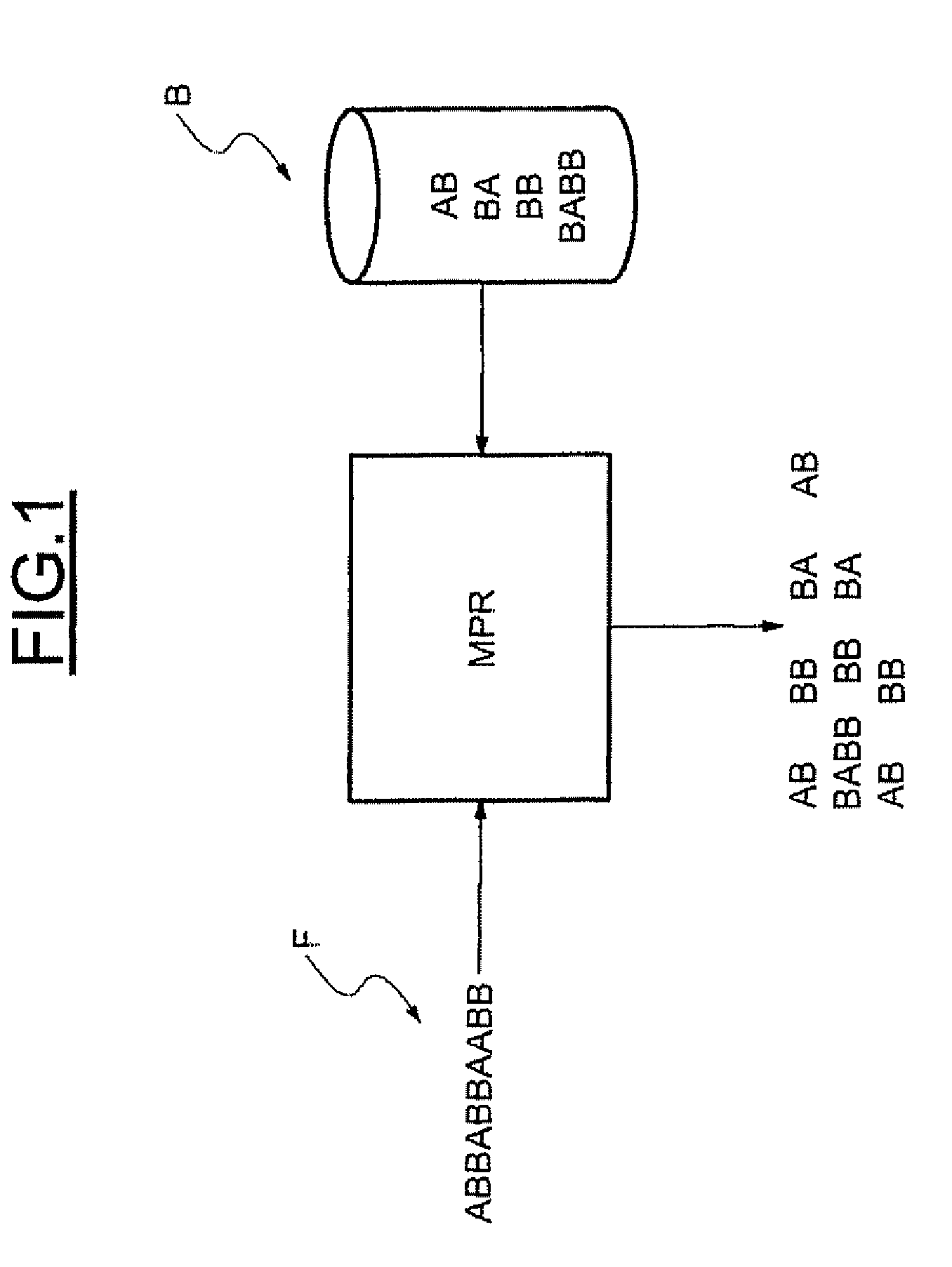
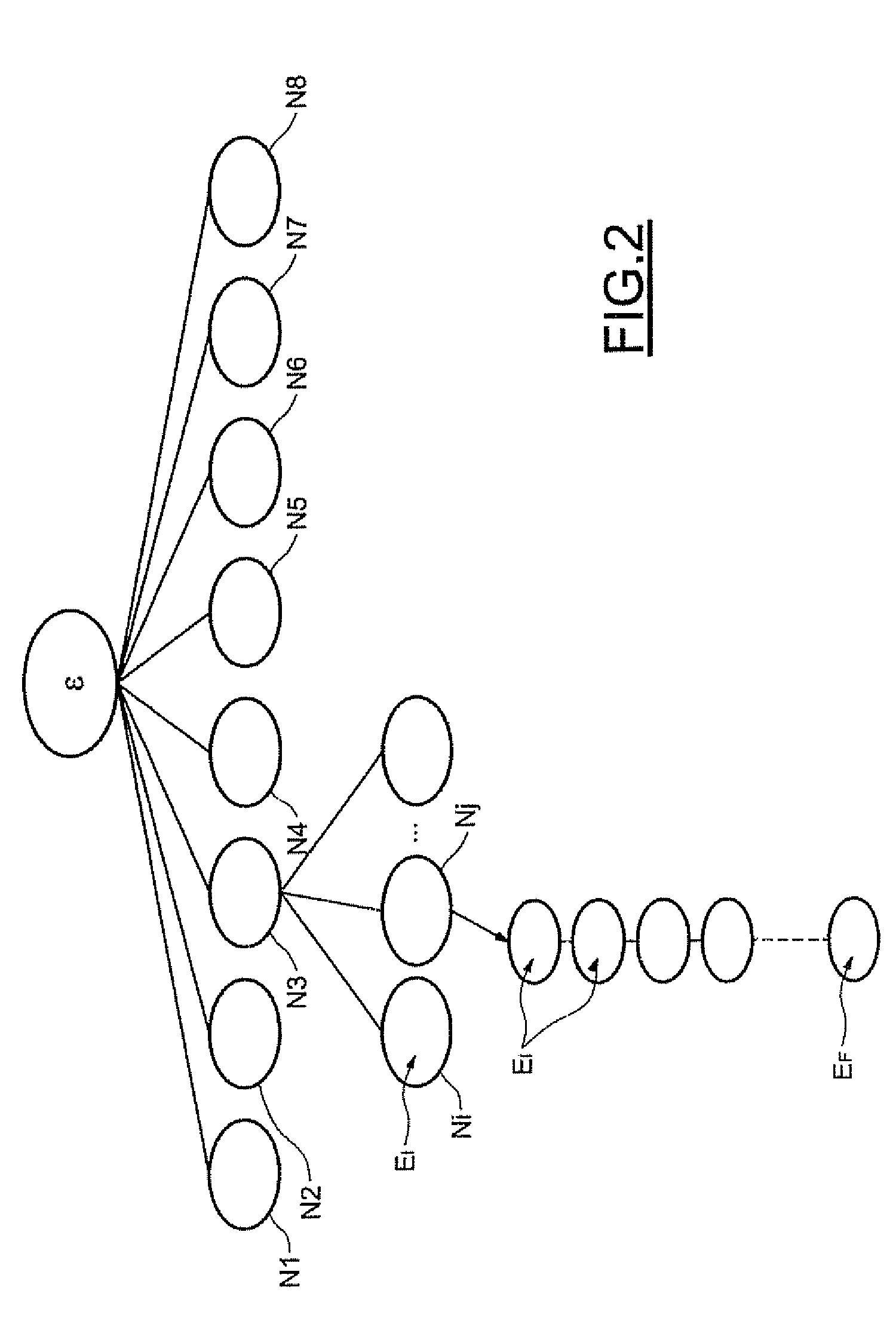
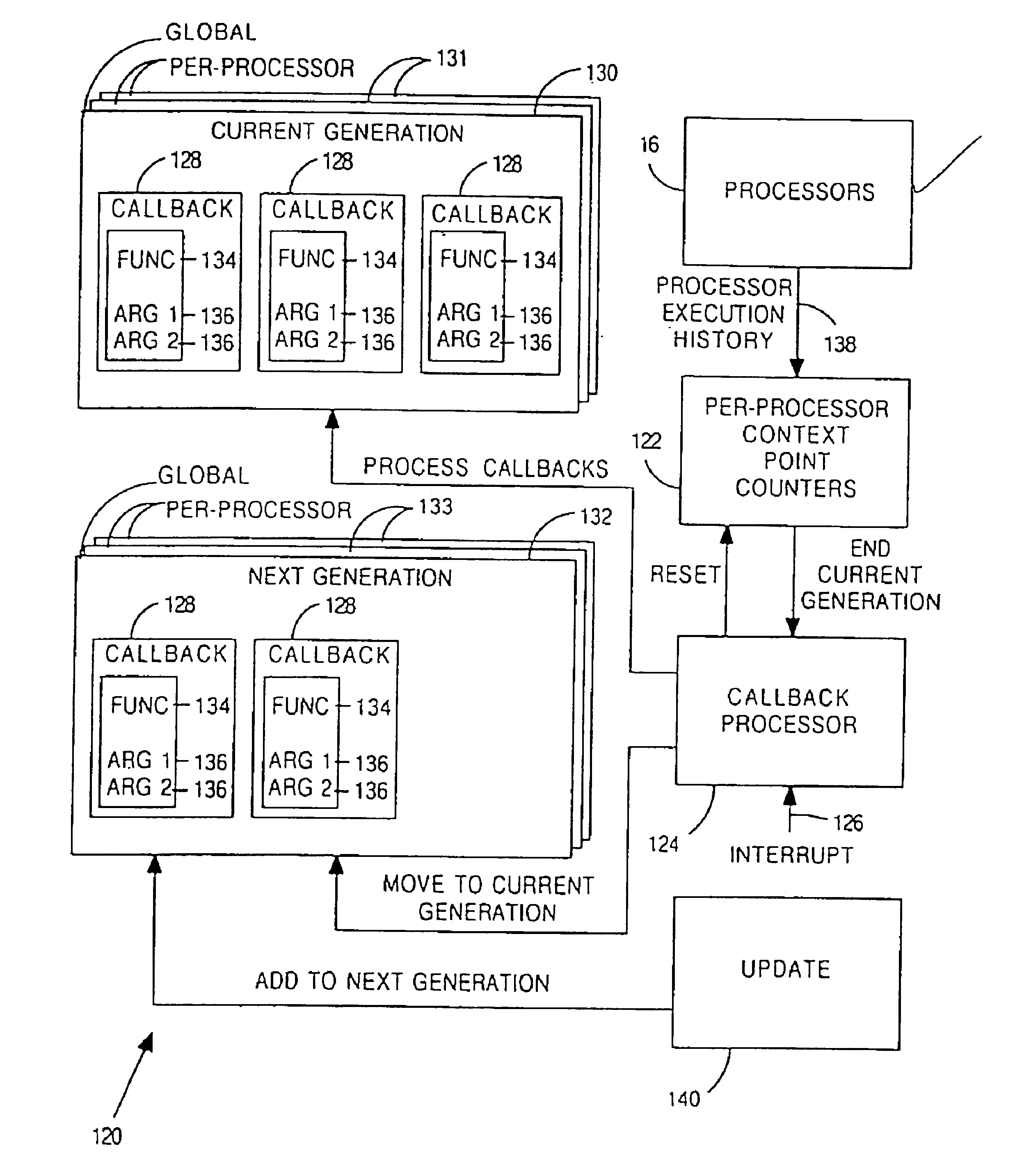
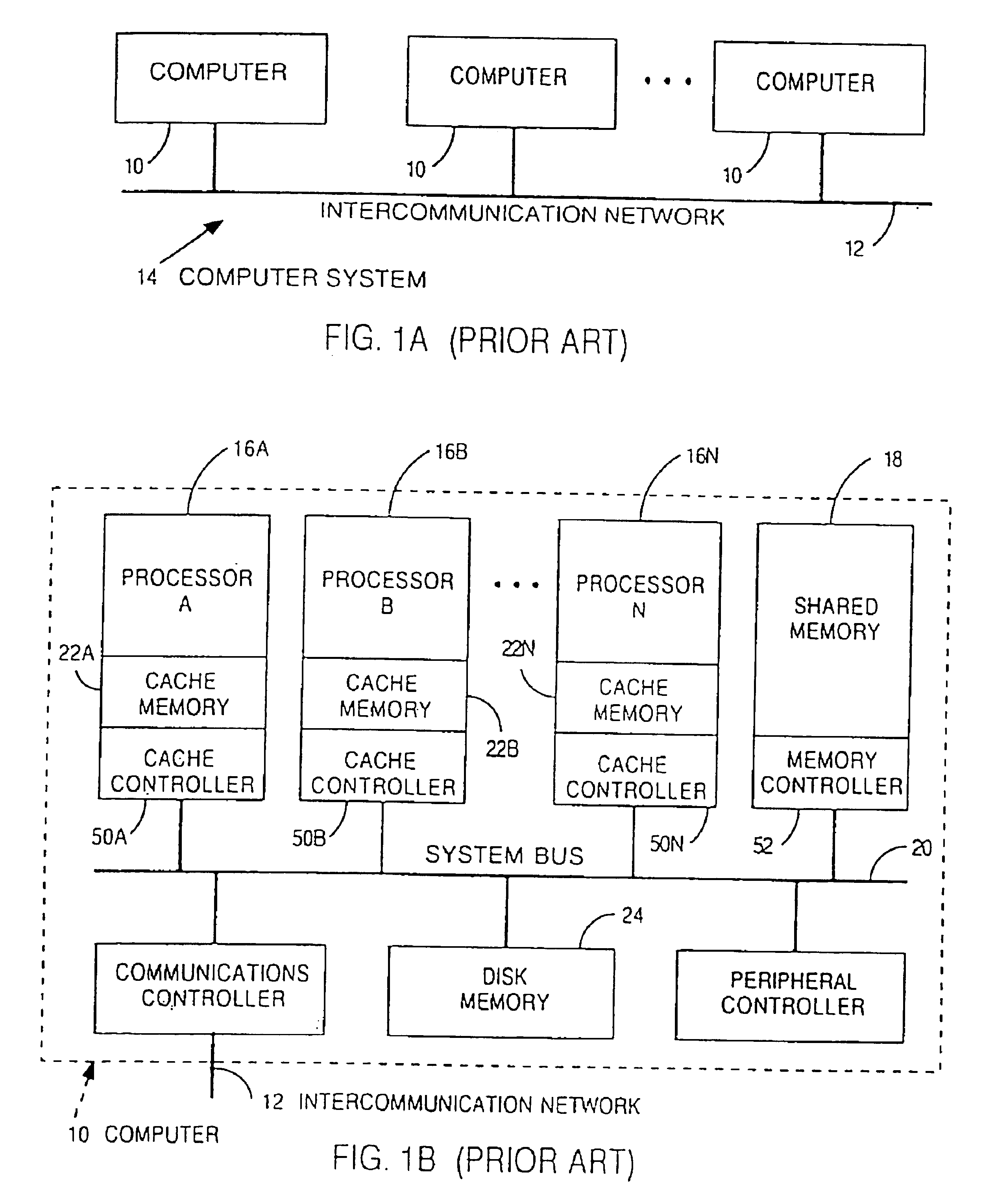
Patents
Literature
2083 results about "Multiple node" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
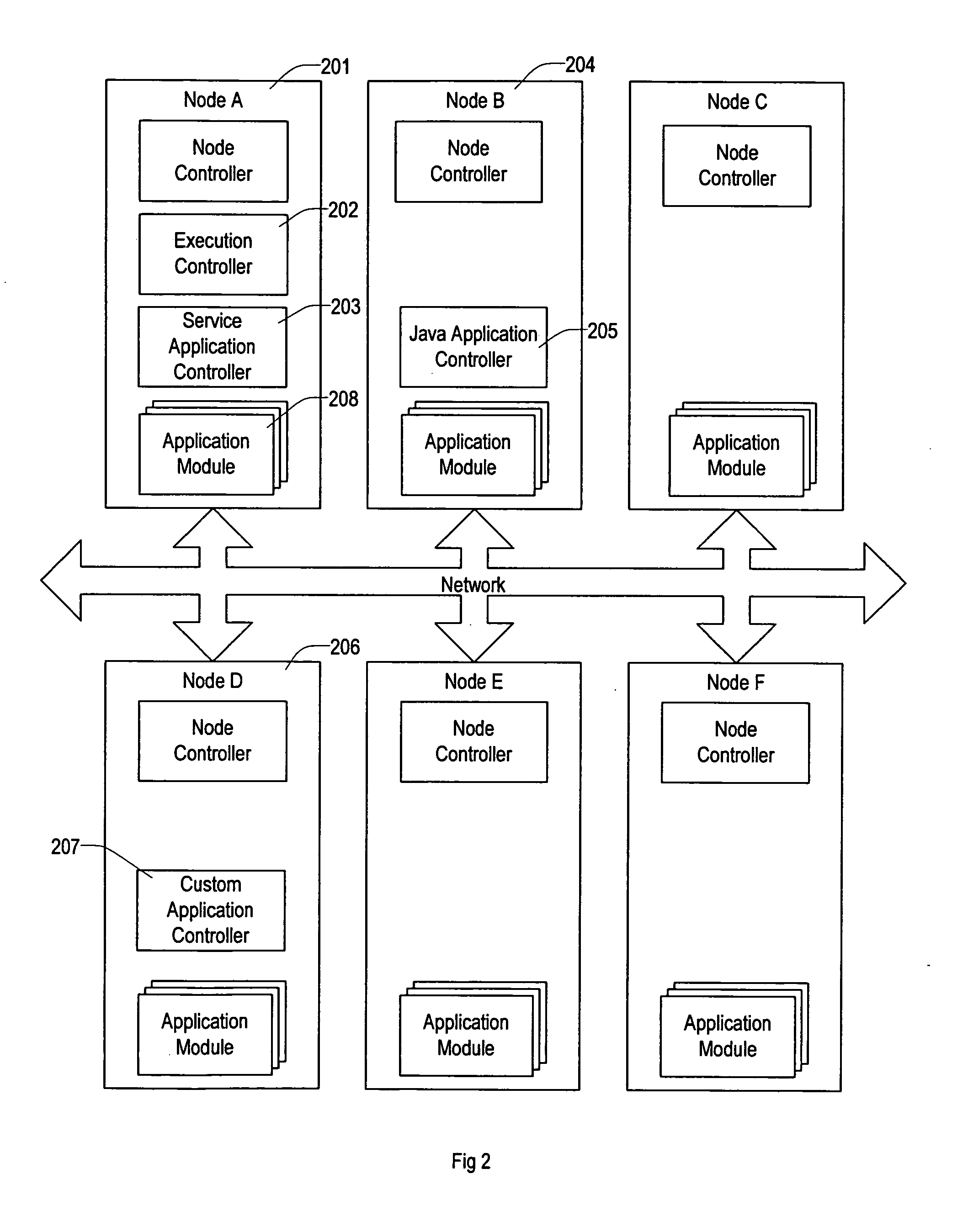
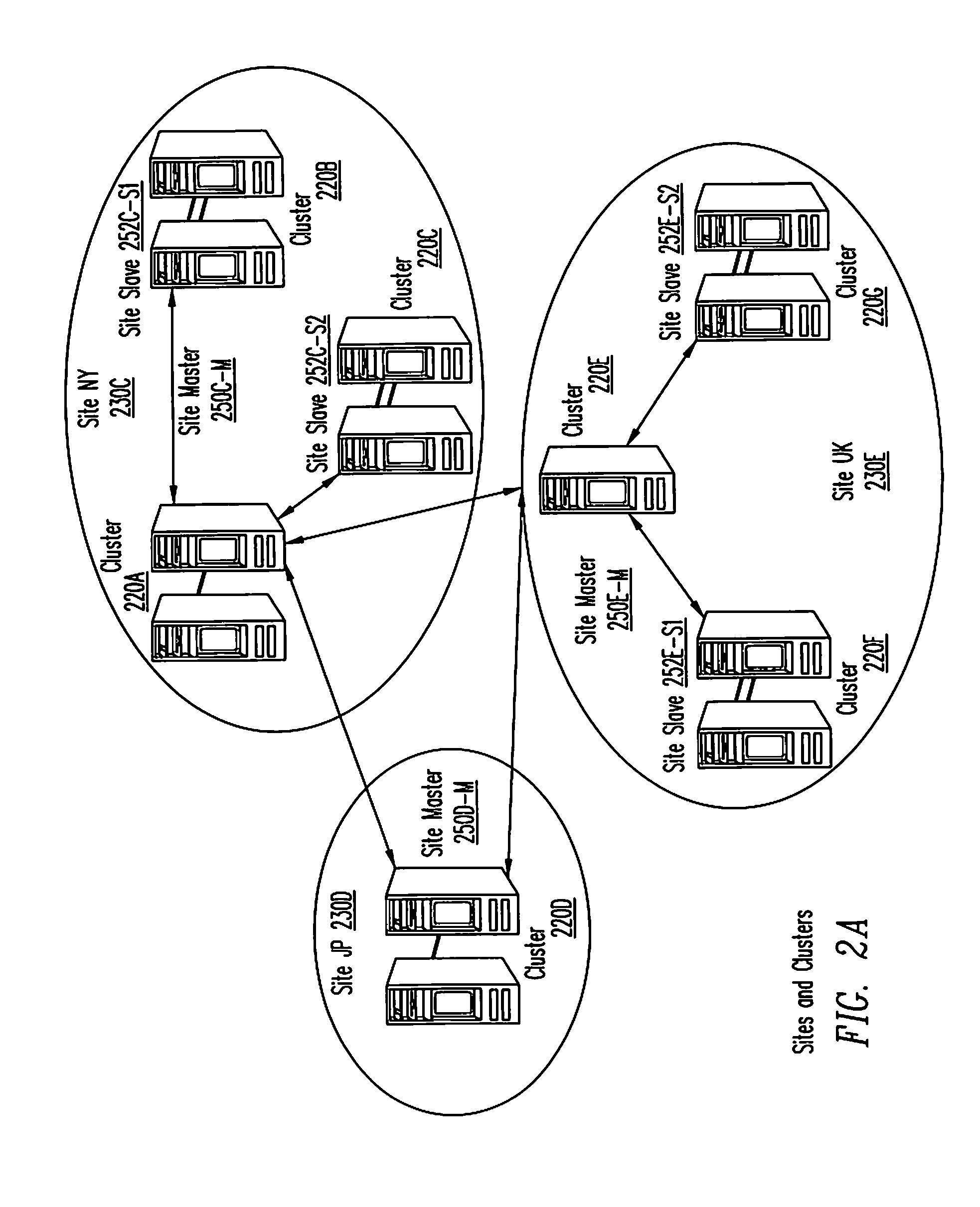
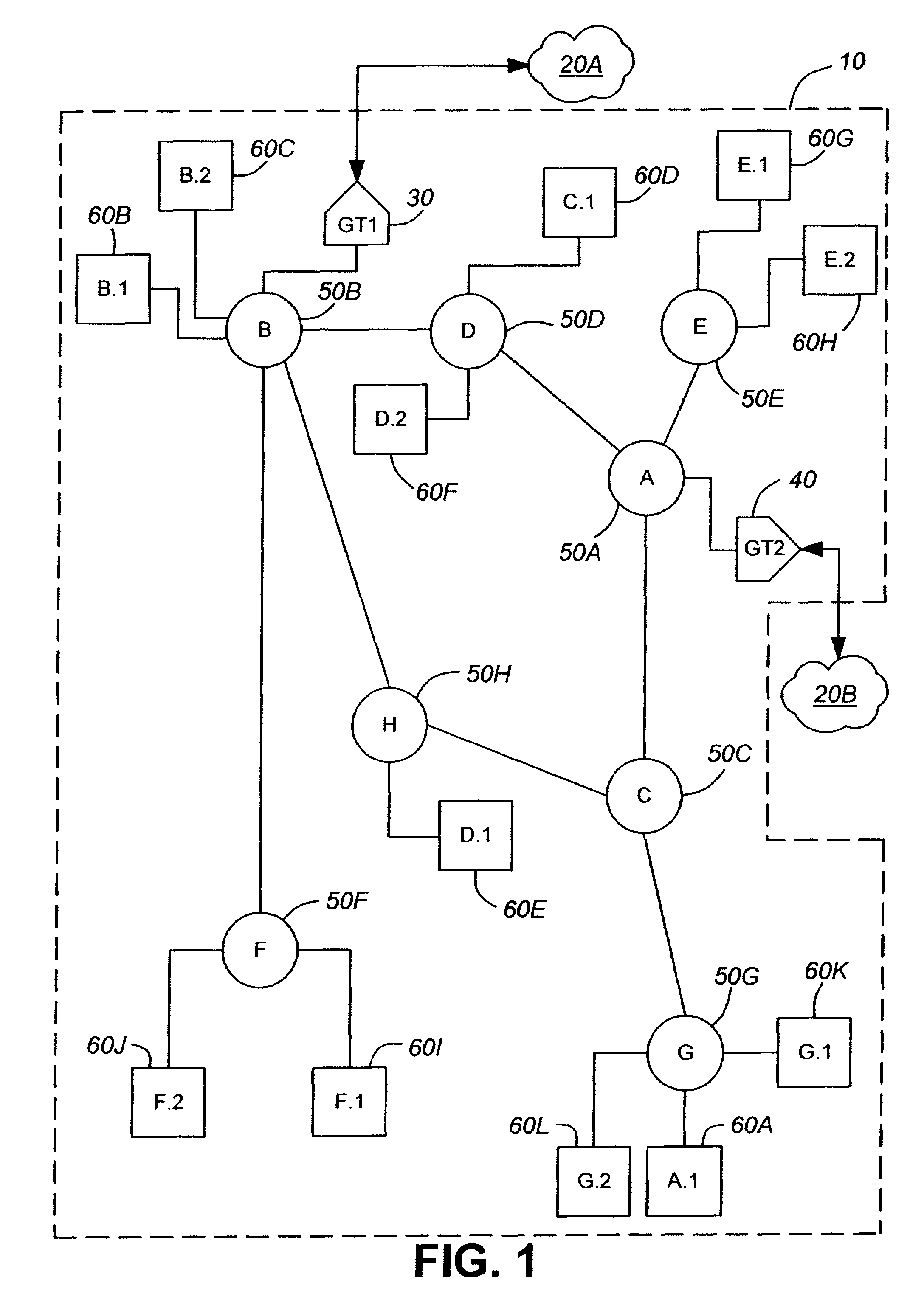
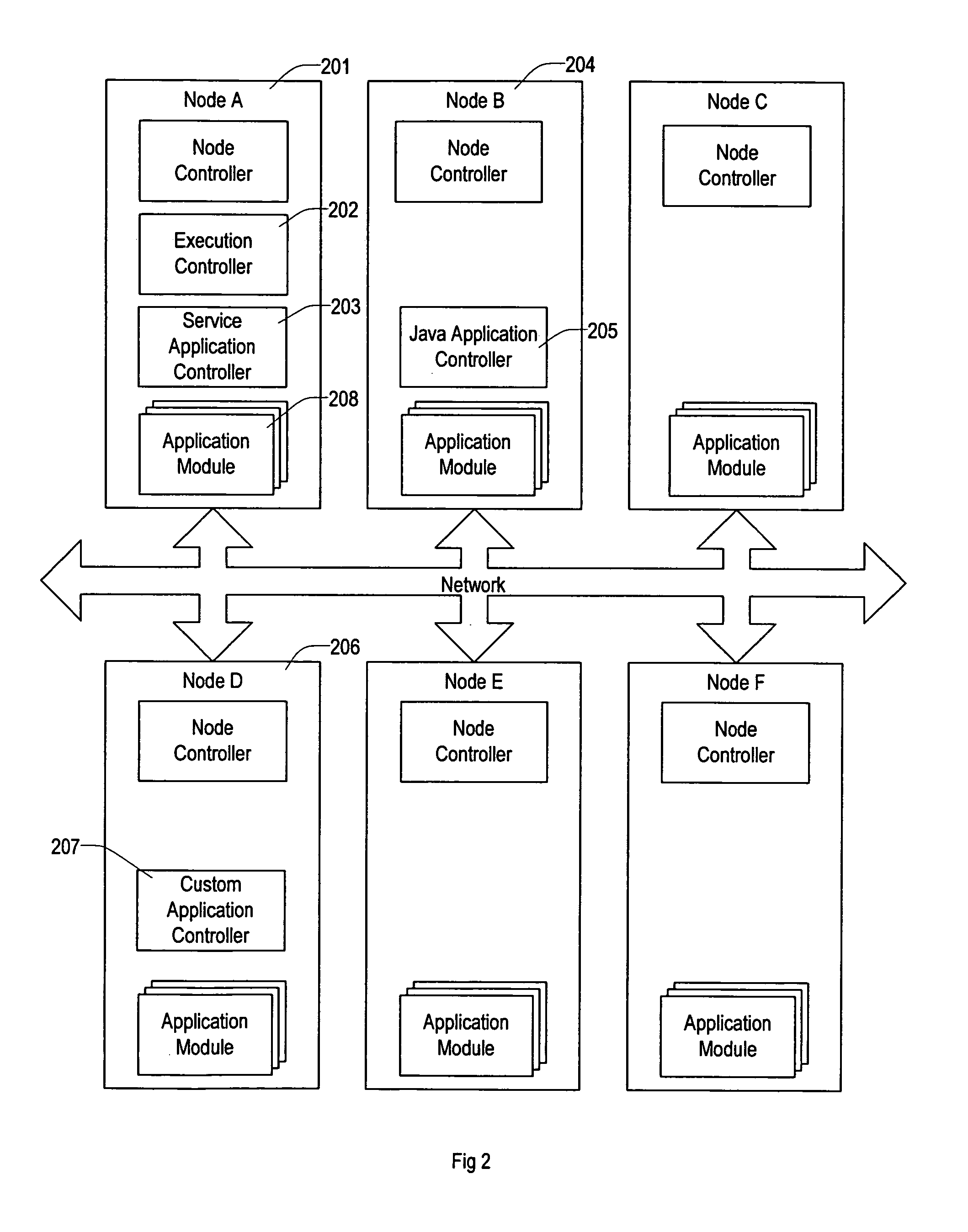
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
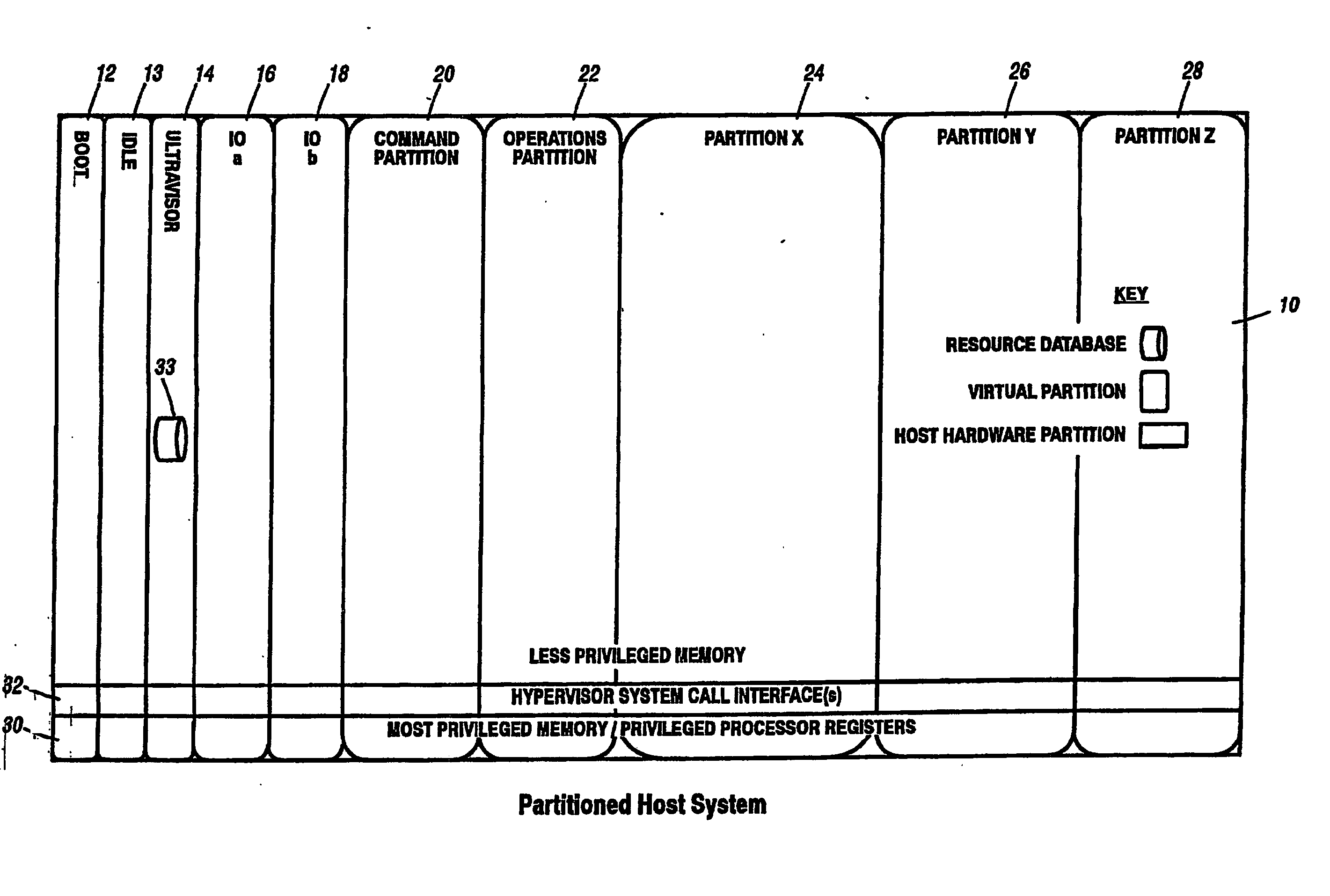
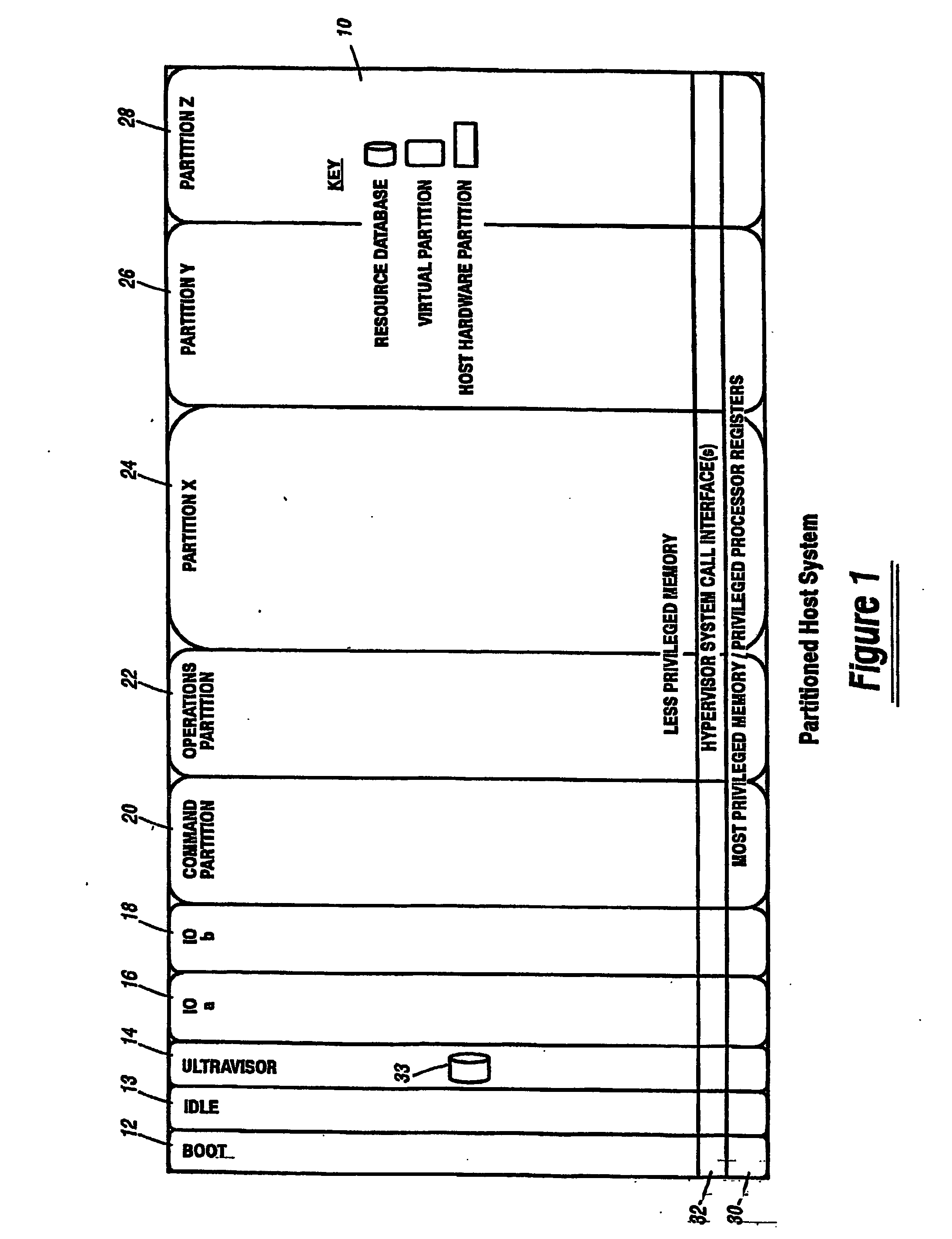
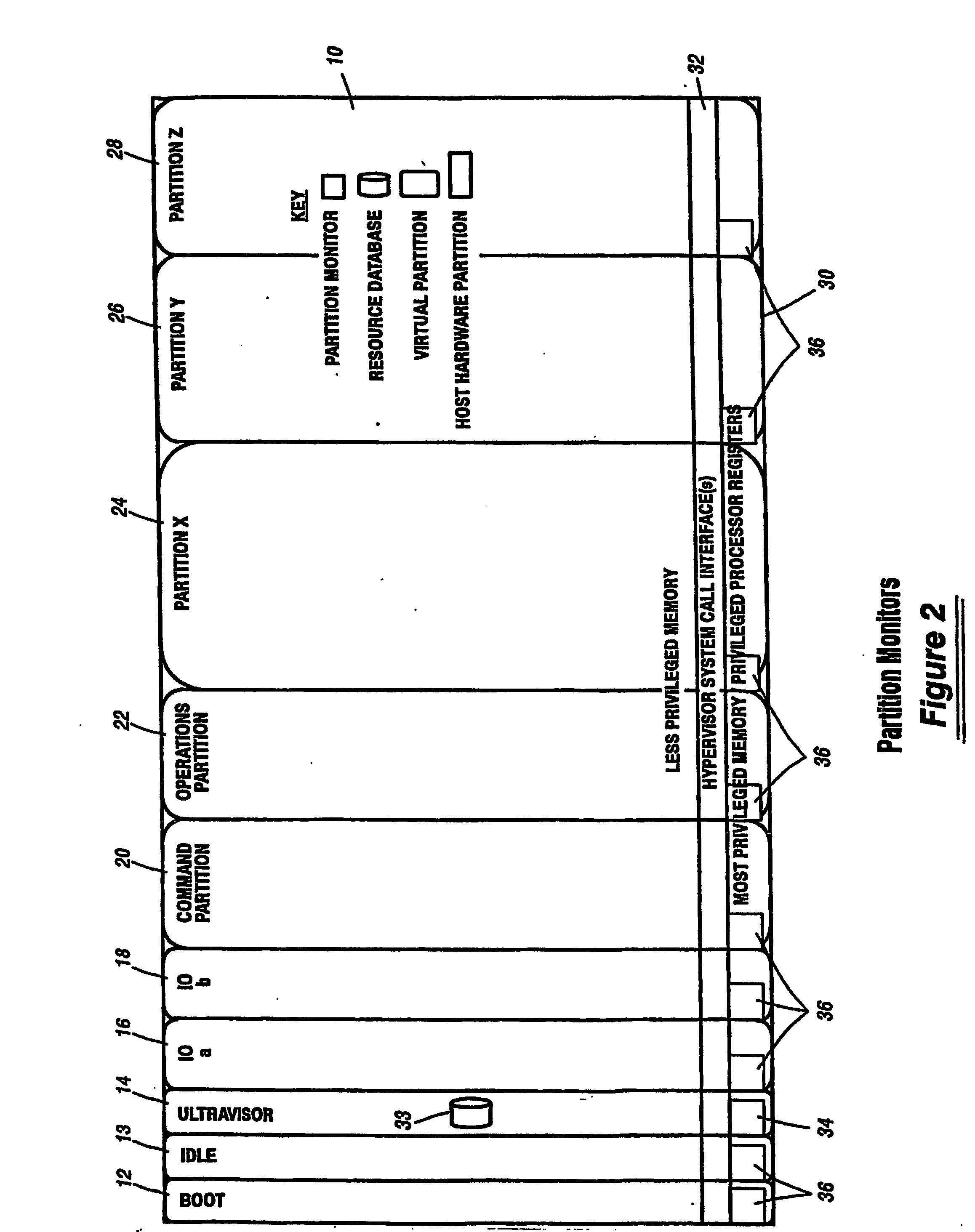
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
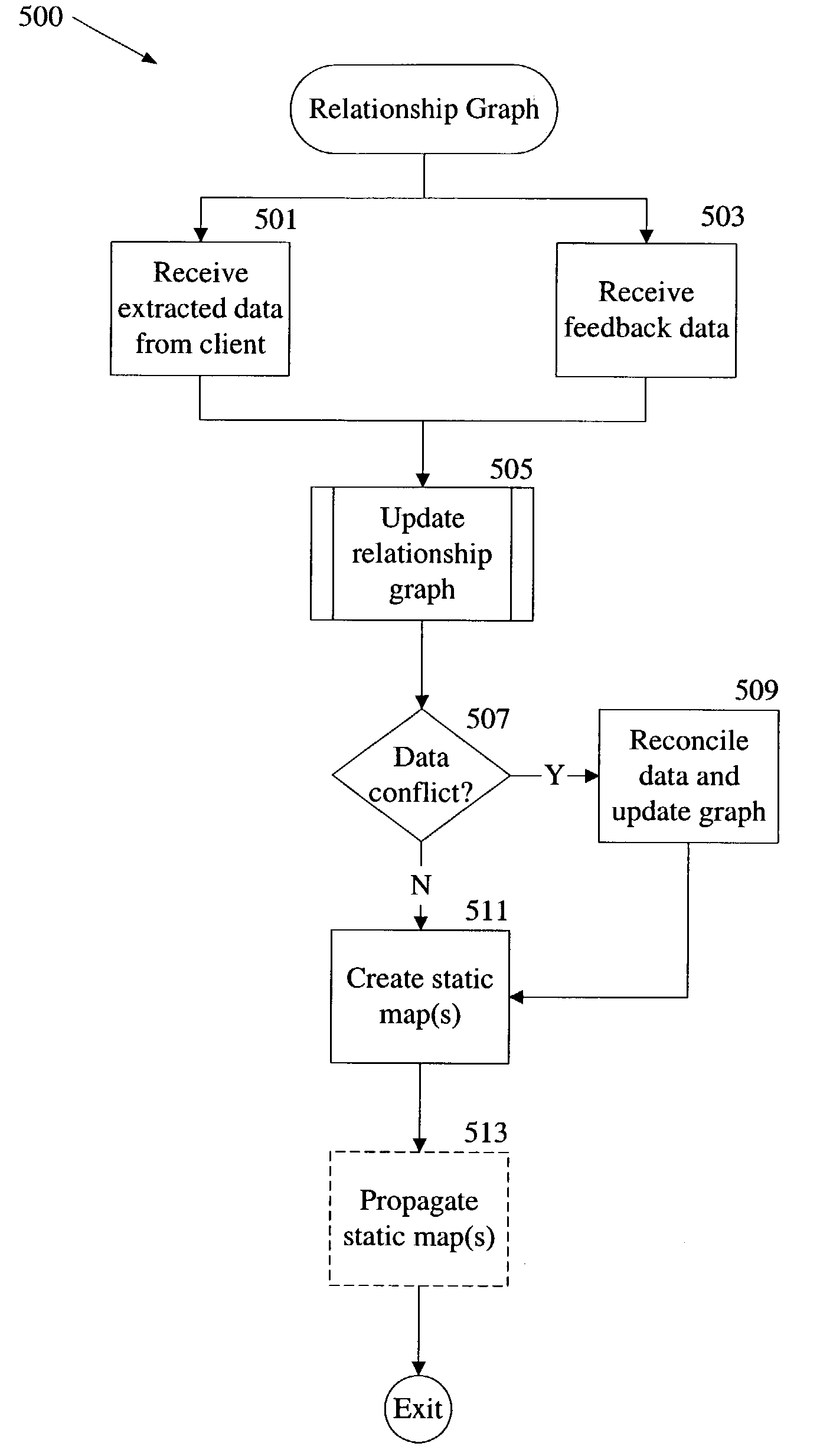
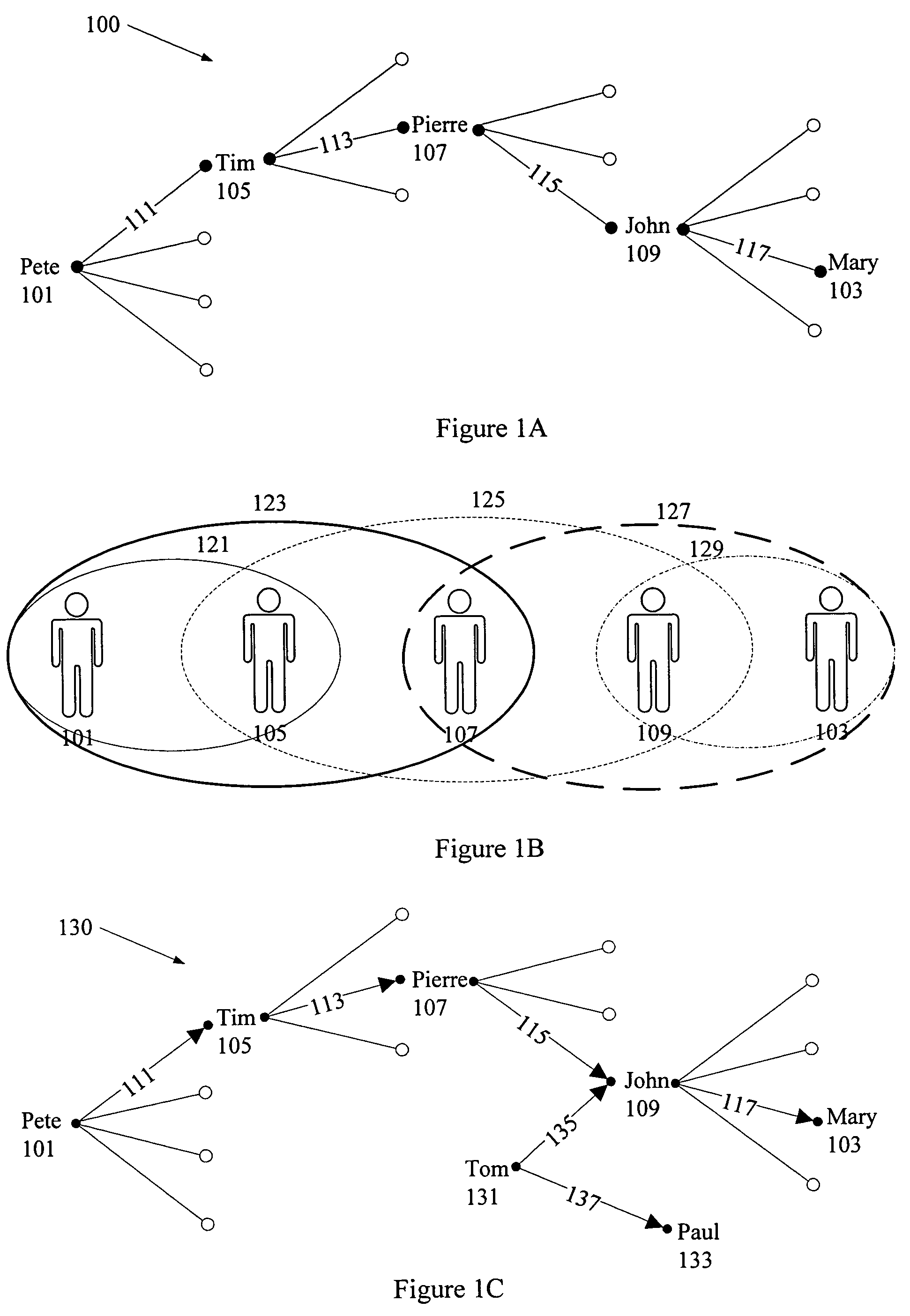
Creation and maintenance of social relationship network graphs
InactiveUS7539697B1Data processing applicationsDigital data information retrievalData sourceSocial web
A relationship graph representing a social network connecting multiple entities is created and maintained as nodes and edges. Data received for an entity is used to create a new node. A strength of relationship value is calculated for each relationship between the new entity and an entity represented by an existing node and assigned to an edge is created to represent each relationship. Data received for an existing node causes the node to be updated, and the strength of relationship values for each of its relationships to be recalculated and assigned to the appropriate edge. More than one node may exist for an entity and conflicts among the data of the multiple nodes are reconciled. The received data may be extracted from data sources owned by a user in accordance with privacy criteria for the user, or may result from processing data in the relationship graph.
