Patents
Literature
239 results about "Function table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
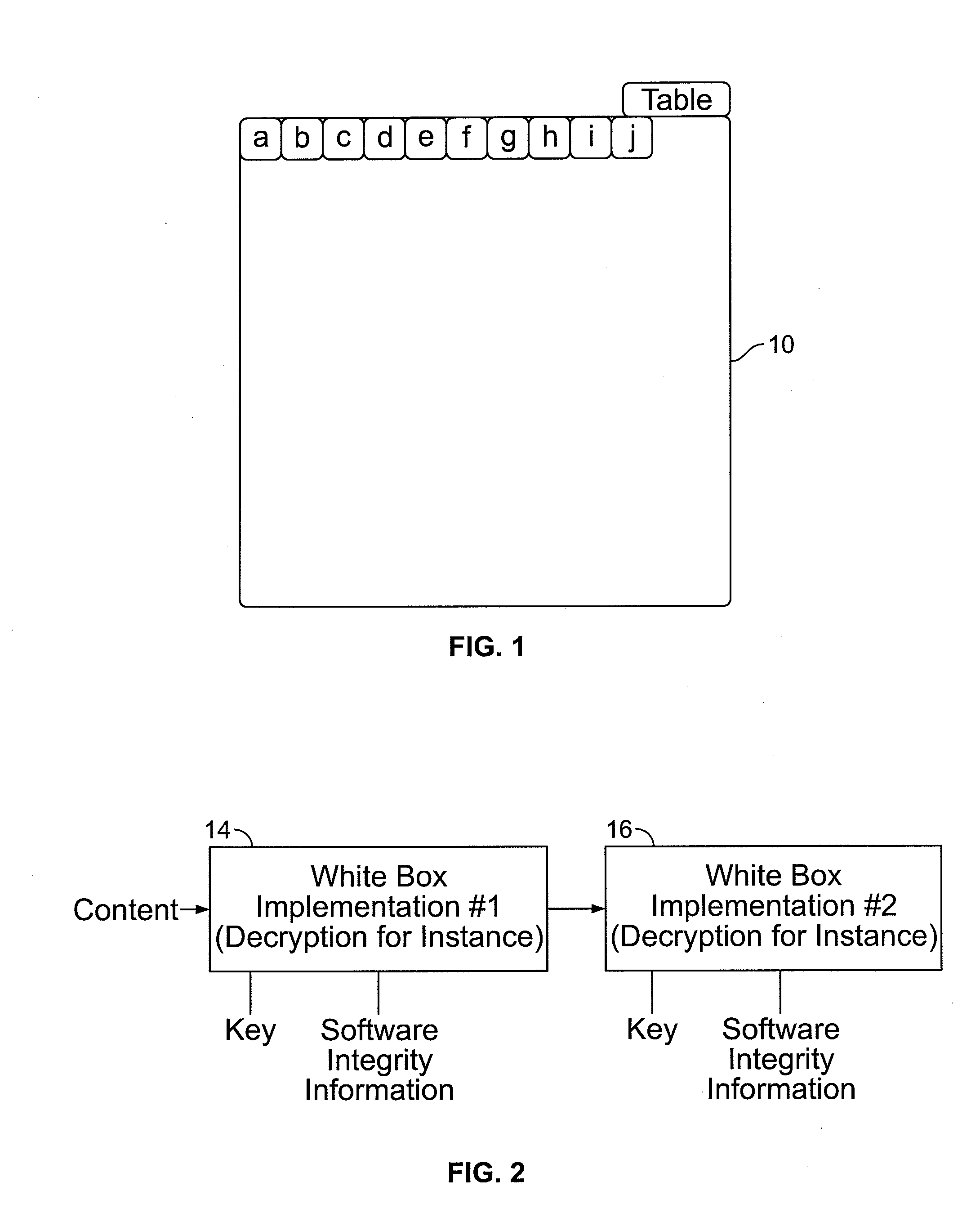
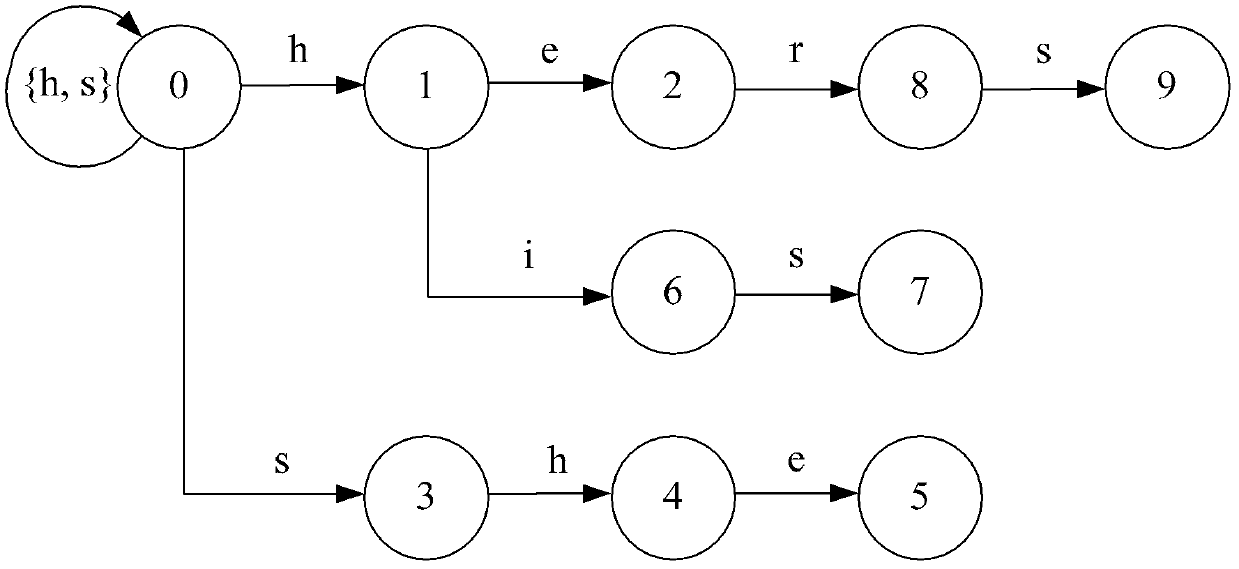
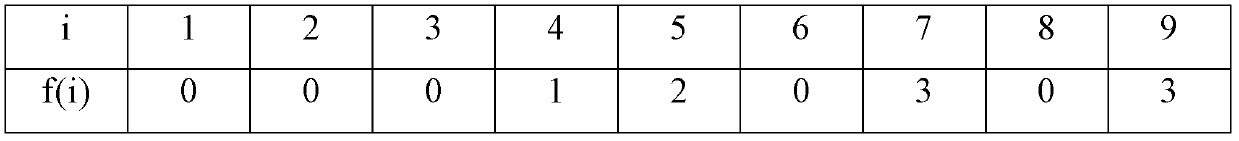
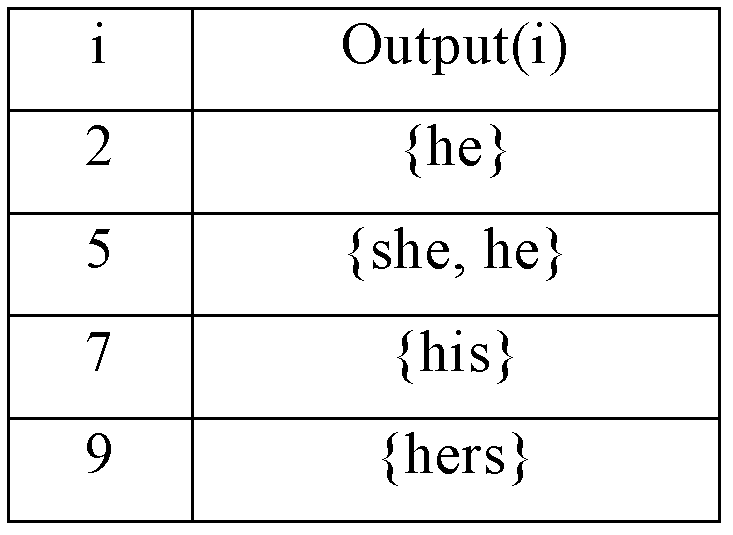
Function Tables. Function tables are simply lists of possible values of a variable and the function's result. Pictured is a simple function table that lists a series of possible grades in the class and then applies the f(x) = x + 3 function to them. To create a function table, simply list a bunch of values in the left column.
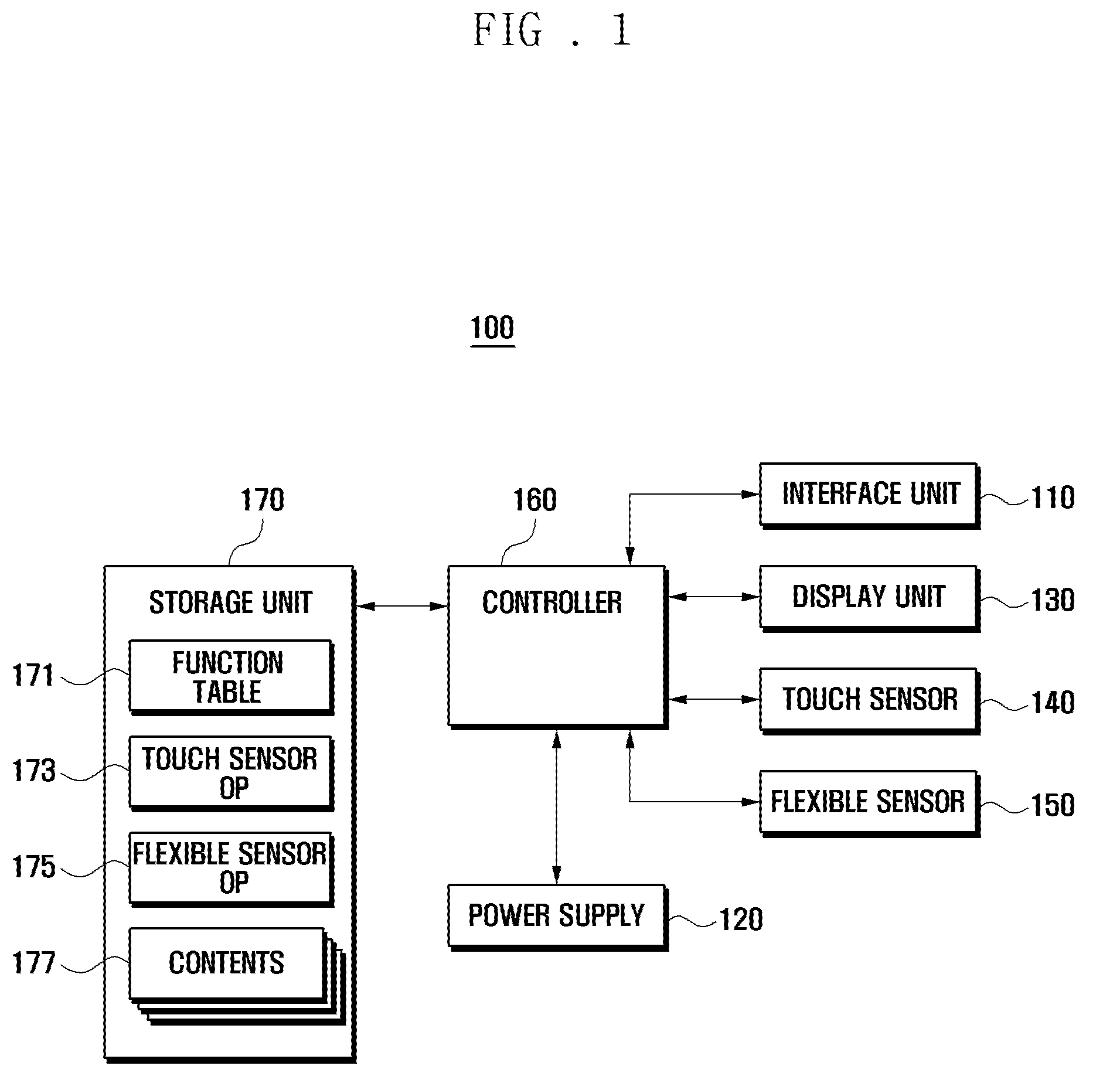
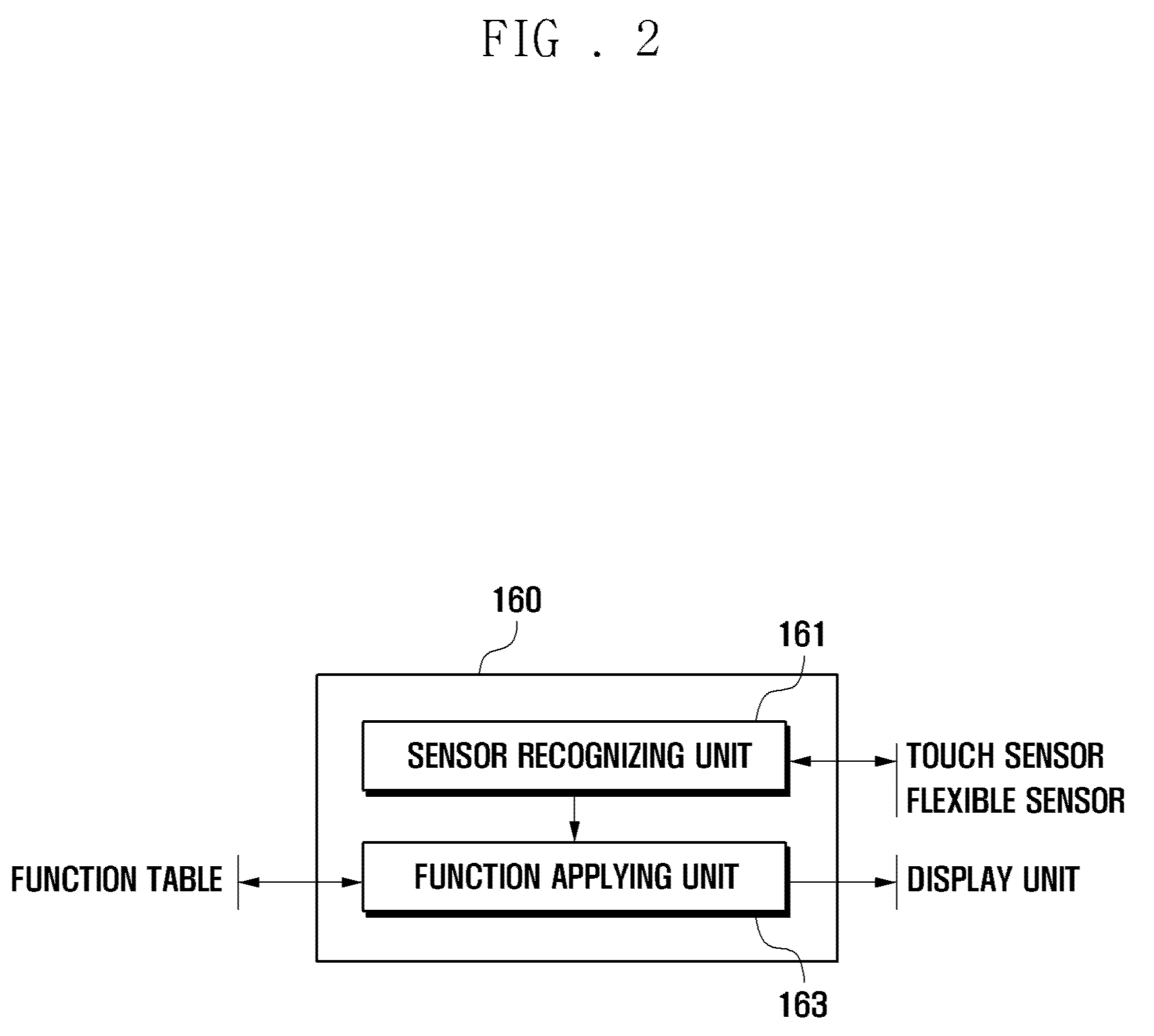
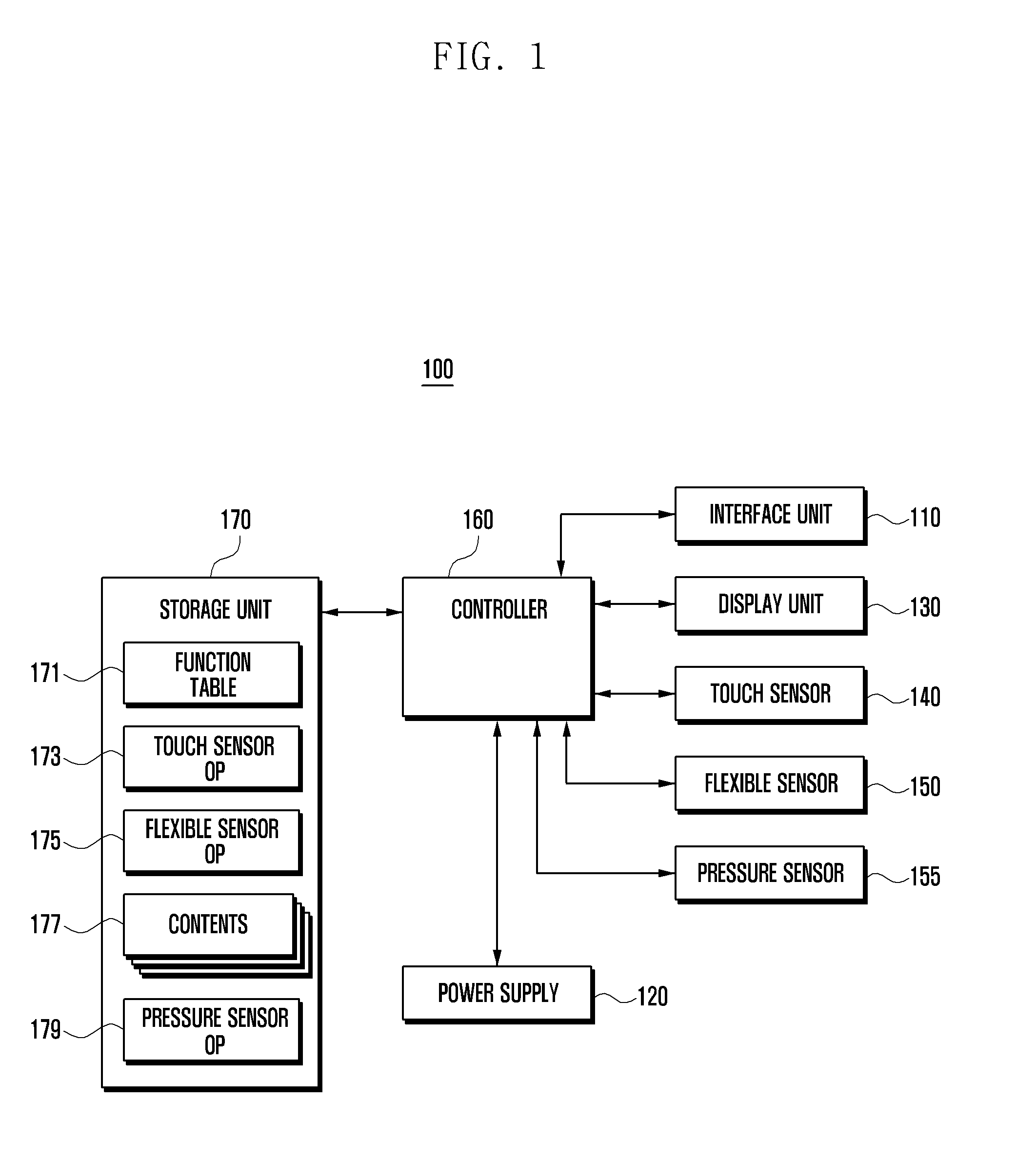
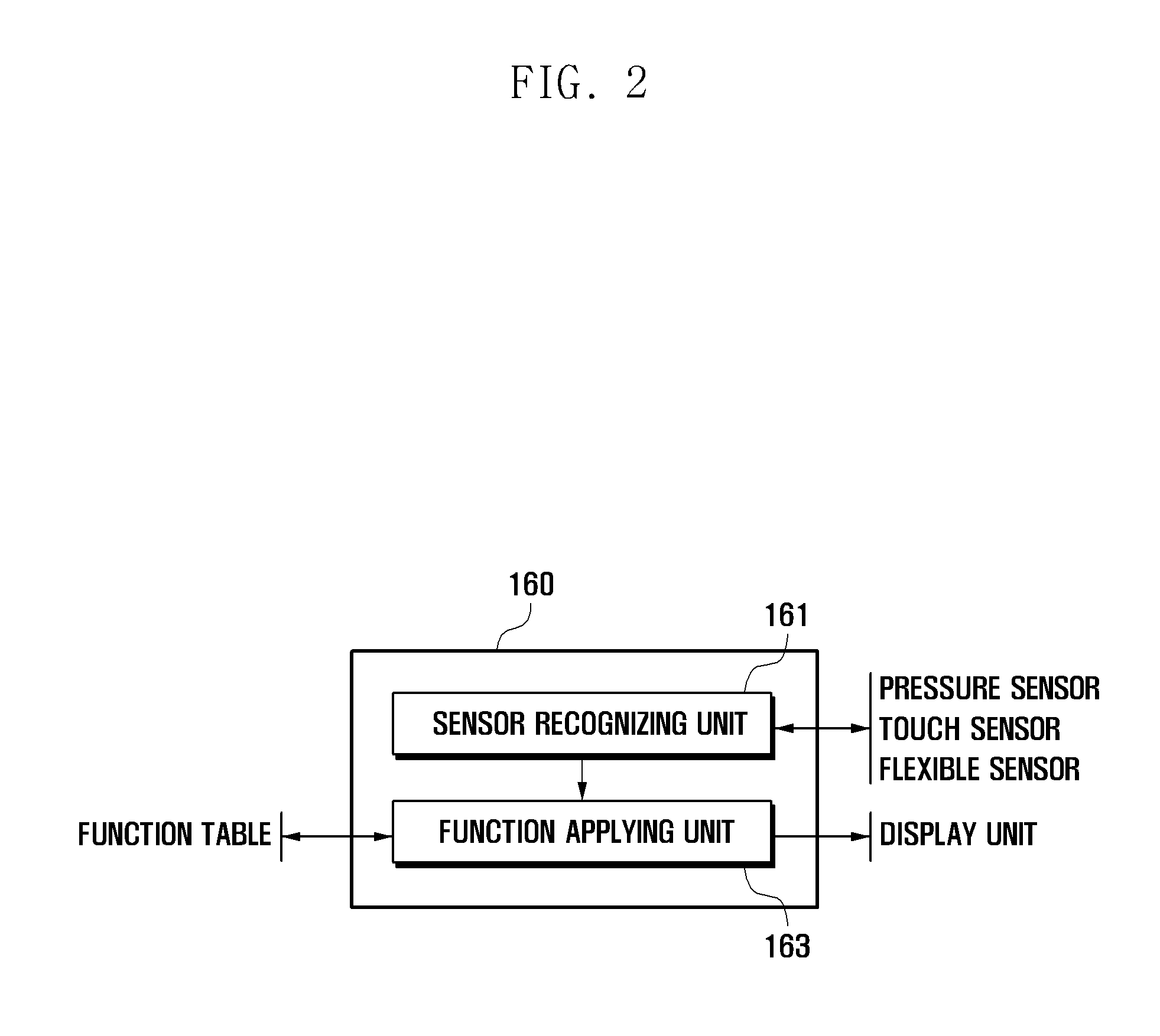
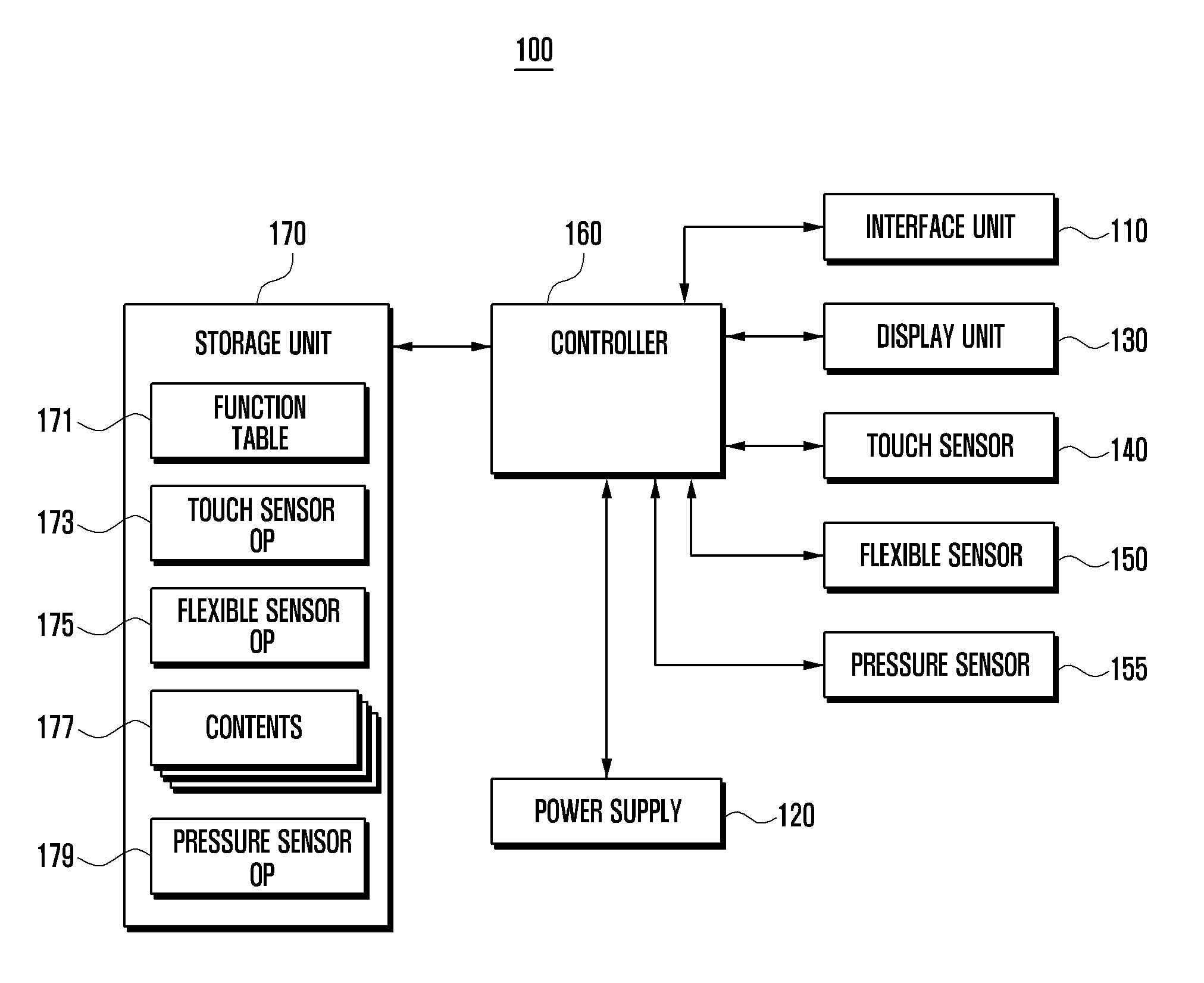
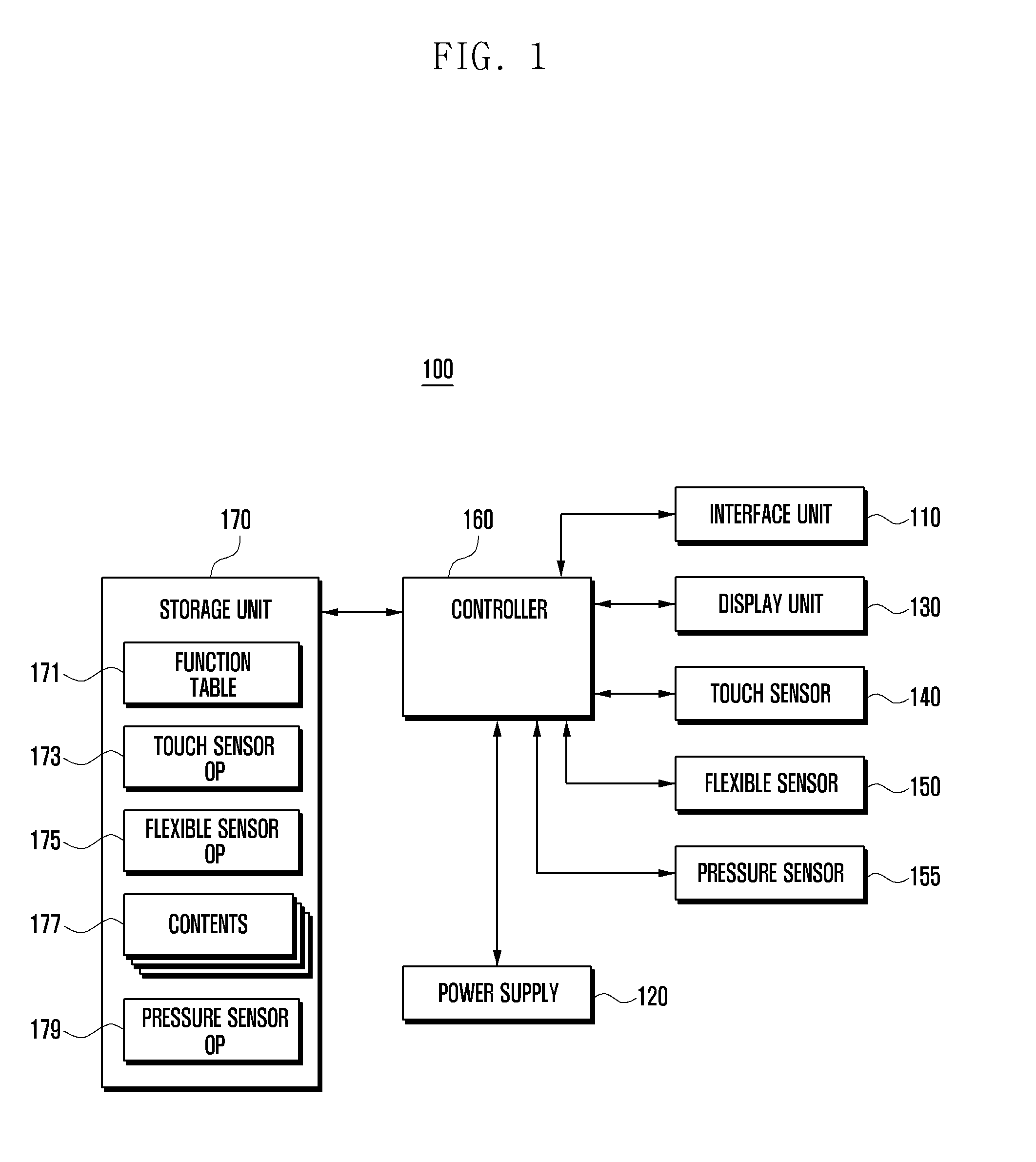
Flexible display device and data displaying method thereof
ActiveUS20100141605A1Digital data processing detailsSubstation equipmentData displayHuman–computer interaction
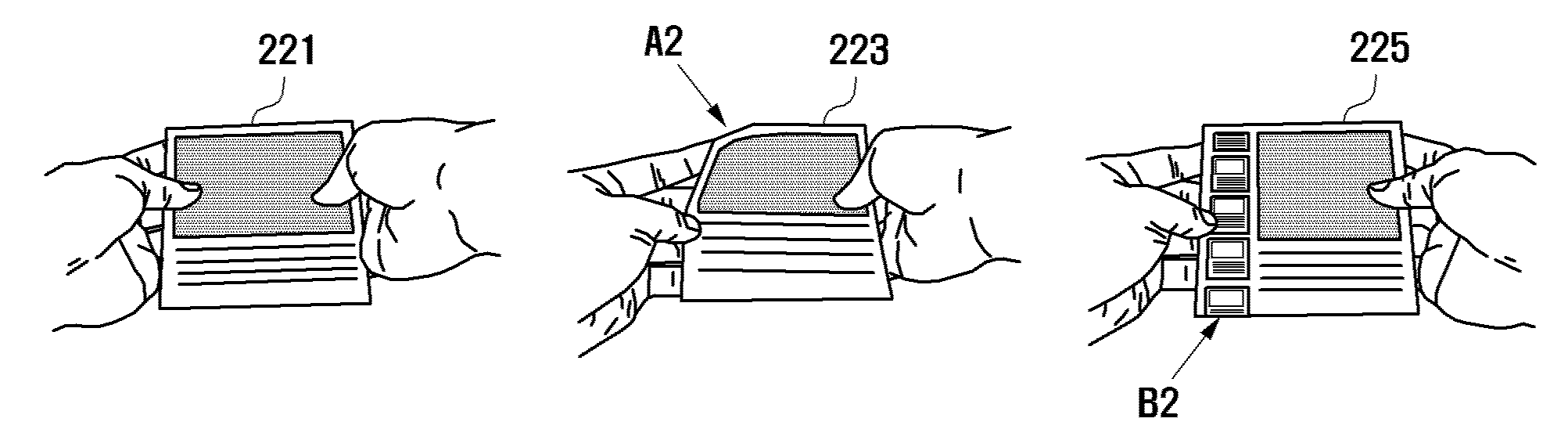
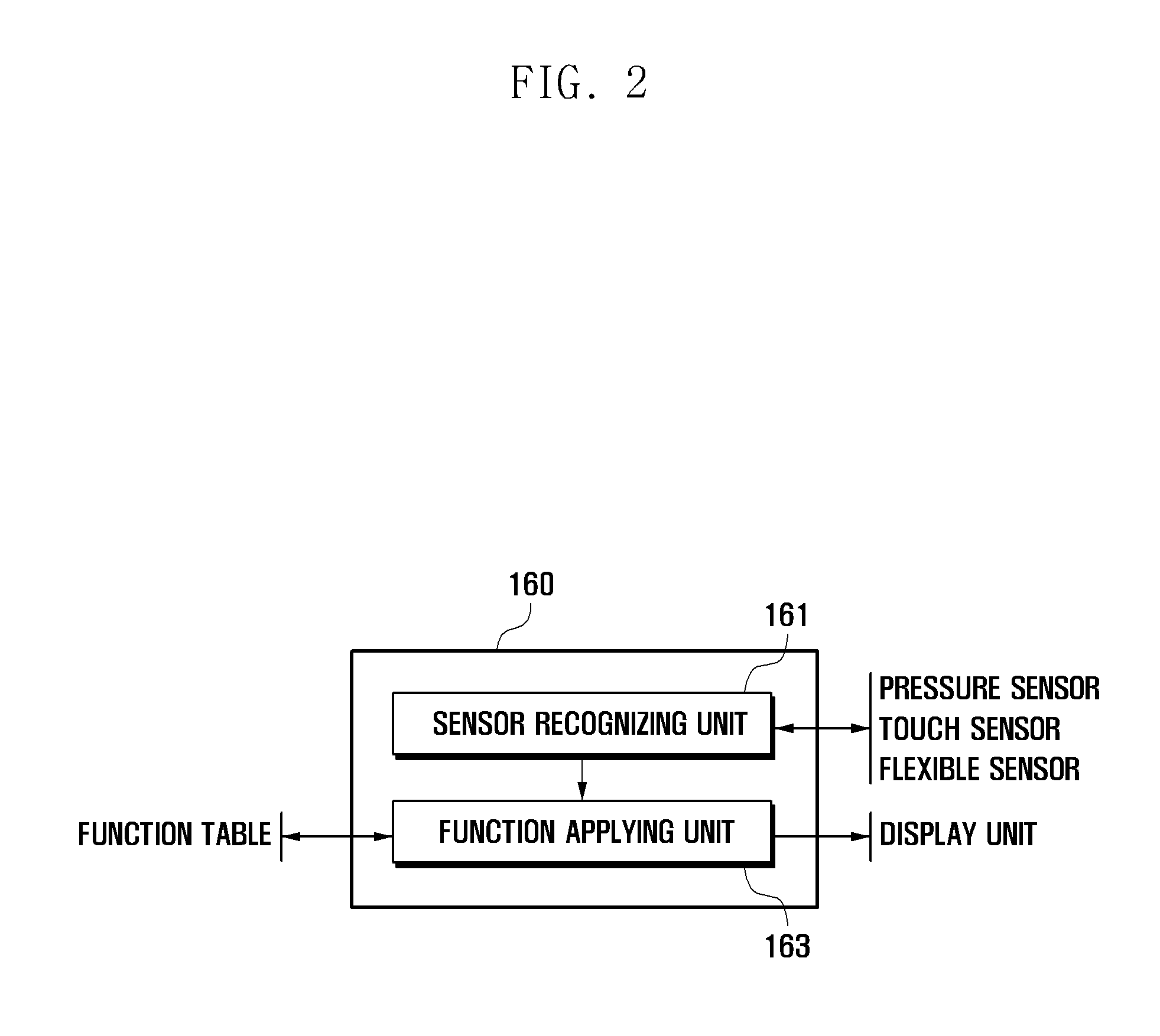
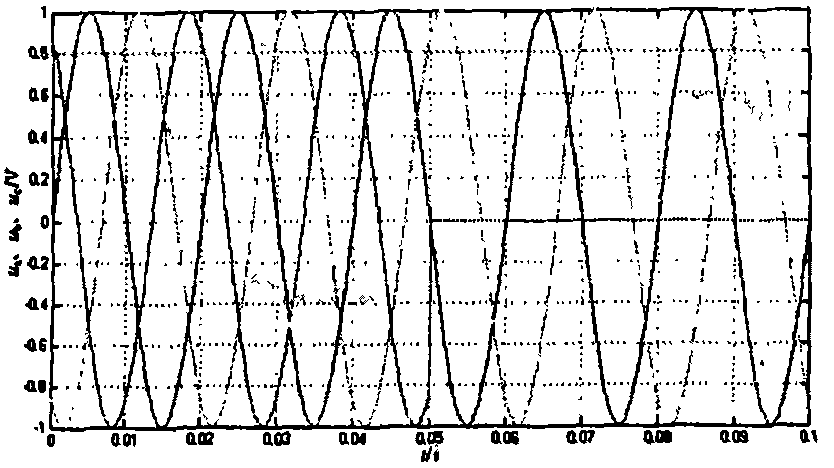
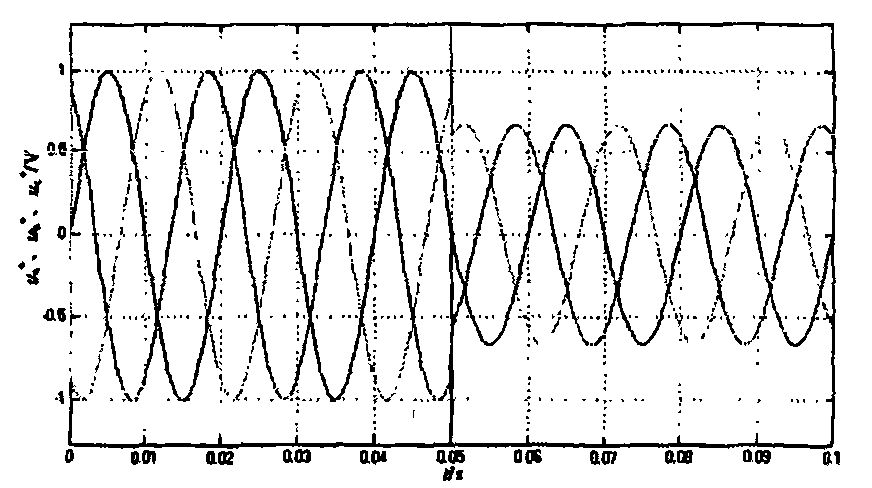
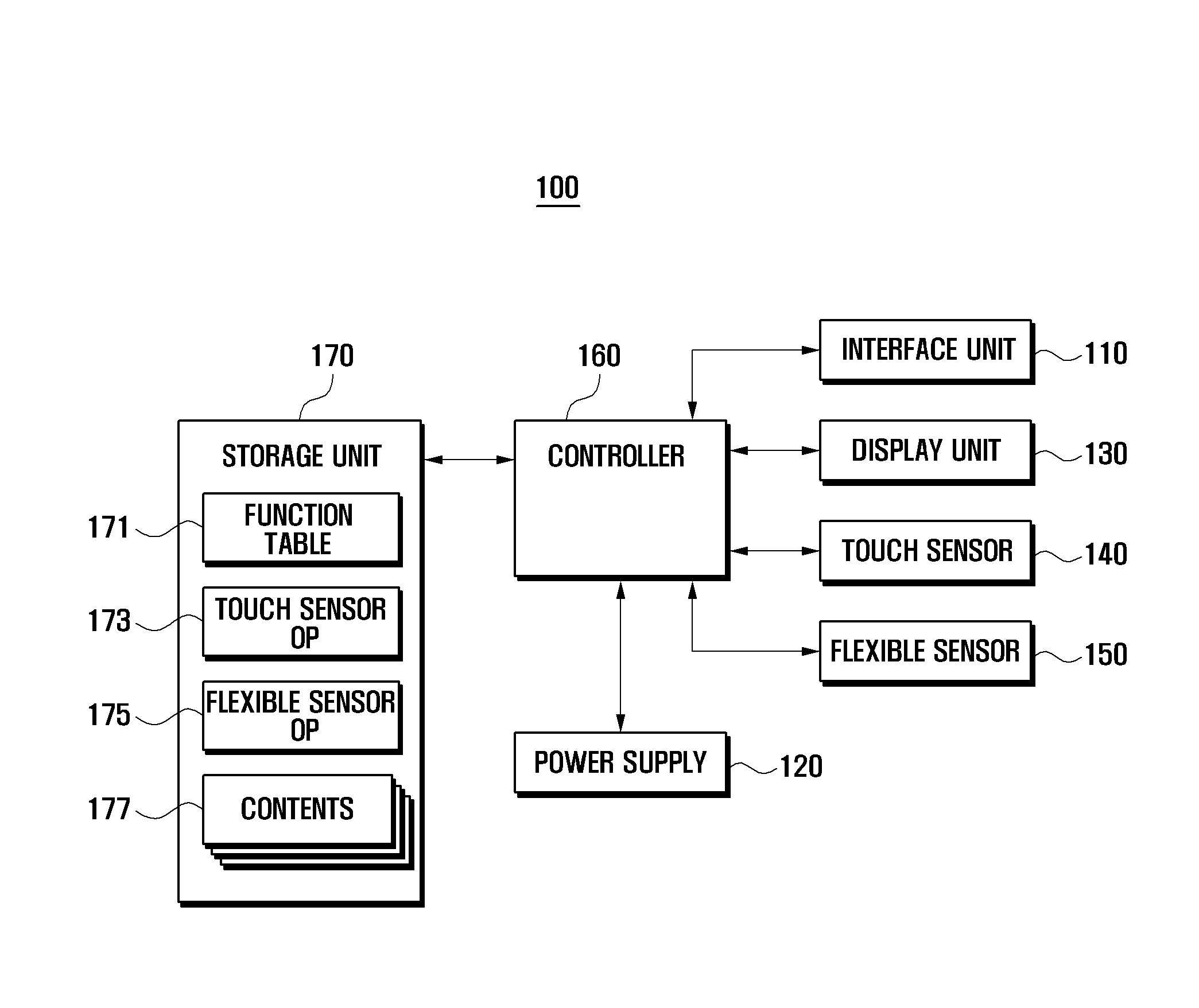
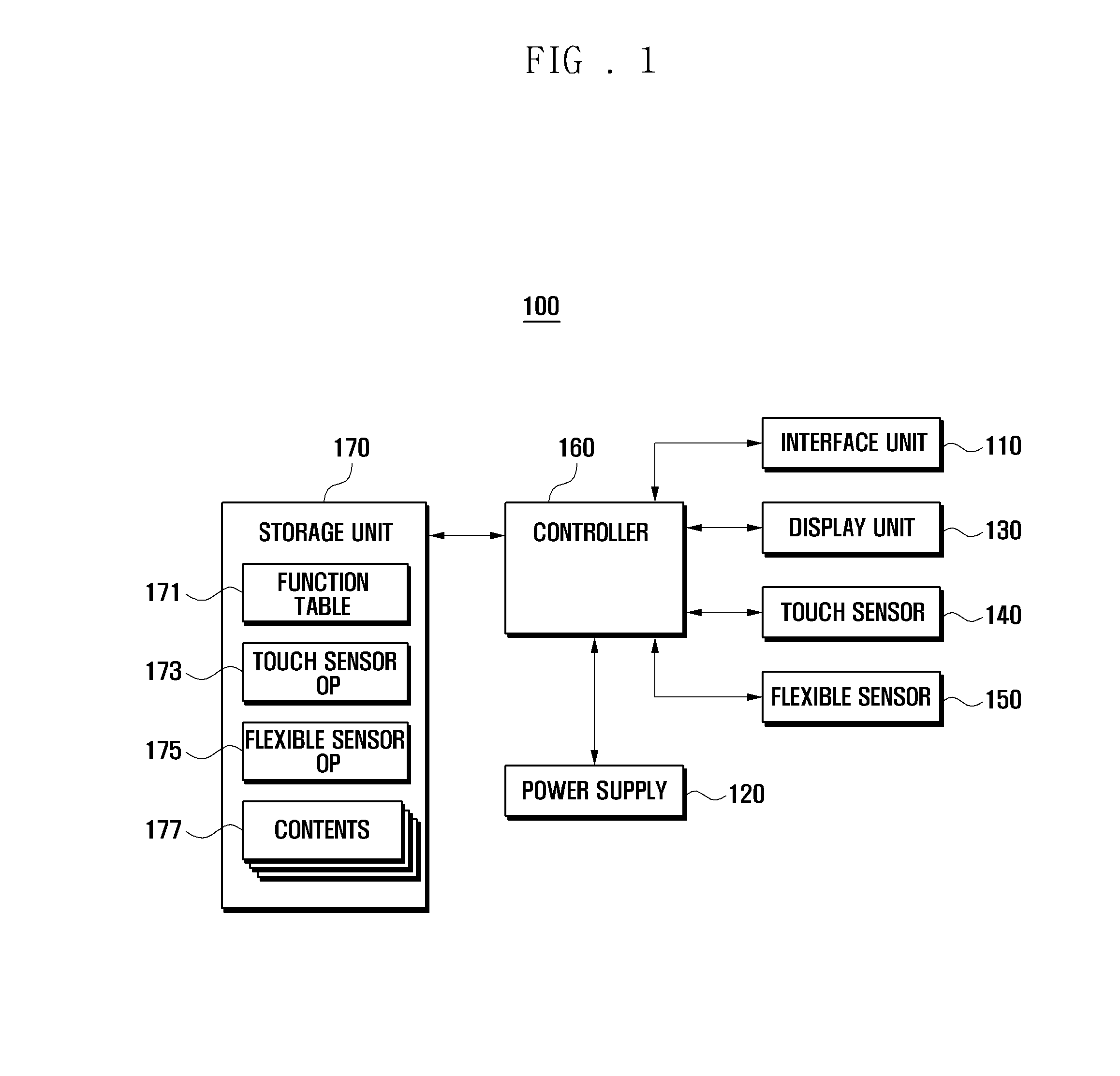
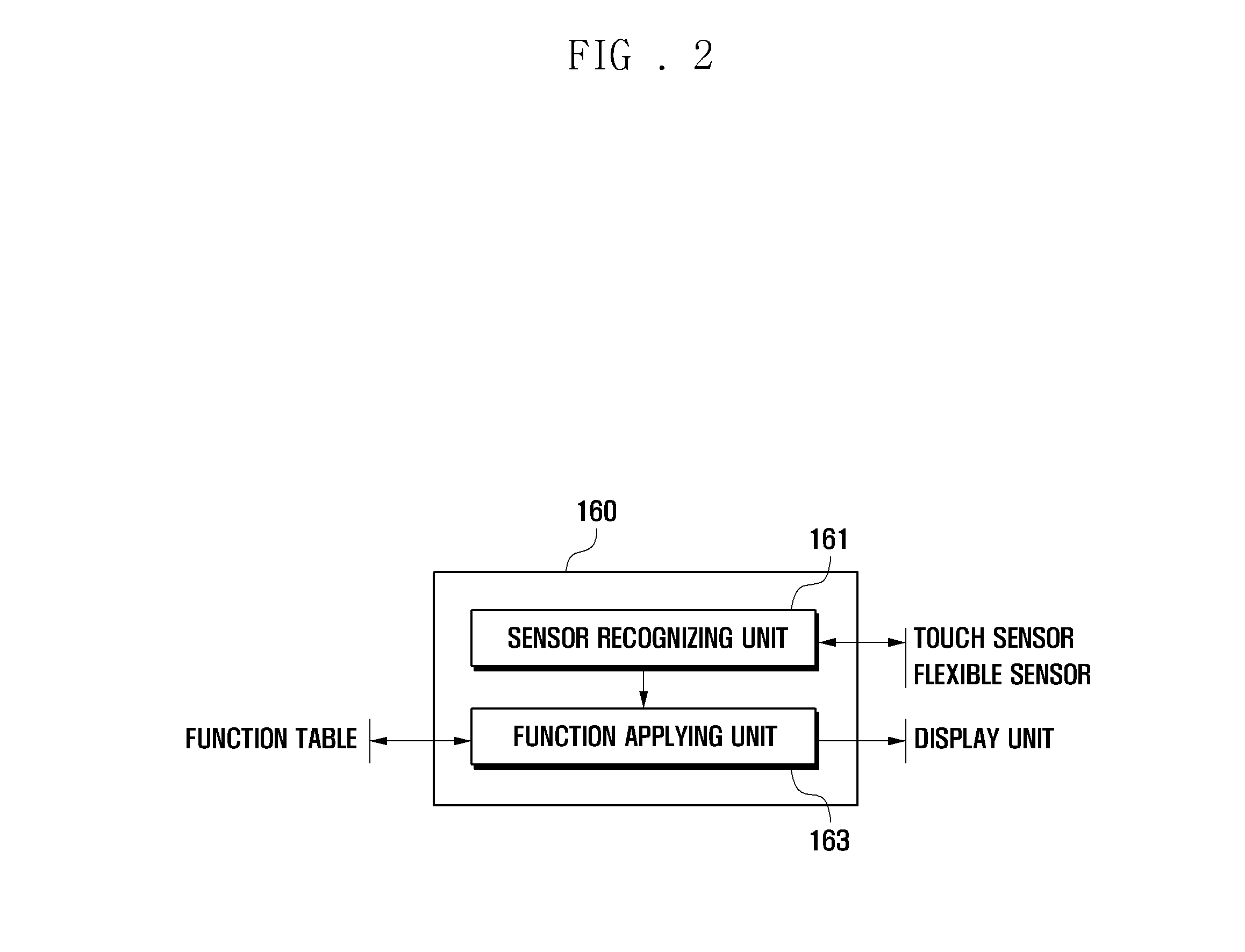
A flexible display device and a data displaying method thereof are disclosed. The device includes a touch sensor to generate touch events according to touch actions, a flexible sensor to generate a bend signal as one side of the device is bent, a storage unit to store a function table, and a controller to control the components of the device. The function table is configured to define control operations to reproduce currently output contents based on the touch events and the bend events.
Owner:SAMSUNG ELECTRONICS CO LTD
Display device and data displaying method thereof
ActiveUS8638311B2Digital data processing detailsGreenhouse cultivationData displayArtificial intelligence
Owner:SAMSUNG ELECTRONICS CO LTD
Display device and data displaying method thereof
