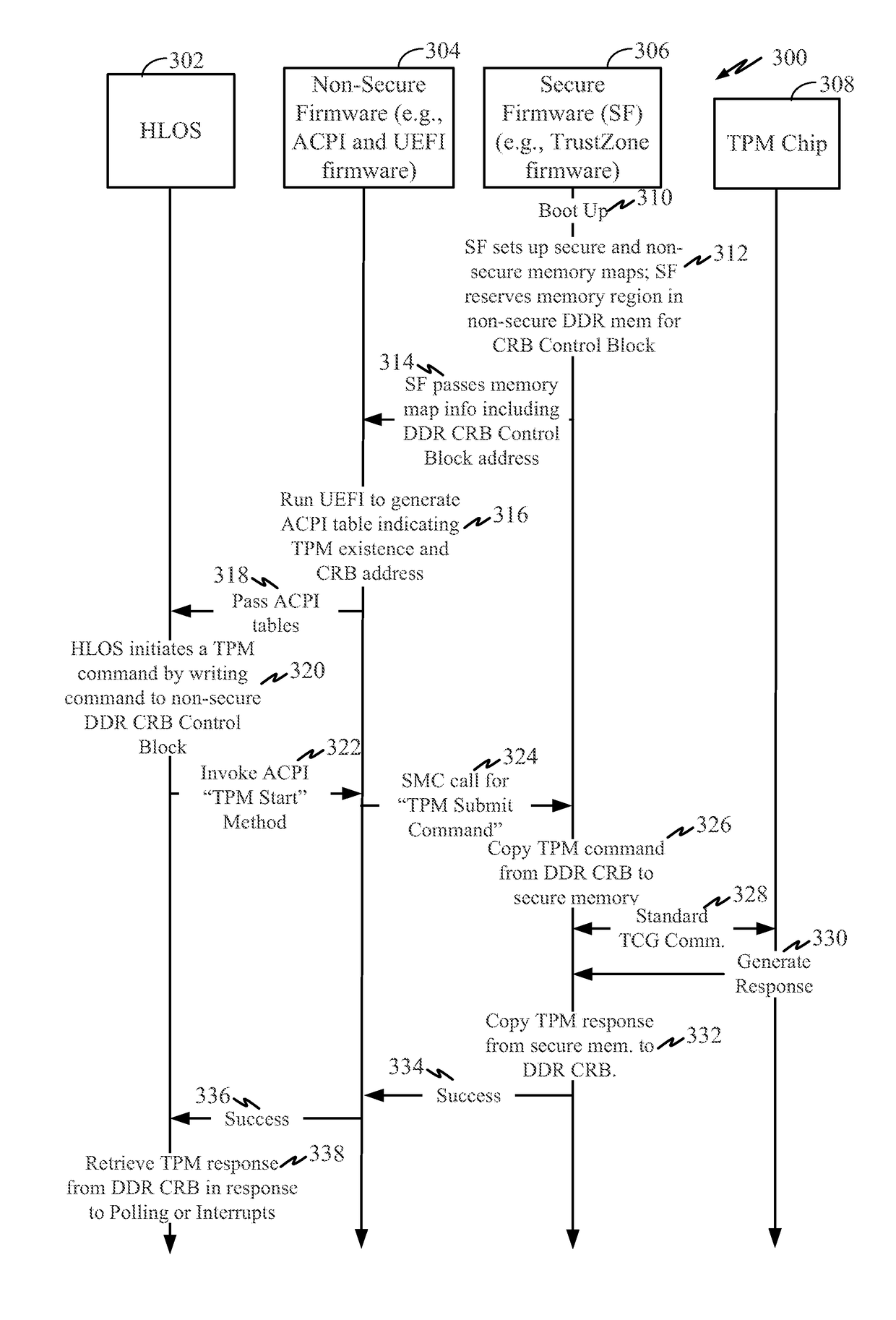
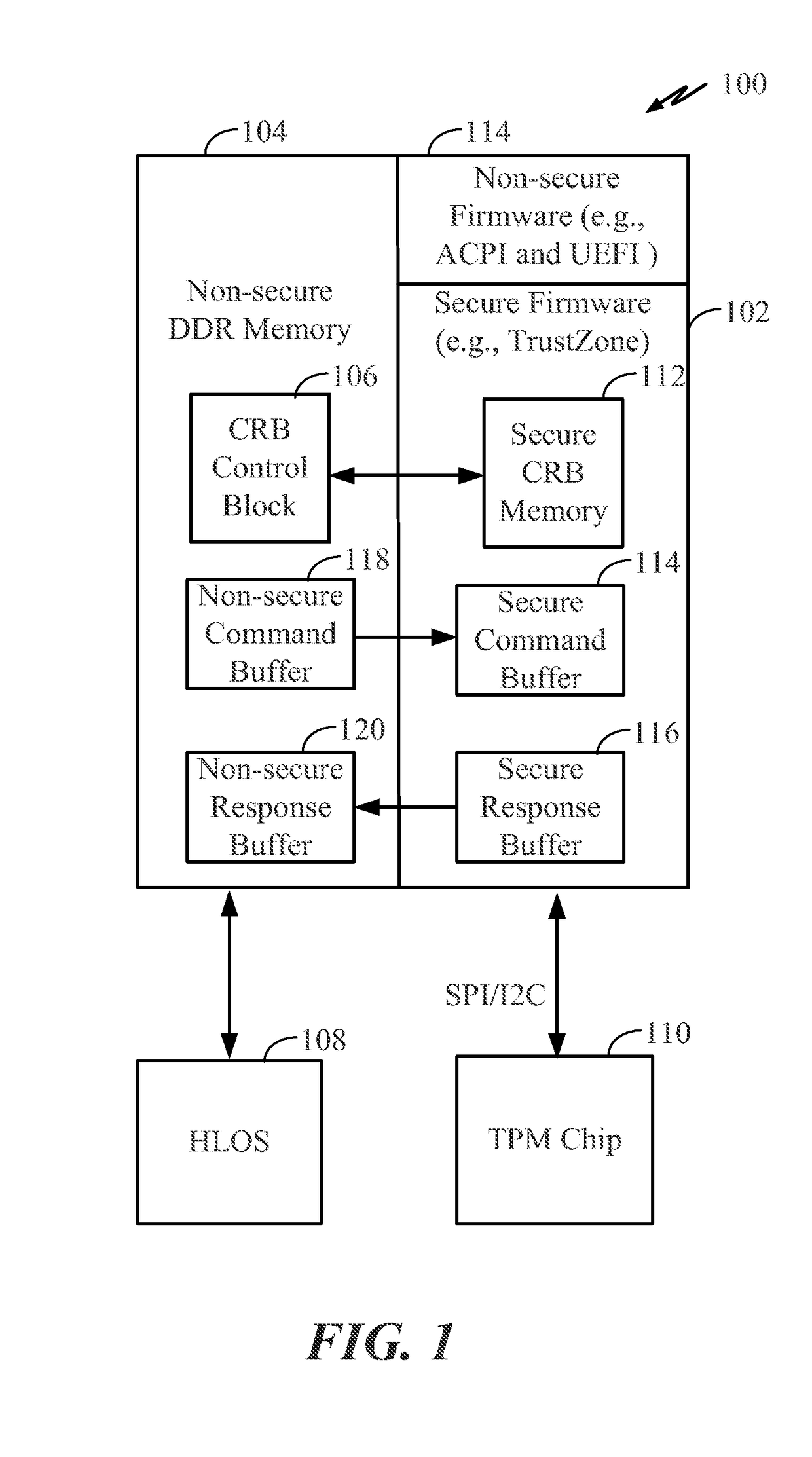
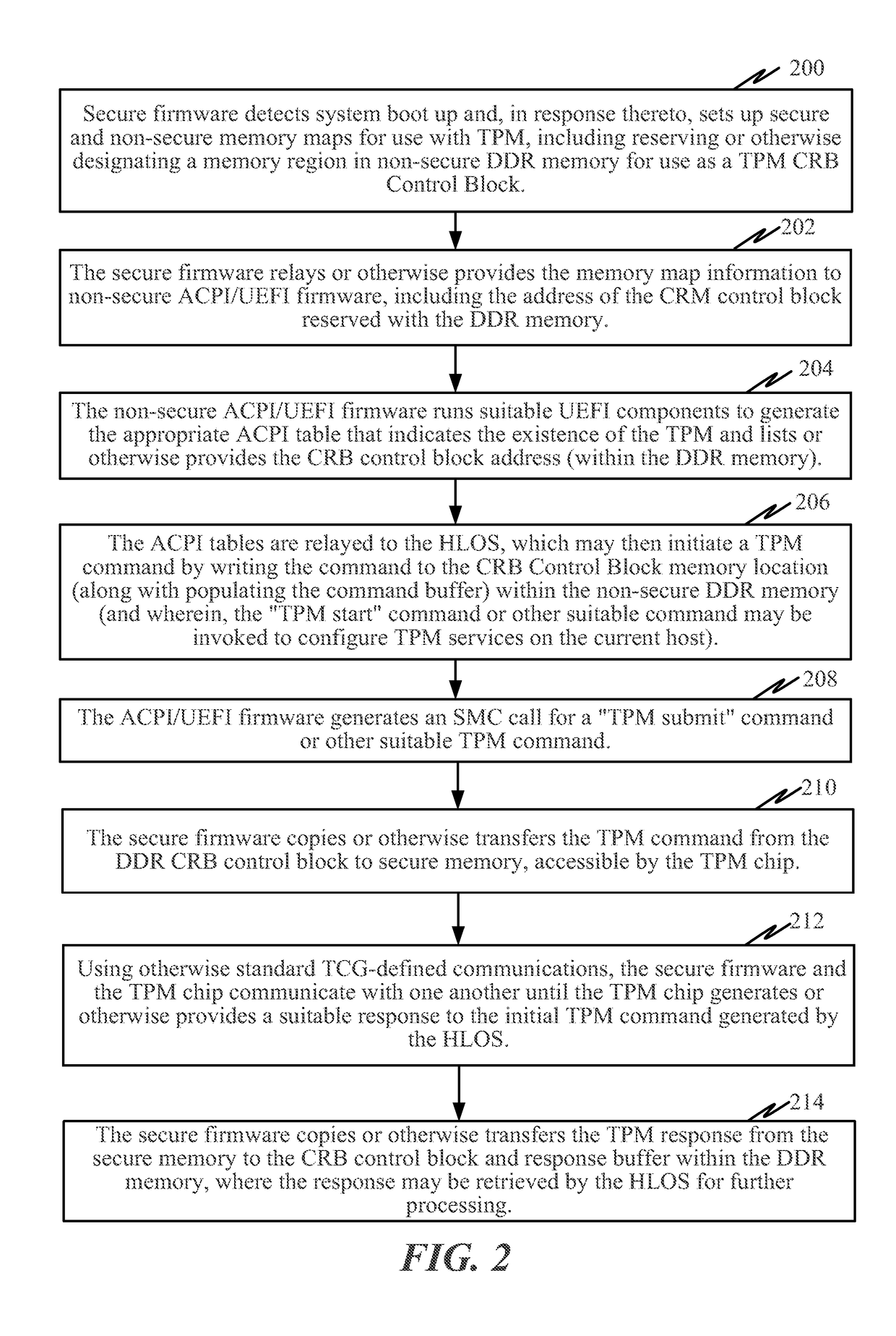
Exemplary features pertain to providing trusted platform module (TPM) support for ARM®-based systems or other Reduced Instruction Set Computing (RISC) systems. In some examples, secure firmware (e.g., TrustZone firmware) operates as a shim between an unsecure high level operating system (HLOS) and a discrete TPM chip or other trusted execution environment component. The secure firmware reserves a portion of non-secure memory for use as a command response buffer (CRB) control block accessible by the HLOS. The secure firmware translates and relays TPM commands / responses between the HLOS and the TPM via the non-secure CRB memory. The system may also include various non-secure firmware components such as Advanced Configuration and Power Interface (ACPI) and Unified Extensible Firmware Interface (UEFI) components. Among other features, the exemplary system can expose the TPM to the HLOS via otherwise standard UEFI protocols and ACPI tables in a manner that is agnostic to the HLOS.
