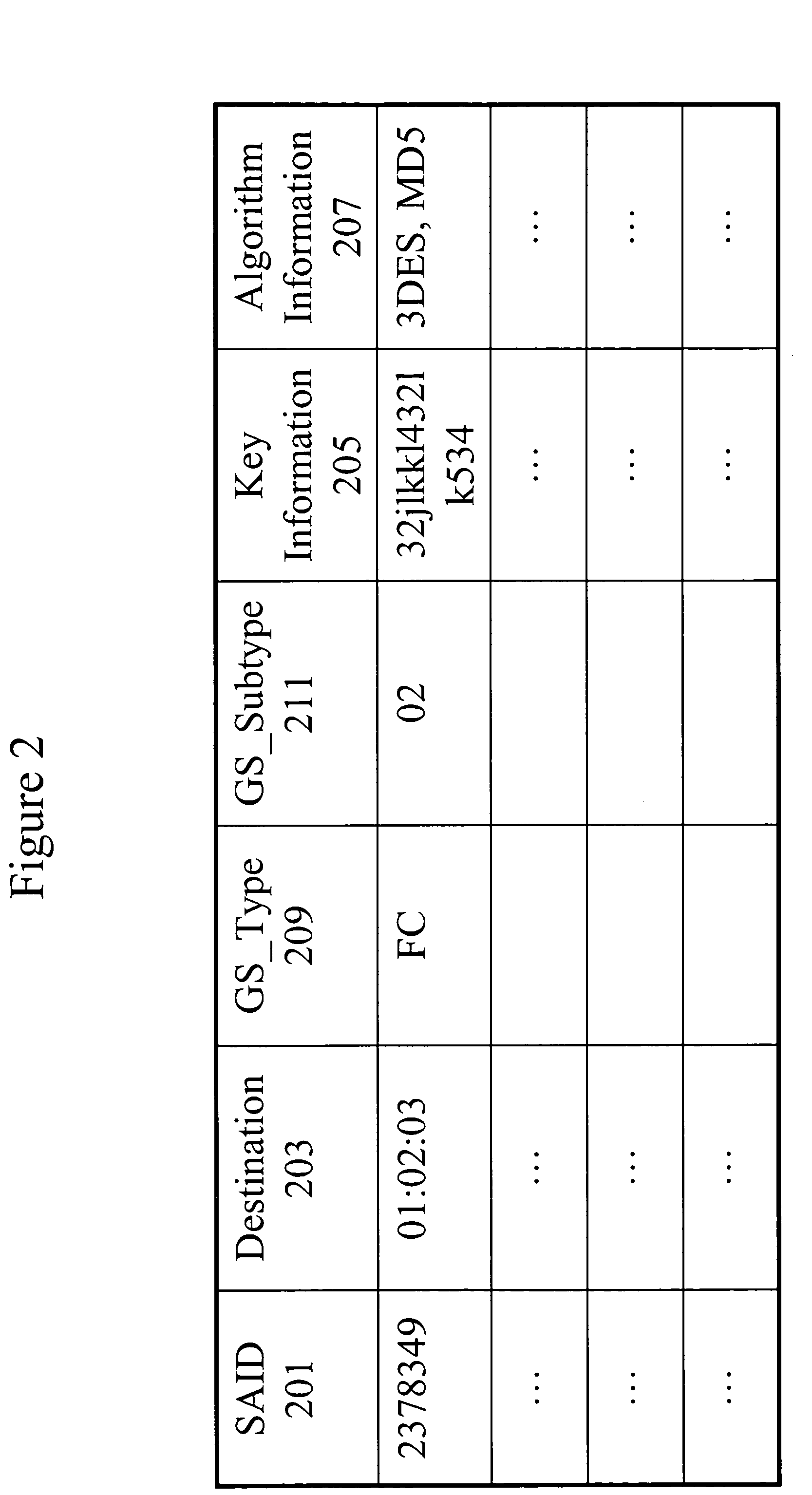
Patents
Literature
82 results about "Confidentiality protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Confidentiality is the protection of personal information. Confidentiality means keeping a client’s information between you and the client, and not telling others including co-workers, friends, family, etc. Examples of maintaining confidentiality include: individual files are locked and secured.
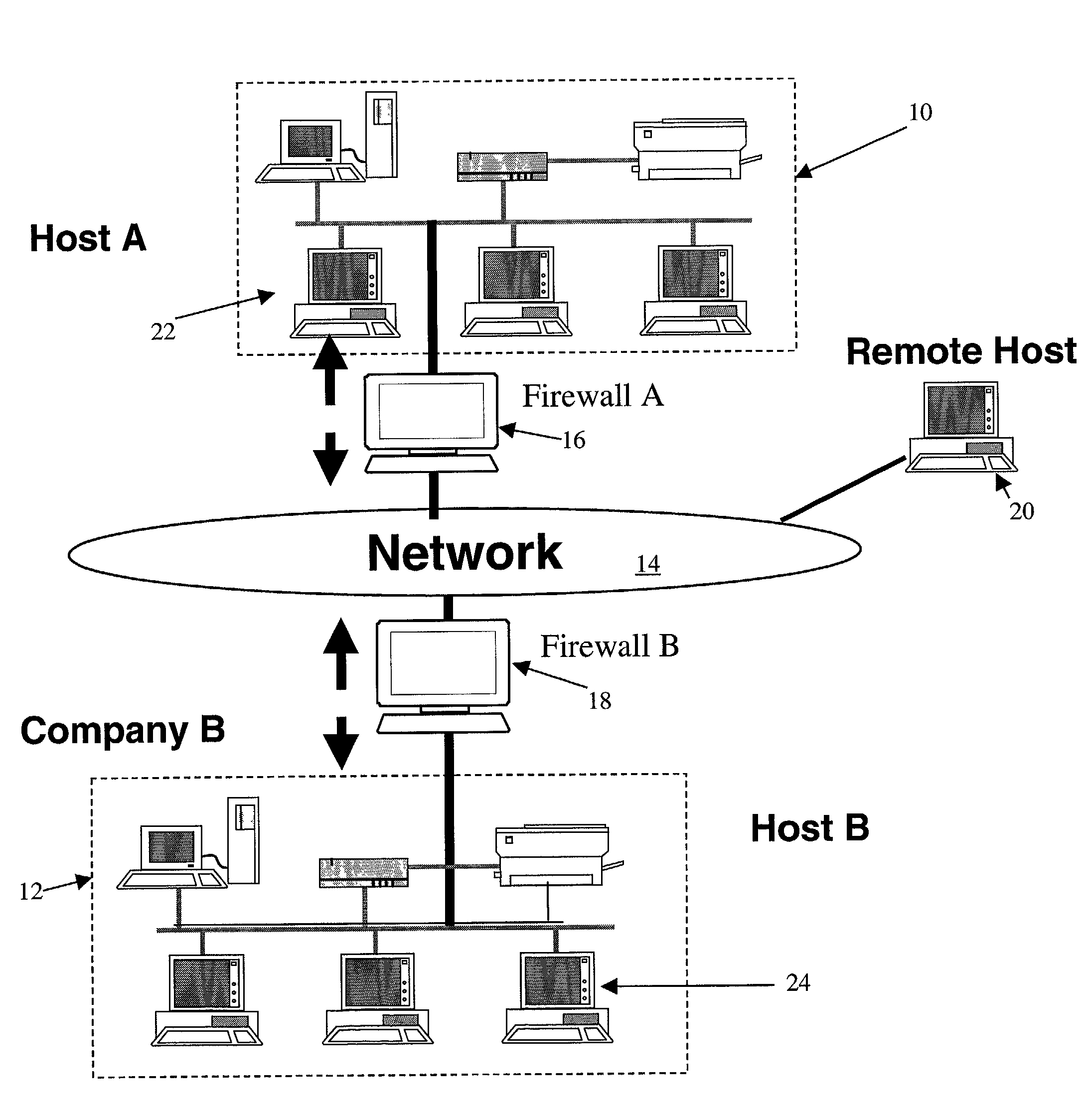
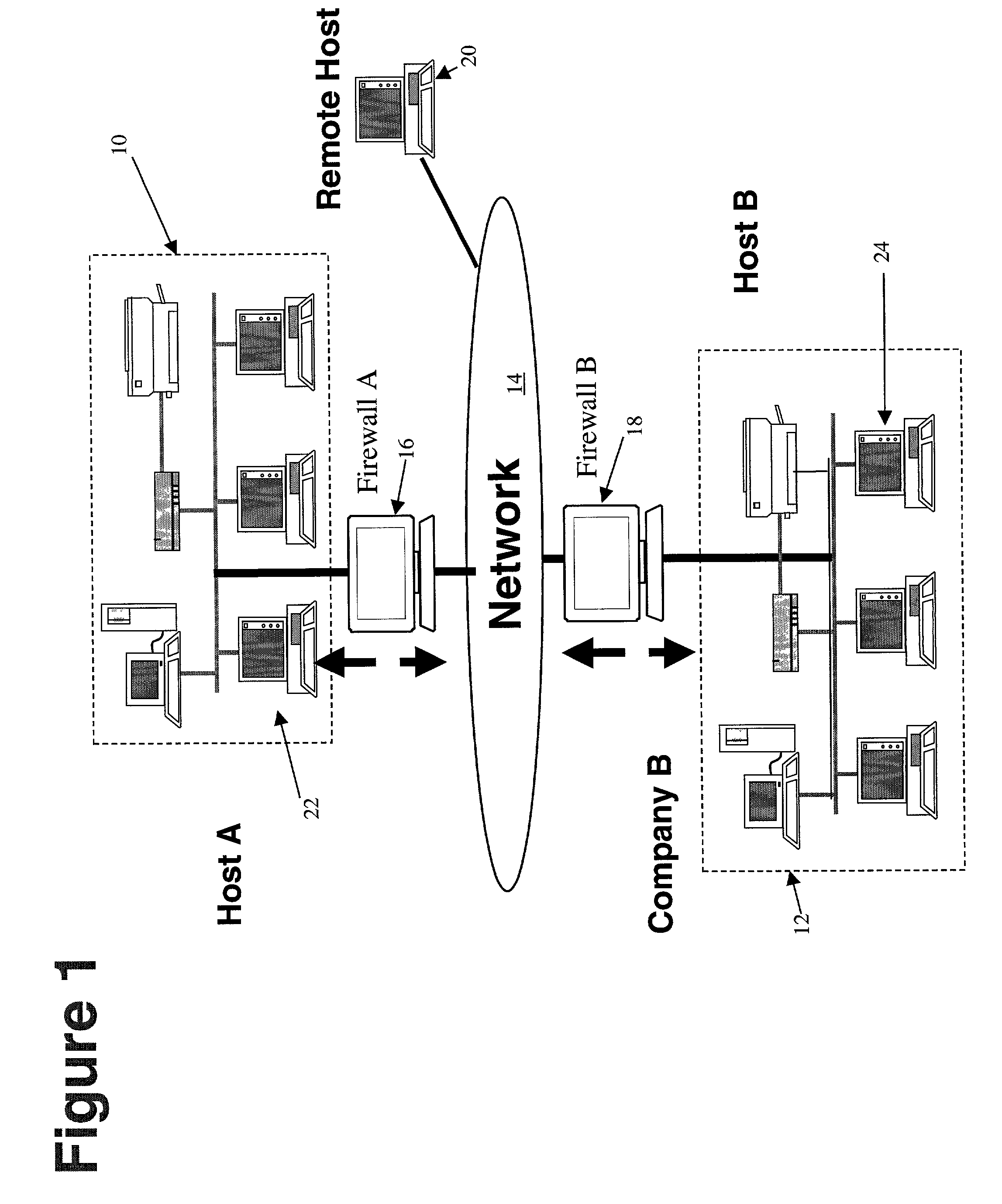
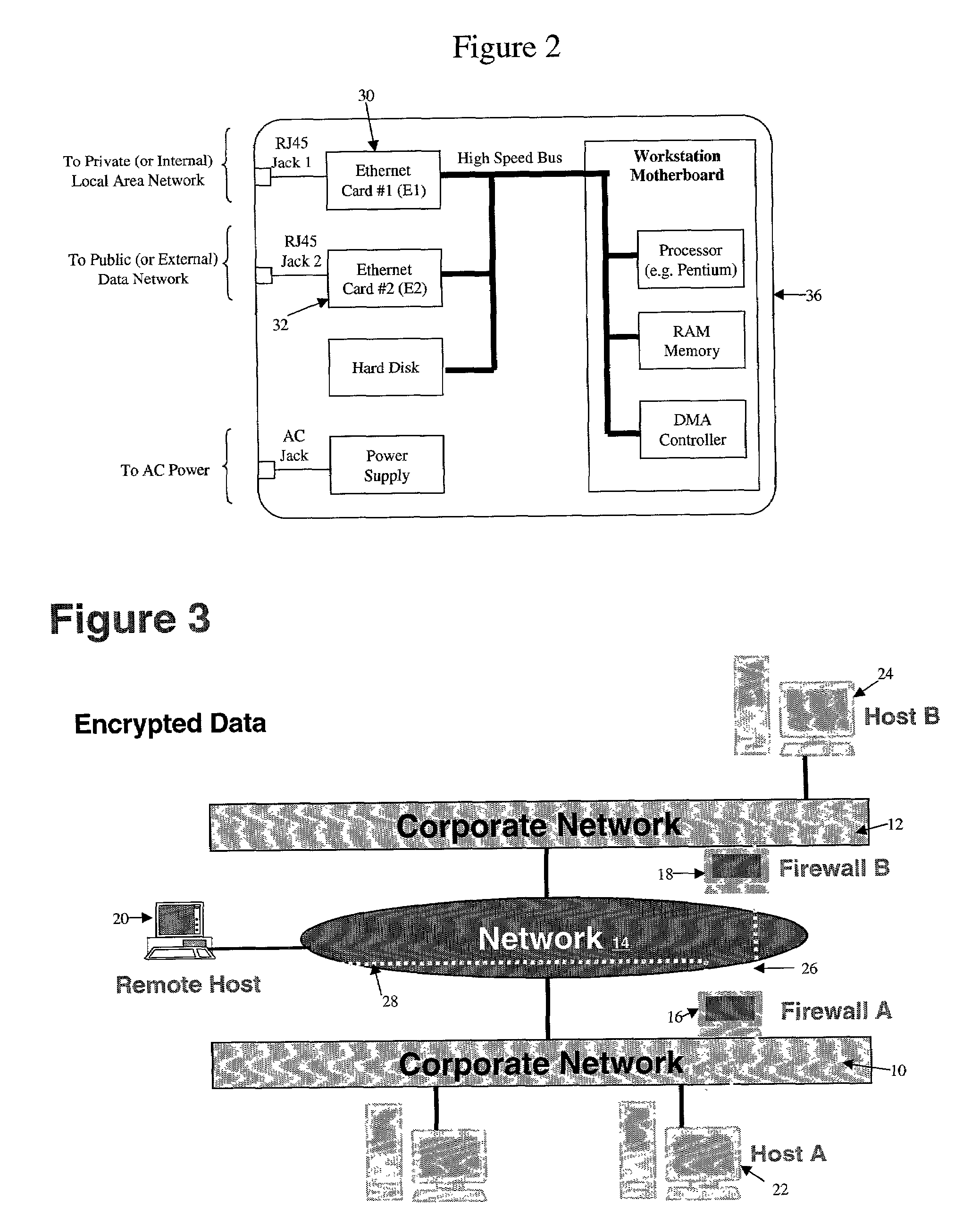
Method and apparatus for securely transmitting encrypted data through a firewall and for monitoring user traffic
InactiveUS7516485B1More scalable solutionLow costComputer security arrangementsMultiple digital computer combinationsTraffic capacityConfidentiality protection
A technique for enabling a firewall device to allow encrypted data to securely pass between networks, and at the same time allow the firewall to selectively monitor the encrypted traffic that is allowed to pass is disclosed. In one embodiment, the technique is realized by detecting an exchange of a first encryption key between a host device and a remote device, and the first encryption key supports confidentiality protection of a first security policy between the host device and the remote device. Next, a second encryption key is exchanged with the host device when the exchange of the first encryption key is detected, and the exchange of the second encryption key supports confidentiality protection of a second security policy between the firewall and the host device. Next, based at least in part upon the second security policy, the first encryption key is requested and the first encryption key is sent under the protection of the second security key and in accordance with the second security policy. Finally, encrypted data is passed when it is determined that the first encryption key is received.
Owner:F5 NETWORKS INC
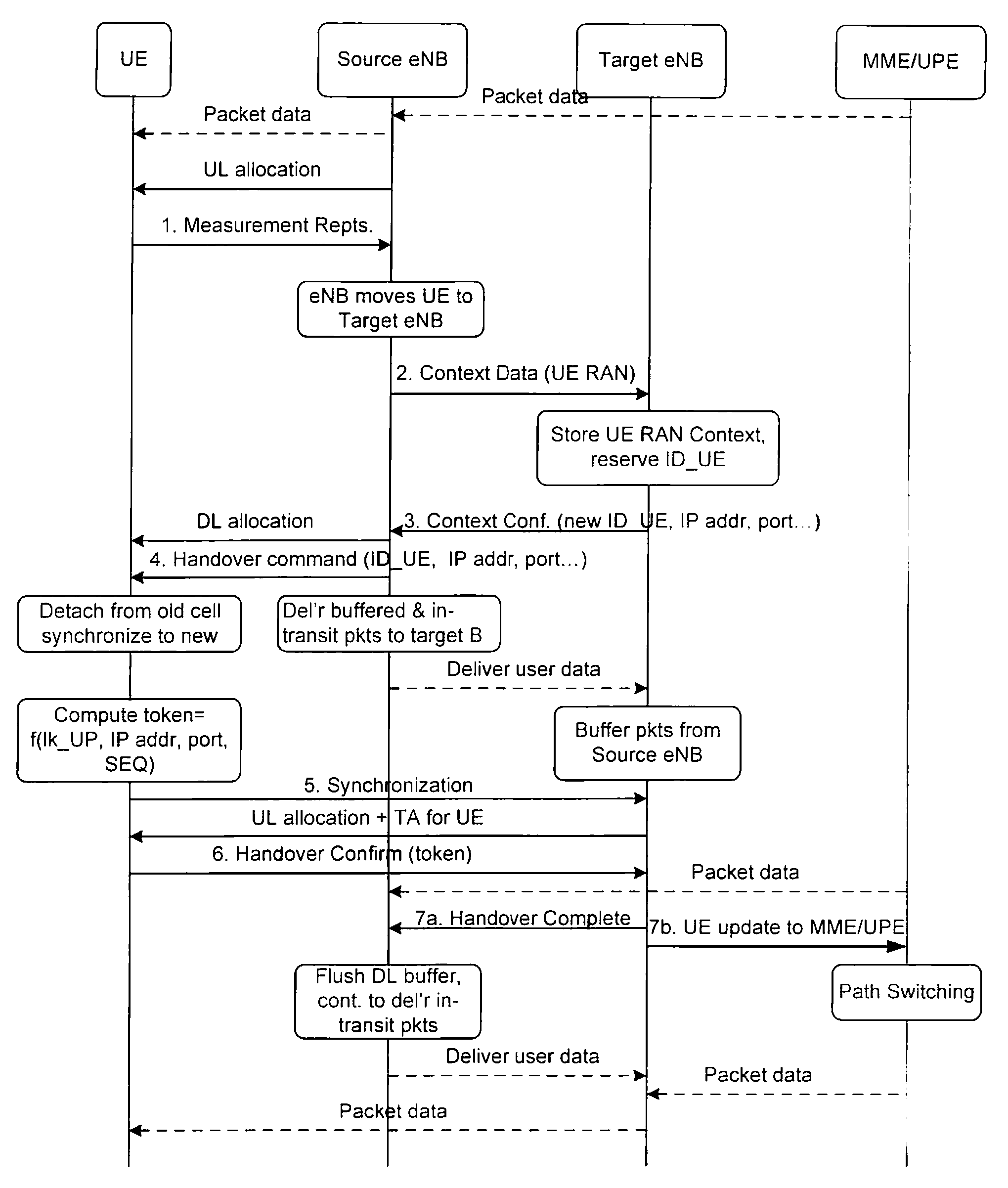
Method and system for protecting signaling information
InactiveUS20080181411A1Key distribution for secure communicationOrthogonal multiplexAccess networkComputer hardware
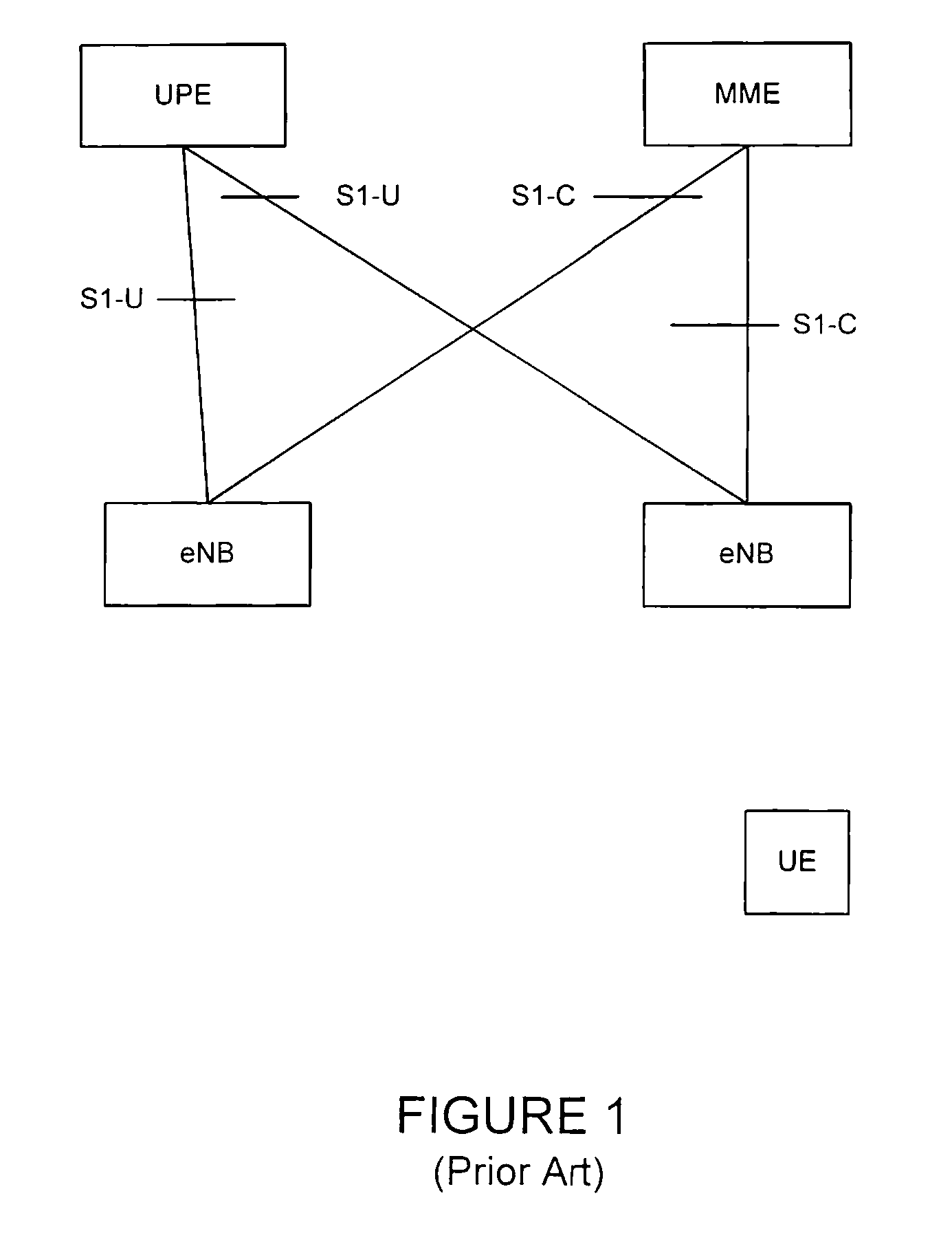
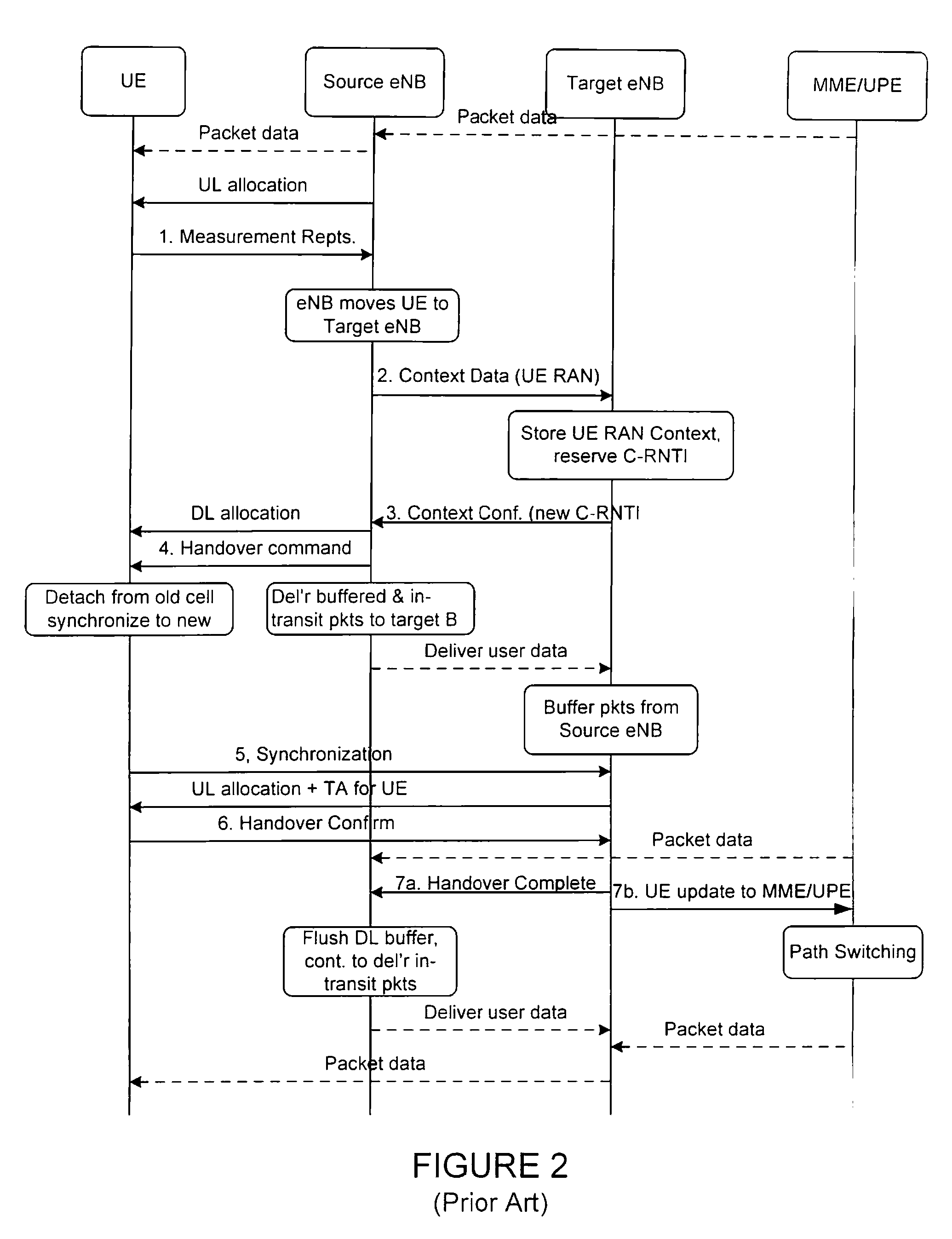
A path switch message in a mobile radio access network is protected as the message is sent over a user plane interface that may be insecure (e.g. lacks integrity and / or confidentiality protection). According to the invention a UE provides an AP with a fresh integrity key over an already existing and secure RAN channel enabling AP to use the integrity key to integrity protect information sent to a UPN. Specifically, UE derives locally at least a user plane key K1. The key derivation is done at authentication e.g. when performing an AKA procedure. On the network side CPN derives the same key K1 for delivery to UPN. At handover, the UE generates a fresh integrity key K3 by applying a Key Derivation Function (KDF) with at least the UP key K1 and a nonce, e.g. a sequence number.
