Patents
Literature
506results about How to "Meet security needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
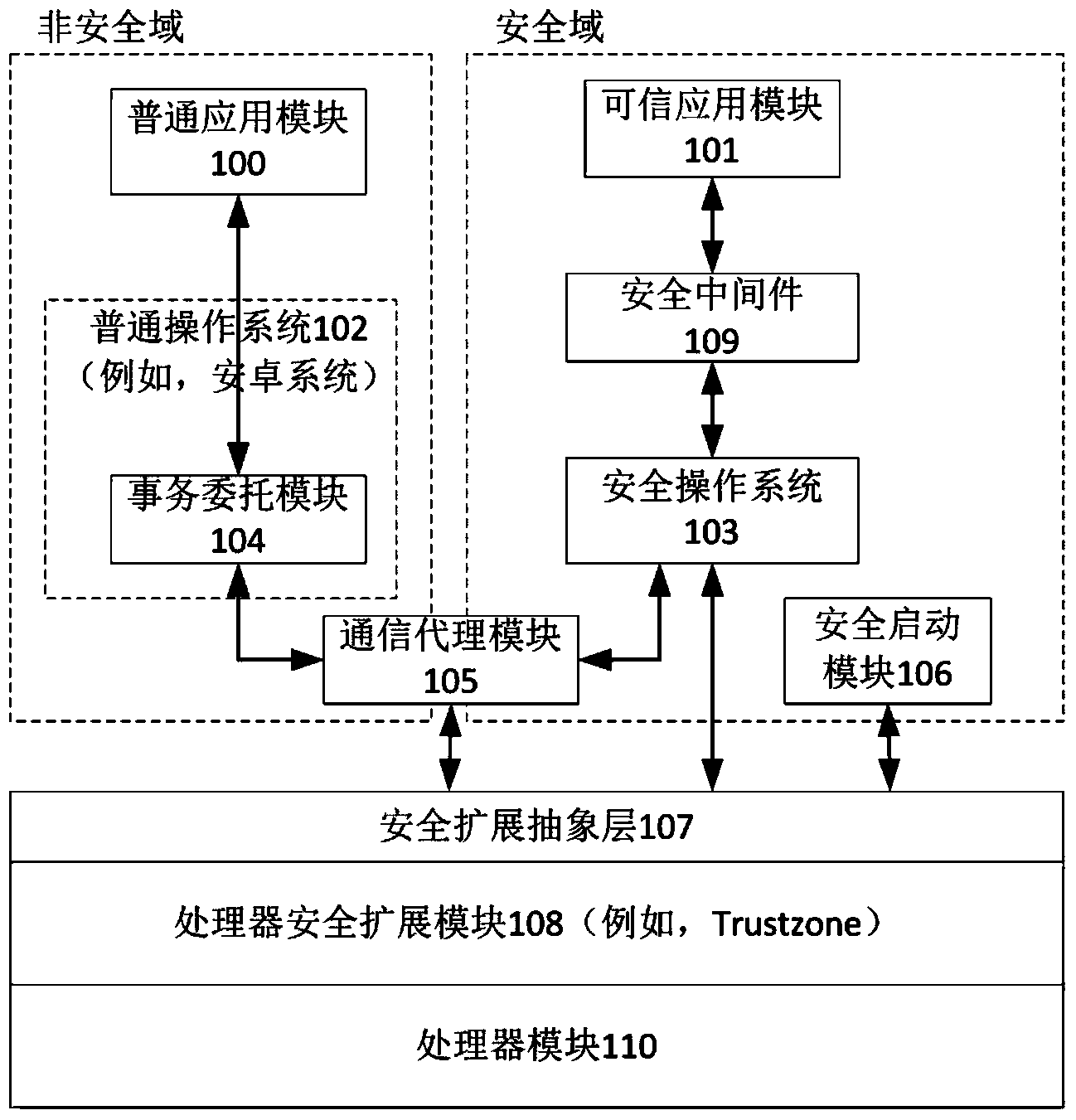
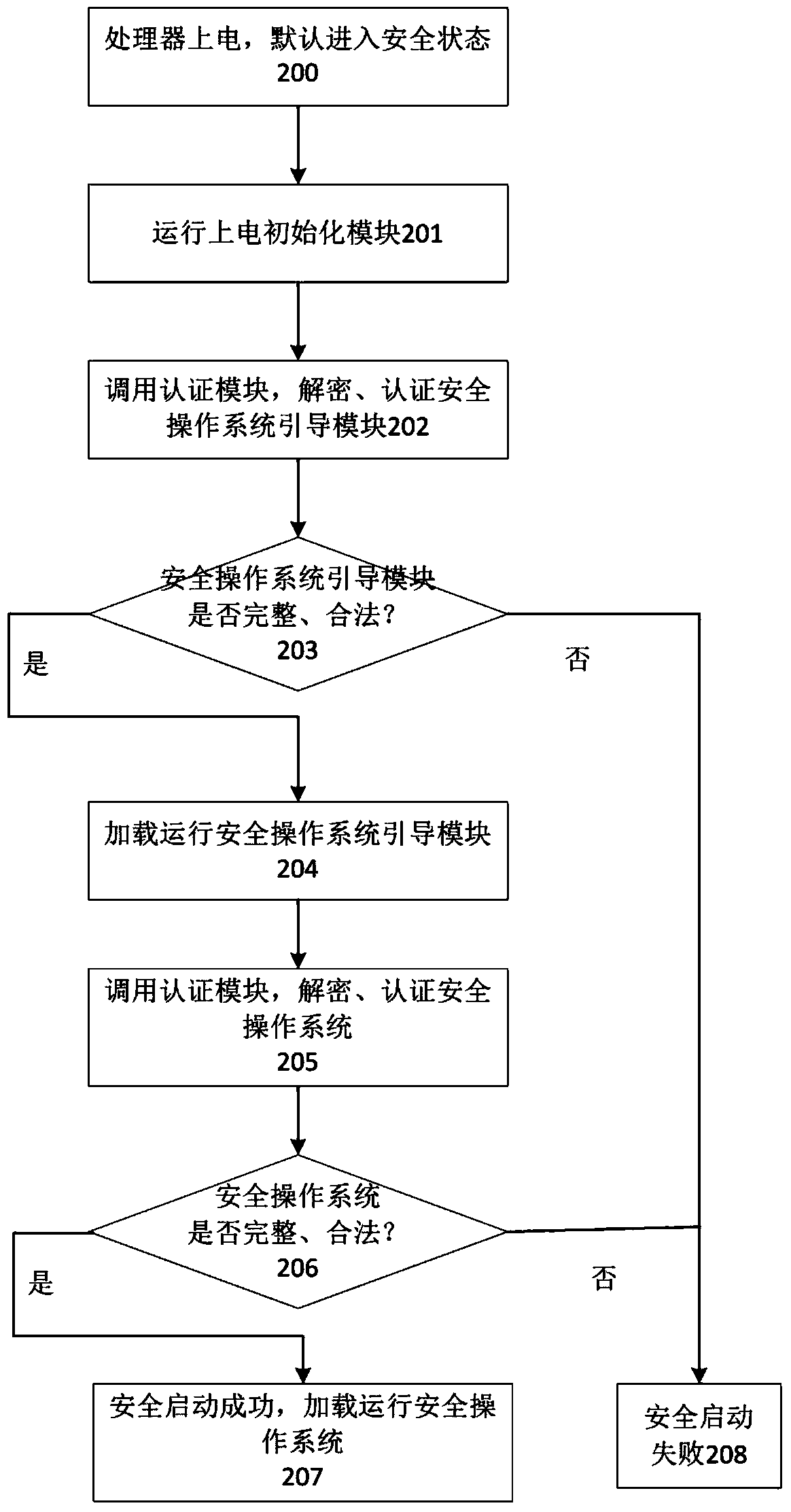
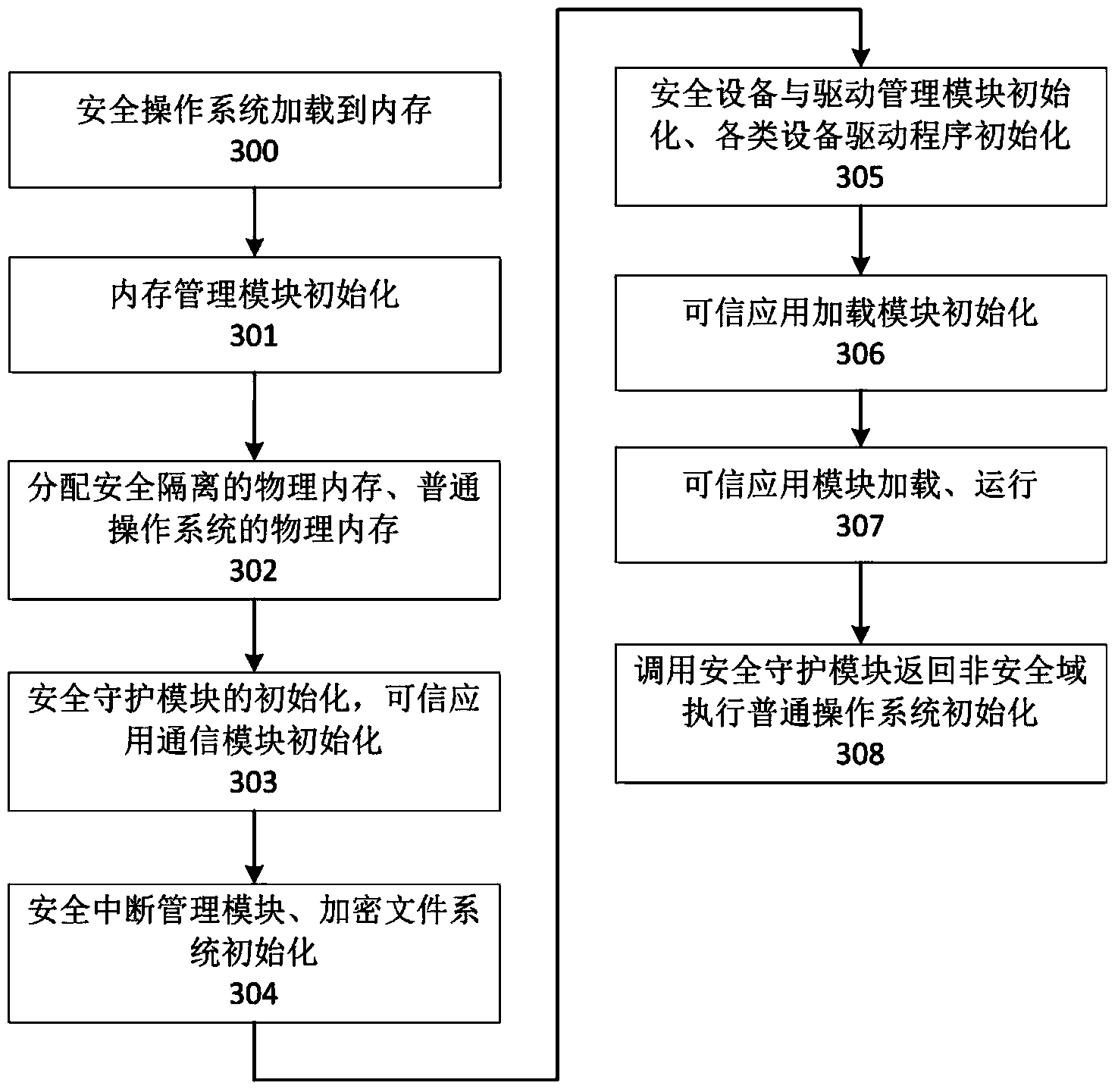
Intelligent terminal isolation system and intelligent terminal isolation method both based on processor safety extension
InactiveCN104318182AAchieve security isolationEnsure safetyInternal/peripheral component protectionSubstation equipmentAbstraction layerOperational system
Disclosed are an intelligent terminal isolation system and an intelligent terminal isolation method both based on processor safety extension. The intelligent terminal isolation system comprises a safety starting module, a transaction commission module, a communication agent module, a safety extension abstraction layer, a safety operating system, safety middleware, credible application modules and a common application module. The safety starting module simply initializes hardware environment of an intelligent terminal, and authenticates and guides the safety operating system. The communication agent module is responsible for encapsulation and communication of bottom layer data of the credible application modules and the common application module. The safety extension abstraction layer provides a uniform calling interface to the safety operating system. The safety operating system provides mutually independent operation space for the credible application modules in a whole safety domain and manages all software and hardware resources in the safety domain. The safety middleware is a core library related to implementation of safety functions and transaction commissions and provides related functional interfaces to credible applications. The intelligent terminal isolation system and the intelligent terminal isolation method aim to provide a complete safety isolation mechanism to the intelligent terminal and improve safety of software operation environment.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
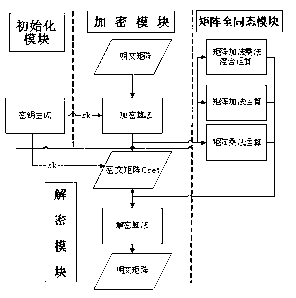
Matrix fully homomorphic encryption method
InactiveCN103259643AInput protectionSatisfy the requirement of full homomorphismSecuring communicationComputer hardwareCiphertext
The invention discloses a matrix fully homomorphic encryption method. The matrix fully homomorphic encryption method comprises an initialization module, an encryption module, a decryption module and a matrix fully homomorphic module. The initialization module is used for generating secret keys needed by encryption and decryption according to dimensions of matrices to be encrypted, encryption types and ranges of matrix element values. The encryption module is used for utilizing encryption algorithms and the secret keys to conduct encryption on plaintext matrices and outputting ciphertext matrices according to the given plaintext matrices. The decryption module is used for utilizing the secret keys and decryption algorithms to conduct decryption on ciphertext matrices and outputting the plaintext matrices according to the given ciphertext matrices. According to the matrix fully homomorphic module, additive operation and multiplying operation of the matrices meet homomorphic properties of the matrices, output generated by the additive operation and the multiplying operation of the matrices still meets the homomorphic properties, namely, fully homomorphic properties of the matrices are met. The matrix fully homomorphic encryption method has the advantages of meeting safety requirements, meeting fully homomorphic requirements of the matrices and remarkably increasing the operating rate of the ciphertext matrices.
Owner:SUZHOU UNIV
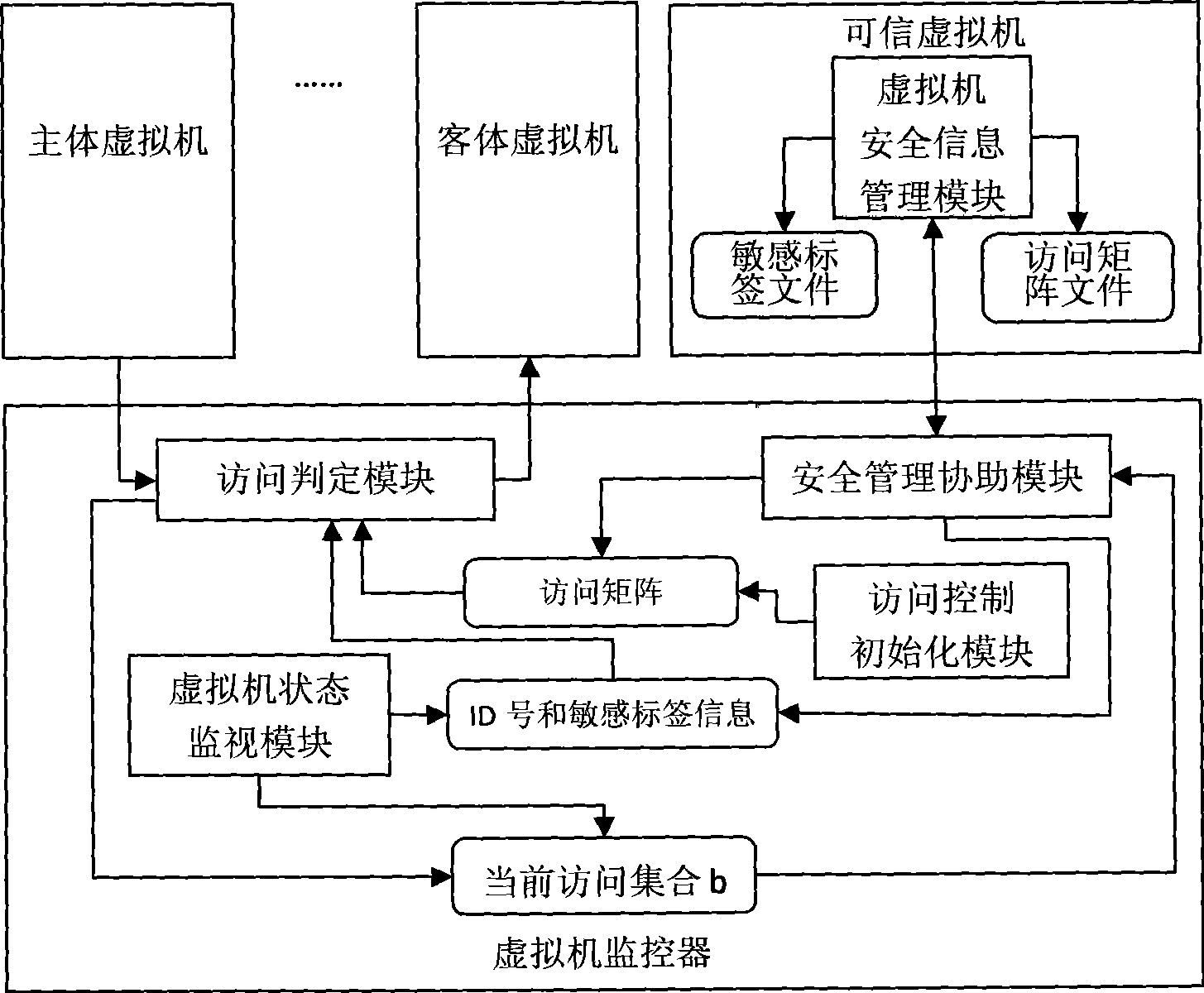
Forced access control method and apparatus in virtual environment
InactiveCN101452397AMeet security needsShare blockingSoftware simulation/interpretation/emulationVirtualizationSecurity level
The invention relates to a forced access control method and a device applied to a virtual environment in the technical field of computer application. The method comprises: designating a virtual machine in a virtual environment as a credible virtual machine with security management authority, in which, the credible virtual machine uses security classification and security category as a sensitive label to identify the security level of a single virtual machine; establishing an access matrix and setting the access type set of each virtual machine to other virtual machines; and when a certain virtual machine main body gets access to a certain virtual machine object in a certain access type, judging whether the access is permitted according to the sensitive label of both the main body and the object and the access type set of the main body to the object in the access matrix. The device comprises an access control initializing module, a virtual machine state monitoring module, an access judgment module, a security management assisting module and a virtual machine security information management module in the credible virtual machine. The forced access control method and the device can effectively control communication and resource sharing between virtual machines in a virtual environment of multilevel security.
Owner:SHANGHAI JIAO TONG UNIV
Communication method and communication system of novel network
ActiveCN101917492AAvoid delayMeet security needsSpecial service provision for substationTelecommunications linkCommunications system
The invention discloses a communication method of a novel network. The novel network is a network with a centralized control function and comprises a main control server and subordinate network equipment, and the subordinate network equipment comprises terminals. The method comprises the following steps that: the main control server configures downlink communication link for a current service; and the main control server sends the current service data packet sent by a source terminal to a target terminal according to the downlink communication link. Through the communication method and the communication system, the stability and smoothness of the transmission channel are ensured, the delay of multimedia services is prevented, the requirements for the state information security are met, the hardware resources are saved and the network transmission quality is guaranteed.
