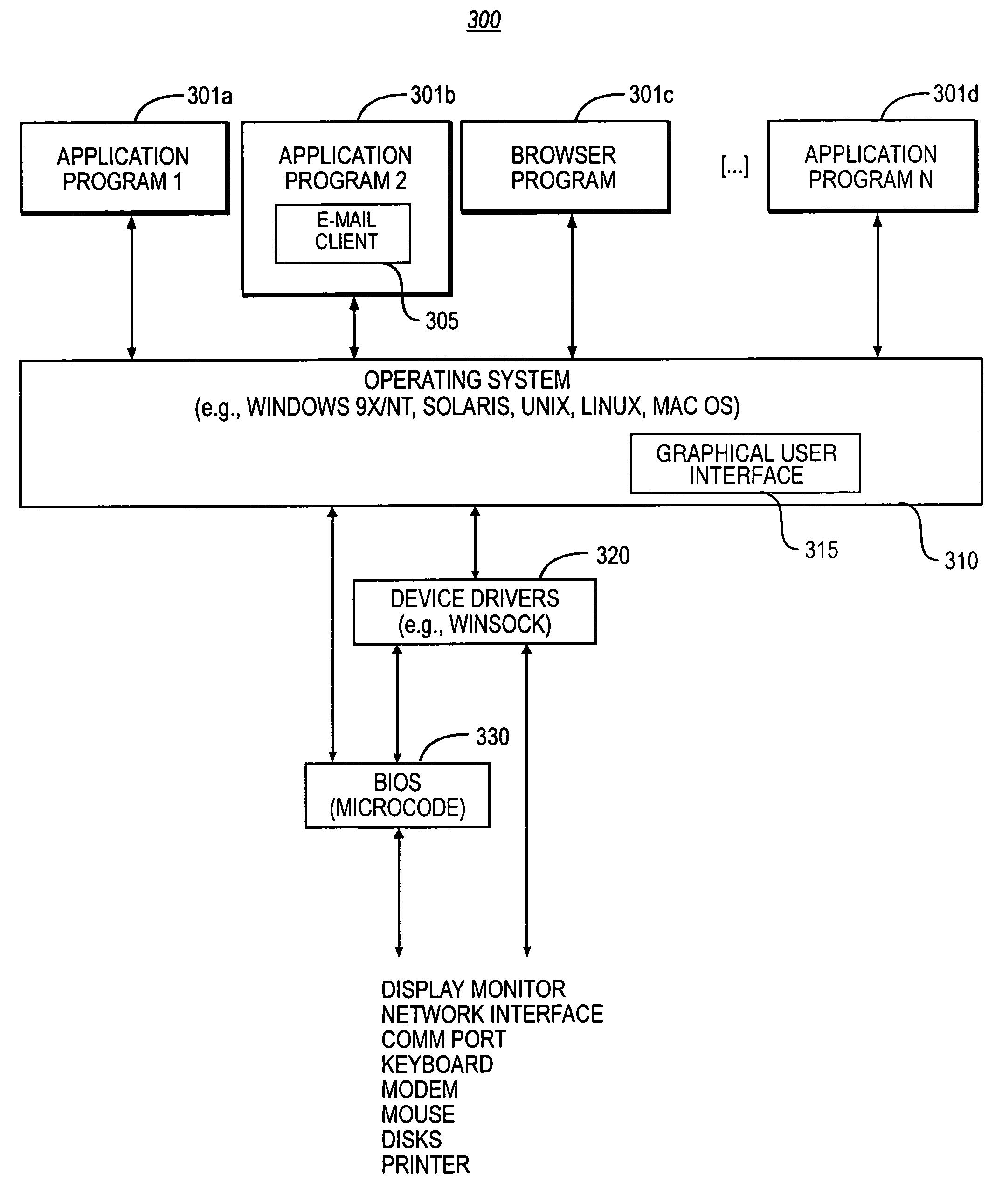
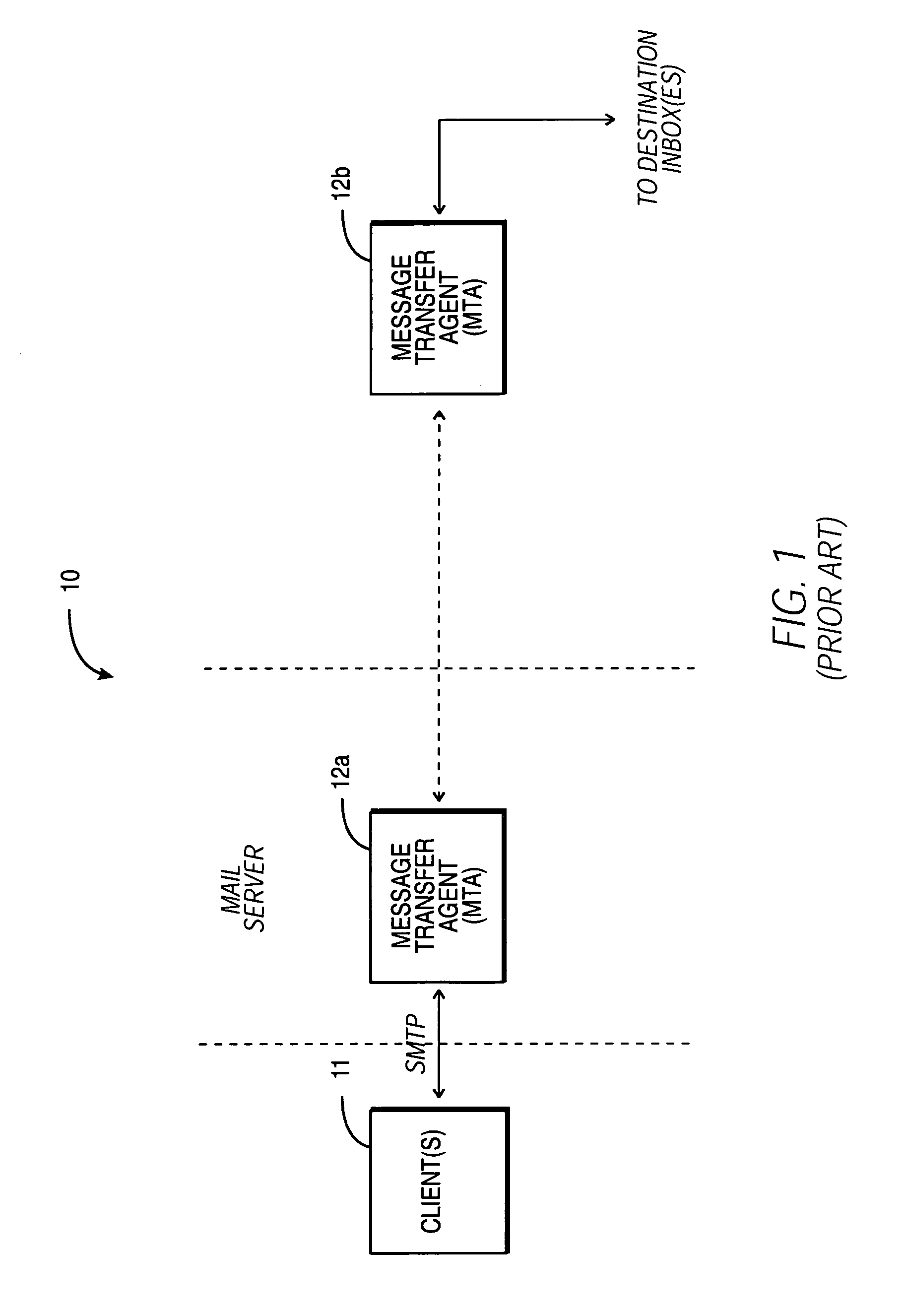
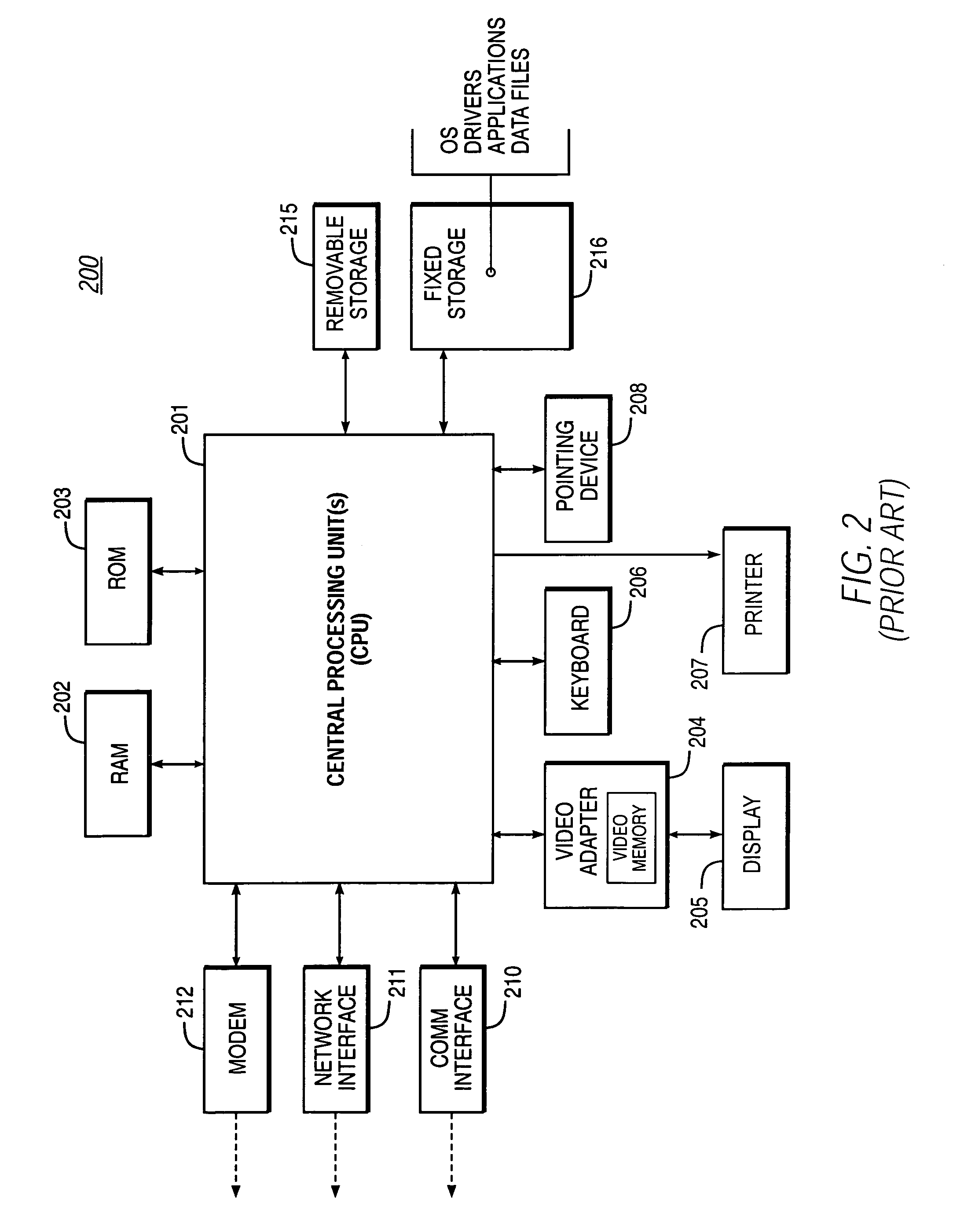
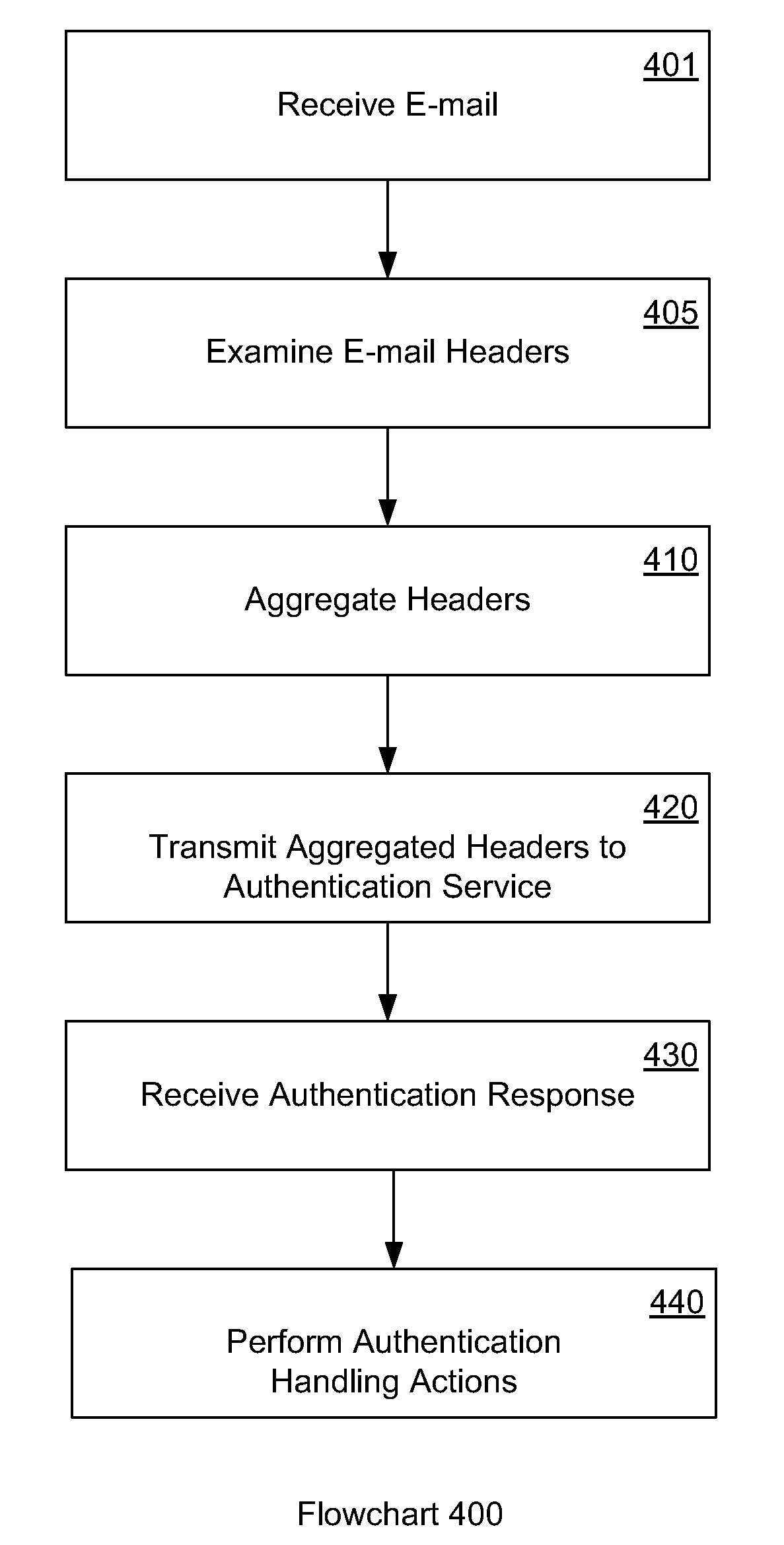
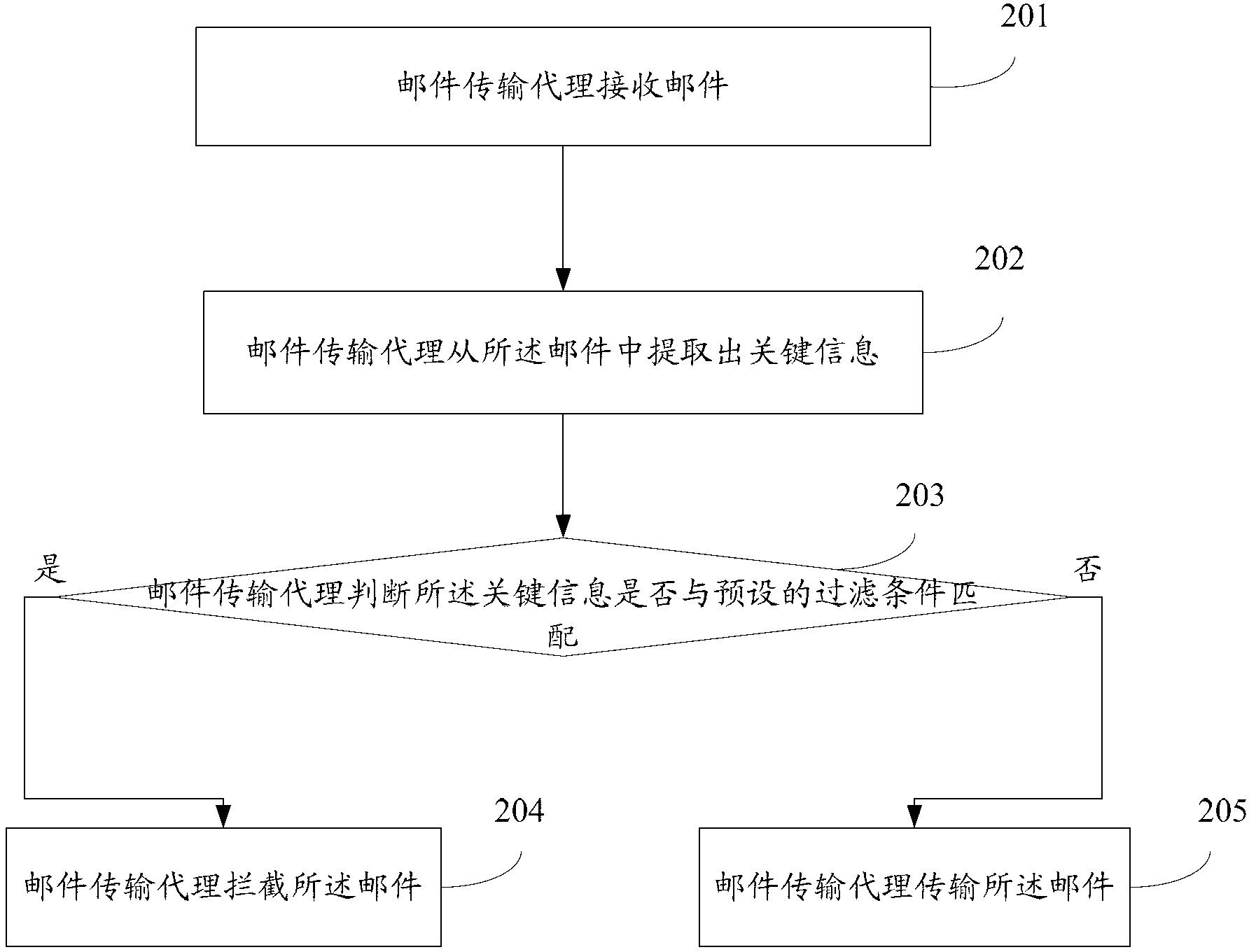Patents
Literature
71 results about "Message transfer agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
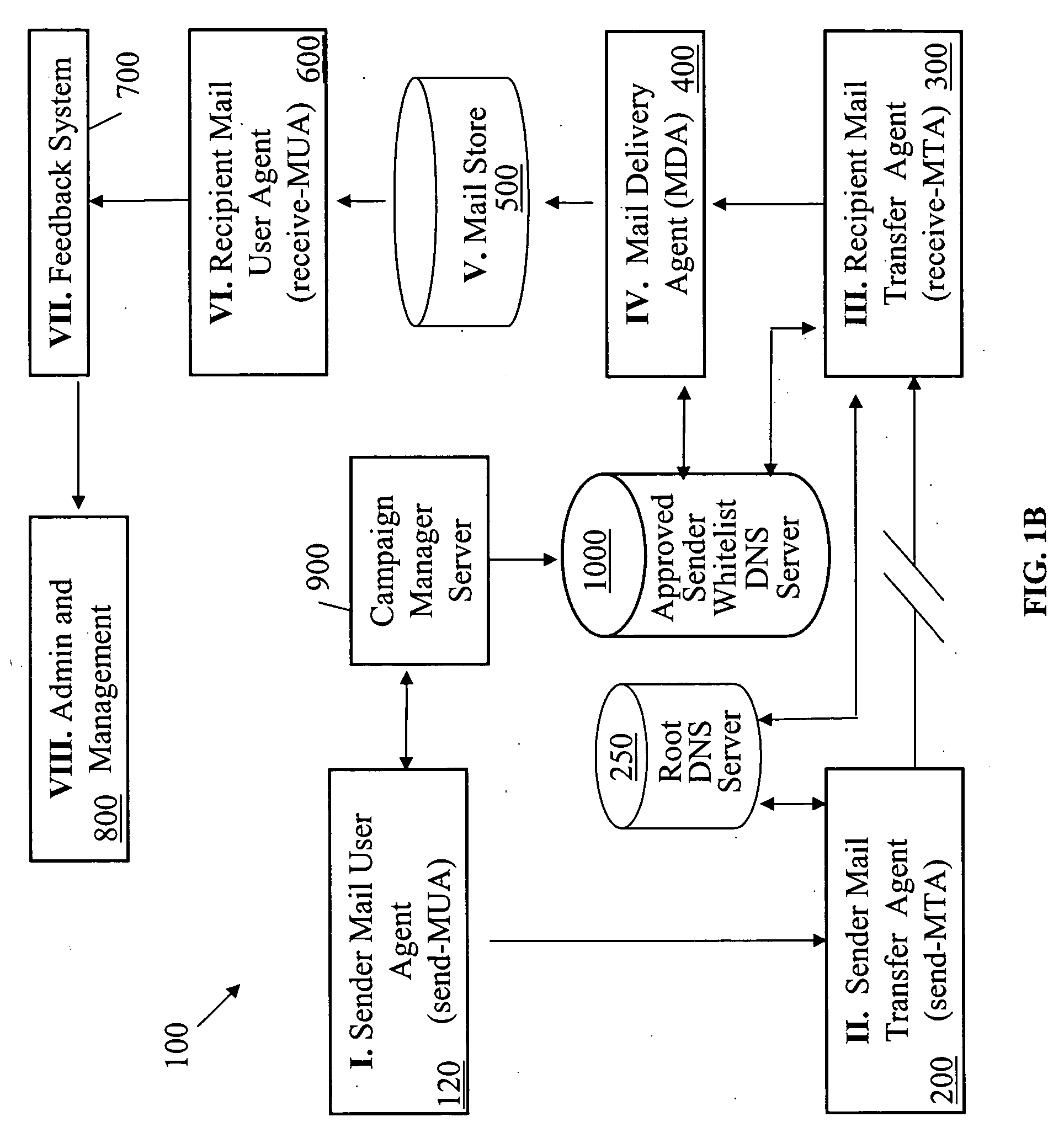
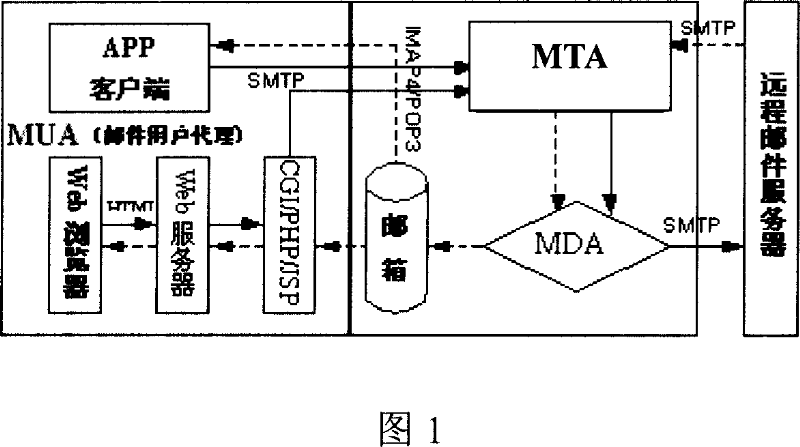
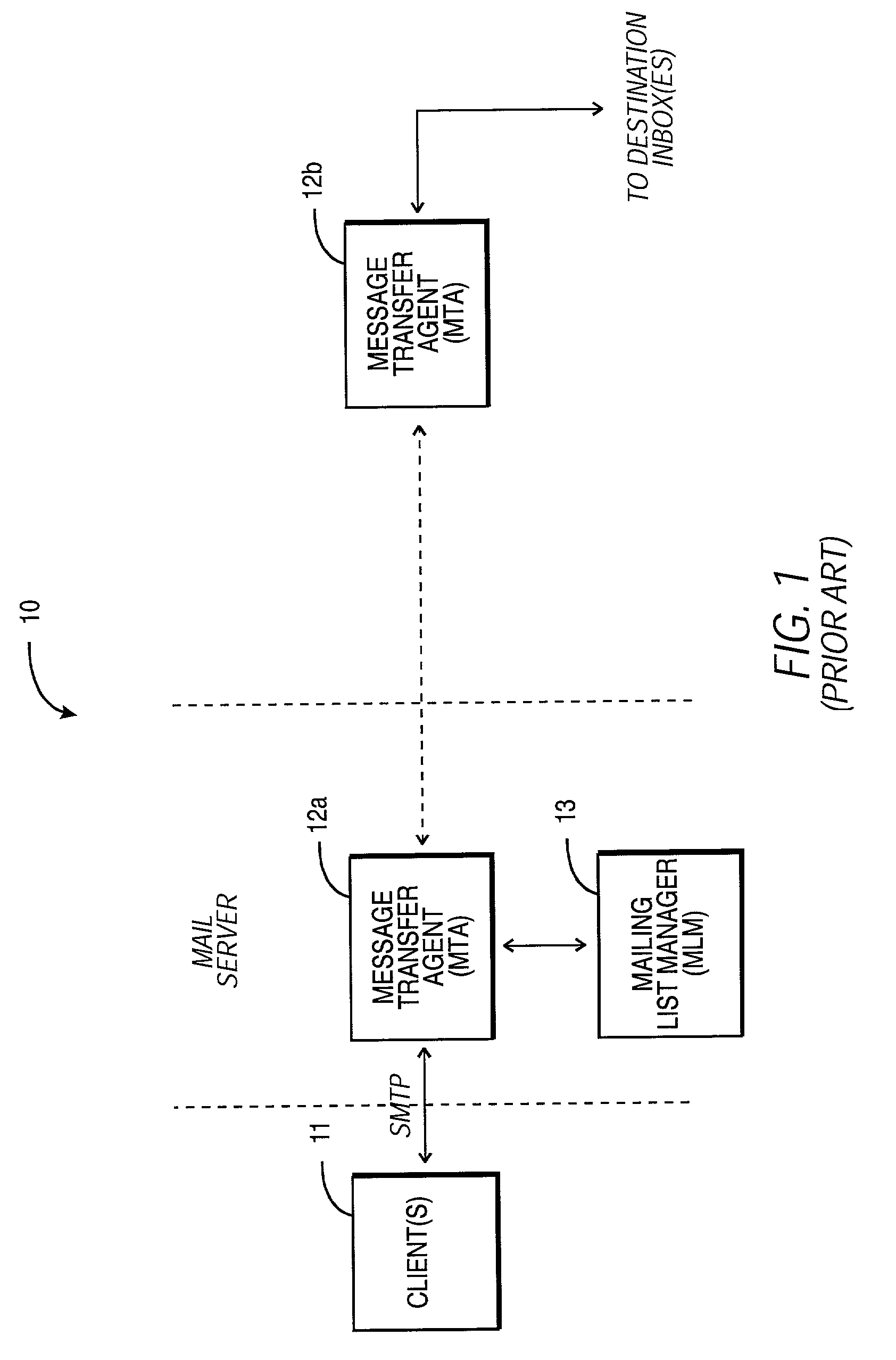
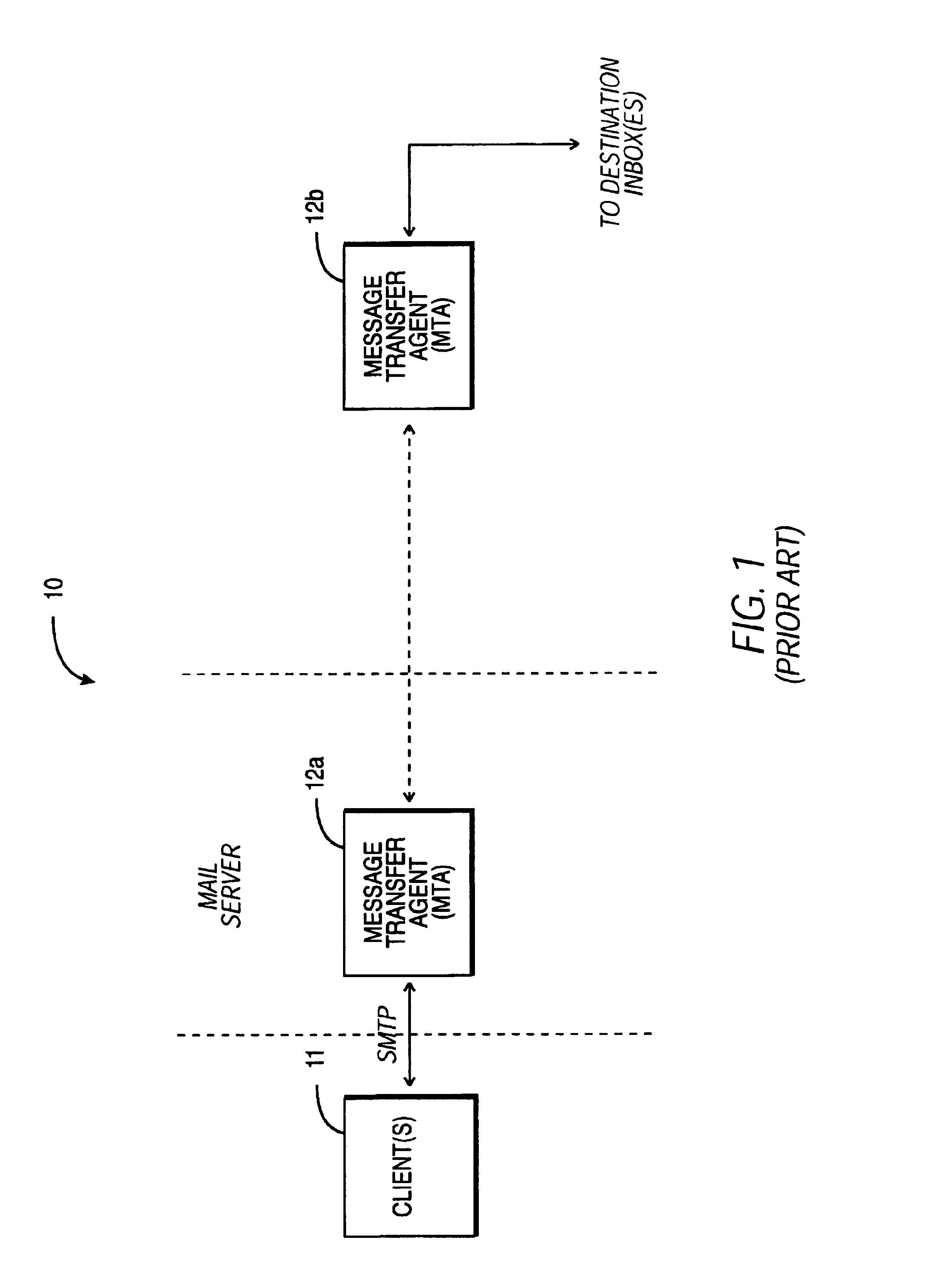
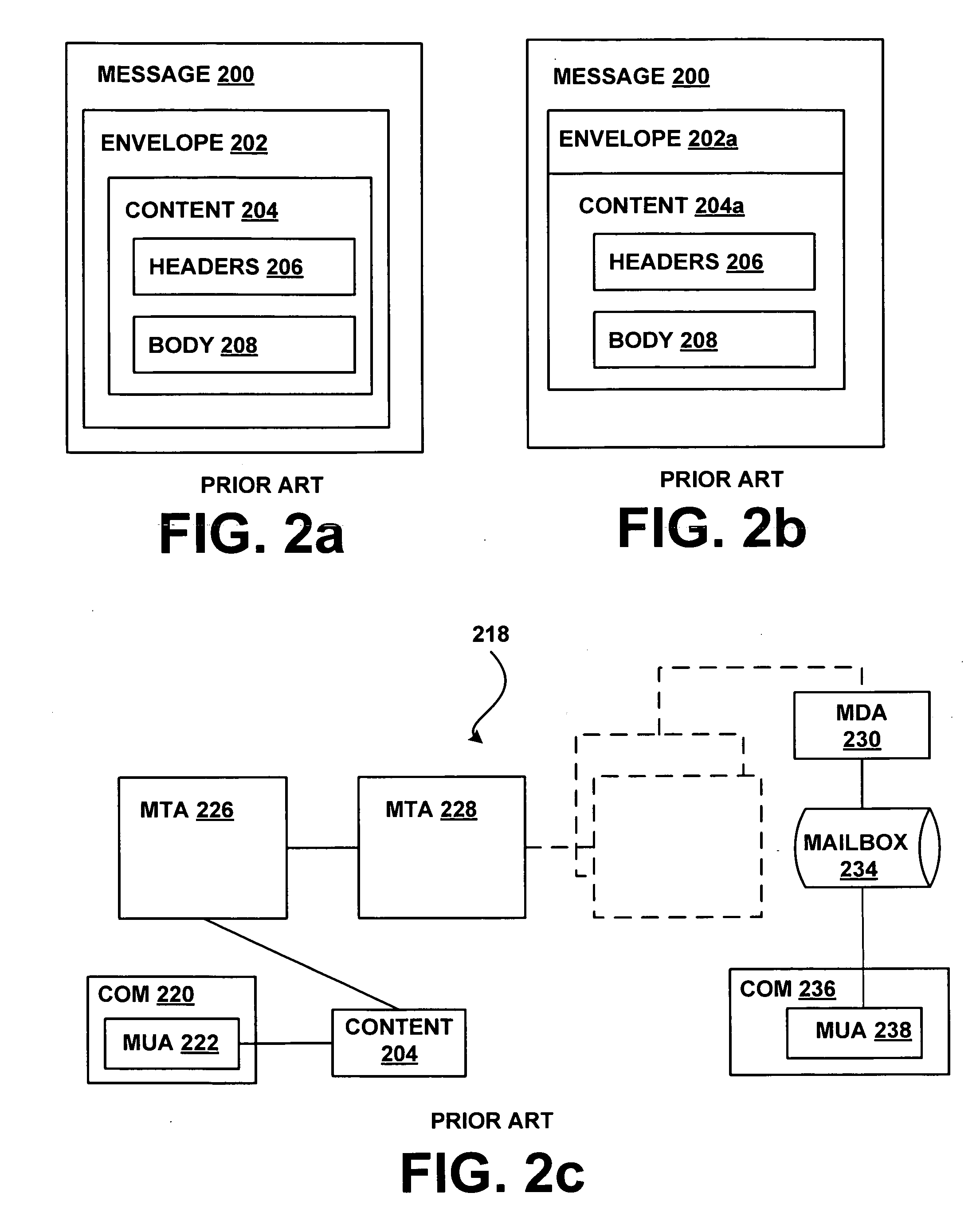
Within the Internet email system, a message transfer agent or mail transfer agent (MTA) or mail relay is software that transfers electronic mail messages from one computer to another using SMTP. The terms mail server, mail exchanger, and MX host are also used in some contexts.