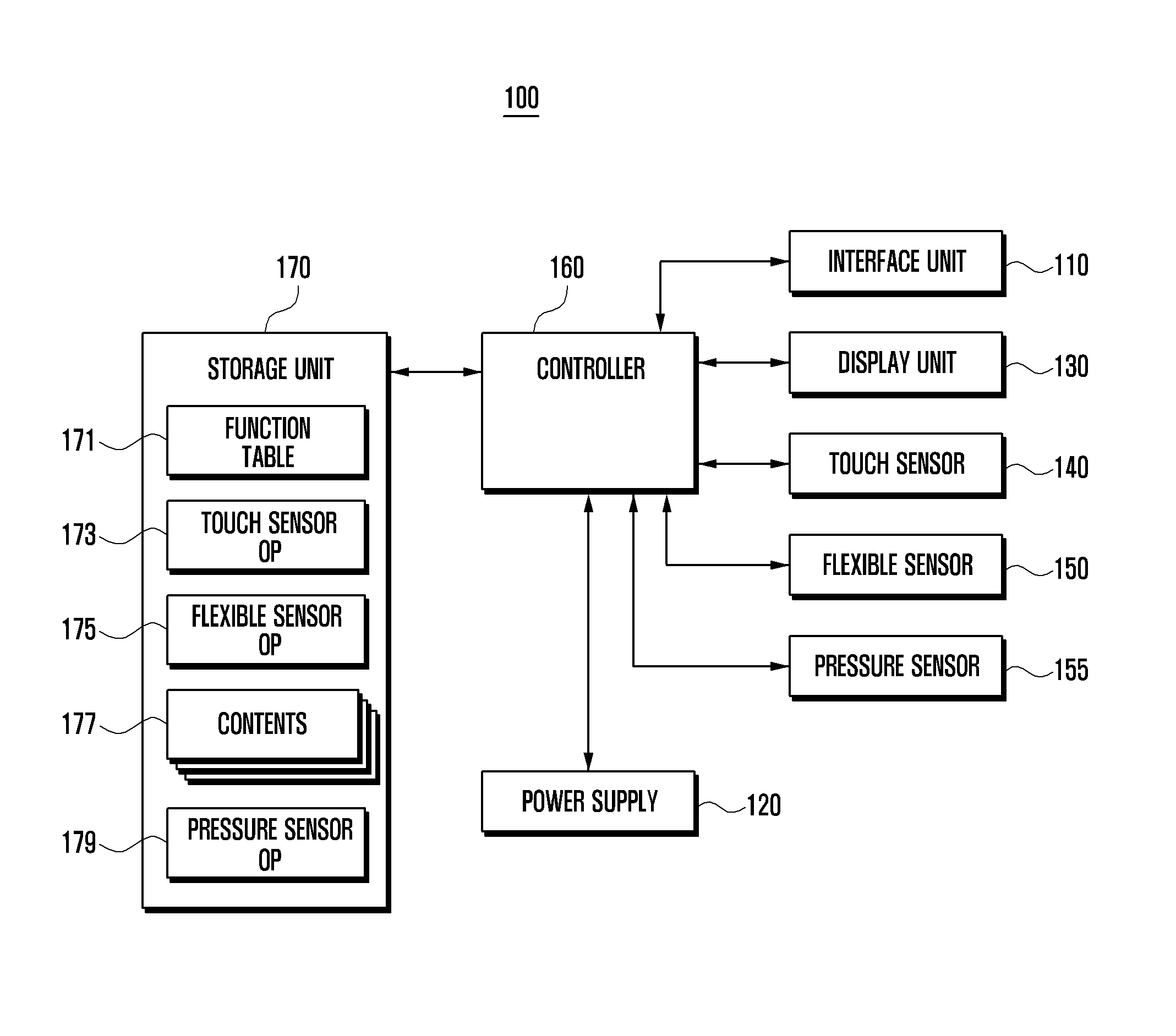
ActiveUS20130120302A1Digital data processing detailsInput/output processes for data processingData displayDisplay device
A display device and a data displaying method thereof are disclosed. The device includes at least one sensor including a touch sensor to generate touch events according to touch events, a flexible sensor to generate a bend signal to detect bend events, and a pressure sensor to generate a pressure signal to detect pressure events, a storage unit to store a function table, and a controller to control the components of the device. The function table is configured to define control operations to reproduce currently output contents based on the touch events, the bend events, the pressure events, and events combined thereof.
Owner:SAMSUNG ELECTRONICS CO LTD
Sdn-based service chaining system
ActiveUS20160080263A1Easy to chargeGood serviceDatabase updatingData switching by path configurationService Request BlockNetworked system
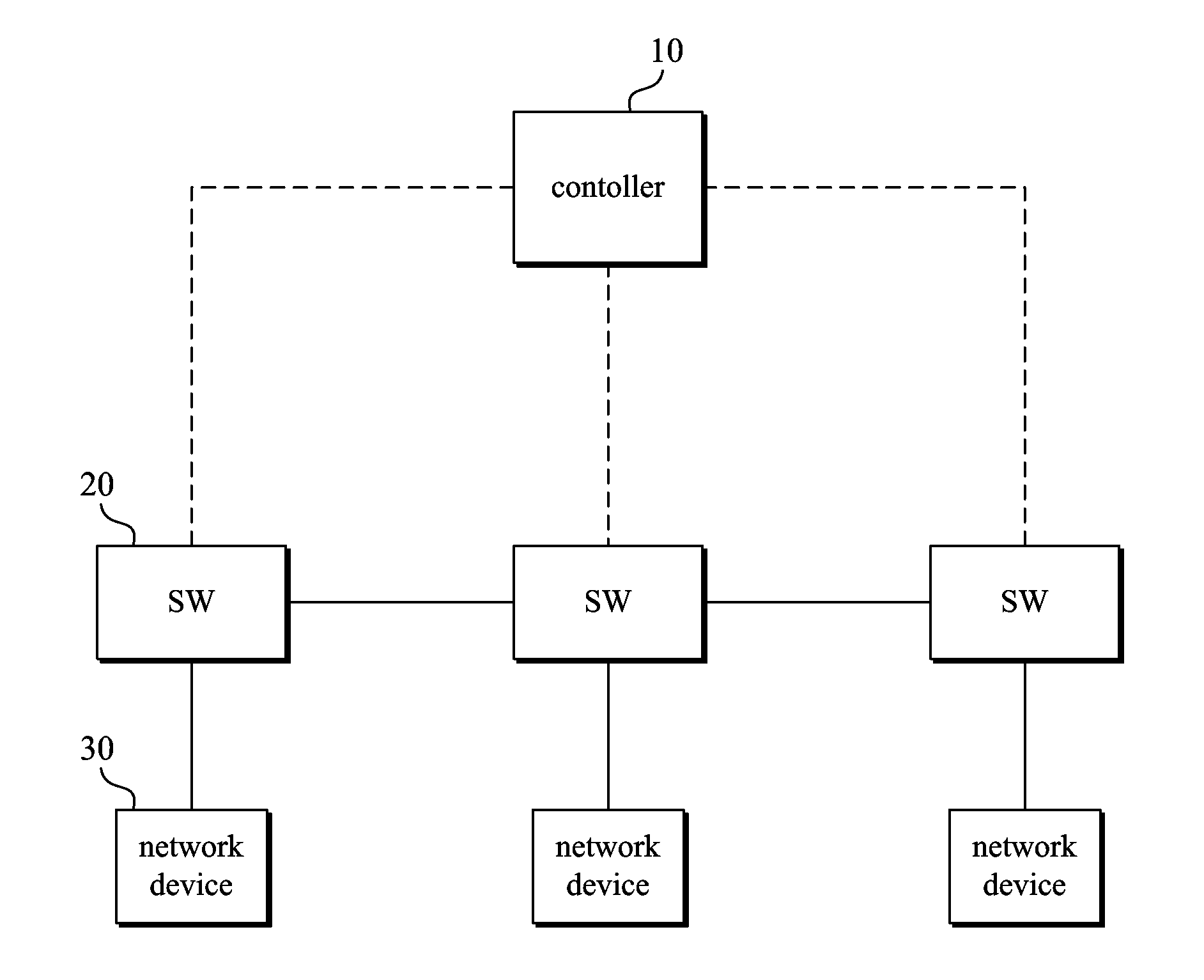
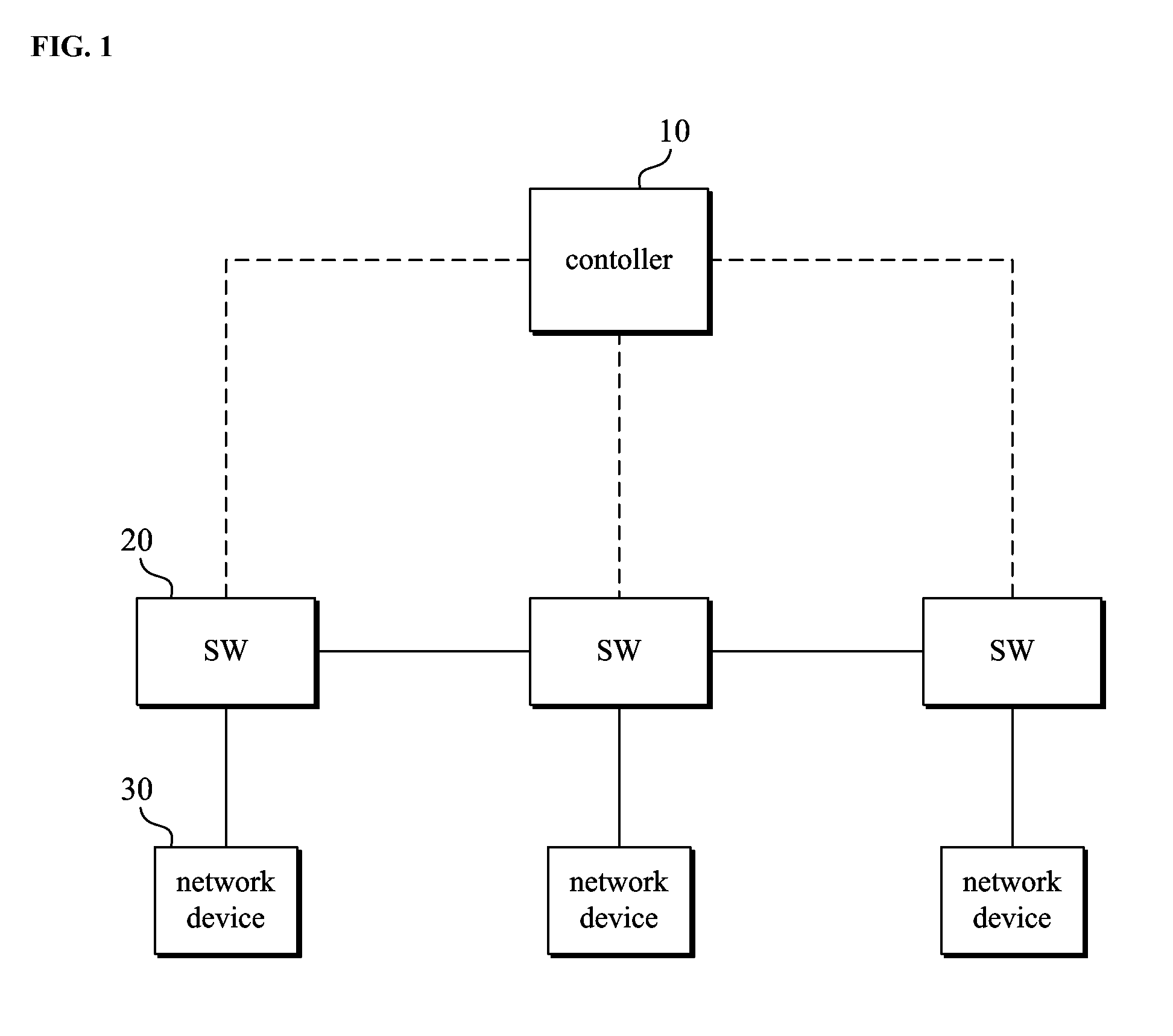
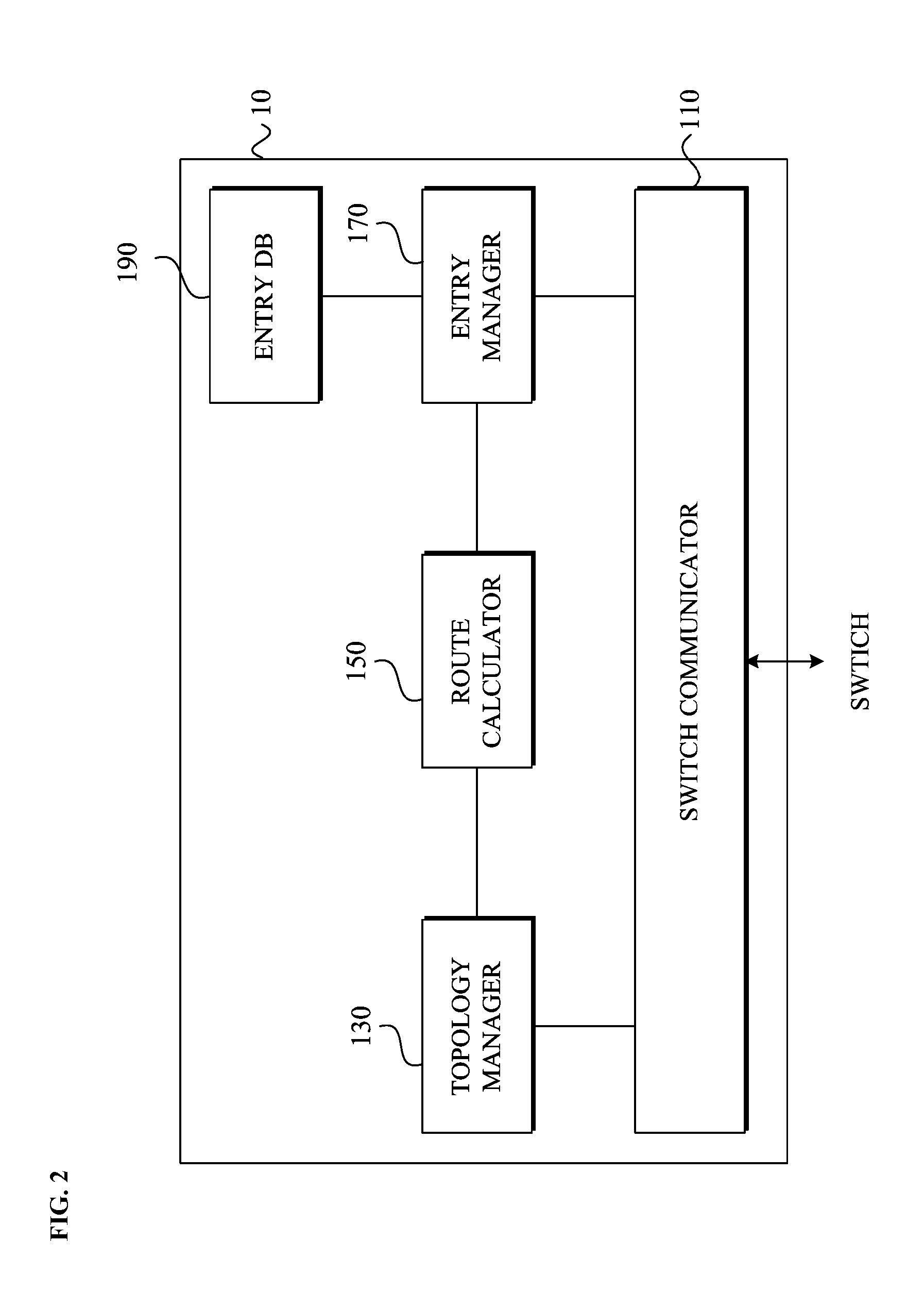
A method for providing service chaining in a software-defined network (SDN)-based network system, the method including: receiving, at a controller, a first packet-in message from a first switch of a plurality of switches, which has received a service request packet from a user, to indicate that the first switch does not have a corresponding entry in a field extracted from the service request packet; extracting from the packet-in message both a service identifier that identifies a type of a service requested through the service request packet and a user identifier that identifies the user; and searching an entry database for an entry list that enables the service request packet to be forwarded to a network function list that corresponds to the service identifier and the user identifier, with reference to a service table, a user table, and a network function table which are associated with one another.
