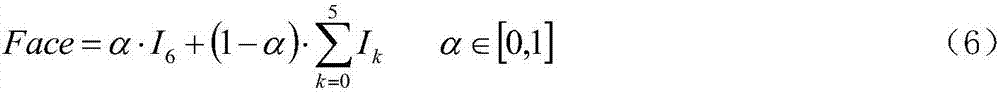Patents
Literature
1385 results about "System hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
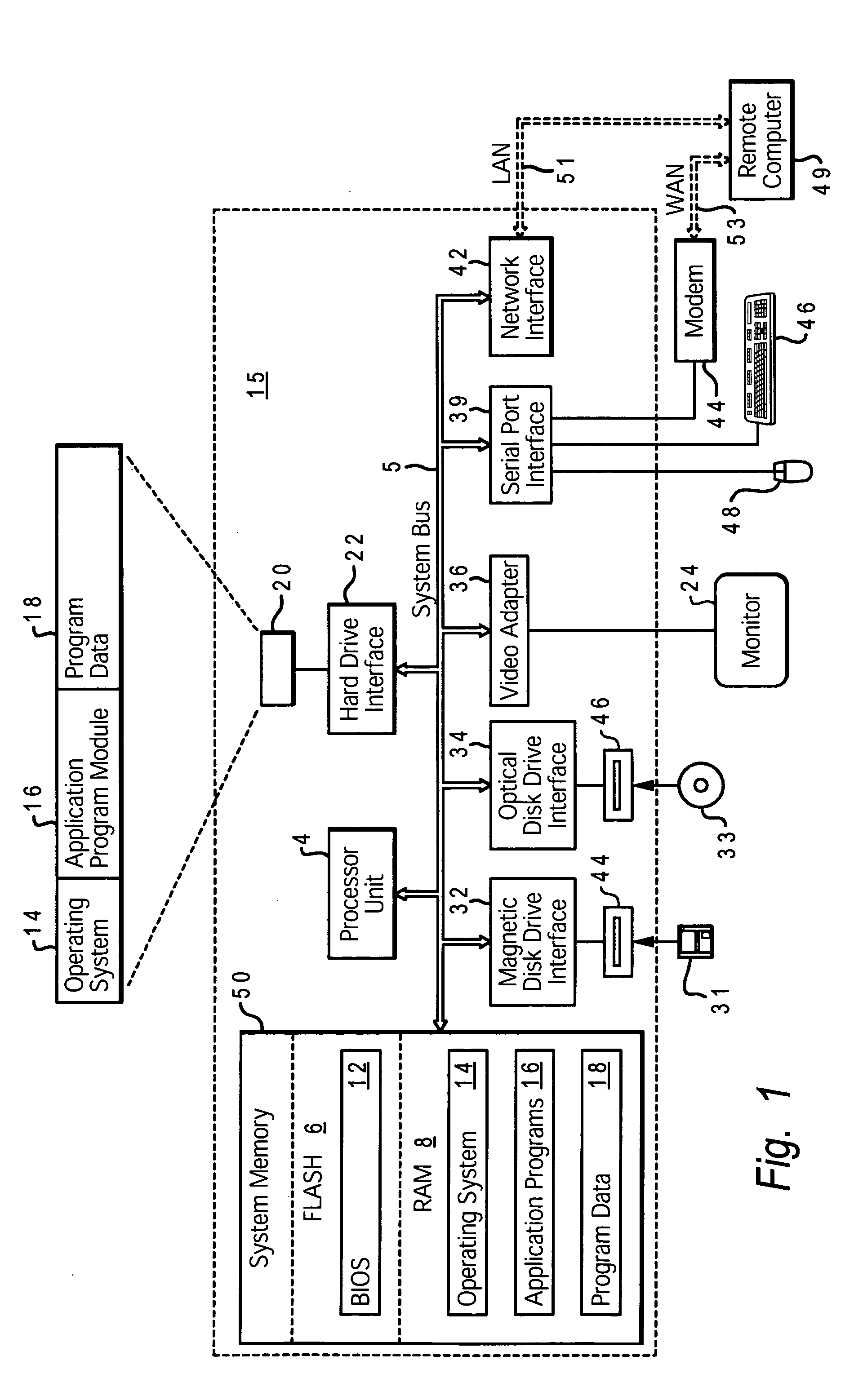
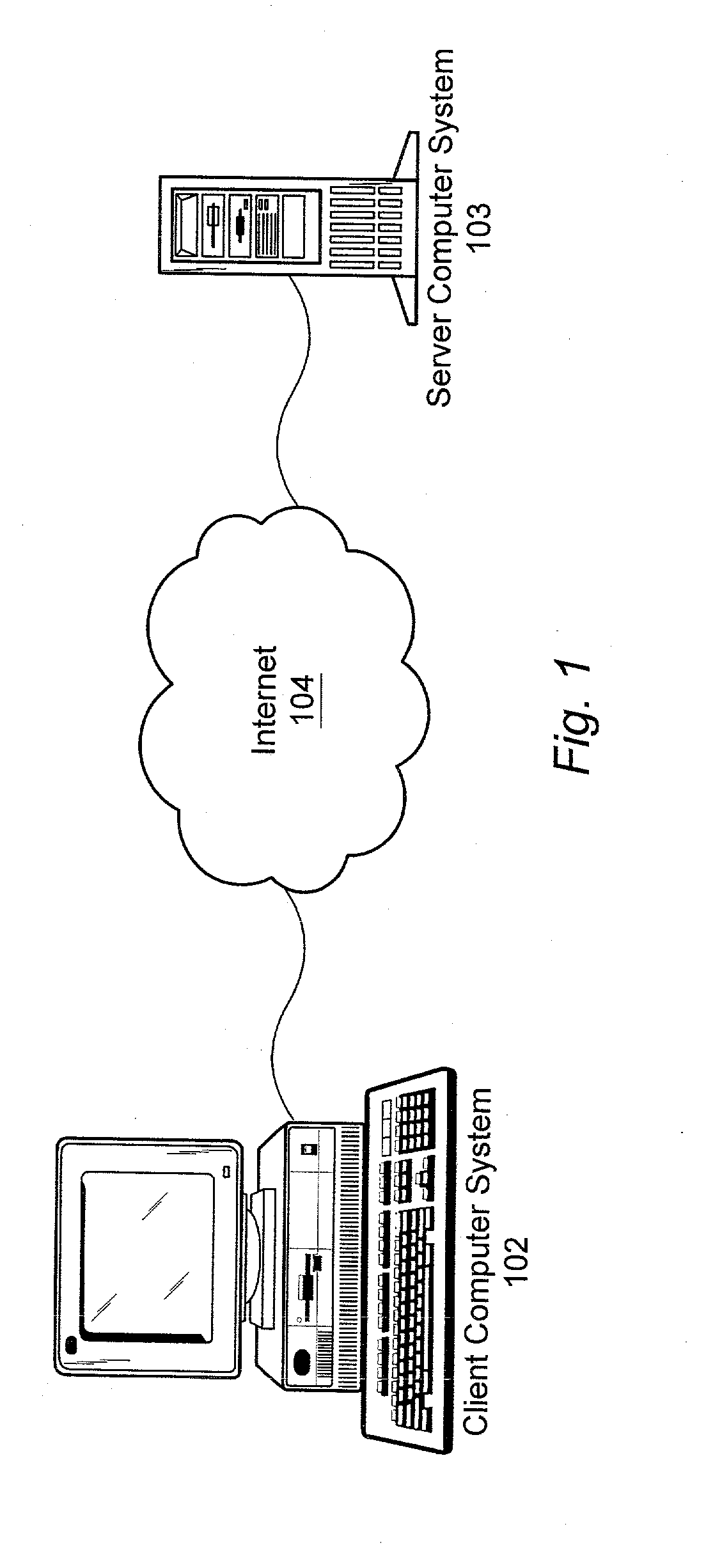
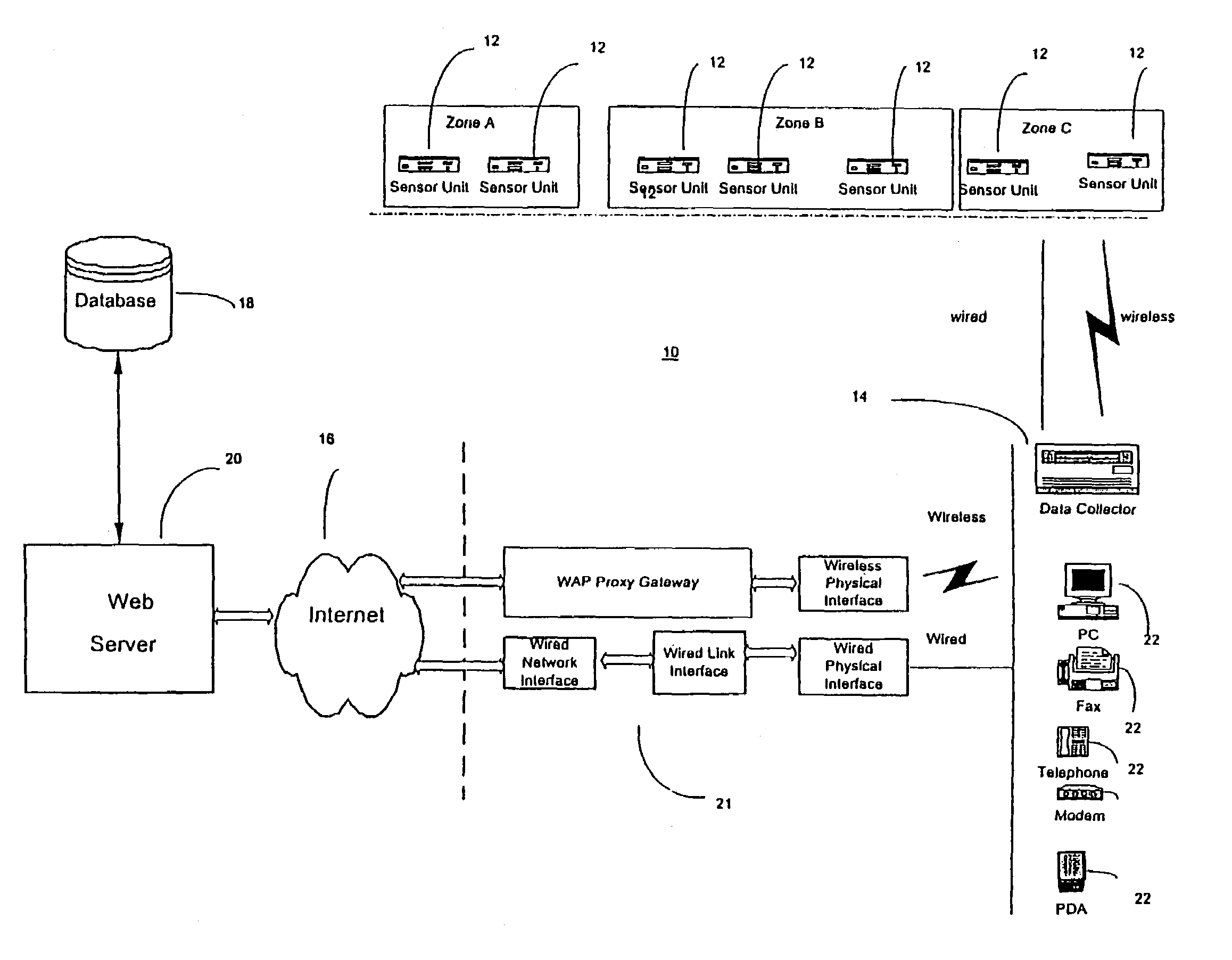
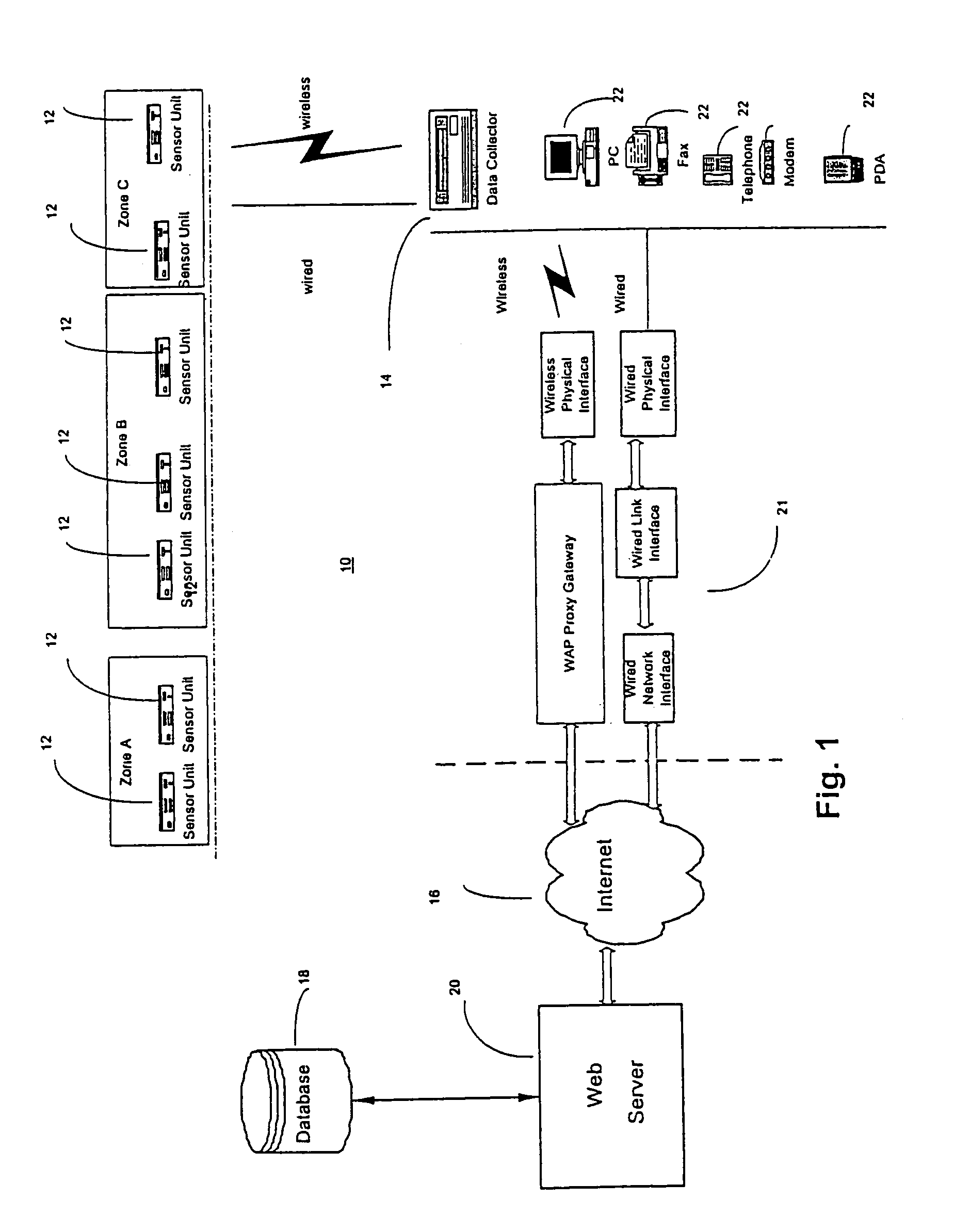
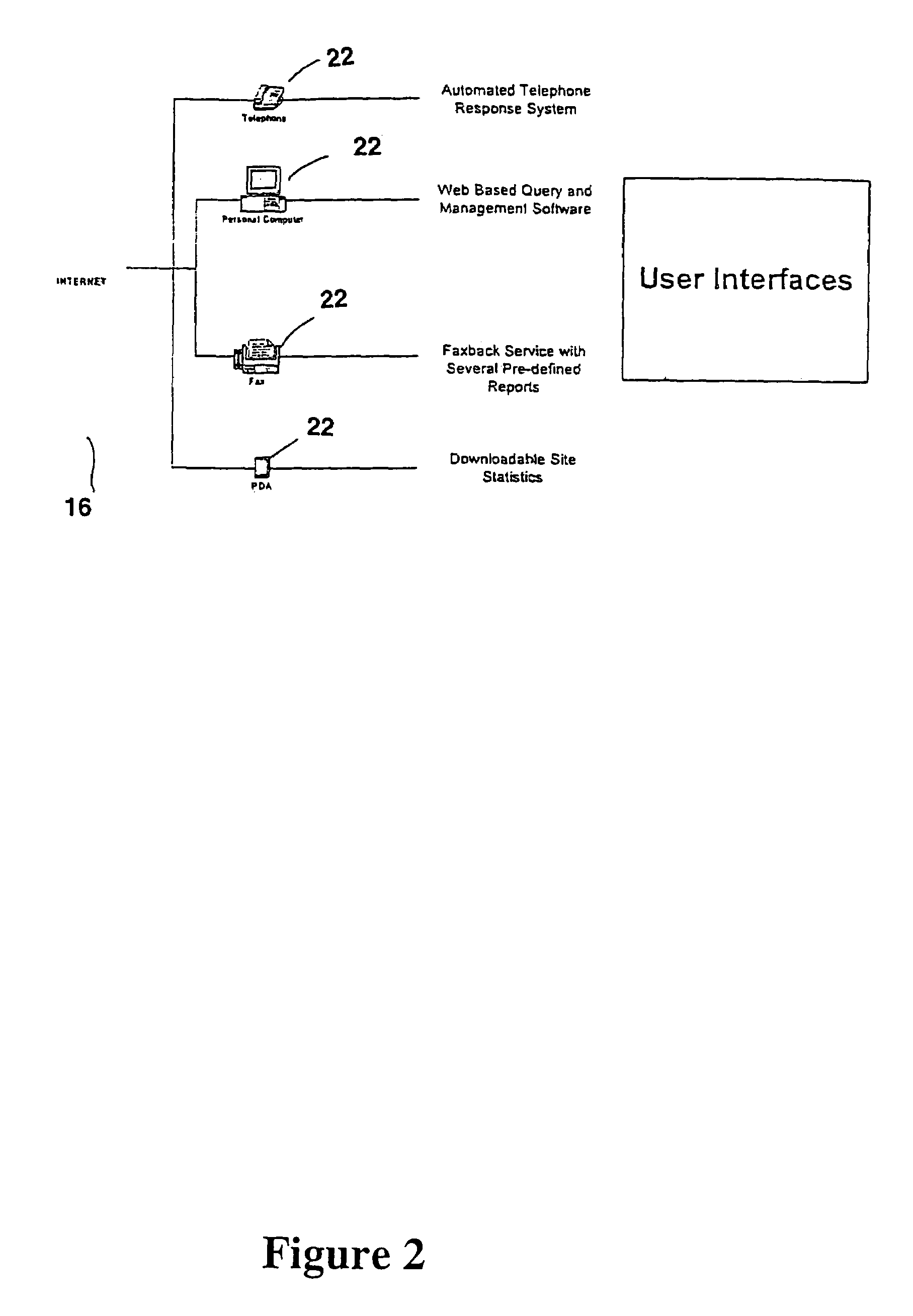
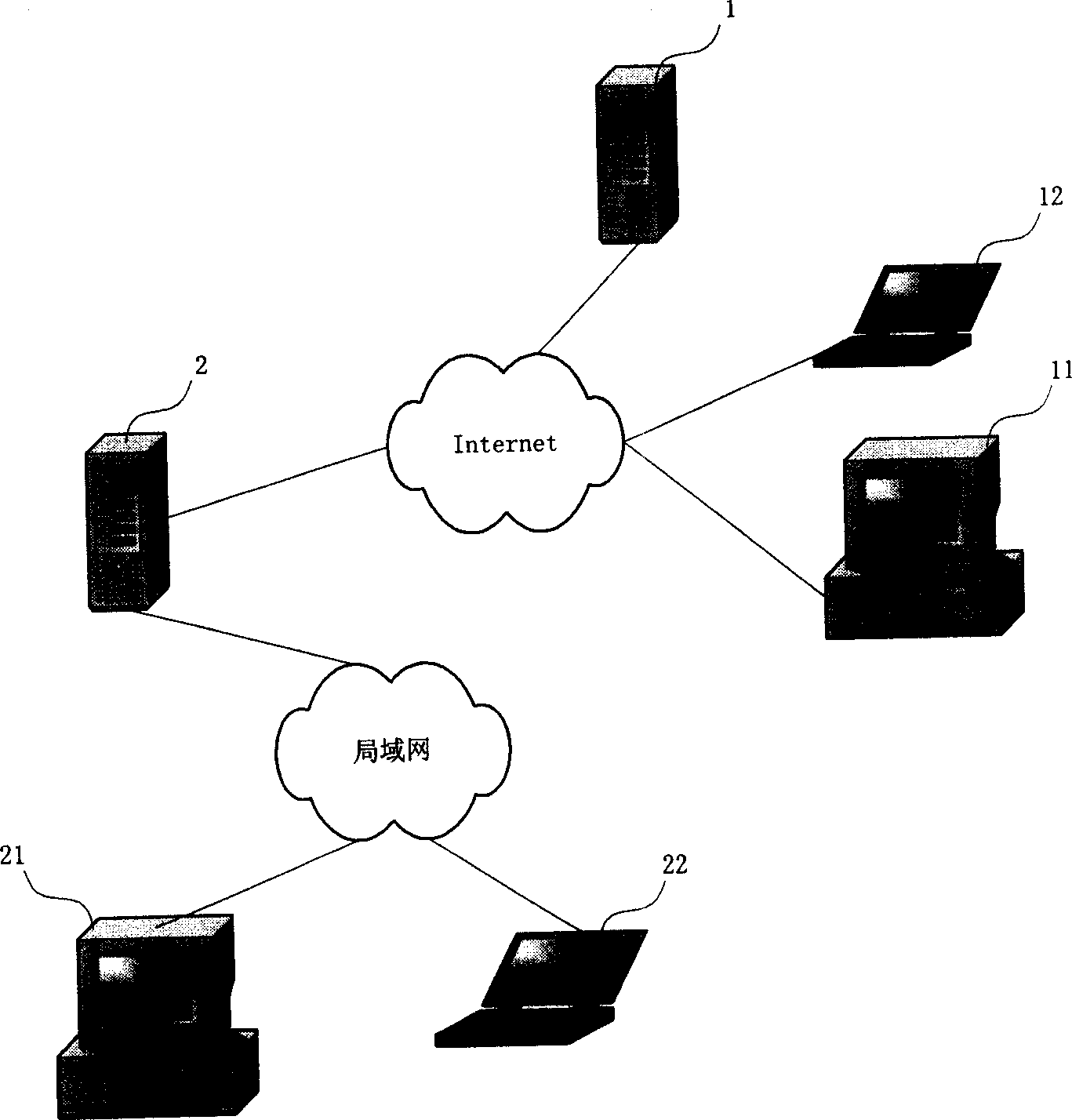
System hardware is a general term for various physical components of a computer system. It includes all the parts inside the computer case such as the CPU, hard disk drive, graphic cards, sound cards, RAM, power supply unit, motherboard, etc. Computer hardware is what you can physically touch.
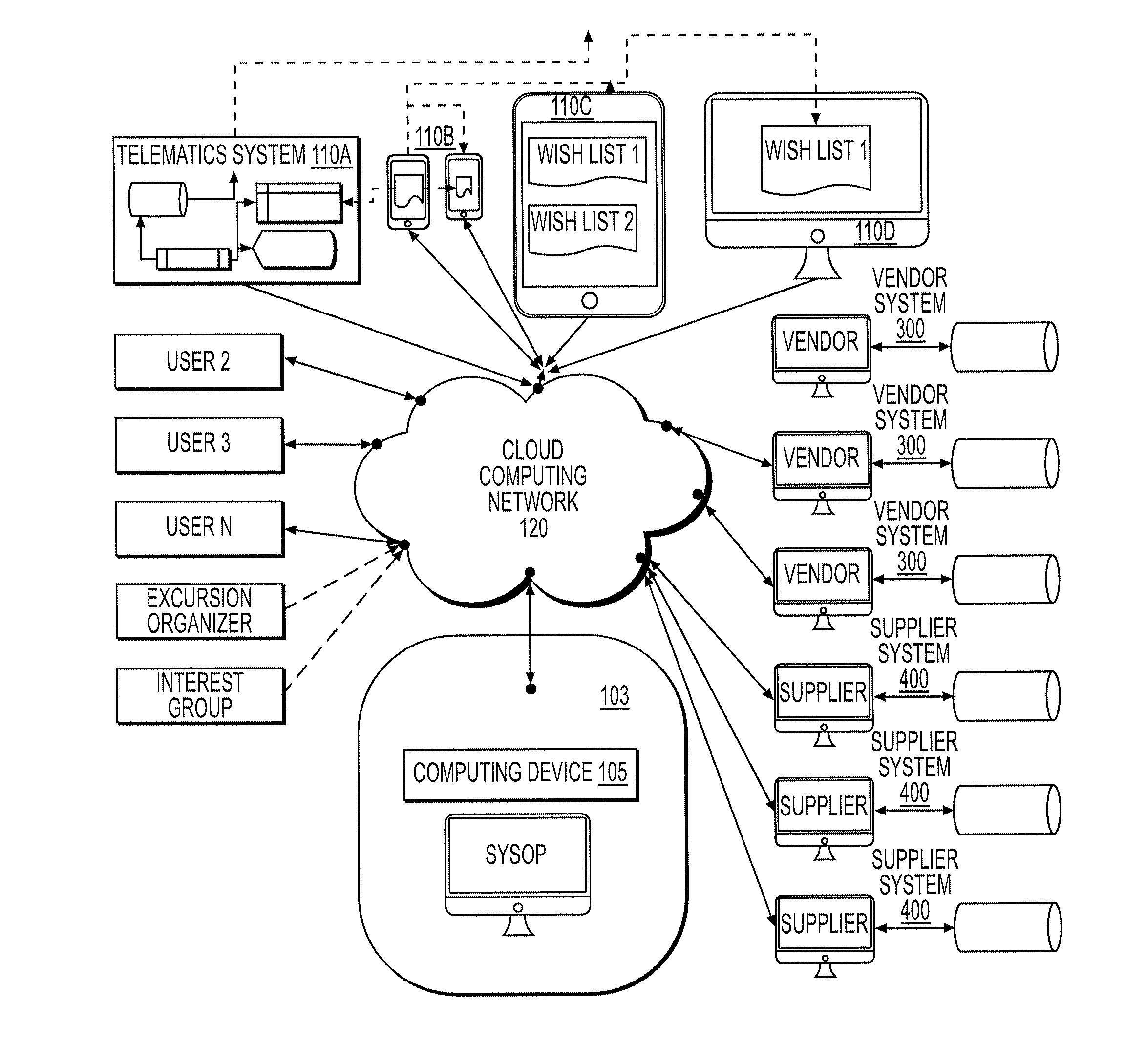
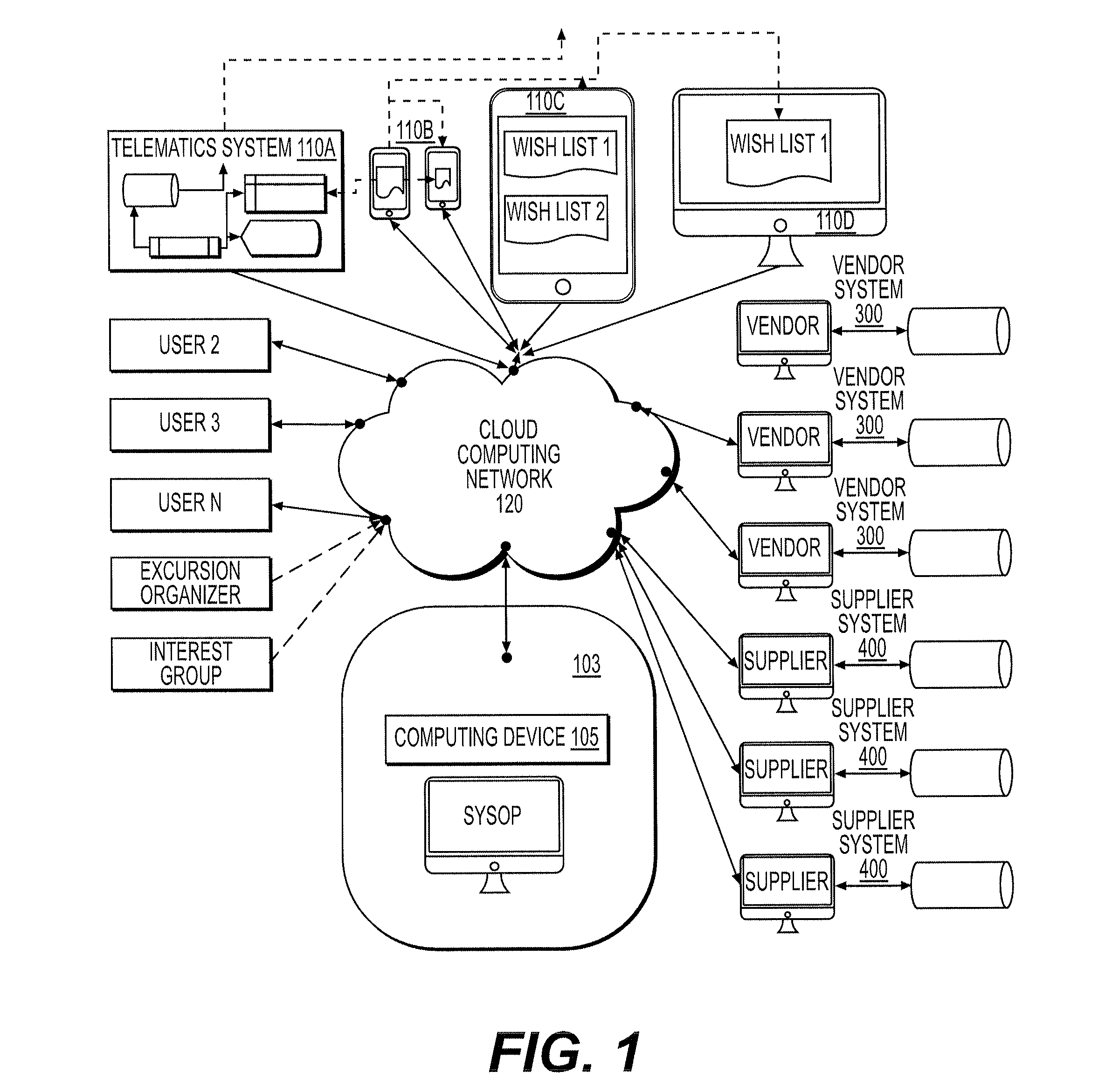
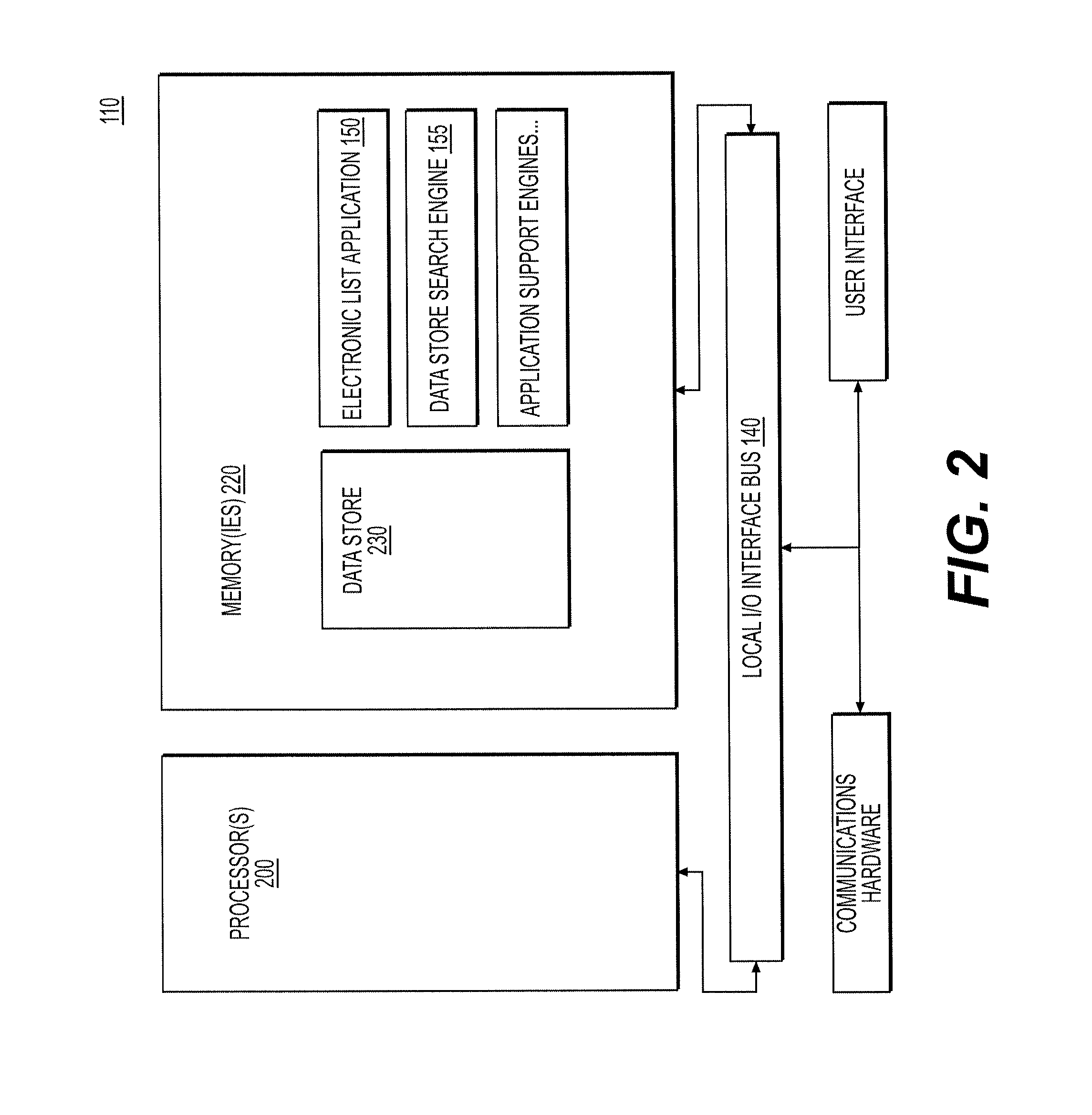
Communications system and smart device APPS supporting segmented order distributed distribution system
InactiveUS20150227890A1Without compromising anonymityFacilitating commerceBuying/selling/leasing transactionsLogisticsControl communicationsControl signal
The communication hardware of the system is controlled by software processes that are preferably grouped as engines that also retrieve process and store data using system hardware. The engines control the communication system hardware to send and receive signals to and from users of the system. The communication signals may include data and control signals for exchanging information and also control signals for remote hardware that, for example, generate displays on user hardware such as smart devices. The communications system allows coordination of segmented order deliveries in a segmented order distributed distribution system. The infrastructure described supports efficient communication to a network of couriers and smart device APPS. Systems, methods and applications for using electronic lists to facilitate commerce, excursion organization and political discourse are also described. Lists stored within the system may be used to facilitate a distributed distribution system using trusted drivers and authorized affiliates.