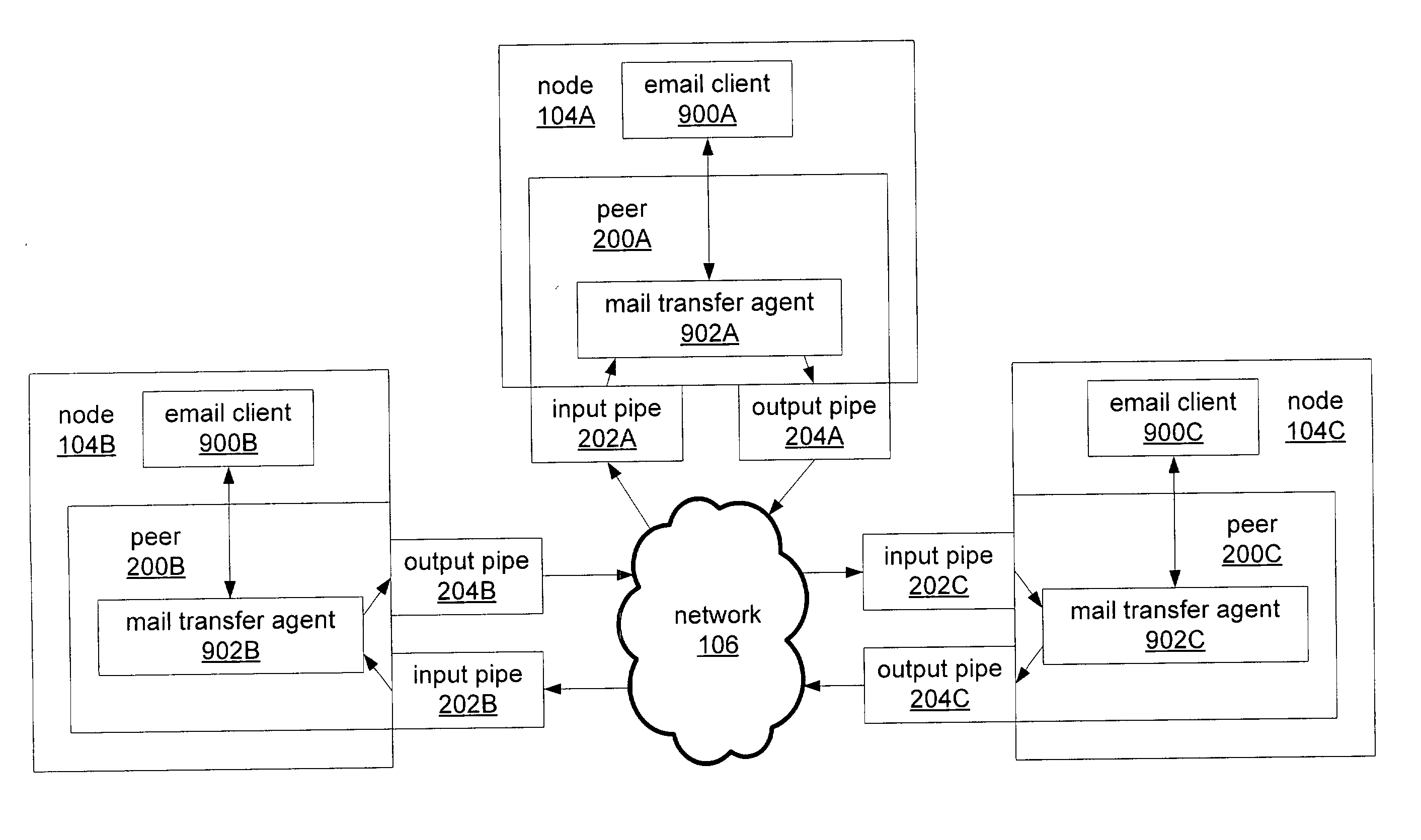
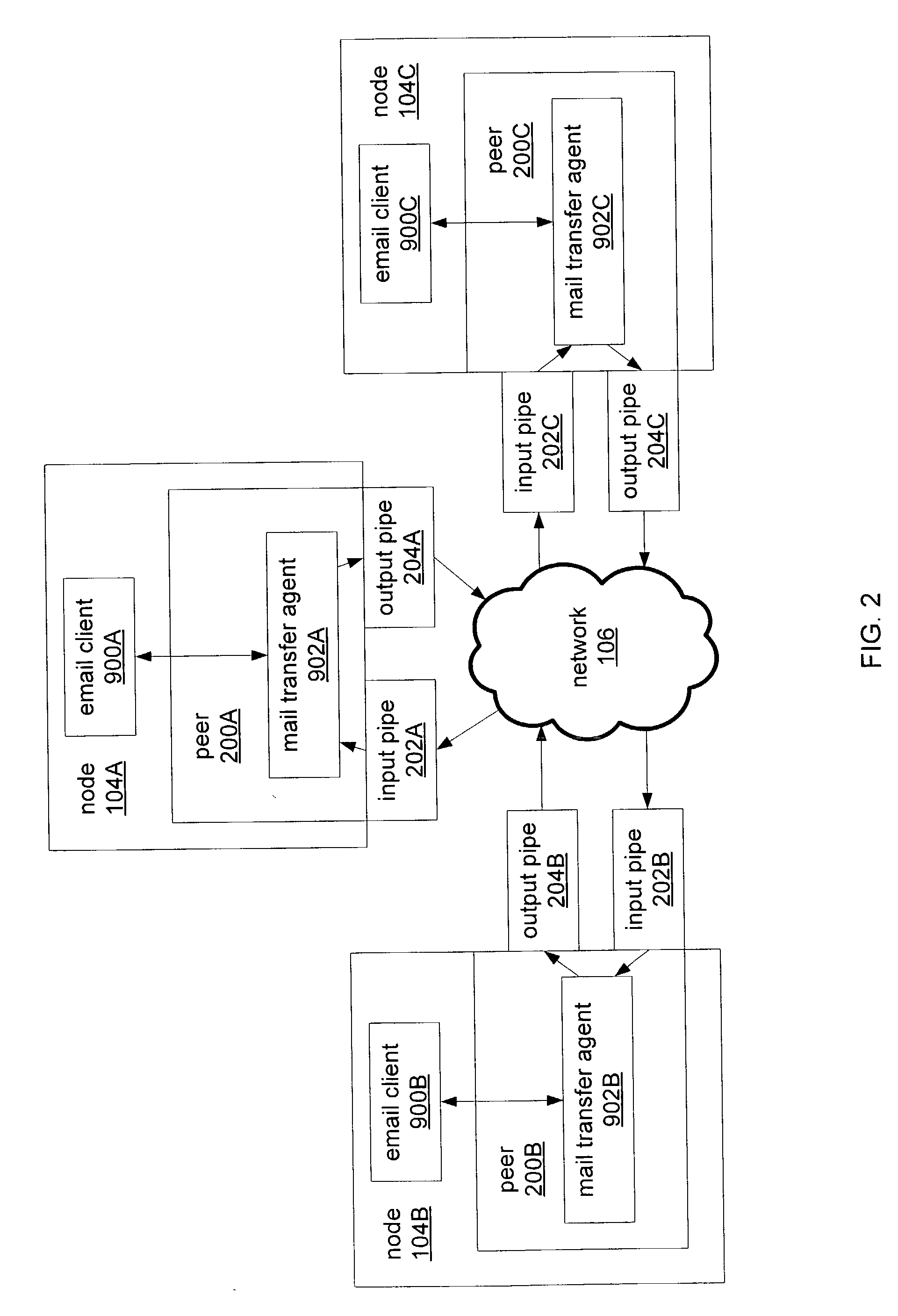
Peer-to-peer email messaging
ActiveUS20040064511A1Multiple digital computer combinationsData switching networksClient-sideDistributed computing
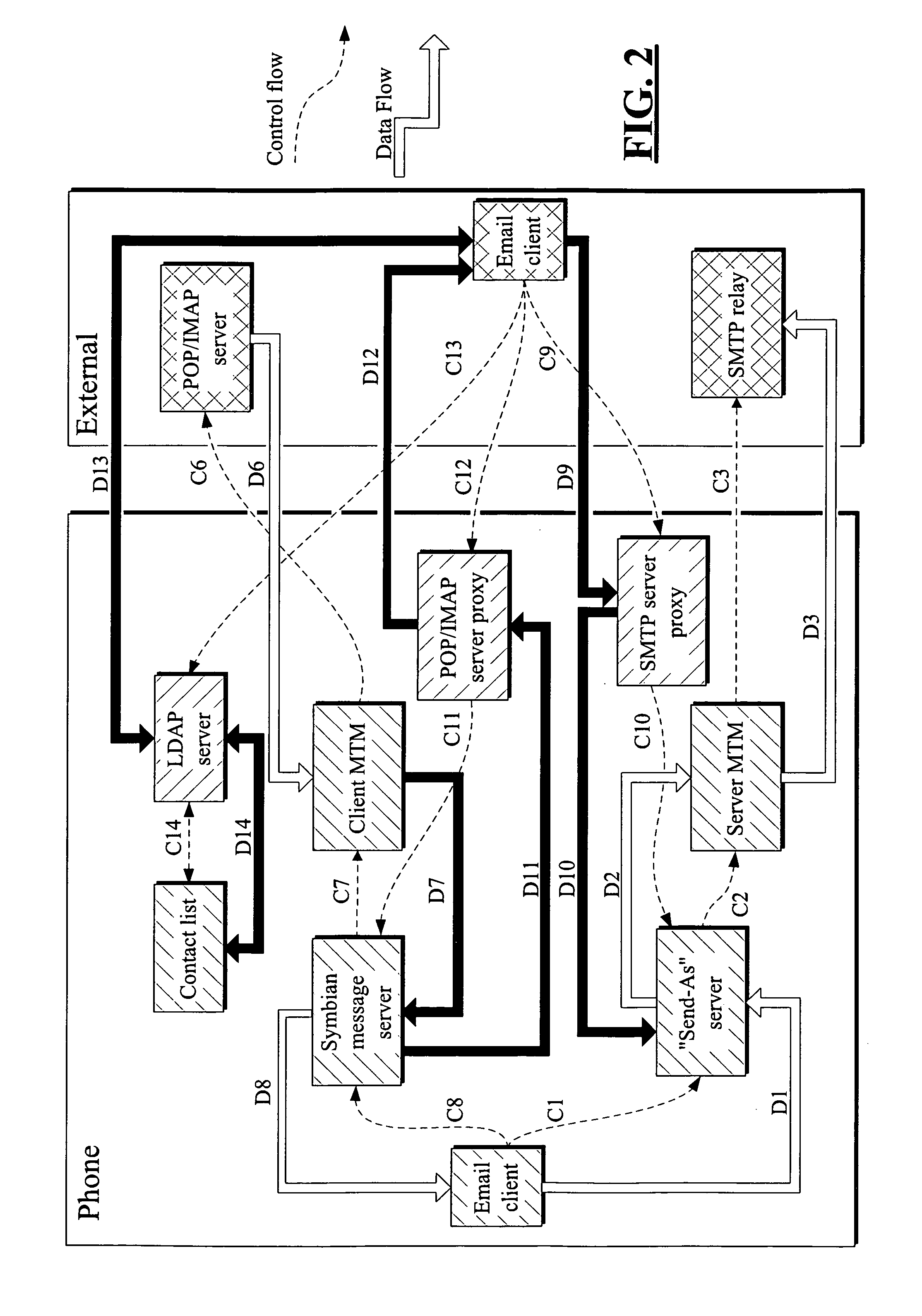
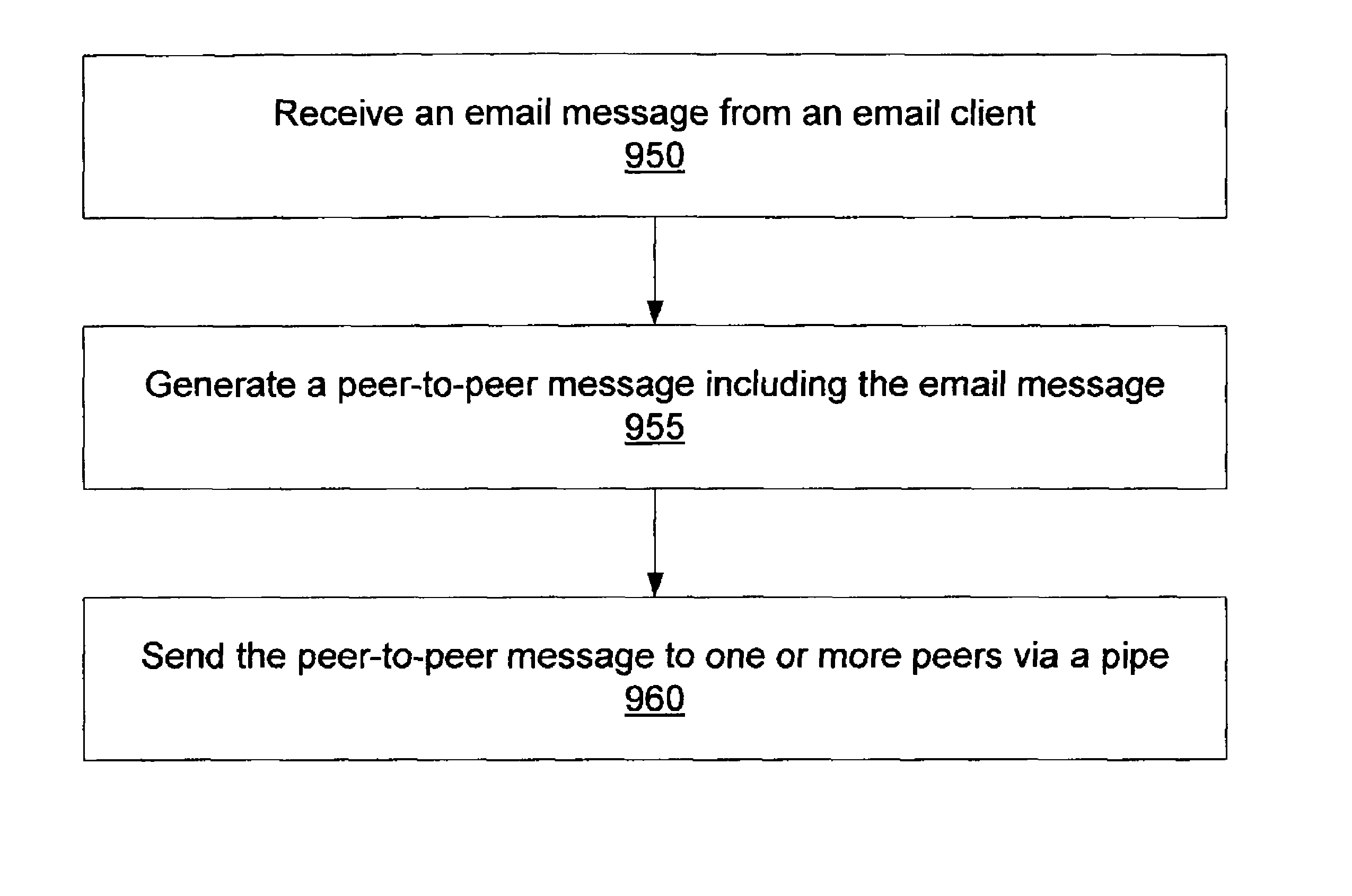
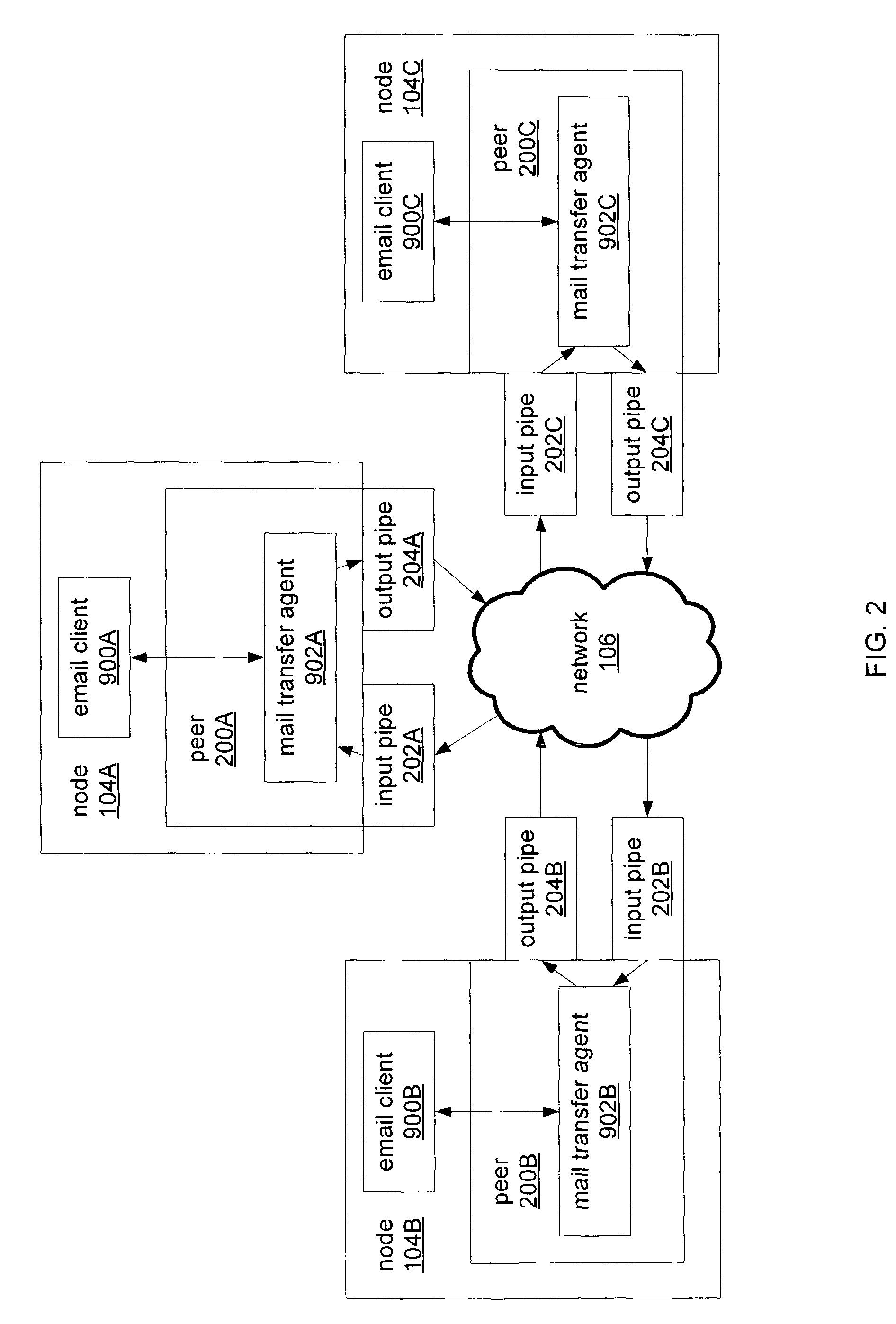
System and method for facilitating communications between peers in a peer-to-peer environment and network email clients. In one embodiment, network nodes including peer nodes may host mail transfer agents. The mail transfer agents may act as bridges between peer-to-peer protocols and email communication protocols. The mail transfer agents may communicate with peers according to peer-to-peer protocols and with email clients according to email communications protocols. Peers may communicate with mail transfer agents to send peer-to-peer messages to email clients. Email clients may communicate with the mail transfer agents to send email messages to and receive email messages from other email clients via the peer-to-peer network and to obtain peer-to-peer messages from peers.
