Data security implementation method capable of resisting timing attacks and devices
A technology for data security and timing attack, applied in the field of modern cryptography, it can solve problems such as timing attack, achieve the effect of resisting timing attack, confidentiality protection and integrity protection, and is conducive to popularization and application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
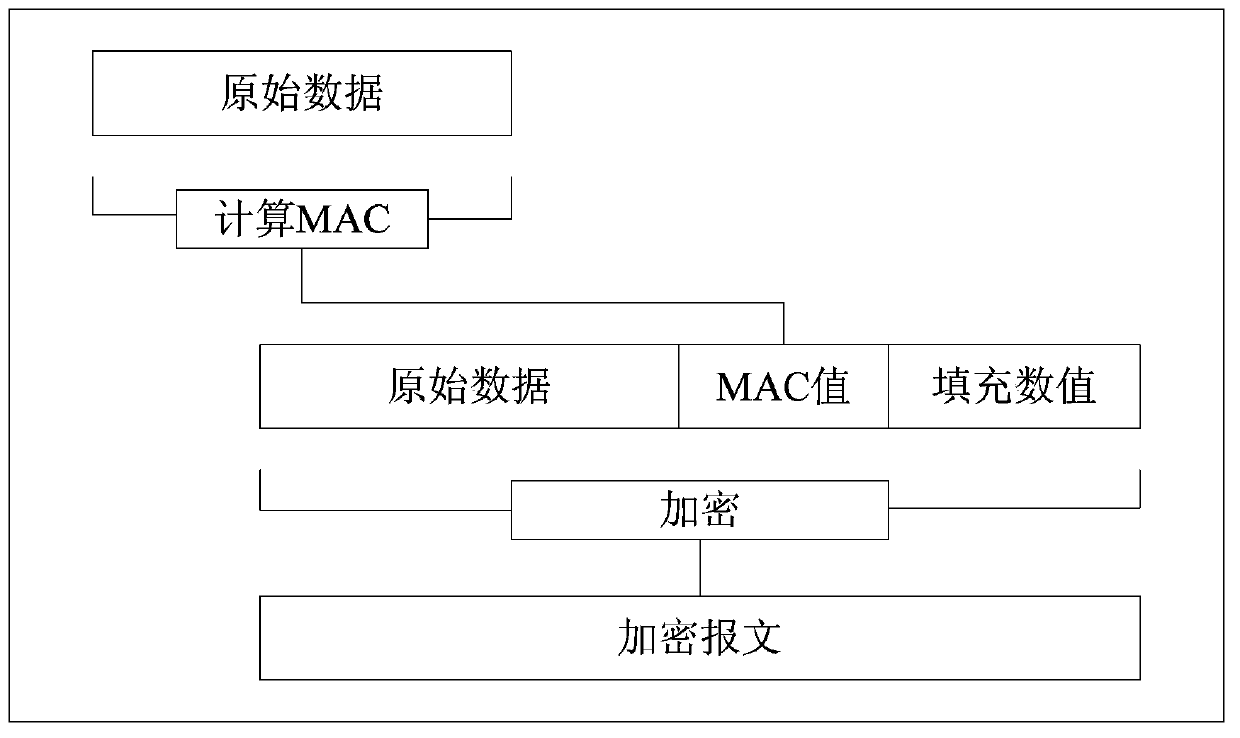
[0048] In this embodiment, it is assumed that the original message is 100 bytes, the MAC algorithm is HMAC-SHA (the output MAC length is 20 bytes), and the encryption algorithm is AES in CBC mode (the packet length is 16 bytes).
