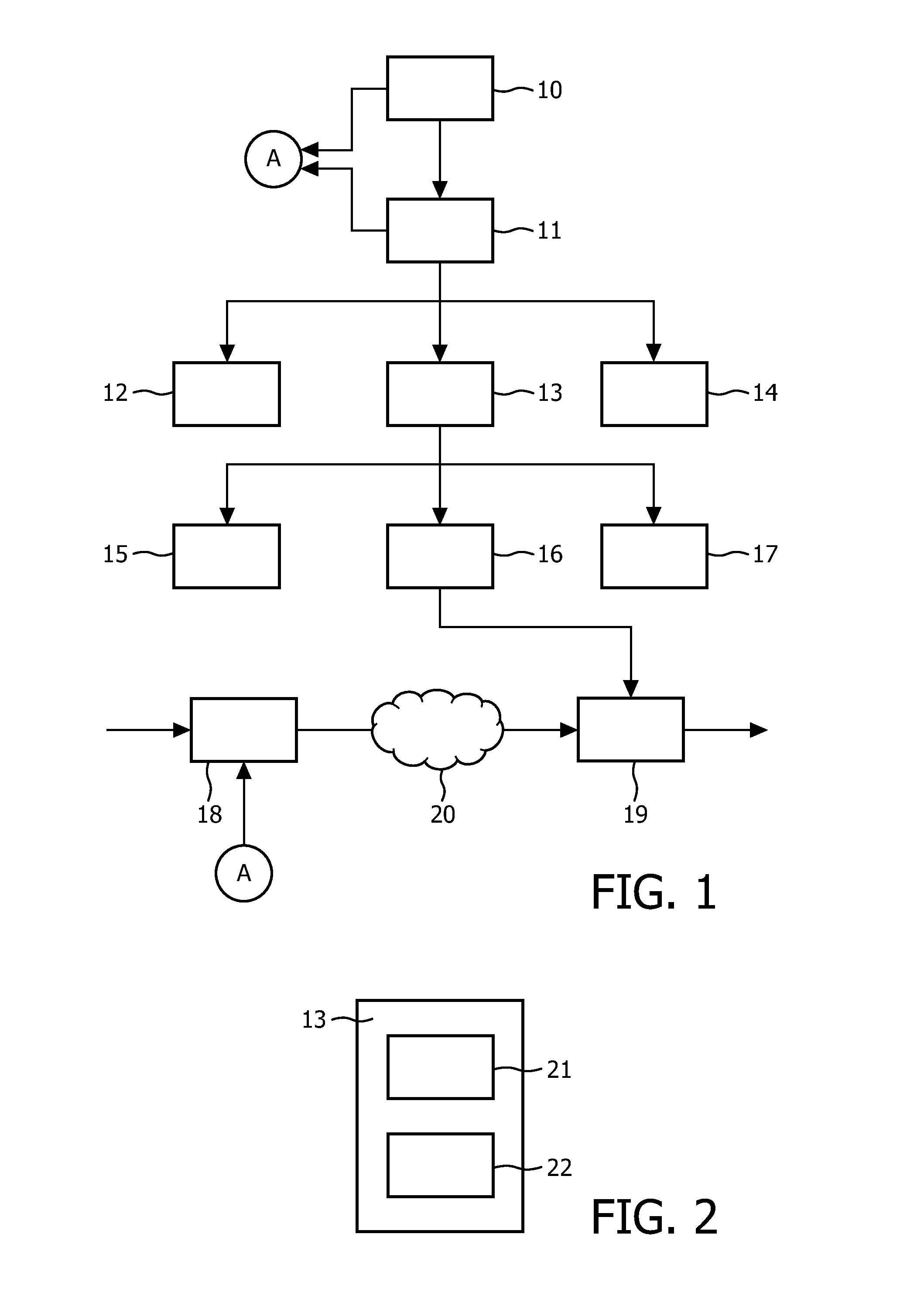
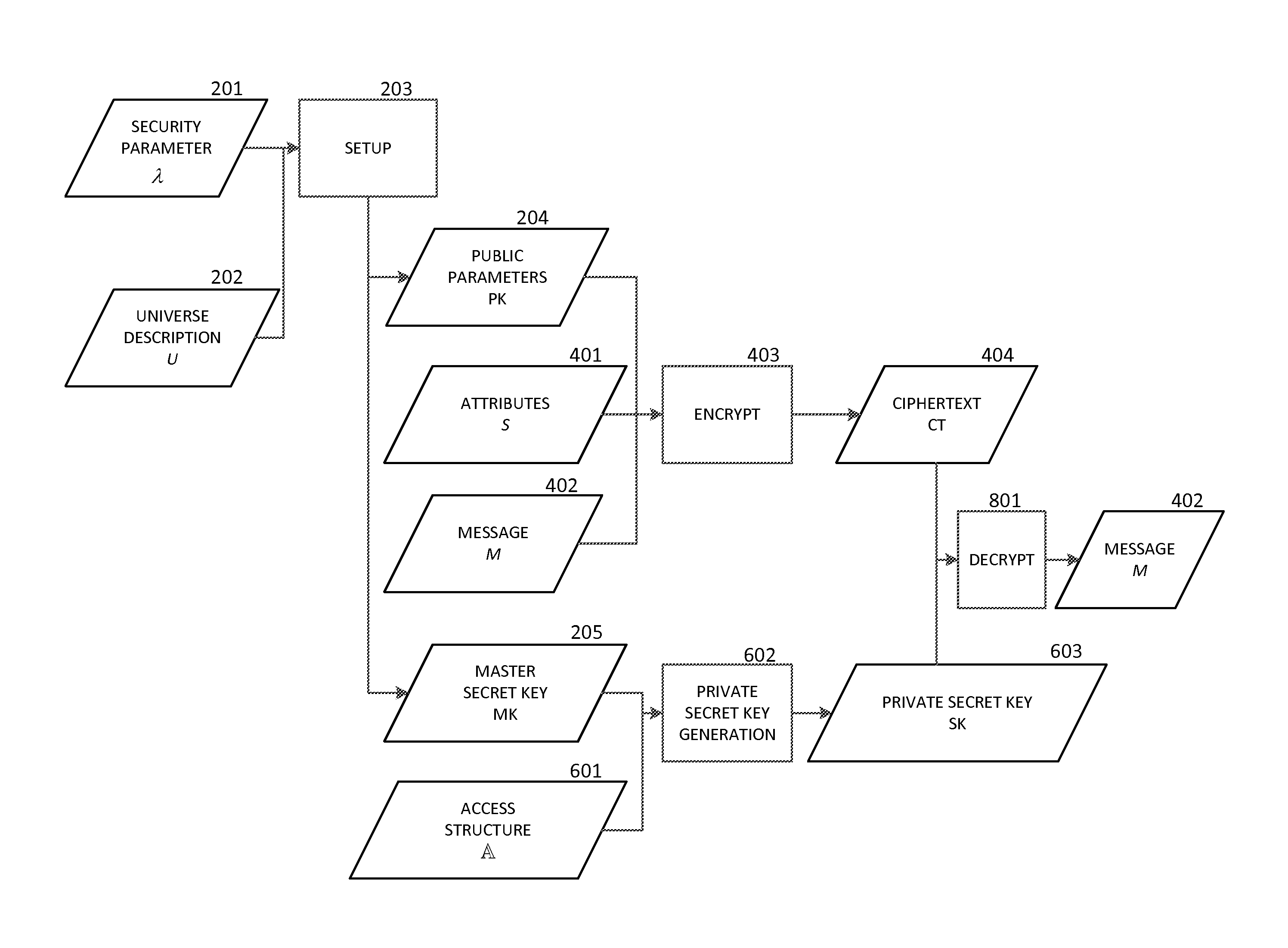
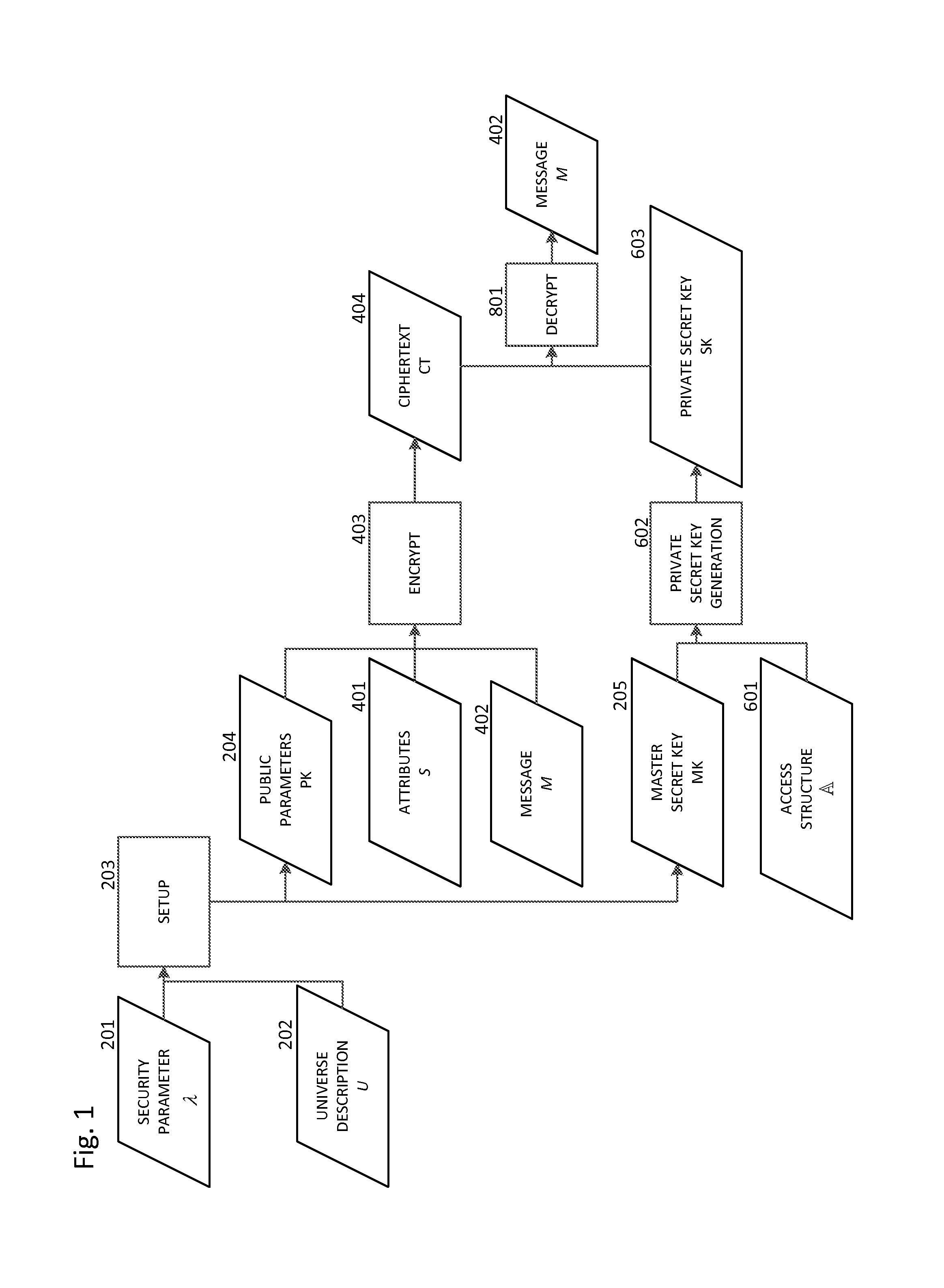
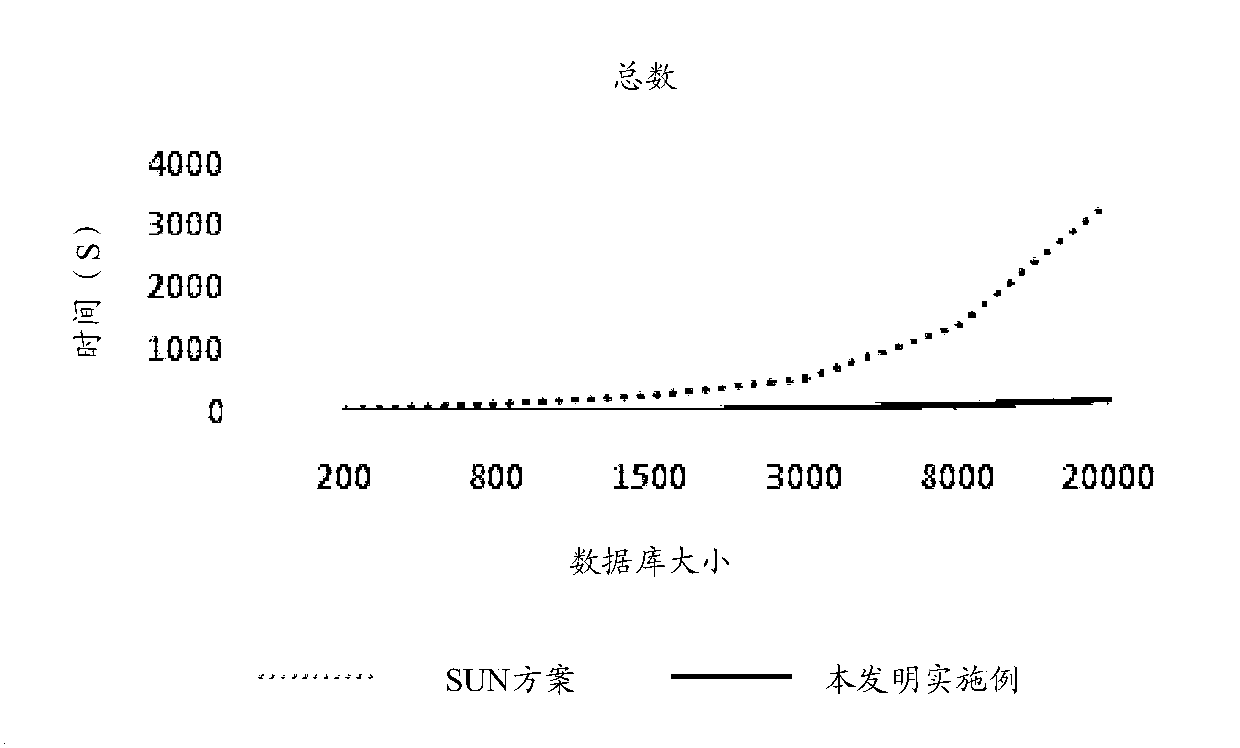
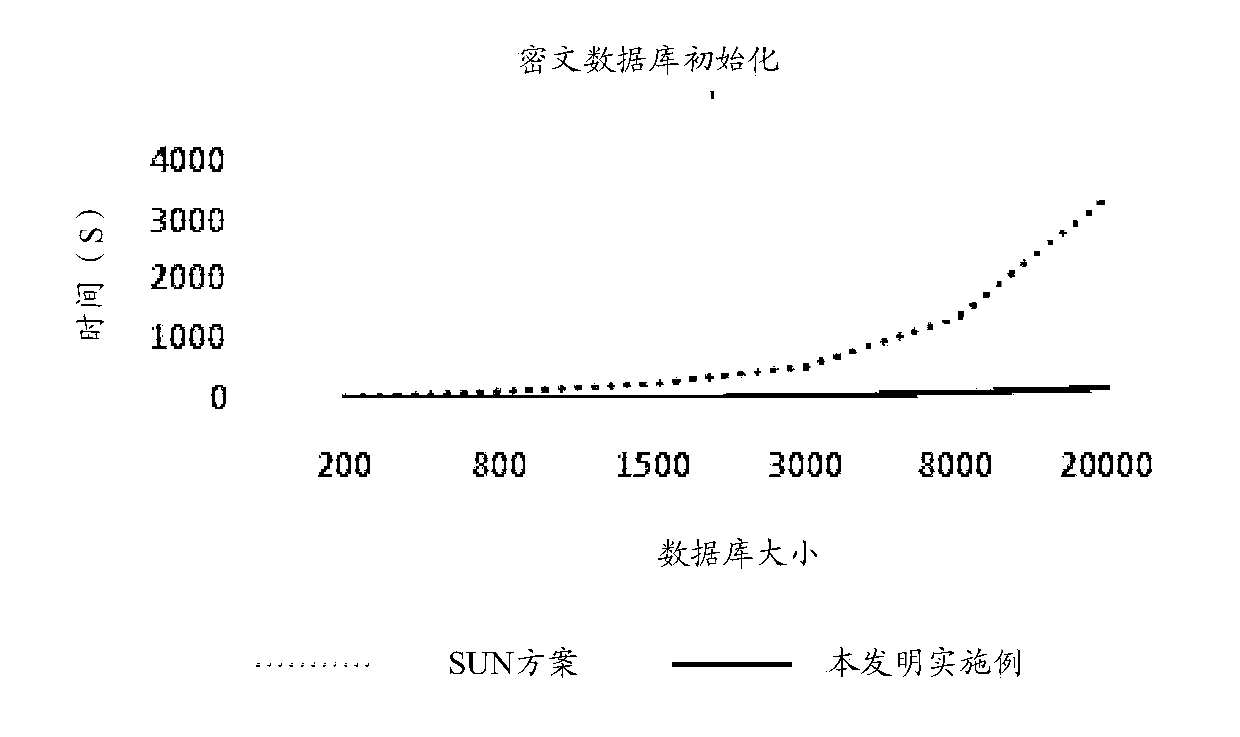
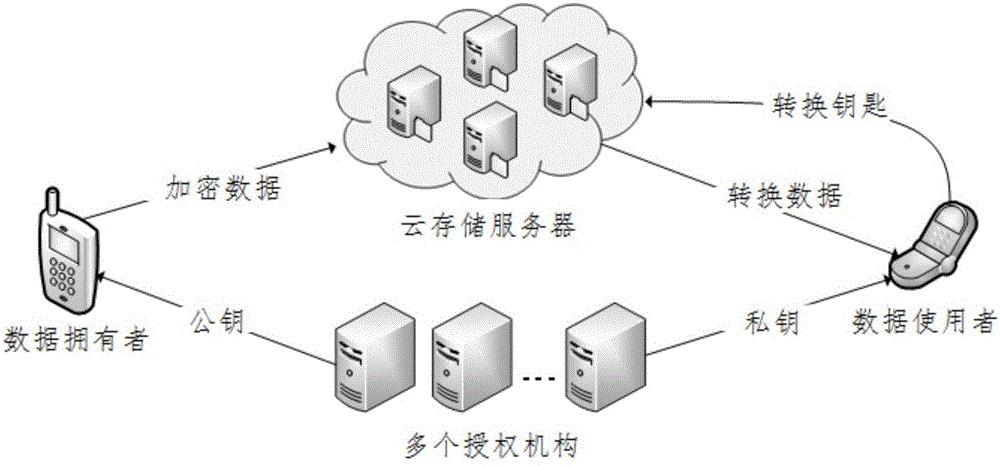
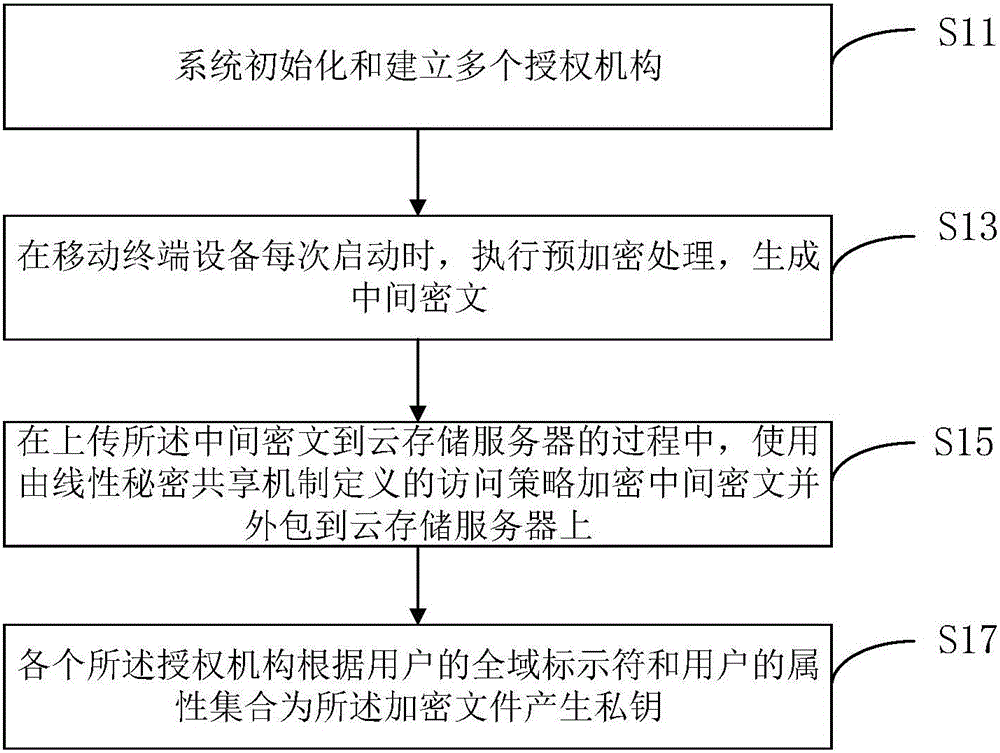
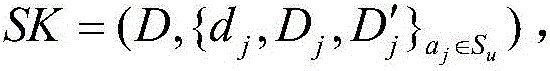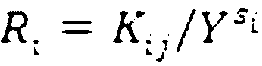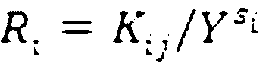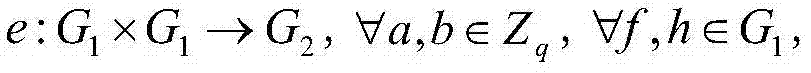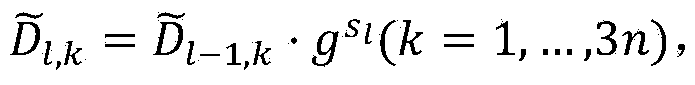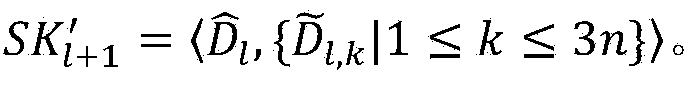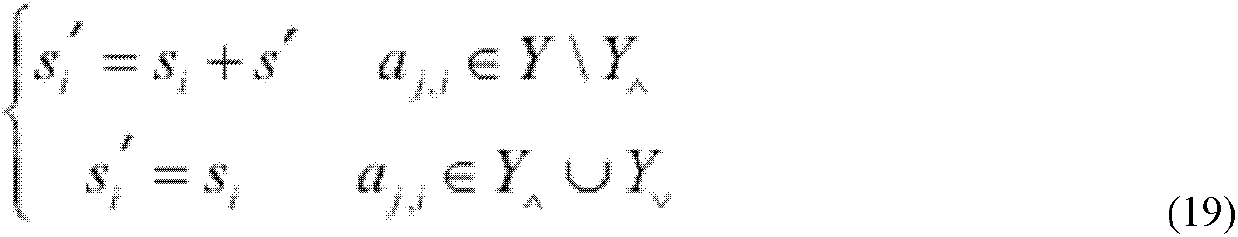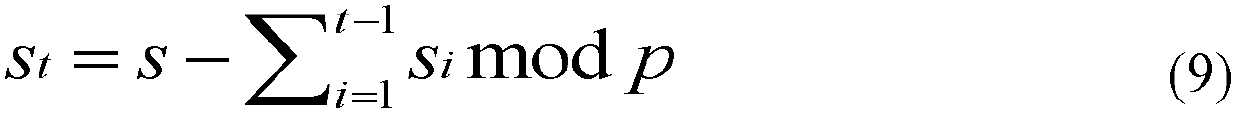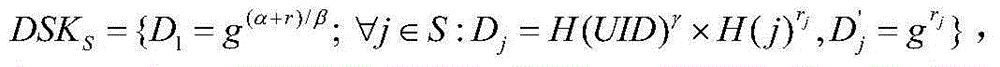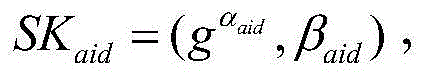Patents
Literature
184 results about "Attribute-based encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
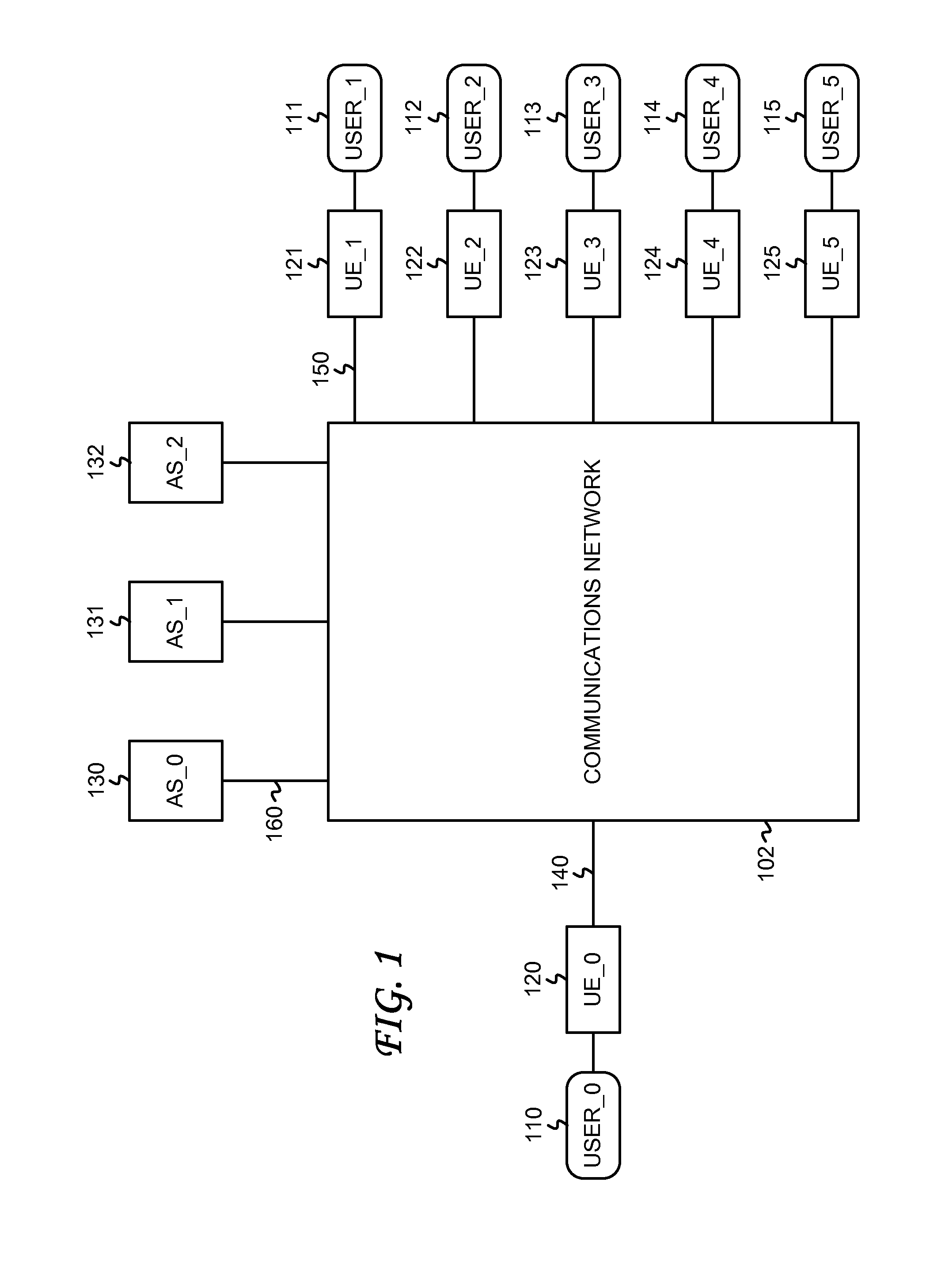
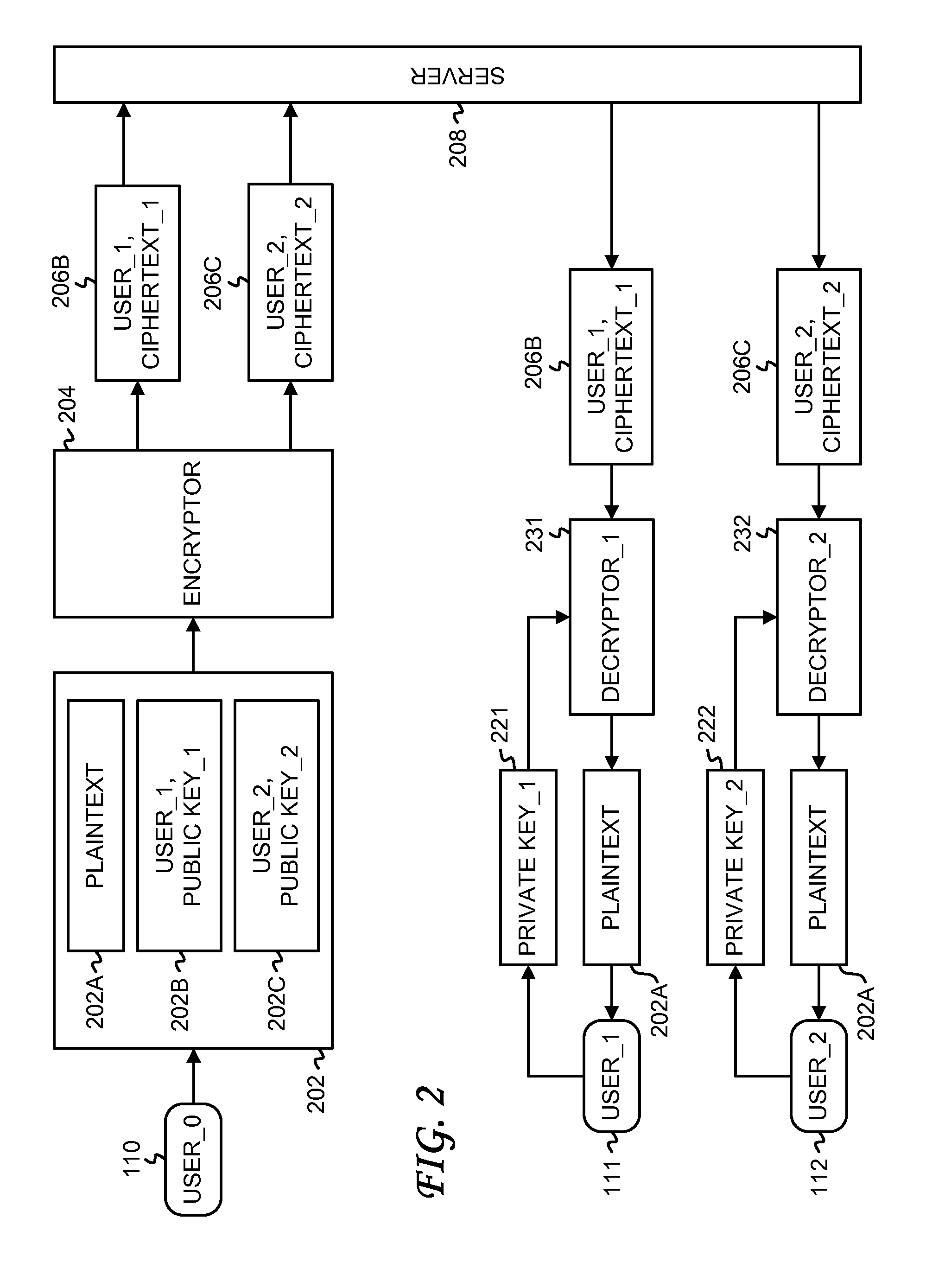
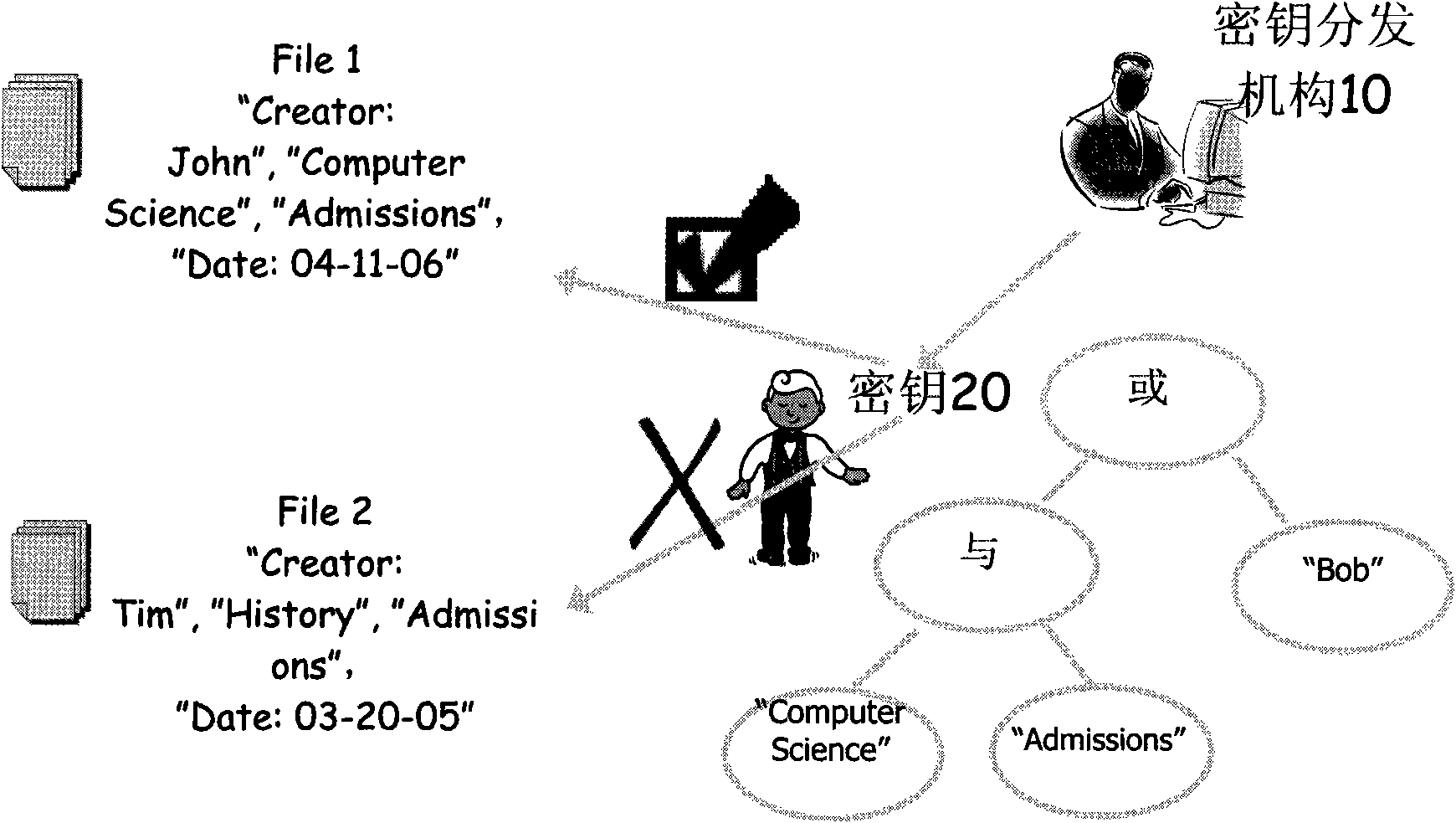
Attribute-based encryption is a type of public-key encryption in which the secret key of a user and the ciphertext are dependent upon attributes (e.g. the country in which he lives, or the kind of subscription he has). In such a system, the decryption of a ciphertext is possible only if the set of attributes of the user key matches the attributes of the ciphertext.
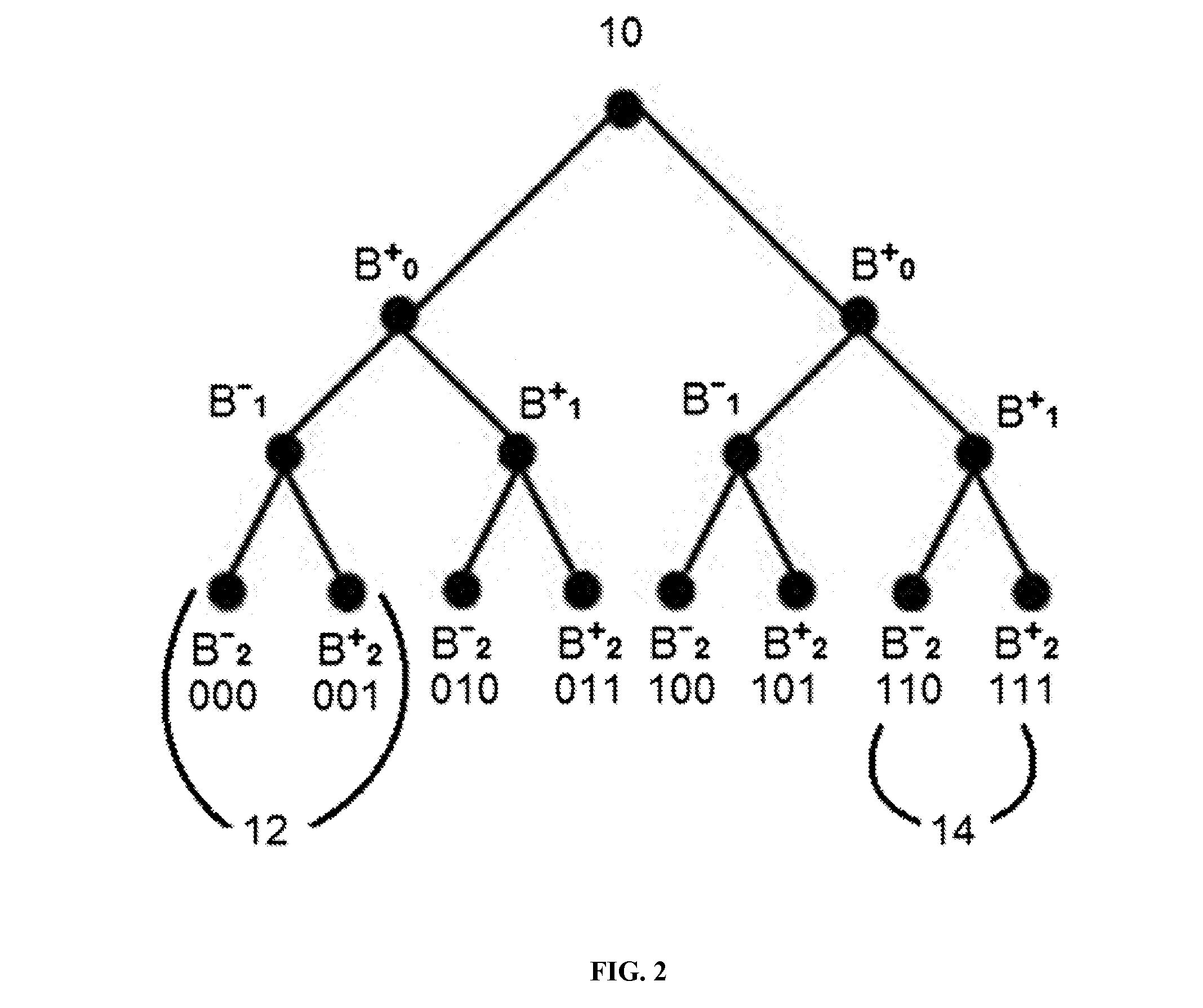
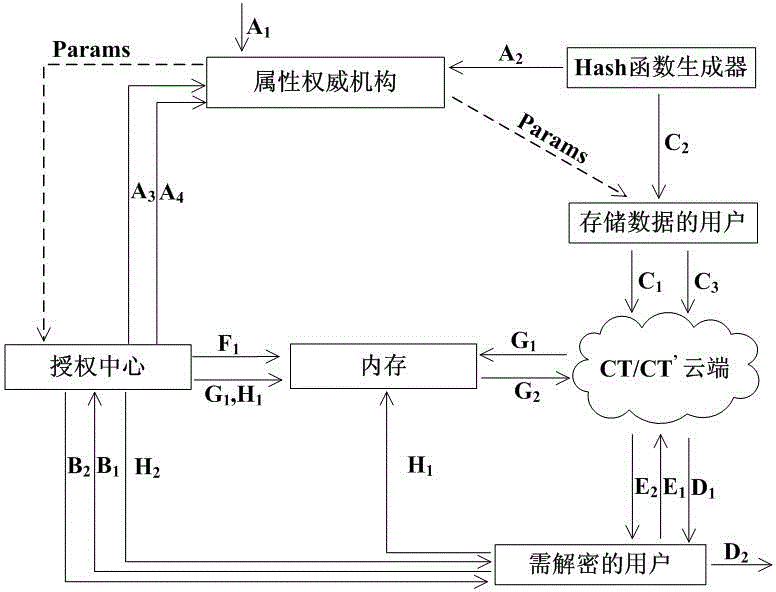
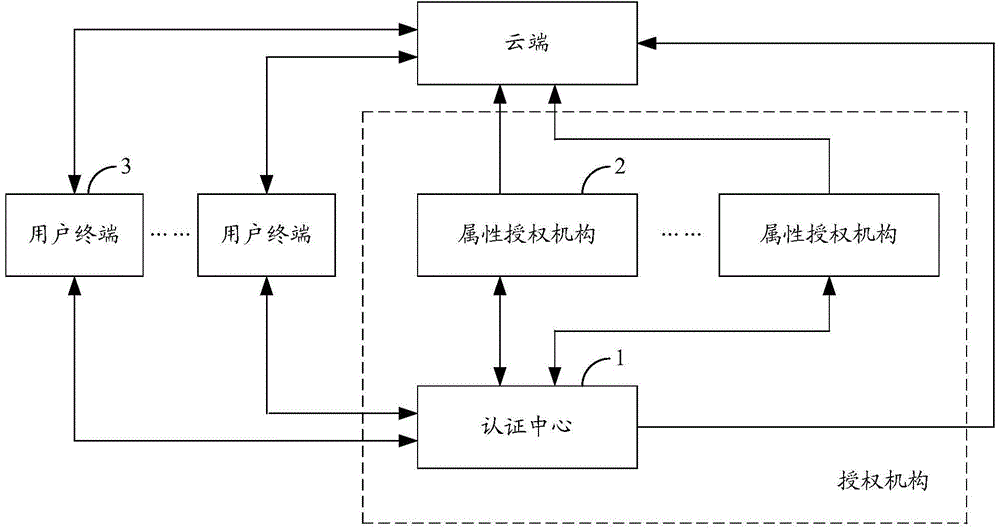
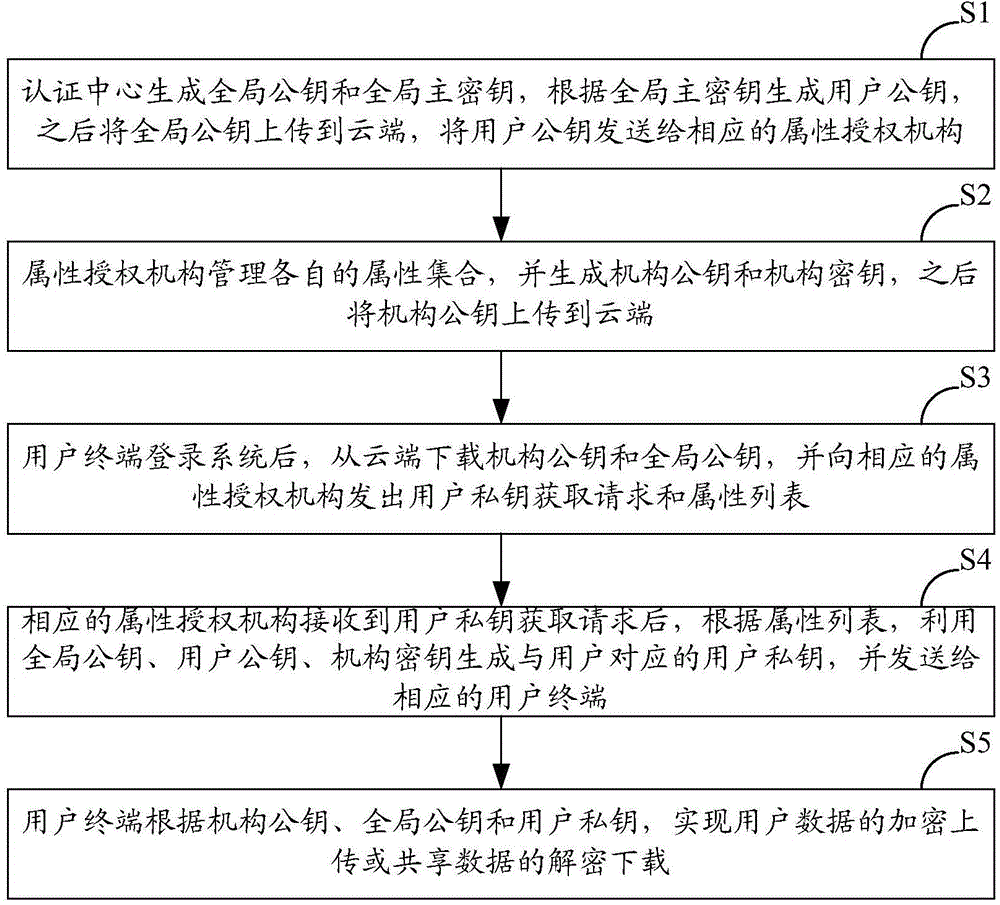
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
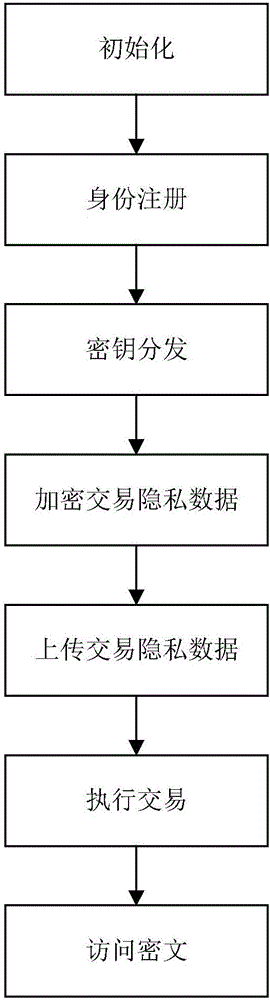
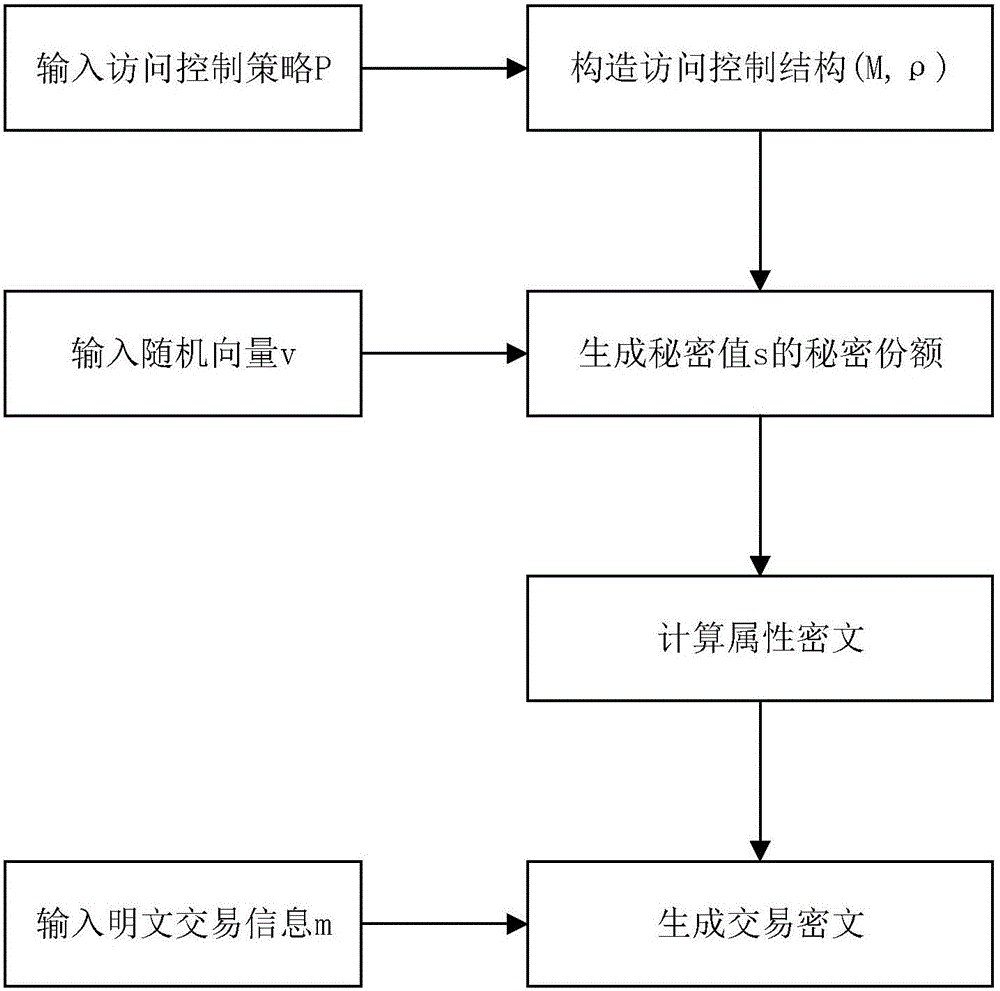
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
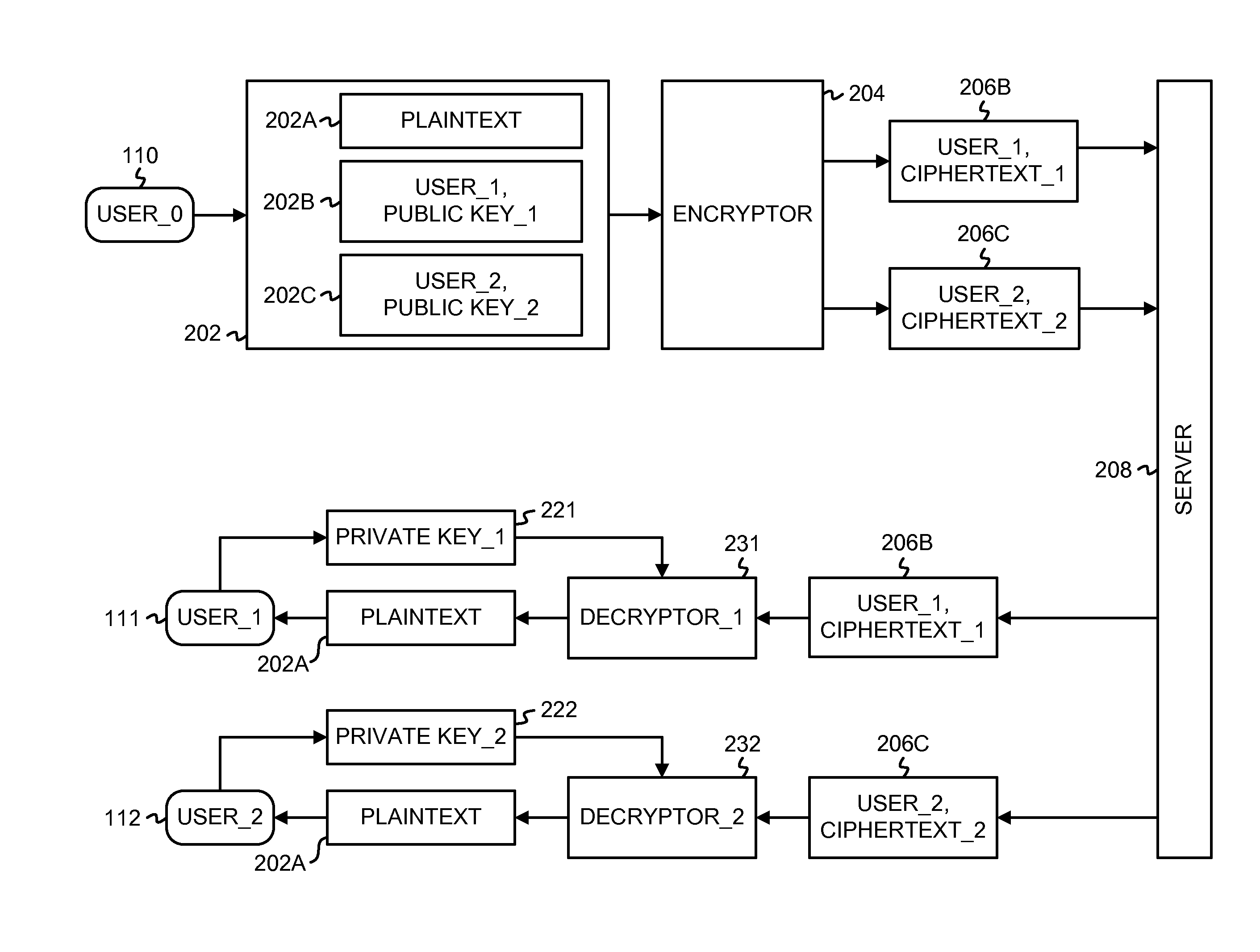
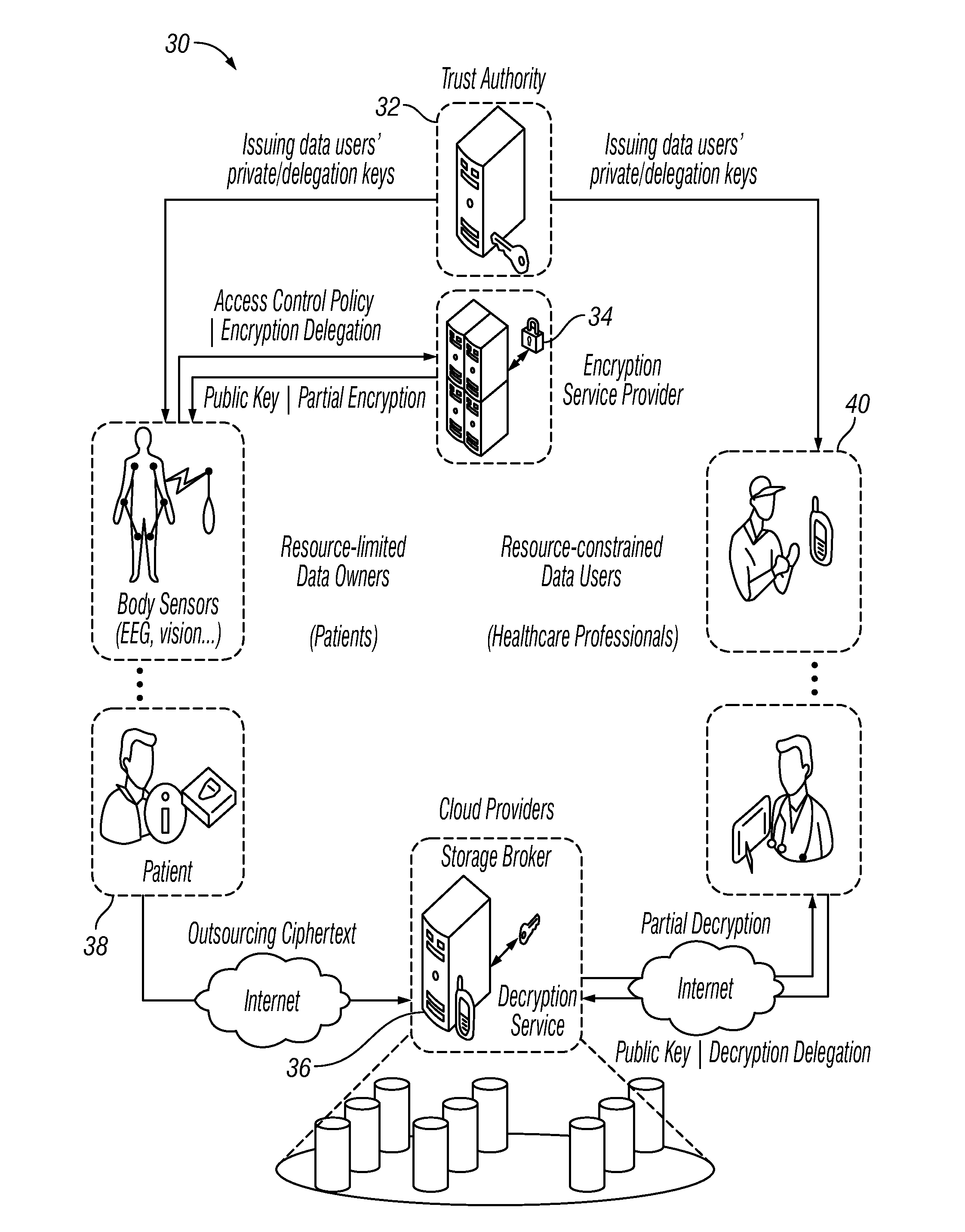
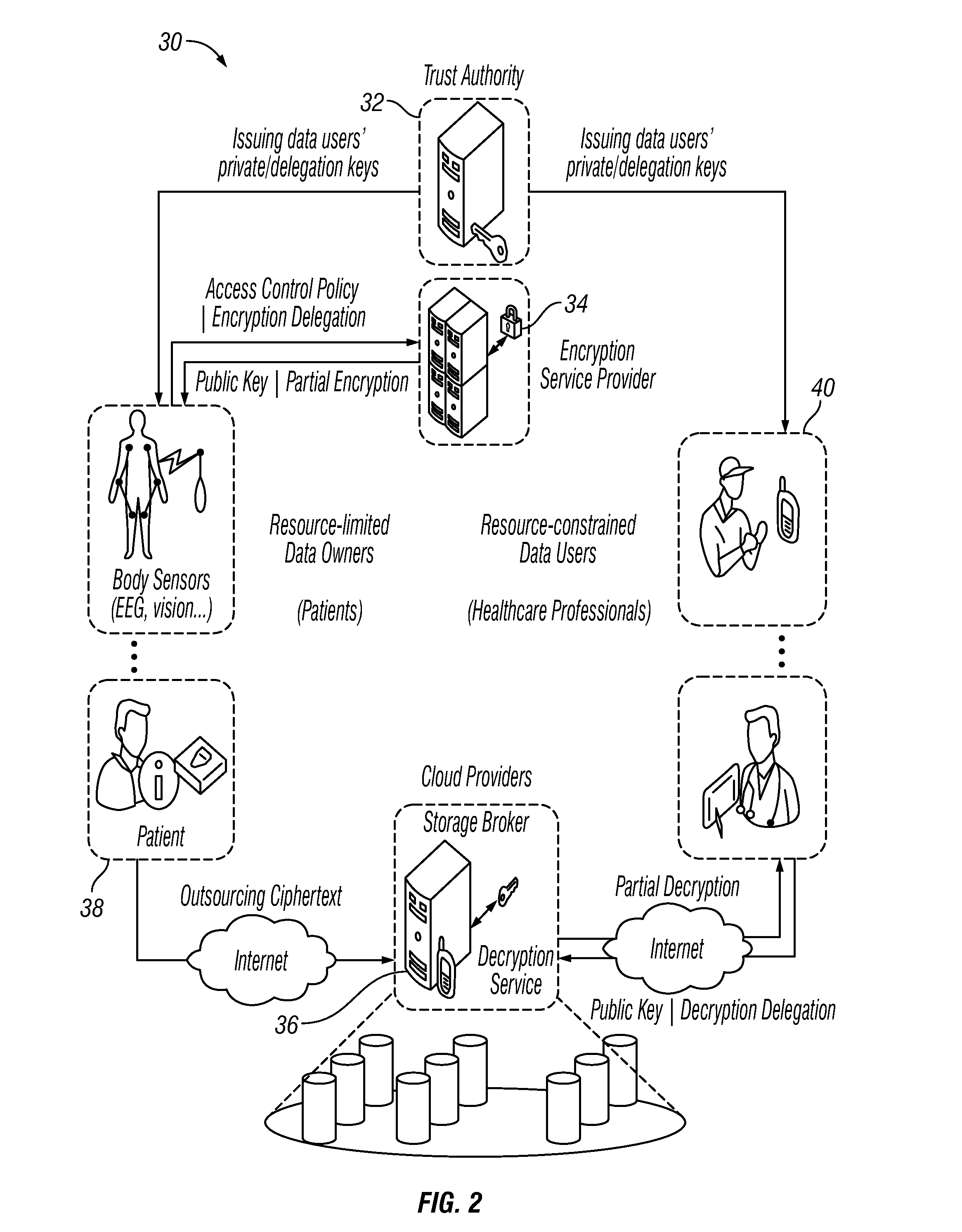
Outsourcing the Decryption of Functional Encryption Ciphertexts
ActiveUS20120300936A1Short bit lengthKey distribution for secure communicationFunctional encryptionAttribute-based encryption
