Patents
Literature
526 results about "Password protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
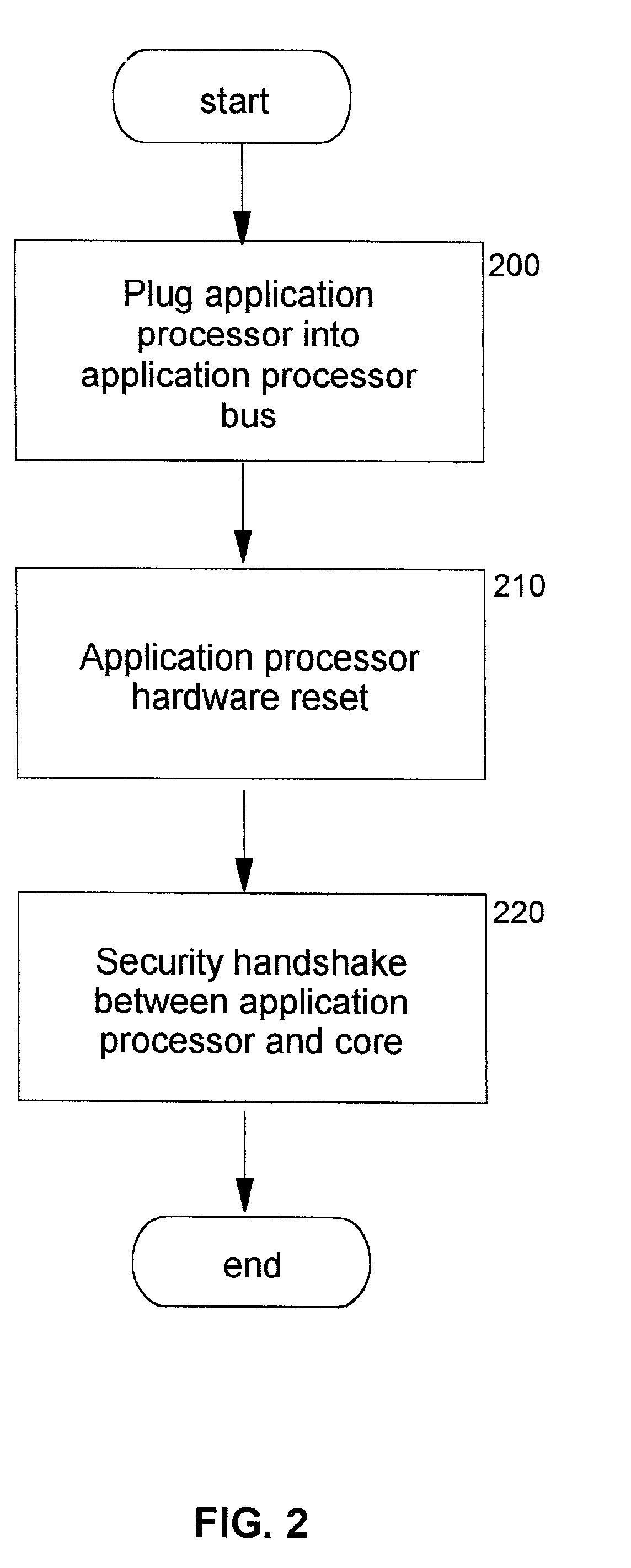
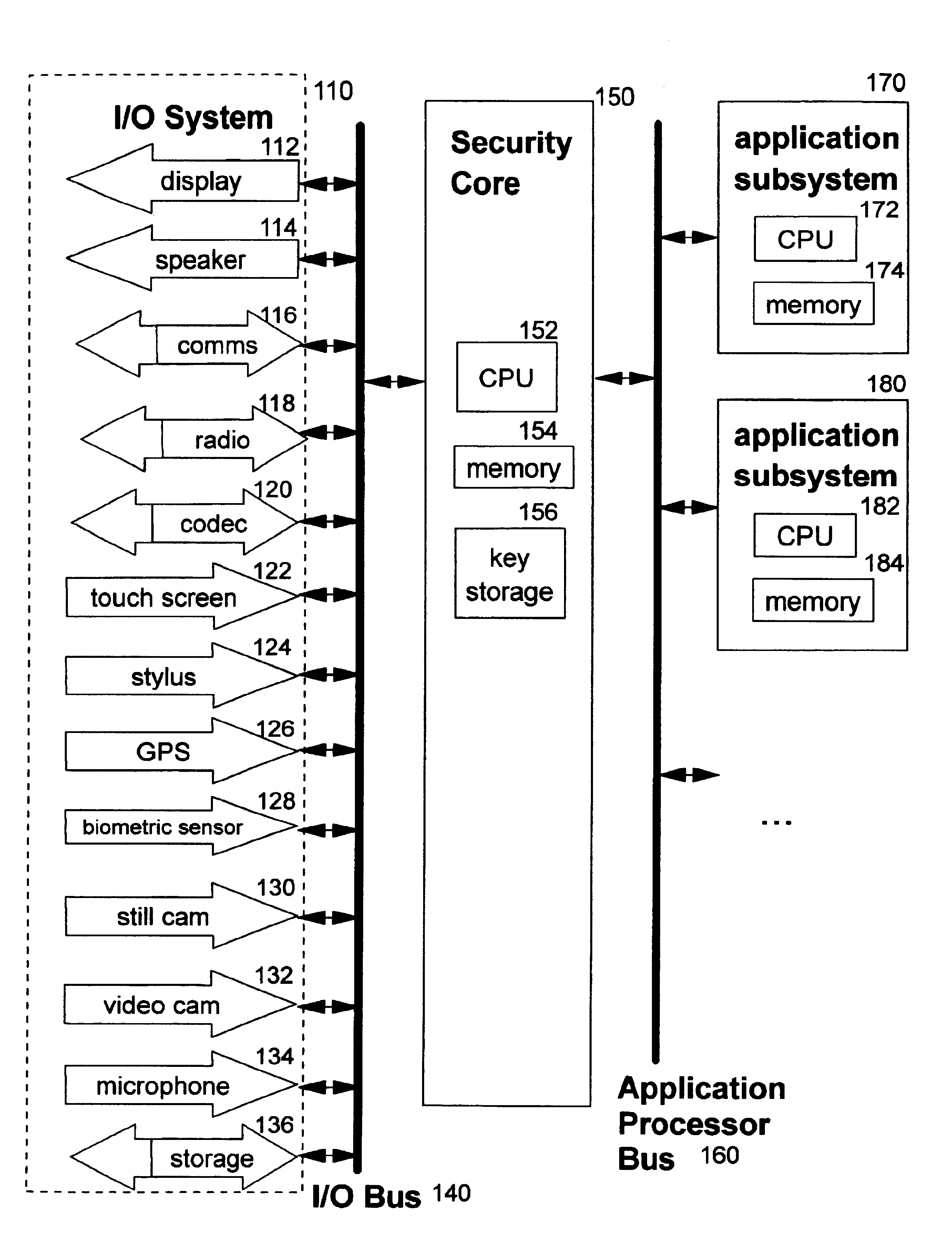
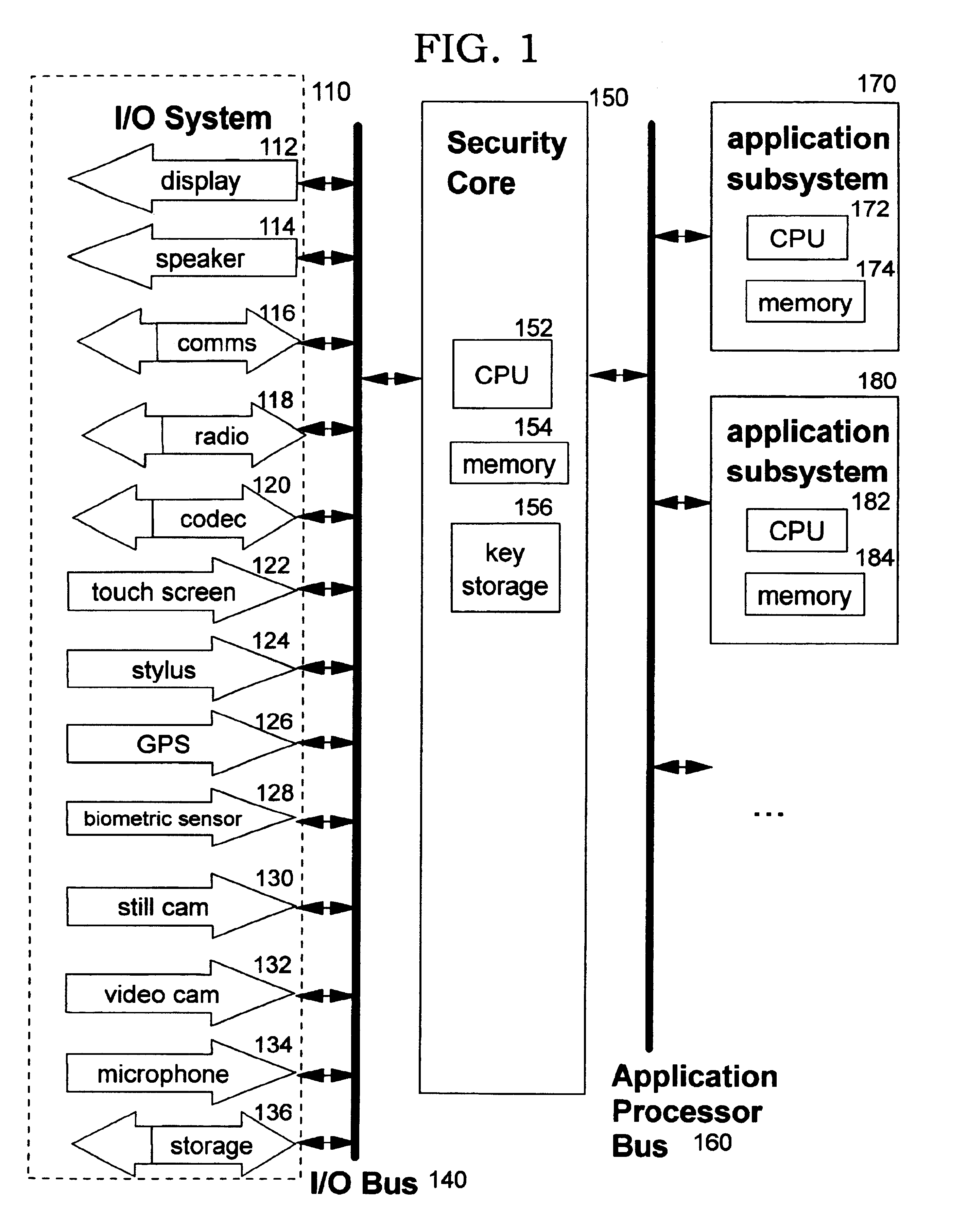
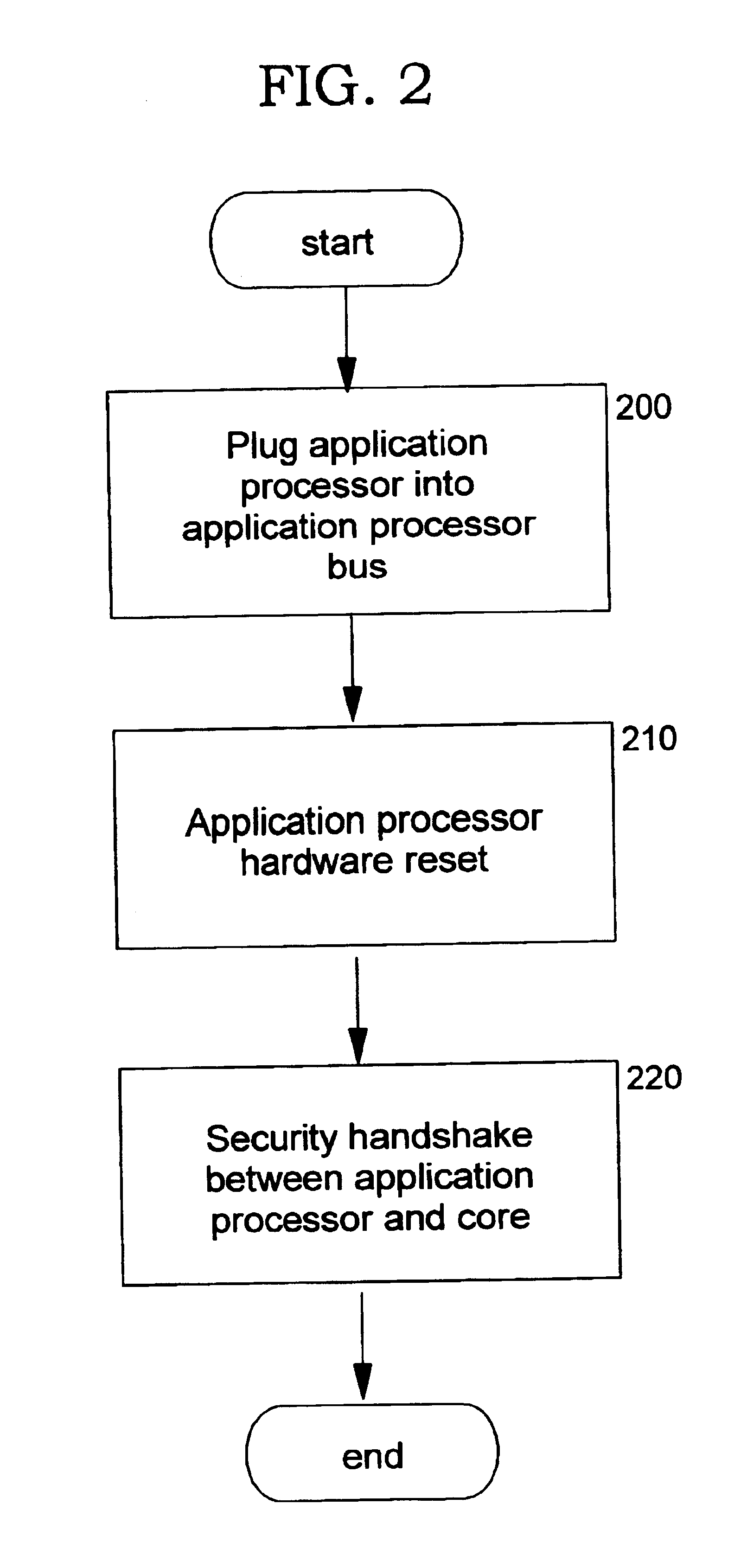
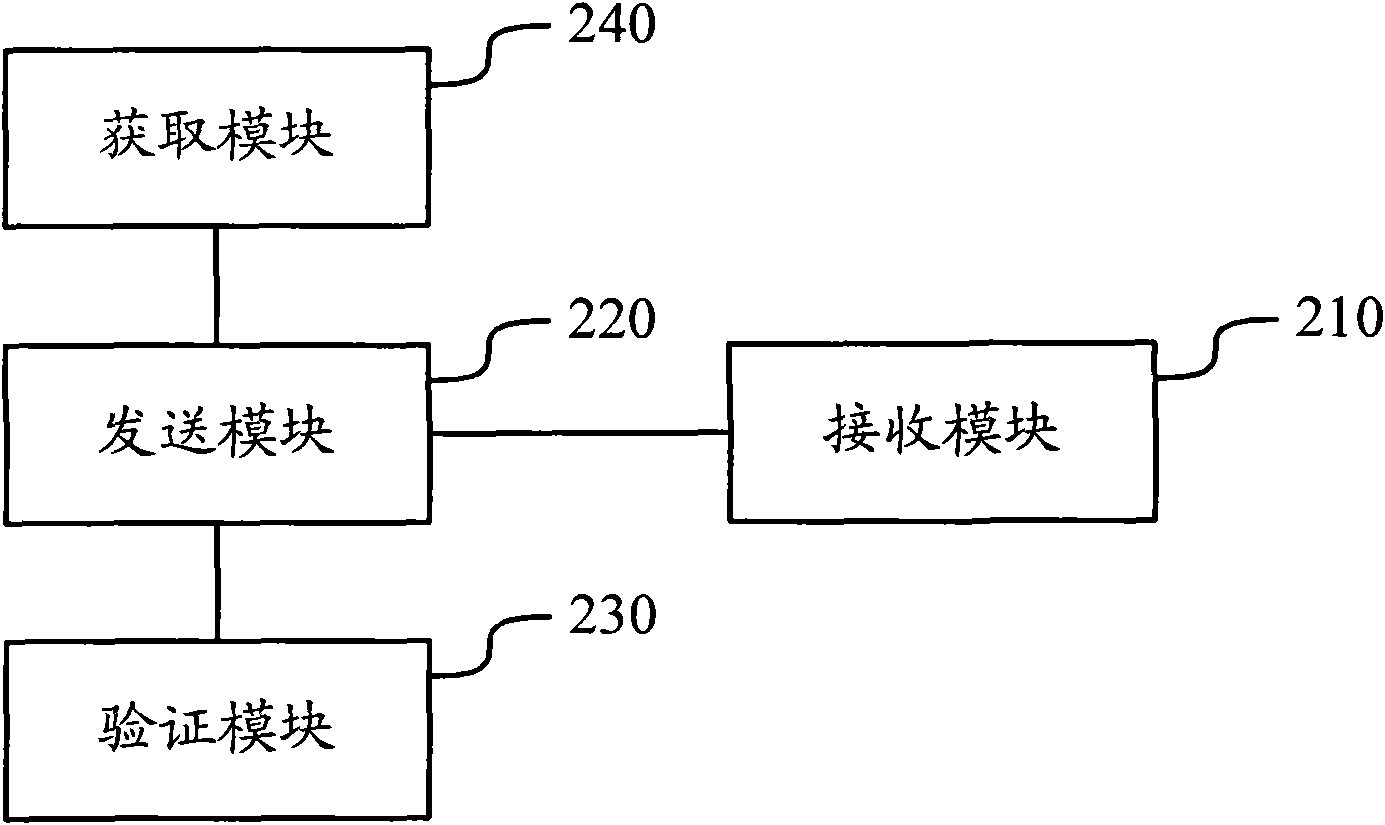
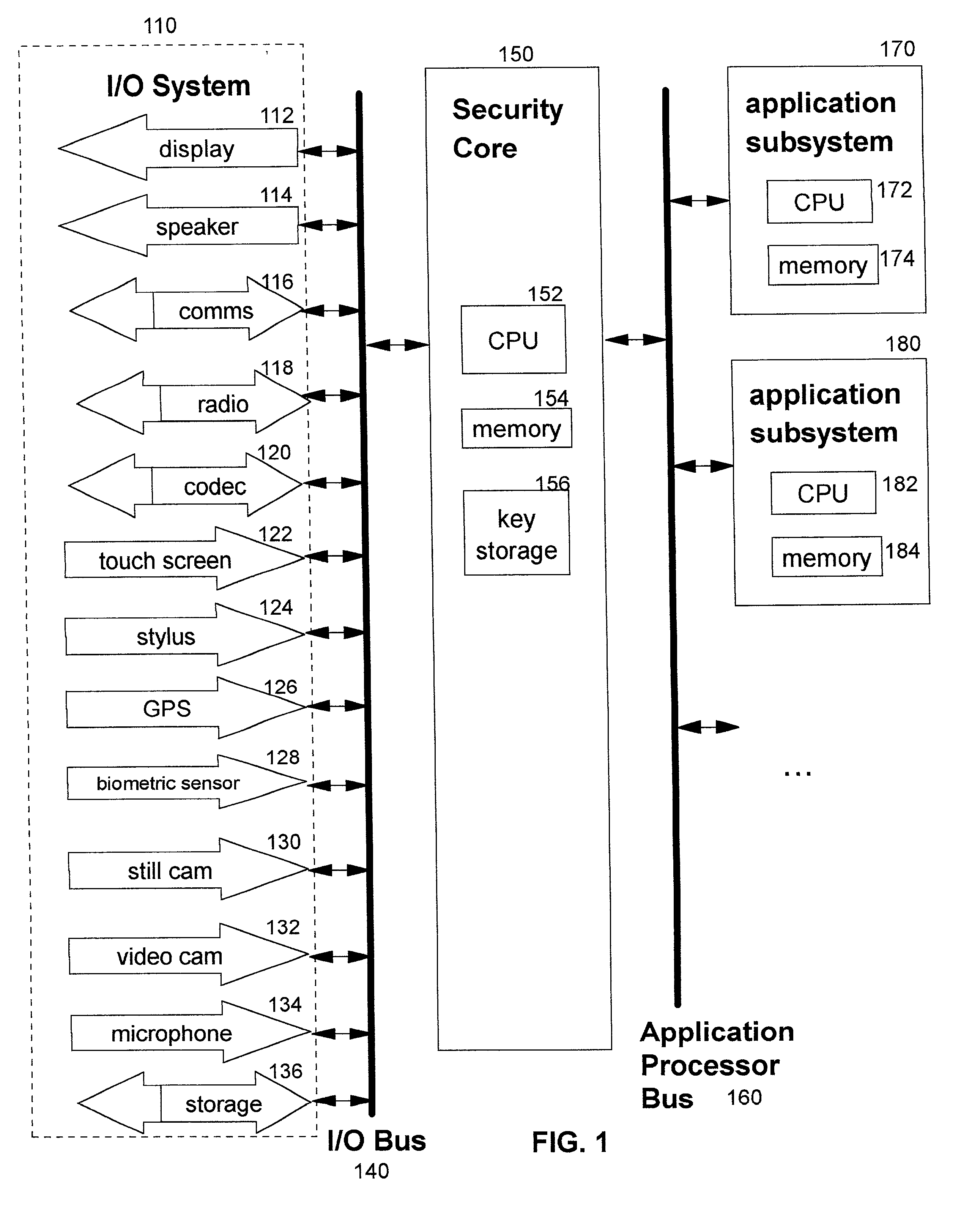
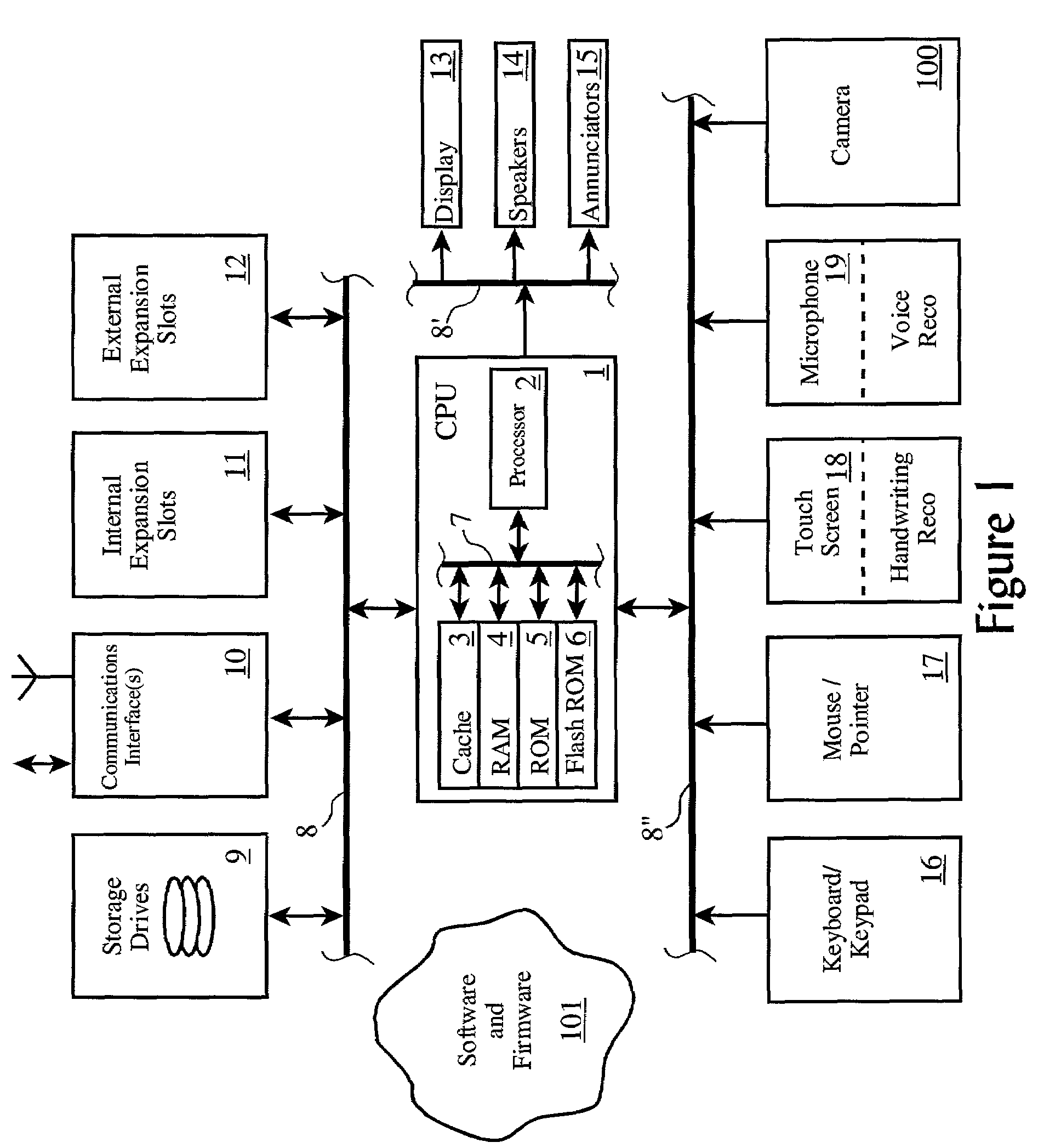
Password-protection module
ActiveUS20060041759A1Key distribution for secure communicationDigital data processing detailsMutual authenticationPassword protection
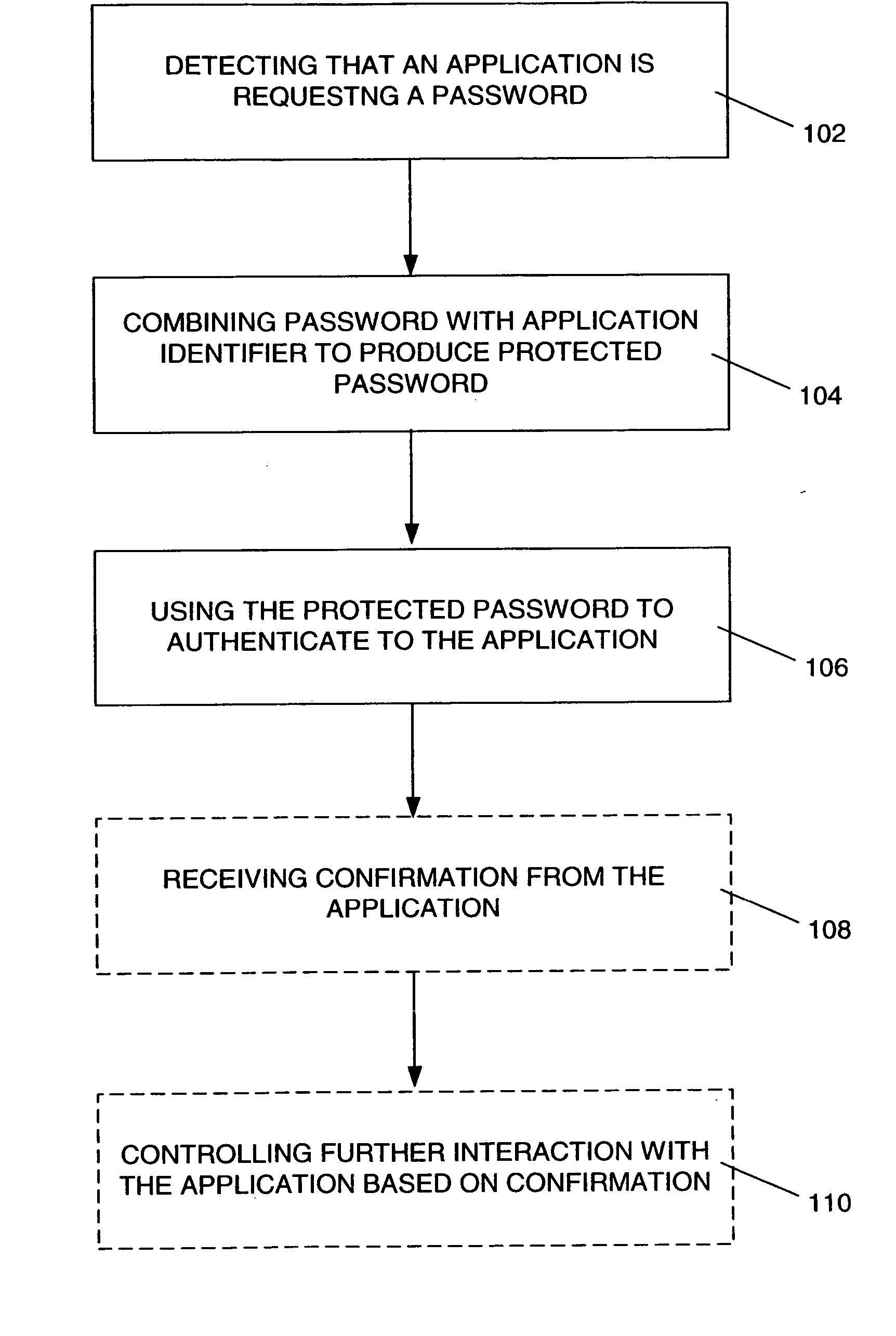
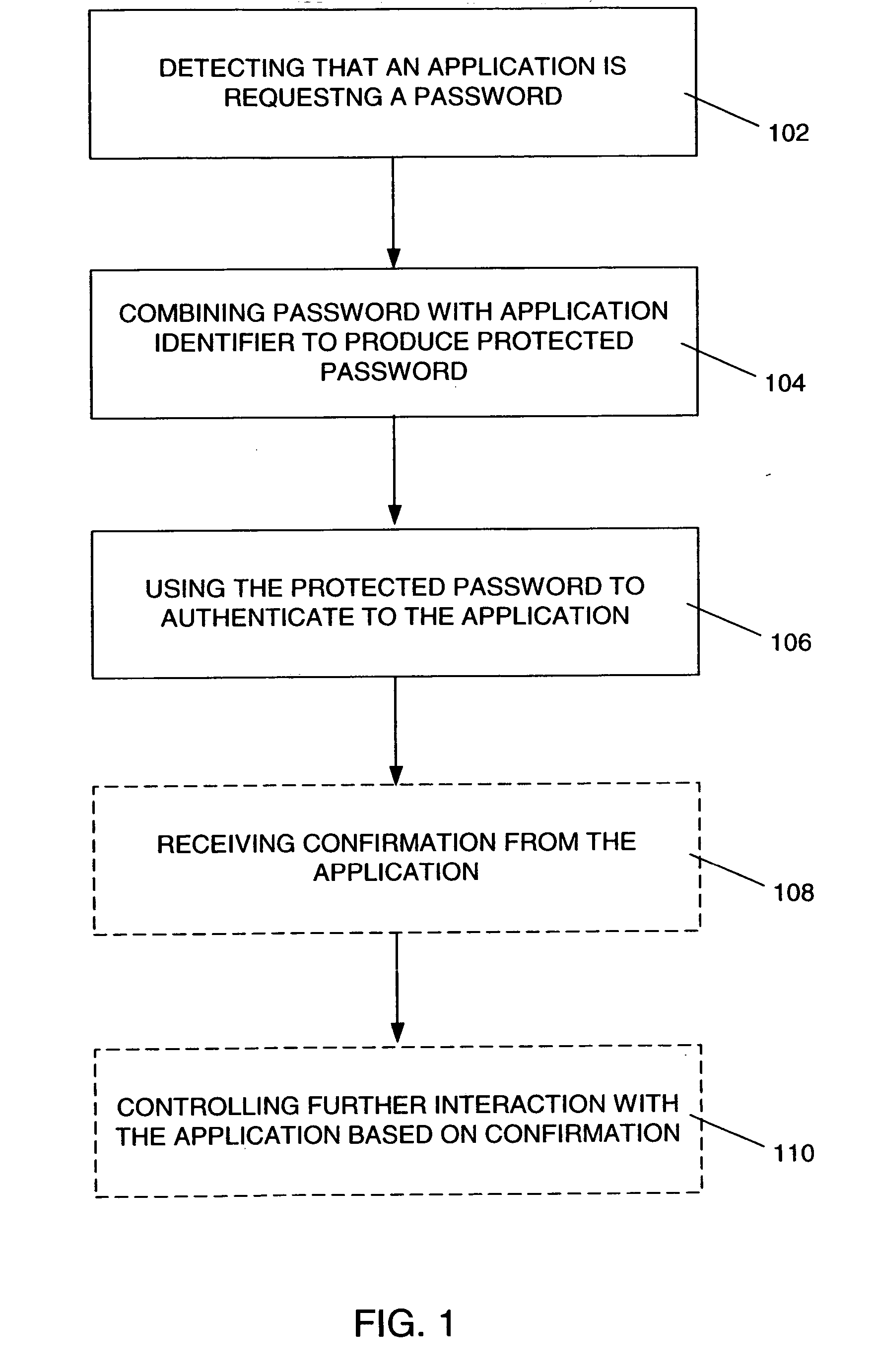
A method of protecting a password being used to establish interaction between a user and an application includes detecting a request for the password from the application by receiving a notification from the user indicating the request. The method further includes combining the password with information identifying the application, so as to produce a protected password, and authenticating to the application using the protected password. The method may also include a mutual authentication capability between user and the application.
