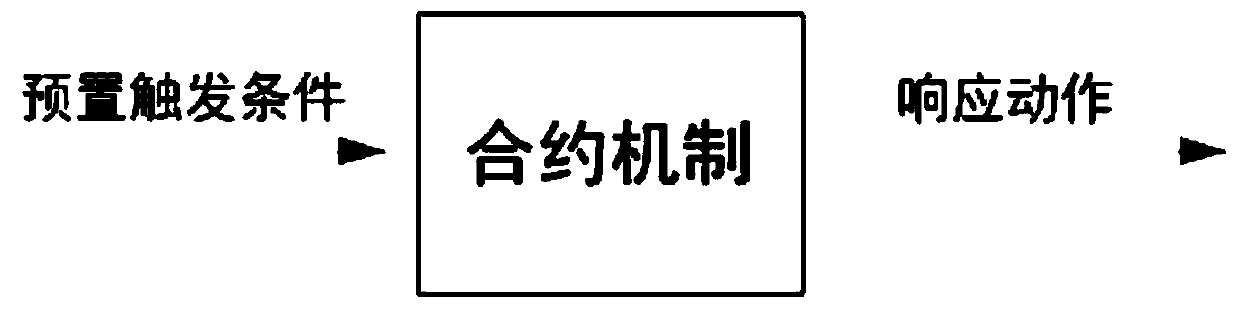
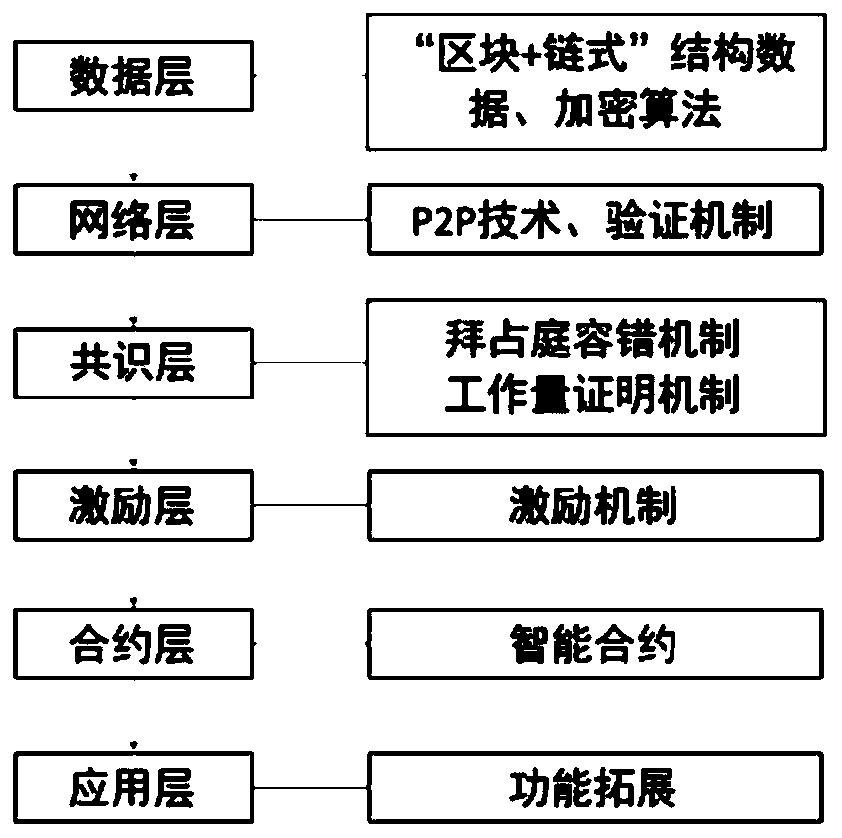
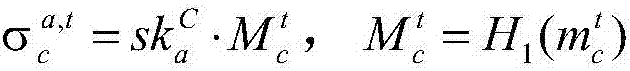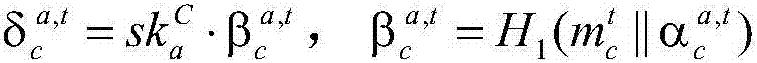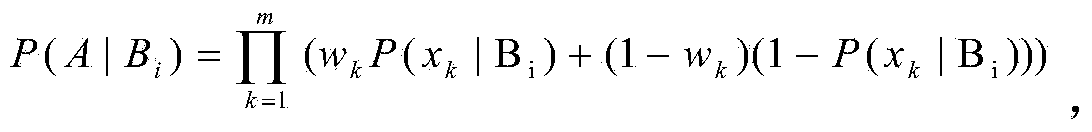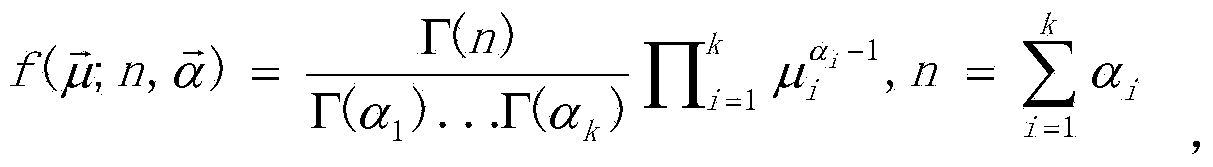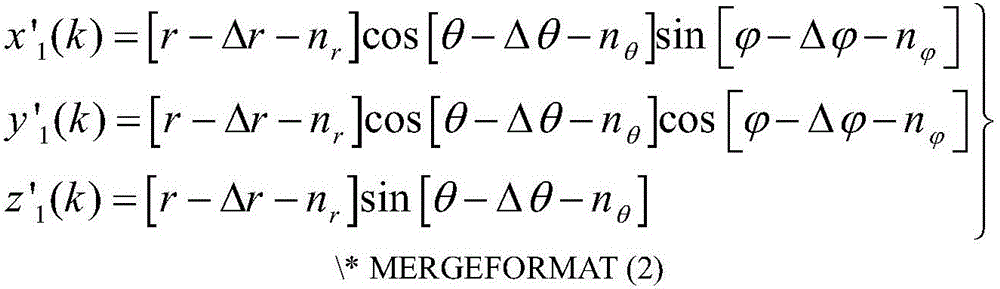Patents
Literature
168results about How to "Guaranteed safe storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multi-signature transaction information processing method for data transaction platform based on block chain
ActiveCN107038578AEnsure information securityEnsure safetyPayment protocolsInformation processingPayment
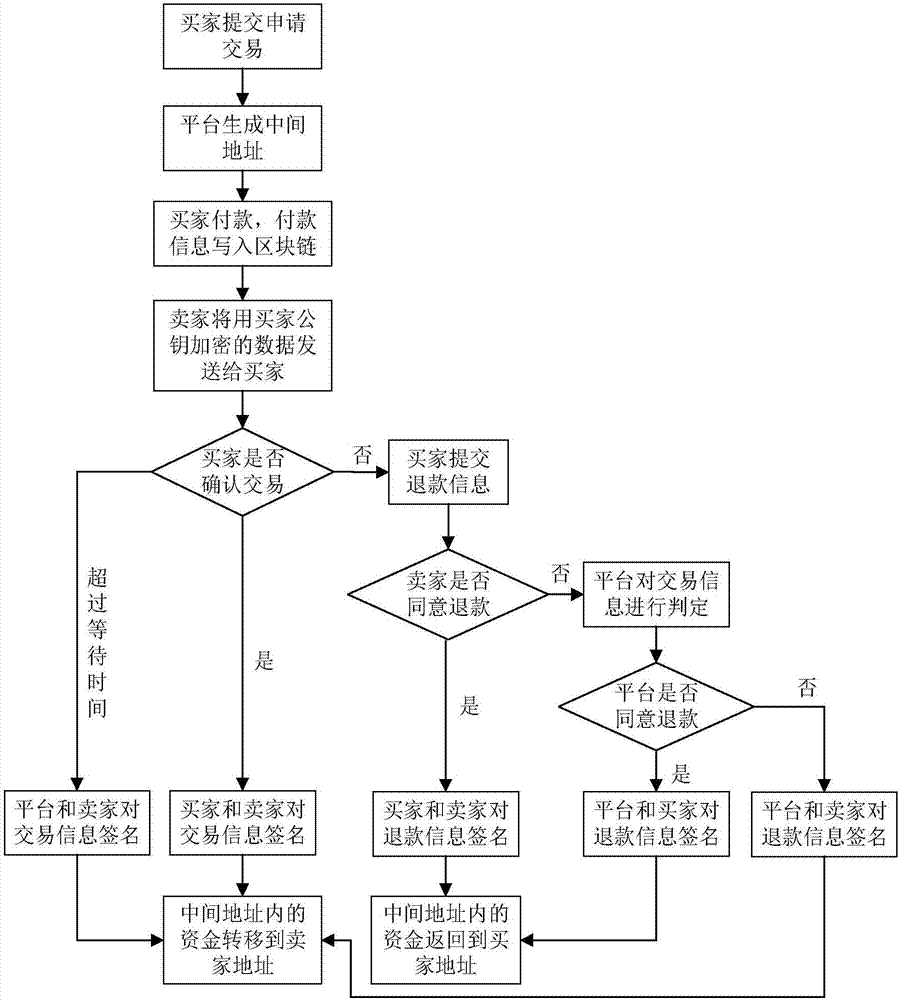
The invention discloses a multi-signature transaction information processing method for a data transaction platform based on a block chain. Each of a buyer and a seller generates a transaction key pair at self client, and the data transaction platform generates and distributes a single transaction key pair for each transaction process; the seller releases data to be transacted on the block chain via the data transaction platform; after the buyer submits a transaction application, an intermediate address is generated according to a three-party public key, money is transferred to the intermediate address after payment, and the seller receives the money, writes the money into the block chain, then encrypts data and sends the encrypted data to the buyer; after the buyer receives the data, if transaction is acknowledged, the double parties sign, and the money is transferred to the address of the seller; and if objection exists, the data transaction platform makes a judgment, and determines to transfer the money to the buyer or the seller according to the judgment result. Data and transaction information during transaction of the double parties are processed in a special regional chain manner, and meanwhile, the data transaction platform cannot embezzle the transaction money, so that the security of digital assets during transaction is further guaranteed.
Owner:浙江数秦科技有限公司
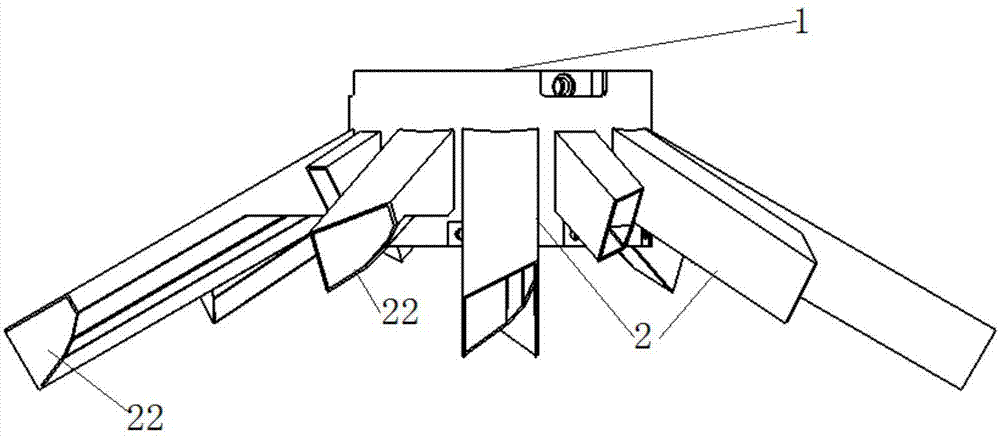
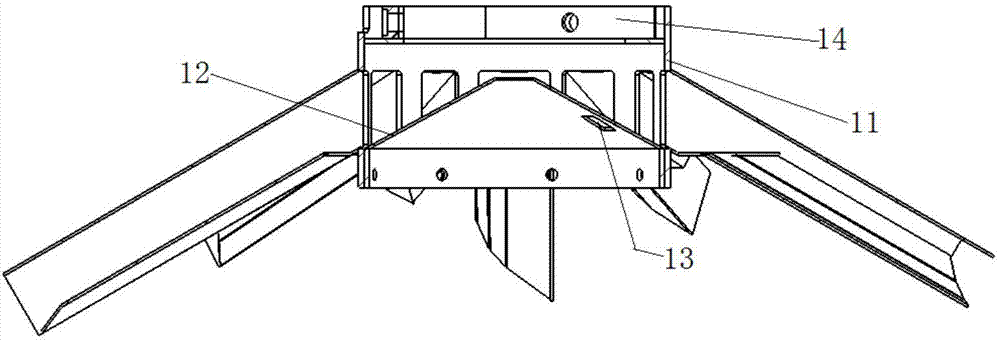
Rotating-type grain distributor and granary provided with grain distributor
InactiveCN104709729AGuaranteed safe storageReduce accumulationLoading/unloadingTangential forceEngineering
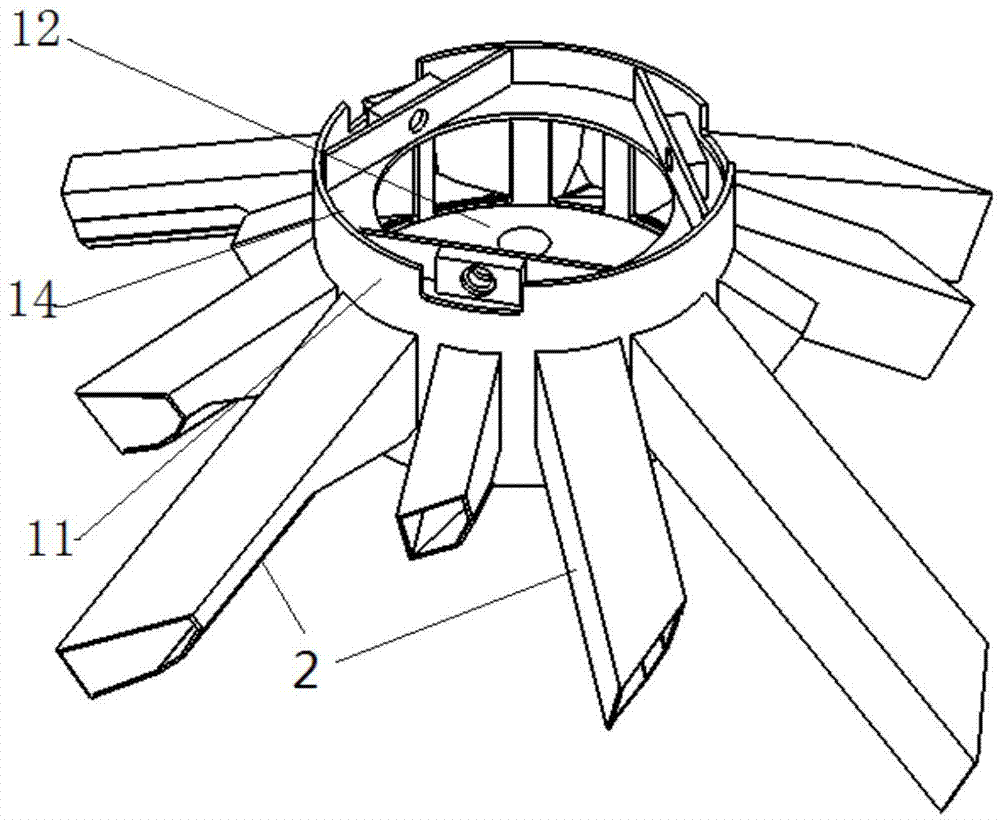
The invention discloses a rotating-type grain distributor and a granary provided with the grain distributor, and belongs to the technical field of granaries. The rotating-type grain distributor comprises a grain collecting barrel. The grain collecting barrel comprises a barrel wall and a barrel bottom. The outer side of the barrel wall of the grain collecting barrel is provided with two downward-inclined grain sliding pipes. The bottom face and one side face of each grain sliding pipe are curved surfaces which are of an integral structure. When the rotating-type grain distributor is used, the rotating-type grain distributor is arranged at a grain inlet of the granary, after grain enters the grain collecting barrel, the grain flows into the grain sliding pipes, and when the rotating-type grain distributor rotates, the grain sliding pipes rotate along with the rotating-type grain distributor. Due to the fact that the bottom face and one side face of each grain sliding pipe are curved surfaces which are of the integral structure, when the rotating-type grain distributor rotates, under the effect of centrifugal force and tangential force generated by the curved surfaces, the grain is scattered and flows out of the grain sliding pipes, and the grain falls onto a circular cross section of the granary. According to the rotating-type grain distributor, the impurity accumulation caused by automatic grading formed by concentrated falling of the grain is alleviated, and the safe storage of the grain is guaranteed.
Owner:BEIJING U PRECISION TECH
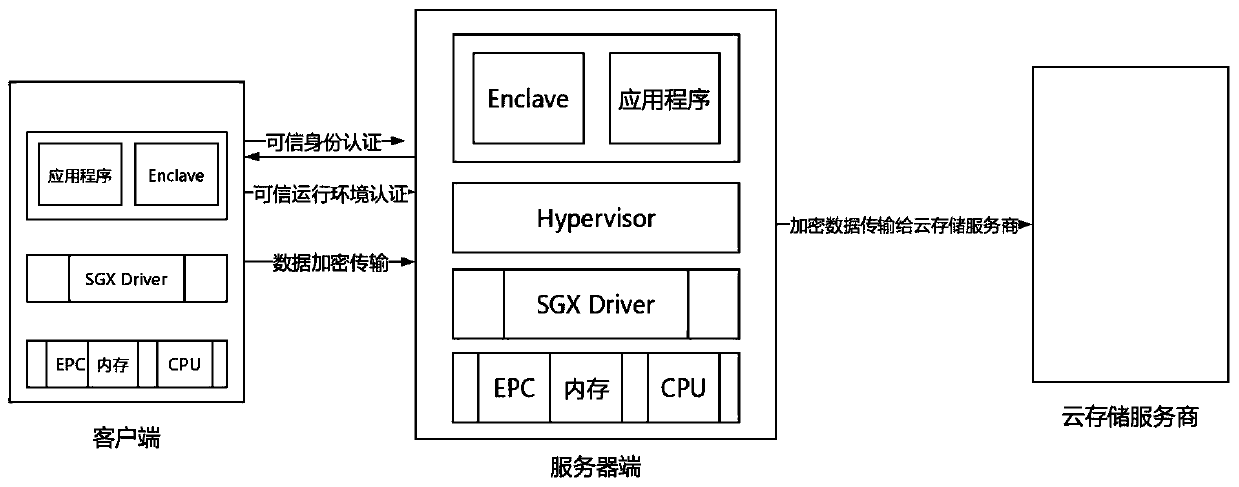
Secure cloud storage method based on SGX
The invention belongs to the technical field of trusted cloud computing, and particularly relates to a secure cloud storage method based on SGX. The method is suitable for a client / server architecturesystem based on SGX, and comprises the following steps: a trusted identity authentication step: a client performs bidirectional authentication of a trusted identity with a server through a trusted identity authentication module of the server, and establishes a session with the server after the trusted identity authentication is completed; a credible operation environment authentication step: after the client passes the credible identity authentication, the client verifies the legality of the operation environment of the server to the server through a credible operation environment authentication module of the server; a credible execution step: the client transmits the data to an endclave of the server through a credible channel, and the endclave encrypts the data; and a cloud storage step: the server side sends the encrypted data to a cloud storage service provider. According to the method, the problems of trusted authentication and key packaging of the client and the server are solved.