Owner:SPOKE SOFTWARE
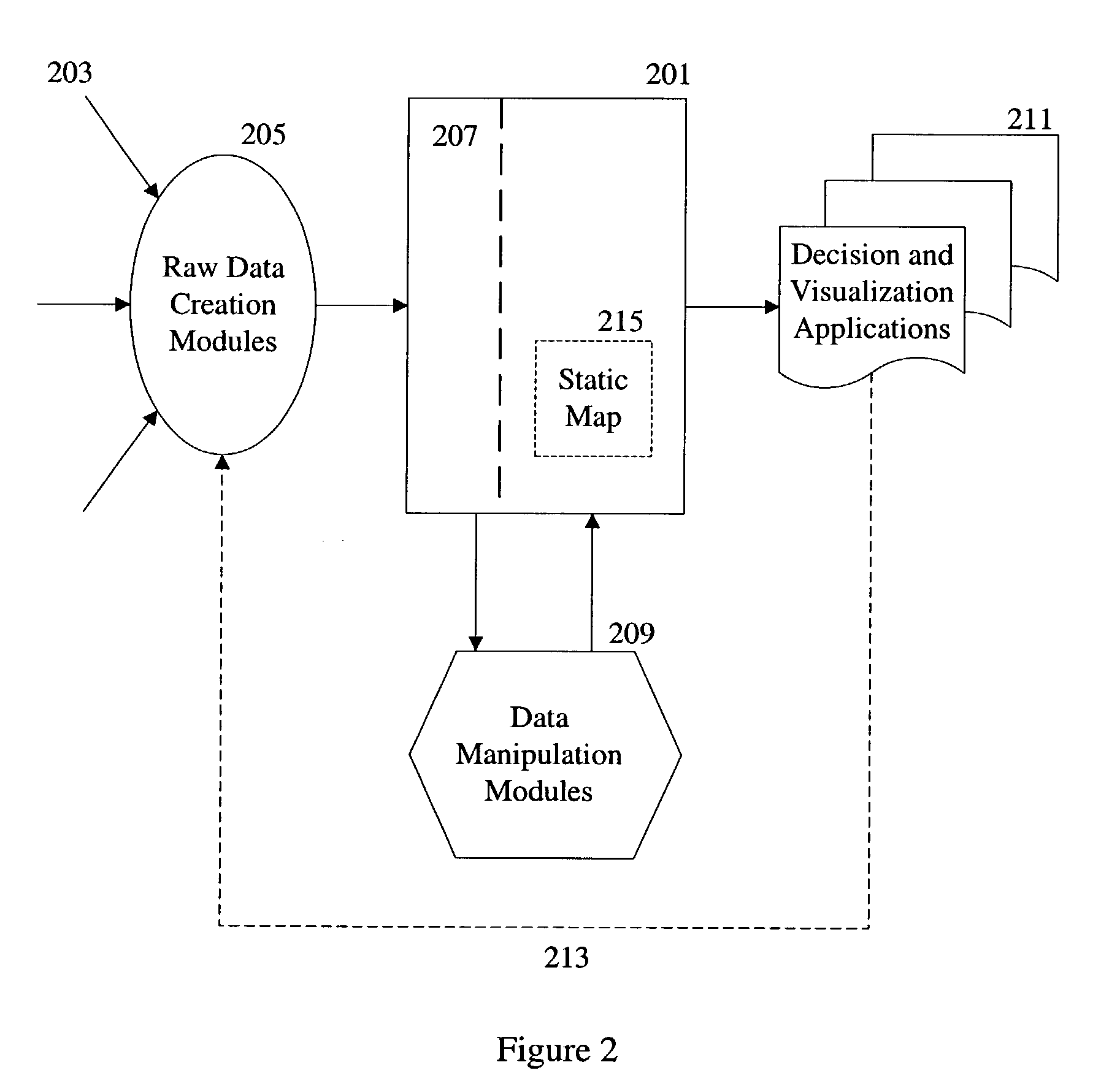
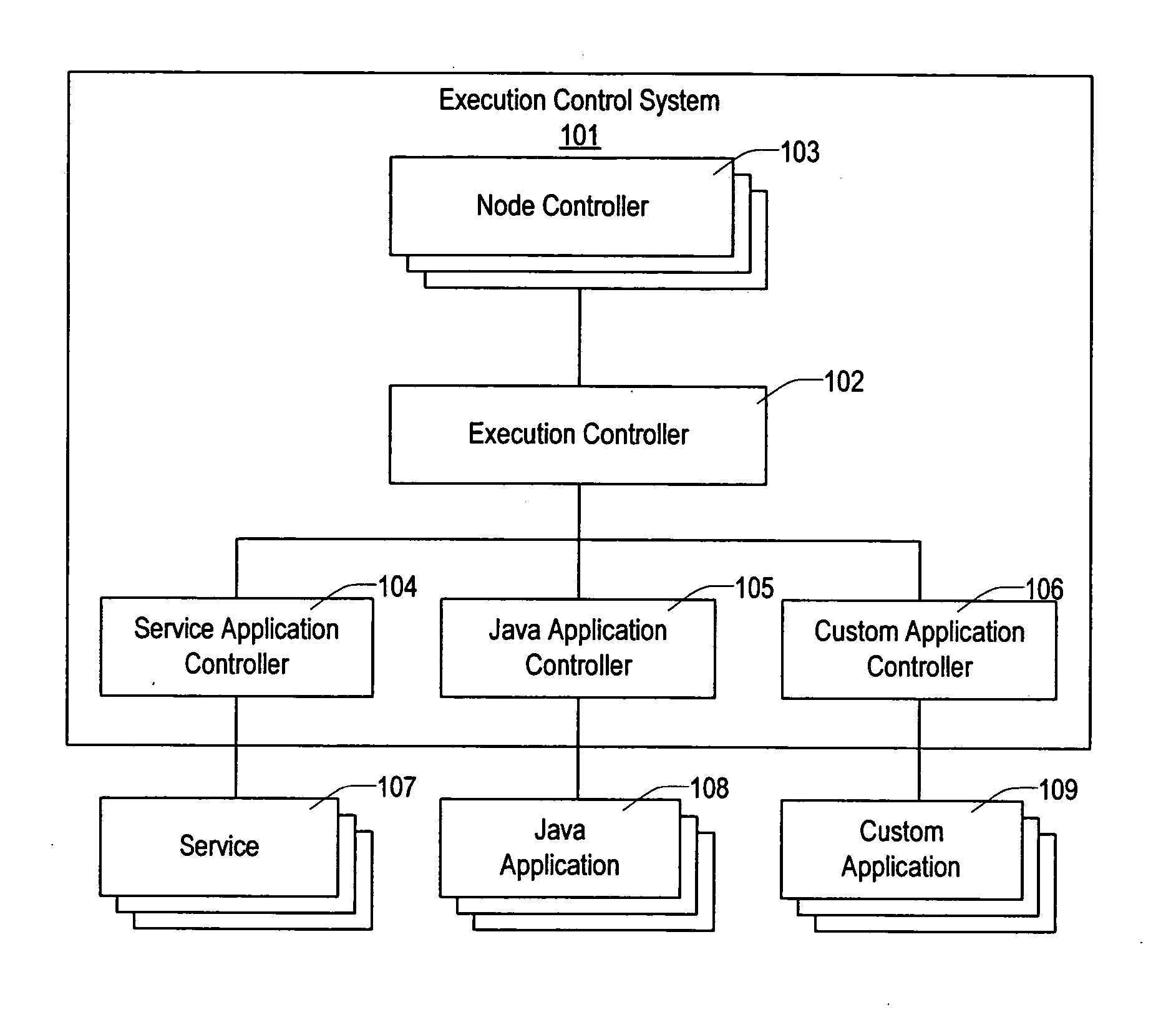
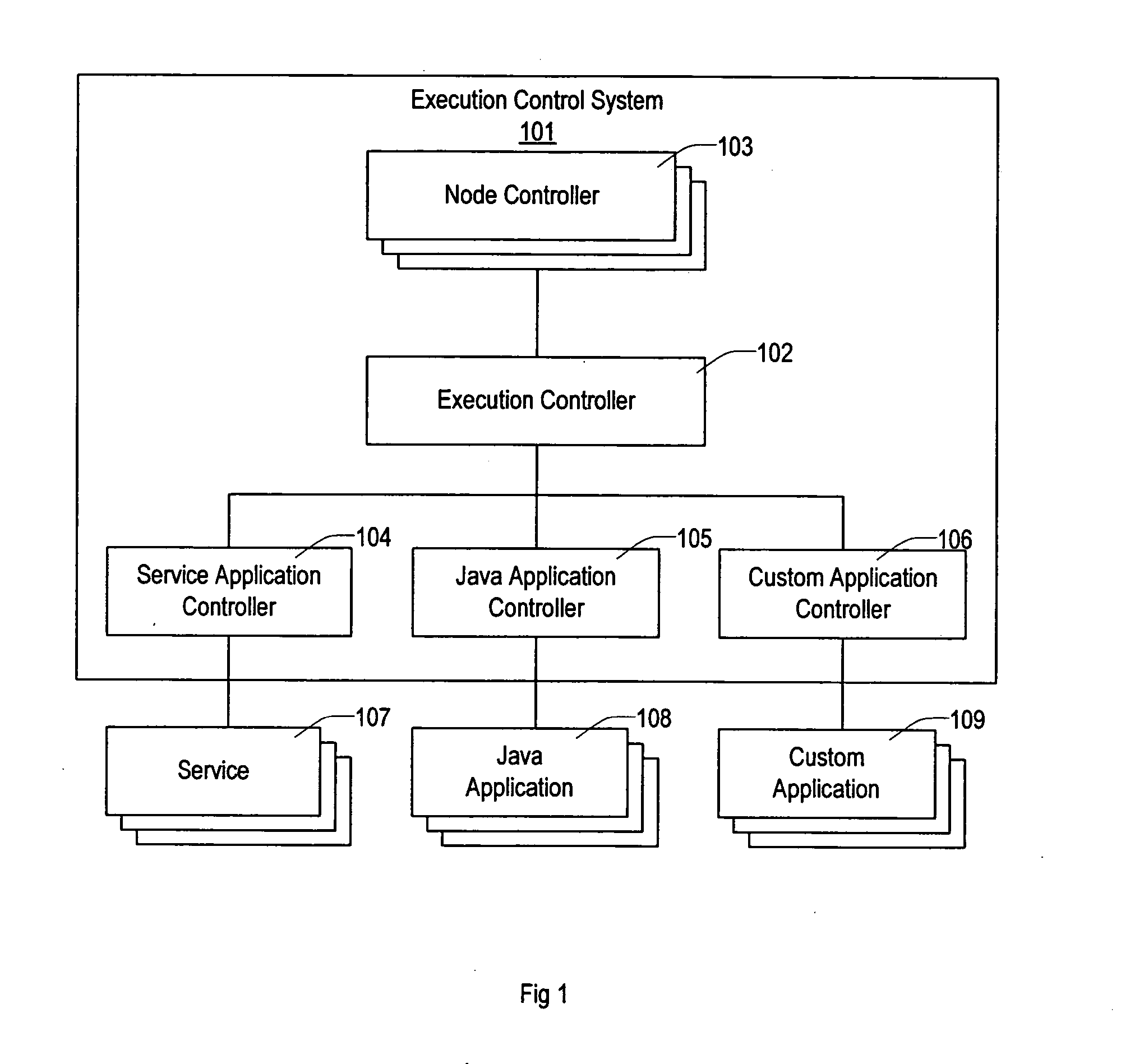
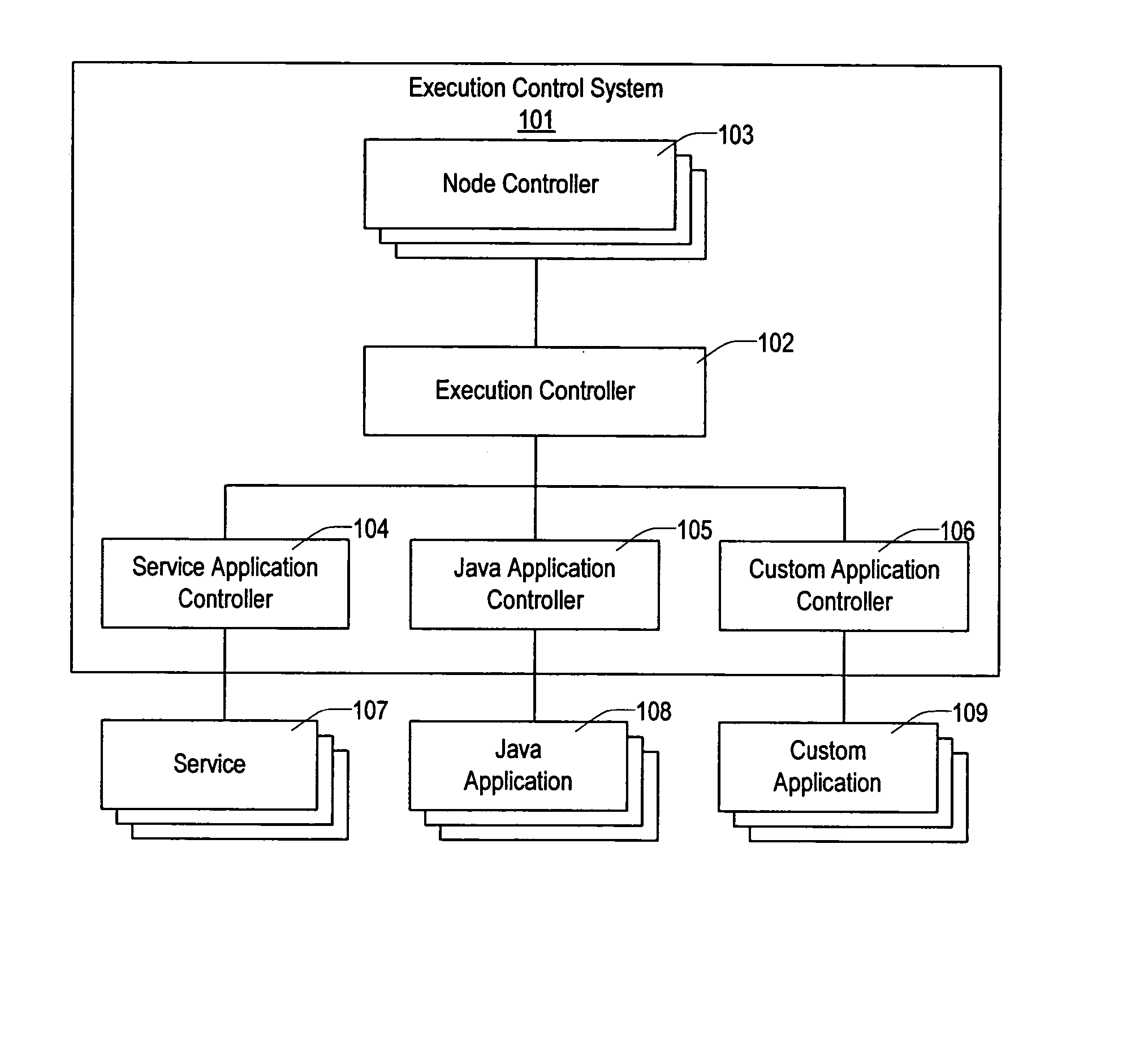
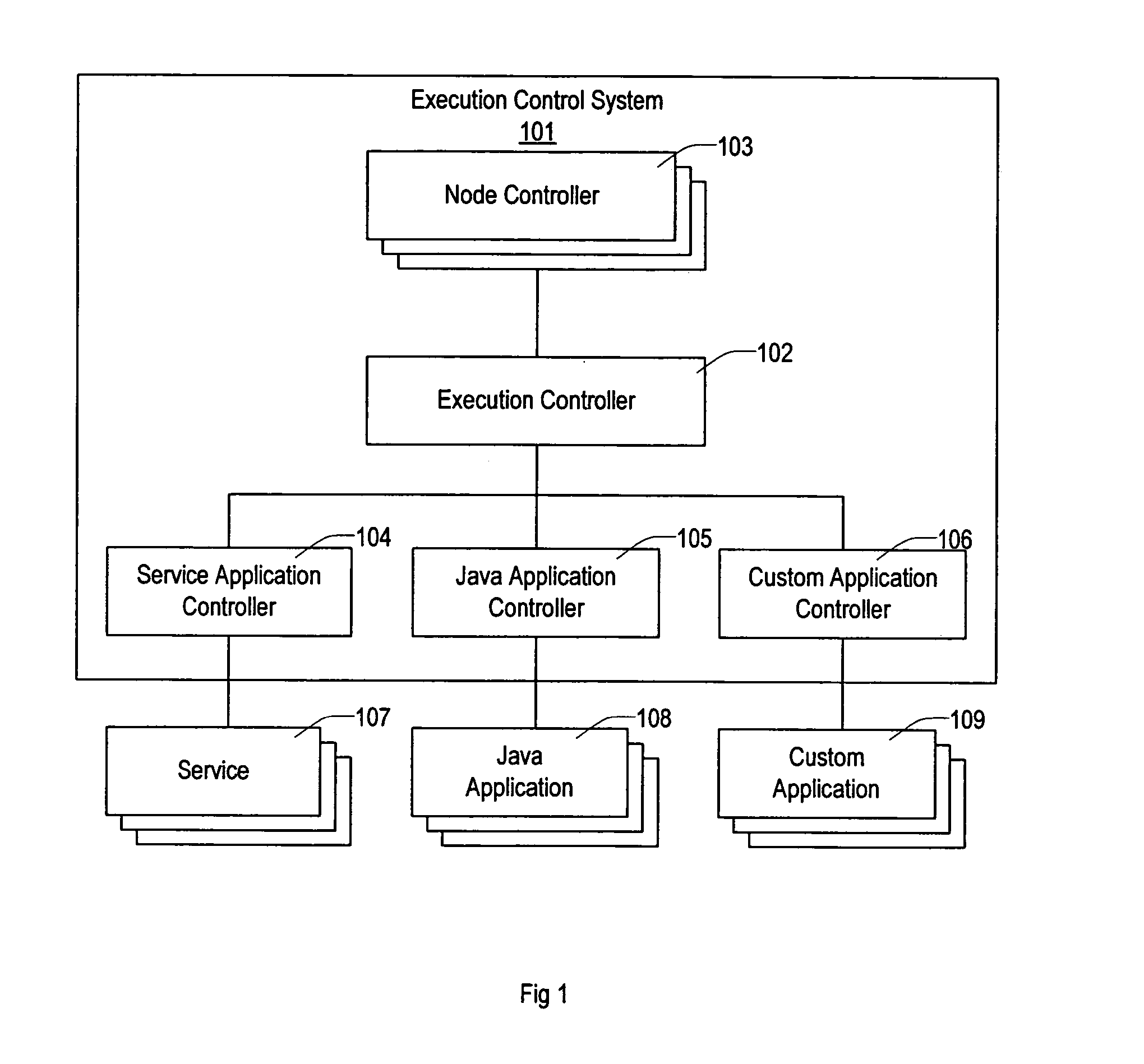
Method and apparatus for executing applications on a distributed computer system
ActiveUS20050005200A1Simplify the management processEasy to manageError detection/correctionDigital data processing detailsControl systemSoftware failure
The present invention provides a flexible and extensible execution control system for distributed computer systems including multiple nodes interconnected through a network. Distributed computer systems that include an execution control system consistent with the present invention can be used for more types of applications than systems using prior art. The applications running on a distributed computer system that includes an execution control system consistent with the present invention can achieve better protection from hardware and software failures than systems using prior art systems and methods.