Owner:QUALCOMM INC
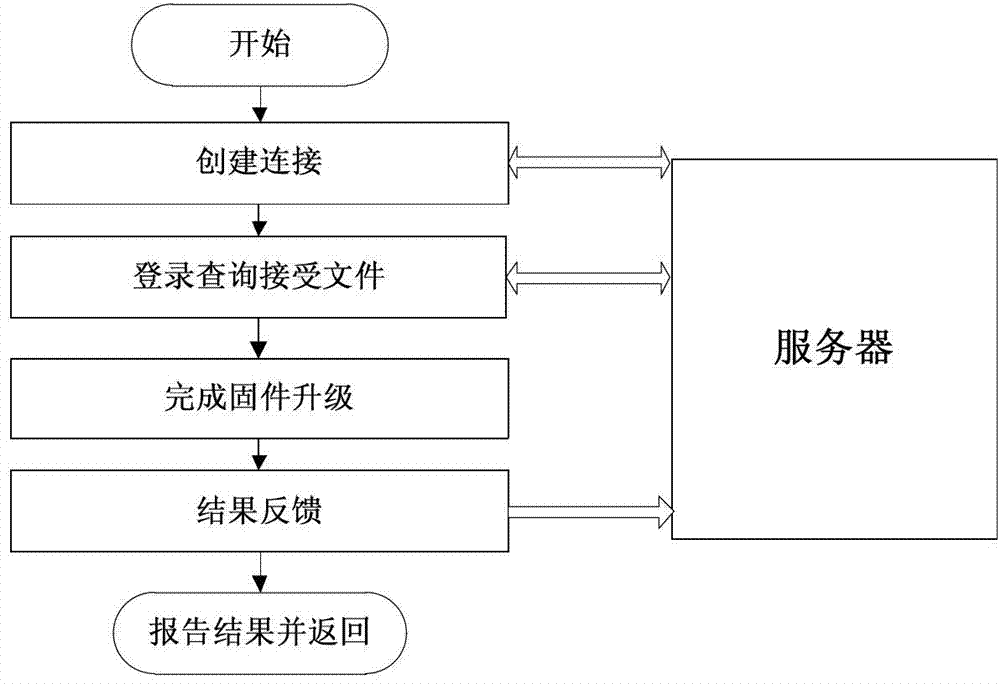
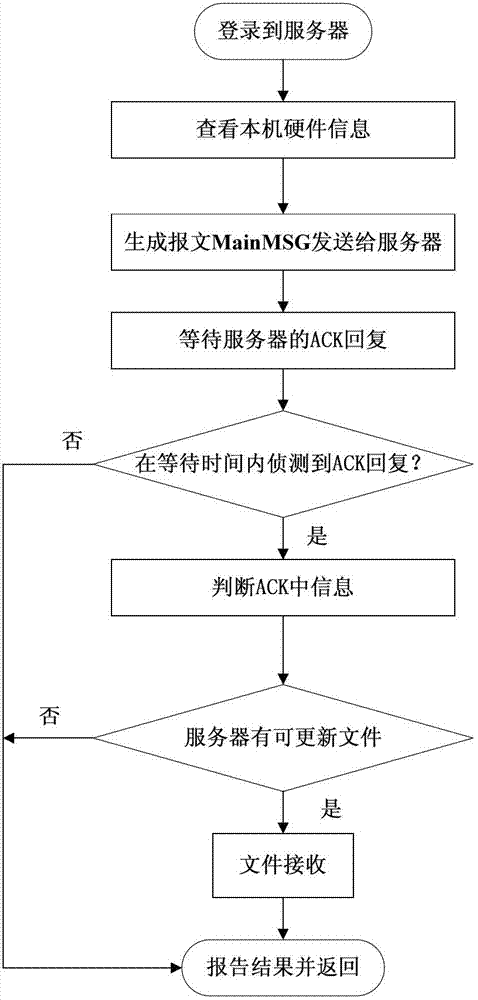
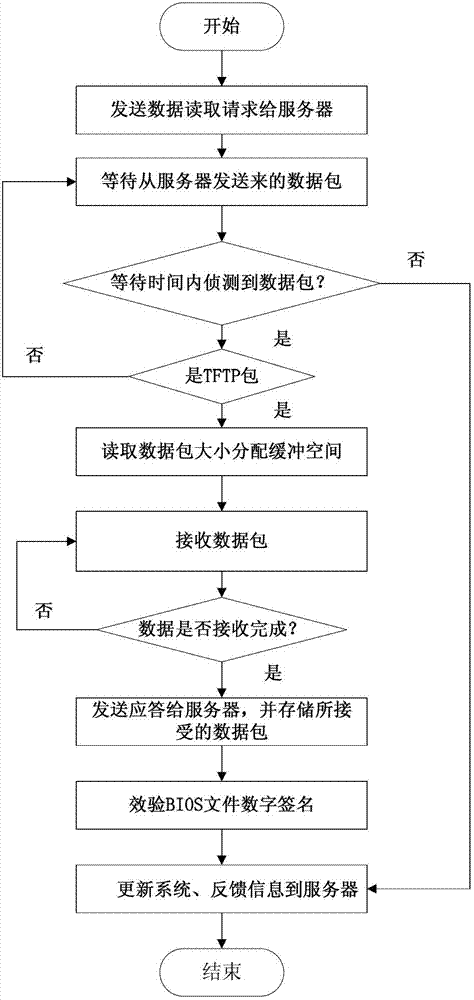
Firmware system long-distance updating methods based on unified extensible firmware interface
InactiveCN103164244AEfficient managementSave human effortProgram loading/initiatingTransmissionStructure of Management InformationData transmission
The invention provides firmware system long-distance updating methods based on a unified extensible firmware interface. A client server structure is adopted by the methods. The client server structure comprises a server and a client machine. A network protocol stack is achieved on UEFIBIOS by the client server structure, and data transmission is carried out by the client machine through a network and the server. The number of the long-distance updating methods is two. One method is that a client machine UEFIBIOS long-distance updating method is started by the server, and the other method is that UEFIBIOS long-distance updating method is started by the client machine. According to the long-distance updating methods, no assistance of mobile devices is needed, long-distance updating of UEFIBIOS is achieved through the network by the server, labor power and cost is reduced, and good control of the upgrading of UEFIBIOS is achieved.