Owner:EMC IP HLDG CO LLC
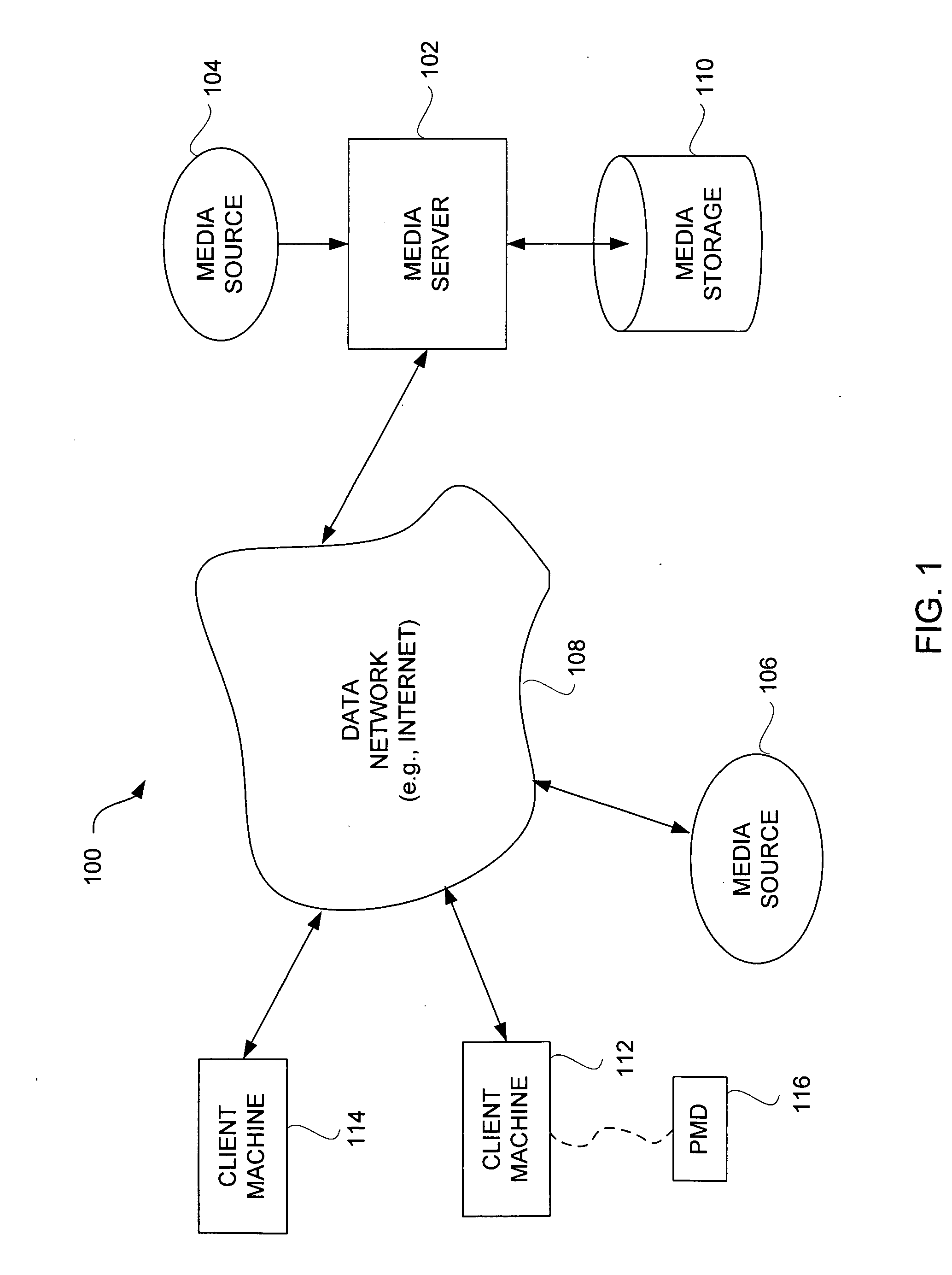
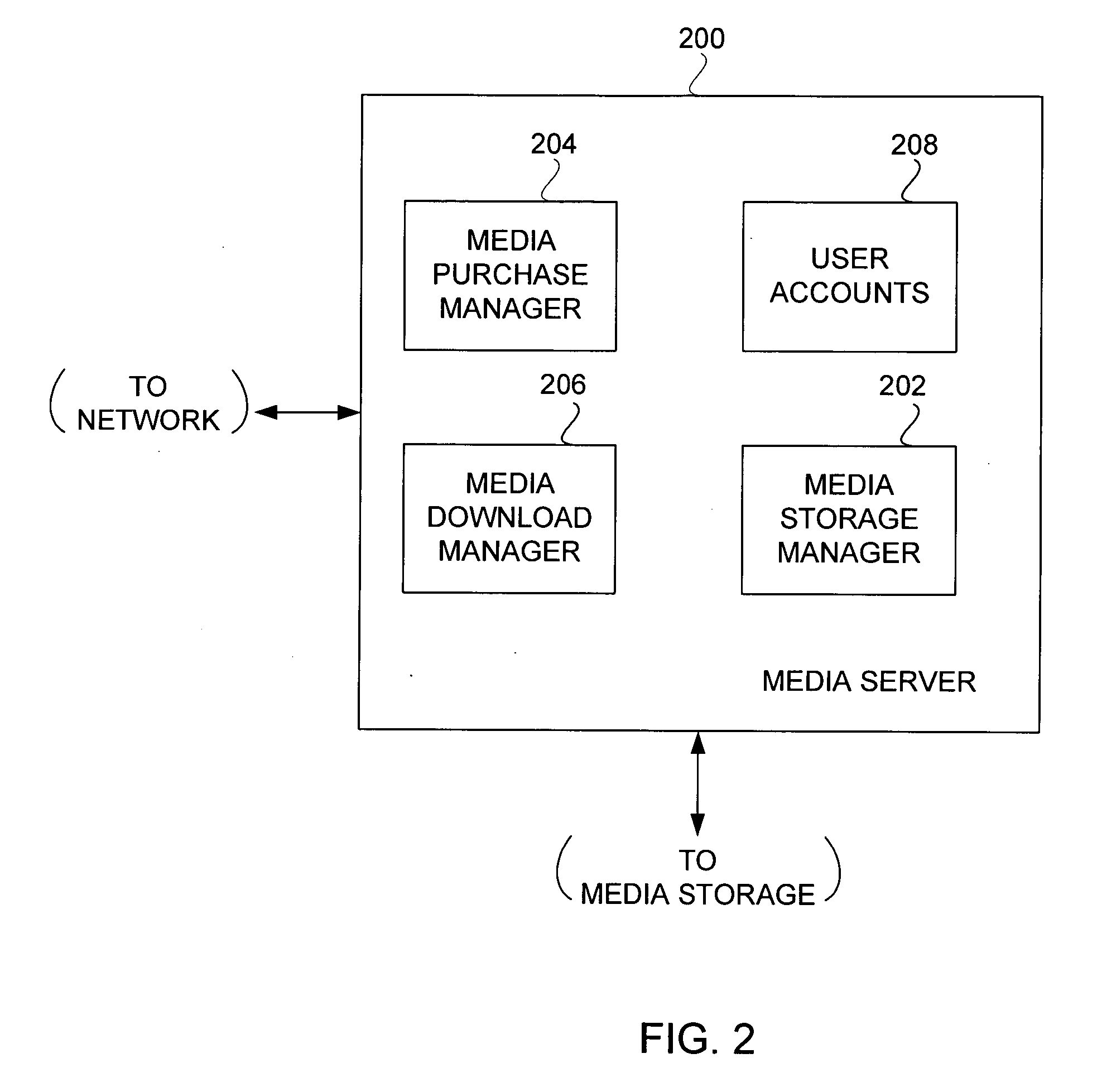
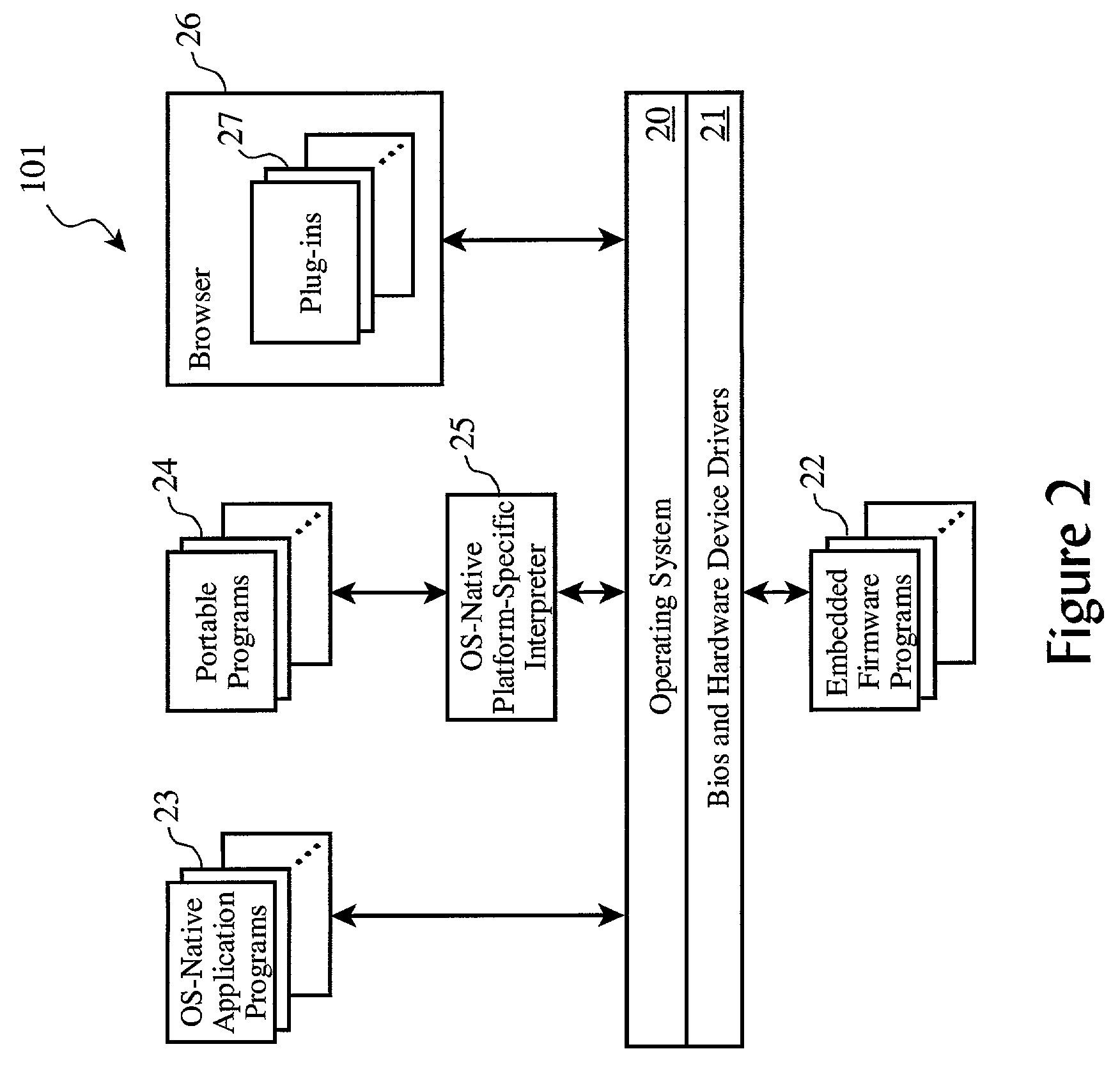
Partial encryption techniques for media data
InactiveUS20070083467A1Fast decryptionEfficient executionData processing applicationsRecord information storageComputer hardwareClient-side
Improved techniques to partially encrypt media files are disclosed. The encryption serves to cryptographically secure only a portion of the media data within a media file, while the remaining portion of the media data is not cryptographically secured. Although only partial encryption is used, the portion being encrypted serves to substantially disrupt usefulness of other parts of the media file which are not encrypted. In other words, the partial encryption renders the media file substantially unusable by unauthorized users. In one embodiment, the partial encryption is performed by a host device and thereafter the partially encrypted media file is delivered to a client device. The client device, if authorized, can subsequently decrypt the partially encrypted media file and utilize (e.g., play) the media file. However, since the media files are only partially encrypted, the decryption is likewise also only partial, which makes decryption faster and less resource intensive.
Owner:APPLE INC
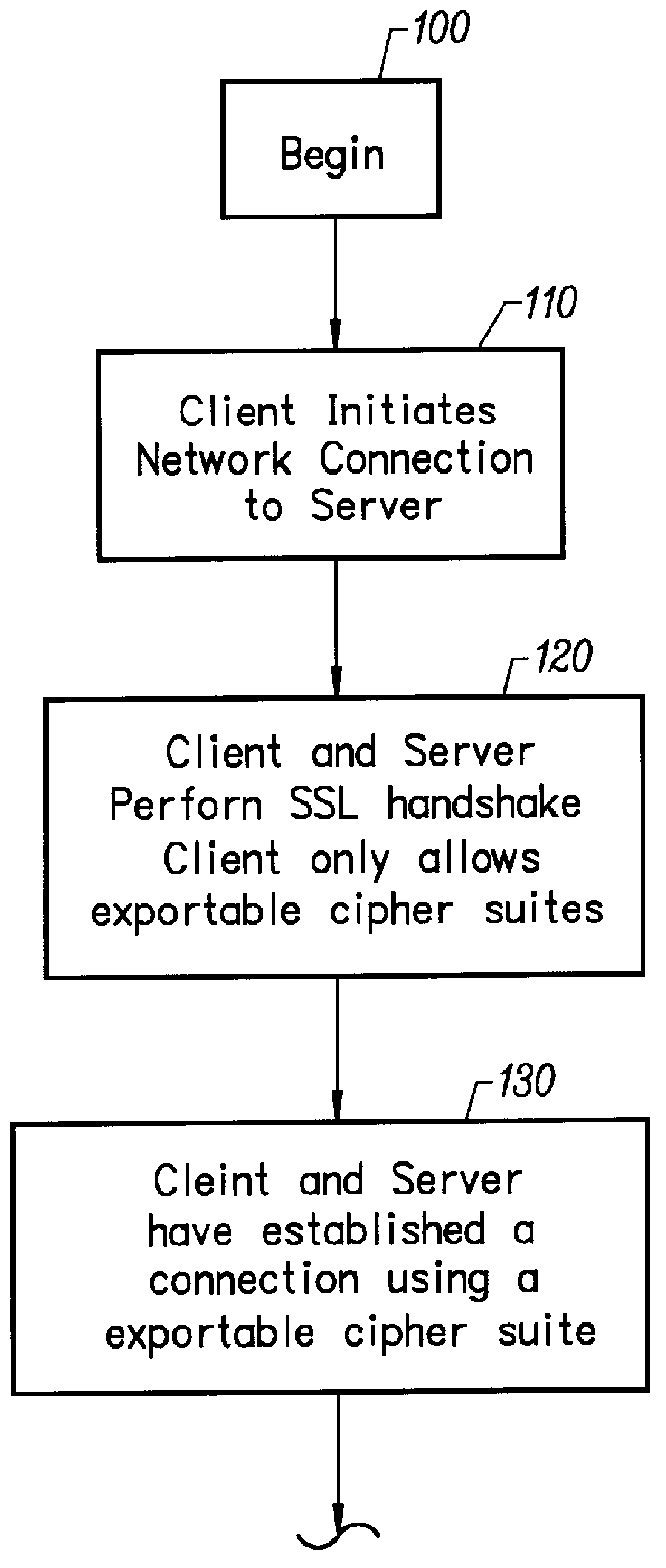
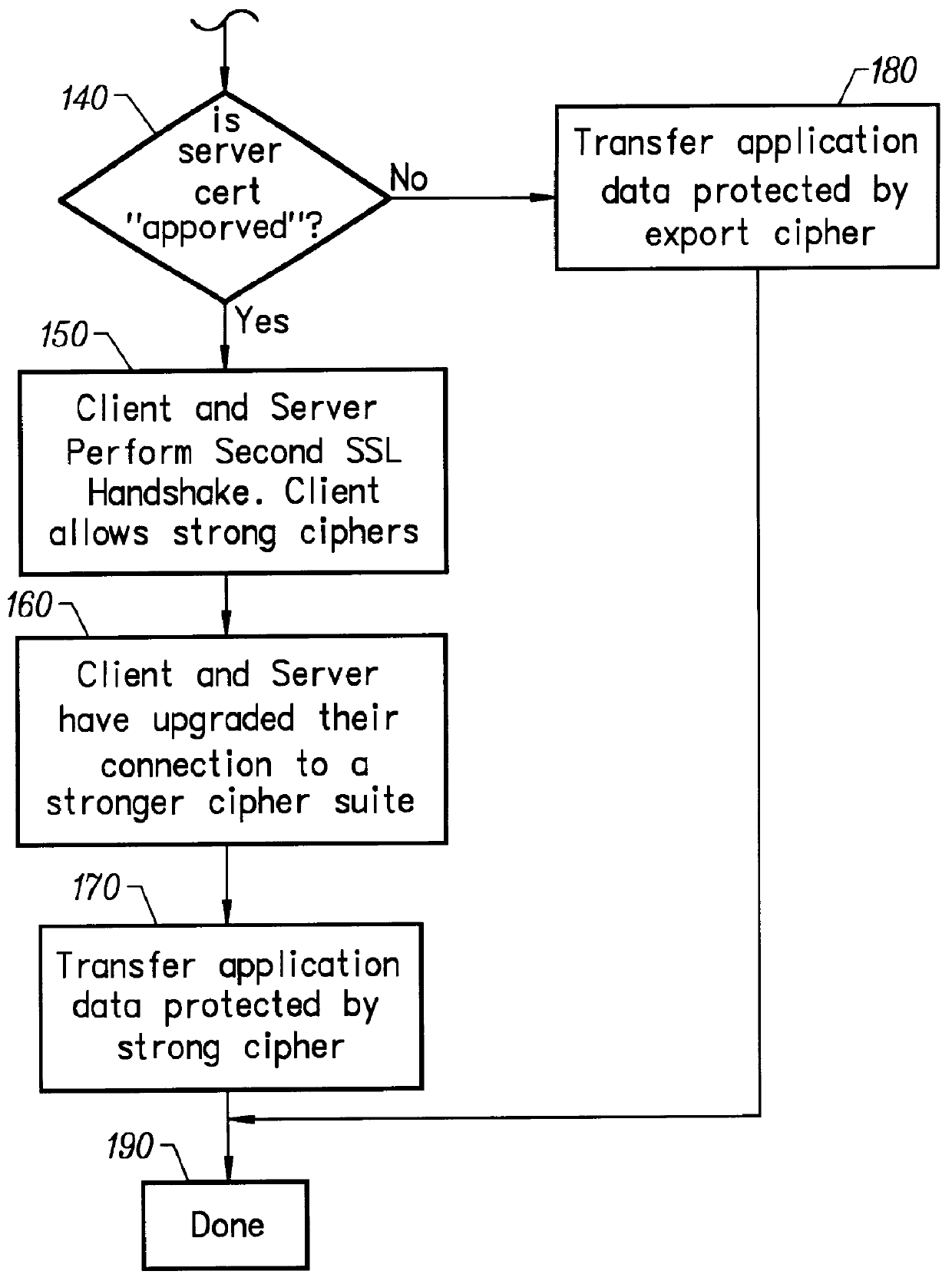
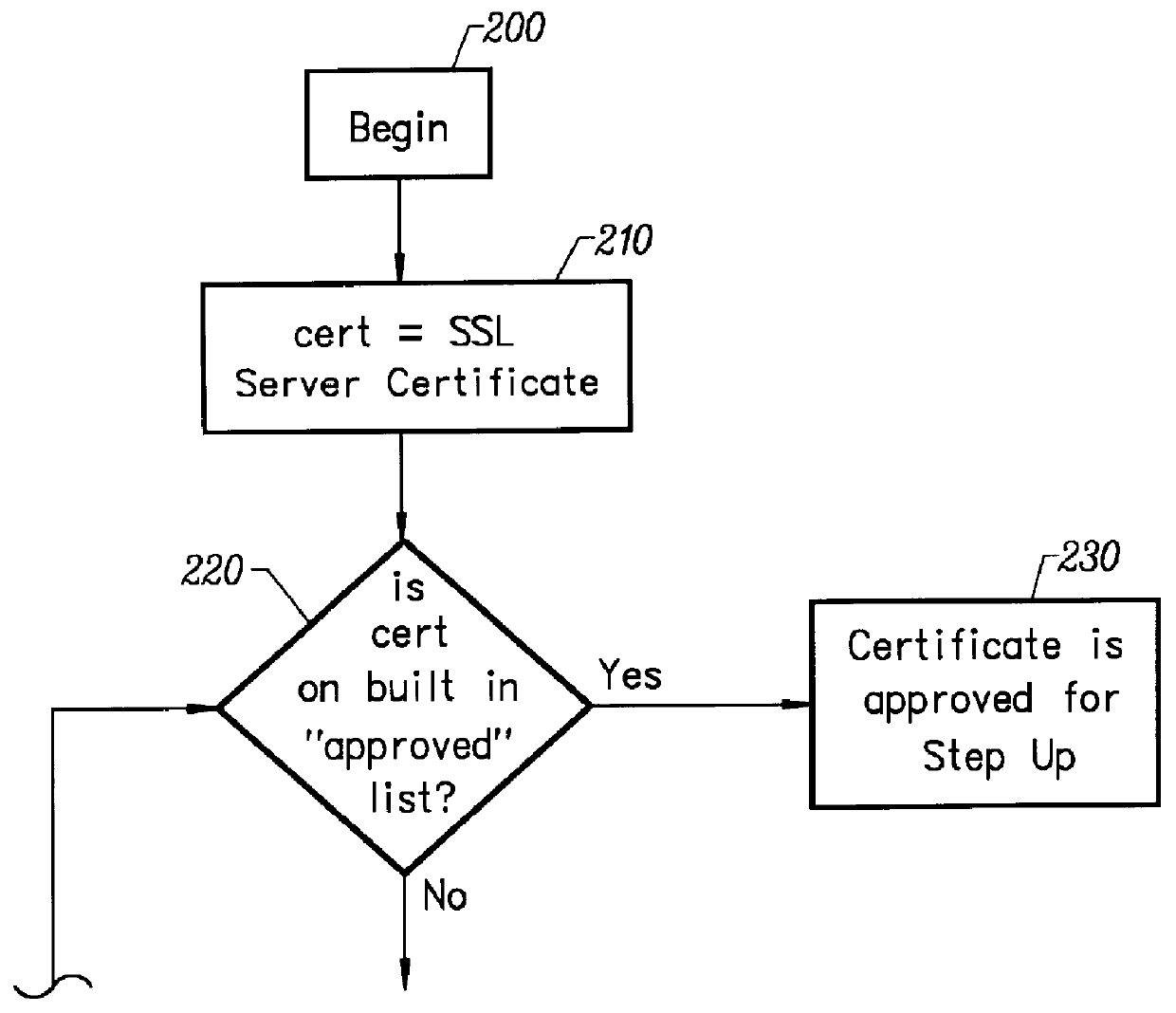
SSL step-up
InactiveUS6094485APublic key for secure communicationMultiple digital computer combinationsClient-sideKey size
A process is provided that allows an exportable SSL client to negotiate an encrypted session using strong encryption with a server if the server is allowed to use strong encryption. With this process, the SSL client is normally limited to export strength encryption. But, when it is communicating with an approved server, it is able to expand the available set of encryption algorithms to include stronger algorithms / key lengths. The process involves performing an SSL handshake twice. The process begins when a client, i.e. a user, wants to establish a session with a server. The client first initiates a network connection to the server. The first handshake between an export client and an approved server results in an SSL session that uses export strength encryption. This establishes a connection using an exportable cipher suite. The client examines the server's certificate obtained as part of the first handshake. If the server is not approved, the SSL session transfers application data that are protected by the export cipher. If the server is approved, then the client initiates a second handshake, this time allowing stronger cipher suites. The result of the second handshake is an SSL session that uses strong encryption. The SSL session may then be used to transfer application data that are protected by the strong cipher suite. At this point, the process is complete.
Owner:META PLATFORMS INC
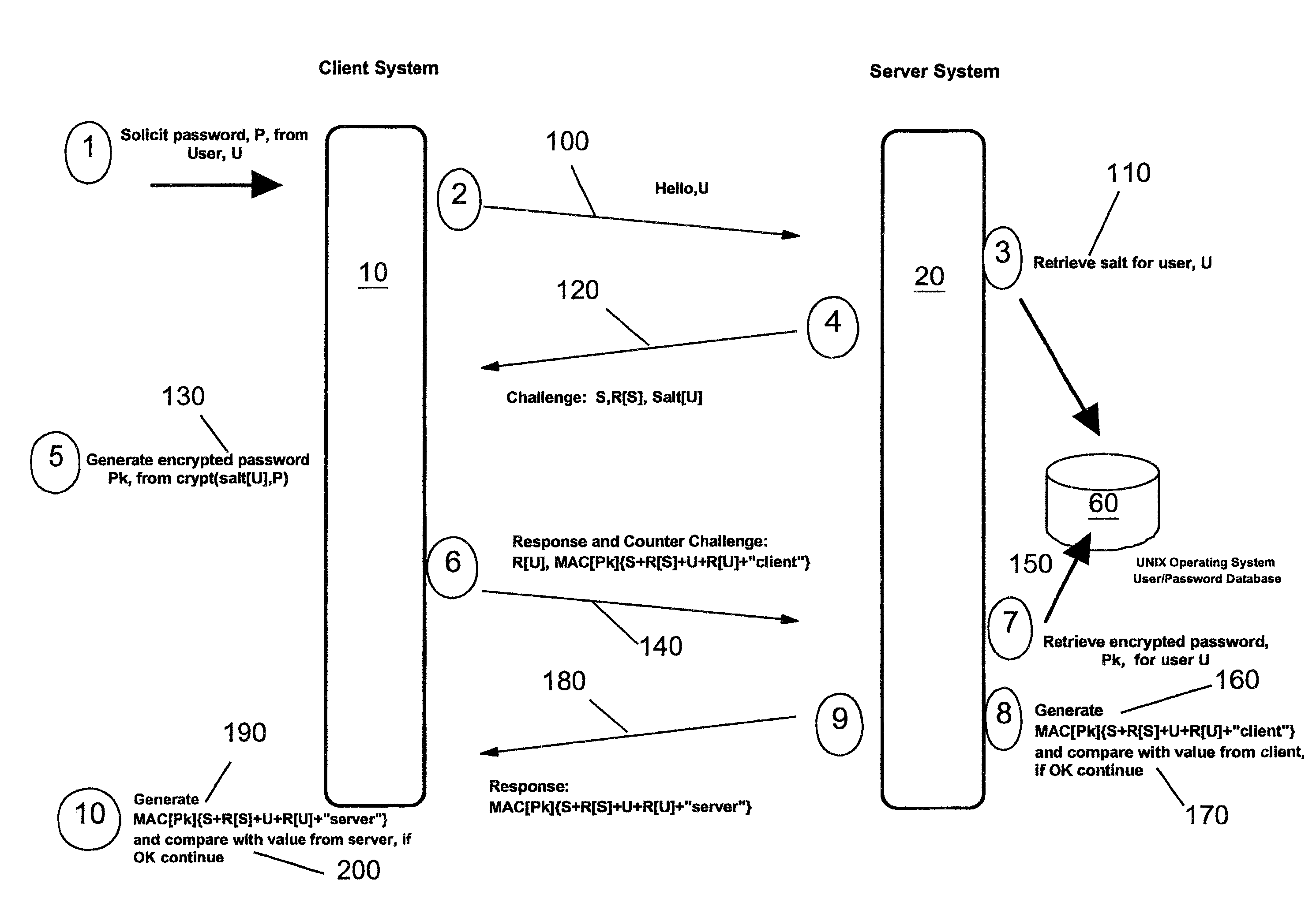
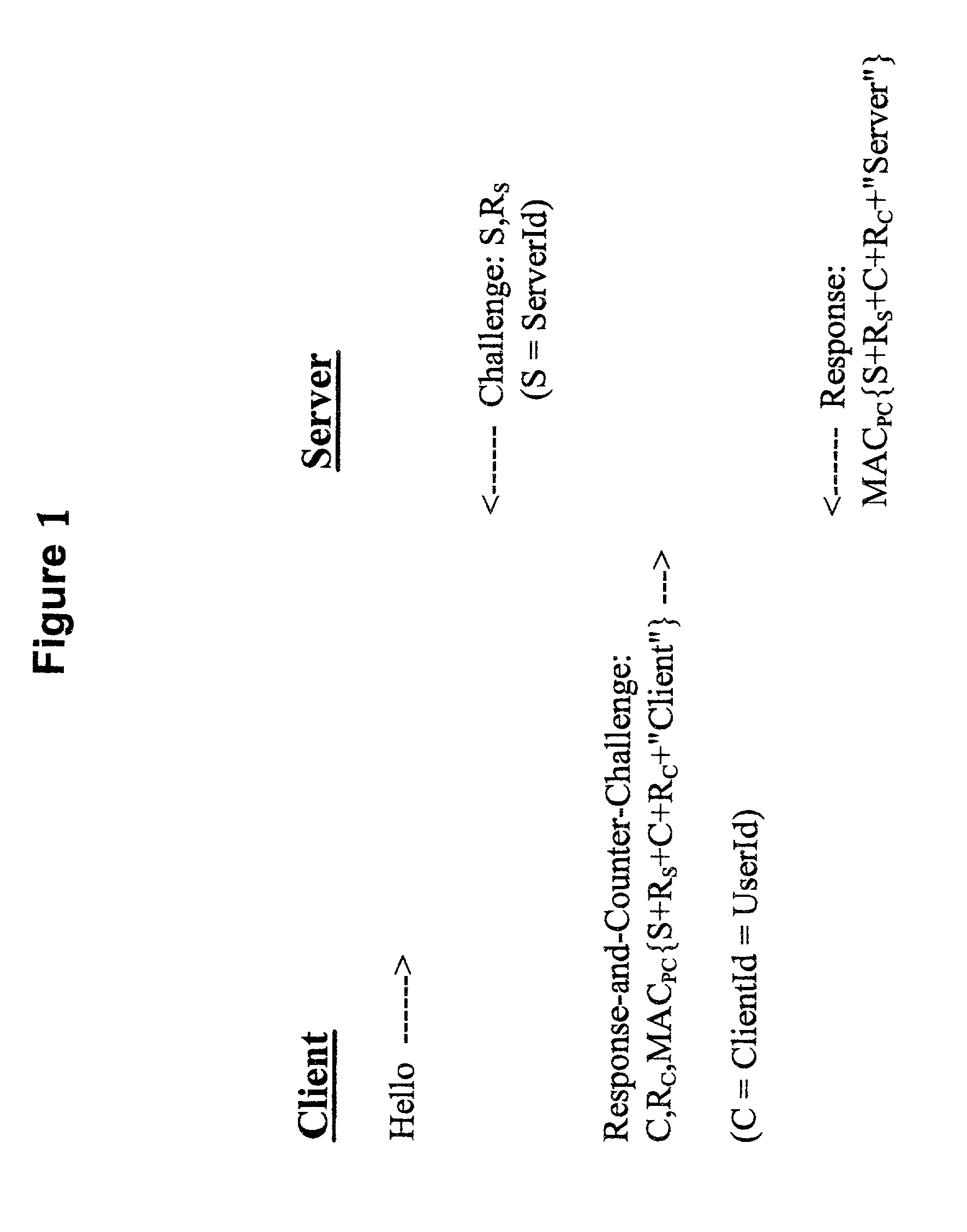
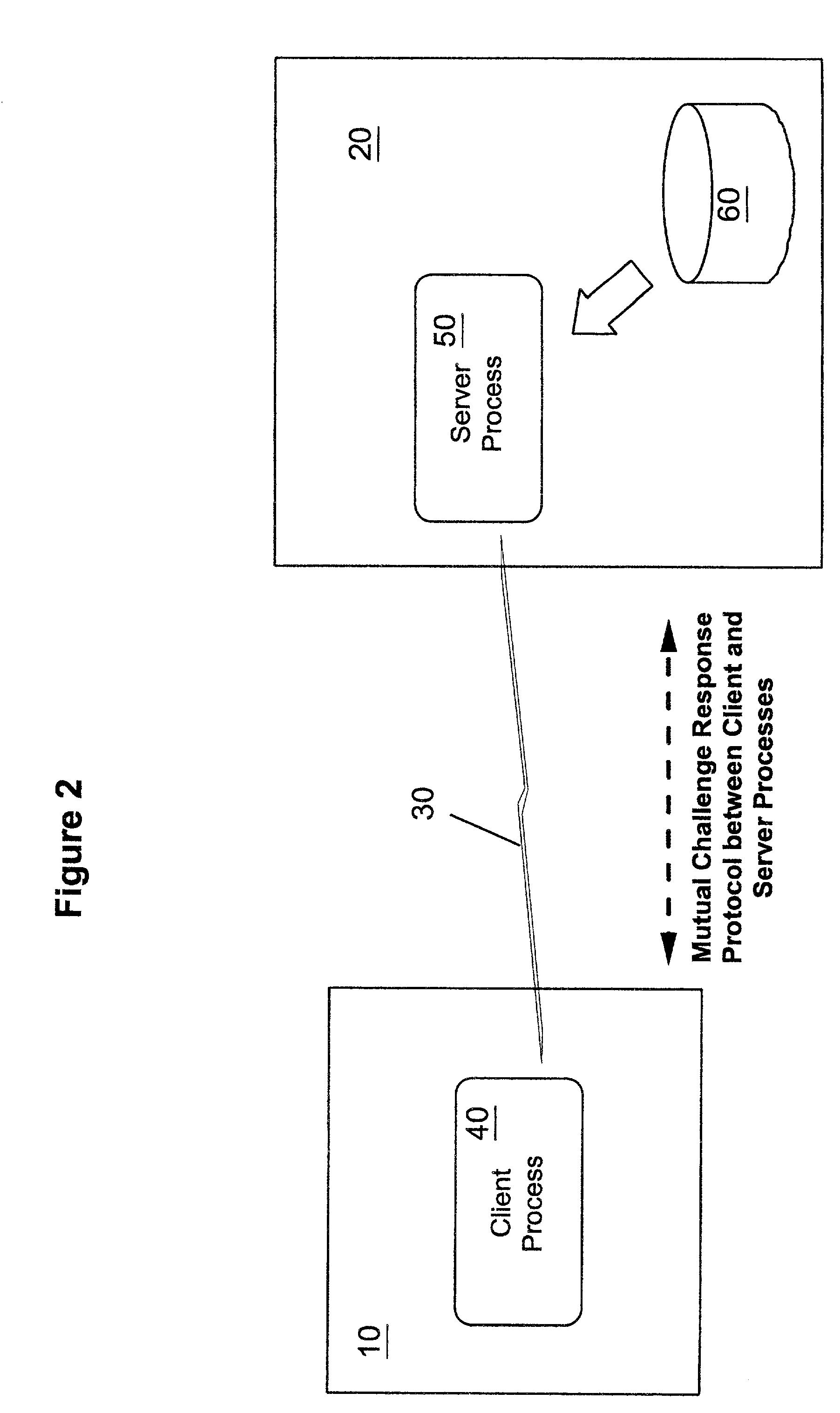
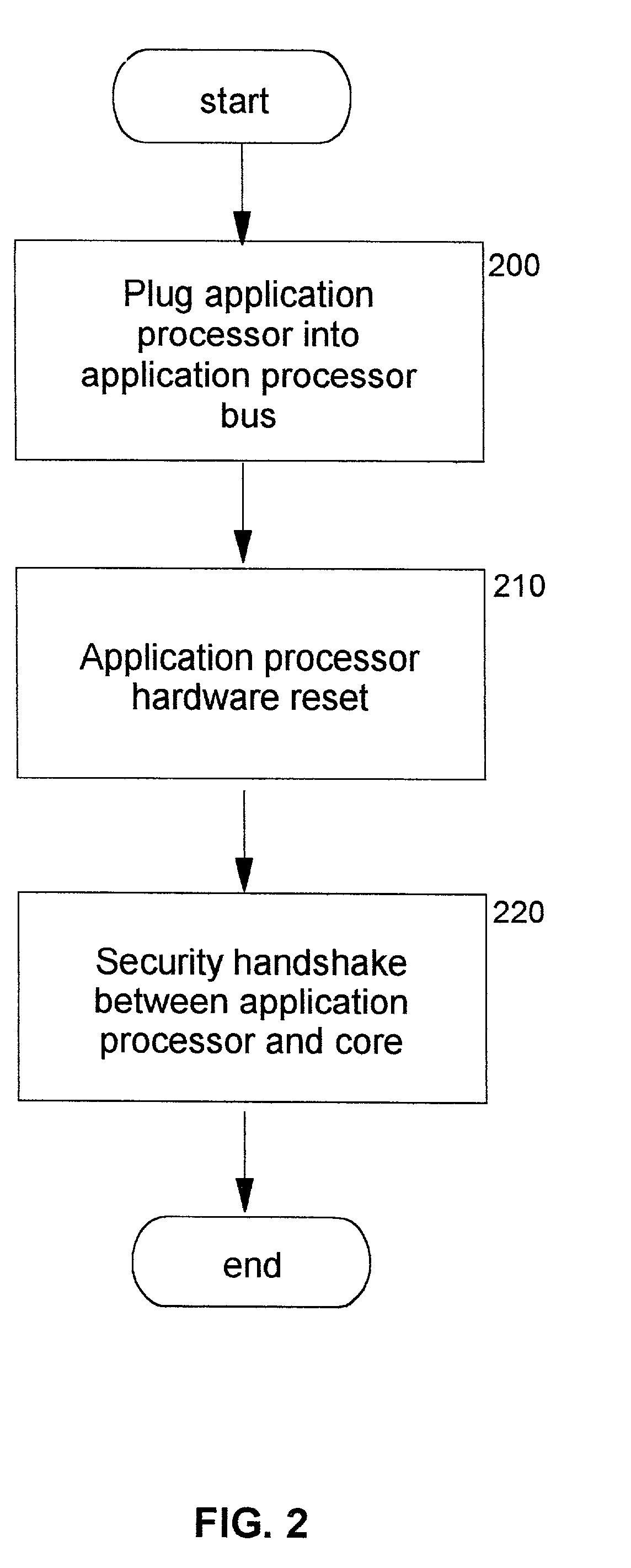
Methods, apparatus and computer programs performing a mutual challenge-response authentication protocol using operating system capabilities
InactiveUS20030093680A1Avoids security exposureMeet growth requirementsKey distribution for secure communicationDigital data processing detailsOperational systemCrypt
A client-server authentication method for use where a server process has access to a repository storing cipher-protected client passwords. The method includes applying the same cipher function to the client's copy of its password as was previously applied to generate the stored cipher-protected client passwords. This ensures that both the client and server have access to an equivalent cipher-protected client password-providing a shared secret for driving a mutual challenge-response authentication protocol without having to convert the password into cleartext at the server. The invention can be implemented without significant additional software infrastructure in a UNIX environment. Client passwords are typically stored in the UNIX password repository under the protection of the crypt( ) function applied to the combination of the password and a random number (a "salt'). By sending the salt to the client system together with the server's initial challenge of the authentication protocol, a process at the client is able to apply the crypt( ) function to the client password with the same salt such that the client and server have a shared secret for use as, or to generate, a common session key for the authentication.