Owner:ORACLE INT CORP
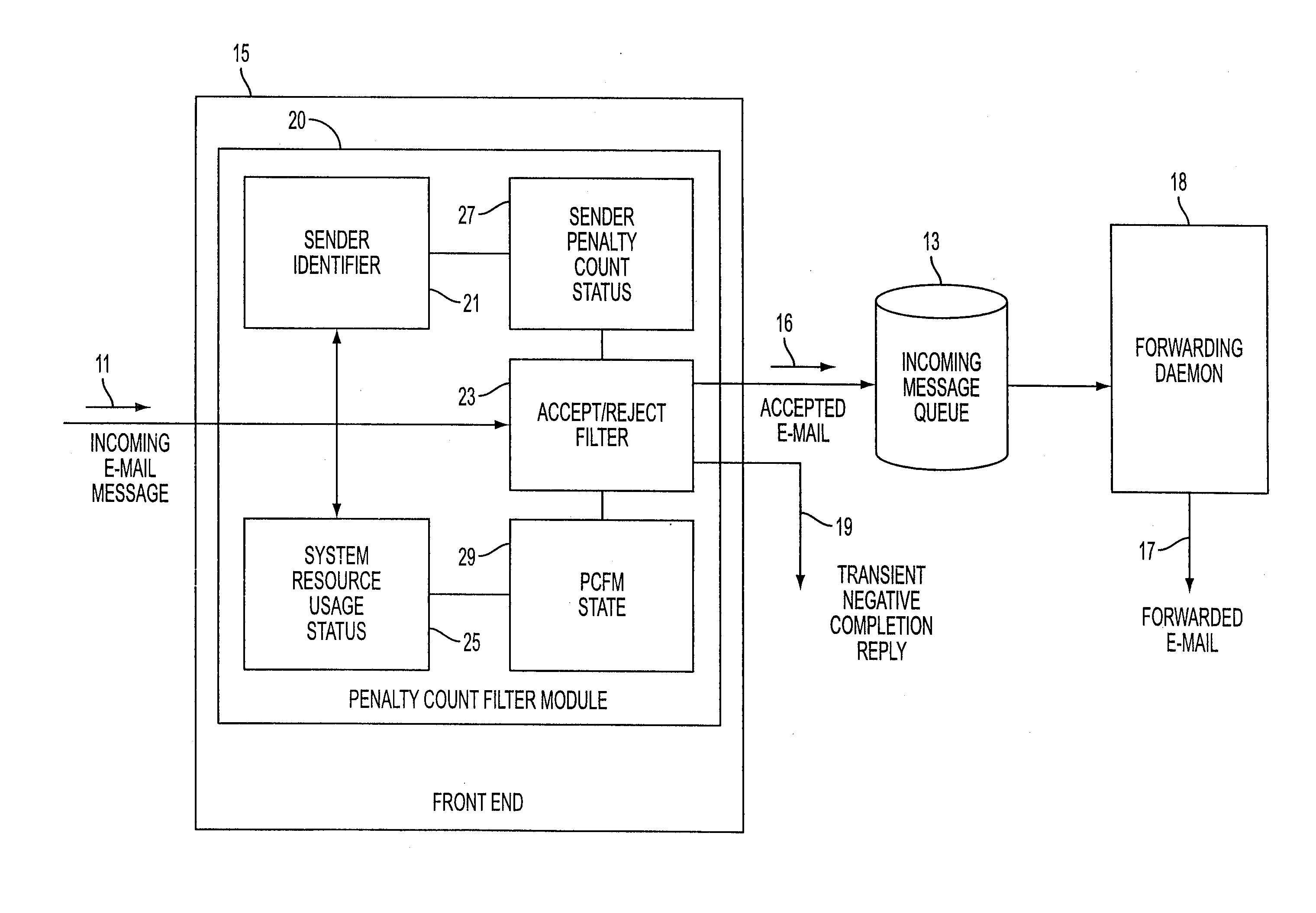
Apparatus and method for handling electronic mail
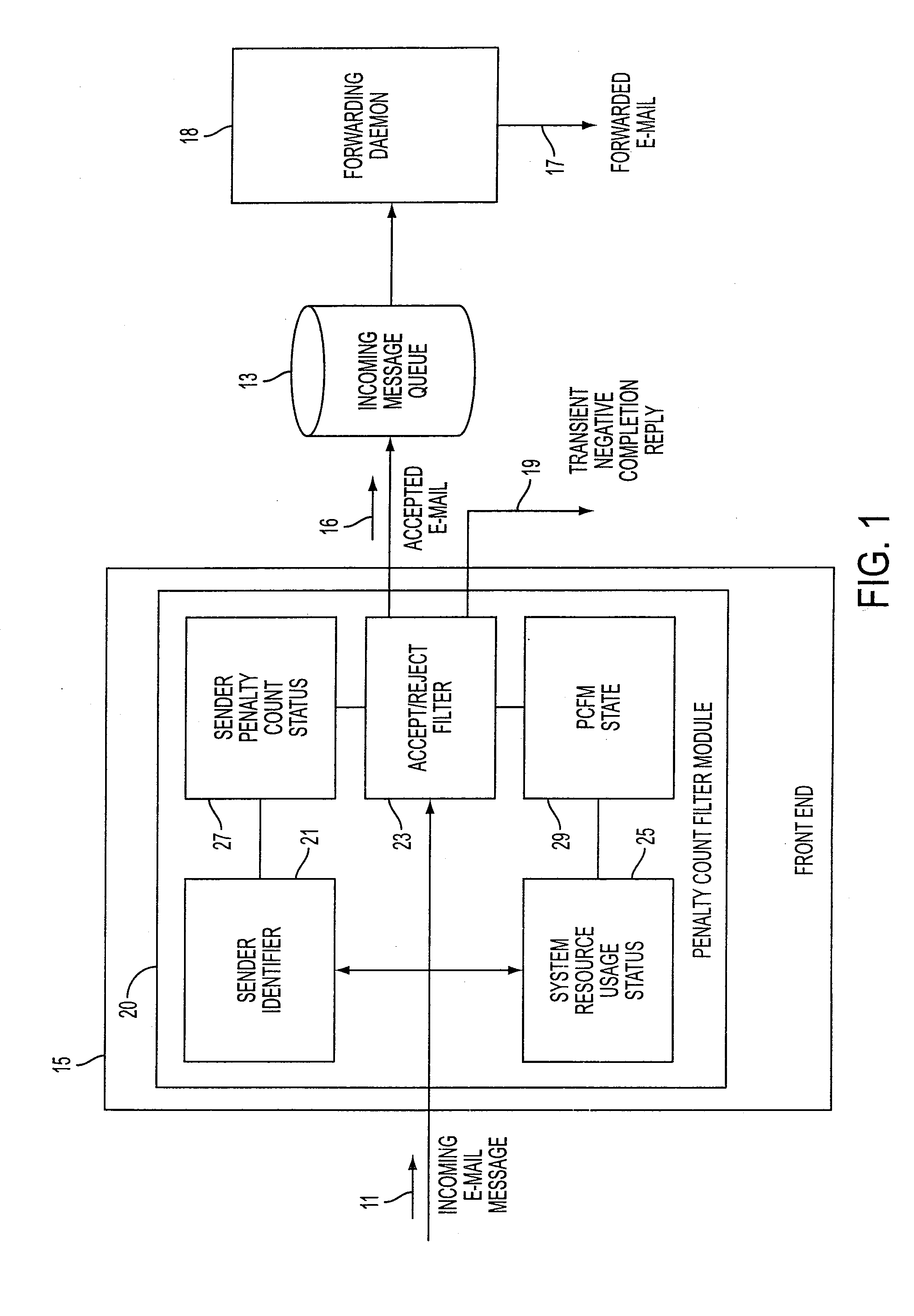
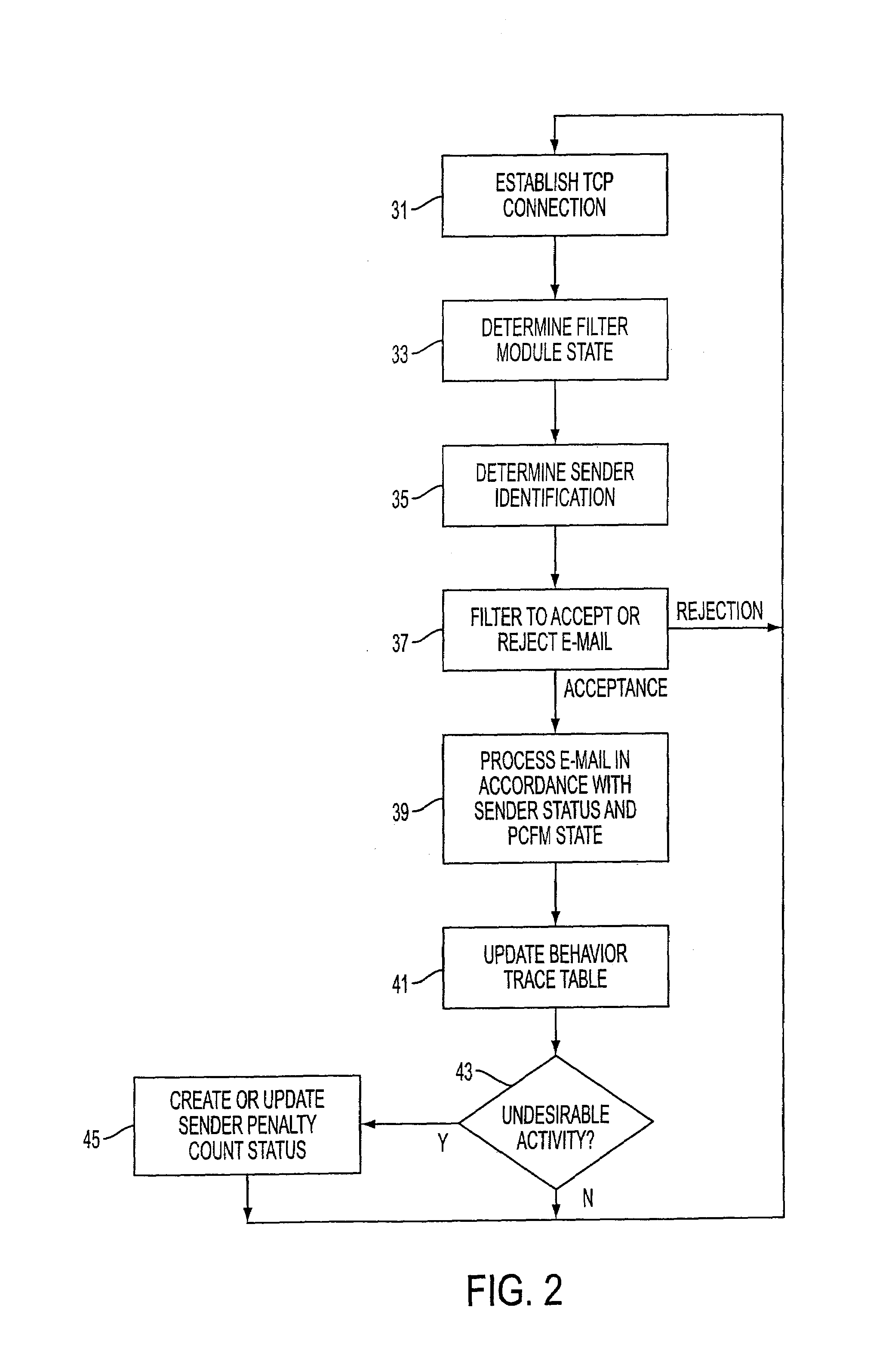
InactiveUS7328250B2Reduce disruptionHigh scrap rateMultiple digital computer combinationsData switching networksCommunications systemRejection rate
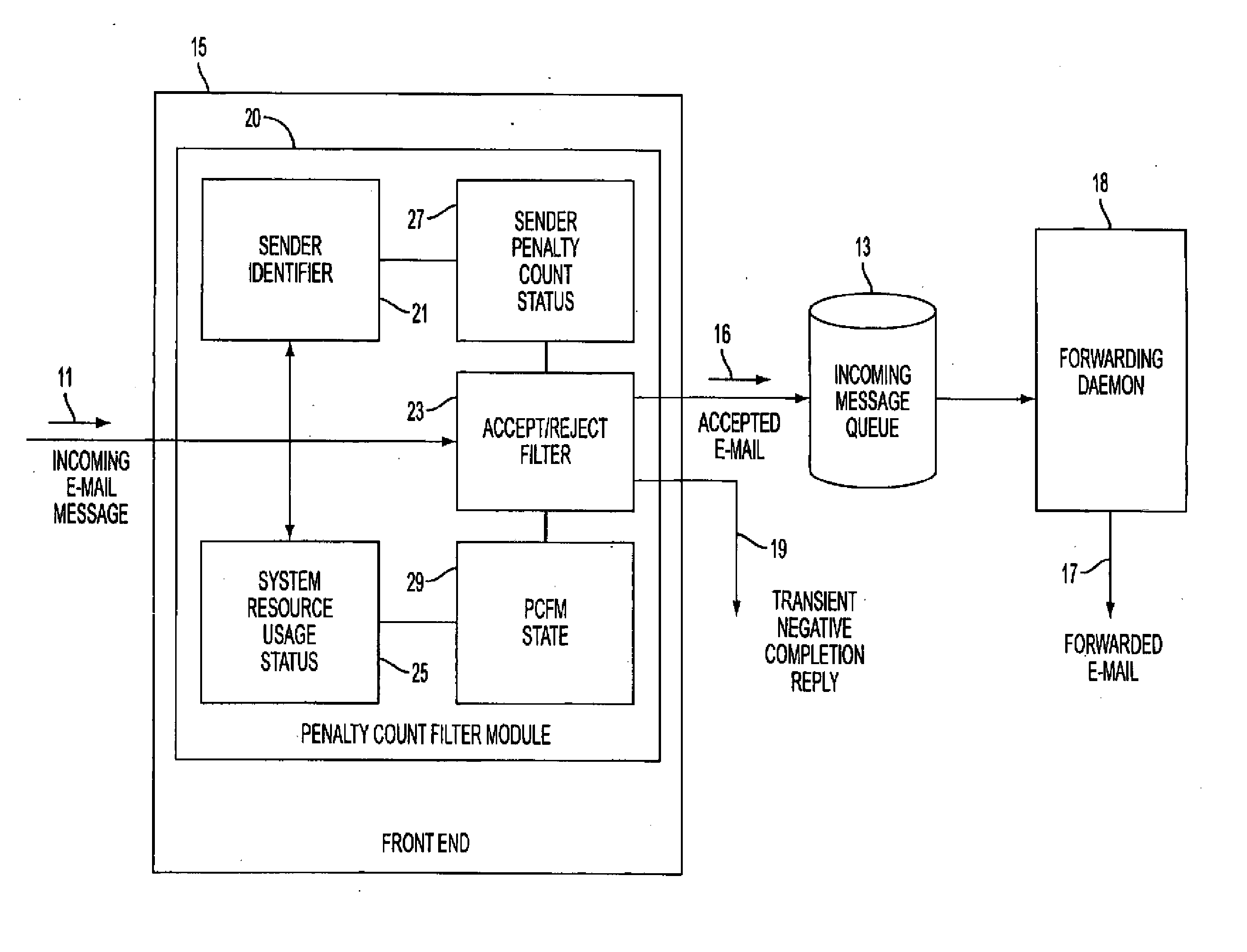
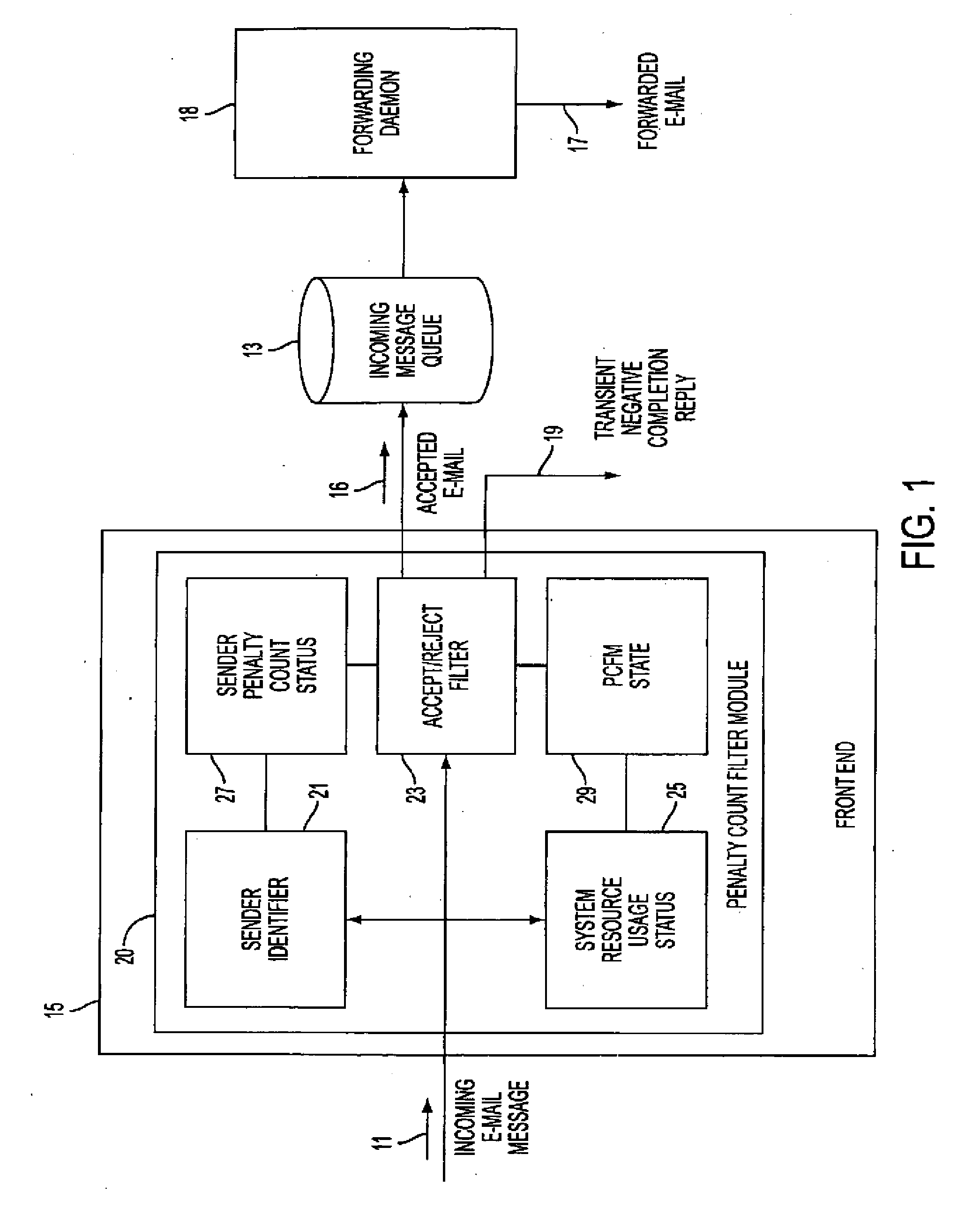
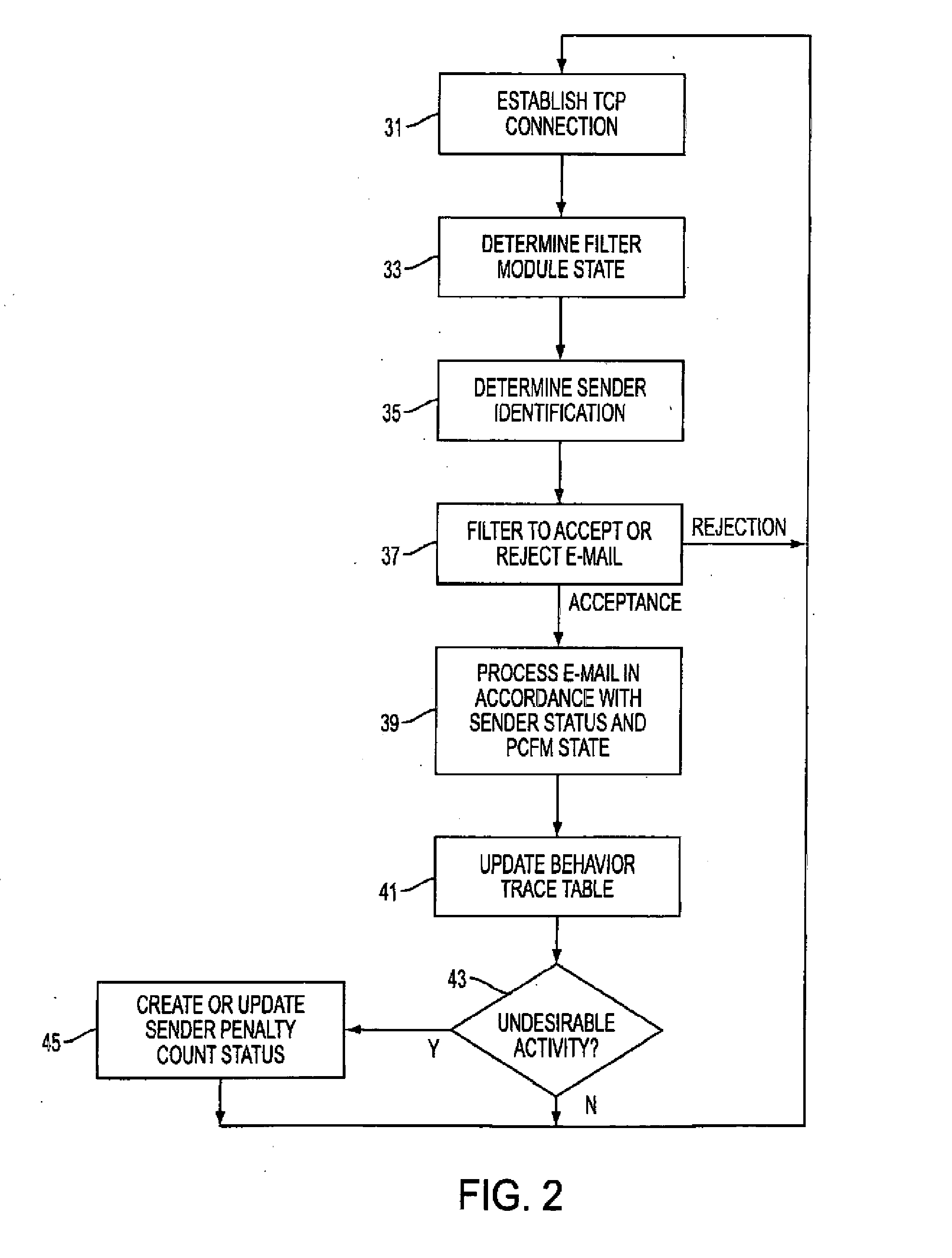
A mail transfer agent adapted for determining the disposition of incoming e-mail from a sender includes a penalty count filter module which functions on the basis of current communication system resource usage, such as the number of concurrent TCP connections being maintained, and penalty counts assigned for cumulative undesirable sender activity such as sending large e-mail files. The penalty count filter module can operate in a selective-rejection state accepting e-mail from senders without a penalty count and randomly accepting other e-mail, and in a random-rejection state rejecting all e-mail from senders with a penalty count and randomly rejecting other e-mail. The rejection rates can be increased or decreased in response to a detected increase or decrease in the usage of system resources.
Owner:NOKIA INC
Method and system for enhanced electronic mail processing
InactiveUS20060168057A1Improved electronic mail deliverabilityMultiple digital computer combinationsData switching networksProxy serverTransfer agent
An asynchronous proxy server system interposed between sender and recipient mail transfer agents, or other agent on the sender side, is configured to classify outgoing mail. Message and message header information is processed and compared against a set of business rules. The message header is modified to reflect an assertion based on an outcome of the comparison. The modified outgoing message is then routed to its destination.
Owner:HABEAS
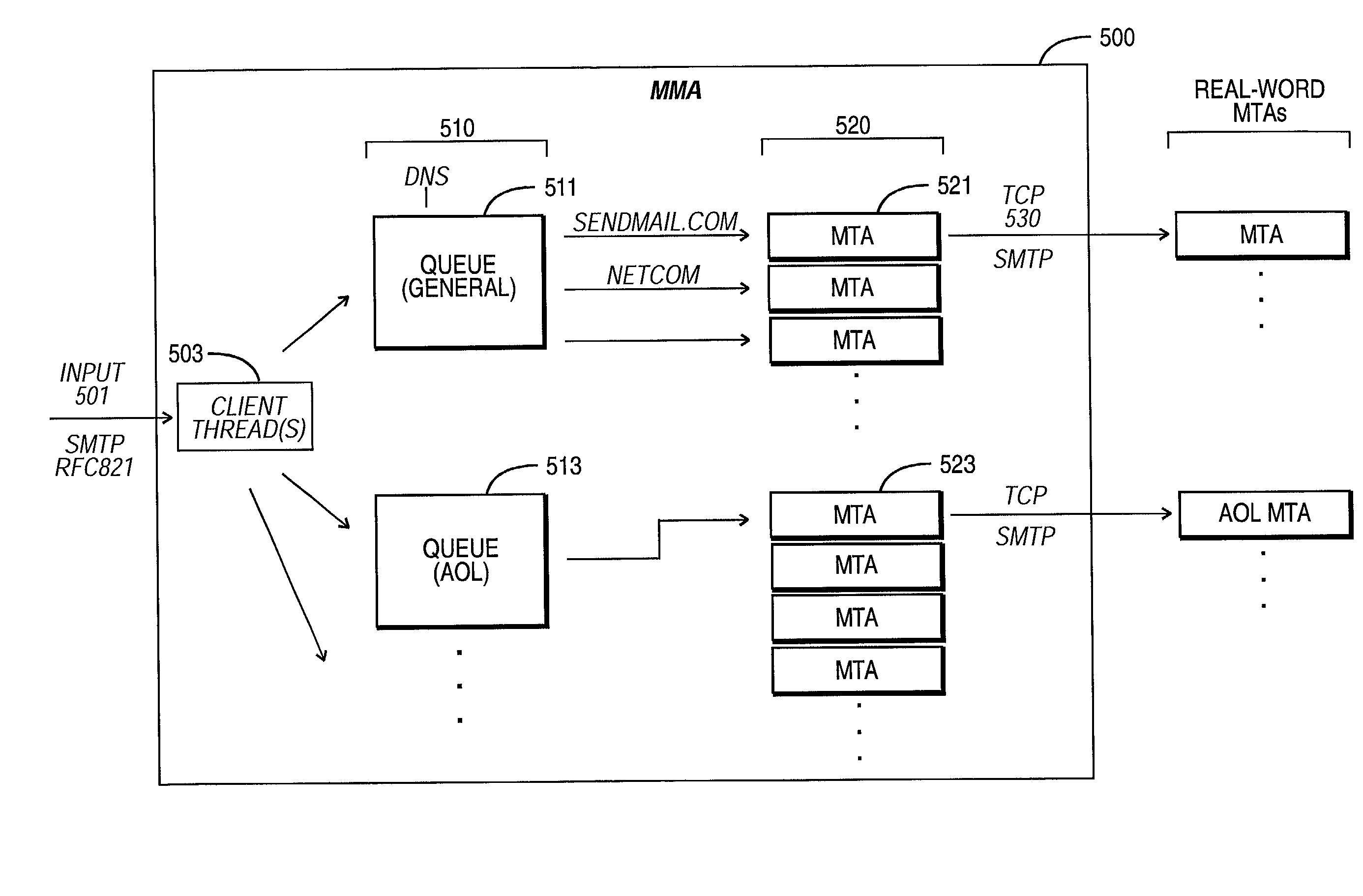
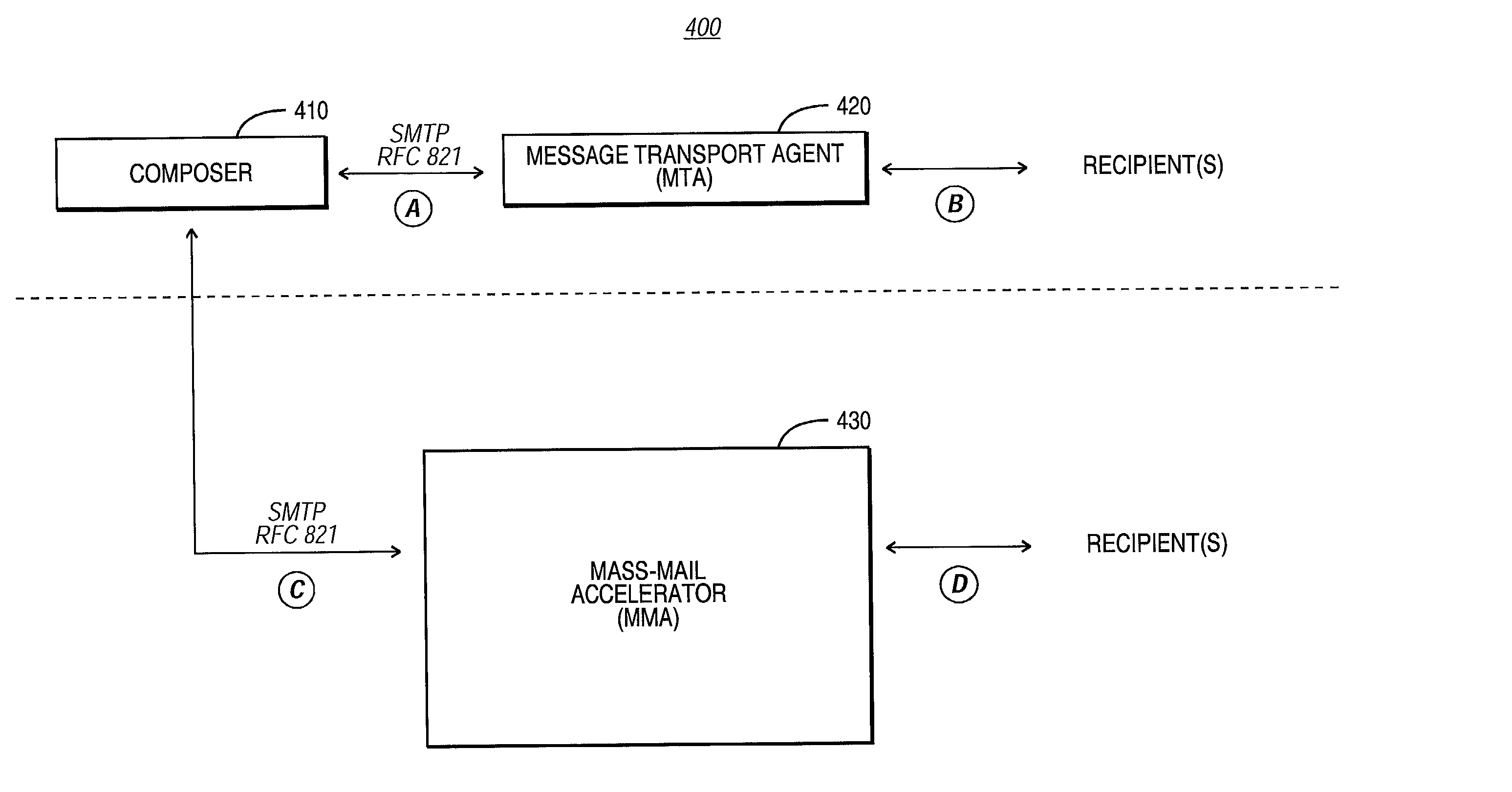
E-mail system with methodology for accelerating mass mailings
InactiveUS20030028580A1Special service provision for substationMultiprogramming arrangementsMessage passingMessage transfer agent
An e-mail system is described that includes a mass-mail accelerator (MMA), which is particularly suited for processing mass e-mailings. Instead of being posted to a message transfer agent (MTA), outgoing messages are instead passed to the MMA for carrying out highly parallel e-mail delivery / routing. The MMA employs a plurality of queues, which may either be general or specific. A specific queue is configured to handle only e-mail destined for a particular domain, such as the AOL.com domain; a general queue is configured to handle all other e-mail. Each queue manages a pool of MTA threads. During MMA operation, once a message has been passed to a queue, that queue examines its MTA threads to see if one is ready to accept the message. If an MTA thread is ready, the queue will assign the message to that MTA. The MTA thread proceeds to handle the work of the SMTP exchange between the MMA and the target real-world MTA (e.g., an AOL MTA). While a given MTA thread is waiting for a reply from the real-world (destination) MTA (e.g., the AOL MTA), the MMA can proceed to do other work. In this manner, the bottleneck usually encountered with processing mass e-mailings is removed.