Owner:VLADIMIR MATENA +1
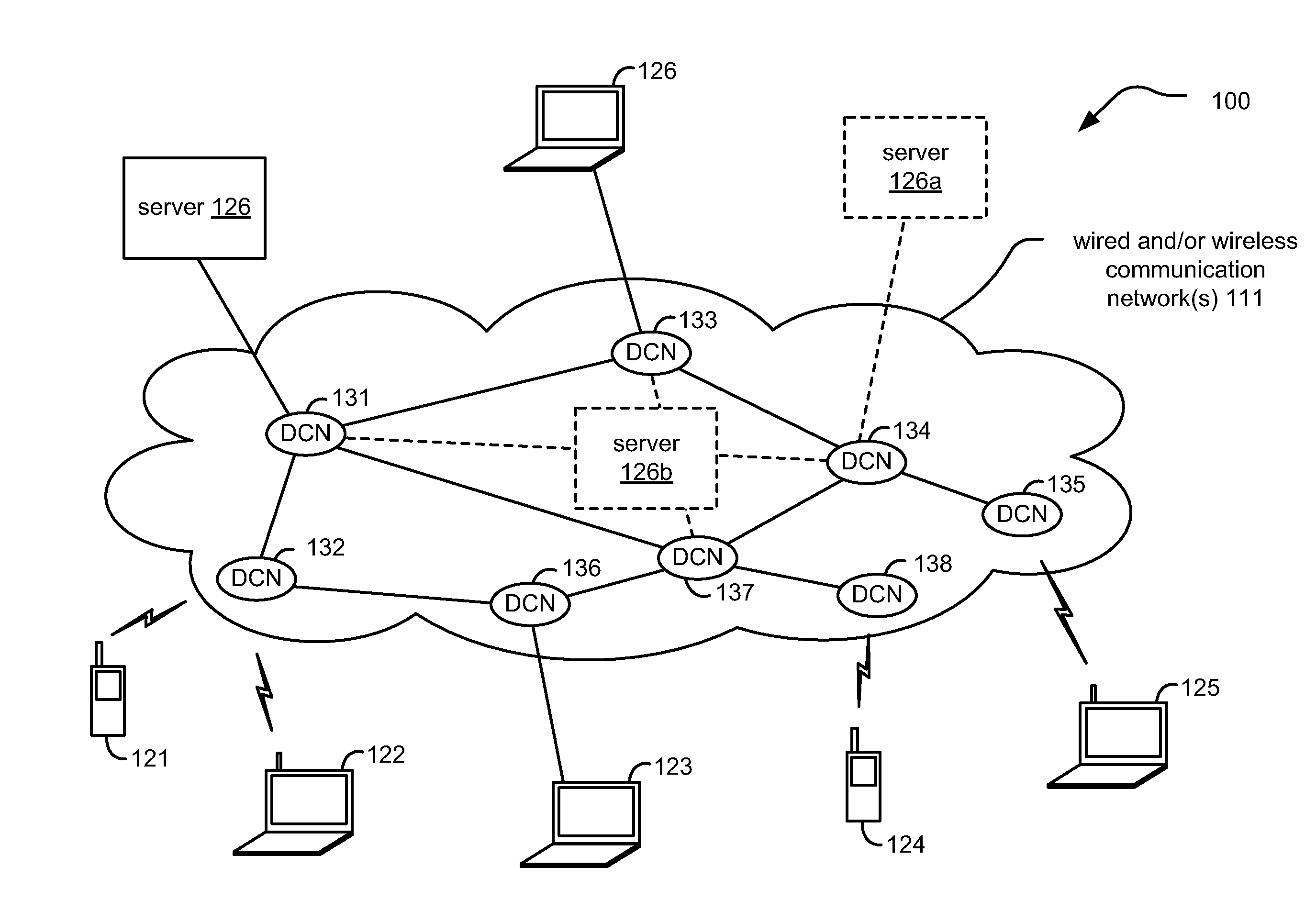
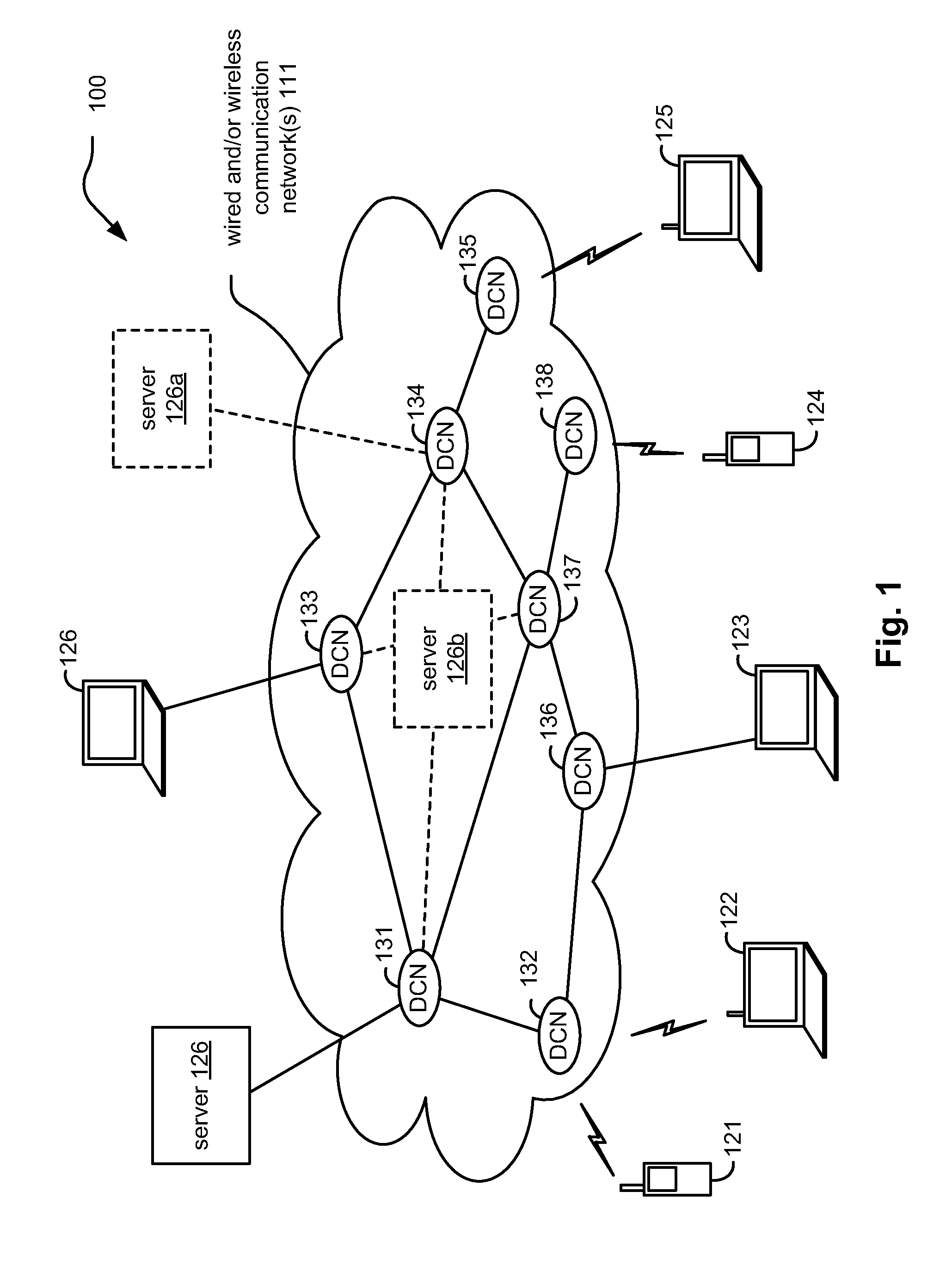
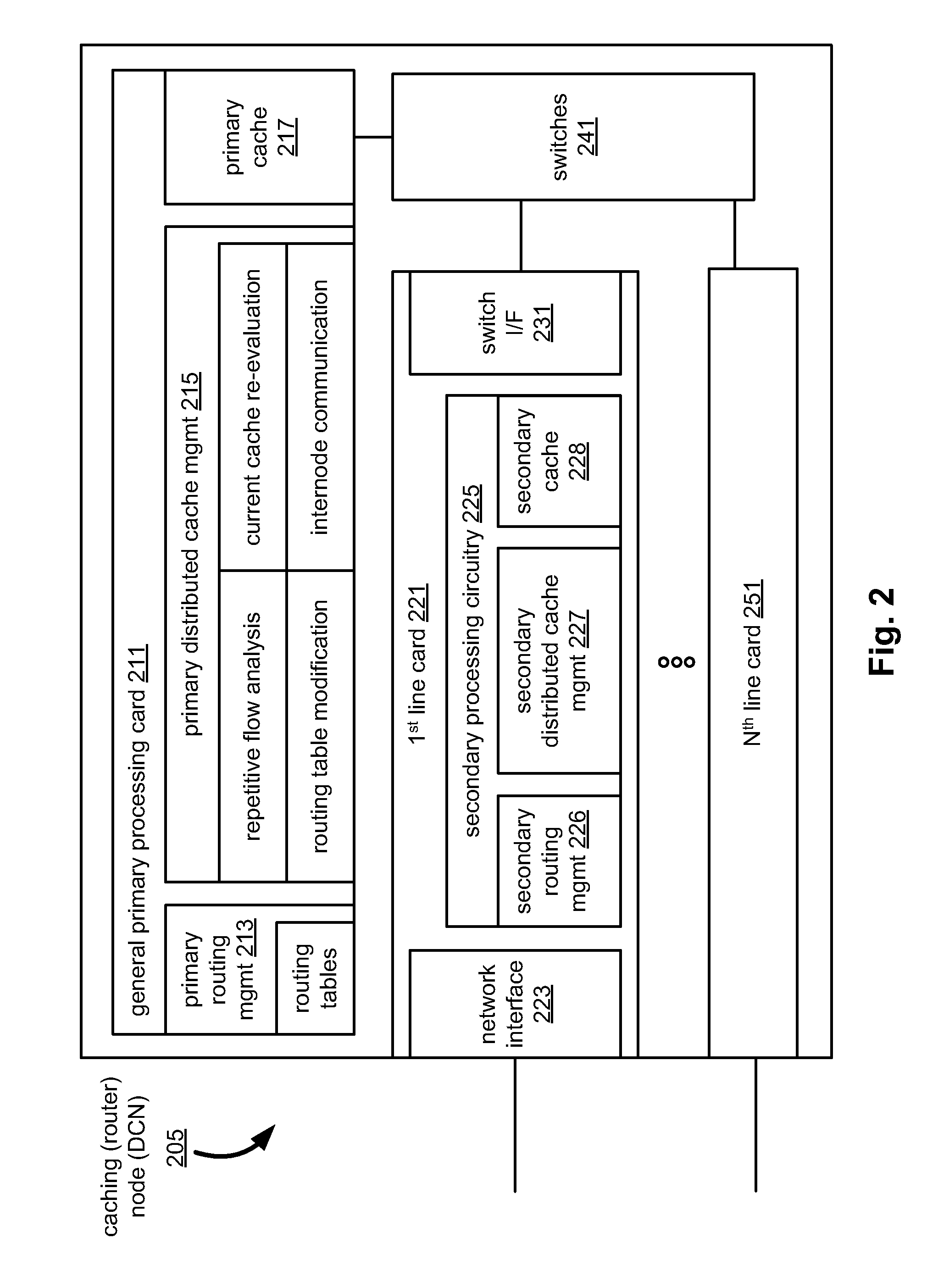
Distributed Internet caching via multiple node caching management
InactiveUS20110040893A1Digital computer detailsTransmissionCommunications systemTelecommunications link
Distributed Internet caching via multiple node caching management. Caching decisions and management are performed based on information corresponding to more than one caching node device (sometimes referred to as a distributed caching node device, distributed Internet caching node device, and / or DCN) within a communication system. The communication system may be composed of one type or multiple types of communication networks that are communicatively coupled to communicate there between, and they may be composed of any one or combination types of communication links therein [wired, wireless, optical, satellite, etc.]). In some instances, more than one of these DCNs operate cooperatively to make caching decisions and direct management of content to be stored among the more than one DCNs. In an alternative embodiment, a managing DCN is operative to make caching decisions and direct management of content within more than one DCNs of a communication system.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
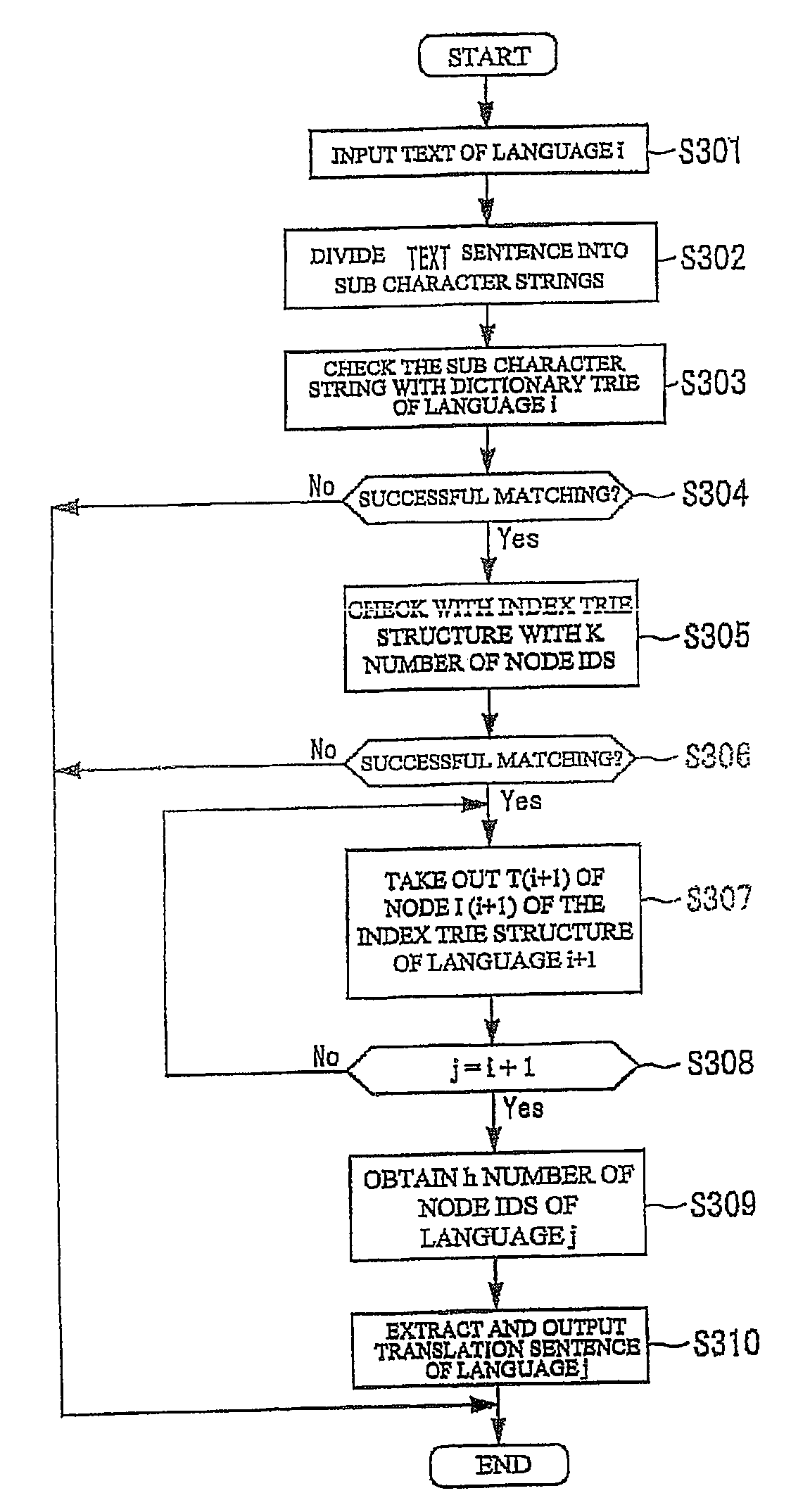
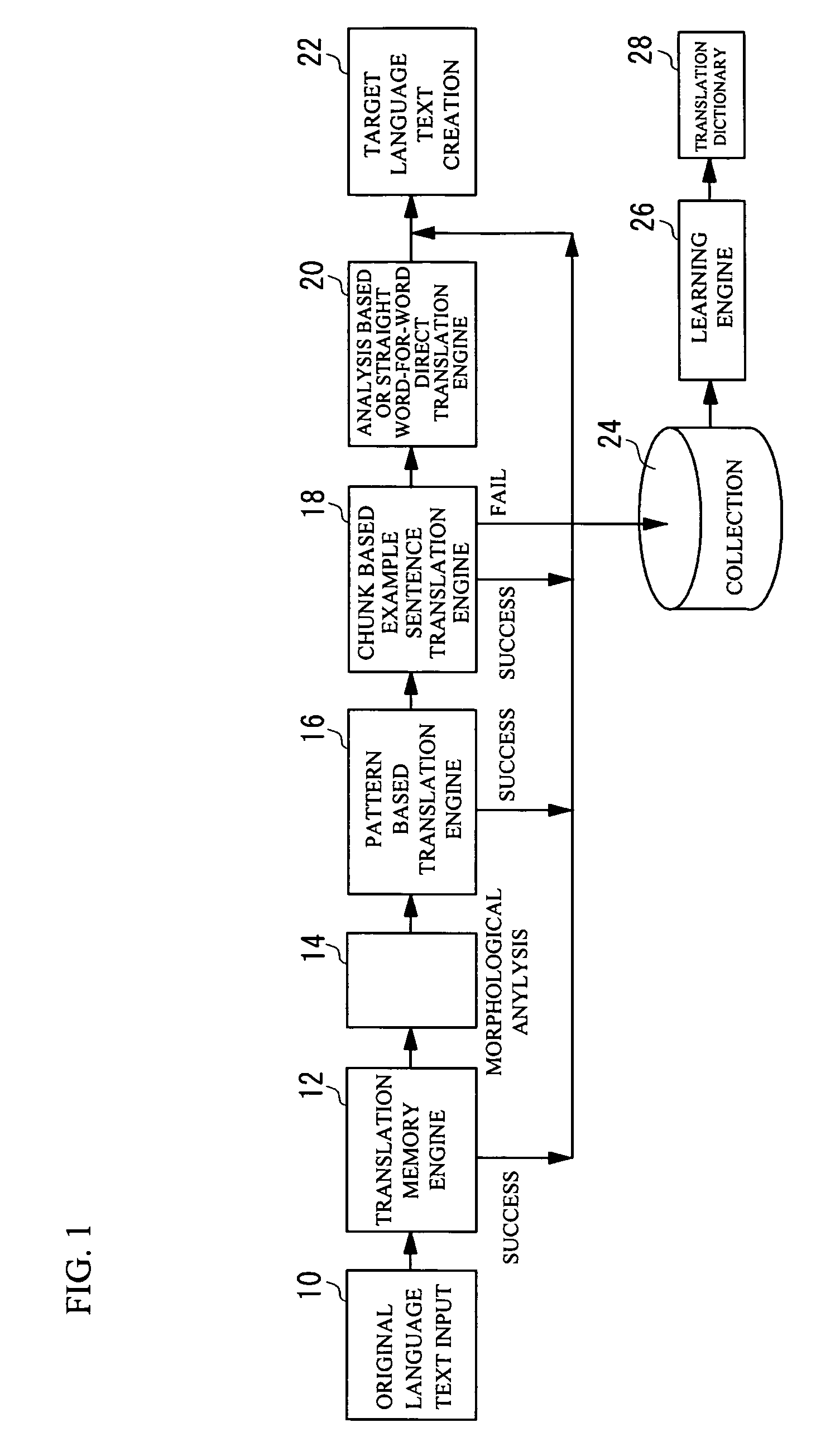
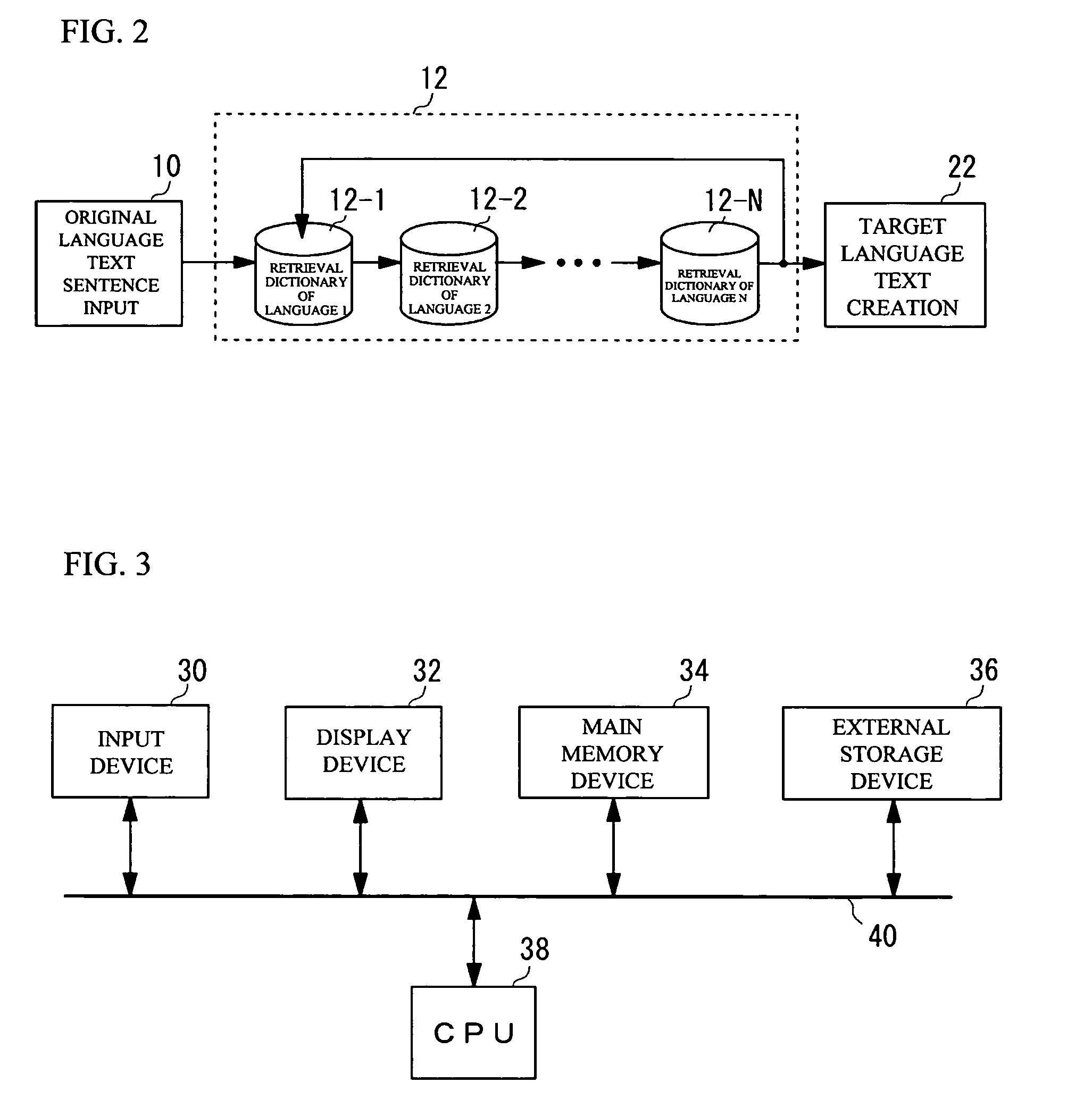
Multilingual translation memory, translation method, and translation program
InactiveUS7707026B2Accurate translationReduce memory capacityNatural language translationSpecial data processing applicationsNatural language processingTranslation memory
A translation memory adapted to sentence-based translation includes a first retrieval dictionary of a first language having a first dictionary TRIE structure and a first index TRIE structure, and a second retrieval dictionary of a second language having a second dictionary TRIE structure and a second index TRIE structure. The first and second dictionary TRIE structures respectively store sub character strings on respective paths from roots to multiple nodes thereof. The first and second index TRIE structure respectively store index information to specify the sub character strings stored in the first and second dictionary TRIE structures. The index information stored in the first retrieval dictionary includes identification information that identifies the index information to specify the sub character strings in the second retrieval dictionary that are translations of those in the first retrieval dictionary.
Owner:FUJIFILM BUSINESS INNOVATION CORP
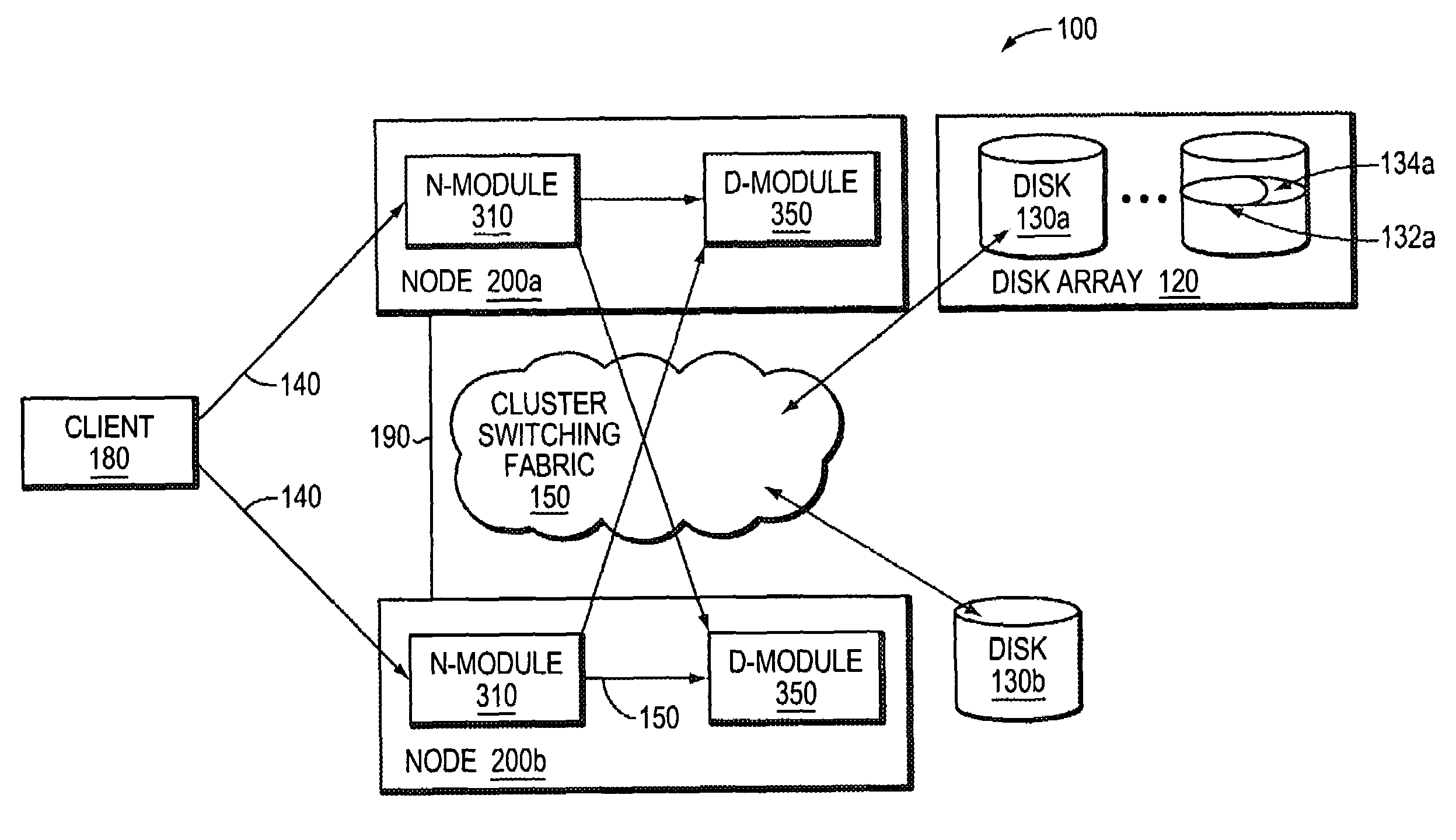
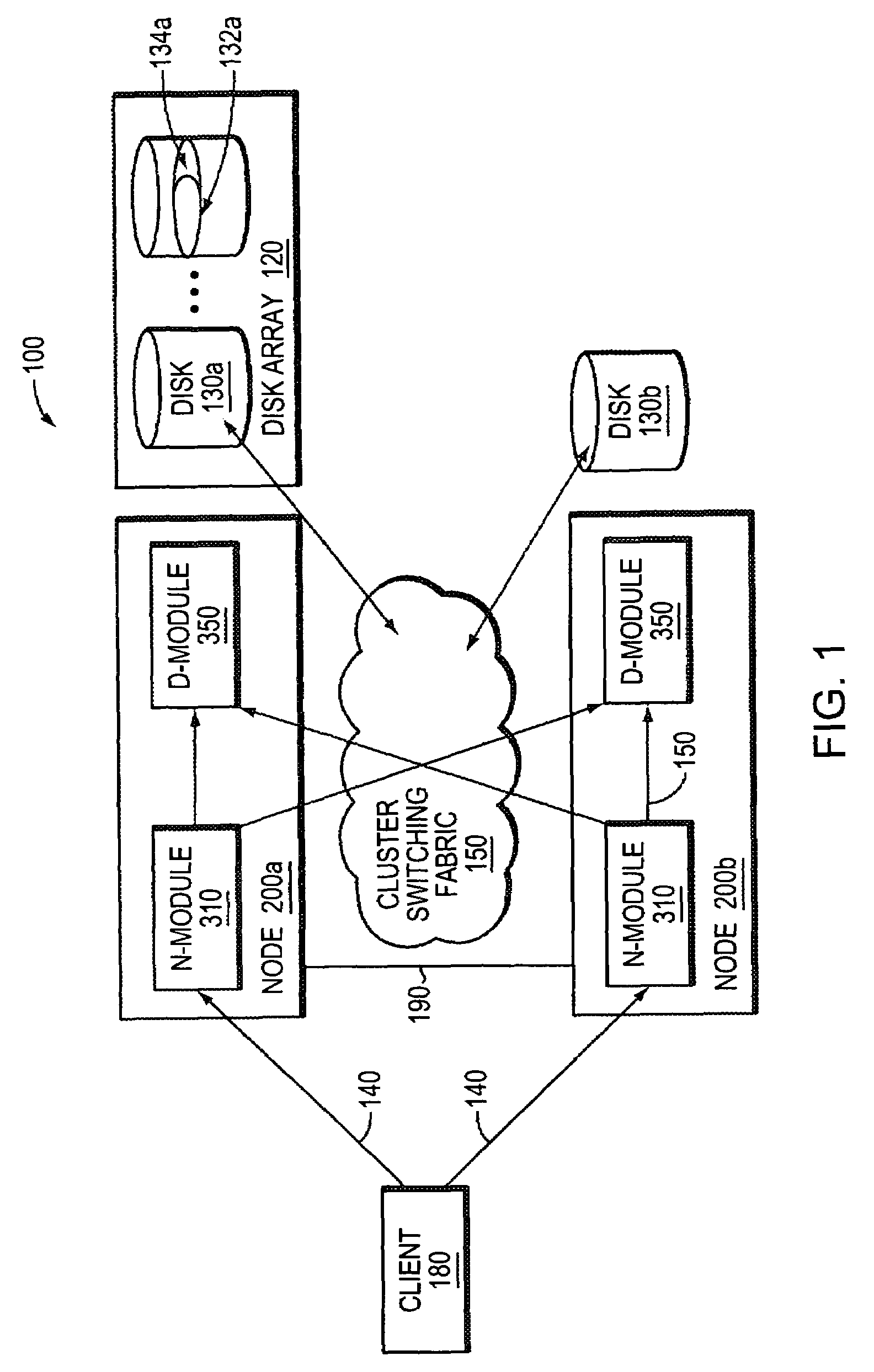
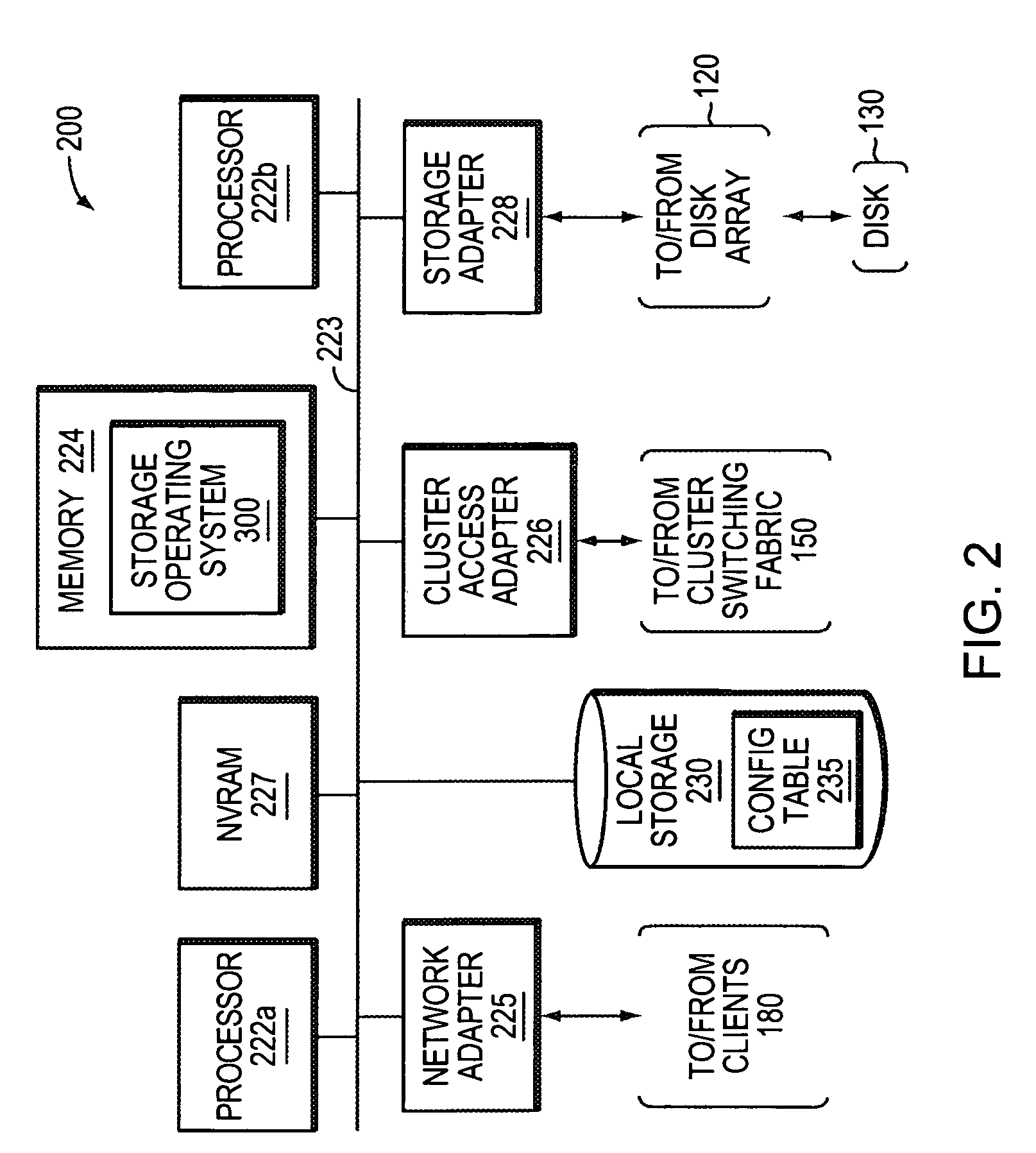
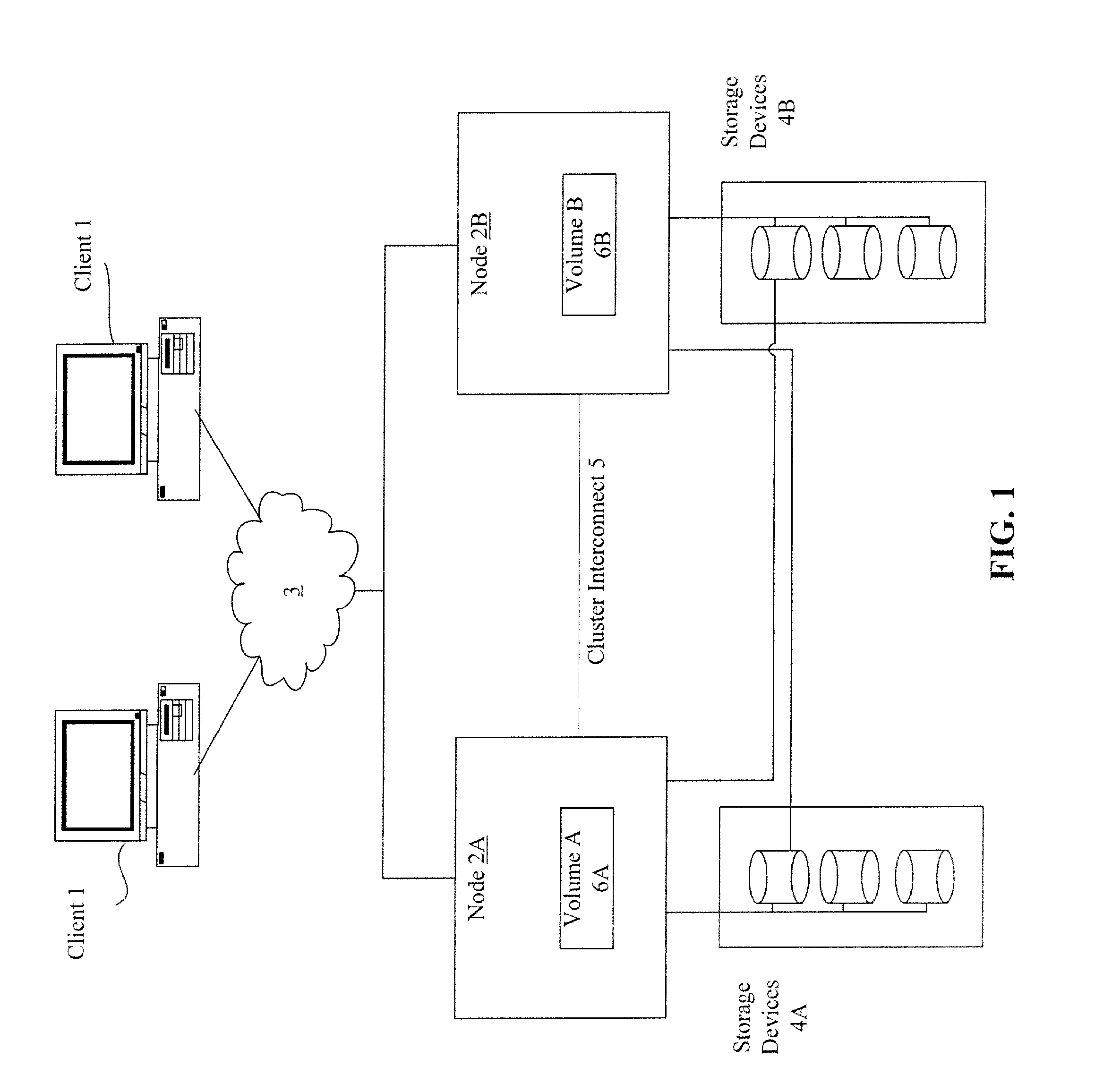
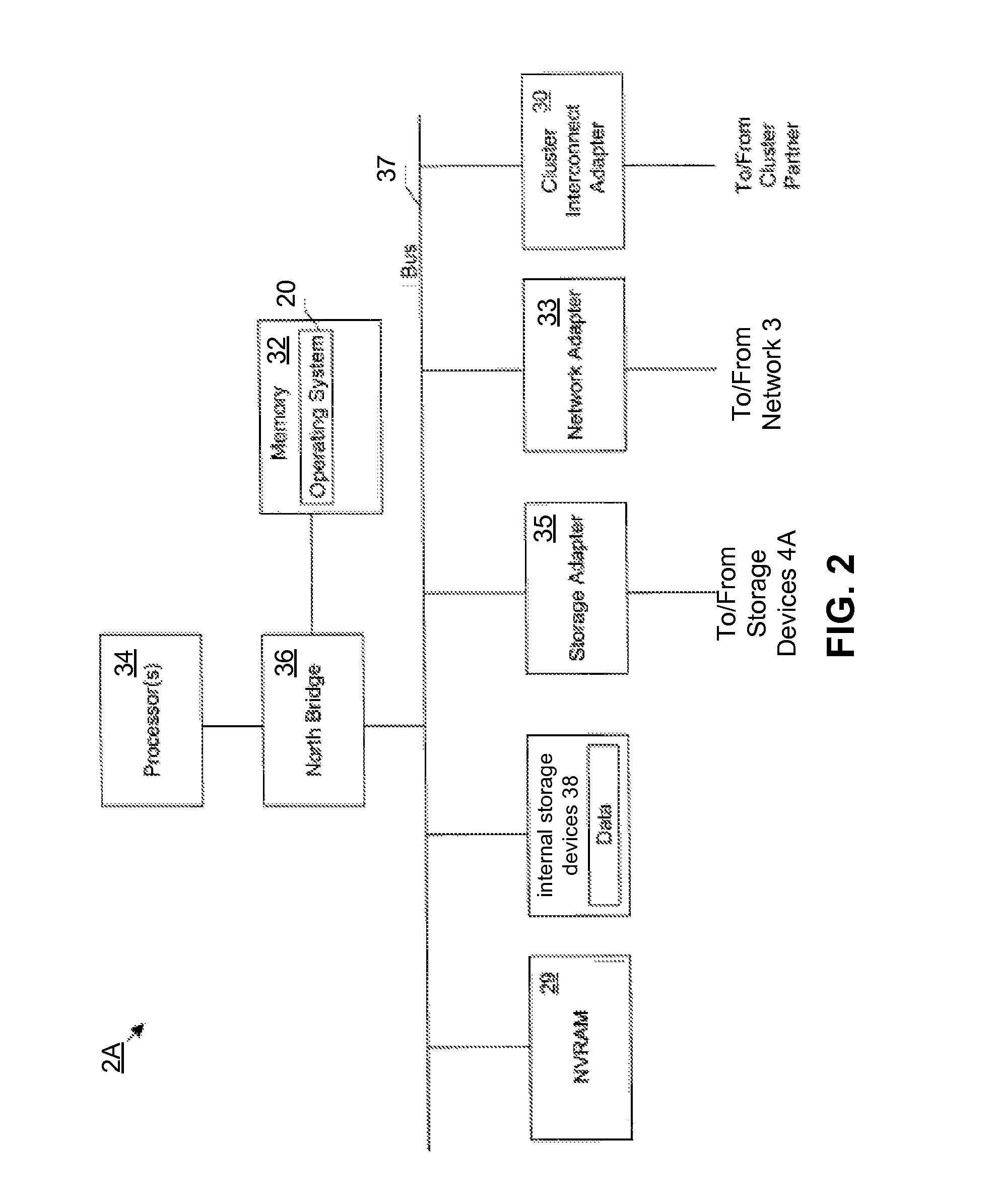
System and method for storage takeover
A takeover system and method for high availability in the face of component failures for a multiple-node storage system cluster is provided. When a takeover is triggered either through a loss of cluster heartbeat, or through a user-initiated command, the system of the present invention is configured such that one or more surviving nodes asserts ownership on one or more of the failed node's disks such that all of the disks become locally owned by one of the surviving nodes. An assimilation of the disks into one or more aggregates is performed, and any duplicated file system identification numbers are corrected to avoid errors. As the disks thus appear to be locally owned by the surviving nodes, one or more newly assimilated aggregates are thus exposed to any N-module that interfaces with the surviving nodes.
Owner:NETWORK APPLIANCE INC
Framework for managing clustering and replication
The present invention provides a framework for managing both clustering and data replication in a software system distributed across multiple nodes. The framework includes at least one agent running at nodes comprising the distributed system. The framework also includes a master to coordinate clustering and replication operations. The framework further includes a library of software programs, called primitives, that are used by agents to communicate with the master. The agent(s) obtain cluster status information and replication status information, which are used by the master to manage clustering and replication operations. The framework is designed to work with existing cluster management applications and data replication facilities. The framework provides status information needed for coordinating clustering and replication operations to ensure that applications and data remain in a consistent state for disaster recovery purposes.