Functional encryption (FE) ciphertext is transformed into partially-decrypted (PD) ciphertext. The PD ciphertext has a shorter bit length than the FE ciphertext, or the decryption time of the PD ciphertext is less than the decryption time of the FE ciphertext. The FE ciphertext can be an attribute-based encryption ciphertext. The transformation can be performed with a transformation key generated by an authority with a master key or by a user with a decryption key. The transformation can also be performed, without a transformation key, based on unencrypted components of the FE ciphertext and on auxiliary information associated with the unencrypted components of the FE ciphertext. The PD ciphertext can require less transmission time across a network than the FE ciphertext. The PD ciphertext can require less time to decrypt than the FE ciphertext, particularly when the computational resources performing the decryption are limited.
Owner:NTT RES INC
Multistage authority management method for cloud storage enciphered data sharing
ActiveCN103107992AReduce complexityEasy to implementTransmissionAttribute-based encryptionCiphertext
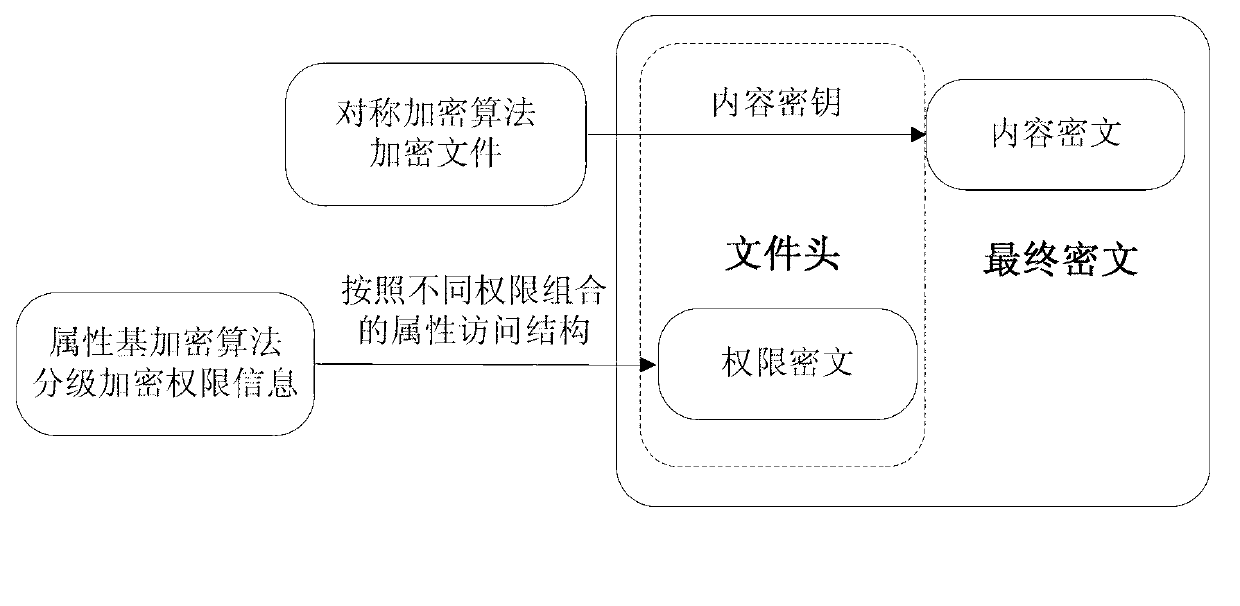
The invention relates to a multistage authority management method for cloud storage enciphered data sharing. The methods such as attribute based encryption, access control and authority management are used for providing a reliable method for access and multistage authority management of a shared cipher text in the cloud storage environment. Through mixing encrypt system, the multistage authority management method for cloud storage enciphered data sharing comprises steps: firstly applying a symmetric encryption algorithm to encrypt data, and generating a content cipher text; then adopting the attribute based encryption to encrypt according to different authority information, and generating an authority cipher text; adopting the attribute based encryption scheme to encrypt a symmetric key and the authority cipher text, regarding the symmetric key and the authority cipher text as a file header of the content cipher text, and generating a final cipher text. The