Patents
Literature
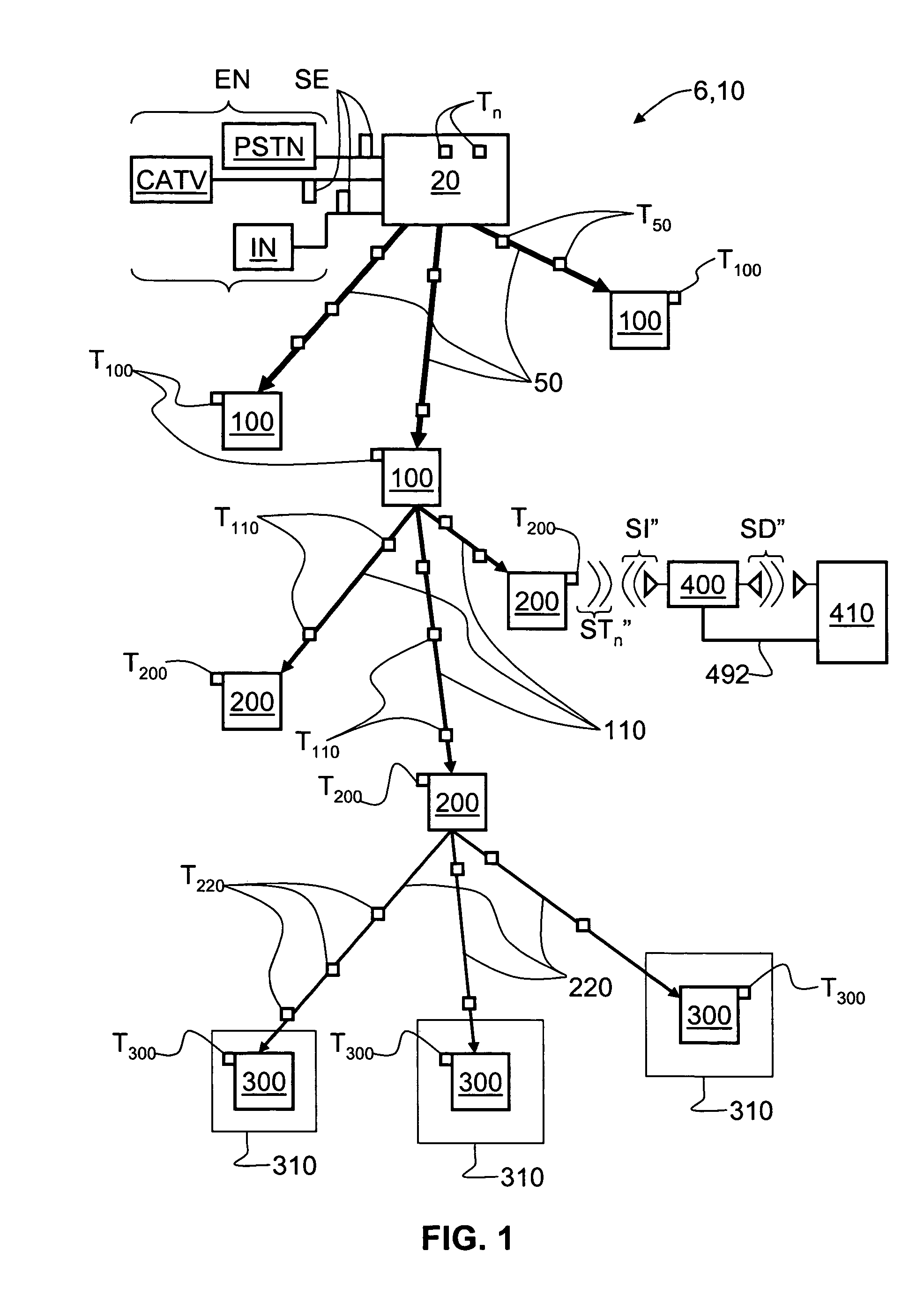
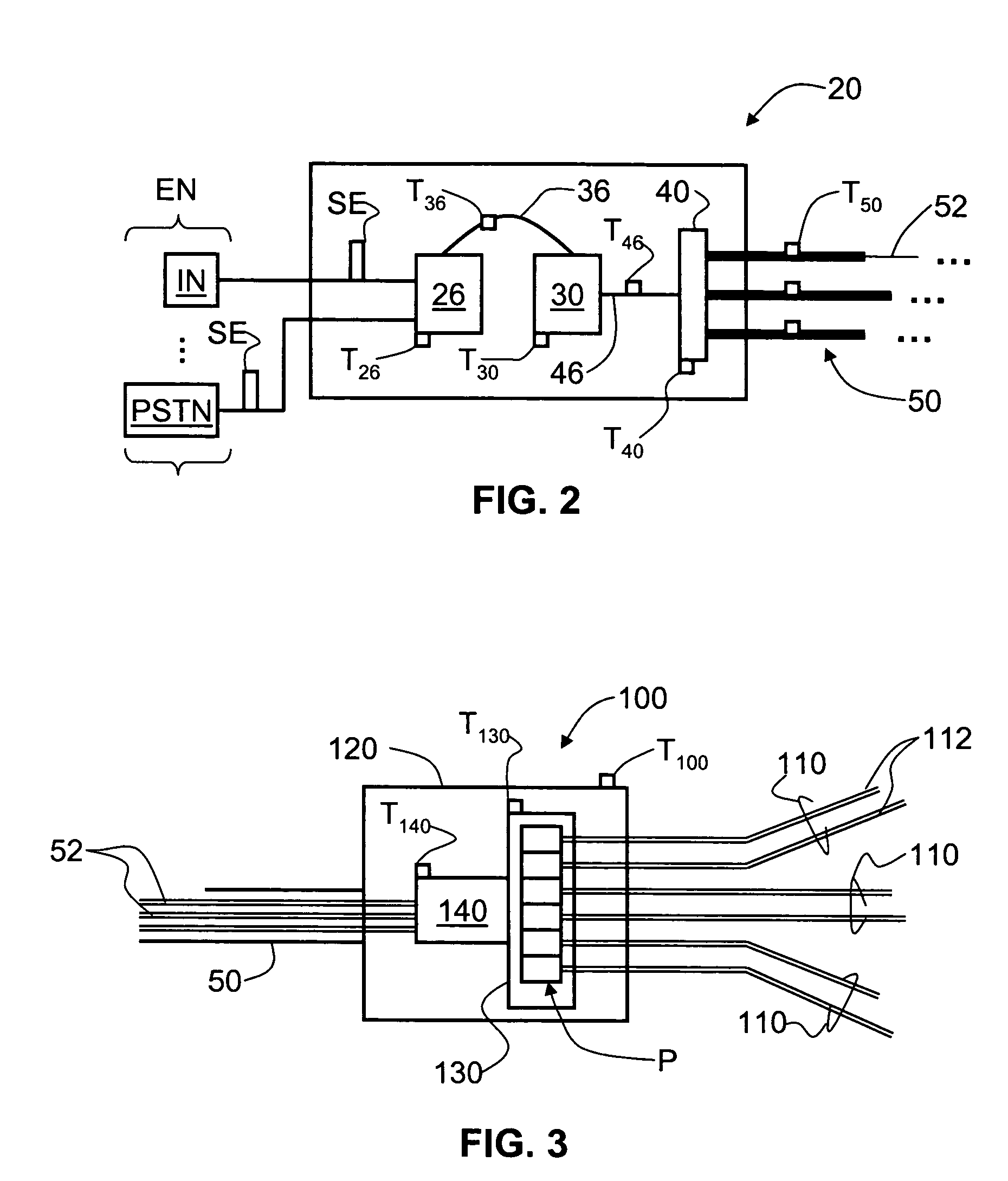
813 results about "System deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
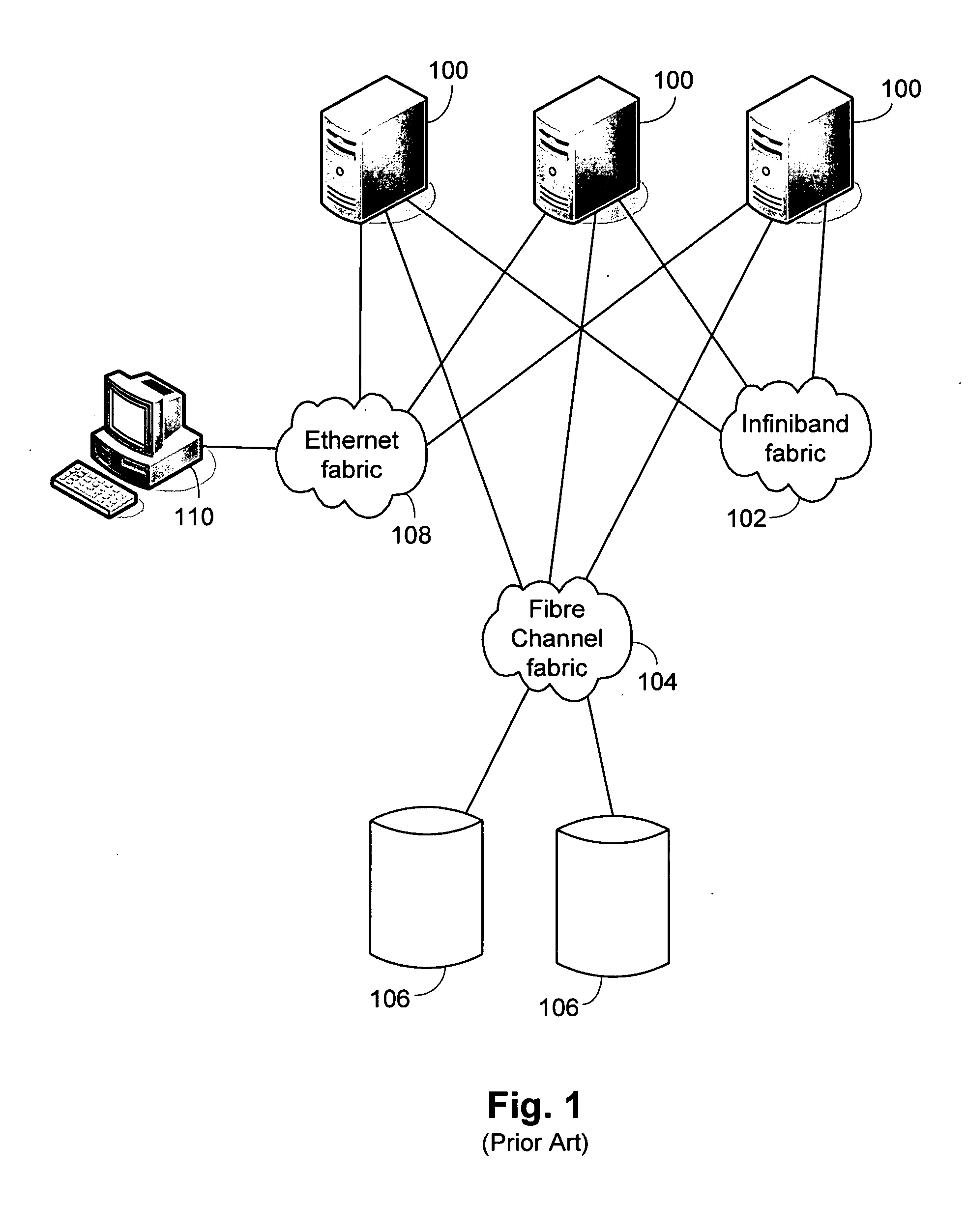
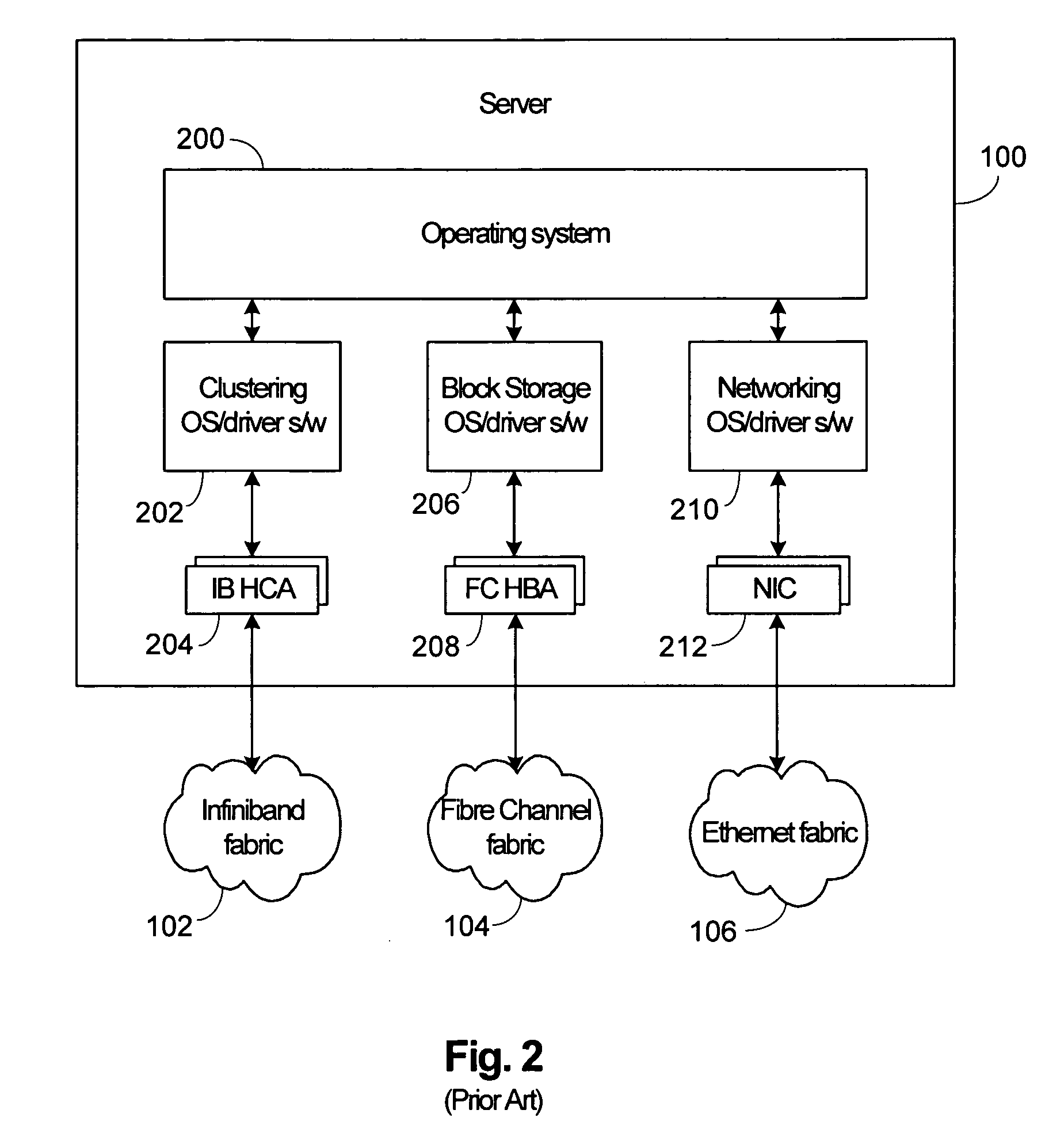
The deployment of a mechanical device, electrical system, computer program, etc., is its assembly or transformation from a packaged form to an operational working state. Deployment implies moving a product from a temporary or development state to a permanent or desired state.
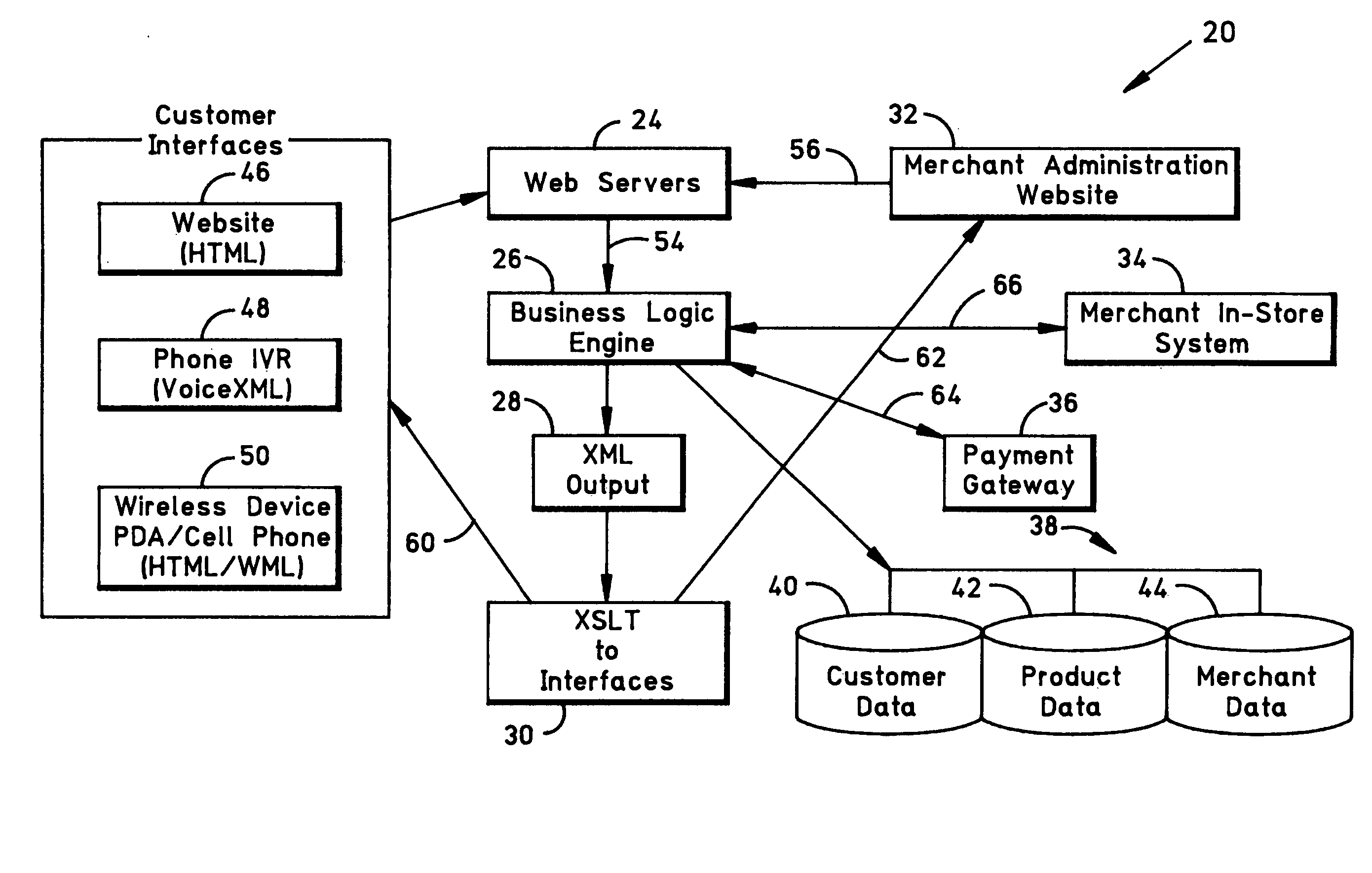
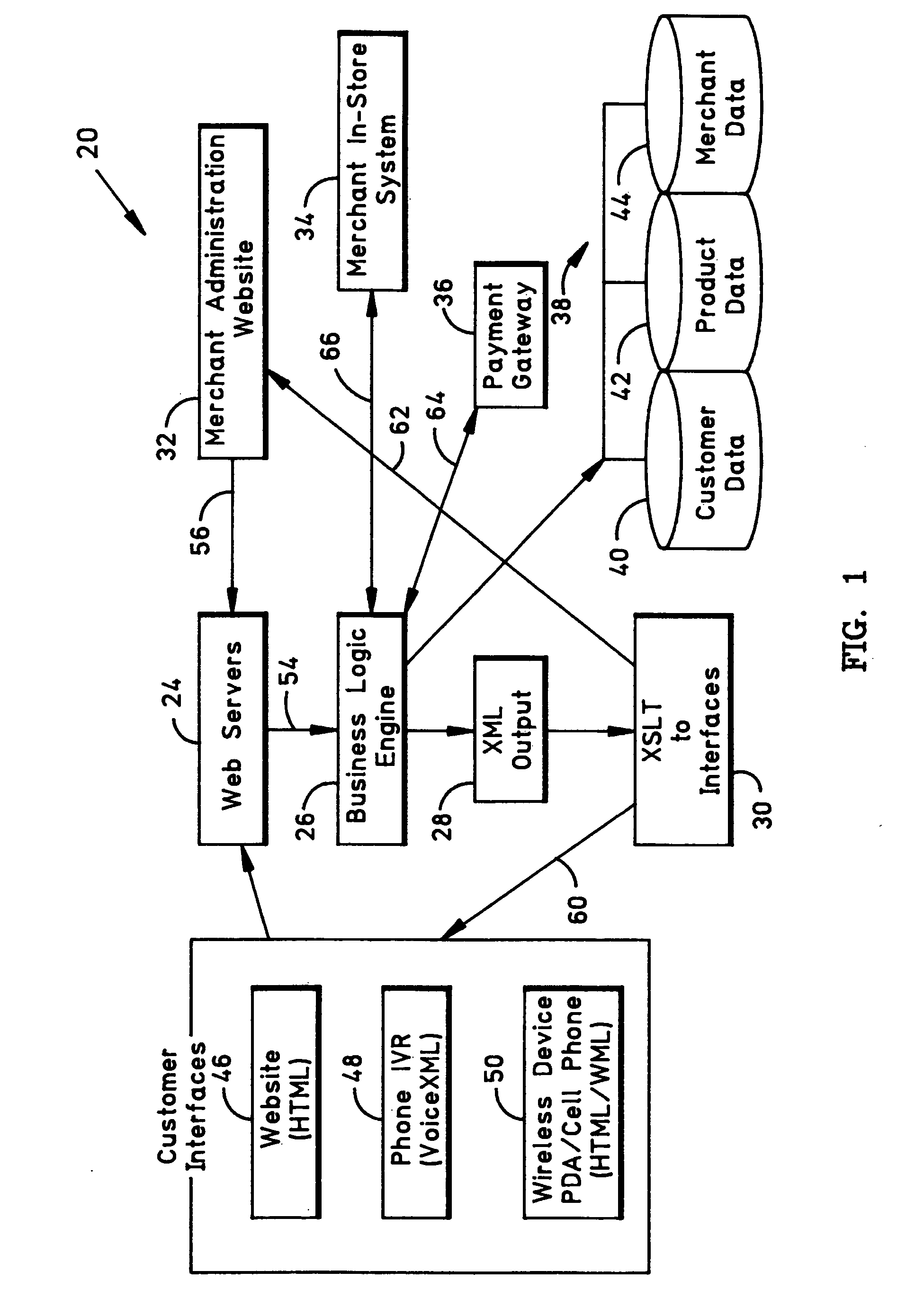
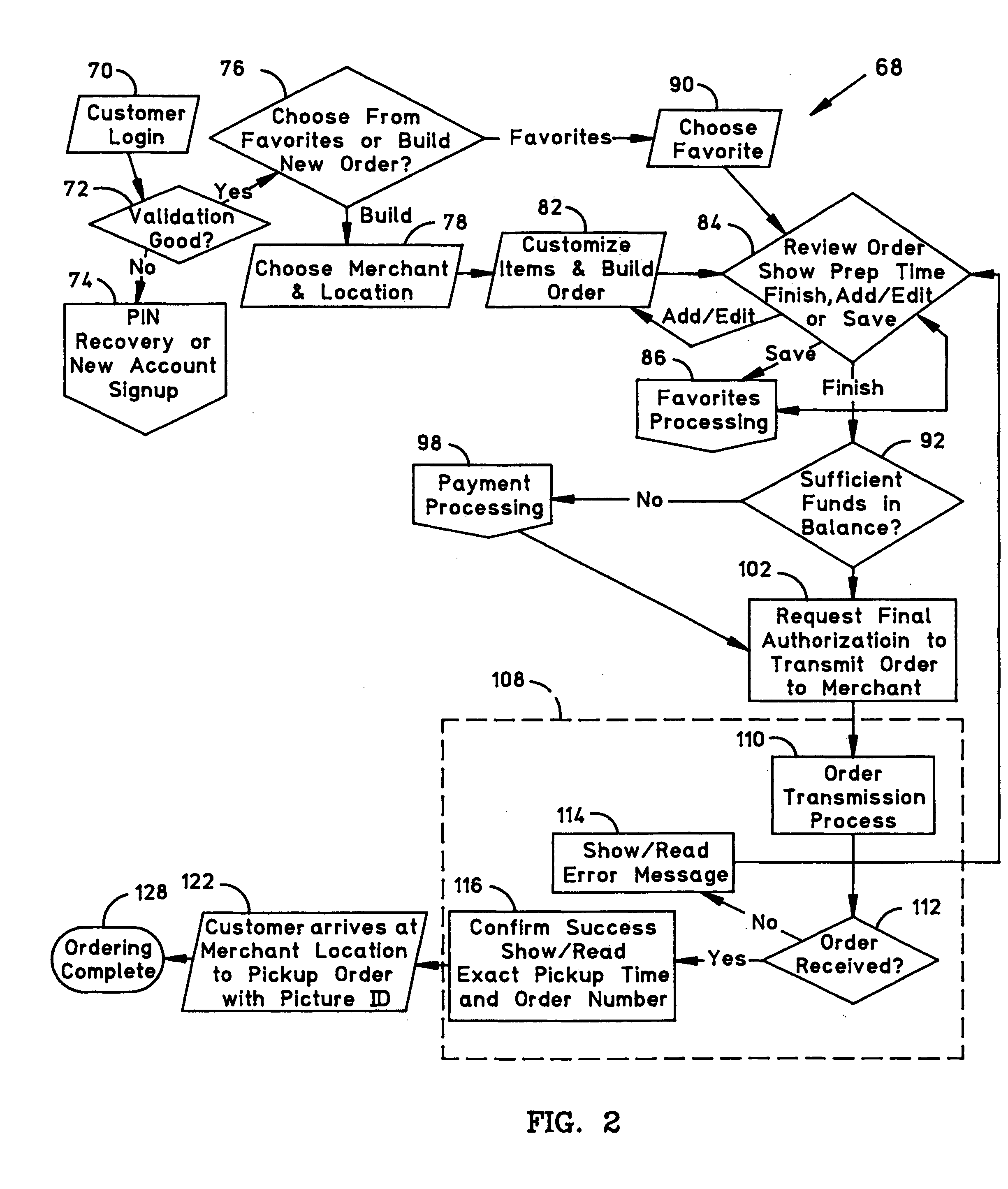
Food order fulfillment system deploying a universal in-store point-of-sale (POS) for preparation and pickup scheduling
InactiveUS20060178943A1Eliminate fulfillment delayEliminate delaysCommerceLogisticsOrder fulfillmentInteractive Voice Response Technology
A remote ordering system including a universal in-store point-of-sale (POS) system deployed to allow a remote-ordering user to customize, pay and transmit a food order to a vending merchant and to provide means for transmitting to the user a confirmation of receipt of the food order in real time together with a merchant commitment to a precise pickup time, thereby facilitating food order fulfillment immediately upon user arrival at the committed pickup time. One aspect of the invention allows a “curb-side” remotely-ordering user to notify the vending restaurant of arrival for fulfillment through a telephone call to an interactive voice response element, which then transmits an arrival notification message to the restaurant.