Owner:SYMANTEC OPERATING CORP
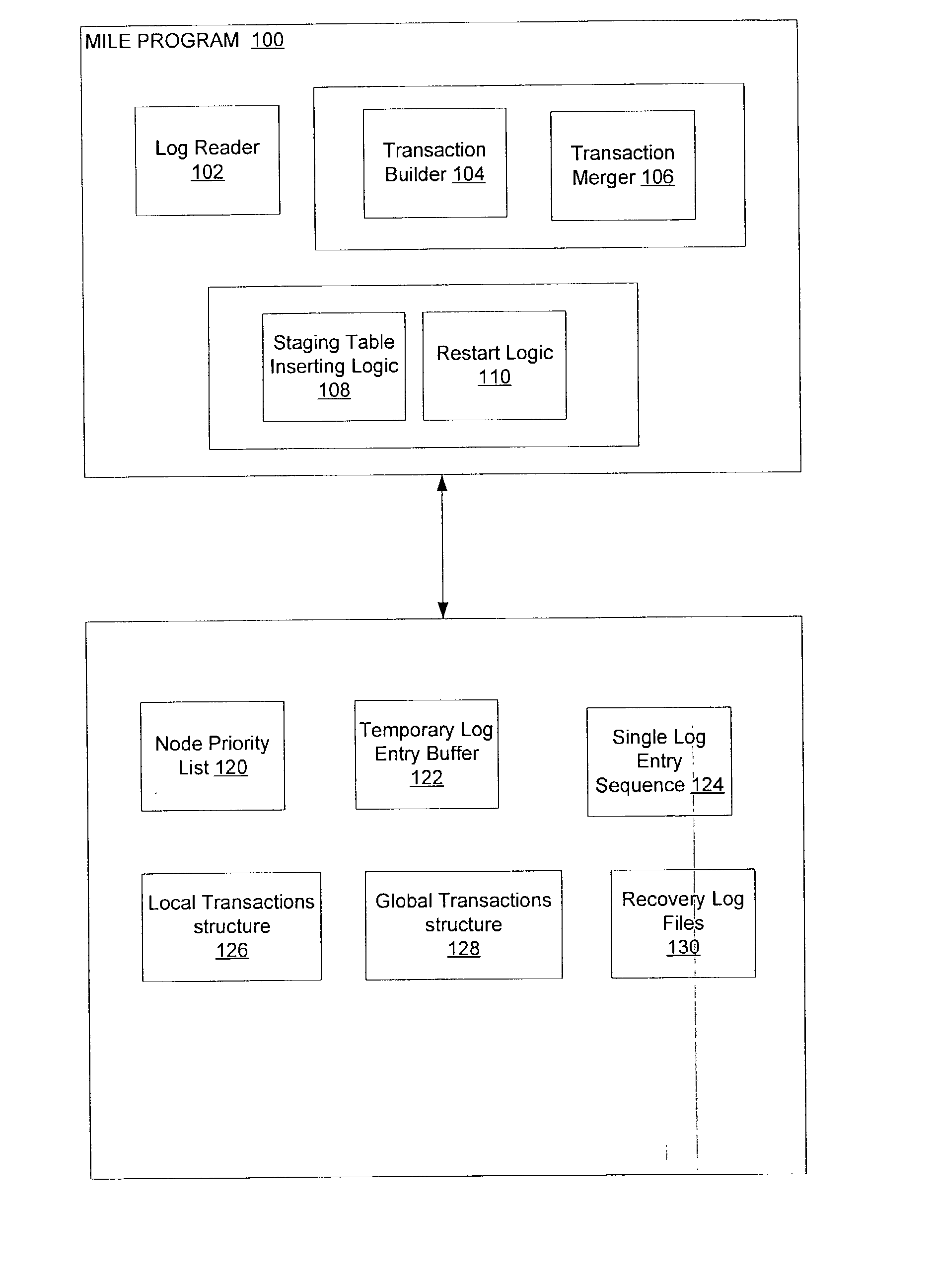
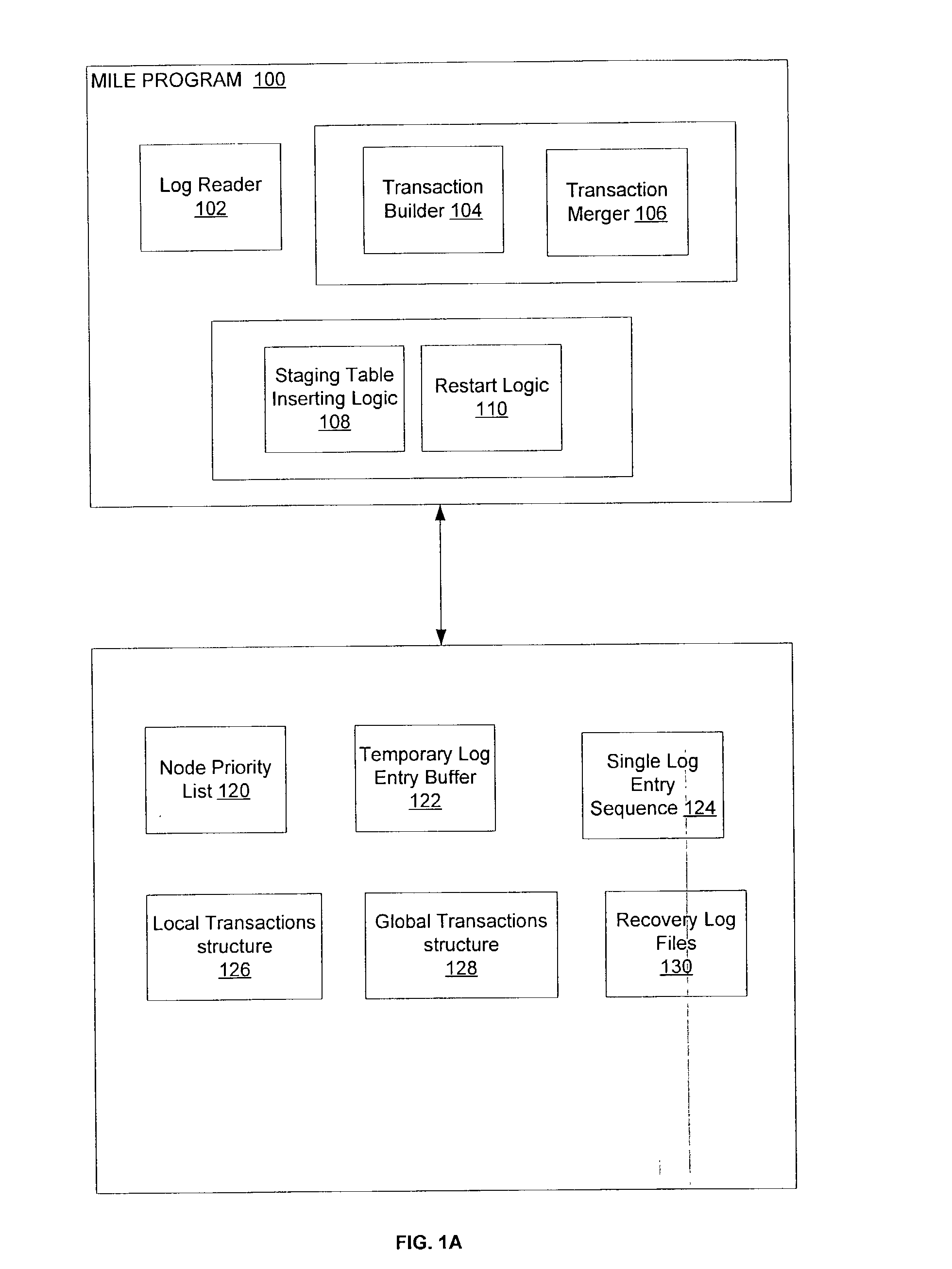
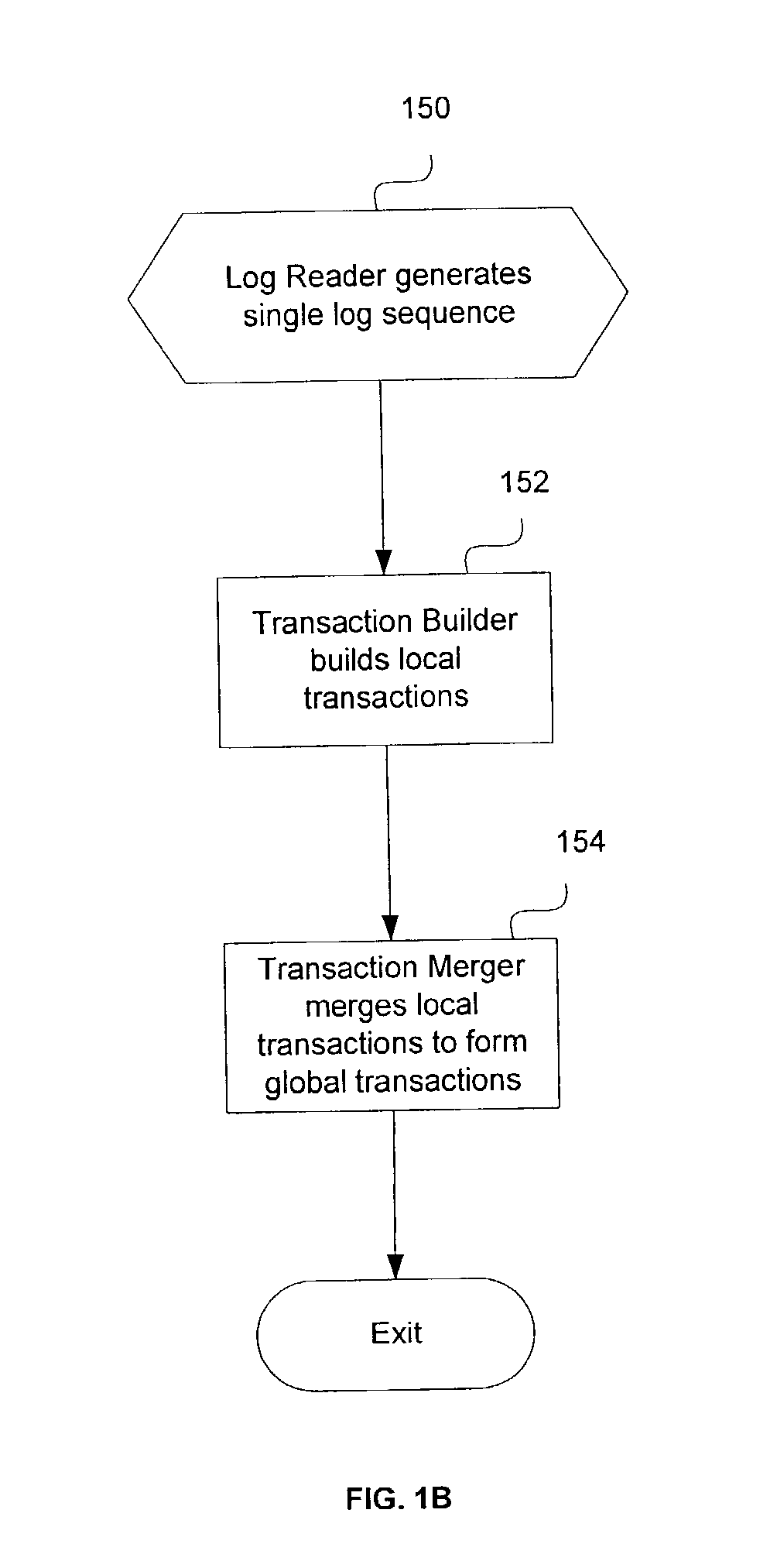
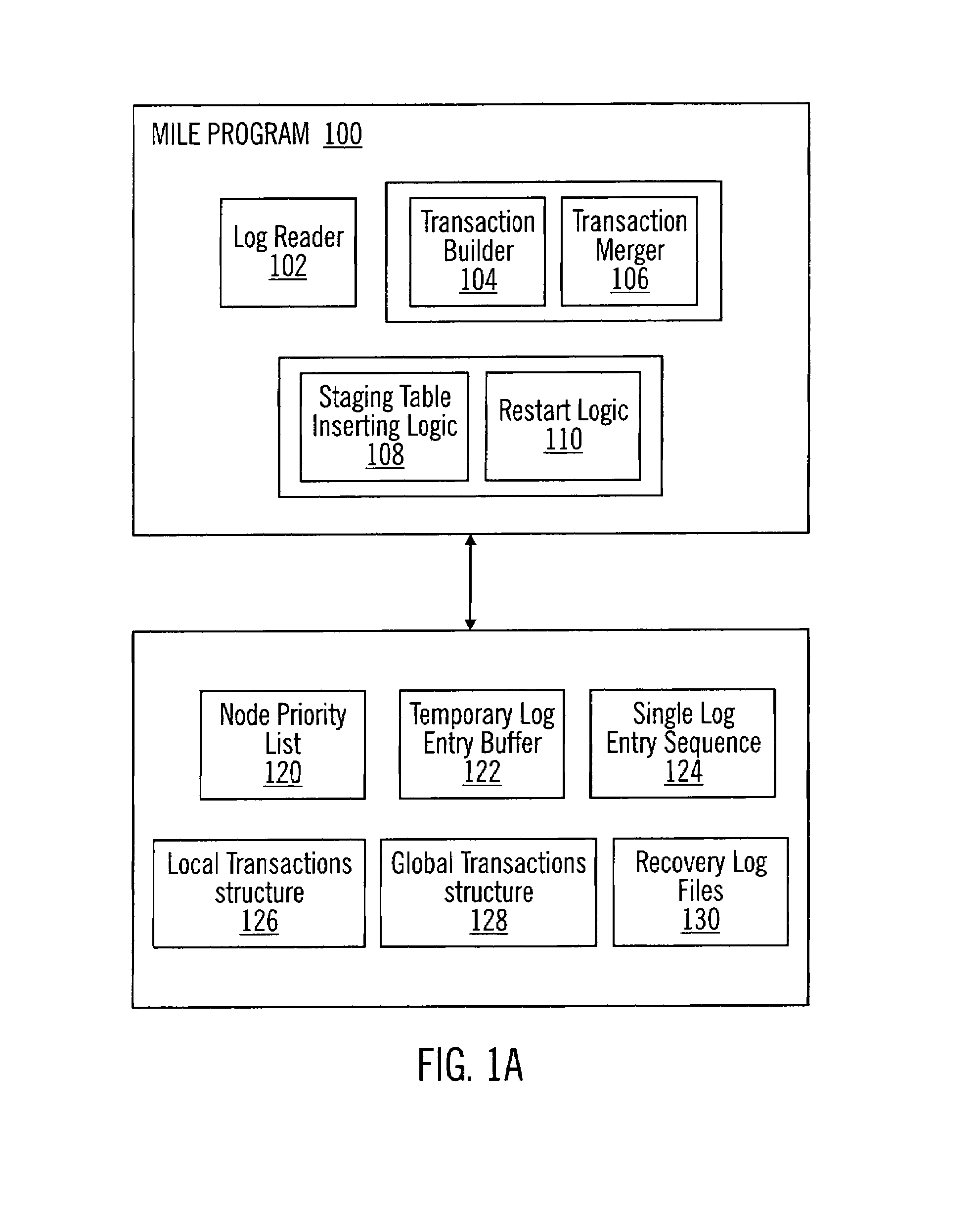
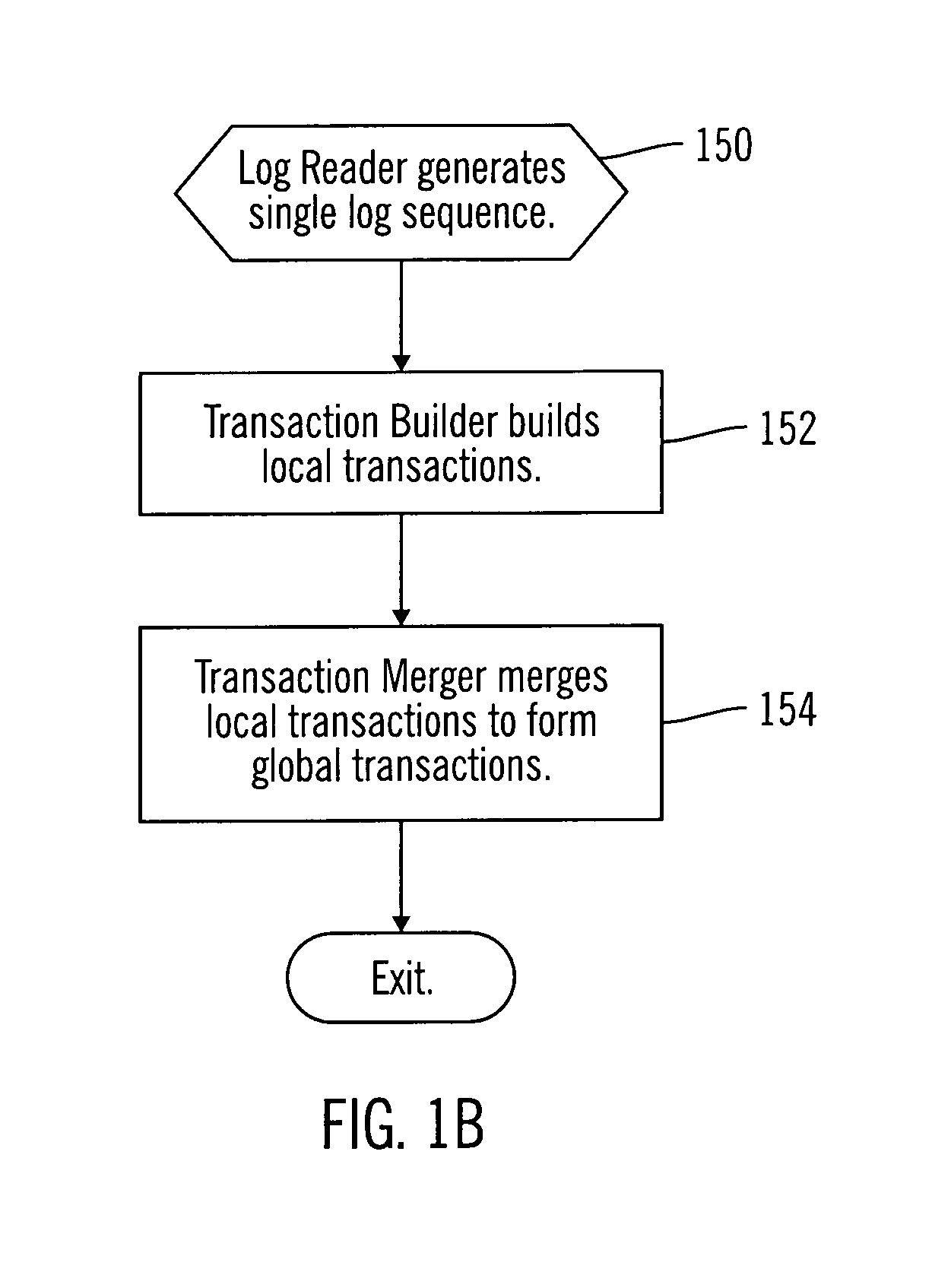
Method, system, and program for merging log entries from multiple recovery log files
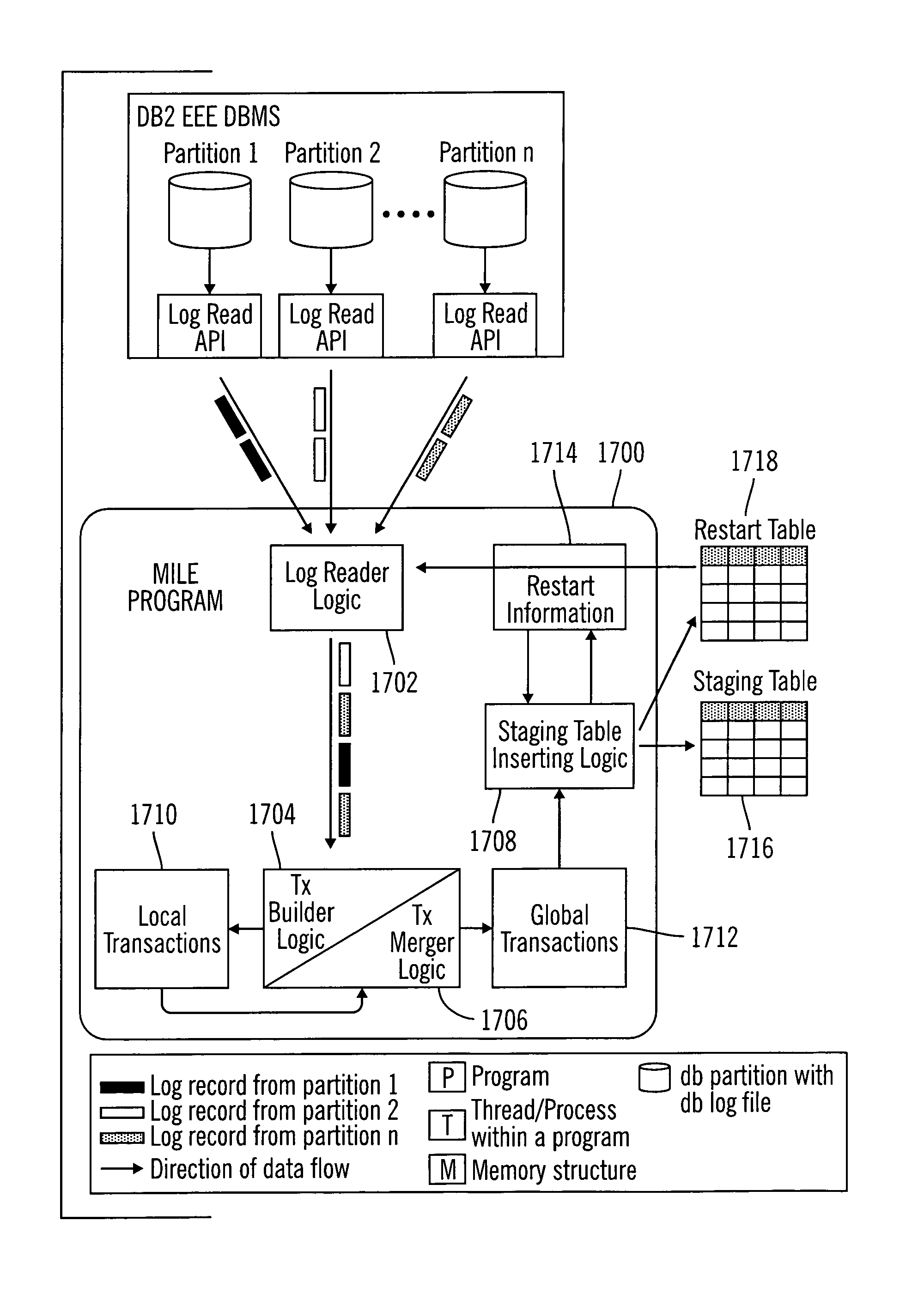
InactiveUS20040030703A1Minimize overheadAvoid reprocessingData processing applicationsDigital data information retrievalDatabaseMultiple node
Provided are a method, system, and program for merging independent log entries in a multiple node shared nothing DBMS. Initially, log entries from multiple log entries are combined to form a single log entry sequence. Local transactions are generated from the single log entry sequence and stored in a local transactions structure. In particular, log entries with the same local transaction identifier form a local transaction. Then, local transactions having the same global identifier are merged to form global transactions.
Owner:IBM CORP
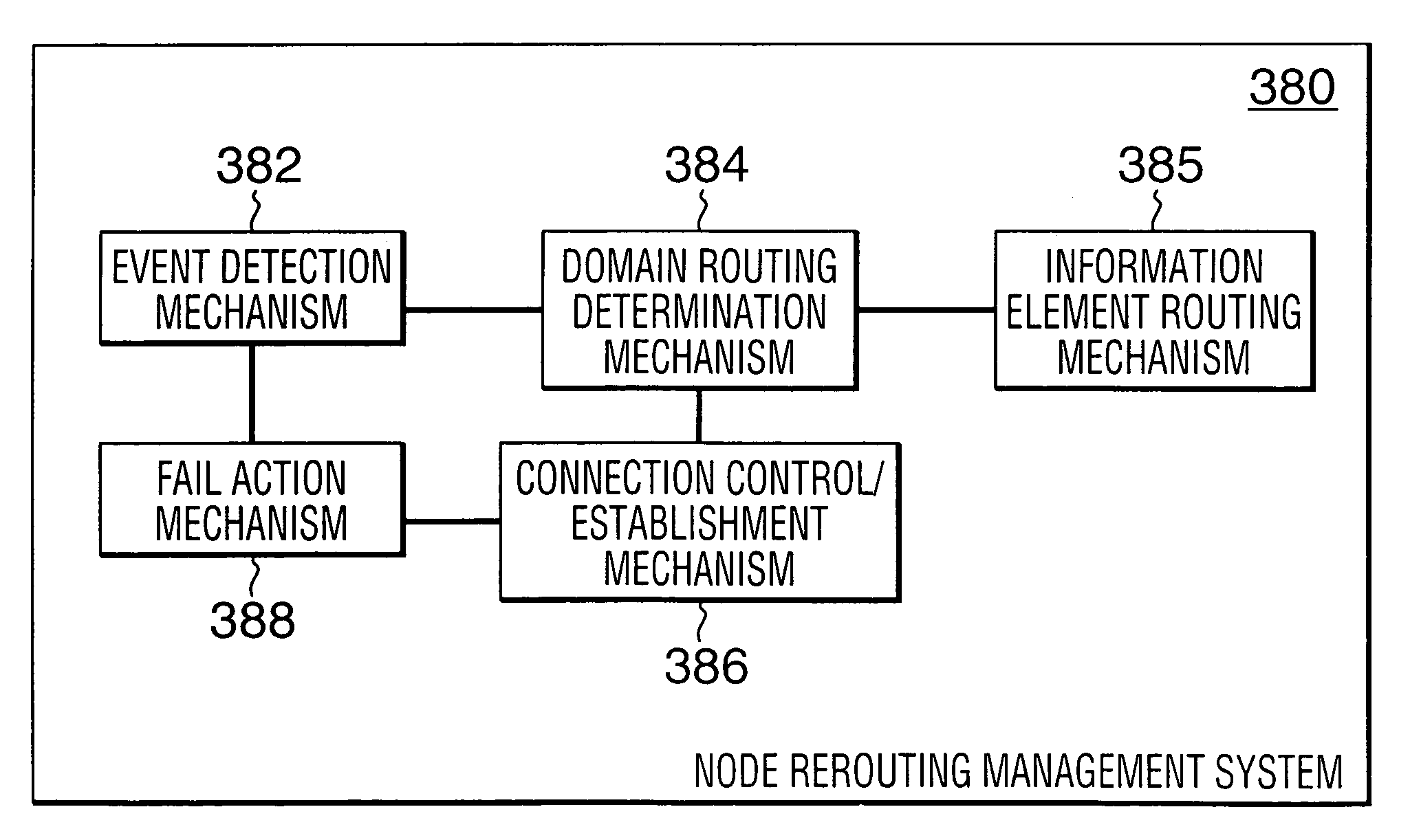
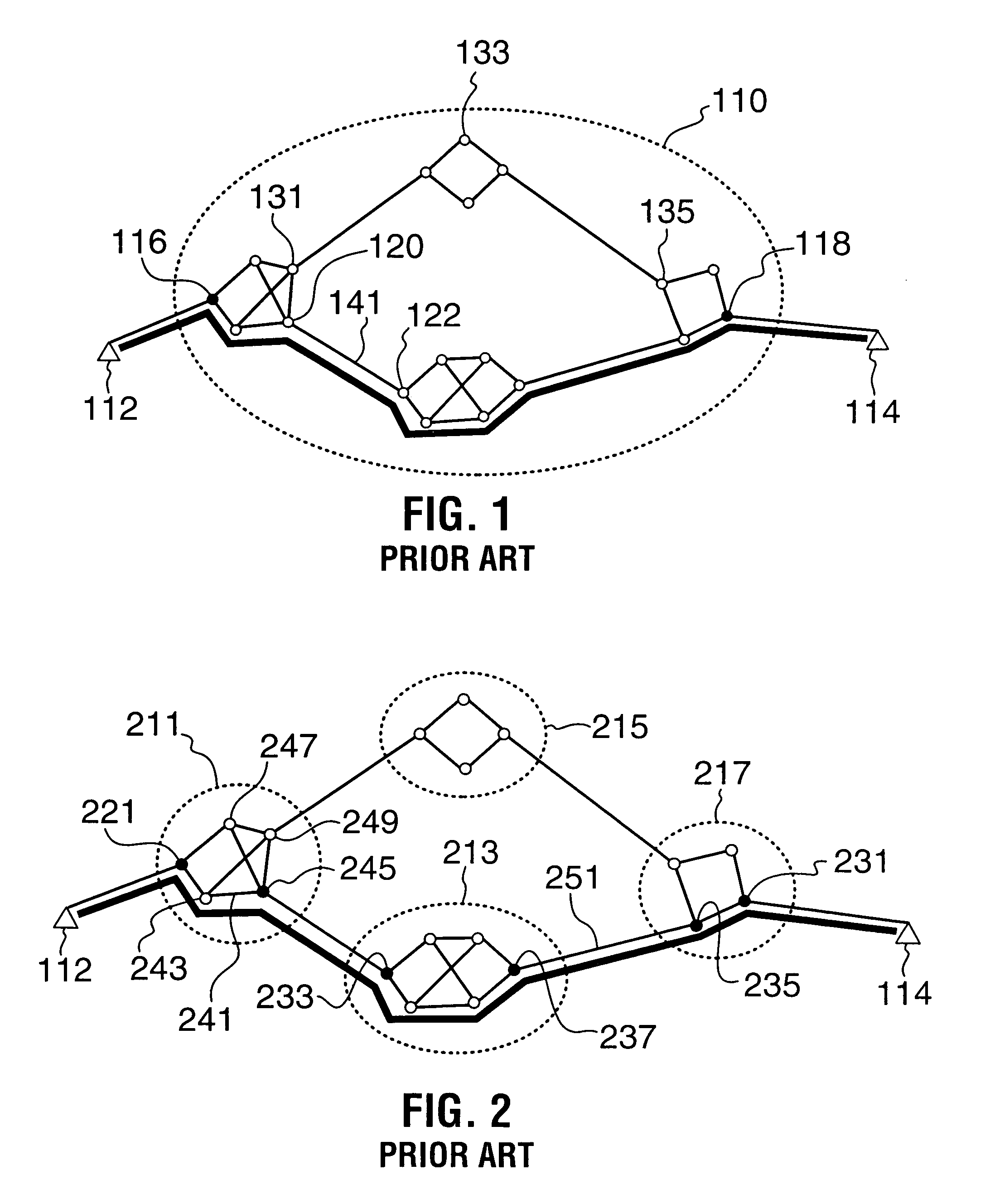
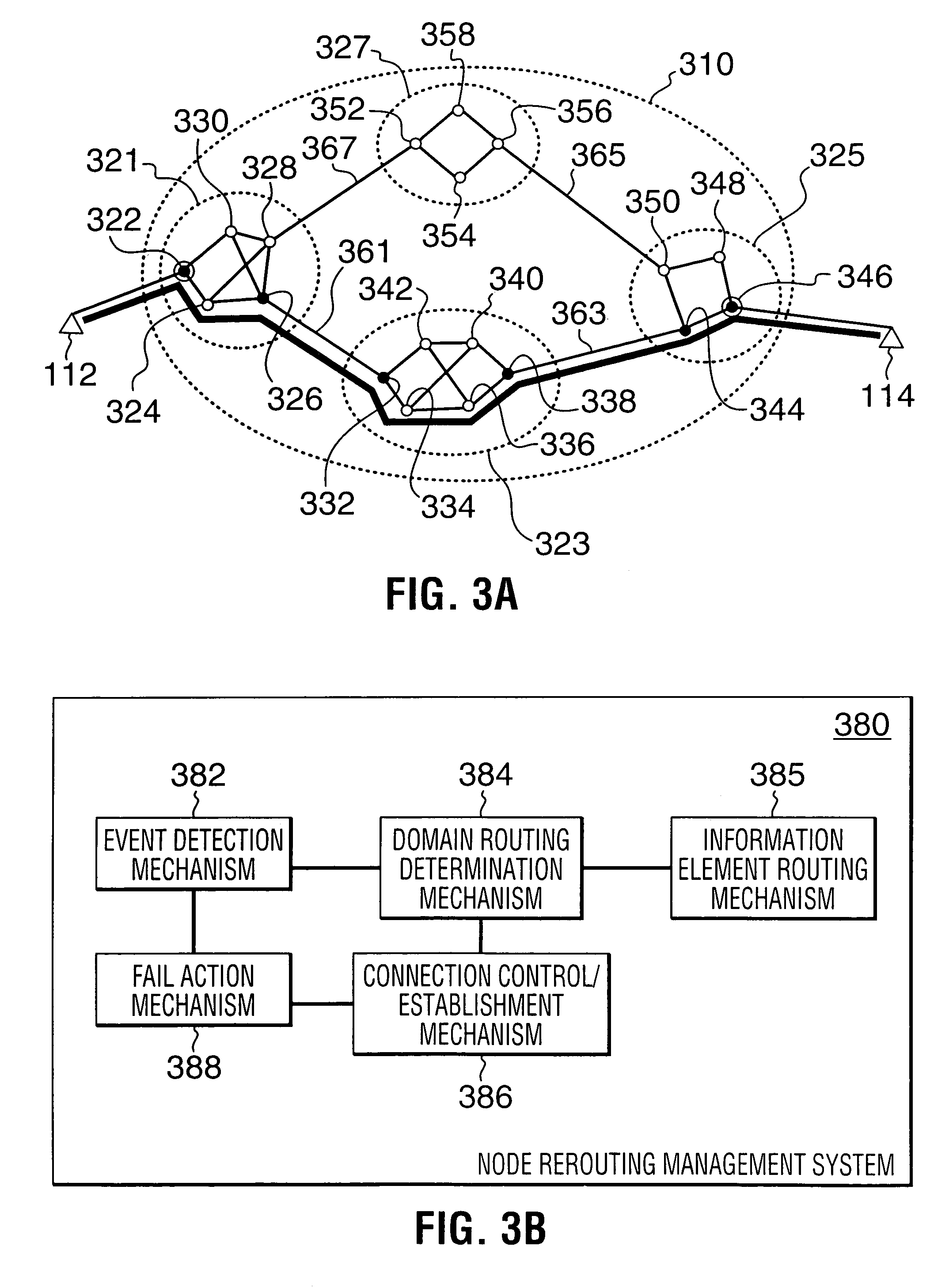
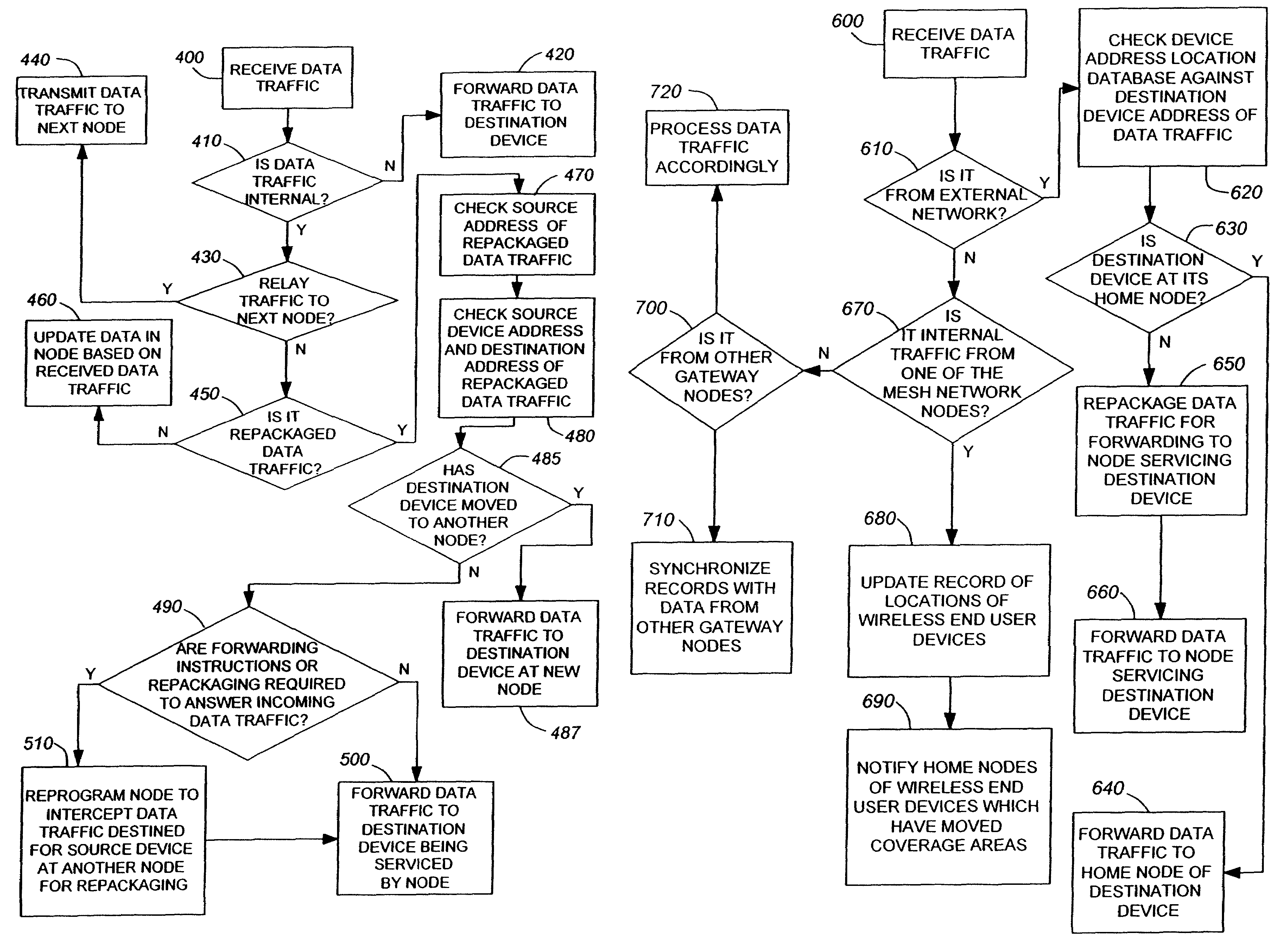
Rerouting in connection-oriented communication networks and communication systems
InactiveUS7180866B1Multiplex system selection arrangementsError preventionDouble faultCommunications system
A Private Network-Network Interface (PNNI) network including interconnected nodes is defined as a single rerouting domain (“global domain”) and the global domain is further defined by multiple divided domains (“local domains”). Each of the local domains is defined to include multiple nodes that are included in the network. Connection recovery and path optimization in the global domain (the entire PNNI network) are performed in accordance with a global rerouting protocol. The global rerouting protocol is a modification of the standard Domain-Based Rerouting (DBR) protocol, by adding information elements of domain identifier, rerouting for the global domain. The DBR protocol does not support the connection recovery from a link failure between local domains (“inter-domains”) and the global path optimization. The global rerouting method is capable of connection recovery and path optimization outside of any rerouting local domains. The global rerouting provides double fault recovery within the rerouting domain (“intra-domain”) as covered by the DBR and outside of the domains (“inter-domain”) or when the initial fault recovery within the domain has failed. Also, the global rerouting method provides maximum path optimization across all domains and within the rerouting local domain.
