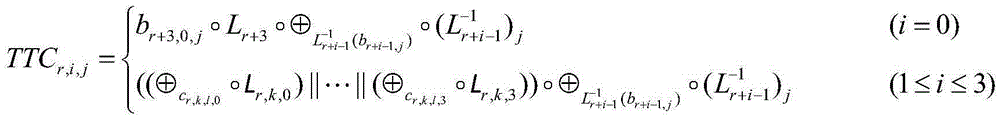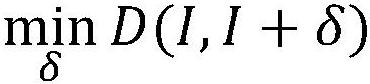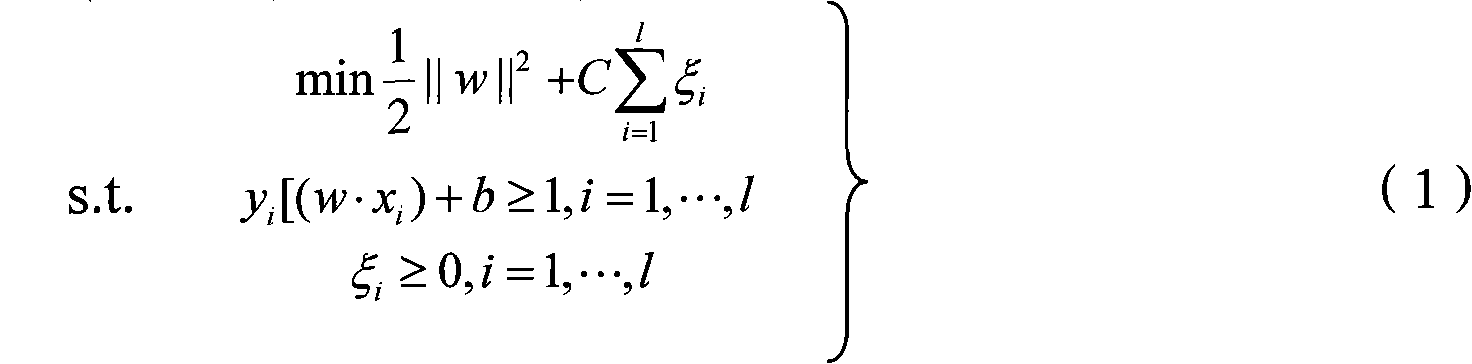Patents
Literature
267 results about "White box" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A white box (or glass box, clear box, or open box) is a subsystem whose internals can be viewed but usually not altered. Having access to the subsystem internals in general makes the subsystem easier to understand but also easier to hack; for example, if a programmer can examine source code, weaknesses in an algorithm are much easier to discover. That makes white-box testing much more effective than black-box testing but considerably more difficult from the sophistication needed on the part of the tester to understand the subsystem.
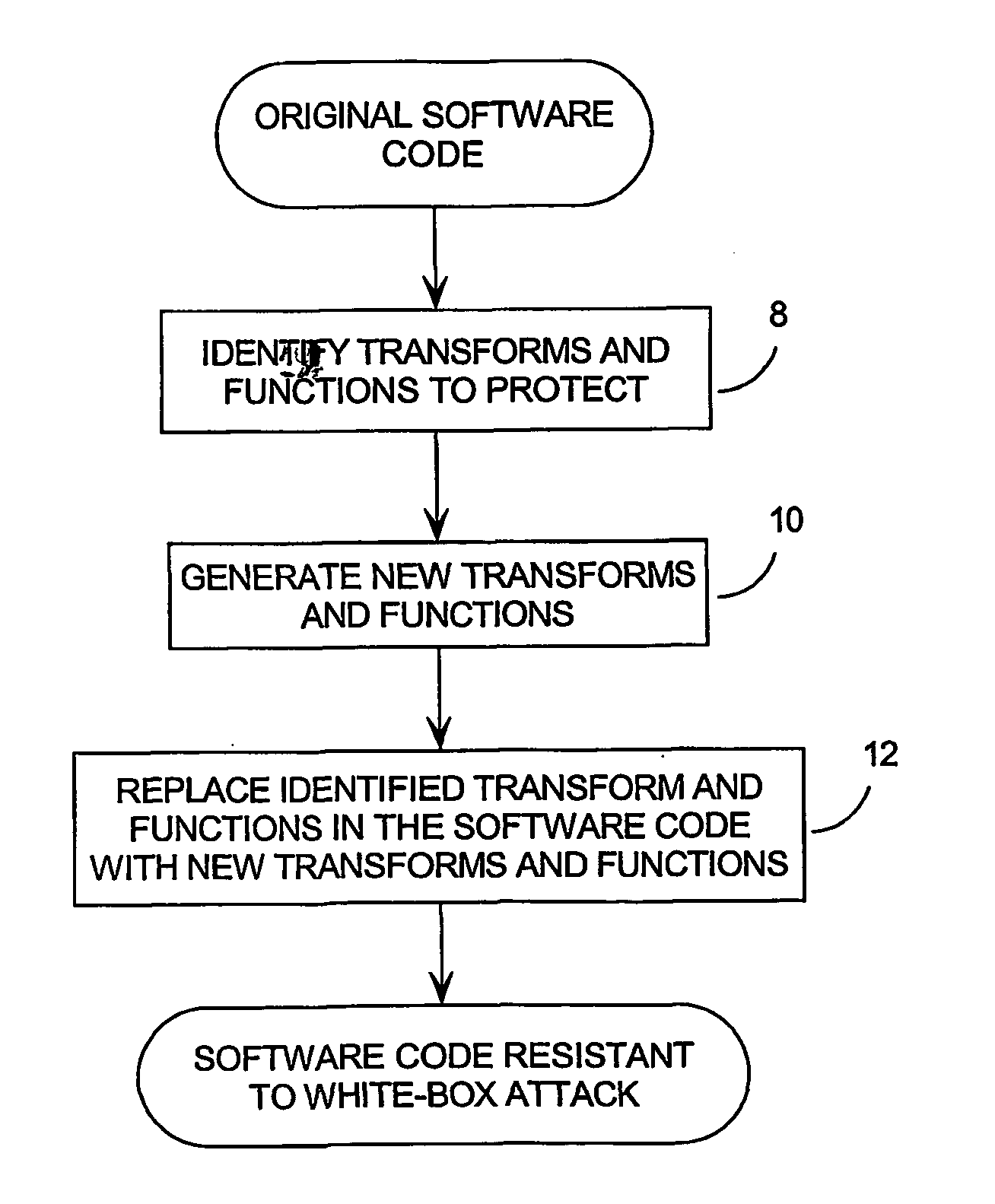
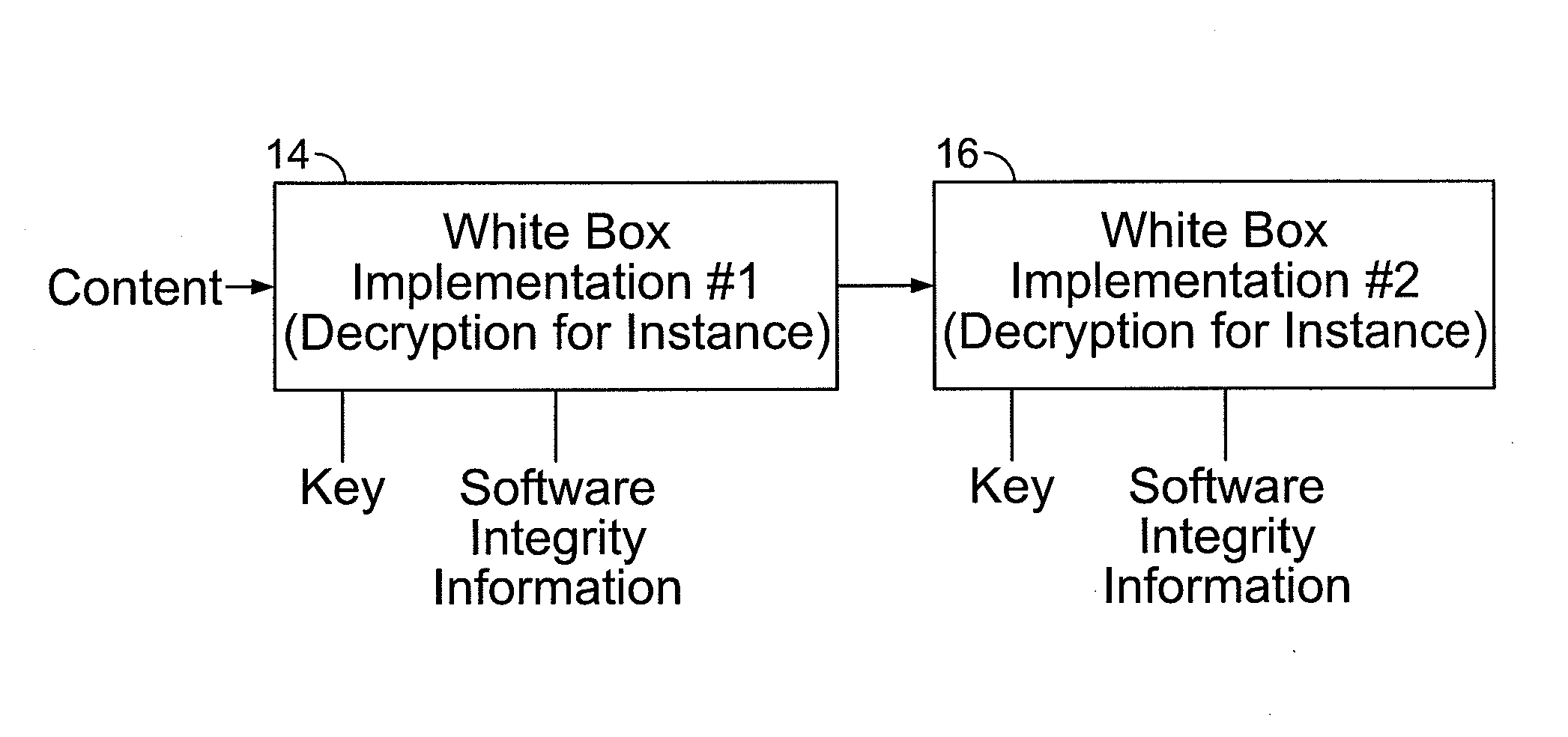
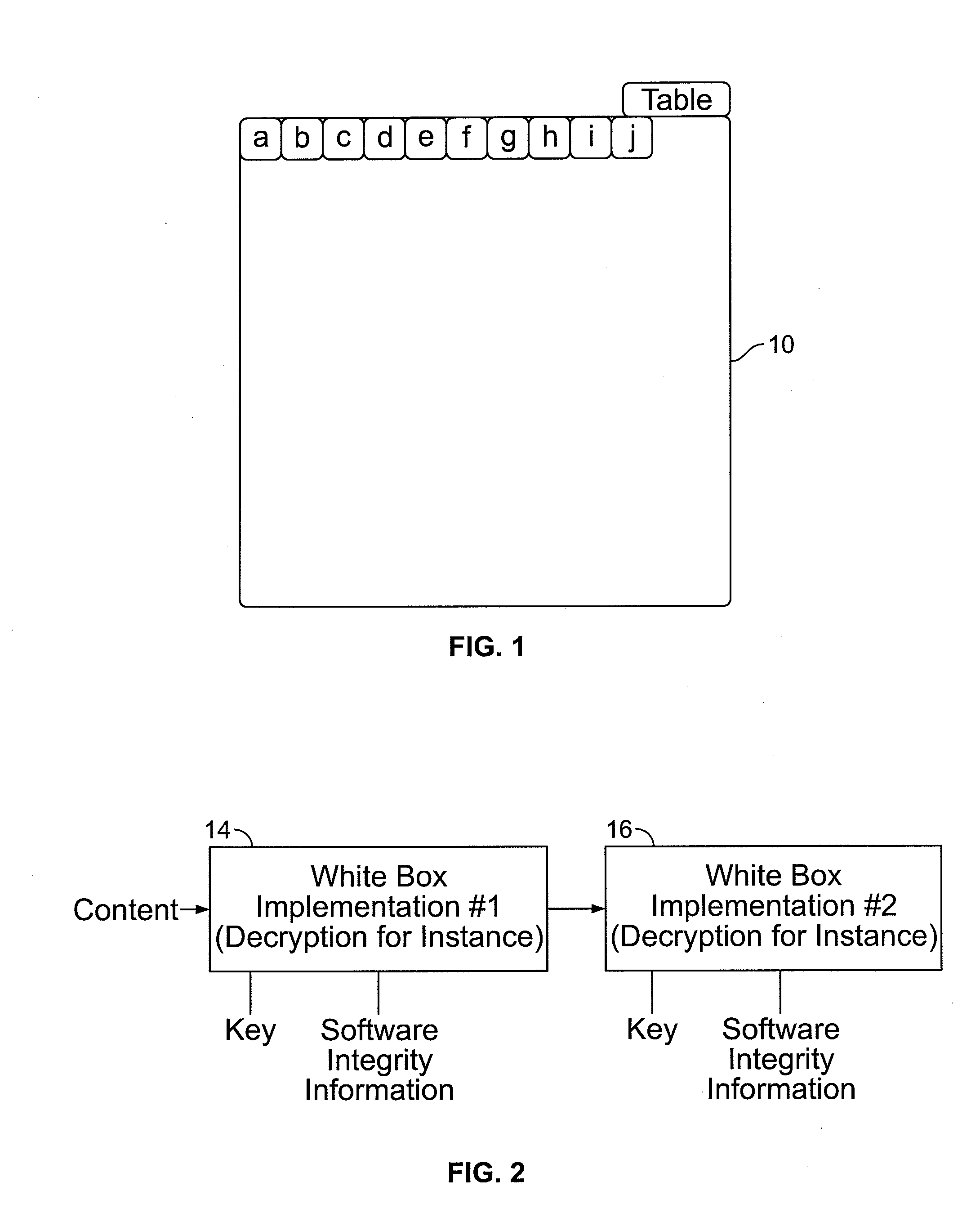
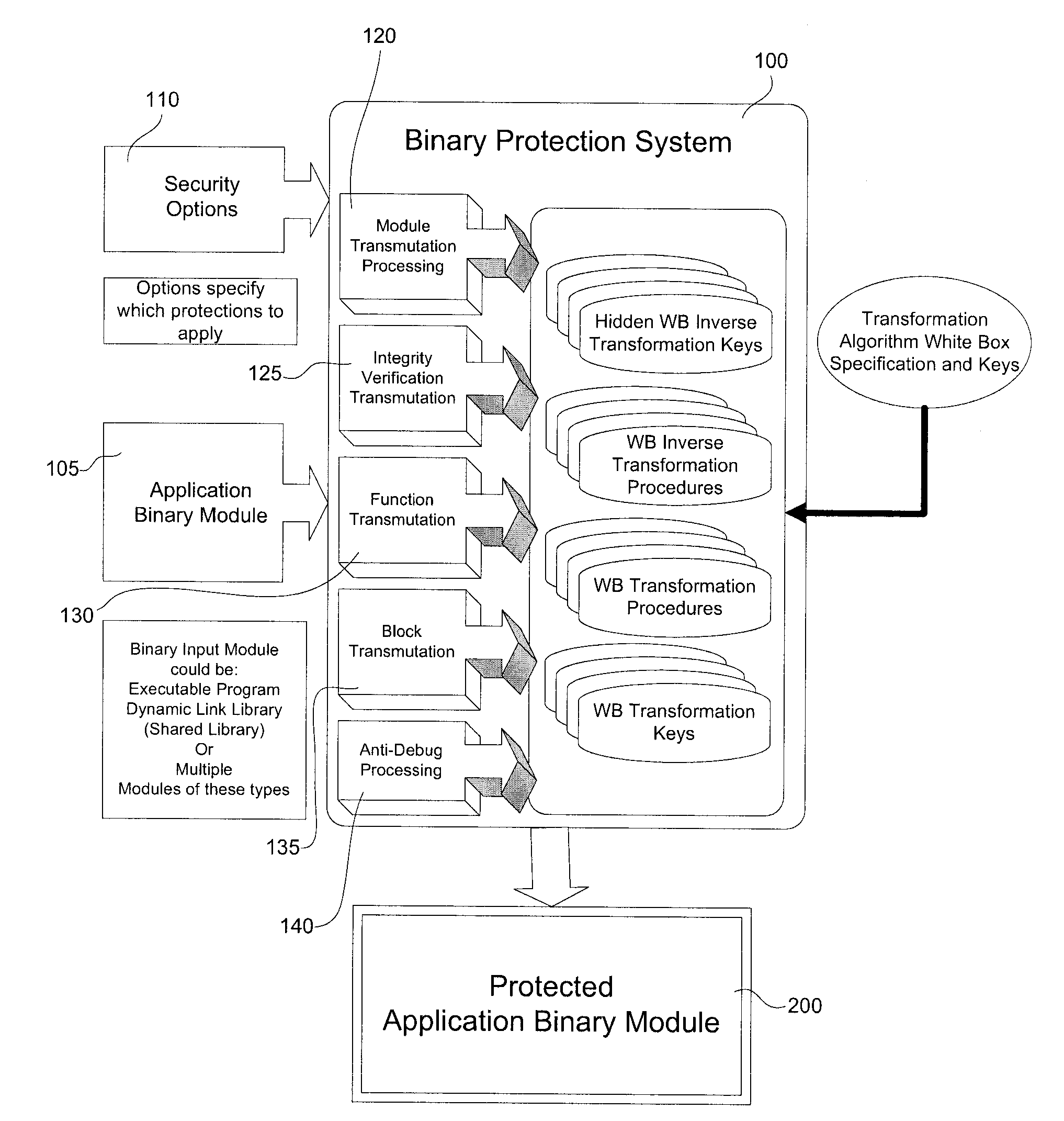
System and method for protecting computer software from a white box attack
InactiveUS20040139340A1Small costLow costUnauthorized memory use protectionHardware monitoringEncryption systemVisibility
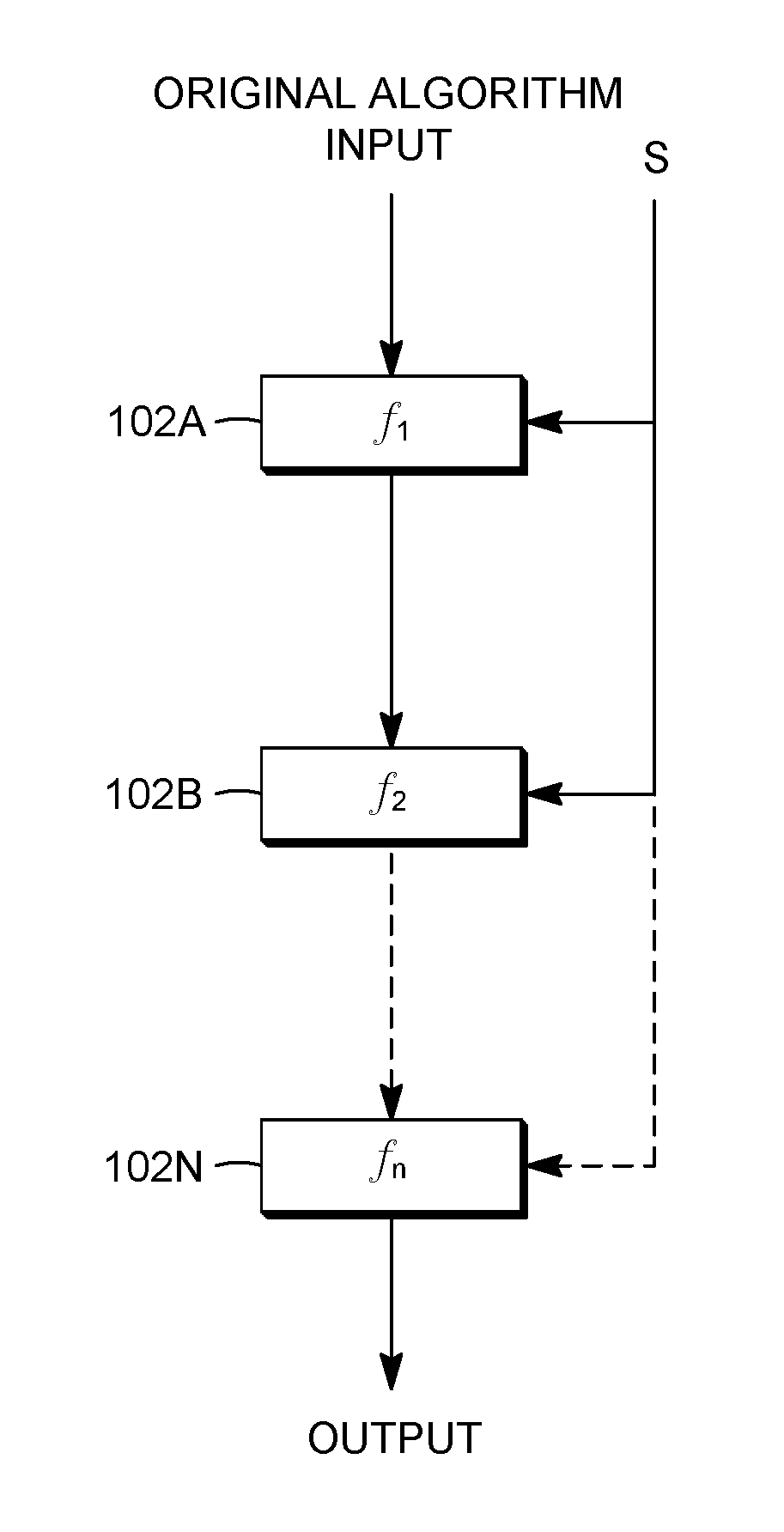
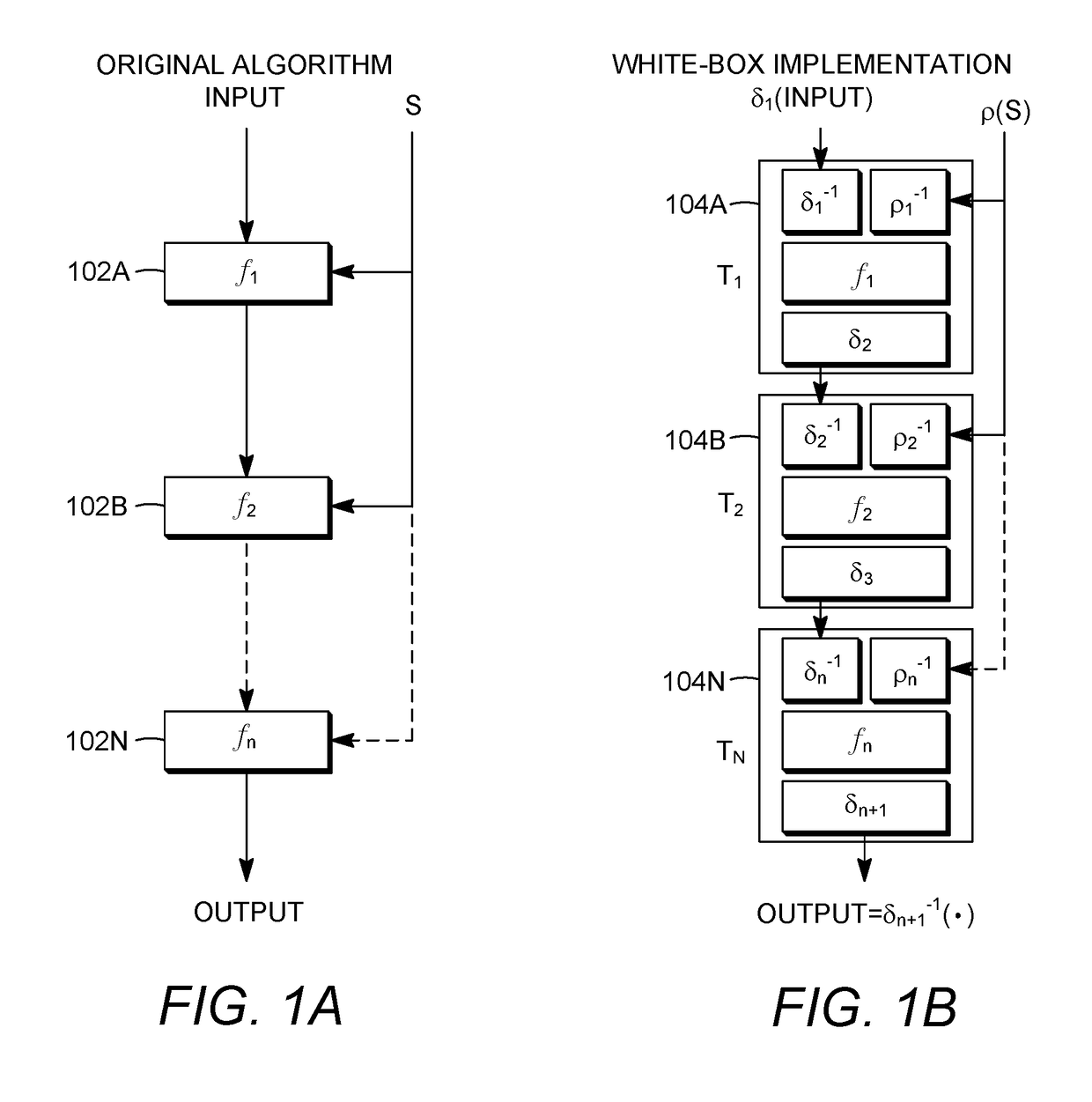
Existing encryption systems are designed to protect secret keys or other data under a "black box attack," where the attacker may examine the algorithm, and various inputs and outputs, but has no visibility into the execution of the algotitm itself. However, it has been shown that the black box model is generally unrealistic, and that attack efficiency rises dramatically if the attacker can observe even minor aspects of the algorithm's execution. The invention protects software from a "white-box attack", where the attacker has total visibility into software implementation and execution. In general, this is done by encoding the software and widely diffusing sites of information transfer and / or combination and / or loss. Other embodiments of the invention include: the introduction of lossy subcomponents, processing inputs and outputs with random cryptographic functions, and representing algorithmic steps or components as tables, which permits encoding to be represented with arbitrary nonlinear bijections.