Owner:TELEFON AB LM ERICSSON (PUBL)
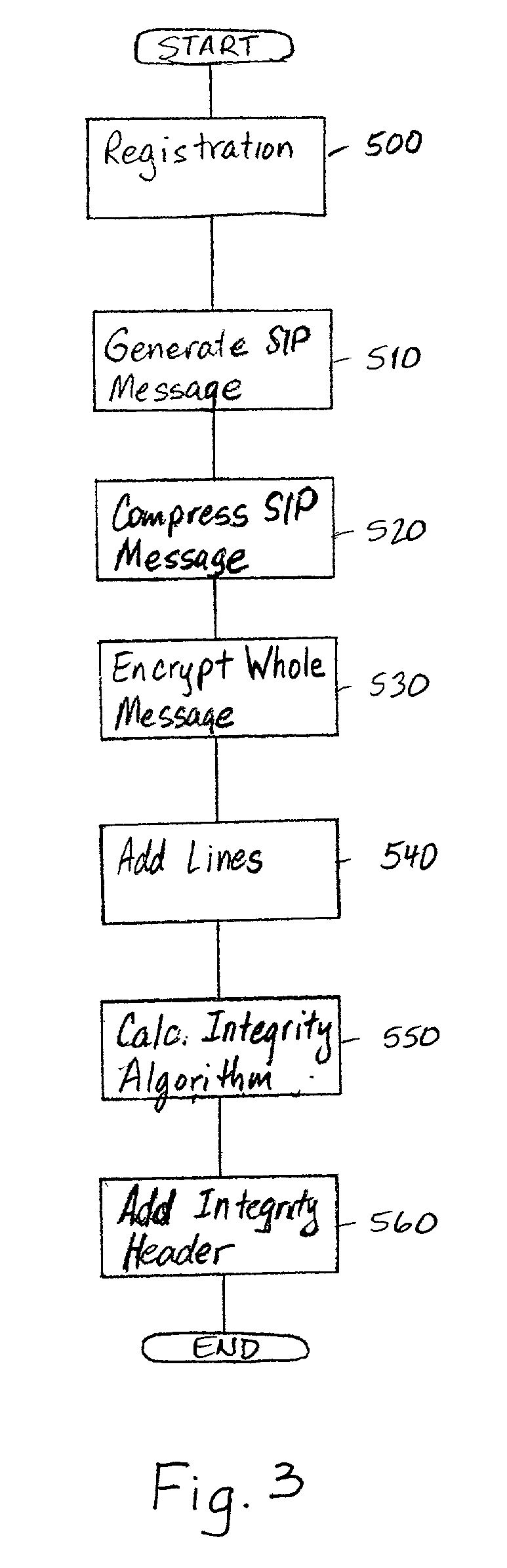
SIP-level confidentiality protection
InactiveUS20030097584A1Digital data processing detailsMultiple digital computer combinationsSession Initiation ProtocolConfidentiality protection
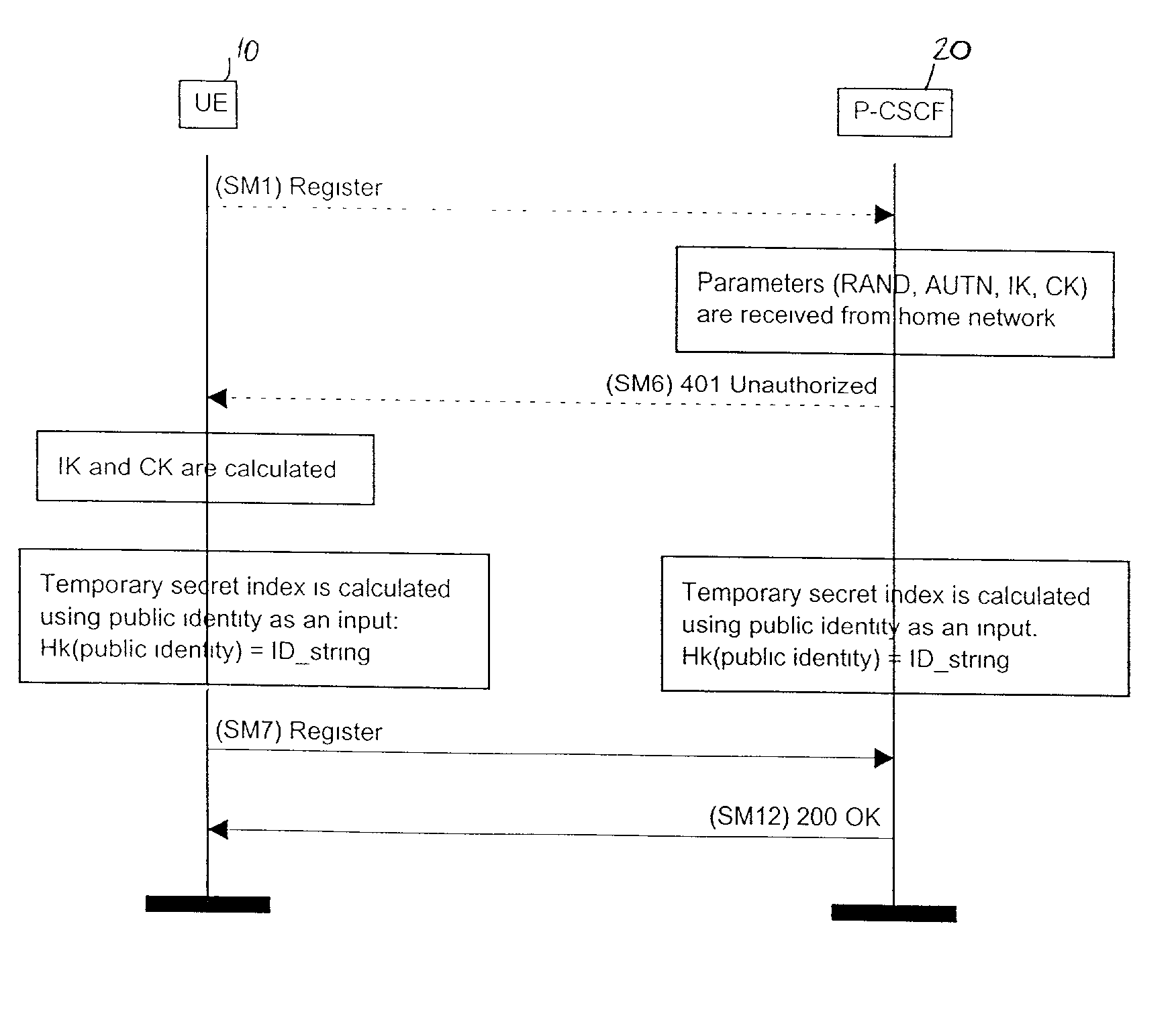
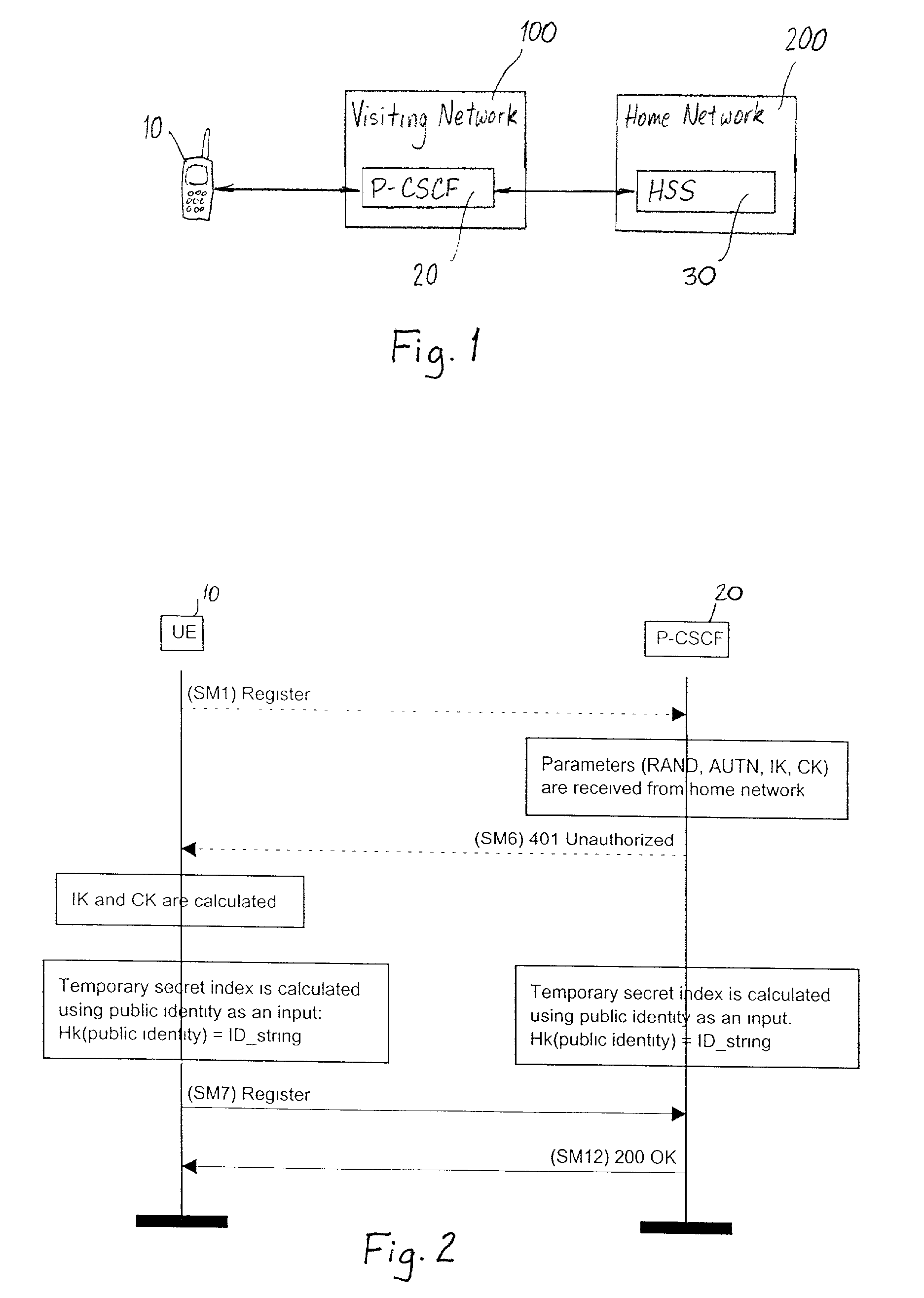
A session initiation protocol message includes confidentiality protection in that the sender of the message is identified using a temporary identity index generated by calculating a hash function for a private key and public information which indicates the sender. The result of the calculation of the hash function is the temporary identity index and is associated with a specific sender-receiver pair.
Owner:NOKIA CORP
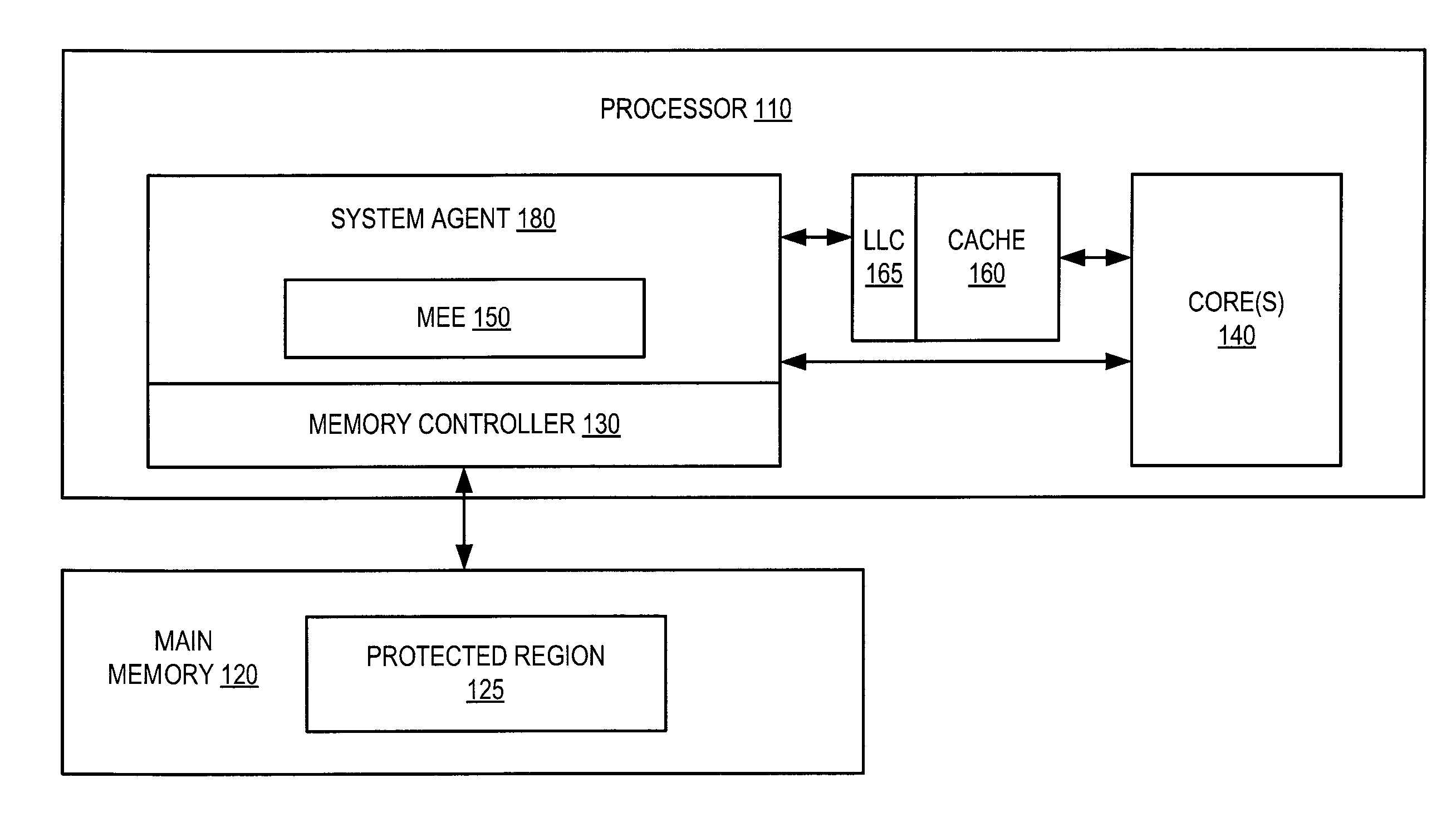
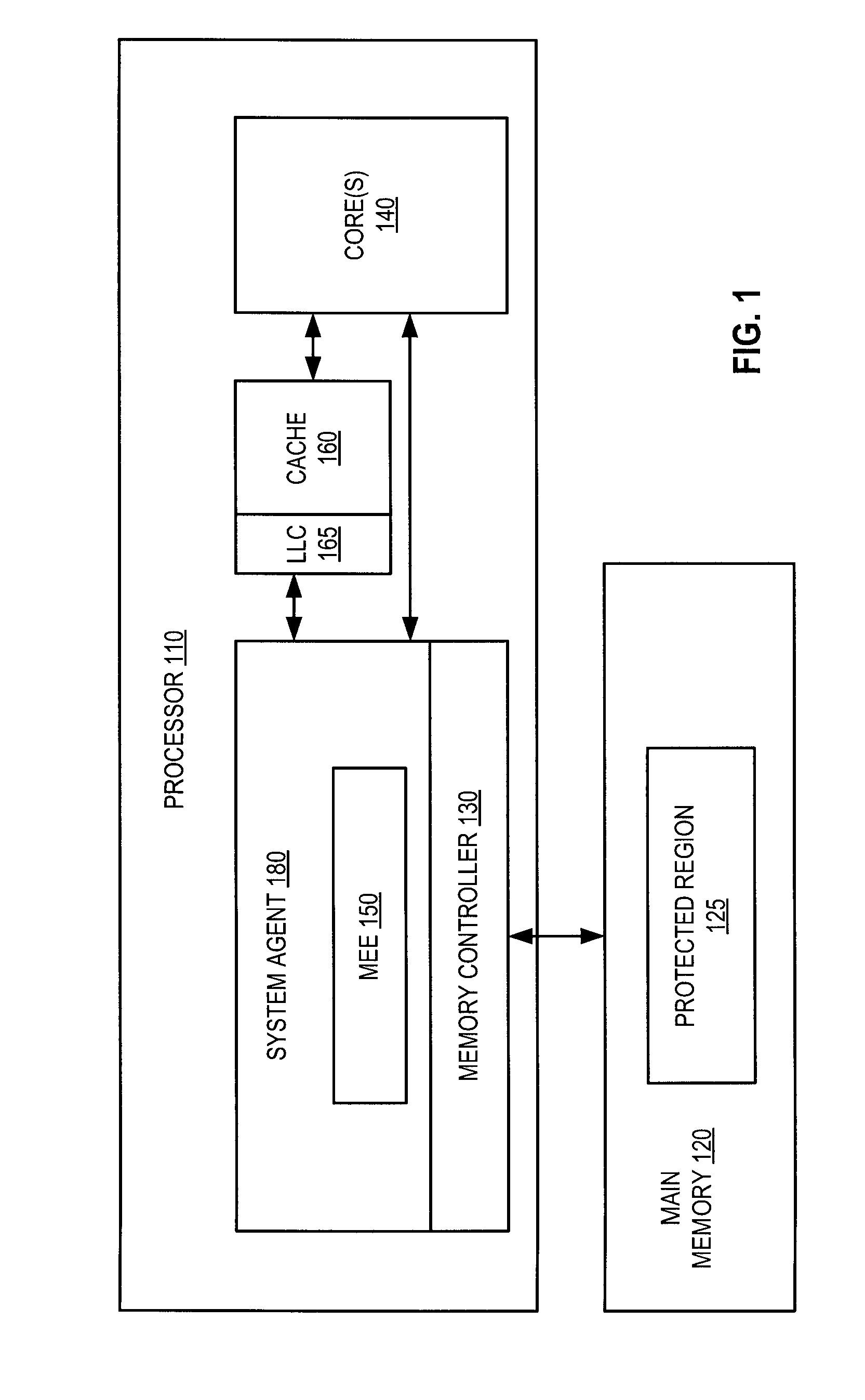
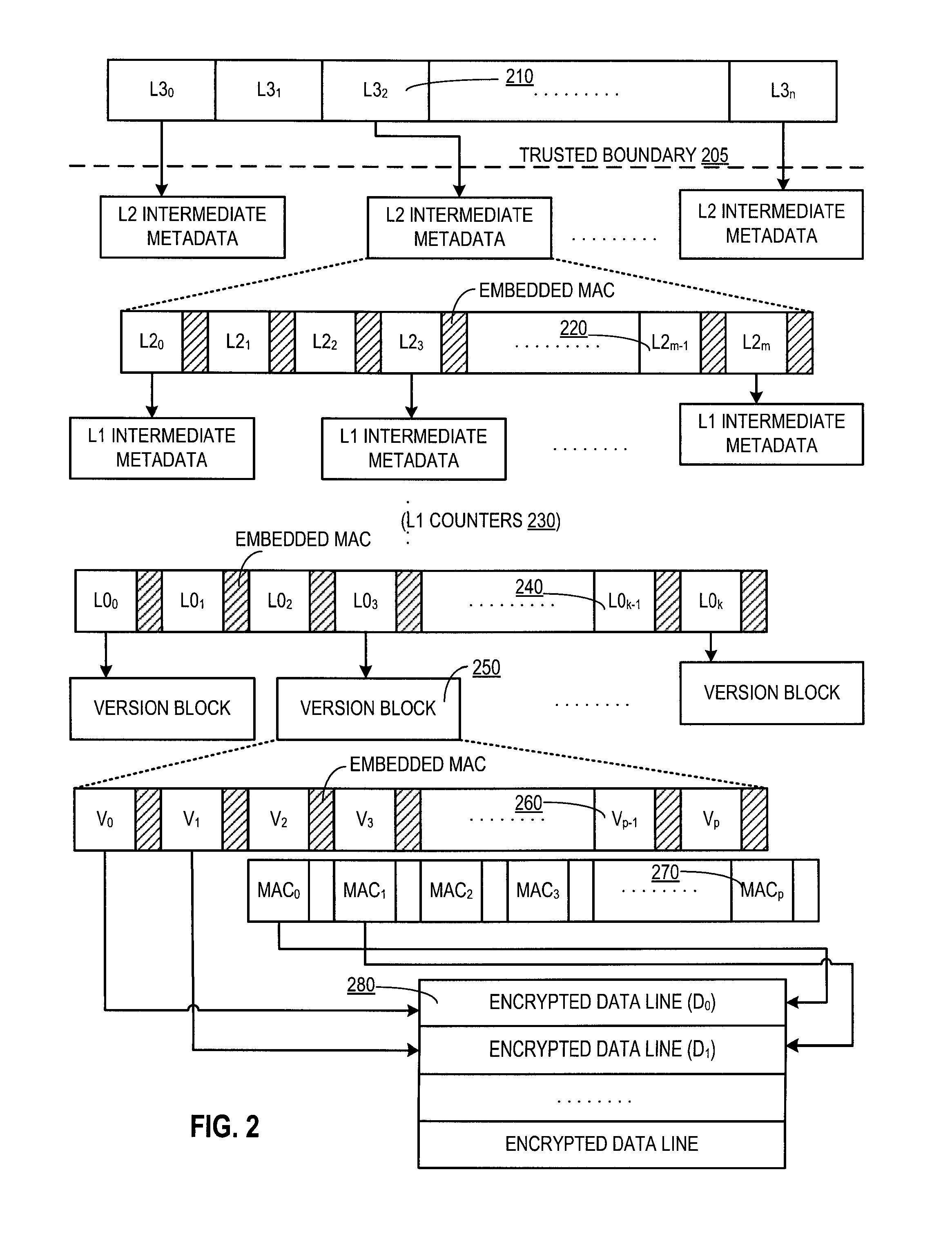
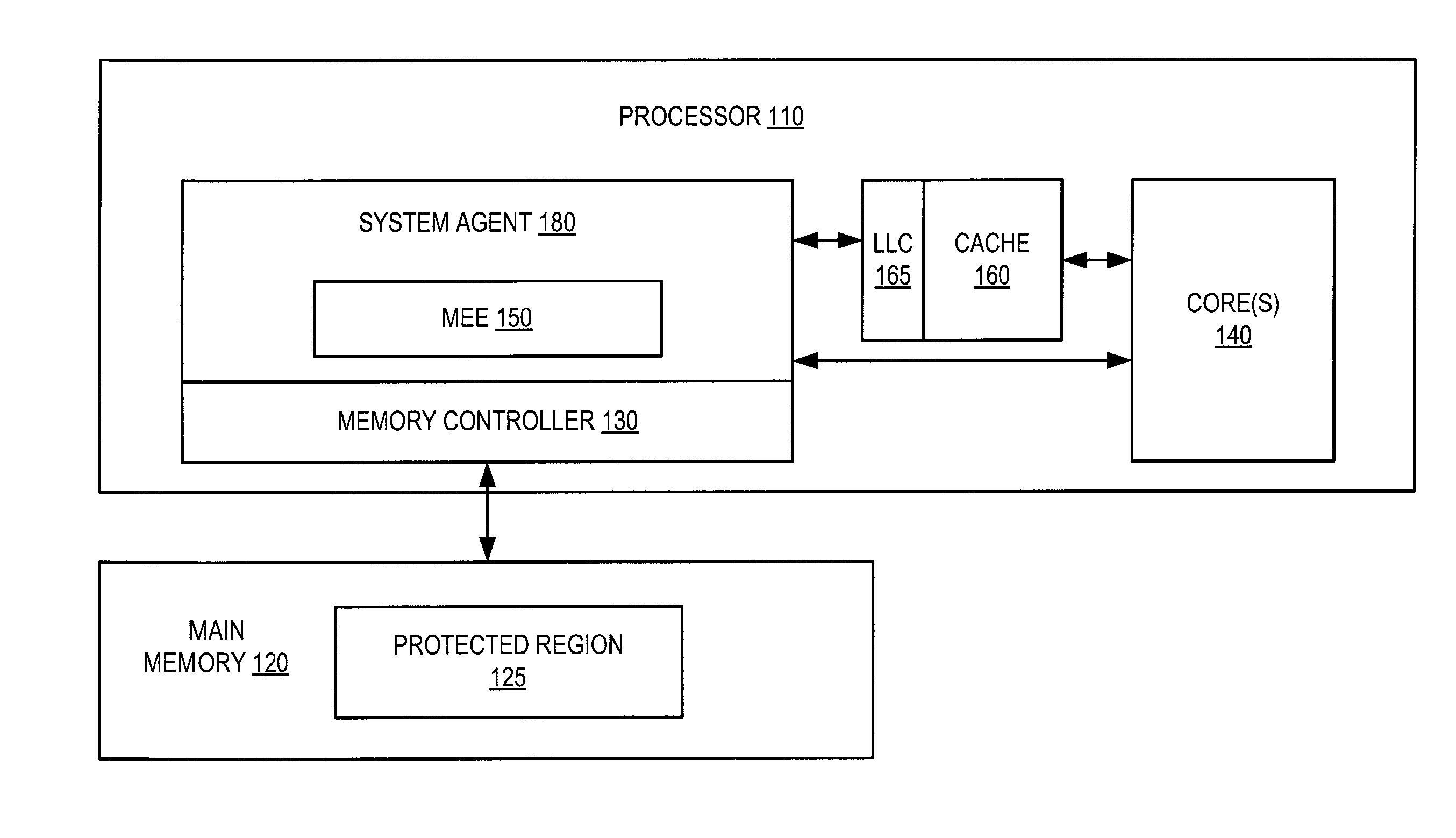
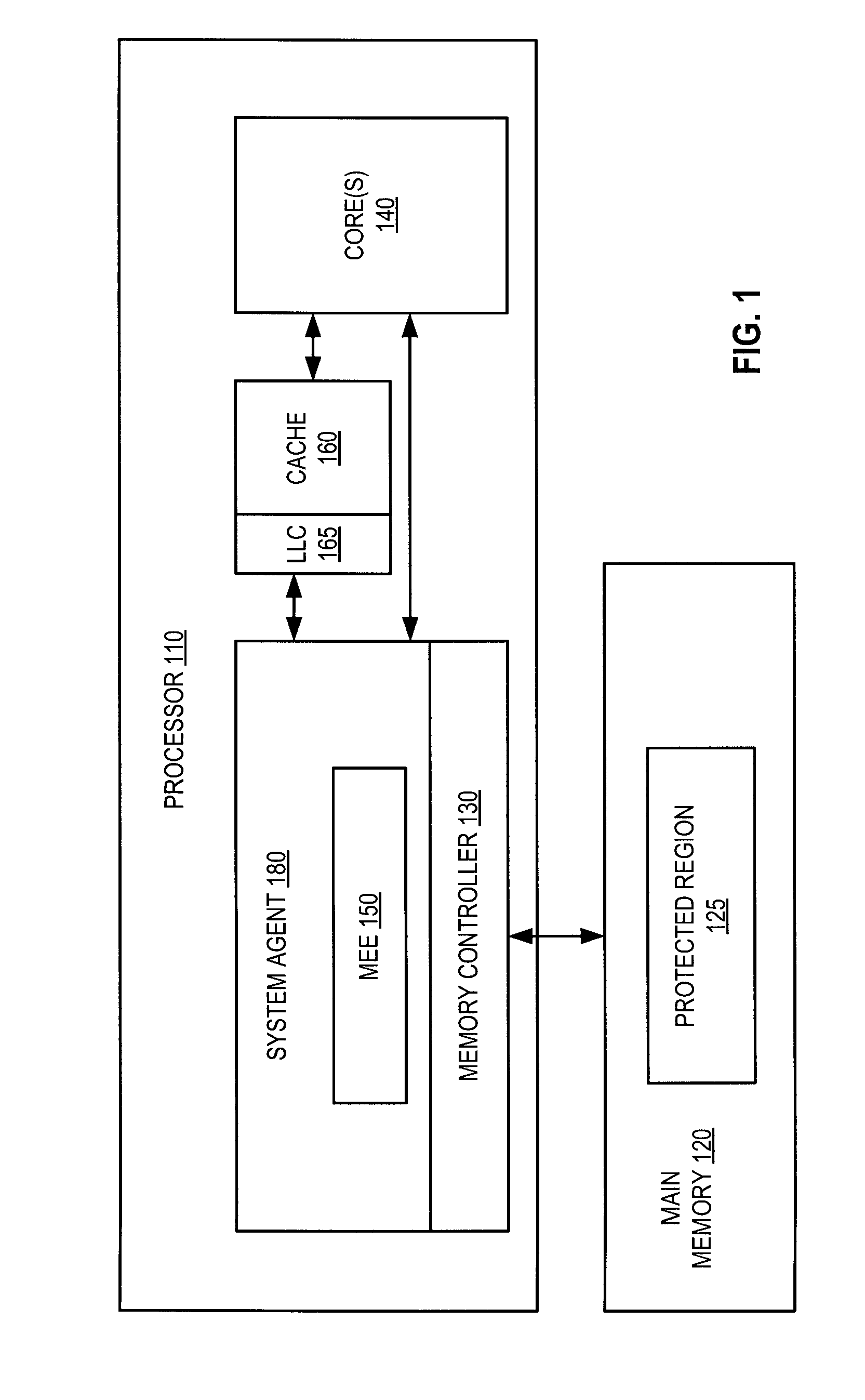
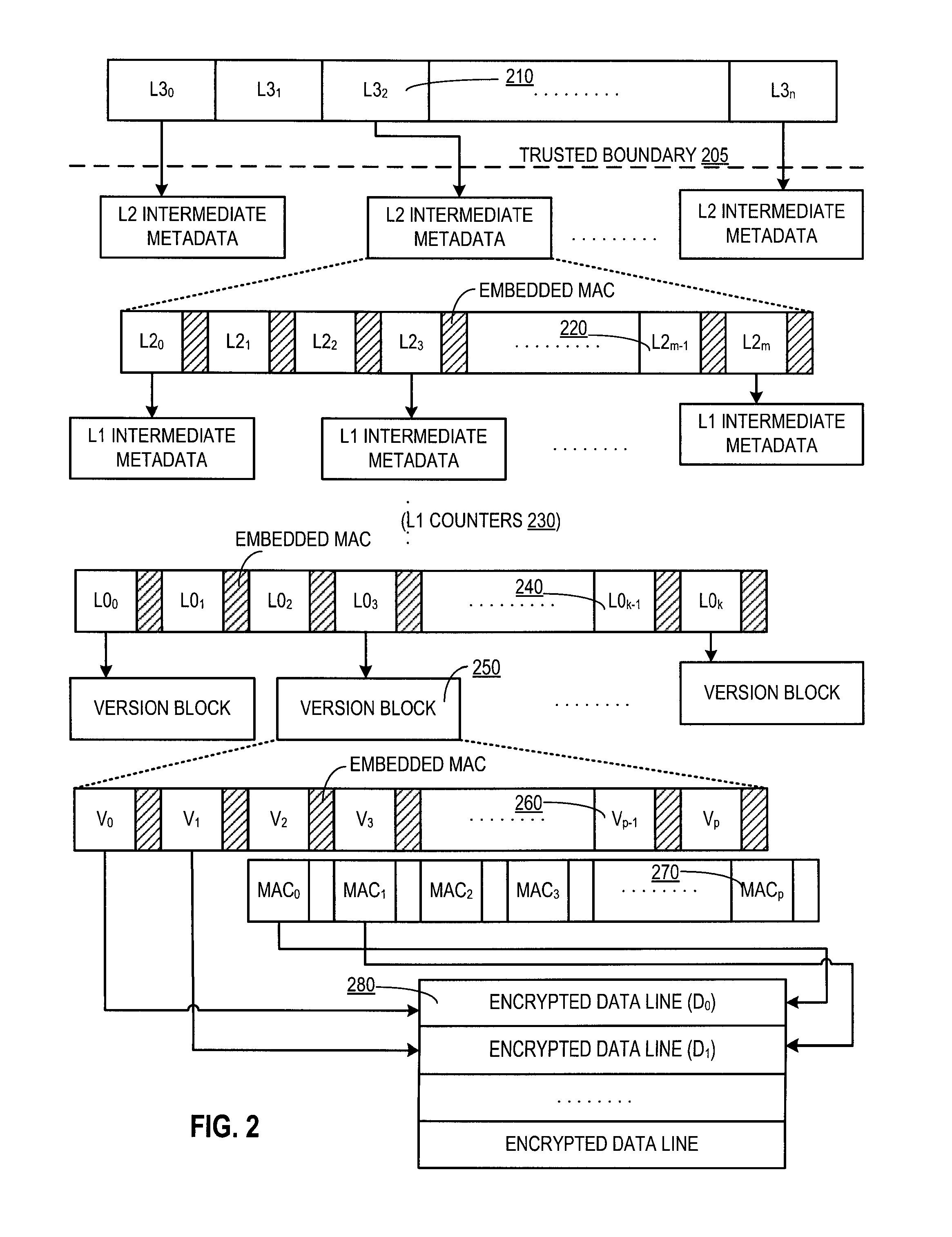
Parallelized counter tree walk for low overhead memory replay protection
ActiveUS8819455B2Unauthorized memory use protectionHardware monitoringComputer hardwareConfidentiality protection
A processor includes a memory encryption engine that provides replay and confidentiality protections to a memory region. The memory encryption engine performs low-overhead parallelized tree walks along a counter tree structure. The memory encryption engine upon receiving an incoming read request for the protected memory region, performs a dependency check operation to identify dependency between the incoming read request and an in-process request and to remove the dependency when the in-process request is a read request that is not currently suspended.
Owner:TAHOE RES LTD
Parallelized counter tree walk for low overhead memory replay protection
ActiveUS20140101461A1Unauthorized memory use protectionHardware monitoringComputer hardwareConfidentiality protection
A processor includes a memory encryption engine that provides replay and confidentiality protections to a memory region. The memory encryption engine performs low-overhead parallelized tree walks along a counter tree structure. The memory encryption engine upon receiving an incoming read request for the protected memory region, performs a dependency check operation to identify dependency between the incoming read request and an in-process request and to remove the dependency when the in-process request is a read request that is not currently suspended.