Owner:RPX CLEARINGHOUSE
Mobile station traffic routing
InactiveUS7545782B2Data switching by path configurationWireless network protocolsMobile stationData traffic
Owner:ERICSSON WIFI +1
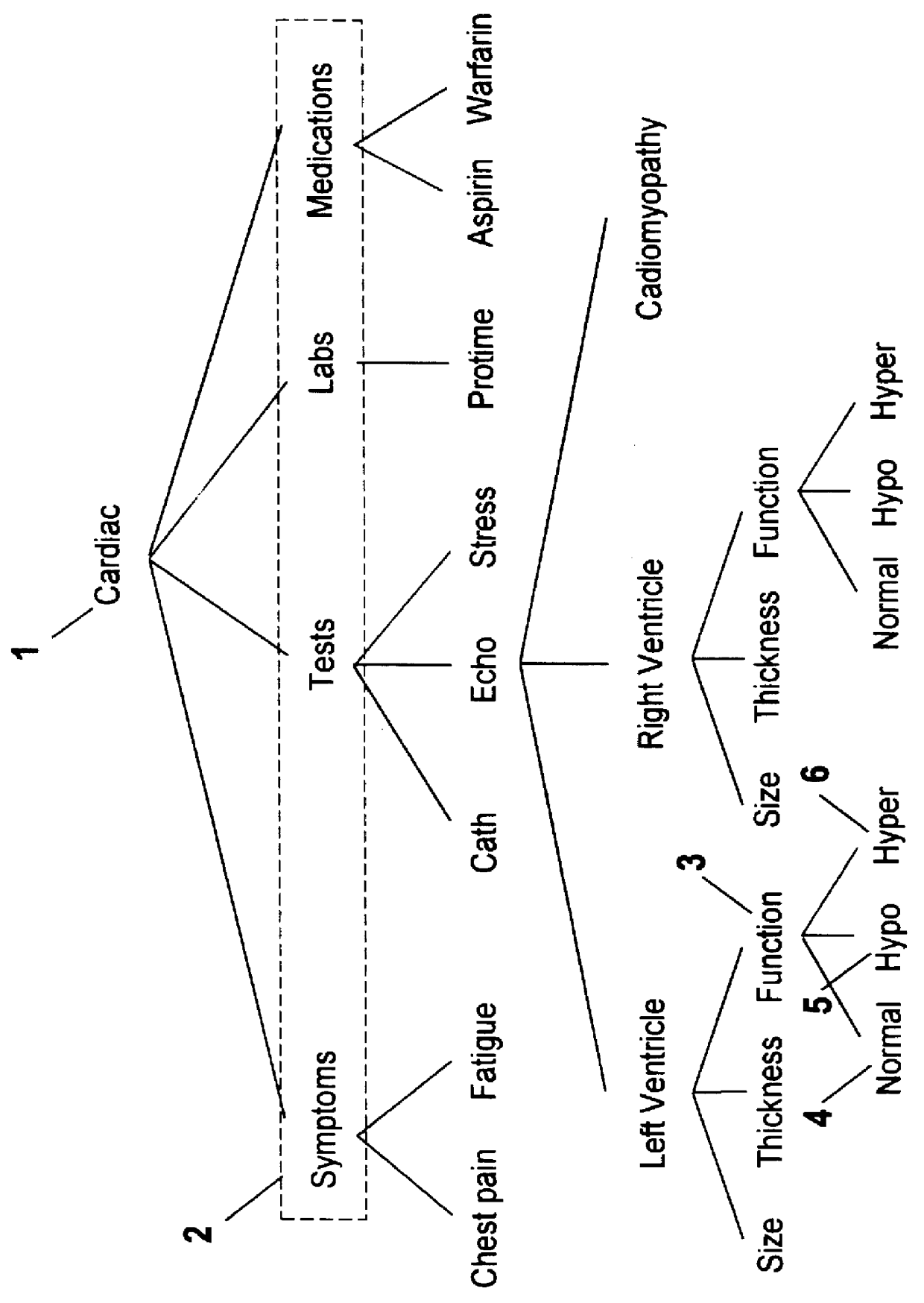
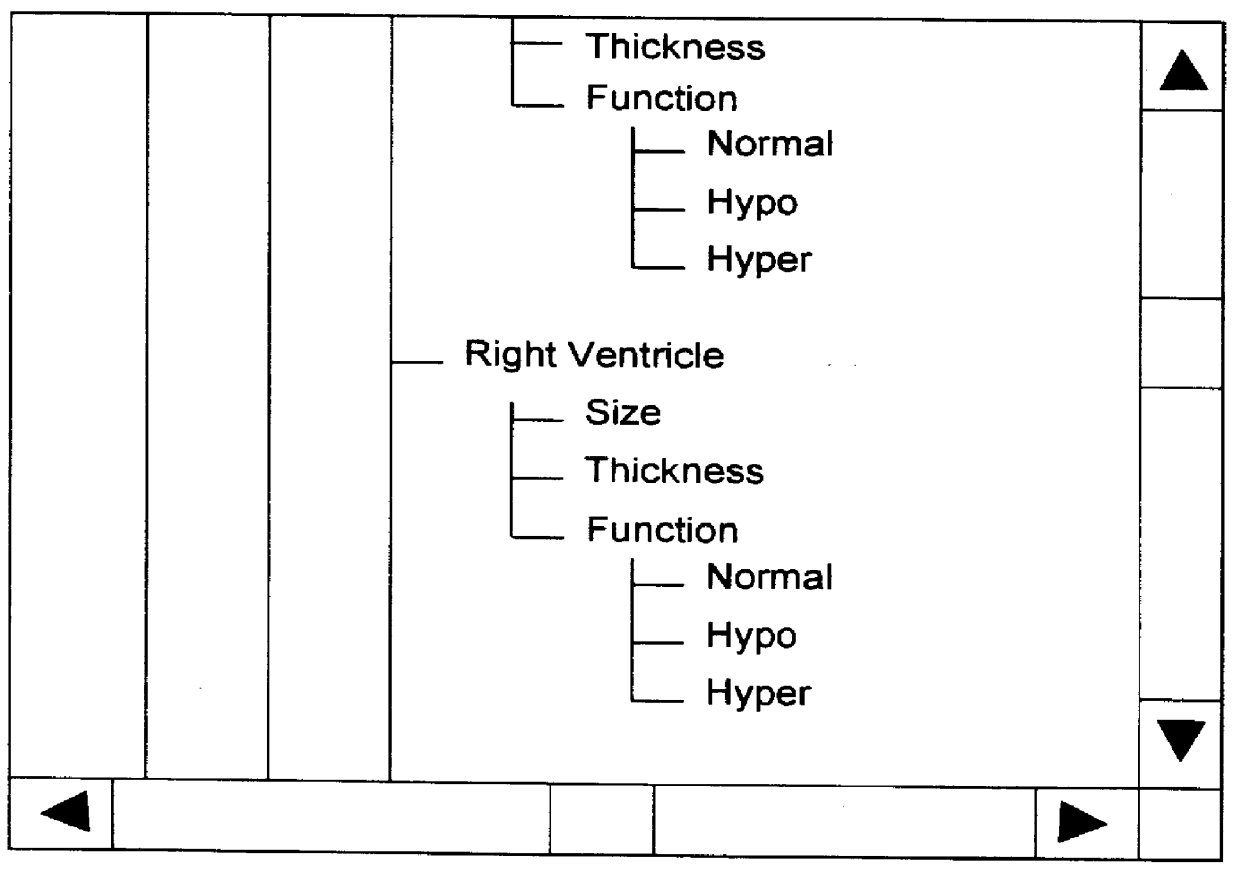
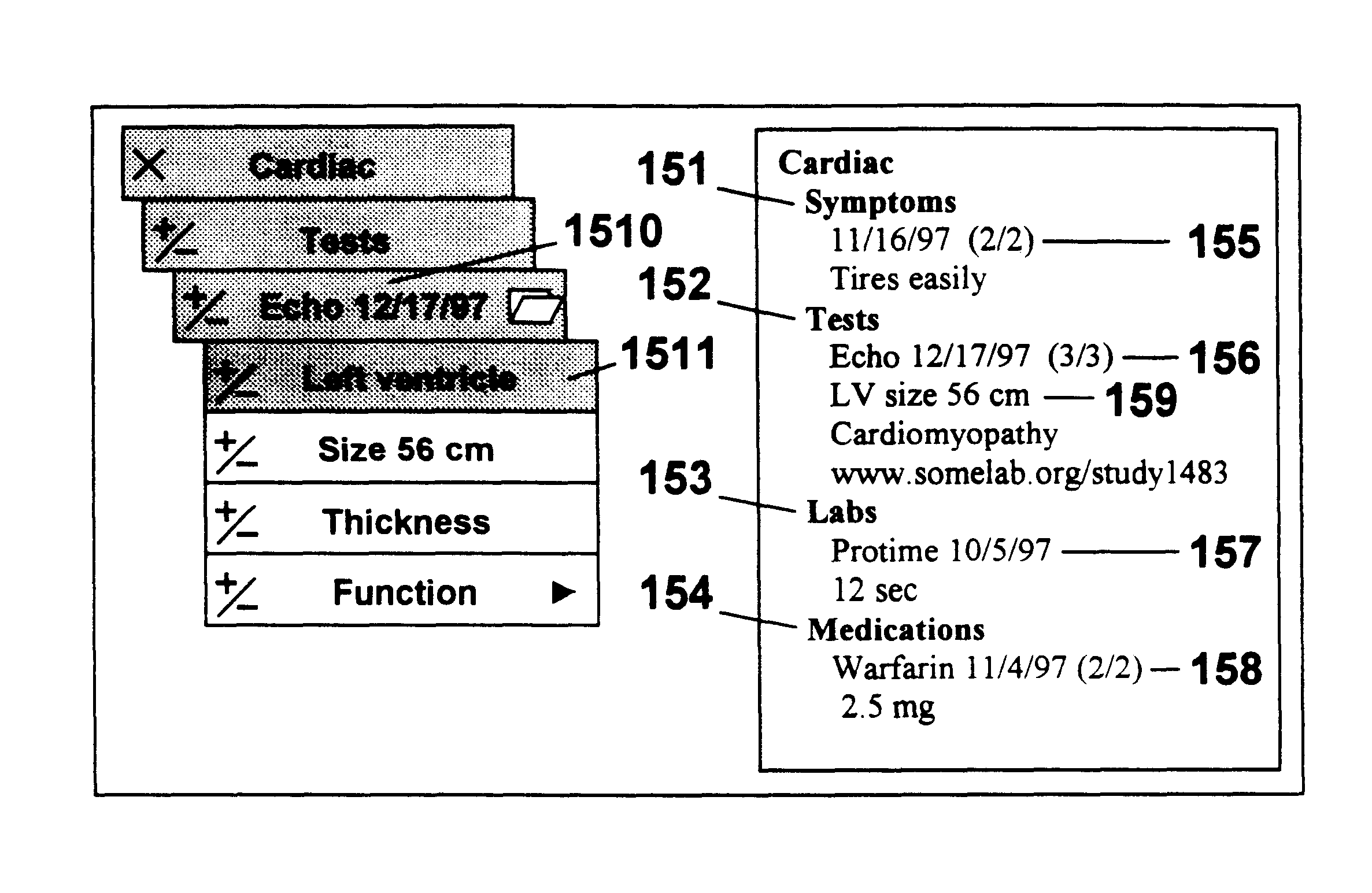
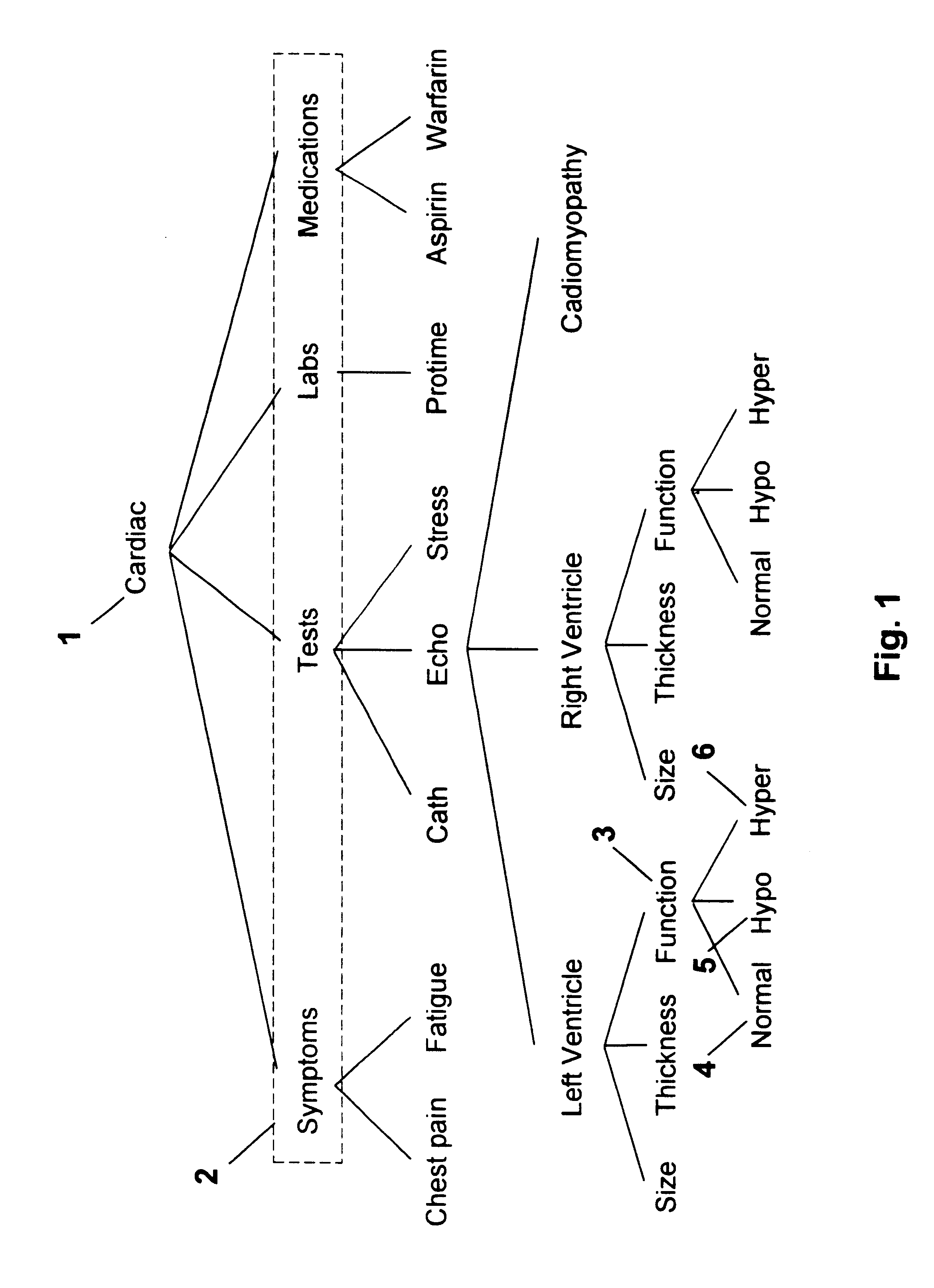
Method and system for navigation and data entry in heirarchically-organized database views
InactiveUS6154750AIncrease entryIncrease updateData processing applicationsOther databases browsing/visualisationDisplay deviceComputer science
A method and system for navigating hierarchical database views that supports the efficient entry, review, and updating of data using a navigation display that is clear and efficient-yet compact in terms of the screen area used. At any point in the navigation process, the navigation display consists of buttons corresponding to the nodes that lie along the path to the last node visited (the set of previously made choices) and the children of this node (the set of current choices). Unselected and unselectable choices are culled and do not clutter the display. The user navigates up and down the hierarchy and enters data by selecting these buttons. An important feature of the invention is support for multiple instances of database subhierarchies within this navigation process and display. In addition, multiple nodes can be composed to form a single database entry, thereby reducing the size and complexity of the hierarchical database views. Finally, database views that are directed acyclic graphs are also supported-including both serial and parallel traversal techniques.
Owner:ASCEND HIT LLC
Network data distribution system and method
ActiveUS20060271617A1GHz frequency transmissionMultiple digital computer combinationsData packPacket loss
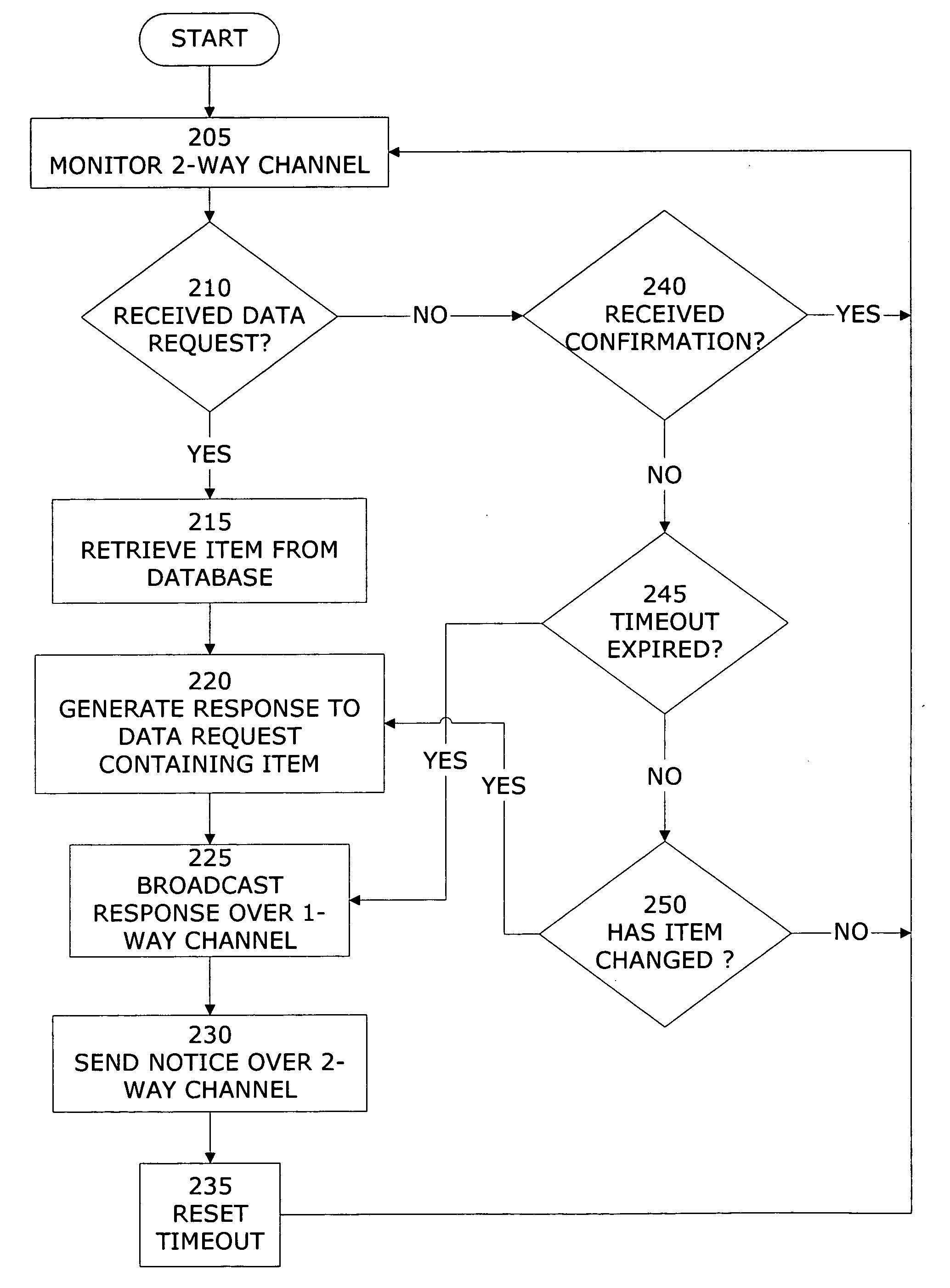
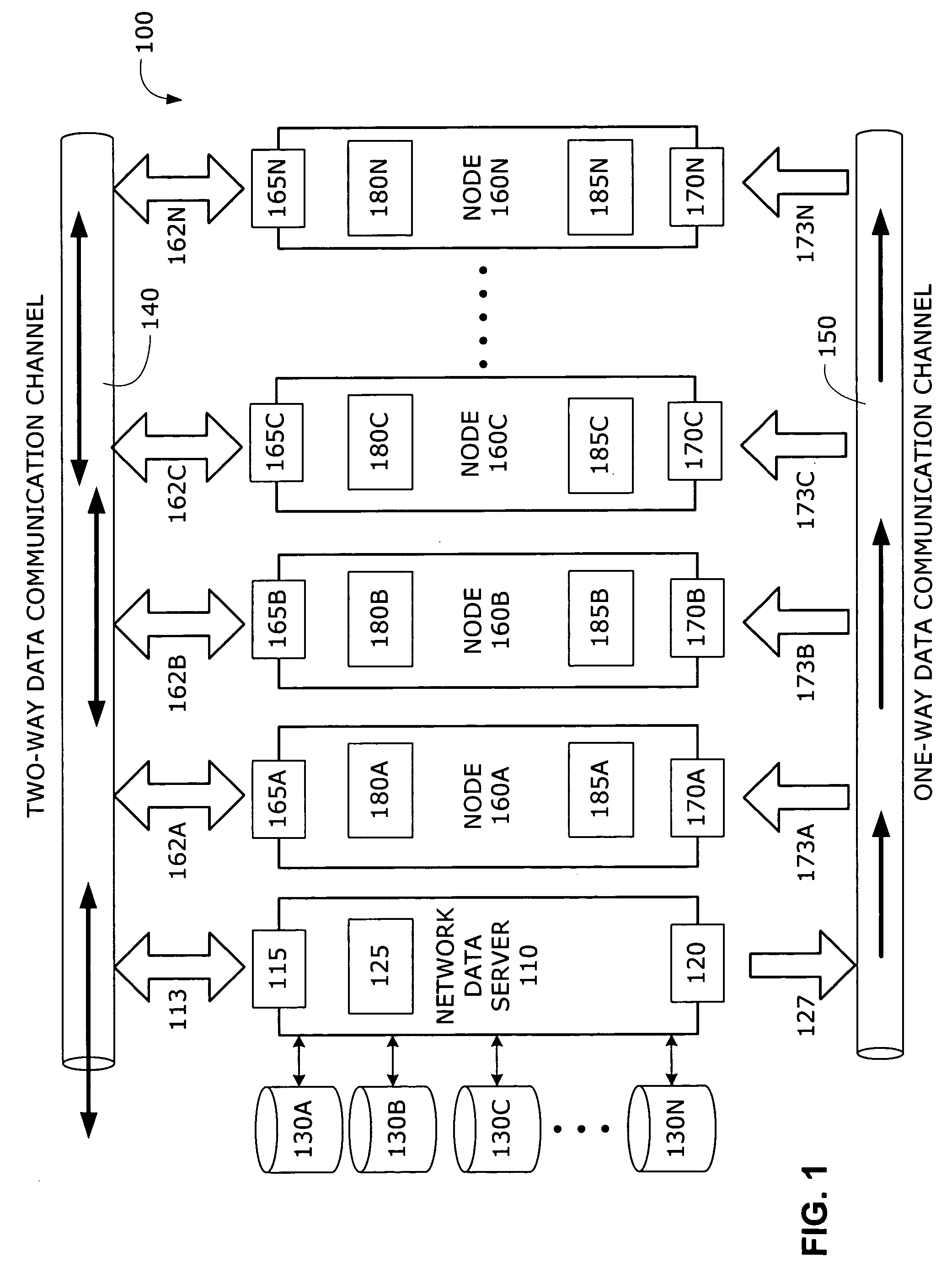
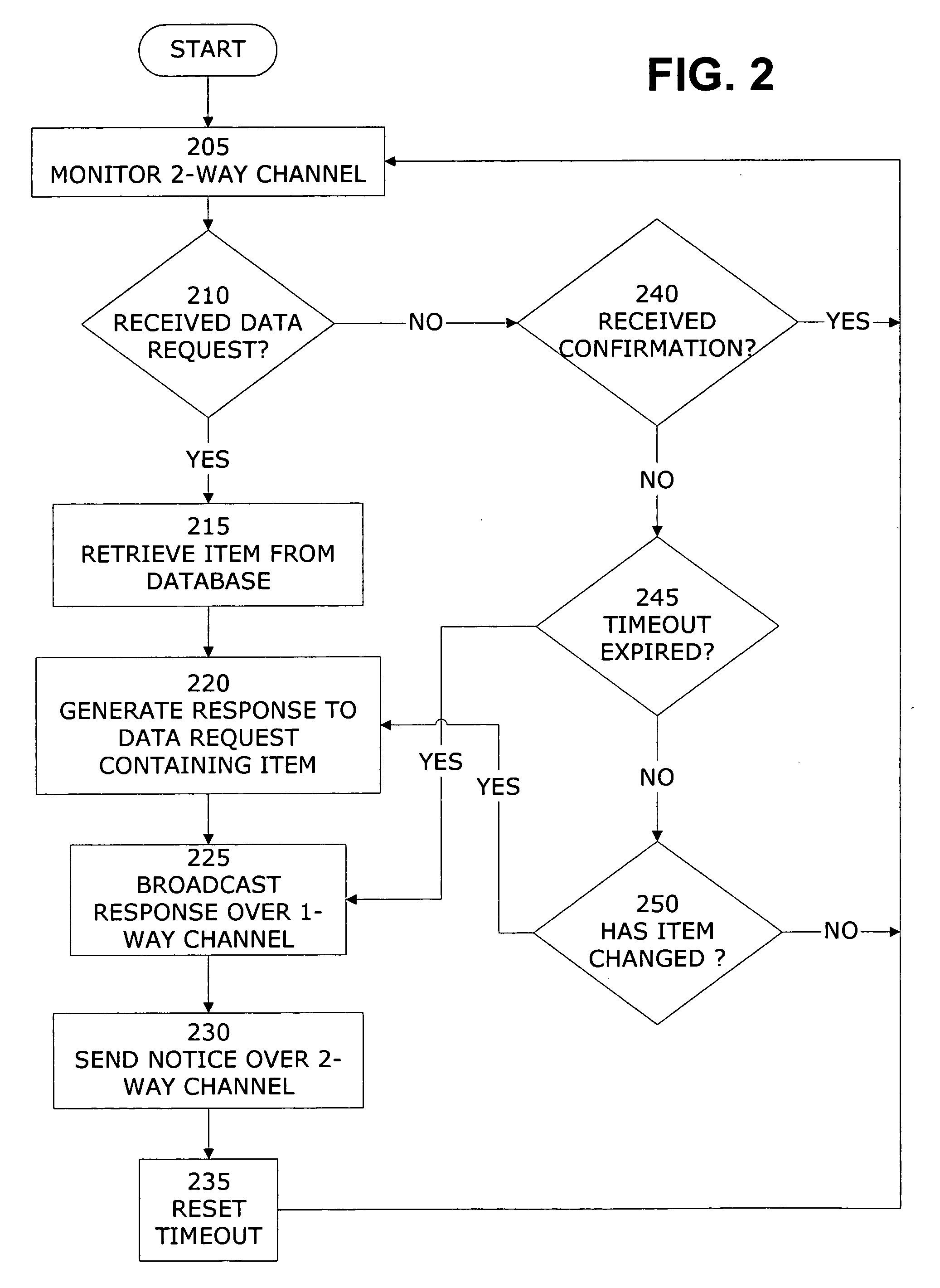
Embodiments of a system and method for distributing network data to multiple nodes in a data communications network is described. Two data communication channels are provided for each node in the network. While one of the communication channels carries routing and flow control protocol messages, as well as data, in both directions between network nodes, the other communication channel is configured to transmit data traffic—and only data traffic—in a single direction from the network data server toward all of the other nodes in the network. By using 100% of the available bandwidth for data traffic only, the speed at which data may be distributed throughout the network is maximized and the performance degradation caused by the congestion, collisions or packet loss that typically occurs in two-way data communication channels is avoided.
Owner:VERIZON PATENT & LICENSING INC
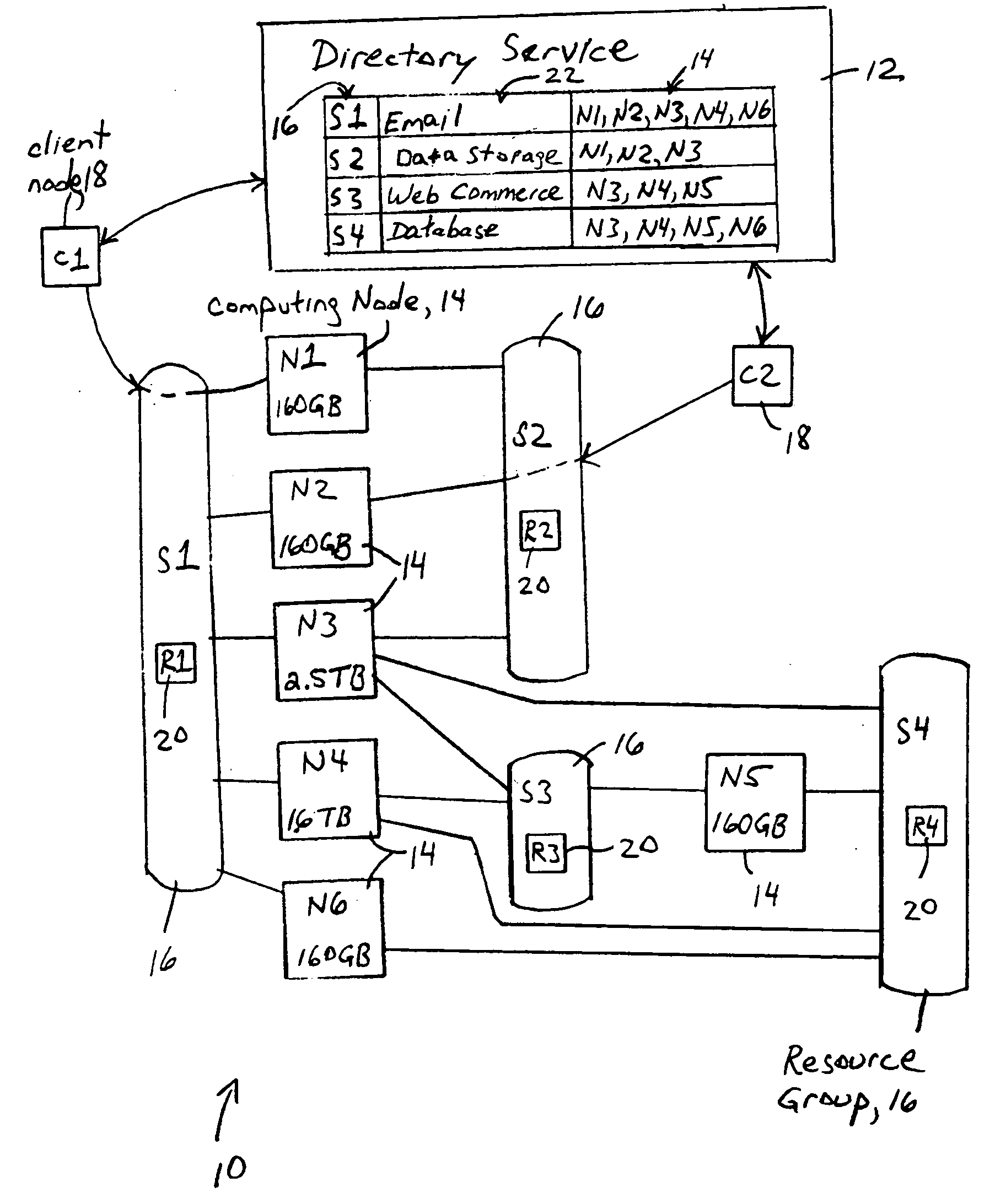
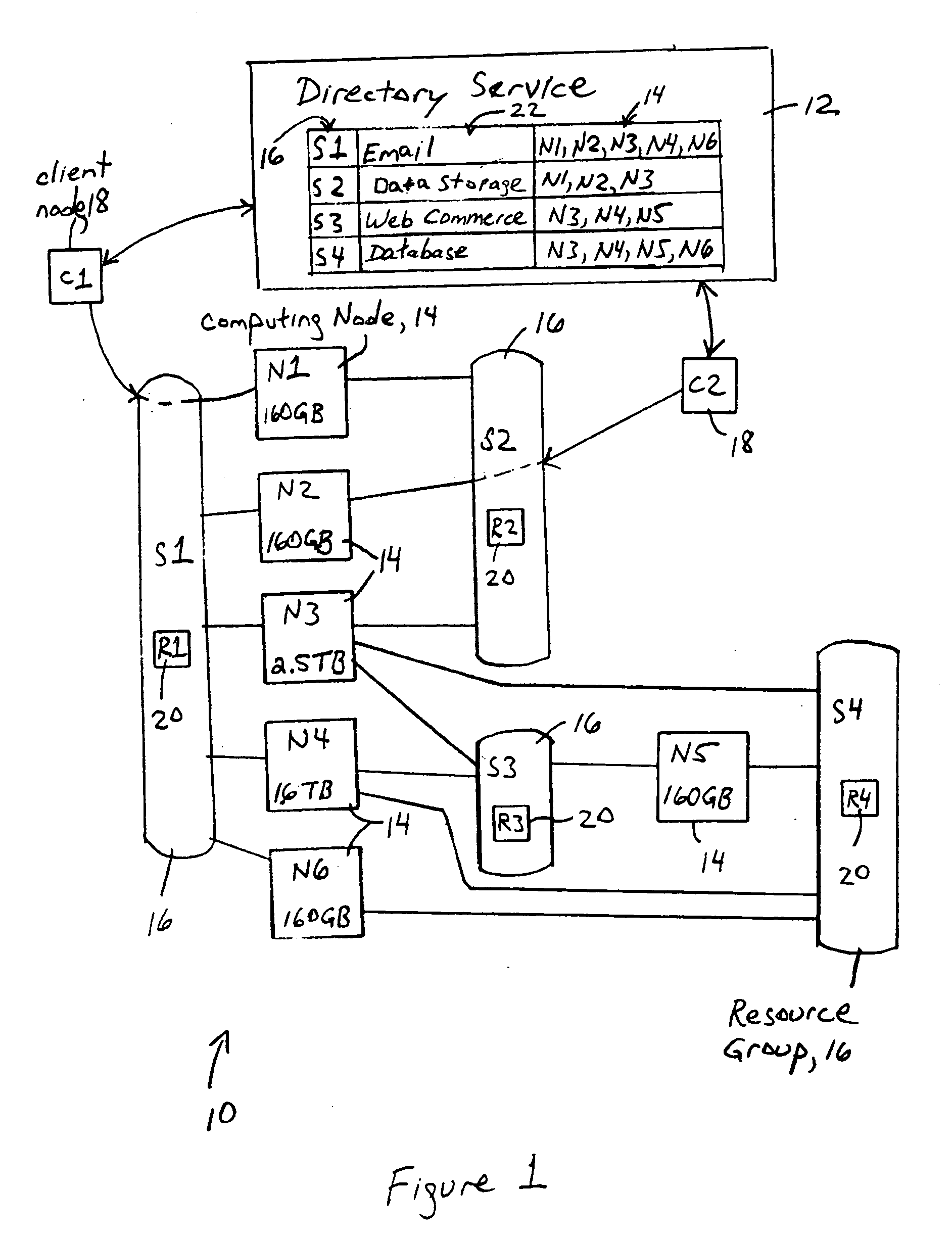
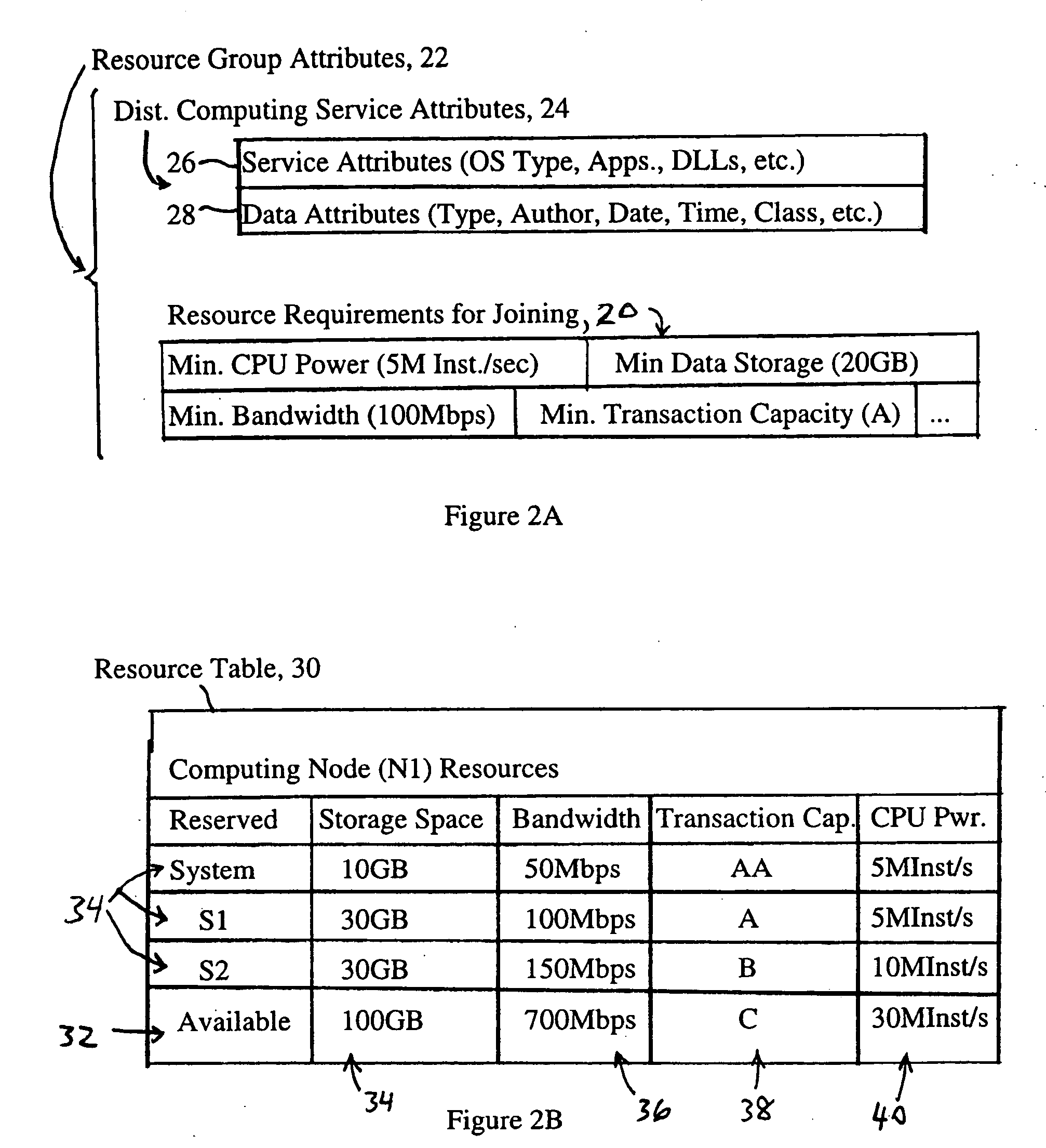
Distributed client services based on execution of service attributes and data attributes by multiple nodes in resource groups
InactiveUS20060179143A1Reduce necessityMultiprogramming arrangementsMultiple digital computer combinationsResource basedClient-side
A network provides distributed client services based on participation in respective resource groups by computing nodes, each resource group including a corresponding resource requirement for any computing node that joins the corresponding resource group for execution of the corresponding distributed client service. Each computing node, in response to determining its corresponding available node capacity, is configured for selectively creating and joining at least one new resource group for execution of a corresponding distributed client service having a corresponding resource requirement, and / or selectively joining at least one of the available resource groups, based on the corresponding available node capacity satisfying the corresponding resource requirement. Each distributed client service also includes service attributes that define parameters for execution of the distributed client service, and data attributes that define the attributes required for data to be used in the distributed client service.
Owner:CISCO TECH INC
Method, system, and program for merging log entries from multiple recovery log files
InactiveUS7076508B2Digital data information retrievalData processing applicationsDatabaseMultiple node
Provided are a method, system, and program for merging independent log entries in a multiple node shared nothing DBMS. Initially, log entries from multiple log entries are combined to form a single log entry sequence. Local transactions are generated from the single log entry sequence and stored in a local transactions structure. In particular, log entries with the same local transaction identifier form a local transaction. Then, local transactions having the same global identifier are merged to form global transactions.