Owner:KULCLOUD
Communication Control Method and Wireless Communication Apparatus
ActiveUS20080261640A1Assure compatibilityNetwork traffic/resource managementAssess restrictionCommunication controlCommunication device
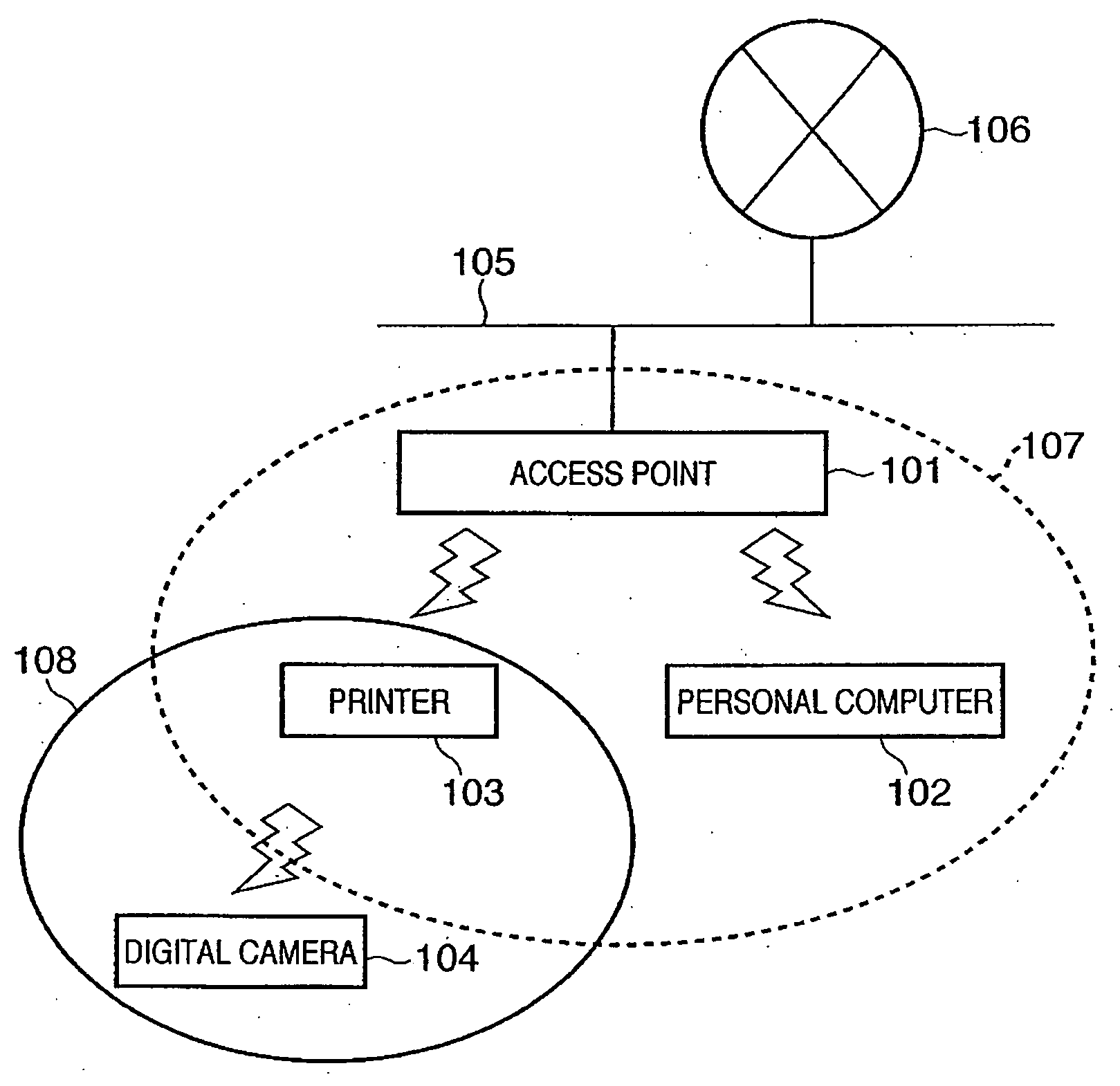
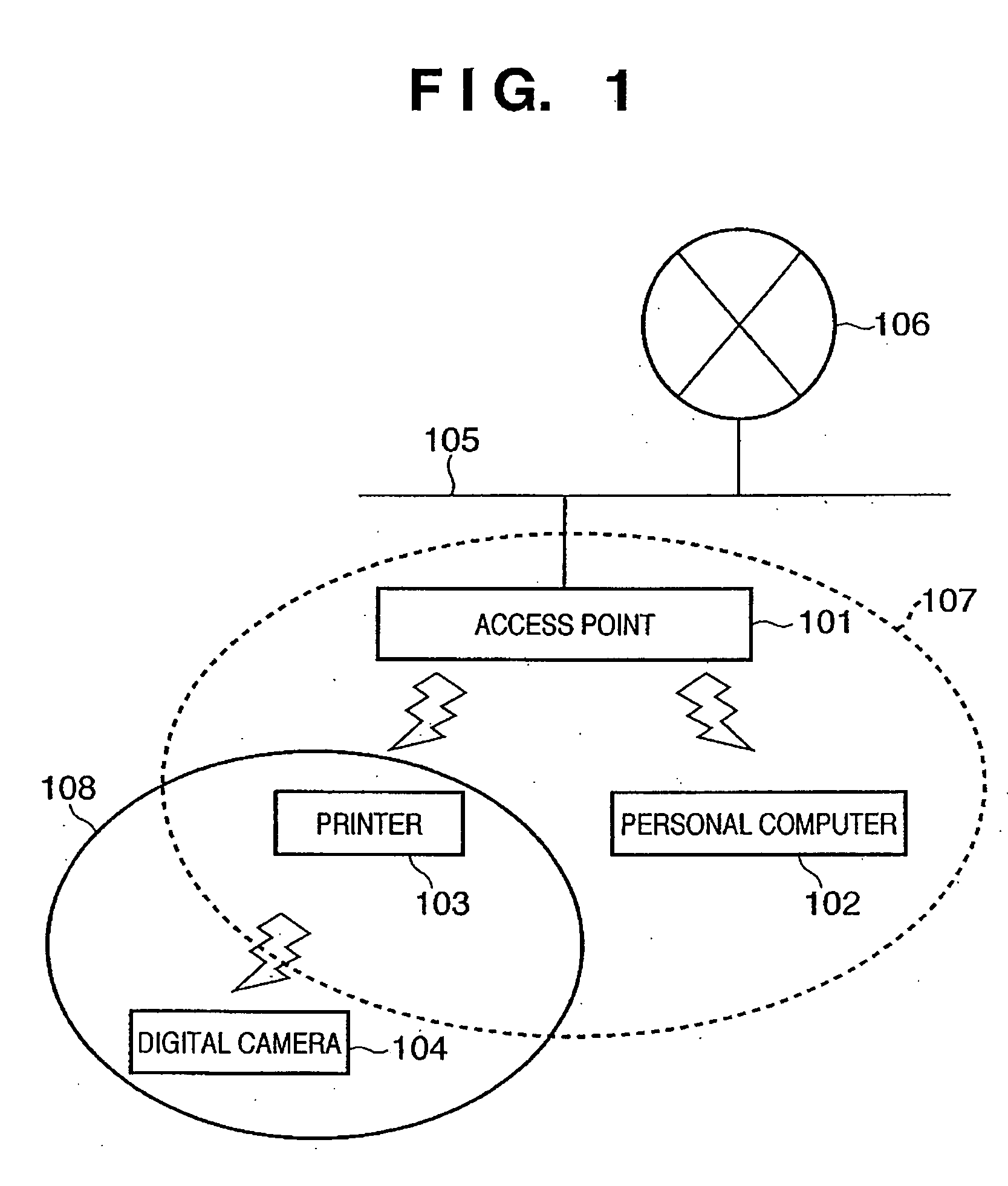
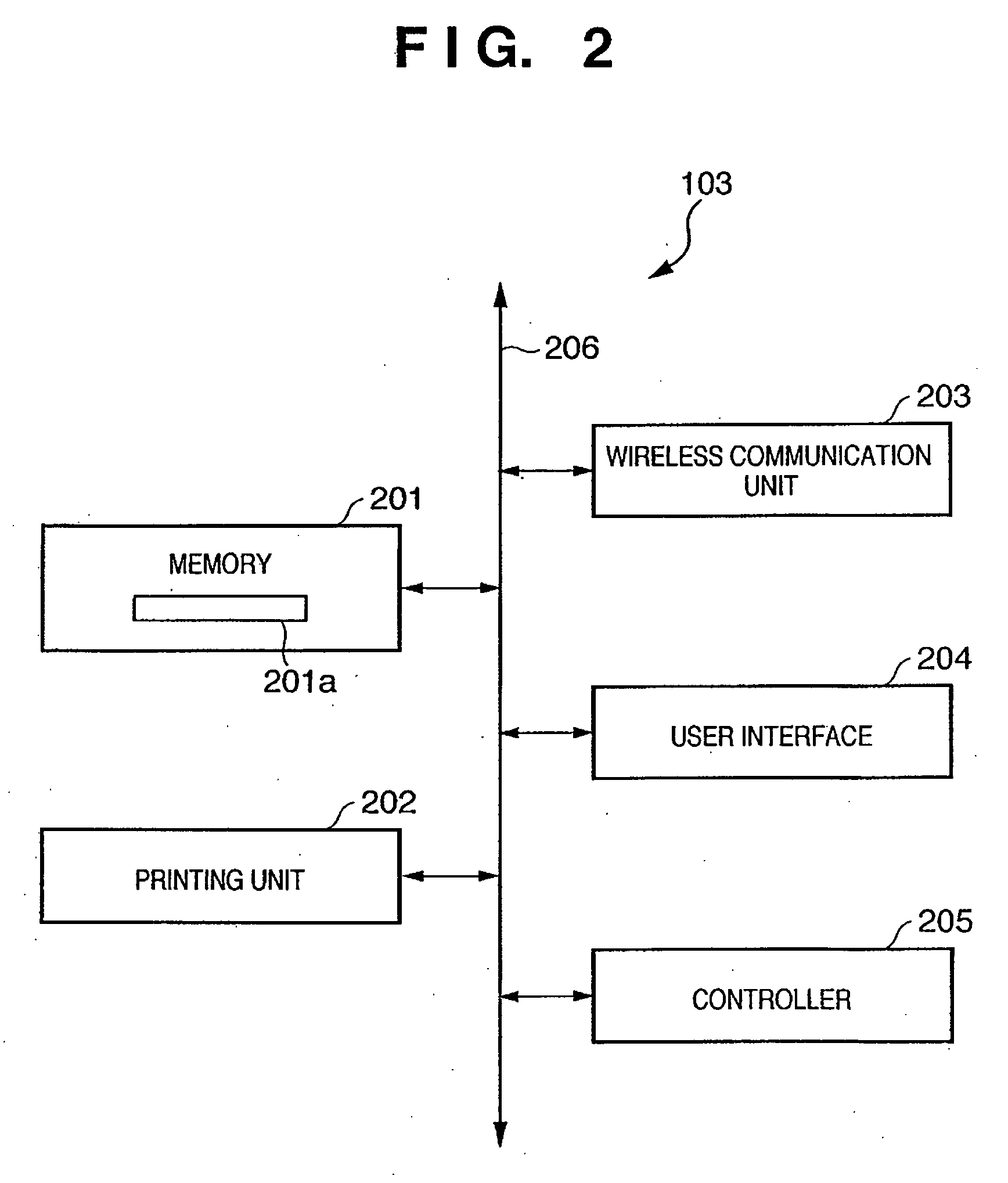
A printer (103) belongs to a service set (107) and communicates via an access point (101) in the infrastructure mode. The printer (103) searches for a beacon periodically. If a beacon is received from a terminal such as a digital camera (104), the printer registers the terminal address, service-set identifier and communication mode, which are contained in the beacon, in a function table. The printer sends each terminal, which has been registered in the function table, a frame that is for searching for a terminal that has a required function. If the response to the frame is positive, then the printer registers the fact that the search succeeded in the function table. A similar function search is conducted also by a digital camera (104) for which a print command has been issued, and the digital camera creates a function table. If there is a terminal (a printer) having the required function, the digital camera (104) transmits print data to this terminal.
Owner:CANON KK
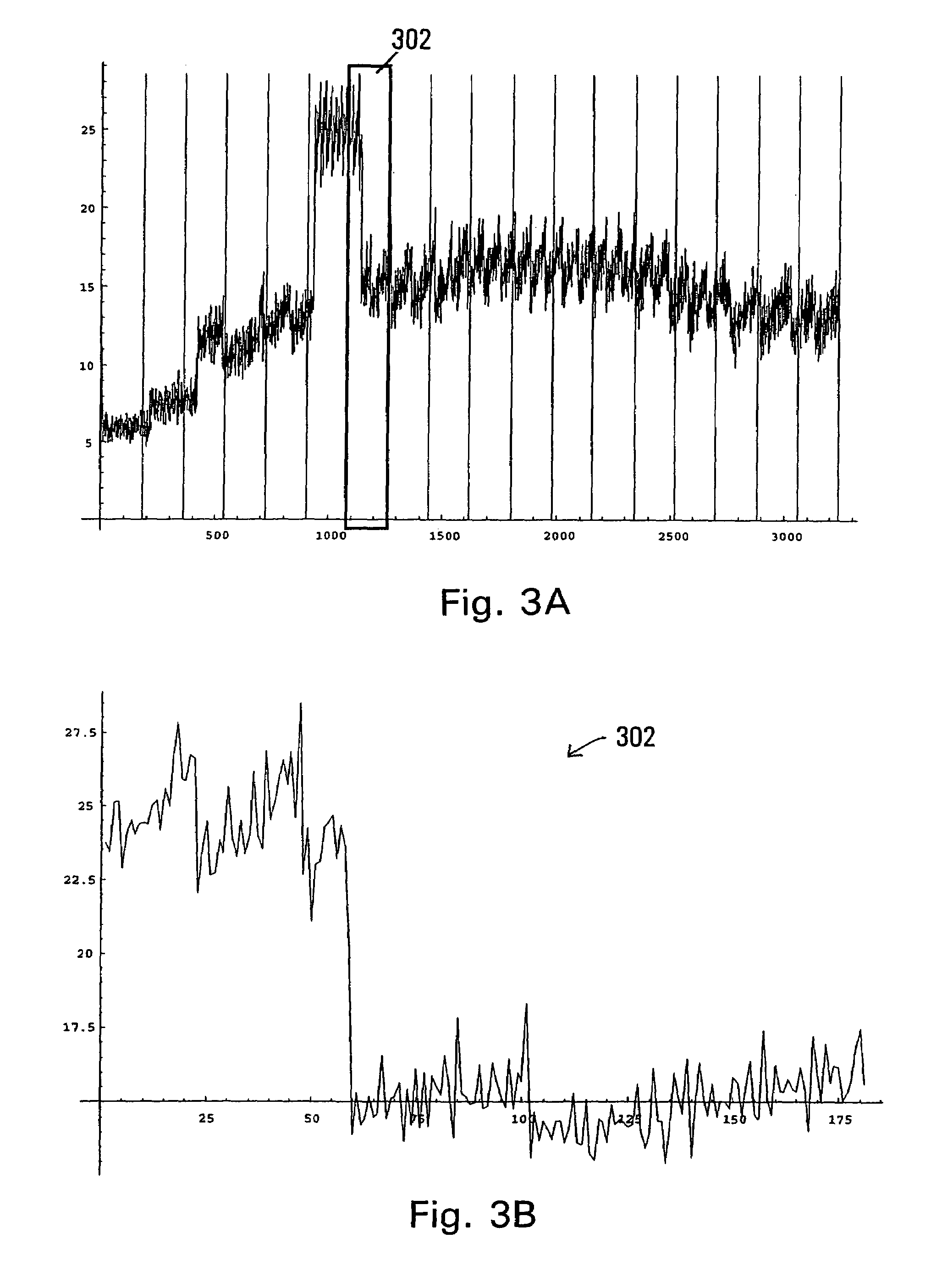
System and methods for display of time-series data distribution
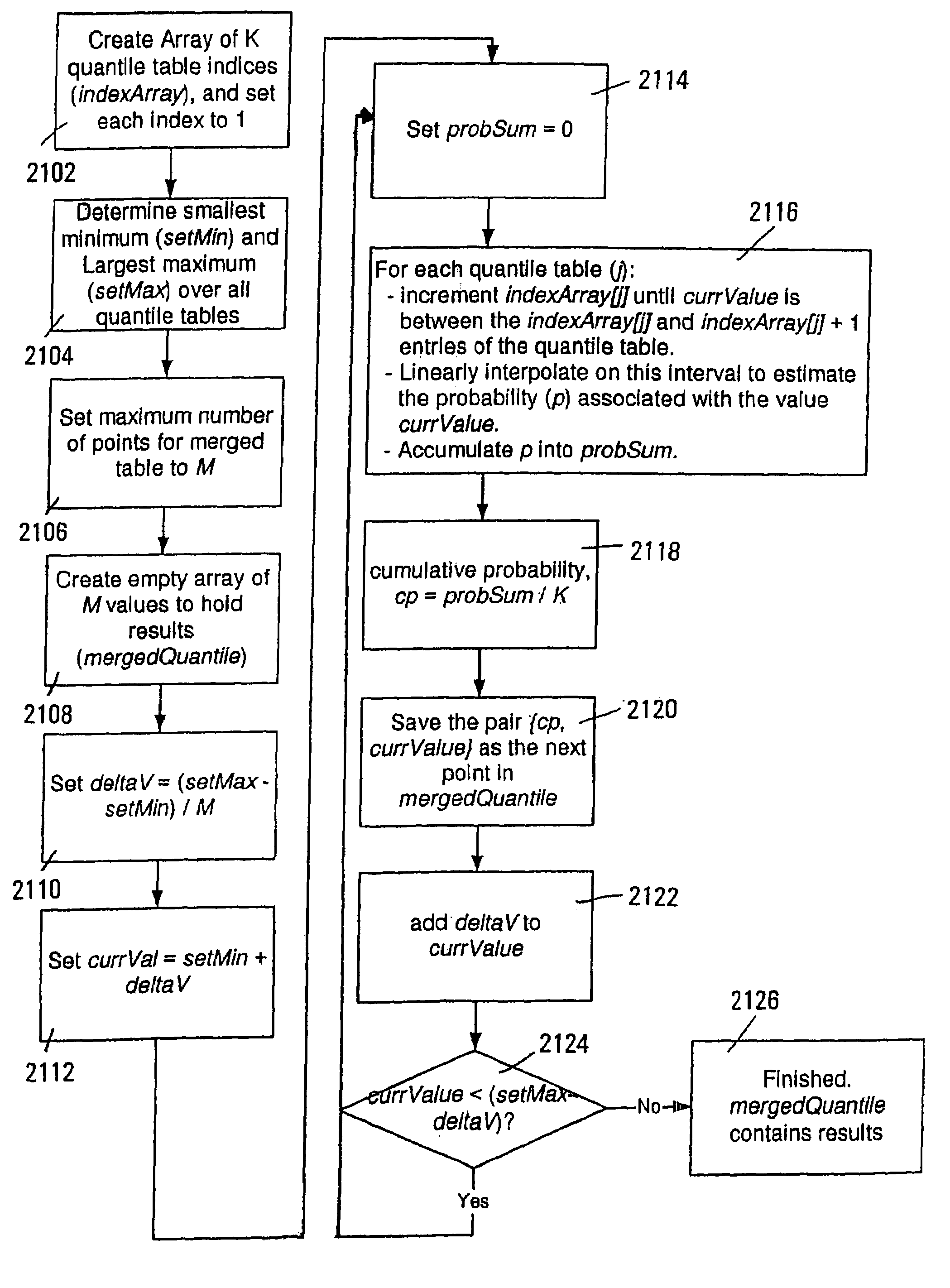
A system and methods for displaying data distribution information for time-series data is described. The methods include computing a condensed quantile function that may be used to generate approximate histograms for the time-series data, while decreasing the data storage requirements for generating a series of histograms for time-series data. The methods further include displaying the data distribution information using stack-bar histograms, many of which may be shown in a single display to permit a user to discern trends in the data distribution information. Methods for merging condensed quantile function tables are also described.
Owner:ATERNITY LLC
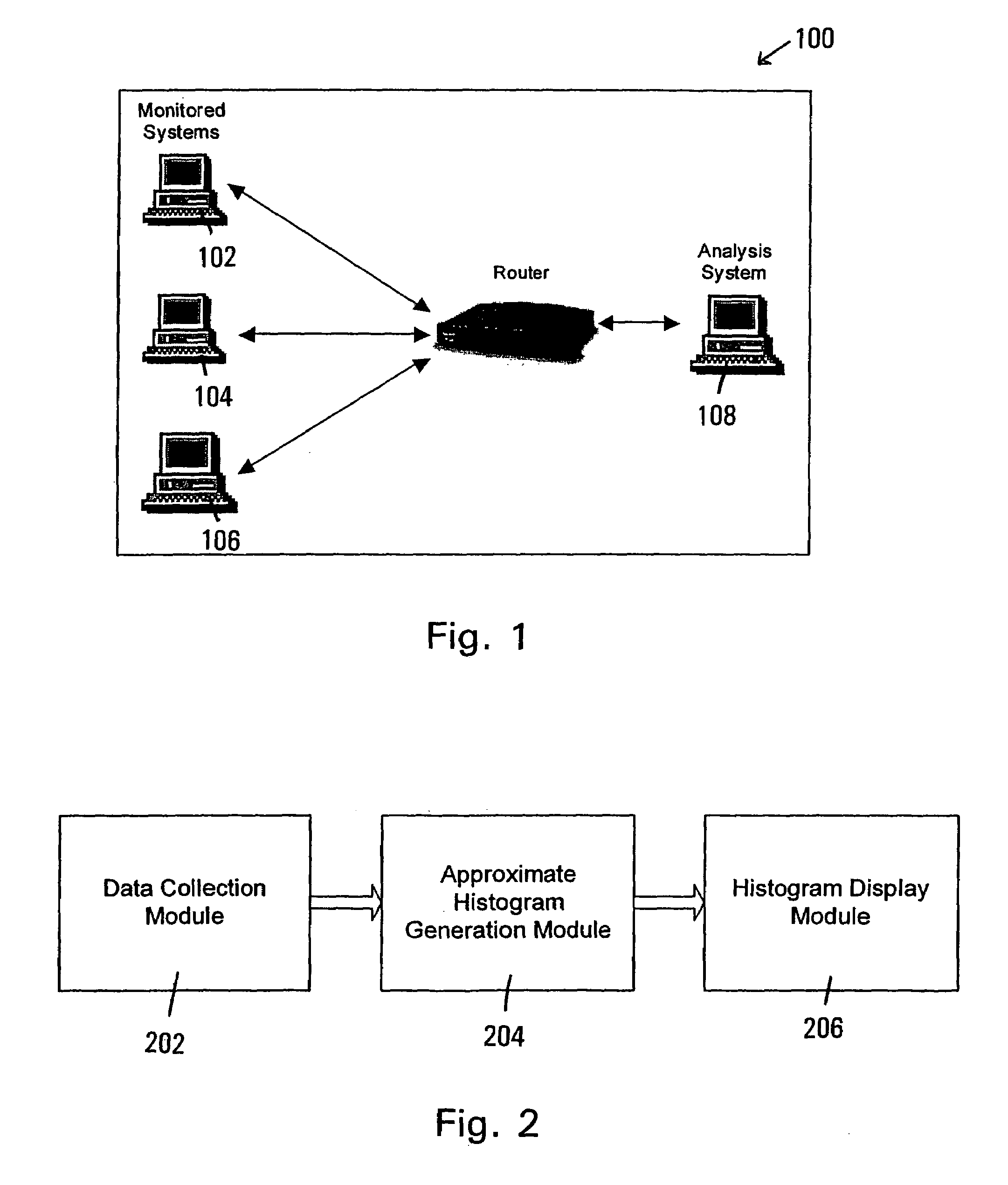
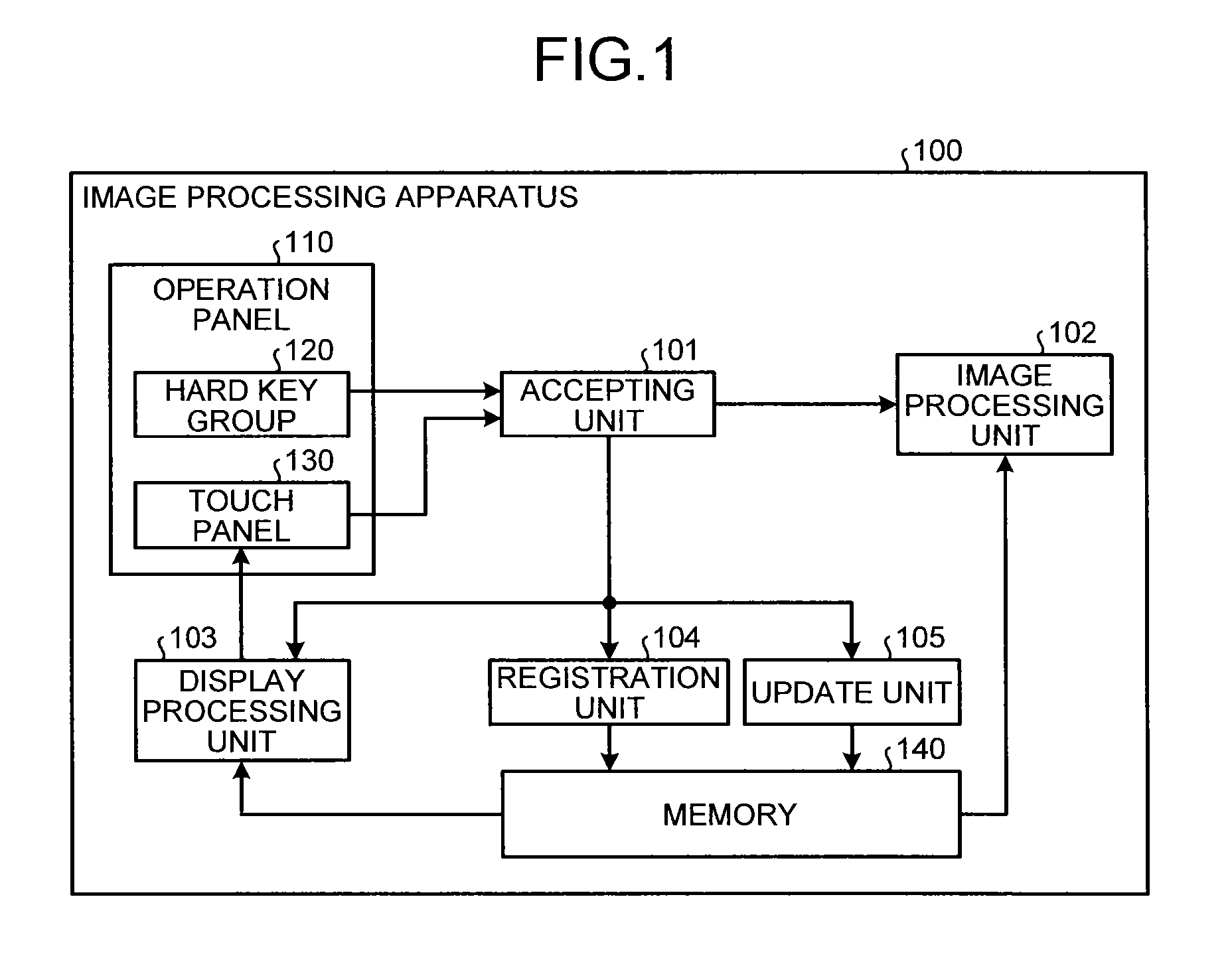
Image processing apparatus, image processing method, and computer program product
ActiveUS20130074008A1Electrographic process apparatusInput/output processes for data processingValue setImaging processing
An image processing apparatus having functions includes an image processing unit that executes the functions; a memory that stores a function table including function identification information identifying the functions, initial values preset for the functions, and registered values set for the functions by a user, in a corresponding manner to each other; a display processing unit that displays a function list screen on which initial value buttons for calling up an initial value function screen accepting an input of an instruction from the user to execute the function using the initial values, and first registered value buttons for calling up a registered value function screen accepting an input of the instruction from the user to execute the function using the registered values are arranged; and an accepting unit accepting a selection of the initial value button or the first registered value button on the function list screen from the user.
