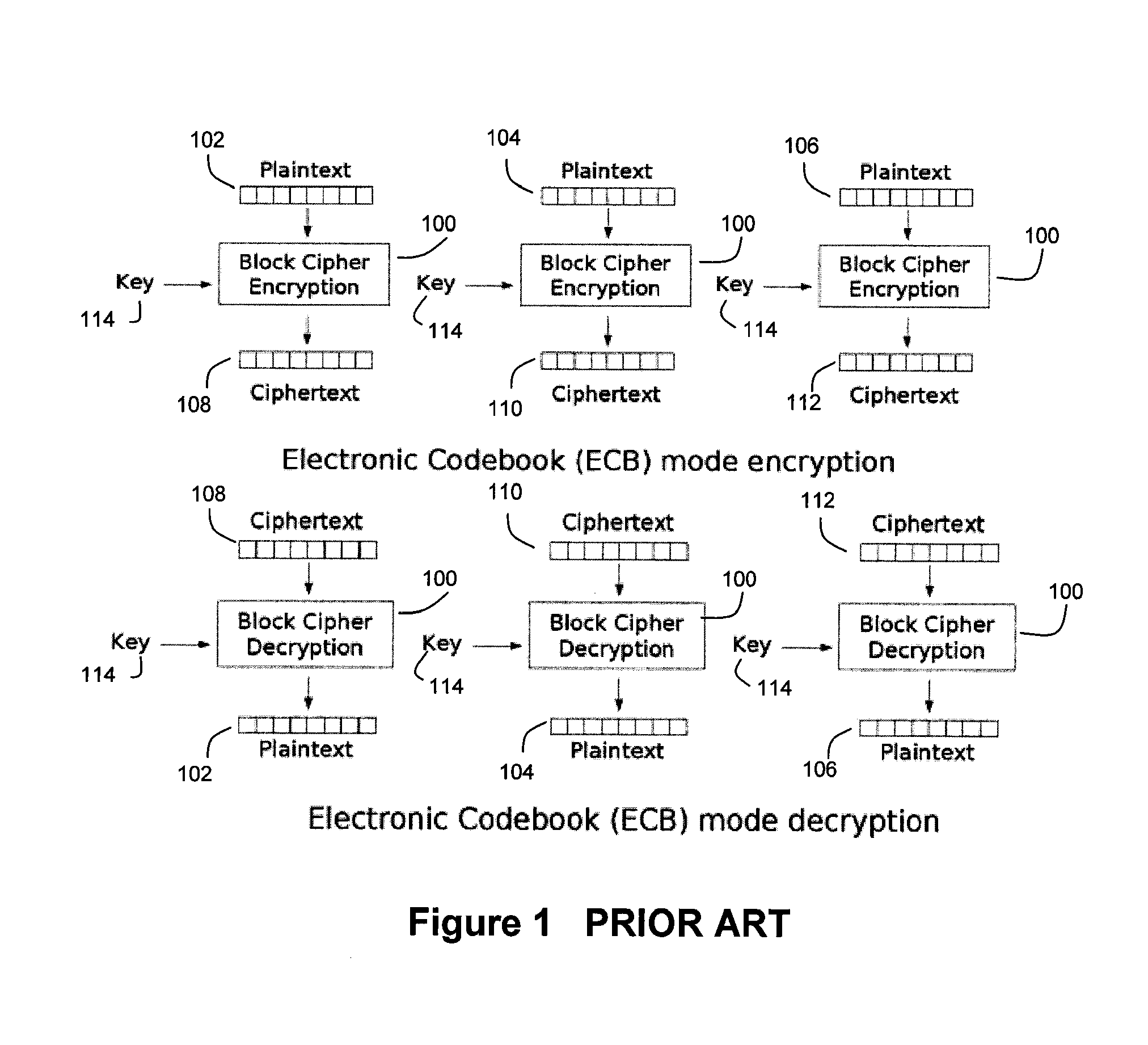
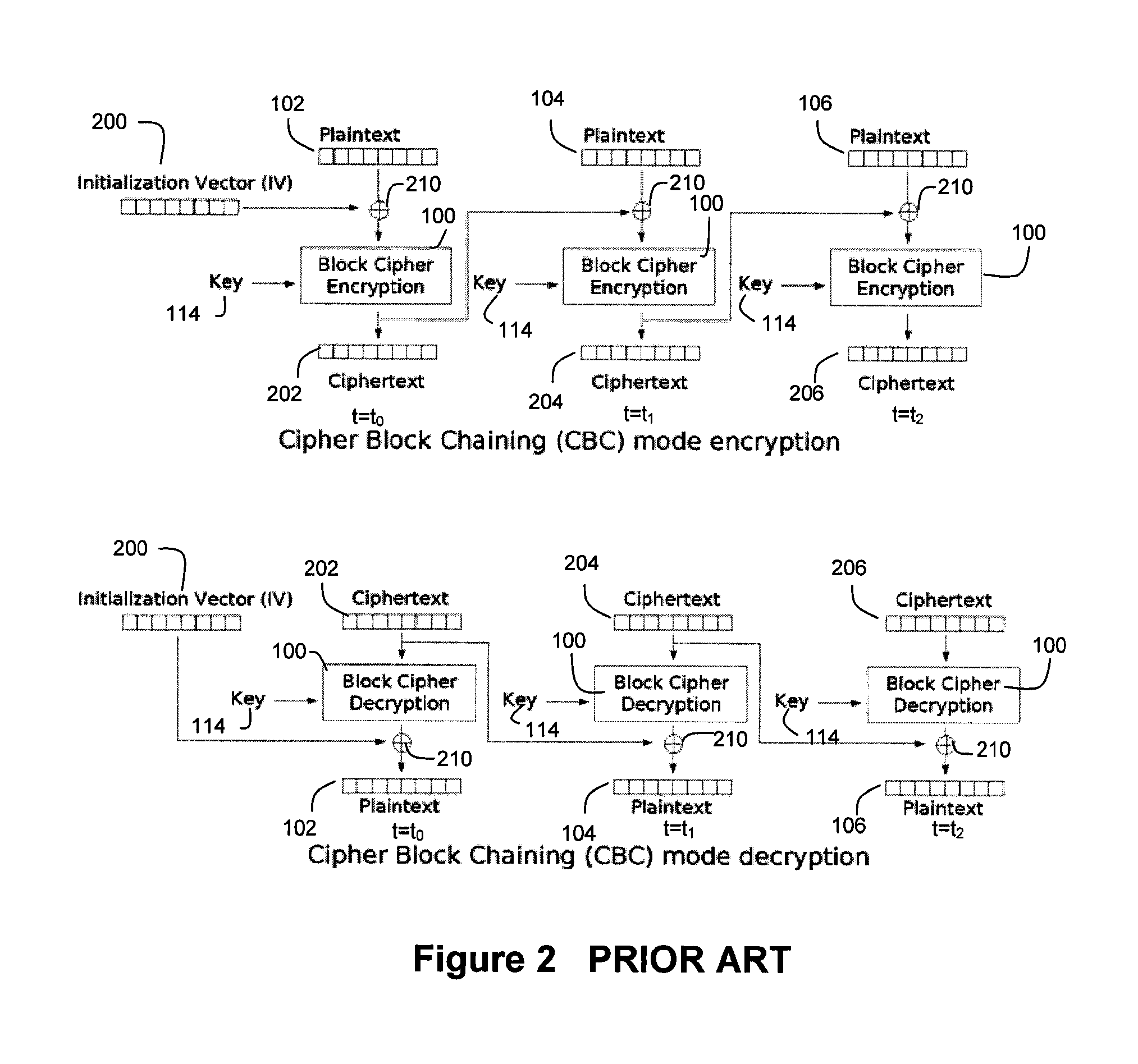
Patents
Literature
1268 results about "Encryption decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Definition of Decryption. Decryption inverts the encryption process in order to convert the message back to its real form. The receiver uses a decryption algorithm and a key to transform the ciphertext back to original plaintext, it is also known as deciphering.
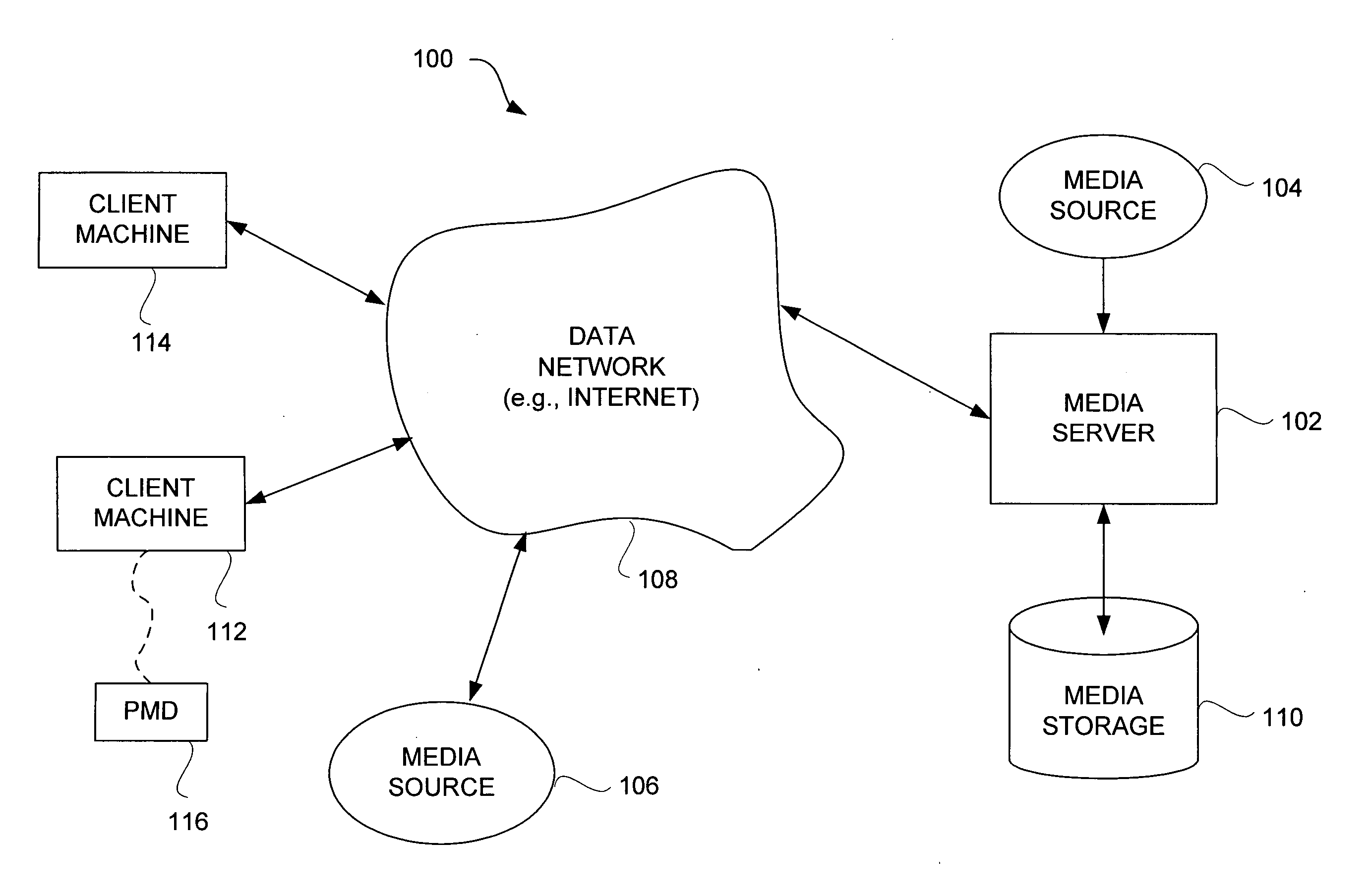
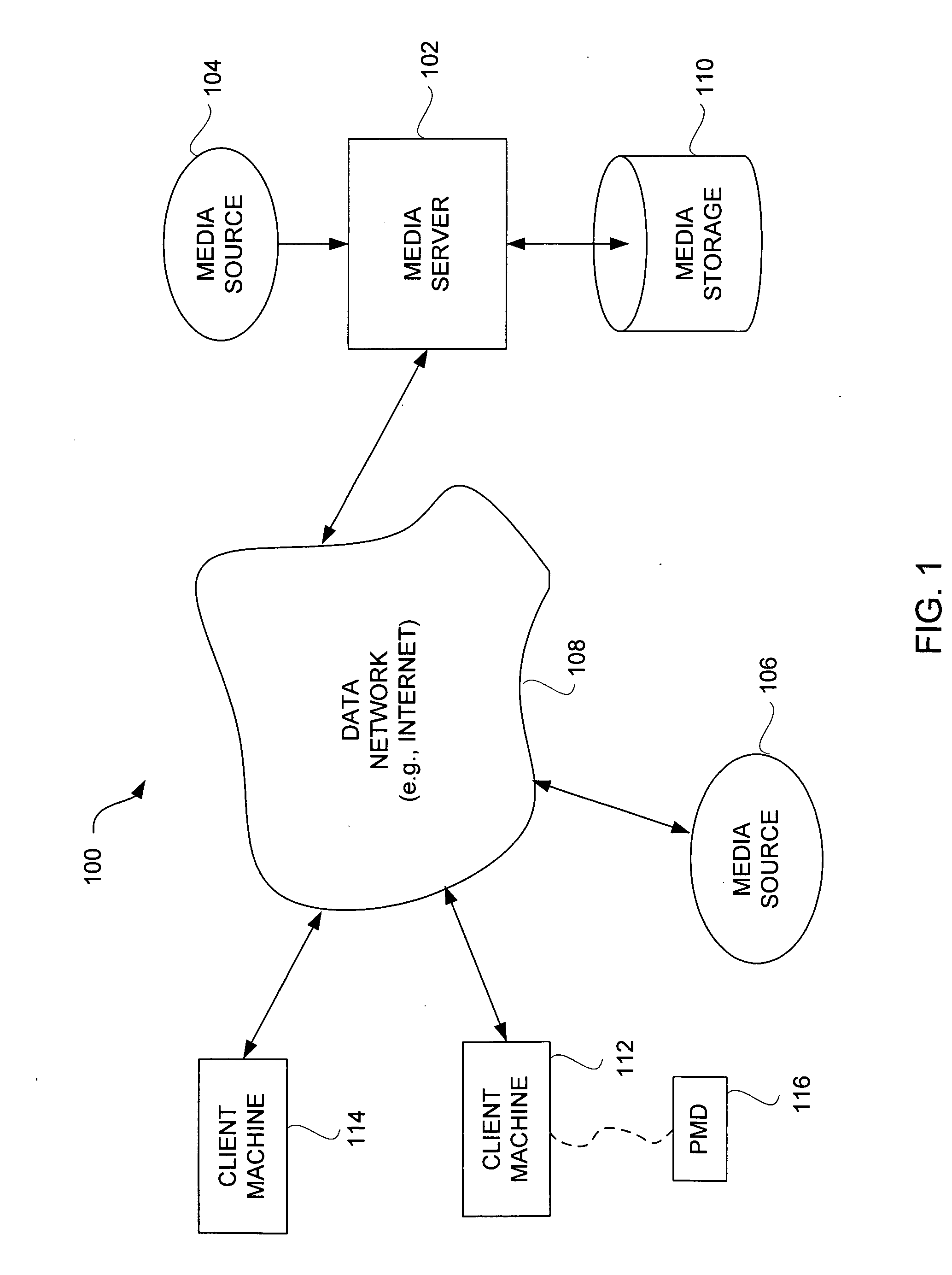
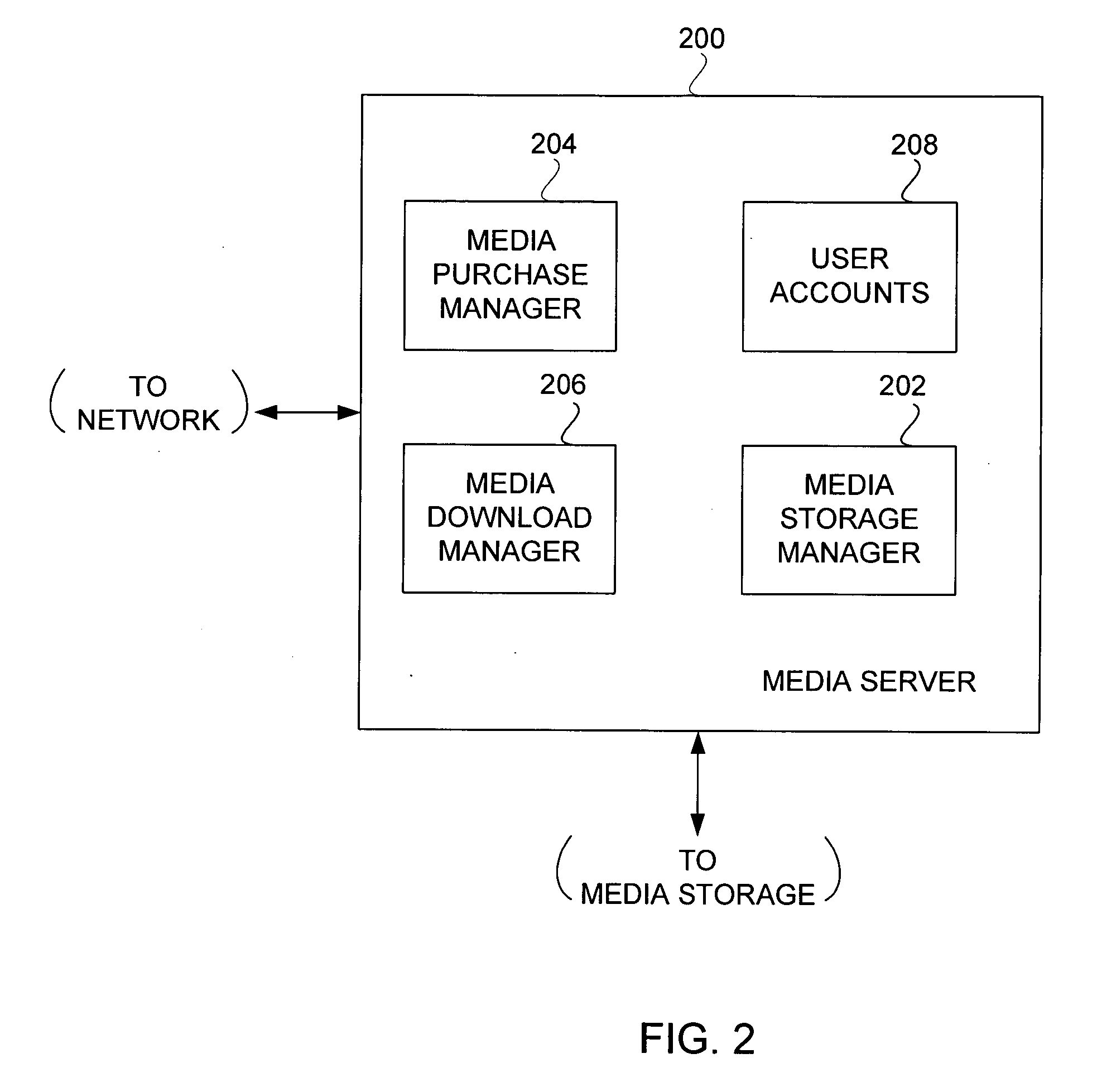
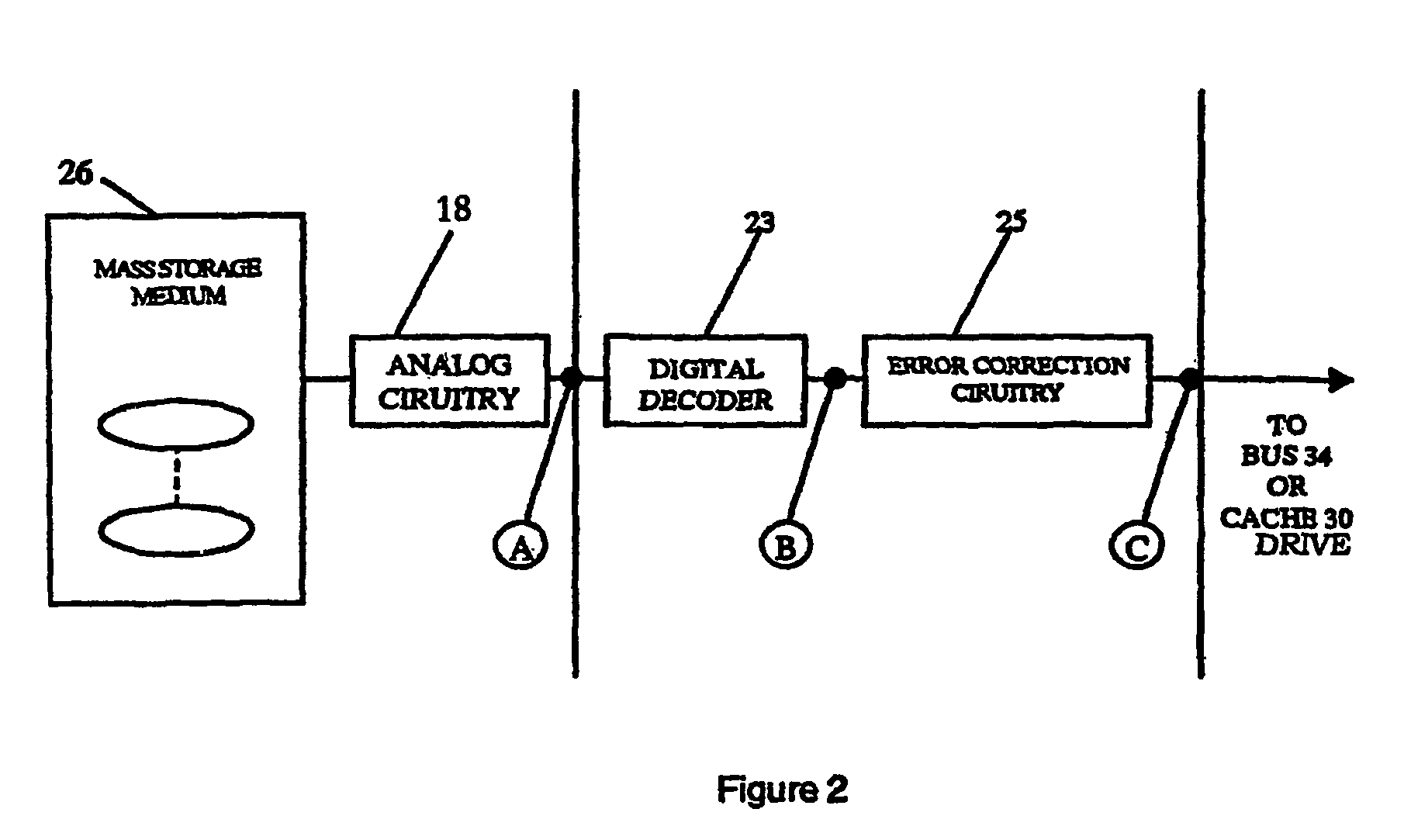
Partial encryption techniques for media data
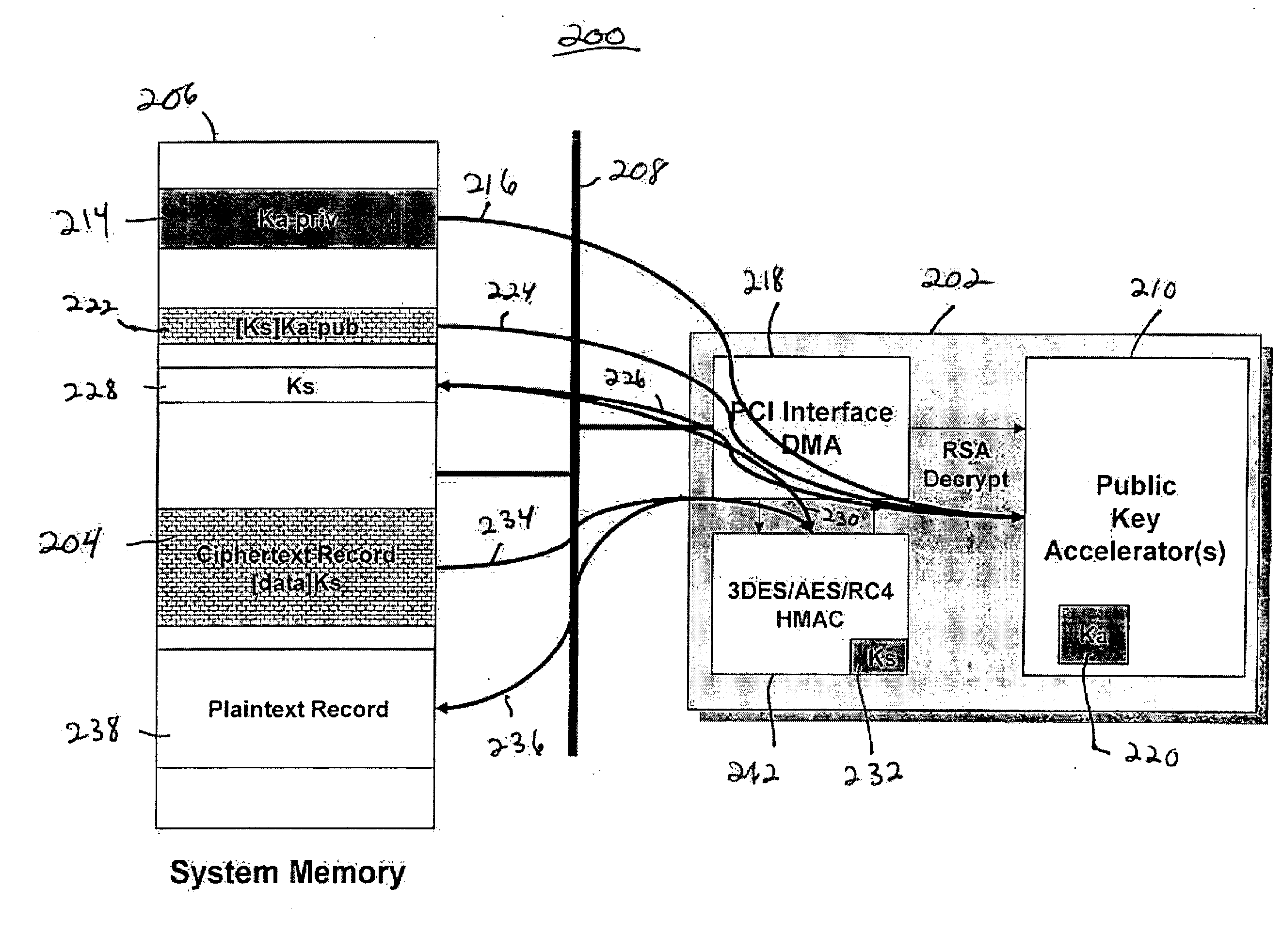
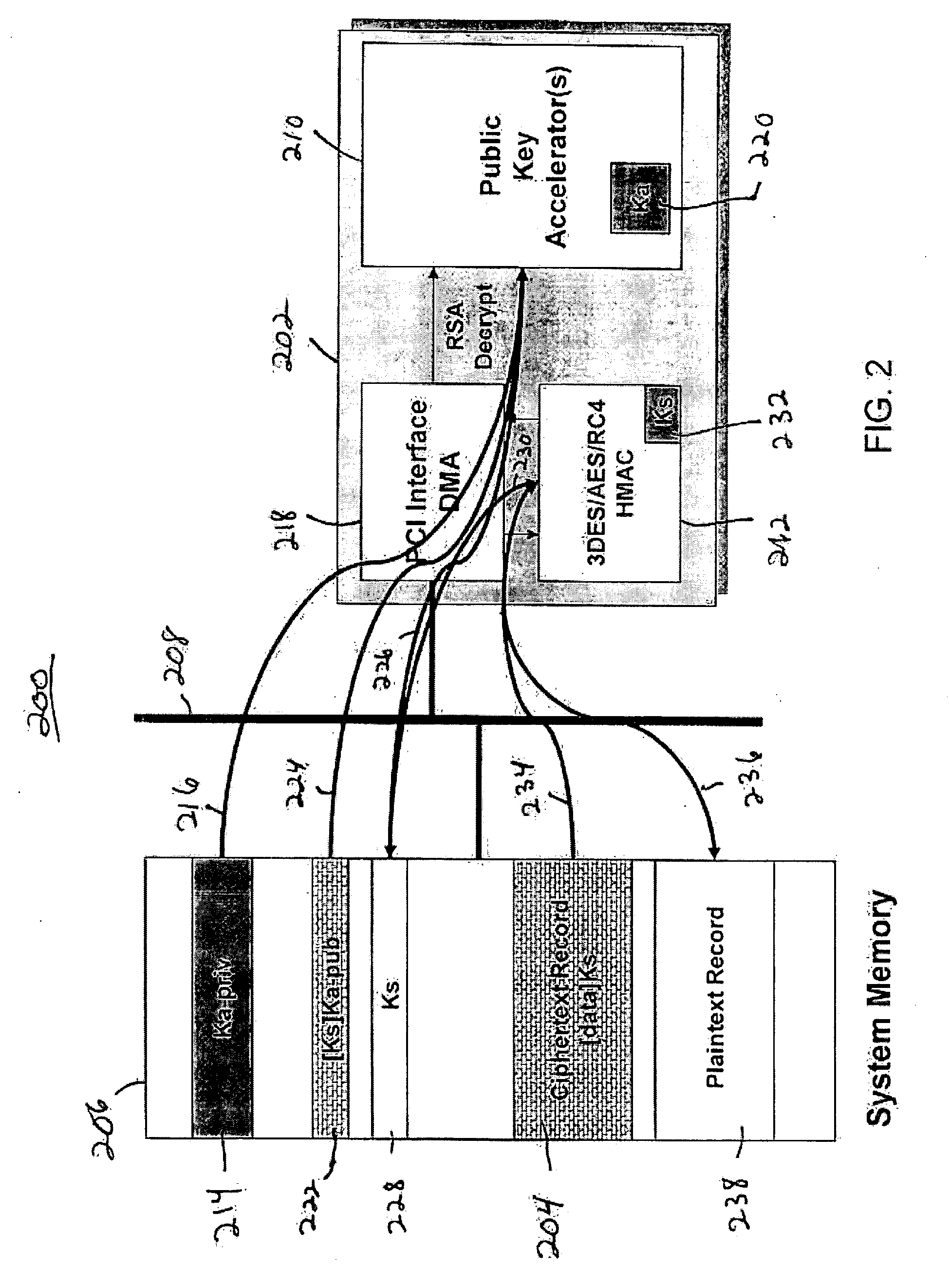
InactiveUS20070083467A1Fast decryptionEfficient executionData processing applicationsRecord information storageComputer hardwareClient-side
Improved techniques to partially encrypt media files are disclosed. The encryption serves to cryptographically secure only a portion of the media data within a media file, while the remaining portion of the media data is not cryptographically secured. Although only partial encryption is used, the portion being encrypted serves to substantially disrupt usefulness of other parts of the media file which are not encrypted. In other words, the partial encryption renders the media file substantially unusable by unauthorized users. In one embodiment, the partial encryption is performed by a host device and thereafter the partially encrypted media file is delivered to a client device. The client device, if authorized, can subsequently decrypt the partially encrypted media file and utilize (e.g., play) the media file. However, since the media files are only partially encrypted, the decryption is likewise also only partial, which makes decryption faster and less resource intensive.