Owner:ROLLINSON JOSEPH R +1
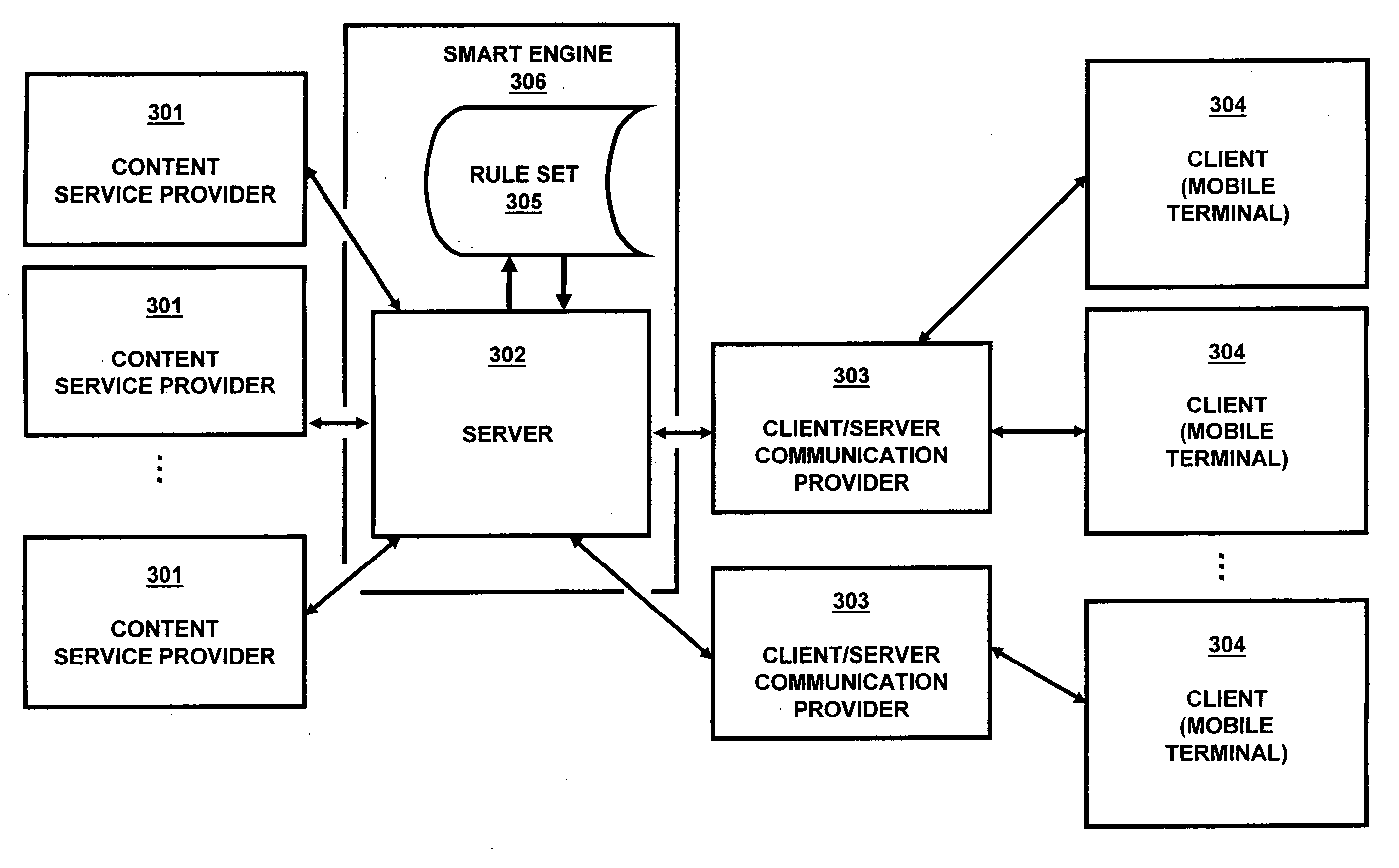
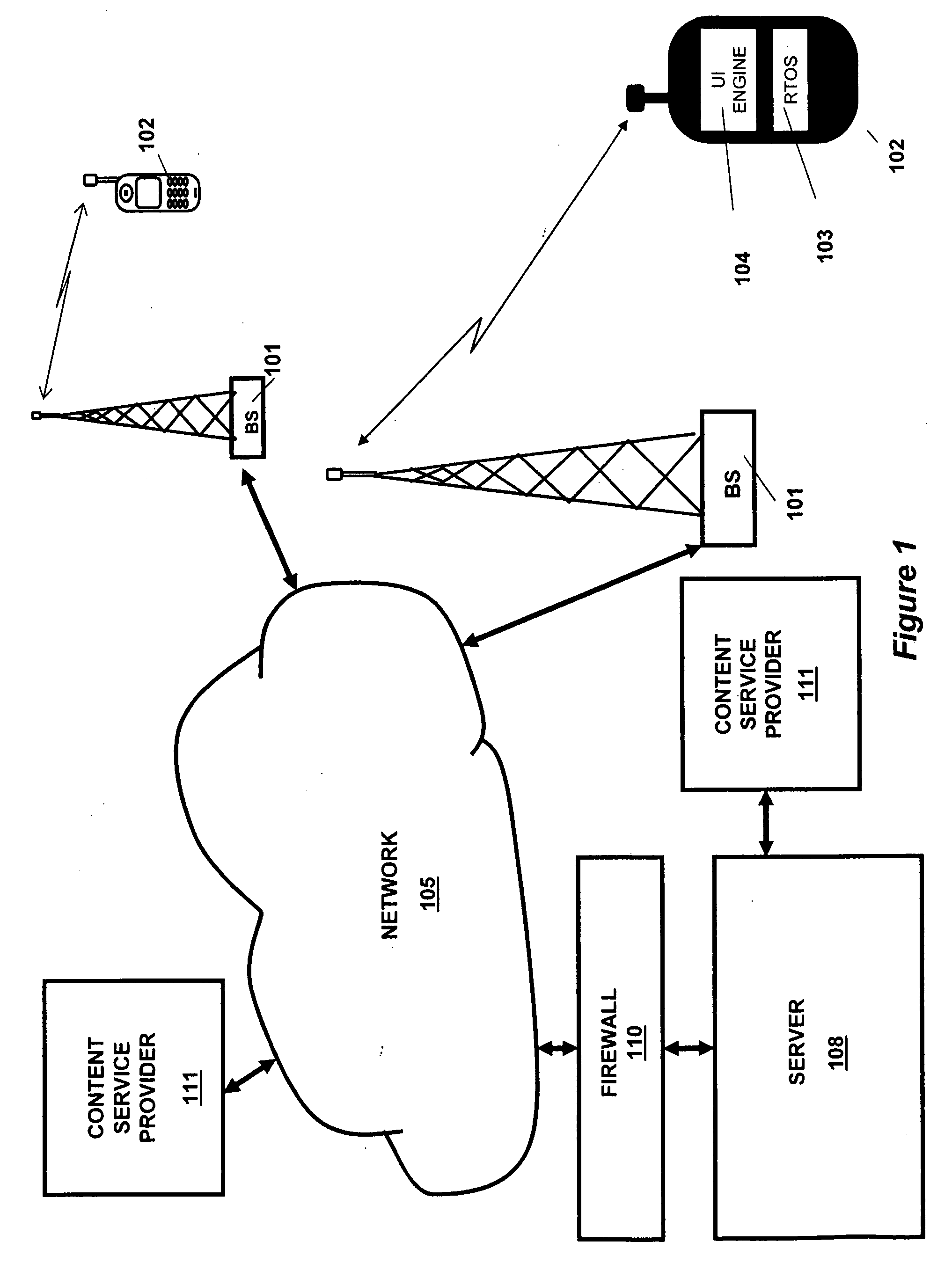
System and method for flexible user interfaces
InactiveUS20070061488A1Reduces application software developmentReduce maintenance costsDigital data information retrievalMultiple digital computer combinationsApplication program softwareSoftware update
A method and system for implementing a user interface for providing a data service in a mobile client using a server with knowledge of the client's hardware and software capabilities to modify data content and display rules for an improved user interface on the client. Data may be cached on the client to improve application response time and provide a standalone application capability for the client. The automatic conversion of newly developed applications to a plurality of clients with differing hardware and software capabilities reduces application software development and maintenance costs. Software updates and bug fixes can be deployed with the same method and system. An interoperable array of adapters for reporting, billing, and format conversions is also described.
Owner:TRILIBIS
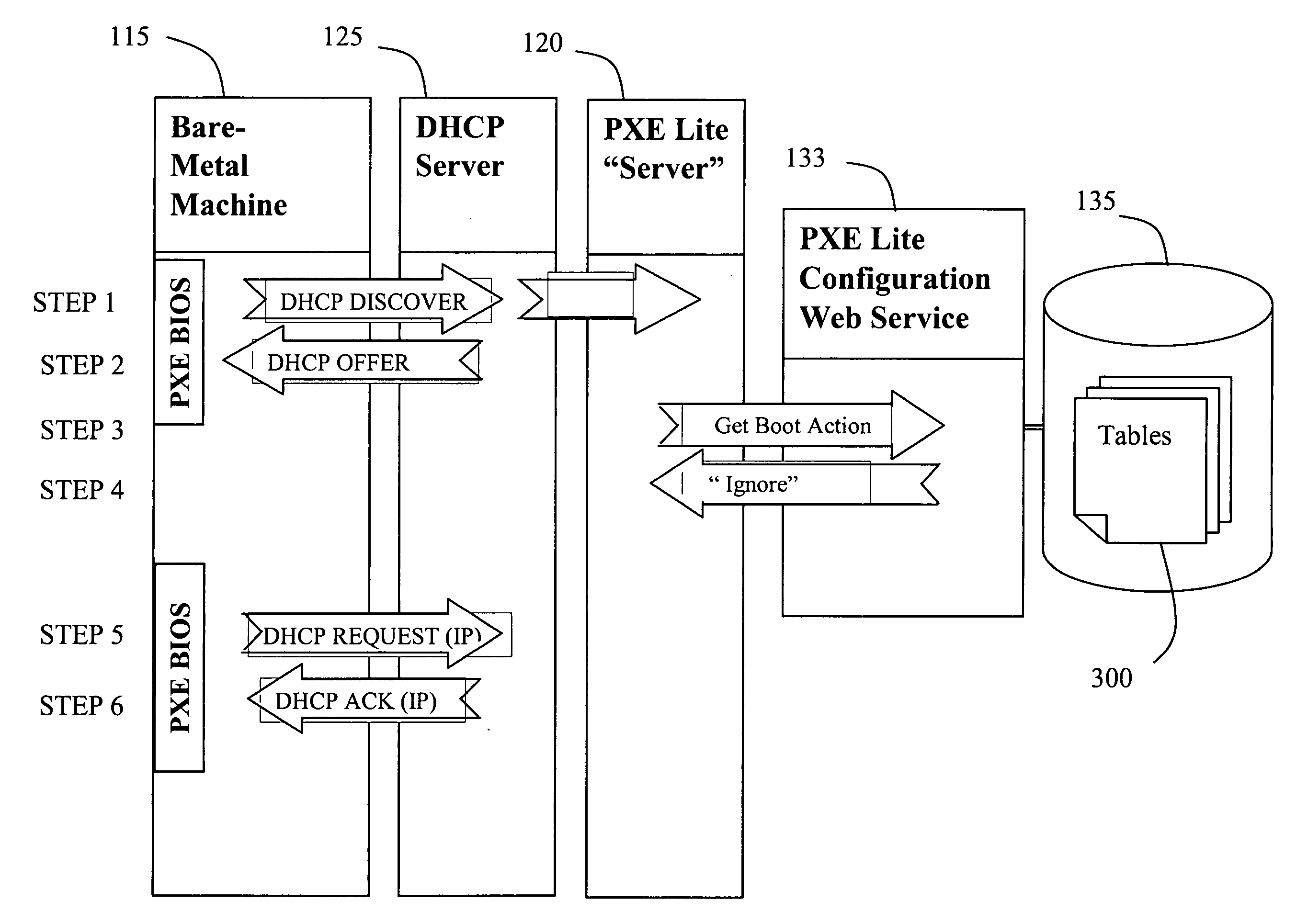
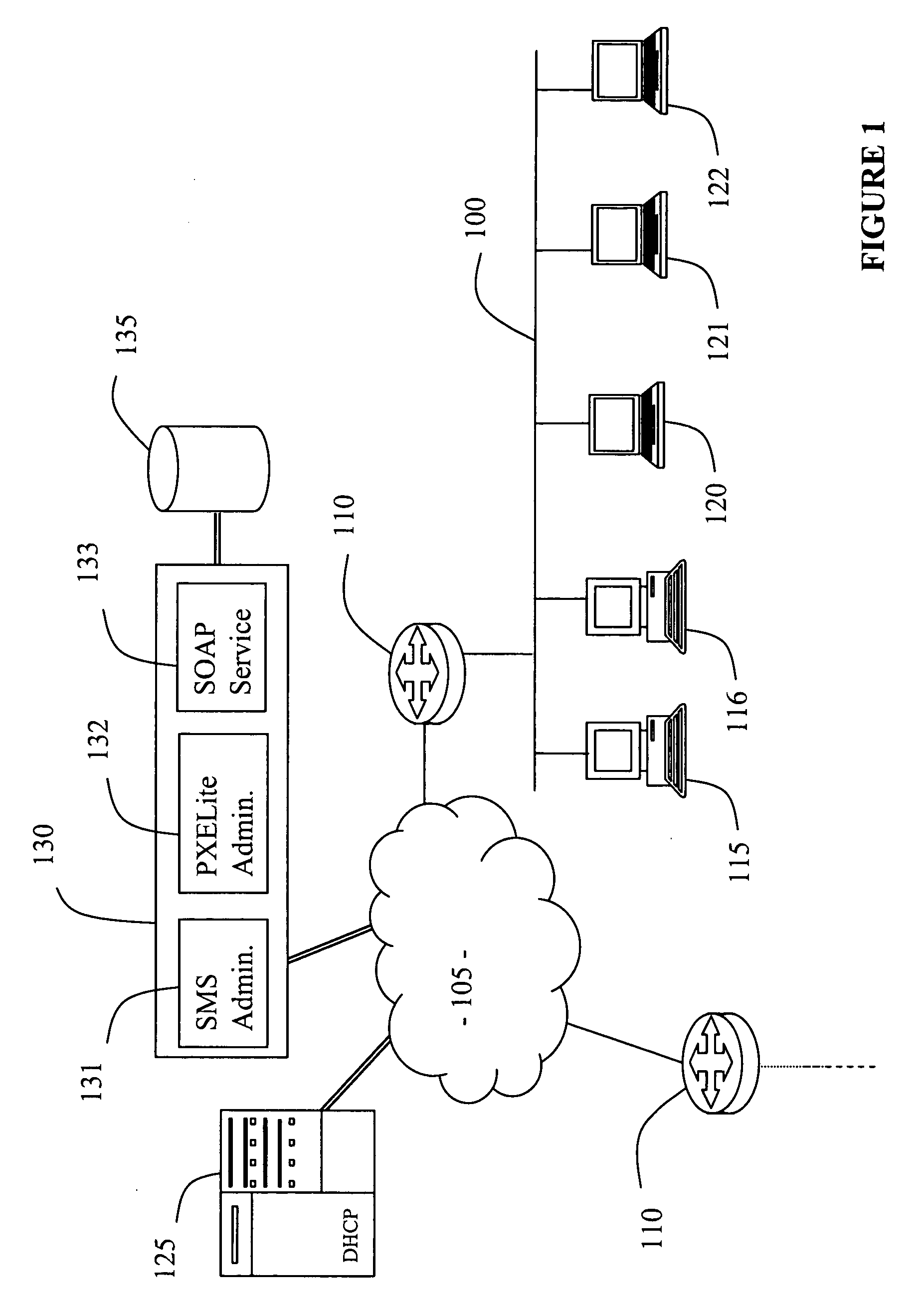
Network booting apparatus and method
ActiveUS20080155245A1Avoid problemsEasy to solveDigital computer detailsProgram controlOperational systemNetwork booting
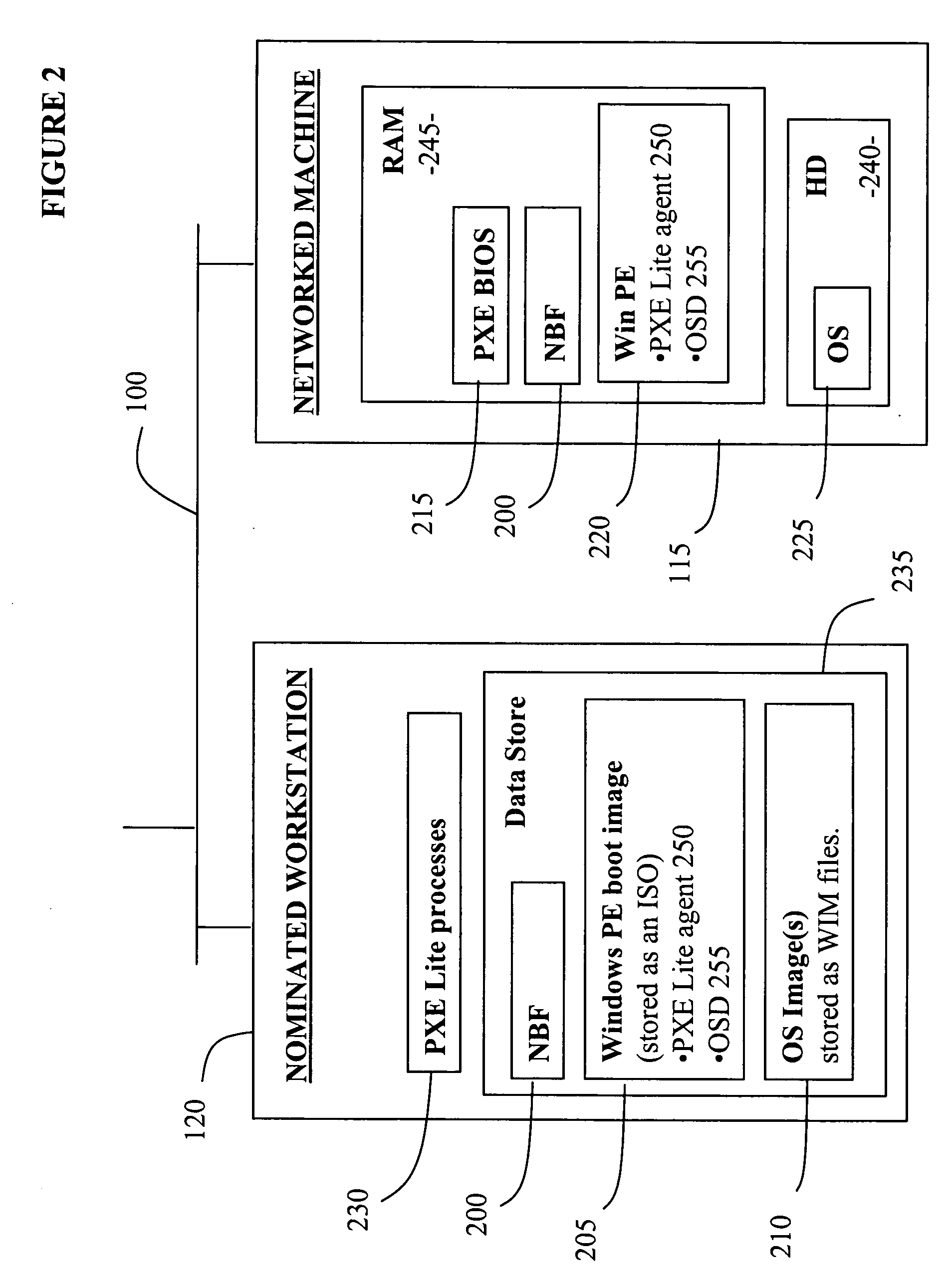
An operating system deployment arrangement provides a database connected to a network for use in monitoring the boot status of machines connected to sub-networks of the network. A workstation connected to a sub-network is adapted to act as a server for a pre-installation environment to machines newly connecting to the sub-network or at the same geographical location. The workstation carries a program for detecting boot initiation messages broadcast on the sub-network and for progressing booting of newly connecting machines in accordance with boot action data held by the database. In particular, the workstation also sends a software agent and operating system deployment processes to a newly connected machine and the agent takes over progression of the booting process from the workstation. The data held in the database for any one machine is updated as booting progresses. Flexibility is provided both in administration of the boot action data held in the database and by means of user interaction software loaded to a newly connected machine in the course of booting.
Owner:1E LTD
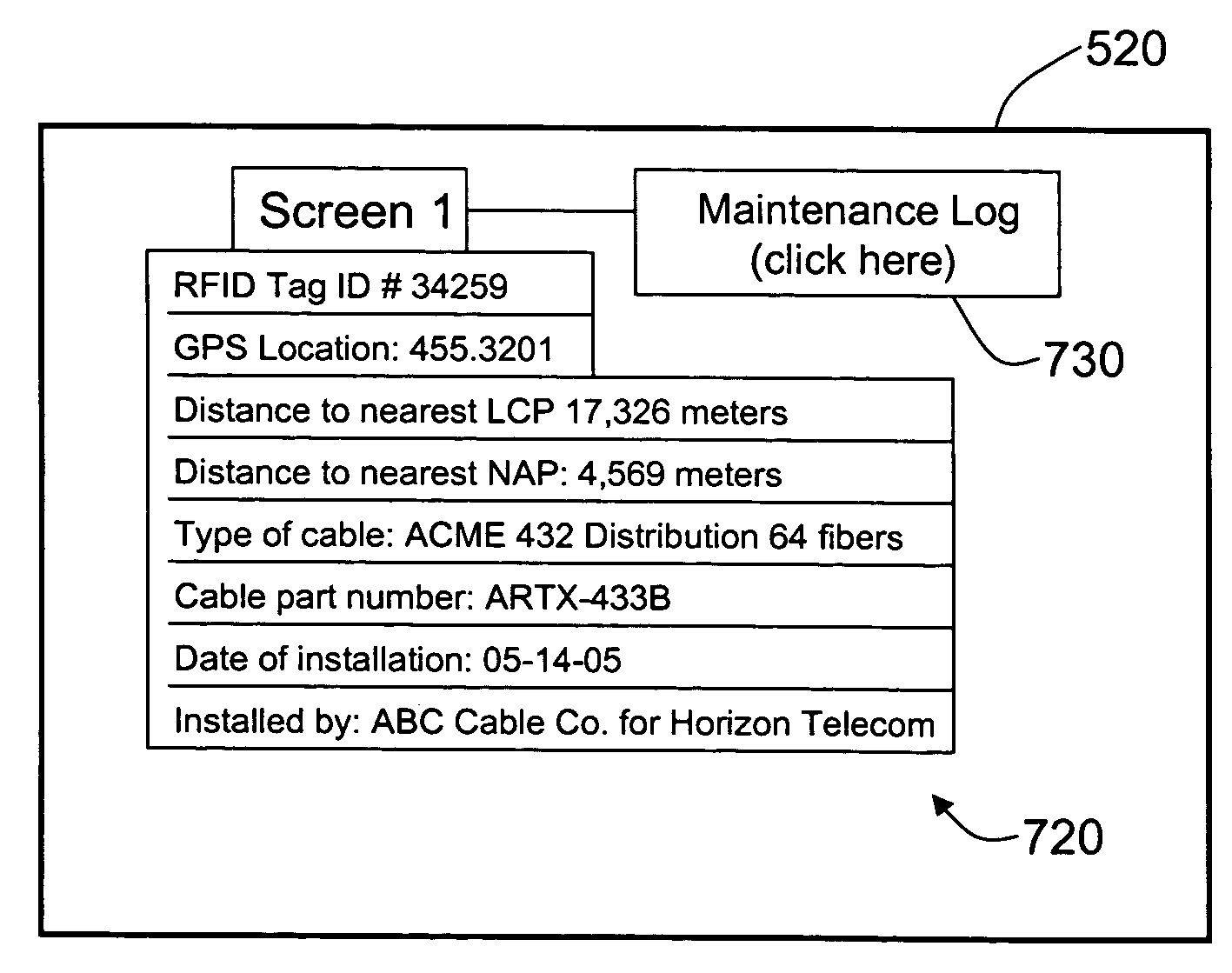
RFID Systems and Methods for Optical Fiber Network Deployment and Maintenance
InactiveUS20090097846A1Multiplex system selection arrangementsElectromagnetic network arrangementsNetwork deploymentService personnel
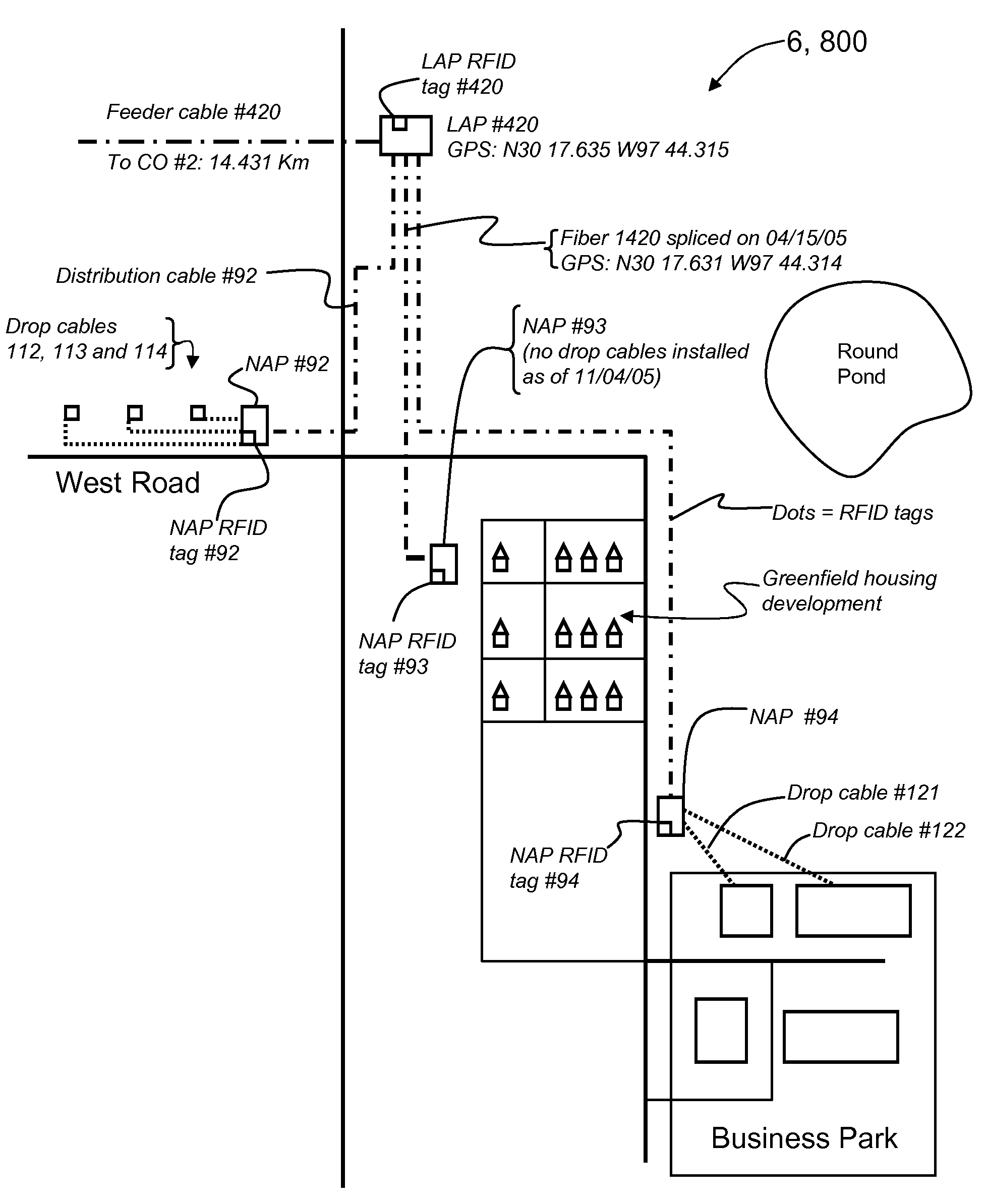
An optical-fiber-network (OFN) radio-frequency identification (RFID) system for deploying and / or maintaining and / or provisioning service and / or locating faults in an OFN. The system includes a plurality of OFN components, and at least one RFID tag that includes RFID tag data that has at least one property of the OFN component associated with the RFID tag. The RFID tag data is written to and read from the RFID tags using one or more mobile RFID readers either prior to, during or after deploying the OFN components. An OFN-component-data database unit is used to store and process the RFID tag data and is automatically updated by the one or more mobile RFID readers. This allows for different maps of the OFN to be made, such as an inventory map and a maintenance map, and for the maps to be automatically updated. The OFN-RFID system allows for mobile automated operations and management of OFN components by service personnel, and provides for faster and more accurate OFN system deployment and maintenance.
