Computer security access control system and method
A computer security and access control technology, applied in the field of information security, can solve the problems of low reliability, insecure storage of user identity information, lack of identity protection, etc., to increase security, increase access control security, and achieve secure storage protection. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
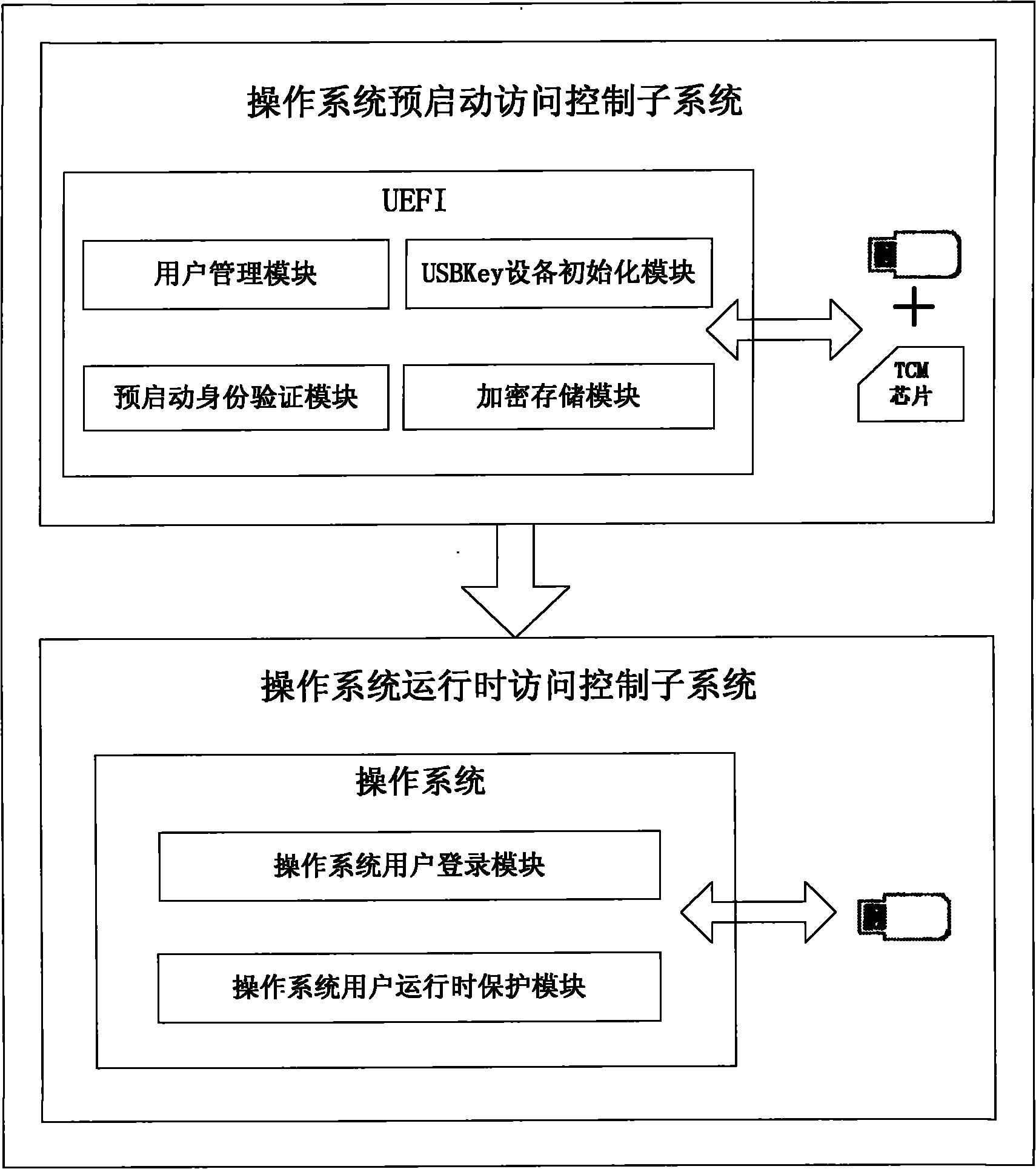
[0054] A computer security access control system and control method of the present invention include a UEFI chip and a TCM chip.