Owner:NORTHEASTERN UNIV
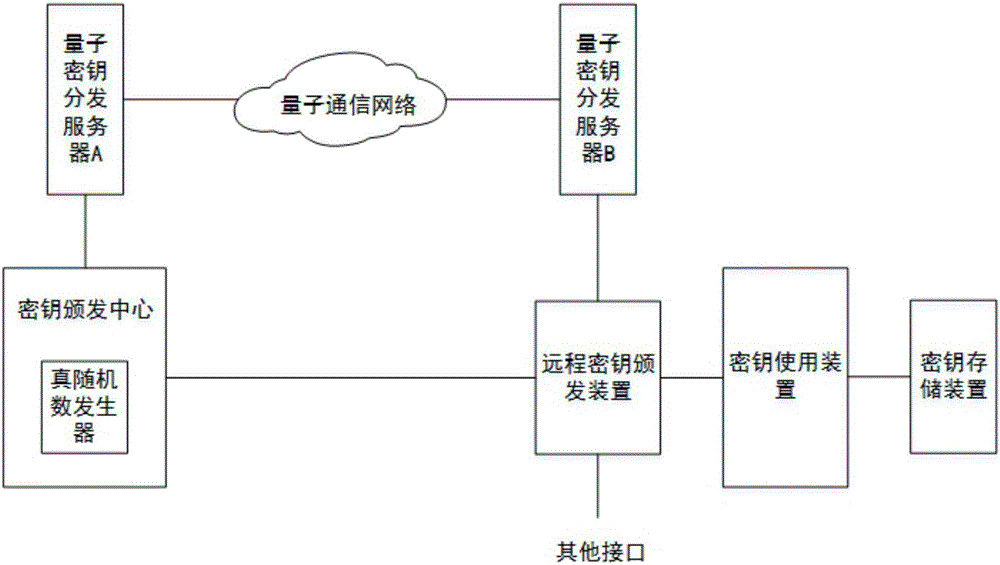
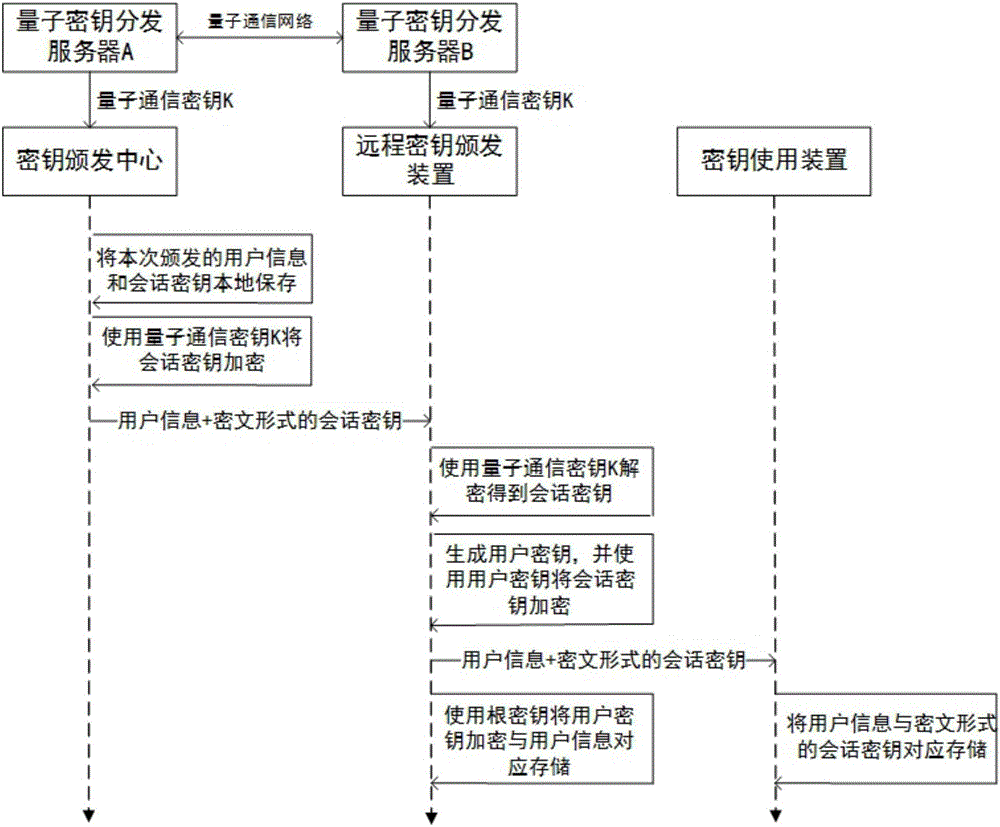
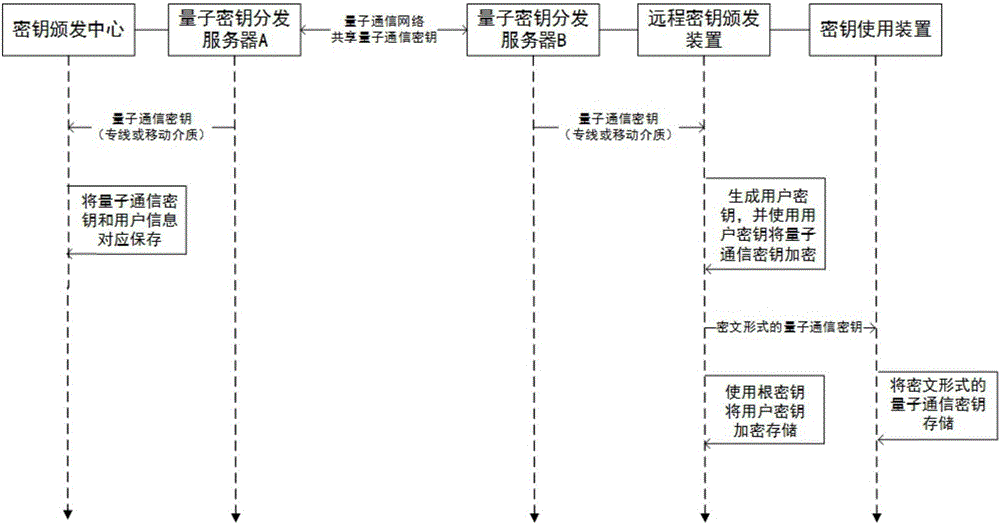
Remote key distributing system based on quantum communication network and application method of remote key distributing system
ActiveCN106789052AEnsure safetySave human effortKey distribution for secure communicationPhotonic quantum communicationTransfer procedureDistributed servers
The invention discloses a remote key distributing system based on a quantum communication network and an application method of the remote key distributing system. The remote key distributing system based on the quantum communication network comprises a remote key distributing device, a key using device, a key storing device, a key distributing center and a quantum key distributing server, wherein the remote key distributing device can be directly connected with the key distributing center to receive a distributed session key, or the remote key distributing device and the key distributing center distribute the session key through the quantum communication network. According to such a key distributing manner, not only safety of the distributed session key in the transmission process is ensured, but also labor force and time for distributing the key at a remote distance are saved. According to the invention, the distributed session key can be either a true random number key generated by a quantum random number generator or a quantum communication key shared in different areas and generated between two arbitrary quantum key distributing service stations in the quantum communication network through a key distribution protocol.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
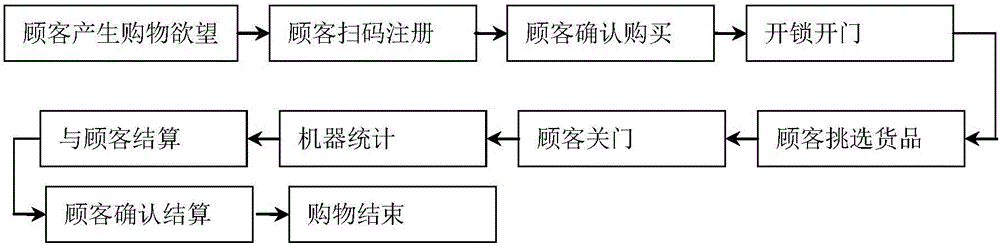
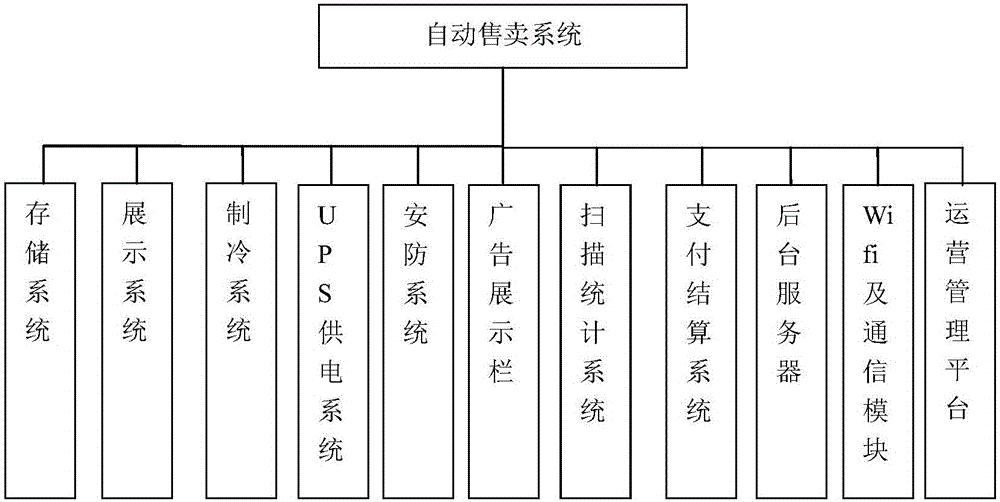
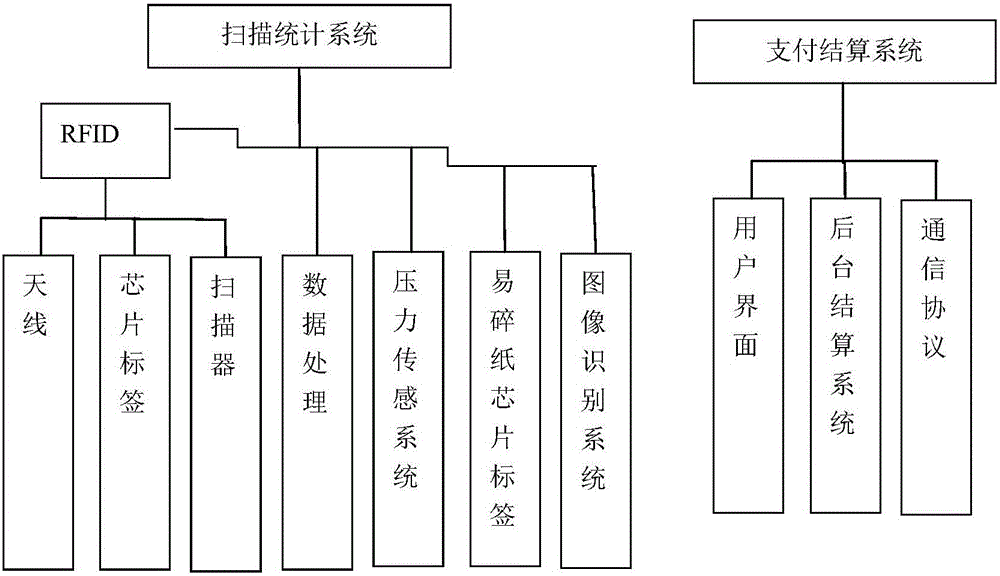
Vending system with function of radio-frequency chip recognition
ActiveCN106710071AGuaranteed safety without lossReal-time selectionBuying/selling/leasing transactionsRecord carriers used with machinesElectromagnetic lockComputer module
The invention particularly relates to the technical field of vending, discloses a vending system with a function of radio-frequency chip recognition and solves defects of low space utilization rate and low intelligent level of an existing vending system which adopts complex feed passages and mechanical mechanisms or a traditional cell cabinet form. The vending system comprises a box and a door, the door is provided with an electromagnetic lock, and the box is provided with a scanner, a control module and a communication module. The scanner is used for scanning wireless radio-frequency identification codes of goods in the box one by one, scanned and identified goods information is uploaded to the control module, and the control module controls and processes the goods information, counts quantity and category information of the goods in the box and transmits information acquired by statistics to a data output end and a background server.
Owner:AUCMA
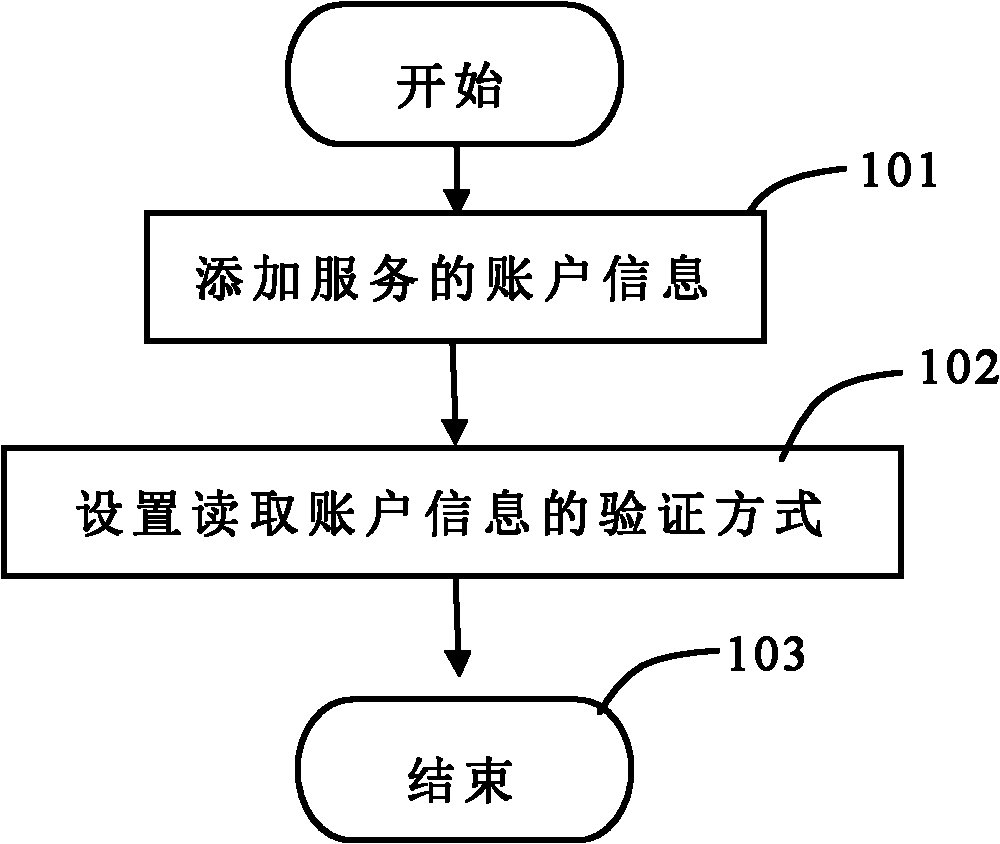
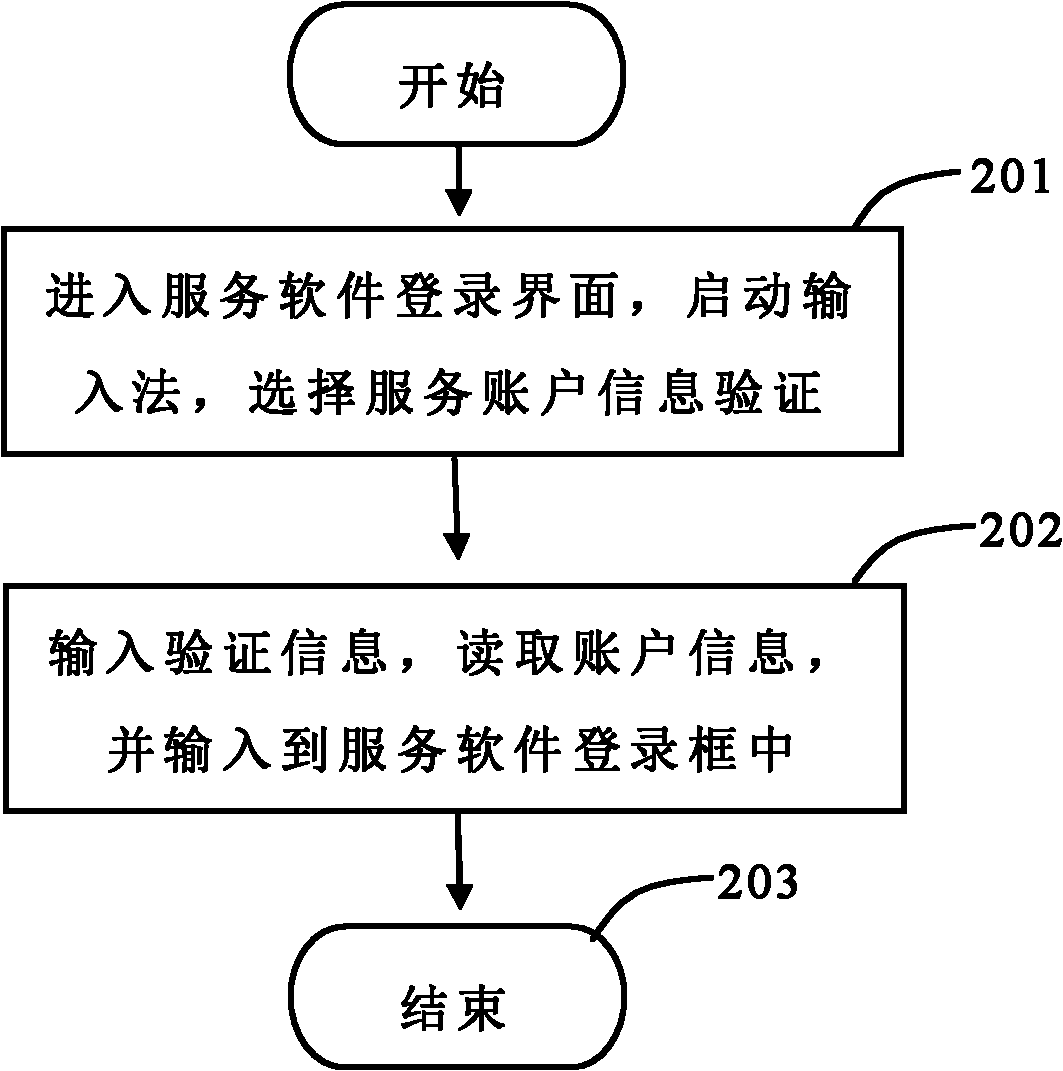
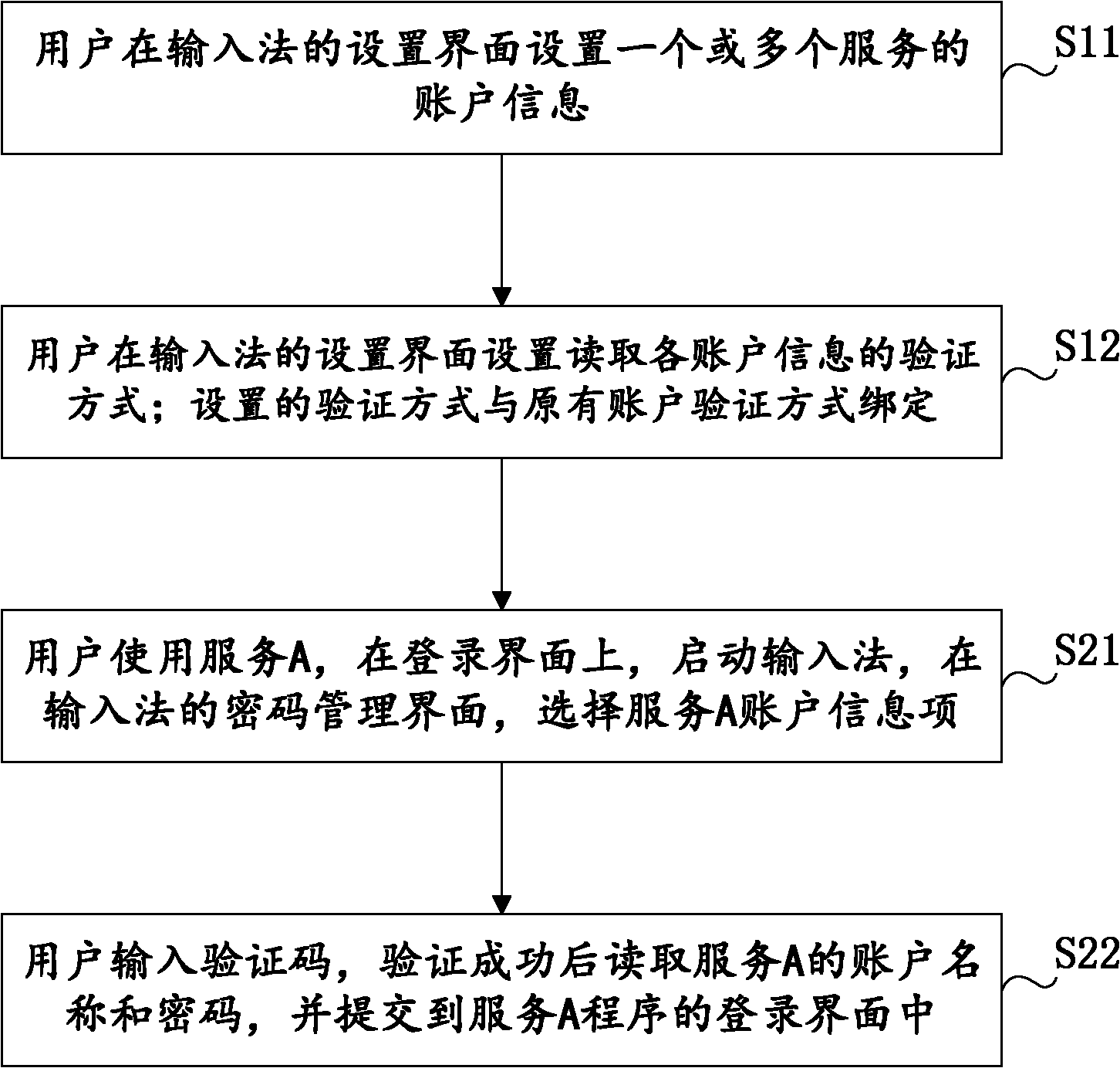
Method for integrating account management function in input method software
ActiveCN102073810AFast inputEnsure safetyDigital data authenticationDigital output to display deviceProgramming languageSoftware engineering
The invention discloses a method for integrating account management function in input method software. The method comprises the following steps of: setting account information of one or more services on a setting interface of an input method by a user; setting a verification mode for reading the account information on the setting interface of the input method by the user; binding the set verification mode and the original account verification mode; starting the input method on a login interface and selecting an account information item of a service A on a password management interface of the input method by using the service A through the user; and inputting a verification code by the user, reading the account name and the password of the service A after the verification is successful, and submitting the account name and the password to the login interface of a service A program. By the method, safe storage of the account password is guaranteed, and the account password is quick and convenient to input.
