vTPM private information protection method based on label
A technology for private information and encrypted information, which is applied in the field of trusted computing and virtualization security, can solve the problems of not considering the security of private information, the weak relationship between vTPM and virtual machine, and the non-migration of vTPM, so as to protect the integrity and facilitate management , the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
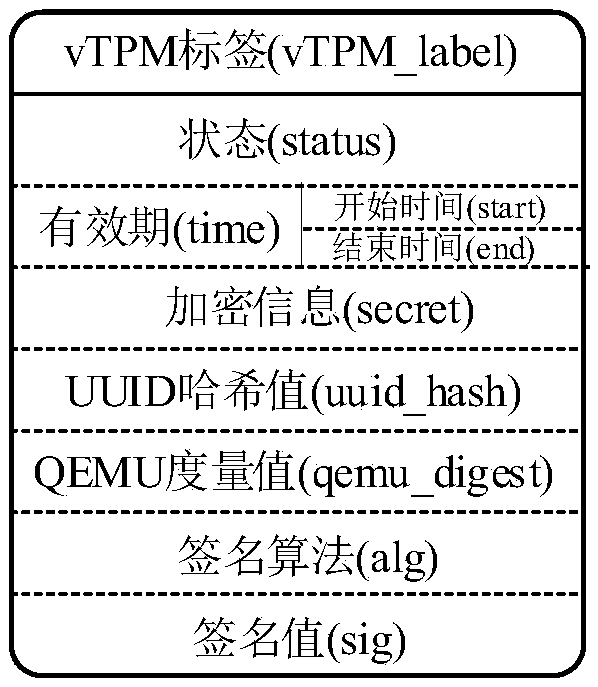
[0047] figure 1 Describes the detailed structure of the vTPM label, including: status field (status), validity period field (time, including start time start and end time end), encryption information field (secret), UUID hash value field (uuid_hash), QEMU measurement value field (qemu_digest), signature algorithm field (alg), signature value field (sig).
[0048] (1) Status (status): vTPM labels have two states of existence, local state and migration state; (2) Validity period (time): vTPM labels are valid within the time period [start, end], expired vTPM labels need (3) Encrypted information (secret): the ciphertext of the symmetric encryption key used for vTPM private information protection, which is encrypted with the key RSA_local of the physical Trusted Platform Module; (4) UUID Hash value (uuid_hash): UUID is the unique identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com