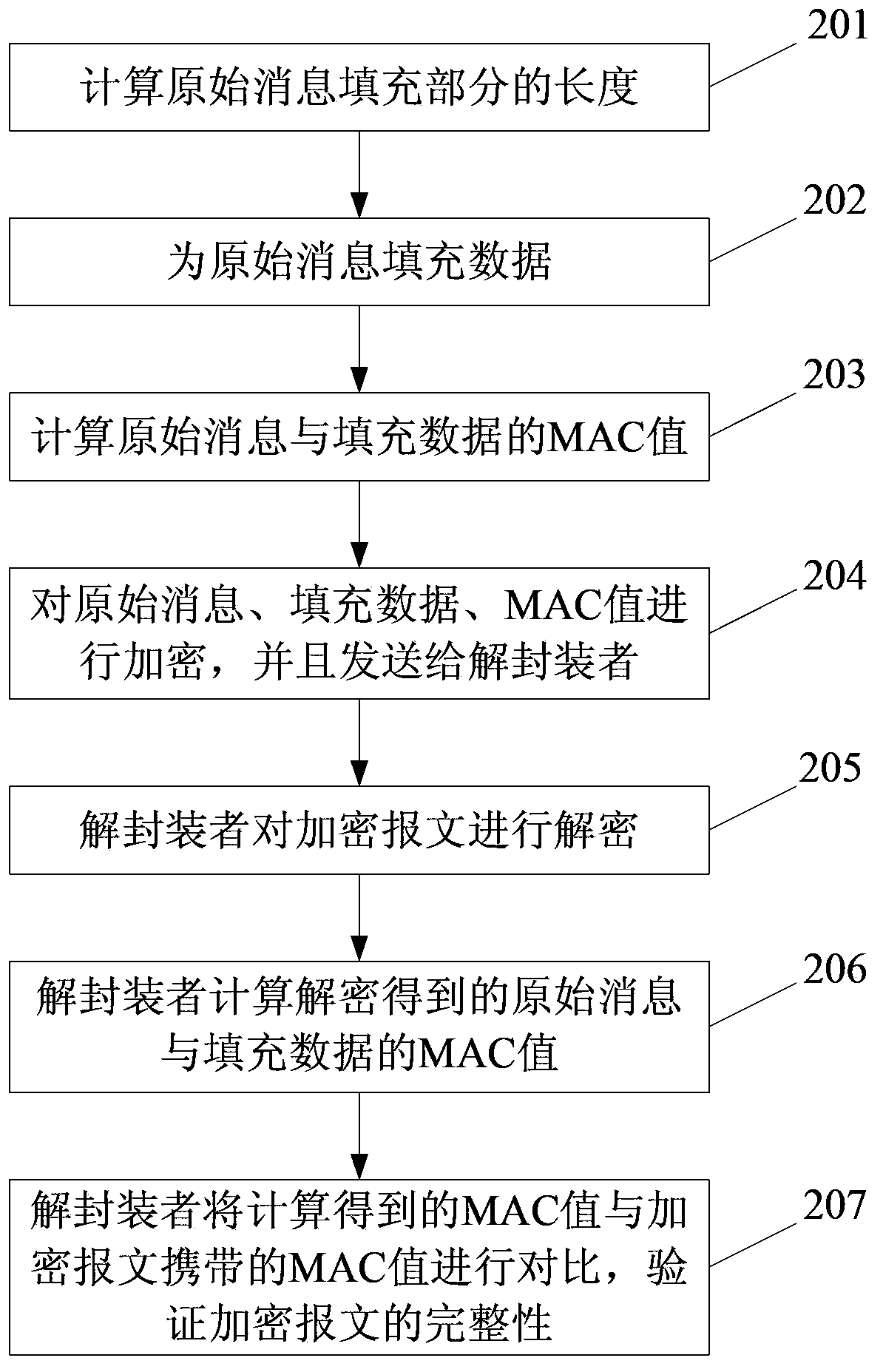
[0049] figure 2 It is a flow chart of this embodiment, and the technical solution of the present invention is described by taking the case of an algorithm suite applicable to all MEE-CBC types as an example, as figure 2 As shown, this embodiment includes the following steps:
[0050] Step 201: Calculate the length of the padding part of the original message.
[0051] In this step, the original message is 100 bytes, the MAC length is 20 bytes, the packet length of the encryption algorithm is 16 bytes, and the closest integer multiple of the encryption algorithm packet length is 128 bytes, so the data length of the padding part is 8 bytes.
[0052] Step 202: Fill data for the original message.
[0053] In this step, 8 bytes of stuffing data are f...
