Encryption method applied to MQTT-SN protocol
An encryption method and protocol technology, which is applied in the encryption field of the MQTT-SN protocol, can solve problems such as unguaranteed messages, invisible payloads, and unrealized authentication of publishers and subscribers, so as to improve security and protect privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Hereinafter, the preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings.
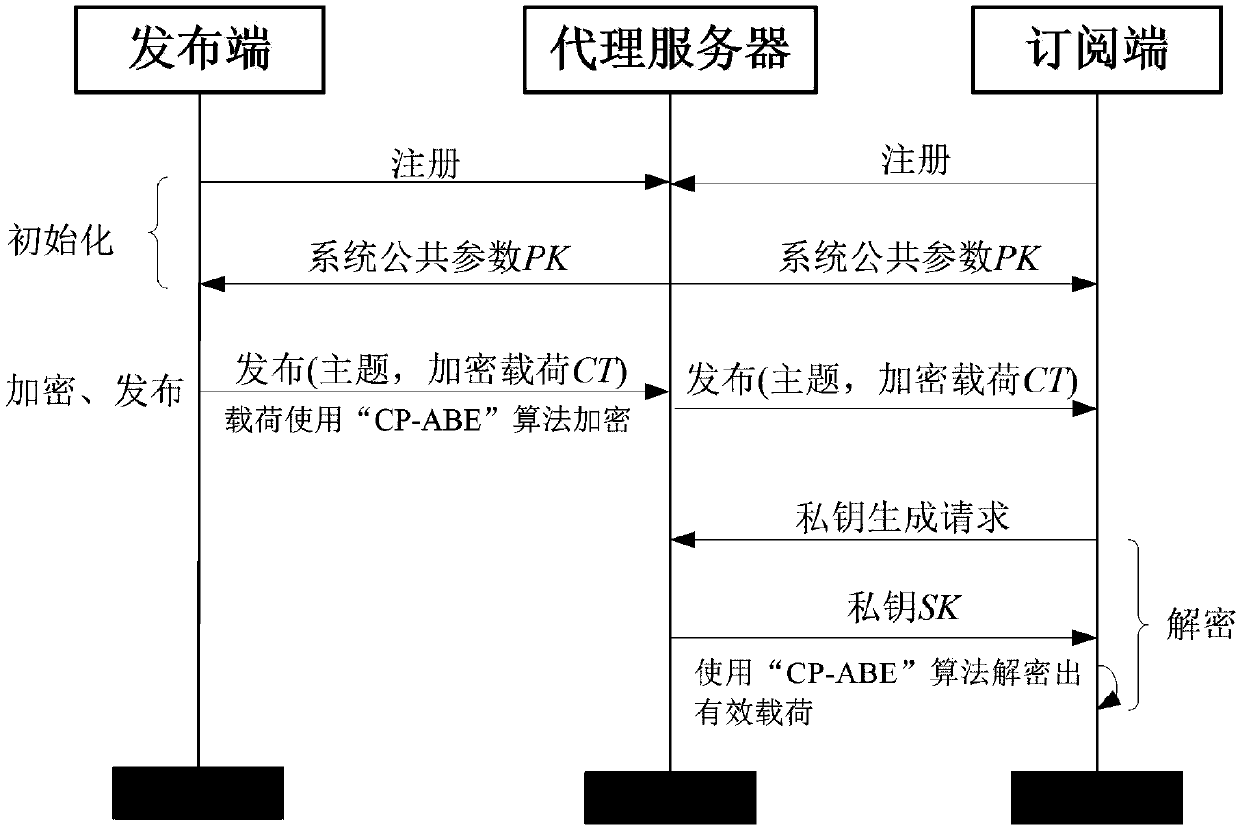
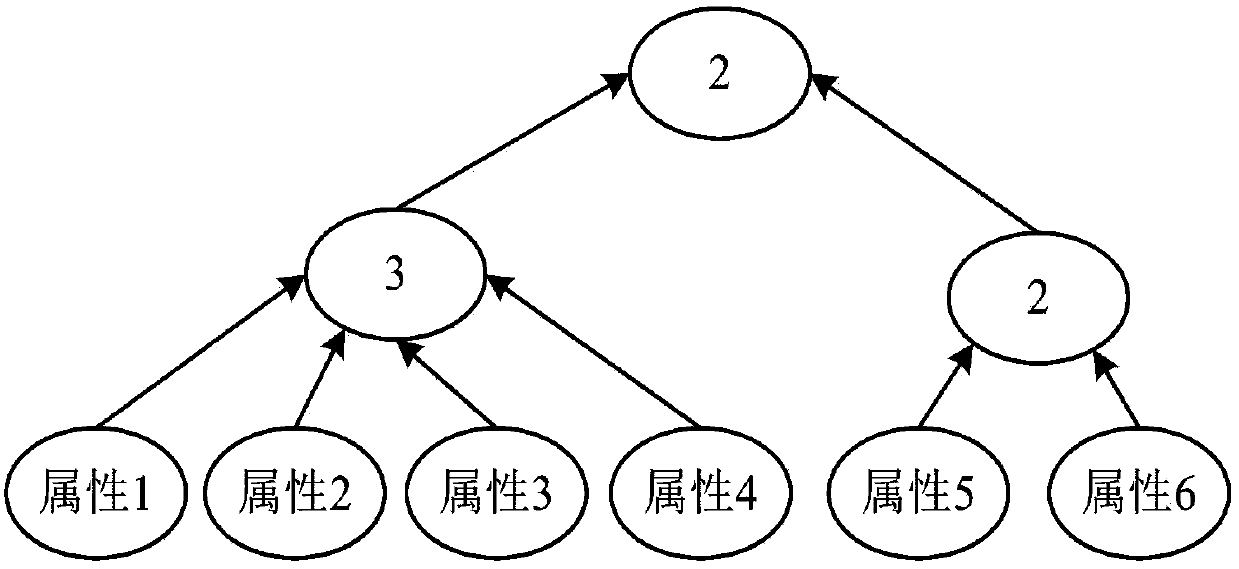
[0046] The present invention uses "0X1E" as the new message type, which means that the published payload data is encrypted using the CP-ABE algorithm, and the overall process is as follows figure 1 As shown, it specifically includes four stages: initialization, encryption, release, and decryption.