Owner:PROOFPOINT INC
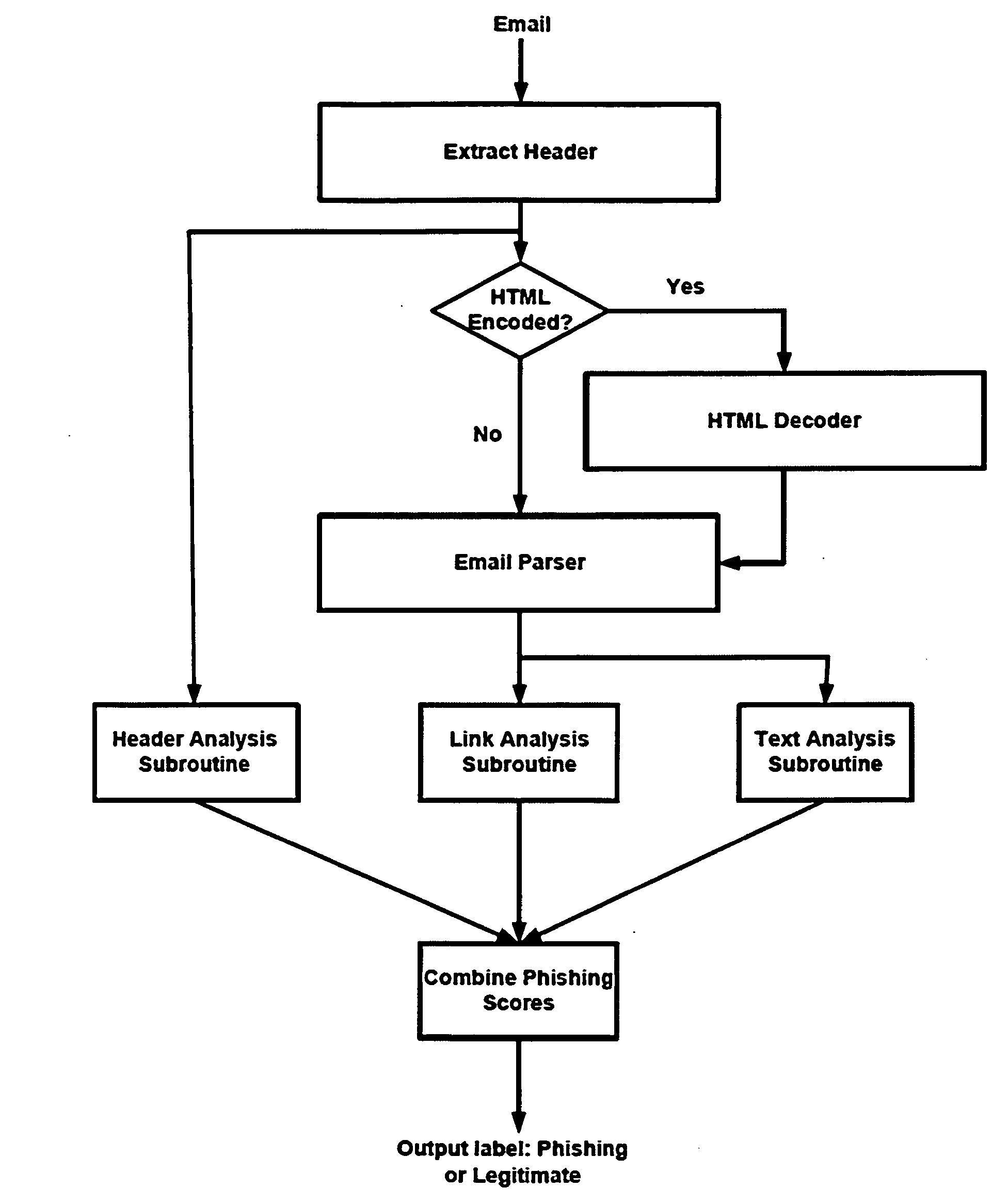
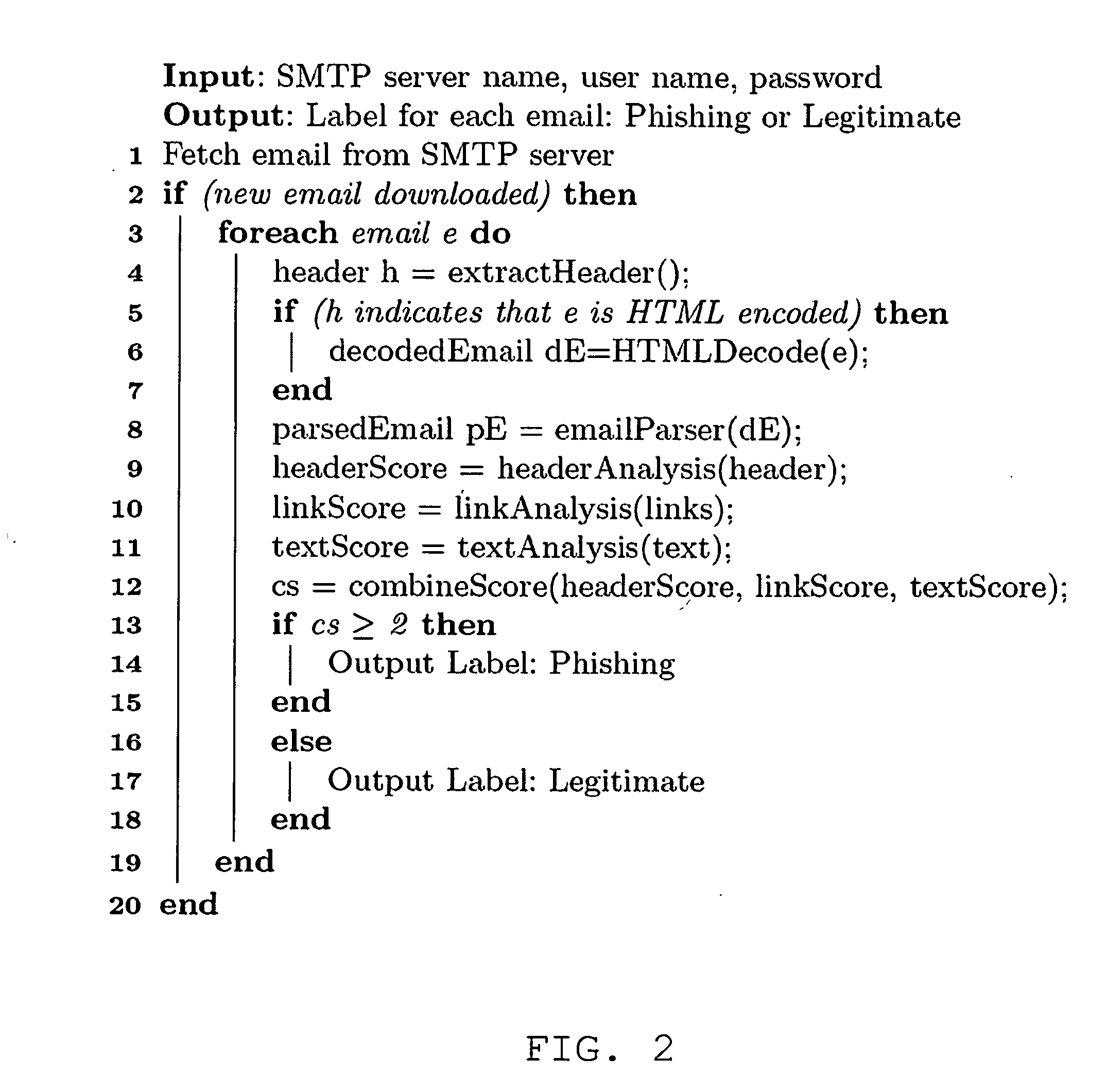
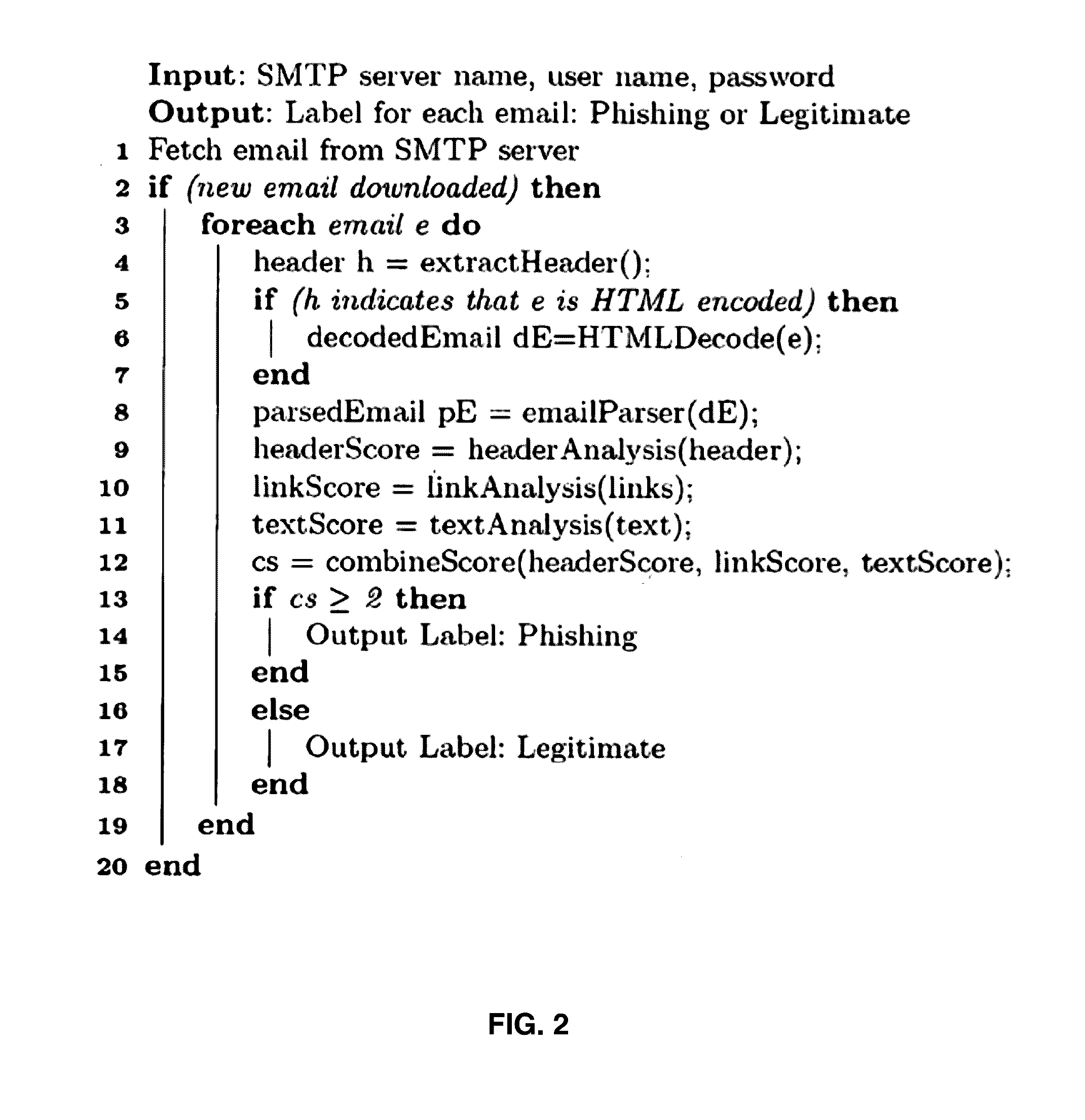
Automatic phishing email detection based on natural language processing techniques
InactiveUS20150067833A1Improve performanceMinimize timeMemory loss protectionError detection/correctionStatistical analysisPhishing
A comprehensive scheme to detect phishing emails using features that are invariant and fundamentally characterize phishing. Multiple embodiments are described herein based on combinations of text analysis, header analysis, and link analysis, and these embodiments operate between a user's mail transfer agent (MTA) and mail user agent (MUA). The inventive embodiment, PhishNet-NLP™, utilizes natural language techniques along with all information present in an email, namely the header, links, and text in the body. The inventive embodiment, PhishSnag™, uses information extracted form the embedded links in the email and the email headers to detect phishing. The inventive embodiment, Phish-Sem™ uses natural language processing and statistical analysis on the body of labeled phishing and non-phishing emails to design four variants of an email-body-text only classifier. The inventive scheme is designed to detect phishing at the email level.
Owner:SHASHIDHAR NARASIMHA +2
Automatic Phishing Email Detection Based on Natural Language Processing Techniques
ActiveUS20160344770A1Improve performanceMinimize detection timeEnsemble learningData switching networksPhishingLink analysis
A comprehensive scheme to detect phishing emails using features that are invariant and fundamentally characterize phishing. Multiple embodiments are described herein based on combinations of text analysis, header analysis, and link analysis, and these embodiments operate between a user's mail transfer agent (MTA) and mail user agent (MUA). The inventive embodiment, PhishNet-NLP™, utilizes natural language techniques along with all information present in an email, namely the header, links, and text in the body. The inventive embodiment, PhishSnag™, uses information extracted form the embedded links in the email and the email headers to detect phishing. The inventive embodiment, Phish-Sem™ uses natural language processing and statistical analysis on the body of labeled phishing and non-phishing emails to design four variants of an email-body-text only classifier. The inventive scheme is designed to detect phishing at the email level.
Owner:VERMA RAKESH +3
System, methods, software, and devices employing messaging
ActiveUS20070083600A1Reduce needIncreased messaging usageMultiple digital computer combinationsSubstation equipmentMostly TrueMobile device
A mobile device is shown in the role of a centralized message transfer agent wherein it manages all messaging for a user for most if not all the time so as to provide a unified messaging approach across all messaging platforms. Other platforms are shown using the mobile device in this unified way. Related systems, methods, integrated circuits, and software are also shown.
Owner:NOKIA TECHNOLOGLES OY
Peer-to-peer email messaging
ActiveUS7849140B2Multiple digital computer combinationsData switching networksClient-sideDistributed computing
System and method for facilitating communications between peers in a peer-to-peer environment and network email clients. In one embodiment, network nodes including peer nodes may host mail transfer agents. The mail transfer agents may act as bridges between peer-to-peer protocols and email communication protocols. The mail transfer agents may communicate with peers according to peer-to-peer protocols and with email clients according to email communications protocols. Peers may communicate with mail transfer agents to send peer-to-peer messages to email clients. Email clients may communicate with the mail transfer agents to send email messages to and receive email messages from other email clients via the peer-to-peer network and to obtain peer-to-peer messages from peers.
Owner:ORACLE INT CORP
Electronic mail system with authentication/encryption methodology for allowing connections to/from a message transfer agent
InactiveUS6986037B1User identity/authority verificationSecret communicationComputer hardwareClient-side
An electronic mail (“e-mail”) system is described that enforces authentication or encryption to / from Mail Transfer Agents and from Mail User Agents. In one embodiment, for example, an electronic mail (e-mail) system is described that comprises: a message transfer agent (MTA) available for a client to connect to; program logic for authenticating the client, through use of a certificate, in order to identify the client as approved for establishing a secured connection with the MTA; program logic for establishing a secured connection between the client and the MTA in instances where the client can be authenticated; program logic for testing encryption strength of the secured connection; and program logic for terminating the secured connection in instances where the secured connection has inadequate encryption strength.
Owner:PROOFPOINT INC
Authenticating and confidence marking e-mail messages
ActiveUS20080189770A1Synchronising transmission/receiving encryption devicesDigital data processing detailsTransfer agentAuthentication
Methods and systems for authenticating and confidence marking e-mail messages are described. One embodiment describes a method of authenticating an e-mail message. This method involves extracting a plurality of e-mail headers associated with the e-mail message, and identifying a sending edge mail transfer agent (MTA). The method then calls for determining if the sending edge MTA is authorized to send the e-mail message.
Owner:ICONIX INC
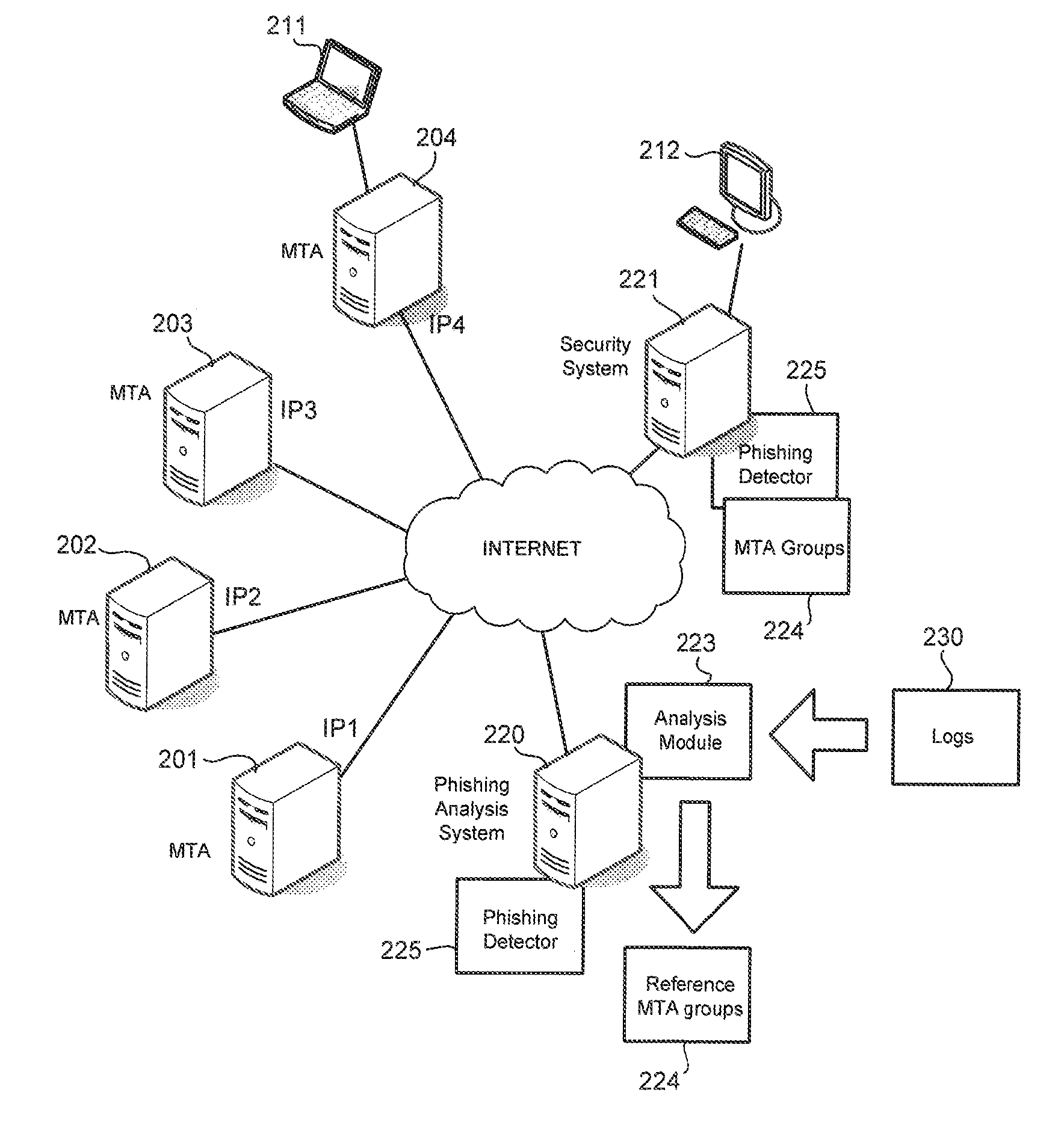
Methods and apparatus for detecting phishing attacks
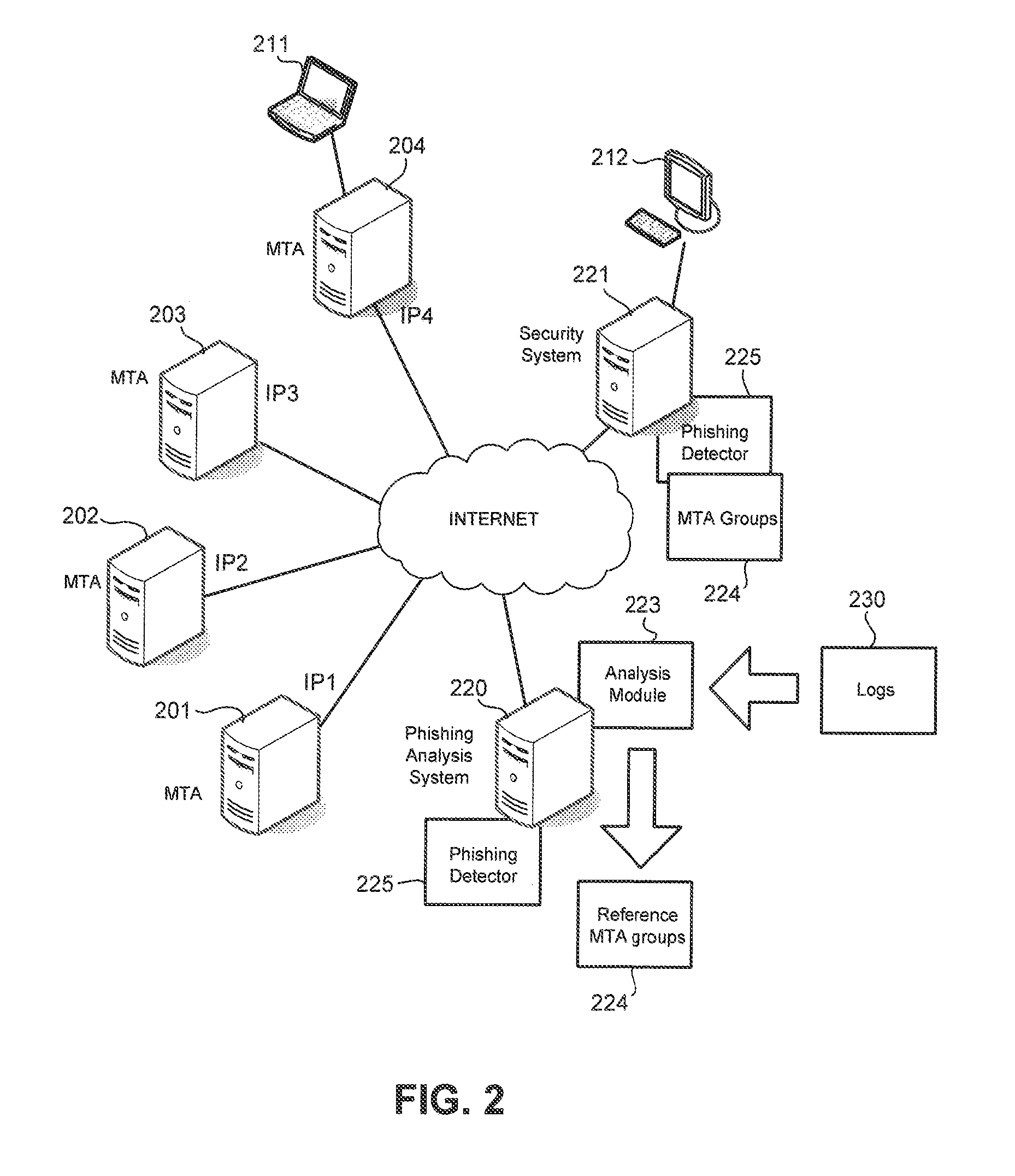
Phishing is detected by creating a message transfer agent (MTA) map, with each point on the MTA map referencing an MTA. Points on the MTA map are connected based on a number of emails with same signature sent by MTAs represented on the MTA map. Reference MTA groups are identified from the map. Phishing is detected when an MTA sent an email with the same signature as that of emails sent by MTAs belonging to a reference MTA group but the MTA is not a member of the reference MTA group.
Owner:TREND MICRO INC
Fax transmission over the packet network
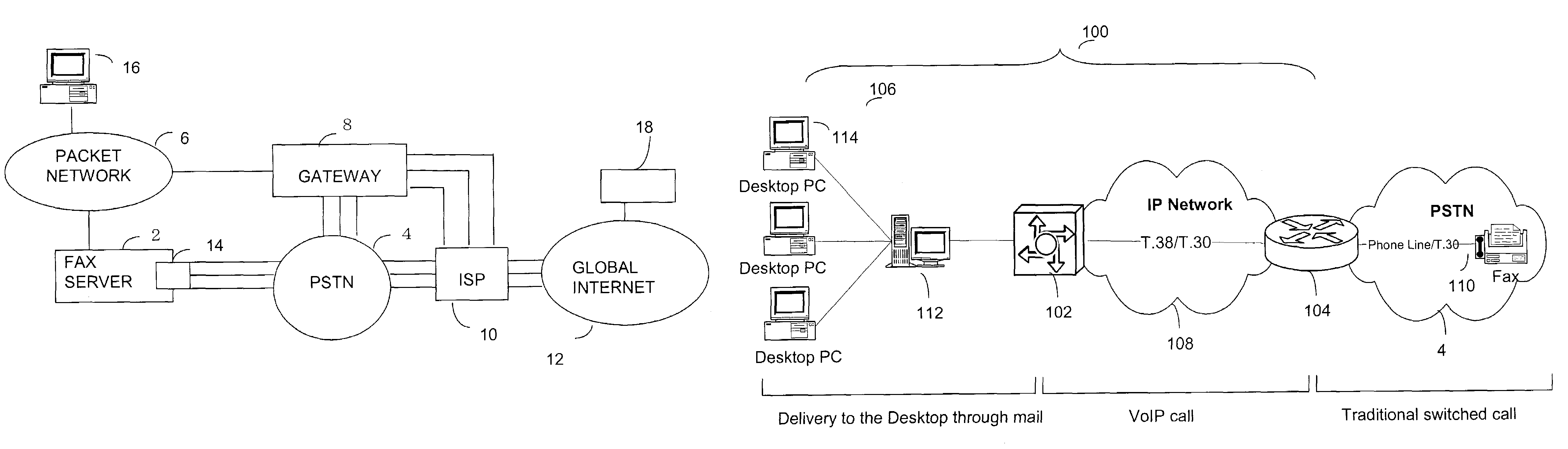
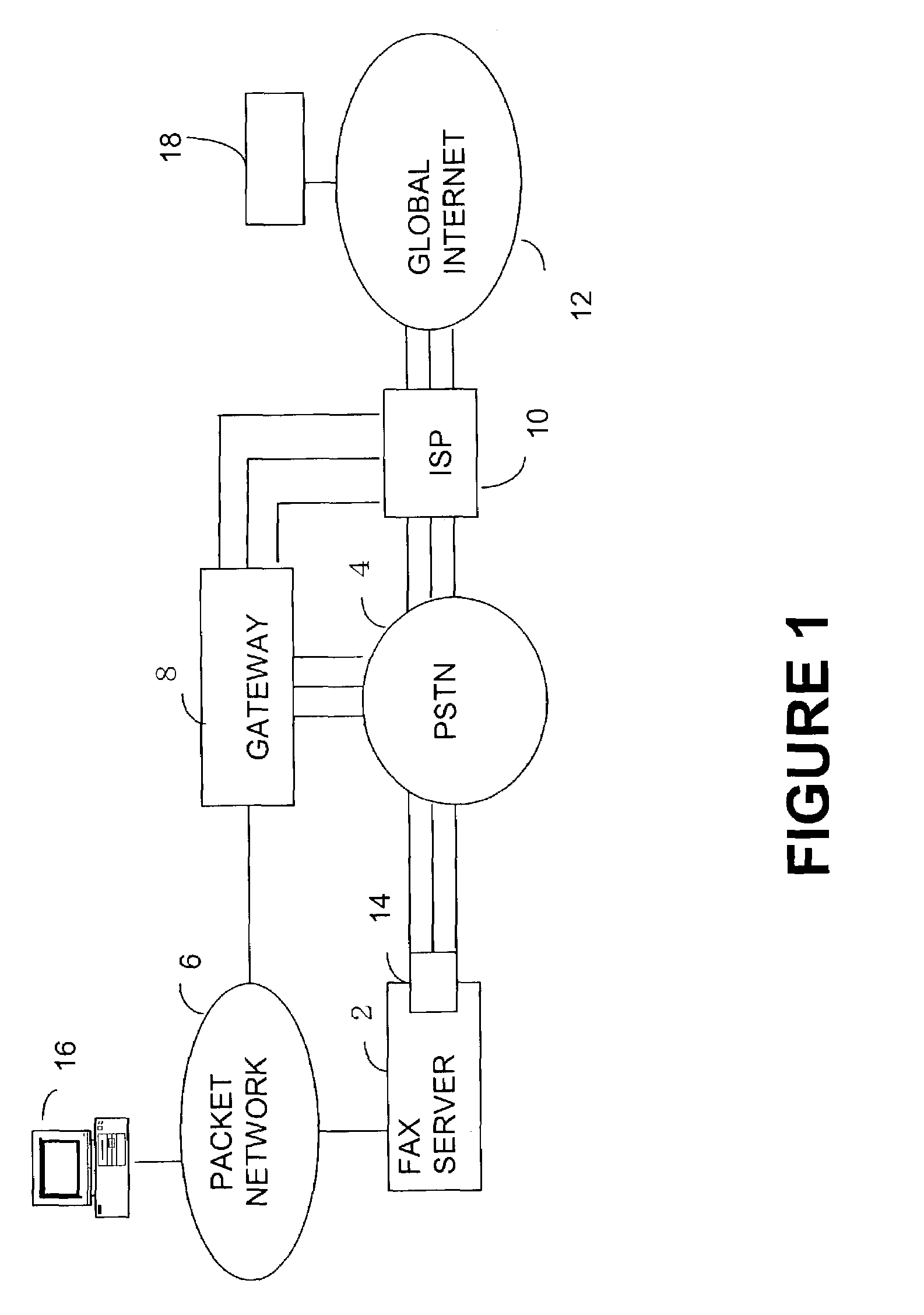
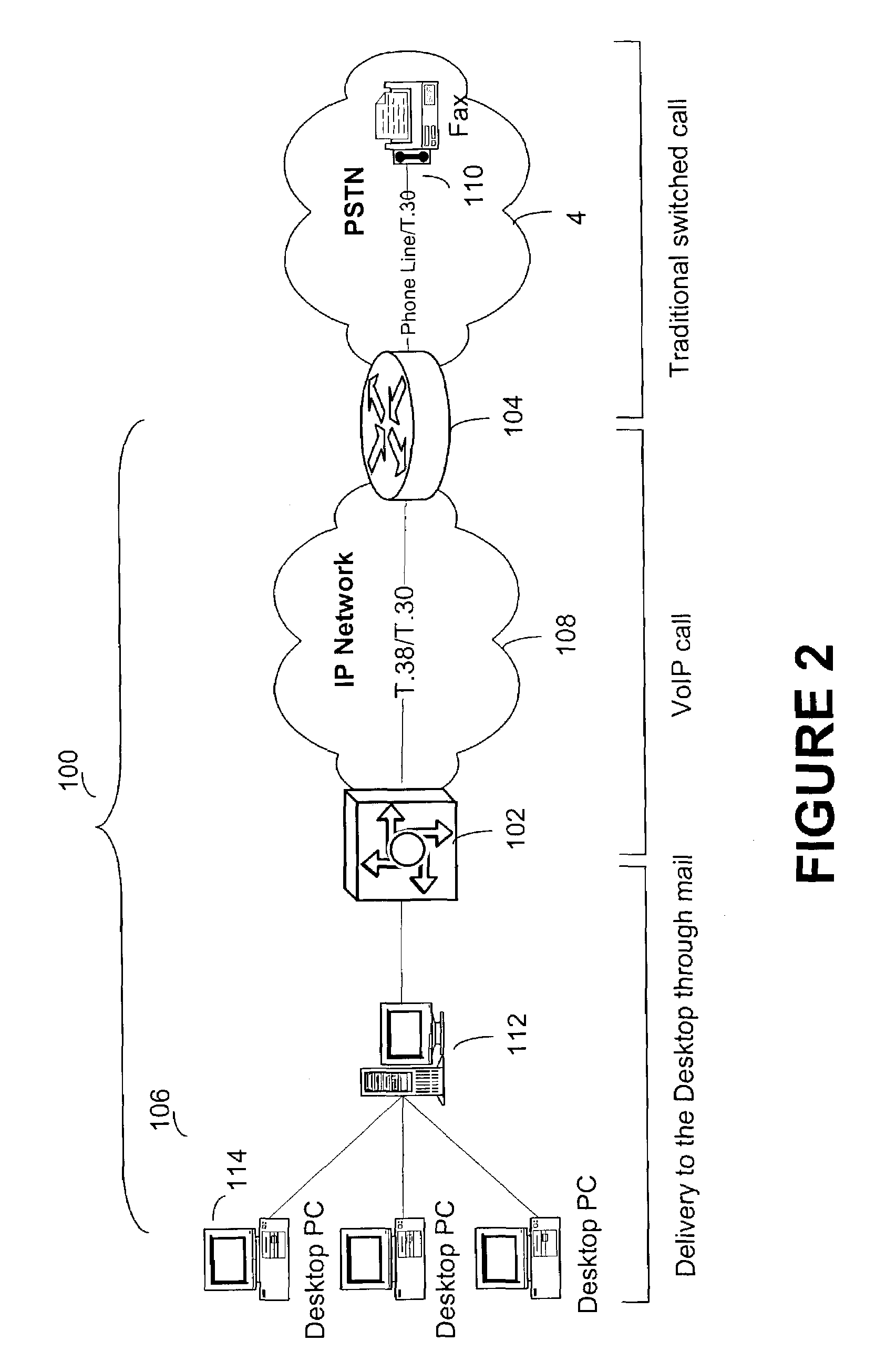
ActiveUS7283270B2Digitally marking record carriersTelephonic communicationCustomer relationship managementWeb service
A FoIP server mediating fax communication between gateways and enterprise backend systems. The gateways are VoIP capable, connected to the PSTN and the enterprise network, and mediate between the PSTN fax call and fax over IP calls. The FoIP Server mediates between the FoIP calls and enterprise backend systems, such as message transfer agent (MTA), Customer Relationship Management CRM, document management, web services, mainframe, or a specialized application requiring faxing capabilities.
