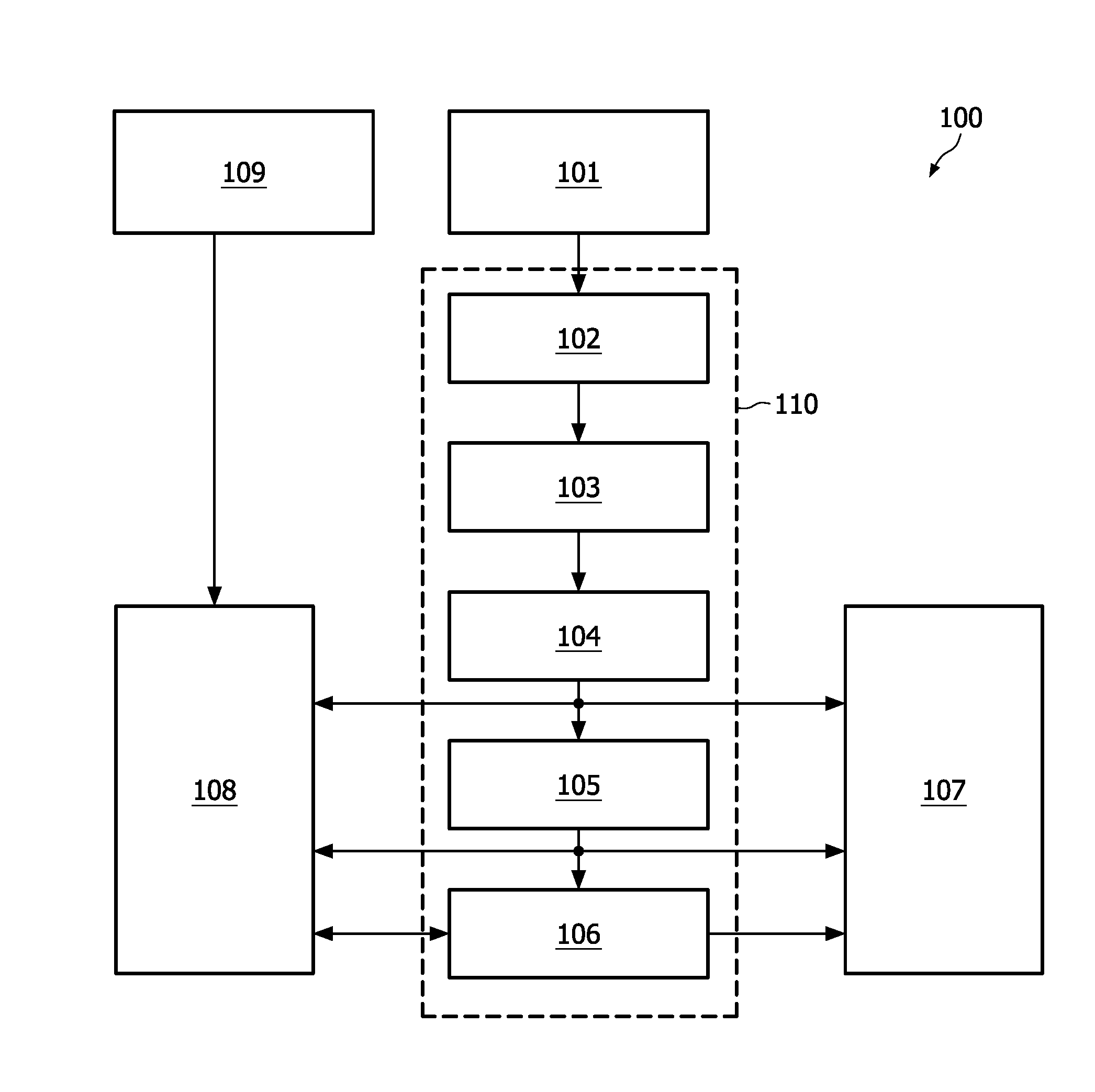
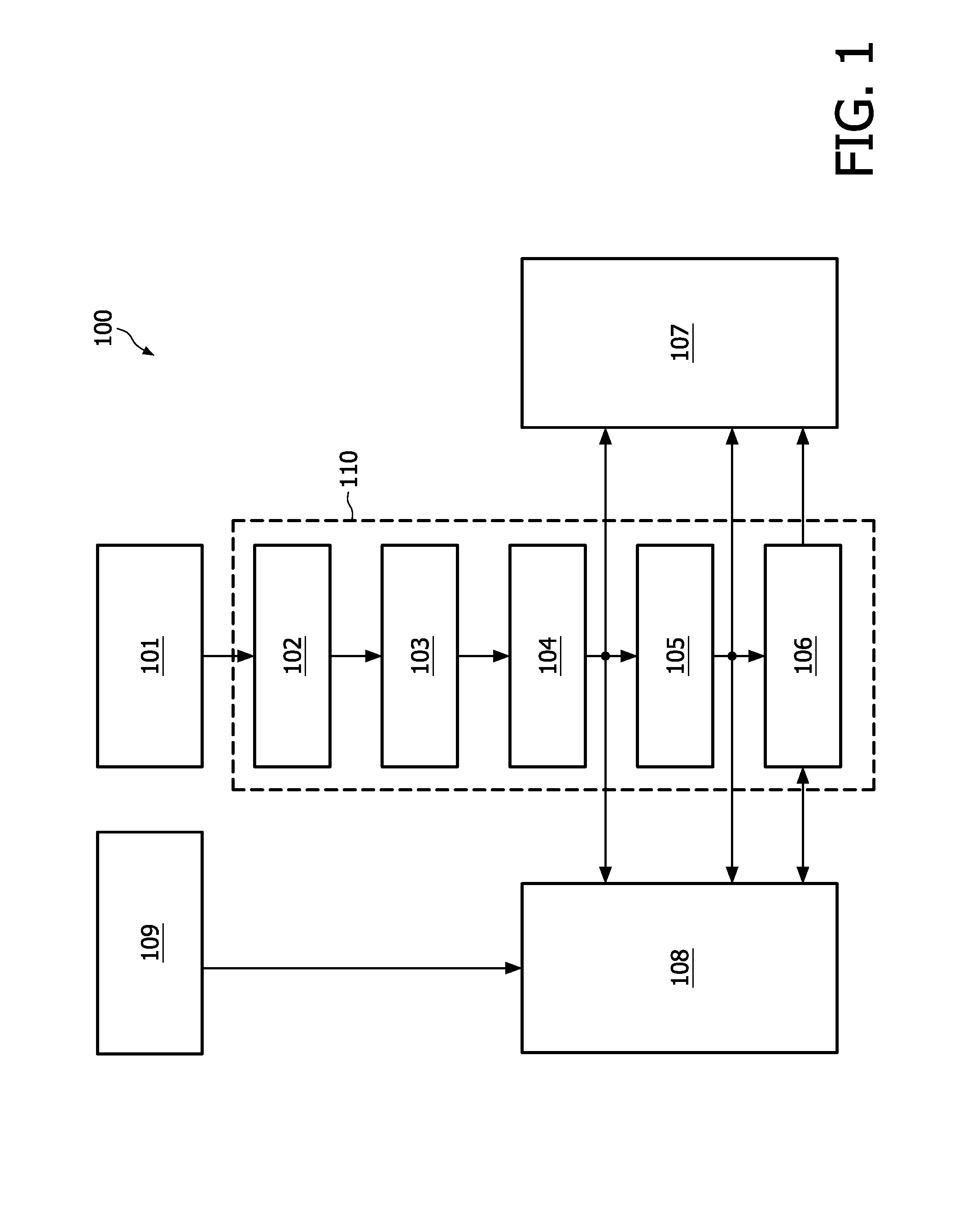
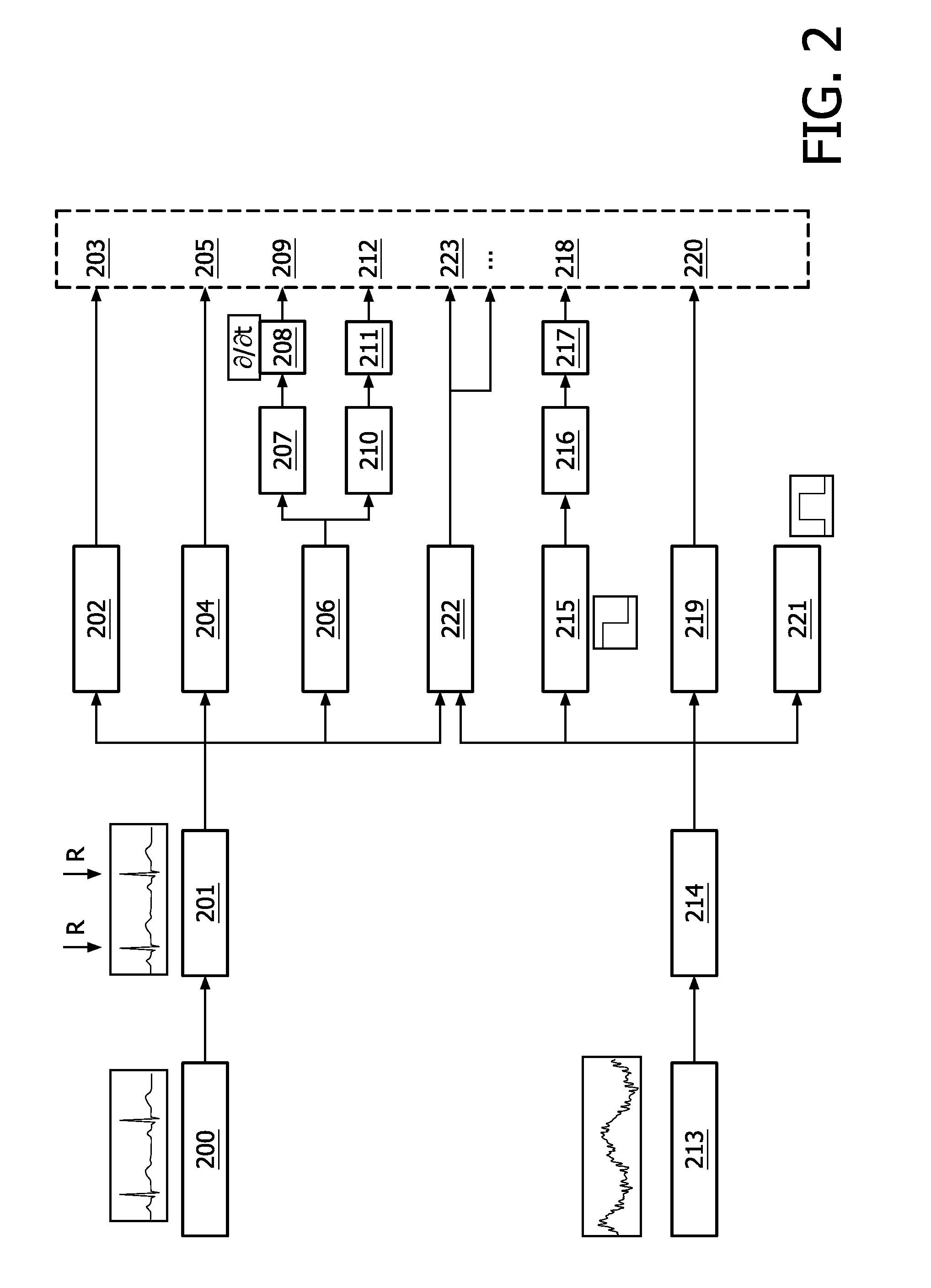
Patents
Literature
469 results about "Mostly True" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A subjective response indicating that something is mostly true.
Conveyor system
InactiveUS6450757B1Increase resistanceAccurately and surely carrying a workpieceProgramme-controlled manipulatorMechanical apparatusMostly TrueHeat resistance
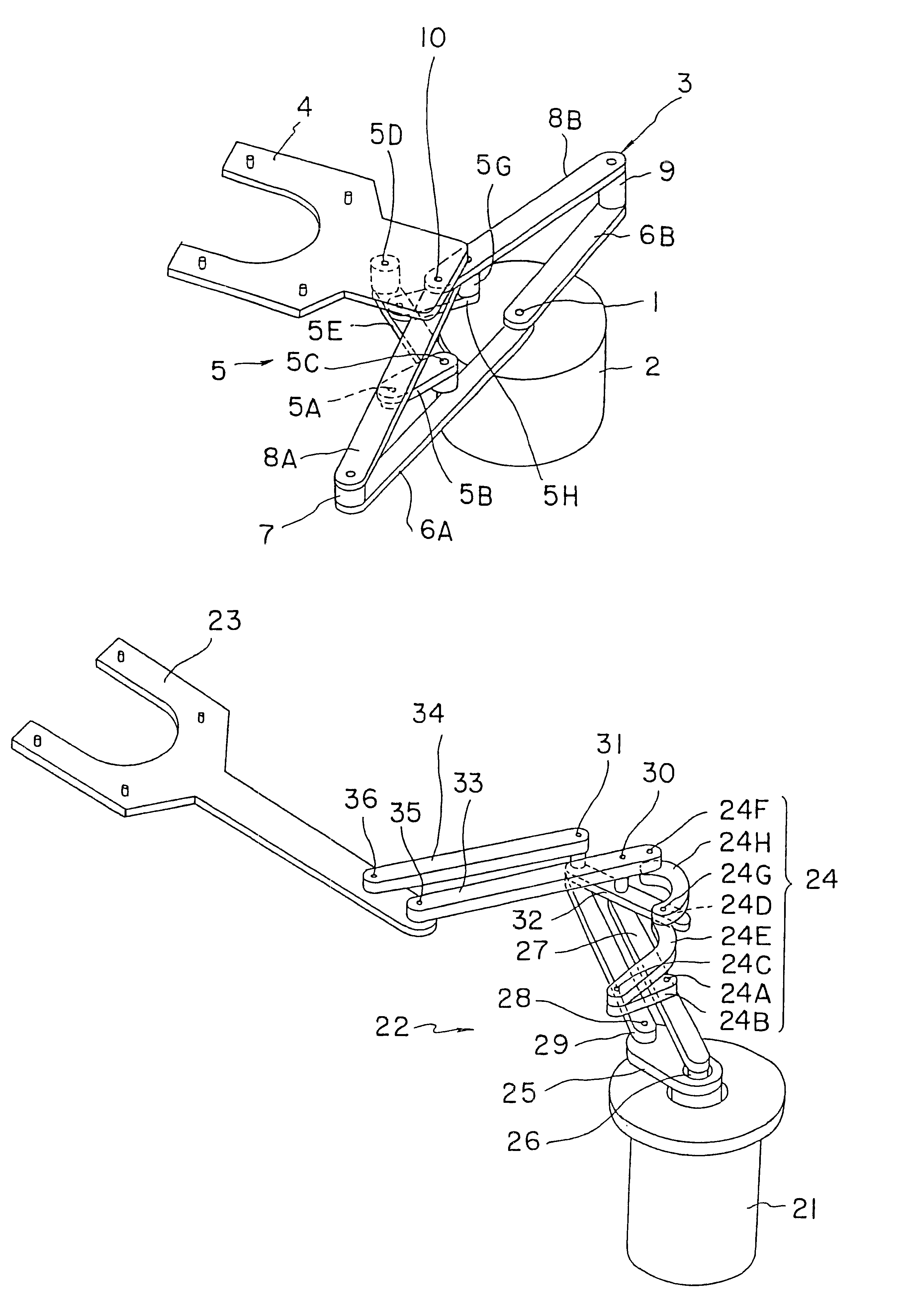
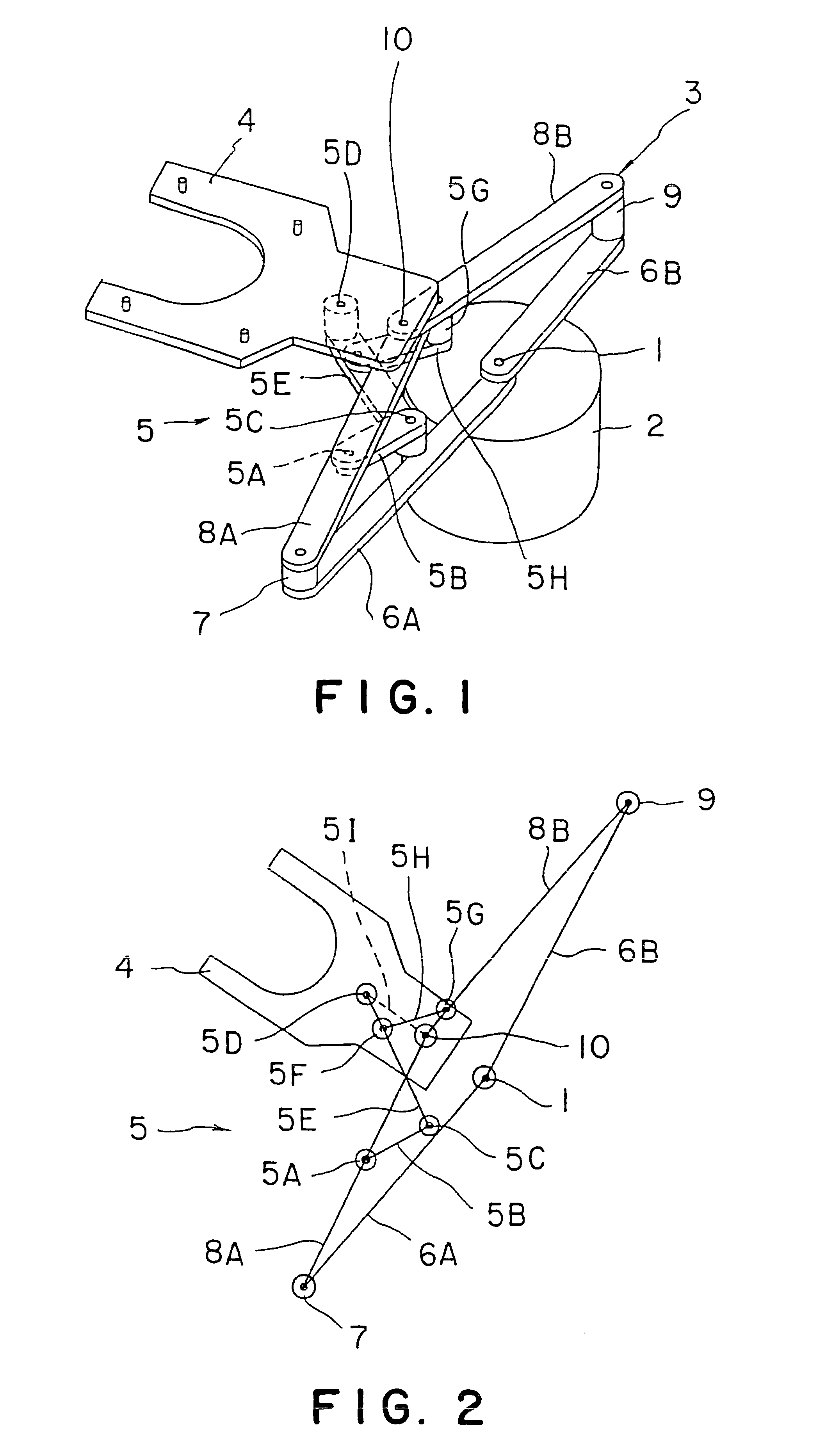
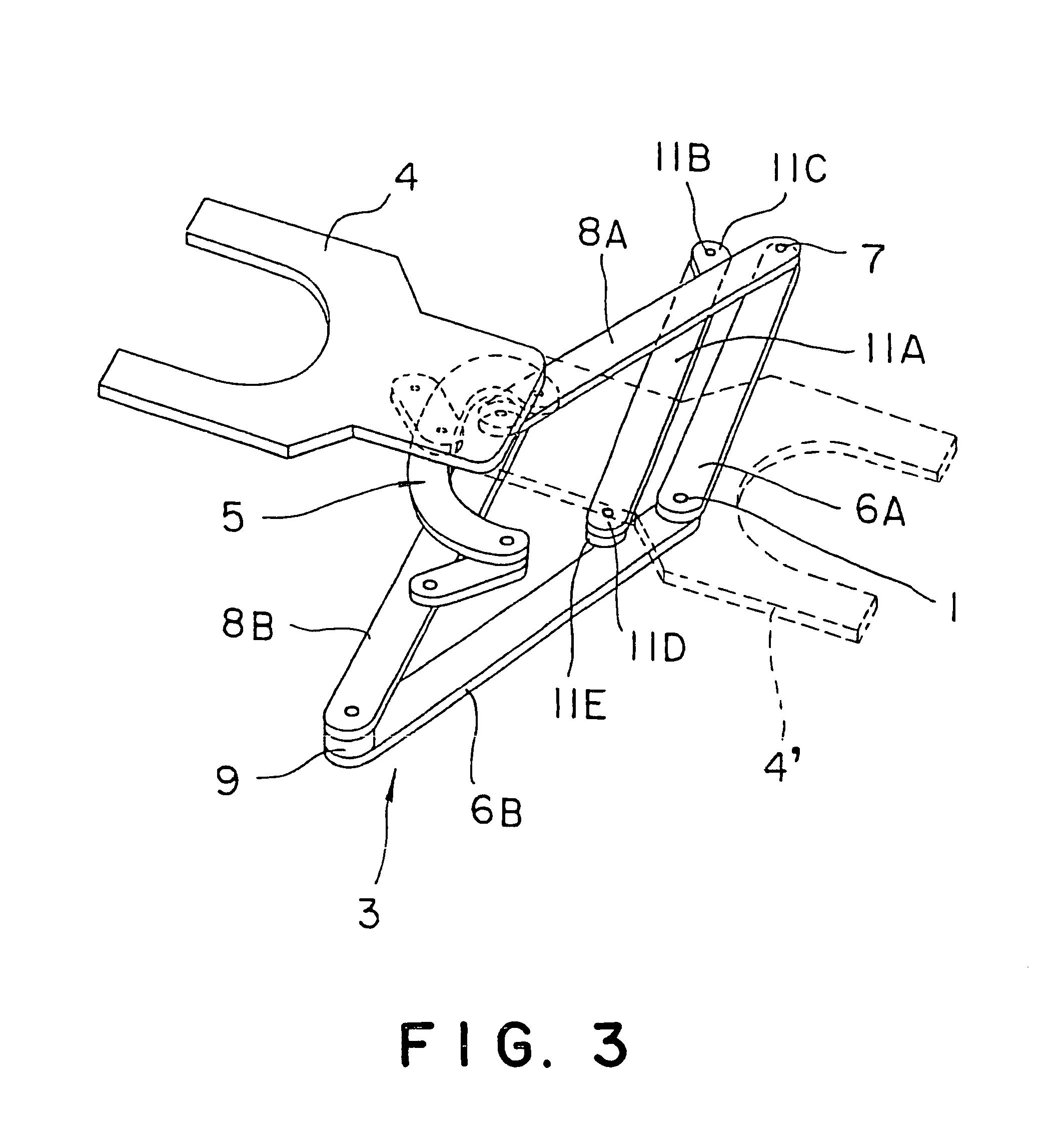
In most cases, a hot, corrosive atmosphere is created in, for example, a semiconductor wafer processing chamber. When an arm including belts, such as steel belts, is moved into such a semiconductor wafer processing chamber, the belts are exposed to the hot, corrosive atmosphere. Belts, such as steel belts, have limited heat resistance and corrosion resistance and the hot, corrosive atmosphere in the processing chamber shortens the life of the belts. A carrying device of the present invention has a frog leg type arm (3) and a wafer holder (4) connected to the frog leg type arm (3). The wafer holder (4) is pivotally connected to front end parts of a first front arm (8A) and a second front arm (8B) by coaxial joints (10). The wafer holder (4) is linked to the first front arm (8A) and the second front arm (8B) by a posture maintaining linkage (5) including two antiparallel linkages capable of controlling the turning of the wafer holder (4) relative to the first and the second front arms (8A, 8B).