Owner:SHANGHAI HEHE INFORMATION TECH DEV
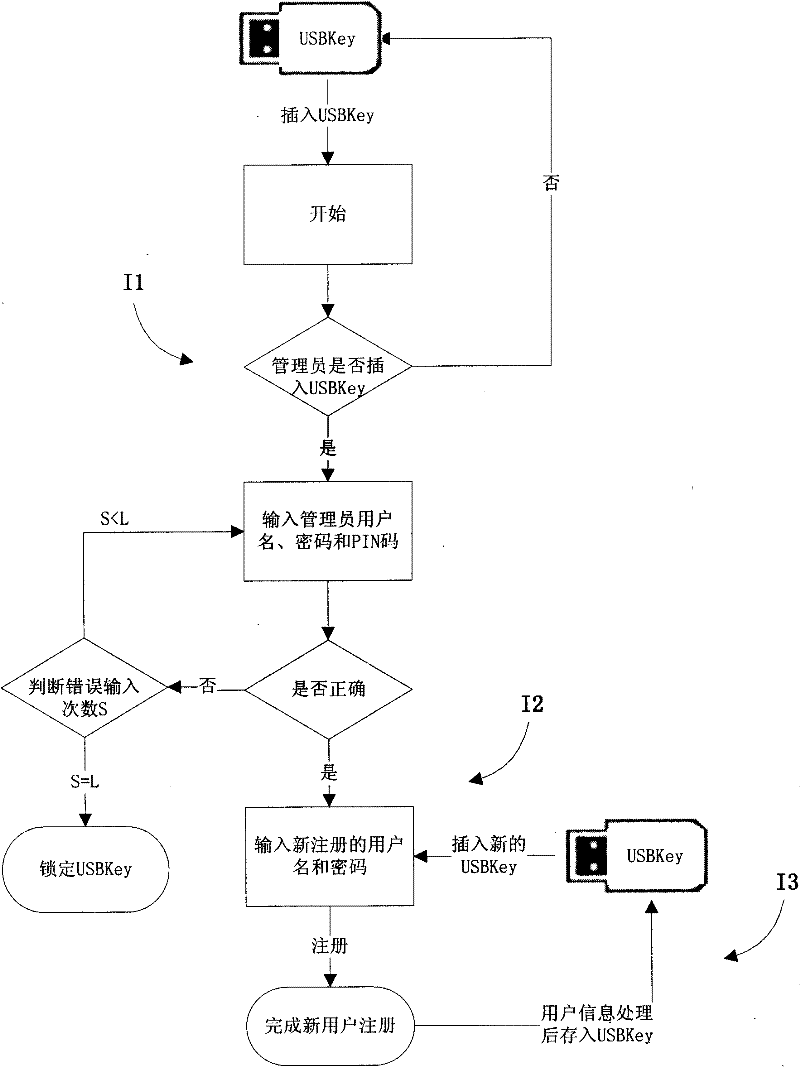
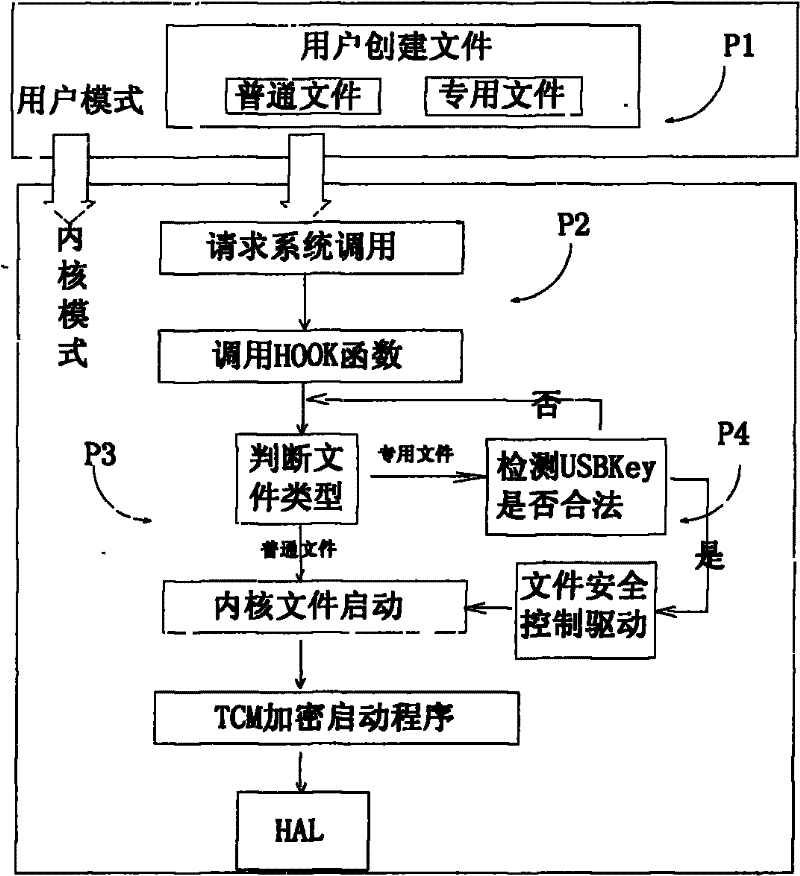
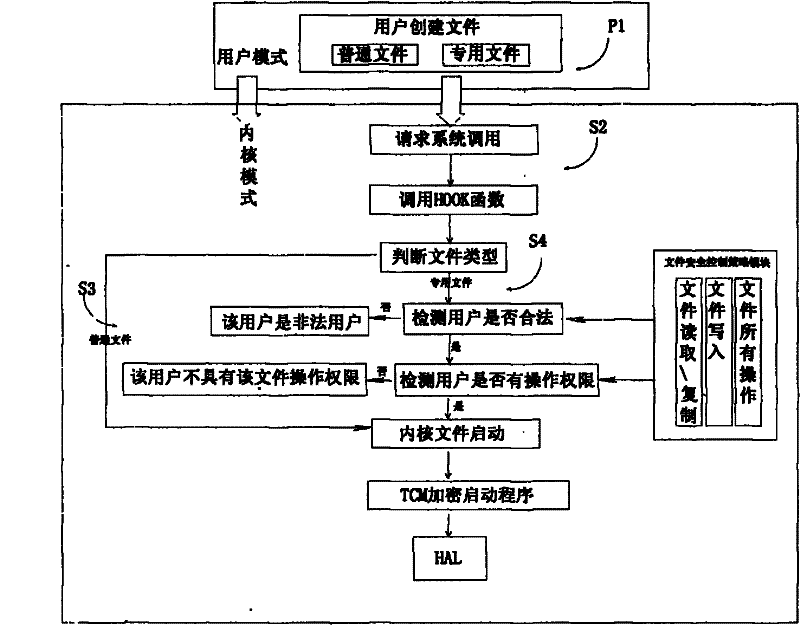
One-machine multi-user security access control method
InactiveCN102236755AImplement secure storage protectionLow costDigital data authenticationOperational systemCiphertext
The invention aims to provide a one-machine multi-user security access control method based on a trusted computing module (TCM) and a universal serial bus (USB) key, and solves the problems of multi-user information storage insecurity, absence of running data security after the login of a user with legal identity, resource wasting of a plurality of hard disks required by a plurality of users and the like under an identical operating system. In the method, security file access control over the users is realized in a kernel mode by combining USBKey hardware equipment and a TCM chip, user identity information is stored in the security storage area of the USBKey hardware equipment in form of cipher text, an encryption process is finished in the TCM chip by adopting a standard cryptographic algorithm, the security of private keys is protected by an SMK, the USBKey hardware equipment can be carried along by the user, and the security storage of private information of the user is realized.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
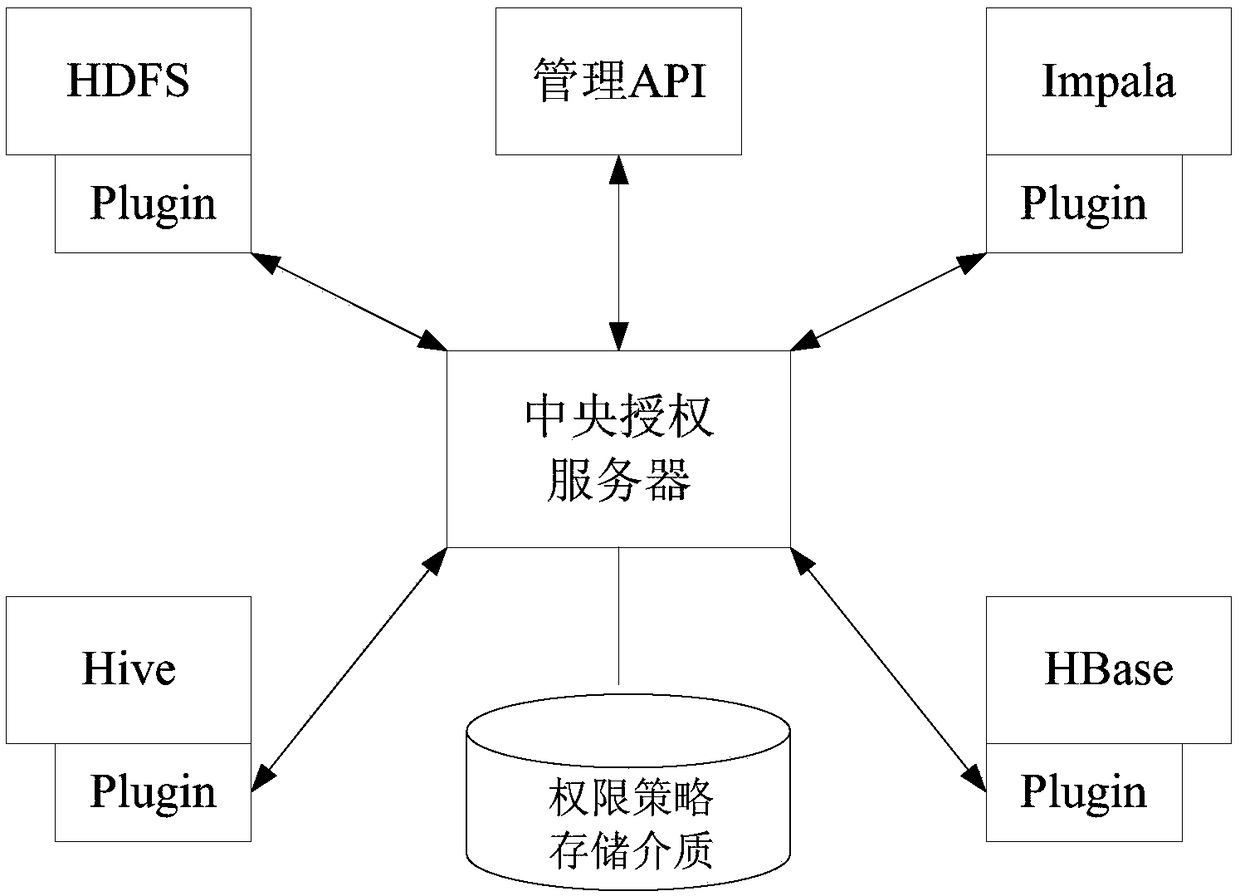
Cloud storage fine grit access control method and data uploading and data accessing method
ActiveCN108900483ATo achieve the purpose of fine-grained access controlGuaranteed safe storageTransmissionAttribute-based encryptionData access control
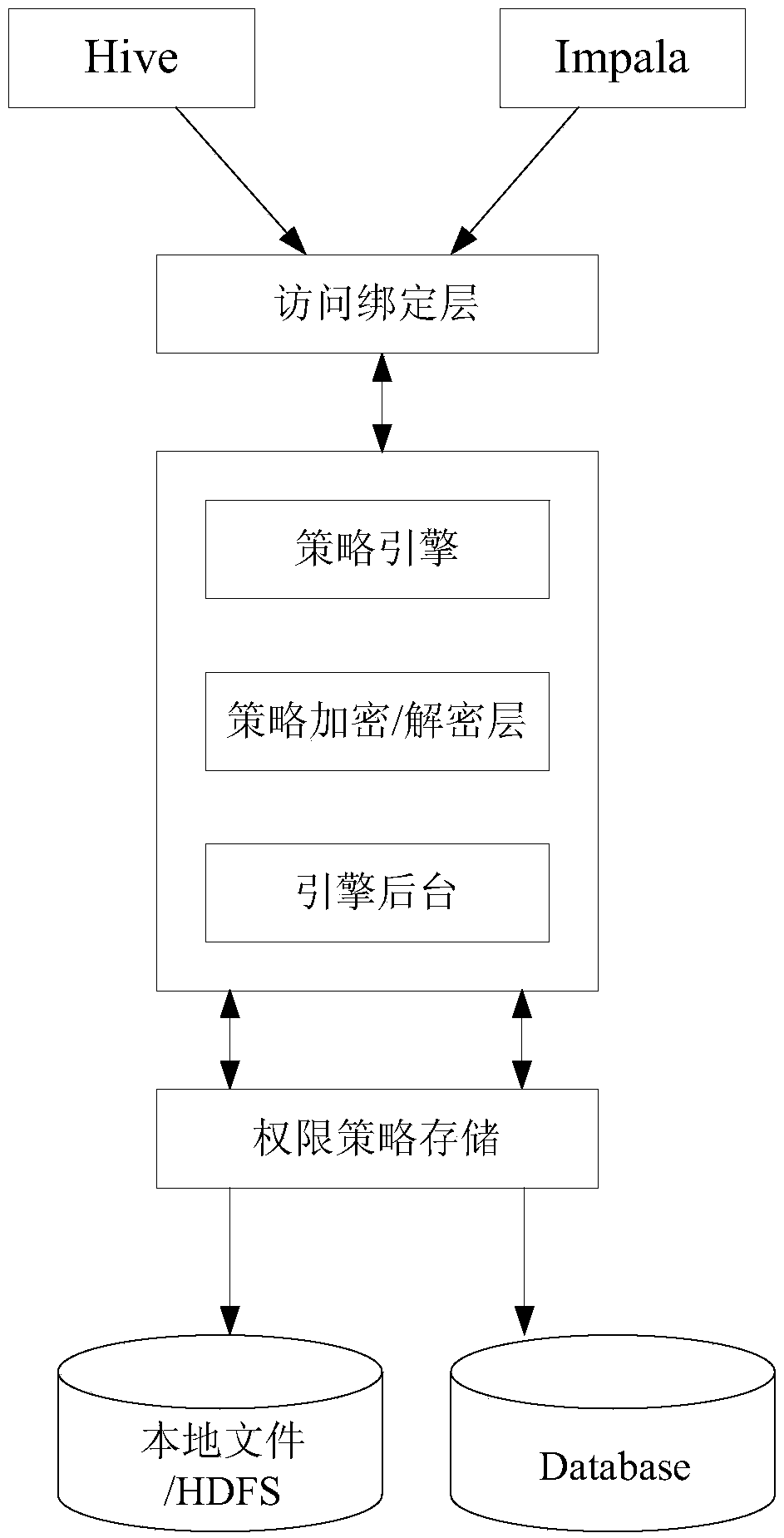
The invention provides a cloud storage fine grit access control method. The method is compatible to access control of a Hadoop assembly in a Plugin way and access control is performed through a central authorization server. Requests intercepted and sent to the central authorization server from the Plugins are accessed to a strategy engine by accessing a binding layer. Authority strategies are encrypted / decrypted through a strategy encryption / decryption layer, finally, through an engine background, storage and reading of the authority strategies are finished, and the storage form is authority encryption ciphers. The decrypted authority strategies are analyzed by the strategy engine, and authorities which can be identified by each Plugin are obtained through the analysis and returned to thecorresponding Plugins. Verification of the authorities is finished by the Plugins and whether user requests of this time are permitted is judged through the Plugins. According to the invention, by introducing autonomous access control, access control authorization of data by a data uploader is achieved; and by introducing a method based on attribute-based encryption, self-description of an accesscontrol structure is performed through attribute labels of data.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
Mobile device encrypted USB key
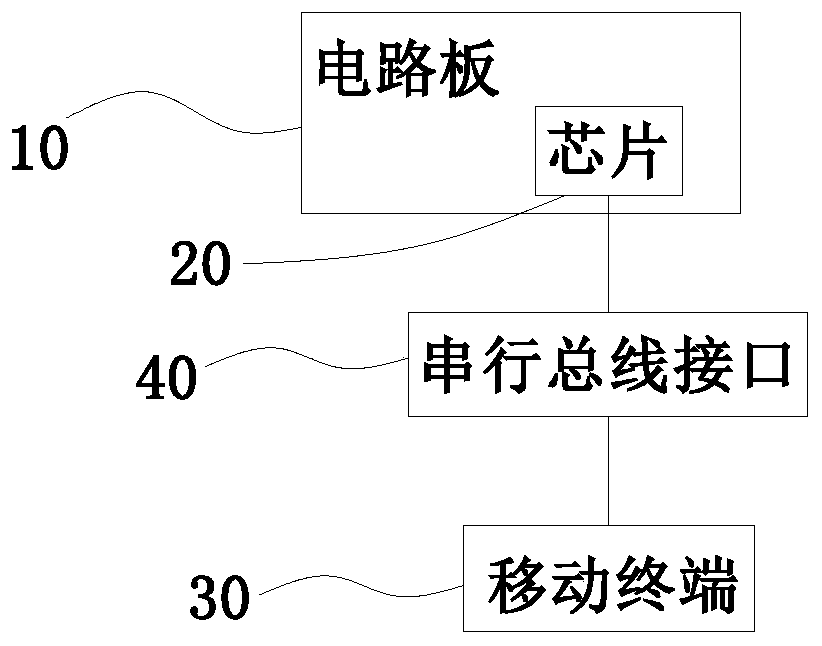
ActiveCN110263524AGuaranteed safety certificationGuaranteed safe storageDigital data protectionDigital data authenticationThird partyBus interface
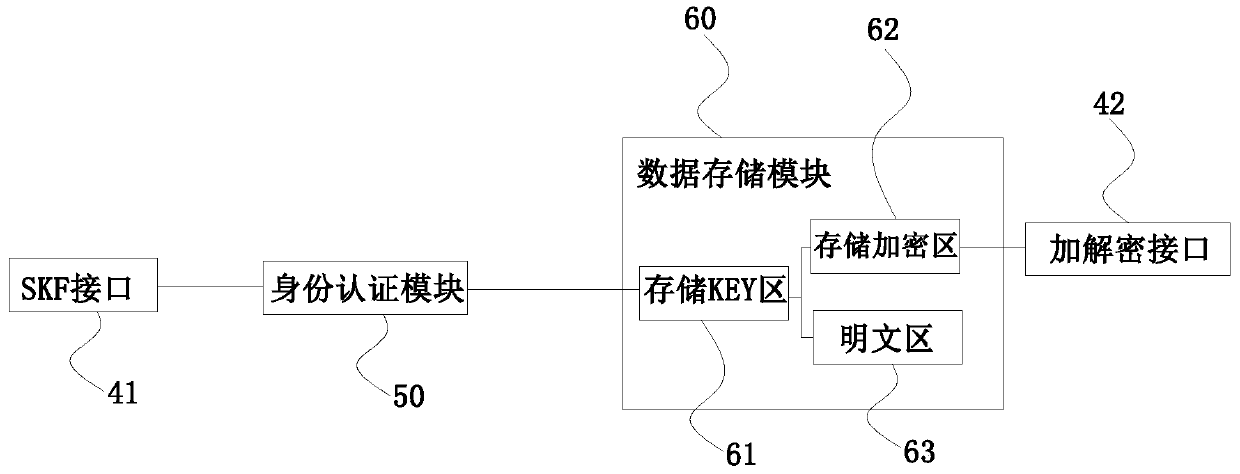
The invention relates to a mobile device encrypted USB key. The encrypted USB key comprises a circuit board and an intelligent card chip arranged on the circuit board, the encrypted USB key is also provided with a serial bus interface connected with the mobile terminal and used for realizing communication with a third-party APP; the serial bus interface comprises an SKF interface and an encryption and decryption interface. The intelligent card chip comprises an identity authentication module and a data storage module, the identity authentication module is in communication connection with a mobile terminal through an SKF interface; and the data storage module is used for detecting the user PIN code and the application characteristic value, realizing communication connection with the mobile terminal through the encryption and decryption interface, and realizing encryption and decryption storage of encrypted data in the data storage module through the encryption and decryption interface after the user identity authentication is passed. According to the invention, the security authentication of a user and the secure storage of information in mobile operation can be ensured, so that the personal mobile phone can be safely used in a general network environment.