Owner:APPLE INC
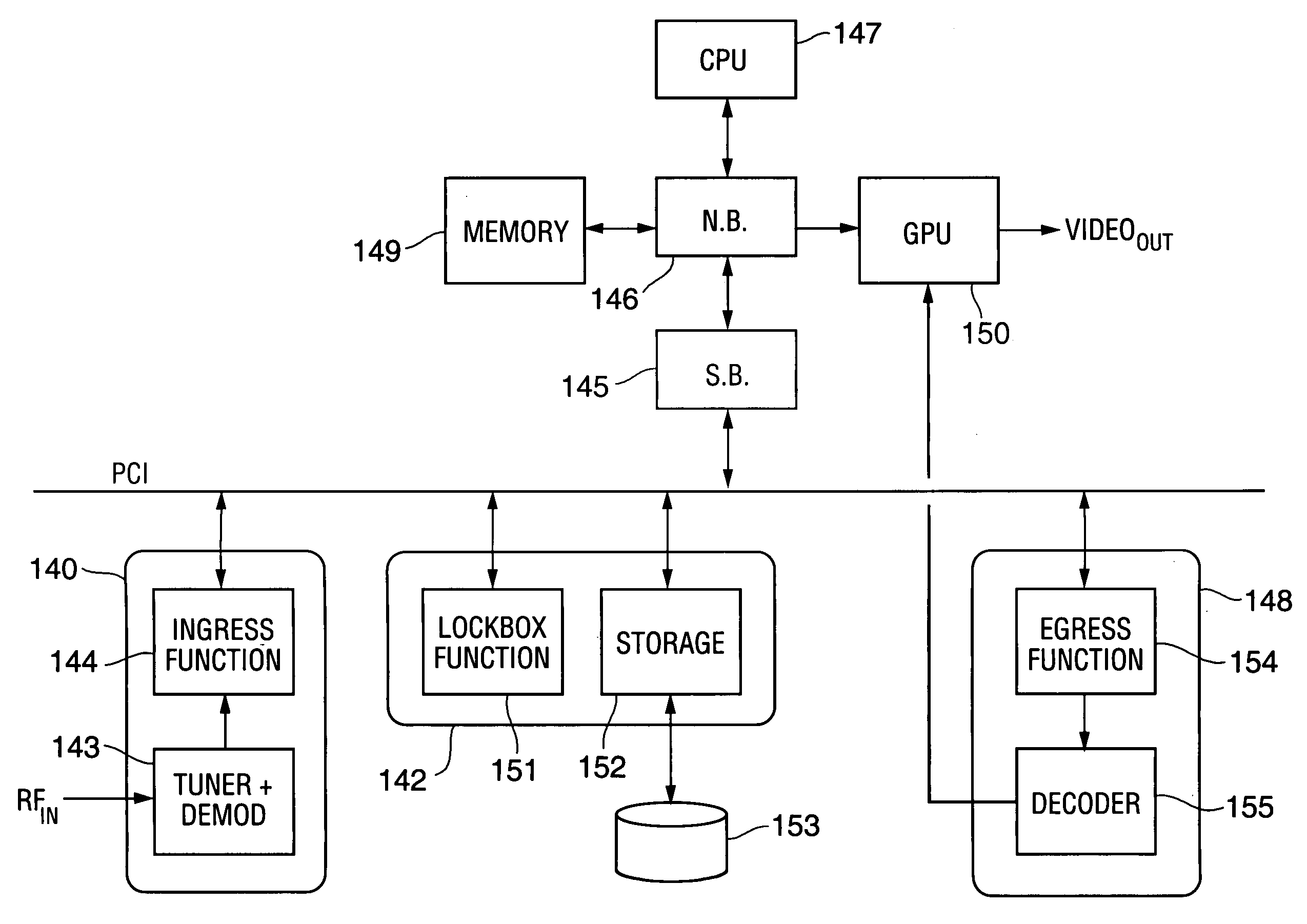
Method and apparatus for content protection in a personal digital network environment
InactiveUS20050144468A1Easy to disassembleReliable lockingTelevision system detailsUser identity/authority verificationGraphicsVideo processing
In some embodiments, the invention is a personal digital network (“PDN”) including hardware (sometimes referred to as Ingress circuitry) configured to transcrypt encrypted content that enters the PDN. Typically, the transcryption (decryption followed by re-encryption) is performed in hardware within the Ingress circuitry and the re-encryption occurs before the decrypted content is accessible by hardware or software external to the Ingress circuitry. Typically, transcrypted content that leaves the Ingress circuitry remains in re-encrypted form within the PDN whenever it is transferred between integrated circuits or is otherwise easily accessible by software, until it is decrypted within hardware (sometimes referred to as Egress circuitry) for display or playback or output from the PDN. Typically, the PDN is implemented so that no secret in Ingress or Egress circuitry (for use or transfer by the Ingress or Egress circuitry) is accessible in unencrypted form to software or firmware within the PDN or to any entity external to the PDN. Other aspects of the invention are methods for protecting content in a PDN (e.g., an open computing system) and devices (e.g., multimedia graphics cards, set top boxes, or video processors) for use in a PDN.
Owner:OPTIMUM CONTENT PROTECTION
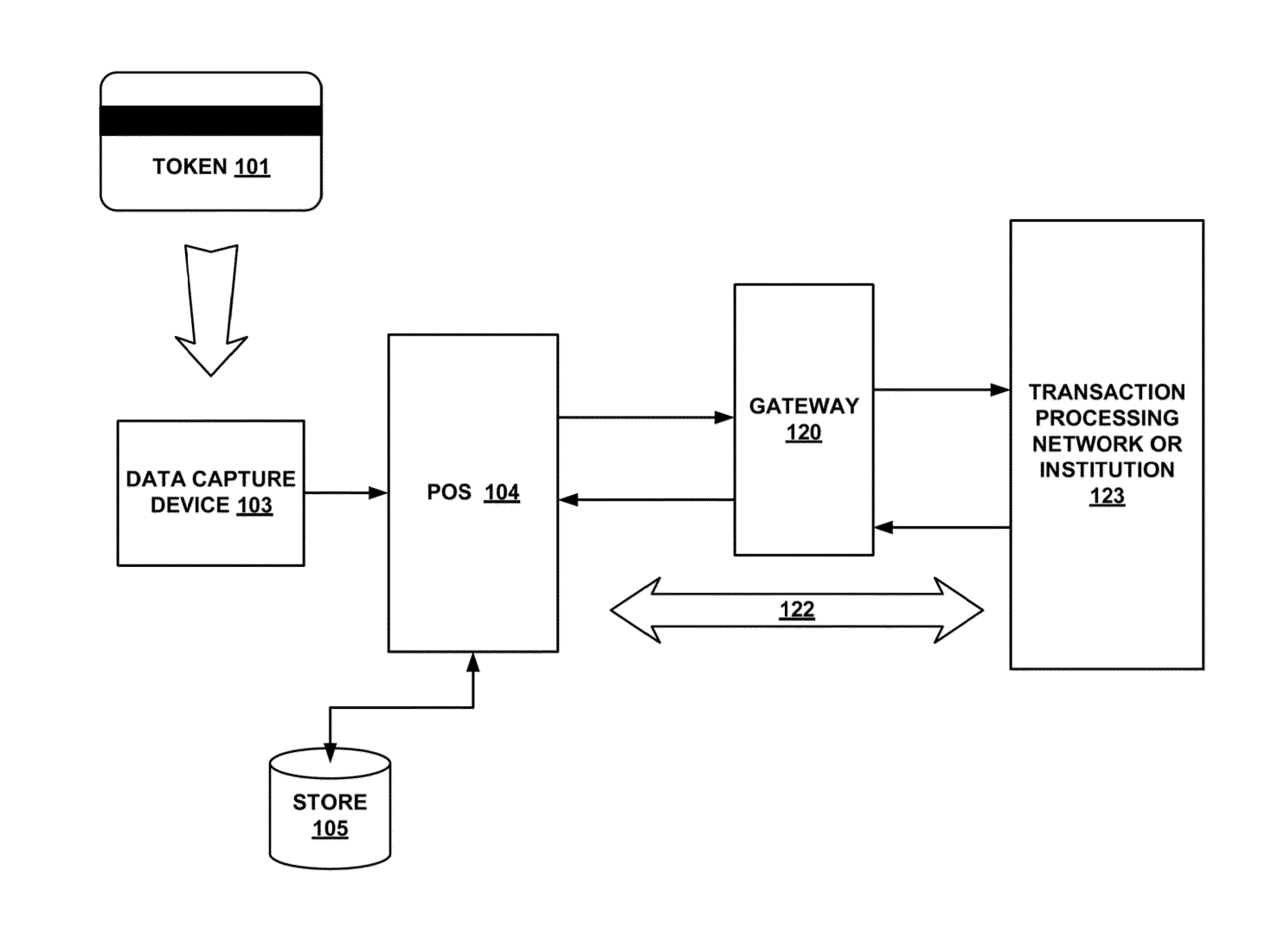
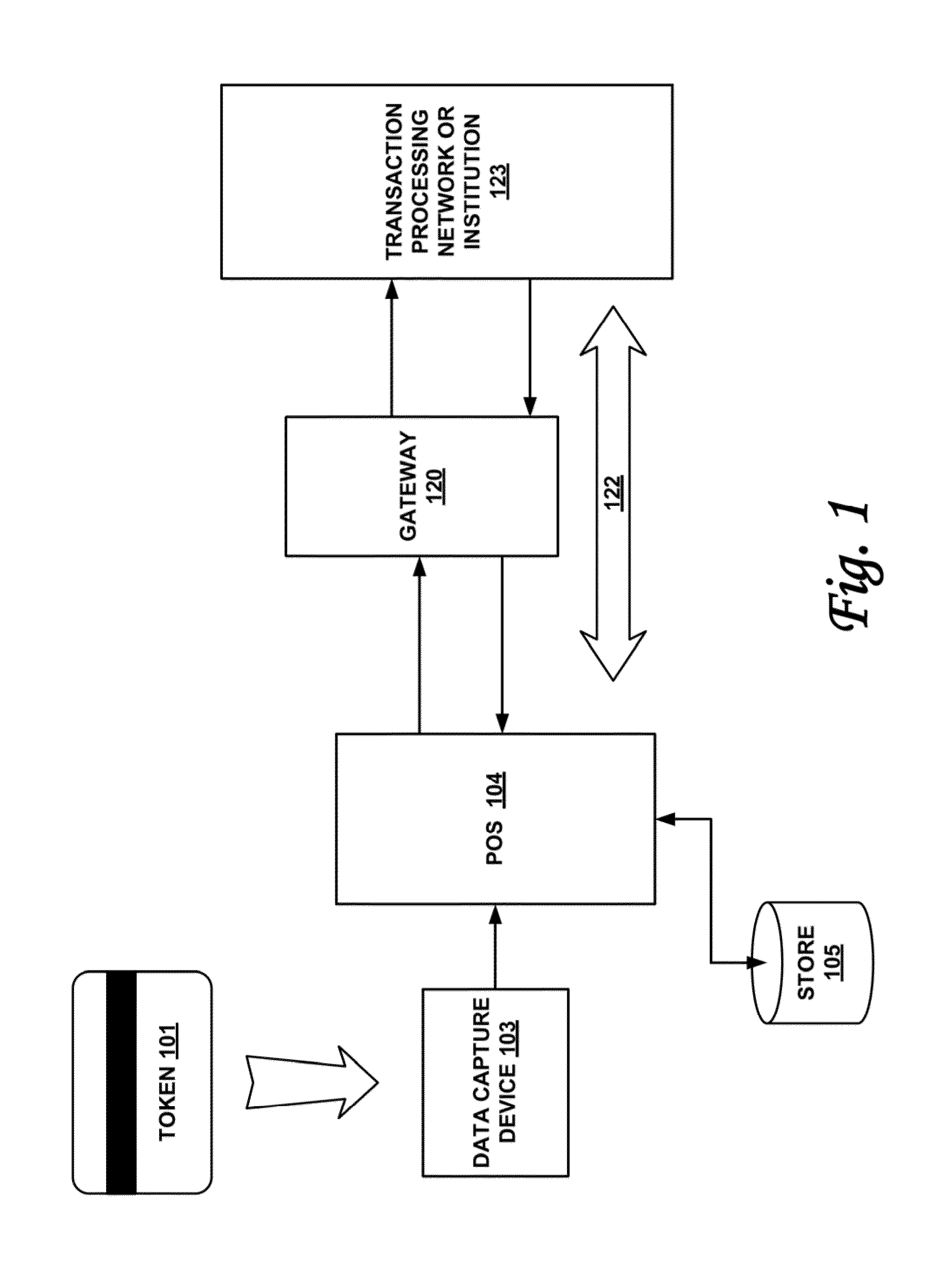
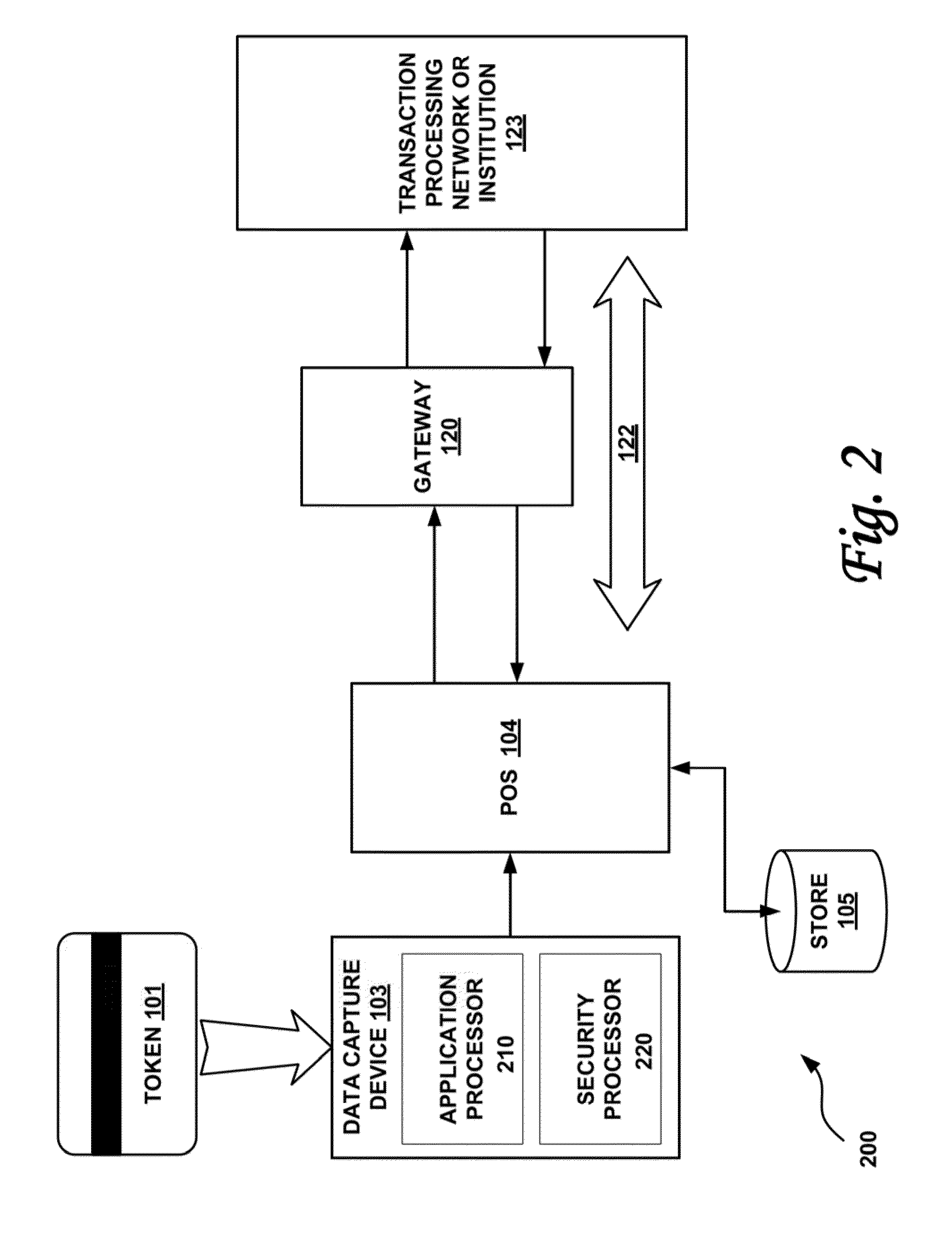
Secured transaction system and method
InactiveUS20130254117A1Reduce riskEasy to optimizePayment protocolsInternet privacyEncryption decryption
Systems and methods for performing financial transactions are provided. In one embodiment, the invention provides for method for bank card transactions, including: reading the token information at the point of swipe for traditional and non-traditional POS platforms; performing a low-security task on the token information using a first microprocessor, wherein the non-security task includes one or more tasks from the group of encryption determination, encryption-decryption request, key management, token information delivery, or transactional data delivery; and performing a security-related task on the token information using a second microprocessor based on a request from the first microprocessor, wherein the security-related task includes one or more tasks from the group of token information authentication, token information decryption, or token information encryption. Formatting the encrypted information such that it is compatible with the format of the current POS system.
Owner:VON MUELLER CLAY W +1
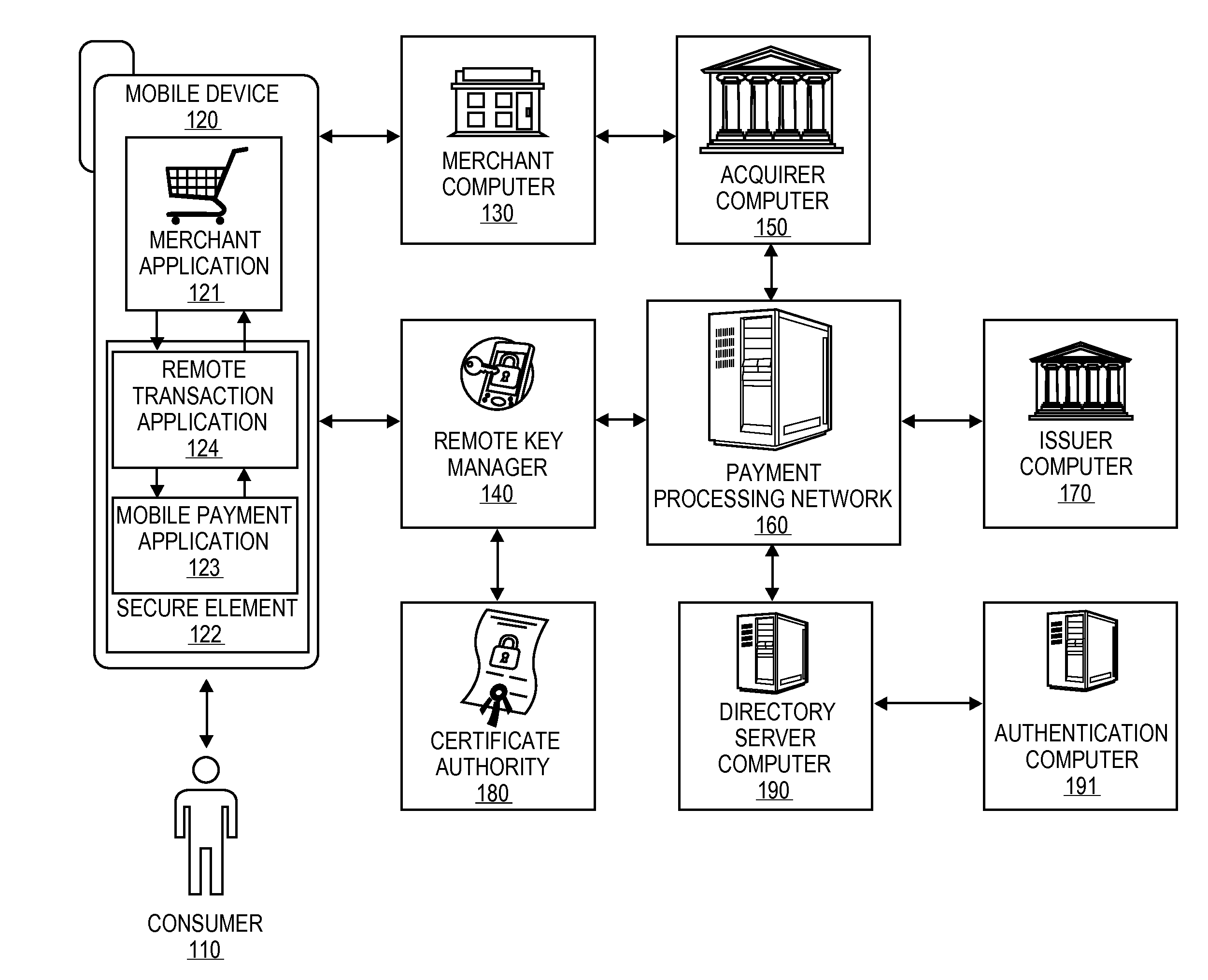
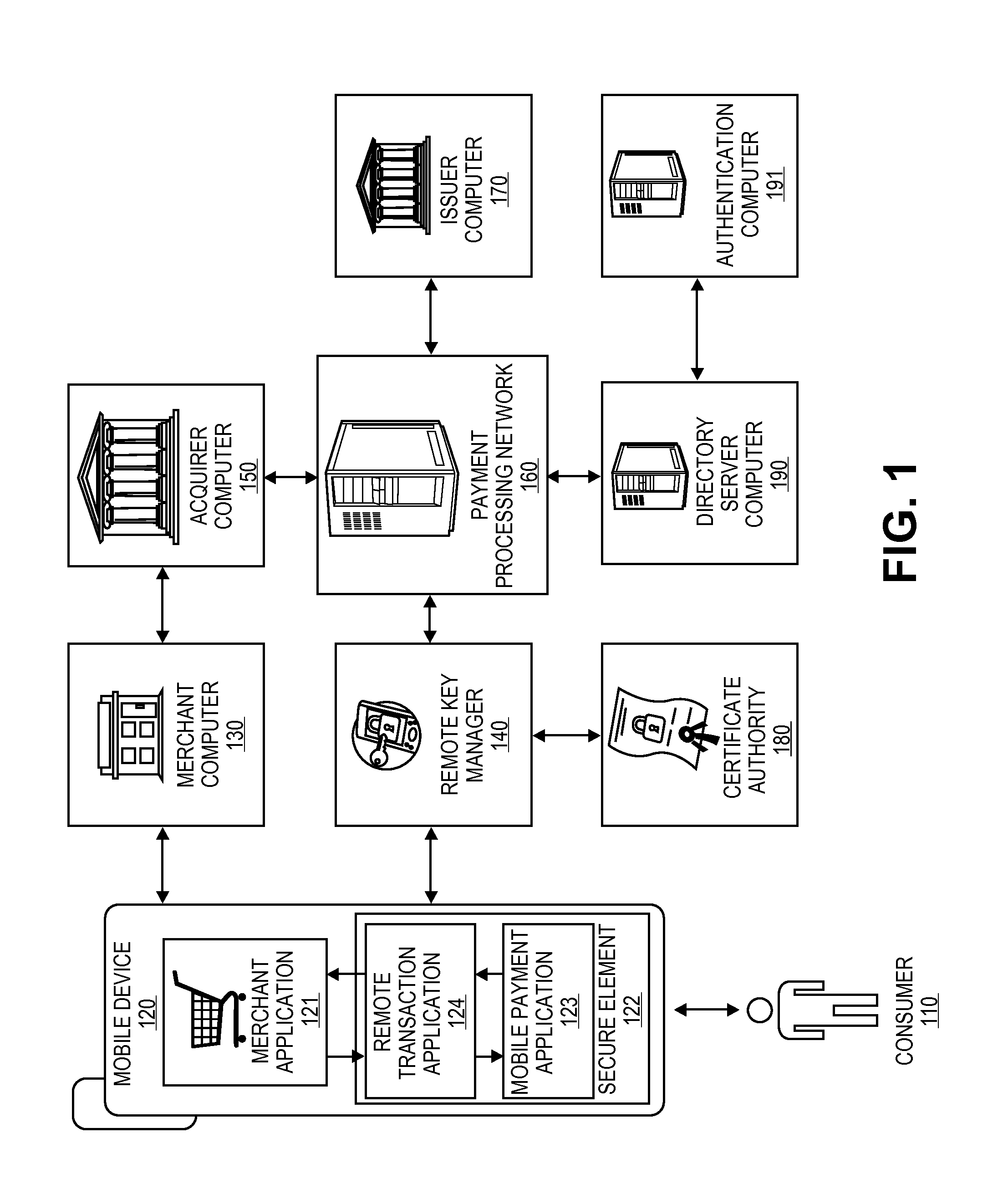
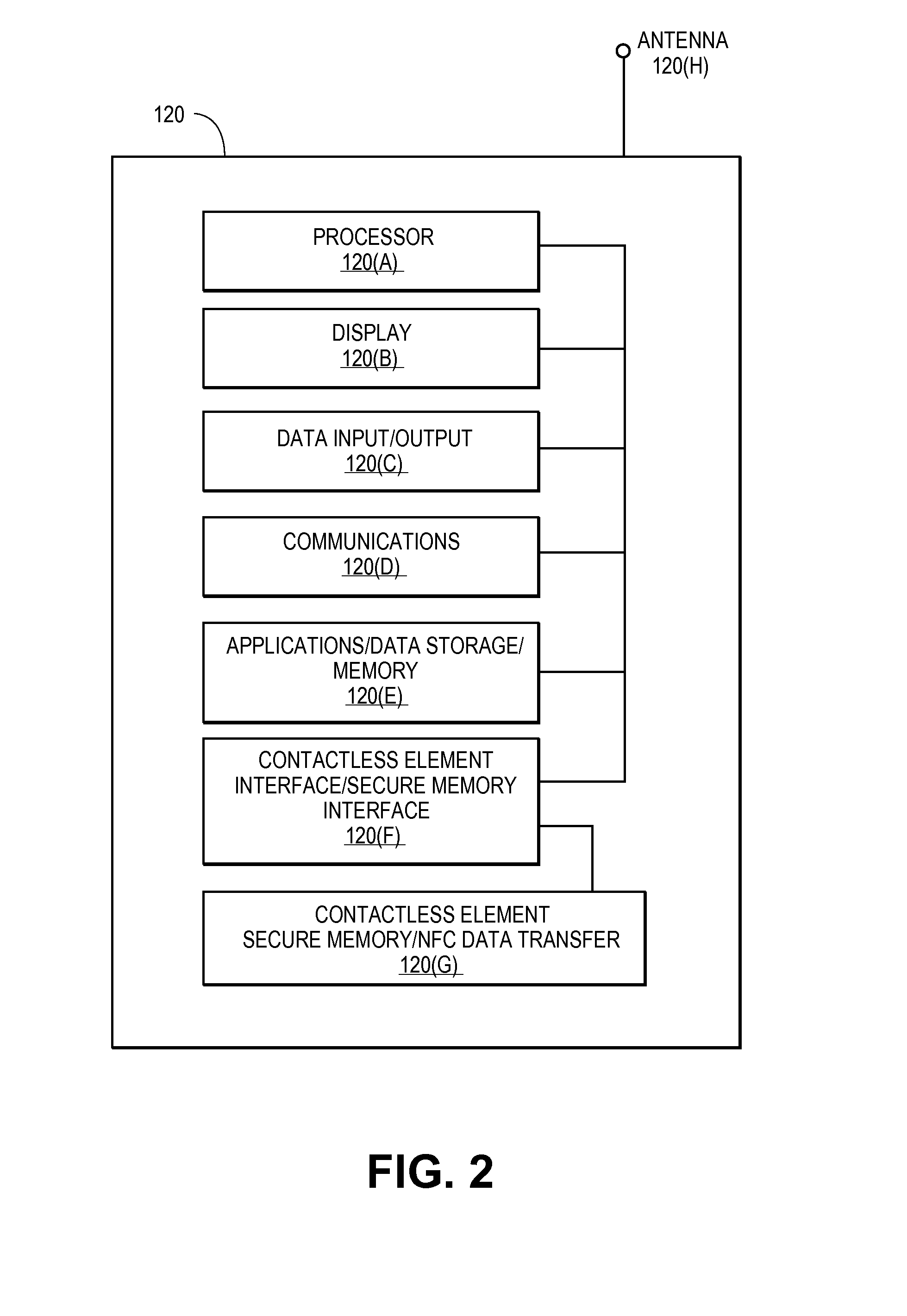
Secure Remote Payment Transaction Processing Including Consumer Authentication
ActiveUS20150088756A1Improve security levelProtocol authorisationPayment transactionEncryption decryption
Embodiments of the invention are directed to methods, apparatuses, computer-readable media, and systems for securely processing remote transactions. One embodiment is directed to a method of processing a remote transaction initiated by a communication device. The method comprising a server computer receiving a payment request including encrypted payment information that is encrypted using a first key. The encrypted payment information including security information. The method further comprises decrypting the encrypted payment information using a second key, obtaining an authentication response value for the remote transaction from an authentication computer associated with an issuer, updating the decrypted payment information to include the authentication response value, re-encrypting the decrypted payment information using a third key, and sending a payment response including the re-encrypted payment information to a transaction processor. The transaction processor decrypting the re-encrypted payment information using a fourth key and initiating a payment transaction using the decrypted payment information.