Owner:NANJING UNIV OF TECH
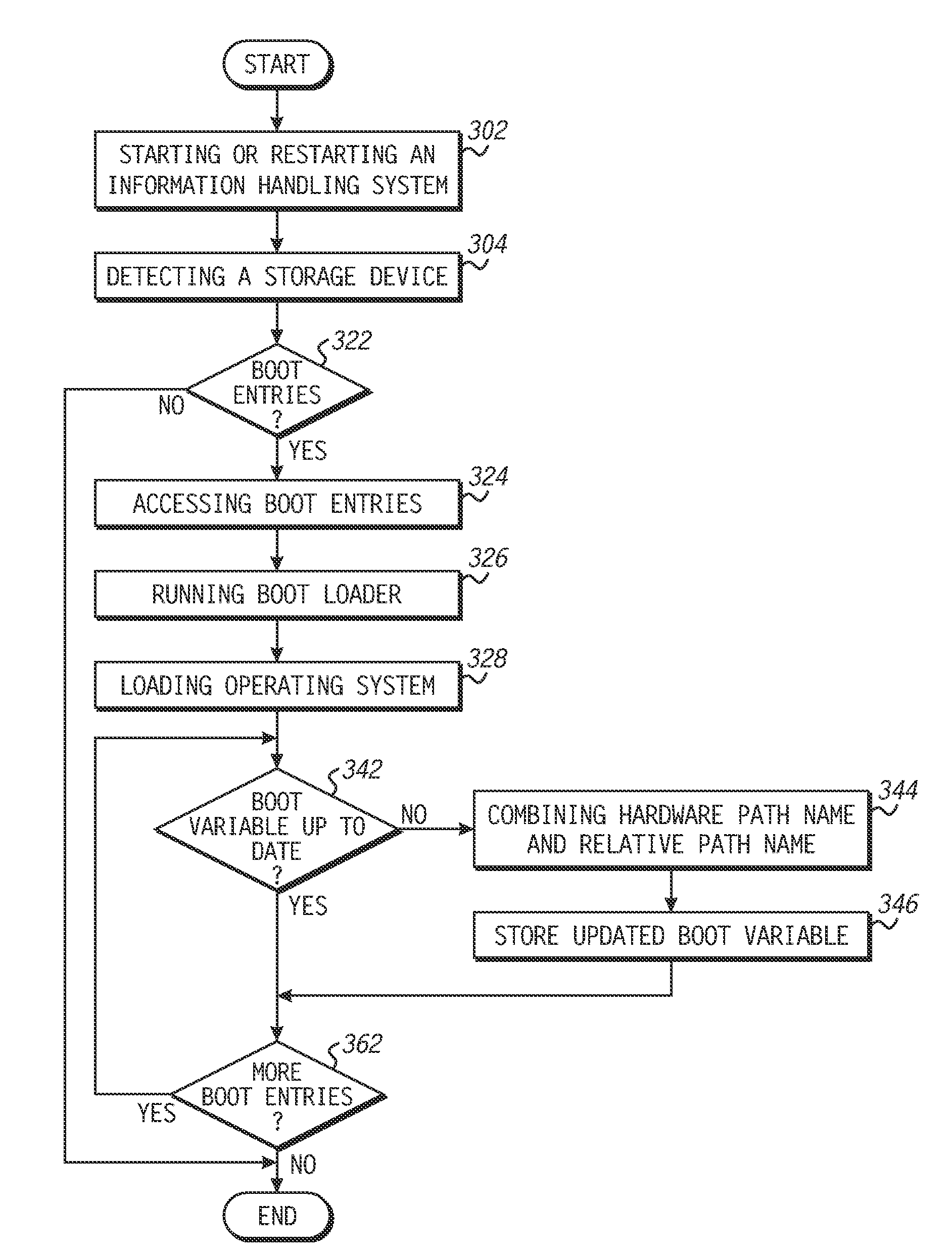
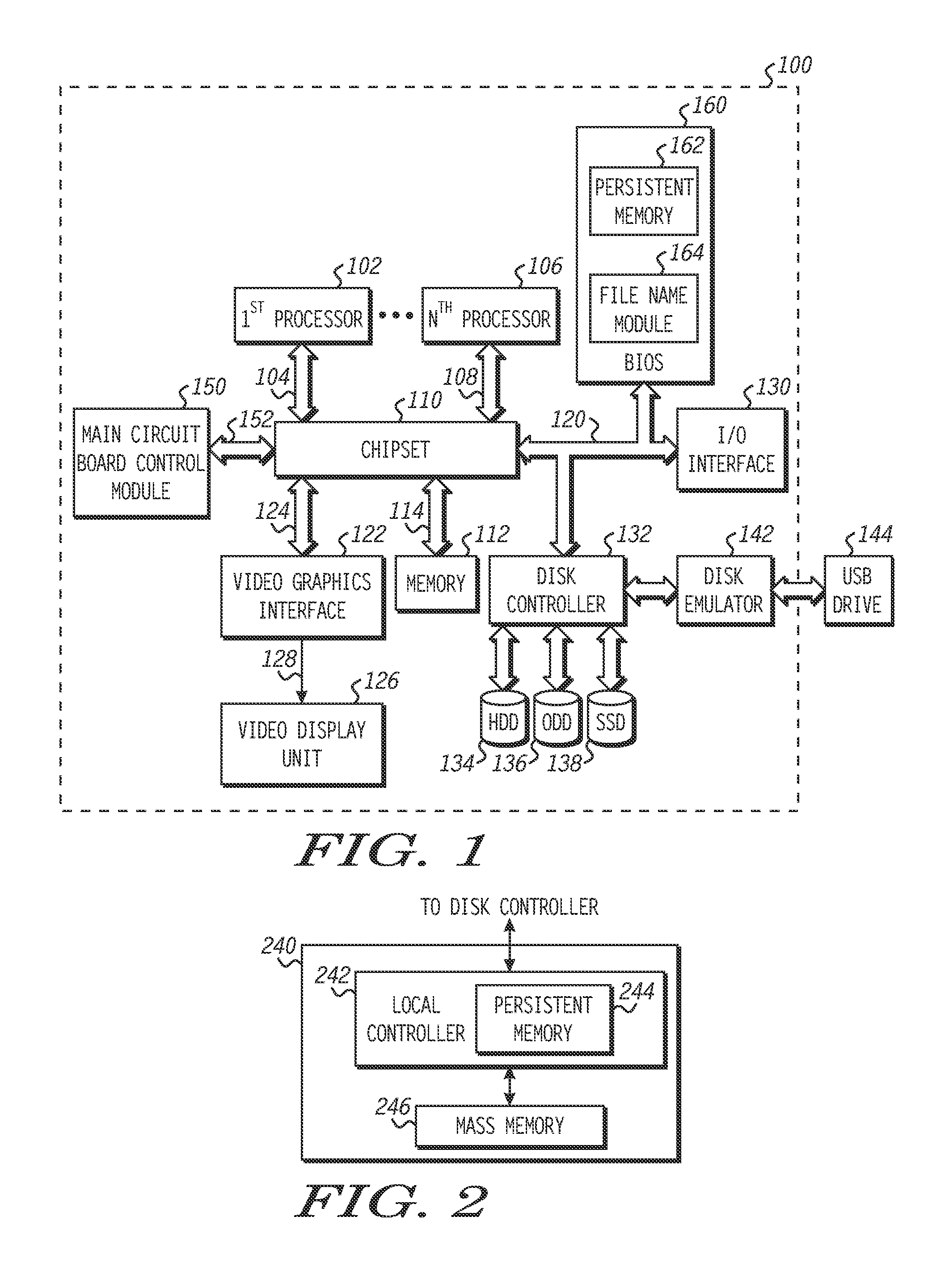
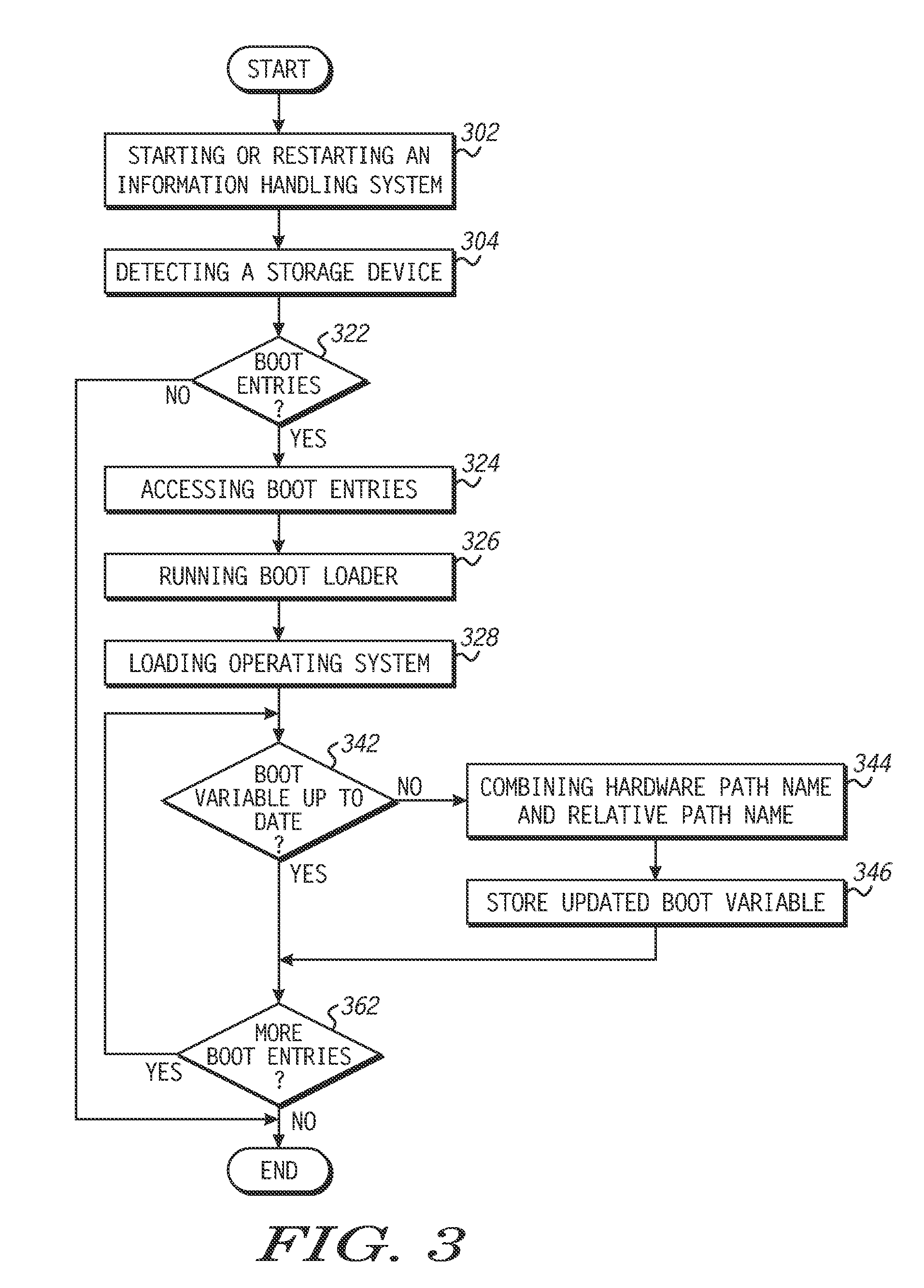
Method of using an information handling system having a boot file, and an information handling system and machine-executable code for carrying out the method
An information handling system and a method of using it can allow the information handling system to be started or restarted and have an operating system loaded, even if a boot variable within a persistent memory is currently invalid. The method can detect and determine a hardware path name to a new drive that has an operating system. The new drive can have a relative path name to boot entries that include a pointer to a boot file. The boot file can be executed to run a boot loader that loads the operating system. During loading of the operating system, other boot entries within the drive can provide boot parameters. The boot variable within persistent memory, and potentially the relative path name or boot parameter(s) can be updated on the new drive. In a particular embodiment, the information handling system can include a unified extensible firmware interface (UEFI).