Owner:CORNING CABLE SYST LLC
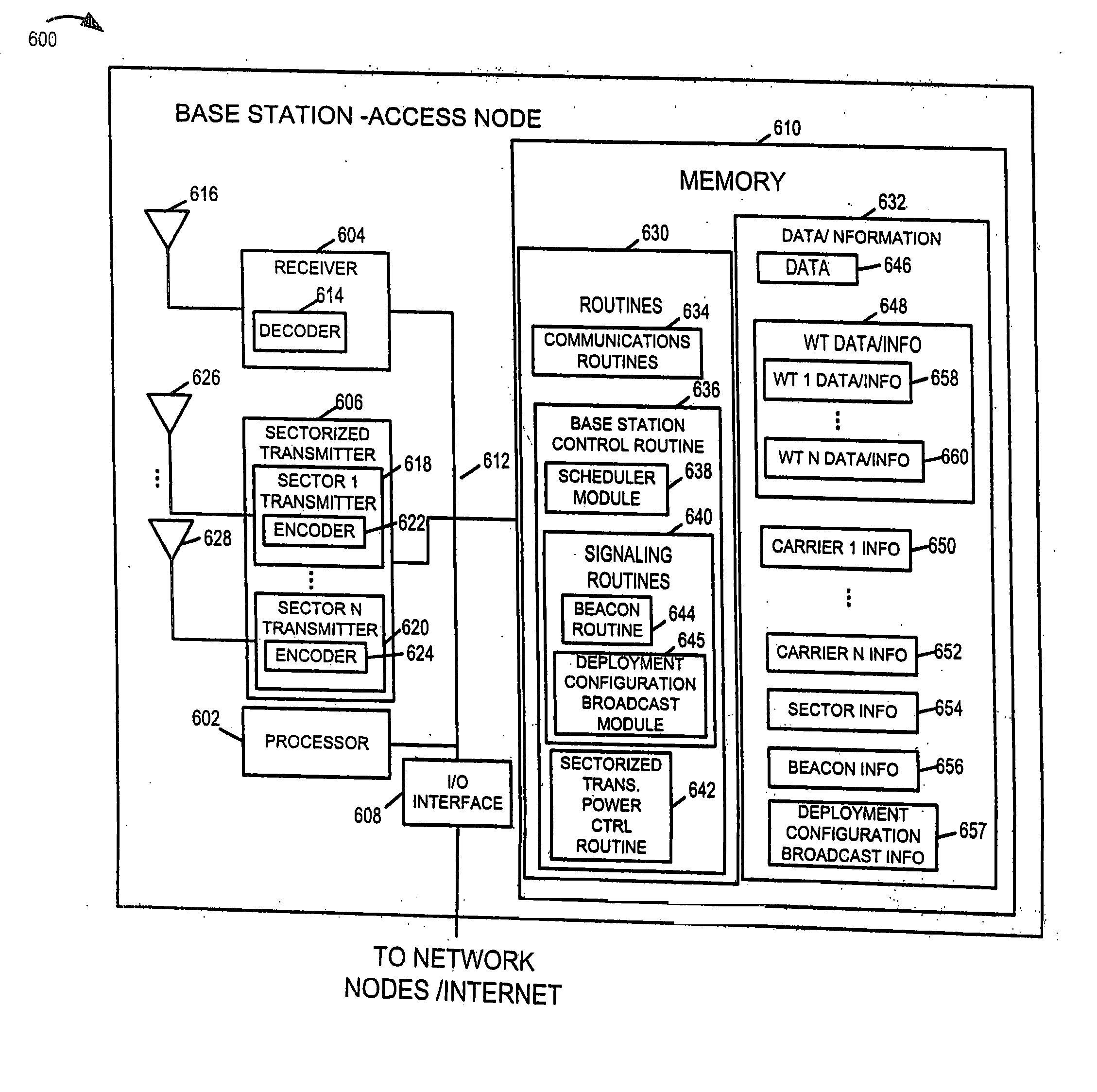
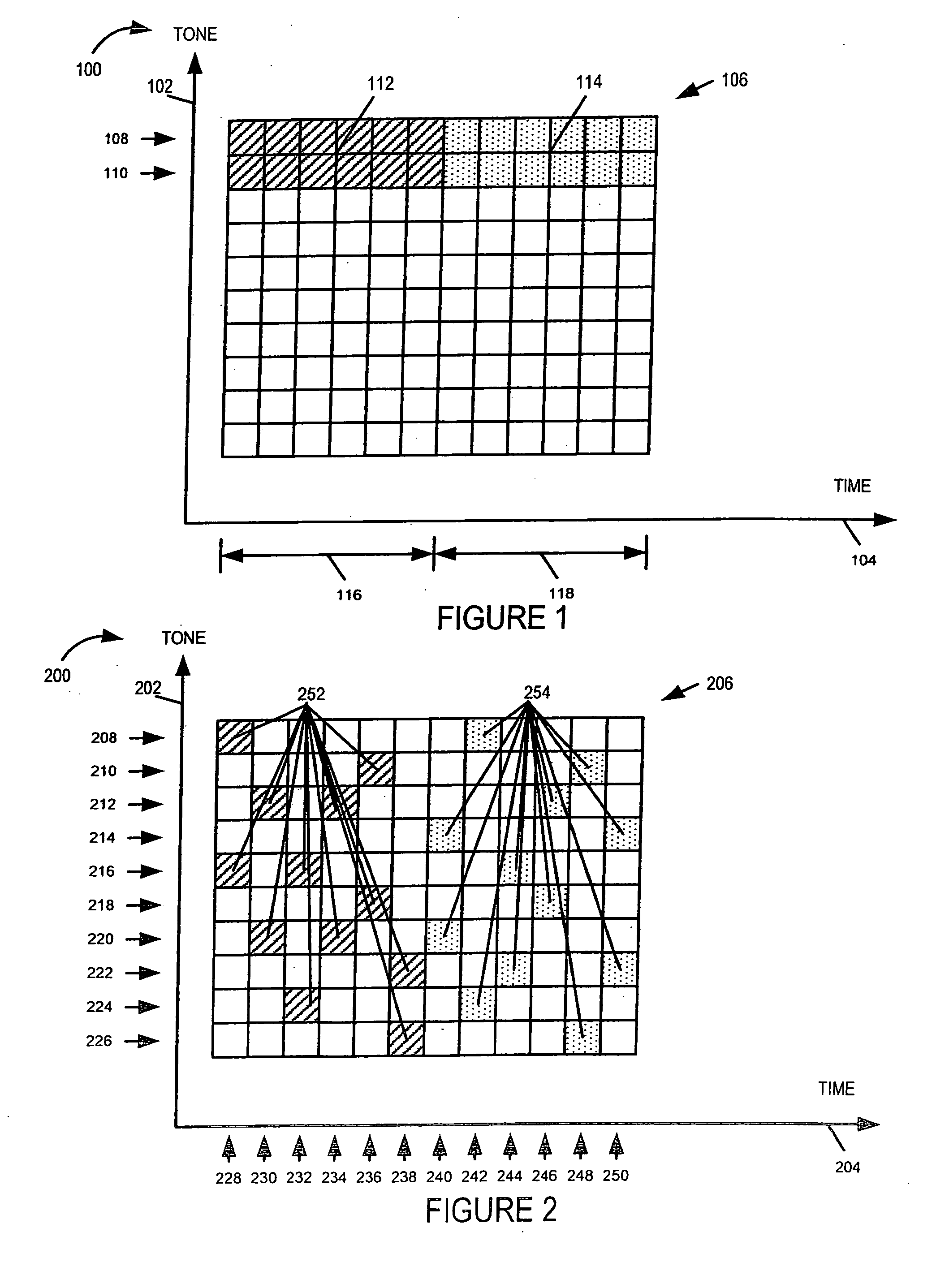
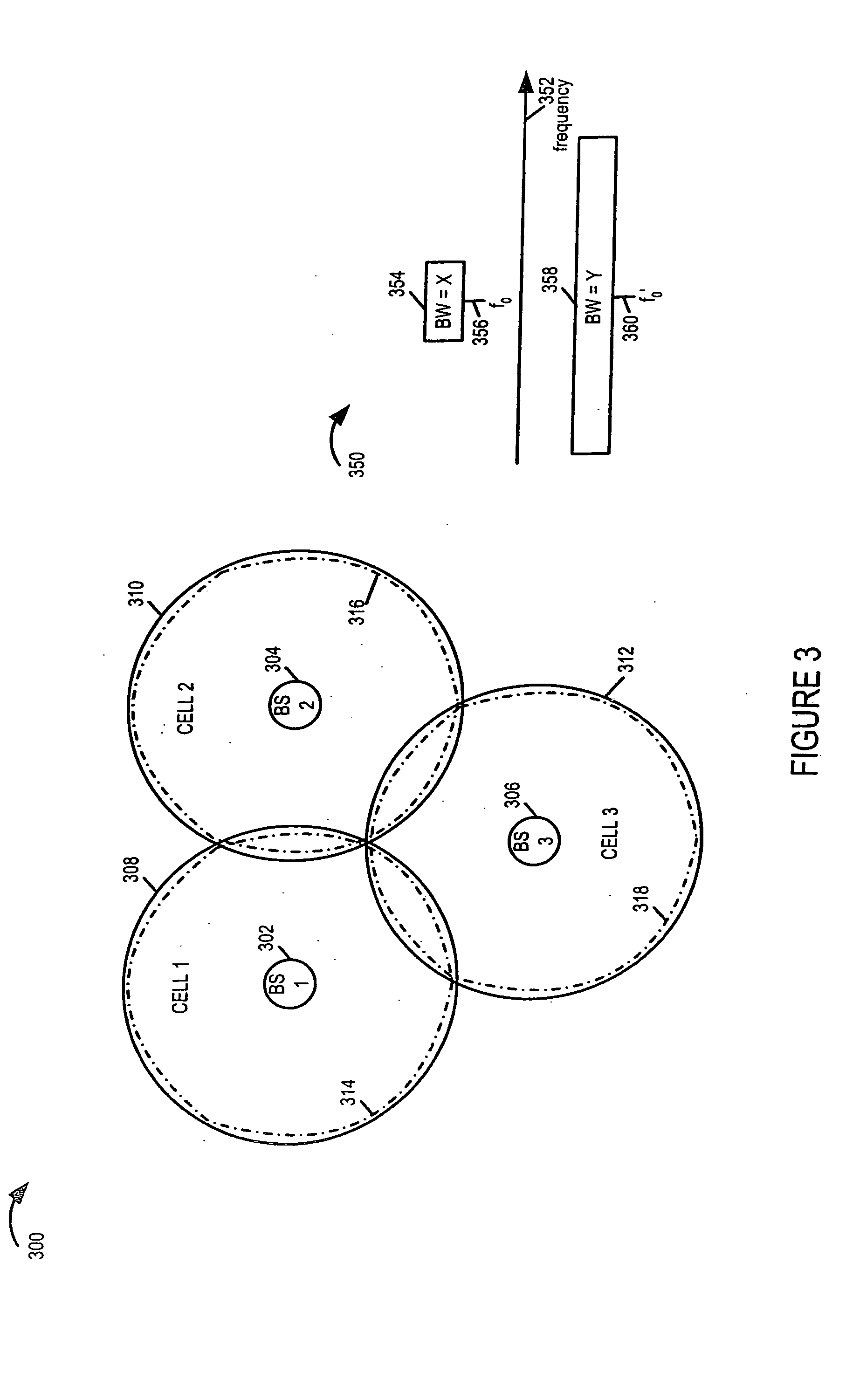
Multi-carrier communications methods and apparatus
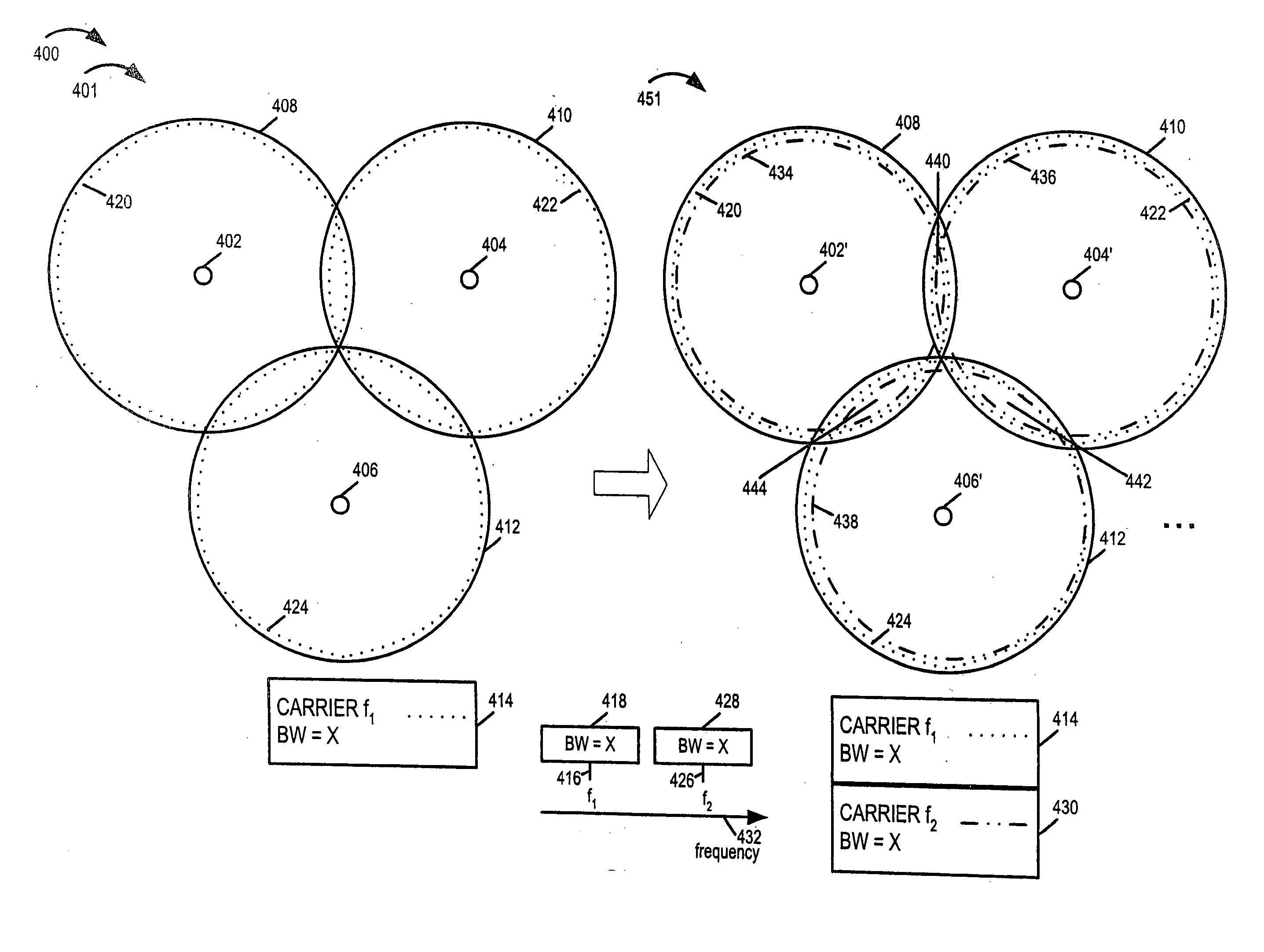
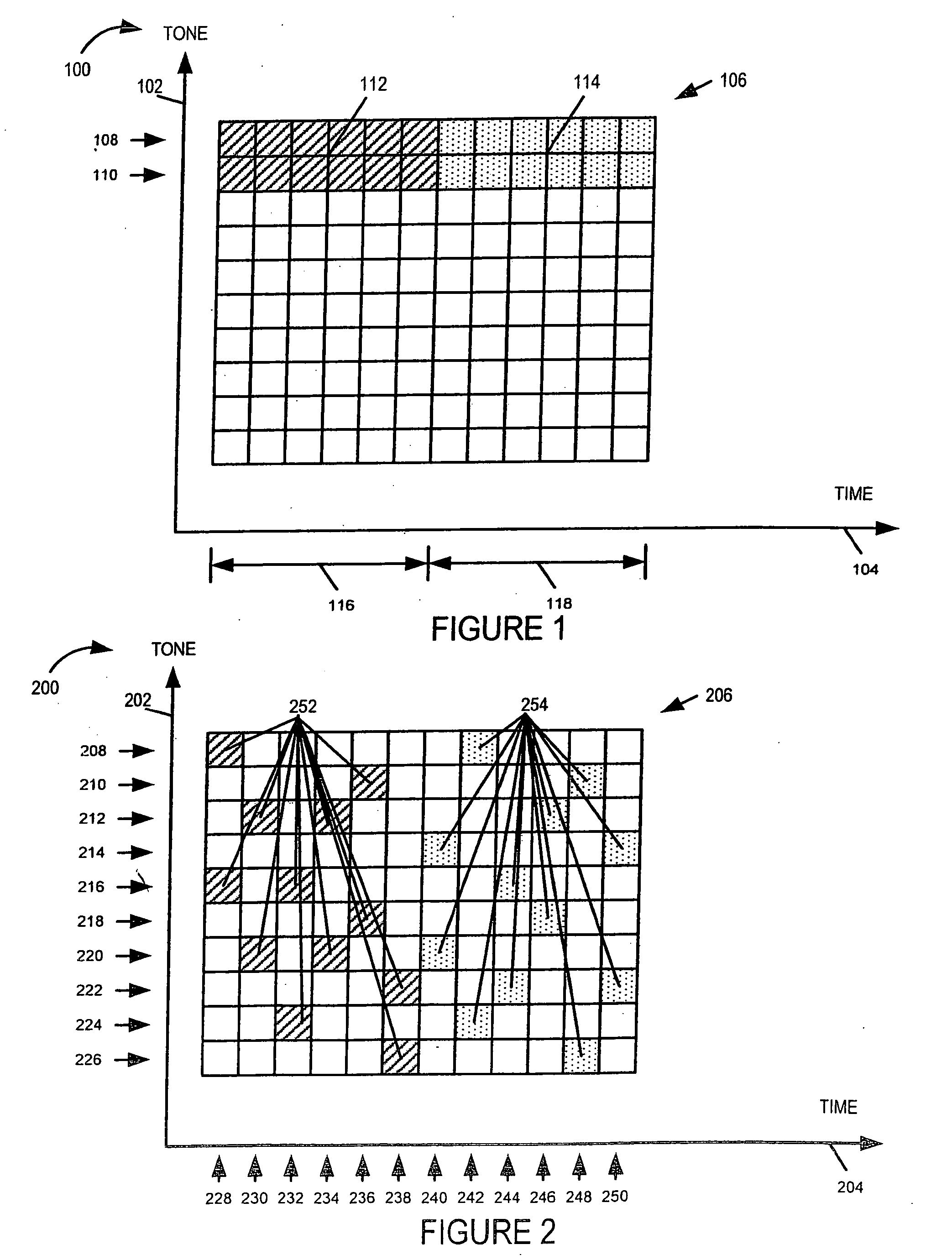
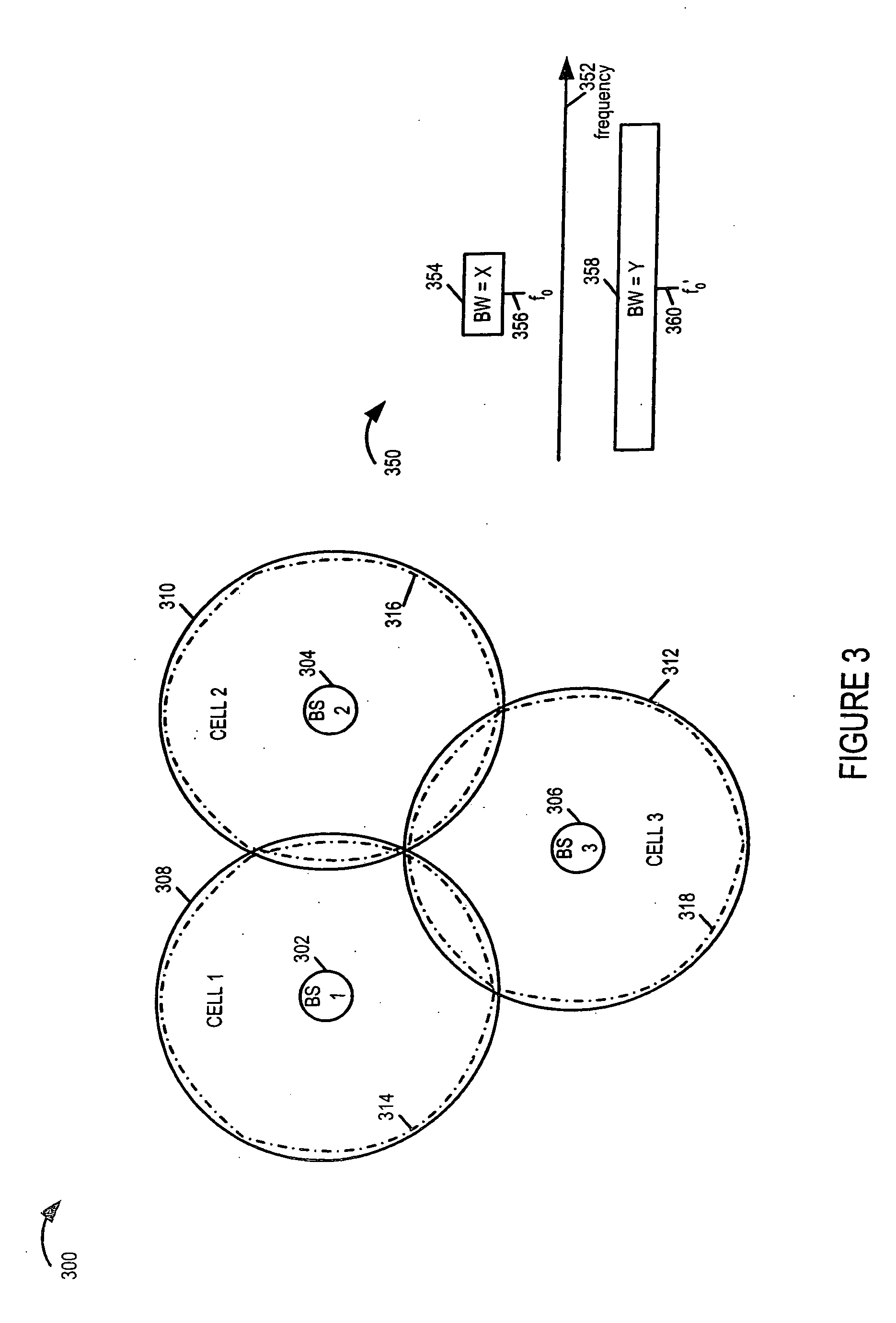
InactiveUS20050233752A1Reduce distractionsImprove robustnessTransmission path divisionCriteria allocationCommunications systemEngineering
Methods and apparatus for implementing a multi-carrier communications system are described. Various approaches to a phased system deployment and system configurations resulting from different levels of deployment are described. In addition mobile node and methods of operating mobile nodes in communications systems that may have different levels of deployment in different cells are described.
Owner:QUALCOMM INC
Automated building exterior cleaning apparatus
InactiveUS20060048800A1Easily and safely securedModulate activityPhotovoltaic supportsEnergy efficient ICTSystem configurationHigh rise
An automated exterior building cleaning system particularly well suited for cleaning the window exteriors on a high rise building. By way of example the system is deployed on a rooftop rail system traversed by a movable platform from which a washing head is deployed over the edges of the building and lowered on cables for cleaning the window surfaces and other building elements. The system is configured for remote monitoring and control and provides a number of novel elements and safety features.