Owner:BEDNAREK KRISTIN KAYE +2
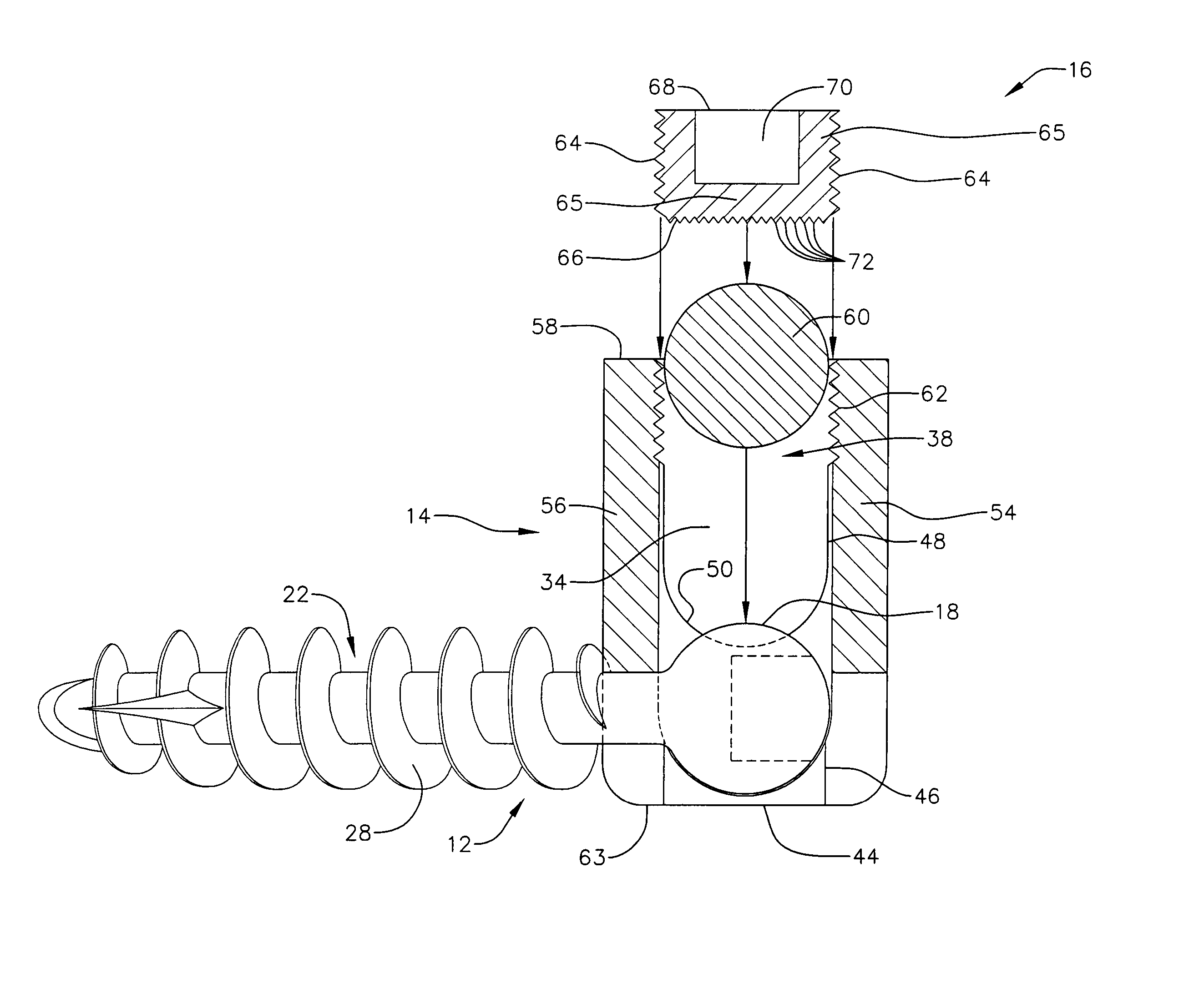
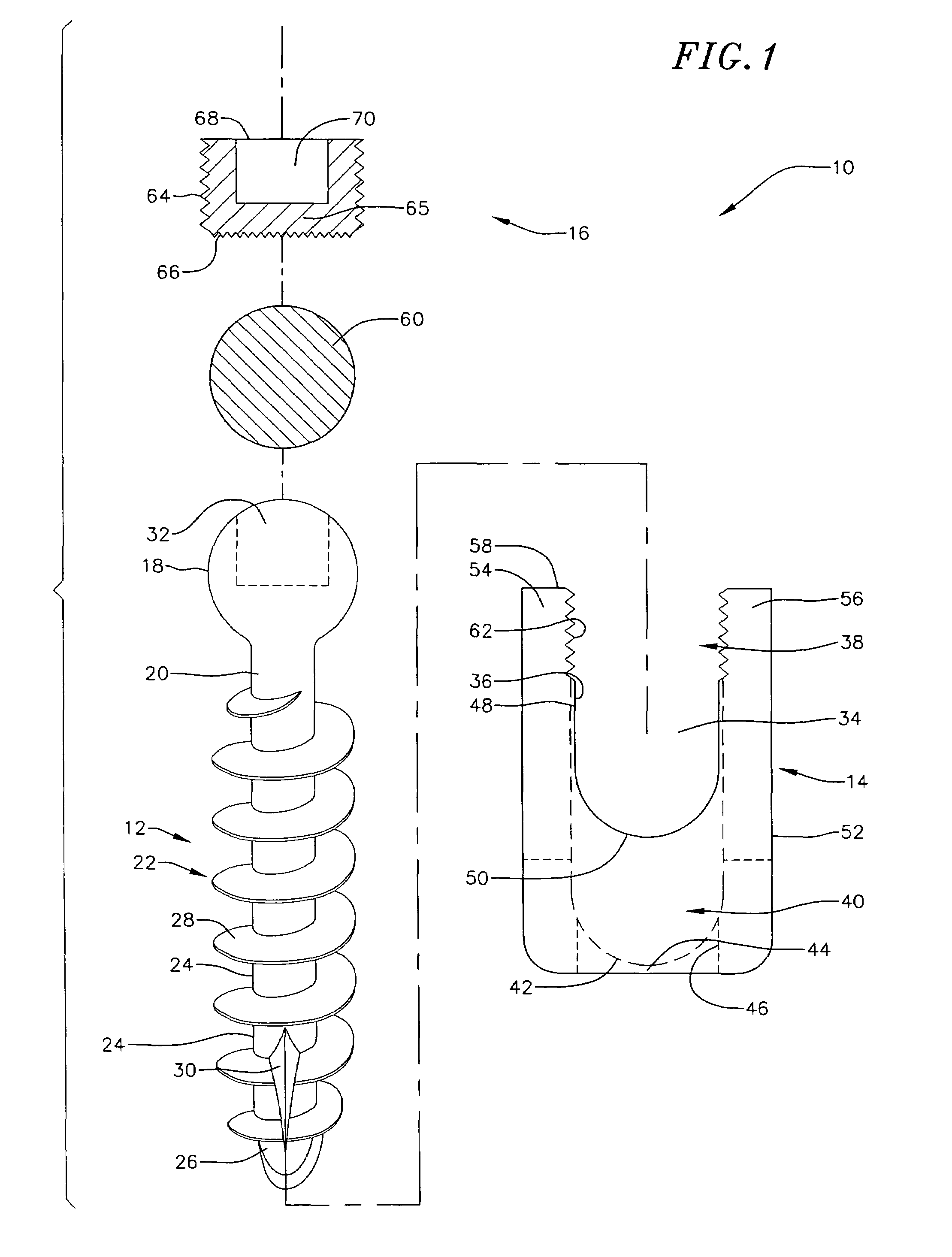
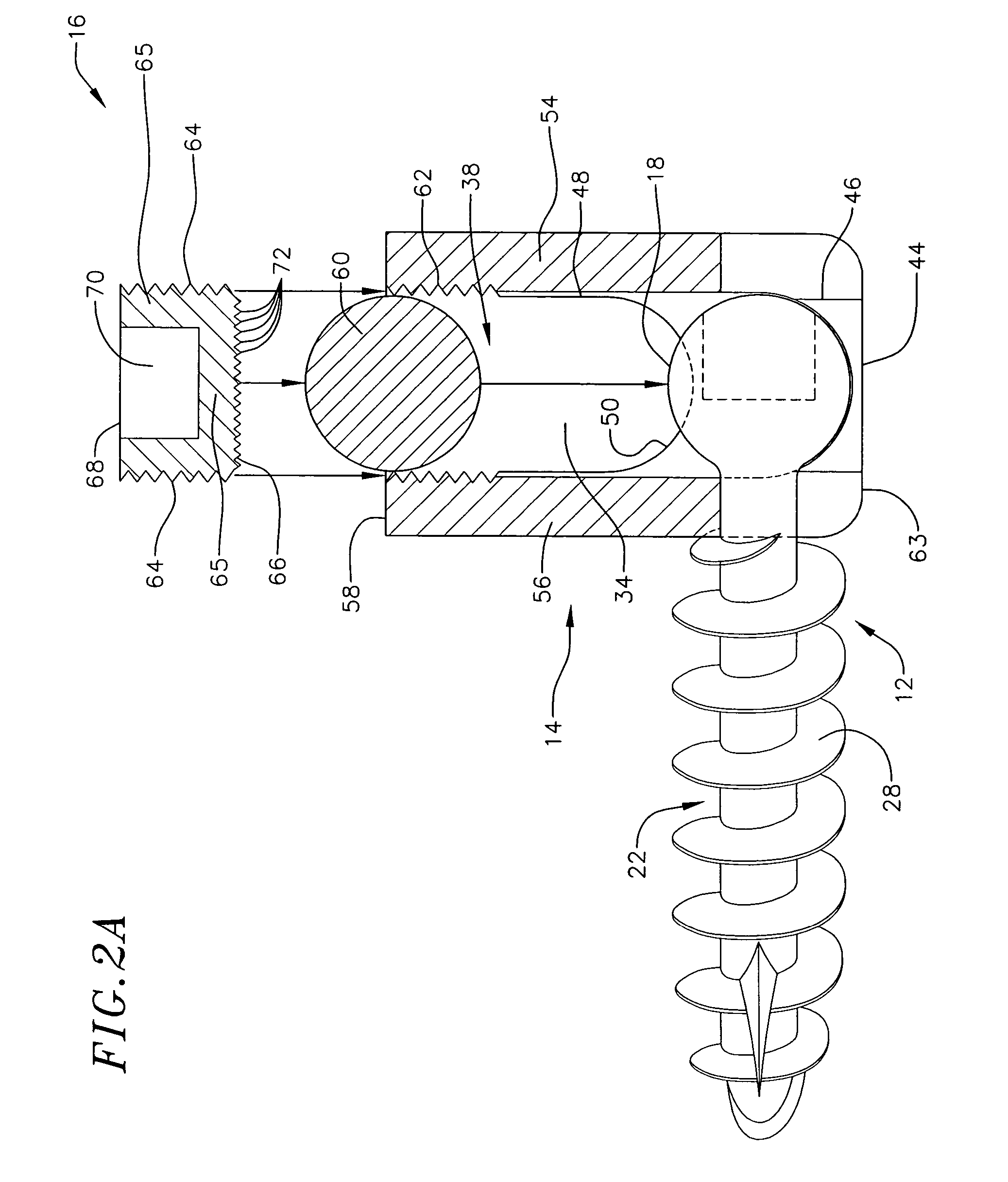
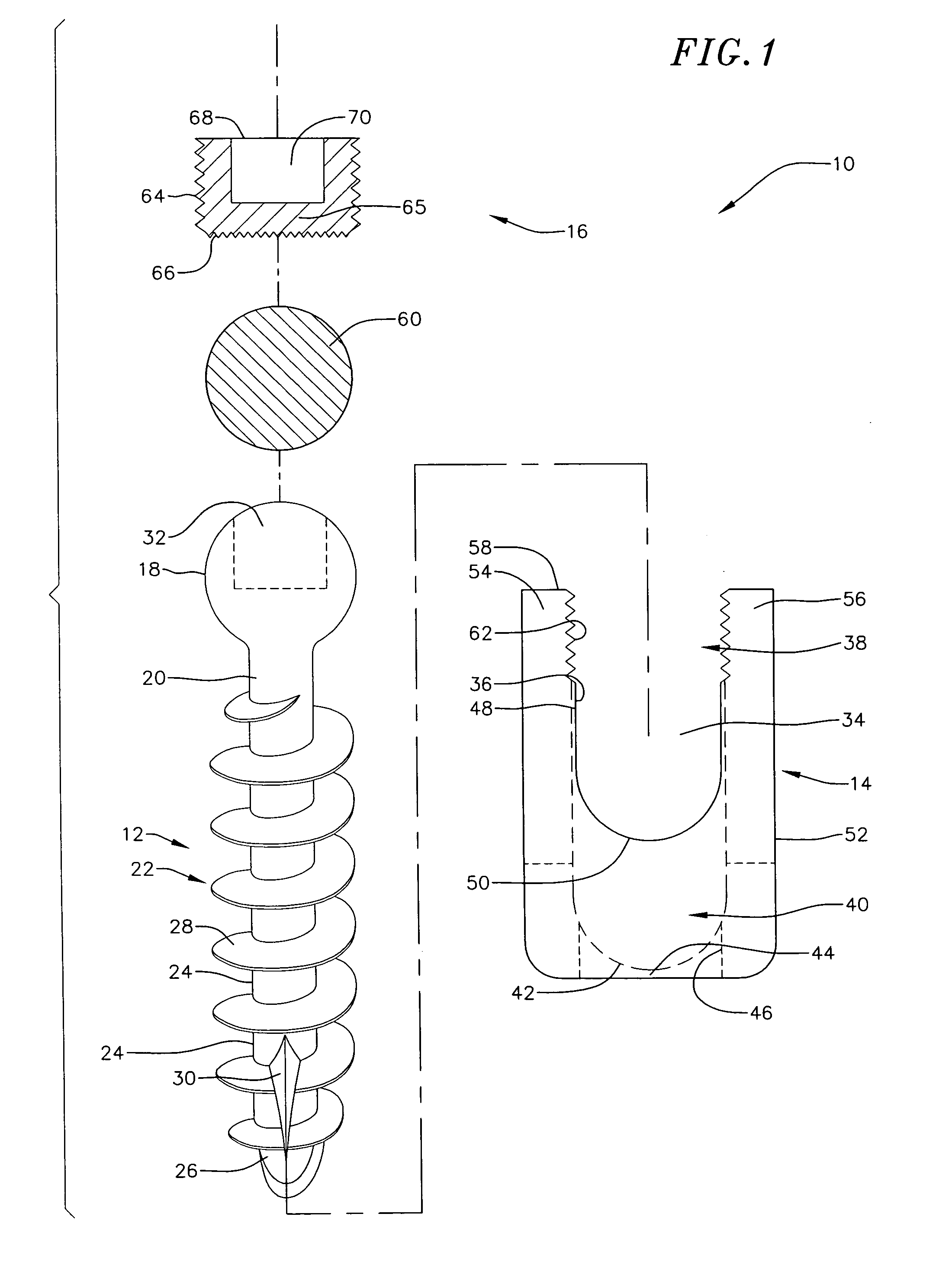
Low profile vertebral alignment and fixation assembly
InactiveUS6981973B2Easy to insertImprove gripInternal osteosythesisJoint implantsCouplingEngineering
A method and apparatus for aligning and fixing vertebral bodies is provided. The low profile vertebral alignment / fixation assembly of the current invention comprises a hemispherical headed pedicle screw disposed within a slotted coupling unit designed to allow angular adjustment of the pedicle screw up to 90° and which may be securely locked into position via a single internal locking nut once a standard alignment rod has been inserted into the slotted coupling unit. The low profile vertebral alignment / fixation assembly enabling the angular adjustment of the fixation system hardware after final placement and insertion of the pedicle screw into the vertebral body. A system and method for aligning and fixing vertebral bodies using the low profile vertebral alignment / fixation assembly of the invention is also provided.
Owner:ZIMMER BIOMET SPINE INC
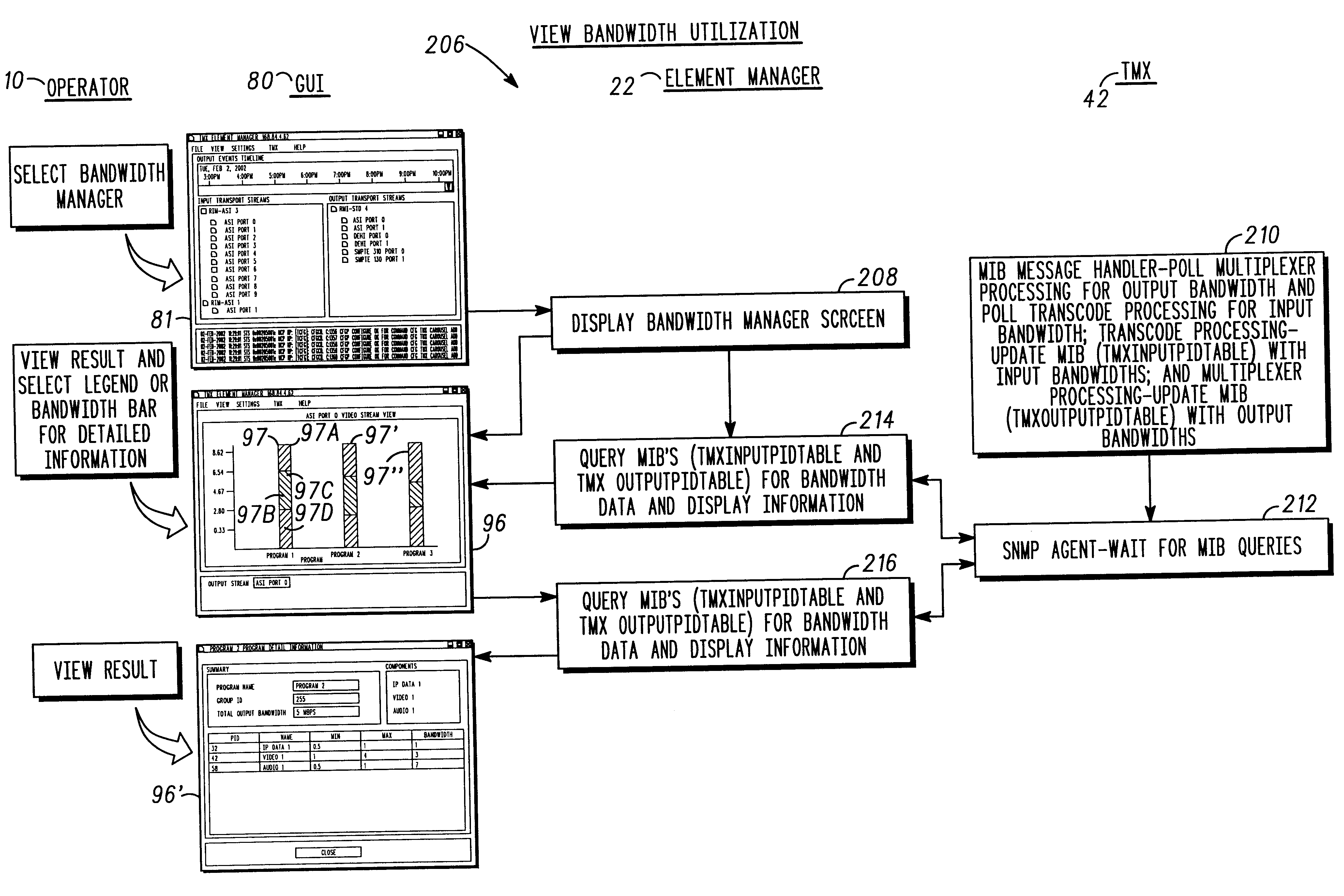
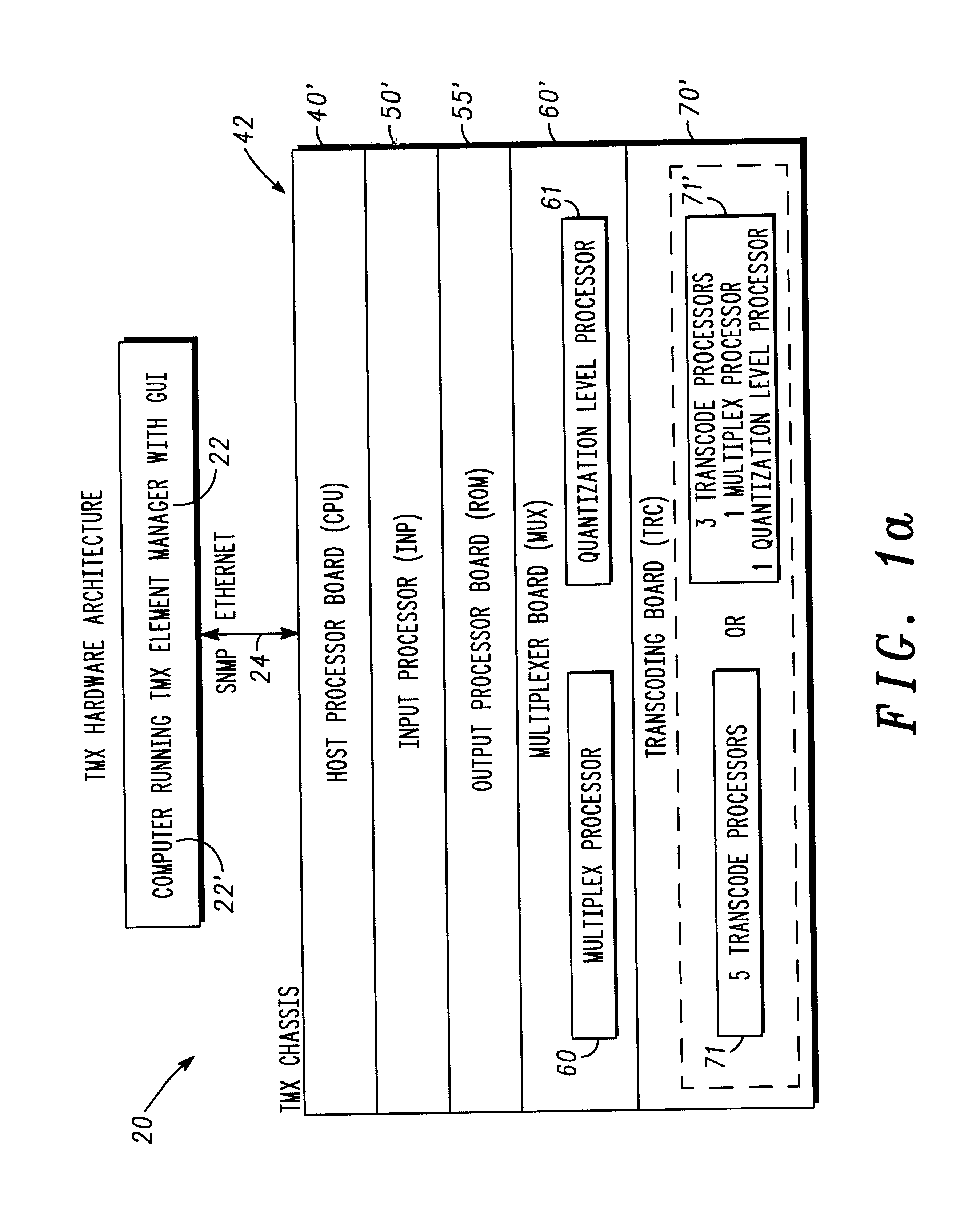
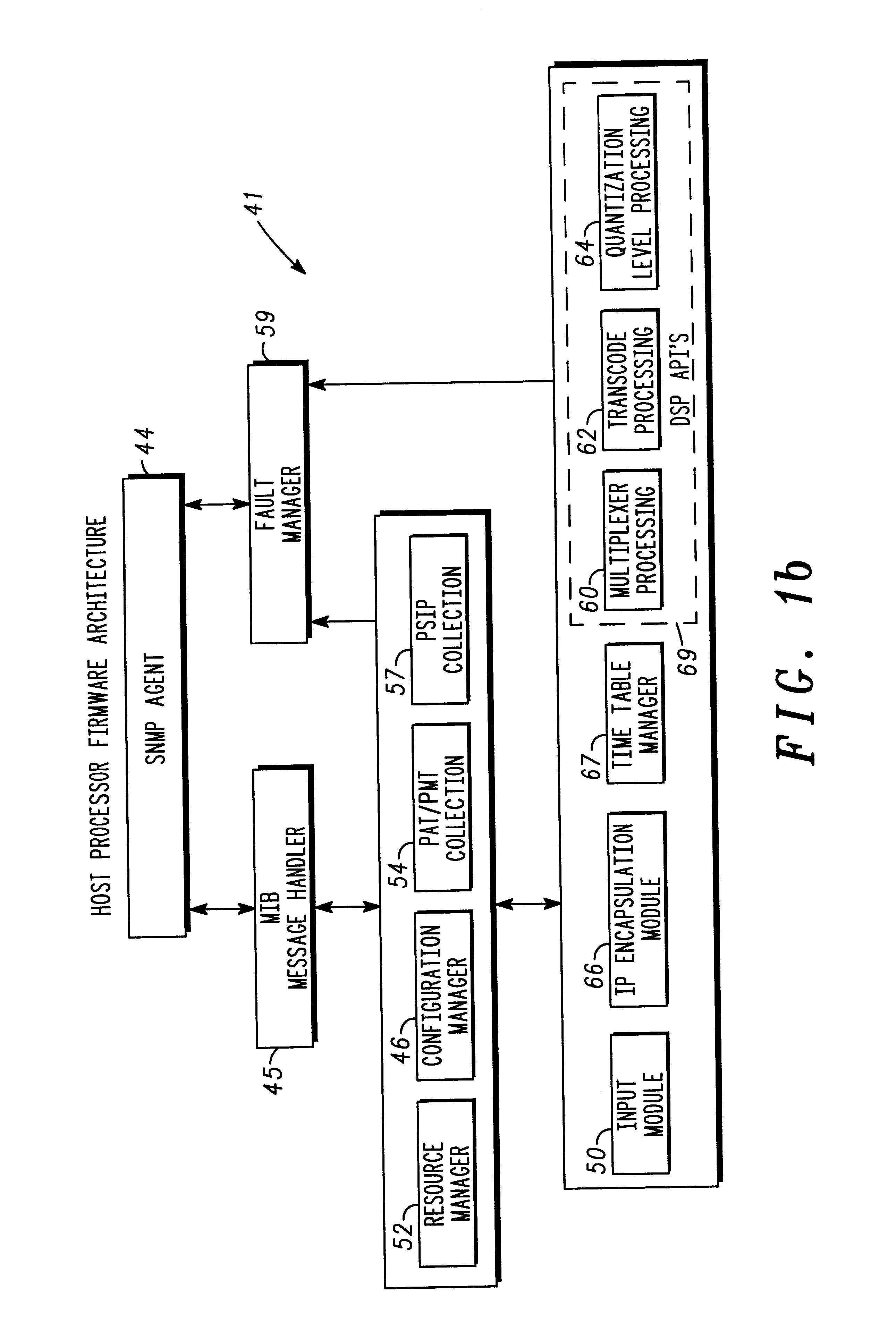
Real-time display of bandwidth utilization in a transport multiplexer
InactiveUS6839070B2Improve effectivenessEasy to displaySpecial service provision for substationDrawing from basic elementsDrag and dropData stream
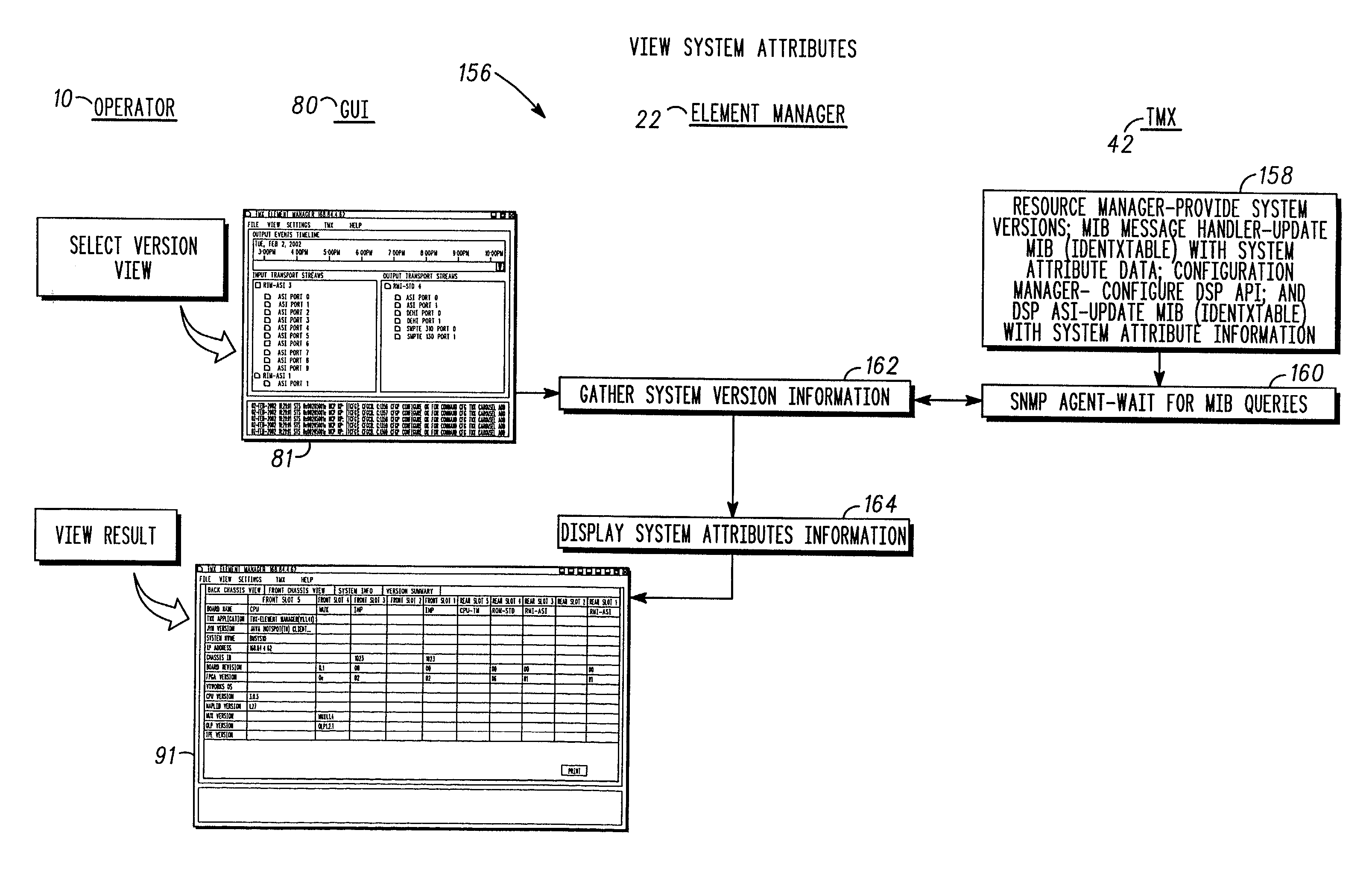
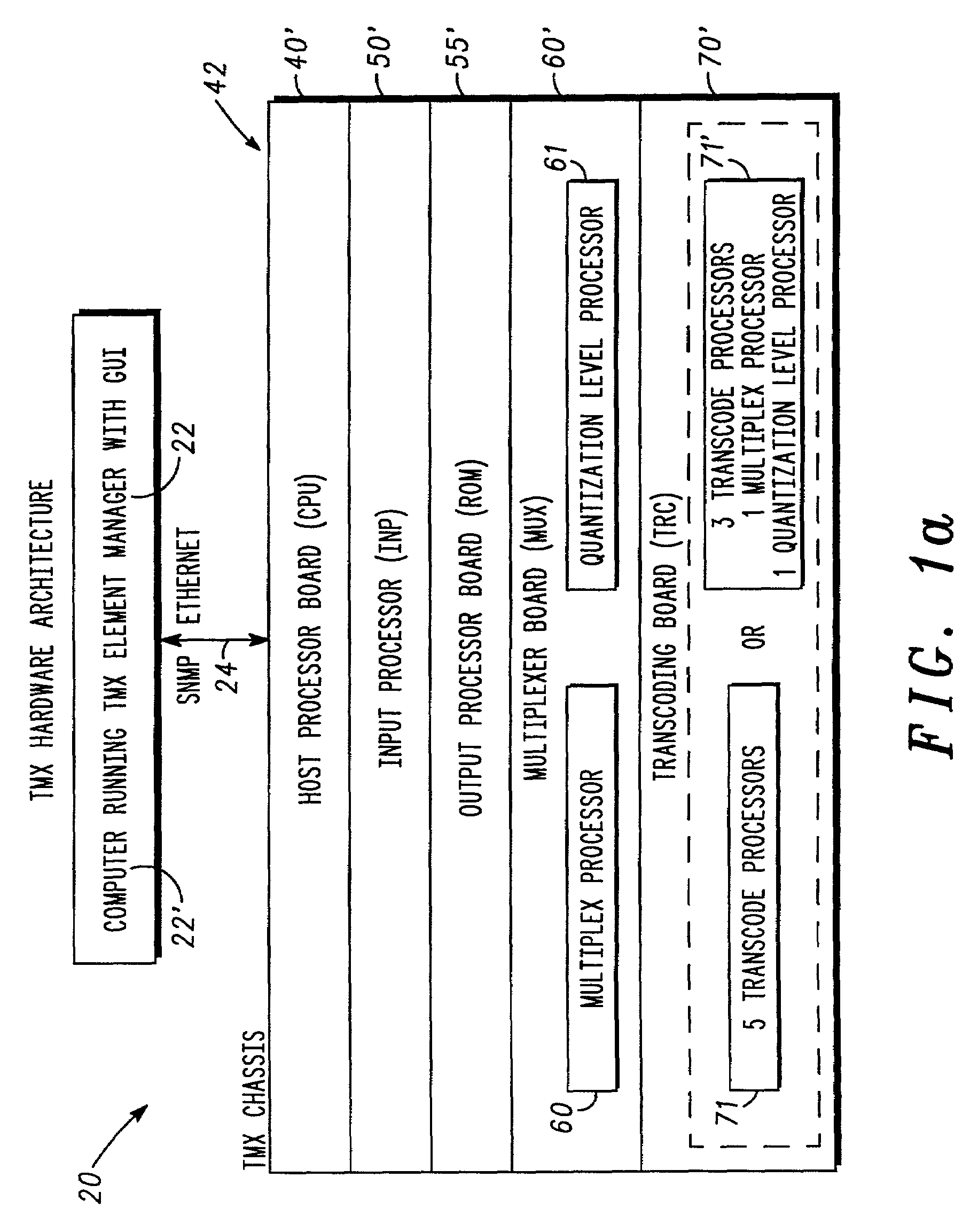
A feature-rich transport multiplexer and a number of associated methods, systems, subsystems, software features, graphical user interfaces and control systems are disclosed. The disclosure includes GUI's that enable operators to easily monitor and manipulate content streams flowing through a transport multiplexer in real-time. The disclosed interfaces include screens that supply operators with identity, structure, configuration, bandwidth utilization and / or status information for system hardware and software. The disclosed features also provide computer assisted routing configuration for present and future routing events through simple manipulation, such as drag and drop operations, of graphical objects. Routing control is further simplified by permitting operators to configure routing control of individual content stream components as well as groups of such components simultaneously. Further flexibility is permitted by predetermination of future routing events, thereby enabling the automatic execution of configuration changes at a future time. Various types of content, such as video, audio, IP data can be manipulated to achieve various results such as one or more multiplexed MPEG data streams.