Owner:DELL PROD LP
Design method of firmware GUI based on SVG
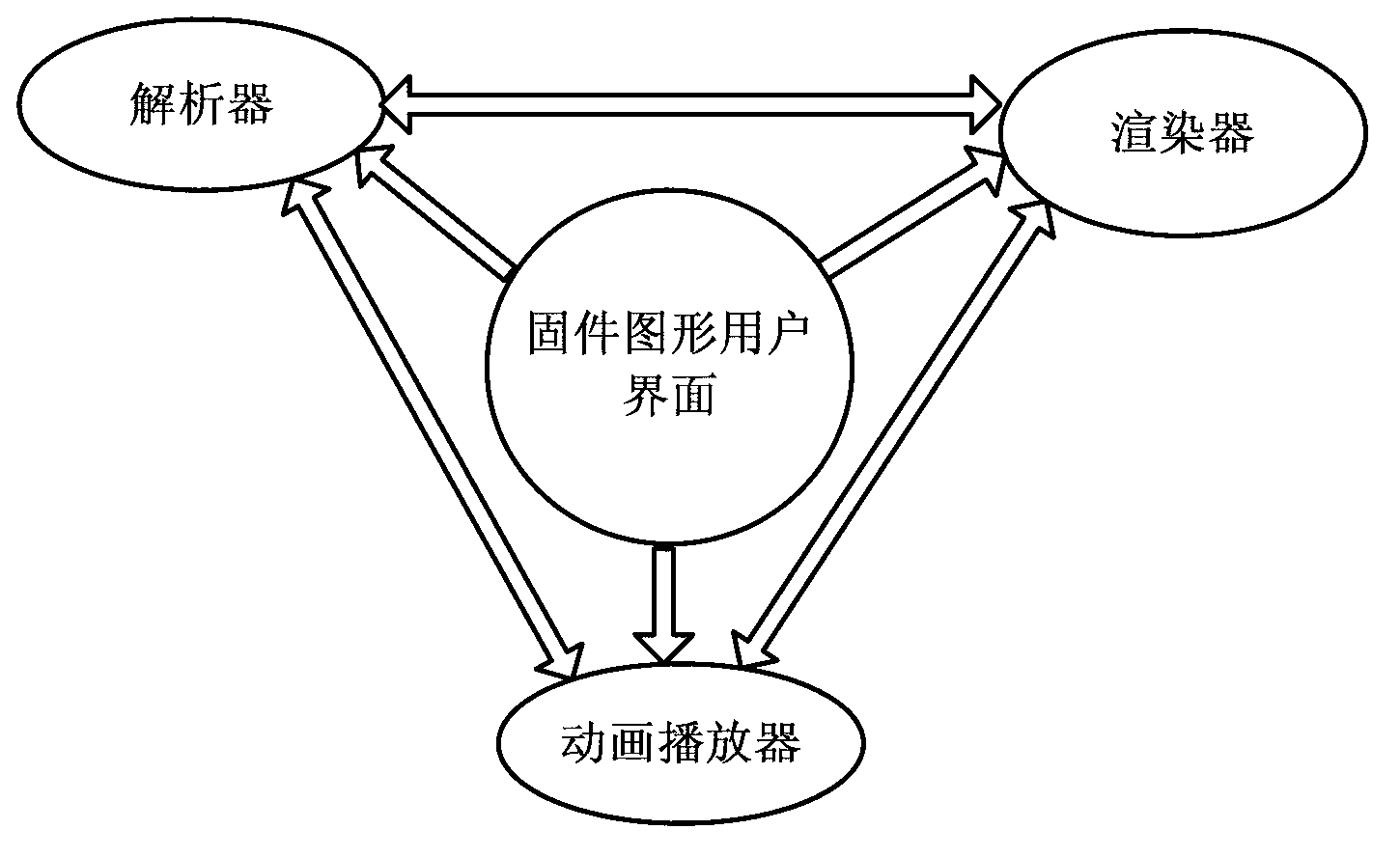
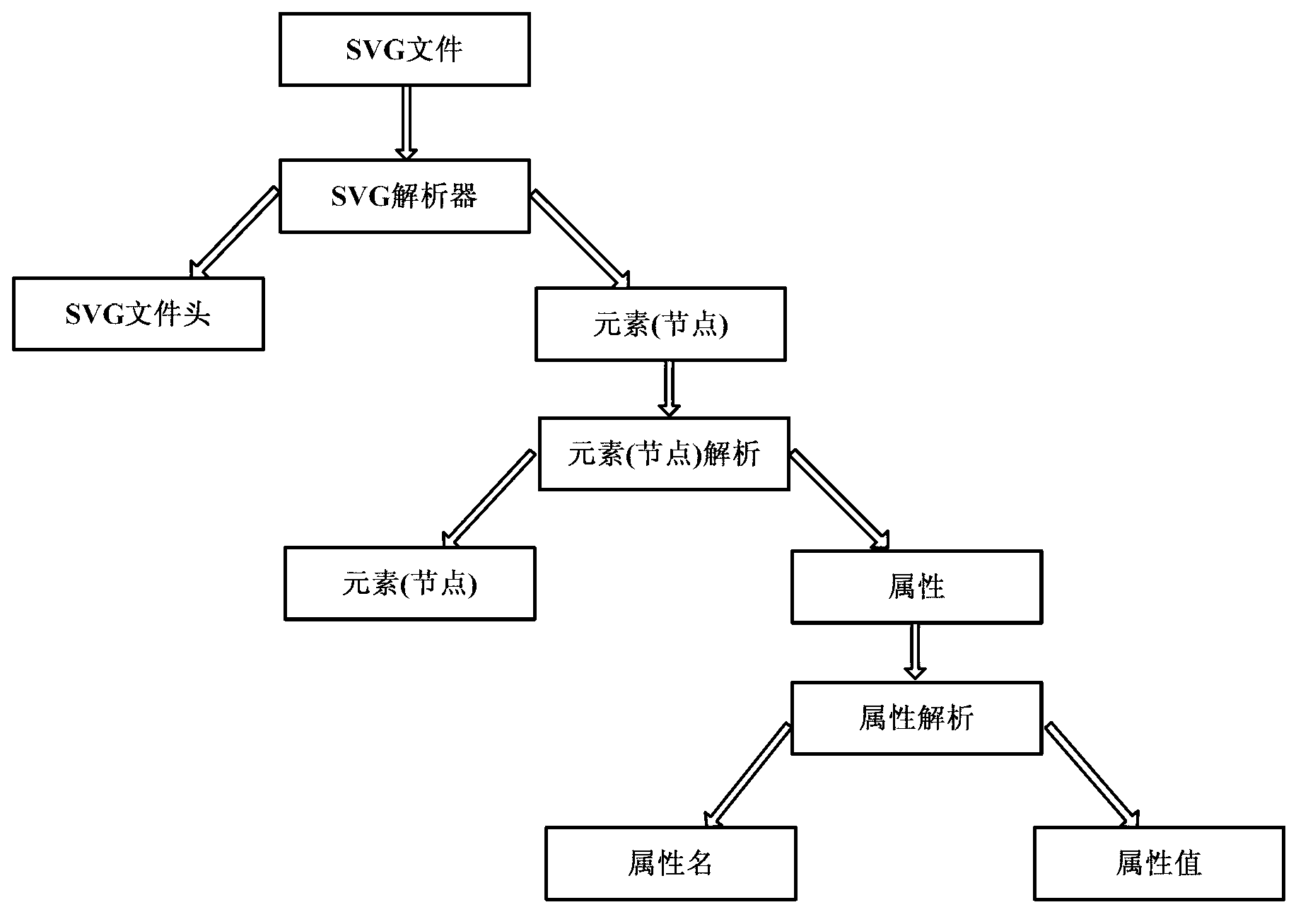
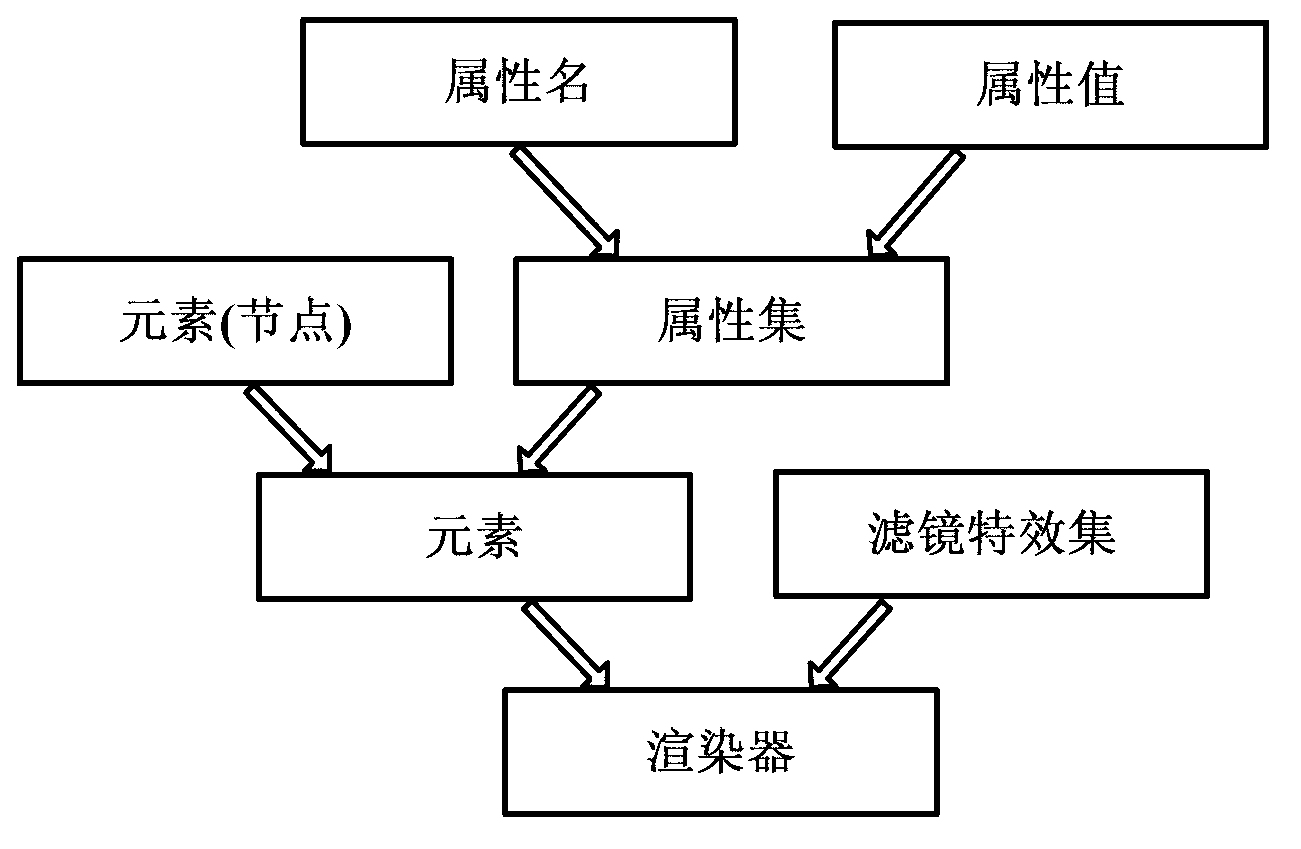
InactiveCN103226471AEasy to operateIntuitive configurationSpecific program execution arrangementsGraphicsGraphical user interface
The invention discloses a design method of a firmware GUI (graphical user interface) based on SVG (scalable vector graphics). The method comprises the steps that the SVG of an extensible markup language is used for indicating constituent elements of the firmware GUI; an interface file described by the SVG is obtained; an SVG resolver is called for resolving the described file of the firmware GUI; basic elements of the SVG are extracted; an interface element structure tree is generated; and the extracted elements of the SVG are drawn and displayed according to a graphic output protocol provided by a UEFI (unified extensible firmware interface). With the adoption of the firmware GUI designed by the method, configuration and management of hardware are more visual and quicker; interface customization is individual; an interface indication file occupies a small space; the interface can play an animation effect; and compared with the traditional BIOS (basic input output system) textual interface, the firmware GUI based on the SVG has the characteristics that the firmware GUI is visual, friendly and easy to operate.