Owner:IBM CORP
Powerhead of a power injection system
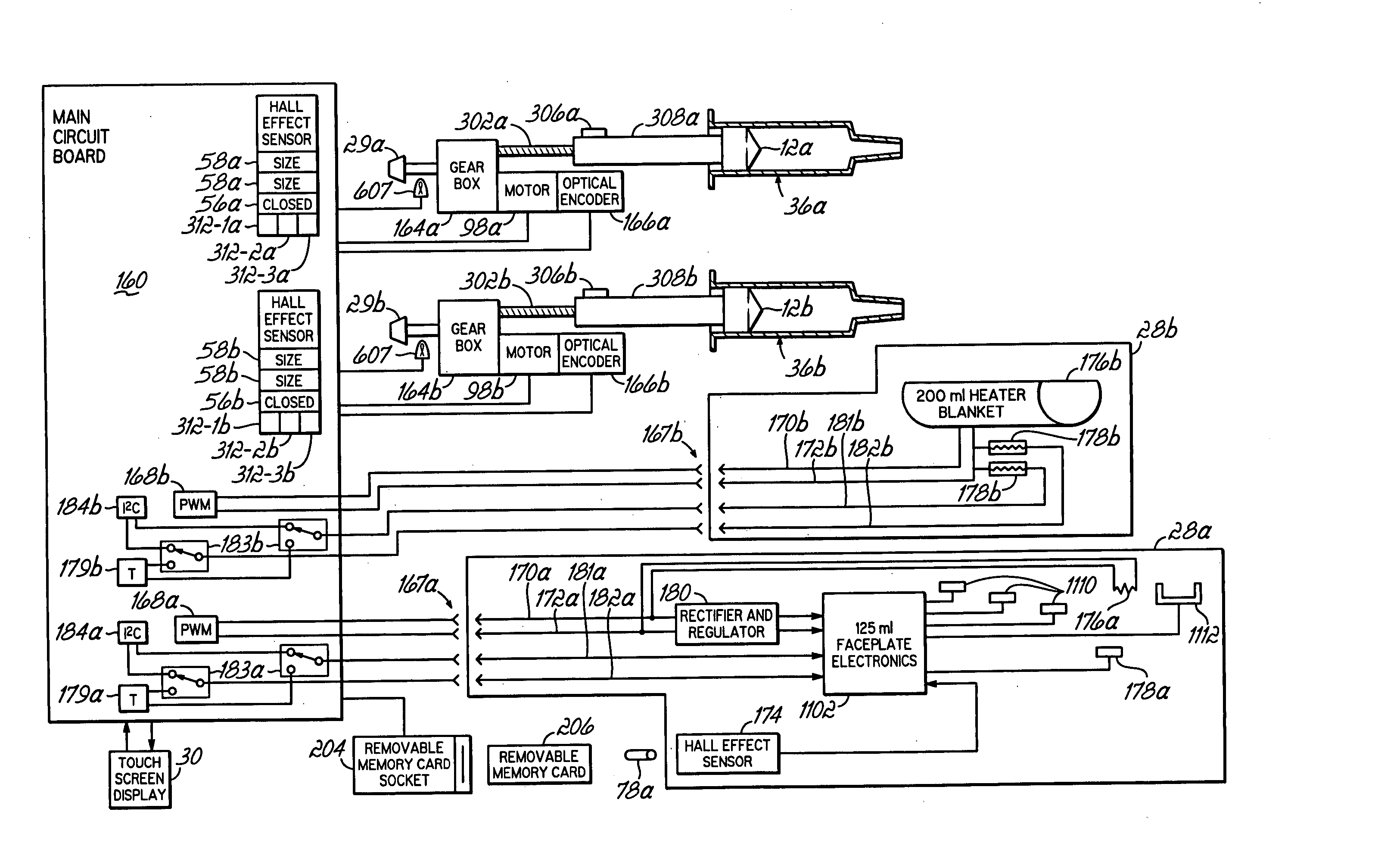
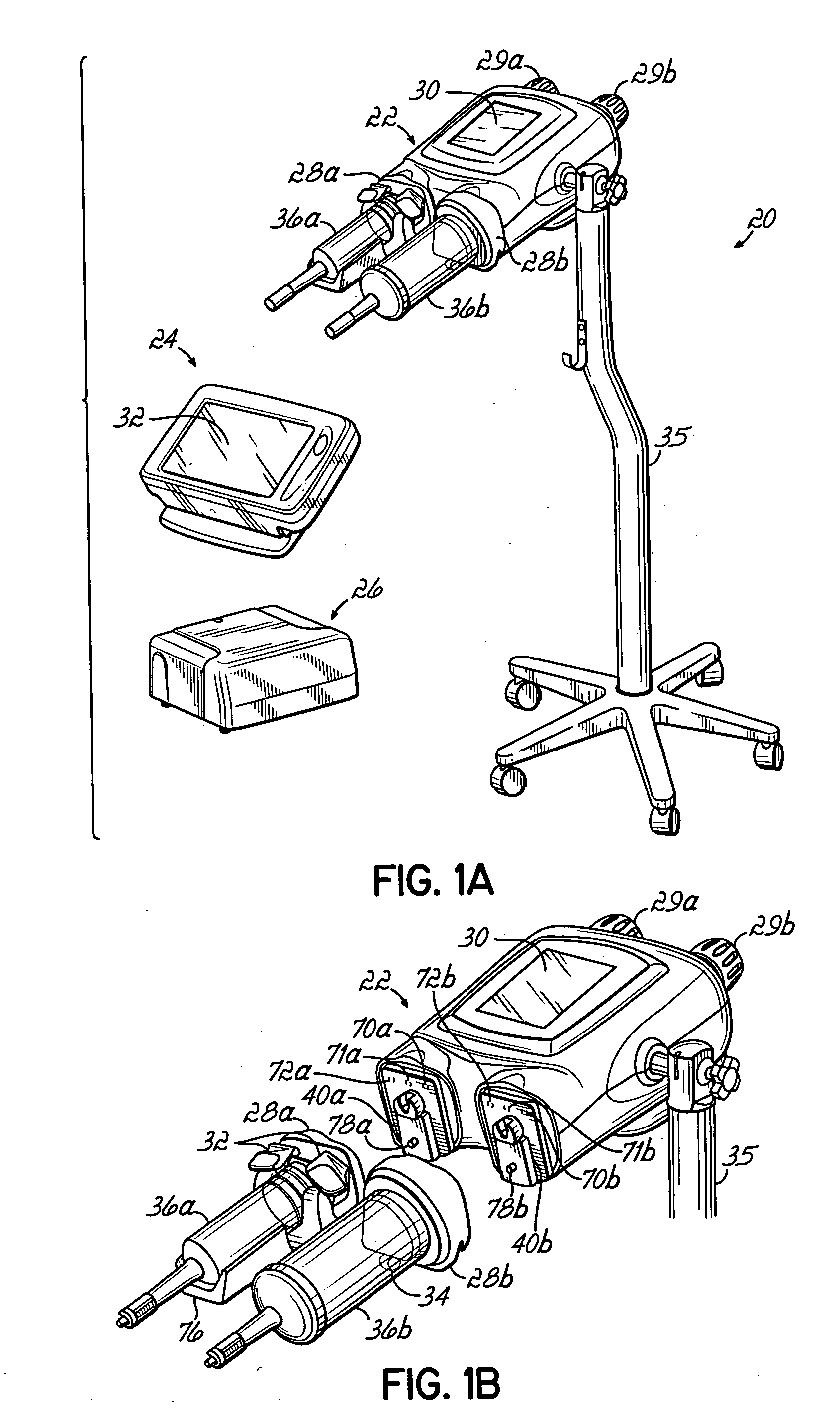
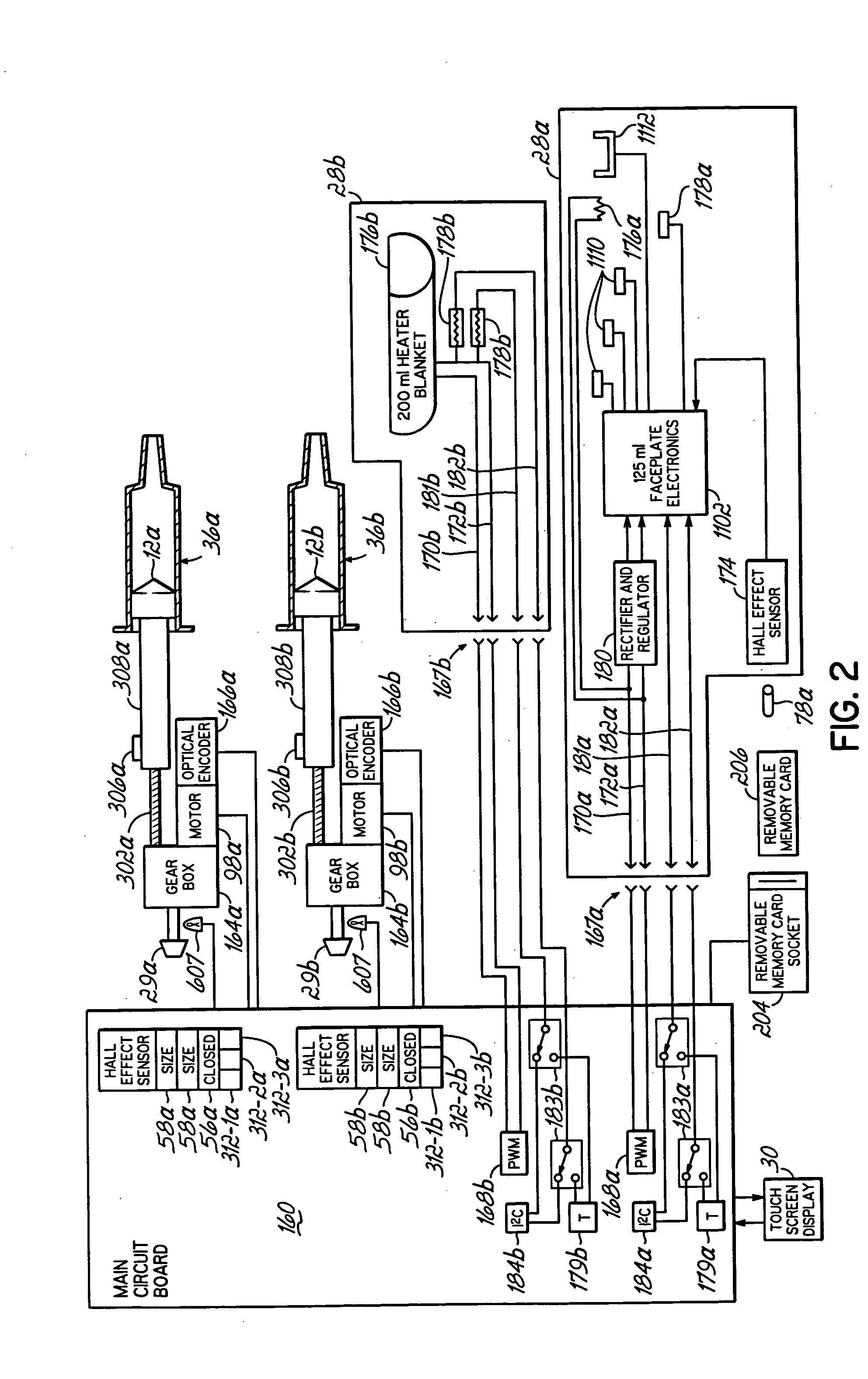
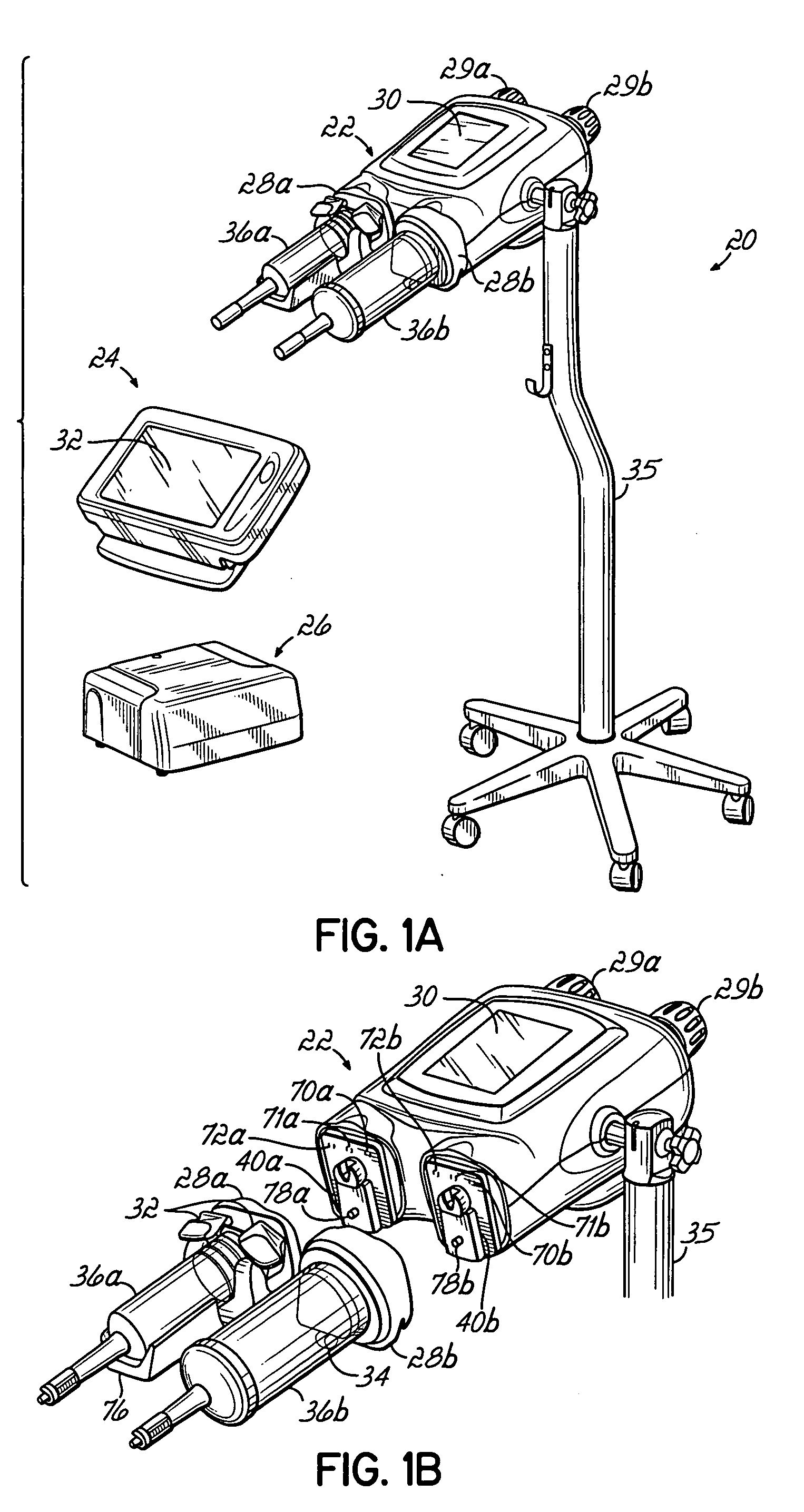
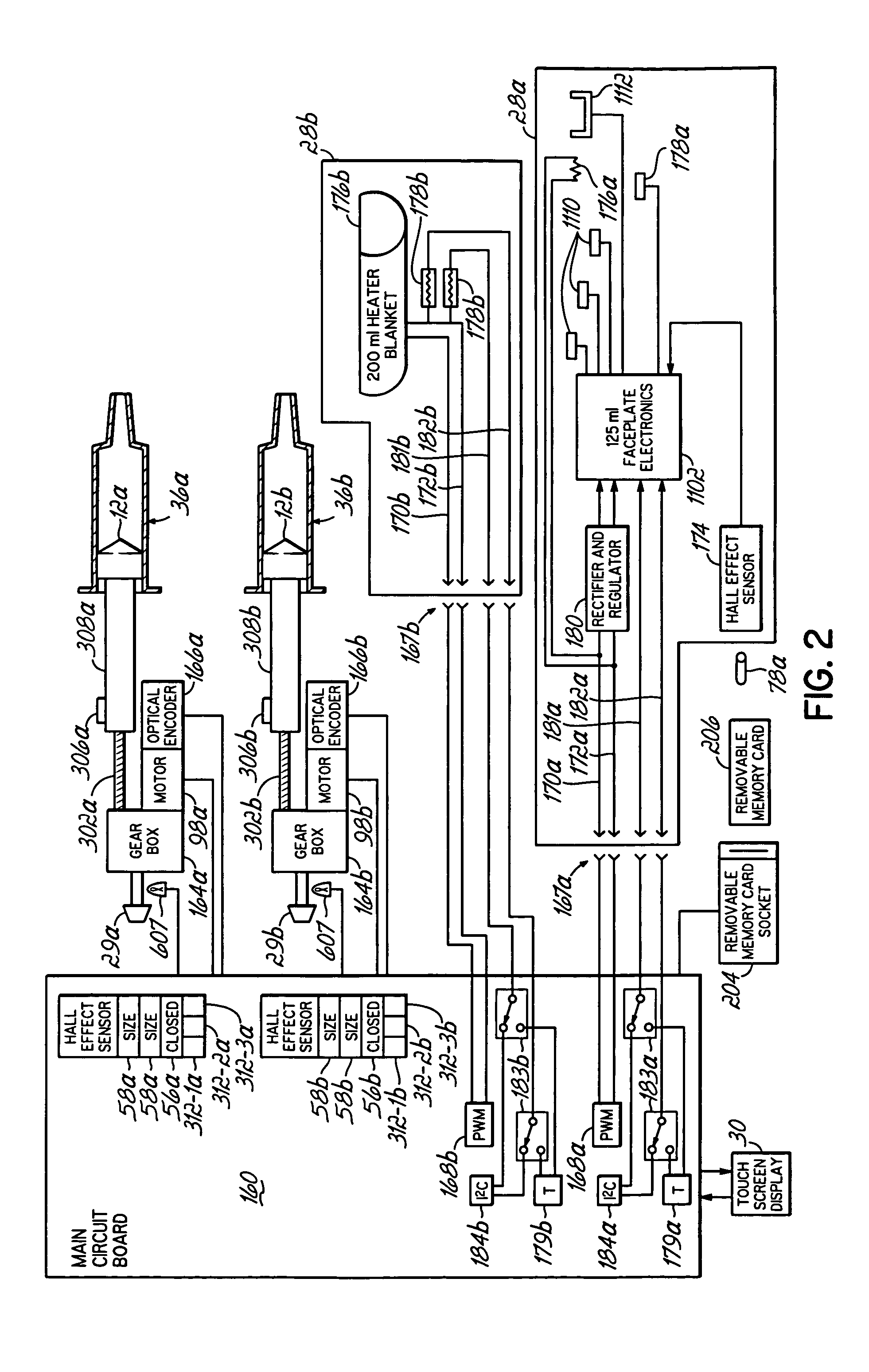
InactiveUS20060079765A1Increase powerImprove accuracyMedical devicesIntravenous devicesEngineeringPassword protection
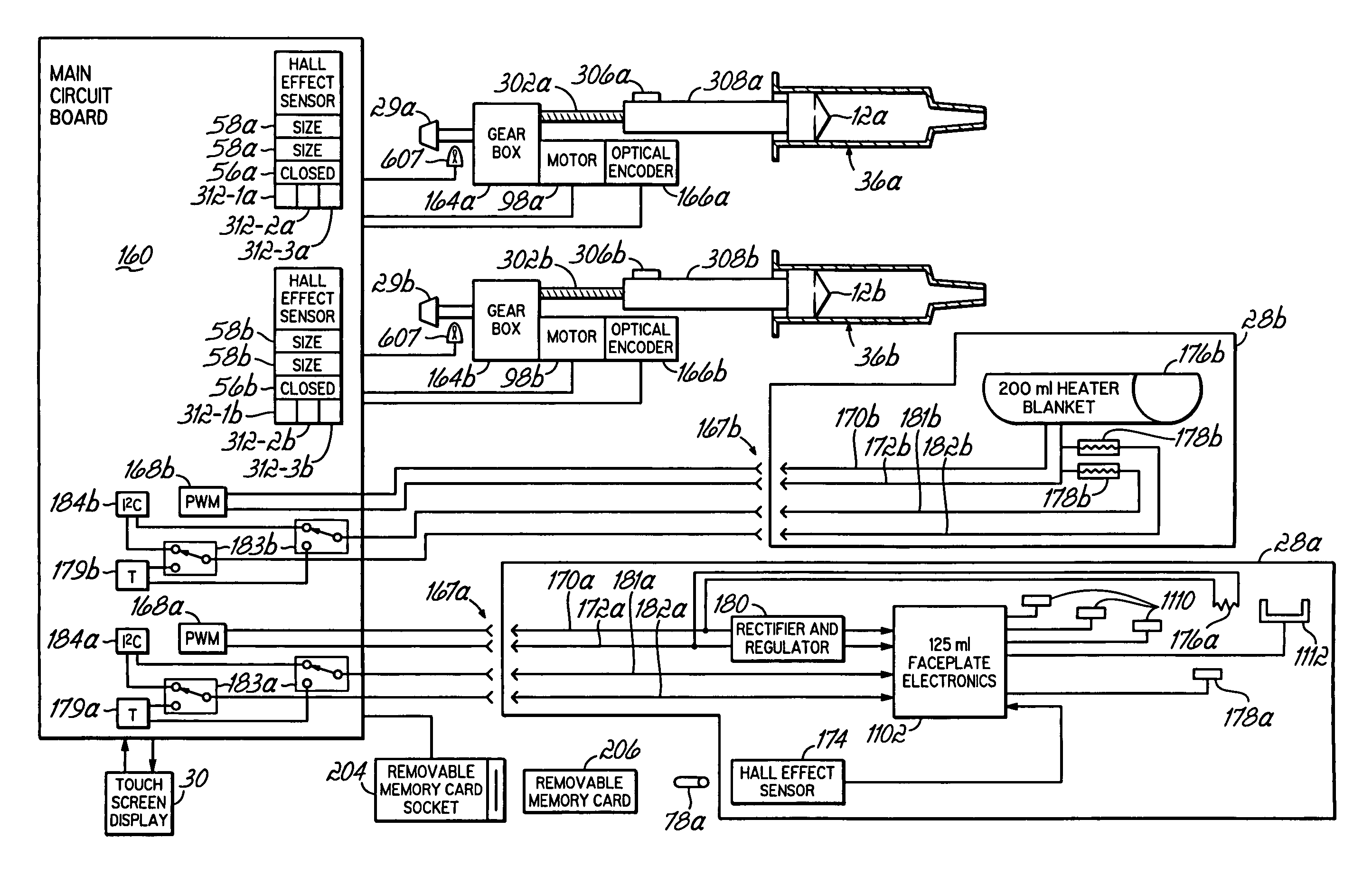
A contrast media injection system includes detects the absolute position of the syringe ram using a non-contact sensor. A series of magnets and Hall-Effect sensors may be used or an opto-reflective system. Illuminated knobs that are connected to the drive mechanism for the syringe ram rotate with the drive and provide visual feedback on operation through the illumination. Analog Hall-Effect sensors are used to determine the presence or absence of magnets that identify the type of faceplate being used. The faceplates include control electronics, connected to the powerhead through connectors, which may be interchangeably used by the two faceplates. The faceplate electronics include detectors for automatically detecting the capacity of pre-filled syringes. Additional features include using historical data to provide optimum pressure limit values during an injection protocol, a removable memory device for storing and transferring information such as injection protocols and injector statistics, and password protection of such protocols.
Owner:LIEBEL FLARSHEIM CO
Systems and methods of securing resources through passwords
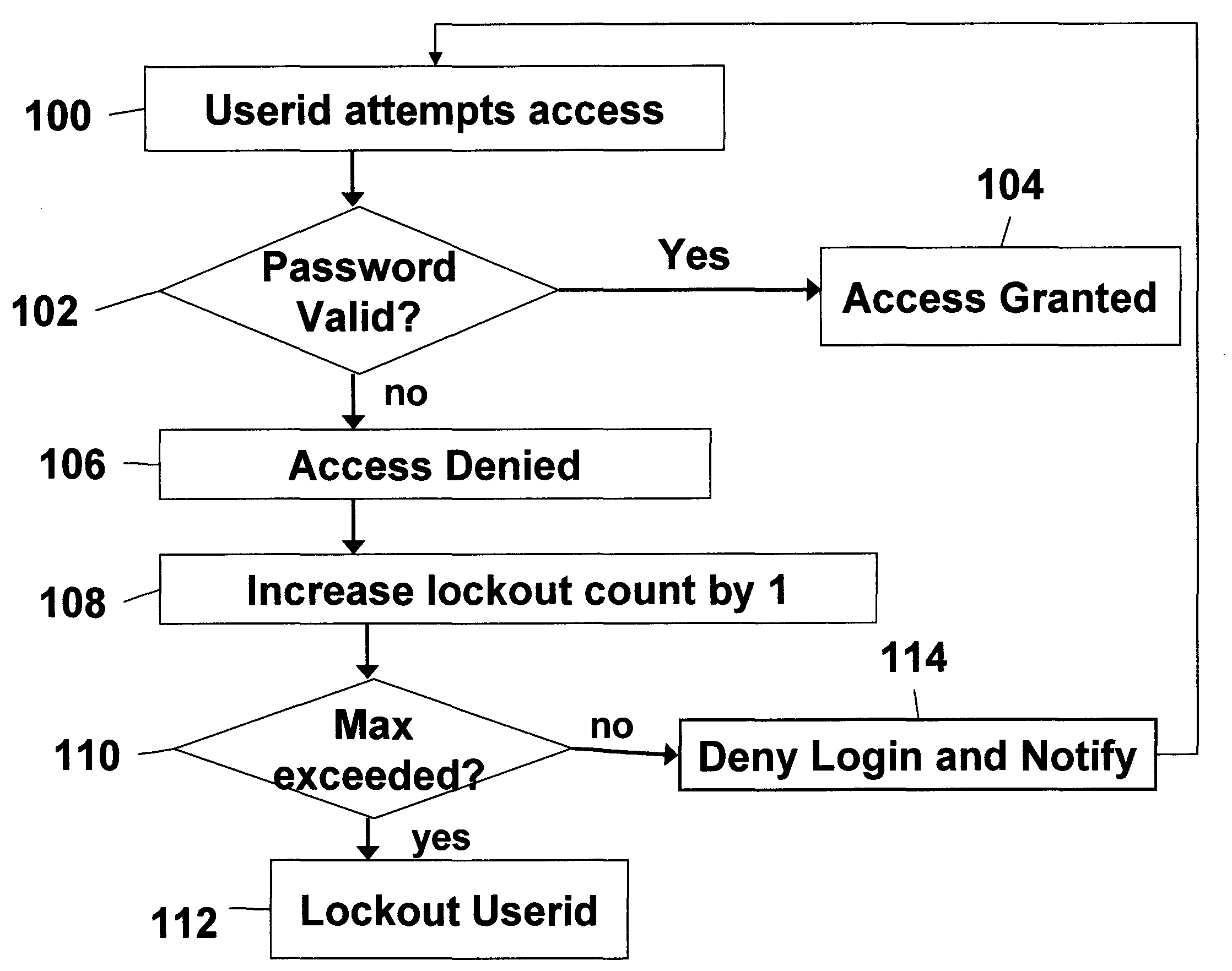
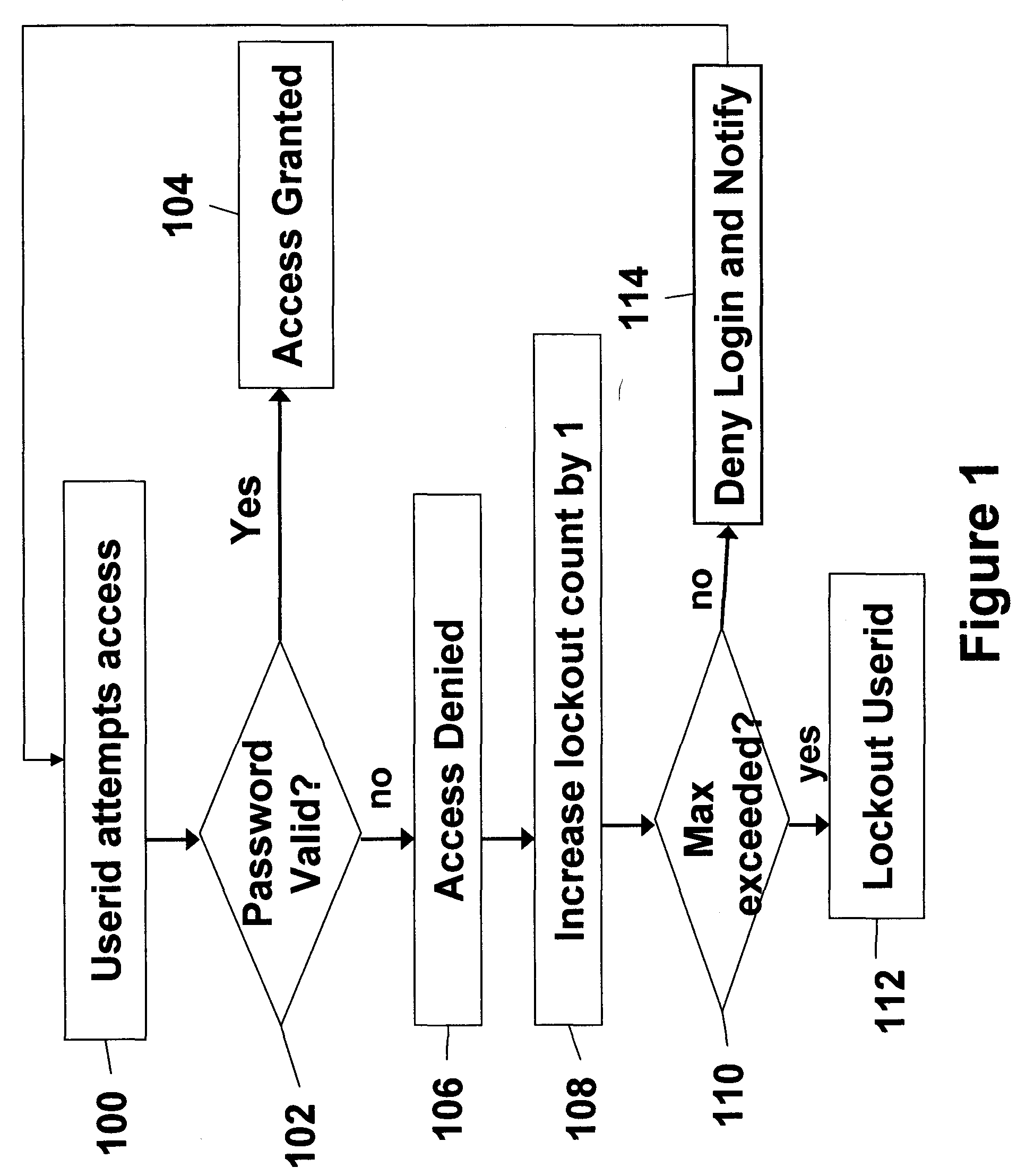
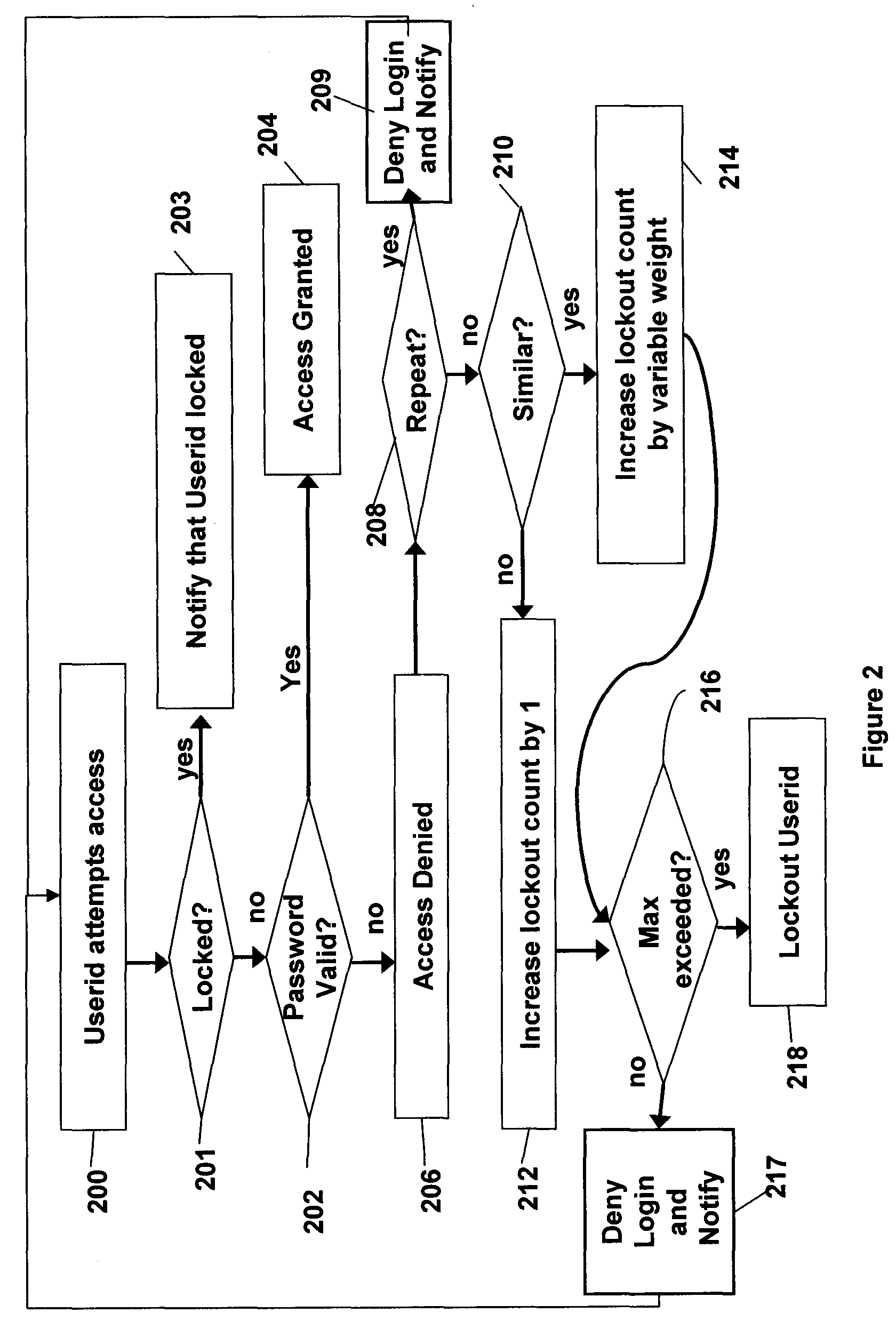
InactiveUS20060041756A1Mitigates password coordination problemMitigating password coordination problemDigital data processing detailsUser identity/authority verificationPasswordData file
Disclosed is a method of authorizing access to an item that maintains a lockout count and blocks access to the item if the lockout count exceeds a predetermined value. One feature is that the invention “variably” increments the lockout count if the presented password fails to exactly match the stored password. In this process the invention increments the lockout count different amounts depending upon how closely the presented password matches the stored password. The invention also provides a methodology that allocates a plurality of the same passwords to a plurality of users who share the same userid. The invention allows continuous operation of the item being accessed by providing that each of the passwords has a different expiration date. Also, when dealing with situations where a plurality of users who share the same userid also share the same password, the invention maps information associated with the users to the password in a data file and periodically updates the data file.