multistage authority management method for cloud storage enciphered data sharing has the advantages of being convenient to achieve, strong in user information protectiveness, fine in authority control grit and the like. Under the premise that a server is not credible, the flexible and extensible authority management to the shared enciphered data is supported, the privacy and the security of the user data and authority information are effectively ensured, and the multistage authority management method for cloud storage enciphered data sharing has good practical value and wide application prospect in the cloud storage field.
Owner:HANGZHOU YUANTIAO TECH CO LTD
Outsourcing decryption method of attribute-based encryption based on ciphertext policy
InactiveCN104022868AReduce the burden onEfficient and safe decryptionKey distribution for secure communicationUser identity/authority verificationThird partyCiphertext
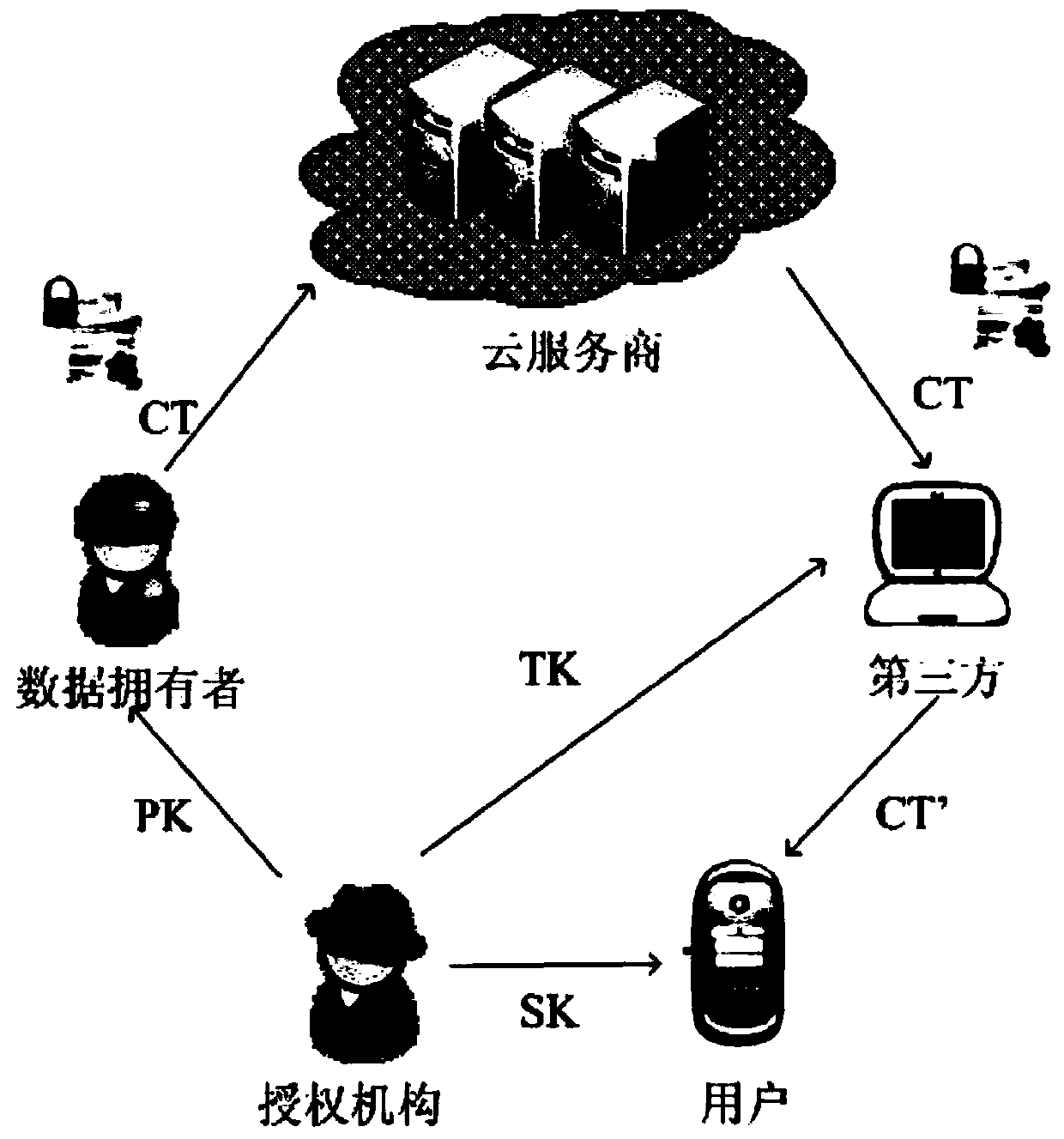
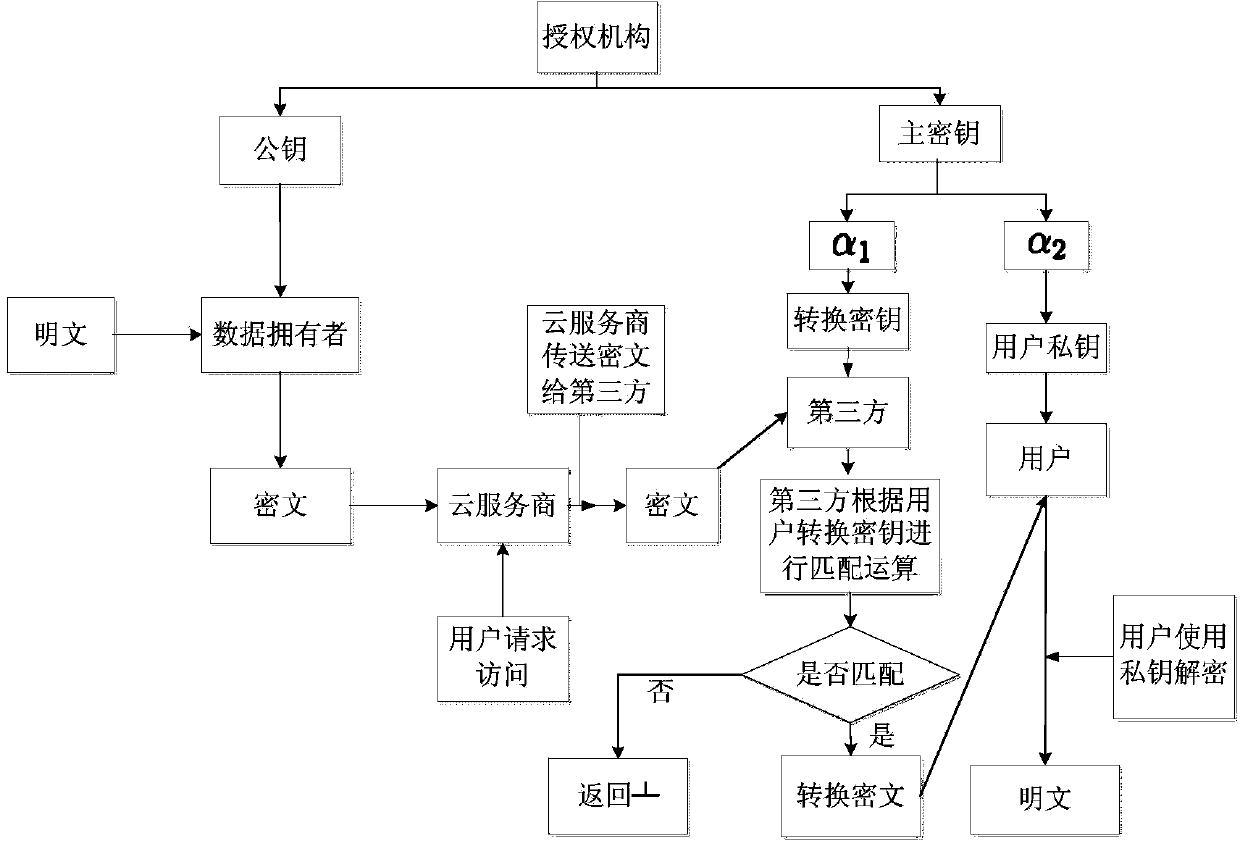
The invention provides a highly-efficient safe outsourcing decryption method based on the attribute encryption in mobile cloud computing environment. The method comprises the following steps: system initialization; a data owner encrypting a file and uploading the file to a cloud service provider; an authorization organization generating secret keys; a third party transforming ciphertexts; and a mobile terminal user decrypting the file. According to the method, targeted for the mobile cloud computing environment, by utilizing a ciphertext policy attribute-based encryption shared data method, according to the requirement of limited operation and storage capacity of a mobile terminal, and under the premise of guaranteeing data security, a portion of complex decryption tasks are outsourced to the third party; and by utilizing outsourcing decryption, secret key decomposition technique and matching algorithm, unnecessary bilinearity pairing operation is reduced, and a reliable method is provided for the mobile terminal to carry out rapid decryption.
