Searchable encryption system with traitor tracing function in mobile electronic healthcare
A mobile electronics and electronic medical technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems that are not suitable for large-scale electronic medical systems, cannot be used according to needs, and cannot support traitor tracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
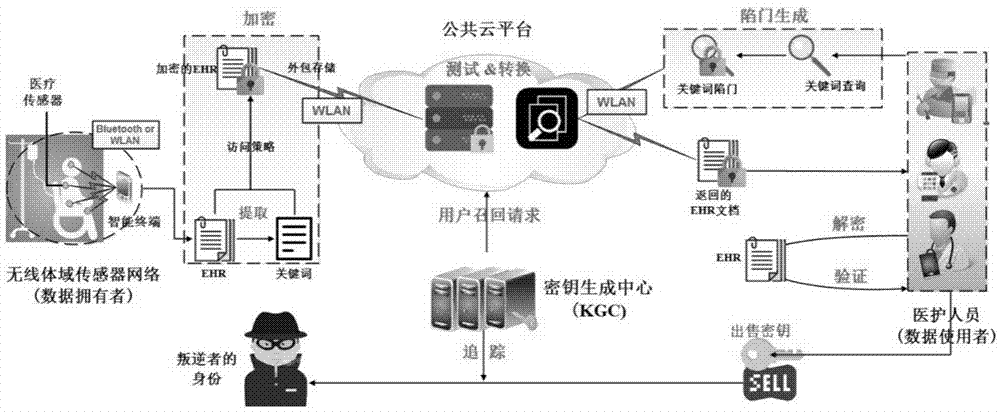
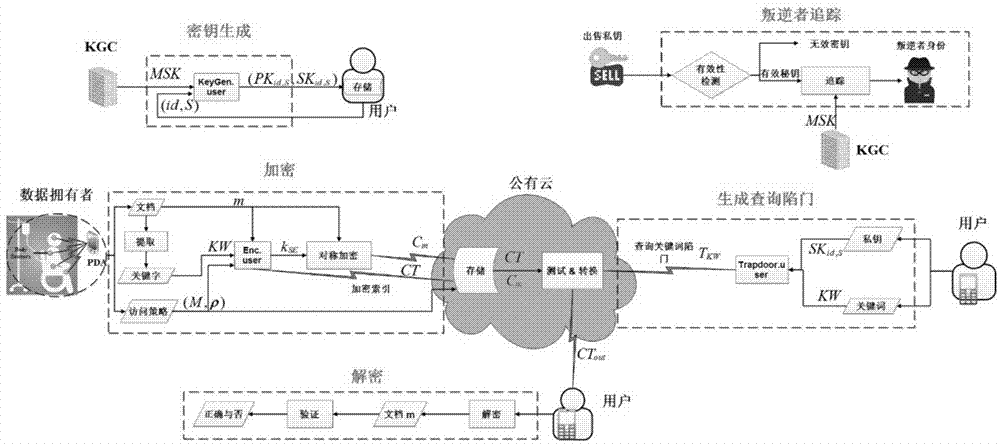
[0026] The present invention is a searchable encryption system with traitor tracking function in mobile electronic medical treatment, figure 1 The system framework in this embodiment mainly consists of four entities: wireless body sensor network (WBSN) as data owner, medical staff as data user, public cloud and key generation center (KGC).
[0027] (1) When the electronic medical data (EHR) is generated in the wireless body area sensor network, the data owner will extract keywords to describe the EHR. Then, the EHR and keywords are encrypted using a lightweight encryption algorithm. During the encryption process, the access policy specified by the data owner will be embedded in the encrypted EHR. The ciphertext is then outsourced to a public cloud via a wireless local area network (WLAN).
[0028] (2) When authorized medical personnel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com