Owner:IBM CORP
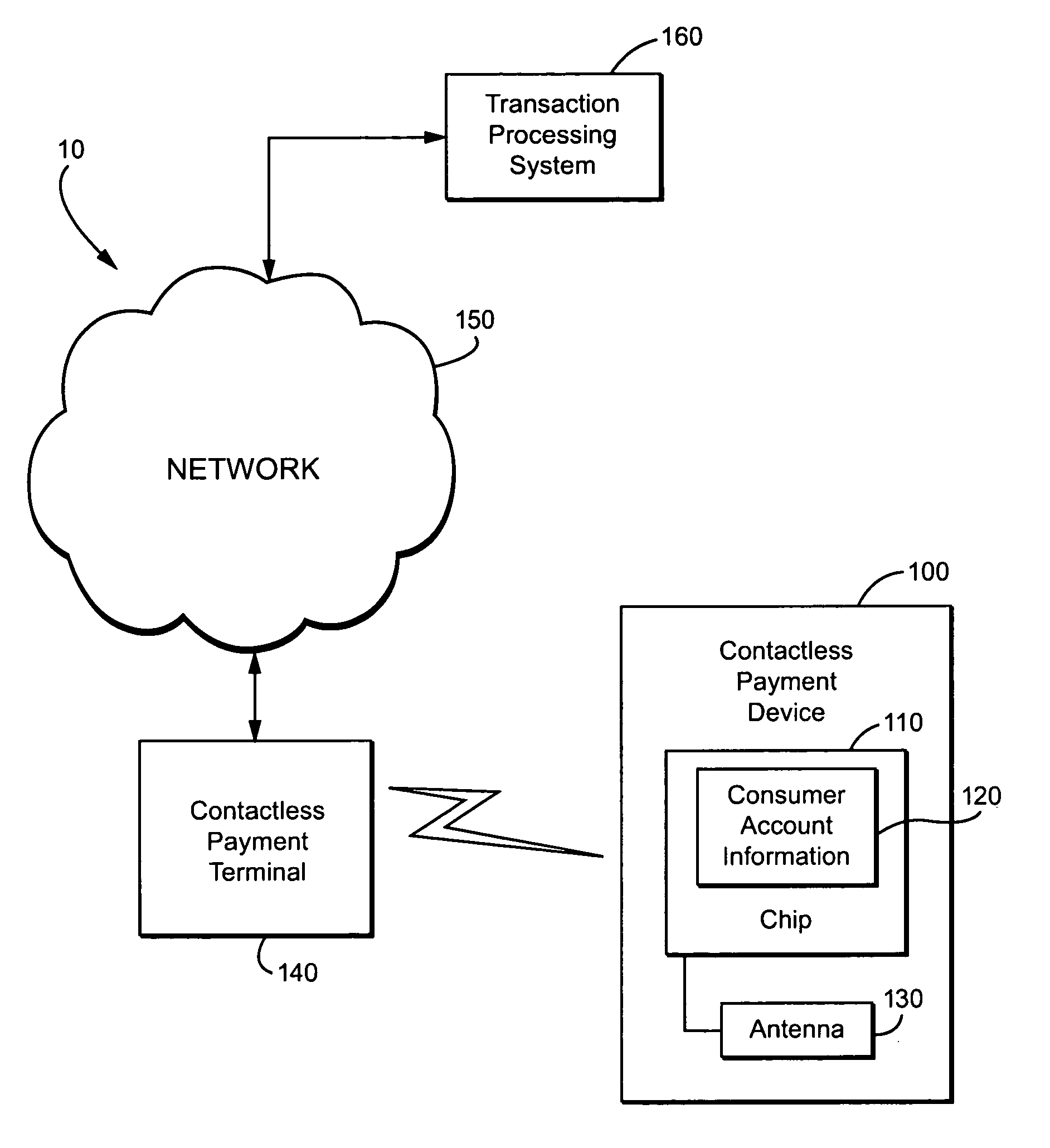
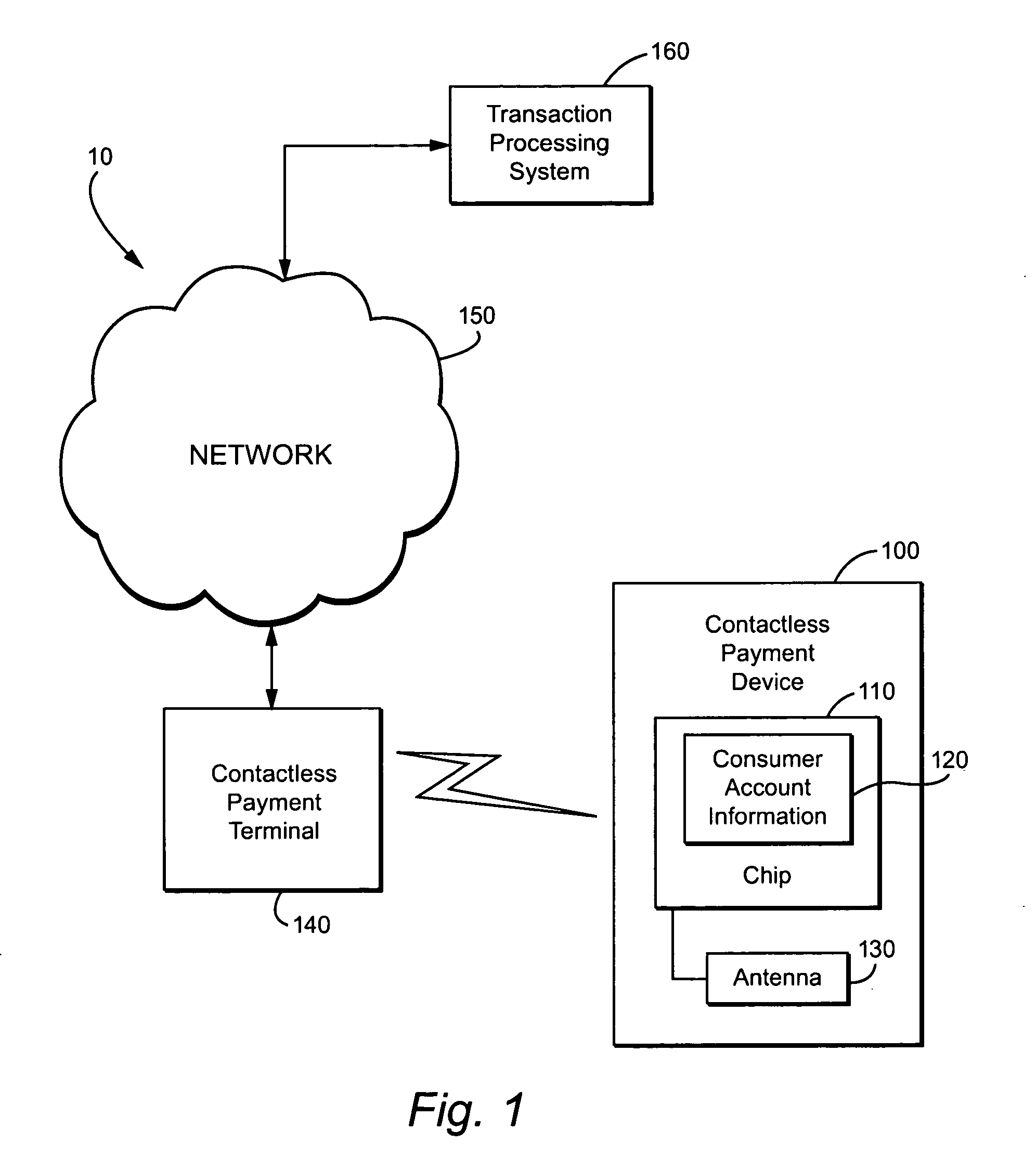
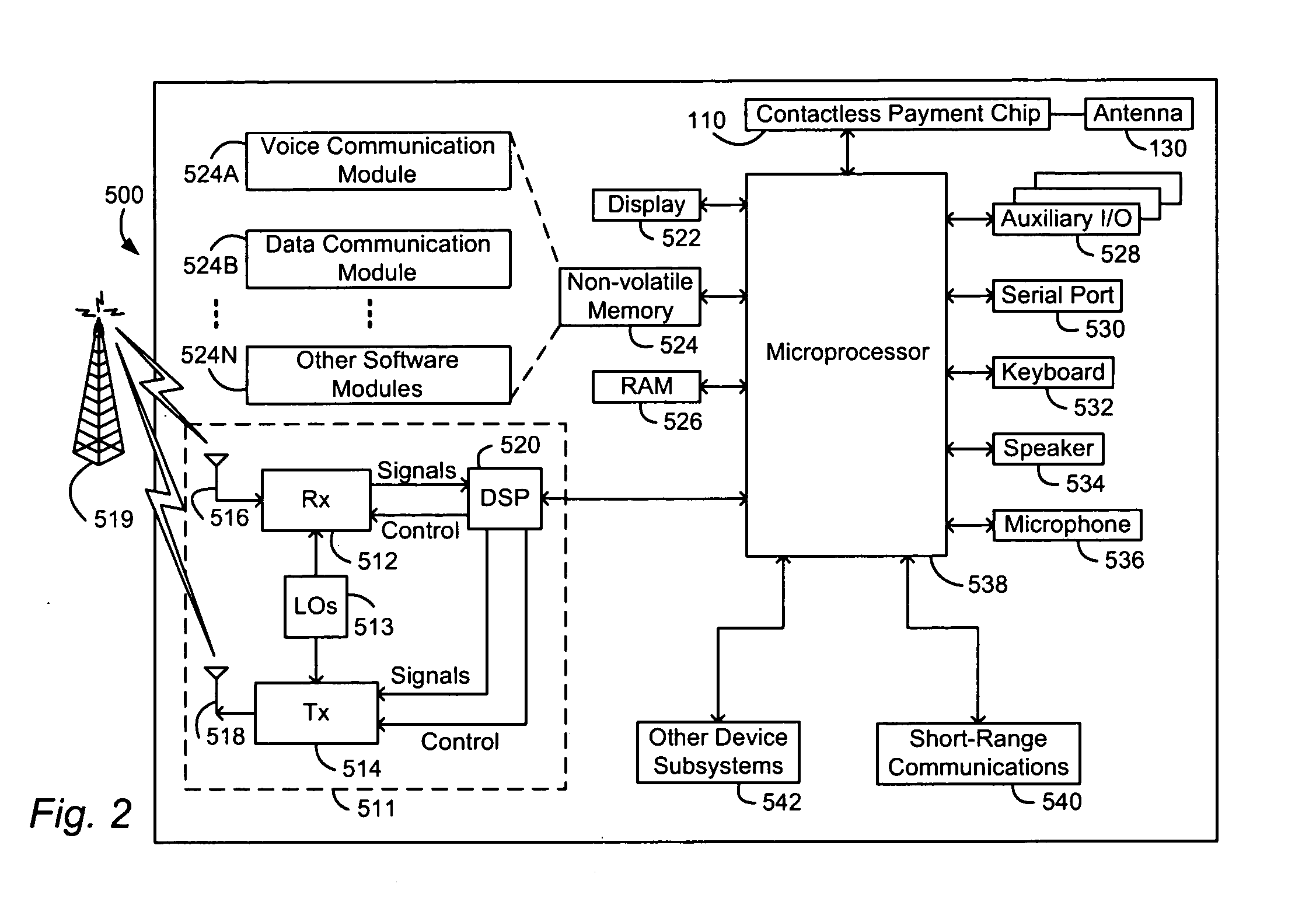
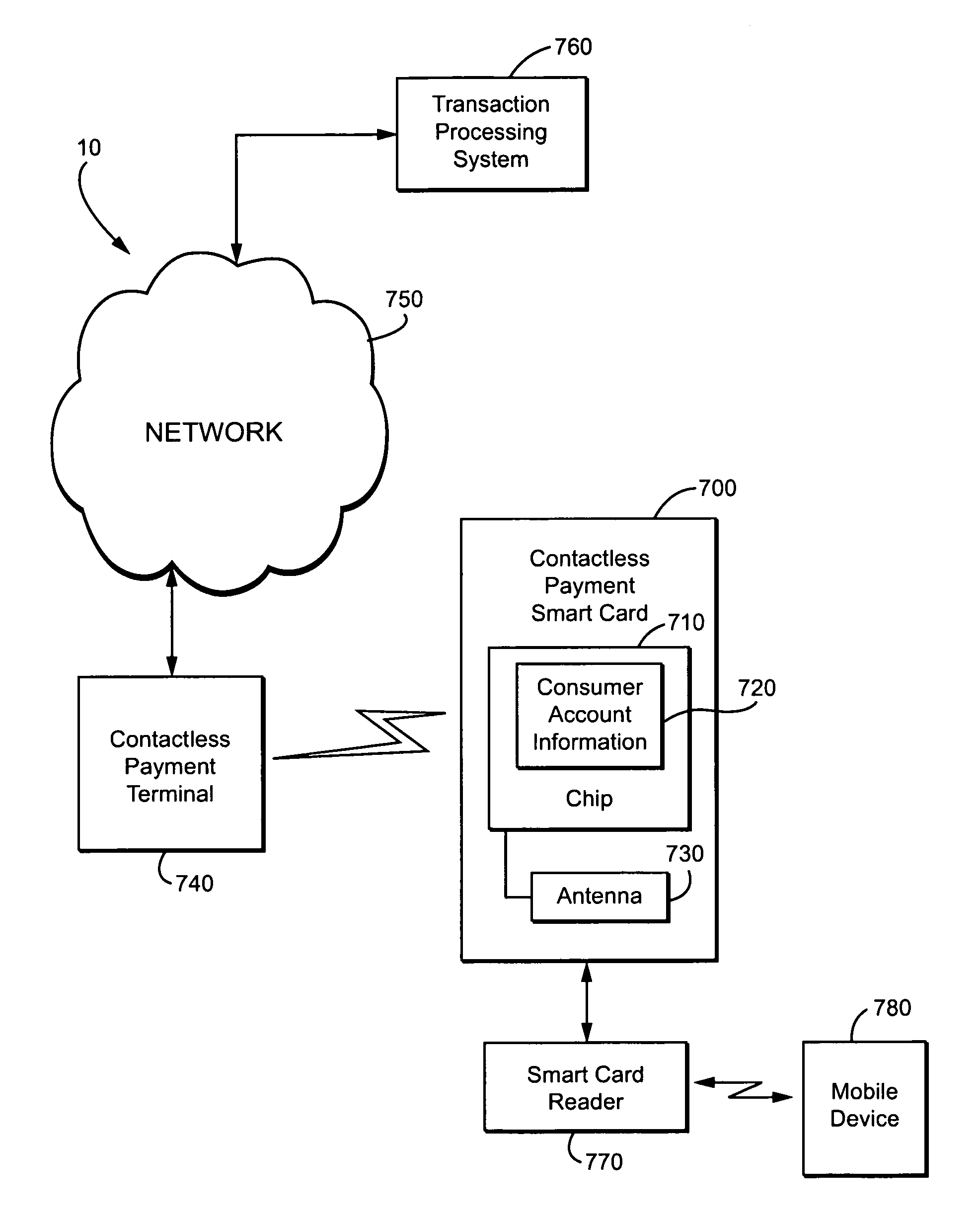
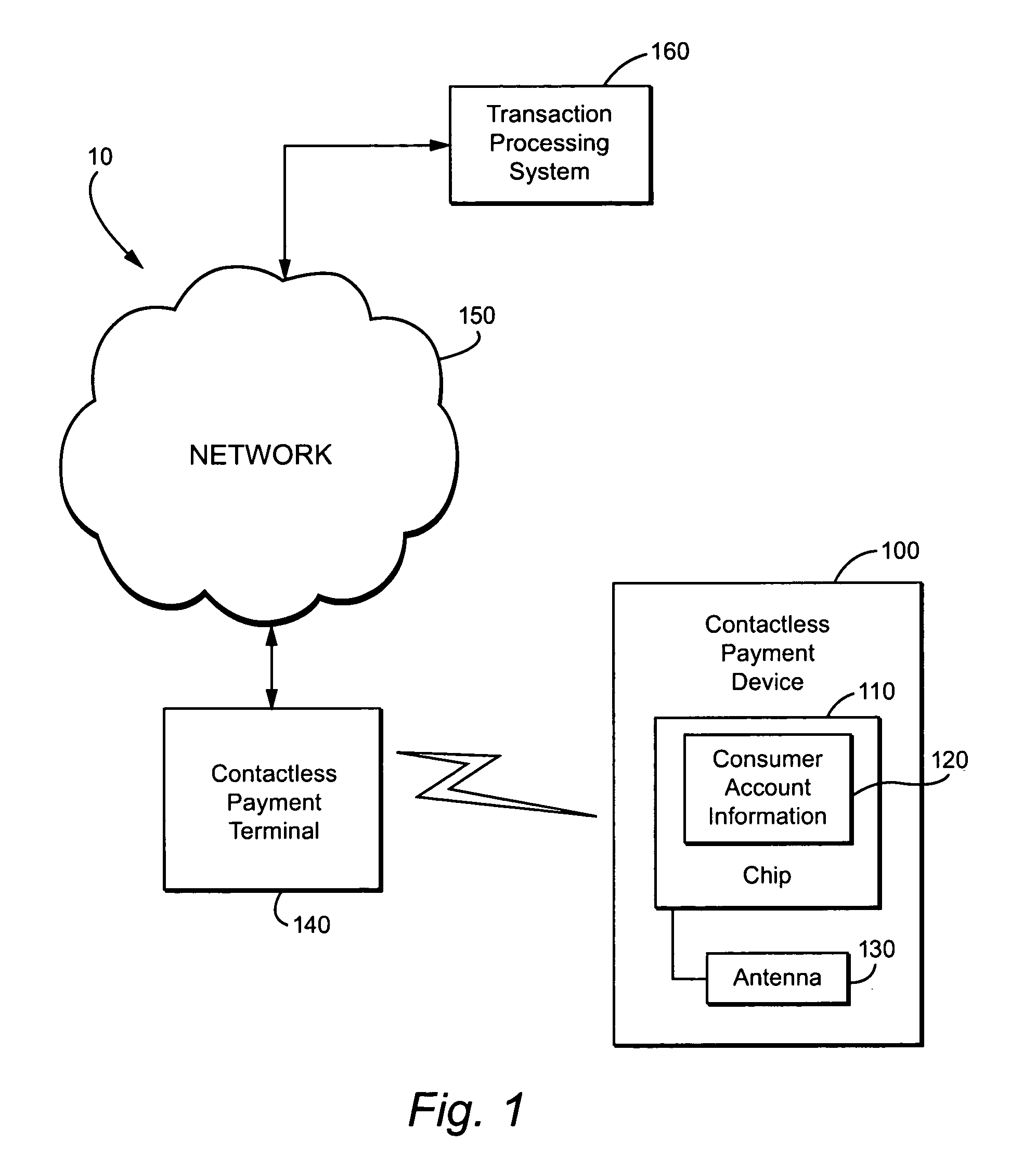
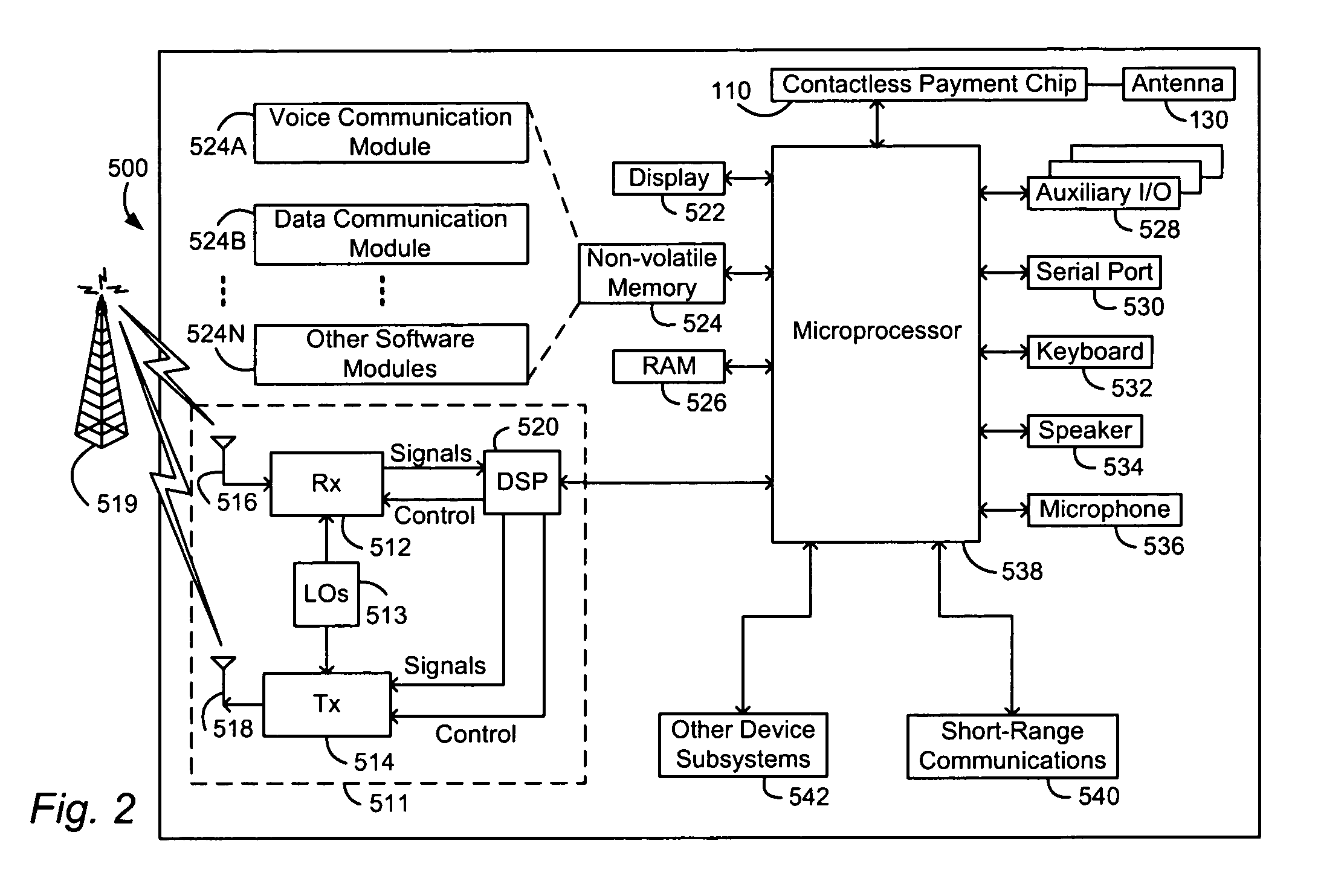
Method and apparatus for contactless payment authentication
ActiveUS20070152035A1Efficient and accurate and easy to implementMaintain conveniencePayment architectureSensing record carriersPaymentPassword protection
The present disclosure relates generally to the authentication of contactless payments attempted by a device having embedded contactless payment functionality. In particular, the disclosure is directed to systems and methods that utilize authentication schemes that already exist on a device in which the contactless payment functionality is embedded. One example of such authentication schemes is the use of password protection to lock or unlock the device in which the contactless payment functionality is embedded. Using the password protection functionality may provide varying levels of authentication protection based on the desires of the user. A number of exemplary uses of such a method and apparatus are disclosed herein.