Owner:XIAMEN GREAT POWER GEO INFORMATION TECH +1
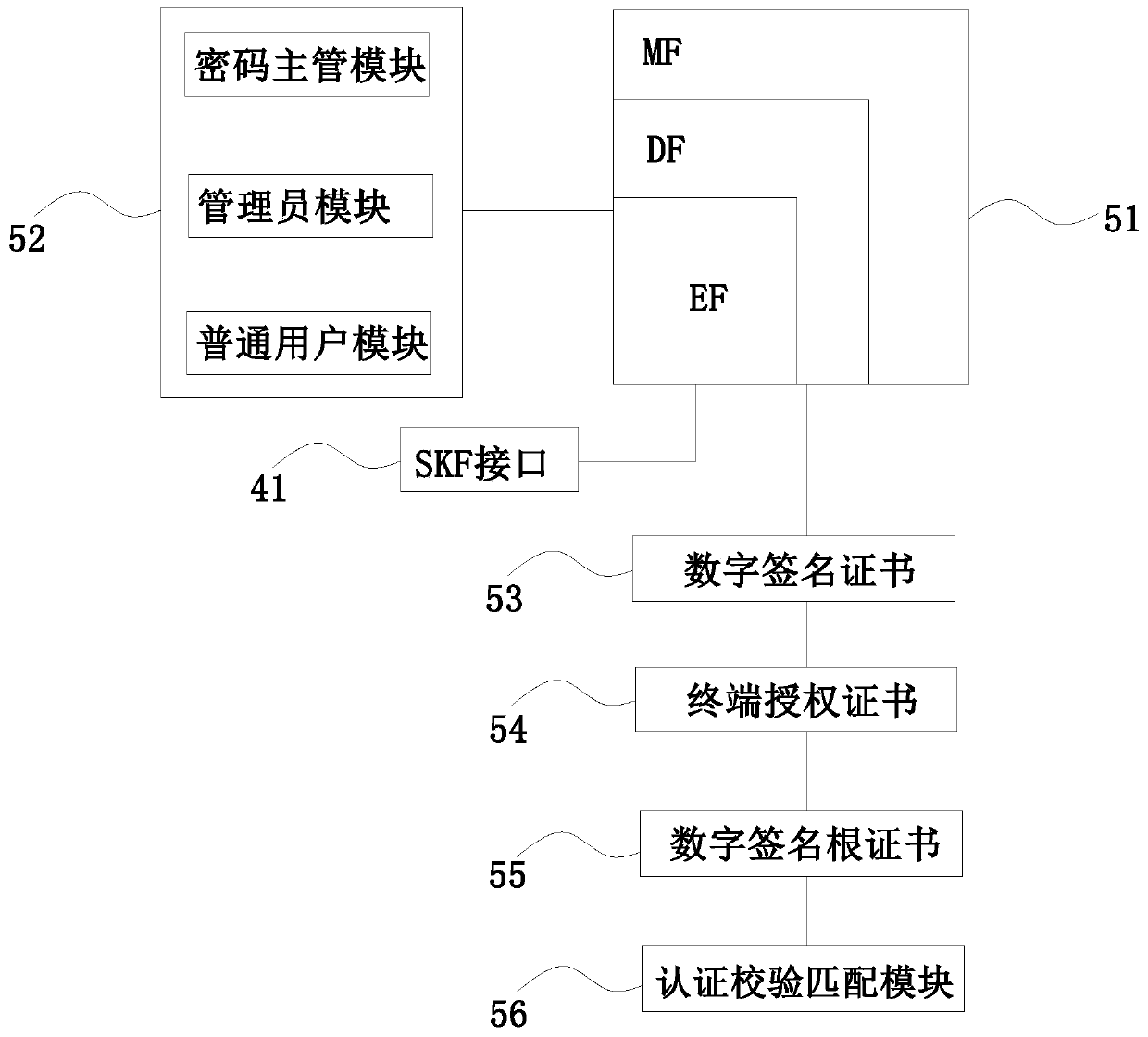
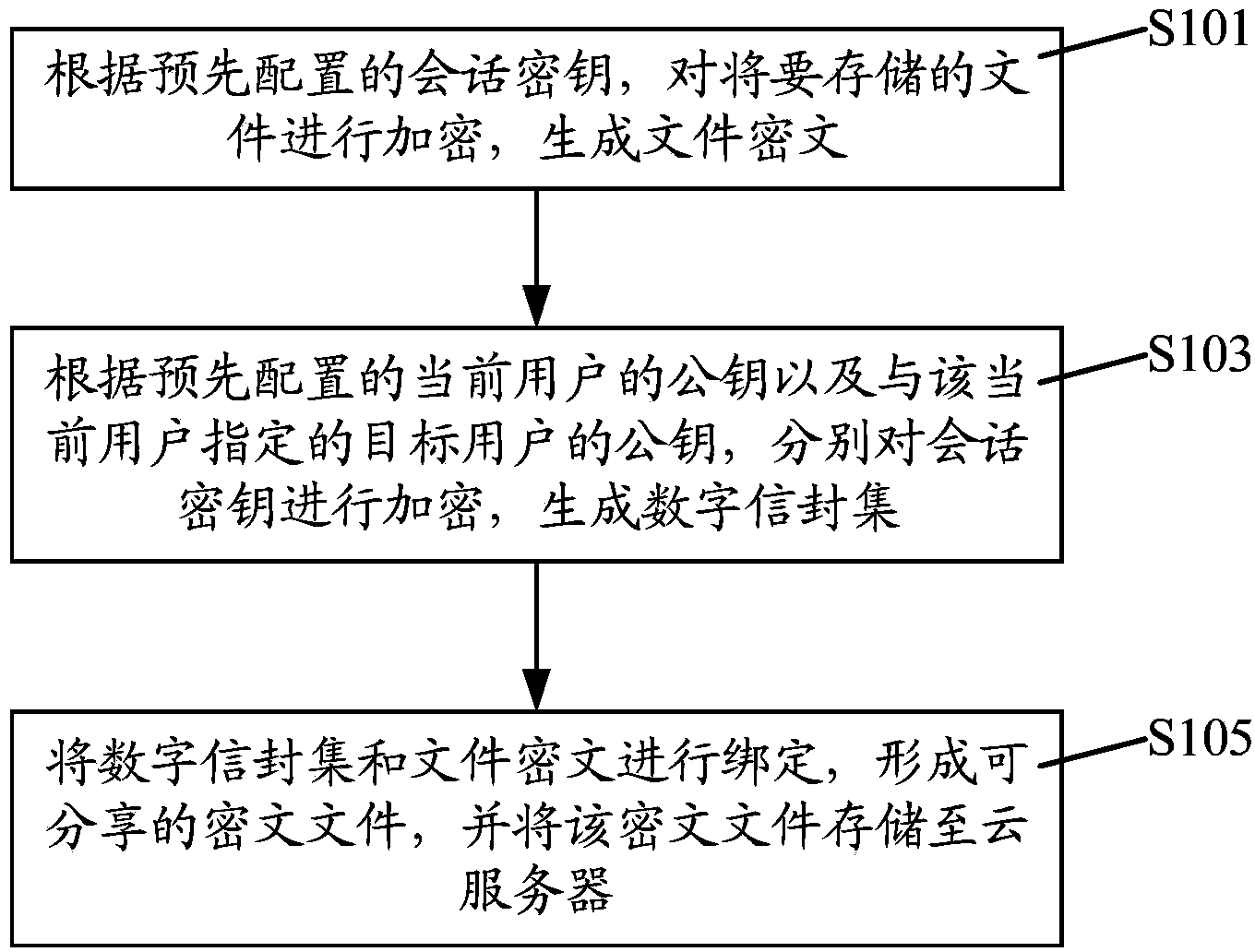
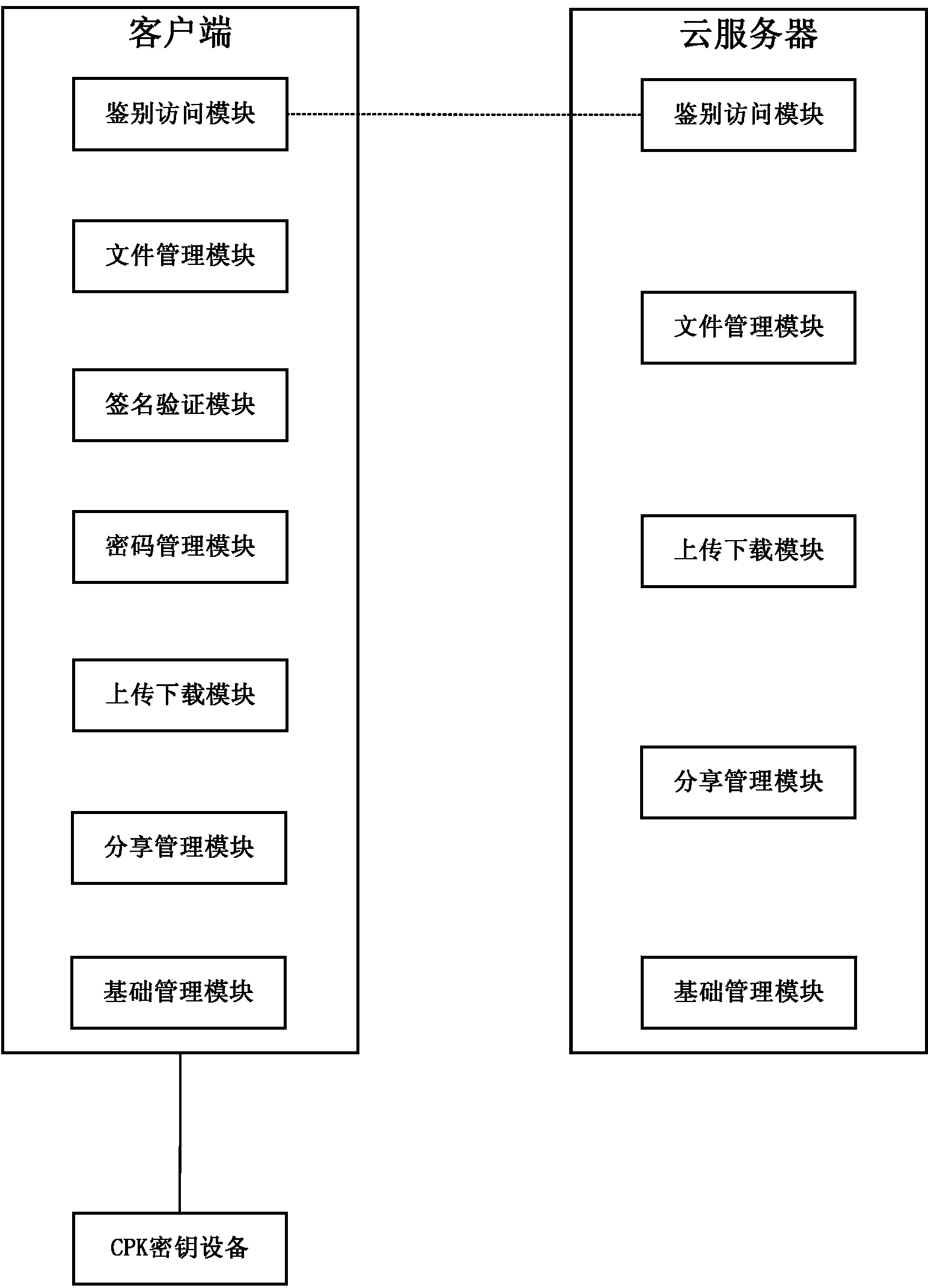
File cloud security management method and system based on CPK
InactiveCN103973440AAchieve securityAchieve sharingPublic key for secure communicationDigital data protectionCiphertextControllability
The invention discloses a file cloud security management method and system based on a CPK. The method comprises the steps that a file to be stored is encrypted according to pre-configured session keys, and file ciphertext is generated; the session keys are respectively encrypted according to a pre-configured public key of a current user and a public key of a target user assigned by the current user, and a digital envelope set is generated; the digital envelope set and the file ciphertext are bound, a ciphertext file capable of being shared is formed, and the ciphertext file is stored in a cloud server. According to the method and system, a CPK combined public key system is adopted as the basis, the key transmitting technology of the CPK is utilized, the local file of the current user is encrypted, the file capable of being decrypted only by the current user and the target user assigned by the current user is generated, the file is stored in the cloud server, and therefore cloud security storage and sharing of the file are achieved, and automatic controllability of cloud security storage and sharing is built.
Owner:东方斯泰克信息技术研究院(北京)有限公司
Attribute-based searchable encrypted block chain medical data sharing method
PendingCN112765650AImprove efficiencyReduce computational overheadDigital data protectionCiphertextPrivacy protection
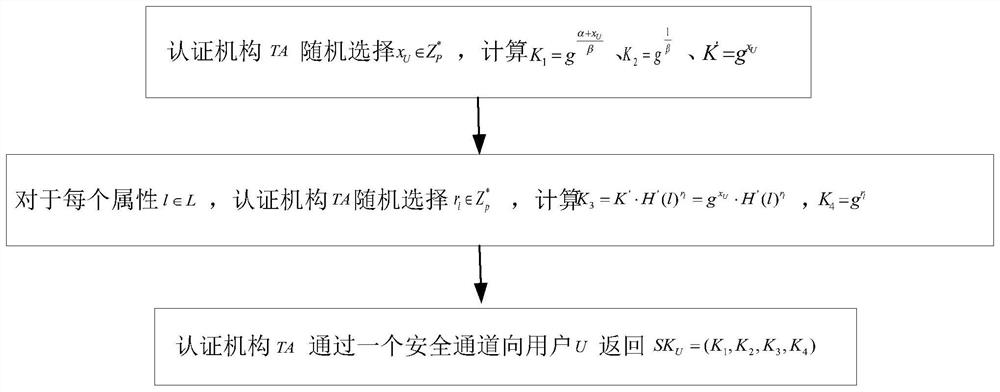
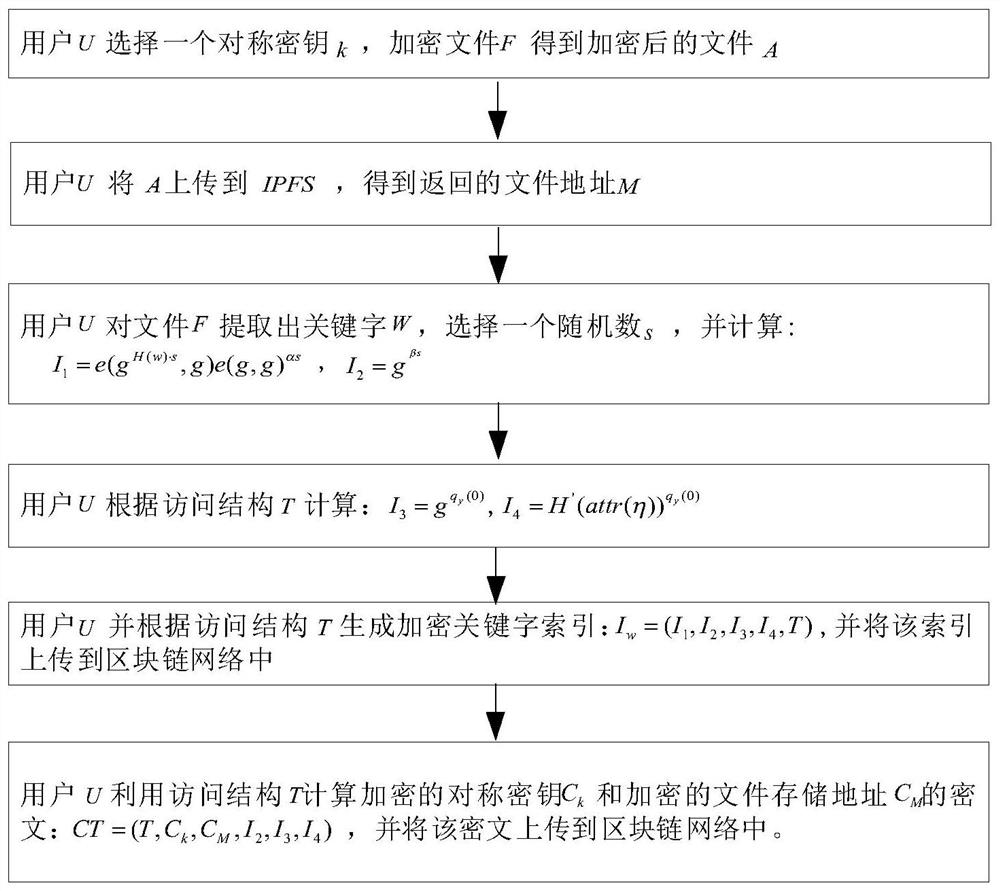
The invention discloses a block chain medical data sharing method with a searchable and encrypted attribute base, and mainly solves the problem that secure sharing cannot be realized in the prior art. The method comprises the following implementation steps: 1) performing system initialization by a certification authority TA; 2) the authentication authority TA generates a key SKU of the user U according to the attribute of the user; 3) the user U encrypts the medical file, uploads the encrypted medical file to an interstellar file system IPFS, encrypts a file encryption key and a file storage address, and uploads the encrypted file encryption key and file storage address to a block chain; 4) the user U generates a search trap door Tq according to the own key SKU and the keyword q, and calls a search algorithm to obtain a file encryption key and a ciphertext of a file storage address; and 5) the user U decrypts to obtain the medical file. The method has the advantages of high efficiency, tampering prevention, access control, privacy protection, no single-point fault and higher practicability, and can be used for secure sharing of data in cloud environments such as education, service and medical treatment.
Owner:XIDIAN UNIV
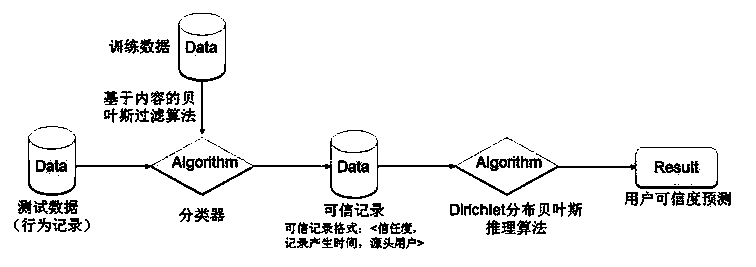
Credibility measuring method combining Bayesian algorithm and MapReduce
InactiveCN103455842AImprove filtering effectReduce complexityBiological modelsTransmissionHigh performance computationBayesian inference
The invention relates to a credibility measuring method combining a Bayesian algorithm and a MapReduce. The credibility measuring method combining the Bayesian algorithm and the MapReduce comprises the following steps that S01, a Bayesian filter algorithm is used for carrying out credibility evaluation on behavior records generated in the process of mobile terminal interaction, statistics is carried out on the prior probability of training data centralization, the posterior probability of the behavior records is calculated through a Bayes formula, and the maximum posterior probability is selected to serve as the credibility of the behavior records; S02, probability distribution evaluation is carried out on credible records through a Bayesian inference algorithm with a Dirichlet process, and prediction of the credibility of mobile terminals can be obtained; S03, selection of a characteristic value is achieved through an information gain algorithm. The credibility measuring method combining the Bayesian algorithm and the MapReduce achieves high efficiency, safety and neutrality in the process of calculation and storage of the credibility with the help of a cloud computing platform, and safe storage and high-performance calculation of data are ensured.
Owner:FUZHOU UNIVERSITY
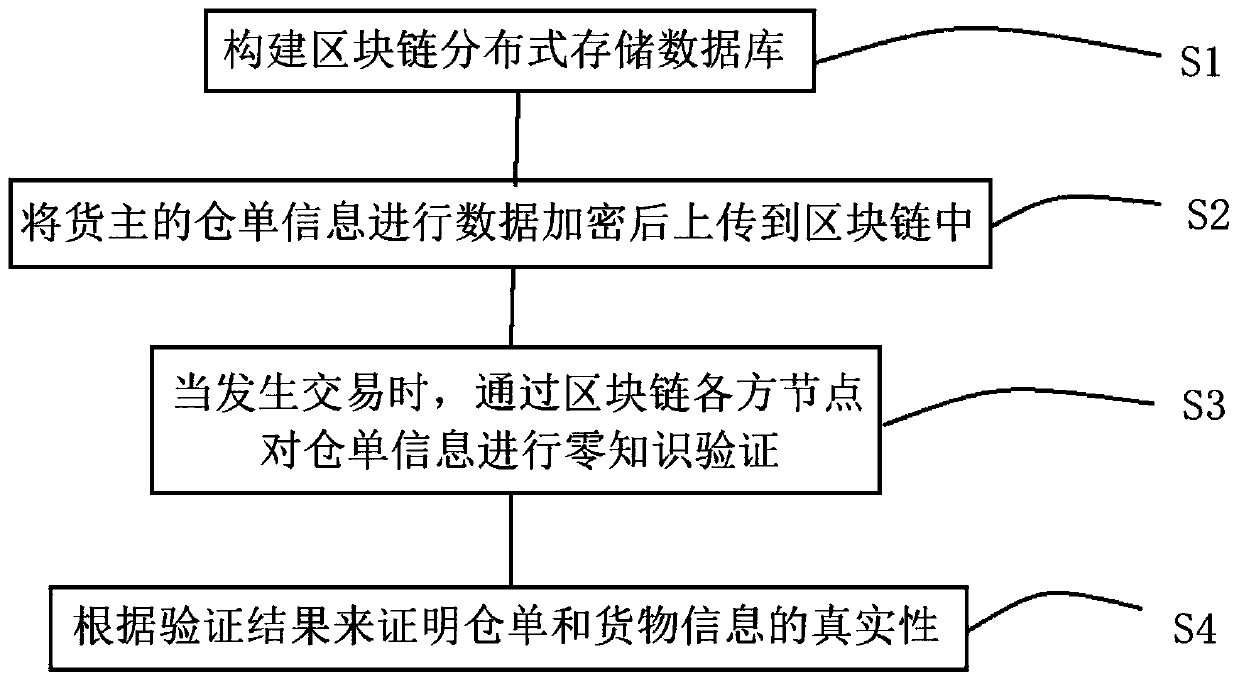
Warehouse receipt verification method based on block chain and zero knowledge proof
ActiveCN109858852AIncrease credibilityGuaranteed safe storagePayment protocolsLogisticsValidation methodsZero-knowledge proof
The invention discloses a warehouse receipt verification method based on a block chain and zero knowledge proof. The warehouse receipt verification method comprises the following steps: constructing ablock chain distributed storage database; the warehouse receipt information of the cargo owner is subjected to data encryption and then is uploaded to the block chain; when a transaction occurs, zero-knowledge verification is carried out on warehouse receipt information through nodes of each party of the block chain; the authenticity of the warehouse receipt and the cargo information is proved according to a verification result; and the authenticity, accuracy and privacy of warehouse receipt information in the transaction market can be ensured.