Owner:VISA INT SERVICE ASSOC
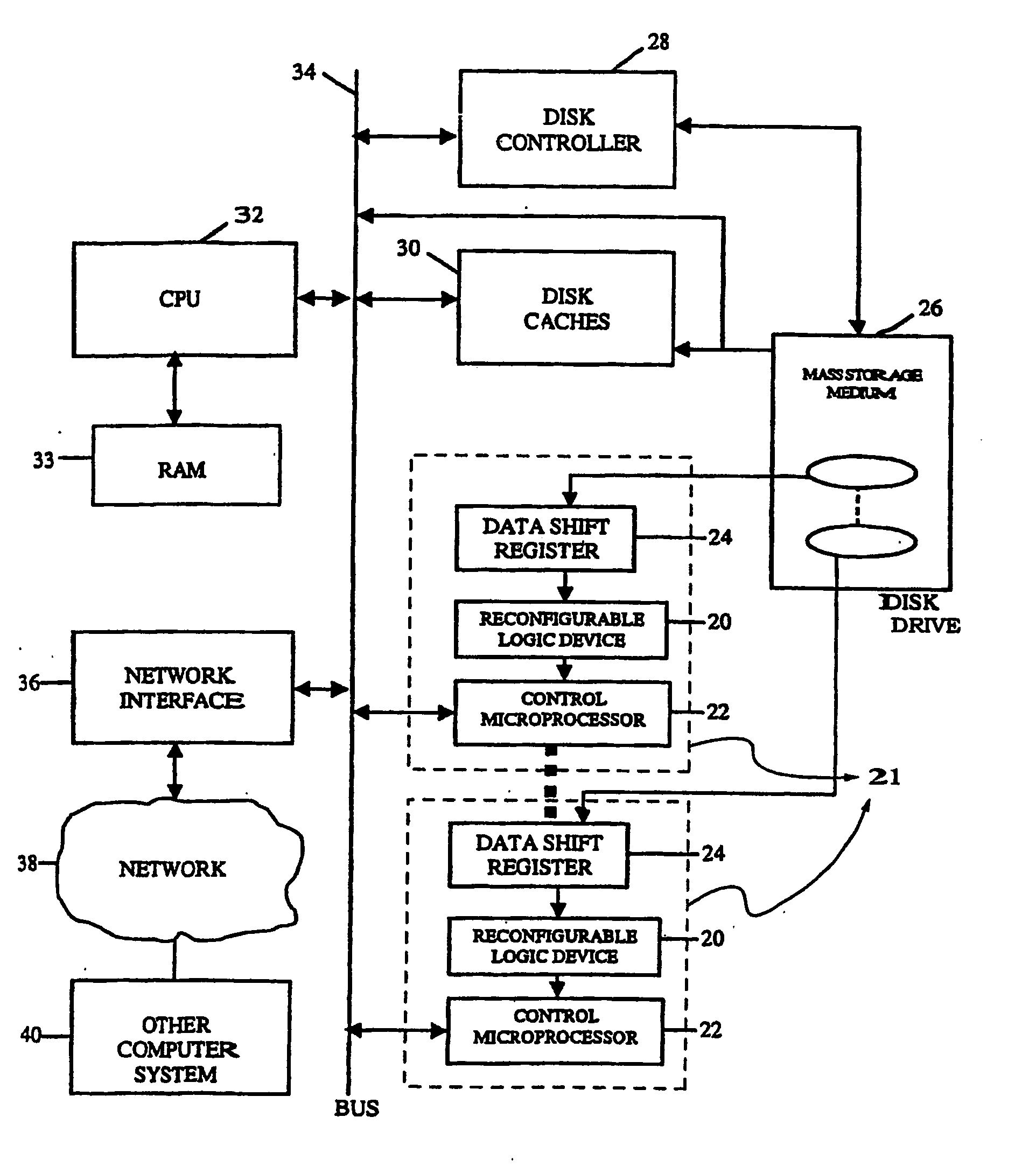
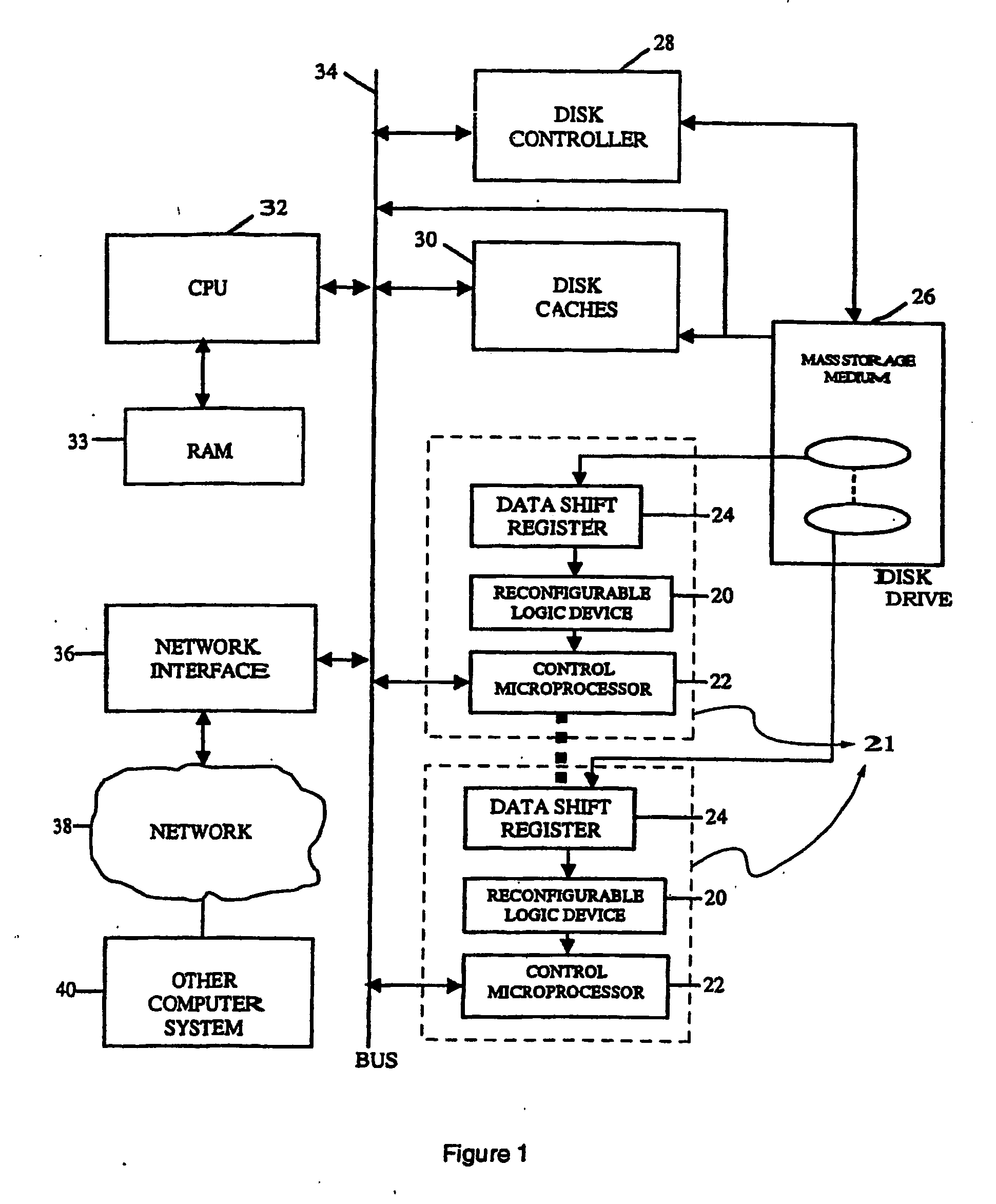
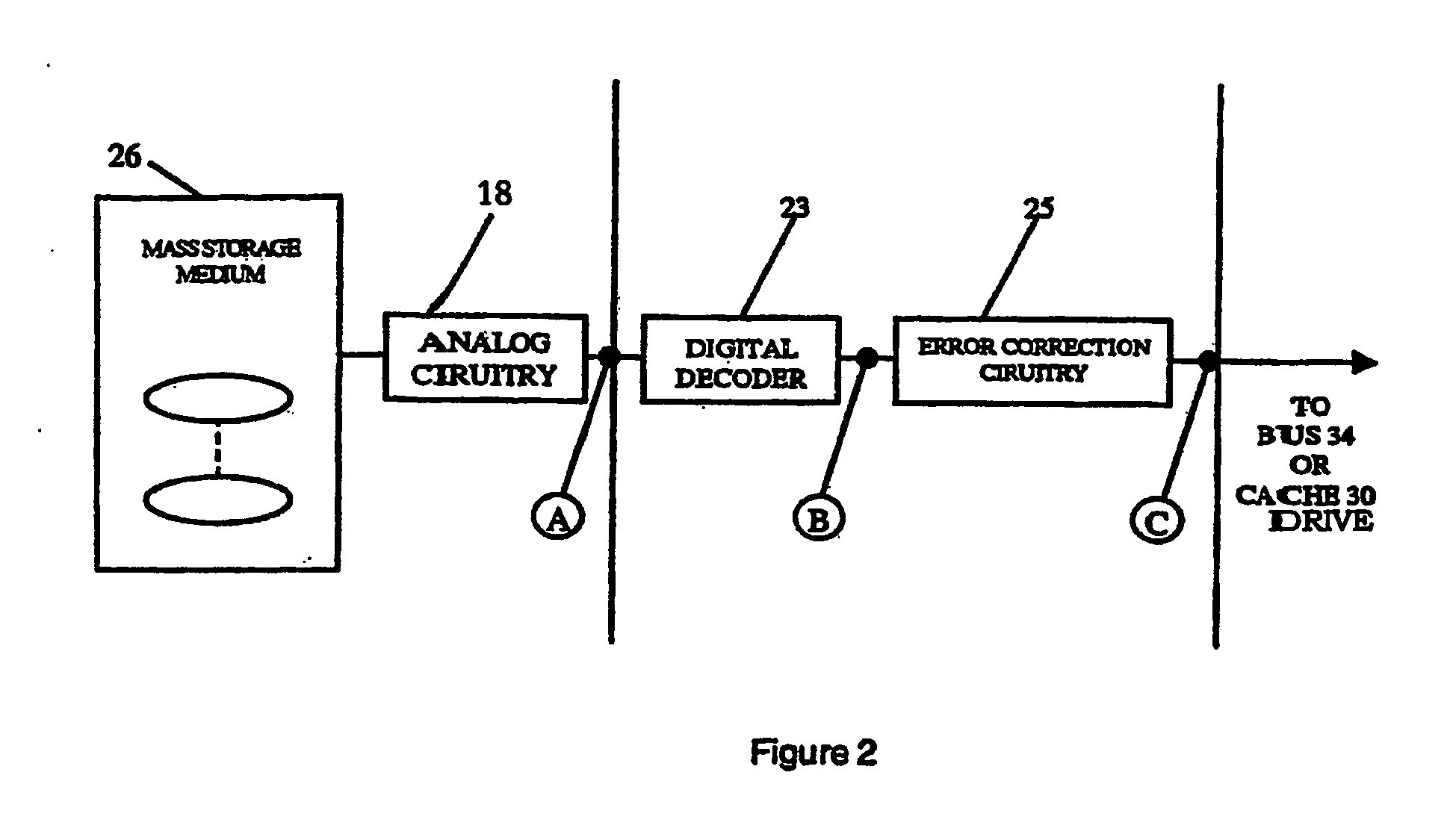
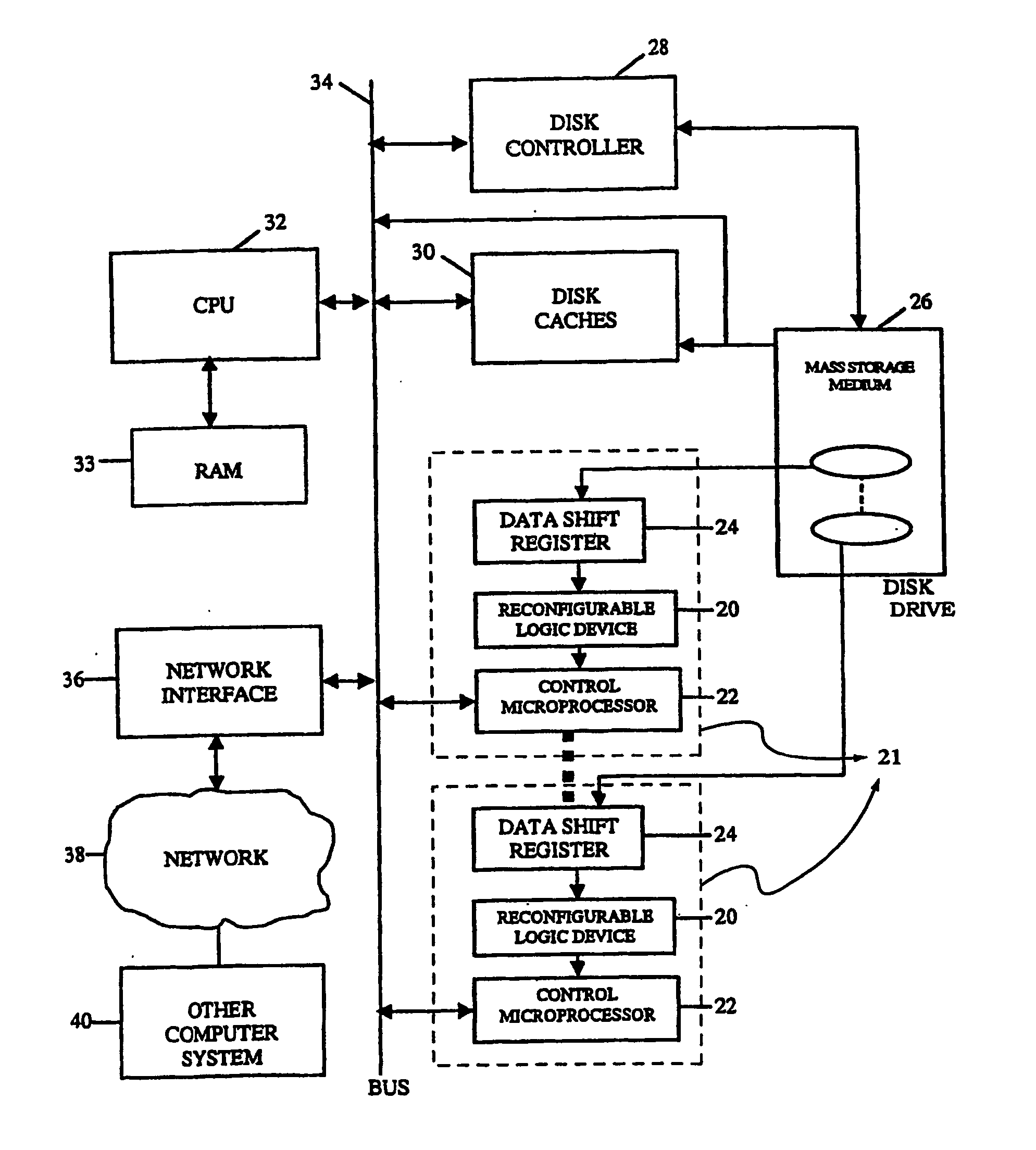
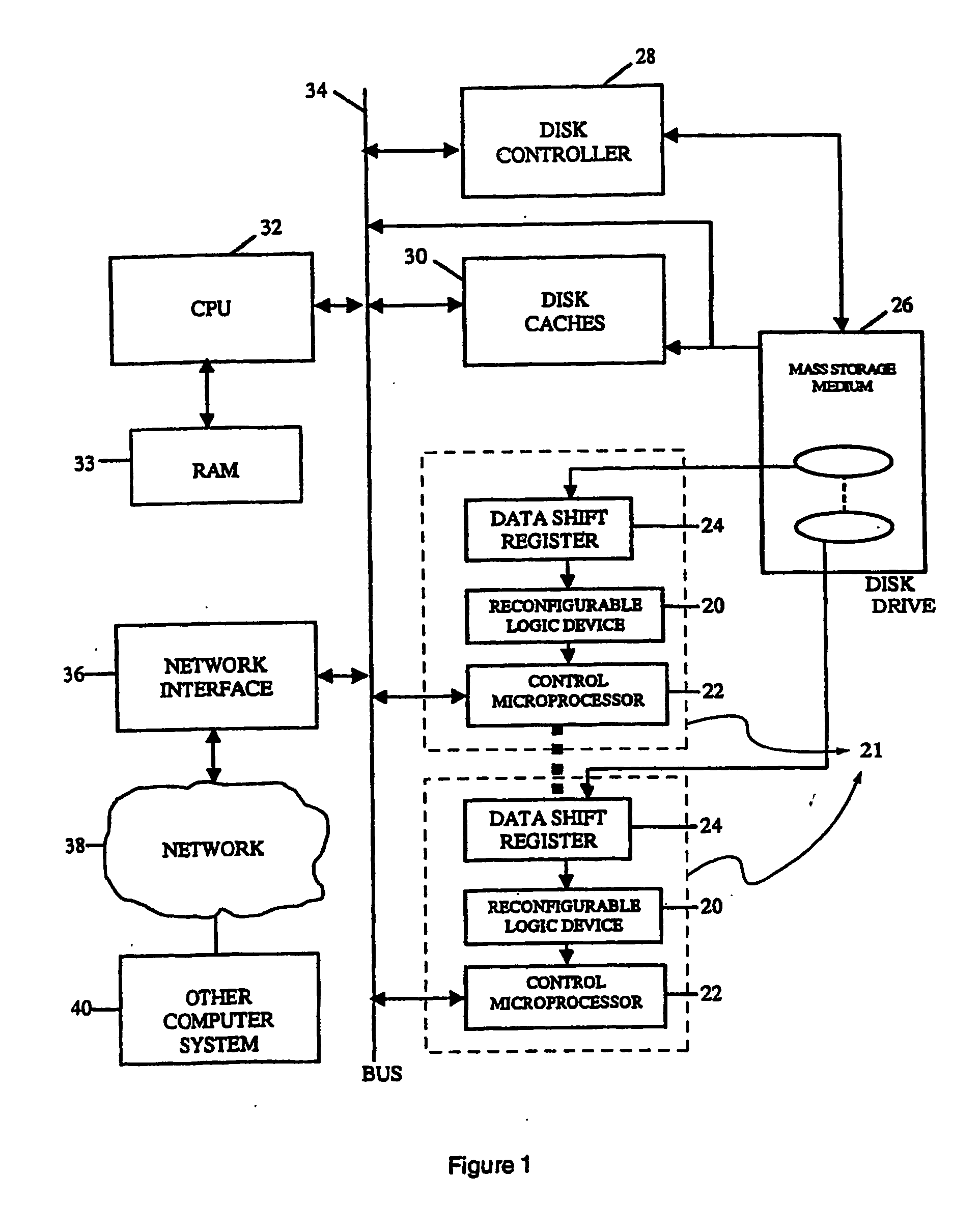
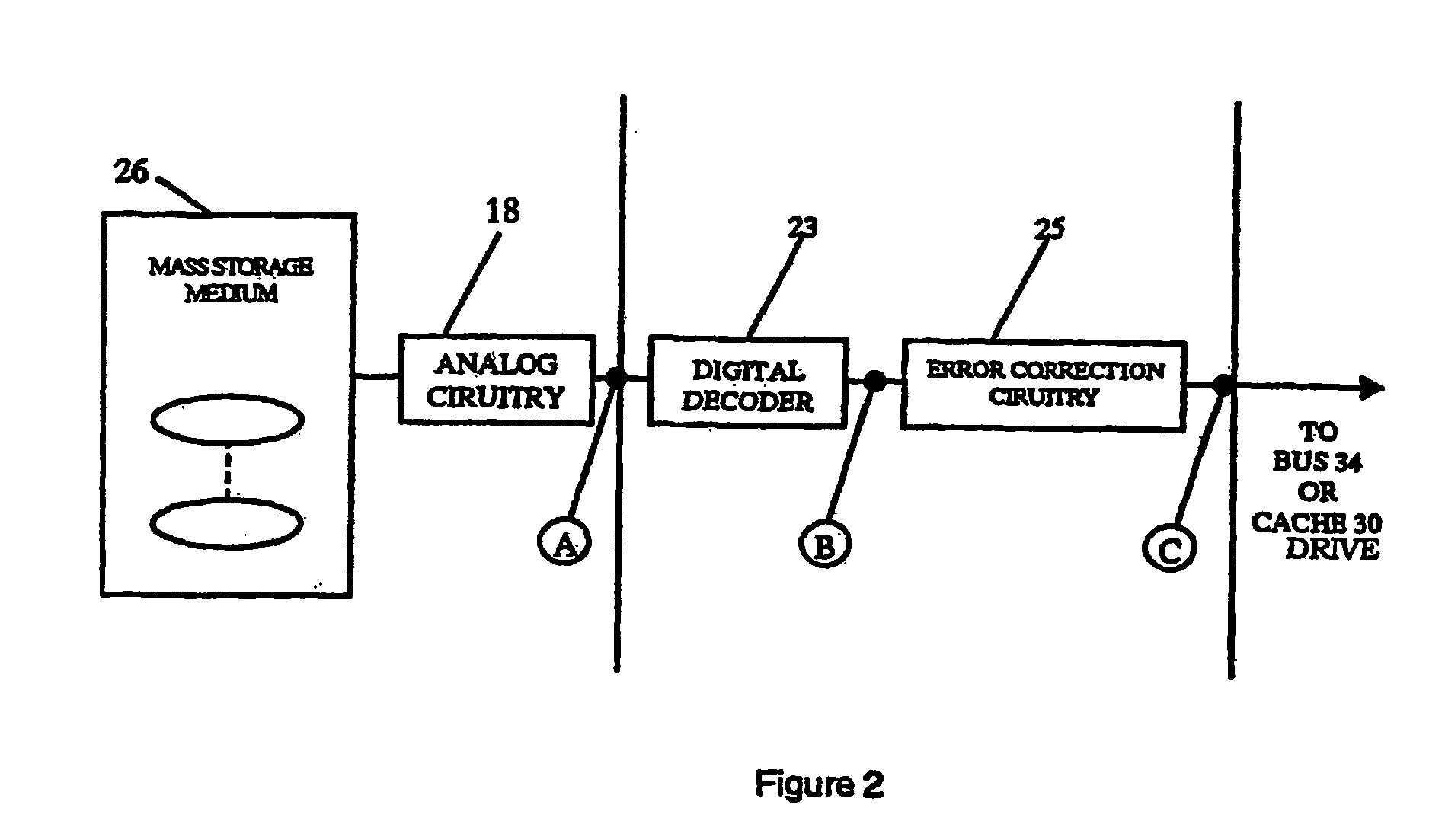
Intelligent data storage and processing using fpga devices
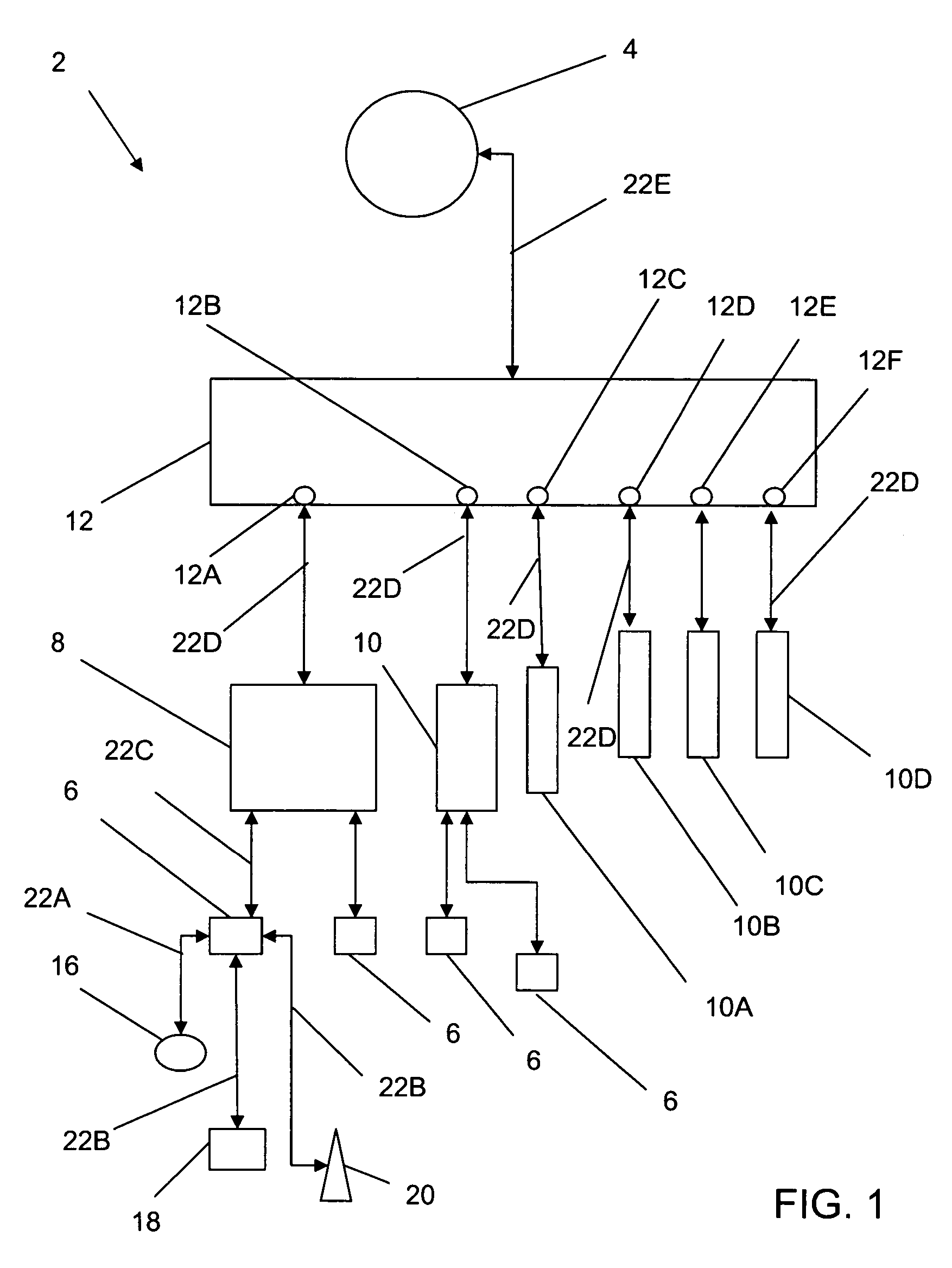
InactiveUS20070277036A1Improve data securityIncrease speedInput/output to record carriersDigital data information retrievalMagnetic storageComputerized system
A data storage and retrieval device and method is disclosed. The device includes at least one magnetic storage medium configured to store target data and at least one re-configurable logic device comprising an FPGA coupled to the at least one magnetic storage medium and configured to read a continuous stream of target data therefrom, having been configured with a template or as otherwise desired to fit the type of search and data being searched. The re-configurable logic device is configured to receive at least one search inquiry in the form of a data key and to determine a match between the data key and the target data as it is being read from the at least one magnetic storage medium. This device and method can perform a variety of searches on the target data including without limitation exact and approximate match searches, sequence match searches, image match searches and data reduction searches. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN. In addition to performing search and data reduction operations, this device may also be used to perform a variety of other processing operations including encryption, decryption, compression, decompression, and combinations thereof.
Owner:IP RESERVOIR
Method and system for the information protection of digital content
ActiveUS20050086501A1Add supportImprove securityDigital data processing detailsUser identity/authority verificationData packDigital content
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
Method and apparatus for securing documents using a position dependent file system
ActiveUS8312064B1Provide securityEasy to manageUnauthorized memory use protectionHardware monitoringInternet privacyFile system
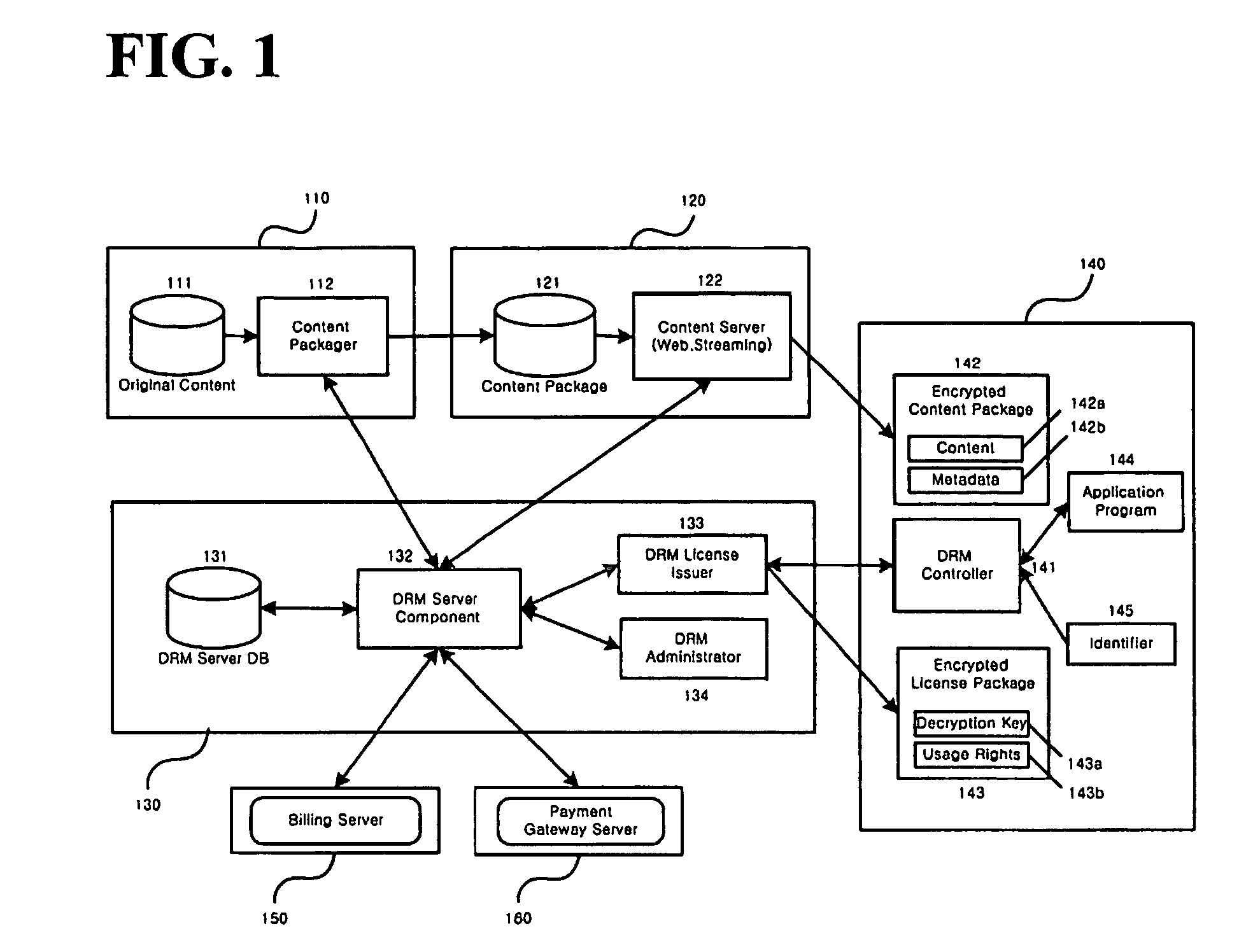
Access to information or a document is secured by a central global positioning authority that evaluates access requests in accordance with predefined policies. One component of an access request includes location information regarding at least one of the requesting entity and location of the requested resource. Access is either allowed or denied as a function of at least the requesting entity, position information and the applicable policy or policies. An encryption / decryption scheme is implemented where the encryption key is a function of the resource's position.