Owner:INT BUSINESS MASCH CORP
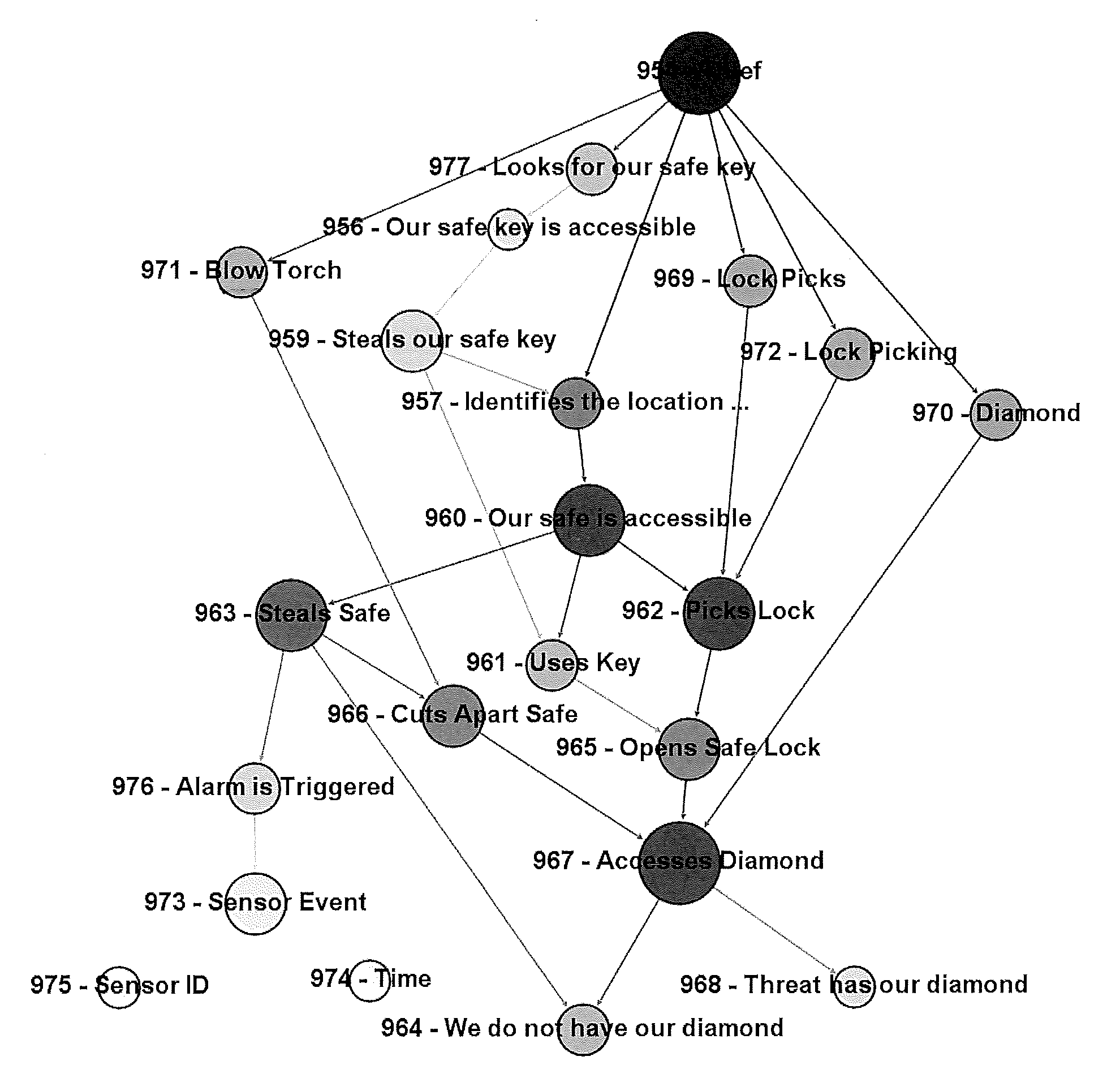
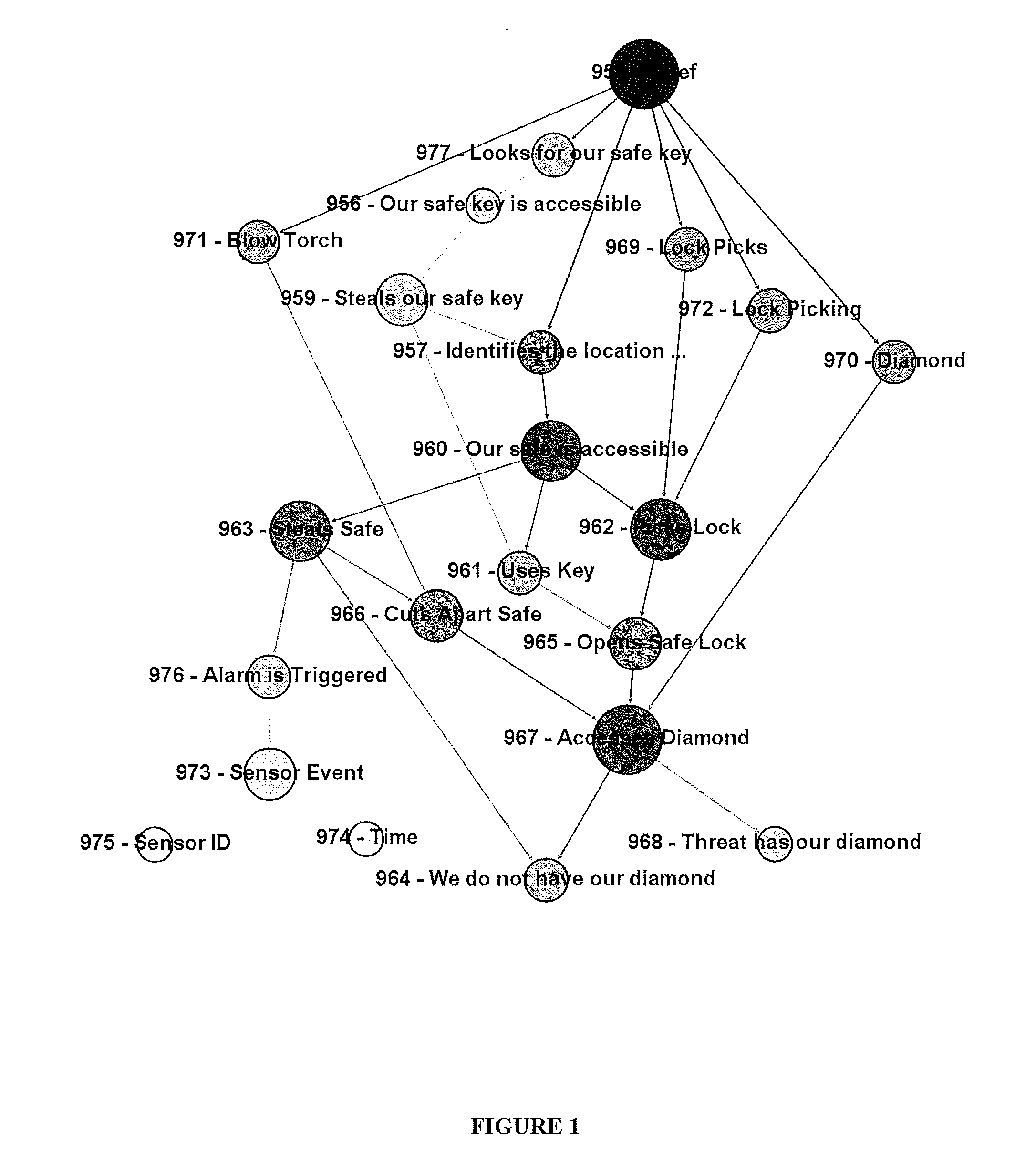
System and Method for Cyber Security Analysis and Human Behavior Prediction
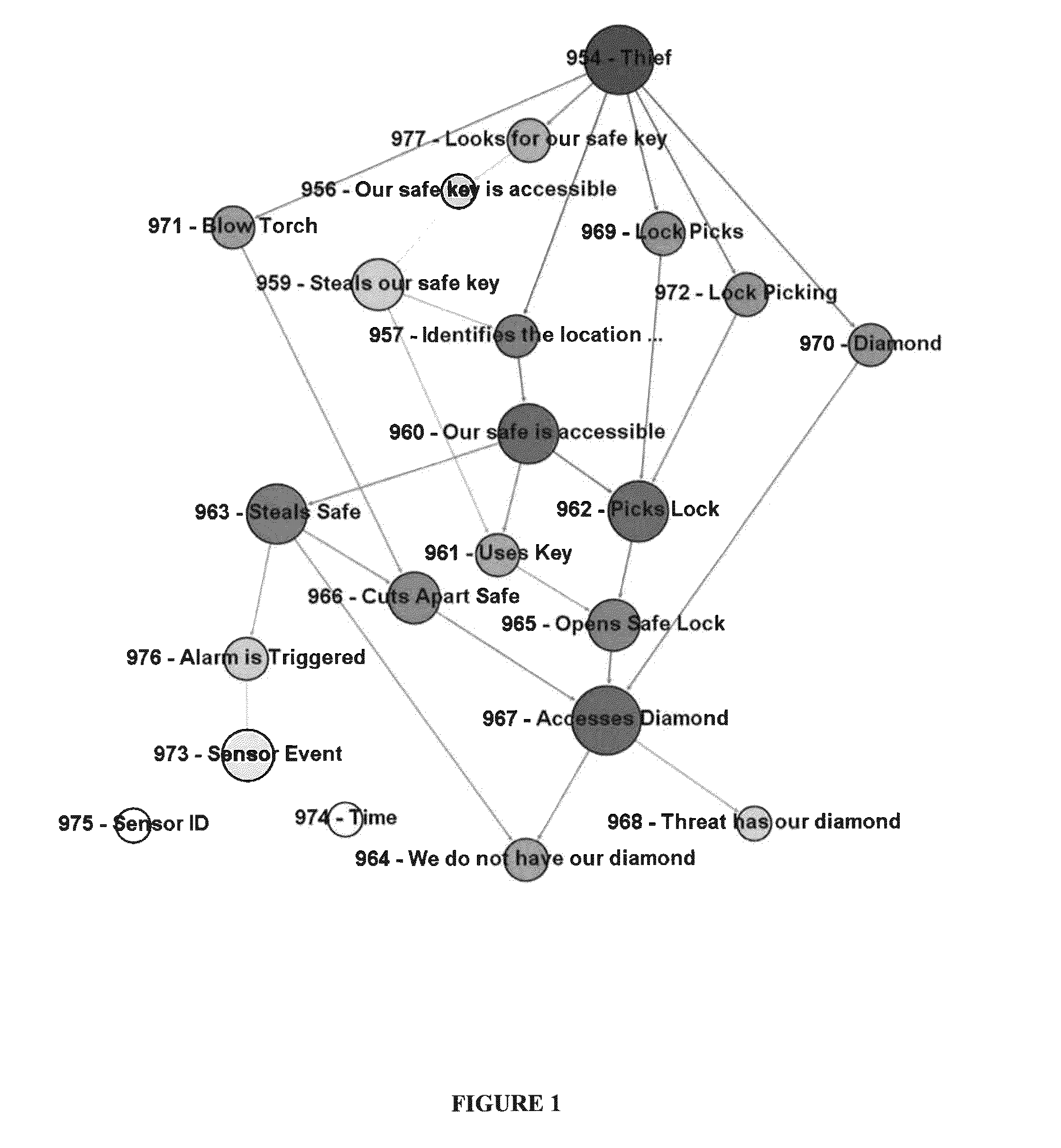
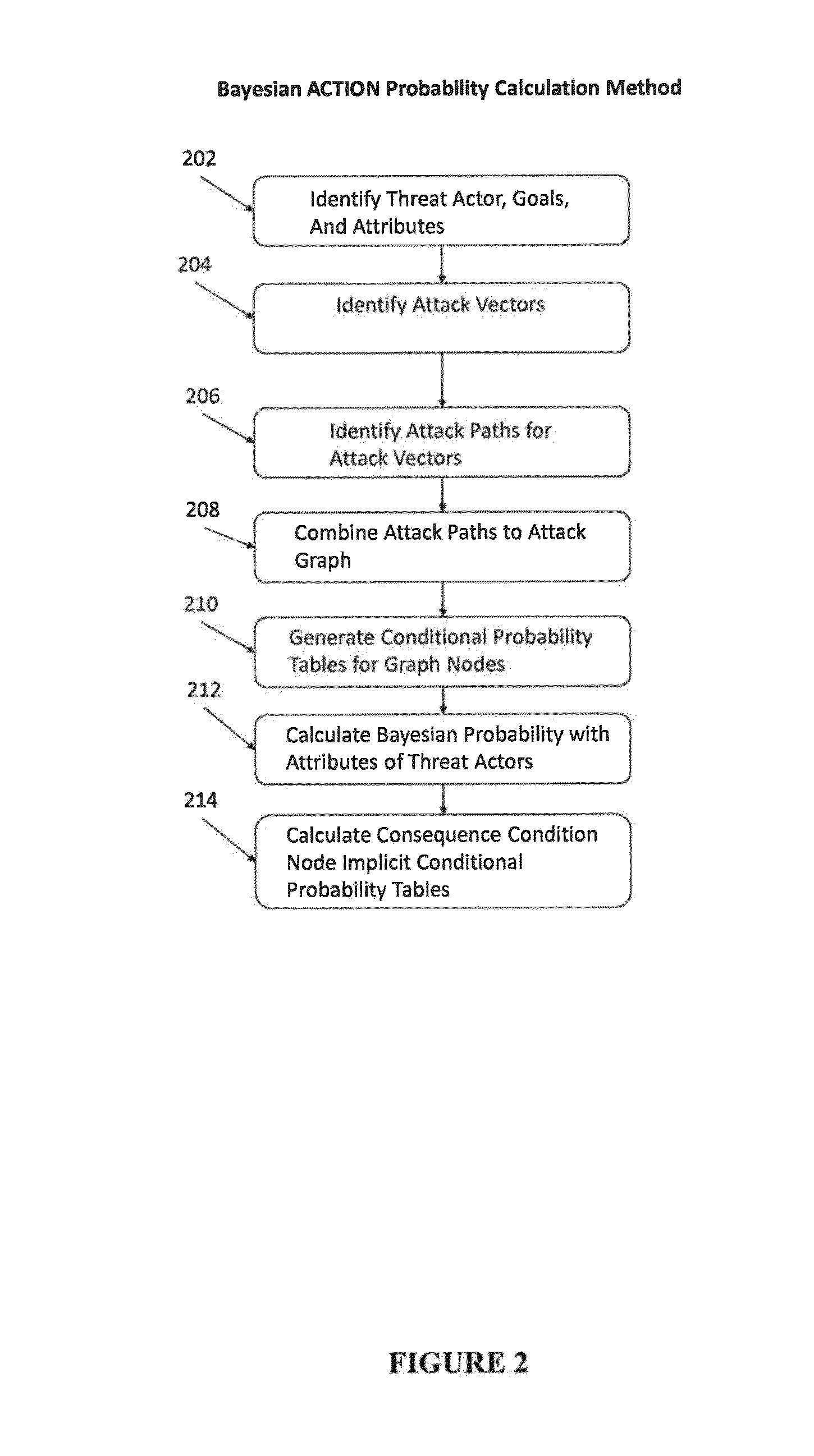
ActiveUS20160205122A1Simple conditionsMemory loss protectionError detection/correctionHuman behaviorAttack graph
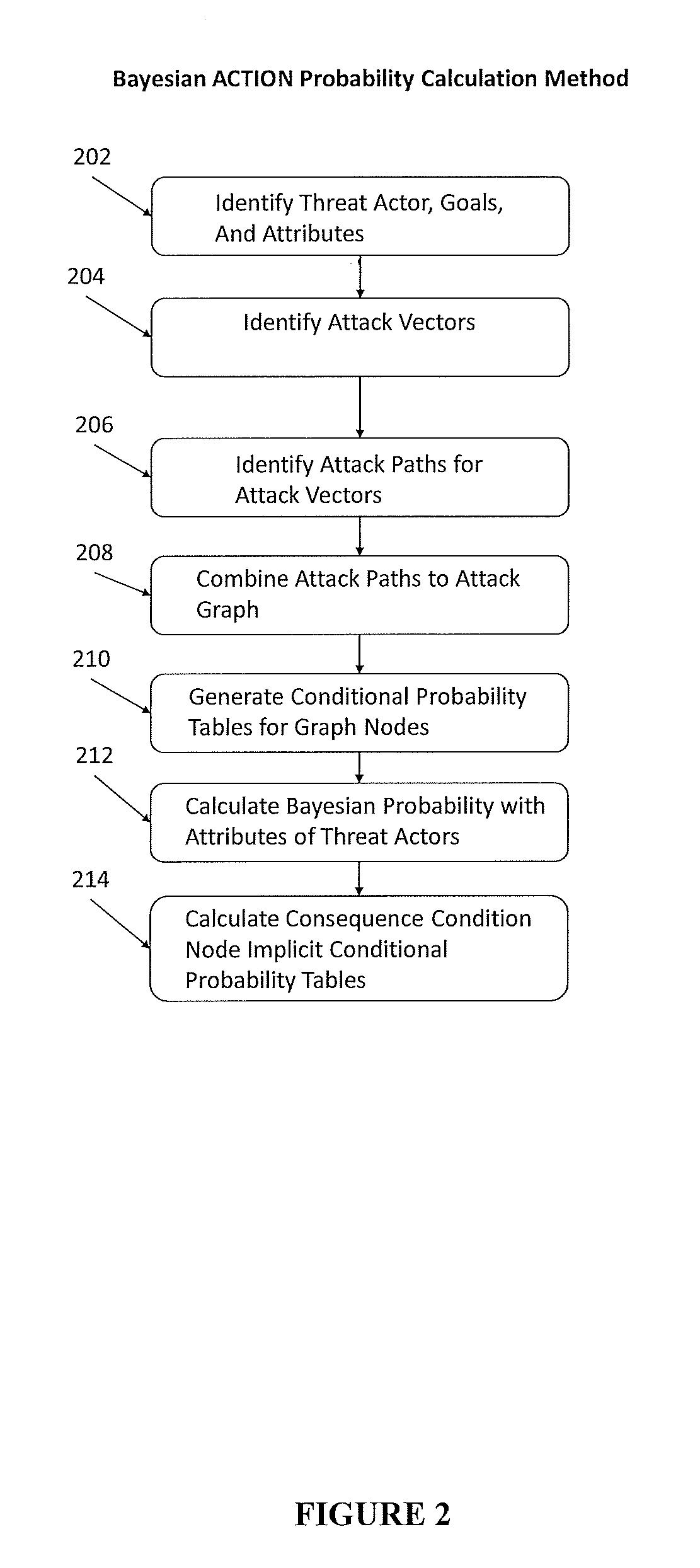
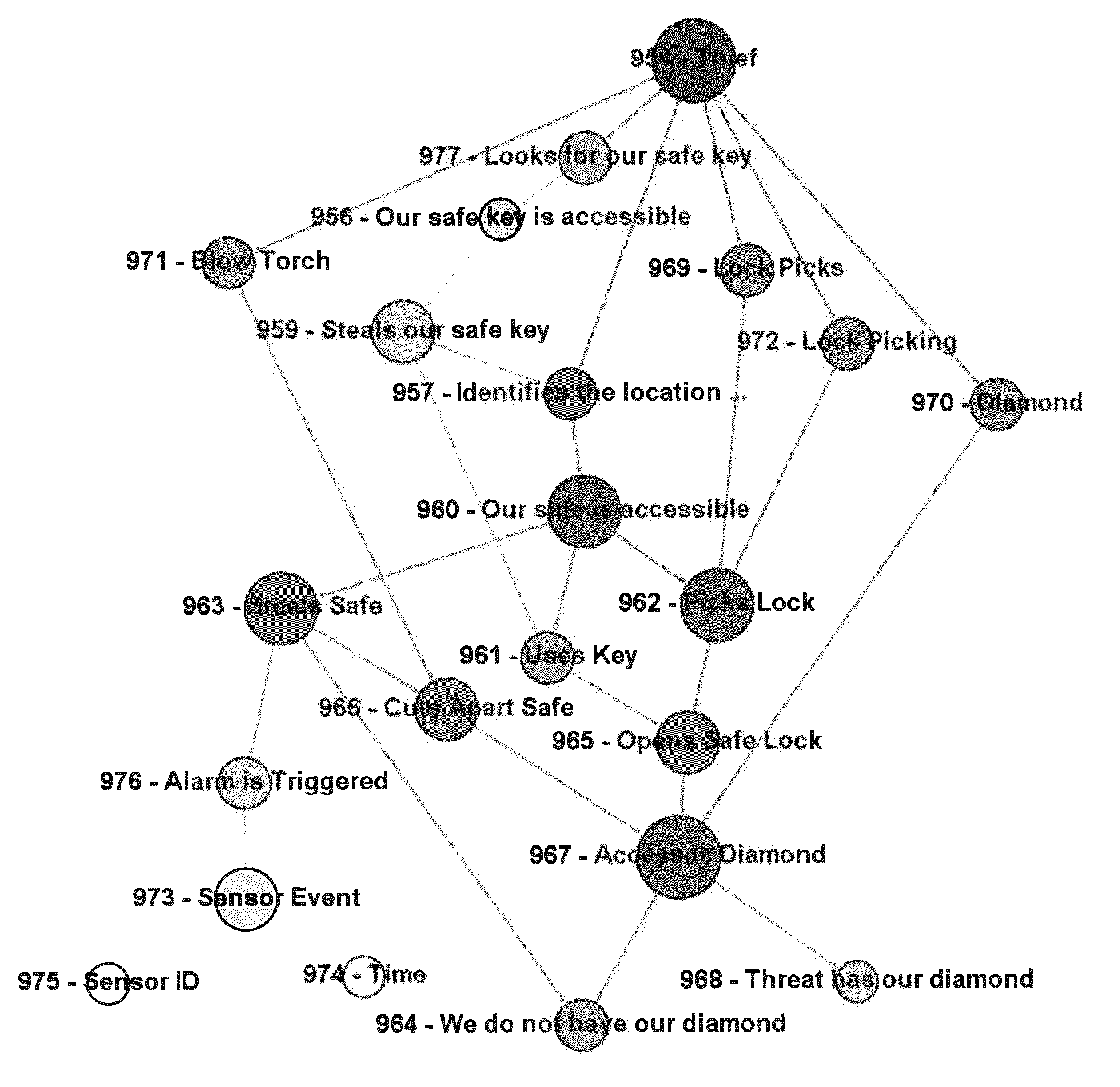
An improved method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the ease of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Next, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions. Finally, attacks are detected with physical sensors on the network, that predict the events and conditions. When an attack is detected, security alerts are generated in response to the attacks.
Owner:BASSETT GABRIEL
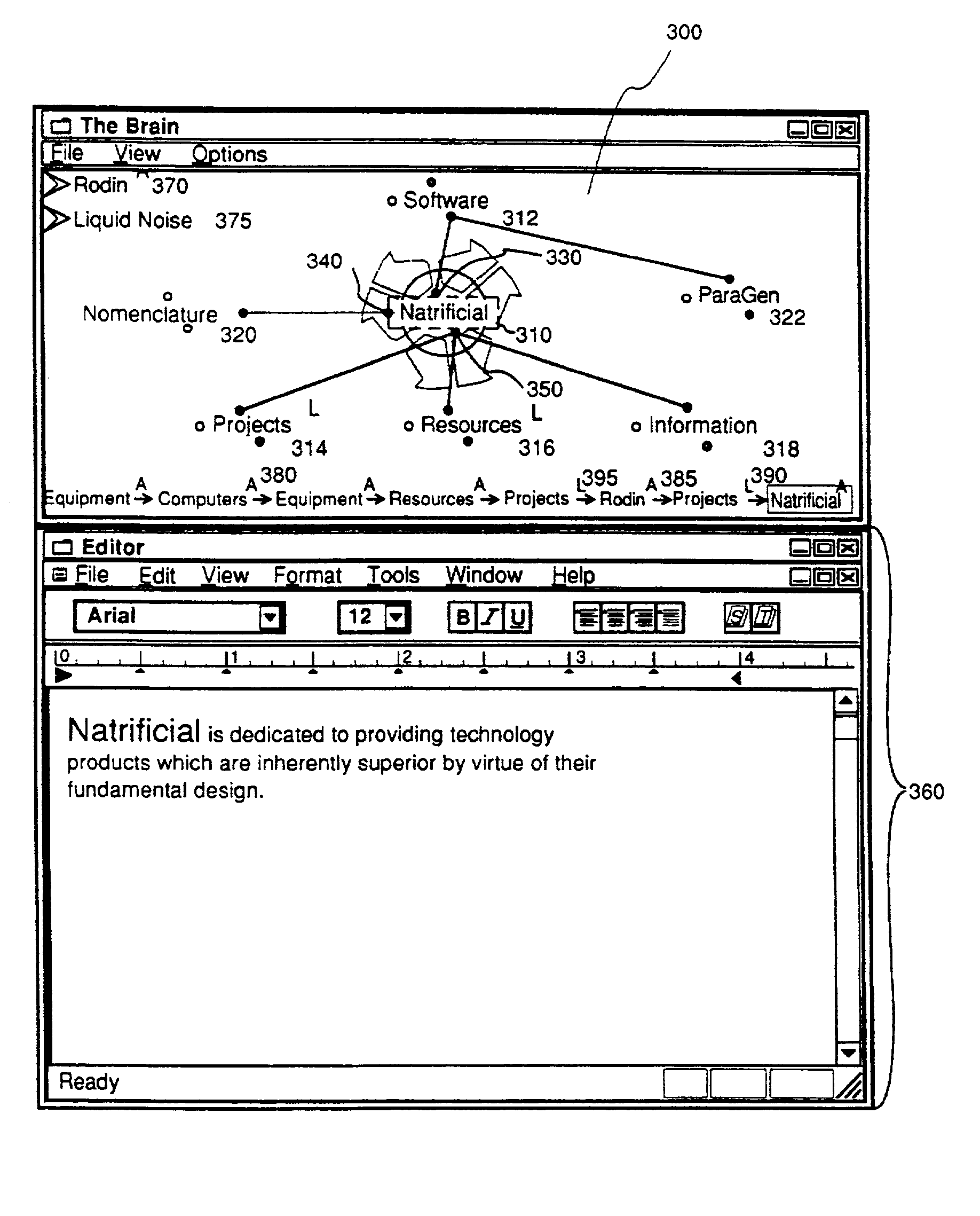
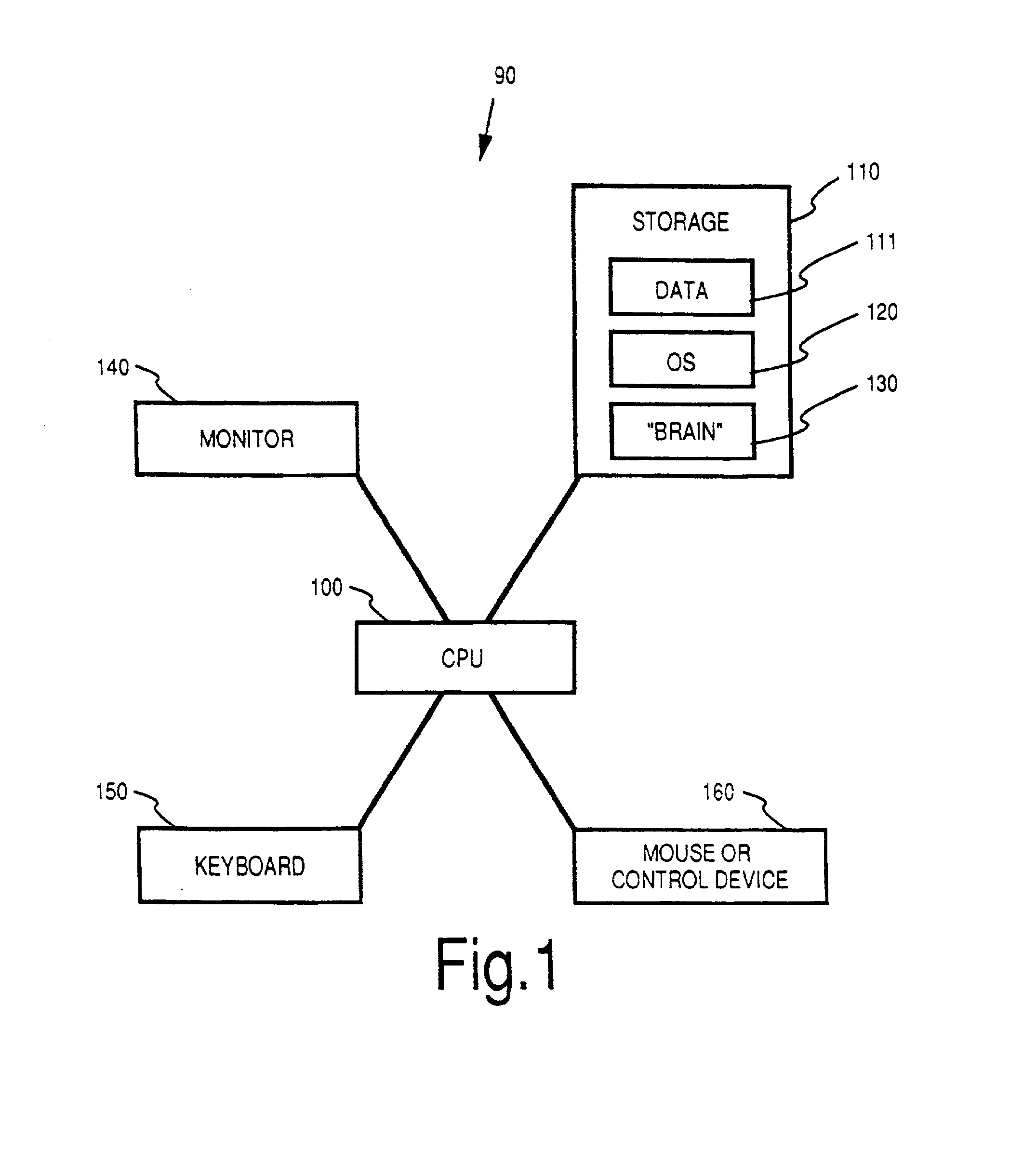
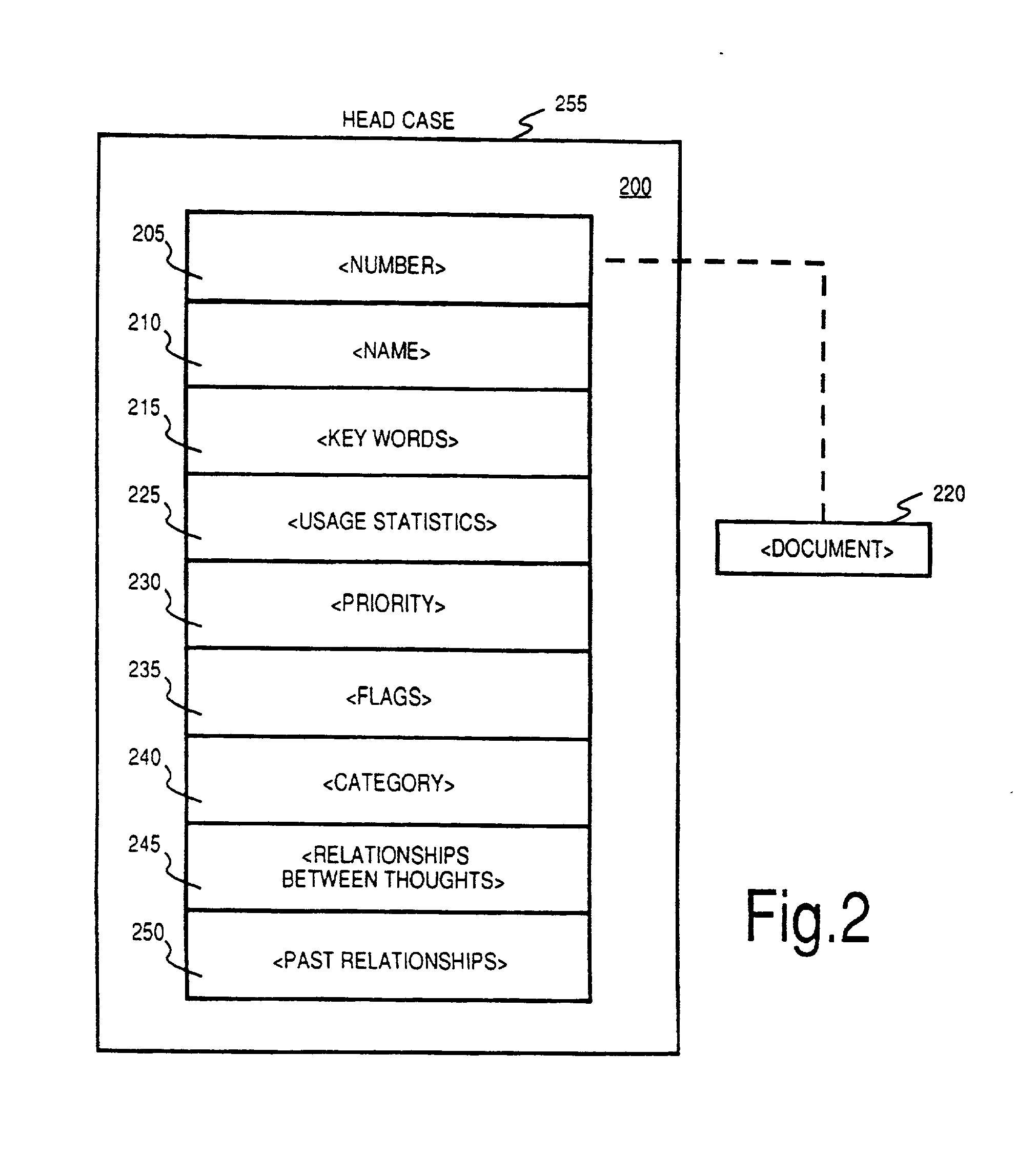
Method and apparatus for sharing many thought databases among many clients
InactiveUS7076736B2Increase flexibilityReduce loadData processing applicationsDatabase distribution/replicationDocumentation procedureDigital storage
Owner:THEBRAIN TECH LP
Method and system for detecting distributed internet crime
InactiveUS8560413B1Investigated betterWide viewingFinanceComputer security arrangementsDomain nameGeotargeting
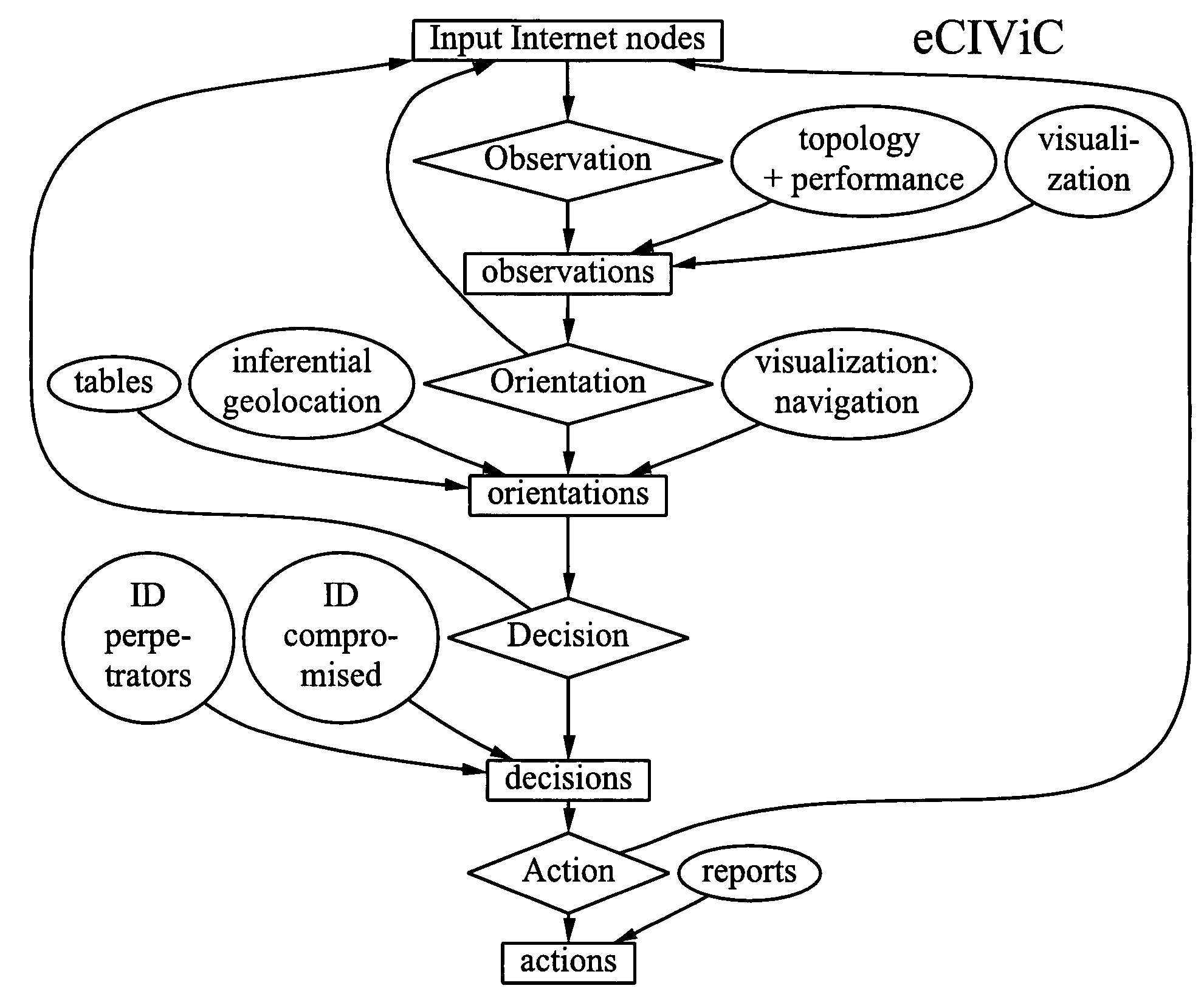
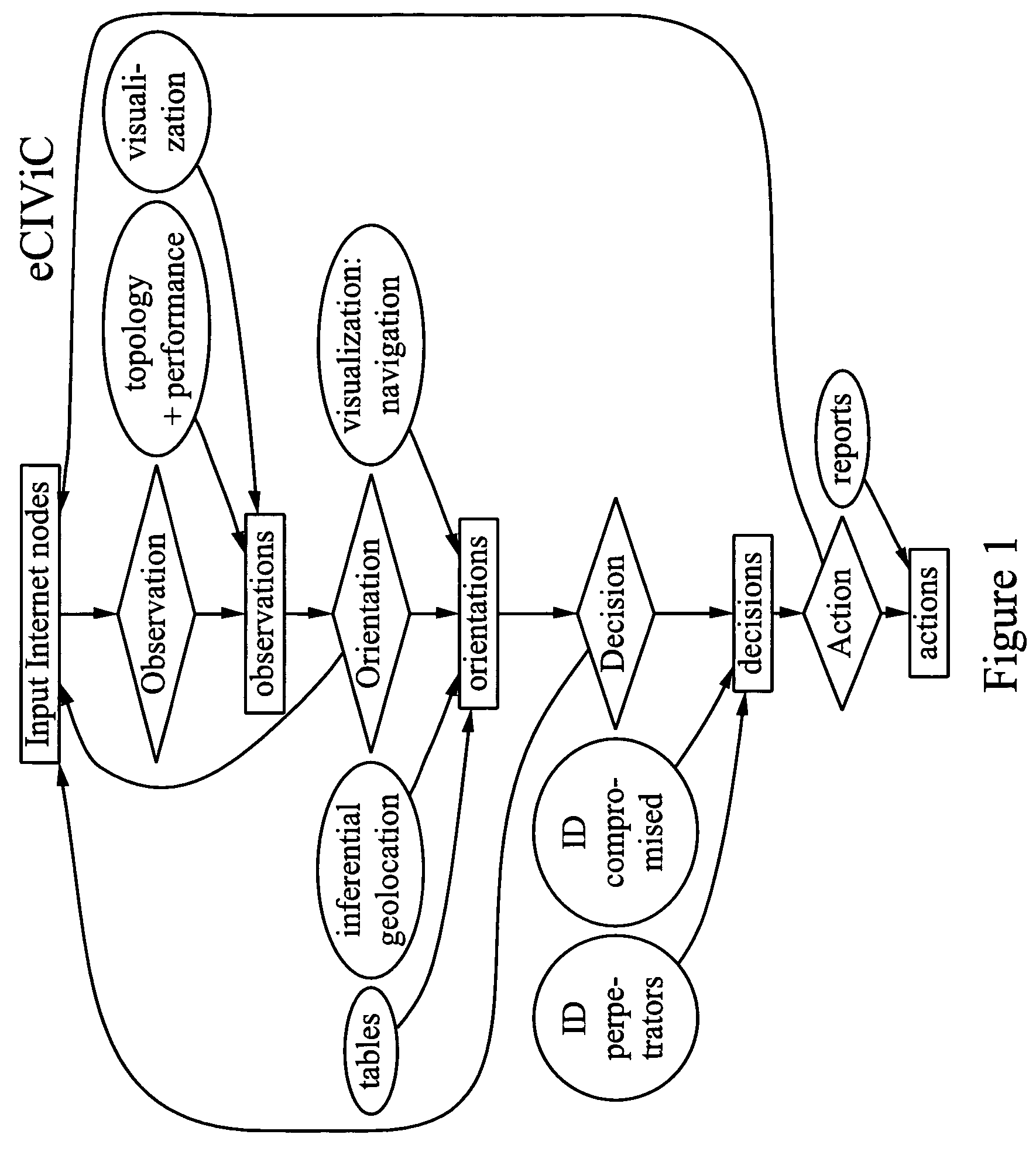
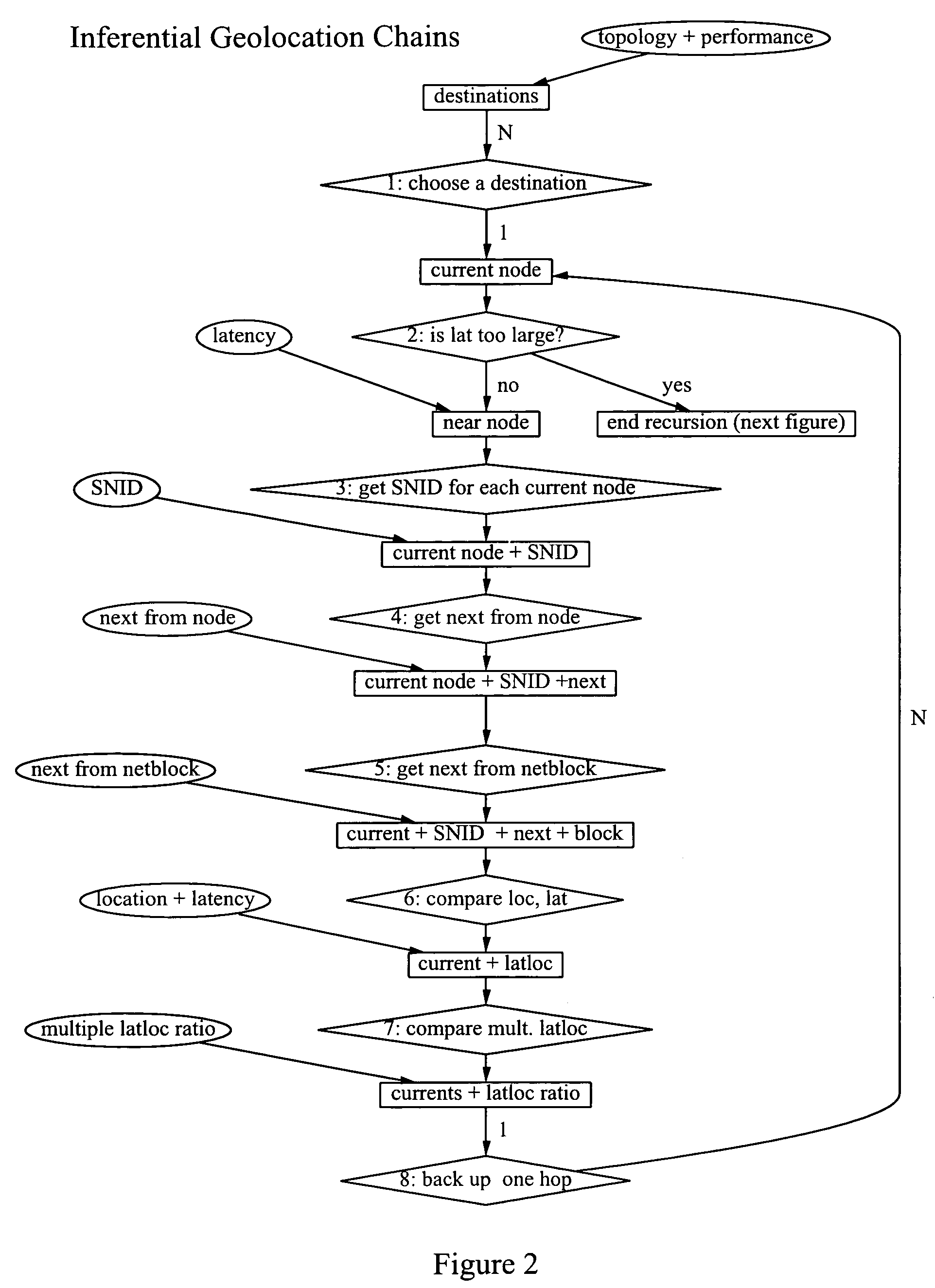
The invention broadly comprises a method and service of visualization of Internet nodes involved in distributed electronic crime in order to see patterns of actionable intelligence, such as multiple phishing nodes hosted at the same hosting center, or domain names registered in one country that are actually in another country or nodes related by one or more aspects, such as specific criminal attack campaign, target or technical weakness exploited to ease commandeering of the node. The invention involves collecting topological and latency data including changes over time and using the data to determine probable topological and geographical locations of single or multiple nodes, as well as inferential geolocation.
Owner:QUARTERMAN JOHN S +2
System and method for cyber security analysis and human behavior prediction
ActiveUS9292695B1Attacked easilyError detection/correctionPlatform integrity maintainanceHuman behaviorAttack graph
A method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the case of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Finally, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions.