Owner:CLOAKWARE CORP
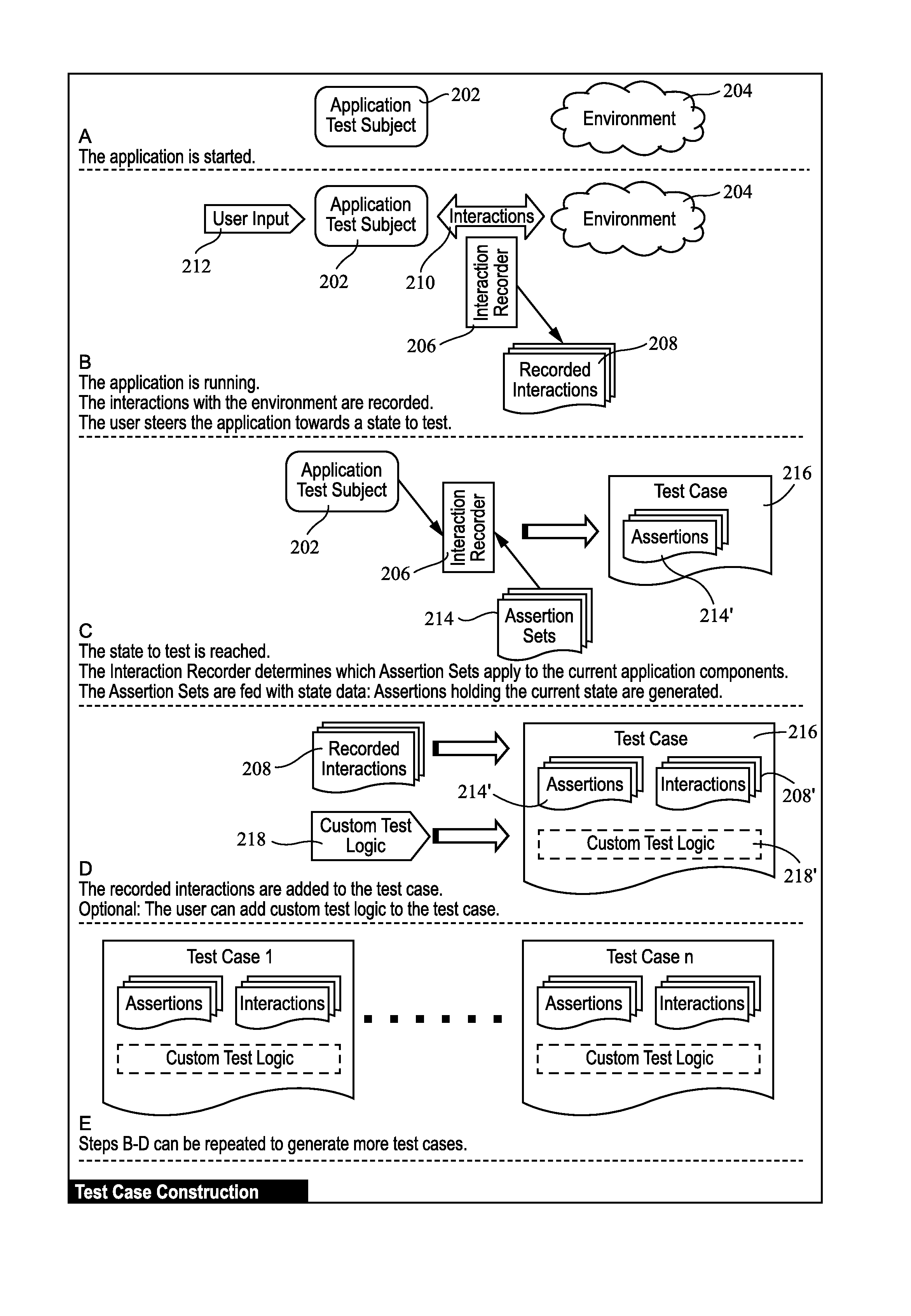
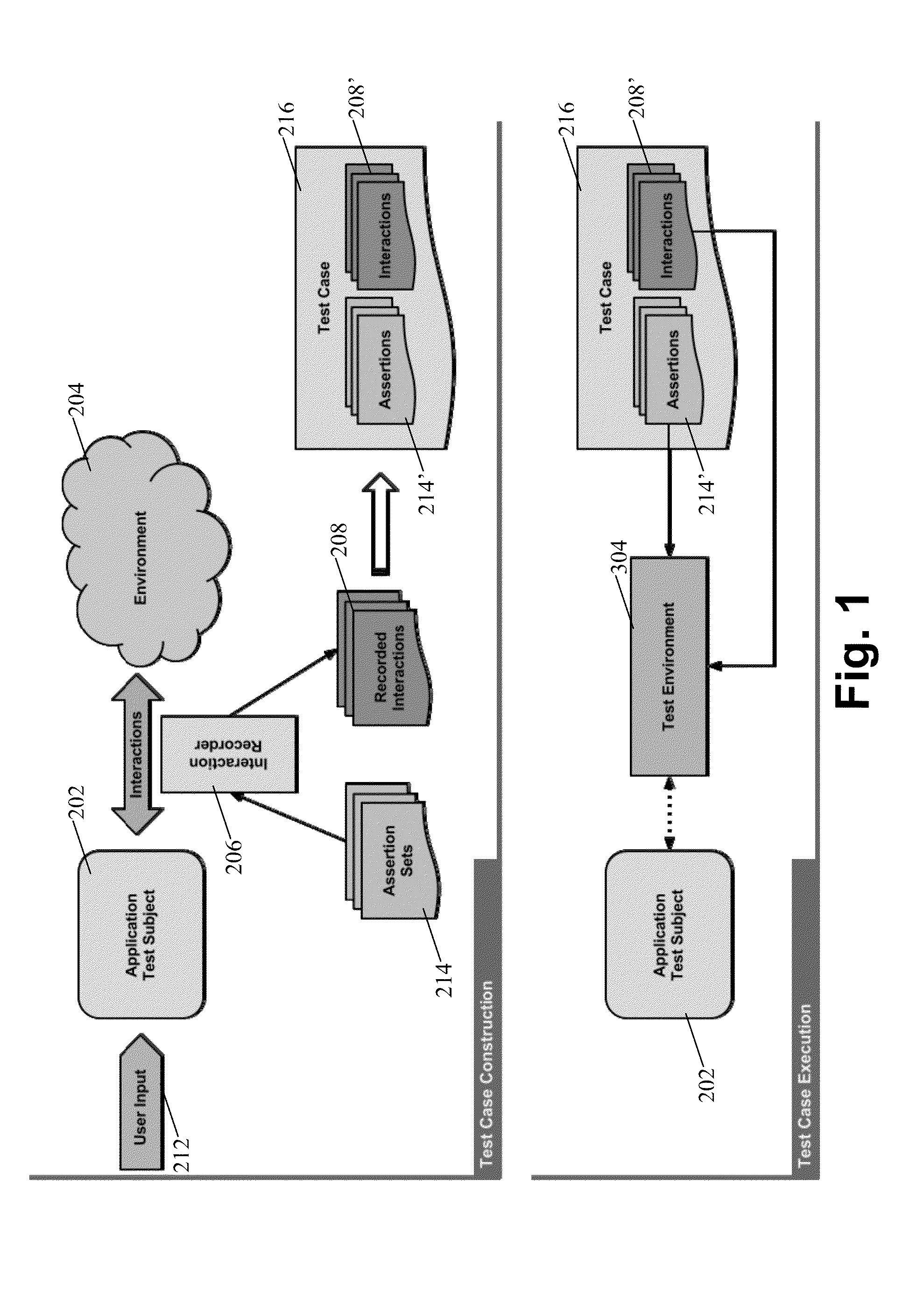
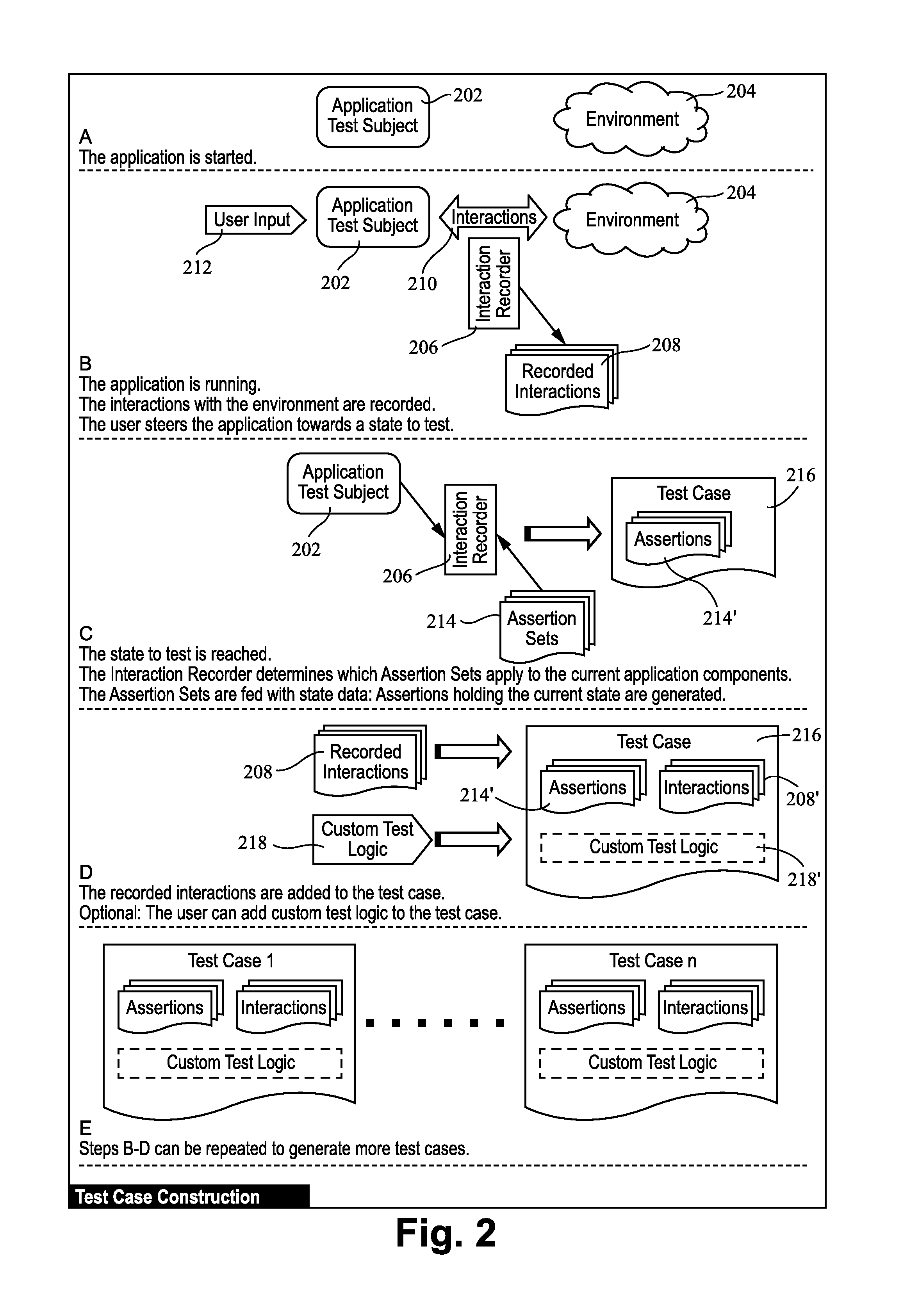
White-box testing systems and/or methods for use in connection with graphical user interfaces
ActiveUS20140101640A1Reduce dependenceGood reproducibilityError detection/correctionSpecific program execution arrangementsProspective dataGraphical user interface
Certain example embodiments relate to white-box testing techniques, e.g., for graphical user interfaces (GUIs). A test case to be run on the application includes interactions between the application and external components that were gathered as the application ran and received user input from a user until a desired test state was reached, and assertions to be made to the application once that state is reached. A test environment replaces a normal environment in which the application runs. An adapter executes interactions on the test environment's GUI dedicated thread(s). The application is fed with interactions, through the adapter, until the application reaches the desired state. Once the application reaches that state, the application is fed with assertions. Expected data associated with the assertions is compared with data actually being generated by the application. A determination is made regarding whether the test case resulted in success or failure.
Owner:SOFTWARE AG
Code tampering protection for insecure environments
ActiveUS20140101458A1Unauthorized memory use protectionHardware monitoringTheoretical computer scienceEngineering
In the field of computer software (code) security, it is known to include verification data such as hash values in or associated with the code to allow subsequent detection of tampering by a attacker with the code. This verification technique is used here in a “White Box” cryptographic process by tying the verification data to the content of functional table lookups present in the object (compiled) code, where values in the table lookups are selectively masked (prior to the source code being compiled into the subject code) by being subject to permutation operations.
Owner:APPLE INC
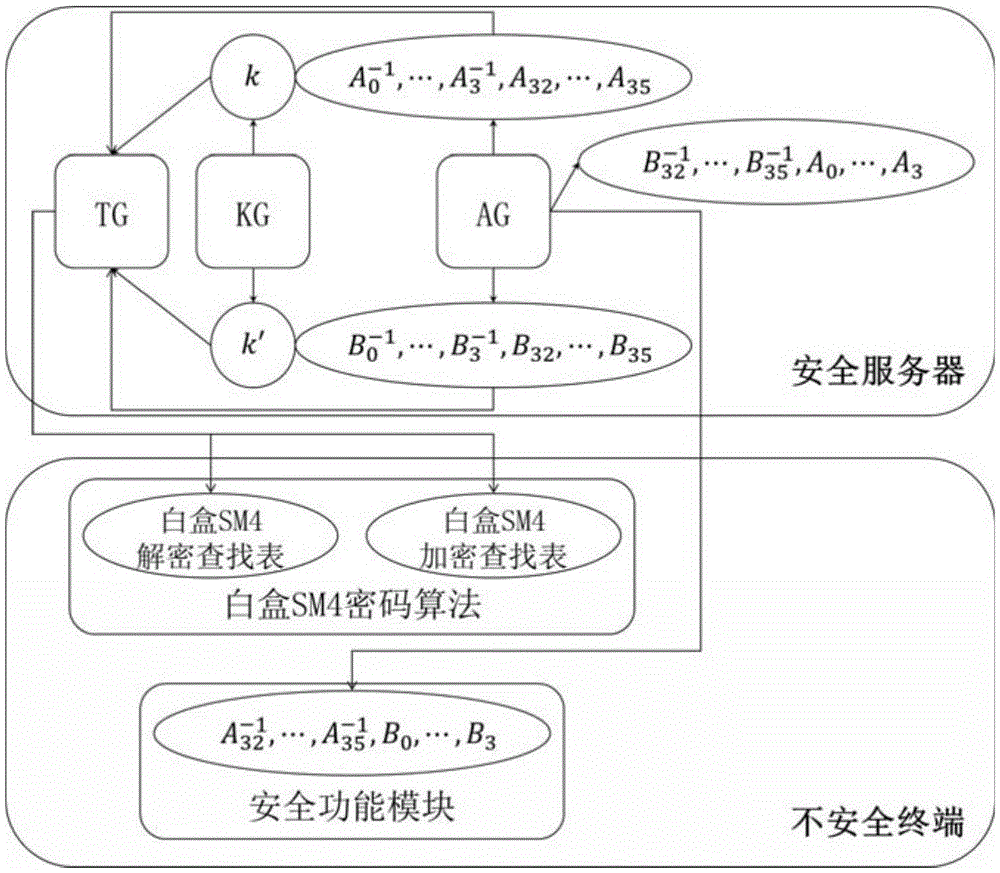
Security white box realizing method and device for national cipher standard algorithm SM4
InactiveCN105681025AEnsure safetySecurity advantageEncryption apparatus with shift registers/memoriesPasswordComputer terminal
The present invention discloses a security white box realizing method and device for the national cipher standard algorithm SM4, discloses essential components of equipment required by the white box SM4 algorithm, and belongs to the technical field of information security. With adoption of the method and the device, secret keys embedded into cipher software can be effectively protected in untrusted computer terminals. The white box SM4 password algorithm provided by the present invention achieves safe realization of the China commercial block cipher standard SM4. Secret keys are embedded into lookup tables, randomly selected affine codes are used for protecting the lookup tables, and thus the secret keys embedded in the lookup tables are protected. A TTC lookup table and a TRT lookup table are used in the algorithm, the last xor operation of output data of the TTC lookup table is embedded into the TRT lookup table, and output data of the TRT lookup table is protected by new 32-bit affine codes, so the situation of offsetting 32-bit affine codes embedded in the lookup tables by combining lookup tables can be prevented, thereby preventing reduction of code cracking difficulty, and realizing the protection aim.
Owner:INST OF INFORMATION ENG CAS
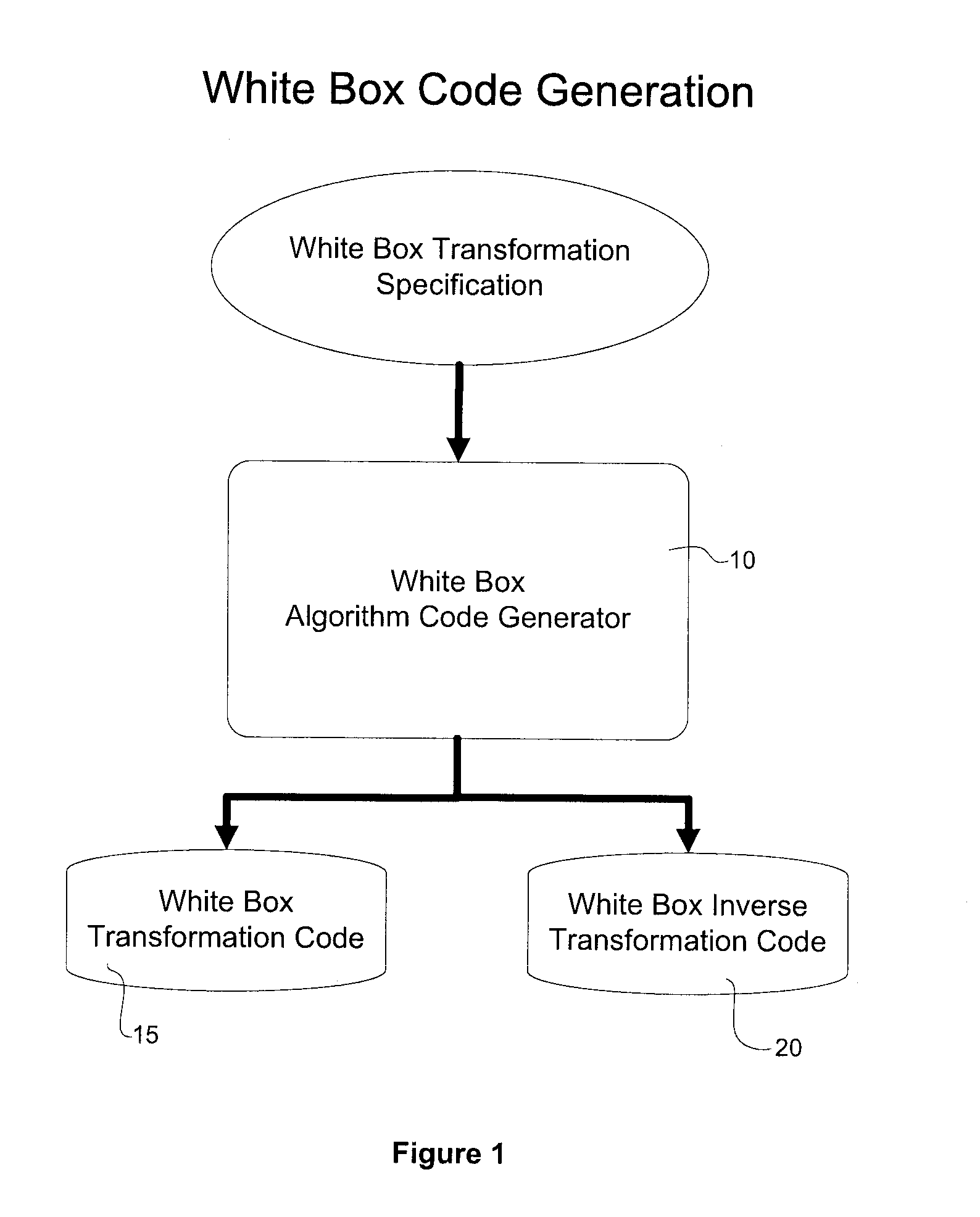
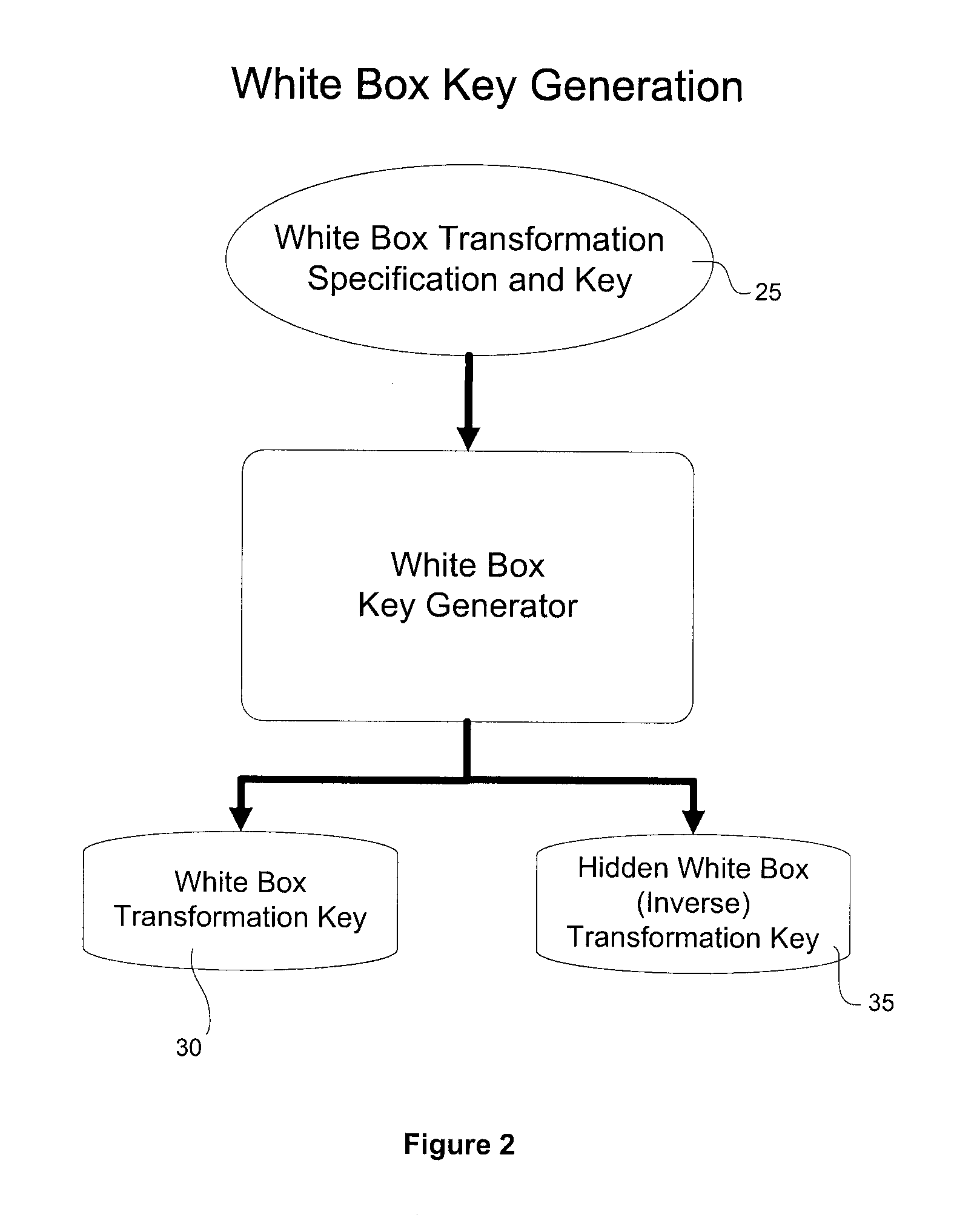
Interlocked Binary Protection Using Whitebox Cryptography
ActiveUS20120192283A1Digital data processing detailsAnalogue secracy/subscription systemsSAFERAttack
A system and method for transforming a software application comprising binary code and optionally associated data, from an original form to a more secure form. The method includes performing a combination of binary transmutations to the application, and interlocking the transmutations by generating and placing interdependencies between the transmutations, wherein a transmutation is an irreversible change to the application. Different types of the transmutations are applied at varied granularities of the application. The transmutations are applied to the application code and the implanted code as well. The result is a transformed software application which is semantically equivalent to the original software application but is resistant to static and / or dynamic attacks.