Owner:GEN DIGITAL INC
System and method for controlling and enforcing access rights to encrypted media
InactiveUS20010029581A1Digital data processing detailsUser identity/authority verificationComputer hardwareNetwork connection
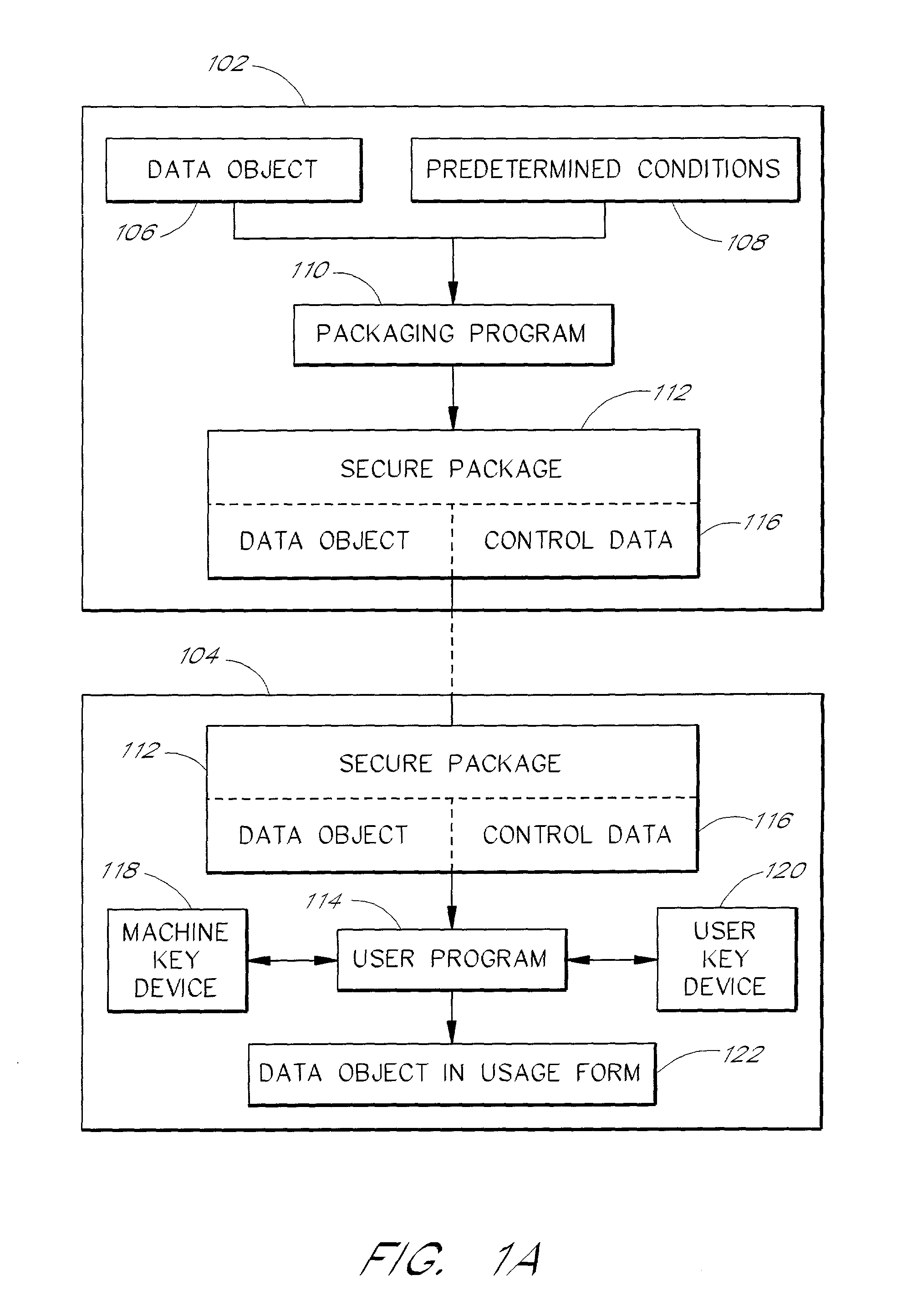
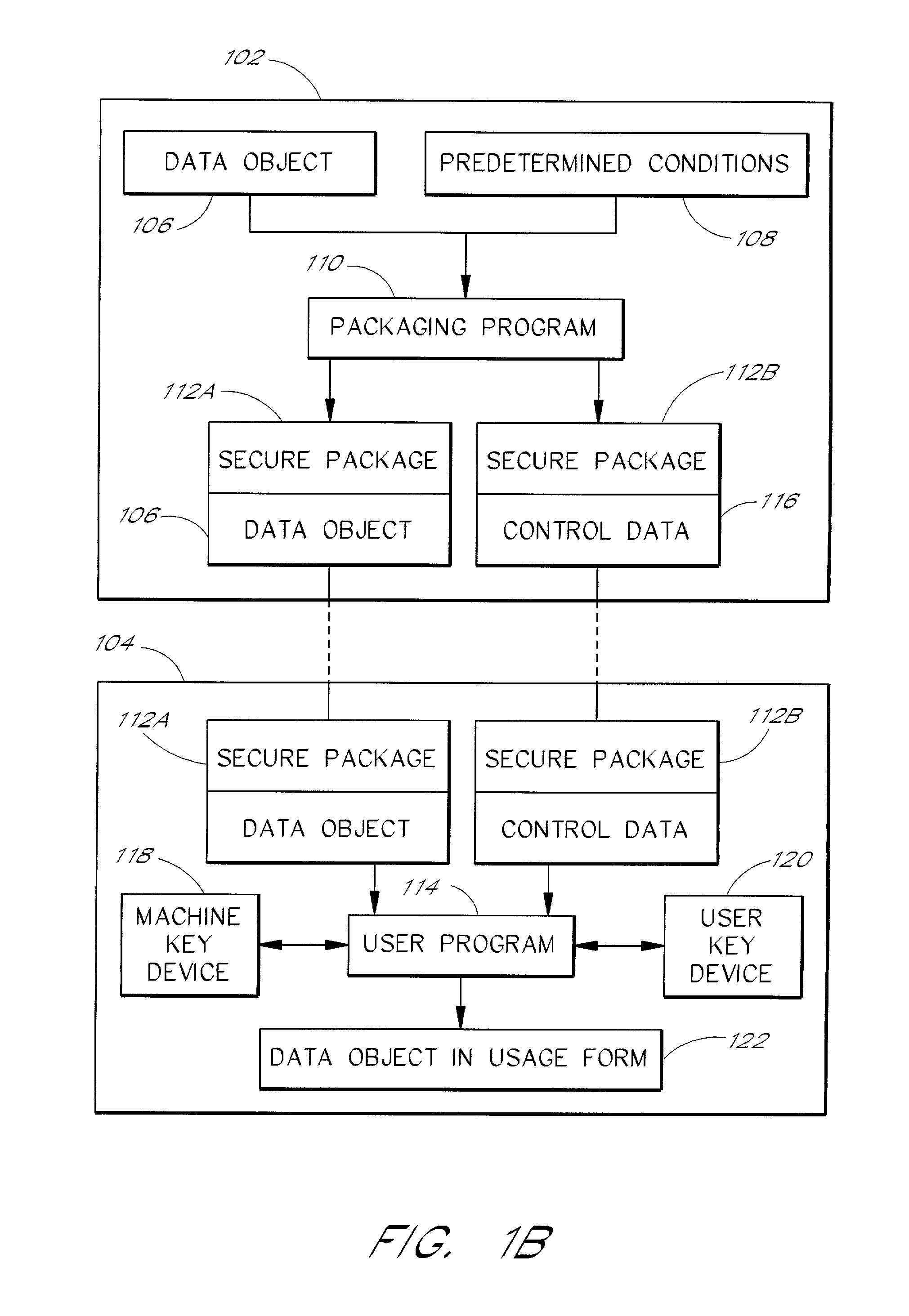
A system for providing rights controlled access to digital media comprises a server data processor and a client data processor connected by a communications network. The user data processor provides access to a data object in accordance with rules associated with the data object by the server data processor. The client data processor comprises a machine key device and a user key device. The machine key device is preferably an installed component of the client data processor that provides encryption, decryption, and authentication functionality for the client data processor. The user key device is preferably a removable, portable device that connects to the client data processor and provides encryption, decryption, and authentication functionality for the user. A method restricts the use of a data object to a particular user and a particular data processor through the use of additional layers of encryption. The method preferably comprises encrypting a data object such that the it can be decrypted by the machine key device, and further encrypting the data object such that it can be decrypted by the user key device. A method restricts the use of a data object to a particular user and a particular data processor through the use of rules that require authentication of the machine key device and the user key device.
Owner:MARKING OBJECT VIRTUALIZATION INTELLIGENCE LLC
Method and System for High Throughput Blockwise Independent Encryption/Decryption
ActiveUS20070237327A1Computational complexity increaseReduce throughputMultiple keys/algorithms usageSecret communicationData segmentLogical block addressing
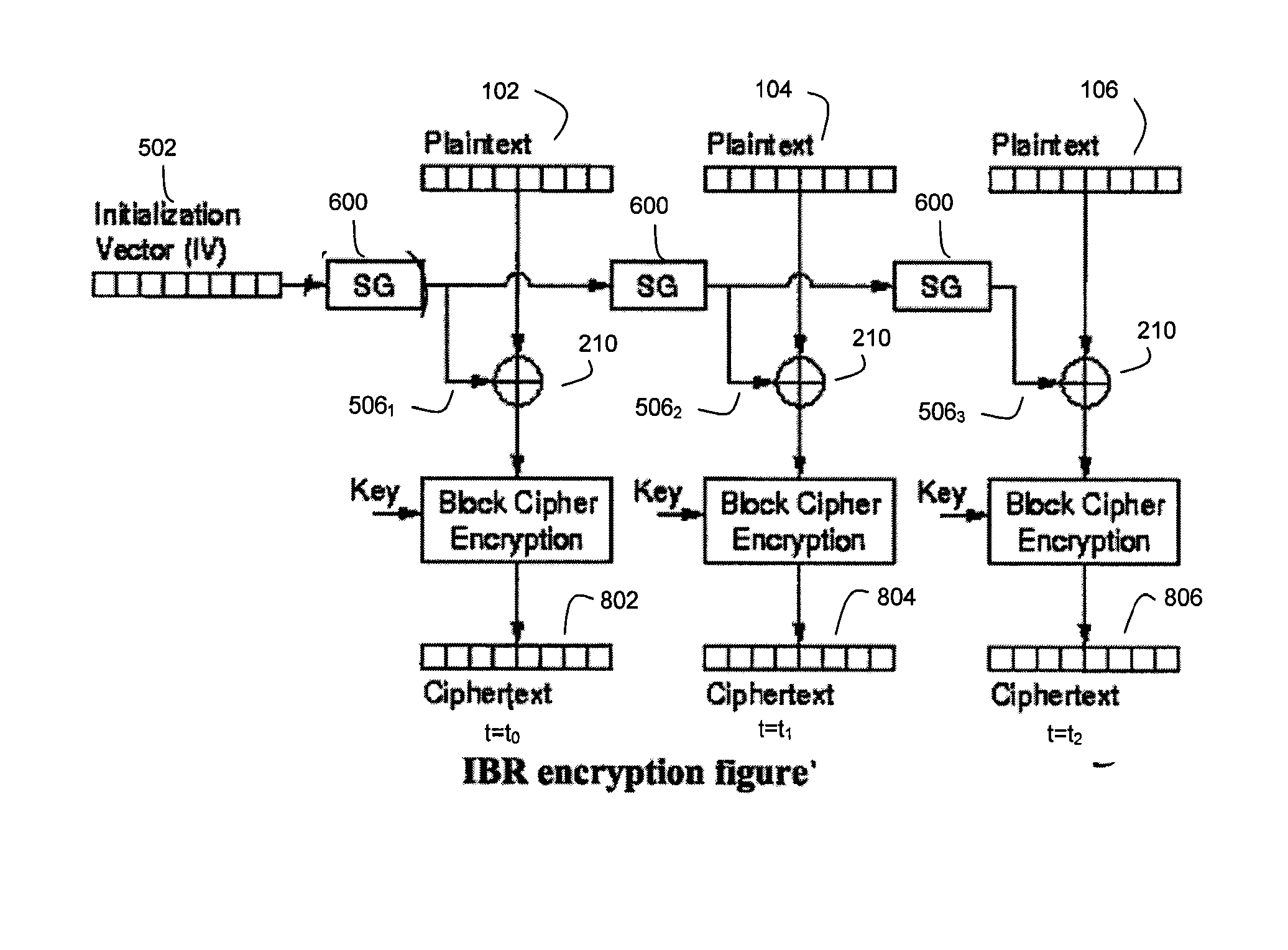
An encryption technique is disclosed for encrypting a data segment comprising a plurality of data blocks, wherein the security and throughput of the encryption is enhanced by using blockwise independent bit vectors for reversible combination with the data blocks prior to key encryption. Preferably, the blockwise independent bit vectors are derived from a data tag associated with the data segment. Several embodiments are disclosed for generating these blockwise independent bit vectors. In a preferred embodiment, the data tag comprises a logical block address (LBA) for the data segment. Also disclosed herein is a corresponding decryption technique as well as a corresponding symmetrical encryption / decryption technique.
Owner:IP RESERVOIR
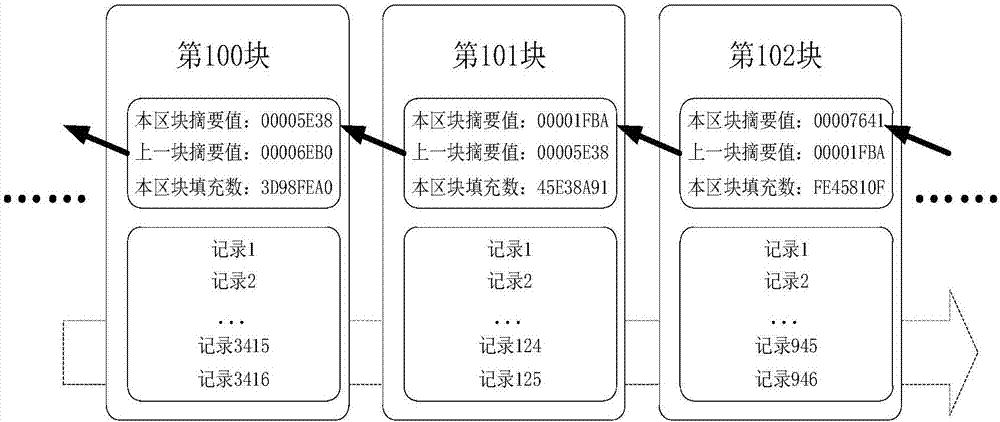
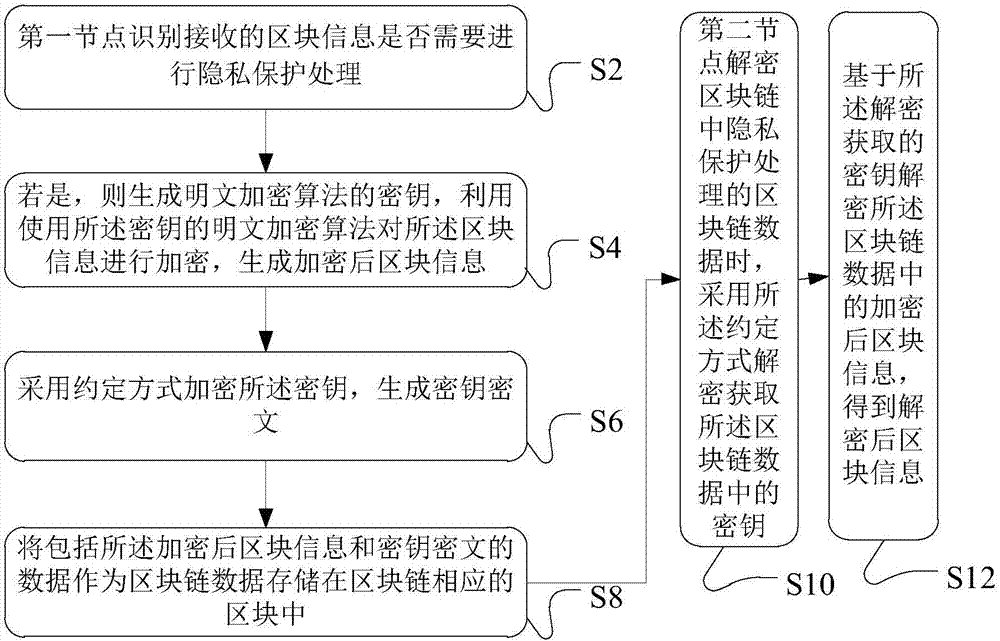
Blockchain data processing method, device and system
InactiveCN107294709ATo achieve the purpose of privacy protectionPrivacy protection is safe and reliableKey distribution for secure communicationCiphertextPrivacy protection
The invention discloses a blockchain data processing method, device and system. The blockchain data processing method comprises that a first node identifies whether received block information needs privacy protection processing; if the received block information needs privacy protection processing, a secret key of a plaintext encryption algorithm is generated, the block information is encrypted by means of the plaintext encryption algorithm employing the secret key, and encrypted block information is generated; the secret key is encrypted in a stipulated way, a secret key ciphertext is generated, the stipulated way comprises an algorithm through which a second node associated with the first node in the first node and the blockchain encrypts and decrypts the secret key ciphertext according to a preset mode; and data including the encrypted block information and the secret key ciphertext is stored a corresponding block of the blockchain as blockchain data. According to each embodiment of the invention, information data stored in the blockchain can be encrypted, so that only specific members can decrypt and check the information data, and the aim of carrying out privacy protection on special transaction information is achieved.
Owner:ADVANCED NEW TECH CO LTD
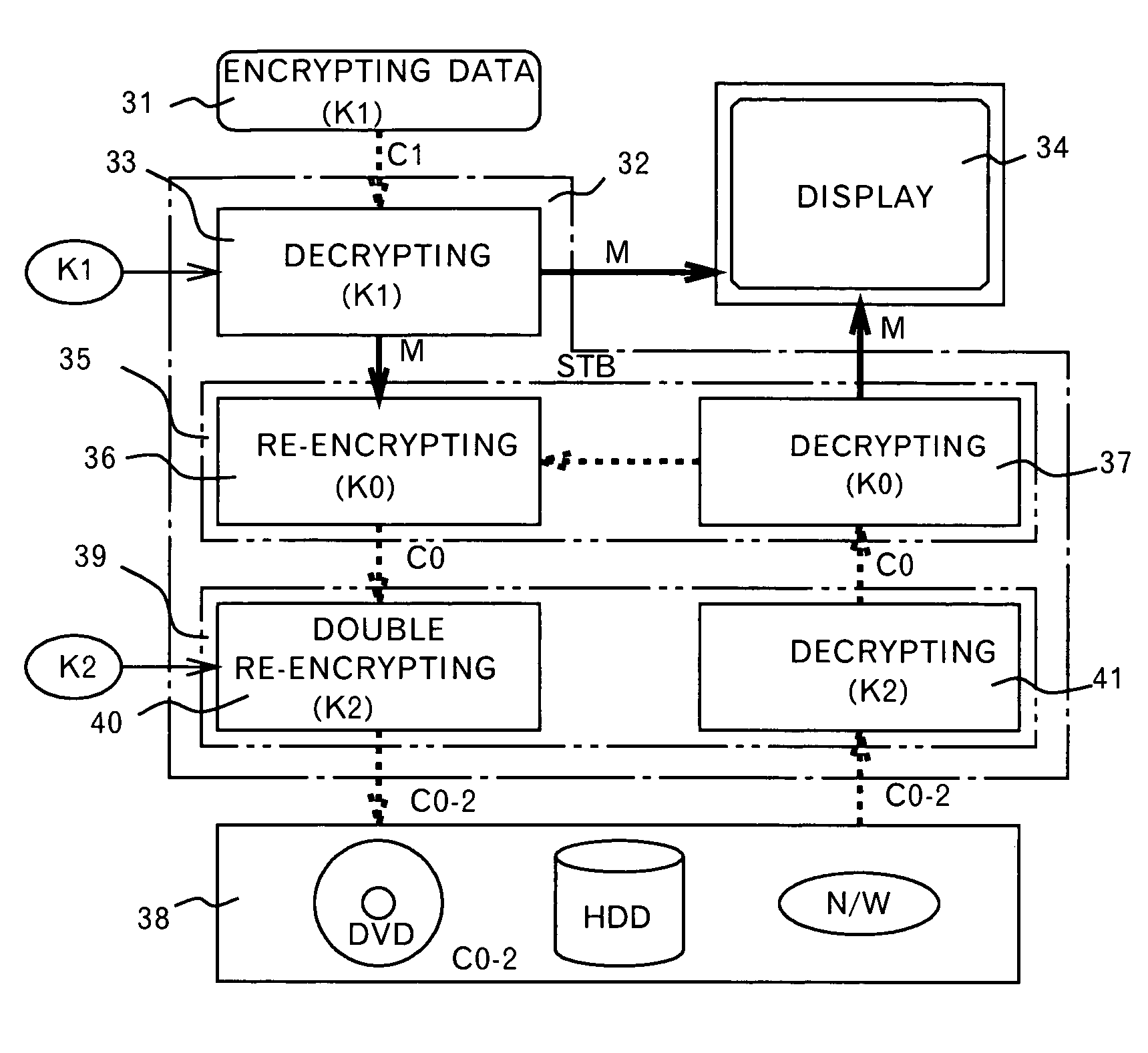
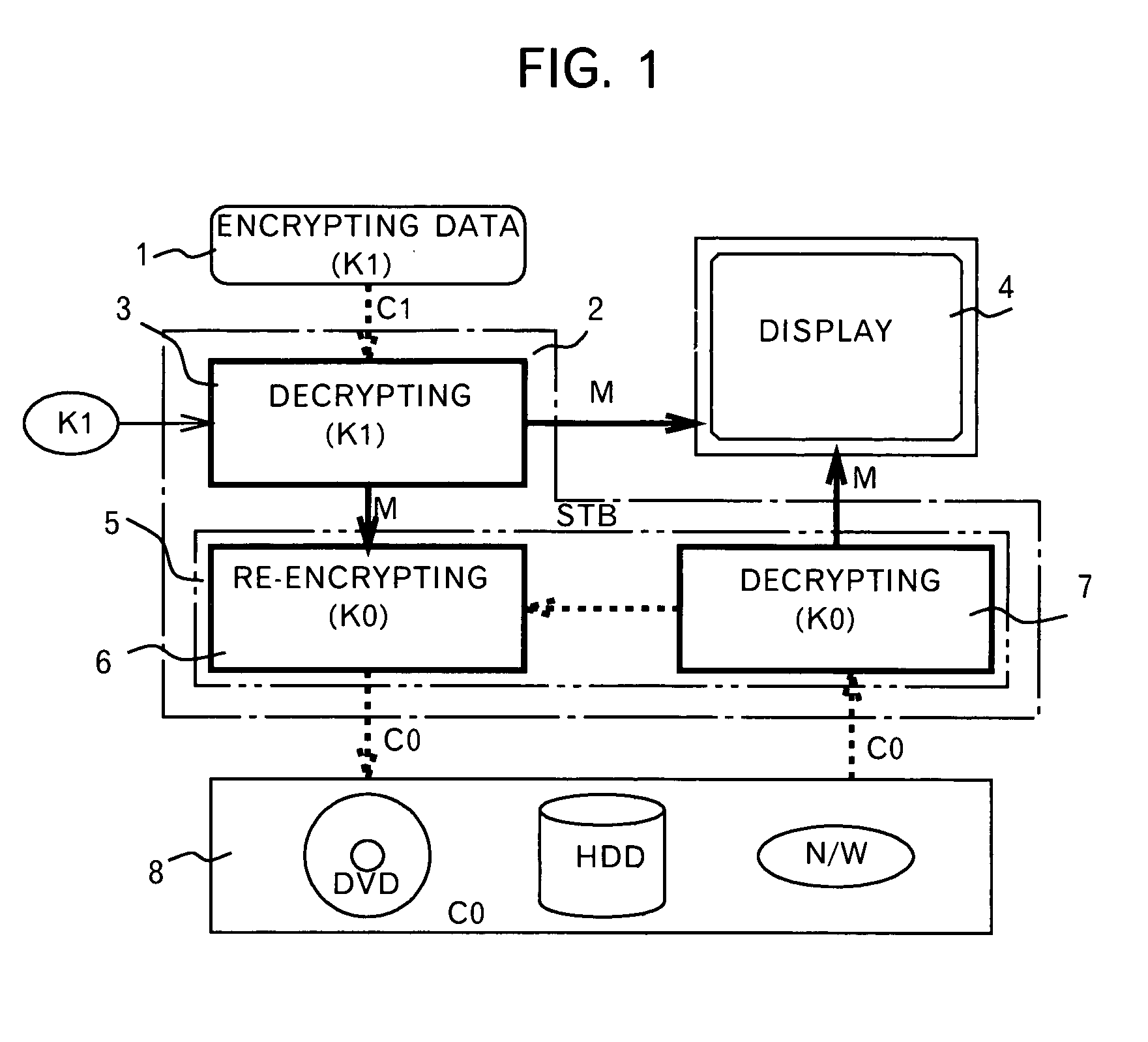
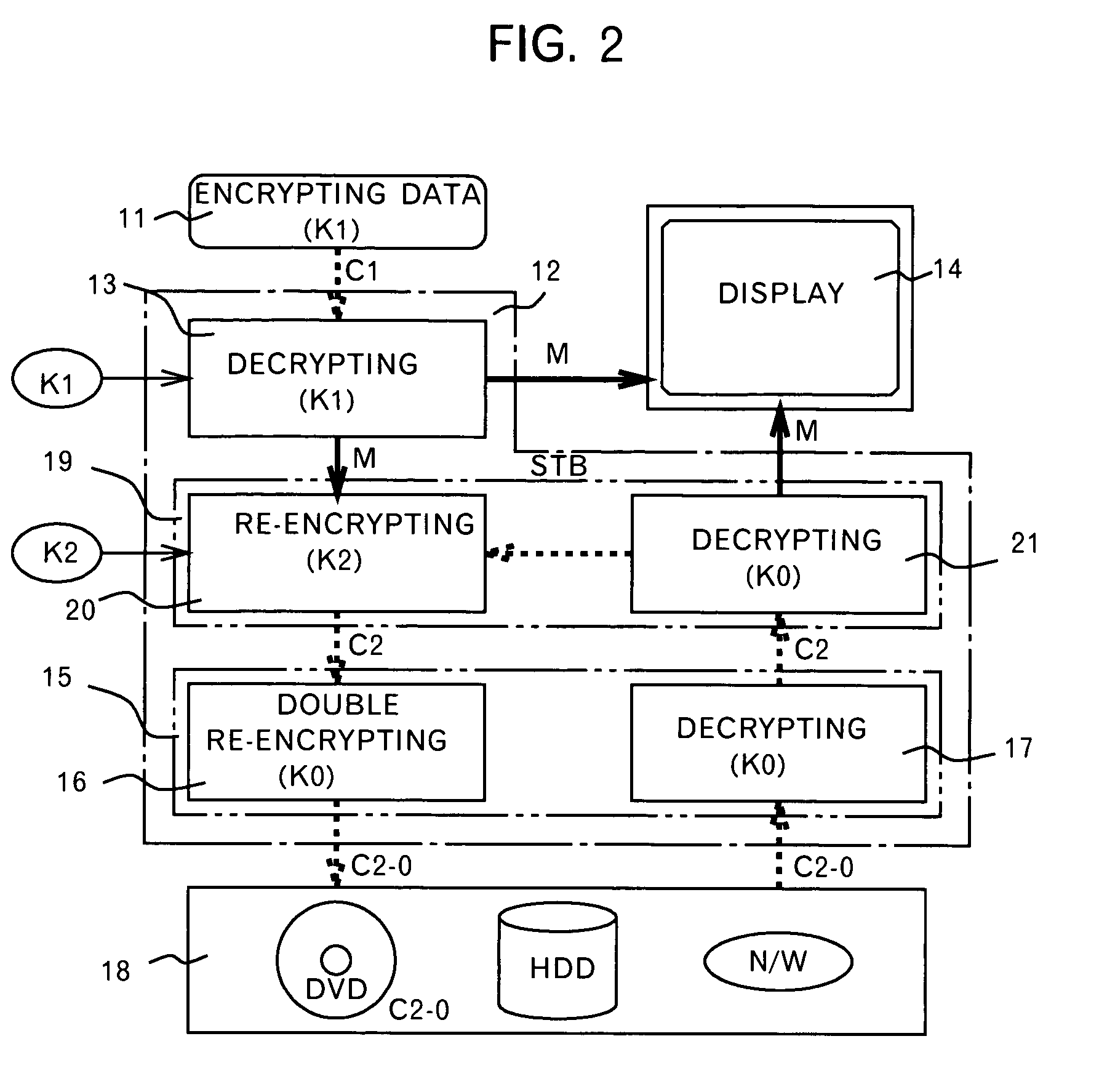
Method and device for protecting digital data by double re-encryption
InactiveUS7093295B1Television system detailsKey distribution for secure communicationDigital videoDigital data
A method and an apparatus ensuring protection of digital data are provided. In addition to re-encrypting the data using an unchangeable key, the data is double re-encrypted using a changeable key. The changeable key is used first and the unchangeable key is then used, or in another case, the unchangeable key is used first, and the changeable key is then used. In the aspect of embodiments, there is a case adopting a software, a case adopting a hardware, or a case adopting the software and the hardware in combination. The hardware using the unchangeable key developed for digital video is available. In adopting the software, encryption / decryption is performed in a region below the kernel which cannot be handled by the user to ensure the security for the program and for the key used. More concretely, encryption / decryption is performed with RTOS using a HAL and a device driver, i.e., a filter driver, a disk driver and a network driver, in an I / O manager. Either one of two filter drivers, with a file system driver between them, may be used. Further, both filter drivers may be used.
Owner:KIOBA PROCESSING LLC
Intelligent data storage and processing using fpga devices
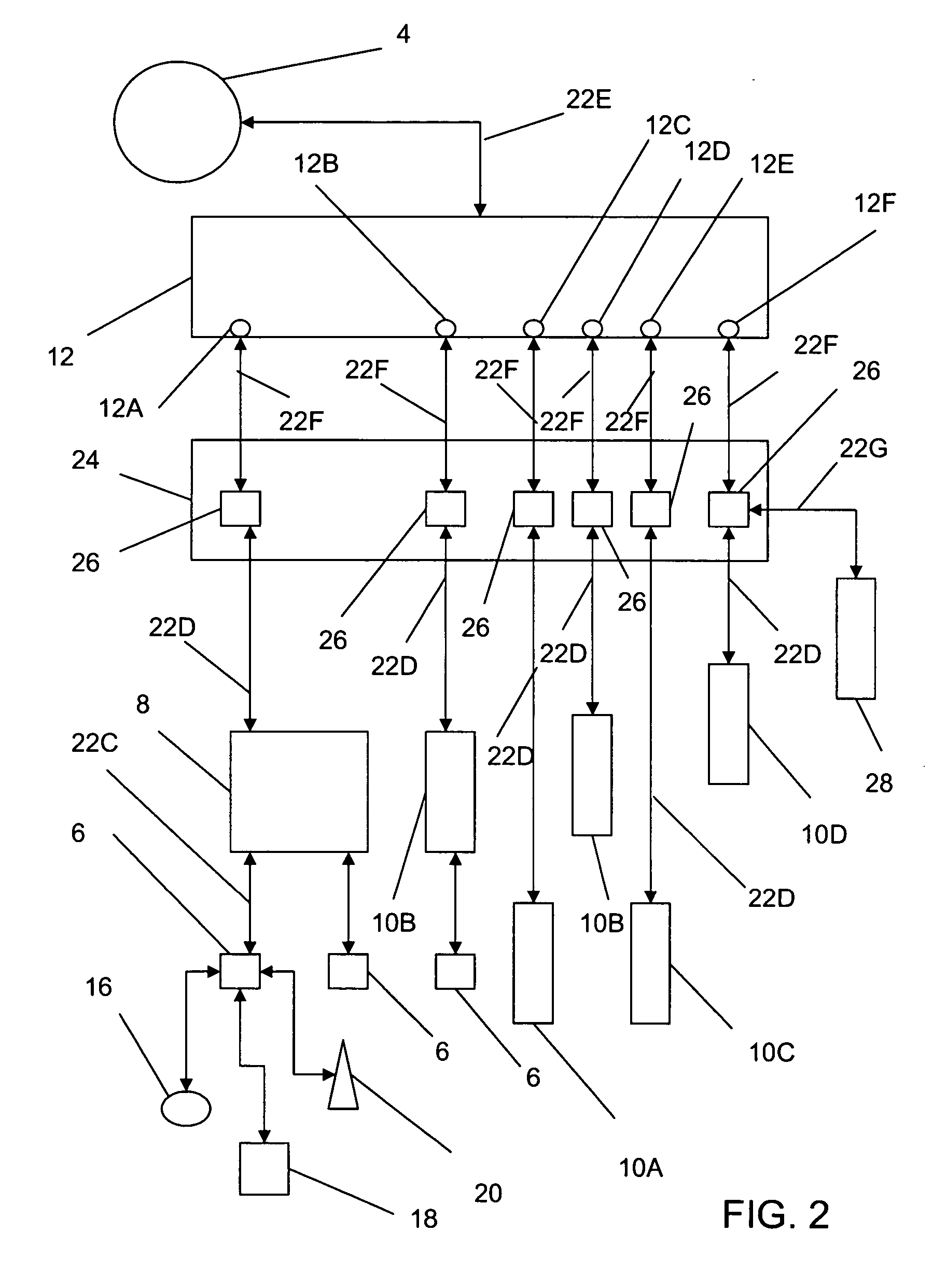
InactiveUS20060294059A1Improve performanceDigital data information retrievalDigital data processing detailsComputer hardwareMagnetic storage
A data storage and retrieval device and method is disclosed. The device includes at least one magnetic storage medium configured to store target data and at least one re-configurable logic device comprising an FPGA coupled to the at least one magnetic storage medium and configured to read a continuous stream of target data therefrom, having been configured with a template or as otherwise desired to fit the type of search and data being searched. The re-configurable logic device is configured to receive at least one search inquiry in the form of a data key and to determine a match between the data key and the target data as it is being read from the at least one magnetic storage medium. This device and method can perform a variety of searches on the target data including without limitation exact and approximate match searches, sequence match searches, image match searches and data reduction searches. This device and method may be provided as part of a stand-alone computer system, embodied in a network attached storage device, or can otherwise be provided as part of a computer LAN or WAN. In addition to performing search and data reduction operations, this device may also be used to perform a variety of other processing operations including encryption, decryption, compression, decompression, and combinations thereof.