Owner:XMEDIUS SOLUTIONS
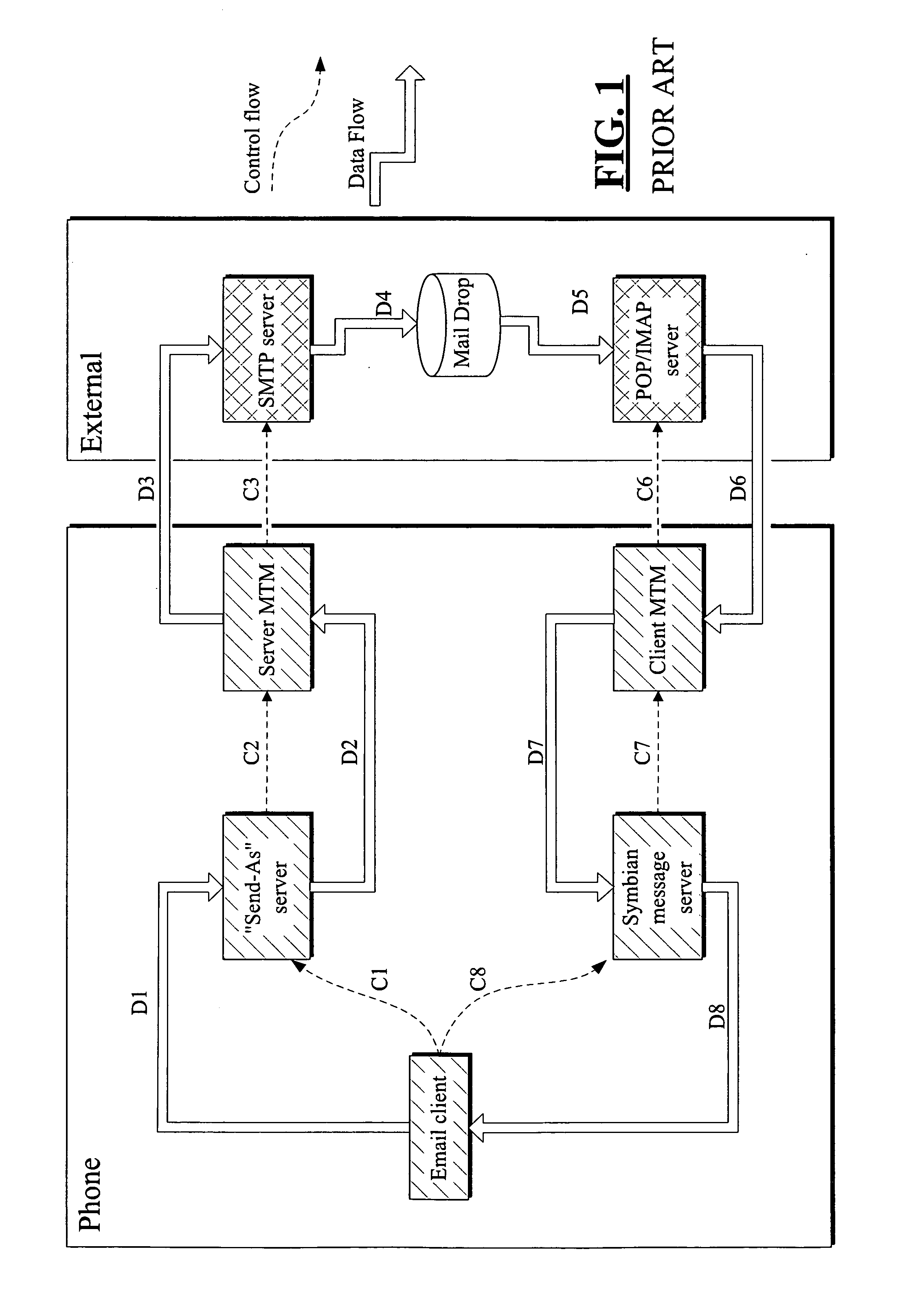
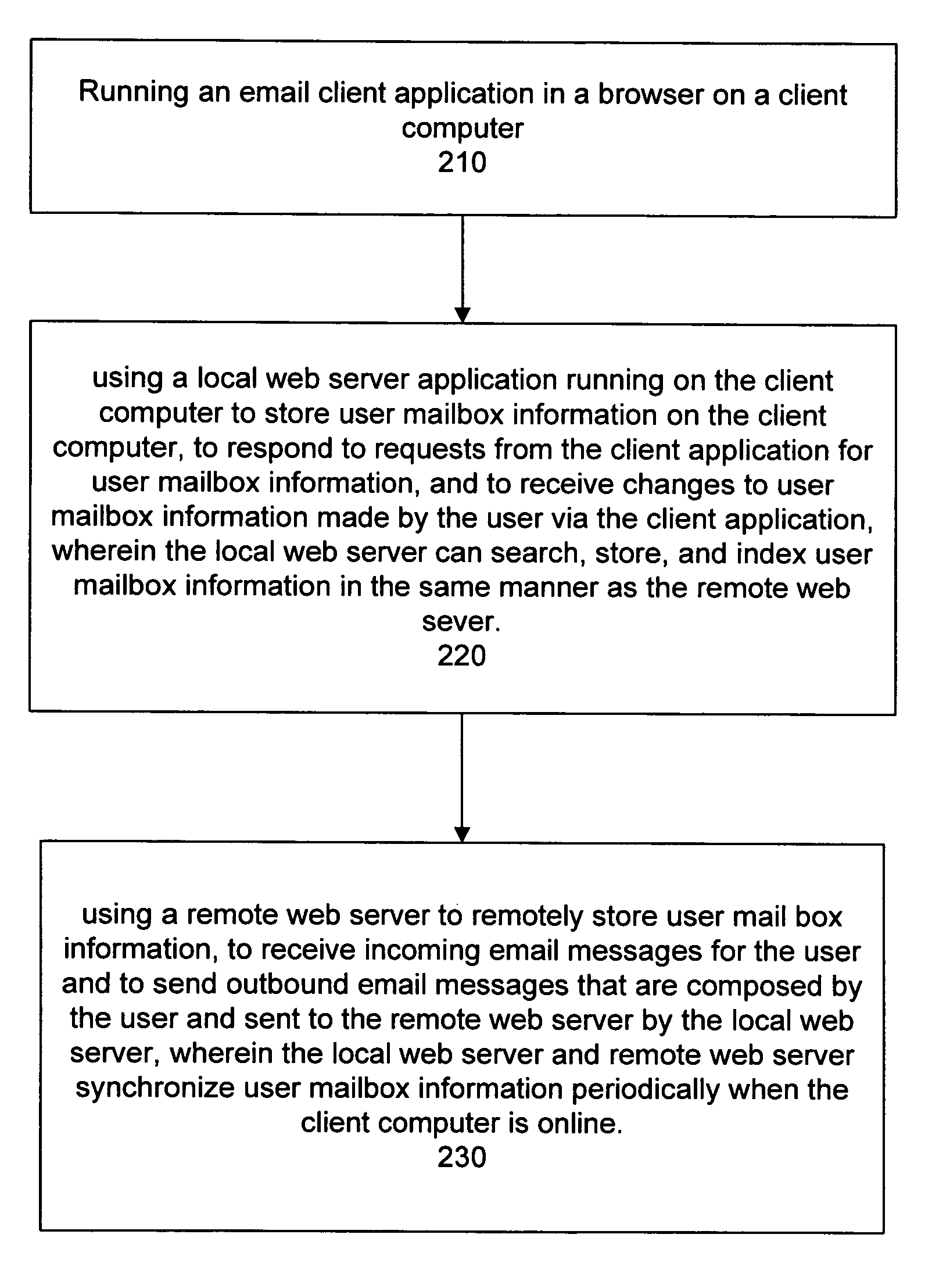
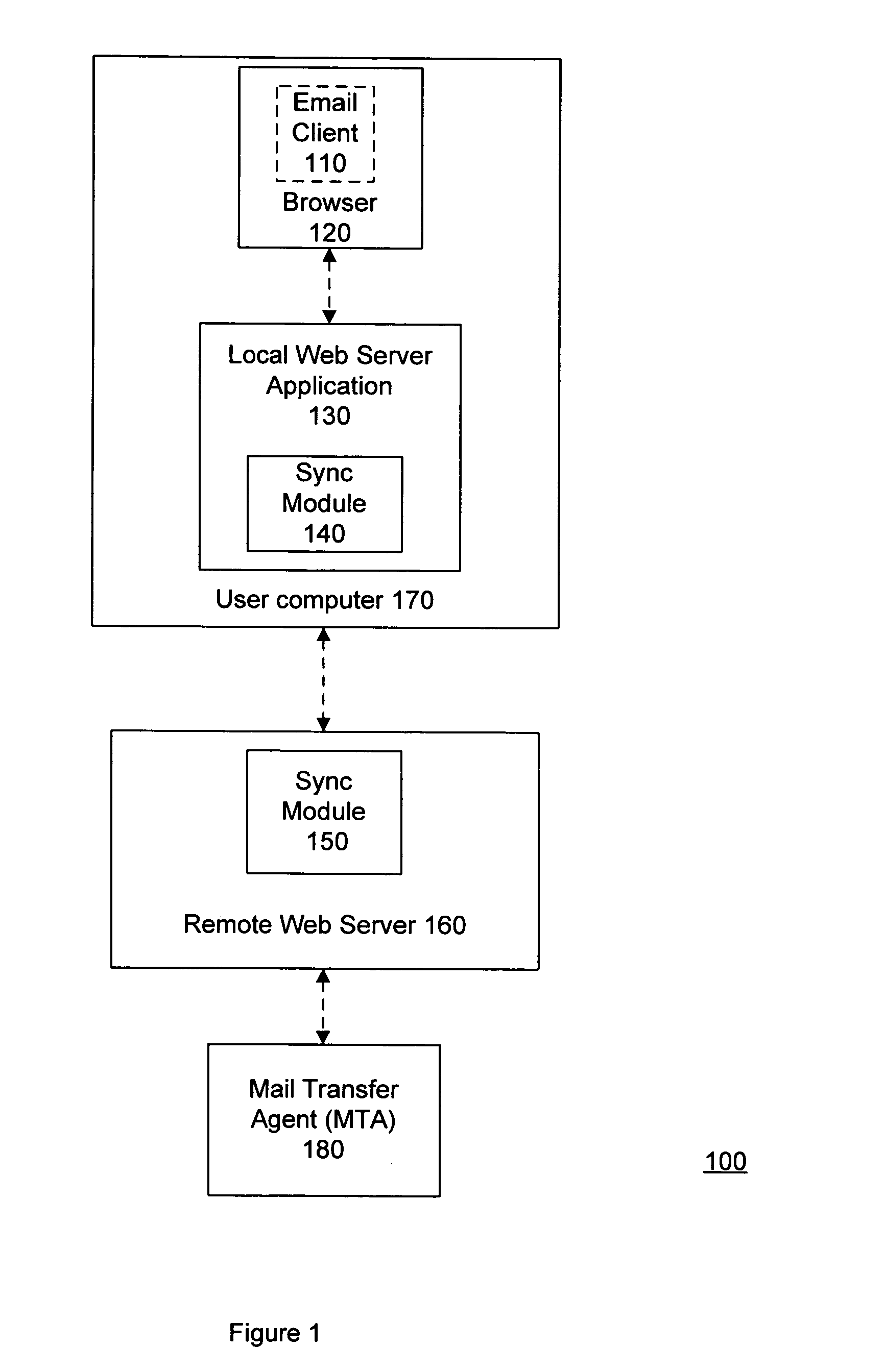
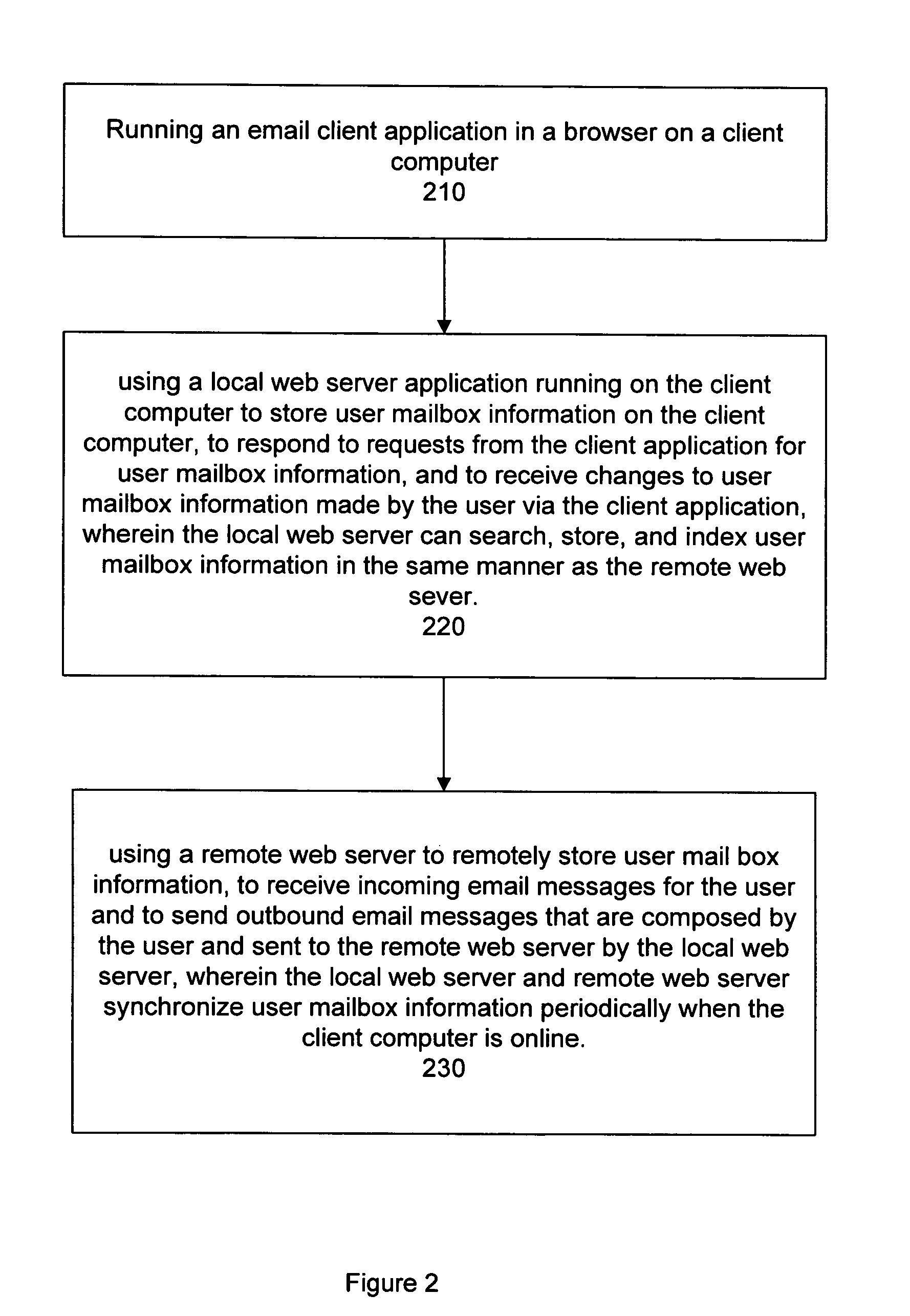
System and method for enabling offline use of email through a browser interface
InactiveUS20090094332A1Data processing applicationsMultiple digital computer combinationsWeb serviceOnline and offline
A system and method provide online and offline collaboration suite functionality. A local web server application running on the user's computer serves an email client on the user's computer, where the email client executes within a browser. Because the local web server application executes on the user's computer, it is able to serve the email client regardless of whether the user's computer is online or offline. The local web server application also communicates with a remote web server, where the remote web server has the capability to receive incoming messages from, and send outbound messages to, a Mail Transfer Agent. When the user's computer is online, the remote web server and local web server application periodically (although not necessarily at regular intervals) synchronize their user mailbox information. The local web server application and remote web server application store, search, and index user mailbox information in the same manner.
Owner:VMWARE INC
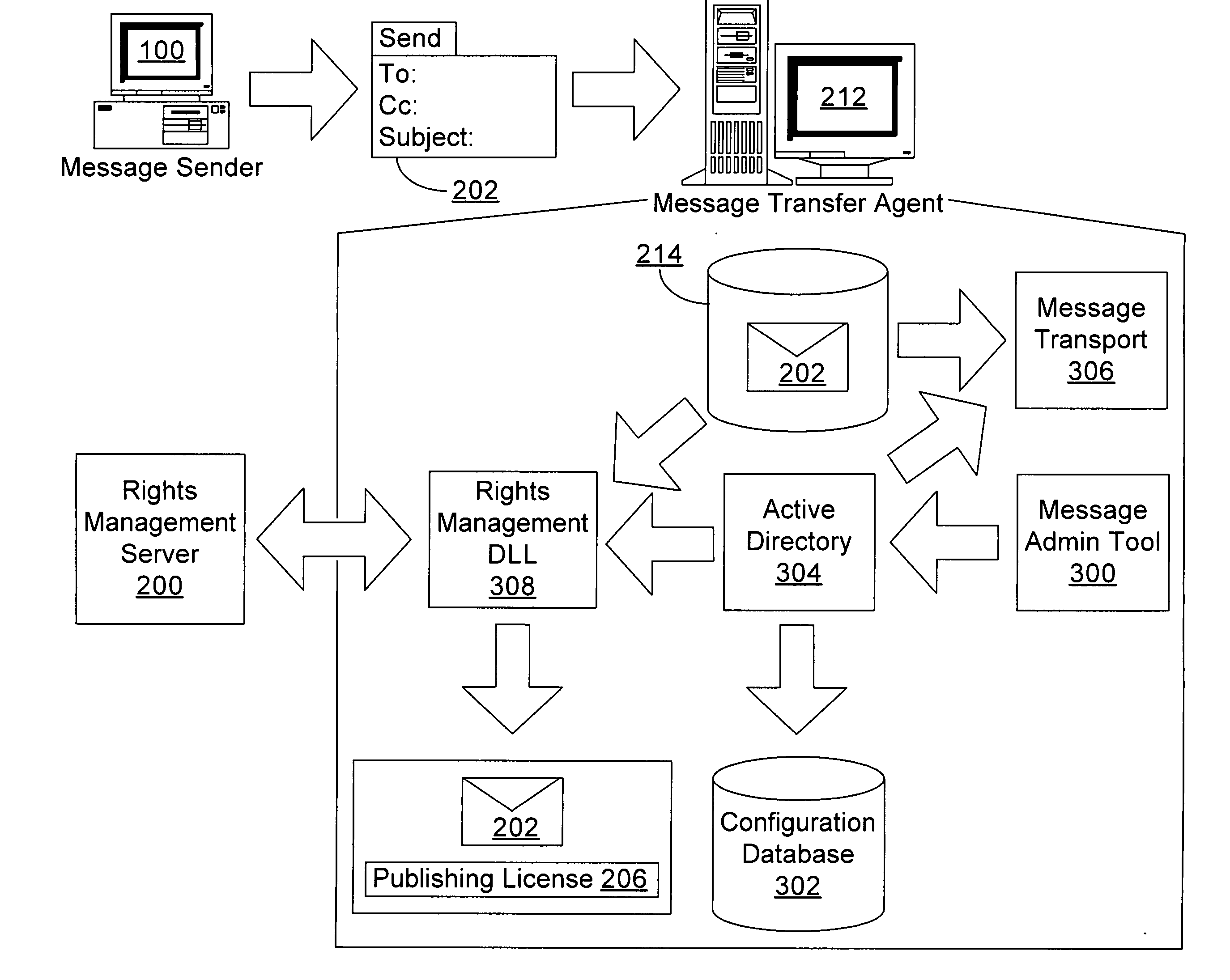
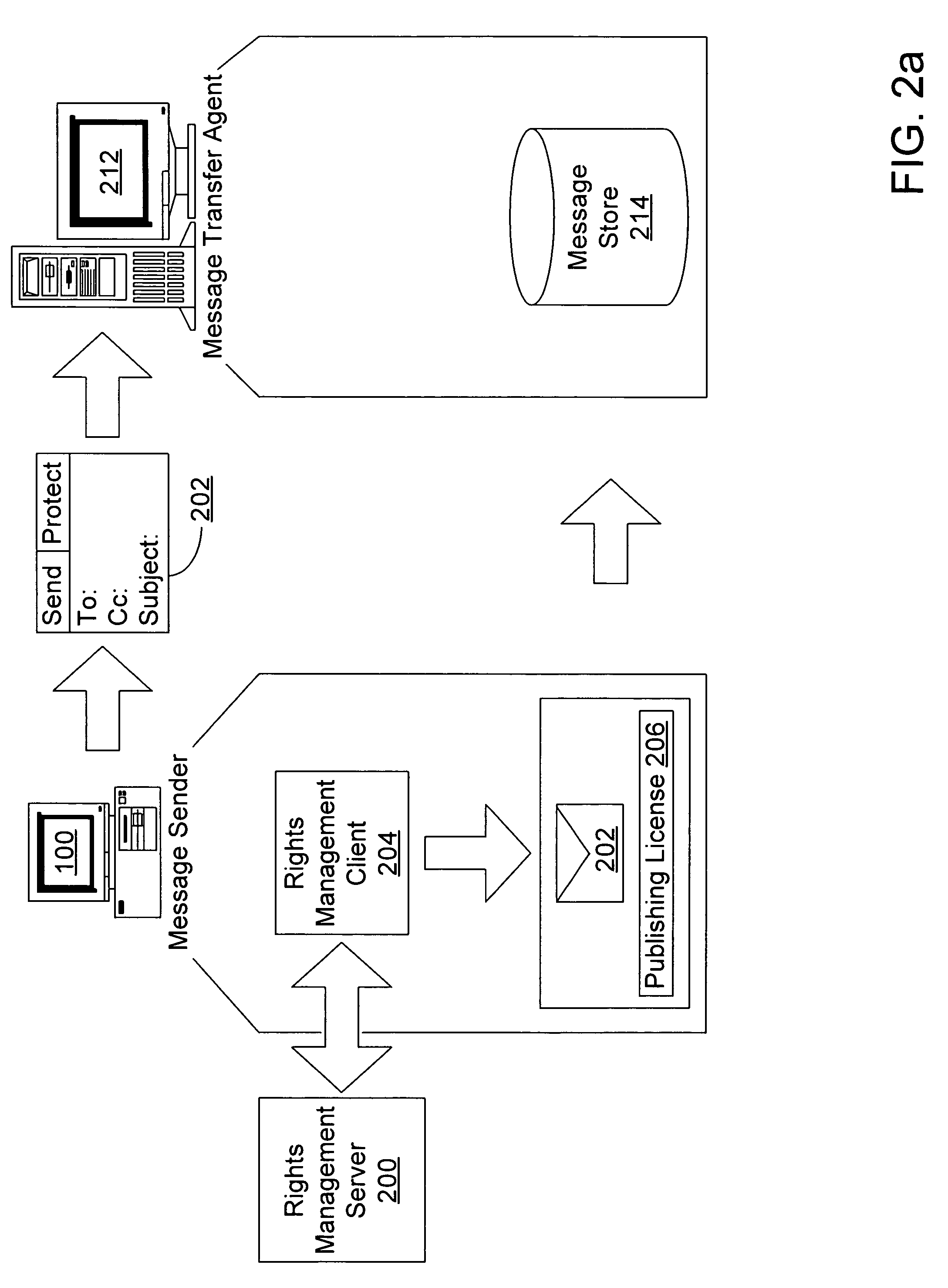
Enforcing rights management through edge email servers
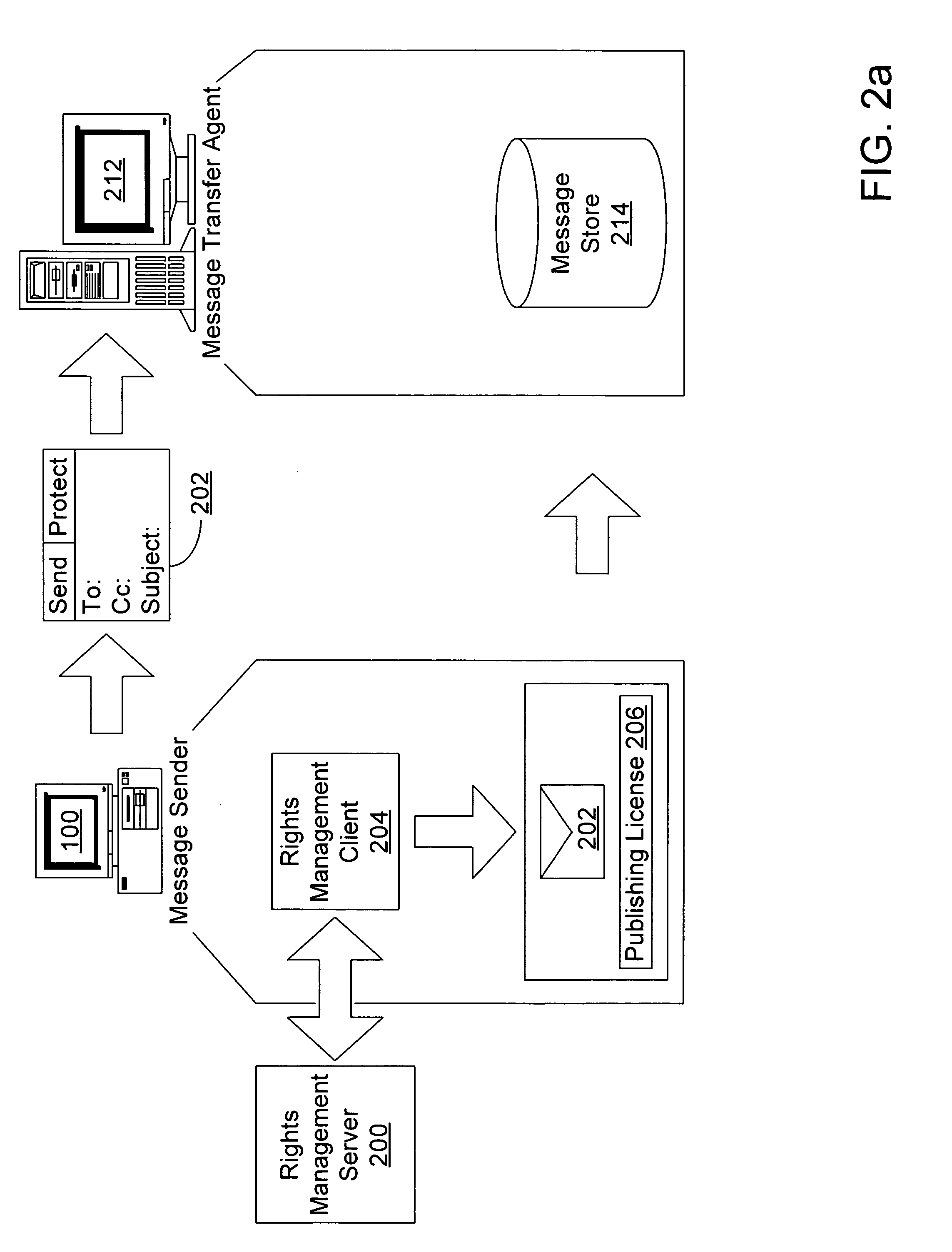
ActiveUS7454778B2Data processing applicationsDigital data processing detailsInternet privacySubject matter
Owner:MICROSOFT TECH LICENSING LLC
Method for dynamic application of rights management policy
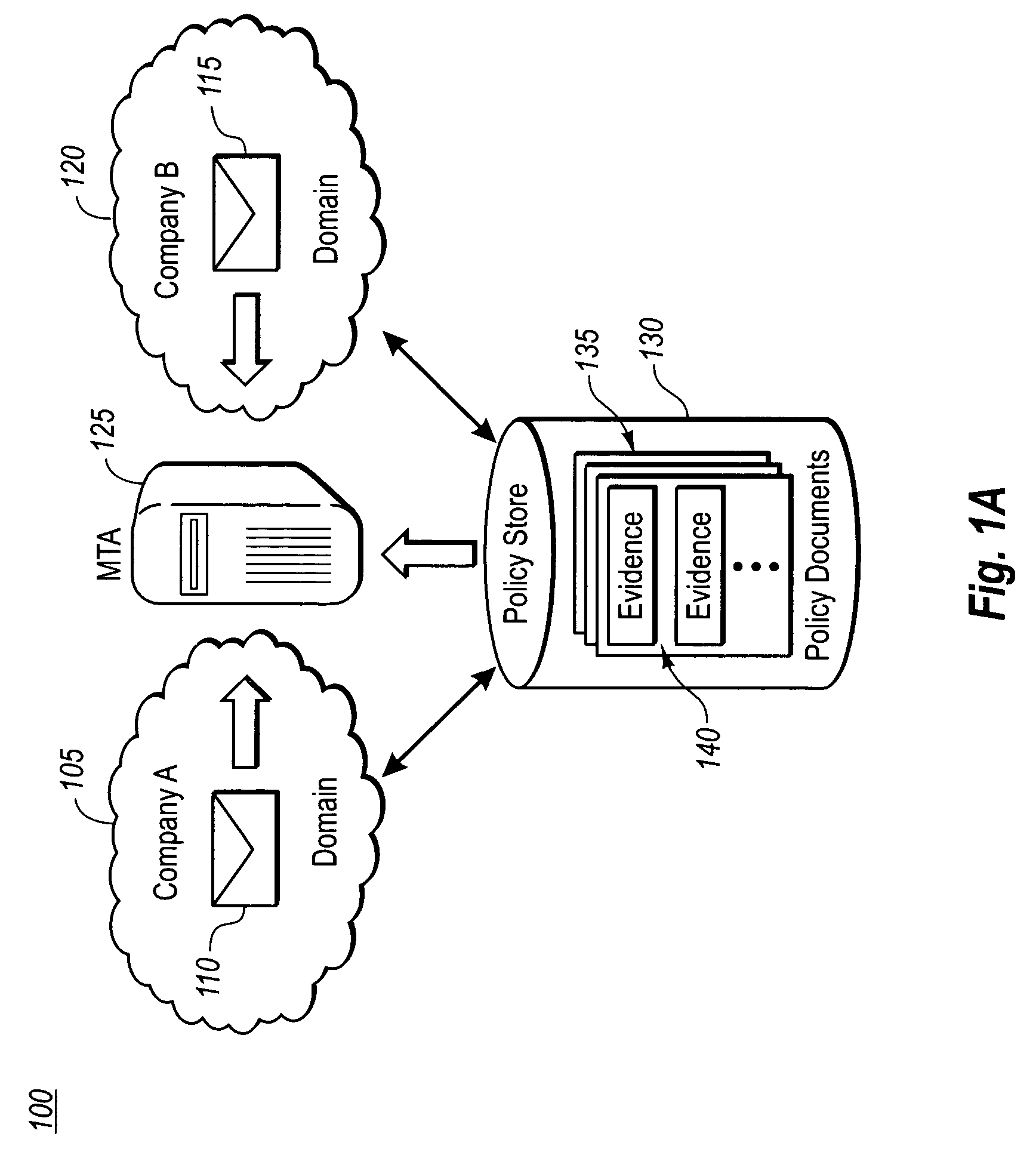
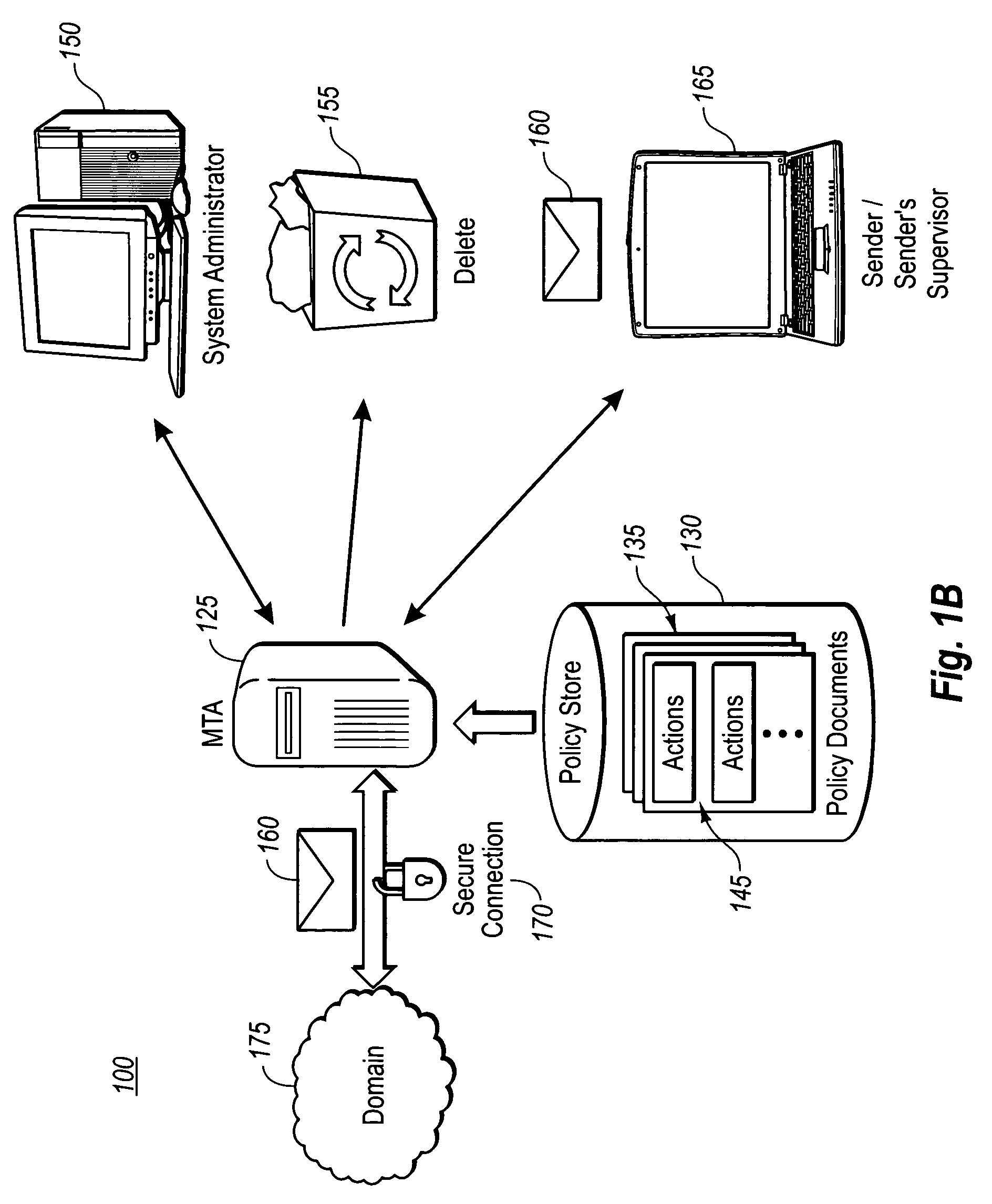
ActiveUS20050216745A1Computer security arrangementsSecret communicationInternet privacyRights management
Disclosed is a method for dynamically applying a rights management policy to a message by allowing an administrator to associate certain rights management policies with certain senders and recipients of messages, with groups of users possessing certain common criteria which define the users and groups of users, with certain attributes of the message, and with certain environmental attributes. Also disclosed is a method for allowing an administrator to automatically update a rights management protected message as it passes through a message transfer agent. The administrator may determine either on a regular interval or an ad-hoc basis that the message transfer agent scan the messages stored to determine whether or not the content has expired. If the content has indeed expired the administrator may take steps to have the expired content deleted entirely, refreshed with more current content, or replaced with a tombstone indicating that the original content has expired.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for selective email processing
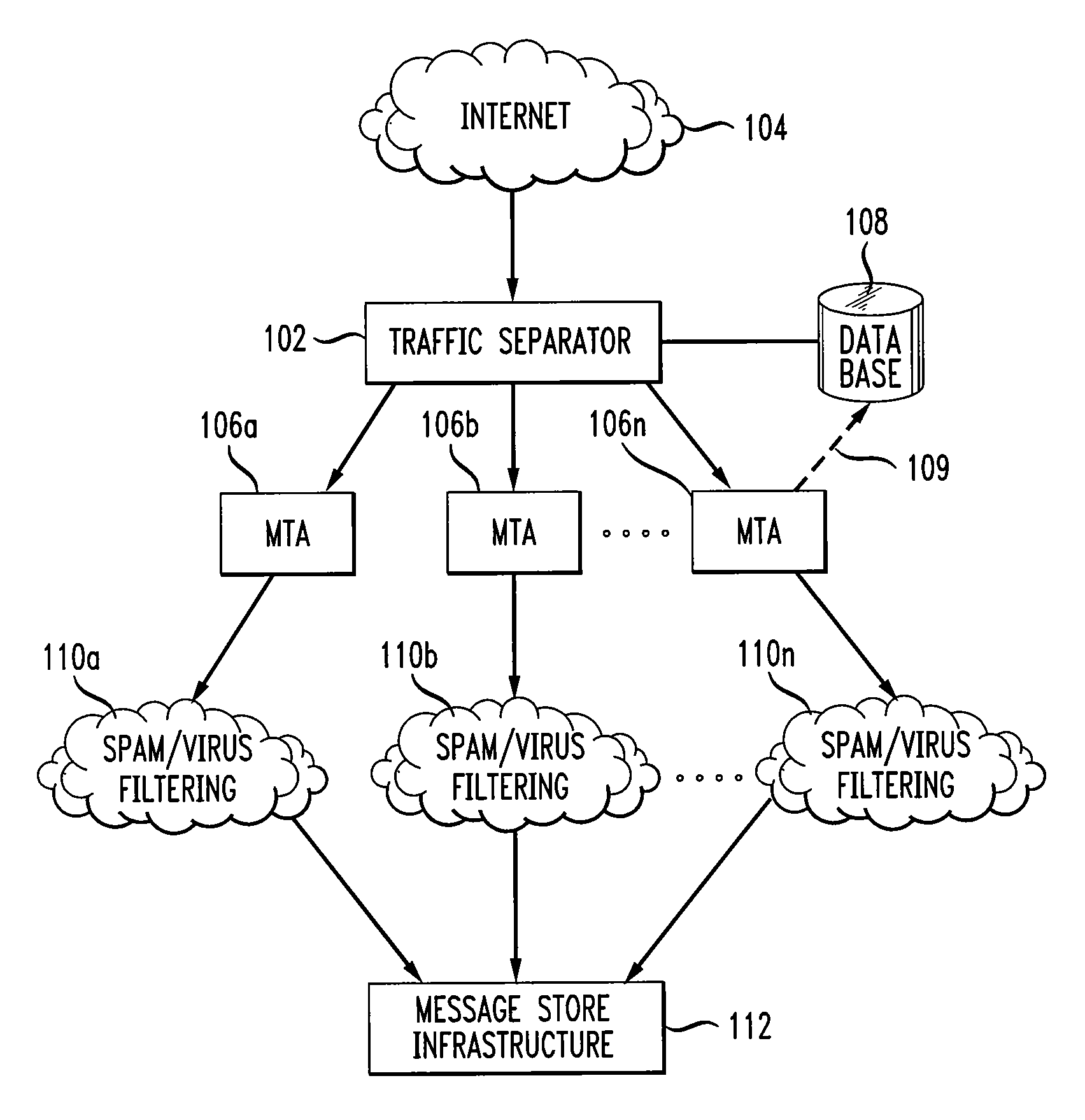
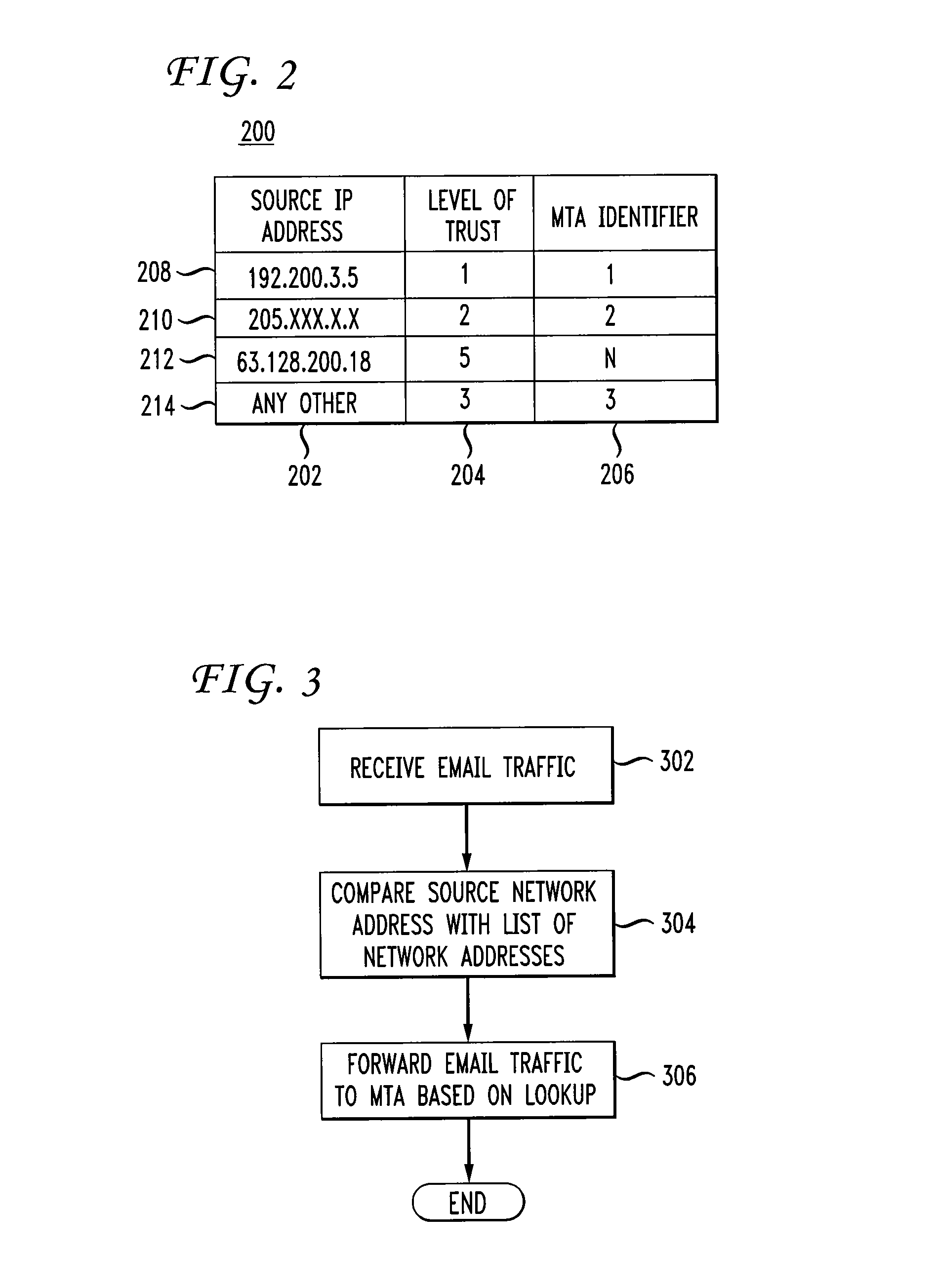
InactiveUS8224902B1Readily availableMultiple digital computer combinationsProgram controlTraffic capacityNetwork addressing
Disclosed is a system and method for selective email processing. A traffic separator includes an interface for receiving electronic mail traffic from a source network address. The traffic separator also includes a processor for comparing the source network address to a stored list of network addresses to determine a categorization of the network source address. The traffic separator also includes at least one interface for forwarding the electronic mail traffic to one of many message transfer agents (MTAs) based upon said determination. A database stores the list of network addresses. In one embodiment, one or more network addresses in the stored list are network address ranges.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
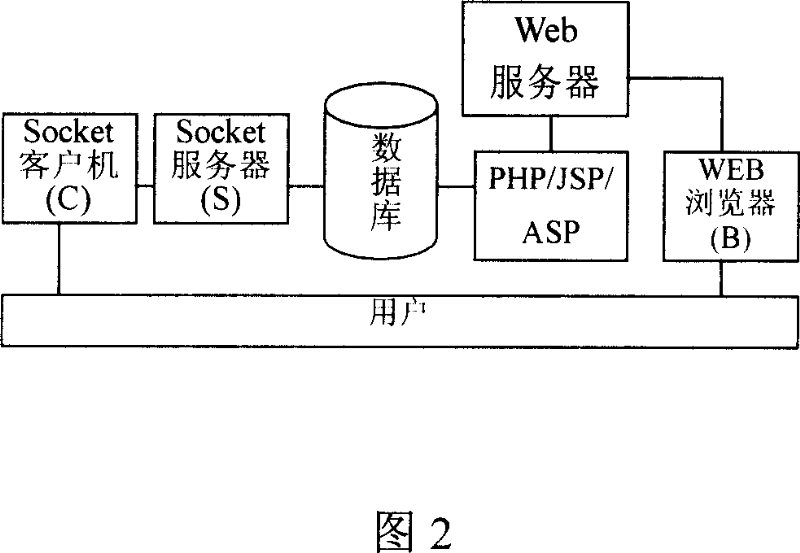
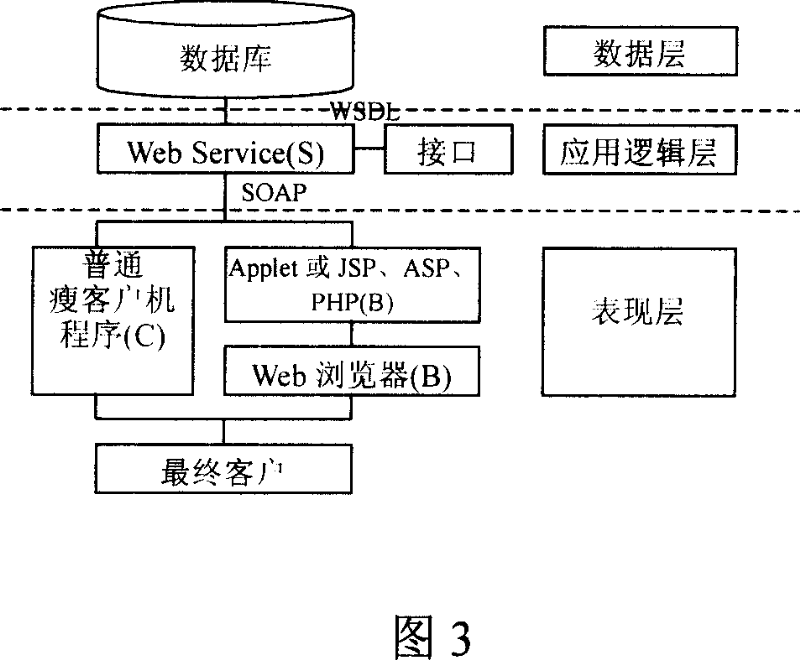
Electronic mail system
The disclosed E-mail system comprises: a server, including a user proxy module with a Web Service container, a mail transmission proxy module, and a mail distribution proxy module; and a client. Wherein, the Web Service container comprises a main package sub-module, a mail transmission sub-module, a mail receiving sub-module, a mail decomposition sub-module, a user key management sub-module, an enciphering / deciphering sub-module, and some corresponding calling interfaces. This invention avoids repeated development, and has wide application, such as PC, palm PC, and mobile phone.