Owner:IRDETO ACCESS
Neural network black box aggressive defense method based on knowledge distillation
ActiveCN111027060AGuaranteed successful attackReduce the pitfalls of losing variance between classesPlatform integrity maintainanceNeural architecturesData setSample sequence
The invention discloses a neural network black box aggressive defense method based on knowledge distillation, and the method comprises the steps: selecting a plurality of sub-networks to construct a teacher network, softening the input vectors of softmax layers of all sub-networks, and then reloading the model parameters of the sub-networks for training to obtain a new sub-network; obtaining a prediction label of each sub-network, and taking all prediction labels as soft labels after averaging or weighted averaging; inputting the Image Net data set into a student network, and guiding student network training by adopting a soft label, a data set hard label and a black box model special label to obtain a substitution model; adopting a white box attack algorithm to attack the substitution model to generate an adversarial sample sequence, adopting the adversarial sample sequence to attack the black box model, and selecting an adversarial sample successfully attacked in the adversarial sample sequence; and adding the successfully attacked countermeasure sample into a training set of the black box model, and performing countermeasure training by adopting the updated training set to generate the black box model with attack defense.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
White-box testing systems and/or methods in web applications
ActiveUS20150169434A1Meet the requirementsSoftware testing/debuggingSpecific program execution arrangementsGraphicsComputer hardware
Owner:SOFTWARE AG
Enabling object oriented capabilities in automation systems
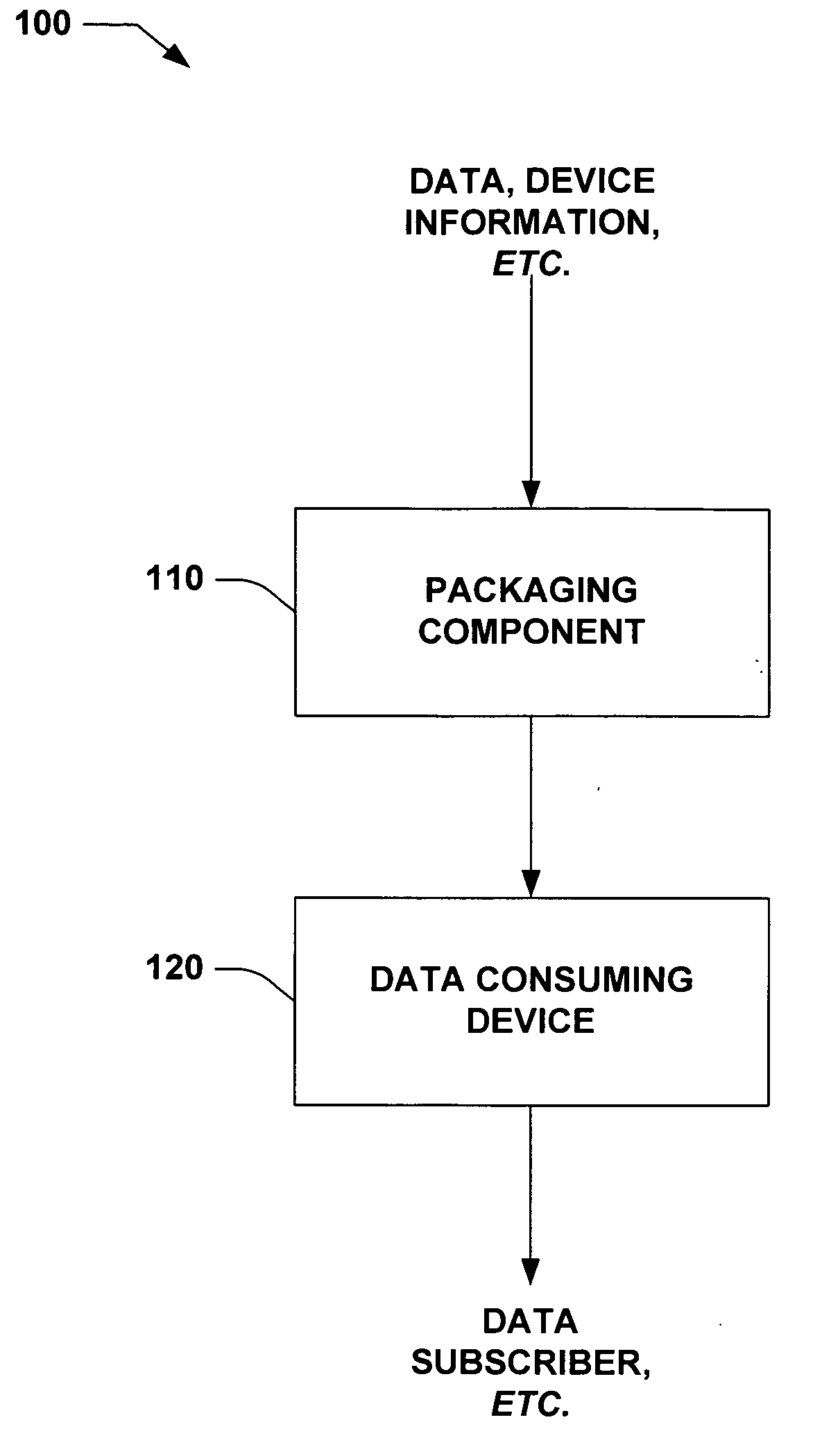
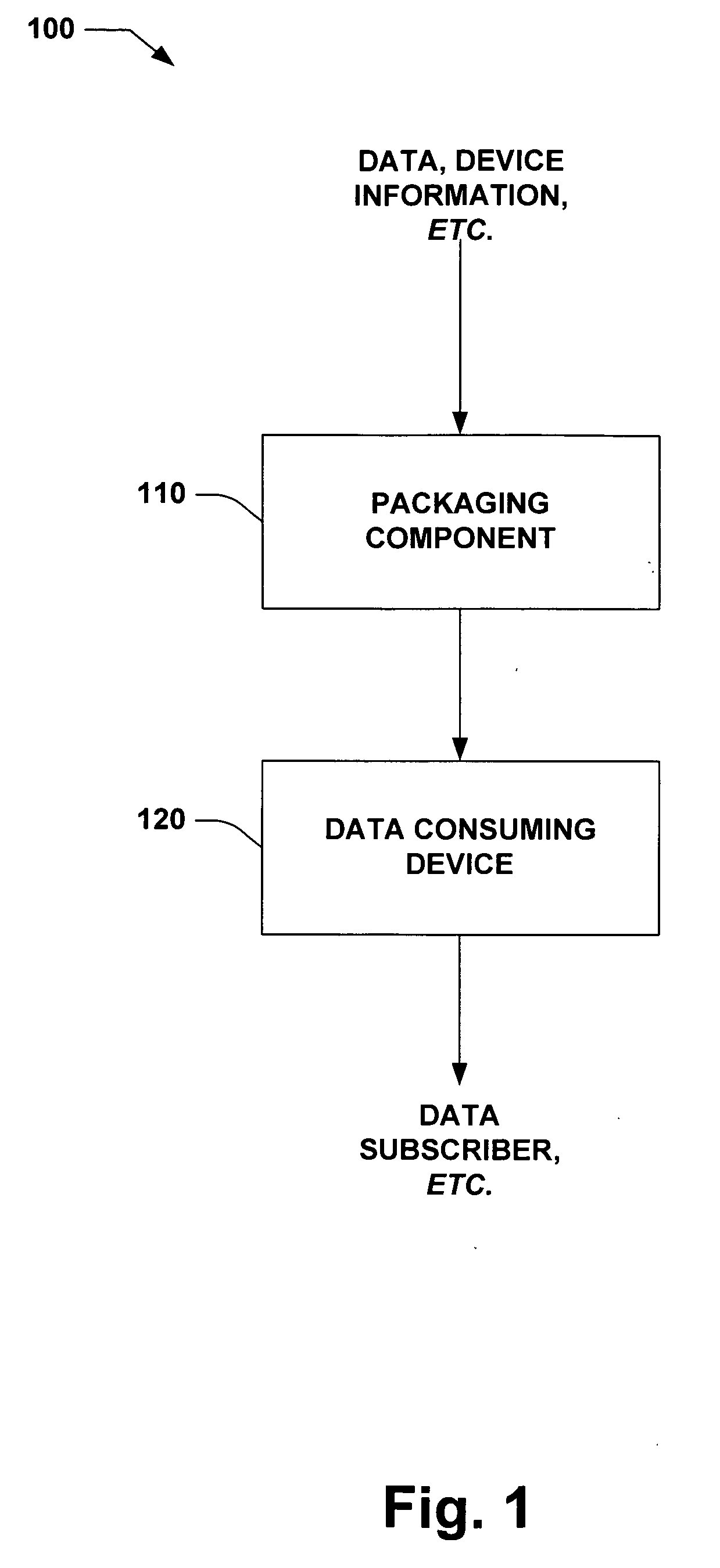
ActiveUS20060074498A1Reduce needEasy accessElectric signal transmission systemsTeeth fillingEncapsulated dataData access
The invention relates to systems and methods that support object oriented access to information at multiple levels in a control architecture, for example. Such data access can be facilitated as a layer adjacent to or part of an MES system or as a white box cooperating to encapsulate data such as in the controller or the MES layer, for example. In addition, such object oriented data access can be built into a controller as a standard behavior of controller data types and tags of those data types. In this manner, data can be encapsulated as a data object to expose properties and / or methods related to the data utilizing a common interface with each data consumer. Thus, the data consumer can employ object oriented concepts, such as properties, methods, scope qualifiers, access qualifiers (private, protected, public enterprise), polymorphism, inheritance and the like directly with their automation system components.
Owner:ROCKWELL AUTOMATION
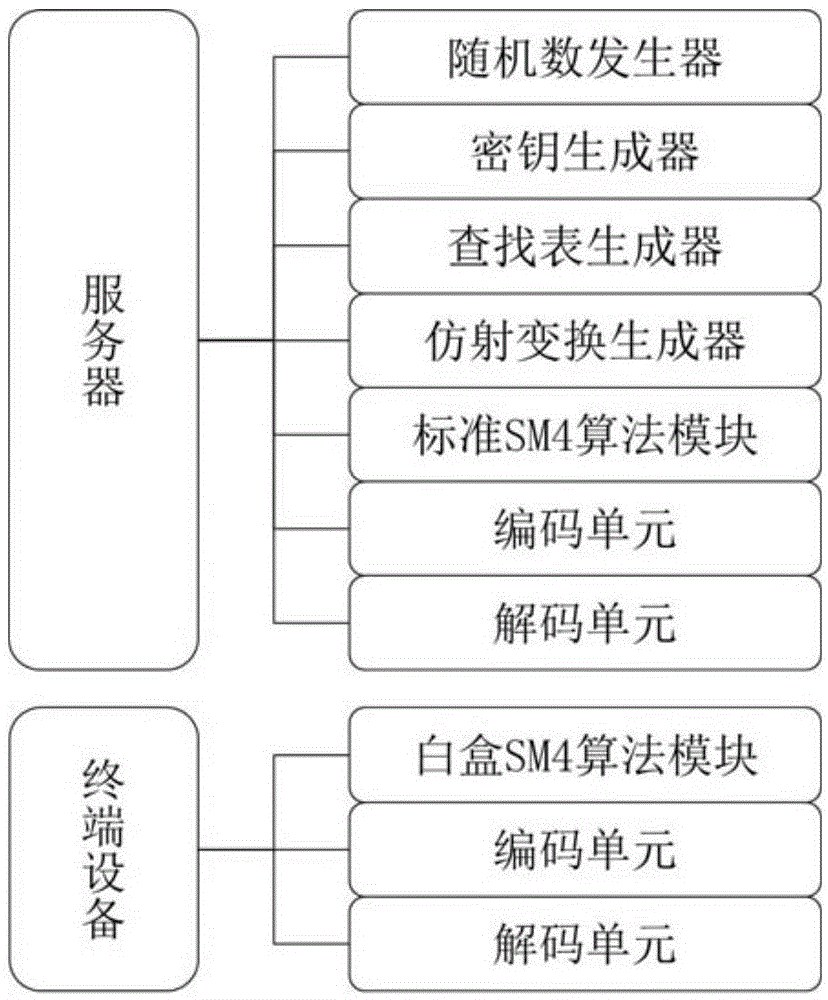
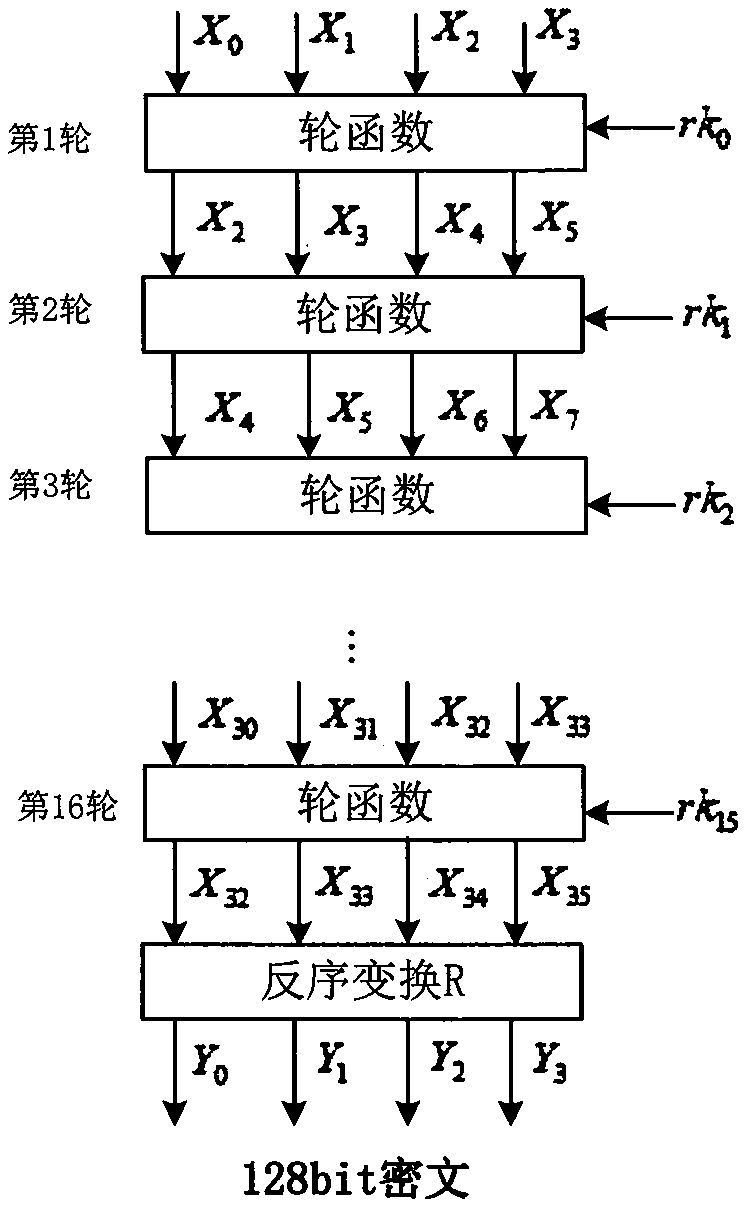
16-wheel SM4-128/128 white box password implementation method
InactiveCN110278072AImprove computing efficiencyIntegrity guaranteedEncryption apparatus with shift registers/memoriesComputer hardwarePassword
In an unsafe environment, a cryptographic analyzer can implement attacks on an algorithm and a secret key by tracking a binary system operated by a program, reading the secret key in a memory and a program execution intermediate result, carrying out static analysis and the like, and a white-box cryptographic algorithm can protect the secret key in the unsafe environment. The invention discloses a 16-round SM4-128 / 128 white box password implementation method, which describes a new mode of improving an SM4 password algorithm when the encryption round number is 16, and the mode improves the structure of a round function, namely the iterative process of the encryption algorithm. An improved SM4 white-box cryptographic algorithm is provided, and the whole encryption and decryption process can be converted into a form of calculating randomly selected affine transformation and lookup tables. The principle is that the internal state of a coding hiding algorithm is input and output scrambled, the secret key is embedded into a lookup table in a coding mode, and meanwhile, a block matrix is used for reducing the scale of the lookup table.
Owner:BEIJING ELECTRONICS SCI & TECH INST
Homomorphic white box system and method for using same
ActiveUS20180198613A1Performance maximizationReduce expertiseKey distribution for secure communicationPublic key for secure communicationCryptographyKey (cryptography)
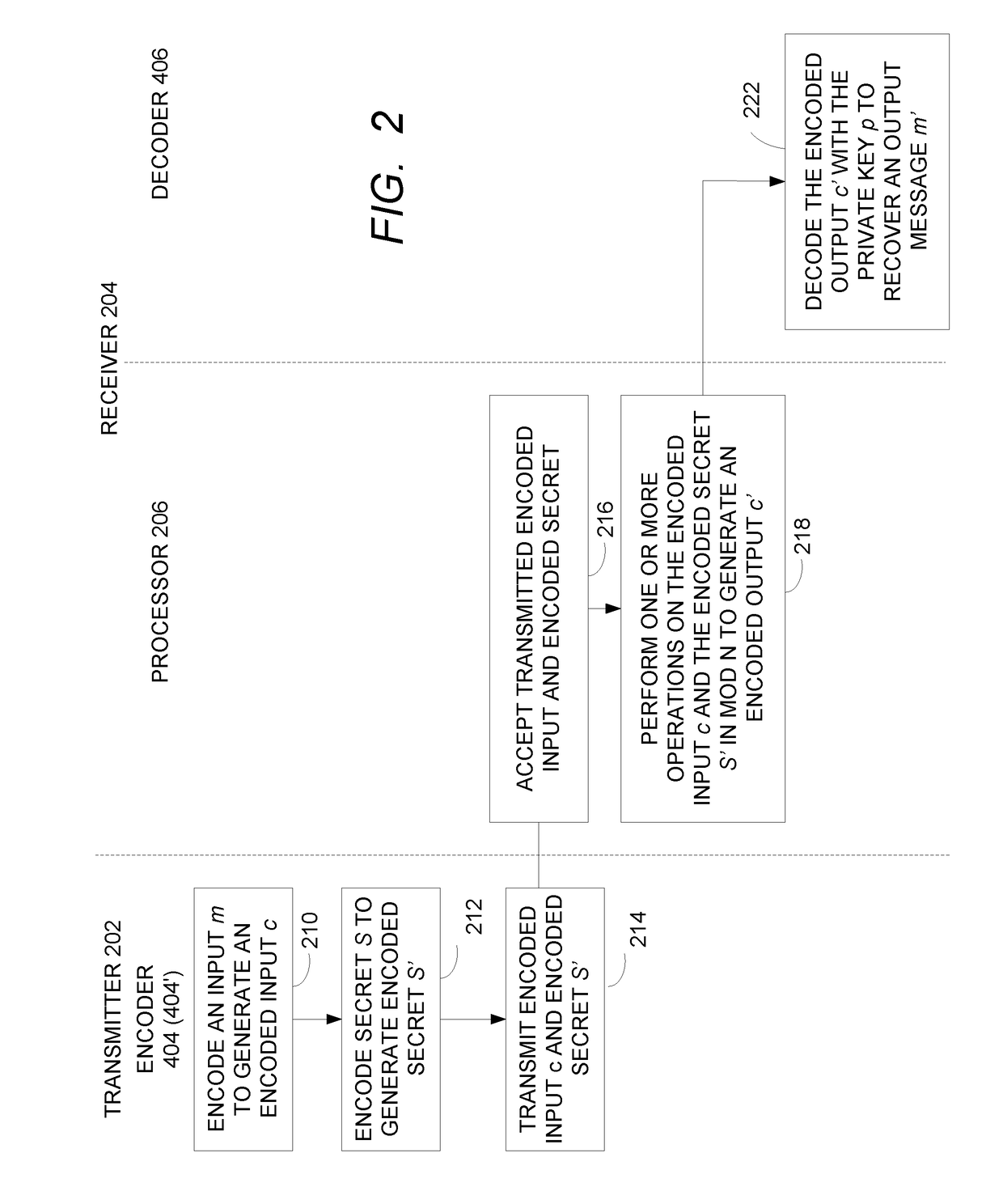
A method for whitebox cryptography is provided for computing an algorithm (m,S) with input m and secret S, using one or more white-box encoded operations. The method includes accepting an encoded input c, where c=Enc(P,m); accepting an encoded secret S′, where S′=Enc(P,S); performing one or more operations on the encoded input c and the encoded secret S′ modulo N to obtain an encoded output c′; and decoding the encoded output c′ with the private key p to recover an output m′ according to m′=Dec(p,c′), such that m′=(m,S).
Owner:ARRIS ENTERPRISES LLC
Securing webpages, webapps and applications
ActiveUS20180373849A1Reduce the possibilityMinimize consequencesDigital data protectionPlatform integrity maintainanceComputer hardwareControl system
A method for securing a webpage or a webapp processed by a browser executing on a client system, the method comprising the browser executing an instance of white-box protected code, wherein execution of the instance of white-box protected code causes the client system to: generate a message comprising message data for use by a control system to perform one or more security tests, the control system communicably connected to the client system via a network; send the message to the control system to enable the control system to perform the one or more security tests using the message data; receive a response from the control system based, at least in part, on the message; and process the response.
Owner:IRDETO ACCESS
System and Method for Protecting Cryptographic Assets From a White-Box Attack
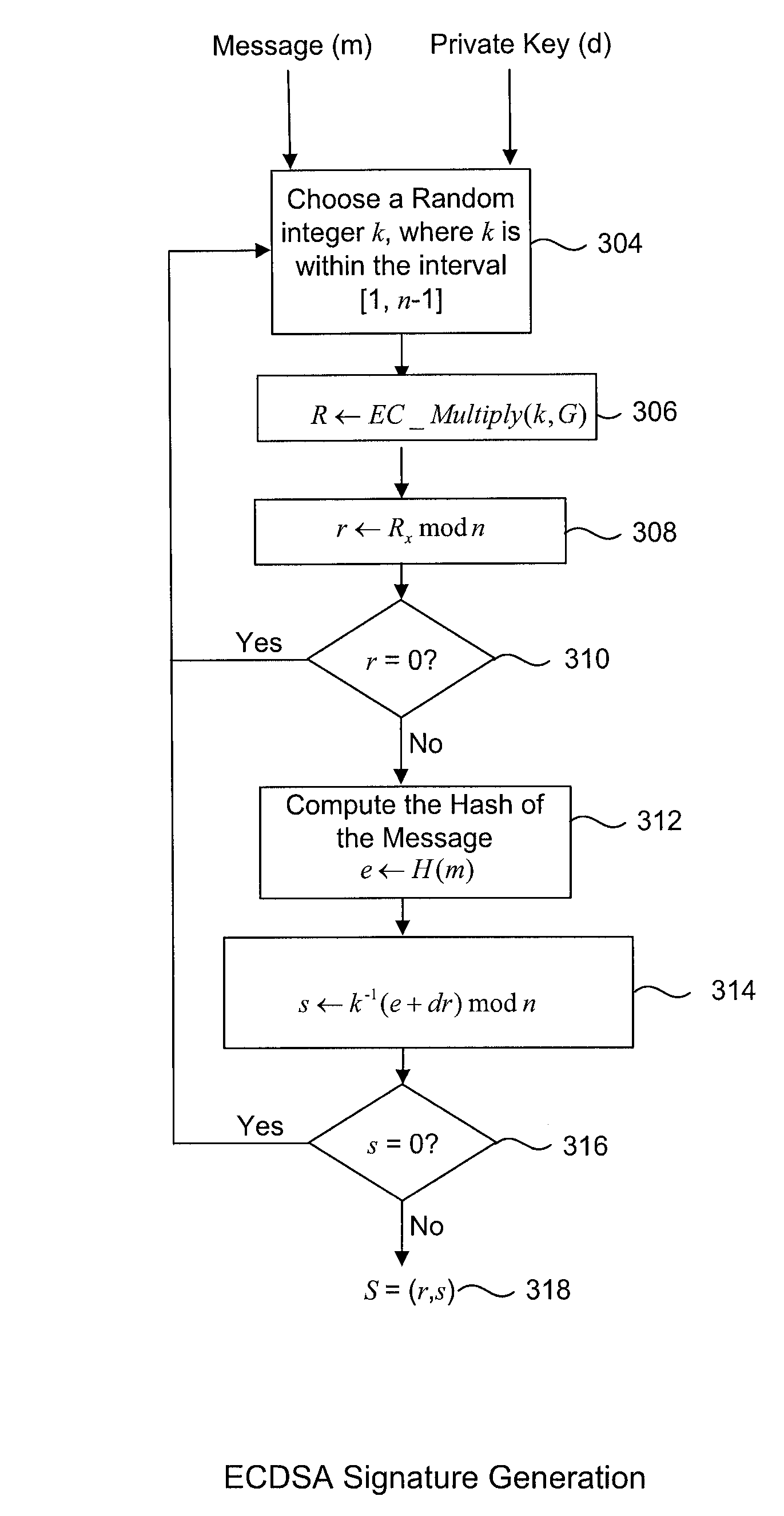
ActiveUS20130024699A1Improve interoperabilityUser identity/authority verificationCryptographic attack countermeasuresGeneration processData transformation
A digital signature generation (DSG) process which provides resistance against white box attackers is disclosed. This is done by applying specially selected data transformations to the inputs, outputs and internal parameters of the algorithm. In particular, the signatory's private key does not appear in the clear in our protected implementation. Our new white box implementation produces signatures that are compatible with signatures created by conventional implementations; thus our solution facilitates interoperability and can be used as a drop-in replacement for conventional implementations. In particular, we describe transformations to the key (d) and the generator domain parameter (usually denoted G or g) of the digital signature generation processes, such that embodiments of the invention can produce signed messages which appear to a verifier as if the key (d) was used, without actually ever using the key (d). This makes it impossible for an adversary to ever observe the key (d), as it is not actually used. Further embodiments include additional protections to make it even harder for an adversary to deduce the key (d) by observing the process which generates the digital signature.