Owner:TOKYO ELECTRON LTD
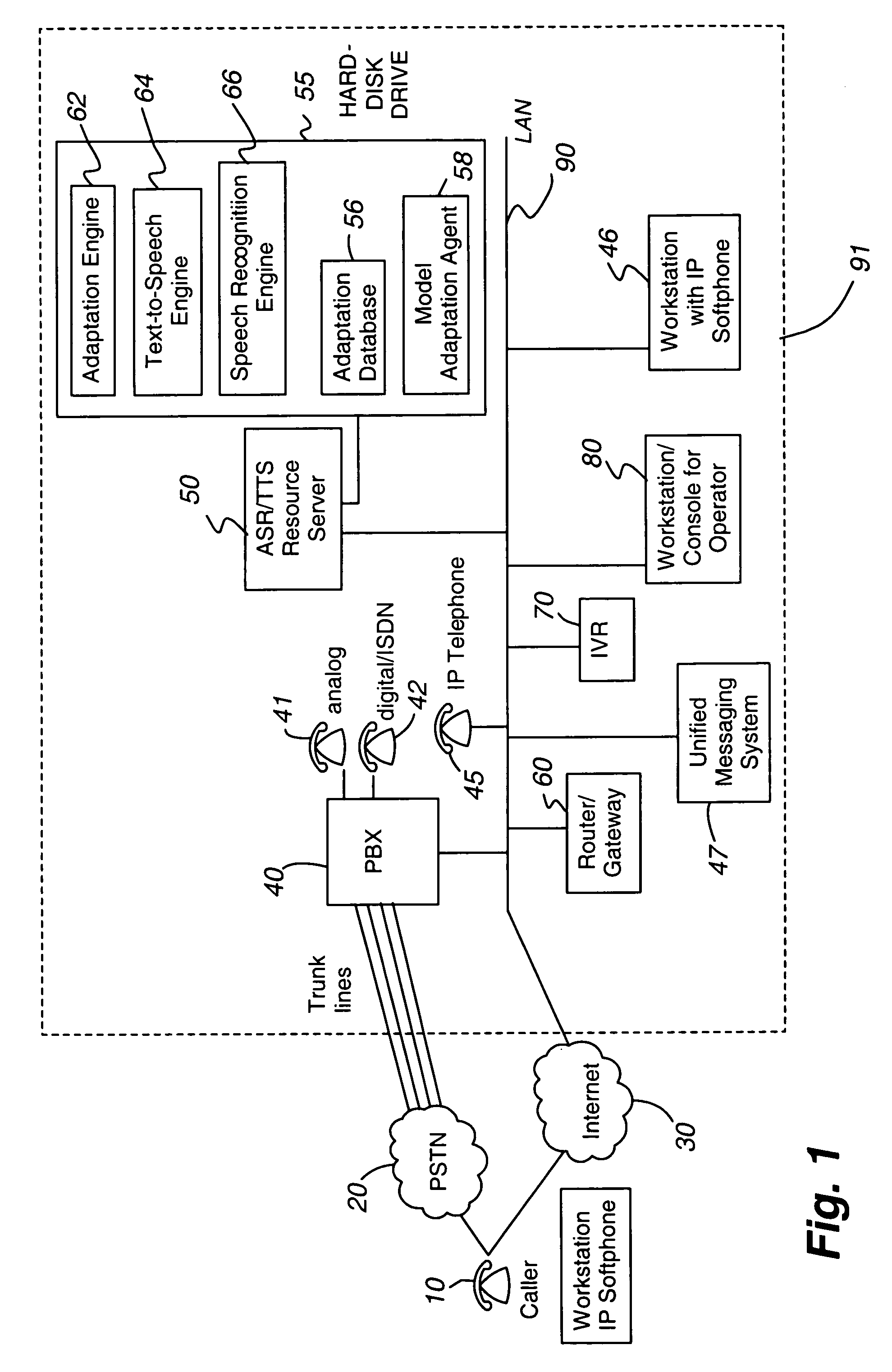
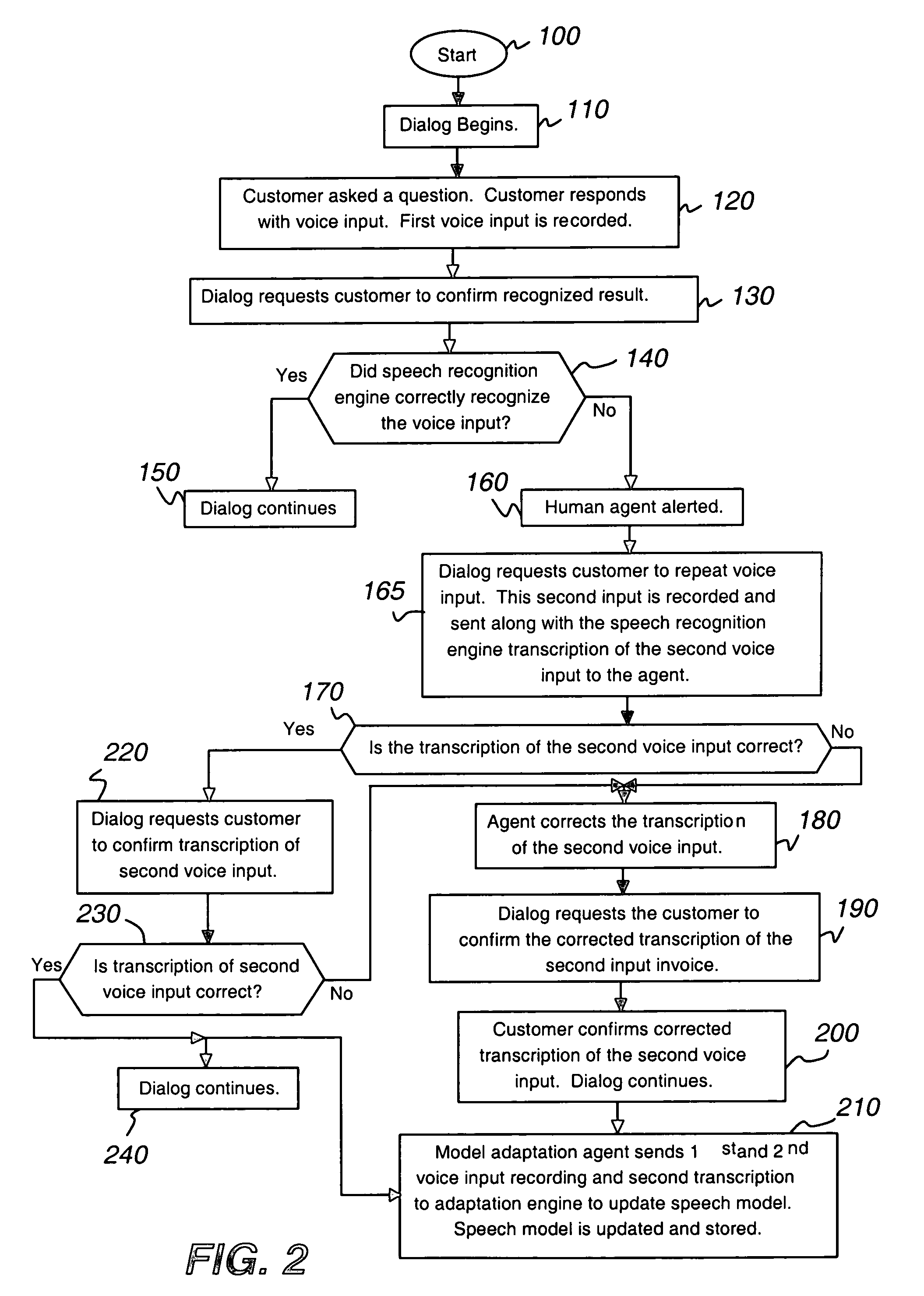
Transparent monitoring and intervention to improve automatic adaptation of speech models
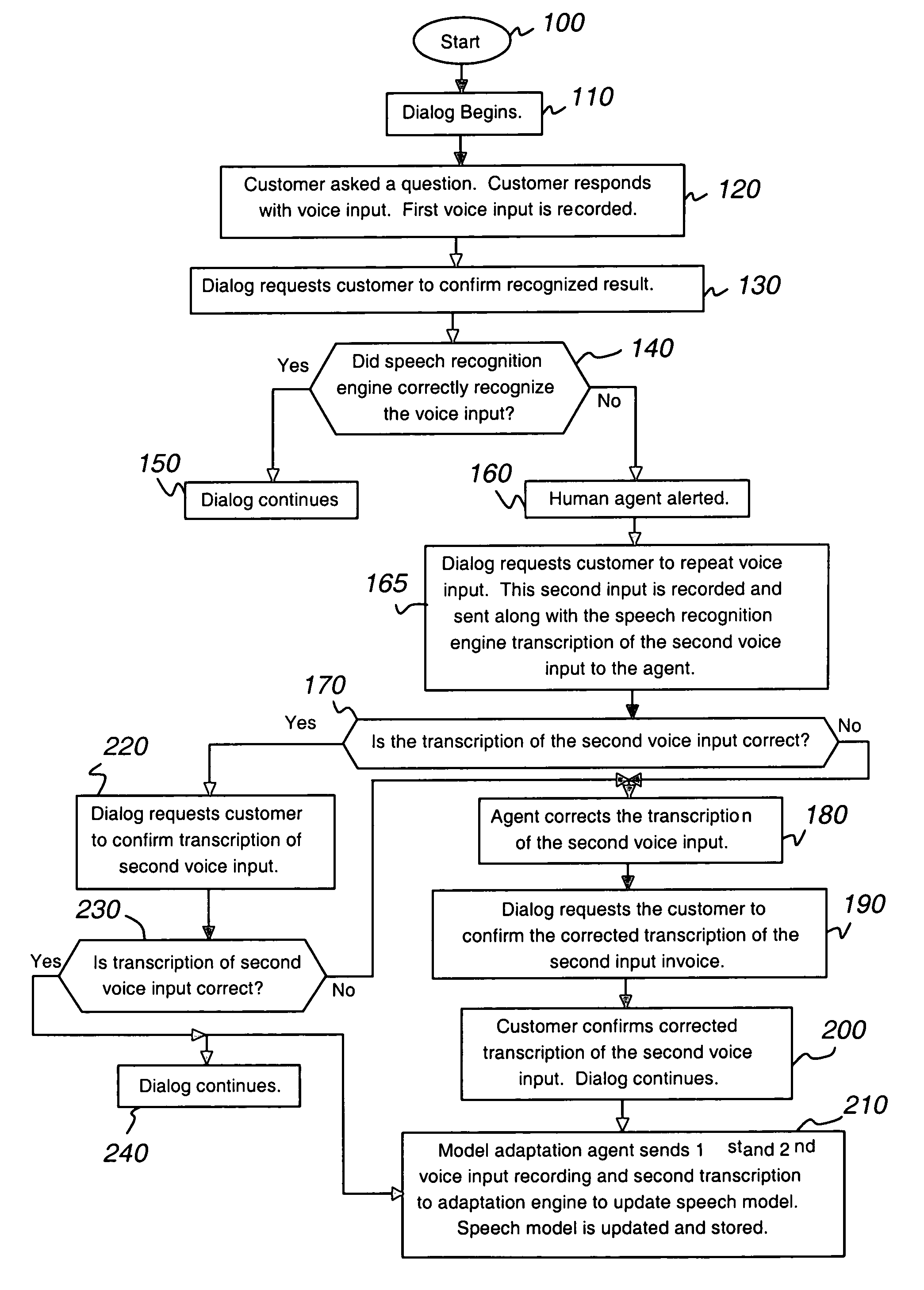
ActiveUS7660715B1Improve speech recognition accuracyQuality improvementSpeech recognitionFrustrationMostly True
A system and method to improve the automatic adaptation of one or more speech models in automatic speech recognition systems. After a dialog begins, for example, the dialog asks the customer to provide spoken input and it is recorded. If the speech recognizer determines it may not have correctly transcribed the verbal response, i.e., voice input, the invention uses monitoring and if necessary, intervention to guarantee that the next transcription of the verbal response is correct. The dialog asks the customer to repeat his verbal response, which is recorded and a transcription of the input is sent to a human monitor, i.e., agent or operator. If the transcription of the spoken input is correct, the human does not intervene and the transcription remains unmodified. If the transcription of the verbal response is incorrect, the human intervenes and the transcription of the misrecognized word is corrected. In both cases, the dialog asks the customer to confirm the unmodified and corrected transcription. If the customer confirms the unmodified or newly corrected transcription, the dialog continues and the customer does not hang up in frustration because most times only one misrecognition occurred. Finally, the invention uses the first and second customer recording of the misrecognized word or utterance along with the corrected or unmodified transcription to automatically adapt one or more speech models, which improves the performance of the speech recognition system.
Owner:AVAYA INC
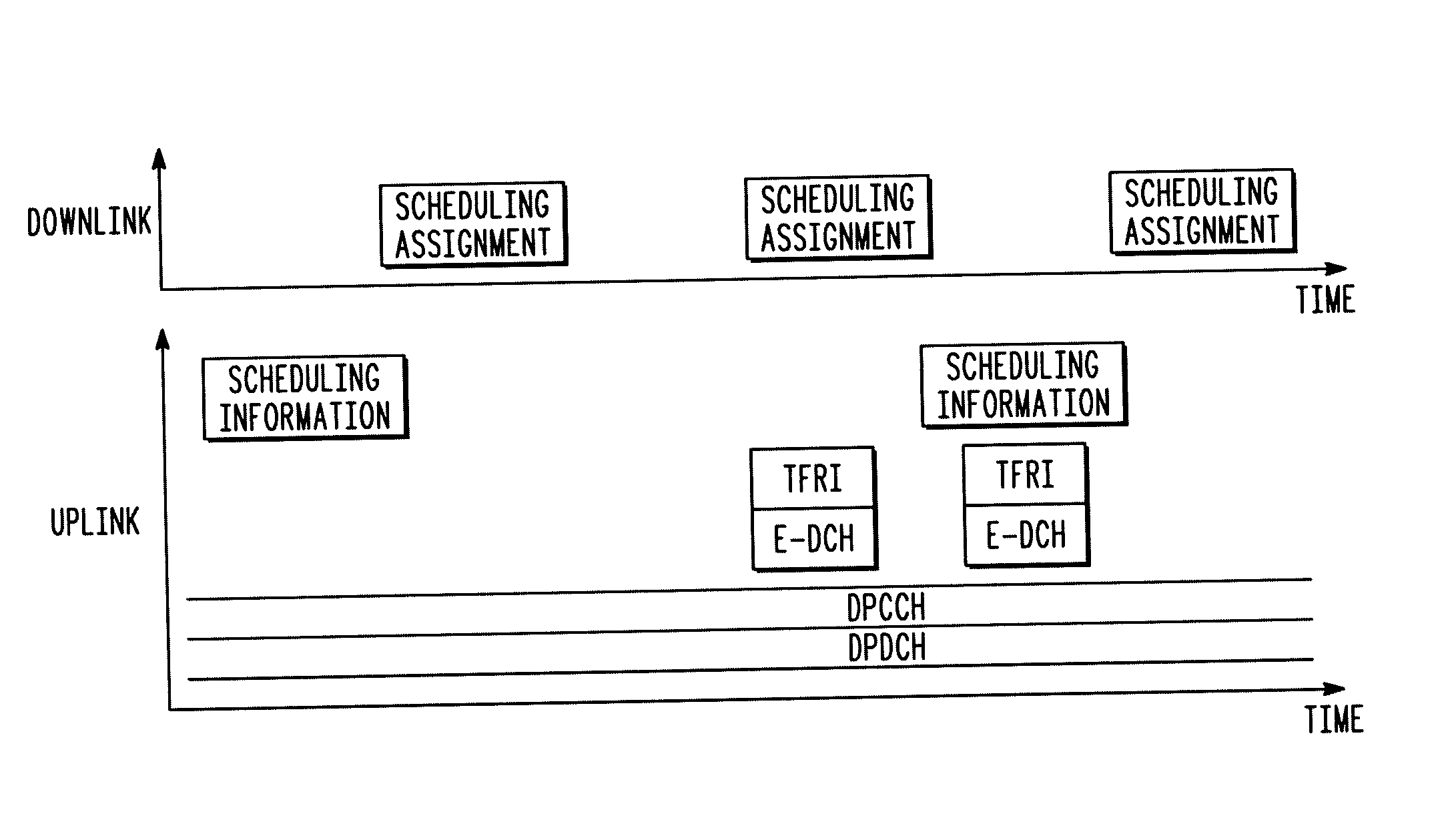
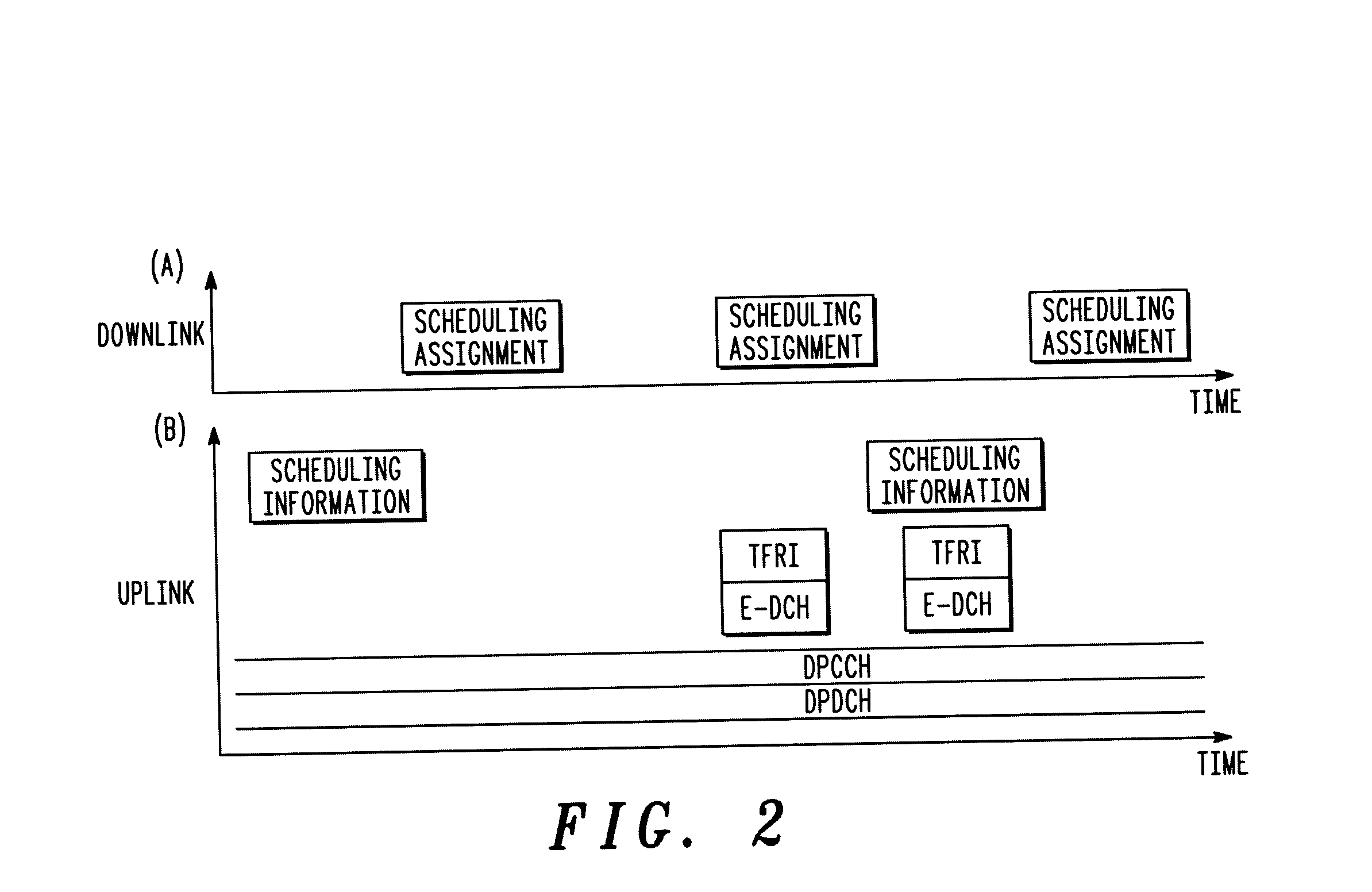
Management of uplink scheduling modes in a wireless communication system
InactiveUS20040219919A1Radio/inductive link selection arrangementsWireless commuication servicesCommunications systemMostly True
The present invention provides an advantageous method for transitioning reliably between scheduling modes on an uplink in a wireless communication system. Transitions between scheduling modes are effected as far as possible using signaling between a wireless communication device and a base station, providing low delay transitions in the majority of cases. Advantageously, signaling direct between the wireless communication device and a network control element may be employed. In addition, the method may operate effectively even when the wireless communication device is in communication with a number of base stations in a soft handoff situation because the network control element may act to ensure that all base stations correspond to the current scheduling mode employed by the wireless communication device.
Owner:GOOGLE TECH HLDG LLC +1
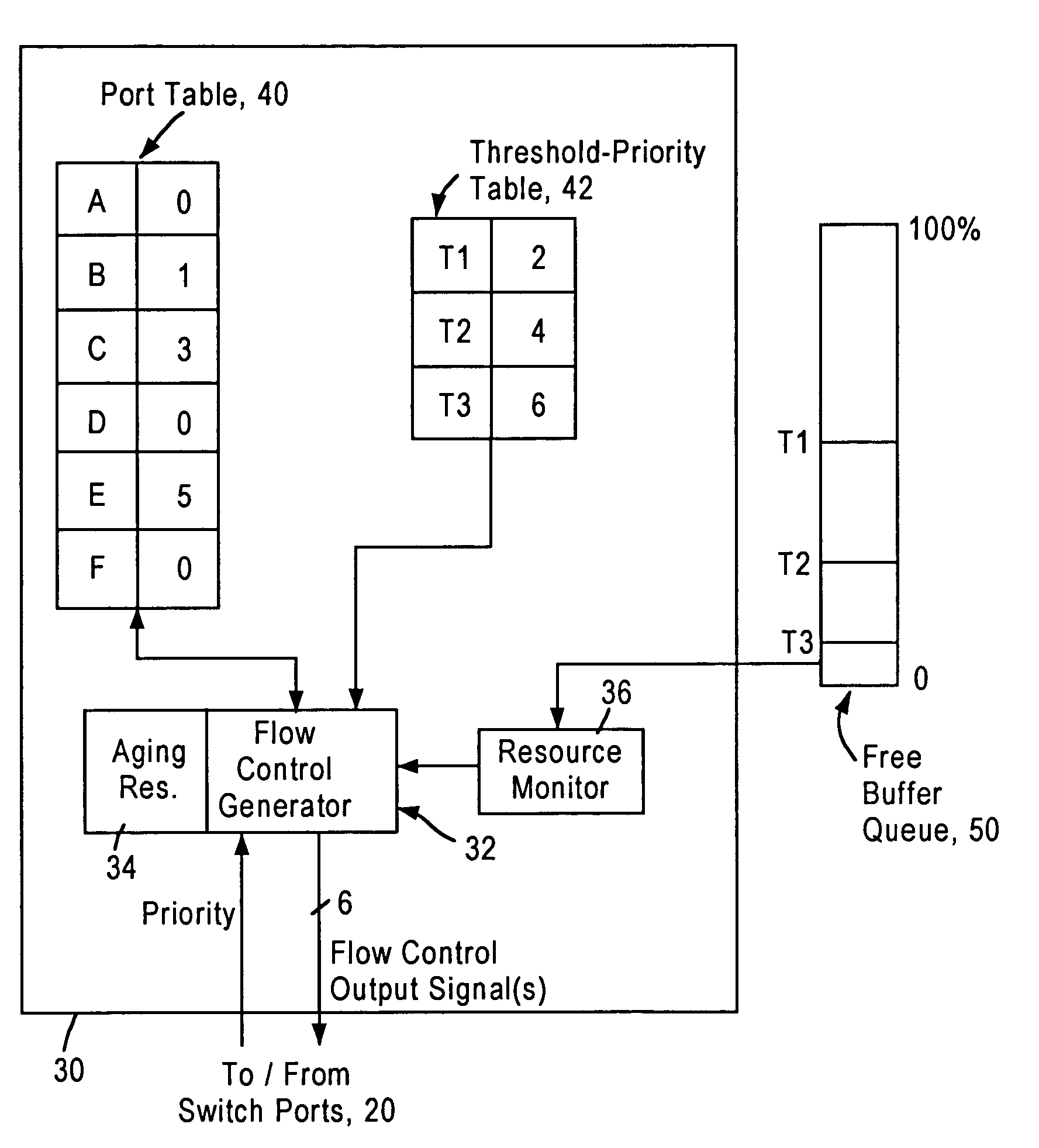
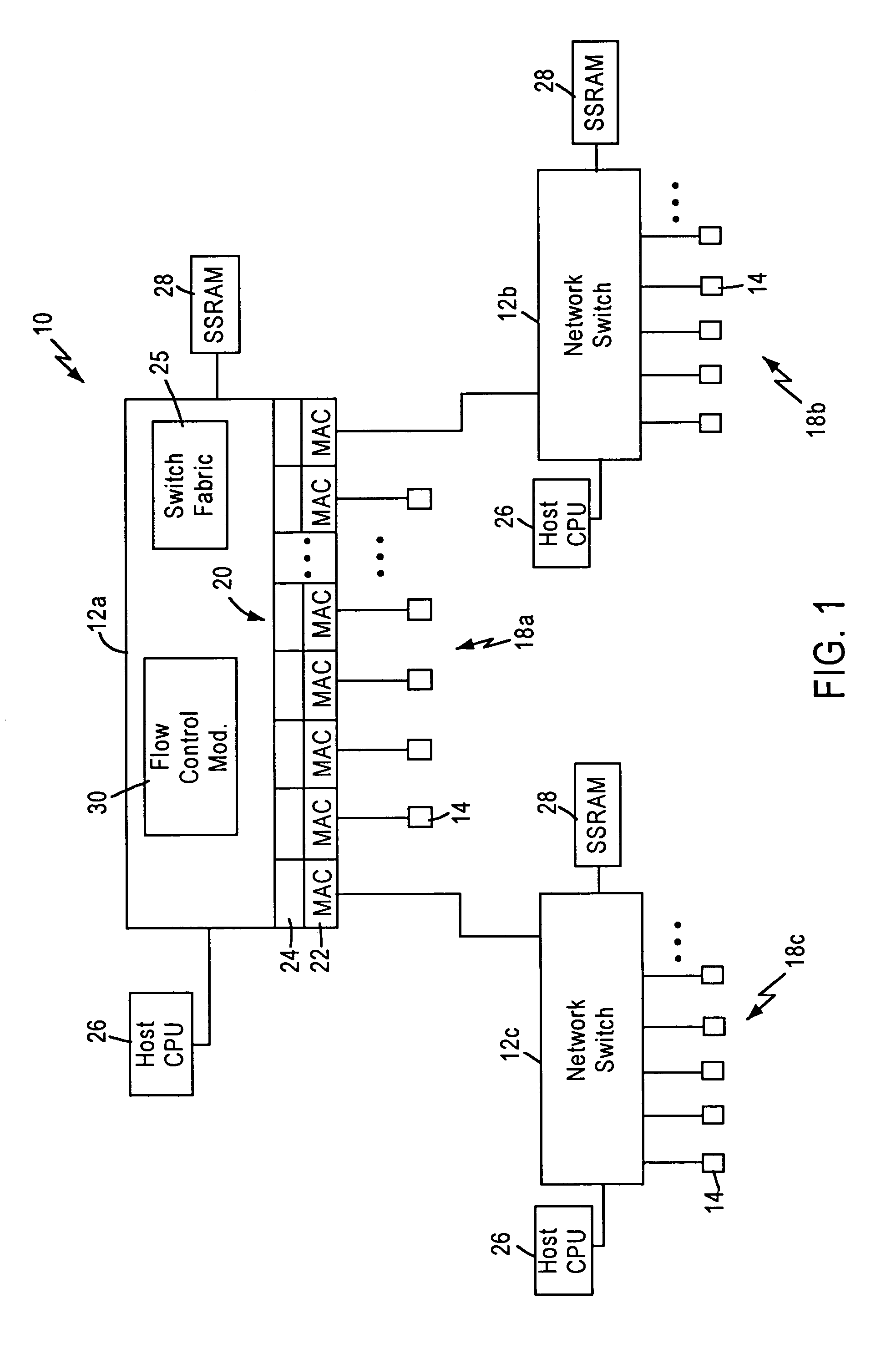
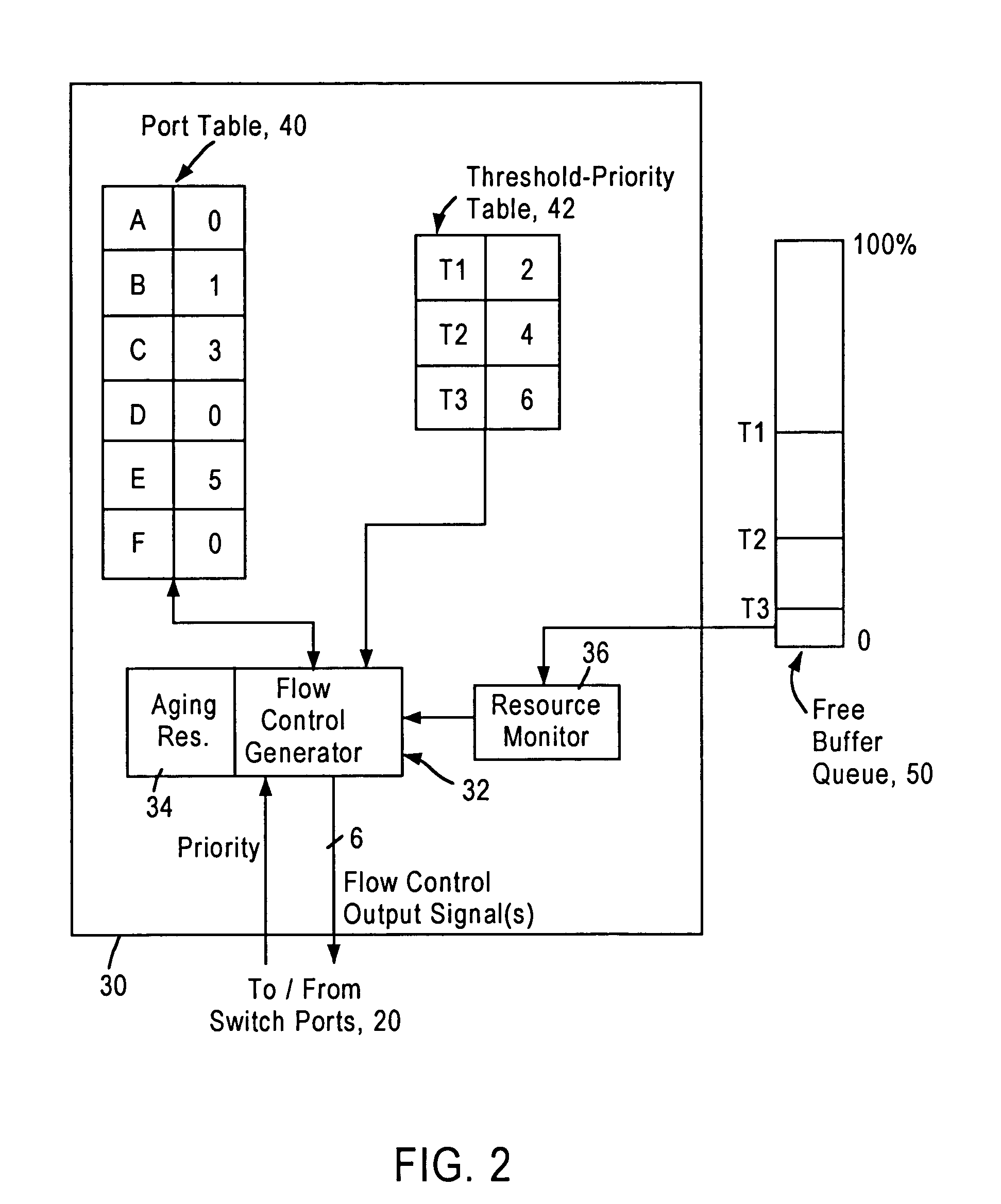
Flow control arrangement in a network switch based on priority traffic
InactiveUS6981054B1Avoid congestionMaintain reliabilityError preventionFrequency-division multiplex detailsTraffic capacityFrame based
A network switch includes network switch ports, each including a port filter configured for detecting user-selected attributes from a received layer 2 frame. Each port filter, upon detecting a user-selected attribute in a received layer 2 frame, sends a signal to a switching module indicating the determined presence of the user-selected attribute, for example whether the data packet has a prescribed priority value. The network switch includes a flow control module that determines which of the network switch ports should output a flow control frame based on the determined depletion of network switch resources and based on the corresponding priority value of the network traffic on each network switch port. Hence, any network switch port that receives high priority traffic does not output a flow control frame to the corresponding network station, enabling that network station to continue transmission of the high priority traffic. In most cases, the congestion and depletion of network switch resources can be alleviated by sending flow control frames on only those network switch ports that receive lower priority traffic, enabling the network switch to reduce congestion without interfering with high priority traffic.
Owner:GLOBALFOUNDRIES US INC
Fixed abrasive tools and associated methods
InactiveUS20050227590A1Easy to remove debrisAdequate material removal rateAbrasion apparatusPlane surface grinding machinesScreen printingMostly True
A fixed abrasive tool incorporating nanodiamond particles is described and disclosed. A fixed abrasive tool can include a polishing layer on a substrate. The polishing layer can include an organic matrix with nanodiamond particles therein. The polishing layer can be formed in a wide variety of configurations, depending on the specific polishing application. Most often, the polishing layer can include a plurality of projections which can have a wide variety of configurations in order to achieve a particular polishing performance. Nanodiamond particles used in the present invention can have a particle size from about 1 nm to about 50 nm, and preferably about 2 nm to about 10 nm. Optionally, the nanodiamond particles can include a carbonaceous coating. Such fixed abrasive tools can be formed by screen printing of a slurry of nanodiamond particles and an organic binder to form a predetermined three-dimensional pattern. Other methods can also be used to form the disclosed nanodiamond fixed abrasive tools. These fixed abrasive tools are particularly suitable for polishing expensive workpieces such as silicon wafers, integrated circuitry, gemstones, and hard drive platters.