Owner:HANGZHOU NORMAL UNIVERSITY
Method for cloud data confidentiality protection and access control
InactiveCN104378386AEnsure safetyEnable secure sharingTransmissionAttribute-based encryptionCloud service provider
The invention discloses a method for cloud data confidentiality protection and access control. The method includes the specific implementation processes: adopting a symmetric cryptosystem correlation algorithm for realizing encryption of sensitive data, and storing the data in a cloud server in an encrypted form; and adopting a ciphertext-policy attribute-based encryption mechanism to realize protection of a data encryption key. An encrypted access policy can be formulated by a data owner as required, and only the data user satisfying conditions of the access policy can access to the encrypted sensitive data by decryption. Compared with the prior art, the method has the advantages that security of the data in a cloud storage system under the open environment is guaranteed under the premise that a cloud server provider is untrusted, security sharing of the sensitive data is realized, and huge computation overhead brought to the data owner by key distribution and data management can be reduced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Efficient Privacy-Preserving Ciphertext-Policy Attribute Based Encryption and Broadcast Encryption
InactiveUS20160241399A1Key distribution for secure communicationPublic key for secure communicationCommunications systemAttribute-based encryption
A new construction of CP-ABE, named Privacy Preserving Constant CP-ABE (PPC-CP-ABE) that significantly reduces the ciphertext to a constant size with any given number of attributes is disclosed. PPCCP-ABE leverages a hidden policy construction such that the recipients' privacy is preserved efficiently. A Privacy Preserving Attribute Based Broadcast Encryption (PP-AB-BE) scheme is disclosed. PP-AB-BE is flexible because a broadcasted message can be encrypted by an expressive hidden access policy, either with or without explicit specifying the receivers. PP-AB-BE significantly reduces the storage and communication overhead. Also, PP-AB-BE attains minimal bound on storage overhead for each user to cover all possible subgroups in the communication system.
Owner:ARIZONA STATE UNIVERSITY
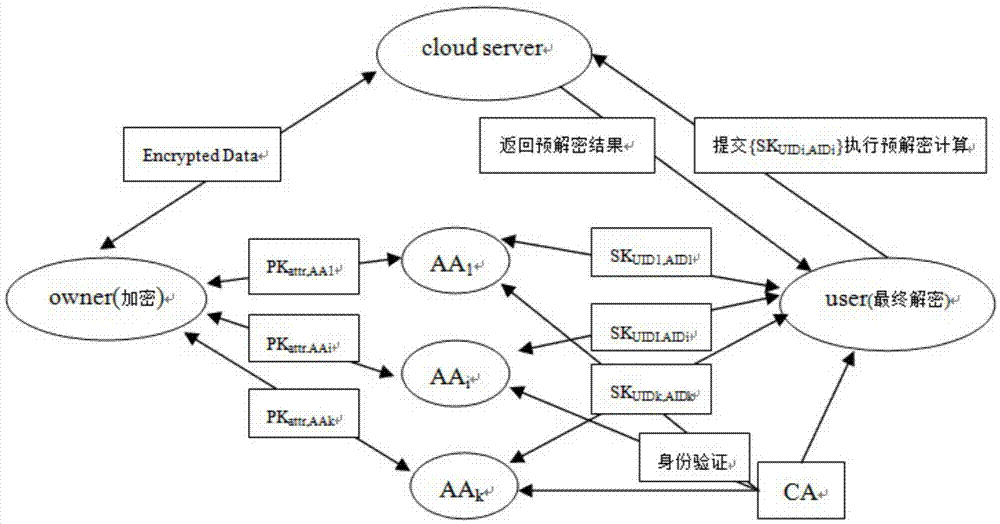
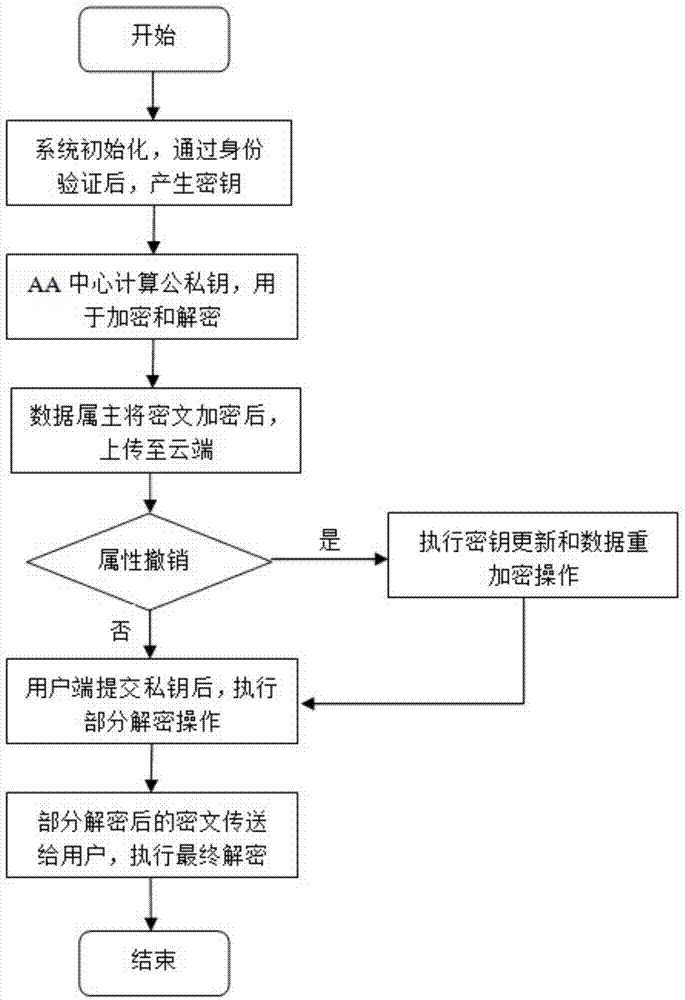
Attribute-based encryption method for multiple authority centers
ActiveCN103618728AImprove securityImprove efficiencyKey distribution for secure communicationAttribute-based encryptionCiphertext
The invention discloses an attribute-based encryption method for multiple institutional centers. According to the method, CP-ABE is expanded to a plurality of authorities, and trust and workload of single authority are dispersed to all the authorities of a system, so that the safety and decryption efficiency of the system are improved. The method comprises the steps that system initialization is conducted, namely, a generated secret key is initialized after authentication of a CA center is passed; secret key calculation is conducted, namely, an AA center calculates a public / private key pair of a user, wherein the public / private key pair is used for data encryption and decryption operation; encryption is conducted, namely, a data owner uploads the ciphertext to a cloud terminal after conducting encryption operation; decryption is conducted, a user terminal executes pre-decryption processing after submitting a part of private keys, the processed ciphertext is sent to the user terminal, and finial decryption operation is executed; the attribute is cancelled, namely, after the attribute of one user is cancelled, secret key update and data re-encryption operation are executed, and it is ensured that the data are not be obtained illegally.
Owner:NANJING UNIV OF POSTS & TELECOMM
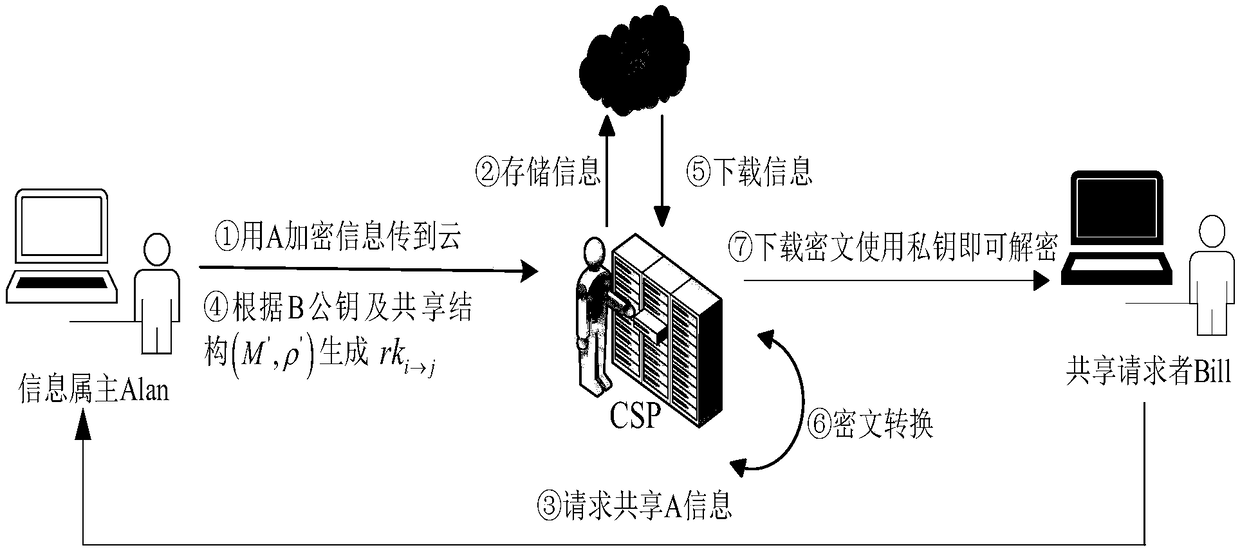
A block chain ciphertext cloud storage sharing method based on attribute proxy re-encryption
ActiveCN109189727AImprove securityImprove sharing efficiencyDigital data protectionFile access structuresAttribute-based encryptionCloud storage
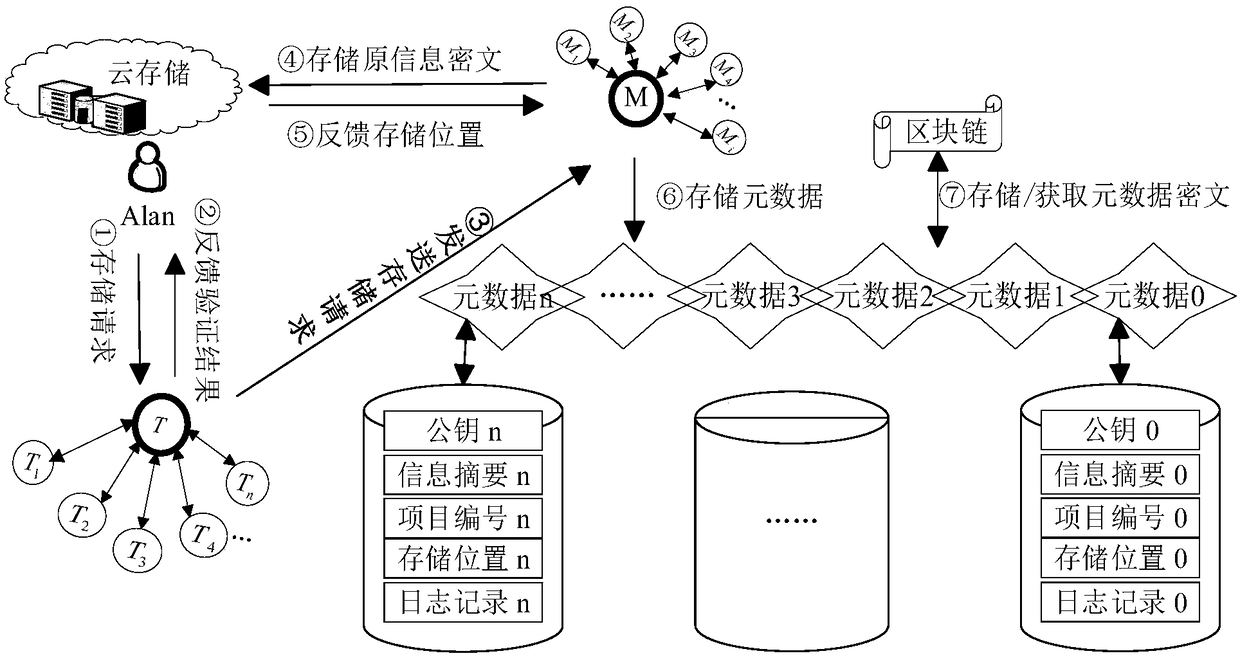
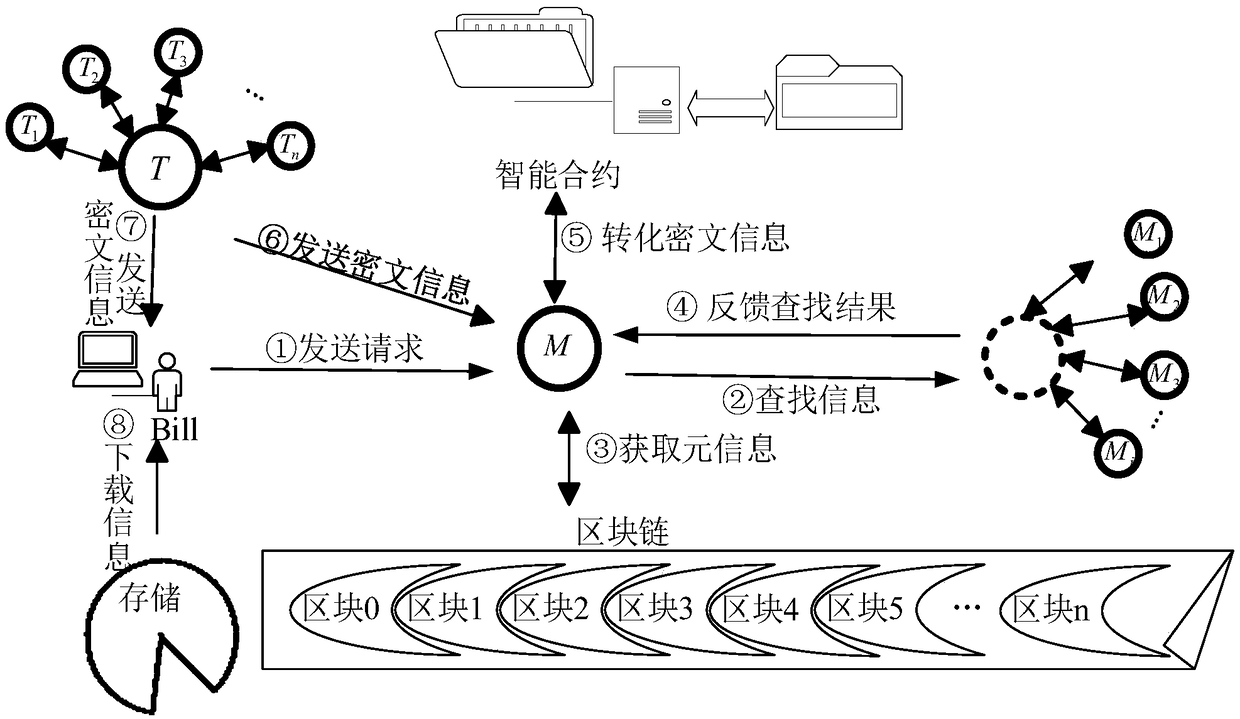
A block chain ciphertext cloud storage sharing method based on attribute proxy re-encryption is provided. On the basis of proxy re-encryption and attribute-based encryption technology, the invention proposes a block chain ciphertext storage sharing idea based on attribute proxy re-encryption for keyword retrieval. The metadata ciphertext is stored separately from the original information ciphertext by the attribute proxy re-encryption algorithm, the pool verification pool mechanism of block chain technology is used to determine the bookkeeping weight of the node, the information interaction contract is introduced to audit the identity of the user, and the transaction cost is automatically cleared. The security and the experimental analysis show that the invention shortens the encryption and decryption time, and reduces the high-frequency access pressure of the cloud memory. When the number of attributes is 100, the time consuming of re-encryption and decryption is 1.69 s, and the efficiency of the system is improved by 19.04%-49.68%. The method has stronger anti-collusion aggression, and has good application prospect in the field of internet of things.
Owner:南方电网互联网服务有限公司
Hierarchical attribute-based encryption and decryption
ActiveUS20140229736A1Easy to optimizeImproved hierarchical attribute-based cryptographic systemPublic key for secure communicationUser identity/authority verificationAttribute-based encryptionCiphertext
A domain authority 13 for use in a hierarchy of domain authorities in a hierarchical cryptographic system. The domain authority 13 comprises a user secret key generator 21 for generating a user secret key based on a domain secret key and one or more attribute representations, to obtain a user secret key associated with a set of attributes corresponding to the attribute representations, and wherein the domain secret key is based on a domain secret key of a parent domain authority or a root secret key of a root authority of the hierarchy of domain authorities, and wherein the attribute representations are independent of the hierarchy. A decrypter makes use of the user secret key. An encrypter generates ciphertext decryptable by the decrypter.
Owner:KONINKLJIJKE PHILIPS NV
Systems and methods for efficient decryption of attribute-based encryption
ActiveUS8559631B1Key distribution for secure communicationPublic key for secure communicationAttribute-based encryptionPairing
Systems and methods for attribute-based encryption systems that support more efficient decryption are provided. The disclosed systems and methods can be configured to decrypt data using a constant number of pairings while the number of attributes used during encryption or decryption can be selected and scaled arbitrarily.