Owner:BEIJING QIANTANG NETWORK TECH
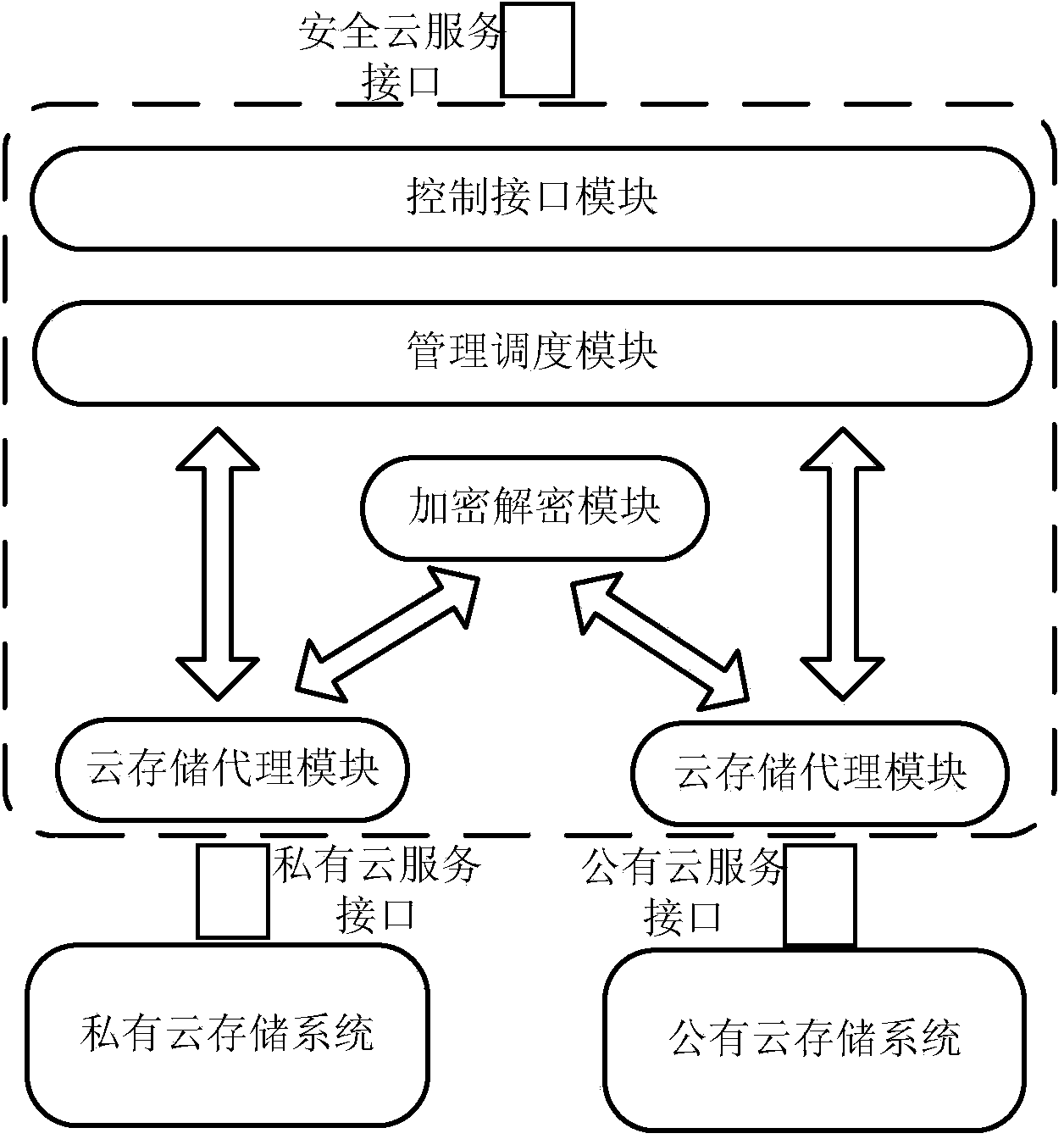
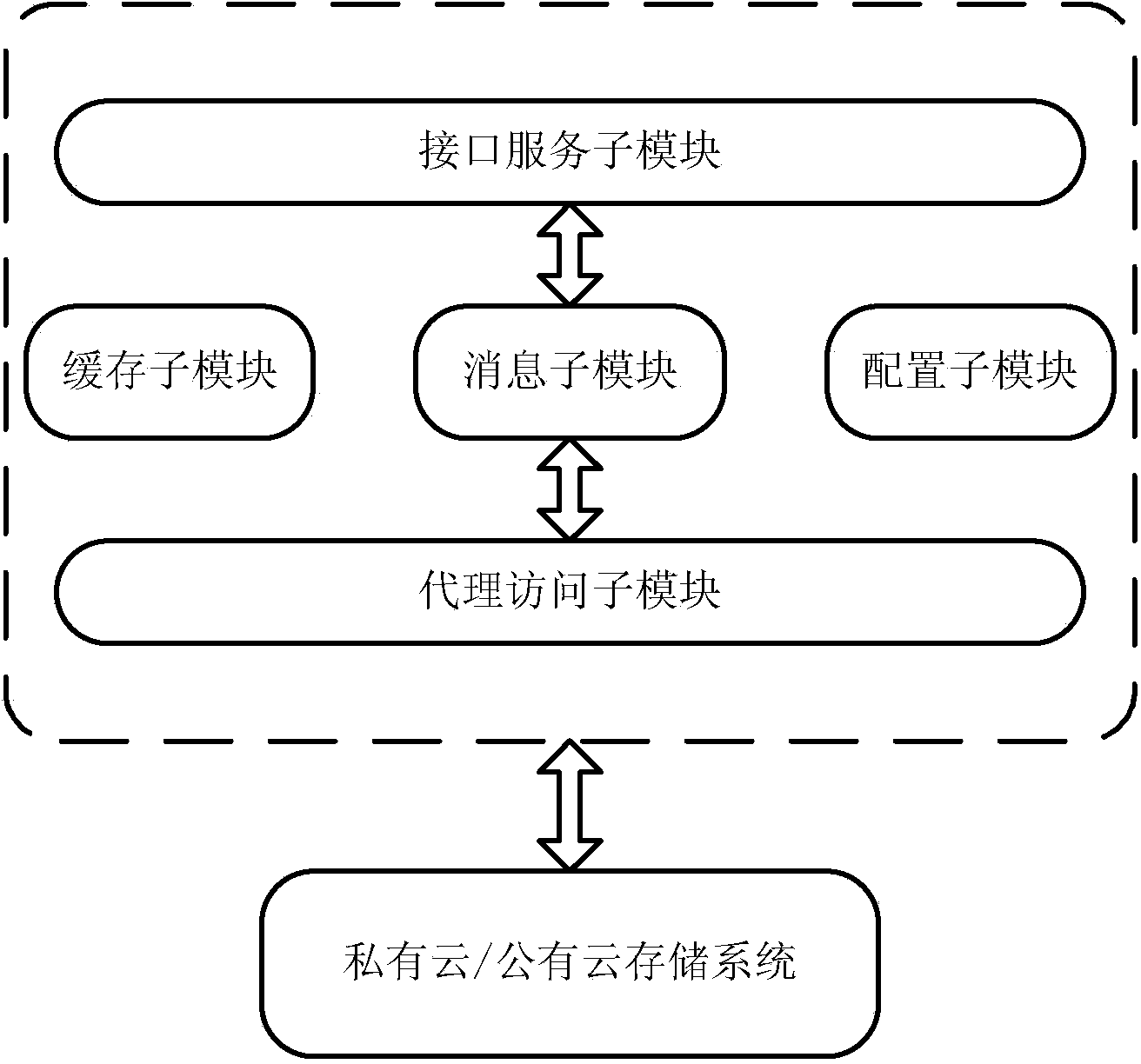
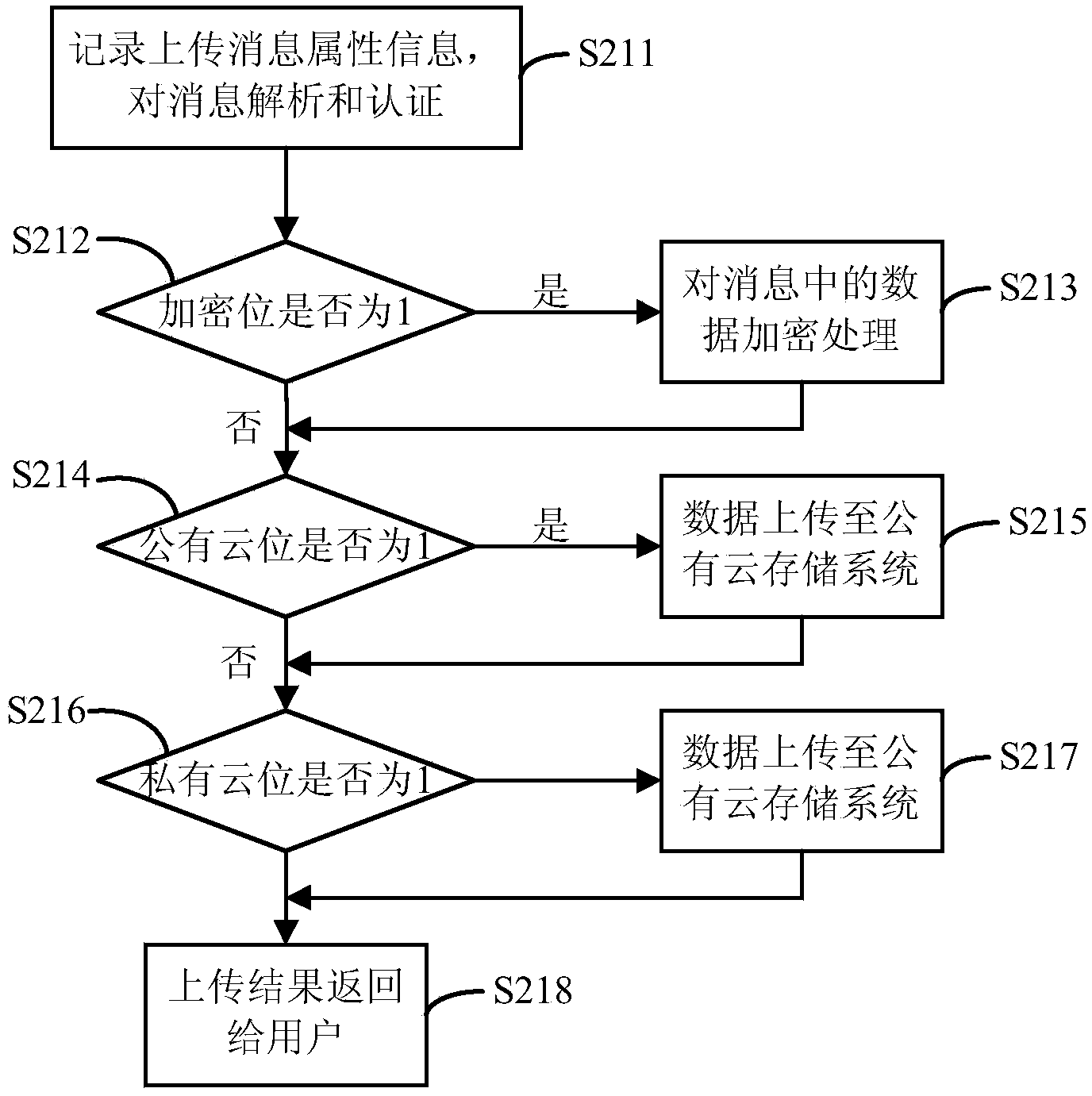
Mixed cloud storage system and method based on safety grading
The invention discloses a mixed cloud storage system and method based on safety grading and relates to the field of data storage. The system includes a control interface module, a management and scheduling module, an encryption and decryption module and two cloud storage agent modules. The control interface module is used for receiving data operation request of a user. The management and scheduling module is used for recording data attribute information. The encryption and decryption module is used for encryption and decryption of data. One cloud storage agent module is sued for communication with a public cloud storage system and the other cloud storage agent module is used for communication with a private cloud storage system. The mixed cloud storage system and method based on safety grading combines public cloud storage and private cloud storage so that different safety demands are met.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
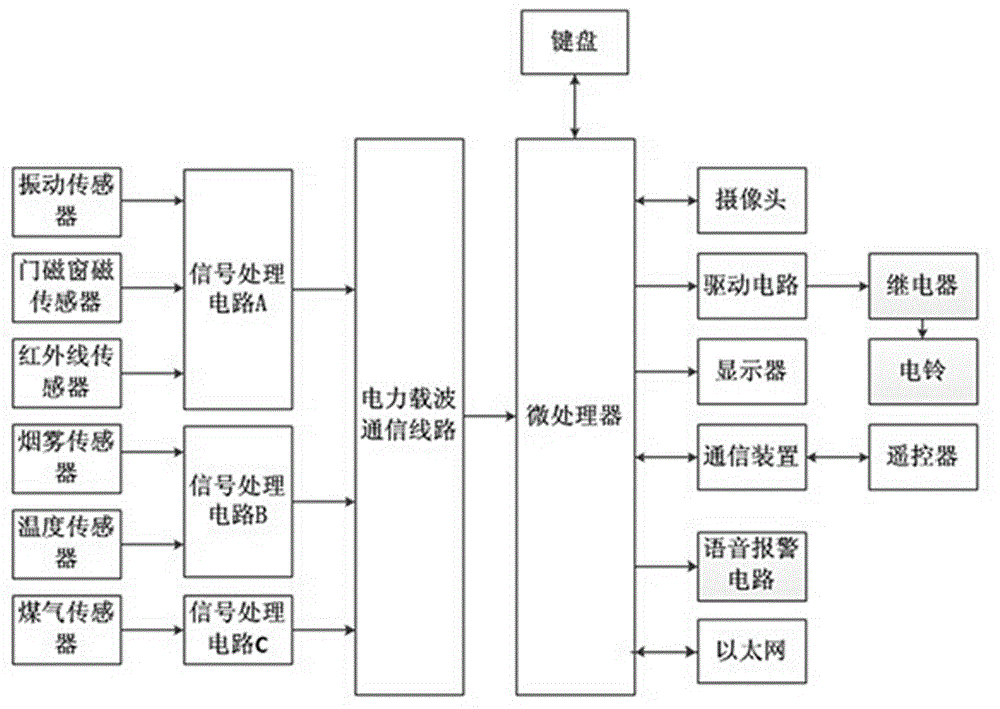
Smart home security system
InactiveCN104157091AMeet security needsGuarantee the safety of lifeClosed circuit television systemsAlarmsSignal processing circuitsGas poisoning
The invention discloses a smart home security system. The smart home security system comprises a vibration sensor, a door and window magnetic sensor, an infrared sensor, a smoke sensor, a temperature sensor and a gas sensor, wherein the vibration sensor, the door and window magnetic sensor and the infrared sensor are connected with a signal processing circuit A respectively; the smoke sensor and the temperature sensor are connected with a signal processing circuit B respectively; the gas sensor is connected with a signal processing circuit C; the signal processing circuit A, the signal processing circuit B and the signal processing circuit C are connected with a power line carrier communication circuit respectively; the power line carrier communication circuit is connected with a microprocessor; the microprocessor is connected with a keyboard, a camera, a driving circuit, a display, a communication device, a voice alarm circuit and an Ethernet respectively; the driving circuit is connected with a relay; the relay is connected with an electric bell; the communication device is connected with a remote controller. The smart home security system can meet needs of people on theft prevention, fire prevention and gas poisoning prevention, is free of mistaken alarm and has an on-spot snapshot function.
Owner:CHENGDU XINXIN INFORMATION TECH
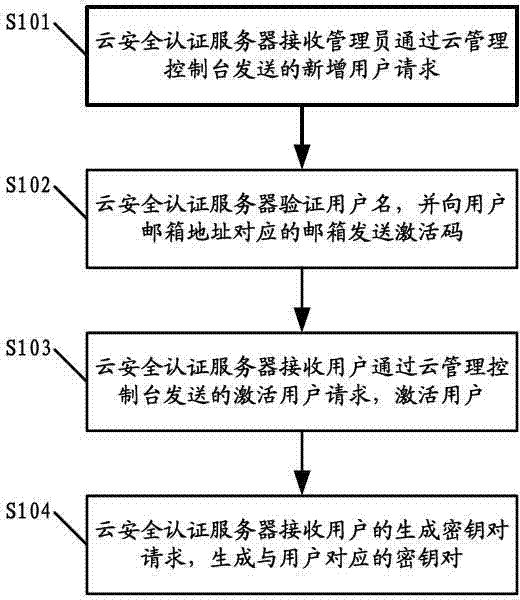
Security control method of virtual machine
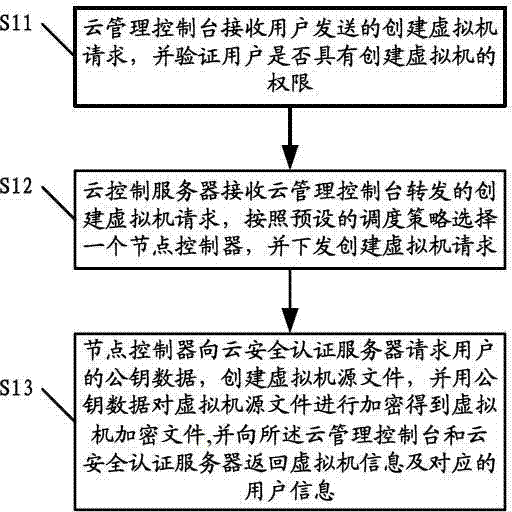
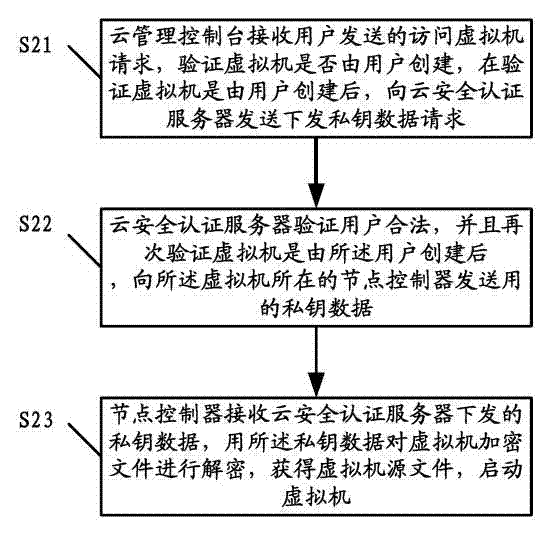
The invention discloses a security control method of a virtual machine. The method includes that a cloud management console receives a virtual machine establishing request sent by a user; a cloud control server receives the virtual machine establishing request forwarded by the cloud management console, selects a node controller according to a preset scheduling policy, and sends the virtual machine establishing request; and the node controller requests public key data in a key pair generated in advance by the user from a cloud security authentication server, builds a virtual machine source file, encrypts the virtual machine source file by using the public key data to obtain a virtual machine encrypted file, and returns virtual machine information and corresponding user information back to the cloud management console and the cloud security authentication server. According to an embodiment of the method, the public key data of the user is used for encrypting the configured virtual machine file, the user who builds the virtual machine can achieve decryption only through applying for private key data of the user who possesses the virtual machine when accessing the virtual machine, and binding of the virtual machine with the user can be achieved.
Owner:GCI SCI & TECH
User identity secret-keeping method in communication system
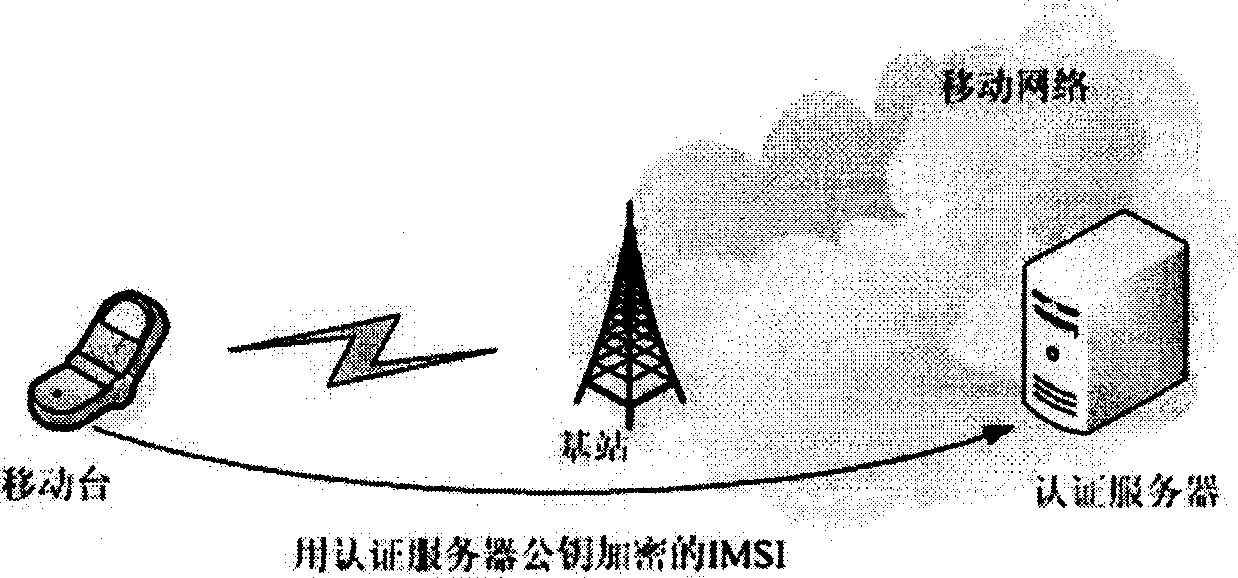
ActiveCN1790984AStrong confidentialityMeet security needsUser identity/authority verificationWeb authenticationNetwork identification
The disclosed secret method for ID in communication system with at least a user terminal and an identification server comprises: the user terminal accesses into network; the provide network identification server asks user to provide ID information; the user terminal enciphers self ID information with public key from server to send to server; the server deciphers the ID information with self private key to identify ID and provide service and charge. This invention uses asymmetric cryptography technology to satisfy security request.
Owner:ZTE CORP
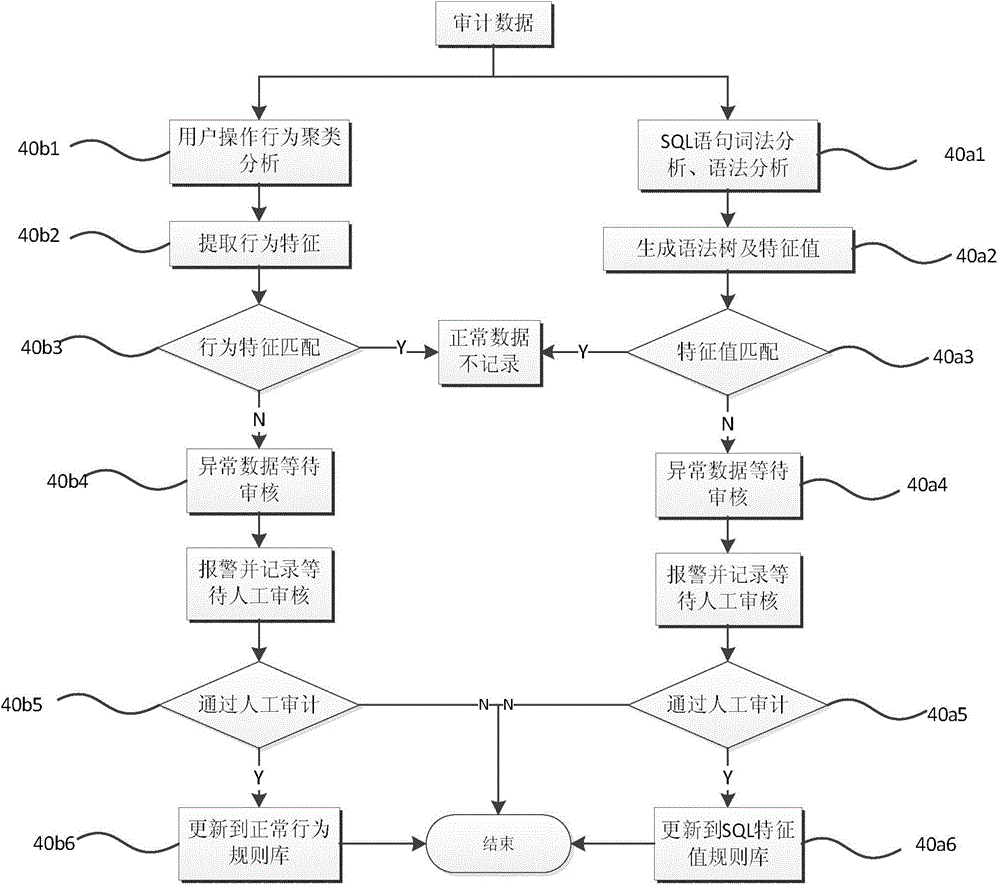
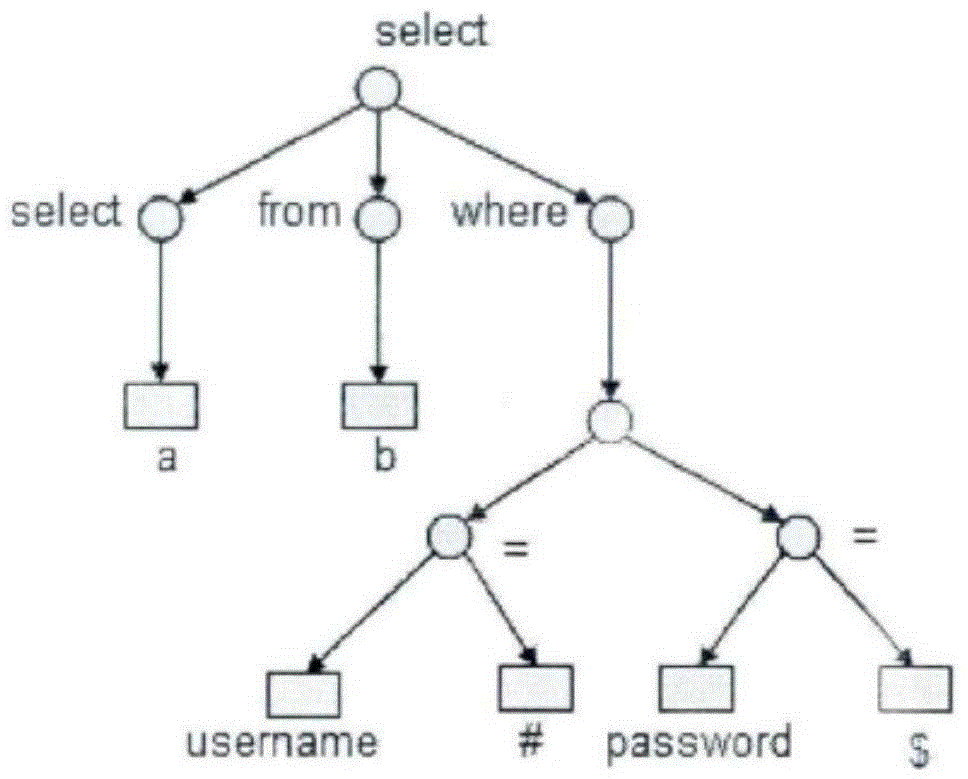
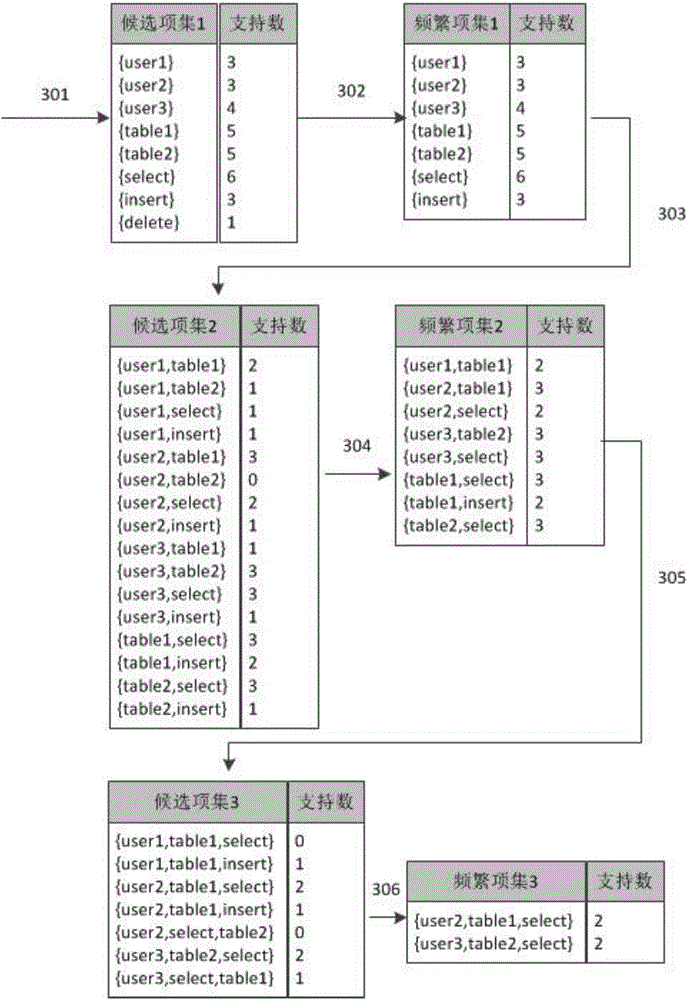
Database auditing system and database auditing method
InactiveCN104090941ARealize audit automatic learningEasy to detectDigital data protectionSpecial data processing applicationsData miningFalse detection
The invention provides a database auditing system which comprises a database statement auditing module and a database user behavior auditing module. The database statement auditing module is used for analyzing collected auditing data, obtaining an SQL statement and detecting the obtained SQL statement. The database user behavior auditing module is used for analyzing the collected auditing data, obtaining user behavior and detecting the user behavior. The invention further relates to an auditing method based on the database auditing system. According to the database auditing system and the database auditing method, universality is high, detection efficiency is high, maintenance is convenient, a rule base is updated continuously to ensure that the false detection rate is reduced, the requirements for database safety of different users can be practically met, and the system and the method have the wide application prospect in the database auditing industry.