Owner:IRDETO ACCESS
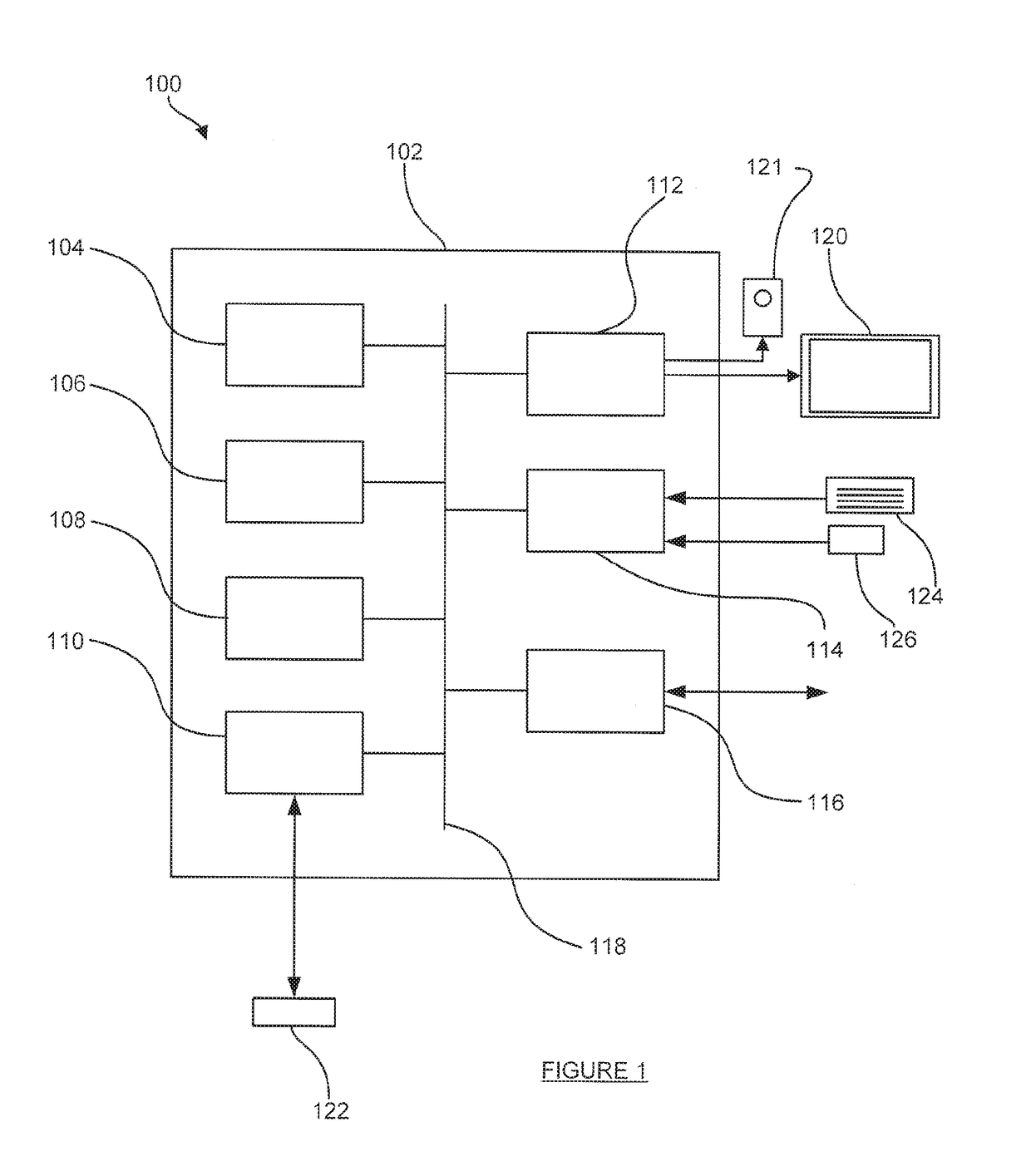
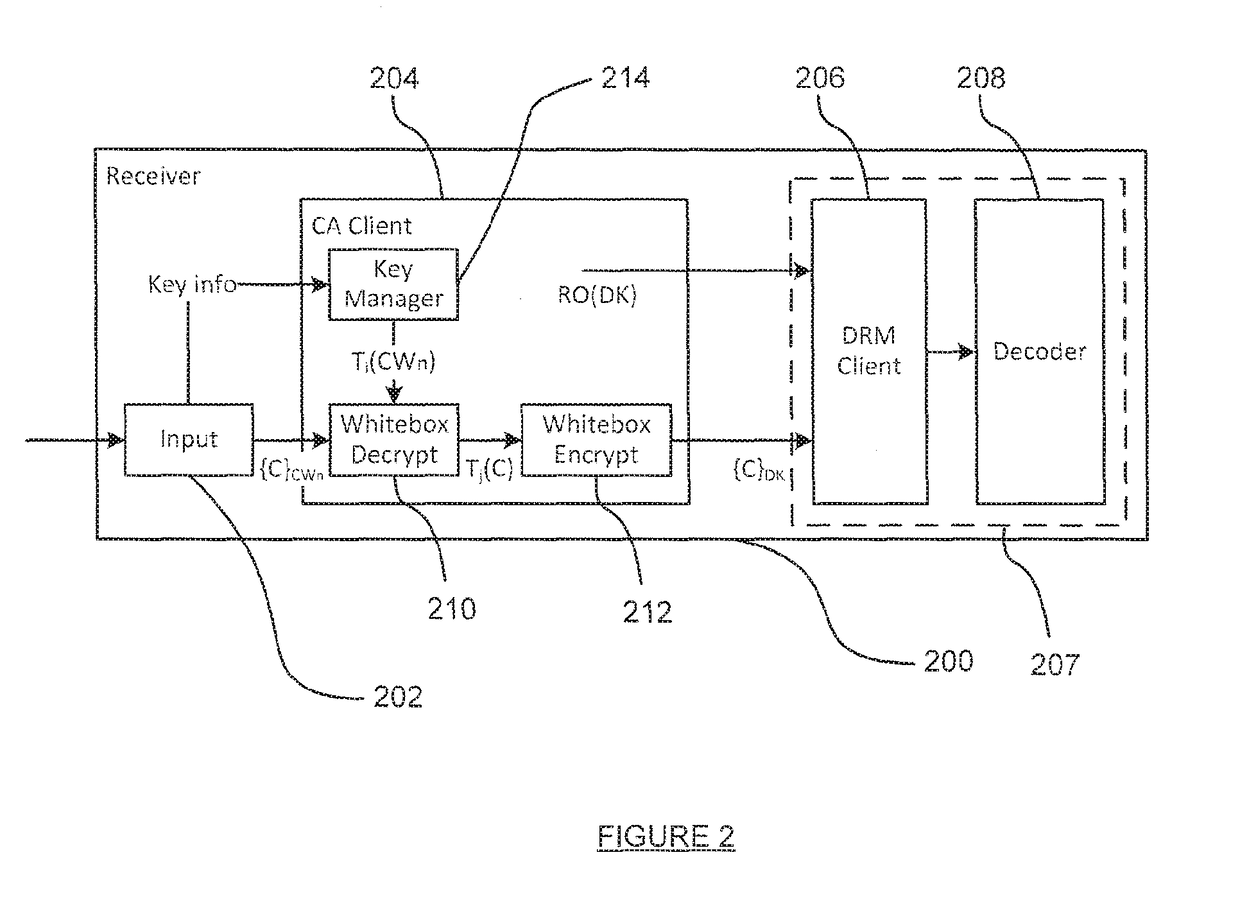
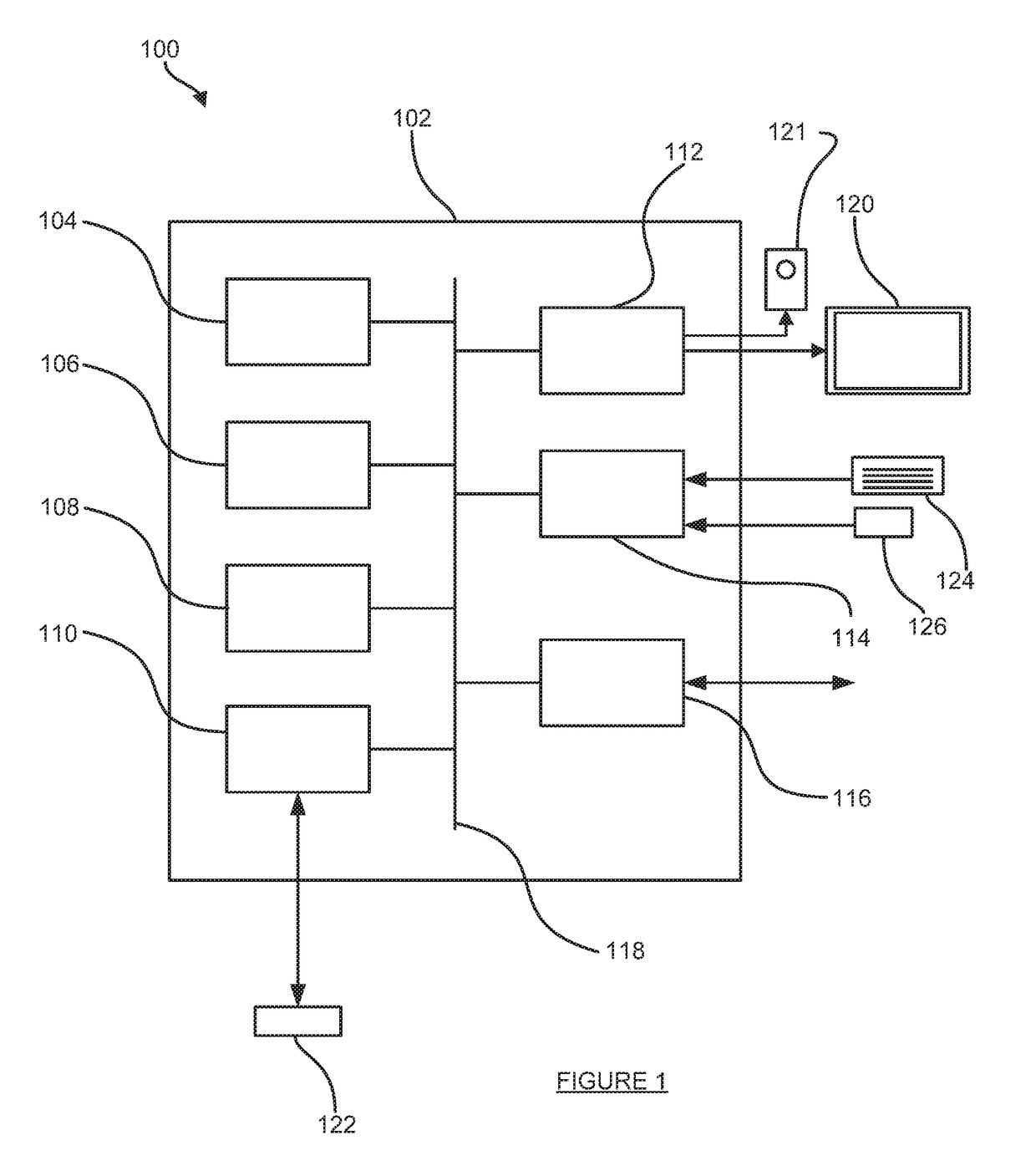
Providing access to content
ActiveUS20170237551A1Limit range of contentLimited rangeCryptographic attack countermeasuresProgram/content distribution protectionClient-sideSoftware
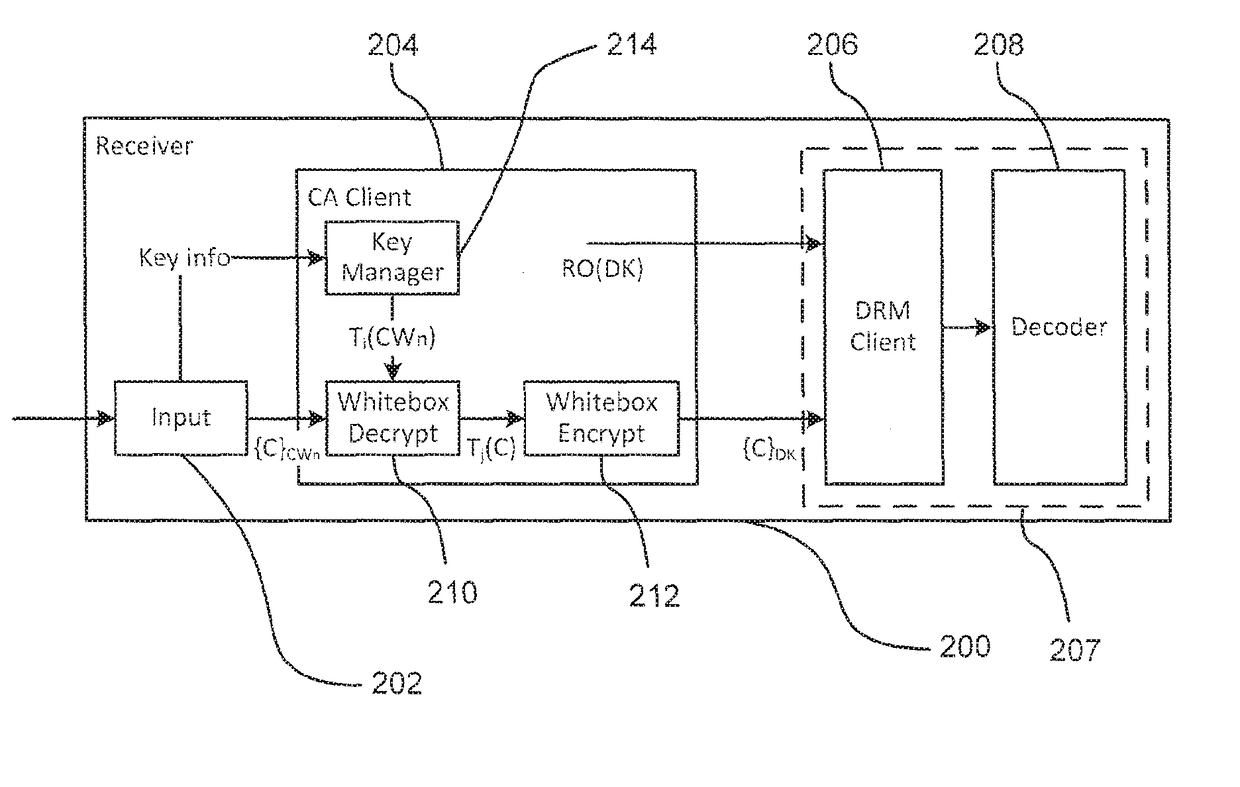
A method of providing access to content at a first device, the method comprising: receiving an item of content, wherein at least part of the item of content is encrypted, the encrypted at least part of the item of content being decryptable using at least one decryption key; in a first software client: obtaining a transformed version of the at least one decryption key; performing a decryption operation on the encrypted at least part of the item of content based on the at least one decryption key to obtain an intermediate version of the at least part of the item of content, wherein said performing the decryption operation uses a white-box implementation of the decryption operation that forms part of the first software client and that operates using the transformed version of the at least one decryption key; and performing an encryption operation on at least a portion of the intermediate version based on at least one encryption key to obtain re-encrypted content, wherein said performing the encryption operation uses a white-box implementation of the encryption operation that forms part of the first software client; and providing, to a digital rights management client that executes on the first device, (a) a rights object that enables the digital rights management client to obtain one or more second decryption keys corresponding to the at least one encryption key, the one or more second decryption keys enabling the digital rights management client to decrypt the re-encrypted content and (b) the re-encrypted content.
Owner:IRDETO ACCESS
Software protection
InactiveUS20170116410A1Improve securityEasy to useSoftware maintainance/managementDigital data protectionComputer hardwareScripting language
A method comprising: providing a protected item of software to a device, wherein the protected item of software is in a scripted language or an interpreted language or source code, wherein the protected item of software, when executed by the device, is arranged to perform a security-related operation for the device, wherein the security-related operation is implemented, at least in part, by at least one protected portion of code in the protected item of software, wherein the at least one protected portion of code is arranged so that (a) the at least one protected portion of code has resistance against a white-box attack and / or (b) the at least one protected portion of code may only be executed on one or more predetermined devices.
Owner:IRDETO ACCESS
Data encoding and decoding apparatus and method thereof for verifying data integrity
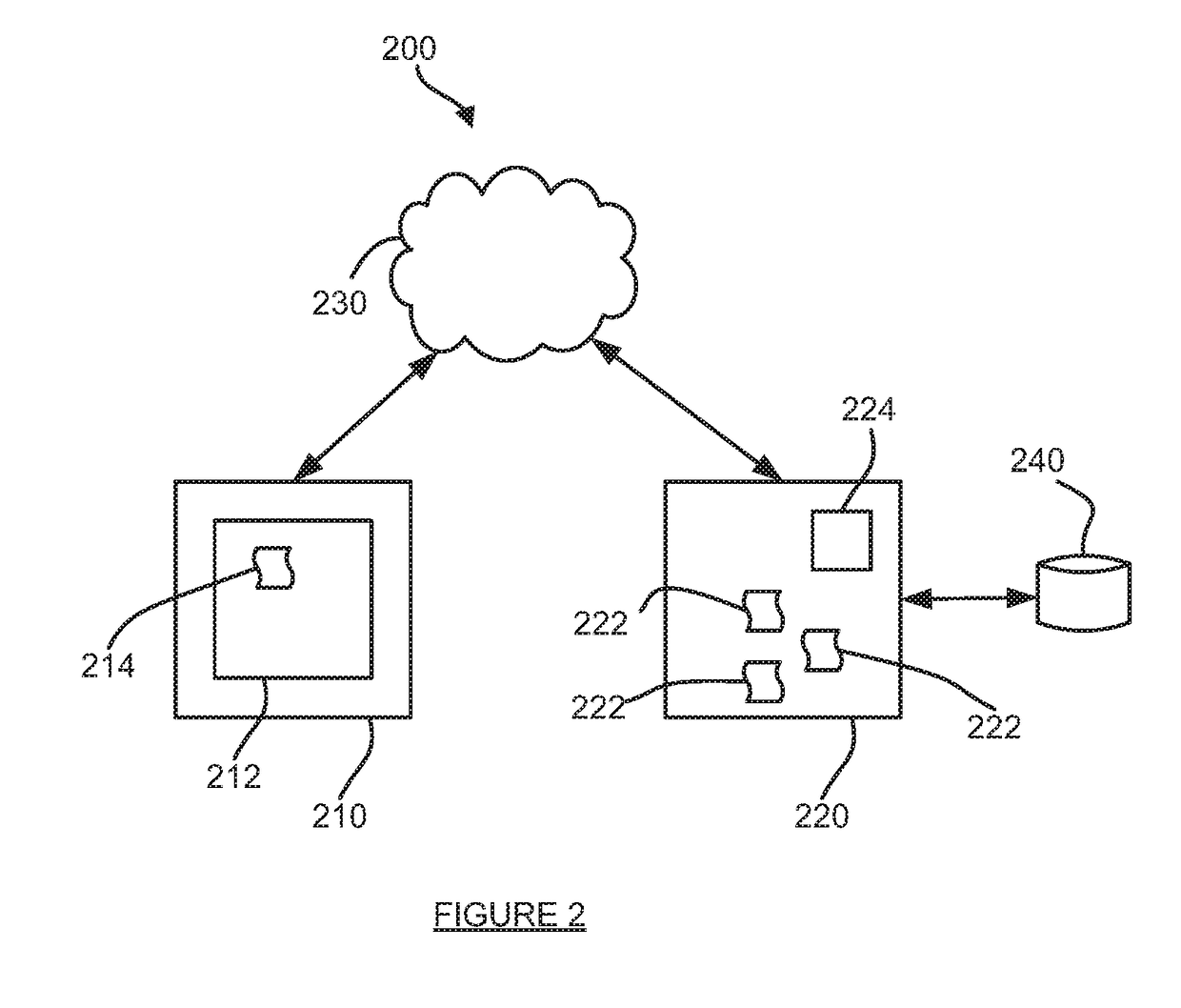
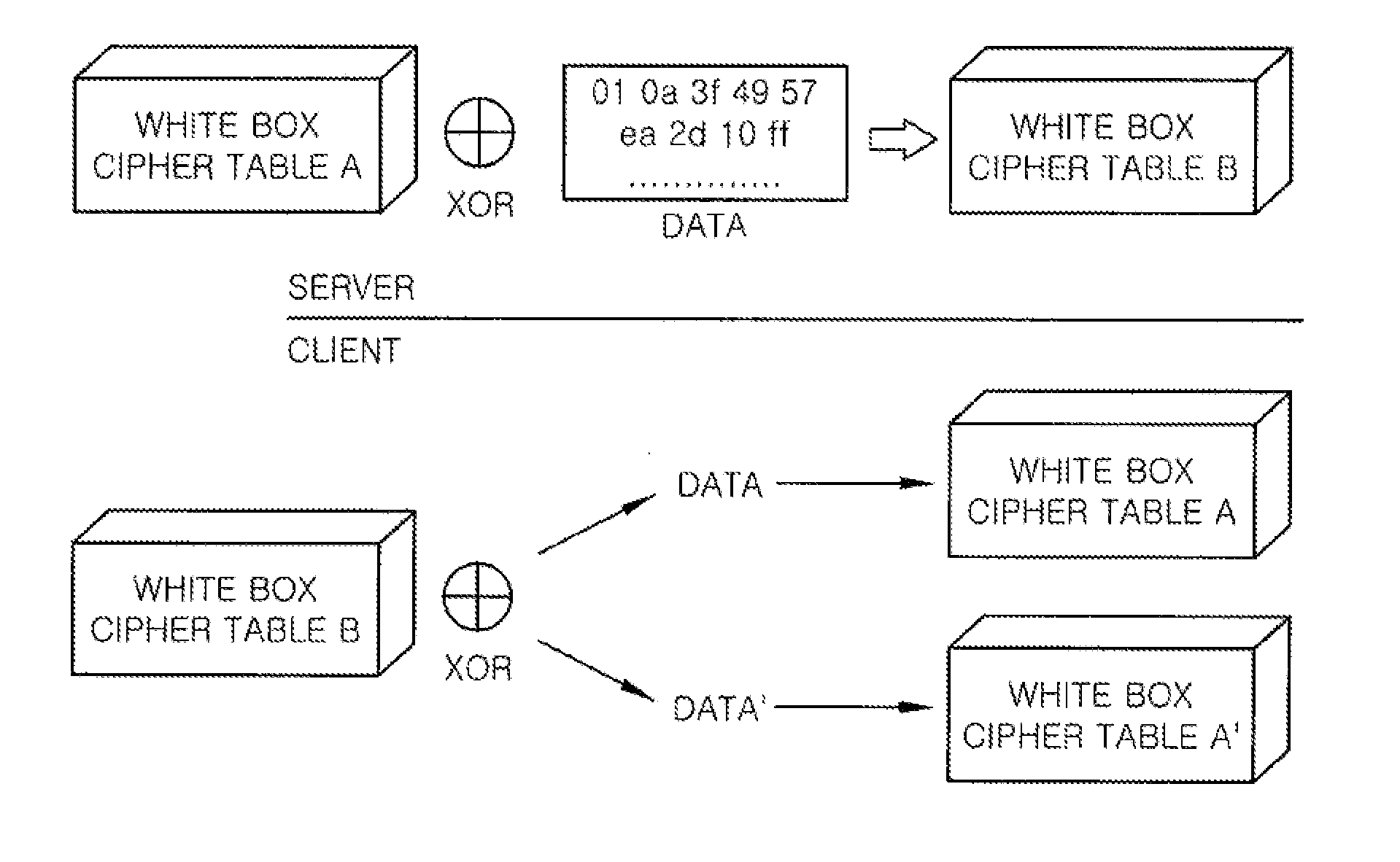
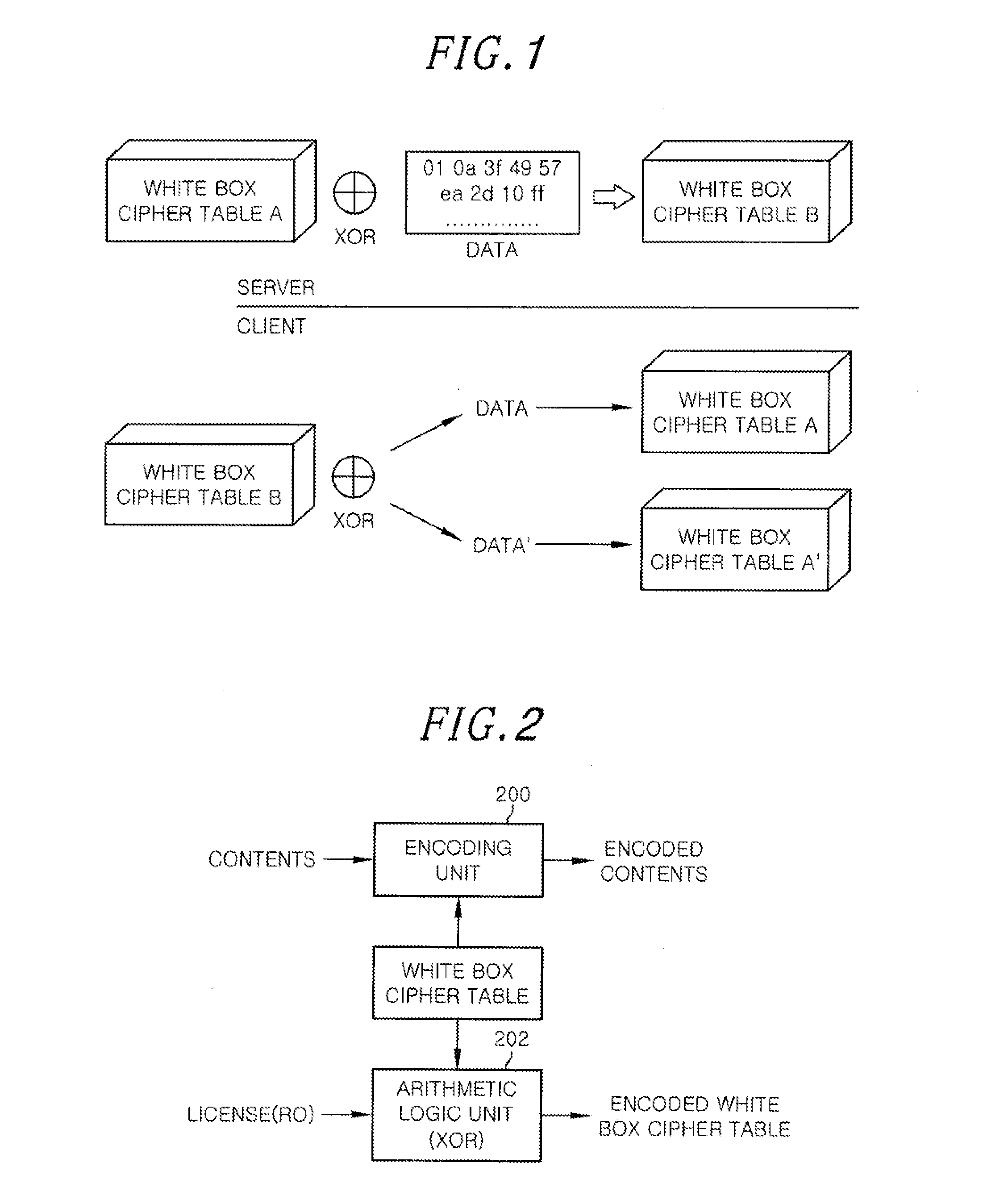
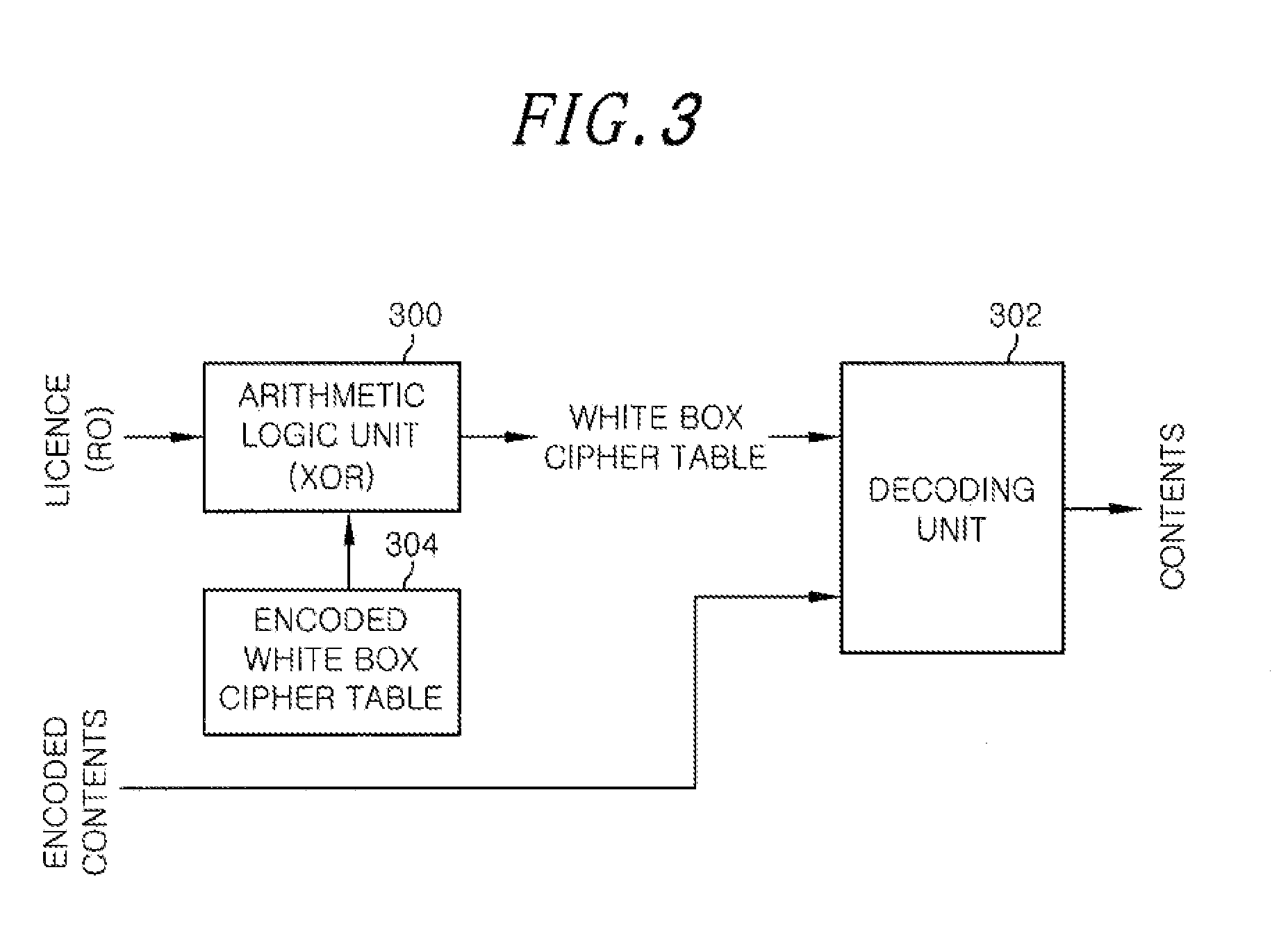
InactiveUS20120163582A1Secret communicationSecuring communicationArithmetic logic unitData integrity
A data encoding apparatus for verifying data integrity by using a white box cipher includes: an encoding unit for encoding content by using a white box cipher table; and an arithmetic logic unit for performing an arithmetic logic operation on the white box cipher table and content information to output an encoded white box cipher table. The arithmetic logic operation is an exclusive OR operation. The content information is license information of the content or hash value of the license information of the content.