Owner:NTT RES INC
Ciphertext policy based revocable attribute-based encryption method and equipment and system utilizing same
InactiveCN102546161AThe ability to undo is not affectedPublic key for secure communicationUser identity/authority verificationAttribute-based encryptionCiphertext
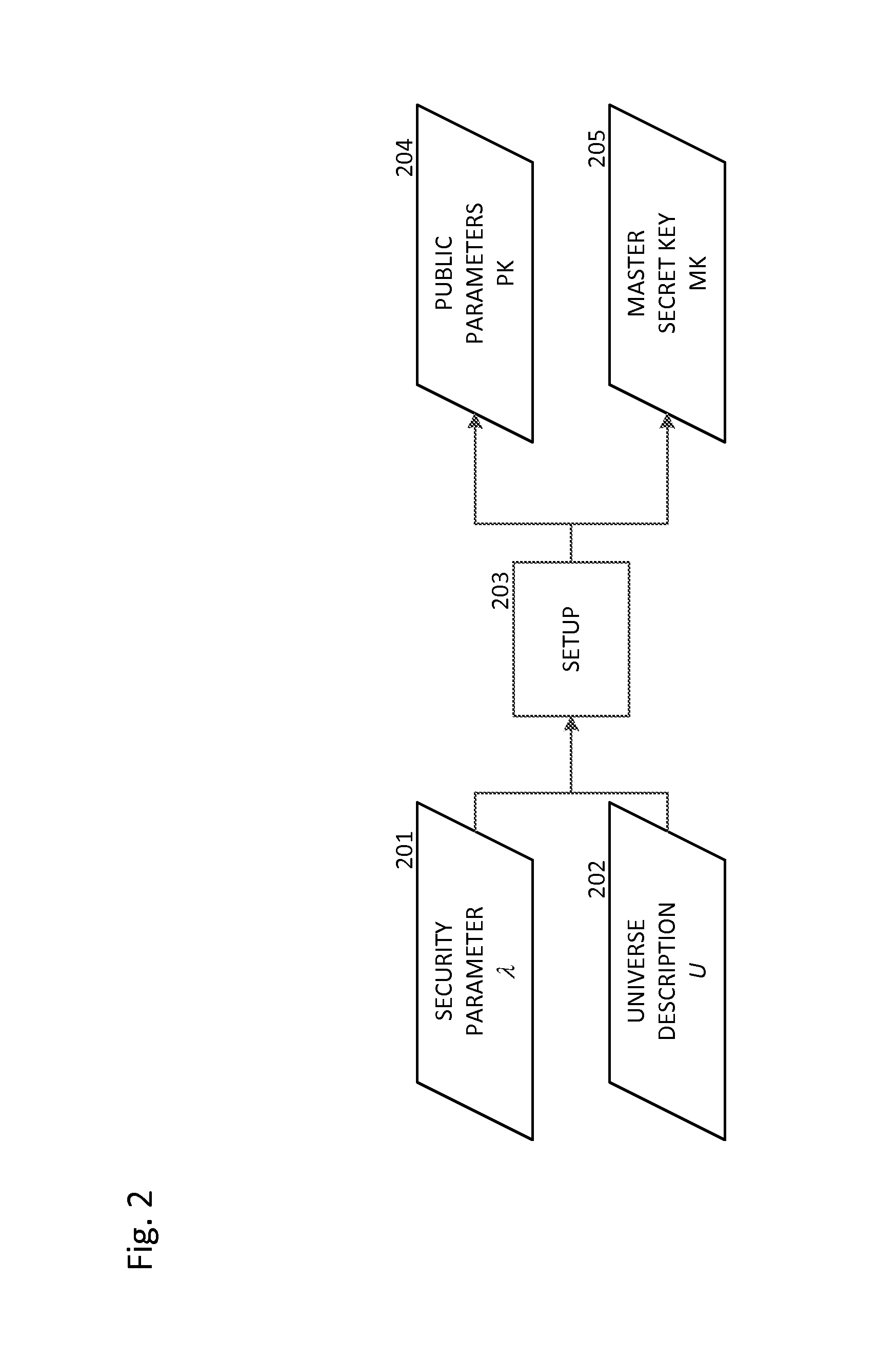
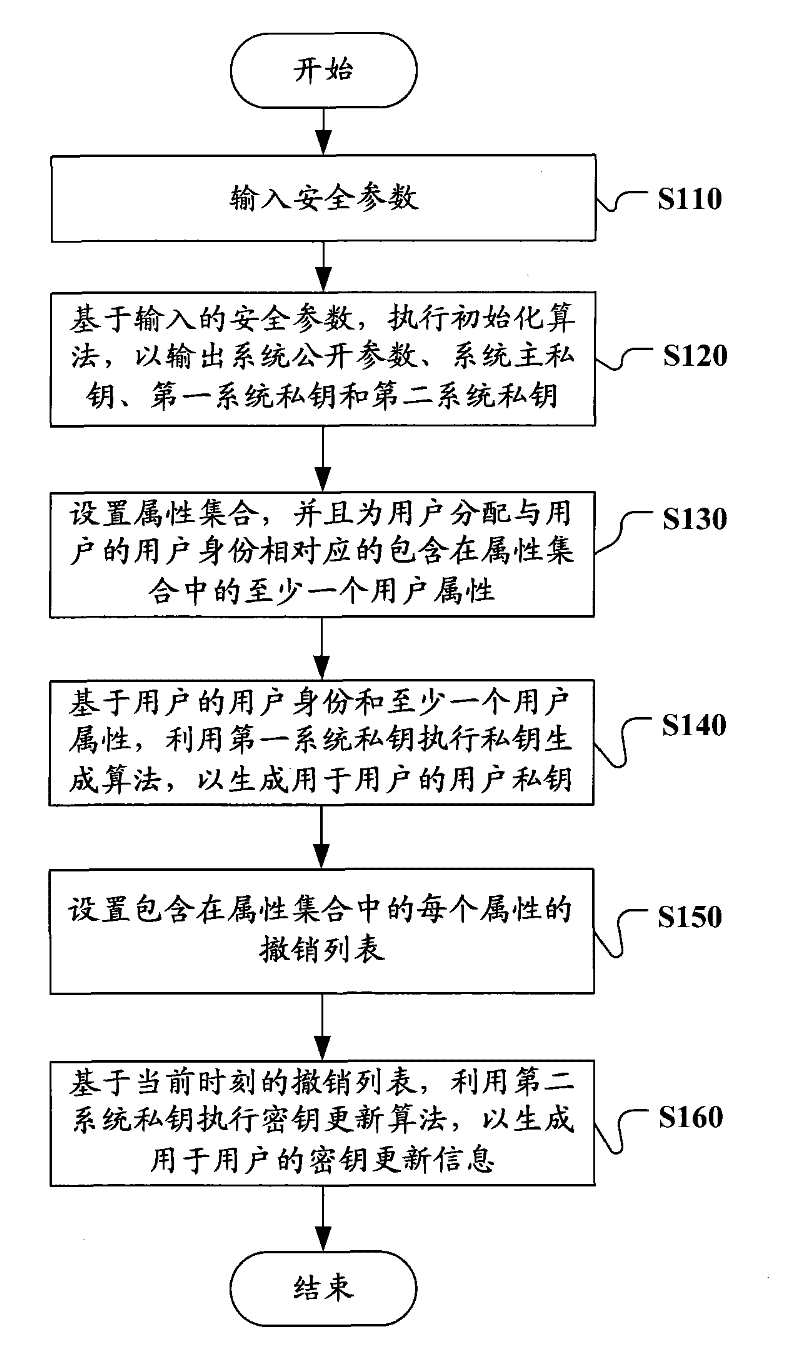
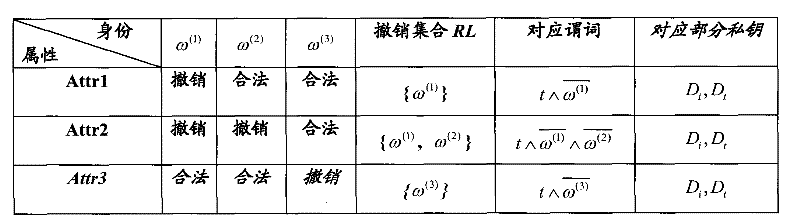
The invention discloses a ciphertext policy based revocable attribute-based encryption method and equipment and a system utilizing same. A key generation method includes of inputting safety parameters; executing the initializing algorithm according to the input safety parameters to output system public parameters, a main system private key, a first system private key and a second private key by an output system; setting an attribute set, distributing at least one user attribute, which corresponds to the user identity and belongs to the attribute set, for users; executing the private key generation algorithm according to the user identity and the at least one user attribute to generate a user private key; setting a revocation list of each attribute belonging to the attribute set to reflect corresponding relation between each attribute and the user identity of the user, of the attribute, revoked at the current moment; and executing the private key updating algorithm by the second system private key on the basis of the current revocation list so as to generate private key updated information.
Owner:SONY CORP
Enabling Comparable Data Access Control for Lightweight Mobile Devices in Clouds
ActiveUS20140289513A1Less-flexible attribute structureEfficient implementationKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
A new efficient framework based on a Constant-size Ciphertext Policy Comparative Attribute-Based Encryption (CCP-CABE) approach. CCP-CABE assists lightweight mobile devices and storing privacy-sensitive sensitive data into cloudbased storage by offloading major cryptography-computation overhead into the cloud without exposing data content to the cloud. CCP-CABE extends existing attribute-based data access control solutions by incorporating comparable attributes to incorporate more flexible security access control policies. CCP-CABE generates constant-size ciphertext regardless of the number of involved attributes, which is suitable for mobile devices considering their limited communication and storage capacities.
Owner:ARIZONA STATE UNIVERSITY
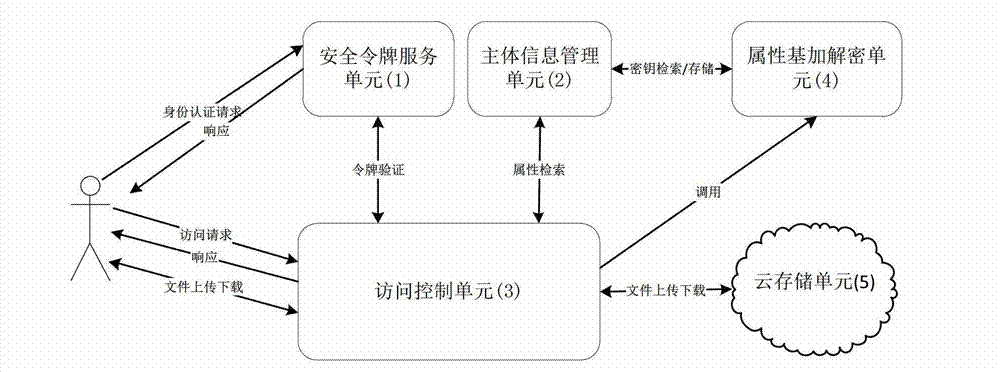
Cloud storage access control system based on attribute
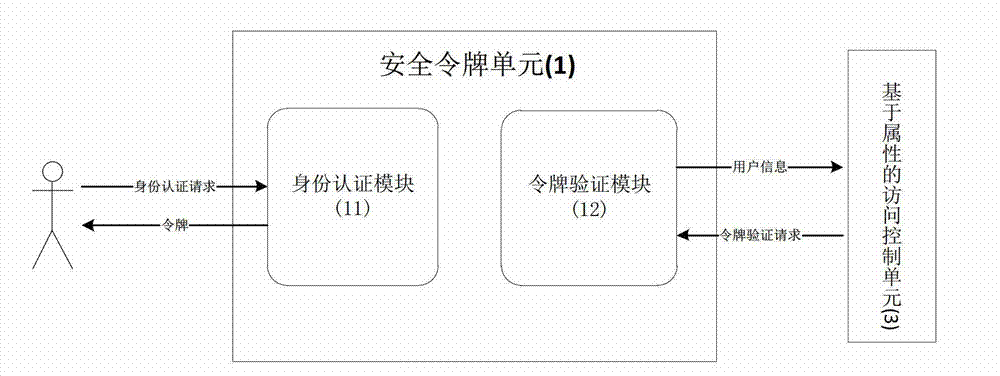
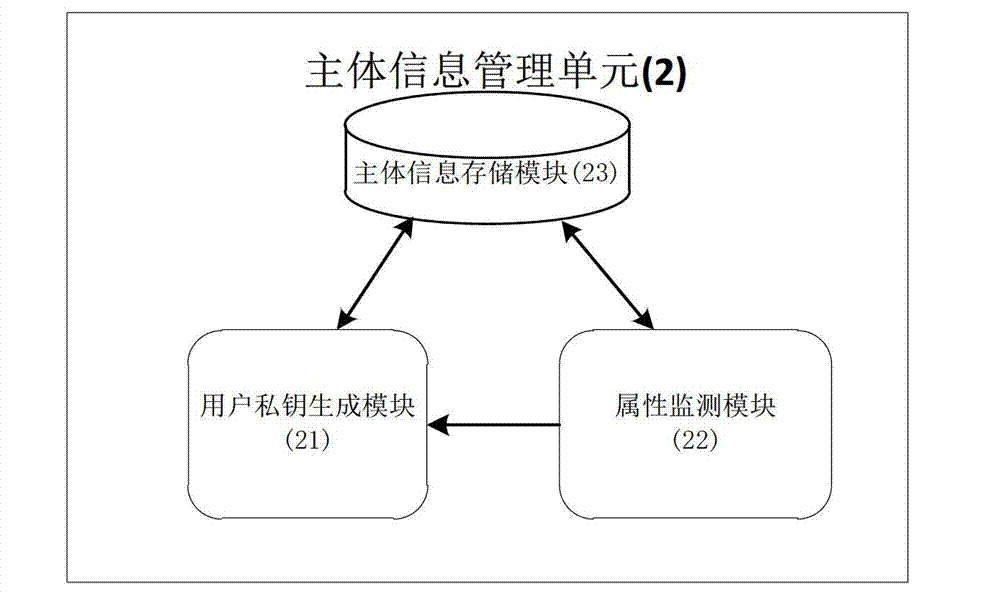
The invention provides a cloud storage access control system based on an attribute. The cloud storage access control system based on the attribute comprises a security token unit (1), a main body information management unit (2), an access control unit (3), an attribute base encryption and decryption unit (4) and a cloud storage unit (5), wherein the security token unit (1) is used for achieving the function of identity authentication, the function of token distribution and the function of token verification, the main body information management unit (2) is used for achieving the function of generating a user private key, the function of storing user attribute information and the user private key, and the function of symmetric keys after encryption of an access control policy, the access control unit (3) is used for achieving the function of access control based on the attribute, and the function of user customization of the access control policy, the attribute base encryption and decryption unit (4) is used for achieving the function of encryption and decryption of files, and the function of using the access control policy and the user private key to carry out encryption and decryption on the symmetric keys, and the cloud storage unit (5) is used for achieving the function of storage of plaintext and ciphertext. The cloud storage access control system based on the attribute has the advantages of being fine in grit, real-time, dynamic, extensible, safe and the like, and can be used for achieving access control in the cloud storage environment.
Owner:XIDIAN UNIV
Ciphertext policy attribute-based encryption system and method
ActiveCN101807991AEnsure safetyKey distribution for secure communicationUser identity/authority verificationPlaintextAttribute-based encryption
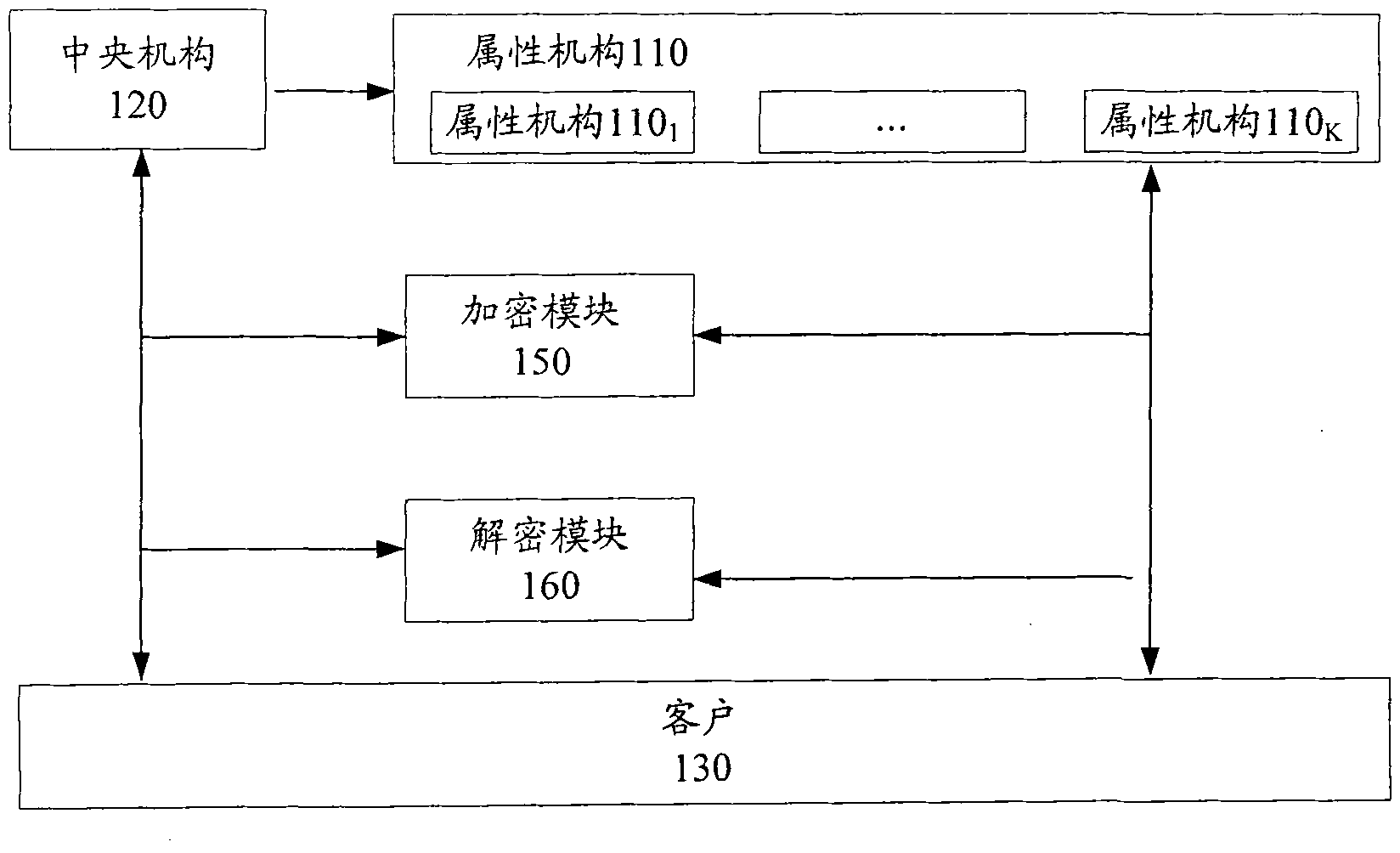
The invention provides a ciphertext policy attribute-based encryption system and a ciphertext policy attribute-based encryption method, which comprise ciphertext policy attribute-based encryption systems with a central mechanism and without the central mechanism and a ciphertext policy attribute-based encryption method. The ciphertext policy attribute-based encryption system with the central mechanism comprises a plurality of attribute mechanisms of the central mechanism, an encrypting component and a client. The plurality of attribute mechanisms of the central mechanism initialize the system together, publish a system public key, and generate a system private key, a local private keys of an attribute mechanism and local public keys; the encrypting component encrypts a cleartext based on the system public key, each local public key and a universal access tree; and the client inputs a client identifier, client attribute sets and the like so as to generate client private key used for decrypting the encrypted ciphertext. Due to the implementing mode of the invention, a multi-mechanism ciphertext policy attribute-based encryption system is designed. The scheme is based on the ciphertext policy, so the scheme better meets the access control requirement in an actual information safety system.
Owner:SHANGHAI JIAO TONG UNIV
User privacy protection method based on attribute and homomorphism mixed encryption under cloud environment
ActiveCN104079574AGuaranteed fair accessEnsure safetyTransmissionAttribute-based encryptionInternet privacy
The invention provides a user privacy protection method based on attribute and homomorphism mixed encryption under a cloud environment. The method is mainly used for solving the safety problem of user privacy under the cloud environment. Firstly, a user sends the information of the user to a cloud service provider, and the cloud service provider clarifies the user privacy. Secondly, the user adopts different encryption modes for different types, namely a homomorphism encryption mode and an encryption mode based on the attribute. It is guaranteed that important privacy information is more difficult to be leaked out and stolen through the homomorphism encryption mode for the user, and the user can conduct operation on the privacy information of the user. Through the encryption mode based on the attribute, it is guaranteed that certain network resources can be shared with other users. Finally, the user downloads and decodes cryptograph. Through the mixed encryption mode, safety of the user data privacy is further guaranteed. Meanwhile, the user can operate important service data of the user conveniently. Moreover, coding efficiency and decoding efficiency are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
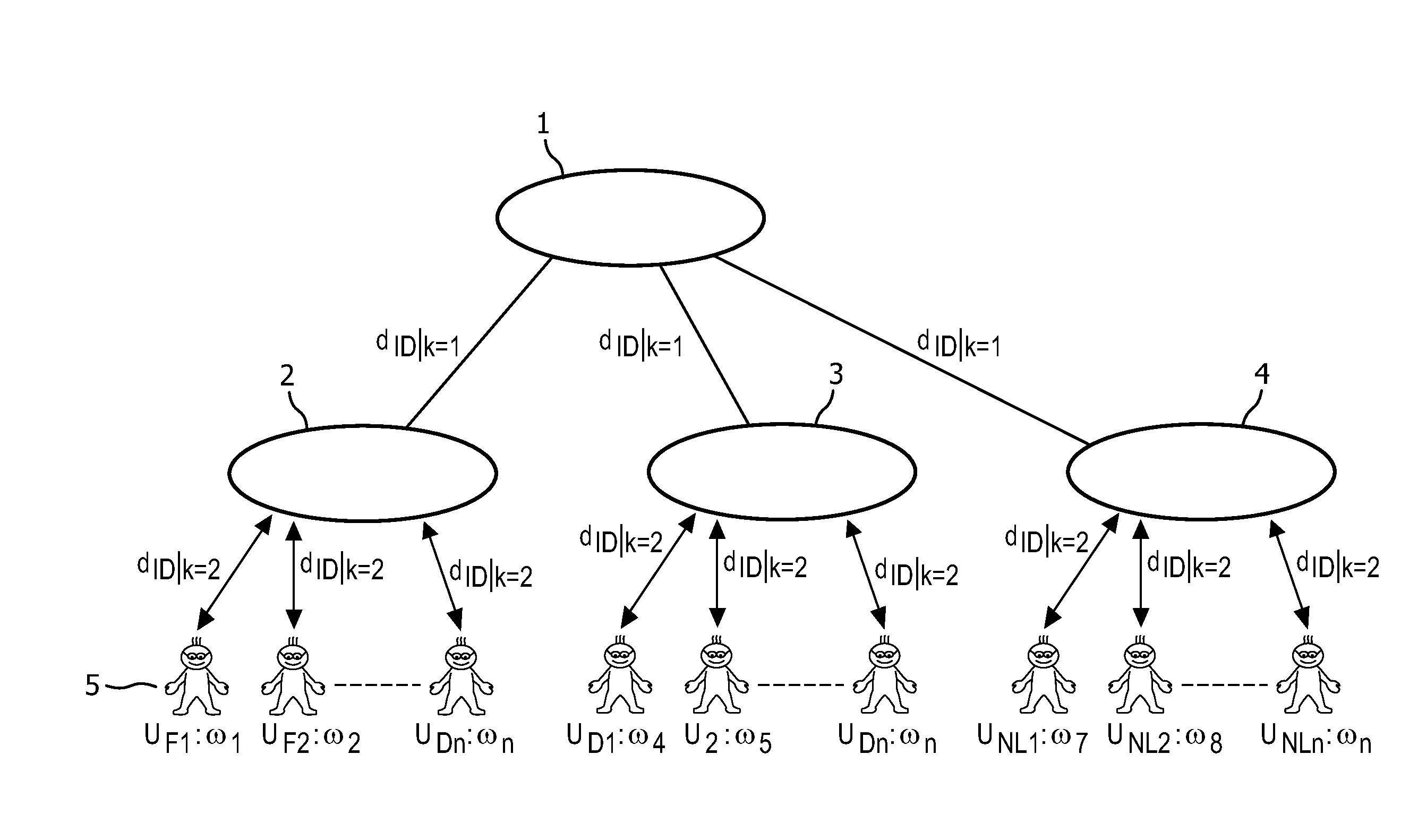
Multi-mechanism hierarchical attribute-based encryption method applied to cloud storage
InactiveCN103618729AFlexible Access Control PolicyReduce workloadPublic key for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses a multi-mechanism hierarchical attribute-based encryption method applied to cloud storage. The method comprises the steps that authorization centers determine recursion depths, select bilinear mappings and bilinear groups, generate a system MK and a PK, reserve the MK, and disclose the PK; the authorization centers allocate a master key authorized at the next stage (the step is executed when a subcenter exists); the central authorization center receives a user identity file and generates an attribute set A for the user identity file; the authorization centers generate a secret key SK for a user and distribute the SK to the user; a data owner DO generates an access strategy tree, the file is encrypted through an Encrypt method, and a ciphertext CT is uploaded to the cloud end; the user sends a request to the cloud end to have access to the file, the CT of the file is sent back through the cloud end, the user decrypts the file by means of the SK, and only when the attribute in the user SK meets an access control strategy of the file, complete decryption can be achieved; if decryption succeeds, a plaintext M is obtained by the user; if decryption does not succeed, it is shown that the user has no right to have access to the file.
