Method for mobile phone information safety protection
A technology for security protection and mobile phone information, which is applied in security devices, telephone communications, wireless communications, etc., and can solve problems such as setting passwords and not trusting them
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
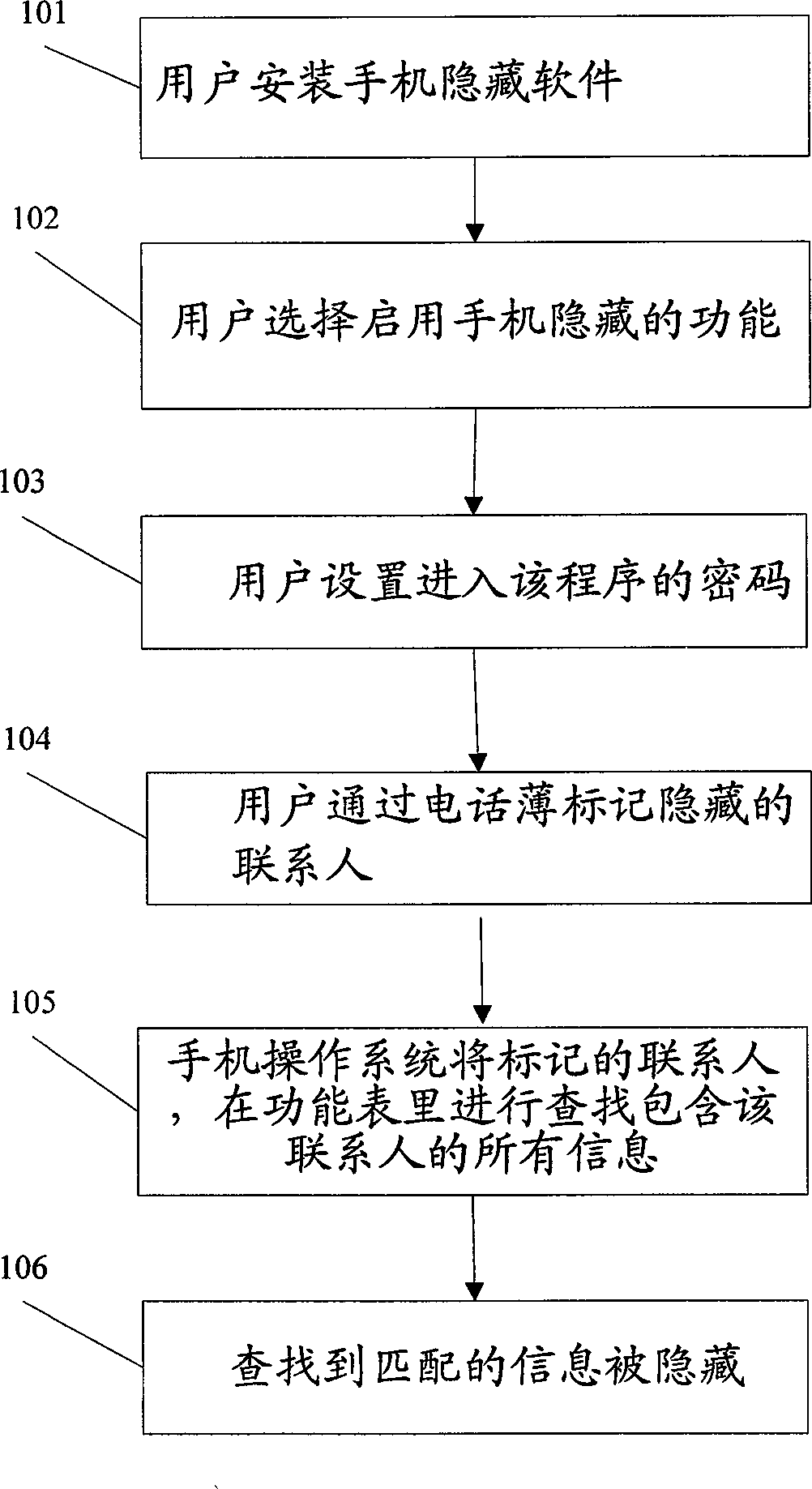
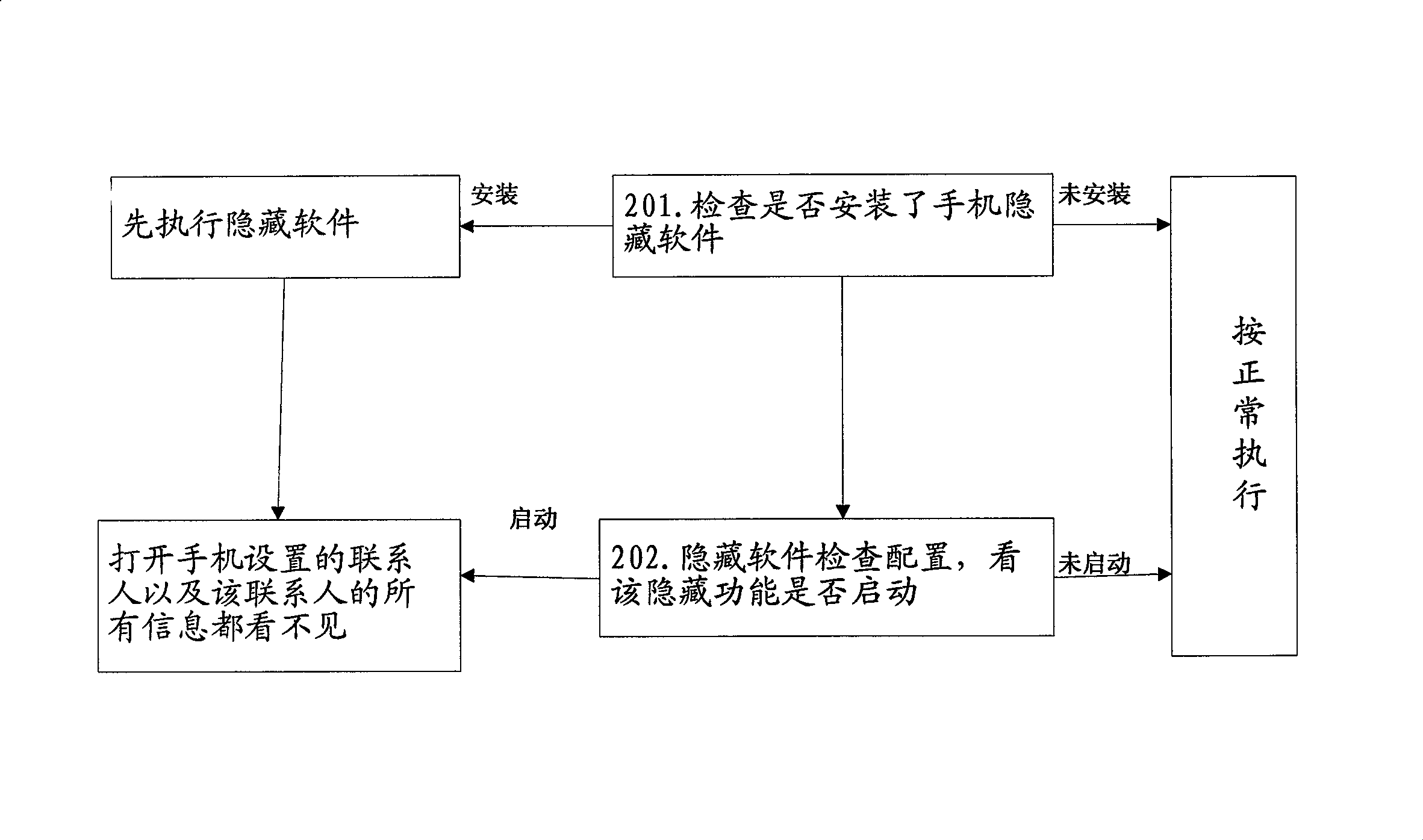
[0024] The function realized by the invention: the user sets the hiding function for the contacts in the phone book, finds all the information related to the contact, and then hides all the information, so that other people cannot find all the information of the contact even if they open the mobile phone.
[0025] Will describe in detail below in conjunction with accompanying drawing,
[0026] Such as figure 1 As shown, the steps for the user to set the contact hiding function:
[0027] 101. User installs mobile phone hidden software:
[0028] This software adds a layer of shell before the program launcher of the mobile phone operating system, that is to say, the mobile phone operating system needs to run the software before starting the mobile phone function program.
[0029] 102. The user chooses to enable the hidden function of the mobile phone:
[0030] 103. The user sets the password, which is the password to enter the program. The default password is 1234. If it is no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com