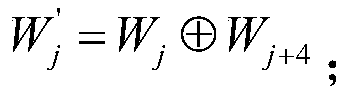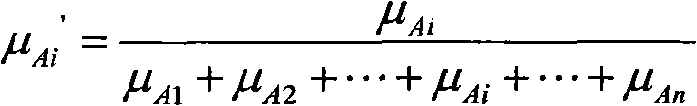Patents
Literature
386results about How to "Achieve authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
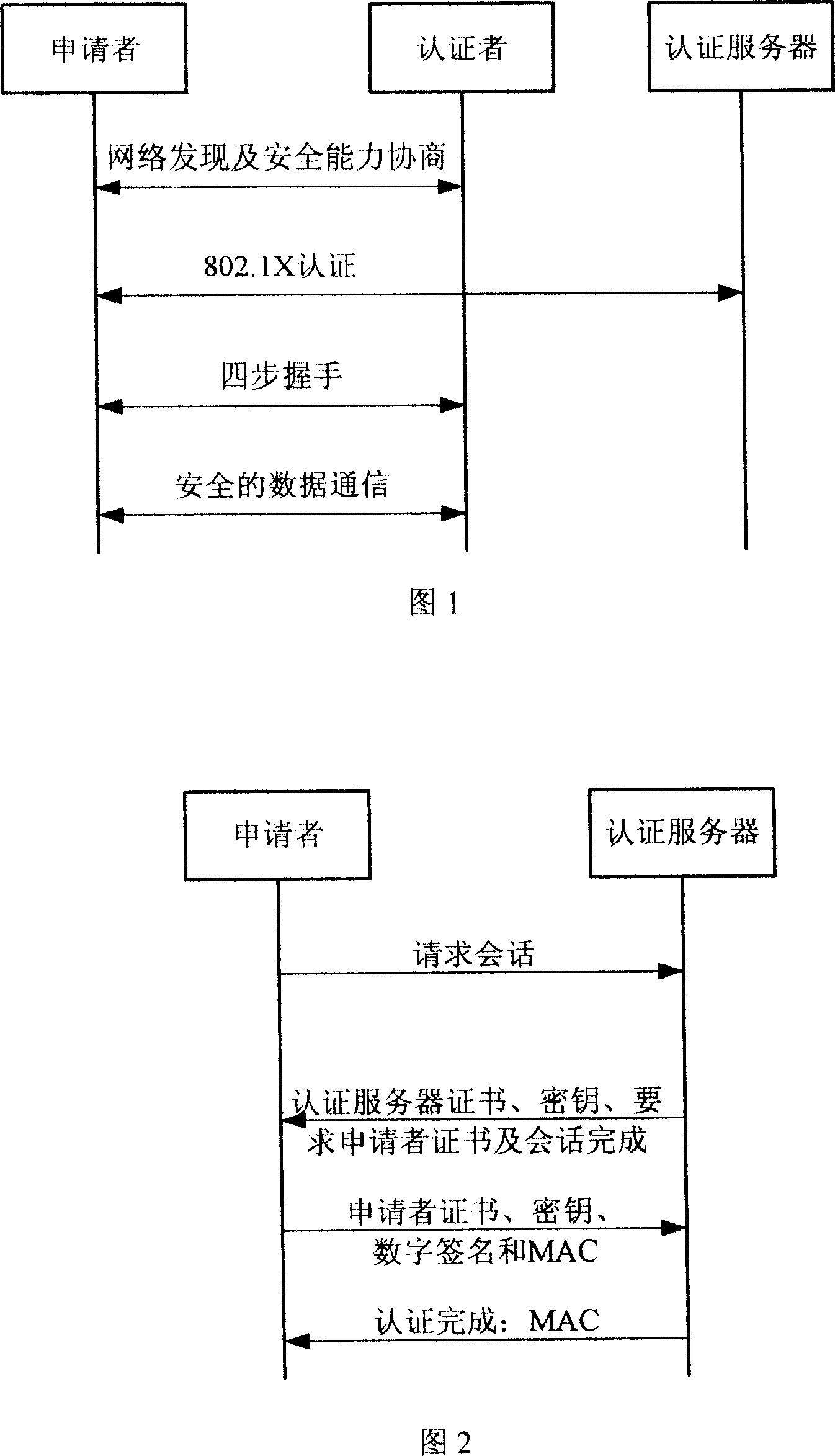
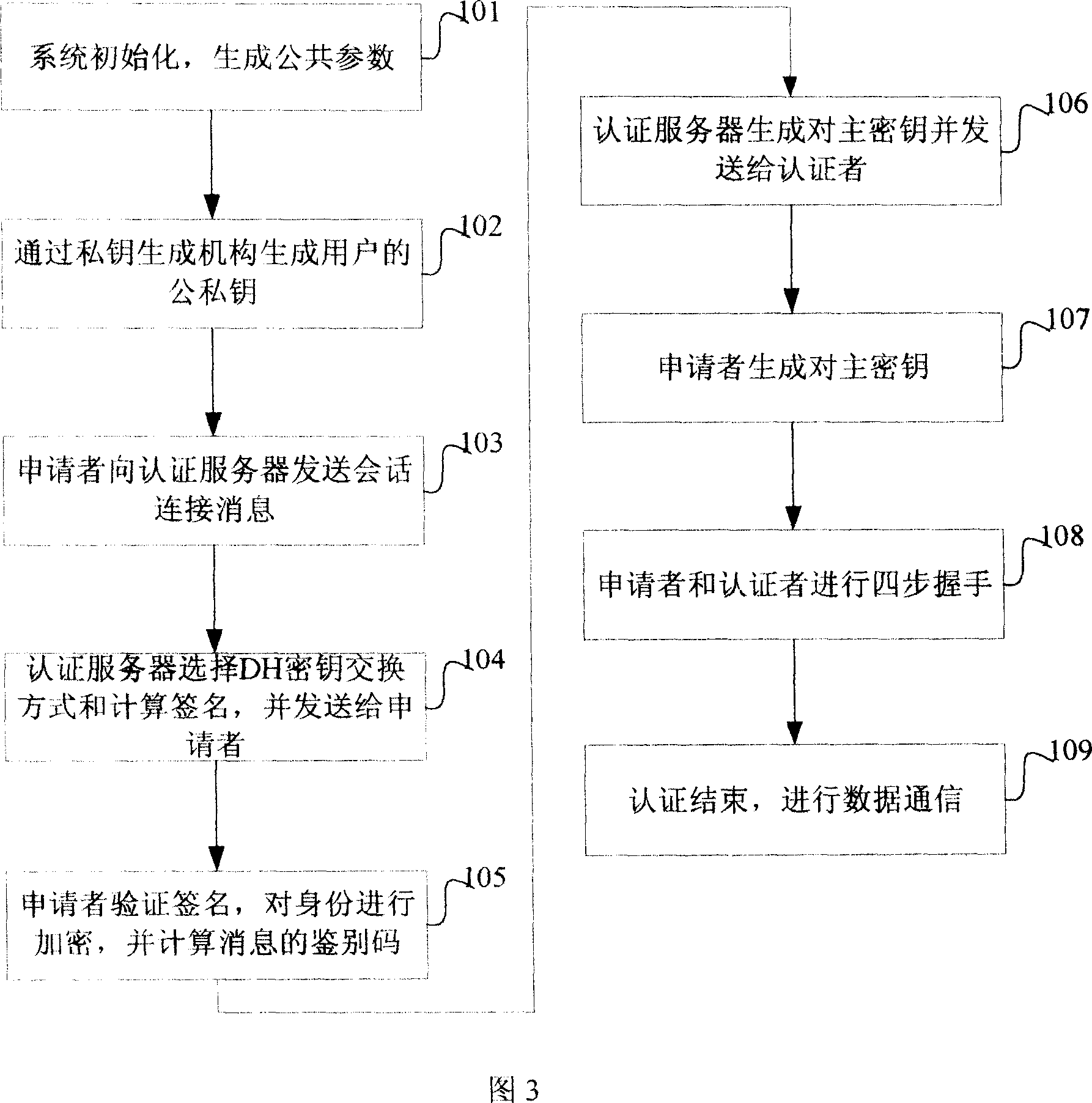
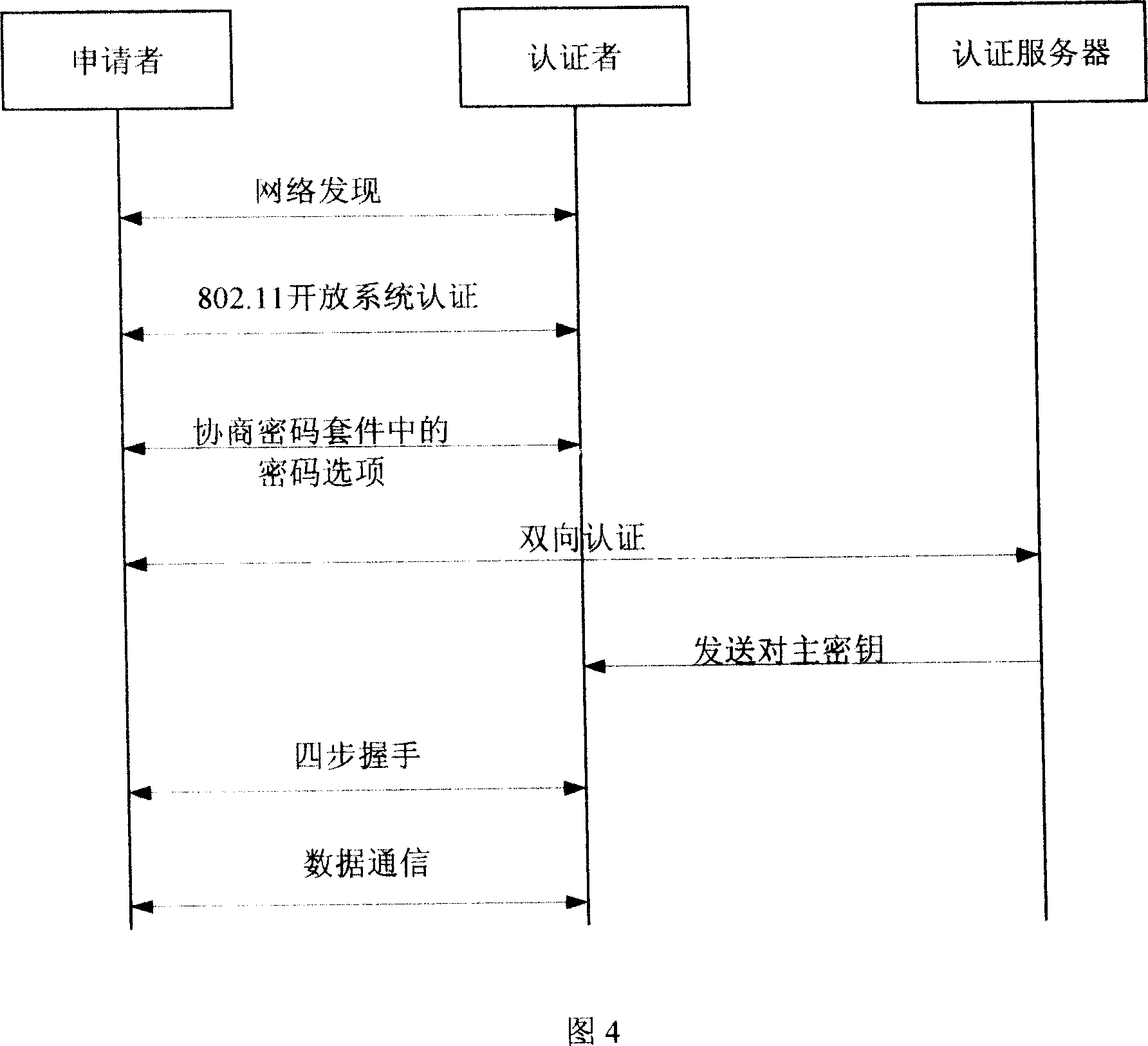
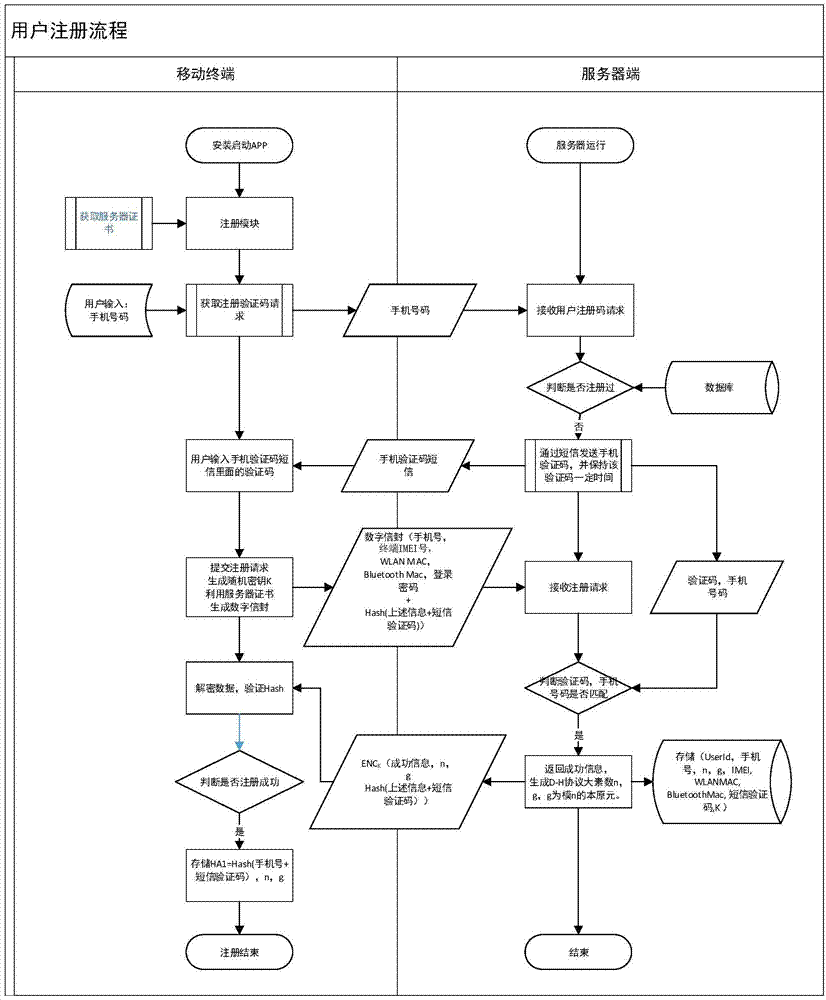
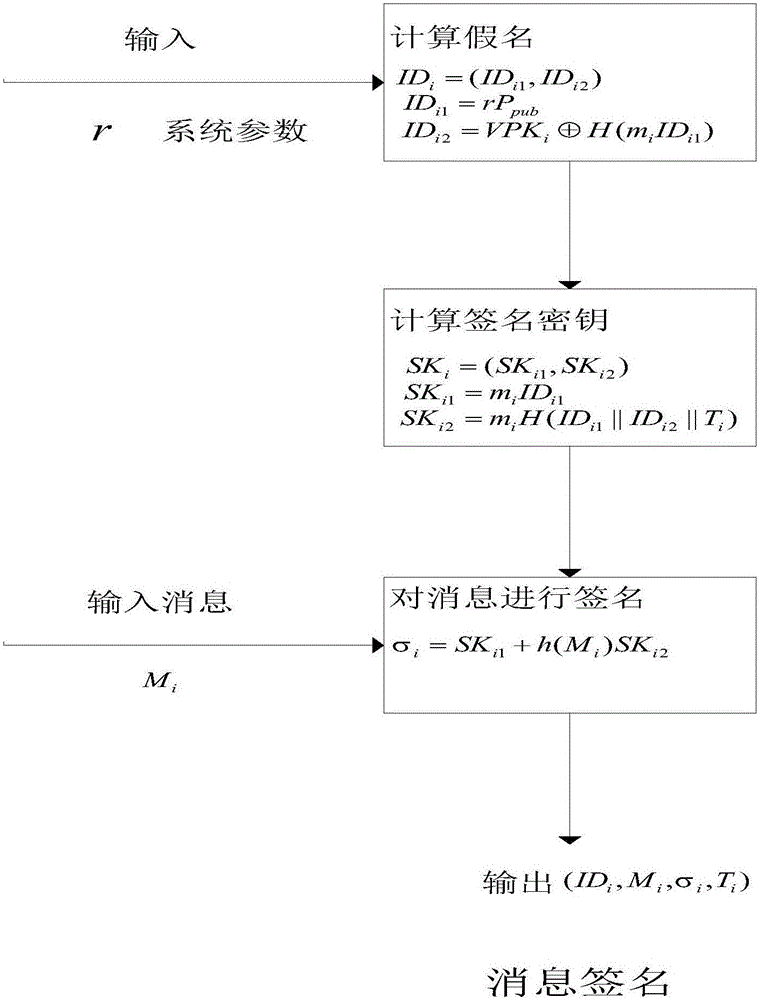
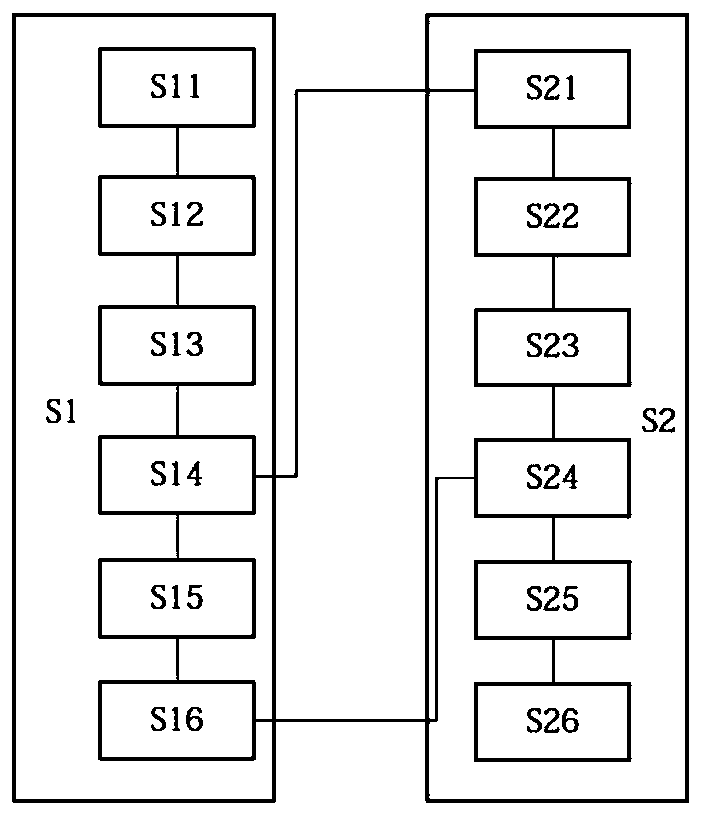
Bidirectional identification method and system
InactiveCN101119196AEffective calculationImprove security strengthUser identity/authority verificationHand shakesNetwork communication
The present invention provides a bi-direction authentication method and system which belongs to the field of network communication. The present invention aims at solving the problems that certificate management in present private key authority technology is complex and the certificate management can not protect the identity of the users. The present invention provides a bi-direction authority method. The present invention includes the procedures of the system initialization and generating system parameters, an applicant initializing a dialogue request to establish connection with an authorization server, the applicant and the authorization server mutually check identity and generate a pair of main key which is used for the four-procedure-hand-shaking. The present invention also provides a bi-direction authorization system. The system includes a parameter initialization module, an establishing dialogue connecting module, a server identity verification module and an applicant identify verification. Applications of the technical proposal of the present invention can reduce the establishing and maintenance cost of the system, to enhance the running efficiency of the system, and to realize the target of protecting applicants.