Owner:GOOGLE TECH HLDG LLC
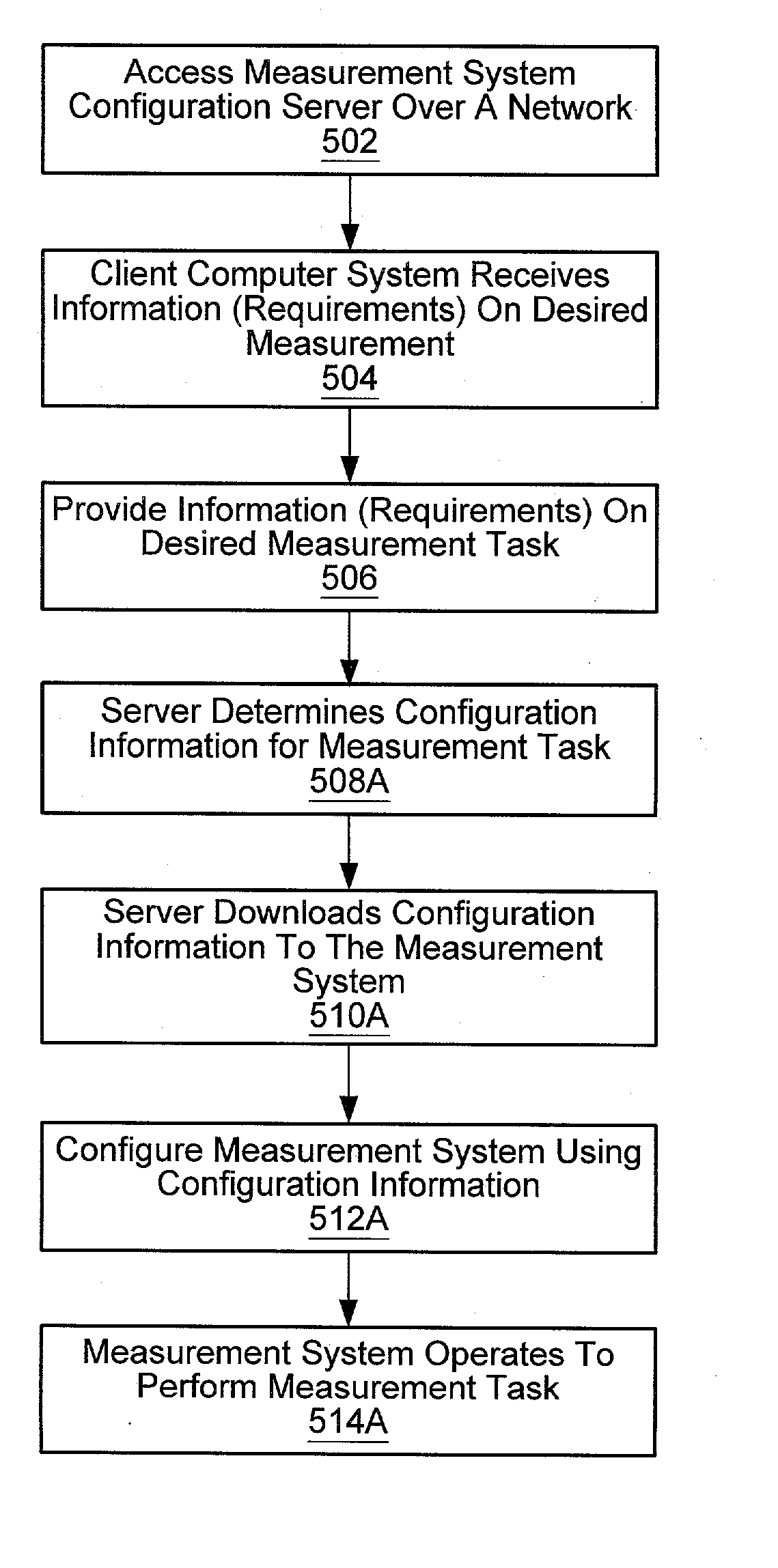
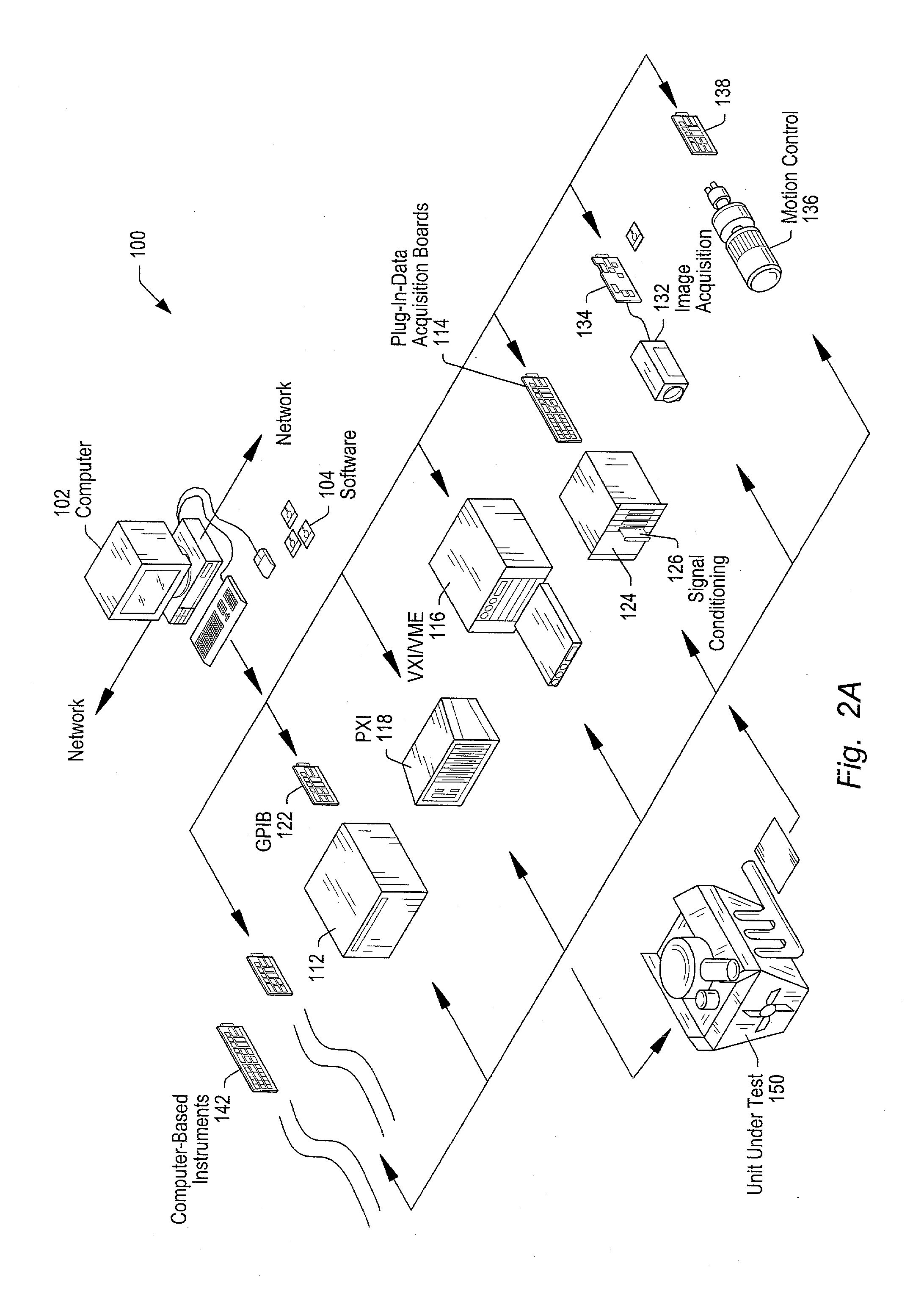
Network-based system for configuring a measurement system using configuration information generated based on a user specification
InactiveUS20030036876A1Measurement arrangements for variableStructural/machines measurementComputer hardwareAuto-configuration
System and method for online configuration of a device for a measurement system. The user accesses a server with a client computer over a network and specifies a task. If the user lacks the hardware to perform the task, hardware specifications are sent to a manufacturer, who sends the hardware to the user. The hardware may be re-configurable hardware (a programmable hardware element or processor / memory based device). Software products (programs and / or data) for configuring measurement system hardware (and / or software) to perform the task may be sent to the user. The hardware may be configured automatically or by the user. The software products may include programs usable by the measurement system to perform the task, configuration information for configuring the client computer or other measurement device, and / or hardware configuration program(s) for configuring a programmable hardware element. Thus, hardware and / or software specific to the user's application are be provided to the user.
Owner:NATIONAL INSTRUMENTS
Multiple operating system and disparate user mass storage resource separation for a computer system
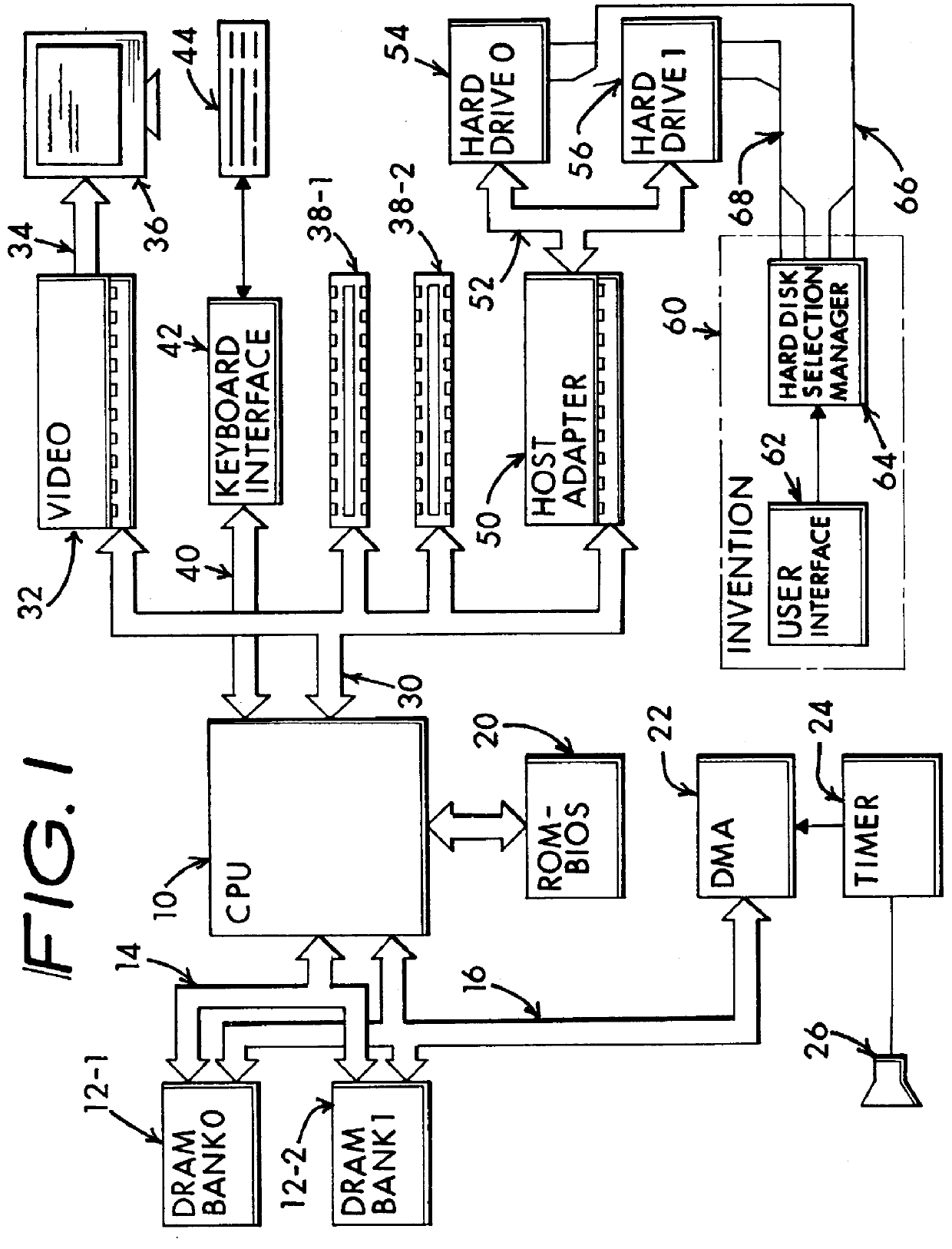
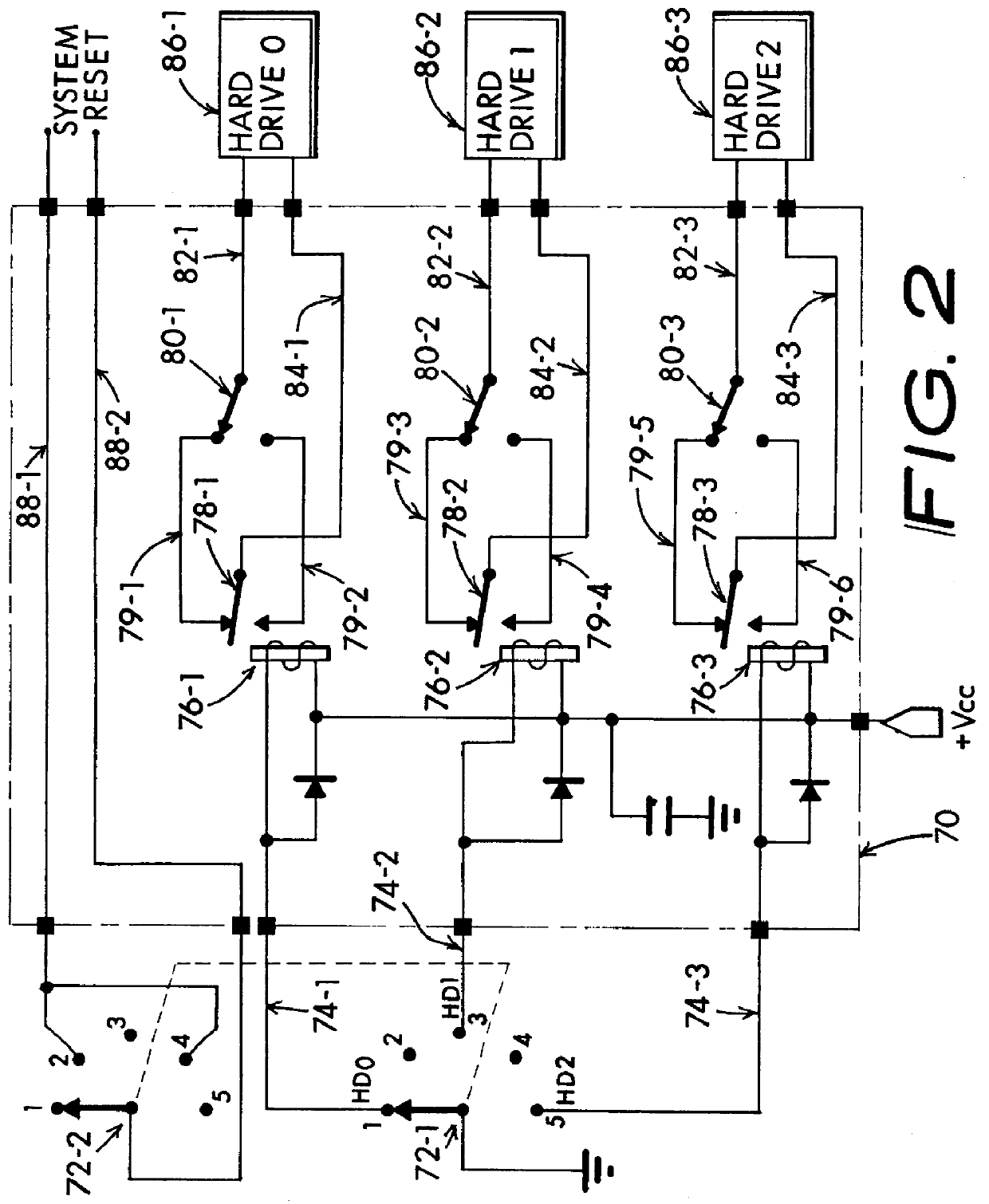
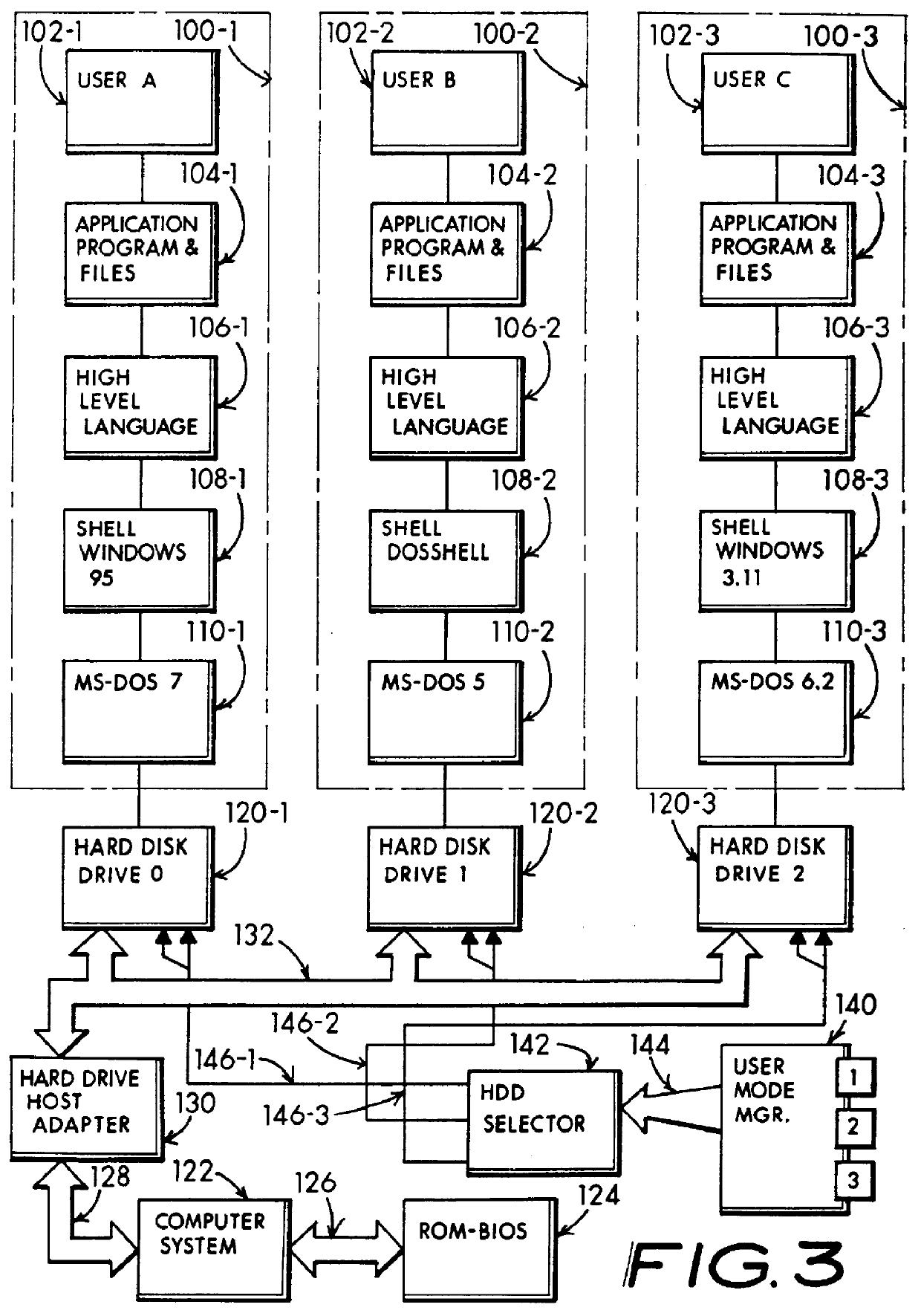
InactiveUS6067618AIsolate userAvoid possibilityDigital data processing detailsDigital computer detailsMass storageHard disc drive
A computer system including several nonconcurrently active hard disk drives ordinarily loaded with unique software bundles. Each active hard drive introduces an especial operating system setup and applications installation which is unconditionally denied access by activities obtained under another hard disk drive's software instructions. An absolute isolation between two or more user's application programs and data files is achieved while sharing a common set of computer system hardware and peripherals. Each category of nonconcurrent user operates independently without a threat of corruption from activities of another prior or subsequent user utilizing the same computer system for another disparate activity. In an IDE / ATA interface environment, a typical arrangement includes a setting of ROM-BIOS to only recognize a MASTER drive with a subsequent user determined swapping of MASTER and SLAVE modes between at least two hard drives utilizing a manual switch-over to obtain operation under operating system and programs uniquely installed on each of the intently selected MASTER drives, while denying access to the alternant SLAVE drive. In an SCSI interface environment, several drives set with the same SCSI-ID number are selected between by manually controlling a completion of the SCSI bus SEL line to the active intended drive and interrupting the SEL line to designated inactive drives. Virus corruption of one primary drive is fire-walled against inadvertent transfer into an alternate primary drive thereby assuring system operating integrity for one user category in spite of virus contamination, command errors, or careless or malicious hacking introduced by another user category.
Owner:HANGER SOLUTIONS LLC
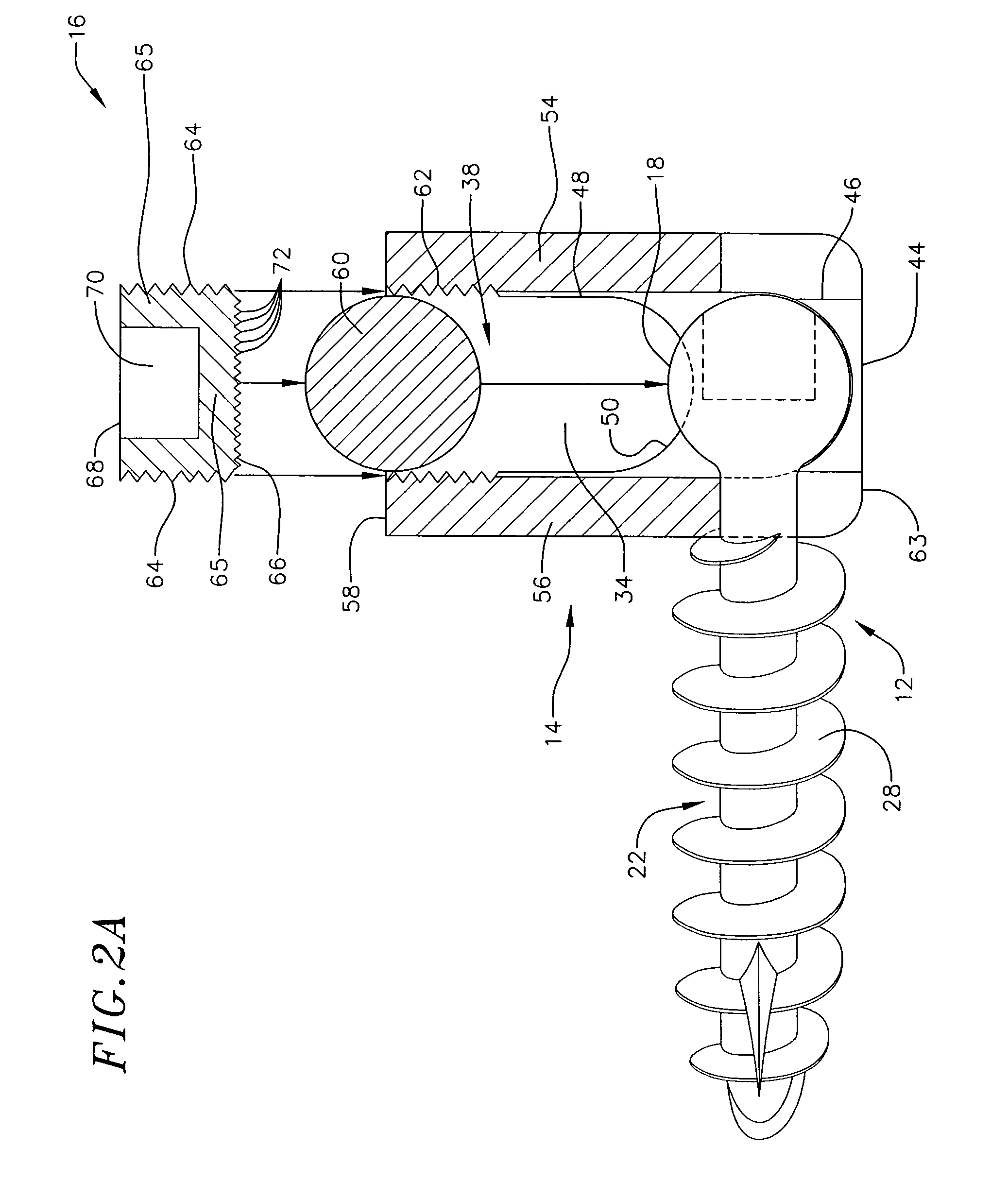
Low profile vertebral alignment and fixation assembly
InactiveUS20050038430A1Easy to insertImprove gripInternal osteosythesisJoint implantsCouplingEngineering
A method and apparatus for aligning and fixing vertebral bodies is provided. The low profile vertebral alignment / fixation assembly of the current invention comprises a hemispherical headed pedicle screw disposed within a slotted coupling unit designed to allow angular adjustment of the pedicle screw up to 90° and which may be securely locked into position via a single internal locking nut once a standard alignment rod has been inserted into the slotted coupling unit. The low profile vertebral alignment / fixation assembly enabling the angular adjustment of the fixation system hardware after final placement and insertion of the pedicle screw into the vertebral body. A system and method for aligning and fixing vertebral bodies using the low profile vertebral alignment / fixation assembly of the invention is also provided.
Owner:ZIMMER BIOMET SPINE INC
Virtual operating system device communication relying on memory access violations
InactiveUS20060259292A1Reducing permissionInternal/peripheral component protectionSoftware simulation/interpretation/emulationVirtualizationOperational system
Attempts by drivers of a virtualized legacy computer game to communicate with nonexistent legacy game system hardware are converted into calls to actual hardware of the host computer game system. An access control list (ACL) restricting and / or reducing page permissions is used to explicitly forbid the drivers of the legacy computer game operating on the virtualized legacy computer game platform from writing to the MMIO addresses of the legacy computer game system. When the operating system of the virtualized legacy computer game platform attempts to touch its driver memory by writing to the MMIO addresses, the operating system of the host computer game system perceives a memory access violation, suspends the virtual machine implementing the virtualized computer game platform, and passes the intended write to an exception handler of the host operating system. The exception handler of the host operating system translates the attempted hardware access command into the command language of the host operating system and then returns control to the operating system of the virtualized legacy computer game platform. The legacy game is completely unaware of this address translation in that it sees only a successful hardware result and proceeds.
