Method for managing USBKey unlocking secret key intensively and safely
A security management and unlocking technology, which is applied in the field of management and unlocking keys, can solve the problems of USBKey security risks and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make it easy to understand the technical means, creative features, objectives and effects achieved by the present invention, the present invention will be further explained below in conjunction with specific drawings.
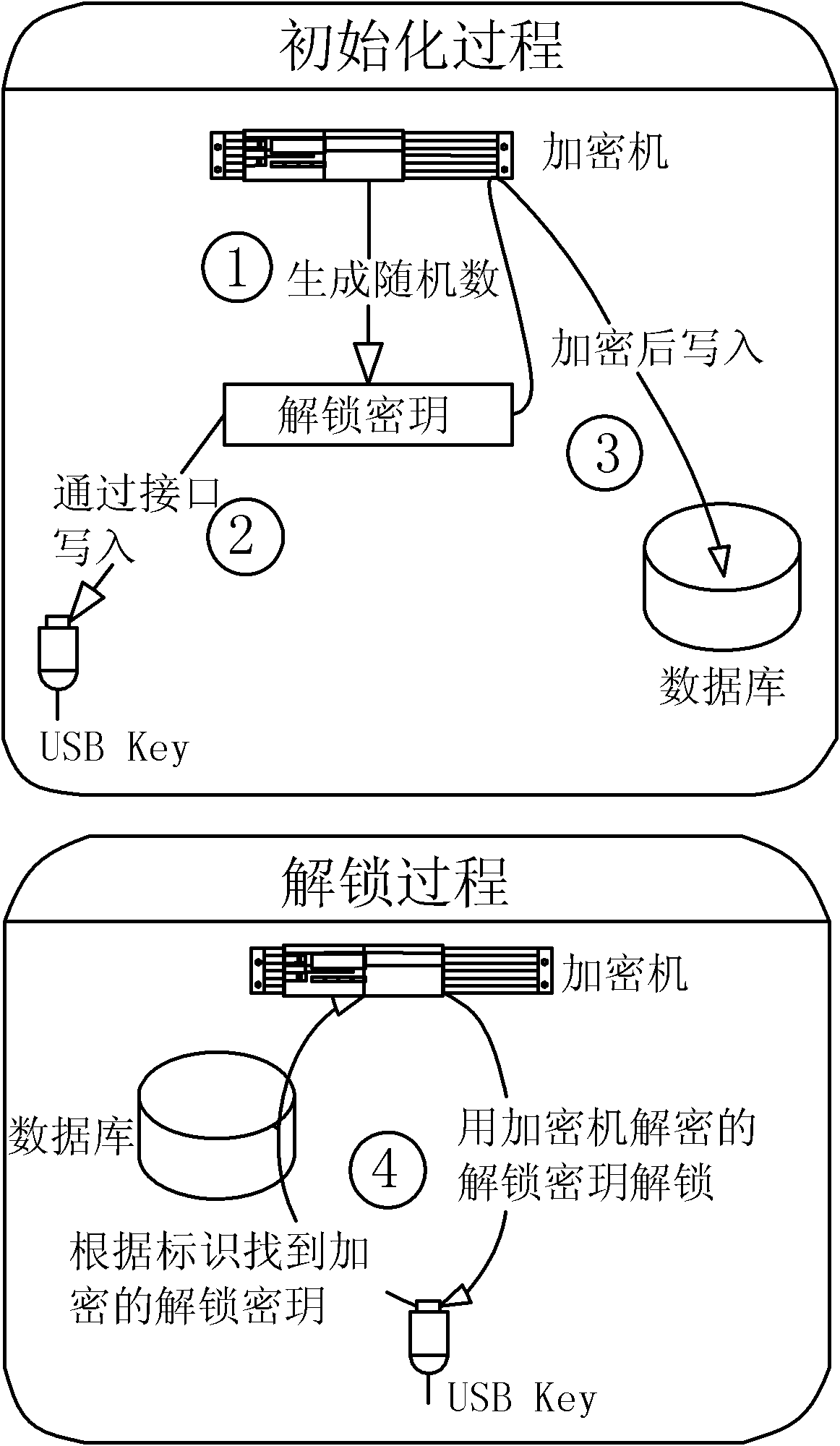
[0026] Such as figure 1 As shown, the method for centralized and safe management of USB Key unlocking keys of the present invention includes the following steps:
[0027] 1) Generate a random number through the encryption machine as the unlocking key;
[0028] 2) Before the USB Key is delivered to the user, write the unlock key generated in step 1) into the USB Key through the Microsoft CSP interface extension;
[0029] 3) The unlocking key generated in step 1) is encrypted with an encryption machine, and together with the unique identifier of the obtained USB Key, it is encrypted and written into the database;
[0030] 4) If the USB Key is locked, the corresponding encrypted unlocking key is found through the unique identification of the USB Key, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com