Owner:北京华电天益信息科技有限公司
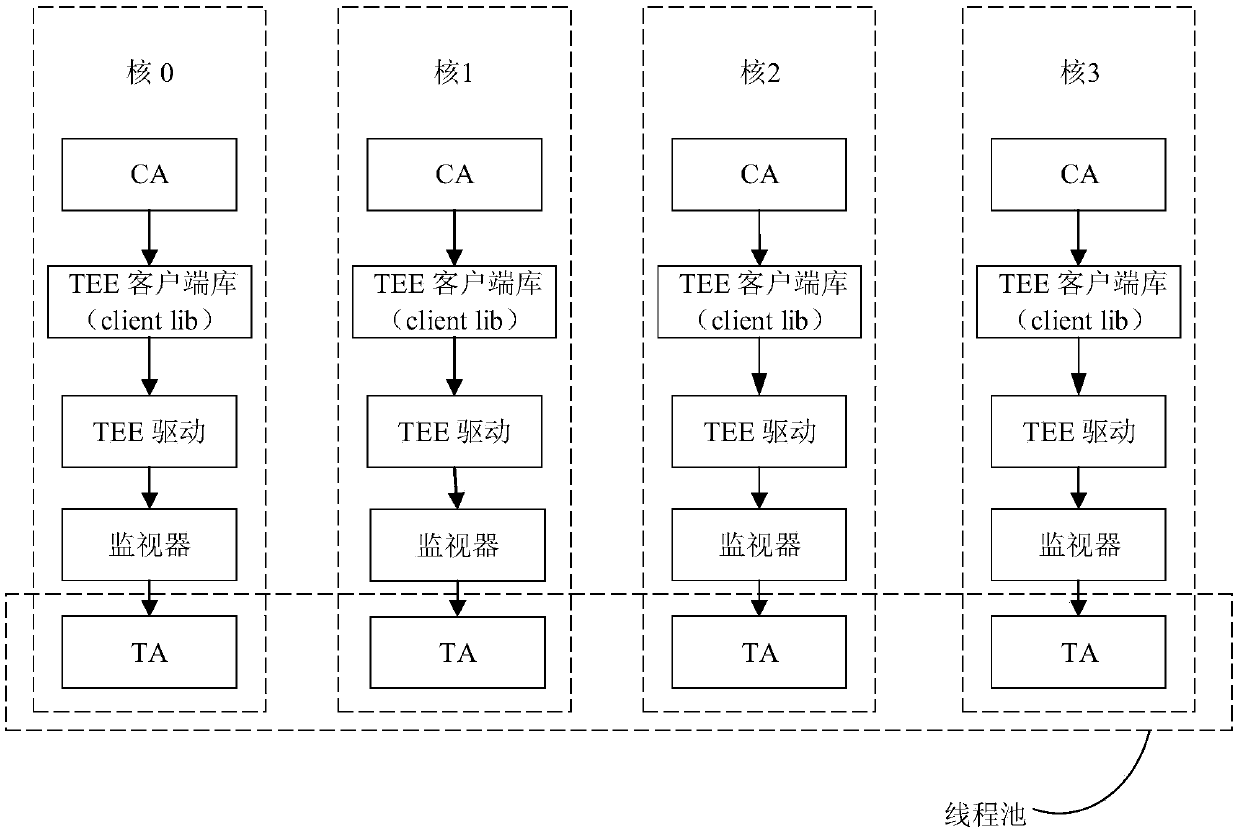
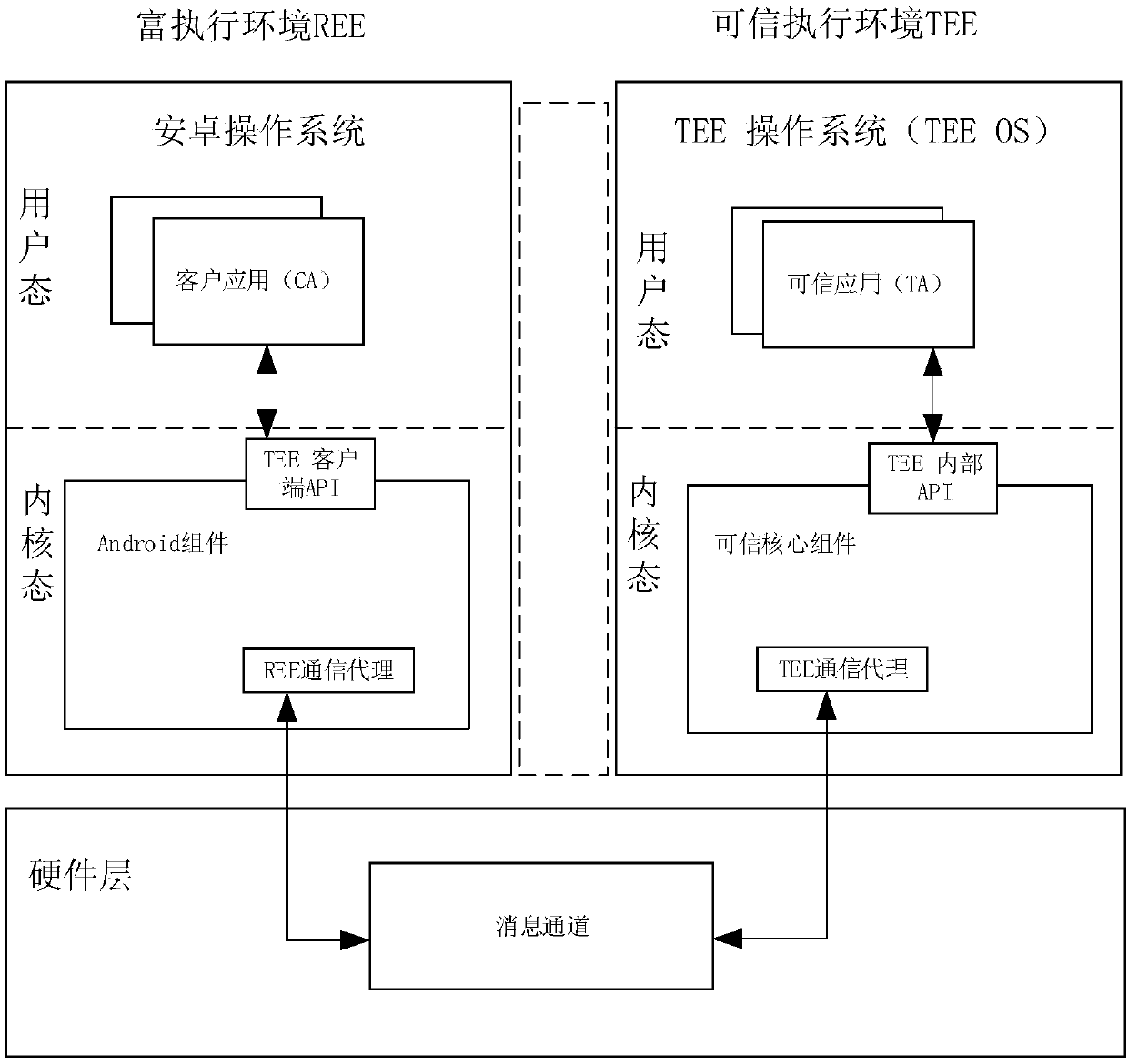
Method, device and system for realizing multi-core parallel at TEE side
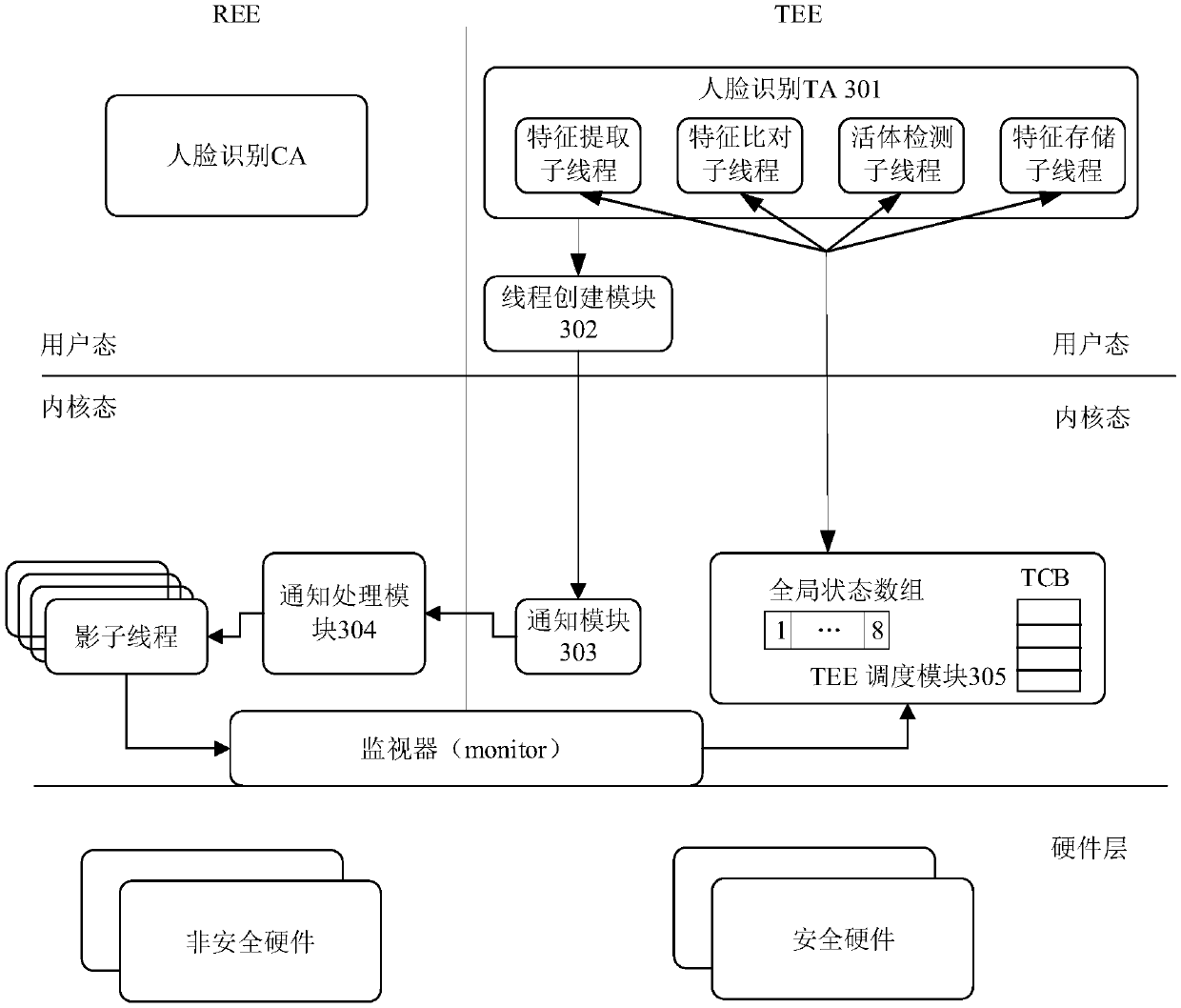
ActiveCN109960582AImplement the callImprove performanceResource allocationInternal/peripheral component protectionParallel computingComputerized system
The invention provides a method and a device for realizing multi-core parallel at a TEE side, a computer system and the like. The method comprises the following steps: a TEE creates a plurality of sub-threads, wherein the sub-threads are used for realizing sub-functions of a TA deployed at a TEE side; for each sub-thread, the TEE triggers a rich execution environment (REE) to generate a shadow thread corresponding to the sub-thread, and the operation of the shadow thread promotes a core running the shadow thread to enter the TEE; and the TEE schedules the created sub-thread to the core where the corresponding shadow thread is located for execution. By utilizing the method, a plurality of service logics in the service with high performance requirements can be operated in parallel in the TEE, and the TEE triggers the REE to generate the thread and automatically enters the TEE side, so that active kernel adding at the TEE side is realized, and the parallel flexibility of the TEE side is improved.
Owner:HUAWEI TECH CO LTD
Dynamic generation and maintenance method of heterogeneous cloud host
ActiveCN107196803AImprove resistance to attackMeet security needsData switching networksSoftware simulation/interpretation/emulationIsomerismsCloud data center
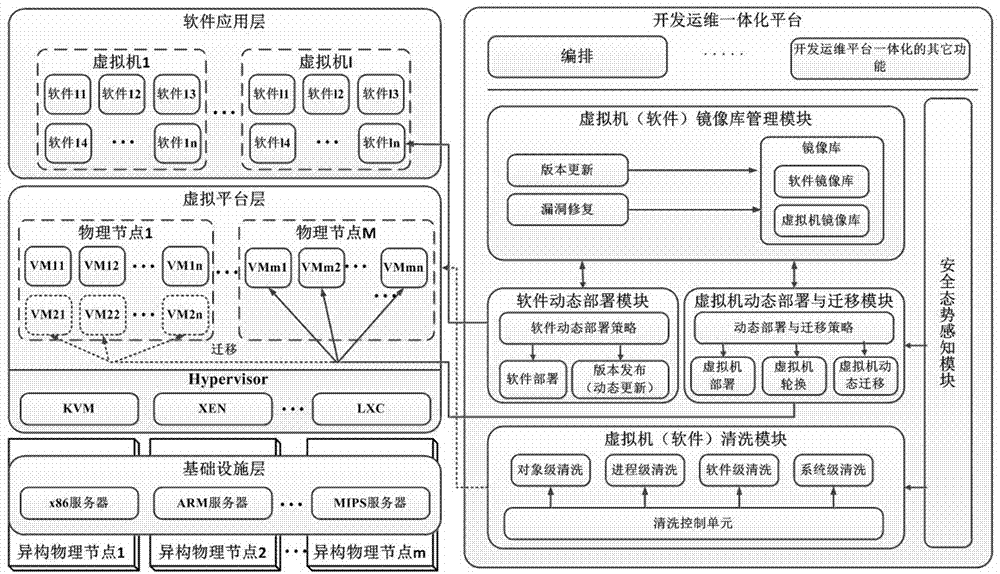
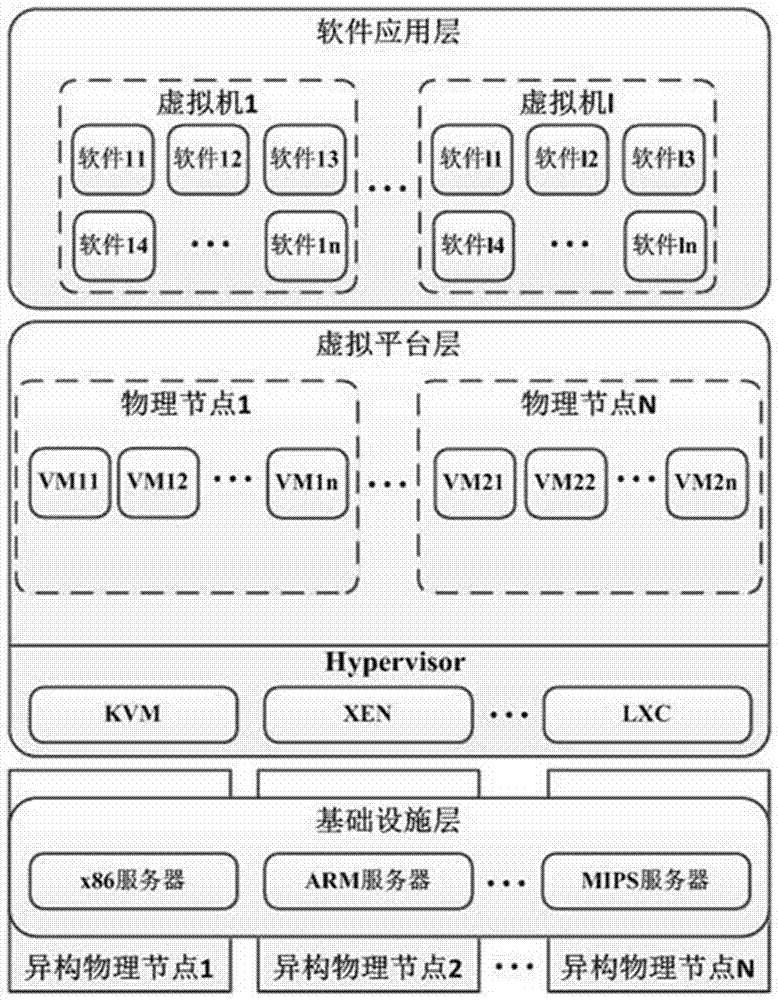
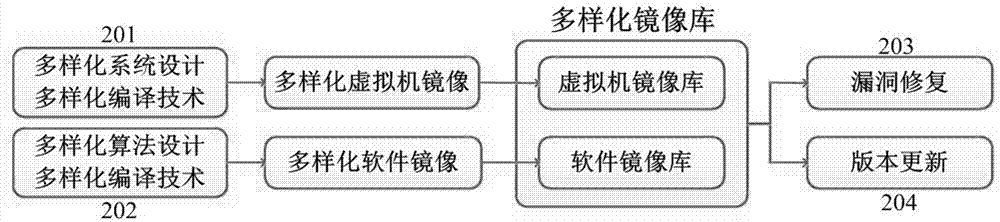
The invention relates to the technical field of network security, and especially relates to a dynamic generation and maintenance method of a heterogeneous cloud host. The method comprises the following steps: 1) a heterogeneous cloud host node whose isomerism is embodied by the diversified physical facilities, virtual machines and software; 2) a mirror image library management system comprising creating diversified virtual machines and software mirror images; 3) dynamic deployment of a heterogeneous virtual machines and software: when the virtual machine or the software is instantiated, generating virtual machines or software of different versions according to physical nodes and application attributes, and deploying the virtual machines or software on the physical nodes; 4) dynamic virtual machine migration mechanism: a development operation and maintenance unit performs security posture estimation on the current virtual machine and its operation environment, and performs initiative migration on the virtual machine according to a strategy; and 5) a dynamic virtual machine and software cleaning mechanism: cleaning the online virtual machines according to the security posture or periodically. By adoption of the method, the anti-attack ability of a cloud data center is improved, and higher security requirements of users and providers for cloud services and infrastructure are satisfied.
Owner:THE PLA INFORMATION ENG UNIV
Data storage method and equipment base on flash memory, as well as data fetch method and apparatu
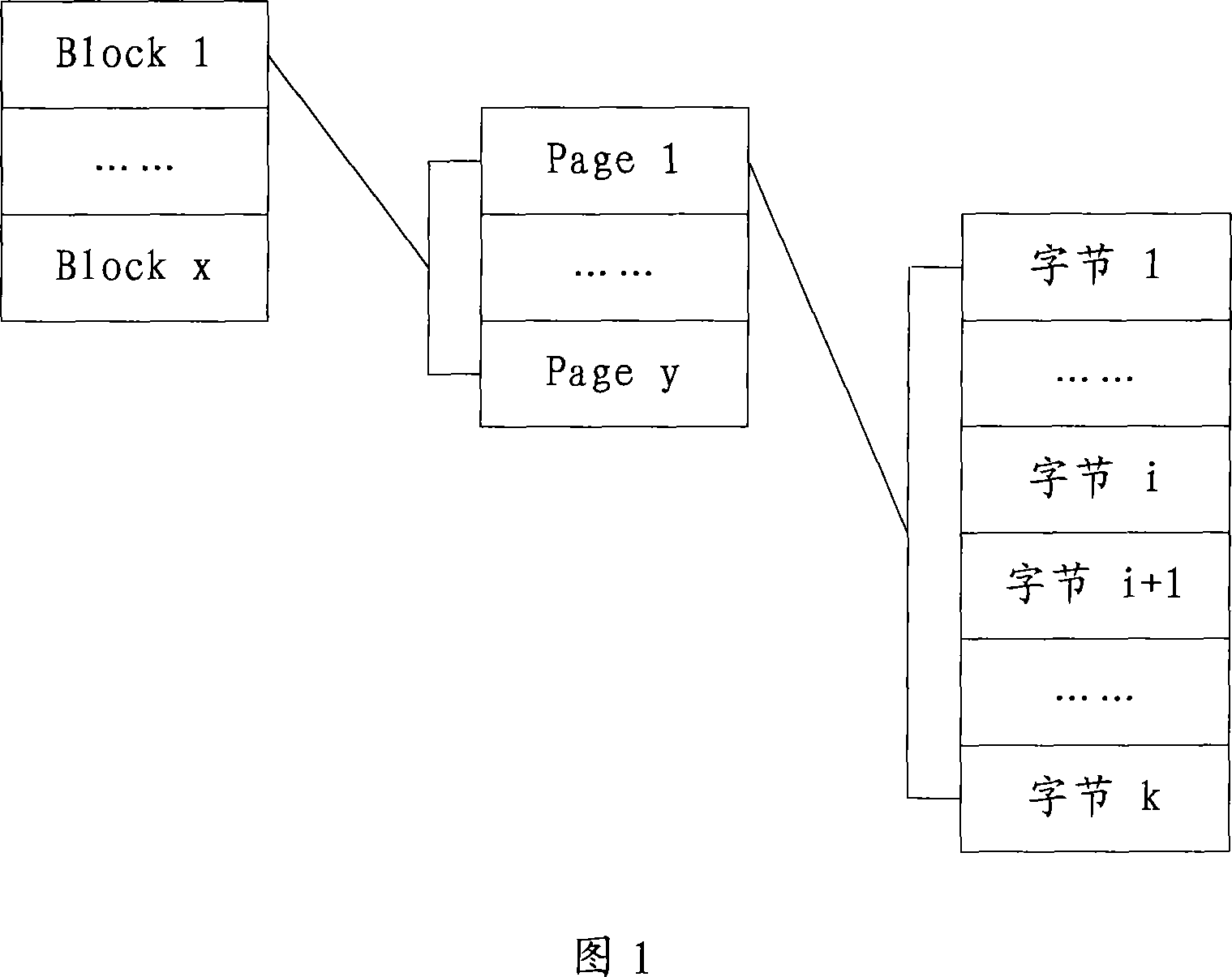
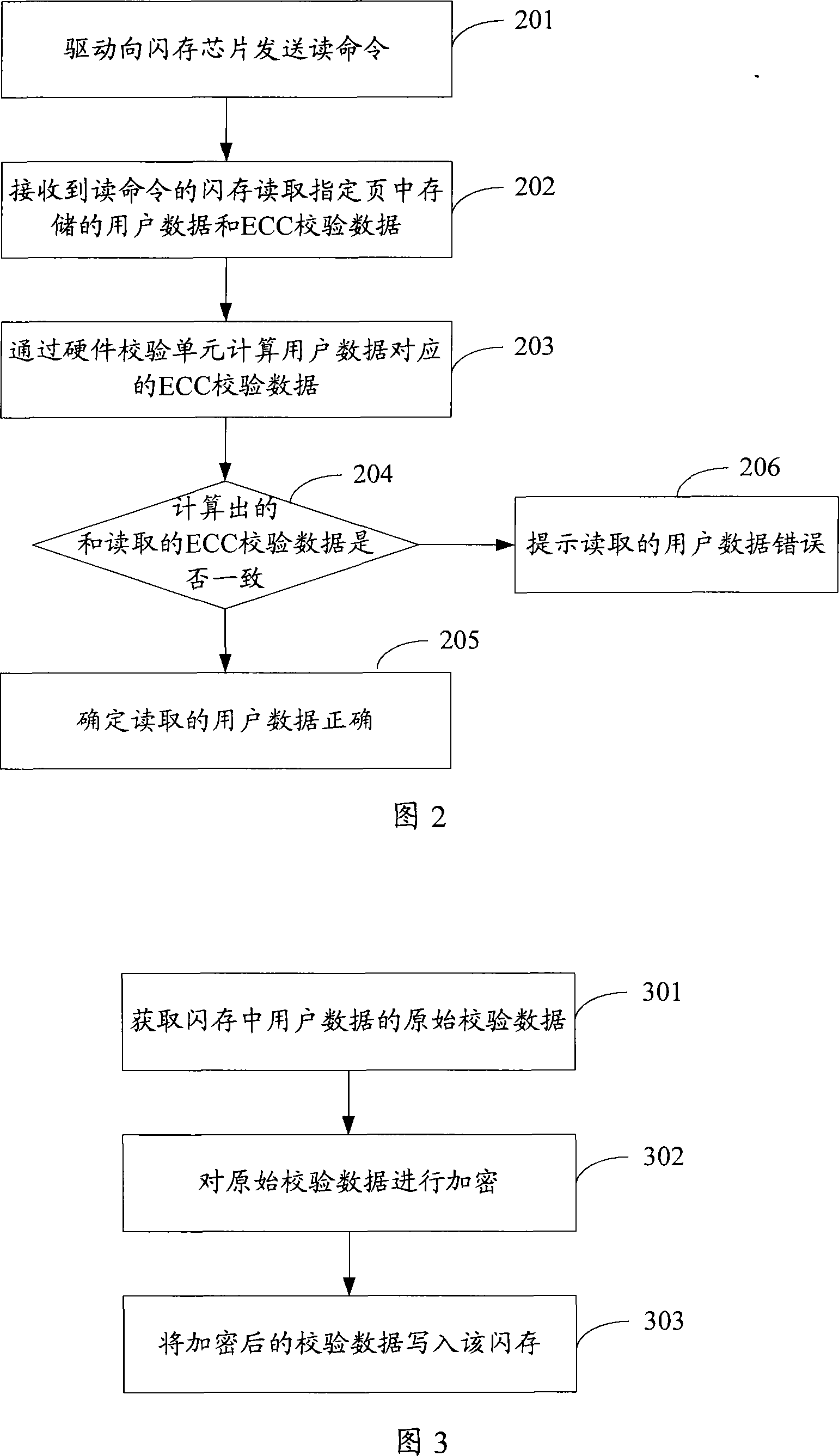
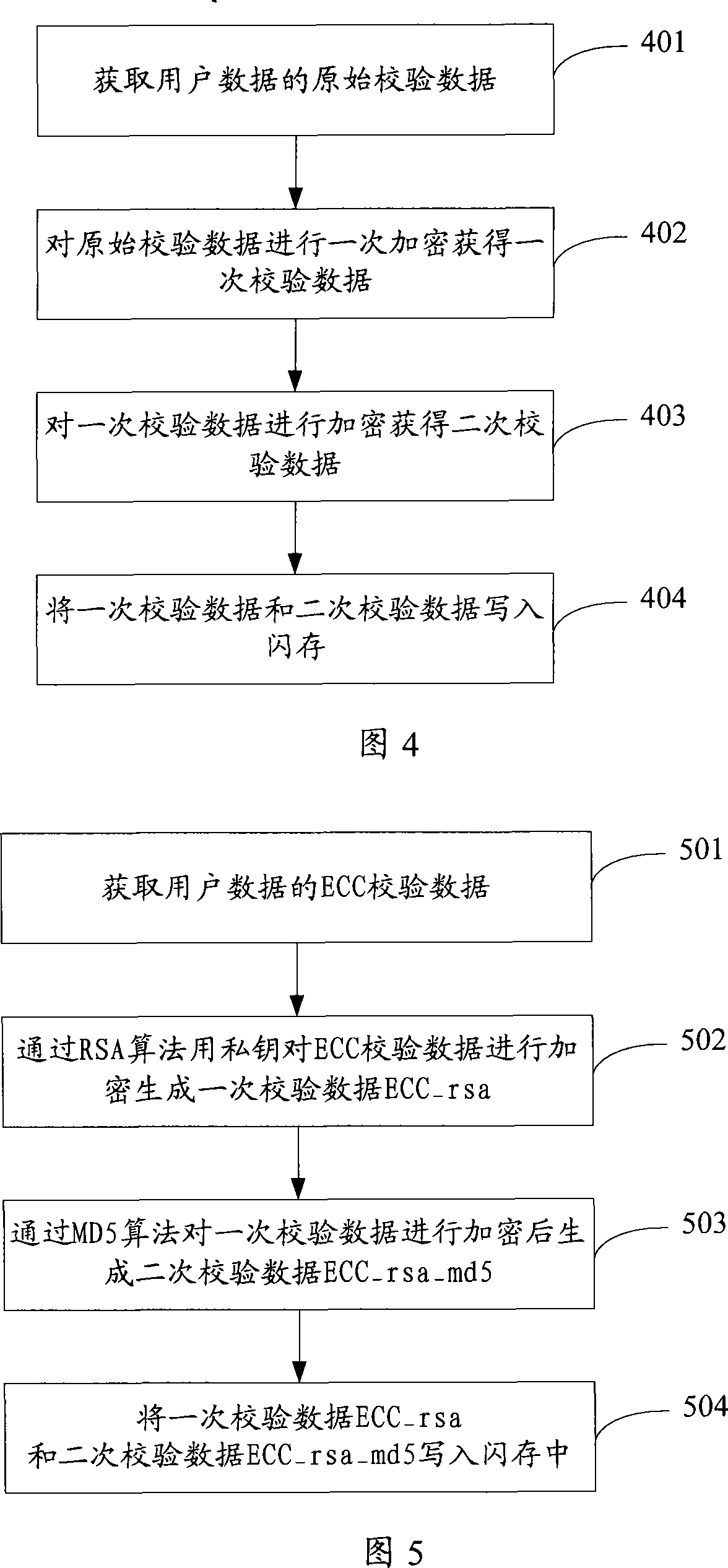
ActiveCN101231622AImprove securityAvoid the problem of illegal copyingUnauthorized memory use protectionData storeFlash memory
The invention discloses a data storage method which is based on a flash memory. The method comprises the following steps that: the original calibration data of user data in the flash memory are obtained; the original calibration data are encrypted, and the encrypted calibration data are written into the flash memory. The invention also discloses a data storage device which is based on the flash memory, as well as a data reading method and a data reading device. Applying the data storage method and the data reading method of the invention, the security of the user data in the flash memory is effectively improved through encrypting the original calibration data, the problem that the user data are illegally copied due to the tampering of the original calibration data is avoided, and the requirement to the security of the flash memory is greatly satisfied.