Owner:MICROSOFT TECH LICENSING LLC
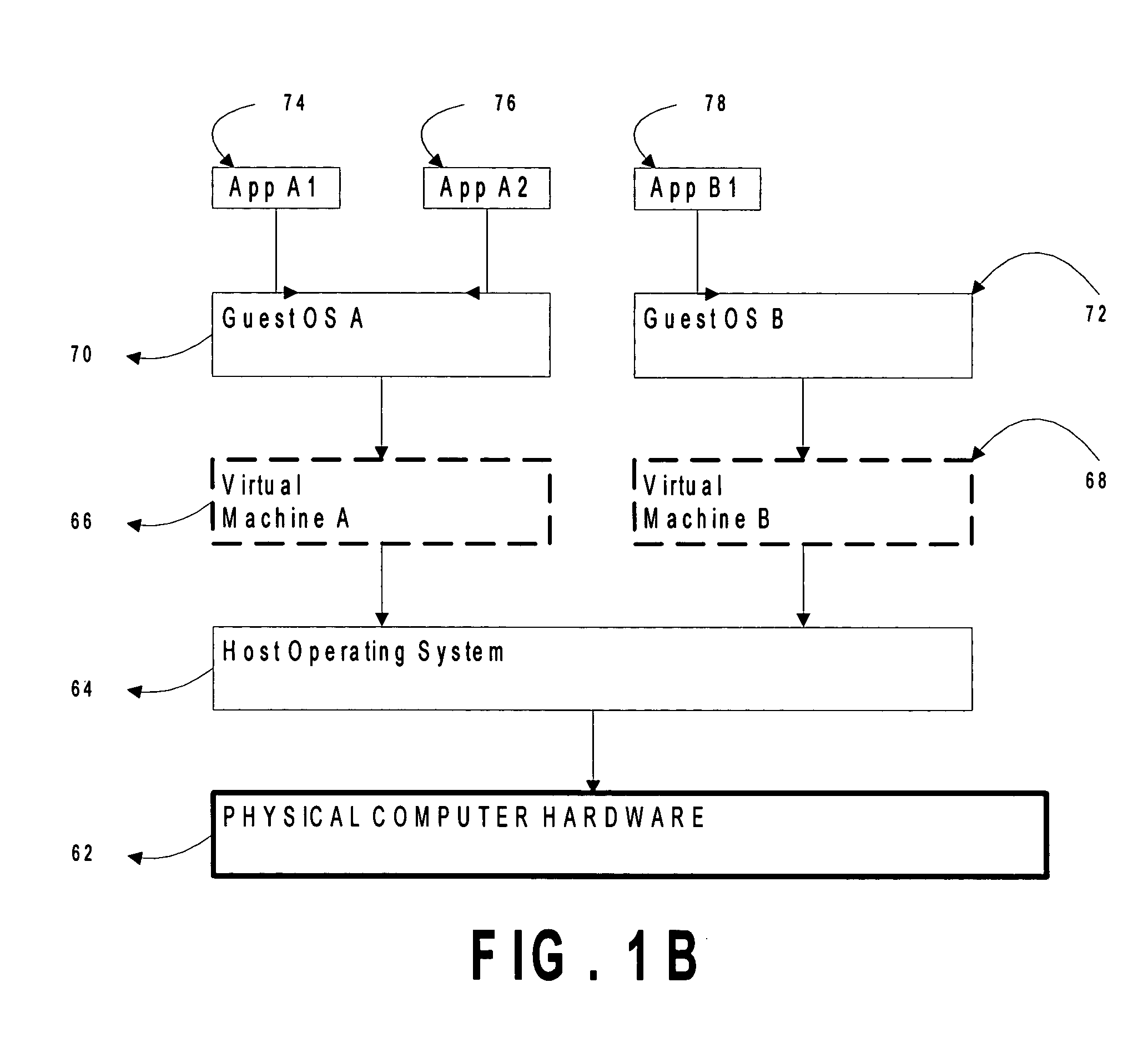
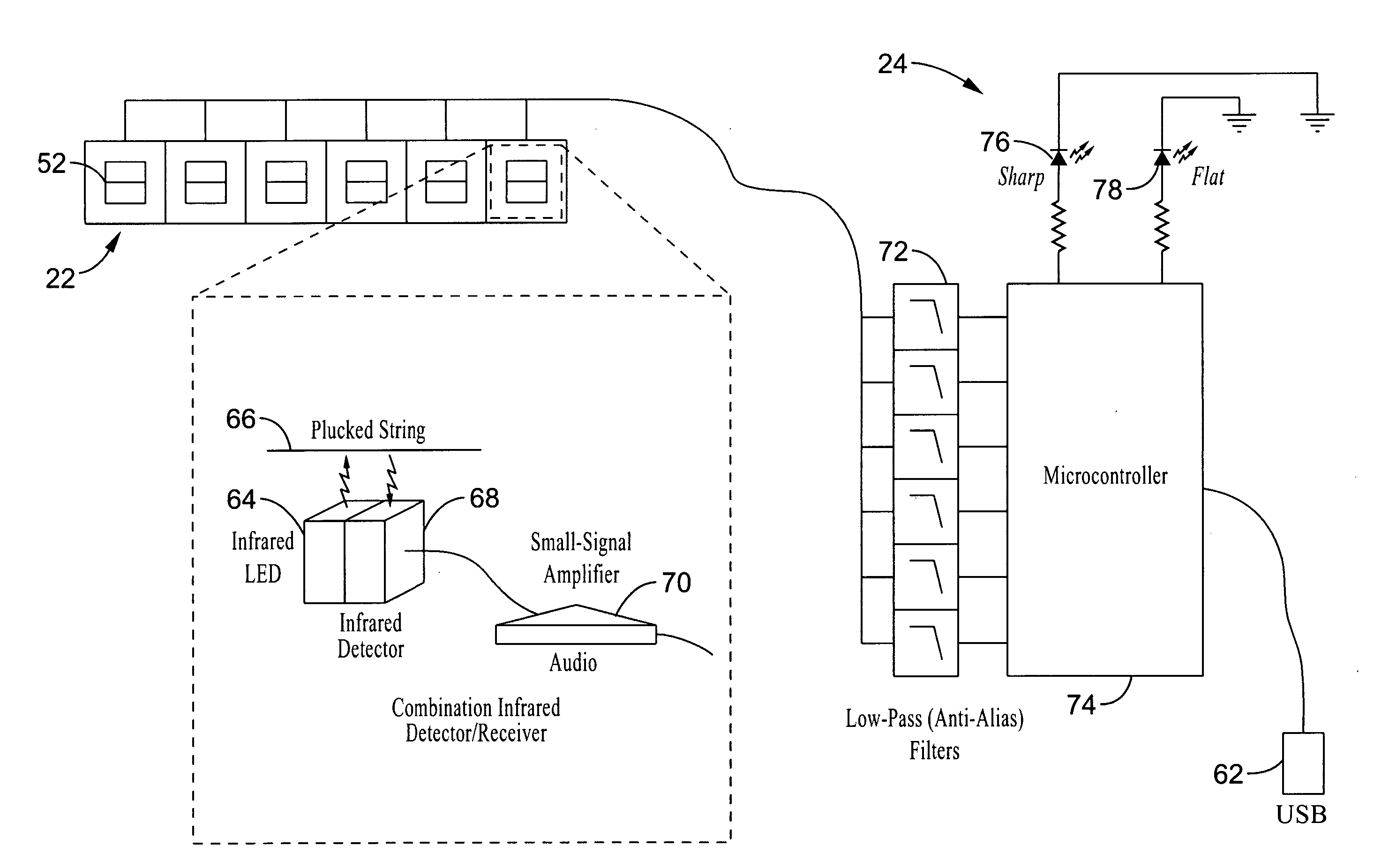
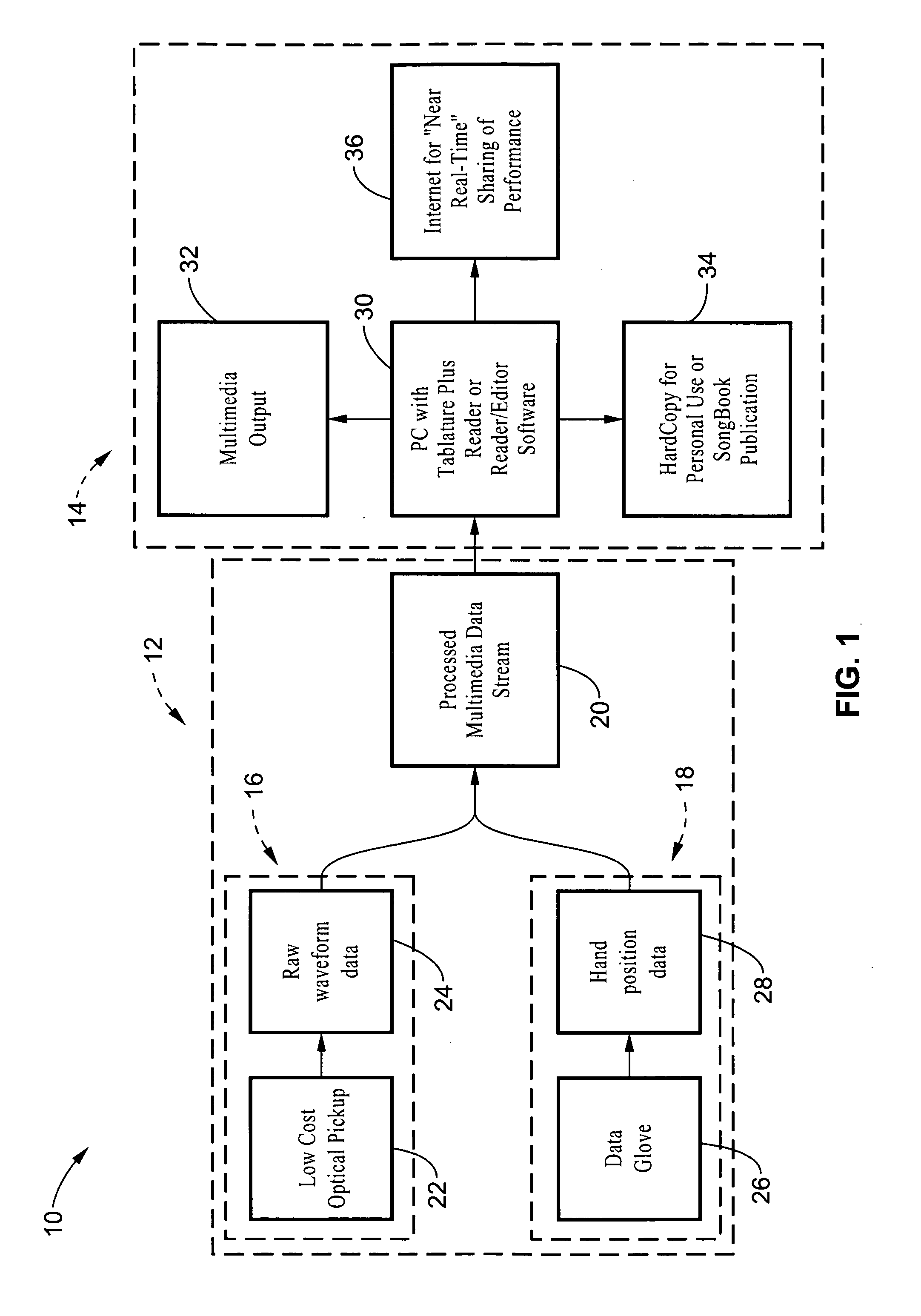
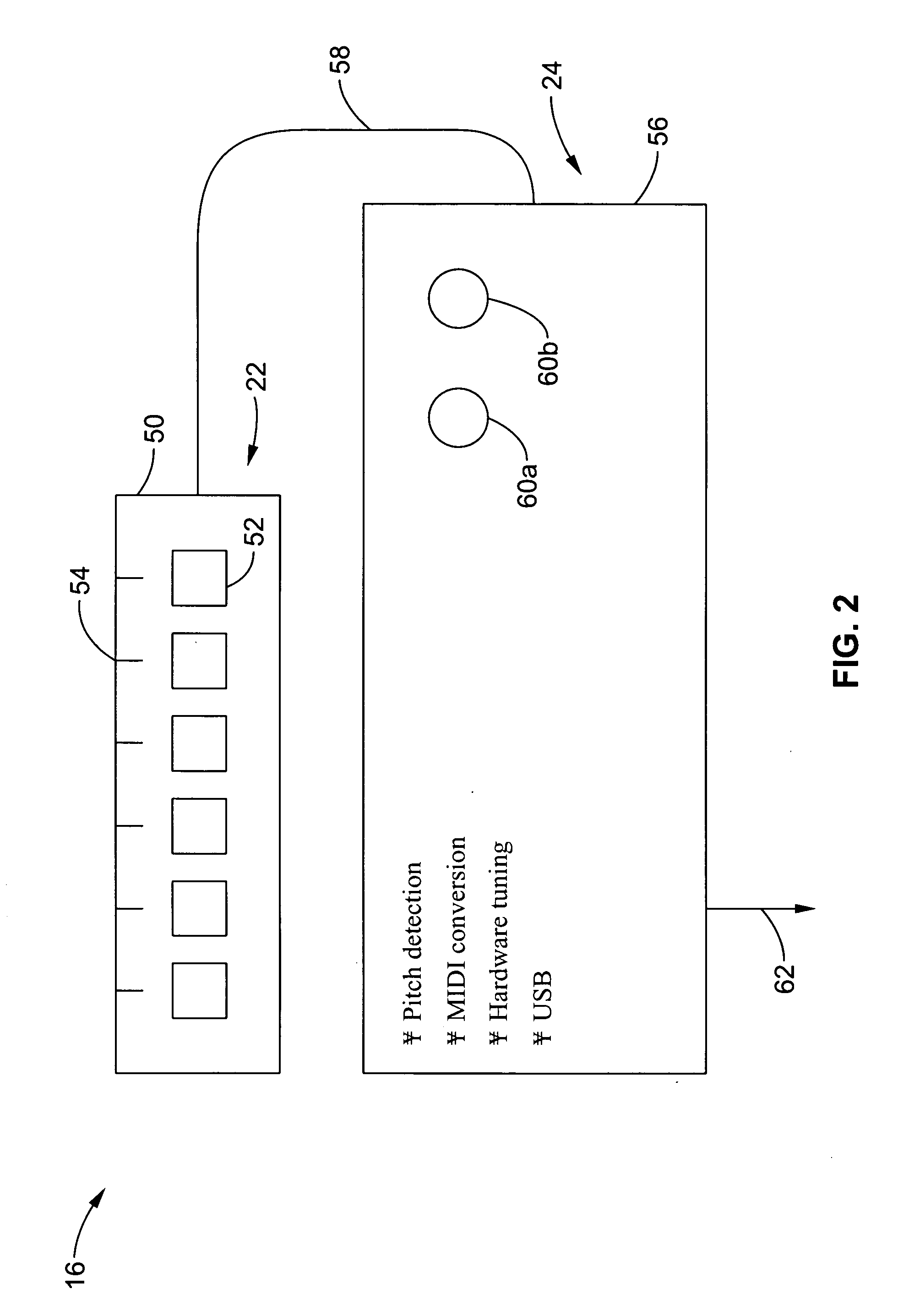
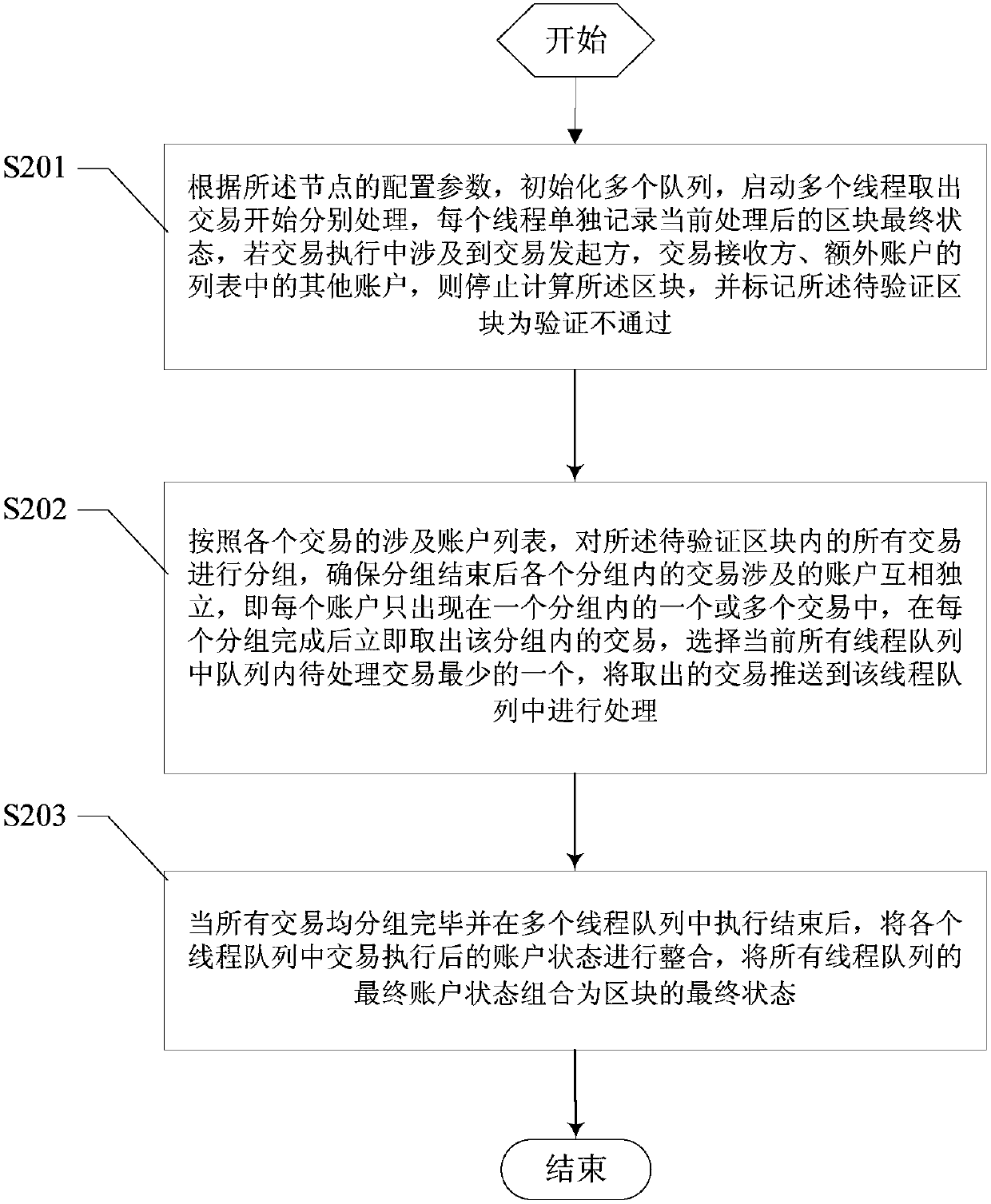
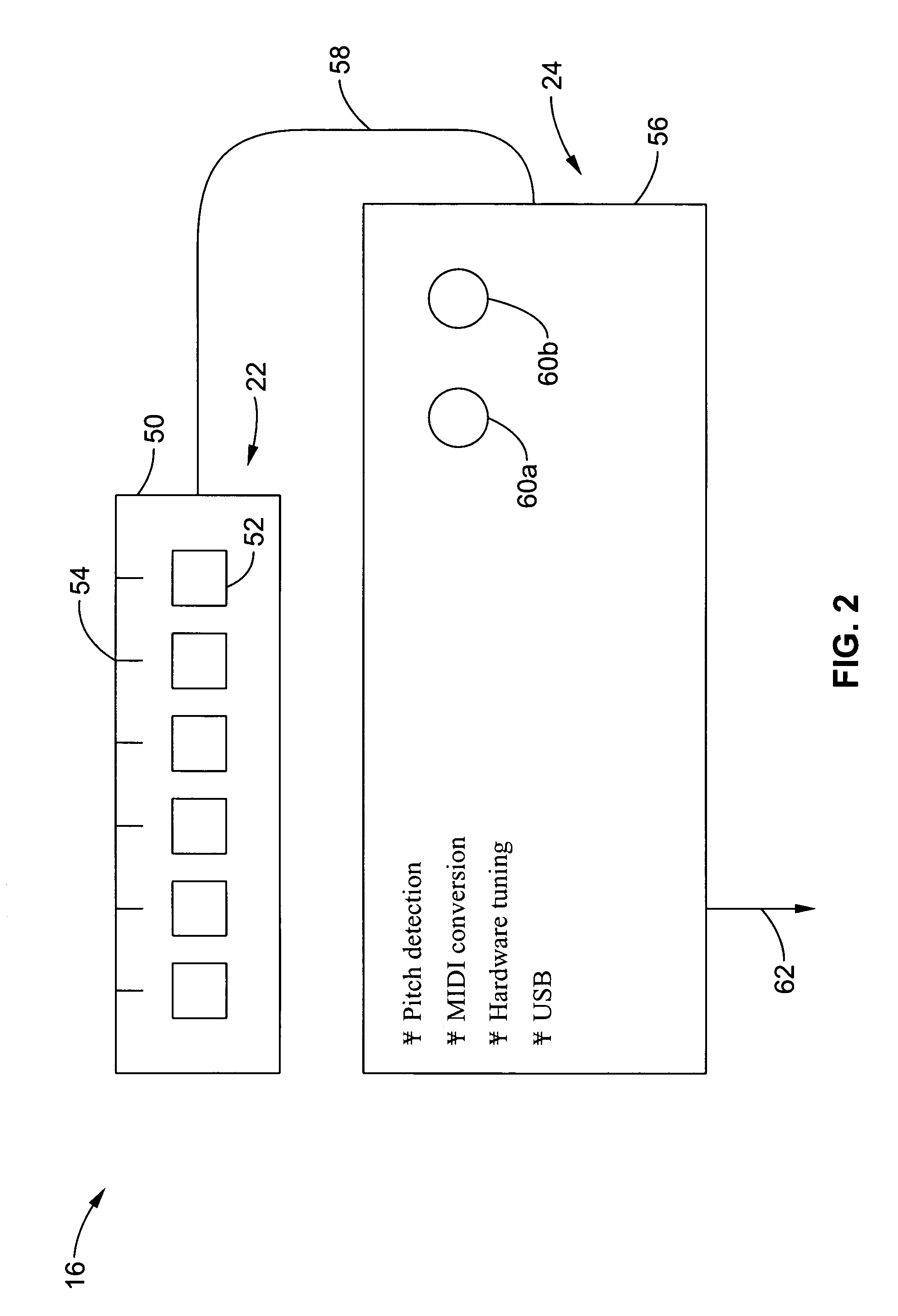
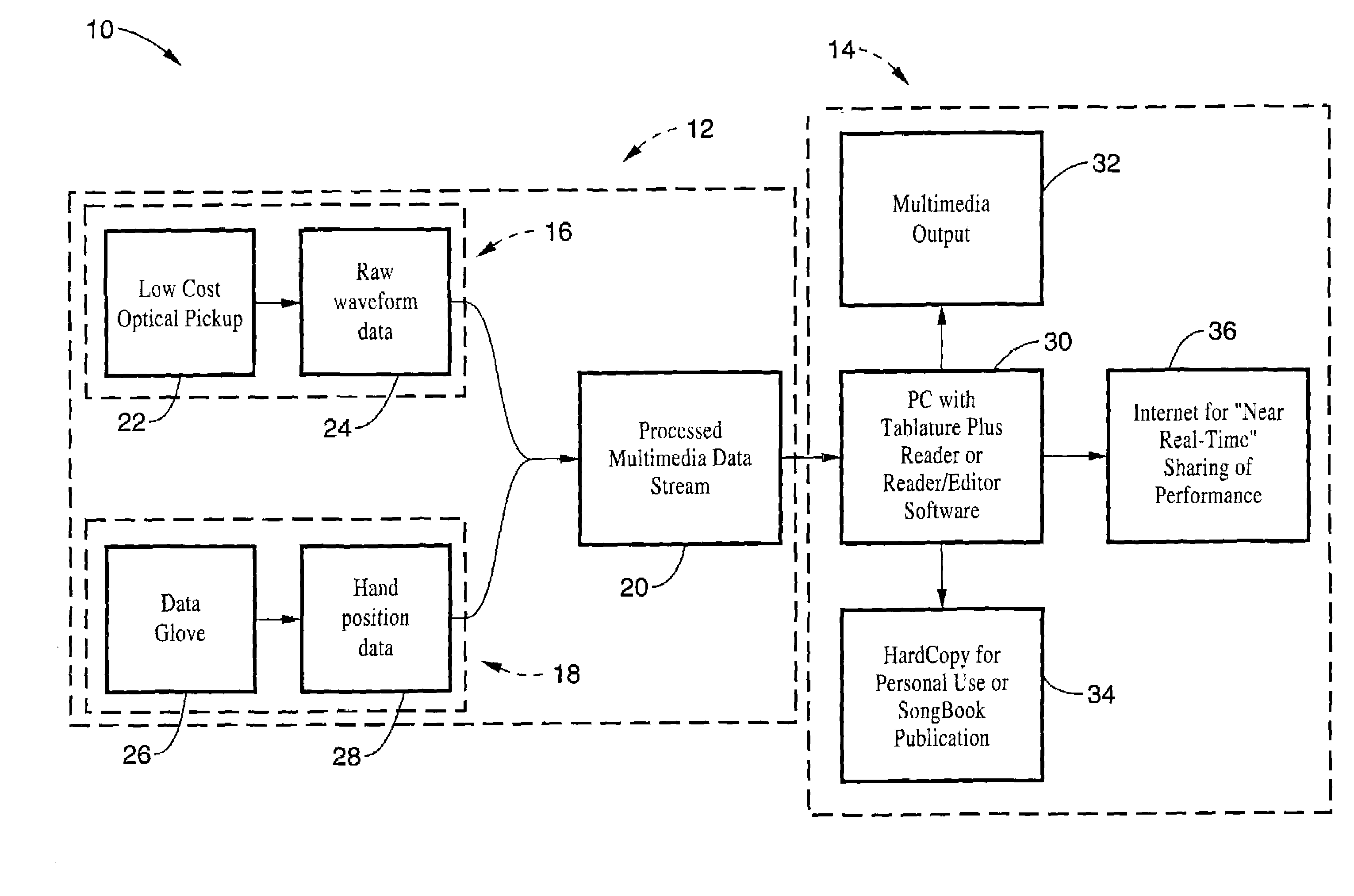
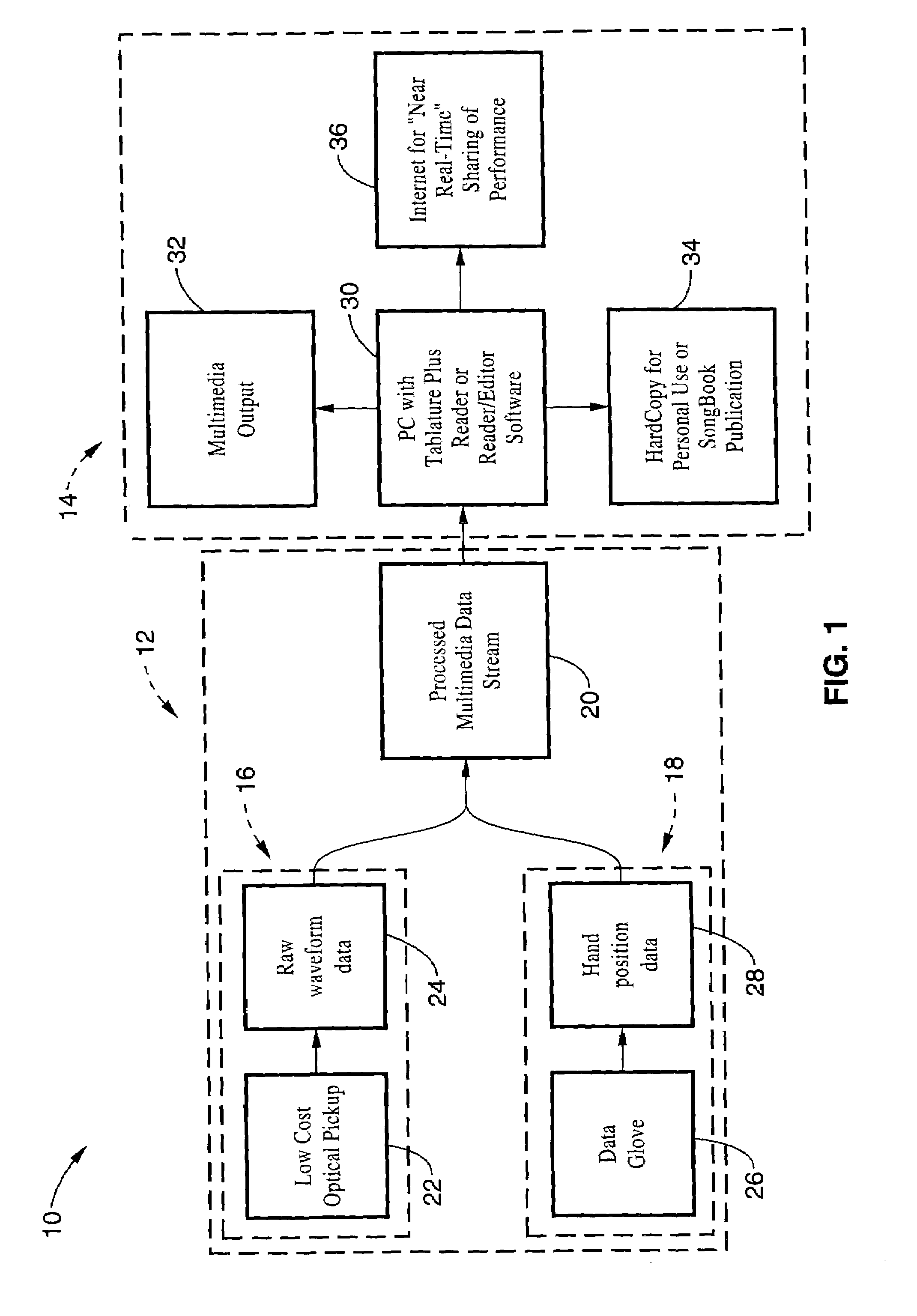
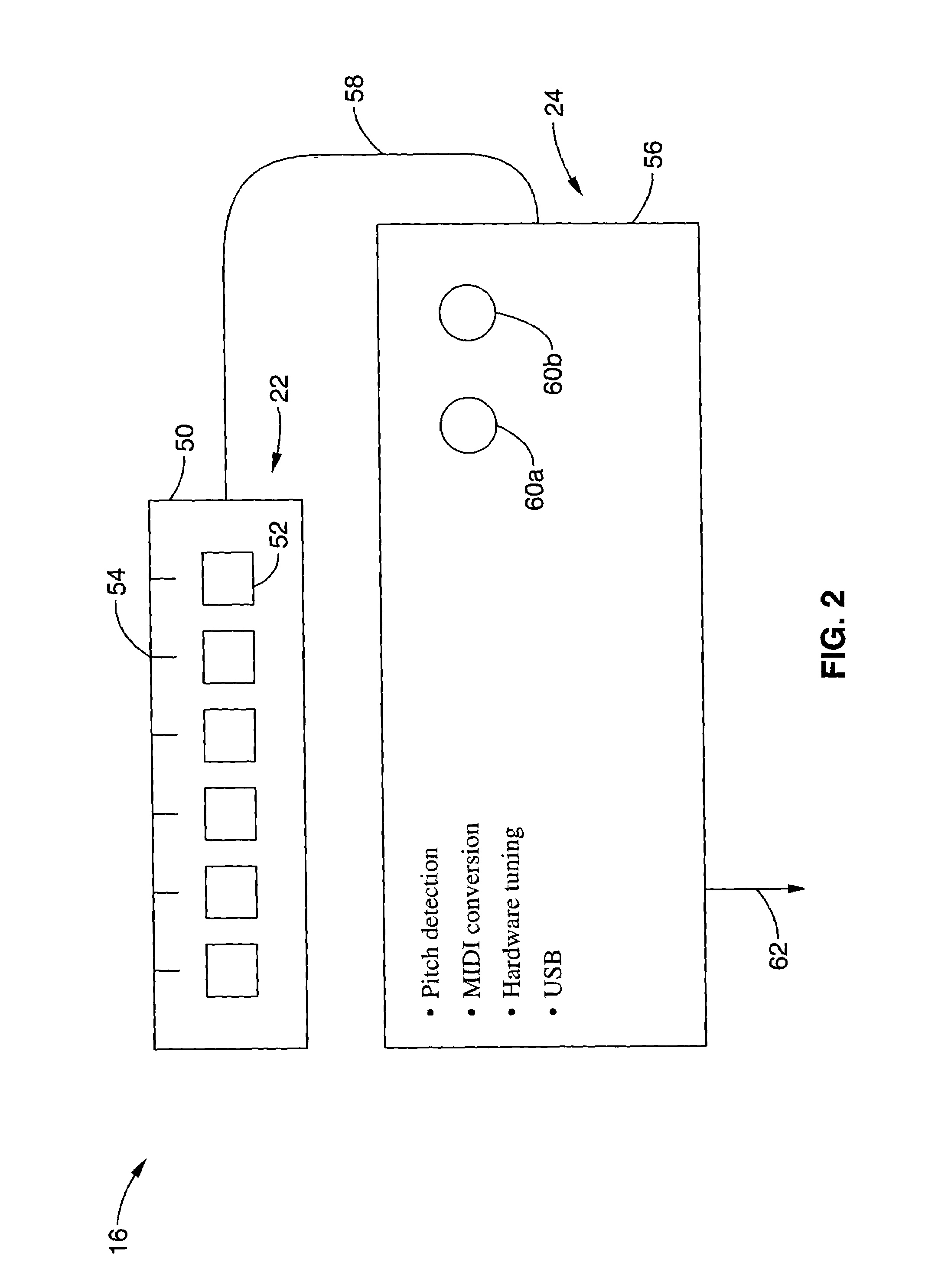
Method and apparatus for sensing and displaying tablature associated with a stringed musical instrument
InactiveUS20060107826A1Readily learn how to playIncrease speedElectrophonic musical instrumentsMusicTablatureMotion capture
A system and method of enhancing guitar instruction based on Tablature Plus encoding of playing techniques within a MIDI file or other data structure, that may be rendered on an associated player application that provides multimedia output of the piece being played including a number of playing techniques. The system hardware for encoding the information includes string motion monitoring, and optionally a hand motion and finger positioning sensor, such as a data glove or a video motion capture system, for simultaneously registering the actions of the guitarist while playing the piece. The software comprises algorithms for determining note pitch and duration, and for extracting playing techniques from the data being collected. Multimedia player software is also described which renders a visual and audio output for the Tablature Plus encoded file, wherein the encoded playing techniques are represented within the display output. The system is adaptable to instruction for any instrument.
Owner:VMUSICSYSTEM GUITARVISION +1
Multisource perception positioning system suitable for smart networked car
InactiveCN109405824ASolve the "last mile" problemReal-time centimeter-level positioning accuracyNavigation by speed/acceleration measurementsFingerprintSystem hardware
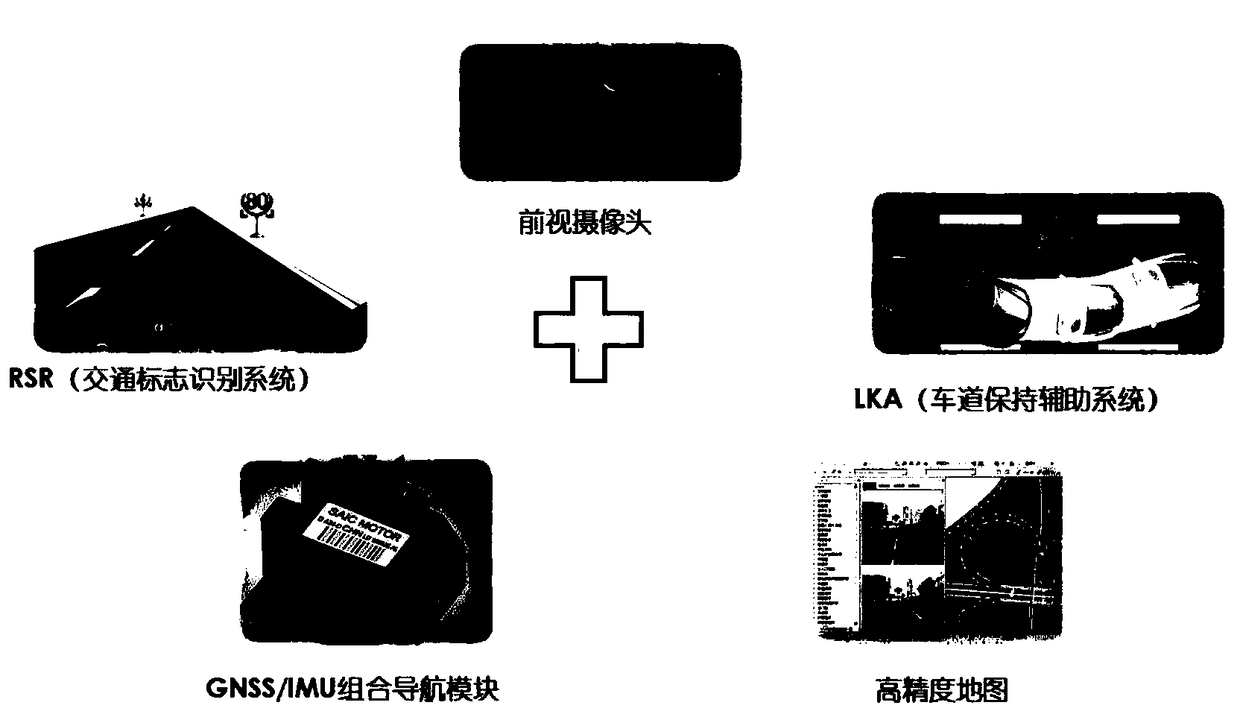
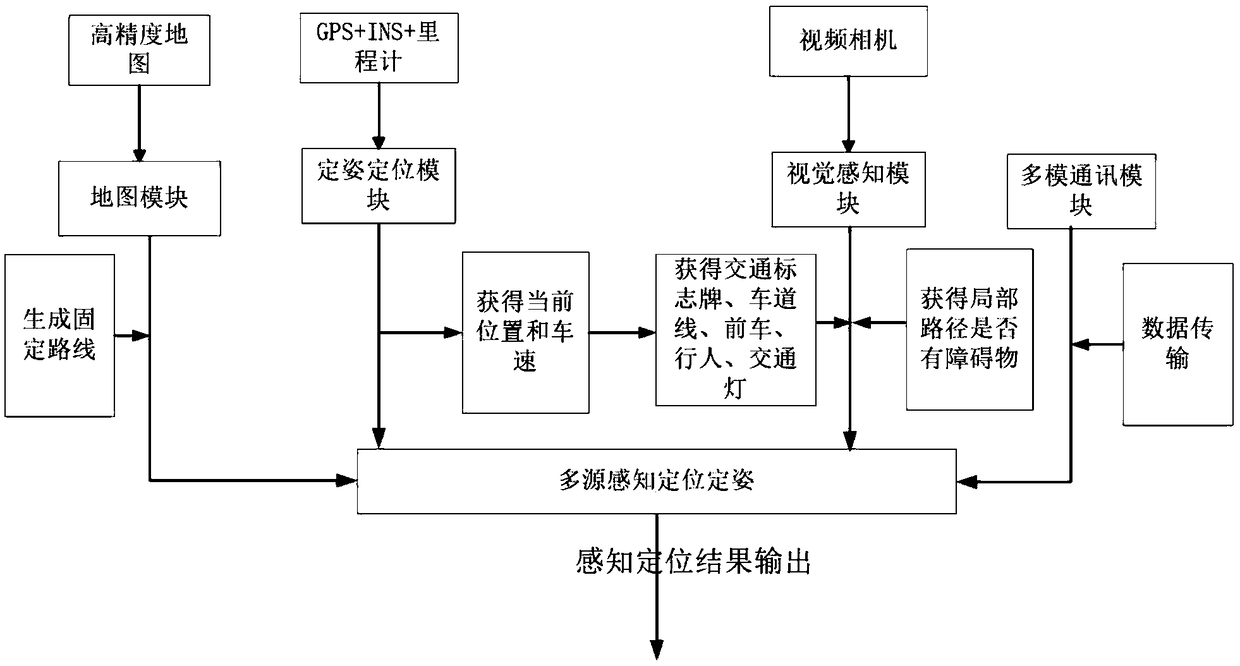
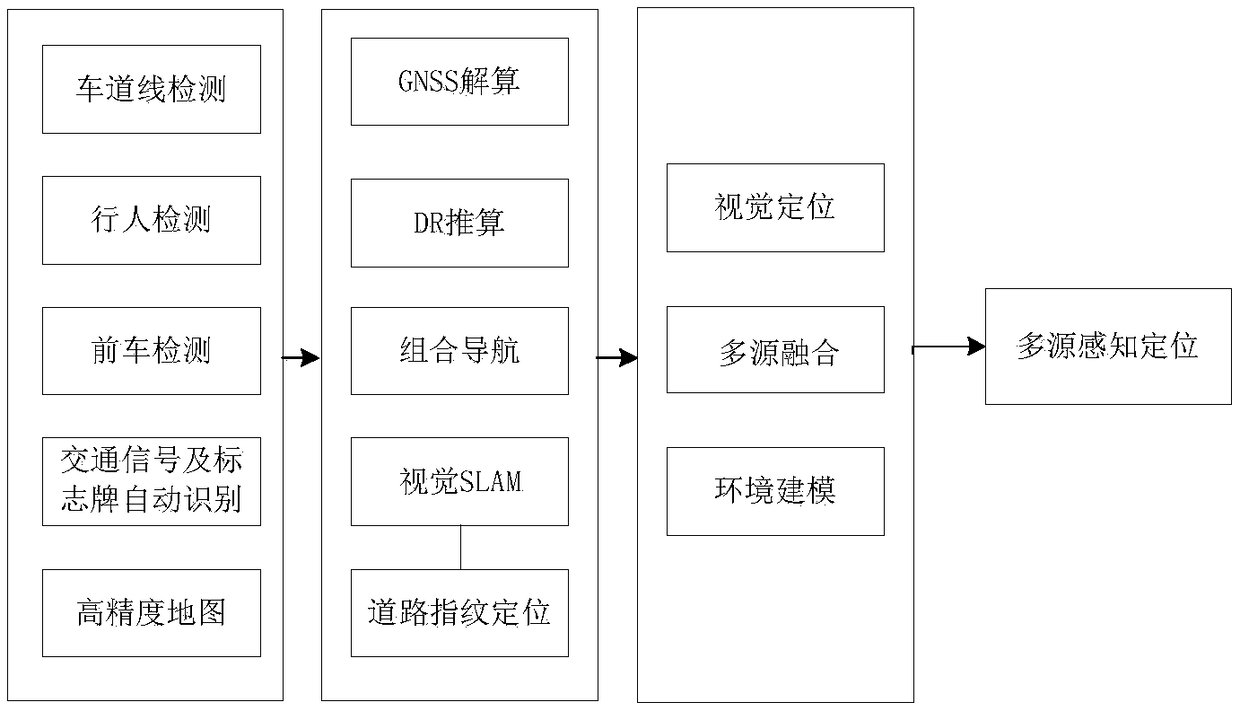
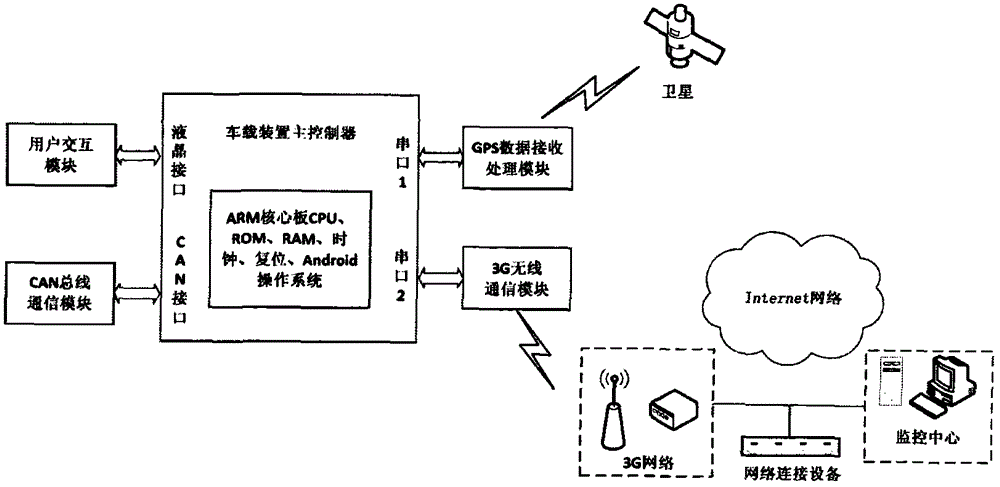
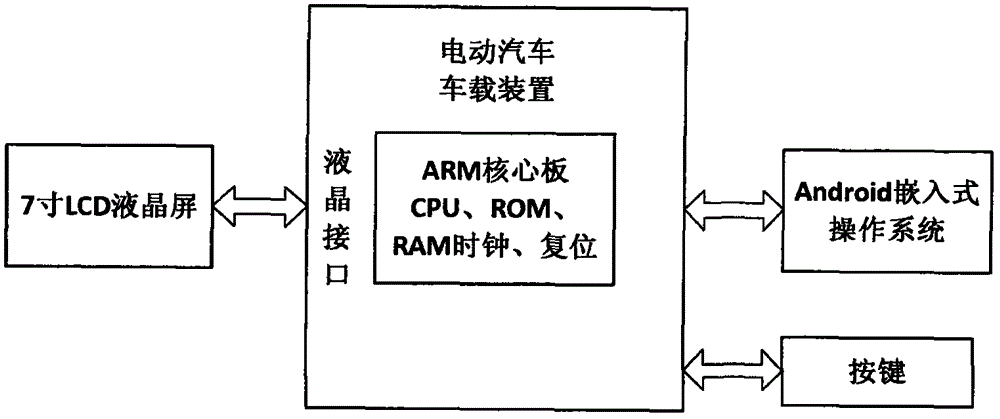
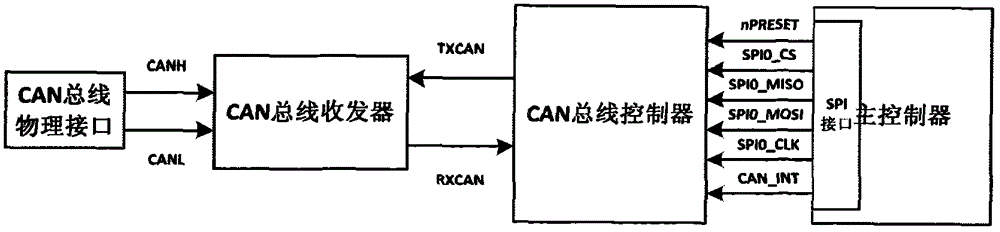
A multisource perception positioning system suitable for smart networked car. In a multisource perception navigation positioning system, a hardware portion includes a front camera, a GNSS and IMU combined navigation module, a LTE multimode communication module, a multisource data fusion processing module and a speedometer, and a software portion includes a data portion comprising a map and a realscene image. The multisource perception navigation positioning system includes: a positioning module, a lane line detection module, a pedestrian detection module, a preceding car detection module, a traffic signal and sign auto-recognition module, a GNSS calculating module, a DR calculating module, a combined navigation module, a visional SLAM module, a road fingerprint positioning module, and a multisource fusion perception positioning module. In the invention, environment perception technology, visional SLAM and closed loop fusion positioning technology, GNSS / inertial integrated navigation positioning technology, high-precision map making technology and multisource fusion perception positioning technology are combined, thus solving the problem of high-precision positioning of the smart networked car under urban complex road situation and losing lock condition in an underground garage.