Owner:RICOH KK
Write-barrier maintenance in a garbage collector
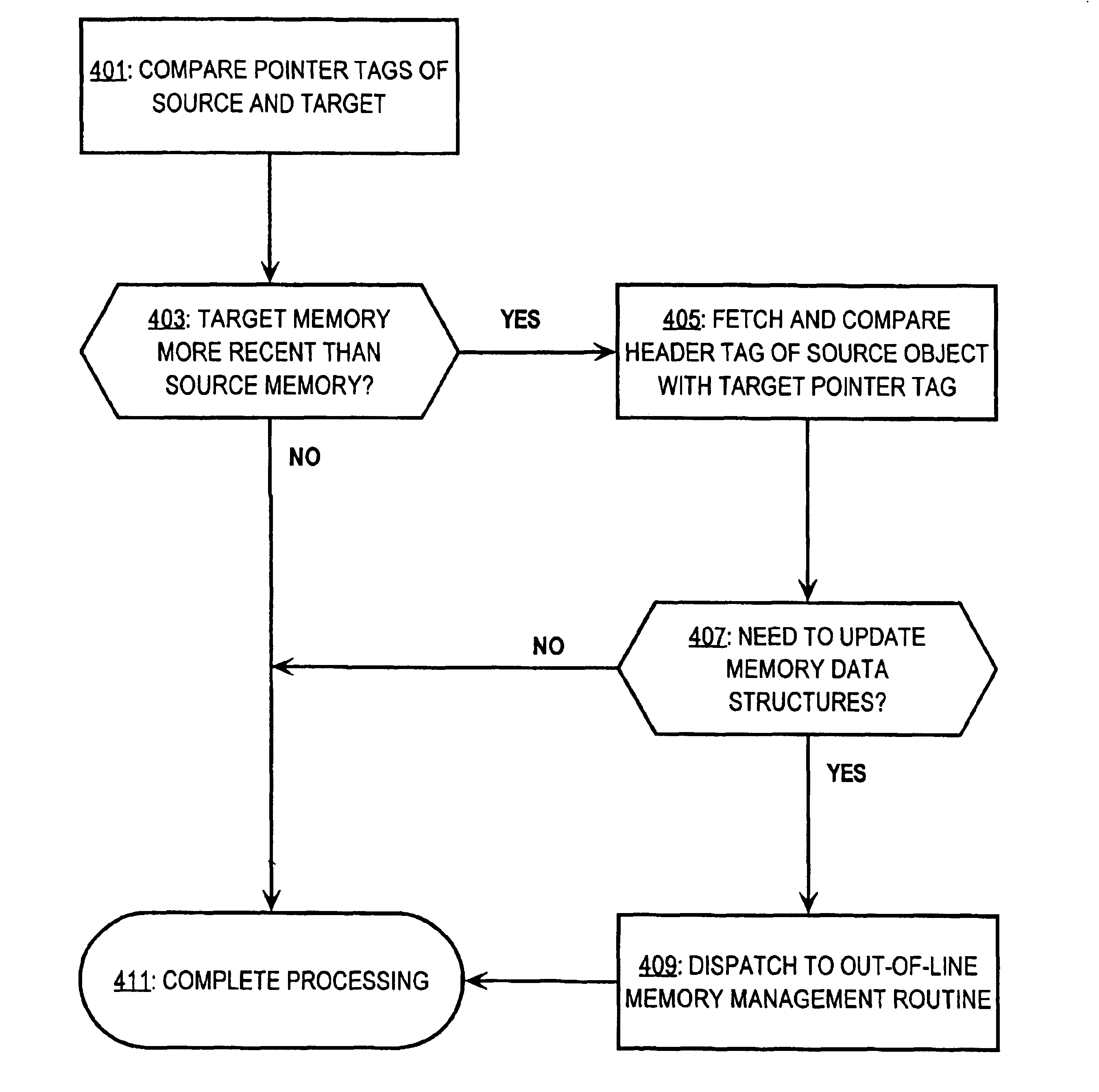
InactiveUS6931423B2Efficiently determinedQuick identificationData processing applicationsMemory adressing/allocation/relocationFunction tableWrite barrier
An approach is provided for maintaining a write barrier during an assignment operation between a source object and a target object. A source tag is obtained from a first reference to the source object, and a target tag is obtained from a second reference to the target object. The source tag and the target tag are compared, such that if the source tag is in a predetermined relationship with the target tag, then a data structure (e.g., a remember table or exit table) associated with the write barrier is updated in accordance with the assignment operation. In one embodiment, the routine to update the data structure is dispatched from a function table based on a tag value in a header associated with the source object.
Owner:ORACLE INT CORP
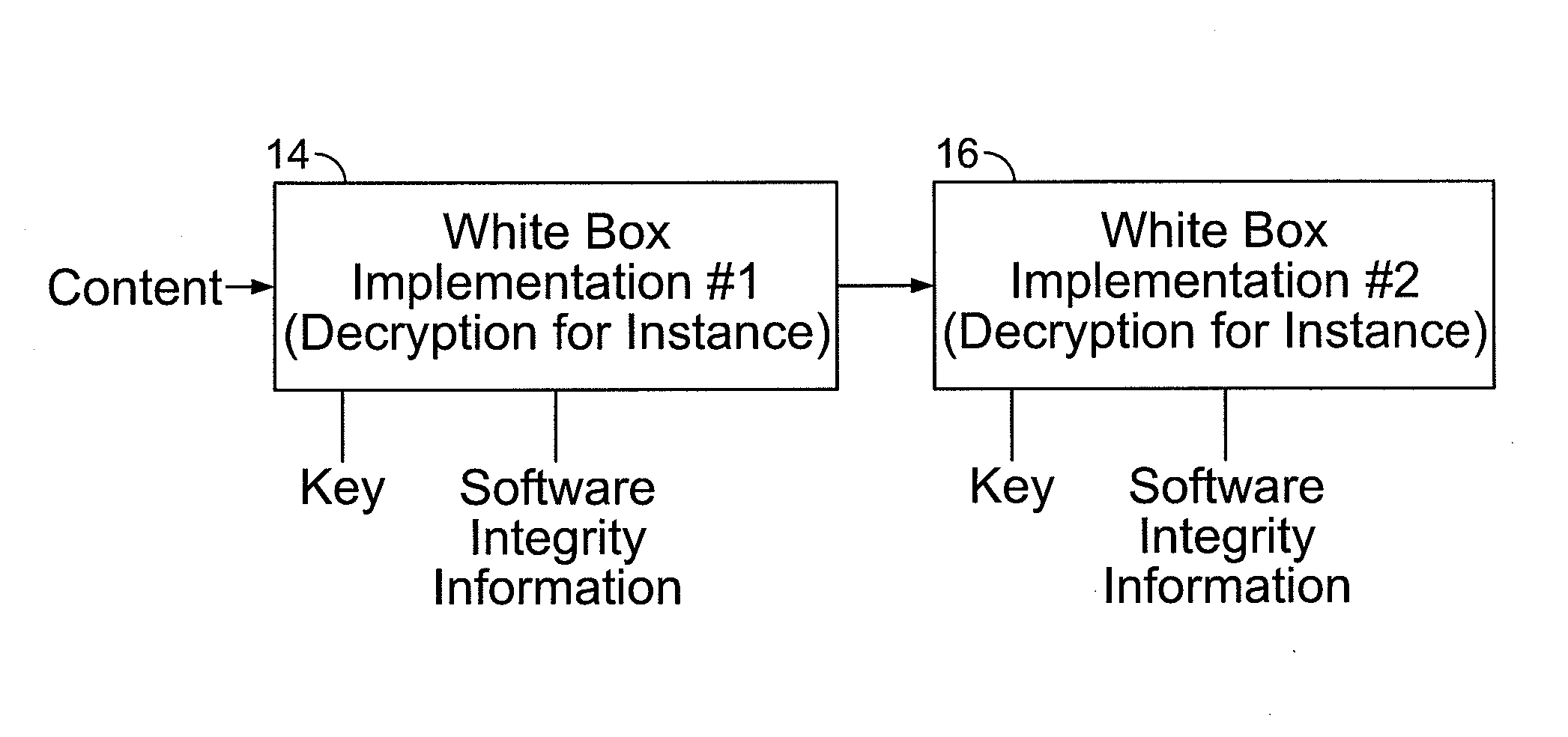
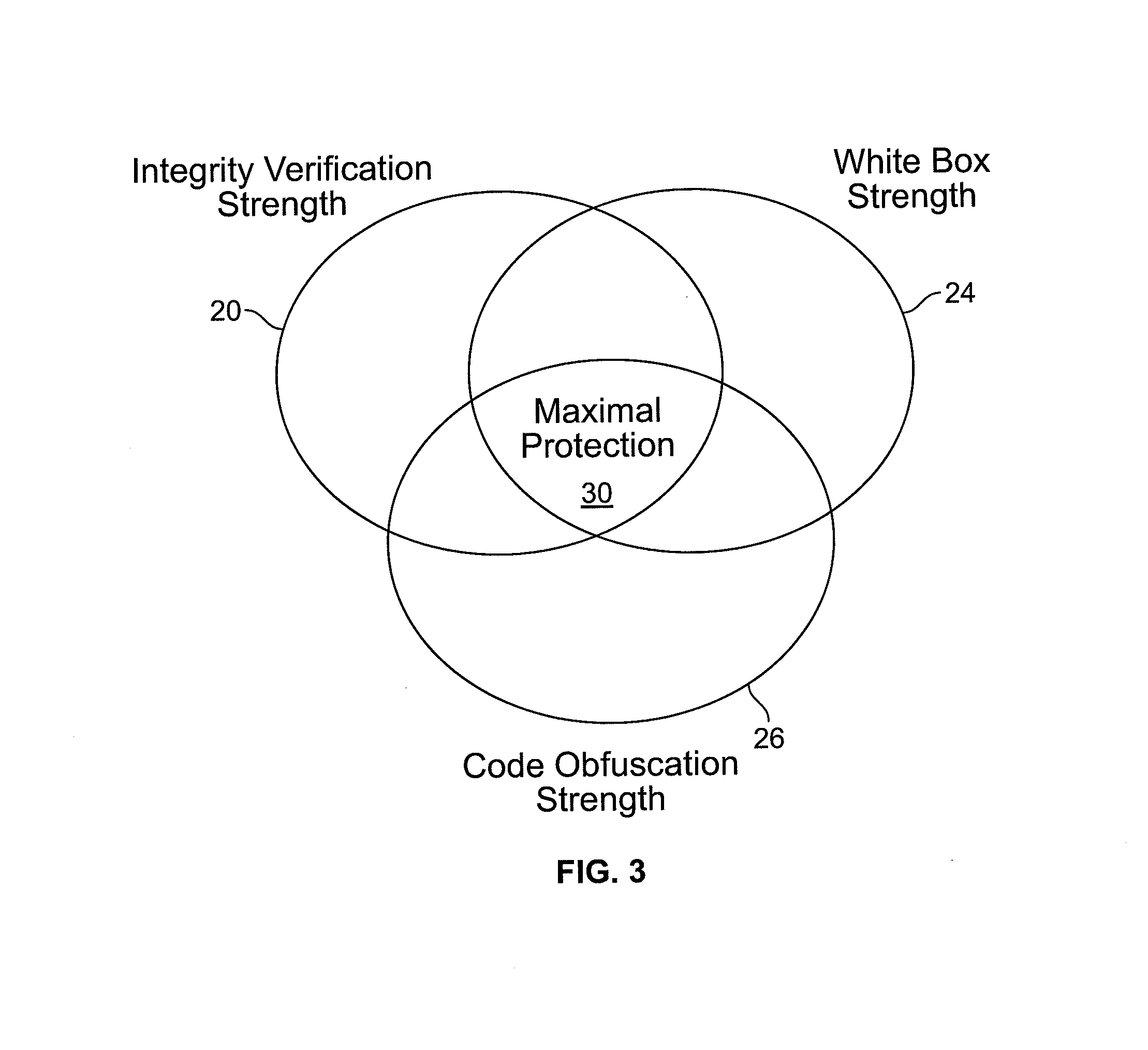
Code tampering protection for insecure environments
ActiveUS20140101458A1Unauthorized memory use protectionHardware monitoringTheoretical computer scienceEngineering
In the field of computer software (code) security, it is known to include verification data such as hash values in or associated with the code to allow subsequent detection of tampering by a attacker with the code. This verification technique is used here in a “White Box” cryptographic process by tying the verification data to the content of functional table lookups present in the object (compiled) code, where values in the table lookups are selectively masked (prior to the source code being compiled into the subject code) by being subject to permutation operations.
Owner:APPLE INC
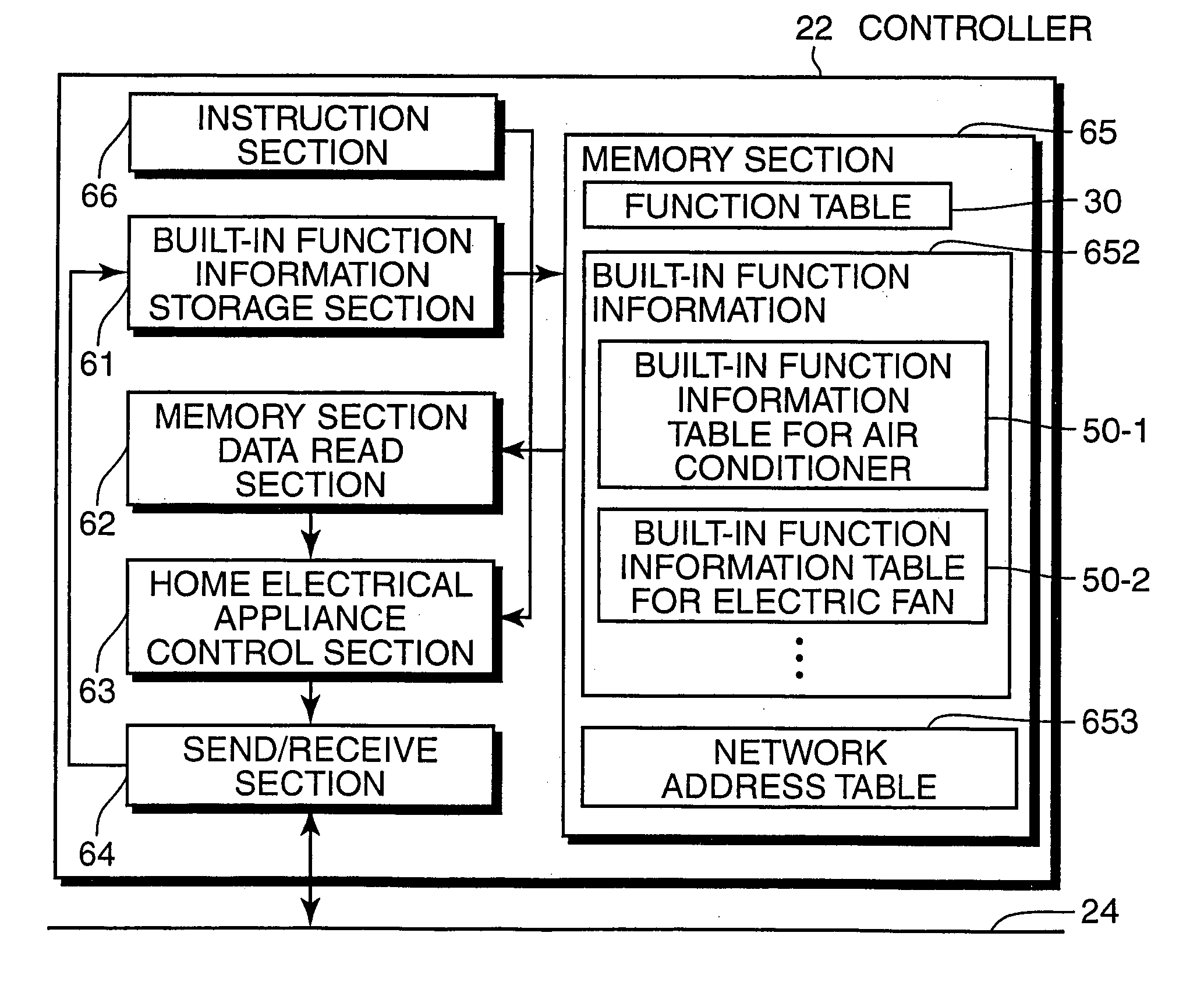
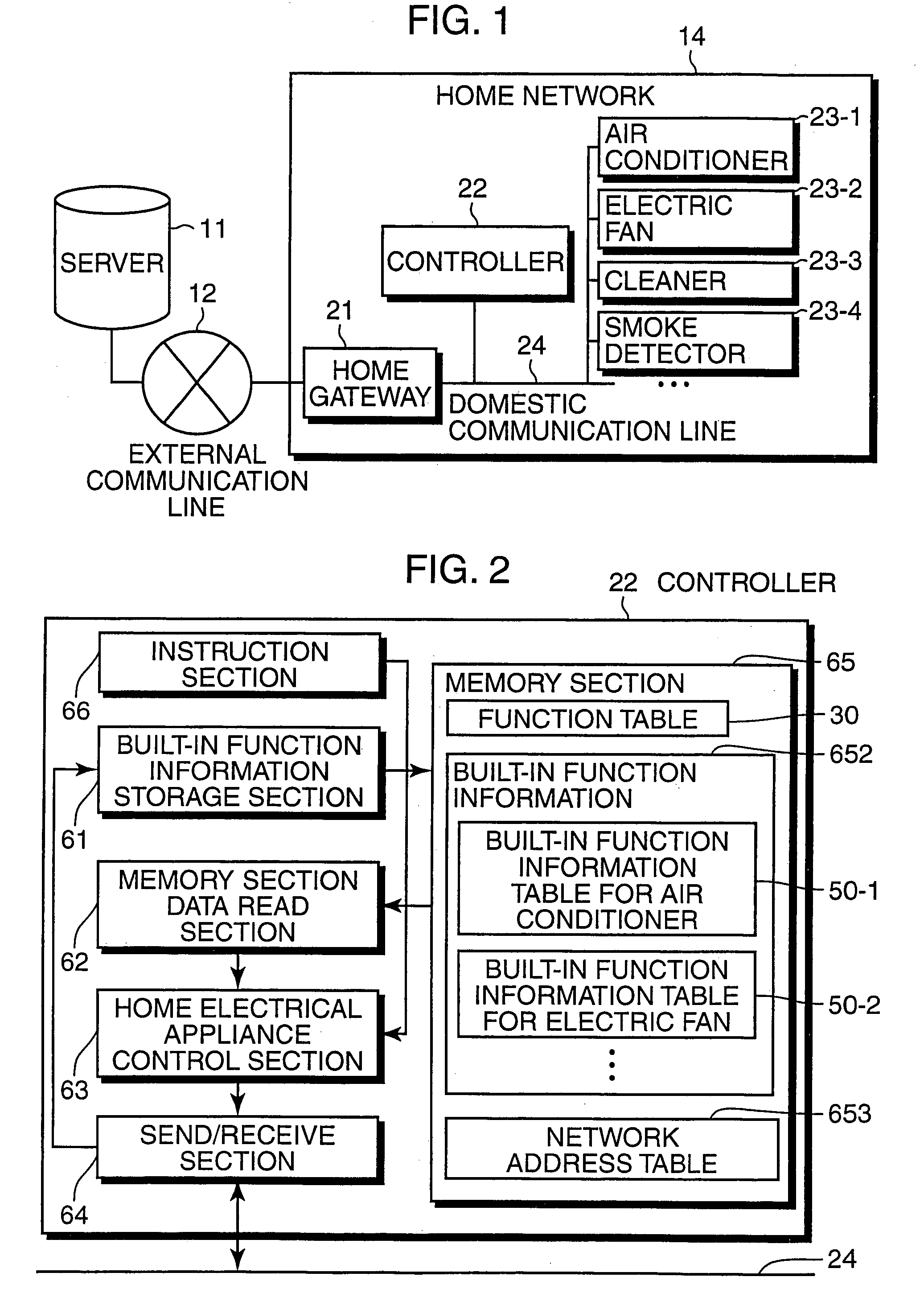
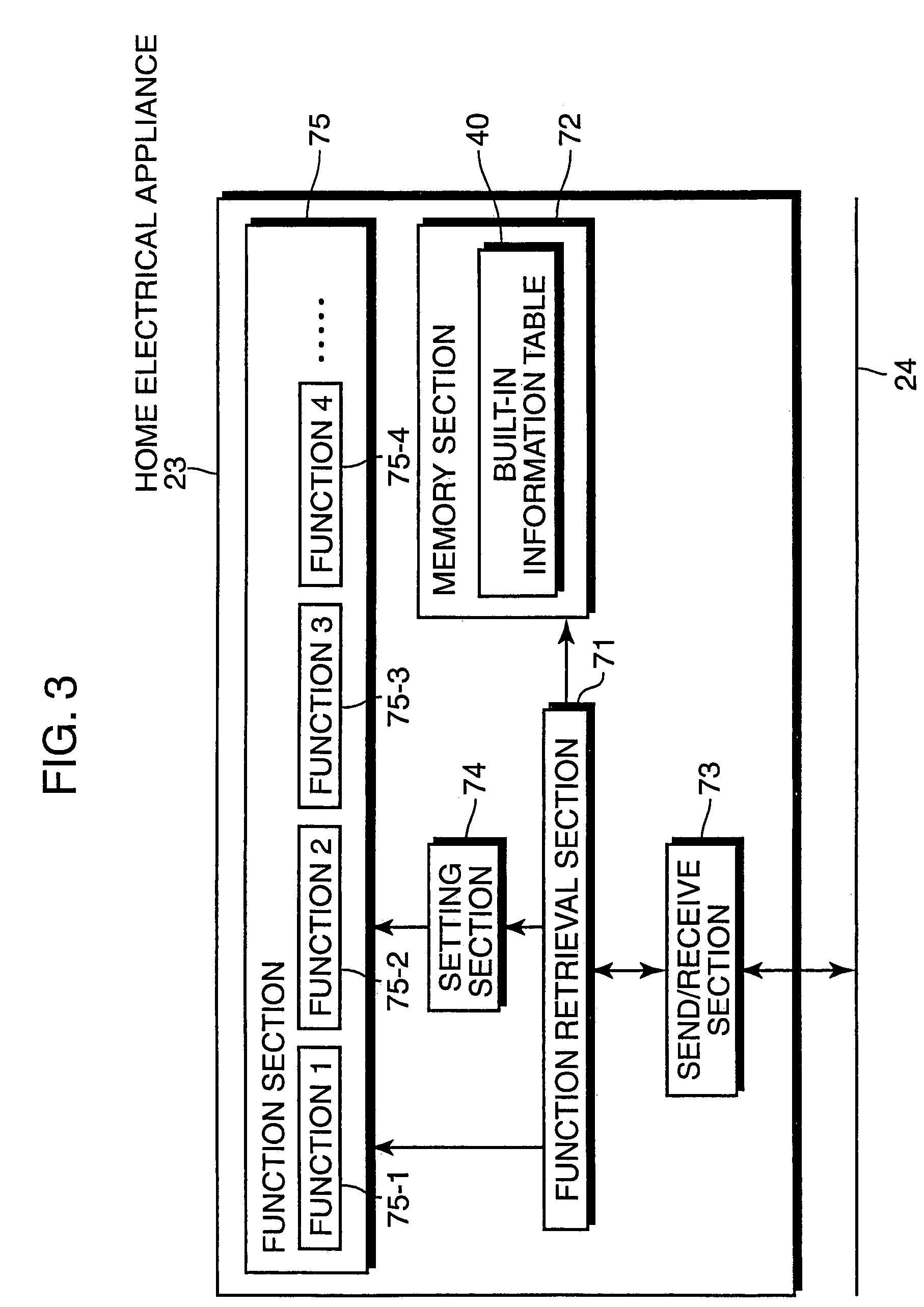
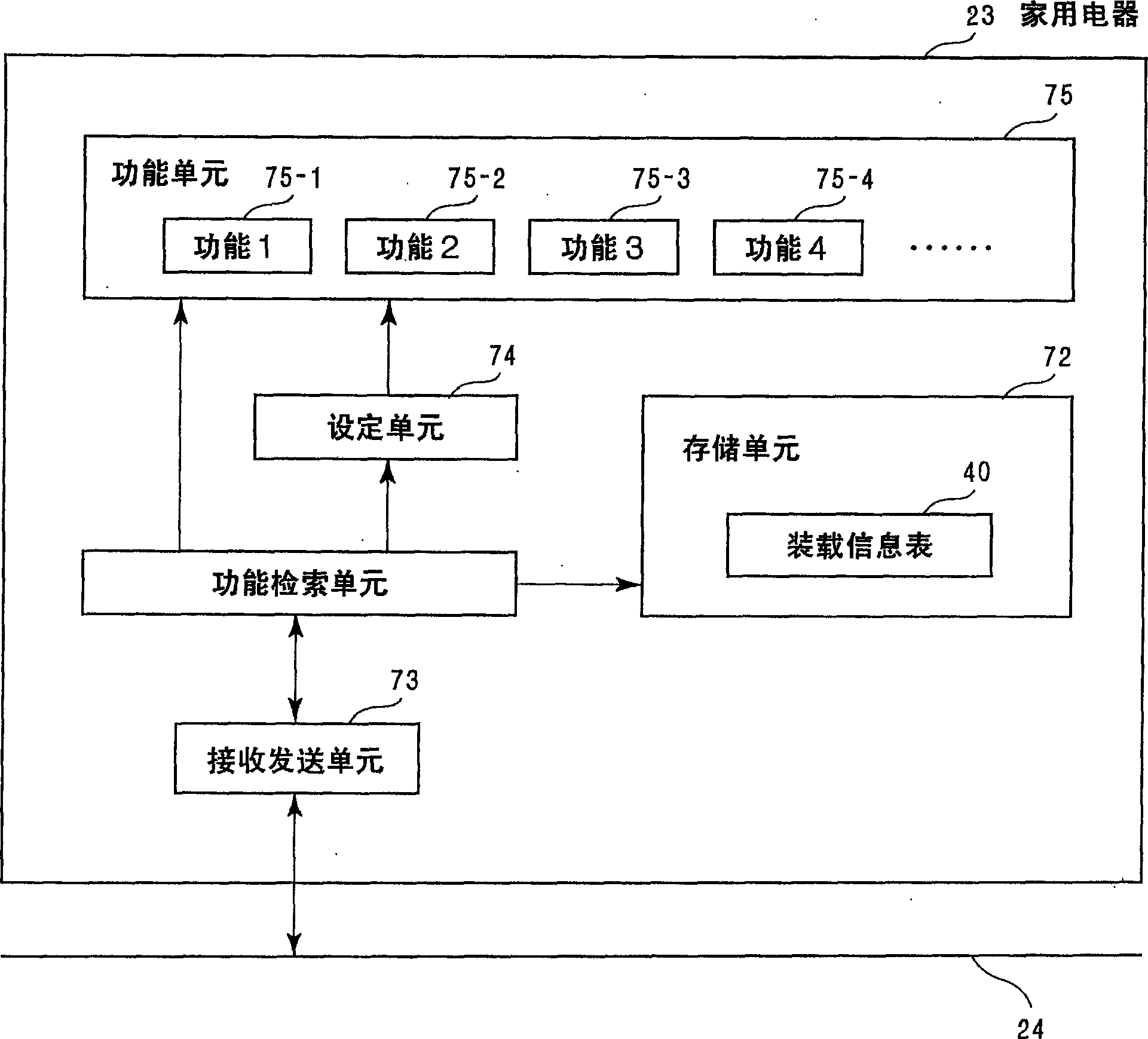
Home electrical appliance control device, control method, control program and home electrical appliance
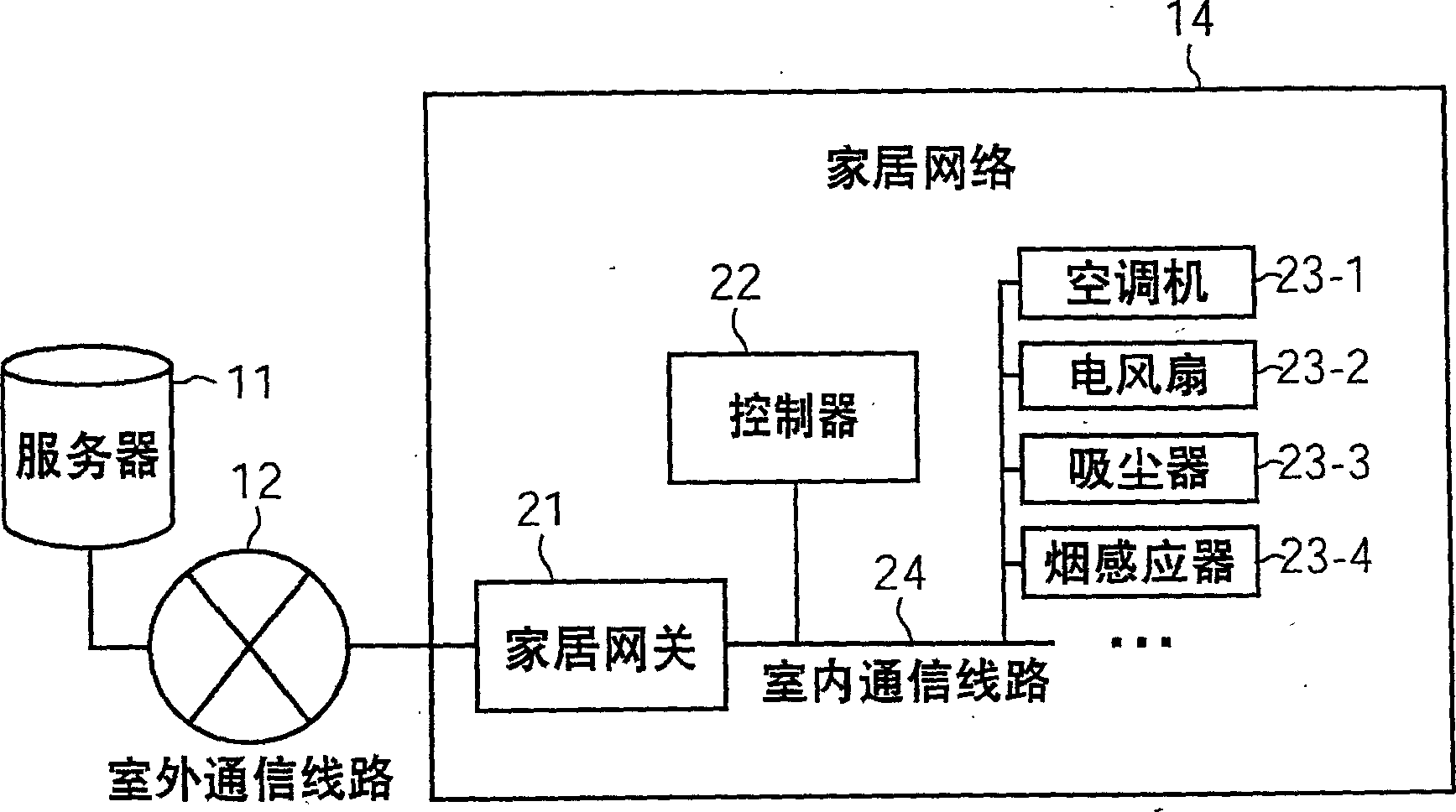
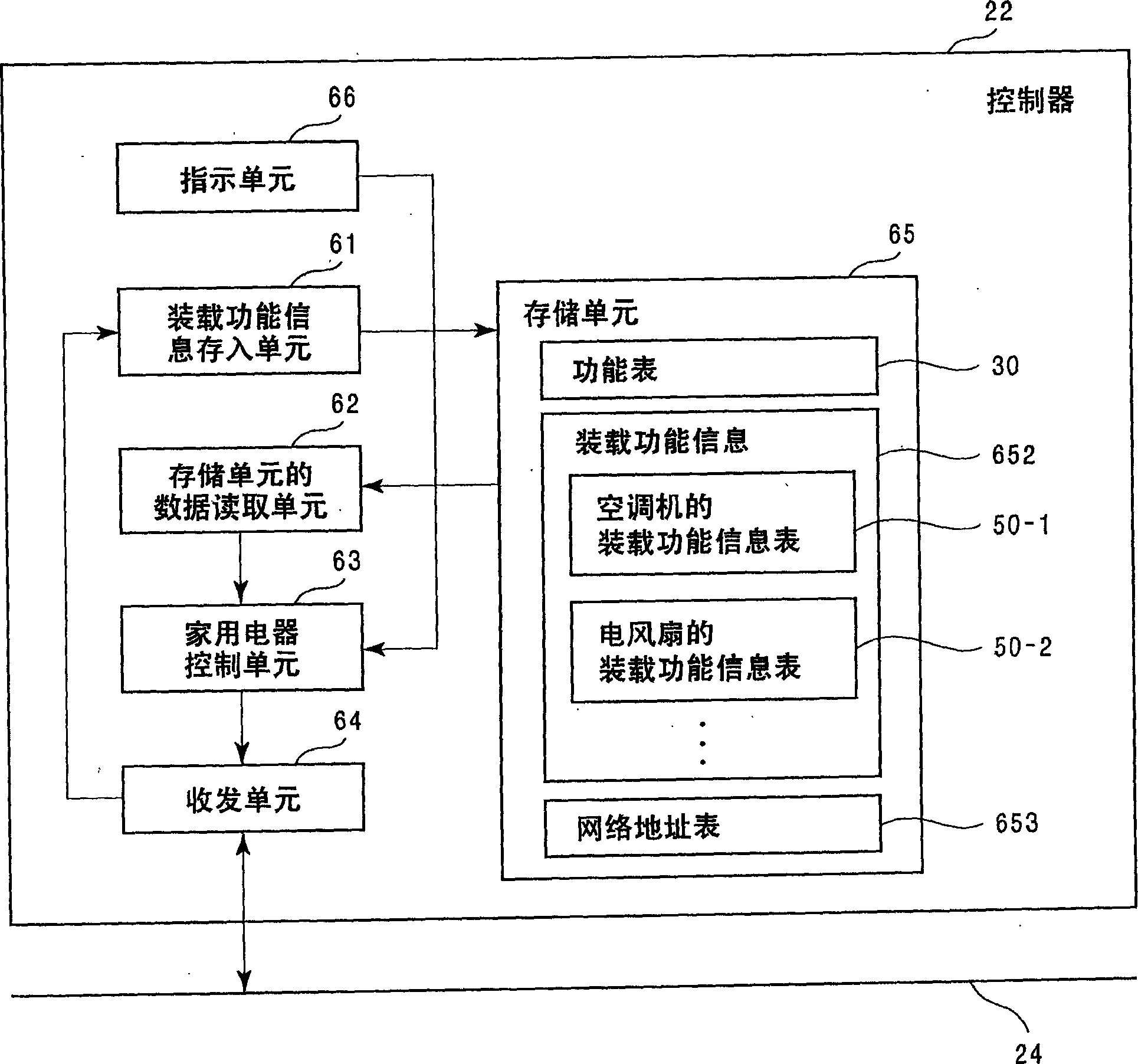
InactiveUS7081830B2Simple compositionSmall needElectric signal transmission systemsComputer controlHome applianceEmbedded system
The present invention provides a control device that controls home electrical appliances via a communication line by using function codes which are set without being specialized for specific home electrical appliances. In particular, the present invention provides a home electrical appliance control device that controls a home electrical appliance connected via a communication line, where the device includes: a memory section for storing a function table for mapping function identifiers, which identify function types allocated with the focus on the function itself to functions with which the home electrical appliance is equipped, with attributes of the functions, and a control section for controlling the home electrical appliance via the communication line based on the function table.