Owner:NANJING UNIV OF TECH
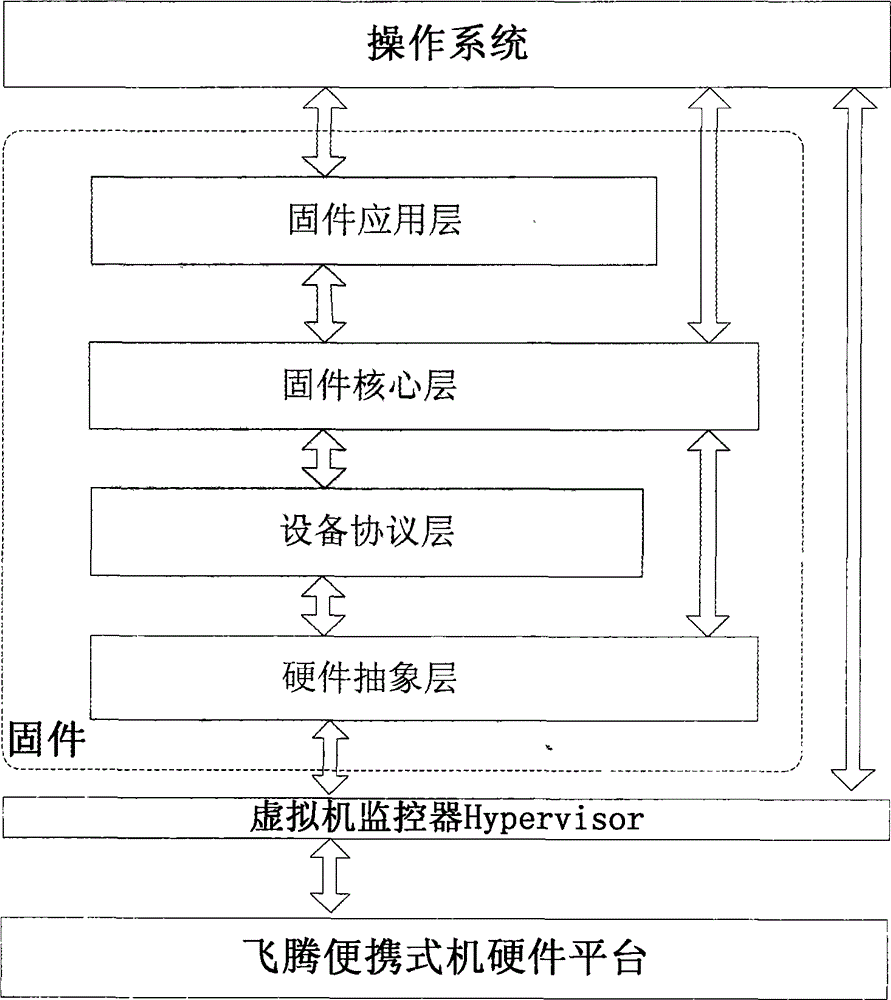
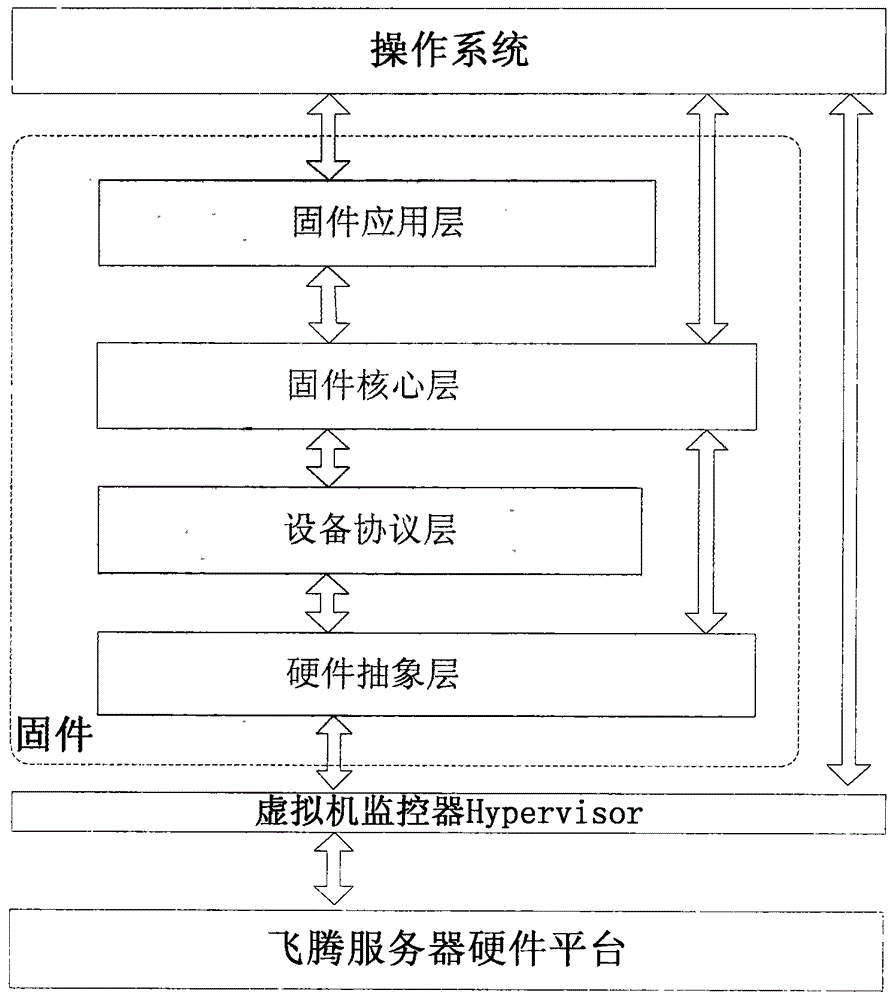
UEFI (Unified Extensible Firmware Interface) firmware implementation method based on Feiteng portable computer
The invention relates to a UEFI (Unified Extensible Firmware Interface) firmware implementation method based on a Feiteng portable computer, and belongs to the technical field of computer firmware. Firmware is divided into a hardware abstraction layer, a firmware core layer, an equipment protocol layer and a firmware application layer, wherein the hardware abstraction layer is used for realizing the initialization of key hardware components such as a processor, an internal memory and a chipset, packaging and abstracting other board-level hardware and realizing the initialization, and also providing a function interface for accessing bottom-layer hardware equipment for an upper module; the firmware core layer is used for establishing a system service table in a UEFI to carry out the unified management of all modules in the firmware and the management of various resources; the equipment protocol layer is used for realizing various standard industrial specifications; the firmware application layer is used for realizing all functions of the firmware, such as interface configuration, system monitoring, file system and operating system guiding. The UEFI firmware implementation method can realize firmware products, with high expandability and perfect functions, meeting international mainstream UEFI firmware specifications on the Feiteng portable computer so as to support the normal start and operation of the Feiteng portable computer.
Owner:昆仑太科(北京)技术股份有限公司
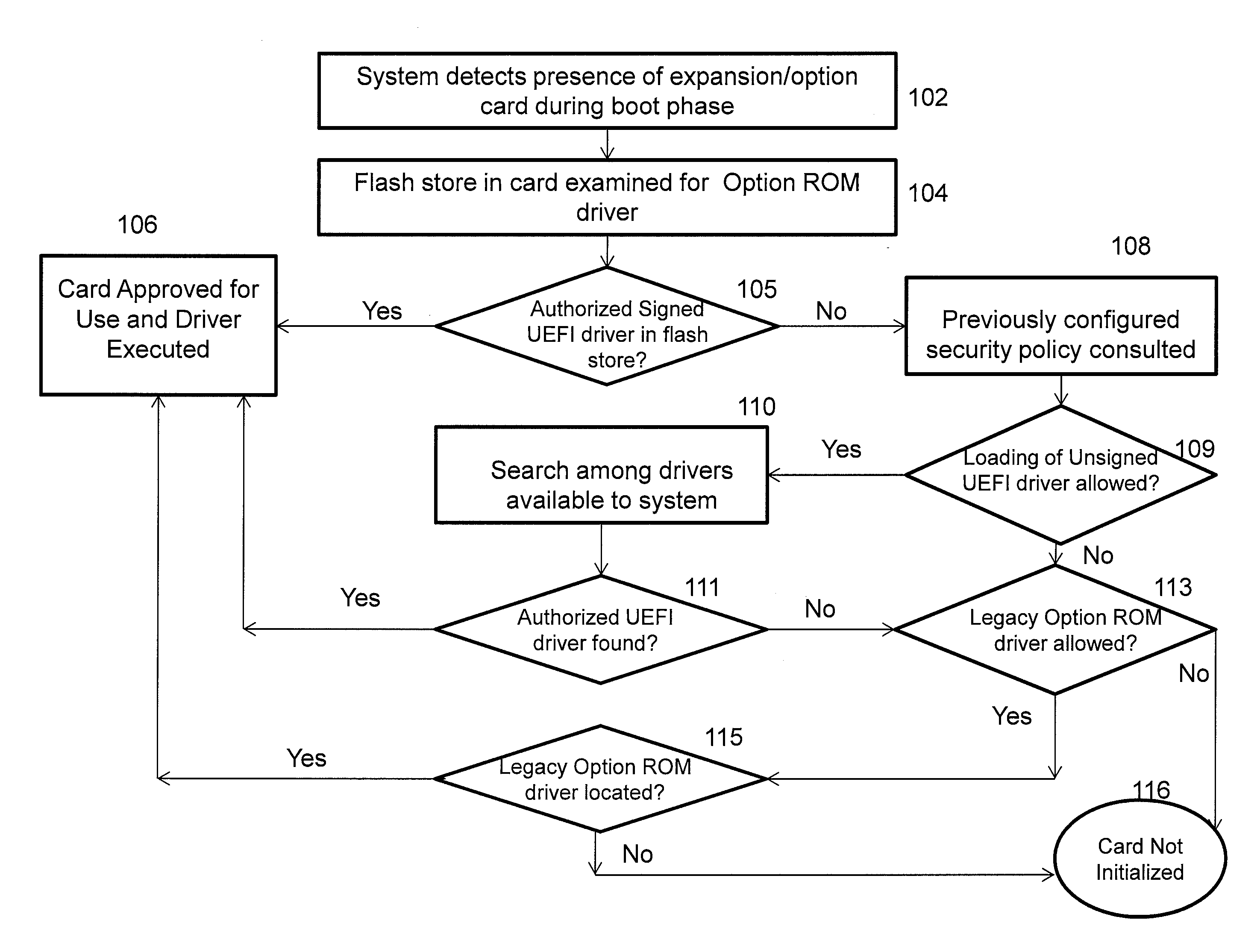
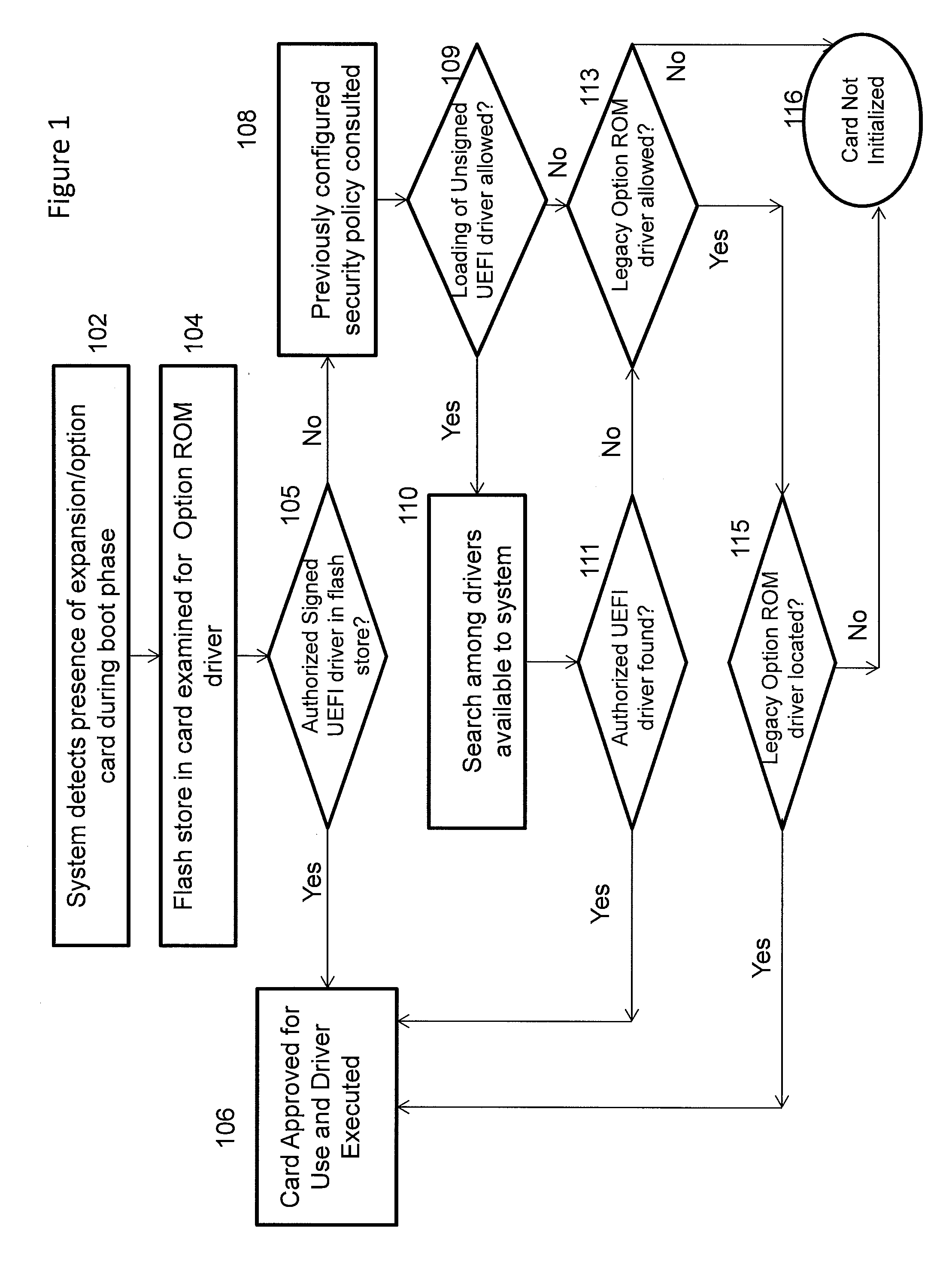
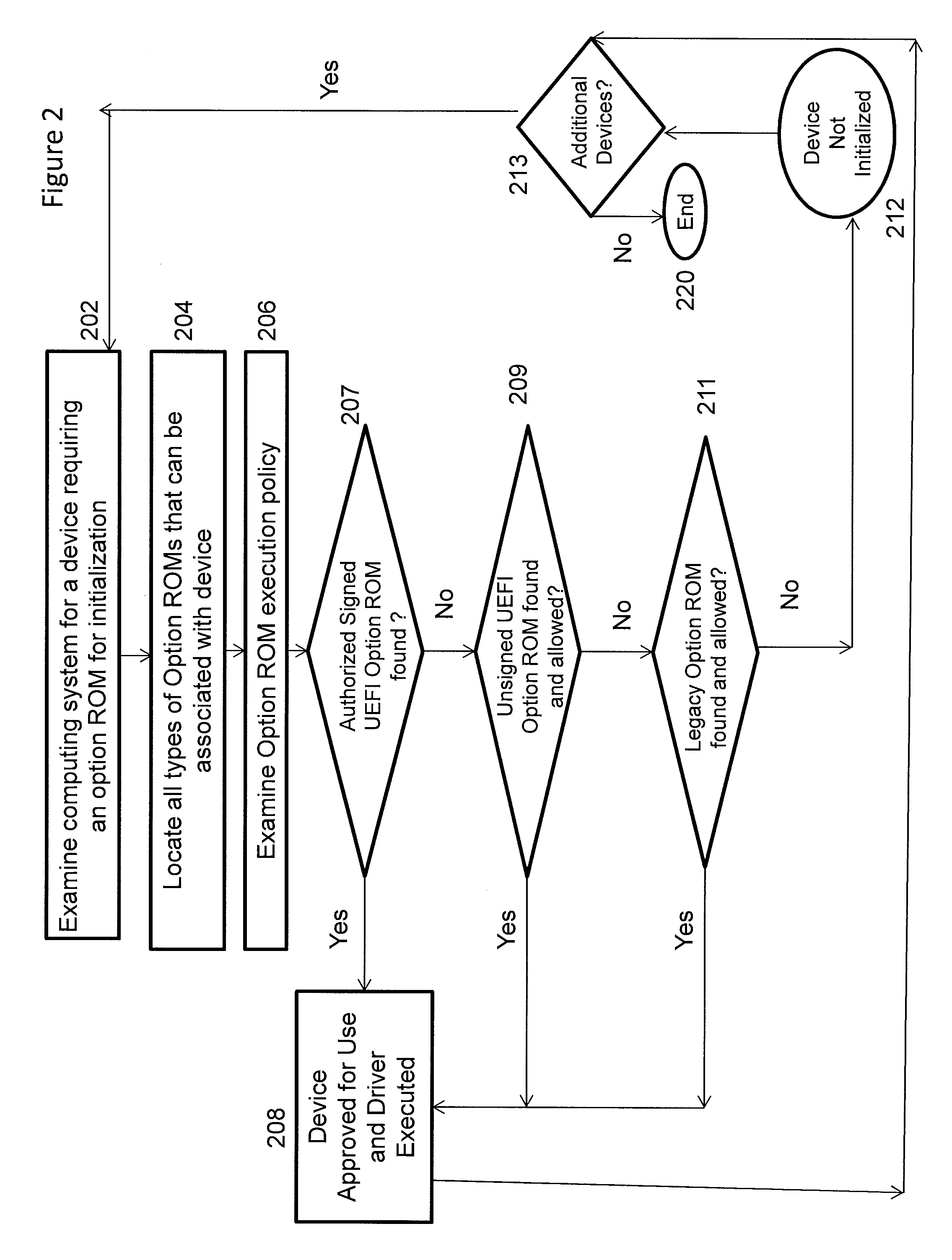
Secure option ROM control
ActiveUS20130104188A1Provide flexibilityPlatform integrity maintainanceTransmissionExpansion cardOption ROM
A mechanism for controlling the execution of Option ROM code on a Unified Extensible Firmware Interface (UEFI)-compliant computing device is discussed. A security policy enforced by the firmware may be configured by the computing platform designer / IT administrator to take different actions for different types of detected expansion cards or other devices due to the security characteristics of Option ROM drivers associated with the expansion card or device. The security policy may specify whether authorized signed UEFI Option ROM drivers, unauthorized but signed UEFI Option ROM drivers, unsigned UEFI Option ROM drivers and legacy Option ROM drivers are allowed to execute on the UEFI-compliant computing device.
Owner:INSYDE SOFTWARE
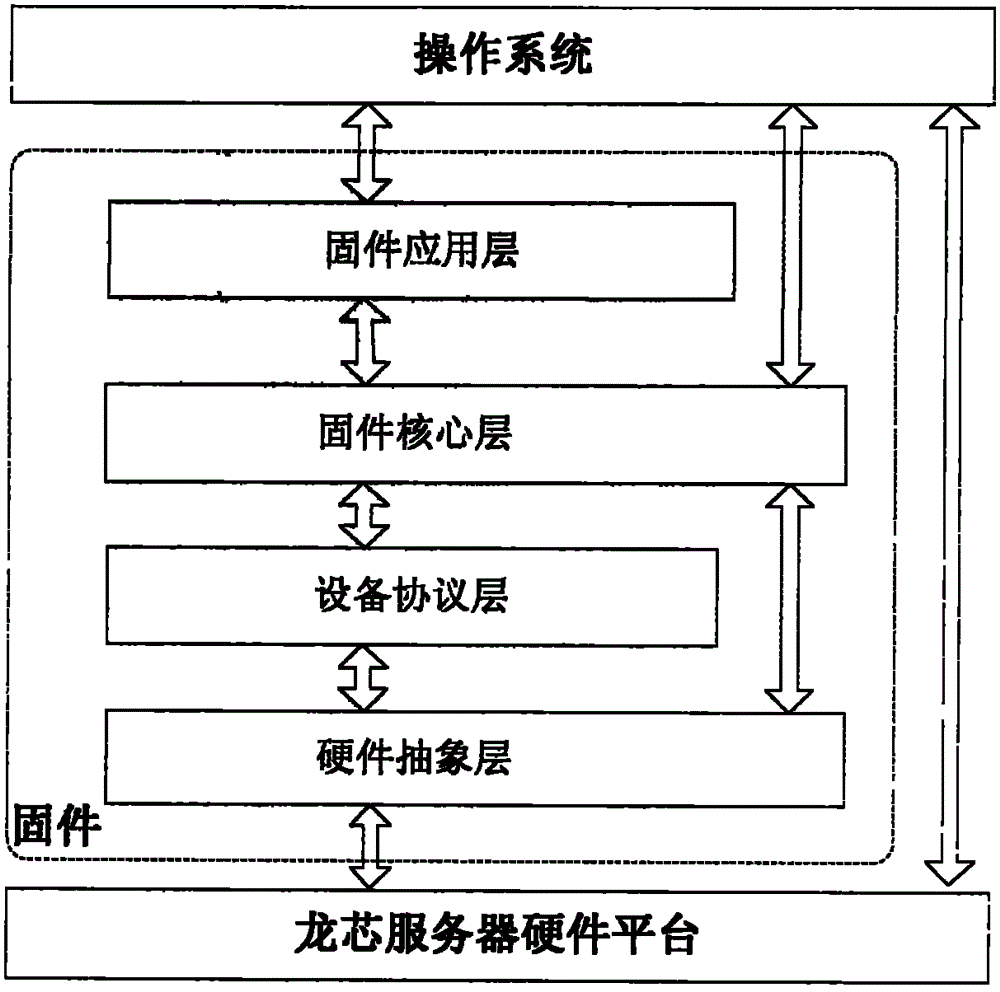
UEFI (Unified Extensible Firmware Interface) firmware implementation method based on Loongson server
InactiveCN104572061ASpeed upAdd supportSpecific program execution arrangementsInternal memoryExtensibility