Owner:ELECTRONICS & TELECOMM RES INST
Software automatically evaluating tool bag
InactiveCN101082876AResolve mismatchQuality improvementSoftware testing/debuggingData warehouseSoftware development
The inveniton discloses an automatic testing and estimating tool of software in the monitoring system of computer software, which comprises the following parts: realizing too of testing and estimating frame of software, unit testing tool, optimizing tool of integrating testing, reliability testing and estimating tool of software, wherein the unit testing tool is simple technique to integrate black box testing and testing routine of testing data generated by random path; the optimizing tool of integrated testing is the testing optimizing model based on component; the reliability testing and estimating tool of software adopts data bin to collect and store ineffective data to build reliable predicting model based on gene expressive formula program, which analyzes the estimating result of multiple models to give perfect qualitative and quantitative reliable analyzing report. The invention solves the contradiction of incomplete mating between commercial testing tool and local software engineering, which affirms high quality to develop software.
Owner:四川华智信息技术有限公司 +1
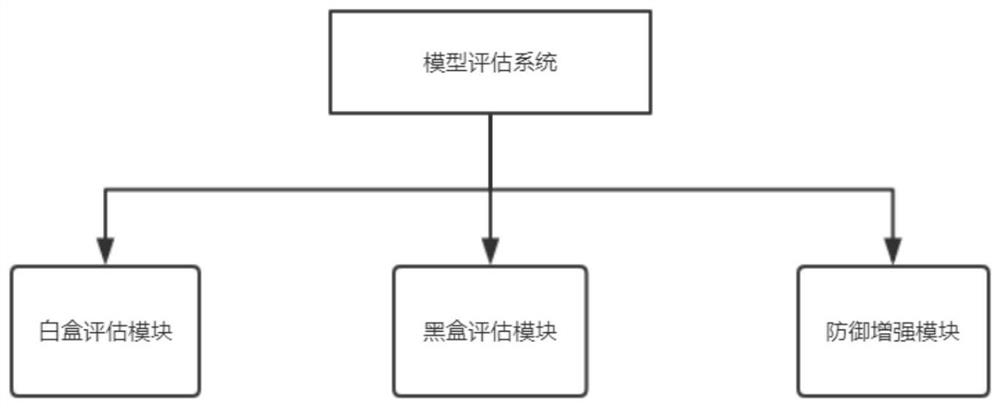
Robustness evaluation and enhancement system of artificial intelligence image classification model
PendingCN111950628AEasy to compareEase of evaluationCharacter and pattern recognitionEvaluation resultAlgorithm
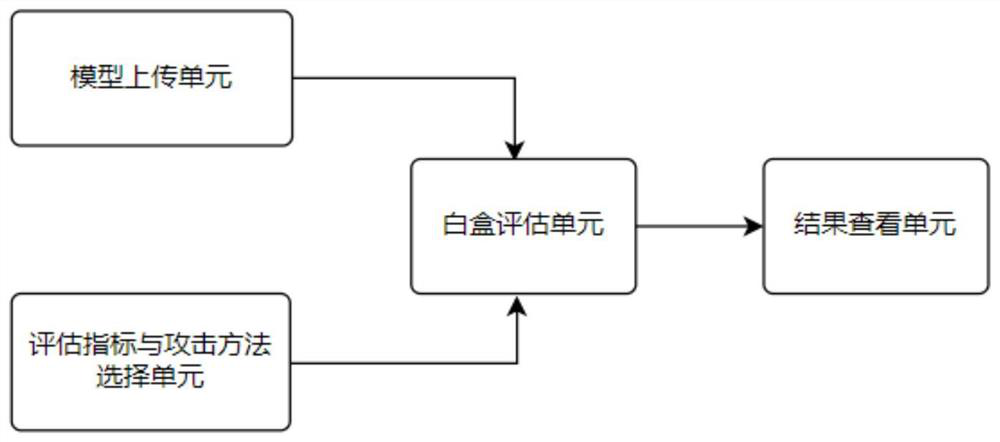
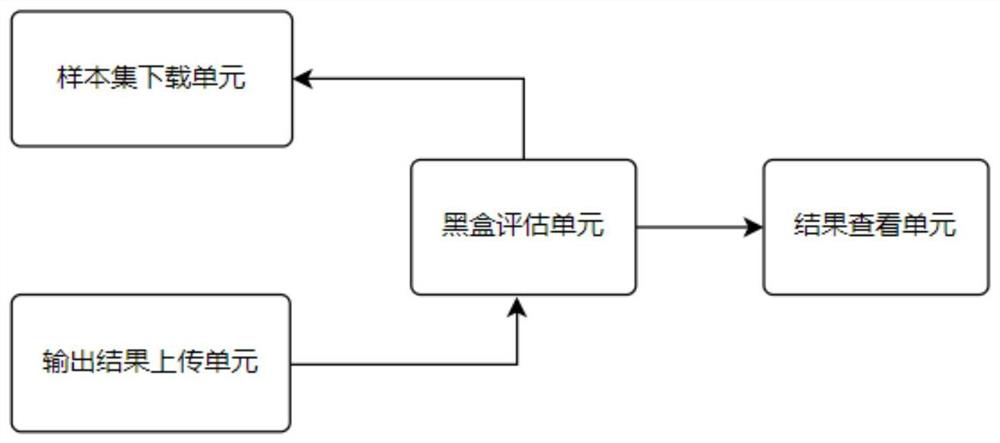
A robustness evaluation and enhancement system of an artificial intelligence image classification model comprises a white box evaluation module, a black box evaluation module and a defense enhancementmodule, the white box evaluation module obtains a to-be-evaluated model and selected evaluation indexes from a user, the attack resistance of the model is evaluated from all aspects according to multiple different indexes, and the defense enhancement module is used for enhancing the robustness of the model and calculating the scores of all indexes and the total score of robustness; and the blackbox evaluation module obtains an output result of the to-be-evaluated model from the user and compares the output result with the correct label to obtain an evaluation result. A plurality of black boxevaluation means is provided, and the robustness of the model is evaluated from the perspective of black boxes; the defense enhancement module is internally provided with a plurality of robustness improvement means. A to-be-enhanced model and selected defense enhancement method information are acquired from the user and robustness enhancement is performed on the model uploaded by the user by using a corresponding defense enhancement method. The robustness evaluation process of the whole model is optimized through multiple robustness evaluation indexes, so that the model is defended through multiple built-in technologies while different methods can be compared and evaluated more conveniently, accurately and comprehensively, and the robustness of the model is improved.
Owner:SHANGHAI JIAO TONG UNIV
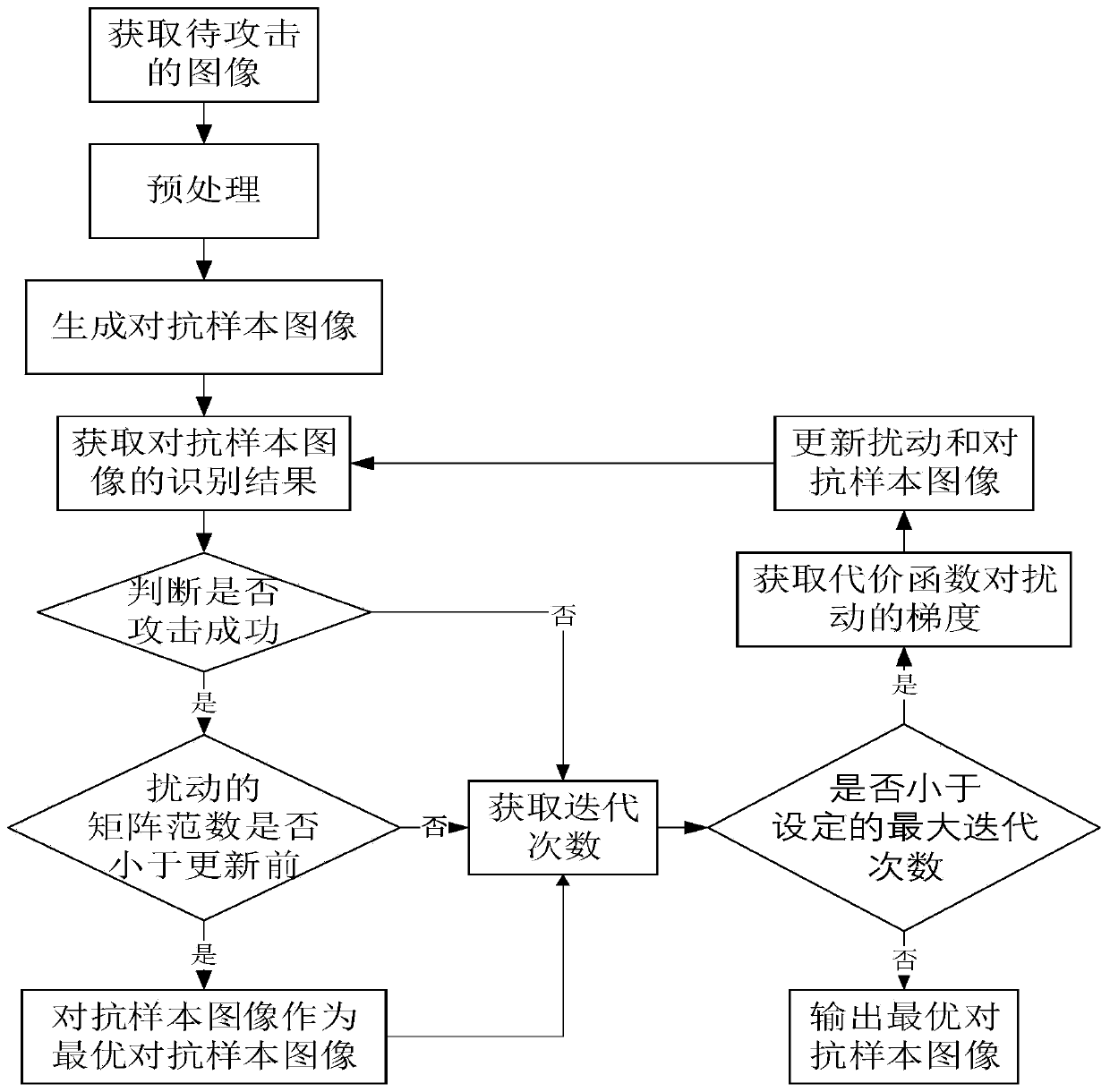
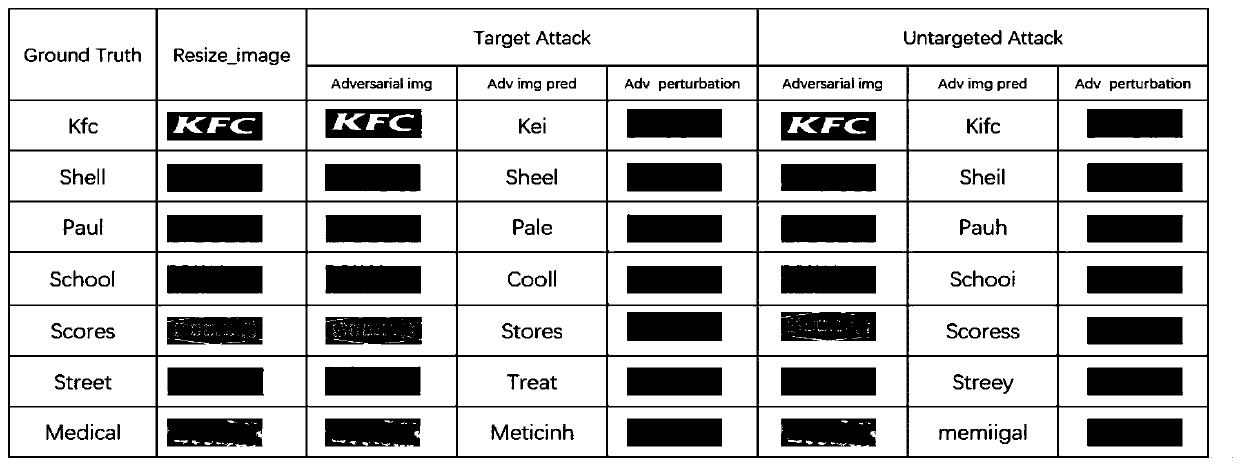
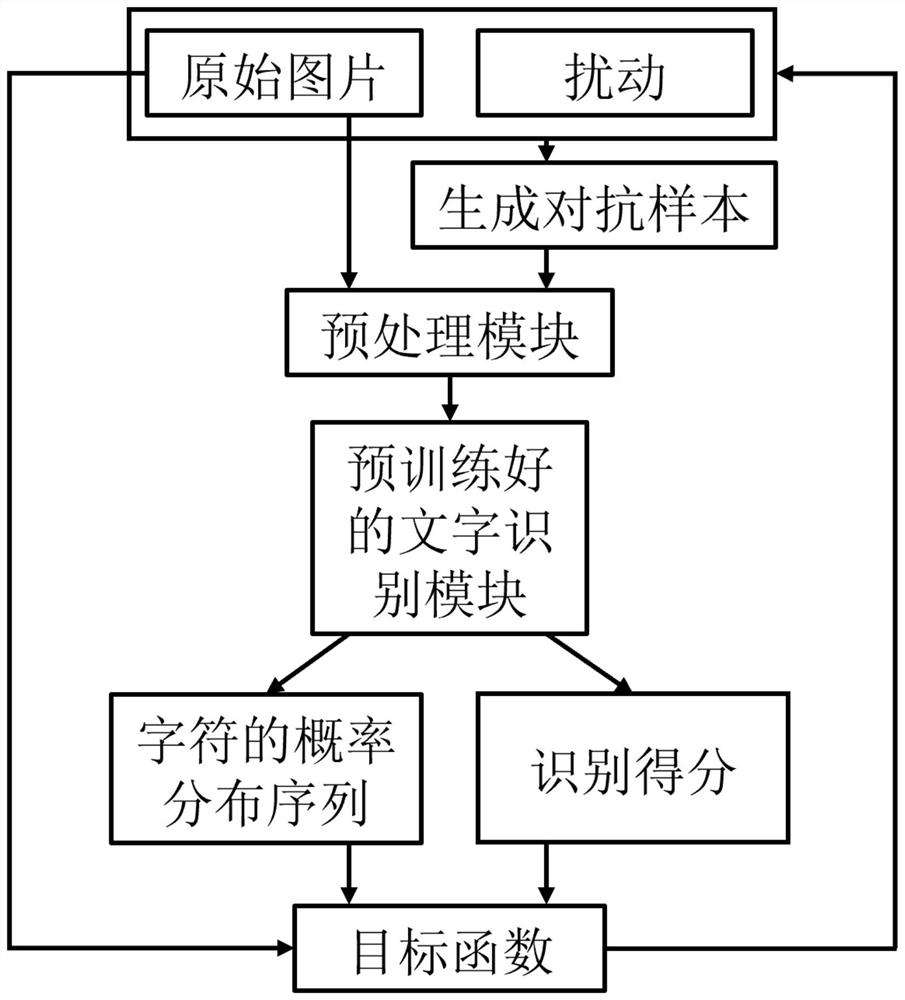
White box adversarial sample generation method for scene character recognition model
PendingCN111476228AAvoid mutationMake sure it's not visibleCharacter and pattern recognitionNeural architecturesAlgorithmEngineering
The invention belongs to the technical field of scene character recognition and white box attack, particularly relates to a white box confrontation sample generation method, system and device for a scene character recognition model, and aims to solve the problems that an existing white box attack algorithm cannot meet requirements and is long in attack time and unstable. The method comprises the following steps: acquiring a to-be-attacked image, and generating an adversarial sample image in combination with disturbance; obtaining a recognition result of the adversarial sample image through a scene character recognition model, judging whether the image is successfully attacked or not based on the result, and taking the image as an optimal adversarial sample image if the image is successfully attacked and the disturbed matrix norm is reduced; otherwise, judging whether the number of iterations is less than a set maximum number of iterations: if so, updating the disturbance and adversarial sample image, and otherwise, outputting an optimal adversarial sample image. According to the method, the white box adversarial sample generation requirement for the scene character recognition model is met, and time consumption and instability of an attack algorithm are avoided through gradient cutting.