Owner:PANASONIC CORP
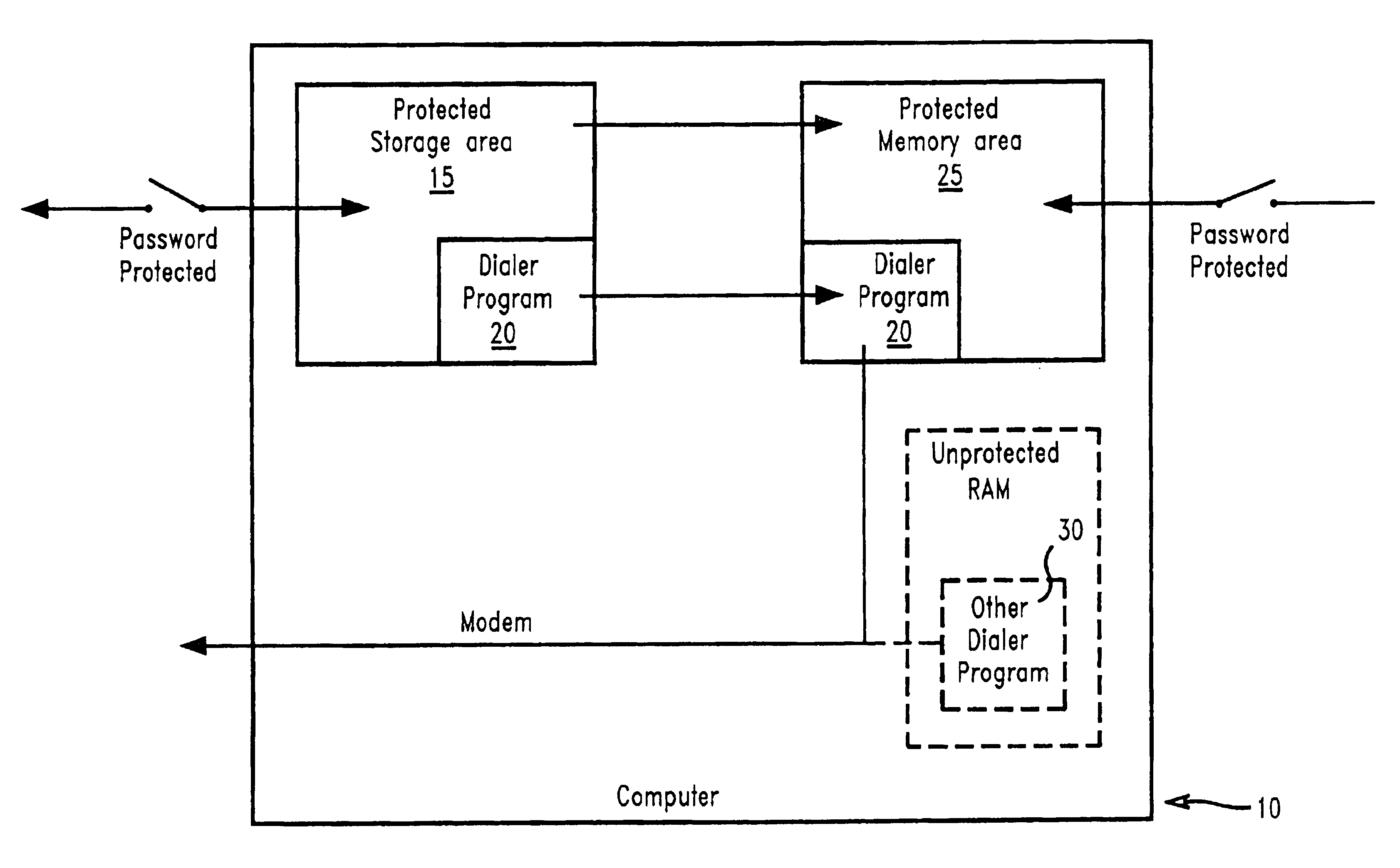
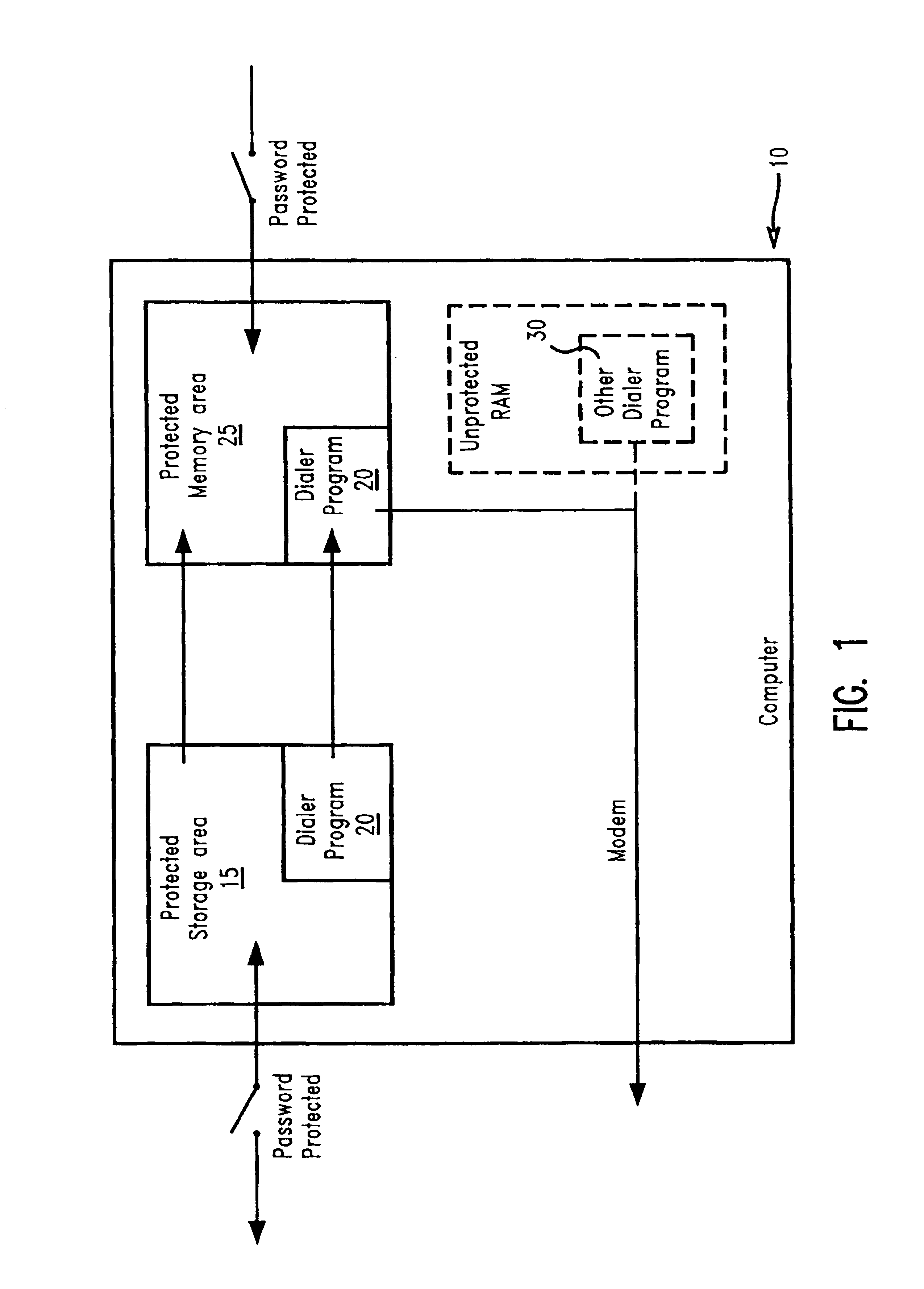
Method of ensuring that the PC is not used to make unauthorized and surreptitious telephone calls
InactiveUS6763465B1Disabling a rogue dialer programDigital data processing detailsUnauthorized memory use protectionHard disc drivePassword
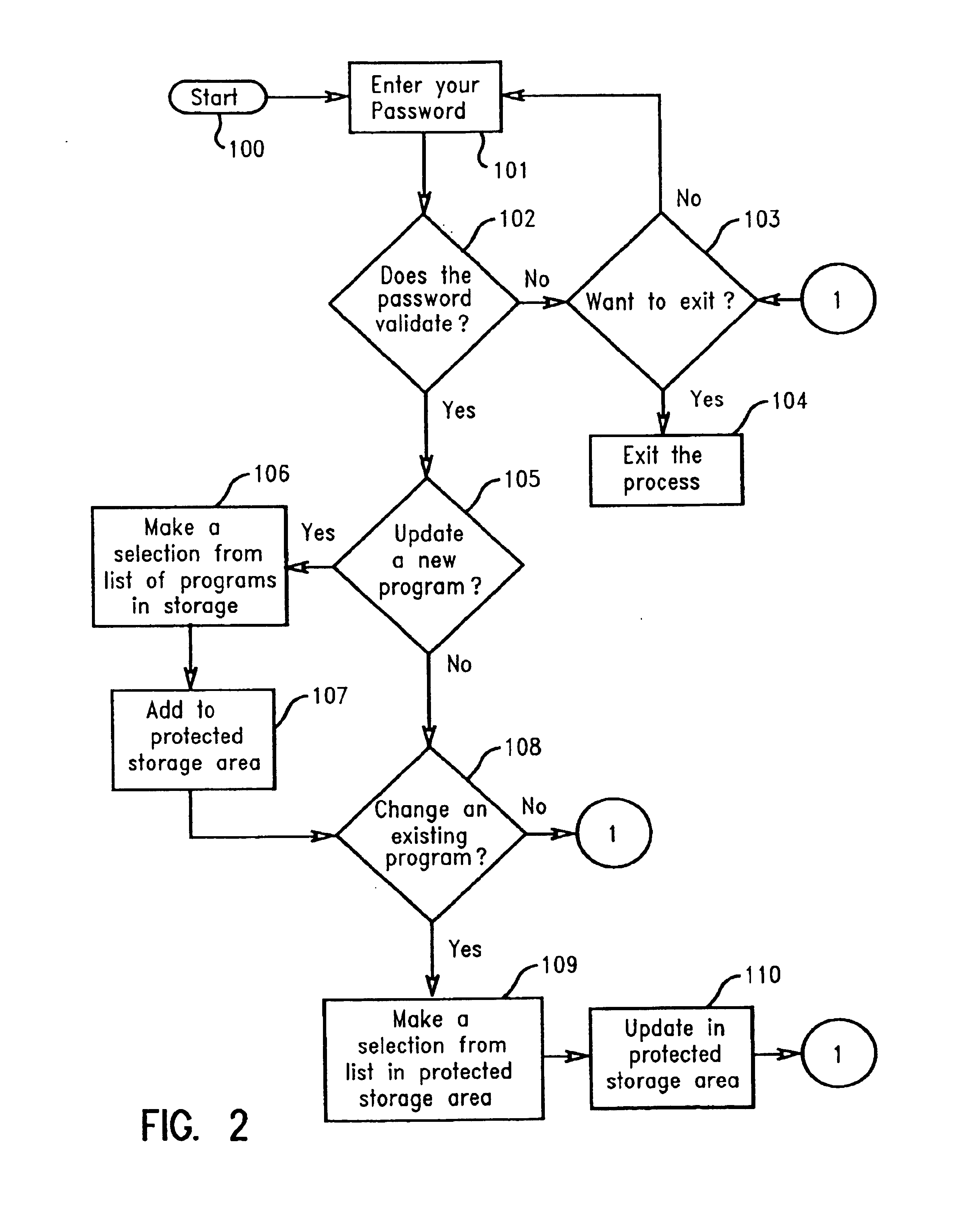
The present invention prevents unauthorized access and modifications to programs and non-executable files, particularly a dialer program, stored on a personal computer system (PC) by providing a protected storage area on a hard drive of the PC wherein access to the protected storage area is controlled by the owner / user of the PC. Attempts to add, remove, or modify any of the programs and non-executable files in the protected storage area will result in an interrupt prompting the user to supply a valid password or other acknowledgement. A preferred embodiment includes a protected memory area as a part of the computer's internal random access memory (RAM) such that upon initialization of a program, the program and non-executable files are copied into the protected memory area from the protected storage area. The protected memory area may also be password protected to provide additional safeguards against unauthorized access. Also disclosed is a method and apparatus for creating and utilizing a program storage table and a program function table for controlling access and modifications of programs and non-executable files, particularly a dialer program, stored in the protected storage area. Preferably, the present invention may be embodied as a computer program product stored on a program storage device.
Owner:LENOVO (SINGAPORE) PTE LTD
Method for improving precision of built-in real-time clock of electric energy meter MCU
ActiveCN103499803ACompensation value is accurateImprove clock accuracyElectrical measurementsReal-time clockCurve fitting
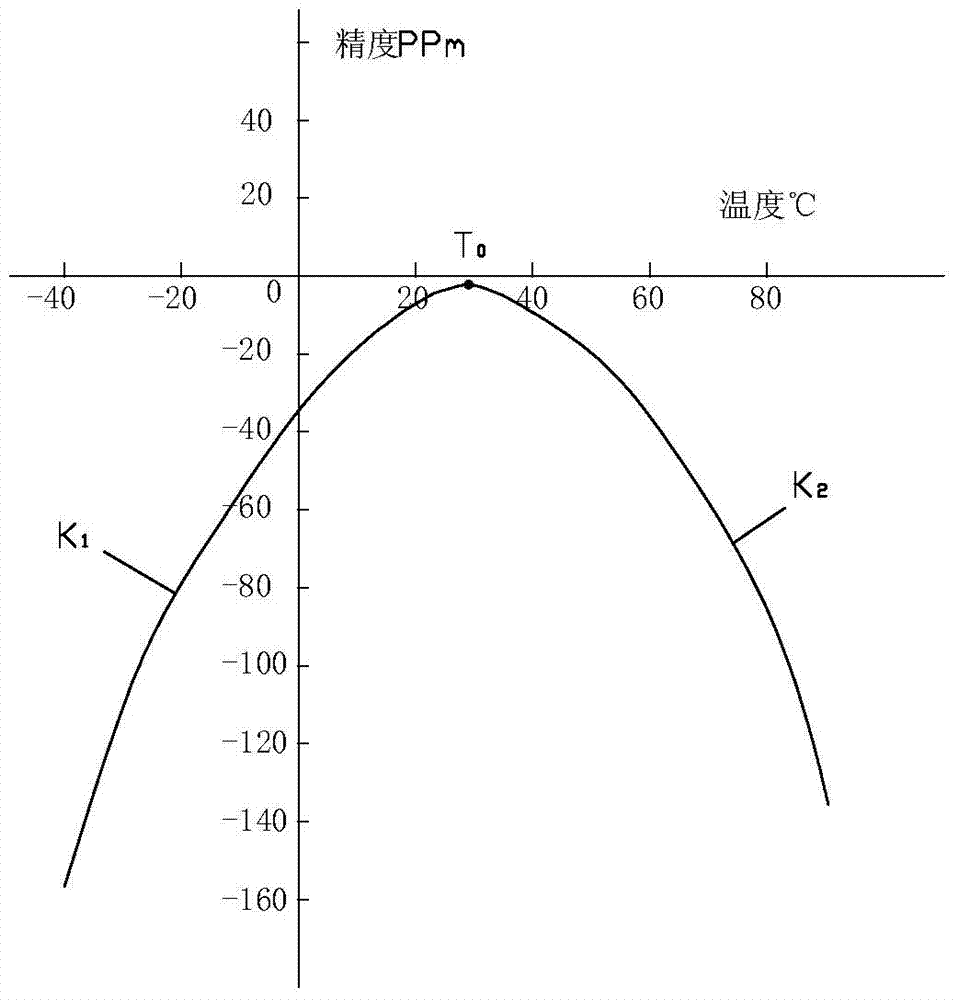
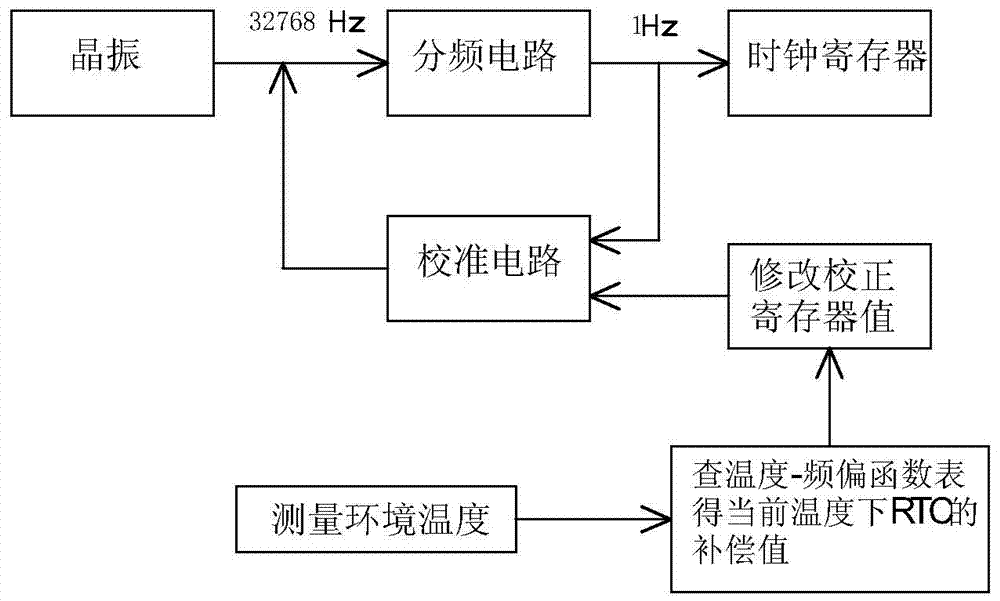
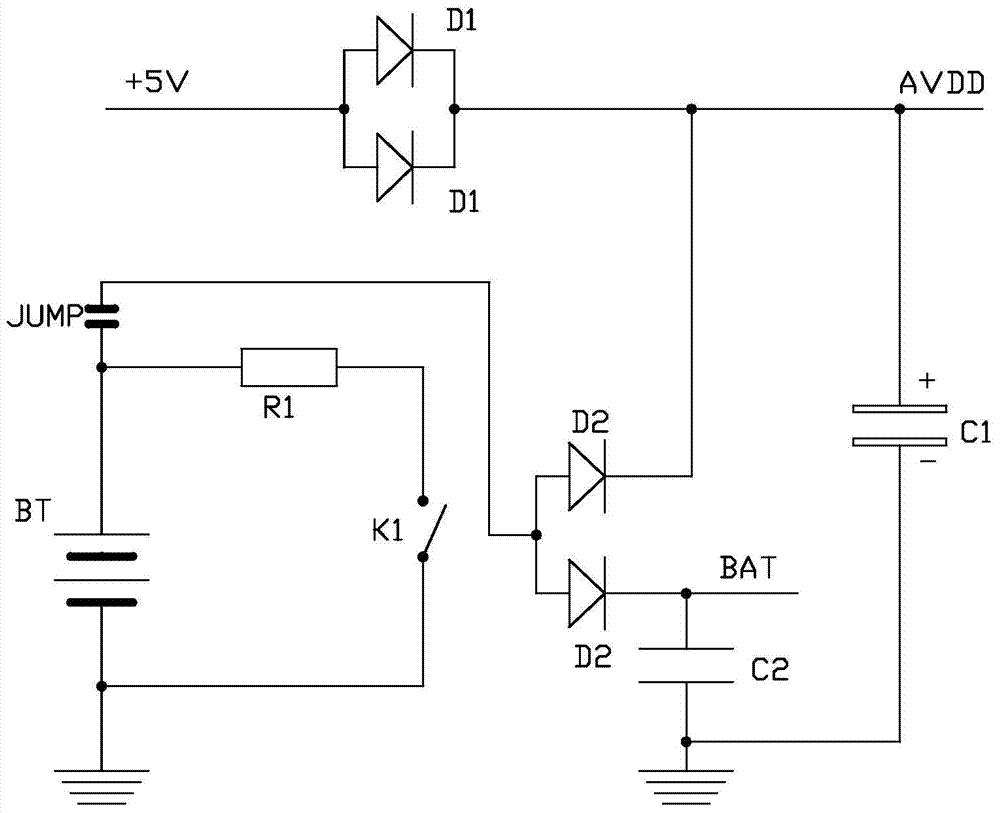
The invention discloses a method for improving the precision of a built-in real-time clock of an electric energy meter MCU. Based on the practical crystal oscillator frequency, fine compensation can be achieved. An electric energy meter comprises the MCU, a crystal oscillator and a power management unit. The method for improving the precision of the built-in real-time clock of the electric energy meter MCU includes the following steps of compensation amount calculation and clock calibration. Compensation amount calculation is performed according to the following processes that firstly, frequency deviations of the practical crystal oscillator under different temperatures are measured; secondly, a temperature-frequency deviation curve sketch is drawn, and the turn temperature T0 is found out; thirdly, the measured frequency deviations of the two sides of T0 undergo curve fitting, and a corresponding buckling constant is obtained; fourthly, a temperature-frequency deviation function table is formed according to a function of the third process, the frequency deviation value of the current temperature can be obtained through the temperature-frequency deviation function table according to the practical environmental temperature, and the frequency deviation value serves as the compensation amount for calibrating the clock under the practical environmental temperature. According to the method for improving the precision of the built-in real-time clock of the electric energy meter MCU, an accurate compensation value can be obtained according to errors of the practical crystal oscillator, and therefore the precision of the clock is improved.
Owner:YANGZHOU WANTAI ELECTRIC TECH CO LTD
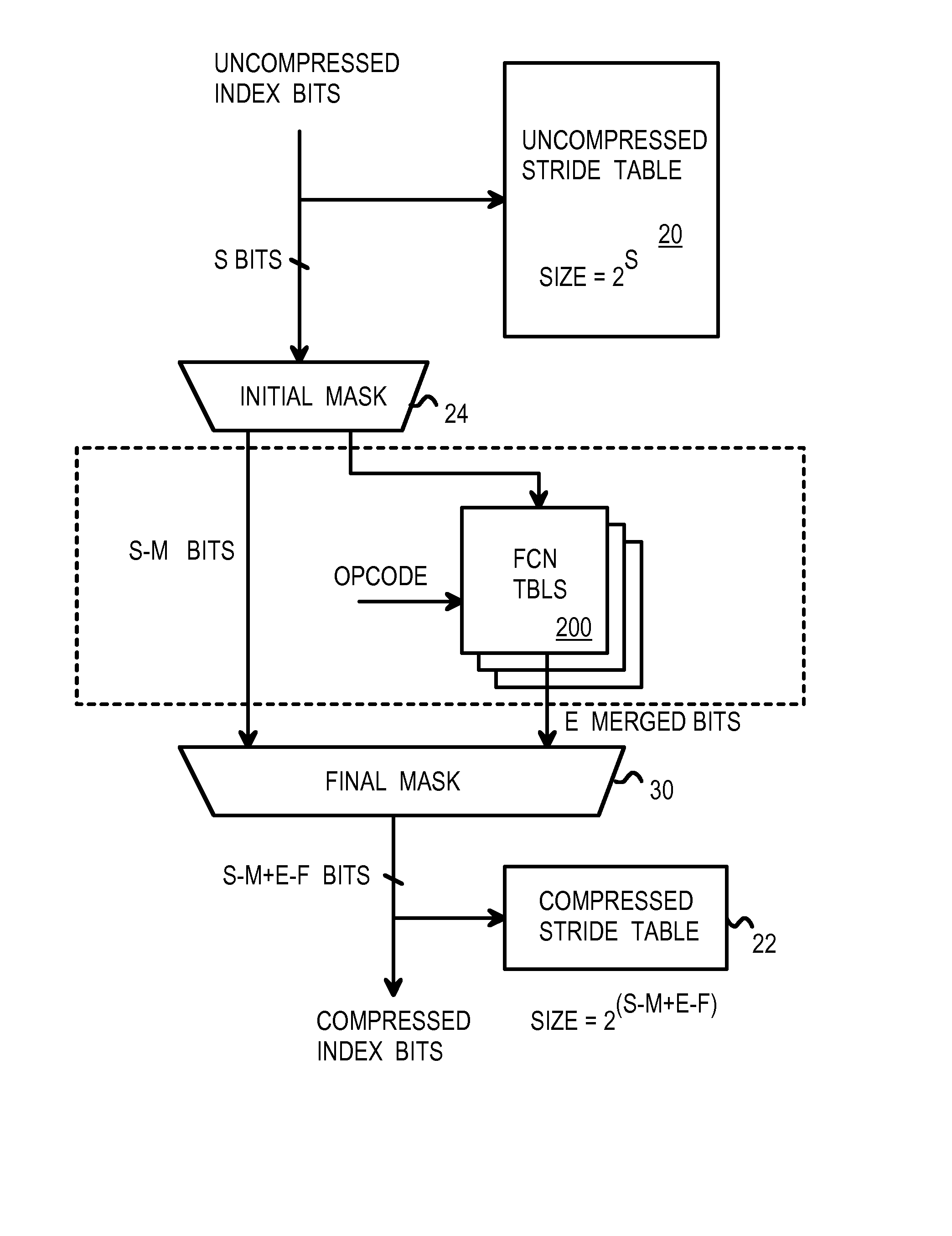
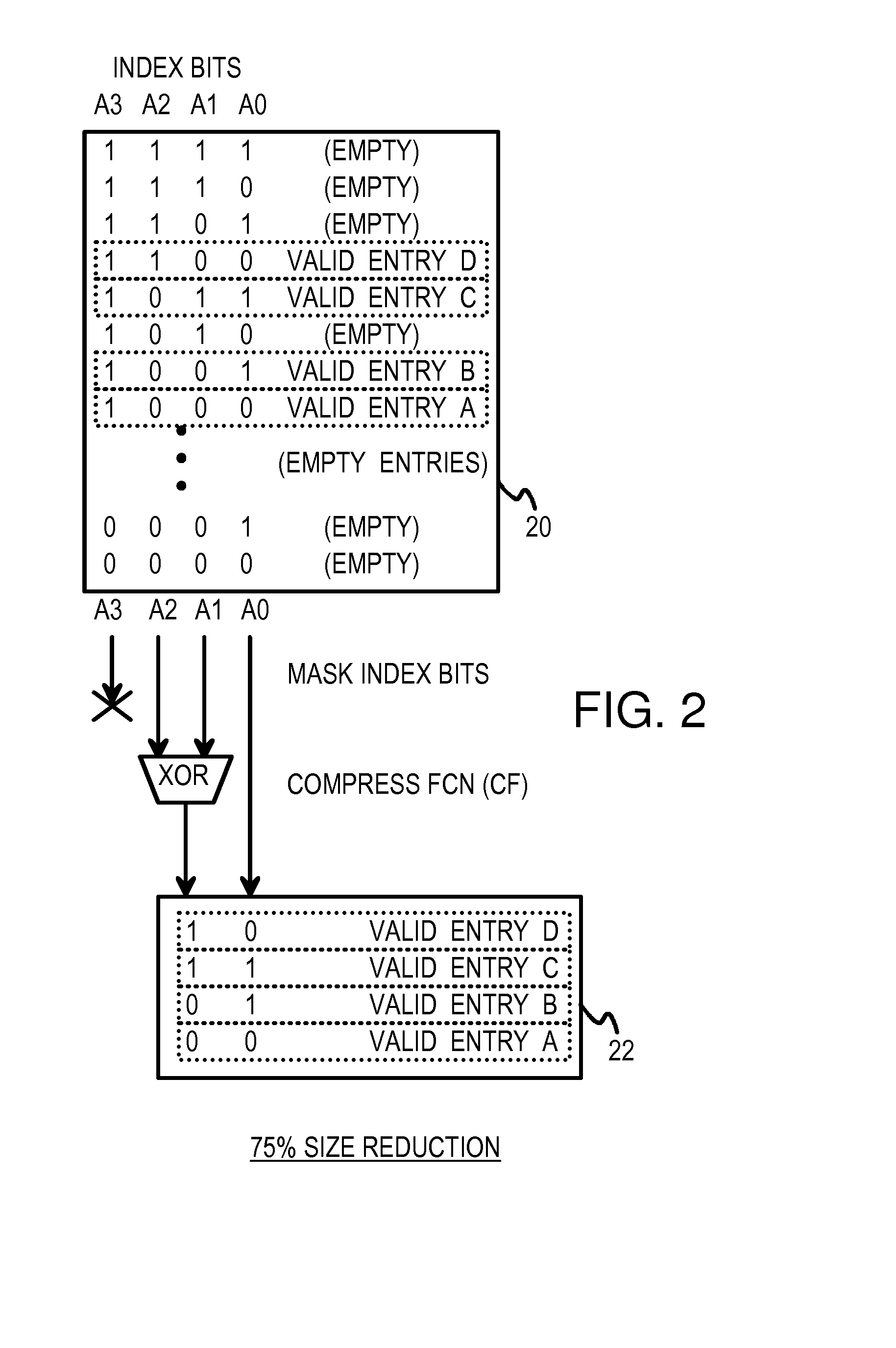
Logical operations encoded by a function table for compressing index bits in multi-level compressed look-up tables
InactiveUS7921088B1Digital data information retrievalDigital data processing detailsTheoretical computer scienceLogical operations
Compressed stride tables in a multi-bit Trie structure perform lookups. An input lookup key is divided into strides including a current stride of S bits. A valid entry in a current stride table is located by compressing the S bits, forming a compressed index of D bits into the current stride table. A compression function logically combines the S bits to generate the D compressed index bits. An entry in a prior-level table points to the current stride table and has an opcode field indicating which compression function and mask to use. Compression functions can include counts of leading-repeated bits, and very complex functions such as hashes, CRC, encryption. A function table stores results of the complex functions that are addressed by the S bits of the current stride. The opcode field in the stride entry selects from among several tables, each storing results for a different function.