[0047] 1. Initialization phase:
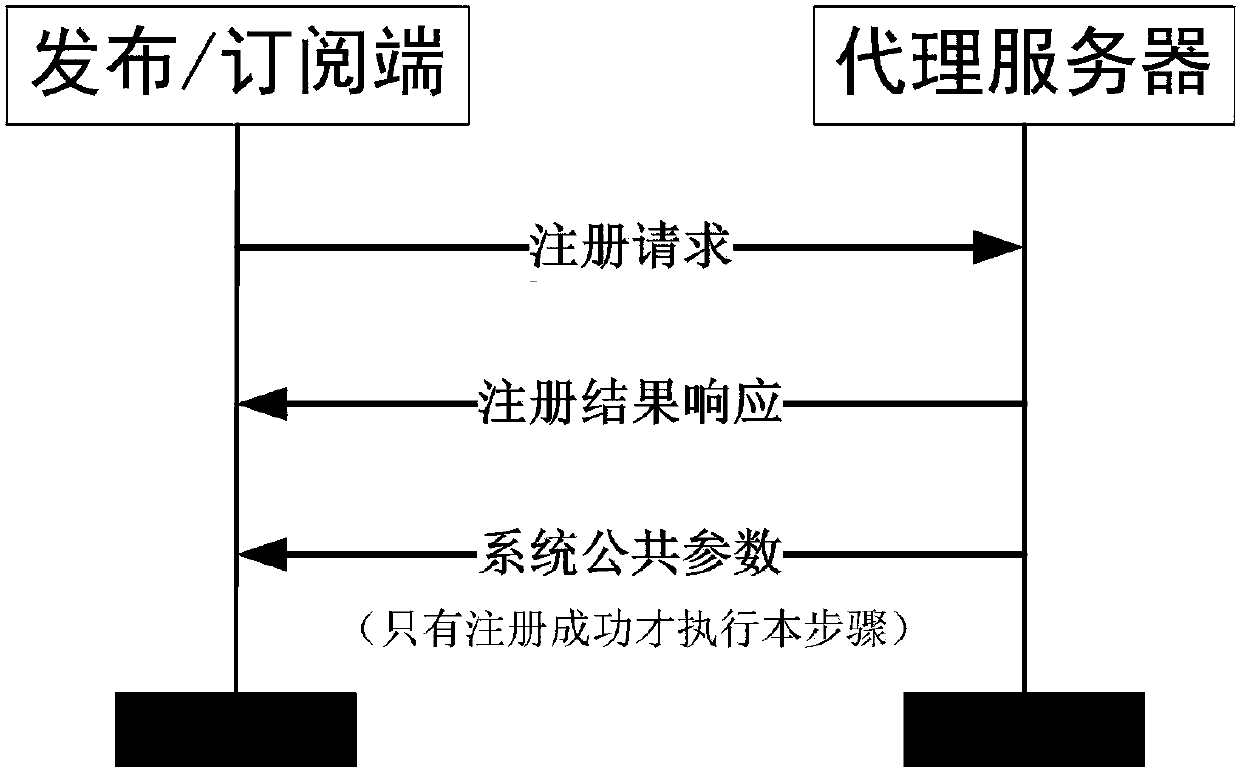
[0048] Before the publish / subscribe client can communicate normally, it needs to be initialized first, that is, the publish / subscribe client completes registration with the proxy server and establishes a connection with the proxy server. The registration process is as figure 2 Shown.
[0049] Step 1-1: The publish / subscribe client sends a registration request to the proxy server, that is, provides identity authentication information. The format of the identity authentication information submitted by the publis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com