Owner:NANJING UNIV OF POSTS & TELECOMM
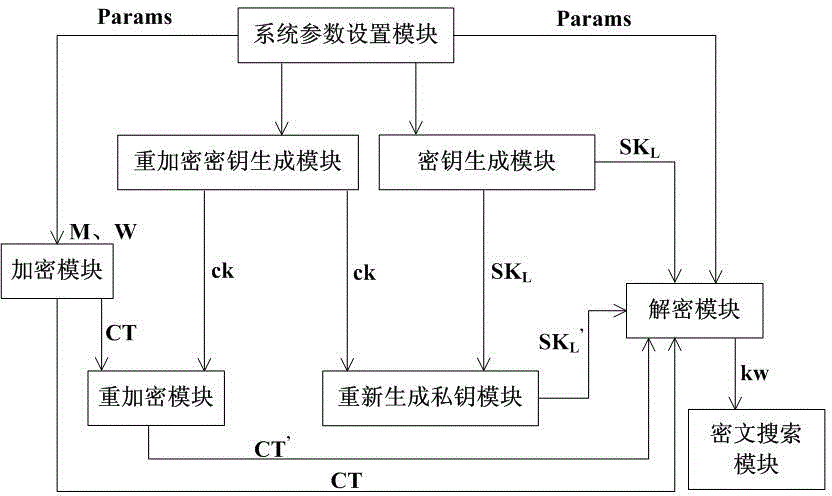
Encryption method and system based on attributes
InactiveCN104363215APrivacy protectionReduce loadPublic key for secure communicationCryptographic key generationAttribute-based encryption
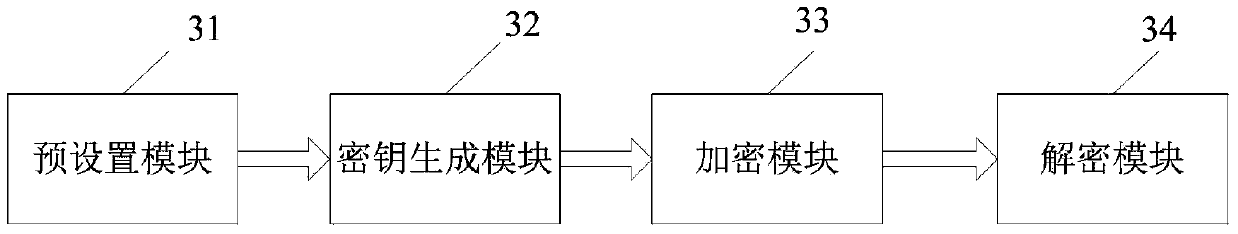
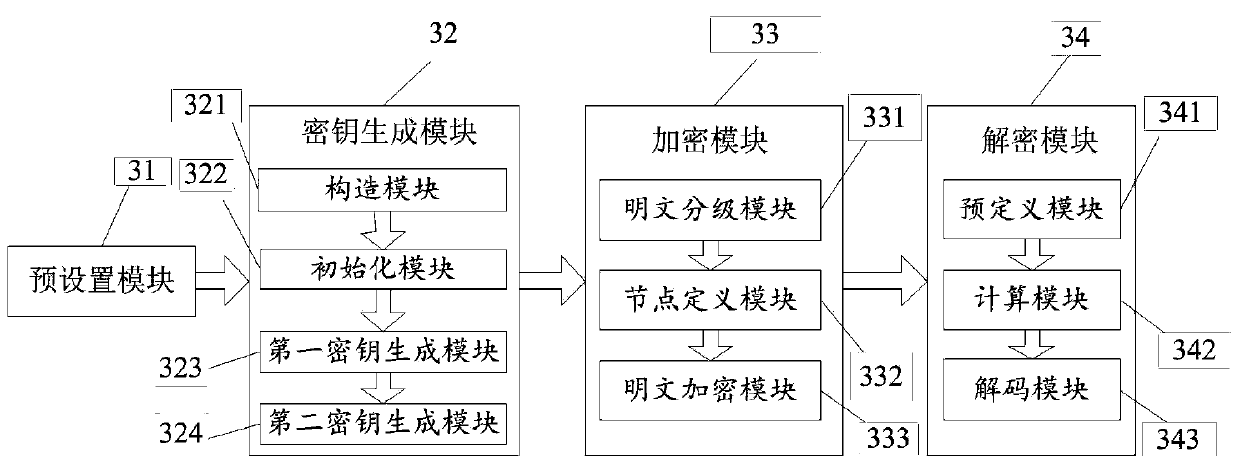
The invention discloses an encryption system based on attributes. The encryption system comprises a system parameter setting module, a key generation module, an encryption module, a decryption module, a cryptograph retrieval module, a re-encryption key generation module, a re-encryption module and a private key re-generation module, wherein the system parameter setting module is used for generating system public parameters, the key generation module is used for generating private keys of users for decrypting messages according to attribute sets of the users; the encryption module is used for encrypting the messages; the decryption module is used for decrypting the messages, the cryptograph retrieval module is used for retrieving the cryptographs; the re-encryption key generation module is used for generating re-encryption keys and updating the cryptographs and the private keys; the re-encryption module is used for re-encrypting the messages on the basis of the original cryptographs; the private key re-generation module is used for updating the private keys of the users. The invention further discloses an encryption method based on the attributes. By the encryption system and method based on the attributes, the problem of privacy protection during cloud computing can be solved, attribute withdrawal and safety retrieval of the cryptographs are supported, and the encryption system is high in flexibility.
Owner:HOHAI UNIV
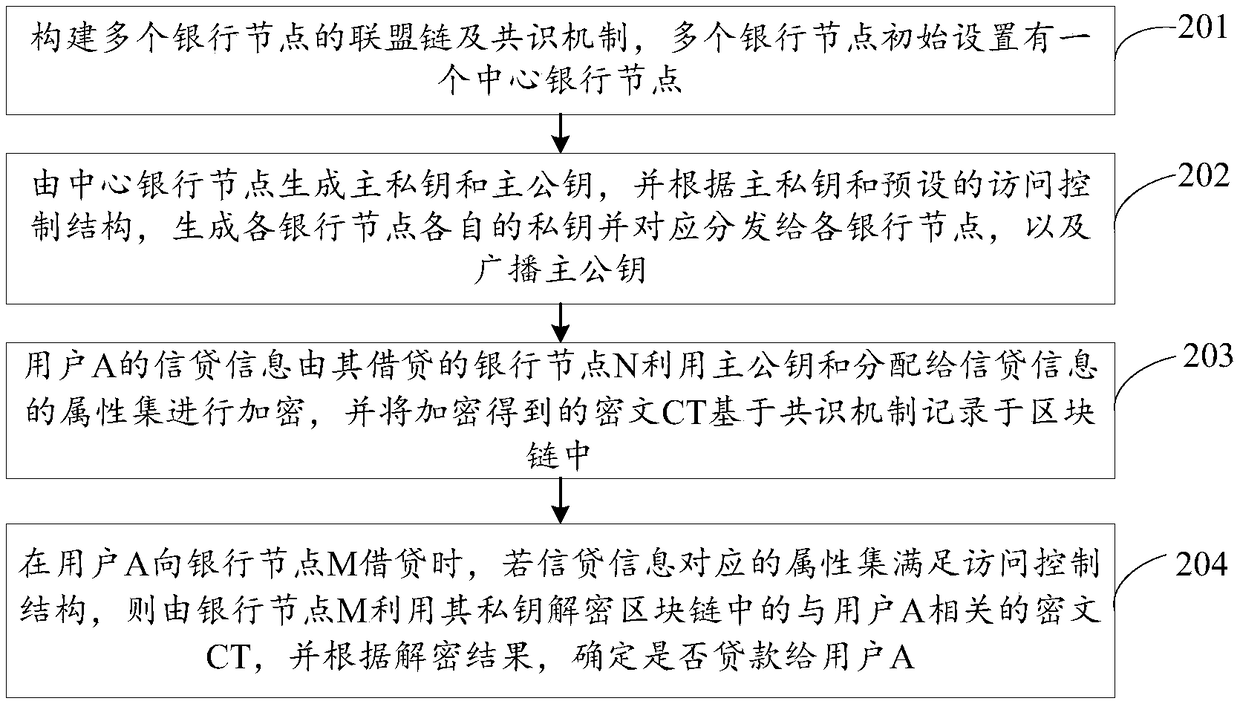
Method and system for implementing credit by using union block chain based on attribute-based encryption
The invention discloses a method and system for implementing credit by using a union block chain based on attribute-based encryption, and relates to the technical field of block chains. The method includes: constructing a union chain and a consensus mechanism of a plurality of bank nodes; allowing a central bank node to generate a master private key and a master public key, generating a private key of each bank node according to the master private key and an attribute set respectively assigned to each bank node and distributing the private key to each bank node correspondingly, and broadcasting the master public key; allowing a lending bank node N of the user A to use the master public key and a preset access control structure to encrypte credit information of a user A, recording a ciphertext CT in a block chain on the basis of the consensus mechanism, allowing a bank node M to use the private key thereof to decrypt the ciphertext CT associated with the user A in the block chain when the user A borrows from the bank node M and if the attribute set of the bank node M satisfies the access control structure, and determining whether to loan to the user A according to the decryption result. The method and system can improve the credit evaluation efficiency and ensure the privacy and security of the credit information.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
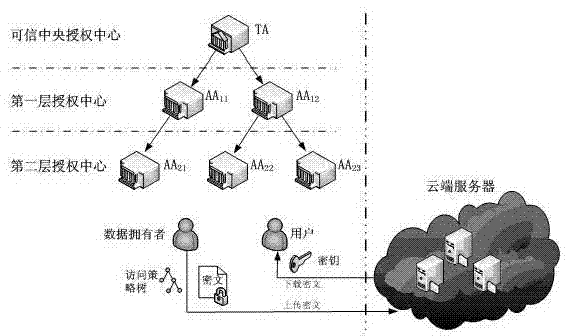
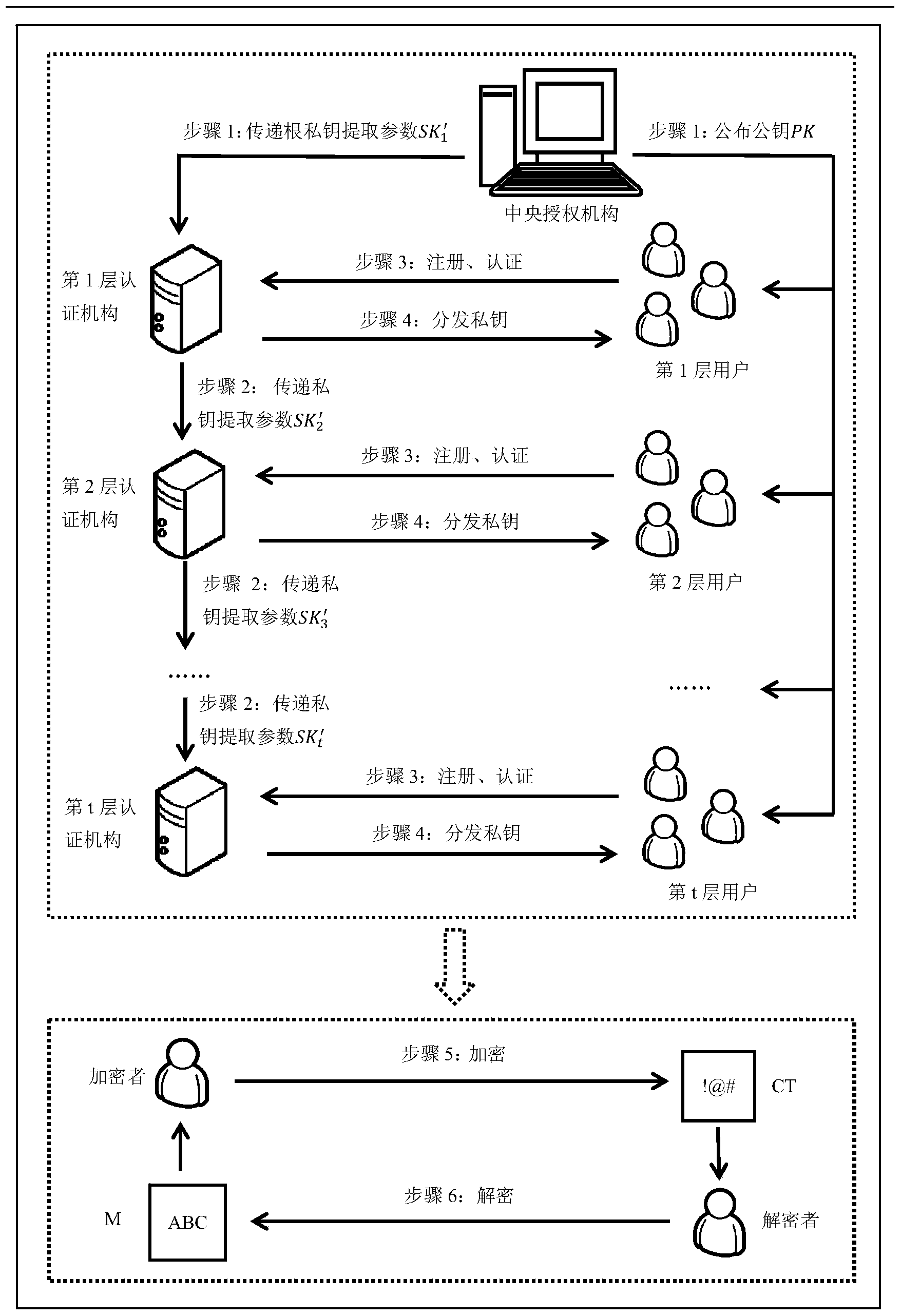
Attribute-based encryption method for achieving hierarchical certification authority
ActiveCN103647644AFacilitate hierarchical distributionEase of distributed managementKey distribution for secure communicationPublic key for secure communicationCiphertextAttribute-based encryption
The invention discloses an attribute-based encryption method for achieving a hierarchical certification authority. The attribute-based encryption method for achieving the hierarchical certification authority mainly comprises the following steps of 1) initialization of a central authority; 2) initialization of multilayer certification authorities; 3) user registration and certification; 4) extraction and distribution of private keys; 5) encryption; 6) decryption. The attribute-based encryption method for achieving the hierarchical certification authority achieves hierarchical distribution of multiple certification authorities on the basis of an attribute-based encryption system of a ciphertext policy, facilitates management of the central authority to the certification authorities, and is applicable to shared data encryption solution in a large organization structure of hierarchical distribution. Besides, during the extraction and distribution process of the private keys, overlapping among attribute sets of different users is allowed, so that the attribute-based encryption method for achieving the hierarchical certification authority has wider adaptability in practical application.
Owner:BEIHANG UNIV
Performing context-rich attribute-based encryption on a host
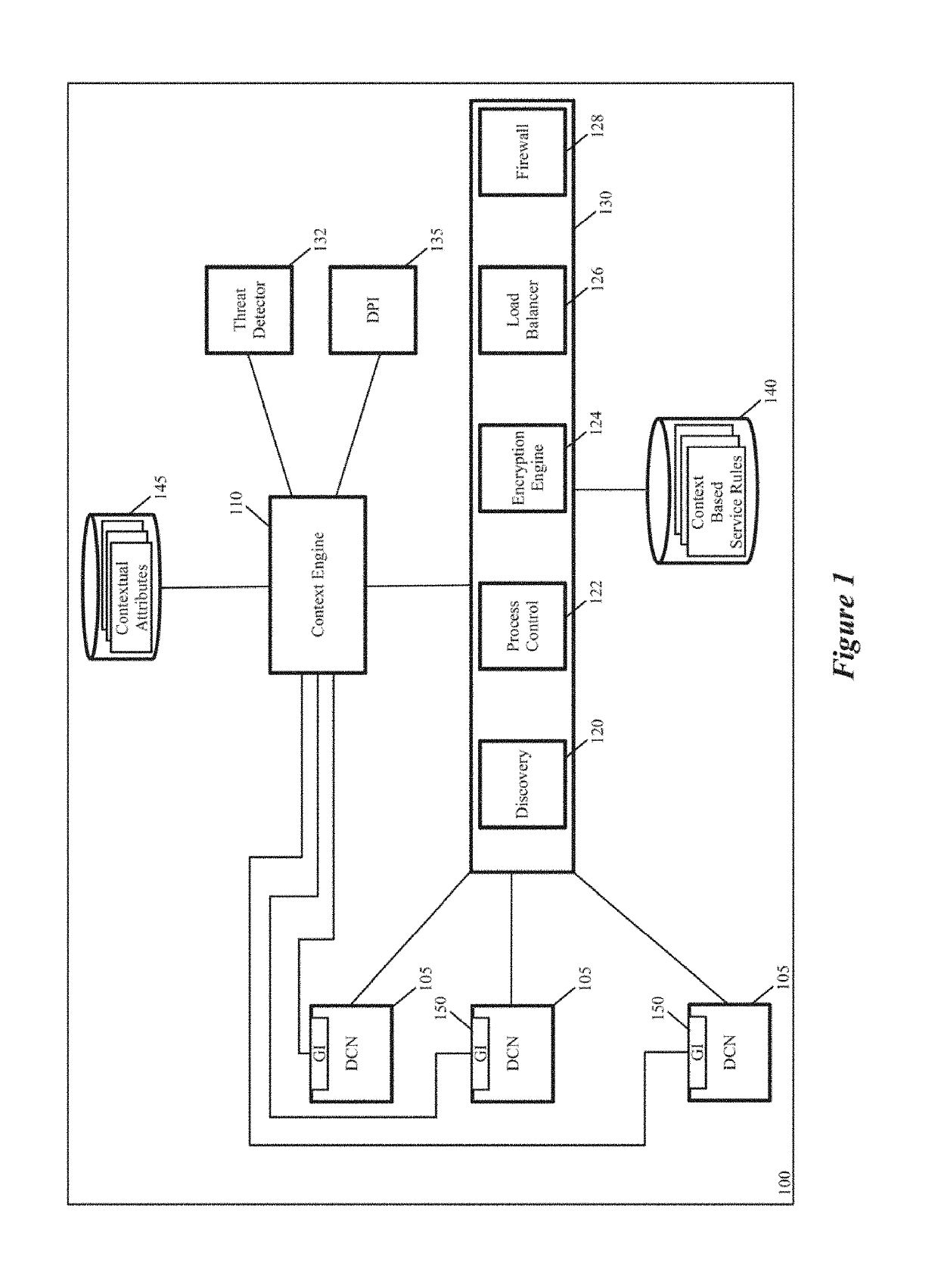
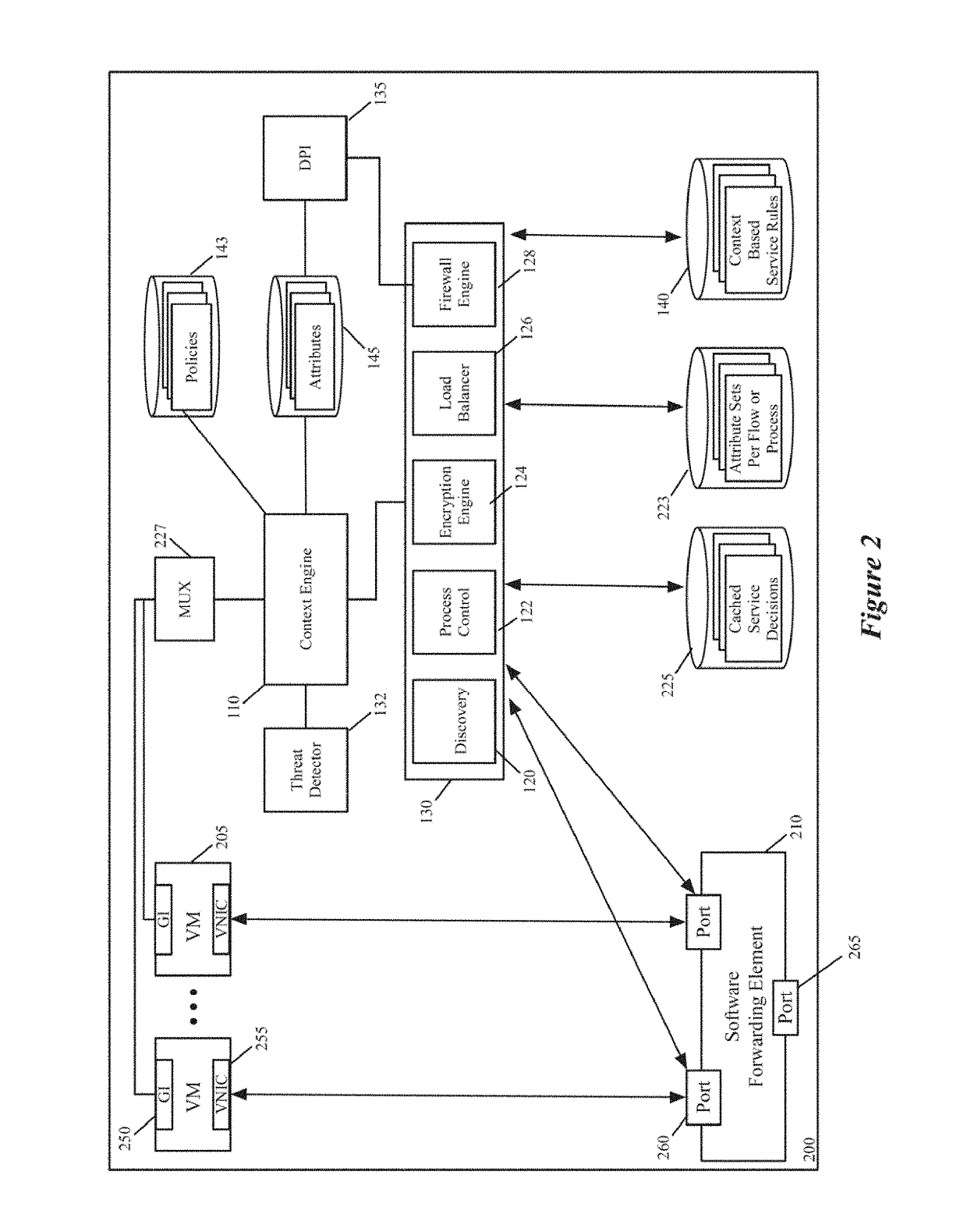
ActiveUS20190149525A1Key distribution for secure communicationSoftware simulation/interpretation/emulationAttribute-based encryptionContext based
Some embodiments provide a context engine that supplies contextual-attributes to several context-based service engines on its host computer. Different embodiments use different types of context-based service engines. For instance, in some embodiments, the attribute-based service engines include an encryption engine that performs context-based encryption or decryption operations to encrypt data messages from the machines, or to decrypt data messages received for the machines.
Owner:NICIRA
Internet of things (IoT) privacy protection method and system for preventing ciphertext from being tampered based on CP-ABE
ActiveCN107070652AImprove interaction efficiencyIncrease flexibilityKey distribution for secure communicationPublic key for secure communicationHash functionAttribute-based encryption
The invention discloses an Internet of things (IoT) privacy protection method and an IoT privacy protection system for preventing ciphertext from being tampered based on CP-ABE. The method provides a ciphertext strategy attribute-based encryption mechanism, a vehicle node sending a message can autonomously develop an access strategy according to the attribute of the vehicle node receiving the message, the access strategy is deployed in the ciphertext, only the attribute of the vehicle node receiving the message is met, successful decryption can be achieved, and extremely strong flexibility is provided. Meanwhile, in order to prevent the sent message from being captured and tampered, a credible authorization center maps the ciphertext and a related parameter into a random number by using a Hash function, when performing decryption, a message accepter firstly verifies whether the message is tampered, and then decrypts the message if the message is not tampered. Not too much complex computation is introduced into the scheme; according to the scheme, interaction efficiency between the vehicle nodes is improved, while security of communication between the vehicle nodes in the Internet of things is ensured.