The invention relates to a UEFI (Unified Extensible Firmware Interface) firmware implementation method based on a Loongson server, and belongs to the technical field of computer firmware. Firmware is divided into a hardware abstraction layer, a firmware core layer, an equipment protocol layer and a firmware application layer, wherein the hardware abstraction layer is used for realizing the initialization of key hardware components such as a processor, an internal memory and a chipset, packaging and abstracting other board-level hardware and realizing the initialization, and also providing a function interface for accessing bottom-layer hardware equipment for an upper module; the firmware core layer is used for establishing a system service table in a UEFI to carry out the unified management of all modules in the firmware and the management of various resources; the equipment protocol layer is used for realizing various standard industrial specifications; the firmware application layer is used for realizing all functions of the firmware. The UEFI firmware implementation method can realize firmware products, with high expandability and perfect functions, meeting international mainstream UEFI firmware specifications on the Loongson server so as to support the normal start and operation of the server.
Owner:昆仑太科(北京)技术股份有限公司
UEFI (Unified Extensible Firmware Interface) firmware implementation method based on Feiteng server
The invention relates to a UEFI (Unified Extensible Firmware Interface) firmware implementation method based on a Feiteng server, and belongs to the technical field of computer firmware. Firmware is divided into a hardware abstraction layer, a firmware core layer, an equipment protocol layer and a firmware application layer, wherein the hardware abstraction layer is used for realizing the initialization of key hardware components such as a processor, an internal memory and a chipset, packaging and abstracting other board-level hardware and realizing the initialization, and also providing a function interface for accessing bottom-layer hardware equipment for an upper module; the firmware core layer is used for establishing a system service table in a UEFI to carry out the unified management of all modules in the firmware and the management of various resources; the equipment protocol layer is used for realizing various standard industrial specifications; the firmware application layer is used for realizing all functions of the firmware, such as interface configuration, system monitoring, file system and operating system guiding. The UEFI firmware implementation method can realize firmware products, with high expandability and perfect functions, meeting international mainstream UEFI firmware specifications on the Feiteng server so as to support the normal start and operation of the Feiteng server.
