Enhanced MASK code method for resisting DES (data encryption standard) power consumption attack
A power consumption attack and enhanced technology, applied in the direction of encryption devices with shift registers/memory, etc., can solve the problems of Hamming distance leakage, resistance to DES power consumption attacks, etc., to reduce costs, reduce chip design area, The effect of resolving Hamming distance leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] According to Figure 3 ~ Figure 6 , A detailed description of the preferred embodiments of the present invention.
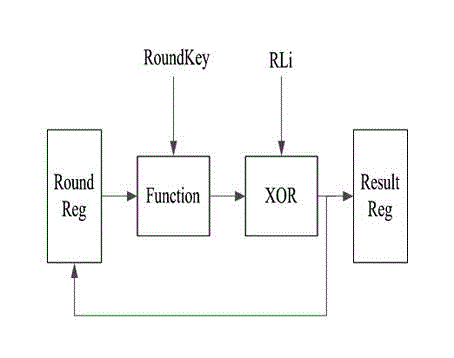
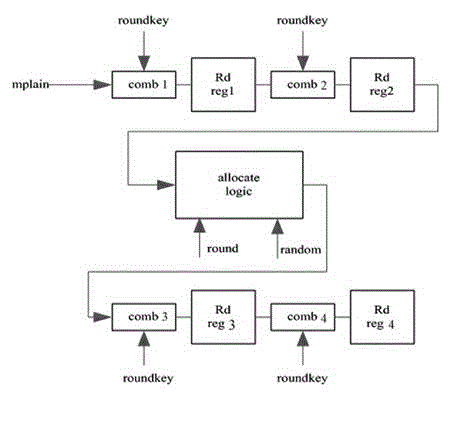
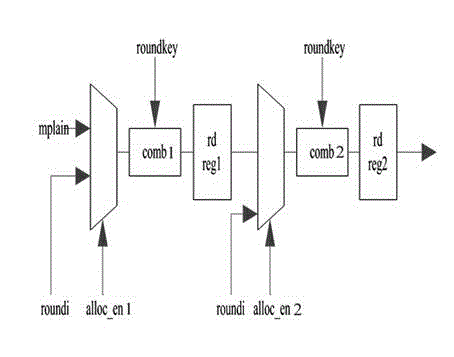
[0043] Such as image 3 As shown, the enhanced MASK masking method for resisting DES power attacks provided by the present invention is an improvement on the basis of the existing DES loop iterative masking scheme. It also includes 16 rounds of calculation processes. The specific steps are as follows Shown:
[0044] Step 1. Start two rounds of DES calculations to be implemented by pipeline calculation, and the calculation circuit is implemented by two independent and unrelated first calculation circuits and second calculation circuits;
[0045] Step 2. The middle twelve rounds, that is, the third to fourteenth rounds of the DES operation process are realized by random positioning logic operation;
[0046] Step 3. The last two rounds of DES operations are implemented by pipeline operation, and the calculation circuit is implemented by using two other independent a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com