Owner:IP RESERVOIR
Method and system for encrypting and decrypting data using an external agent
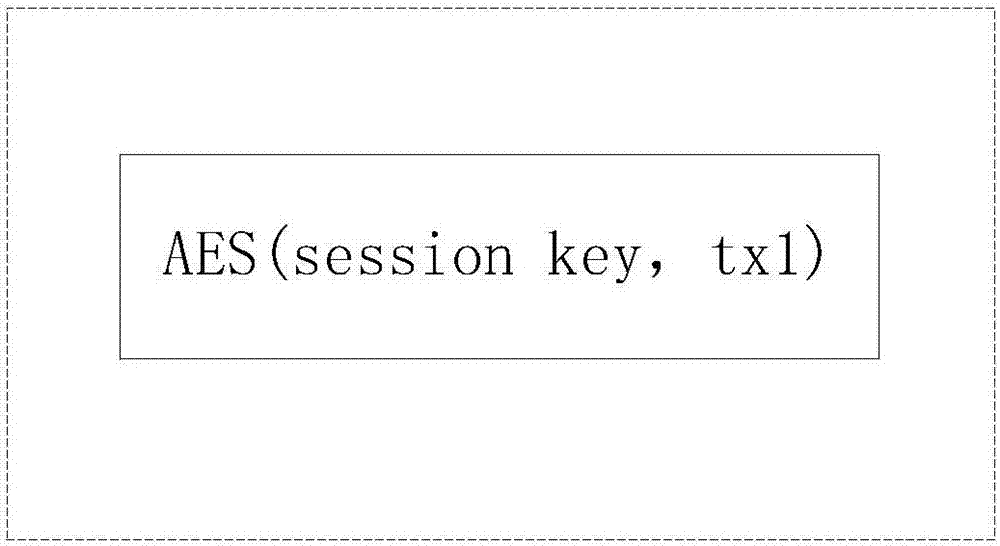
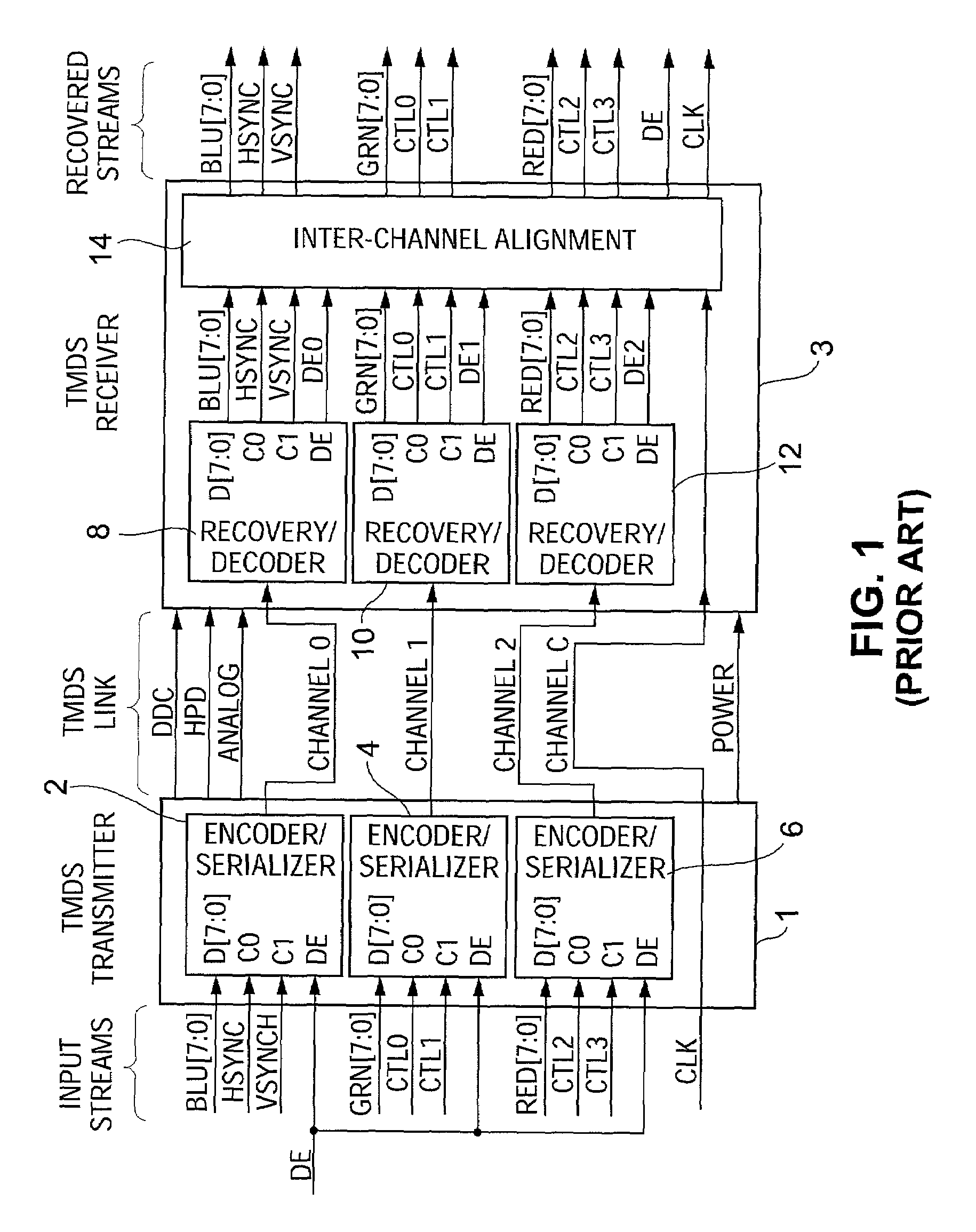
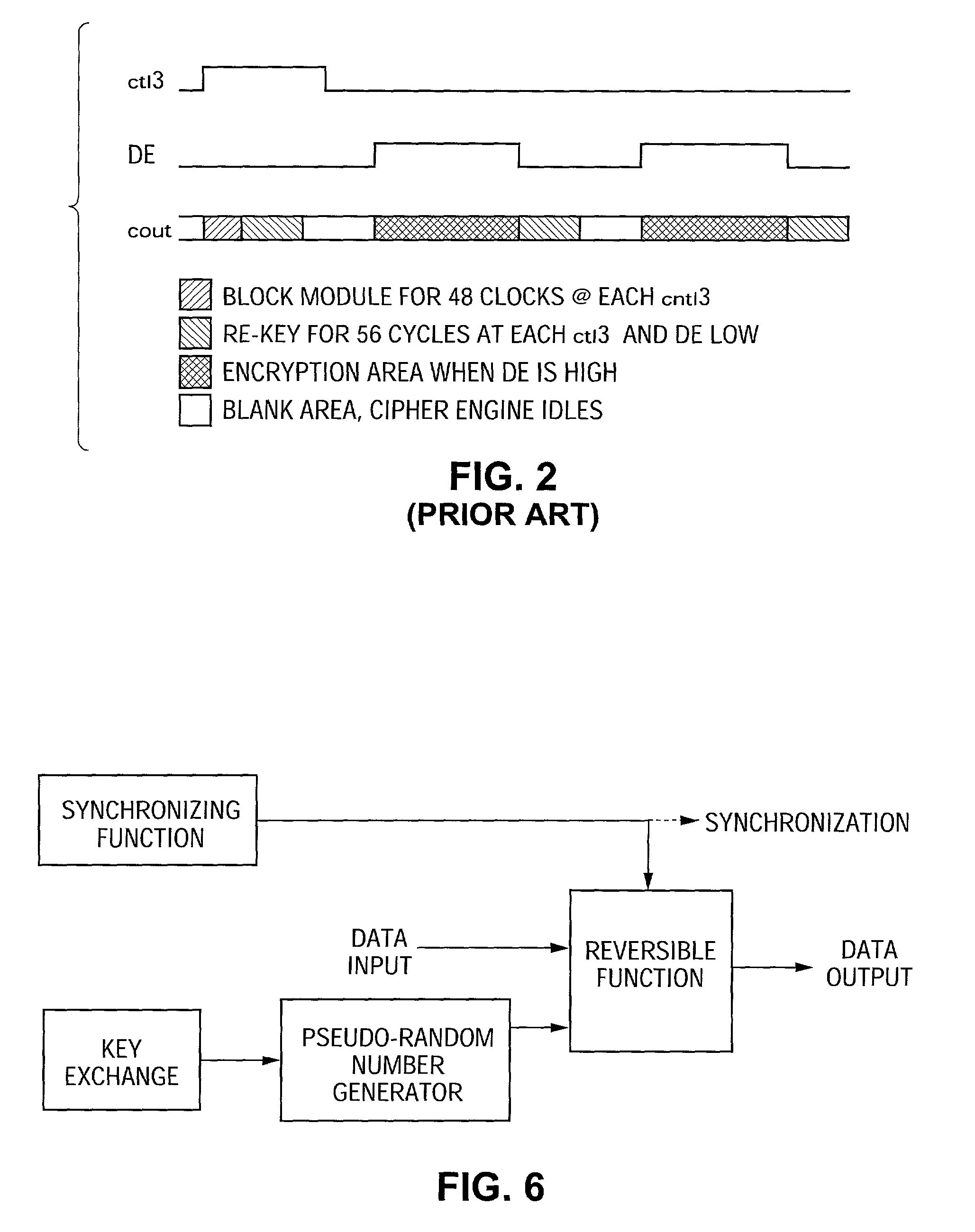
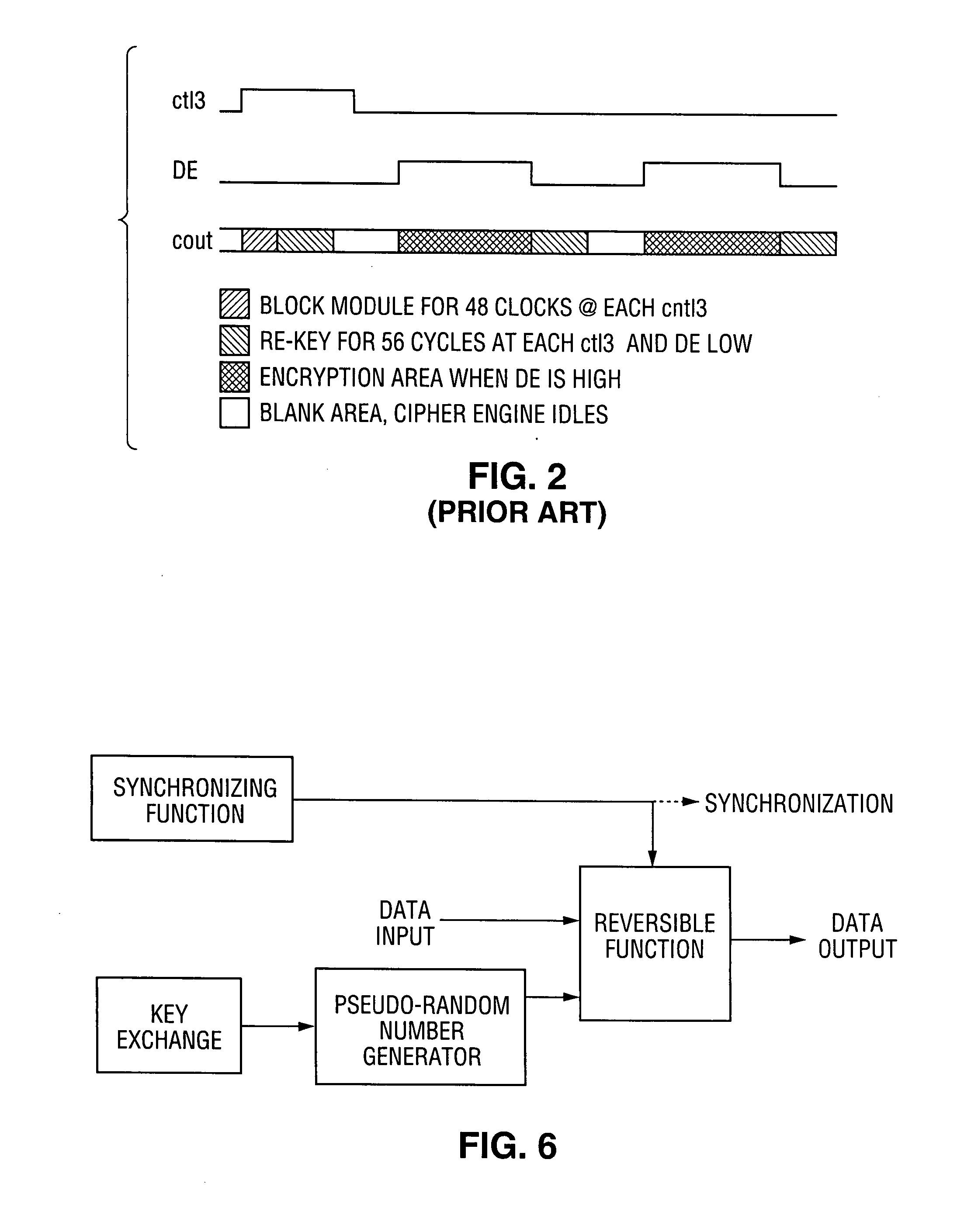
ActiveUS7242766B1Improve securitySynchronising transmission/receiving encryption devicesSecret communicationResponse processTelecommunications link
A communication system including a transmitter, a receiver, a communication link (for example, a TMDS-like link), and preferably also an external agent with which the transmitter and receiver can communicate, in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such a system, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for distributing keys to the transmitter and receiver. The receiver can be a player coupled to a downstream receiver by a TMDS-like link, and configured to re-encrypt the decrypted data (for example, using an AES or HDCP protocol) and send re-encrypted data over the link to the receiver. Optionally, the player is a repeater which translates the decrypted data from the transmitter, and then re-encrypts the translated data for transmission to the downstream receiver. The transmitter can itself be a player that receives and decrypts encrypted data from an upstream source. In preferred embodiments, the system implements a content protection protocol including a challenge-response procedure. After a new key is supplied to the receiver (and the same new key should have been supplied to the transmitter) and before the receiver can use the new key, the challenge-response procedure requires that the receiver validate the transmitter by verifying that the transmitter has proper knowledge of the new key.
Owner:LATTICE SEMICON CORP
Methods and systems for providing access control to secured data
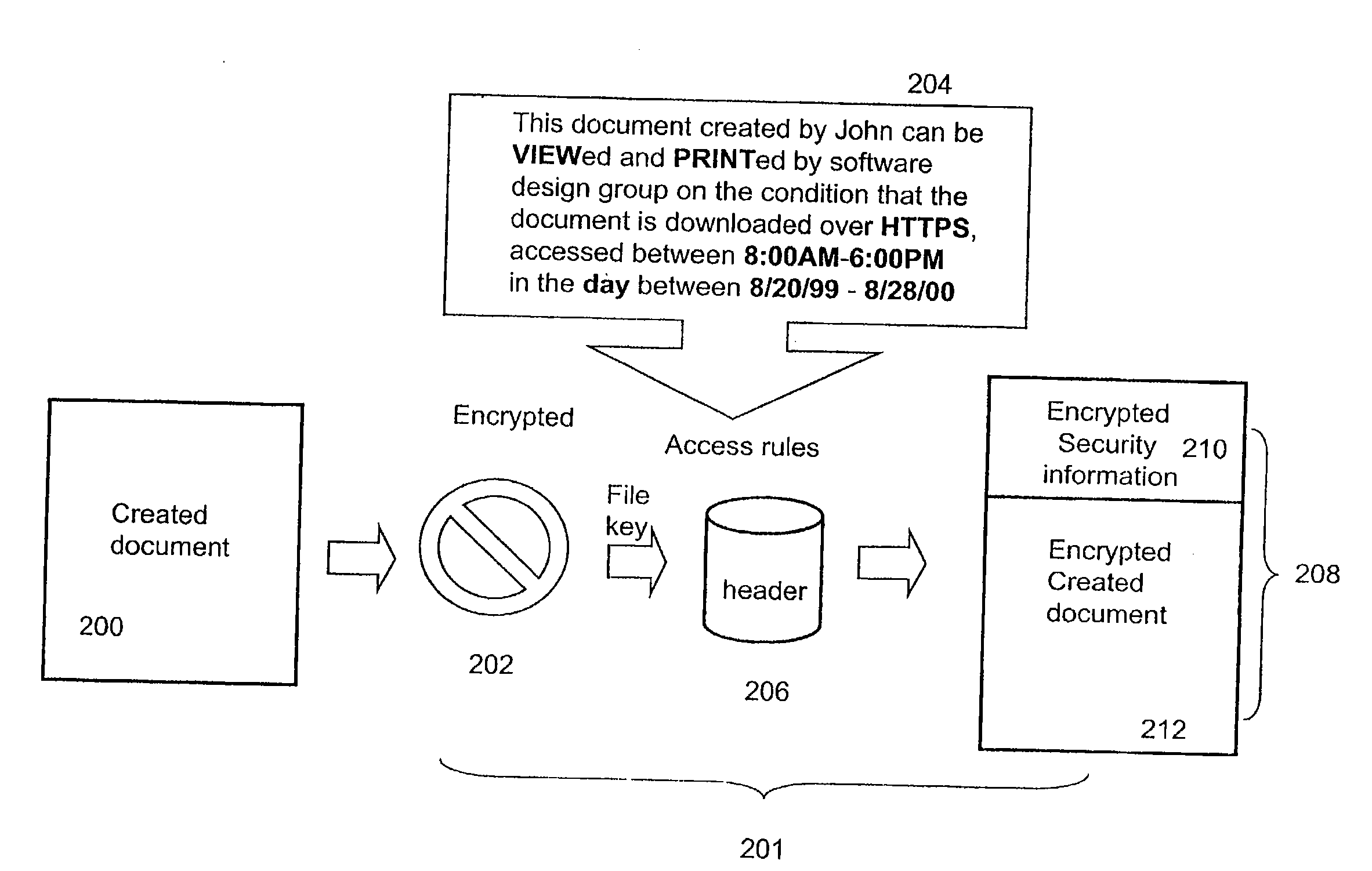
ActiveUS20090100268A1Ensures dependabilityEnsure reliabilityDigital data processing detailsUser identity/authority verificationEngineeringEncryption decryption
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
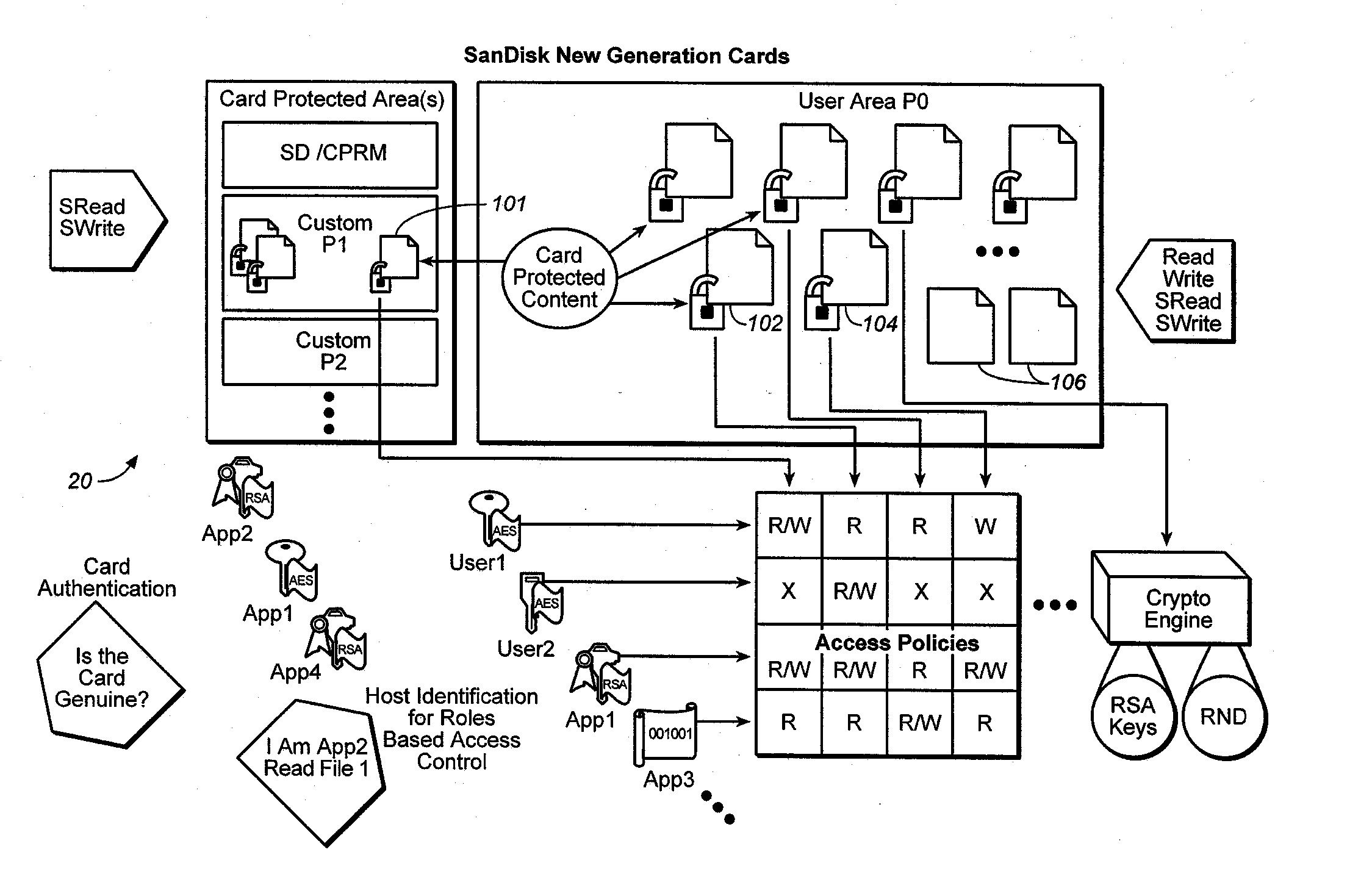
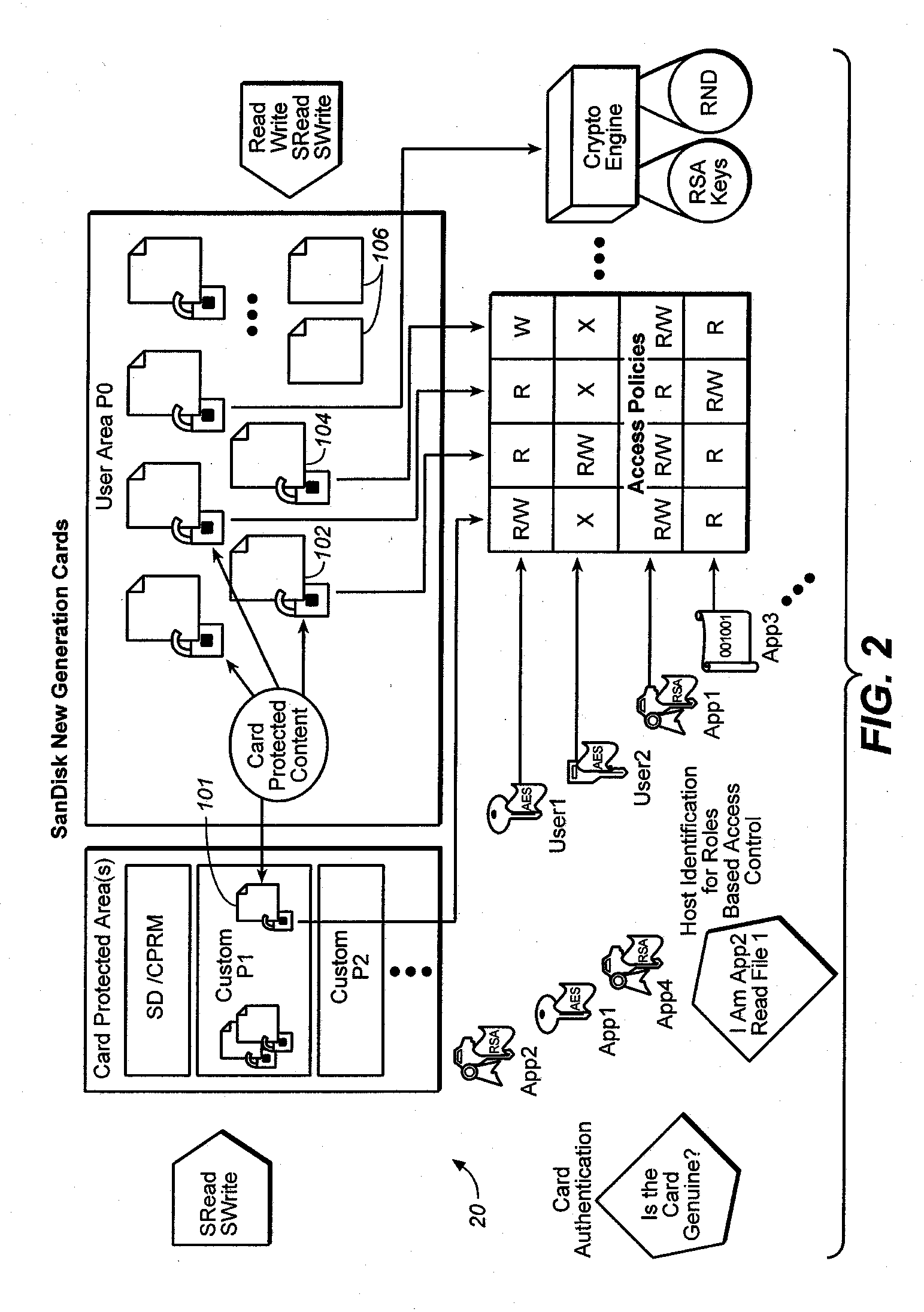
Method forversatile content control
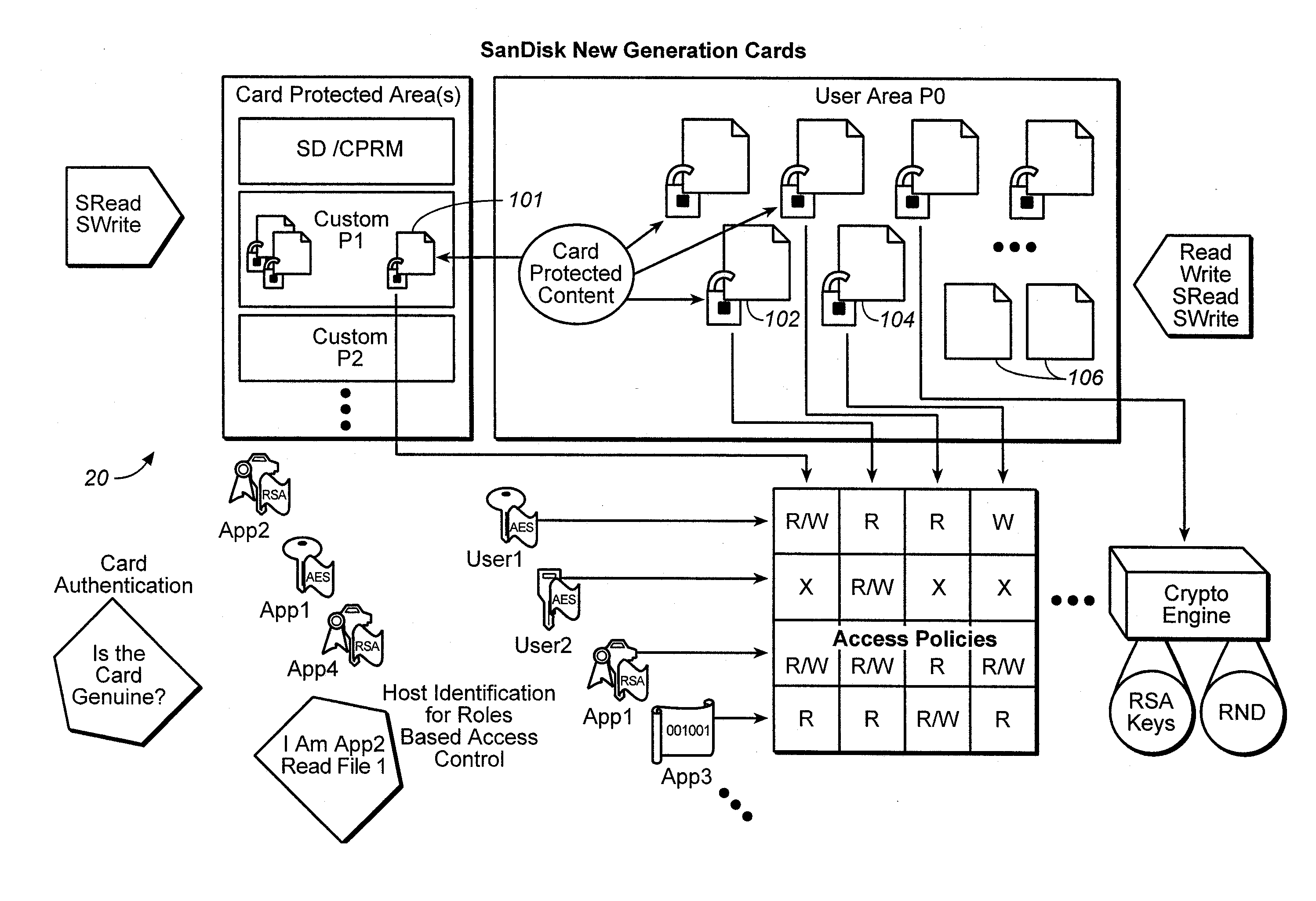
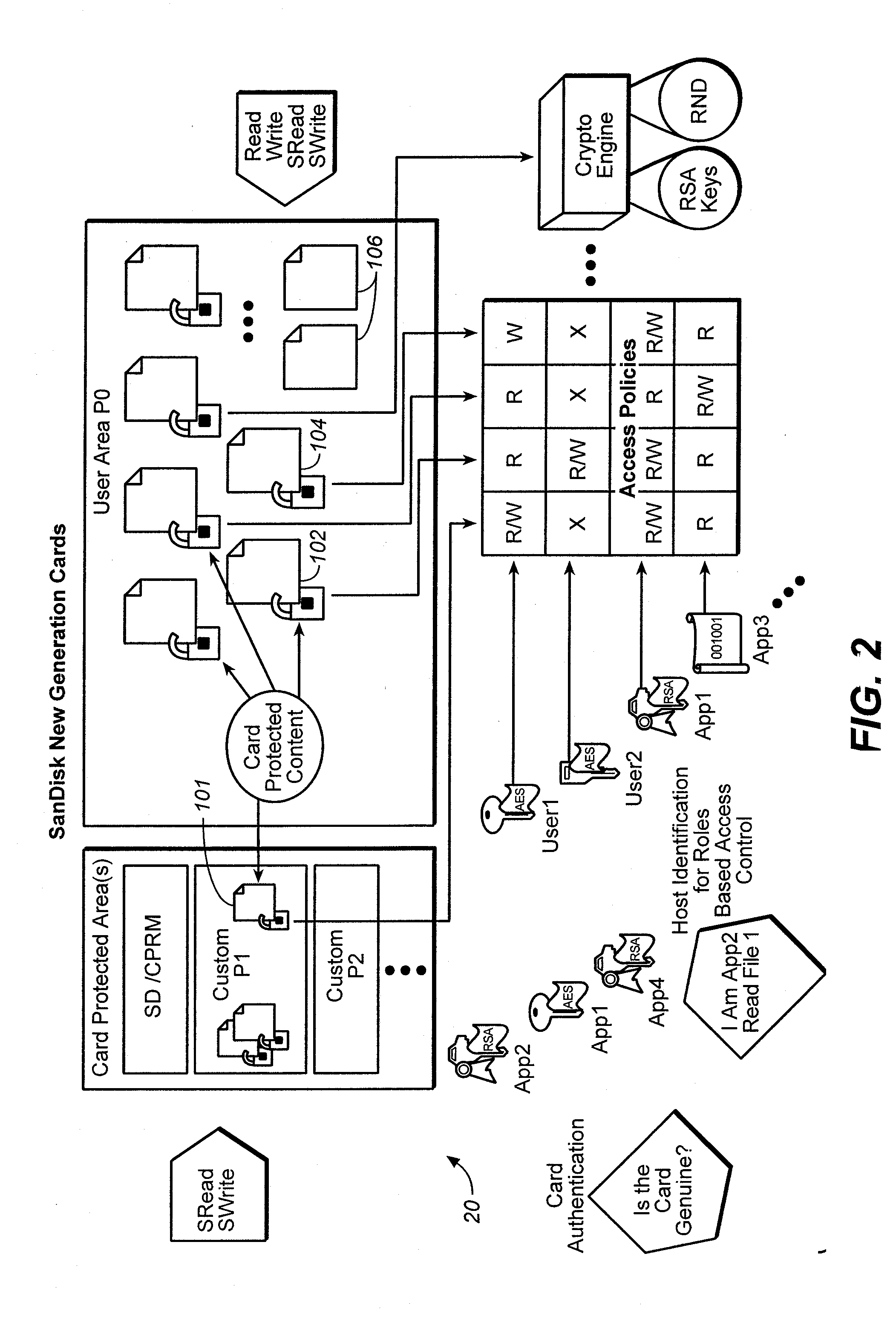
ActiveUS20060242068A1Easy to optimizeImprove versatilityData processing applicationsDigital data processing detailsFile systemEncryption decryption
The owner of proprietor interest is in a better position to control access to the encrypted content in the medium if the encryption-decryption key is stored in the medium itself and substantially inaccessible to external devices. Only those host devices with the proper credentials are able to access the key. An access policy may be stored which grants different permissions (e.g. to different authorized entities) for accessing data stored in the medium. A system incorporating a combination of the two above features is particularly advantageous. On the one hand, the content owner or proprietor has the ability to control access to the content by using keys that are substantially inaccessible to external devices and at the same time has the ability to grant different permissions for accessing content in the medium. Thus, even where external devices gain access, their access may still be subject to the different permissions set by the content owner or proprietor recorded in the storage medium. When implemented in a flash memory, the above features result in a particularly useful medium for content protection. Many storage devices are not aware of file systems while many computer host devices read and write data in the form of files. The host device provides a key reference or ID, while the memory system generates a key value in response which is associated with the key ID, which is used as the handle through which the memory retains complete and exclusive control over the generation and use of the key value for cryptographic processes, while the host retains control of files.