Owner:HUAWEI DEVICE CO LTD
Safety on-demand supply method and system, and service type acquisition method
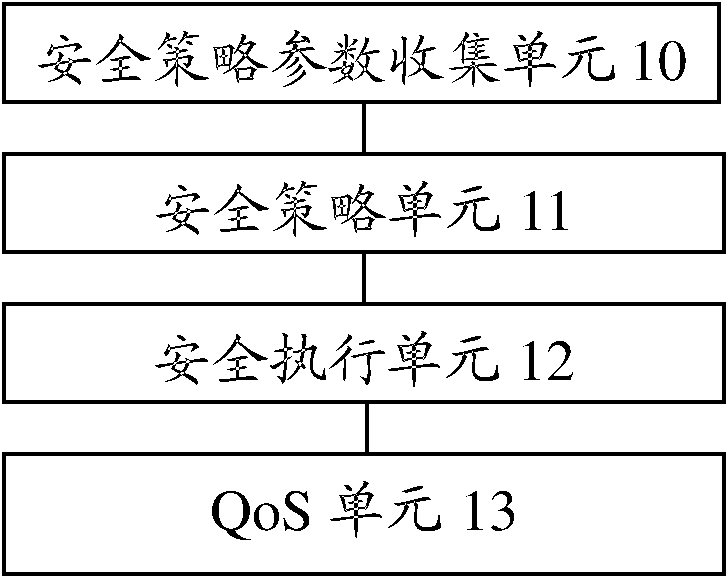
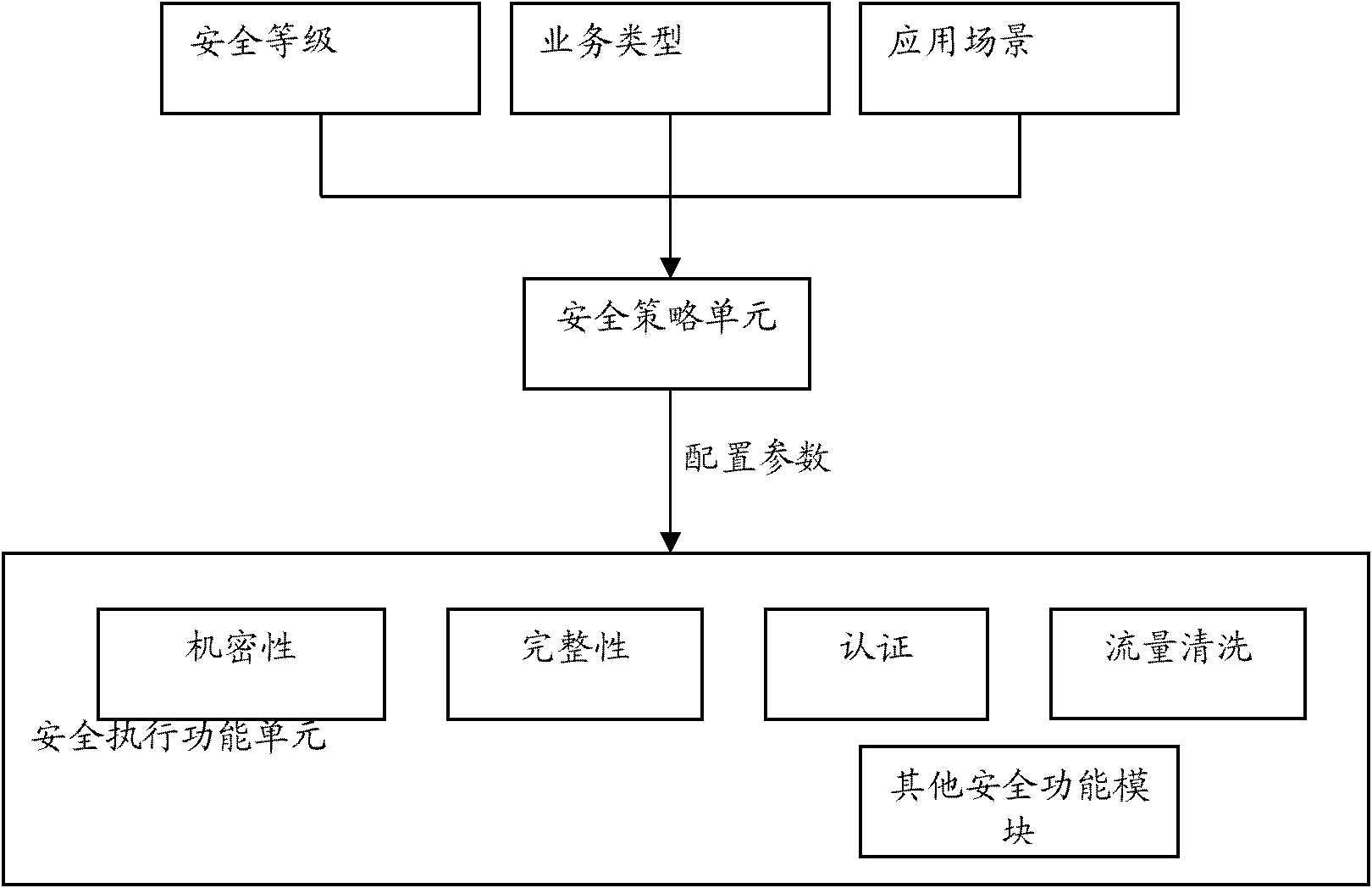
ActiveCN102932382AImprove experienceMeet security needsTransmissionSecurity arrangementPersonalizationQuality of service
The invention discloses a safety on-demand supply method. The method comprises the following steps of: determining configuration parameters of a safety function module according to a safety level which is set for service request by a user, an application scene in which a user terminal is positioned, and / or service type; and configuring the safety function module according to the configuration parameters, and safely protecting service data of the user. The invention also discloses a service type acquisition method for safely protecting a specific user and / or a service. Service identifiers of data are acquired by using a service type classification function of a quality of service (QoS) function module, so the specific user and / or the service are safely protected. The invention also discloses a safety on-demand supply system and the service type acquisition method. By the invention, according to safety requirements of different users on different services, different service safety guarantee can be provided. The safety on-demand supply system meets the safety requirements of various users and various services, personalized safety guarantee is provided for the users, and a user experience effect is improved.
Owner:ZTE CORP
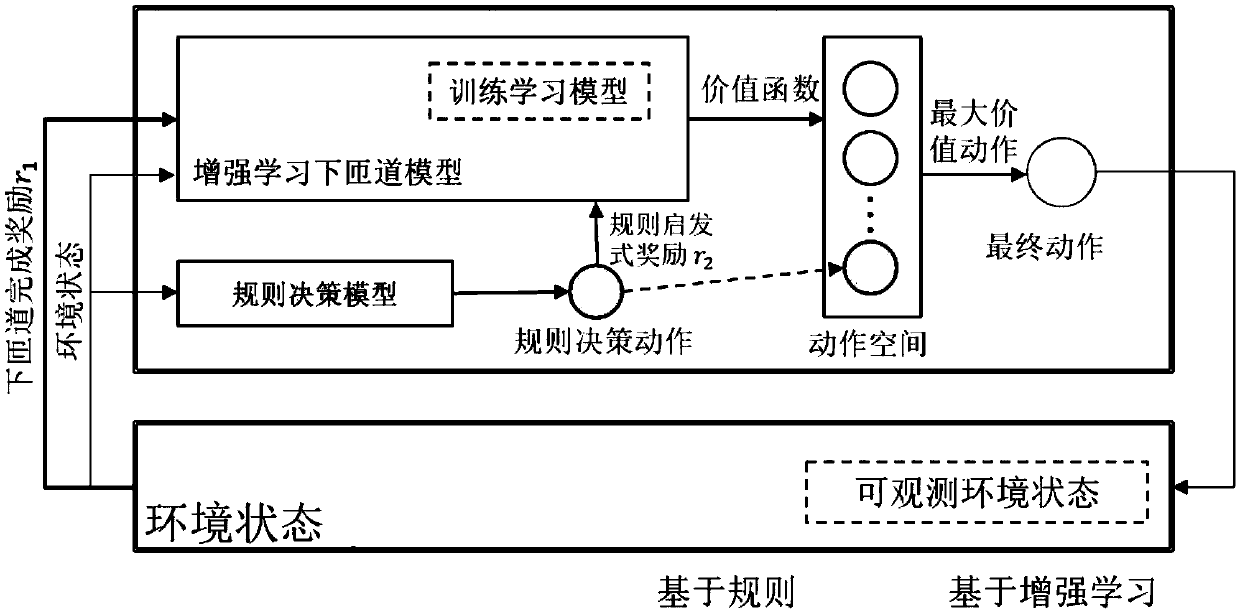
Rule and learning model-based highway leaving method for driverless cars
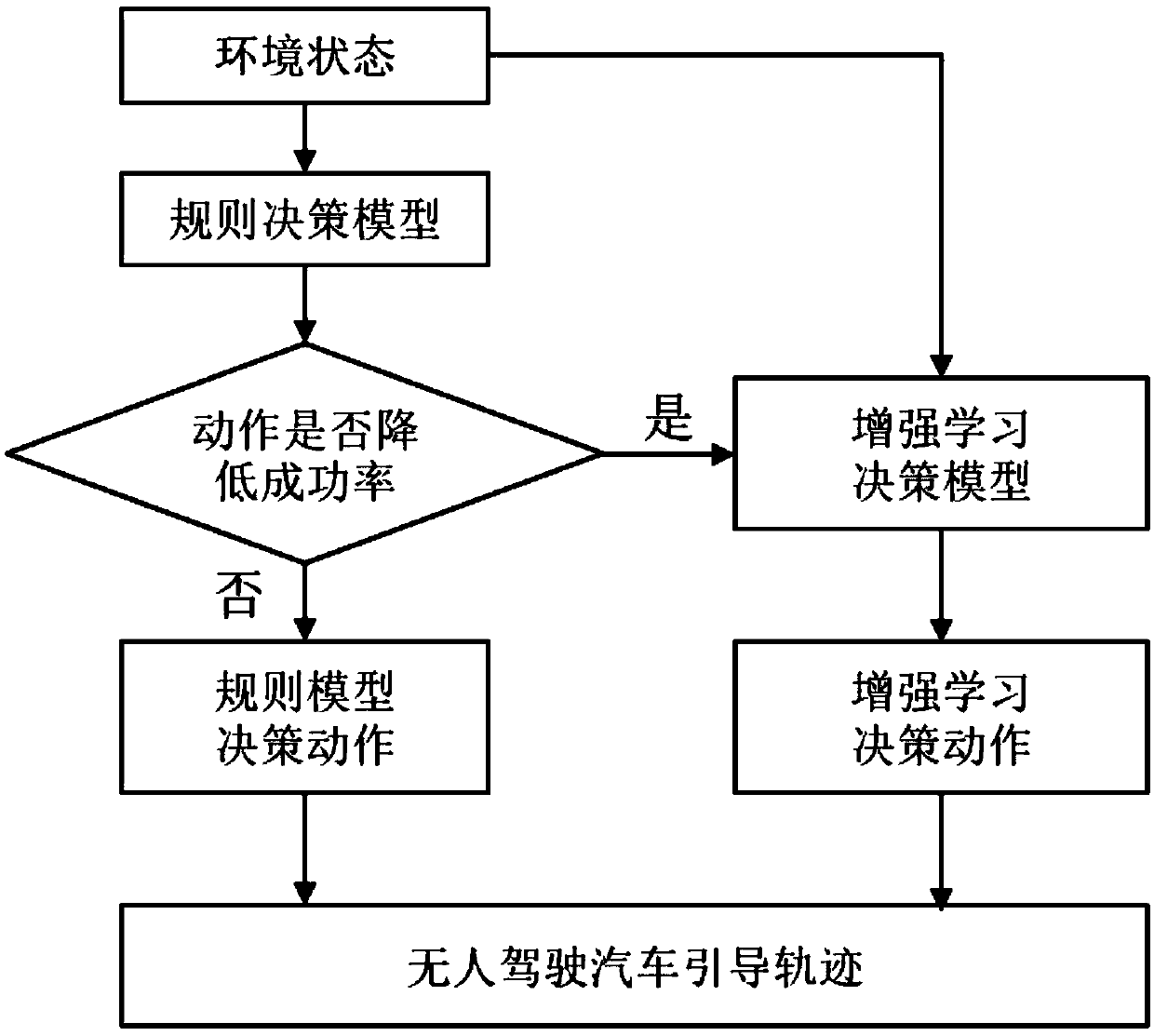
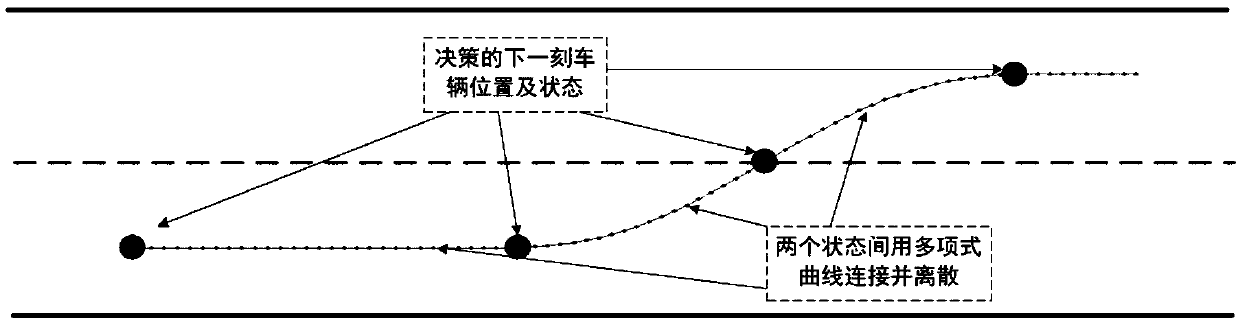
ActiveCN109598934AIncrease success rateMeet security needsDetection of traffic movementPosition/course control in two dimensionsDecision modelDecision-making
The invention relates to a rule and learning model-based highway leaving method for driverless cars. The method comprises the steps of: in a process that a driverless car runs on a highway, generatingan off-ramp motivation at a distance before a ramp according to a navigation system, trying to get off the ramp by utilizing a rule model, judging whether off-ramp decided by a rule-based decision making model reduces the success rate or not, if the judging result is negative, adopting an action decided by the rule model, and otherwise, entering the next step; and establishing a rule and reinforcement learning mixed hybrid decision making model and a training method thereof on the basis of a framework of reinforcement learning, wherein the hybrid decision model is capable of adopting a rule model for running when being far away from the ramp, and utilizing the reinforcement learning decision making model to adjust the vehicle action according to off-ramp urgency in the process of drivingto the ramp. The method is capable of enhancing the running efficiency and stability of driverless cars in the off-ramp process, and realizing efficient and high-stability off-ramp decision making ofdriverless cars under the condition that the perception range is limited and the environment vehicles are difficult to predict.
Owner:北京超星未来科技有限公司
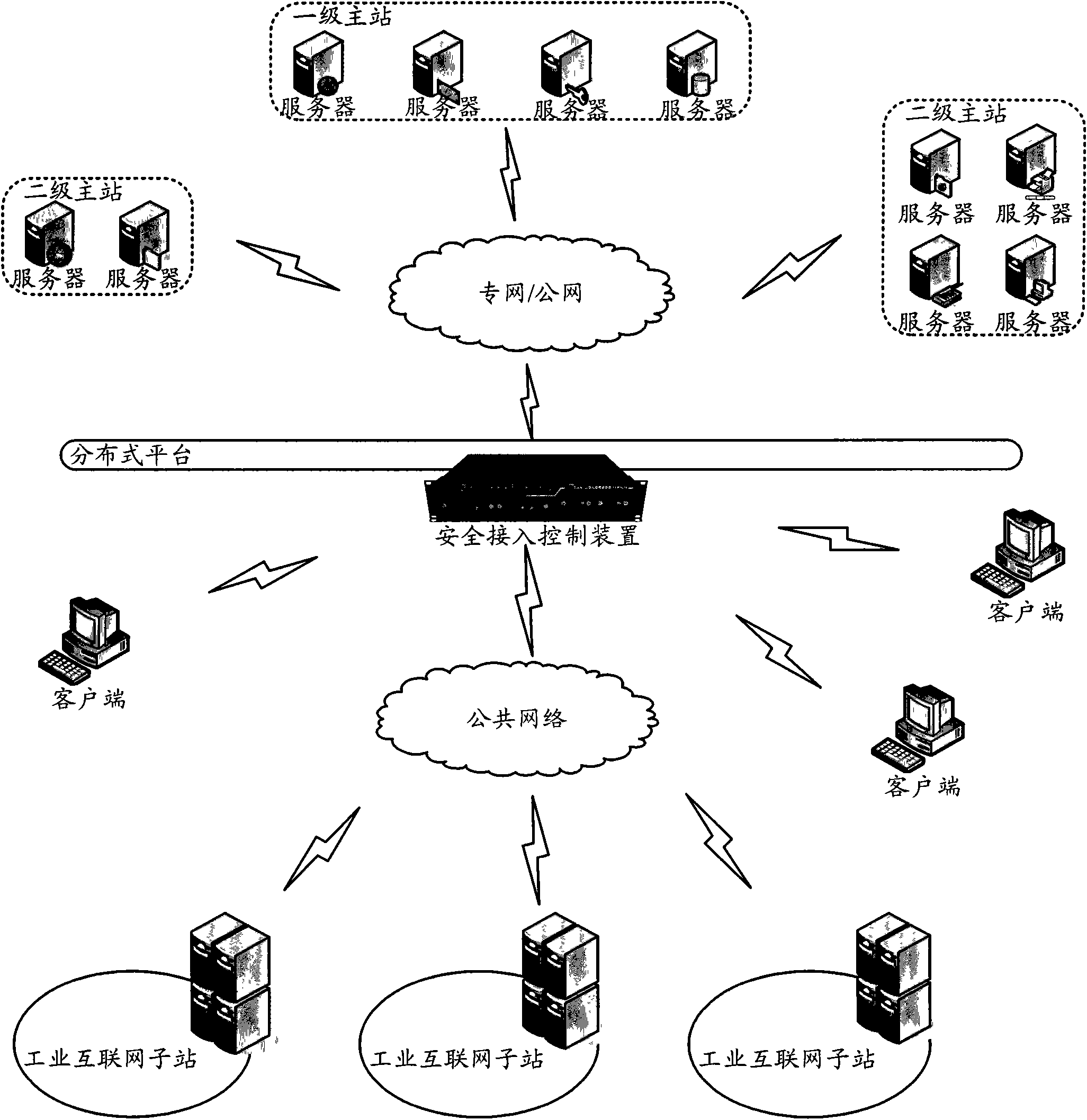
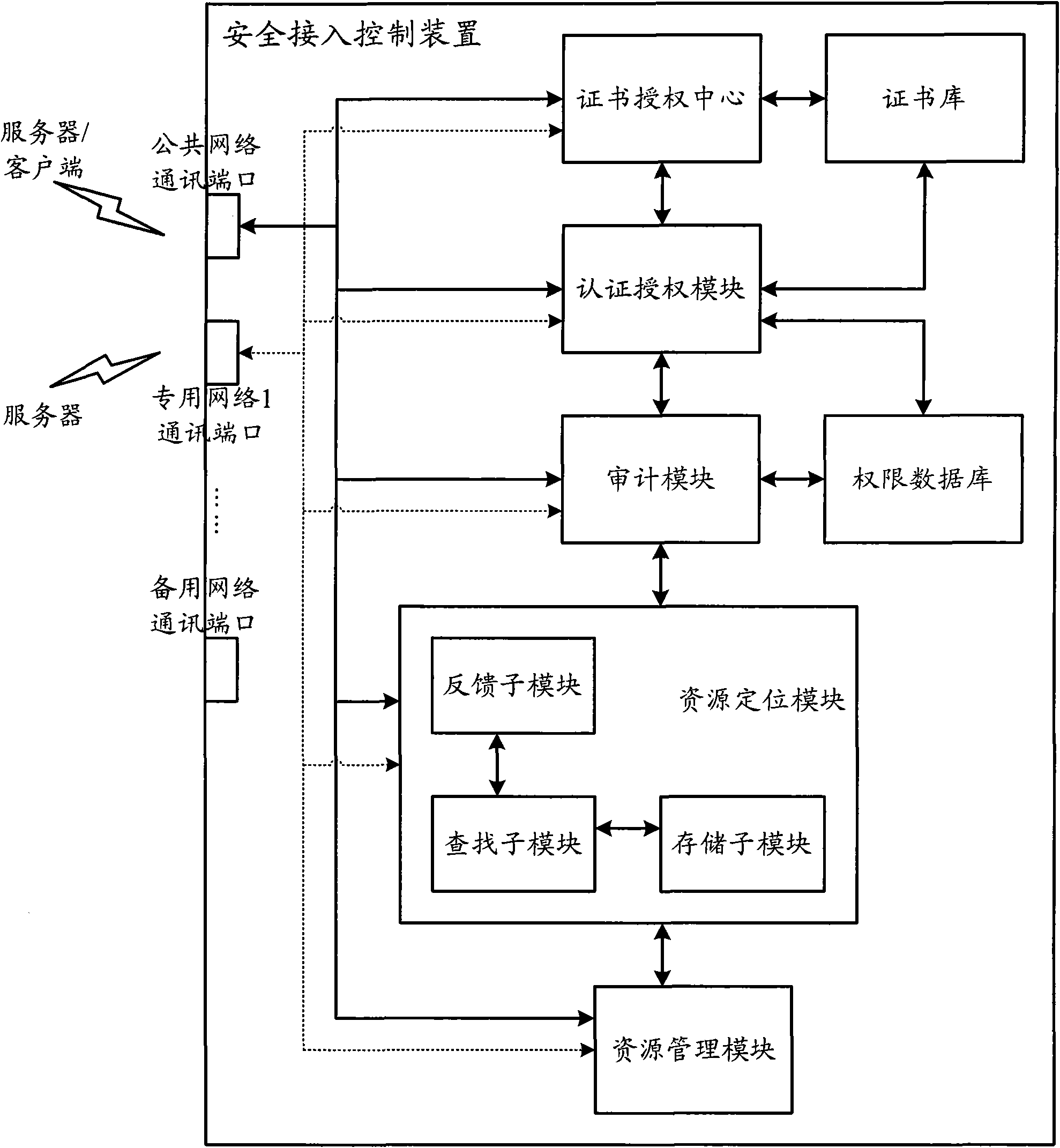
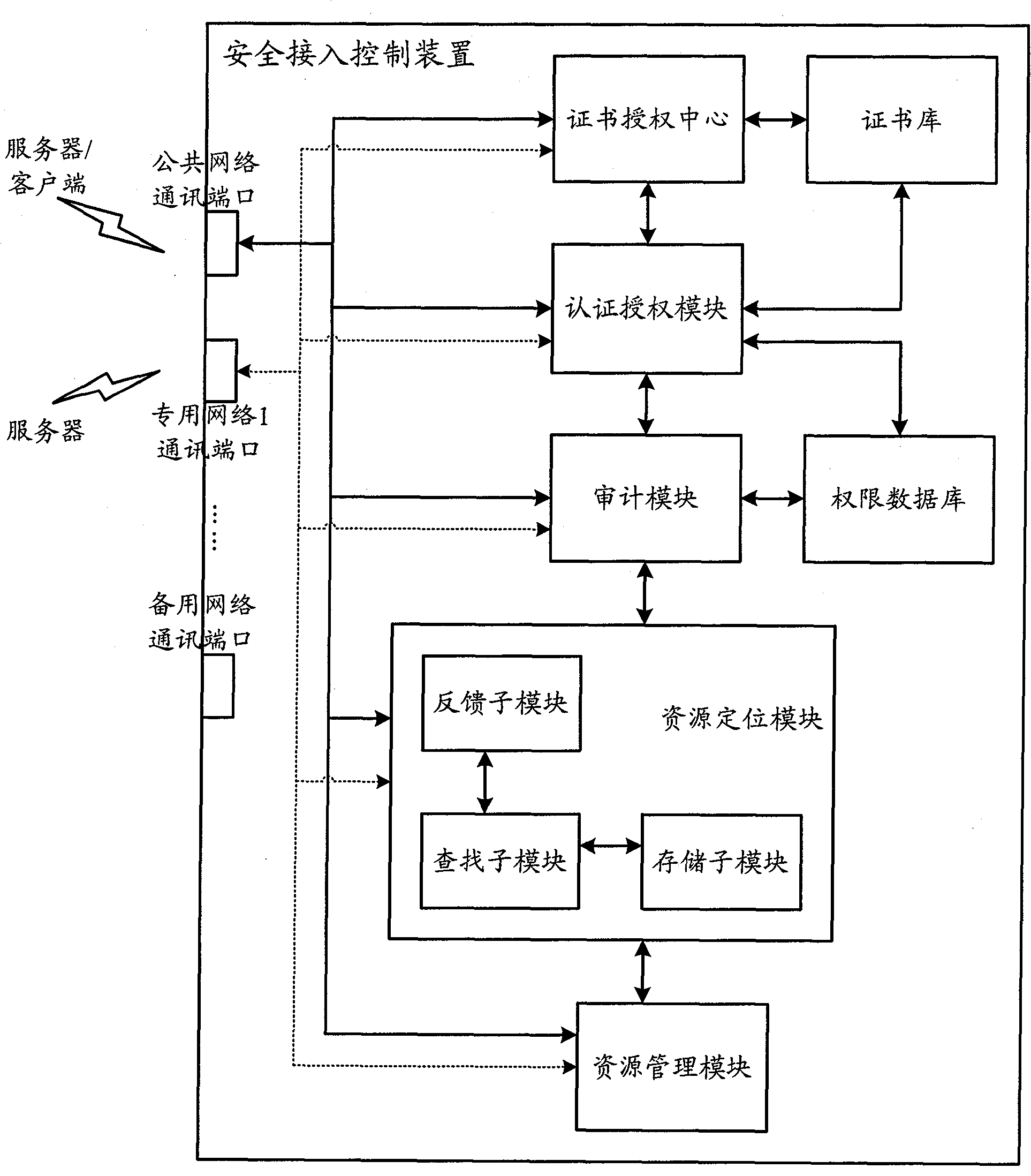
Industrial Internet distributed system safety access control device
ActiveCN102487383AGuaranteed legalityPrevent theftUser identity/authority verificationThe InternetIndustrial Internet
The invention discloses an industrial Internet distributed system safety access control device. The device integrates a module which is used to carry out authentication and authorization to identities and access operations of a user and a server, the module which is used to audit the access operations of the user and the server and the module which is used to carry out uniform resource positioning to object resources accessed by the user and the server. Identity security and authority validity of the user or the server which access to the industrial Internet distributed system and acquire information / service can be effectively ensured. In addition, the user and the server in the industrial Internet do not need to know an actual storage position of the needed object resources. Through a uniform resource positioning platform of the distributed system, the corresponding server can be positioned and the needed object resources can be acquired. A demand in a distributed environment can be rapidly and conveniently satisfied.