Owner:MALIKIE INNOVATIONS LTD
Method for preventing malicious software installation on an internet-connected computer
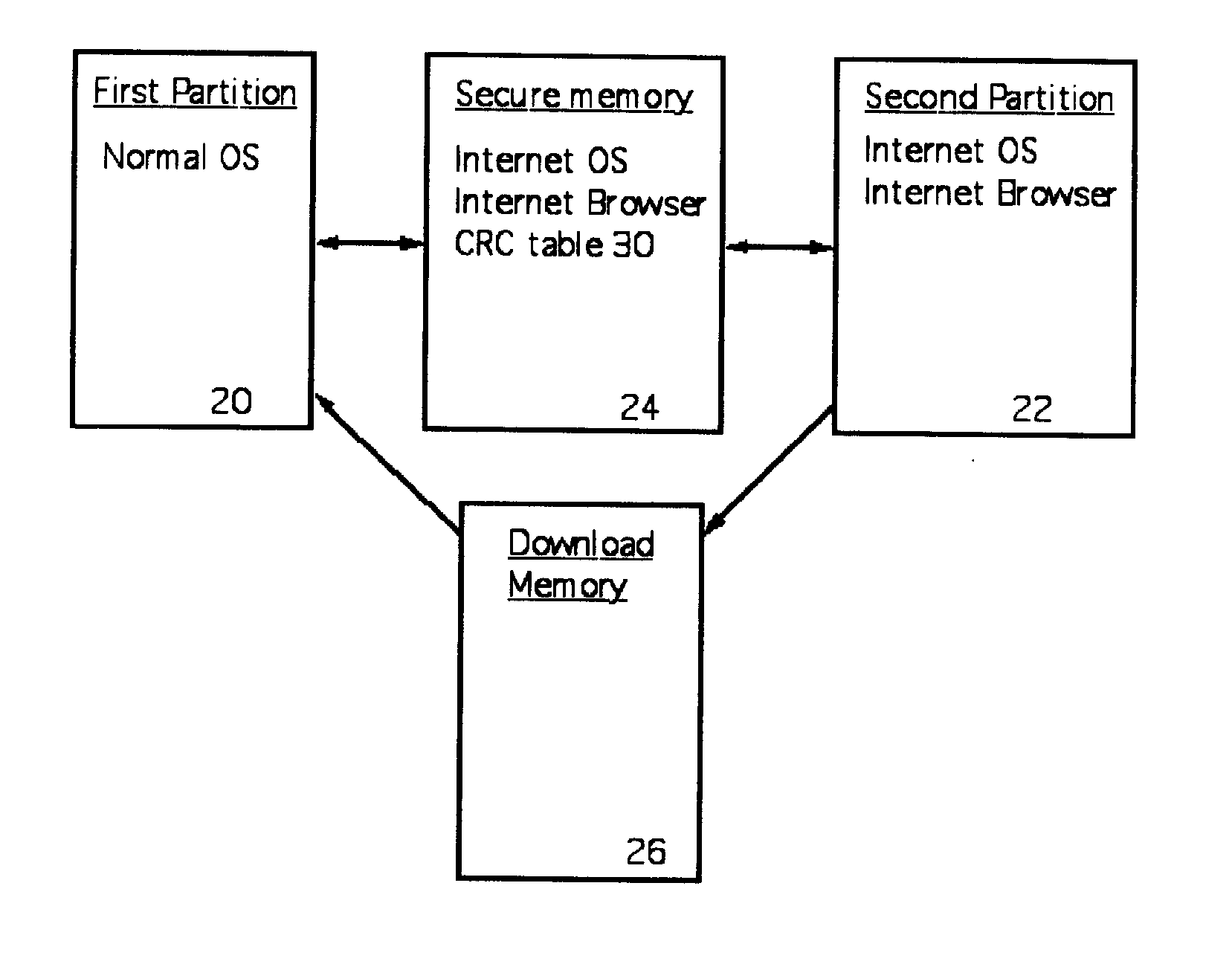
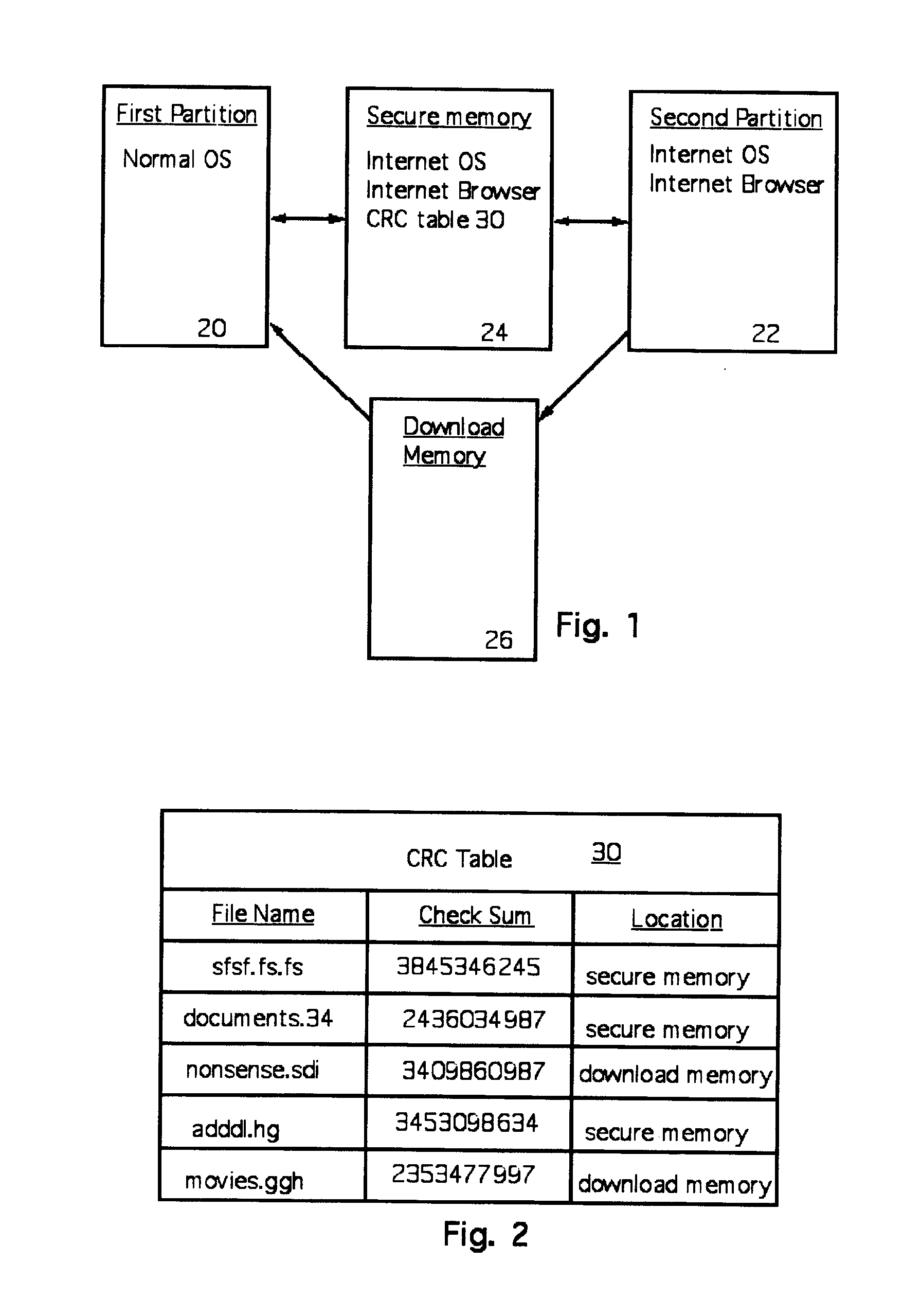
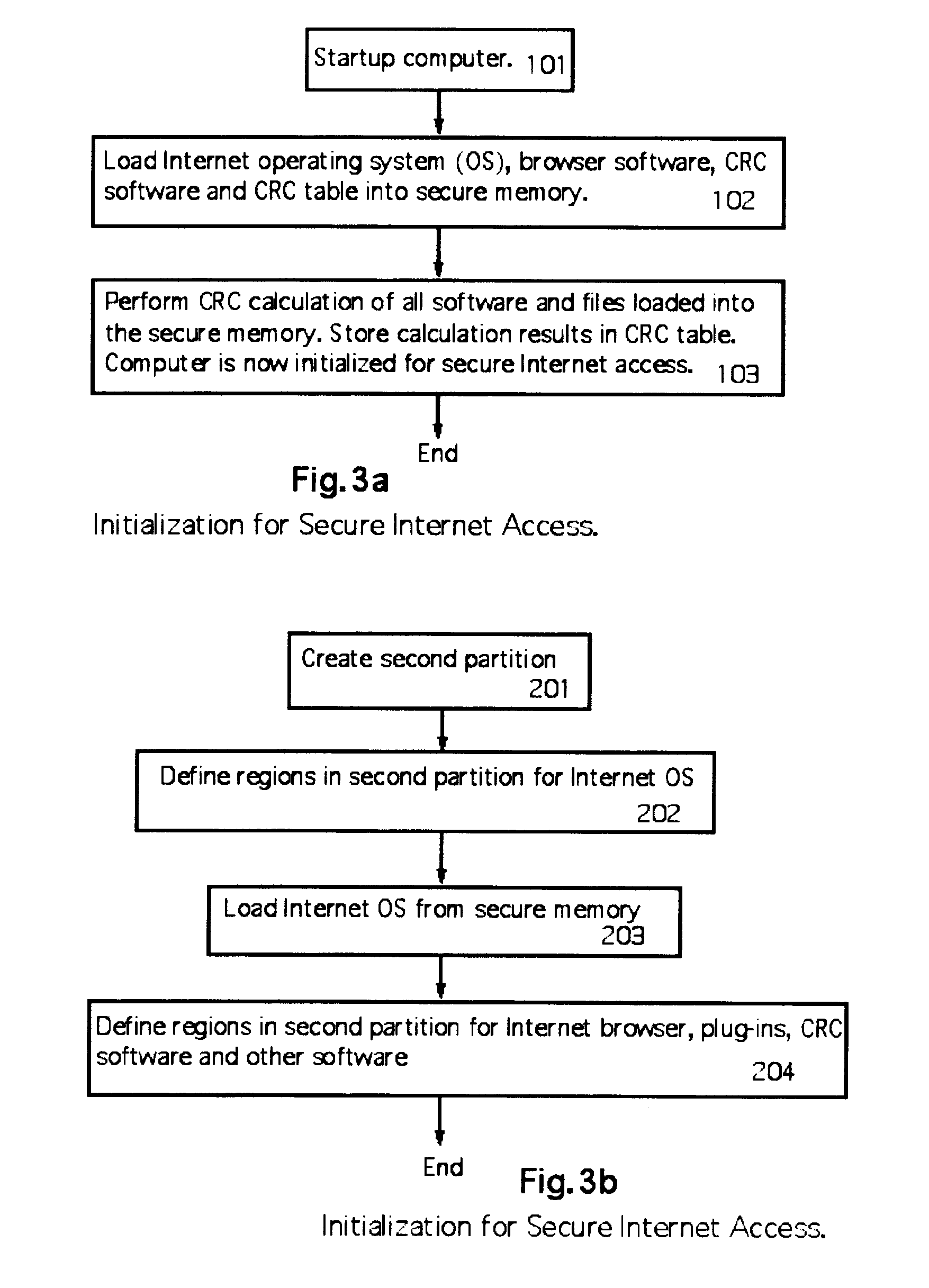
ActiveUS20070192854A1Prevents gaining accessAvoid accessMemory loss protectionDigital data processing detailsOperational systemTerm memory
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
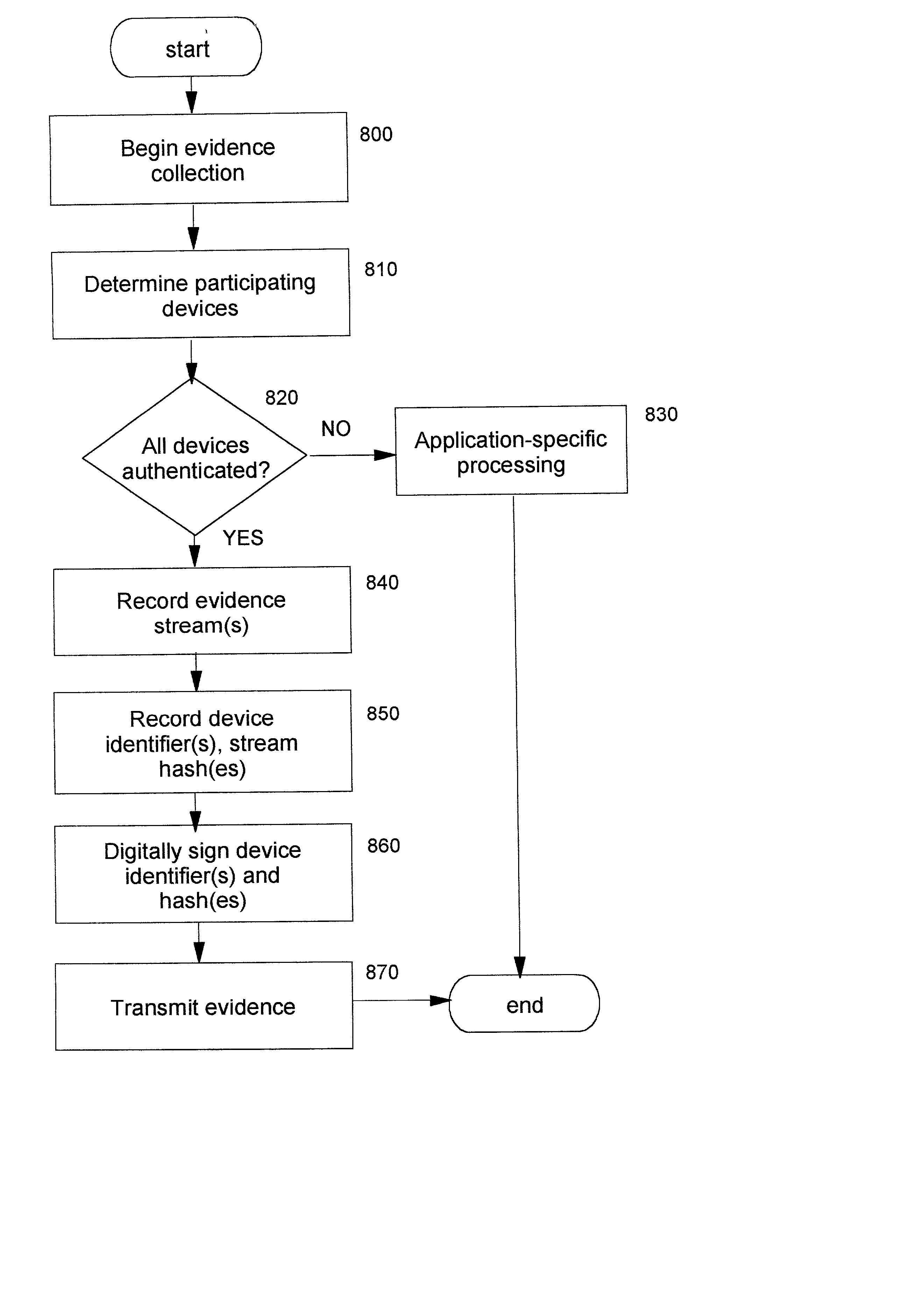
Technique for establishing provable chain of evidence
InactiveUS20020095601A1IntegrityMemory loss protectionError detection/correctionData streamDigital signature
A method, system, computer program product, and method of doing business by providing a provable chain of evidence for data stream(s) created by one or more components (such as input / output devices and application processing components). Components that create the evidence collection are authenticated. A unique identifier of each such component is included within cryptographically-protected information that is added to the evidence collection. A digital signature is preferably used for the cryptographic protection, thereby digitally notarizing the evidence collection. The authenticity and integrity of the evidence collection can be verified. In preferred embodiments, the authenticated identities of components providing the evidence can also be determined from the cryptographically-protected information. One or more data streams may be included within the evidence collection to establish information such as the date and time the evidence collection was captured, the geographic location where the capture was performed, an identification of a person performing the evidence capture, and so forth. When present in a provable chain of evidence, these types of additional evidence are provided by authenticated components which are identified within the cryptographically-protected information.
Owner:IBM CORP
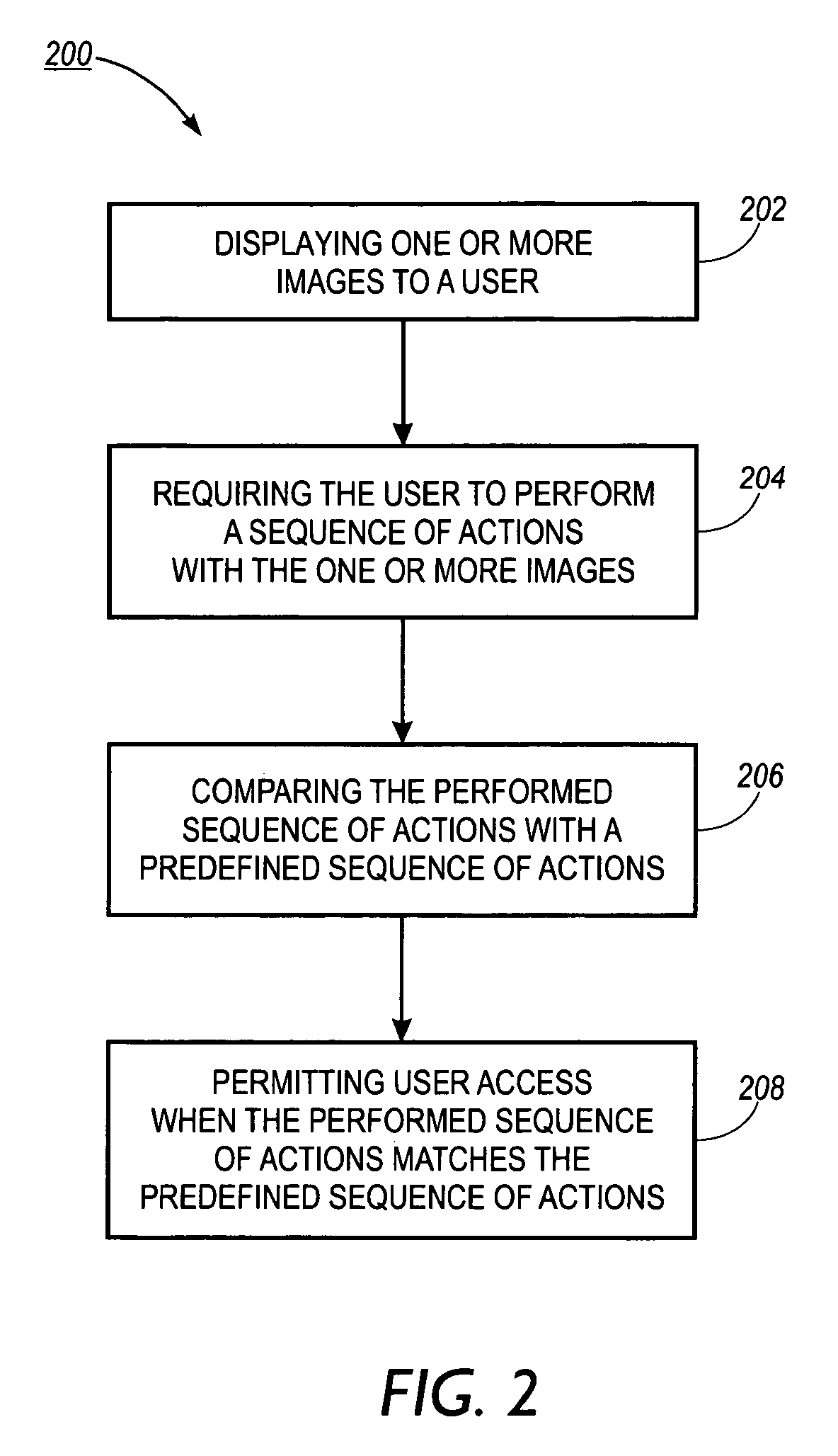
System, method and article of manufacture for knowledge-based password protection of computers and other systems
InactiveUS6934860B1User identity/authority verificationUnauthorized memory use protectionPasswordSoftware engineering
A system, method and article of manufacture are provided for password protecting user access to a computer system. One or more images are displayed to a user. The user is then required to perform a sequence of actions involving the images. The performed sequence of actions is compared with a predefined sequence of actions. If the performed sequence of actions matches the predefined sequence of actions, user access is permitted.
Owner:XEROX CORP
Methods, systems, and computer program products for securely transforming an audio stream to encoded text
InactiveUS6990444B2Easy to compressDigital data processing detailsSpeech recognitionText streamEngineering
A method, system, computer program product, and method of doing business by providing improved audio compression wherein an audio stream is securely transformed to an encoded text stream (such as an ASCII, EBCDIC, or Unicode text stream). One or more components which are involved in the transformation process are authenticated. A unique identifier of each such component is included within cryptographically-protected information that is provided for the encoded text stream. A digital signature is preferably used for the cryptographic protection, thereby digitally notarizing the encoded text stream. The authenticity and integrity of the encoded text stream can therefore be verified. In preferred embodiments, the authenticated identities of components performing the transformation can also be determined from the cryptographically-protected information. The encoded text stream will typically require much less storage space than the audio stream, and providing the digital notarization along with the encoded text stream serves to reliably establish evidence of the contents of the audio stream (even though a perfect speech-to-text transformation might not be achieved).
Owner:MICROSOFT TECH LICENSING LLC
Technique for establishing provable chain of evidence
InactiveUS6948066B2IntegrityMemory loss protectionError detection/correctionData streamDigital signature
A method, system, computer program product, and method of doing business by providing a provable chain of evidence for data stream(s) created by one or more components (such as input / output devices and application processing components). Components that create the evidence collection are authenticated. A unique identifier of each such component is included within cryptographically-protected information that is added to the evidence collection. A digital signature is preferably used for the cryptographic protection, thereby digitally notarizing the evidence collection. The authenticity and integrity of the evidence collection can be verified. In preferred embodiments, the authenticated identities of components providing the evidence can also be determined from the cryptographically-protected information. One or more data streams may be included within the evidence collection to establish information such as the date and time the evidence collection was captured, the geographic location where the capture was performed, an identification of a person performing the evidence capture, and so forth. When present in a provable chain of evidence, these types of additional evidence are provided by authenticated components which are identified within the cryptographically-protected information.
Owner:IBM CORP
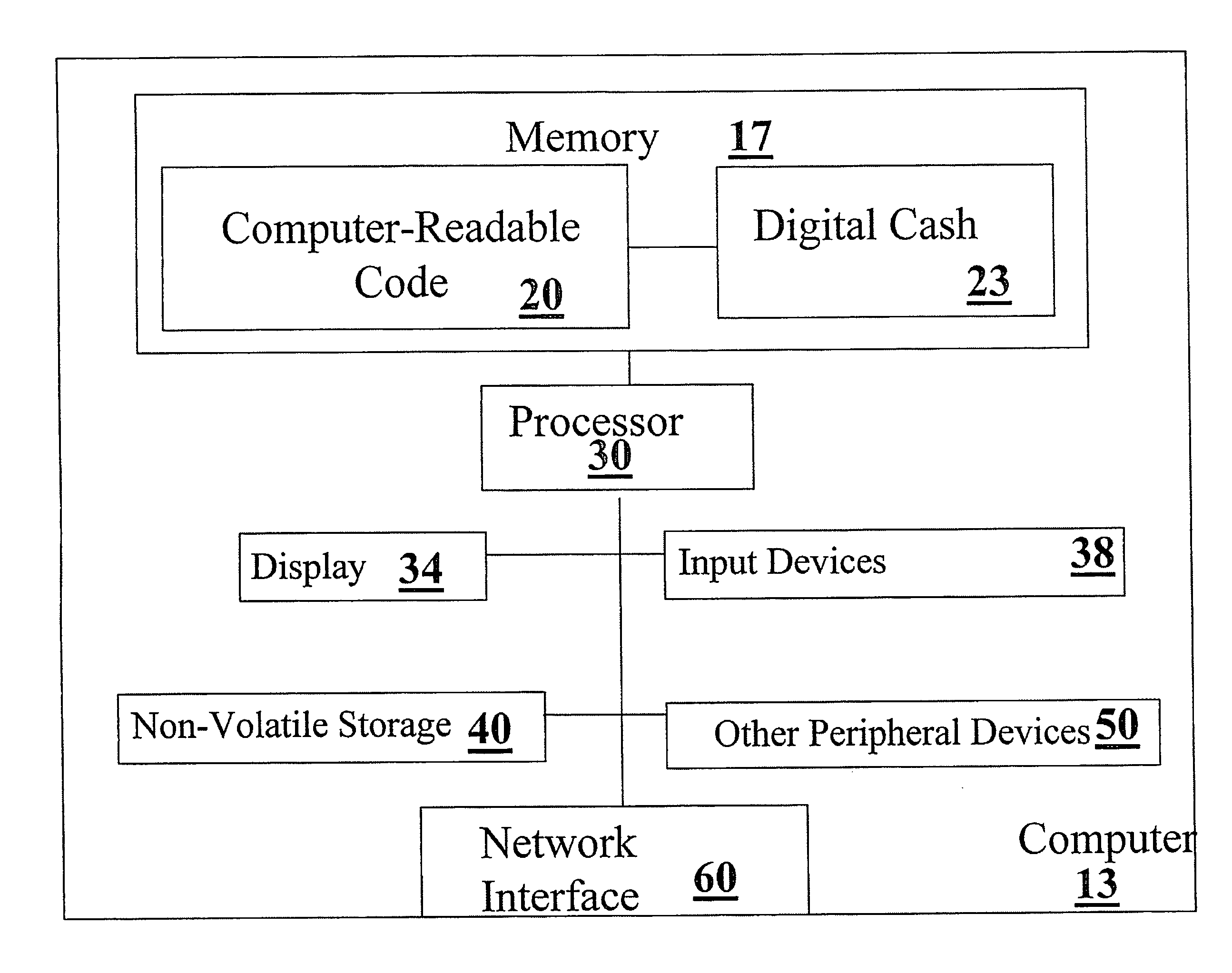
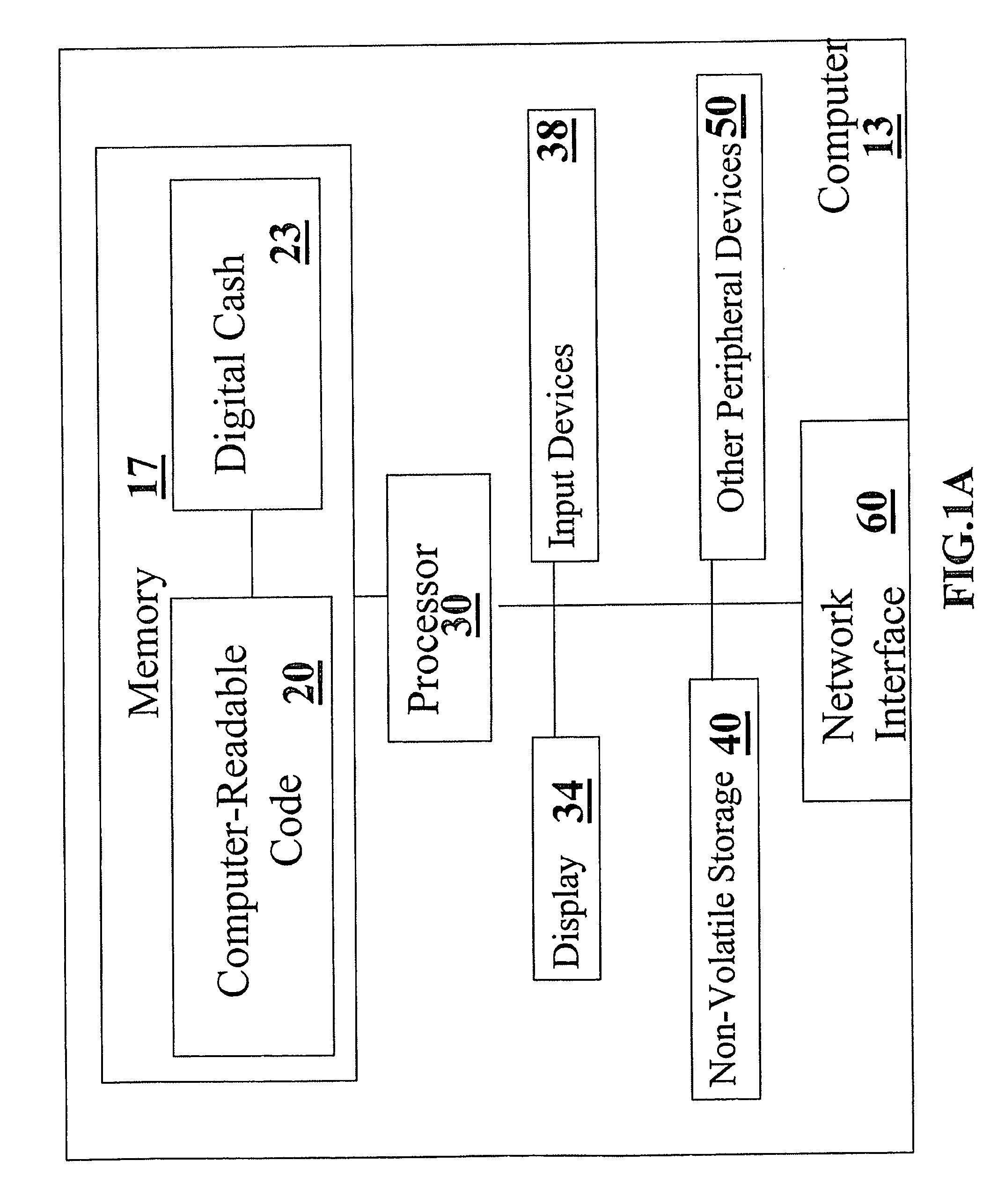
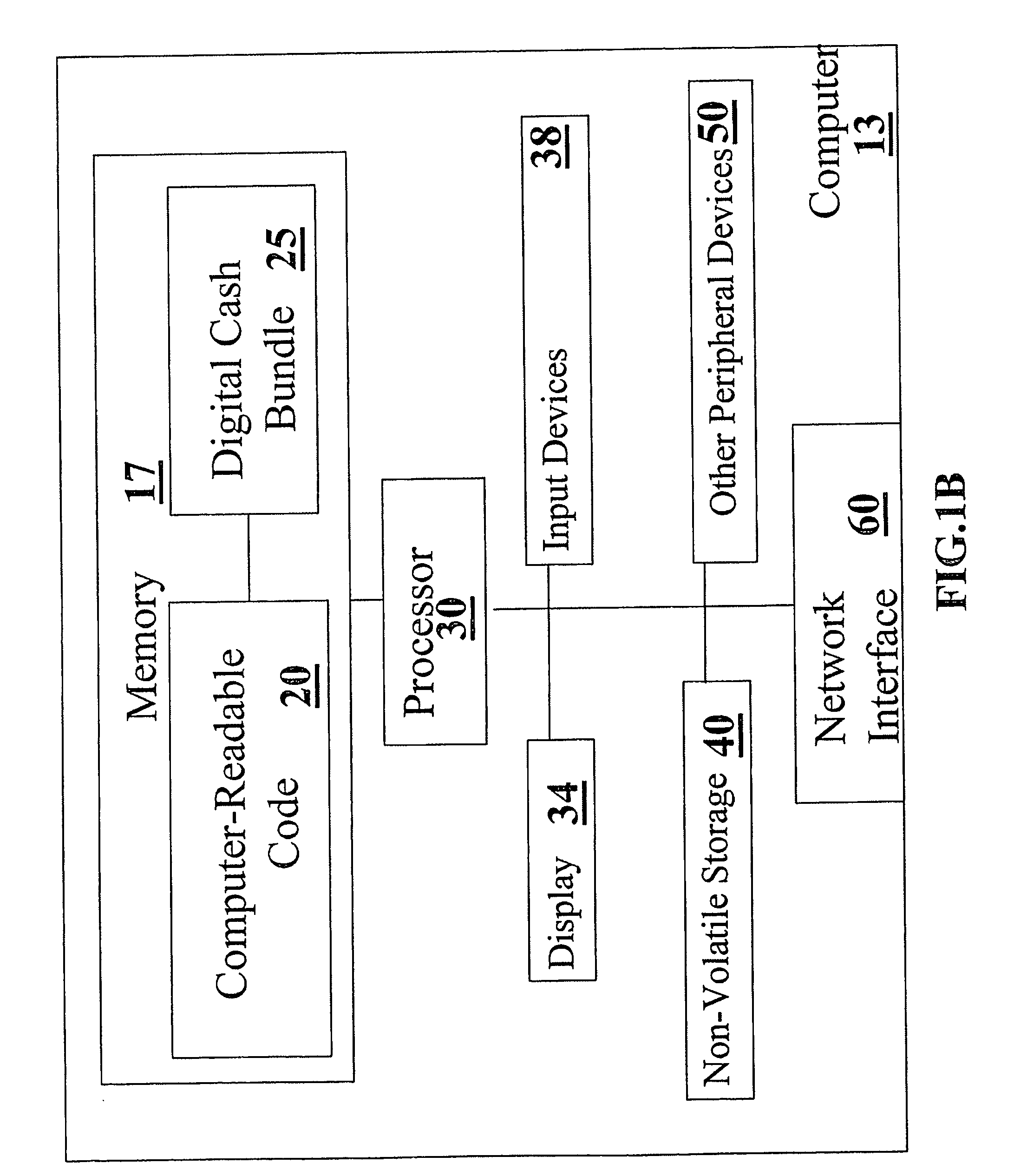
Systems, methods and computer readable code for visualizing and managing digital cash
Systems, methods and computer readable code for handling (for example, visualizing and / or managing) digital cash are provided. According to some embodiments, digital cash bundles are each represented as graphical icons associated a visual indication of at least one digital cash attribute of the respective digital cash bundle. Exemplary digital cash attributes include but are not limited to an earliest valid redeeming time, a multi-redeeming parameter, an acceptance condition parameter, a password protection status, and a currency parameter. Methods systems and computer-readable code for generating, redeeming and / or dispensing digital cash are disclosed. Methods of doing business involving digital cash are provided. Methods and systems for facilitating the installation of software on a user machine in accordance with operations involving digital cash are disclosed. Methods for simulating drag-and-drop notification icons from the taskbar of a Microsoft Windows system are provided.
Owner:DIGICASH
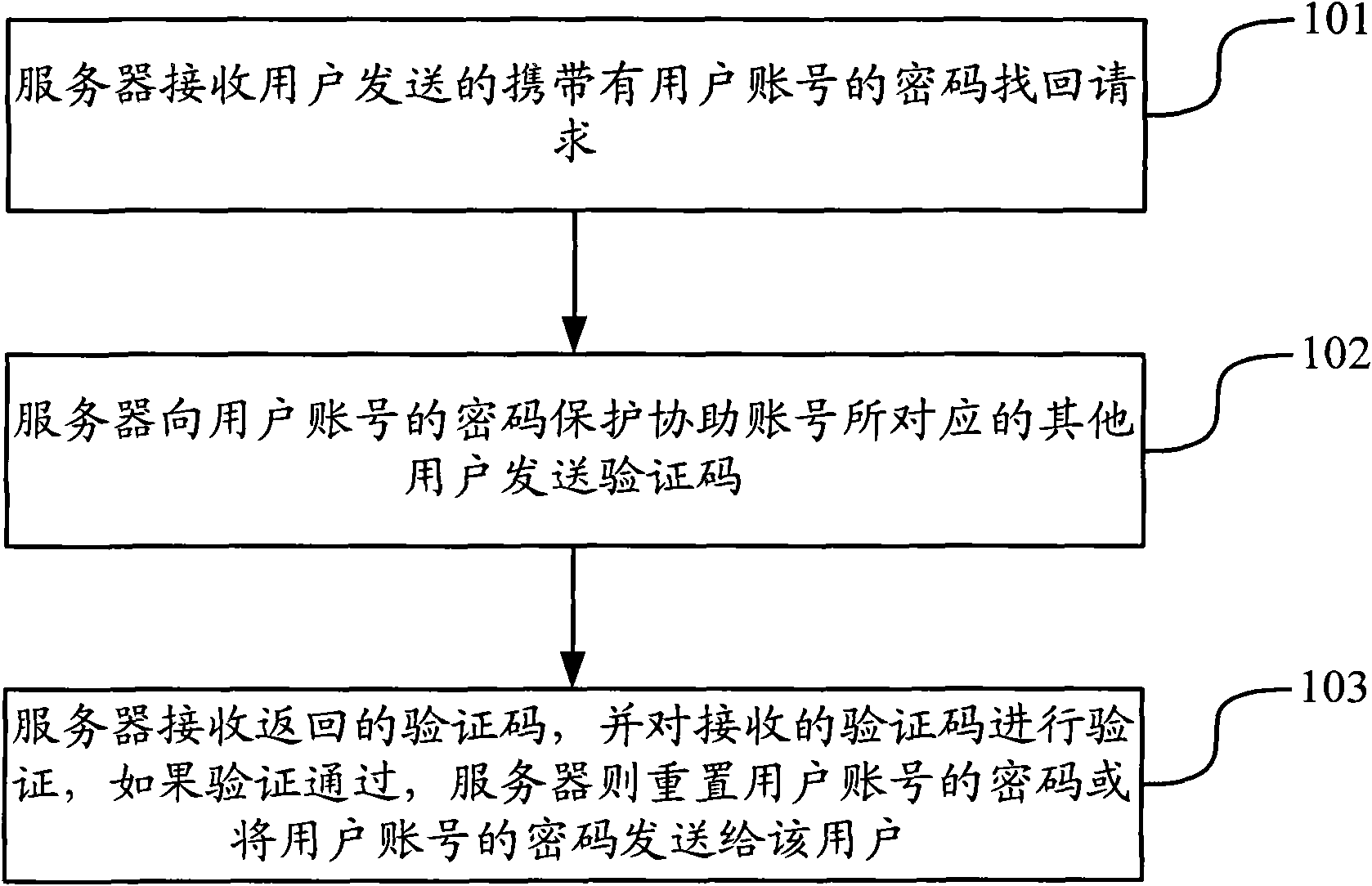
Method and device for retrieving password of network account number
The application discloses a method and device for retrieving a password of a network account number. A server acquires a password protection assistant account number corresponding to a user account number in advance. The method comprises the steps that: the server receives a password retrieving request with a user account number sent from a user; the server sends verification codes to other users corresponding to the password protection assistant account number of the user account number; and the server receives the returned verification codes and verifies the received verification codes, and if the verification passes, resets the password of the user account number or sends the password of the user account number to the users. By applying application, occupation of network resource in the password retrieving process of the network account number can be reduced.