Owner:RAST RODGER H +1
User interface system and method for implementation on multiple types of clients
InactiveUS20060077941A1Reduces application software developmentReduce maintenance costsInformation formatContent conversionApplication program softwareSoftware update
A method and system for implementing a user interface for providing a data service in a mobile client using a server with knowledge of the client's hardware and software capabilities to modify data content and display rules for an improved user interface on the client. Data may be cached on the client to improve application response time and provide a standalone application capability for the client. The automatic conversion of newly developed applications to a plurality of clients with differing hardware and software capabilities reduces application software development and maintenance costs. Software updates and bug fixes can be deployed with the same method and system.
Owner:TRILIBIS
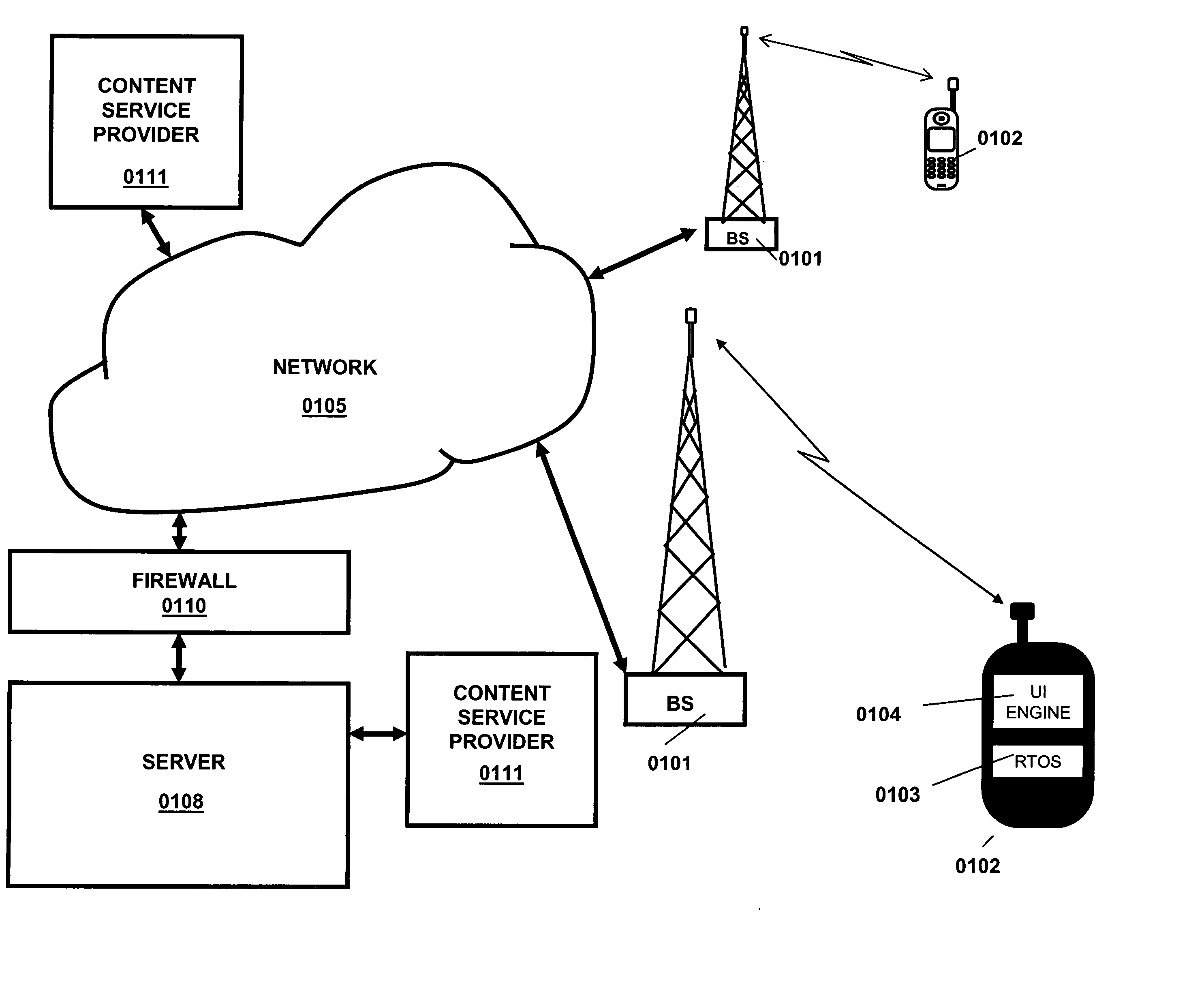
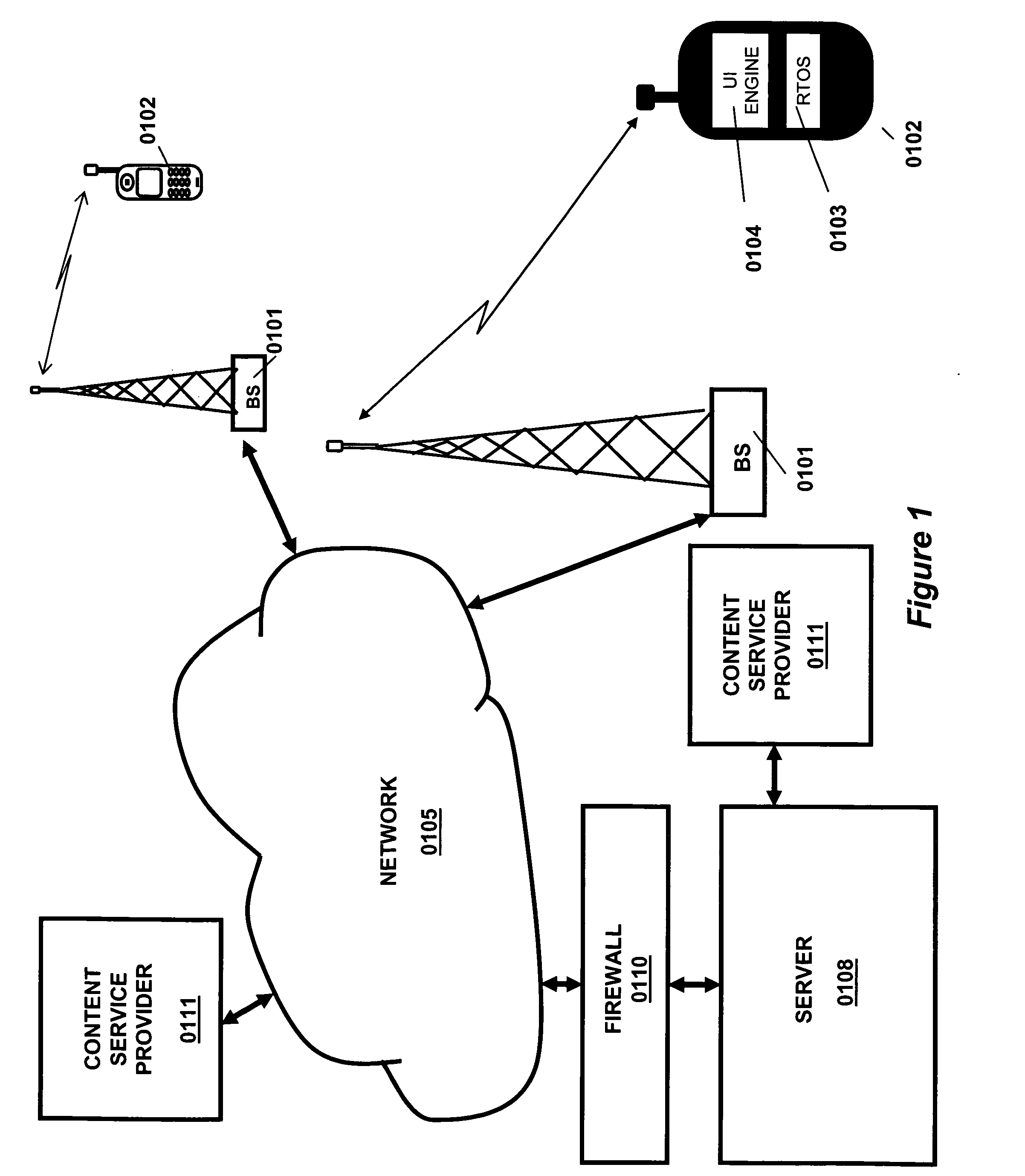
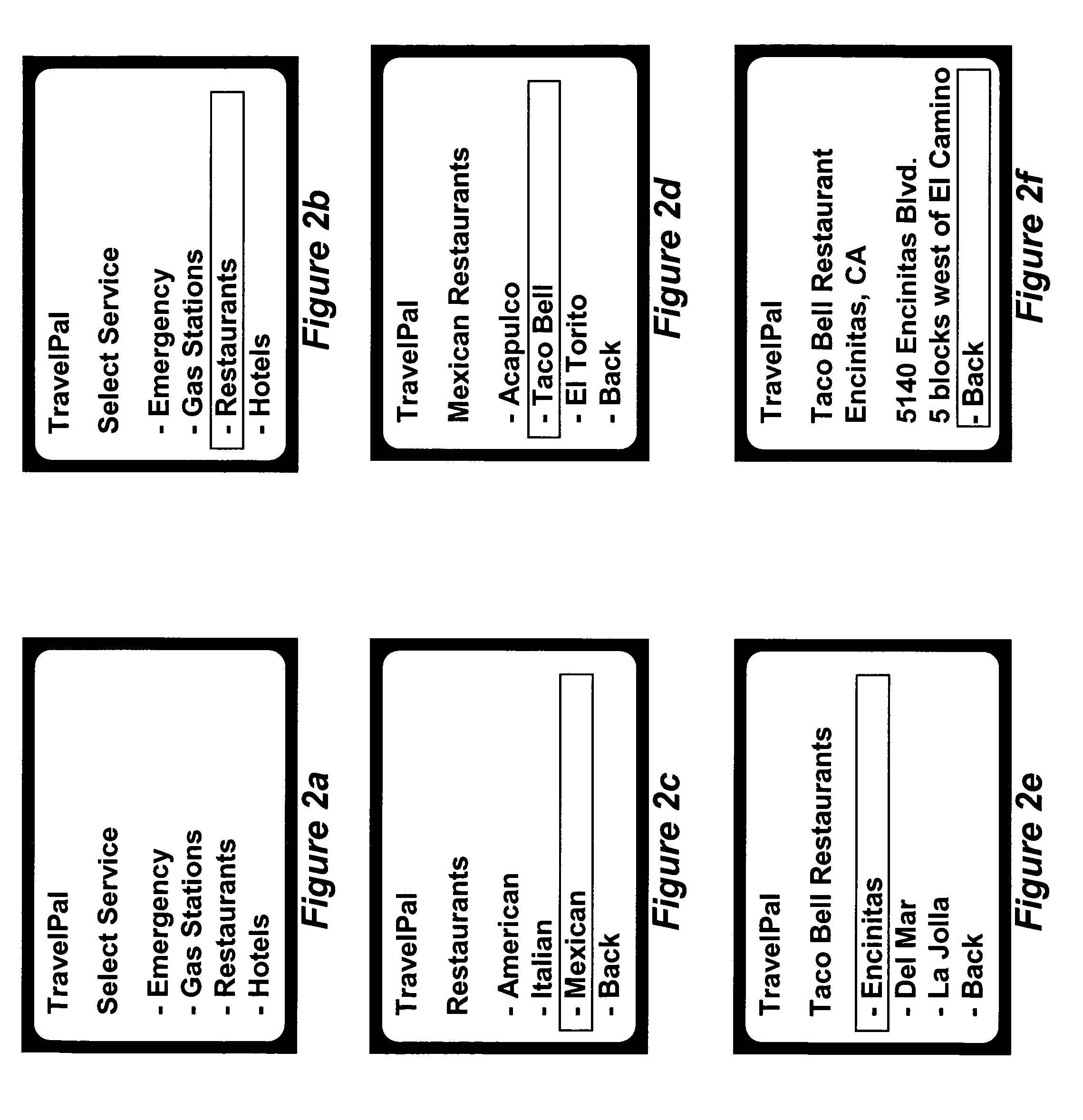
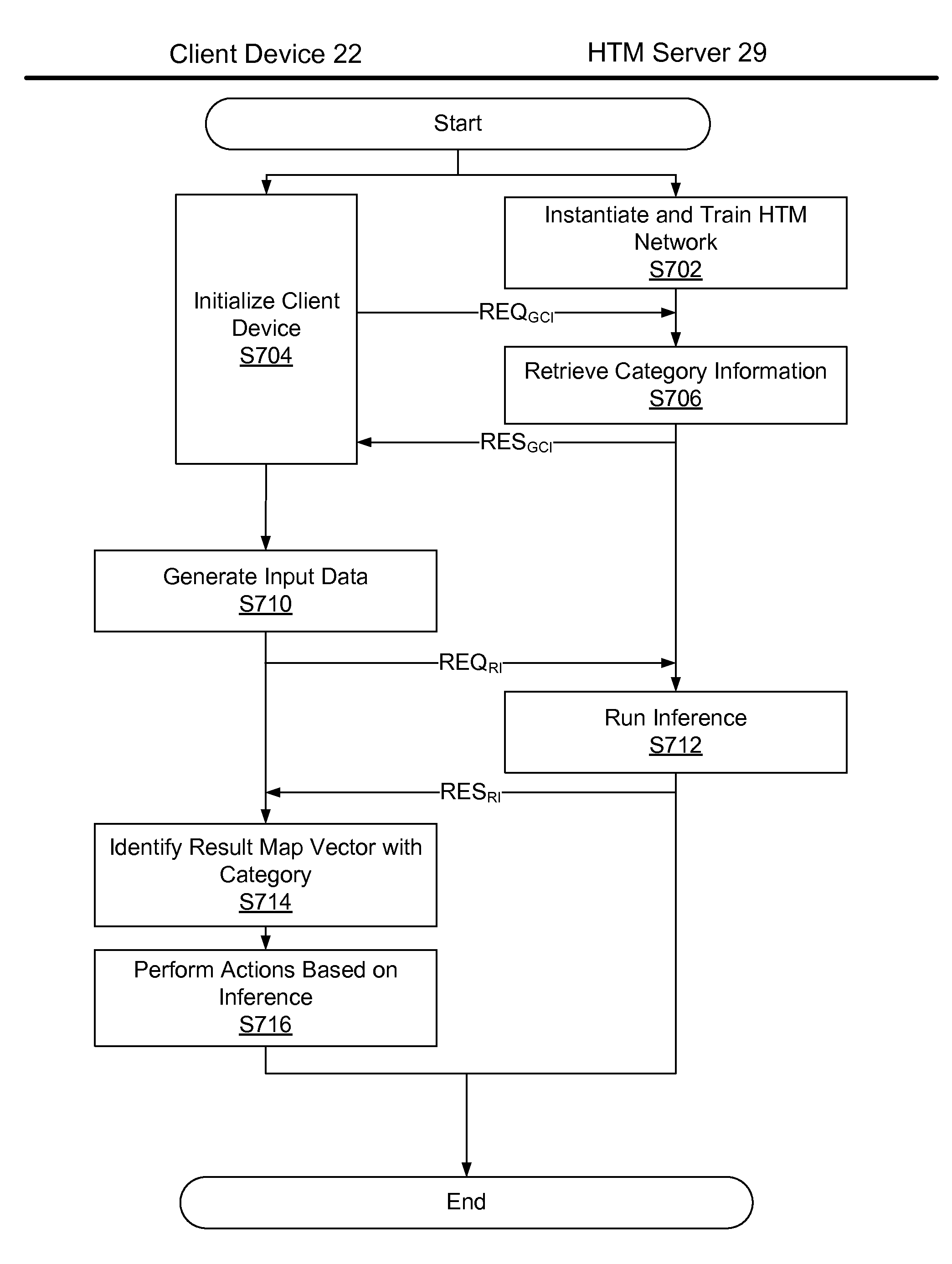
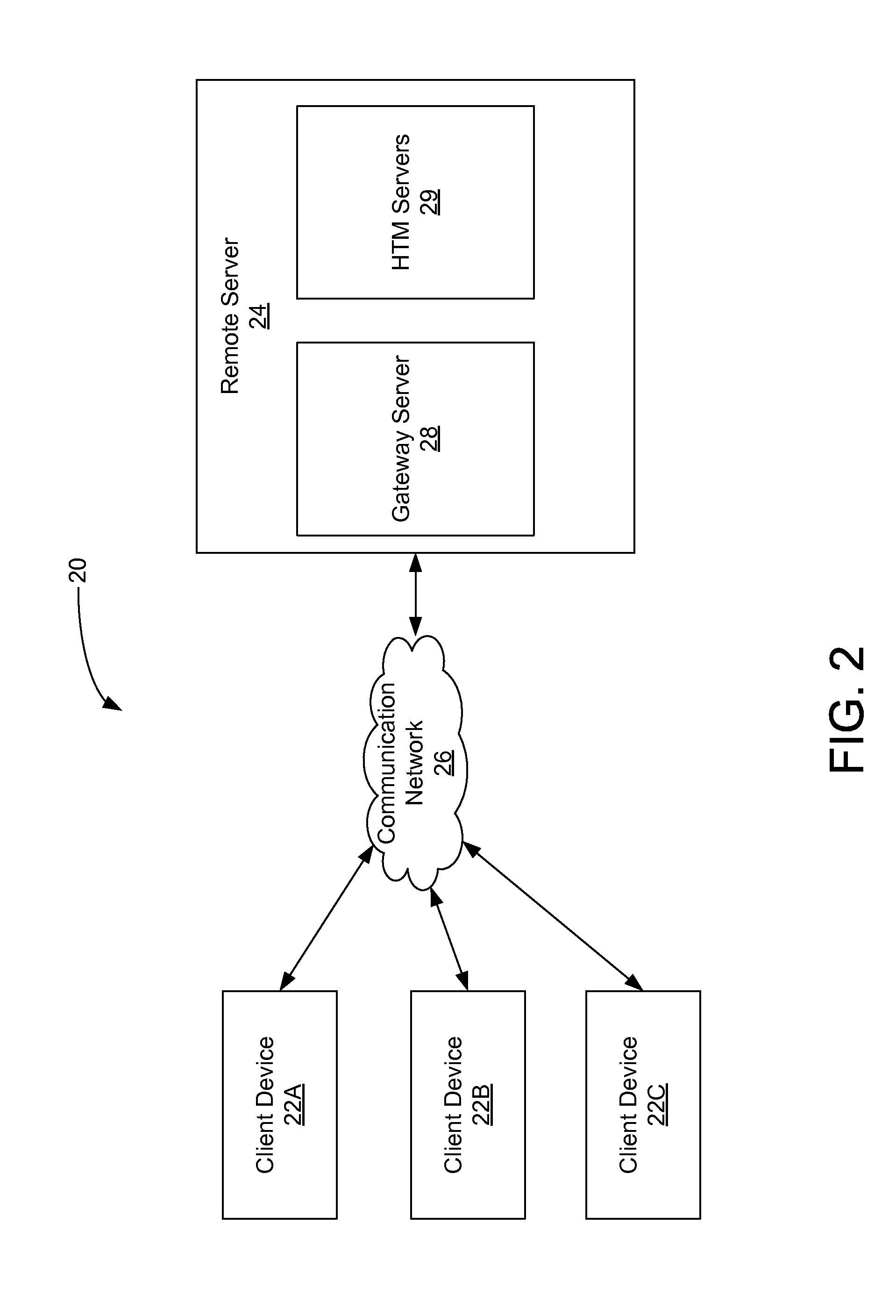
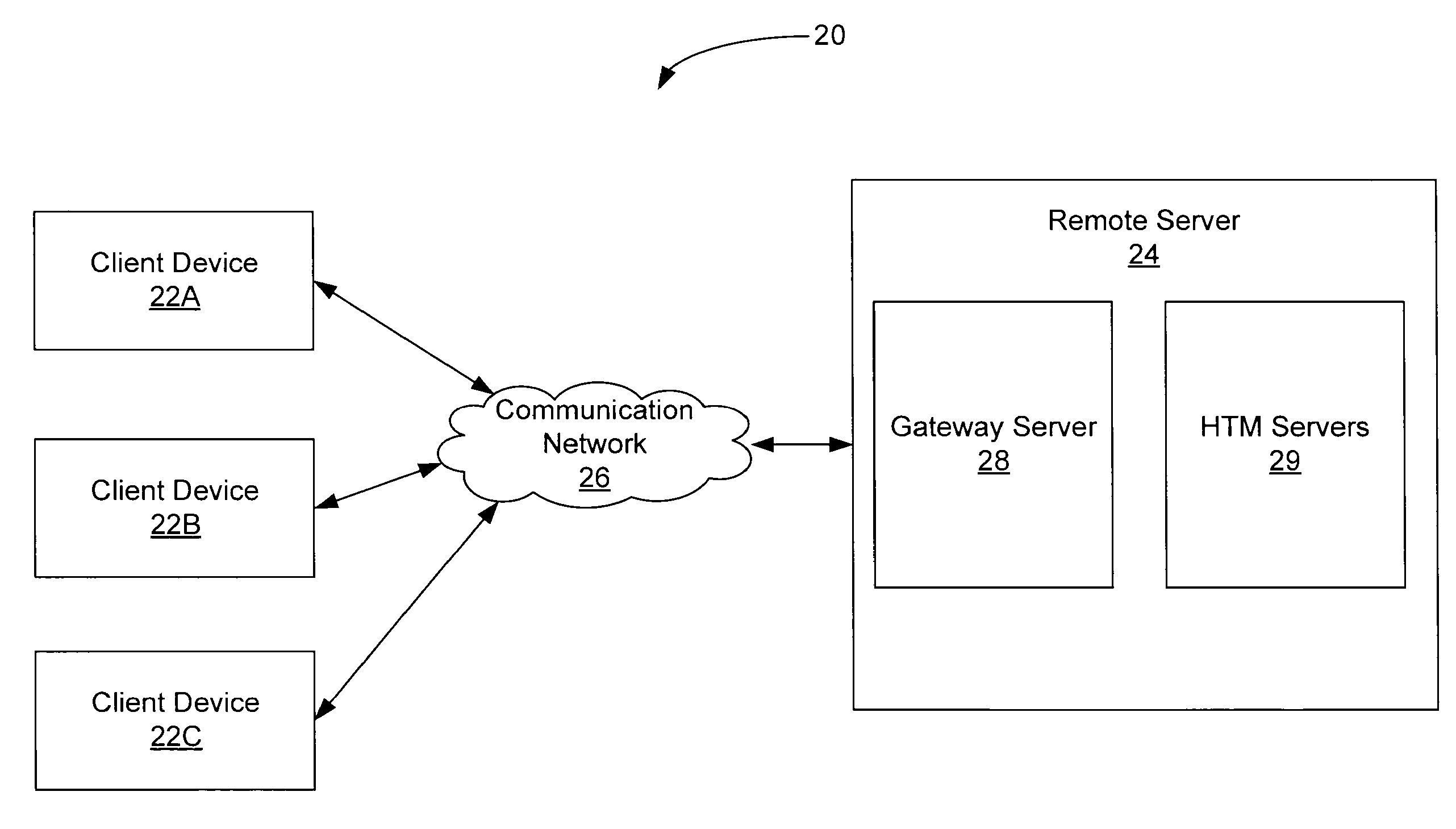
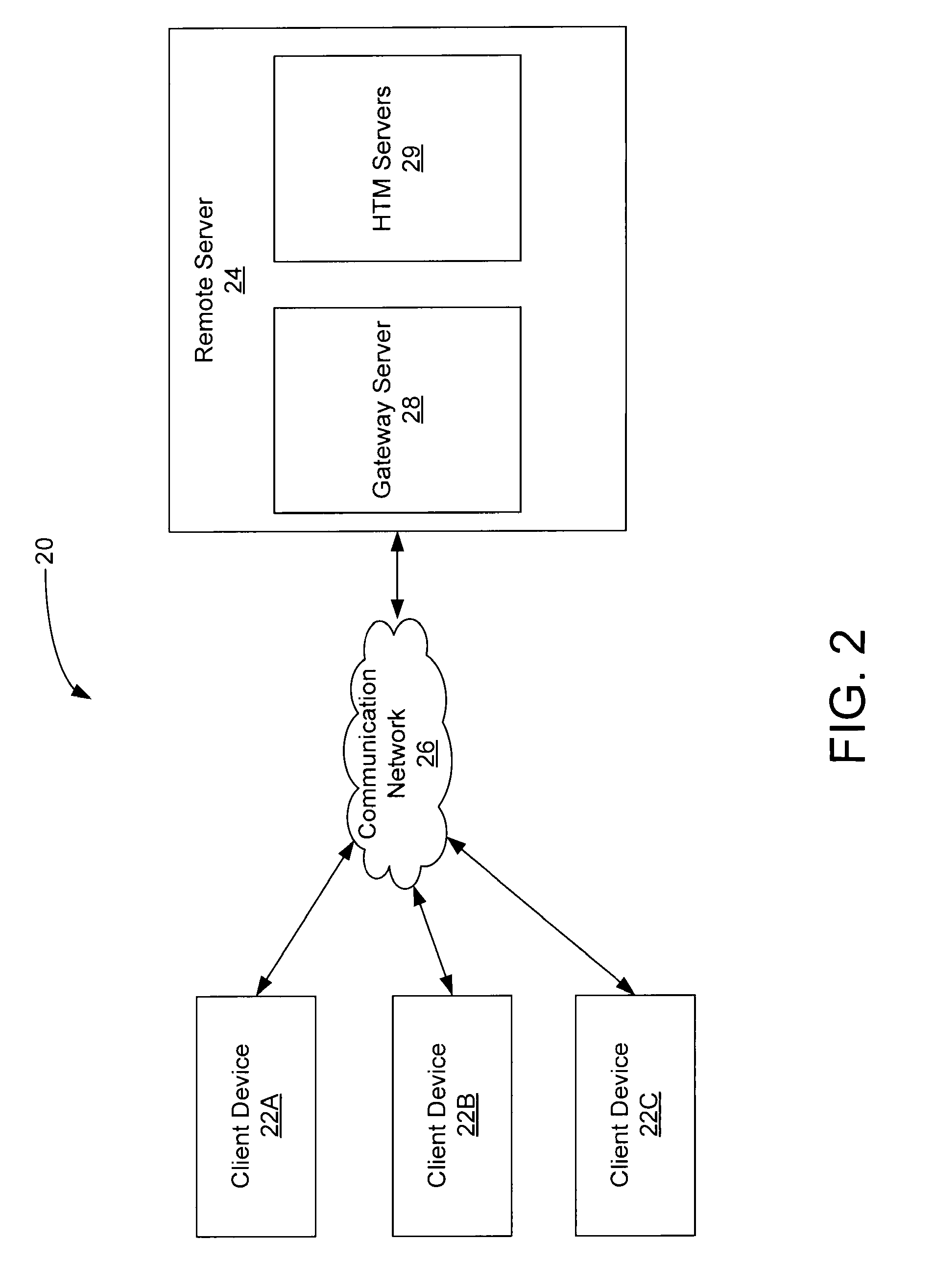
Hierarchical Temporal Memory (HTM) System Deployed as Web Service
ActiveUS20120166364A1Accurately inferredCharacter and pattern recognitionMultiple digital computer combinationsWeb serviceClient-side
A web-based hierarchical temporal memory (HTM) system in which one or more client devices communicate with a remote server via a communication network. The remote server includes at least a HTM server for implementing a hierarchical temporal memory (HTM). The client devices generate input data including patterns and sequences, and send the input data to the remote server for processing. The remote server (specifically, the HTM server) performs processing in order to determine the causes of the input data, and sends the results of this processing to the client devices. The client devices need not have processing and / or storage capability for running the HTM but may nevertheless take advantage of the HTM by submitting a request to the HTM server.