Owner:HUNAN UNIV OF SCI & ENG
Ciphertext access control method and system based on cloud computing platform
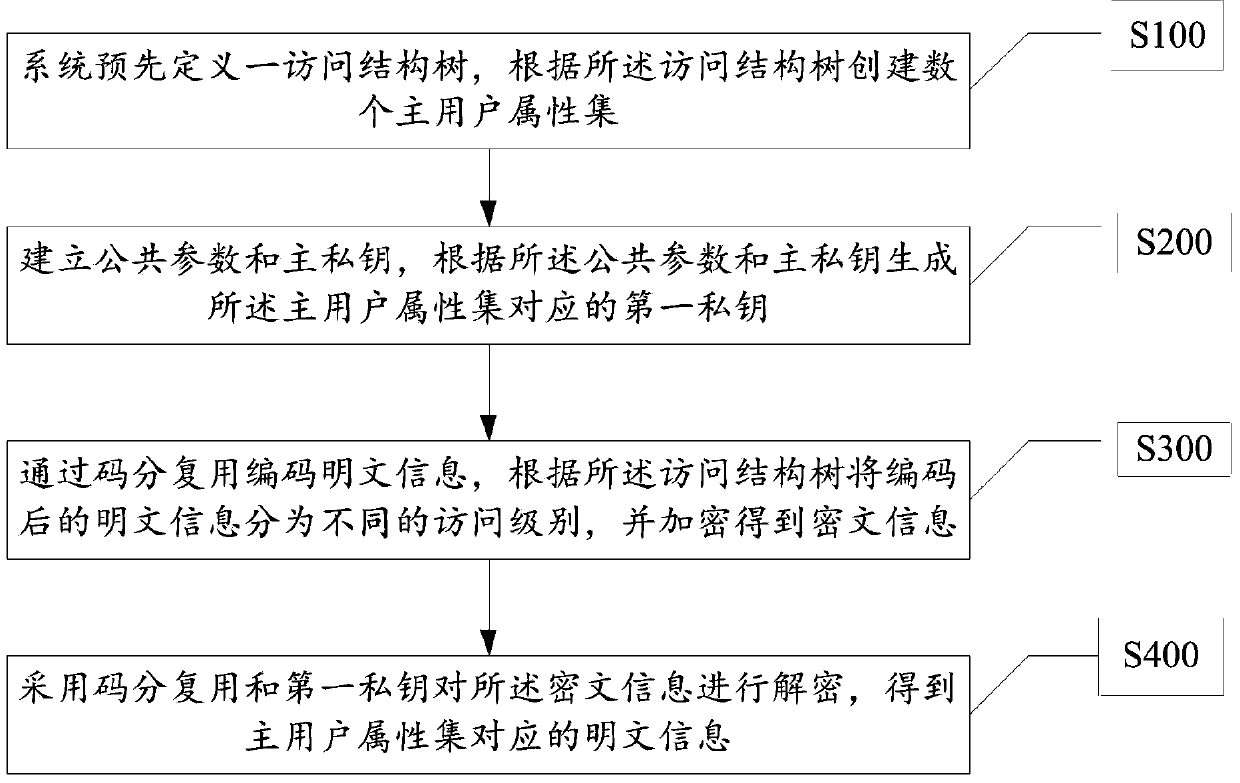
The invention discloses a ciphertext access control method and system based on a cloud computing platform. The method and the system have the beneficial effects that the efficiency of access control is improved by controlling the ciphertext access control systems under existing cloud computing by grades; the ciphertext storage space is reduced by coding plaintexts and ciphertexts by utilizing the code division multiplexing technology; meanwhile, the quantity of private keys kept by users is reduced by adopting the ciphertext-policy attribute-based encryption scheme, thus improving the overall performance of the system and reducing the consumption of the storage space.
Owner:SHENZHEN UNIV
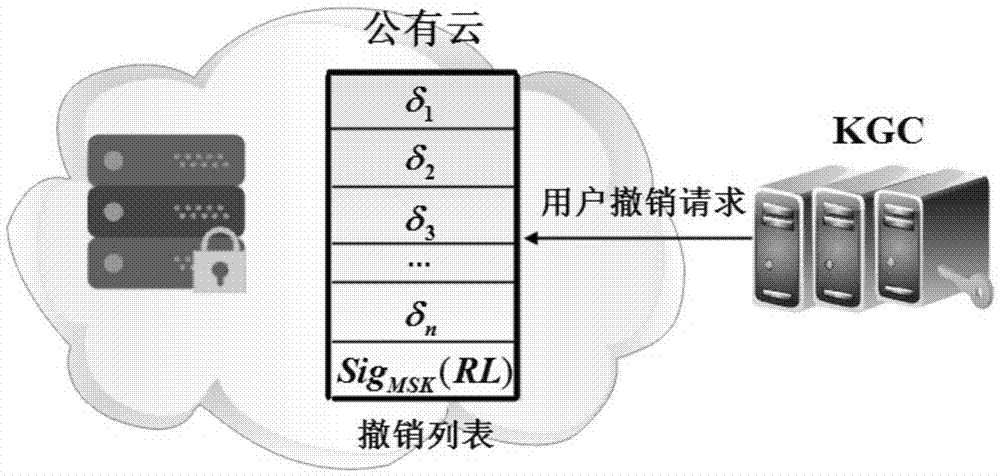
Revocable attribute base encryption method
InactiveCN107566386AGuaranteed confidentialityAchieving forward and backward securityKey distribution for secure communicationAttribute-based encryptionCiphertext
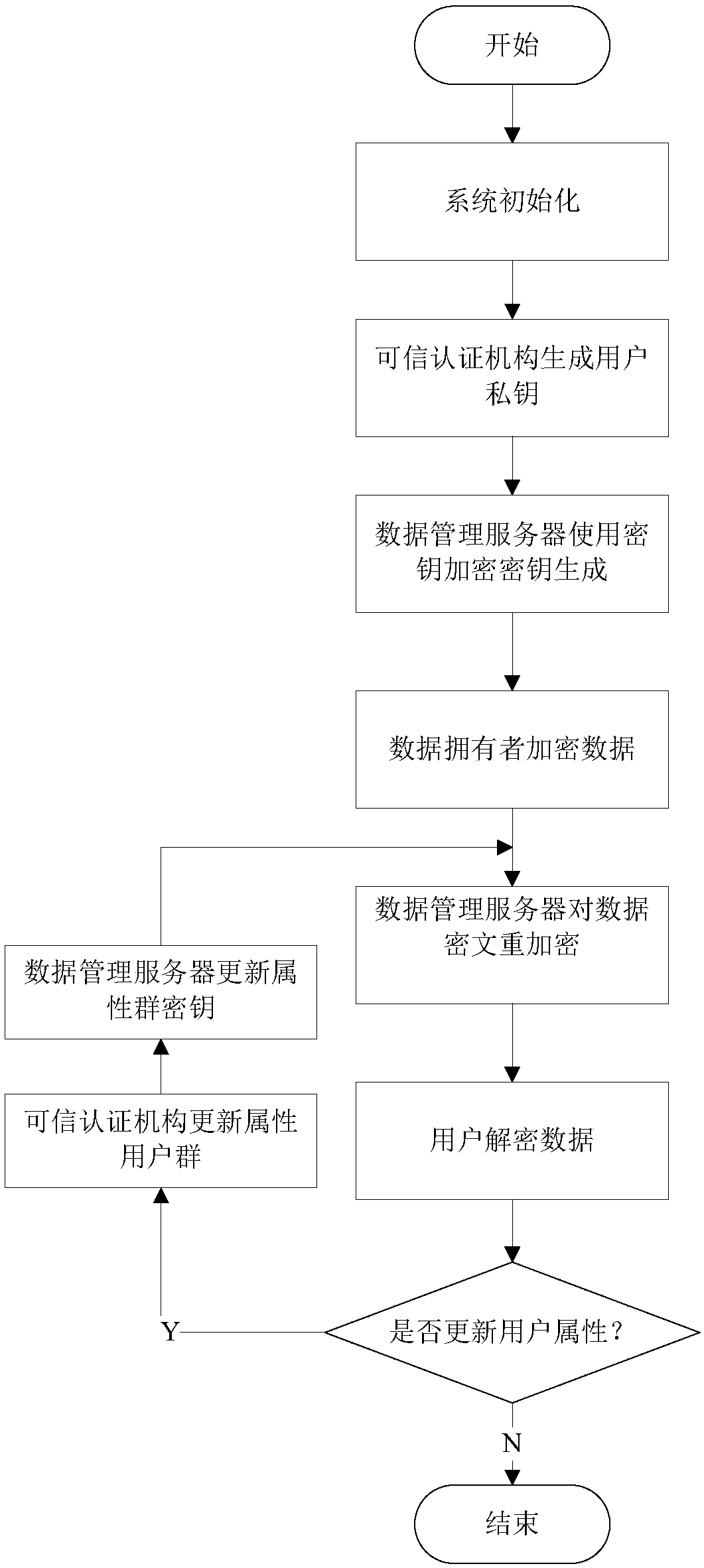
The invention discloses a revocable attribute base encryption method. A master public key and a master key are generated for a system through a trusted authentication mechanism, and an attribute usergroup corresponding to each attribute is transmitted to a data management server after user attributes needing to be registered are verified and corresponding private keys are generated. The data management server generates a corresponding KEK two binary tree for each user, distributes an attribute group key, re-encrypts a cipher text encrypted by a data owner, and sends data use requests of the users the users after receiving the data use requests. When the trusted authentication mechanism receives a request of updating a user attribute group, the user attribute group can be updated in time,the data management server is informed of an updated user list, and the data management server performs key update of the user attribute group. If and only if a user is not revoked from an attribute group and is granted permission, the user can perform decryption. Through adoption of the revocable attribute base encryption method, flexible expression of an access strategy is implemented, and the forward and backward security of encrypted data is ensured. The method has high expansibility and practicability.
Owner:SHANGHAI MARITIME UNIVERSITY
Data access control method in cloud
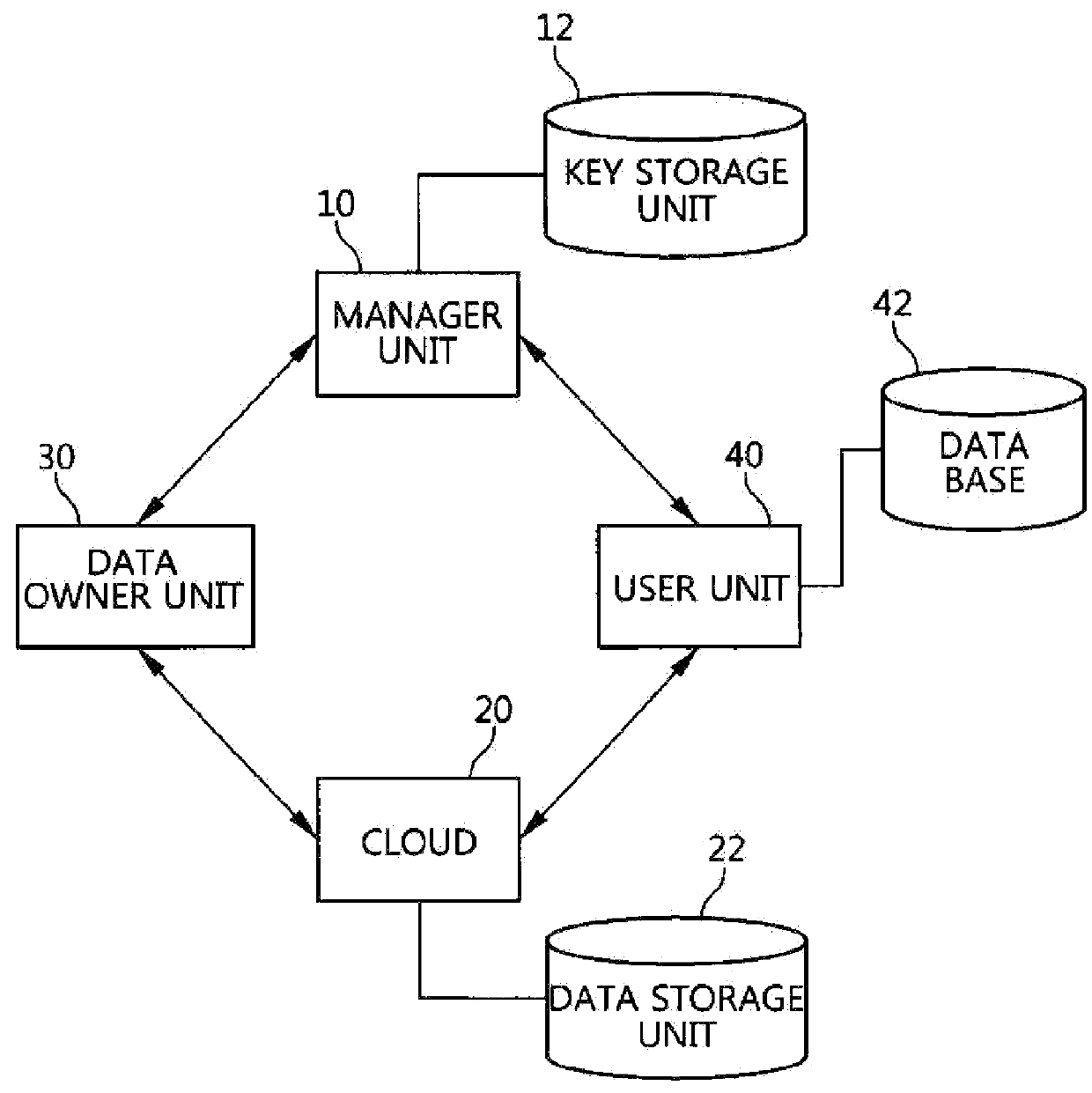
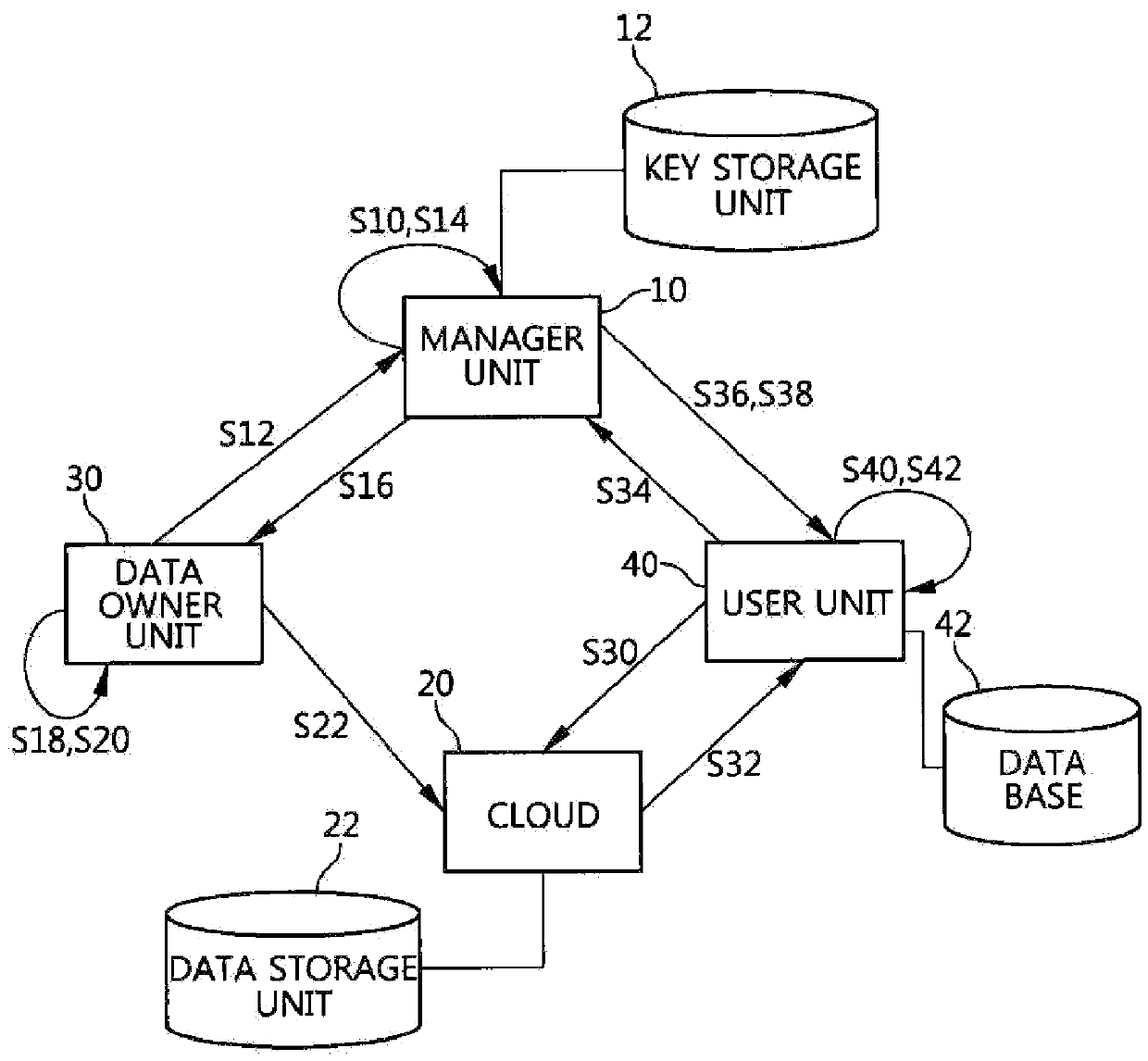
ActiveUS20160055347A1Key distribution for secure communicationPublic key for secure communicationAttribute-based encryptionCiphertext
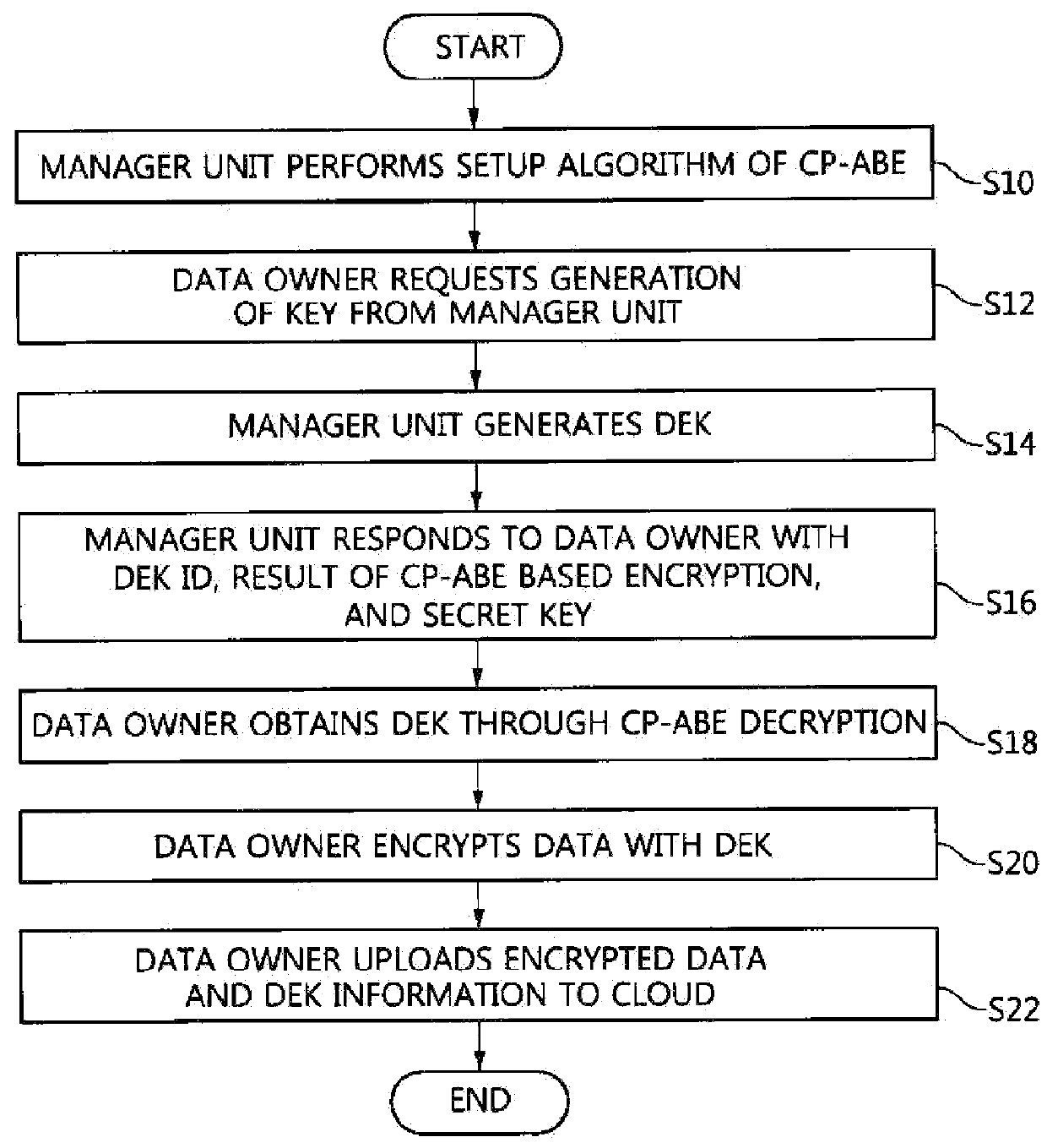
A data access control method includes requesting, by the data owner unit, the generation of a data encryption key (DEK) from the manager unit, generating, by the manager unit, the DEK, generating, by the manager unit, the result of the Ciphertext Policy-Attribute Based Encryption (CP-ABE) of the DEK and a secret key used to decrypt the result of the CP-ABE encryption, and then responding, by the manager unit, to the data owner unit, obtaining, by the data owner unit, the DEK by performing the CP-ABE decryption of the result of the CP-ABE encryption using the secret key, encrypting, by the data owner unit, data with the obtained DEK, and uploading, by the data owner unit, the encrypted data and DEK information to the cloud.