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD
E-mail system with methodology for accelerating mass mailings
InactiveUS7058687B2Improve parallelismEliminate bottlenecksSpecial service provision for substationMultiprogramming arrangementsMessage passingMessage transfer agent
An e-mail system is described that includes a mass-mail accelerator (MMA), which is particularly suited for processing mass e-mailings. Instead of being posted to a message transfer agent (MTA), outgoing messages are instead passed to the MMA for carrying out highly parallel e-mail delivery / routing. The MMA employs a plurality of queues, which may either be general or specific. A specific queue is configured to handle only e-mail destined for a particular domain, such as the AOL.com domain; a general queue is configured to handle all other e-mail. Each queue manages a pool of MTA threads. During MMA operation, once a message has been passed to a queue, that queue examines its MTA threads to see if one is ready to accept the message. If an MTA thread is ready, the queue will assign the message to that MTA. The MTA thread proceeds to handle the work of the SMTP exchange between the MMA and the target real-world MTA (e.g., an AOL MTA). While a given MTA thread is waiting for a reply from the real-world (destination) MTA (e.g., the AOL MTA), the MMA can proceed to do other work. In this manner, the bottleneck usually encountered with processing mass e-mailings is removed.
Owner:PROOFPOINT INC
Datacenter mail routing
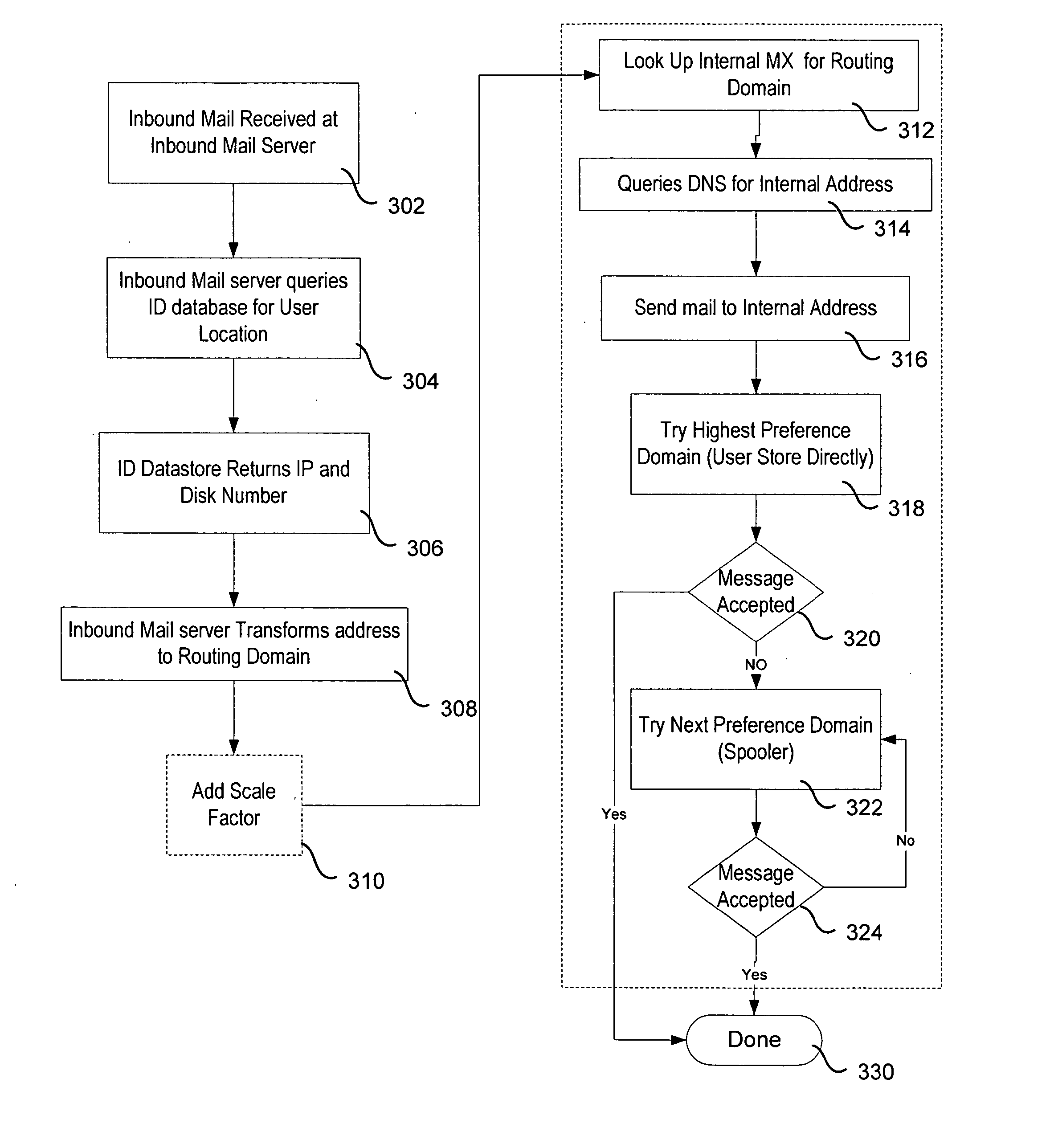
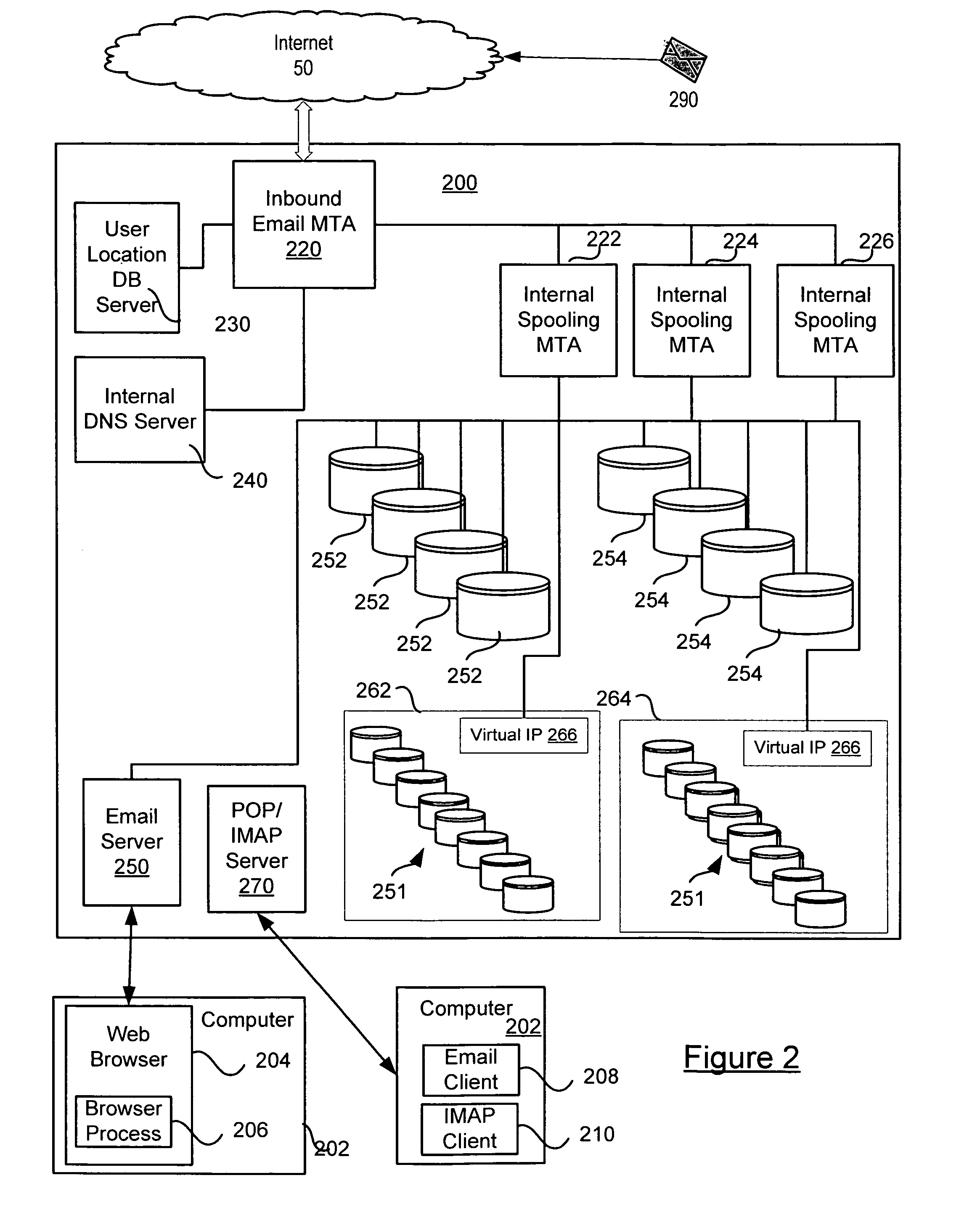
ActiveUS20060174033A1Multiple digital computer combinationsData switching networksMX recordData center
A system and method for providing email using a flexible routing technique based on MX records. The method includes the steps of creating an MX record for a user, the MX record identifying a storage location for the user within the system; and routing mail within the enterprise email system using the information contained in the MX record. A system may include an inbound mail transfer agent coupled to an external network and an internal network; user email data storage having an address within the internal network; a user location database server containing a unique user token identifying a storage location for user email data in the user email data storage; and an internal DNS server including MX records for storage domains on the internal network.
Owner:MICROSOFT TECH LICENSING LLC
Method for dynamic application of rights management policy
ActiveUS7430754B2Computer security arrangementsSecret communicationInternet privacyRights management
Disclosed is a method for dynamically applying a rights management policy to a message by allowing an administrator to associate certain rights management policies with certain senders and recipients of messages, with groups of users possessing certain common criteria which define the users and groups of users, with certain attributes of the message, and with certain environmental attributes. Also disclosed is a method for allowing an administrator to automatically update a rights management protected message as it passes through a message transfer agent. The administrator may determine either on a regular interval or an ad-hoc basis that the message transfer agent scan the messages stored to determine whether or not the content has expired. If the content has indeed expired the administrator may take steps to have the expired content deleted entirely, refreshed with more current content, or replaced with a tombstone indicating that the original content has expired.
Owner:MICROSOFT TECH LICENSING LLC
Electronic mail system with authentication methodology for supporting relaying in a message transfer agent
InactiveUS6865671B1Multiple digital computer combinationsSecret communicationPrimitive operationInternet privacy
An electronic mail (“e-mail”) system is described that provides a methodology that allows the system to determine when it is appropriate to relay e-mail messages, particularly from “roaming” users. In basic operation, the methodology of the present invention first checks whether the client has been authenticated. If not, the decision of whether relaying is allowed may be subject to other rules in the system, such as whether the user currently resides behind the company's firewall. Of interest herein is a case where the client has been authenticated. In that case, the system can allow relaying for everyone who has a certificate (“cert”) signed by certain certificate authorities (“CAs”). Additionally, the system can require specific cert subjects.