[0055] Such as figure 1 As shown, the control system includes an operating system pre-start access control subsystem and an operating system runtime access control subsystem;
[0056] The operating system pre-boot access control subsystem includes:
[0057] USBKey device: As a login user authentication key, the USBKey stores PIN code data and encrypted user identity information;
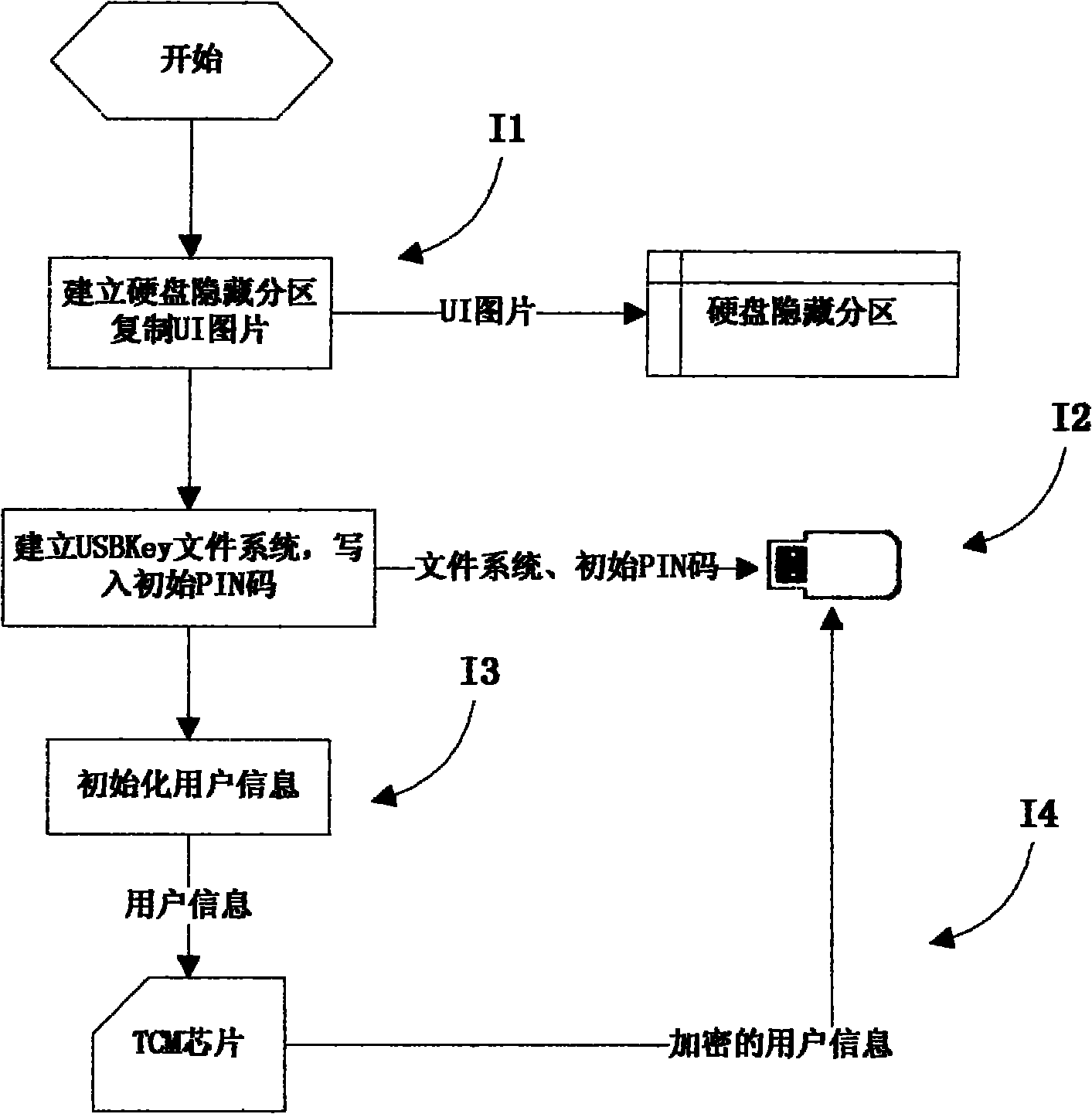
[0058] USBKey device initialization module: Embedded in the UEFI chip, it is used to establish the USBKey file system, set the initial PIN code, and create initial user information;
[0059] User management module: embedded in the UEFI chip, used to manage user information. Including two levels of user management rights, user information can be added, deleted, and modified.