Owner:TAHOE RES LTD
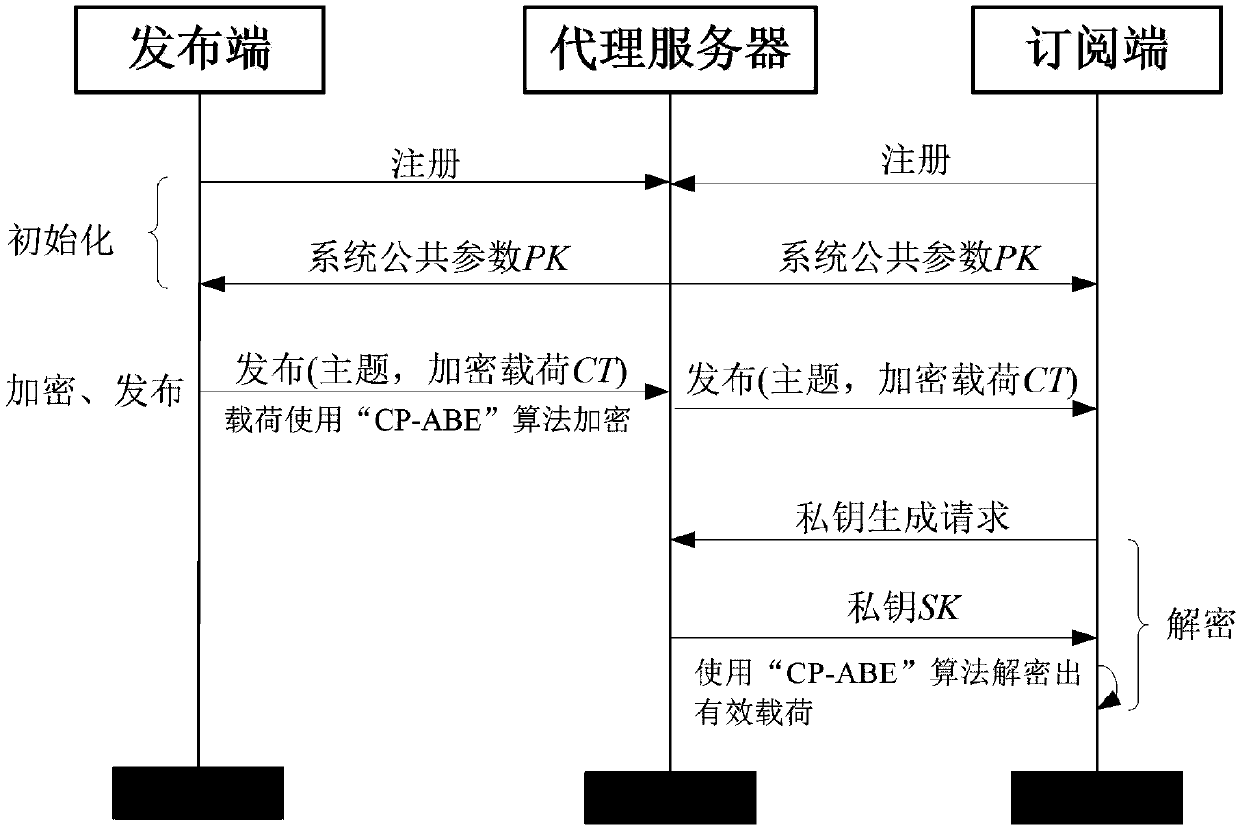
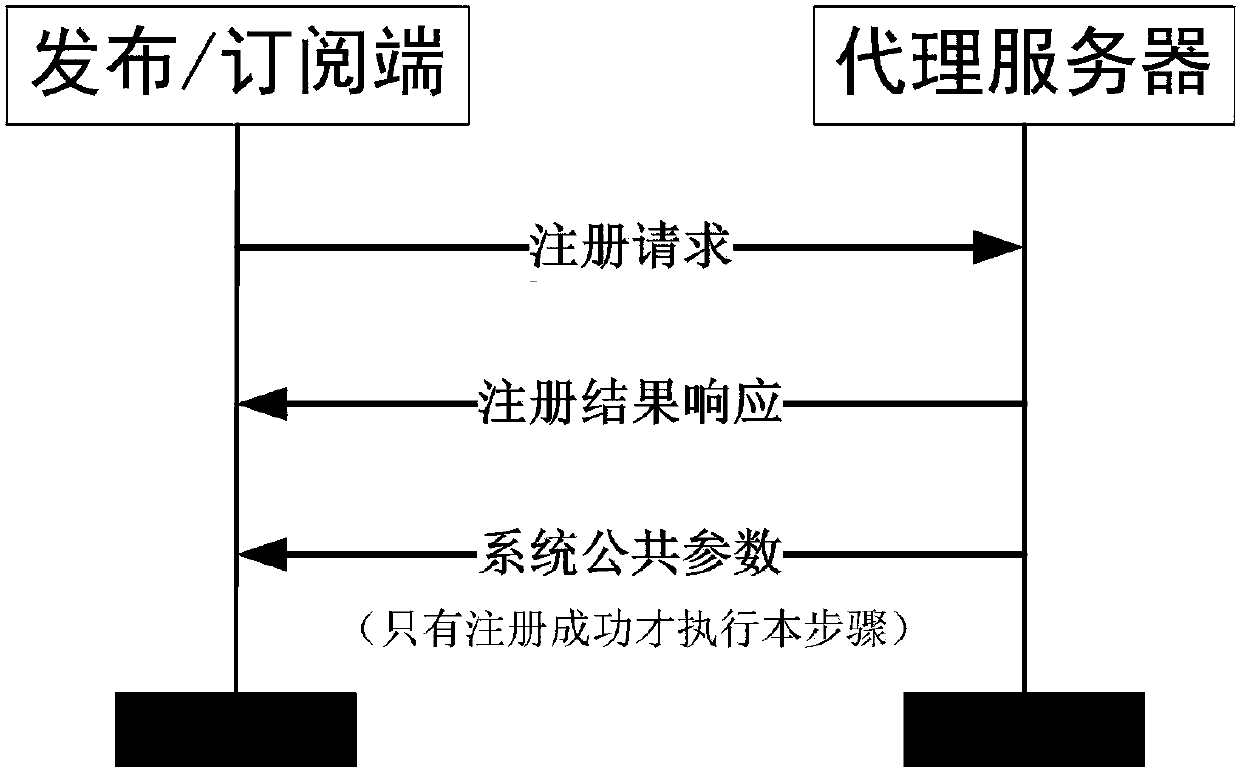
Encryption method applied to MQTT-SN protocol
InactiveCN107708112AImplement encryptionAchieve authenticationNetwork topologiesTransmissionComputer hardwarePlaintext
The invention relates to an encryption method applied to a MQTT-SN protocol, and relates to the field of communication. The method employs a harsh algorithm and ciphertext-policy attribute-based encryption method, so that a publishing terminal, an agent server and one or a plurality of subscription terminals can complete encrypted communication. The method herein includes the following steps: an agent server verifying the identity of a publishing / subscription terminal, performing registration of the publishing / subscription terminal, and generating a system common parameter; the publishing terminal encrypting a plaintext load by using the ciphertext-policy attribute-based encryption method; the publishing terminal transmitting the encrypted load to the agent server, the agent server forwarding the encrypted load to one or a plurality of subscription terminals; and the subscription terminal applying for a secrete key from the agent server, decrypting the encrypted load, obtaining a plaintext. According to the invention, the method can implement identity verification of a MQTT-SN protocol publishing / subscription terminal, data integrity verification, and data confidentiality protection, and better addresses the safety issues faced by the MQTT-SN protocol in terminals of wireless sensor network applications.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
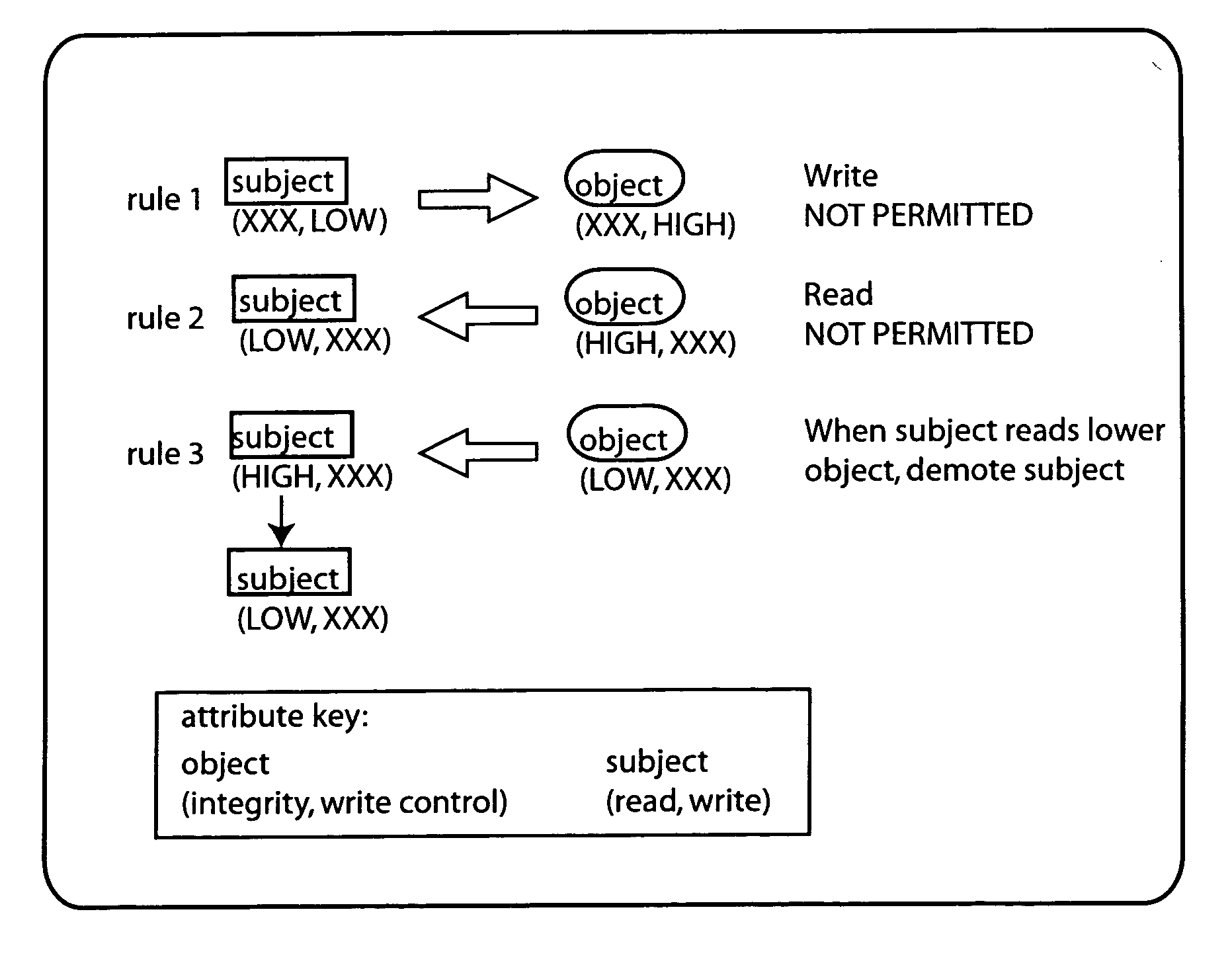
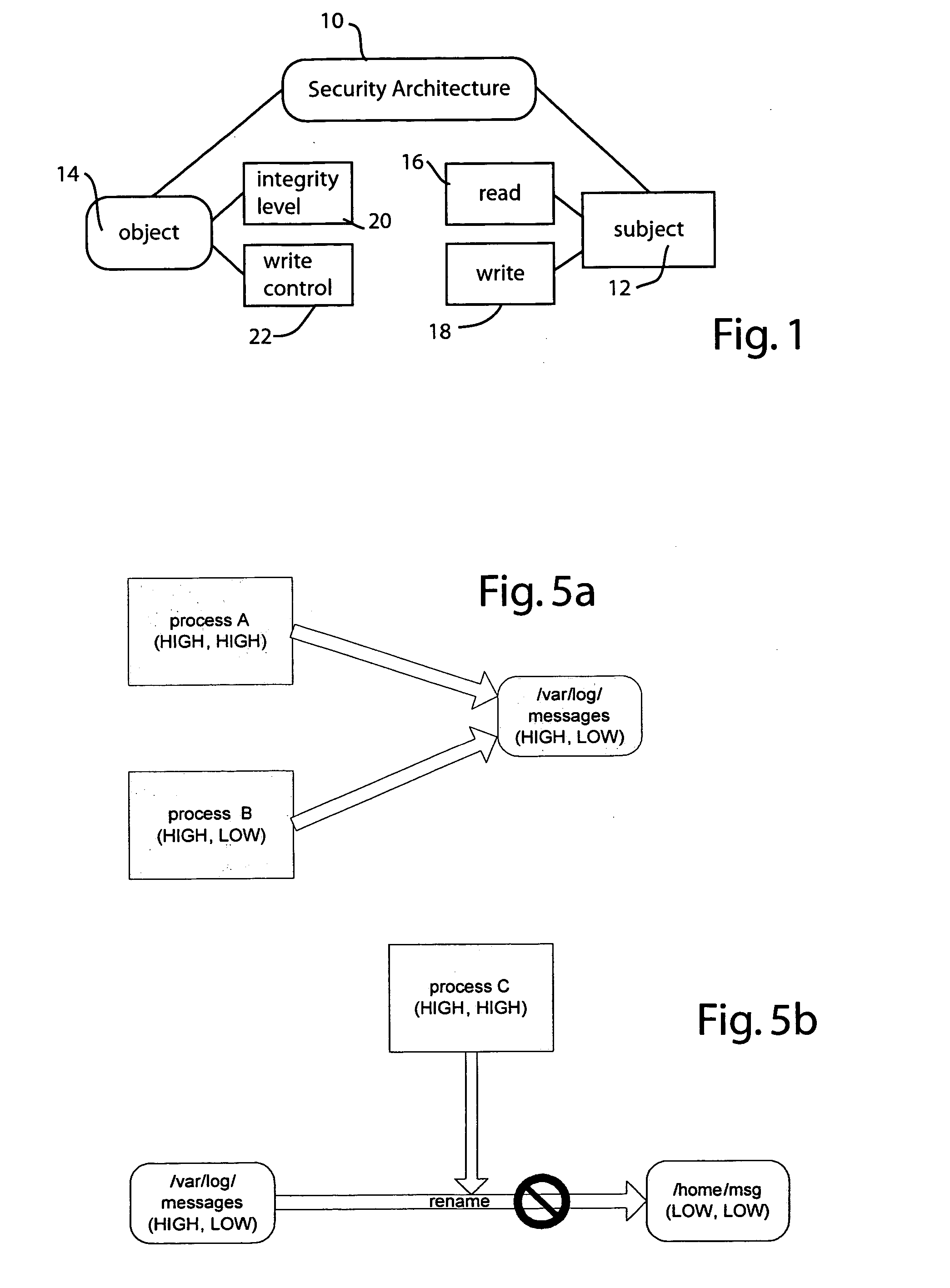
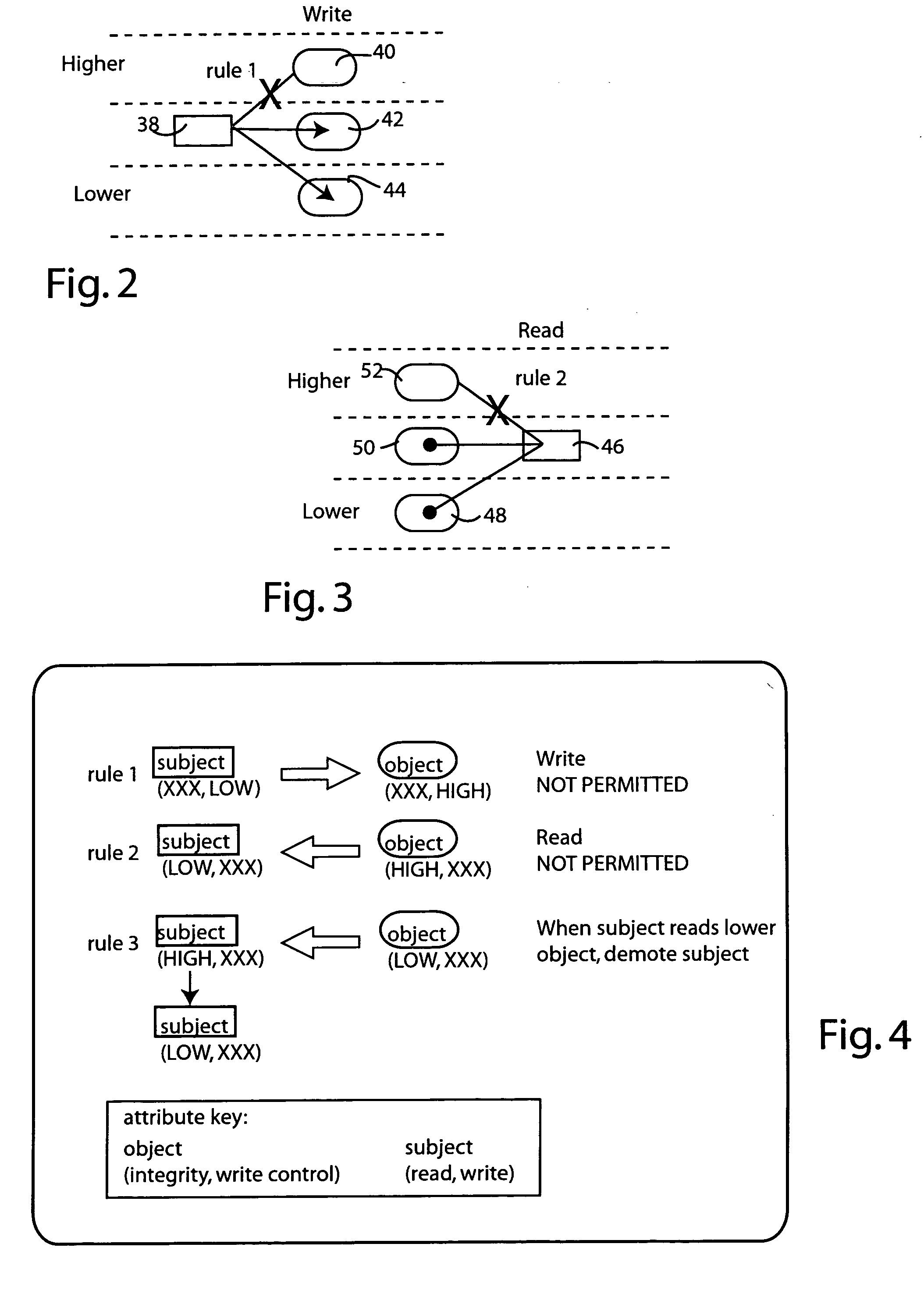
Mandatory access control scheme with active objects
InactiveUS20060075508A1Digital data processing detailsUser identity/authority verificationConfidentiality protectionAccess control
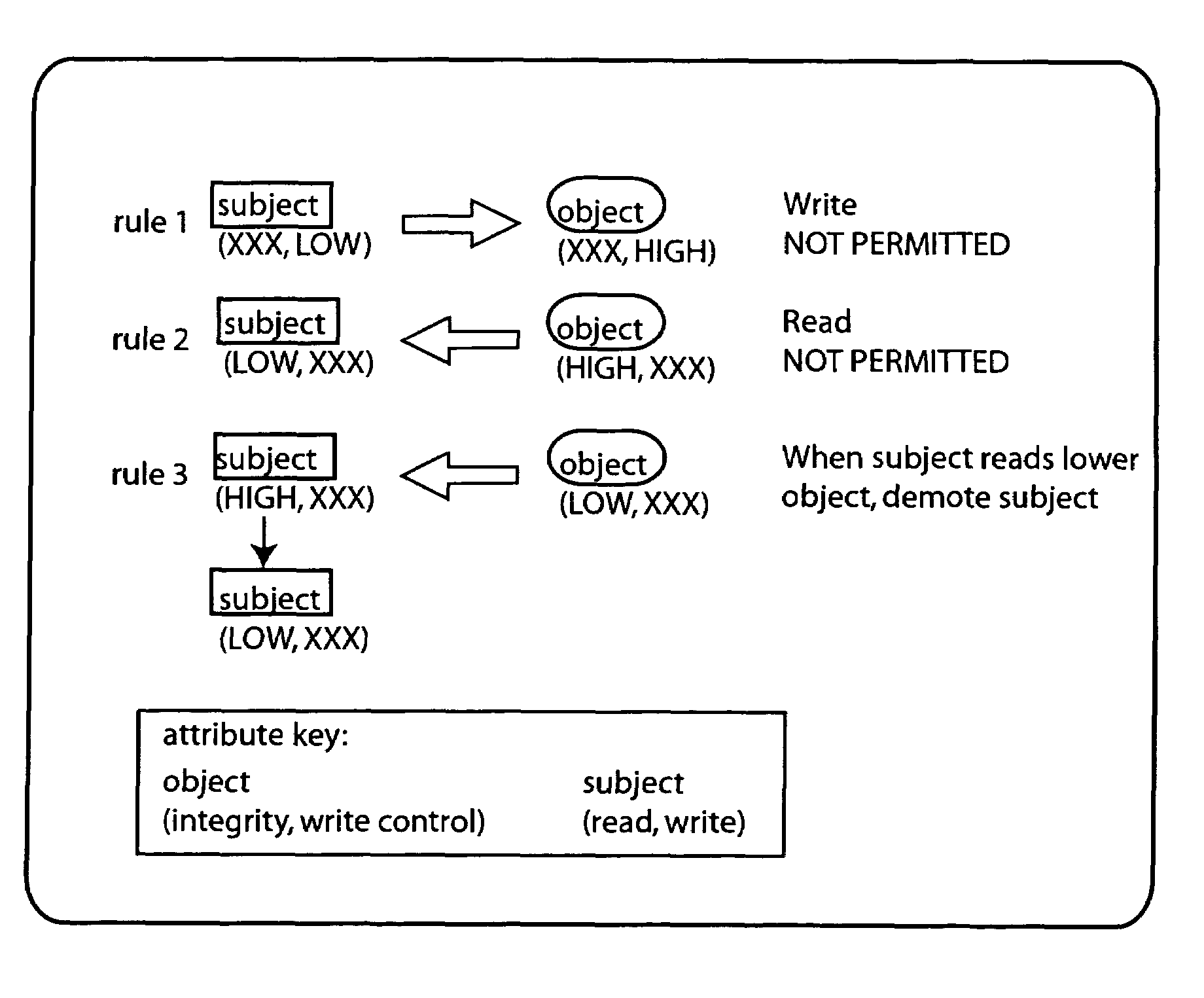
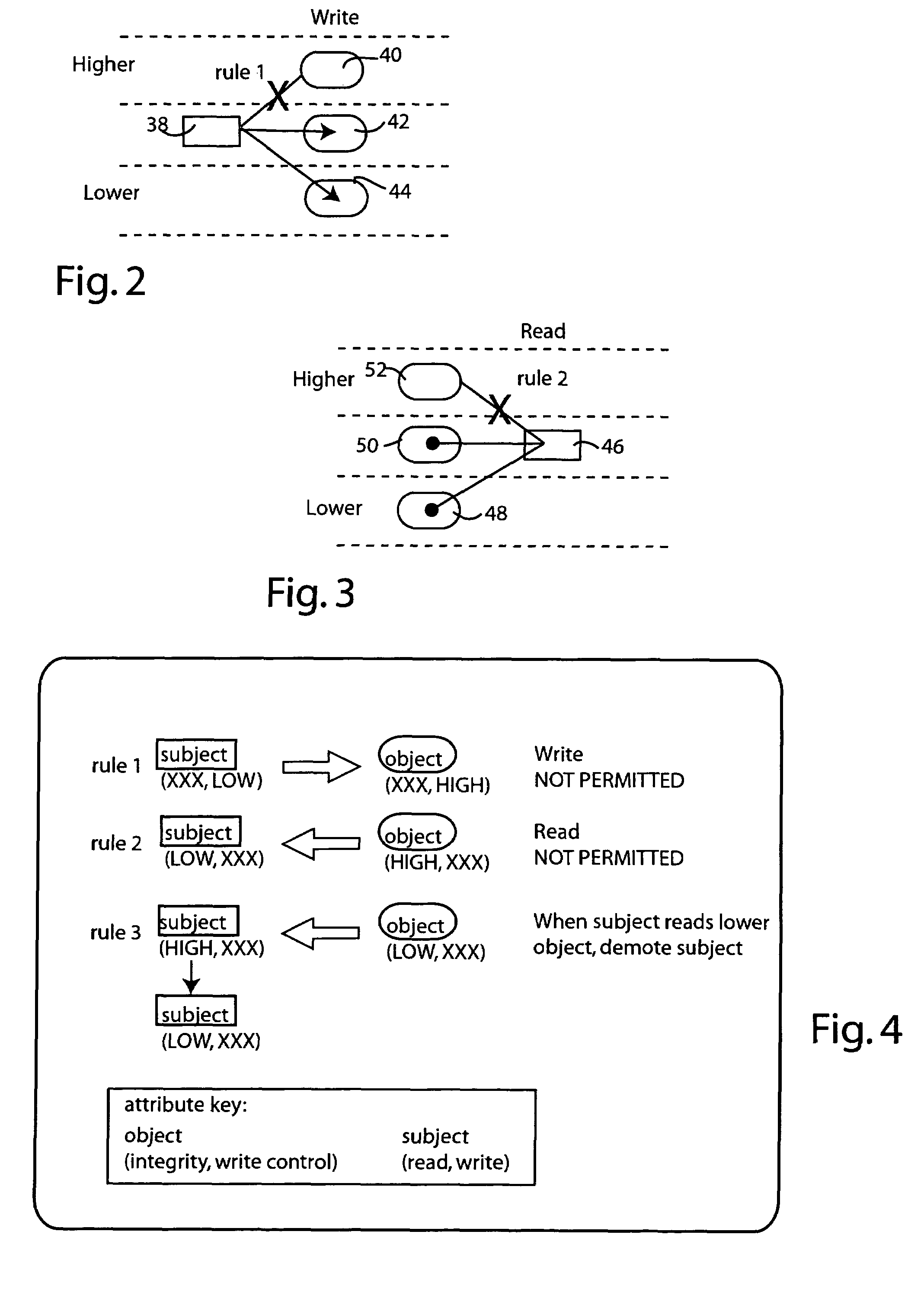
Access control is mediated by a set of 2-tuple labels or attributes which are associated with subject and object entities, respectively. Subject entitles, such as processes, have separate read and write attributes, while object entities, such as files, have separate integrity and write control attributes. The system implements a set of rules to provide both integrity control and confidentiality protection. Specifically, write operations to an object are inhibited where the subject's write attribute is lower than the write control attribute of the object. Read operations from an object are inhibited where the subject's read attribute is lower than the object's integrity attribute. When a subject reads from an object having a lower integrity level than the subject's read attribute, the subject's read attribute is demoted.
Owner:PANASONIC CORP
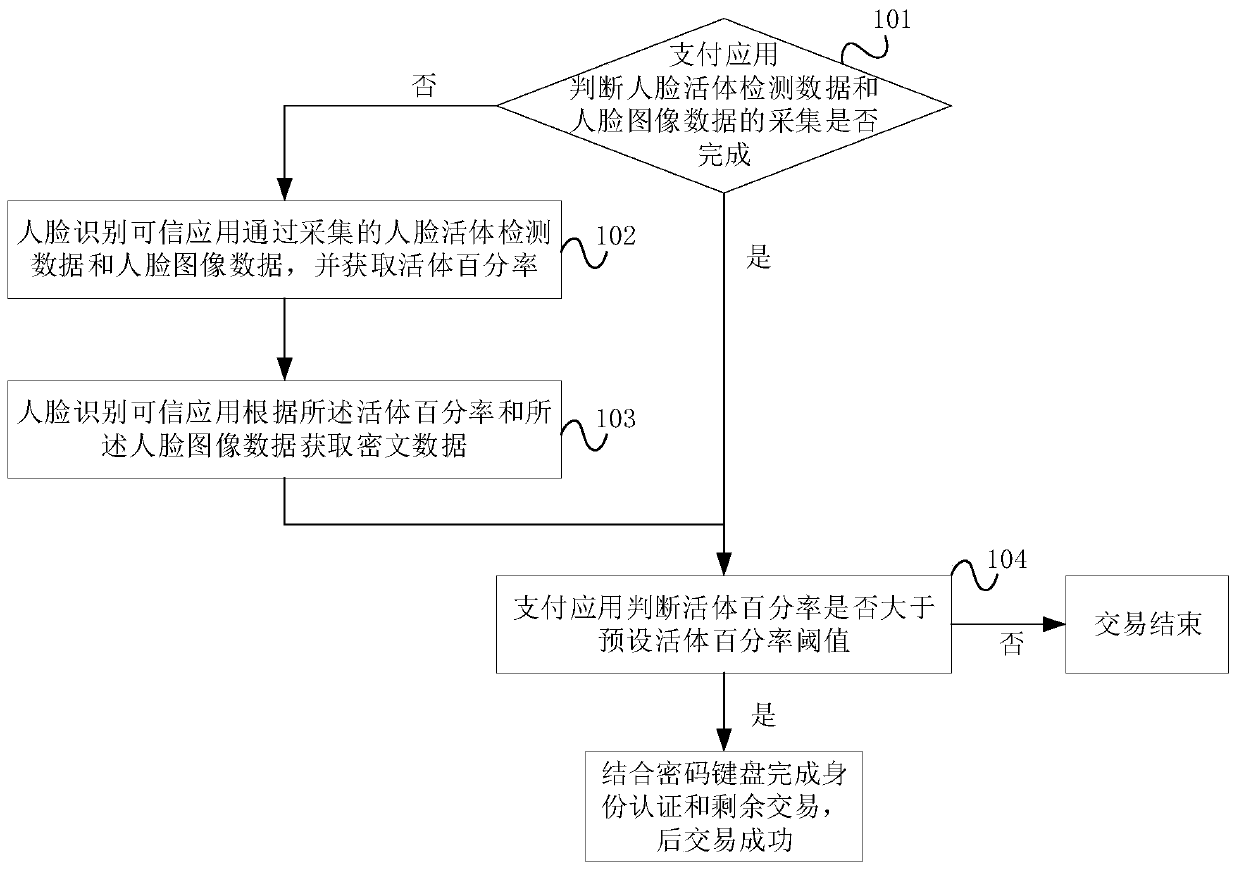
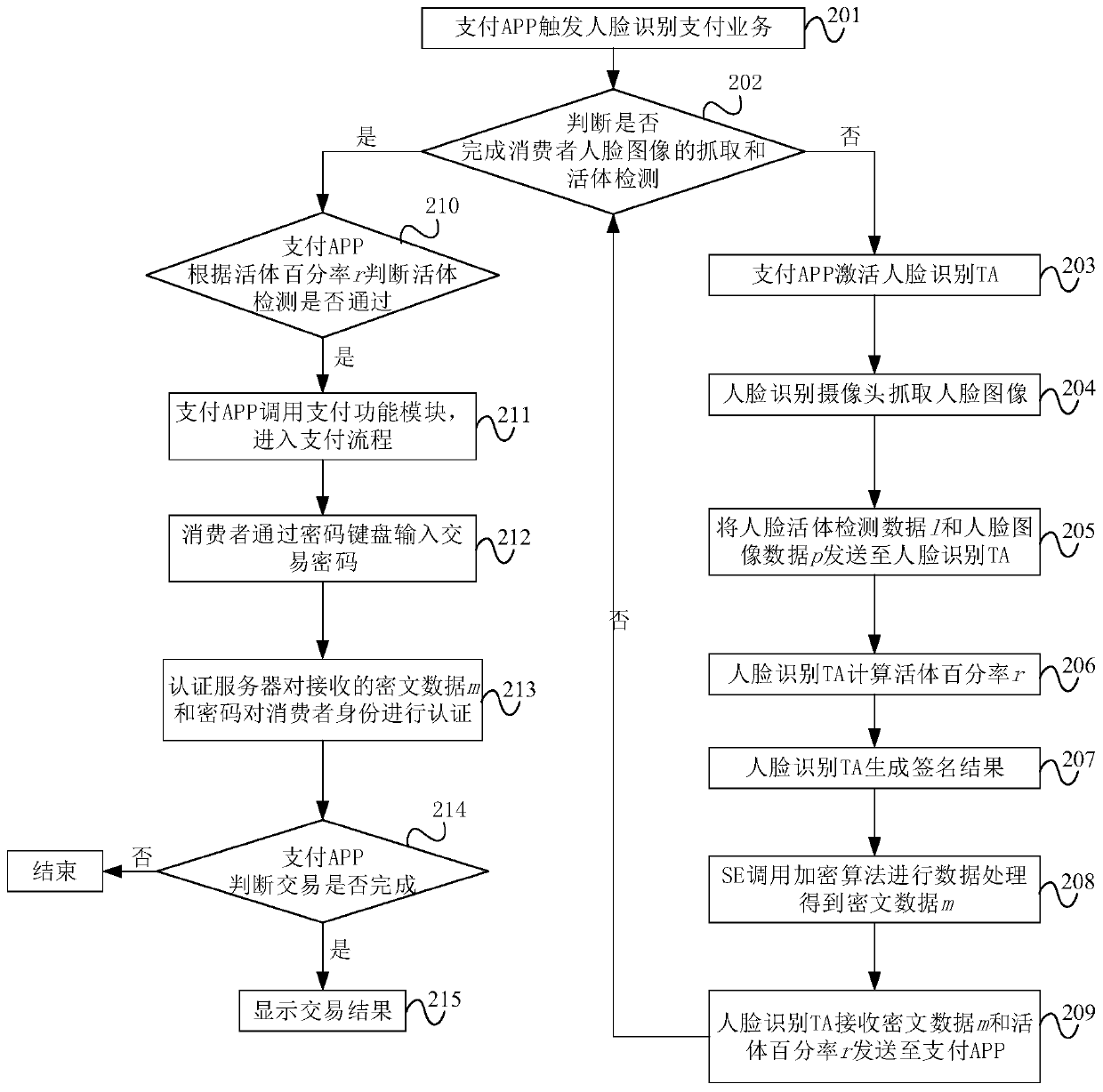
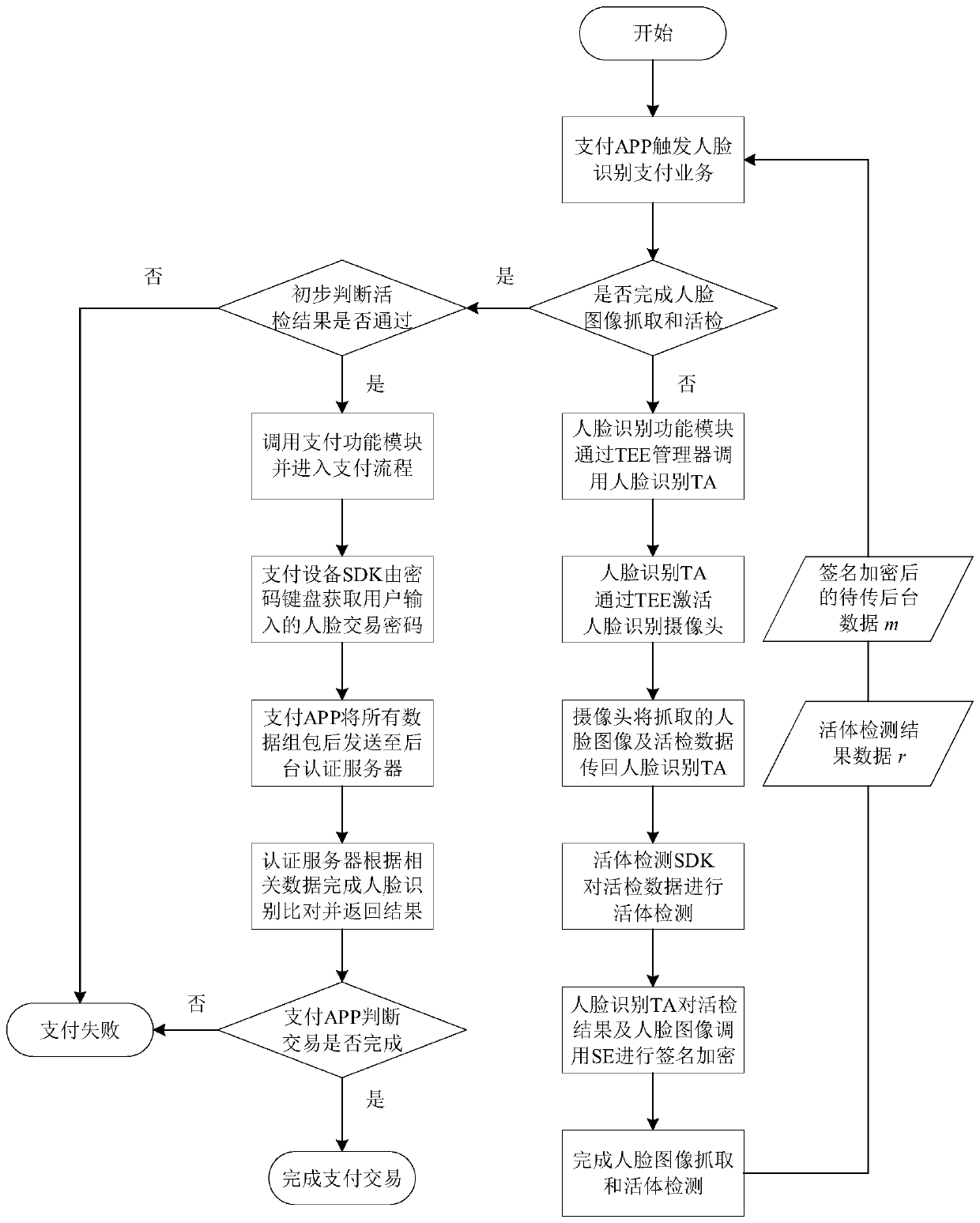
Face payment security method and platform based on security unit and trusted execution environment
PendingCN110555706AProtect data accuracyImprove integrityProtocol authorisationPaymentPattern recognition
The invention provides a face payment security method and platform based on a security unit and a trusted execution environment. Human face living body detection data and human face image data are collected through a human face recognition trusted application and a human face recognition camera; after the trusted execution environment calculates and obtains the living body percentage, the securityunit is called to obtain a percentage signature result and ciphertext data, the payment application judges whether the living body percentage is larger than a preset living body percentage thresholdvalue or not, and if yes, user identity authentication and remaining transaction are conducted in the rich execution environment in combination with the password keyboard. In the scheme, the securityunit provides a secure cryptographic algorithm service and a face recognition data protection key, the trusted execution environment ensures the secure execution of a face living body detection algorithm, and the integrity, authentication and confidentiality protection of each piece of data in the face payment process is ensured through direct connection with the face recognition camera.