Owner:BEIJING YUNJIANG TECH CO LTD
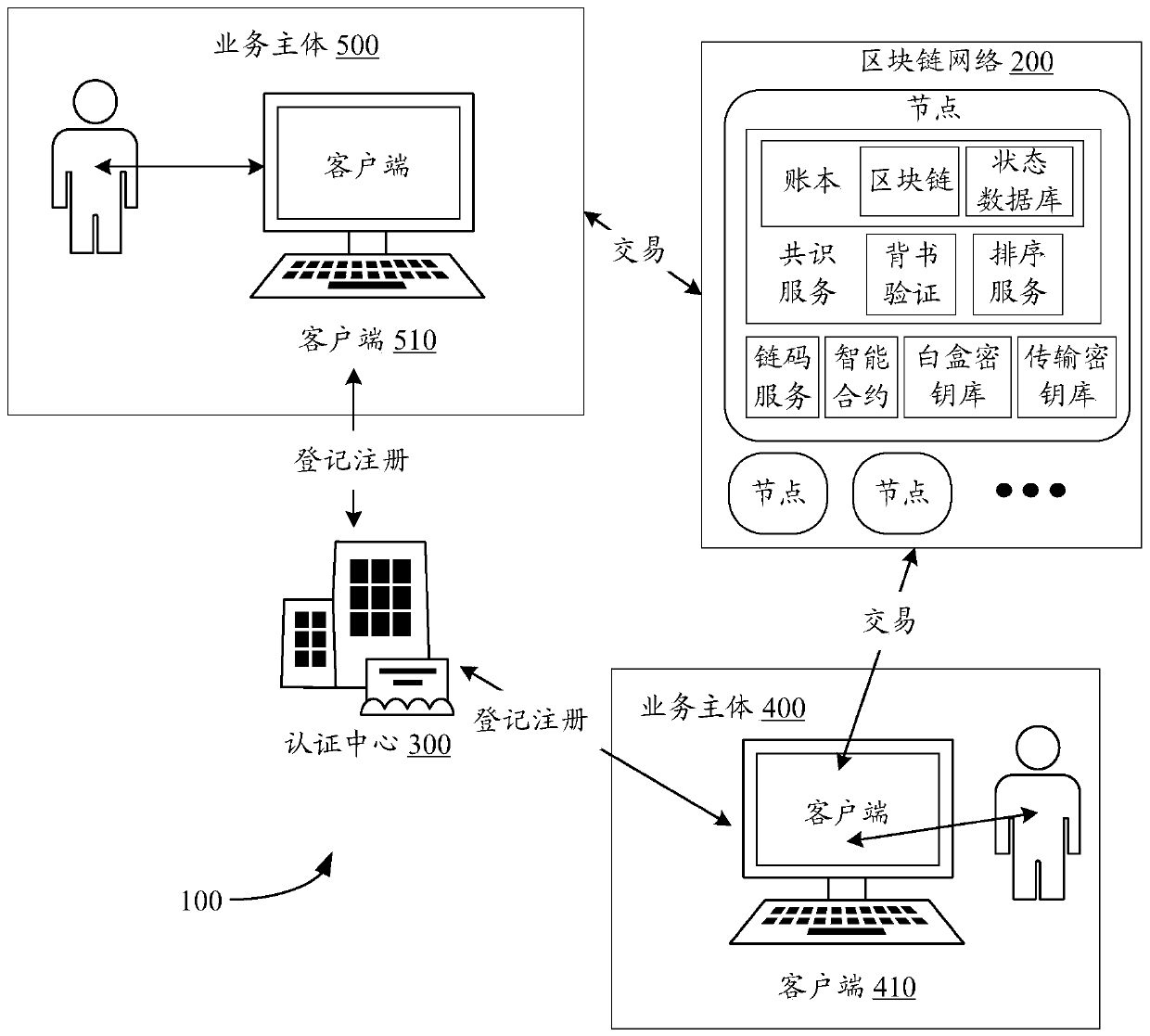
Data processing method and device based on blockchain network, electronic equipment and storage medium
ActiveCN110933108AEnsure safetyEasy for business logicFinanceUser identity/authority verificationEngineeringFinancial transaction
Owner:TENCENT TECH (SHENZHEN) CO LTD
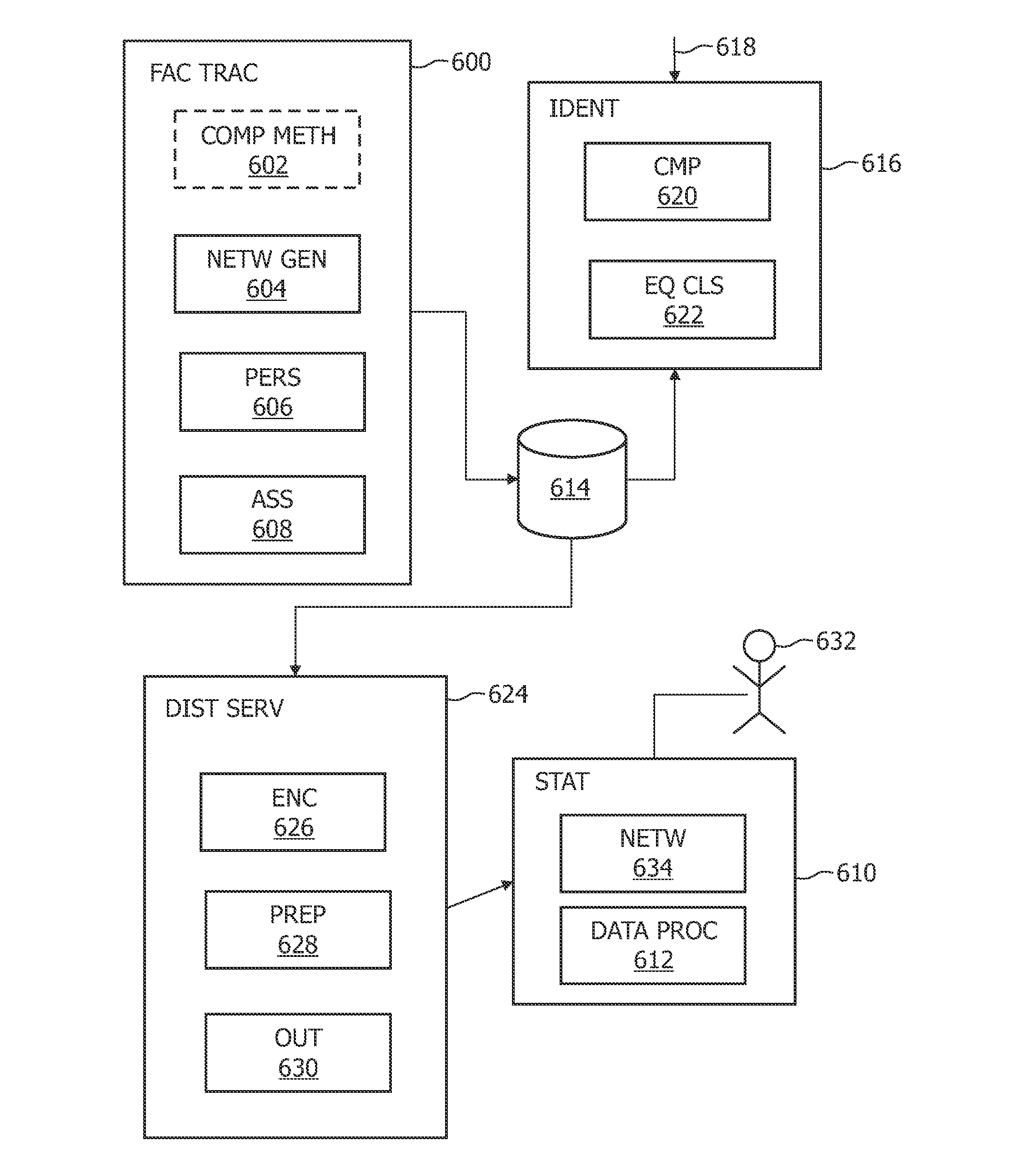
Method and system for tracking or identifying copy of implementation of computational method, and computation system
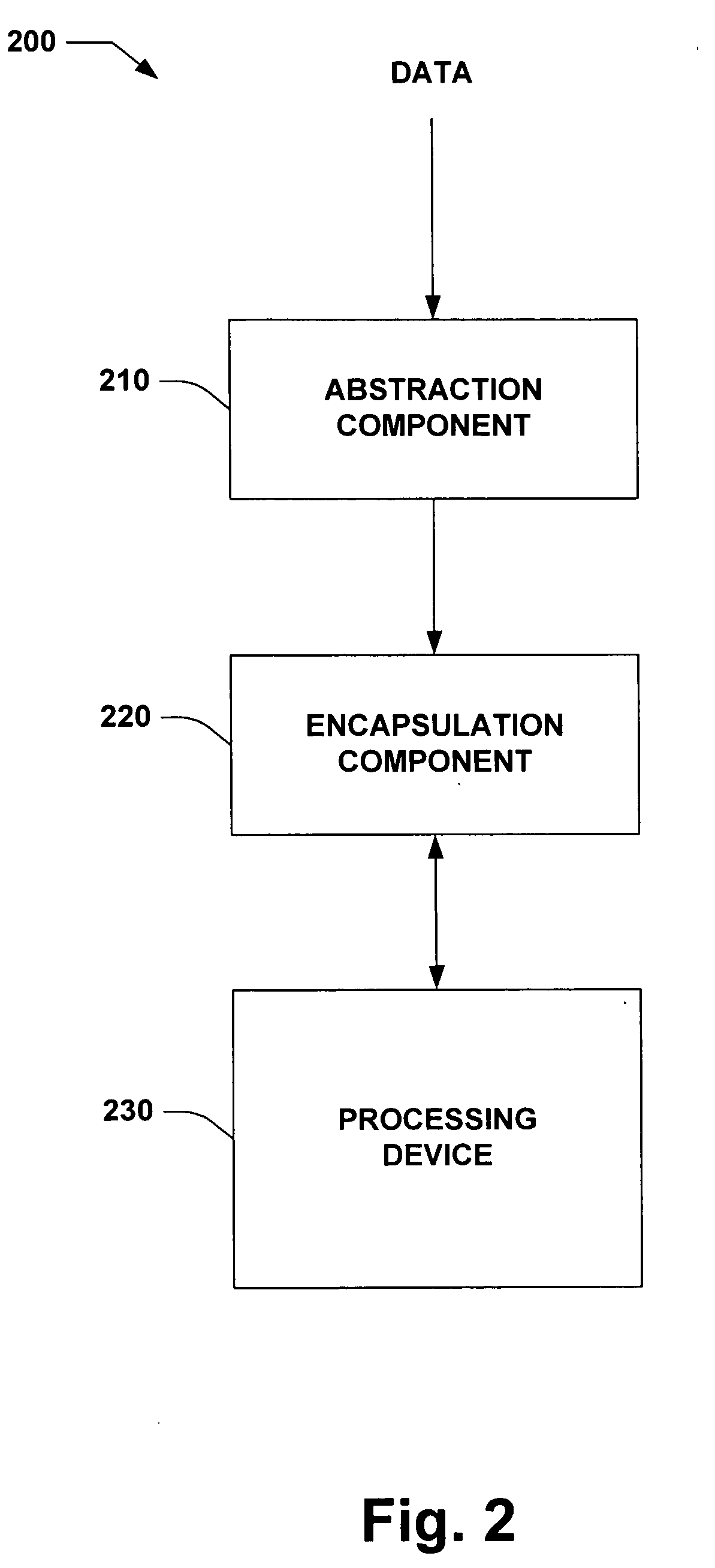
InactiveUS8306216B2Efficient use ofEfficient integrationHandling data according to predetermined rulesAnalogue secracy/subscription systemsAlgorithmTheoretical computer science
A method and system is provided facilitating tracing copies of an implementation of a computational method where different versions of a network of look-up tables representing steps of the computational method are generated, and stored in a memory, each version being unique so that output encodings and / or input decodings of the white-box implementations of the computational method are different in the different versions. The network is formed by using an output value of a first look-up table as an input value of a second look-up table. The different versions are generated by changing at least one value in the network, end results of the version corresponding to a relevant domain of input values being substantially the same for each version. A method and system for computation for a user with the corresponding version in the memory, and / or for identifying a copy of an implementation of the computational method is provided.
Owner:IRDETO ACCESS
AMBSE method suitable for aircraft airborne system architecture design
PendingCN112380625AReduce iterative processAvoid Subversive ModificationsGeometric CADDesign optimisation/simulationSystems designSystem requirements
The invention discloses an aMBSE method suitable for aircraft airborne system architecture design, and the method comprises the steps: converting the demands of stakeholders into system demands, defining system cases, and carrying out the case planning; translating the confirmed use case into an executable black box model, and verifying the model and related system requirements through dynamic behavior simulation of the model; providing a series of alternative schemes meeting requirements for system requirements, and seeking an optimal architecture scheme; gradually expanding a system-level black box model for function analysis into a subsystem-level white box model, and integrating mutually independent subsystems into a complete system architecture in an incremental iteration mode. Smalliteration is added in the system development process, large iteration is reduced, the model is tested in the early stage of design, a reasonable architecture design thought is determined, problems inearly-stage design are prevented from being brought into the verification stage, the complexity of system design is reduced, and the problem of demand change in system engineering is effectively solved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
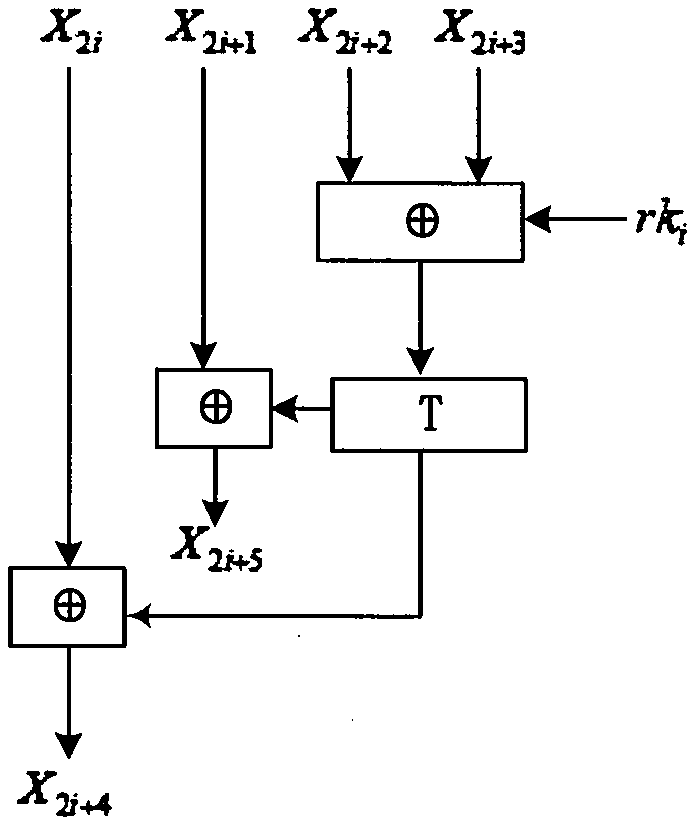
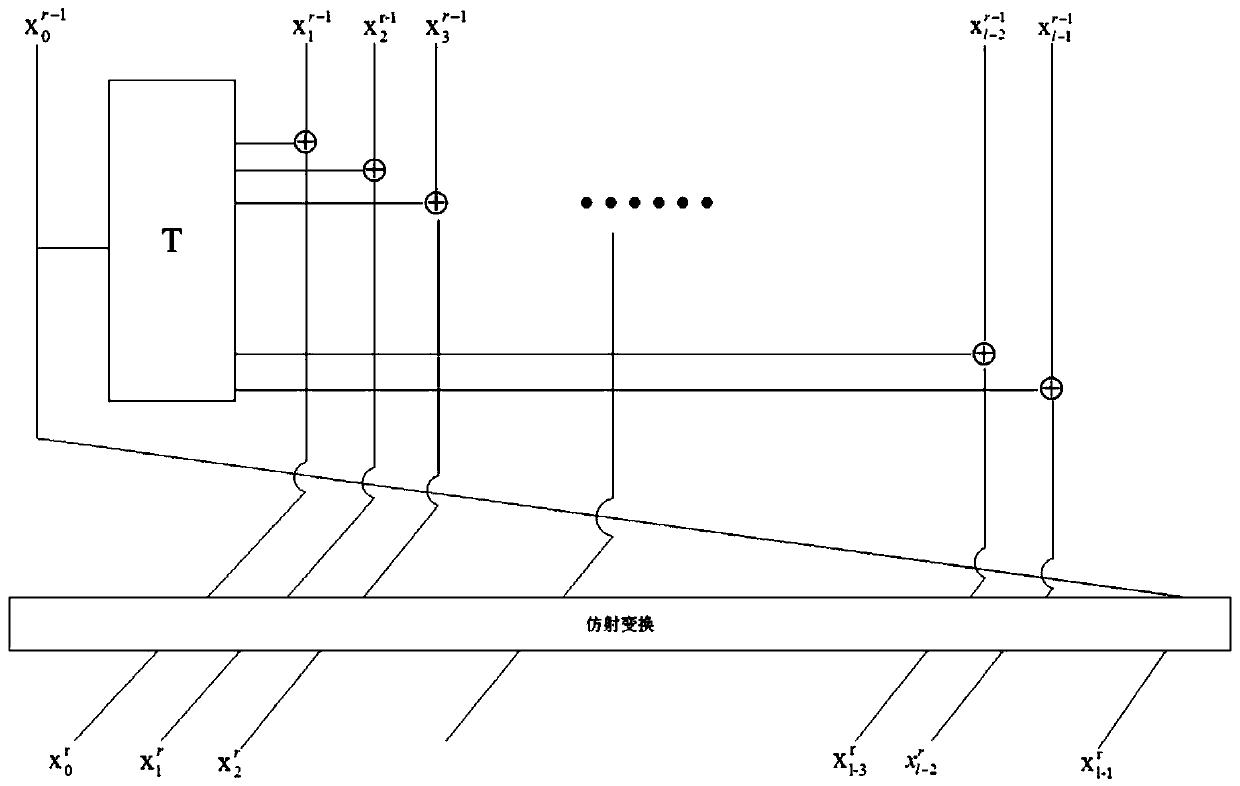
White box block cipher construction method and system based on FeisiteBox Box structure
ActiveCN109981256AImprove securityAffine Transform EliminationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordCiphertext
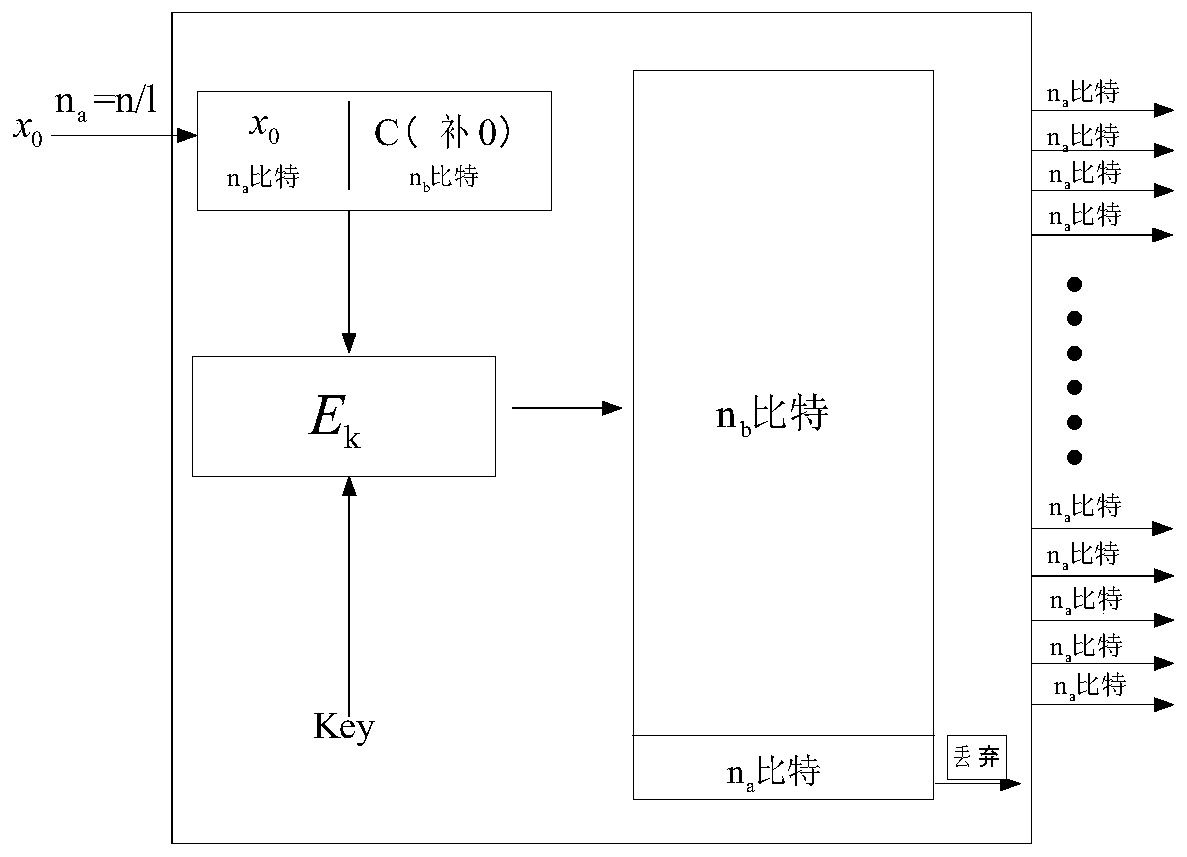
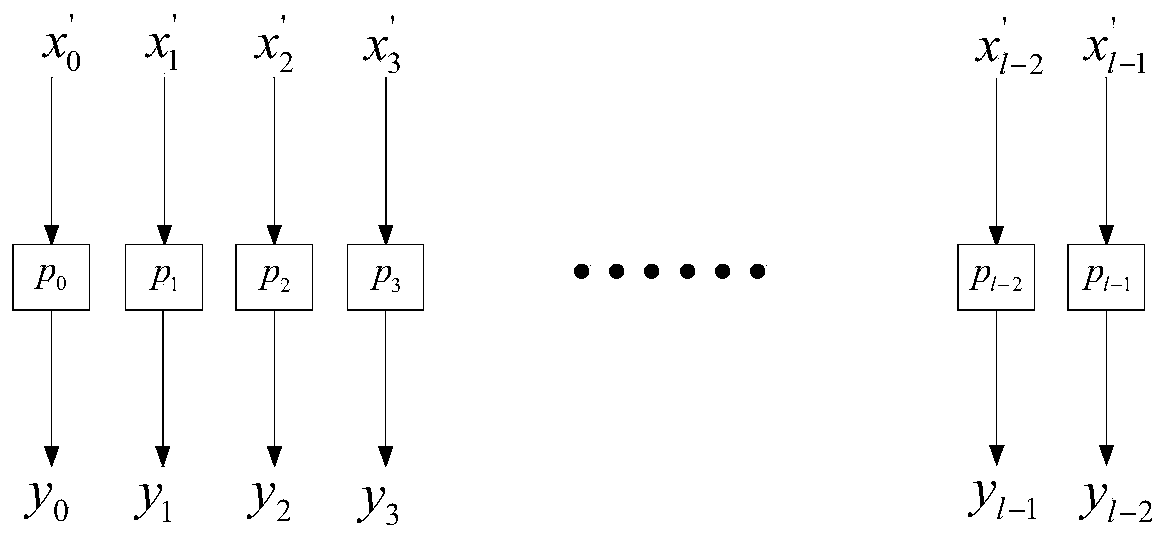
The invention discloses a white box block cipher construction method and system based on a FeisiteBox Box structure. The method comprises the steps that an n-bit plaintext is input, the size na of a block and the iteration processing round number r of a FistelBox structure are set, bit conversion is conducted through a T function, input na-bit bits are converted into nb-bit bits to be output, andna + nb = n; affine transformation is added between the wheels of the iteration processing wheel number, chain connection is performed, the operation of each round is tightly connected with the operation of the previous round and the operation of the next round, the inverse transformation of the affine transformation of the previous round is embedded into the lookup table operation of the round, the affine transformation of the previous round is applied to the result of the lookup table, and the affine transformation layer adopts the reversible affine transformation matrix; S1-S2 encryption operation is executed to obtain an encryption result; the system comprises a bit conversion module, an affine transformation module and an operation execution module. According to the invention, an attacker cannot obtain the information of the ciphertext, the password cracking difficulty of the attacker is increased, and the security of key storage is enhanced.
Owner:SOUTH CHINA NORMAL UNIVERSITY
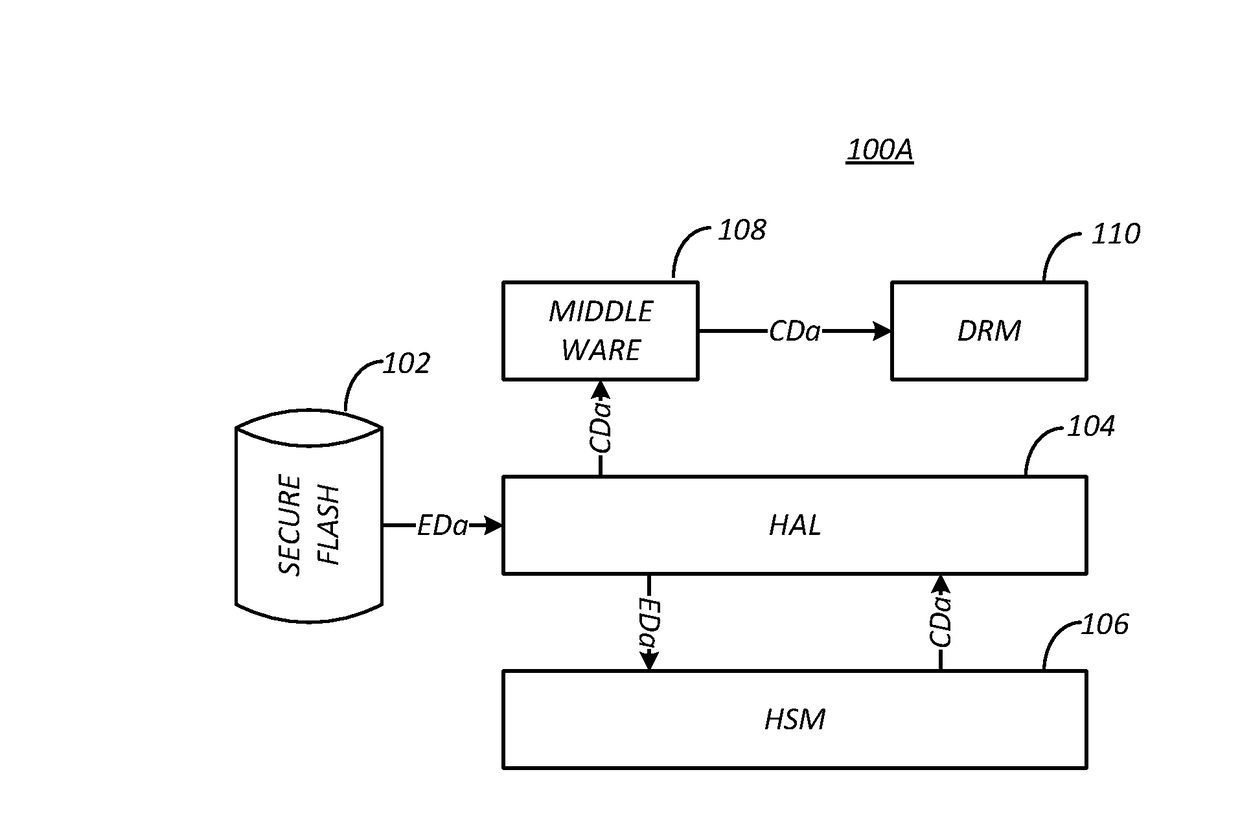
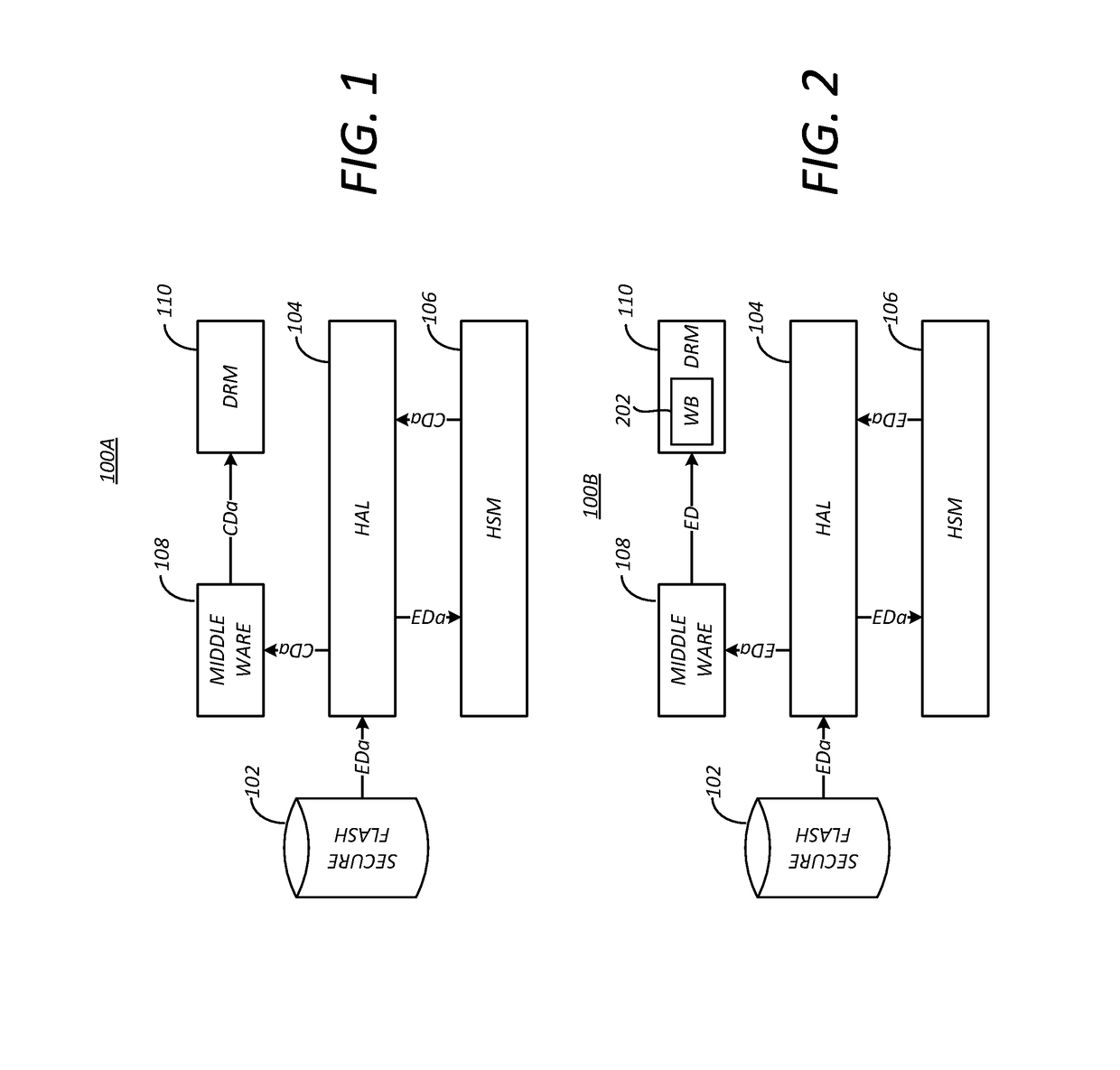
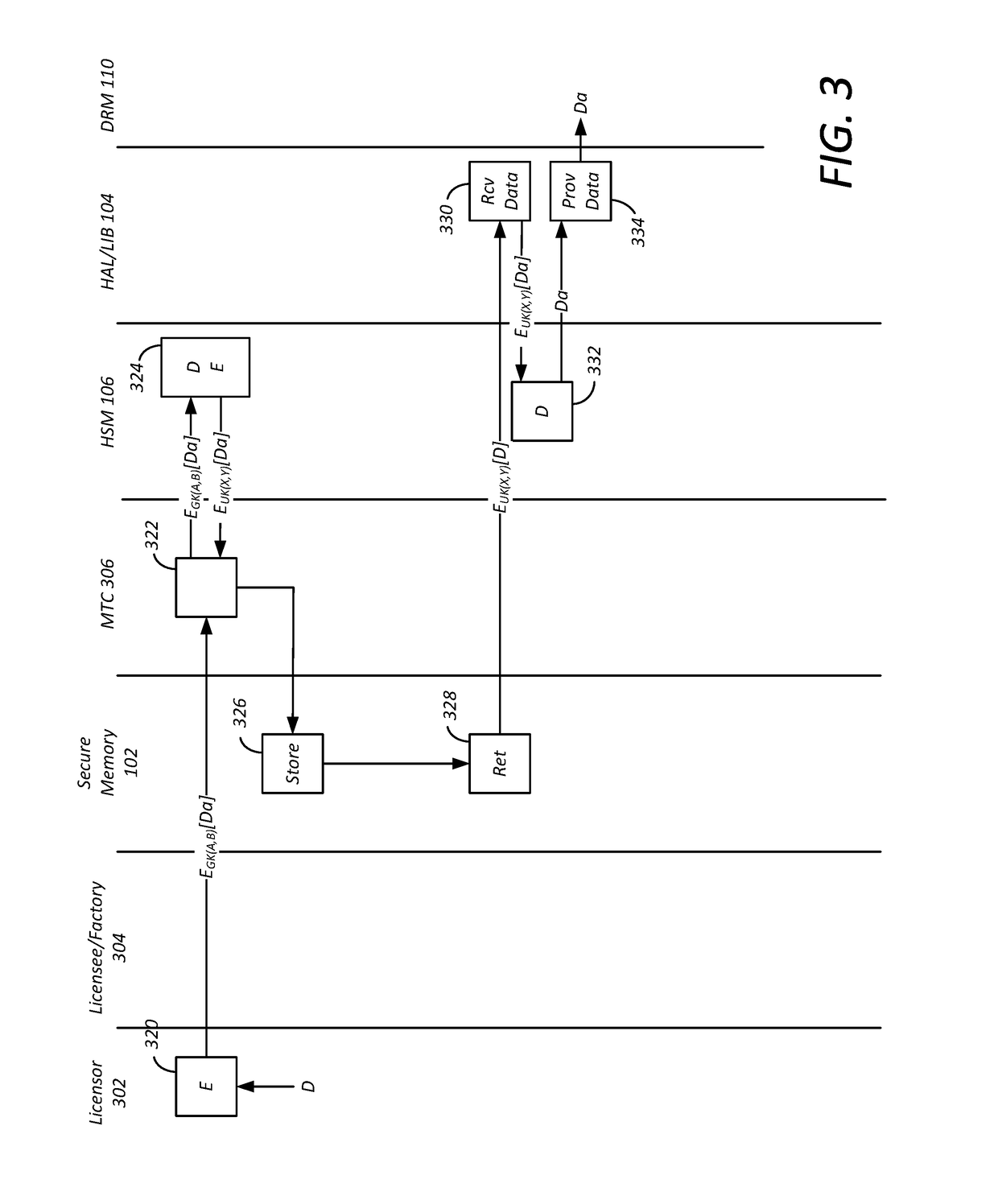
Method and apparatus for protecting confidential data in an open software stack
A method is provided for securely providing data for use in a consumer electronics device having a processor performing instructions defined in a software image. The method includes receiving the data encrypted according to a global key, further encrypting the data according to a device-unique hardware key, storing the further encrypted data in a secure memory of the consumer electronics device, providing the global key to a whitebox encoder for encoding according to a base key to generate a whitebox encoded global key, and transmitting the software image to the consumer electronics device for storage in an operating memory of the consumer electronics device, the software image having a whitebox decoder utility corresponding to the whitebox encoder and the whitebox encoded global key.