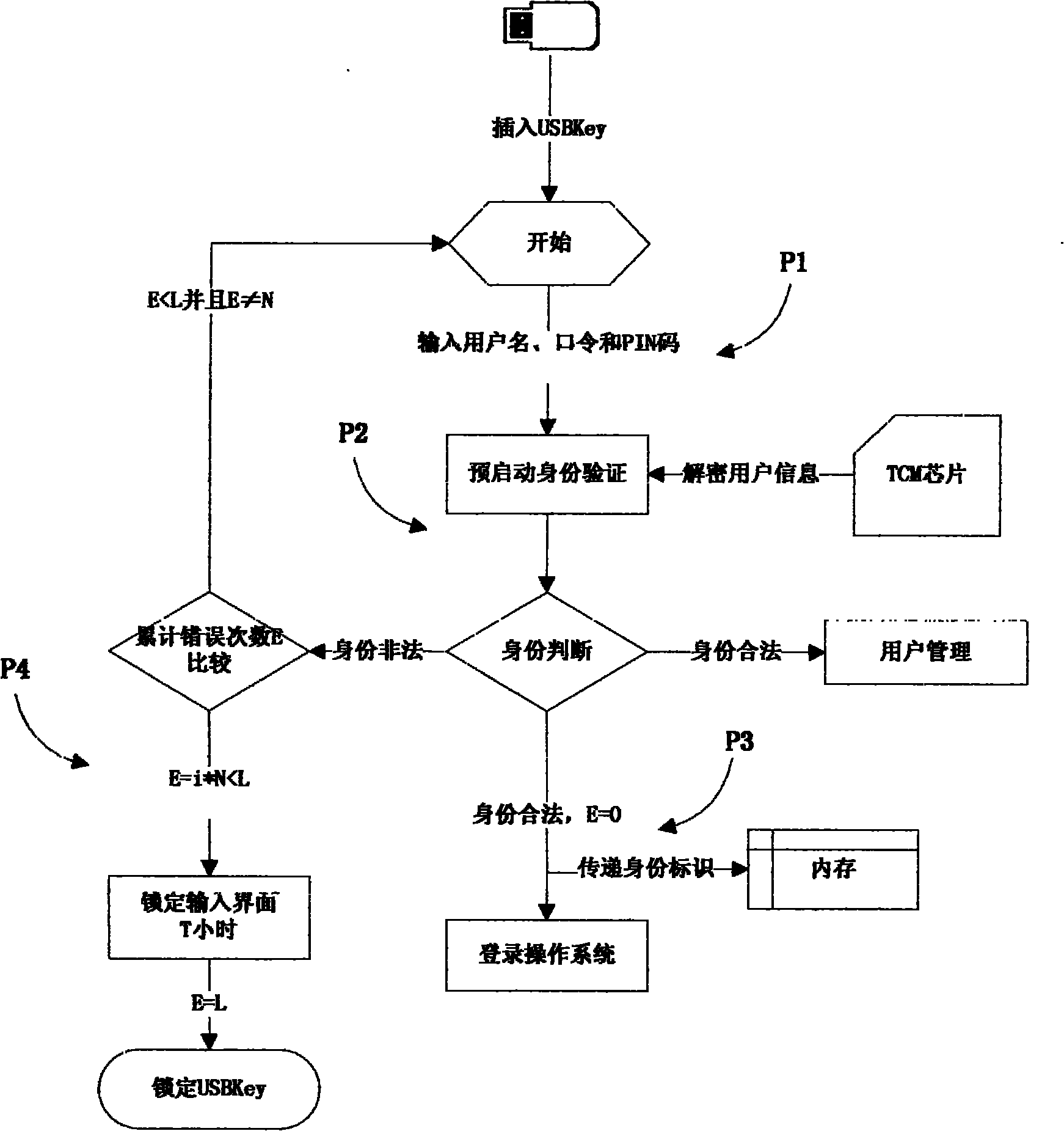
[0060] Operating system pre-boot authentication module: embedded in UEFI chip, used to verify...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com