Owner:XIDIAN UNIV +1
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
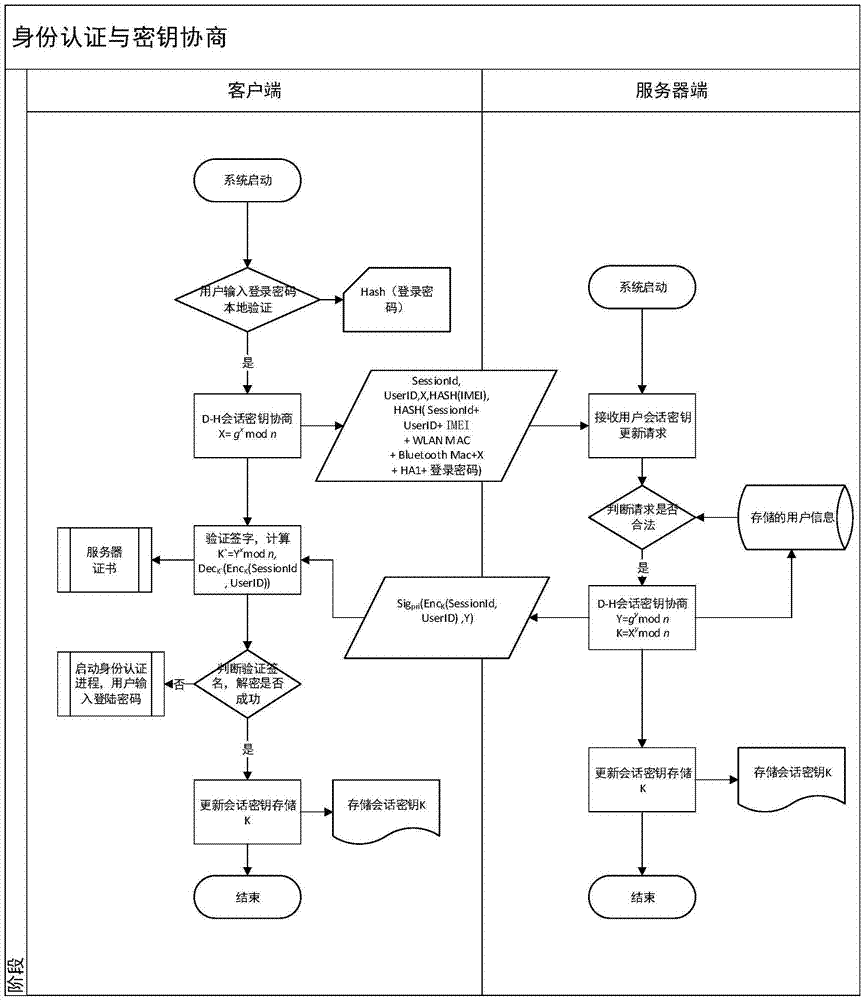
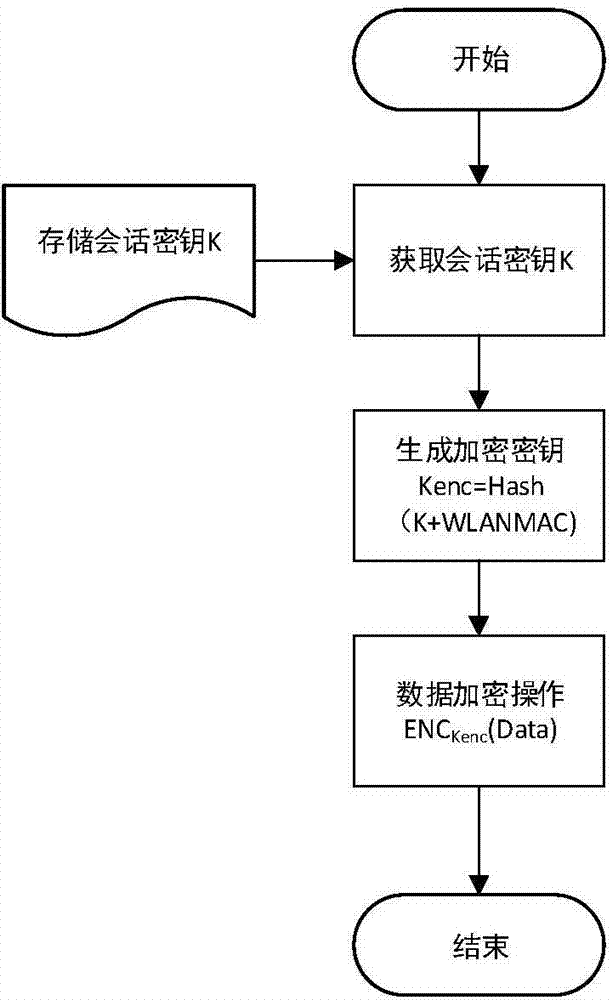
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
Identity based efficient anonymous batch authentication method in IOV (Internet of Vehicles) environment
ActiveCN105847235AAchieve authenticationImprove securityUser identity/authority verificationTrusted authorityTamper resistance
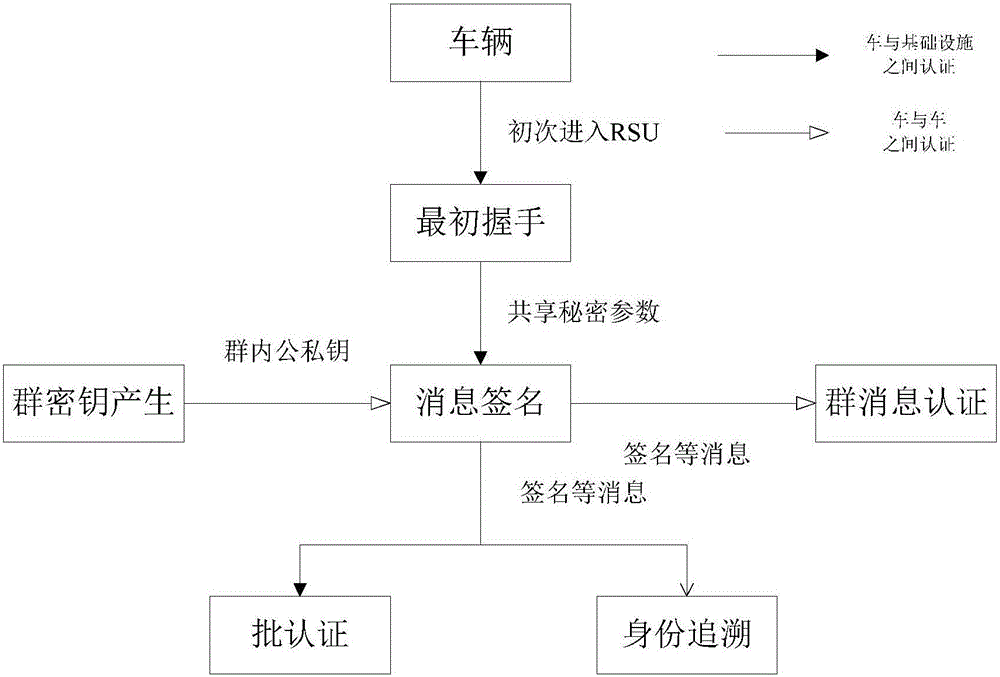
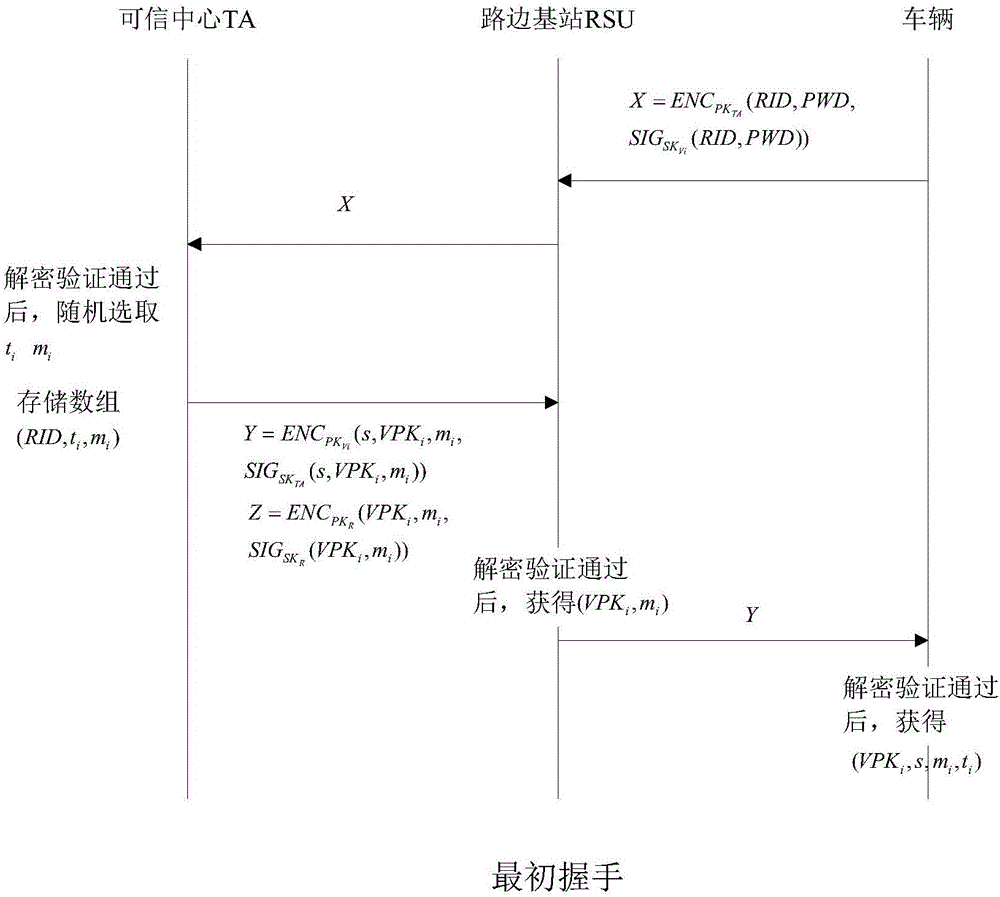
The invention discloses an identity based efficient anonymous batch authentication method in an IOV (Internet of Vehicles) environment. The identity based efficient anonymous batch authentication method in the IOV environment comprises an initial handshake module, a message signature module, a batch authentication module, an identity tracing module, a group key generation module and a group message signature and authentication module. According to the identity based efficient anonymous batch authentication method in the IOV environment, authentication between vehicles and infrastructures and authentication between vehicles can be realized, no tamper-proofing device is depended, privacy protection is realized by utilizing a pseudonymous name, conditional privacy protection is realized as a TA (Trusted Authority) can trace the real identity of each vehicle if necessary, the efficiency is improved as batch authentication is adopted, and the authentication process is simple and efficient. The message signature process and the group message signature process are same, the operating cost is low, and a replay attack can be borne as a time stamp is added.
Owner:南京秉蔚信息科技有限公司
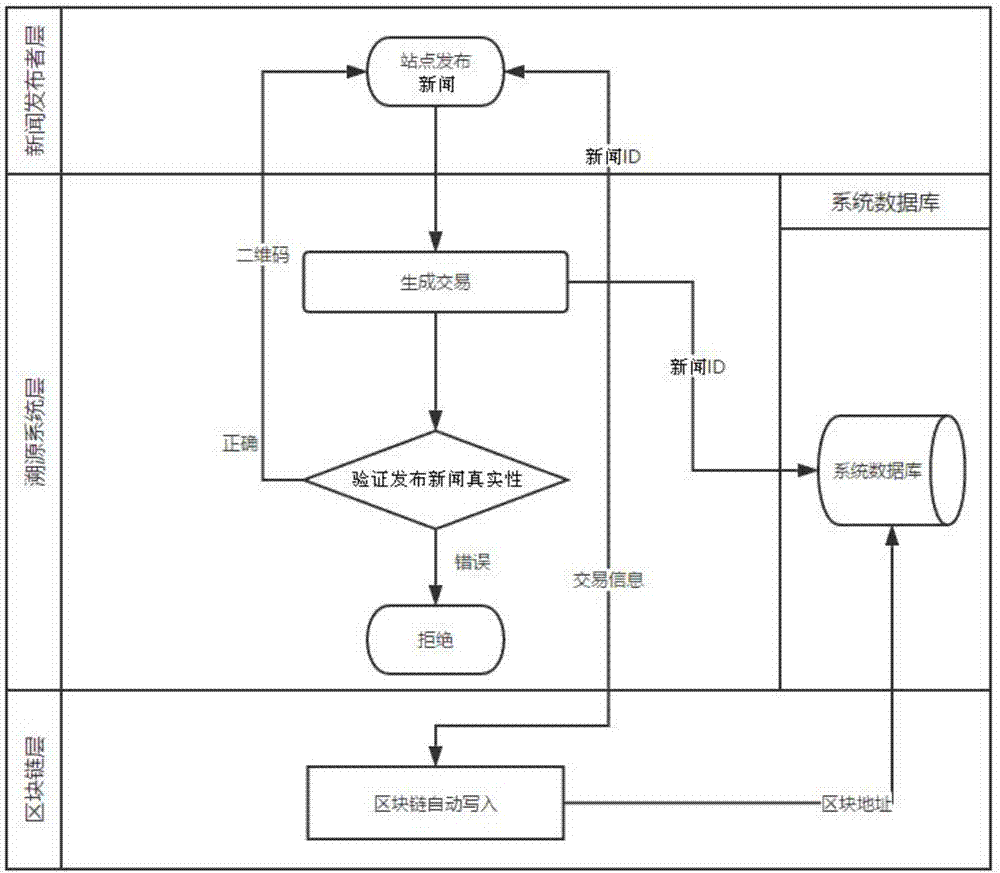
Block chain-based information-authenticating and source-tracing method and system
InactiveCN107316239AAchieve authenticationRealize traceabilityFinanceDigital data protectionVoucherSource tracing
The invention discloses a block chain-based information-authenticating and source-tracing method. The method comprises the steps of (1) acquiring the copy of the original information to be issued by an original information publishing end; (2) generating the hash value of the copy and picking the content information of the copy at the same time; (3) creating the first transaction information based on the content information of the copy and the hash value of the copy; (4) writing the first transaction information into a center database and a block chain, or writing the first transaction information into the block chain; (5) acquiring the transshipment information released by a information transshipment end, and generating the hash value of the transshipment information; (6) comparing the hash value of the transshipment information with the hash value of the copy; if the two hash values are the same, returning a first voucher for representing the information to be true or non-tampered; if the two hash values are not the same, not returning the first voucher or returning a second voucher for representing the information to be not true or tampered. The invention further discloses a corresponding system. According to the invention, the information authentication and the source tracing can be reliably realized.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
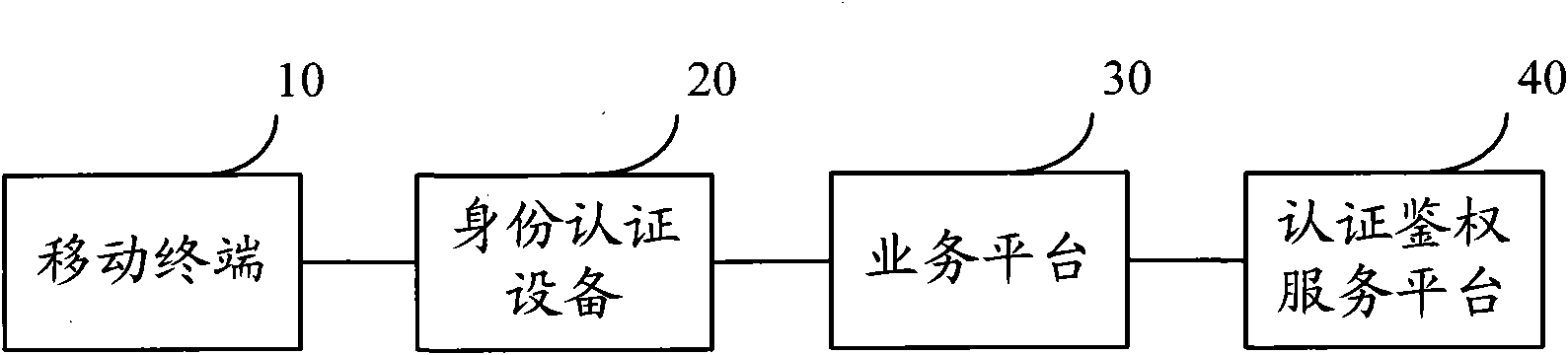
Identity authentication method, device and system
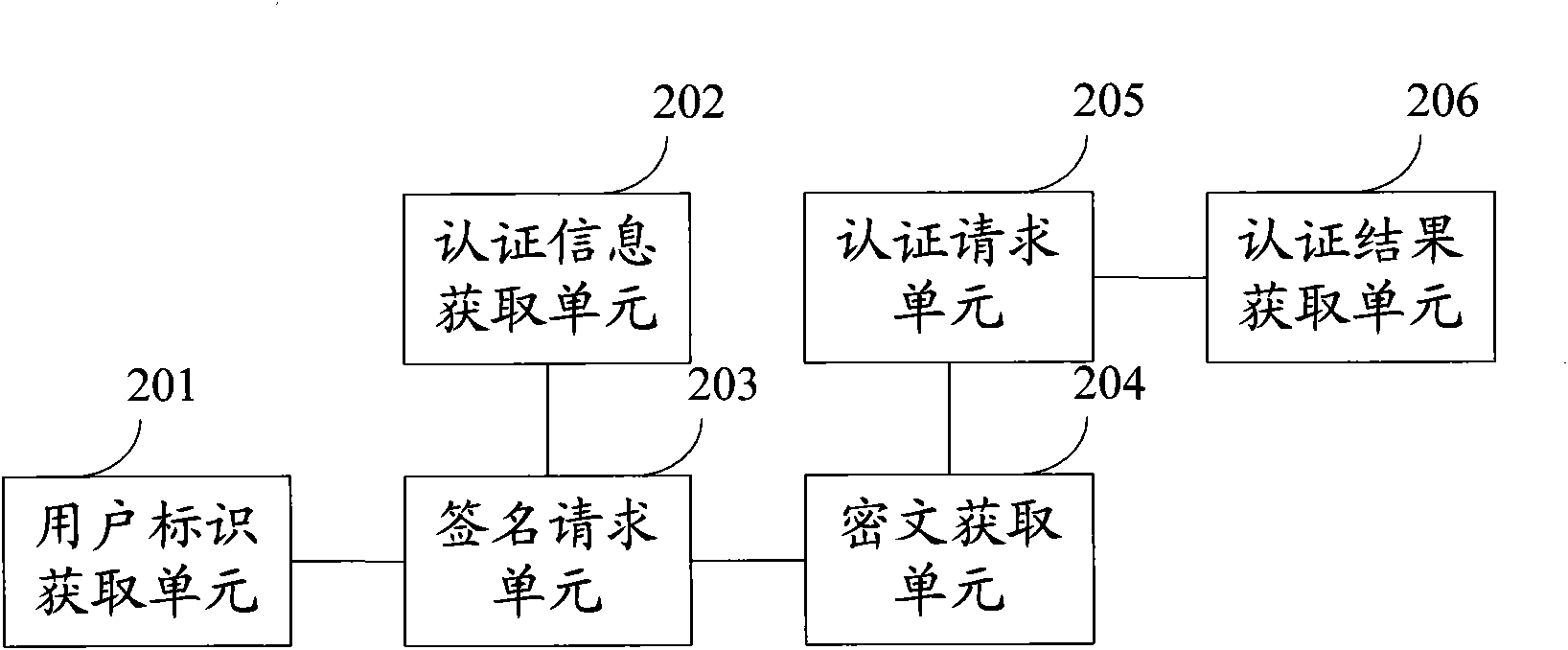
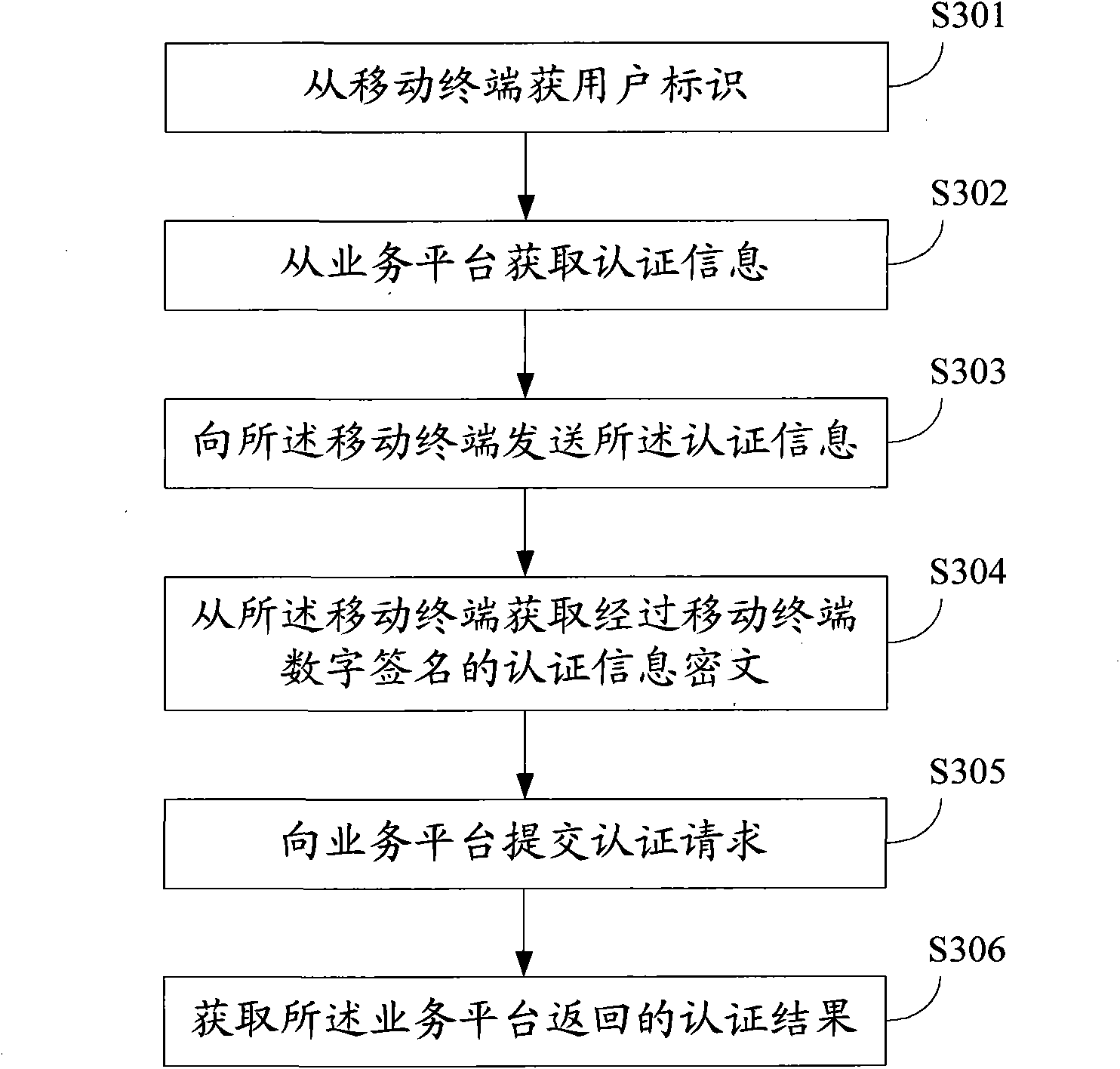
InactiveCN101778380AAchieve authenticationAvoid security risksUser identity/authority verificationSecurity arrangementCiphertextSerial code
The embodiment of the invention provides an identity authentication method, which comprises the steps of acquiring a user identification from a mobile terminal; acquiring identification information including an authentication serial number and authentication time from a service platform; sending the identification information to the mobile terminal; acquiring authentication information cipher text digitally signed via the mobile terminal form the mobile terminal; submitting an authentication request including the user identification, the authentication information and the authentication information cipher text to the service platform; and acquiring authentication results returned by the service platform. Accordingly, the embodiment of the invention also discloses an identity authentication device and an identity authentication system. With the invention, the user identity is authenticated, and various safety risks and losses brought by fake or alternative identity and the like are avoided.
Owner:卓望数码技术(深圳)有限公司
Method, system and equipment for authentication
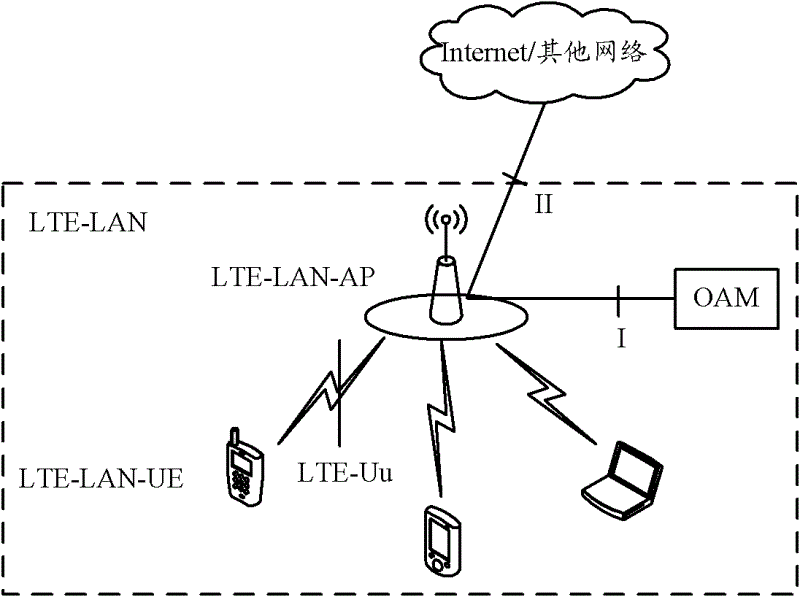
The embodiment of the invention, which relates to the wireless communication technology field, discloses a method, a system and equipment for authentication, so that a problem of how to carry out authentication between a terminal and an access point (AP) device can be solved. According to the invention, a terminal sends identification information of the terminal to an AP device; the AP device sends an authentication request carrying the identification information of the terminal to a home subscriber server (HSS) through gateway (GW) equipment; the HSS determines a root key that is arranged for the terminal corresponding to the terminal identification in advance; according to the root key and an authentication and key agreement (AKA) algorithm, an AKA authentication vector is obtained by calculation; the AKA authentication vector is sent to the AP device through GW equipment; and the AP device sends the AKA authentication vector to the terminal and the terminal uses the AKA algorithm to carry out verification on the AKA authentication vector and determines whether the AP device is legal or not according to the verification result. Therefore, the authentication on the AP device by the terminal is realized.
Owner:CHINA ACAD OF TELECOMM TECH
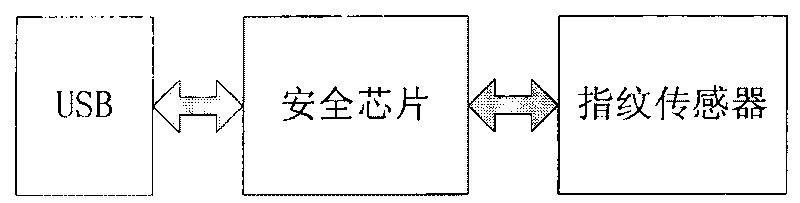
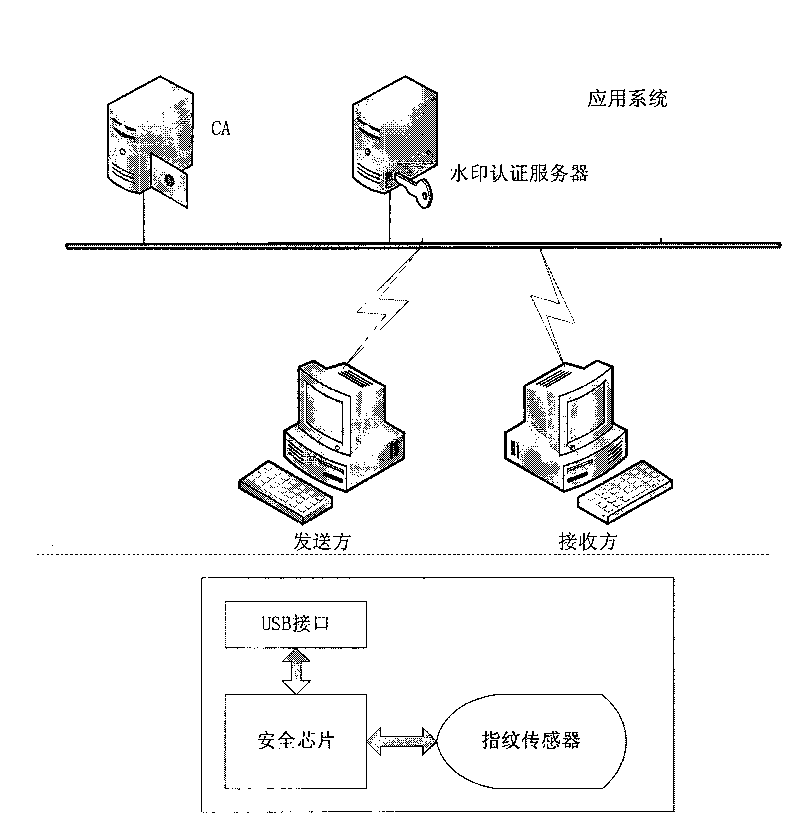
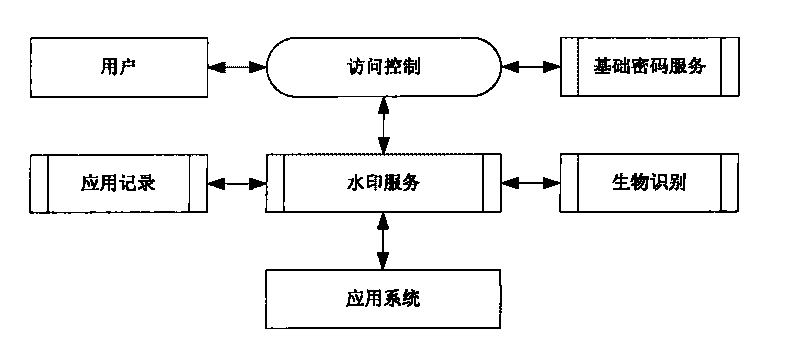
Security certificate method based on fingerprint, cryptographic technology and fragile digital watermark
ActiveCN101729256AAuthenticityAvoid the risk of being stolenUser identity/authority verificationImage data processing detailsDigital signatureSecure authentication
The invention discloses a security certificate method based on fingerprint, cryptographic technology and fragile digital watermark, comprising the following steps: a sender collects a fingerprint image, calculates summary information of the fingerprint image and inserts the summary information, a secret key and digital information which is digitally signed and encrypted into the fingerprint image as a watermark; the fingerprint of the sender is collected, the fingerprint image inserted with the watermark is sent to a receiver after the fingerprint of the sender is qualified; after receiving information, the receiver firstly detects and verifies whether the fingerprint image is inserted with the digital watermark and whether the digital watermark is right or not so as to indentify identity authenticity; digital watermark information is extracted from the received image; the summary information of the fingerprint image from which the watermark is extracted is calculated; and the summary information is compared with the summary information of the fingerprint image recorded in the watermark information to approve information authenticity. The invention can effectively overcome the defects that the existing digital signature security certificate can not approve the legal KEY holder and the fingerprint in the fingerprint certificate is easy to clone and embezzle.