Owner:北京银联金卡科技有限公司
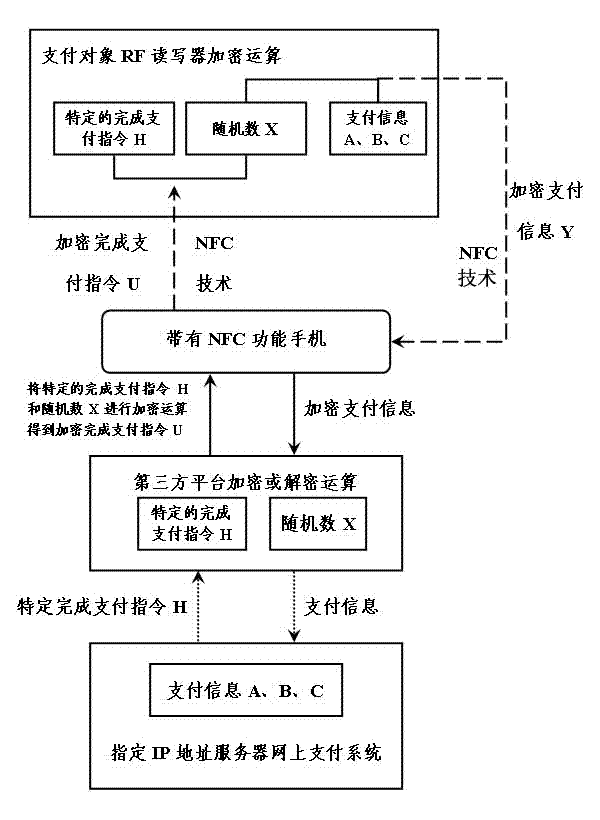
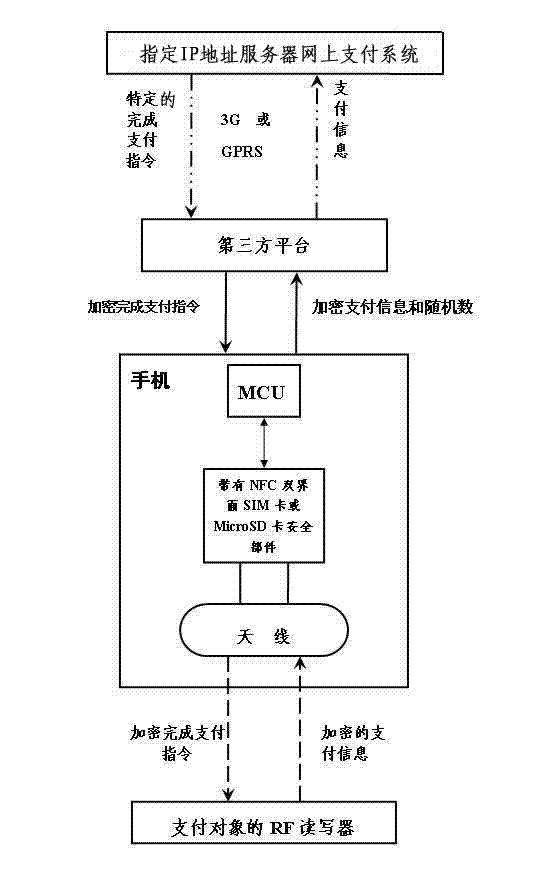
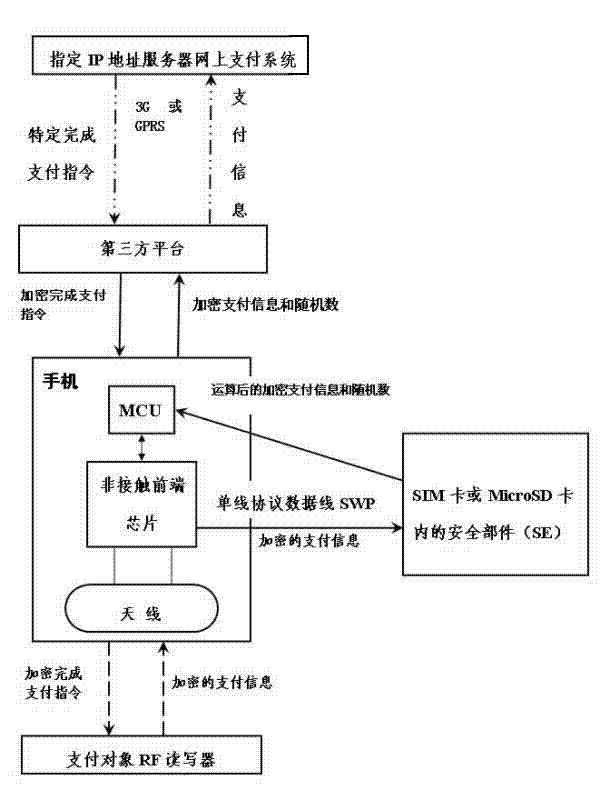
Near field payment and payment completion confirming method for NFC (Near Field Communication) functional mobile phone
ActiveCN102810189AImprove convenienceImprove practicalityTelephonic communicationTransmissionComputer hardwareIp address
The invention relates to a near field payment and payment completion confirming method for an NFC (Near Field Communication) functional mobile phone to solve the defect of existing near field payment and the difficulty that payment completion authenticity can not be confirmed. The encrypted payment information of a payment object is received by the NFC functional mobile phone through an NFC technology, a third-party platform is connected with an internet banking system of an appointed IP (Internet Protocol) address server, and the payment information needed by the internet banking system is filled in by the third-party platform so as to realize near field payment; and an encrypted payment completion instruction is verified through the third-party platform and an RF (radio frequency) reader-writer of the payment object so as to confirm the method for completing the payment. According to the technical scheme of the invention, the user account information and the payment password needing secret protection are preserved in the mobile phone of the user, the leak that the user account and payment password information preserved on a POS (point-of-sale) machine in the near field payment mode of the prior art is plugged, and the security of the user account information and fund is greatly improved; and because the internet access function of the mobile phone of the user is fully utilized, the POS machine with a high cost is replaced by the RF reader-writer with a low cost, and the investment cost of hardware used for the near field payment is greatly reduced.
Owner:黄志军
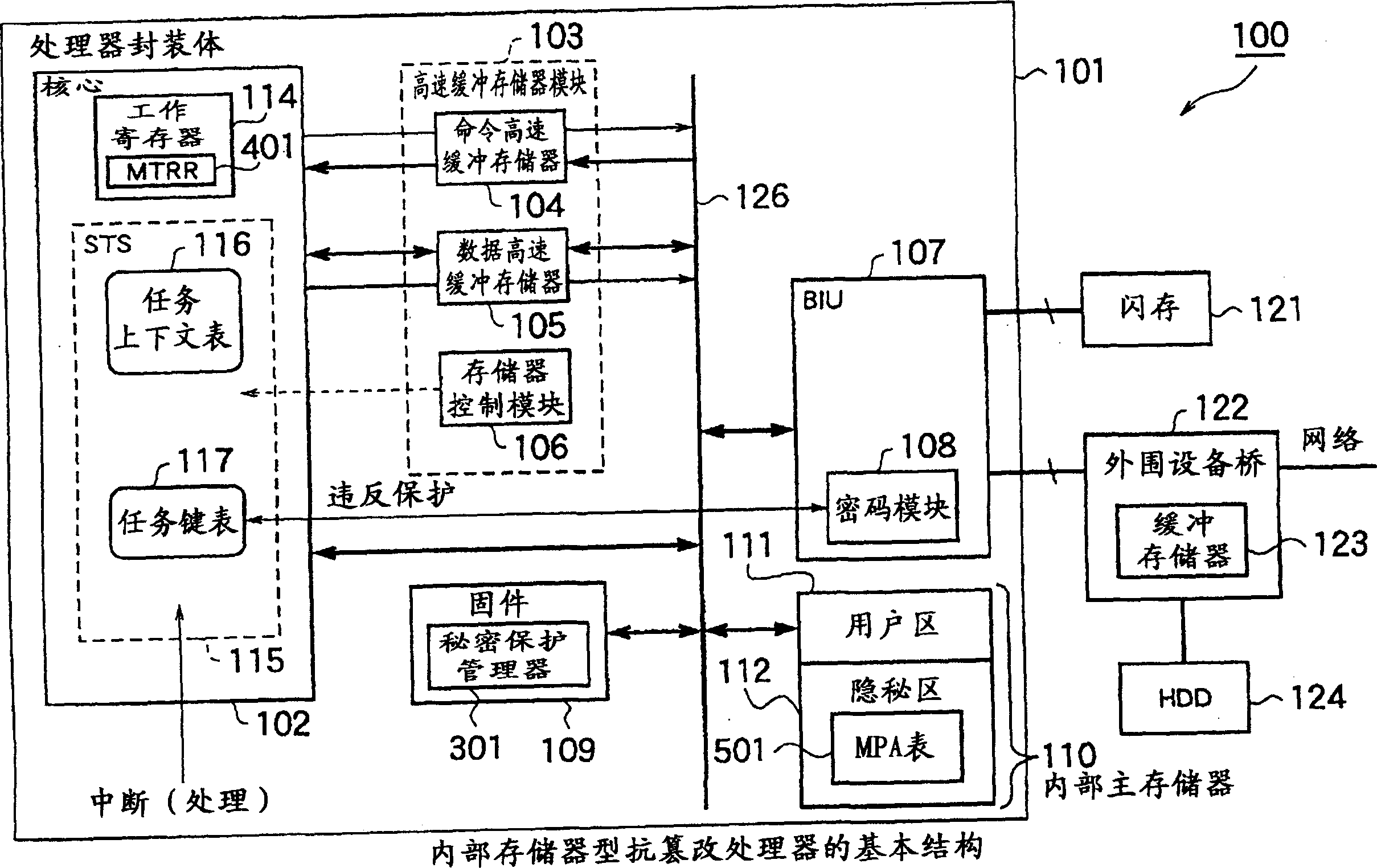
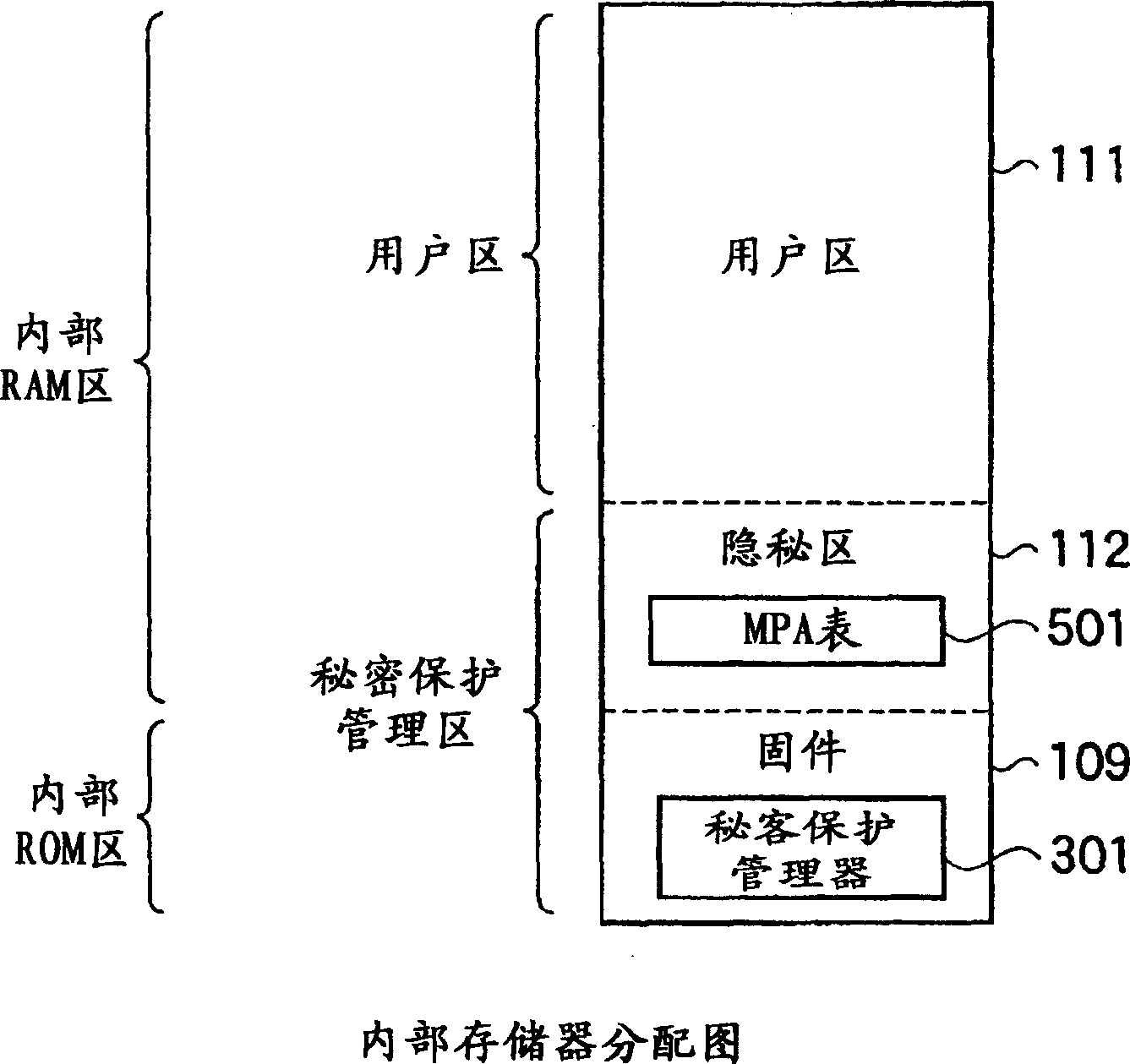
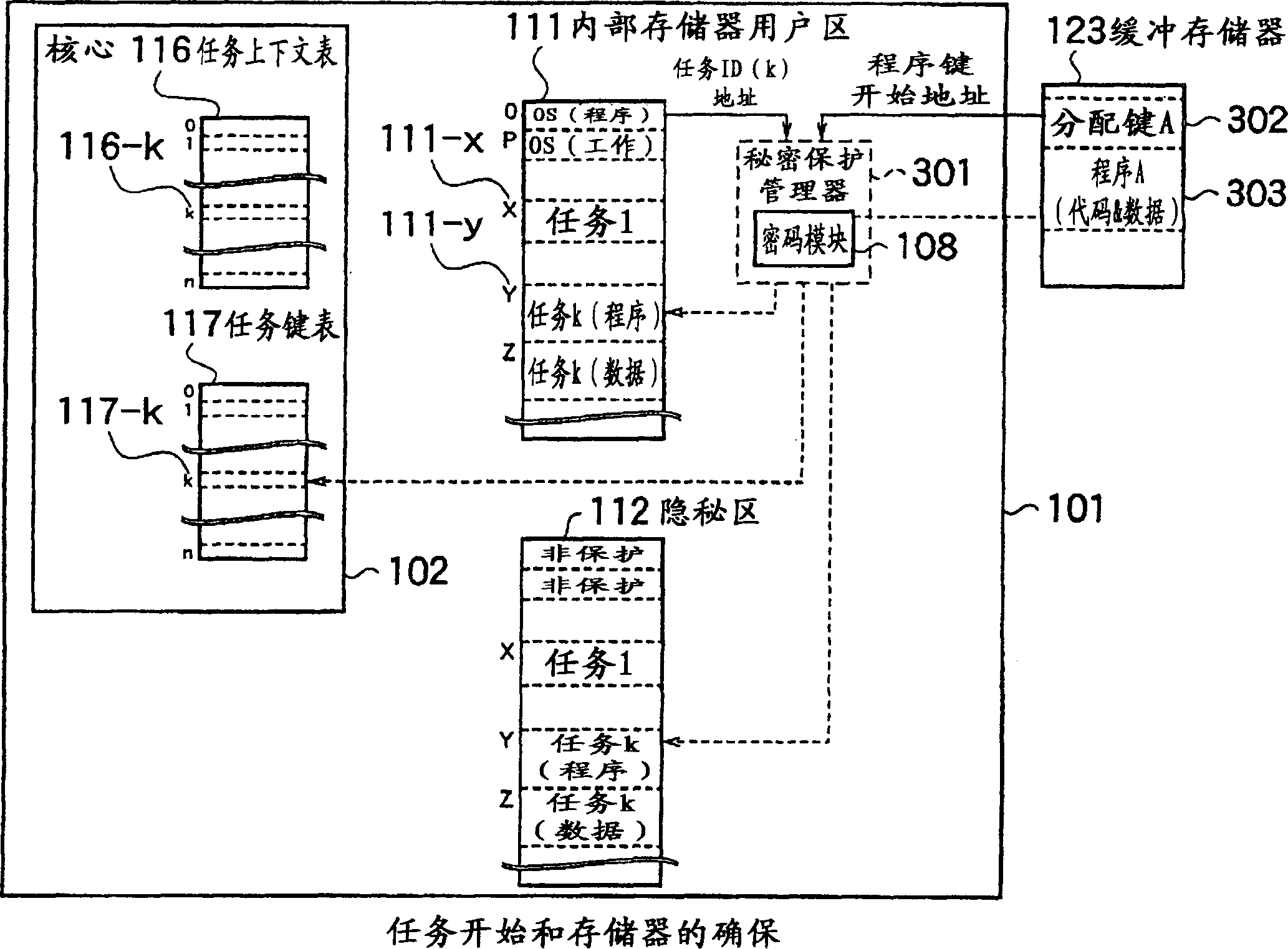
Internal memory type anti-falsification processor and security method
InactiveCN1445680AEnsure normal communicationKeep secretMemory adressing/allocation/relocationUnauthorized memory use protectionInternal memoryConfidentiality protection
The anti-tampering processor with large-capacity internal memory and the security method of the present invention can realize efficient internal data management that prevents illegal changes in a multi-task environment. The tamper-resistant processor has: a decoding unit that decodes a plurality of programs encrypted with different encryption keys; Memory; the required confidentiality attribute required by the setting task for each memory page of the access object is exclusive, and the required confidentiality attribute storage component stored; for each memory page, the memory confidentiality attribute for storing the memory confidentiality attribute of the memory page is stored Parts; when executing a task, the task is to the memory page of the access object, and the secret management part of setting the memory security attribute in the memory protection attribute preservation part; the requirement secrecy attribute stored in the requirement secret attribute preservation part and stored in the memory protection The memory protection component to which the memory protection attributes in the attribute holding component are compared.
Owner:KK TOSHIBA
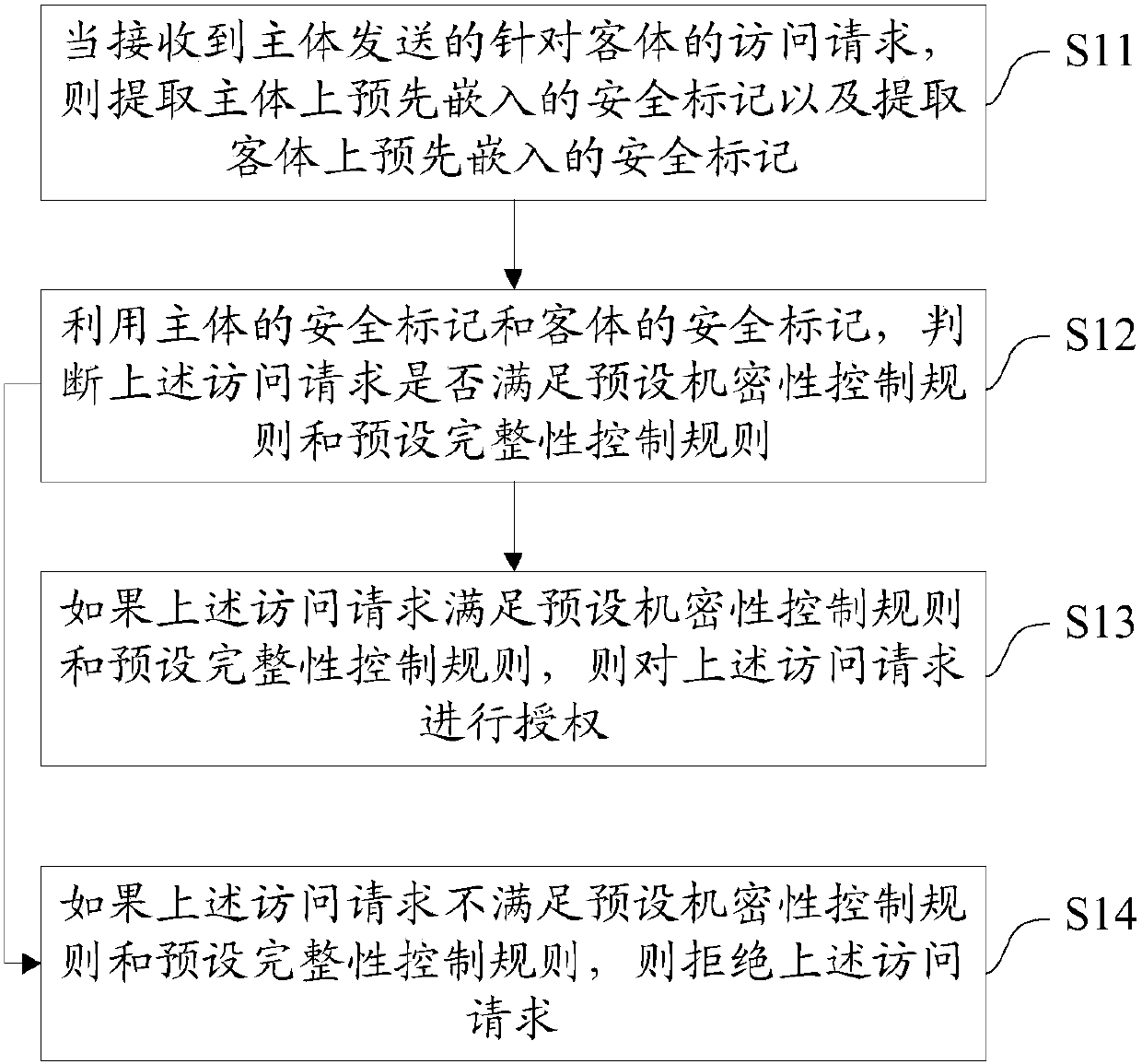
Mandatory access control method and system based on fusion of multiple protection strategies
The application discloses a mandatory access control method and system based on fusion of multiple protection strategies. The method comprises the steps of: when receiving an access request which is sent by a subject and aims at an object, extracting security labels embedded in advance on the subject and extracting security labels embedded in advance on the object, wherein both the security labels of the subject and the security labels of the object comprise confidentiality labels and completeness labels; by utilizing the security labels of the subject and the security labels of the object, judging whether the access request meets a preset confidentiality control rule and a preset completeness control rule, if yes, carrying out authorization on the access request, and if no, refusing the access request. According to the application, the confidentiality protection strategy and the completeness protection strategy are fused to carry out access control on the access request, so that data access security can be effectively promoted.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
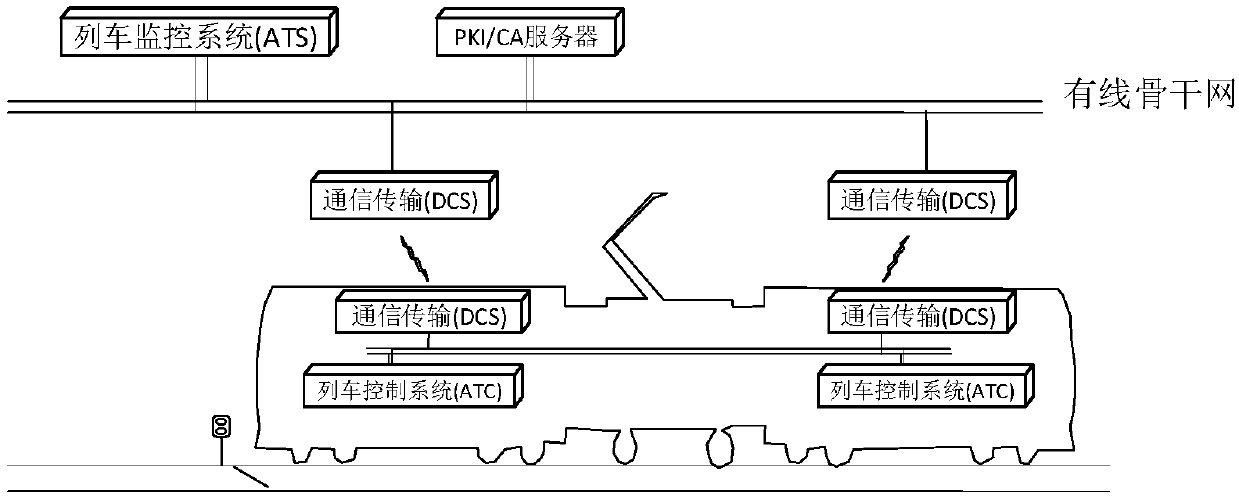
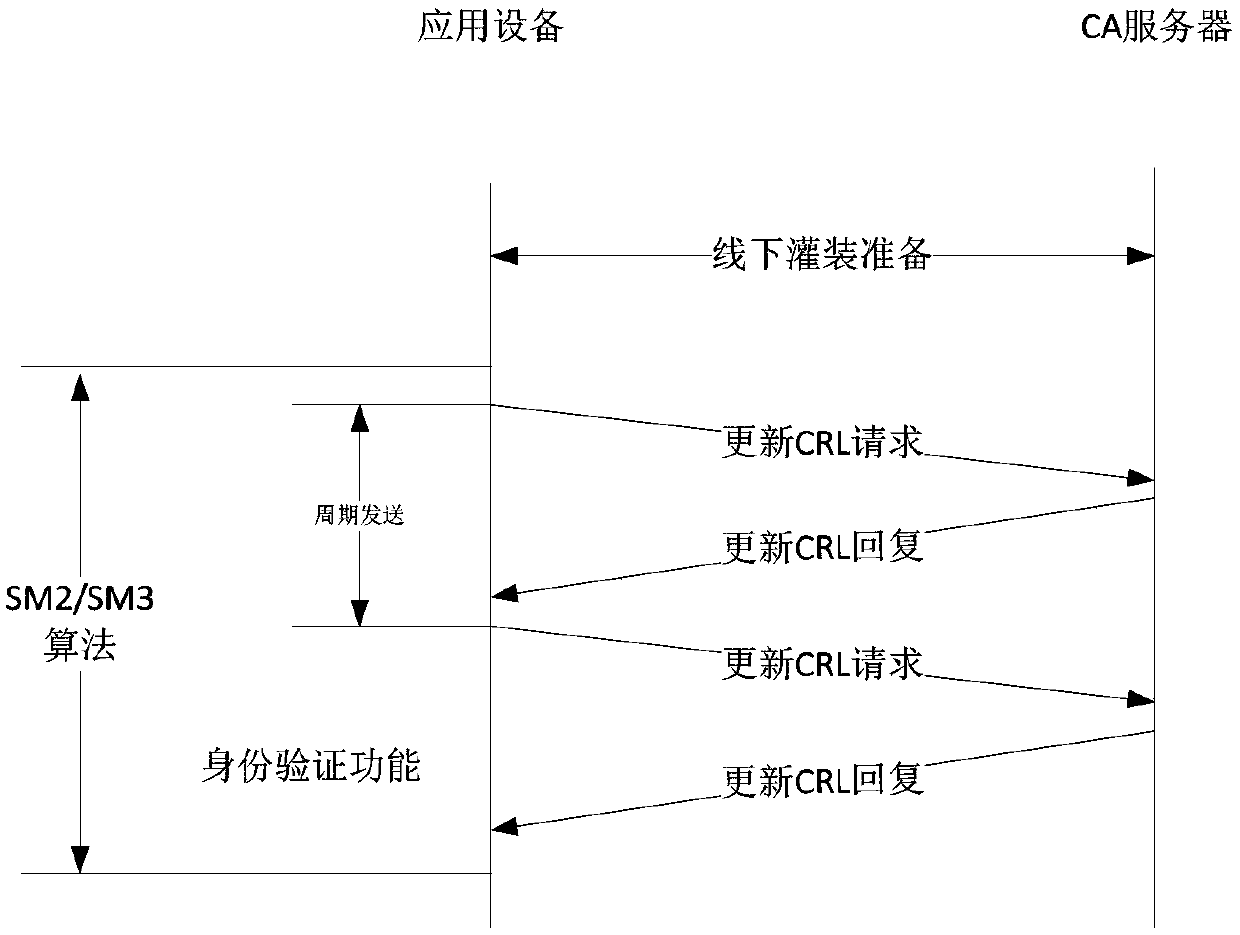
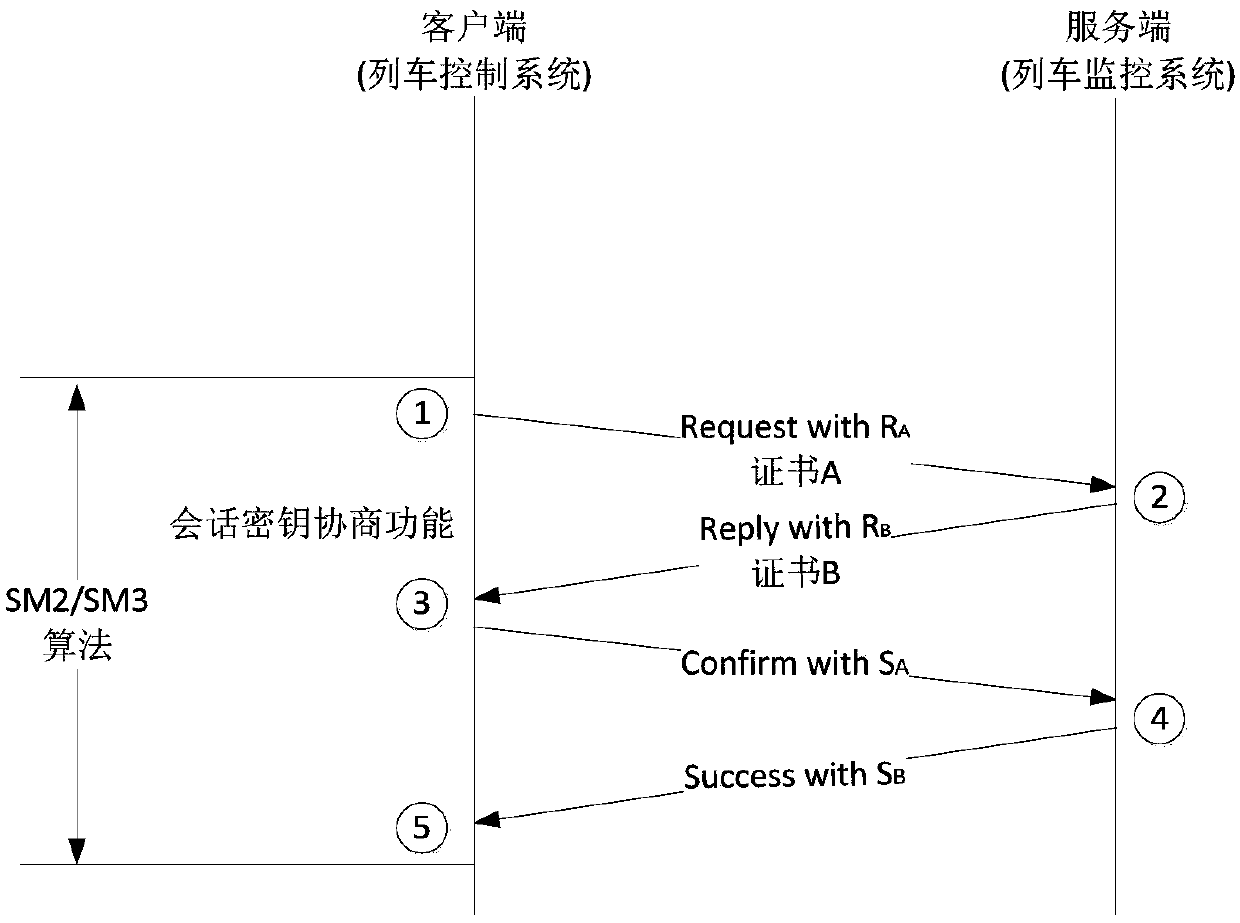
Vehicle-ground wireless communication encryption method and device applied to train monitoring system
PendingCN109688585AImprove information security protection capabilitiesSelf-controllableKey distribution for secure communicationUser identity/authority verificationConfidentiality protectionMonitoring system
The invention relates to a vehicle-ground wireless communication encryption method and device applied to a train monitoring system. The method comprises the following steps: establishing a communication association relationship and communication authentication by using a SM2 algorithm, and implementing management by adopting a dynamic key; encrypting and decrypting vehicle-ground wireless communication data by using a SM1 algorithm; and implementing integrity verification on the vehicle-ground wireless communication data by using a SM3 algorithm in order that the vehicle-ground wireless communication data are under identifiability protection, non-repudiation protection, confidentiality protection and integrity protection. Compared with the prior art, the vehicle-ground wireless communication encryption method has the advantages that a data encryption technology is applied to application layer equipment of the train monitoring system, so that the information safety protection performance of the vehicle-ground wireless communication is improved greatly.