Owner:NUMENTA INC
Method and apparatus for using a single multi-function adapter with different operating systems
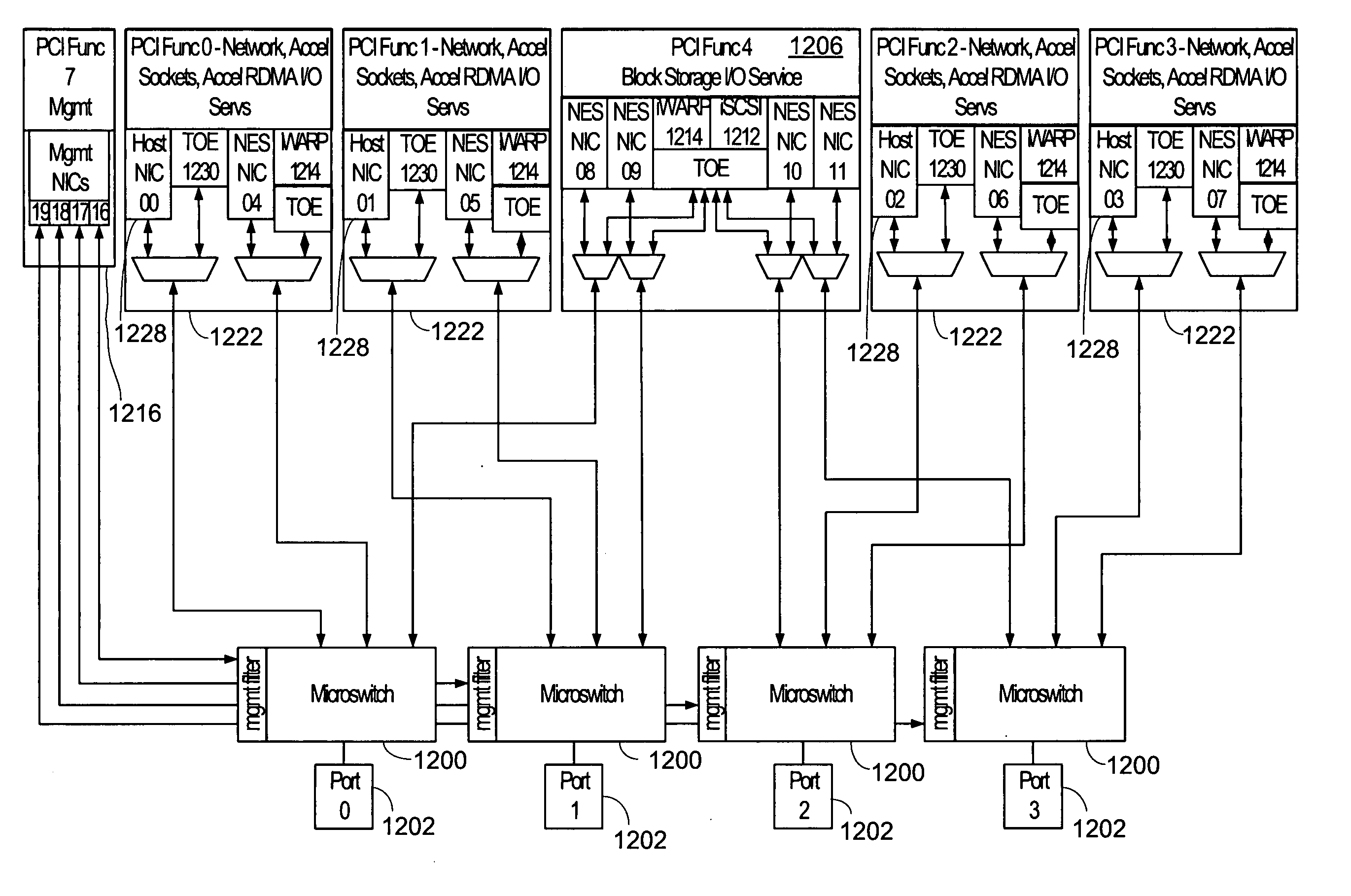
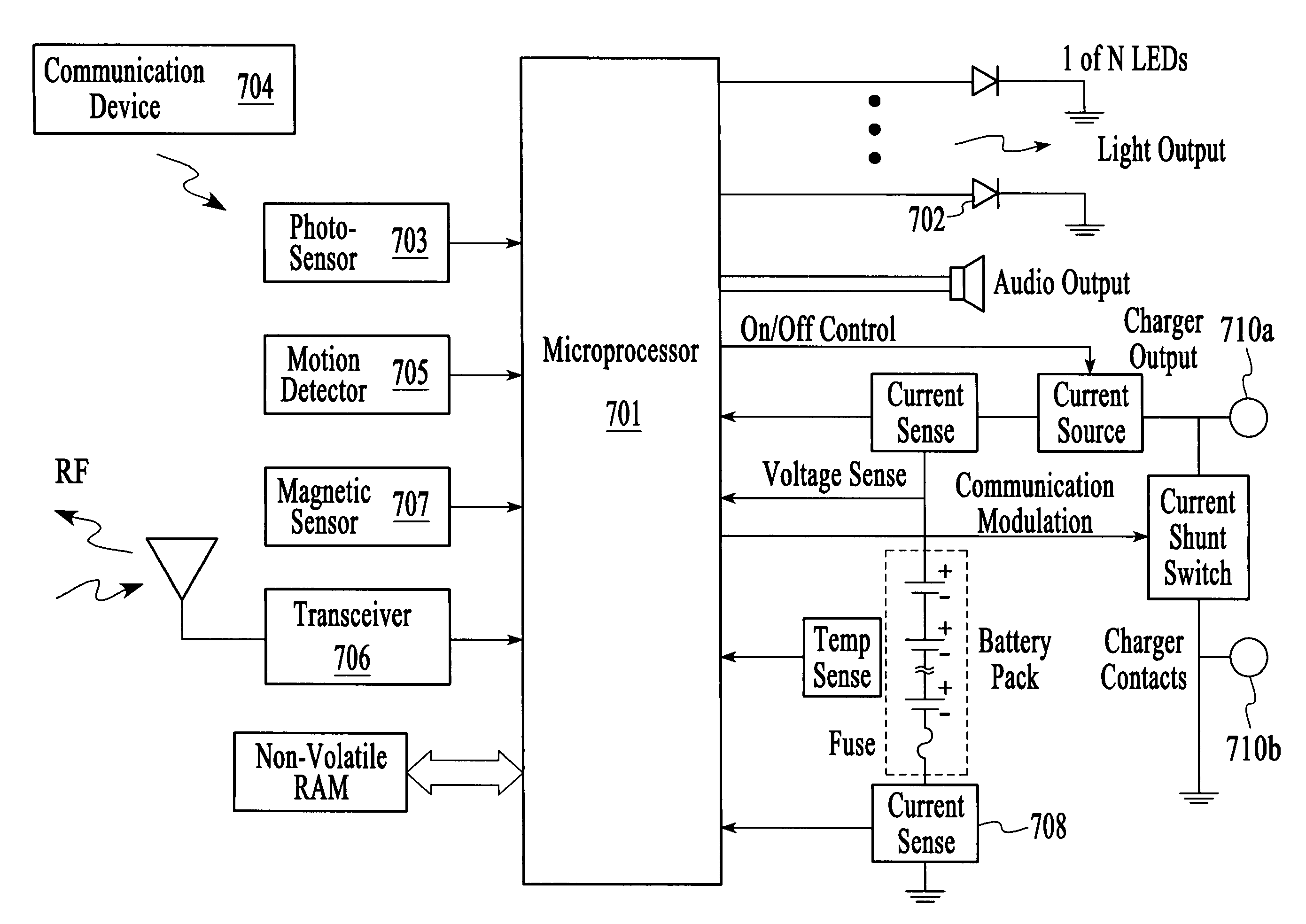
ActiveUS20070226386A1Precise processingDigital computer detailsMultiprogramming arrangementsSystem deploymentMultiple function
A flexible arrangement allows a single arrangement of Ethernet channel adapter (ECA) hardware functions to appear as needed to conform to various operating system deployment models. A PCI interface presents a logical model of virtual devices appropriate to the relevant operating system. Mapping parameters and values are associated with the packet streams to allow the packet streams to be properly processed according to the presented logical model and needed operations. Mapping occurs at both the host side and at the network side to allow the multiple operations of the ECA to be performed while still allowing proper delivery at each interface.
Owner:TAHOE RES LTD
Multi-carrier communications methods and apparatus
ActiveUS20050250502A1Reduce distractionsImprove performanceTransmission path divisionCriteria allocationCommunications systemEngineering
Methods and apparatus for implementing a multi-carrier communications system are described. Various approaches to a phased system deployment and system configurations resulting from different levels of deployment are described. In addition mobile node and methods of operating mobile nodes in communications systems that may have different levels of deployment in different cells are described.
Owner:QUALCOMM INC
Landslide real-time monitoring and warning system
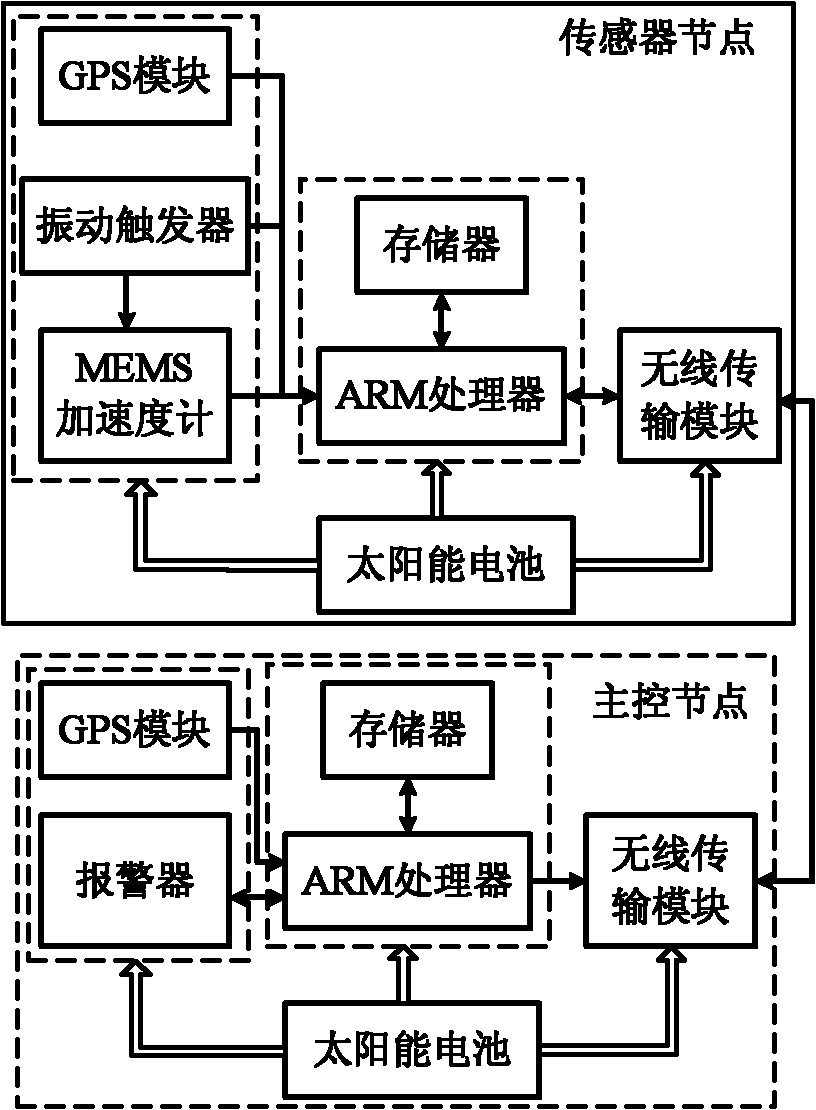
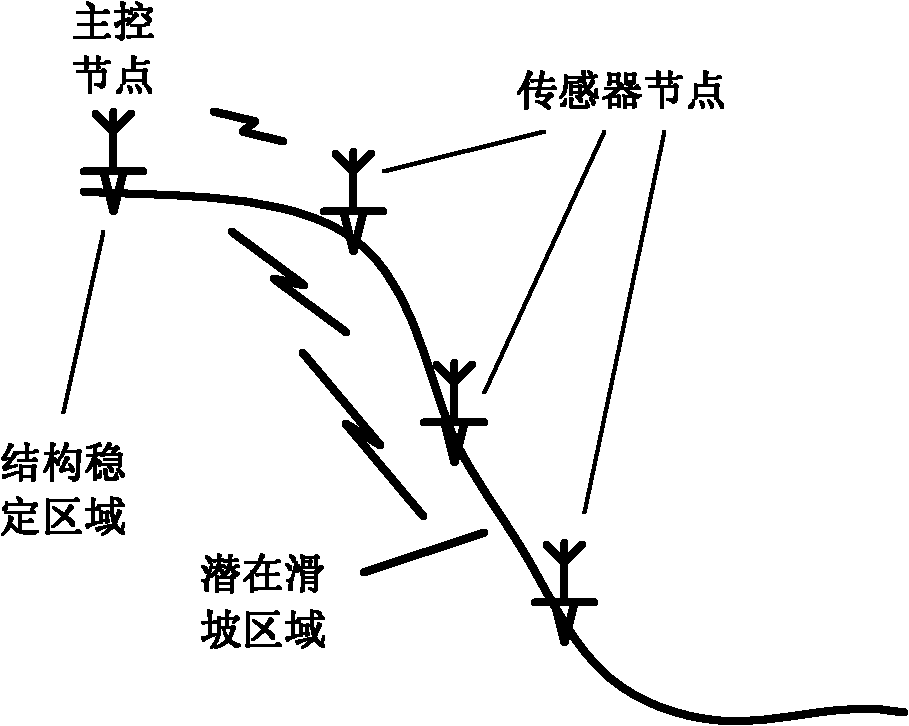
InactiveCN102163363AAccurate detectionOvercome the cycleSeismologyAlarmsAccelerometerWireless transmission
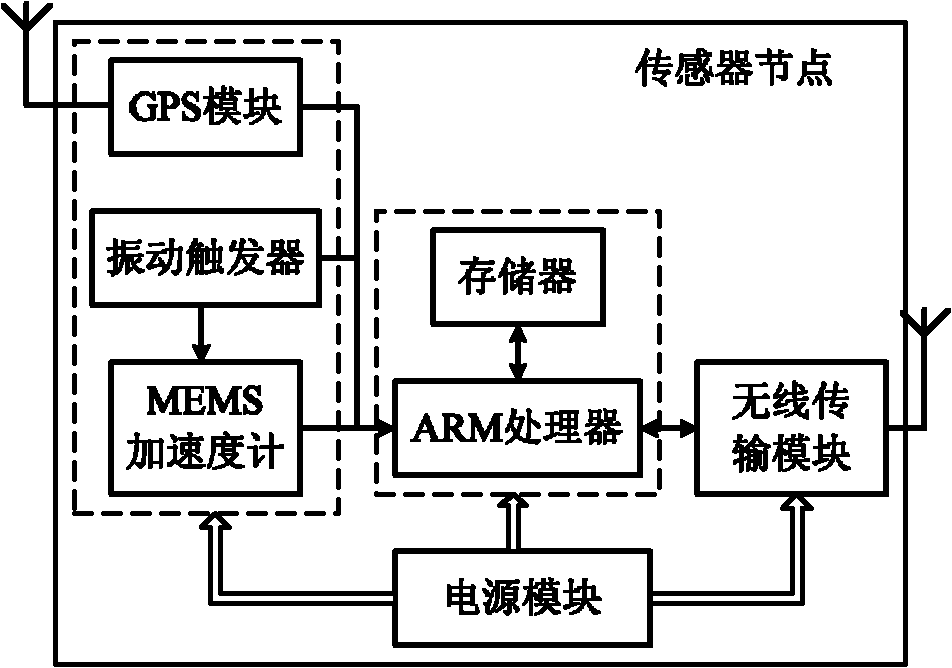
The invention discloses a landslide real-time monitoring and warning system. The system comprises a main control node and a plurality of sensor nodes; each sensor node comprises a global positioning system (GPS) module, a vibration trigger module, a micro electro mechanical system (MEMS) accelerometer, a memory, an advanced reduced instruction-set computer (RISC) machine (ARM) processor, a wireless transmission module and a power supply module; the main control node consists of a GPS module, a wireless transmission module, a memory, an ARM processor and an alarm; the sensor nodes acquire mountain deformation parameters through the GPS modules, acquire an instantaneous abnormal underground vibration signal through the MEMS accelerometer, and send data to the main control node through the wireless transmission modules; the main control node receives the mountain deformation parameters and the instantaneous abnormal vibration data of the sensor nodes through the wireless transmission modules, comprehensively analyzes the mountain deformation parameters and the instantaneous abnormal vibration data, and sends landslide warning information to the alarm. The system can be used for monitoring the state of a mountain in real time and timely detecting premonition of landslides and has the advantages of flexible deployment and convenience for use.
Owner:BEIHANG UNIV
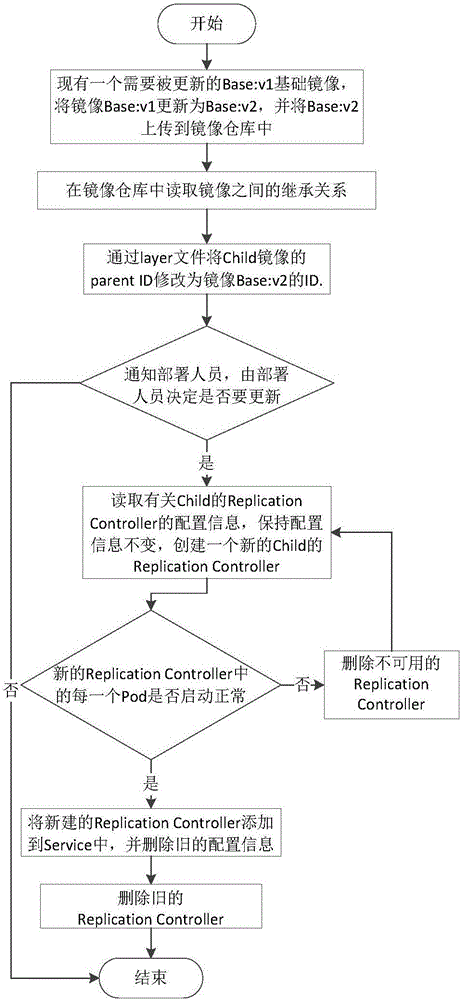
Container-based distributed storage system deployment method
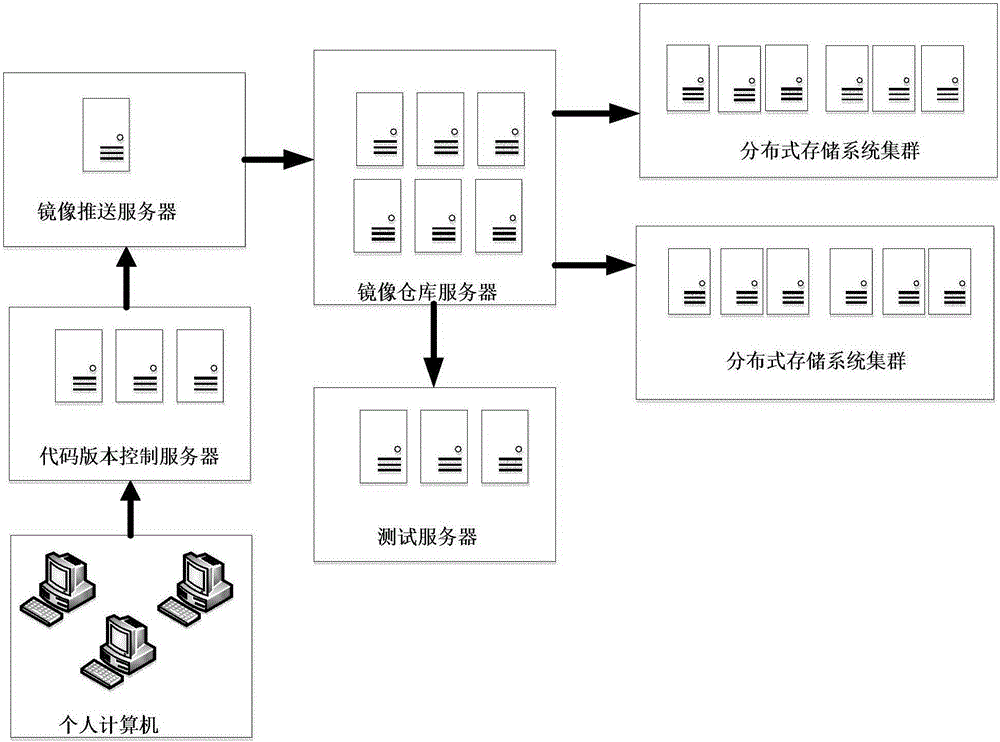
The invention discloses a container-based distributed storage system deployment method. A developer packs and pushes a distributed storage system to a mirror image warehouse in a mirror image manner through a container warehouse, and a person responsible for testing, operation and maintenance obtains the mirror images of the distributed storage system from the mirror image warehouse to complete the deployment of cluster nodes.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Transponder systems and methods for radio-over-fiber (ROF) wireless picocellular systems
ActiveUS20080186143A1Enhanced antenna directivityImprove directivityTelemetry/telecontrol selection arrangementsSensing record carriersRadio over fiberCombined use
Transponder systems and methods for radio-over-fiber (RoF) wireless picocellular system are disclosed. One type of transponder system includes a RoF transponder used in combination with at least one radiation-reflector assembly to provide for enhanced antenna directivity of the transponder. Another type of transponder system is a transponder node assembly, wherein two or more transponders are integrated into a single assembly, thereby reducing cost while facilitating RoF wireless picocellular system deployment. Another type of transponder system provides one or more transponders in a RoF wireless picocellular system with radio-frequency identification (RFID) tags, and uses an RFID tag reader to locate and read information from the transponders, as well as to perform transponder mode selection. Another type of transponder system is directed to a tether cable assembly that includes a dispensible / retractable coiled tether cable housed in a protective housing for connecting the tether cable to a transponder.