Owner:SHENZHEN POKA ELECTRONICS EQUIP +1
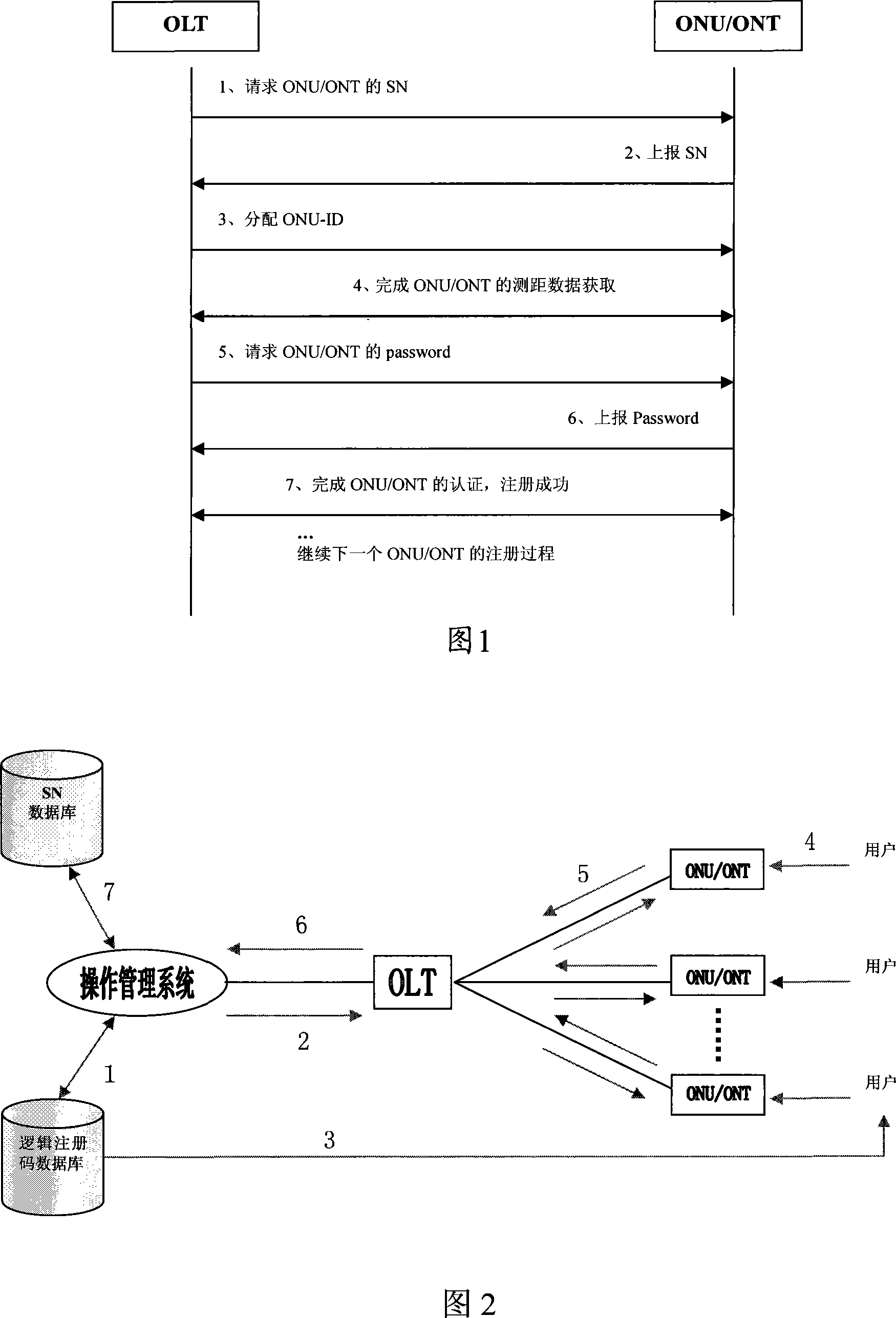
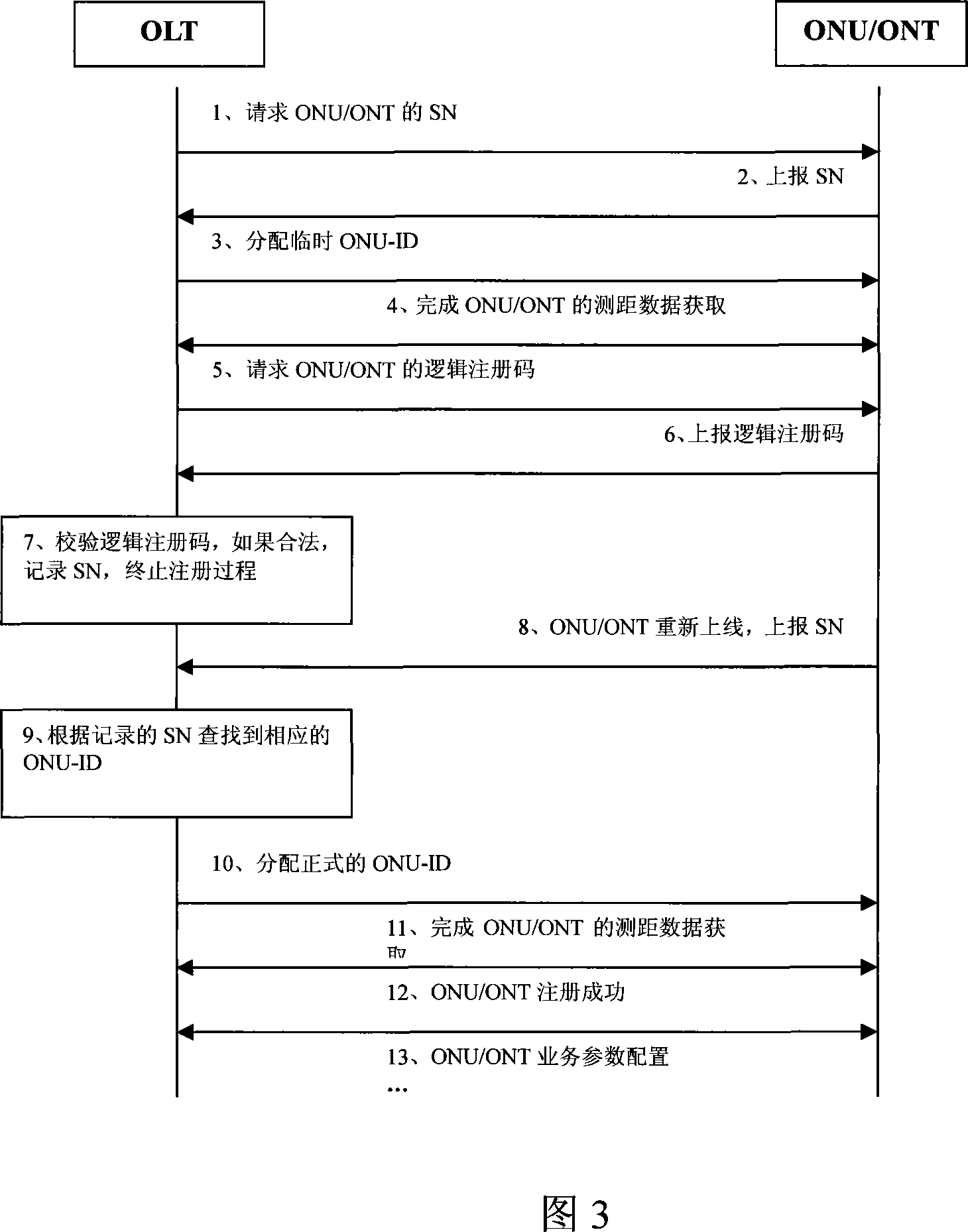
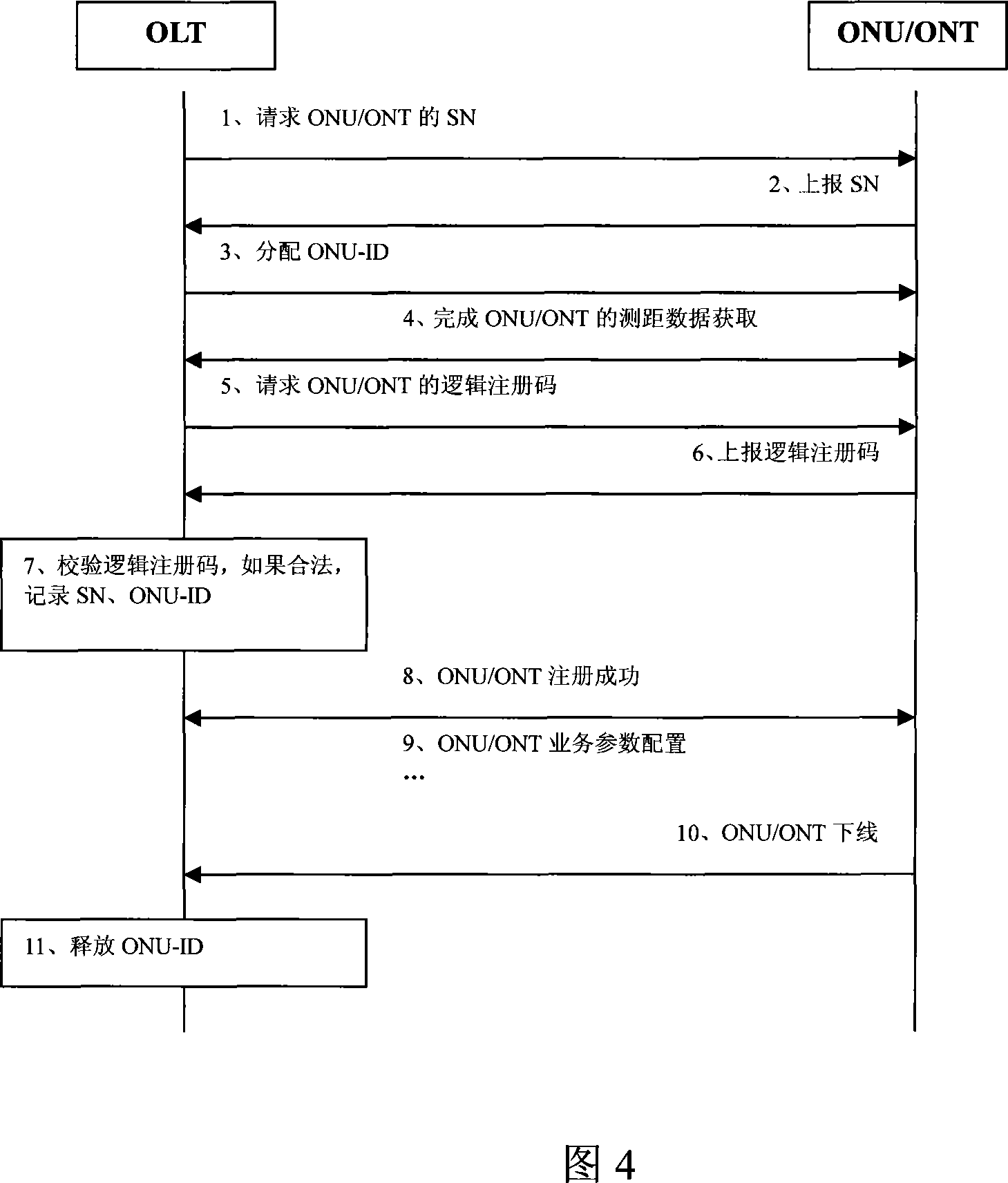
Terminal detection authentication process, device and operation administrative system in passive optical network
ActiveCN101083589AReduce maintenance costsIncrease flexibilityMultiplex system selection arrangementsUser identity/authority verificationComputer hardwareMaintainability
The invention relates to terminal detecting certifying method, device and operational management system in passive optical network. The method includes the following steps: the terminal has logic poll code; the local terminal will confirm the received logic poll code matches with stored one to check it is legal; recording the legal terminal sequence code as terminal mark. The invention can reduce maintenance cost, increase detecting certifying flexibility and maintainability.
Owner:HUAWEI TECH CO LTD
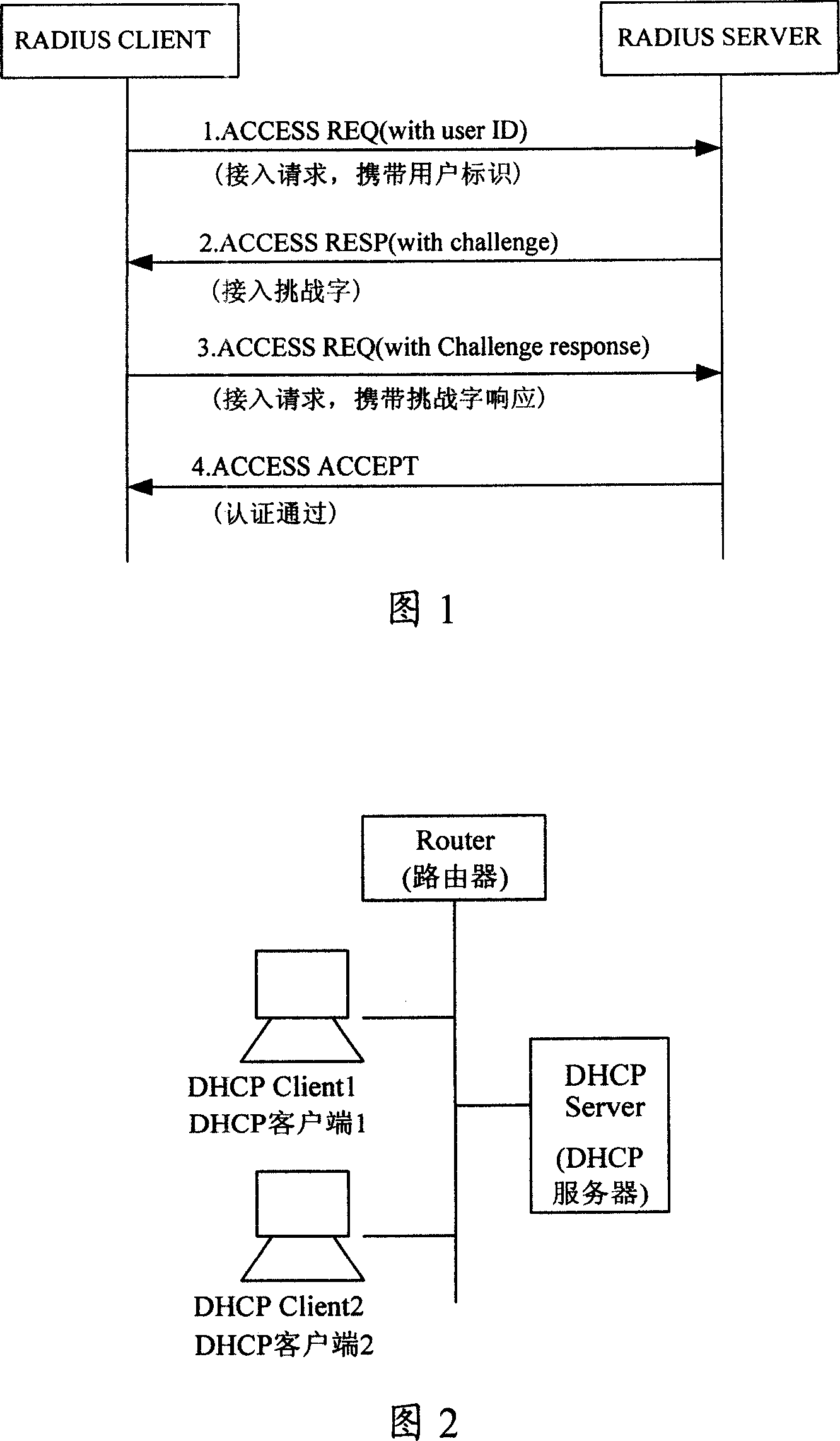
Implementing authentication method and system
InactiveCN101141253AEnsure safetyAchieve authenticationUser identity/authority verificationUser deviceInternet privacy
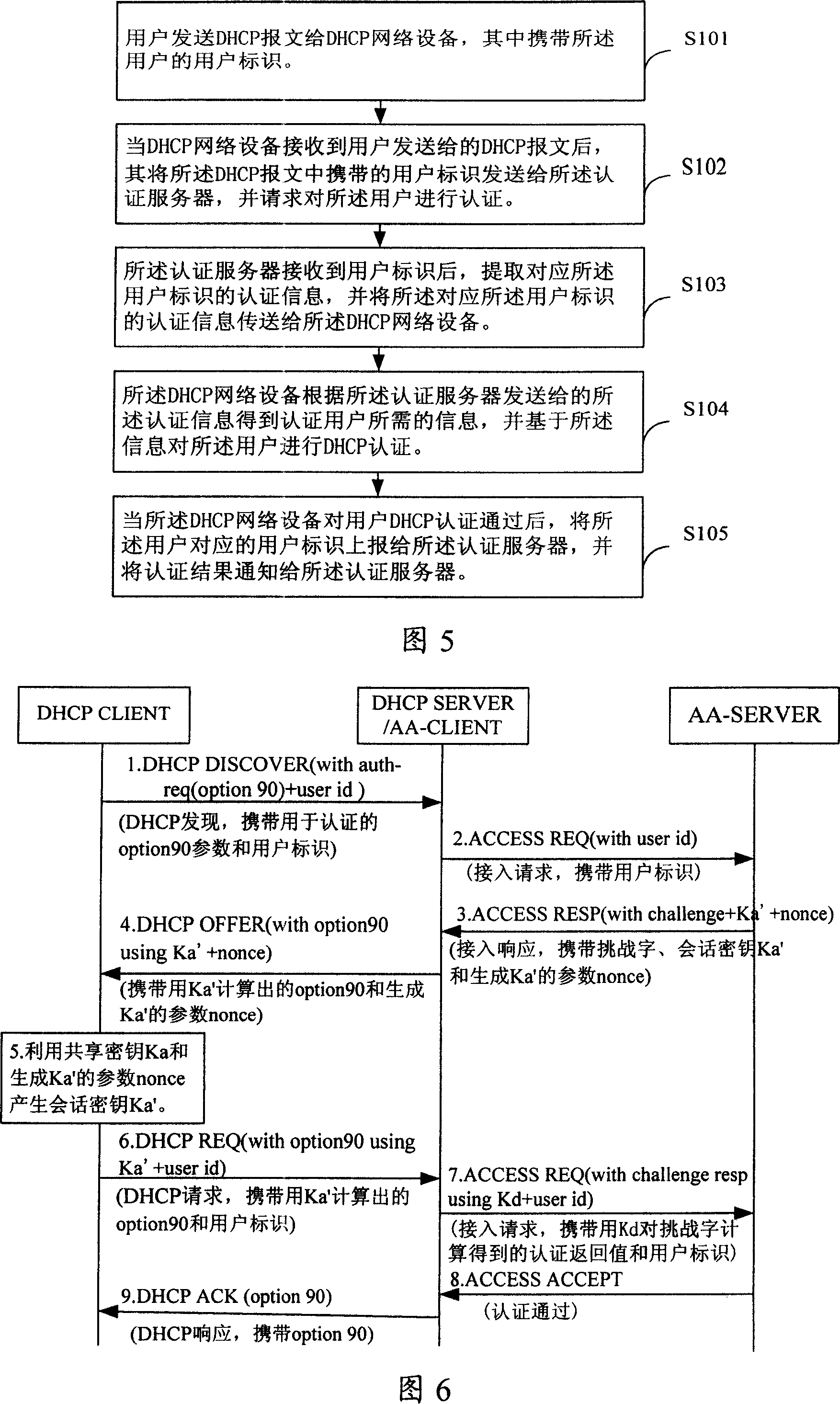
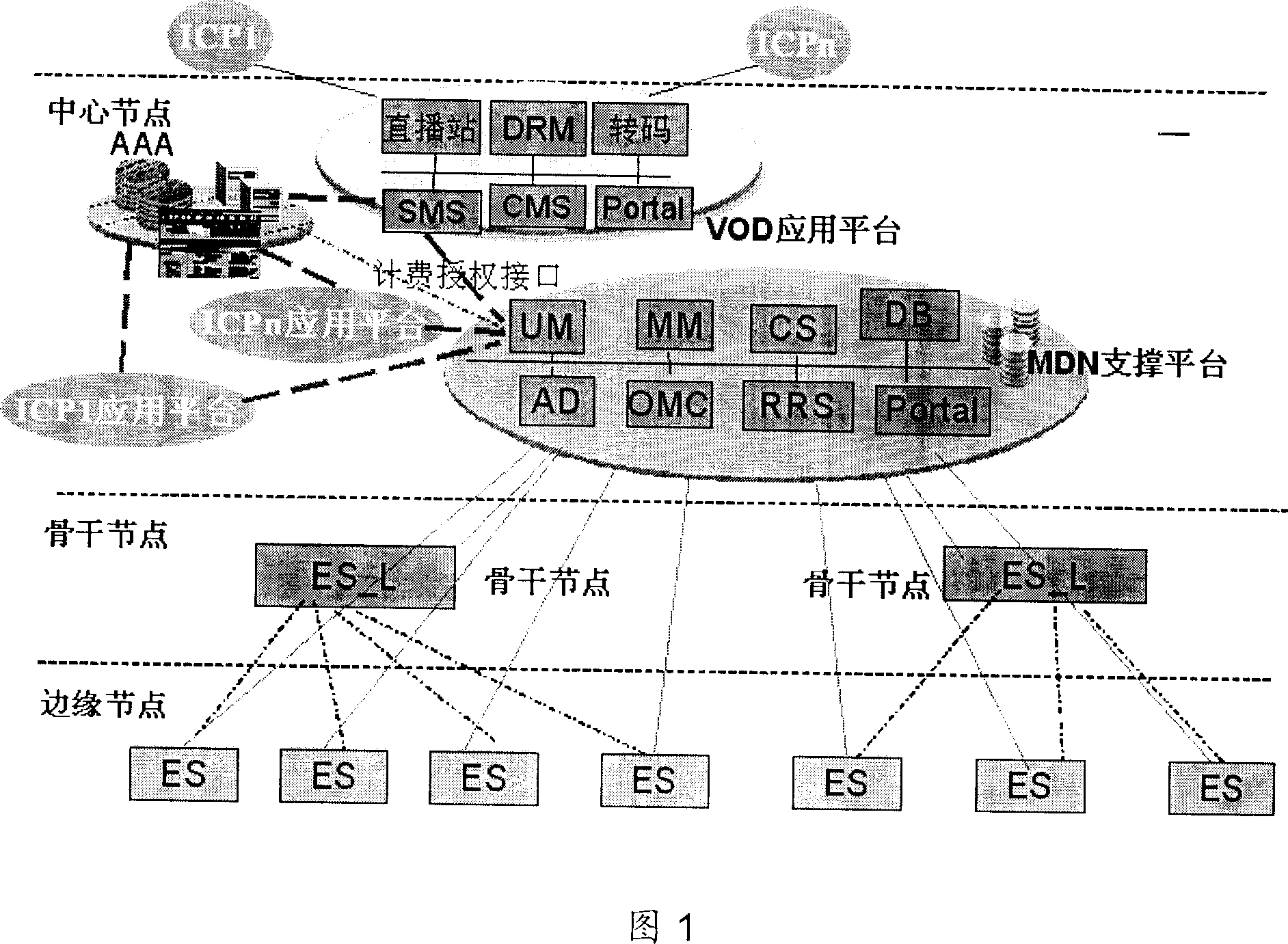
The utility model discloses an authentication method and a authentication system. The core thereof is that when the DHCP network equipment receives the DHCP message sent by the user, the authentication information for the user can be obtained through the interaction with the authentication server. Based on the information needed by the authentication client, the DHCP network equipment can conduct the DHCP authentication for the user. Also, the utility model provides another authentication method as well as a certified server, a DHCP network device and a user device. The utility model guarantees not only the user's safety, but also the network equipment's reliability. Meanwhile, based on the DHCP authentication mechanism, the user can conduct the network authentication. As the relay certified server is added, the user can be effectively certified. The authentication server can launch the re-authentication process, so that the network is supported to conduct the re-authentication for the user.