Owner:BASSETT GABRIEL
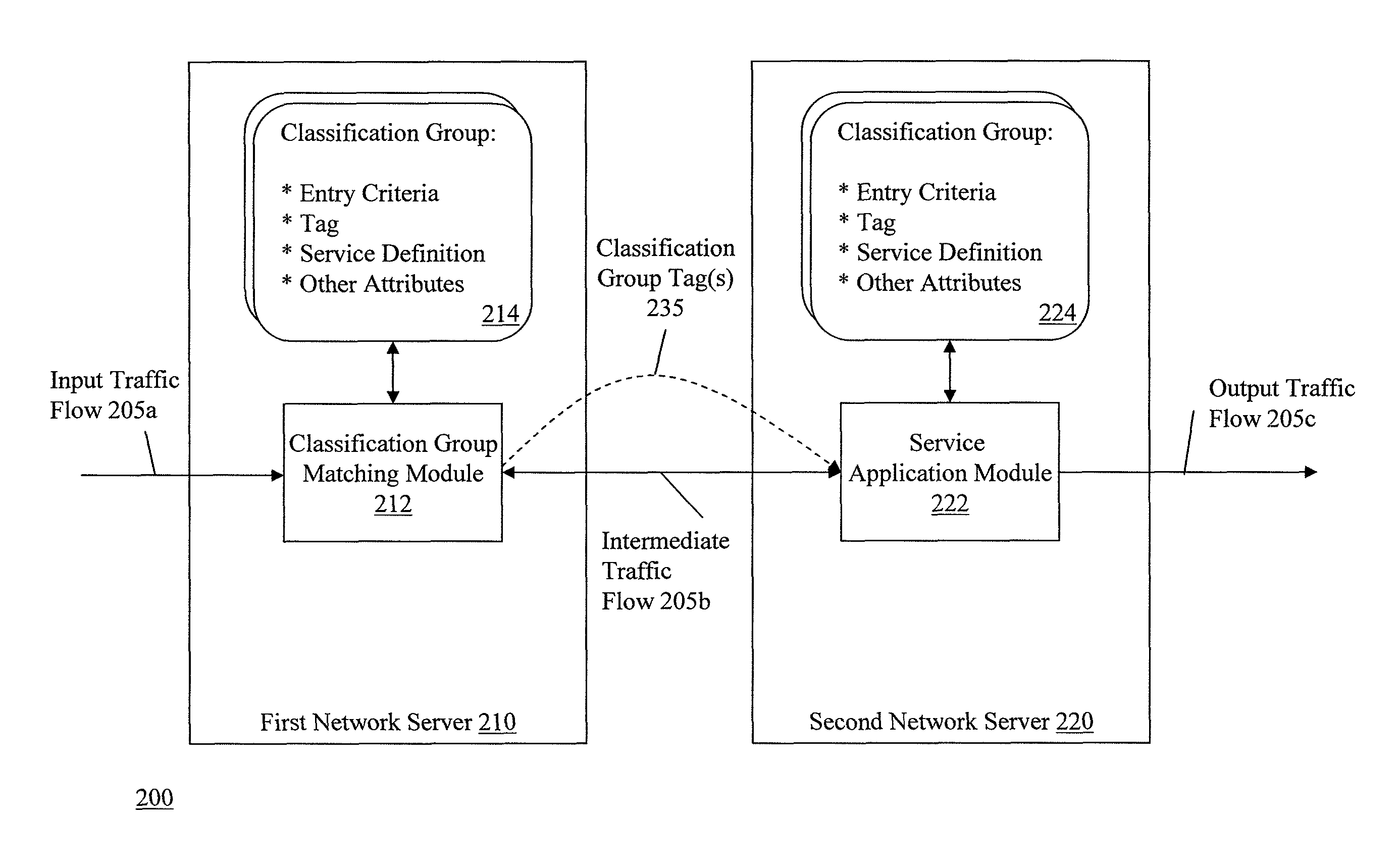
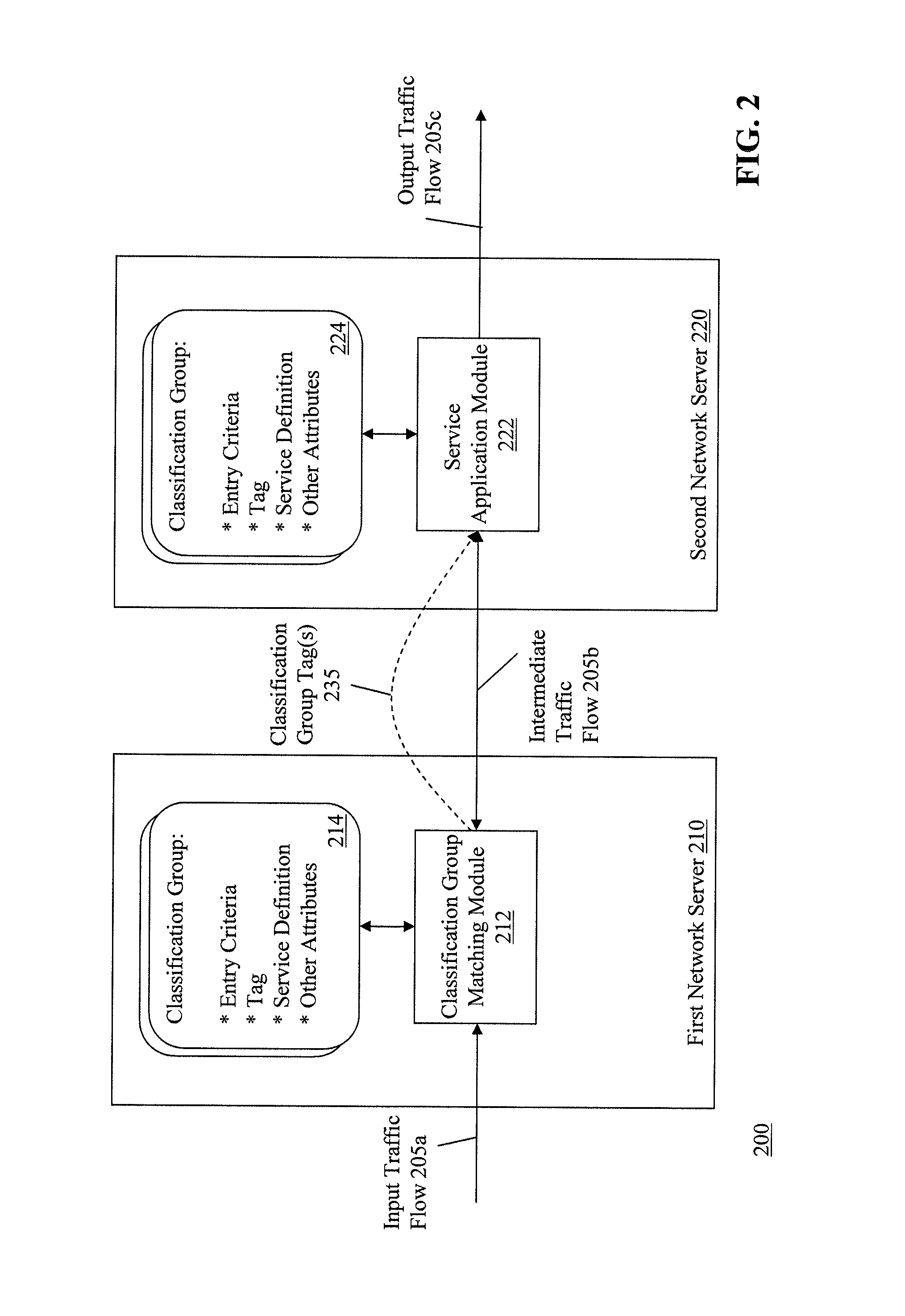
Dynamic classification and grouping of network traffic for service application across multiple nodes
ActiveUS8352630B2Data switching by path configurationMultiple digital computer combinationsNODALTraffic capacity
Methods and apparatuses, including computer program products, are described for applying service based on classification and grouping of traffic flows. The method includes receiving a traffic flow, and matching the traffic flow to classification groups. The matching includes determining a first event associated with the traffic flow, comparing attributes of the first event with entry criteria of the classification groups, and assigning the first event to one or more classification groups where the first event meets the entry criteria of the one or more classification groups. The method includes identifying one or more service definitions for the traffic flow based on the classification groups assigned to the traffic flow, reconciling the one or more service definitions for the traffic flow, and providing a service to the traffic flow based on the reconciled service definitions.
Owner:RIBBON COMM OPERATING CO INC
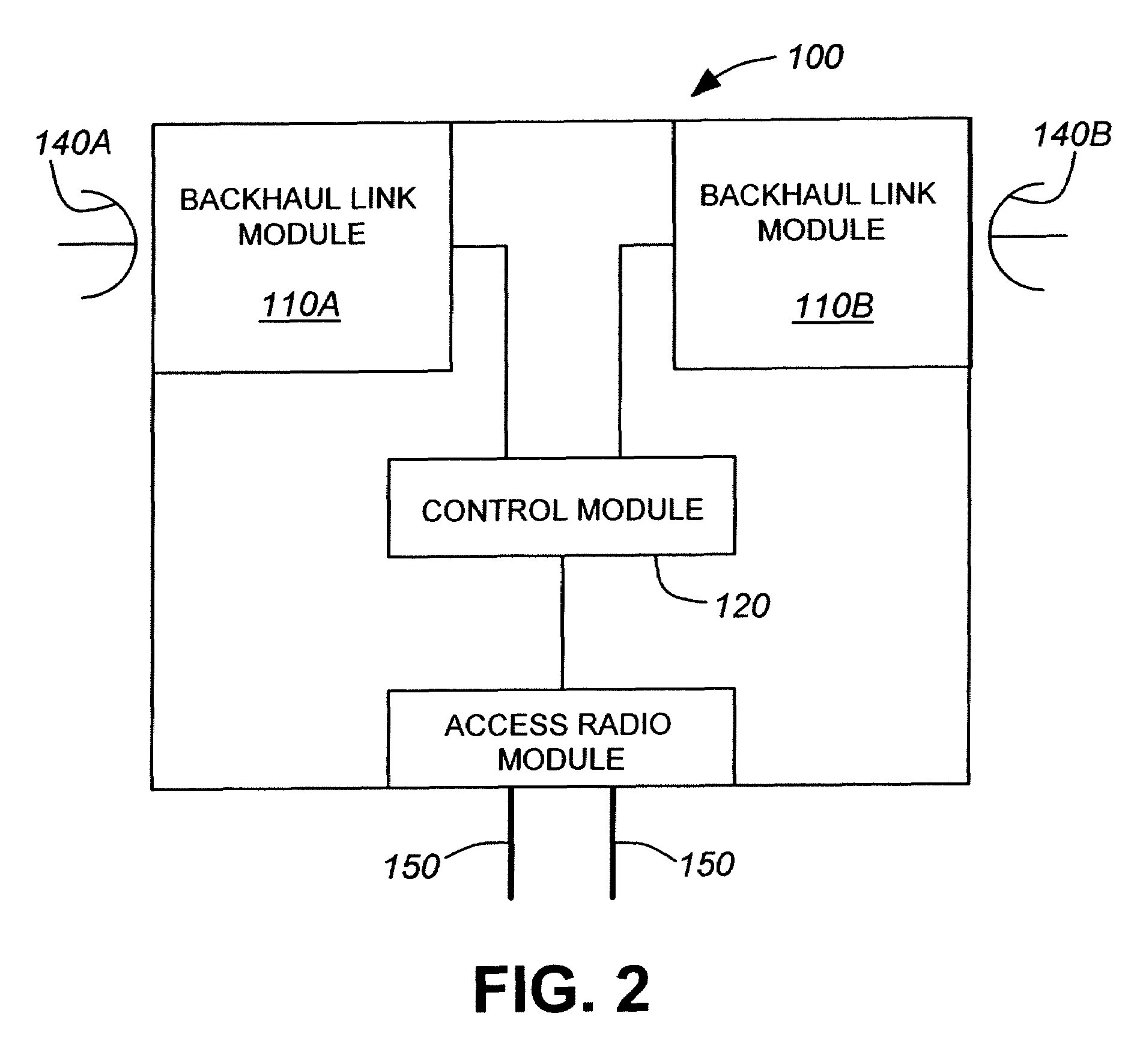
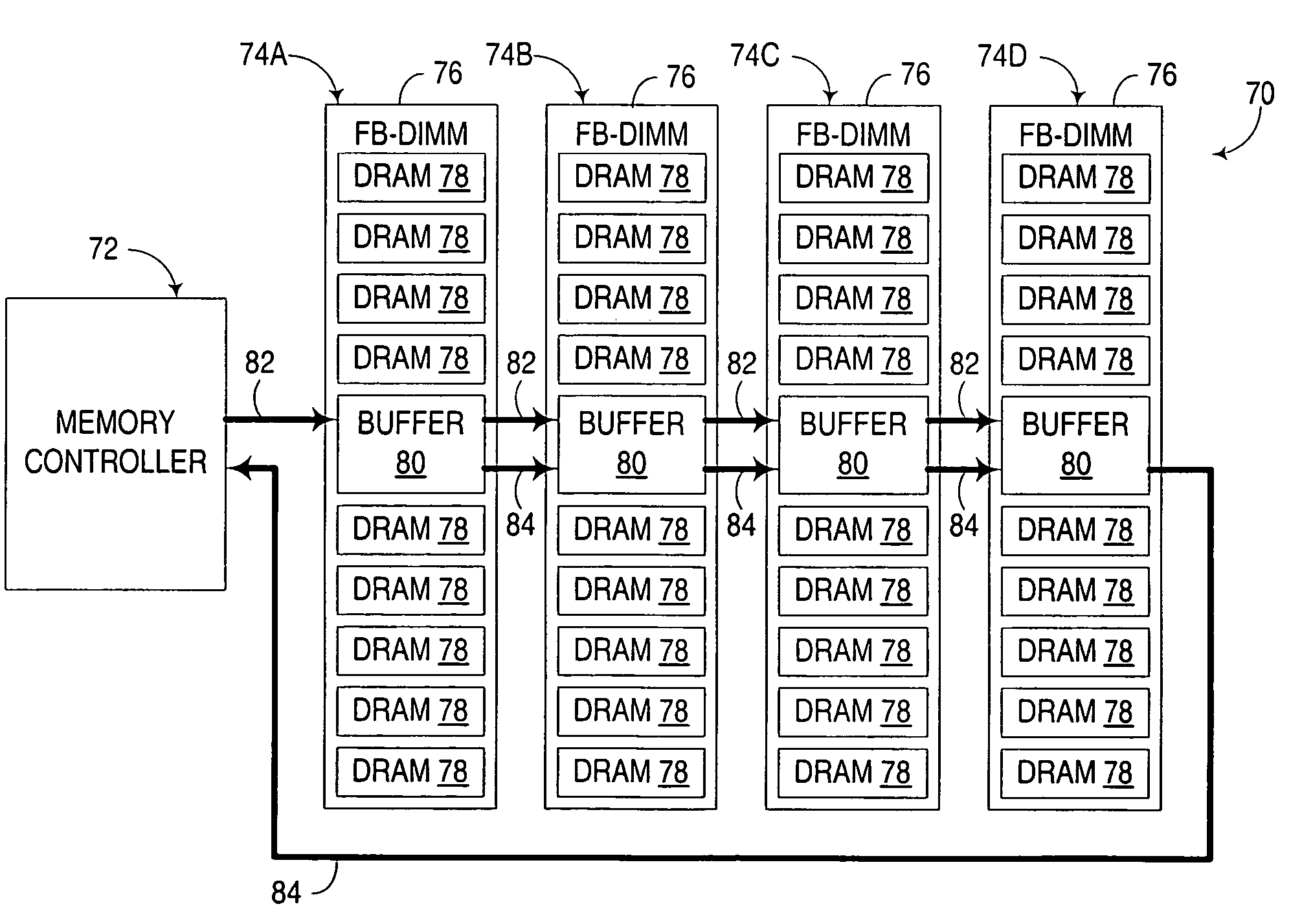
Multi-node architecture with daisy chain communication link configurable to operate in unidirectional and bidirectional modes
InactiveUS20060020740A1Error detection/correctionUnauthorized memory use protectionTelecommunications linkCommunication link
A circuit arrangement, method and apparatus utilize communication links that are selectively configurable to operate in both unidirectional and bidirectional modes to communicate data between multiple nodes that are interconnected to one another in a daisy chain configuration. As a result, in many instances communications may be maintained with nodes located both before and after a discontinuity in a daisy chain configuration.
Owner:IBM CORP
Method and apparatus for acceleration by prefetching associated objects
ActiveUS20080222244A1Multiple digital computer combinationsTransmissionMostly TrueUniform resource locator
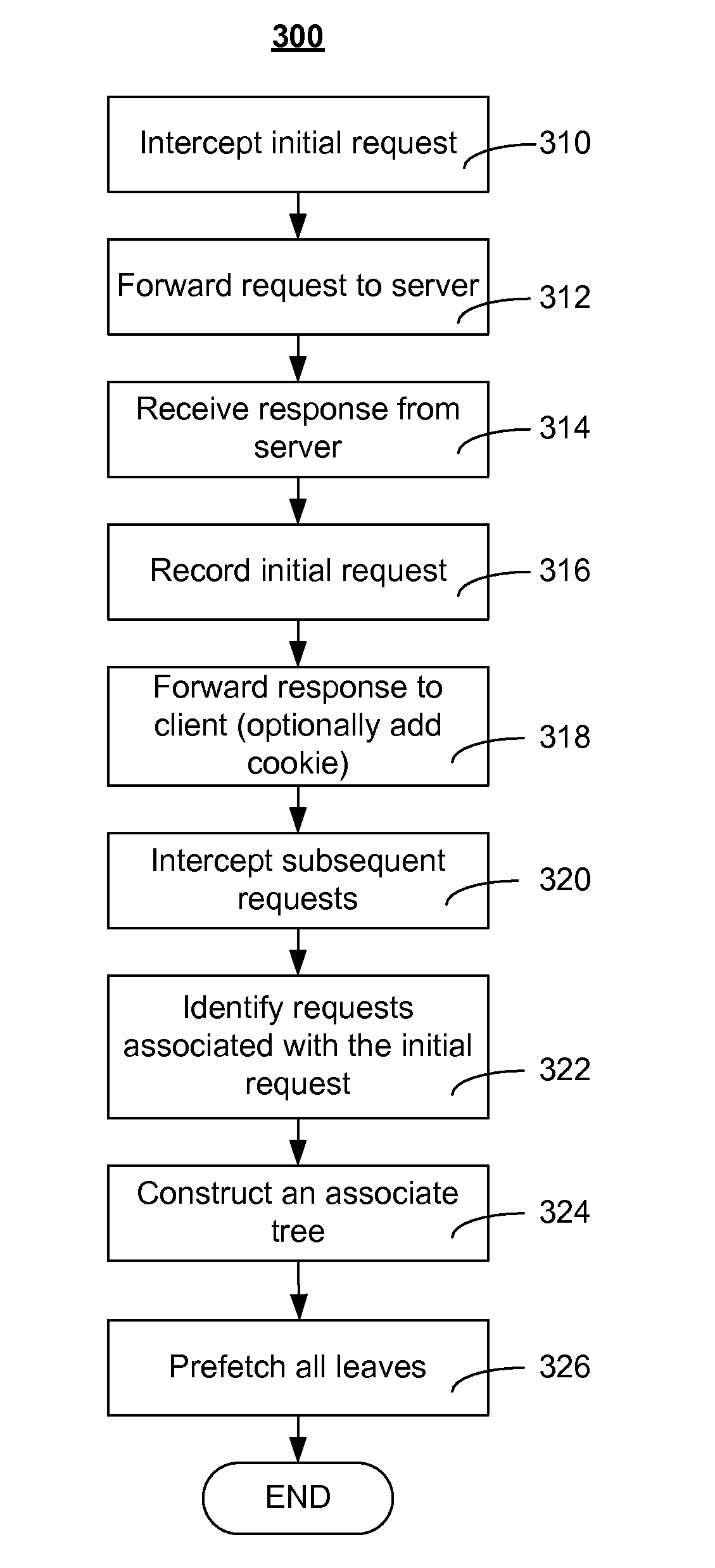
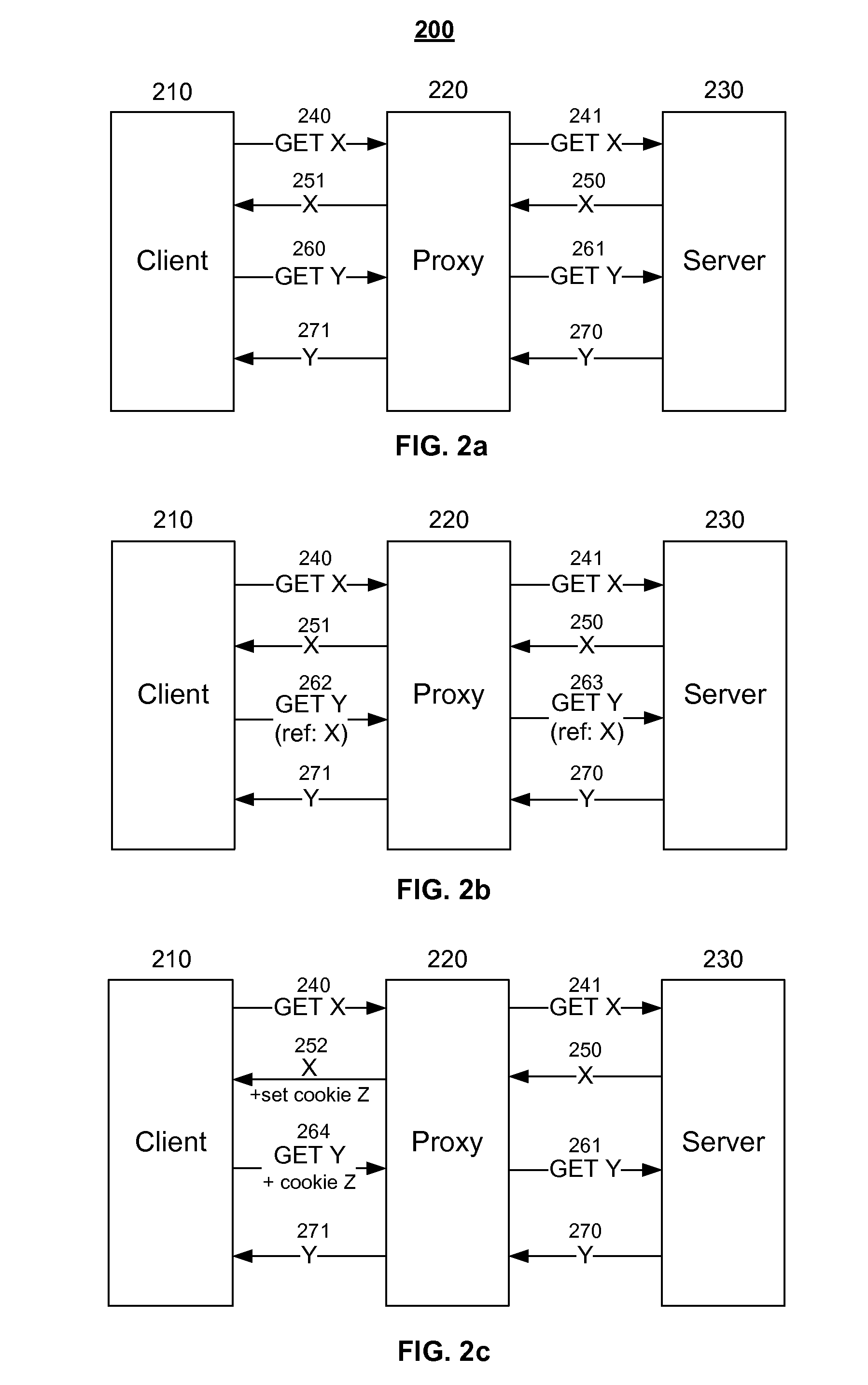
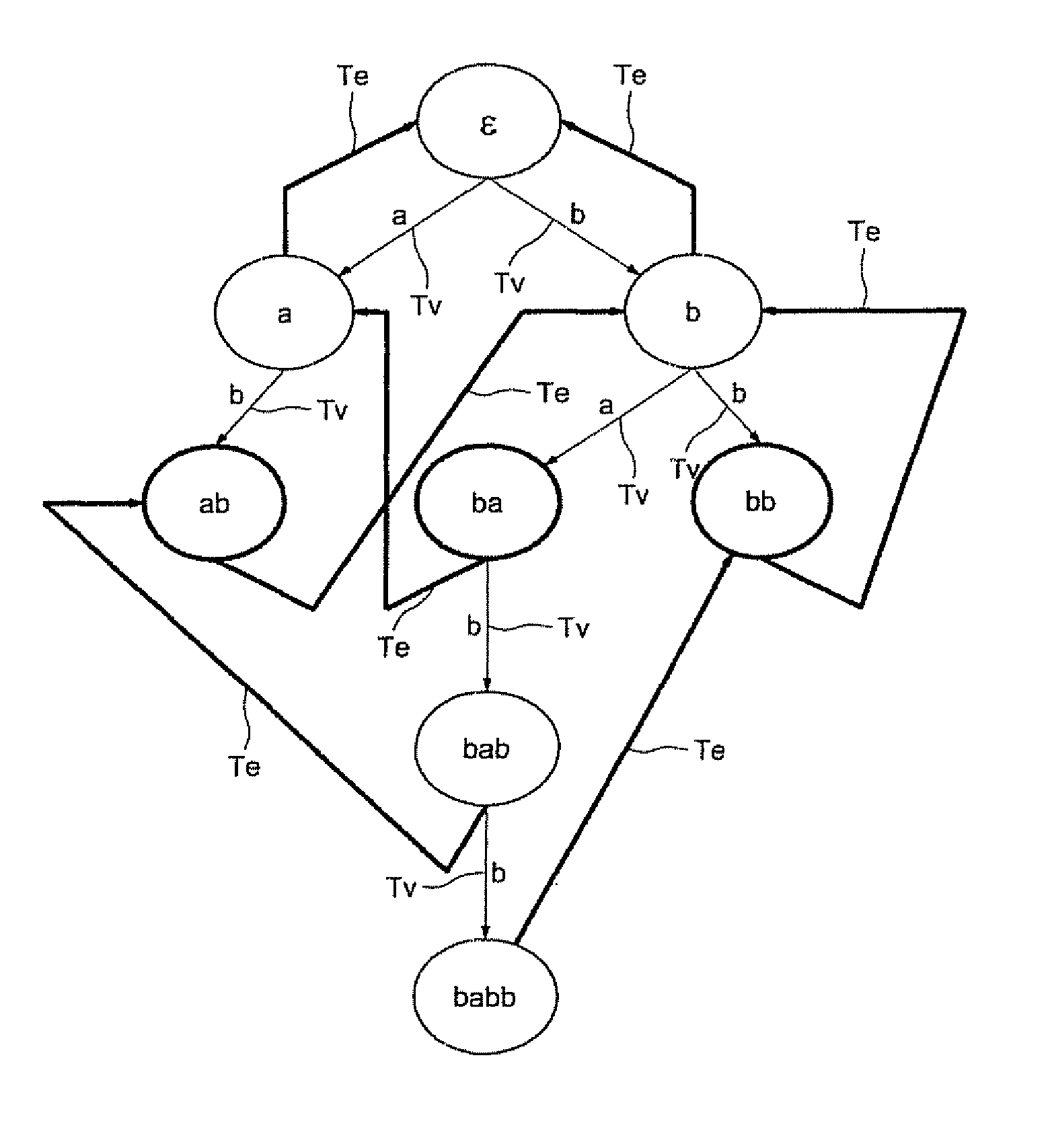
Association information is used to build association trees to associate base pages and embedded objects at a proxy. An association tree has a root node containing a URL for a base page, and zero or more leaf nodes each containing a URL for an embedded object. In most cases, an association tree will maintain the invariant that all leaves contain distinct URLs. However, it is also possible to have an association tree in which the same URL appears in multiple nodes. An association tree may optionally contain one or more internal nodes, each of which contains a URL that is an embedded object for some other base page, but which may also be fetched as a base page itself. Given a number of association trees and a base-page URL, a prefetch system finds the root or interior node corresponding to that URL (if any) and traverses the tree from that node, prefetching URLs until the URL of the last leaf node is prefetched. The prefetching starts the process of bringing over the various embedded objects before the user or program would ordinarily fetch them.
Owner:RIVERBED TECH LLC
Memory circuit for aho-corasick type character recognition automaton and method of storing data in such a circuit
ActiveUS20070075878A1Number of bitDigital data information retrievalCode conversionMemory addressData stream
A memory circuit for an Aho-Corasick type character recognition automaton uses a node tree for recognizing predetermined strings of characters in an incoming data stream. The recognization is based upon successive transitions in the node tree stored in memory in which each node corresponds to a recognized sequence of a character string. At least part of the nodes are related to a consecutive node by a valid transition, from an initial state to terminal states, with each one corresponding to a recognized character string This memory circuit includes first sets of consecutive memory addresses defining respectively strings of consecutive nodes accessible sequentially during successive transitions to a terminal state, and second sets of memory addresses defining multiple nodes each pointing to several states.
Owner:STMICROELECTRONICS SRL
High speed methods for maintaining a summary of thread activity for multiprocessor computer systems
InactiveUS6886162B1Reduce in quantityMultiprogramming arrangementsMemory systemsQuiescent stateProcessor node
A high-speed method for maintaining a summary of thread activity reduces the number of remote-memory operations for an n processor, multiple node computer system from n2 to (2n−1) operations. The method uses a hierarchical summary of-thread-activity data structure that includes structures such as first and second level bit masks. The first level bit mask is accessible to all nodes and contains a bit per node, the bit indicating whether the corresponding node contains a processor that has not yet passed through a quiescent state. The second level bit mask is local to each node and contains a bit per processor per node, the bit indicating whether the corresponding processor has not yet passed through a quiescent state. The method includes determining from a data structure on the processor's node (such as a second level bitmask) if the processor has passed through a quiescent state. If so, it is then determined from the data structure if all other processors on its node have passed through a quiescent state. If so, it is then indicated in a data structure accessible to all nodes (such as the first level bitmask) that all processors on the processor's node have passed through a quiescent state. The local generation number can also be stored in the data structure accessible to all nodes. If a processor determines from this data structure that the processor is the last processor to pass through a quiescent state, the processor updates the data structure for storing a number of the current generation stored in the memory of each node.
Owner:SEQUENT COMPUTER SYSTEMS
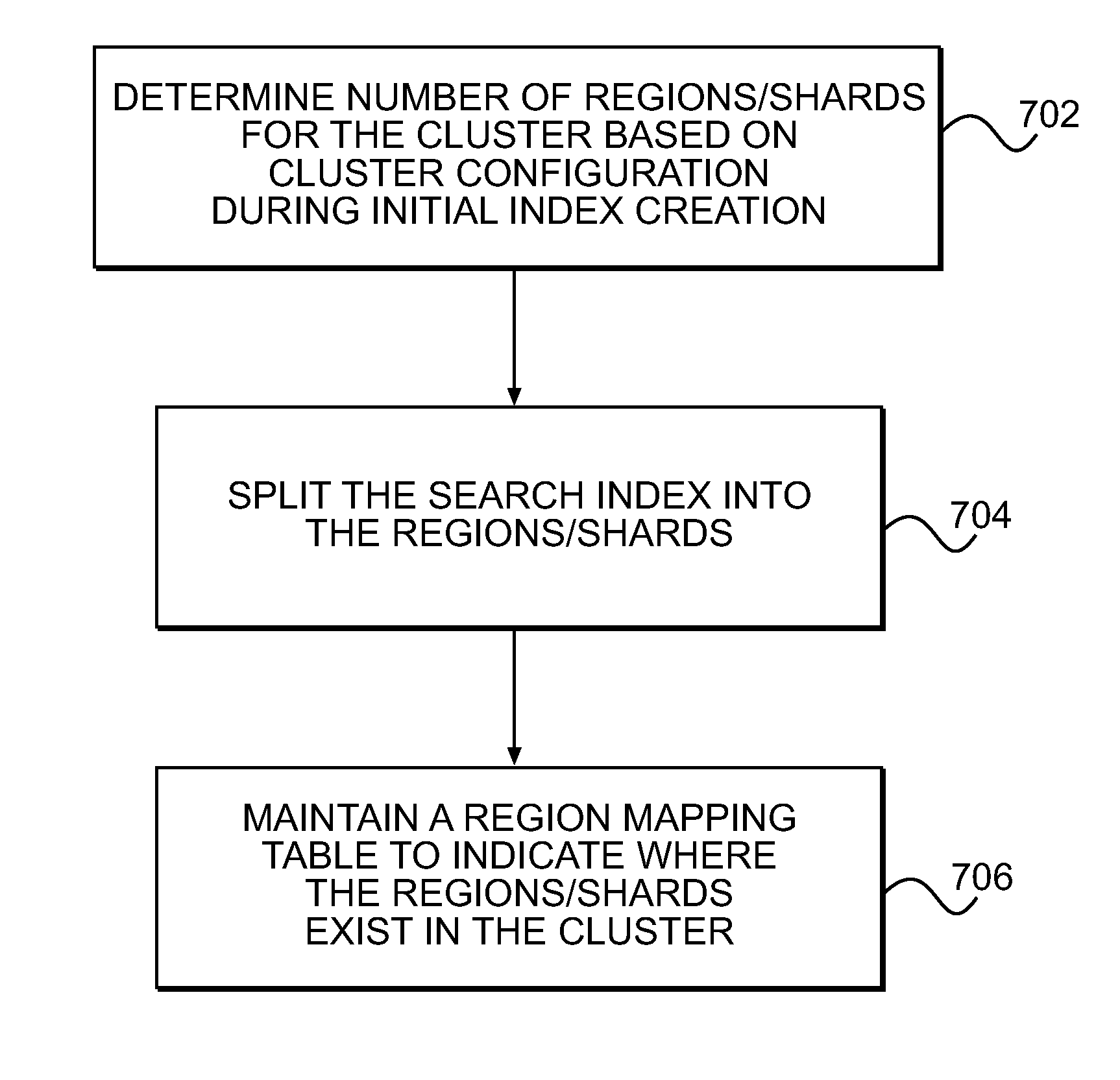
Highly available search index with storage node addition and removal
ActiveUS20140330785A1Facilitate new region distributionAddressing slow performanceDigital data processing detailsTransmissionObject basedTheoretical computer science
A redundant array of independent nodes are networked together. Each node executes an instance of an application that provides object-based storage. The nodes are grouped into systems each having multiple nodes. A search index is provided in each system for locating objects within the system. A method of managing the search index comprises splitting the search index into shards to be divided among a plurality of regions (704). The regions are larger in number than the nodes in the system. Each region has a master and at least one backup copy of one of the shards. A shard core is a master or backup copy of a shard. The method further comprises distributing the shard cores to the nodes, and providing a region mapping table in each node in the system to map the shard cores to the nodes in which the shard cores are stored (706).
Owner:HITACHI VANTARA LLC
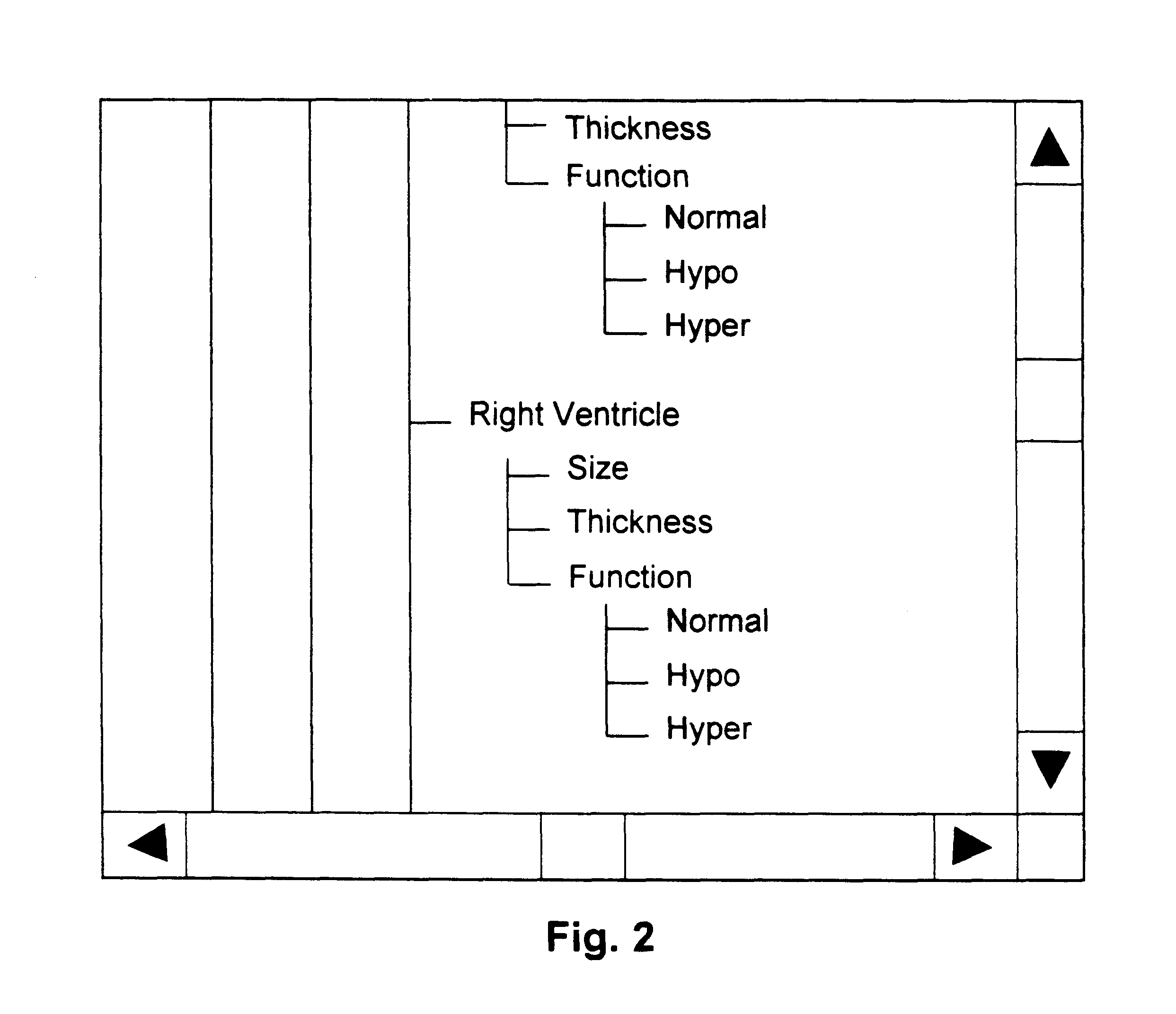
Method and system for navigation and data entry in hierarchically-organized database views
InactiveUS6381611B1Increase entryIncrease updateData processing applicationsDigital data processing detailsEngineeringData mining
A method and system for navigating hierarchical database views that supports the efficient entry, review, and updating of data using a navigation display that is clear and efficient-yet compact in terms of the screen area used. At any point in the navigation process, the navigation display consists of buttons corresponding to the nodes that lie along the path to the last node visited (the set of previously made choices) and the children of this node (the set of current choices). Unselected and unselectable choices are culled and do not clutter the display. The user navigates up and down the hierarchy and enters data by selecting these buttons. An important feature of the invention is support for multiple instances of database subhierarchies within this navigation process and display. In addition, multiple nodes can be composed to form a single database entry, thereby reducing the size and complexity of the hierarchical database views. Finally, database views that are directed acyclic graphs are also supported-including both serial and parallel traversal techniques.