Owner:SUNG CHIEN MIN
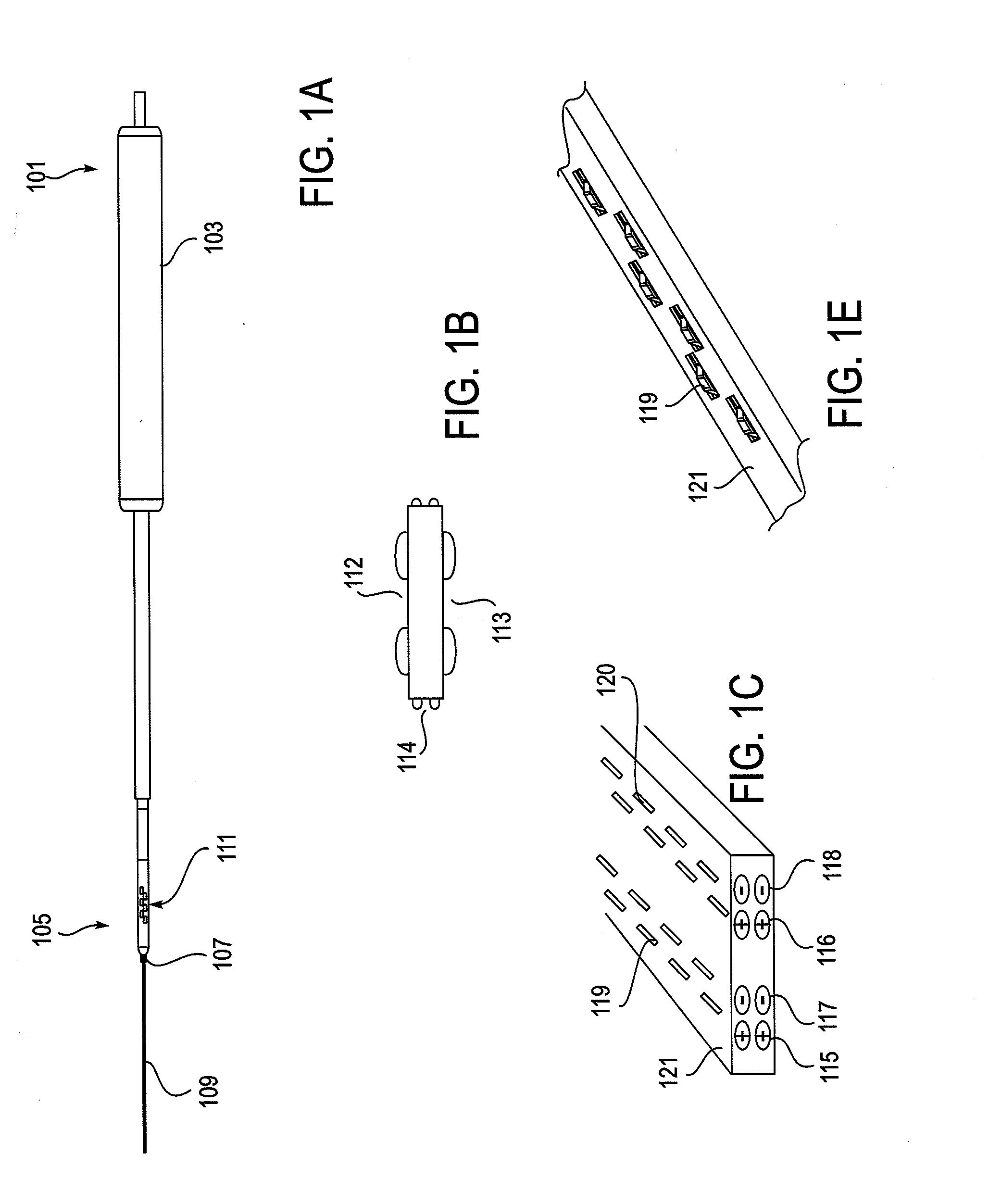
Flexible Neural Localization Devices and Methods
InactiveUS20110004207A1Control spreadAvoid damageSpinal electrodesInternal osteosythesisMedicineNeural foramen
Described herein are devices, systems and methods for determining if a nerve is nearby a device or portion of a device. The neural stimulation tools described herein are configured to be flexible and low-profile, so that they can be used within body regions that may be tortuous or difficult to reach, such as within a compressed or partially occluded neural foramen. In most cases, these tools described herein are ribbon-shaped and adapted to be manipulated bimanually, for example, by applying force to the ends of the devices from separate locations outside of the patient's body. Thus, in some of the exemplary neural localization devices described herein, the distal end region of the device are configured to couple to the proximal end of a guidewire. One or more surfaces of the devices may include an electrode or multi-polar network of electrodes configured to stimulate only nerves within a predetermined distance of a particular face of the device.
Owner:BAXANO SURGICAL
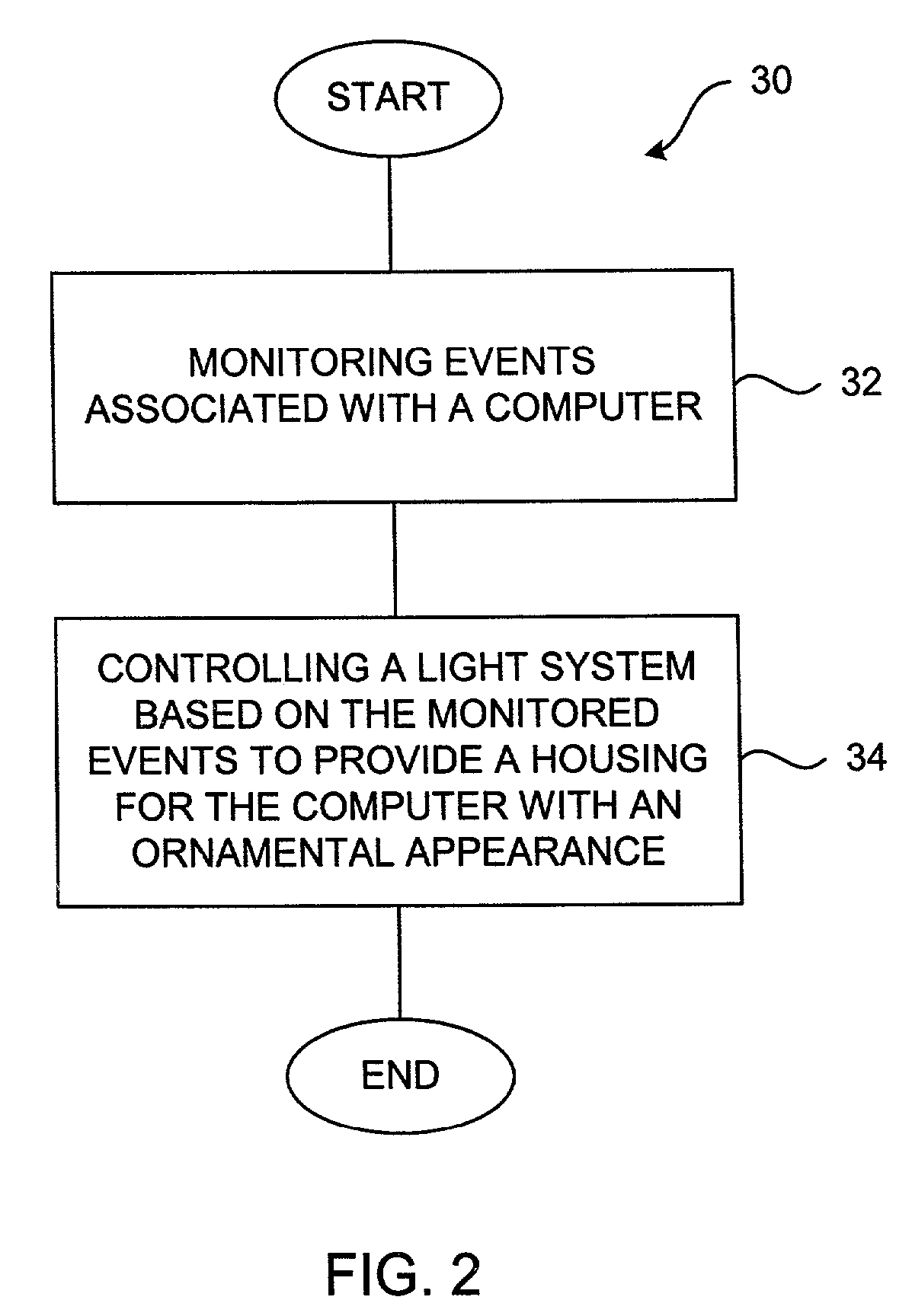
Computing device with dynamic ornamental appearance
The invention pertains to electronic devices capable of dynamically changing their ornamental or decorative appearance, i.e., the outer appearance as seen by a user. The electronic devices generally include an illuminable housing. The illuminable housing, which includes at least one wall configured for the passage of light, is configured to enclose, cover and protect a light arrangement as well as functional components of the electronic device. The light arrangement, which generally includes one or more light sources, is configured to produce light for transmission through the light passing wall(s) of the illuminable housing. The transmitted light illuminates the wall(s) thus giving the wall a new appearance. That is, the transmitted light effectively alters the ornamental or decorative appearance of the electronic device. In most cases, the light is controlled so as to produce a light effect having specific characteristics or attributes. As such, the electronic device may be configured to provide additional feedback to the user of the electronic device and to give users the ability to personalize or change the look of their electronic device on an on-going basis. That is, a housing of the electronic device is active rather than passive, i.e., the housing has the ability to adapt and change. For example, the light may be used to exhibit a housing behavior that reflects the desires or moods of the user, that reflects inputs or outputs for the electronic device, or that reacts to tasks or events associated with operation of the electronic device.
Owner:APPLE INC
Cryptographic key update management method and apparatus
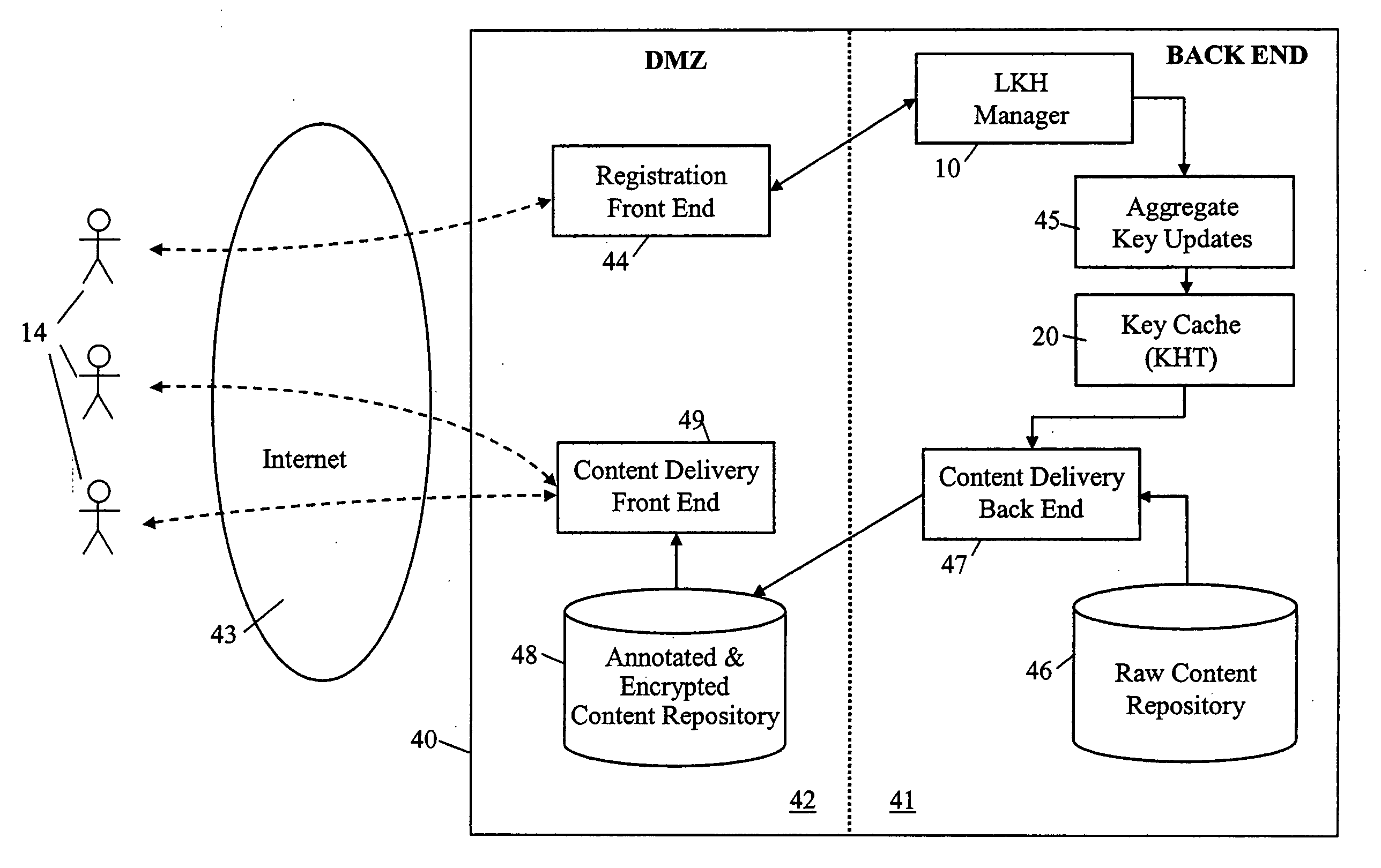
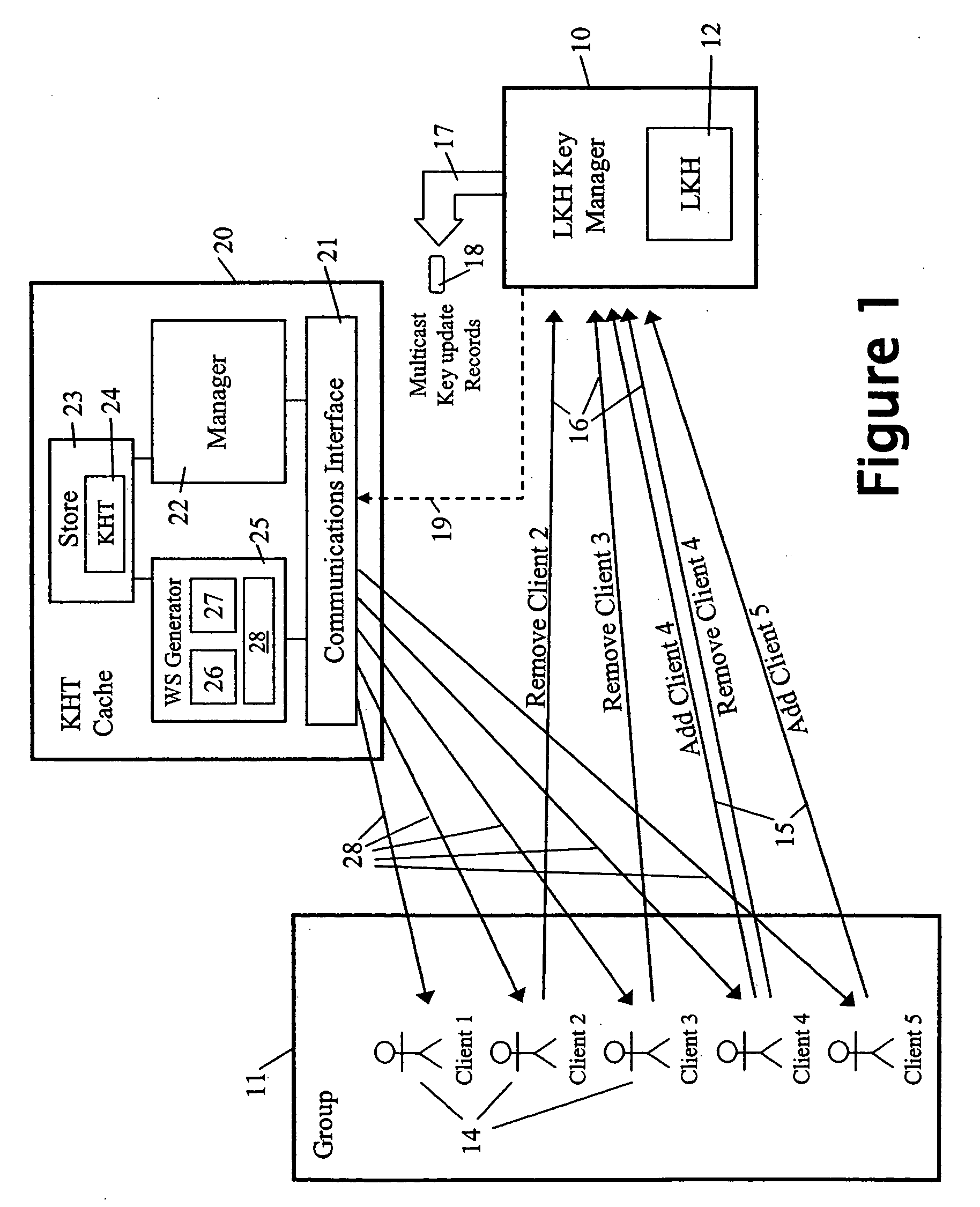
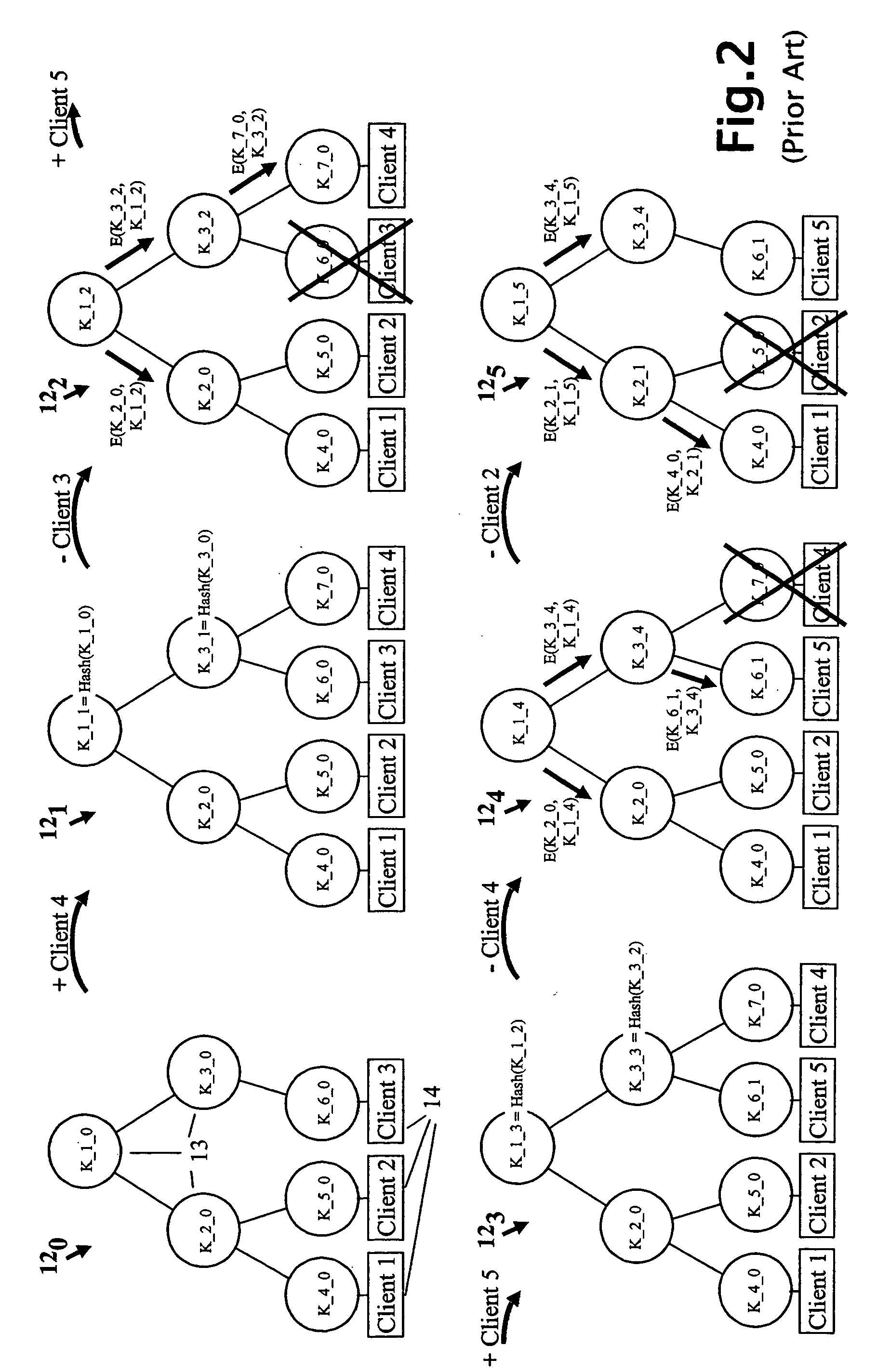
ActiveUS20050018853A1Key distribution for secure communicationPublic key for secure communicationMostly TrueRekeying
A method and apparatus is provided for consolidating cryptographic key updates, the consolidated update information enabling, for example, a returning member of a secure group who has been offline, to recover the current group key, at least in most cases. The unconsolidated key updates each comprise an encrypted key, corresponding to a node of a key hierarchy, that has been encrypted using a key which is a descendant of that node. The key updates are used to maintain a key tree with nodes in this tree corresponding to nodes in the key hierarchy. Each node of the key tree is used to store, for each encrypting key used in respect of the encrypted key associated with the node, the most up-to-date version of the encrypted key with any earlier versions being discarded. The key tree, or a subset of the tree, is then provided to group members.
Owner:MICRO FOCUS LLC
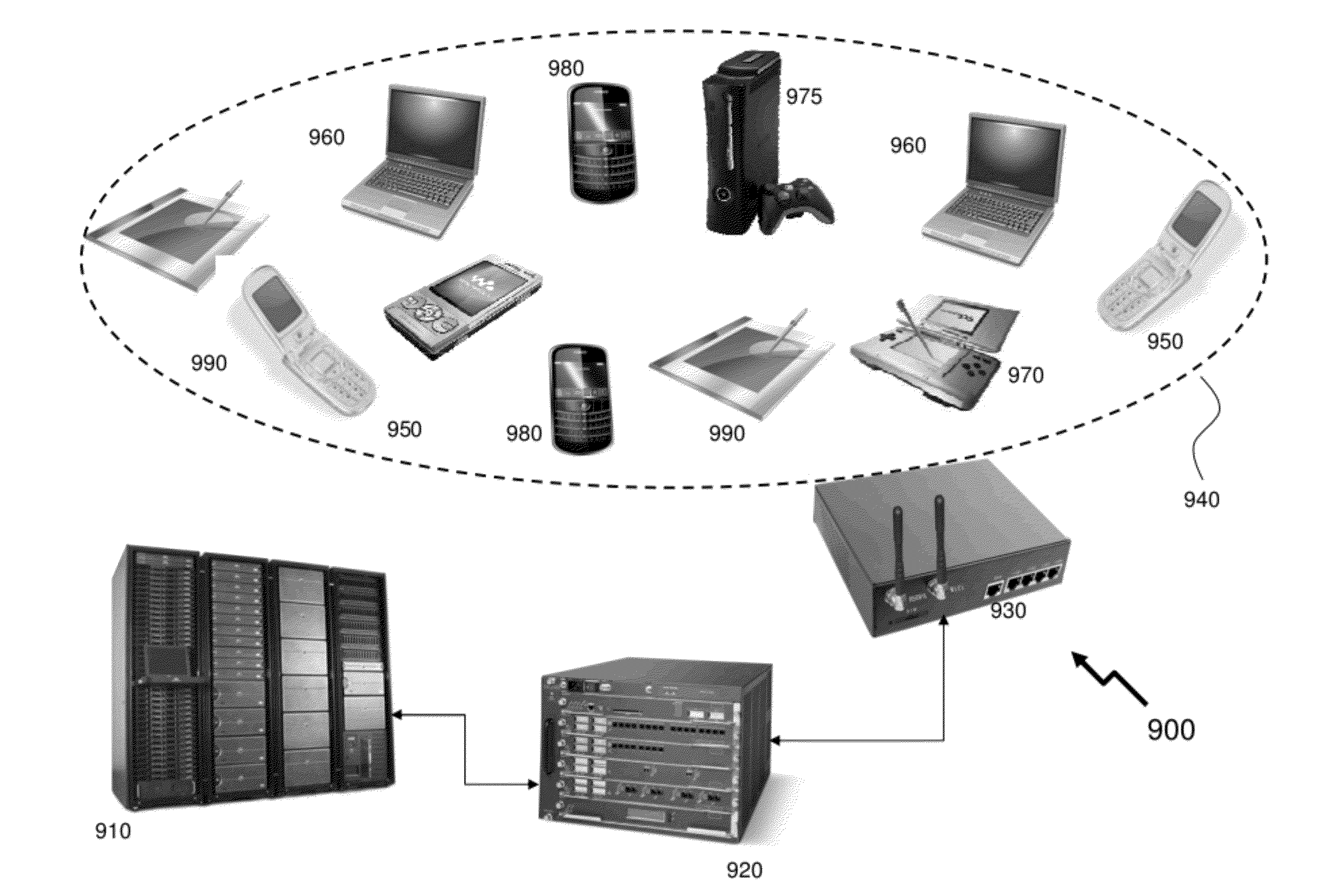
Traffic management in distributed wireless networks
InactiveUS20120224484A1Error preventionTransmission systemsService-level agreementInterference ratio
Wireless networks and devices are ubiquitous today. For service providers to offer customers QoS and Service Level Agreements (SLAs) means in part providing resilient connectivity of wireless devices with good signal strength, good Signal to Noise and Interference Ratio (SNIR), and adequate useable bandwidth. Doing so requires that devices transmitting and receiving packets use over-the-air bandwidth efficiently and manage over-the-air congestion. According to embodiments of the invention QoS measurements and controls are incorporated only in the network (i.e. APs or controllers) and therefore QoS and SLAs can be achieved with all deployed client stations versus standards based approaches that require additional capabilities in network nodes, client stations and in most cases modifications to the applications. SLAs can be provided exploiting embodiments of the invention for traffic prioritization, capacity improvements through load distribution, and adjacent channel interference mitigation discretely or in combination with standards based mechanisms.