Owner:HUAWEI TECH CO LTD
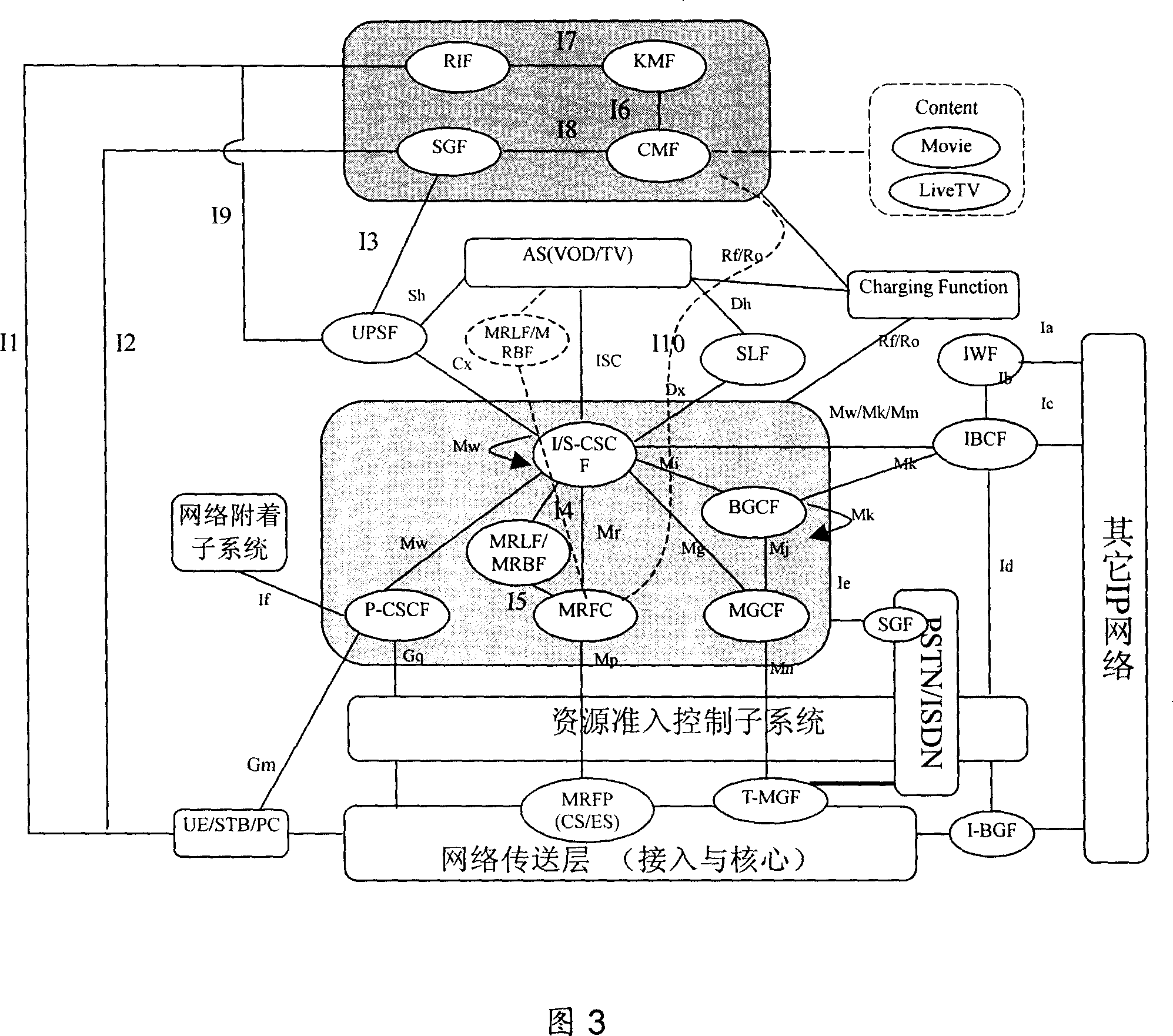
IMS-based flow media network system
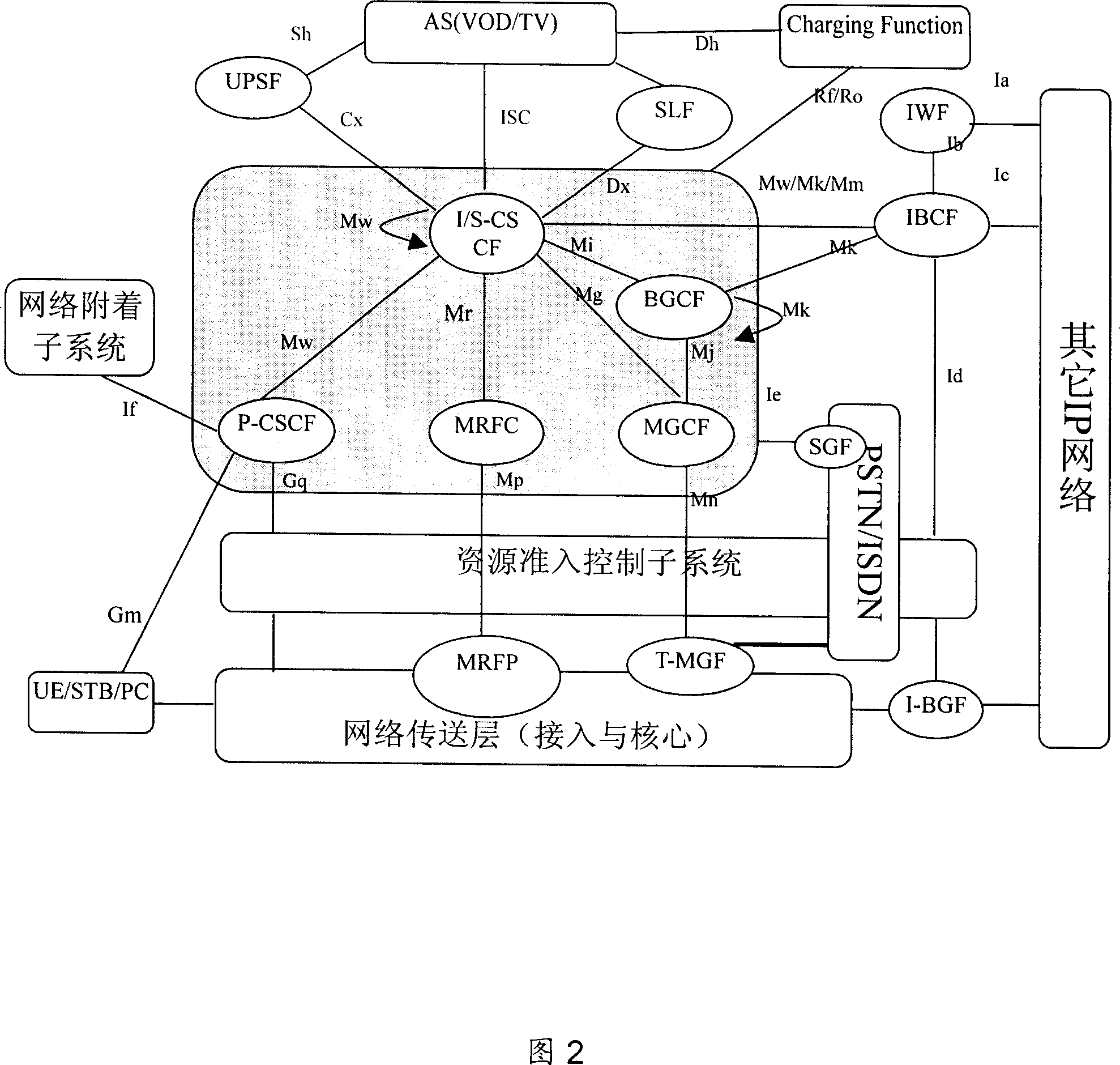
ActiveCN101026615AAchieve authenticationRealize billingAutomatic exchangesTwo-way working systemsApplication serverSession control
The system includes following parts: P-CSCF, S-CSCF, and I-CSCF in use for implementing controlling session, routing, and service triggering functions; entity for enabling stream media service (SMS) is in use for implementing supporting function needed by SMS; media resources functional (MRF) entity is in use for implementing function of media server; media resources locating function (MRLF) entity, or media resources broker function (MRBF) entity is in use for implementing function of distributing and dispatching media resource; application server AS is in use for implementing function of logic controlling SMS; user signed data service function (UPSF) is in use for saving user information of signed stream media user, authority information, and selectable SMS information; and user equipment UE. Comparing prior art, the invention realizes united authentication, charging, managing supporting functions for users, and guarantees QoS.
Owner:HUAWEI TECH CO LTD
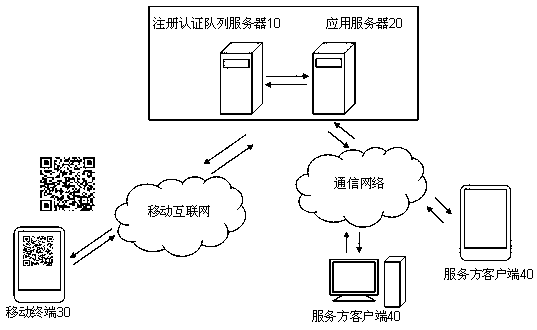
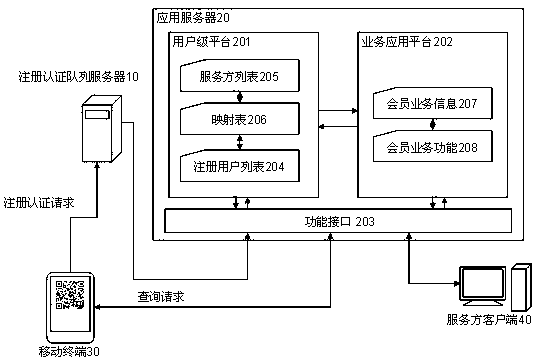
Two-dimension code user registration certification system and method thereof
ActiveCN103236935AImprove experienceImplement user registration methodUser identity/authority verificationCommerceApplication serverSoftware engineering
The invention discloses a two-dimension code user registration certification system and a method of the two-dimension code user registration certification system. The system is characterized in that a mobile terminal shoots a two-dimension code and obtains a service provider ID in the two-dimension code, and the mobile terminal sends a registration certification request containing the service provider ID and the mobile terminal number to a registration certification array server; an application server extracts and analyzes the registration certification request from the request array of the registration certification array server, and verifies whether the mobile terminal number is registered as a registered user corresponding to the service provider ID; if not, registering the mobile terminal number as the registered user corresponding to the service provider ID; and if so, activating a corresponding service provider client to execute member service functions on the registered user. According to the invention, the user registration and user certification operations are finished by the flexible and easy manner with high experience of shooting the two-dimension code, thereby being convenient for the user to register as a member and enjoy the member service.
Owner:重庆瑞迅宏成信息技术有限公司
Vehicle authentication method, device and system
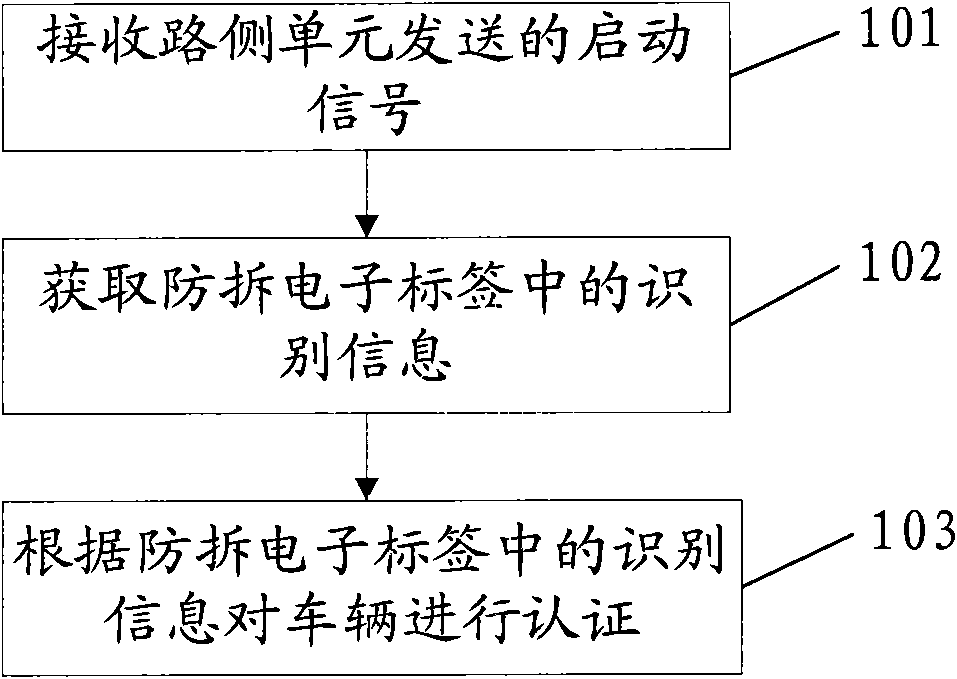
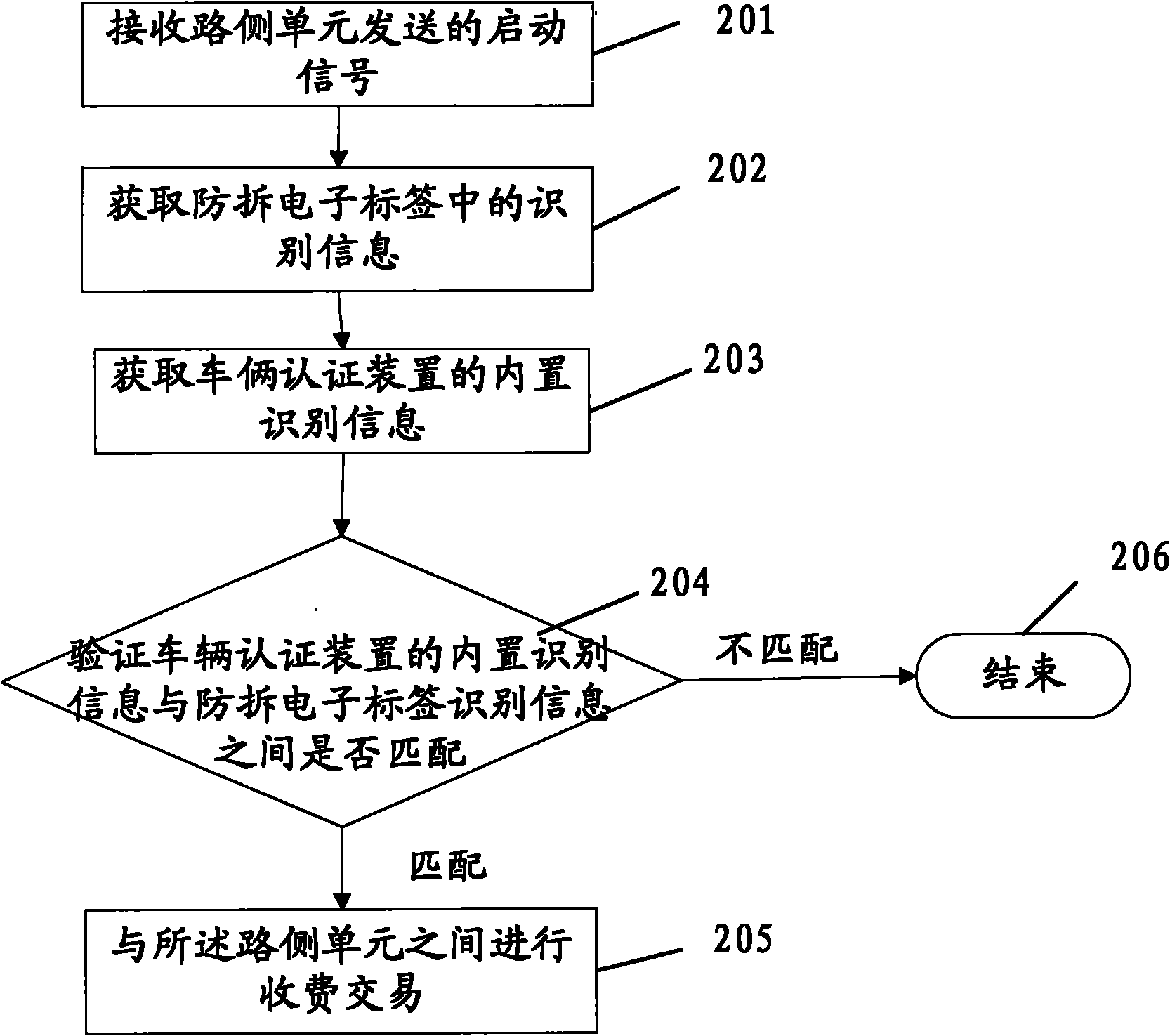
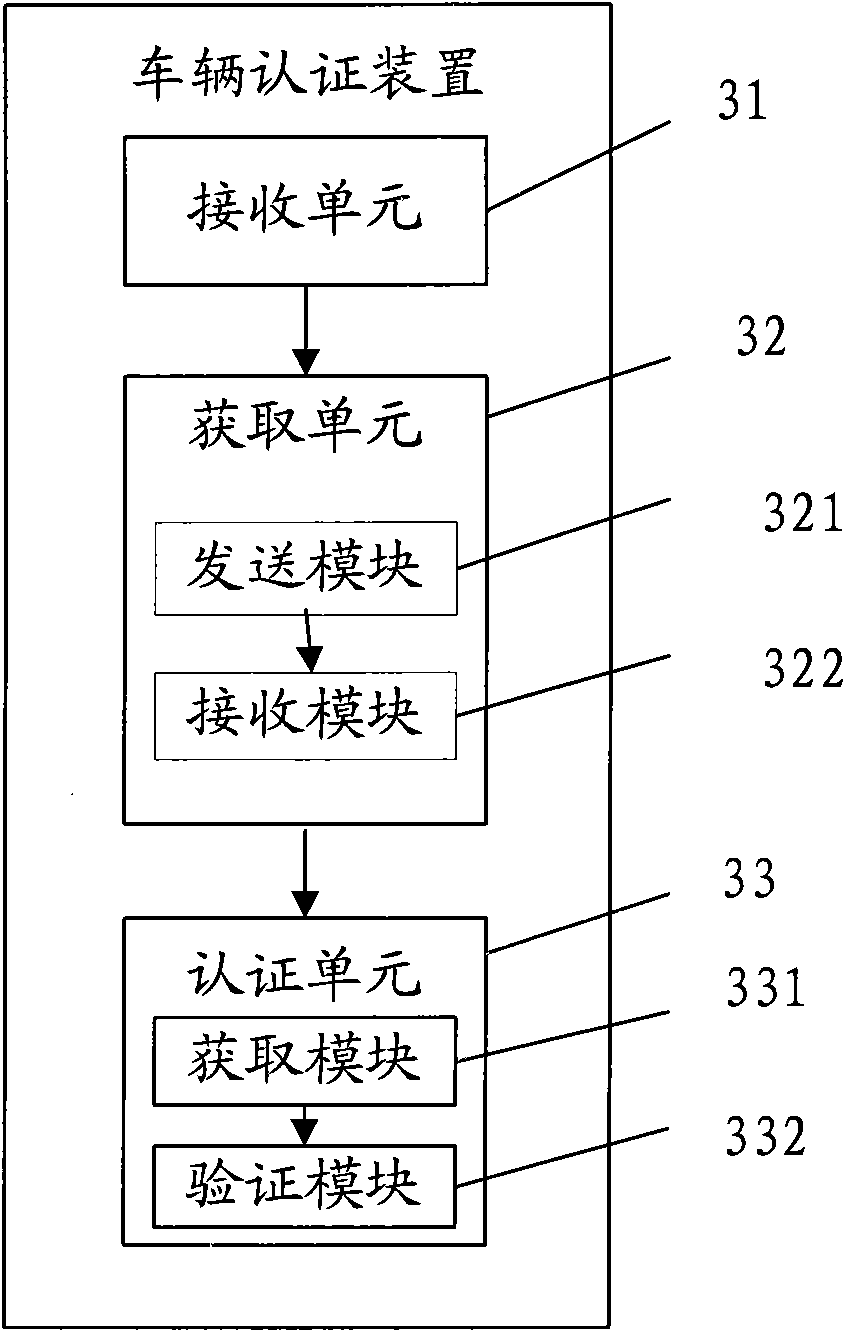
InactiveCN101859446AAchieve authenticationTicket-issuing apparatusElectronic taggingElectronic toll collection system
The embodiment of the invention discloses vehicle authentication method, device and system and relates to the technical field of vehicle authentication. The invention can effectively authenticate vehicles and can not bring inconvenience to vehicle owners. The vehicle authentication method comprises the following steps of: receiving starting signals sent from a road side unit; acquiring identifying information in an anti-dismantle electronic tag fixed on a vehicle; and authenticating the vehicle according to the identifying information in the anti-dismantle electronic tag. The invention is mainly used for authenticating vehicles, especially used in an electronic toll collection system to authenticate the vehicles.