Owner:ALIBABA GRP HLDG LTD
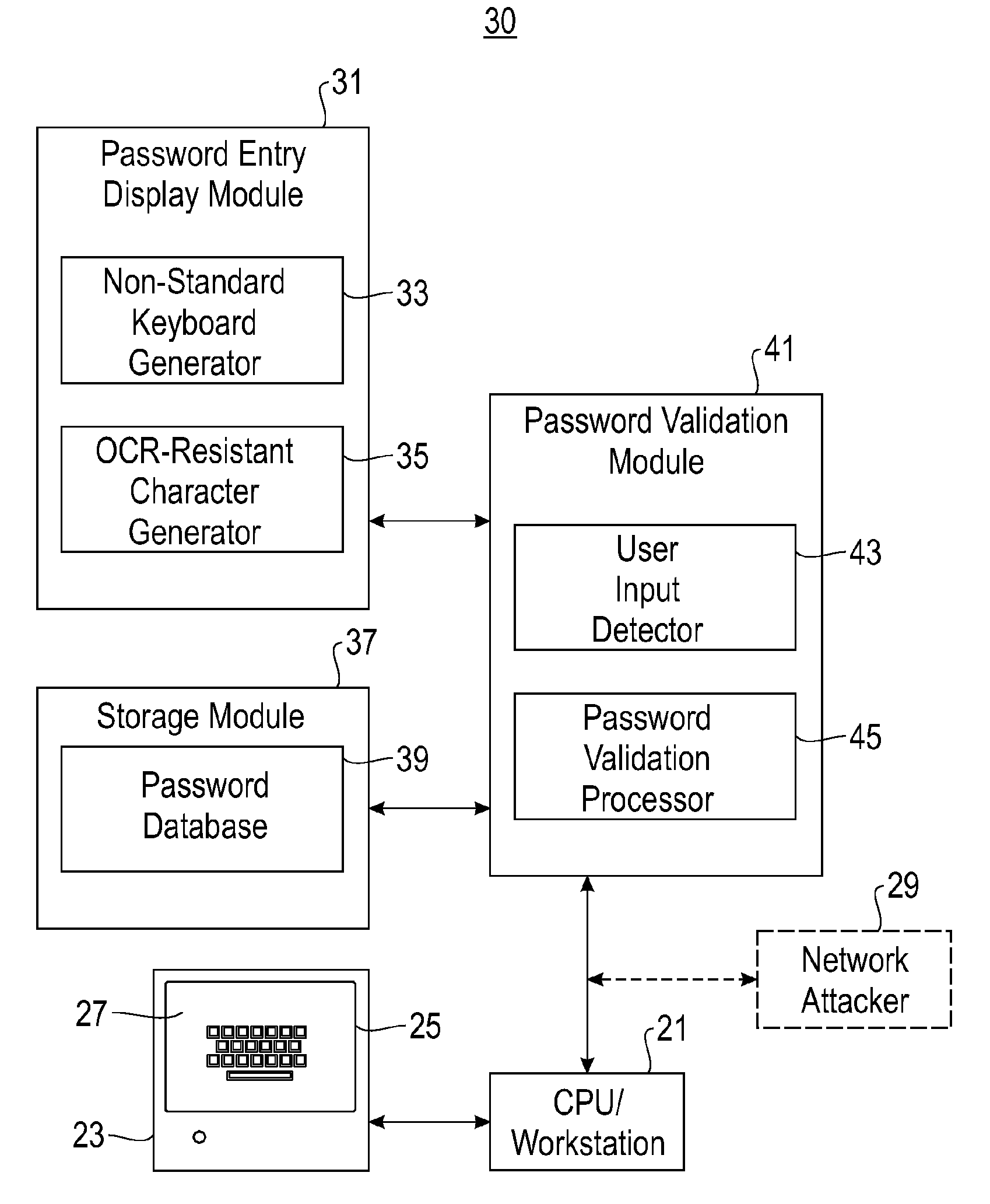
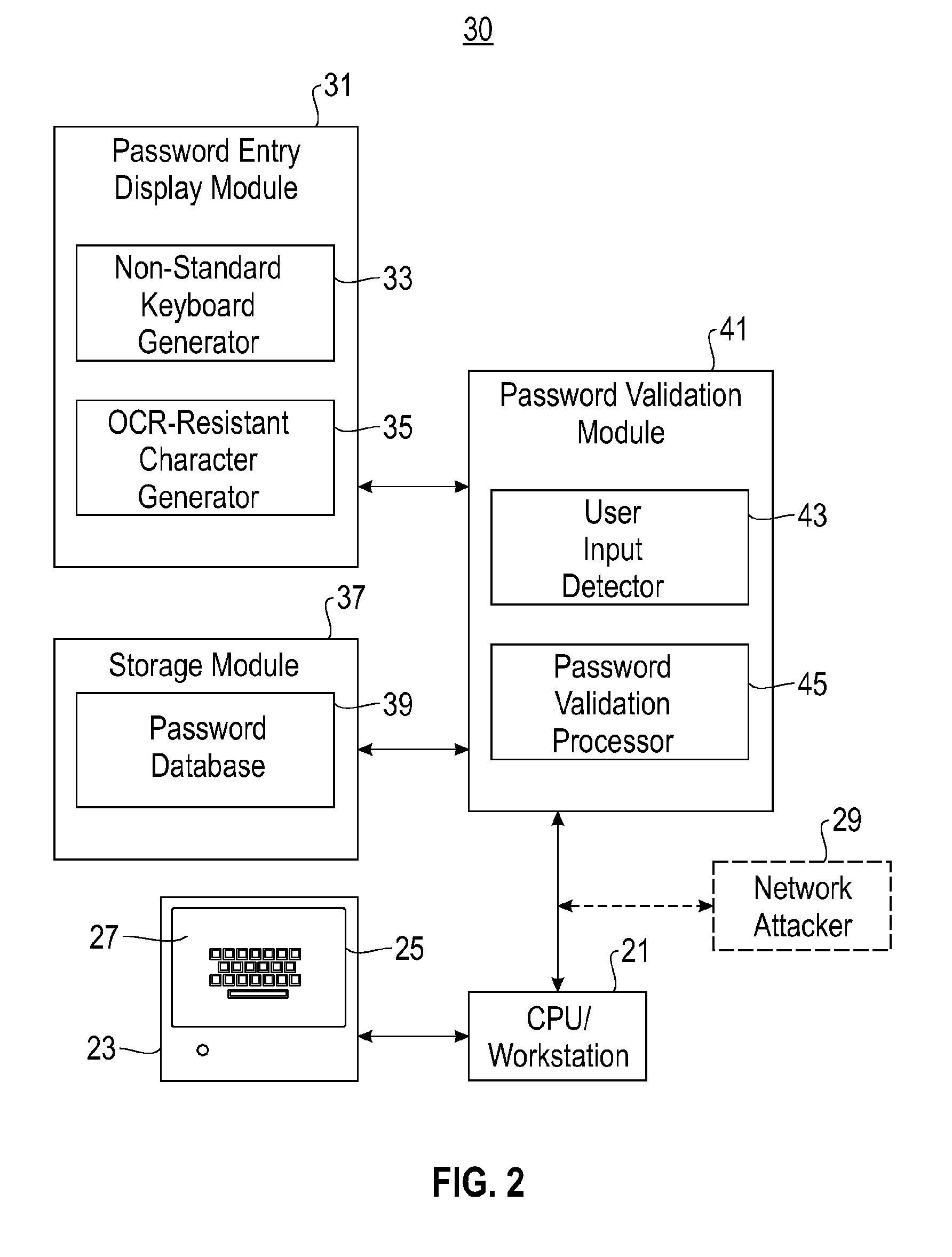
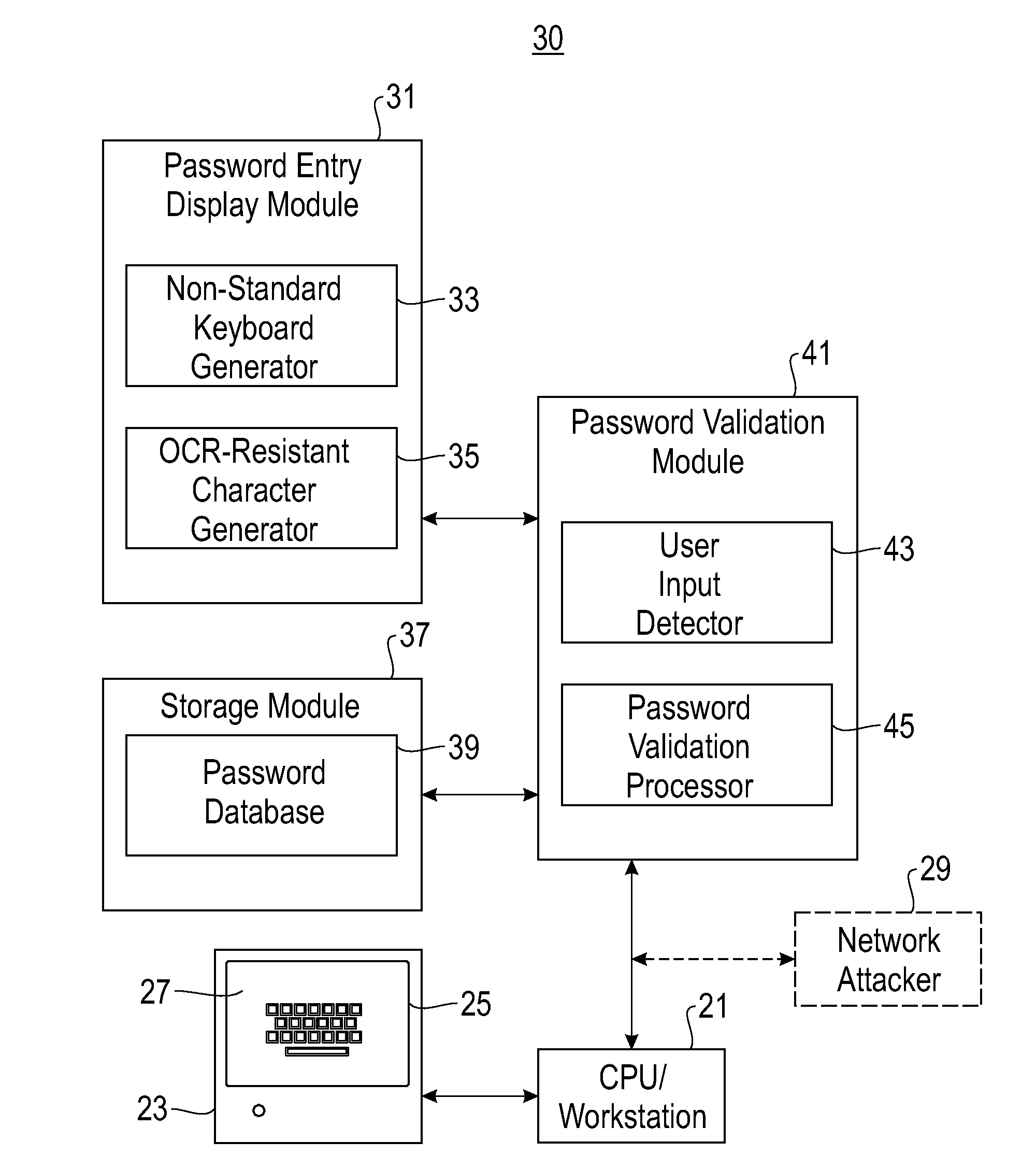
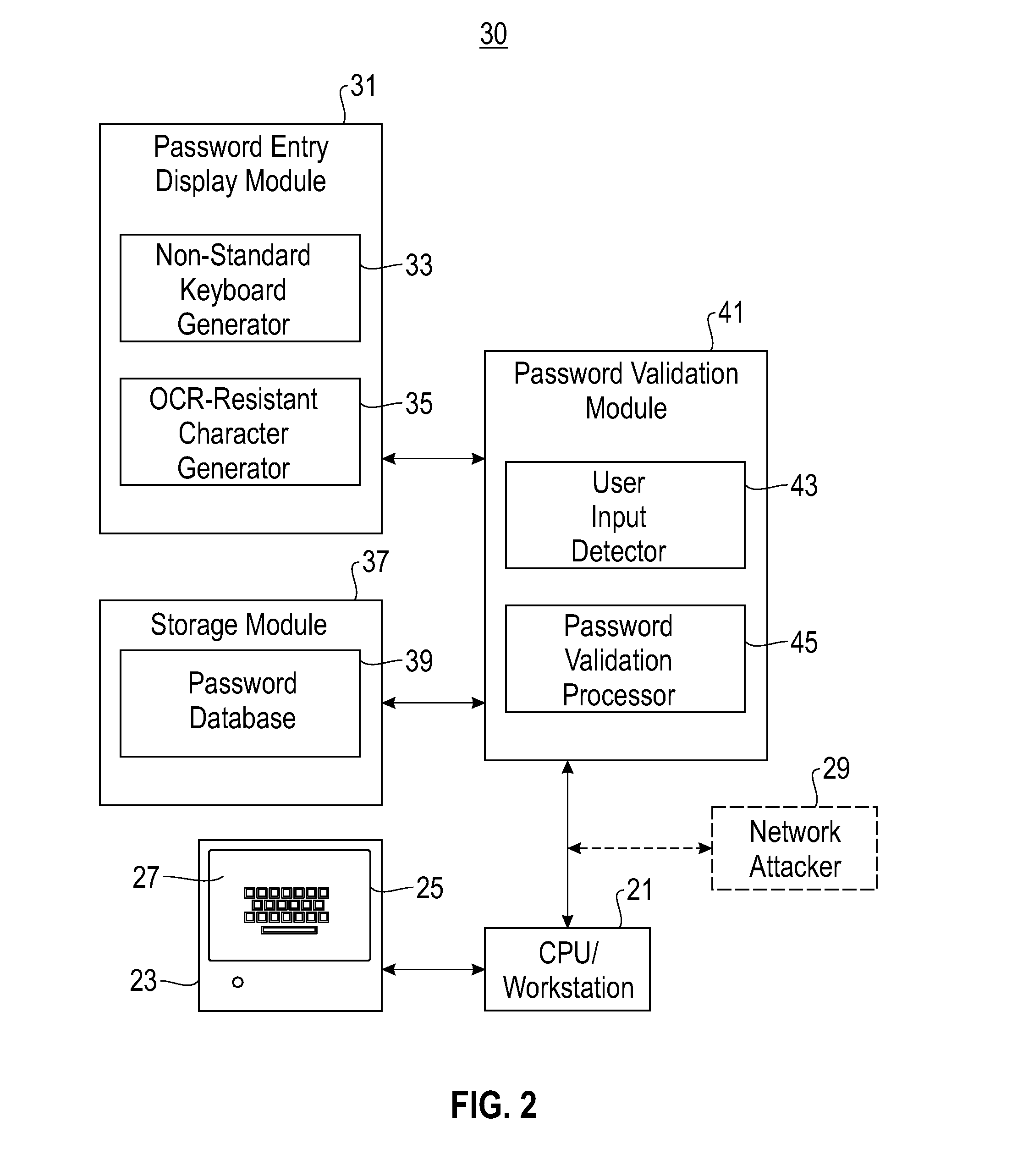
System and method for user password protection
InactiveUS20090106827A1Digital data processing detailsUser identity/authority verificationPassword protectionComputer program
A system and method are disclosed for protecting a password assigned to a user, the method comprising: providing a password entry screen having a virtual keyboard, the virtual keyboard including a plurality of character keys arranged in a non-QWERTY format; authenticating the user if a password submitted by the user accessing the password entry screen matches a user password retrieved from a password database; and denying access to the user if the submitted password does not match the retrieved user password. The system comprises a storage module and a computer program for performing the method.
Owner:IBM CORP
System and method for remote reset of password and encryption key
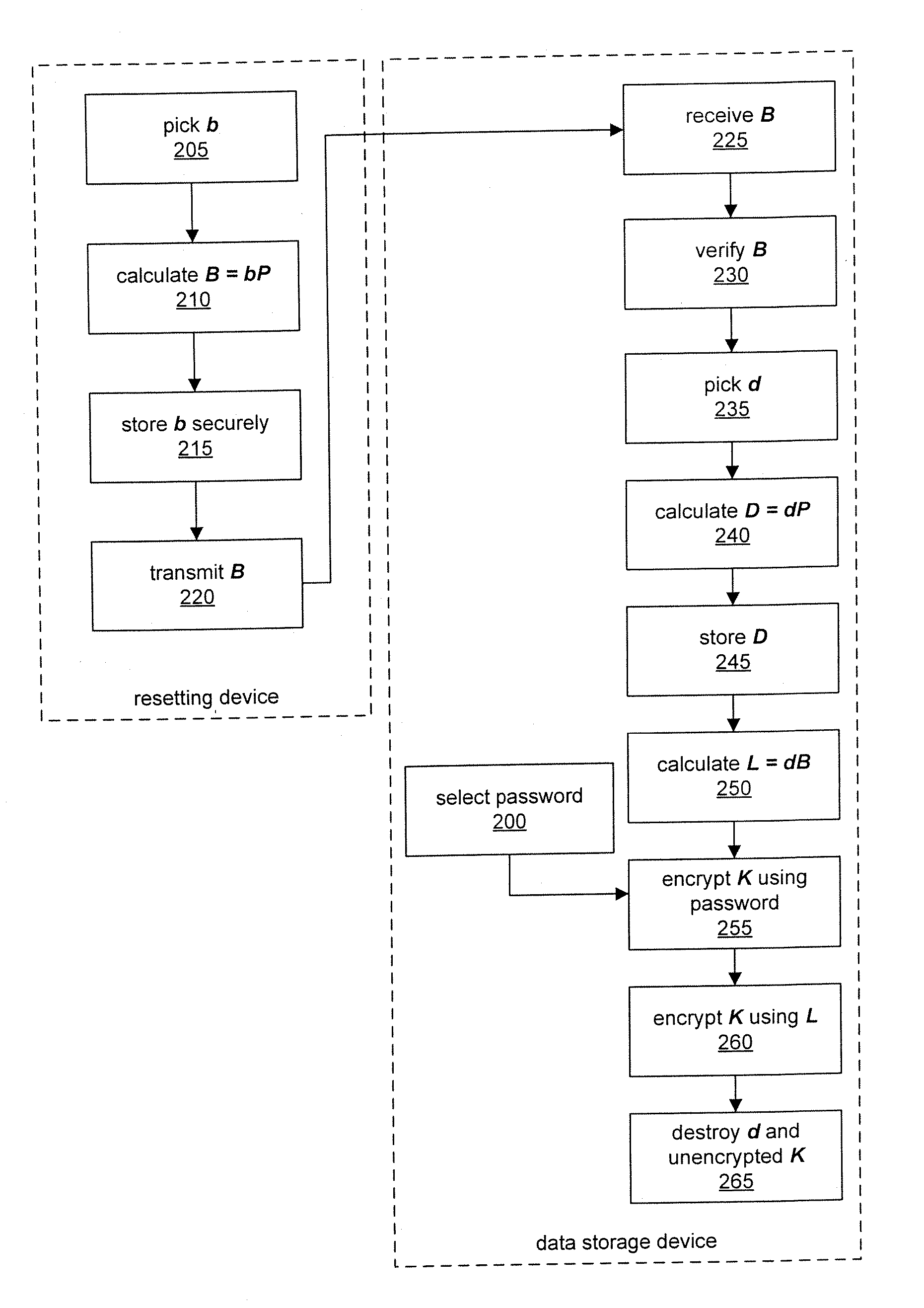
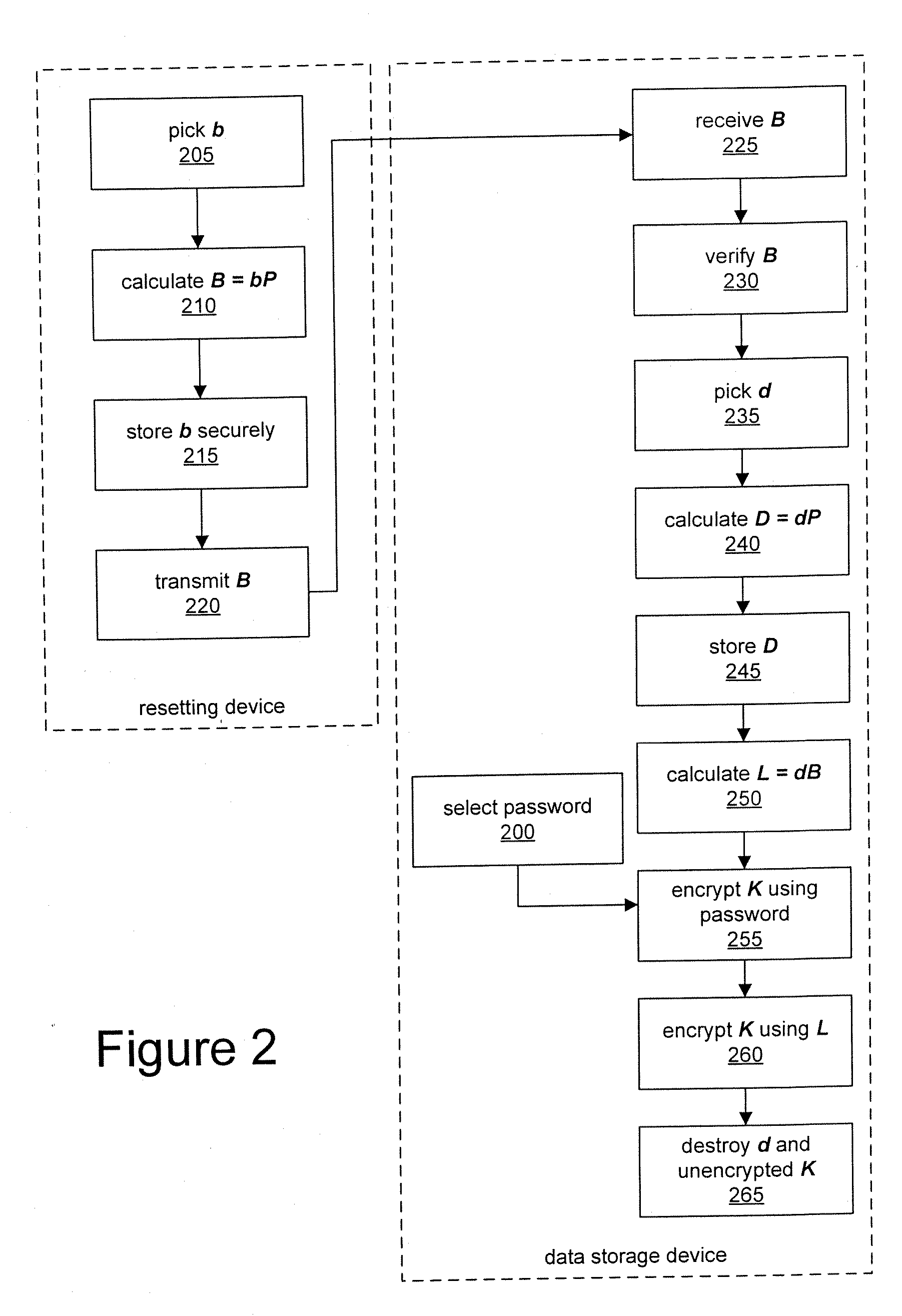
ActiveUS20070266258A1Multiple keys/algorithms usageDigital data processing detailsPasswordCollaboration
A method for securing data and resetting a password using a content protection key is provided, in which the content protection key itself is protected by a password. A content protection key is also protected at a data storage device with a key encryption key generated in collaboration with an additional device such as a server. The server stores a private key required to regenerate the key encryption key, but this private key is not provided from the server to the data storage device; rather, a public key derived from the private key is provided by the server. The data storage device combines the received public key and a further private key to derive the key encryption key; the further private key itself is not stored by the data storage device, but rather its matching public key is stored. The content protection key is then encrypted using a password and the derived key encryption key. If the password is lost, data from the server and from the data storage device may be combined to recreate the key encryption key.
Owner:MALIKIE INNOVATIONS LTD
Technique for improved audio compression
ActiveUS20020095296A1Easy to compressDigital data processing detailsSpeech recognitionTheoretical computer scienceText stream
A method, system, computer program product, and method of doing business by providing improved audio compression wherein an audio stream is securely transformed to an encoded text stream (such as an ASCII, EBCDIC, or Unicode text stream). One or more components which are involved in the transformation process are authenticated. A unique identifier of each such component is included within cryptographically-protected information that is provided for the encoded text stream. A digital signature is preferably used for the cryptographic protection, thereby digitally notarizing the encoded text stream. The authenticity and integrity of the encoded text stream can therefore be verified. In preferred embodiments, the authenticated identities of components performing the transformation can also be determined from the cryptographically-protected information. The encoded text stream will typically require much less storage space than the audio stream, and providing the digital notarization along with the encoded text stream serves to reliably establish evidence of the contents of the audio stream (even though a perfect speech-to-text transformation might not be achieved).
Owner:NUANCE COMM INC
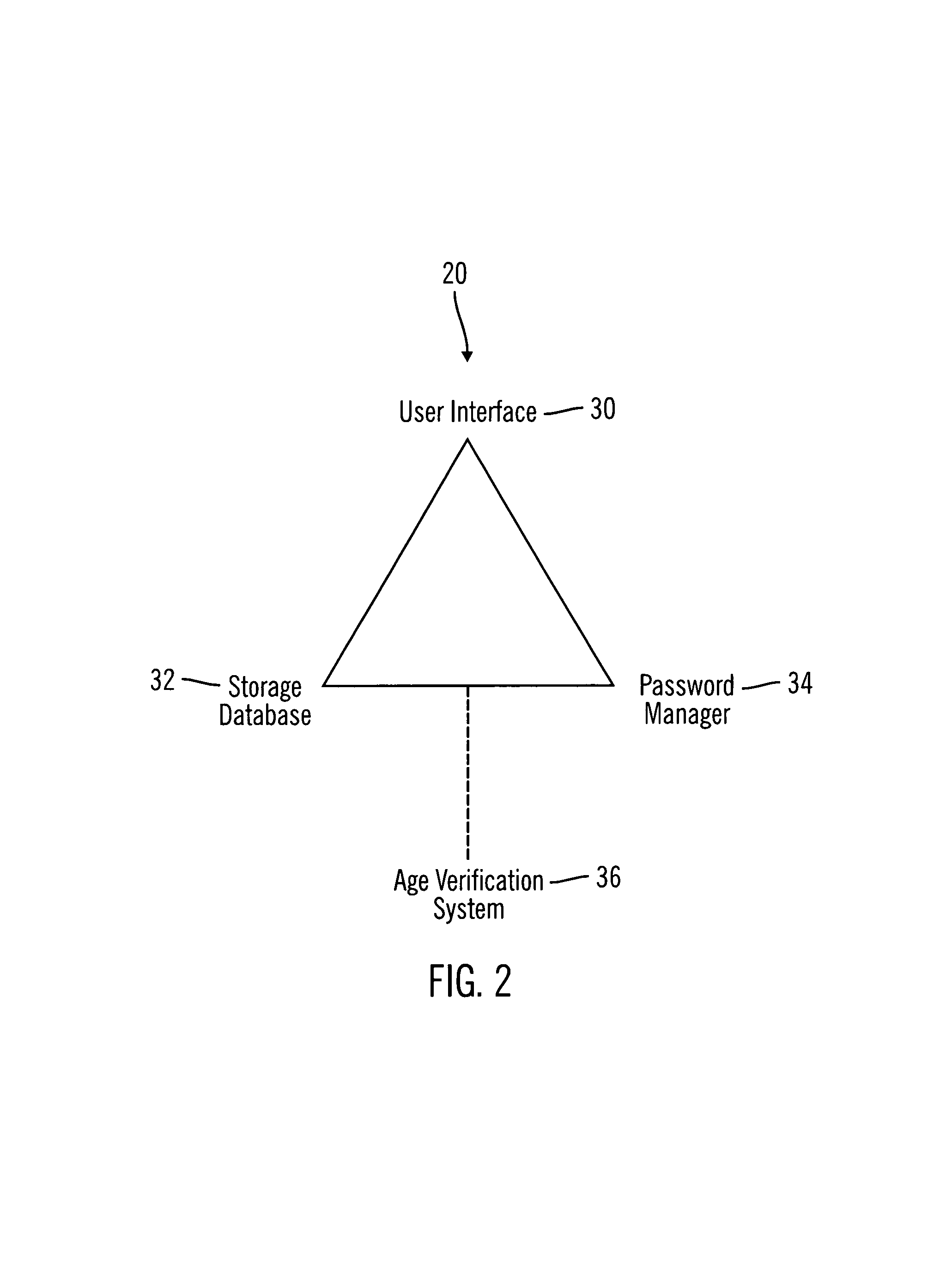
Password protection system and method
ActiveUS7734779B1Multiple digital computer combinationsTransmissionPassword protectionAge appropriate
A system and method for providing a password to a user on a network, the network having provider computer and a user computer, the provider computer comprising a password system configured to issue a password to a user of the user computer for use in accessing age-restricted content once a determination has been made that the user is age appropriate.
Owner:GULA CONSULTING LLC
Multi-source powered audio playback system
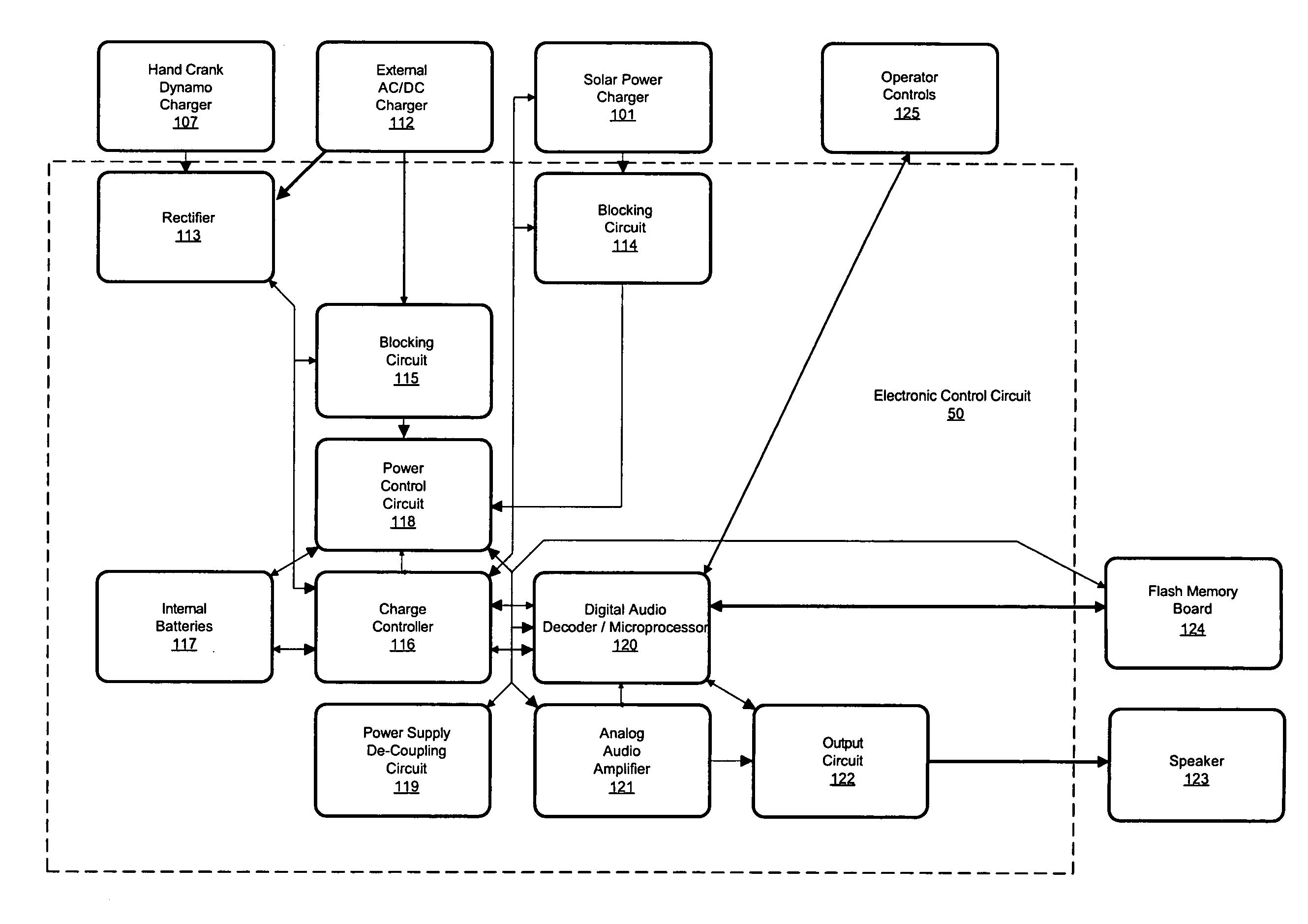
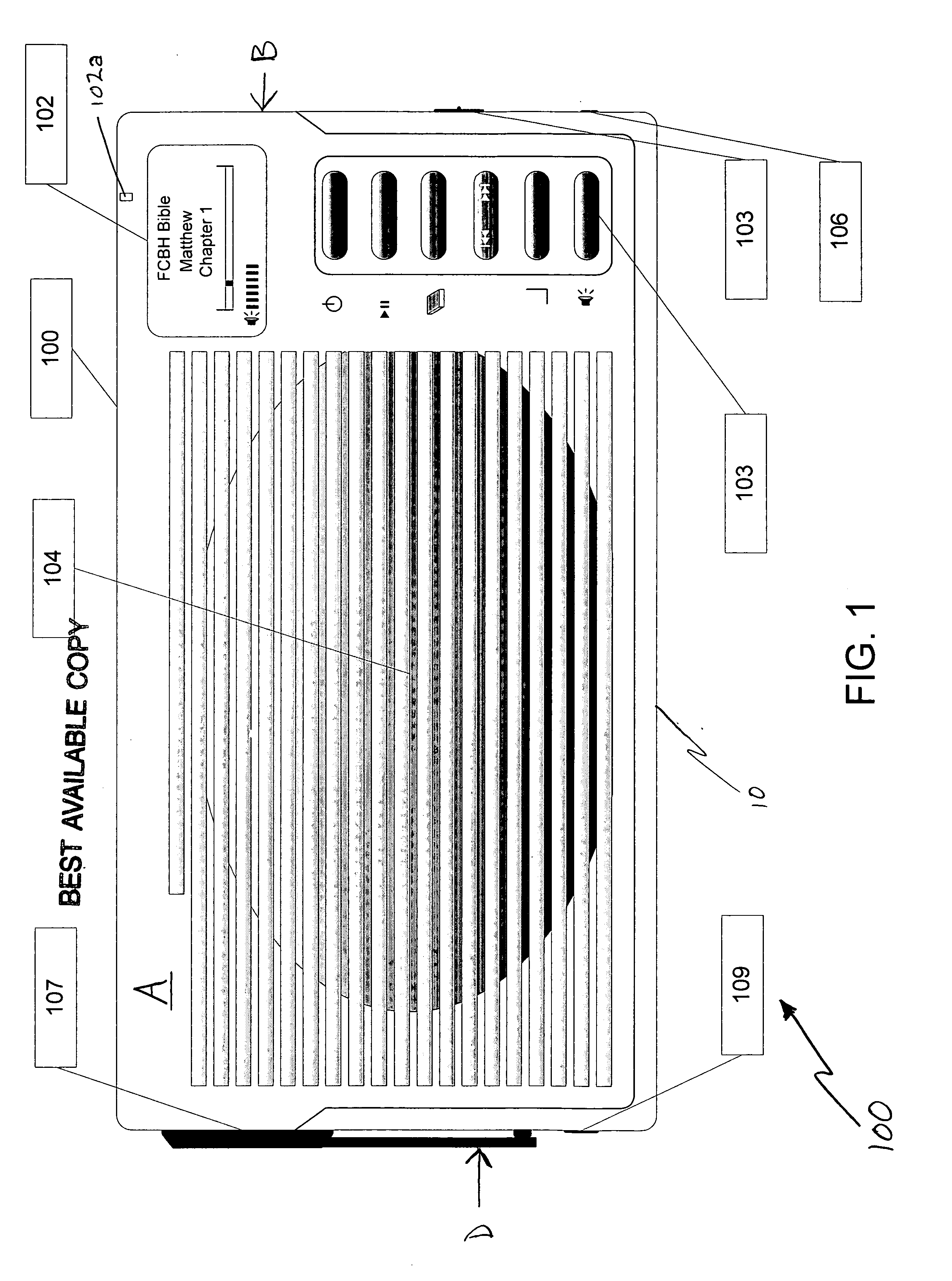
InactiveUS20060155545A1Easy to understandSpeech analysisRecord information storageElectrical batteryEngineering
The present invention is a multi-source powered audio playback system which integrates multiple energy charging sources that charge an internal battery, with a digital audio player and an analog audio amplifier and multiple audio outputs. In one embodiment, the present invention includes a mechanical power generating means, rectifier, solar power cell, blocking circuit, external AC / DC charger, blocking circuit, charge control circuit, at least one rechargeable battery pack, a power control circuit, a digital audio player, at least one mass memory device with secure content, voltage regulator circuit, power supply de-coupling circuit, analog audio amplifier, output circuit and a waterproof speaker. The audio content is secured by the elimination of a consumer usable data port and / or password protection. The invention optimally provides an audio output signal that is sufficient for private, room or group use.
Owner:HOSANNA
Method and apparatus for contactless payment authentication
ActiveUS7641111B2Efficient and accurate and easy to implementMaintain conveniencePayment architectureSensing record carriersPaymentPassword protection
The present disclosure relates generally to the authentication of contactless payments attempted by a device having embedded contactless payment functionality. In particular, the disclosure is directed to systems and methods that utilize authentication schemes that already exist on a device in which the contactless payment functionality is embedded. One example of such authentication schemes is the use of password protection to lock or unlock the device in which the contactless payment functionality is embedded. Using the password protection functionality may provide varying levels of authentication protection based on the desires of the user. A number of exemplary uses of such a method and apparatus are disclosed herein.