Owner:3INOVA NETWORKS
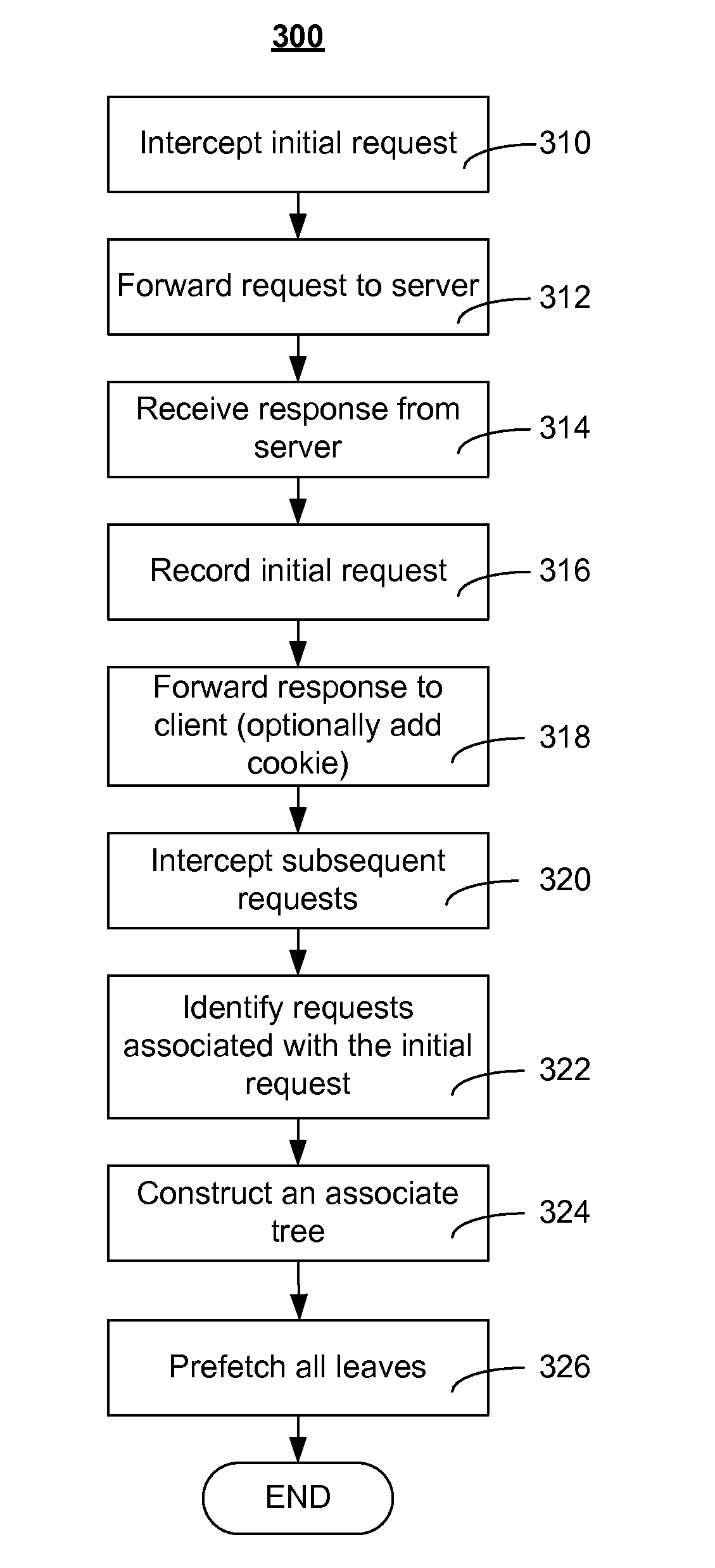
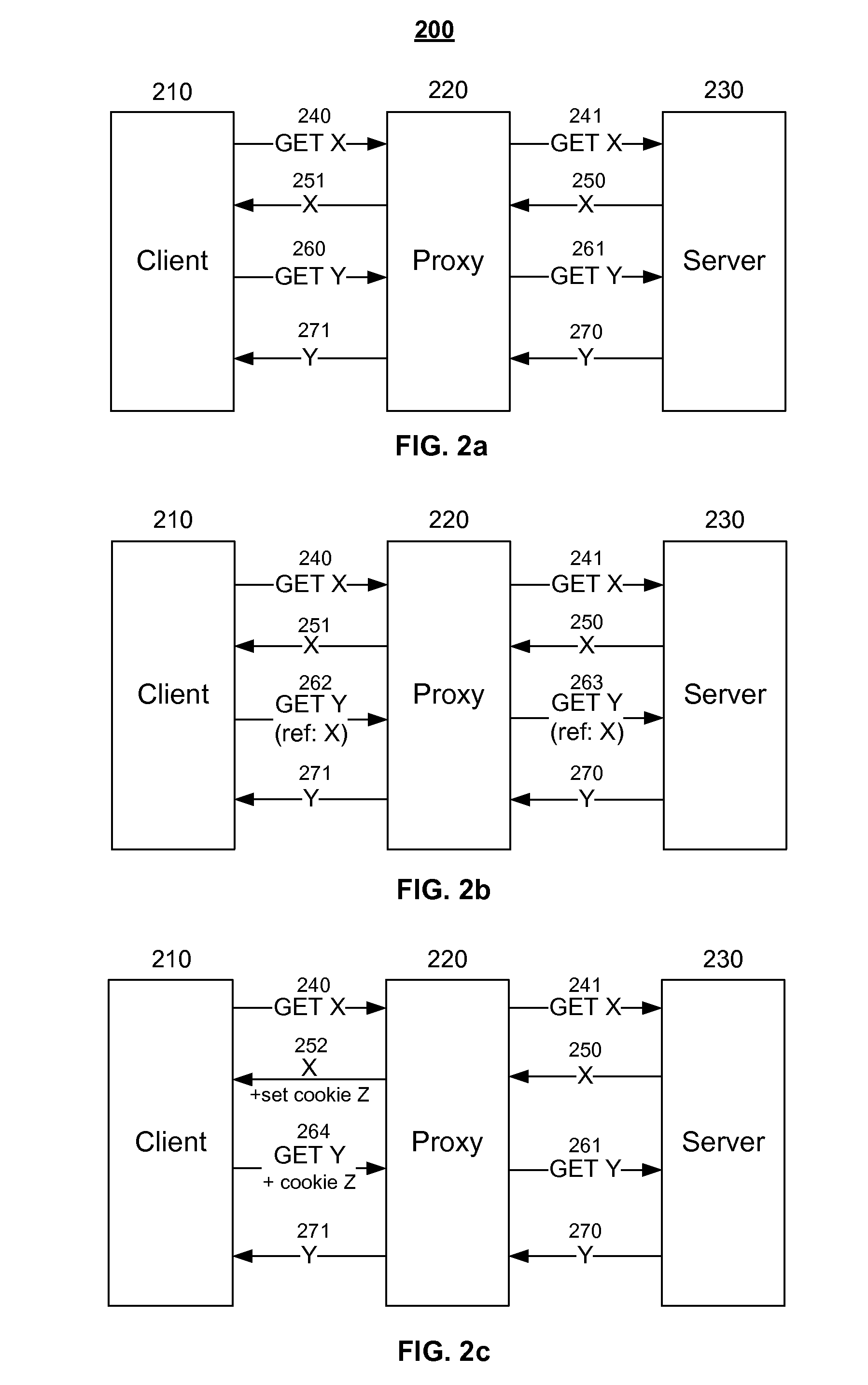
Method and apparatus for acceleration by prefetching associated objects
ActiveUS20080222244A1Multiple digital computer combinationsTransmissionMostly TrueUniform resource locator
Association information is used to build association trees to associate base pages and embedded objects at a proxy. An association tree has a root node containing a URL for a base page, and zero or more leaf nodes each containing a URL for an embedded object. In most cases, an association tree will maintain the invariant that all leaves contain distinct URLs. However, it is also possible to have an association tree in which the same URL appears in multiple nodes. An association tree may optionally contain one or more internal nodes, each of which contains a URL that is an embedded object for some other base page, but which may also be fetched as a base page itself. Given a number of association trees and a base-page URL, a prefetch system finds the root or interior node corresponding to that URL (if any) and traverses the tree from that node, prefetching URLs until the URL of the last leaf node is prefetched. The prefetching starts the process of bringing over the various embedded objects before the user or program would ordinarily fetch them.
Owner:RIVERBED TECH LLC
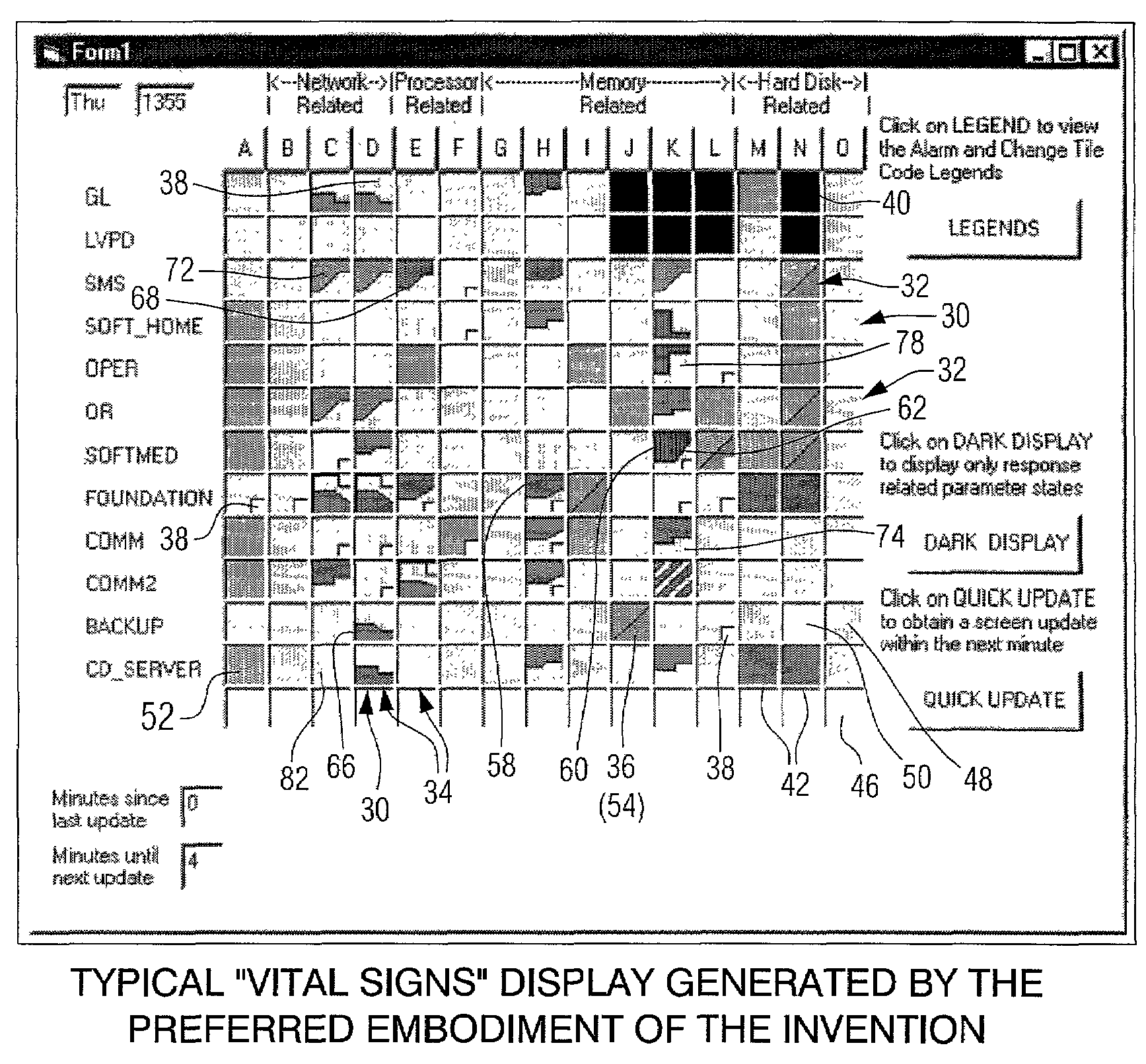
Display to facilitate the monitoring of a complex process
A display organized with the various components of a complex process represented by the rows, and selected parameters to be monitored listed in columns. The fields of the display which represent a particular “vital sign” for a particular component present two types of information: (1) alarms which indicate whether the parameter is in or out of limits and how close it is to failure; and (2) trends which indicate changes and types of changes, but do not pose a threat to the system. The alarms, in most part, are represented by solid colors. The trends are shown by the interface line between two contrasting colors or shades of colors defining the trend line and showing the direction of the trend and type of change.
Owner:IMPINK JR ALBERT J +3
Traffic management in distributed wireless networks
InactiveUS20120224481A1Error preventionTransmission systemsService-level agreementInterference ratio
Wireless networks and devices are ubiquitous today. For service providers to offer customers QoS and Service Level Agreements (SLAs) means in part providing resilient connectivity of wireless devices with good signal strength, good Signal to Noise and Interference Ratio (SNIR), and adequate useable bandwidth. Doing so requires that devices transmitting and receiving packets use over-the-air bandwidth efficiently and manage over-the-air congestion. According to embodiments of the invention QoS measurements and controls are incorporated only in the network (i.e. APs or controllers) and therefore QoS and SLAs can be achieved with all deployed client stations versus standards based approaches that require additional capabilities in network nodes, client stations and in most cases modifications to the applications. SLAs can be provided exploiting embodiments of the invention for traffic prioritization, capacity improvements through load distribution, and adjacent channel interference mitigation discretely or in combination with standards based mechanisms.
Owner:3INOVA NETWORKS
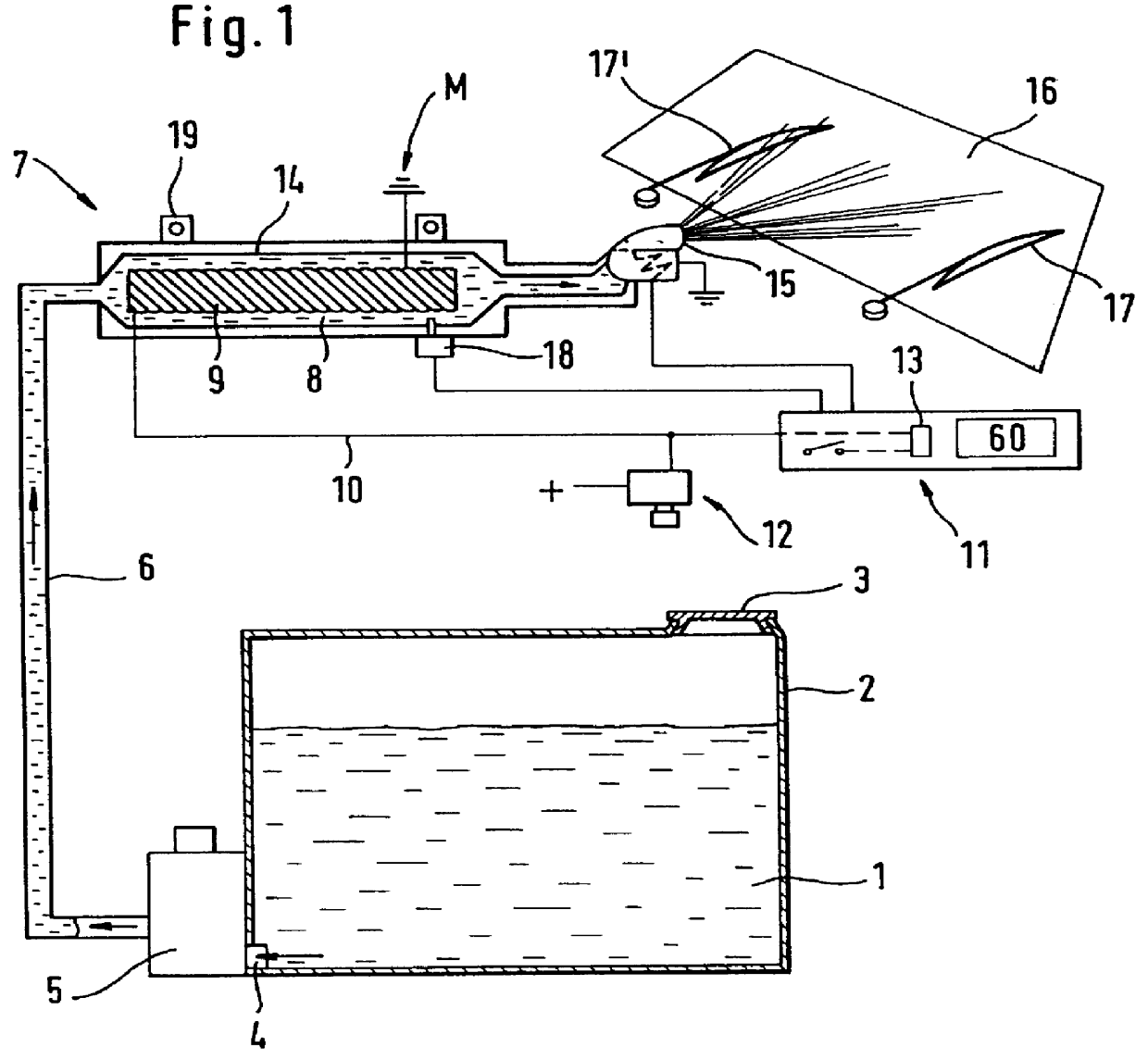
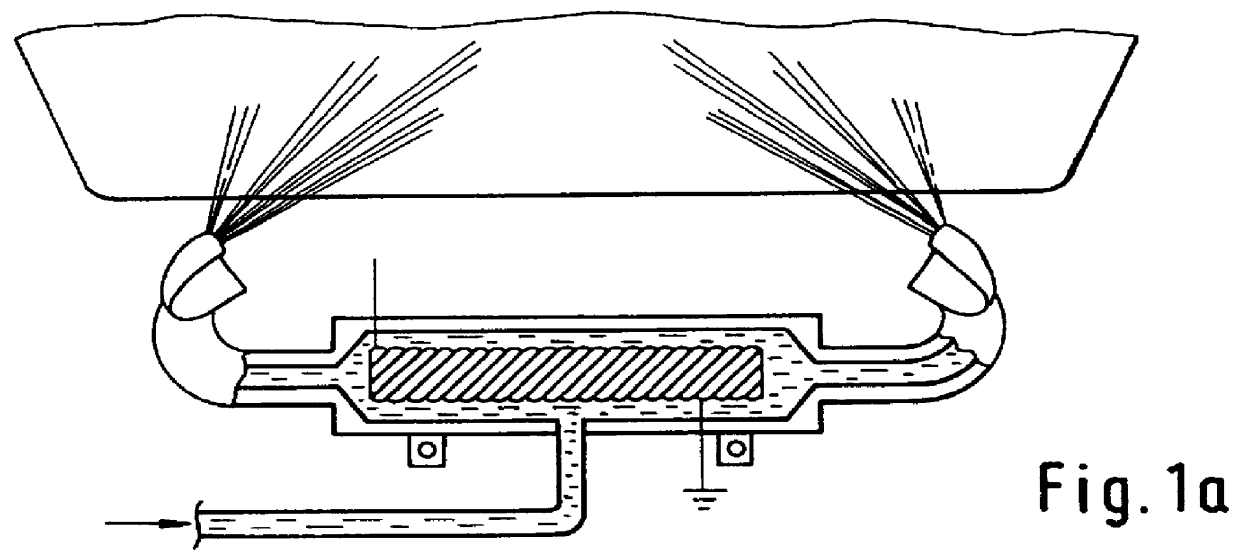
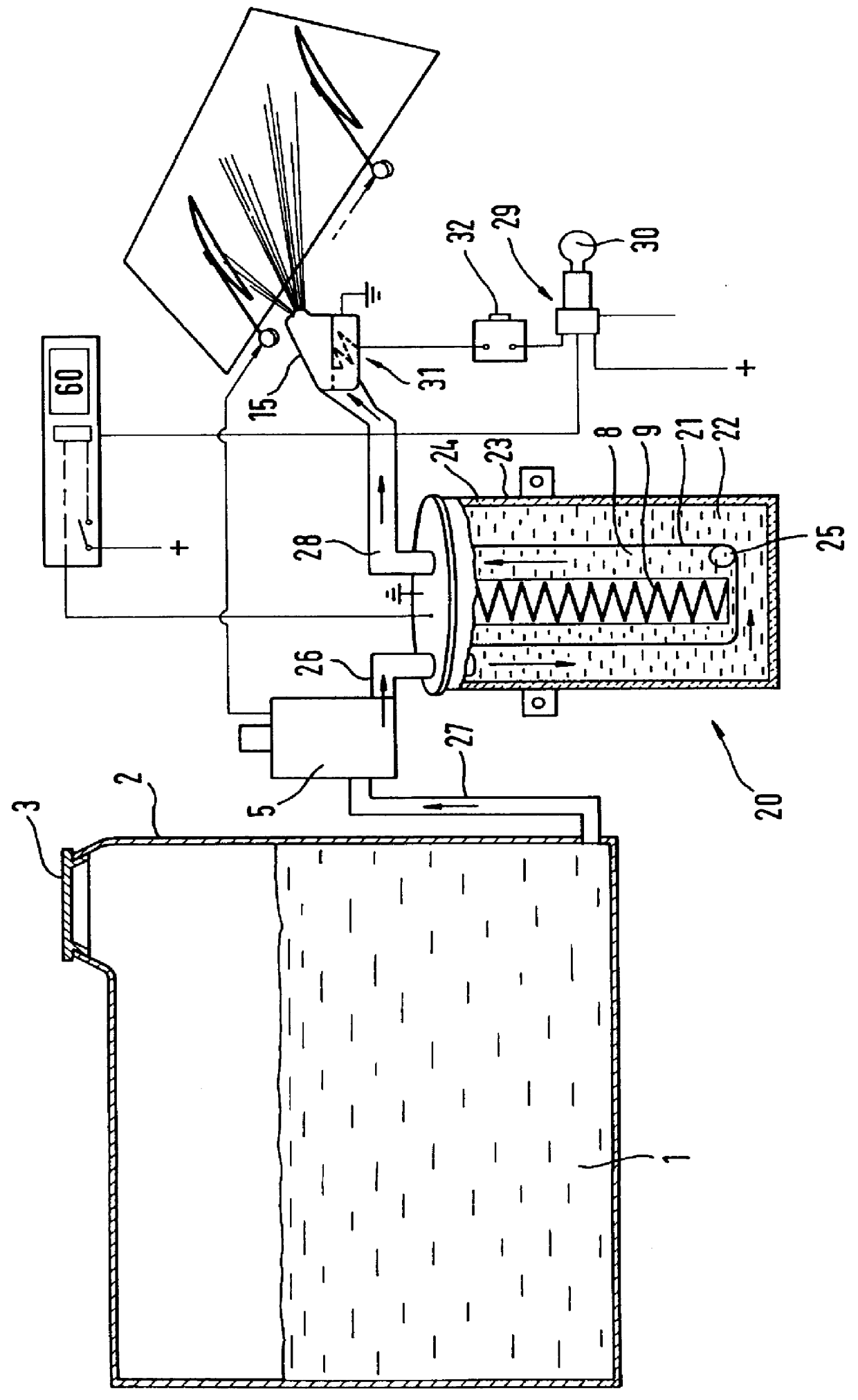
Process and device for heating windscreen washer liquid
PCT No. PCT / EP97 / 02902 Sec. 371 Date Apr. 12, 1999 Sec. 102(e) Date Apr. 12, 1999 PCT Filed Jun. 4, 1997 PCT Pub. No. WO97 / 46431 PCT Pub. Date Dec. 11, 1997Only a small useful quantity of washing water as close as possible to the spray nozzles of the windshield wiper system is heated. As a result of corresponding miniaturization, the heating time can be reduced to 5 to 10 seconds. A sufficient cleaning effect can be achieved in most cases by hot water after the windshield spray system is actuated two or three times. Additional cleaning can be carried out either by rinsing with colder or cold water or by repeating after 10 to 20 seconds. The water is heated via an instant heating element which, with a content of, for example, 10 to 50 cm3, can be installed even in a secondary chamber. Some of the heat energy is therefore stored in a larger thermal reserve tank of, for example, 1 dl.
Owner:RASHPAL BAINS
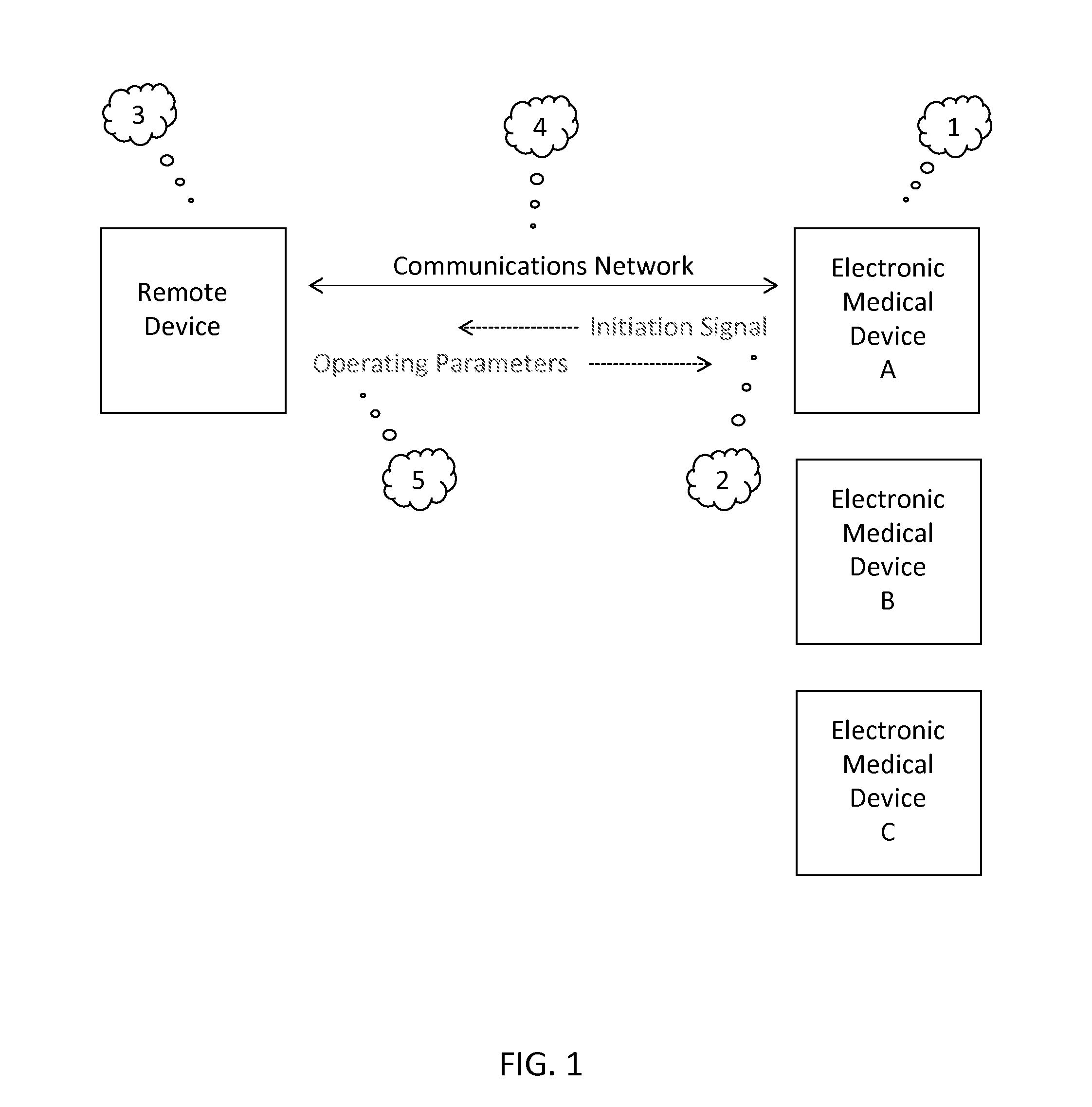
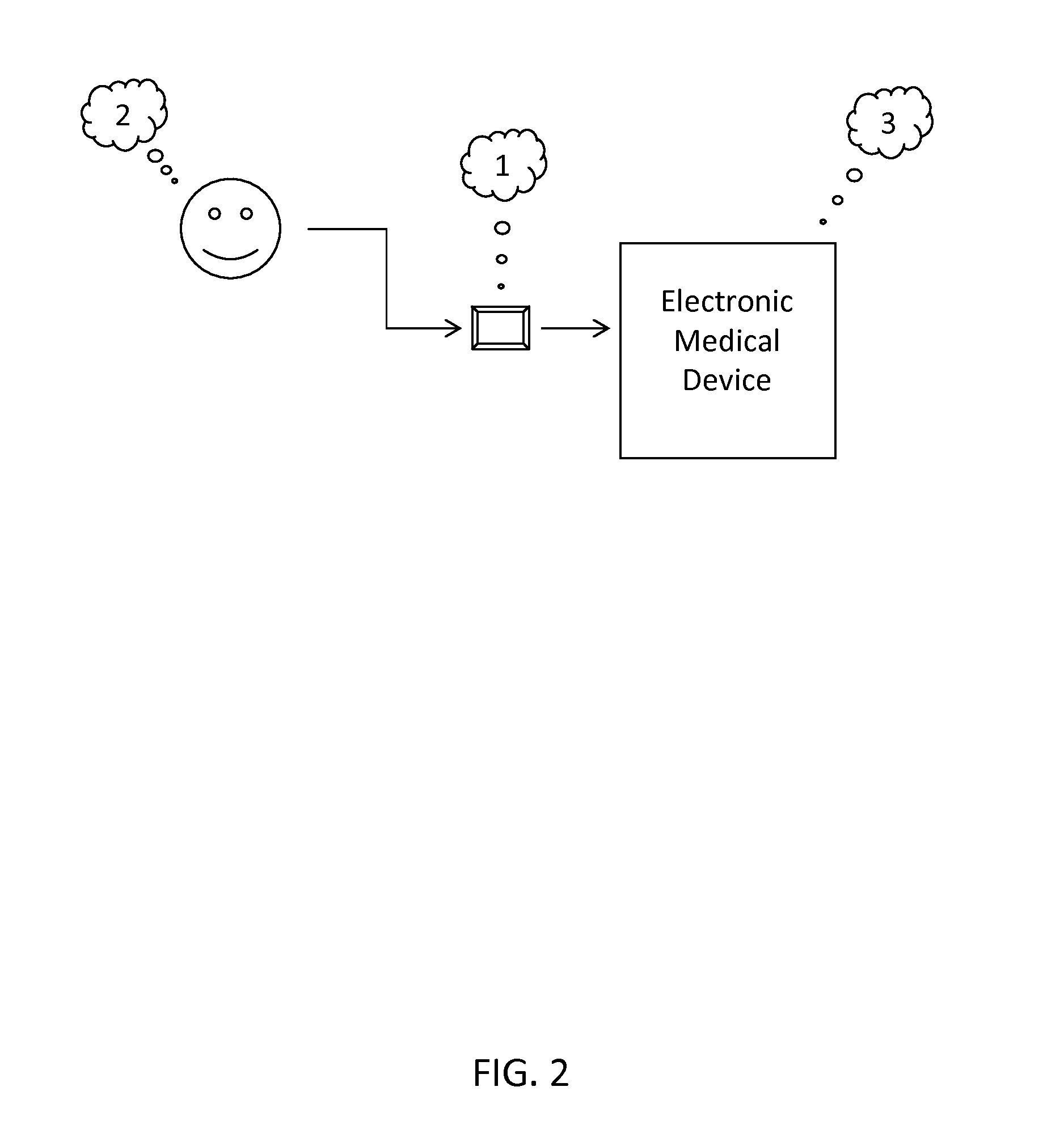
Method for External Storage of Medical Device Program Design Parameters
ActiveUS20130291116A1Easy to findPreserving a greater degree of design secrecyDigital data processing detailsAnalogue secracy/subscription systemsExternal storageMostly True
Many electronic medical devices include program design features that direct the operation of the device. The program design features of most electronic medical devices reside in the device itself and therefore are easily discovered by reverse engineering. In most cases, however, these features can be introduced into the device from an external source for only so long as necessary for each operation of the device, thereby making the reverse engineering of these features more difficult (or even impossible) and preserving a greater degree of design secrecy.