Owner:PROOFPOINT INC
Unsolicited message rejecting communications processor
InactiveUS7490128B1Apparent advantageMultiple digital computer combinationsData switching networksComputer hardwareIp address
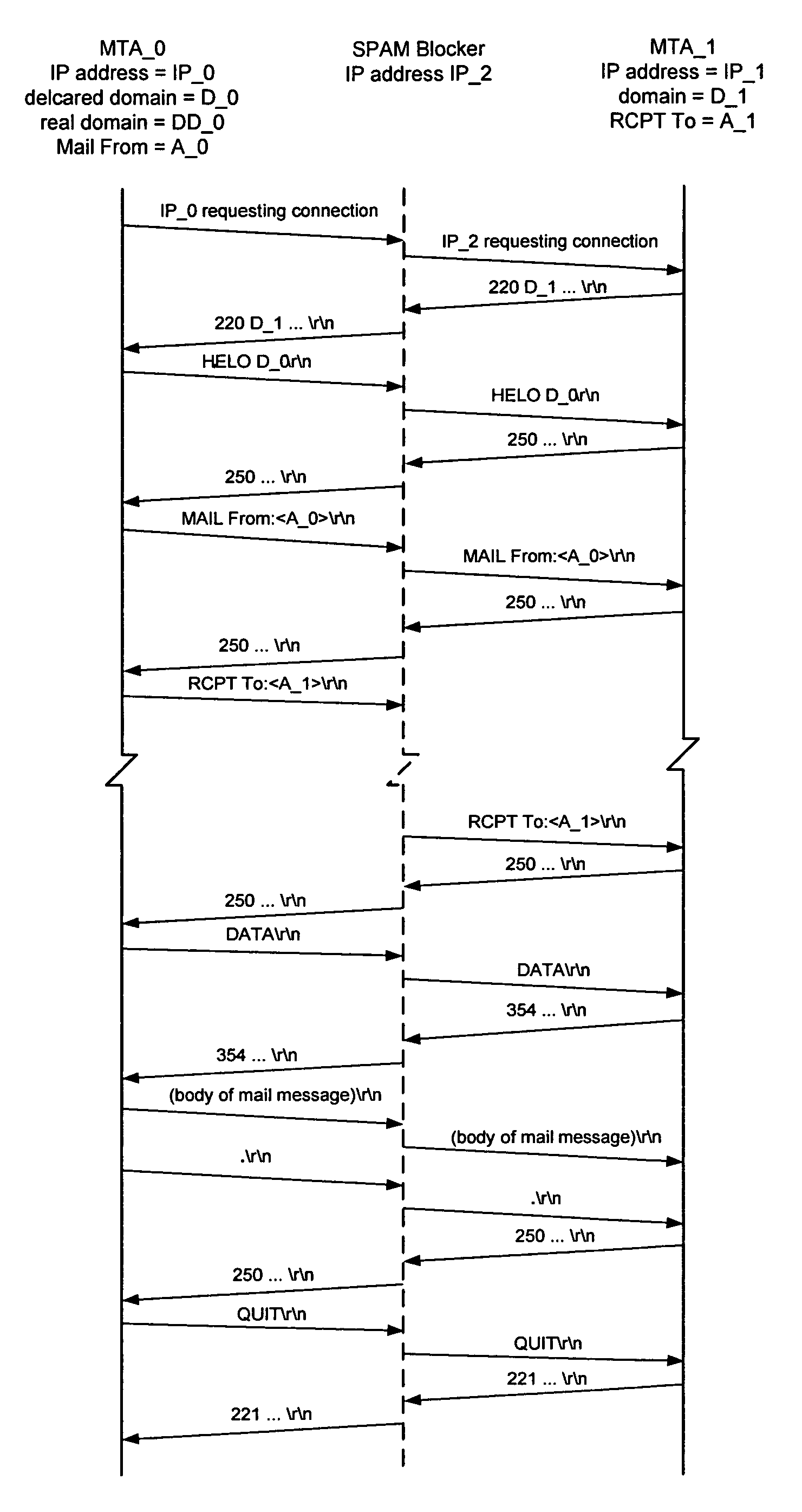
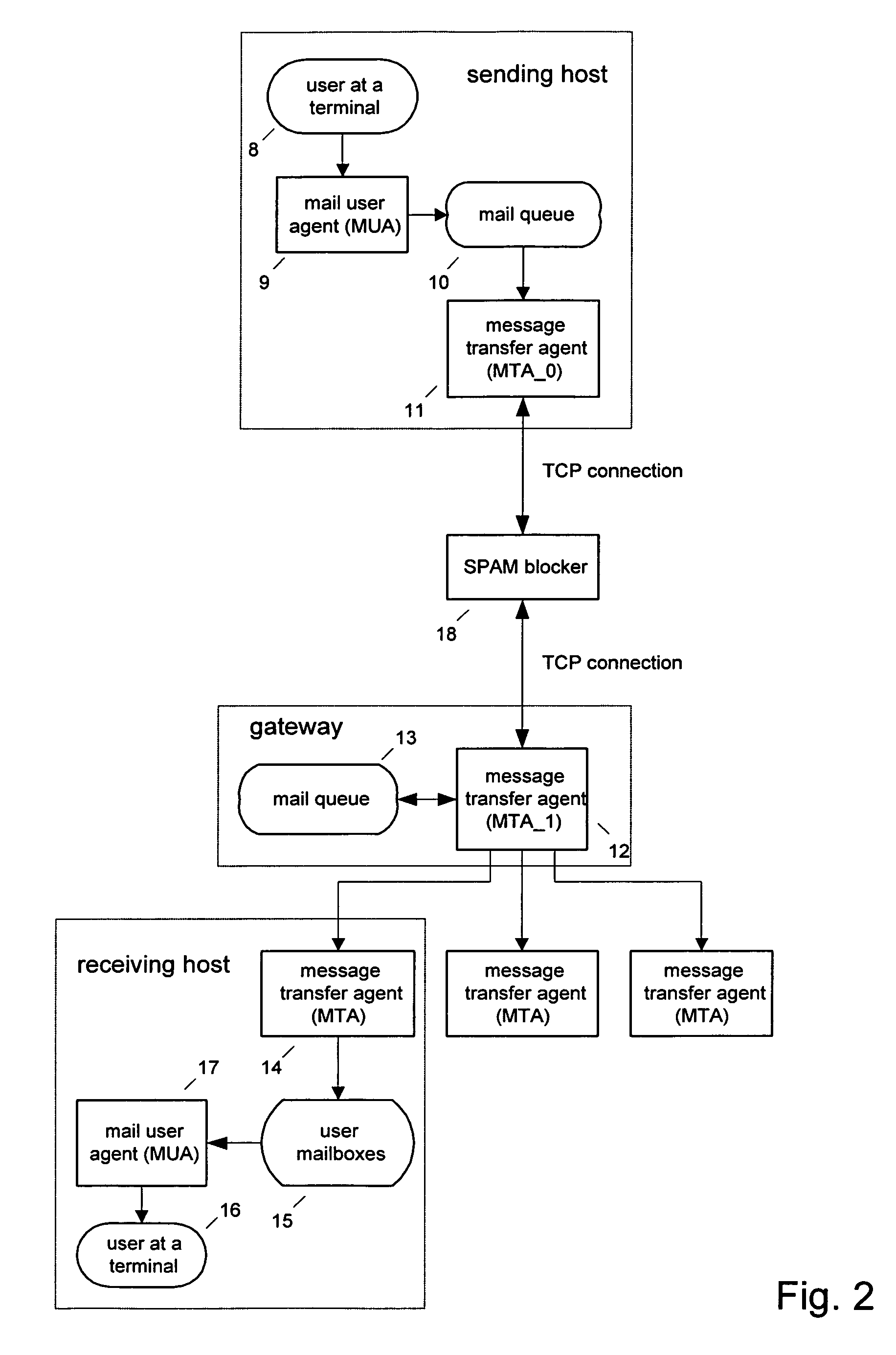
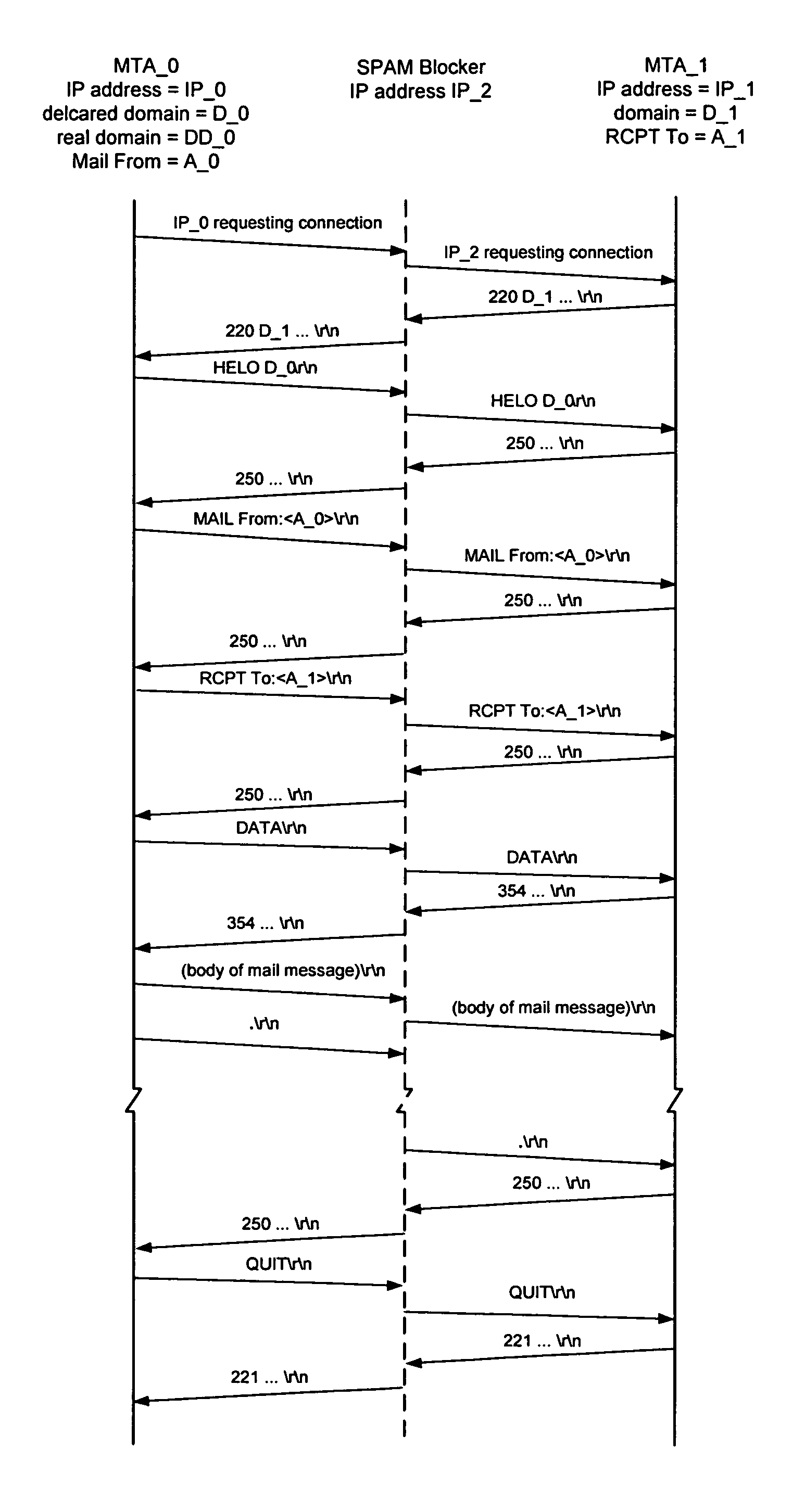
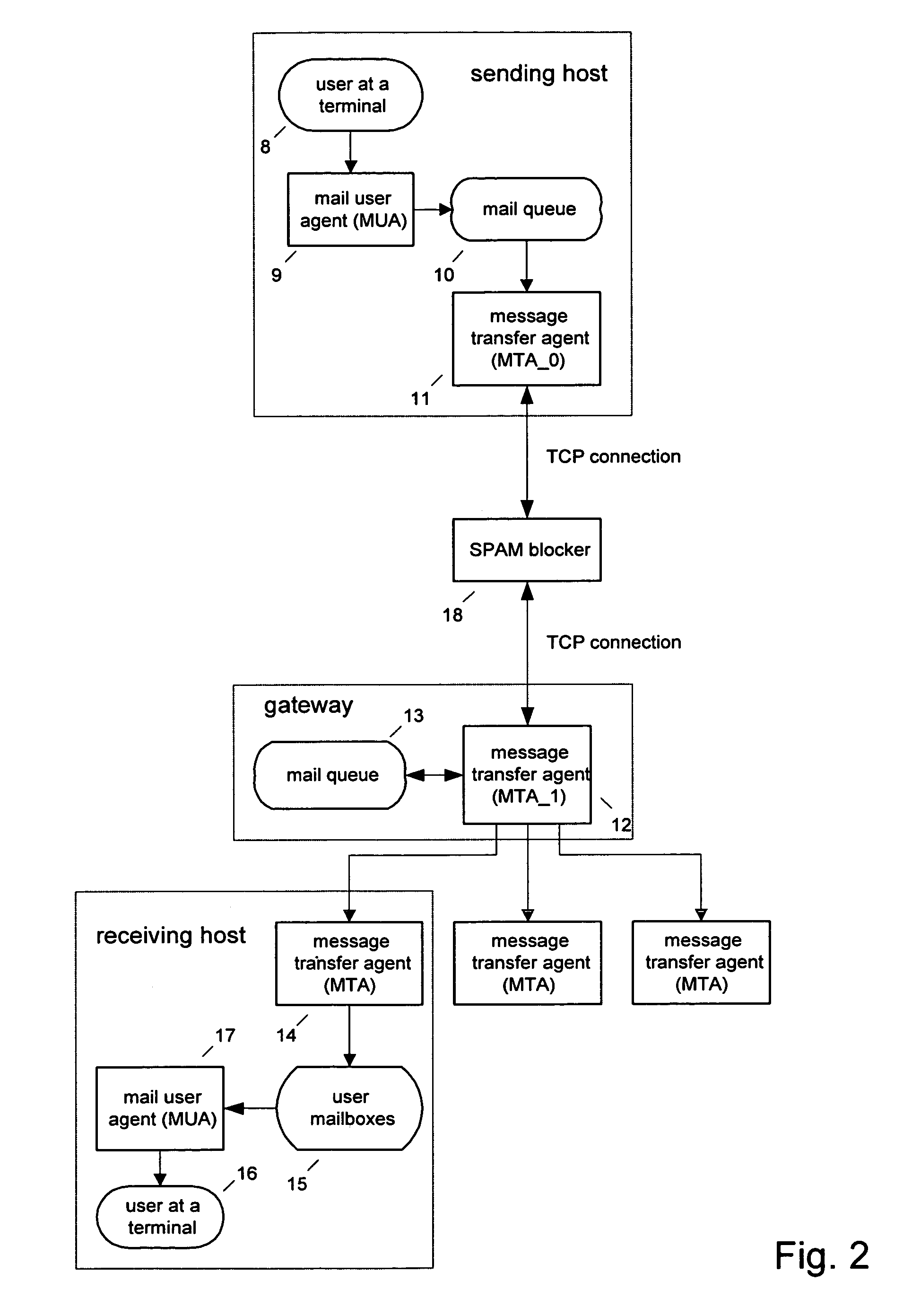
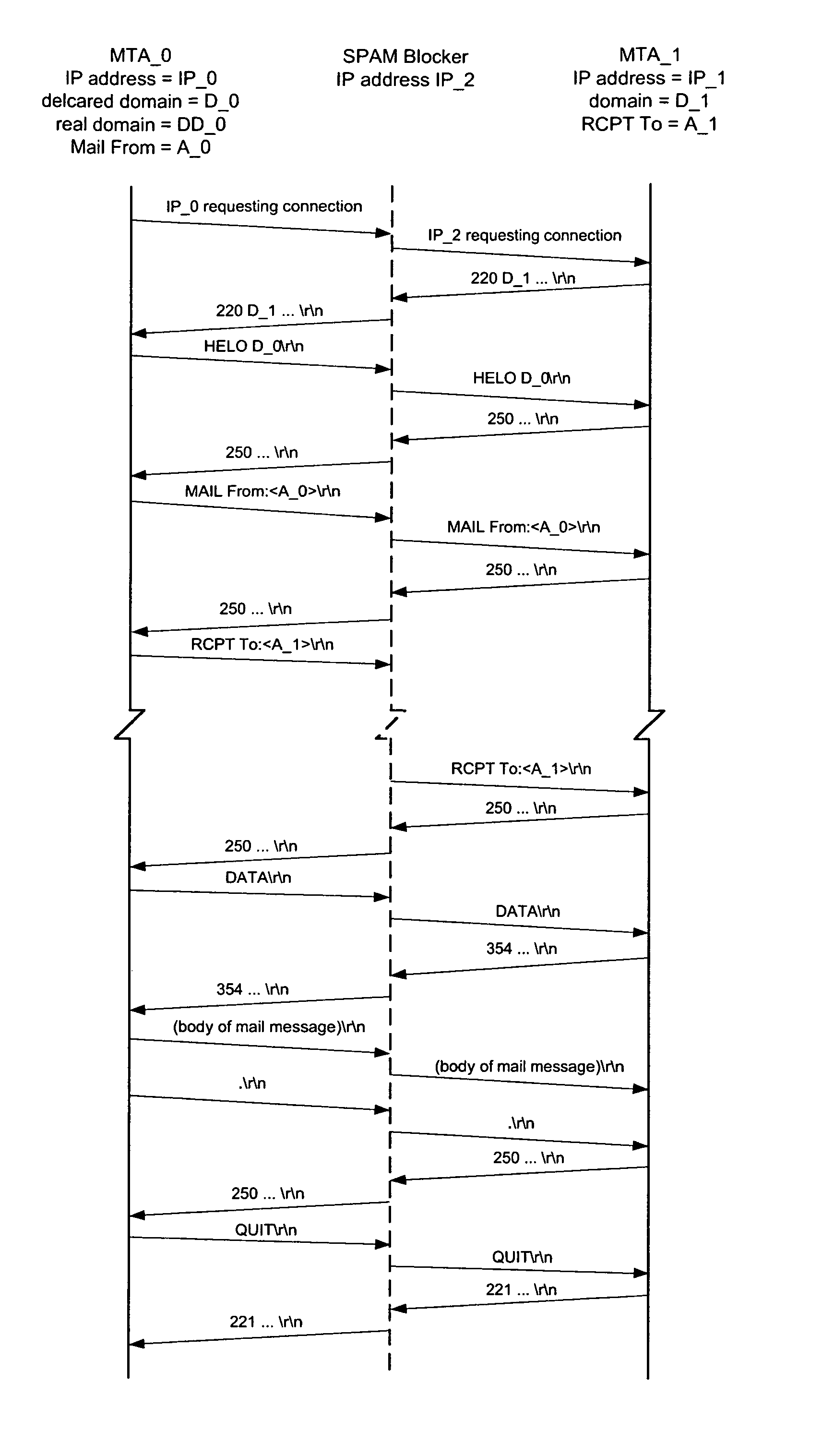
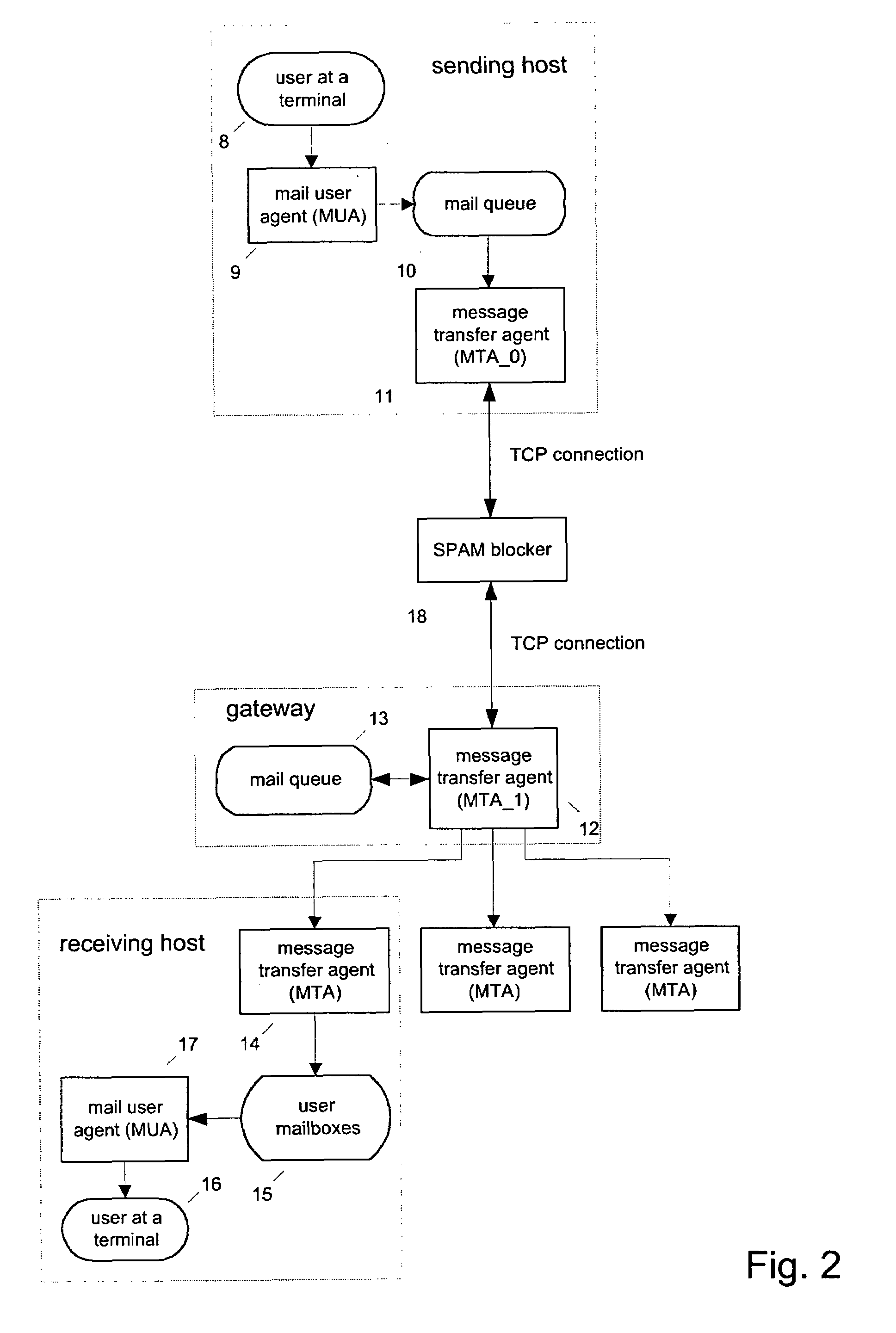
The spam blocker monitors the SMTP / TCP / IP conversation between a sending message transfer agent MTA—0 and a receiving message transfer agent MTA—1; catches MTA—0's IP address IP—0, MTA—0's declared domain D—0, sender_address A—0; and recipient A—1; and uses this source and content based information to test for unsolicited messages. It interrupts the conversation when MTA—0 sends a command specifying the recipient (an “RCPT” command) and uses the various test results to decide if the message is suspected of being unsolicited. If the message is suspected of being unsolicited then it logs the rejected message, sends an error reply to MTA—0 which forces MTA—0 to terminate the connection with MTA—1 before the body of the message is transmitted; else it logs the allowed message, releases the intercepted RCPT command which allows the conversation between MTA—0 and MTA—1 to proceed.
Owner:ENGATE TECH CORP
System and method for deferring the delivery of an e-mail
InactiveUS20050108343A1Avoid readingMultiple keys/algorithms usageMultiple digital computer combinationsThe InternetData transmission
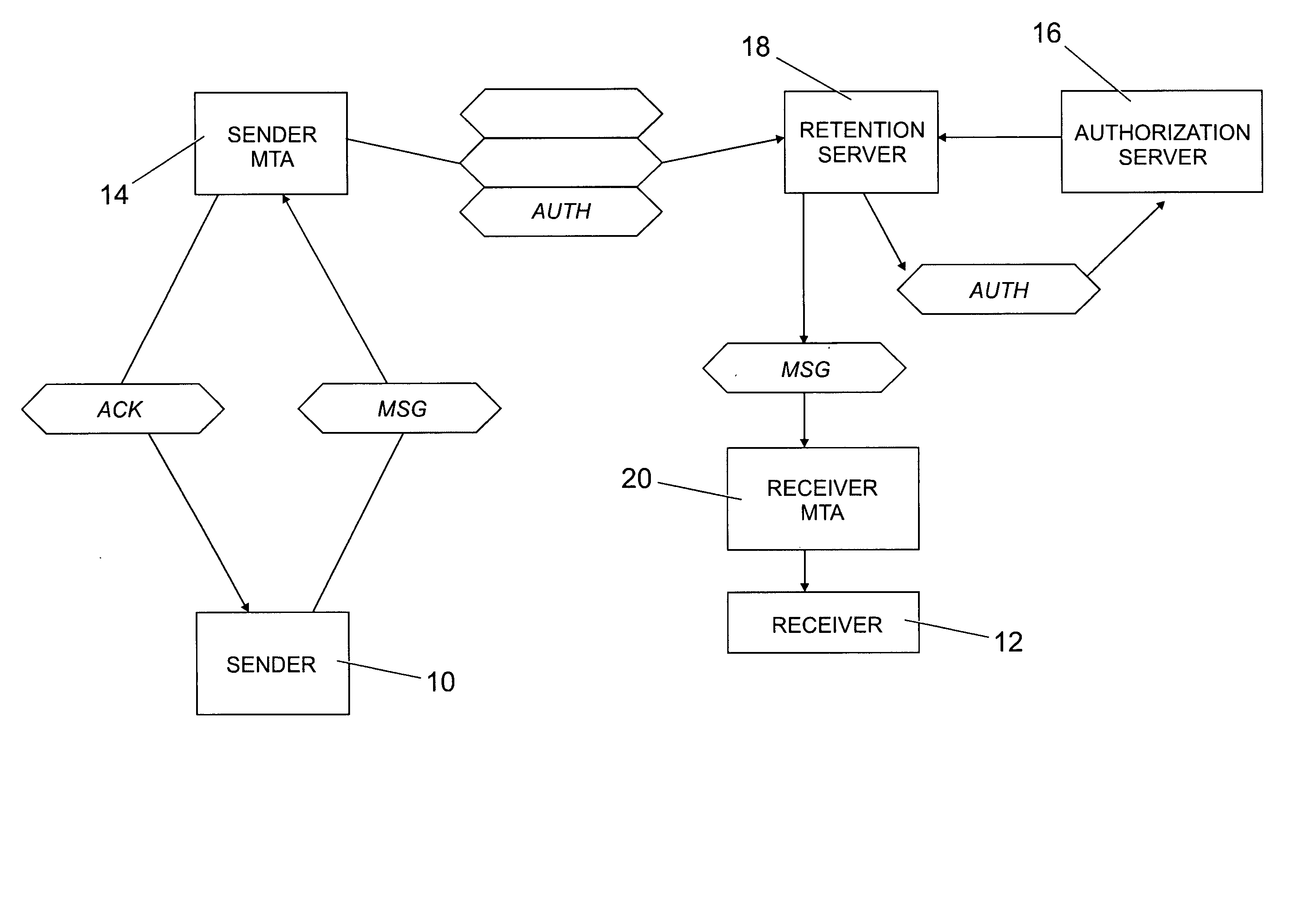
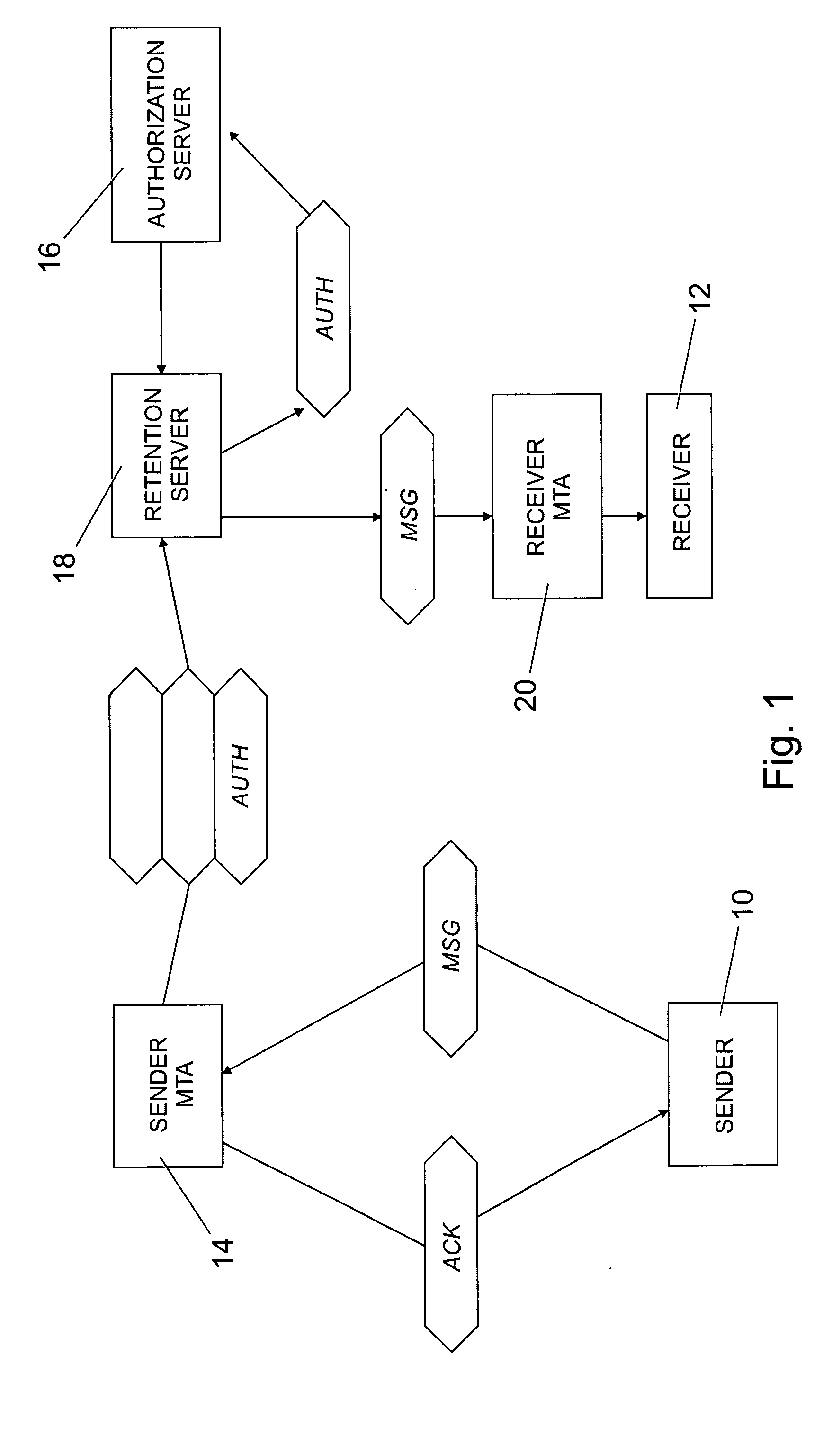
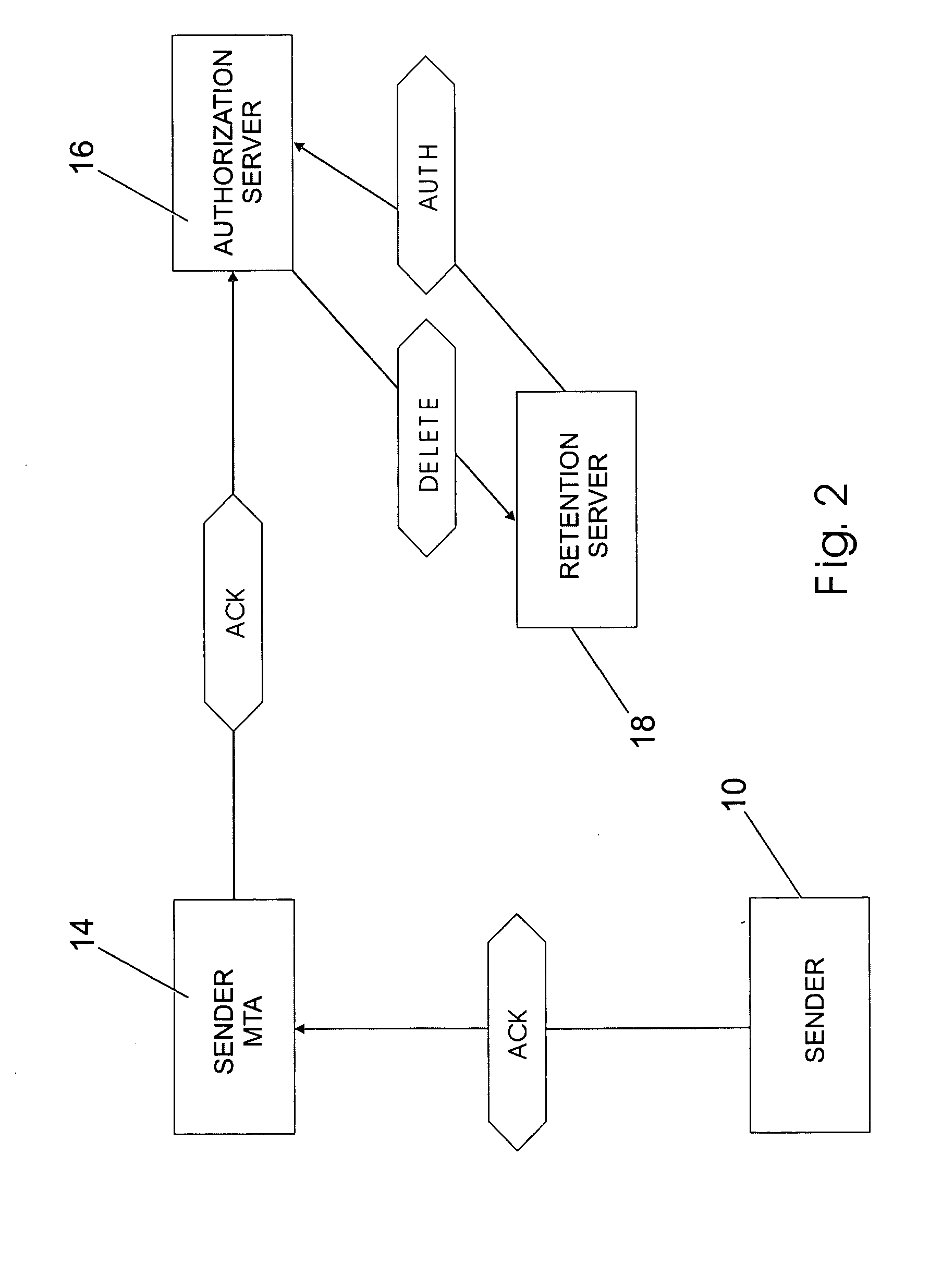
System for deferring the delivery of an e-mail sent by a sender to a receiver through a data transmission network such as Internet wherein a Message Transfer Agent (MTA) associated with the sender is in charge of transmitting over the network any e-mail being sent by the sender. The system comprises a retention server for storing the e-mail whose delivery is to be deferred and an authorization server for giving the retention server the authorization to deliver the stored deferred e-mail to the receiver when predetermined criteria are met. The MTA associated with the sender includes a retention enabling program for sending the deferred e-mail to the retention server when there is an indication in the e-mail that it is to be deferred.