Owner:ASAT CHINA TECH
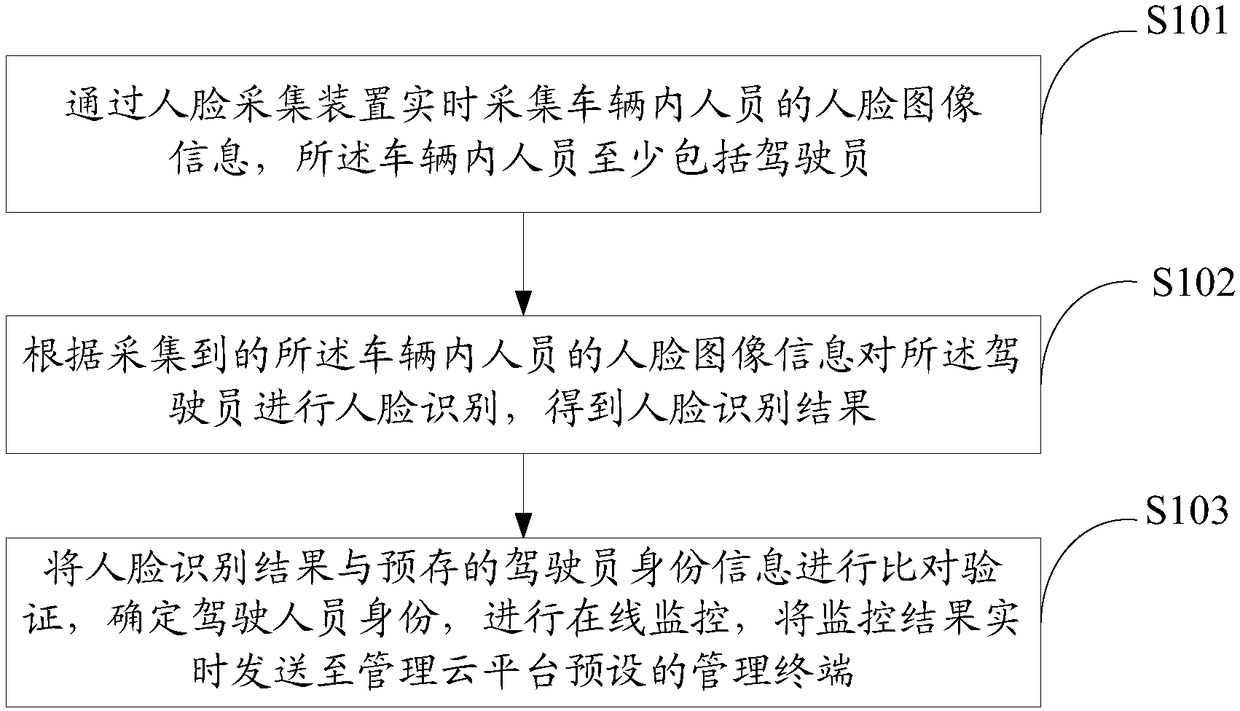
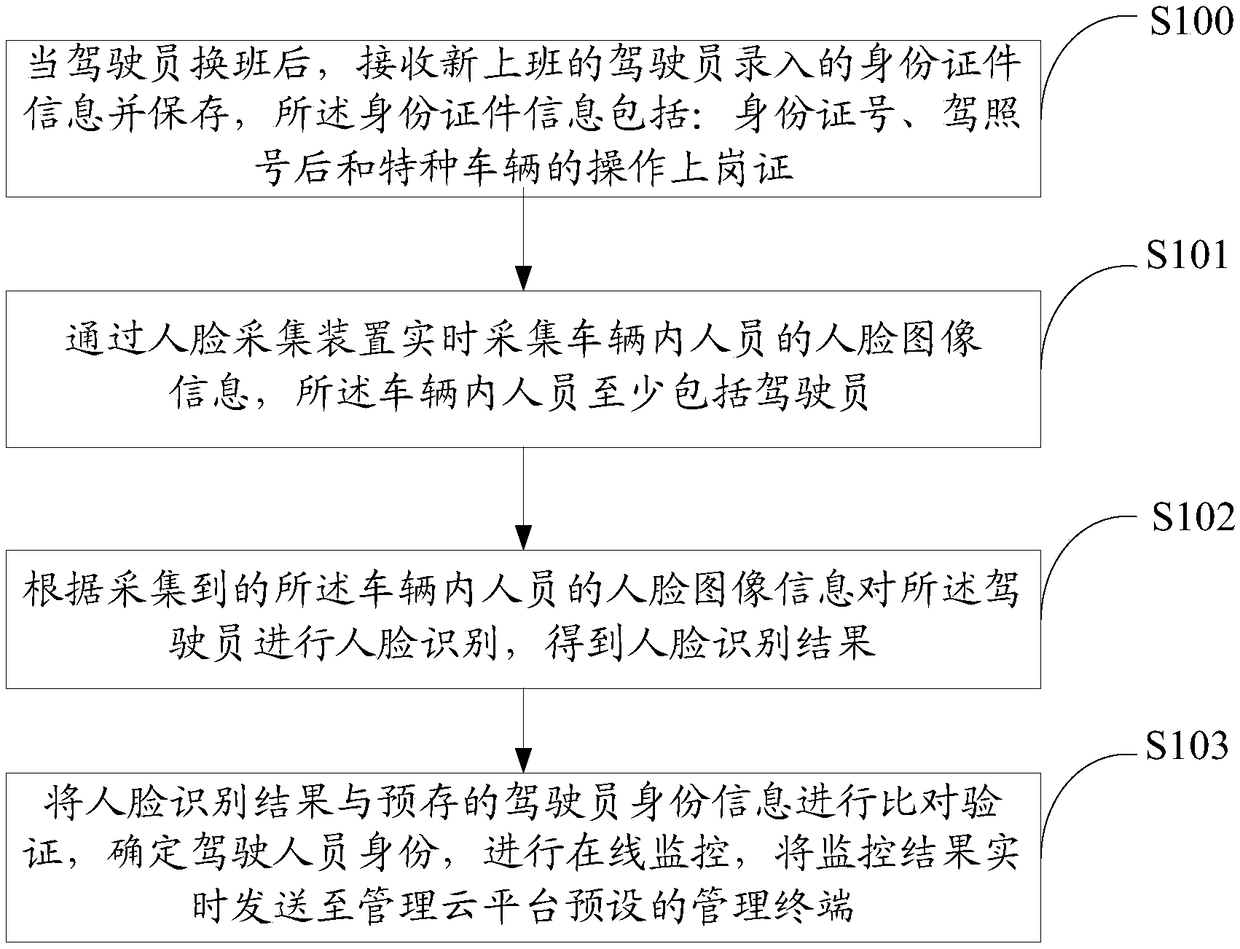
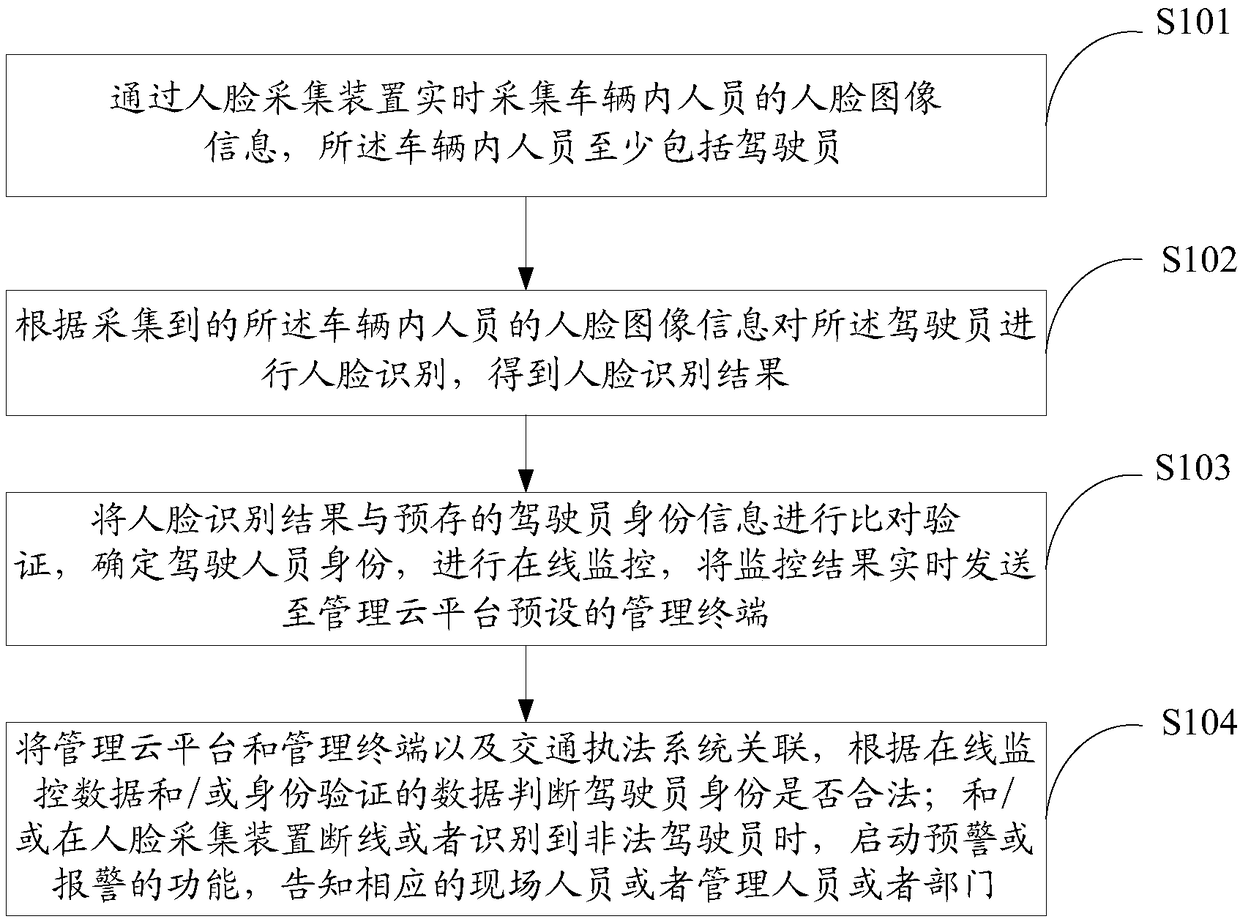
Online monitoring method and device for identities of personnel in vehicle, and storage medium
ActiveCN108304830AEasy to detectImprove efficiencyCharacter and pattern recognitionDriver/operatorIn vehicle
The invention discloses an online monitoring method and an online monitoring device for identities of personnel in a vehicle, and a storage medium. The online monitoring method comprises the steps of:acquiring face image information of the personnel in the vehicle in real time by means of a face acquisition device, wherein the personnel in the vehicle at least comprises a driver; and performingface recognition on the driver according to the acquired face image information of the personnel in the vehicle, transmitting a recognition result and an acquired face picture to a management cloud platform in real time through wireless communication, querying personnel identity in a database and performing personnel identity online monitoring by means of the management cloud platform, and transmitting a monitoring result to a preset management terminal of the management cloud platform in real time. The online monitoring method, the online monitoring device and the storage medium realize the flexible and convenient real-time online monitoring of the identities of the driver and passengers in the vehicle, improve the intelligence and efficiency of personnel detection, satisfy the security requirements in special occasions, can completely eradicate the substitution of the driver in the midway, can analyze the driving time of a certain driver by using online data, and performs fatigue driving early warning.
Owner:XIAN IRAIN IOT TECH SERVICES CO LTD
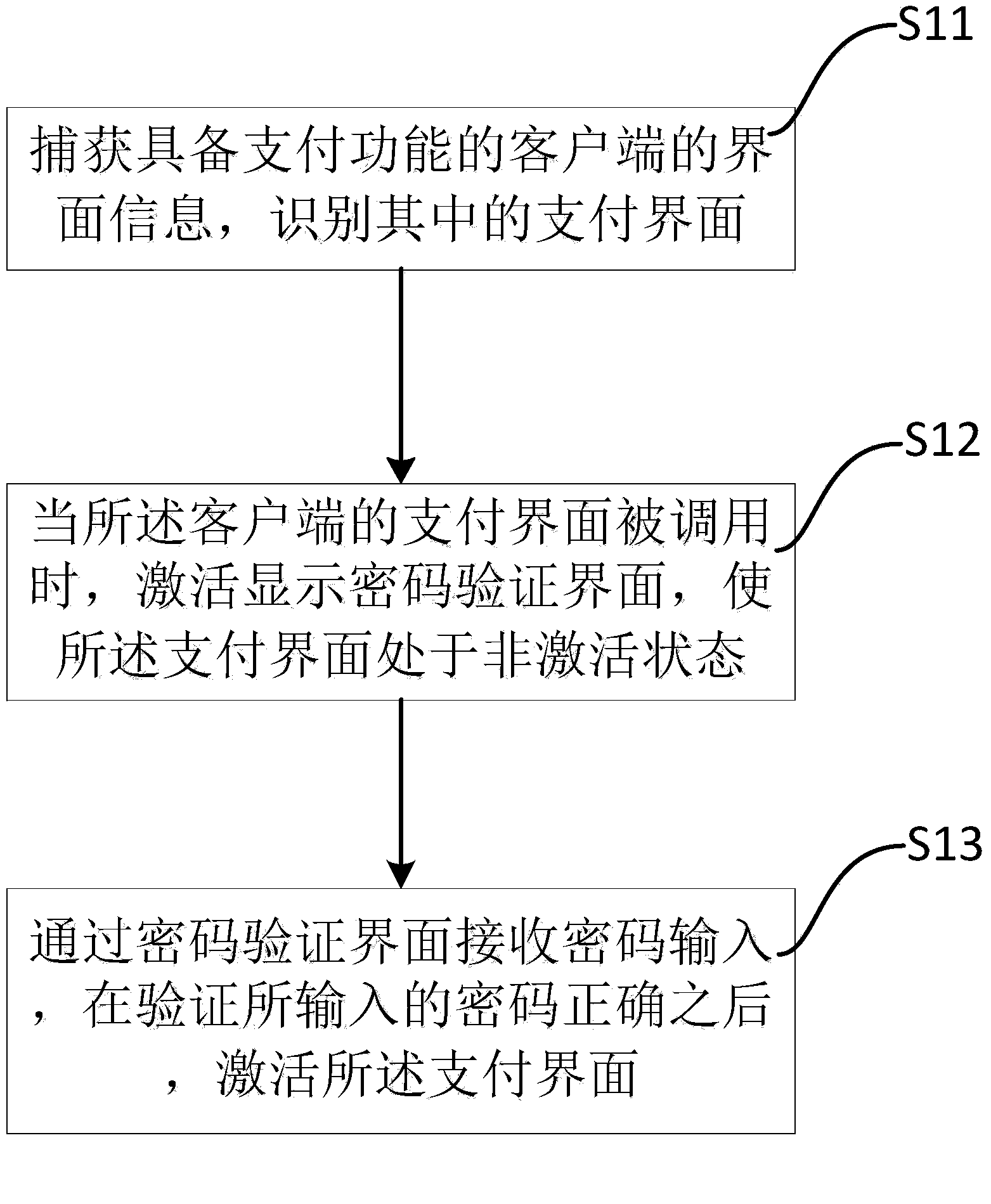
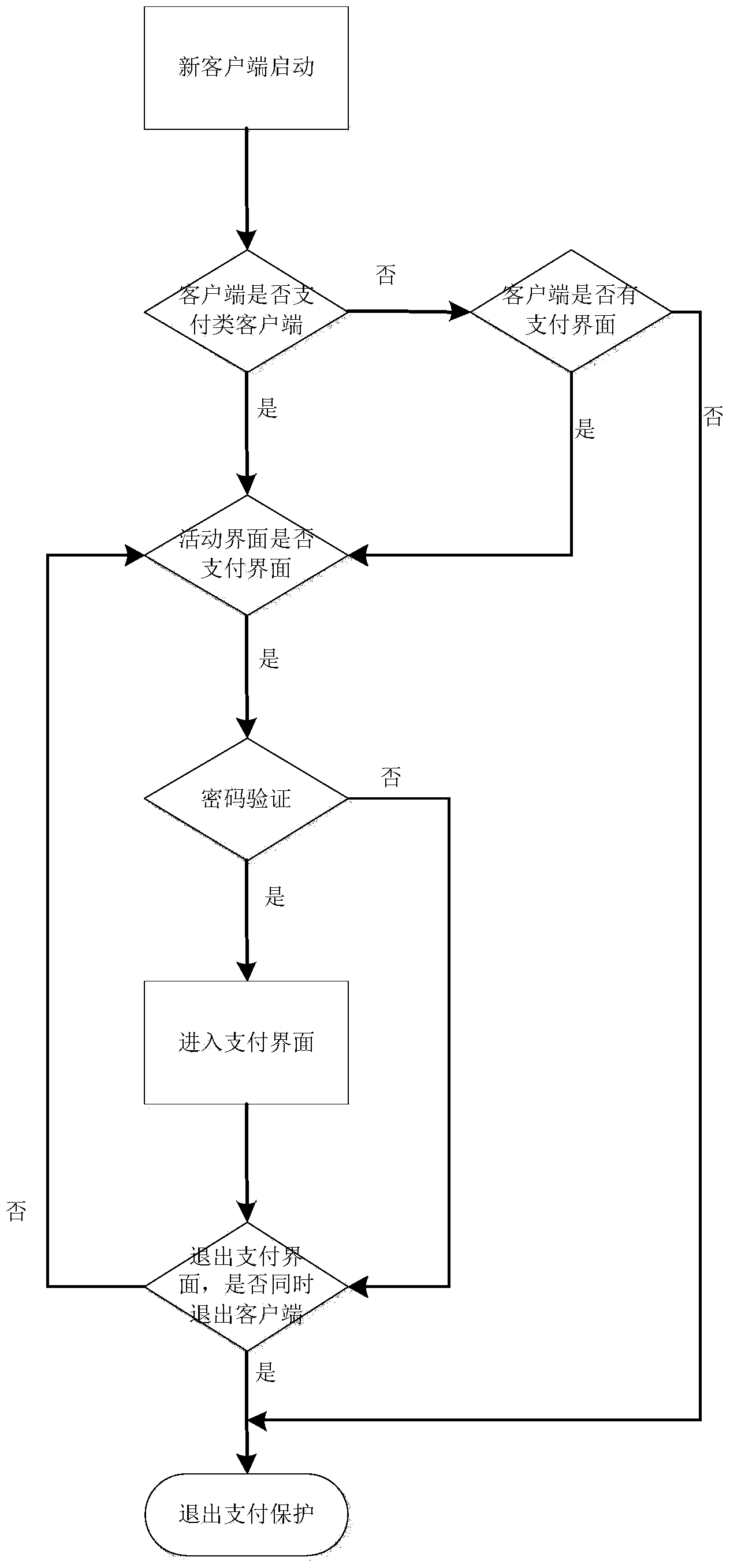
Mobile terminal payment interface protection method and device
ActiveCN104376274AHigh degree of intelligenceFree from pop-up harassmentDigital data protectionDigital data authenticationPaymentPassword
The invention discloses a mobile terminal payment interface protection method. The method comprises the following steps that interface information of a client terminal having a payment function is captured, and a payment interface in the interface information is recognized; when the payment interface of the client terminal is called, a password authentication interface is activated and displayed, so that the payment interface is in an inactive state; password input is received through the password authentication interface, and the payment interface is activated when an input password is authorized to be correct. The invention further discloses a mobile terminal payment interface protection device which can implement the method. The mobile terminal payment interface protection method and device concretize recognition for payment scenes to the active interface of the client terminal, namely make recognition for payment scenes be corresponding to active components of the client terminal, improve the intelligent degree of recognition and can be applied to non-payment type application programs which are compatible with the payment function.
Owner:BEIJING QIHOO TECH CO LTD
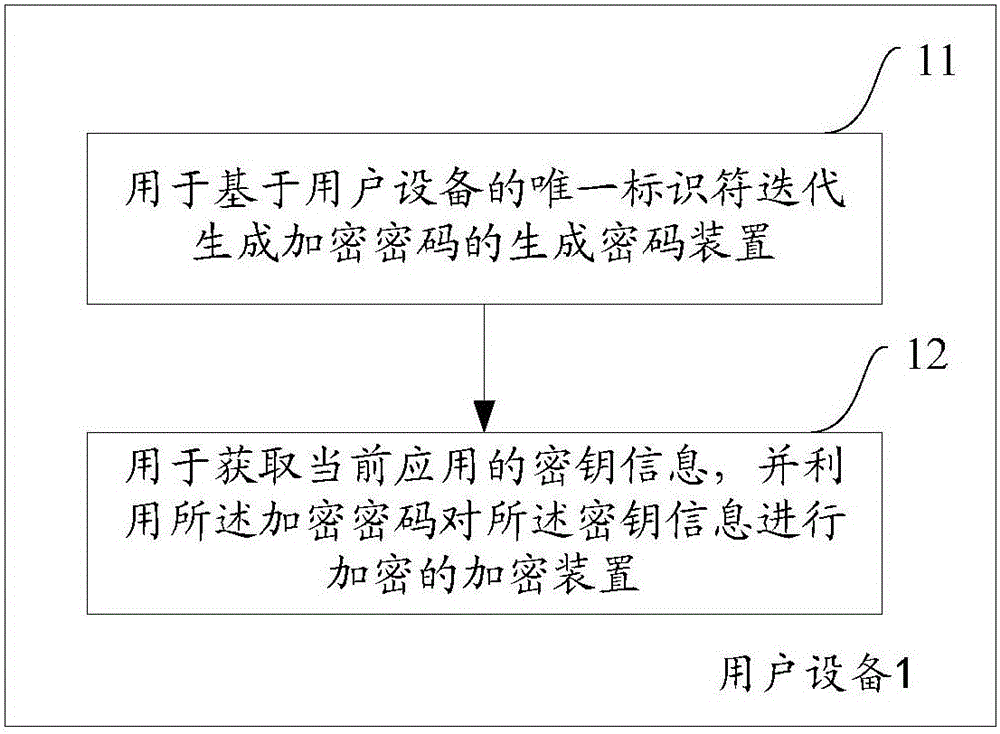
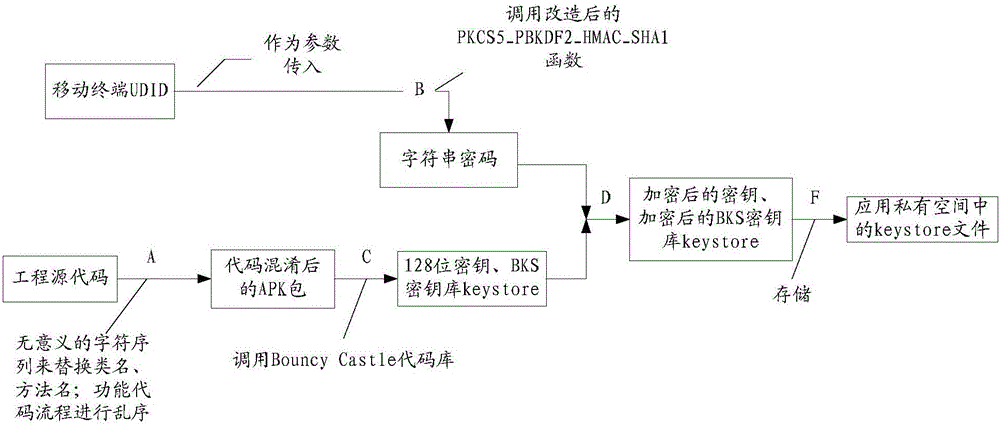
Method and device for secret key generation and corresponding decryption
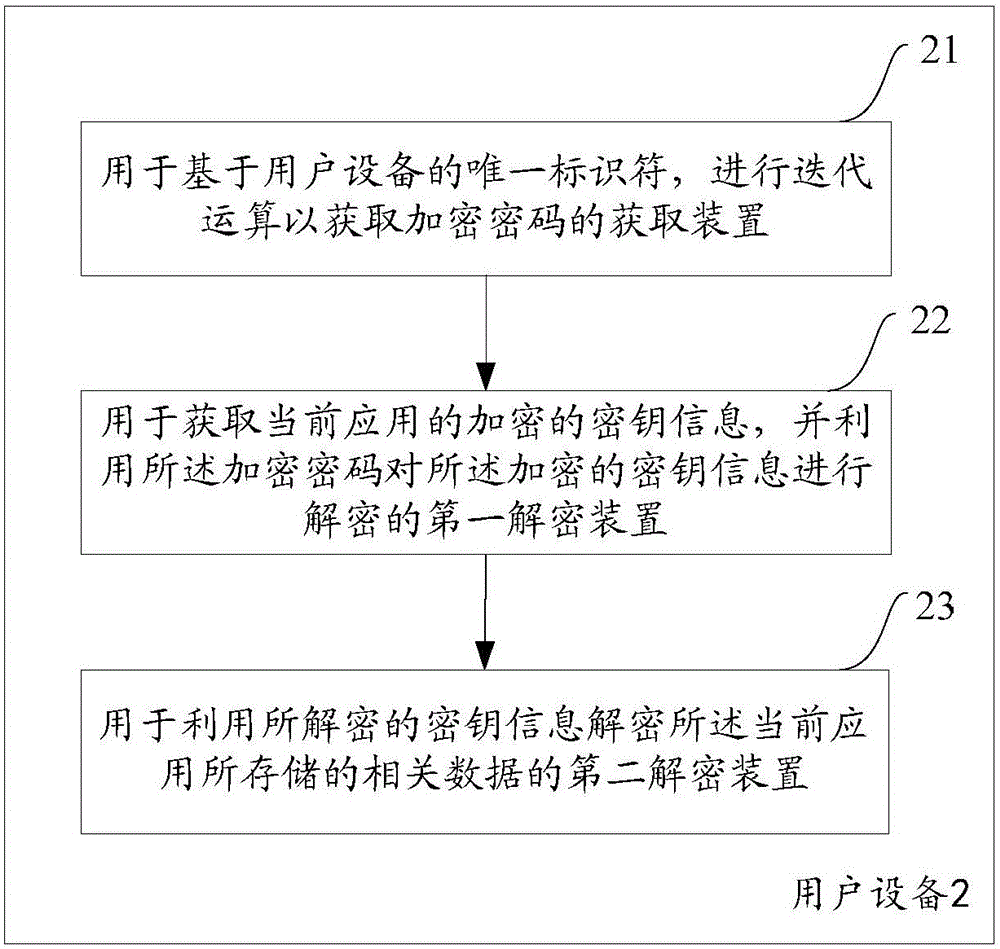
ActiveCN105681039AMeet security needsSatisfy Application BindingKey distribution for secure communicationSecurity arrangementPasswordUnique identifier
The invention aims to provide a method and device for secret key generation and corresponding decryption. The method comprises the steps that: an encryption password is generated in an iterative manner based on a unique identifier of user equipment; current applied secret key information is obtained and the encrypted password is utilized to encrypt the secret key information, so that the secret key can only be called by a specific application and cannot be called by other applications or terminals, which meets the requirements of application binding and device binding; iterative calculation is performed to obtain the encrypted password based on the unique identifier of the user equipment when the user equipment starts a current application; the encrypted secret key information of the current application is obtained, and the encrypted password is utilized to decrypt the encrypted secret key information; and the encrypted secret key information is utilized to decrypt relevant data stored in the current application, so that the secret key is only enabled to be used when the user uses the application, and the secret key security requirement approved by the user is met.