Owner:ARRIS ENTERPRISES LLC
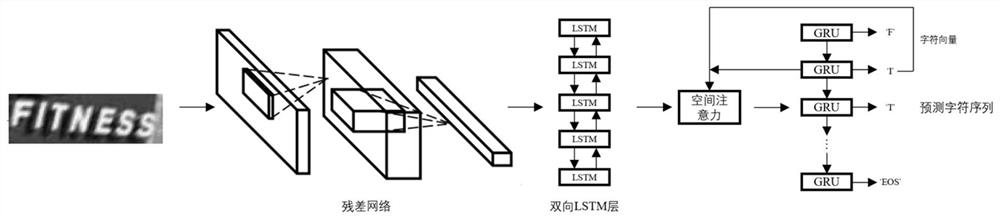
Non-directional white-box attack resisting method for scene character recognition
InactiveCN112836798ALittle noise disturbanceOptimizing Noise SizeCharacter and pattern recognitionNeural architecturesText recognitionNetwork model
The invention discloses a non-directional white-box attack resisting method for scene character recognition, which is characterized in that noise which is difficult to perceive by human eyes is added into an input image, so that a character recognition algorithm obtains a recognition result which is totally different from the original recognition result, and the effect of attacking a scene character recognition network model is achieved. Different from common object recognition, a character recognition result is a character sequence, so that an existing adversarial attack method cannot be directly applied to scene character recognition. Therefore, the method comprises the following steps: firstly, an objective function in a single object classification adversarial attack algorithm is modified into a sequence form; in order to accelerate generation of an adversarial sample, a step function is introduced in, and once a character is different from the recognition result of the original image in the recognition result of the adversarial sample, the penalty of the target function is zero; besides, in consideration of different attack difficulty levels of different samples, the more easily recognized correctly the samples are, the more difficultly attacked the samples are, recognition scores are introduced into the target function, so that adversarial samples with smaller disturbance are obtained.
Owner:HUAZHONG UNIV OF SCI & TECH
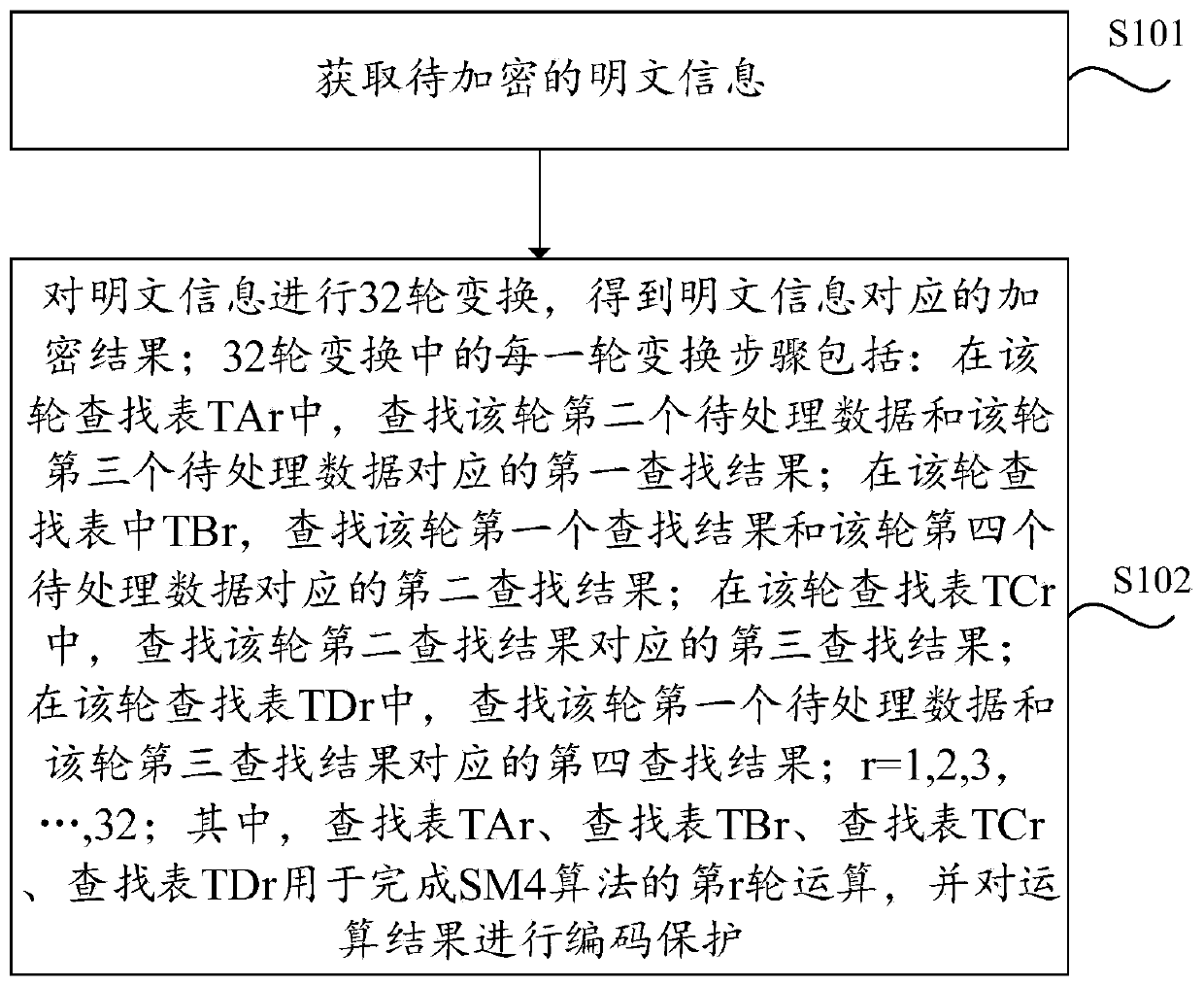
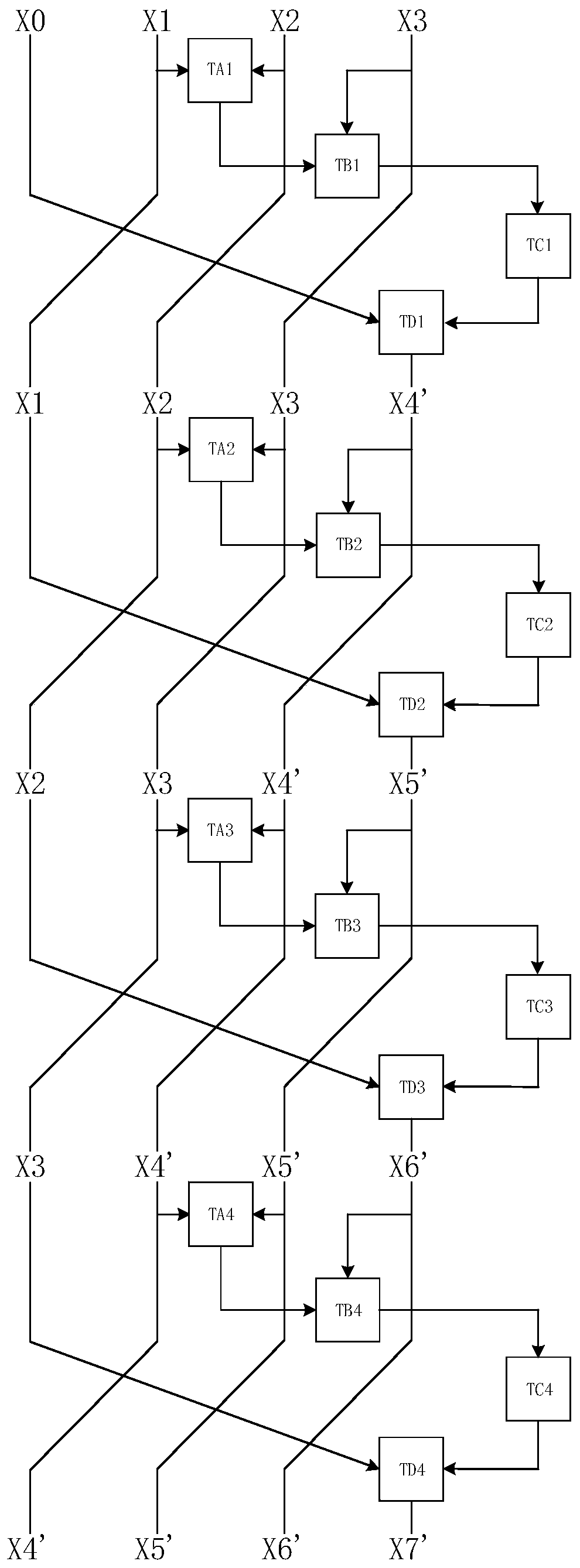
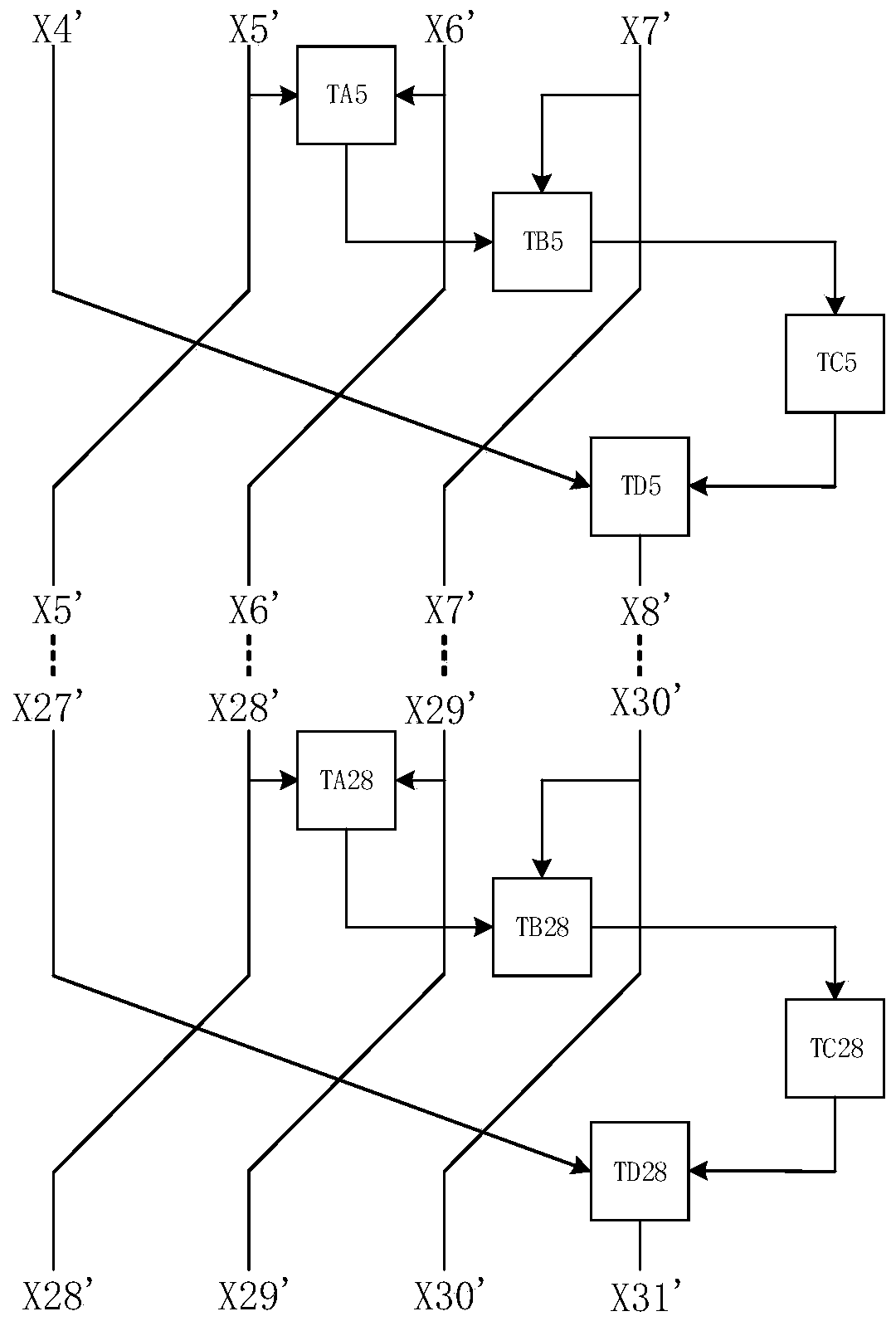
SM4 algorithm white box implementation method and device, electronic equipment and computer medium
PendingCN110784306AImprove smoothness of interactionImprove securityEncryption apparatus with shift registers/memoriesAlgorithmParallel computing
The invention provides an SM4 algorithm white box implementation method and device, electronic equipment and a computer medium. The method comprises the steps of obtaining plaintext information to beencrypted; performing 32 rounds of transformation on the plaintext information to obtain an encryption result corresponding to the plaintext information, wherein each round of transformation in the 32rounds of transformation comprises the following steps: in the round of lookup table TAr, searching a first lookup result corresponding to the second round of data to be processed and the third roundof data to be processed; searching a first search result of the round and a second search result corresponding to fourth to-be-processed data of the round in the round search table TBr; searching a third search result corresponding to the second search result in the round of lookup table TCr; in the round of lookup table TDr, searching a fourth lookup result corresponding to the first round of data to be processed and the third round of lookup result, wherein r is equal to 1, 2, 3,..., 32, the lookup table TAr, the lookup table TBr, the lookup table TCr and the lookup table TDr are used for completing the rth round of operation of the SM4 algorithm, and encoding protection is carried out on an operation result; and the key has high security.