Owner:GULA CONSULTING LLC
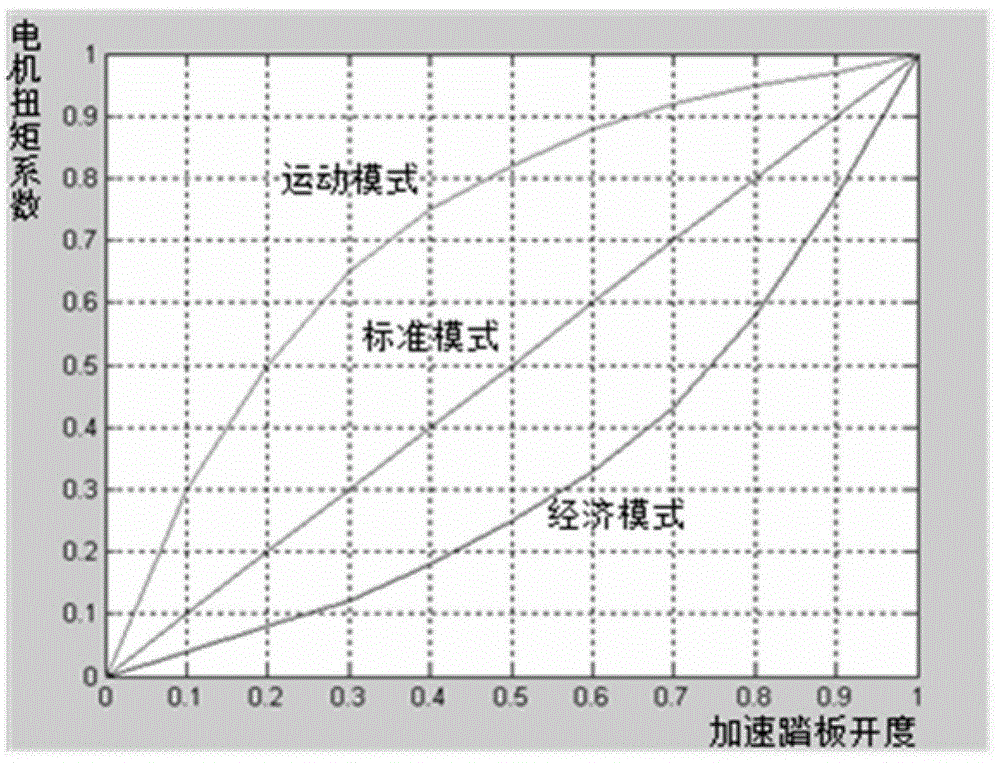
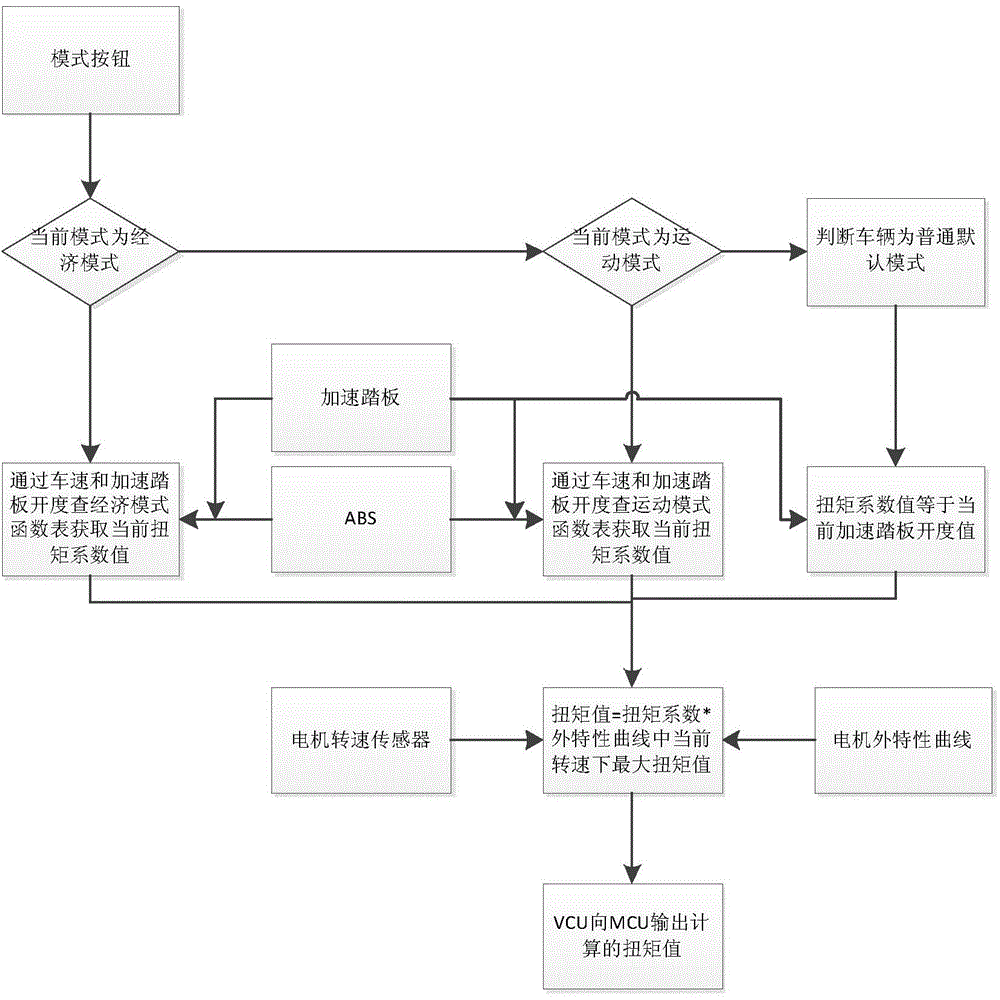
Multimode drive control method for pure electric vehicle
ActiveCN104648184AAvoid the disadvantages of insufficient torqueOptimize workspaceSpeed controllerElectric energy managementElectric machineryPeak value
The invention provides a multimode drive control method for a pure electric vehicle. The method comprises the steps that an overall vehicle controller judges the state of a driving mode of the vehicle, a torque parameter value is obtained by searching a function table through an input value in accordance with that different driving modes correspond to different function tables and input values of the function tables are current vehicle speed and openness of an accelerator pedal, and finally, a torque output value is determined by a product of the obtained torque parameter value and a peak torque value, which can be reached at a current revolving speed, of a motor. According to the method, through introducing a camber control strategy formulated through vehicle speed signals in various modes, the disadvantages resulting from the deficiency of torque of a rear segment of the driving motor are effectively avoided, the working interval of the driving motor is optimized, and the economical efficiency of the whole vehicle is increased.
Owner:BEIJING ELECTRIC VEHICLE
Method for operation of pen function and electronic device supporting the same
ActiveUS20140055426A1Easily and more convenientlyInput/output for user-computer interactionGraph readingHuman–computer interactionStorage cell
An apparatus and method for operation of a pen function in an electronic device. A pen recognition panel recognizes a touch pen according to a set mode. A control unit collects pen status information including at least one of information on an arrangement state between a pen recognition panel and a touch pen and a state information on whether a button of the touch pen is pushed, type information on a currently activated application program, and a gesture recognition information according to a gesture input operation of the touch pen, or collects the pen status information and the gesture recognition information. A storage unit stores a pen function table providing a pen function command corresponding to collected information according to the set mode, and a display panel displays information according to performing of a function corresponding to the pen function command.
Owner:SAMSUNG ELECTRONICS CO LTD
Gesture operation control method, gesture operation control device and intelligent display terminal
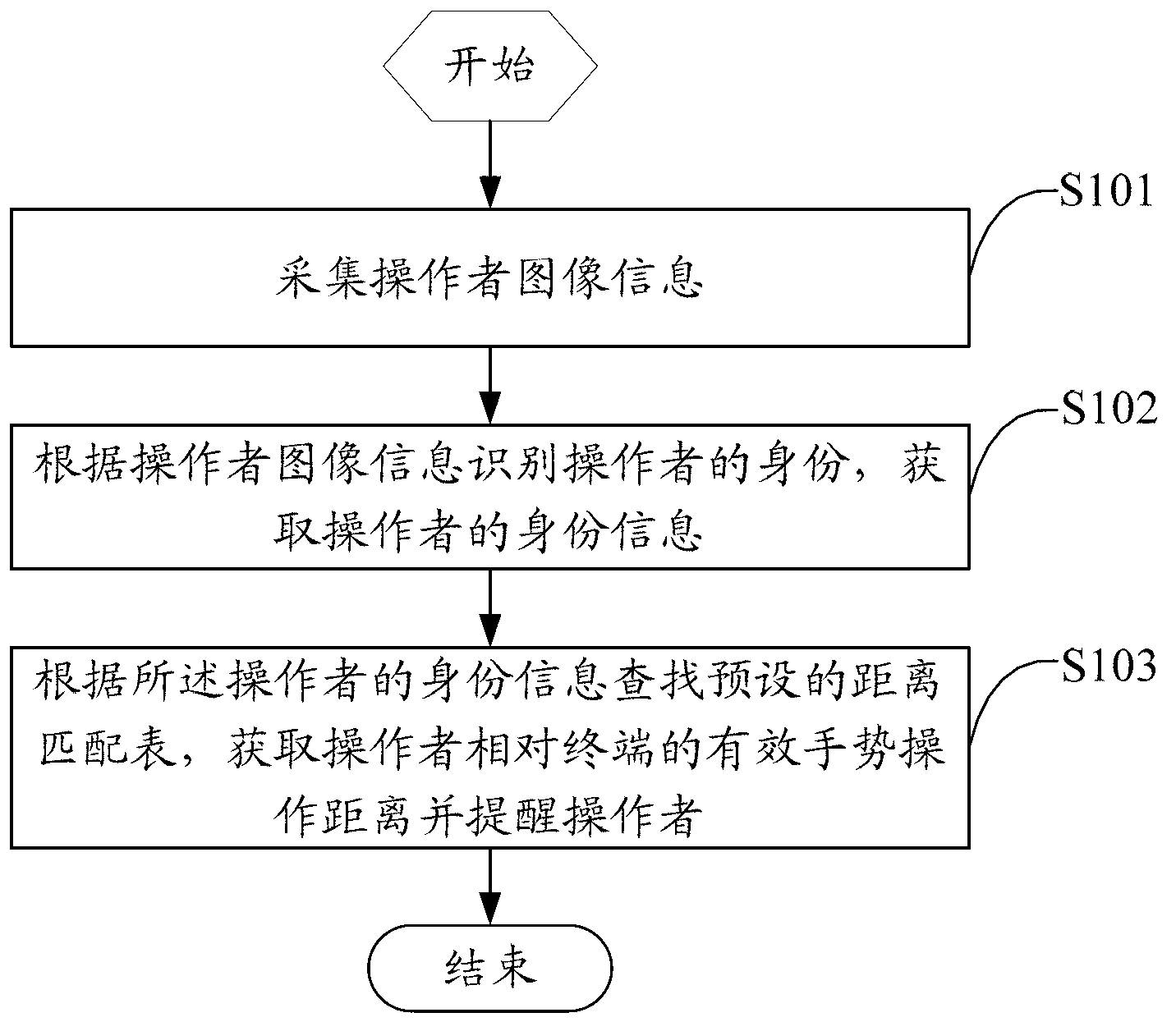
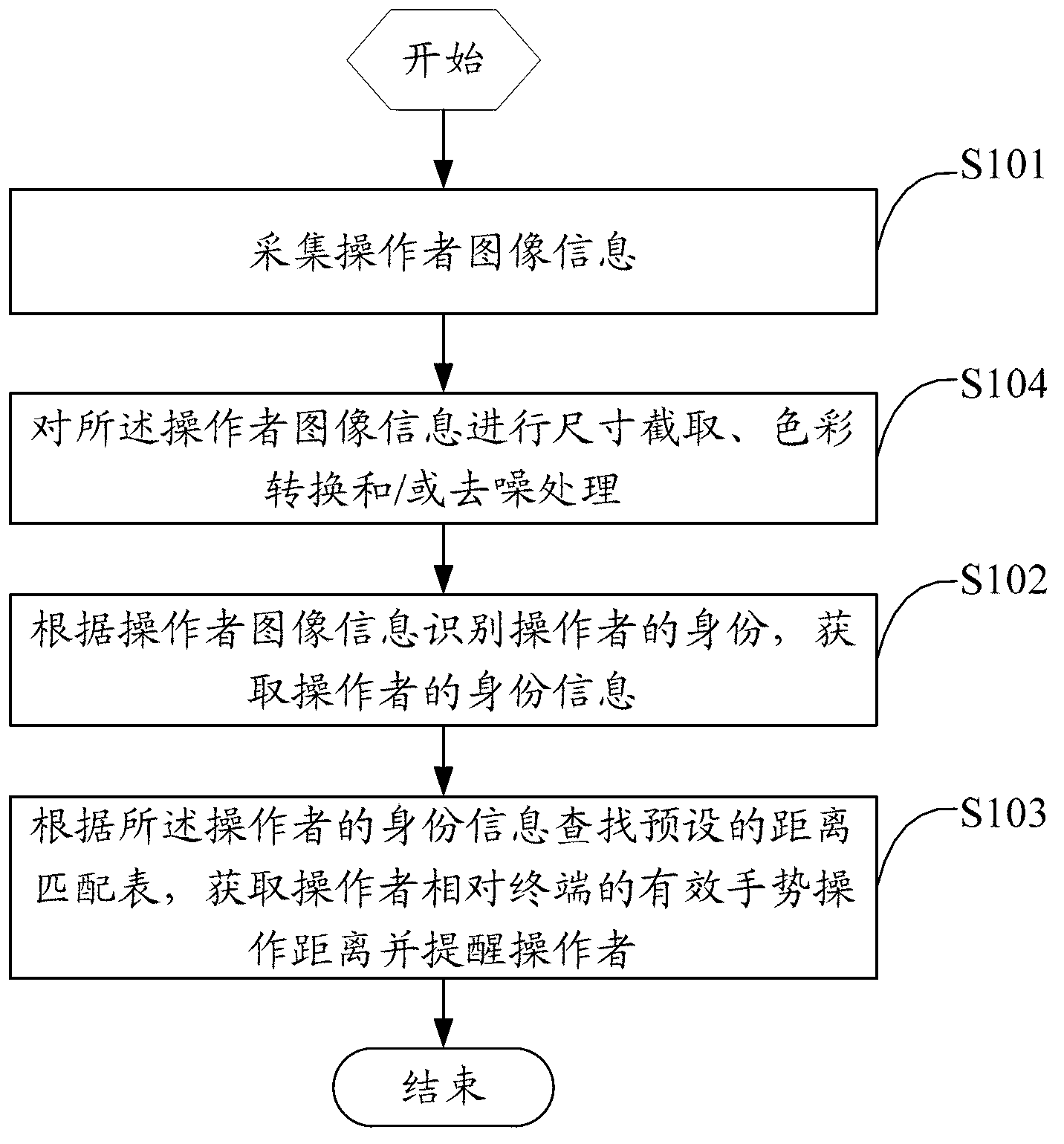
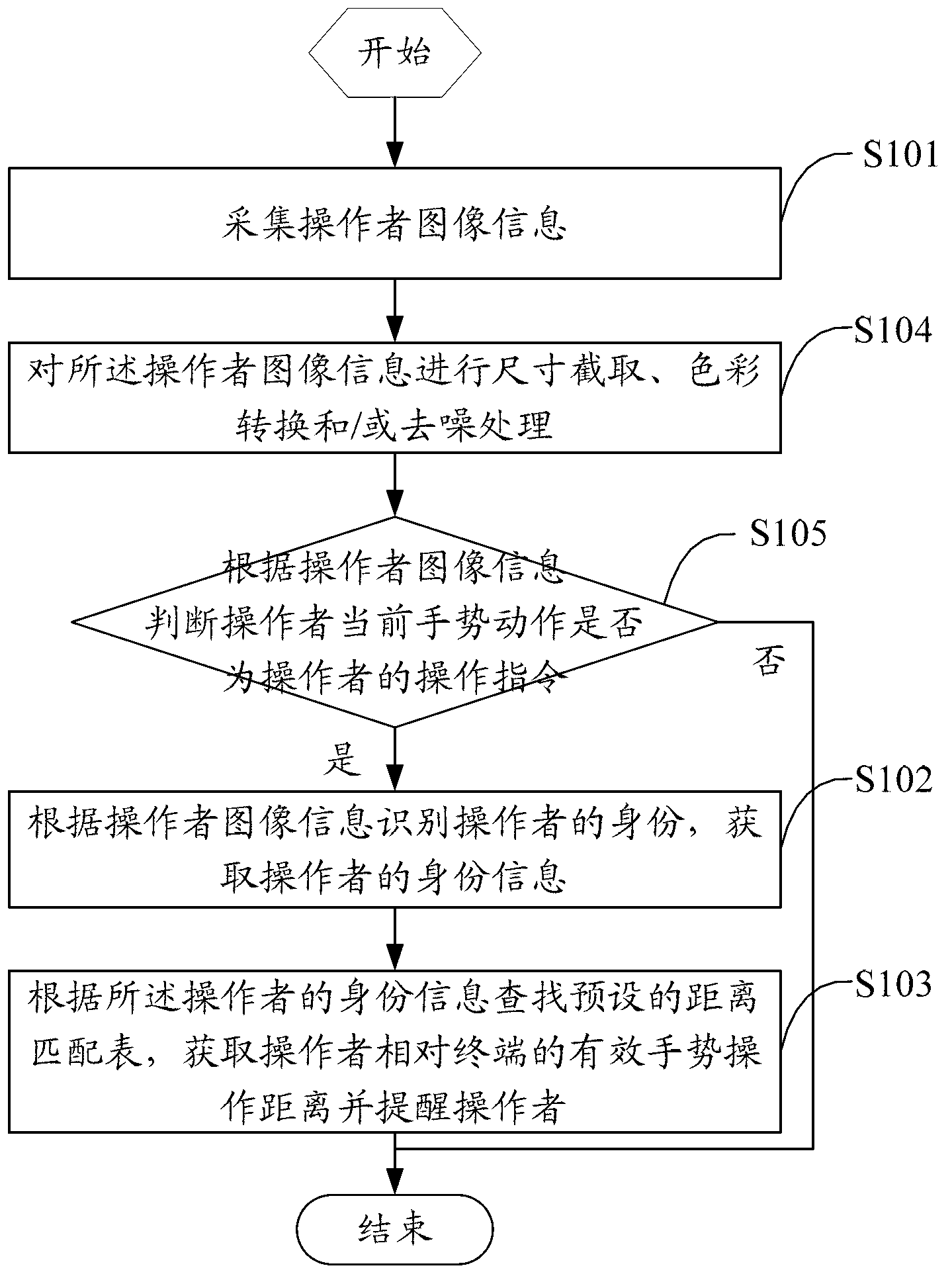
ActiveCN103295028AHigh precisionAvoid Handling InjuriesInput/output for user-computer interactionCharacter and pattern recognitionFunction tableCable television
The invention discloses a gesture operation control method, a gesture operation control device and an intelligent display terminal. The method includes: collecting operator image information; identifying the identity of an operator according to the operator image information, and acquiring identity information of the operator; and searching a preset distance matching table according to the identity information of the operator, acquiring an effective gesture operation distance of the operator relative to the terminal and reminding the operator. A gesture control system is capable of automatically reminding the effective distance of the operator relative to the intelligent display terminal, operator gesture action recognition precision of the gesture control system is improved, and operation injuries to the operator are avoided. Besides, a gesture recognition function table can be searched according to the acquired operator image information, corresponding functions of the terminal are adjusted correspondingly according to search results, and the purpose for control television functions through operator gestures is achieved.
Owner:SHENZHEN TCL NEW-TECH CO LTD
Instantaneous symmetrical component method-based current detection method for distribution static synchronous compensator (DSTATCOM)
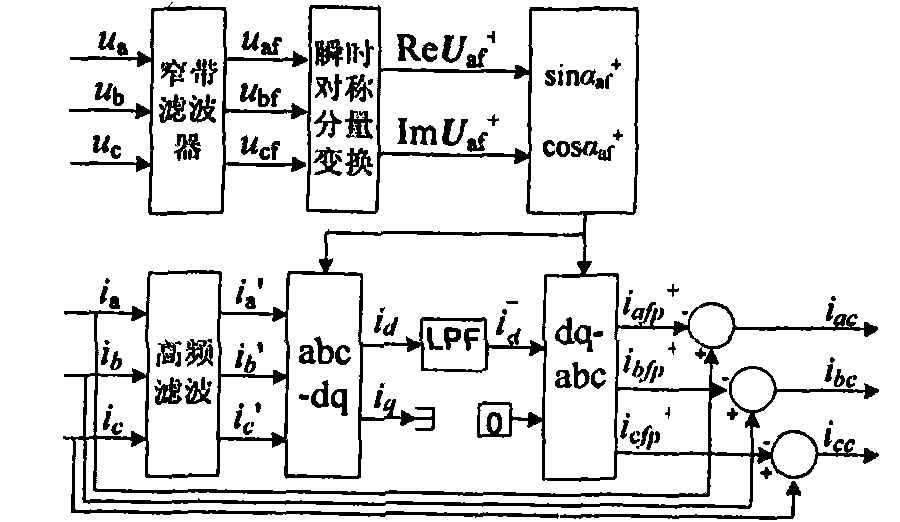
InactiveCN102081114AAvoid look-up processQuick checkReactive/real component measurementsPhase locked loop circuitSymmetrical components
The invention discloses an improved instantaneous symmetrical component method-based current detection method for a distribution static synchronous compensator (DSTATCOM), which comprises the following steps of: 1, determining a symmetrical component method and a method for expressing an instantaneous value in a phasor time domain; 2, determining the instantaneous value; 3, implementing the improved instantaneous symmetrical component method; 4, establishing a model by adopting a MATLAB simulation tool to perform simulation analysis on a conclusion; 5, filtering, converting and processing data; and 6, subtracting obtained three phases of positive fundamental active currents iafp<+>, ibfp<+> and icfp<+> from a load current to obtain required comprehensive compensation command currents iac, ibc and icc comprising harmonic components, negative sequence components and reactive components. The method avoids a complex phase shift circuit, a phase locked loop circuit, and an address generator and a table lookup process of sine and cosine function table, and eliminates errors and faults caused thereby.
Owner:STATE GRID CORP OF CHINA +3
Flexible display device and data displaying method thereof
ActiveUS20130342509A1Digital data processing detailsSubstation equipmentData displayHuman–computer interaction
Owner:SAMSUNG ELECTRONICS CO LTD
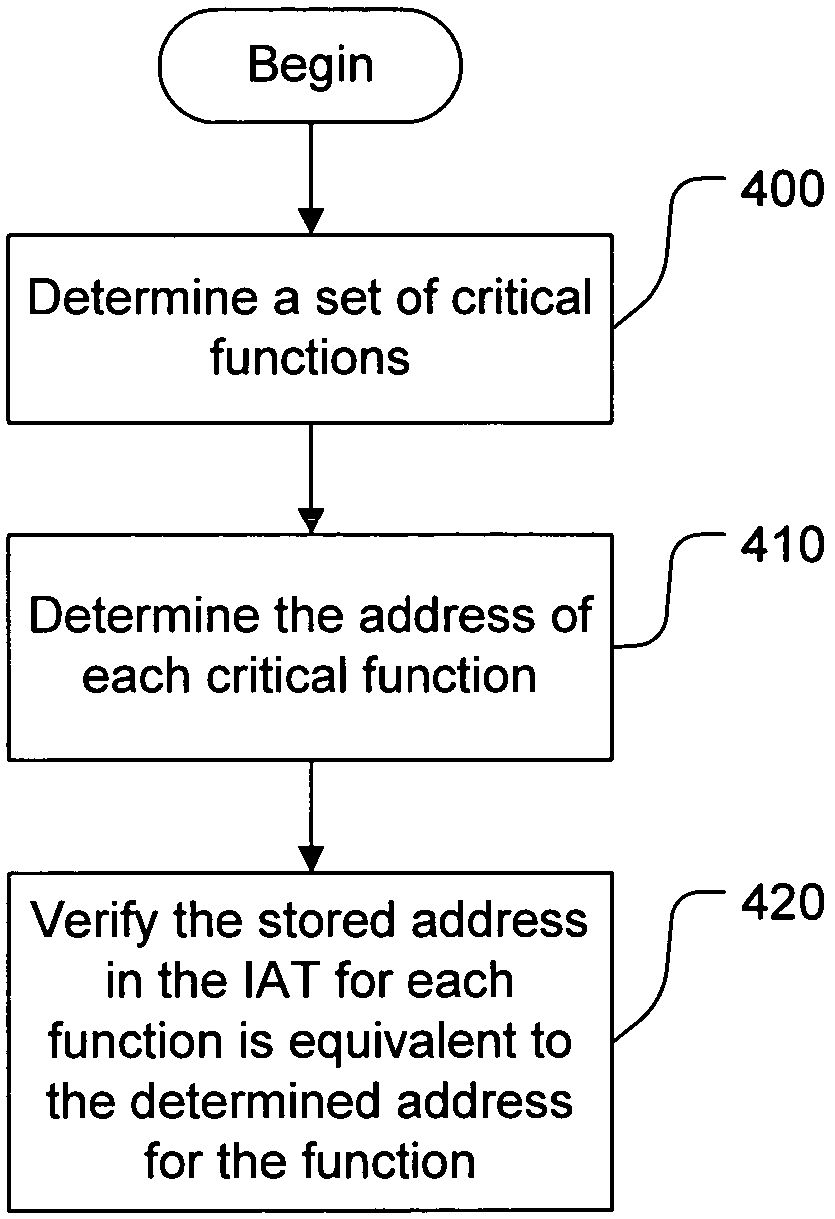
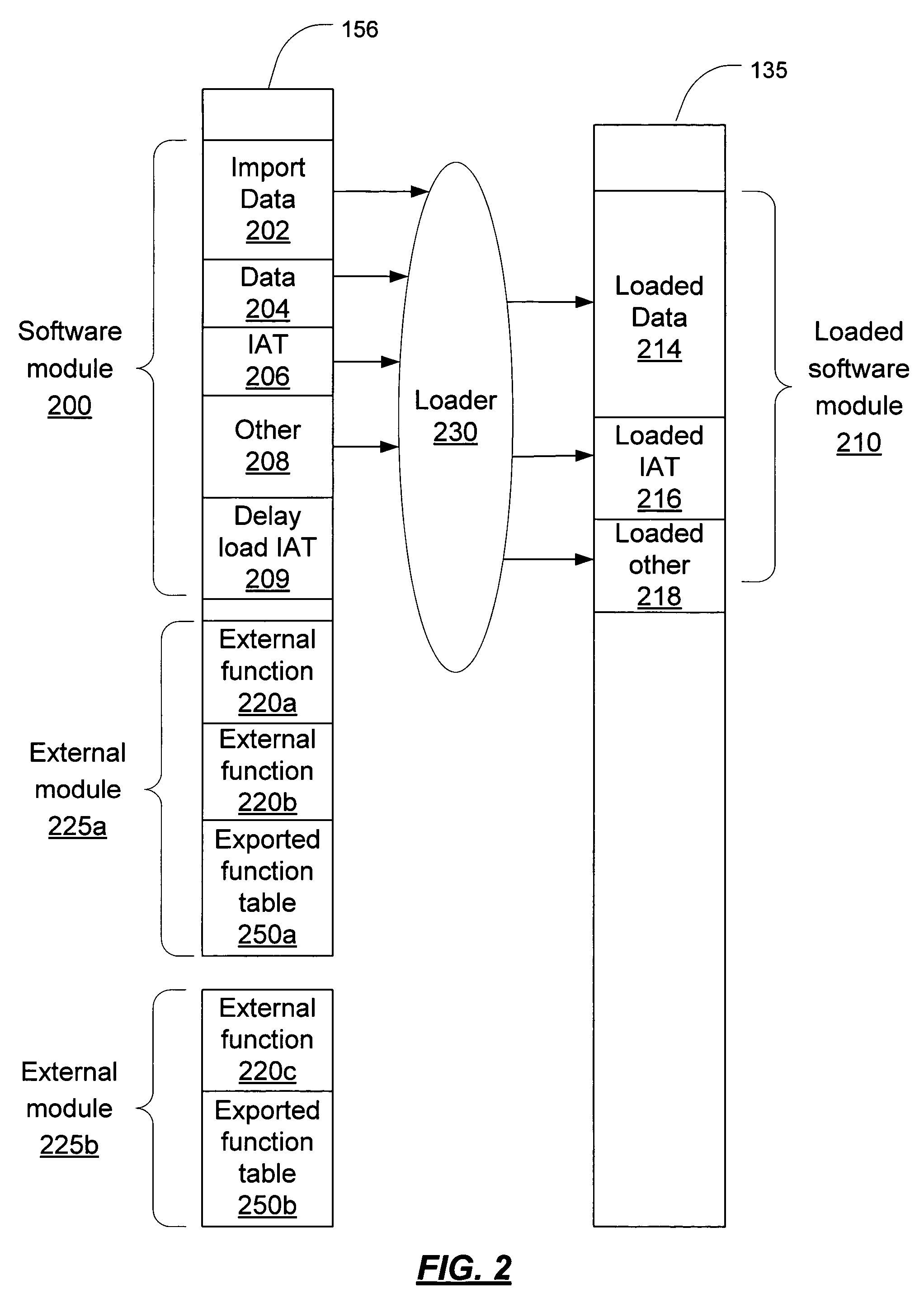
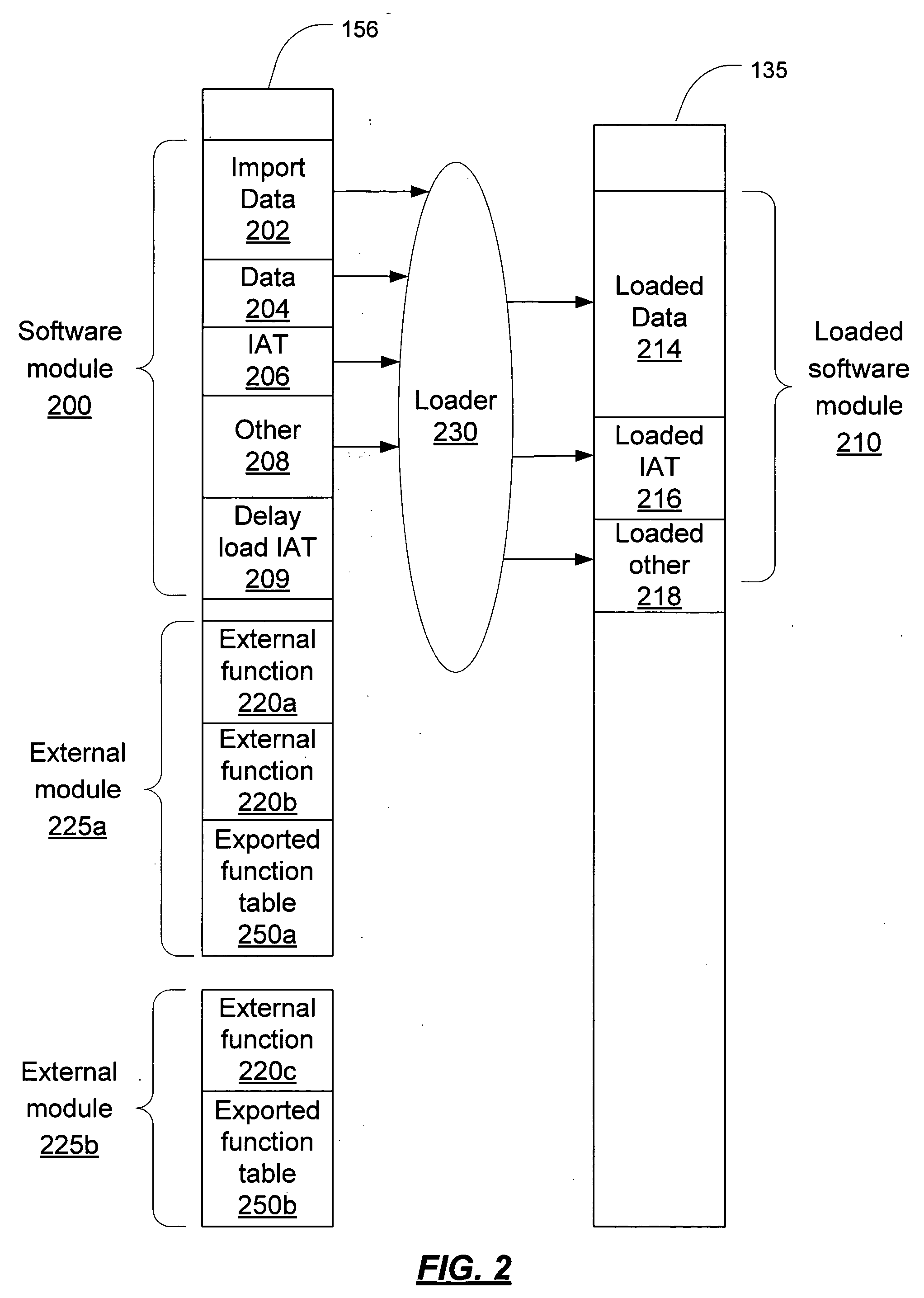
Import address table verification
ActiveUS7739516B2User identity/authority verificationUnauthorized memory use protectionComputer scienceSoftware modules
The import address table of a software module is verified in order to prevent detouring attacks. A determination is made regarding which entries in the IAT must be verified; all of the entries may be verified or some subset of the entries that are critical may be verified. For each external function, the external module containing the external function is loaded, if it is not already loaded. The function address in the exported function table is found. That address is compared to the address for the function in the IAT. Additionally, the external module, in one embodiment, is verified to ensure that it has not been modified. For a delay load IAT, a similar procedure is followed; however the delay load IAT may be periodically checked to ensure that the delay load IAT entries are either valid (indicating that the external function has been bound) or in their initial state (indicating that no binding has yet occurred).