Owner:HOMER GREGG S
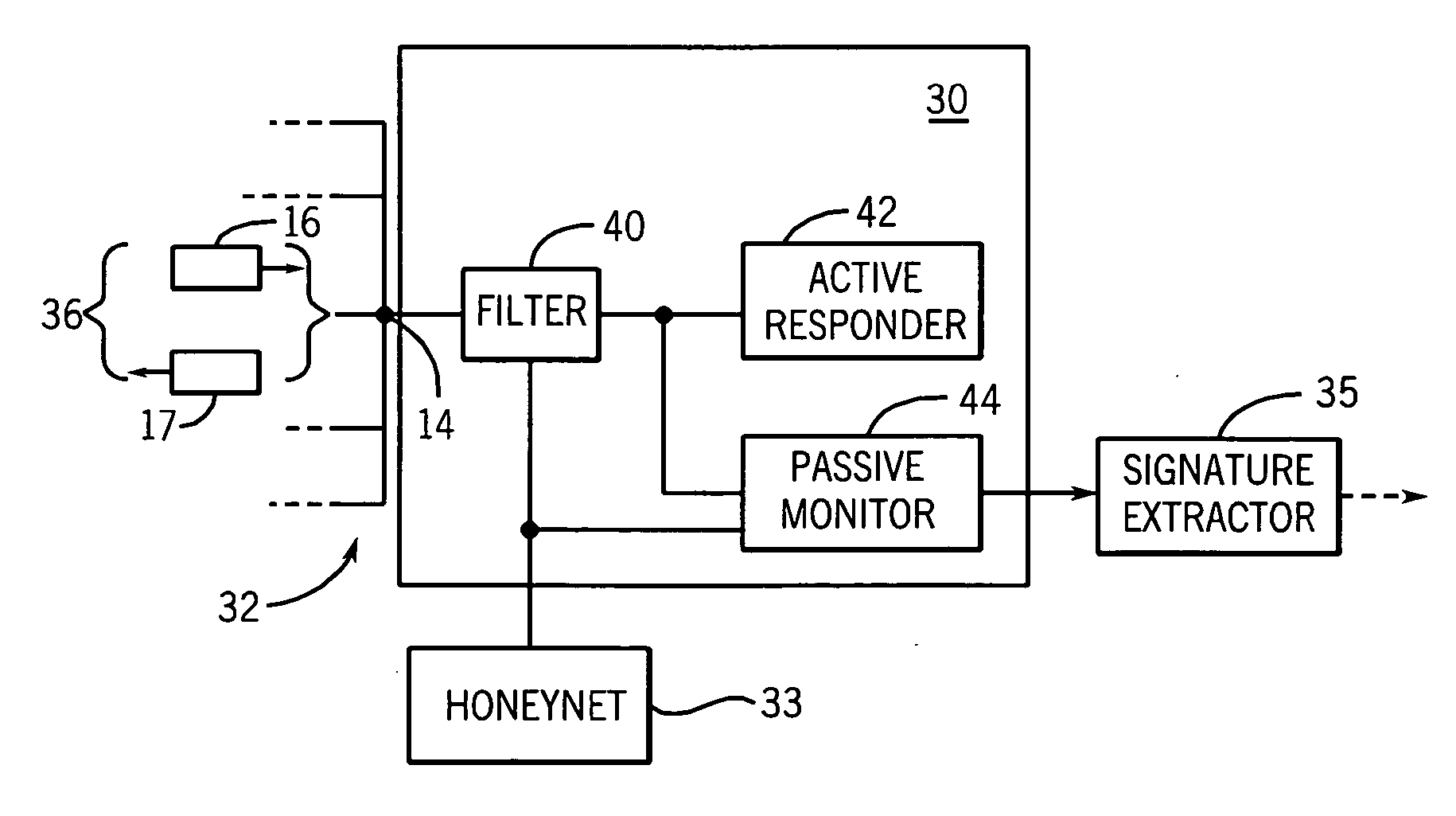
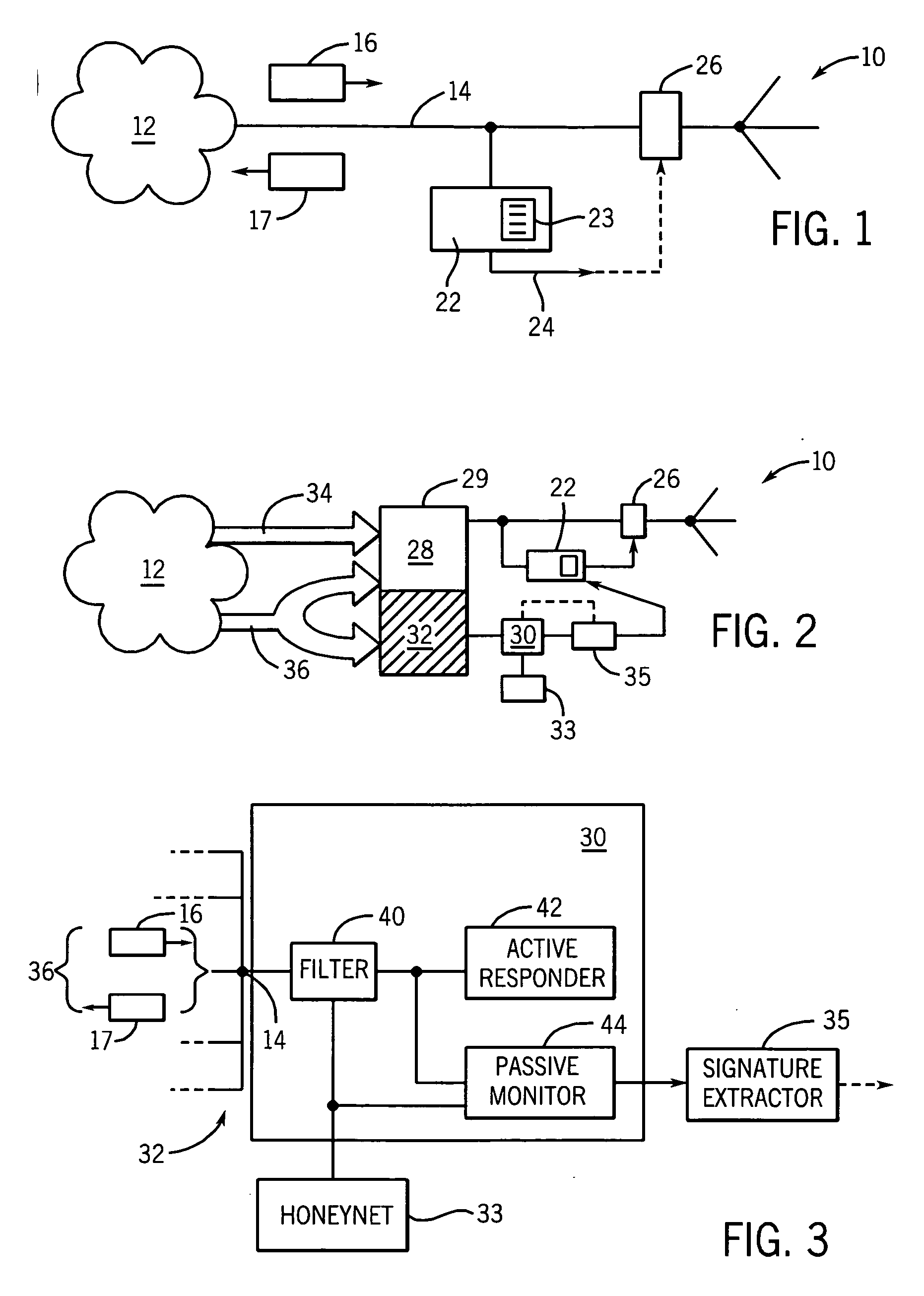
Scalable monitor of malicious network traffic
ActiveUS20070067841A1Memory resource is reducedHigh degreeMemory loss protectionUnauthorized memory use protectionExtensibilityMostly True
A monitor of malicious network traffic attaches to unused addresses and monitors communications with an active responder that has constrained-state awareness to be highly scalable. In a preferred embodiment, the active responder provides a response based only on the previous statement from the malicious source, which in most cases is sufficient to promote additional communication with the malicious source, presenting a complete record of the transaction for analysis and possible signature extraction.
Owner:WISCONSIN ALUMNI RES FOUND
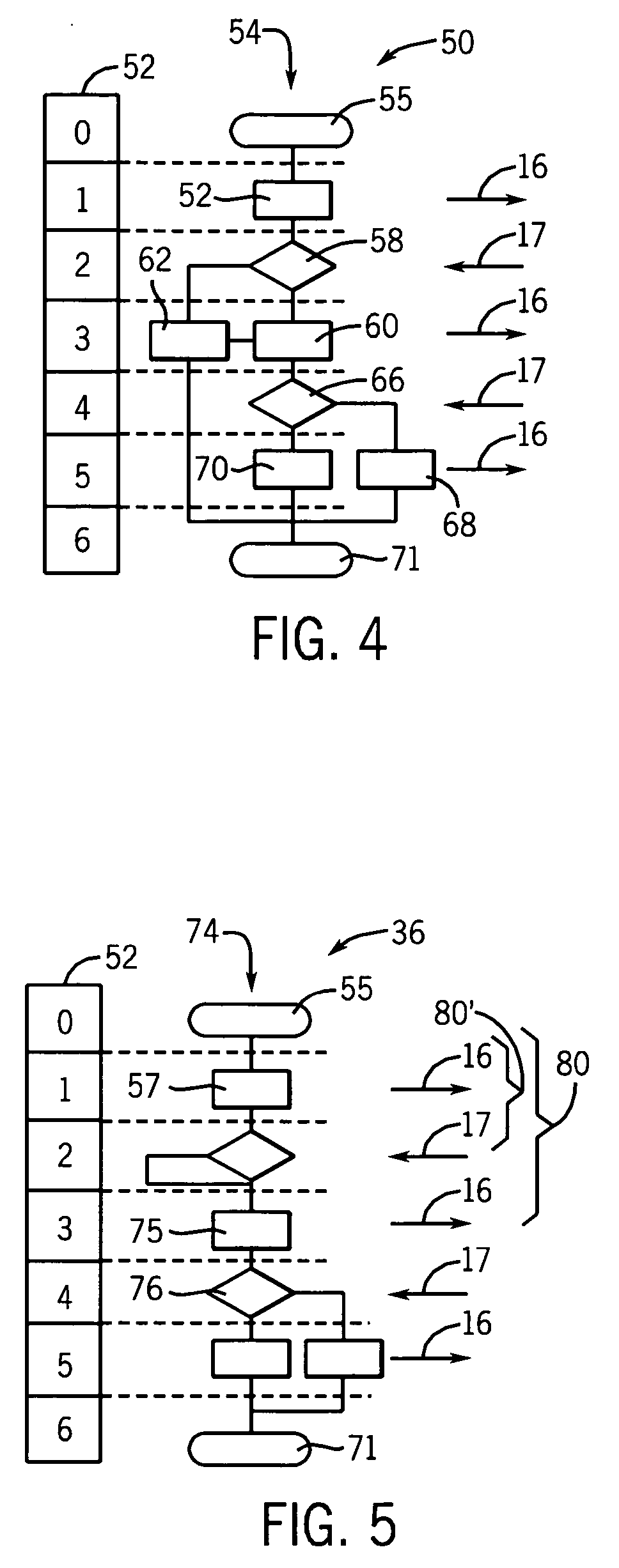
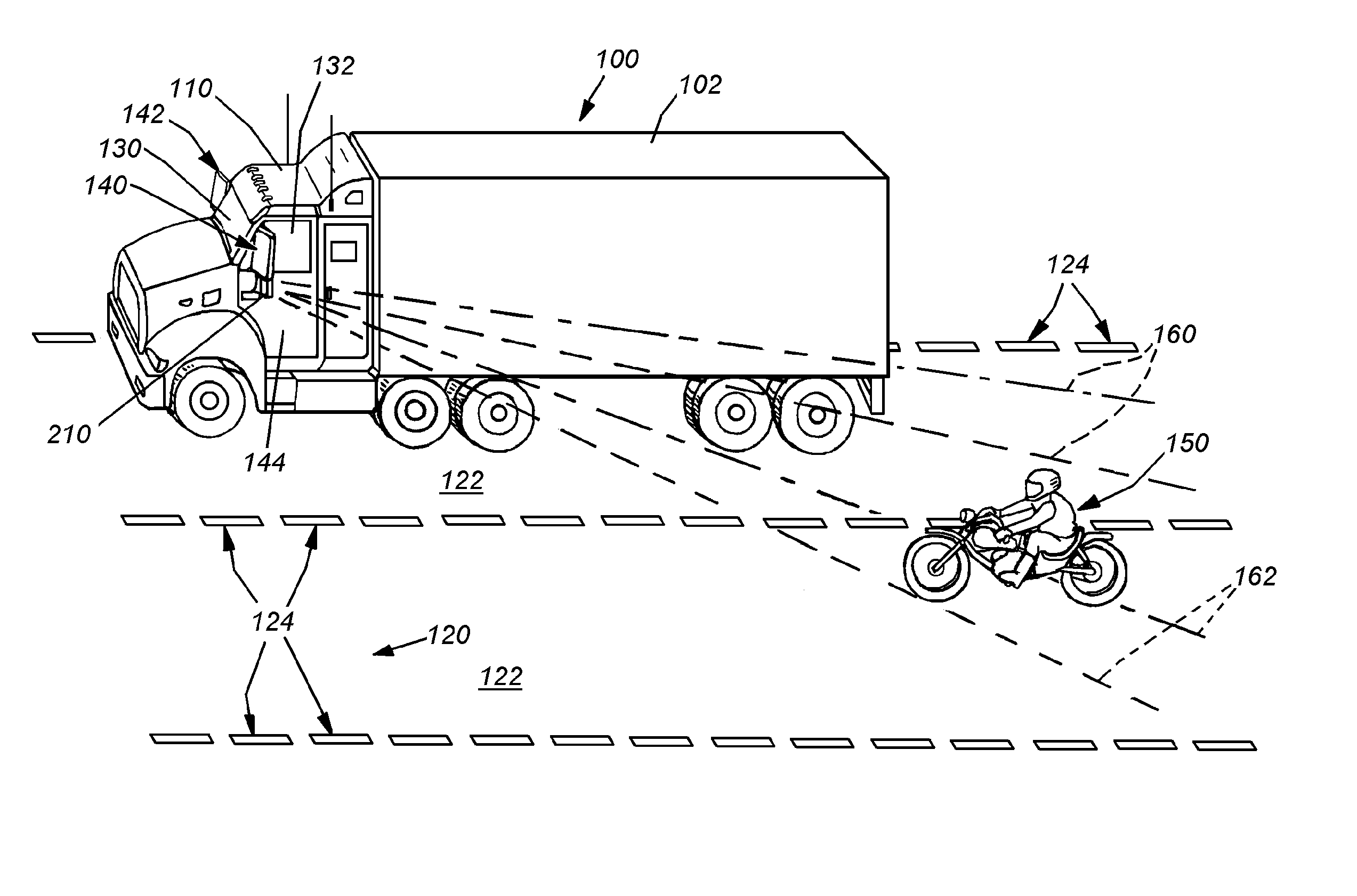
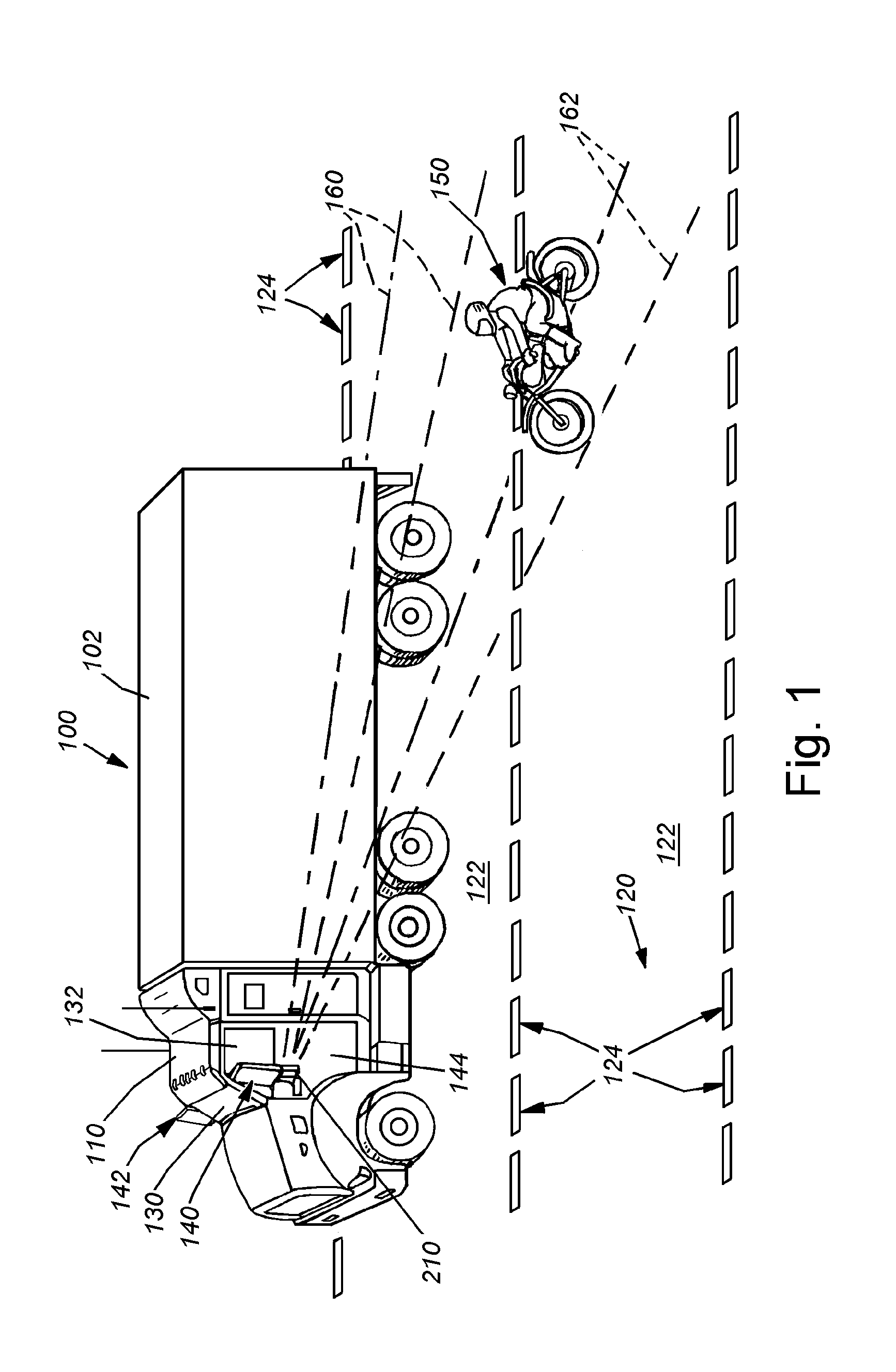
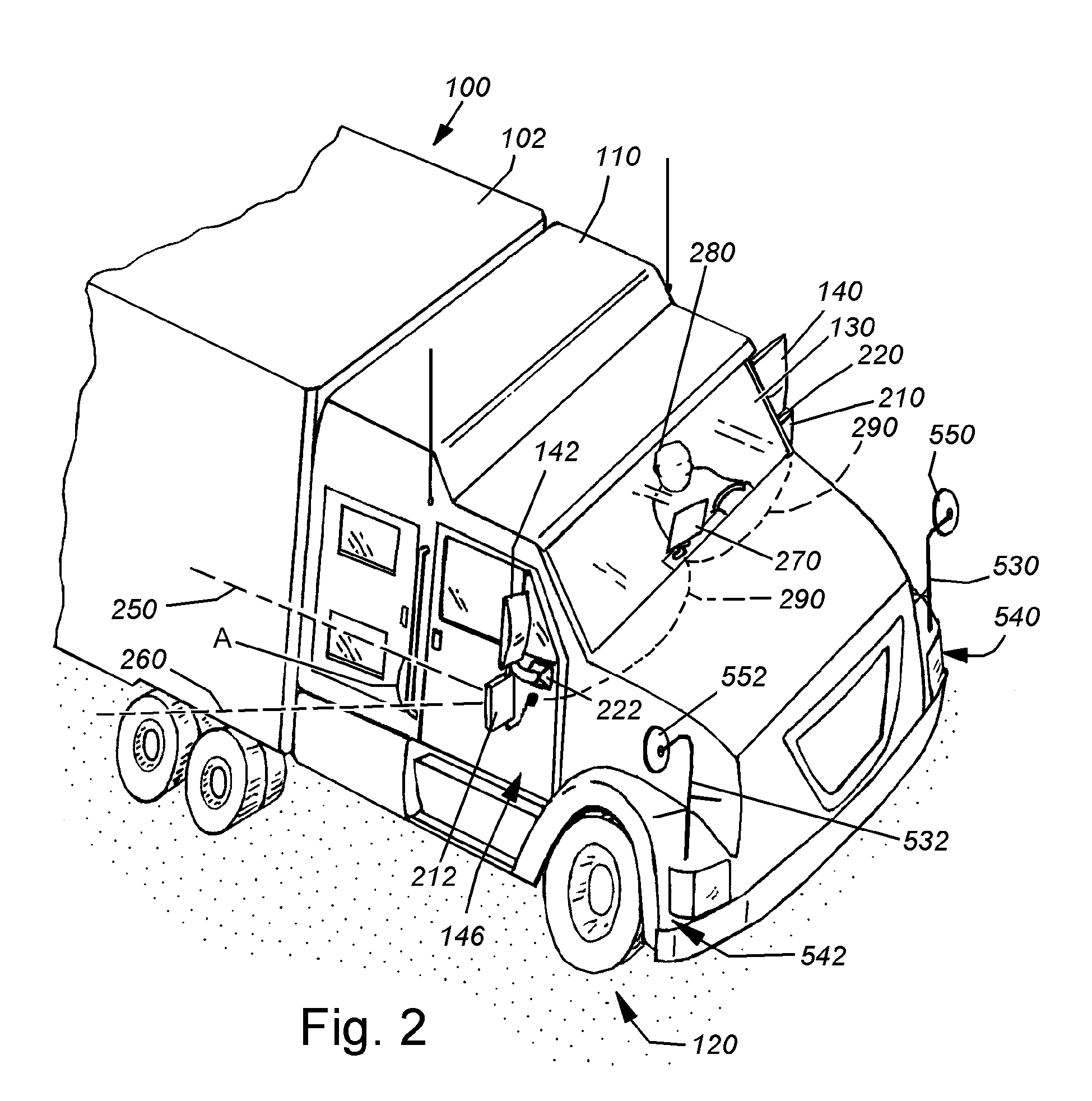
System and method for side vision detection of obstacles for vehicles
InactiveUS20080304705A1Reliable detectionGood range discriminationTelevision system detailsImage enhancementParallaxMostly True
This invention provides a system and method for object detection and collision avoidance for objects and vehicles located behind the cab or front section of an elongated, and possibly tandem, vehicle. Through the use of narrow-baseline stereo vision that can be vertically oriented relative to the ground / road surface, the system and method can employ relatively inexpensive cameras, in a stereo relationship, on a low-profile mounting, to perform reliable detection with good range discrimination. The field of detection is sufficiently behind and aside the rear area to assure an adequate safety zone in most instances. Moreover, this system and method allows all equipment to be maintained on the cab of a tandem vehicle, rather than the interchangeable, and more-prone-to-damage cargo section and / or trailer. One or more cameras can be mounted on, or within, the mirror on each side, on aerodynamic fairings or other exposed locations of the vehicle. Image signals received from each camera can be conditioned before they are matched and compared for disparities viewed above the ground surface, and according to predetermined disparity criteria.
Owner:COGNEX CORP
Apparatus and method for freezing the states of a receiver during silent line state operation of a network device
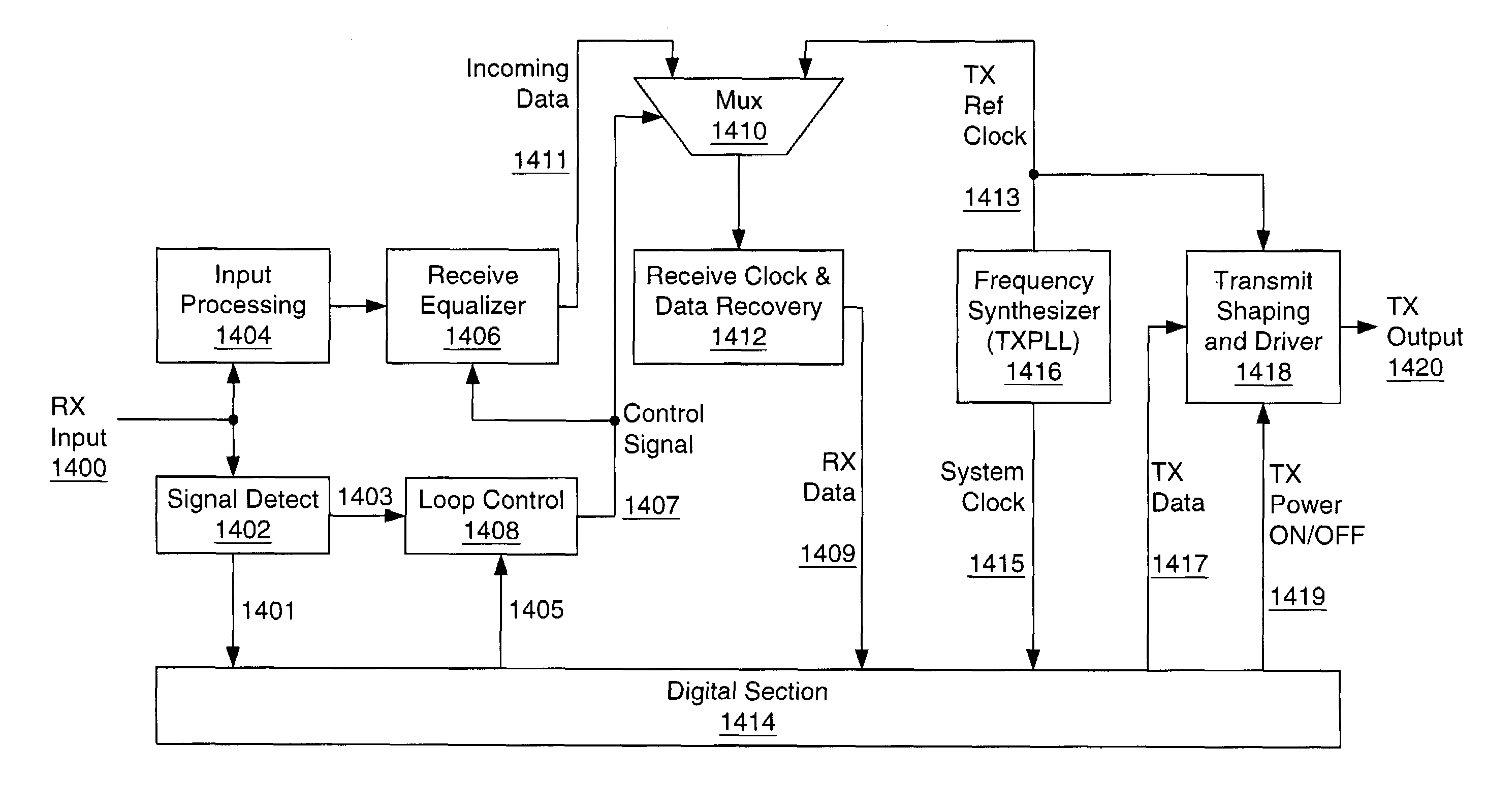
InactiveUS7327754B2Reduce the required powerAvoid data lossEnergy efficient ICTVolume/mass flow measurementMostly TrueLoop bandwidth
A method for maintaining the states of a receiver during the silent line state of a network device operating in a low power link suspend mode is presented. Accordingly, a method of freezing the states of the equalizer and keeping the receiver clock locked to a frequency that is approximately equal to that of the input data while providing for rapid adjustment to the phase and thus recovery of the input data is presented. During Silent Line State (SLS), the receiver states are frozen using methods that avoid parasitic decay. Also, the receive clock phase lock loop is locked onto the local transmit clock since the local transmit clock has a frequency approximating the incoming data frequency. During the SLS, the transmitter of the remote network device may have been turned off to conserve power therefore the receiver has no way of immediately knowing the phase of an incoming data. Thus, in order to prevent loss of data, the receiver loops of the receiving network device are trained to the frequency of the transmitting remote network device using periodic Link Suspend packets. Thus, in most cases, only the phase of the incoming signal need be acquired when data arrives. The phase may be quickly acquired using loop bandwidth shift methods whereby the receive clock phase lock loop bandwidth is increased to a value that aids rapid acquisition of the input clock and then, after acquisition, the bandwidth is shifted to a low value to enhance noise rejection during tracking.