Owner:CASCO SIGNAL
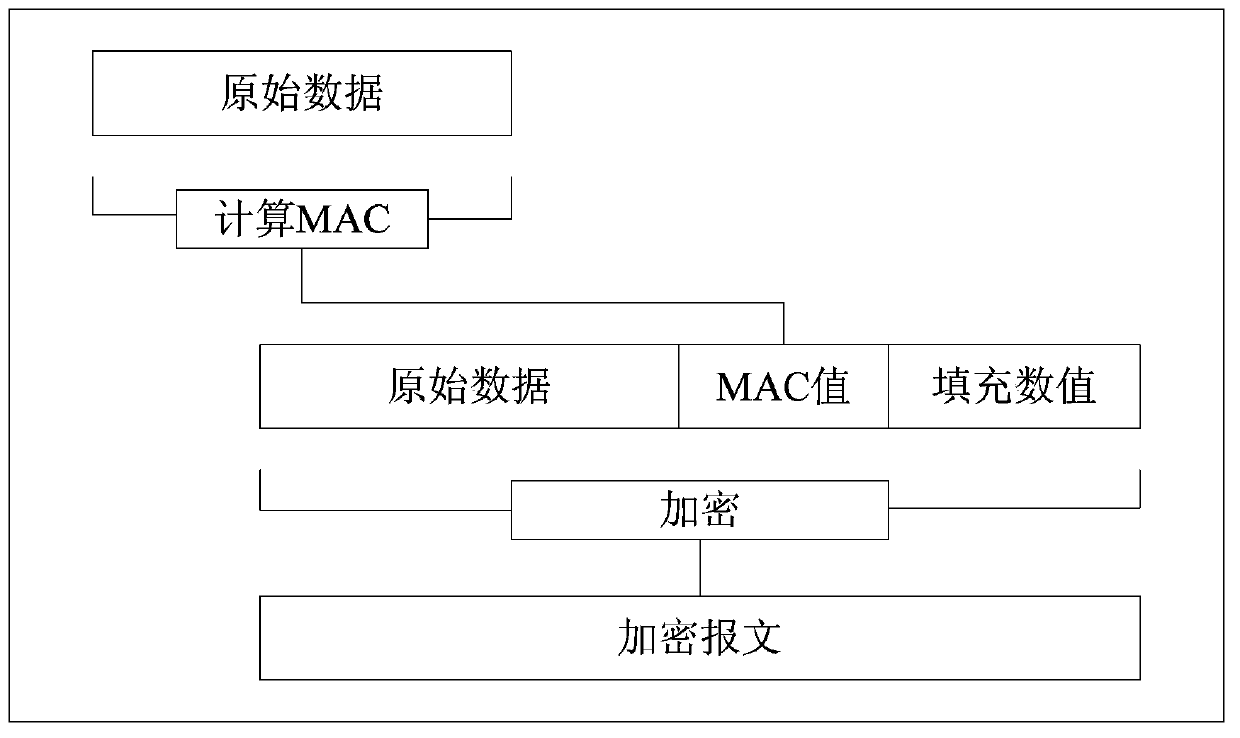
Data security implementation method capable of resisting timing attacks and devices
ActiveCN103428204AAvoid modificationImprove protectionTransmissionComputer hardwareConfidentiality protection
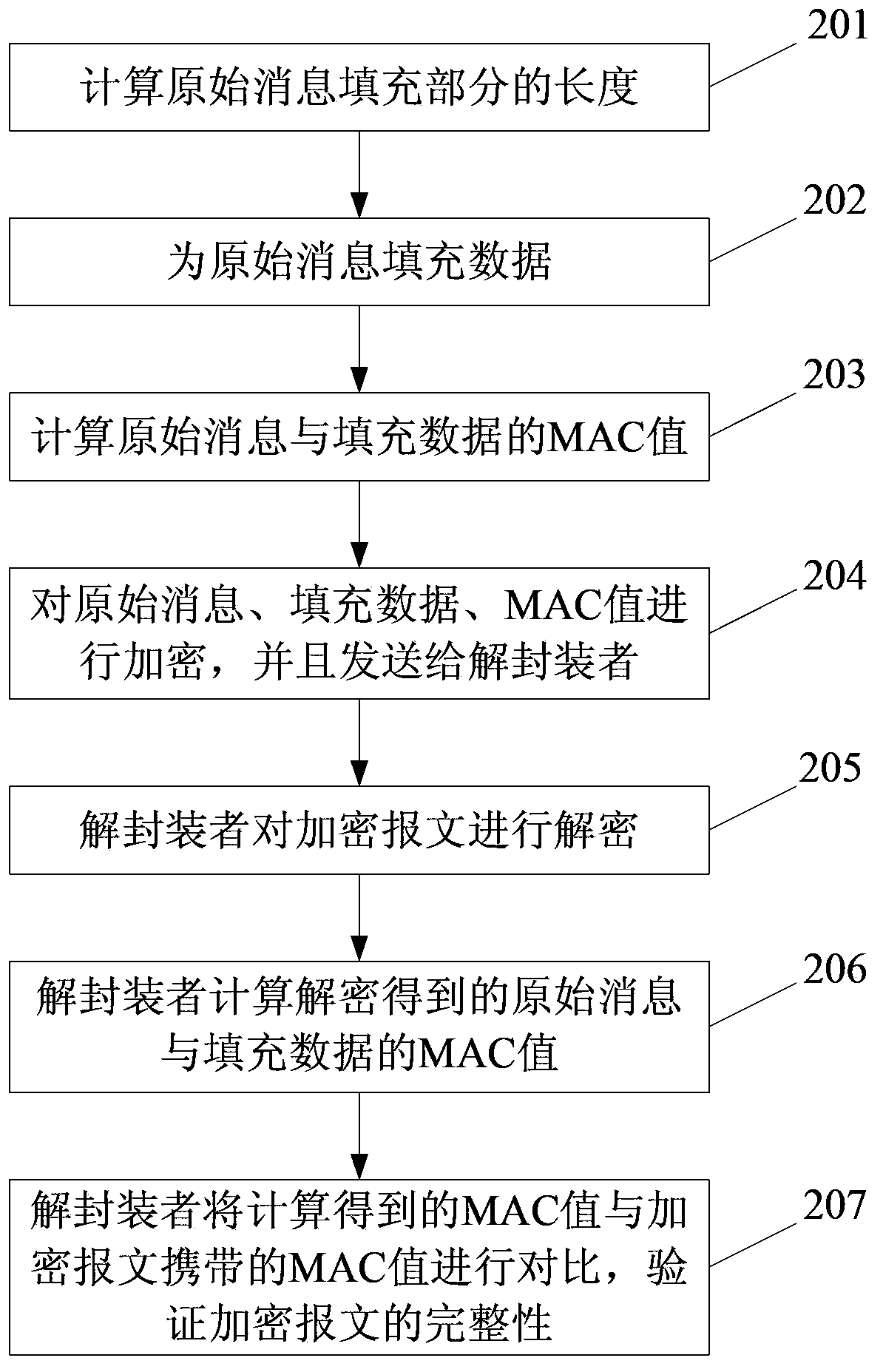
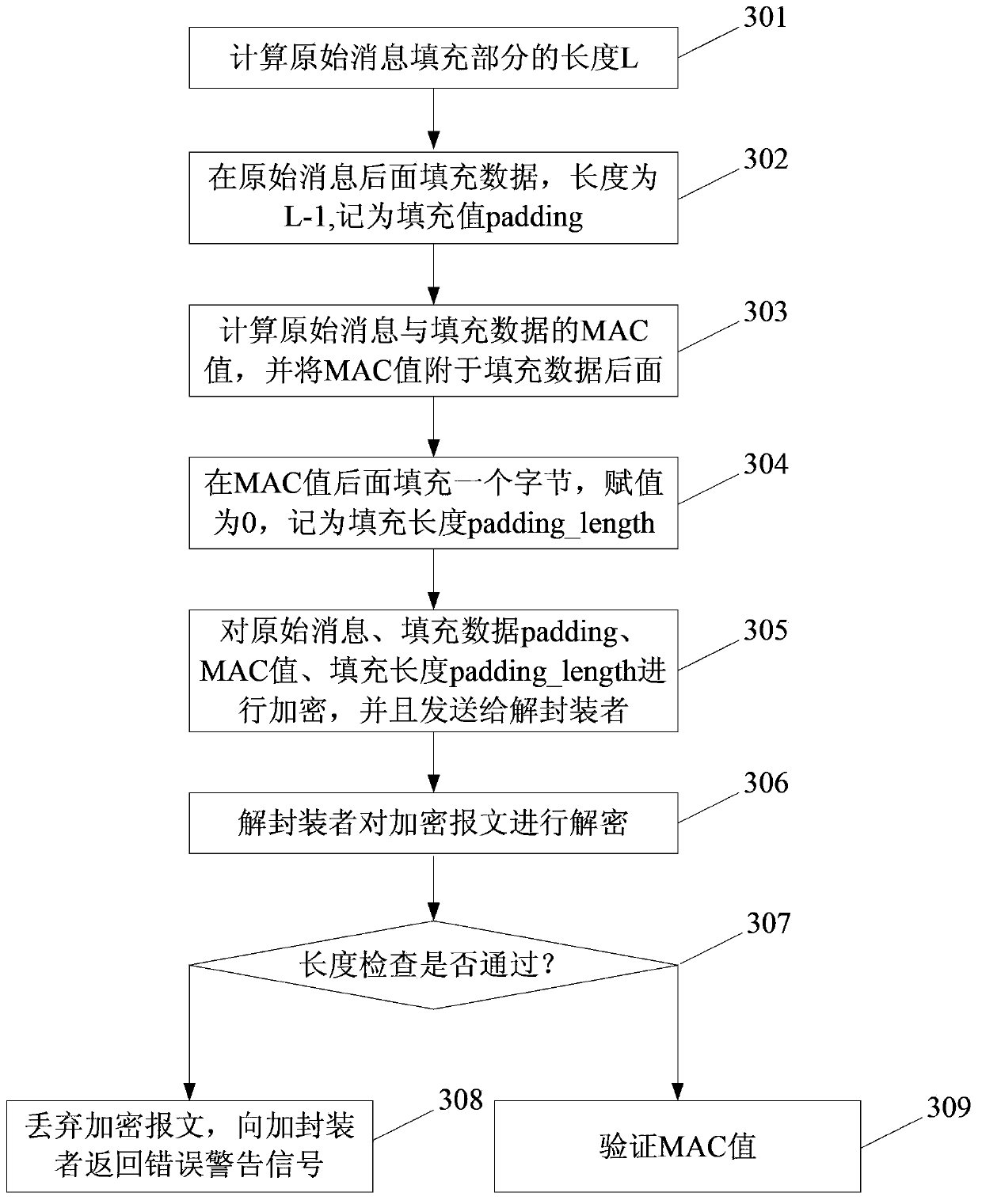
The invention discloses a data security implementation method capable of resisting timing attacks and devices. The method is suitable for calculating a message authentication code MAC value for a raw message prior to encryption, and an algorithm kit in a cipher block chaining mode is adopted as an encryption algorithm. The method includes that an encapsulation device connects raw information, padding data and MAC values sequentially in series, the MAC values are MAC values of the raw information and the padding data, the sum of lengths of the raw information, the padding data and the MAC values is an integral multiple of the encryption algorithm block length, a message is encrypted and then sent to a de-encapsulation device, and the de-encapsulation device receives the encrypted message, decrypts the message, then extracts the raw message and the padding data, calculates the MAC value of the message, compares the MAC value to the MAC value carried by the encrypted message, judges that the message is not tampered if the MAC value and the MAC value carried by the encrypted message are the same, discards the message and returns error warning information to the encapsulation person otherwise. By the aid of the technical scheme, total time consumed by the de-encapsulation device for processing the encrypted message can be ensured to be the same, so that the timing attacks are resisted effectively, and confidentiality protection and integrality protection of the encrypted message are guaranteed.
Owner:NEW H3C TECH CO LTD
Sensitive data grading protection method and system based on numerical control system
InactiveCN111726353AControl network flowControl flowDigital data protectionTransmissionSecurity domainInformation security
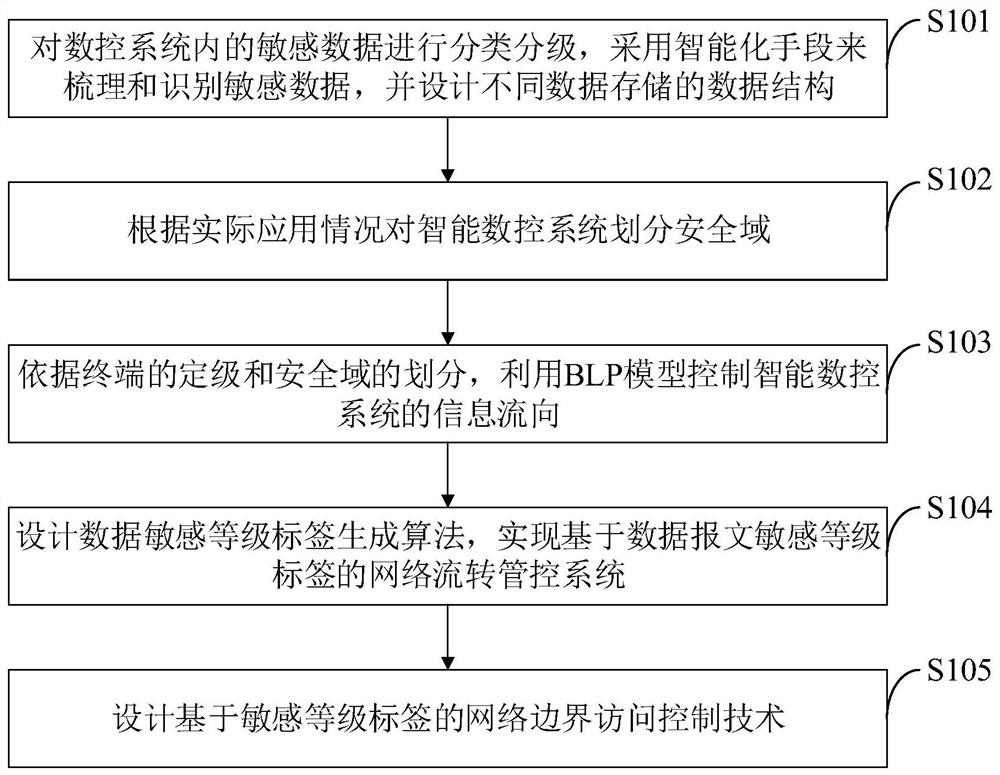
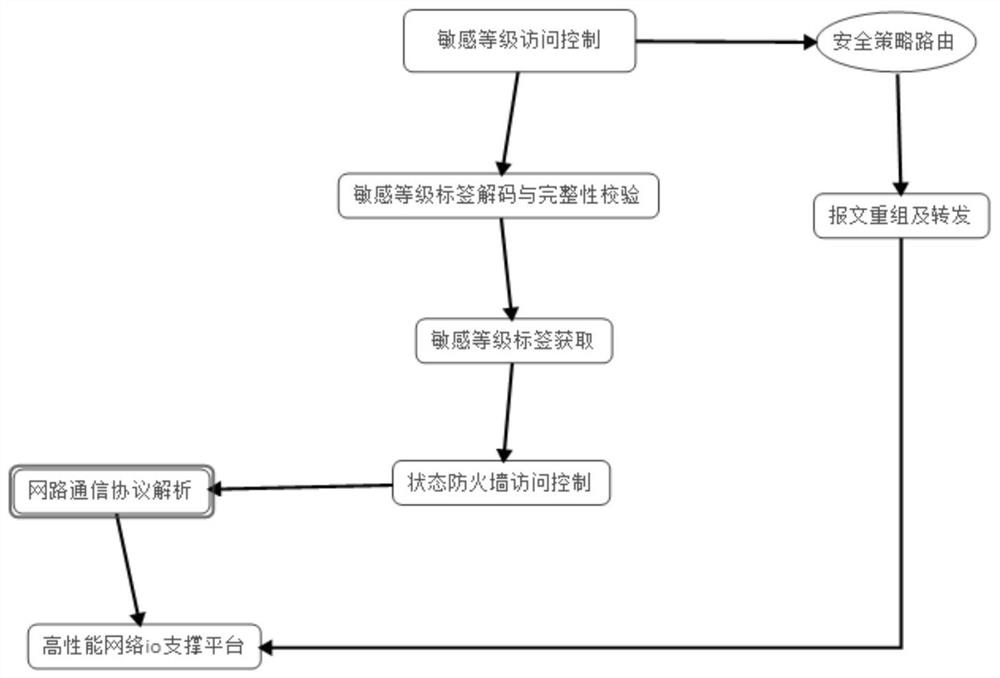
The invention belongs to the technical field of computer network security, and discloses a sensitive data grading protection method and grading protection system based on a numerical control system. The method comprises steps of classifying and grading sensitive data in the numerical control system, carding and identifying the sensitive data by adopting an intelligent means, and designing data structures for storing different data; dividing a security domain for the intelligent numerical control system; controlling the information flow direction of the intelligent numerical control system by using the BLP model according to the grading of the terminal and the division of the security domain; designing a data sensitivity level label generation algorithm, and realizing a network flow management and control system based on the data message sensitivity level label; and designing a network boundary access control technology based on the sensitivity level label. Sensitive data of the intelligent numerical control system can be subjected to confidentiality protection, the network flow direction of the sensitive data is controlled, the situation that the data illegally flows into a low-security-level area due to routing errors and other reasons is eradicated, and the industrial information security requirement of the intelligent numerical control system is met.
Owner:HUAZHONG UNIV OF SCI & TECH
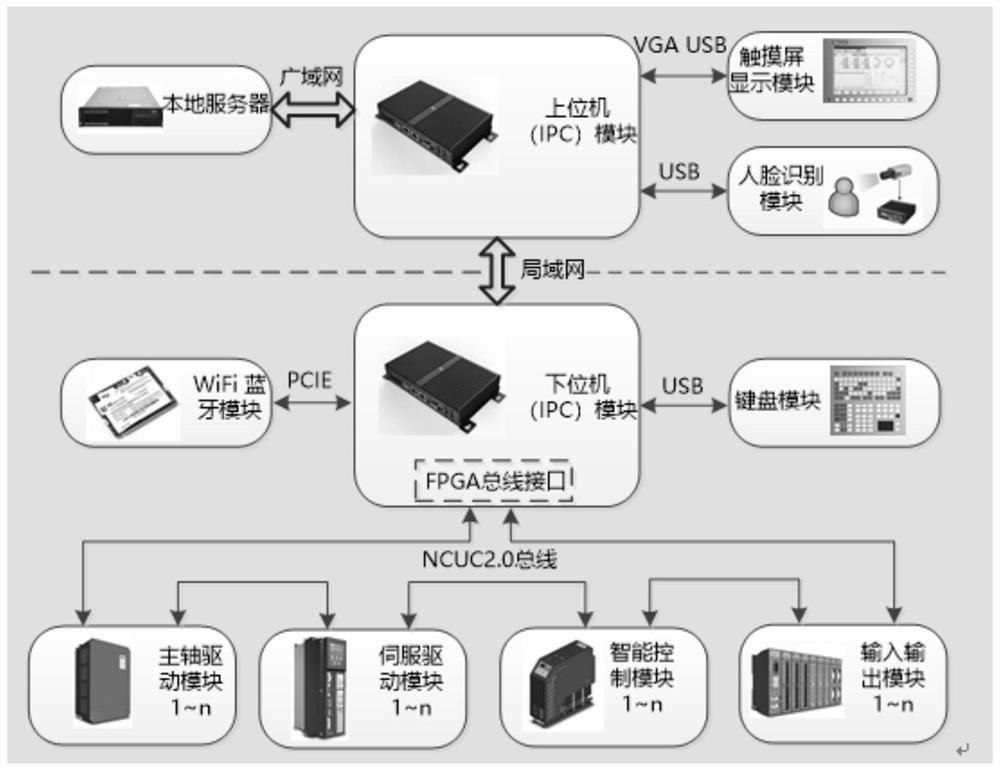
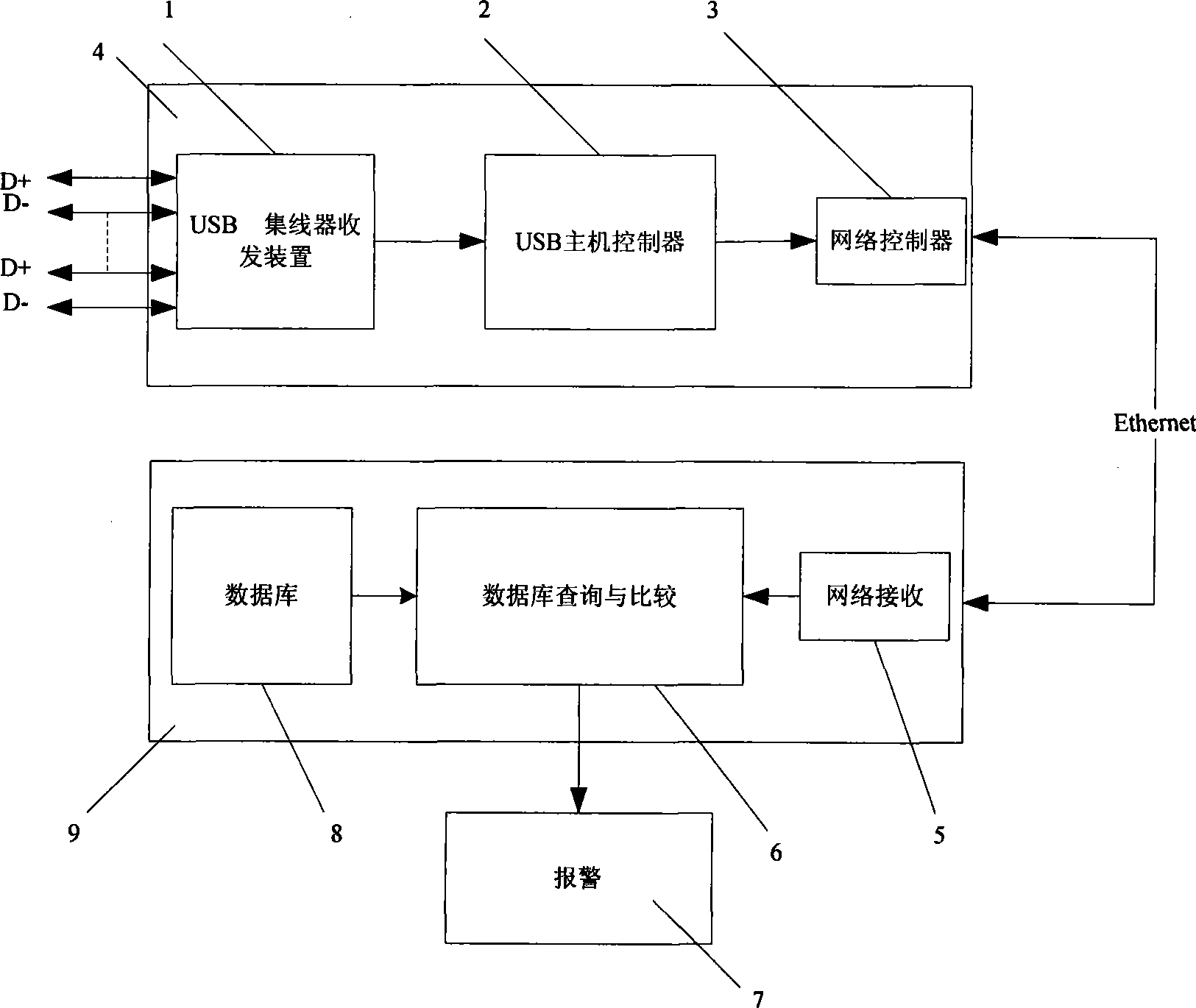
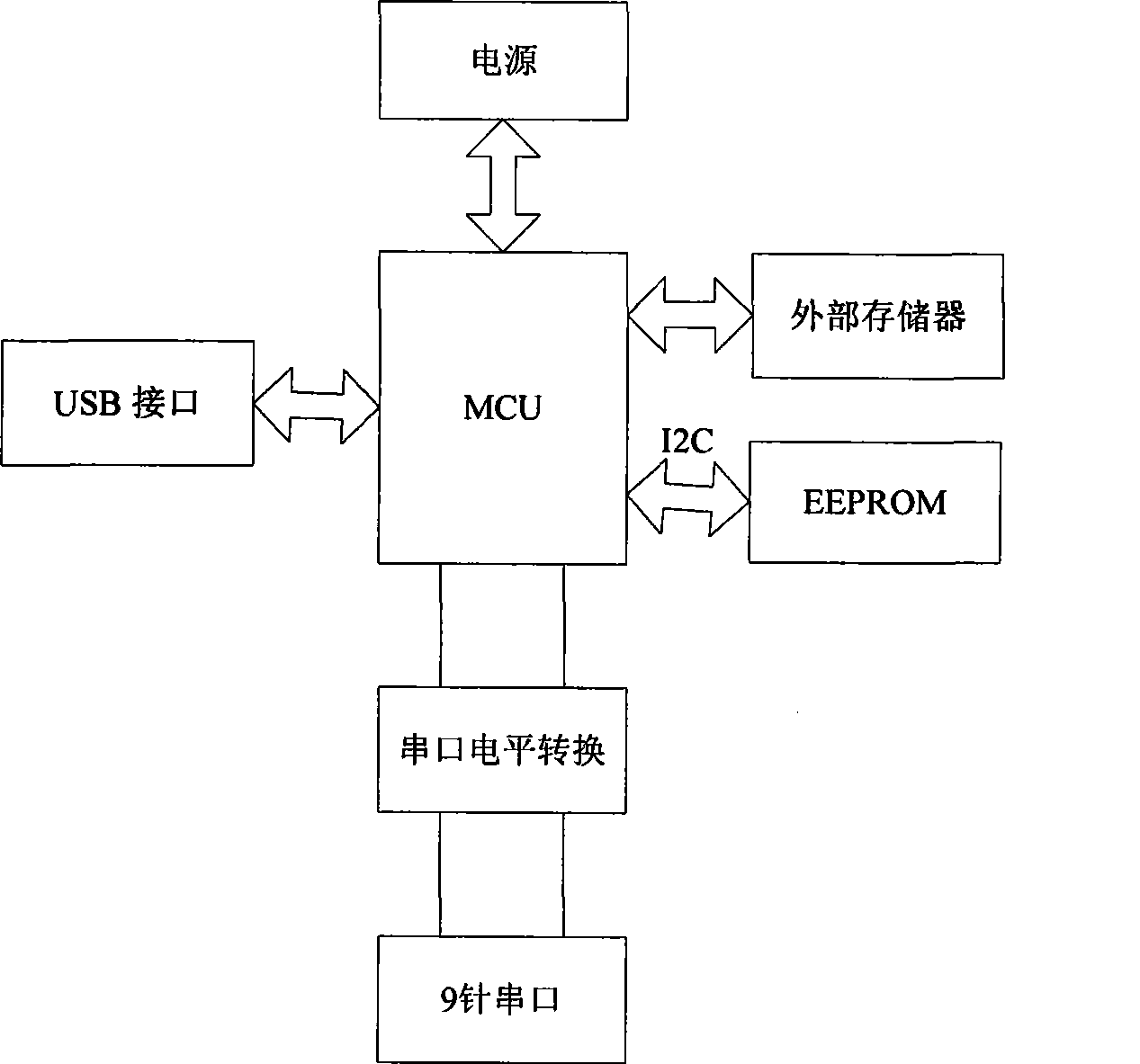
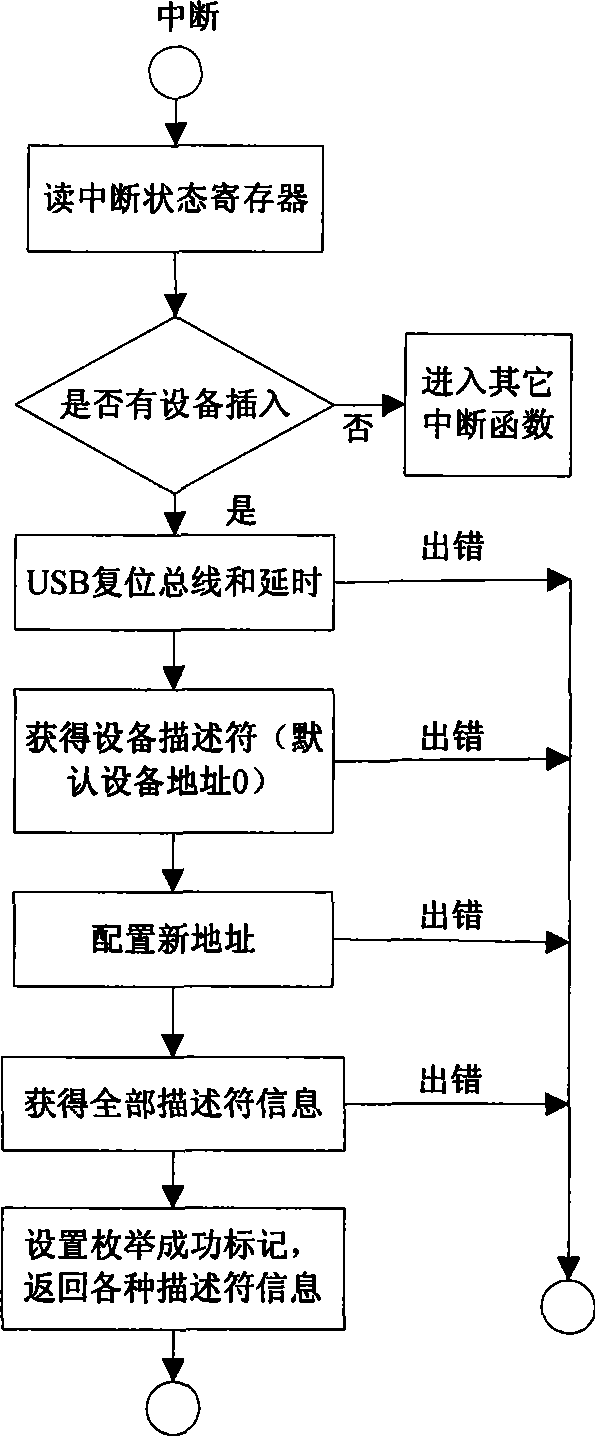
Confidential U-disk remote monitoring system and method thereof
InactiveCN101521662AImprove supervisionReduce volumeTransmissionInstrumentsTransceiverConfidentiality protection
The invention provides a confidential U-disk remote monitoring system and a method thereof. The invention constructs a unique identification for U-disks based on USB and MSC protocols, adopts a hub transceiver for expanding USB interface slots, and uses an embedded-type storing device for obtaining and identifying the unique identification of the U-disk in each USB slot; through the remote transmission realized by network and the encapsulation of network transmission data, the unique identification of the U-disk is led to be bound with the information of users; and a remote monitor center can effectively control the lending and return of the U-disk all the time and give an alarm or a notice according to the alarm rule. The confidential U-disk remote monitoring system has small volume, easy installation, good reliability and strong confidentiality protection capability, and can realize the unified management of the confidential U-disks of a unit through the network.