Owner:DISCRETIX TECH +1
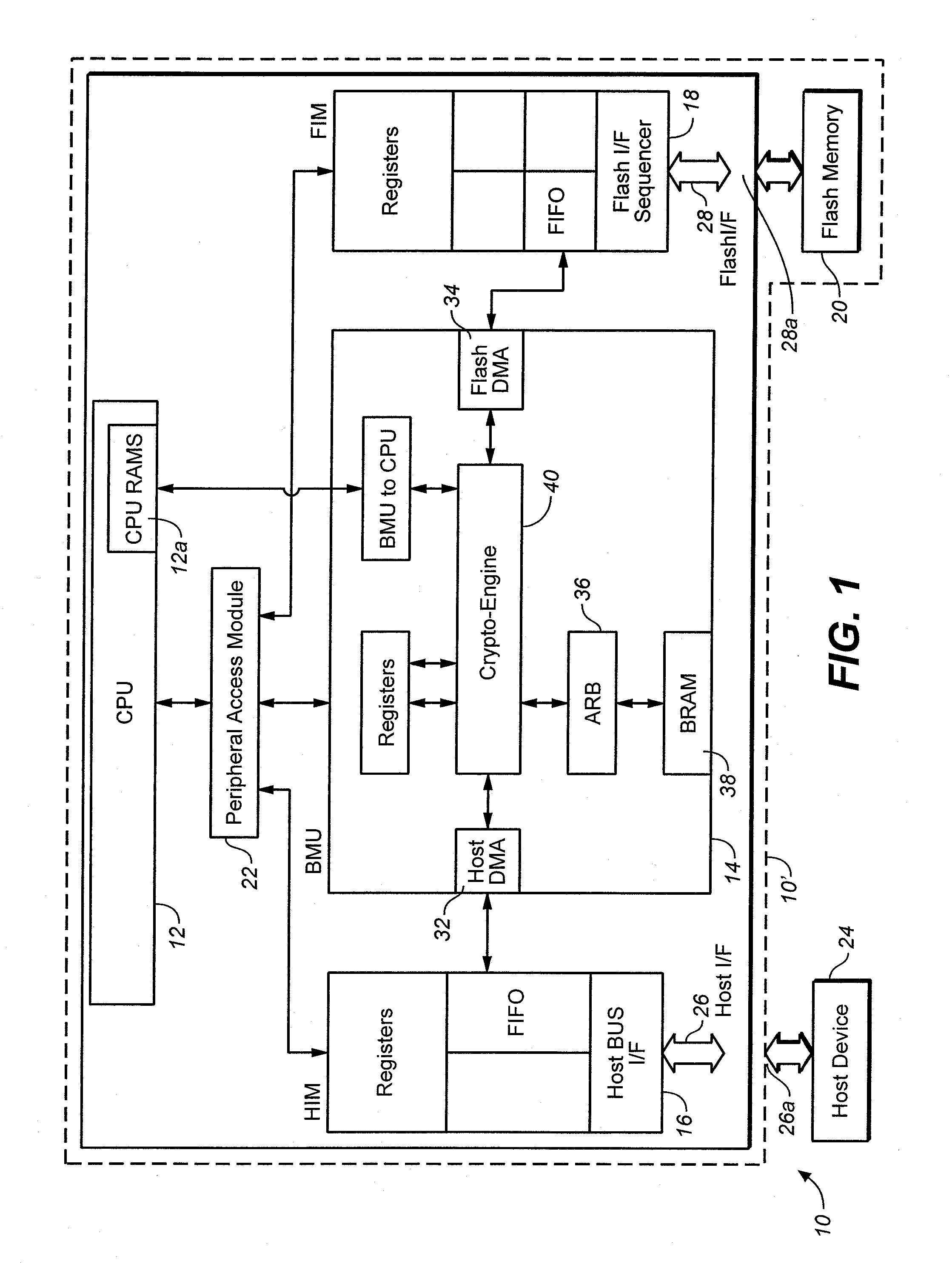
Programmable security platform
InactiveUS20060117177A1Internal/peripheral component protectionSecuring communicationRandom access memoryEncryption decryption
A dynamically programmable security device. The device includes: a secure nonvolatile read only memory (NVMROM) for securely storing a unique device cipher key; a secure interface for dynamically loading authenticated application code; a cryptographic engine for encrypting, decrypting data and authenticating the application code; a secure random access memory (RAM) for storing the authenticated application code and application data; and a processor for executing the authenticated application code.
Owner:BROADCOM CORP
Method and system for transparent in-line protection of an electronic communications network
InactiveUS20060190997A1Improve performanceDigital data processing detailsUser identity/authority verificationComputing systemsAggregate data
The invention provides a method and system for enabling in-line communications channels between a plurality of computational systems and a switch, and / or a plurality of switches and a router. In a first version of the invention an in-line system receives uplinks of aggregated data from a plurality of switches and applies policies to the each aggregated data stream prior to transmission of the aggregated data streams from the in-line system to the router. At least one computational system provides a user identification associated with a user profile to the in-line system. The user profile informs indicates to the in-line system of the constraints imposed upon and activities permitted to the computational system originating the user identification. The constraints may include (a) one or more customized policies, (b) policies applicable to a group associated with the user identification, (c) virus / worm detection & protection, (d) a firewall, (e) virtual private network rules, and / or (f) encryption / decryption. In a second version the in-line system is configured to communicate directly with one or more computational systems as well as one or more switches.
Owner:NEVIS NETWORKS INC
Intelligent data storage and processing using FPGA devices
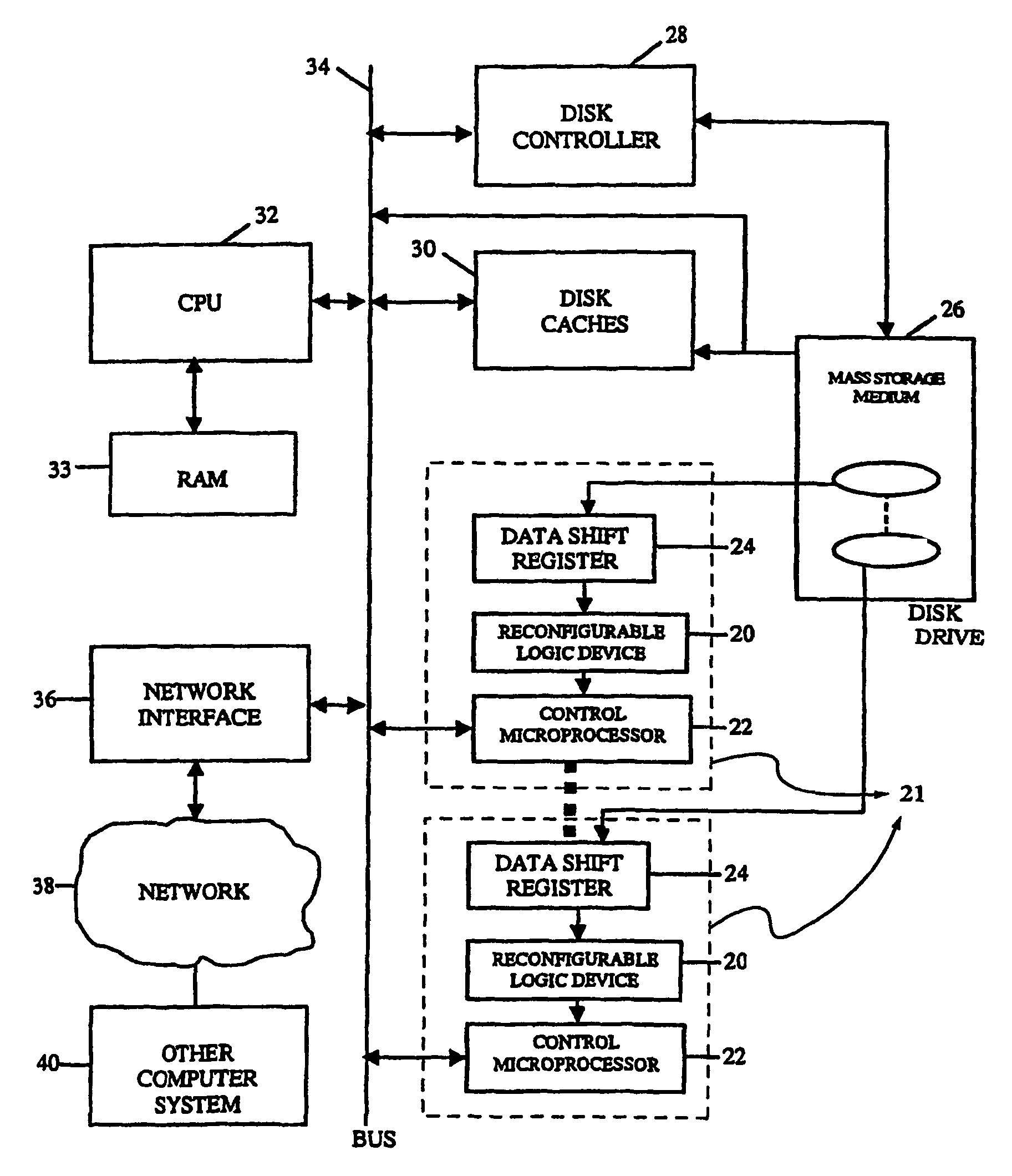
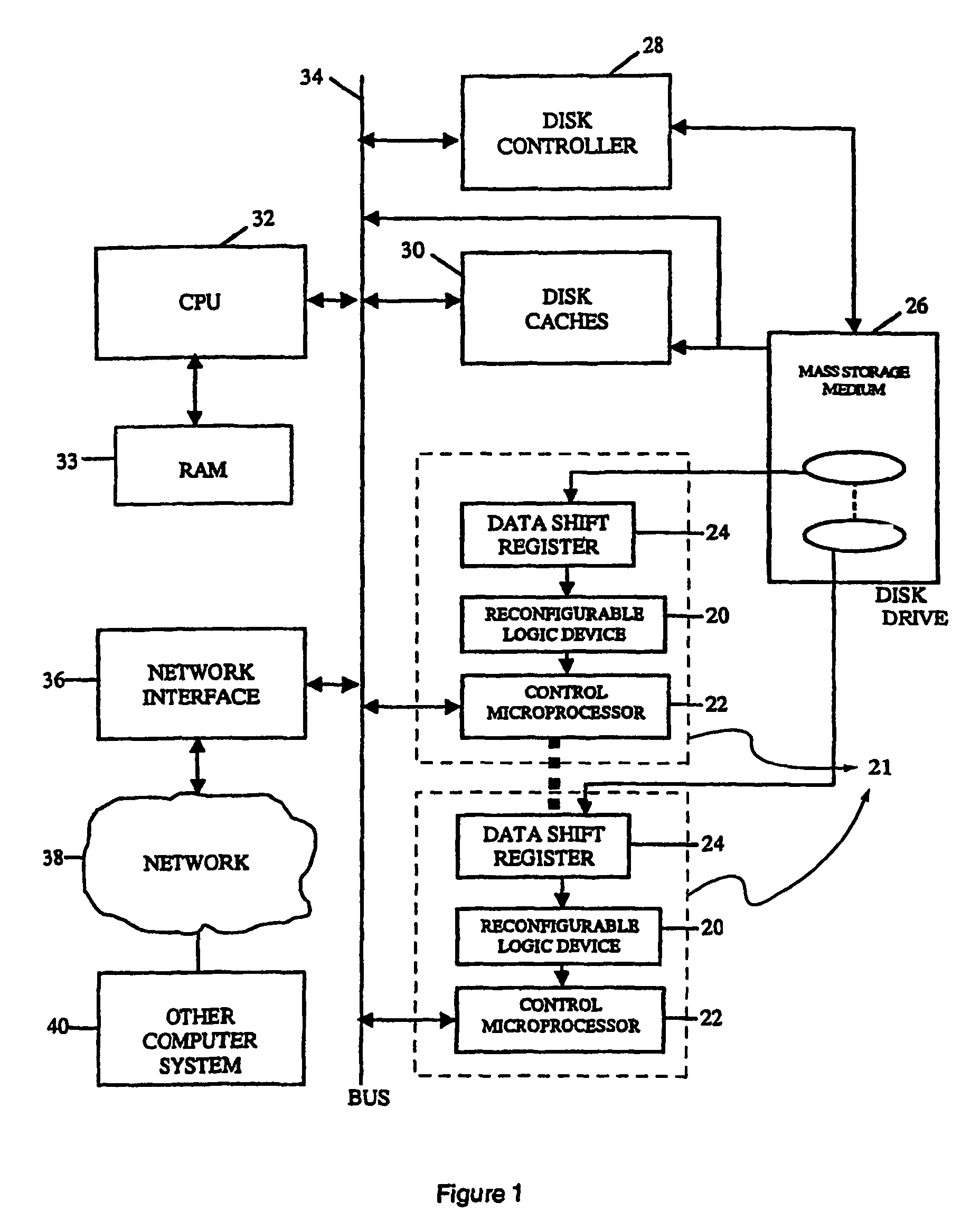
InactiveUS8095508B2Improve performanceDigital data information retrievalDigital data processing detailsComputer hardwareMagnetic storage
Owner:IP RESERVOIR
System and method that provides for the efficient and effective sanitizing of disk storage units and the like
InactiveUS6993661B1Efficient and effective sanitizingWithout risking the confidentiality of data previously stored thereonUnauthorized memory use protectionHardware monitoringDigital dataData storing
An arrangement sanitizes a digital data storage unit, such as a disk data storage unit, by encrypting the information that is stored thereon. When the previously-stored information is retrieved from the digital data storage system storage unit, the information is decrypted prior to being provided to the device that requested retrieval of the data. If the digital data storage unit is to be sanitized, the key or keys that used to at least decrypt the data stored on the digital data storage unit are discarded or made unavailable for use in decrypting the encrypted digital data, thereby making the unencrypted data unavailable. Any of a number of types of encryption / decryption methodologies can be used, including a symmetric key methodology, an asymmetric key methodology such as a public key / private key methodology, or any of a number of other encryption / decryption methodologies.
Owner:GARFINKEL SIMSON L
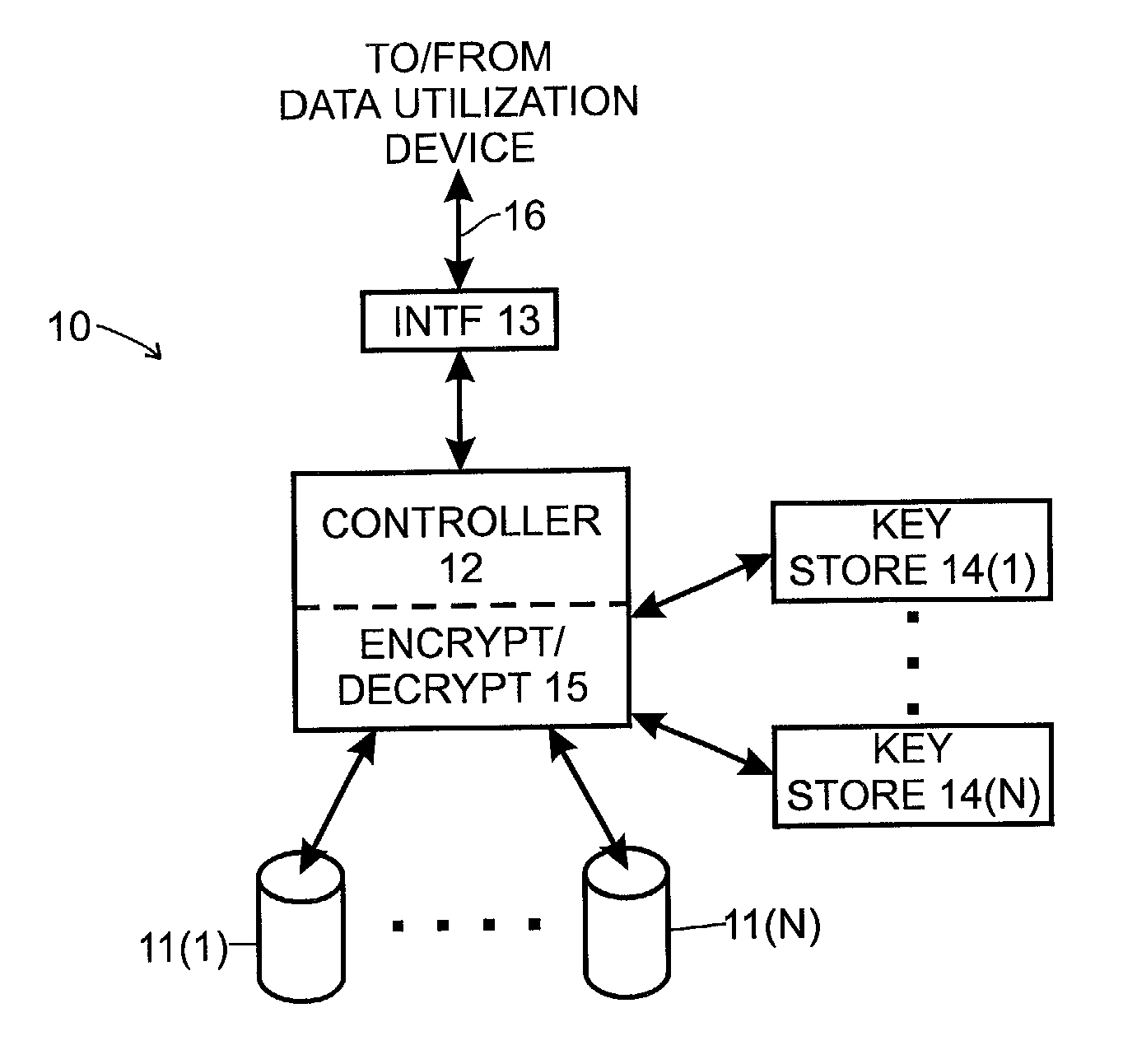
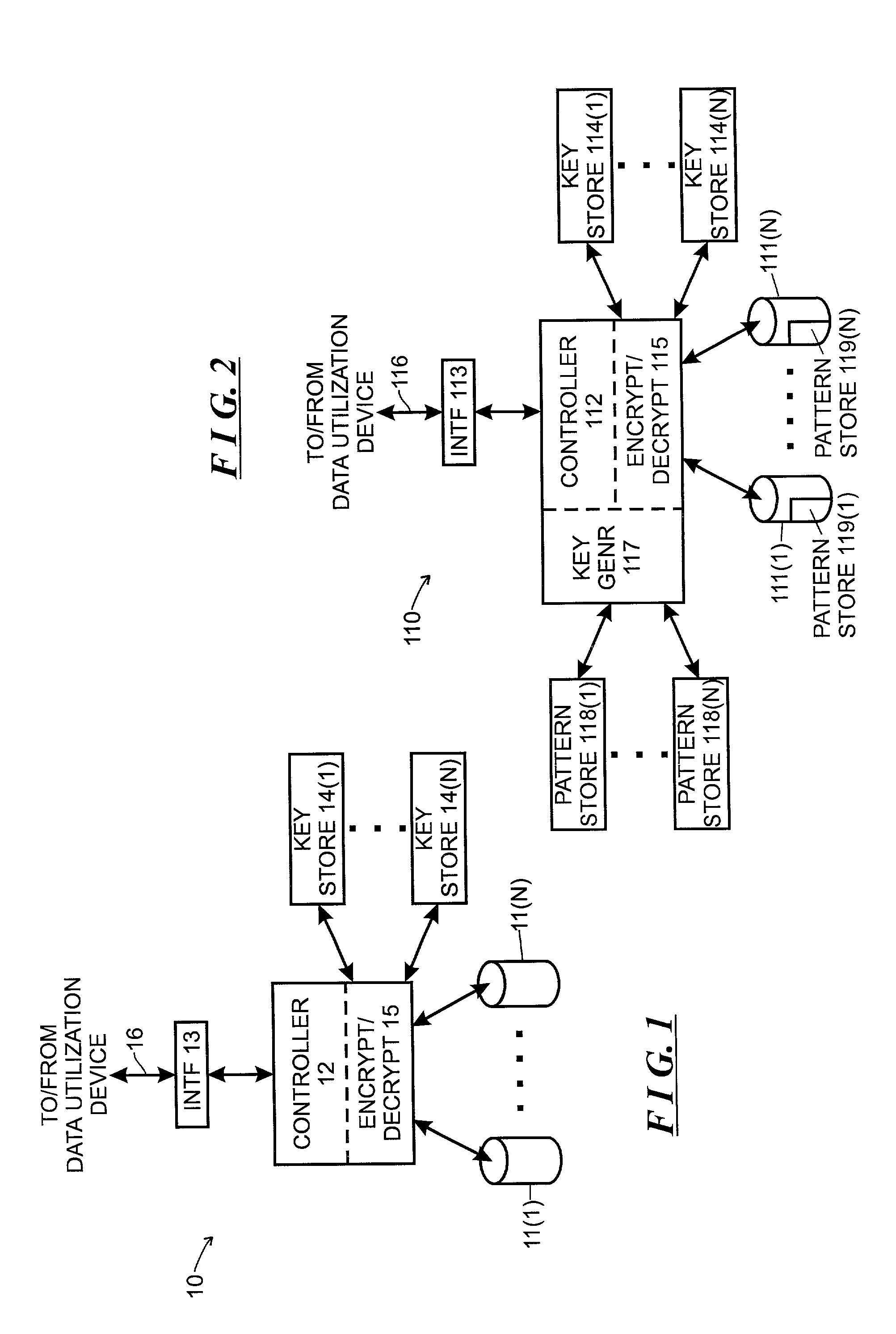
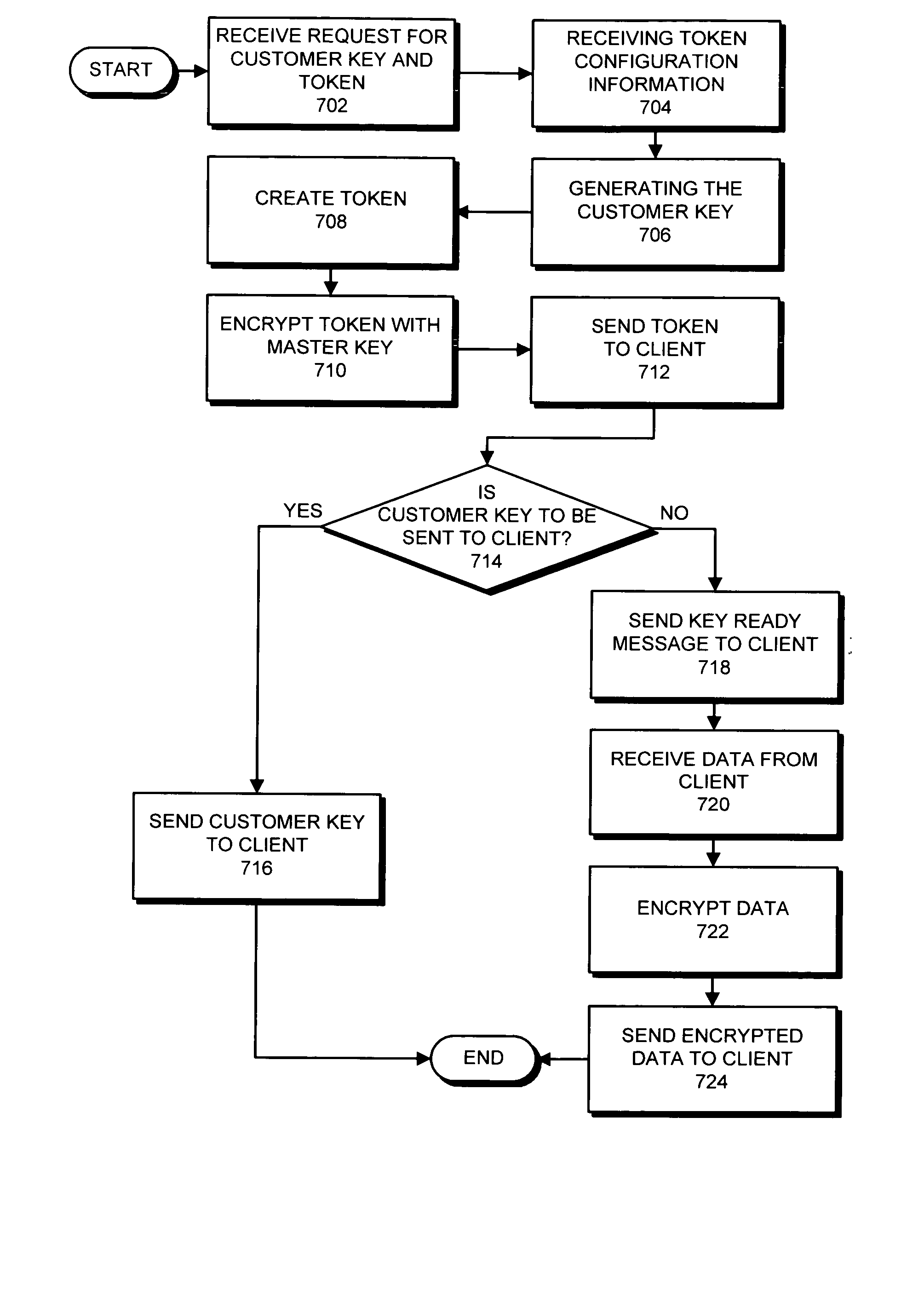
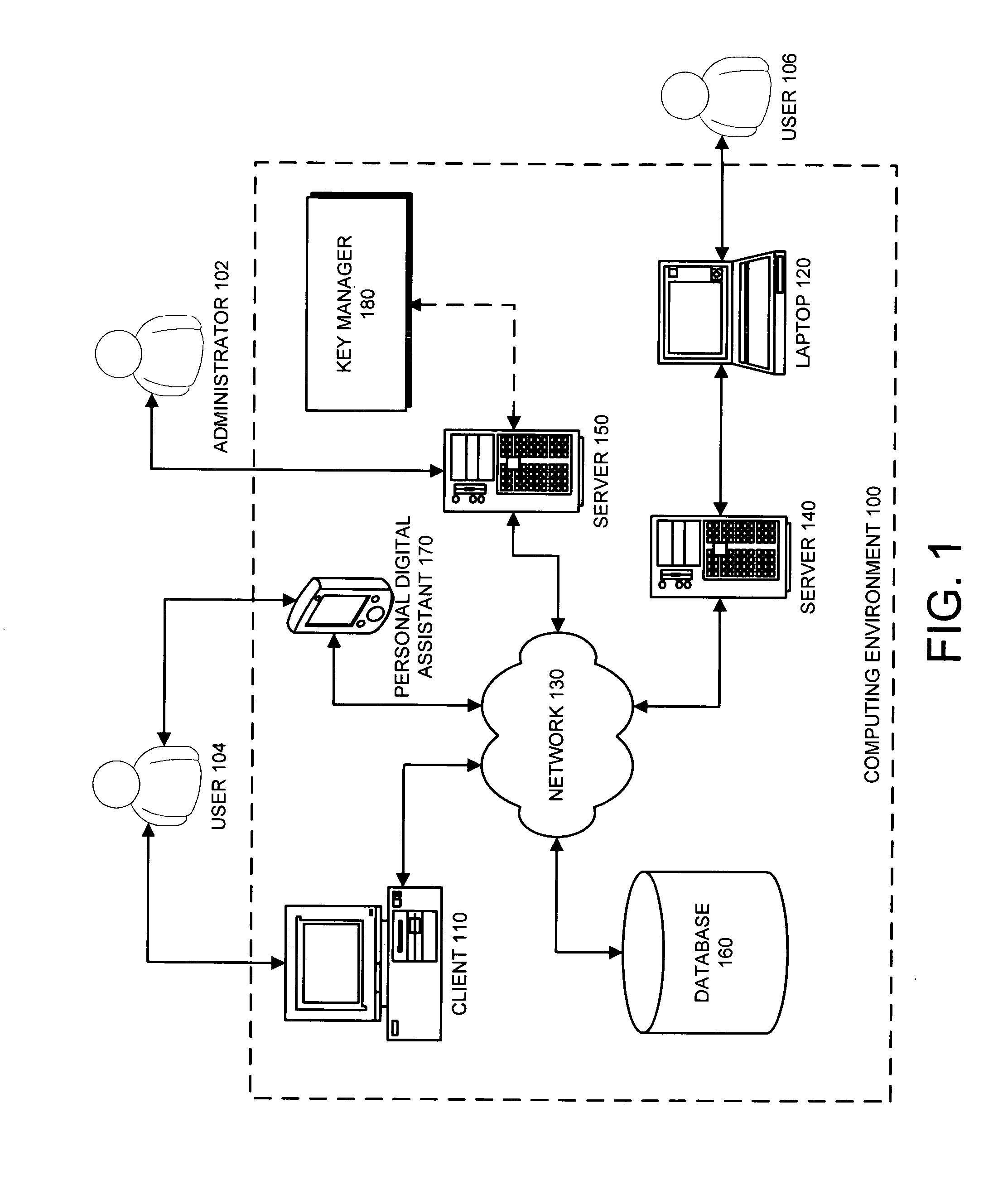
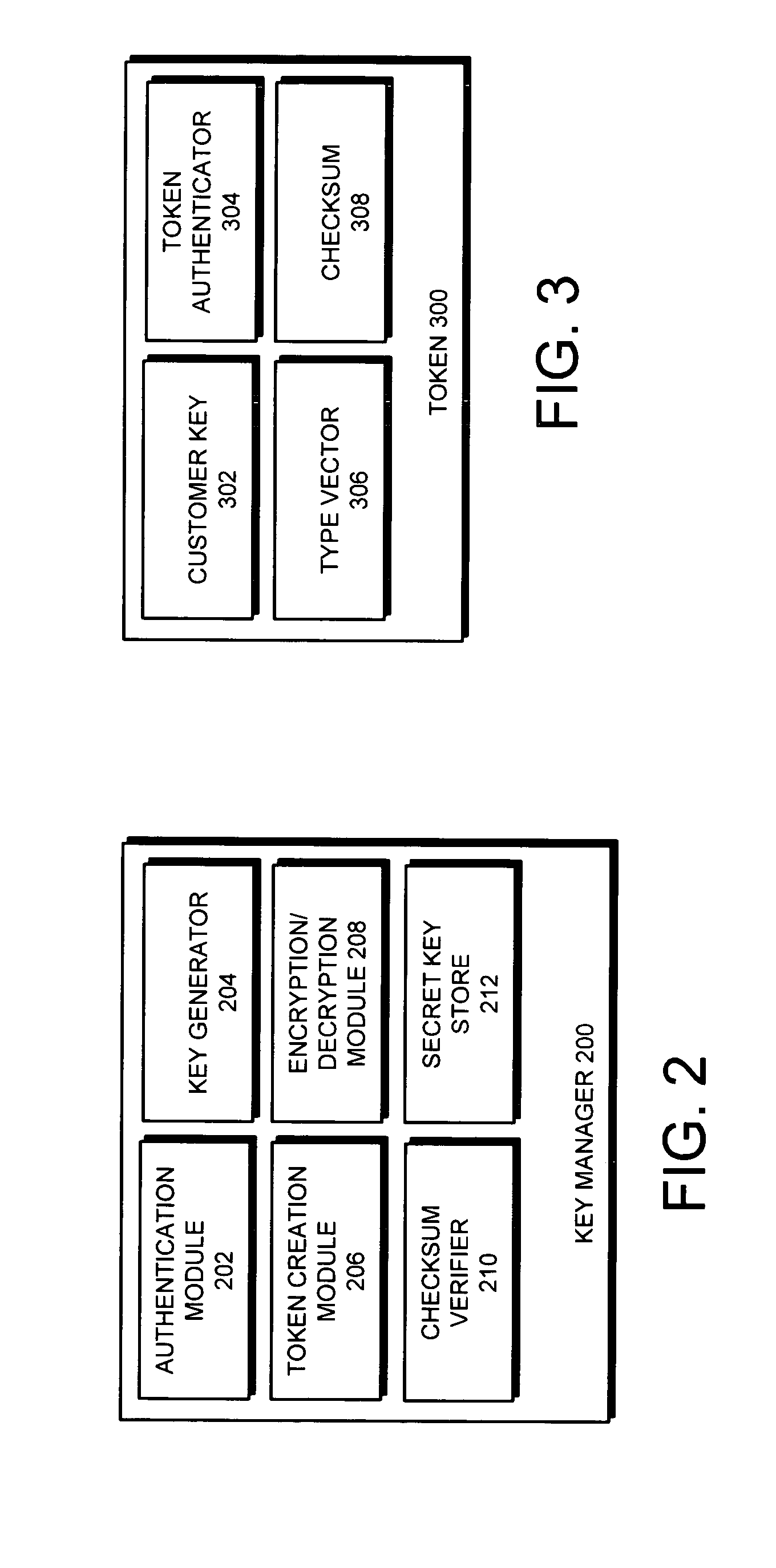
Method and apparatus for managing cryptographic keys
ActiveUS20080019527A1Easy to identifyKey distribution for secure communicationEncryption decryptionMaster key
One embodiment of the present invention provides a system for managing keys. During operation, the system authenticates a client at a key manager. Next, the system receives a token from the client at the key manager, wherein the token is associated with a customer key, and includes a token authenticator. This token authenticator comprises one-half of an authenticator pair which is used to determine if the client is the owner of the customer key. Next, the system decrypts the token using a master key. The system then verifies a client authenticator, which comprises the other half of the authenticator pair which is used to determine if the client is the owner of the customer key. If the client is the owner of the customer key, the system sends the customer key to the client, which enables the client to encrypt / decrypt data. Finally, the client deletes the customer key.