Owner:CORNING OPTICAL COMM LLC
Method for disposing inbreak detection system
InactiveCN101465770AReduce loadImprove accuracyData switching networksNetworked systemVirtual switch
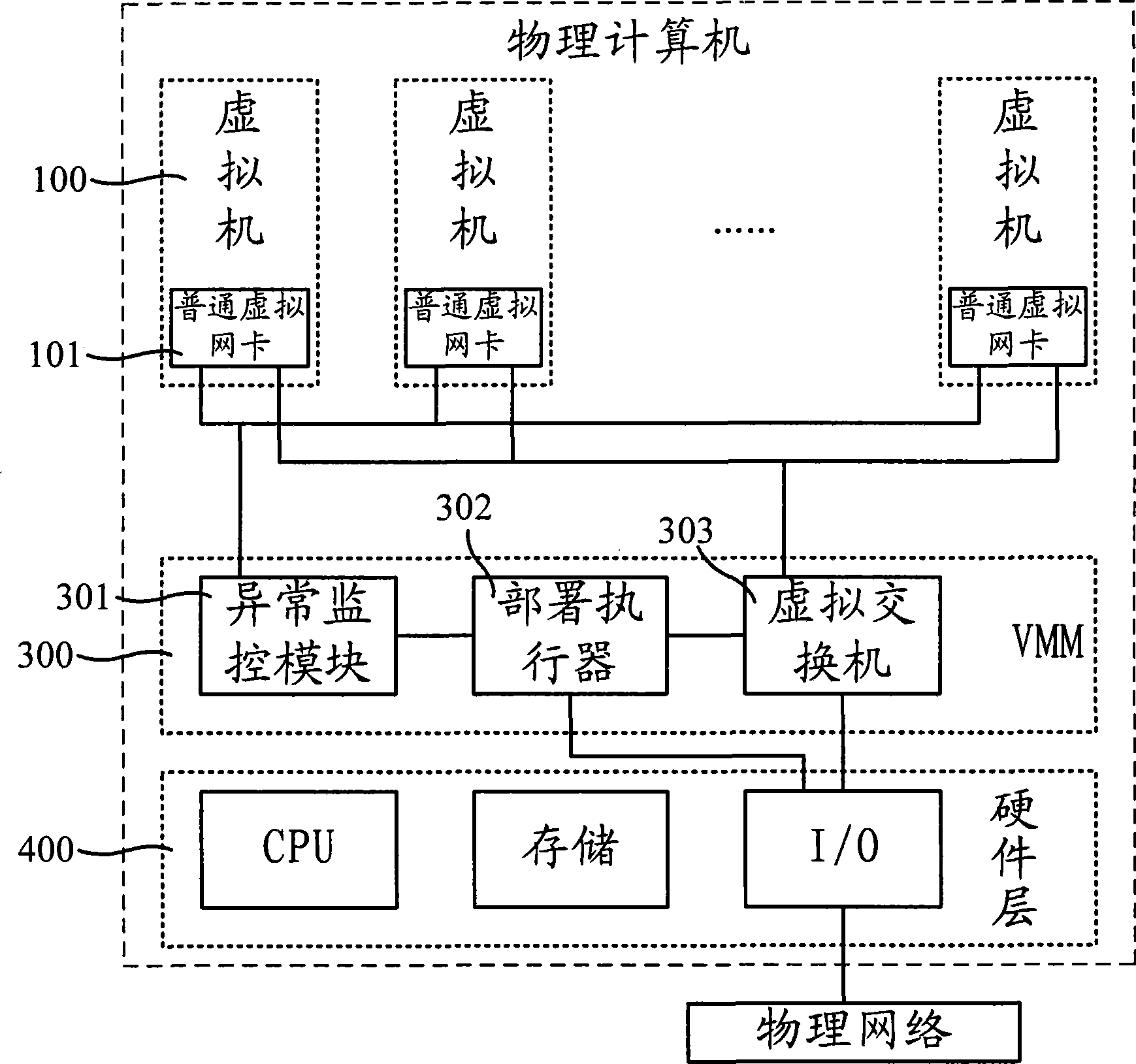
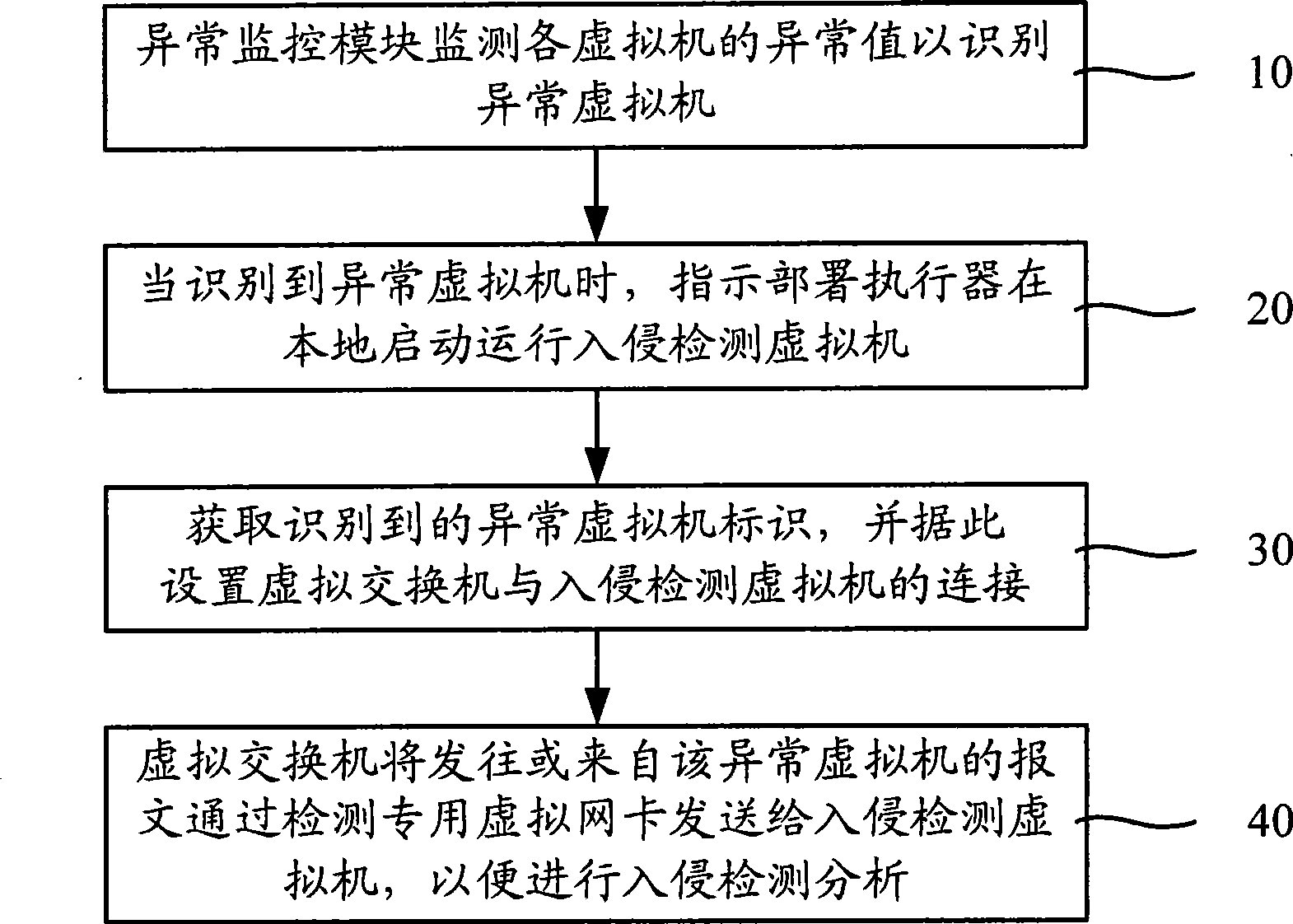
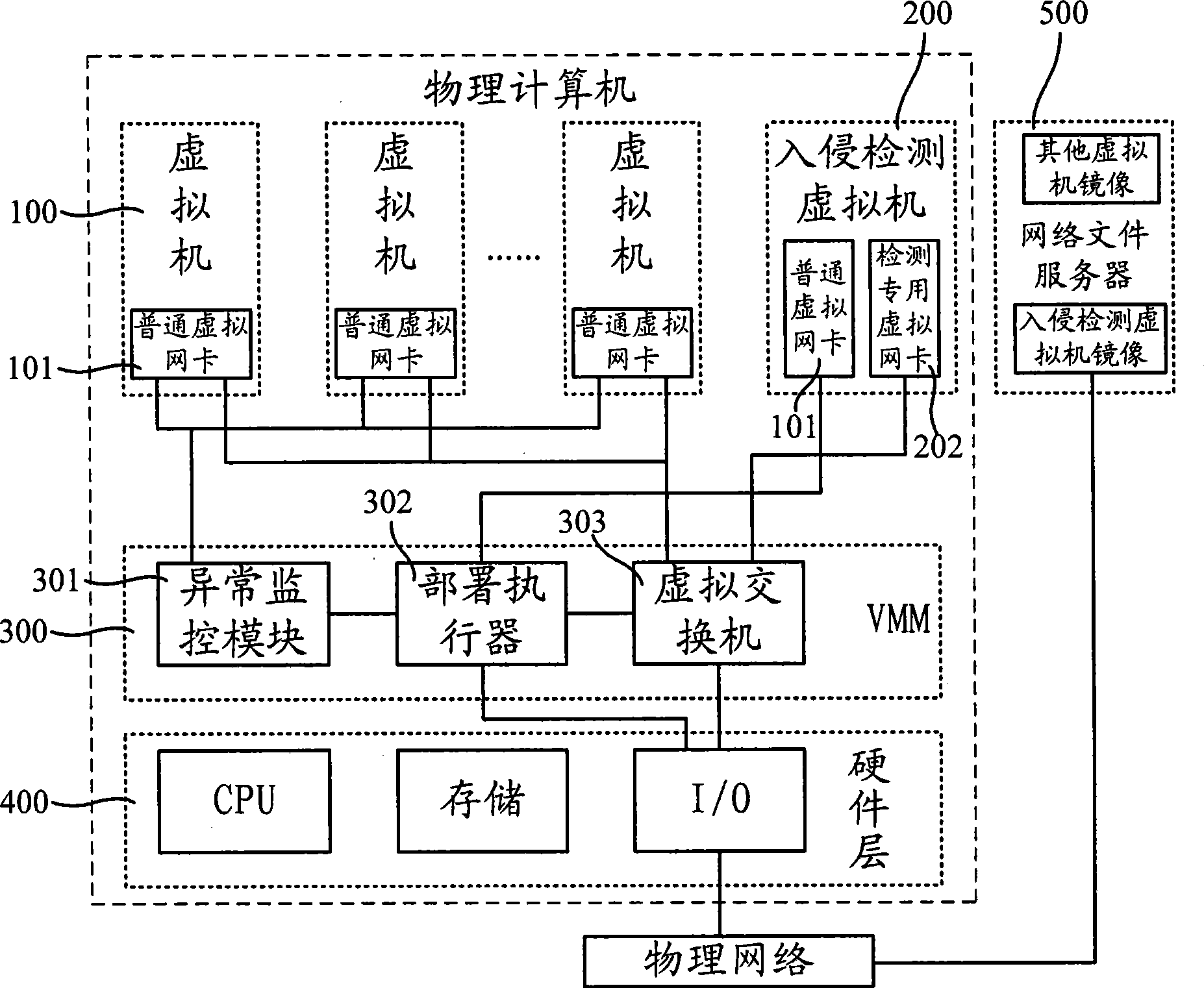
The invention relates to an intrusion detection system deployment method, including that: an abnormity monitoring module monitors and identifies an abnormal virtual machine; when abnormity is identified, a deployment actuator is indicated to locally start up and operate an intrusion detection virtual machine; the deployment actuator acquires an abnormal virtual machine mark from the abnormity monitoring module and sets up the connection between a virtual switcher and an intrusion detection virtual machine according to the abnormal virtual machine mark; and the virtual switcher sends the message sending to or coming from the abnormal virtual machine to the intrusion detection virtual machine through a special detection virtual network card so as to carry out intrusion detection analysis. The intrusion detection system deployment method, based on virtual machine technology, realizes the flexible deployment of the intrusion detection system and identifies the abnormal virtual machine by monitoring the abnormity values of the virtual machines so as to pertinently start up the intrusion detection virtual machine to conduct intrusion detection to the massage transmitted by the intrusion detection virtual machine. The intrusion detection system can be deployed more flexibly in a network system, thus reducing the intrusion detection load and improves intrusion detection accuracy and efficiency.
Owner:BEIHANG UNIV
Integrated system of mobile application platform and Intranet-Internet data security exchange platform
InactiveCN106209801AGet rid of limitationsSafe exchange fastTransmissionSystem deploymentData format
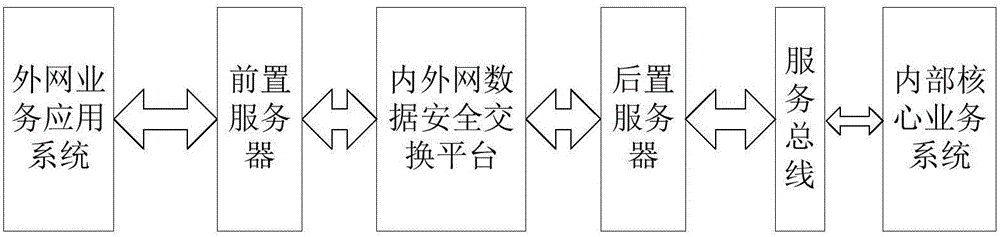
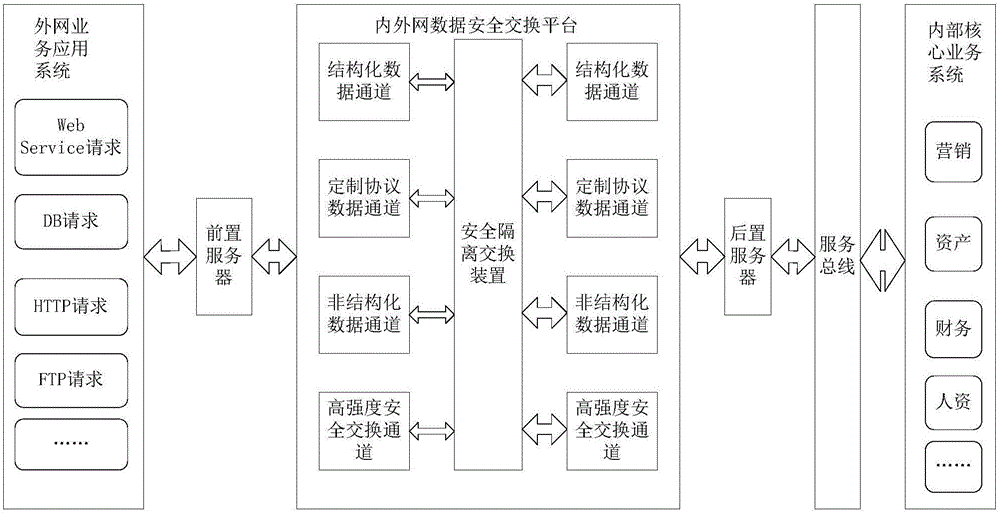
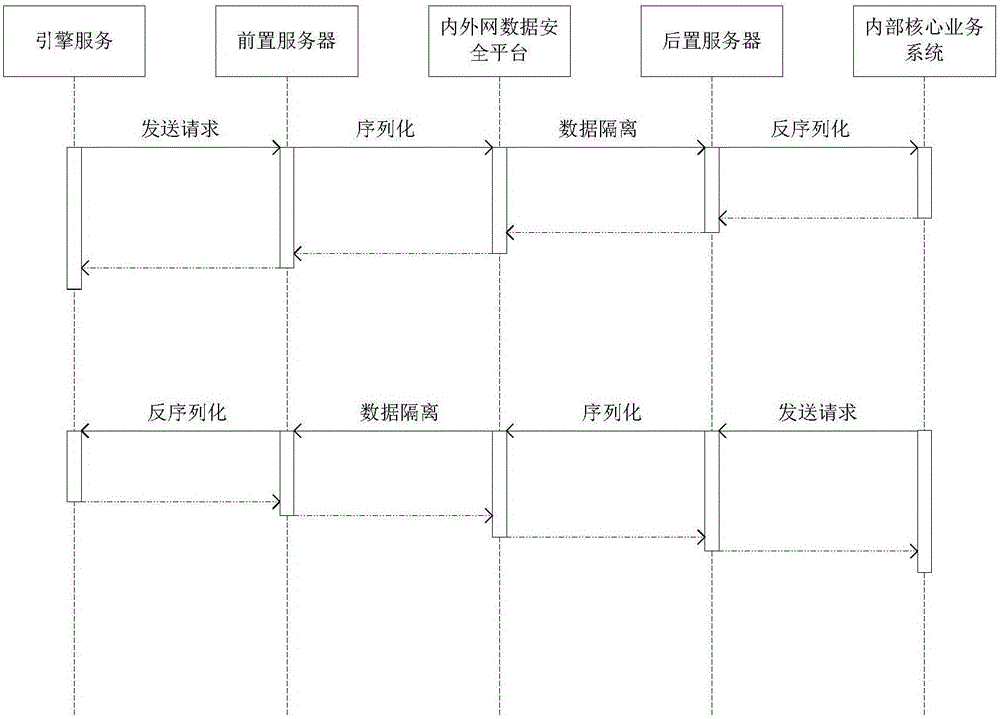
The invention relates to an integrated system of a mobile application platform and an Intranet-Internet data security exchange platform. The integrated system comprises an Internet service application system, a preposed server, a postposed server and the Intranet-Internet data security exchange platform, wherein the Internet service application system is connected with the mobile application platform; the preposed server is connected with the Internet service application system of the mobile application platform, and used for providing an interface for an engine service of the Internet service application system to call, providing an interface service for the Intranet-Internet data security platform to call, converting data formats, and performing data exchange with the Intranet-Internet data security platform; the postposed server is connected with an internal core service system through an enterprise service bus, and used for providing an interface for the Intranet-Internet data security platform to call, converting the data formats and performing data exchange with the Intranet-Internet data security platform; and the Intranet-Internet data security platform exchange platform is used for establishing data exchange security management and control and network isolation defense between the Internet and information Intranet to defend network attacks of the Internet. Through adoption of the integrated system, the construction cost is lowered, and the deployment capability of the Internet service application system is enhanced.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
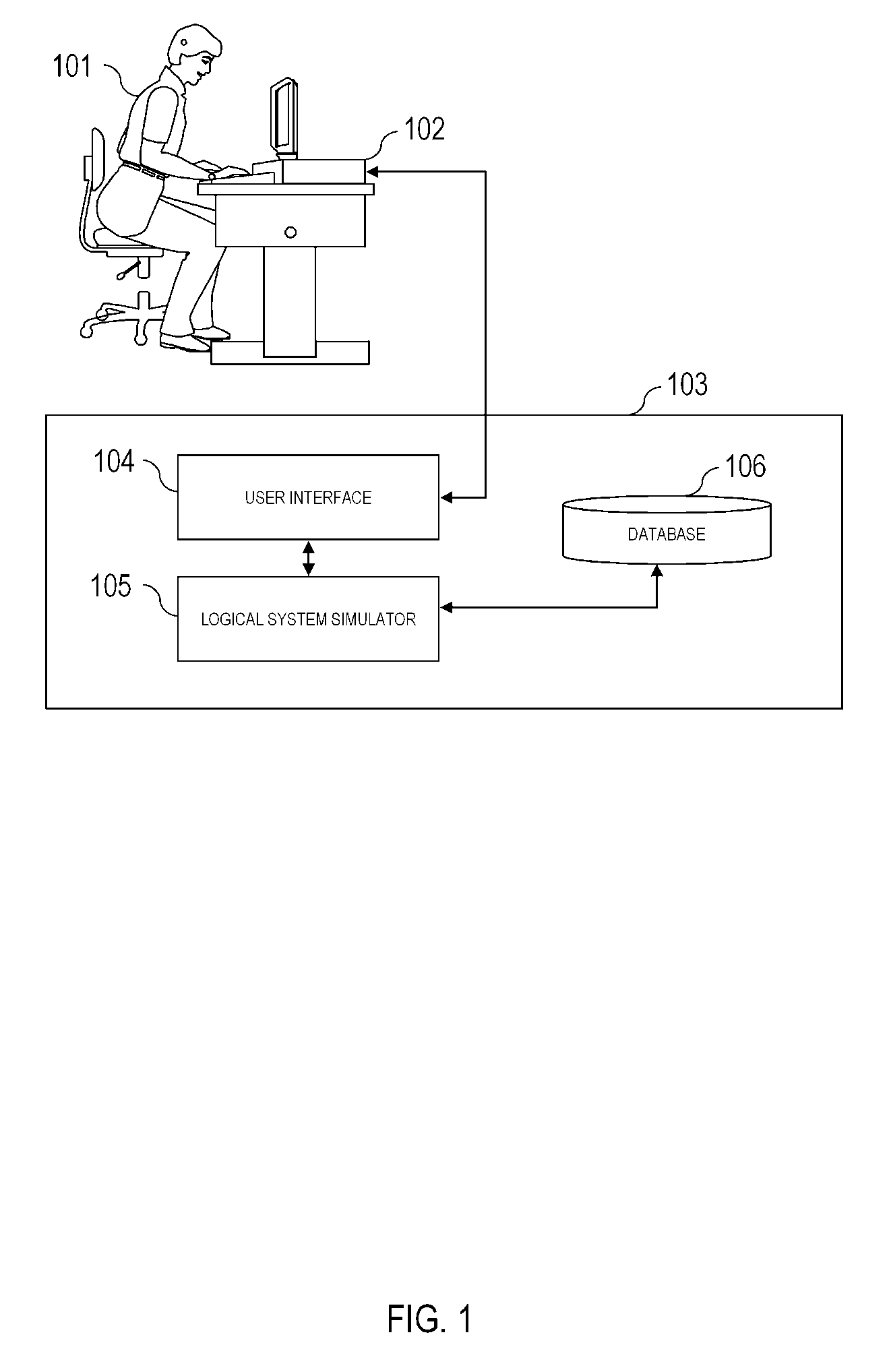
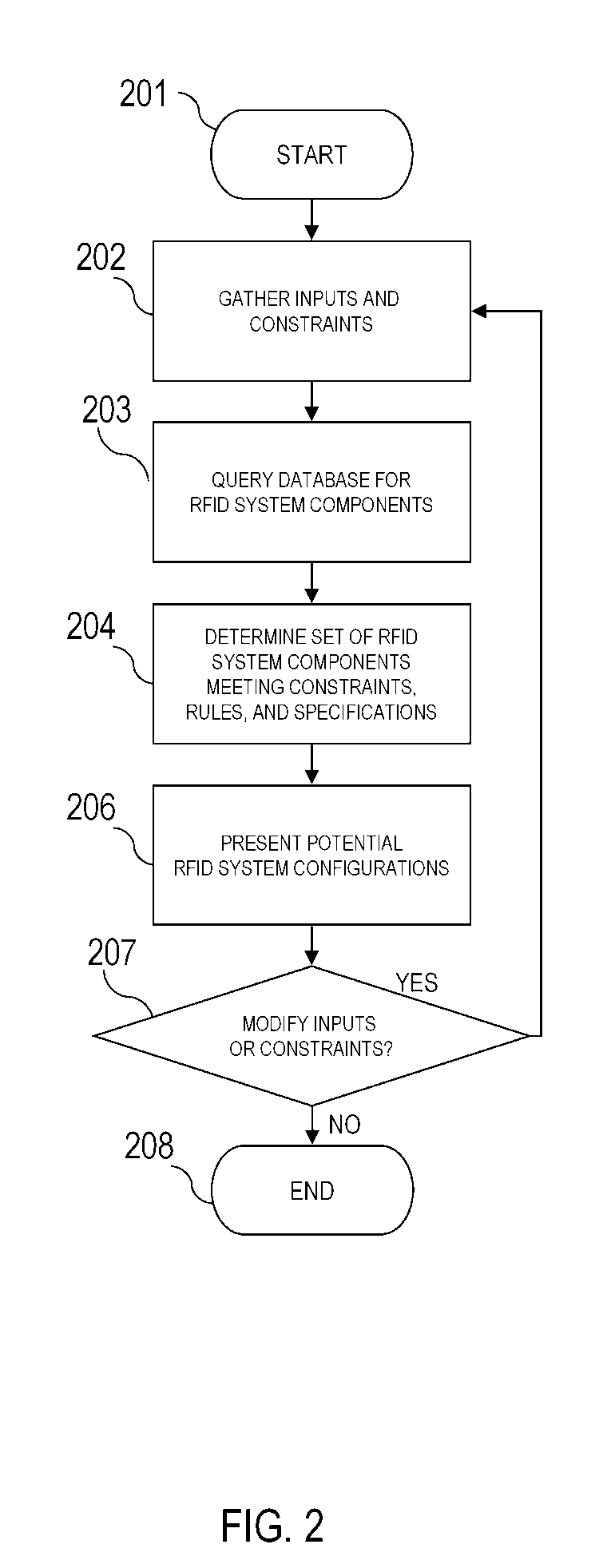
Radio frequency identification simulator and tester
InactiveUS20050154572A1Analogue computers for electric apparatusCo-operative working arrangementsUser inputTester device
A method and system for simulating radio frequency identification (RFID) systems. The system determines RFID system configurations and components that meet user constraints to facilitate planning for RFID system deployment. The simulator updates a database on the basis user input and radio frequency interrogator data from deployed systems.
Owner:QUAKE GLOBAL
Hierarchical Temporal Memory (HTM) System Deployed as Web Service
InactiveUS20080208966A1Accurately inferredMultiple digital computer combinationsData switching networksWeb serviceComputer science
A web-based hierarchical temporal memory (HTM) system in which one or more client devices communicate with a remote server via a communication network. The remote server includes at least a HTM server for implementing a hierarchical temporal memory (HTM). The client devices generate input data including patterns and sequences, and send the input data to the remote server for processing. The remote server (specifically, the HTM server) performs processing in order to determine the causes of the input data, and sends the results of this processing to the client devices. The client devices need not have processing and / or storage capability for running the HTM but may nevertheless take advantage of the HTM by submitting a request to the HTM server.