Owner:MAXIM INTEGRATED PROD INC
Method for operating a wind park
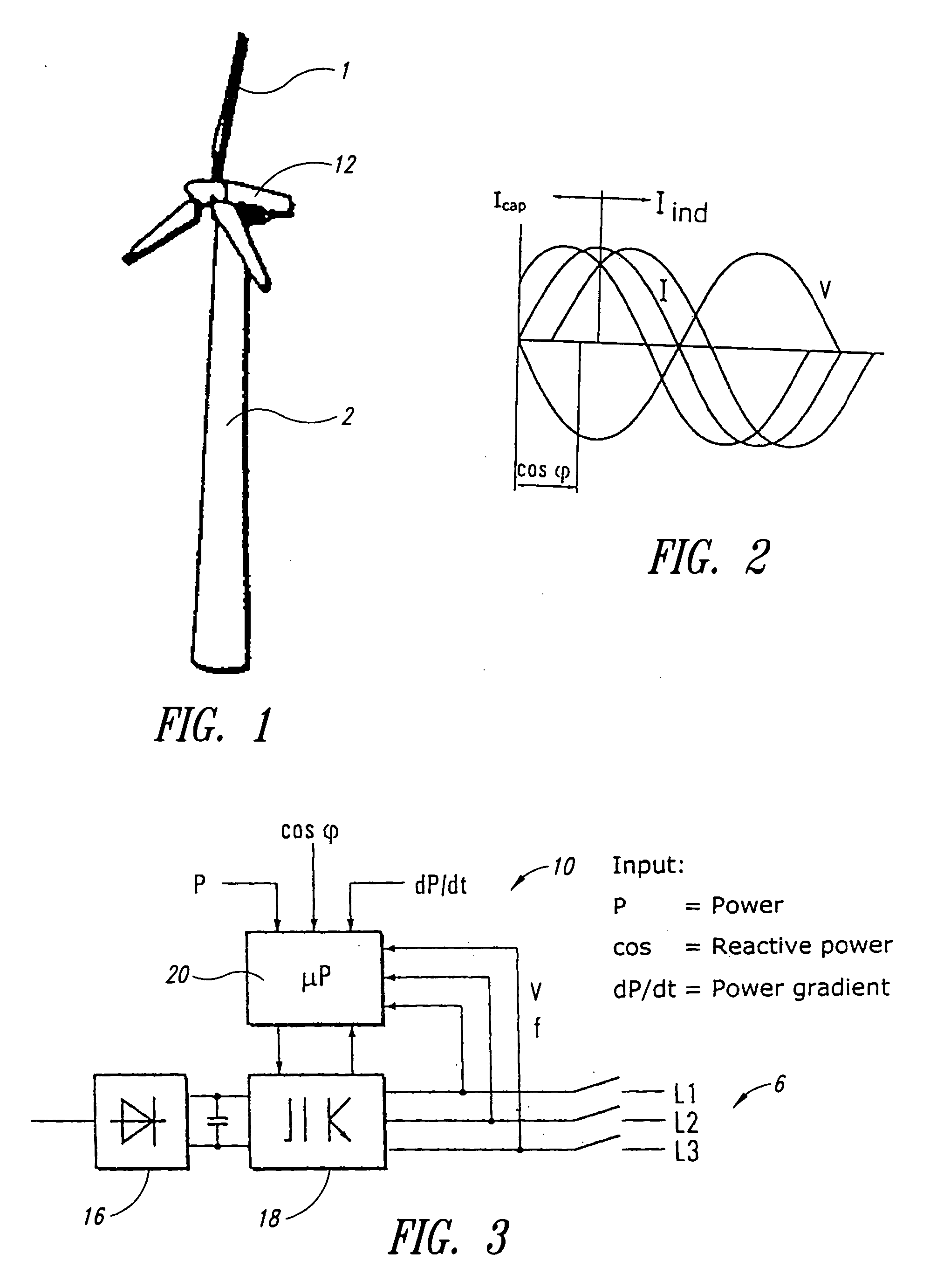
InactiveUS20050042098A1Intuitive effectEasy to adaptPropellersPump componentsWind potentialElectric power
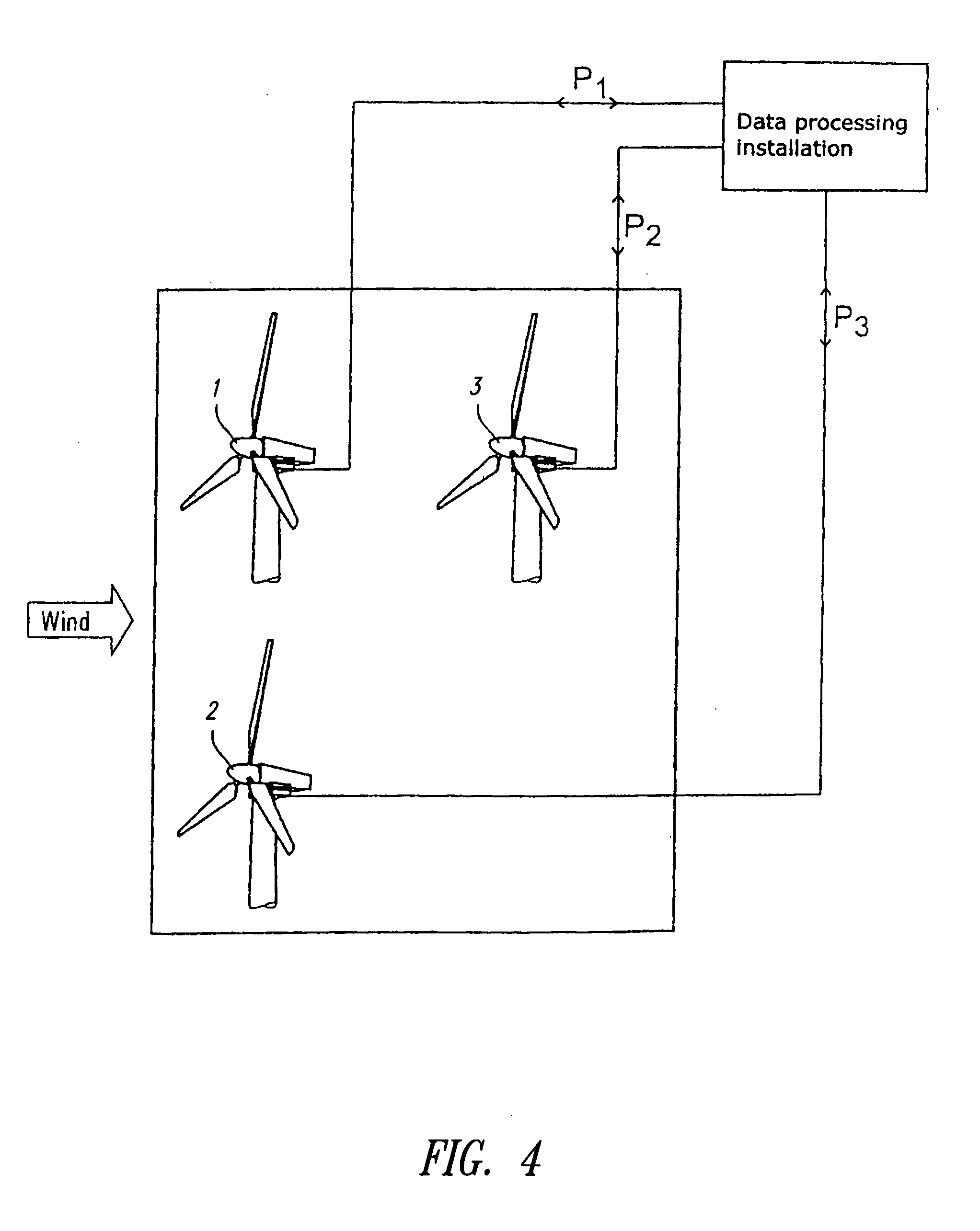
Wind power installations were initially always erected in the form of individual units and it is only in recent years that, caused also by administrative and building regulations, wind power installations are frequently installed in wind parks. In that respect a wind park in its smallest unit is an arrangement of at least two wind power installations, but frequently markedly more. By way of example mention may be made of the wind park at Holtriem (East Frisia) where more than 50 wind power installations are set up in an array. It is to be expected that the number of units and also the installed power of the wind power installations will also increase greatly in the forthcoming years. In most cases the wind potential is at its greatest in regions of the power supply networks with a low level of short-circuit power and low population density. It is precisely there that the technical connection limits are quickly reached by the wind power installations, with the result that it is then no longer possible for further wind power installations to be set up at such sites._A method of operating a wind park comprising a plurality of wind power installations, wherein the wind park is connected to an electrical power supply network into which the electrical power produced by the wind park is fed and the wind park and / or at least one of the wind power installations of the wind park has a control input, by means of which the electrical power of the wind park or one or more individual wind power installation or installations can be set in a range of between 0 and 100% of the respective power to be made available, in particular the nominal power, and that there is provided a data processing apparatus which is connected to the control input and by means of which the setting value is set in the range of between 0 and 100%, depending on how great is the power that the overall wind park provides at its output for feeding into the energy network and wherein the operator (PSU) of the electrical supply network to which the wind park is connected can adjust the power delivered by the wind park by way of the control input.
Owner:WOBBEN ALOYS
Method and system for efficiently retrieving information from a database
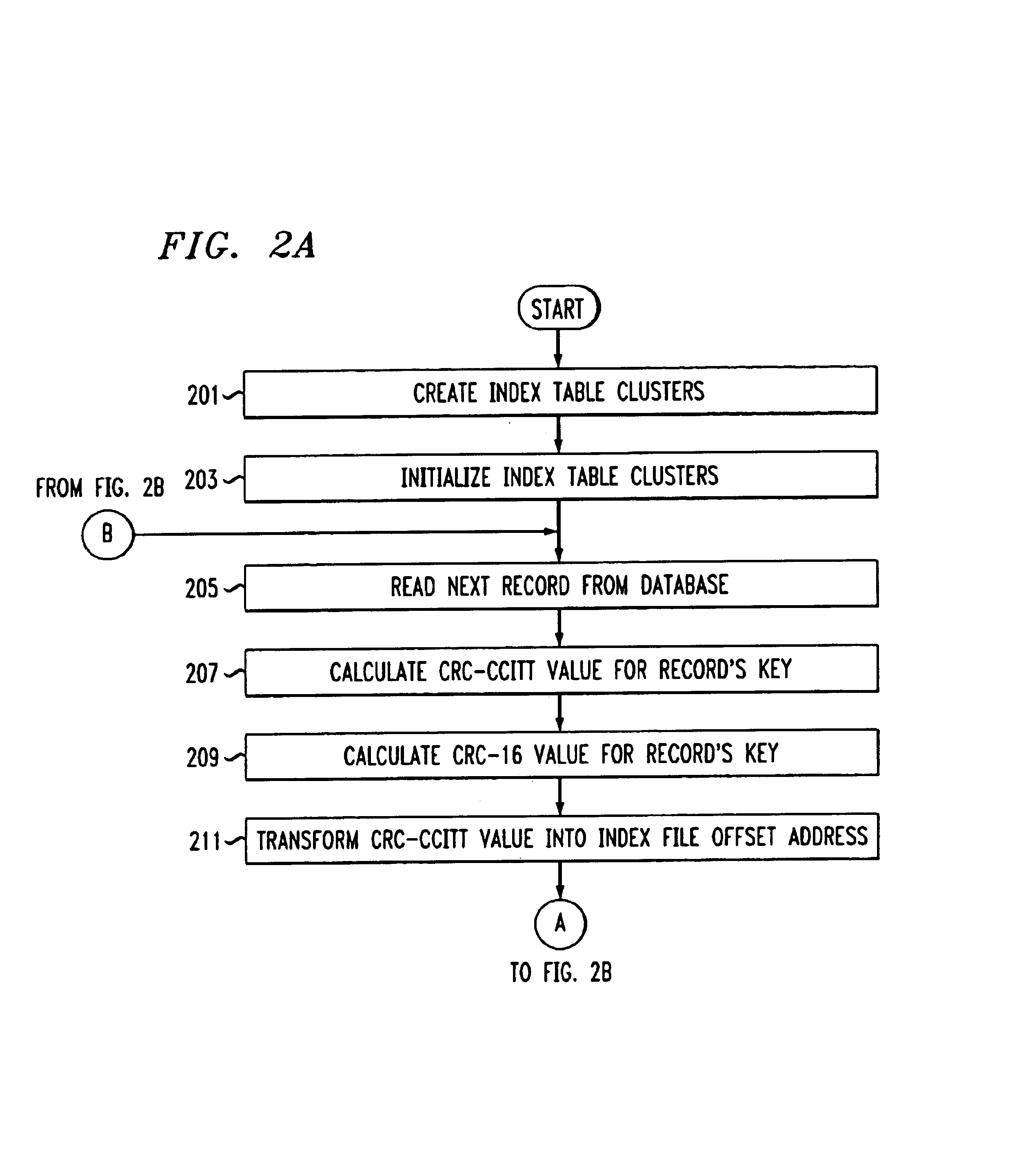
InactiveUS6865577B1Easy to handleSpace minimizationData processing applicationsDigital data information retrievalMostly TrueS/KEY
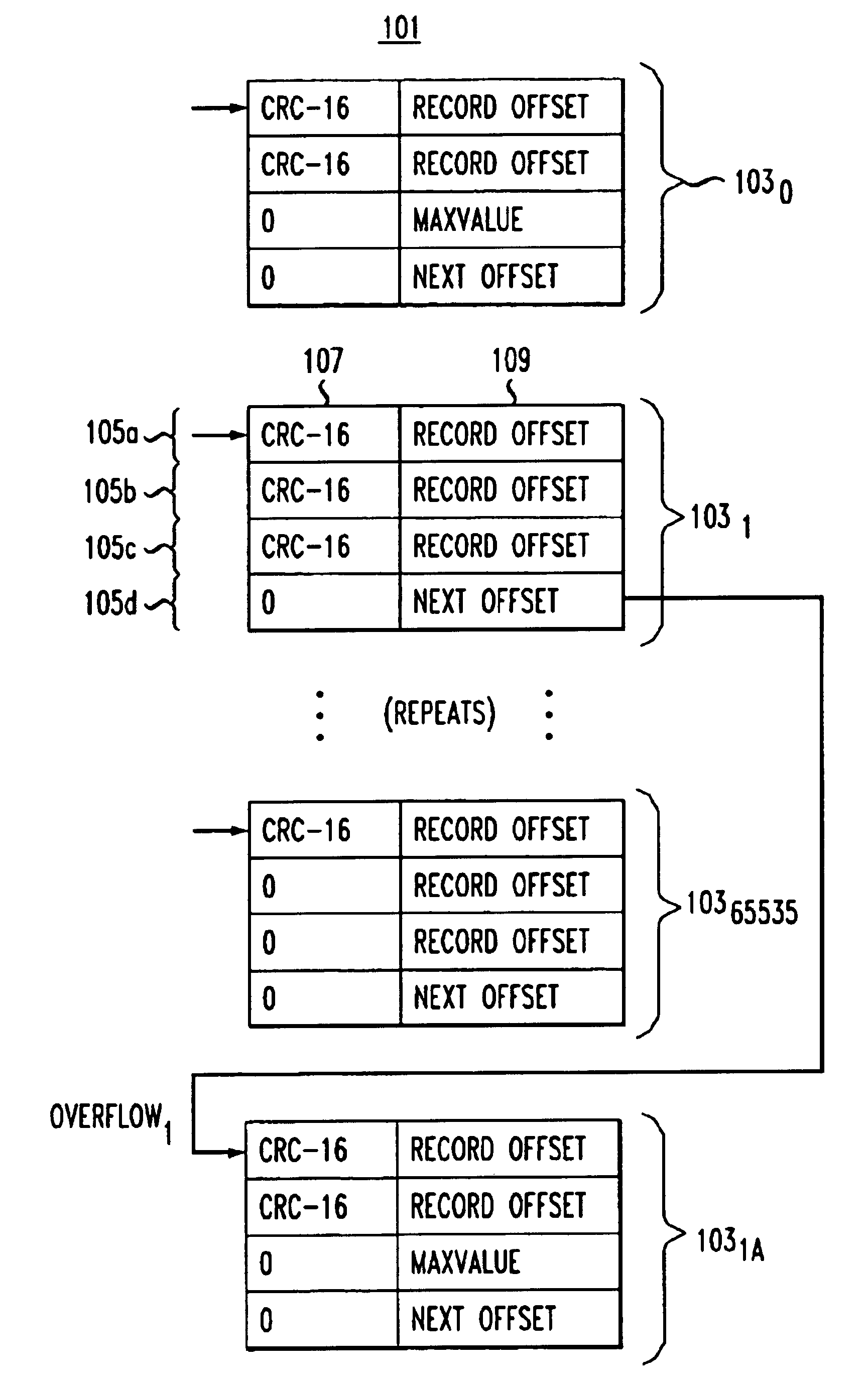
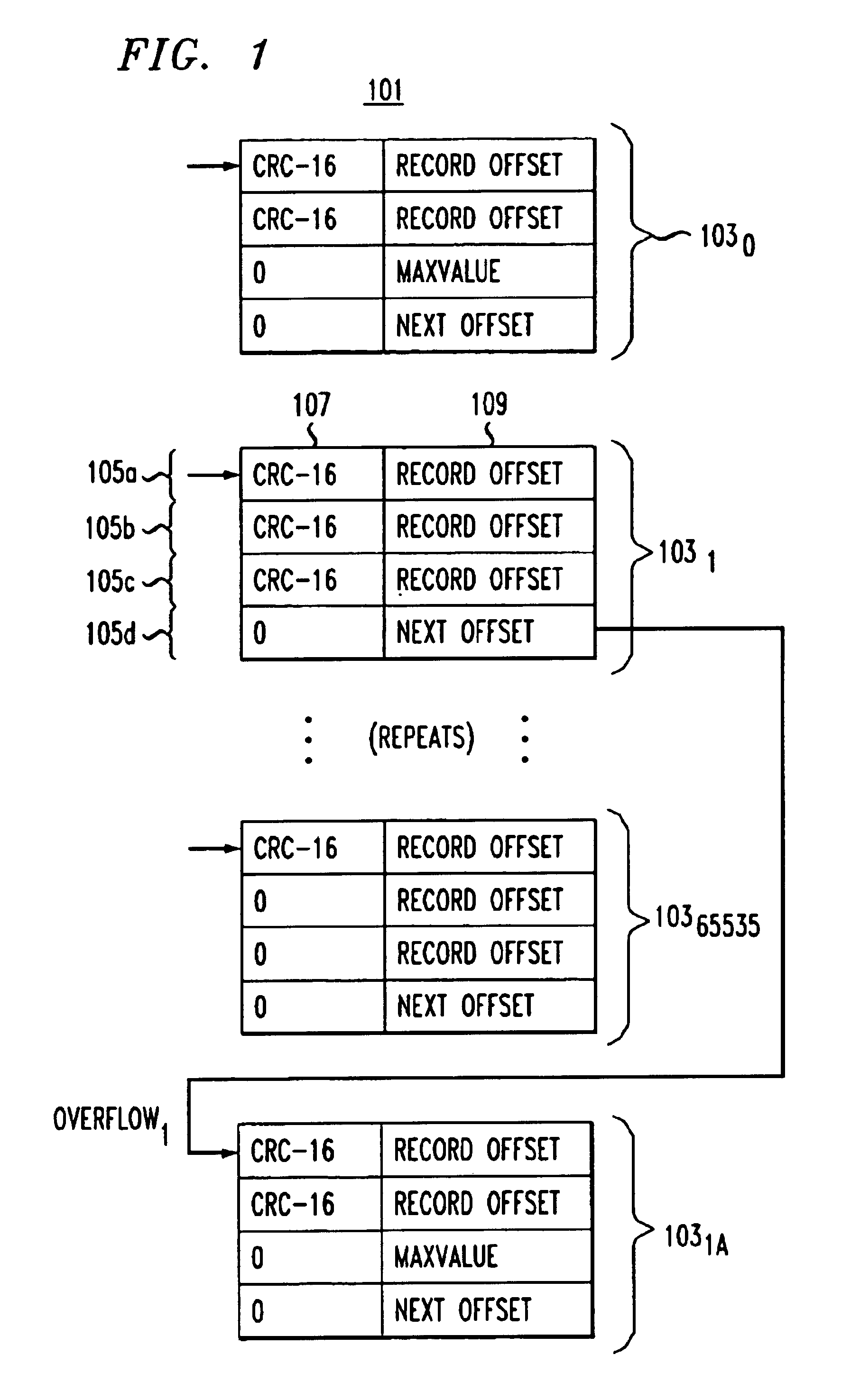
A method for fast and efficient record retrieval in large databases using cyclical redundancy check (CRC) computations as hash functions. Two hash values are computed for each record's key using the CRC-CCITT and CRC-16 generator polynomials. The two CRC values then are combined into a four-byte composite hash value that represents a binary signature of the record's key. Alternately, a single CRC-32 value can be used as a four-byte hash value. In most cases, this four-byte hash value uniquely identifies the record's key. An index file is constructed using a hybrid search method, part hash table and part linear search. The index file is searched to find a match for the four-byte hash value and the record's offset is obtained. The record's offset is used to retrieve the record from the database.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Method and system for name and address validation and correction
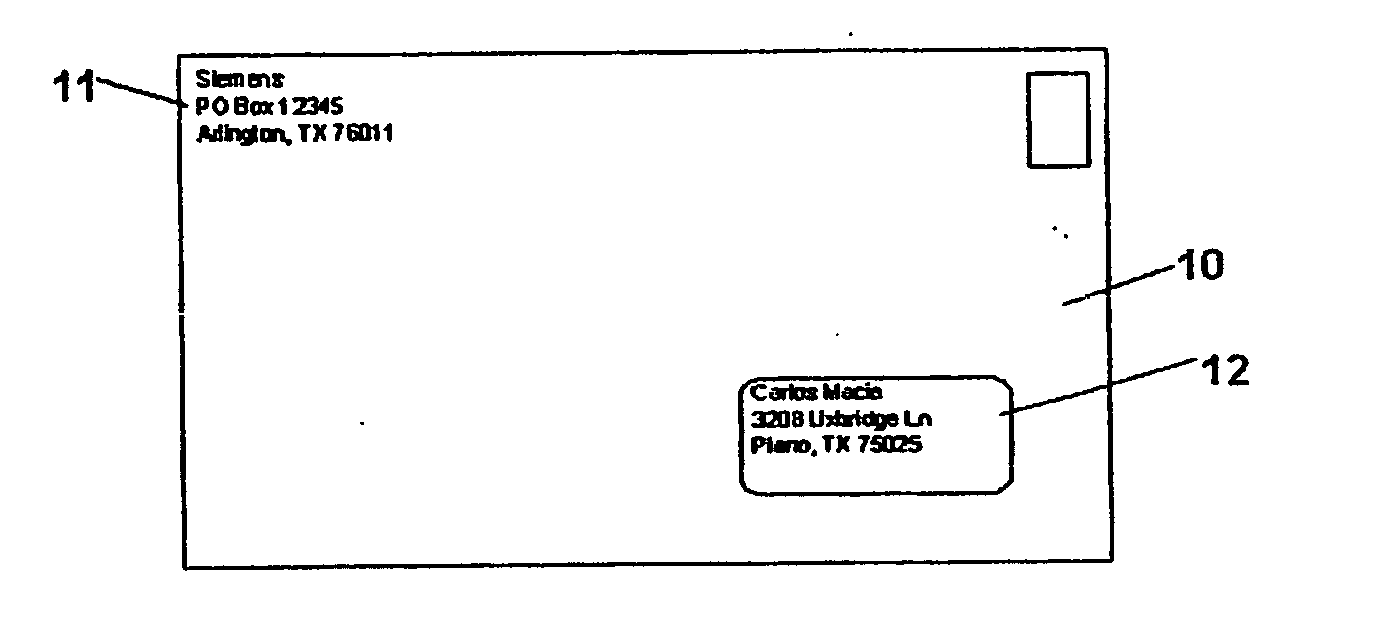
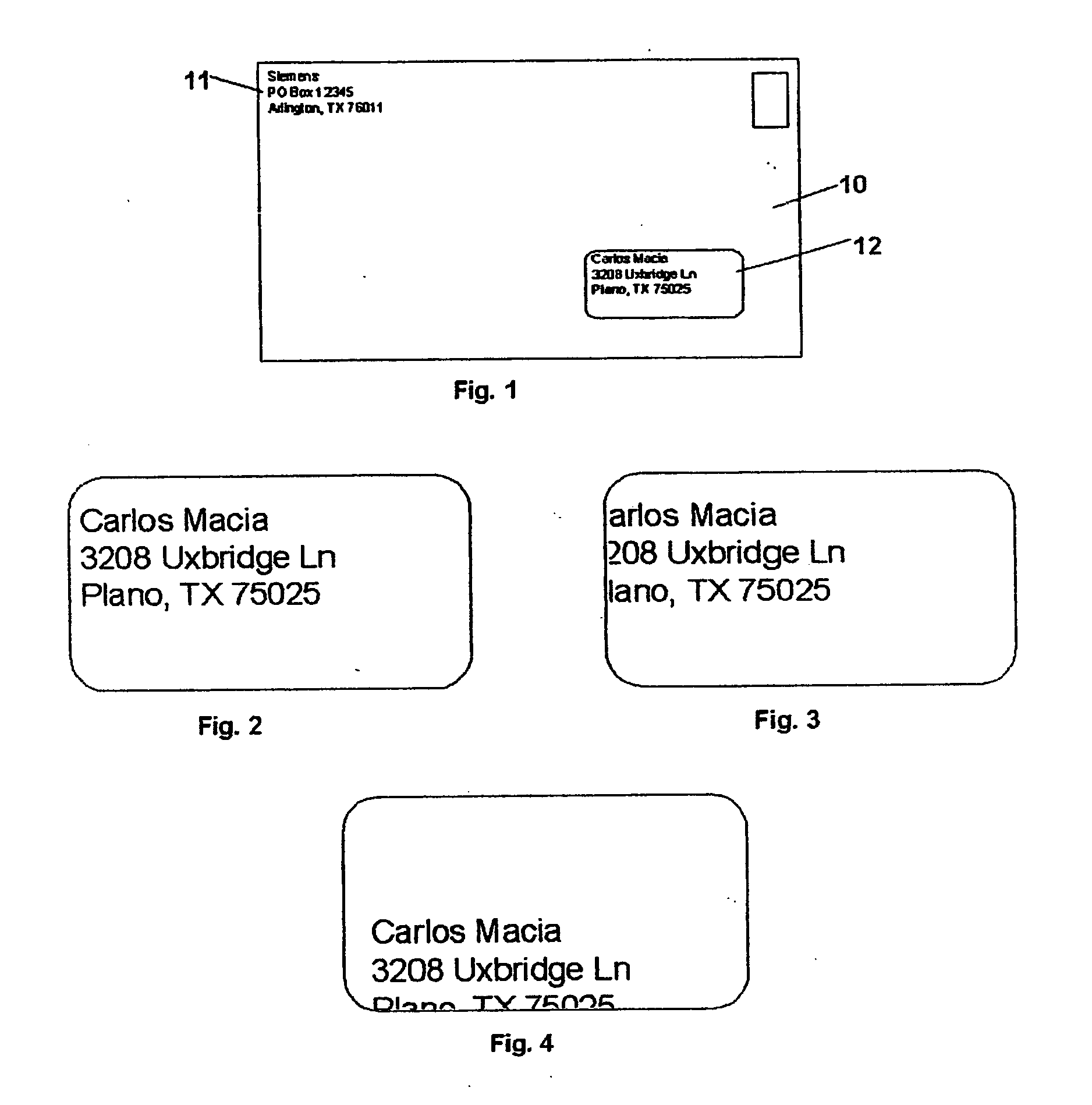
InactiveUS20050137991A1Improve efficiencyAccurate informationProgram controlSortingMostly TrueComputer data storage
A method of correcting postal name and address information according to the invention includes the step of comparing the name and address information to at least one database of known names and associated addresses to determine if the name and address information matches a known postal recipient. if no match is found, the name and address information is corrected by comparing fields of the name and address information with corresponding fields from the database of known names and addresses, and deducing an incorrect or missing field in the name and address information. An action is then taken using the corrected name and address information, depending on the setting in which the method is used. In most cases, the corrected name and address information will be saved to a computer data storage medium for future use. If a series of name and address records are being read from mail pieces being processed on a postal sorting machine, the final step may comprise sorting a mail piece using the corrected name and address information.
Owner:SIEMENS LOGISTICS & ASSEMBLY SYST
Mixed entertainment application
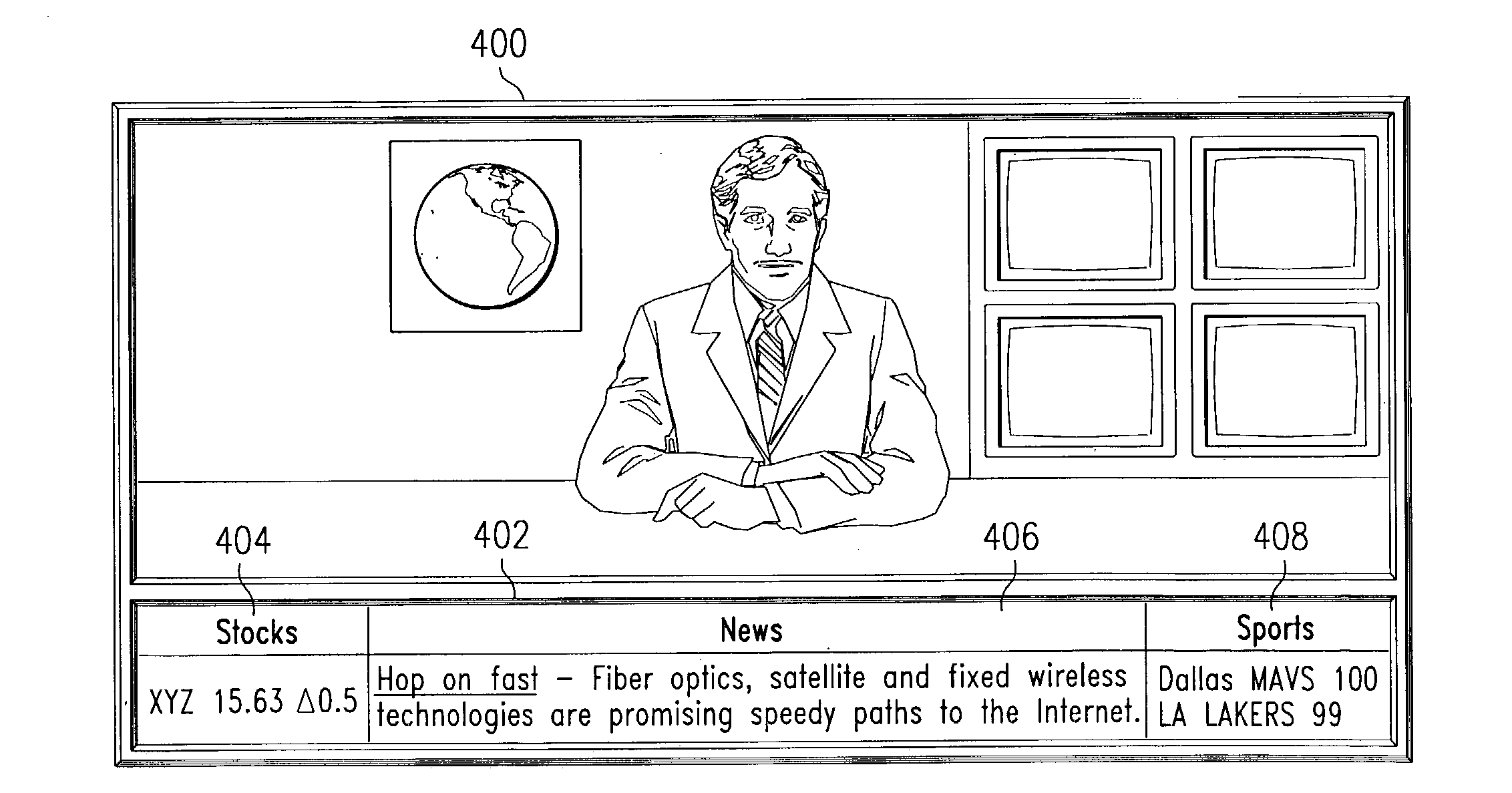
InactiveUS20030084456A1Easy accessEasily presentableTelevision system detailsPicture reproducers using cathode ray tubesMostly TrueThe Internet
A software application, which presents aggregated content including broadcast, Internet, and local media on a single HDTV display screen. For the most part, this information is pulled from existing databases and supplied by means of an entertainment portal, and then synchronized, resized, and displayed on a single HDTV display screen. This allows mixed entertainment content from creators, broadcasters, advertisers, manufactures, websites, and home consumers to be viewed on a single HDTV display screen, thereby creating a single-screen home entertainment experience. In operation, the screen is divided into multiple areas 200, 202 where web content, which can be continuously updated, is displayed at the same time live video is being aired. This can include any and all types of content; such as news, stock quotes, weather forecast, sports scores, on-line shopping, on-line multi-player games, local community information, etc.