Owner:武汉契友科技股份有限公司
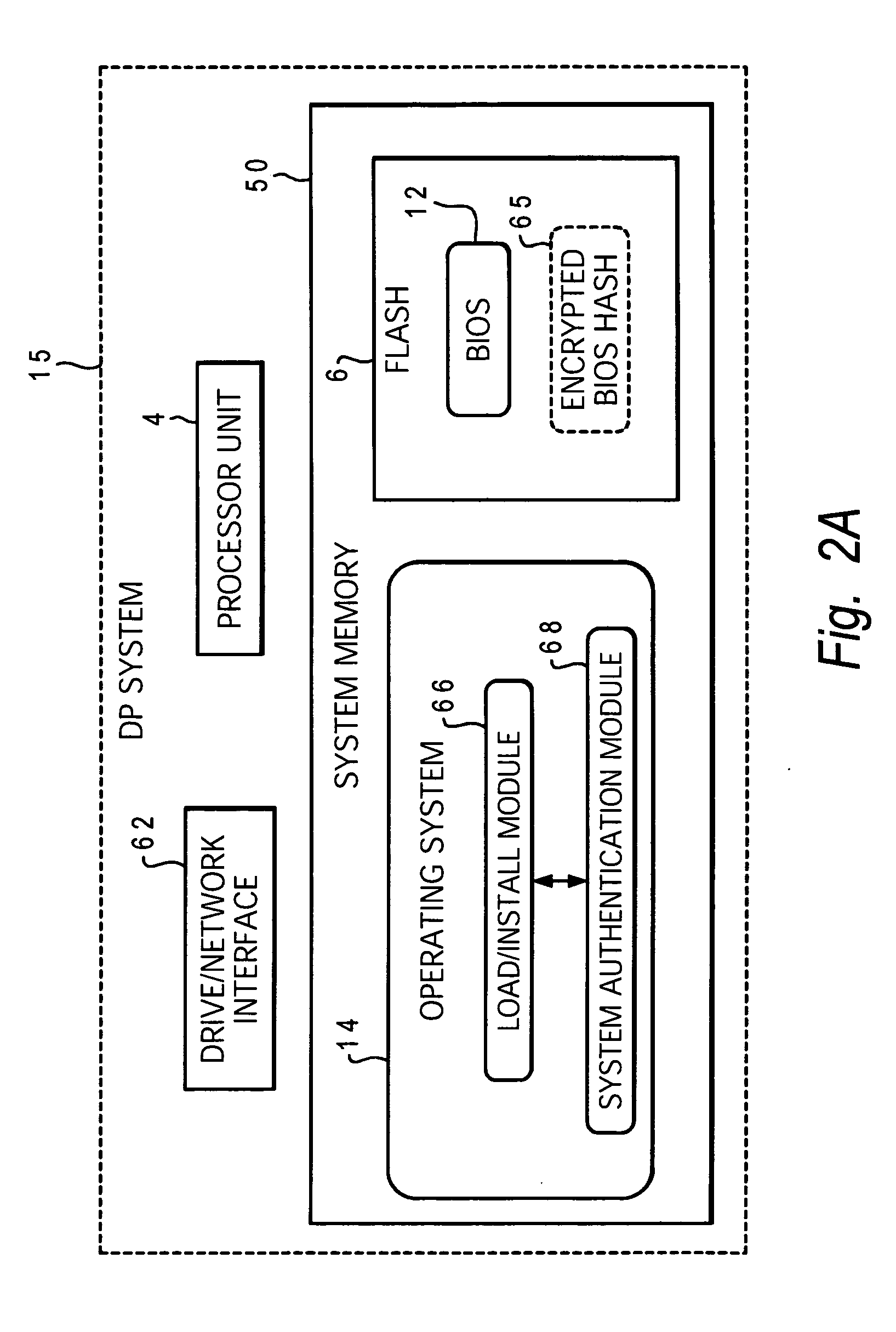
System and method for data processing system planar authentication
InactiveUS20060020821A1Unauthorized memory use protectionHardware monitoringData processing systemVerification system
A system and method for providing a system planar specific pre-load authentication that enables a supplier of system hardware and software components to detect assembly of unauthorized systems. The method includes authenticating a data processing system having a hardware inventory device that is uniquely associated with the data processing system. First, an identifier code that uniquely identifies the data processing system and an encrypted hash of the identifier code are stored in non-erasable memory within a hardware inventory device prior to the device being mounted on a system board. After mounting the hardware inventory device on the system board, software preload is authenticated by generating a hash of the identifier code, decrypting the encrypted hash of the identifier code, and comparing the decrypted identifier code hash with the generated identifier code hash to authenticate the system. The entities providing the hardware and / or software components, maintains a record of the system specific identifier codes enabling hardware inventory control tracking by comparing the number of hardware inventory devices issued to a specified system manufacturer with the number of system boards ordered by the manufacturer.
Owner:LENOVO PC INT
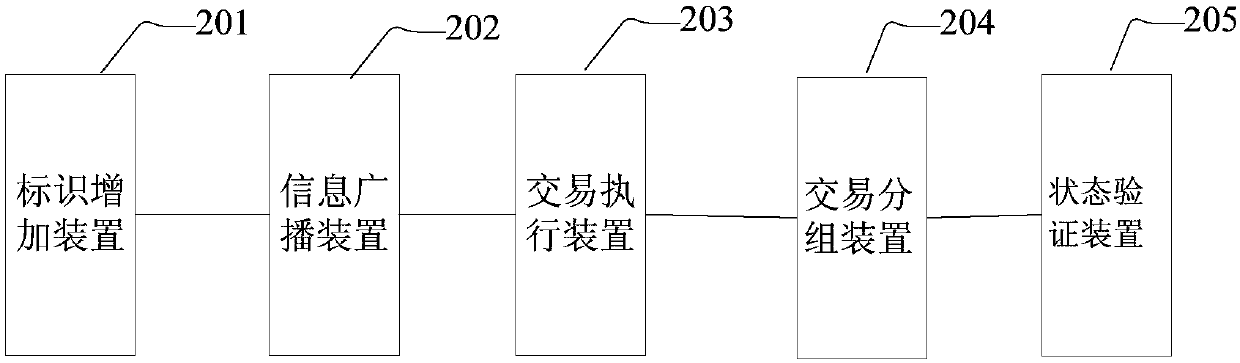
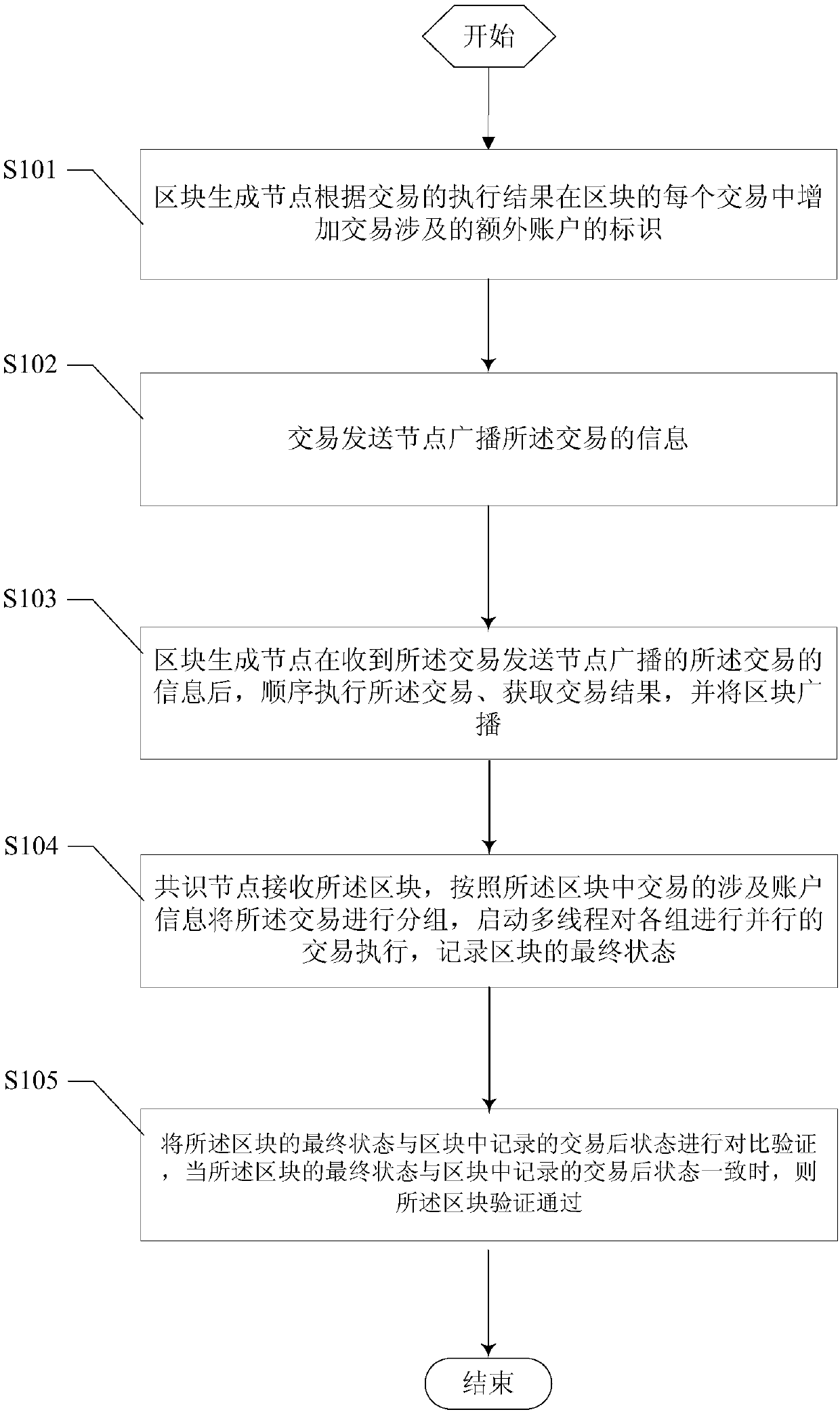
Transaction grouping-based block chain verification method and system
InactiveCN107678865AImprove performanceEnhanced authenticationProgram initiation/switchingInterprogram communicationValidation methodsFinancial transaction
The invention provides a transaction grouping-based block chain verification method and system, a computer device and a computer readable storage medium, and relates to the technical field of data processing. The method comprises the steps that a block generation node adds identifiers of additional accounts involved by transactions into the transactions of a block according to executive results ofthe transactions; a transaction sending node broadcasts information of the transactions; the block generation node sequentially executes the transactions, obtains transaction results, and broadcaststhe block; a consensus node performs grouping on the transactions according to account information involved by the transactions in the block, starts multiple threads to perform parallel transaction execution on groups, and records a final state of the block; and when the final state of the block is consistent with an after-transaction state recorded in the block, block verification is passed. Theblock verification and synchronization speed is increased by expanding system hardware; and finally the overall performance of a block chain transaction network can be greatly improved.
Owner:BANK OF CHINA
Method and apparatus for sensing and displaying tablature associated with a stringed musical instrument
InactiveUS7223913B2Readily learn how to playImprove learning experienceElectrophonic musical instrumentsMusicApplication softwareMotion capture
A system and method of enhancing guitar instruction based on Tablature Plus encoding of playing techniques within a MIDI file or other data structure, that may be rendered on an associated player application that provides multimedia output of the piece being played including a number of playing techniques. The system hardware for encoding the information includes string motion monitoring, and optionally a hand motion and finger positioning sensor, such as a data glove or a video motion capture system, for simultaneously registering the actions of the guitarist while playing the piece. The software comprises algorithms for determining note pitch and duration, and for extracting playing techniques from the data being collected. Multimedia player software is also described which renders a visual and audio output for the Tablature Plus encoded file, wherein the encoded playing techniques are represented within the display output. The system is adaptable to instruction for any instrument.
Owner:VMUSICSYSTEM GUITARVISION +1
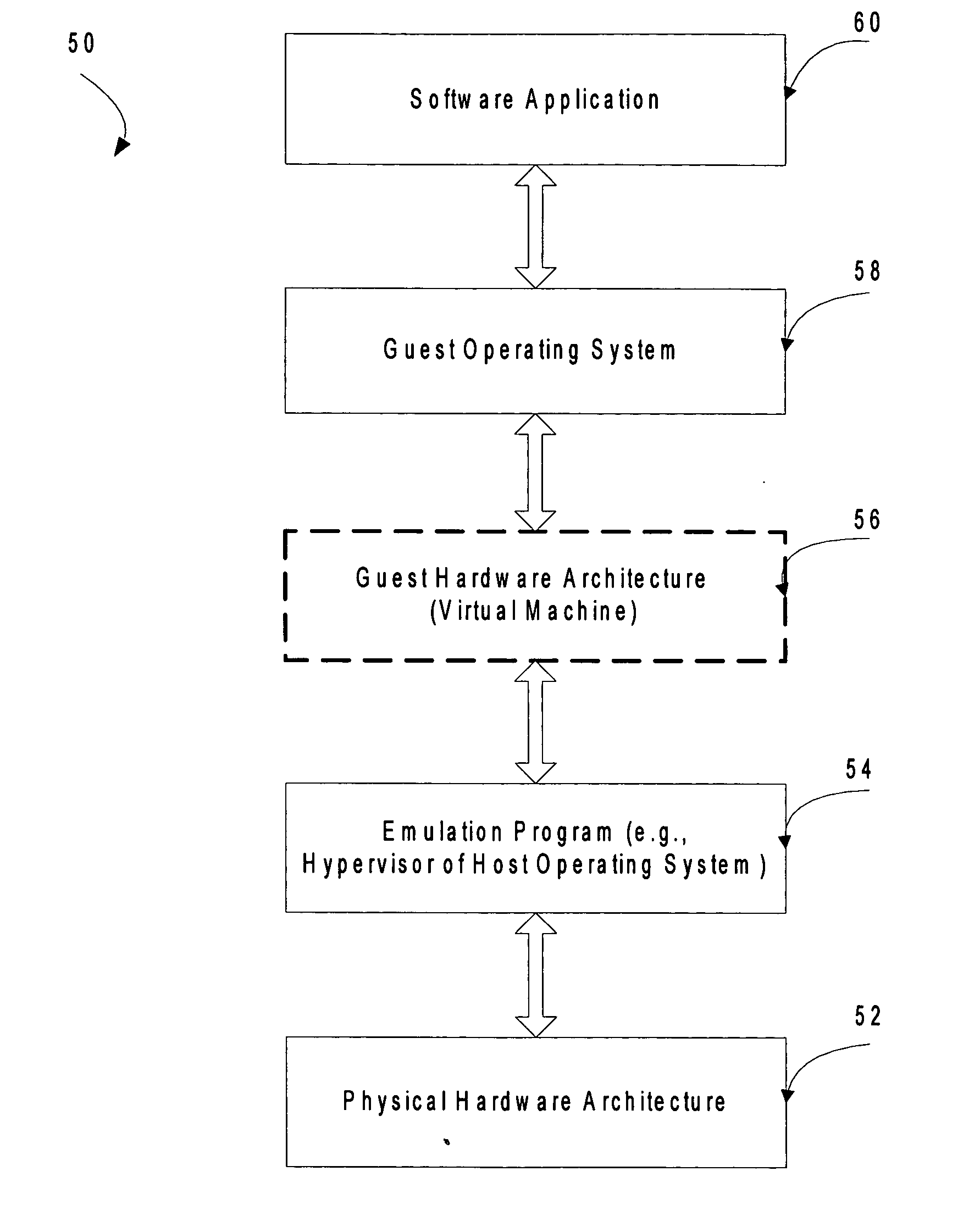
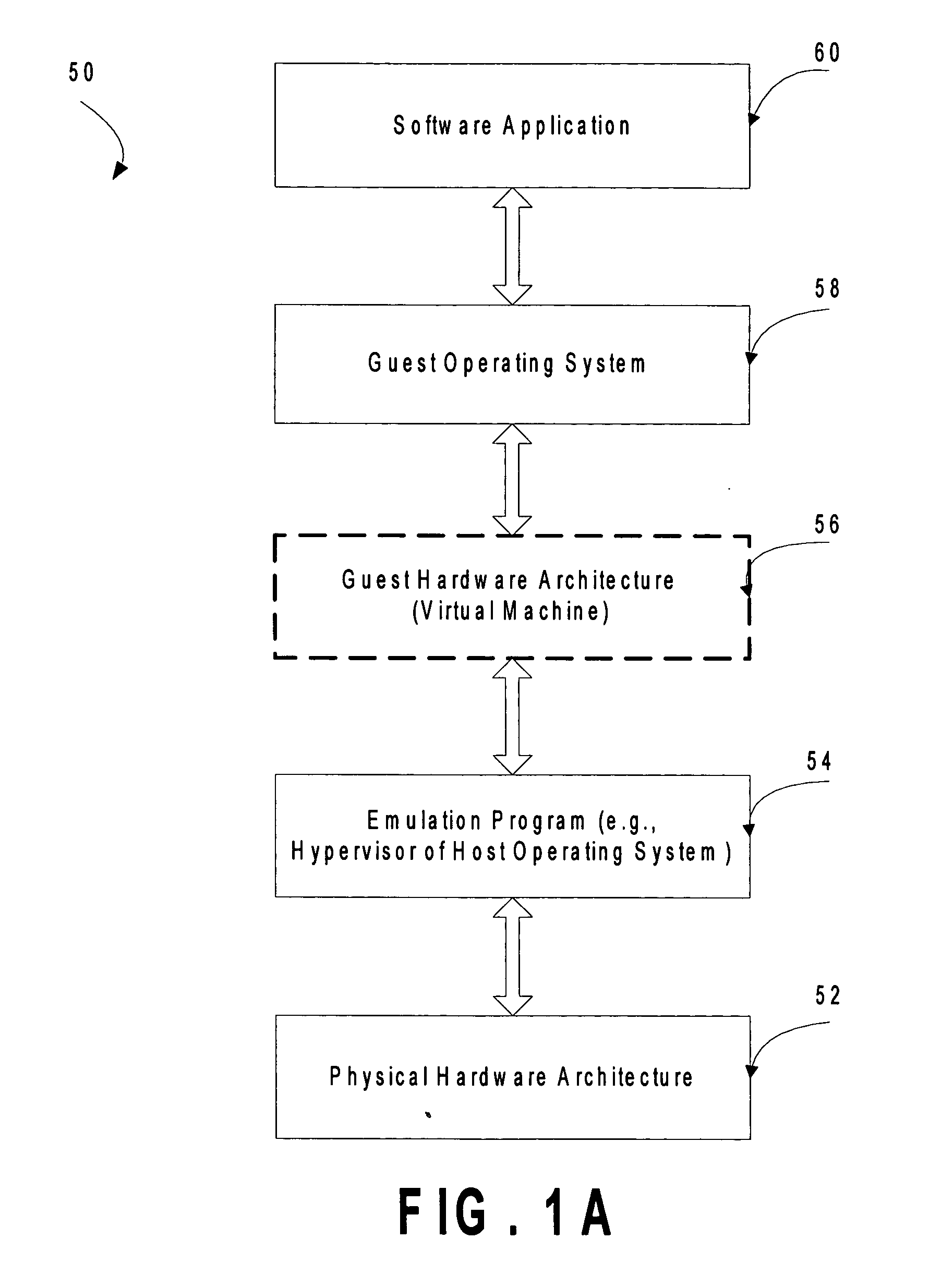
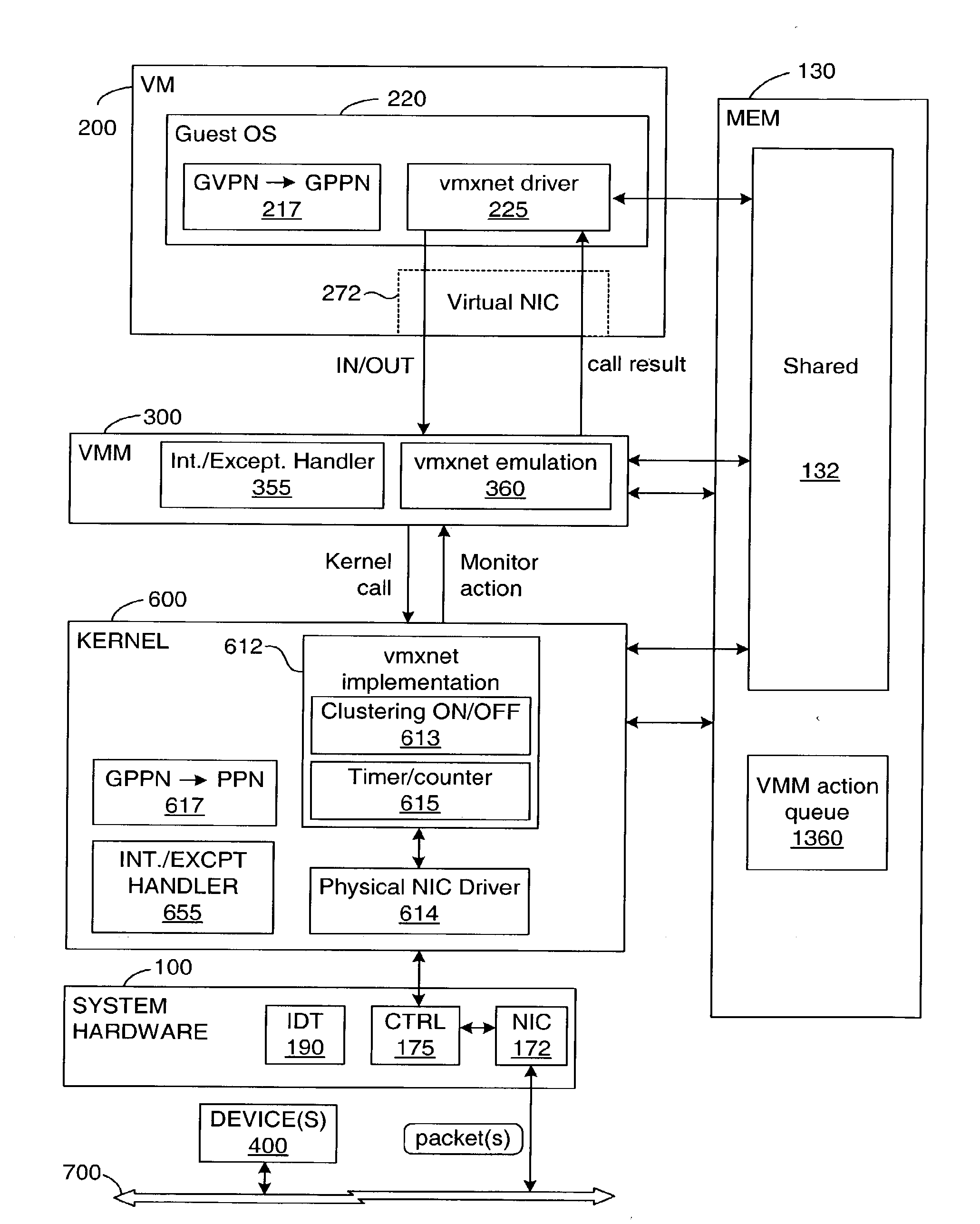
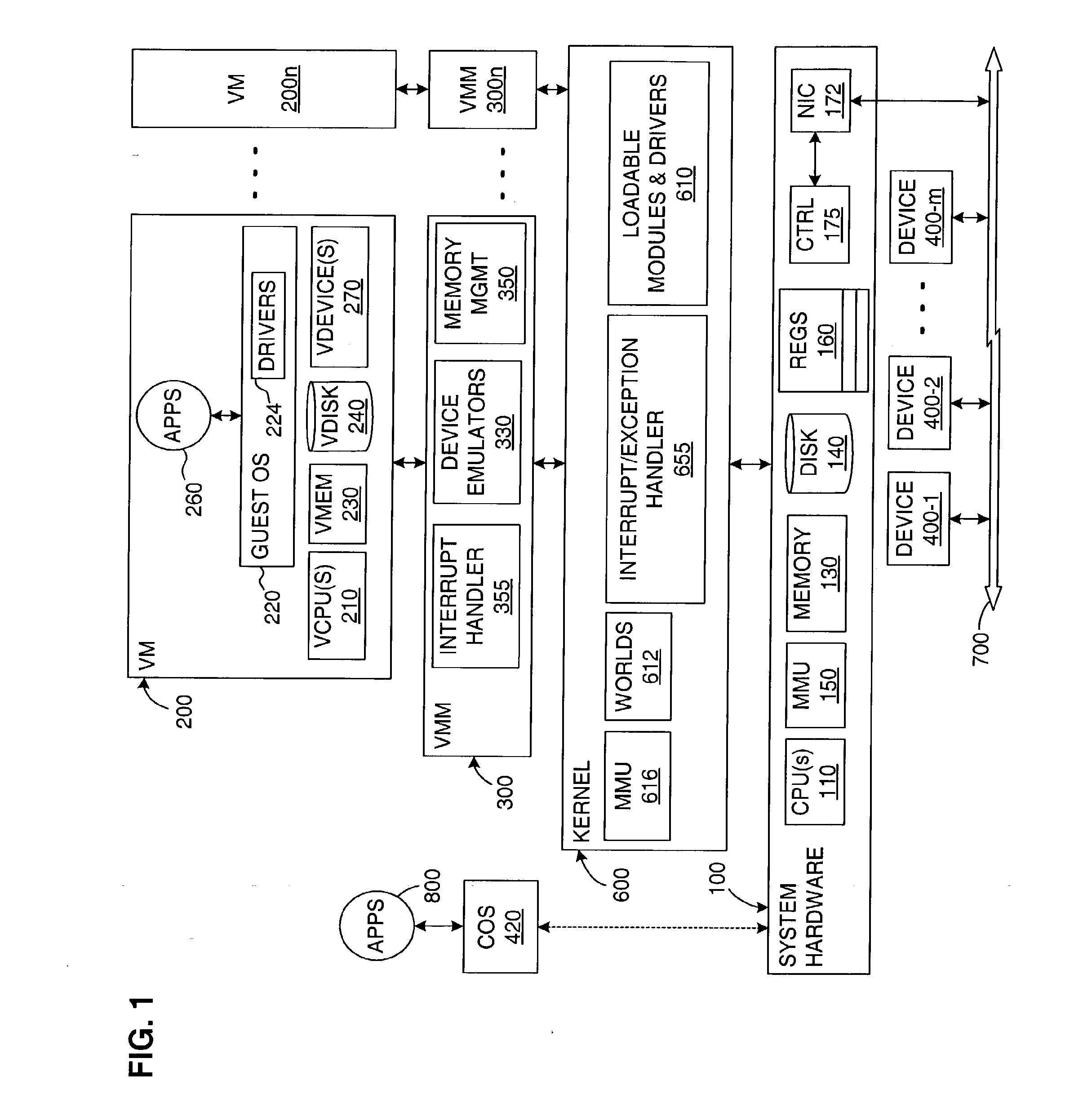
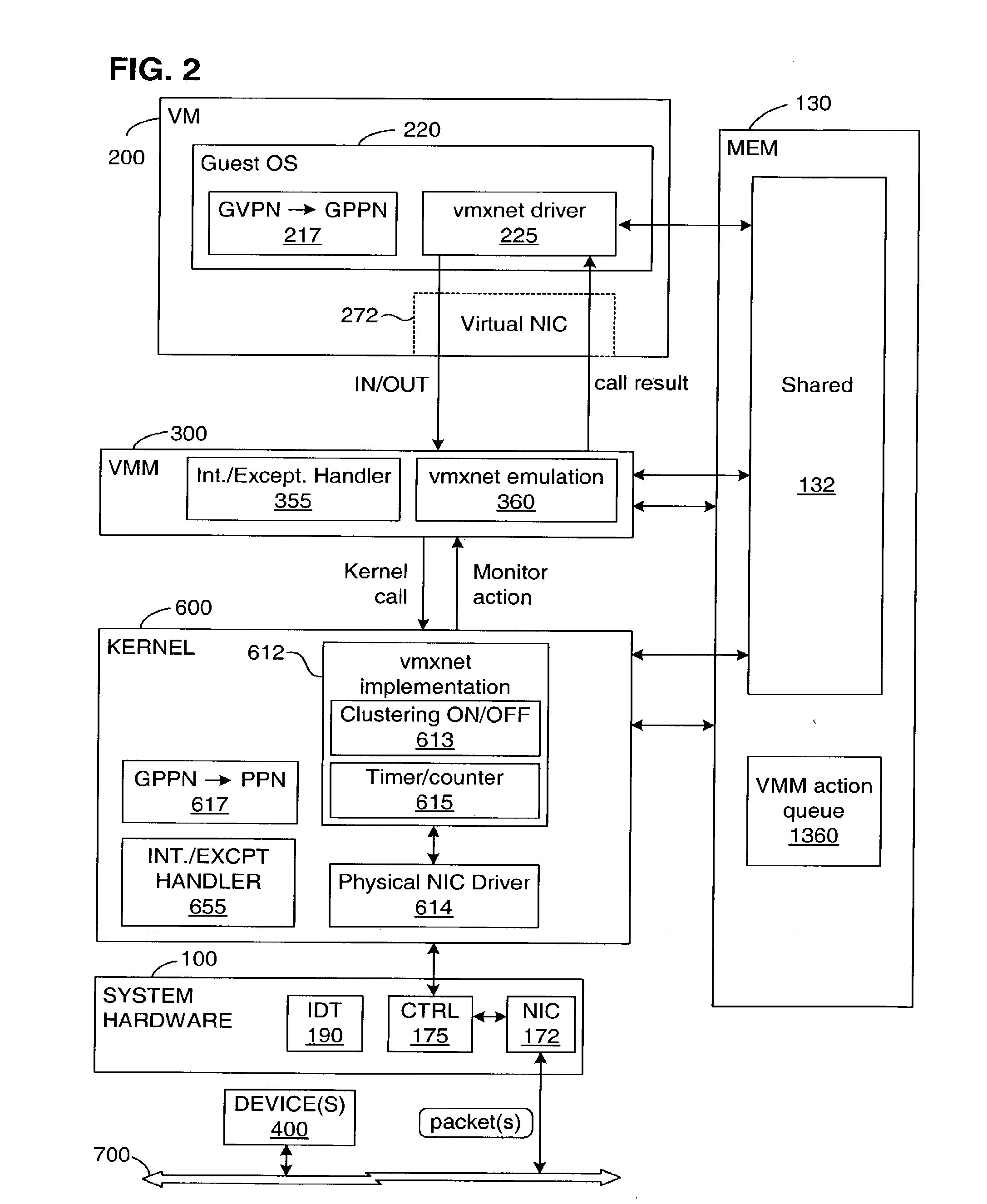
High-performance virtual machine networking
InactiveUS20090183180A1Software simulation/interpretation/emulationMemory systemsData packMulti processor
A virtual machine (VM) runs on system hardware, which includes a physical network interface device that enables transfer of packets between the VM and a destination over a network. A virtual machine monitor (VMM) exports a hardware interface to the VM and runs on a kernel, which forms a system software layer between the VMM and the system hardware. Pending packets (both transmit and receive) issued by the VM are stored in a memory region that is shared by, that is, addressable by, the VM, the VMM, and the kernel. Rather than always transferring each packet as it is issued, packets are clustered in the shared memory region until a trigger event occurs, whereupon the cluster of packets is passed as a group to the physical network interface device. Optional mechanisms are included to prevent packets from waiting too long in the shared memory space before being transferred to the network. An interrupt offloading mechanism is also disclosed for use in multiprocessor systems such that it is in most cases unnecessary to interrupt the VM in order to request a VMM action, and the need for VMM-to-kernel context transitions is reduced.
Owner:VMWARE INC
System and method for online specification of measurement hardware
InactiveUS20030036871A1Error preventionFrequency-division multiplex detailsComputer hardwareGraphics
A system and method for online configuration of a measurement device for a measurement system. The user accesses a server with a client computer over a network and specifies a desired measurement task. If the user lacks the hardware required to perform the task, hardware specifications and configuration software and / or data specific to the user's application, i.e., to perform the task, are sent to a manufacturer, who pre-configures the hardware with the configuration software and / or data to perform the task and sends the pre-configured hardware to the user. The hardware may be re-configurable hardware, such as a programmable hardware element or processor / memory based device. Configuration software and / or data for configuring the user's measurement system hardware (and / or software) to perform the desired task may also be sent to the user. The configuration software sent to the user may comprise a graphical program usable by the measurement system to perform the task.