Owner:SHANGHAI YUANLU JIAJIA INFORMATION SCI & TECH CO LTD
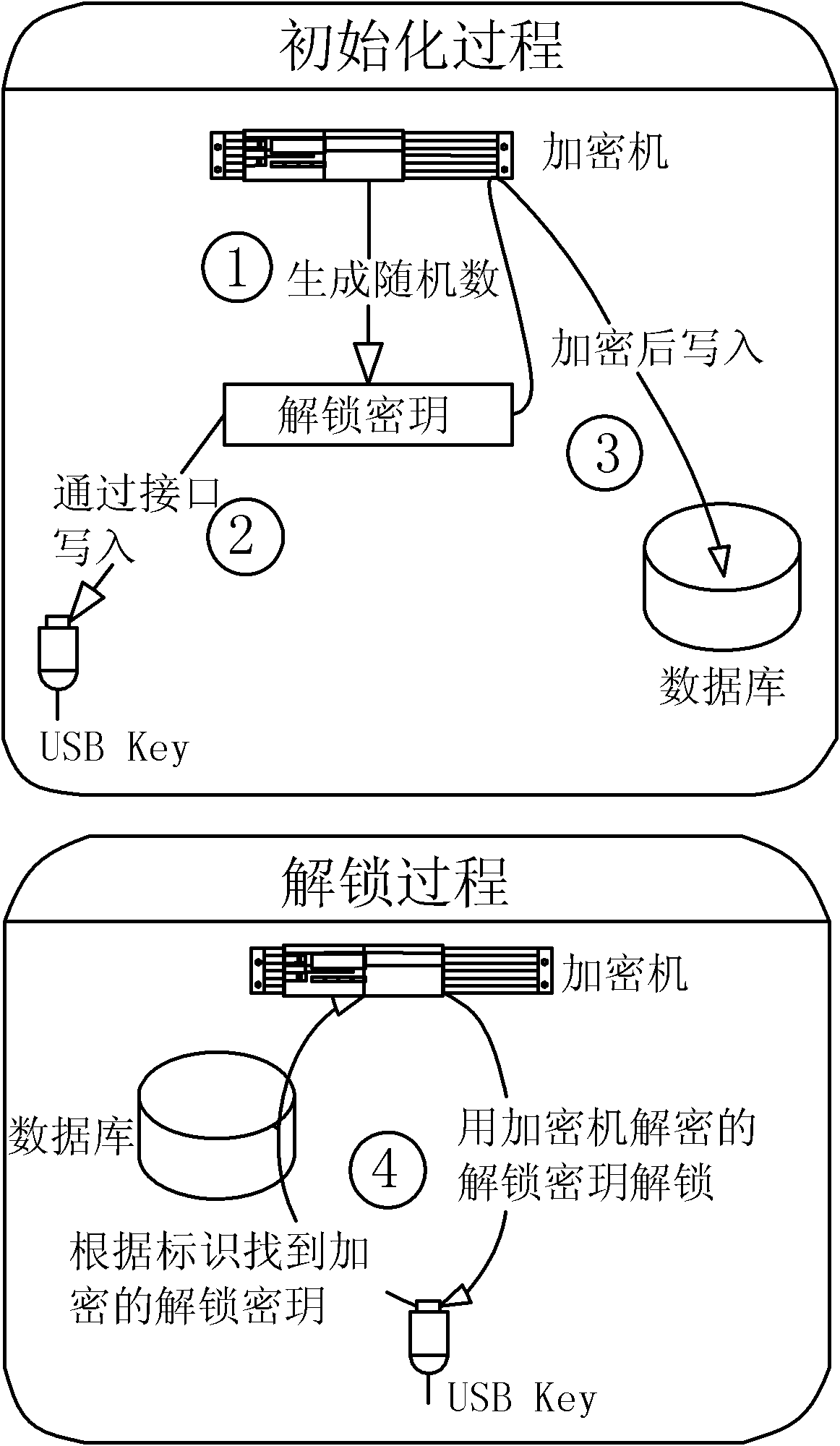
Method for managing USBKey unlocking secret key intensively and safely
ActiveCN102571327AWon't leakEnsure securityKey distribution for secure communicationComputer security
Owner:上海格尔安信科技有限公司
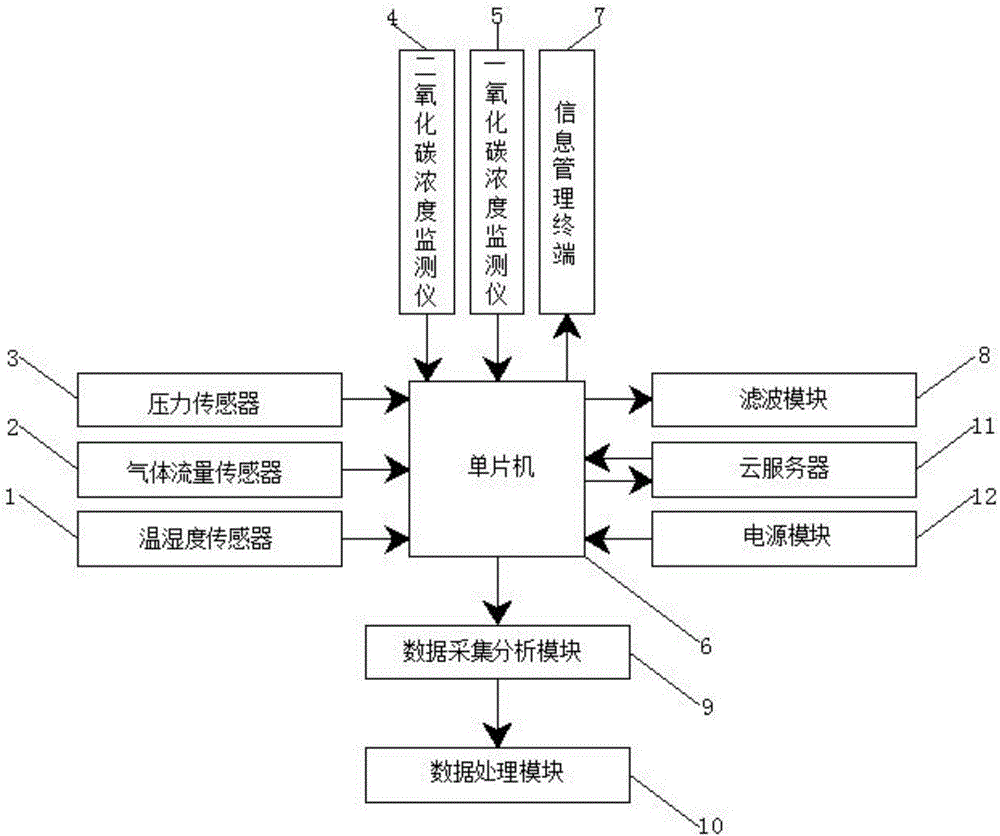
Cement enterprise carbon emission real-time on-line monitoring management system
InactiveCN106647514AQuick collectionGuaranteed safe storageProgramme controlComputer controlMicrocontrollerData acquisition
The invention relates to a cement enterprise carbon emission real-time on-line monitoring management system. A cement enterprise carbon emission real-time on-line monitoring management system comprises a single-chip microcomputer, which is in a wired connection with a temperature and humidity sensor, a gas flow sensor, a pressure sensor, a carbon dioxide concentration monitor, a carbon monoxide concentration monitor, and is used for analyzing and processing received data; an information management terminal, which is in the wired connection with the single-chip microcomputer, and is used for storing operation data; a filtering module, which is in the wired connection with the single-chip microcomputer, and is used for eliminating interference signals; a data processing module, which is in the wired connection with the single-chip microcomputer by a data acquisition analysis module, and is used for analyzing, processing, and counting the monitoring data; and a cloud server, which is in a wireless connection with the single-chip microcomputer by a GPRS wireless network, and is used for data transmission and exchange. The cement enterprise carbon emission real-time on-line monitoring management system is advantageous in that various sensors and various monitors are used for real-time on-line monitoring of carbon emission, and the monitoring data is accurate, and the confusion and missing problems of the acquired data are prevented.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
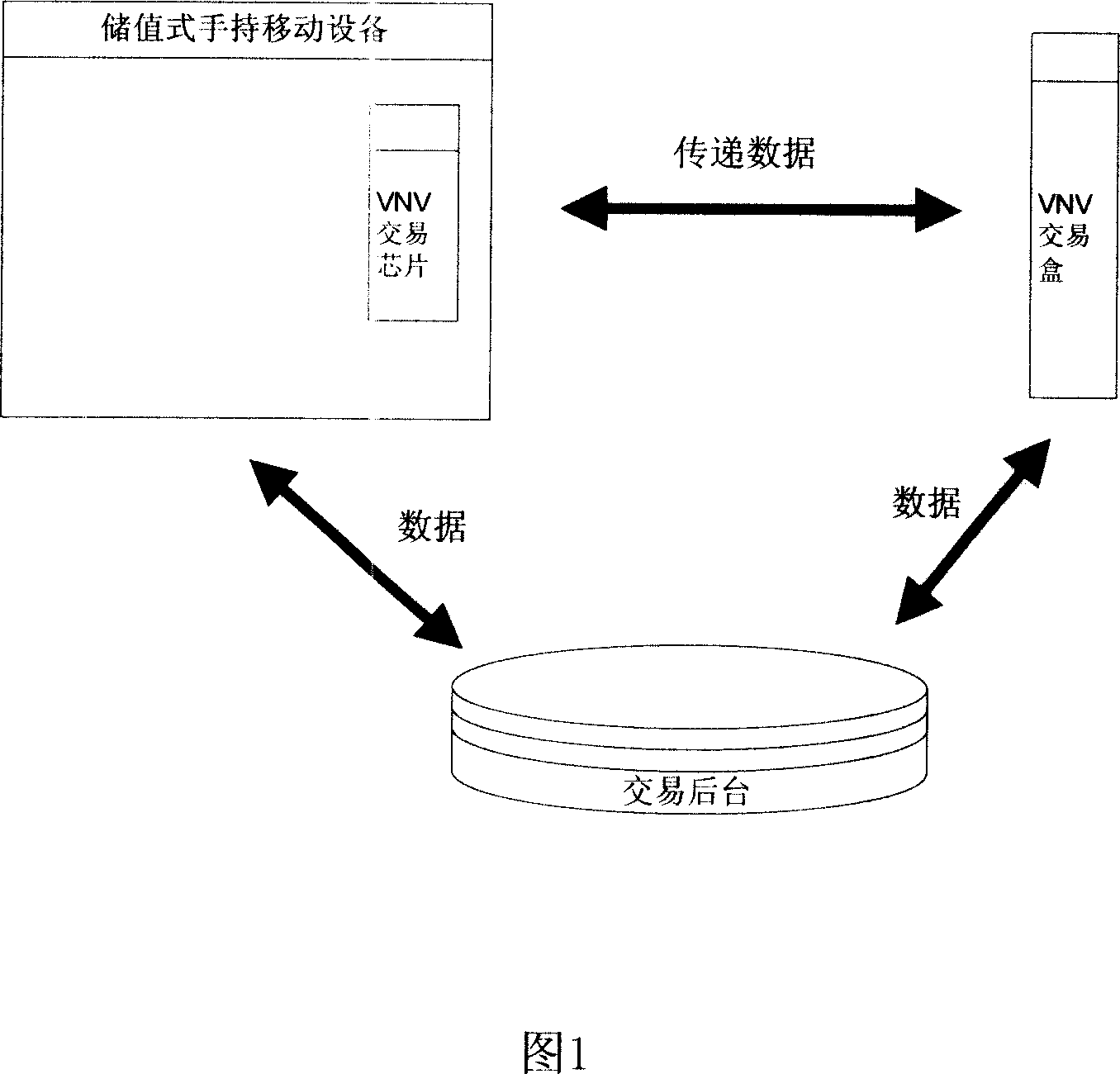
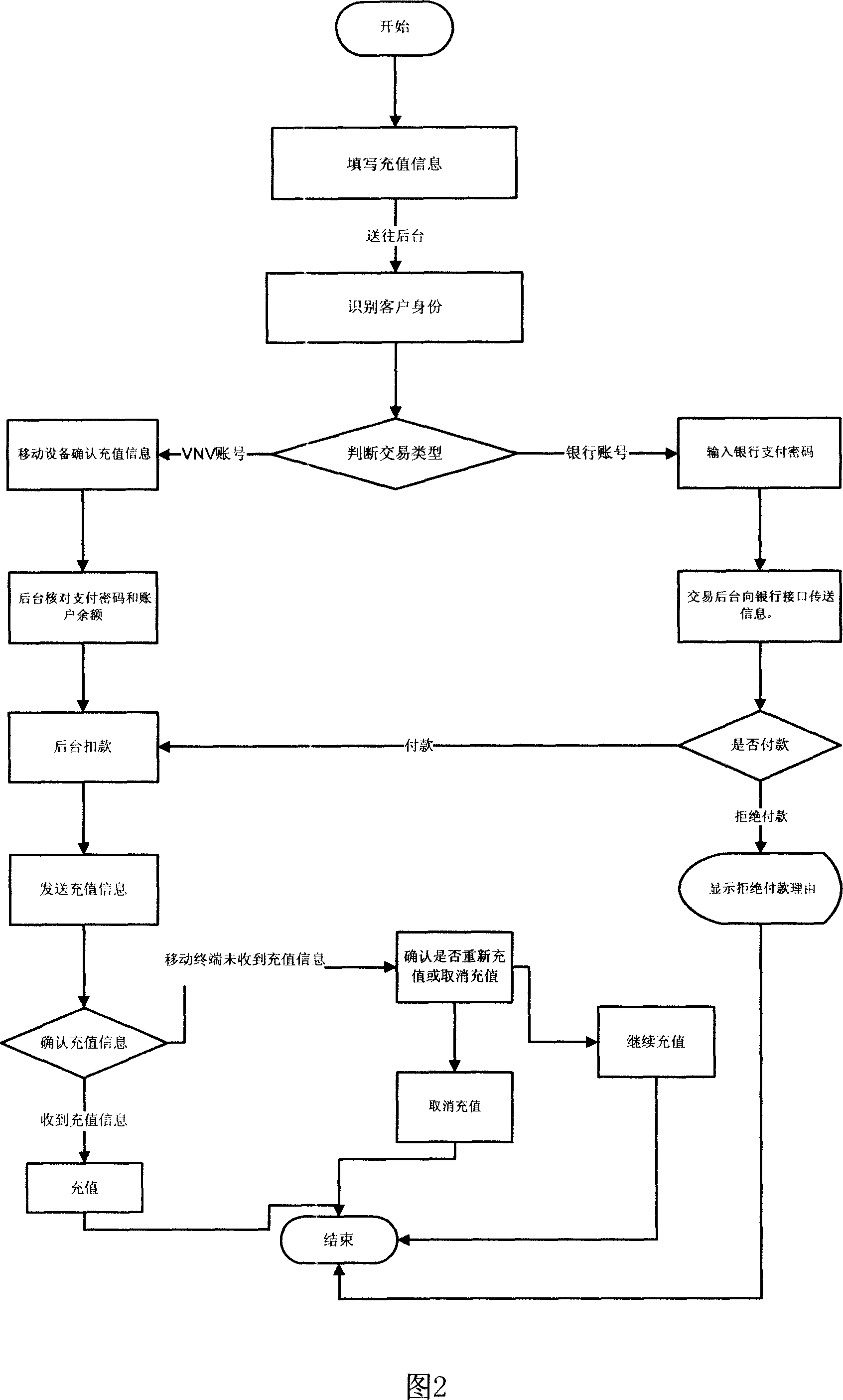
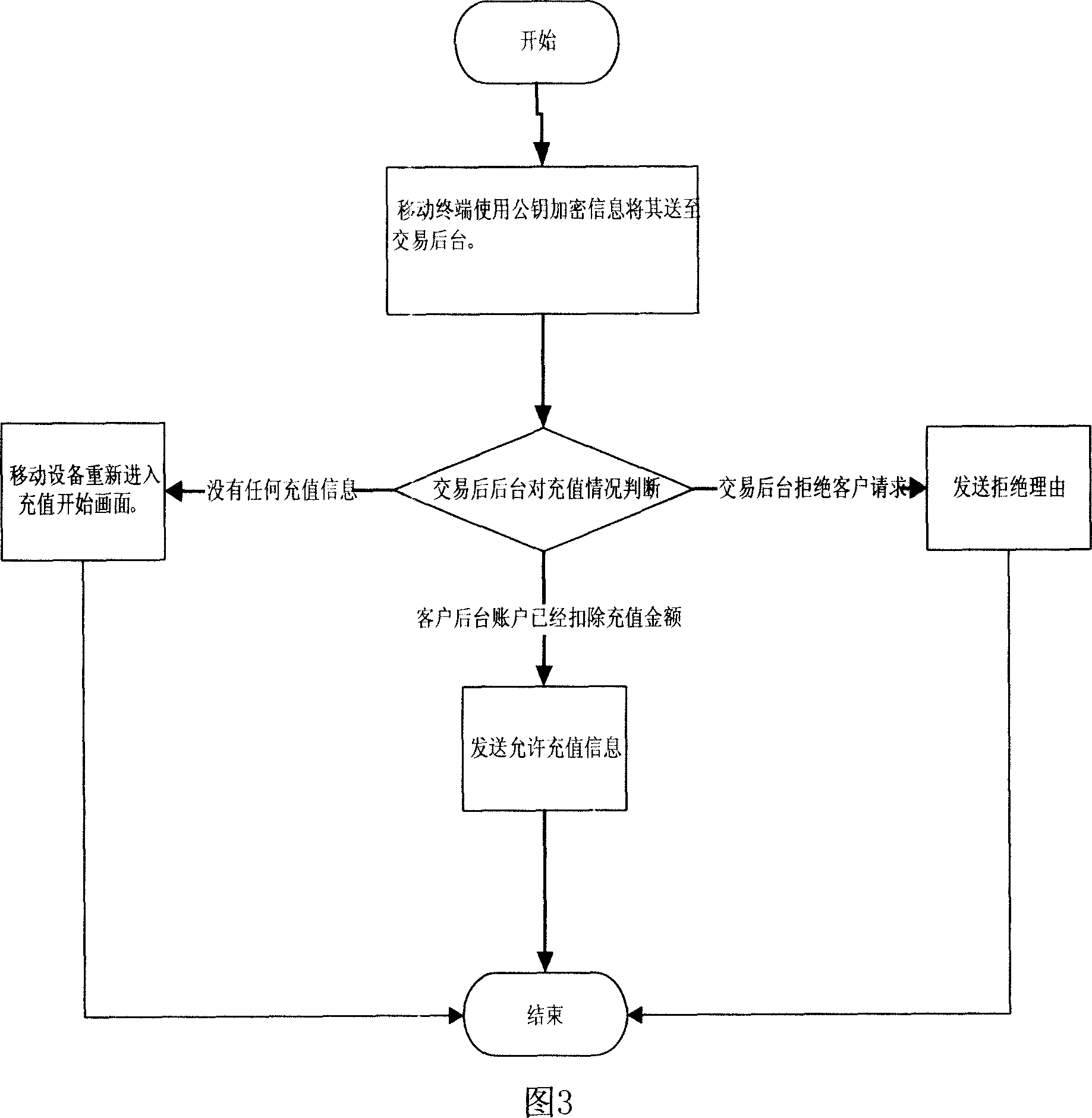
Method for charging using saving type handhold mobile equipment
InactiveCN101136092AFast paymentGuaranteed safe storagePre-payment schemesPrepayment telephone systemsMobile phonePassword
The method comprises: writing the mobile phone pre-paid information; identifying user's ID; deciding the type of transaction; the mobile device confirms the pre-paid information, checks the payment password and the balance of his account; sending the pre-paid information; confirming the pre-paid information; confirming if needing to make the pre-paid again or to cancel the pre-paid; displaying the reason of rejecting a payment on the mobile device; ending the pre-paid.
Owner:上海银生宝电子支付服务有限公司
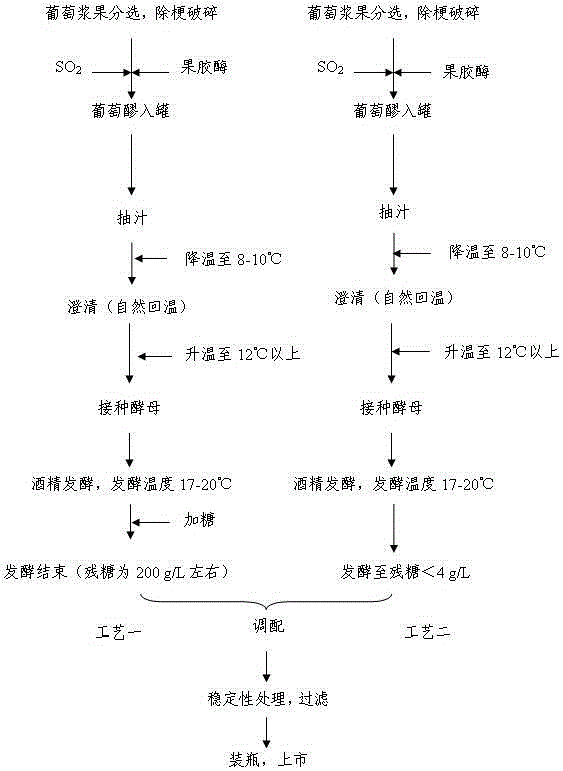
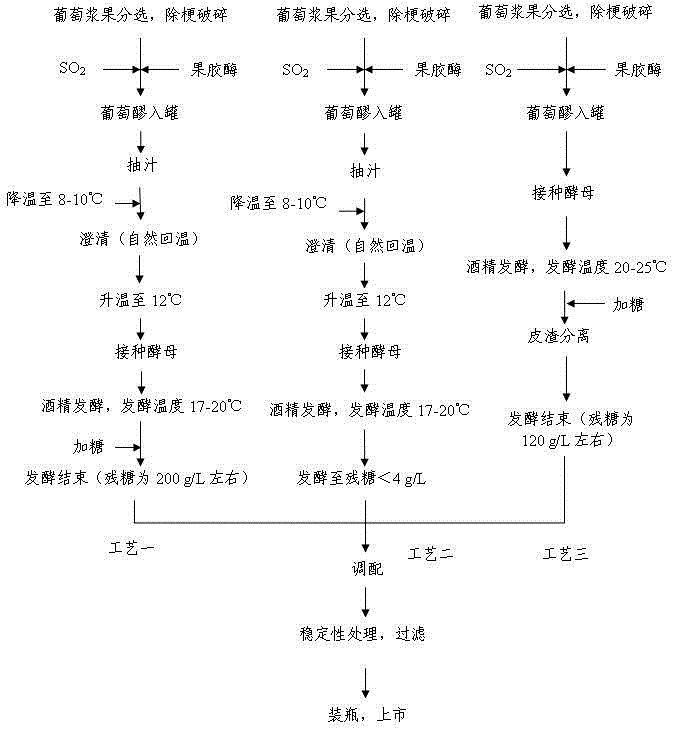
Soft pink fresh wine brewing technology
ActiveCN105176722AMaximize potential qualityReduce waste of resourcesWine preparationVitis viniferaVintage
The invention discloses a soft pink fresh wine brewing technology and belongs to the technical field of wine brewing. The soft pink fresh wine brewing technology includes using two brewing technologies for brewing two kinds of raw wine respectively and blending the two kinds of raw wine. The soft pink fresh wine brewing technology includes the steps of (1) brewing sweet pink wine; (2), brewing dry pink wine; (3) blending the two kinds of raw wine; (4) performing rapid aftertreatment; (5) filling to come into the market. The soft pink fresh wine brewing technology has the advantages that the soft pink fresh wine brewing technology solves the use problem of poor-quality grapes in special years, makes full use of potential quality of the grapes, is easy to operate and has no difficulty in implementation basically since related required equipment is possessed by fine wine producers, thereby being popularized extensively easily; the time from fermentation to bottling to come into the market is short, so that long-time bottle storage is unneeded, and capital is saved.