Owner:BEIJING WATCH DATA SYST
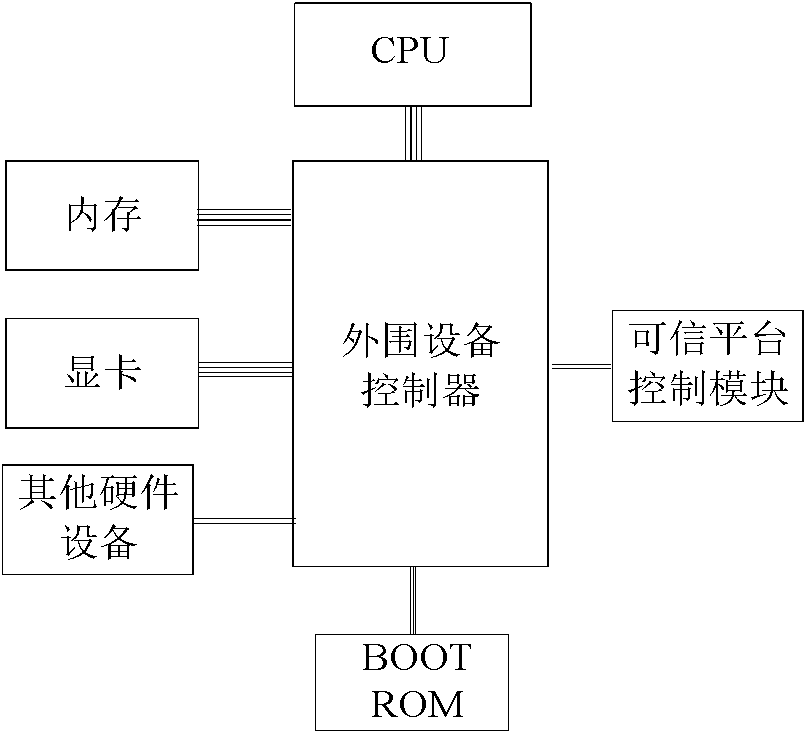
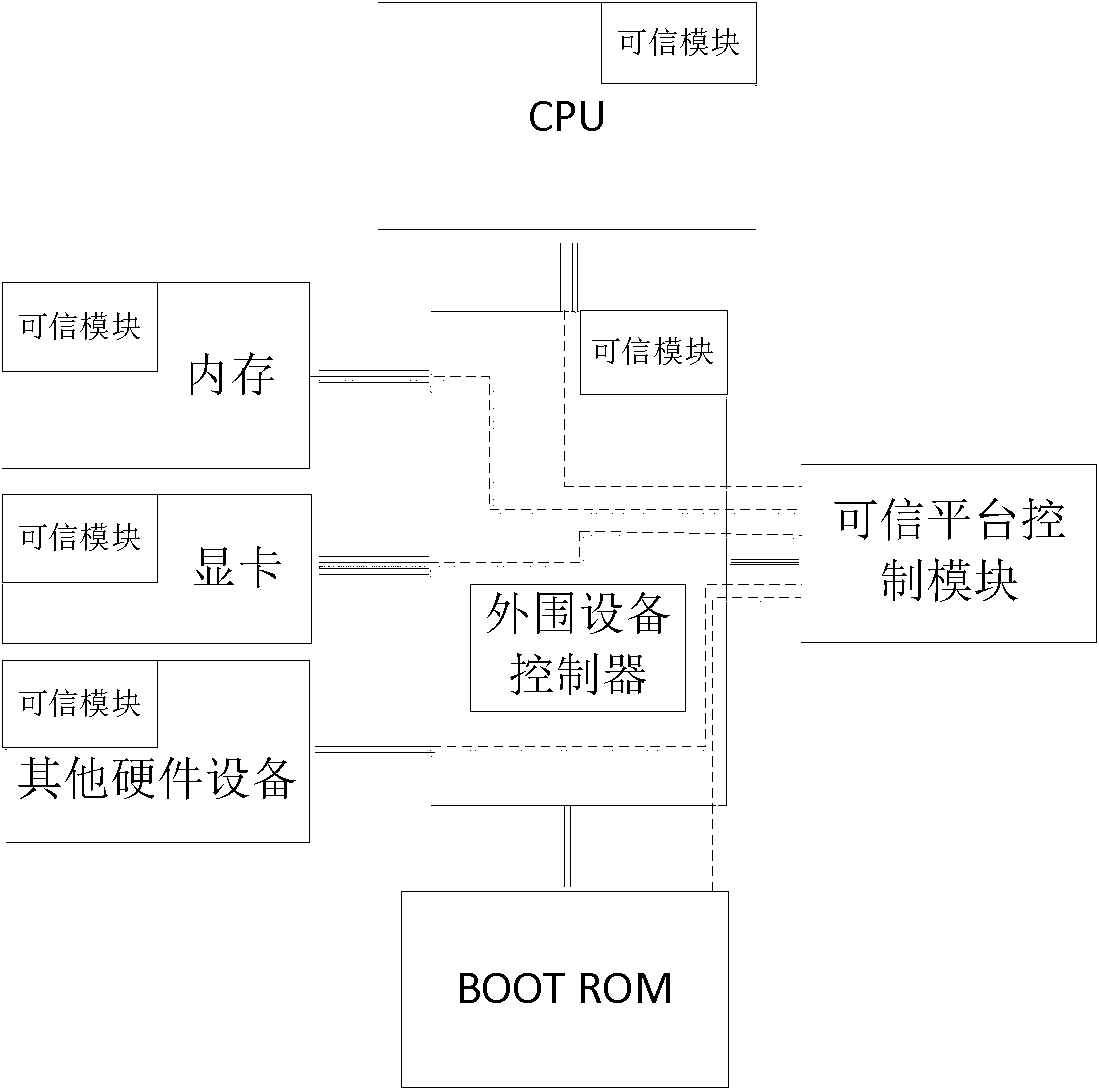
Credible device with active control function and authentication method thereof
ActiveCN102063593AEnsure safetyAchieve authenticationPlatform integrity maintainanceApplication softwareActive measurement
The invention discloses a credible device with an active control function and an authentication method thereof, relating to the field of information security. A credible platform control module with the active control function and a hardware device are connected to a credible platform of the credible device with the active control function, wherein the hardware device are separated into a credible hardware device and an incredible hardware device by the credible platform control module through the active control function, and the credible platform control module is internally provided with hardware units such as an active measurement engine, a control judgment engine, a work mode customizing engine, a credible control policy configuration engine and the like to realize active check on theworking condition configuration information of the hardware device, control policy configuration information, a firmware code and the working condition of a circuit. Mutual binding between the credible platform and the credible hardware is realized through combing the credible platform control module and a credible pipeline technology, the binding process of the credible platform control module and the credible hardware is completely transparent to an operating system and an application program, and the operating system cannot bypass or intervene the process of binding the credible hardware by the credible platform.
Owner:BEIJING UNIV OF TECH
Heterogeneous Internet of Things authentication method based on edge computing and Internet of Things security platform
ActiveCN109873815AImplement anonymous authenticationAchieve authenticationPublic key for secure communicationThe InternetHeterogeneous network
The invention belongs to the technical field of computer network security, and discloses a heterogeneous Internet of Things authentication method based on edge computing and an Internet of Things security platform. By deploying the edge server on the edge side and managing massive Internet of Things terminal authentication information by the edge server, the defects of an existing cloud-end-basedauthentication mechanism are overcome, the core network load is reduced, and the authentication efficiency is improved. The edge equipment generates a unified virtual IPv6 address for the heterogeneous network equipment according to the address information of the heterogeneous network equipment, so that the unified security authentication of the heterogeneous Internet of Things equipment is realized. And the lightweight and high efficiency of the authentication protocol are ensured by using the random number and the hash value. According to the Internet of Things authentication architecture based on edge computing provided by the invention, the authentication information of mass Internet of Things terminals is managed by the edge equipment, so that the core network load can be effectivelyreduced, and the authentication efficiency is improved. The identity authentication of the Internet of Things terminal is simply and efficiently realized by using the random number and the hash value,and the cross-network security authentication of the heterogeneous Internet of Things terminal is realized.
Owner:XIDIAN UNIV
Encryption method applied to MQTT-SN protocol
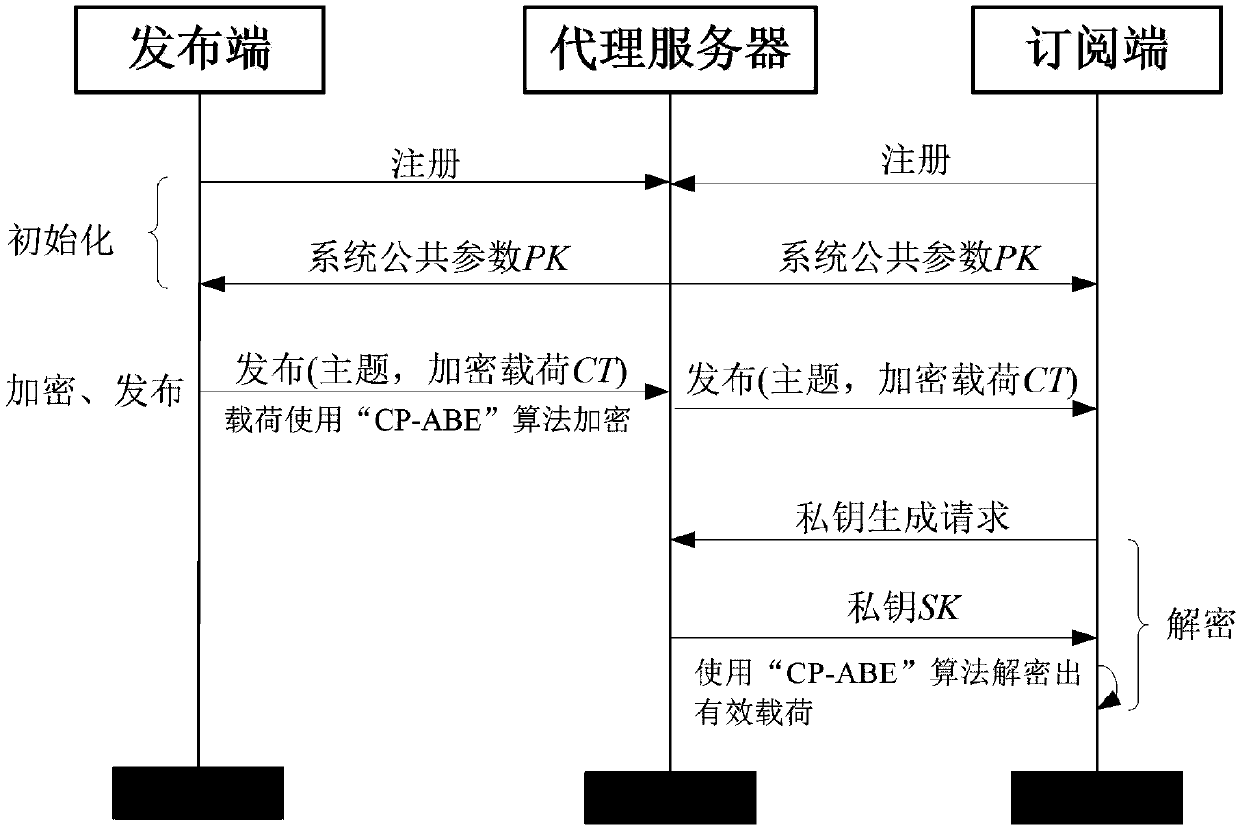
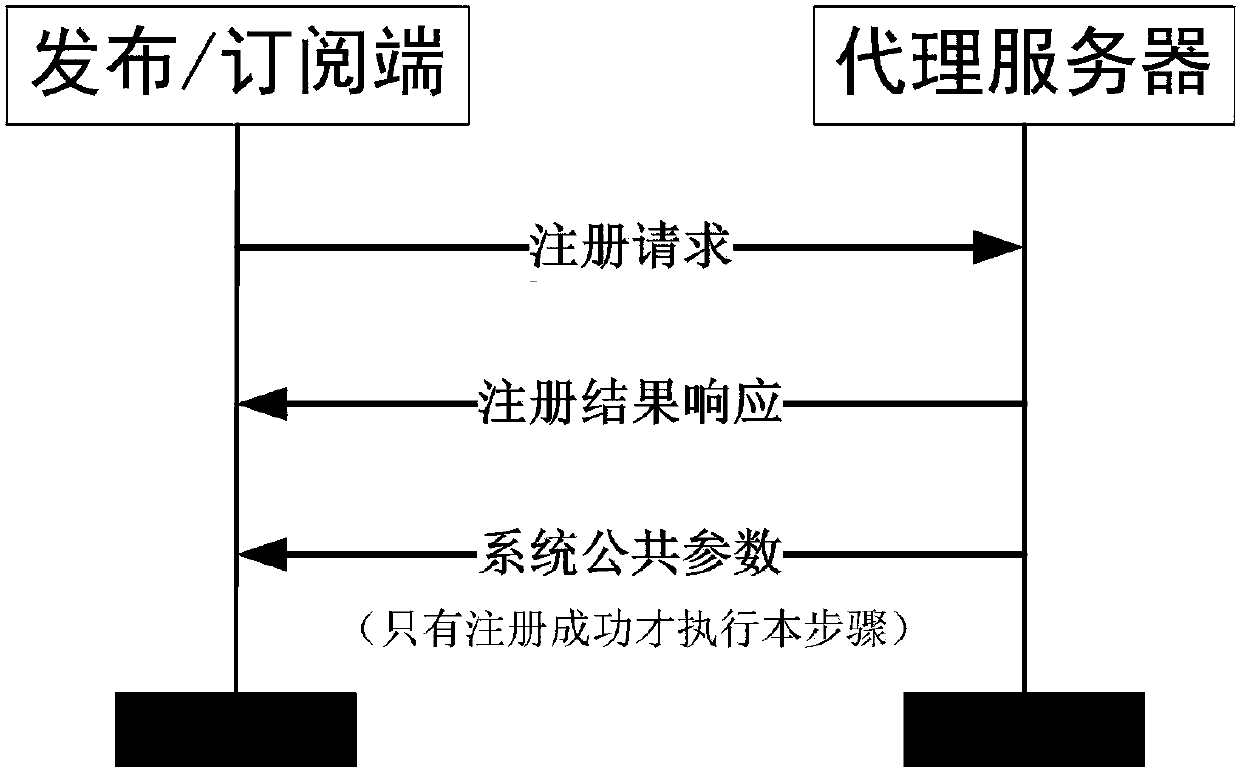
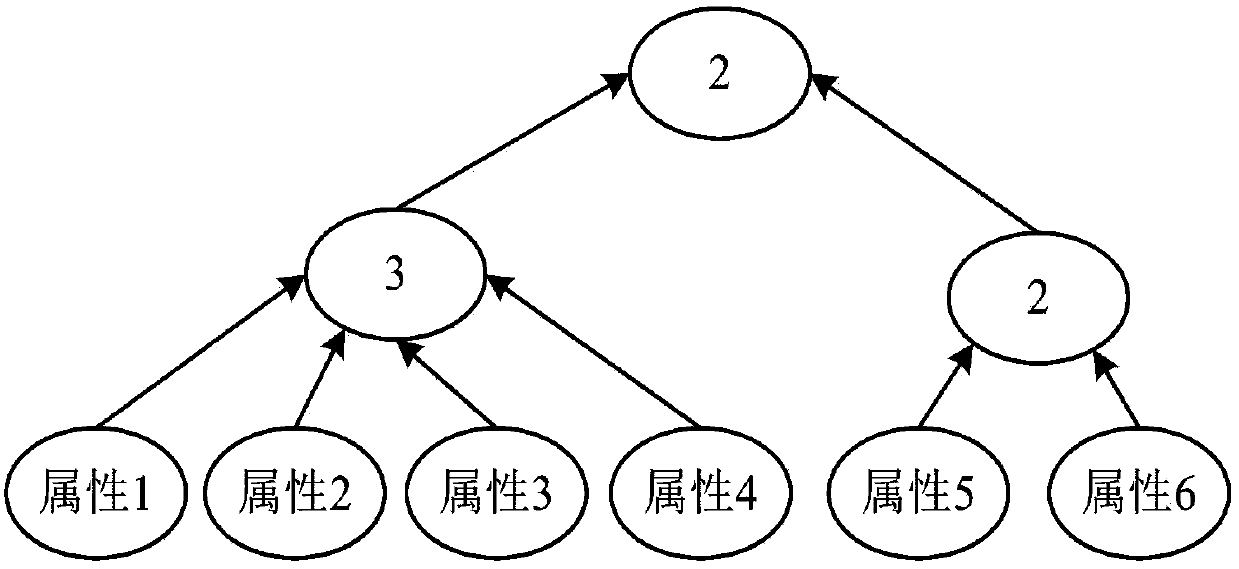
InactiveCN107708112AImplement encryptionAchieve authenticationNetwork topologiesTransmissionComputer hardwarePlaintext
The invention relates to an encryption method applied to a MQTT-SN protocol, and relates to the field of communication. The method employs a harsh algorithm and ciphertext-policy attribute-based encryption method, so that a publishing terminal, an agent server and one or a plurality of subscription terminals can complete encrypted communication. The method herein includes the following steps: an agent server verifying the identity of a publishing / subscription terminal, performing registration of the publishing / subscription terminal, and generating a system common parameter; the publishing terminal encrypting a plaintext load by using the ciphertext-policy attribute-based encryption method; the publishing terminal transmitting the encrypted load to the agent server, the agent server forwarding the encrypted load to one or a plurality of subscription terminals; and the subscription terminal applying for a secrete key from the agent server, decrypting the encrypted load, obtaining a plaintext. According to the invention, the method can implement identity verification of a MQTT-SN protocol publishing / subscription terminal, data integrity verification, and data confidentiality protection, and better addresses the safety issues faced by the MQTT-SN protocol in terminals of wireless sensor network applications.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Authenticated encryption method and encryption system based on symmetric encryption
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
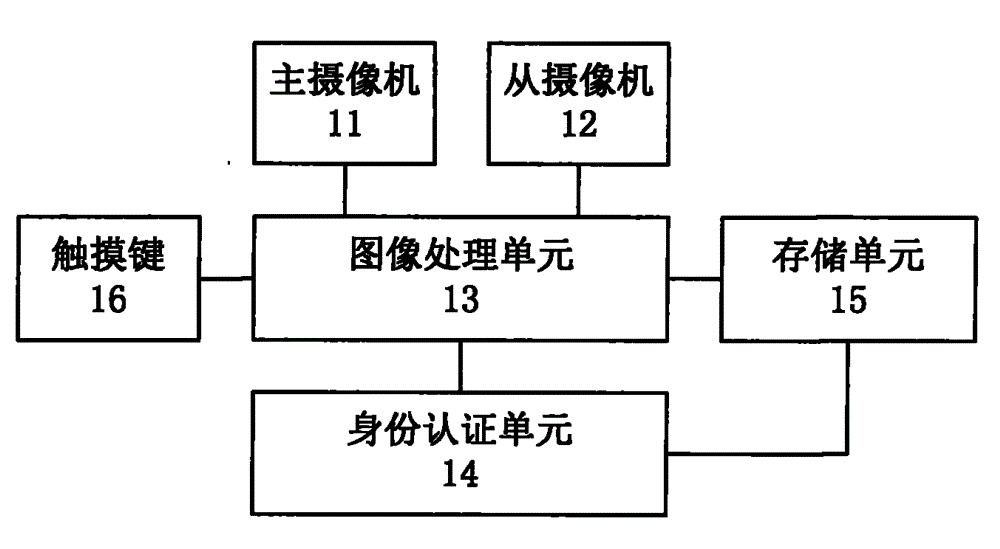
Identity recognition device and method based finger veins
ActiveCN104933389AAchieve authenticationImprove accuracyCharacter and pattern recognitionDigital data authenticationVeinImaging processing
The invention discloses an identify recognition device and method based finger veins, and the device comprises a main camera, a slave camera, an image processing unit, an identity authentication unit, a storage unit, a touch key, a glass filter, and an ultraviolet surface light source, wherein the main and slave cameras are used for respectively transmitting obtained main and slave finger vein images to the image processing unit. The image processing unit is used for extracting three-dimensional characteristic information of finger veins from the main and slave finger vein image signals, and carrying out normalizing, thereby obtaining the reference characteristic information of the finger veins. The identity authentication unit is used for comparing the obtained reference characteristic information of to-be-recognized finger veins with characteristic template information, and completing the identity recognition and authentication of the finger veins. Through the extraction and normalization of the three-dimensional characteristic information of the finger veins, the device and method effectively solve a problem of wrong recognition caused by the change of a finger posture, and remarkably improve the recognition accuracy and safety level.
Owner:北京细推科技有限公司
Head-wearing display equipment
ActiveCN103455746AReliable interactionAchieve authenticationDigital data authenticationHead worn displayBiometric trait
The invention provides head-wearing display equipment. The head-wearing display equipment comprises a biological feature scanning unit and a certification interface unit: the biological feature scanning unit is used for scanning the biological features of a user wearing the head-wearing display equipment; the certification interface unit is used for receiving a biological feature scanning result from the biological feature scanning unit and sending the biological feature scanning result to a remote server, so the remote server can certificate the biological features of the user.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
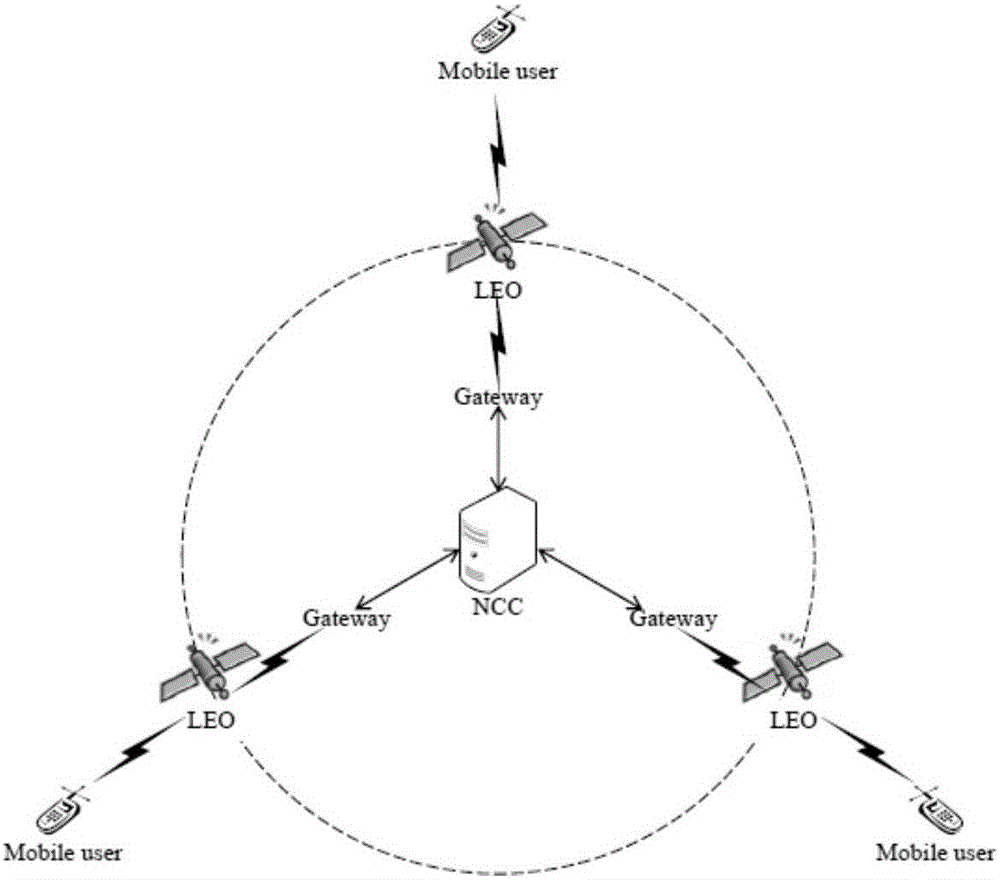
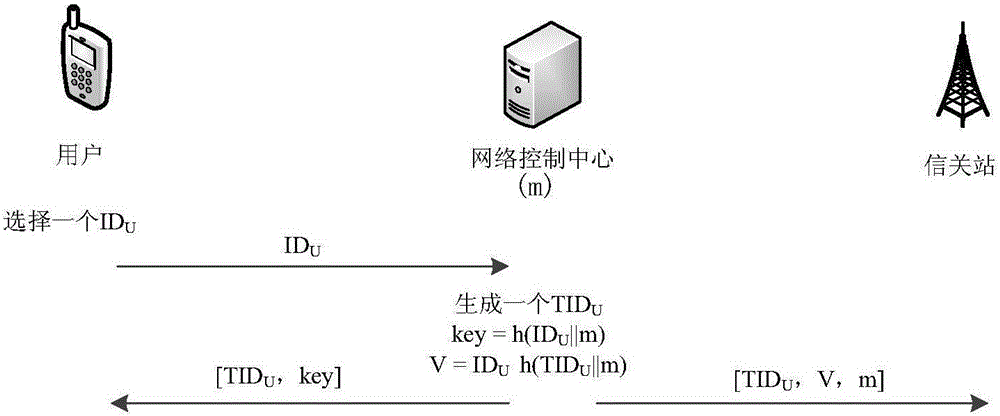
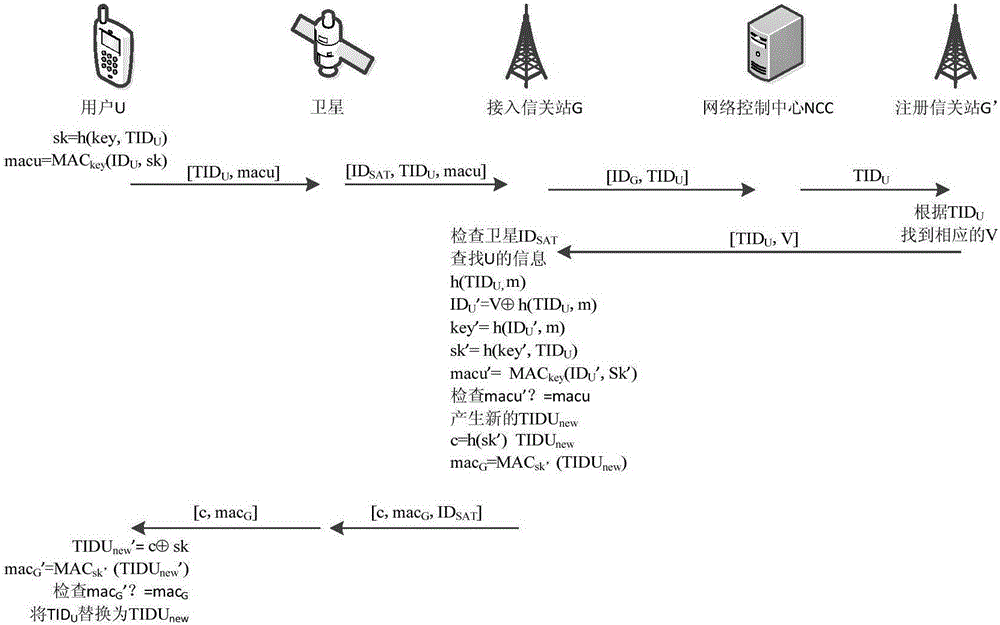
Gateway station-based satellite network anonymous authentication method
ActiveCN105827304AImprove securityImplement anonymous authenticationRadio transmissionSecurity arrangementNetwork controlAnonymous authentication
The present invention provides a gateway station-based satellite network anonymous authentication method. The conventional satellite network authentication methods all adopt a network control center (NCC) to authenticate users, and in order to reduce the authentication calculation amount of the NCC, the gateway station-based satellite network anonymous authentication method of the present invention enables an authentication function to transfer to a gateway station G, thereby relieving the burdens of the NCC. The gateway station-based satellite network anonymous authentication method of the present invention adopts a message authentication code (MAC) during an authentication process, thereby realizing the anonymous authentication of the users, and protecting the privacy of the users. According to the present invention, after the security authentication of a satellite network to the users is realized, the security authentication of the users to the satellite network is finished, thereby achieving a bidirectional authentication purpose, and further improving the network security. The authentication method of the present invention mainly comprises two stages, namely a registration stage and an authentication stage.