Owner:MALIKIE INNOVATIONS LTD
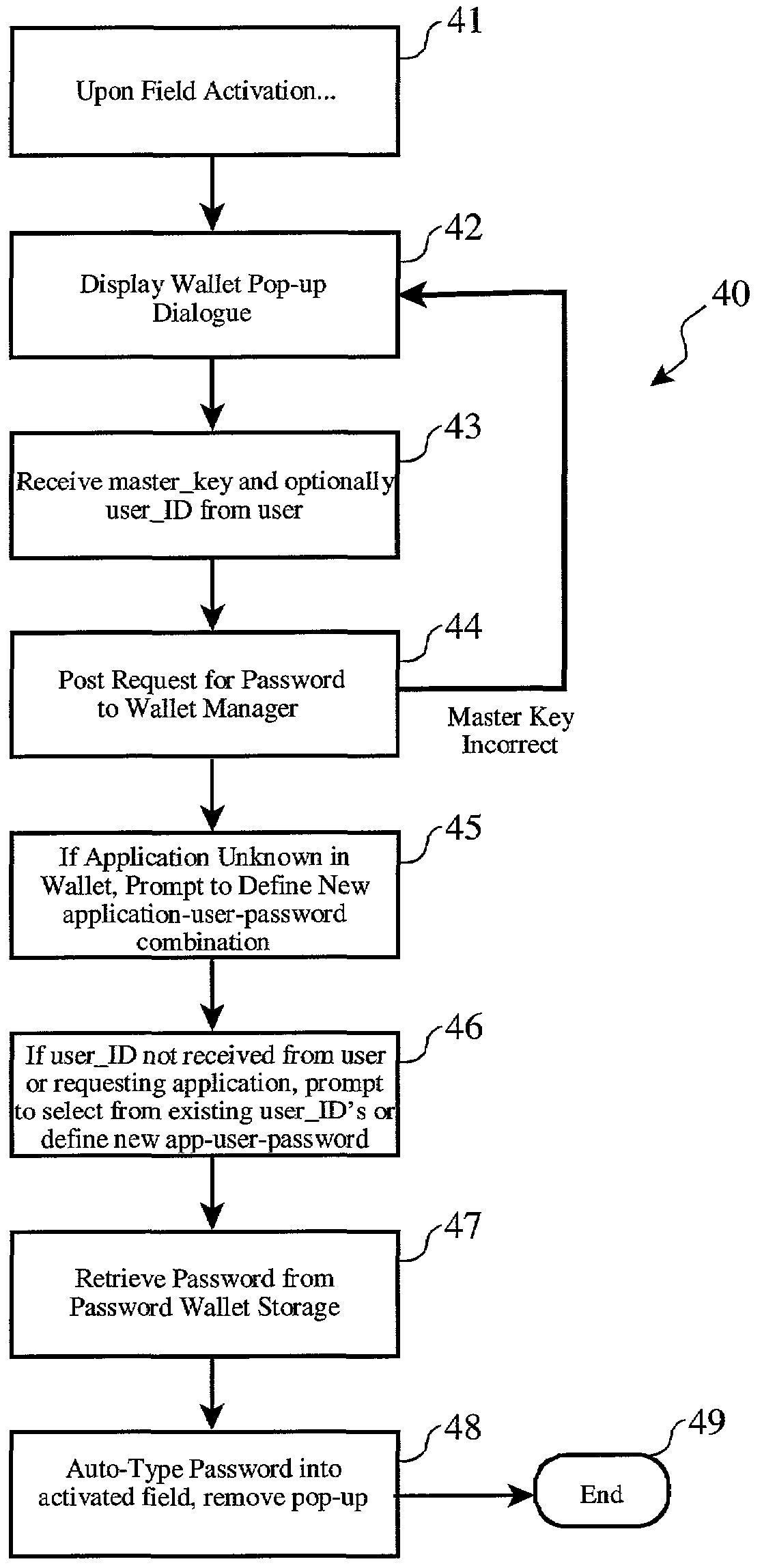
Electronic password wallet
InactiveUS7136490B2Easy and fast accessKey distribution for secure communicationDigital data processing detailsWeb siteDisplay device
A convenient and secure system and method for access to any number of password-protected computer applications, web sites and forms without adding to the user cognitive load and without circumventing the inherent security of such password-protection schemes. An existing password field on a device display is overlaid with password wallet pop-up field which allows a wallet “master” key to unlock the wallet. An application-specific and / or user-specific password is automatically retrieved from the wallet and entered into the password field with no other user action required.
Owner:LINKEDIN
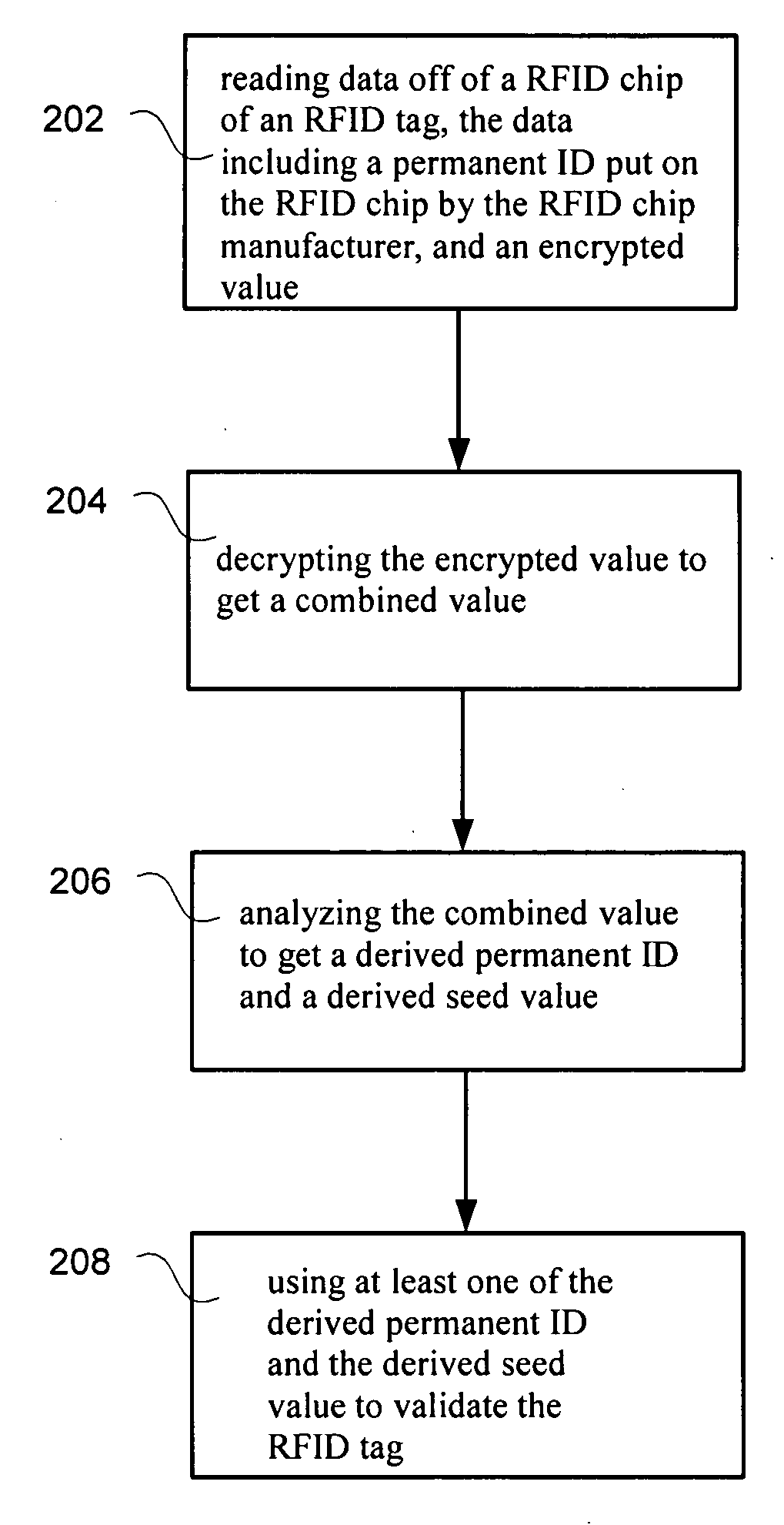
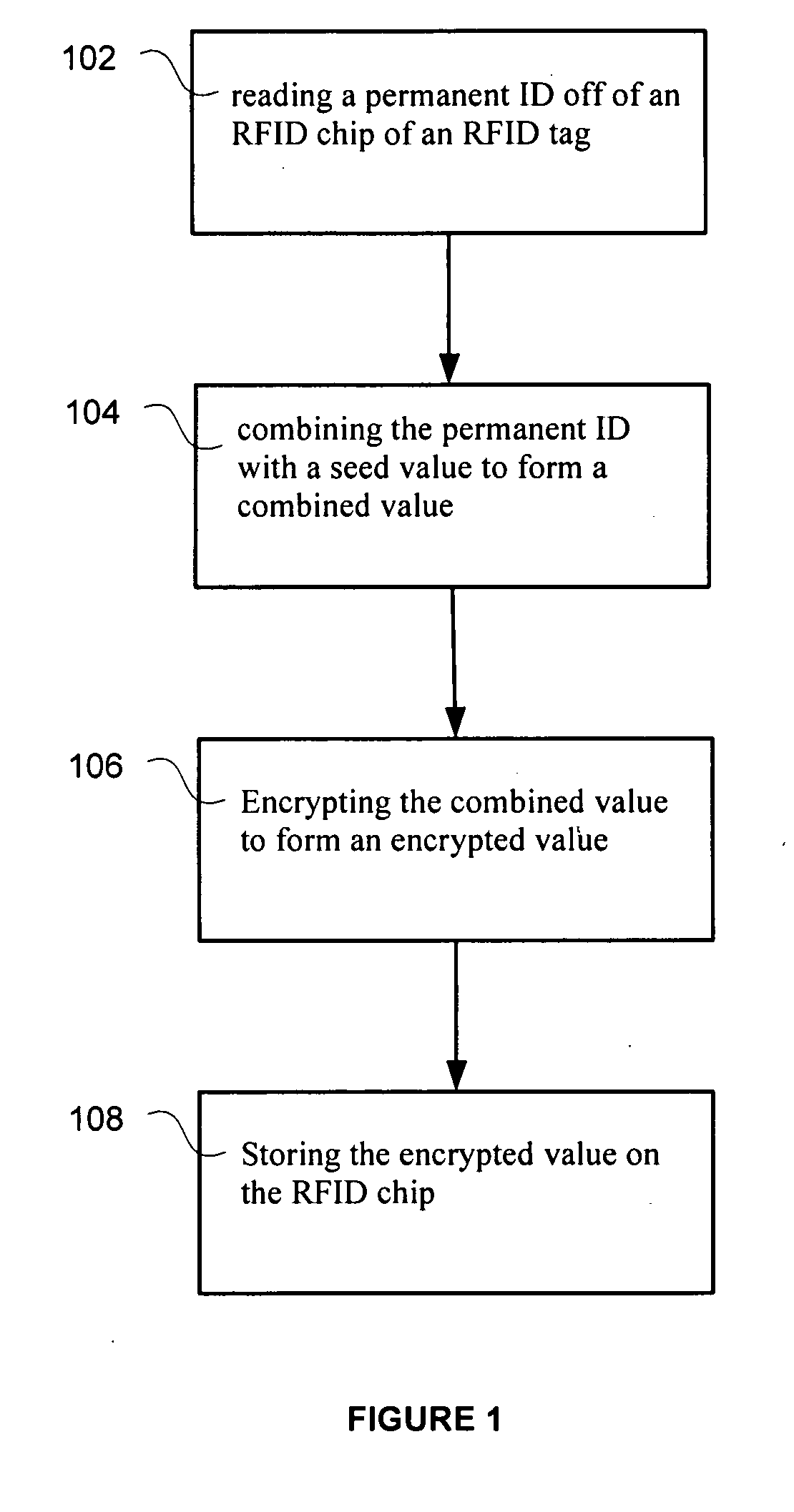
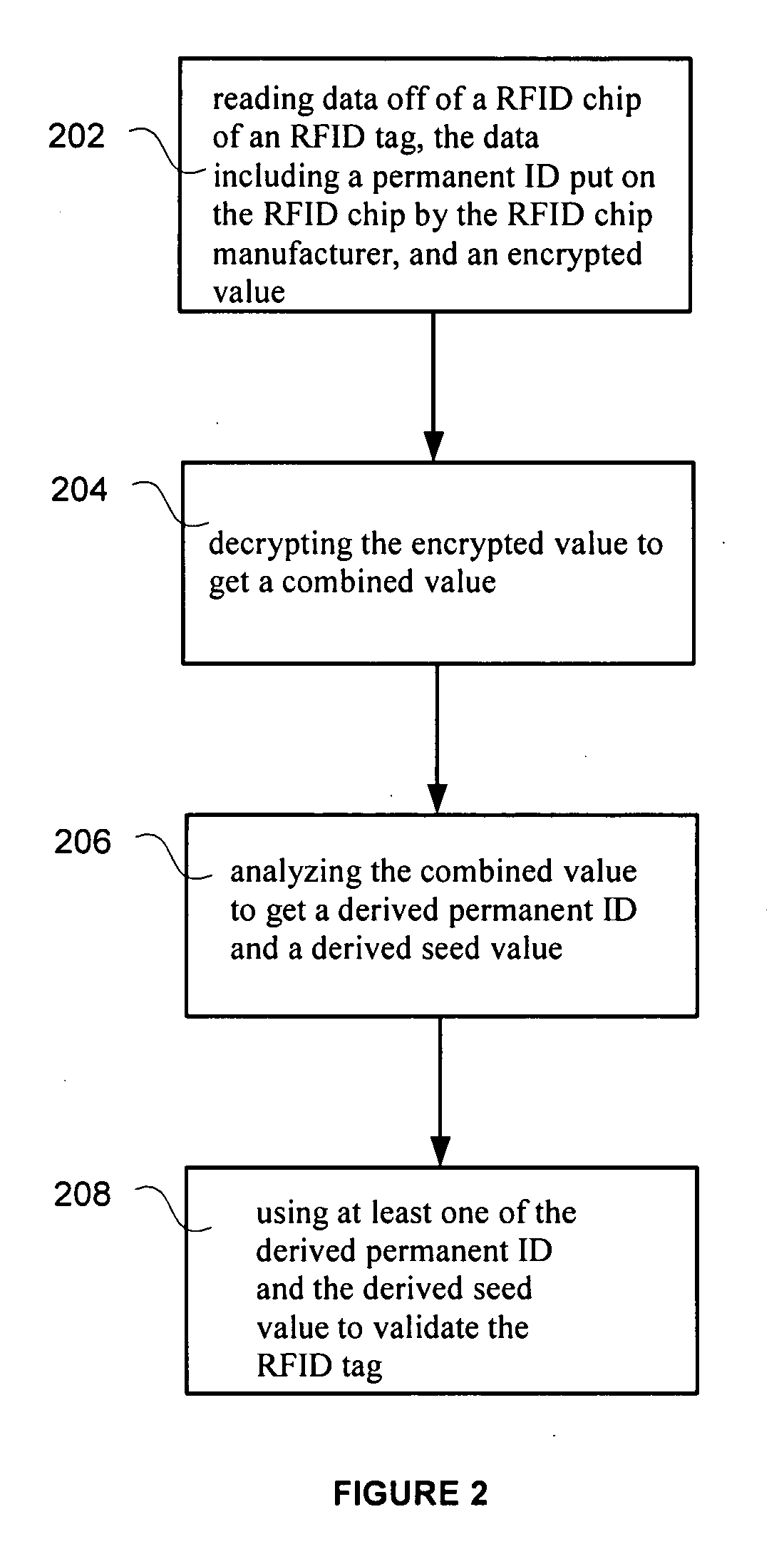
RFID tag using encrypted password protection
InactiveUS20090096574A1Programme controlElectric signal transmission systemsComputer hardwarePassword protection
A permanent ID can be read off of an RFID chip of an RFID tag. The permanent ID can be combined with a seed value to form a combined value. The combined value can be encrypted to form an encrypted value. This encrypted value can be stored on the RFID chip. Later, the RFID tag can be validated using the encryption value.
Owner:RCD TECHNOLOGY
System and method for user password protection
InactiveUS20090106825A1Digital data processing detailsUnauthorized memory use protectionPassword protectionComputer program
A system and method are disclosed for protecting a password assigned to a user, the method comprising: providing a password entry screen having a virtual keyboard, the virtual keyboard including a plurality of character keys arranged in a non-QWERTY format; authenticating the user if a password submitted by the user accessing the password entry screen matches a user password retrieved from a password database; and denying access to the user if the submitted password does not match the retrieved user password. The system comprises a storage module and a computer program for performing the method.
Owner:IBM CORP
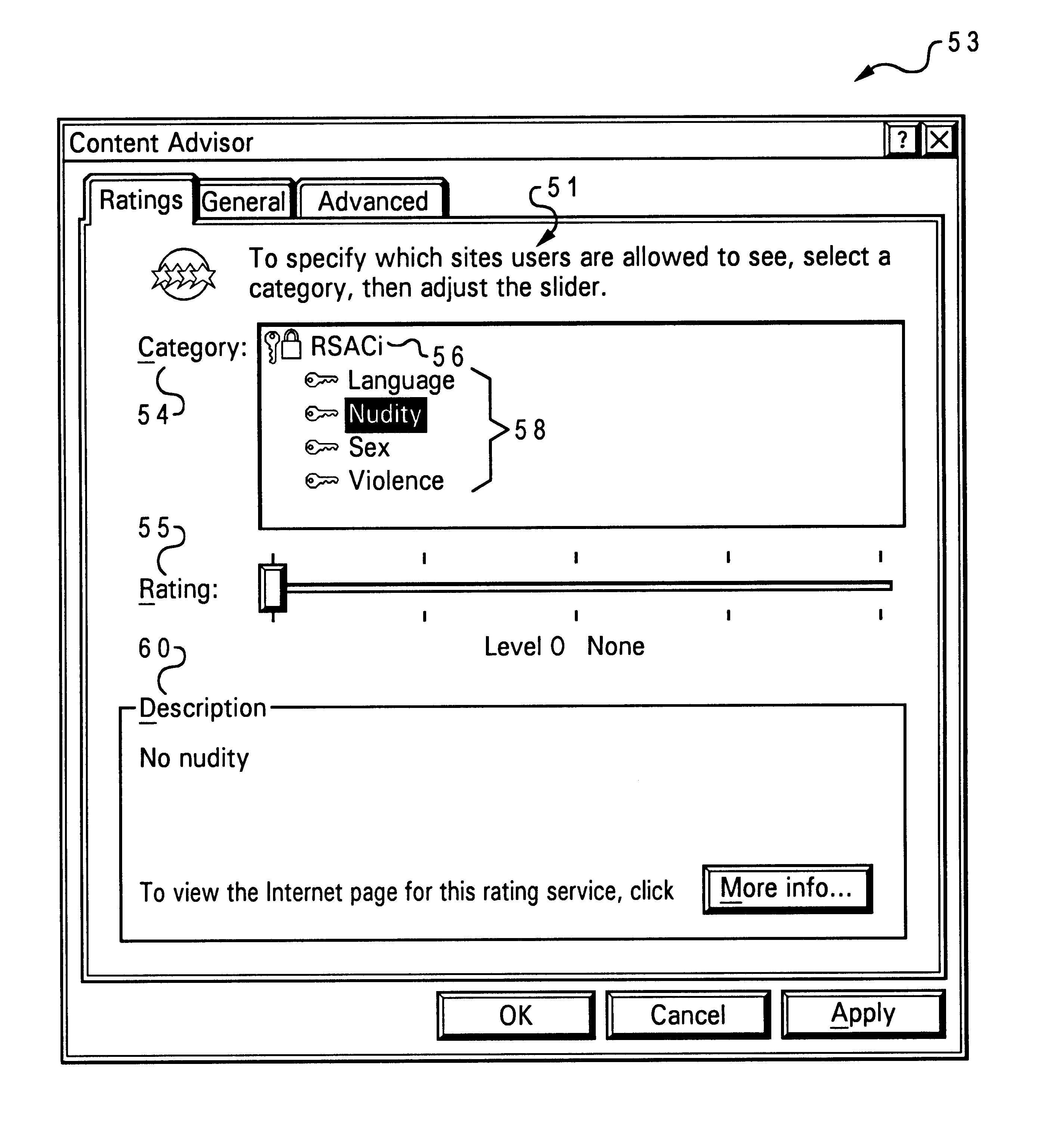
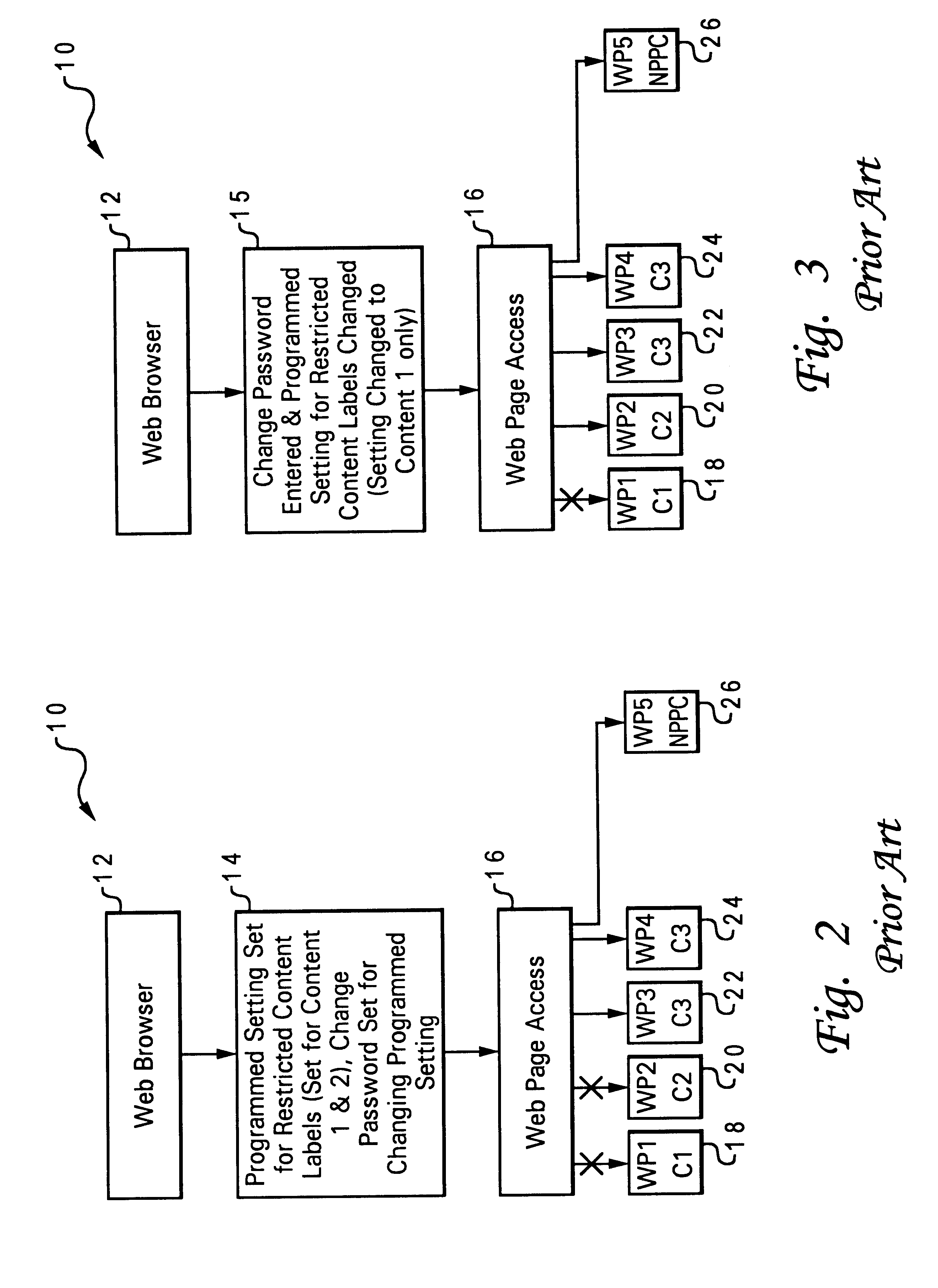
Selective and multiple programmed settings and passwords for web browser content labels
InactiveUS6725380B1Digital data information retrievalUser identity/authority verificationWeb browserPassword
A system and method are disclosed that regulate browsing of web content or content labels and that provide selective and multiple programmed settings and passwords for web content labels. In one embodiment, at least some of the web pages accessible to a web browser are assigned content labels. Programmed settings are established for the content labels that are to be password protected. A content password is assigned to each of the programmed settings. Access to web pages without any content labels is strictly denied by the web browser. Access to web pages with content labels that are not being regulated is allowed. Access to web pages with content labels that are password protected is regulated.
Owner:IBM CORP
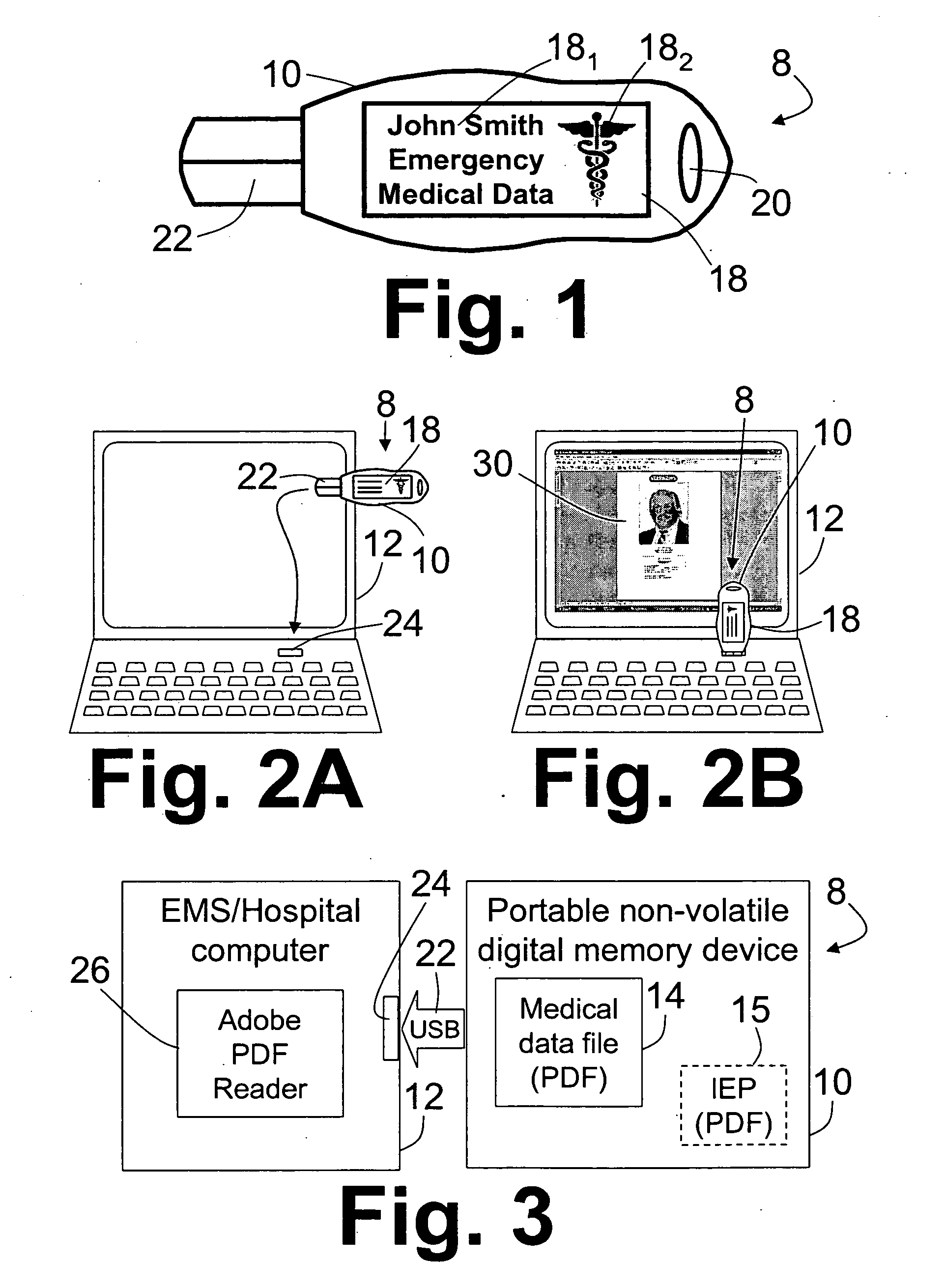
Portable method and device for personal medical record compilation and retrieval
InactiveUS20060015368A1Data processing applicationsPatient personal data managementMedical recordInformation device
A medical information device includes a portable USB memory drive adapted for detachable connection with a USB port of a computer. A current medical profile Portable Document Format (PDF) file is stored on the portable USB memory drive unencrypted and without password protection. The current medical profile PDF file contains information relevant to delivering emergency aid to an associated person in the event of a medical emergency. Visual indicia are coupled with the portable USB memory drive to alert emergency personnel that the portable USB removable memory drive contains information relevant to delivering emergency aid to the associated person.