Owner:山西戎子酒庄有限公司
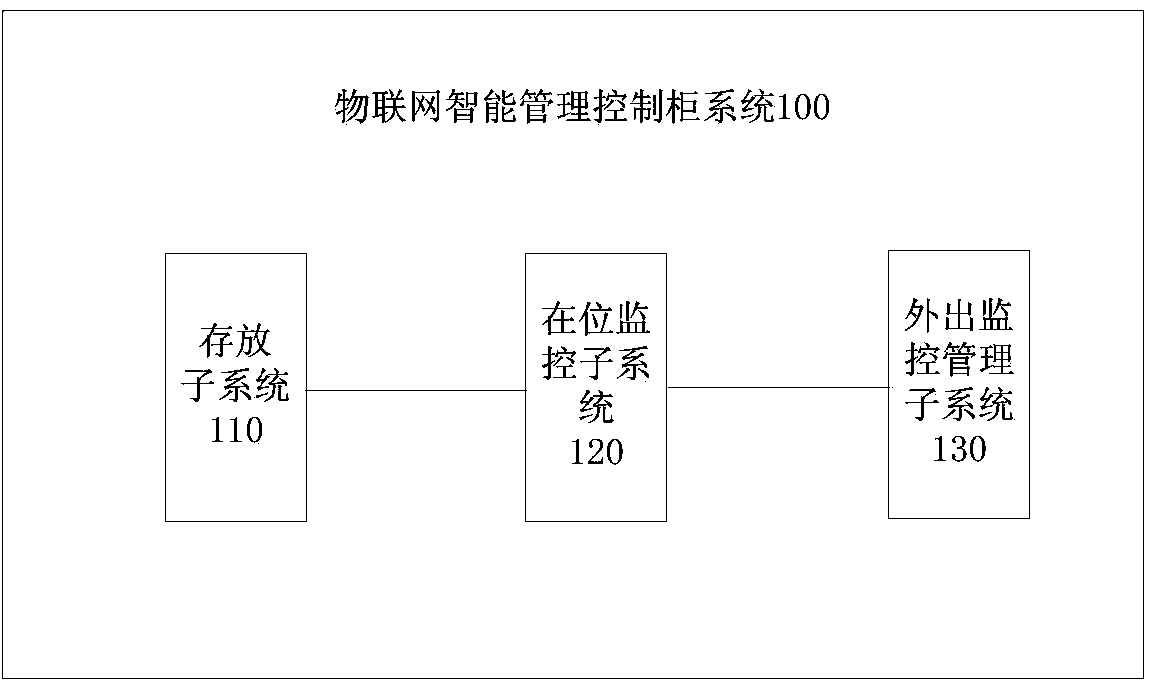
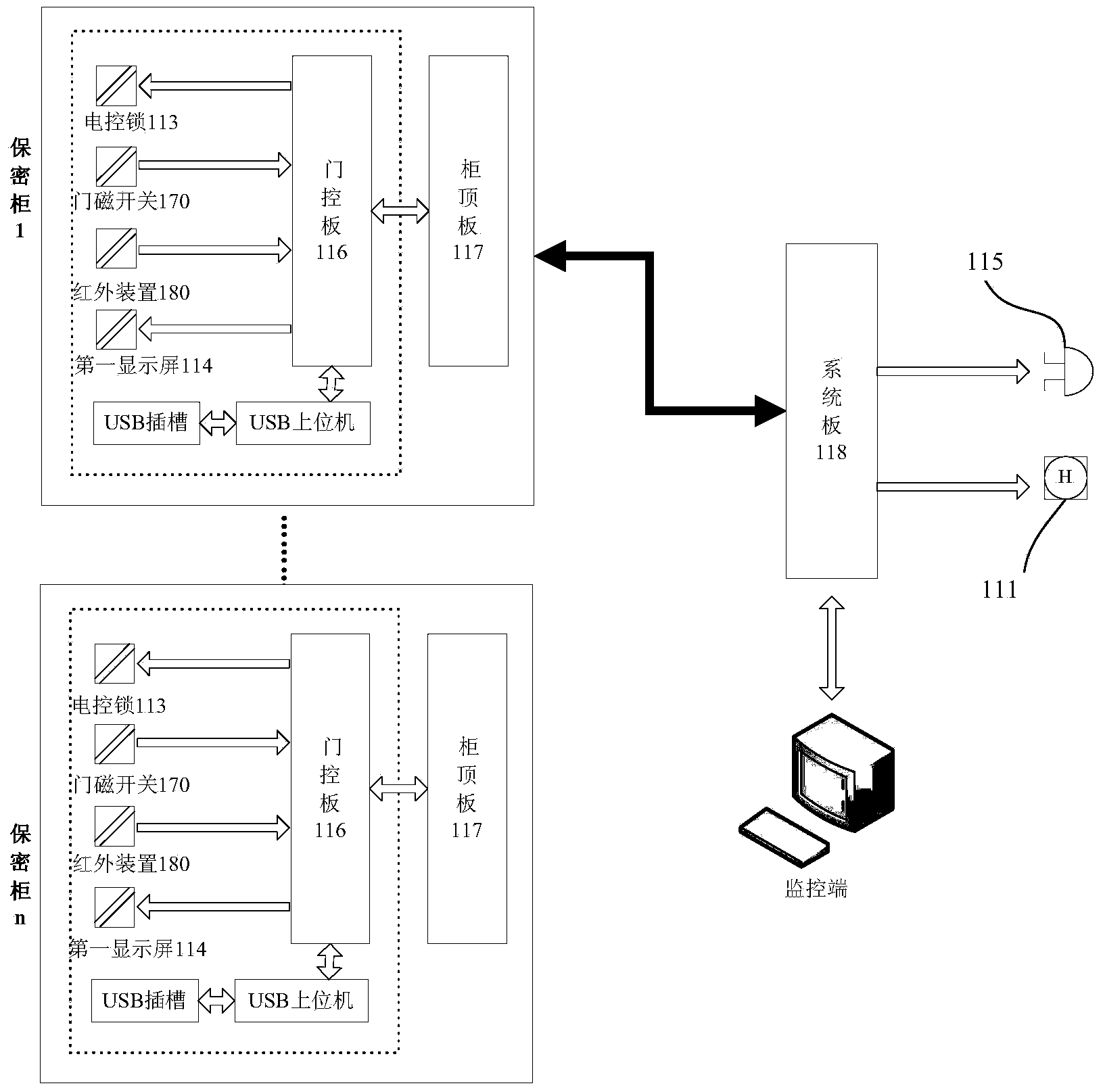
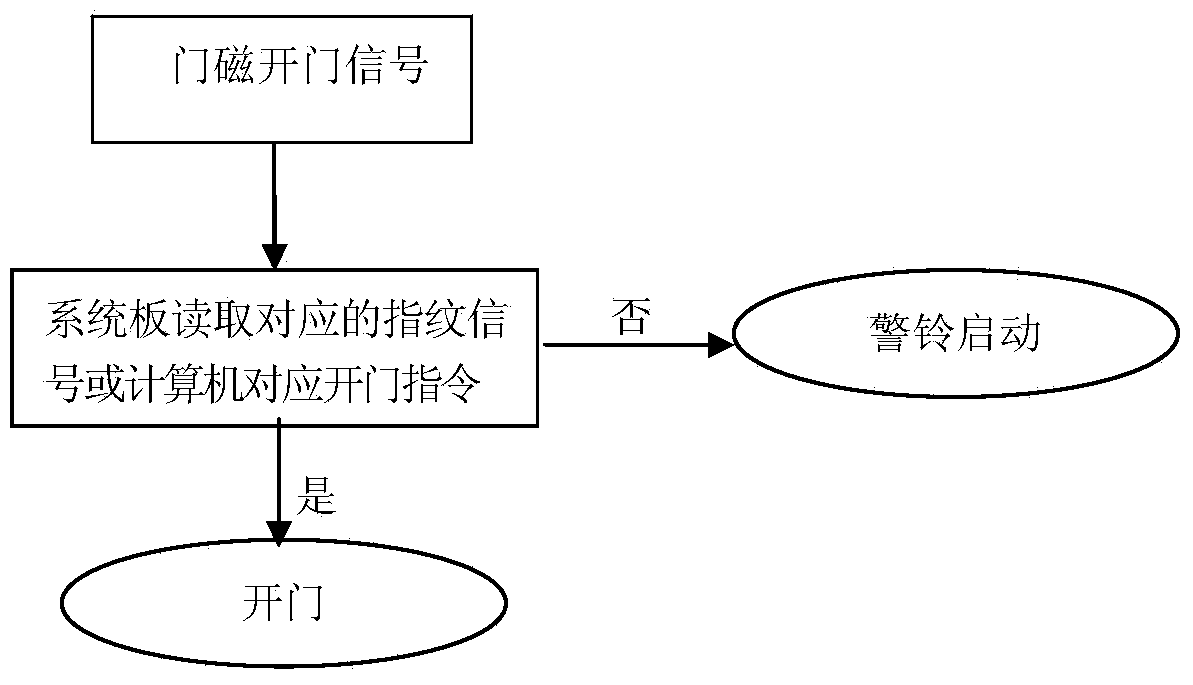
Internet of things intelligent management control cabinet system
ActiveCN103593687ARealize tracking and monitoringGuaranteed safe storageCo-operative working arrangementsAlarmsThe InternetIntelligent management
The invention provides an internet of things intelligent management control cabinet system which comprises a storage subsystem, an in-place monitoring subsystem, a first RFID electronic tag reader and an outdoor monitoring and management subsystem, wherein the storage subsystem is used for placing, protecting, positioning and managing carriers; the in-place monitoring subsystem is used for identifying and tracking all the carriers in the storage subsystem; the first RFID electronic tag reader is located on the external of the storage subsystem and used for reading tag information sent by an RFID beacon to identify and track the carriers corresponding to the tag information; the outdoor monitoring and management subsystem is used for monitoring whether tag information passing through an entrance guard position exists or not, whether the carriers corresponding to the tag information are allowed to pass through the entrance guard position or not is further monitored if the tag information passing through the entrance guard position exists, and an alarm signal is sent out if the carriers corresponding to the tag information are not allowed to pass through the entrance guard position. According to the internet of things intelligent management control cabinet system, storage safety of the carriers can be guaranteed, positions of the carriers can be tracked and monitored, an alarm can be sent out to the system in real time to avoid leakage situations when it is found out that the existing carriers are brought out privately, and safety and reliability of the system are improved.
Owner:烟台锂能环保科技有限公司
Brewage technique of thick sweet red fresh wine
ActiveCN105039044AMaximize potential qualityReduce waste of resourcesWine preparationVitis viniferaVintage
The invention relates to a brewage technique of a thick sweet red fresh wine, belonging to the technical field of wine brewage. The technique comprises three brewage processes for respectively brewing three unblended wines, and the three unblended wines are blended. The technique comprises the following steps: (1) brewing a sweet pink wine; (2) brewing a dry pink wine; (3) brewing a sweet red wine; (4) blending the unblended wines; (5) quickly carrying out after-treatment; and (6) filling and sending to the market. The technique successfully solves the problem of utilization of poor-quality grape raw materials in special years, fully utilizes the potential quality of the grape raw materials, is easy to operate, is easy to implement since every production enterprise has required related equipment, and can easily implement large-scale popularization. The technique requires short time from fermentation to bottling and appearance on the market, and does not need long-time bottle storage, thereby saving the cost.
Owner:山西戎子酒庄有限公司
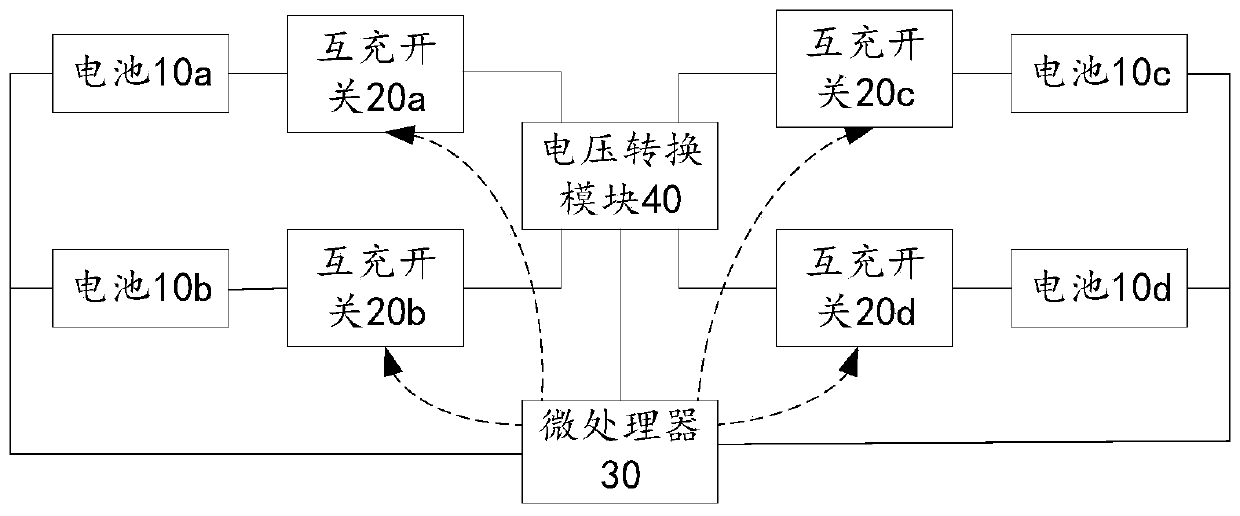
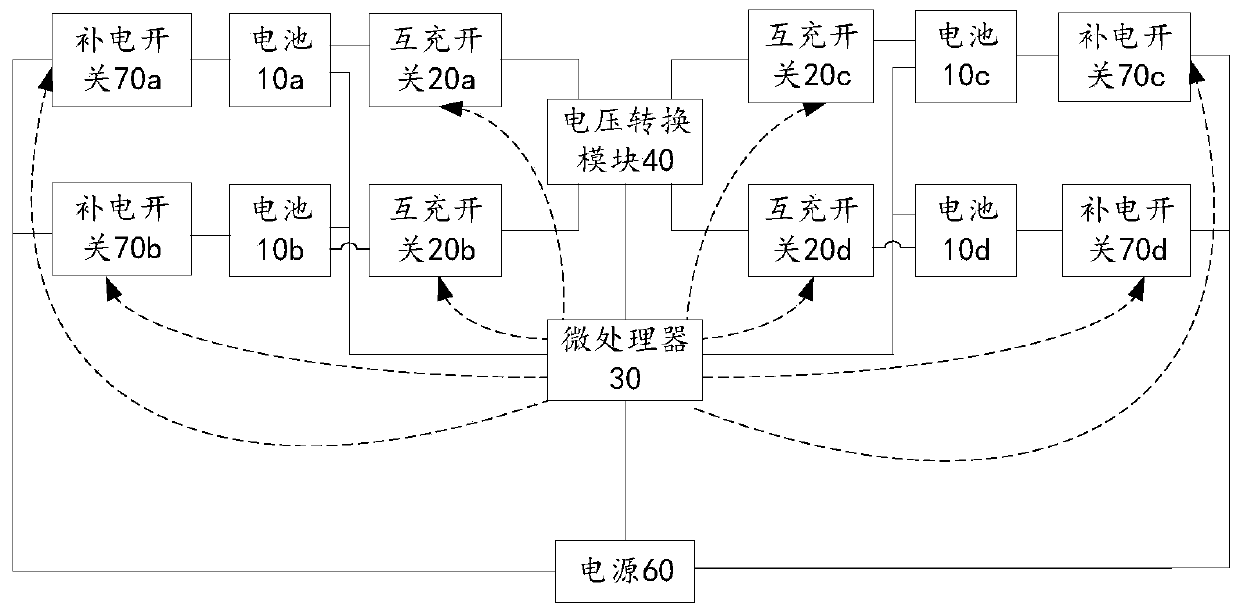
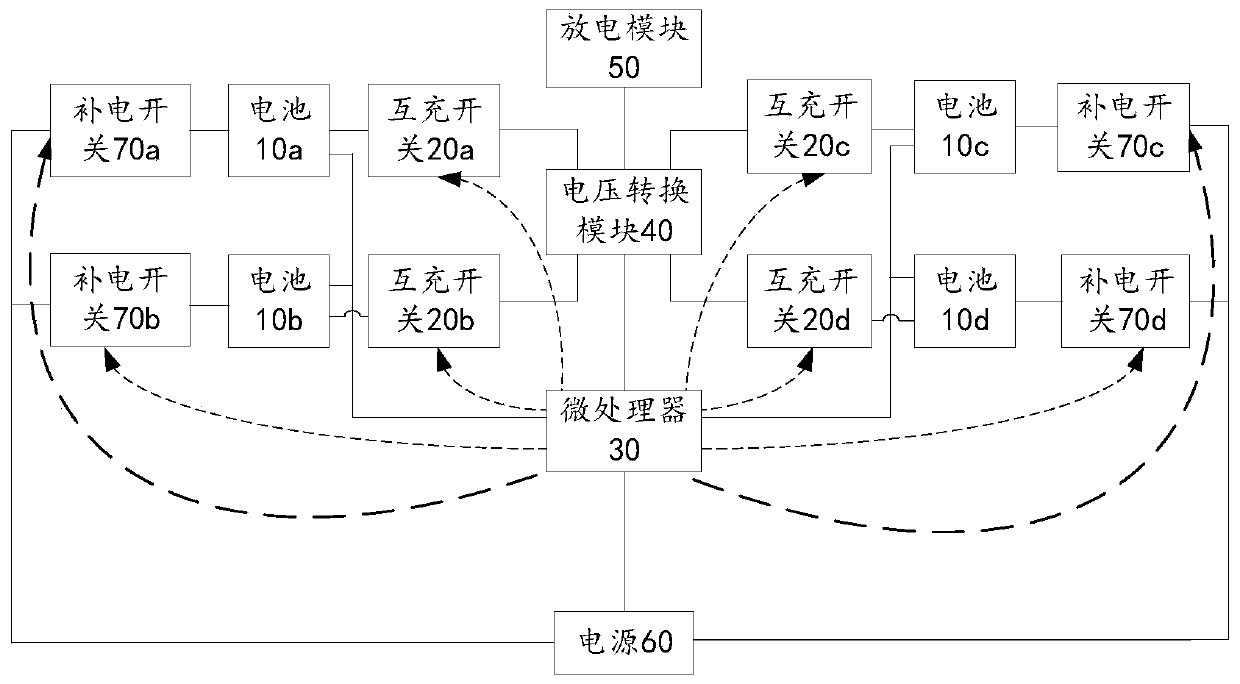
Multi-battery management device and unmanned aerial vehicle
ActiveCN110712529AGuaranteed safe storageReduce wasteElectric power distributionElectric devicesBattery chargeElectrical battery
Owner:SHENZHEN AUTEL INTELLIGENT AVIATION TECH CO LTD
Physically isolated dual-system construction method based on removable storage medium
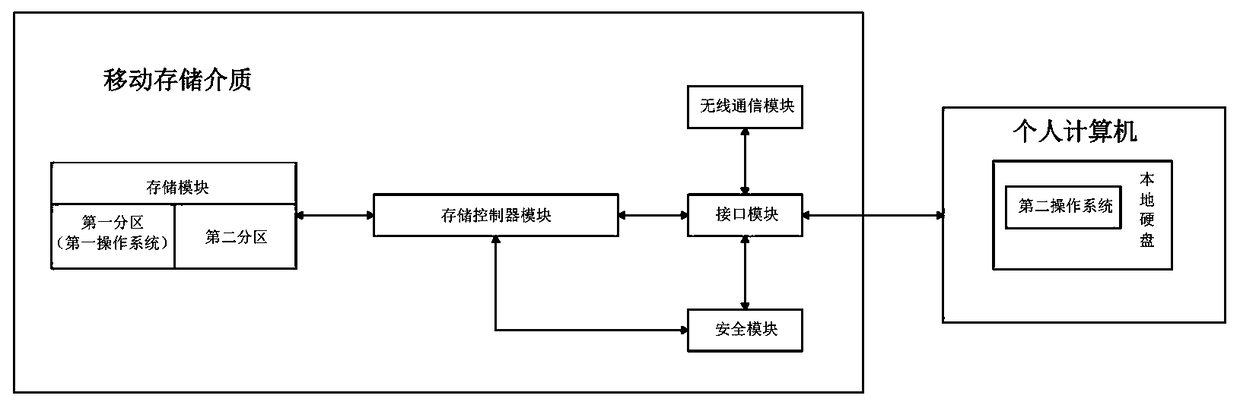
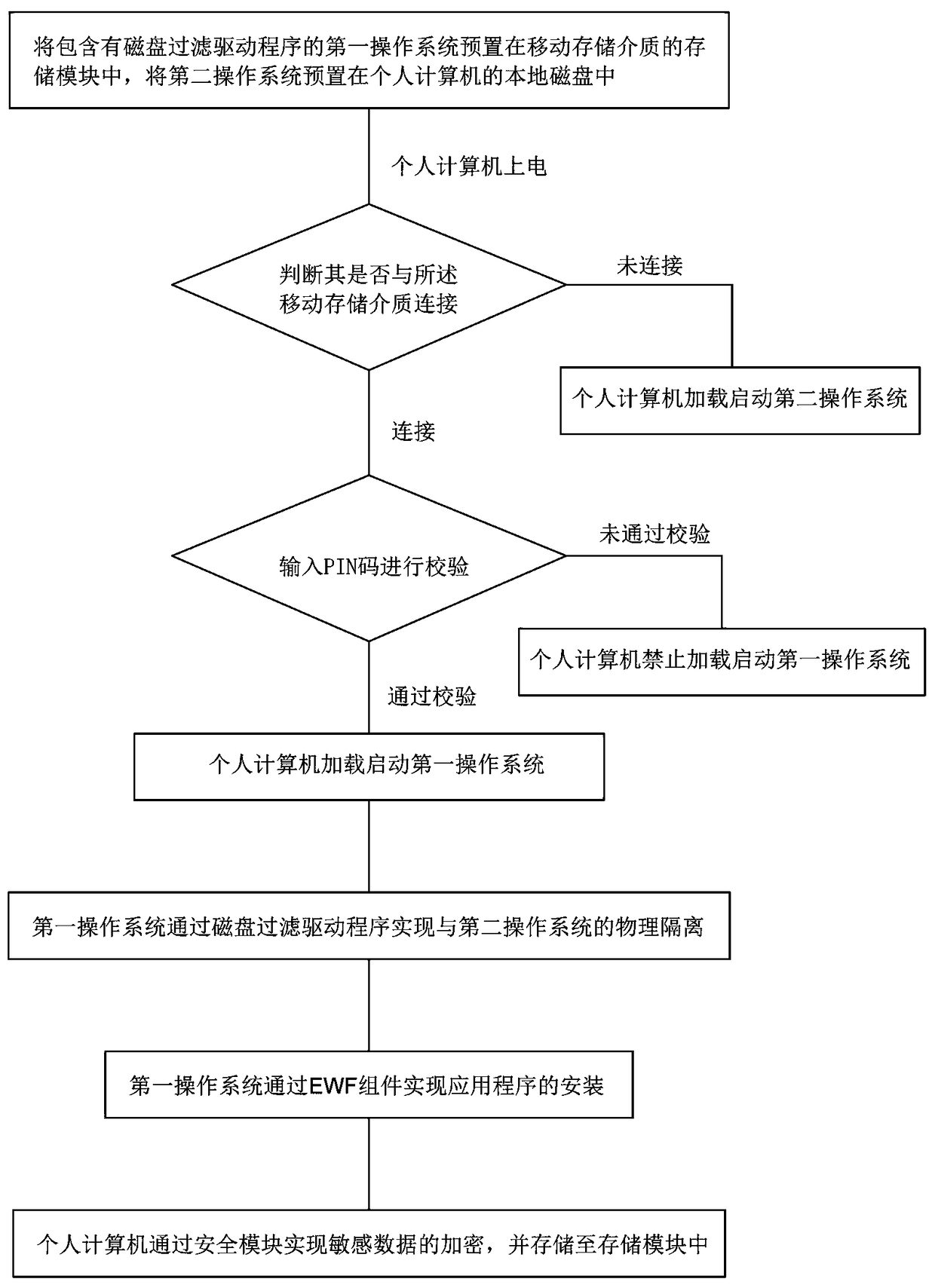
ActiveCN109086620AImprove securityGuaranteed privacy and securityDigital data protectionPlatform integrity maintainanceElectricityOperational system
The invention provides a physical isolation dual system construction method based on a removable storage medium, the removable storage medium includes a storage controller module, a storage module, aninterface module, a security module and a wireless communication module, the memory controller module is respectively connected with the memory module, the interface module is connected with the security module. The interface module is connected with the security module and the wireless communication module. The method comprises the following steps: presetting a first operating system including adisk filter driver in the storage module; presetting a second operating system in a local disk of the personal computer; presetting a second operating system in a local disk of the personal computer;after the personal computer is powered on, when the personal computer is connected with the removable storage medium and the PIN code verification passes, the first operating system being allowed tobe loaded and started. The first operating system realizes physical isolation from the second operating system through the disk filter driver.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Solar environment monitoring vehicle
InactiveCN106707850AUnderstanding Pollution IssuesGuaranteed safe storageProgramme controlMeasurement devicesAir pumpWater quality
The invention discloses a solar environment monitoring vehicle comprising a monitoring vehicle body, an environment monitoring device, and a central processor. A motor is fixedly installed on the top of the monitoring vehicle body. The top of the motor is connected with a rotary platform through a rotating shaft. An air pump is fixedly installed on the rotary platform. The air pump is movably connected with the other end of a solar cell panel through a pneumatic telescopic rod. The environment monitoring device is composed of an atmospheric monitoring device, a water quality monitoring device, and a soil monitoring device. The input end of the central processor is electrically connected with the output ends of the solar cell panel, an input module, a light sensor and a GPS positioning module. The output end of the central processor is electrically connected with the input end of a data processing module through an acquisition data analysis module. The beneficial effects are as follows: the monitoring parameters are diverse; the basic parameters of atmosphere, water quality and soil can be monitored, analyzed and processed; and the angle of the solar cell panel can be adjusted freely.
