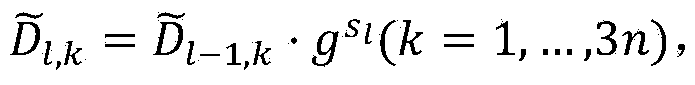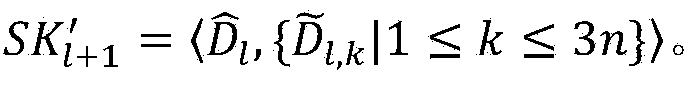Attribute-based encryption method for achieving hierarchical certification authority
An attribute-based encryption and certification authority technology used in public keys and key distribution for secure communications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
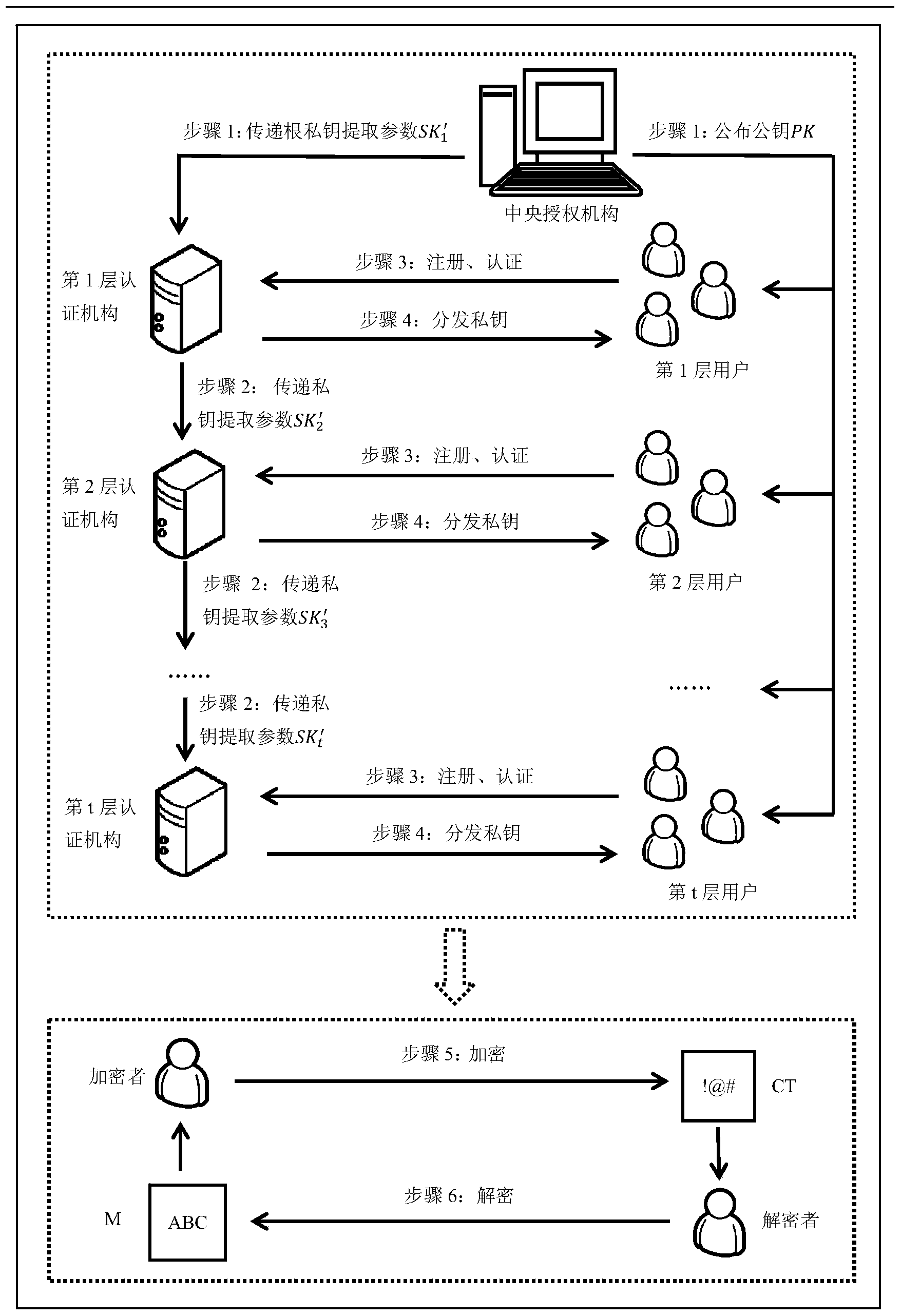
[0049] The attribute-based encryption method for implementing a hierarchical certification authority will be described in detail below in conjunction with the accompanying drawings. The present invention can be divided into four stages of initialization, private key extraction and distribution, encryption, and decryption. There are 6 steps in total, see figure 1 , the specific steps of the method are as follows:
[0050] Phase 1: Initialization phase
[0051] Step 1: Central authority initialization. The central authority first defines the global attribute domain, assuming that N={1,...,n} (n is a certain natural number), and each attribute i∈N and its inverse It all makes sense. Then according to the system security parameter k, select a bilinear group with prime order p and there is a bilinear map choose random number as well as A random generator g of , and then calculate Y=e(g,g) y , T k = g ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com