Owner:昆仑太科(北京)技术股份有限公司
Policy description technique in uefi firmware
InactiveUS20100318962A1Specific program execution arrangementsMemory systemsCore functionPersonal computer
Methods, systems, apparatuses and program products are disclosed for providing parametric policy isolation in builds of Unified Extensible Firmware Interface based Personal Computer firmware, typically but not essentially as BIOS.Policy Description, including means for enabled description of desired system behavior under code execution and operational hardware exigencies are provided through project file statements.Provision is made for direction of policy at a project file that is not embedded in core functions. This allows a less expert and more efficient approach to policy adaptation and evolution in response to evolving PC product requirements.
Owner:KINGLITE HLDG INC
Recovering an information handling system from a secure boot authentication failure
A method, information handling system (IHS) and a recovery system for recovering an IHS from a secure boot authentication failure. The method includes retrieving, via a processor from a first memory device, a first unified extensible firmware interface (UEFI) driver associated with a first component / device of the IHS. The method further includes determining, via a secure boot process, if the first UEFI driver is an authenticated UEFI driver. In response to determining that the first UEFI driver is not an authenticated driver, a previously validated UEFI driver corresponding to the first component / device is retrieved from a second memory device. The method further includes loading the previously validated UEFI driver.
Owner:DELL PROD LP
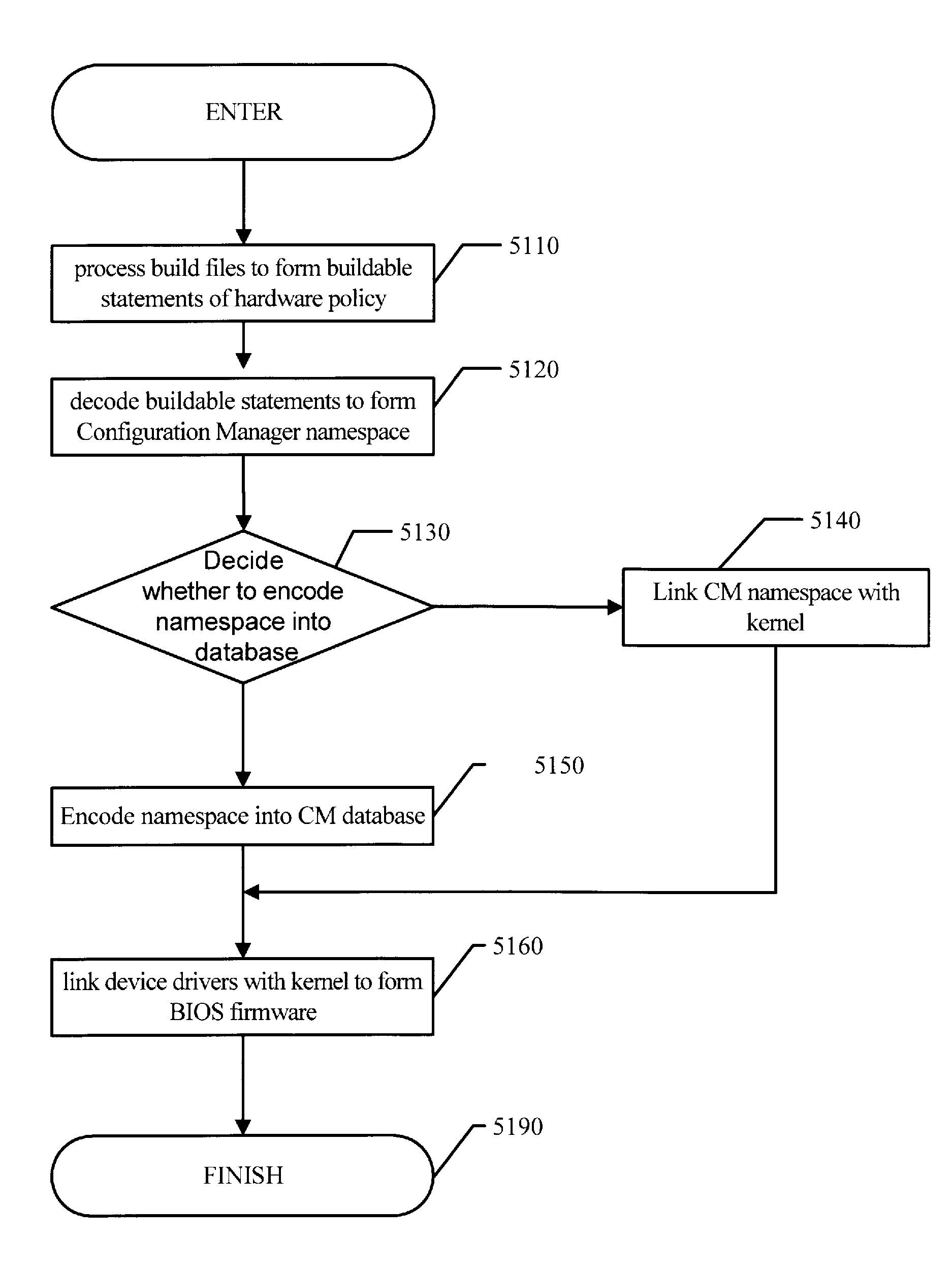
Parametric Build of UEFI Firmware
InactiveUS20100318961A1Specific program execution arrangementsMemory systemsParallel computingPersonal computer
Methods, systems, apparatuses and program products are disclosed for providing parametric driven build of Unified Extensible Firmware Interface based Personal Computer firmware, typically but not essentially as BIOS.Provision is made for source databases providing for multiple configurations, variants, revisions and levels of capabilities including on non-hierarchical bases.
Owner:KINGLITE HLDG INC
Supporting hardware configuration changes in a uefi firmware component
ActiveUS20120254831A1BootstrappingMemory systemsUnified Extensible Firmware InterfaceConfiguration management
A method and apparatus for providing support for customization of a build configuration of a Unified Extensible Firmware Interface (UEFI) compatible component. The method includes modifying the build configuration of the UEFI compatible component to reflect modifications to a first file. A configuration parameter is received. The configuration parameter is used to create a configuration parameter symbol pointing to the first file. The first file is replaced with a second file, which includes modifications to the first file. The modifications support a functionality desired by a user.
Owner:PHOENIX TECH EMEA LTD
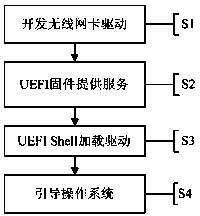
Method of realizing wireless card driver in UEFI (unified extensible firmware interface) layer
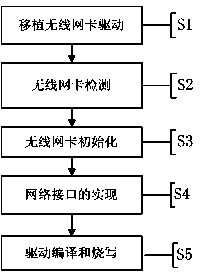
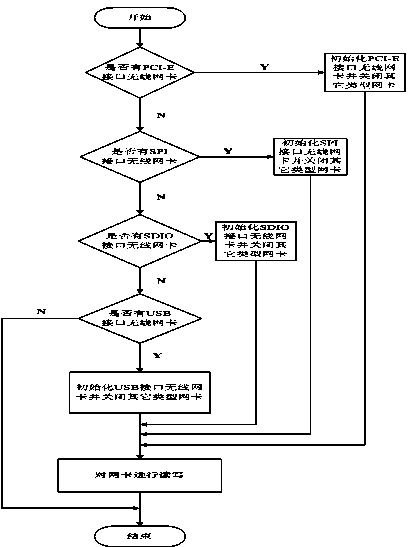
InactiveCN103853586AImplementation supportGet rid of dependenceProgram loading/initiatingTransmissionProtocol for Carrying Authentication for Network AccessNetwork interface controller
The invention discloses a method of realizing a wireless card driver in a UEFI (unified extensible firmware interface) layer. The method comprises the steps of transplanting and modifying the wireless card driver, adding the codes of wireless card driver detection and initiation and realizing a network protocol interface; rewriting, recompiling and programming the codes to a development board; powering on the system, operating the UEFI firmwire, initializing the hardware and realizing all the services defined by all the needed UEFI standards for an upper interface. A UEFI startup manager loads UEFIShell, the UEFIShell loads the wireless card driver and a transmission control protocol / internet protocol (TCP / IP) stack module, a wireless network communication environment is established, and the operating system is remotely booted through the wireless network. The method can realizing the detection, the initiation and the data read-write of the wireless network equipment in an environment without the operating system and the reliance of the wireless network equipment on the operating system is removed.
Owner:CENT SOUTH UNIV
UEFI (unified extensible firmware interface) based server NVME (non-volatile memory express) hard disk back plate function testing method
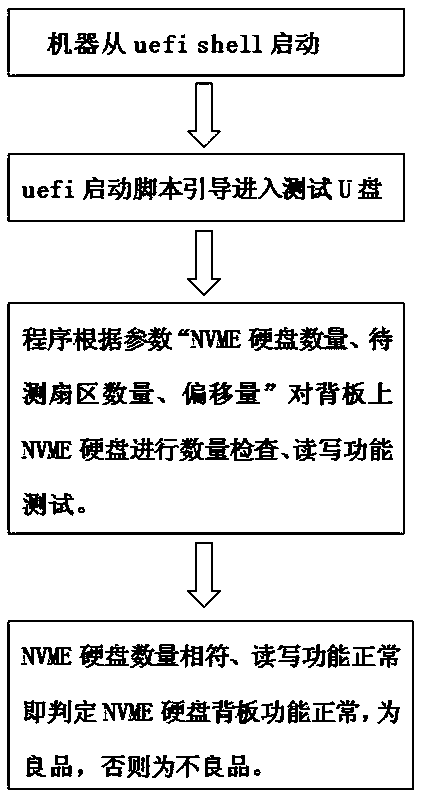
ActiveCN105511993AThe testing process is simpleEasy to testFaulty hardware testing methodsTest fixtureUSB
The invention discloses a UEFI (unified extensible firmware interface) based server NVME (non-volatile memory express) hard disk back plate function testing method. The testing method comprises steps as follows: 1) a machine is started through a uefi shell; 2) a uefi starting script is guided into a testing USB disk; 3) a procedure performs quantity checking and read-write function testing on the NVME hard disks on a back plate according to parameters including 'the number of the NVME hard disks, the number of to-be-tested sectors and the offset'; 4) the function of an NVME hard disk back plate is normal and the NVME hard disk back plate is a non-defective product if the number of the NVME hard disks is consistent and the read-write function is normal, and otherwise, the NVME hard disk back plate is a defective product. By means of the method, the problems that an existing testing method consumes long time and is dependent on a system, an operating system requires daily maintenance and large-scale testing of a factory is hindered are solved, simplicity in operation, fast speed, saving of testing time and test fixtures and high expandability and flexibility during large-scale testing of the NVME hard disk back plate are realized, and testing of the NVME hard disk back plate is simplified and rapid.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Secure boot administration in a Unified Extensible Firmware Interface (UEFI)-compliant computing device
ActiveUS9021244B2Difficult to performDigital computer detailsUnauthorized memory use protectionThird partyUnified Extensible Firmware Interface
Firmware in a UEFI-compliant computing device is used to administer and alter a Secure Boot process for the computing device while continuing to provide protection from unauthorized third-party code.