Owner:NANJING UNIV OF POSTS & TELECOMM
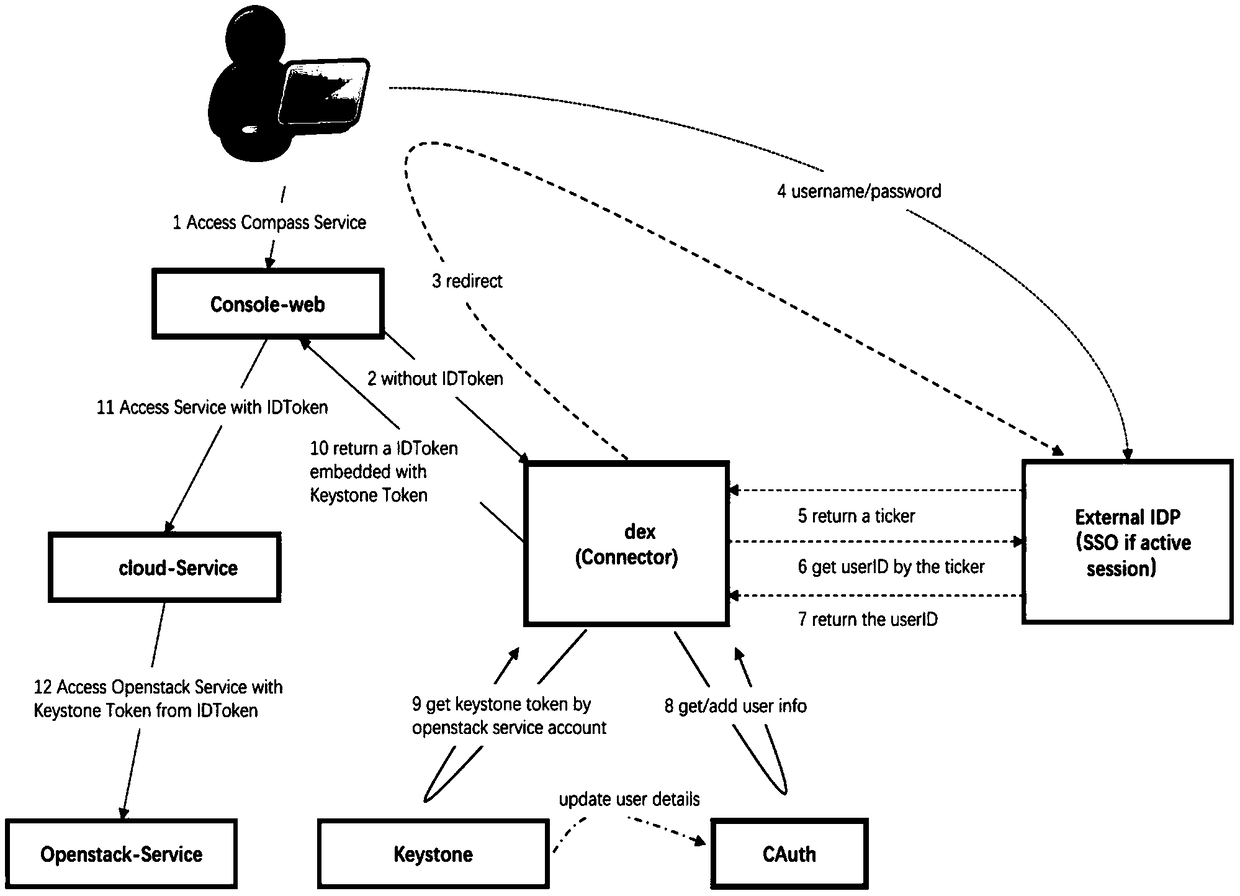
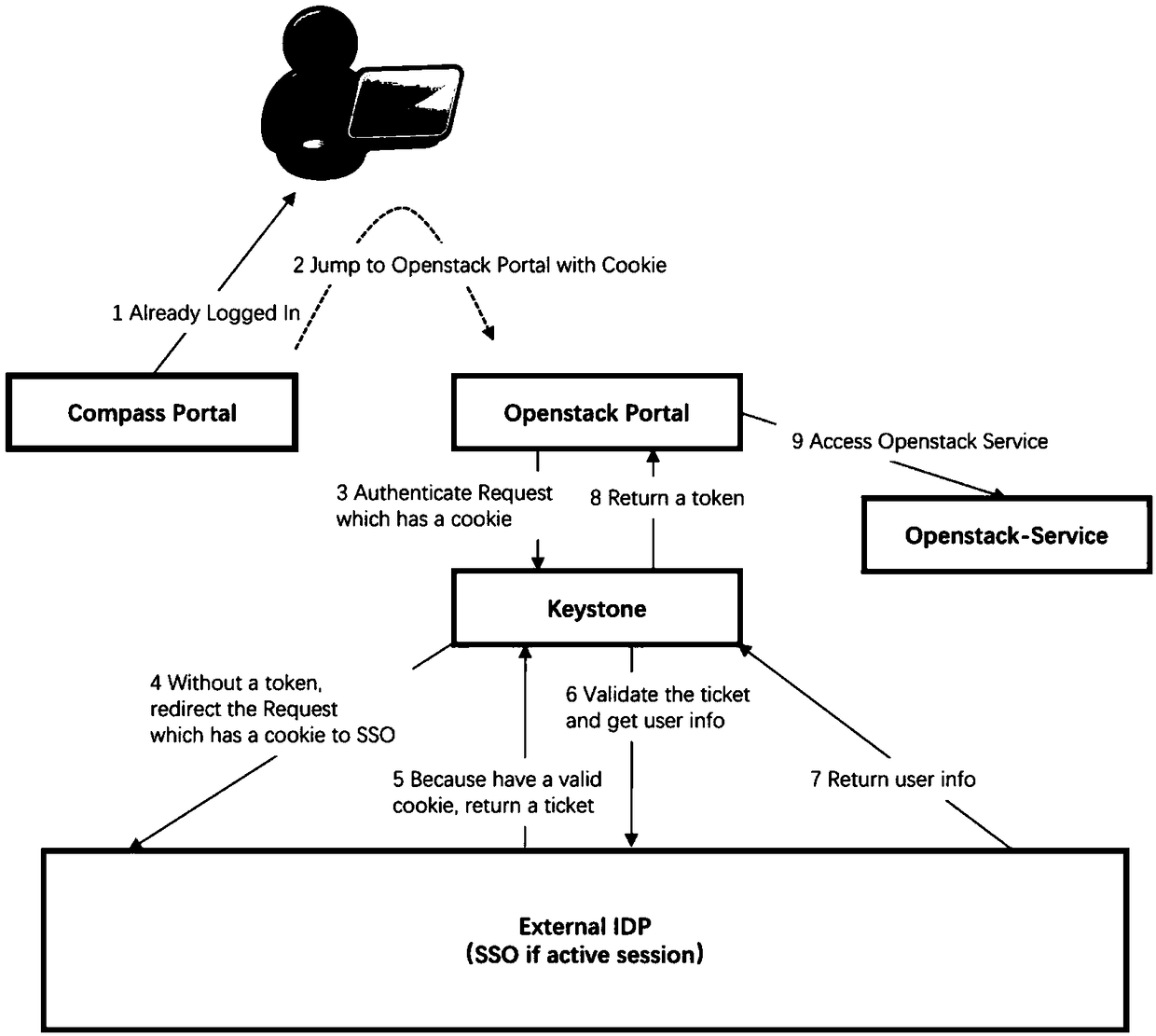
Cross-platform login unify authentication docking method, storage medium, and electronic device
ActiveCN109063457AAchieve authenticationLogin unified authentication implementationDigital data authenticationCross-platformAuthentication
A method for uniformly authenticating and docking cross-platform login includes responding access request by container cloud service, sending redirection request to Dex component, redirecting access page of Dex component to SSO login page, receiving Ticket generated by SSO, and requesting SSO to obtain user identification information through Ticket, redirecting access page to SSO login page by Dexcomponent, and receiving Ticket generated by SSO. The Dex component obtains user information from Cauth through user identification information, sends a request for synchronizing user information, obtains Keystone Token, and generates ID Token according to the user information and Keystone Token; the client accesses the container cloud service through the ID Token, the container cloud platform obtains the Keystone Token through the ID Token, and accesses the Openstack service through the Keystone Token. The invention realizes unified authentication of cross-platform login and synchronizationof user information, and ensures that the user can realize login and authentication from any party of the docking platform.
Owner:SHANGHAI SUIXUNTONG ELECTRONICS TECH CO LTD
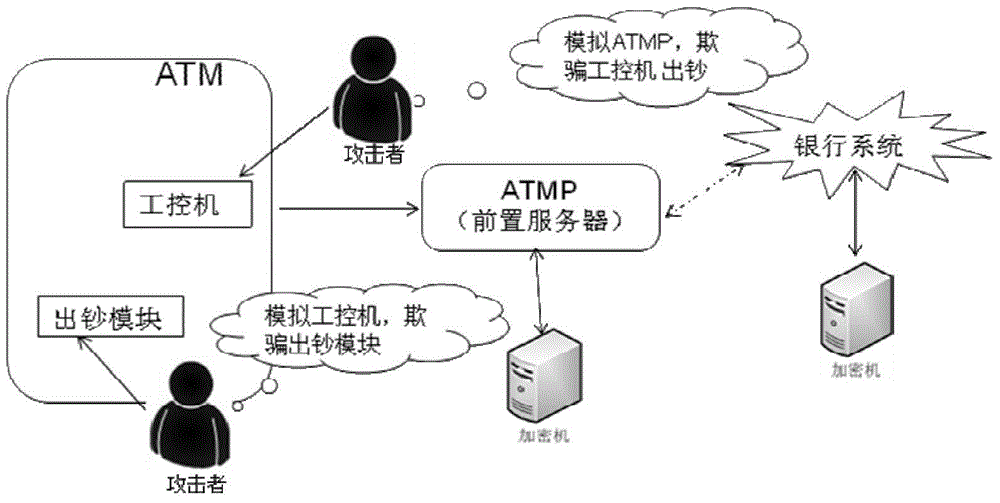
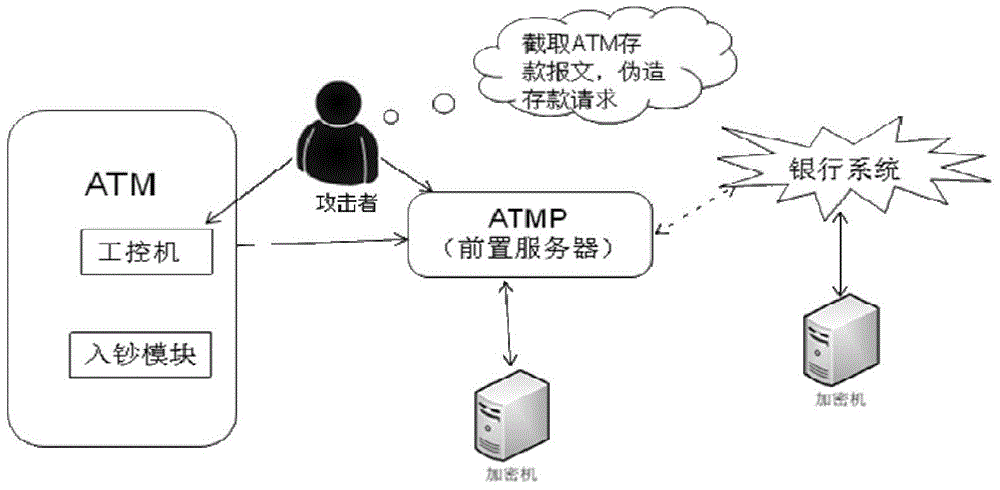
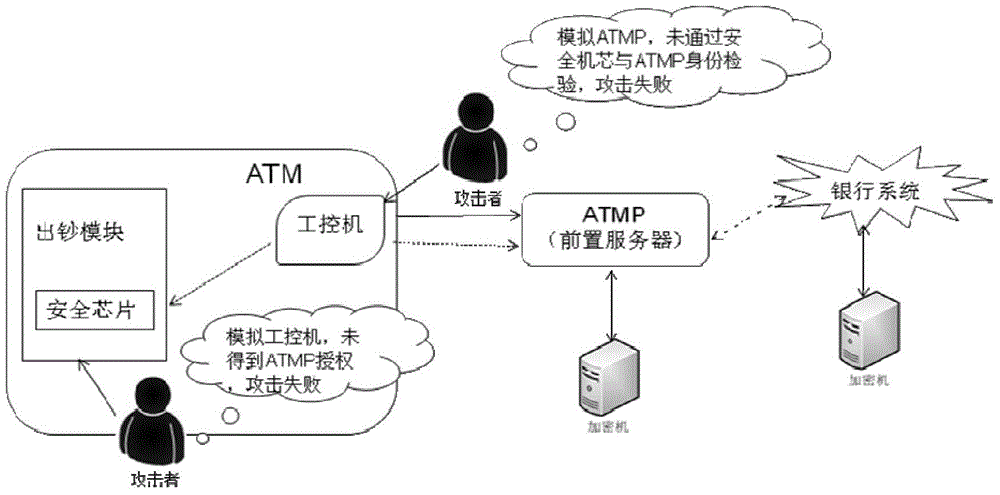
Method and system for controlling depositing and withdrawing safety based on safety core
The invention discloses a method and a system for controlling depositing and withdrawing security based on a security core. A security chip is arranged in a depositing and withdrawing core and put in the safe case of an automatic teller machine. The core safety chip is called the security core for short; the security core communicates with an automatic teller machine pre-system (ATMP); the safe communication of the security core with the ATMP is realized by virtue of certificate issuing and key exchange; the ATMP authorizes the core to dispense cashes, and meanwhile, checks the amount deposited. According to the method and the system for controlling the depositing and withdrawing security based on the security core, due to the safe communication of the security core and the ATMP, the identity is authenticated, an instruction sent out is verified legally and a message sent out is encrypted, and then the ATMP authorizes the core to dispense cashes and checks the amount deposited; the method and the system have the advantages that authentication and encryption / decryption can be effectively authenticated to achieve integrity protection, prevent tampering and prevent replay attack protection, and therefore, the security of the ATM is improved.
Owner:HUNAN GREATWALL INFORMATION FINANCIAL EQUIP
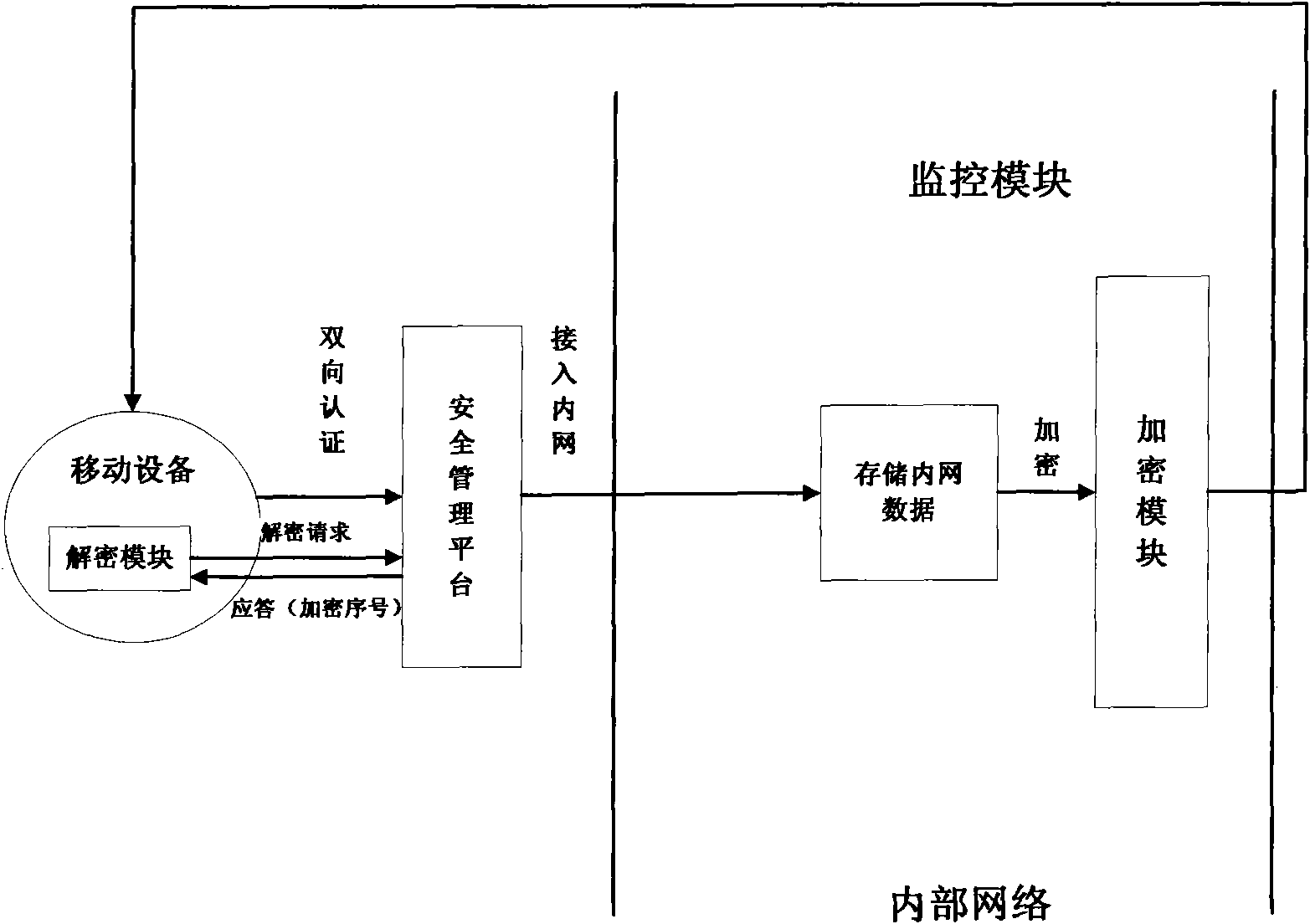
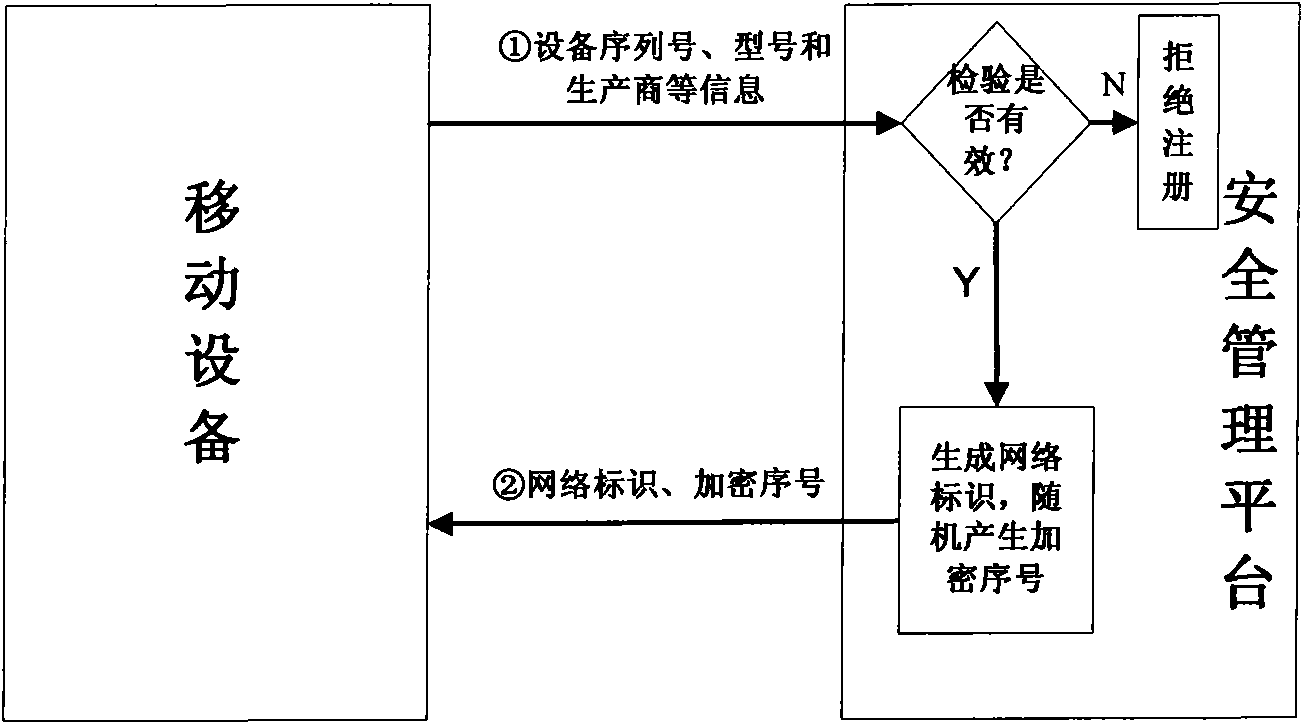
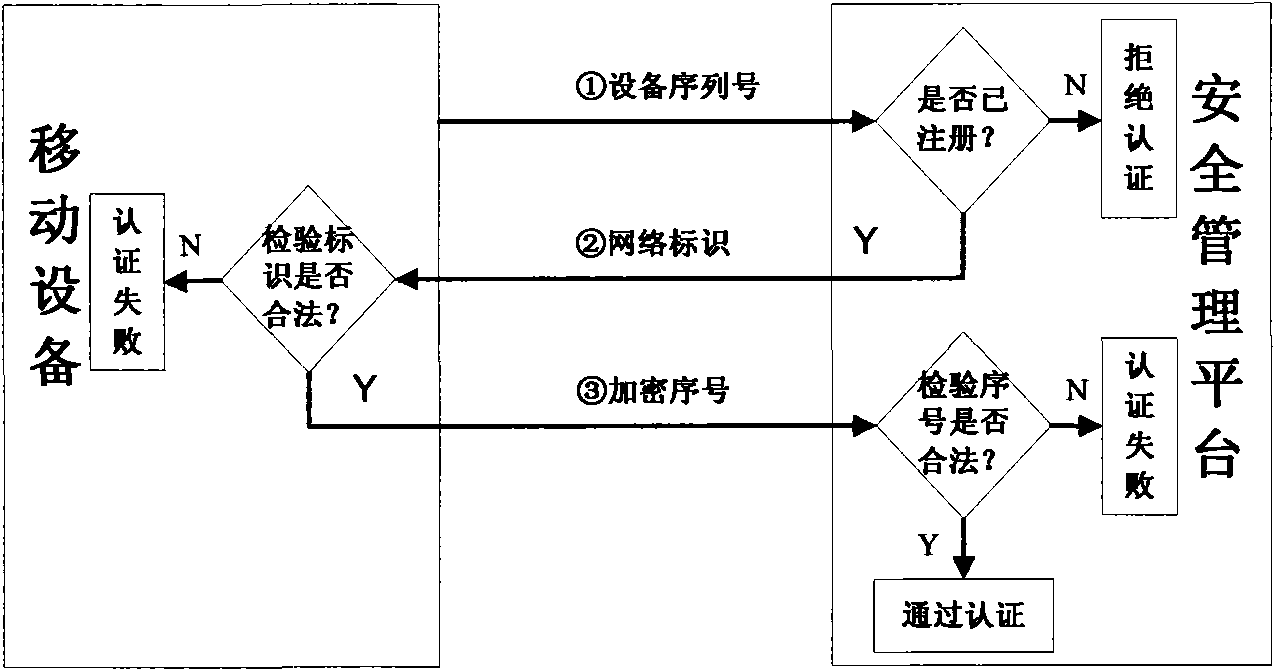
Realization system and method for safely visiting and storing intranet data by mobile equipment
InactiveCN101800738AAchieve authenticationDefend against impersonation attacksUser identity/authority verificationData switching by path configurationConfidentialityMobile device
The invention discloses a realization system and a method for safely visiting and storing intranet data by mobile equipment. The method comprises the following steps: judging whether the mobile equipment is registered or not by a security management platform; carrying out mutual authentication on the registered mobile equipment; allowing the accession to the intranet after the authentication success; rejecting the accession to the intranet of unregistered mobile equipment and authentication failed mobile equipment; invoking an encryption module when a monitoring module discovers that the mobile equipment is about to store the intranet data in the intranet into the mobile equipment per se; selecting corresponding encryption methods by the encryption module under the monitoring of the monitoring module according to the confidentiality levels of the intranet data for encrypting the intranet data to be stored into the mobile equipment; and inquiring whether the encryption data is confidentiality data or not by a decryption module to the monitoring module in the intranet when the encryption data stored in the mobile equipment needs to be decrypted, and then, selecting corresponding methods for decrypting the encryption data. The invention implements different encryption and decryption methods according to different confidentiality levels, improves the encryption and decryption efficiency and data confidentiality, integrally utilizes the mutual authentication method and the encryption and decryption method, and improves the security of the intranet data.