Owner:NATIONAL INSTRUMENTS
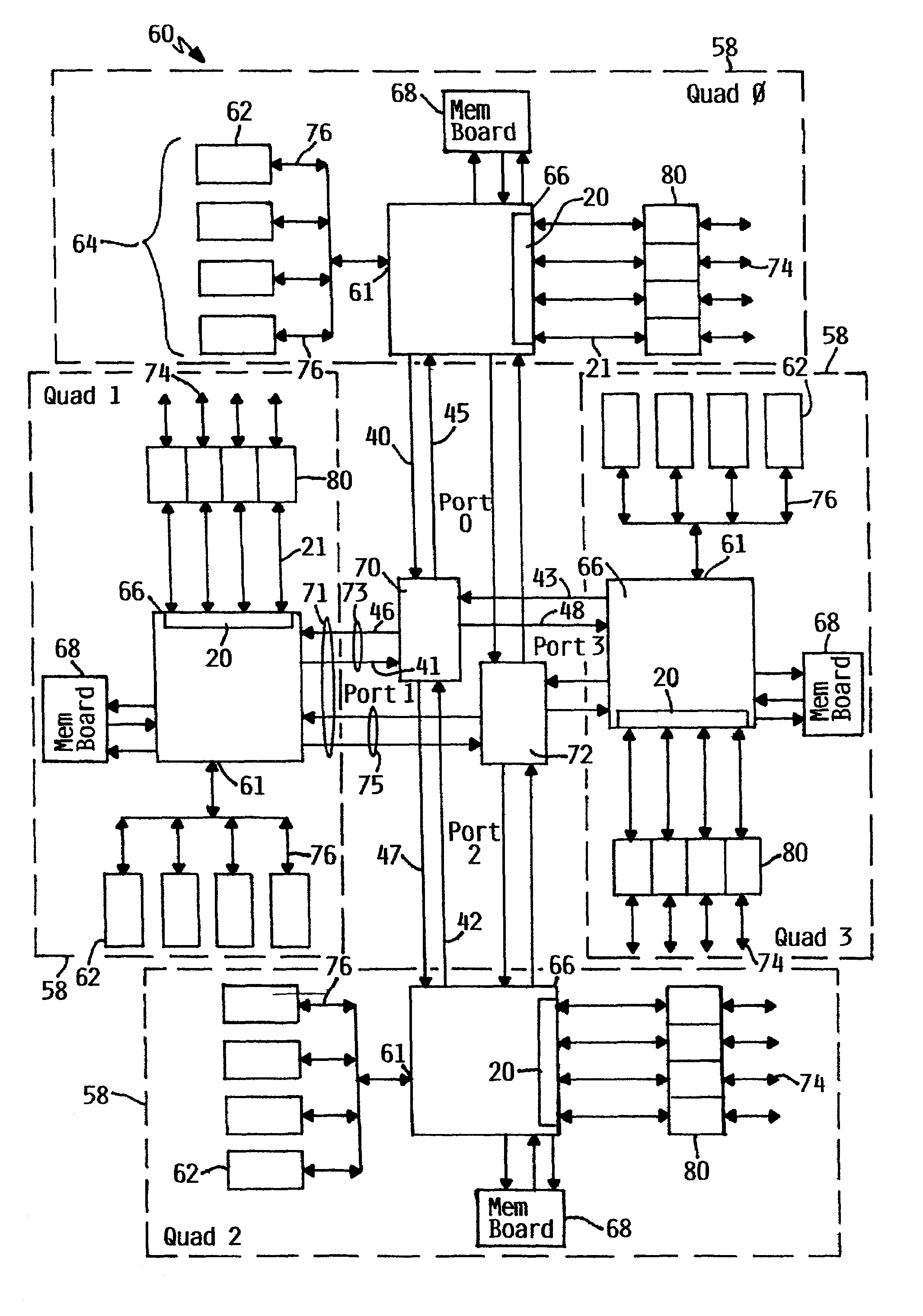
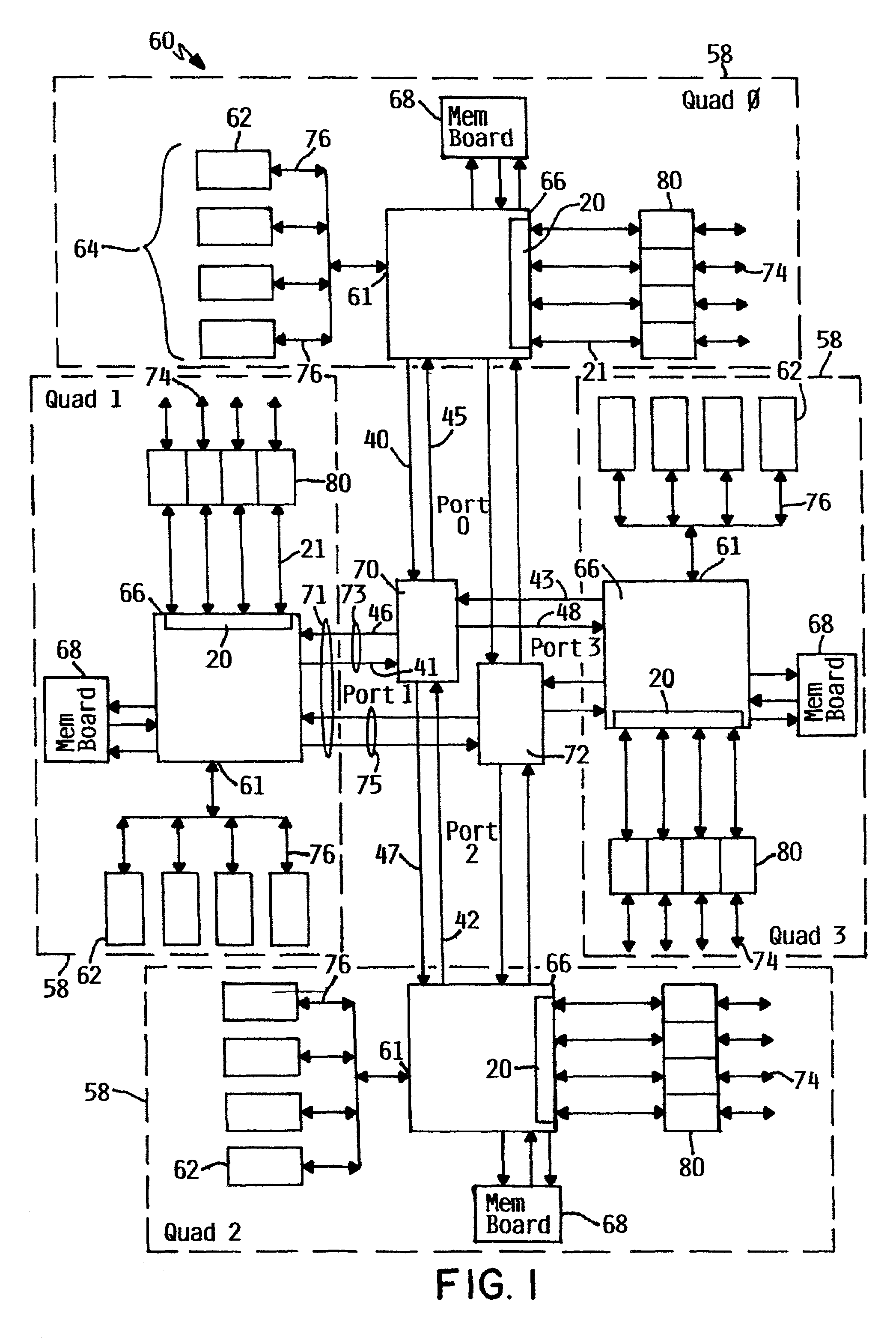
Distributed allocation of system hardware resources for multiprocessor systems
A method is provided for allocating system resources across multiple nodes of a system communicating through a hardware device. The method provides for allocation of transaction units or identifiers in an allocating component for use in a multiple target component which may be in a distinct target node within the multiple node system. Based on the operations or requests that a target node receives from multiple external request source nodes, each requiring the use of target transaction unit objects such as transaction identification bits, the method provides inclusion of such information in the initial request to a target node which allows any data transmission between the source node and the target node, or the target node and the source node to be accomplished without any further intervention by the allocating component. Such component may be a local memory control agent or device.
Owner:IBM CORP
System and method for providing prepaid services via an internet protocol network system
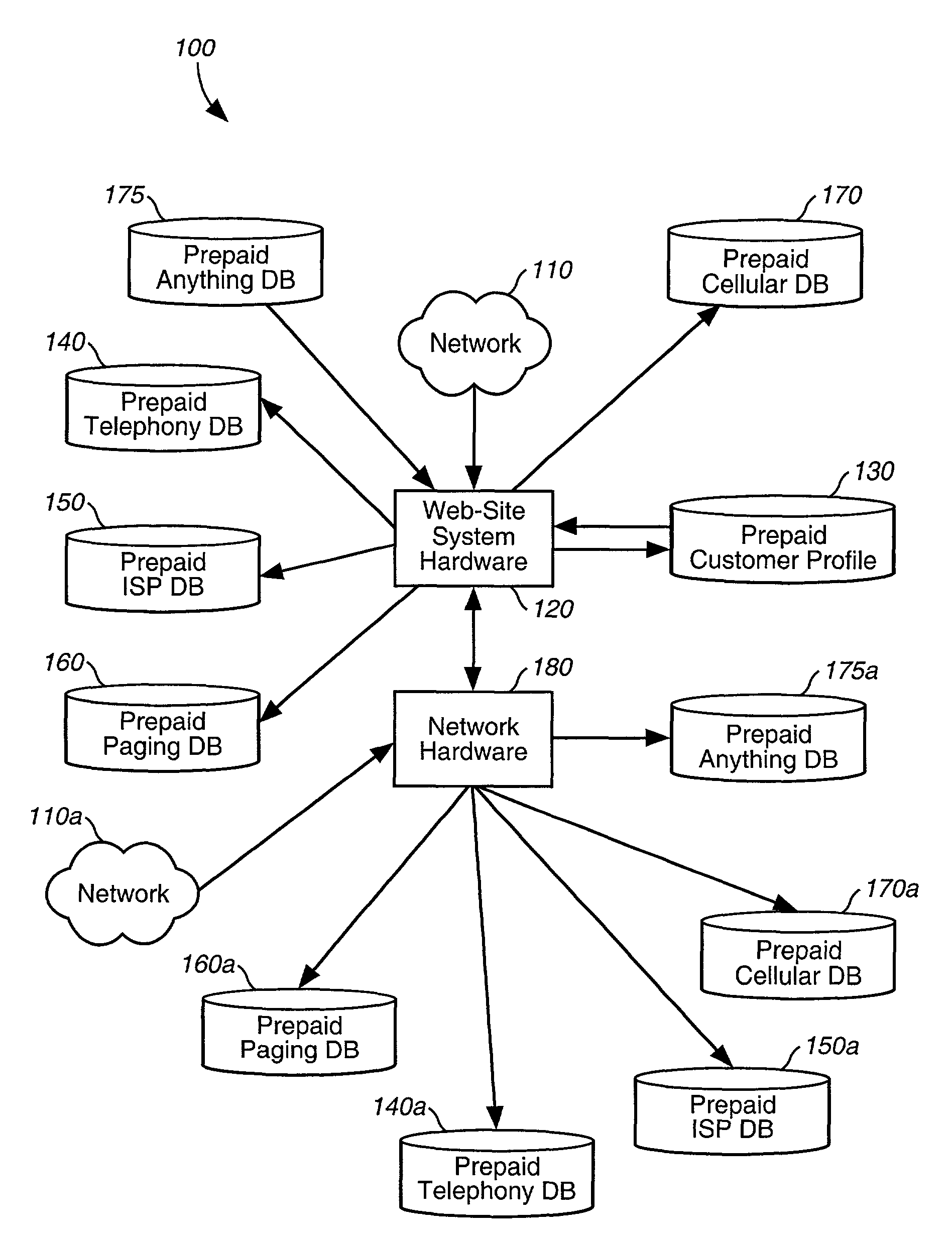
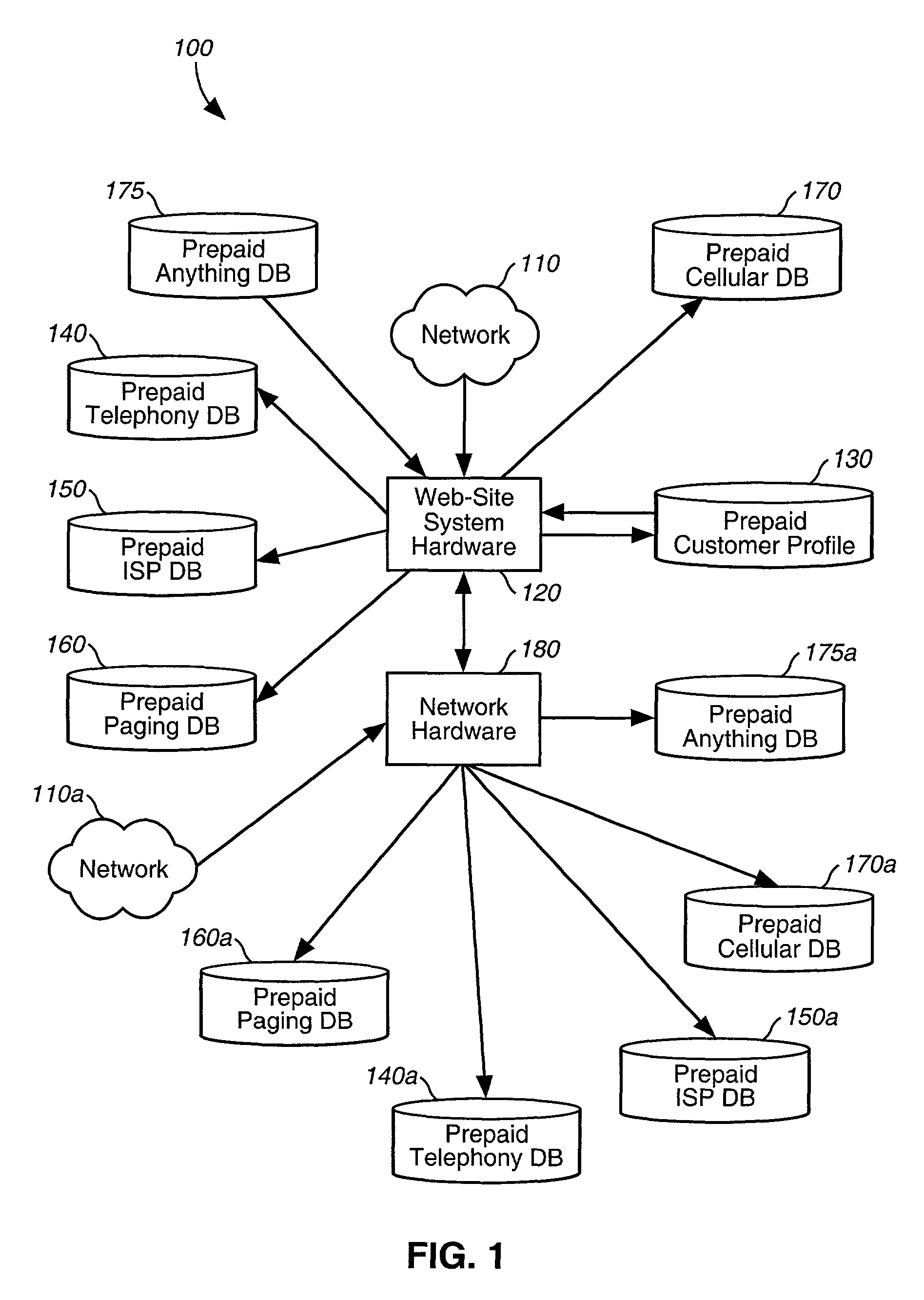
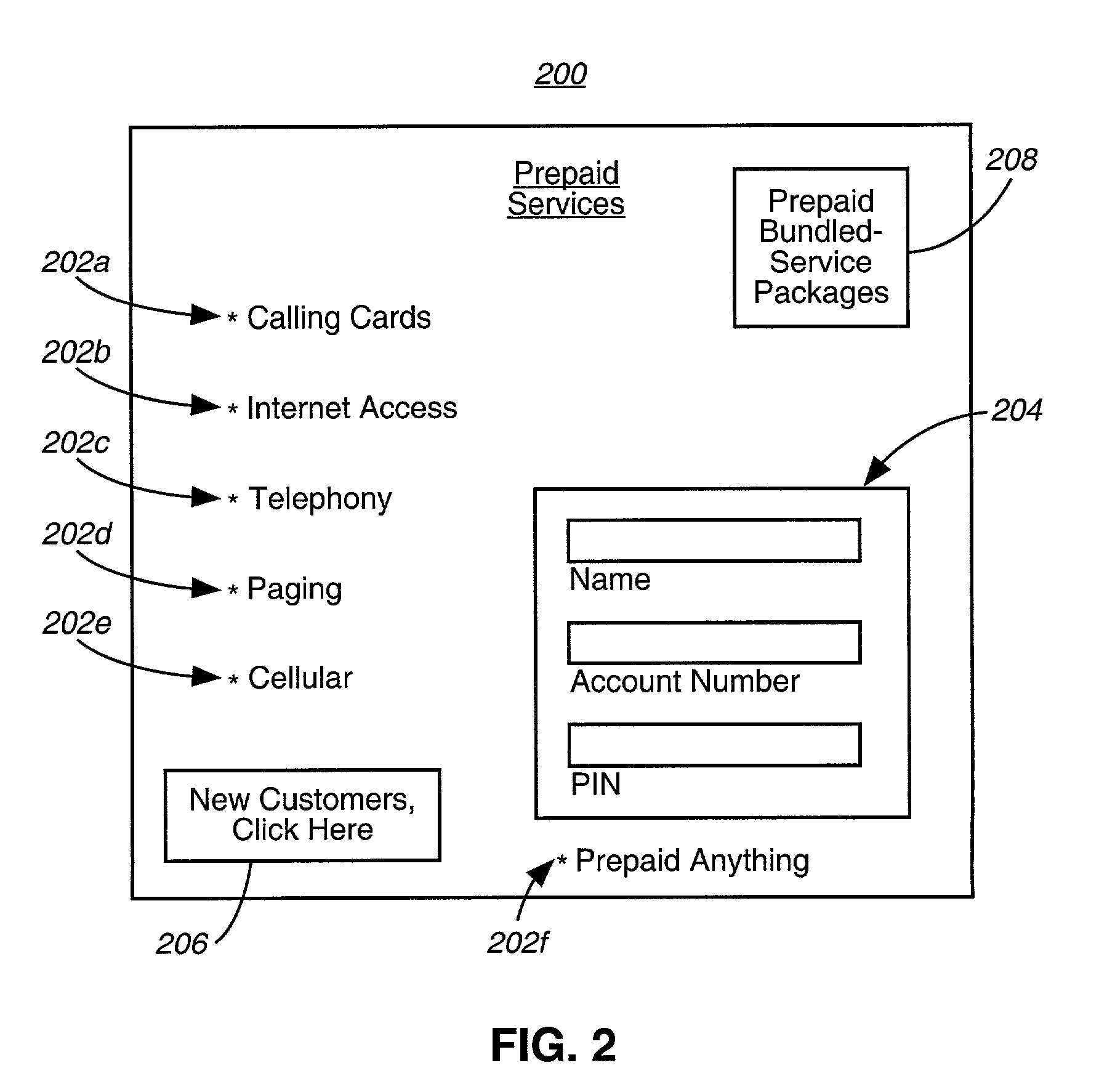
ActiveUS8175965B2Reduce delivery costsOvercomes drawbackCredit registering devices actuationFinanceSystem developmentSystem hardware
A system and method are disclosed for providing prepaid services via an open network architecture system having access to a network, such as the Internet via an Internet protocol. The architecture system is operated by a system operator and includes a customer profile database which stores various customer-related information, such as customer names and their respective payment and contact information, a plurality of databases each storing prepaid accounts for a particular prepaid service, such as telephony, Internet access, paging, and cellular, and web-site system hardware connected to the customer profile database and the plurality of databases and to a network, such as the Internet, for ubiquitously accessing the databases via the Internet for viewing and managing one's prepaid services, as well as purchasing additional prepaid services and / or usage rights. The architecture system further includes network hardware connected to the web-site system hardware for enabling outside system operators, e.g., wholesalers, online retailers, system developers and ISPs, to utilize the architecture system to brand their own prepaid services and offer them through the architecture system.
Owner:GLOBAL TELLINK
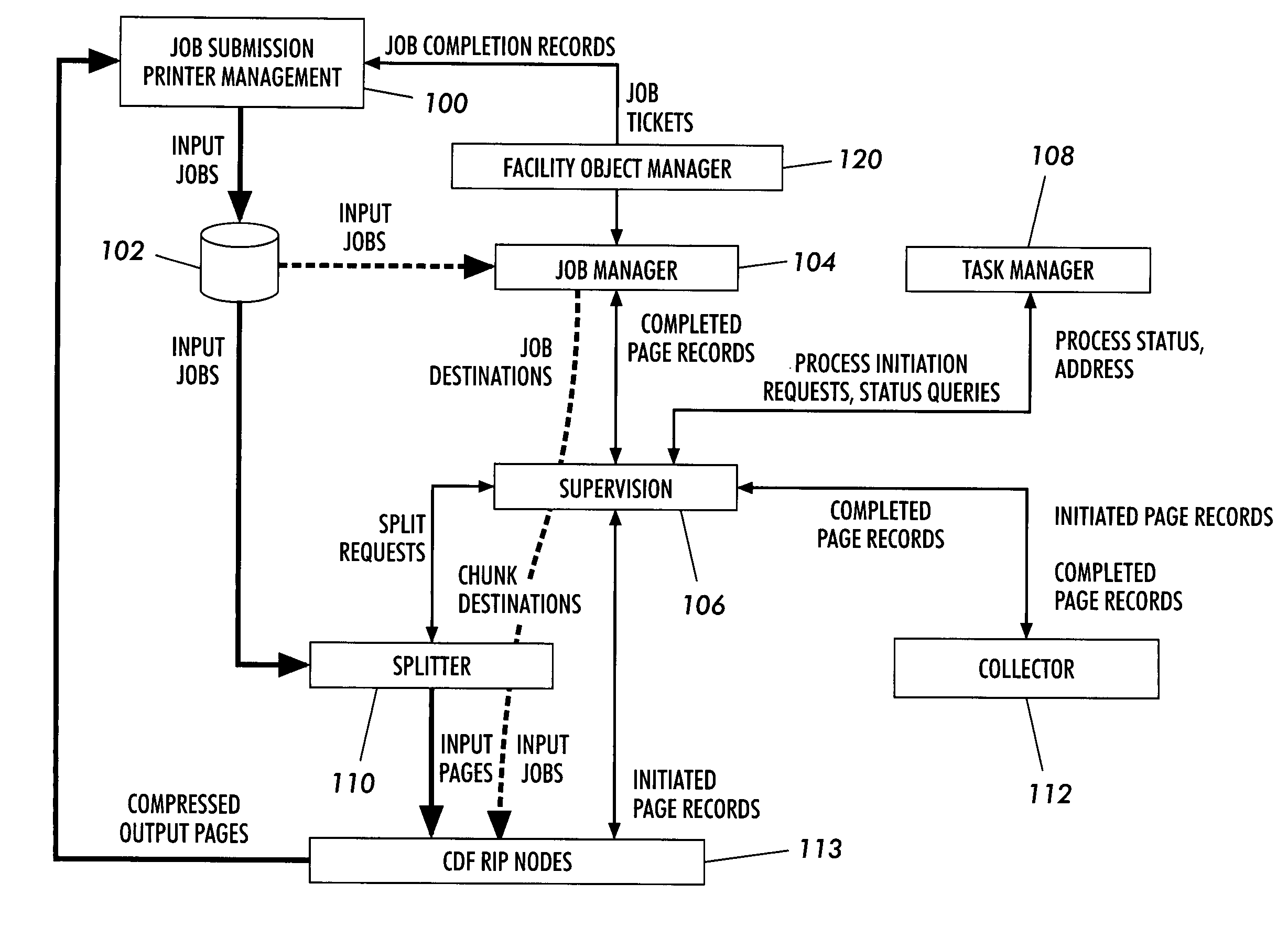
Information management system
InactiveUS7069188B2Avoid problemsAnimal huntingError detection/correctionData processing systemTelecommunications link
A system sends an electrical signal communicated over a communication link. Both a system hardware and communication architecture and a software data processing system are provided to permit gathering, transmission, processing, storage, access, presentation and use of the data gathered by the system of the present invention.
Owner:WALRUS HLDG
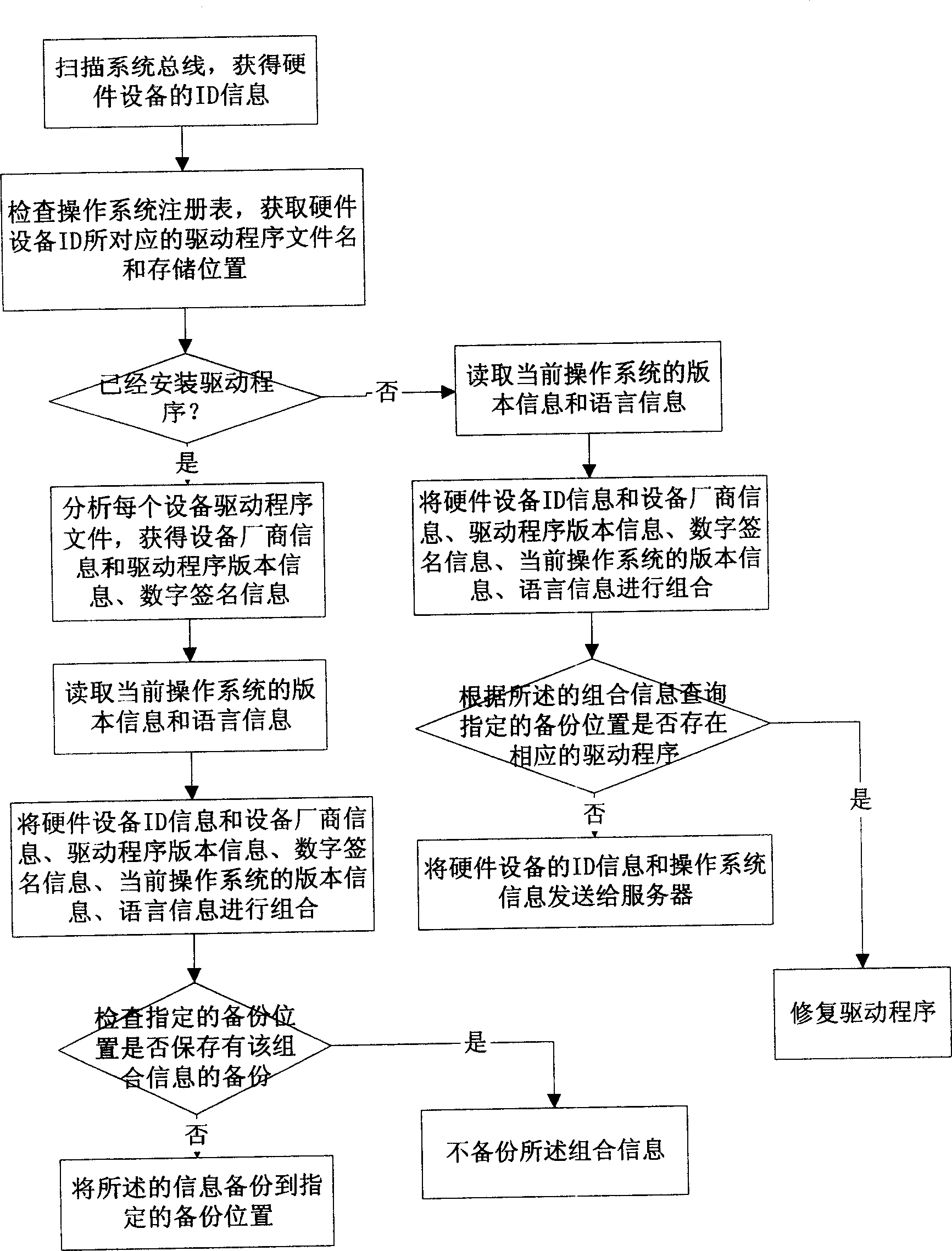
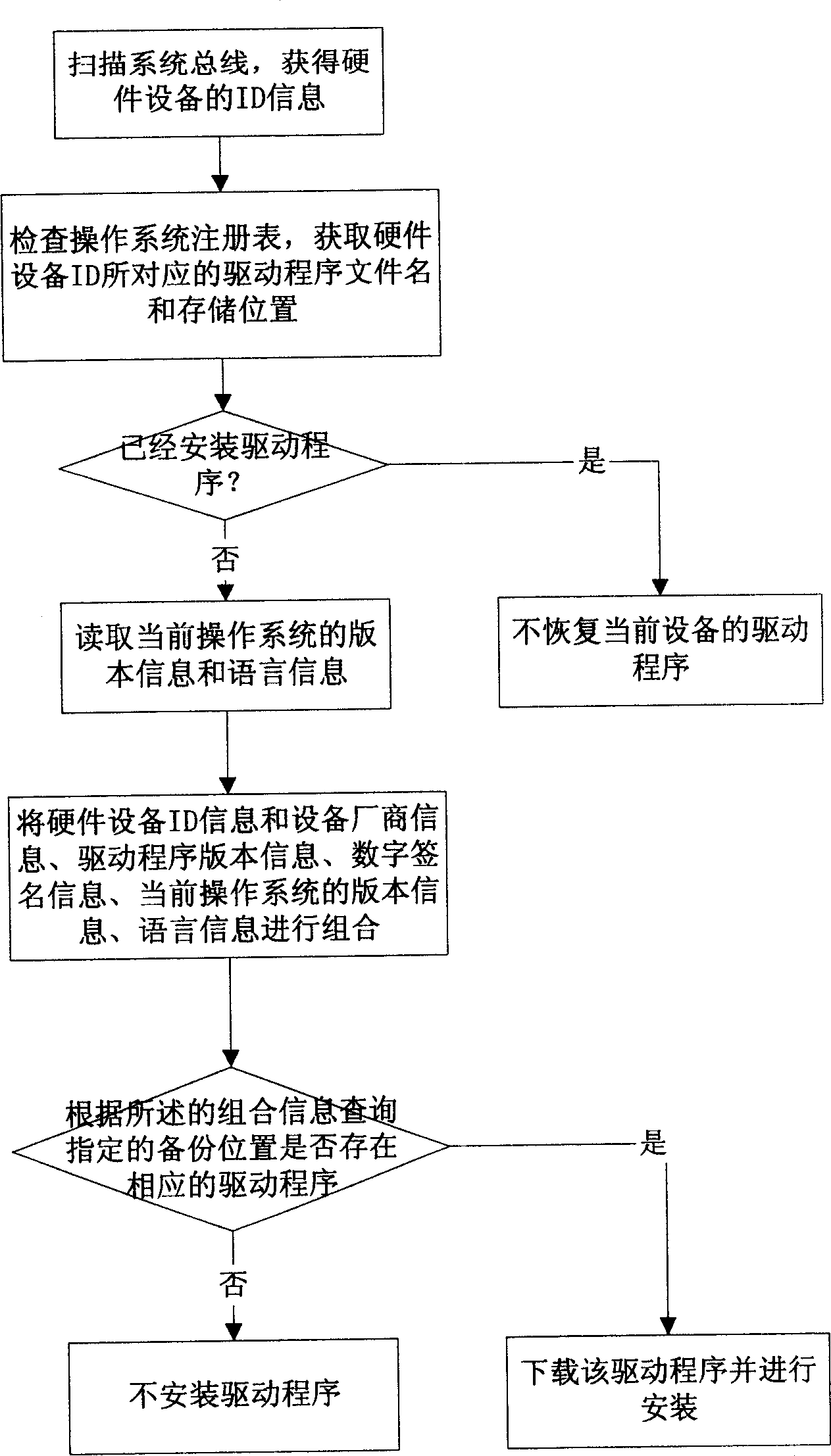
Automatic detesting method for computer system hardware device
The present invention discloses automatic detecting method of computer system hardware devices. The deputy module in computer system is used in detecting computer system hardware devices in computer system and maintaining and managing the hardware devices and the drive program. The detection includes real-time detecting hardware devices and diagnosing the abnormality; issuing hardware device fault report in designated format; and automatically installing, repairing or updating the drive programs of the hardware devices. The present invention realizes the automatic management and maintenance of the hardware devices and the drive programs to reduce back-up cost, raise service efficiency and update the drive programs.
Owner:南通英可达信息技术有限公司
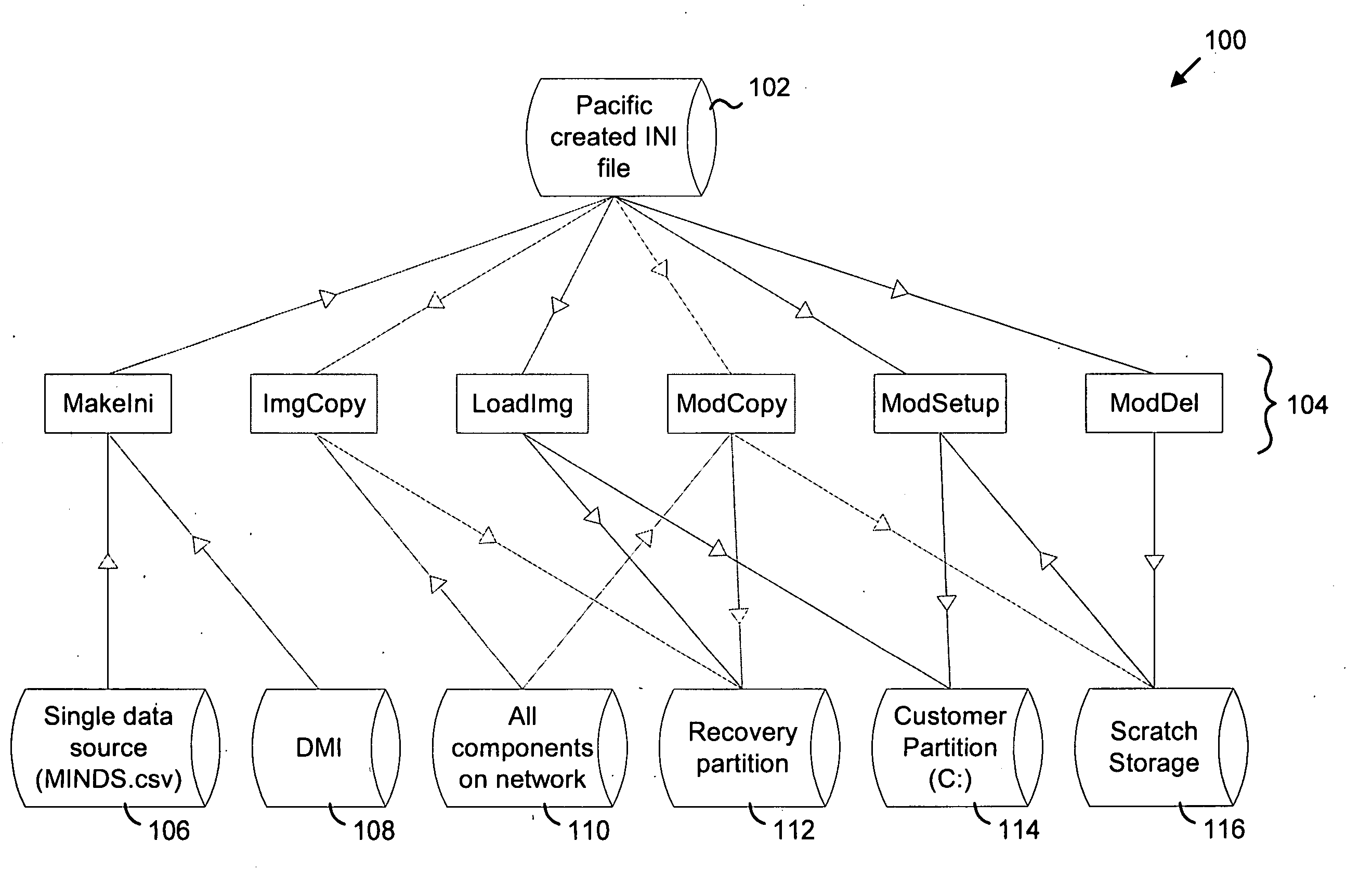
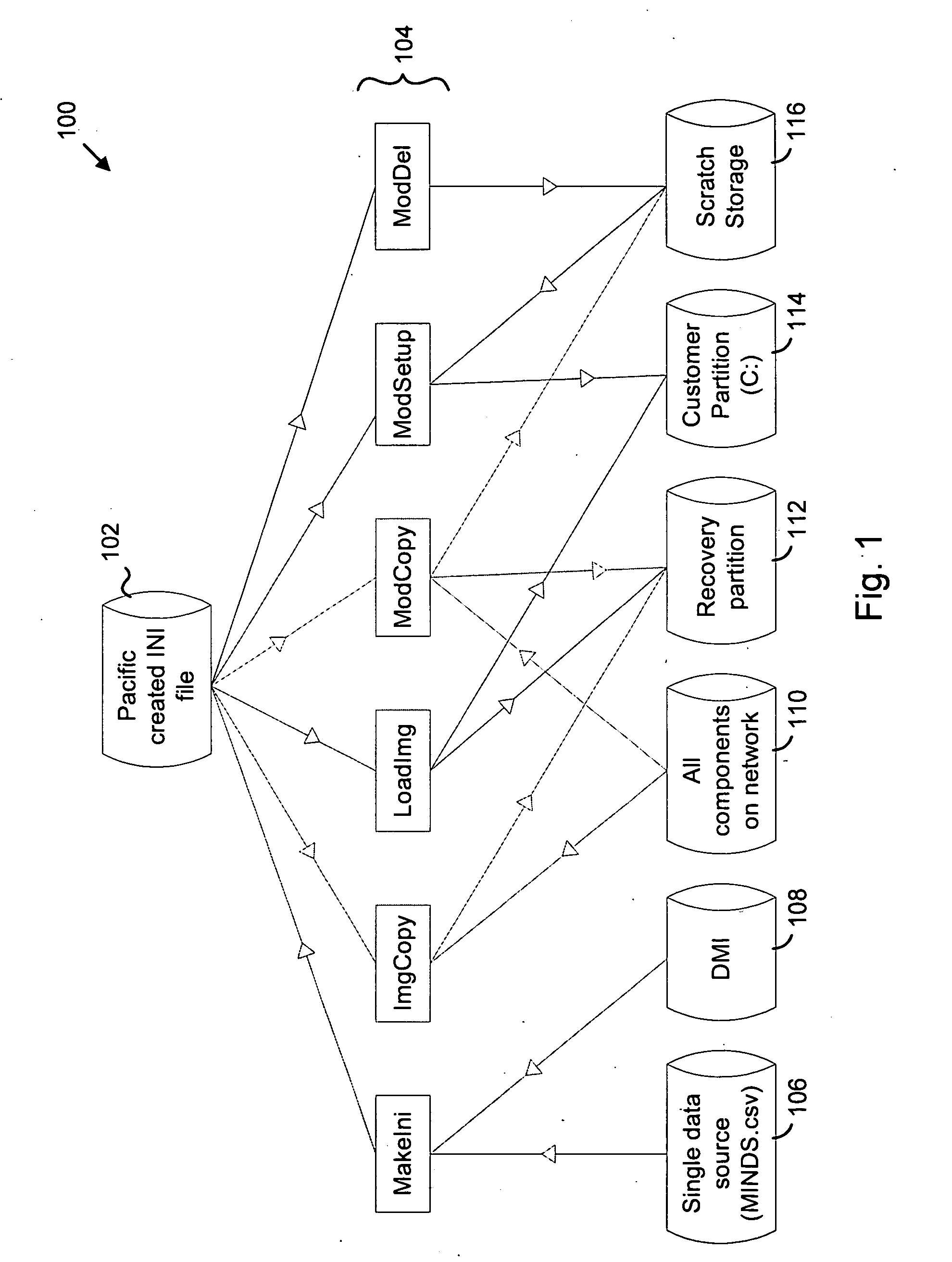
Modular imaging of computer software for system install and restore
InactiveUS20050240815A1Error detection/correctionProgram loading/initiatingDigital videoOperational system
A modular approach to creating a software configuration and to allowing recovery of a configuration. Initial configuration tools can be applied or executed selectively and in different orders at a time of manufacture or shipping of a computer system. Foundation images and modules are stored in a flat directory structure, in one directory, with unique names to make management of, and access to, the images and modules more efficient. Records are used to identify image and module compatibility on specific hardware platforms, or sets (i.e., computer system hardware). In one embodiment a text format is used for the records and other database information to describe and define the images and modules. A hardware set is identified by an identification (ID) code. A recovery set of tools allows a user to selectively restore a system to an original configuration, or to restore selected modules or components. A graphical user interface is described along with facilities for starting and managing a recovery process, application recovery, and Compact Disk (CD) / Digital Video Disk (DVD) media creation from within the computer system's operating system and to recover system and application files and modules; create recovery media and to remind a user to create recovery media.