Owner:INST OF ELECTRONICS ENG CHINA ACAD OF ENG PHYSICS
A virtual machine security migration system
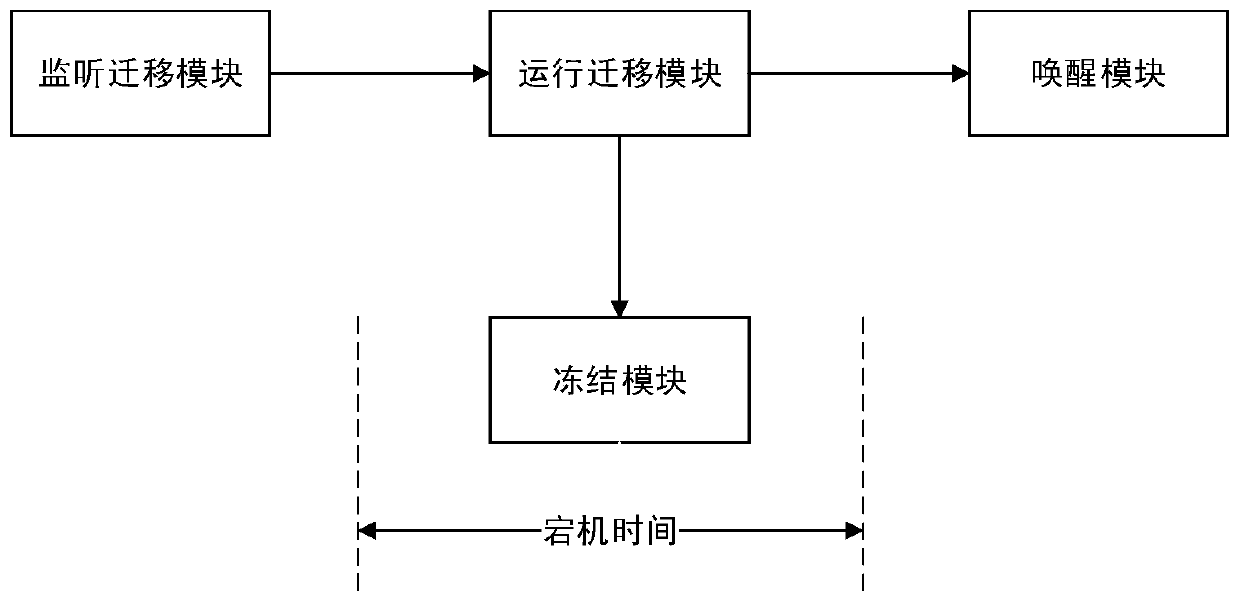
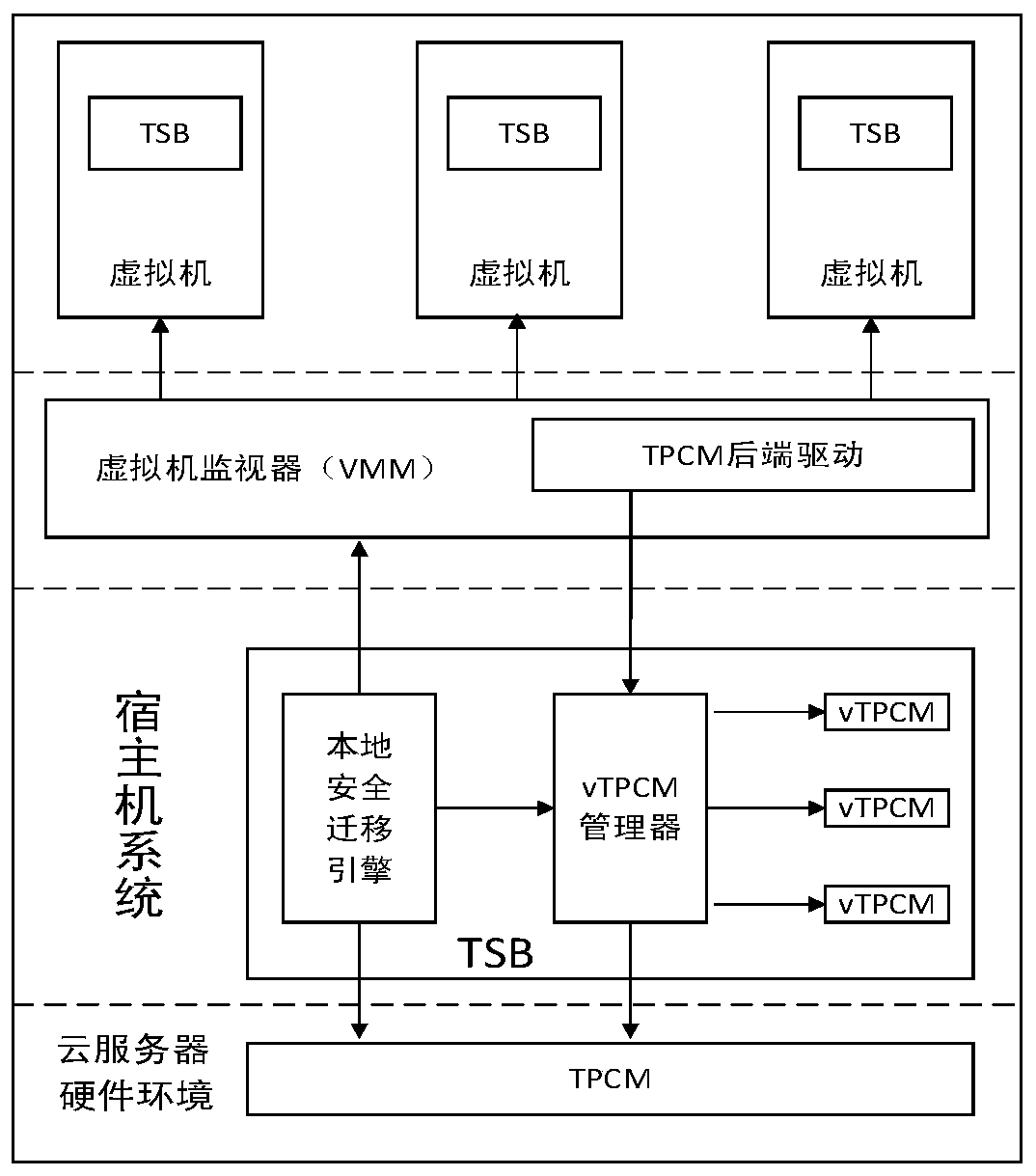
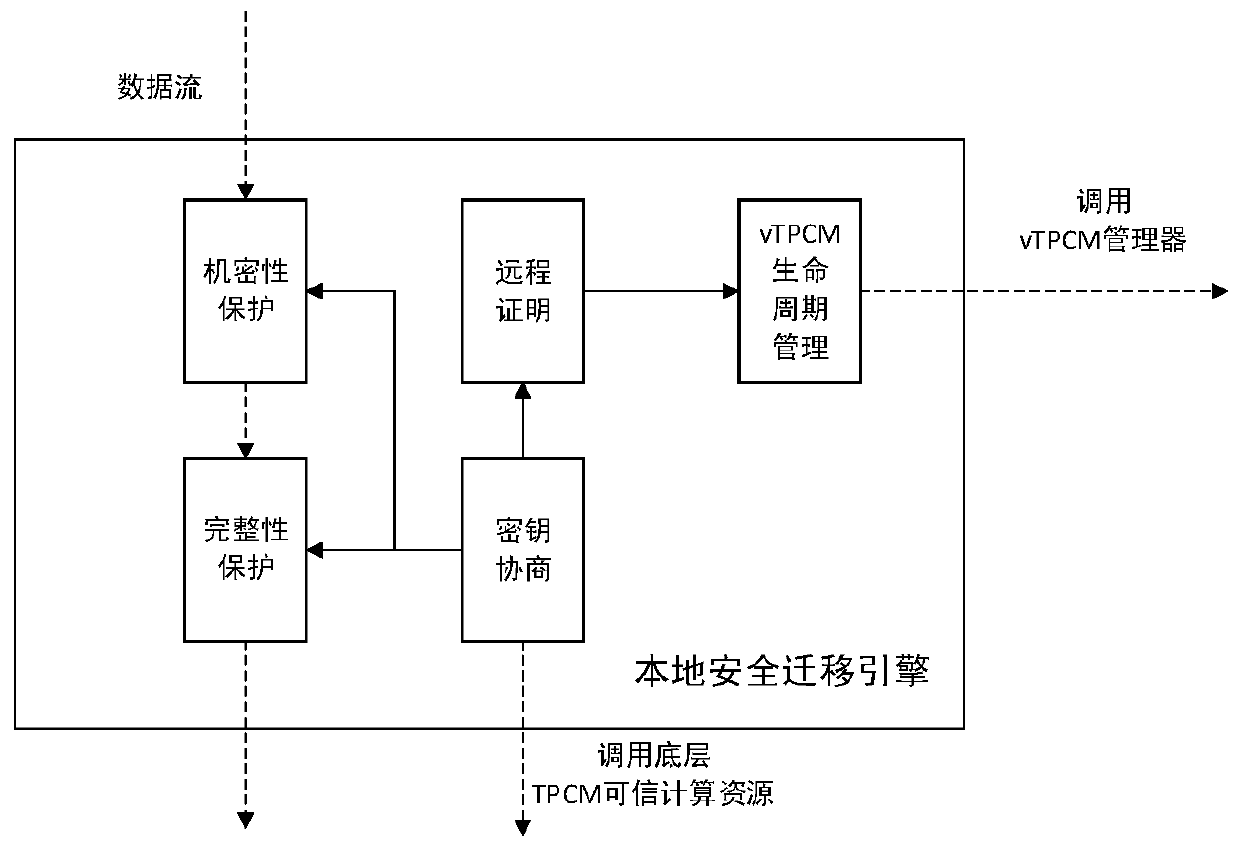
InactiveCN109783192ASafe buildGuaranteed Security AssociationDigital data protectionPlatform integrity maintainanceConfidentiality protectionVirtual machine
The invention relates to a virtual machine security migration system. The virtual machine security migration system includes a sever hardware environment, a host machine system, a virtual machine monitor and one or more virtual machine instances, wherein the host machine system comprises a local security migration engine, the local security migration engine comprises a key agreement module, a remote proof module, a confidentiality protection module, an integrity protection module and a virtual TPCM life cycle management module. the security migration of the virtual machine between a source node and a target can be realized through the virtual machine security migration system provided by the invention.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Multi-layer content protecting microcontroller
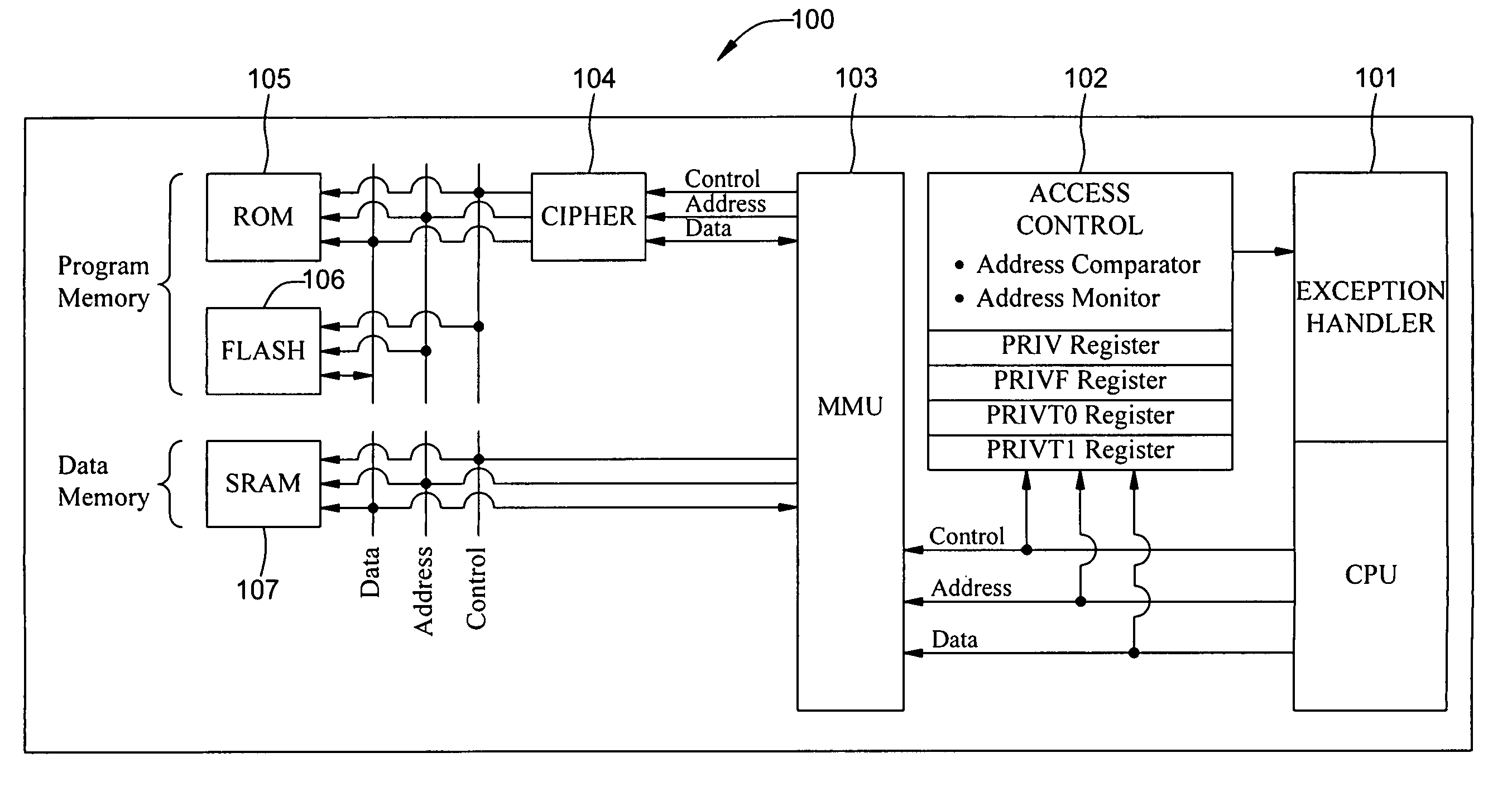
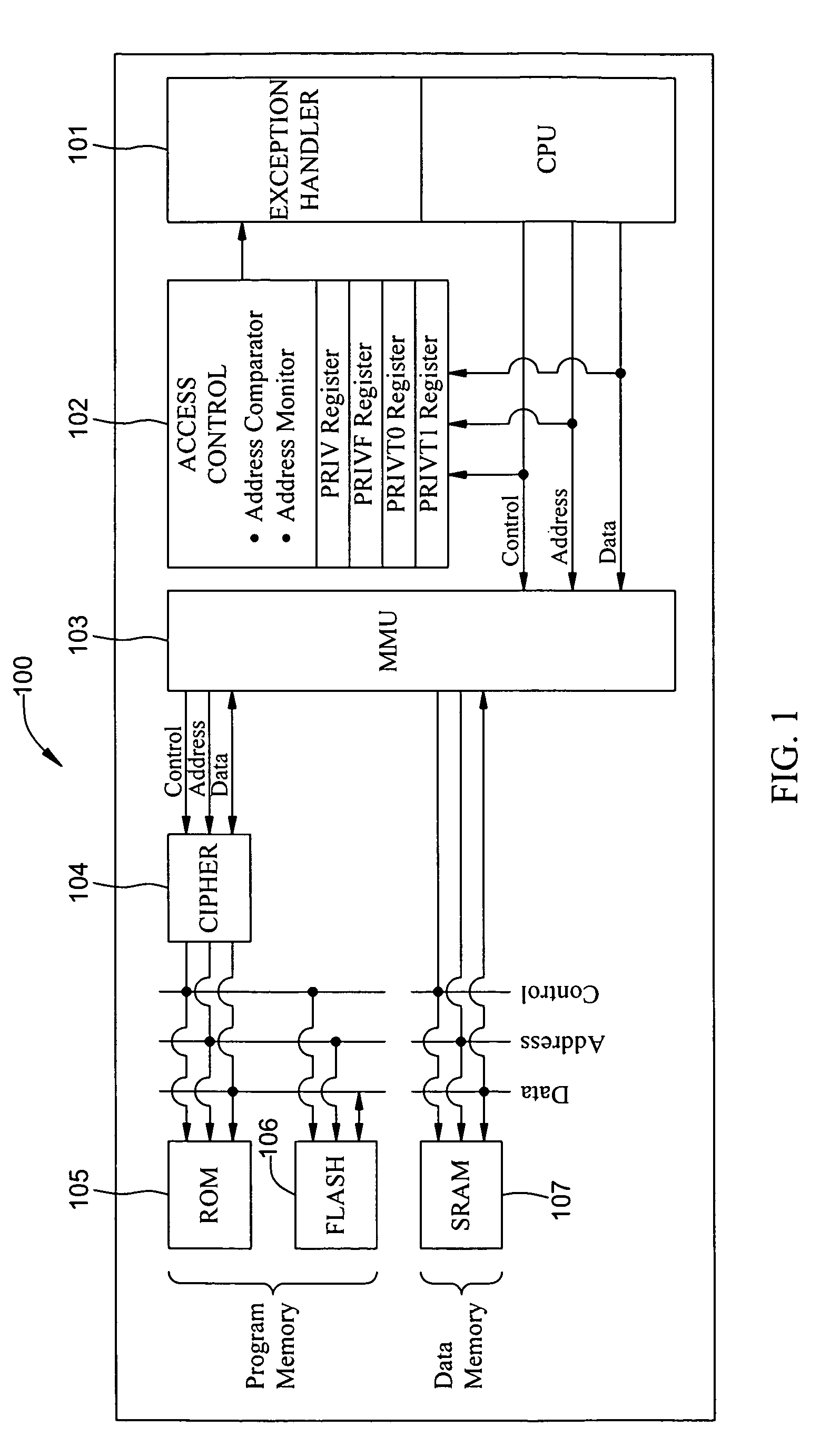
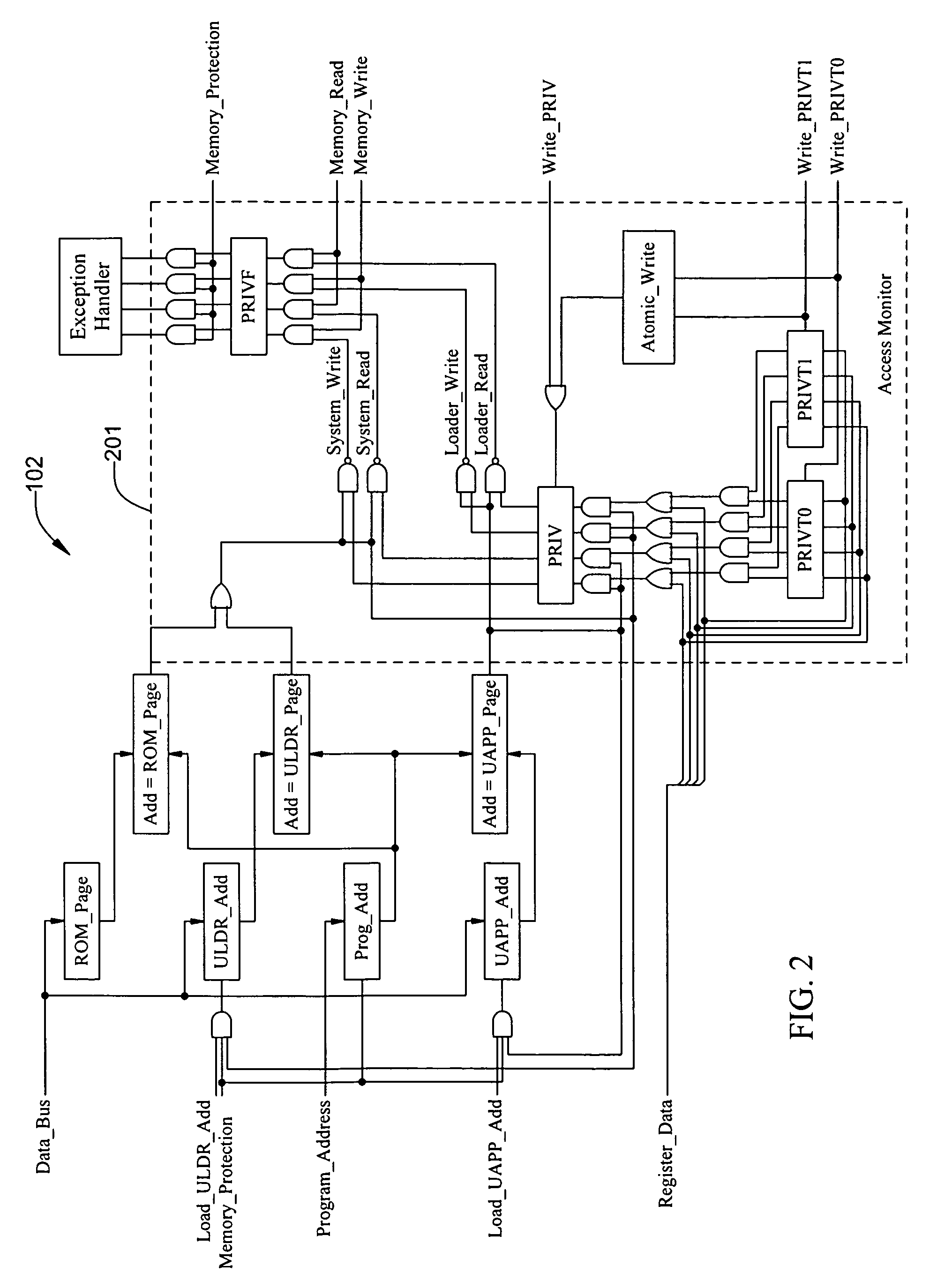
ActiveUS8555015B2Enables confidentiality protectionDigital data processing detailsDigital computer detailsInternal memoryMicrocontroller
The present invention relates to a microcontroller designed for protection of intellectual digital content. The microcontroller includes a secure CPU, a real-time cipher, and a user programmable multi-layer access control system for internal memory realized by programmable nonvolatile memory. Programmable nonvolatile memory allows in-system and in-application programming for the end user. The programmable nonvolatile memory is mainly used for program code and operating parameter storage. The multiple-layer access control is an integral part of the CPU, providing confidentiality protection to embedded digital content by controlling reading, writing, and / or execution of a code segment according to a set of user-programmed parameters. The cipher incorporates a set of cryptographic rules for data encryption and decryption with row and column manipulation for data storage. All cryptographic operations are executed in parallel with CPU run time without incurring additional latency and delay for system operation.
Owner:MAXIM INTEGRATED PROD INC
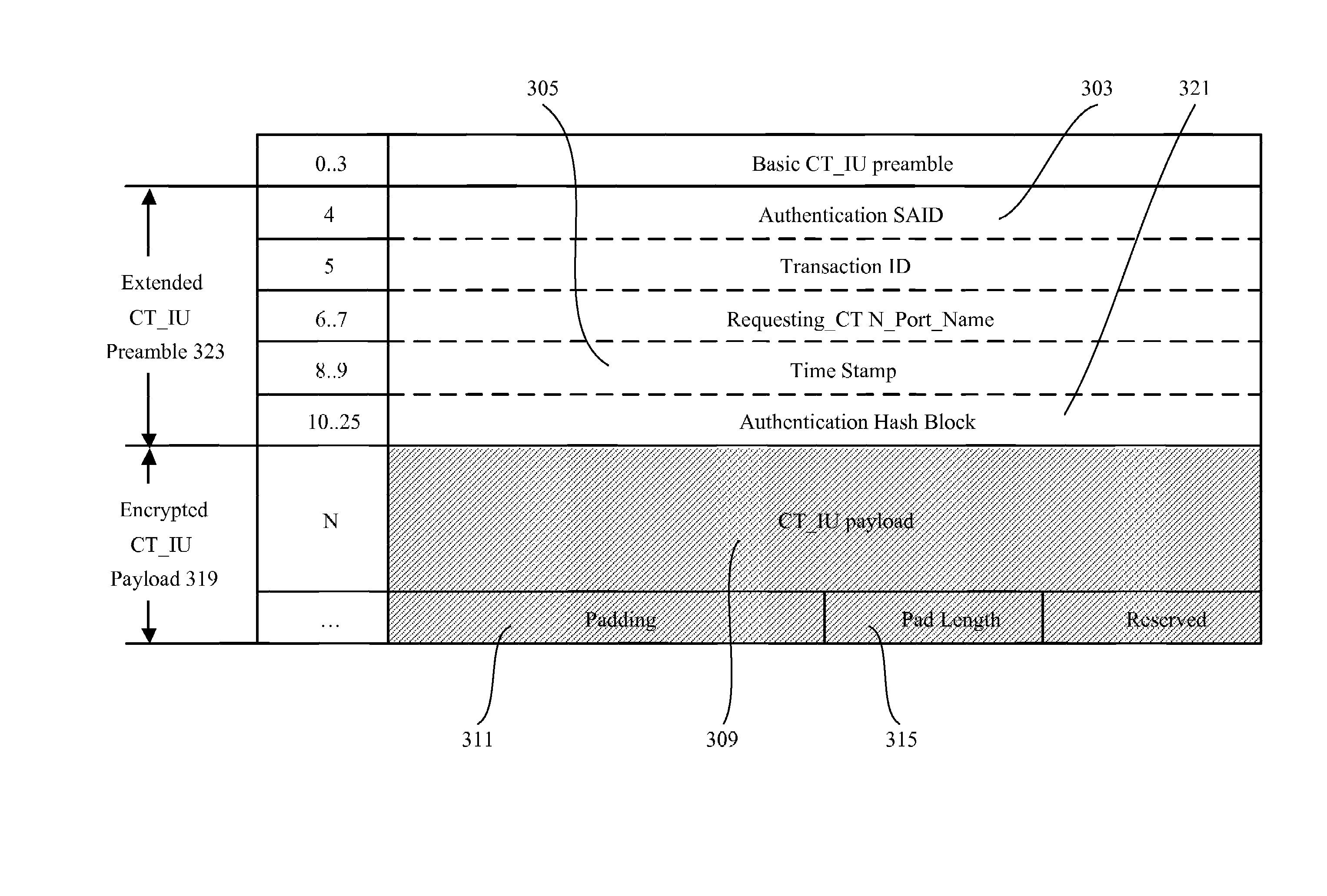
Methods and apparatus for confidentiality protection for Fibre Channel Common Transport
InactiveUS7333612B2Improve confidentialityKey distribution for secure communicationSecret communicationFiberData Origin
Methods and apparatus are provided for improving message-based security in a Fibre Channel network. More specifically, the present invention relates to methods and apparatus for providing confidentiality for Fibre Channel control messages encapsulated within Common Transport Information Units. Control messages transported with the Fibre Channel Common Transport protocol, and passed between Fibre Channel network entities, can be encrypted providing confidentiality combined with data origin authentication, integrity and anti-replay protection provided by existing Fibre Channel security mechanisms.