Owner:JINAN UNIVERSITY
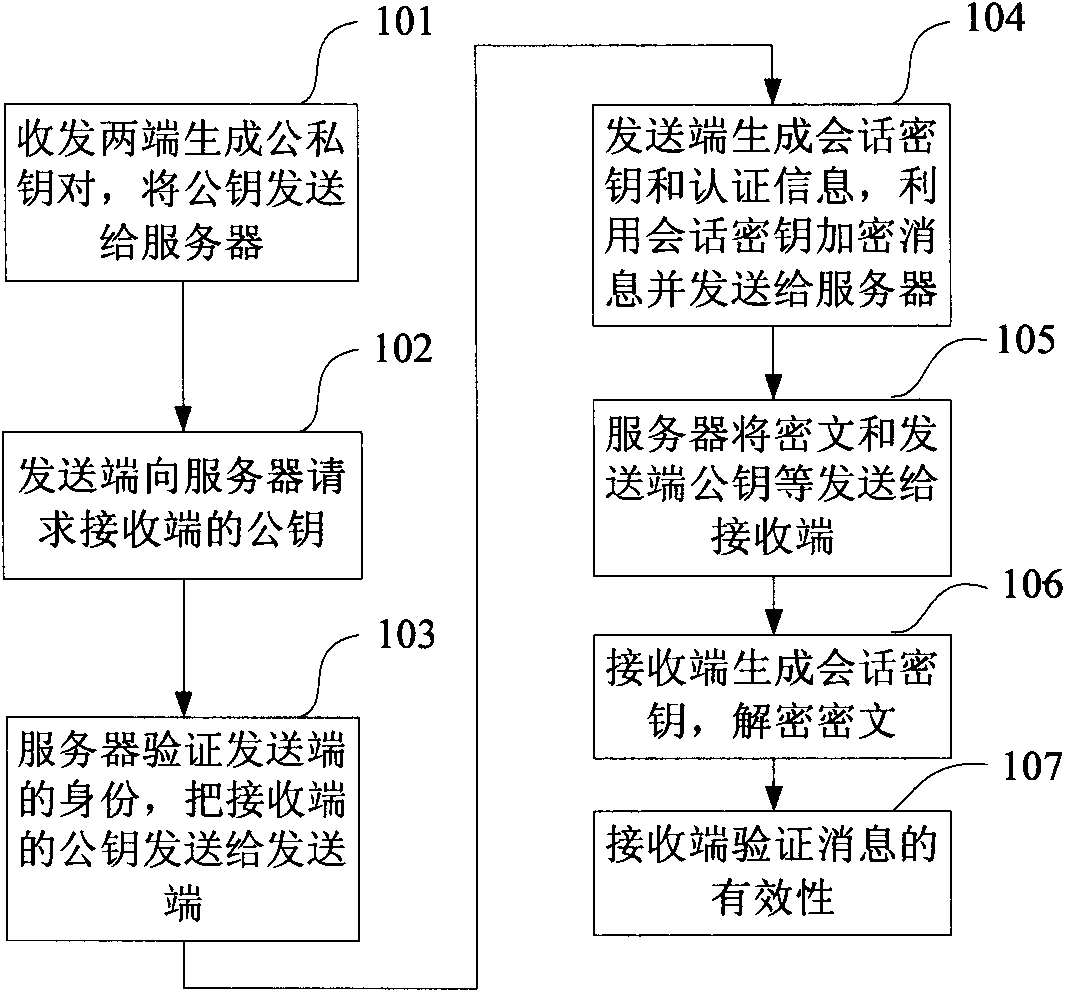
Identity-based wireless sensor network security trust method
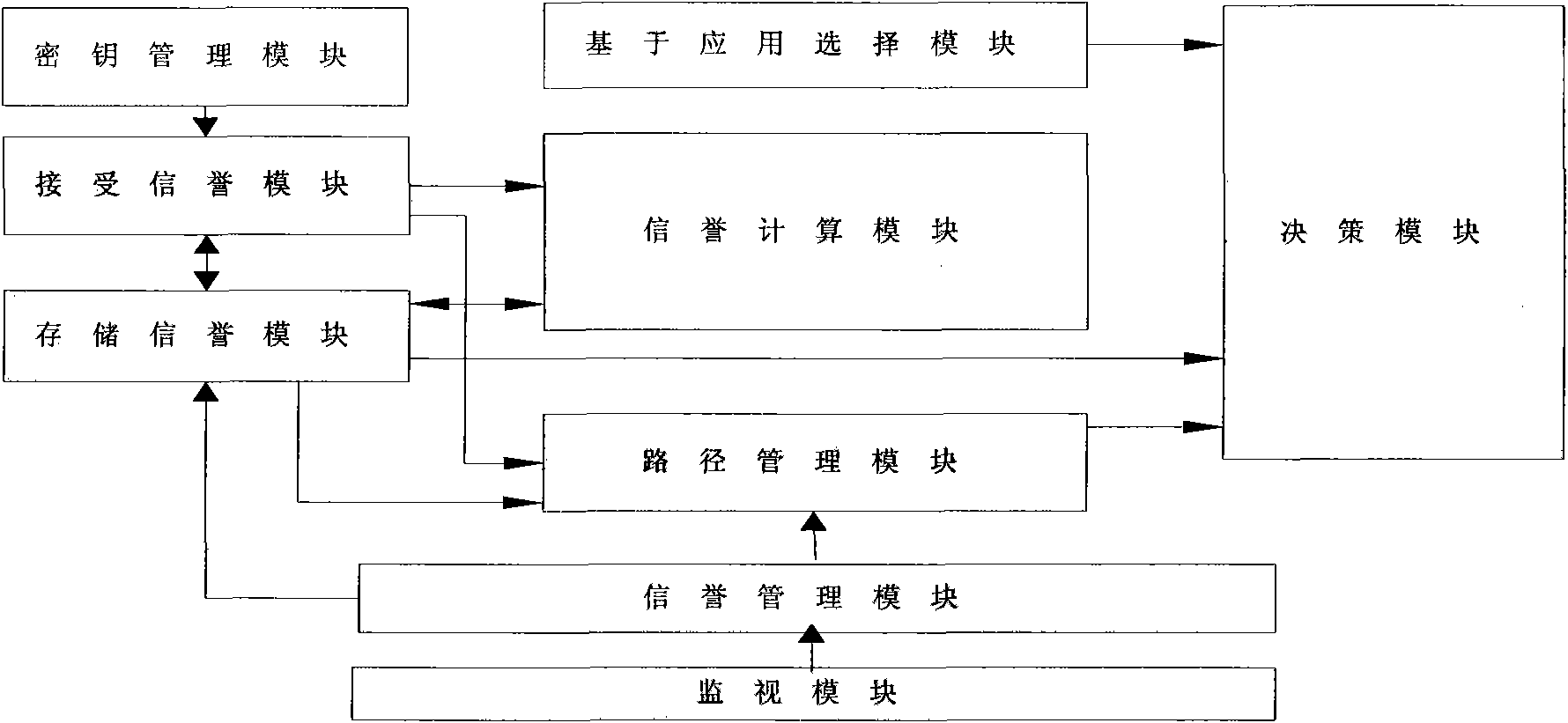
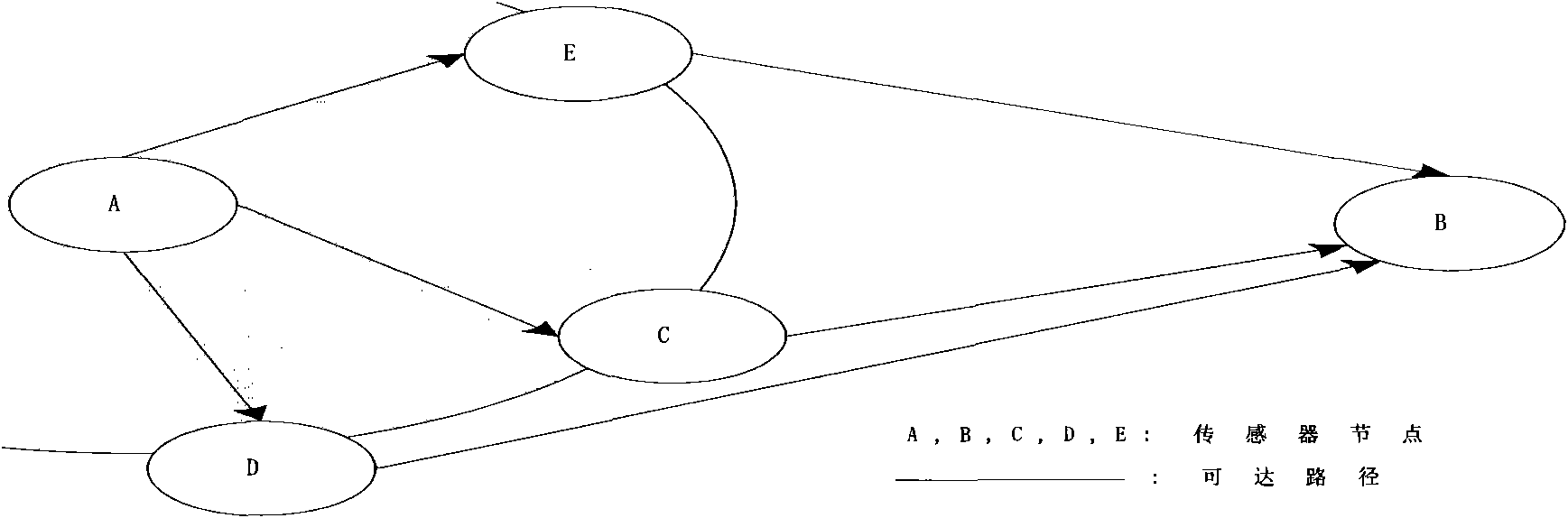
InactiveCN101600198AExchangeImplement encryptionNetwork topologiesSecurity arrangementTrusted systemAuthentication
The invention discloses an identity-based wireless sensor network security trust method. In the method, firstly each node in the network is loaded with a trust management structure; wherein the trust management structure is composed of a secret key management module, a receiving credit module, a storage credit module, a credit calculating module, an application selecting module, a route management module, a decision making module, a credit management module and a monitoring module. On the basis of the trust management structure, a trust communication network is established by broadcasting query node information among nodes, receiving query respond and updating node credit and by identity-based public key password encryption and authentication among nodes, so as to realize safe communication of credit information among nodes. The invention reduces complexity of credit calculation in the wireless sensor network, improves security of communication of the wireless sensor network trust system, solves communication problem of a source node and a destination node under multi-hop condition, and can meet the requirement of large-scale self-organized network application.
Owner:XIDIAN UNIV
Method and system for authenticating image contents
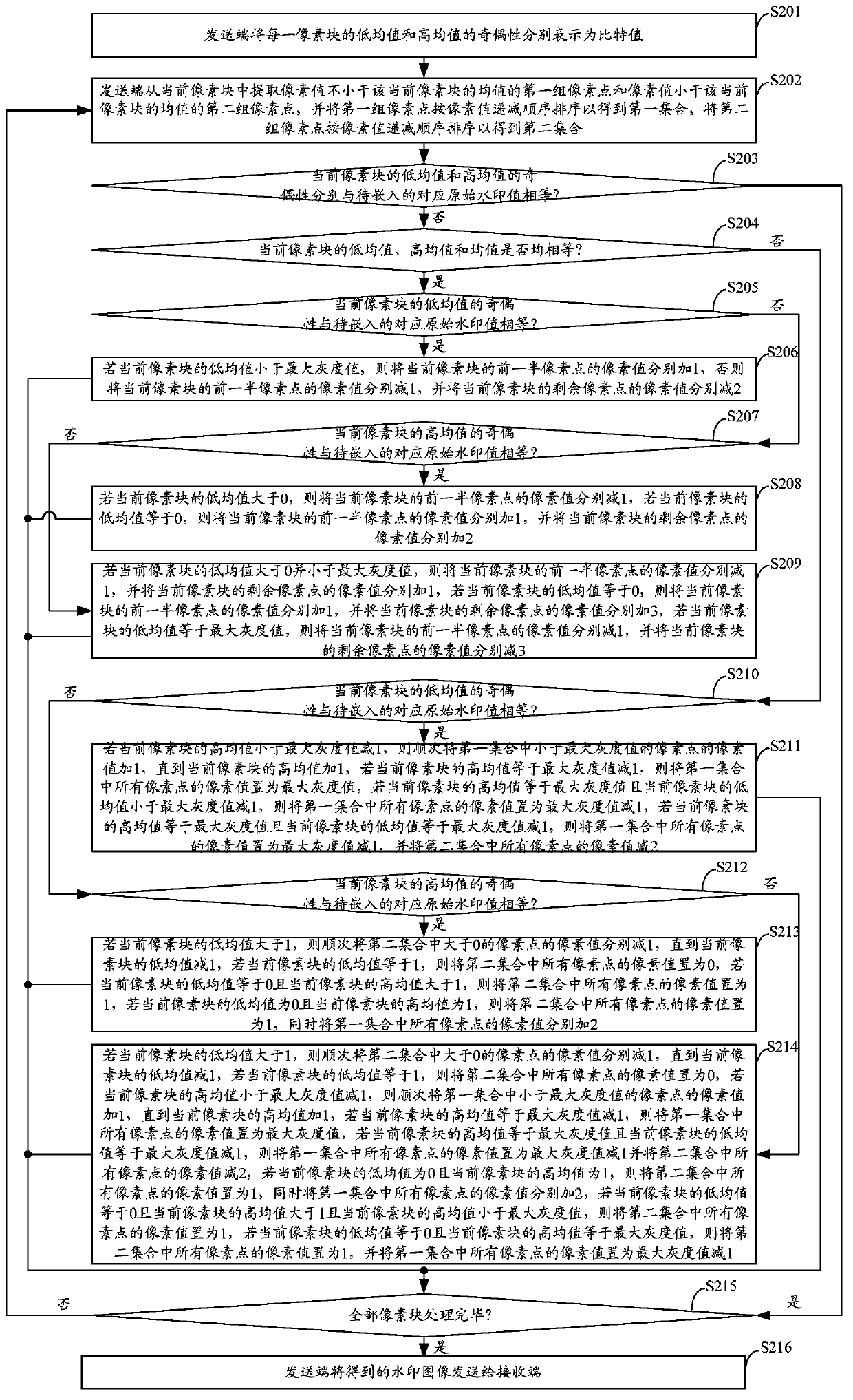
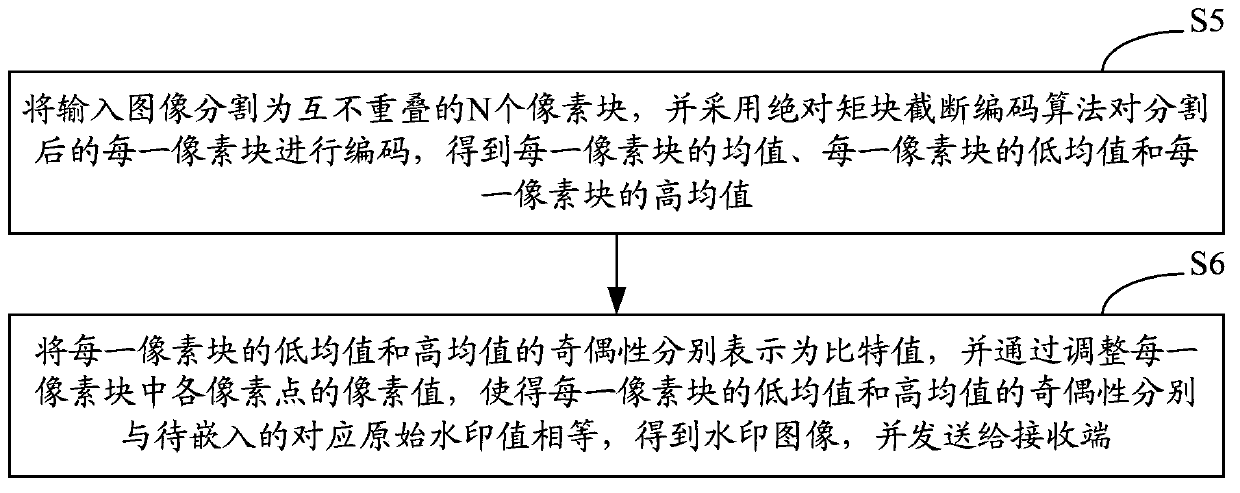
InactiveCN103426141AQuality assuranceAchieve authenticationImage data processing detailsPattern recognitionPixel based
The invention belongs to the technical field of digital watermark technologies, and provides a method and a system for authenticating image contents. According to the method and system, an AMBTC (Absolute Moment Block Truncation Coding) algorithm is utilized for guiding the embedding and extraction of a digital watermark, and the parity of a low mean value and a high mean value of each pixel block is correspondingly equal to a to-be-embedded 2-byte watermark by adjusting the pixel value of each pixel in each pixel block of the input image. The image is not really subjected to BTC (Block Truncation Coding) compression, but the AMBTC quantized data are utilized for guiding the watermark embedding and extraction process, so that image authentication of a semi-fragile watermark is realized while the quality of the image is guaranteed. In addition, as an embedding mechanism based on a pixel domain and an extraction mechanism based on a compression domain are used, the method and system for authenticating the image contents can suppress brightness and contrast change operations efficiently, and have good fragility for the other operations.
Owner:华盾技术(深圳)有限责任公司
Two-way network access authentication method based on digital certificate
ActiveCN103237038AUpdate admin keyReduce riskKey distribution for secure communicationUser identity/authority verificationConfidence regionAuthentication server
The invention relates to the technical field of network security and discloses a two-way network access authentication method based on a digital certificate. The two-way network access authentication method comprises the following steps of step 1, dividing a network access authentication system into an access region and a confidence region and accessing a client to be authenticated to a physical port of a confidence client; step 2, actively initializing the network access authentication to the client to be authenticated after receiving access information of the client to be authenticated by an authentication server; and step 3, after submitting equipment authentication information to the authentication server after the client to be authenticated receives the access authentication, starting the authentication after the authentication server receives the authentication information and feeding the authentication result back to the client to be authenticated. The client to be authenticated is physically connected with the confidence client and the authentication server actively initializes the network access authentication to the client to be authenticated after receiving the access information, so that the authentication of network access identities of router equipment, exchange equipment, security safety equipment and the like is realized and the safety and the practicality of the network are improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Data sharing control method based on block chain
InactiveCN110535833AThere will be no false identity authenticationAchieve authenticationTransmissionData accessData memory
The invention relates to a sharing control method based on a block chain. A data holder uploads a first file package comprising encrypted data resources and index files corresponding to the data resources to a data memory through a private chain created by the data holder; the data accessor downloads the first file package from the data memory; the data accessor can access the private chain corresponding to the data resource based on the obtained management file, wherein the private chain allows the data accessor to acquire a key corresponding to the data resource from the private chain underthe condition that the management file is approved; and the data decryption module is used for decrypting the encrypted data resources, requesting the sharing permission from the data holder based onthe data accessor, generating a management file matched with the index file by the data holder under the condition that the data accessor is matched with the index file, and transmitting the management file to the data accessor.
Owner:CHINA UNIV OF PETROLEUM (BEIJING)
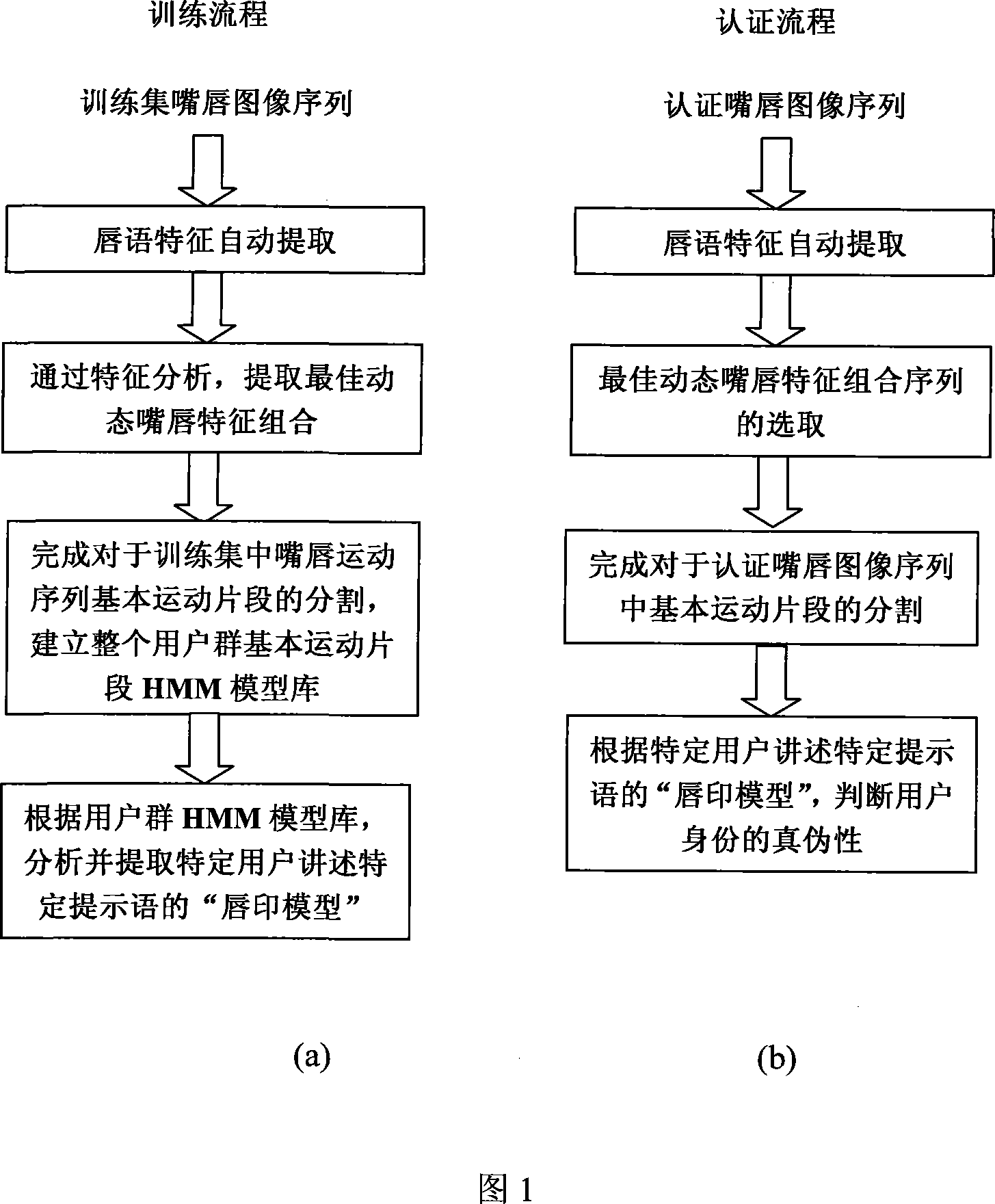
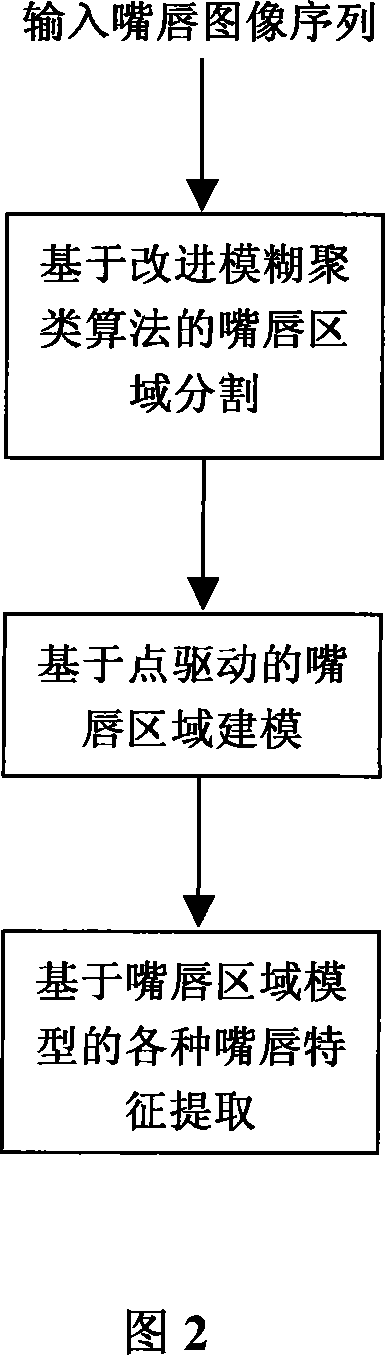
Identity identification method based on lid speech characteristic
InactiveCN101046959AImprove classification accuracyAchieve authenticationCharacter and pattern recognitionSpeech recognitionComputer scienceImage sequence
The present invention relates to a speechmaker identity authentication method based on lip movement in the field of biological characteristics and mode identification technology. Said method includes the following steps: inputting lip image sequence, dividing lip region based on improved fuzzy aggregation algorithm, modeling lip region based on point drive and extracting various lip characteristics based on lip region model.