Owner:SUNINFO INFORMATION TECH
Multi-network environment isolation method and terminal
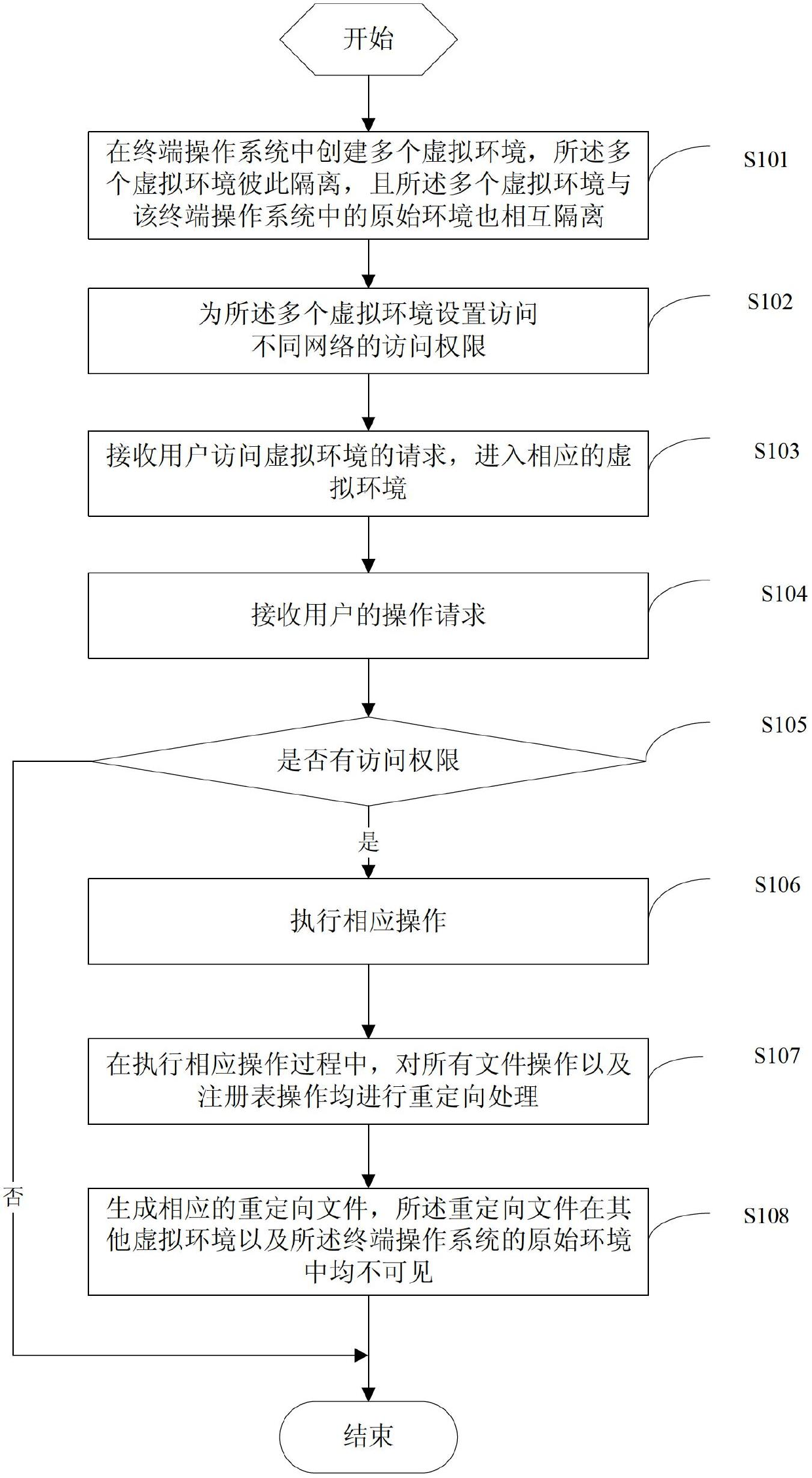
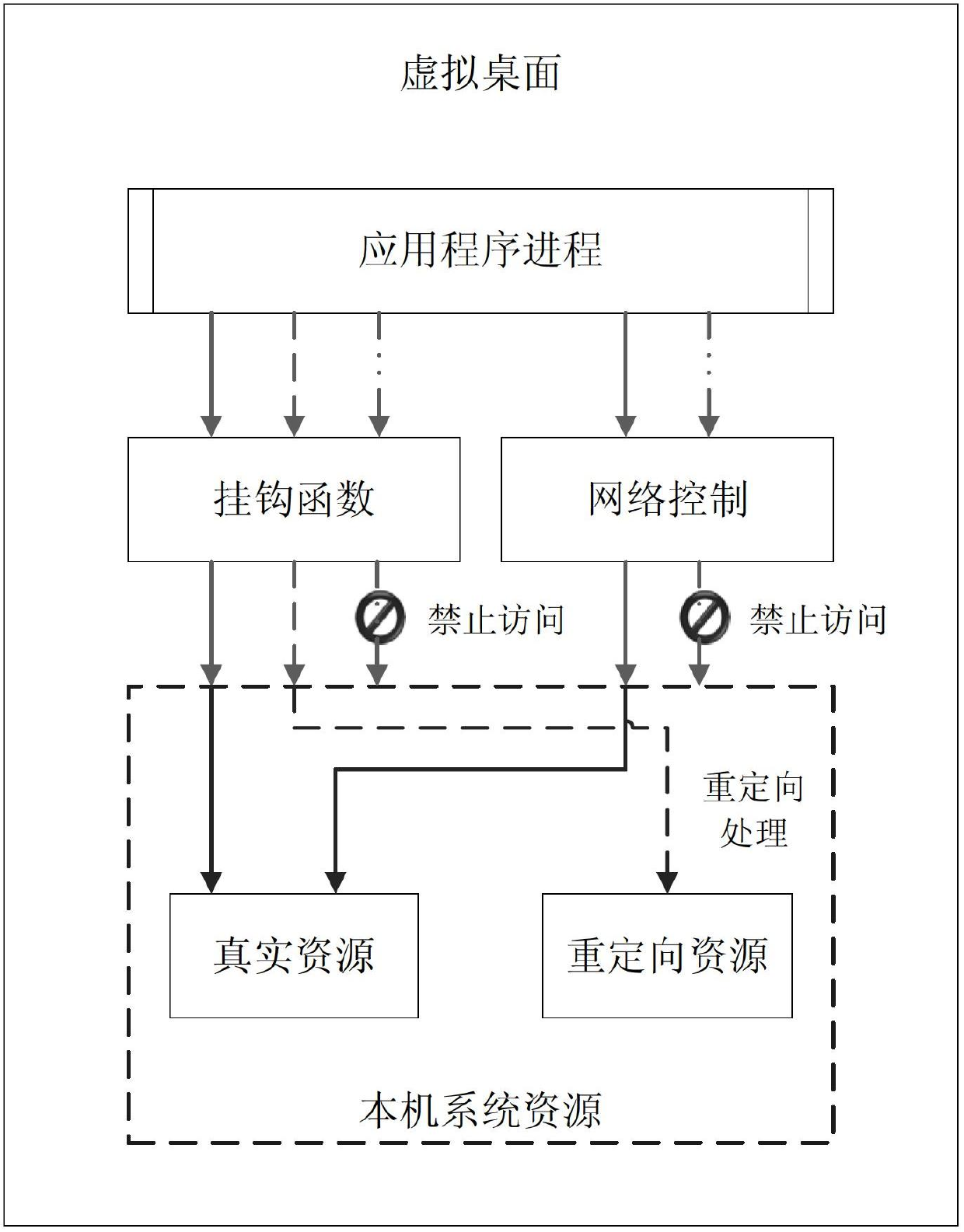
InactiveCN102685136AMeet security isolation requirementsPrevent leakageTransmissionOperational systemTerminal operation
The invention discloses a multi-network environment isolation method and a terminal. The method comprises the following steps of: establishing a plurality of virtual environments in a terminal operation system, wherein a plurality of the virtual environments are mutually isolated and a plurality of the virtual environments are mutually isolated from an original environment in the terminal operation system; and setting access permissions for accessing different networks in a plurality of the virtual environments. The invention realizes a safe network access control and data isolation function in different virtual tabletops, so as to achieve the aims of preventing viruses and preventing data from being leaked; and the realization scheme has the characteristics of low cost, simple arrangement, safety and convenience for use, easiness for maintenance and the like.
Owner:SANGFOR NETWORK TECH SHENZHEN
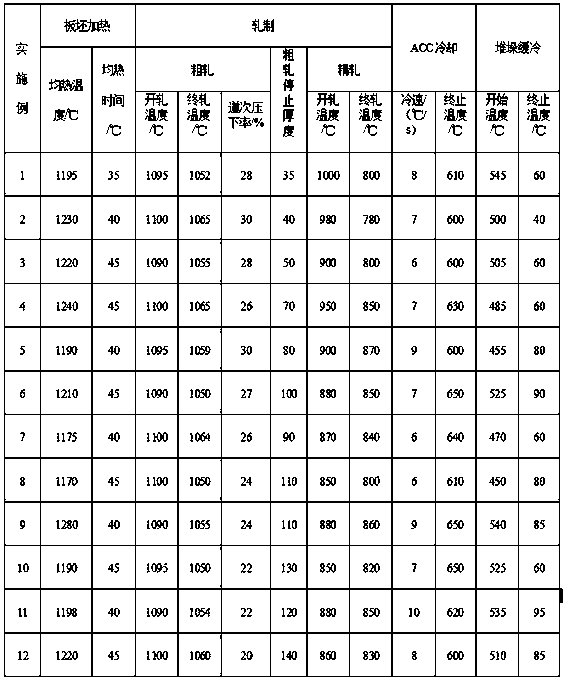
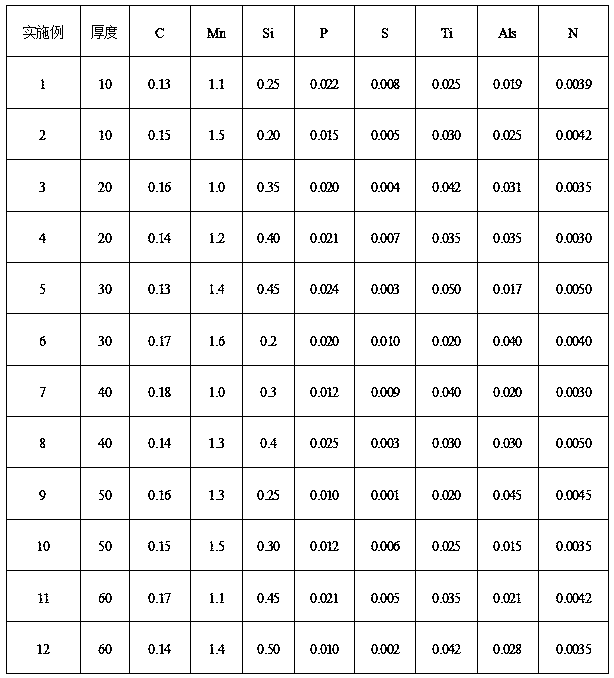
Economical high-plasticity 360MPa grade structural steel plate and manufacturing method thereof
ActiveCN108914008AShort processImprove efficiencyManufacturing convertersProcess efficiency improvementAlloySteel ball
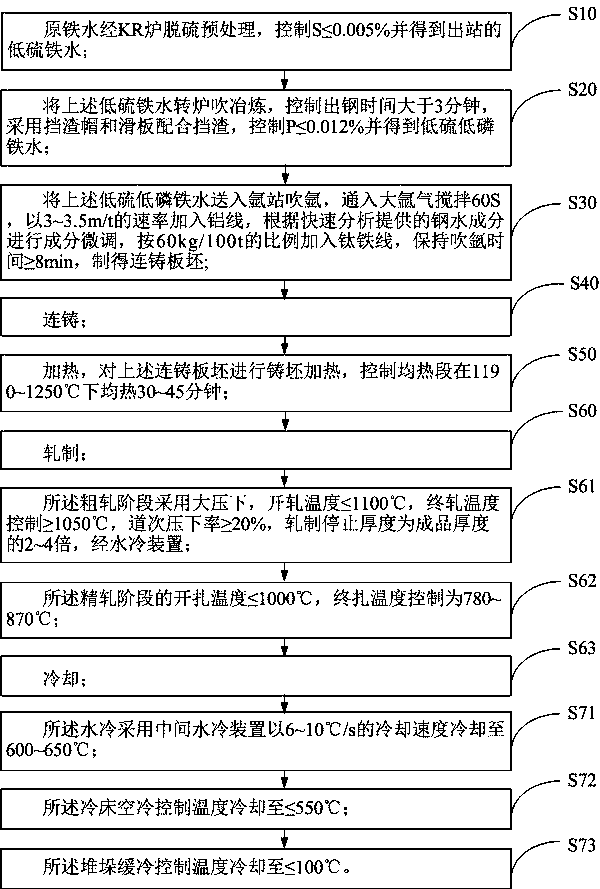
The invention discloses an economical high-plasticity 360MPa grade structural steel plate and a manufacturing method thereof, wherein the economical high-plasticity 360MPa grade structural steel platecomprises the following components in percentage by weight: 0.13-0.18% of C, 1.0-1.6% of Mn, 0.20-0.50% of Si, less than or equal to 0.025% of P, less than or equal to 0.010% of S, 0.020-0.050% of Ti, greater than or equal to 0.015% of Als, less than or equal to 0.005% of N and balance Fe and unavoidable impurity elements. The yield strength of the steel plate provided by the invention at a normal temperature is greater than or equal to 360MPa; the tensile strength is greater than or equal to 500MPa; the ductility is greater than or equal to 30%; the yield ratio is less than or equal to 0.80;the ballistic work at minus 20 DEG C is greater than or equal to 180J; with high strength, high plasticity, low yield ratio and excellent welding performance, the economical high-plasticity 360MPa grade structural steel plate can meet the safety demands of bridge steel well; and with low alloy content, short process flow, high production efficiency and low manufacturing cost, the economical high-plasticity 360MPa grade structural steel plate conforms to the development demands of green and economical steel ball.
Owner:WUHAN IRON & STEEL GRP ECHENG IRON & STEEL CO LTD
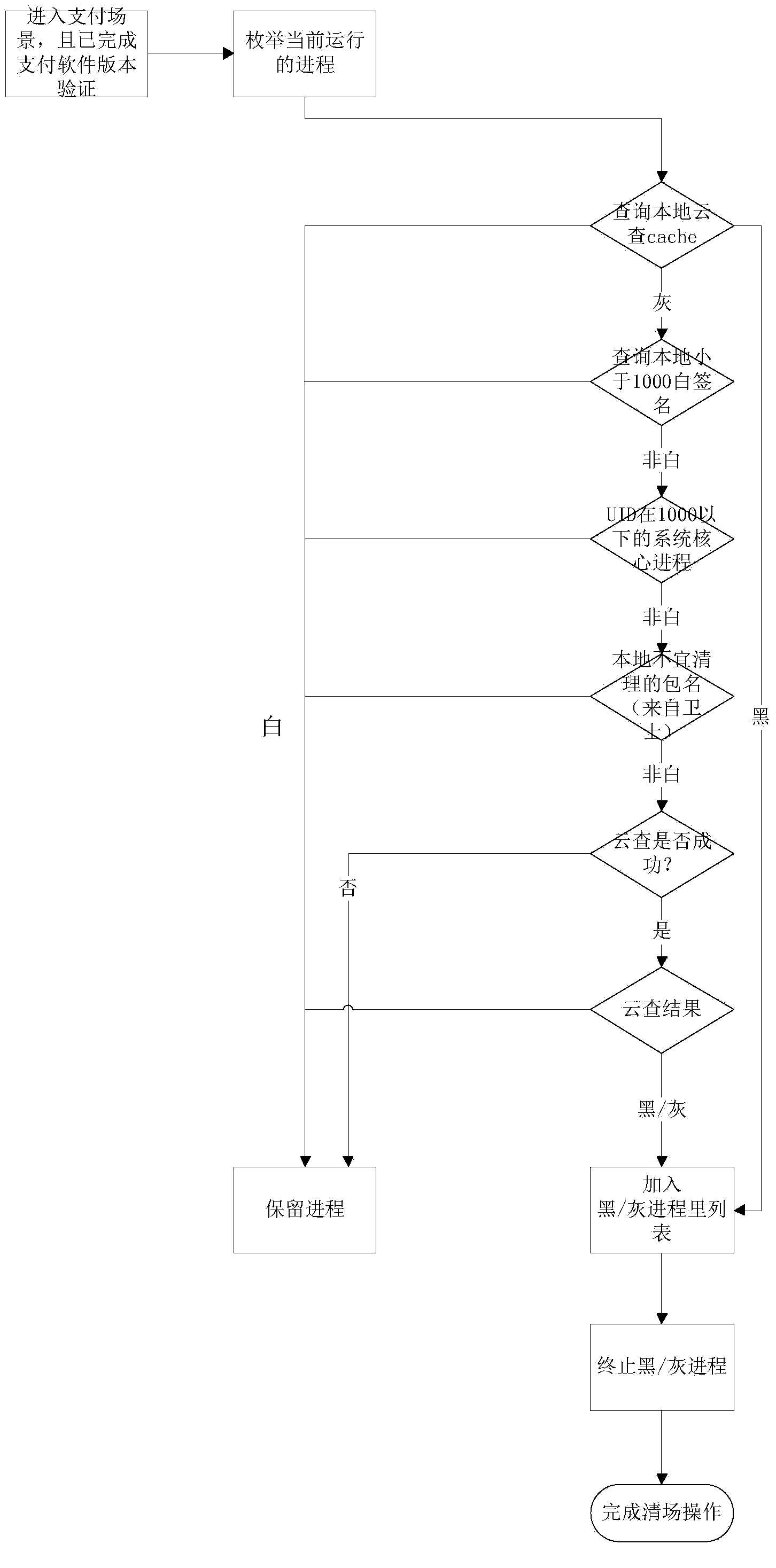
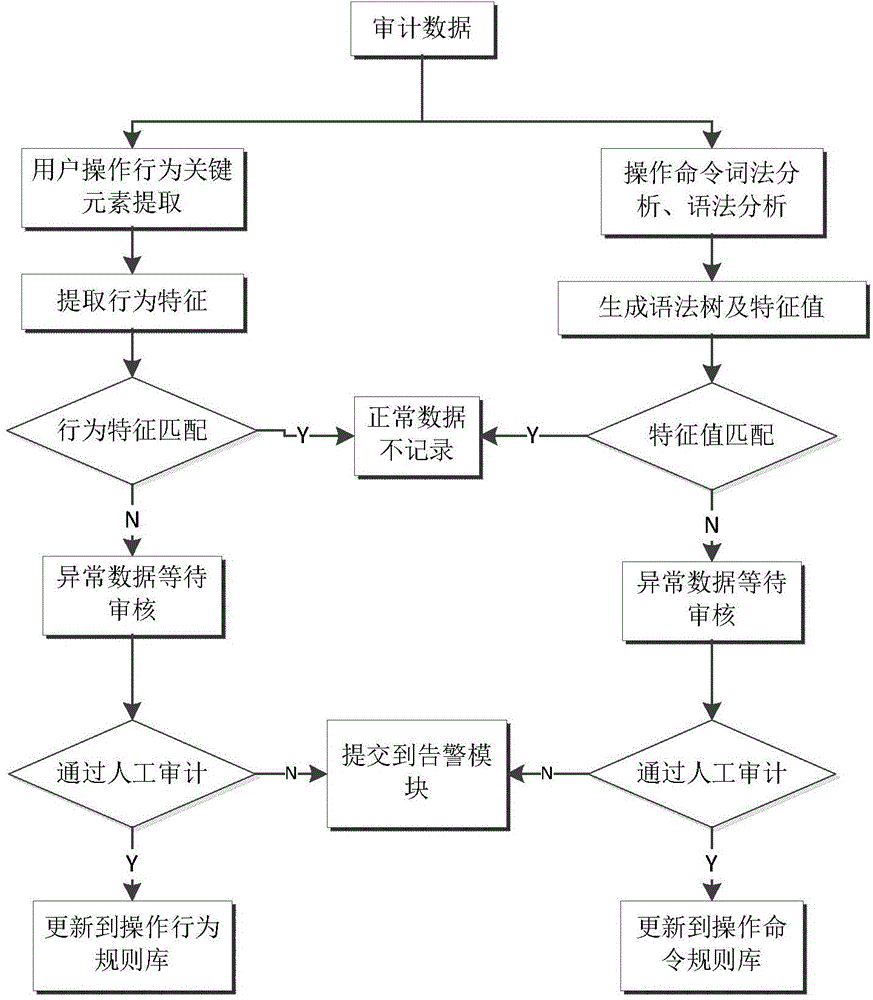
Method for remote intelligent operation and maintenance audit
InactiveCN104156439AEasy to detectMeet security needsData processing applicationsError detection/correctionBehavioral analyticsMatch rule
The invention discloses a method for a remote intelligent operation and maintenance audit. An access gateway is built between a client and a server, operation and maintenance conducted by the client on the server are forwarded by the access gateway to be conducted, and the access gateway collects operation and maintenance data and audits the operation and maintenance data. The method comprises a learning stage and a detecting stage, wherein an operating command rule base and an operating behavior rule base are formed through character command analysis and user behavior analysis in the learning stage; in the detecting stage, whether operation and maintenance operating commands and operating behaviors are normal or not is audited through a matching rule base, and the rule bases can be updated. Compared with the prior art, the method is high in universality and detecting efficiency, detecting can be conducted only after the learning stage lasting for a period of time, maintenance is convenient, and continuous updating of the rule bases guarantees that the false detecting rate is reduced.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
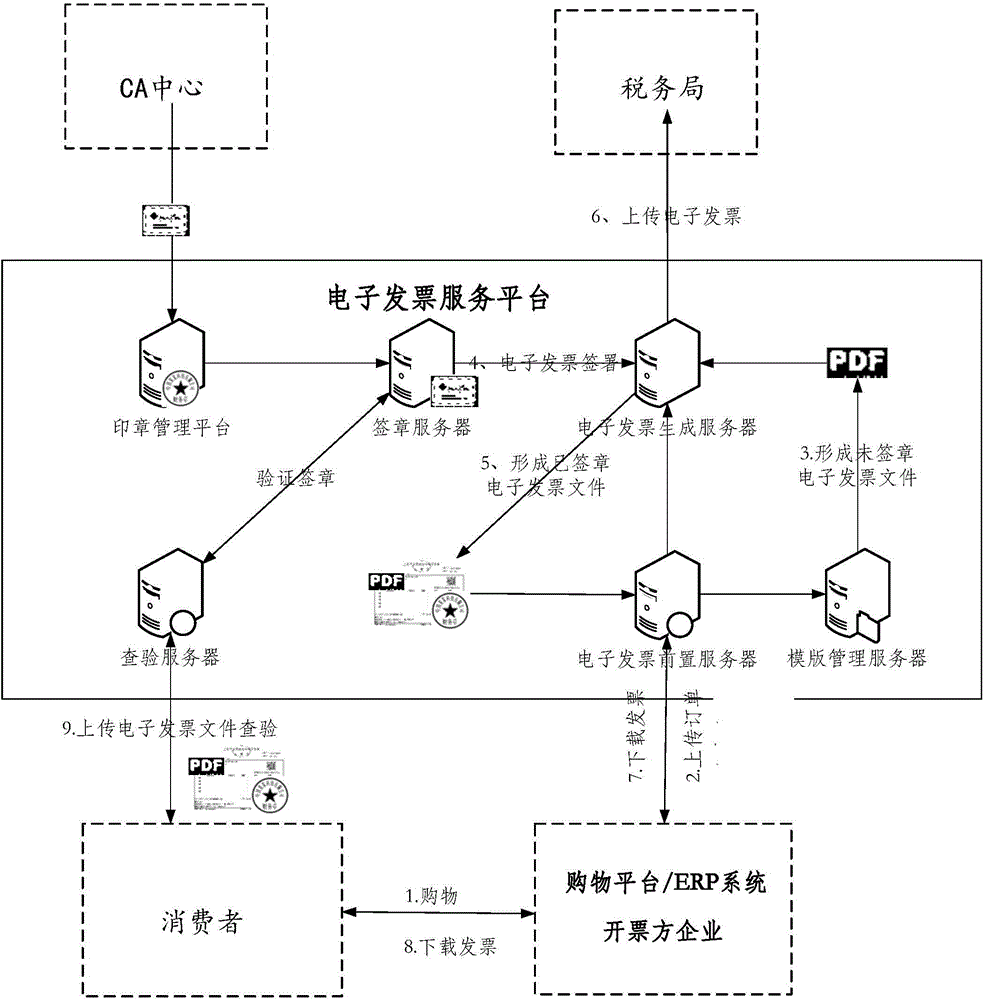
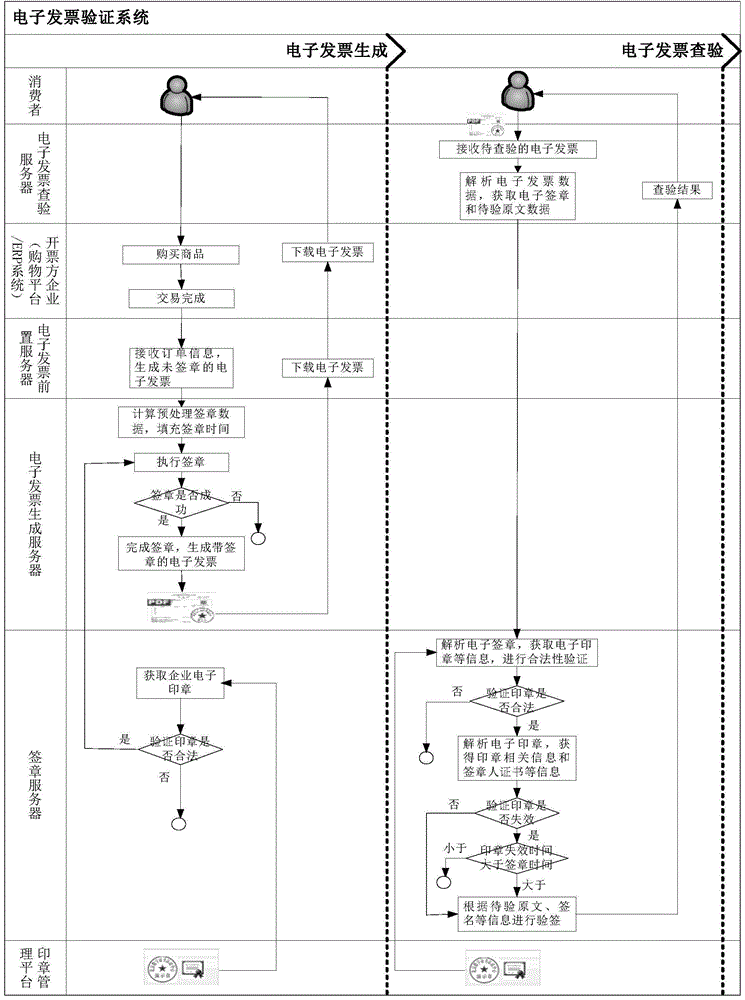
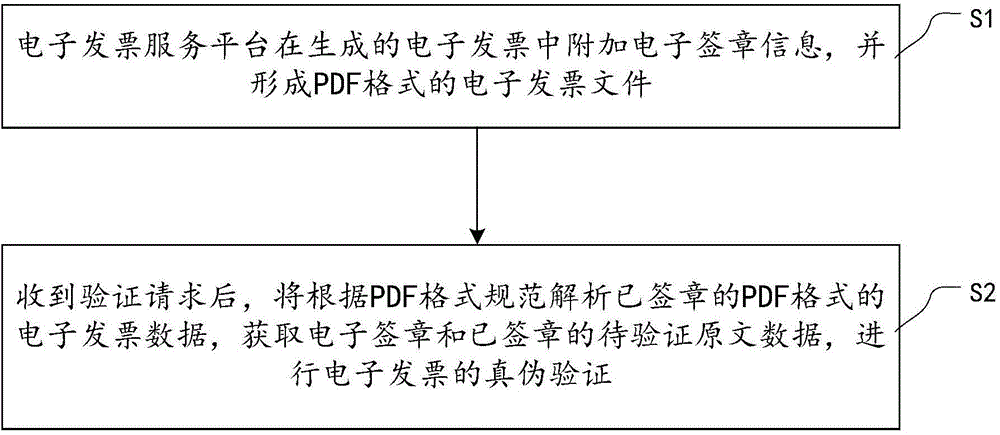
Electronic invoice generation and verification method and system
The invention discloses an electronic invoice generation and verification method which comprises the following steps: electronic signature information is added on a generated electronic invoice, a PDF format electronic invoice file is formed, data of the PDF format electronic invoice with a signature can be parsed according to PDF format specifications via an electronic invoice service platform after a verification request is received, and therefore an electronic signature and original text data with a signature to be verified can be obtained; authenticity of the electronic invoice can be verified. According to the electronic invoice generation and verification method, via use of PDF format files and electronic signature adding technology, authenticity, integrity and non-repudiation of electronic invoice content can be guaranteed; a full nominal value information verifying method which allows for convenience, safety and low cost is provided.