Owner:HOCKEY SANFORD
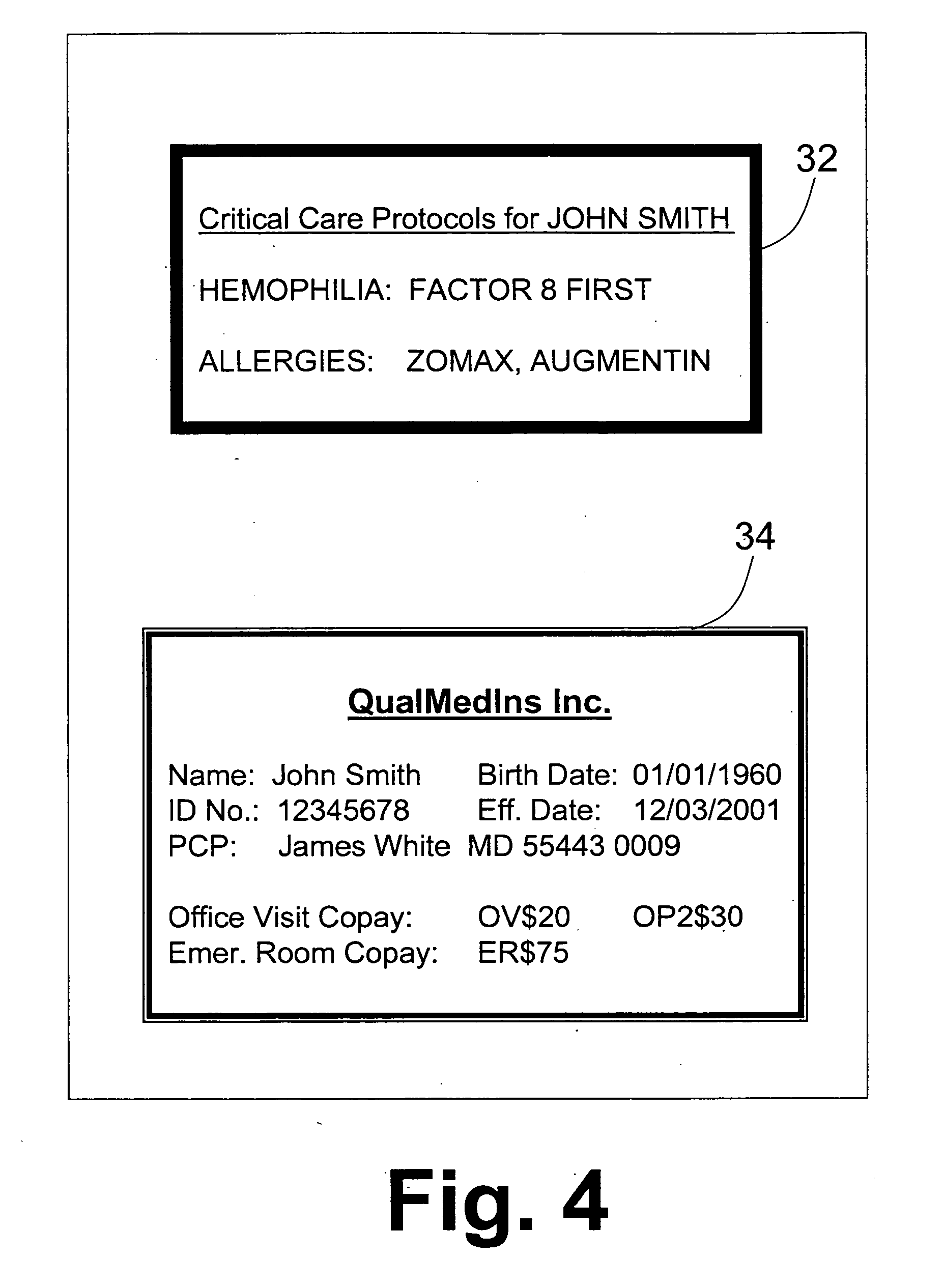
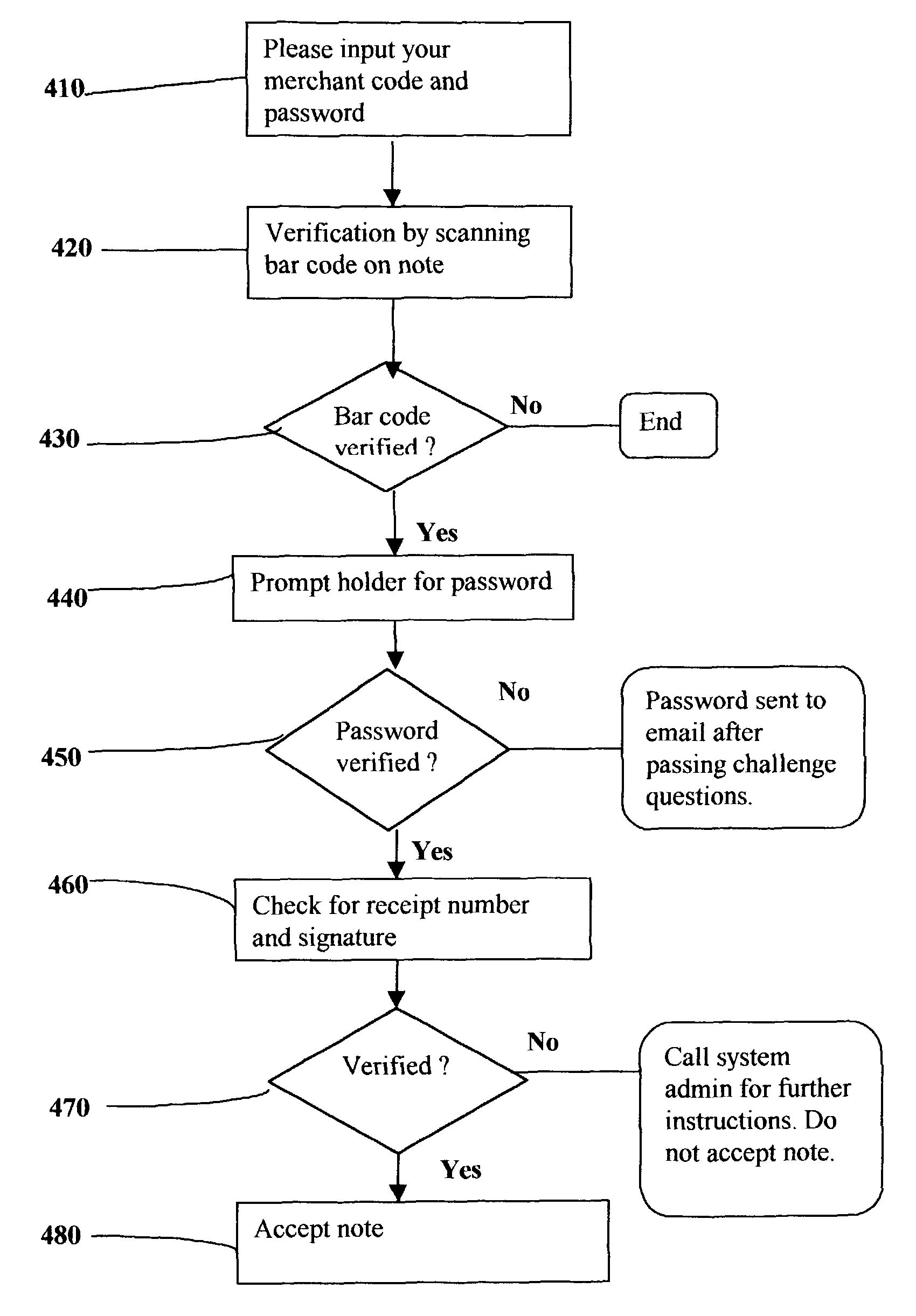
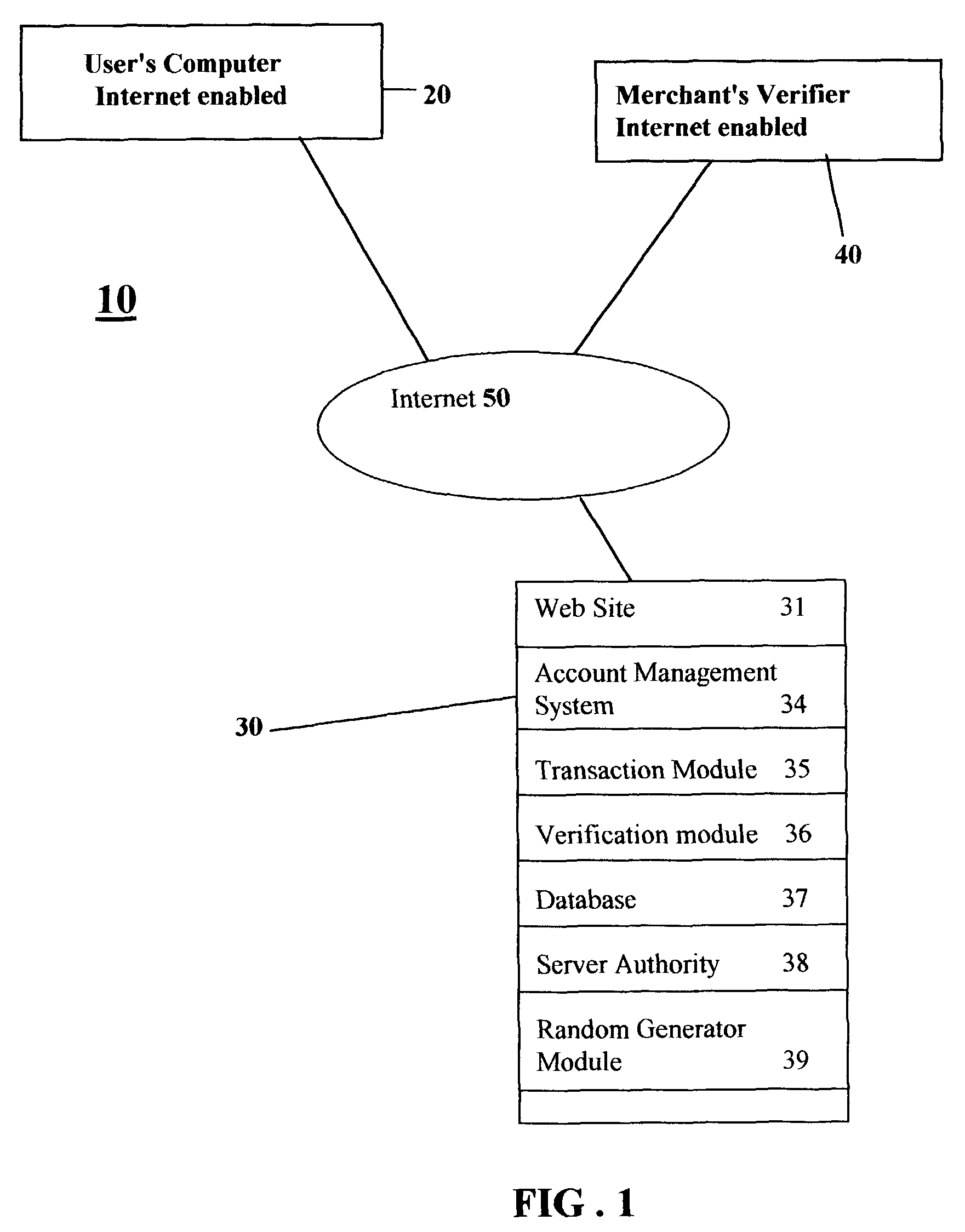
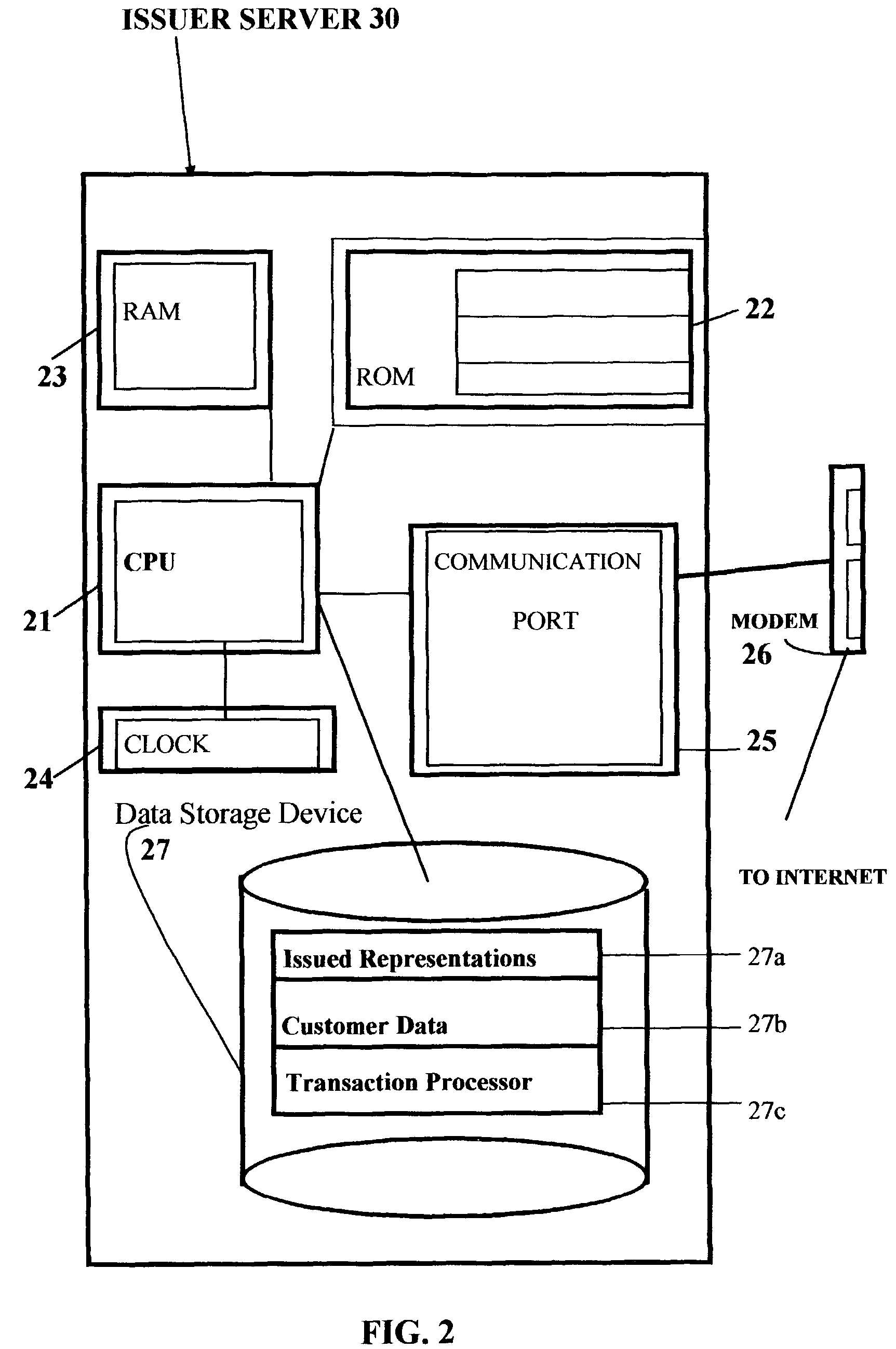
Computer program, system and method for on-line issuing and verifying a representation of economic value interchangeable for money having identification data and password protection over a computer network
InactiveUS7742996B1Safe transferEasy transferSensing record carriersBuying/selling/leasing transactionsDistribution systemPassword protection
An electronic economic value representation distribution system. The potential user may specify the economic value representation. A password is required to lock in the representation and is stored in the issuer server. Information identifying the representation is linked to the password stored in the database. User can create the said representation by downloading from the issuer computer that may be printed on the user's printer connected to his personal computer. On presentation of the said economic value representation at verifier's terminal connected to issuer server, identifying data is transmitted to issuer server for verification. Upon successfully verifying said identifying information, user is requested to present the password locking the representation. Upon successful authentication of presented and successful reconciling with originating account, verifier is to provide user with services or amount valued by the economic representation.
Owner:KWAN KHAI HEE
Computer program for securely viewing a file
InactiveUS20050204130A1Digital data processing detailsUnauthorized memory use protectionPasswordBiological activation
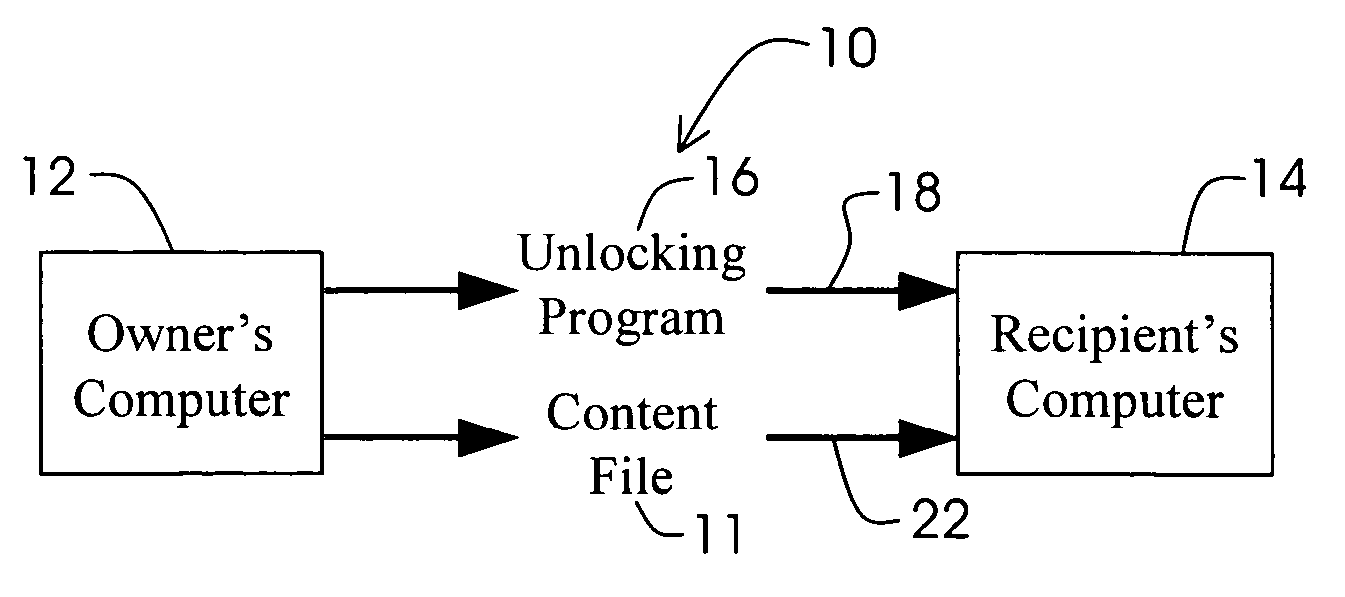
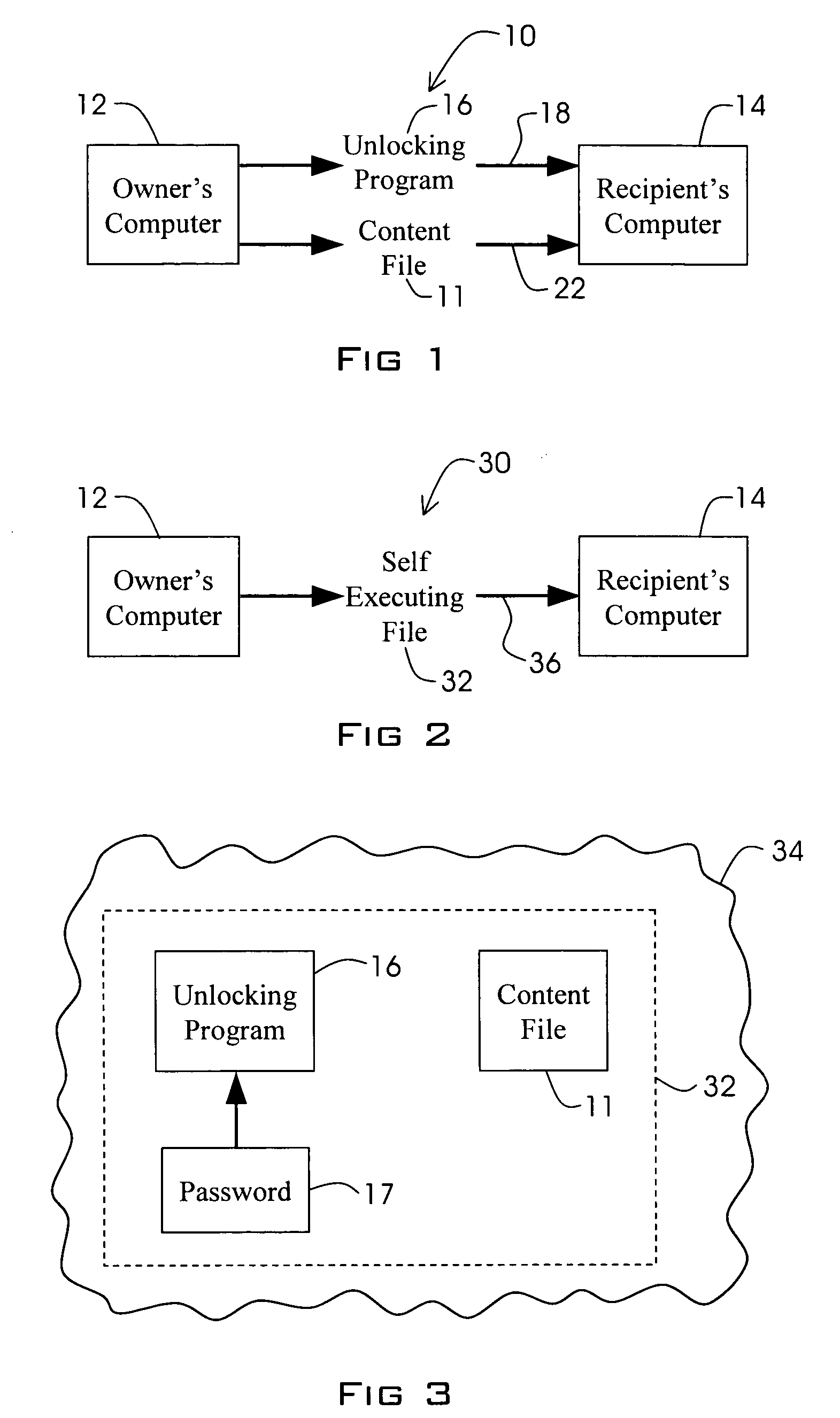
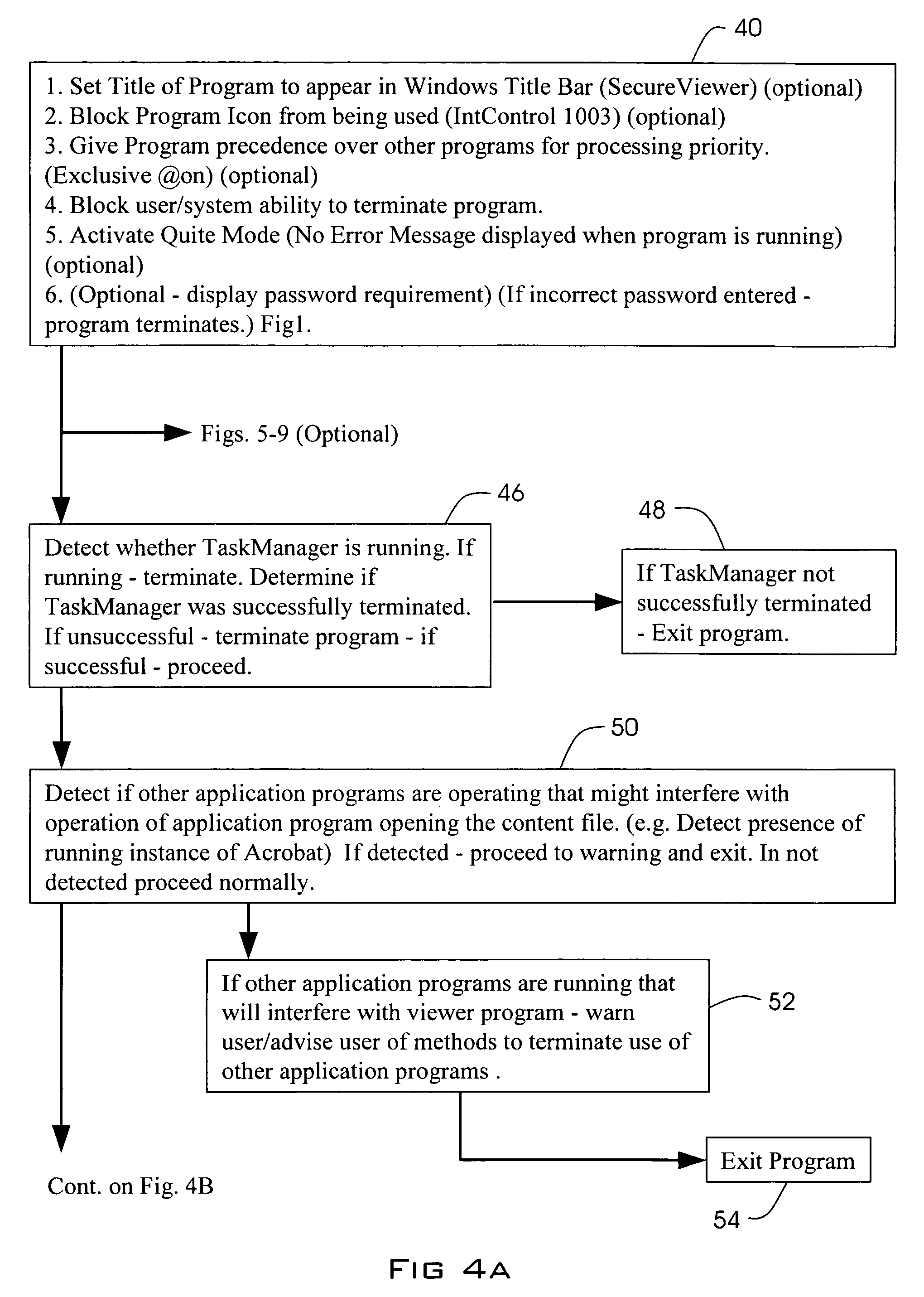
A method for distributing a password protected content file without revealing the password to a recipient. An unlocking program that has access to at least one password corresponding to the password protecting the content file is distributed to the recipient's computer. A password protected content file is distributed to the recipient's computer wherein upon activation of the unlocking program, the unlocking program automatically supplies the at least one password upon loading of the password protected content file.
Owner:HARRIS STEVEN M
Powerhead of a power injection system
InactiveUS20060079767A1Increase powerImprove accuracyMedical devicesIntravenous devicesEngineeringPassword protection
A contrast media injection system includes detects the absolute position of the syringe ram using a non-contact sensor. A series of magnets and Hall-Effect sensors may be used or an opto-reflective system. Illuminated knobs that are connected to the drive mechanism for the syringe ram rotate with the drive and provide visual feedback on operation through the illumination. Analog Hall-Effect sensors are used to determine the presence or absence of magnets that identify the type of faceplate being used. The faceplates include control electronics, connected to the powerhead through connectors, which may be interchangeably used by the two faceplates. The faceplate electronics include detectors for automatically detecting the capacity of pre-filled syringes. Additional features include using historical data to provide optimum pressure limit values during an injection protocol, a removable memory device for storing and transferring information such as injection protocols and injector statistics, and password protection of such protocols.
Owner:LIEBEL FLARSHEIM CO
Method of ensuring that the PC is not used to make unauthorized and surreptitious telephone calls
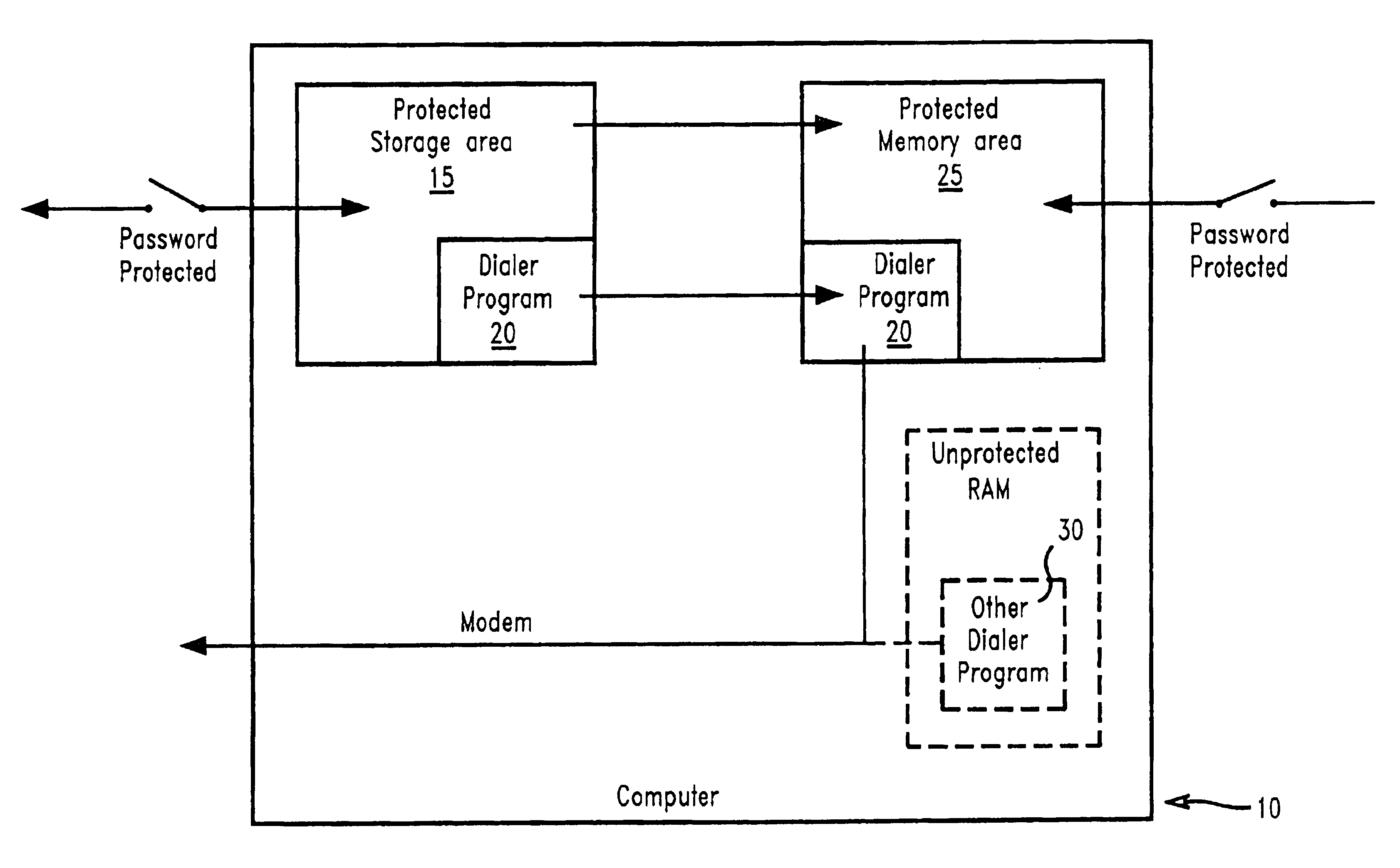
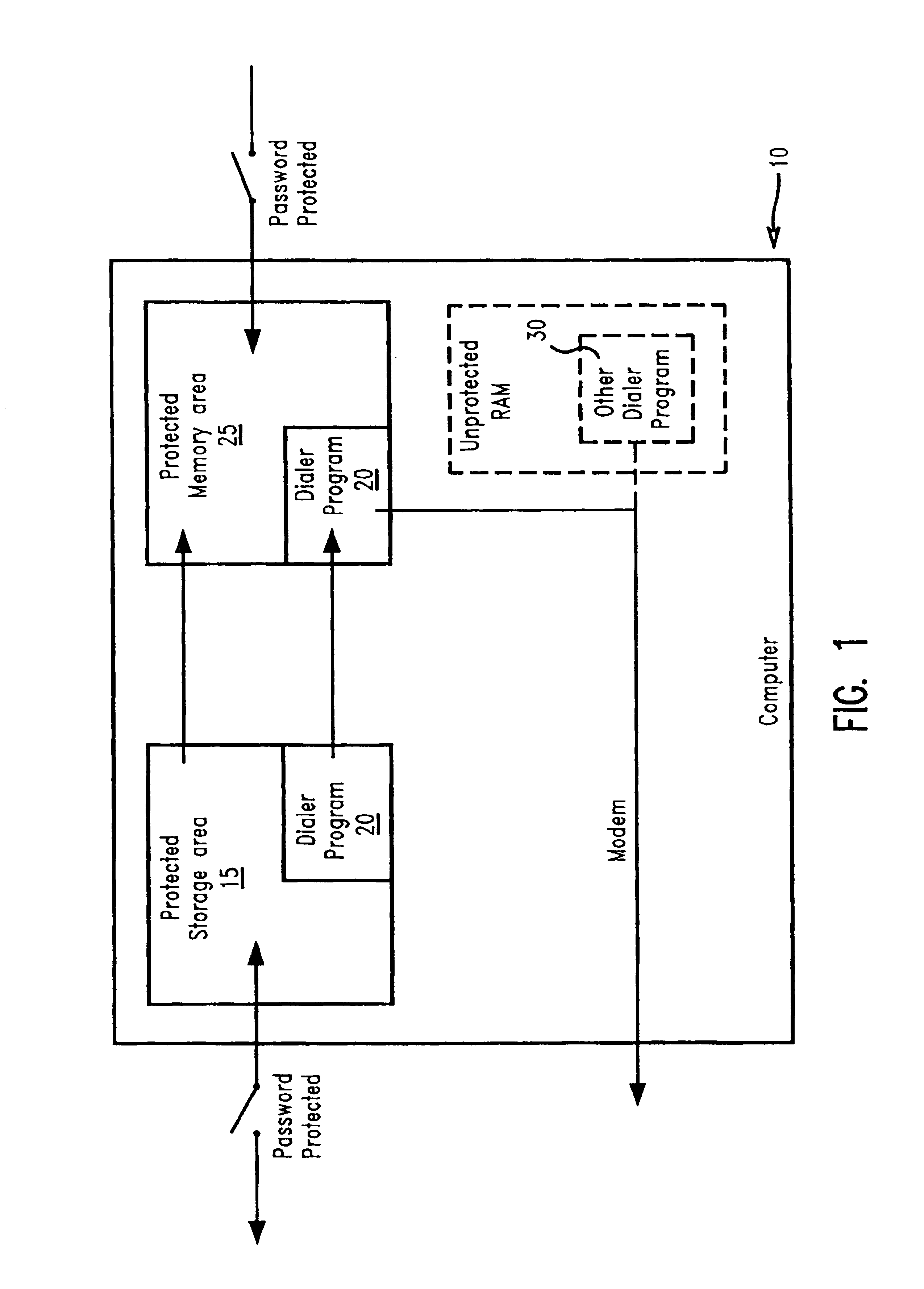
InactiveUS6763465B1Disabling a rogue dialer programDigital data processing detailsUnauthorized memory use protectionHard disc drivePassword
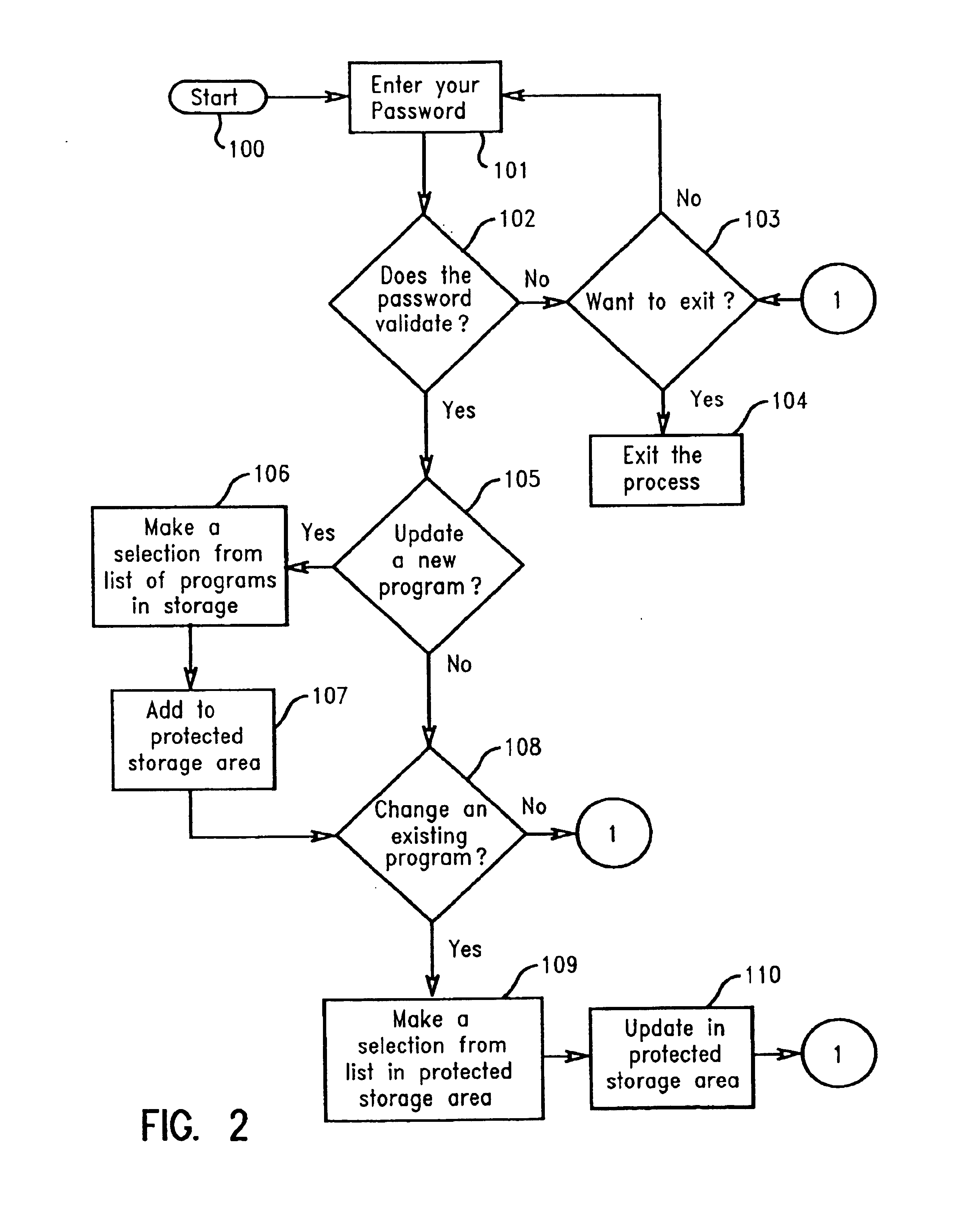
The present invention prevents unauthorized access and modifications to programs and non-executable files, particularly a dialer program, stored on a personal computer system (PC) by providing a protected storage area on a hard drive of the PC wherein access to the protected storage area is controlled by the owner / user of the PC. Attempts to add, remove, or modify any of the programs and non-executable files in the protected storage area will result in an interrupt prompting the user to supply a valid password or other acknowledgement. A preferred embodiment includes a protected memory area as a part of the computer's internal random access memory (RAM) such that upon initialization of a program, the program and non-executable files are copied into the protected memory area from the protected storage area. The protected memory area may also be password protected to provide additional safeguards against unauthorized access. Also disclosed is a method and apparatus for creating and utilizing a program storage table and a program function table for controlling access and modifications of programs and non-executable files, particularly a dialer program, stored in the protected storage area. Preferably, the present invention may be embodied as a computer program product stored on a program storage device.
Owner:LENOVO (SINGAPORE) PTE LTD
Product authentication and anti-counterfeiting method based on block chain technology
InactiveCN107169776AAvoid dependenceAvoid misalignmentCommerceRecord carriers used with machinesTablet computerPassword protection
The invention discloses a product authentication and anti-counterfeiting method based on a block chain technology. A block chain system capable of being authenticated publicly, a block chain gateway system, an intelligent mobile phone, an iPad or a similar tablet computer or another terminal with a photographing or / and NFC (IC) reading and writing function, an NFC anti-counterfeiting label with password protection, and an application APP operating in the intelligent mobile phone or the similar tablet computer are mainly used to store information generated in production and circulation links to the block chain, a pair of public key and private key is generated continuously, the traceability of each link can be ensured through repeatedly authenticating the private keys and the public keys, a password Pass is set for a cipher part according to the series number of the NFC, the public key B and the Hash value of the product, the problem that the whole label content is copied can be solved, and the anti-counterfeiting performance of a single product can be improved.
Owner:无锡井通网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com