Owner:ELECTRONICS & TELECOMM RES INST
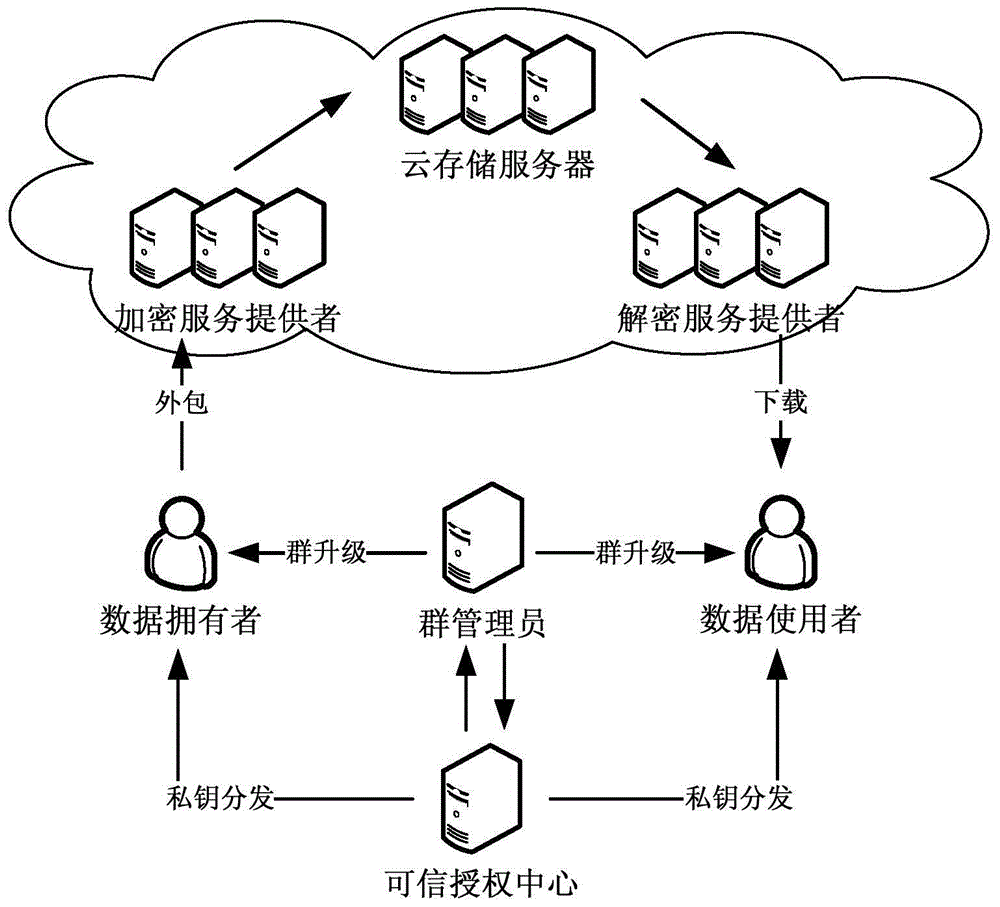
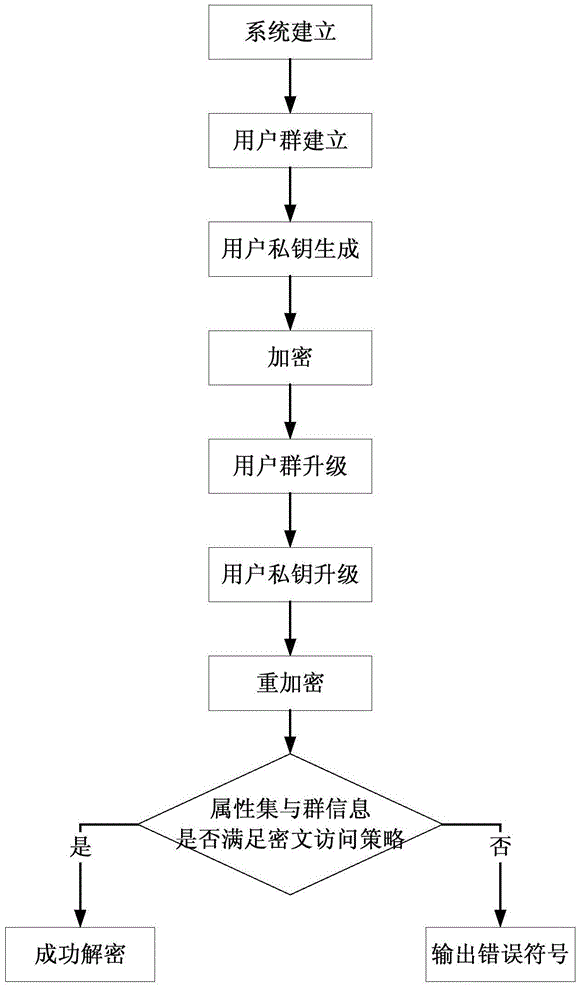
Ciphertext-policy attribute-based encryption method having efficient user revocation capability
The invention discloses a ciphertext-policy attribute-based encryption method having an efficient user revocation capability, and includes the following steps: (1) a system establishment step; (2) a user group establishment step; (3) a user private key generation step; (4) an encryption step; and (5) a decryption step; if a user revocation event occurs in the system, the method should also include: (6) a user group upgrading step; (7) a user upgrading step; and (8) a re-encryption step. The encryption method has the advantages that a revocation process involves few users, revocation cost is low and revocation efficiency is high, and the encryption method has high security, and can resist collusion attacks of multiple types of users. Since the attribute-based encryption scheme has the characteristics of one-time encryption multi-user decryption and fine-grained access control, the encryption method can be applied to a cloud storage environment.
Owner:HOHAI UNIV
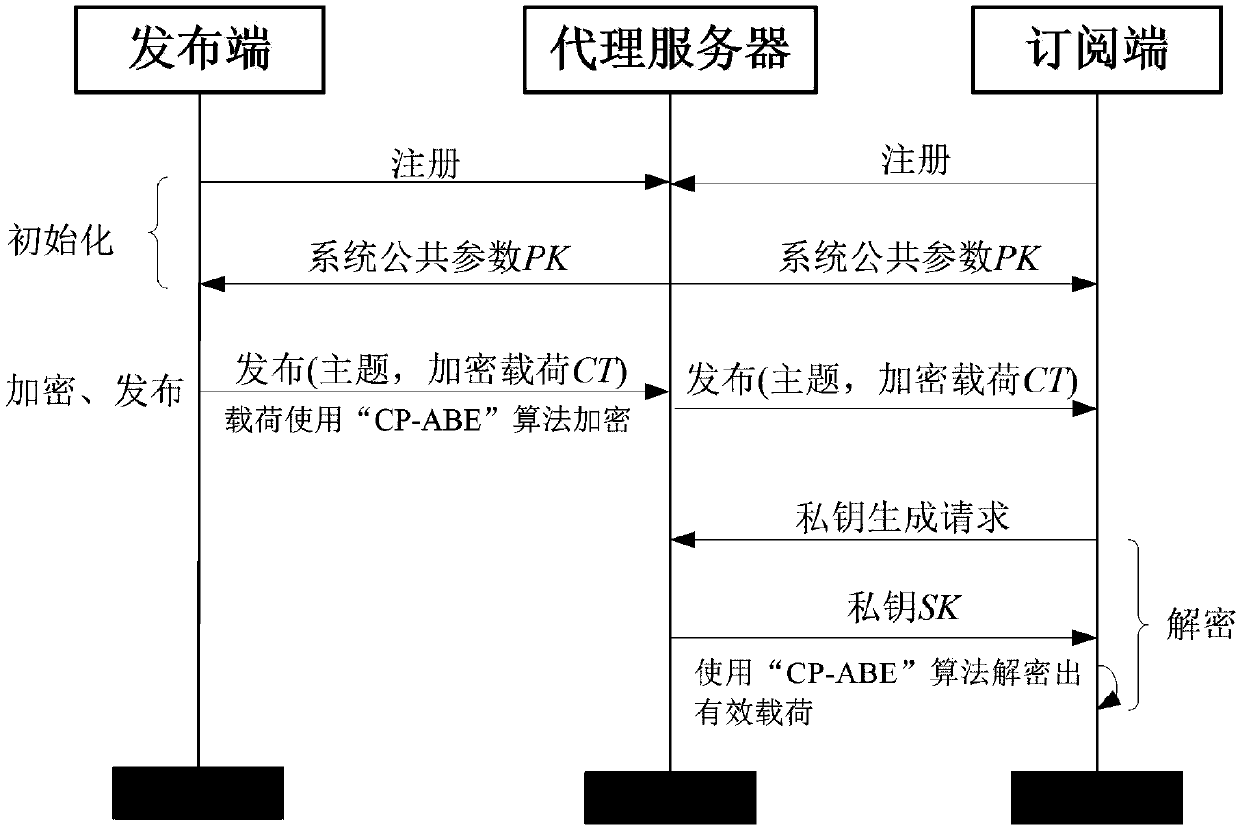
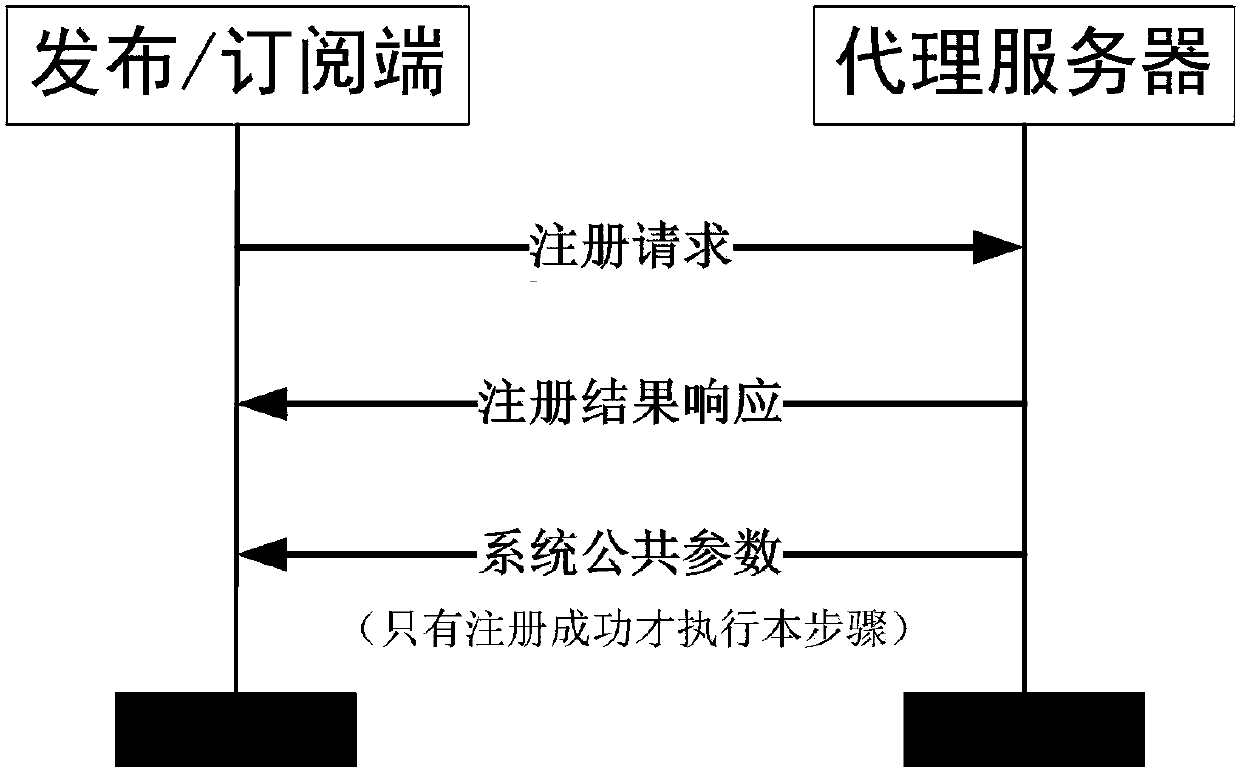
Encryption method applied to MQTT-SN protocol
InactiveCN107708112AImplement encryptionAchieve authenticationNetwork topologiesTransmissionComputer hardwarePlaintext
The invention relates to an encryption method applied to a MQTT-SN protocol, and relates to the field of communication. The method employs a harsh algorithm and ciphertext-policy attribute-based encryption method, so that a publishing terminal, an agent server and one or a plurality of subscription terminals can complete encrypted communication. The method herein includes the following steps: an agent server verifying the identity of a publishing / subscription terminal, performing registration of the publishing / subscription terminal, and generating a system common parameter; the publishing terminal encrypting a plaintext load by using the ciphertext-policy attribute-based encryption method; the publishing terminal transmitting the encrypted load to the agent server, the agent server forwarding the encrypted load to one or a plurality of subscription terminals; and the subscription terminal applying for a secrete key from the agent server, decrypting the encrypted load, obtaining a plaintext. According to the invention, the method can implement identity verification of a MQTT-SN protocol publishing / subscription terminal, data integrity verification, and data confidentiality protection, and better addresses the safety issues faced by the MQTT-SN protocol in terminals of wireless sensor network applications.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
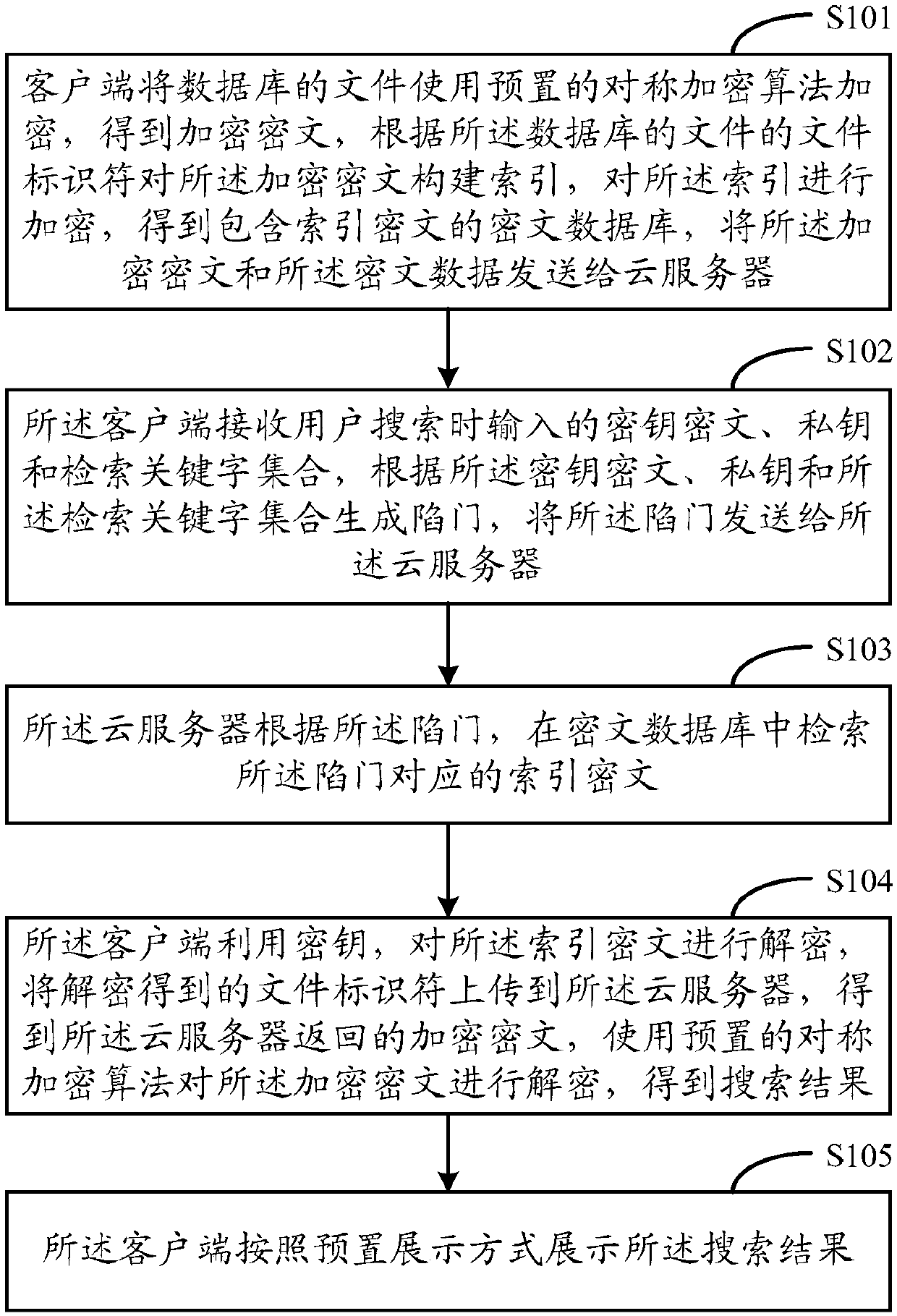
Ciphertext searching method and system supporting access control
ActiveCN108494768ASolve data security issuesReduce computational overheadTransmissionSpecial data processing applicationsAttribute-based encryptionCiphertext
The invention is applicable to the field of data processing, and provides a searching method supporting access control. The searching method comprises the steps that: a client encrypts files of a database to obtain encrypted ciphertexts, and indexes are established and encrypted according to file identifiers to obtain a ciphertext database; the client receives a key ciphertext, a private key and aretrieval keyword set to generate a trap door; a cloud server retrieves the corresponding index ciphertext according to the trap door; the client carries out decryption on the index ciphertext by utilizing a key, uploads the file identifier obtained by decryption to the cloud server to obtain the encrypted ciphertext, and the encrypted ciphertext is decrypted to obtain a search result; and the client shows the search result according to a preset showing mode. In the implementation process of the embodiment of the invention, the ability of a searching client for data access is controlled by adopting attribute-based encryption, but access control is set to be carried out in the overall database instead of the indexes, so that calculation cost when a data owner encrypts the database can be greatly reduced; and meanwhile, in the process that a user acquires the search trap door, the data owner does not need to participate in.
Owner:SHENZHEN UNIV
Multi-authority ciphertext-policy attribute-based encryption method
ActiveCN106230590AEnsure safetyImprove battery lifeKey distribution for secure communicationPublic key for secure communicationAttribute-based encryptionMobile cloud
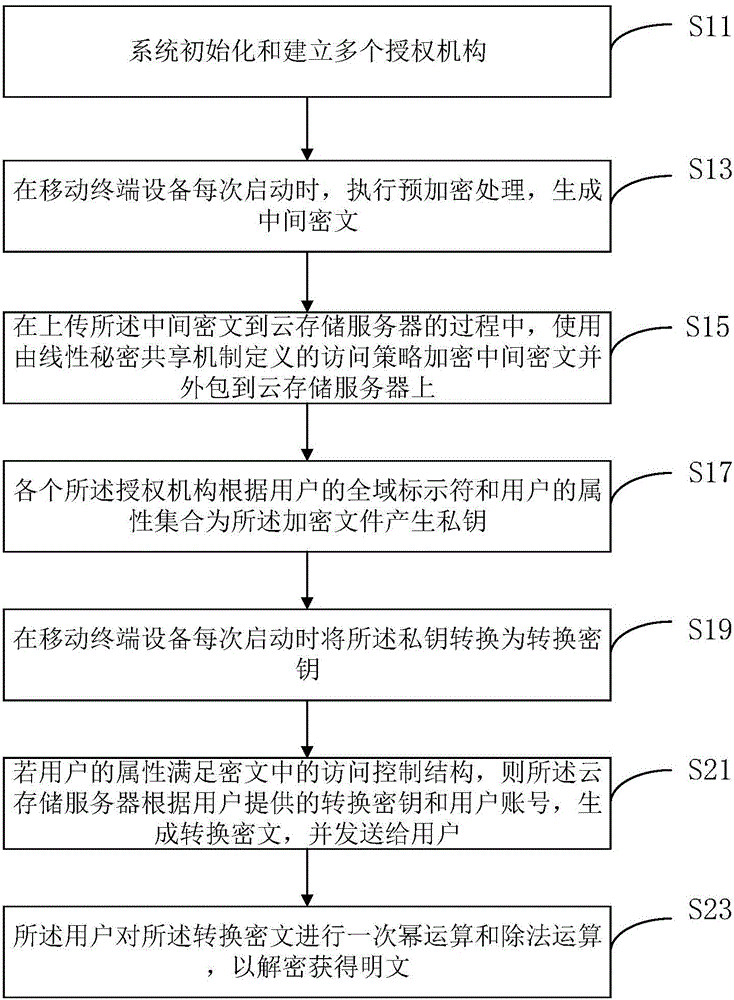
The invention discloses a multi-authority ciphertext-policy attribute-based encryption method. The method includes following steps: step 1, performing system initialization and establishing a plurality of authorities; step 2, before each starting of a mobile terminal device, executing pre-encryption treatment, and generating an intermediate ciphertext; step 3, in a process of uploading the intermediate ciphertext to a cloud storage server, encrypting the intermediate ciphertext by employing an access policy defined by a linear secret sharing mechanism, and outsourcing the intermediate ciphertext to the cloud storage server; and step 4, generating a private key for an encryption file according to global identifiers of users and an attribute set of the users by each authority. According to the method, aiming at the mobile cloud storage environment, on the premise of guaranteeing the data security, a lot of pairing operations are pre-processed in advance by employing the encryption pre-processing technology so that the calculation cost of online encryption is minimum; and by employing the secret key transformation technology and decryption outsourcing, a lot of pairing operations are outsourced to the cloud storage server so that the decryption calculation cost of the mobile terminal is reduced.
Owner:ANHUI UNIVERSITY
Searchable encryption system with traitor tracing function in mobile electronic healthcare
ActiveCN107104982AImplement revocation mechanismKey distribution for secure communicationSpecial data processing applicationsComputer hardwareMobile electronics
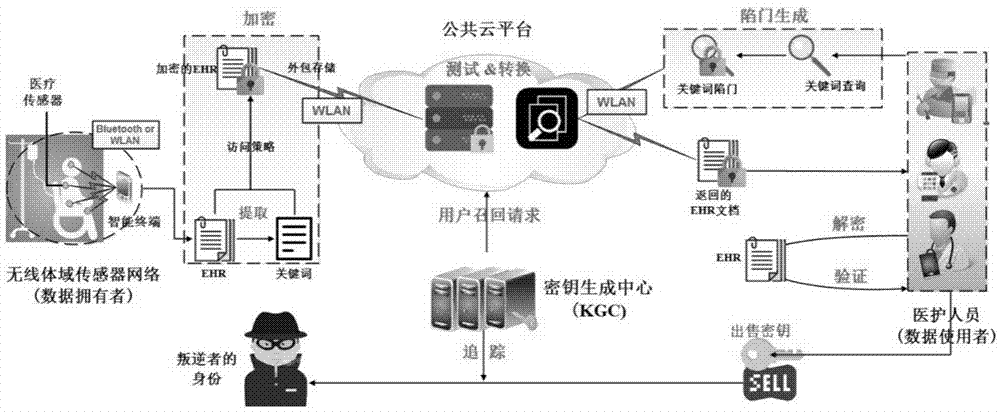
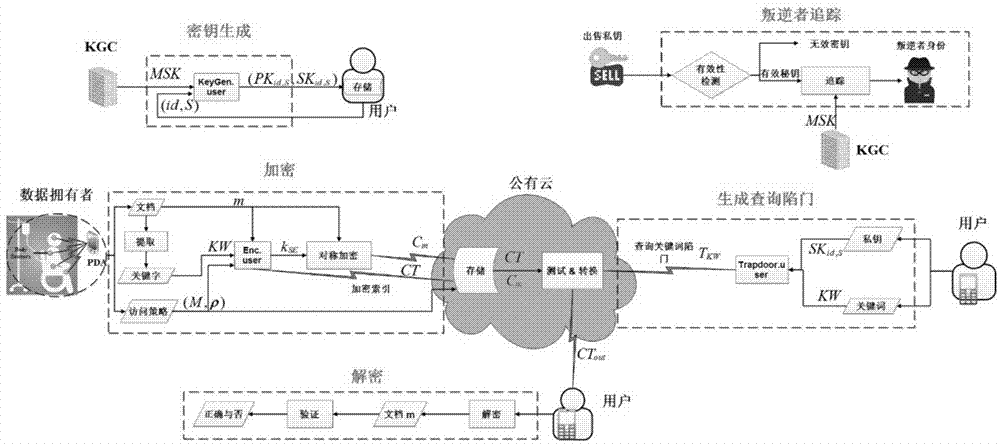
The invention relates to a searchable encryption system with a traitor tracing function in mobile electronic healthcare. In view of the problems that the computation overhead in the existing mobile health (mHealth) system is too large, traitor tracing cannot be supported, and that on-demand revocation of users cannot be realized, a novel lightweight secure electronic health system (LiST) is provided, which can perform data sharing, access authority control and traitor tracing. In addition to realizing fine-grained access control of encrypted electronic heath records (EHR) by using an attribute-based encryption (ABE) mechanism, the LiST also supports keyword search of the encrypted HER, and provides an efficient traitor tracing mechanism and a flexible user revocation mechanism.
Owner:FUZHOU UNIV
Access control system for cloud store service platform and access control method thereof
ActiveCN104917772AImprove securityGuaranteed confidentialityUser identity/authority verificationAccess control matrixConfidentiality
The invention belongs to the field of cloud service information safety, and provides an access control system for a cloud store service platform and an access control method thereof. The system and method are based on a weight attribute encryption mechanism, adopt a multi-mechanism attribute based encryption technique, encrypt the data and then store in the cloud store service platform, thereby improving the safety of cloud store service. In addition, as the attribute and weight are combined, hierarchical management of user attributes is realized, different levels of users with the same attribute have different access authorities, and more flexible and subtle access control is realized. Furthermore, the system and method adopt the multi-mechanism attribute based encryption technique, thereby preventing a single authentication center from having excessively centralized authority, and further improving safety of data store. The system and method are particularly suitable for being deployed on an open storage service (OSS) platform, can effectively guarantee confidentiality of data stored in the OSS platform by users, and can perform fine grit access control on a data sharing range.
Owner:SHENZHEN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com