Owner:MICROSOFT TECH LICENSING LLC
Method and device for constructing AC (aho-corasick) state machine
The invention provides a method and a device for constructing an AC (aho-corasick) state machine. The method comprises the following steps of: setting each wildcard character in each search mode as a specific character; constructing a keyword tree according to each search model; copying a goto function table of wildcard character nodes to brother state nodes, and recording input characters (transferred to the brother state nodes) as to-be-excluded characters; when a recognizing that an uncertain goto function exists, processing the uncertain goto function so as to exclude the uncertain goto function until no uncertain goto function is recognized; and excluding all to-be-excluded characters corresponding to the brother state nodes from the wildcard characters. According to the method and device for constructing the AC (aho-corasick) state machine disclosed by the invention, the AC state machine can deal with wildcard characters.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Import address table verification
ActiveUS20050198507A1User identity/authority verificationUnauthorized memory use protectionComputer scienceSoftware modules
The import address table of a software module is verified in order to prevent detouring attacks. A determination is made regarding which entries in the IAT must be verified; all of the entries may be verified or some subset of the entries that are critical may be verified. For each external function, the external module containing the external function is loaded, if it is not already loaded. The function address in the exported function table is found. That address is compared to the address for the function in the IAT. Additionally, the external module, in one embodiment, is verified to ensure that it has not been modified. For a delay load IAT, a similar procedure is followed; however the delay load IAT may be periodically checked to ensure that the delay load IAT entries are either valid (indicating that the external function has been bound) or in their initial state (indicating that no binding has yet occurred).
Owner:MICROSOFT TECH LICENSING LLC
Image processing apparatus, image processing method, recording medium recorded with image processing program, and image processing system
ActiveUS20090296150A1Improve user convenienceImprove conveniencePictoral communicationDigital output to print unitsComputer hardwareImaging processing
At an extended function server side, user information is received, and a user authentication process is executed. When the authenticity is established, an extended function table is read out, and an extended function list is generated in correspondence with users, based on the extended function table. Then, determination is made as to whether there is an extended function list set in correspondence with a user When there is an extended function list set in correspondence with a user, the extended function list is transmitted. At the MFP side, the extended function list transmitted from the extended function server is received. Then, the received extended function list is registered.
Owner:KONICA MINOLTA BUSINESS TECH INC
Information transmitting method between application and protocol stack and processing device
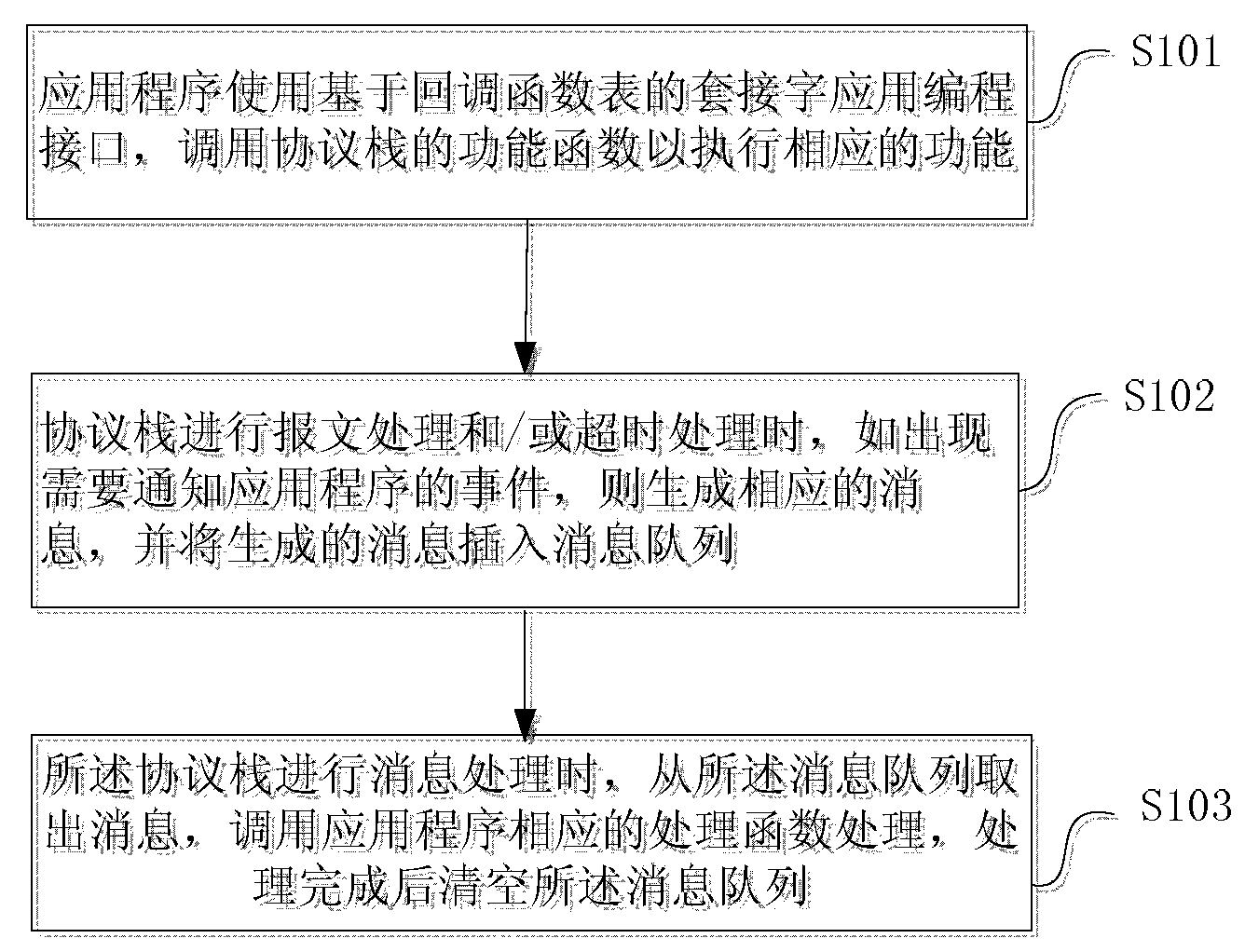
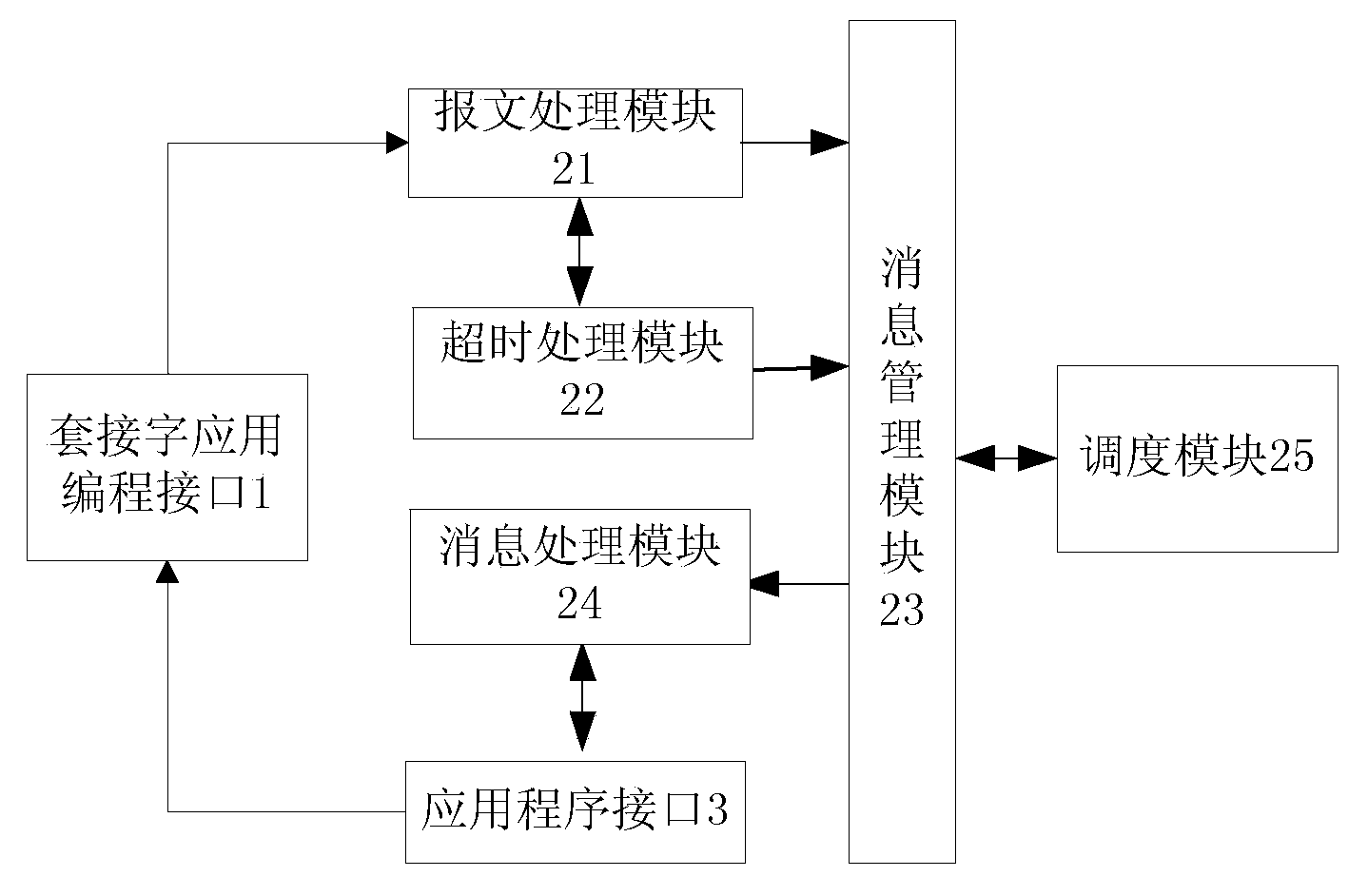
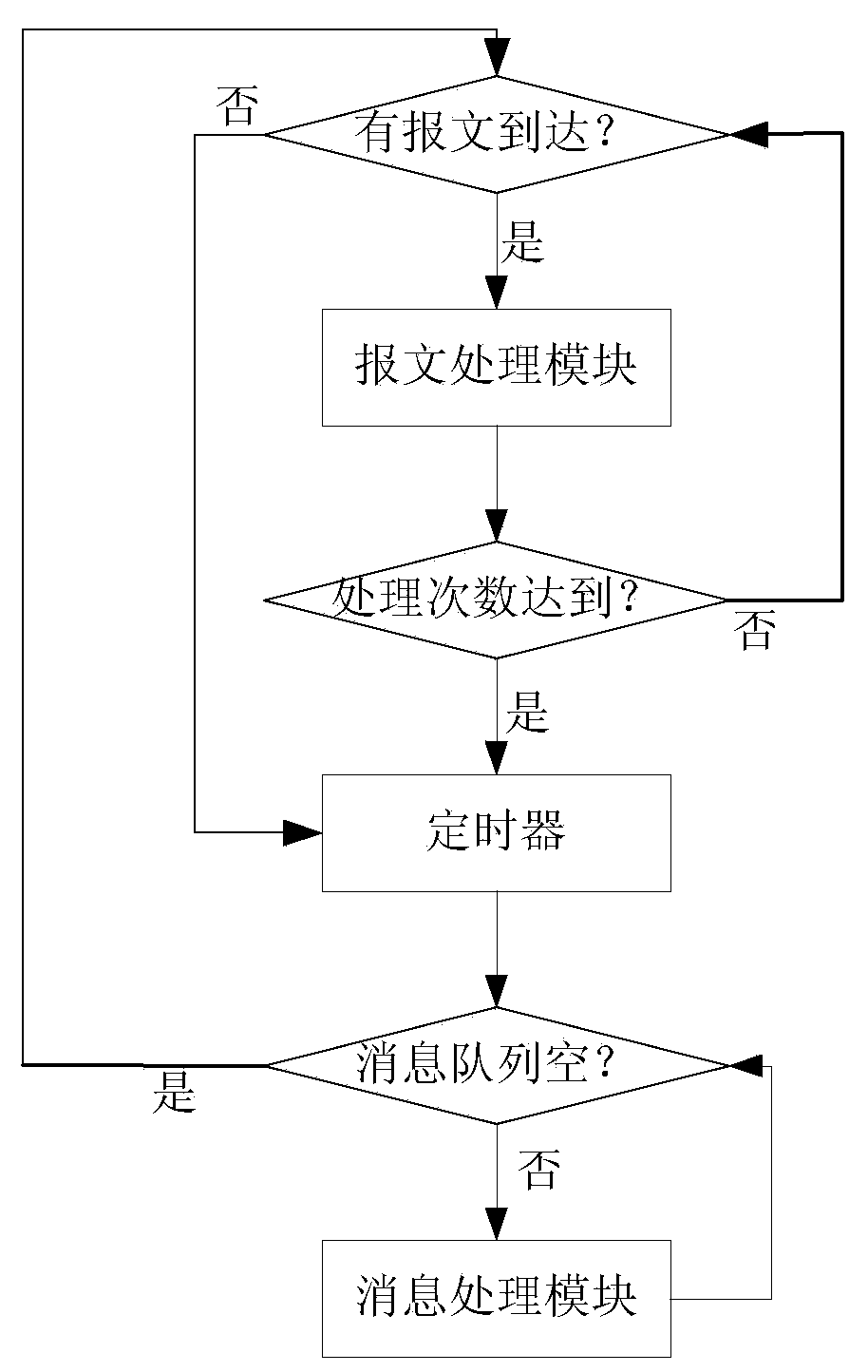
ActiveCN103888441AEasy to handleAvoid switchingProgram initiation/switchingInterprogram communicationComputer hardwarePerformance function
The invention provides an Information transmitting method between an application and a protocol stack and a processing device. The method comprises the steps that (1) an application uses a socket application programming interface based on a callback function table and calls the performance function of a protocol stack to execute a corresponding function, (2) when the protocol stack carries out packet processing and / or timeout processing, if an event that the application is needed to be notified appears, the corresponding message is generated, and the generated message is inserted into a message queue, (3) when the protocol stack carries out message processing, the message is extracted from the message queue,, the processing function corresponding to the application is called to carry out processing, and the message queue is emptied after the processing is completed. According to the method and the device, the system calling is replaced by a single task message queue polling mechanism, and the processing performance of the protocol stack is improved.
Owner:北京太一星晨信息技术有限公司
User authority management system
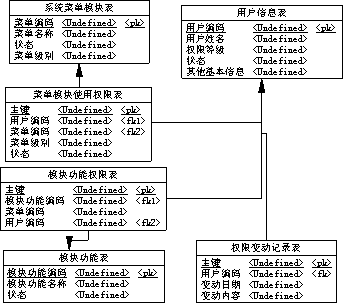
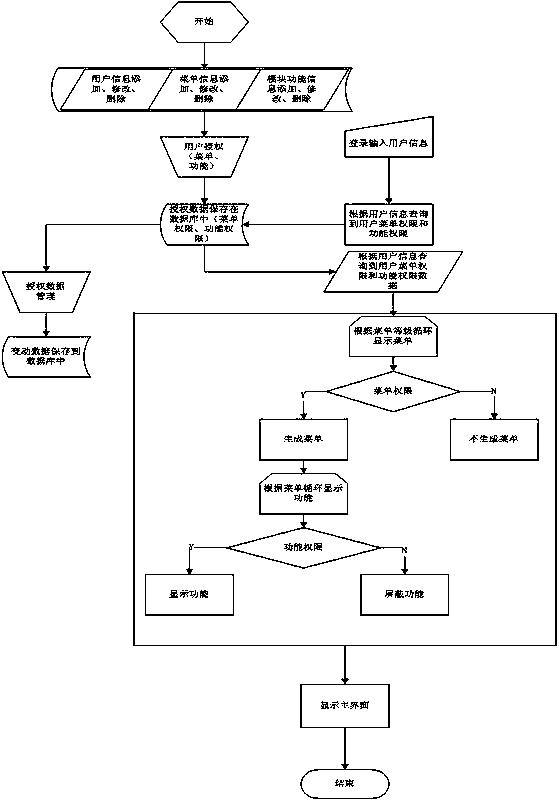
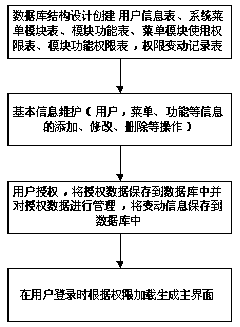
InactiveCN105373726APermissions are intuitiveImprove stabilityDigital data authenticationUser PrivilegeStructure of Management Information
The invention discloses a user authority management system, and belongs to the technical field of medical instruments. The system is characterized by comprising a design database structure and a server, wherein a user information table, a system menu module table, a module function table, a menu module using authority table, a module function authority table and an authority change record table are created in the design database structure; before the register of a user, a system manager maintains the basic information; during the register of the user, authority management is carried out on the user through the user authority data in the database; and the server is used for maintaining the basic data and authorizing the user. The user authority management system has the characteristics of being individualized, layered and simplified, making the user authority be more visual, improving the authorization stability, and being easy to manage and strong in expansibility.
Owner:NANJING PERLOVE RADIAL VIDEO EQUIP
Method and apparatus for reusing a computer software library
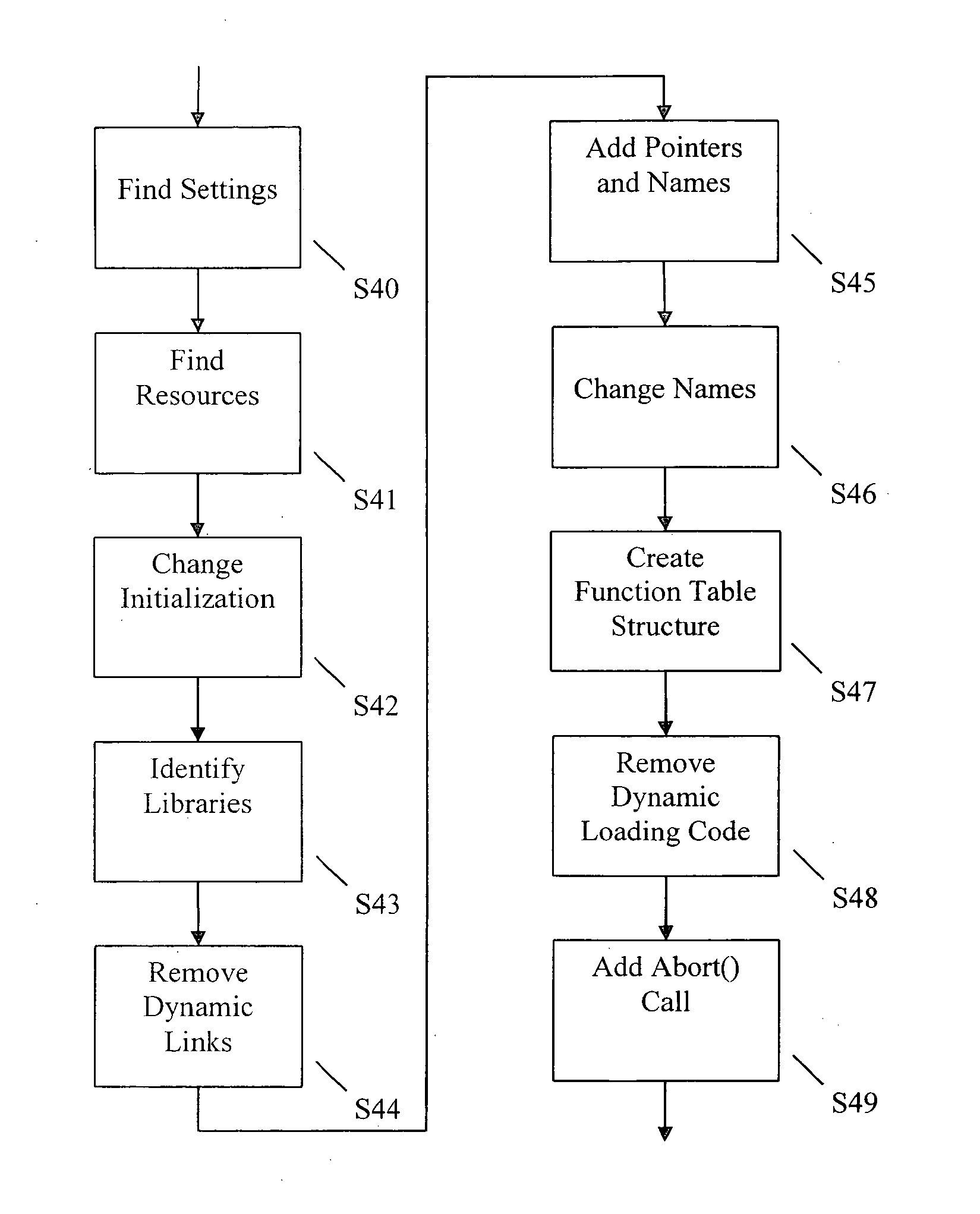
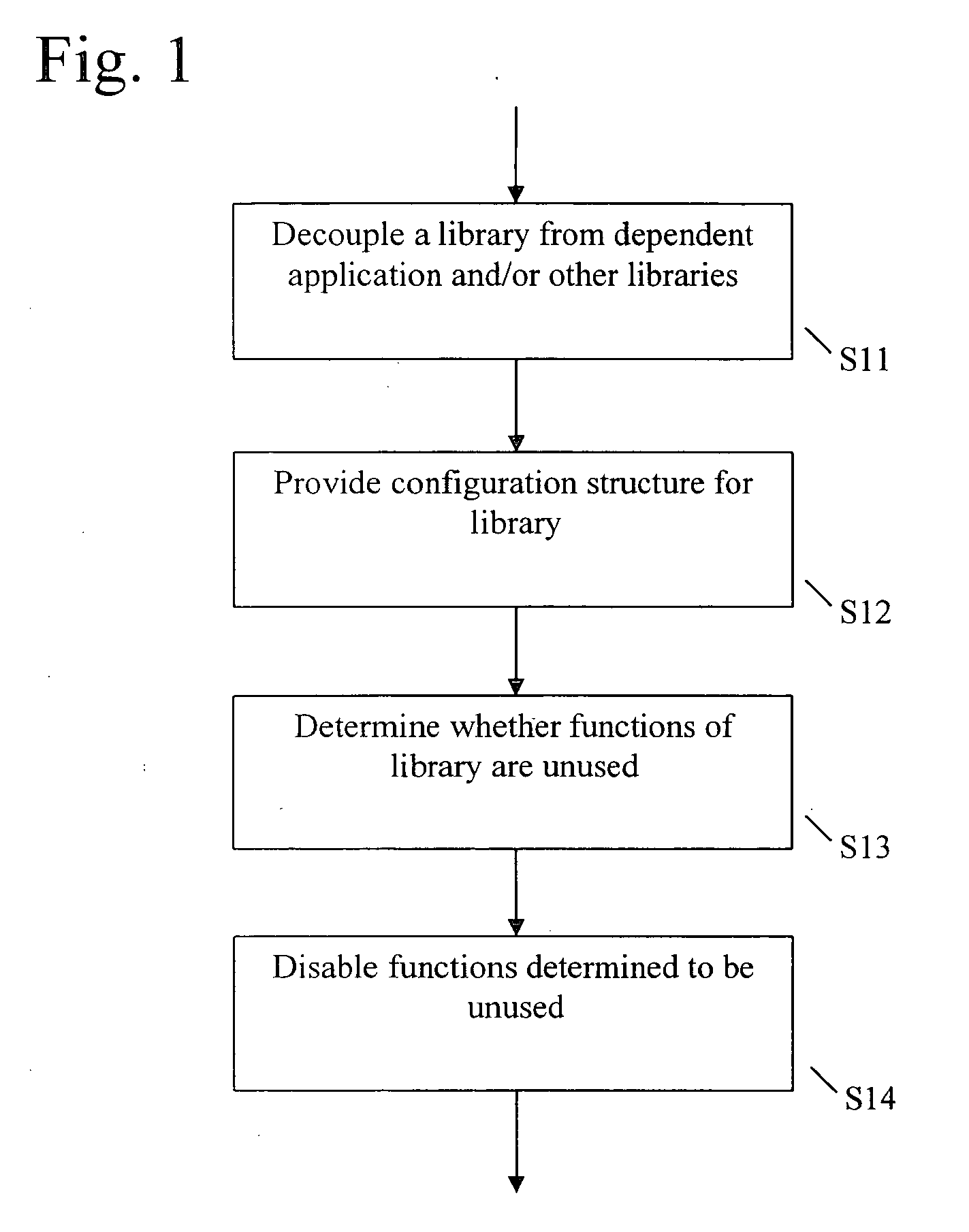
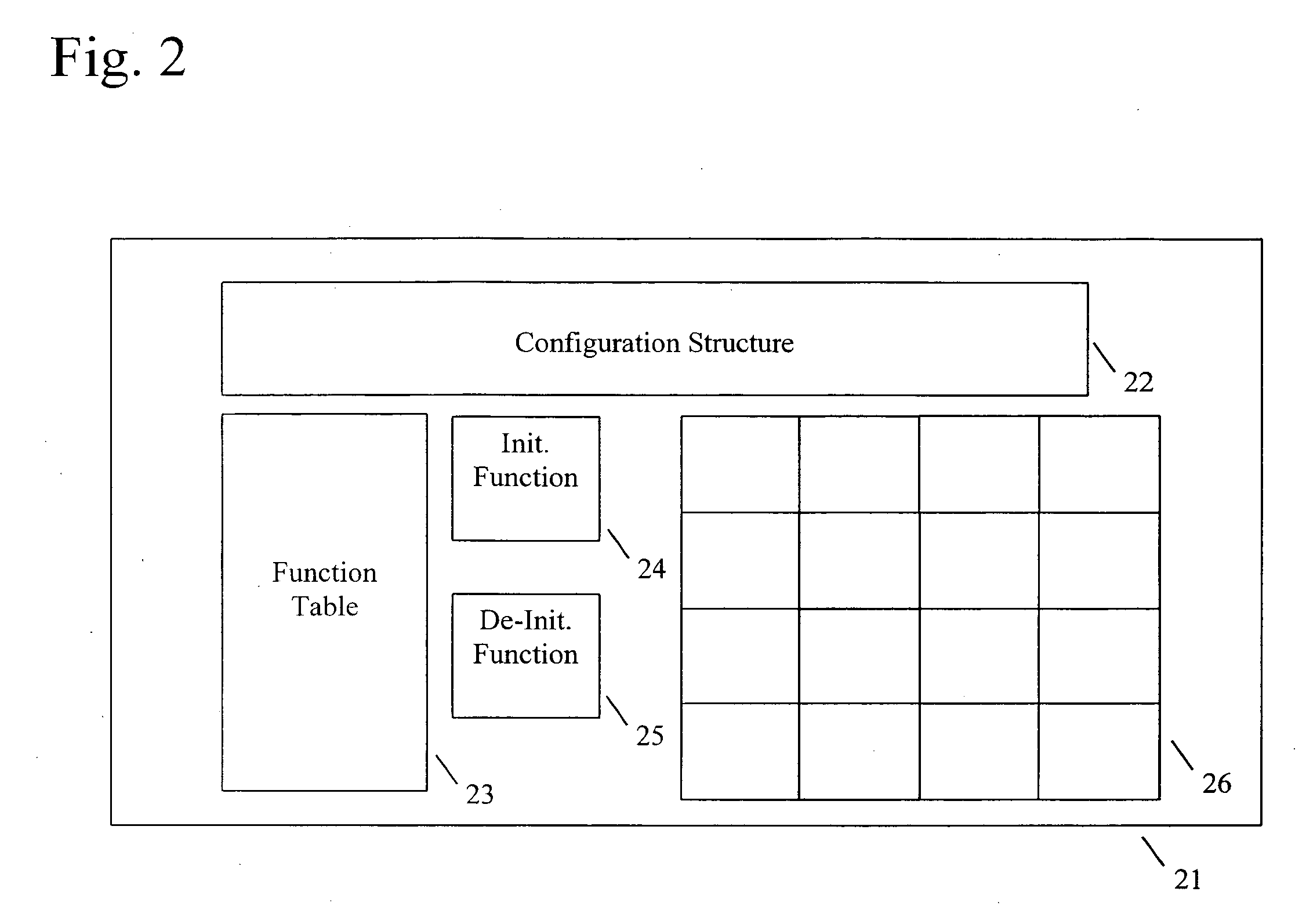
InactiveUS20050262522A1Program loading/initiatingMemory systemsProgramming languageComputer software
A method for creating a reusable library, including providing one or more functions, providing a function table for the provided one or more functions, and providing a configuration structure for communicating values between the provided one or more functions and a program that calls the reusable library. The program that calls the reusable library communicates a function table structure to the reusable library containing information as to which of the one or more functions are desirable. When those of the one or more functions that are not desirable contain dependencies, those dependencies are canceled.
Owner:COMP ASSOC THINK INC
Control equipment, control method and control program for domestic electric devices and domestic electric device products
An object of the present invention is to provide a control device and the like that controls home electrical appliances via a communication line by using function codes which are set without being specialized for specific home electrical appliances. This object is achieved by a home electrical appliance control device that controls a home electrical appliance connected via a communication line, comprising: a memory section for storing a function table for mapping function identifiers, which identify function types allocated with the focus on the function itself to functions with which the home electrical appliance is equipped, with attributes of the functions; and a control section for controlling the home electrical appliance via the communication line on the basis of the function table.