Owner:AEROSPACE INFORMATION
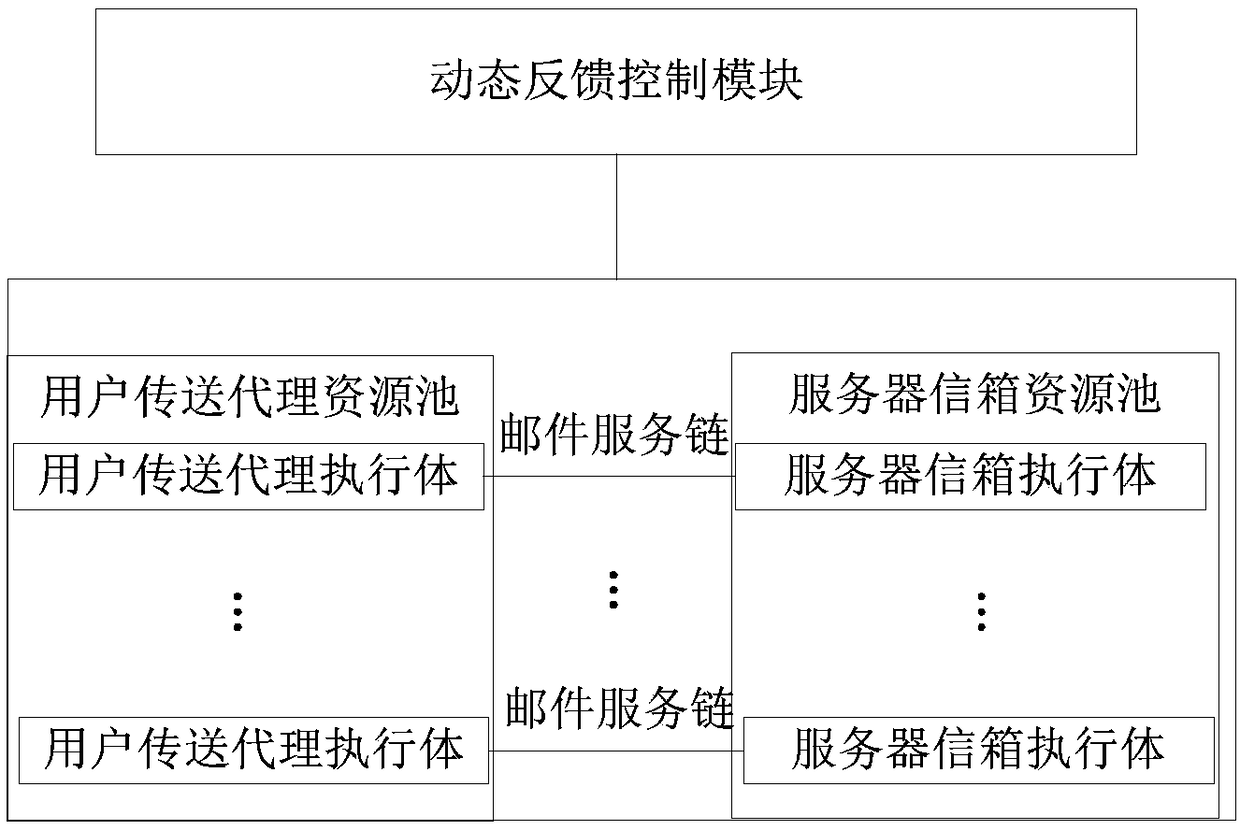
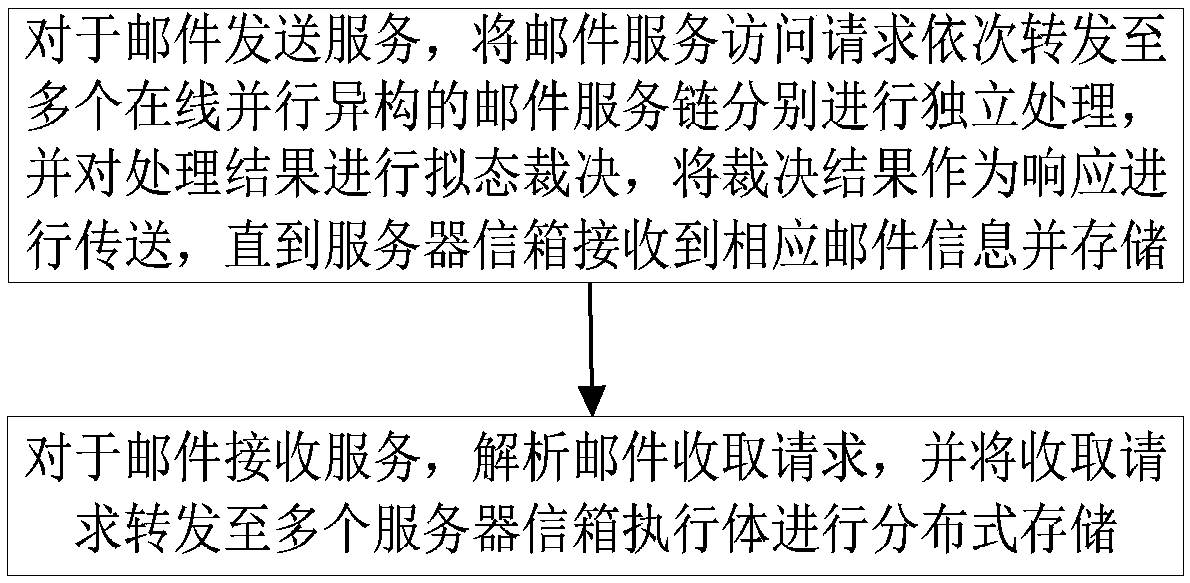
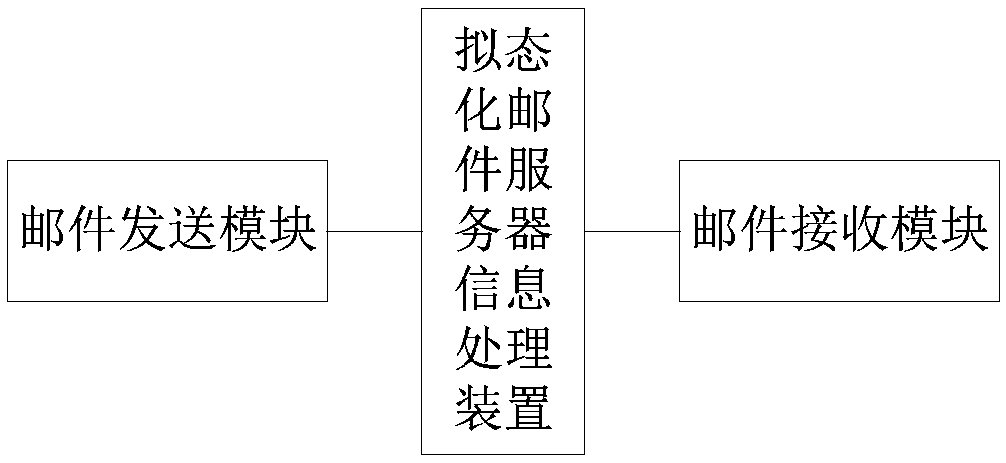
Mimetic mail server information processing device and mail service processing method, device and mail system
ActiveCN108833417AMeet security needsSolve the problem of building homogeneityData switching networksResource poolInformation processing
The invention relates to a mimetic mail server information processing device and a mail service processing method, device and a mail system. The information processing device comprises a resource poolcomposed of a user transfer proxy component and a server mailbox component, multiple parallel heterogeneous mail service chains composed of various components randomly selected from the resource pool, and a dynamic feedback control module, wherein the user transfer proxy component includes a number of heterogeneous user transfer proxy executors, and the server mailbox component includes a numberof server mailbox executors; and the dynamic feedback control module is used to monitor the operation of each executor and perform dynamic scheduling on various components. According to the scheme ofthe invention, the diversified executors are created, multiple processing results are subjected to mimetic decision output, the security performance of the mail system services can be improved, the initiative, variability and randomness of the mail system defense capability can be improved, the problem of privacy protection can be effectively solved, a more secure mail server solution can be provided, and the important guiding significance can be provided for the mail system security technologies.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
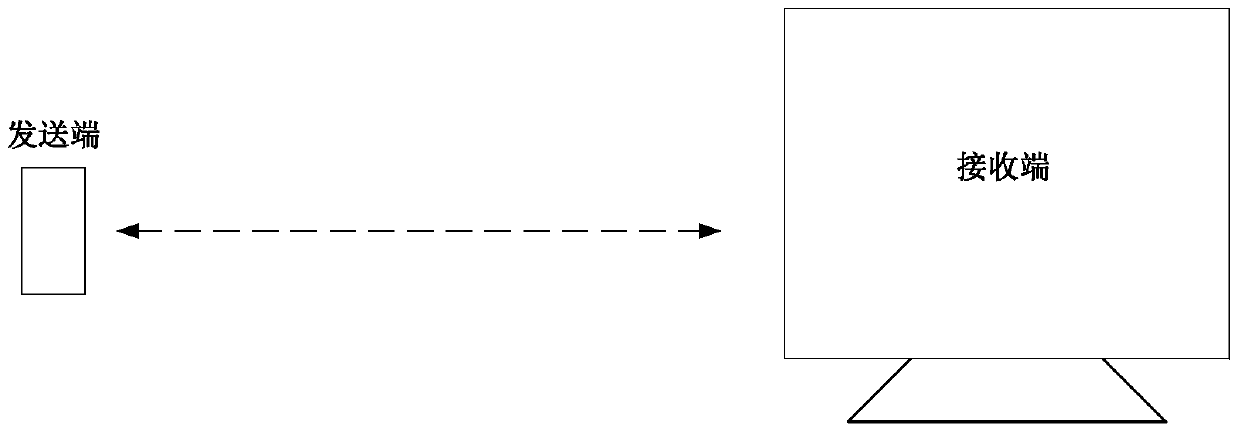
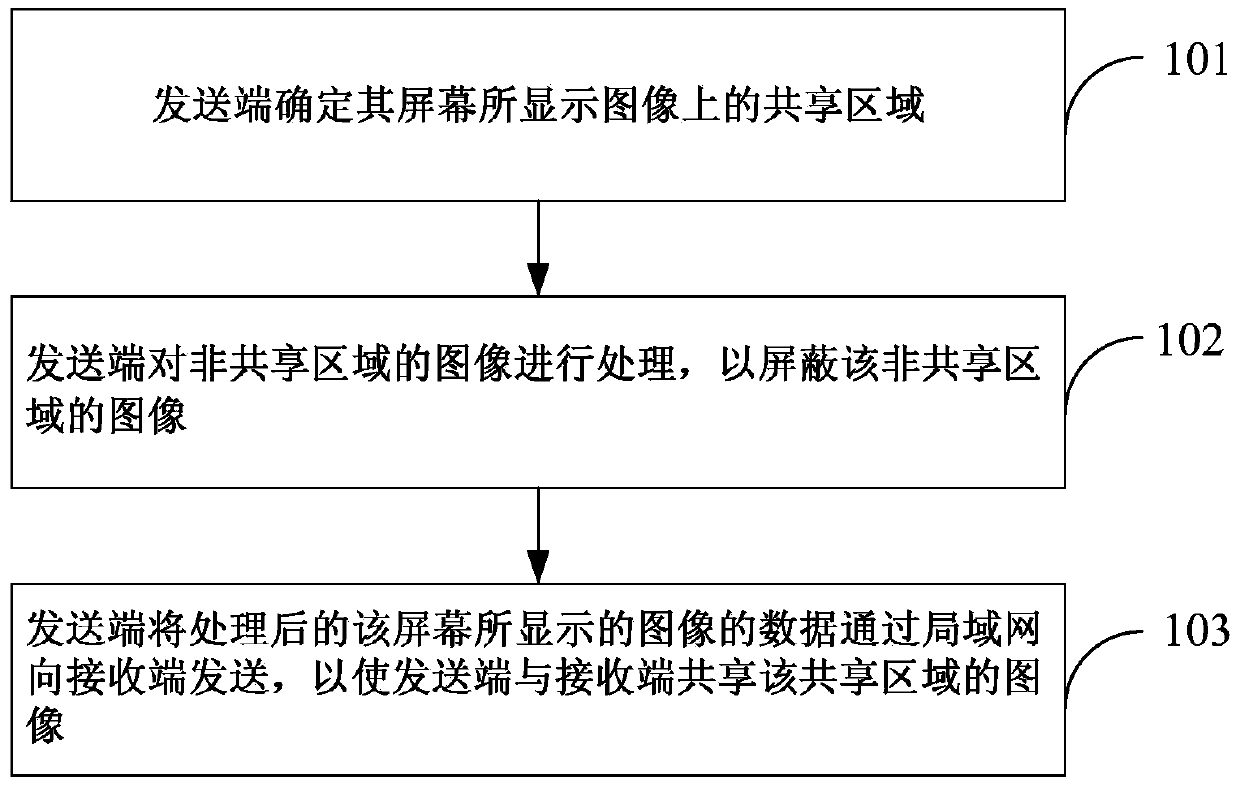
Terminal-to-terminal image sharing method, terminal device and communication system
ActiveCN103701927AAchieve sharingMeet security needsDigital data protectionTransmissionPersonalizationLocal area network
The embodiment of the invention discloses a terminal-to-terminal image sharing method, a terminal device and a communication system. In the method, a transmission terminal is connected with a receiving terminal through a local area network. The method comprises the following steps of determining a share area of an image displayed on a screen of the transmitting terminal; processing the image in a non-share area through the transmitting terminal so as to shield the image in the non-share area, wherein the non-share area is the area excepting the share area in the image displayed on the transmitting terminal screen; transmitting the processed image displayed by the screen to the receiving terminal through the local area network by the transmitting terminal, so that the transmitting terminal and the receiving terminal share the image of the share area. By adopting the terminal-to-terminal image sharing method, the terminal device and the communication system, the share of the local image between two terminals in the local area network can be realized, and the safety and individualization requirement of the user can be met.
Owner:HUAWEI TECH CO LTD
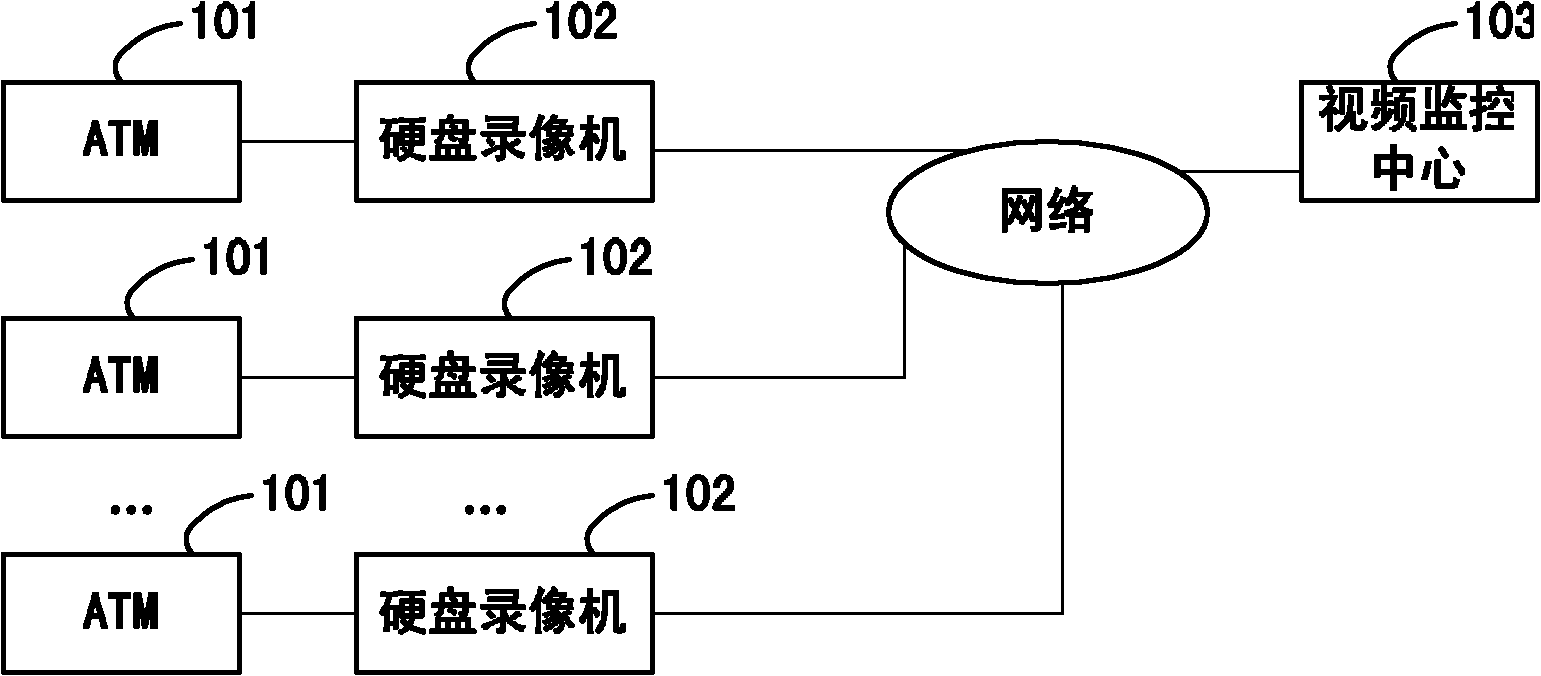
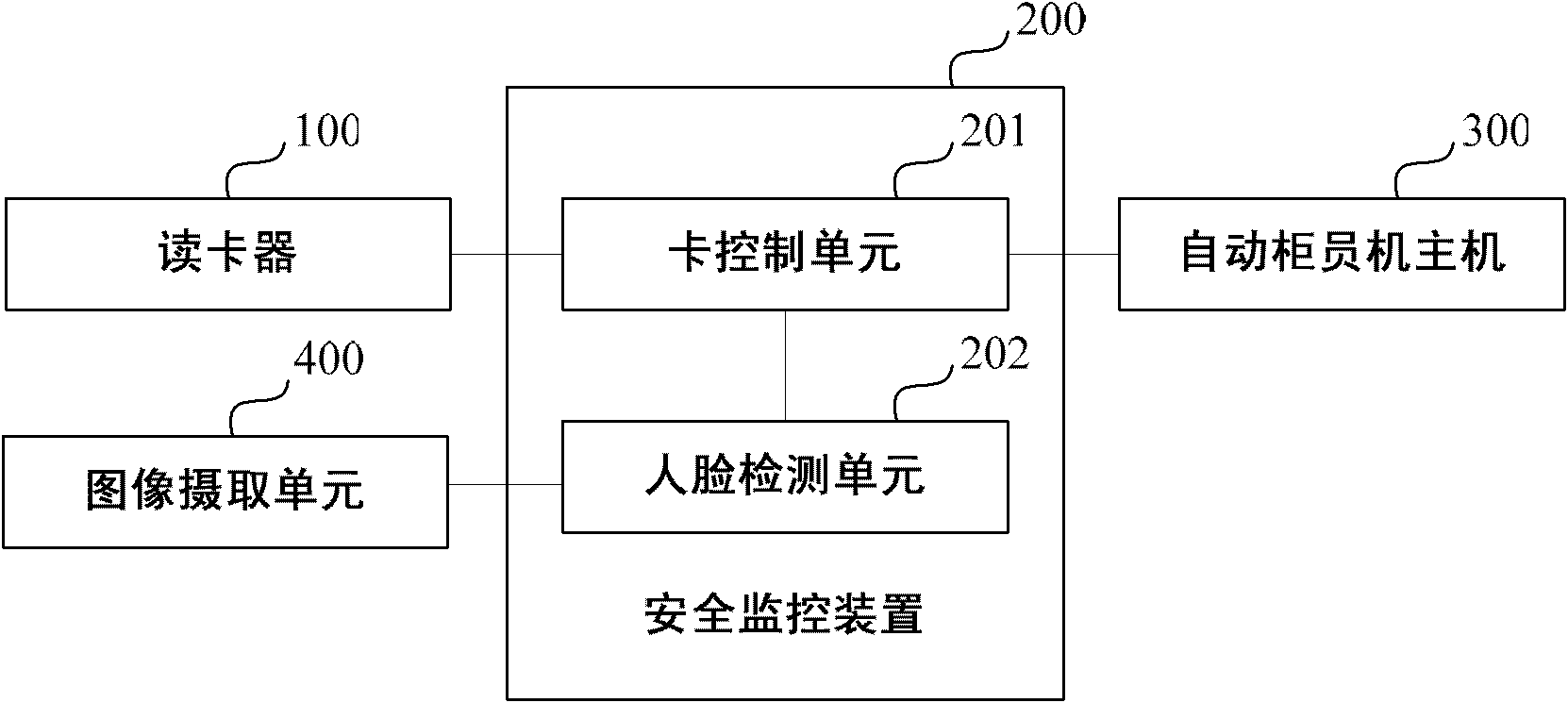
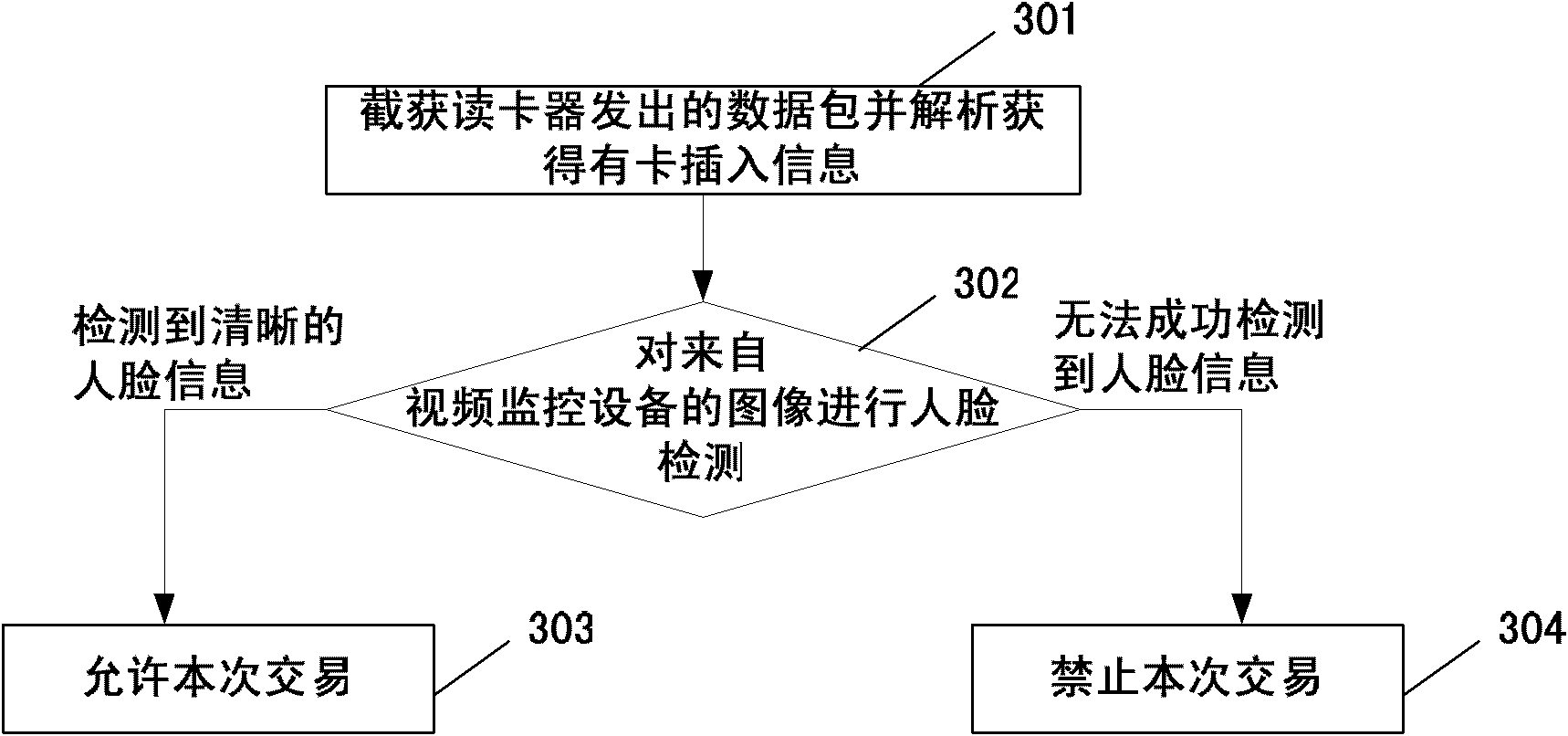
Automatic teller machine-based safe monitoring device and method and automatic teller machine
InactiveCN102004904ASolve the problem of not being able to effectively stop illegal transactionsMake up for the shortcomings of not having the ability to prevent crimes in advanceCharacter and pattern recognitionClosed circuit television systemsFace detectionNetwork packet
The invention discloses an automatic teller machine-based safe monitoring device, an automatic teller machine-based safe monitoring method and an automatic teller machine. The monitoring device is used for monitoring the automatic teller machine, is arranged between a card reader and the automatic teller machine and comprises a card control unit and a human face detecting unit, wherein the card control unit is used for informing the human face detecting unit to start to detect when acquiring a data packet sent by the card reader and resolving the acquired card insertion information, and receiving the detection result from the human face detecting unit, if the detection result is that human face information is undetected, stopping the transaction at the time, and if the detection result isthat human face information is not detected, permitting the transaction at the time and forwarding the data packet sent by the card reader to a host of the automatic teller machine; and the human face detecting unit is used for performing human face detection on an image from an image taking device according to a received detection start notification and informing the card control unit of the detection result. The device, the method and the automatic teller machine of the invention can prevent a masked criminal suspect from drawing money of a loser from the automatic teller machine (ATM).