Owner:TEXAS INSTR INC
System, methods, software, and devices employing messaging
ActiveUS20070083600A1Reduce needIncreased messaging usageMultiple digital computer combinationsSubstation equipmentMostly TrueMobile device
A mobile device is shown in the role of a centralized message transfer agent wherein it manages all messaging for a user for most if not all the time so as to provide a unified messaging approach across all messaging platforms. Other platforms are shown using the mobile device in this unified way. Related systems, methods, integrated circuits, and software are also shown.
Owner:NOKIA TECHNOLOGLES OY
Protective head covering having impact absorbing crumple zone
InactiveUS6996856B2Closer in weight and sizeMinimizing resultant disproportionHatsSport apparatusMostly TrueEngineering
A helmet construction for protecting a user's head, and the brain within the cranium from impact forces, includes a shell contoured to the shape of the user's head, with cushioning along at least part of the shell interior and a chinstrap. The shell consists of three (or more) discrete panels that are physically and firmly coupled together providing rigid protection under most circumstances, but upon impact the panels move relative to one another, but not relative to the user's head, thereby permitting impact forces to be dissipated and / or redirected away from the cranium and brain within. Upon impact to the helmet, there are sequential stages of movement of the panels relative to each other, these movements initially being recoverable, but with sufficient vector forces the helmet undergoes structural changes in a pre-determined fashion, so that the recoverable and permanent movements cumulatively provide a protective ‘crumple zone’ or ‘shear zone’. The first two stages of protection arise from the design of the fasteners that have the ability to invaginate and collapse within themselves, and their design having a 45 degree angle, which will allow movement of a region of connected panels to translate along the fastener shaft. Both of these movements will be recoverable and provide a ‘functional crumple zone’. The final stage of protection arises from the braking function of the pins, as they are forced from one aperture through to the next, the direction and extent of which is determined by the impact force and direction. This final level of panel movement and protection is not recoverable and thus provides a ‘structural crumple zone’. Finally the fastener size and thickness, together with the thickness of webbing and distance between apertures, functions to provide varying degrees of resistance to impact forces, thus making the helmet design suitable for activities with different levels of impact speed and risk potential.
Owner:PUCHALSKI TECHN
Method and system for sleep/wake condition estimation
InactiveUS20110034811A1Easy to handleUnobtrusive for patientCatheterRespiratory organ evaluationNon pharmacologicalSleep restriction therapy
Insomnia is a prevalent sleep disturbance in the general population. As standard diagnostic method for assessing the nature and the severity of the sleep problem, a so-called sleep log or sleep diary, i.e. a questionnaire usually on paper, is used in most cases. The main drawback of this diagnostic tool is that its accuracy is affected by subjective bias of the patient, e.g. for patients it is often difficult to remember sleep and wake periods during the night correctly. The present invention proposes an automatic sleep log that uses vital body signs as input signals for assessing sleep and wake periods during the night. By using objective data, the diagnosis will be more accurate. Furthermore, this system can also be used to sleep restriction therapy, a non-pharmacological method to treat insomnia. Also in this application it can contribute to patients correctly applying this method and thus leading to a better medical outcome.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
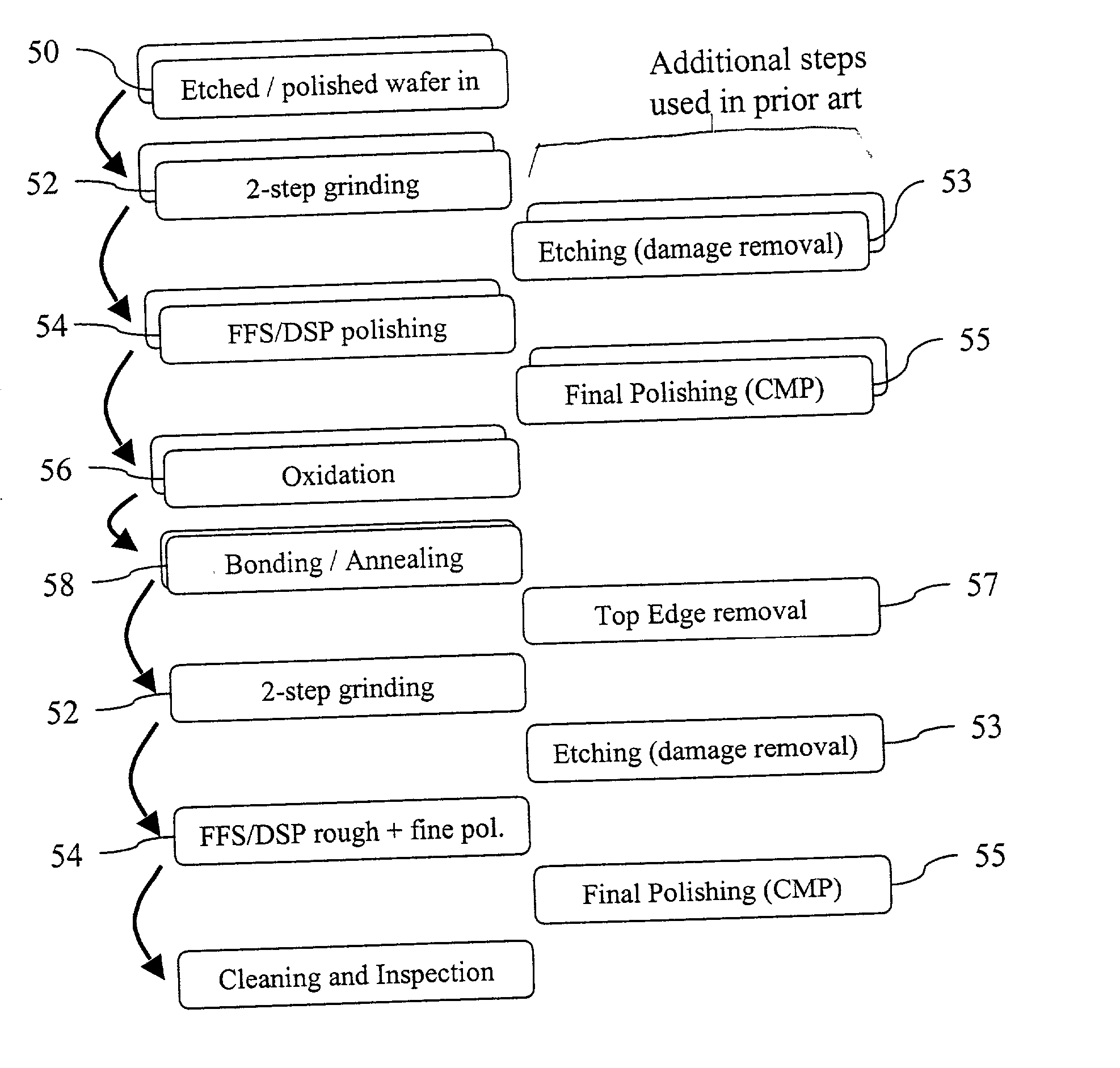
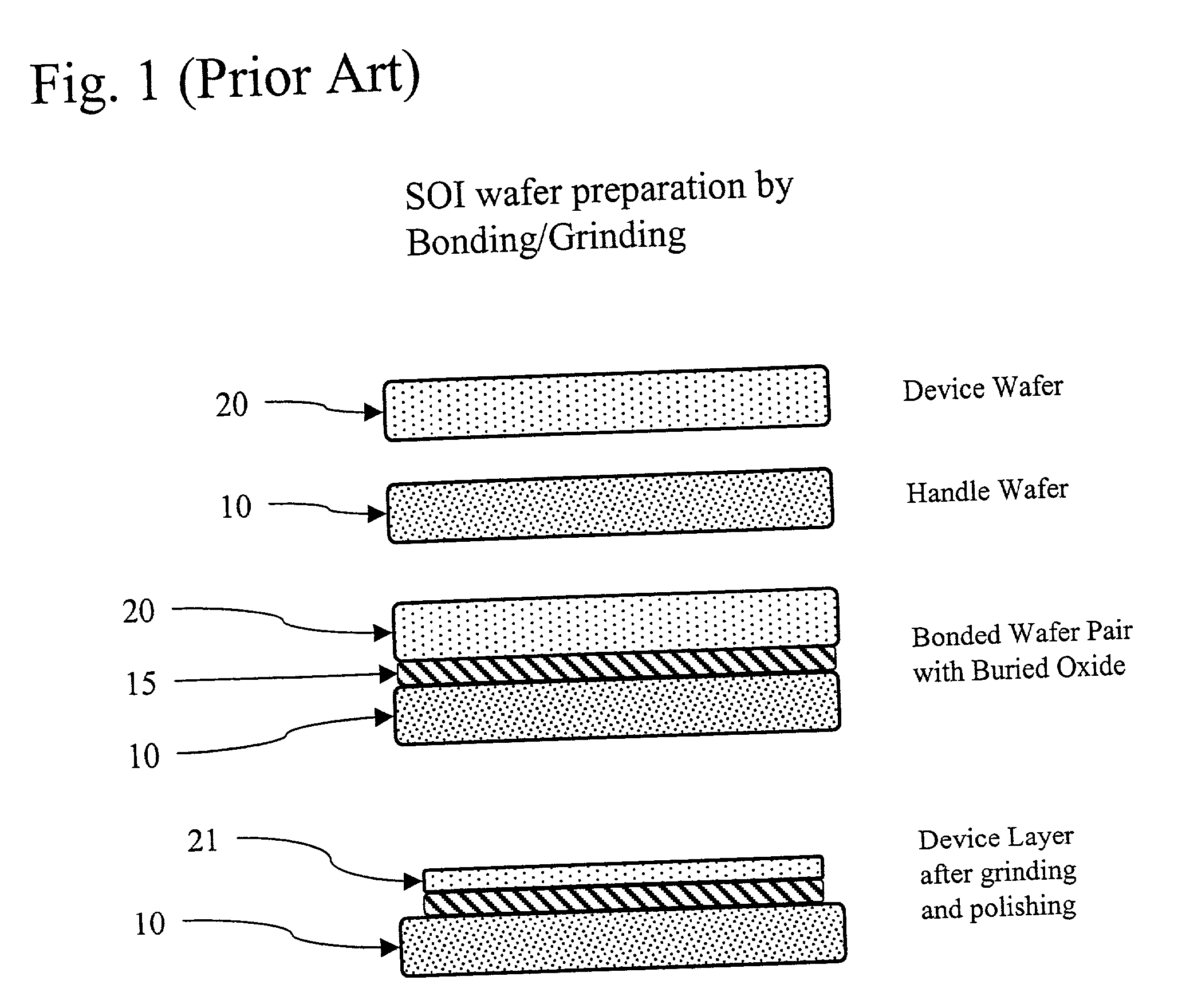
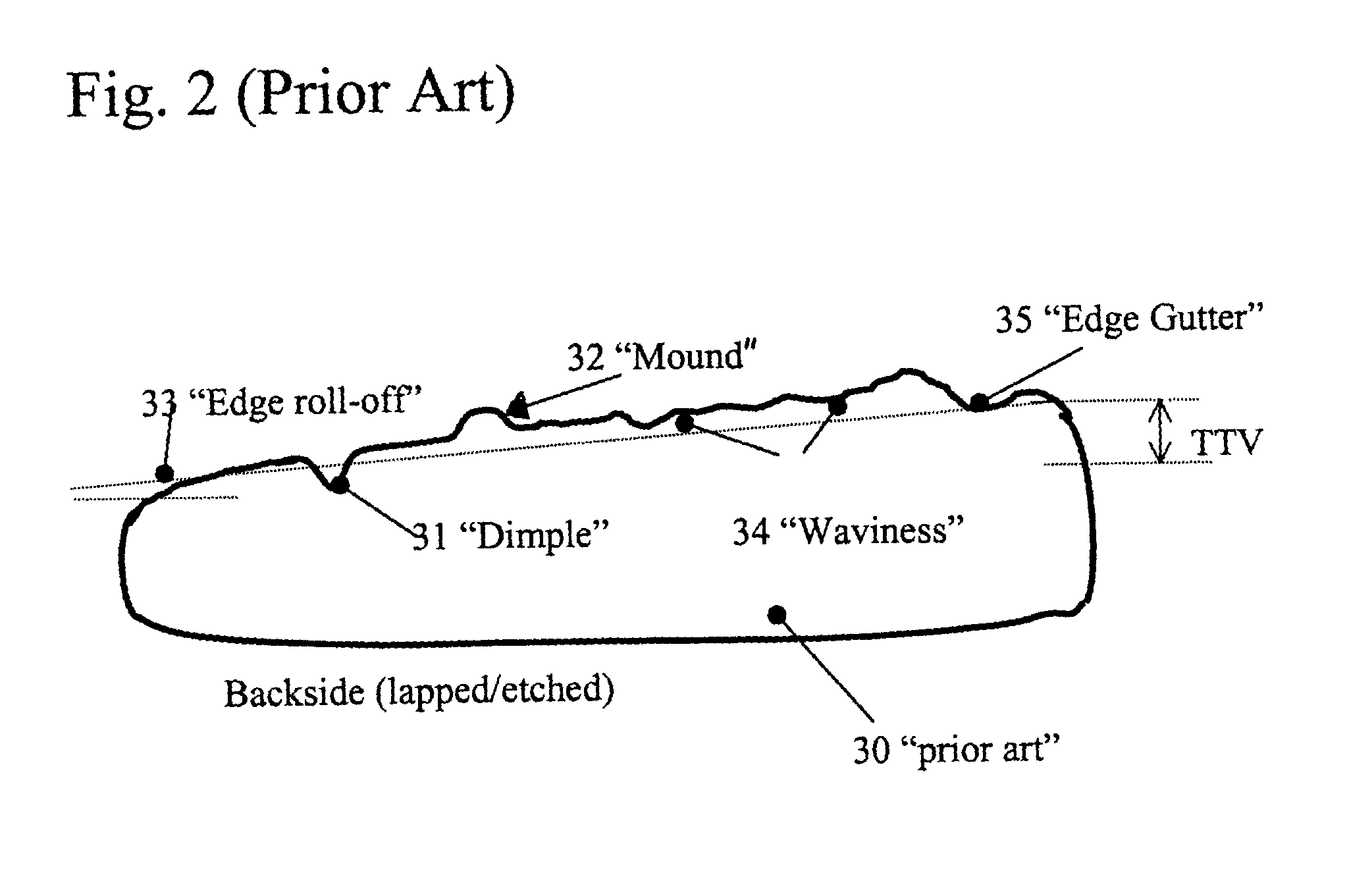
Methods for silicon-on-insulator (SOI) manufacturing with improved control and site thickness variations and improved bonding interface quality
A method for the production of silicon-on-insulator (SOI) wafers for controlling the device layer thickness variations and improvement of bonding quality at the interface of the wafers is disclosed. Using standard etched wafers, a unique sequence of process steps consisting of 2-step front side grinding, free-floating simultaneous double side polishing prepares wafers with low TTV and reduced edge roll off zones. The much smaller unbonded edge zone eliminates the requirements for edge grinding or etching in most cases. When the same s-step grinding / FFS-DSP sequence is applied after bonding and annealing of a Silicon-on-Insulator package, the resulting thickness variation in the device layer is usually smaller than what would be obtained from prior art processes.
Owner:SILICON EVOLUTION
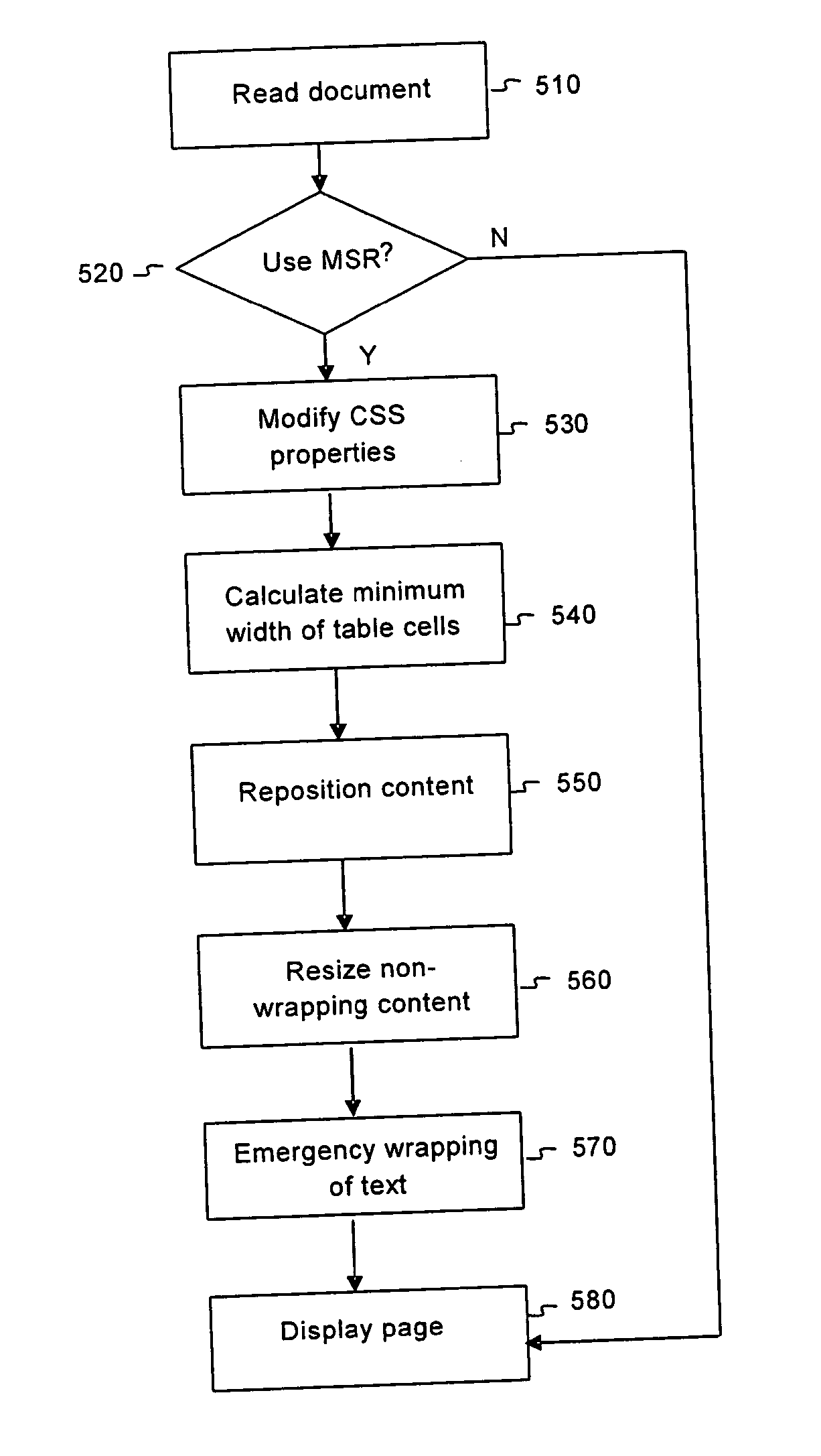
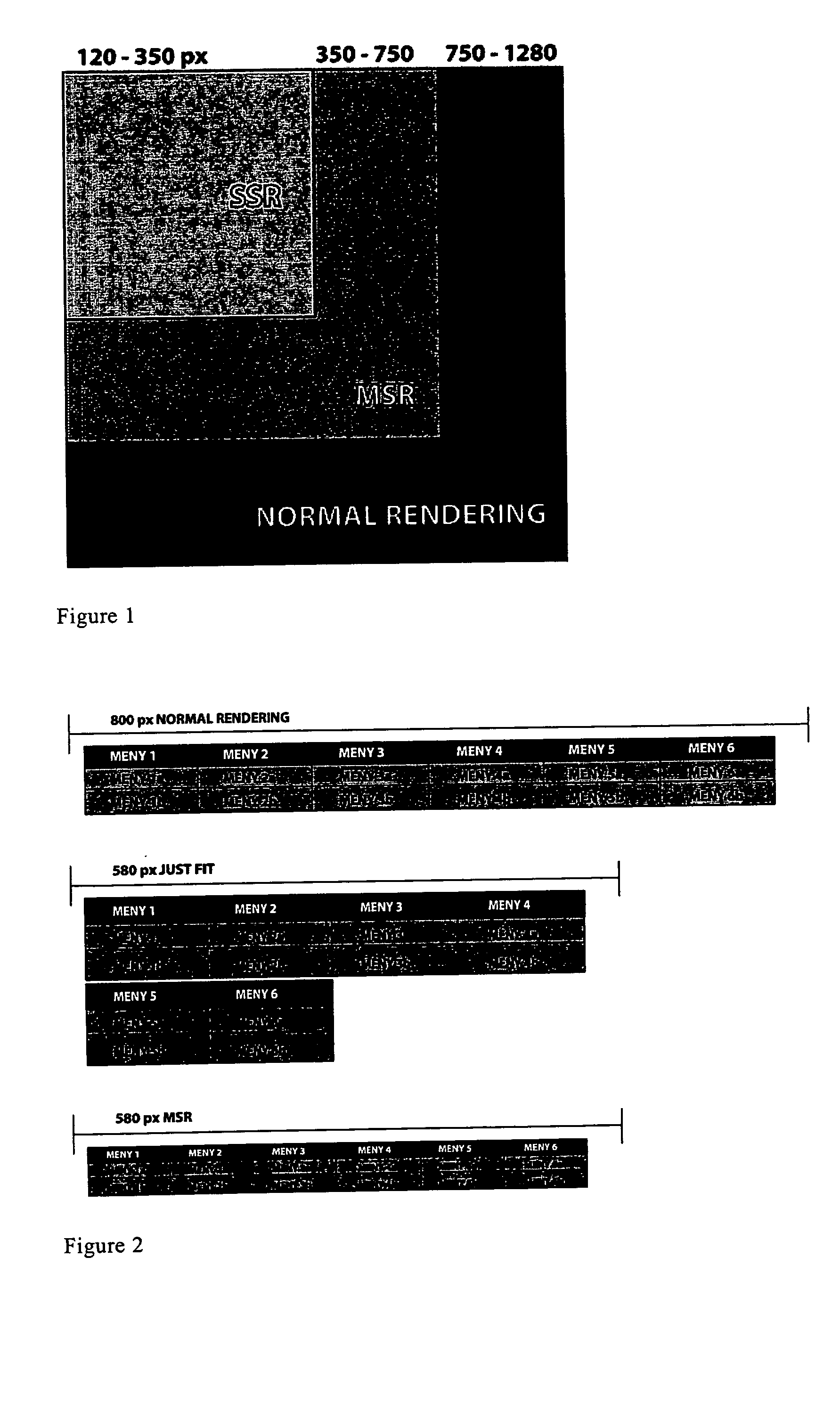
Presenting HTML content on a screen terminal display
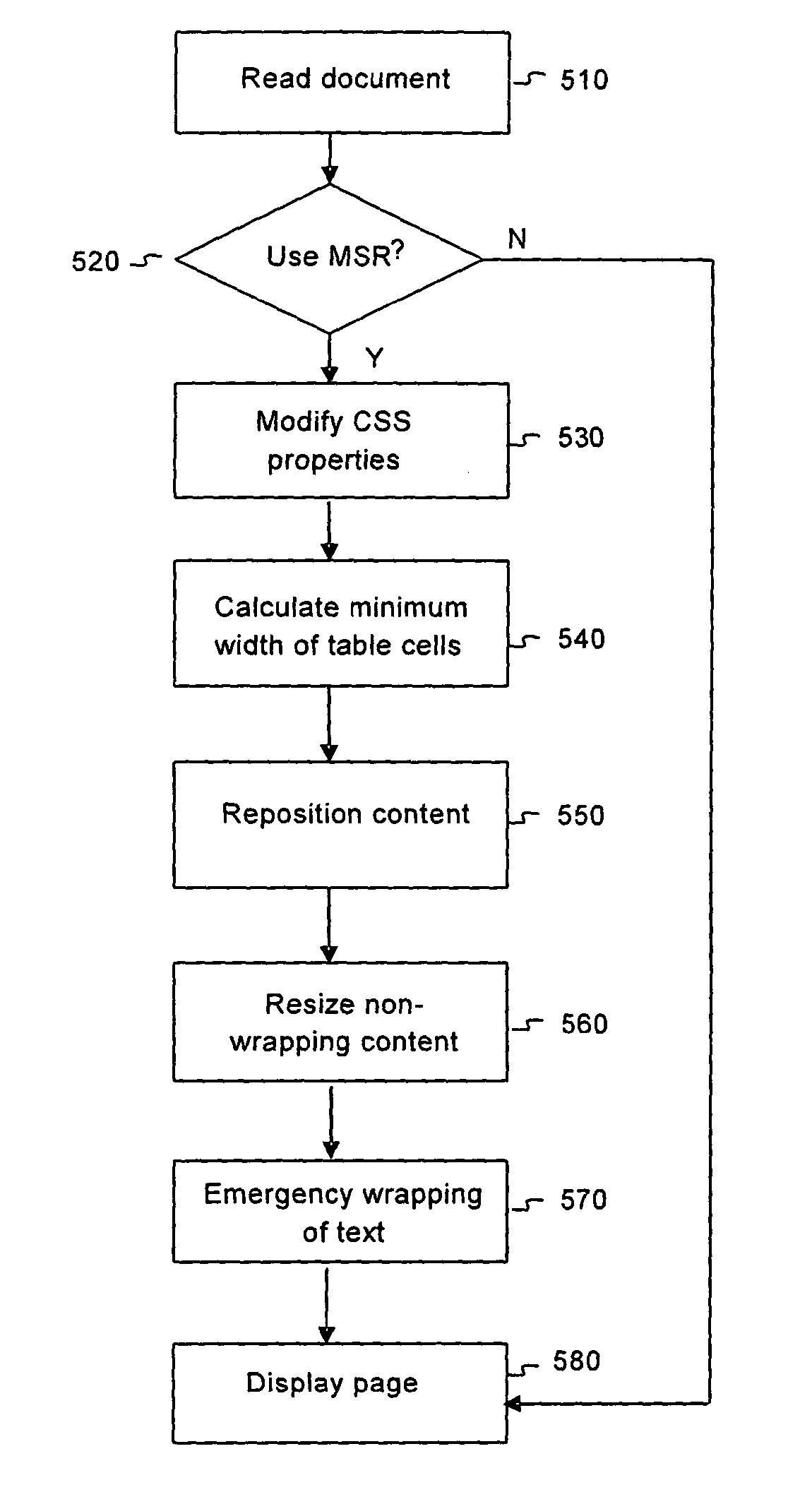
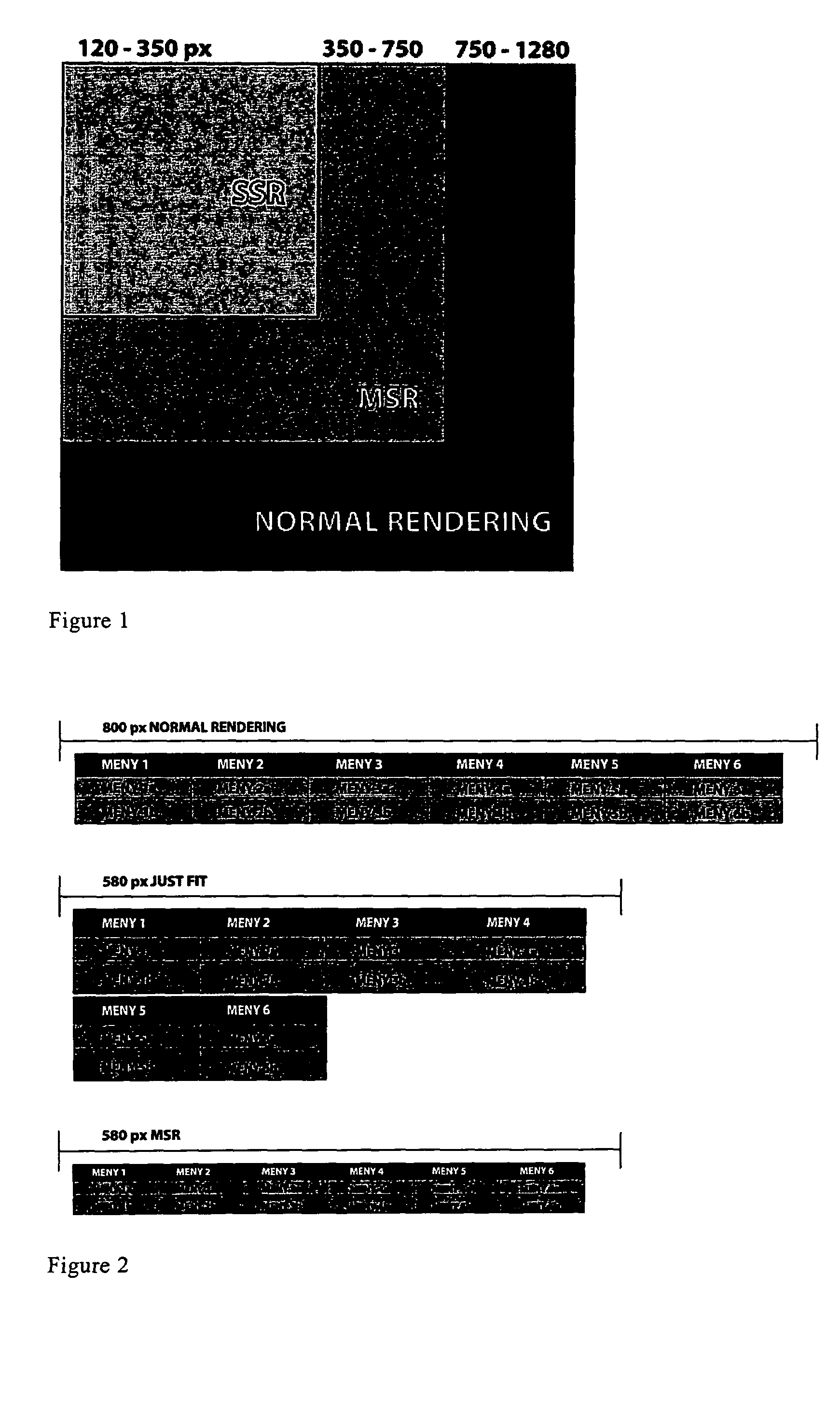
ActiveUS20050097444A1Small resolutionDigital data information retrievalDigital computer detailsImage resolutionMostly True
The object of the present invention is to render markup documents within the limits of resolutions smaller than the resolutions for which the documents were originally designed, in most cases without introducing horizontal scrolling, while keeping the original fonts, colors, design, and style. The object is achieved by finding and selecting only elements that are too big, shrinking them individually, and disallowing certain elements to grow table cells under specific circumstances.
