One-machine multi-user security access control method
A security access control and multi-user technology, applied in the field of single-machine multi-user security access control, can solve the problems of lack of data security and confidentiality, multi-user information storage insecurity, multi-user, multi-hard disk resource waste, etc., and achieve the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the purpose, technical method and advantages of the present invention clearer and easier to understand, the present invention will be further described below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
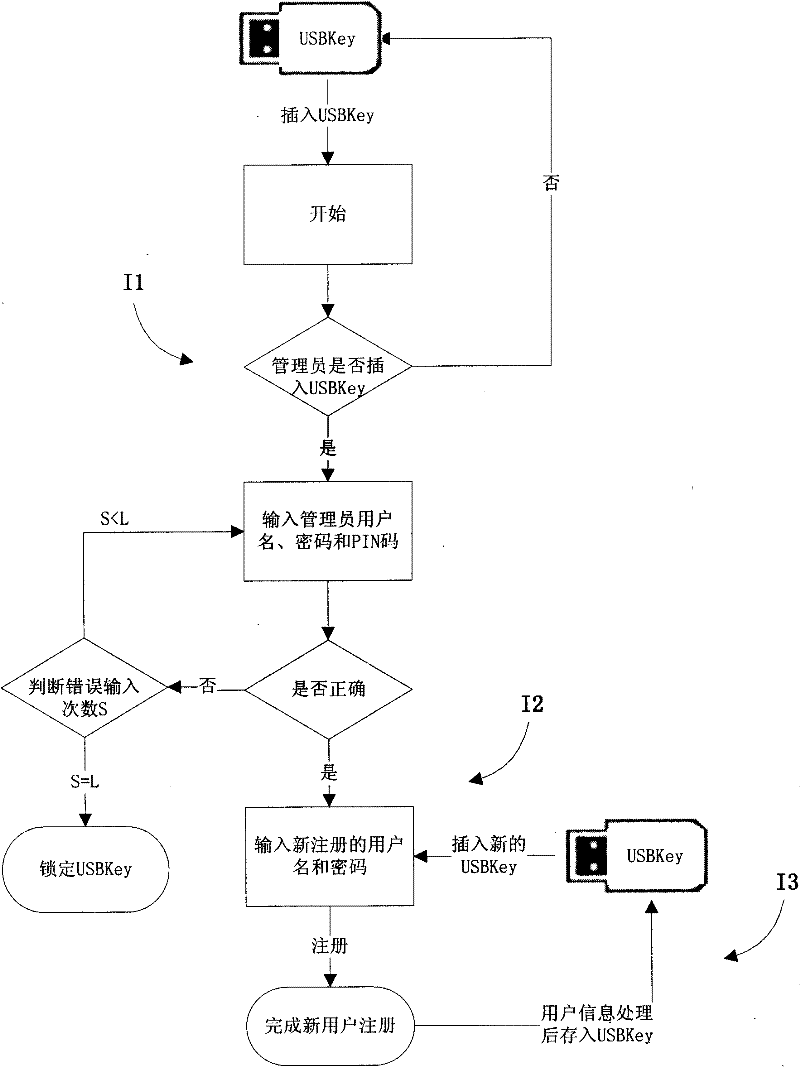
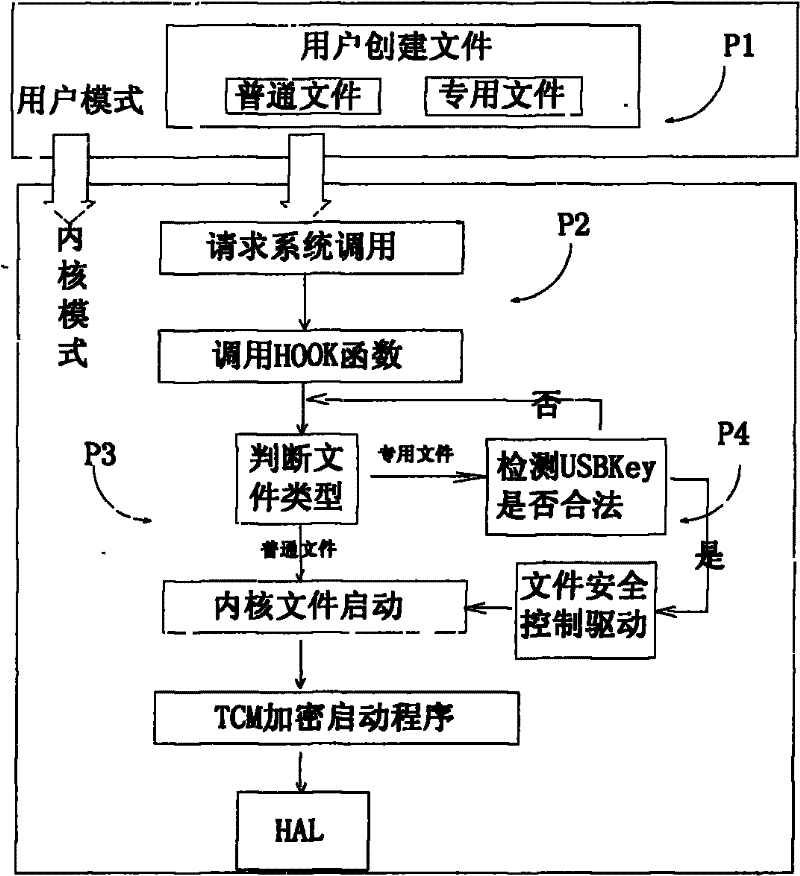
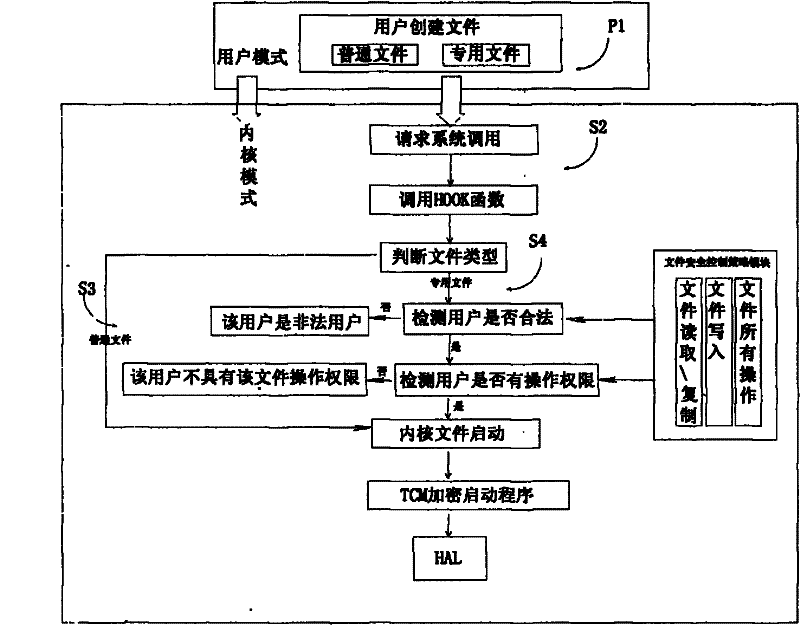
[0038] As an embodiment of the present invention, initialization work needs to be done before deploying the access control system, as shown in the attached figure 1 The implementation steps of the specific method for initializing a new user of the file security control management system shown are as follows:
[0039] Step I1. The administrator user logs in to the file security management system, and needs to input the user name, password and PIN code. The USBKey internally calculates the number of user information verifications. After the verification is passed, the system is logged i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com