Owner:张强
Refrigeration device and control method thereof
InactiveCN107664371AGuaranteed safe storageGuaranteed uptimeLighting and heating apparatusDomestic refrigeratorsTemperature controlEngineering
The invention provides a refrigeration device. The refrigeration device comprises a chamber for storing objects, a first temperature sensor for detecting the temperature of the chamber, an evaporatorfor cooling the chamber, and a second temperature sensor for detecting the temperature of the evaporator; when the first temperature sensor cannot normally work, a control unit controls refrigerationof the chamber based on the temperature, detected by the second sensor, of the evaporator; and when the second temperature sensor cannot normally work, the control unit controls defrosting of the evaporator based on the temperature, detected by the first sensor, of the chamber in the defrosting phase of the evaporator. Before maintainers replace the broken sensor, continuous normal operation of arefrigerator can be guaranteed according to the temperature information measured by the other temperature sensor.
Owner:BSH ELECTRICAL APPLIANCES JIANGSU +1
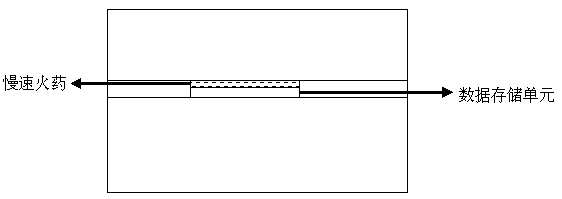
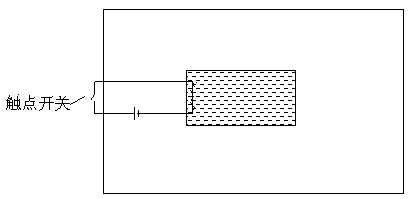
Physical self-destruction method for electronic data
PendingCN107608915AGuaranteed safe storageLow costUnauthorized memory use protectionInternal/peripheral component protectionComputer hardwareLow speed
The invention discloses a physical self-destruction method for electronic data. A low-speed explosive layer is paved on one surface of an electronic data storage medium which does not contact with a circuit, and the low-speed explosive layer is connected with an ignition device, the low-speed explosive is ignited by the ignition device, and the high temperature is produced on the surface of the storage medium, so the physical destruction is generated in the medium so as to achieve the purpose of the data self-destruction. The method is capable of breaking a traditional view of the current logical deleting and physical destruction, ensuring the safety storage while a low-price device is used for the data under the situation of the data safety unexpected destruction at the present stage especially, performing the safety destruction while the data can be leaked, and effectively solving such existing contradiction, and has the advantages of cheap cost and strong operability.
Owner:JIANGSU DU WAN ELECTRONICS TECH CO LTD
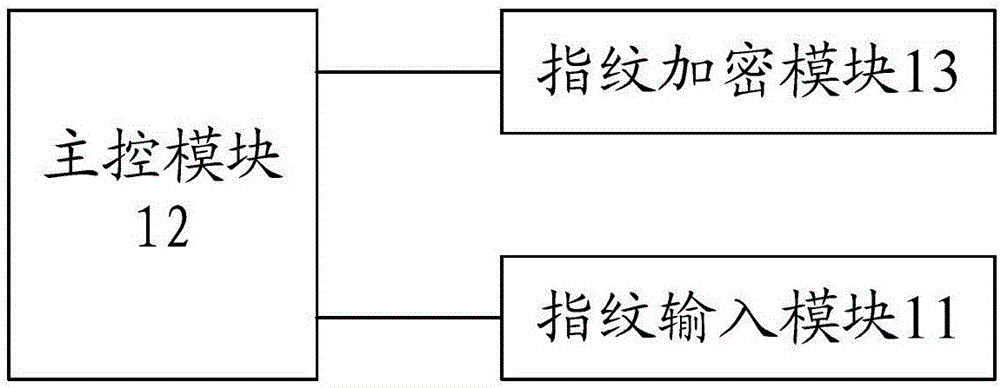
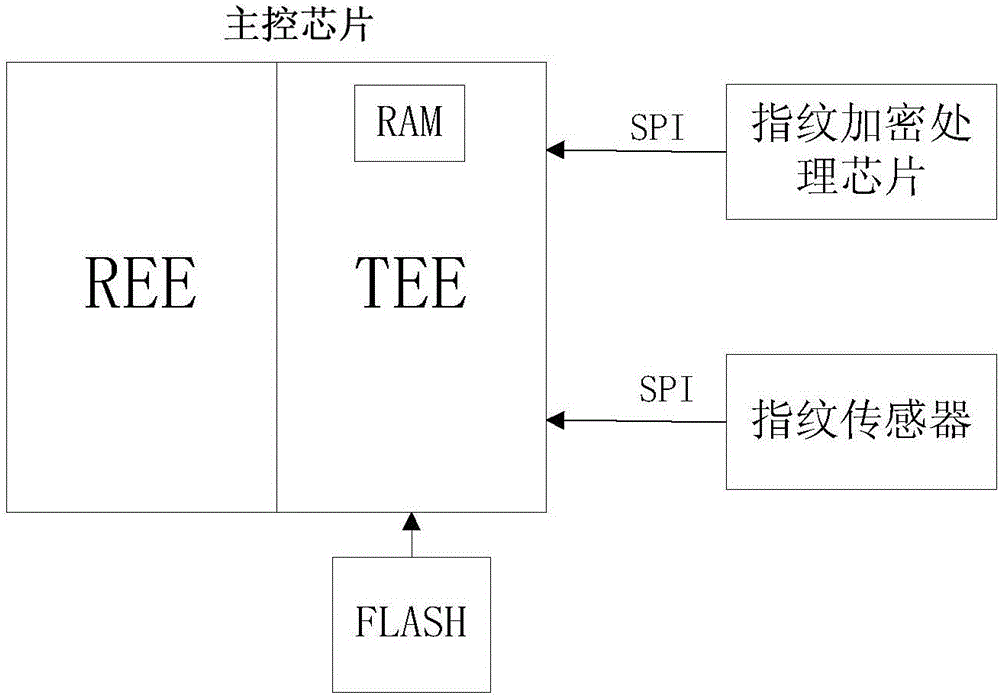
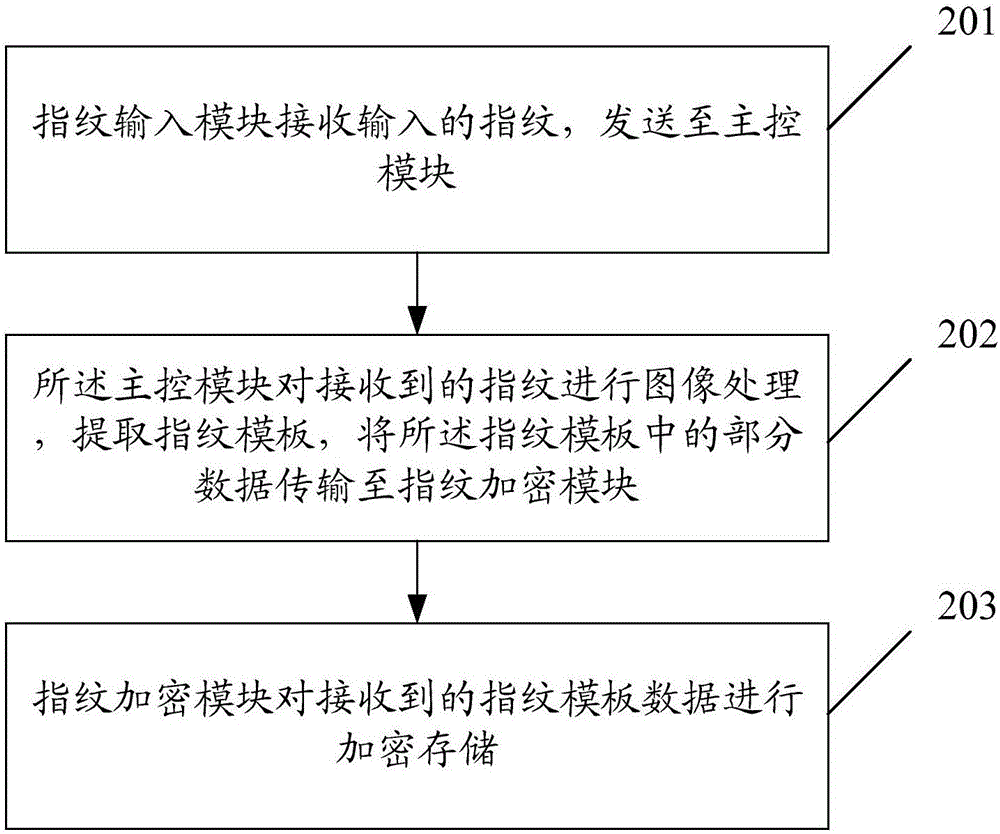
Fingerprint encryption device and implementation method thereof
InactiveCN106682522AGuaranteed safe storageEnsure safetyDigital data protectionDigital data authenticationComputer hardwareImaging processing
The invention discloses a fingerprint encryption device and an implementation method. The fingerprint encryption device is applied to a mobile terminal, and comprises a fingerprint input module, a main control module and a fingerprint encryption module connected in sequence, wherein the fingerprint input module is used for receiving an input fingerprint, and sending the fingerprint to the main control module; the main control module is used for performing image processing on the received fingerprint, extracting a fingerprint template, and transmitting a part of data in the fingerprint module to the fingerprint encryption module; and the fingerprint encryption module is used for storing the received data of the fingerprint template in an encrypted manner. According to the device and the method provided by the embodiment of the invention, the part of data in the fingerprint data is stored in the encrypted manner, so that secure storage of the fingerprint template can be ensured.
Owner:DATANG MICROELECTRONICS TECH CO LTD +1
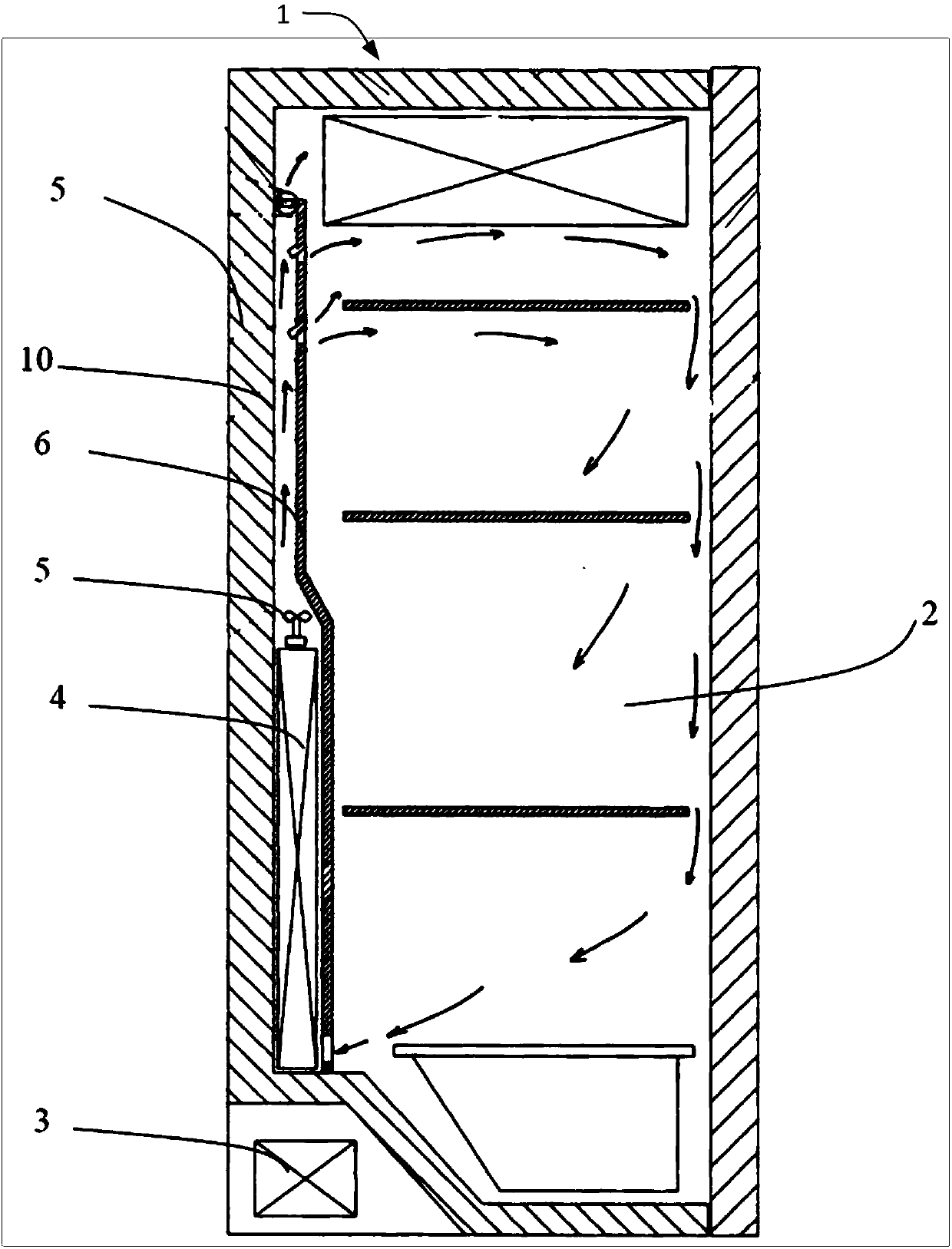
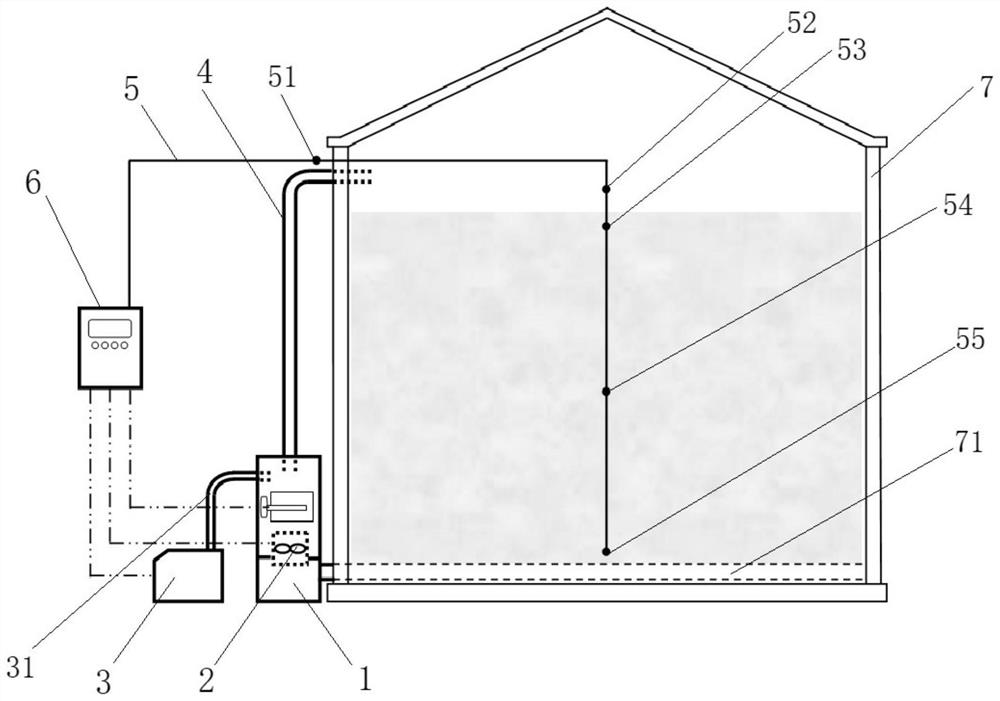
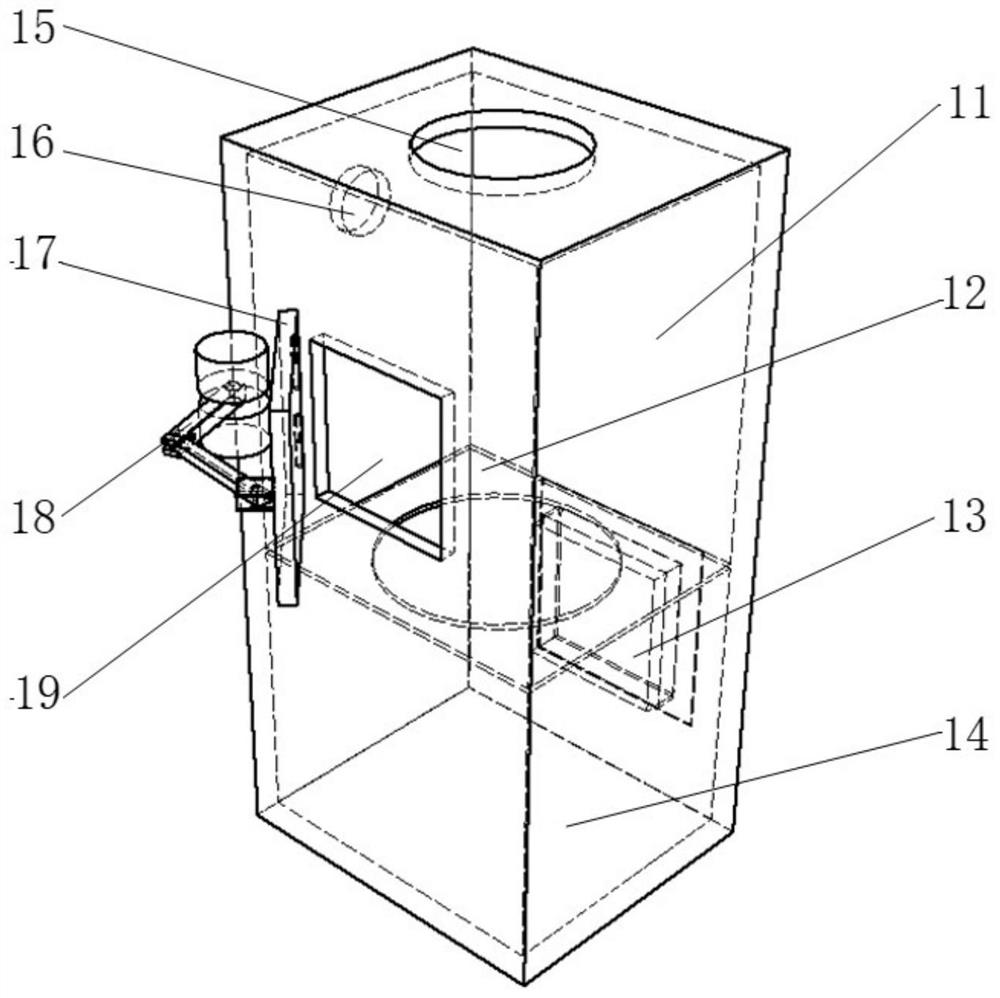
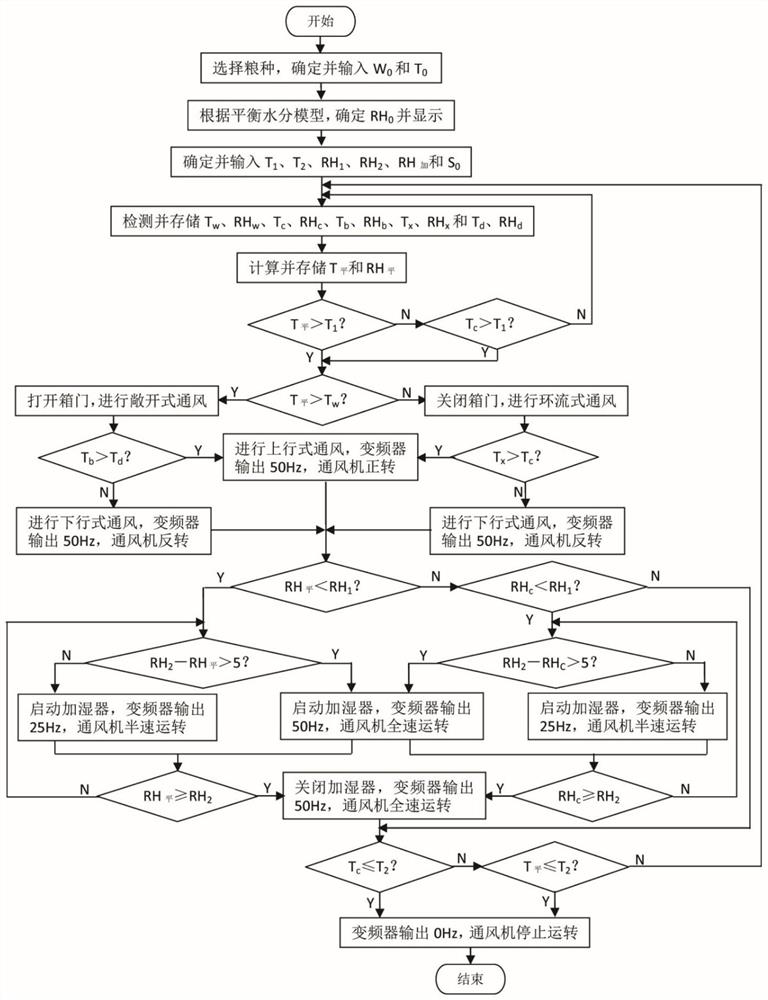
Two-way variable air volume ventilation temperature control and humidification system for granaries and control method of two-way variable air volume ventilation temperature control and humidification system
PendingCN111642256AEasy to operateEasy maintenanceAgriculture tools and machinesMechanical apparatusVariable air volumeTemperature control
The present invention discloses a two-way variable air volume ventilation temperature control and humidification system for granaries and a control method of the two-way variable air volume ventilation temperature control and humidification system. The system comprises an air mixing box, a two-way ventilator, a ventilation pipe, a humidifier, a temperature and humidity detection cable and a measurement and control device. By analyzing temperature and humidity values of inside and outside of the granaries and different depths of grain piles measured by sensors on the temperature and humidity detection cable, when temperature control conditions are met, the system selects an open type or circulating type ventilation method, besides, forward or reverse rotations of the ventilator are utilizedto implement upward type or downward type ventilation, when humidification conditions are met, the humidifier is started, and besides, a frequency converter adjusts rotation of the ventilator to change air volume and humidification volume. The system operation and control method can control space temperature and humidity in the granaries or temperature and humidity of the grain piles within a setsafe storage temperature range and an equilibrium relative humidity range corresponding to safe storage moisture, thereby reducing quality deterioration and water loss during a grain storage period,reducing storage loss and ensuring safe grain storage.