Owner:SONY CORP +1
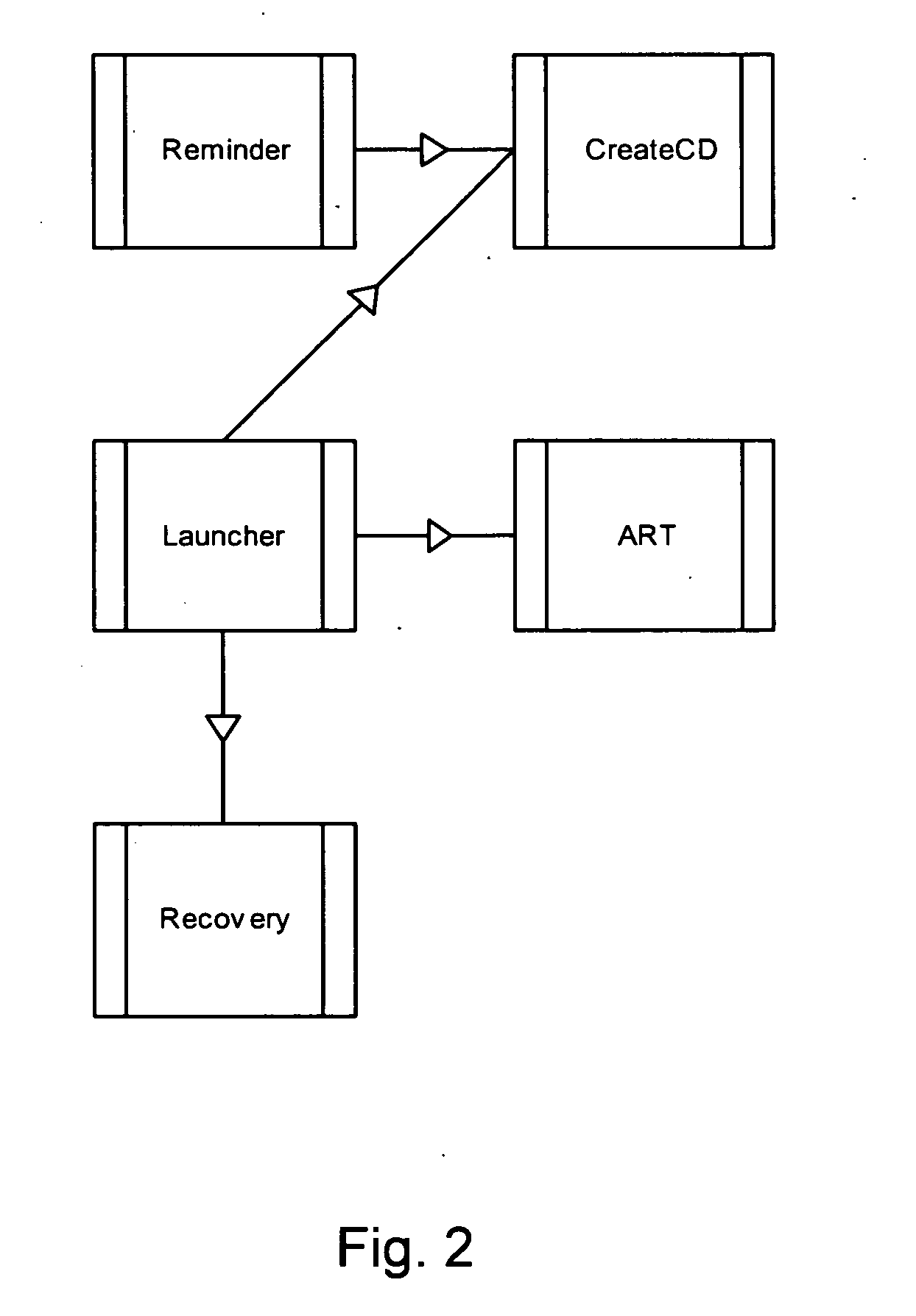
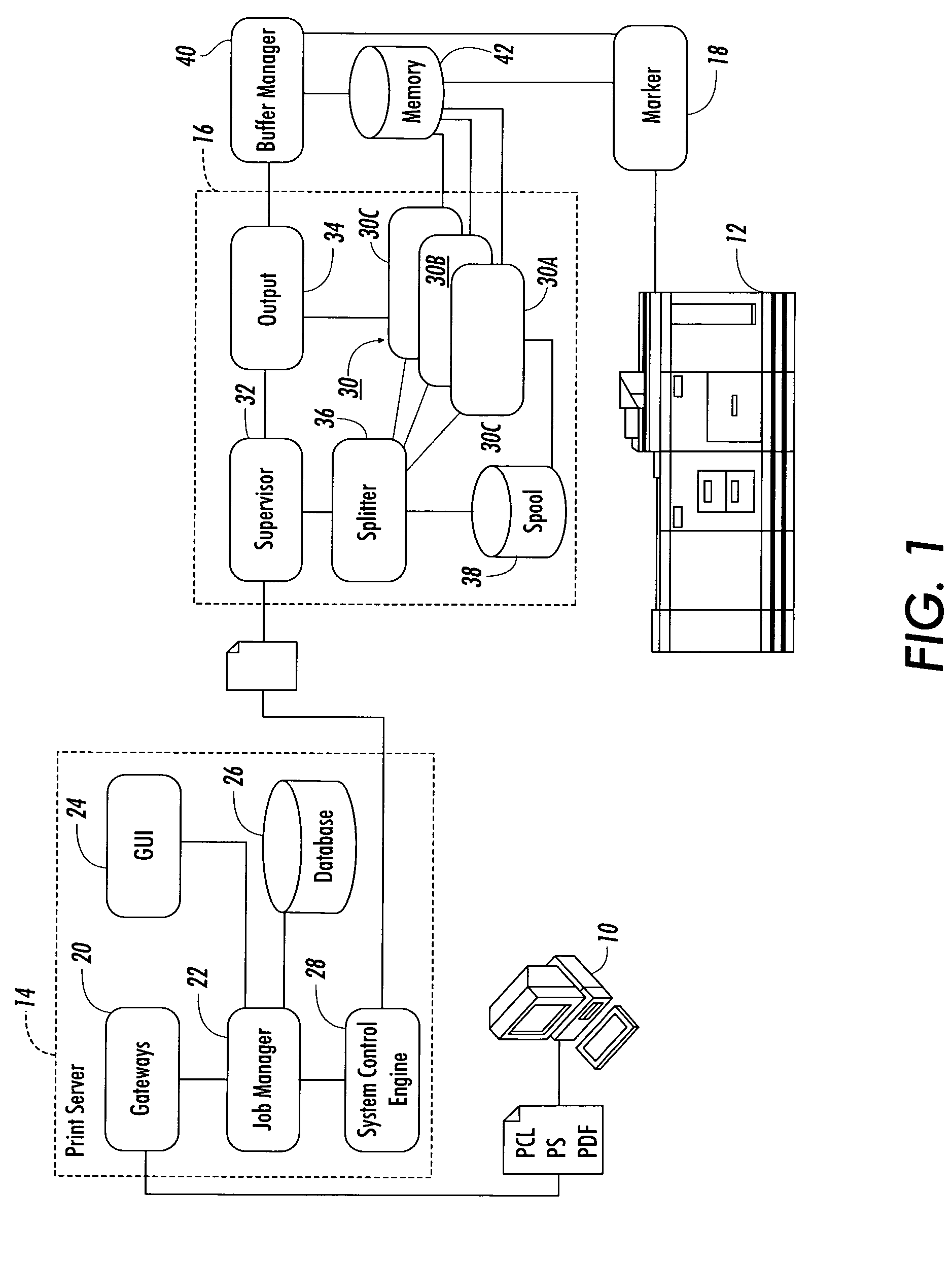
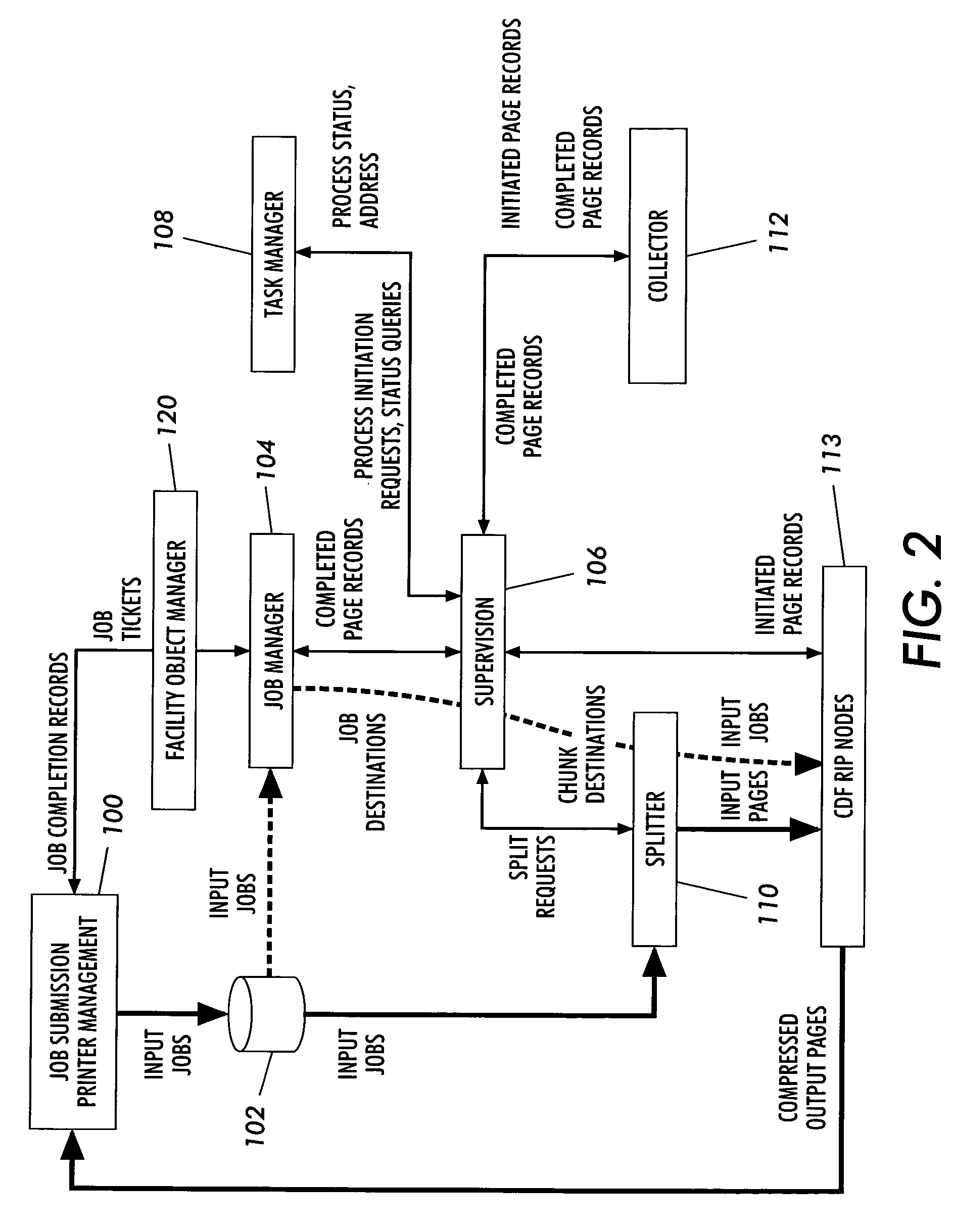
Parallel printing system having modes for auto-recovery, auto-discovery of resources, and parallel processing of unprotected postscript jobs
ActiveUS7161705B2Improve processing efficiencyImprove efficiencyVisual presentationPictoral communicationOperation modeParallel processing
A printing system comprised of a printer, a plurality of processing nodes, each processing node being disposed for processing a portion of a print job into a printer dependent format, and a processing manager for spooling the print job into selectively sized chunks and assigning the chunks to selected ones of the nodes for parallel processing of the chunks by the processing nodes into the printer dependent format. The chunks are selectively sized from at least one page to an entire size of the print job in accordance with predetermined splitting factors for enhancing printer printing efficiency. The operating of the printing system includes a method for parallel processing of a print job with a plurality of processing nodes into a printer-ready format for printing the print job, wherein operating modes are provided for: auto-recovery in response to a page fault by executing an auto recovery in serial mode of operation; auto-discovery of system hardware resources; and parallel processing of protected PostScript print jobs.
Owner:XEROX CORP
Electric vehicle battery pack replacement system composed of computer, Internet and multiple robots
ActiveCN104828028AAccurate operationReduce usageCharging stationsElectric propulsion mountingAutomotive batteryStructure of Management Information
An electric vehicle battery pack replacement system. The hardware of said system consists of computers, a first palletizing robot (608), a second palletizing robot (609), a ferry robot (199), a four-post lift (22), a ferry robot track (198), a first conveyance line (607), and a second conveyance line (610). Connection between said hardware and an electric vehicle onboard device is achieved by means of various forms of computer-based supervisory control software, wired / wireless internet, and a 3G / 4G wireless network, creating a man-machine dialogue system that utilizes supervisory control center computers to control, command, and guide electric vehicle battery replacement. The system is quick, safe, and prevents drivers unskilled at operating battery replacement systems from causing an accident by replacing a battery incorrectly. The system is well-designed, structurally simple, low in cost, and occupies little space.
Owner:岳秀兰
Safety guide device and method for embedded system
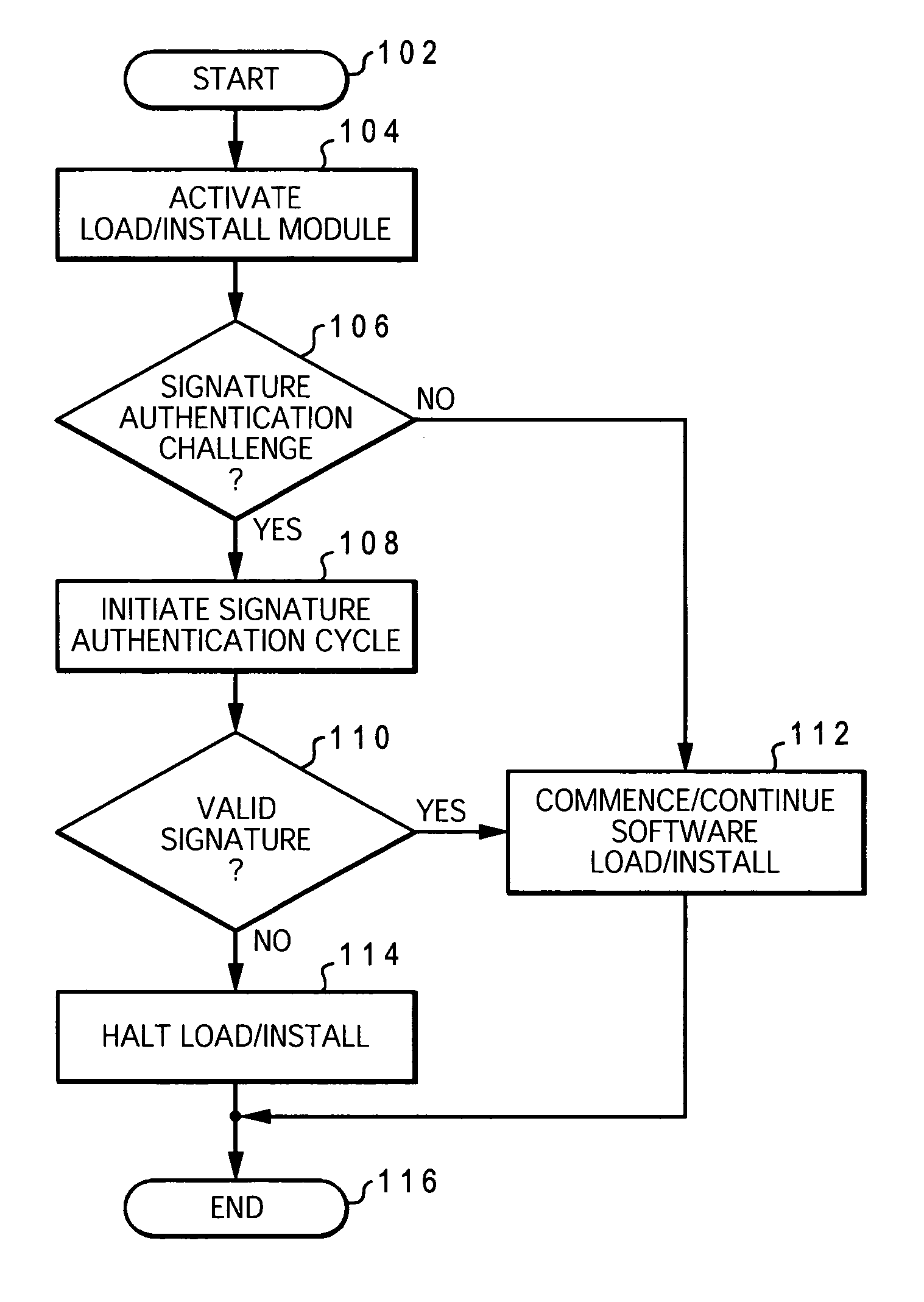
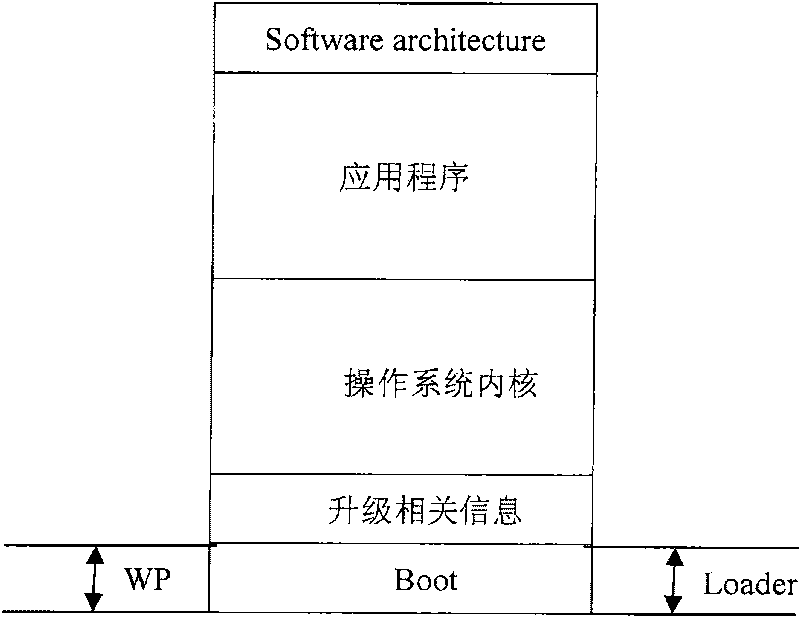
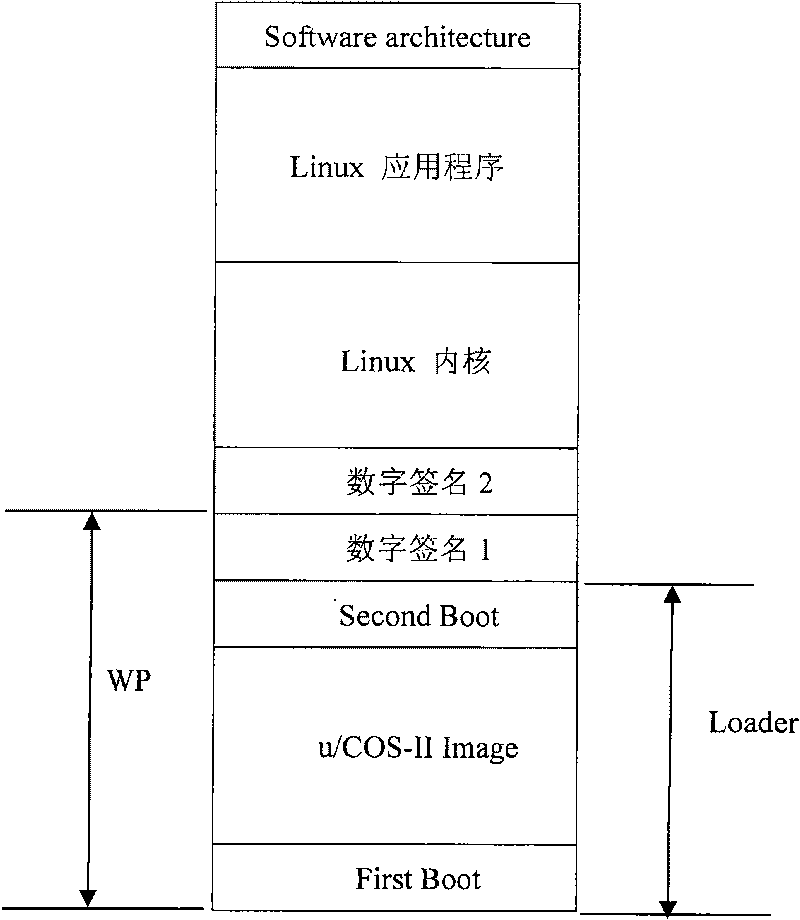
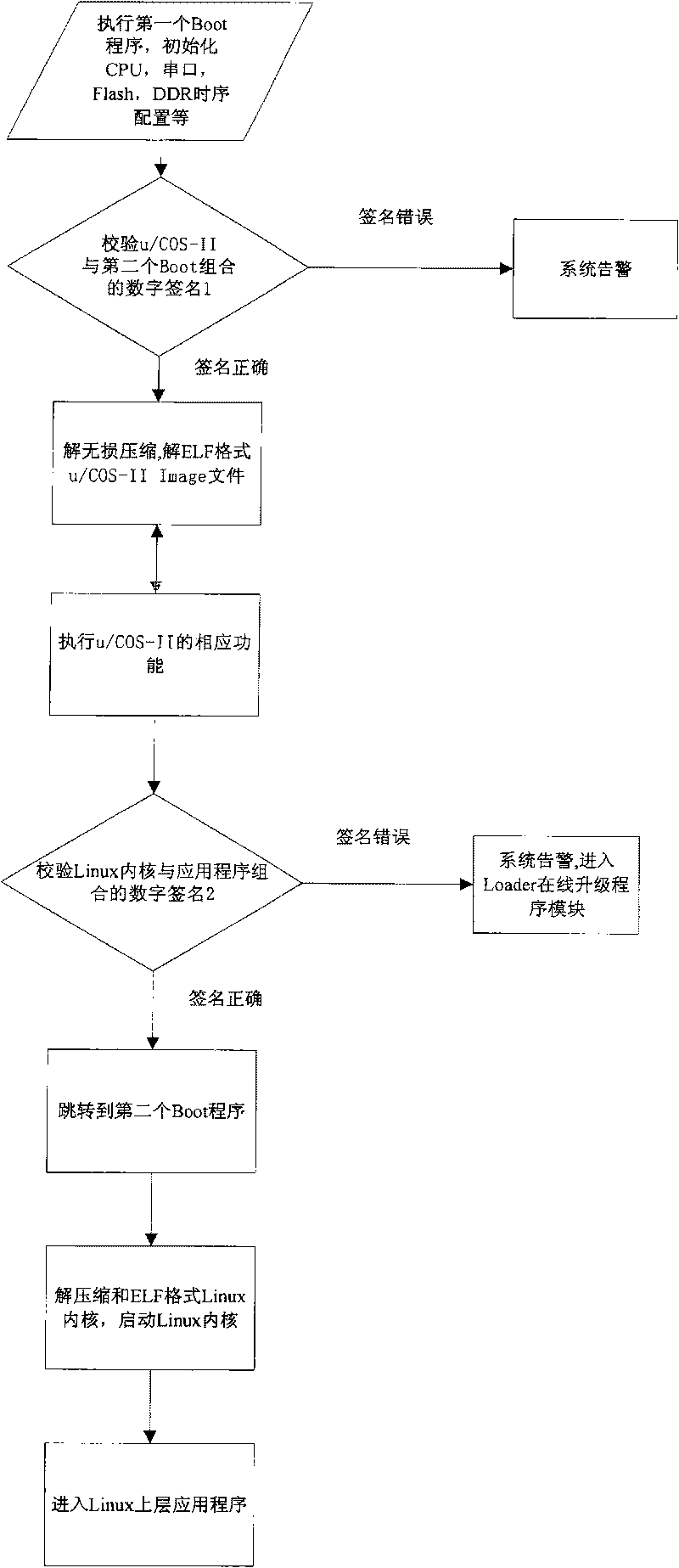
InactiveCN101751273AImplement complex functionsPrevent malicious substitutionProgram loading/initiatingWrite protectionOperational system
The invention provides a safety guide device for an embedded system, which comprises a loading module installed in a memory write protection region and is characterized in that the loading module comprises a first guide program module, a loading region operating system and a second guide program module; the first guide program module is used for initializing system hardware after starting up and then starting a loading region operating system; the loading region operating system is provided with a jump thread, and the jump thread is used for jumping the program to an initial address of the second guide program module after execution of other threads of the loading region operating system; and the second guide program module is used for initializing the system hardware again, and then a main operating system is started. In addition, the invention also provides a corresponding safety guide method. The invention can realize a plurality of complex functions at a safety guide phase. If an upper application program and a main operating system kernel are actively updated online, the invention fast displays a colorful start-up picture, realizes check step by step and the like.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
Graphical user interface for a transport multiplexer
InactiveUS6996779B2Easy to operateEasy to controlSpecial service provision for substationPulse modulation television signal transmissionDrag and dropData stream
A feature-rich transport multiplexer and a number of associated methods, systems, subsystems, software features, graphical user interfaces and control systems are disclosed. The disclosure includes GUI's that enable operators to easily monitor and manipulate content streams flowing through a transport multiplexer in real-time. The disclosed interfaces include screens that supply operators with identity, structure, configuration, bandwidth utilization and / or status information for system hardware and software. The disclosed features also provide computer assisted routing configuration for present and future routing events through simple manipulation, such as drag and drop operations, of graphical objects. Routing control is further simplified by permitting operators to configure routing control of individual content stream components as well as groups of such components simultaneously. Further flexibility is permitted by predetermination of future routing events, thereby enabling the automatic execution of configuration changes at a future time. Various types of content, such as video, audio, IP data can be manipulated to achieve various results such as one or more multiplexed MPEG data streams.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
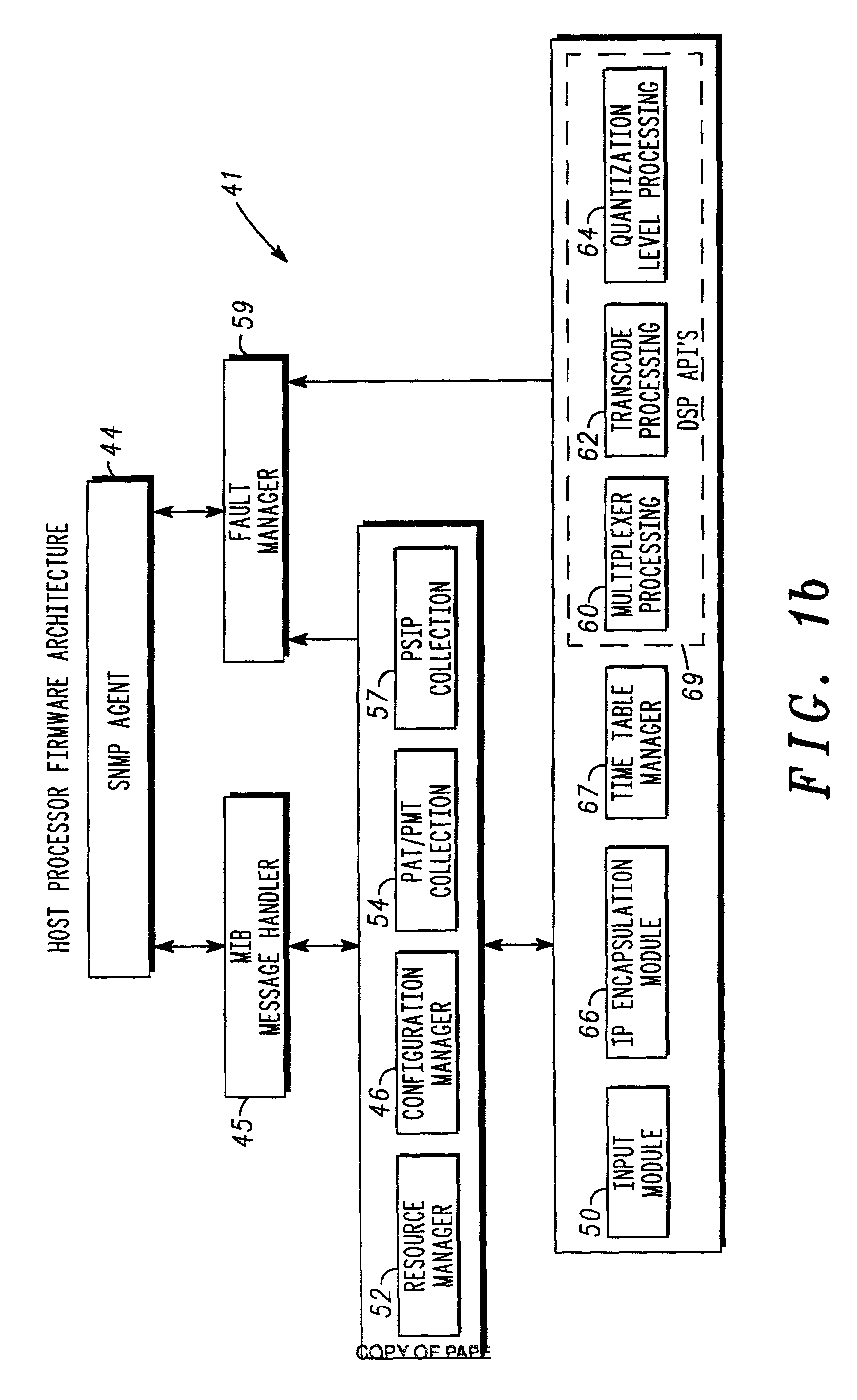
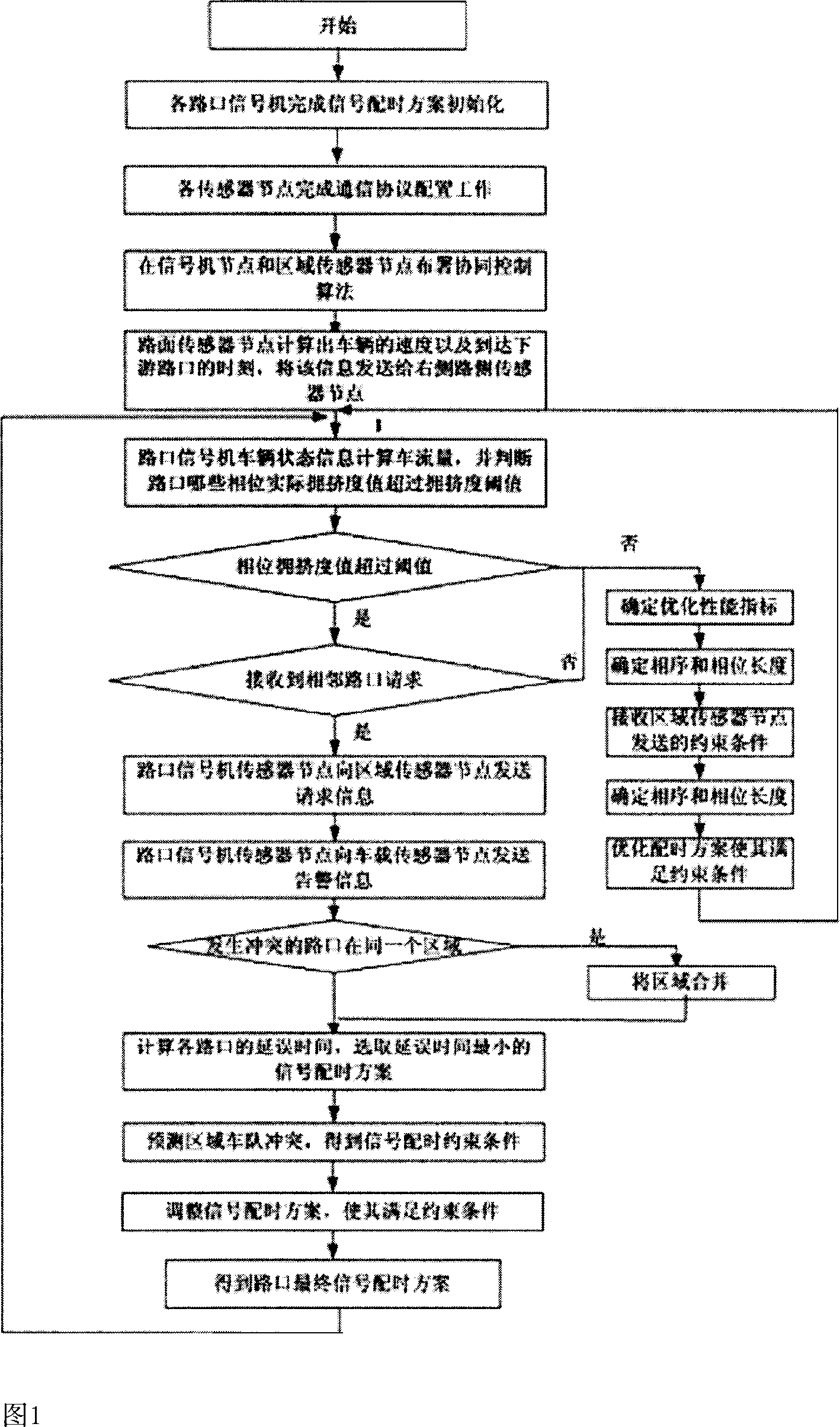
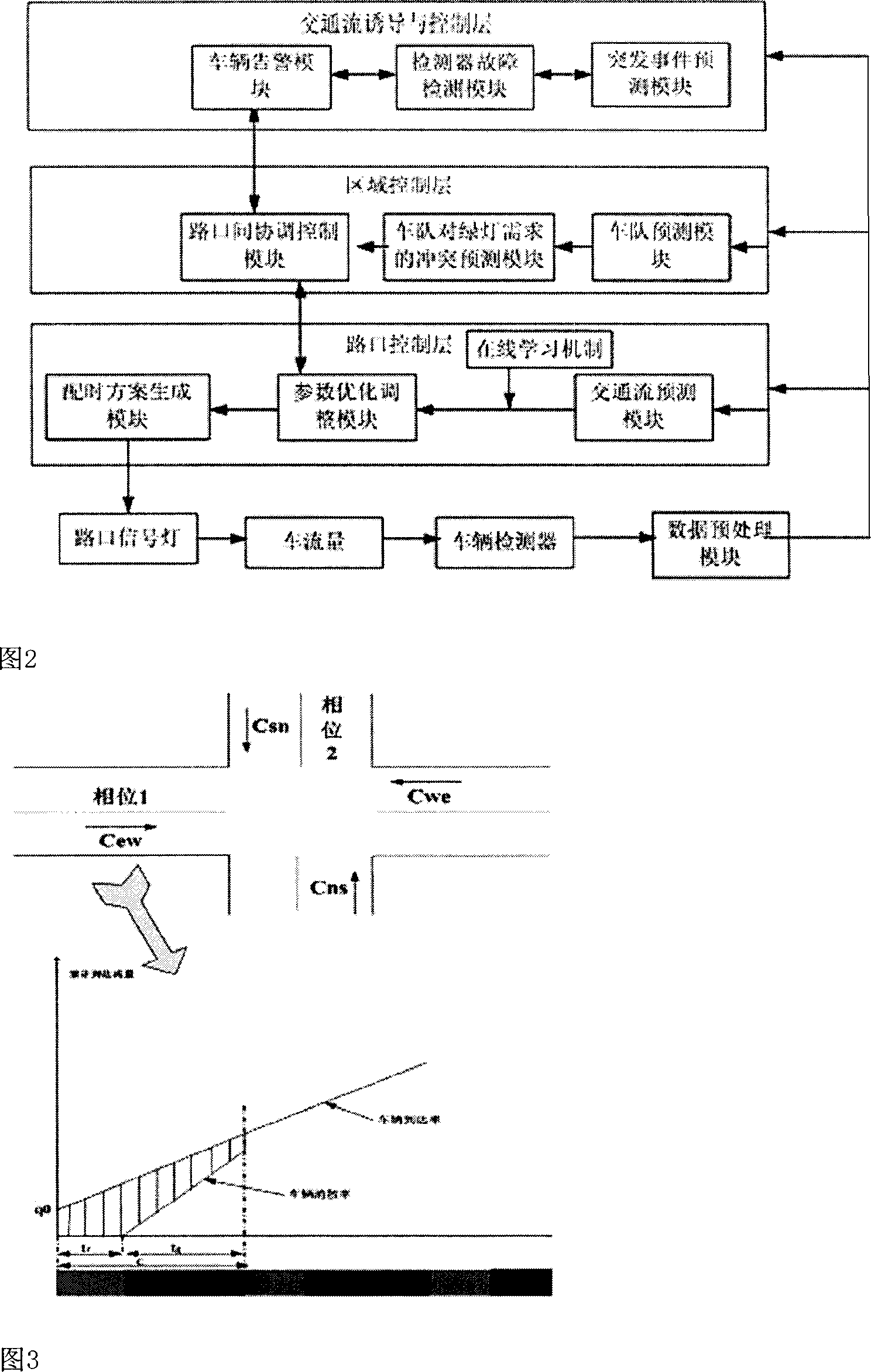
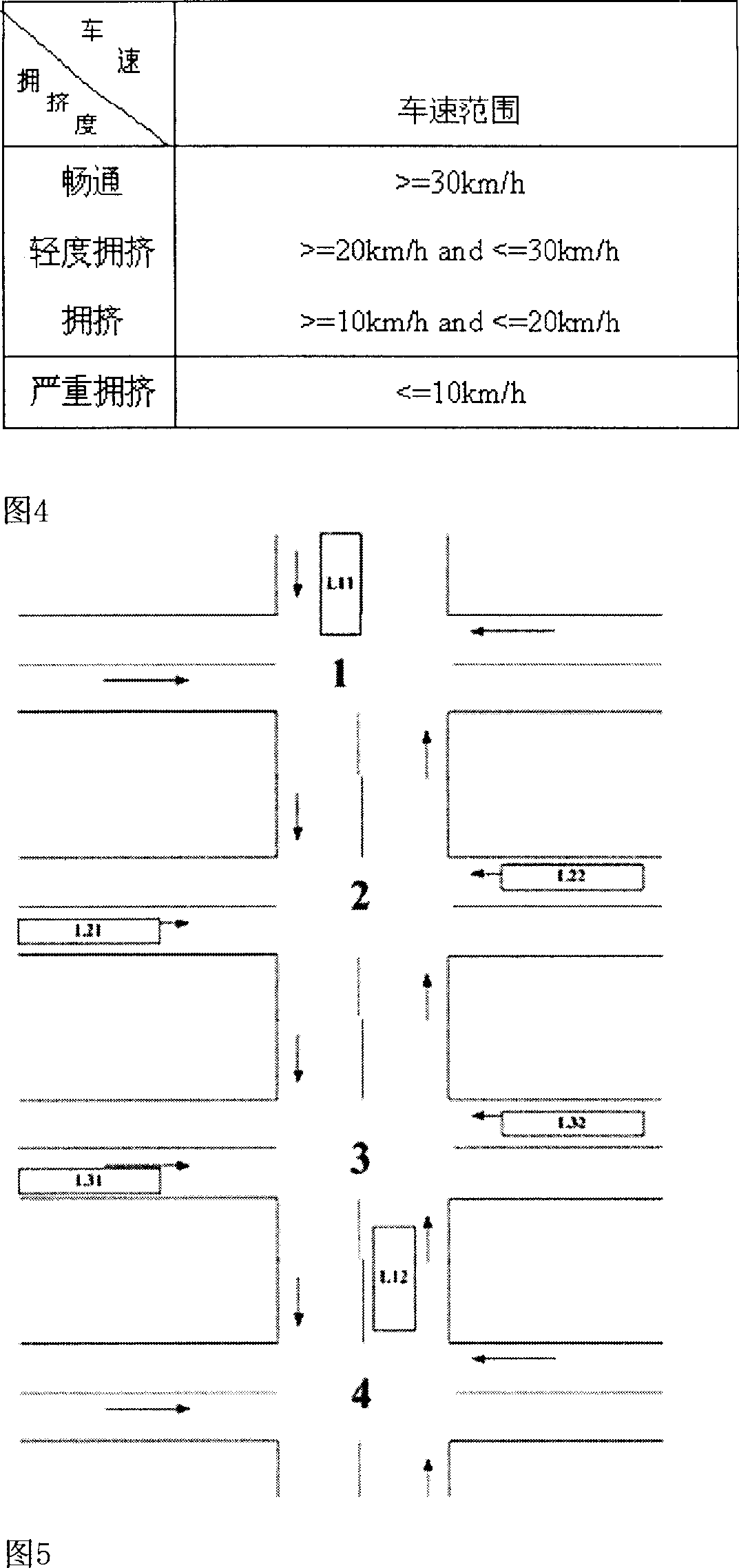
City area-traffic cooperative control method based wireless sensor network
InactiveCN1936999AEasy to installEasy maintenanceControlling traffic signalsDetection of traffic movementEngineeringTraffic flow
Using six types of nodes of radio sensors to structure four types of radio sensor networks, the invention forms cooperation in four layers, and accomplishes four functions. The said cooperation is: cooperation between section of road and vehicles; road junction and road junction; road junction and subarea; subarea and subarea. The said four functions are: using radio sensor networks to collect data of traffic flow in real time, fast and accurately; based on need of real time traffic flow, the invention selects self-contained signal control algorithm or cooperated signal control algorithm dynamically to generate optimal scheme for allocating time of signal for road junction; communication between road junction and vehicles make possible to redistribute spatial traffic flow; remote control end can control schemes for allocating time forcibly. There is good compatibility between the invention and current hardware of signal control system.