Owner:NUMENTA INC
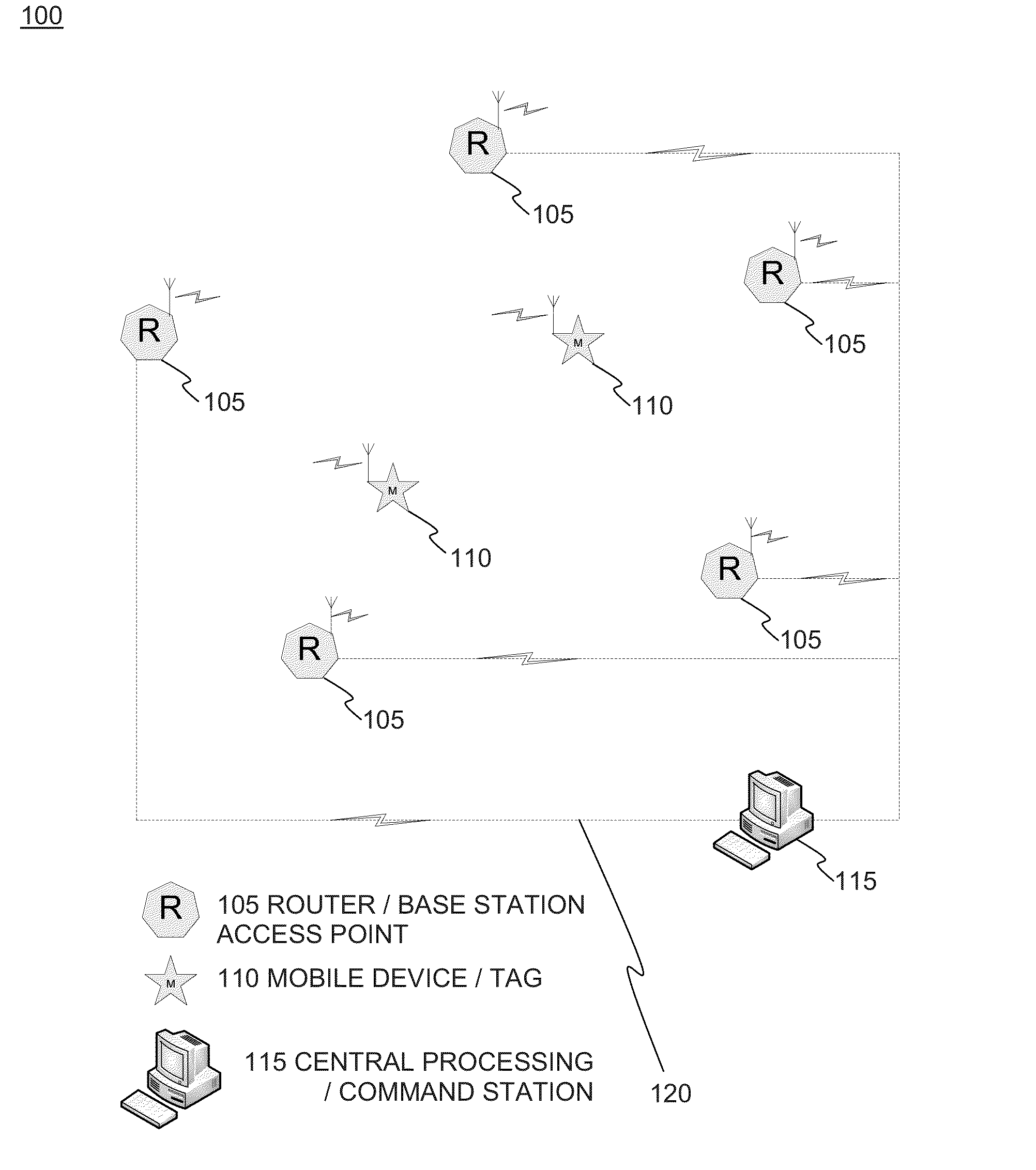
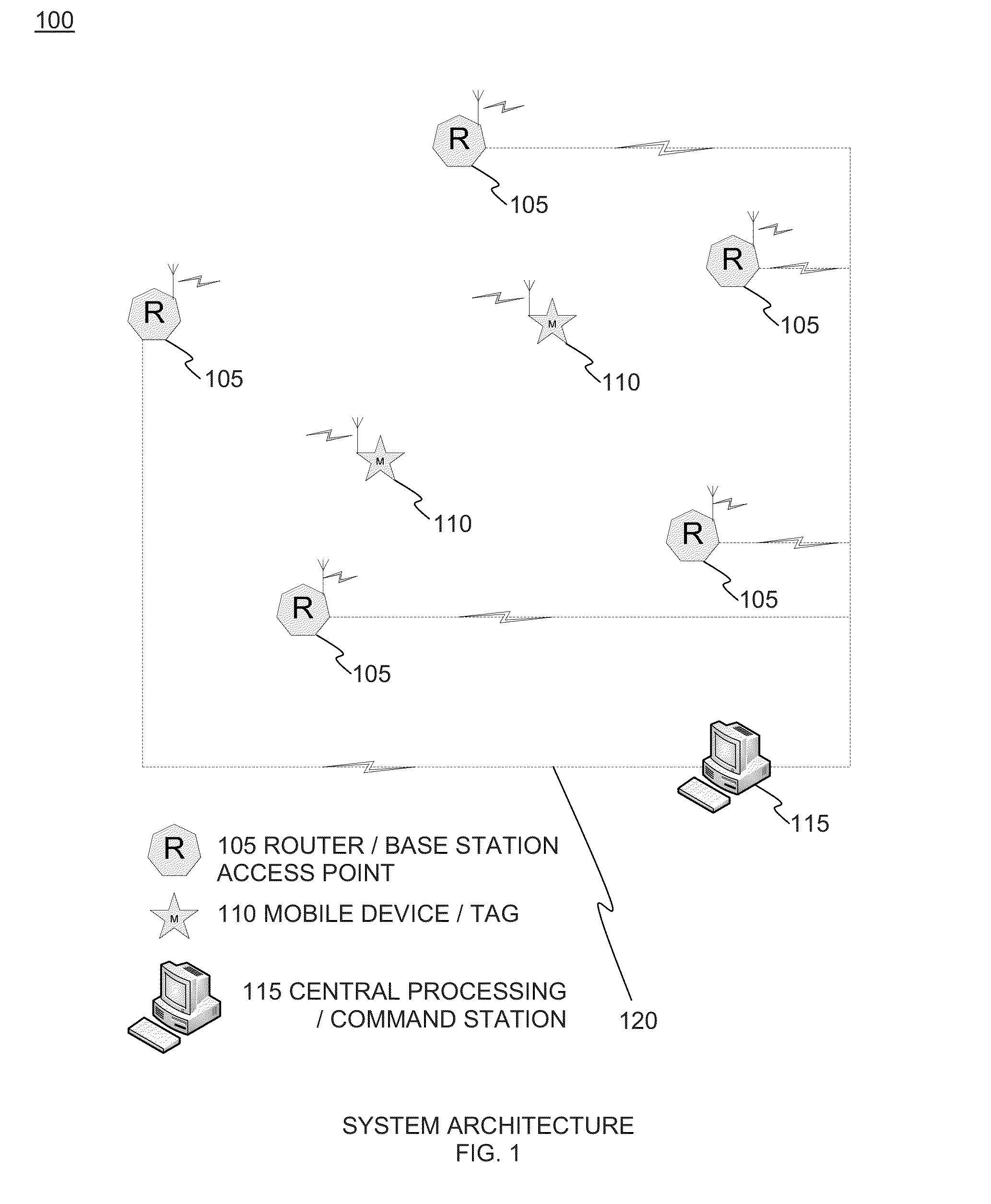
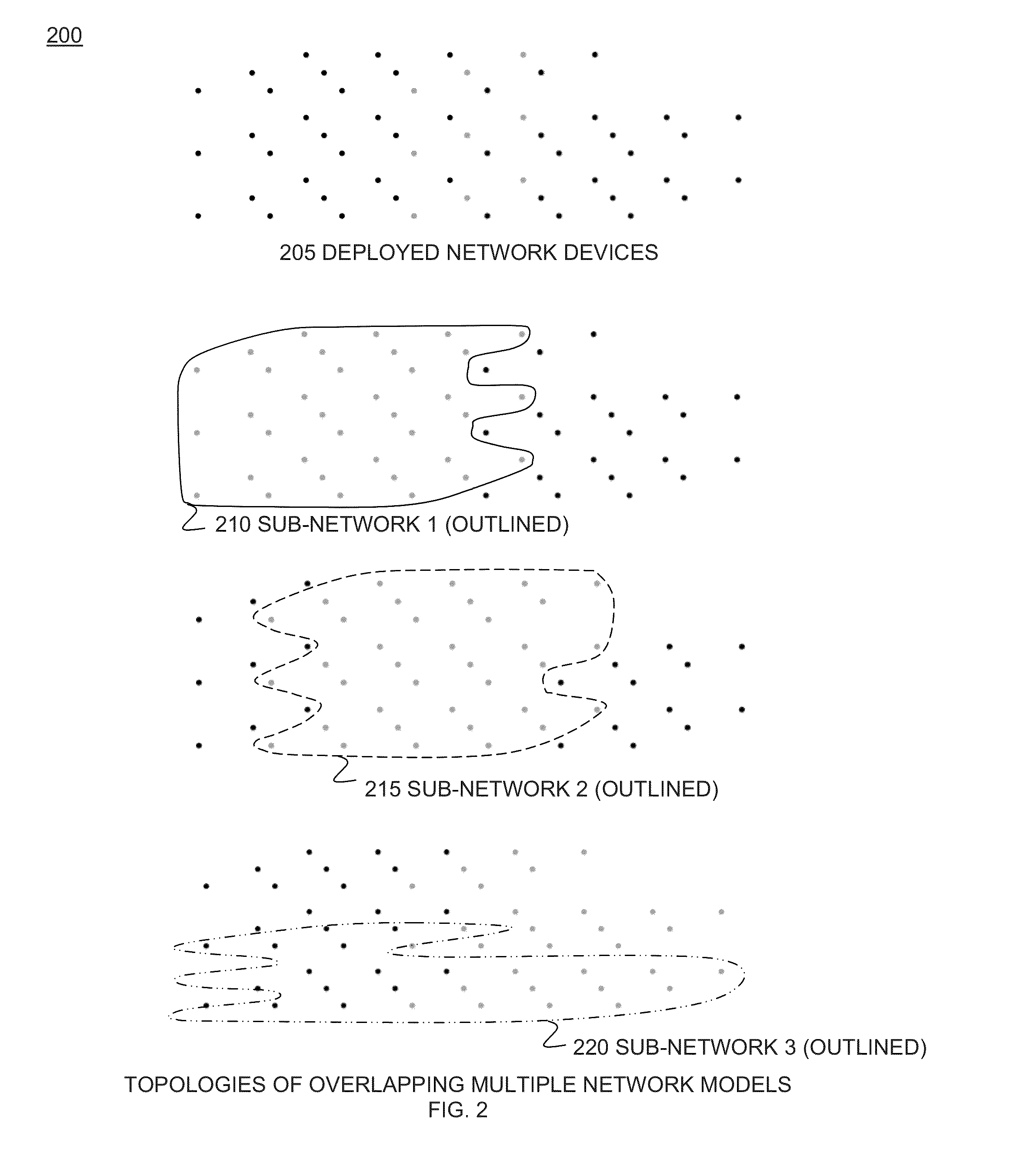
Scalable real-time location detection based on overlapping neural networks
ActiveUS20140329540A1Position fixationLocation information based serviceWireless transceiverTransceiver
A system and method for real-time location detection consists of three groups of components. Mobile subjects to be tracked are equipped with wireless transceivers capable of sending and optionally for receiving data over pre-determined radio frequency (RF) band(s). Router / base station access point devices are equipped with wireless transceivers capable of sending and receiving data over pre-determined radio frequency (RF) band(s) in order to communicate with mobile units. Routers are combined into specific overlapping router groups, with each group forming a spatial sub-network. System central processing and command station(s) perform data processing and implementation of computational models that determine the mobile unit location. System deployment consists of three phases: collection of training and testing data, network training and testing, and network adaptive maintenance.
Owner:CONSORTIUM P
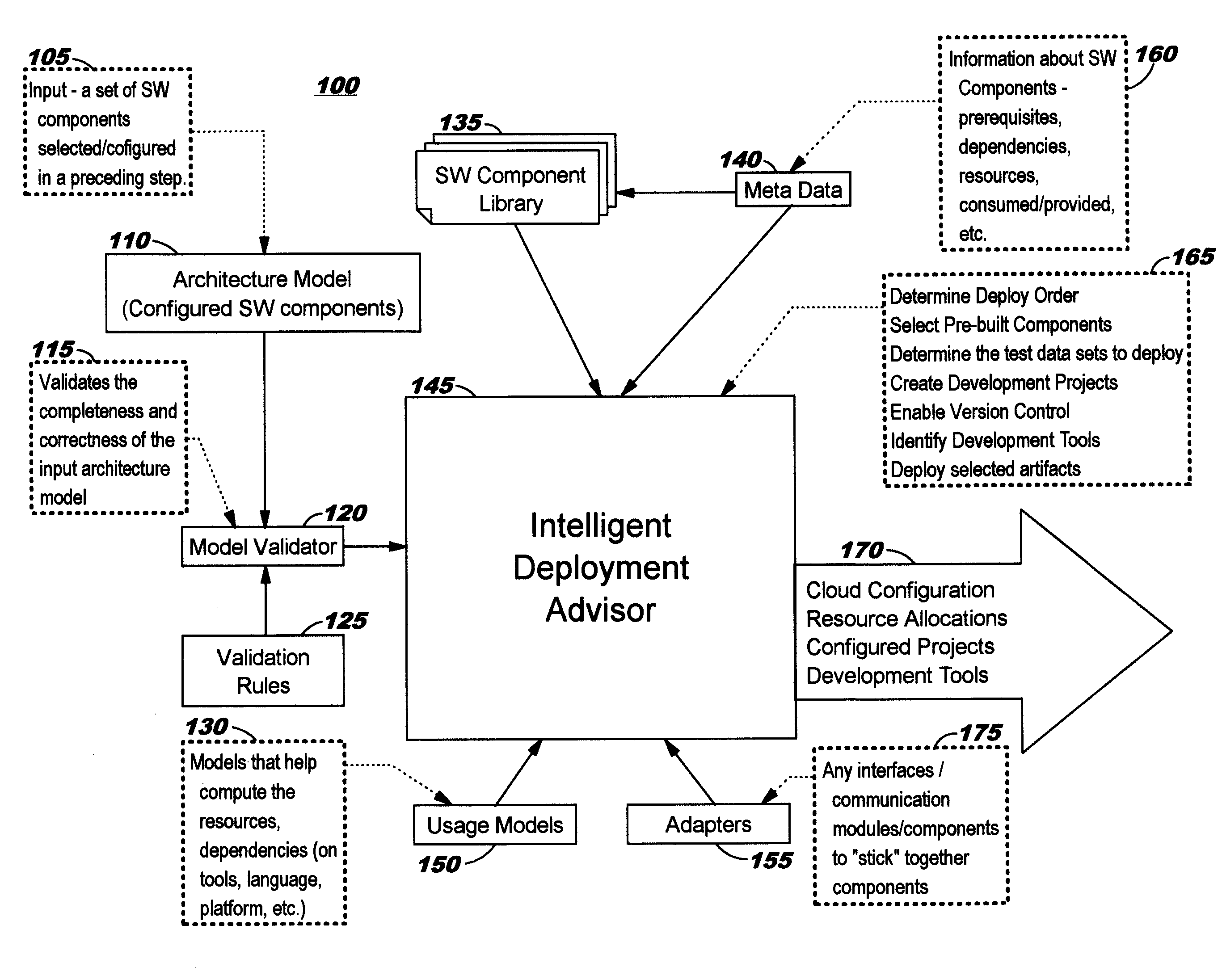
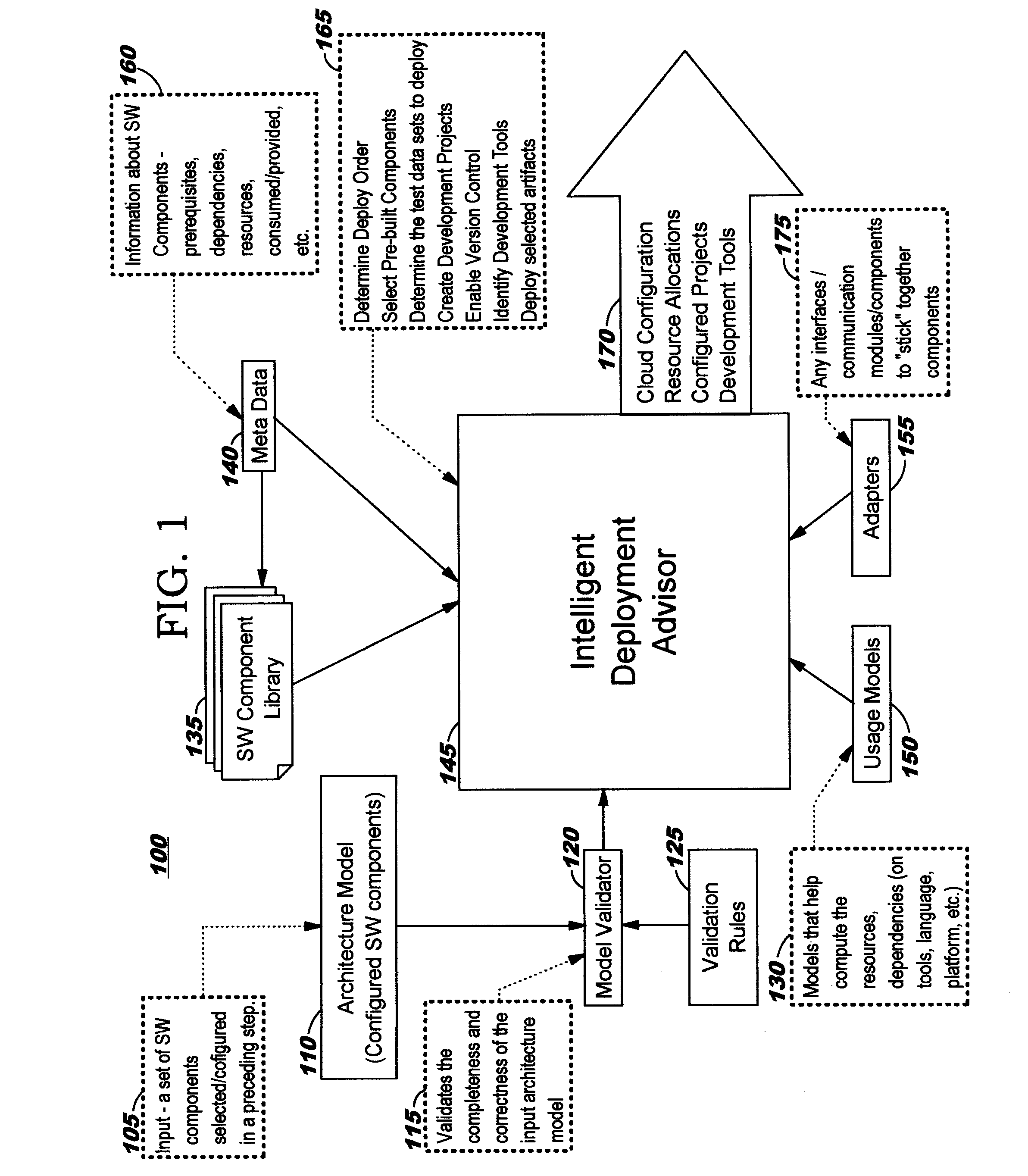
Automated Deployment of a Configured System into a Computing Environment
InactiveUS20140068546A1Specific program execution arrangementsMemory systemsAuto-configurationComputer compatibility
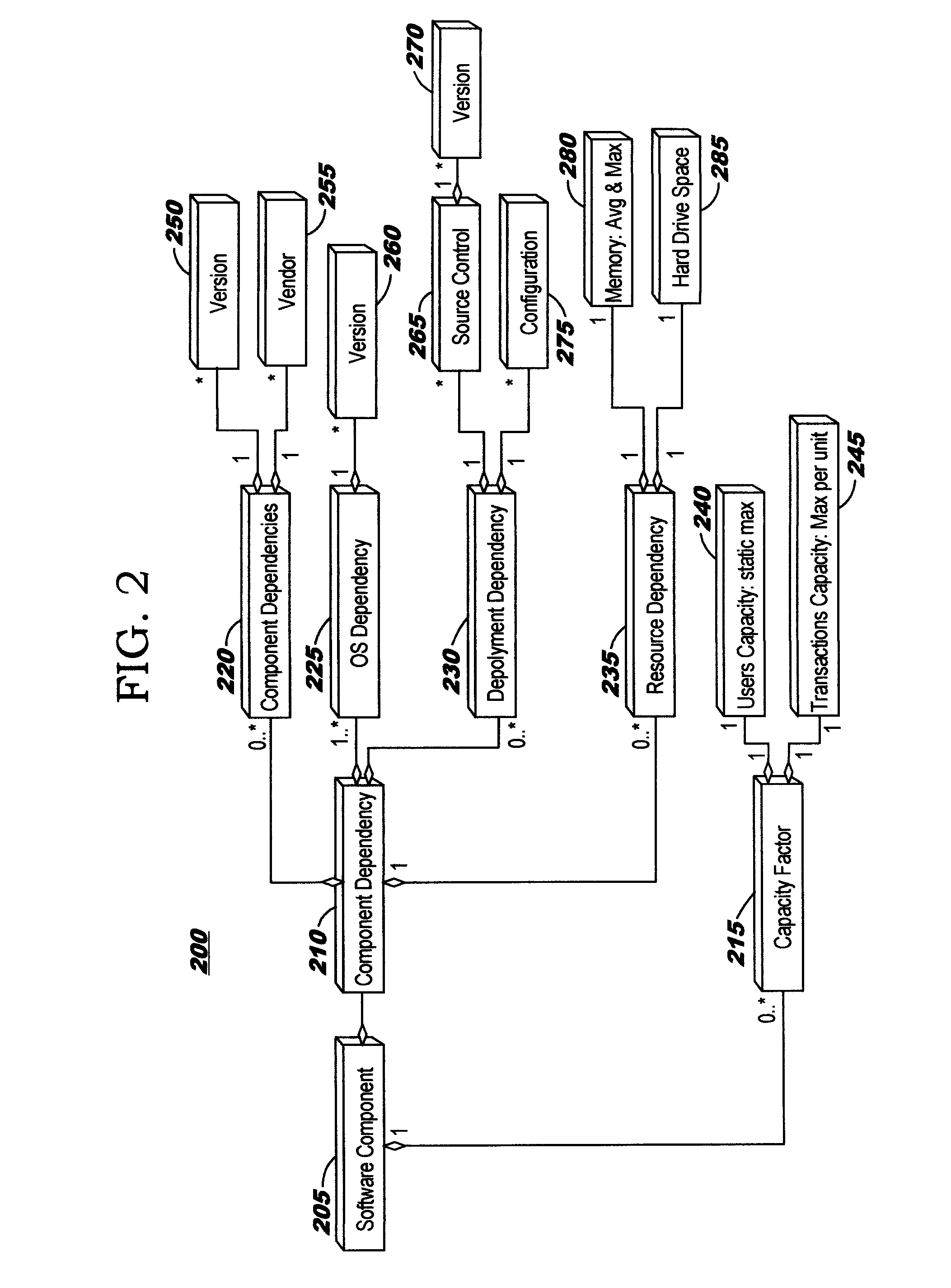
Automatically deploying a configured system into a computing environment (such as a cloud computing environment) for execution therein comprises obtaining a configured architecture model describing the configured system, and iteratively evaluating the model to deploy pre-built components for the system and to create and enable a development environment in the computing environment for development of custom-built components needed for the system according to the model. The automated deployment processing further comprises automatically configuring the system; determining a proper installation sequence; allocating resources in the target environment; and installing the required tools and other software that will be needed for execution once the components of the system are deployed. Component metadata is used during the deployment, enabling automated consideration of various factors such as whether component dependencies, resource requirements, and compatibility issues are met.
Owner:IBM CORP
RFID systems and methods for optical fiber network deployment and maintenance
InactiveUS7760094B1Reduce riskFaster and accurate installationMultiplex system selection arrangementsFibre mechanical structuresNetwork deploymentComputer hardware
Owner:CORNING CABLE SYST LLC
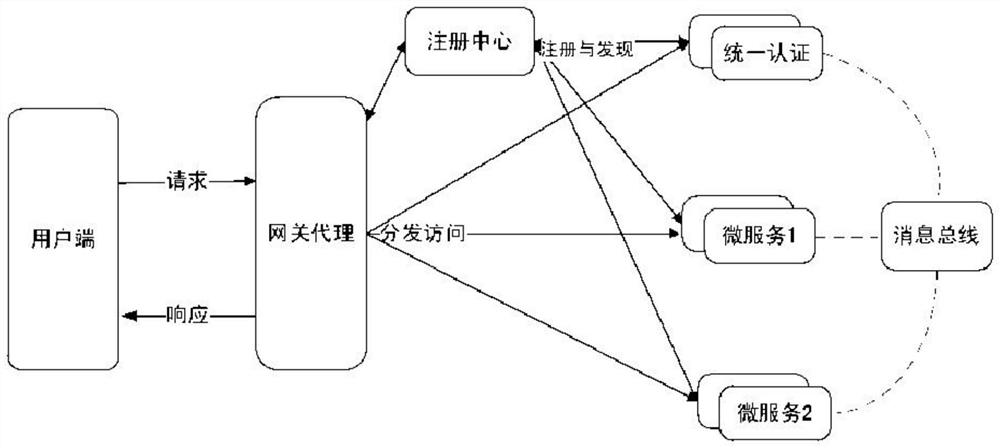
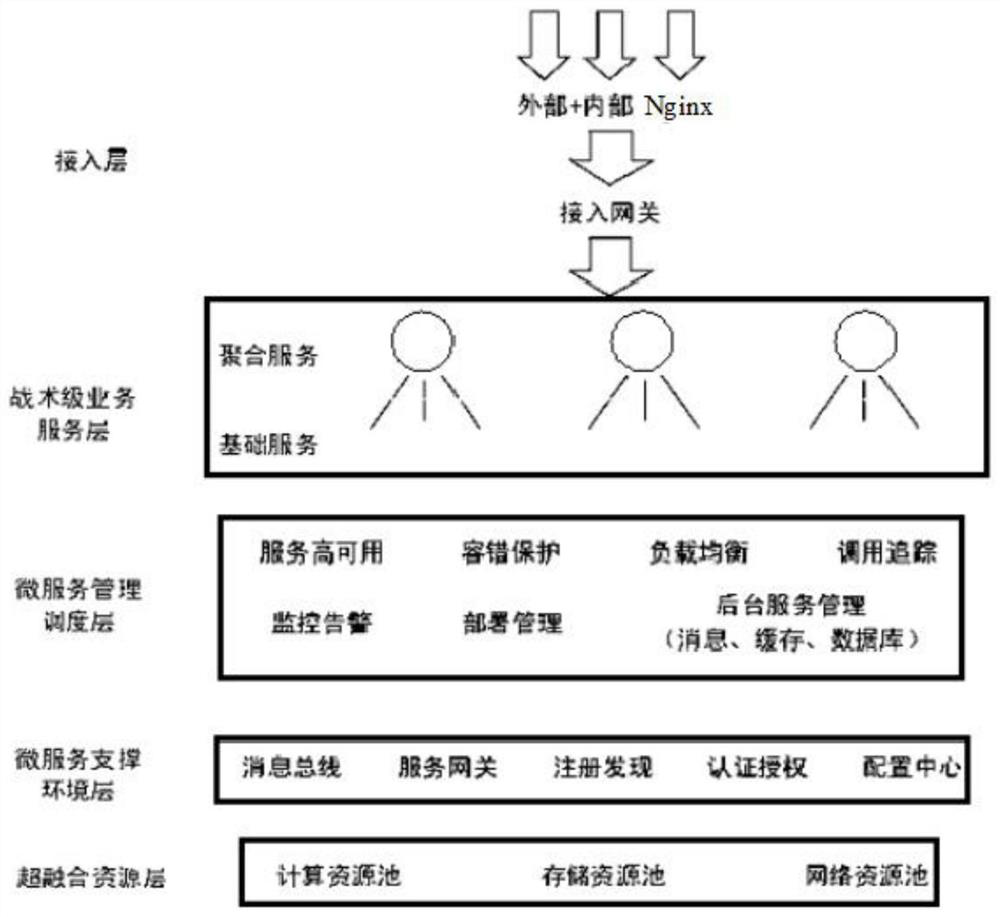
Application management method based on micro-service architecture
PendingCN112000448AGuaranteed operating efficiencyWith access cacheProgram initiation/switchingResource allocationService systemSystem deployment
The invention discloses an application management method based on a micro-service architecture. The method comprises the steps of tactical application-oriented micro-service technology architecture design, lightweight micro-service operation support environment construction, tactical environment-oriented micro-service reliable management technology and information service whole-process dynamic operation and maintenance. According to the invention, a leading-edge micro-service architecture is introduced for application management, a tactical-level service system is split into loosely-coupled and finer-grained service units; based on the application system deployment mode based on the micro-service framework, the method has the advantages of easiness in development and maintenance, quicker starting, easiness in local modification and deployment, telescopic deployment as required and the like; the application system support environment construction based on the micro-service is realized,the military application requirements for light weight and rapid deployment of the tactical environment are met, meanwhile, the project studies reliable management of the micro-service for the battlefield environment, and application operation and maintenance management with higher reliability is achieved through optimization technologies such as high-availability management, load balancing, service fault tolerance and call tracking.