Owner:中电科网络安全科技股份有限公司
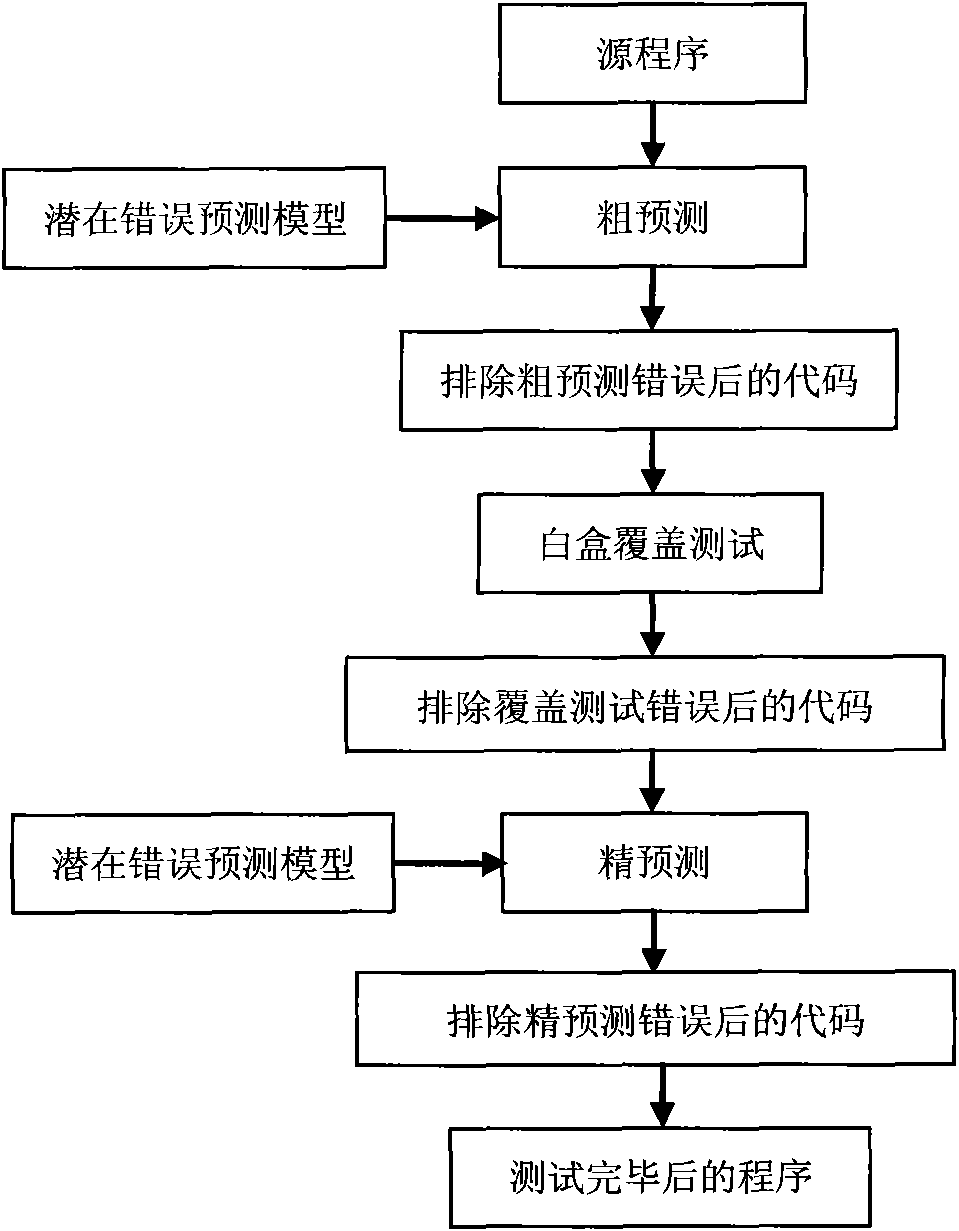
Method for testing improved host-oriented embedded software white box
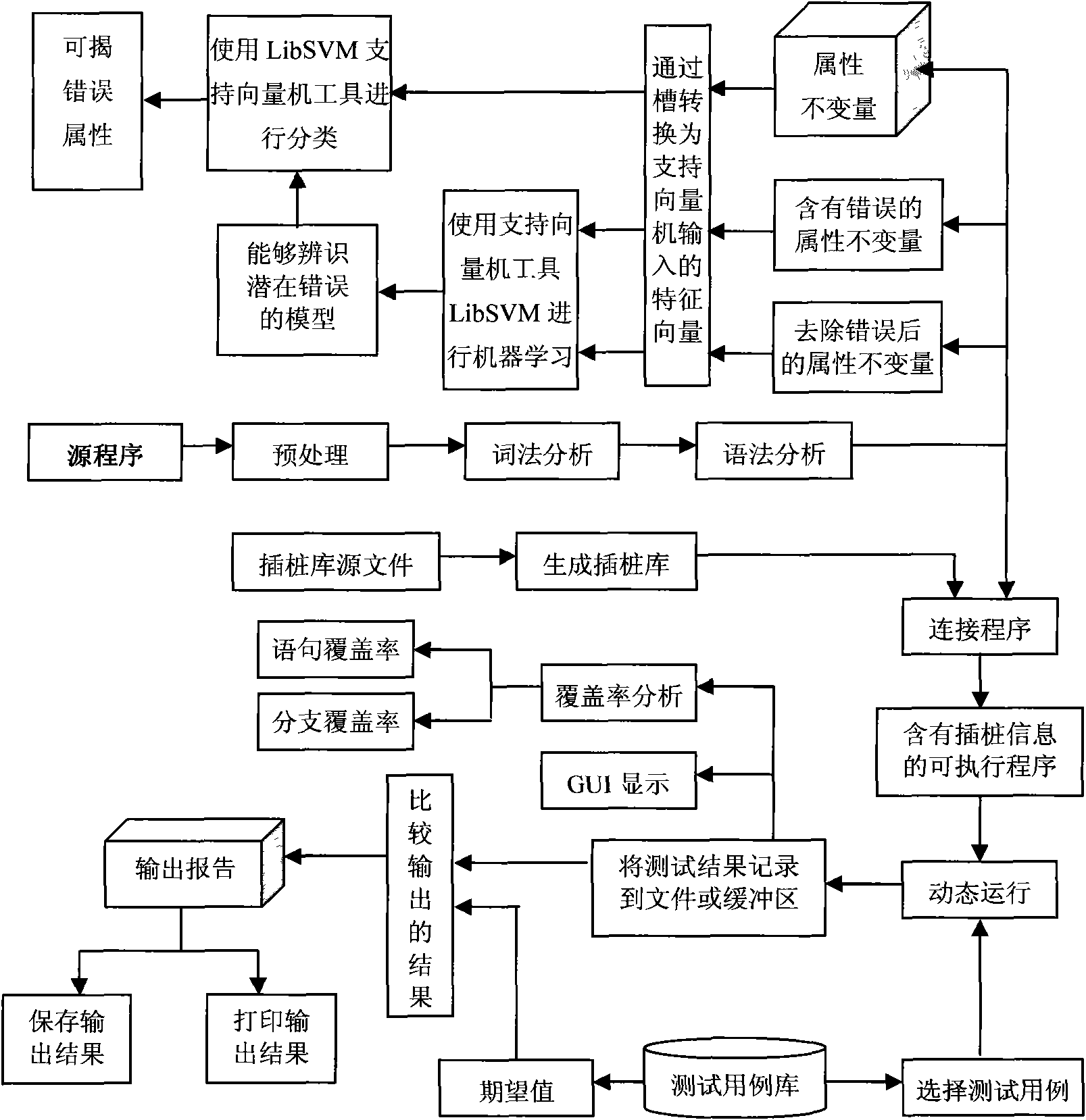
InactiveCN101576850AImprove general performanceSoftware testing/debuggingSupport vector machineSoftware bug
The invention discloses a method for testing an improved host-oriented embedded software white box, and belongs to the technical field of embedded software test. The method comprises the following steps: 1, a first stage test (coarse prediction), comprising extraction of program invariable, machine learning, machine prediction and the like based on a support vector machine, and preliminarily revealing hidden error; 2, a second stage test (prior white box test), namely carrying out embedded software white box coverage test on the program removed with revealed error attribute, and removing problems appearing during removal test, wherein the white box test comprises lexical analysis, grammar analysis, software measurement analysis and coverage rate analysis; and 3, a third stage test (precise prediction), namely identifying the program removed with the problems appearing during coverage test by using a machine predication step in the first stage to acquire possibly hidden deeper program error. The method can be applied to different programs and has strong universality.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
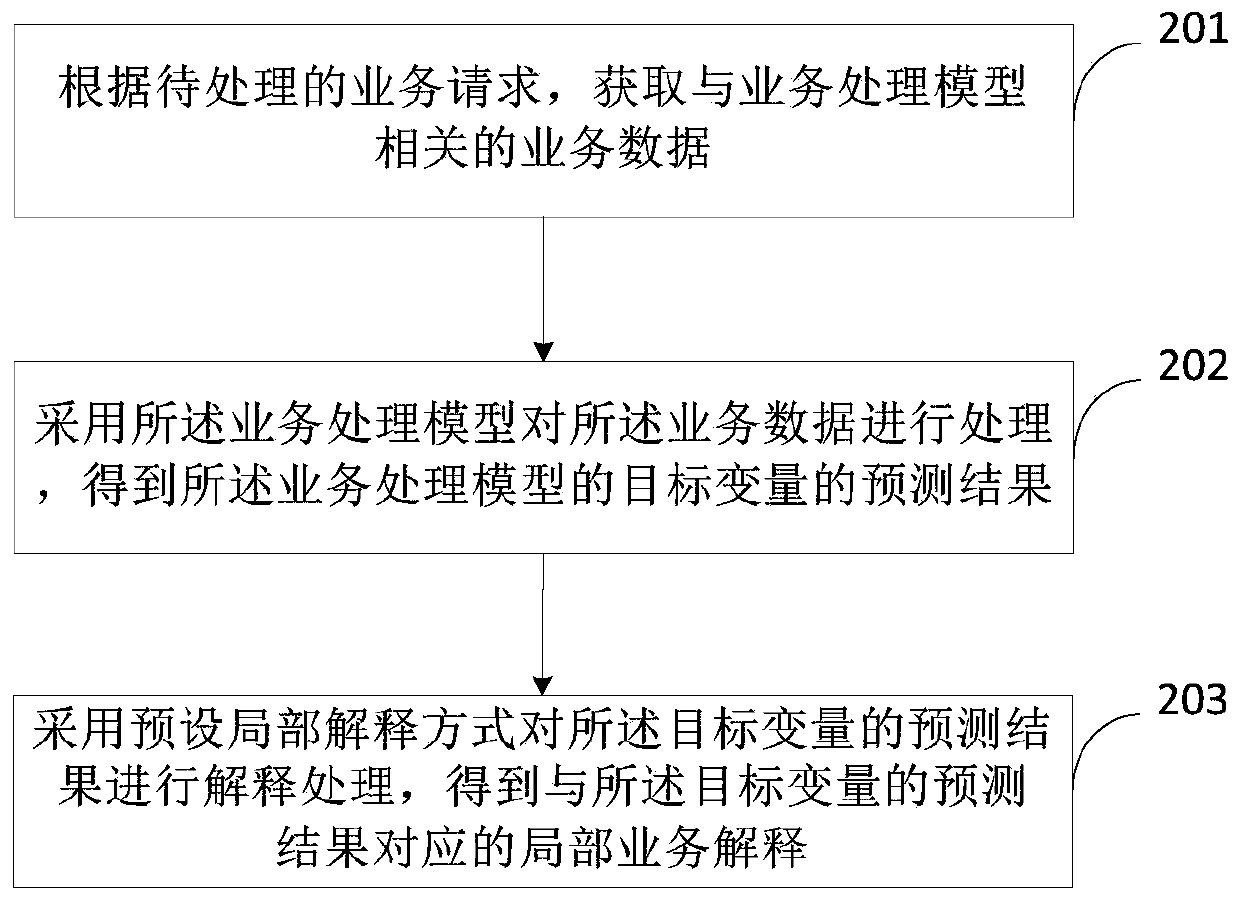
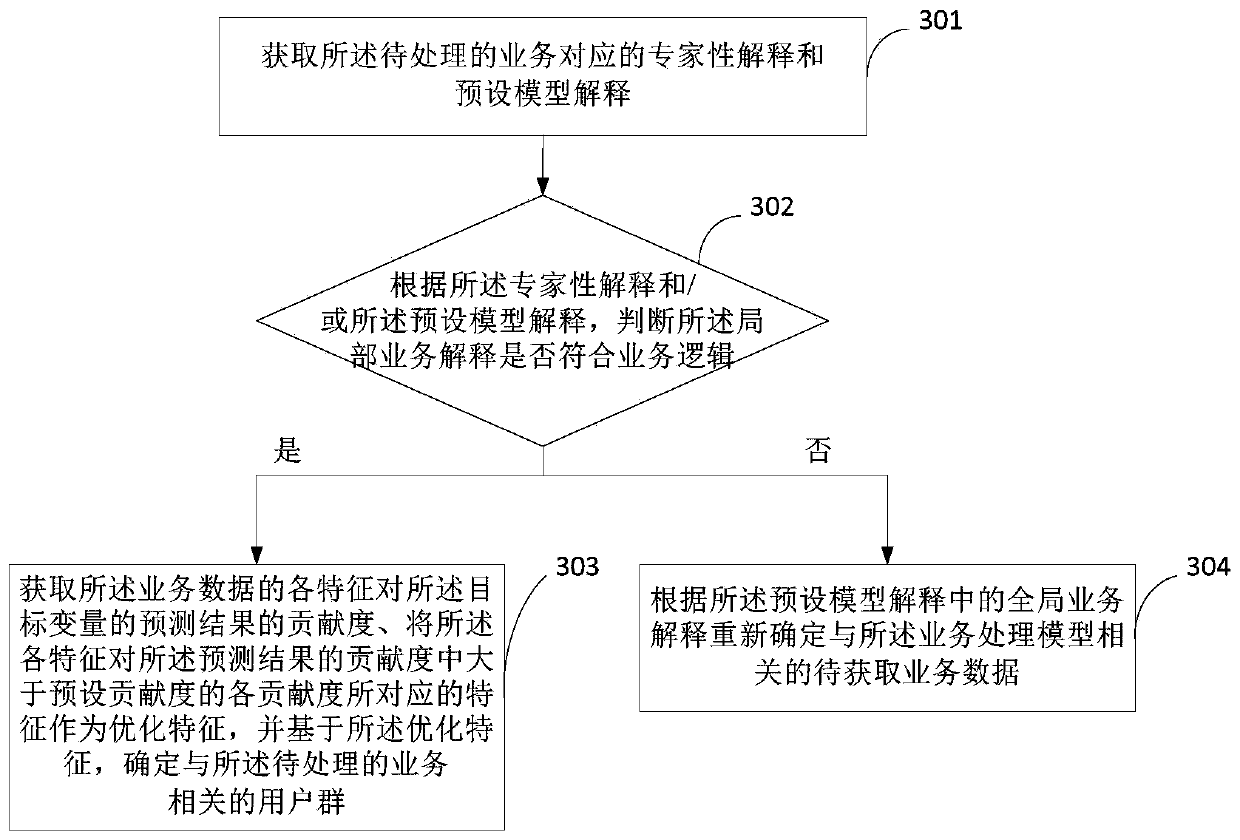
Service processing method and device, equipment and storage medium
The embodiment of the invention provides a service processing method and device, equipment and a storage medium. The method comprises: processing service data corresponding to a to-be-processed service request by adopting a service processing model to obtain the prediction result of the target variable of the service processing model; and interpreting the prediction result of the target variable by adopting the preset local interpretation mode to obtain the local service interpretation corresponding to the prediction result of the target variable. Visibly, in the embodiment of the invention, the machine learning model and the model interpretation are combined so that a machine learning model is made to be a white box, related service interpretation information about the machine learning model is obtained, the interpretability of the machine learning model is improved; on one hand, the credibility of the model is improved, and the utilization rate of the machine learning model in the technical field with the high requirement for the interpretability of the model is increased; and on the other hand, the user group suitable for the to-be-processed service can be determined in combination with the service interpretation information.
Owner:JINGDONG TECH HLDG CO LTD
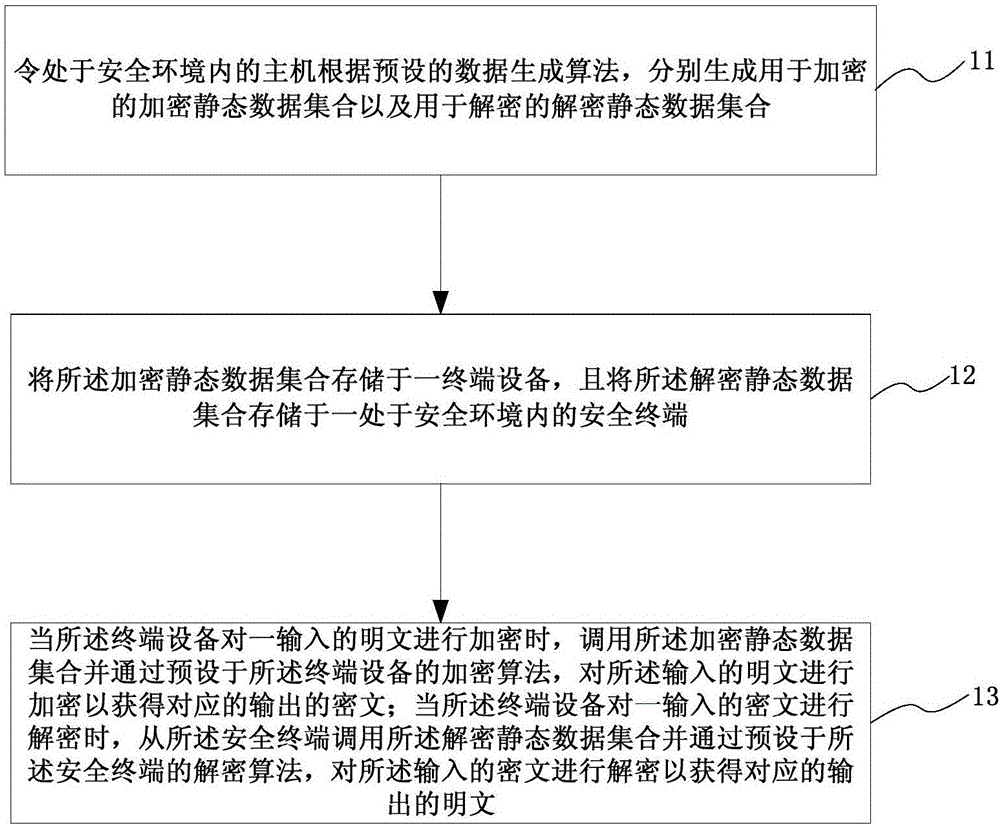
Safety operation method and system based on white box encryption
ActiveCN106603224ASmall static data volumeImprove operational efficiencyEncryption apparatus with shift registers/memoriesEncryptionStatic data
The invention provides a safety operation method and system based on white box encryption. The corresponding encryption algorithm and the decryption algorithm are matched by employing a series of static data as fixed input, lightweight safety operation can be realized, the volume of the static data is small, the operation efficiency is high, and relatively high encryption security can be obtained in a white box attack environment with limited calculating resources.
Owner:TONGJI UNIV
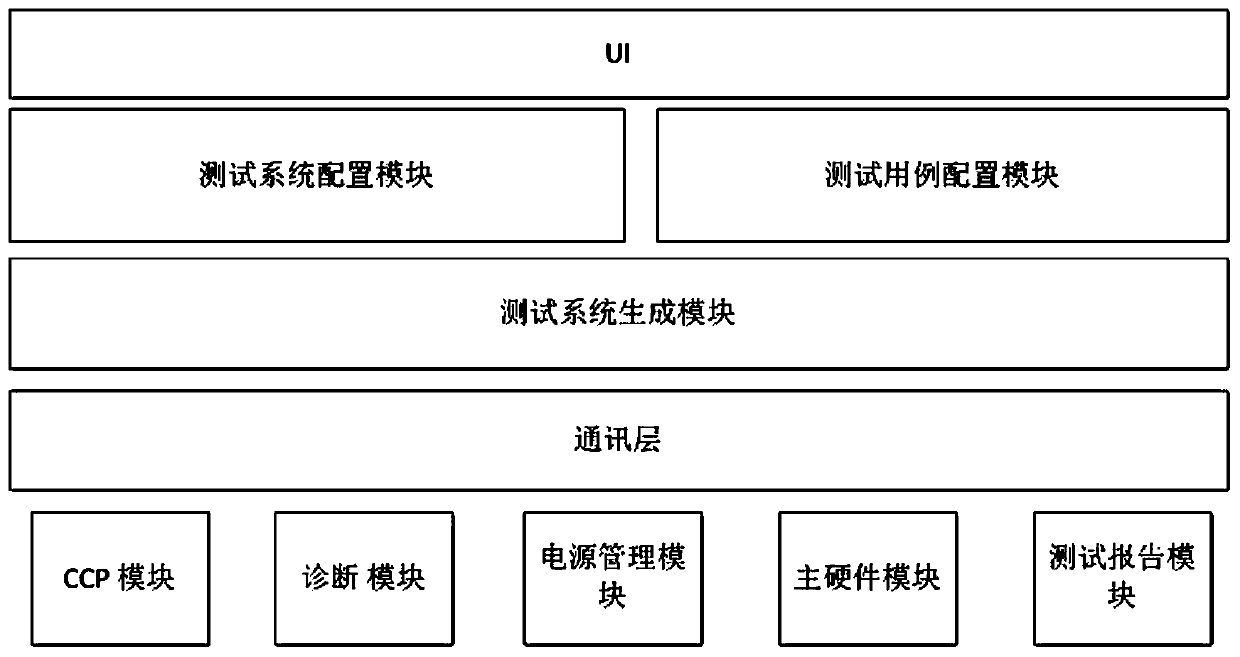
Full-automatic test system for automobile electronic equipment
PendingCN107861874ASolve only manual black box testingSolve the repeatabilitySoftware testing/debuggingComputer configurationSoftware system
The invention relates to the field of automatic testing of automobile embedded software, in particular to a full-automatic test system for automobile electronic equipment. The test system comprises atest platform; the test platform comprises a hardware system, a lower computer detection control software system and an upper computer configuration software system; the hardware system comprises a communication module, a signal module and a programmable power supply module. Compared with the prior art, the test system can be freely matched with test system hardware, and test cases can be automatically generated through simple configuration to conduct white-box testing and black-box testing on embedded software; all signals and results can be fed back in the testing process, and the problems that when automobile embedded software is tested previously, only manual black-box testing can be conducted, and a large number of repetitive tests can not be conveniently conducted are solved.
Owner:NINGBO PREH JOYSON AUTOMOTIVE ELECTRONICS
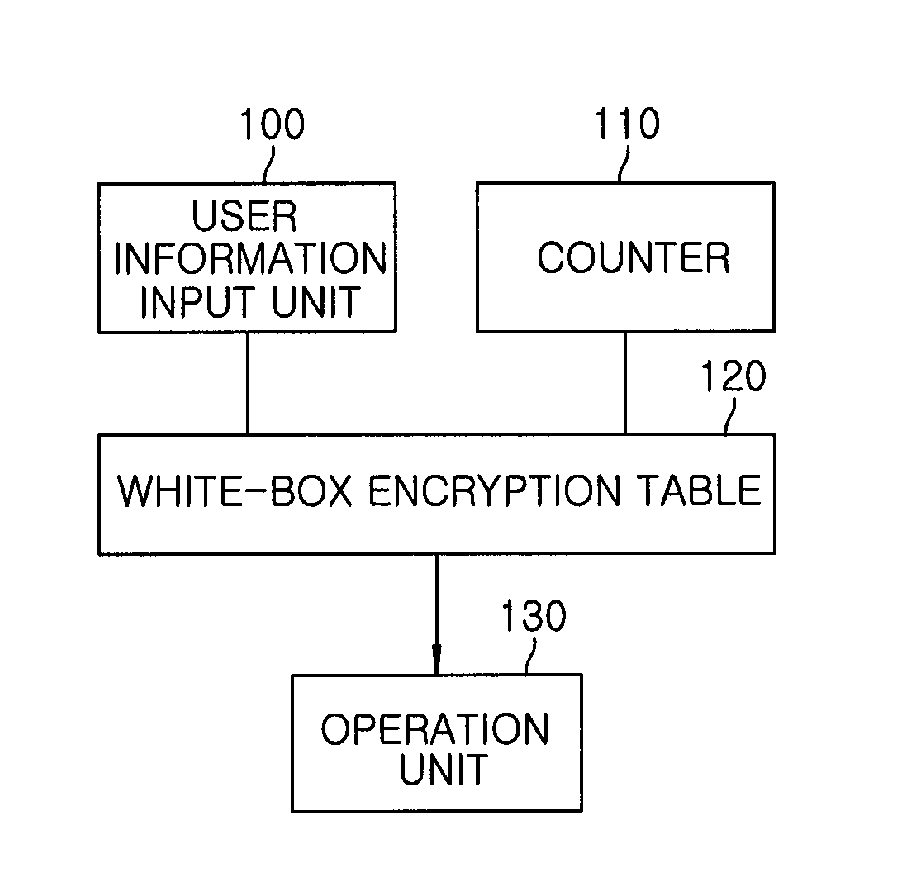
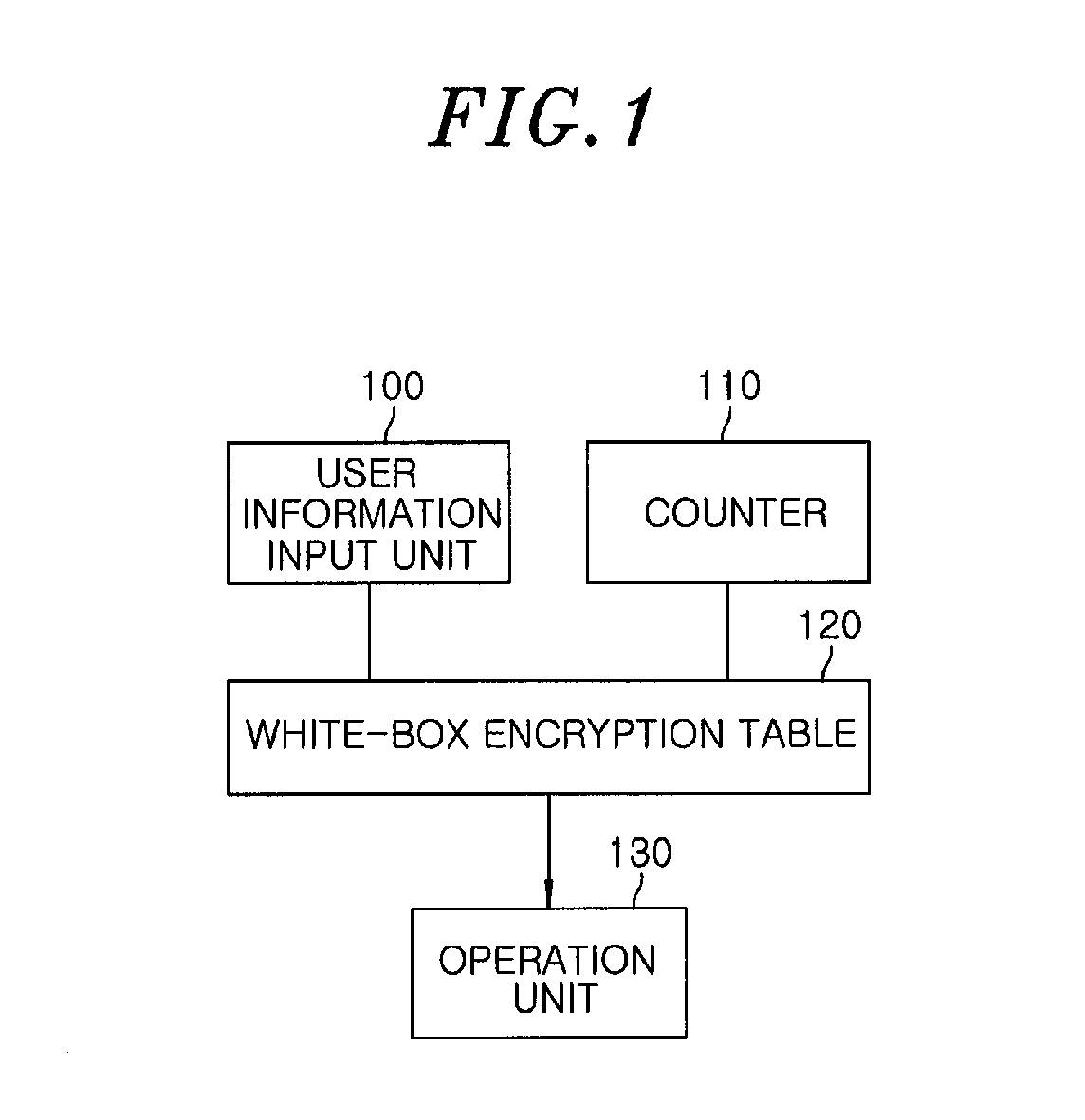
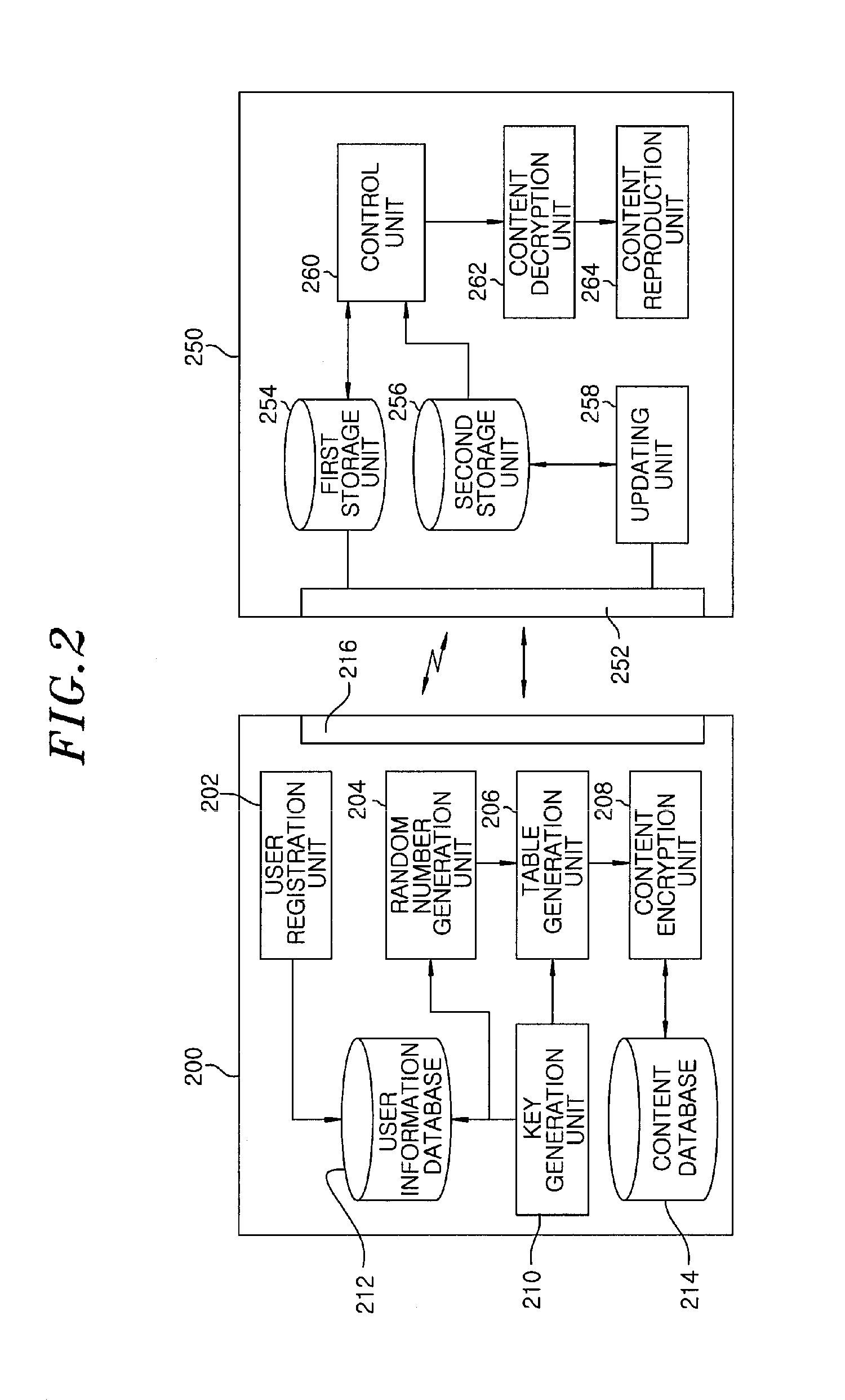
Content protection apparatus and content encryption and decryption apparatus using white-box encryption table
InactiveUS8712041B2Secret communicationProgram/content distribution protectionEncryptionRandom number generation
A content protection apparatus using a white-box encryption table includes: a random number generation unit for generating a random number; a white-box encryption table for encrypting the random number and user information provided from a user to generate an encrypted output value; and an operation unit for performing an operation between the encrypted output value and data inputted from an outside to encrypt or decrypt the data.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com