Owner:LIAONING RES INST OF GRAIN SCI
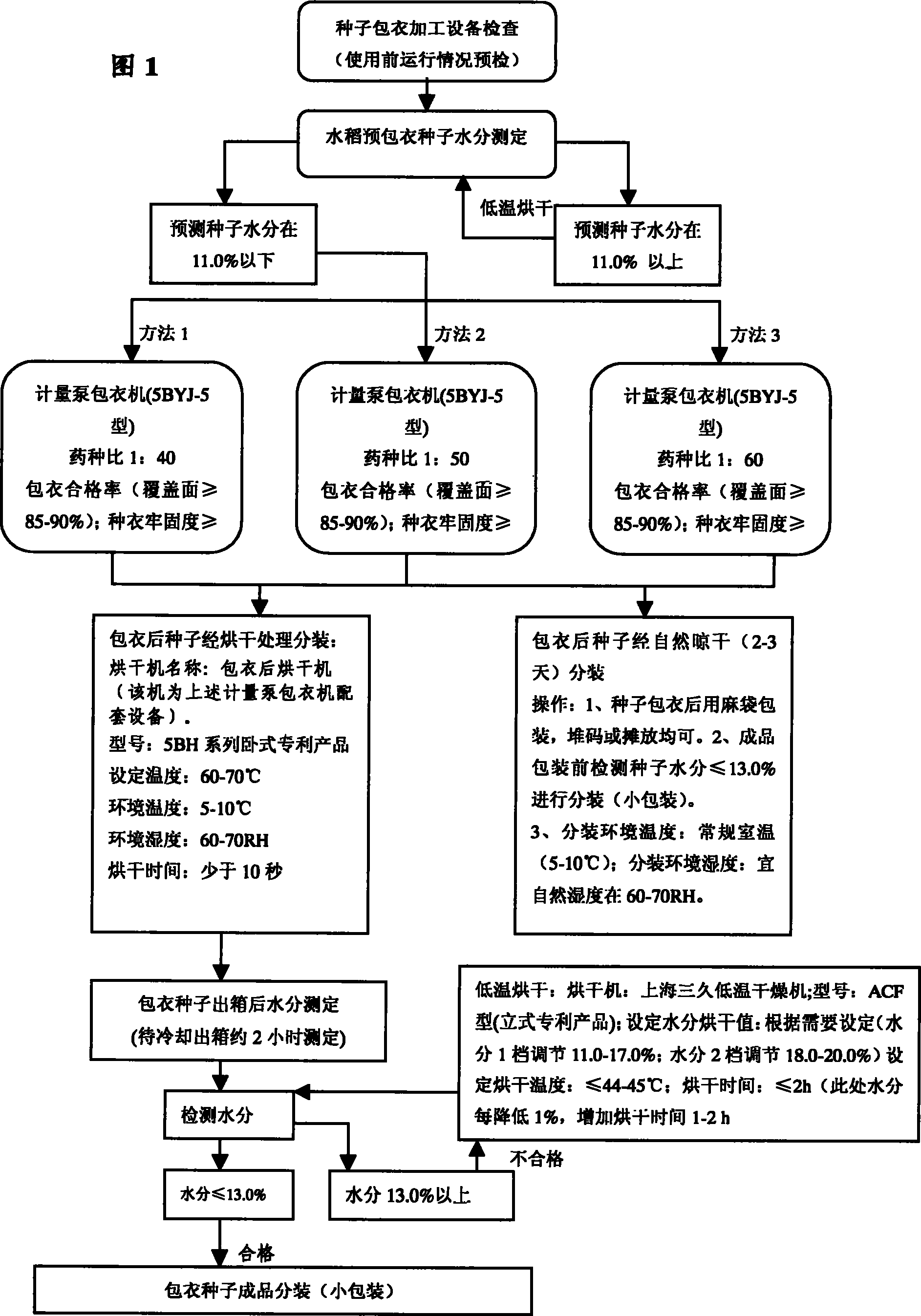
Hybrid rice seed coating agents and method
The present invention is one kind of seed coating agent and its coating process. The hybrid rice seed coating agent consists of the following active components: carbendazim 7-8 weight portions, thiram 7-8 weight portions,paclobutrazol 0.15-1.3 weight portions and prochloraz 0.3-2.66 weight portions. The coating process with the hybrid rice seed coating agent includes the following steps: stoving water content of seed to below 11 %; coating seed in a seed coating machine in the ratio between the seed coating agent and seed of 1 to 40-70; and stoving the coated seed to water content below 13.0 %. Treating rice seed with the seed coating agent can raise the germination rate and rice seedling forming rate obviously, raise rice seedling quality, and result in other positive effects.
Owner:HAINAN SHENNONG DAFENG SEED TECH
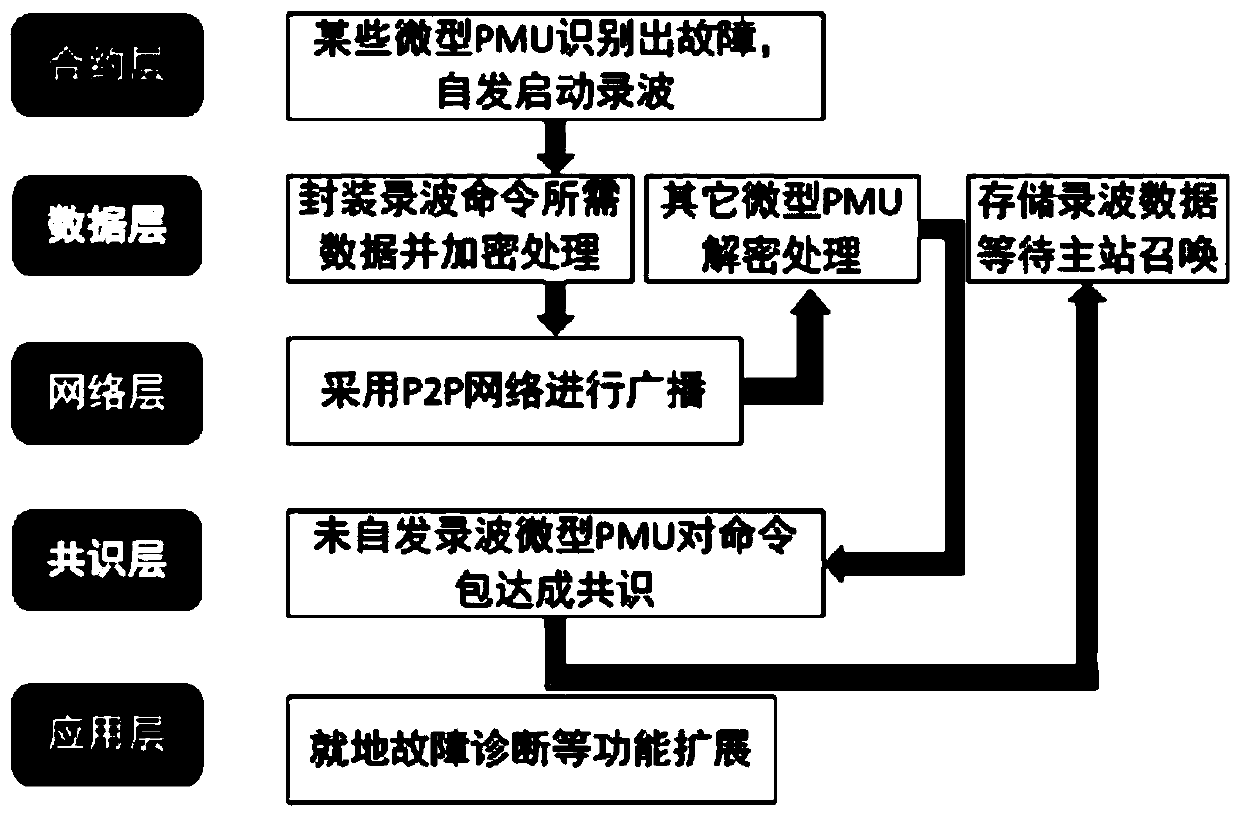
Power distribution network micro PMU fault recording cooperation method and system based on block chain
ActiveCN110187221ALarge storage capacityRealize retrospective queryElectrical testingMaster stationChain network
The invention provides a power distribution network micro PMU fault recording cooperative method and system based on a block chain. All micro PMUs are used as nodes of a block chain network, the blockchain network is constructed, and the judgment process is started: when any micro PMU triggers fault recording, the fault recording is broadcasted to the whole block chain network, other micro PMUs are informed to carry out fault recording in a coordinated mode, and when certain micro PMUs judge the fault according to fault characteristic quantity detected in real time by means of built-in faultcriteria, the fault recording is started, and corresponding operation is automatically executed. The power distribution network micro PMU fault recording cooperative method and system based on the block chain realize decentralized management independent of a master station and coordination and autonomy among the micro PMUs.
Owner:SHANDONG UNIV
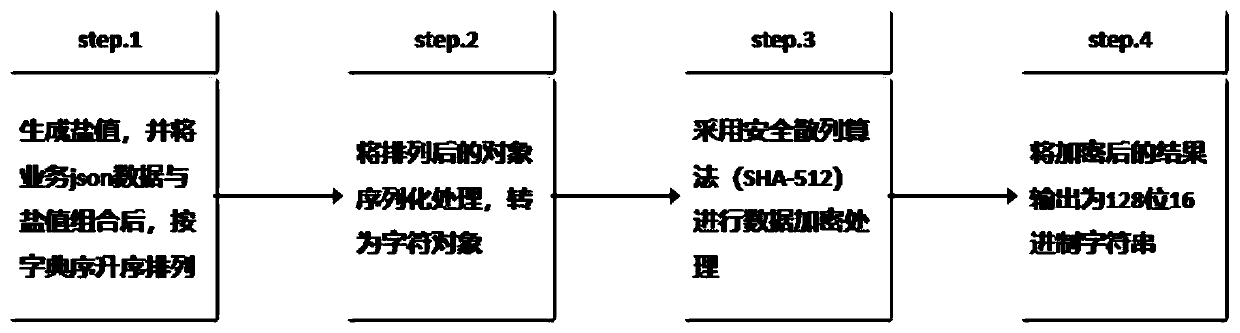
User name and password information encryption and verification method
InactiveCN105897730AAvoid data breachesGuaranteed safe storageTransmissionIp addressValidation methods
The invention discloses a user name and password information encryption and verification method. By encrypting and storing user names and passwords, user names and password information are prevented from being divulged under the condition that a database is attacked and the like. If mismatching appears in the verification process, IP address information is further verified and a relevant measure is taken, so that the security can be further strengthened.
Owner:GUANGXI ZUNDA E COMMERCE CO LTD
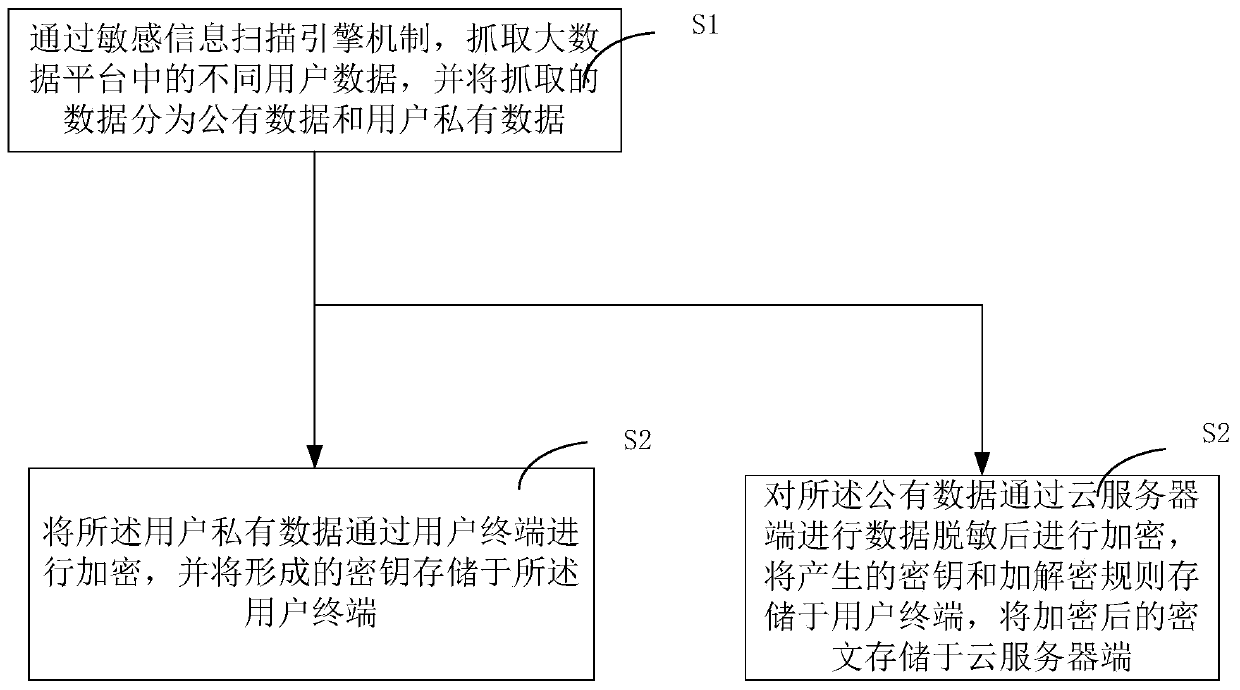
Big data construction storage method and system based on data desensitization
InactiveCN109858277AGuaranteed safe storageReduce the burden onDigital data protectionCiphertextData platform
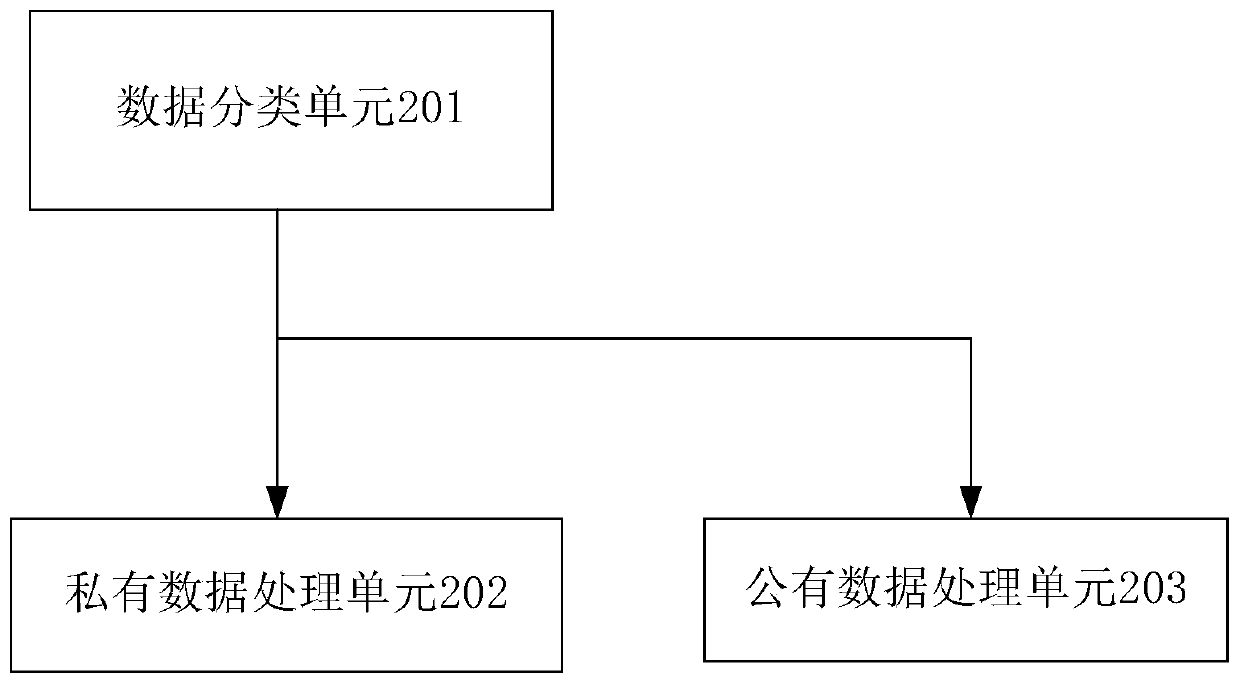
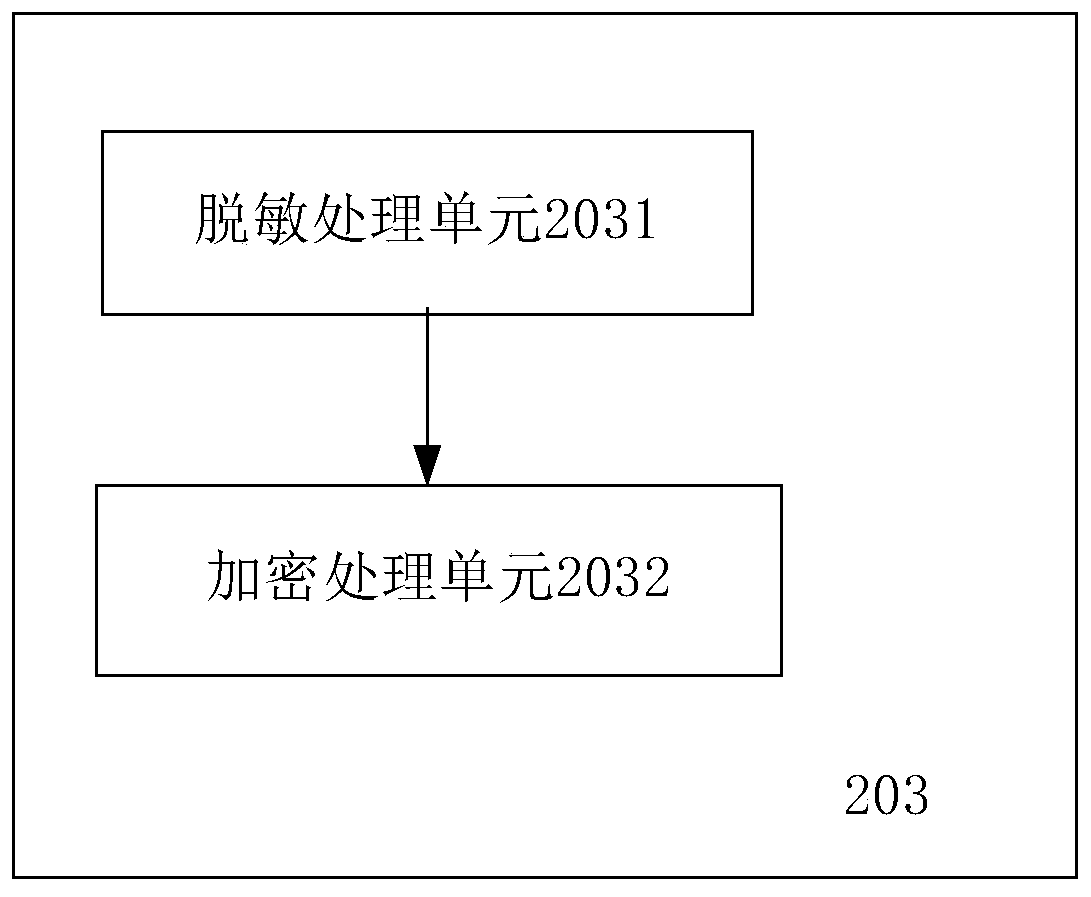
The invention discloses a big data construction storage method and system based on data desensitization, and the method comprises the following steps: S1, capturing different user data in a big data platform through a sensitive information scanning engine mechanism, and dividing the captured data into public data and user private data; S2, encrypting the user private data through a user terminal,and storing a formed secret key in the user terminal; S3, carrying out data desensitization on the public data through a cloud server side and then encrypting the public data; storing the generated key and the encryption and decryption rule in a user terminal. According to the method and the system, the powerful storage capacity of the cloud platform can be utilized, the burden of the cloud servercan be reduced, the private data of the user are stored in the client through an encryption method, and the leakage risk of the private data of the user is greatly reduced.
Owner:GUANGZHOU UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com