Owner:CISCO TECH INC
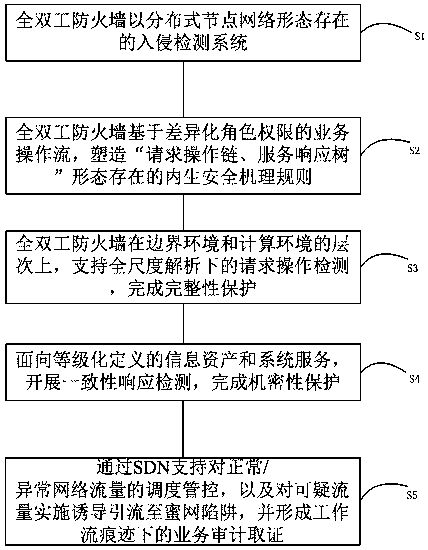
Full-duplex firewall protection method supporting mandatory access control
An embodiment of the invention discloses a full-duplex firewall protection method supporting mandatory access control. The method comprises the following steps of: S1, the full-duplex firewall being an intrusion detection system in a form of a distributed node network; S2, the full-duplex firewall establishing an endogenous security mechanism rule in the form of ''requesting operation chain and service response tree'' based on a business operation flow of a differentiated role authority; S3, the full-duplex firewall supporting a request operation detection under full-scale parsing at the levelof boundary environment and computing environment, and completing an integrity protection; S4, performing a consistency response detection, and completing a confidentiality protection facing information assets and system services which are hierarchically defined; S5, supporting dispatching and control for normal / abnormal network traffic through SDN, inducing suspicious traffic to a honeynet trap,and forming a business audit forensics under workflow trace.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
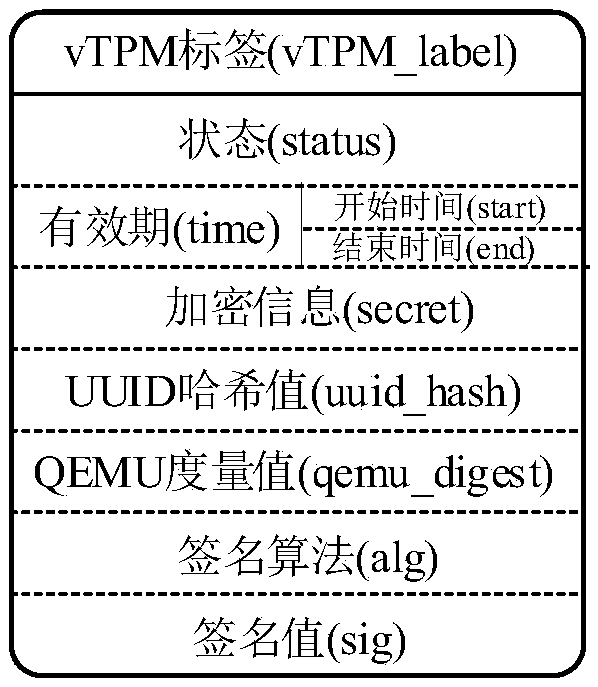
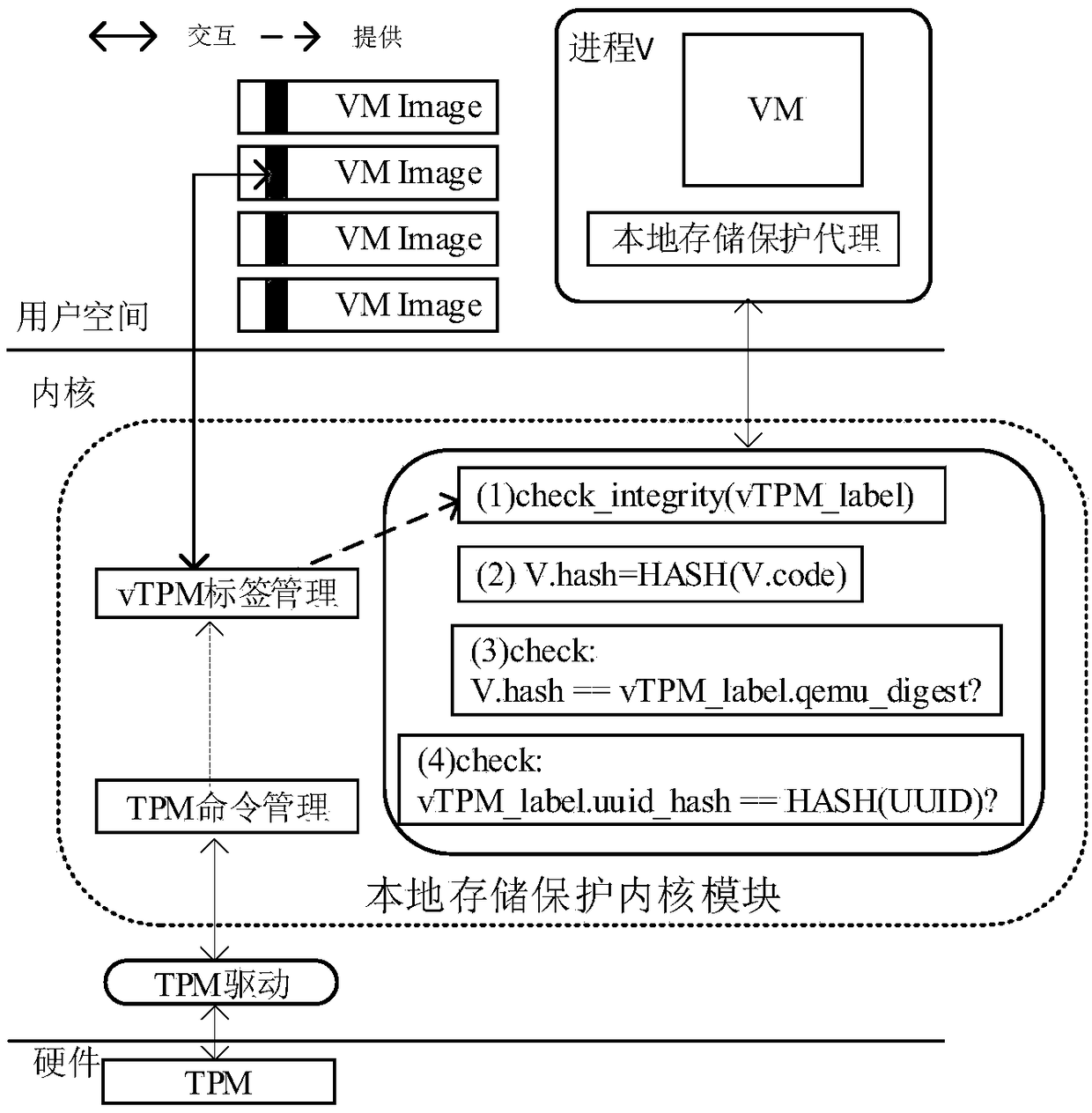
vTPM private information protection method based on label
ActiveCN108804203AImprove confidentialityImprove integrityKey distribution for secure communicationUser identity/authority verificationConfidentiality protectionComputer science
The invention discloses a vTPM private information protection method based on a label. The method comprises the steps of S1, performing initialization work before system deployment; S2, separately building a vTPM label for a vTPM instance of each virtual machine; S3, extracting the vTPM label from an mirror file of the virtual machine, detecting related content of the vTPM label, judging whether acorresponding relationship between the virtual machine and the vTPM is correct, and thus judging whether the virtual machine is started; S4, performing Hash operation, encryption, decryption and Hashvalue verification according to a KEY acquired through decrypting the encryption information field of the vTPM label acquired in the step 3, and performing confidentiality protection and completenessverification on the vTPM private information; and S5, when the virtual machine is in dynamic migration, securely migrating volatility information and private information of the vTPM and the vTPM label. According to the method provided by the invention, the confidentiality and completeness of the vTPM private information and the consistency of the association relationships between the virtual machines and the vTPM instances are protected in real time by using the vTPM labels, and association between the vTPM and the physical credible platform module is built.
Owner:SICHUAN UNIV
A hardware-based dynamic data protection method for embedded system
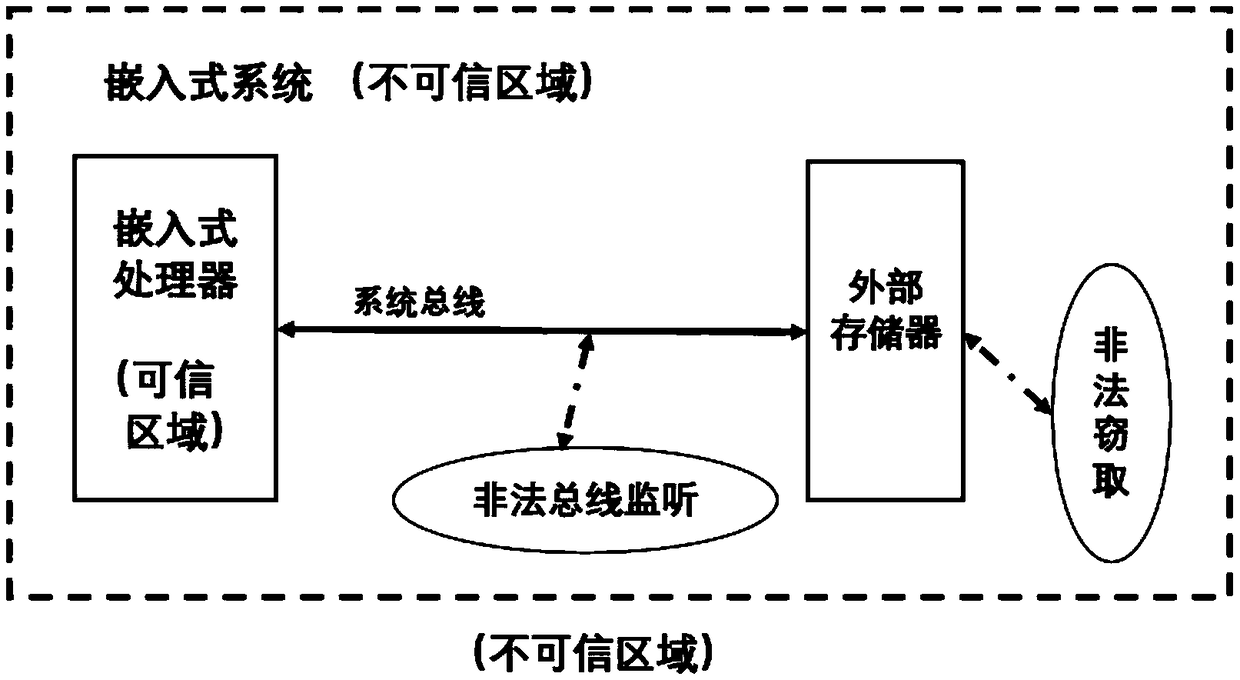
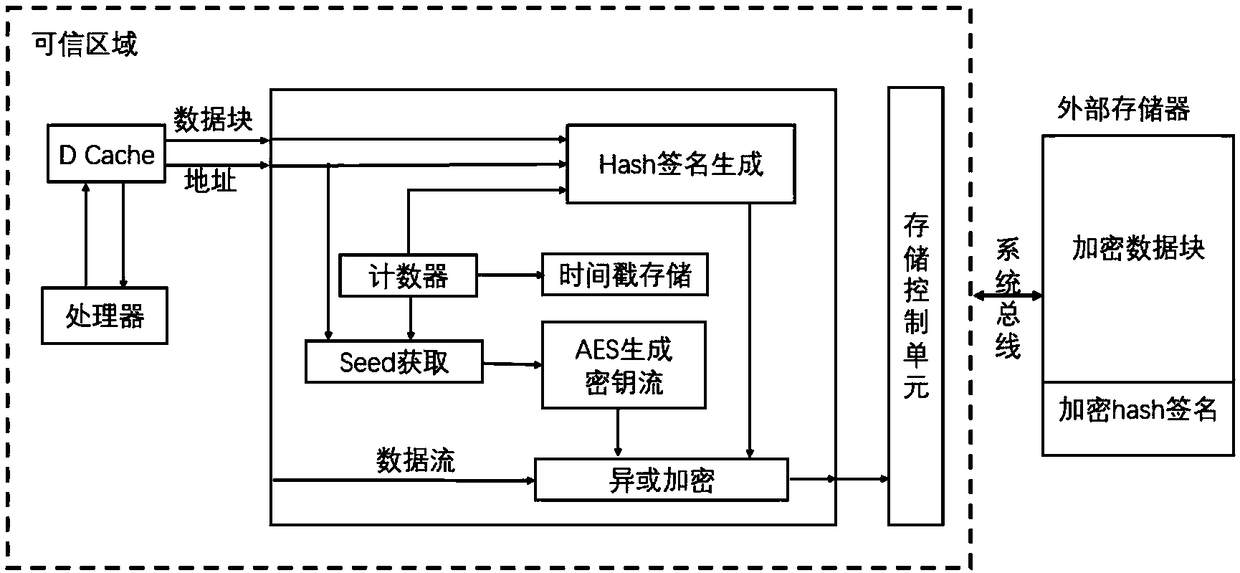
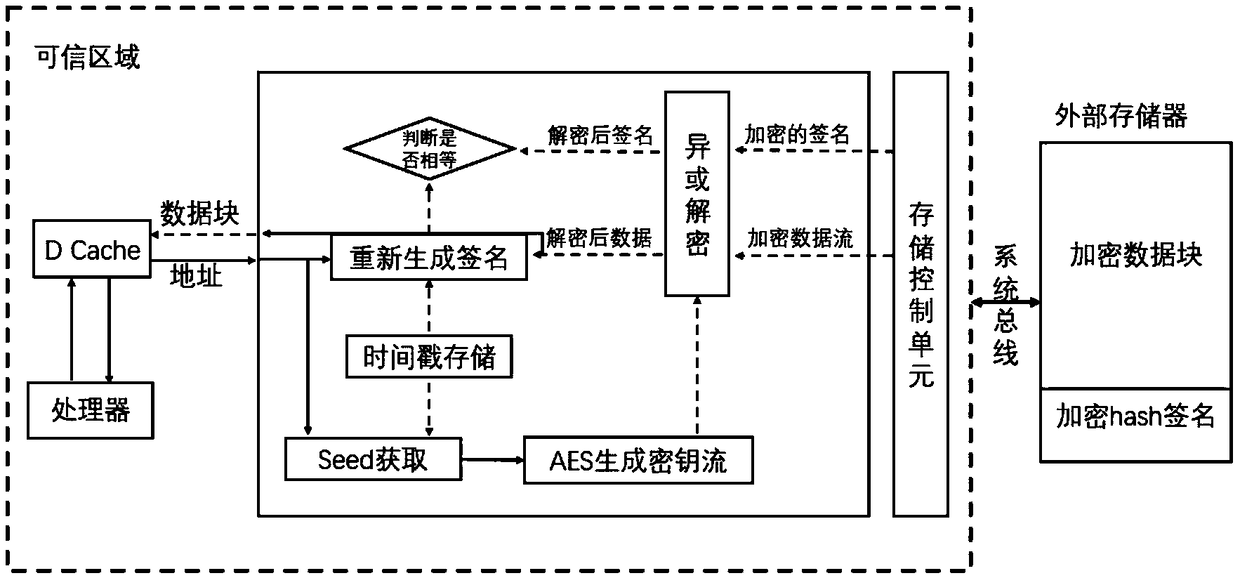
ActiveCN109086612AReduce performance lossReduce latencyDigital data protectionInternal/peripheral component protectionConfidentiality protectionExternal data
The invention provides an embedded system dynamic data protection method based on hardware realization, which comprises the following steps: 1, a safety module caching data blocks to be stored; 2, calculating the check information of the data block by using a hash method; 3, generating a key stream based on an advanced encryption standard, i. E. AES; 4, encrypting the data block and its checking information by use the key stream to realize the confidentiality protection; 5, when the external data is read into the chip, the security module generating a key stream; 6, decrypting the read data and the check information thereof; 7, recalculating the check information of the decrypted data block; 8, comparing the decryption check information in the step 6 with the check information in the step7, and judging whether the integrity of the data is attacked or not. The invention realizes the confidentiality protection and integrity verification of the embedded system data in the non-trusted area, solves the problems that the off-chip data is monitored, stolen, tampered and the like, thereby improving the safety of the embedded system data.
Owner:BEIHANG UNIV
Method for providing confidentiality protection of control signaling using certificate
InactiveUS8452964B2Control safetyPrevent a unique identifierKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCommunications systemConfidentiality protection
Owner:LG ELECTRONICS INC
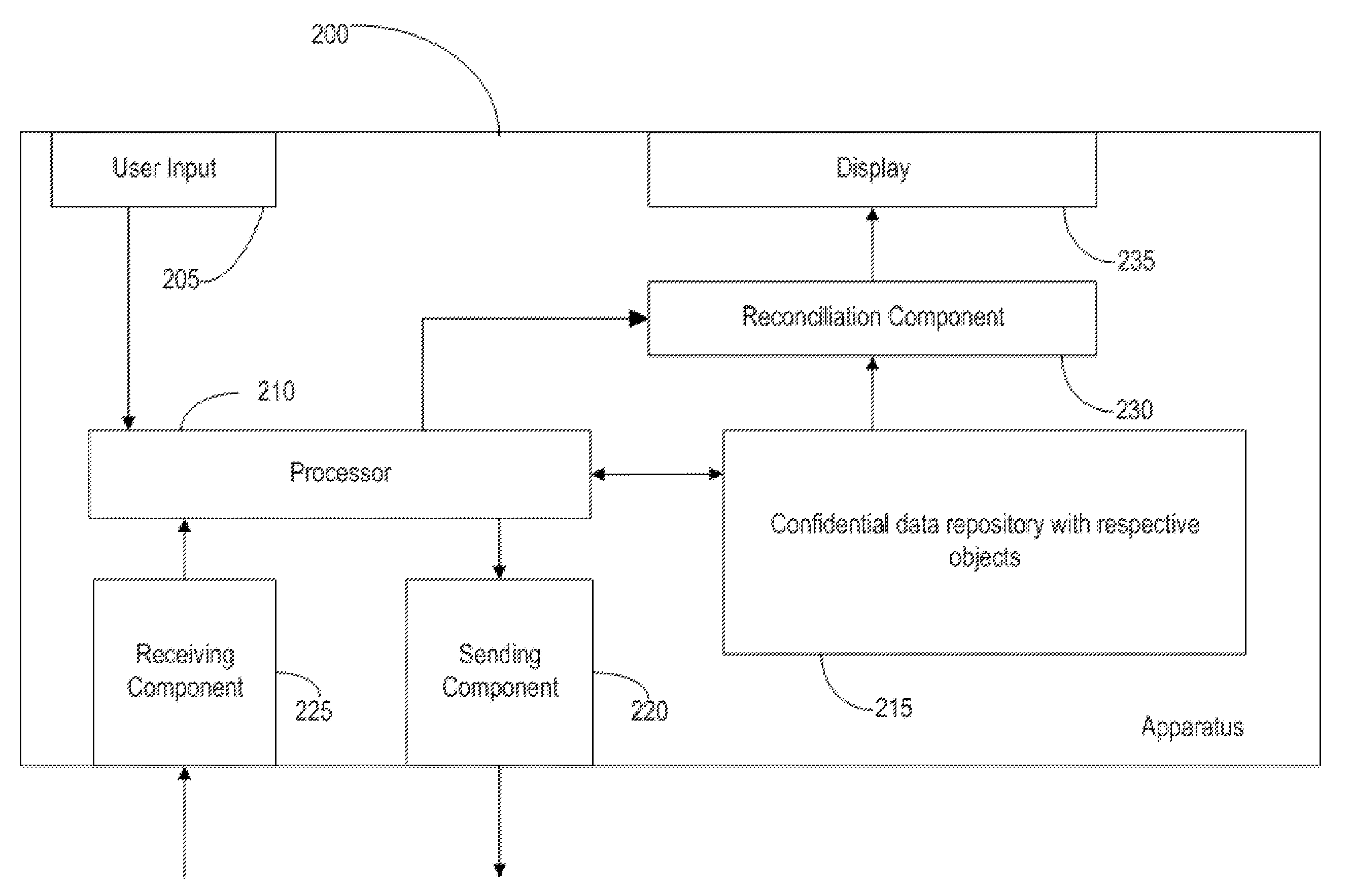
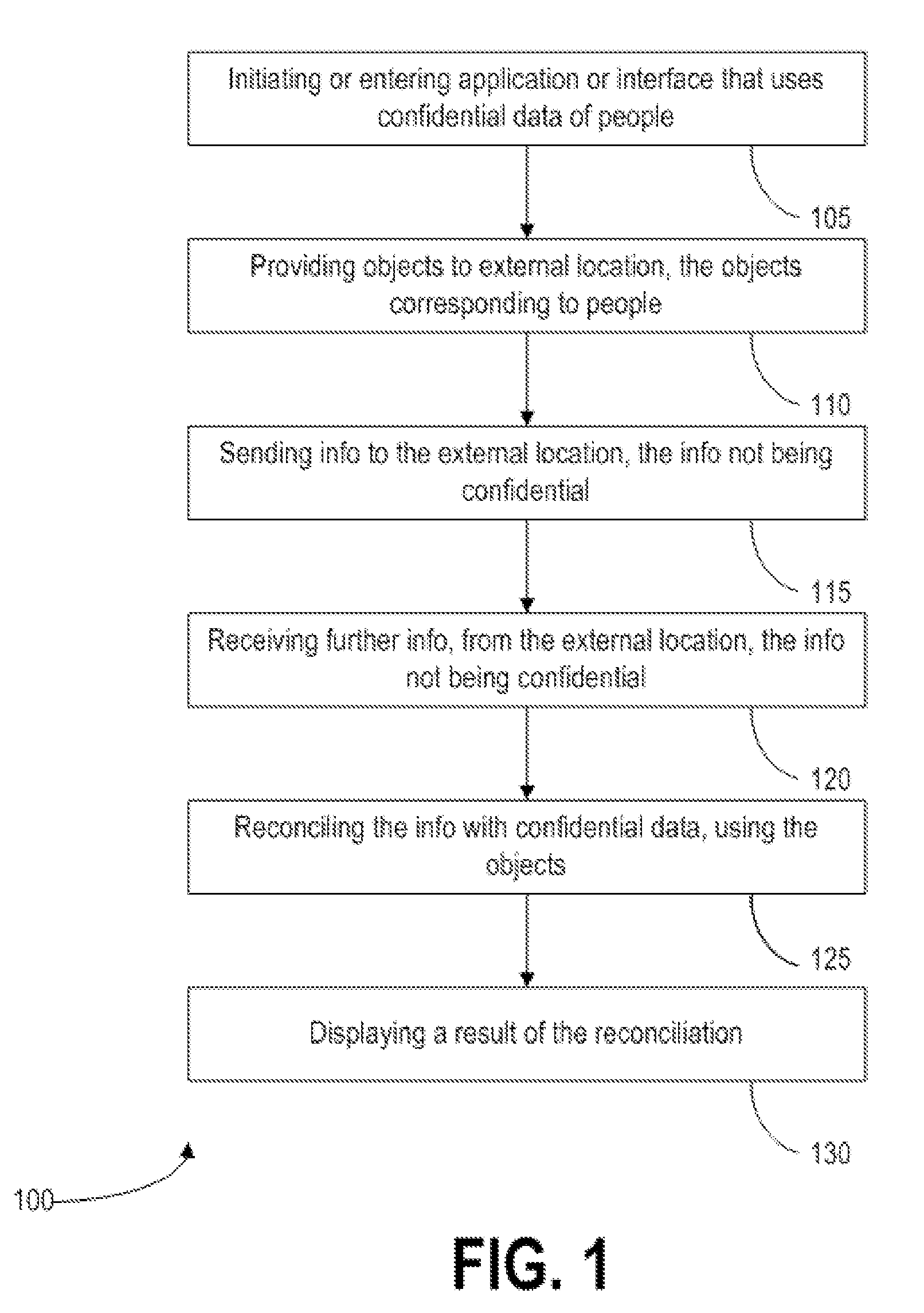
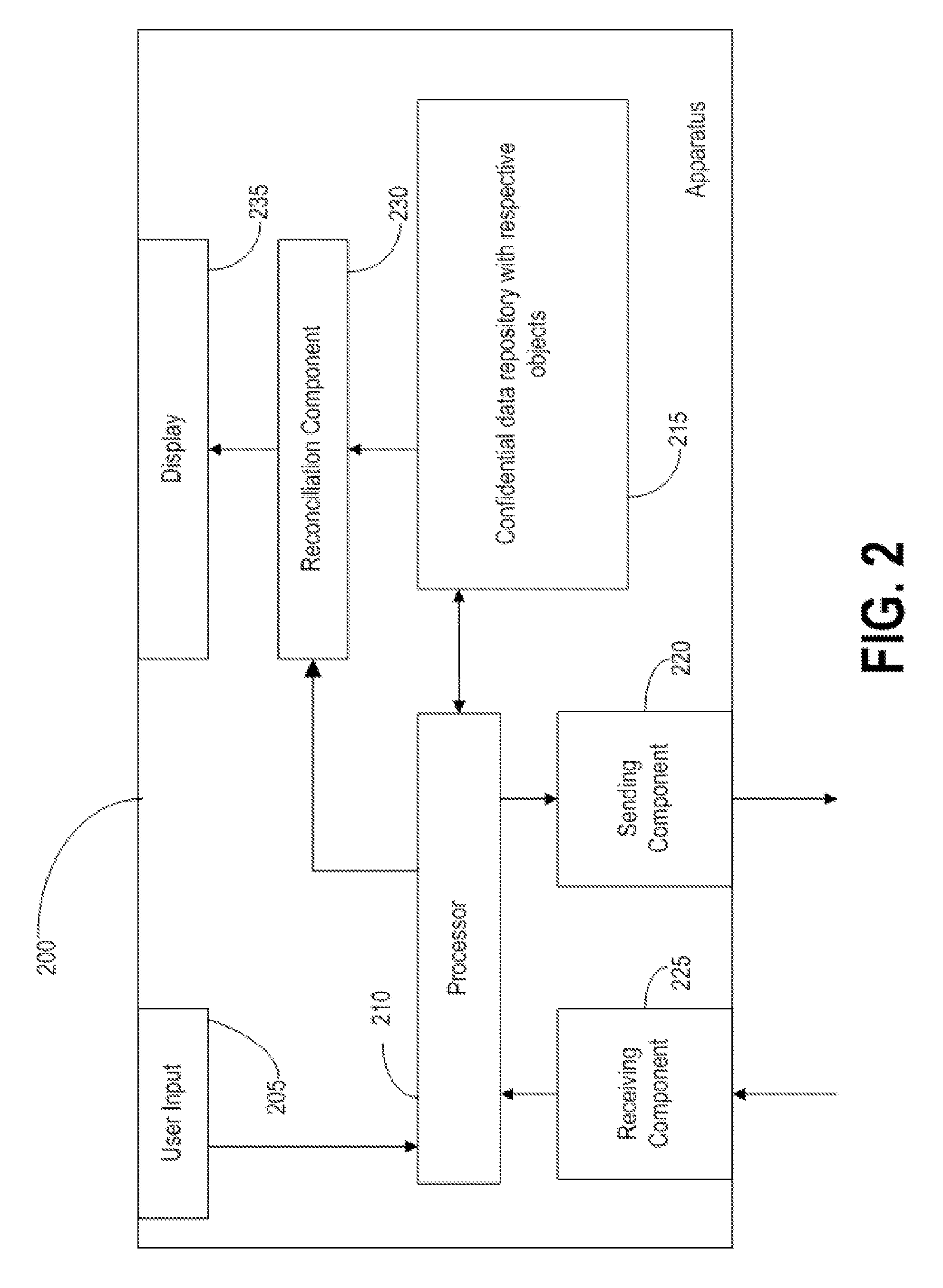
Method, apparatus, and computer program product for isolating personal data
InactiveUS20100077489A1Broaden applicationIncrease opportunitiesDigital data processing detailsUser identity/authority verificationConfidentiality protectionInternet privacy
A method, user equipment, network device, and software product that protects data confidentiality where data transmission is required between distant systems. The invention comprises splitting data into confidential and non-confidential data. The invention further includes an isolating indexation responsible for data transmission, processing and reconciliation. Also, the invention comprises data confidentiality protection where multiple systems are involves.
Owner:AKE JOEL H
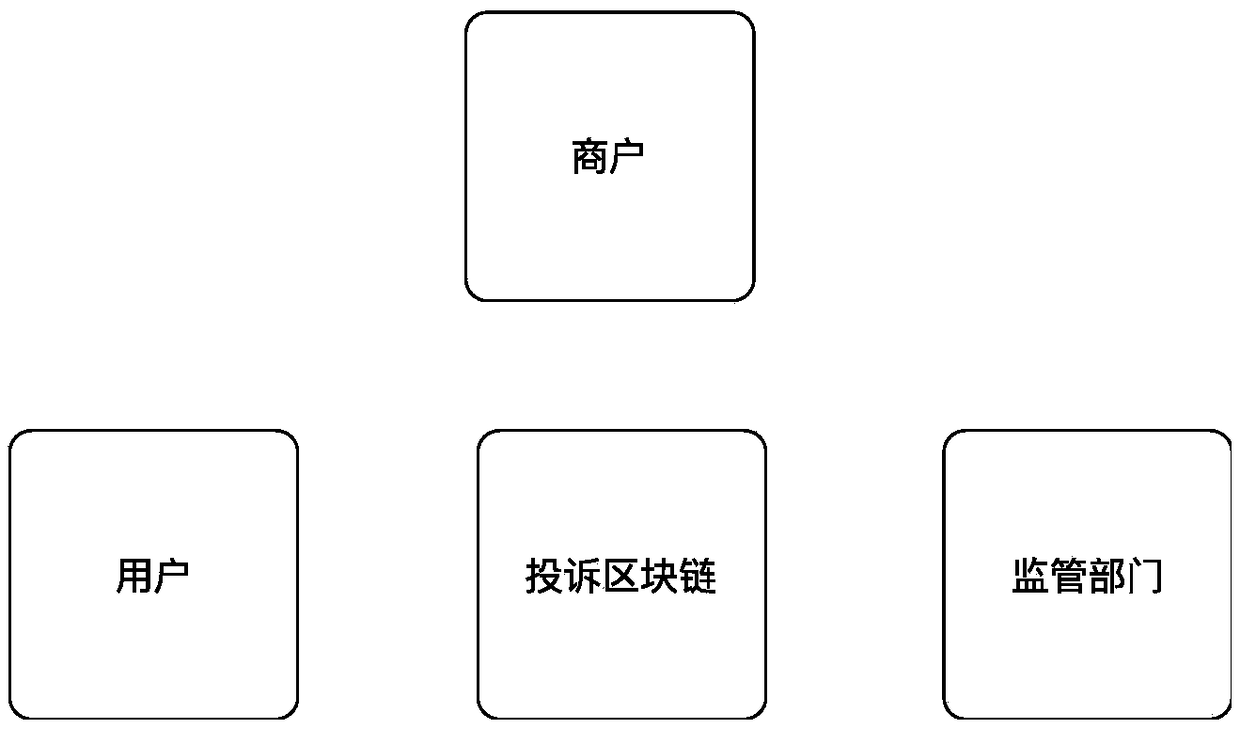
A complaint method and a system based on a block chain
InactiveCN109409903AAvoid artificial deletionDrawbacks of avoiding tamperingDigital data protectionCommerceConfidentiality protectionComputer science
The invention discloses a complaint method and a system based on a block chain, comprising a complaint block chain module, a user complaint client, a merchant complaint processing client and a supervisory department complaint processing client. Among them, the complaint block chain module generates and records the information of users' complaints, and constructs the corresponding block chain. Thesystem of the invention properly manages and maintains the complaint information, the complaint record in the system cannot be tampered with, avoids the disadvantages of artificial deletion or tampering, can justly and fairly carry out the complaint, and utilizes the technology of the block chain to carry out the confidentiality protection to the information of the complainant.