Owner:DALIAN UNIV OF TECH
Method and apparatus for sensing and displaying tablature associated with a stringed musical instrument
InactiveUS6995310B1Enhanced informationReadily learn how to playElectrophonic musical instrumentsMusicApplication softwareVisual perception
A system and method of enhancing guitar instruction based on Tablature Plus encoding of playing techniques within a MIDI file or other data structure, that may be rendered on an associated player application that provides multimedia output of the piece being played including a number of playing techniques. The system hardware for encoding the information comprises a pickup head for registering string motion, and optionally a hand motion and finger positioning sensor, such as a data glove, for simultaneously registering the actions of the guitarist while playing the piece. The software comprises algorithms for determining note pitch and duration, and for extracting playing techniques from the data being collected. Multimedia player software is also described which renders a visual and audio output for the Tablature Plus encoded file, wherein the encoded playing techniques are represented within the display output.
Owner:MTW STUDIOS
Network-based system for configuring a measurement system using software programs generated based on a user specification
InactiveUS20030036873A1Resistance/reactance/impedenceError detection/correctionGraphicsComputer hardware
A system and method for online configuration of a measurement system. The user may access a server over a network and specify a desired task, e.g., a measurement task, and receive programs and / or configuration information which are usable to configure the user's measurement system hardware (and / or software) to perform the desired task. Additionally, if the user does not have the hardware required to perform the task, the required hardware may be sent to the user, along with programs and / or configuration information. The hardware may be reconfigurable hardware, such as an FPGA or a processor / memory based device. In one embodiment, the required hardware may be pre-configured to perform the task before being sent to the user. In another embodiment, the system and method may provide a graphical program in response to receiving the user's task specification, where the graphical program may be usable by the measurement system to perform the task.
Owner:NATIONAL INSTRUMENTS
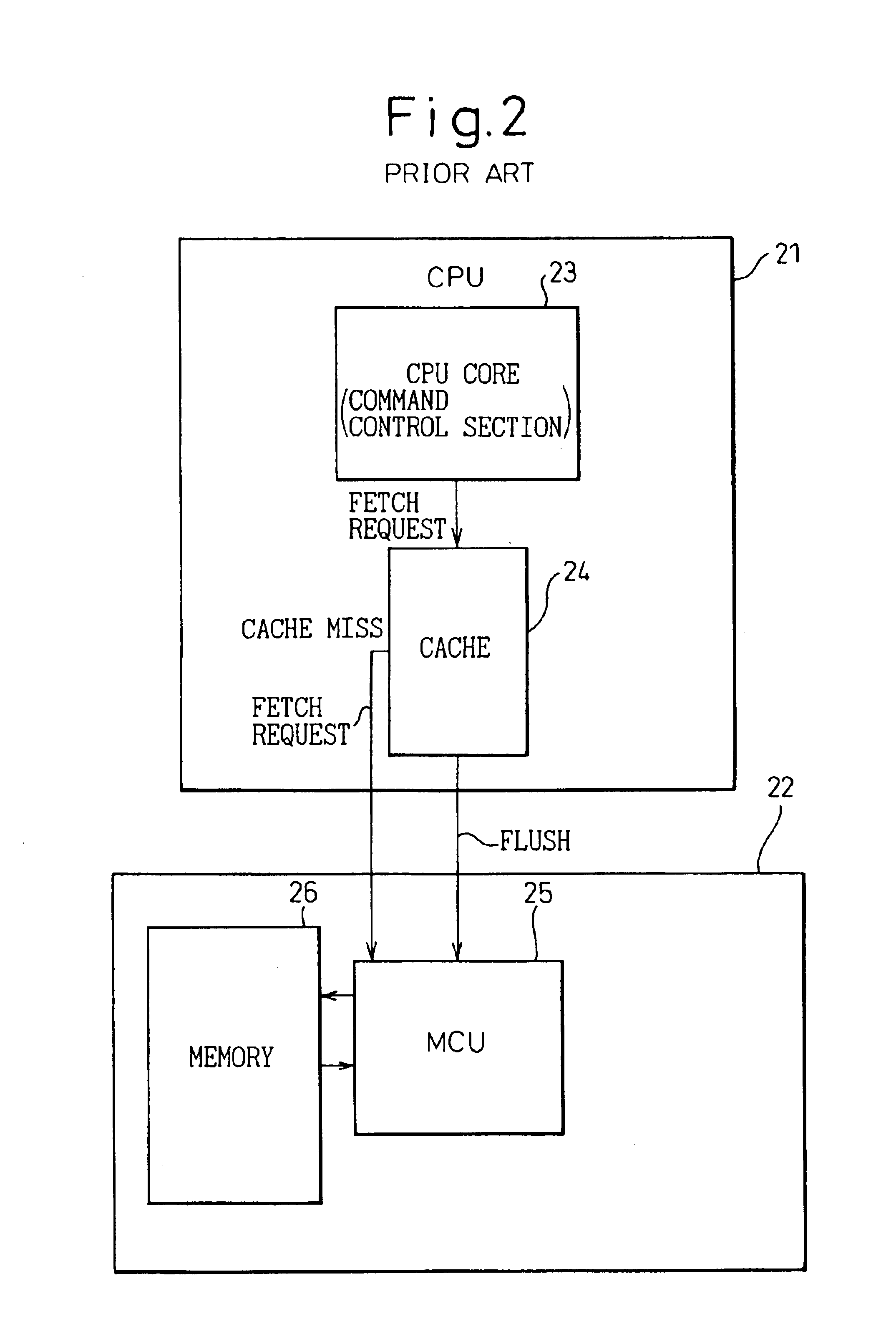
Cache control device and manufacturing method thereof
InactiveUS6883069B2Reliable executionMemory loss protectionMemory adressing/allocation/relocationOperational systemSystem hardware
Owner:FUJITSU LTD
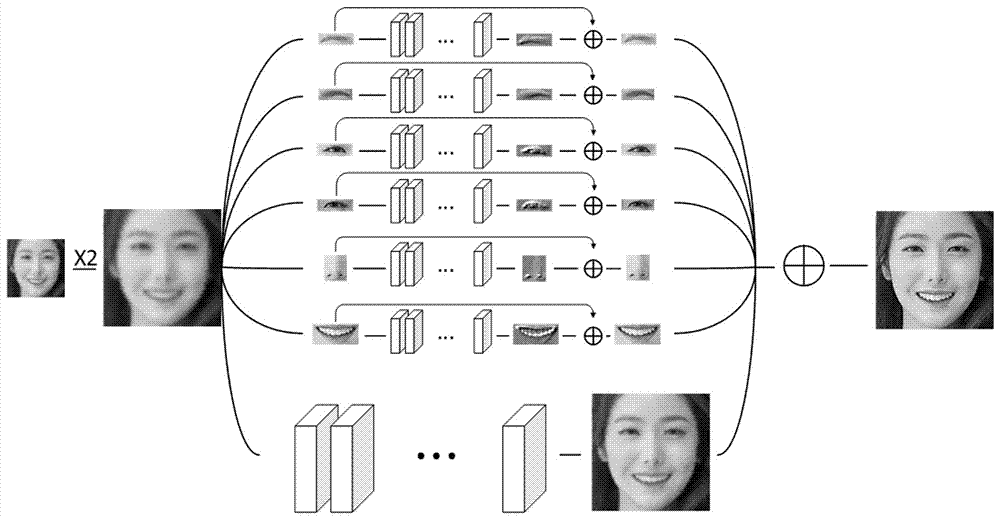
Face super-resolution reconstruction method based on deep learning
The invention discloses a face super-resolution reconstruction method based on deep learning, and aims to utilize the deep learning technology to train low resolution face data, thus obtaining a mapping function from the low resolution face to the high resolution face; the technical keys comprise the following steps: 1, extracting key points of a training face data set; 2, calculating a face angleaccording to the extracted key points, and selecting a relatively right face image; 3, correcting the relatively right face image; 4, segmenting the corrected face image into the left eyebrow, the left eye, the right eyebrow, the right eye, the nose and the mouth, and respectively training said parts; 5, super-resolution processing the eyebrow, eye, nose and mouth images, super-resolution processing the face image, and combining said images so as to obtain the final super-resolution face image. The face super-resolution reconstruction method based on deep learning can effectively improve theobtained face image quality without changing the imaging system hardware equipment.
Owner:GOSUN GUARD SECURITY SERVICE TECH
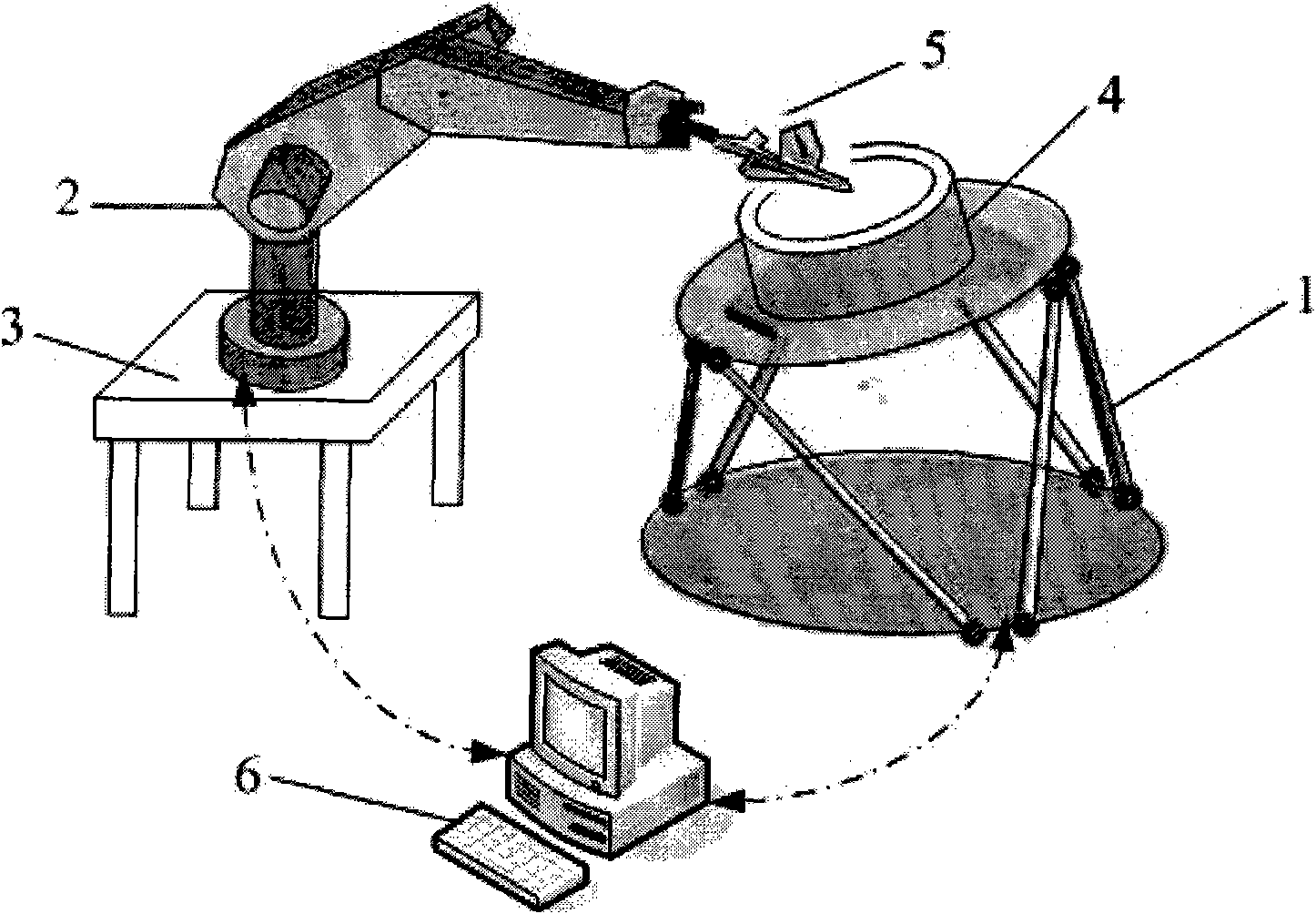
Series-parallel robot combined processing system and control method thereof
InactiveCN101811301AImprove adaptabilityIncrease flexibilityProgramme-controlled manipulatorControl systemEngineering
The invention discloses a series-parallel robot combined processing system and a control method thereof. The system comprises a series robot, a parallel robot, a controller, a platform, workpieces to be processed and a terminal executer. The controller controls the series robot and the parallel robot by adopting a layering control system, the upper controller is used for distributing tasks and controlling movement, and the lower series-parallel robot is used for driving hardware and executing the tasks. The invention combines the system hardware with software, thereby enhancing the automation degree, production efficiency, bearing capability and repetitive positioning accuracy of processing, strengthening the flexibility and adaptability of the system, realizing real-time control on line, and having a certain intelligent performance.
Owner:BEIHANG UNIV
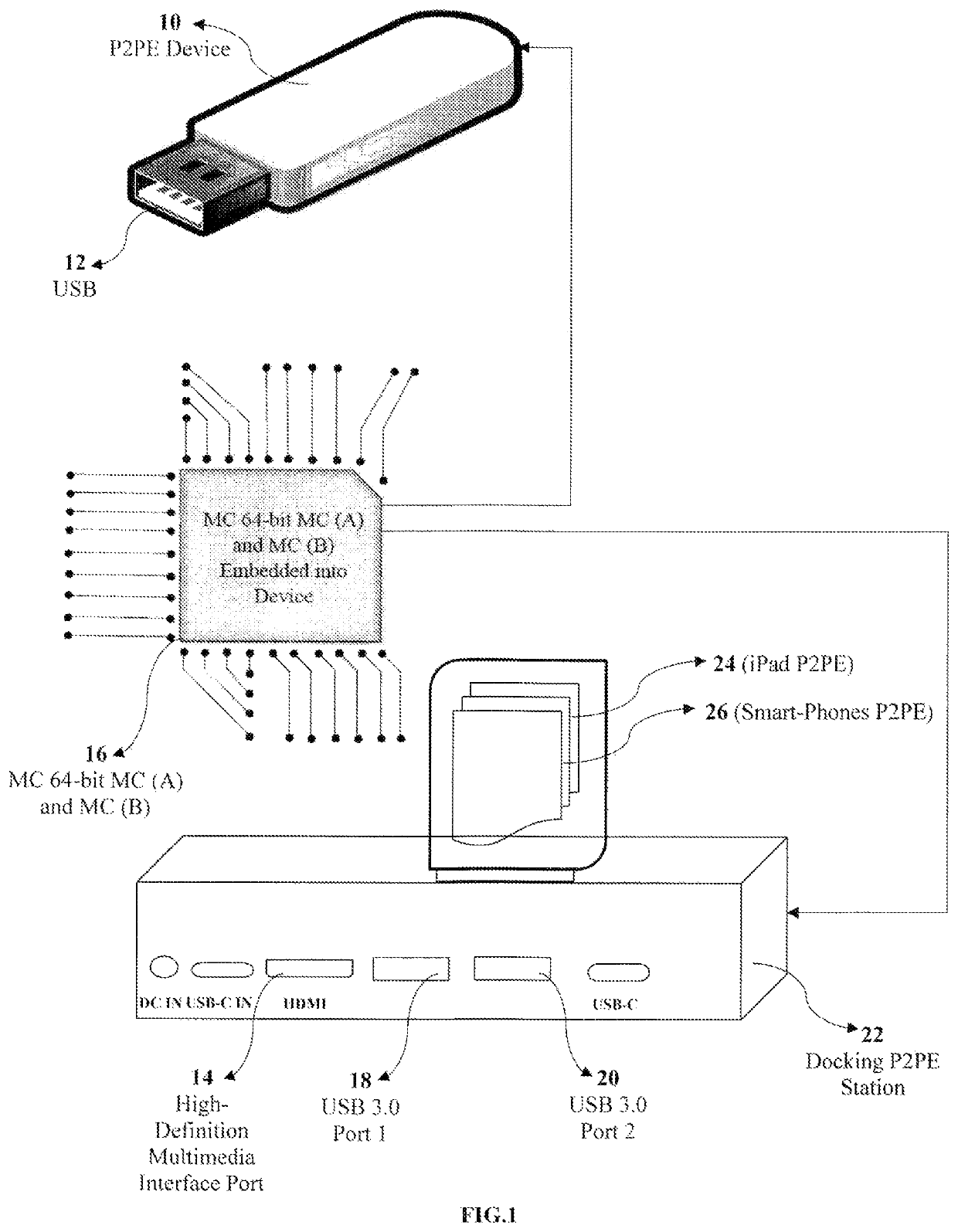
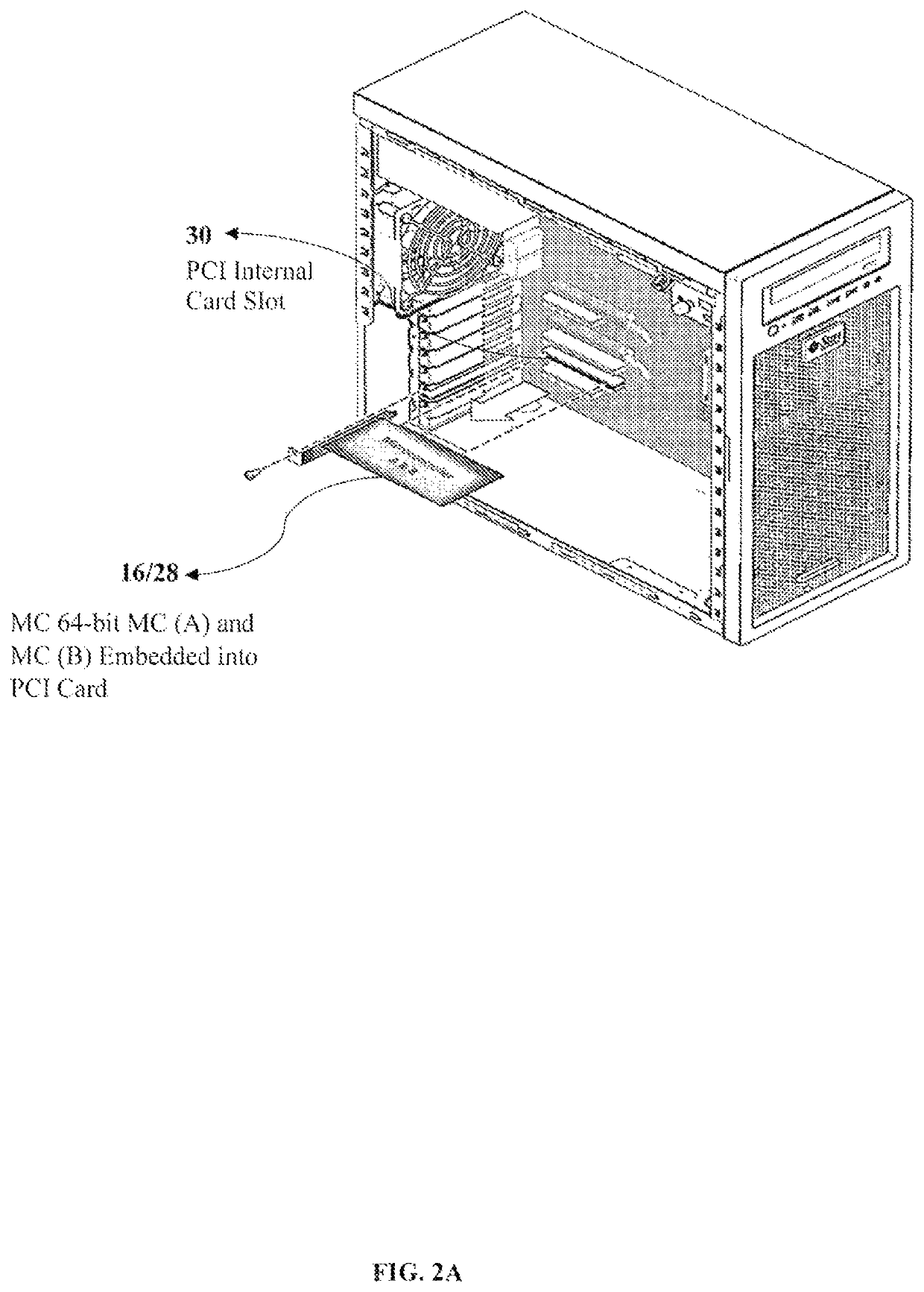
Methods, system and point-to-point encryption device microchip for AES-sea 512-bit key using identity access management utilizing blockchain ecosystem to improve cybersecurity
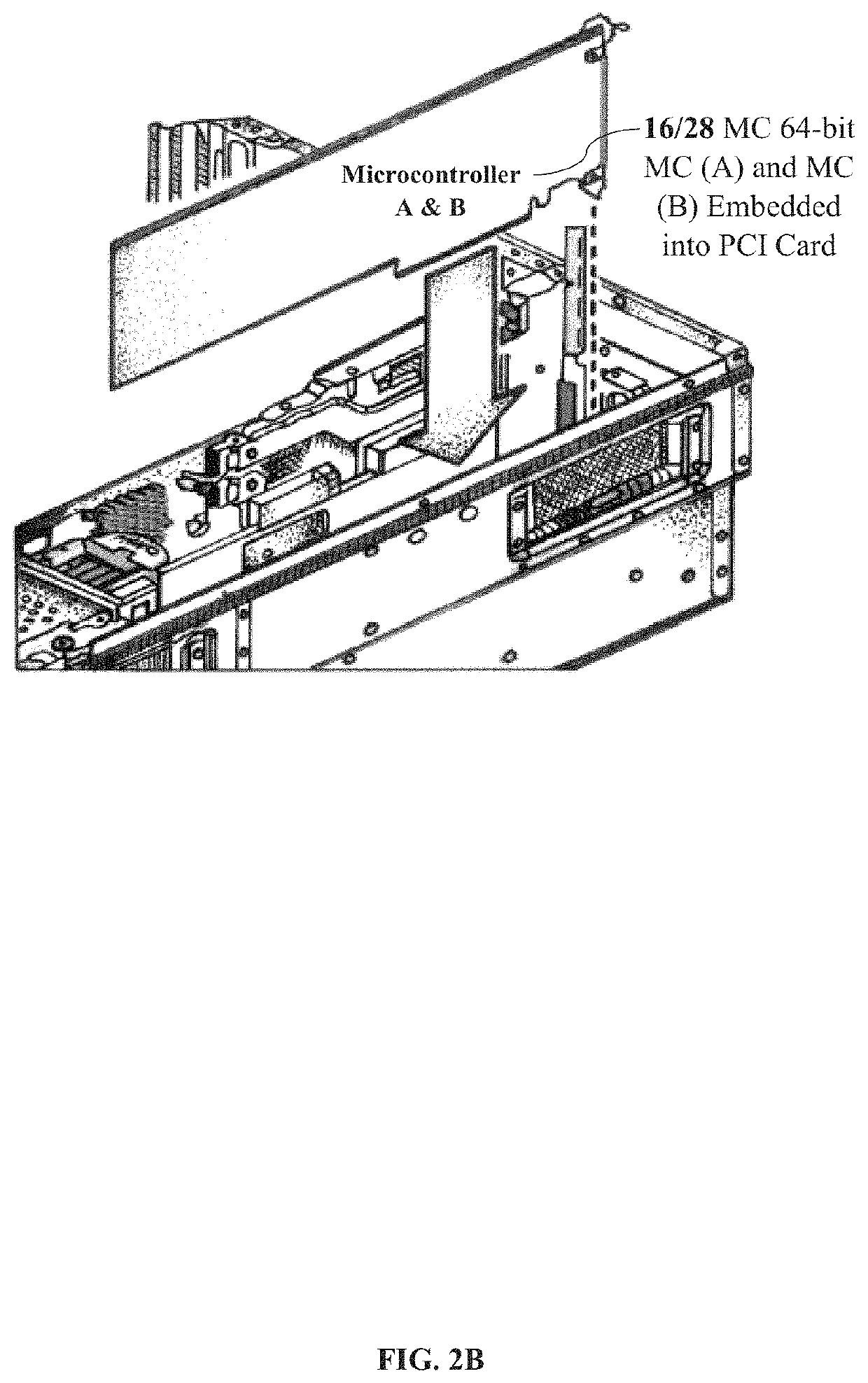
ActiveUS10673617B1Facilitate communicationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMicrocontrollerComputer architecture
A combined system and not a system separately having a complex system hardware architecture and software with levels of complexity of P2PE, IAM, and BCE. A microcontroller (MC) 64-bit using MC (A) and MC (B) embedded into a device using point-to-point encryption (P2PE) to communicate with the novel IAM blockchain software and a central server database to track all registered and non-registered IoT devices in the BCE. The present invention includes a MC 64-bit method of MC (A) and MC (B) having an advanced encryption standards (AES) strong encryption algorithm (SEA) of 512-bit key utilizing the blockchain ecosystem (BCE), IoT identity to validate transactions between the authentication, and identity of the IoT devices. The MC 64-bit of MC (A) and MC (B) employs a novel AES-SEA 512-bit key to generate a real-time randomly validation symmetrical key encryption in rounds of 10 bits, sending data into the central server and the IAM blockchain software to authenticate each device, track IoT devices, MC entries, and validations. Once the encryption AES-SEA 256-bit key is generated in the MC (A) and the encryption AES-SEA 256-bit key is generated in MC (B), the communication between the MC (A) and MC (B) will generate the AES-SEA 512-bit key with 10 bits; the pseudo-random number process is modified using a time based to be programmed with a timer which has an input of the clock frequency. The MC 64-bit of MC (A) and MC (B) is programmed in a master mode and slave mode; therein providing a novel system of circuit hardware using an AES-SEA 512-bit key and AES 2048 algorithm key to generate PKI certifications for validation, authentication, and authorization through the BCE.
Owner:CYBER ALIENS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com