Owner:NEUSOFT CORP
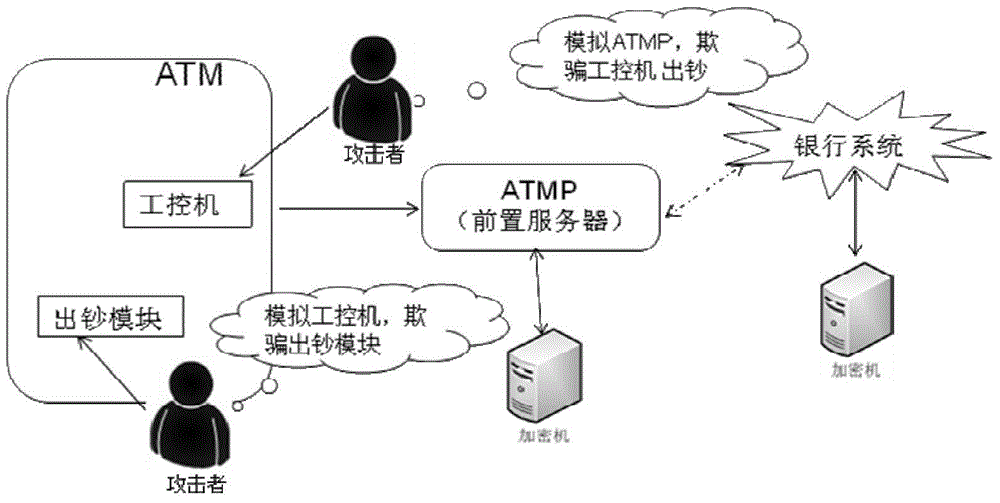
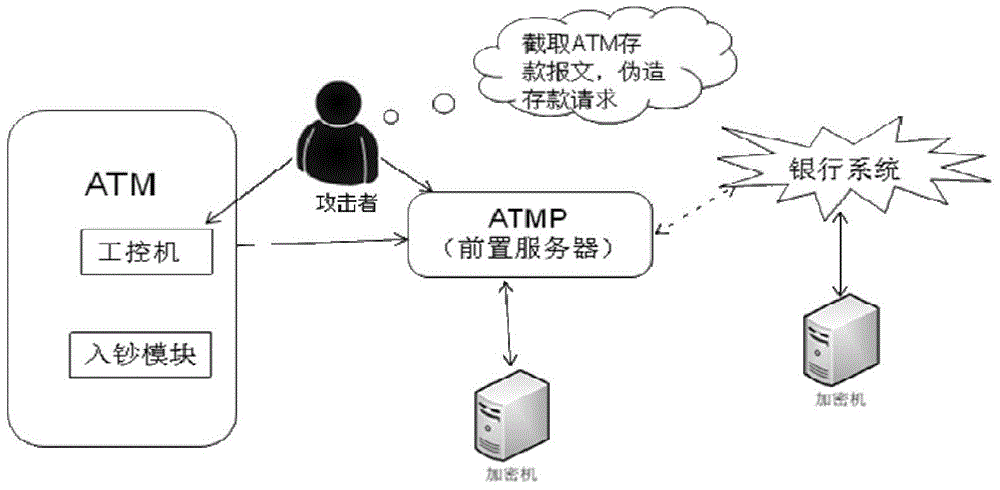
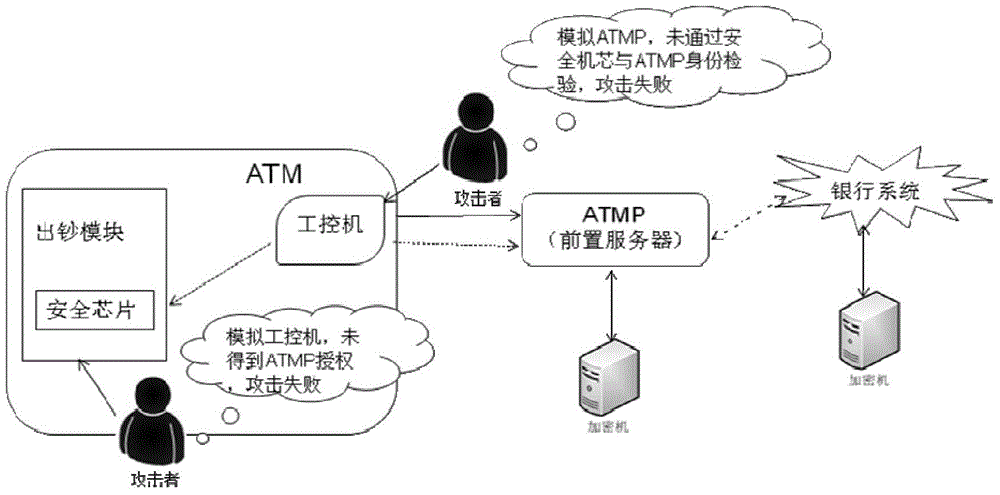
Method and system for controlling depositing and withdrawing safety based on safety core
The invention discloses a method and a system for controlling depositing and withdrawing security based on a security core. A security chip is arranged in a depositing and withdrawing core and put in the safe case of an automatic teller machine. The core safety chip is called the security core for short; the security core communicates with an automatic teller machine pre-system (ATMP); the safe communication of the security core with the ATMP is realized by virtue of certificate issuing and key exchange; the ATMP authorizes the core to dispense cashes, and meanwhile, checks the amount deposited. According to the method and the system for controlling the depositing and withdrawing security based on the security core, due to the safe communication of the security core and the ATMP, the identity is authenticated, an instruction sent out is verified legally and a message sent out is encrypted, and then the ATMP authorizes the core to dispense cashes and checks the amount deposited; the method and the system have the advantages that authentication and encryption / decryption can be effectively authenticated to achieve integrity protection, prevent tampering and prevent replay attack protection, and therefore, the security of the ATM is improved.
Owner:HUNAN GREATWALL INFORMATION FINANCIAL EQUIP
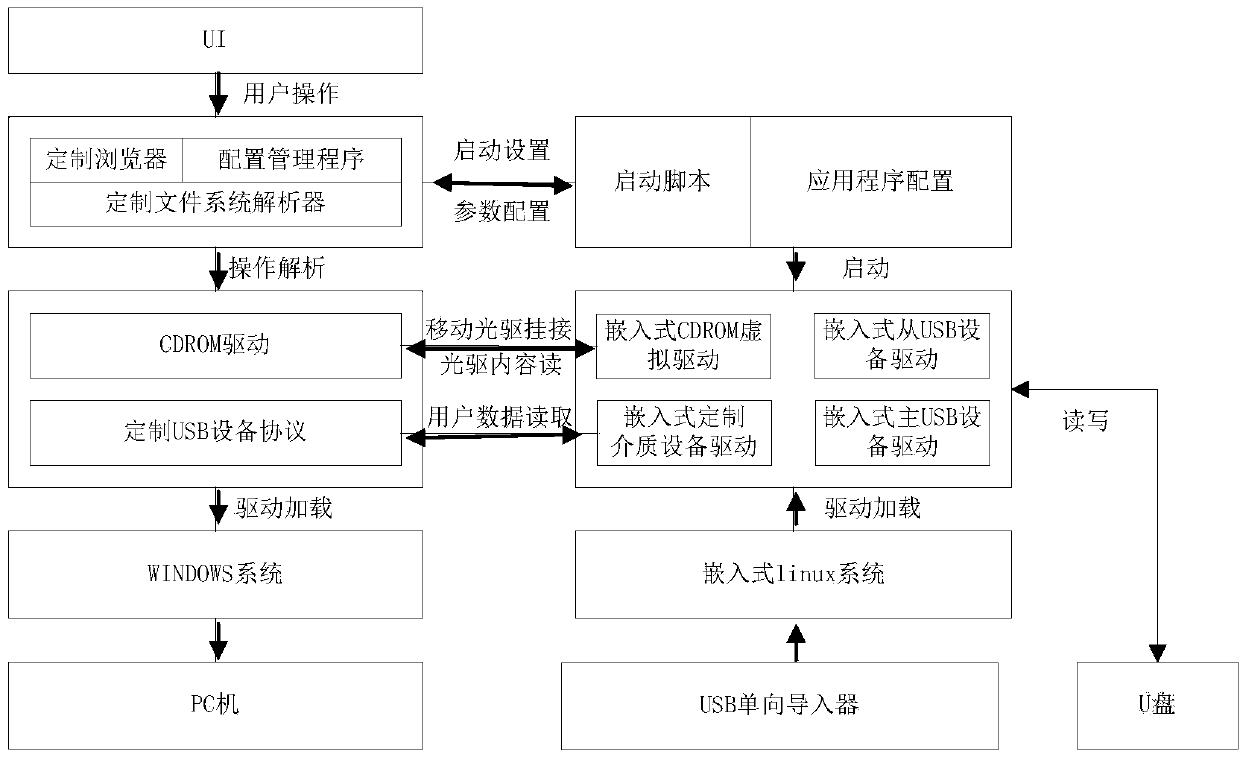
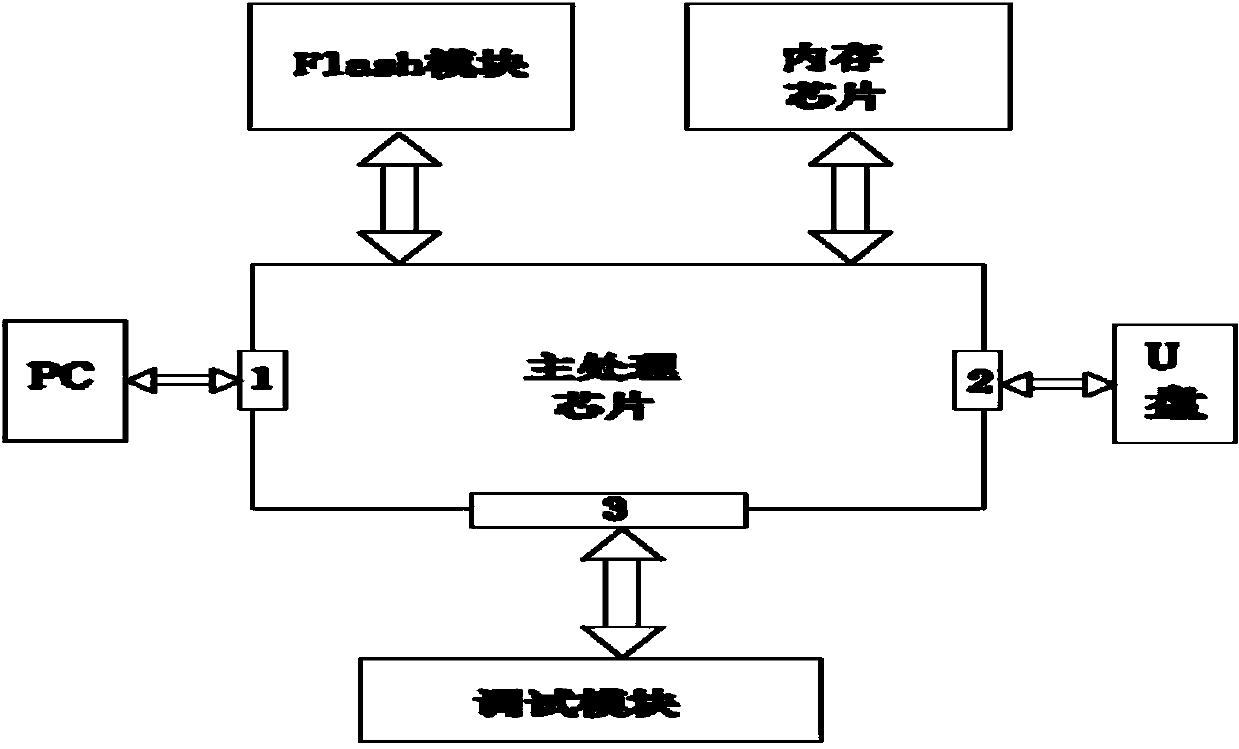
Safe leading-in device, system and method for USB data
ActiveCN104200172AEnsure safetyMeet security needsDigital data protectionPlatform integrity maintainanceInformatizationComputer module
The invention relates to the technical field of information safety, in particular to a safe leading-in device, system and method for USB data. The safe leading-in device for the USB data comprises a main processing chip. The main processing chip comprises a main interface connected with a U disk, an auxiliary interface connected with a PC chip, a serial port connected with a debugging module, a Flash module and an internal storage chip, the Flash module is in bothway signal transmission with the main processing chip, and the Flash module is inserted into the linux system. The invention further provides the safe leading-in system and method for the USB data. Safe, fast and one-way big data leading in can be achieved in the current mobile storage medium safety management field, the efficiency of safely leading extranet data in the intranet is effectively improved on the premise of guaranteeing the safety of the intranet through the technical measures such as identity authentication, behavior auditing, Trojan virus defense and jurisdiction control, and the information safety requirement in the informatization application is met.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
Realization method and device of attachment procedure
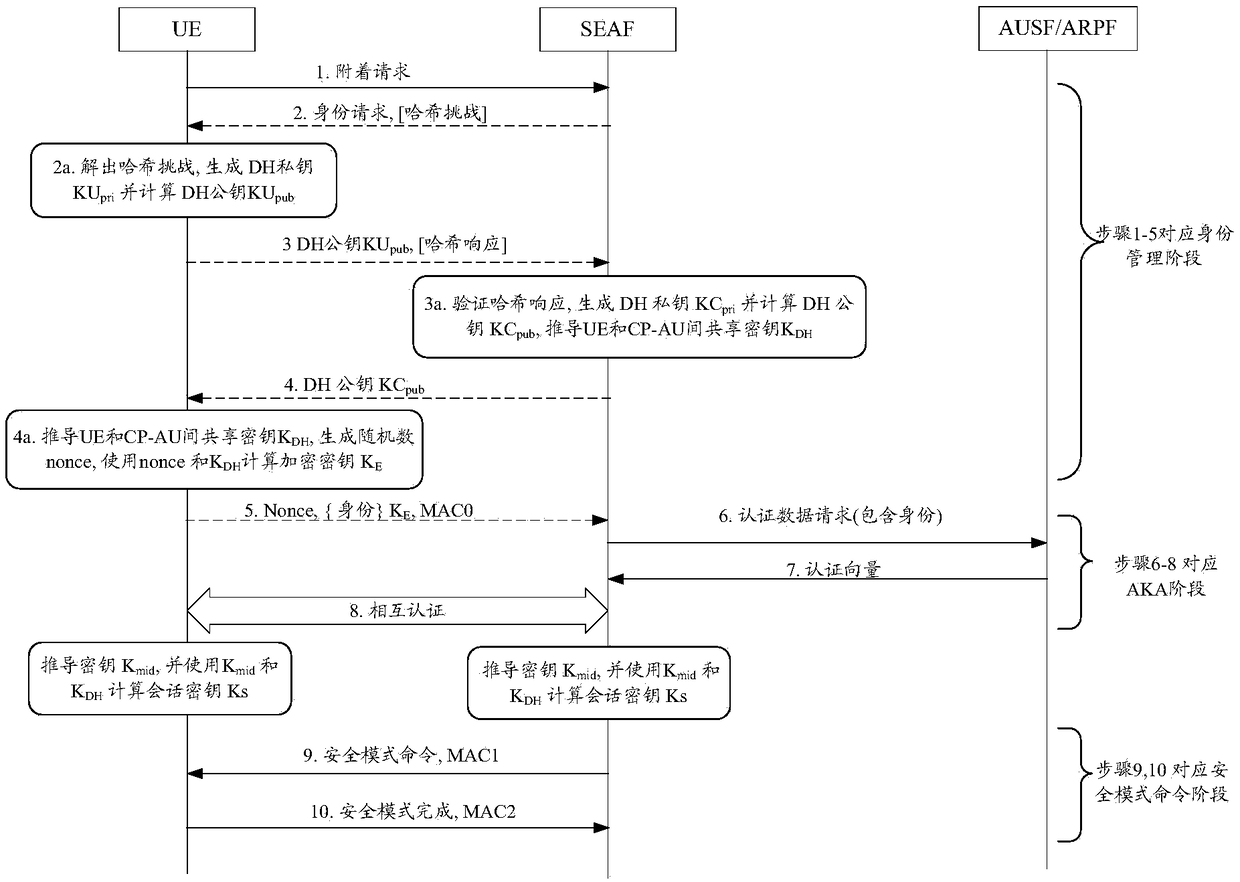
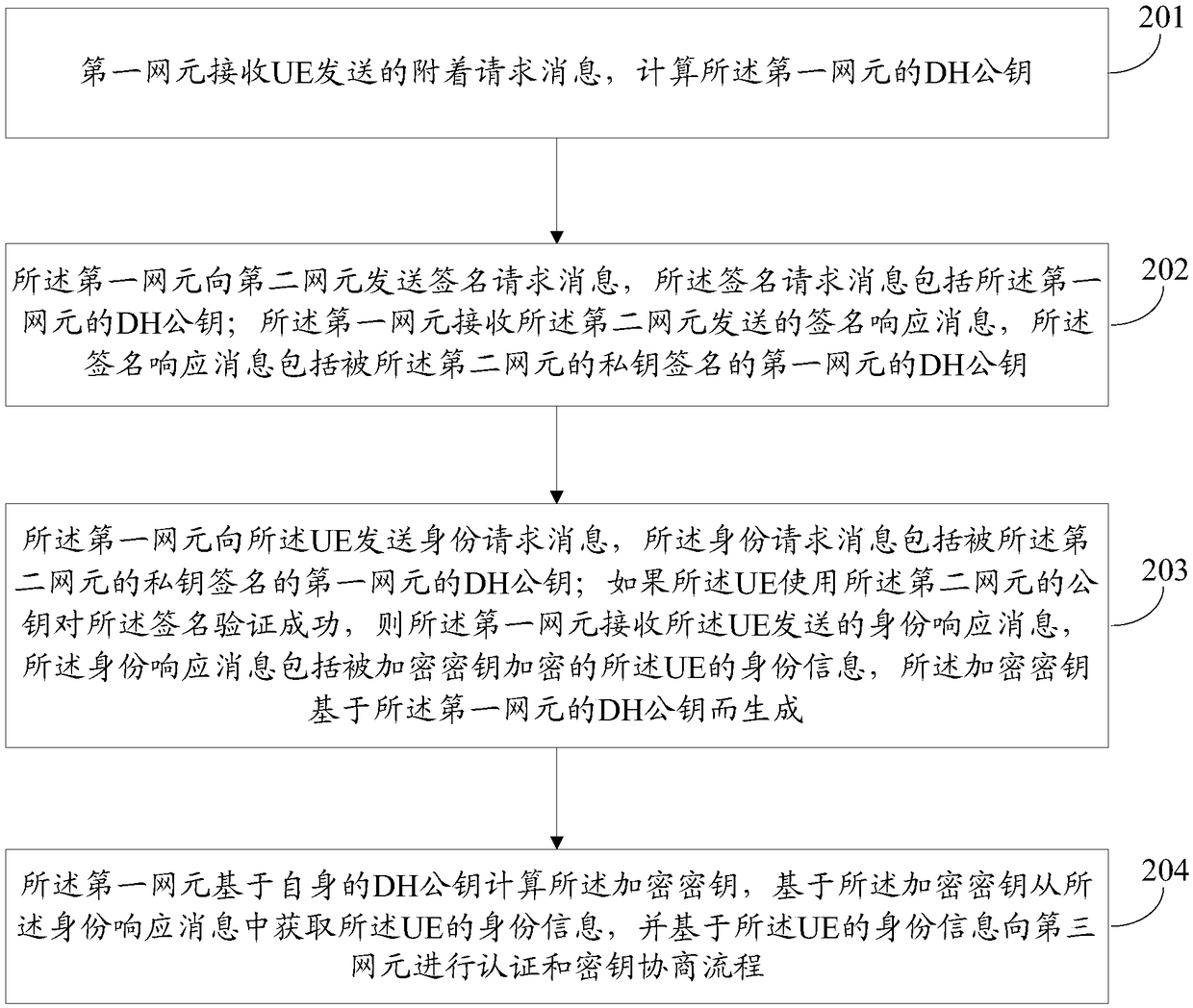
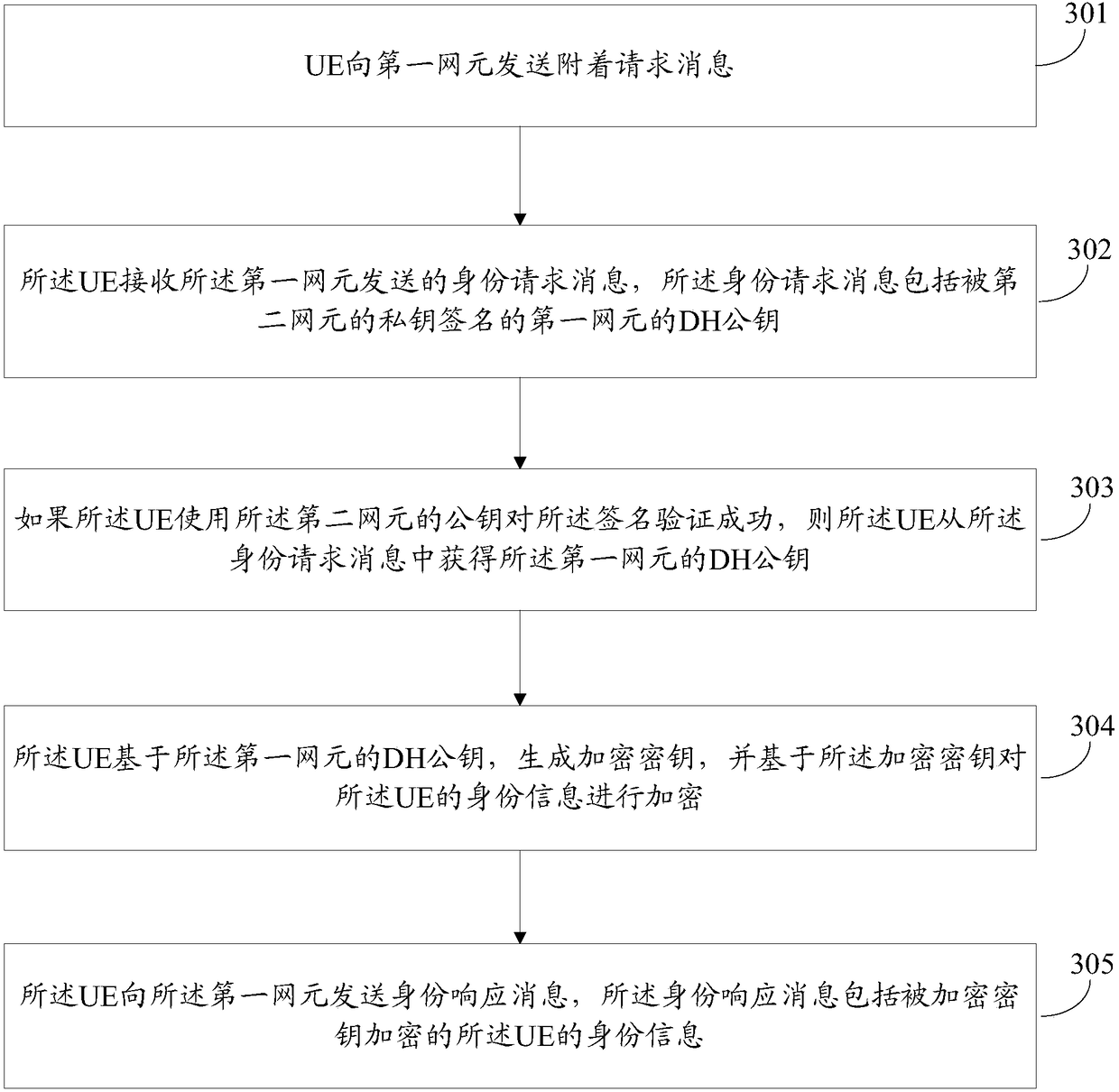
ActiveCN108880813AMeet security needsPublic key for secure communicationUser identity/authority verificationNetwork elementComputer security
The invention discloses a realization method and device of attachment procedure. The method comprises the following steps: receiving an attachment request message sent by UE through a first network element, computing a DH public key of the first network element, and sending a signature request message to the second network element, wherein the signature request message comprises the DH public keyof the first network element; receiving a signature response message sent by the second network element, wherein the signature response message comprises the DH public key of the first network elementsigned by a private key of the second network element; sending an identity request message to the UE, wherein the identity request message comprises the DH public key of the first network element signed by the private key of the second network element; if the UE successfully verifies the signature by using the public key of the second network element, receiving the identity response message sentby the UE, wherein the identity response message comprises the identity information, encrypted by the encrypted key, of the UE; and computing the encrypted key based on the own DH public key, and acquiring the identity information of the UE from the identity response message based on the encrypted key.
Owner:CHINA MOBILE COMM LTD RES INST +1
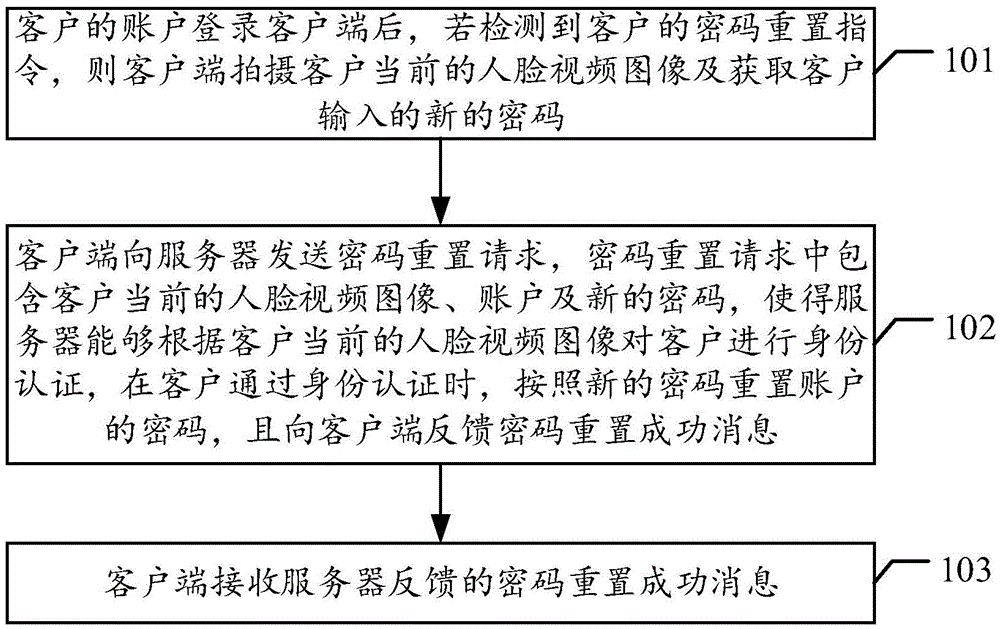
Cipher reset method and system, client and server
ActiveCN105577664AEnsure safetyImprove experiencePayment architectureTransmissionBank accountClient-side
The invention discloses a cipher reset method. The method comprises following steps that: a server receives a cipher reset request sent by a client; the cipher reset request comprises a current face video image of a customer, an account logining the client and a new cipher input by the customer; the server carries out identity authentication to the customer according to the current face video image of the customer, resets the cipher of the account according to the new cipher when the customer passes the identity authentication and feeds back a cipher reset success message to the client. The invention also discloses a cipher reset device and a cipher reset system. According to the method, the system, the device, the client and the server provided by the invention, the account security can be effectively ensured; the security demand for resetting the cipher of the bank account through the bank client is satisfied; the customer is unnecessary to go to the bank for handling the cipher reset service; and the customer experience is improved.
Owner:WEBANK (CHINA)
Wireless network system and communication method thereof
InactiveCN101232402AImprove reliabilitySafe and smoothError preventionData switching networksResource poolDependability
The embodiment of the invention discloses a wireless network system, which comprises a controller resource cell including all or some controllers in a wireless network. The controller resource cell includes a first controller and a second controller. The first controller is used for establishing a master attribution link with a base station, and the second controller is used for establishing a slave attribution link with the base station. When the master attribution link fails, the second controller is used for establishing a new master attribution link with the base station. The embodiment of the invention further discloses a communication method of the wireless network system, a controller and a base station. The scheme provided by the embodiment of the invention improves the reliability of network, increases utilization ratio of device resources and resistance to burst flow, reduces cost, shortens time for disaster-tolerant switching / interrupting service, and can satisfy high reliability requirement of a network operator.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com