Embodiment 2
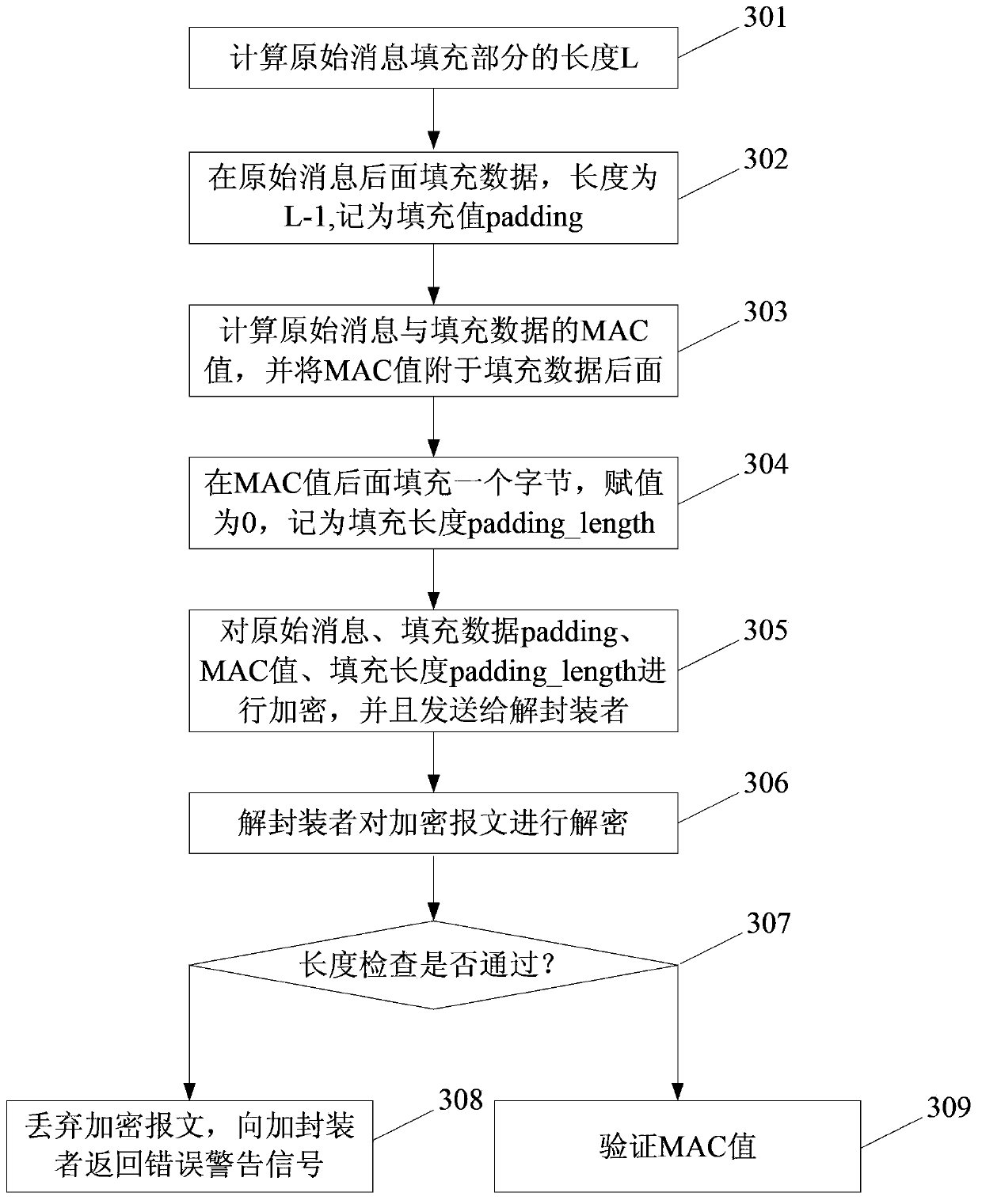
[0066] The technical solution in method embodiment 1 can be extended to a general solution for implementing MEE-CBC type algorithm suites in various security protocols. When it is specific to the application scenario of the TLS / SSL protocol, the present invention also provides an alternative solution to complete the defense timing The purpose of the invention of the attack, this scheme is shown in the second method embodiment, and this embodiment still uses the data parameters of the first method embodiment.
[0067] image 3 It is a flow chart of the method embodiment 2. This embodiment takes the application scenario of a specific TLS / SSL protocol as an example to demonstrate the technical solution of the present invention, including the following steps:
[0068] Step 301: Calculate the length L of the padding part of the original message.
[0069] In this step, the original message is 100 bytes, the MAC length is 20 bytes, the block length of the encryption algorithm is 16 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com