Owner:SHANGHAI JIAO TONG UNIV
Cross-domain anonymous resource sharing platform and implementing method thereof
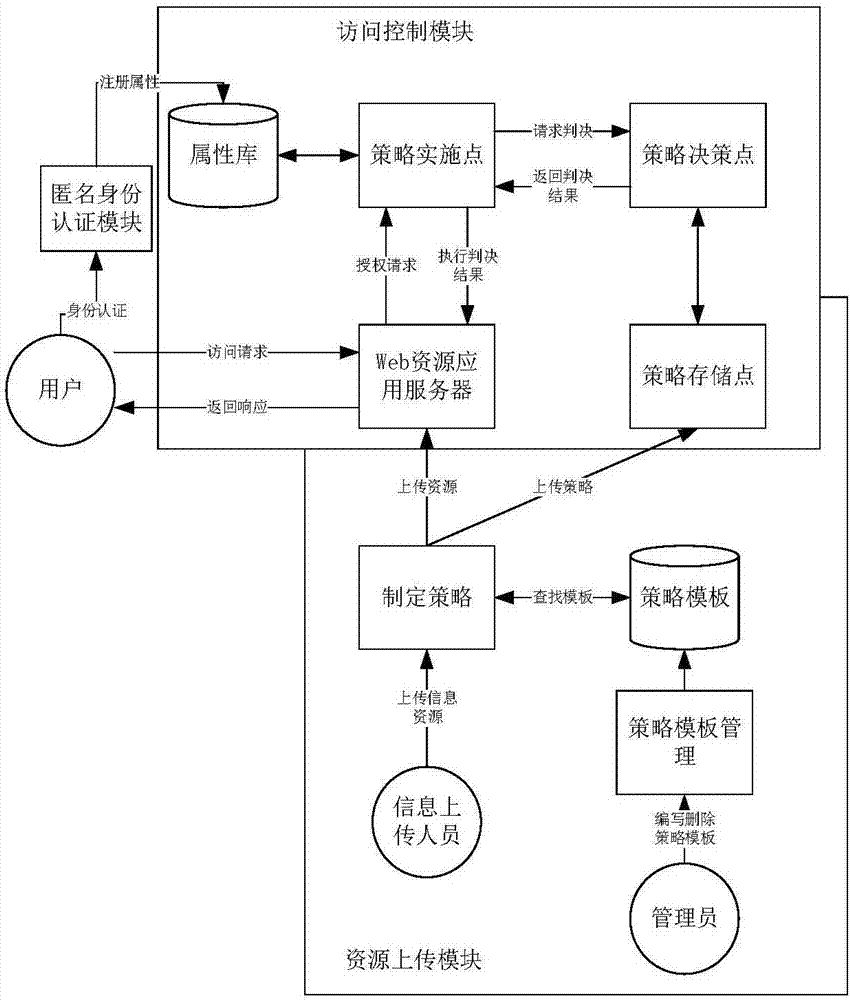
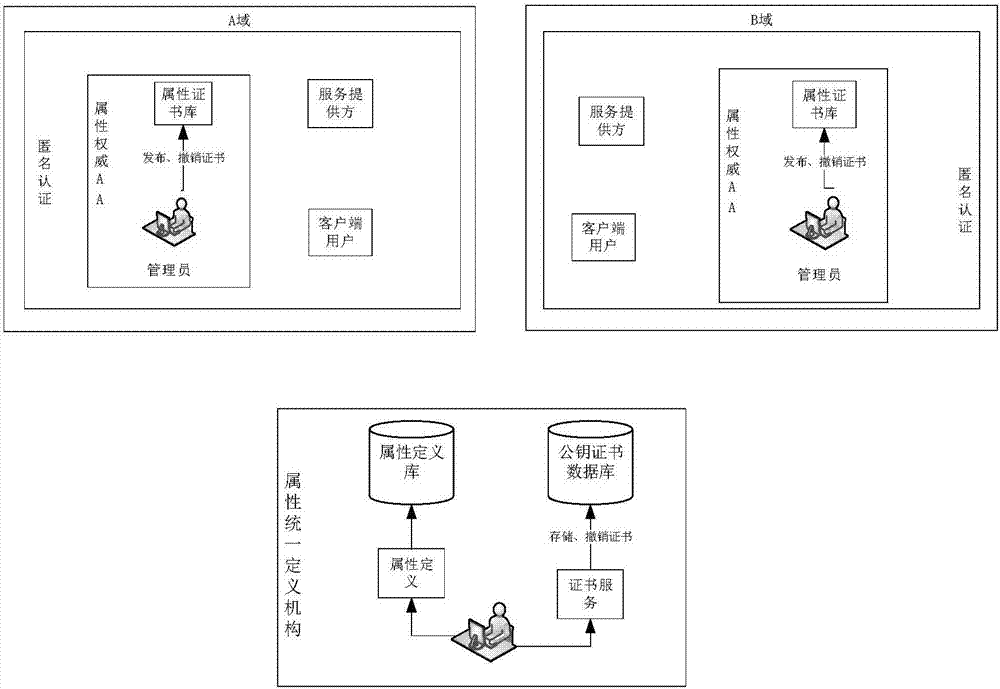
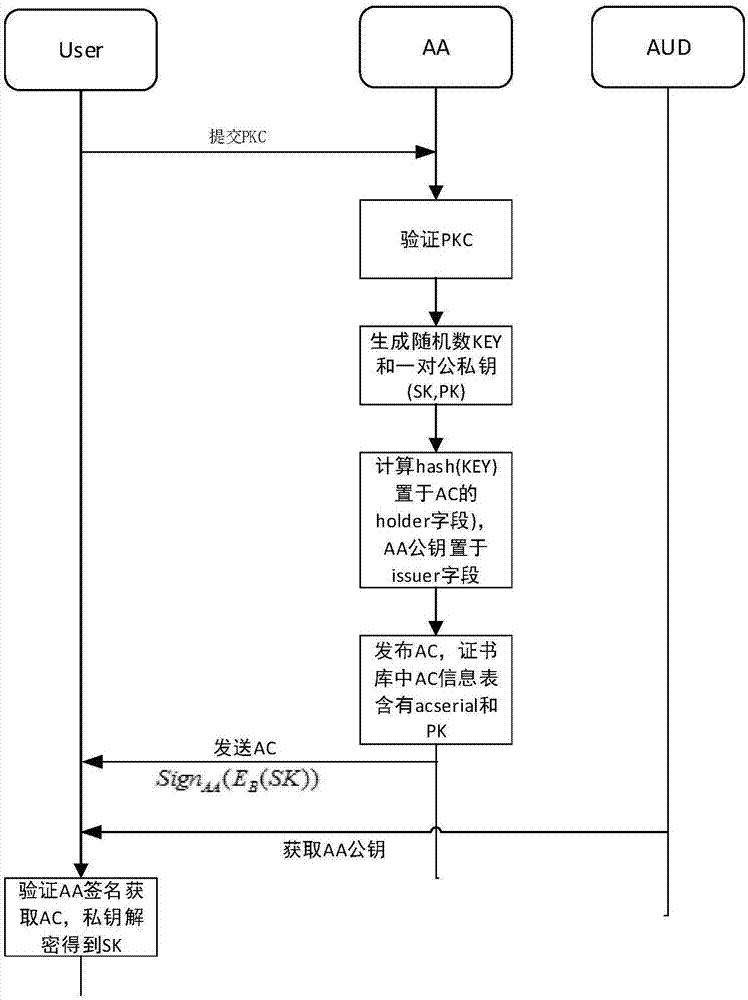
ActiveCN106992988AAchieve authenticationRealize cross-domain authorization managementUser identity/authority verificationInternet privacyStrategy making
The invention discloses a cross-domain anonymous resource sharing platform and an implementing method thereof. The platform comprises an anonymous identity authentication module, a resource uploading module and an access control module. According to the invention, anonymous identity authentication on a user is implemented by the anonymous identity authentication module, and authorization management on the user is implemented by methods of access control and the like. According to the invention, firstly, by analysis on an attribute certification structure, anonymous identity authentication on the user and construction of a user attribute library on the basis of protecting user identity privacy are implemented. Based on identity authentication, access strategy making for uploaded resources is implemented by the resource uploading module, the access control module judges whether a visitor has an access permission according to each entity attribute and strategy so as to ensure security of resources, and finally, anonymous cross-domain authentication management on the user is implemented and a fine-grained resource sharing mode is implemented. Meanwhile, the cross-domain anonymous resource sharing platform and the implementing method thereof have effectiveness, dynamics and the like.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Routing method for wireless sensor network based on LEACH protocol
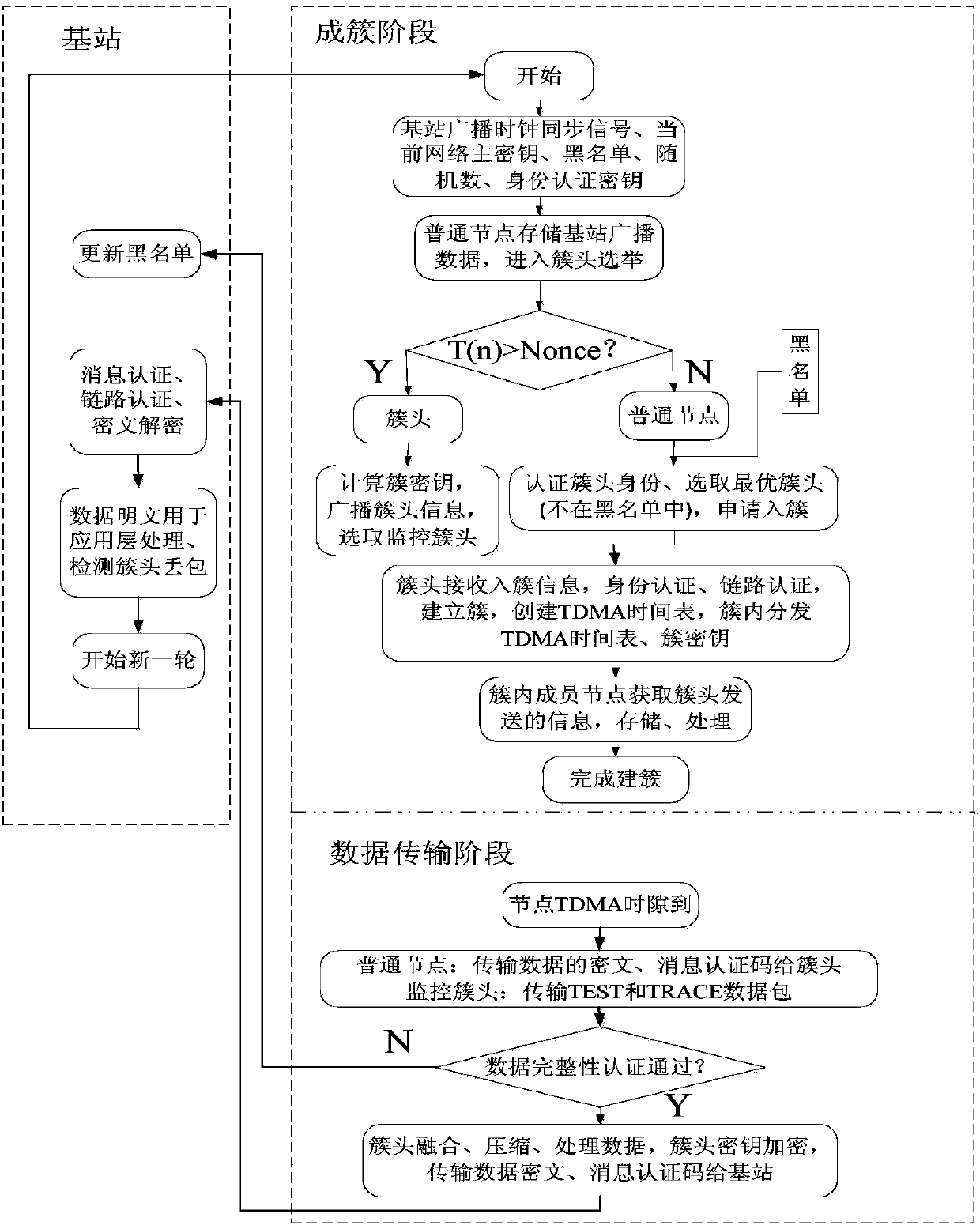
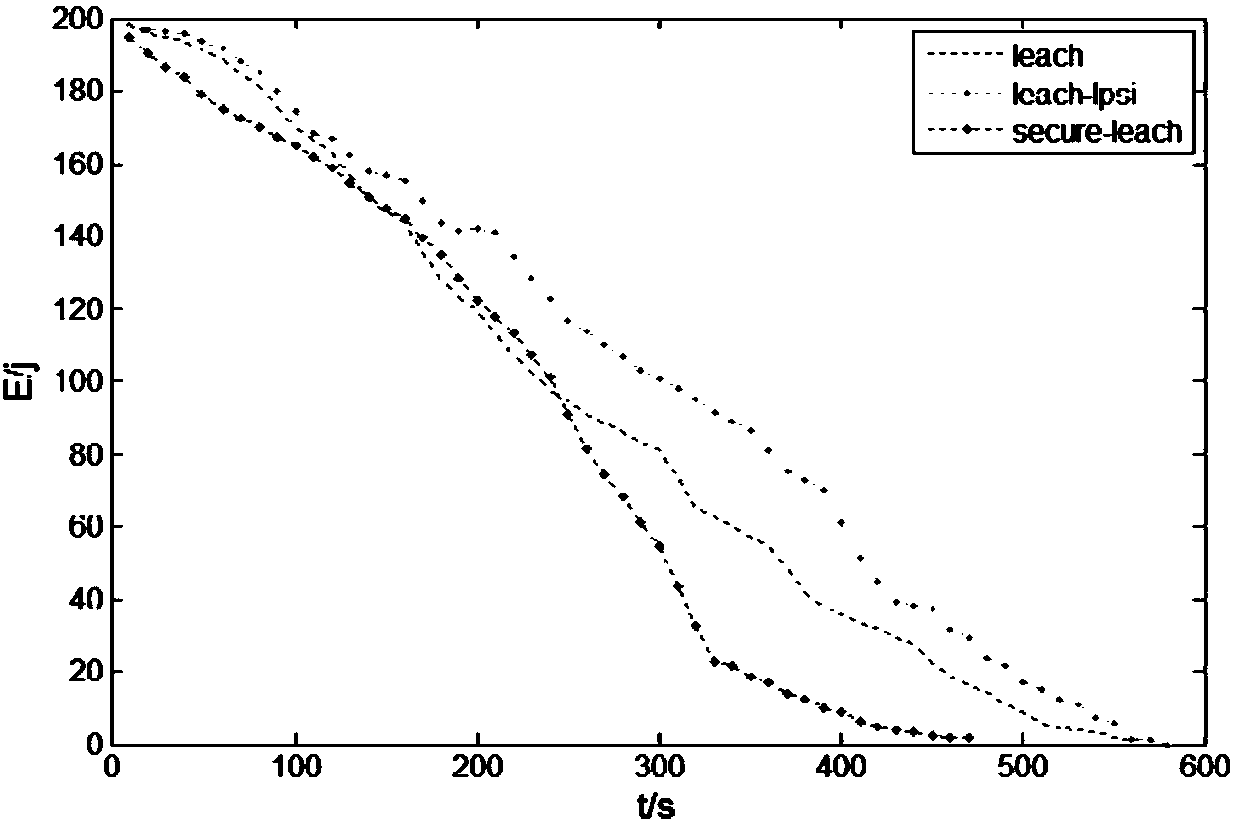
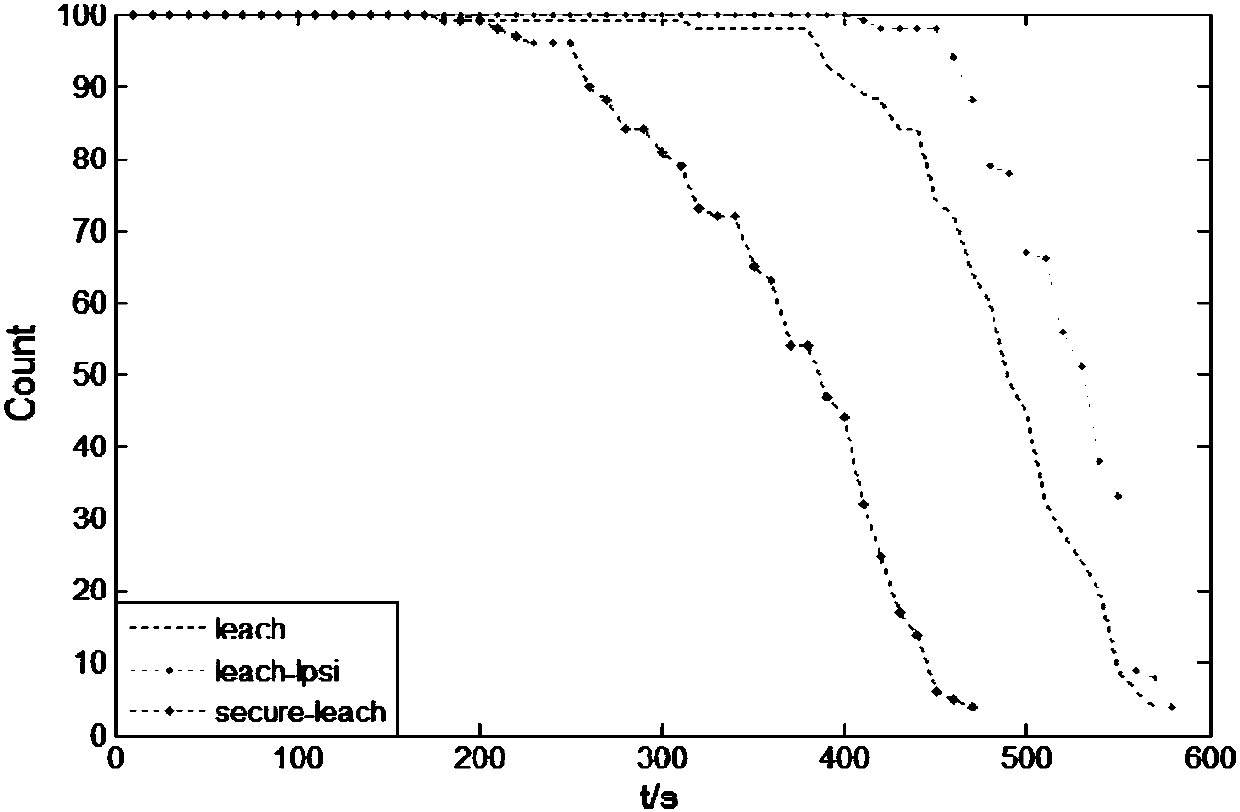
ActiveCN106454815AImplement Link AuthenticationGuaranteed robustnessNetwork topologiesSecurity arrangementWireless mesh networkPacket loss
The invention discloses a routing method for a wireless sensor network based on an LEACH protocol. The method comprises the following steps of carrying out initialized deployment on all nodes in the whole network; entering an authentication broadcast stage; entering a clustering stage; and entering a data transfer stage, wherein the authentication broadcast stage is as follows: a base station broadcasts and updates security control information, and the nodes are updated after obtaining broadcast information; the clustering stage is as follows: a cluster head node is elected and an optimal cluster head node is selected to enter a cluster from common nodes; and each cluster head node selects a monitoring cluster head node and the monitoring cluster head node enters into the cluster; the data transfer stage is as follows: all common nodes transmit data to the cluster heads of the clusters where the common nodes are located; and meanwhile, each monitoring cluster head node transmits a testing data packet to a monitored cluster head node and transmits a tracking data packet to the base station; after the cluster head node receives the data, the cluster head node transmits a random number and the data which received in the base station broadcast stage to the base station; and the base station detects whether the network has attacks, such as tampering and packet loss, through checking the data sent by all cluster heads. According to the method, the security is improved while the system energy consumption is reduced, so that the network can effectively resist the attacks.
Owner:SOUTH CHINA UNIV OF TECH
Data interaction safety protection method based on CPK identity authentication technology
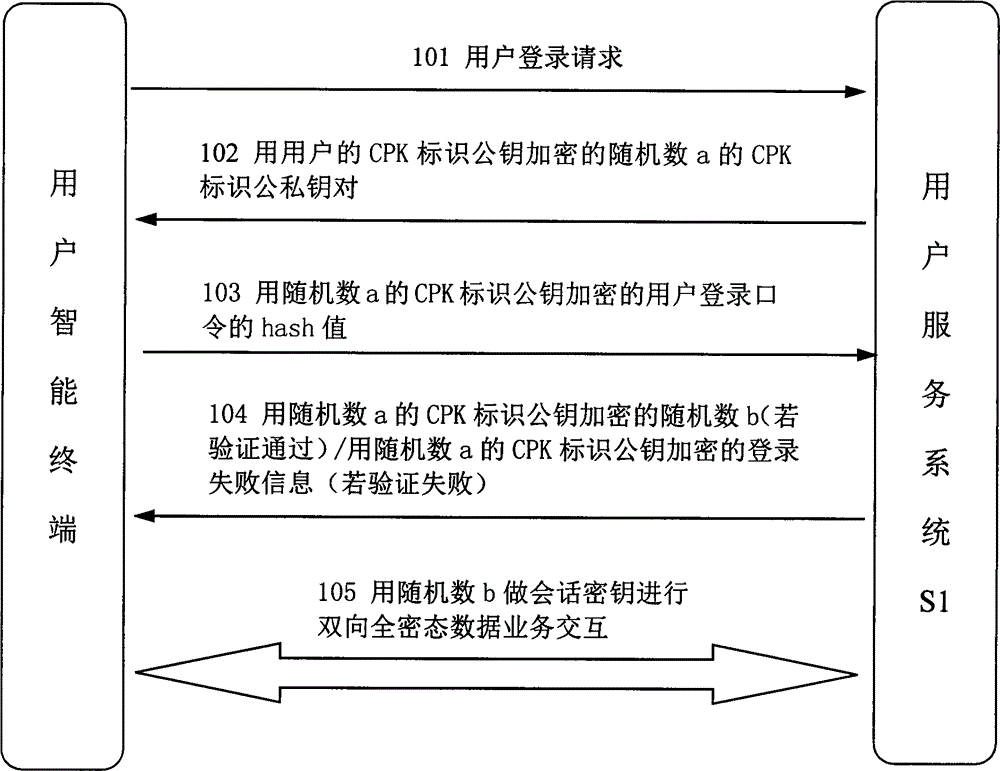
InactiveCN104901803ALow input costAchieve authenticationUser identity/authority verificationUser inputSession key
The invention provides a data interaction safety protection method based on a CPK identity authentication technology. The method is applied to user login security of a user service system (S1) and interactive protection of all service data. The user service system (S1) is used for receiving a login request transmitted by a user intelligent terminal, generating a random number a and generating a CPK identification public-private key pair of the random number a by using the CPK identity authentication technology, and downwardly transmitting to the user intelligent terminal after using the CPK identification public-private key to encrypt the CPK identification public-private key pair of the random number a. A user inputs a user login command on the intelligent terminal and transmits the user service system (S1) to recognize authenticity of a user identity after encrypting the hash value which is obtained by changing the user login command. The user service system (S1) is used for generating a random number b and transmitting to the user intelligent terminal after being encrypted if the verification is passed, otherwise, returning the data of failing login. After the user registers successfully, all service data between the user intelligent terminal and the user service system (S1) uses the random number b as a session key to perform bidirectional whole secret state service data interaction.
Owner:成都腾甲数据服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com