Owner:ASCEND HIT LLC
Method and apparatus for sharing many thought databases among many clients
InactiveUS20030117434A1Increase flexibilityReduce loadData processing applicationsDatabase distribution/replicationDocumentation procedureDigital storage
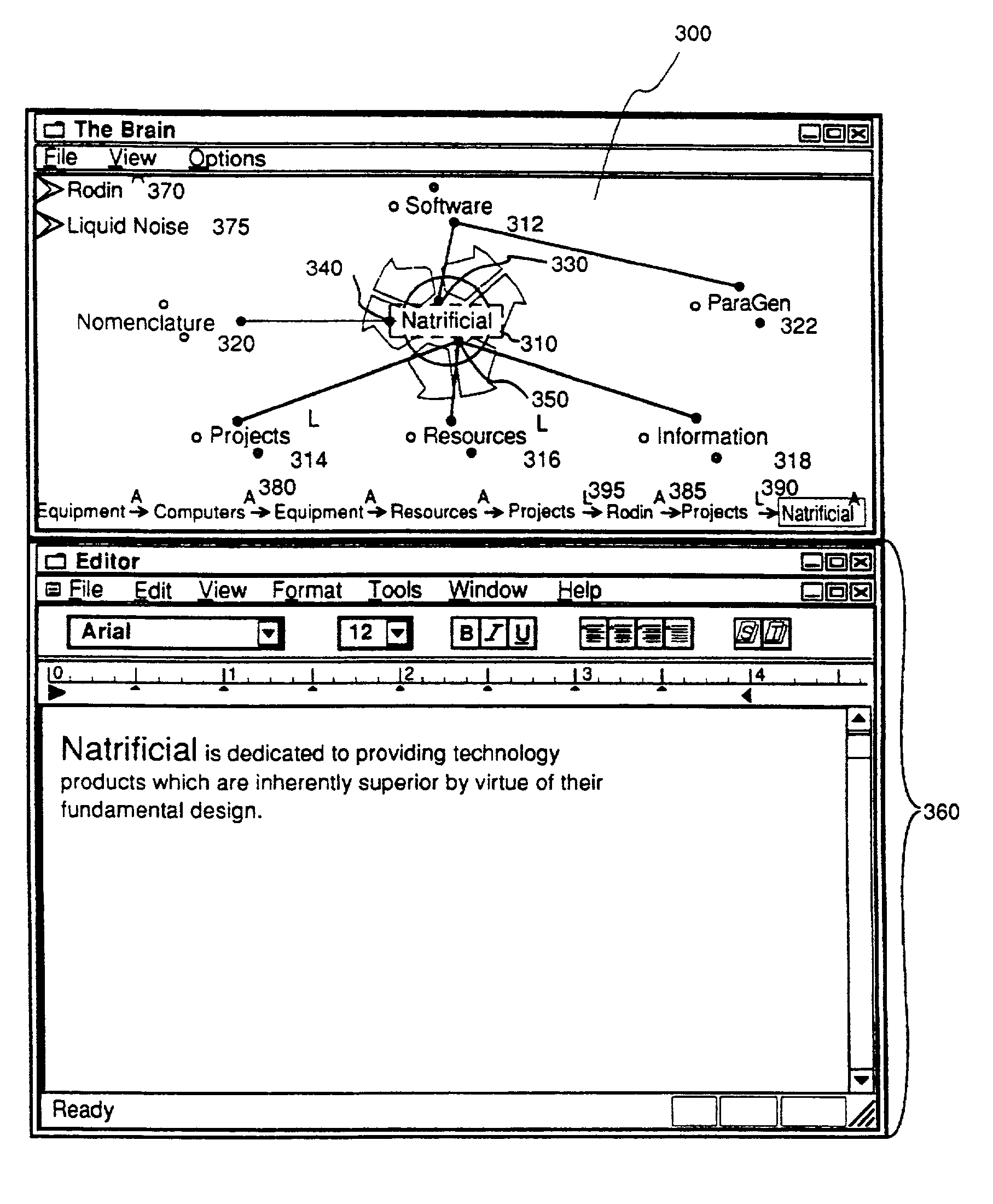
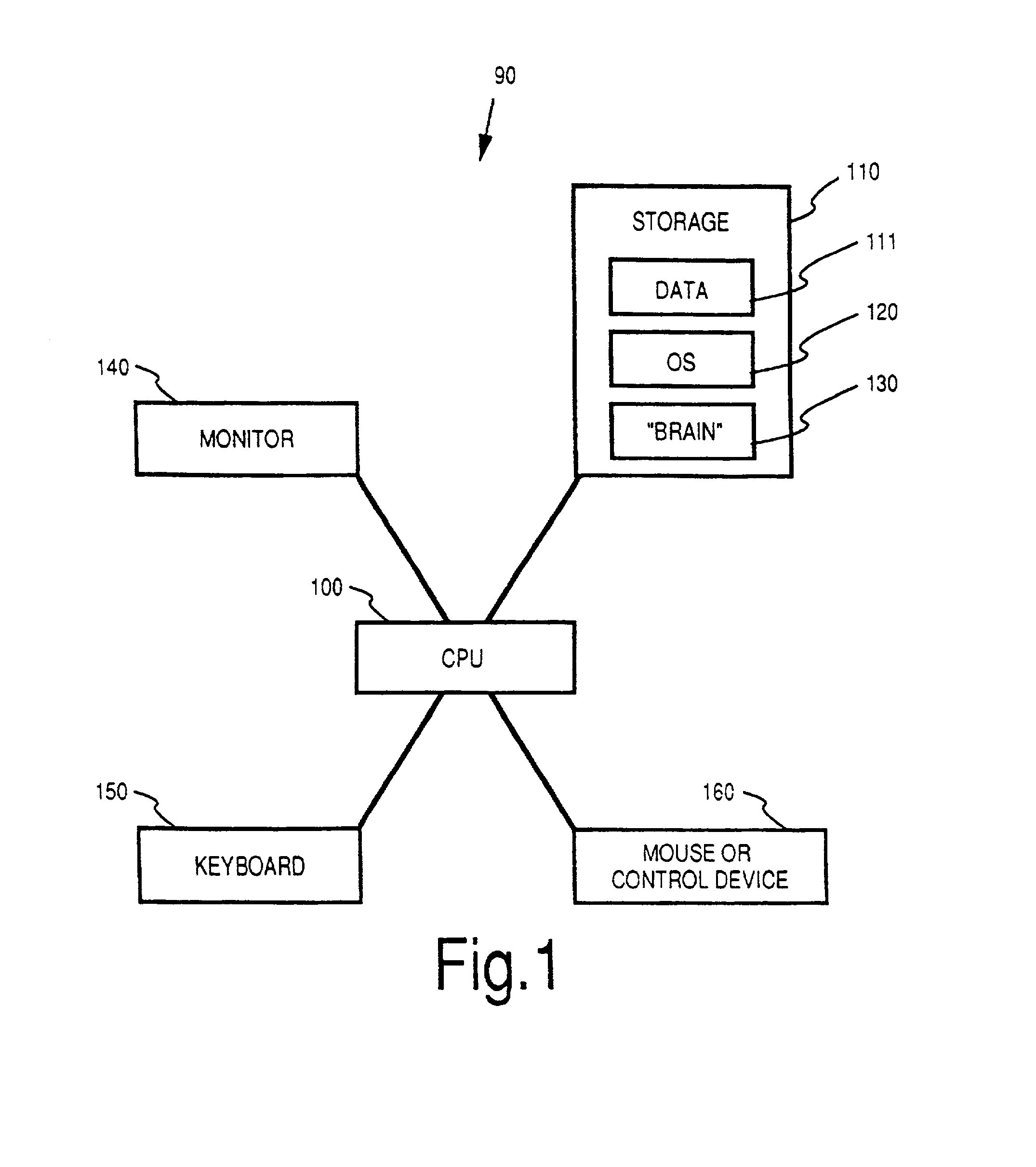
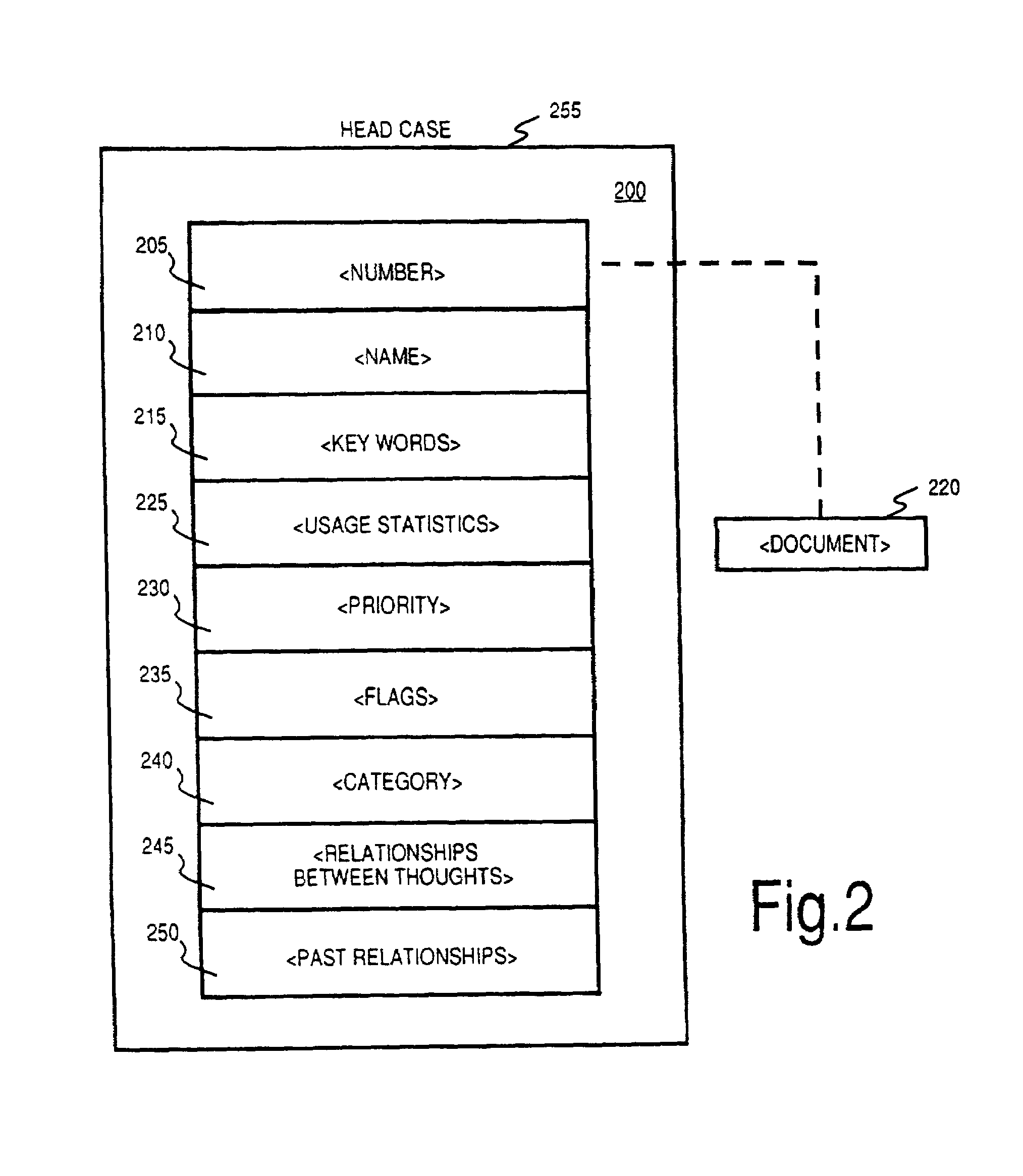
The Brain system employs a graphical user interface to facilitate user interaction with highly flexible, associative "matrices" that enable users to conveniently organize digitally-stored "thoughts" (inter-related information) and their network of inter-relationships. The Brain system offers a solution that facilitates the capture of information from a company's repositories and showcases it in an engaging and dynamic visual interface. The Brain accomplishes this by providing a connector system that serves as an interface between the Brain server and whatever repositories are employed to store data. By use of a special type of connector, the Brain can permit a single user to collaborate with a number of different repositories at different locations and of different sorts under a single associative interface. A client can also interface directly with multiple data stores that are configured for interaction with the associative interface described herein. Multiple nodes on a network can access common sources of associative data in real-time or by way of synchronization techniques. Lastly, methods are further described permitting single items of associative data to reference multiple documents at once.
Owner:THEBRAIN TECH LP
Method and apparatus for executing applications on a distributed computer system
ActiveUS7302609B2Simplify the management processEasy to manageDigital data processing detailsError detection/correctionControl systemComputerized system
Owner:VLADIMIR MATENA +1
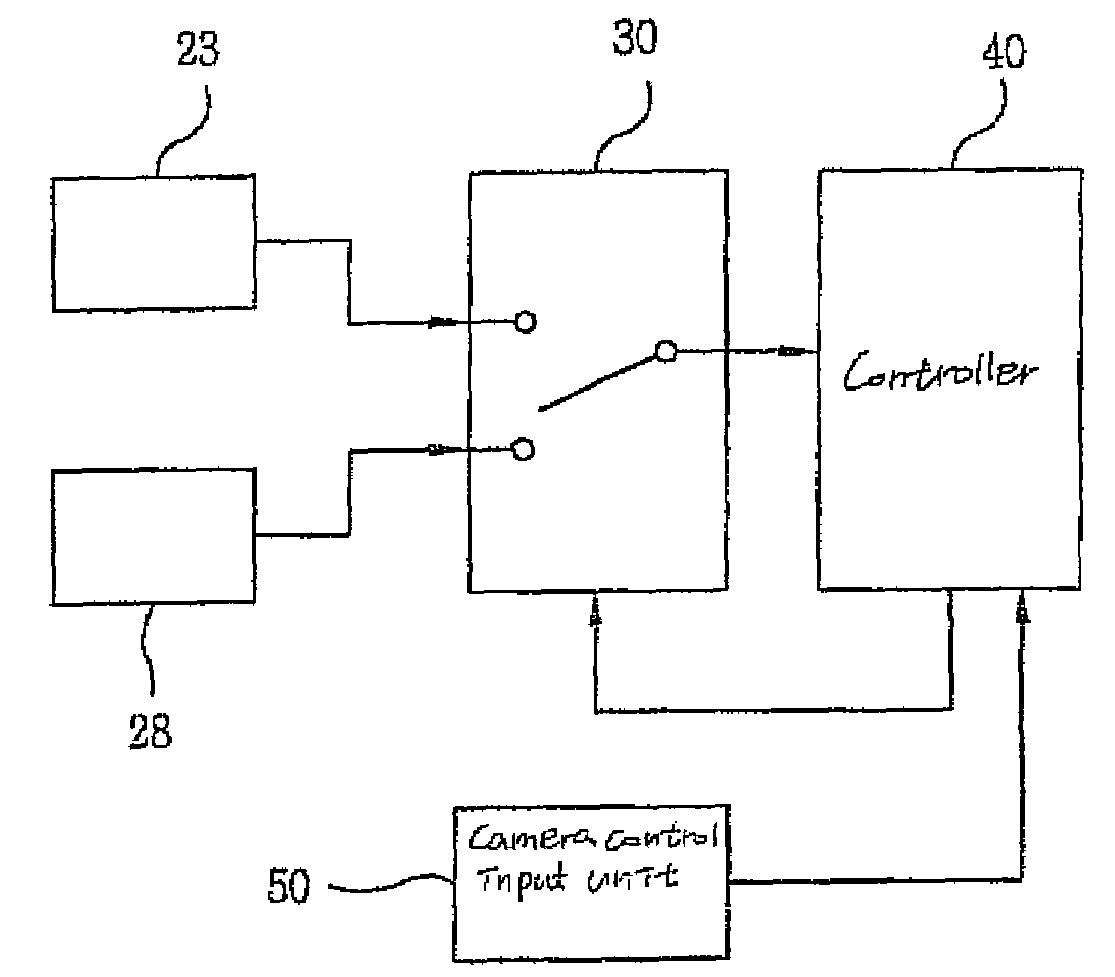
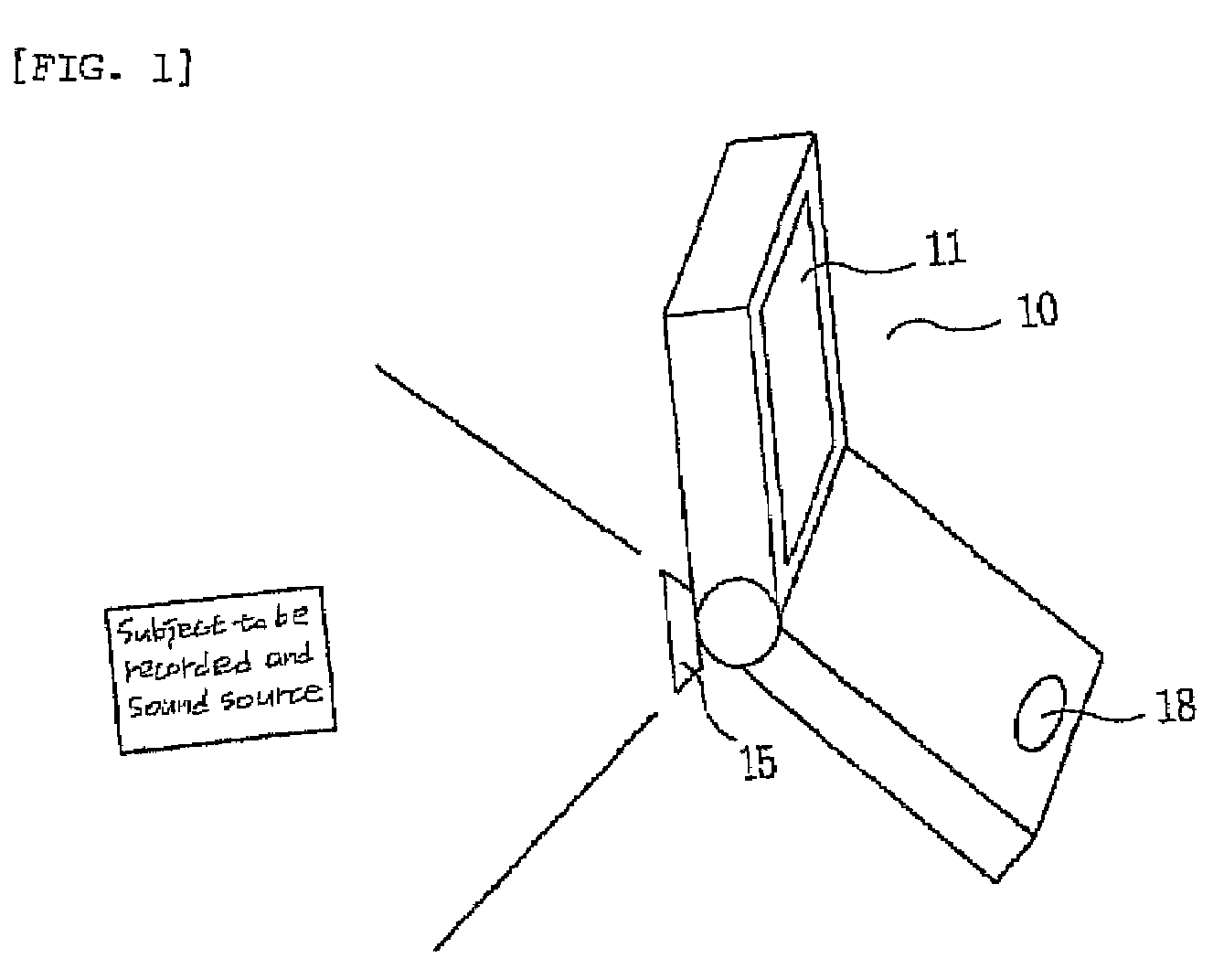
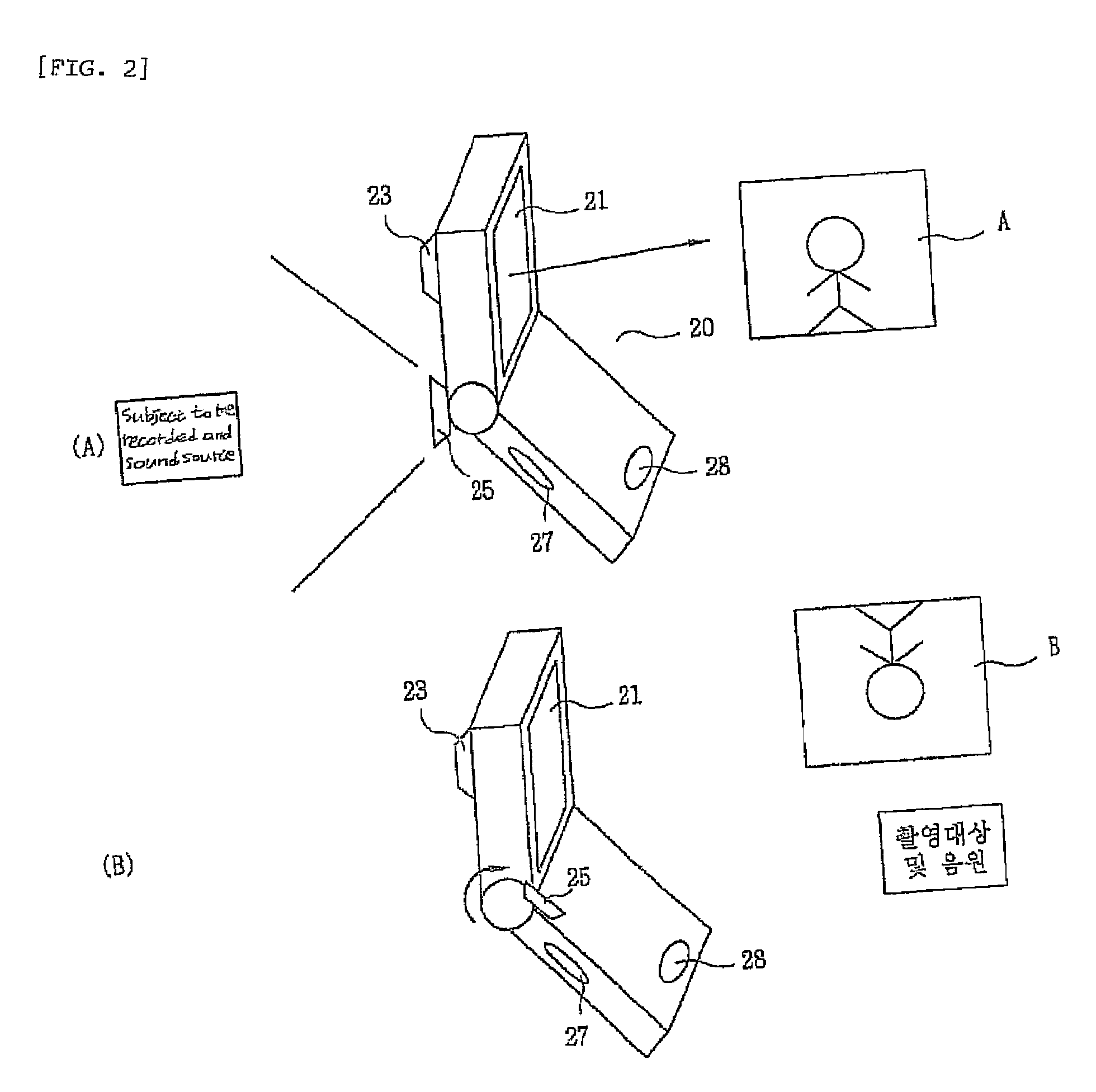
Recording audio and video in a mobile communication terminal
InactiveUS7394480B2Easy to operateReadily apparentTelevision system detailsColor television detailsSound sourcesVoice communication
The present invention relates to a microphone switching apparatus and method for a mobile communication terminal having a camcorder function, and in particular, a mobile communication terminal having a rotational camera so as to record more distinct and clearer sound, by disposing a microphone on the front and rear side of a mobile communication terminal and operating a microphone at a position corresponding to the direction of a subject (an object to be recorded) and a sound source. In a related art mobile communication terminal, a volume of voice / sound from a subject is recorded undesirably low when a subject is located in front direction of a mobile communication terminal and a camera is directed toward the subject, since it is recorded through the microphone located in the rear side of the terminal, wherein the microphone for voice communication is used for recording voice / sound when performing a camcorder function. To solve the aforementioned problems, a microphone switching apparatus and method for a mobile communication terminal has an effect to increase a volume and clearness of voice or sound which is recorded in video, and thereby to greatly improve the quality of video, which additionally disposes a front microphone on a front side of a mobile communication terminal so as to be used when performing a camcorder function, selects automatically or manually either of the front microphone or the rear microphone according to a derection of a camera, which the rear microphone is used for voice communication.
Owner:LG ELECTRONICS INC
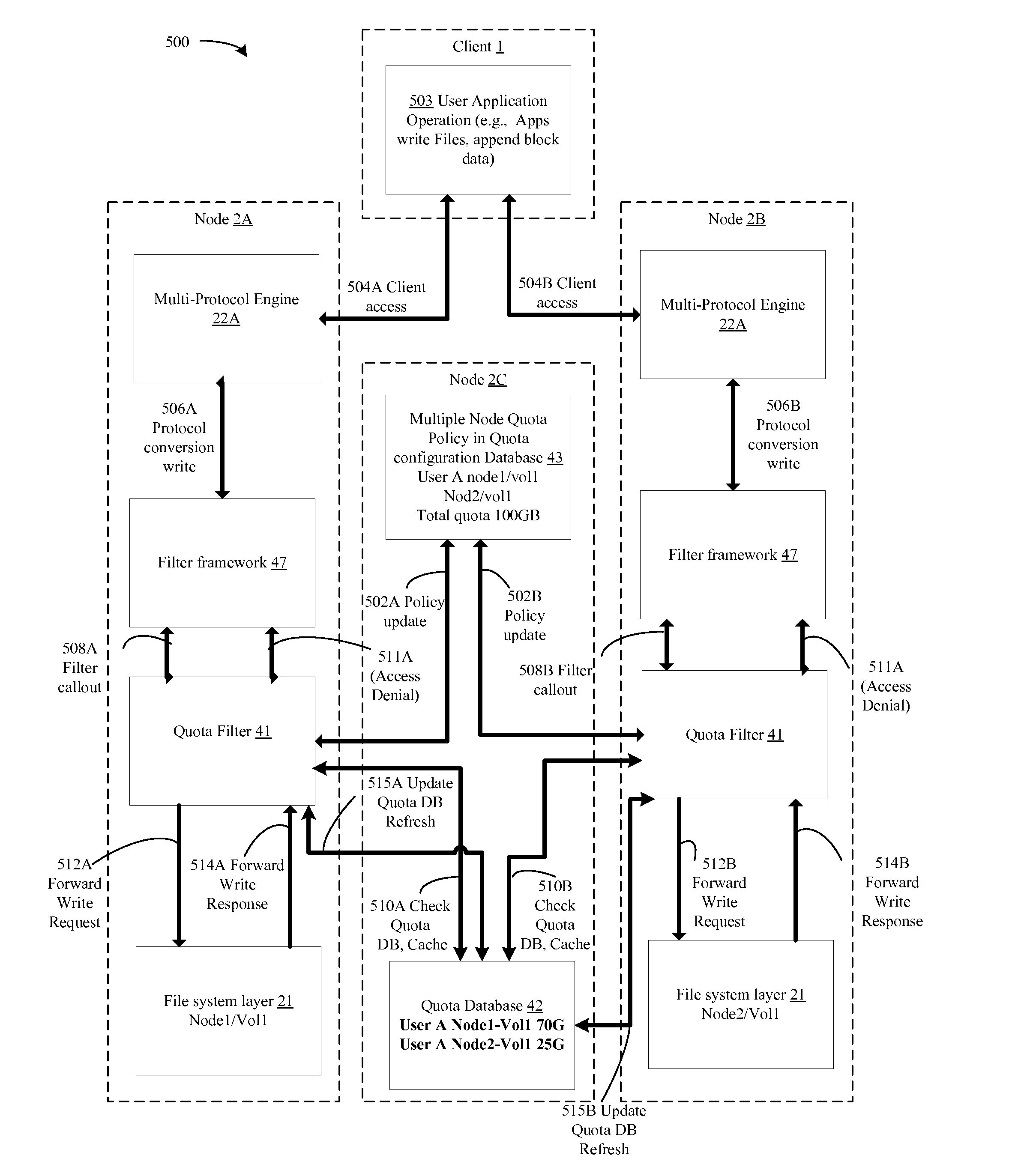
Multiple node quota filter
ActiveUS8131784B1Digital data information retrievalSpecial data processing applicationsData accessMultiple node
An apparatus and a method that allow a quota to be implemented over a data storage system having data associated with the user stored in multiple volumes or directories across multiple storage servers. The quota limits a user or a group of users to a defined amount (e.g., quota) of storage resources of the storage system. The method may include monitoring input-output (IO) data access requests on each of the multiple storage servers, for example, using a pluggable quota filter on each of the storage servers, determining a total usage of storage resources for a particular user over the multiple storage servers, and limiting the user to the quota over the multiple storage servers.
Owner:NETWORK APPLIANCE INC
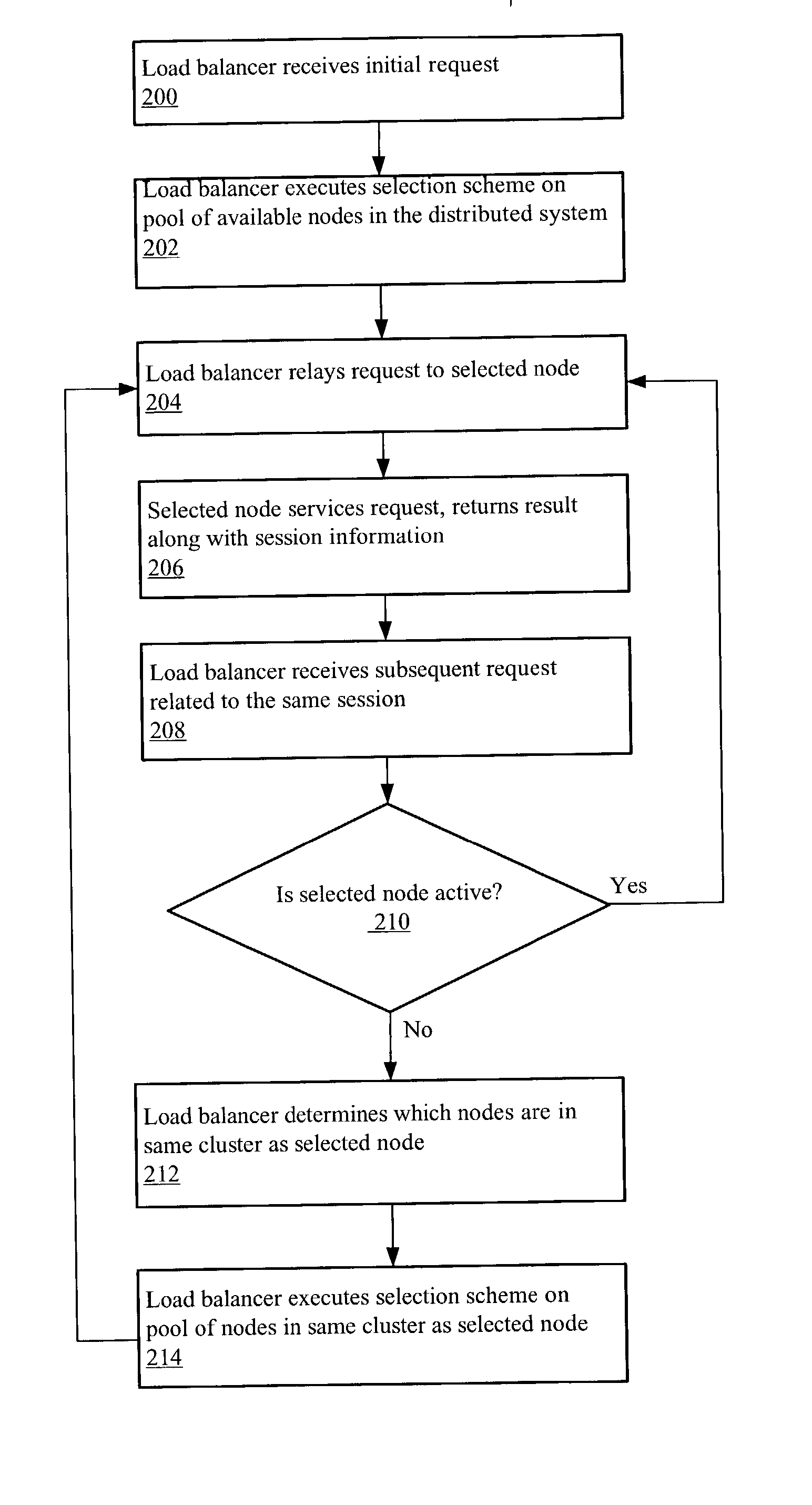
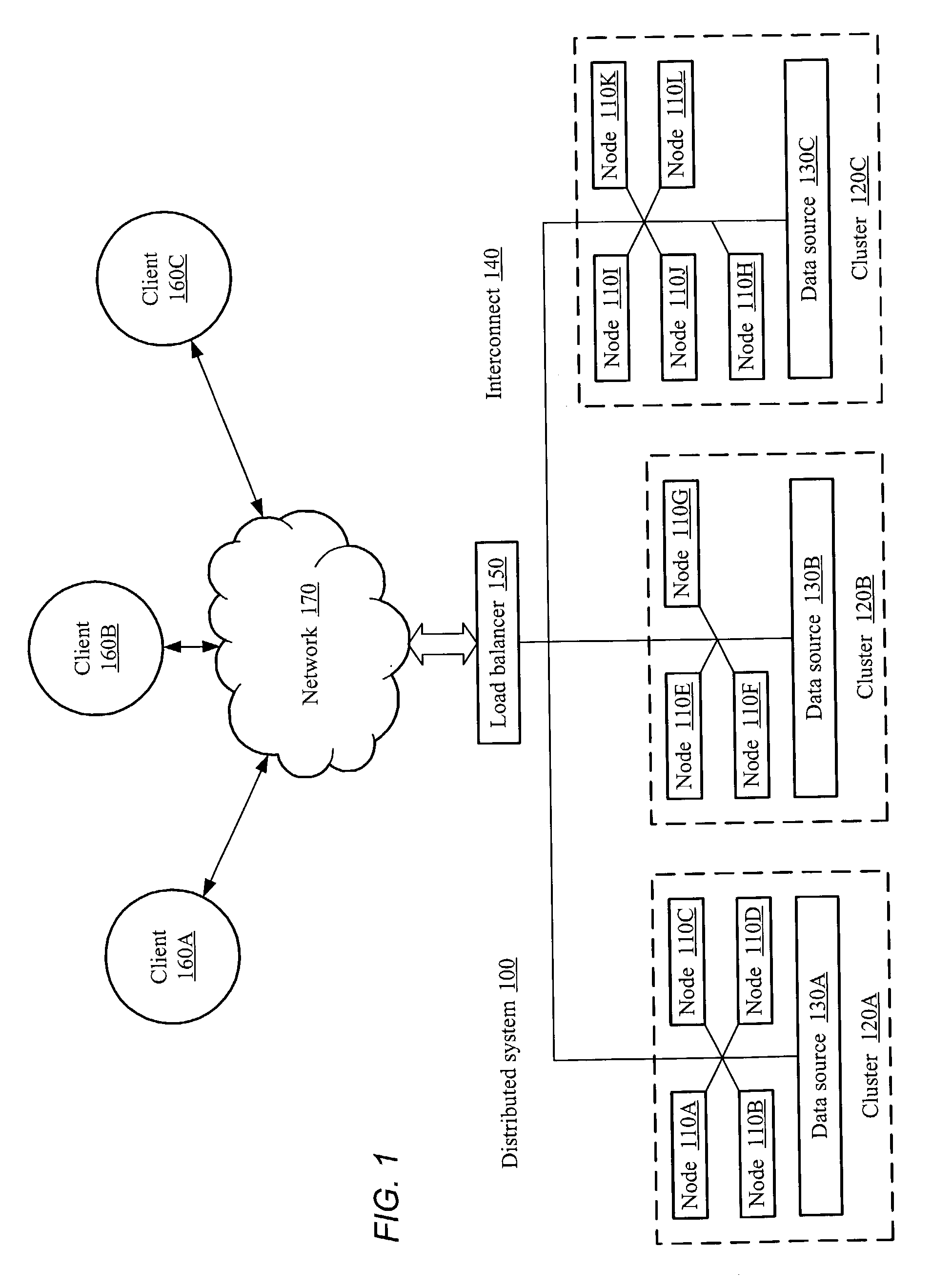
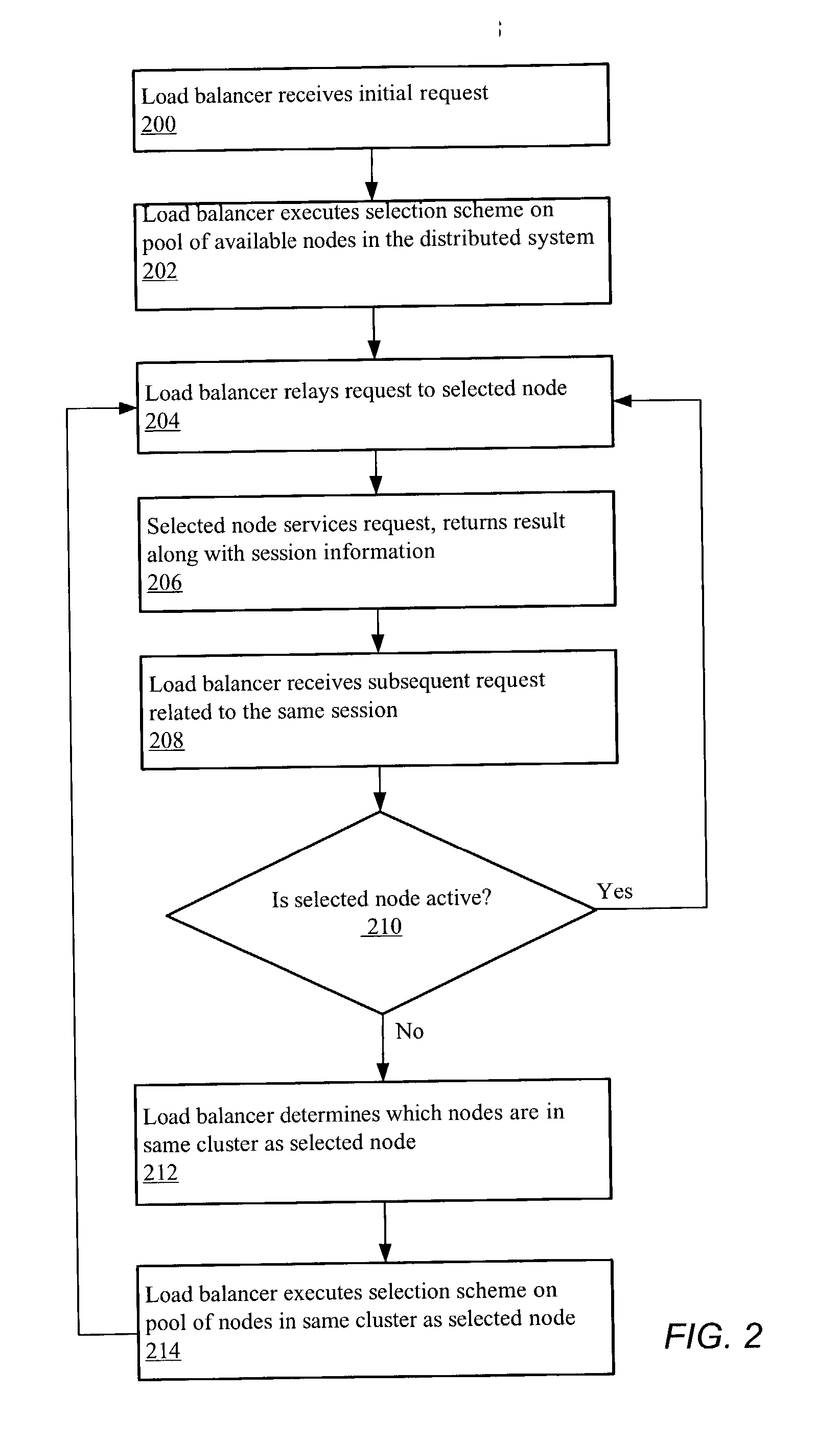
System and method for cluster-sensitive sticky load balancing
A system and method for cluster-sensitive sticky load balancing of server workload may include a load balancer receiving an initial request from a client. A session may be initiated in response to receiving the request. The load balancer may relay the initial request to a selected node, where the selected node may be part of a cluster of multiple nodes. Upon receiving a subsequent request pertaining to the session initiated by the initial request, the load balancer may determine if the selected node is active. If the selected node is active, the load balancer may relay the subsequent request to the selected node. If the selected node is not active, the load balancer may determine for which cluster the selected node was a member, and relay the subsequent request to another node in that same cluster.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com