Owner:ORACLE INT CORP
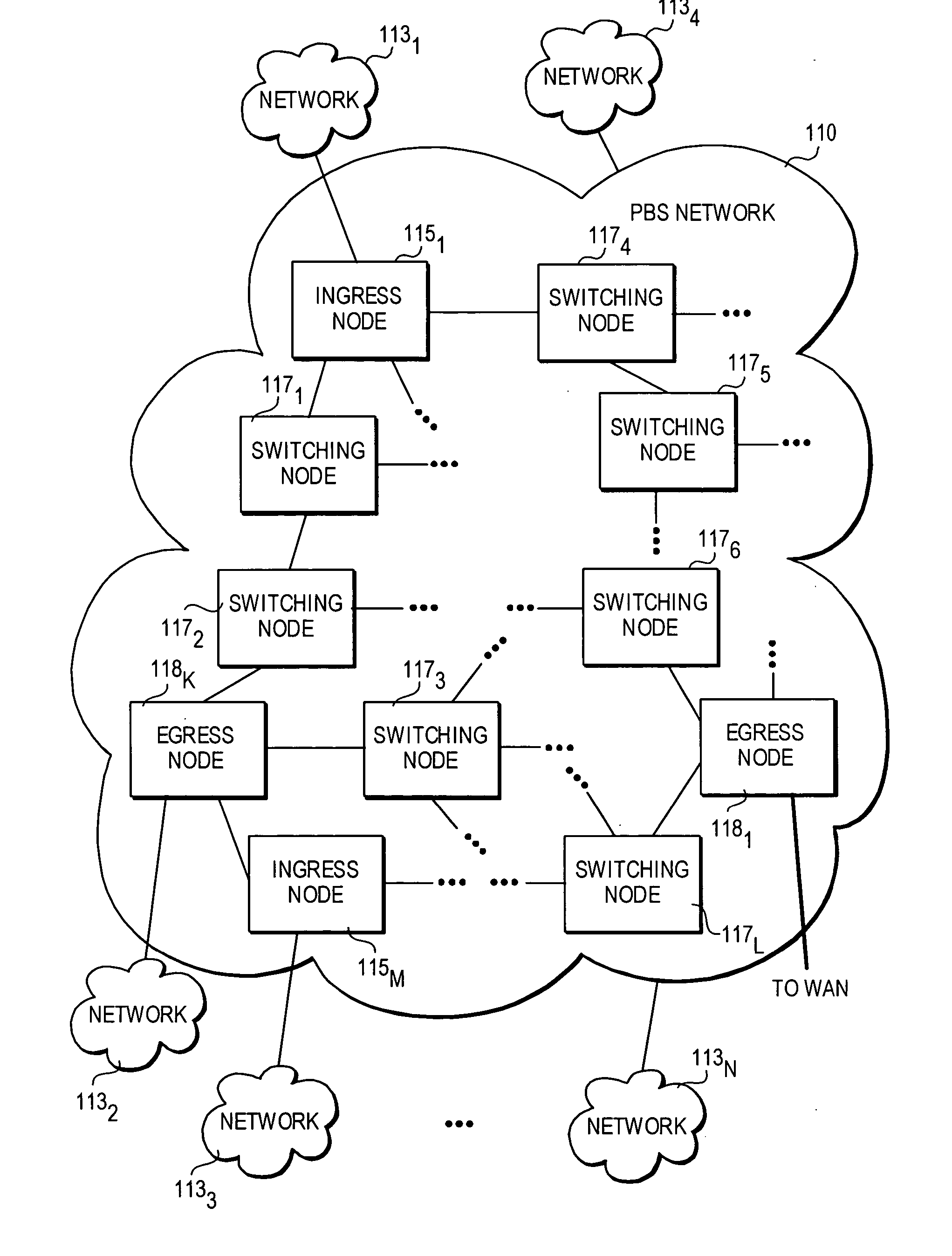
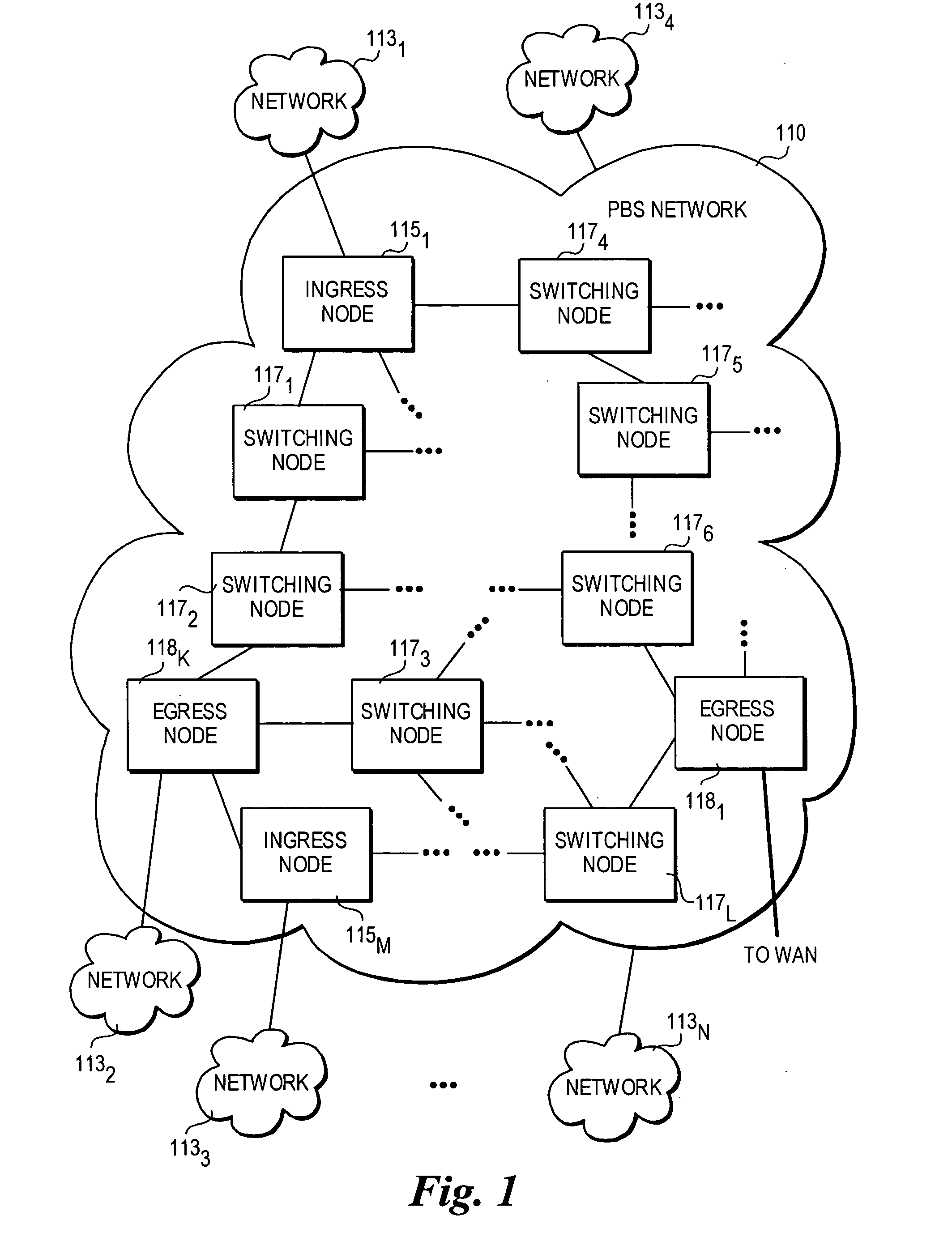
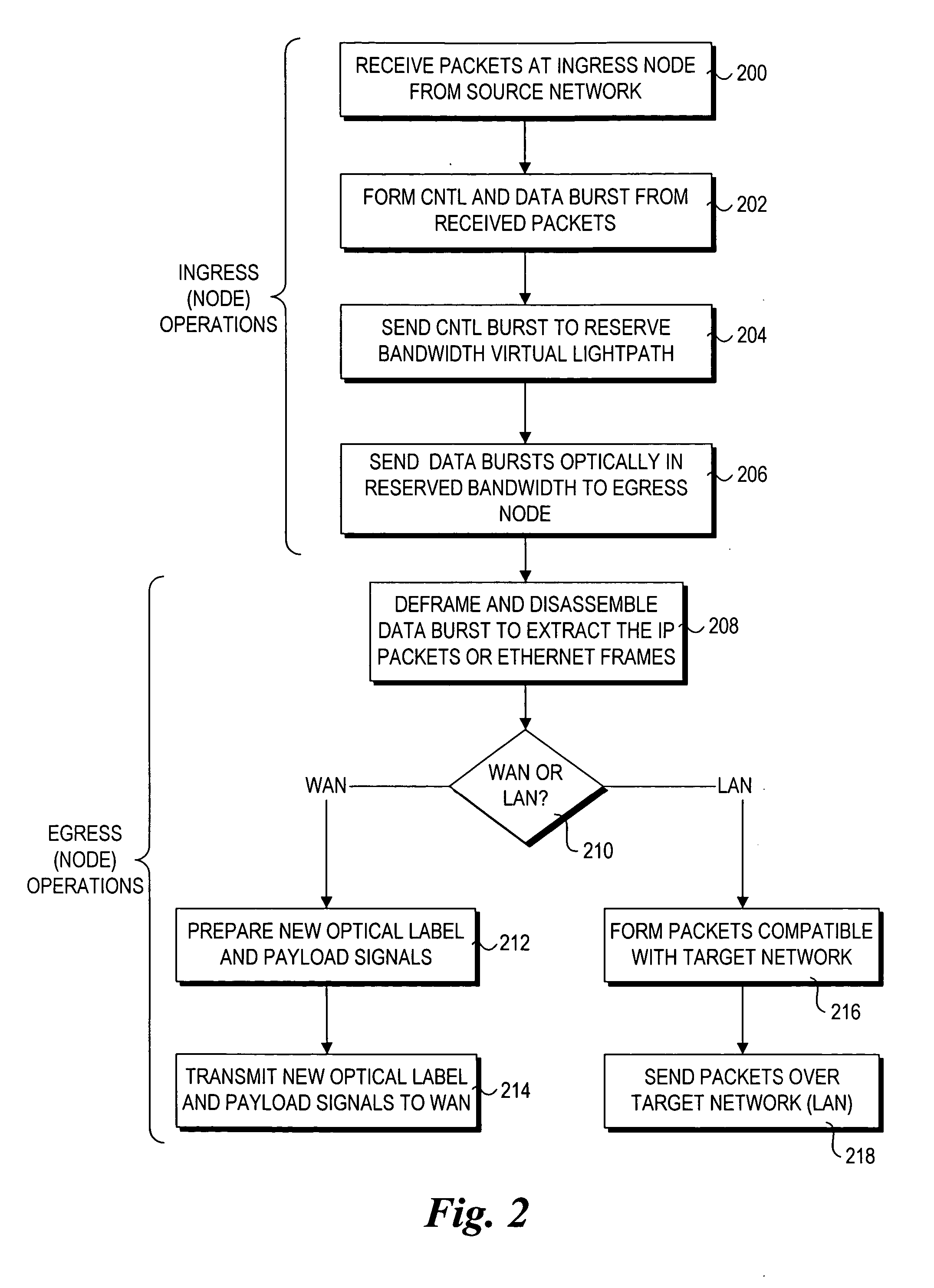
Method and architecture for security key generation and distribution within optical switched networks
InactiveUS20050177749A1Digital data processing detailsUser identity/authority verificationExchange networkEdge node
A method and architecture for secure transmission of data within optical-switched networks. In one embodiment, the optical switched network comprises a photonic burst-switched (PBS) network. Under various schemes, security keys including encryption and decryption keys are generated by edge nodes and the decryption keys are distributed to other edge nodes in a PBS network. In one embodiment, the security keys are dynamically generated by a trusted platform module (TPM). A source edge node uses its encryption key to encrypt selected data bursts to be sent to a destination edge node via a virtual lightpath coupling the source and destination edge nodes. Security data are embedded in a control burst header indicates to the destination node whether corresponding data bursts sent via the virtual lightpath are encrypted. The security data also includes the decryption key and may also identify an encryption / decryption algorithm to be used. In some embodiments, public key infrastructure facilities are used in conjunction with employment of private and public keys and digital certificates.
Owner:TAHOE RES LTD
Memory system with versatile content control
InactiveUS20070168292A1Improve versatilityData processing applicationsComputer security arrangementsFile systemEncryption decryption
The owner of proprietor interest is in a better position to control access to the encrypted content in the medium if the encryption-decryption key is stored in the medium itself and substantially inaccessible to external devices. Only those host devices with the proper credentials are able to access the key. An access policy may be stored which grants different permissions (e.g. to different authorized entities) for accessing data stored in the medium. A system incorporating a combination of the two above features is particularly advantageous. On the one hand, the content owner or proprietor has the ability to control access to the content by using keys that are substantially inaccessible to external devices and at the same time has the ability to grant different permissions for accessing content in the medium. Thus, even where external devices gain access, their access may still be subject to the different permissions set by the content owner or proprietor recorded in the storage medium. When implemented in a flash memory, the above features result in a particularly useful medium for content protection. Many storage devices are not aware of file systems while many computer host devices read and write data in the form of files. The host device provides a key reference or ID, while the memory system generates a key value in response which is associated with the key ID, which is used as the handle through which the memory retains complete and exclusive control over the generation and use of the key value for cryptographic processes, while the host retains control of files.
Owner:DISCRETIX TECH LTD +1
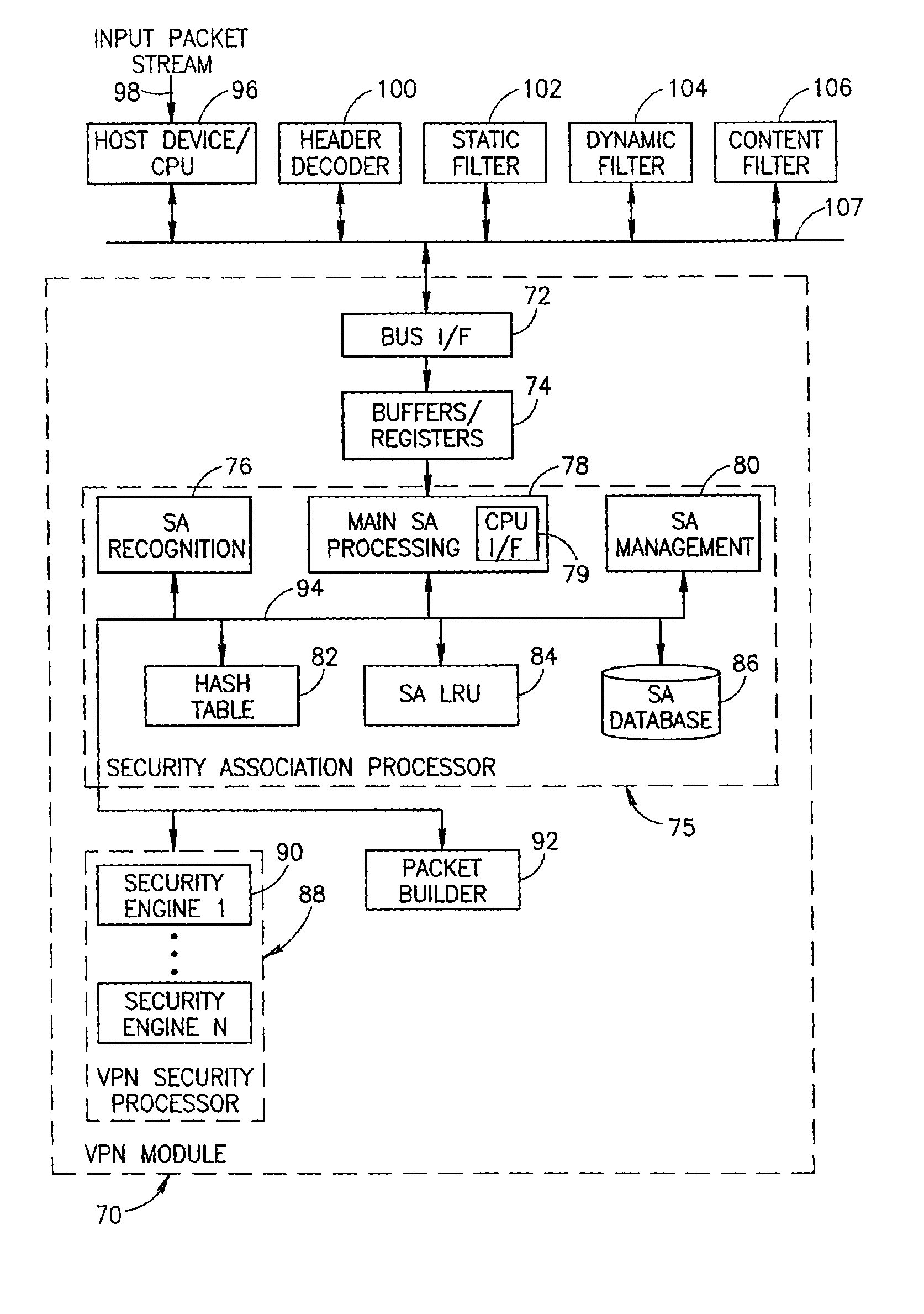
Virtual private network mechanism incorporating security association processor
ActiveUS7107464B2Low costLow-cost implementationMultiple digital computer combinationsProgram controlSecurity associationPrivate network
A novel and useful virtual private network (VPN) mechanism and related security association processor for maintaining the necessary security related parameters to perform security functions such as encryption, decryption and authentication. A security association database (SAD) and related circuitry is adapted to provide the necessary parameters to implement the IPSec group of security specifications for encryption / decryption and authentication. Each security association (SA) entry in the database comprises all the parameters that are necessary to receive and transmit VPN packets according to the IPSec specification.
Owner:TELECOM ITALIA SPA
Flexible automated connection to virtual private networks
InactiveUS20060080441A1Quickly and efficiently configuredUnified interfaceDigital computer detailsNetworks interconnectionPrivate networkEncryption decryption
A network interface unit is provided for use intermediate a LAN and a public or private network, or a combination of both, for establishing secure links to a VPN gateway. Login by a LAN client with the network interface unit, addressing, authentication, and other configuration operations achieved using a web page-based GUI are applied in establishing tunnels from LAN clients to desired VPN destinations. Illustrative network interface units include a DHCP server and provide encryption-decryption and encapsulation-decapsulation of data packets for communication with VPN nodes. Configuration and connection of a client are further enhanced by a built-in DNS server and other functional servers to provide a high degree of autonomy in establishing connections to a desired VPN gateway via an ISP or other public and / or private network links to. The interface unit then performs required authentication exchanges, and required encryption key exchanges.
Owner:CHEN YIHSIU +6
Method and system for encrypting and decrypting data using an external agent
InactiveUS20070237332A1Improve securitySynchronising transmission/receiving encryption devicesTelecommunications linkCommunications system
A communication system including a transmitter, a receiver, a communication link (for example, a TMDS-like link), and preferably also an external agent with which the transmitter and receiver can communicate, in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such a system, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for distributing keys to the transmitter and receiver. The receiver can be a player coupled to a downstream receiver by a TMDS-like link, and configured to re-encrypt the decrypted data (for example, using an AES or HDCP protocol) and send re-encrypted data over the link to the receiver. Optionally, the player is a repeater which translates the decrypted data from the transmitter, and then re-encrypts the translated data for transmission to the downstream receiver. The transmitter can itself be a player that receives and decrypts encrypted data from an upstream source. In preferred embodiments, the system implements a content protection protocol including a challenge-response procedure. After a new key is supplied to the receiver (and the same new key should have been supplied to the transmitter) and before the receiver can use the new key, the challenge-response procedure requires that the receiver validate the transmitter by verifying that the transmitter has proper knowledge of the new key.
Owner:SILICON IMAGE INC
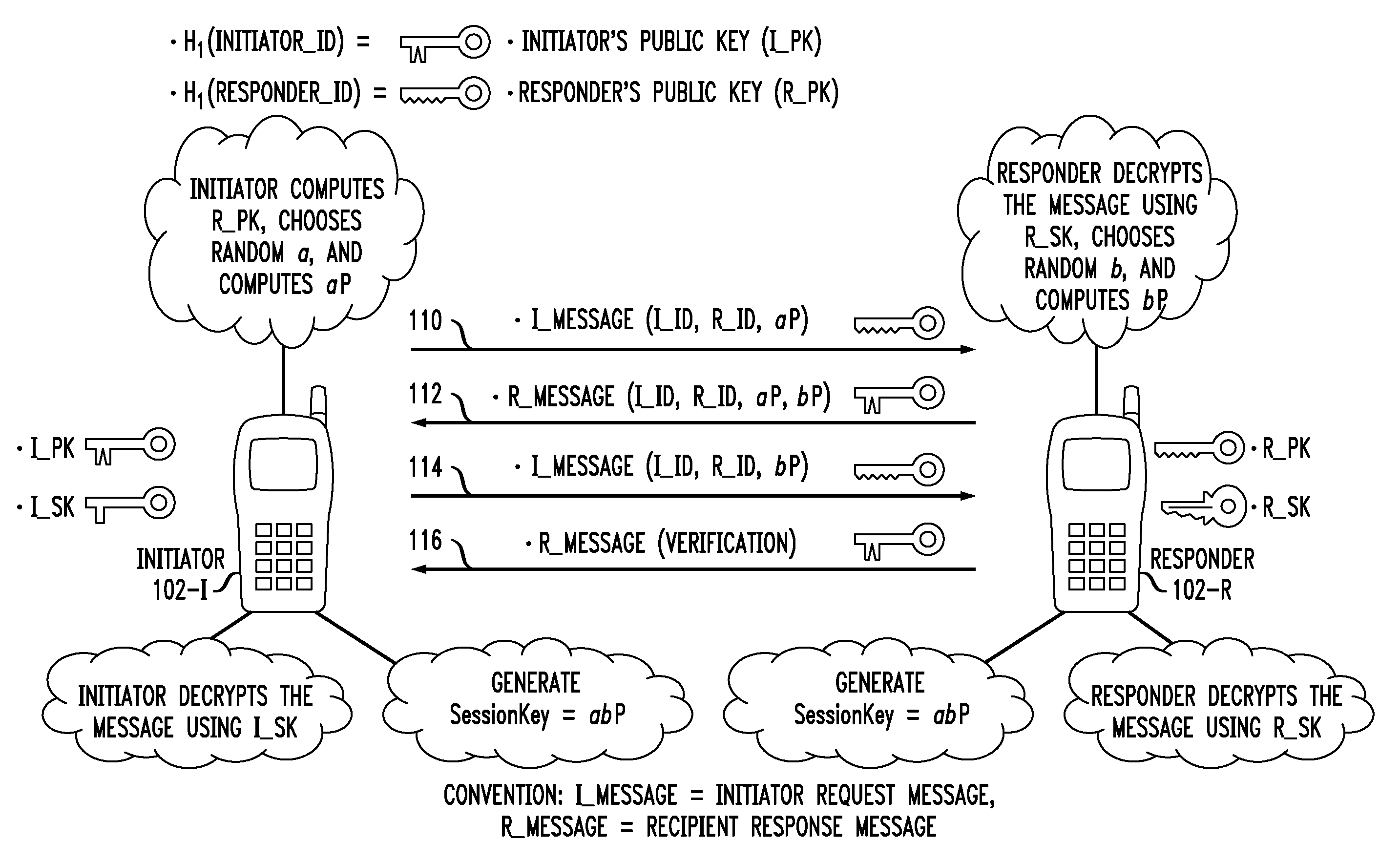
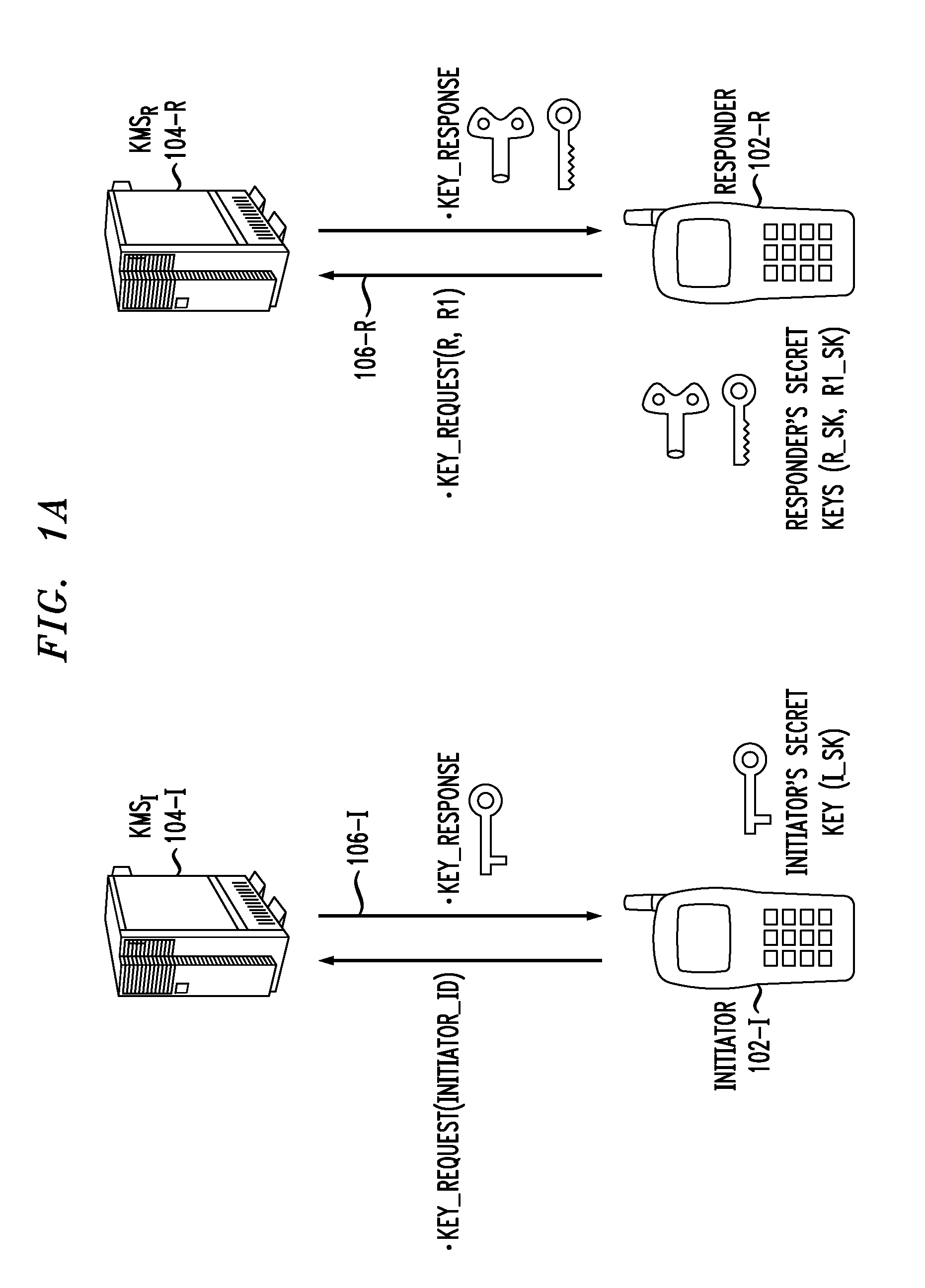
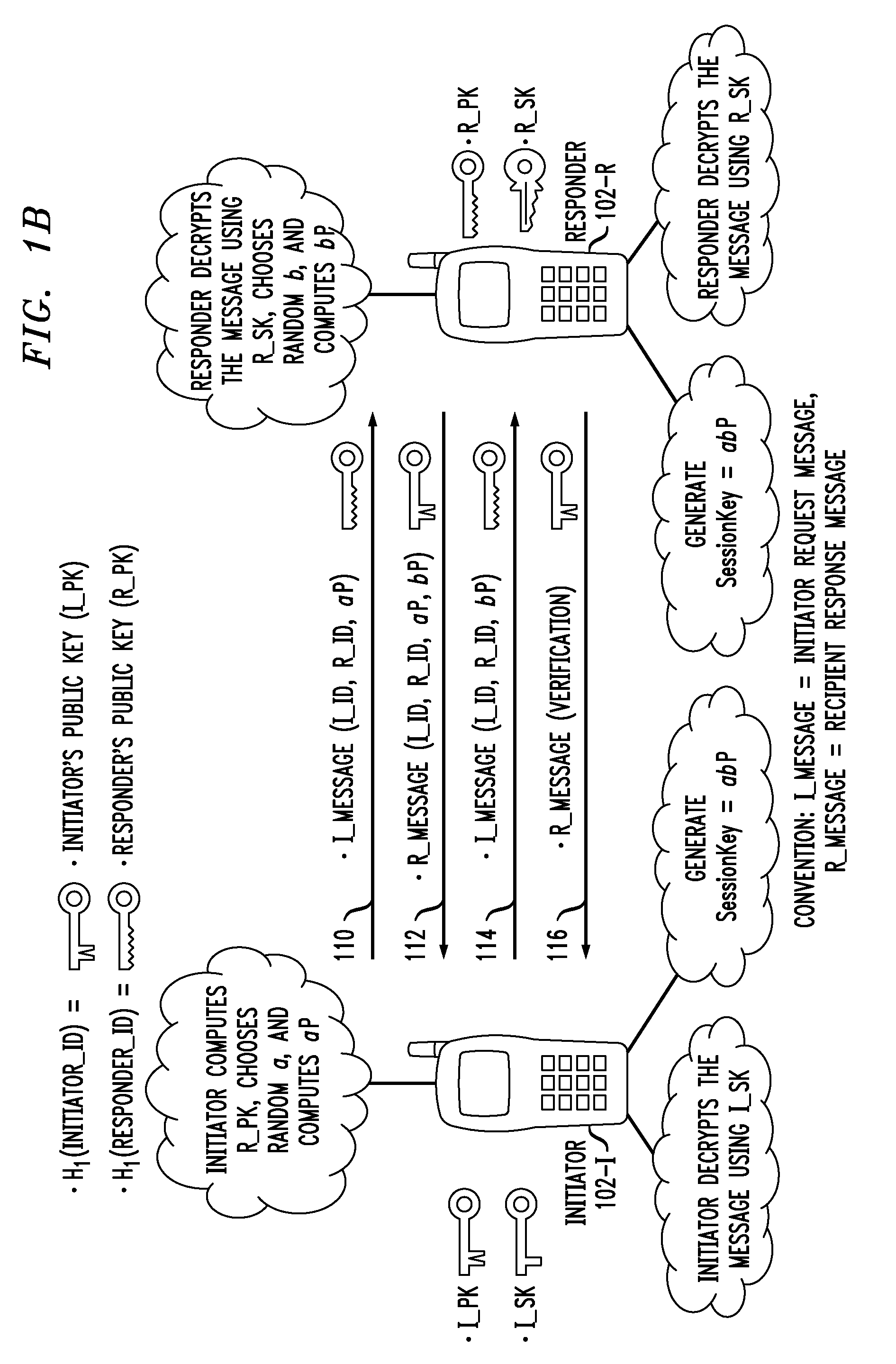
Secure Key Management in Multimedia Communication System
ActiveUS20110055567A1Key distribution for secure communicationMultiple keys/algorithms usageID-based encryptionCommunications system
Principles of the invention provide one or more secure key management protocols for use in communication environments such as a media plane of a multimedia communication system. For example, a method for performing an authenticated key agreement protocol, in accordance with a multimedia communication system, between a first party and a second party comprises, at the first party, the following steps. Note that encryption / decryption is performed in accordance with an identity based encryption operation. At least one private key for the first party is obtained from a key service. A first message comprising an encrypted first random key component is sent from the first party to the second party, the first random key component having been computed at the first party, and the first message having been encrypted using a public key of the second party. A second message comprising an encrypted random key component pair is received at the first party from the second party, the random key component pair having been formed from the first random key component and a second random key component computed at the second party, and the second message having been encrypted at the second party using a public key of the first party. The second message is decrypted by the first party using the private key obtained by the first party from the key service to obtain the second random key component. A third message comprising the second random key component is sent from the first party to the second party, the third message having been encrypted using the public key of the second party. The first party computes a secure key based on the second random key component, the secure key being used for conducting at least one call session with the second party via a media plane of the multimedia communication system.