Owner:INSYDE SOFTWARE CORP
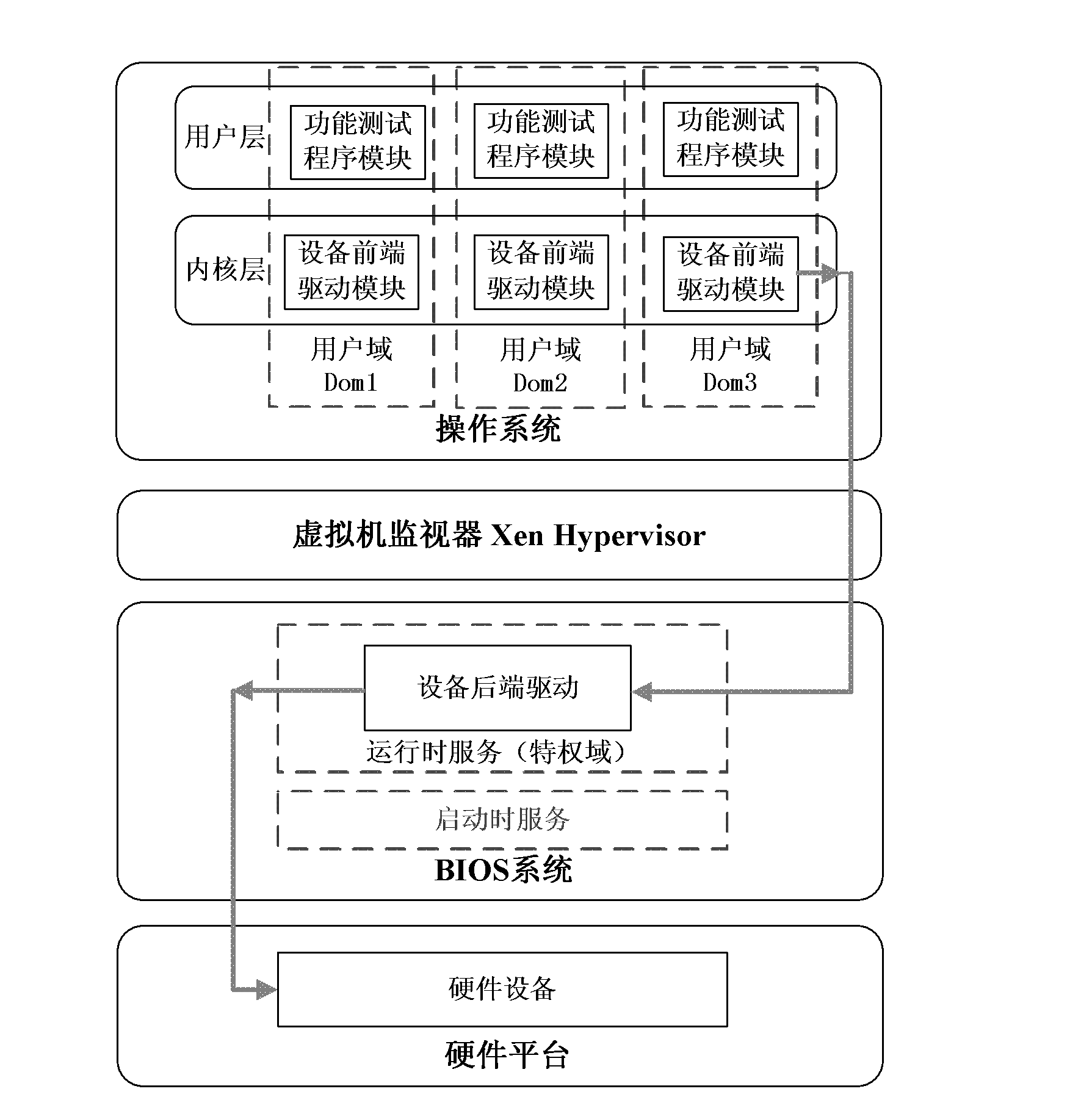
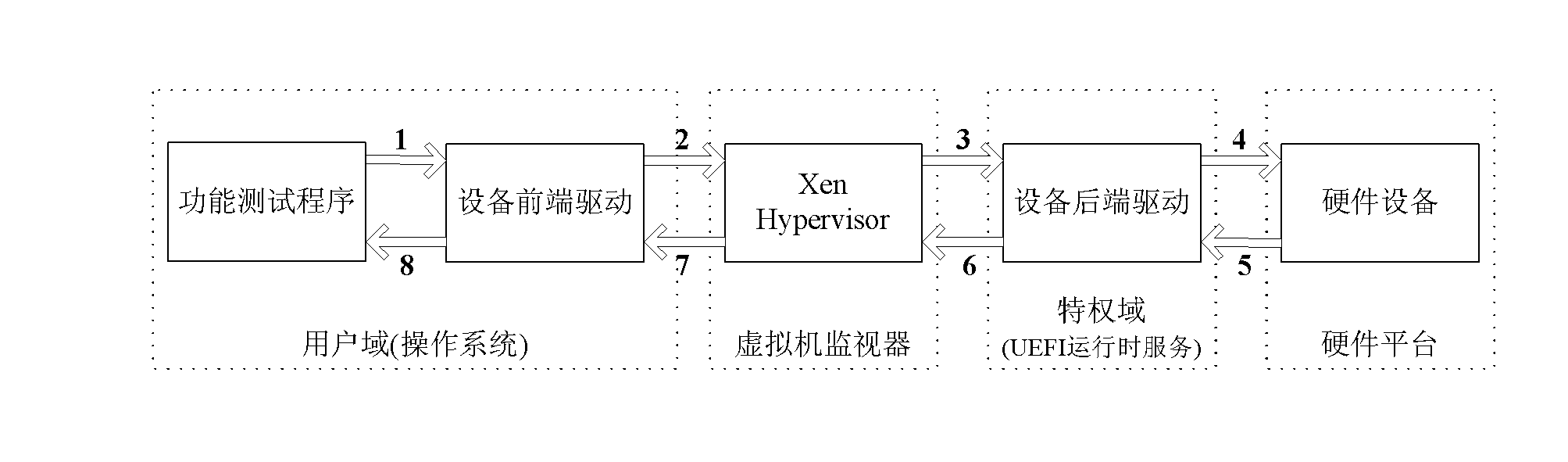
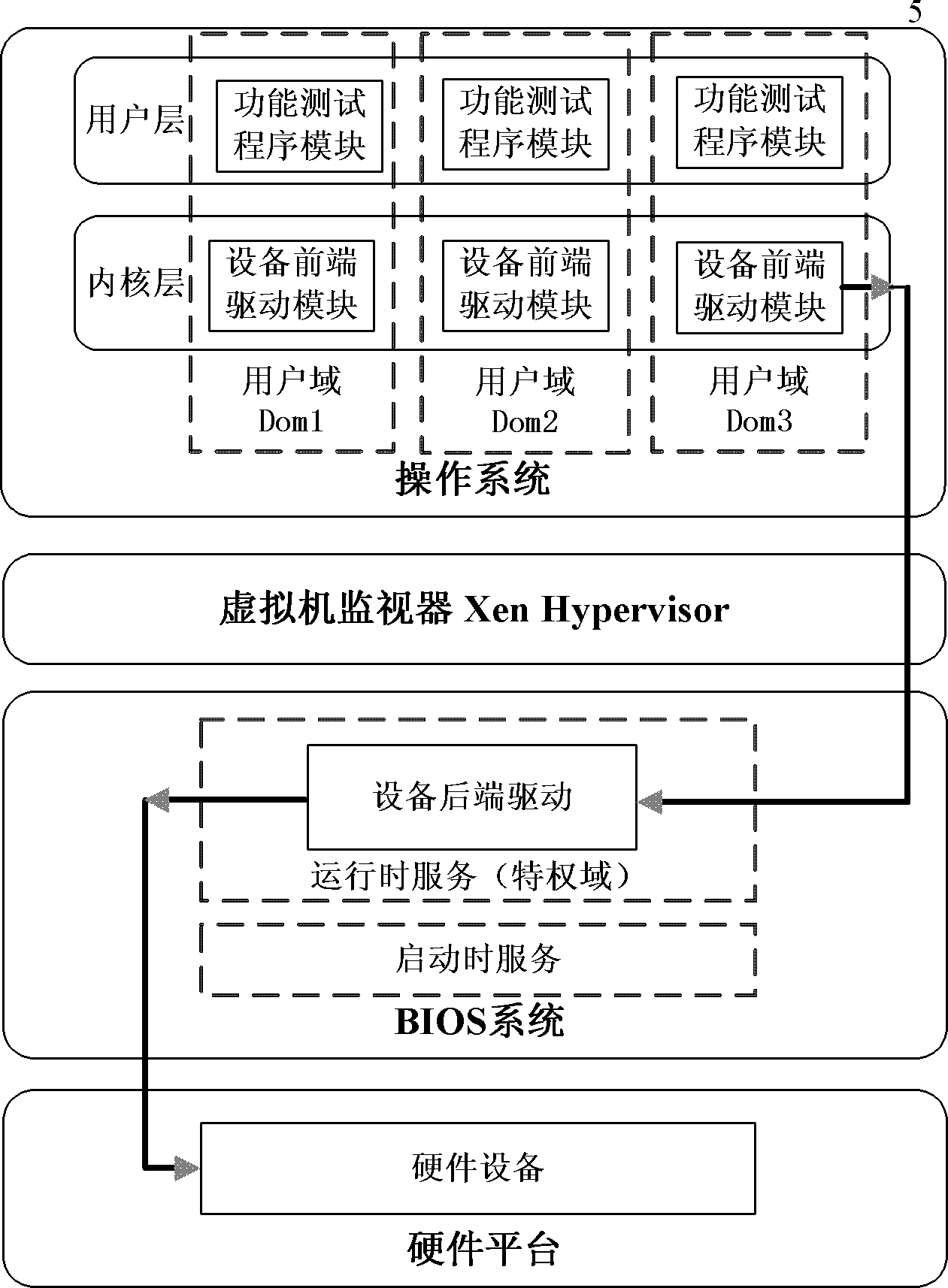
Xen virtual machine framework based on UEFI (unified extensible firmware interface) runtime service and implementation method thereof
InactiveCN102609638ASolve the problem of low security protection levelSimplifyPlatform integrity maintainanceSoftware simulation/interpretation/emulationOperational systemFunctional testing
The invention discloses a Xen virtual machine framework based on UEFI (unified extensible firmware interface) runtime service and an implementation method of the Xen virtual machine framework. The Xen virtual machine framework comprises a hardware platform, a BIOS (basic input / output system) system, a virtual machine monitor and an operating system, wherein the UEFI BIOS comprises a UEFI boot service and a UEFI runtime service; a privilege domain is communicated with a device front drive as one part of the UEFI runtime service in an operation stage of the operating system; the virtual machine monitor is located between the system hardware platform and the operating system software of the virtual computing domain to monitor lower hardware; the operating system comprises a device front drive in an inner nuclear layer and a functional test program in a user layer. Because the privilege domain is not stored in the hardware and is stored in a Flash chip as UEFI runtime service, the Xen virtual machine framework solves the problem that the existing Xen virtual machine framework has low-level safety protection. The simplification of the Xen privilege domain is achieved.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com