Owner:OPERA SOFTVEAR AS
Temperature stable voltage reference circuit using a metal-silicon Schottky diode for low voltage circuit applications
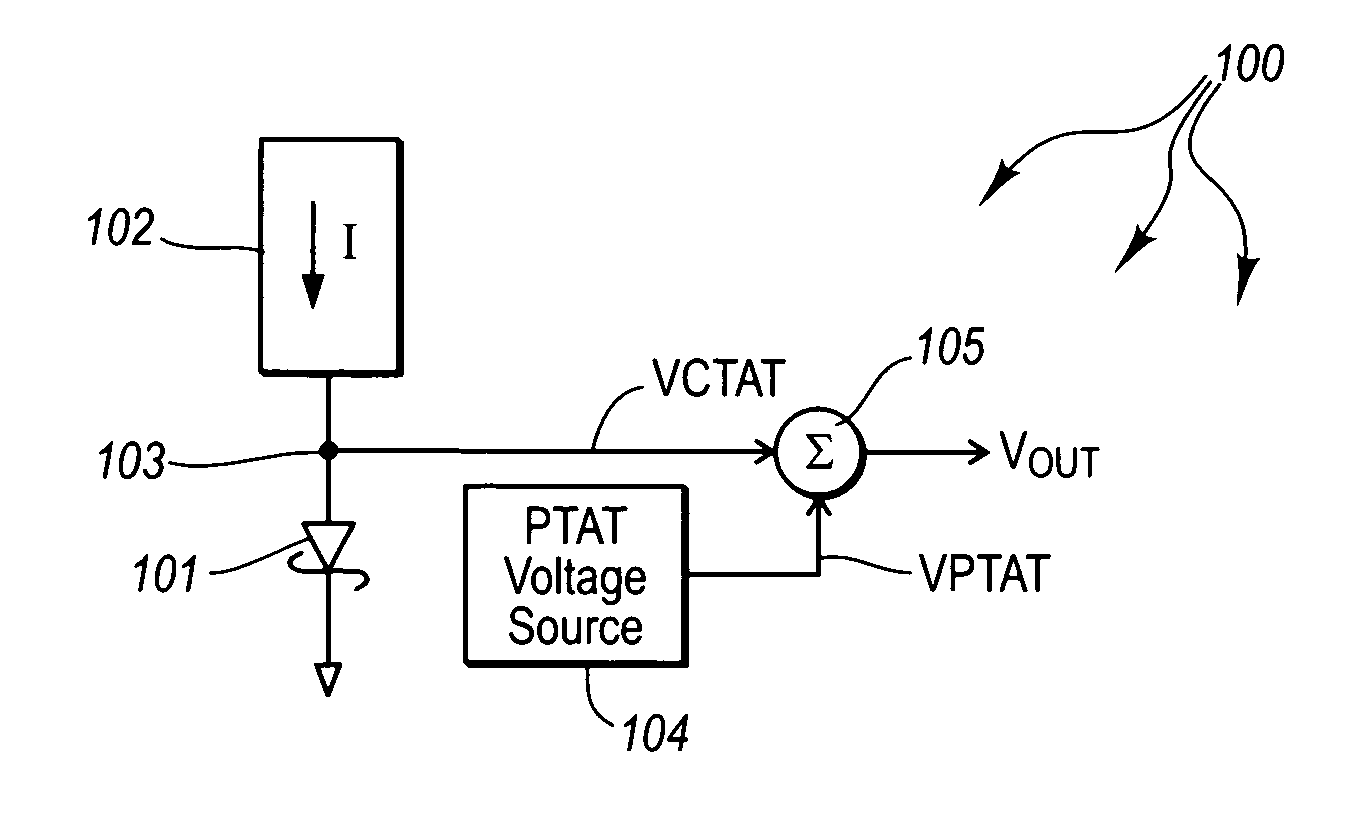
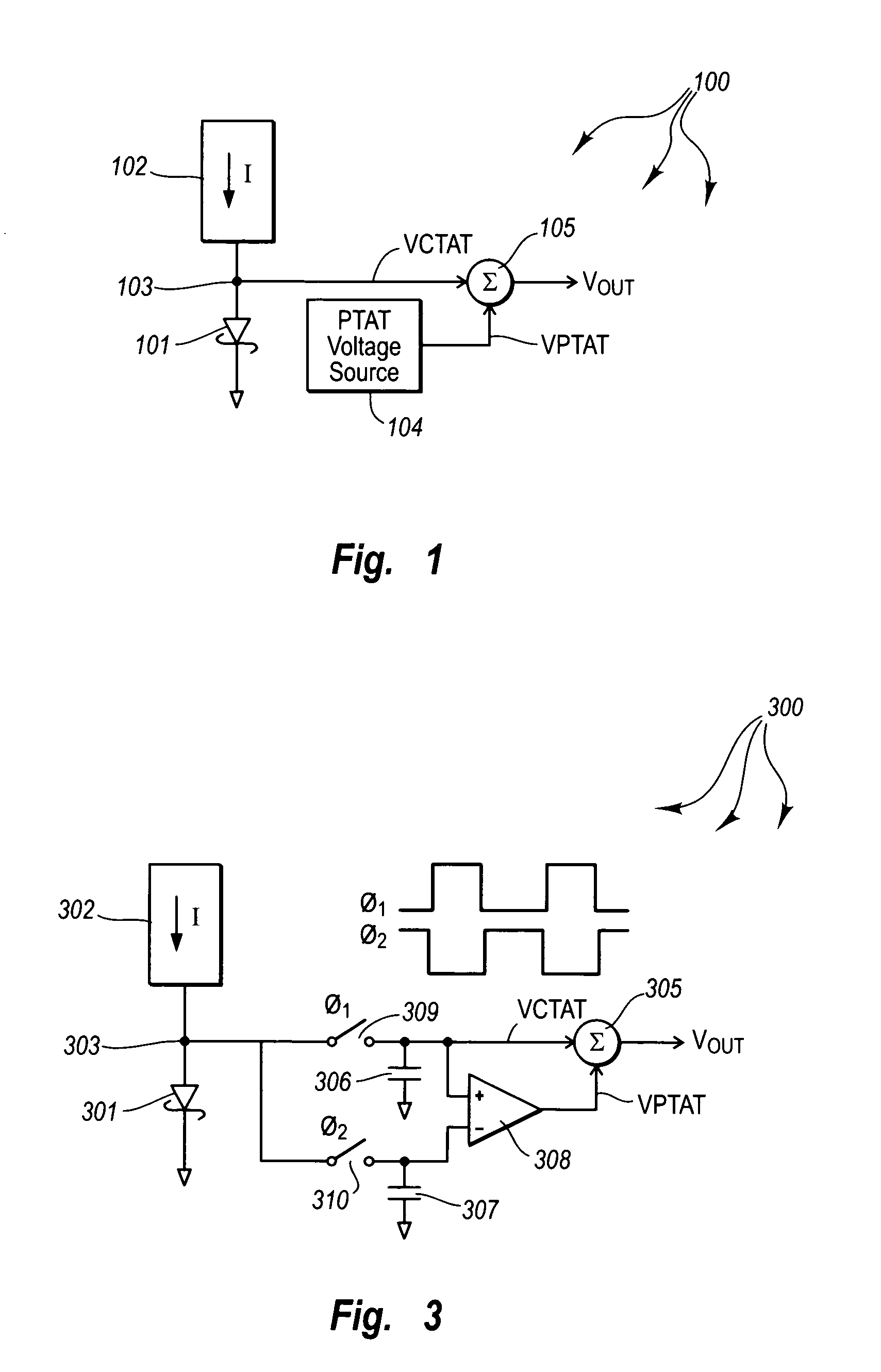
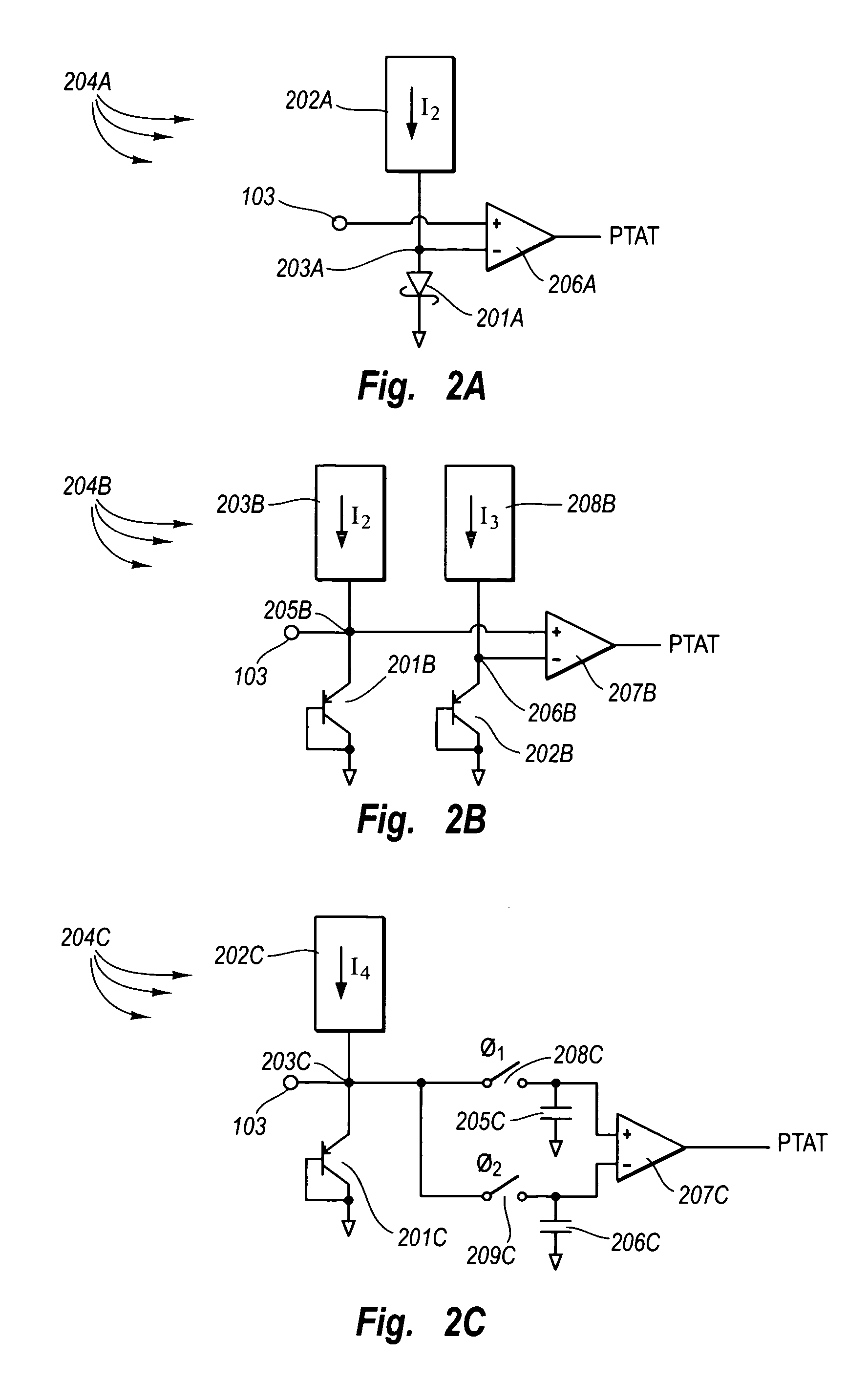
ActiveUS7009444B1Electronic switchingPulse generation by opto-electronic devicesLow voltage circuitsMostly True
Silicon-based voltage reference circuits that generate a temperature independent voltage reference that is less than even the silicon bandgap potential. The voltage reference circuit includes a diode-connected metal-silicon Schottky diode that is biased with a current. In this configuration, the anode terminal of the Schottky diode is a CTAT voltage source in this configuration. The anode terminal has a voltage at zero degrees Kelvin at the barrier height of the Schottky diode, which may differ depending on the metal chosen, but in most cases is less than the bandgap potential of silicon. The voltage reference circuit also includes a PTAT voltage source. The PTAT voltage may be generated in a variety of ways. An amplifier amplifies the PTAT voltage, and a summer adds the CTAT voltage to the amplified PTAT voltage to generate the temperature stable voltage reference.
Owner:SEMICON COMPONENTS IND LLC
Protective head covering having impact absorbing crumple or shear zone
A helmet construction for protecting a user's head, and the brain within the cranium from impact forces, includes a shell contoured to the shape of the user's head, with cushioning along at least part of the shell interior and a chinstrap. The shell consists of three (or more) discrete panels that are physically and firmly coupled together providing rigid protection under most circumstances, but upon impact the panels move relative to one another, but not relative to the user's head, thereby permitting impact forces to be dissipated and / or redirected away from the cranium and brain within. Upon impact to the helmet, there are sequential stages of movement of the panels relative to each other, these movements initially being recoverable, but with sufficient vector forces the helmet undergoes structural changes in a pre-determined fashion, so that the recoverable and permanent movements cumulatively provide a protective ‘crumple zone’ or ‘shear zone’. The first two stages of protection arise from the design of the fasteners that have the ability to invaginate and collapse within themselves, and their design having a 45 degree angle, which will allow movement of a region of connected panels to translate along the fastener shaft. Both of these movements will be recoverable and provide a ‘functional crumple zone’. The final stage of protection arises from the braking function of the pins, as they are forced from one aperture through to the next, the direction and extent of which is determined by the impact force and direction. This final level of panel movement and protection is not recoverable and thus provides a ‘structural crumple zone’. Finally the fastener size and thickness, together with the thickness of webbing and distance between apertures, functions to provide varying degrees of resistance to impact forces, thus making the helmet design suitable for activities with different levels of impact speed and risk potential.
Owner:PUCHALSKI TECHN
Presenting HTML content on a screen terminal display
ActiveUS7900137B2Digital data information retrievalDigital computer detailsImage resolutionMostly True
The object of the present invention is to render markup documents within the limits of resolutions smaller than the resolutions for which the markup documents were originally designed, in most cases without introducing horizontal scrolling, while keeping the original fonts, colors, design, and style. The object is achieved by finding and selecting elements whose content takes up too much space horizontally, determining appropriate widths for rendering such elements, and shrinking or horizontally squeezing such elements individually to fit within their respective determined widths. Further, the invention determines the widths for rendering table cells in such manner as to preserve the layout of the corresponding table.
Owner:OPERA SOFTVEAR AS
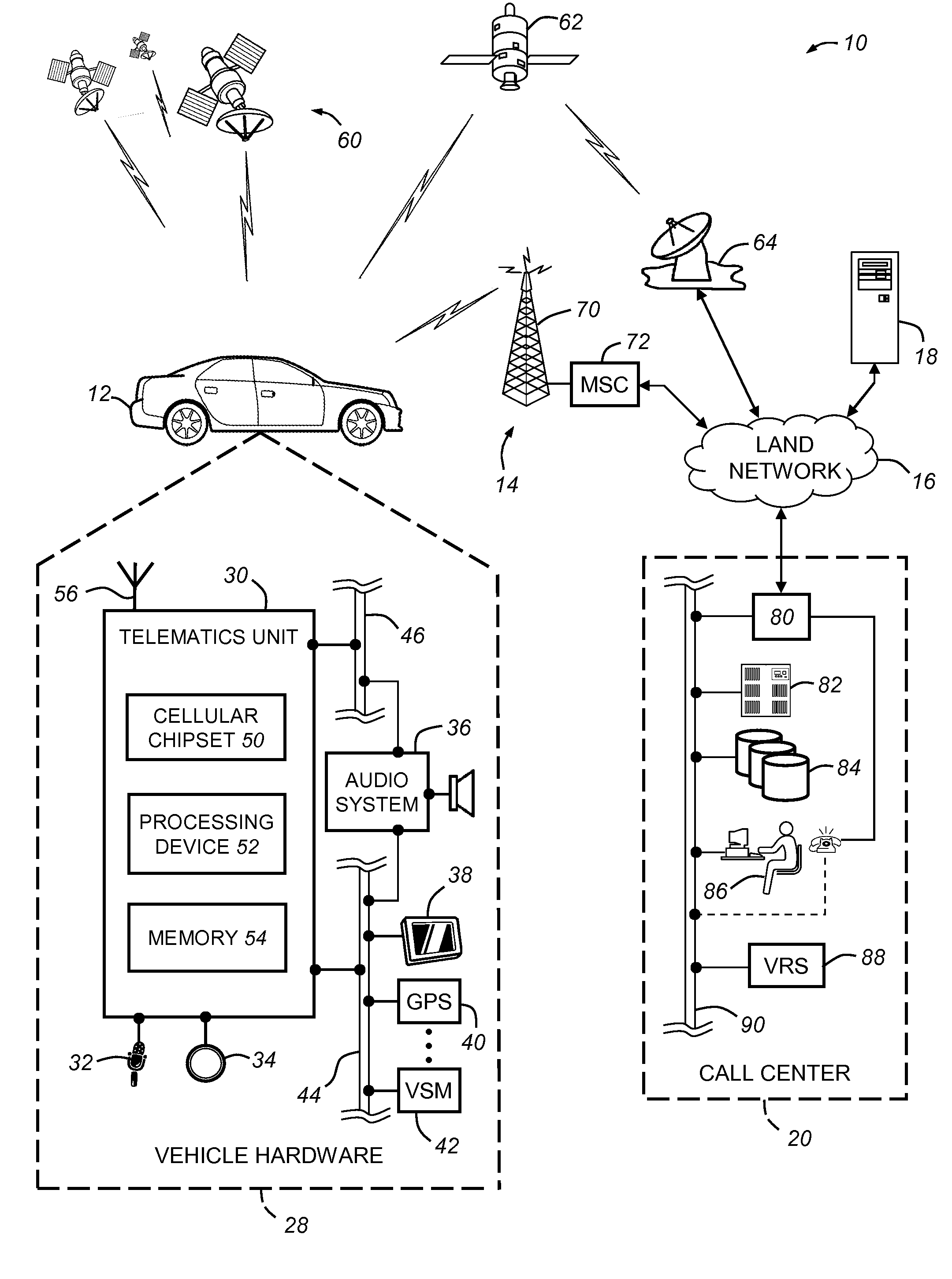
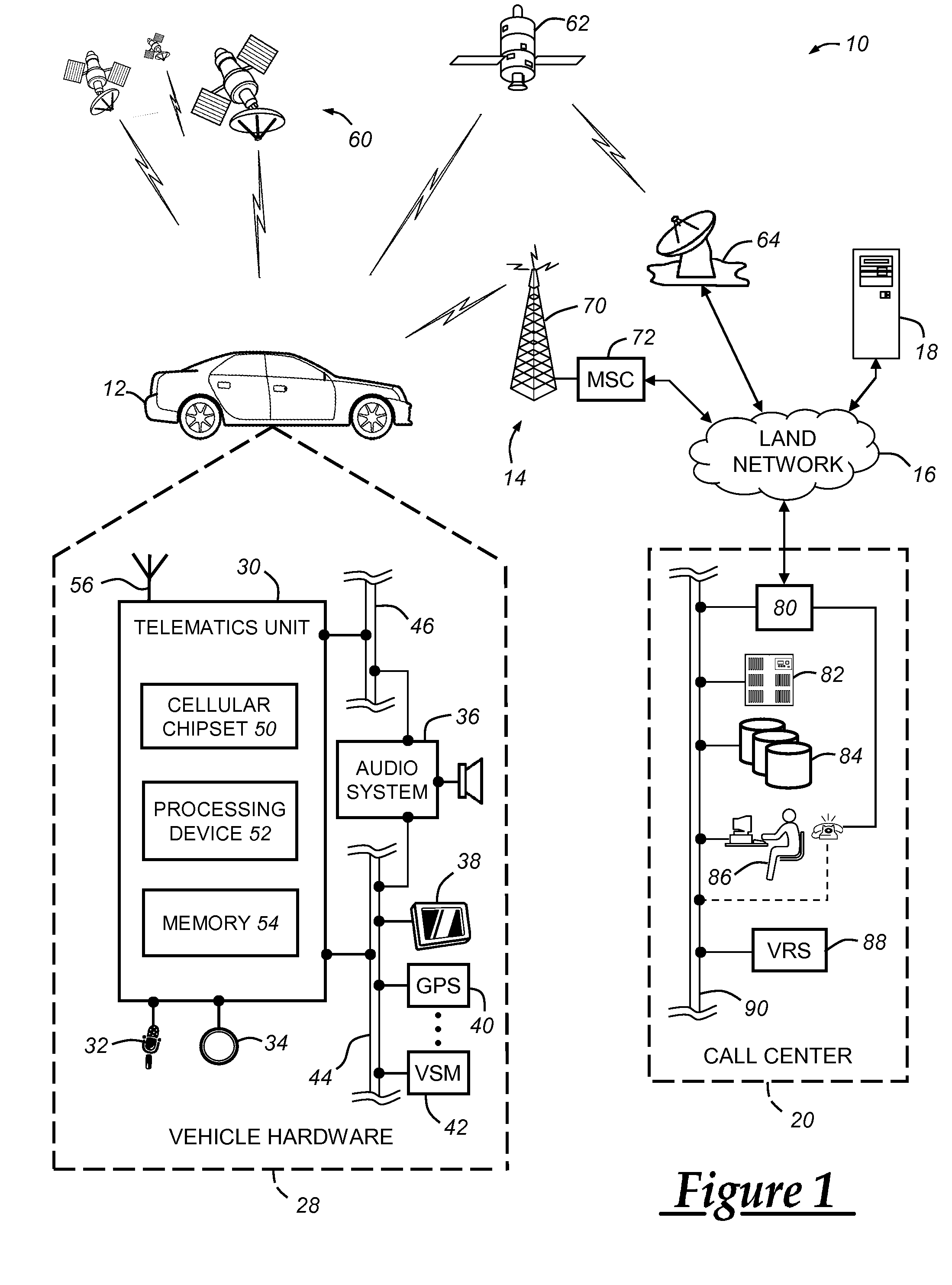
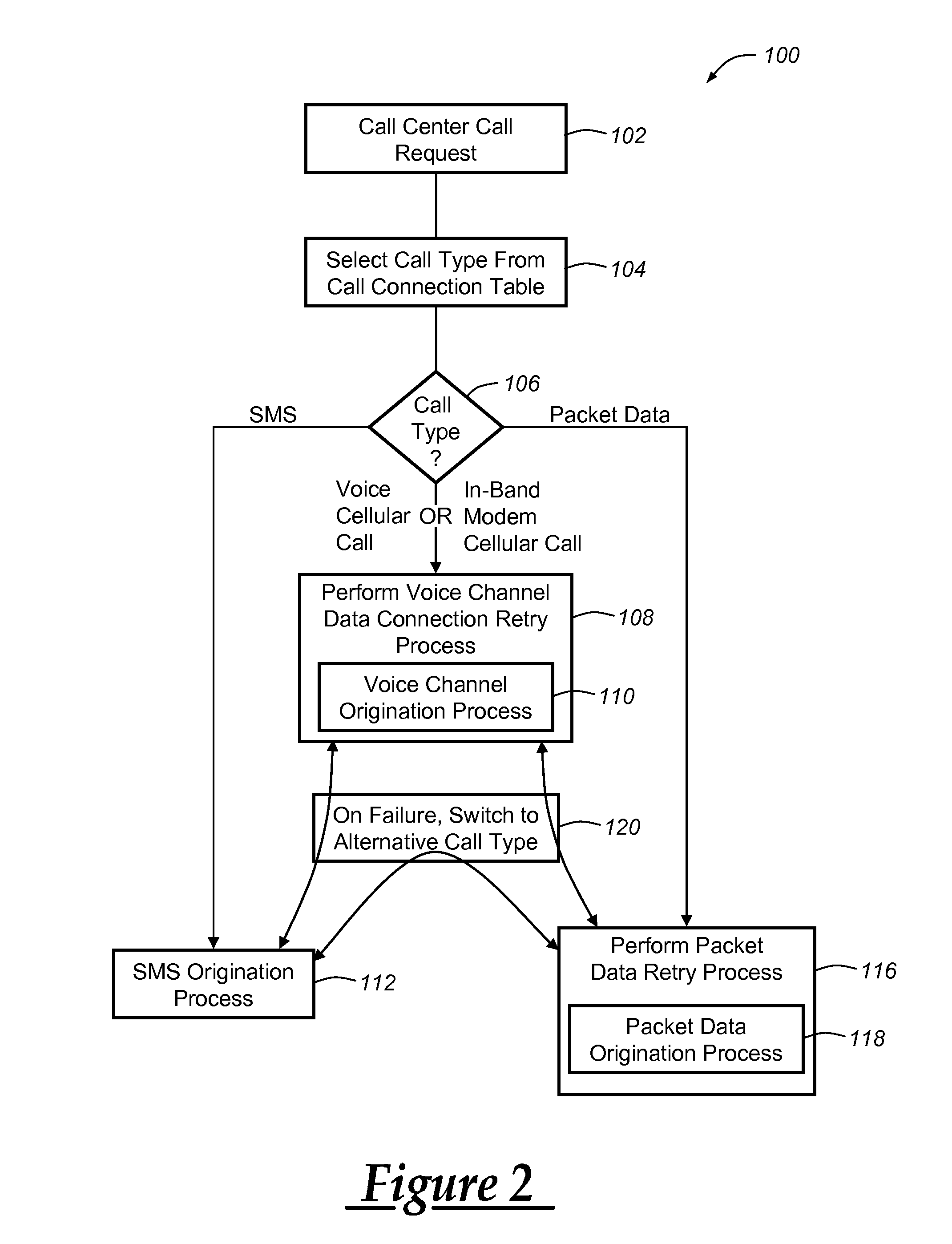
Outgoing binary SMS messaging for vehicle communication with a call center
A system and method for making vehicle originated calls to a telematics service provider or other call center. The method includes identifying a call type associated with a desired wireless communication of speech or data to the call center, and then carrying out one of a number of different call connection processes depending on the call type. For voice channel cellular connections, an in-band modem cellular connection is preferably established in most instances using a connection retry strategy that includes primary, secondary, and possibly tertiary connection attempts each of which utilize at least one of a number of different voice and data call origination processes. The system and method can be carried out in connection with various cellular system technologies, but is especially suited for use with GSM systems.
Owner:GENERA MOTORS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com