A hardware-based dynamic data protection method for embedded system
An embedded system, dynamic data technology, applied in digital data protection, internal/peripheral computer component protection, electrical digital data processing, etc., to achieve the effect of reducing performance loss, system performance loss, and shortening delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
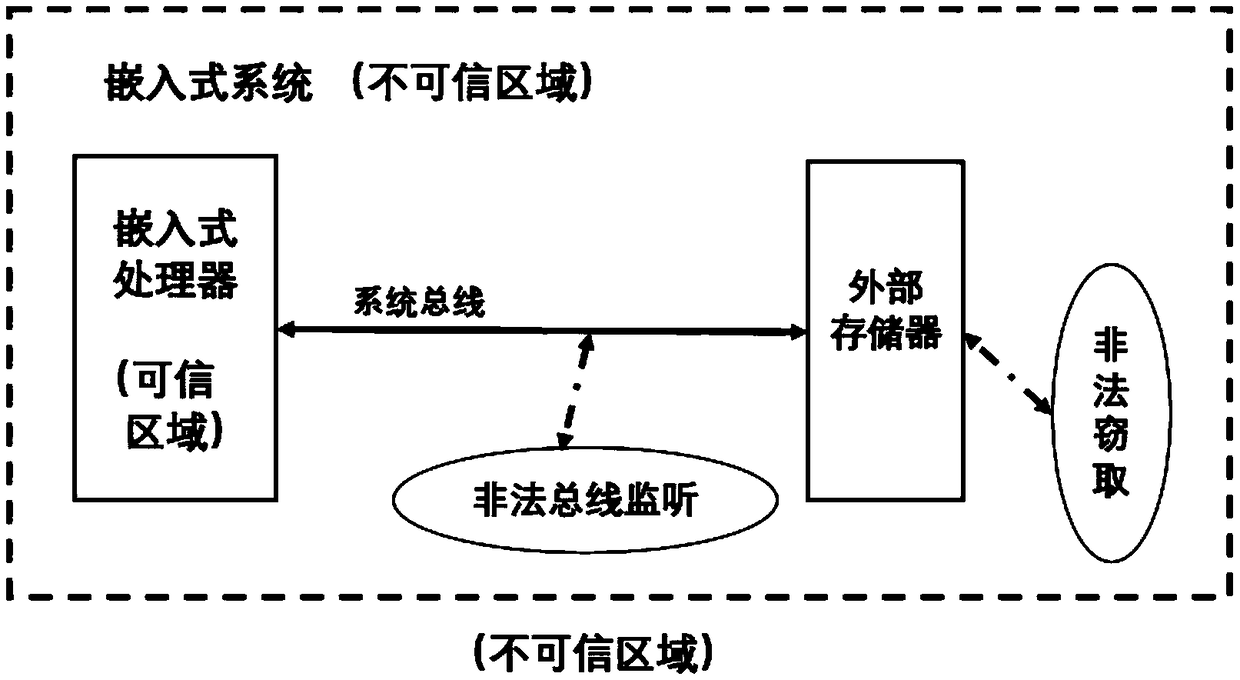
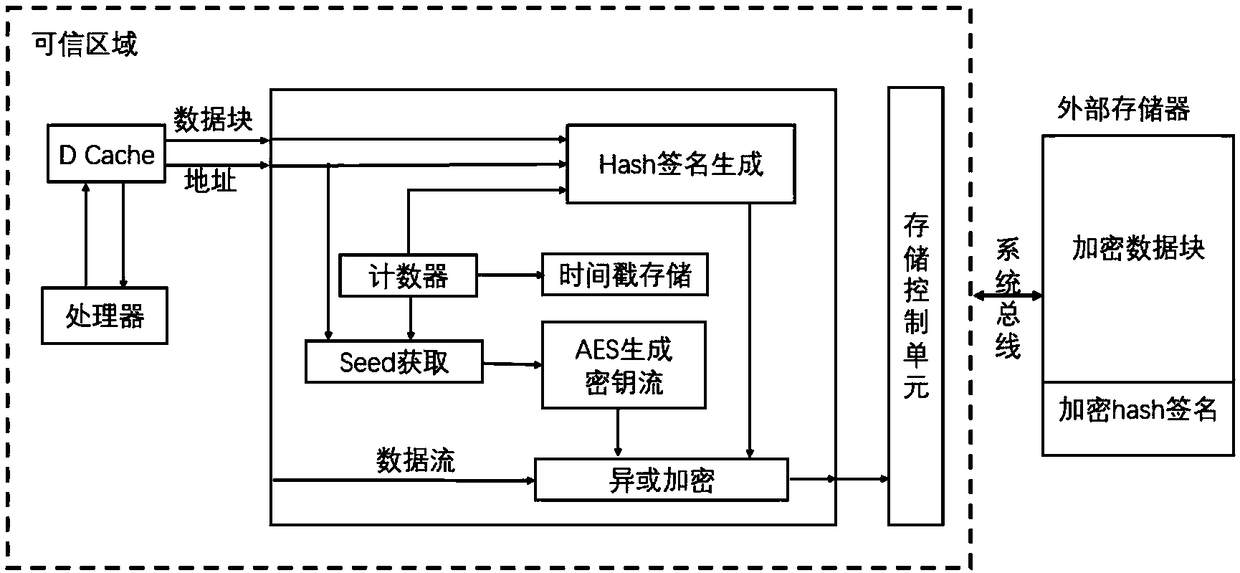
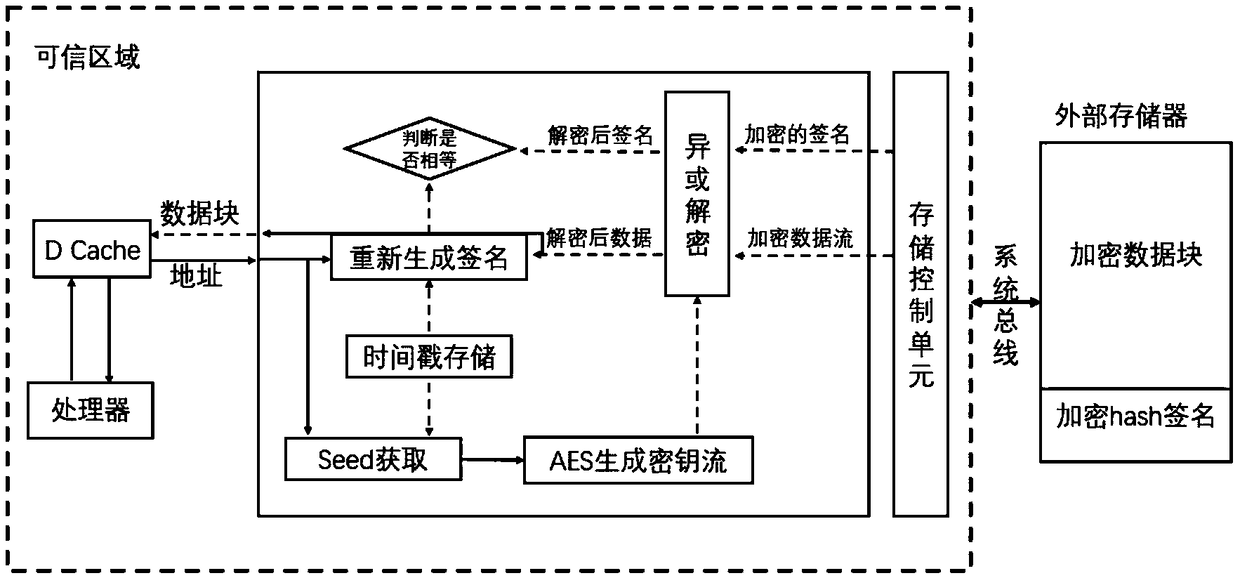
[0049] For the embedded system data threat model proposed by the data protection method in the present invention, see figure 1 As shown, we believe that the processor chip is a trusted area, which mainly defends against attacks that occur off-chip and on the bus, and protects the confidentiality and integrity of on-chip data. It adopts lightweight hash method and stream encryption method, and adds a security protection mechanism between the data buffer of the embedded system and the external memory. The security module is located in the trusted area of the chip. During the program running, when the data cache When the device misses the target and exchanges data blocks with the external memory, the security module provides confidentiality and integrity protection for the data blocks stored off-chip. When the data buffer writes data to the external memory, see figure 2 As shown, the security module calculates the hash value of the data block and uses it as the verification i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com