Secure storage device
A technology for safe storage and equipment, applied in computer security devices, instruments, electrical digital data processing and other directions, can solve the problems of insufficient data encryption key transmission means, no data transmission security measures, etc. Effects of data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
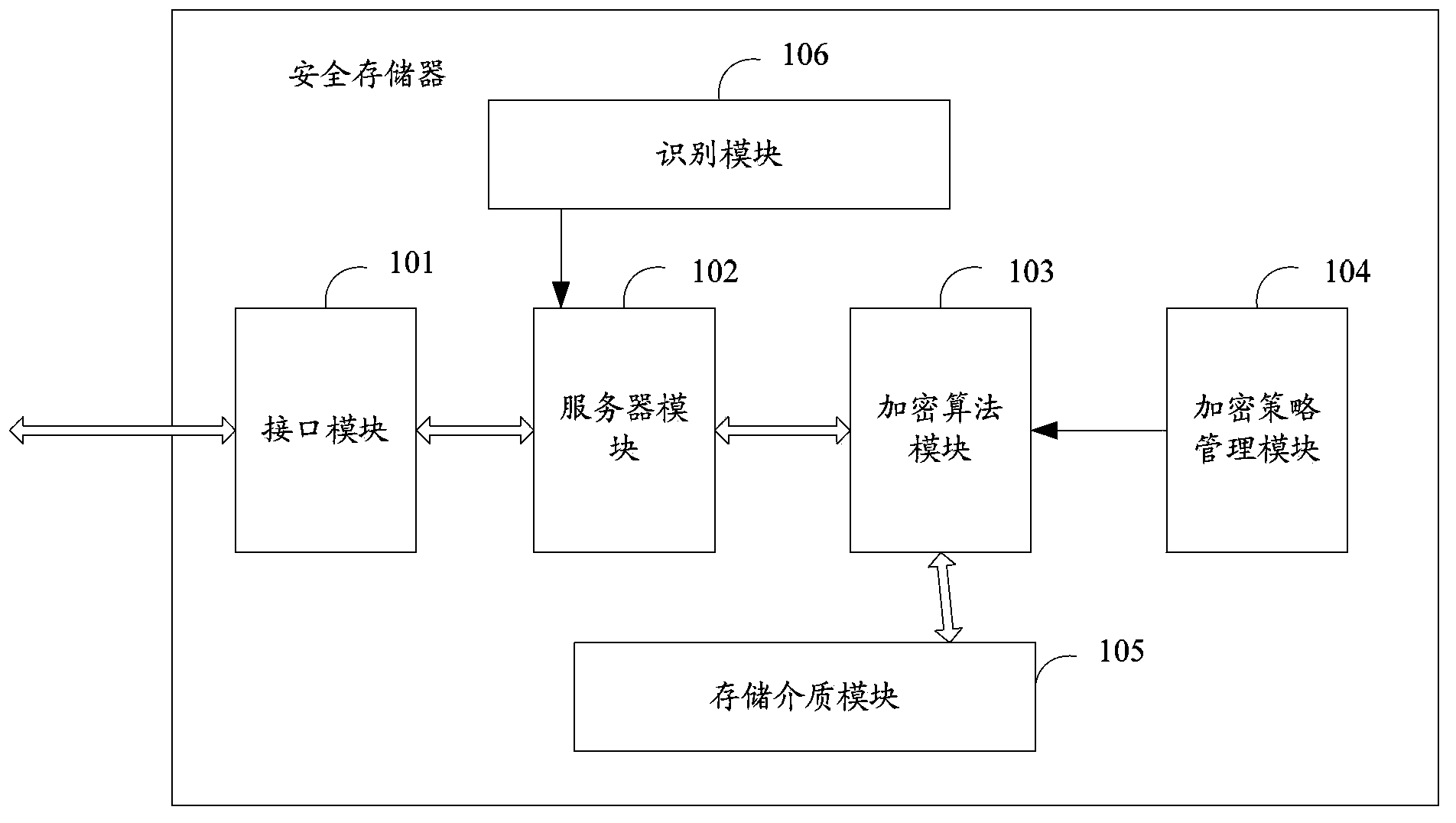
[0058] Embodiment 1 is: (1) the server module 102 supports Hypertext Markup Language 5 (HTML5) or an earlier version of HTML, and the server module 102 can support various file operations in addition to generating traditional pages; (2) when the user When the local computer accesses the storage, it is completed through the HTML browser, and the server module 102 receives the file access request sent by the user's local computer through the HTML browser; when the user's local computer opens the file on the storage, it is equivalent to the server module 102 completing a series of operations , and display the operation results in the form of HTML5 objects or HTML pages.
Embodiment 2
[0059] The second embodiment is: (1) The server module 102 is an X-server, and the user's local computer sends a file access request through the x-client or RDP; (2) When the user's local computer accesses the storage, the local X-client will be opened. All operations are completed by the processor on the memory, and the user's local computer only displays the graphics results after processing. Wherein, X-server refers to that the server is a device that supports client access through a graphics protocol, and the X-client terminal interacts with the server through a graphics protocol.
[0060] In addition, if the method of X-Server or HTML Server is not used, the server module 103 can be implemented by starting a server software program on the safe storage, and the storage provides a client program that can be obtained by the user's local computer, and the program can communicate with The server module interacts. The client program can communicate with the server through secu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com