Owner:GUANGZHOU CHNAVS DIGITAL TECH
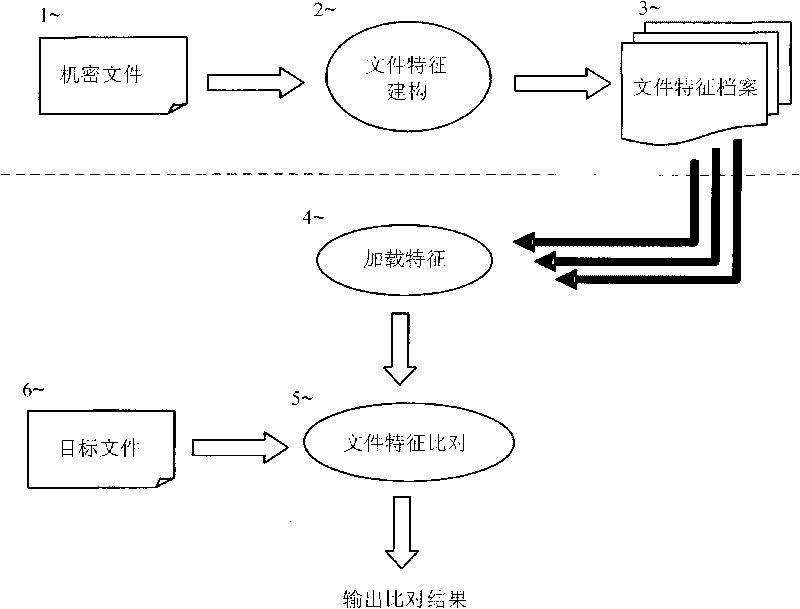
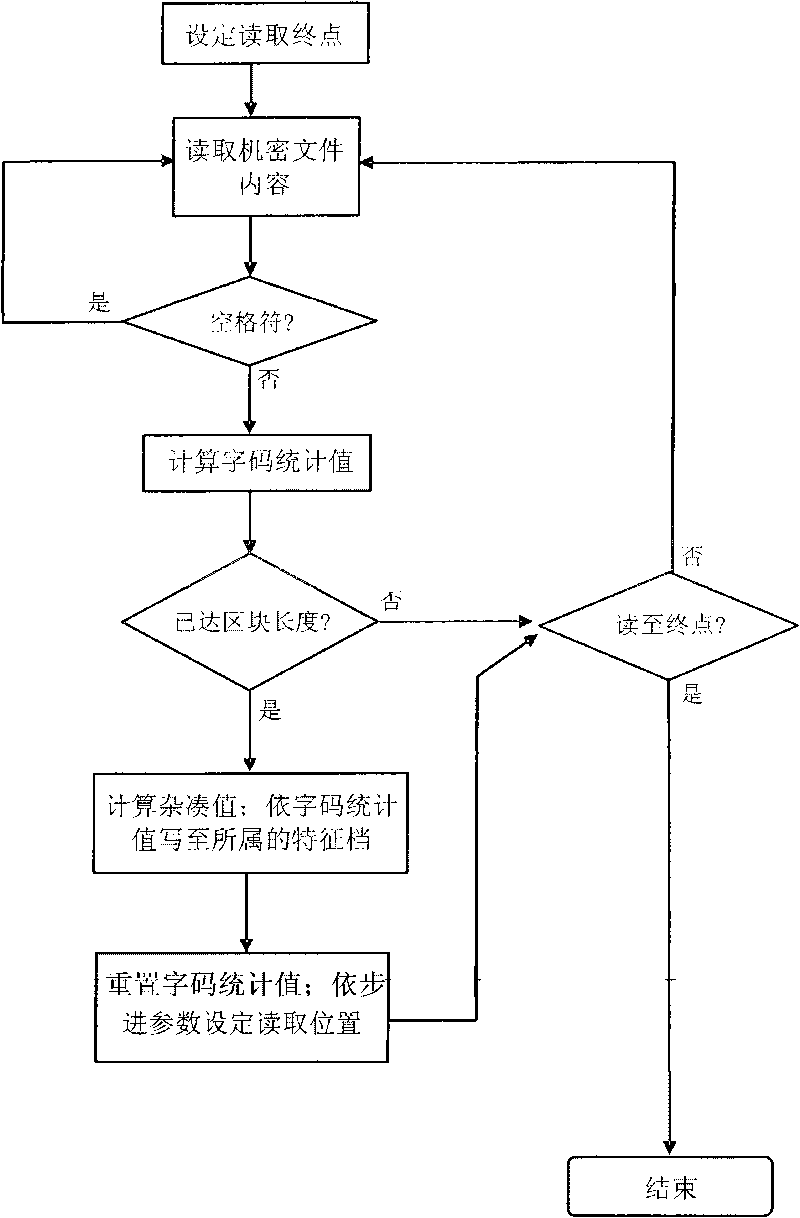
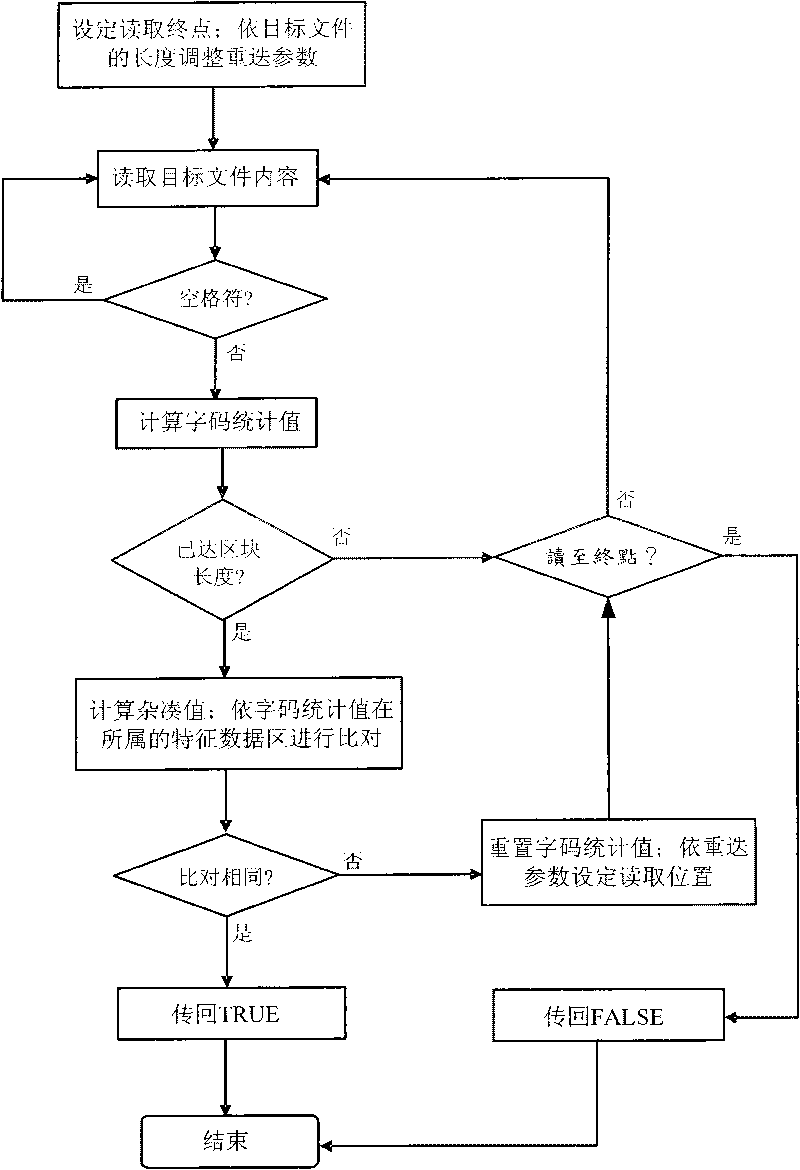
Characteristic value comparison based content analysis method
InactiveCN101699428AReduce the chance of conflictReduce the number of comparisonsSpecial data processing applicationsData spaceContent analytics
The invention discloses a characteristic value comparison based content analysis method, which comprises the following steps: firstly, calculating the characteristic value of a confidential file to be protected, and constructing a corresponding data characteristic file; and later, comparing data contents with fixed length for a suspicious file by using the characteristic data of the file at the content analysis stage of confidential protection operation, wherein if the data accords with the characteristic comparison, the suspicious file is a file containing confidentiality, and the related protection operation appointed by a policy is performed by a protection system, otherwise, the suspicious file is judged as a file which does not contain confidentiality. By improving the confidentiality protection field based partial file comparison technology and using a method for cutting data space, the comparison efficiency and precision of large-sized files are promoted, and the adjustment of related parameters during data comparison is performed according to the length of the target file so as to meet two difficult requirements of confidentiality identification rate and system efficiency.
Owner:CHUNGHWA TELECOM CO LTD
Mandatory access control scheme with active objects
InactiveUS7600117B2Digital data processing detailsAnalogue secracy/subscription systemsConfidentiality protectionSubject matter
Access control is mediated by a set of 2-tuple labels or attributes which are associated with subject and object entities, respectively. Subject entitles, such as processes, have separate read and write attributes, while object entities, such as files, have separate integrity and write control attributes. The system implements a set of rules to provide both integrity control and confidentiality protection. Specifically, write operations to an object are inhibited where the subject's write attribute is lower than the write control attribute of the object. Read operations from an object are inhibited where the subject's read attribute is lower than the object's integrity attribute. When a subject reads from an object having a lower integrity level than the subject's read attribute, the subject's read attribute is demoted.
Owner:PANASONIC CORP
A data security method and system for MapReduce calculation
ActiveCN109684856AAchieve indistinguishabilityDigital data protectionConfidentiality protectionPaired Data
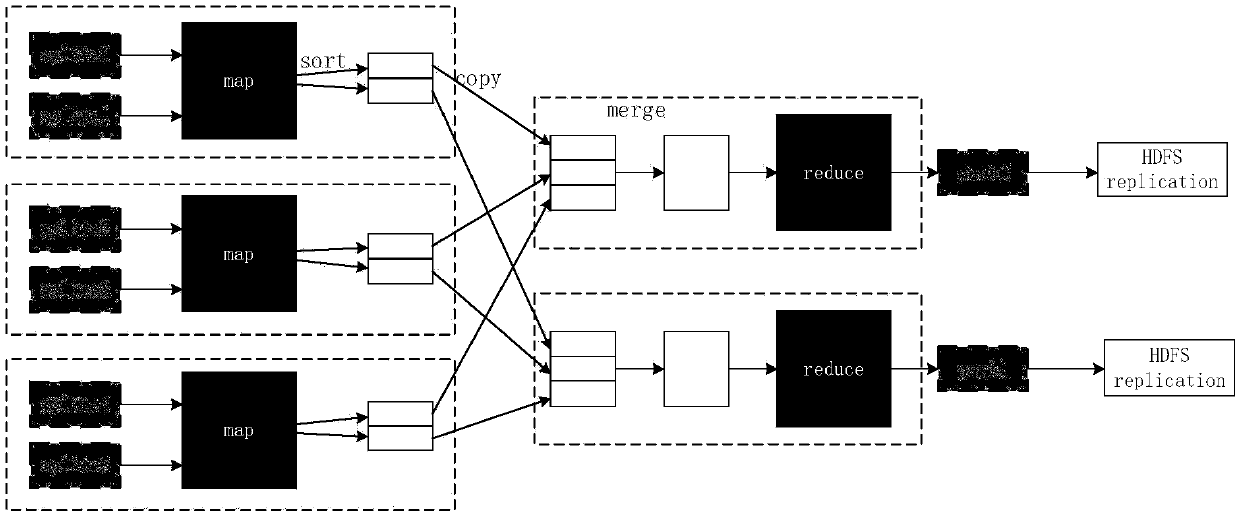
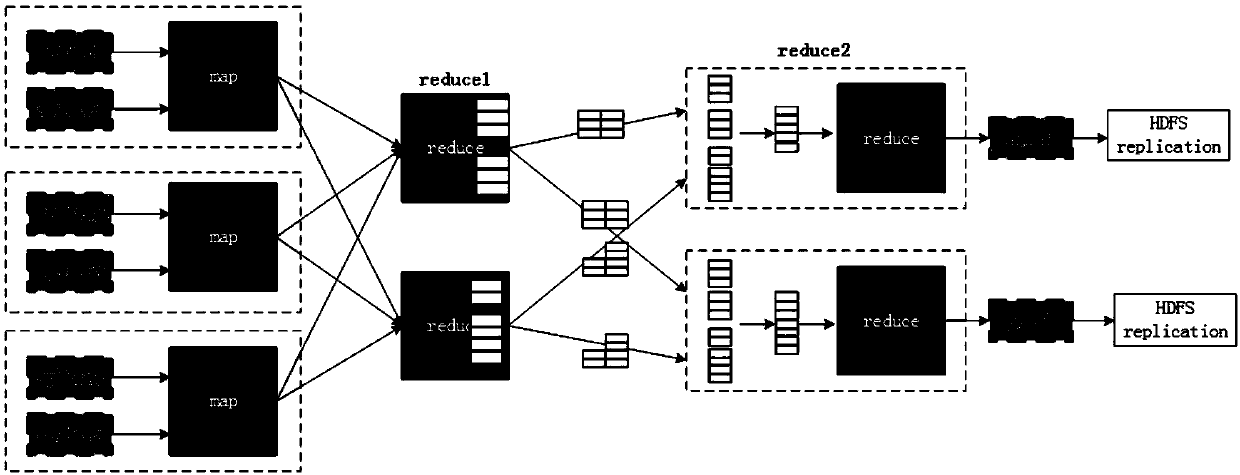
The invention discloses a data security method and system for MapReduce calculation. The method comprises the following steps: adding another reduce stage reduce 1 before a standard reduce stage reduce 2 of MapReduce; Writing a random distribution function into the function of the map stage, and sending the data in each map task of the map stage to each reduce task of the reduce 1 stage on average; Sending the key value pair data combined with each reduce task in the reduce 1 stage to each reduce task in the reduce 2 stage, or adding false key value pair data into the key value pair data and then sending the false key value pair data; And processing the data, and discarding the key value pair data which does not belong to the merging of each reduce task in the reduce 1 stage. According tothe invention, confidentiality protection of the MapReduce operation data in the cloud computing platform is realized.
Owner:XIDIAN UNIV
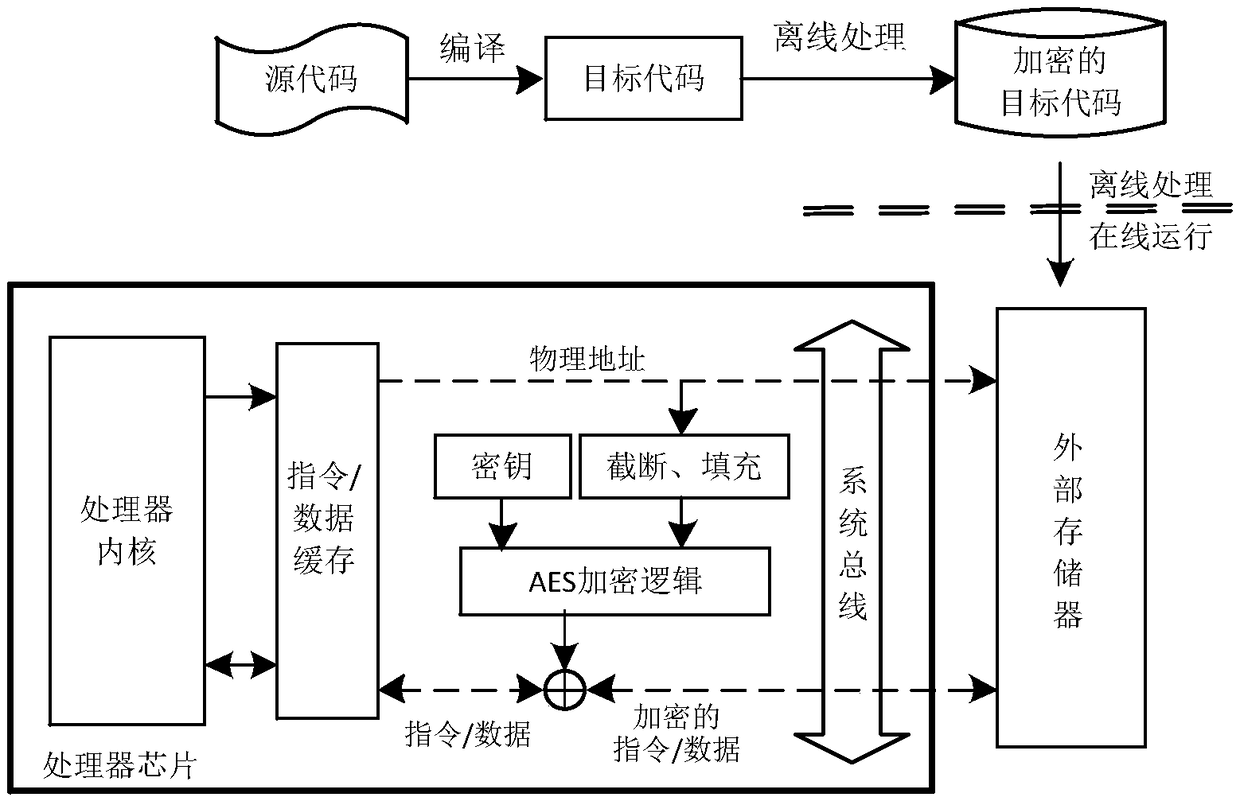
A hardware-based embedded system confidentiality protection method
ActiveCN108959129APrevent unauthorized accessAvoid understandingUnauthorized memory use protectionPower-on resetConfidentiality protection
The invention relates to a hardware-based embedded system confidentiality protection method, which comprises the following steps: 1, generating an object code; 2, encrypting that object code and storing the object code into a non-volatile storage; 3, power-on resetting; 4, executing a program, such as a cache miss or a data cache write-back, and executing step 5; otherwise, executing step 4 untilthe program ends; 5, if that out memory is written, executing step 6; otherwise, executing step 8; 6, carrying out truncating and filling, generating pad with hardware encryption logic, and generating ciphertext with data of exclusive OR cache line; 7, writing that ciphertext into the external memory, and executing the step 4; 8, truncating and filling that physical address corresponding to the cache line, generating the pad by the hardware encryption logic, and exclusively or reading the ciphertext from the external memory to obtain instructions or data; 9, sending instructions or data intothat processor and write corresponding cache lines, and executing step 4. Through the above steps, the method can realize the confidentiality protection of the embedded system with lower performance cost and implementation cost.
Owner:BEIHANG UNIV
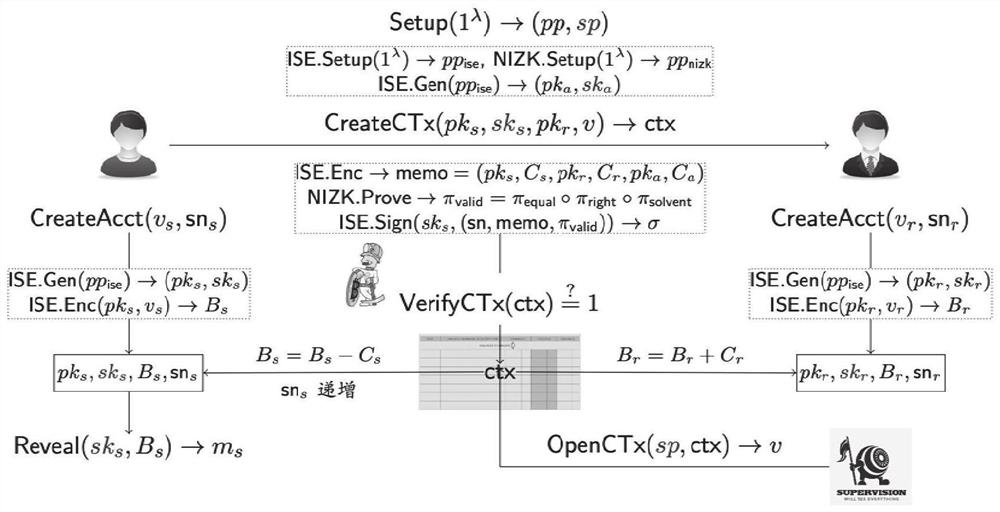
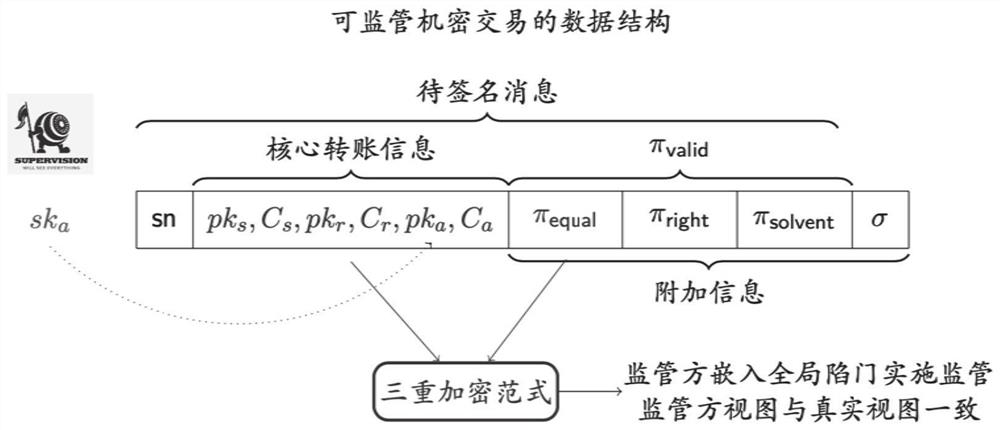
Supervisable distributed confidential transaction system and method
ActiveCN112651742AImprove user experienceRealize penetrating supervisionFinanceProtocol authorisationConfidentiality protectionEngineering
The invention provides a supervisable distributed confidential transaction method and system. A supervisor generates public parameters by using a non-interactive zero-knowledge proof system generation algorithm, generates public and private key pairs by using an integrated encryption signature method, and uses a private key as a global supervision private key; the participant generates a registration request, and sends a public and private key pair, a secret balance and account public information to the supervisor for registration; the supervisor monitors the transaction of the participant transaction party and confirms whether the transaction amount and the account balance of the transaction initiator are in a reasonable interval; and if the confirmation result is passed, confidential transaction is carried out between the participant transaction parties, confidential transaction records passing validity verification is uploaded, and the account state of each participant transaction party is updated by each participant transaction party. According to the invention, confidentiality protection can be provided for a user, and a supervisor is allowed to implement efficient penetration type global supervision.
Owner:SHANDONG UNIV
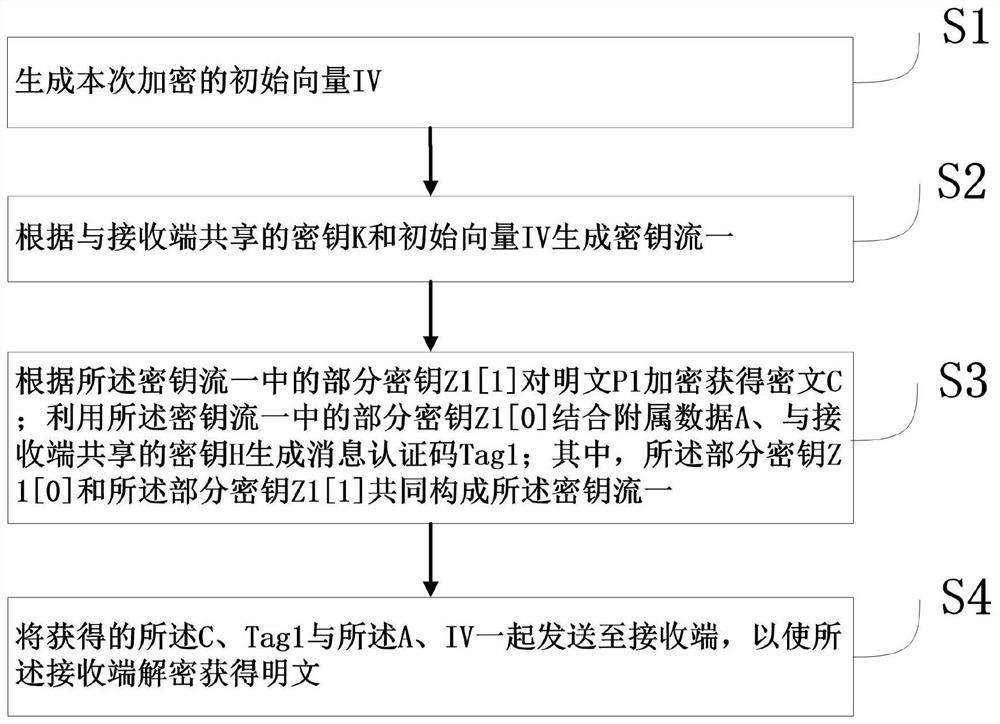
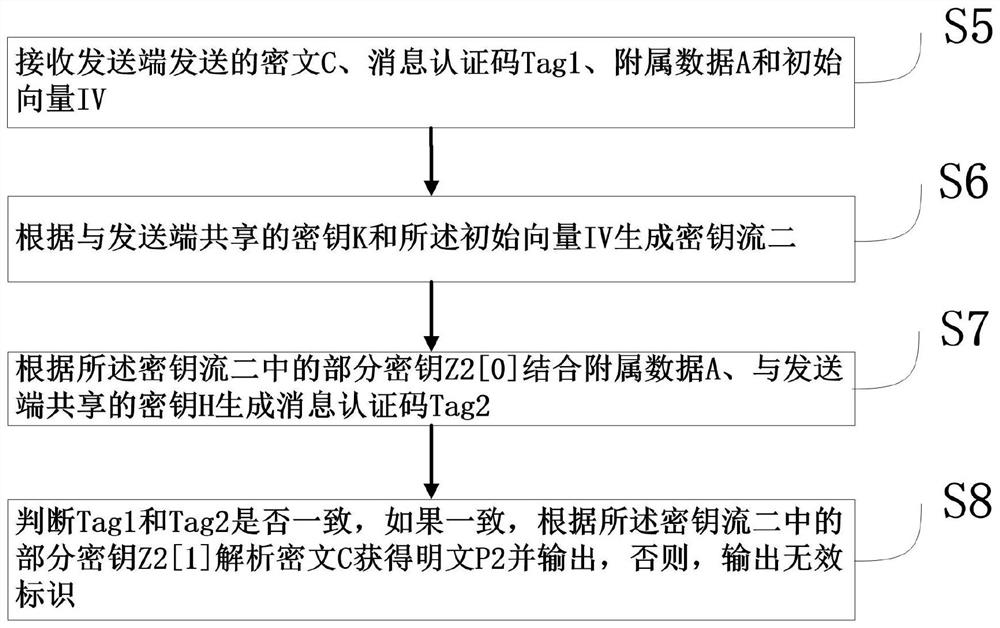
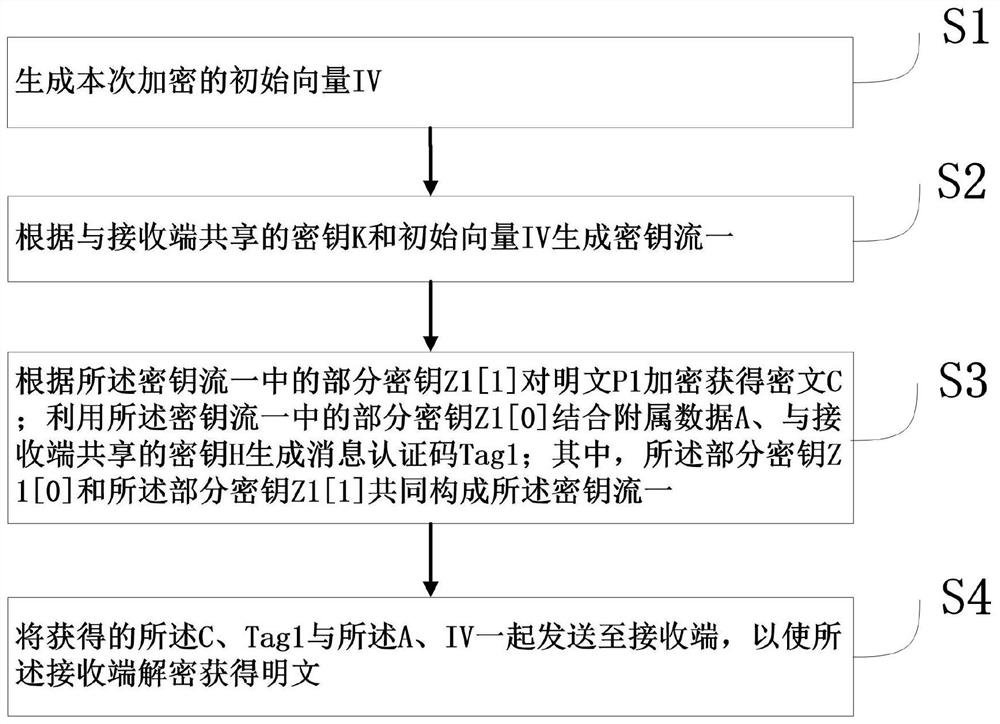
Authentication encryption, verification decryption and communication method
PendingCN112152805AImprove securityImprove communication efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentiality protectionCiphertext
The invention relates to an authentication encryption, verification decryption and communication method, belongs to the technical field of communication, and solves the problems that in the prior art,the operation efficiency and the security boundary are low, and confidentiality protection and integrity protection cannot be provided for data at the same time. The method comprises the following steps: a sending end executing an encryption program, generating an initial vector IV of the encryption, generating a key stream I according to a shared key K and the initial vector IV, encrypting a plaintext P1 according to the key stream I to obtain a ciphertext C, generating a message authentication code Tag1 in combination with affiliated data A and a shared key H, and sending the obtained C, Tag1, A and IV to a receiving end; and the receiving end executes a decryption program, generating a key stream II according to the shared key K and the received IV, generating a message authenticationcode Tag2 according to the key stream II, the received A, C and the received shared key H, judging whether Tag1 and Tag2 are consistent or not, if the Tag1 and Tag2 are consistent, analyzing the ciphertext C according to the key stream II to obtain a plaintext P2, and outputting the plaintext P2 if the Tag1 and Tag2 are or not consistent.
Owner:XINGTANG TELECOMM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com