Owner:ALCATEL LUCENT SAS
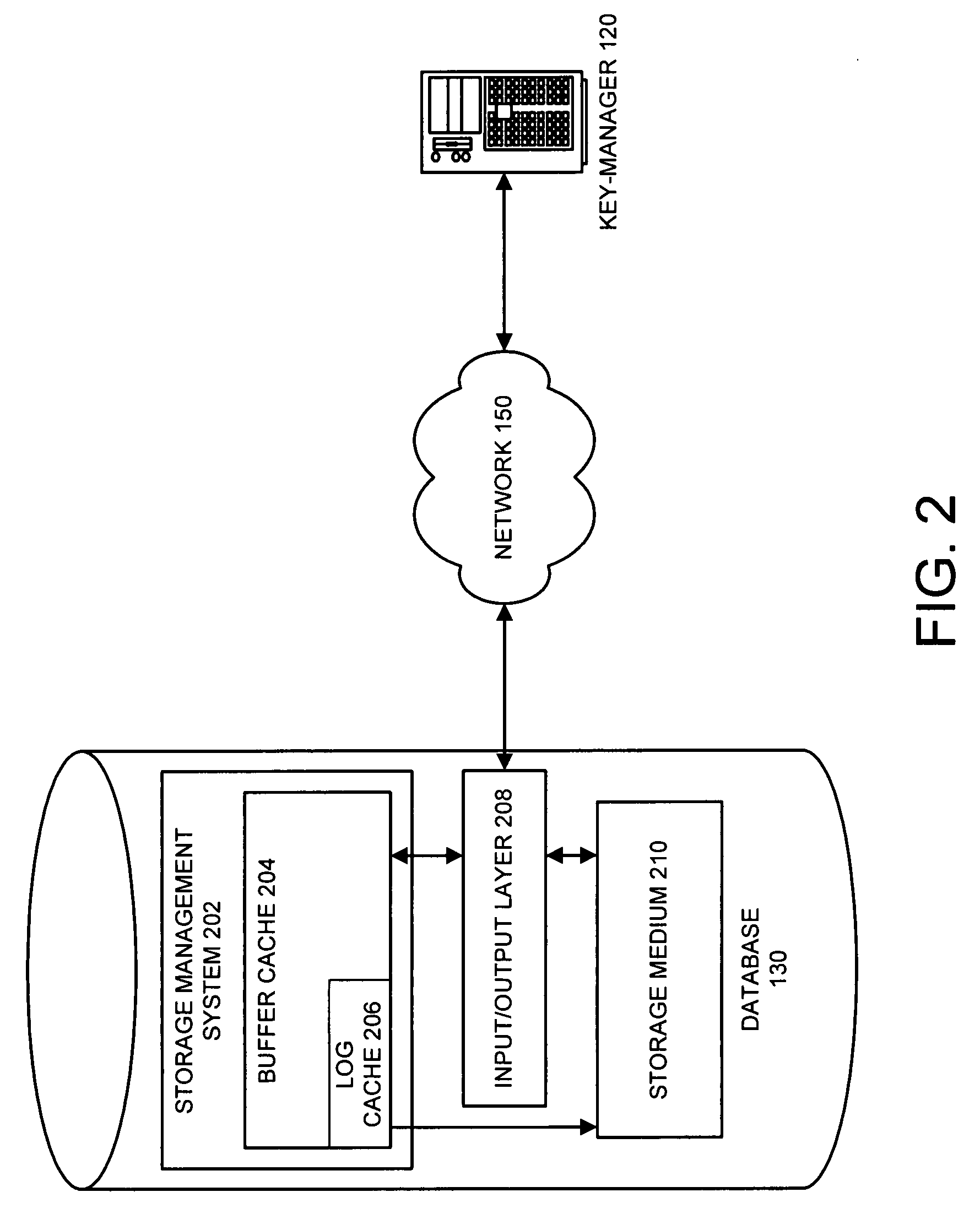
Method and apparatus for performing selective encryption/decryption in a data storage system
One embodiment of the present invention provides a system for performing selective encryption / decryption in a data storage system. During operation, the system receives a data block from a storage medium at an input / output layer, wherein the input / output layer serves as an interface between the storage medium and a buffer cache. Next, the system determines whether the data block is an encrypted data block. If not, the system stores the data block in the buffer cache. Otherwise, if the data block is an encrypted data block, the system retrieves a storage-key, wherein the storage-key is associated with a subset of storage, which is associated with the encrypted data block. Using the storage-key, the system then decrypts the encrypted data block to produce a decrypted data block. Finally, the system stores the decrypted data block in the buffer cache, wherein the data block remains encrypted in the storage medium.
Owner:ORACLE INT CORP
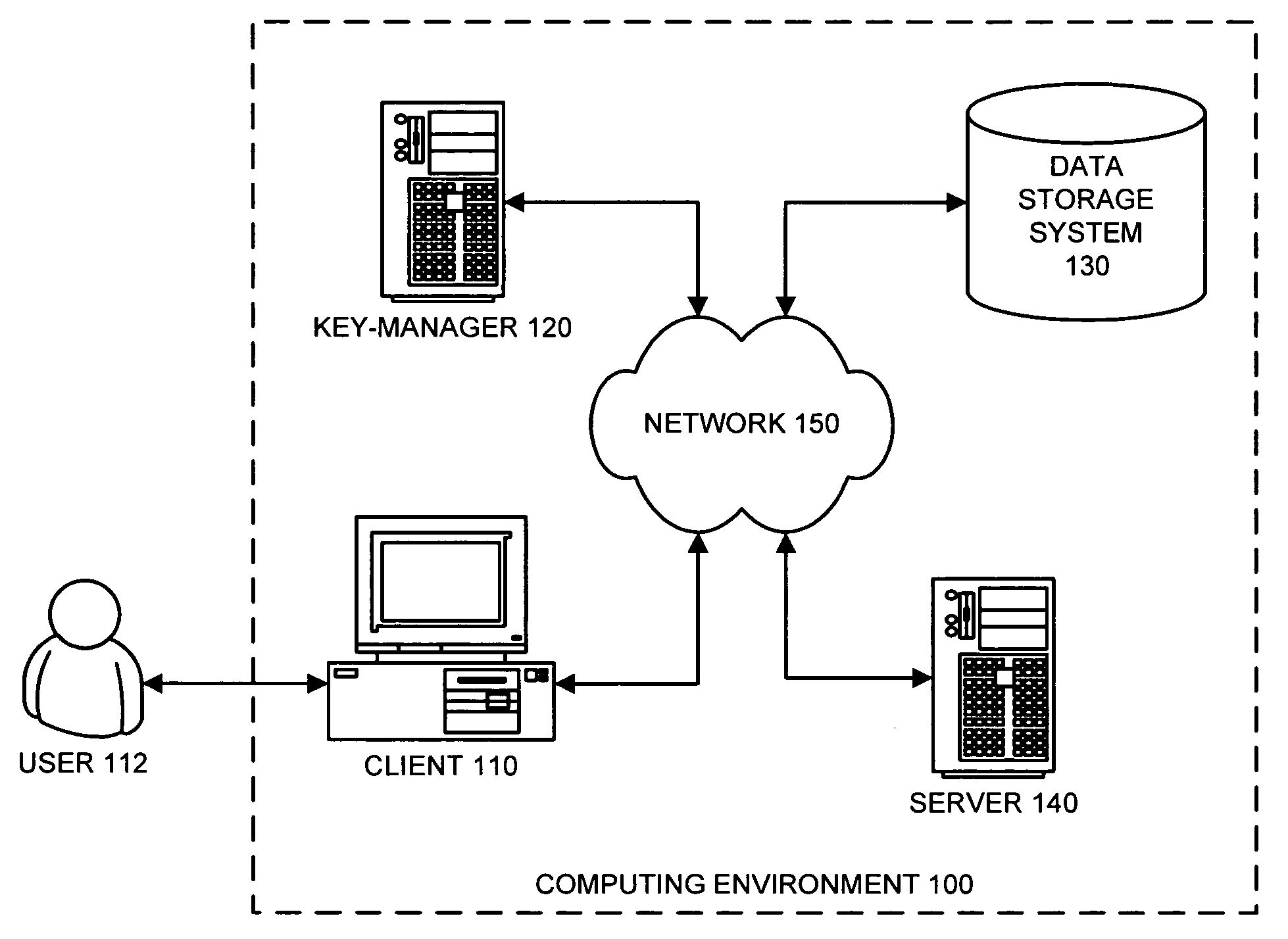
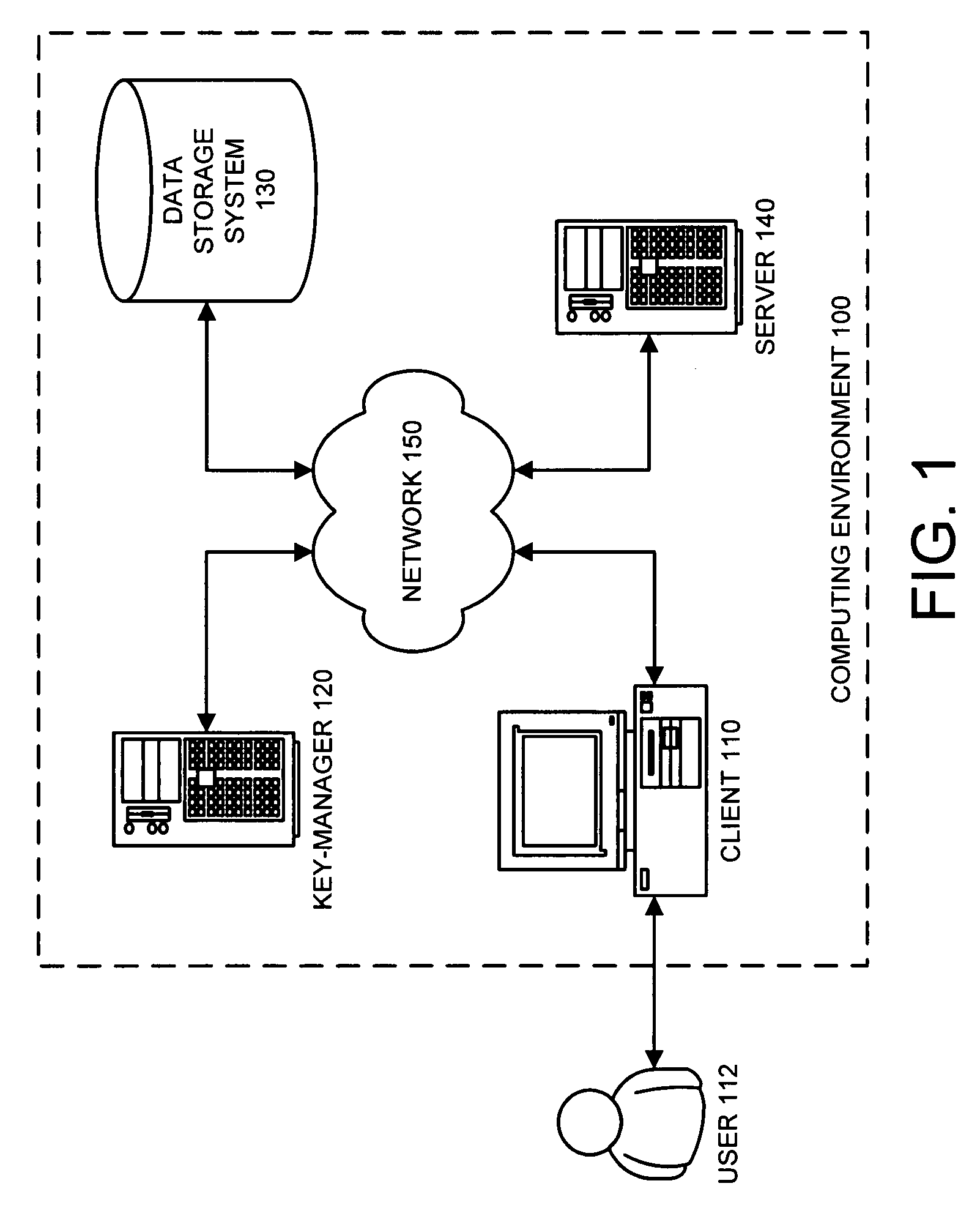
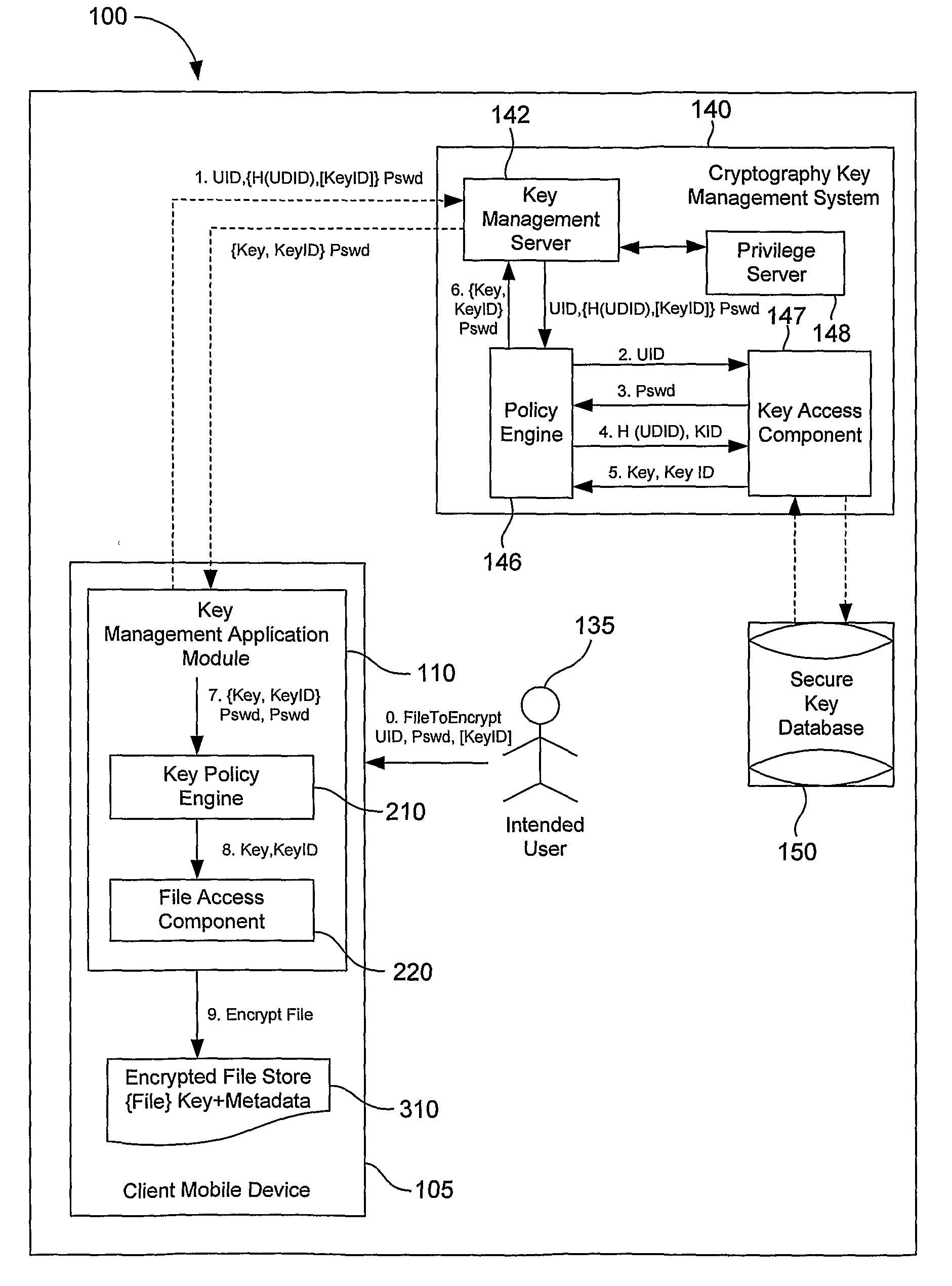
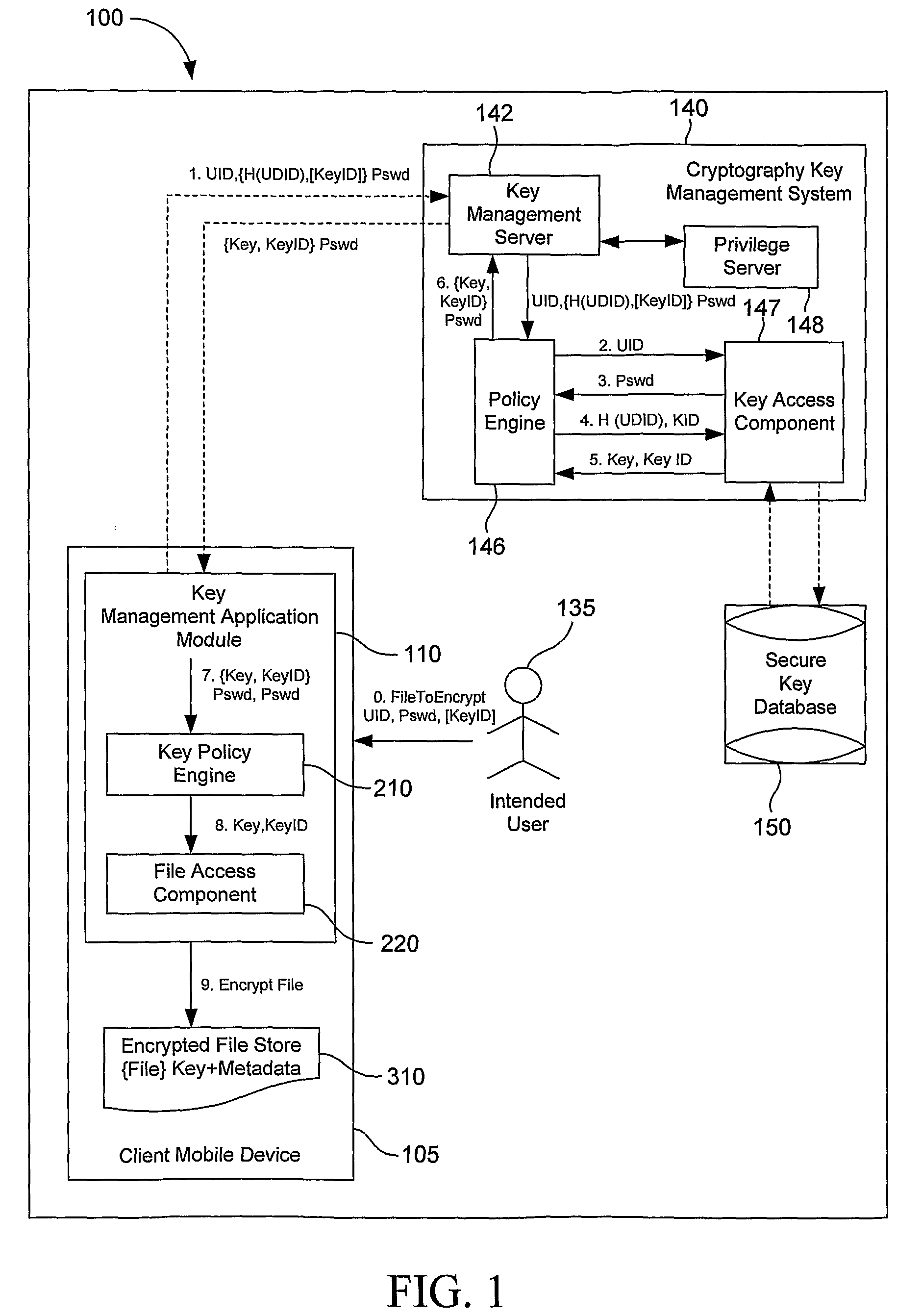
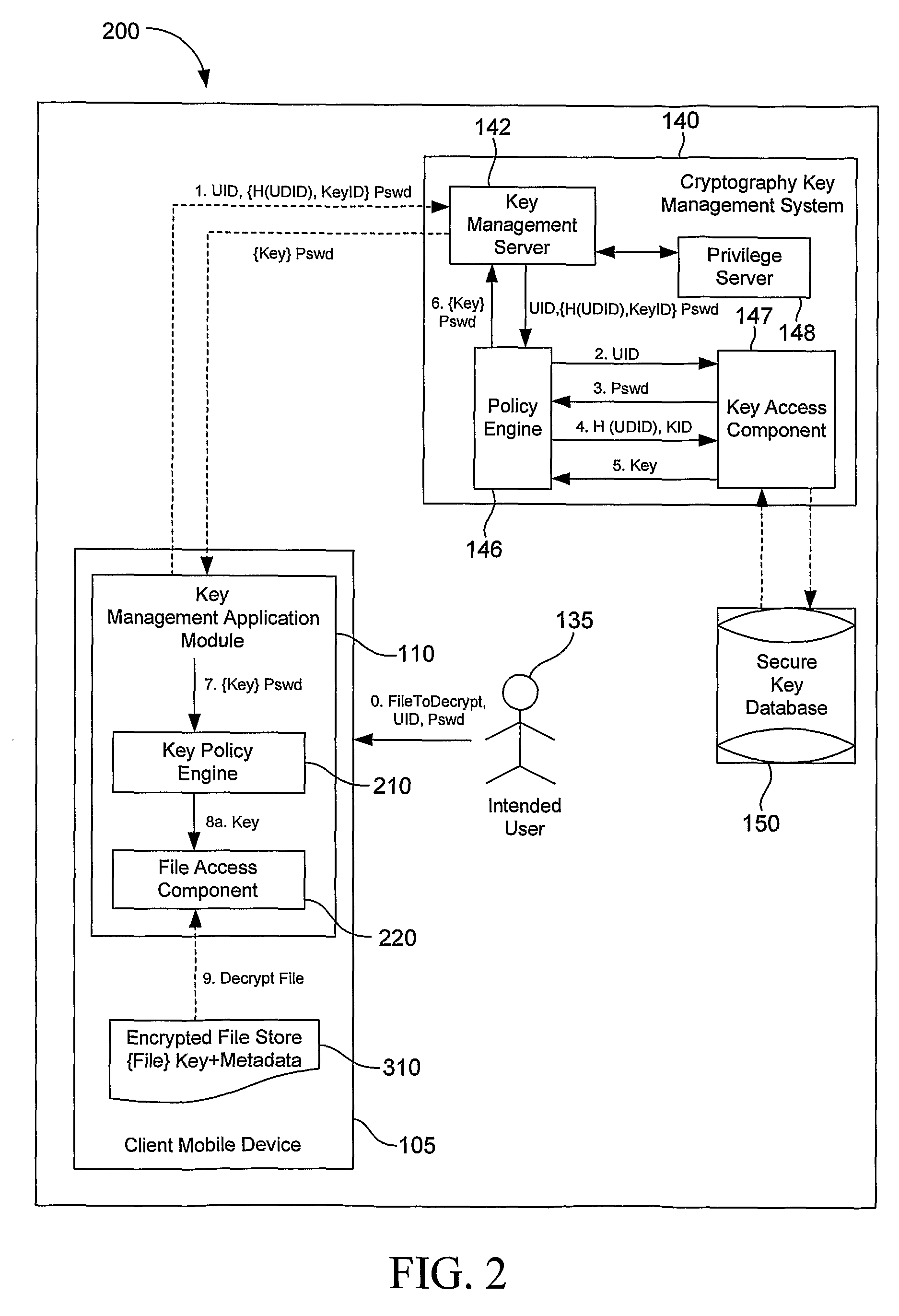
System, Method and Apparatus to Obtain a Key for Encryption/Decryption/Data Recovery From an Enterprise Cryptography Key Management System
ActiveUS20080232598A1Key distribution for secure communicationDigital data protectionPasswordData file
A technique for obtaining a key for encryption / decryption / data recovery from an enterprise key management system. In one example embodiment, this is accomplished by connecting a client mobile device to a cryptography key management using a UID, a UDID, the names of one or more data files to encrypt, a password Pswd, and a KeyID to obtain the key for encryption / decryption / data recovery.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Encryption/decryption system, encryption/decryption equipment, and encryption/decryption method
InactiveUS20050149745A1Adverse of arithmetic operationAdverse effect of loadRandom number generatorsData stream serial/continuous modificationComputer hardwareLogical operations
An object of the present invention is to provide an encryption / decryption system and encryption / decryption equipment which suppress the adverse effect of a load on arithmetic and logic operations to be performed by a computer, whose cipher system is hard to infer, which provide great security, and which eliminate the labor of managing keys or entering a key. A security key that encrypts or decrypts data using random numbers generated by a thermal noise random number generator is detachably attached to a personal computer. When attached to the personal computer, the security key autonomously encrypts or decrypts data to be handled by the personal computer. In other words, encryption / decryption equipment employing the thermal noise random number generator is detachably attached to a computer. The encryption / decryption equipment can be used as easily as keystrokes are made, and great security can be guaranteed.
Owner:BUFFALO CORP LTD
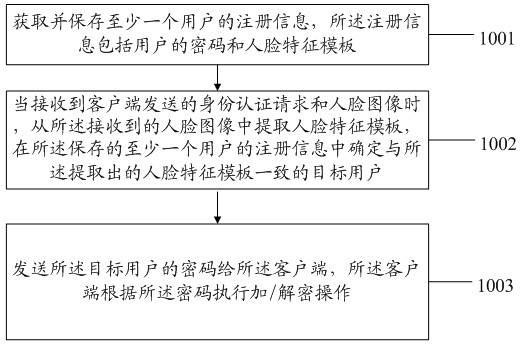
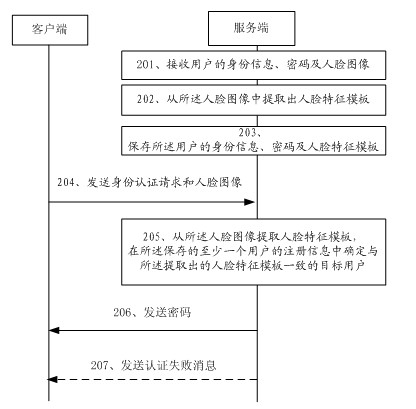
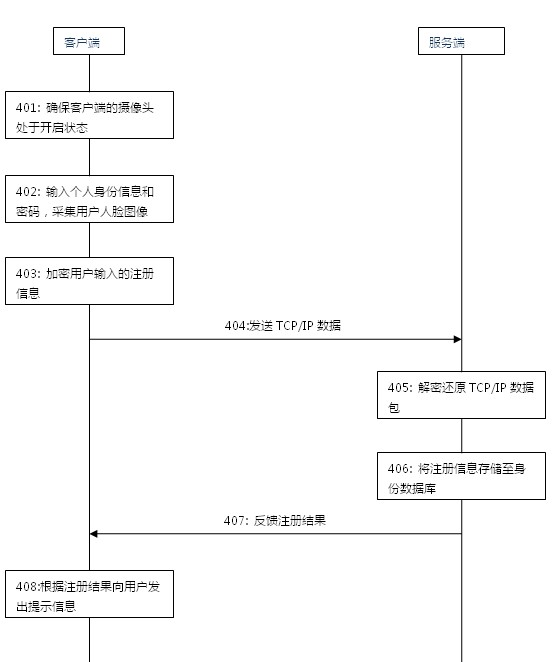
Electronic data protection method, device and system based on face recognition
The embodiment discloses an electronic data protection method, a device and a system based on face recognition, relating to the field of encryption-decryption security technologies of electronic data and improving the safety of data protection. The electronic data protection method comprises the following steps of: obtaining and storing registration information of at least one user, wherein the registration information comprises a password and a facial feature template of the user; extracting the facial feature template from a received face image when receiving an authentication request and the face image sent by a client, and determining a target user consistent with the extracted facial feature template from the stored registration information of the at least one user; and sending the password of the target user to the client, and indicating the client to carry out encryption-decryption operation according to the password. The embodiment is mainly applied to an encryption-decryptiontreatment process of data and utilizes the face recognition technology for authenticating user's identify, thereby improving the safety of the data.
Owner:HANVON CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com