Owner:PANASONIC CORP
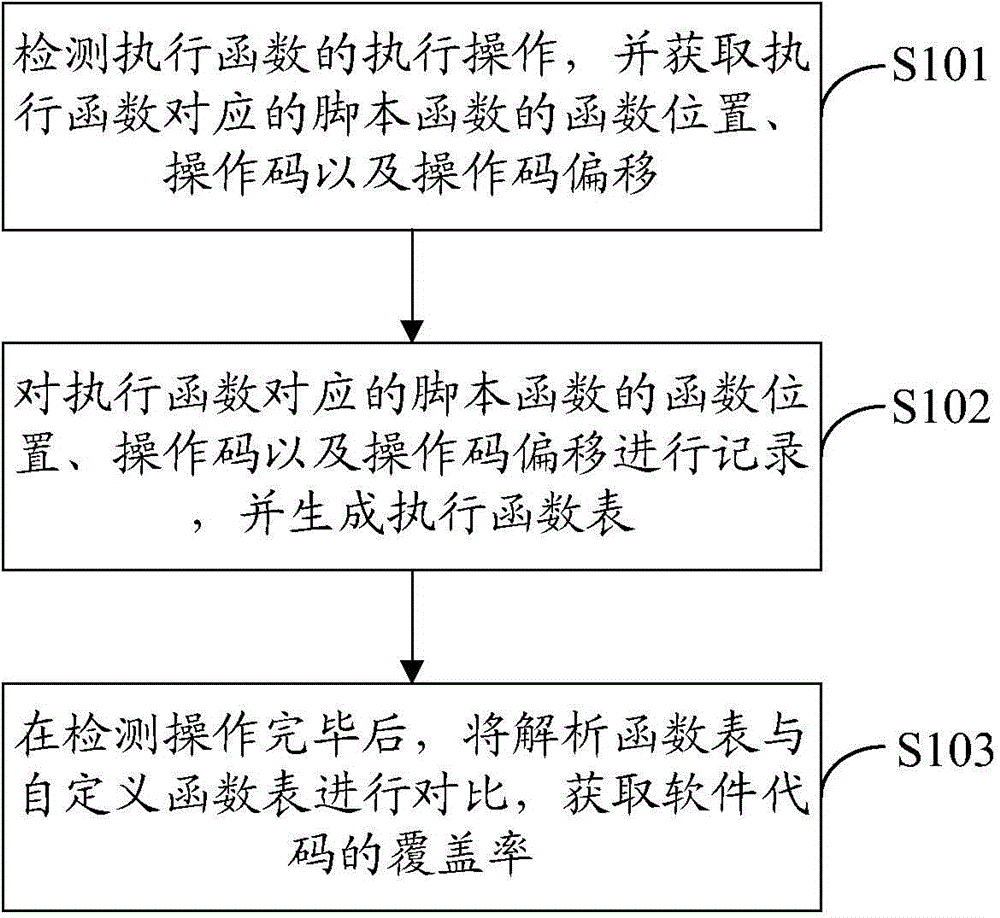
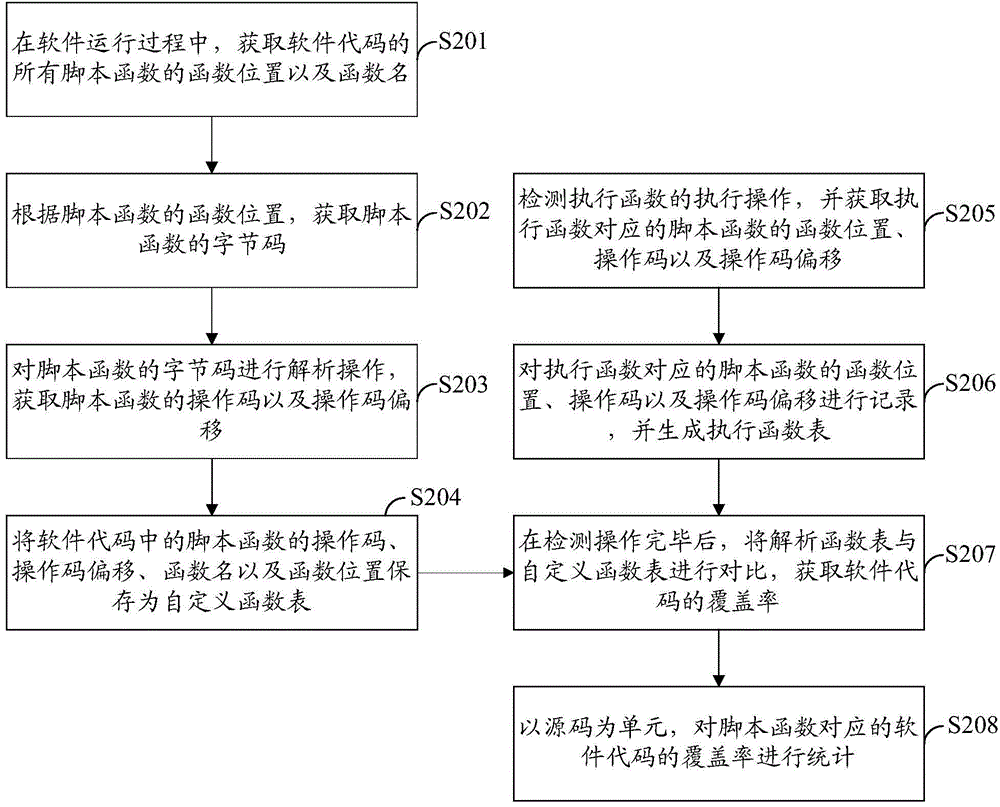
Coverage test method and coverage test device
ActiveCN105468505AThe testing process is simpleSoftware testing/debuggingCode coverageUser-defined function
The invention provides a coverage test method and a coverage test device. The coverage test method comprises the following steps: detecting an execution operation of an execution function, and obtaining a function position, an operation code and an operation code offset of a script function corresponding to the execution function; recording the function position, the operation code and the operation code offset of the script function, and generating an execution function table; and after the detection operation, comparing the execution function table with a user-defined function table to obtain the coverage of a software code. The invention further provides the coverage test device. According to the coverage test method and the coverage test device provided by the invention, the user-defined function table is compared with the execution function table to generate the code coverage, a variety of software codes can be compatible effectively by the user-defined function table, and the entire test process is simple.
Owner:TENCENT TECH (SHENZHEN) CO LTD
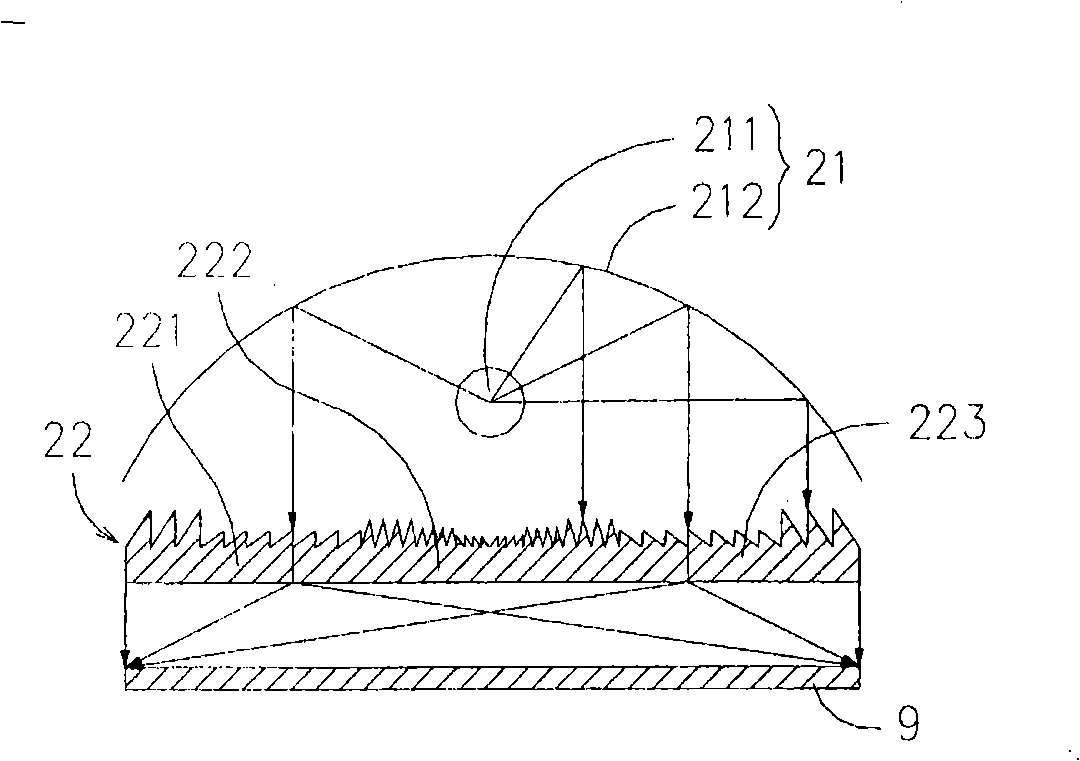
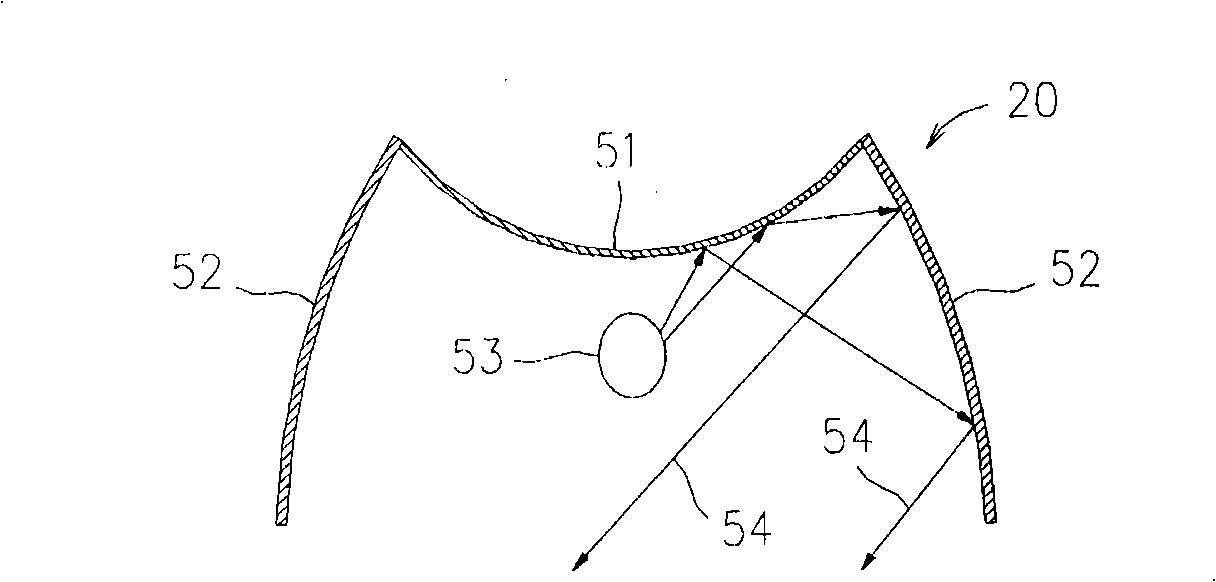
Anti-dazzle function table lamp
The present invention discloses a table lamp with glare preventing function. The table lamp comprises a table lamp main body, a light source and a microstructure light control component. The light source and the microstructure light control component are arranged on the table lamp main body. The microstructure light control component is formed by combining a Fresnel microstructure and a light control structure component. The Fresnel microstructure is used for dispersing or bunching light rays provided by the light source. The dispersing structure is used for controlling the projecting direction of the light rays so as to achieve the aims of preventing the production of the glares and enhancing the uniformity of luminescence.
Owner:IND TECH RES INST
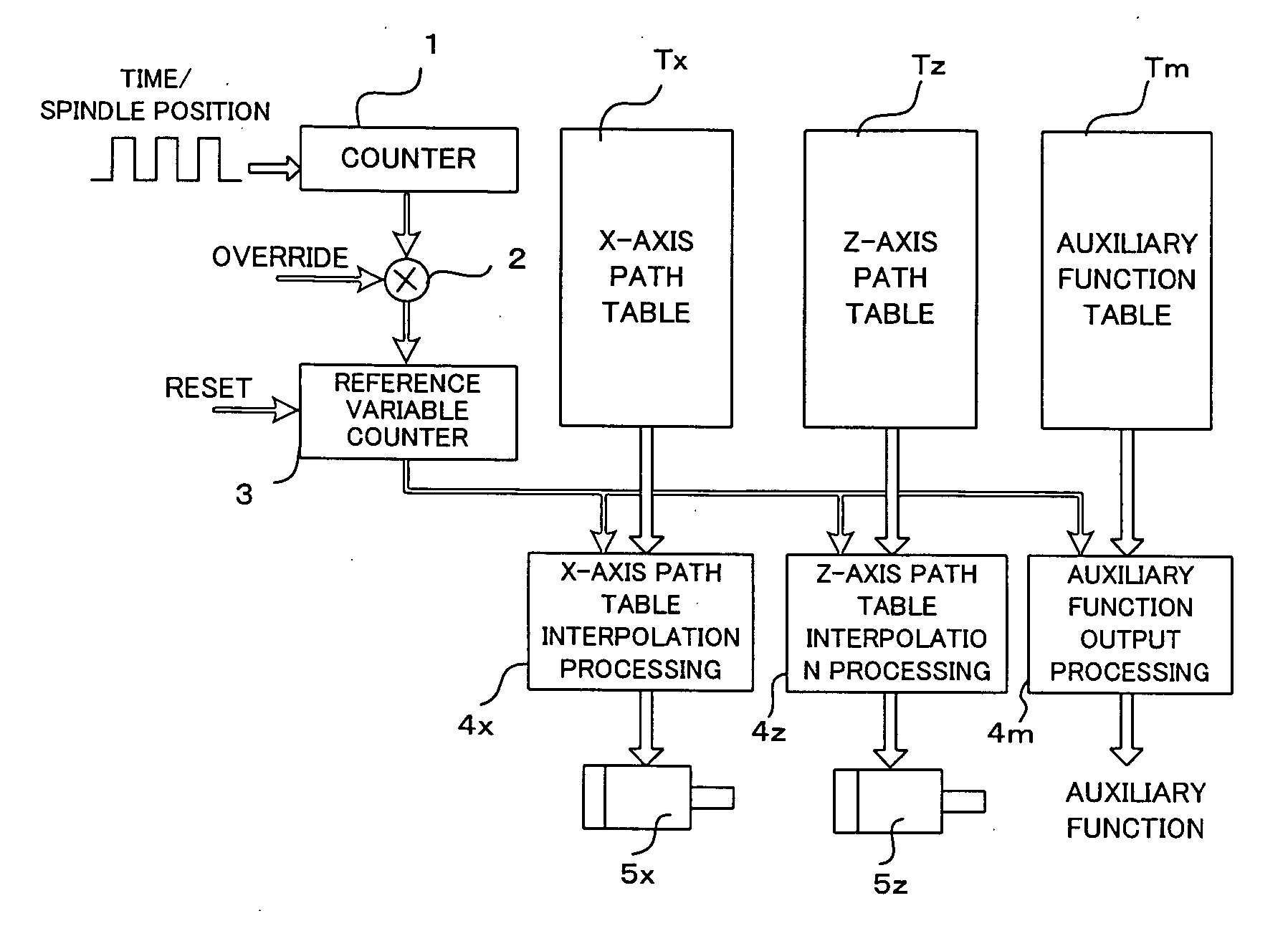
Numerical controller
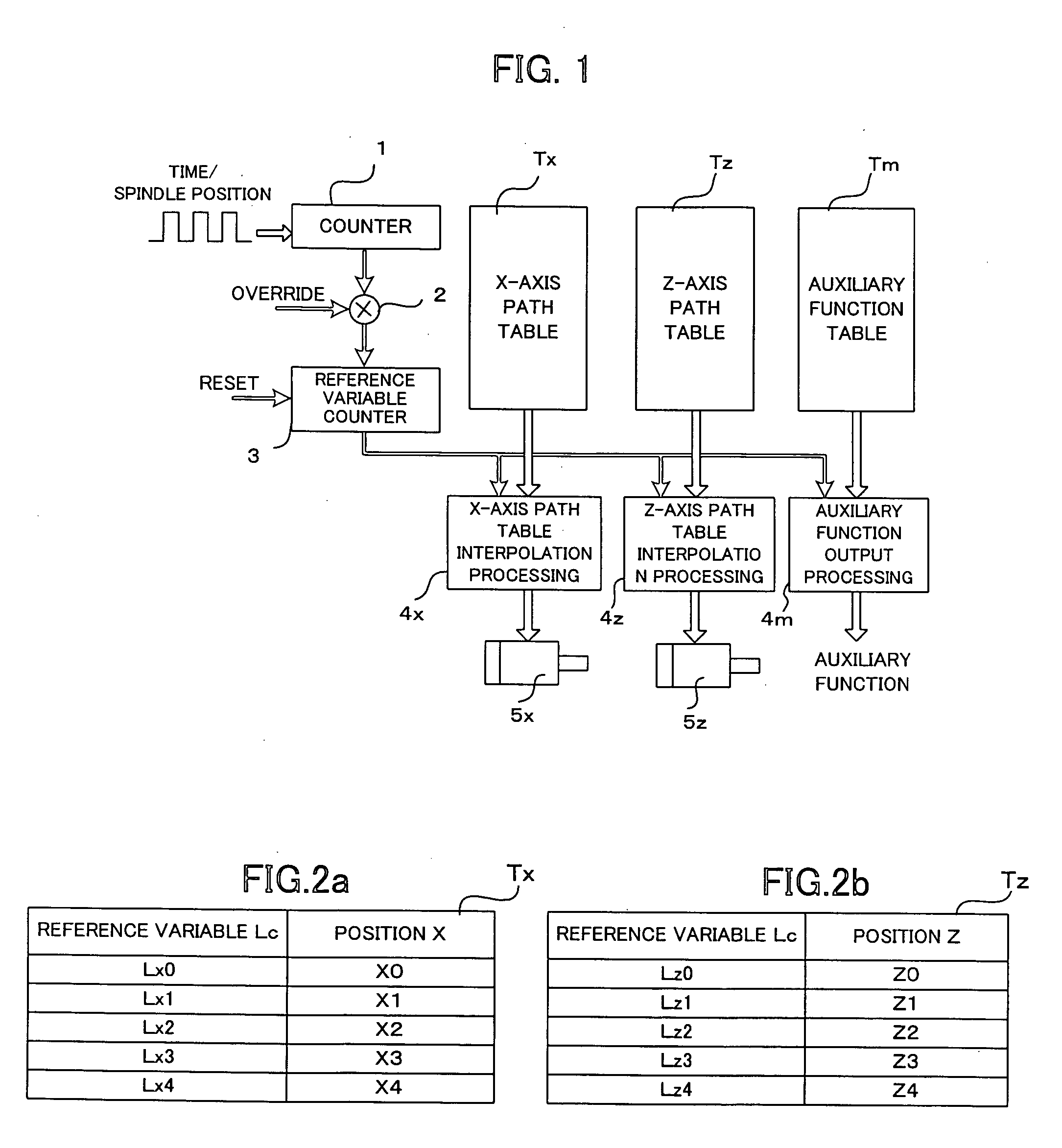
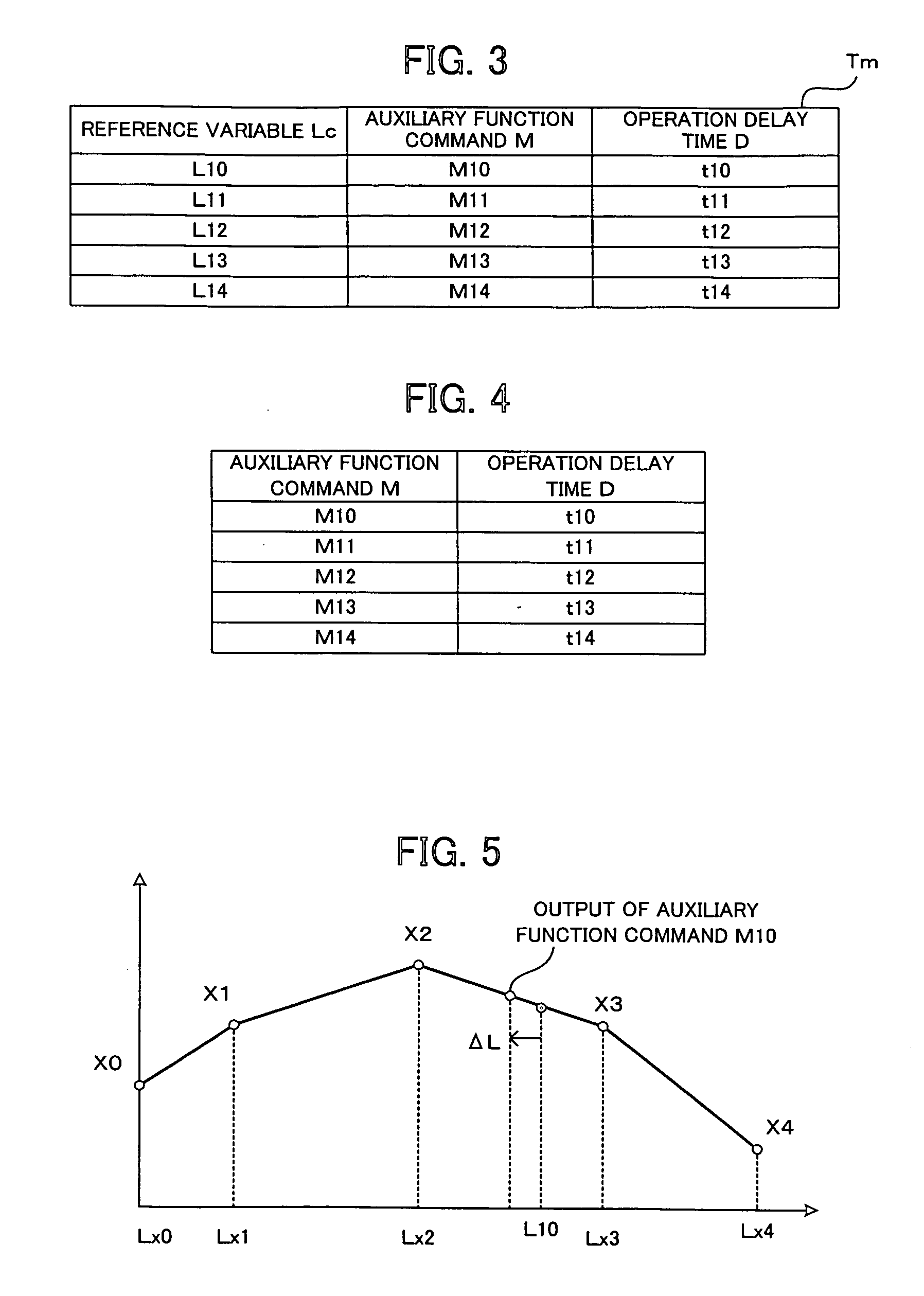
A numerical controller capable of operating an auxiliary function at a target time or spindle position in performing operation based on table format data. An auxiliary function table is stored with auxiliary function commands M to be outputted corresponding to commanded reference times Lc and their corresponding operation delay times D. A reference time L is updated based in accordance with an override value. An auxiliary function command M and its corresponding operation delay time D are read from the auxiliary function table. The delay time D is corrected with the override value, and a reference time prior to a commanded reference time Lc by a margin equivalent to the corrected delay time is set as a command time Lr. If an override is entered, the delay time is corrected for the override amount and modified into an overridden reference time unit, and a command time for an auxiliary function is obtained and outputted based on the reference time unit. Thus, the auxiliary function is performed appropriately at a commanded value Lc of the reference time.
Owner:FANUC LTD
Method for mobile phone information safety protection
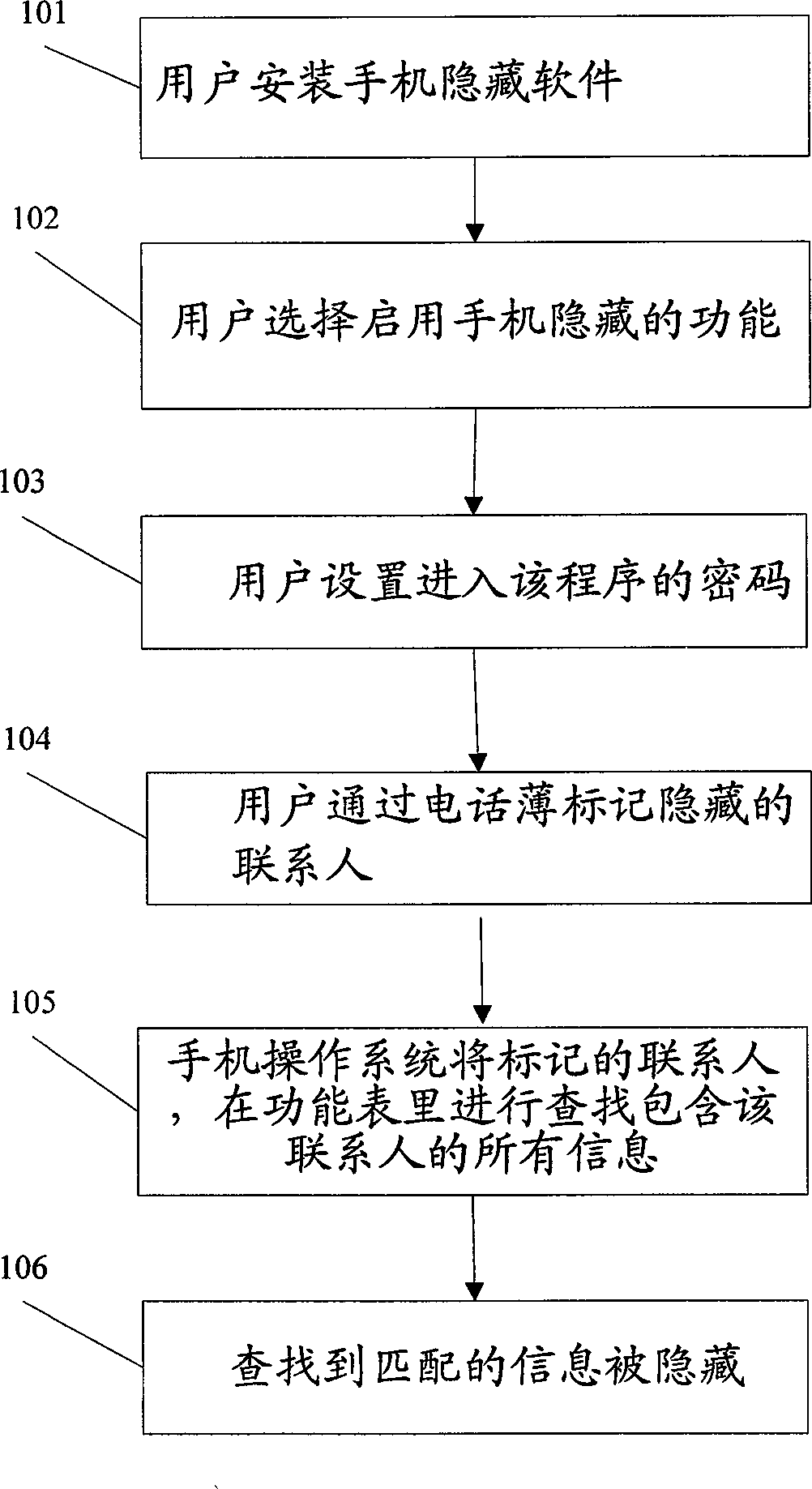
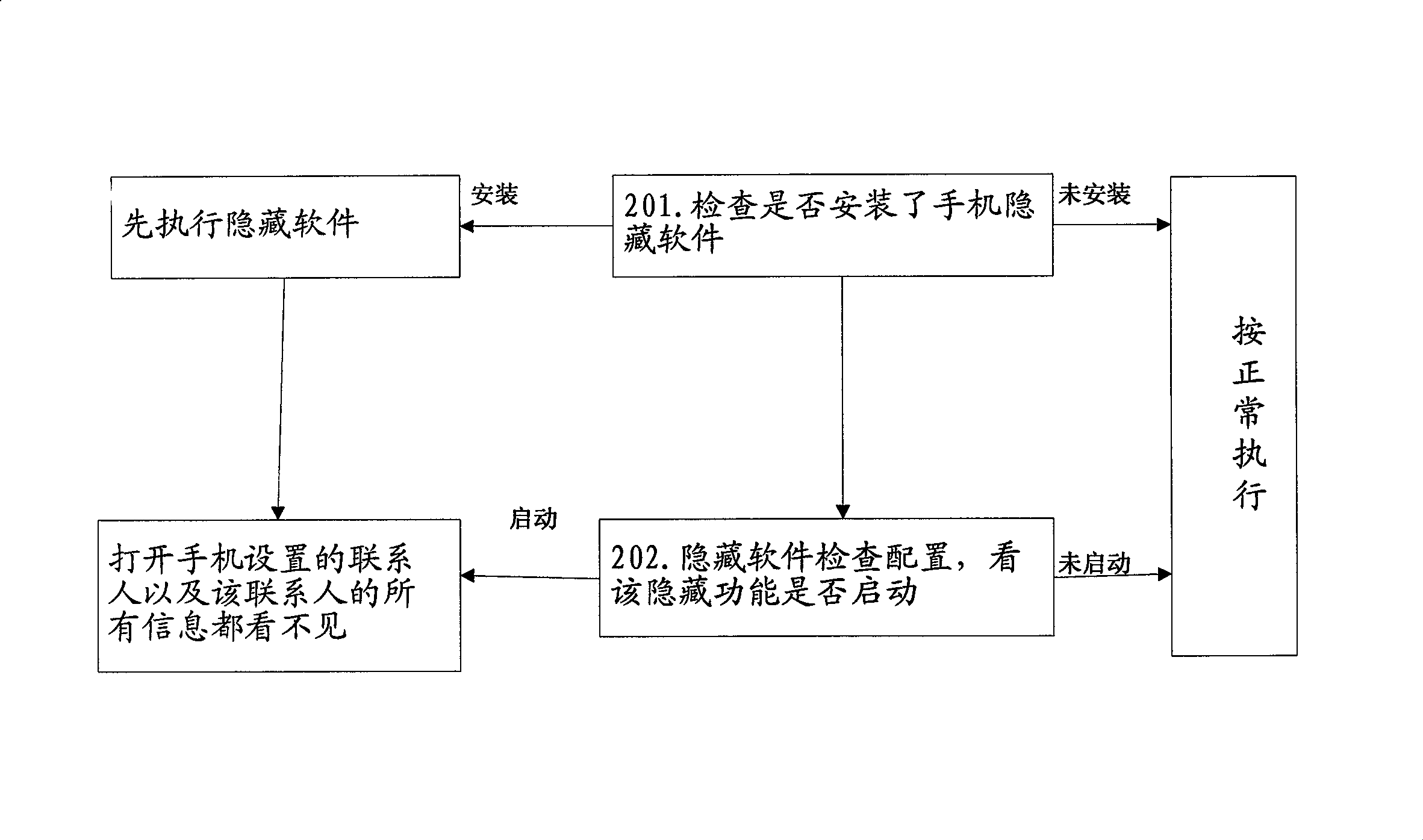
The invention provides a safety protection method for mobile phone information, which comprises the following steps: the user installs mobile phone hiding software; the user opens the function of mobile phone hiding; the user sets a password for entering the program; the user marks the contacts need to be hidden through a telephone directory; the marked contacts and all the information comprising the contacts which can be found in the function table are hidden by the operating system of the mobile phone. After the user sets to hide a certain contact in the telephone directory according to the information needs to be hidden, all the information of the contact is hidden. Therefore, even if the mobile phone is lost or other people are available to the mobile phone under conscious or unconscious conditions or even open the mobile phone and the files inside such as the telephone directory, the information of the set contact cannot be found.
Owner:BEIJING YIQI TELECOMM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com