Realization method and device of attachment procedure
A technology for implementing methods and processes, applied in the field of implementing methods and devices for attaching processes, can solve problems such as lack of integrity protection of public keys, man-in-the-middle attacks, and inability to prevent active attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0120] In order to understand the characteristics and technical contents of the embodiments of the present invention in more detail, the implementation of the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. The attached drawings are only for reference and description, and are not intended to limit the embodiments of the present invention.
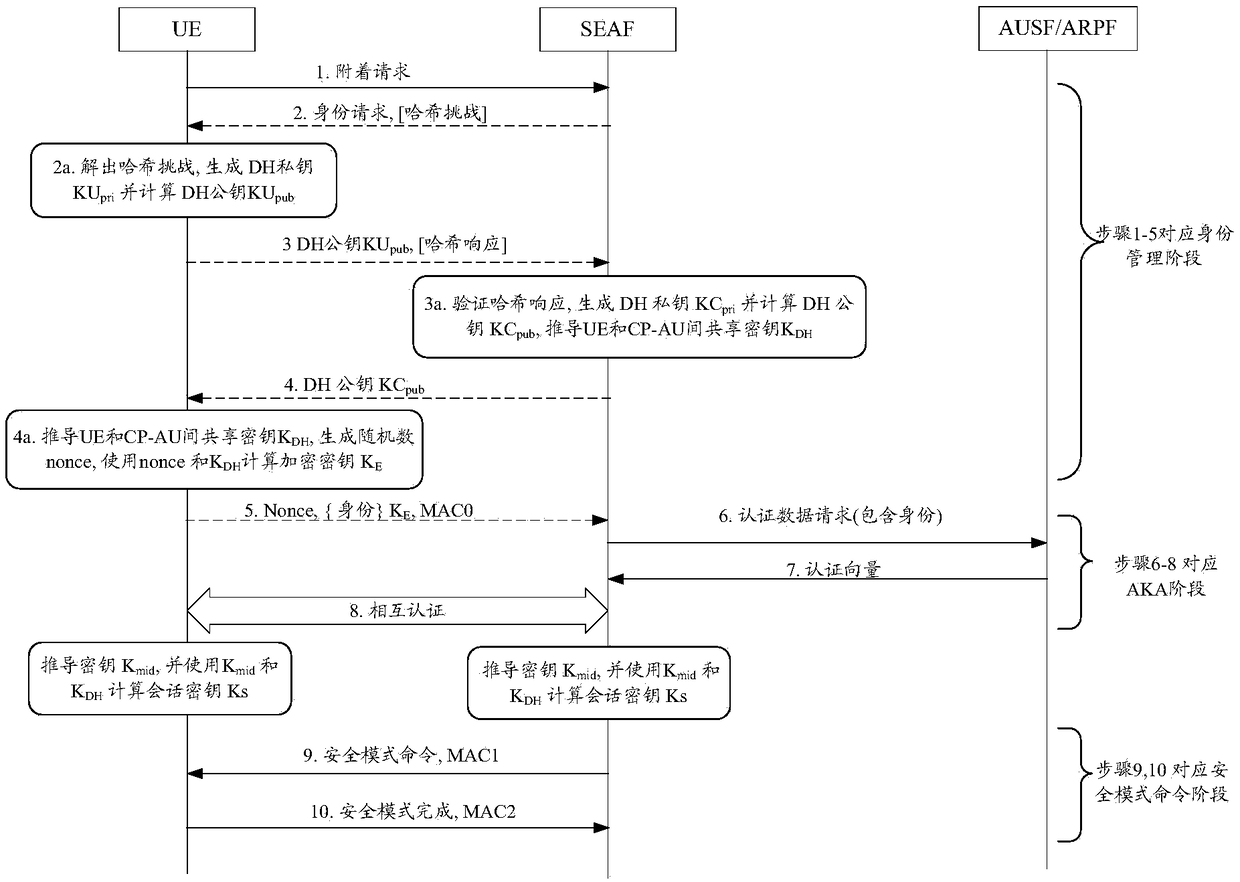
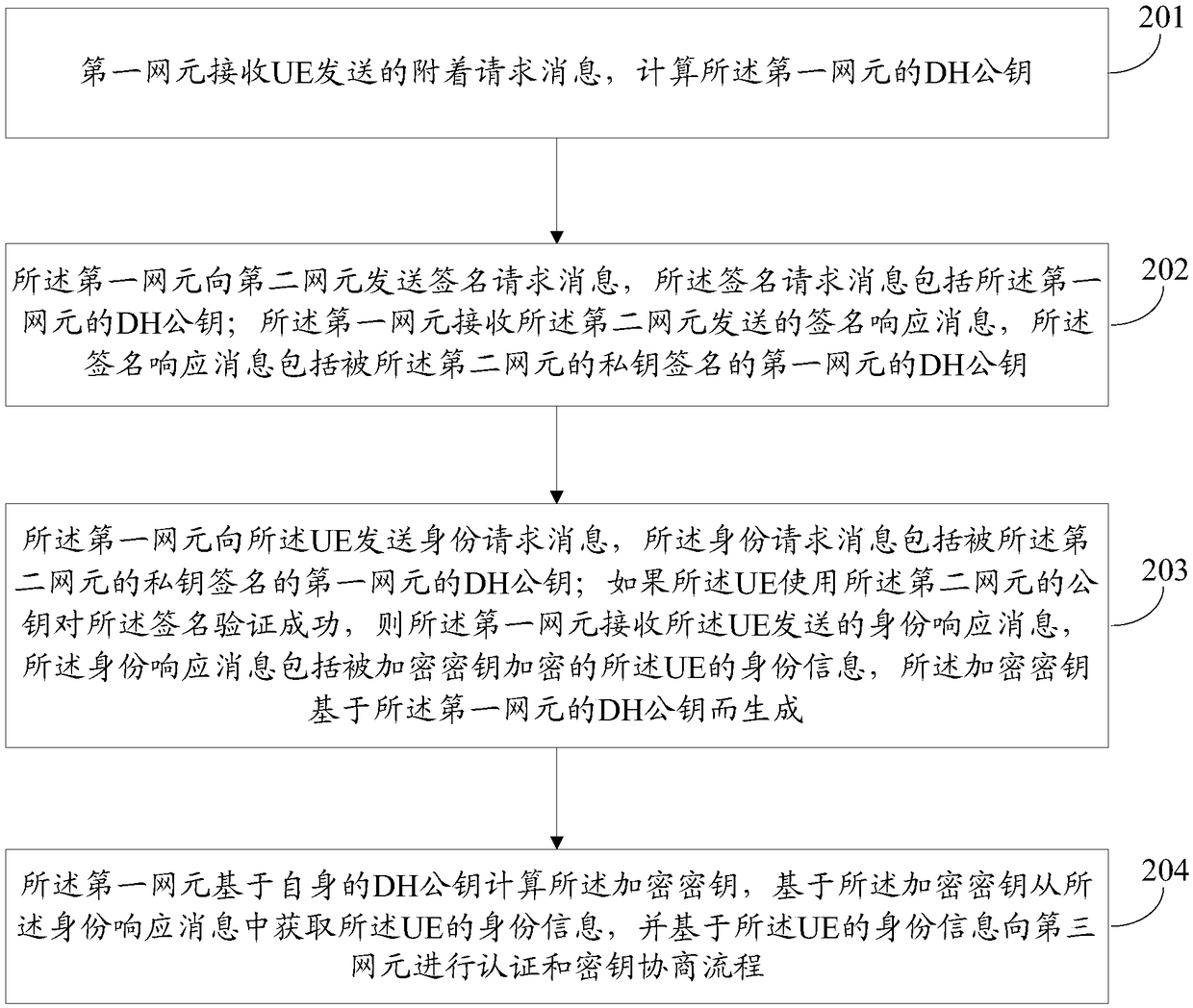
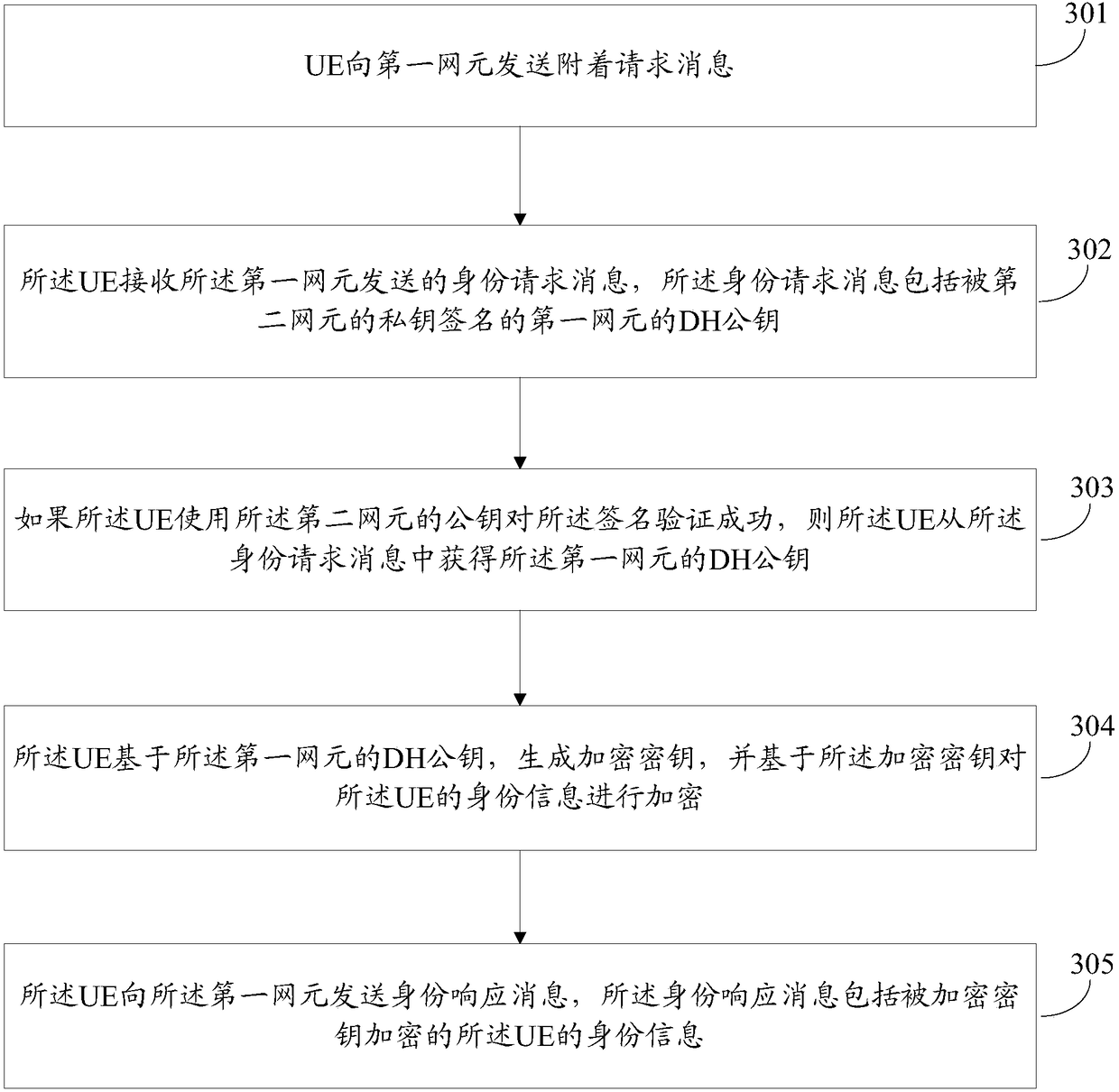
[0121] The attachment process is an important step for the UE to access the network. It can be divided into three stages according to its different functions: (1) identity management, which is used to determine the identity of the UE on the network side, (2) authentication between the UE and the network and key management (AKA, Authentication and Key Agreement), used for mutual authentication and deriving session keys, (3) Security Mode Command (SMC, Security Mode Command), used for negotiation of cryptographic algorithms and protection of activation messages. Although mos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com