Owner:IBM CORP
E-mail filtering method and device thereof
ActiveCN103220213AMeet security needsImprove securityData switching networksInternet privacyA domain
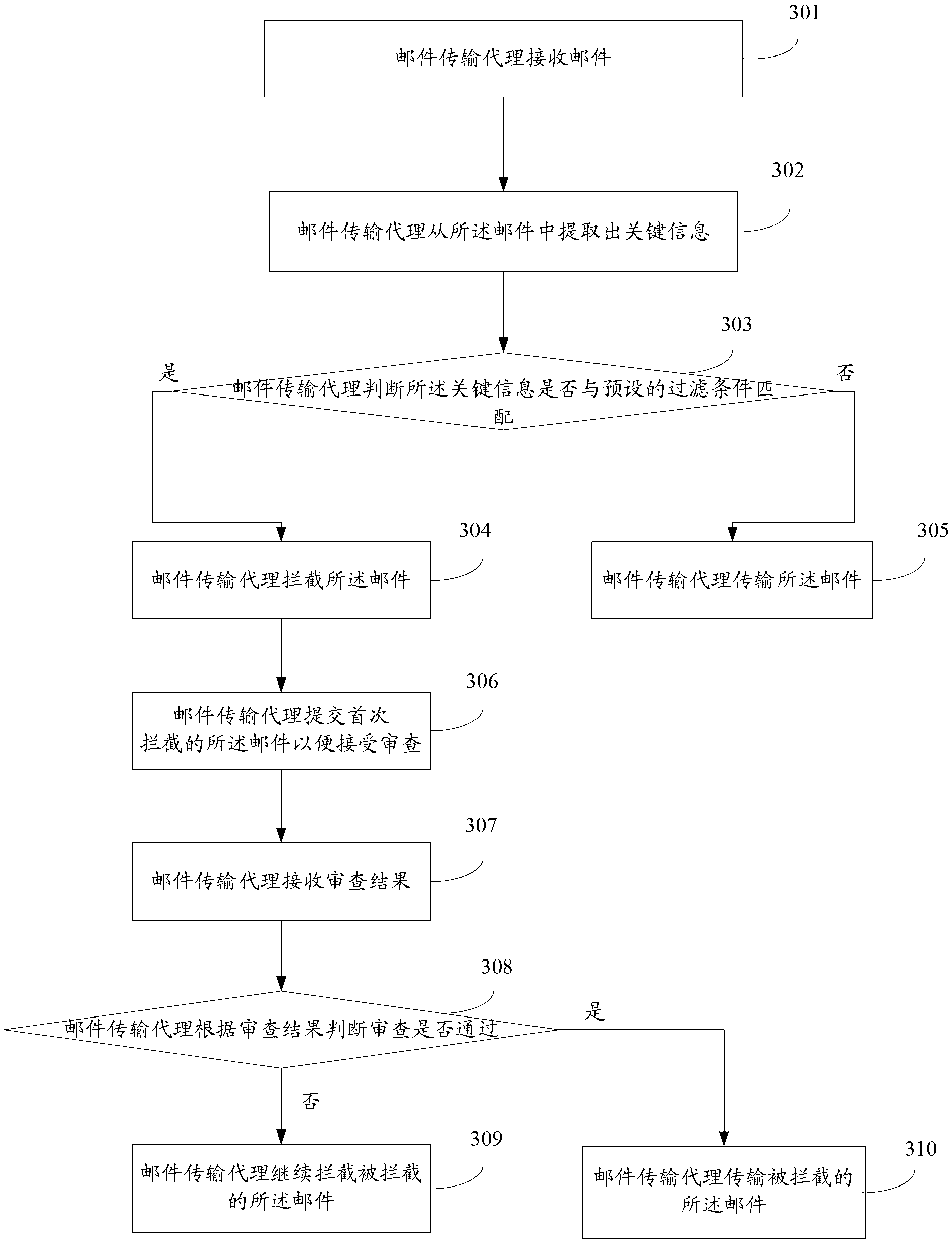
An embodiment of the invention discloses an E-mail filtering method and an E-mail transmission agent, wherein the E-mail filtering method comprises an E-mail transmission agent for receiving an E-mail, the E-mail transmission agent abstracts key information from the an E-mail, the key information comprises an attachment type, a subject, a text, a domain name, addressee number and any one or more combination information in addresser / addressee information, the E-mail transmission agent judges if the key information is matched with a preset filtering condition, if the key information is matched with the preset filtering condition, the E-mail transmission agent intercepts the E-mail, otherwise, the E-mail transmission agent transmits the E-mail. According to the embodiment of the E-mail filtering method and the E-mail transmission agent, safety of the E-mail can be improved.
Owner:STATE GRID CORP OF CHINA +2
Unsolicited message intercepting communications processor
InactiveUS7673058B1Apparent advantageMultiple digital computer combinationsTransmissionComputer hardwareIp address
The spam blocker monitors the SMTP / TCP / IP conversation between a sending message transfer agent MTA—0 and a receiving message transfer agent MTA—1; catches MTA—0's IP address IP—0, MTA—0's declared domain D—0, from-address A—0; to-address A—1, and the body of the message; and uses this source and content information to test for unsolicited messages. It interrupts the conversation when MTA—0 sends a .\r\n end-of-message indicator and uses the various test results to decide if the message is suspected of being unsolicited. If the message is suspected of being unsolicited then it logs the rejected message and sends an error reply to MTA—0 which forces MTA—0 to send a QUIT command before the body of the message is transmitted; else it logs the allowed message and releases the intercepted RCPT command which allows the conversation between MTA—0 and MTA—1 to proceed.
Owner:ENGATE TECH CORP
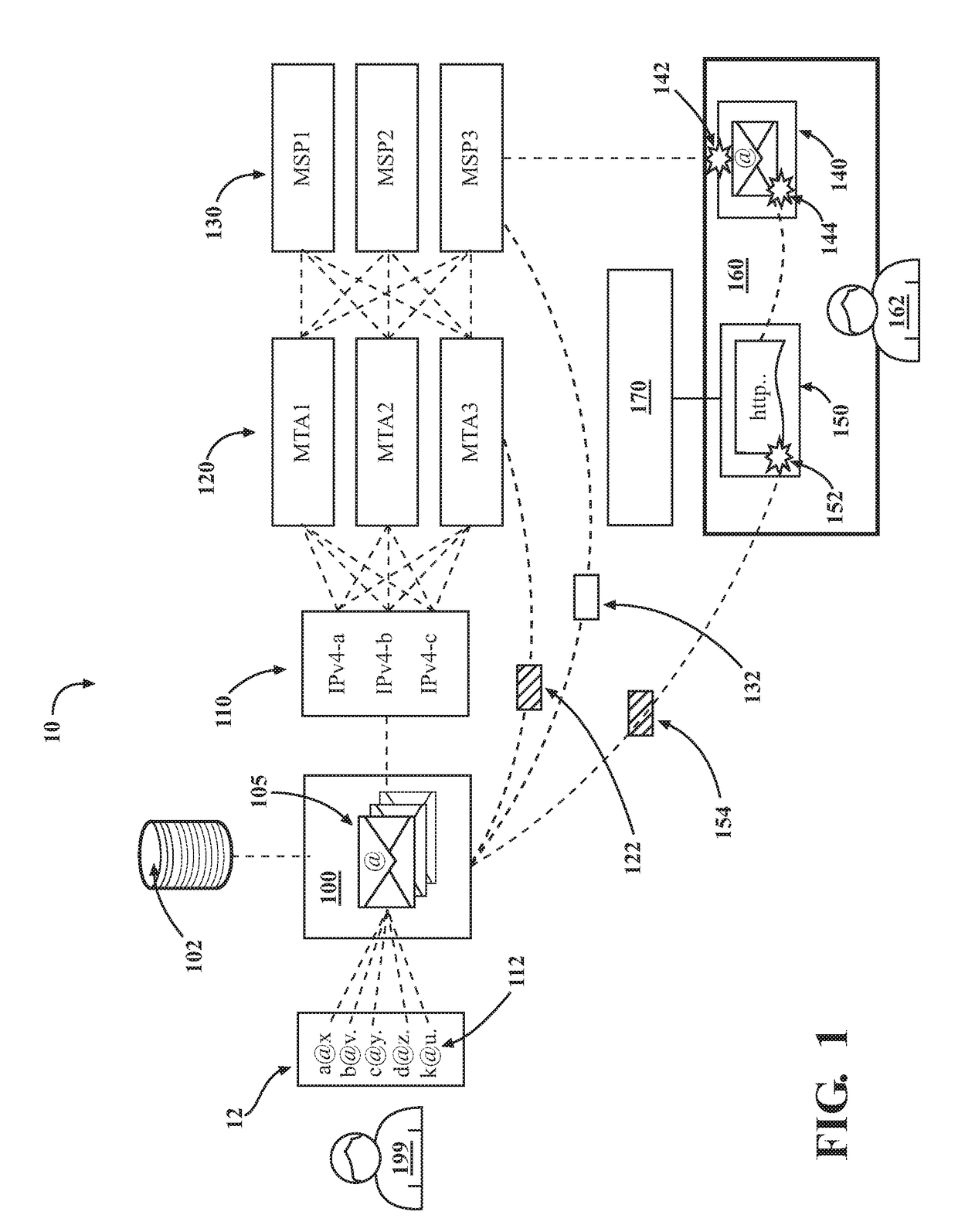
Managing electronic messages with a message transfer agent
ActiveUS20180219819A1Mitigating cross-impactEasy to compareMathematical modelsAdvertisementsSpammingEngineering
Owner:HUBSPOT
Method and system for distributing e-mail messages to recipients
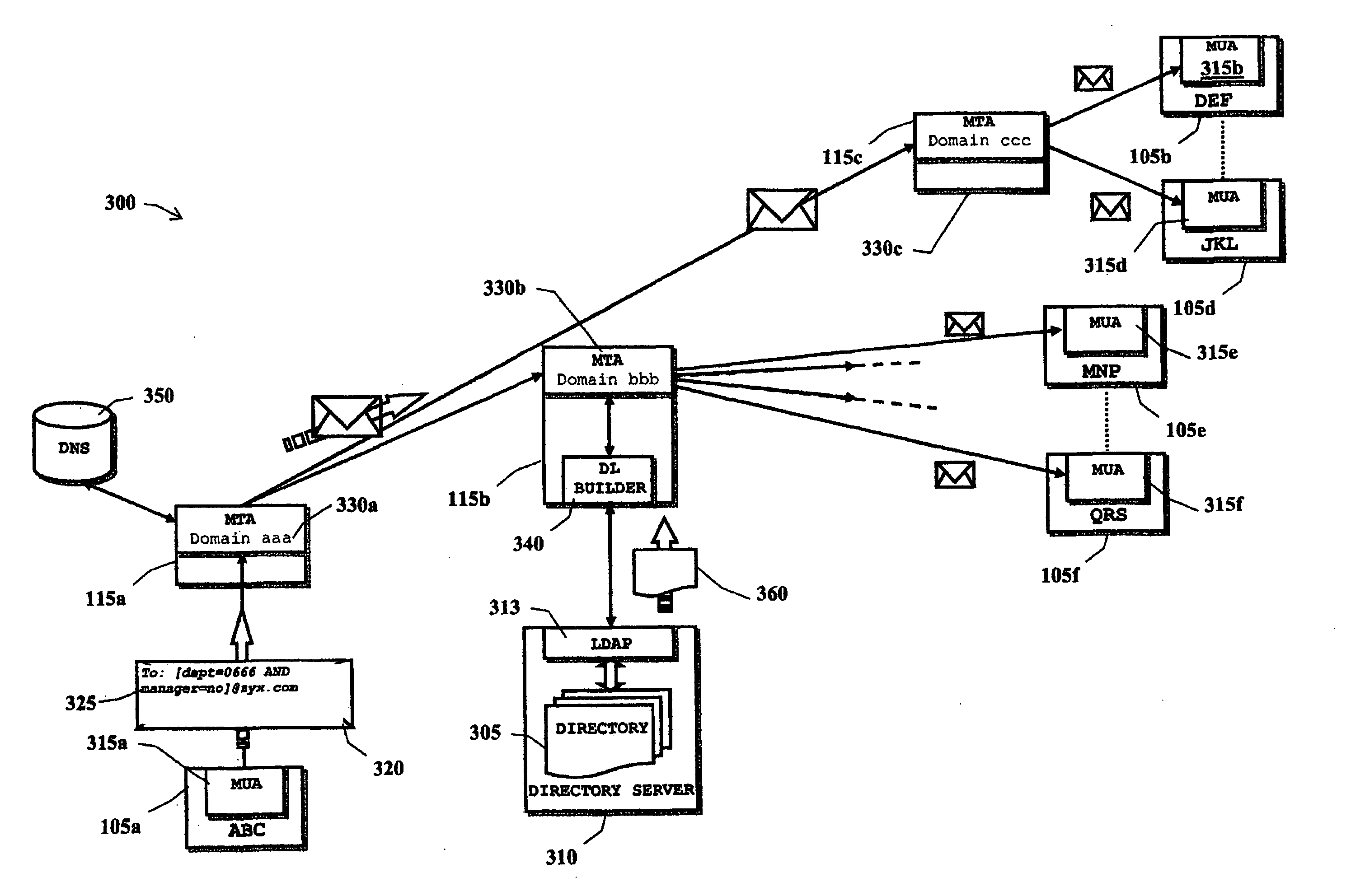
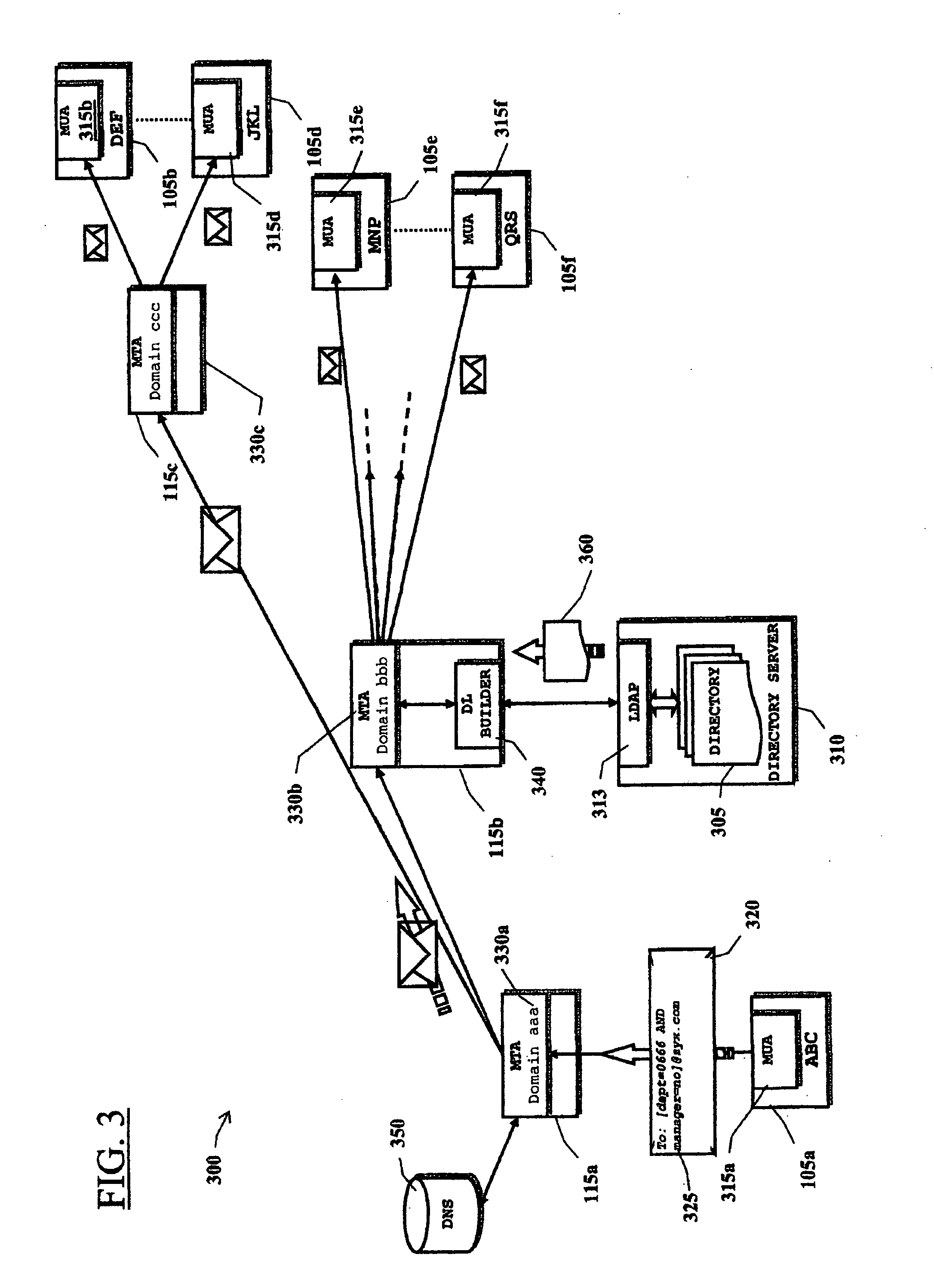
InactiveUS20060143277A1Multiple digital computer combinationsTransmissionData processing systemEmail address
In a data processing system (100) supporting electronic mail (e-mail) messaging, a method, an apparatus and software for distributing an e-mail message from a sender mail user agent (315a) to recipients mail user agents (315b-315f), comprising: providing a remote directory (305) of recipients' contacts including recipients e-mail addresses, the remote directory being located remotely (310) with respect to the sender mail user agent; providing a mail transfer agent (330b) having an interface function (340) with said remote directory, the interface function being adapted to interact with the remote directory so as to perform queries and obtain in reply lists of recipients' e-mail addresses; including in an address field of the e-mail message a pseudo-address, the pseudo-address comprising an address of said mail transfer agent, and at least one directive for the interface function; upon reception of the e-mail message by the mail transfer agent, having the interface function translate the at least one directive into a corresponding query, submitting the query to the directory, and retrieve a list of recipients e-mail addresses; and propagating the e-mail message from the mail transfer agent to the recipients whose e-mail addresses are in the list.
Owner:IBM CORP
Managing working set in an extensible message transfer system
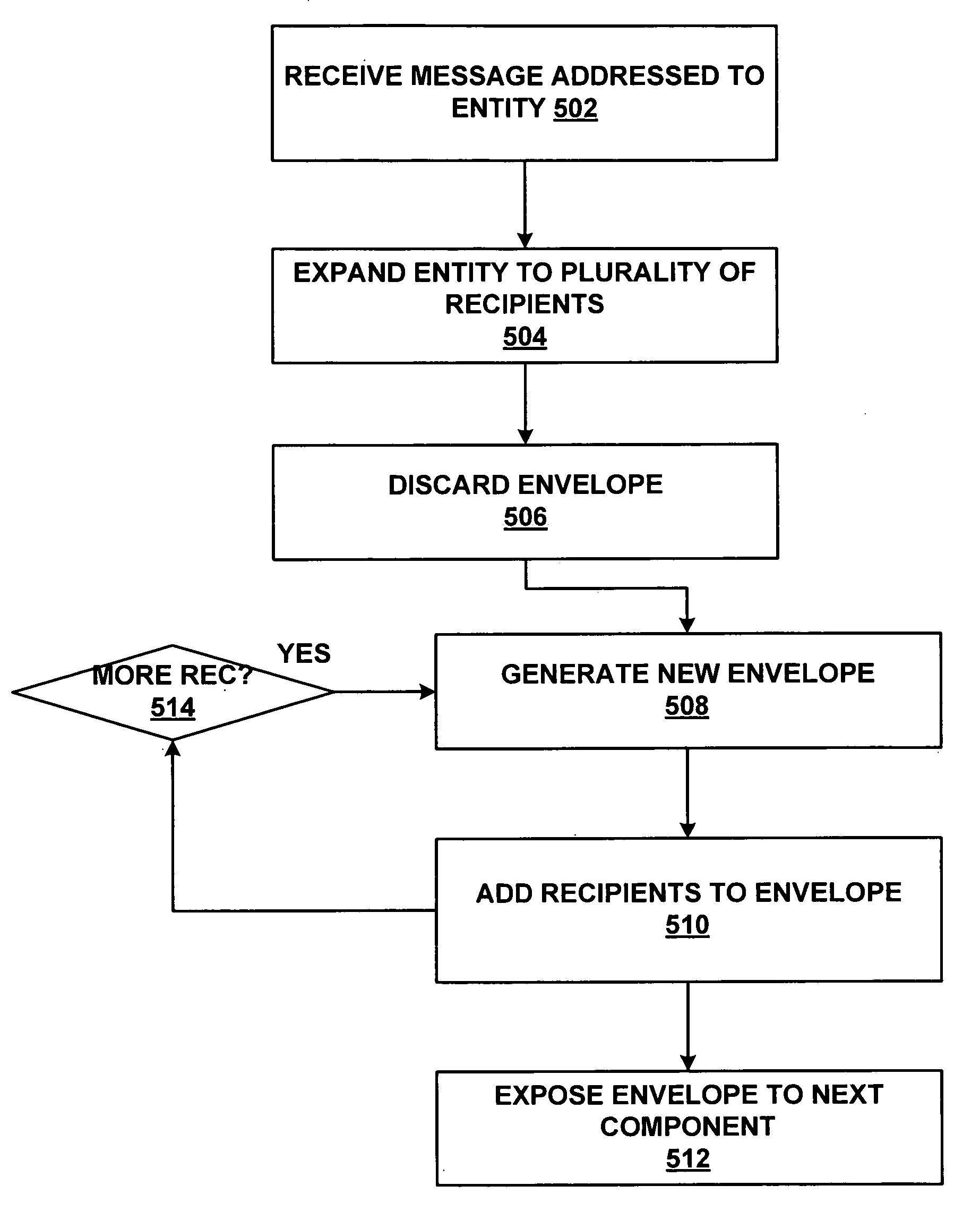
ActiveUS20060195531A1Send efficientlyMultiple digital computer combinationsData switching networksTransfer systemMessage transfer agent
Within a mail transfer agent of a message transfer system, a message is received and if the recipient entity resolves to a number of recipients exceeding a specified quantity, the original message is not processed. Instead, at least two messages are created, with each of the created messages addressed to a subset of the original set of recipients. The created messages are returned to the calling module for processing.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and Method for Handling Electronic Mail
InactiveUS20080040439A1Reduce disruptionHigh scrap rateMultiple digital computer combinationsData switching networksCommunications systemRejection rate
A mail transfer agent adapted for determining the disposition of incoming e-mail from a sender includes a penalty count filter module (20 which functions on the basis of current communication system resource usage, such as the number of concurrent TCP connections being maintained, and penalty counts assigned for cumulative undesirable sender activity such as sending large e-mail files. The penalty count filter module can operate in a selective-rejection state accepting e-mail from senders without a penalty count and randomly accepting other e-mail, and in a random-rejection state rejecting all e-mail from senders with a penalty count and randomly rejecting other e-mail. The rejection rates can be increased or decreased in response to a detected increase or decrease in the usage of system resources.
Owner:NOKIA TECH OY
Unsolicited message diverting communications processor
InactiveUS7716351B1Apparent advantageMultiple digital computer combinationsTransmissionComputer hardwareIp address
The spam blocker monitors the SMTP / TCP / IP conversation between a sending message transfer agent MTA—0 and a receiving message transfer agent MTA—1; catches MTA—0's IP address IP—0, MTA—0's declared domain D—0, from-address A—0; and to-address A—1; and uses this source and content based information to test for unsolicited messages. It interrupts the conversation when MTA—0 sends a RCPT command and uses the various test results to decide if the message is suspected of being unsolicited.If the message is suspected of being unsolicited and to-address is not in the save_spam database then the spam blocker logs the rejected message, sends an error reply to MTA—0 which forces MTA—0 to terminate the connection before the body of the message is transmitted. If the message is suspected of being unsolicited and to-address is in the save_spam database then the spam blocker logs the rejected message, substitutes a diversion address A′—1 for the to-address A—1 in the RCPT command, and send the modified RCPT command to MTA—1 and allows the conversation to continue. If the message is not suspected of being unsolicited then the spam blocker logs the allowed message, releases the intercepted RCPT command which allows the conversation to continue.
Owner:ENGATE TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com