Owner:BEIJING INST OF COMP TECH & APPL
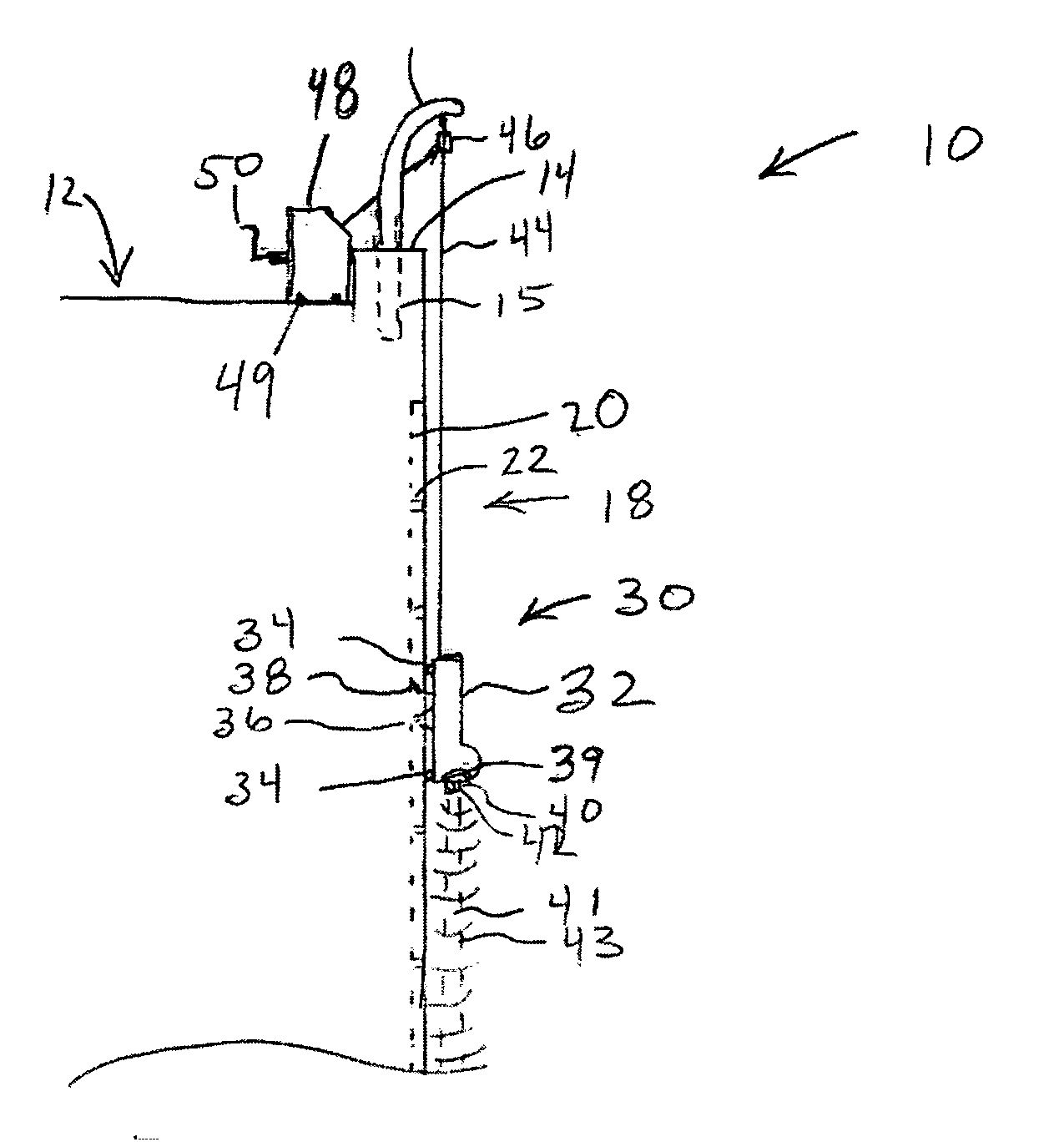
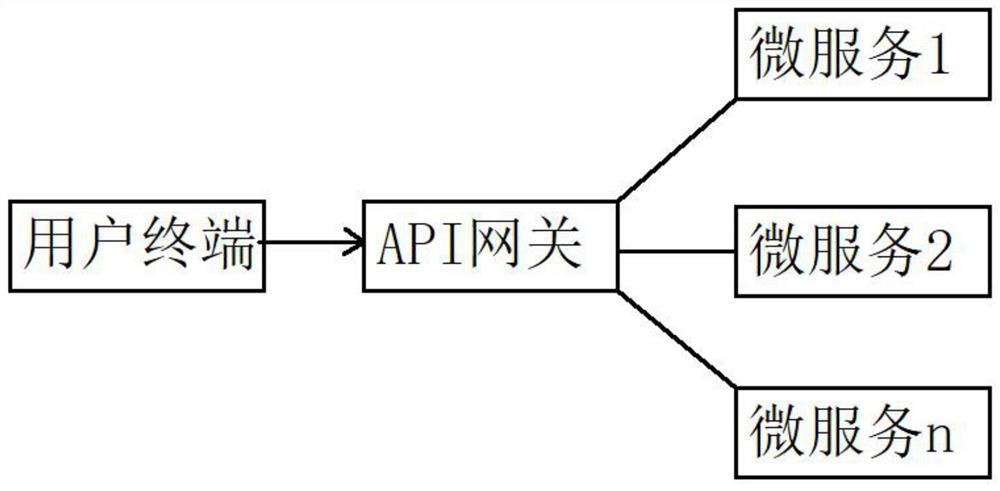
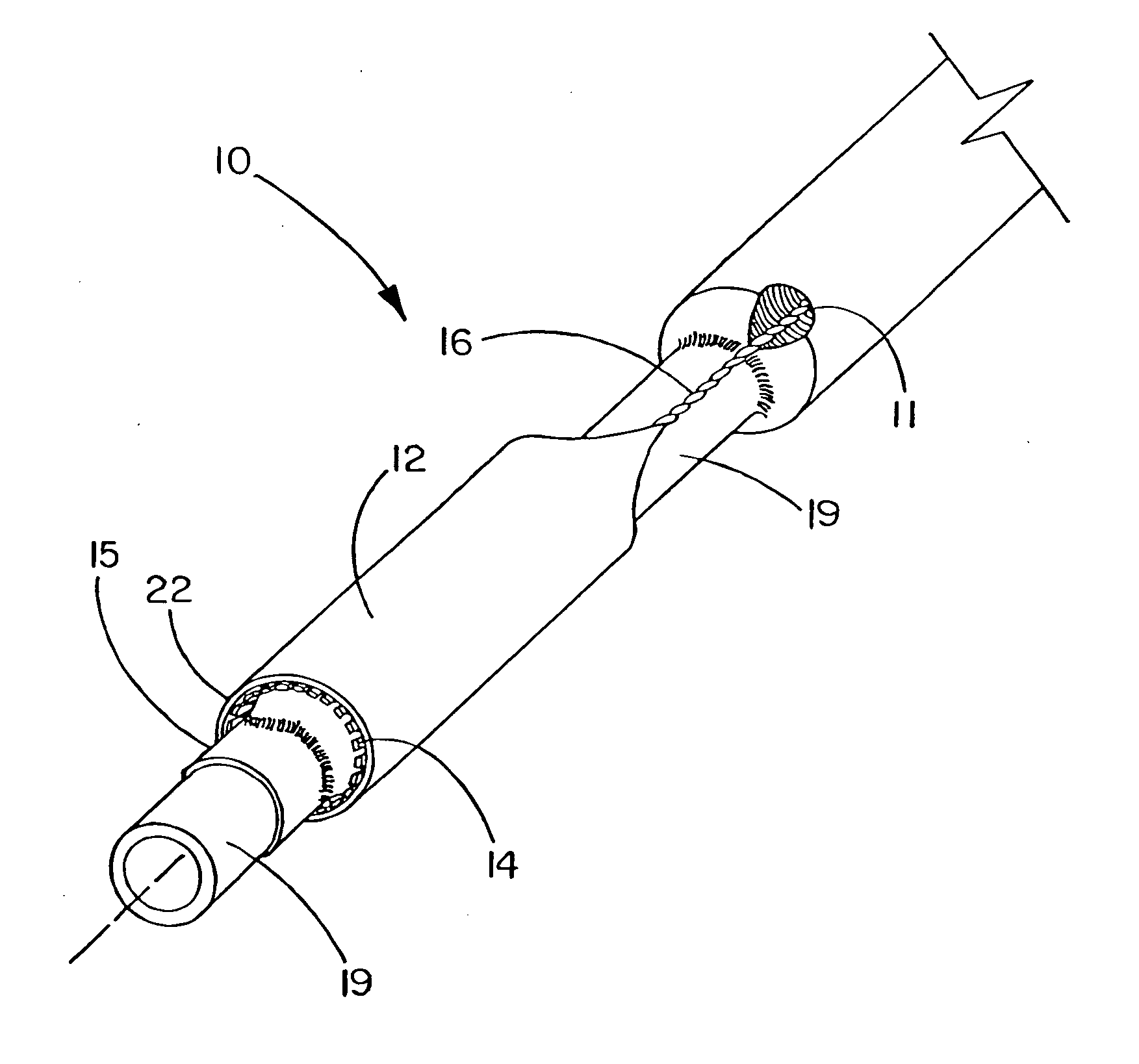
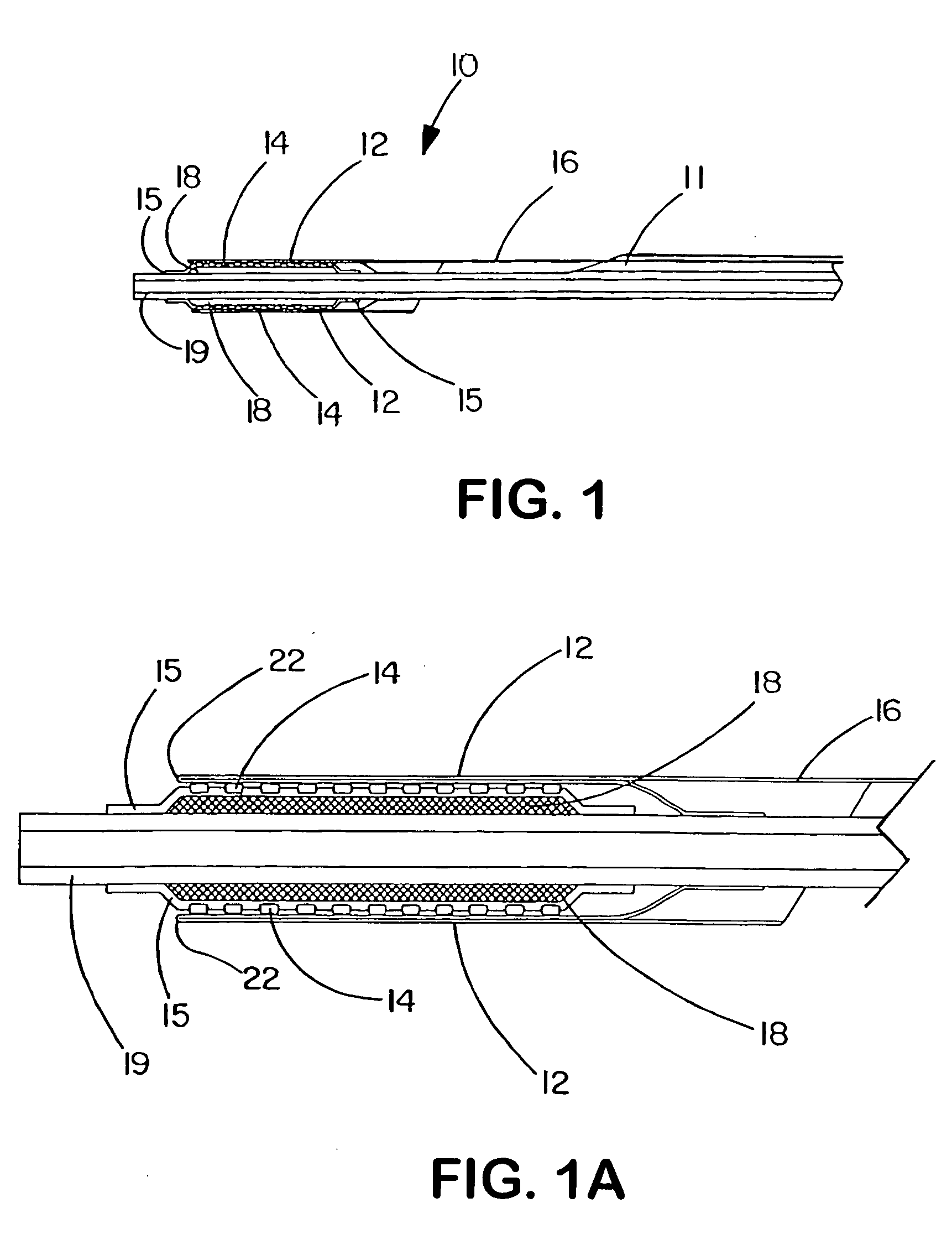
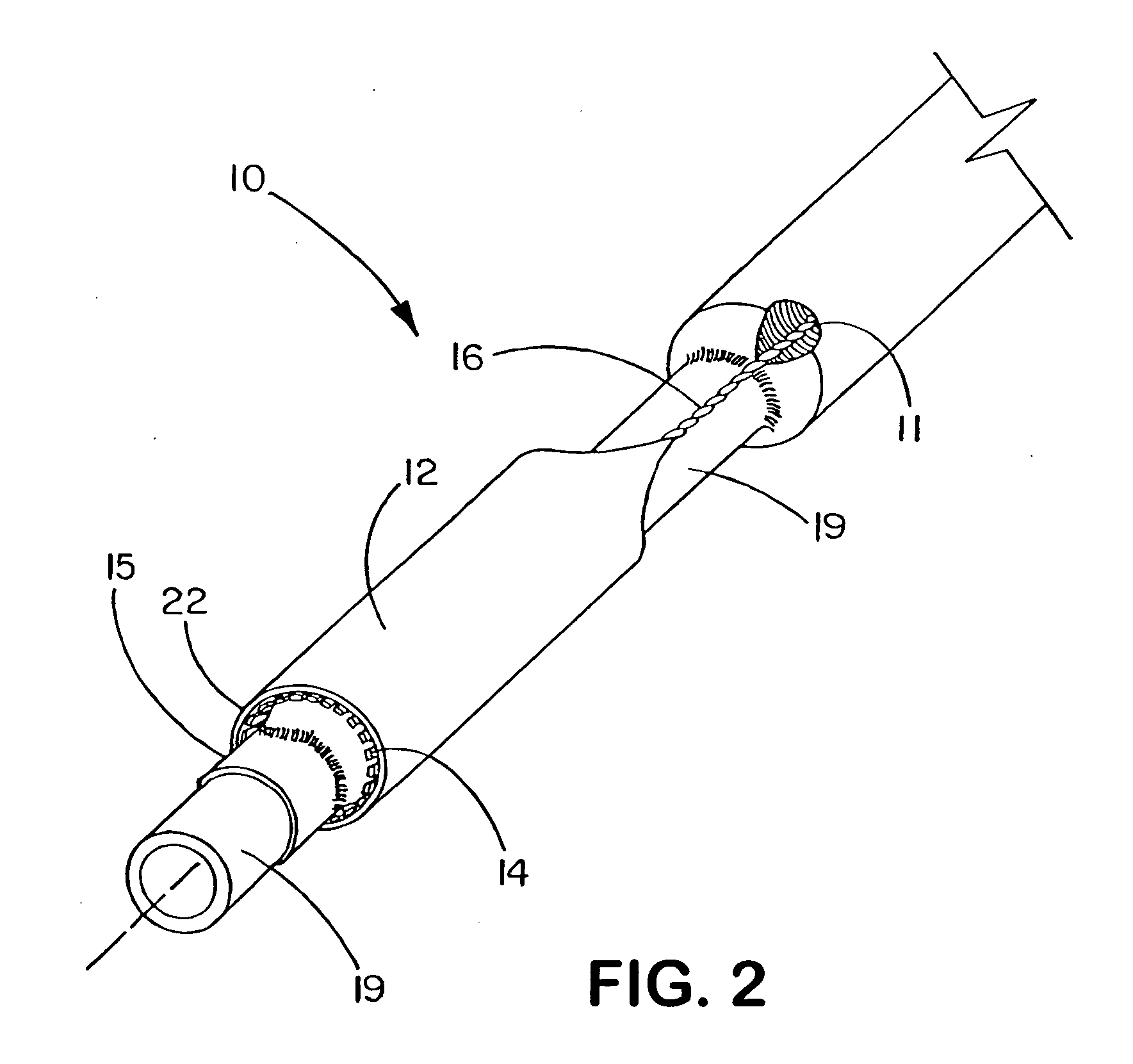
Deployment system for an expandable device
InactiveUS20060058866A1Improve system accuracyImprove deployment accuracyStentsCatheterBiomedical engineeringCatheter device
The present invention is directed to a deployment system for a self-expanding endoluminal device. The deployment system includes a confining sheath placed around a compacted endoluminal device so that upon deployment the sheath is transitioned into an internal deployment line housed within the catheter. The deployment system is configured to prevent rotation of the catheter relative to the deployment line during deployment line actuation.
Owner:WL GORE & ASSOC INC
Data synchronization
InactiveUS7451163B2Digital data processing detailsCathode-ray tube indicatorsData synchronizationControl system
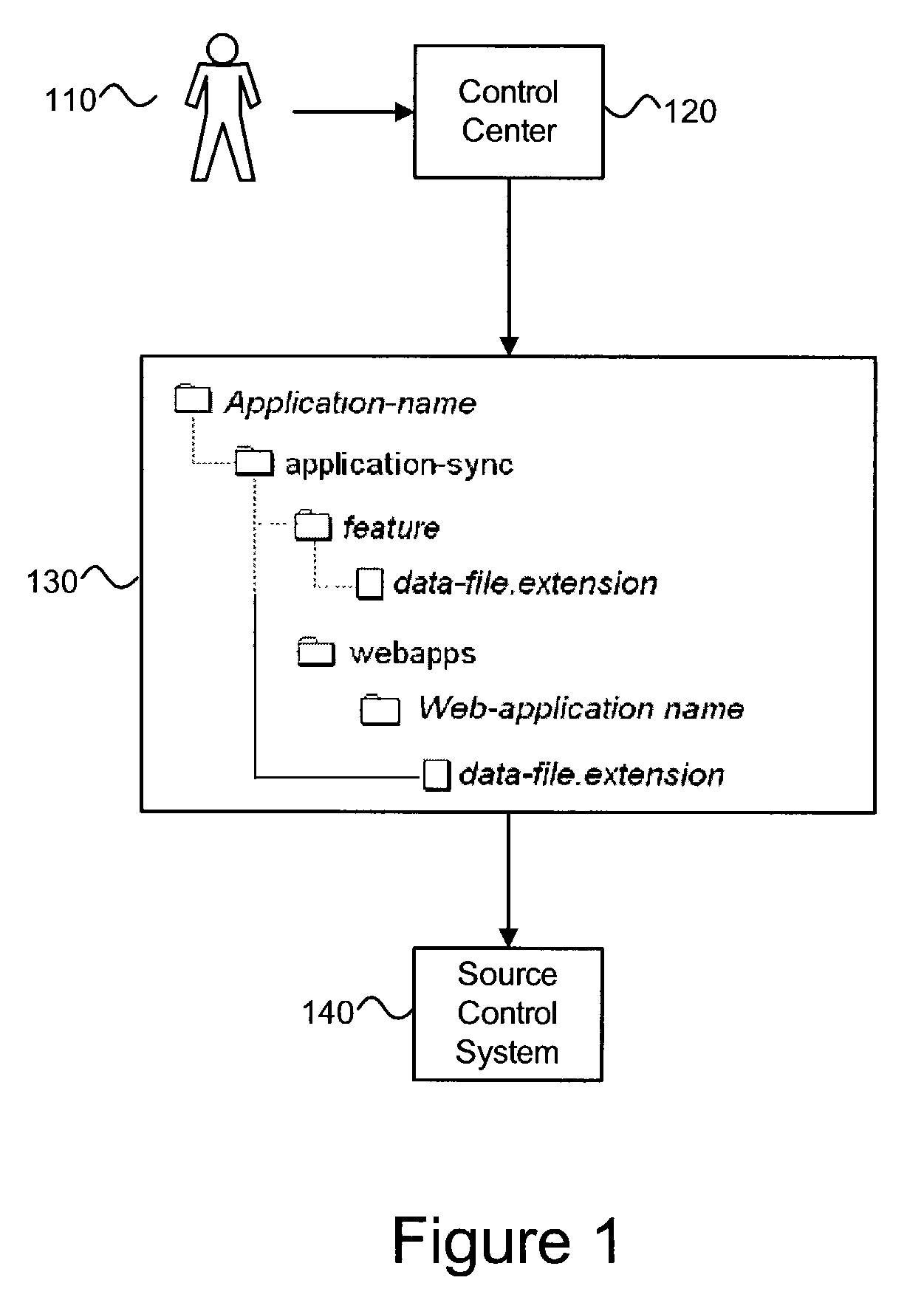
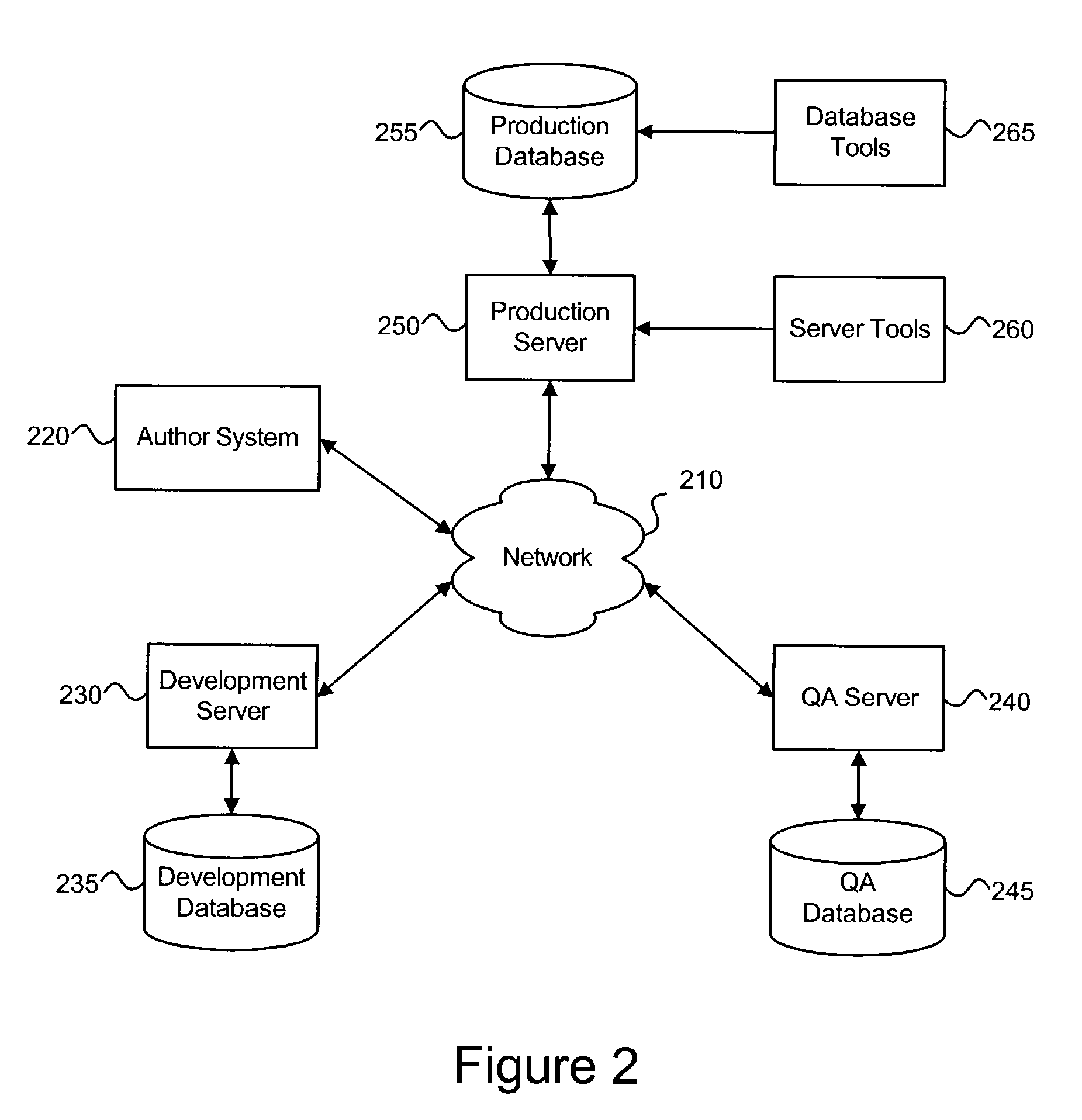
Application data used by enterprise applications running on one or more servers can be synchronized with application data deployed from other locations. Application data can be transmitted as XML files over HTTP to facilitate synchronization with web-enabled servers. Multiple service data repositories can be synchronized with application data residing in a master data repository that runs within an enterprise application. Server-to-server data synchronization functionality is also provided through the use of proxy data repositories. Application data files can be deployed from an author system to remote servers. Newly-authored application data files can be versioned in the author system using a source control system and selectively deployed to various servers by the author in conjunction with a multi-stage testing process in preparation for deployment of the application data to a production server.
Owner:ORACLE INT CORP
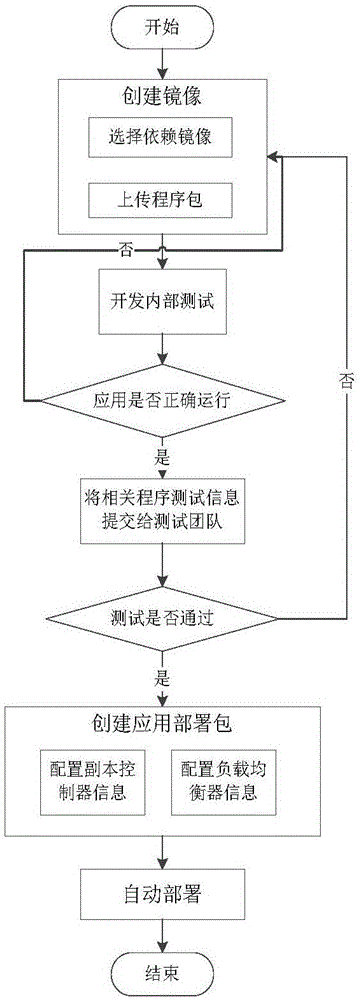
Development, testing, operation and maintenance integration system, deployment and full-quantity and incremental updating method
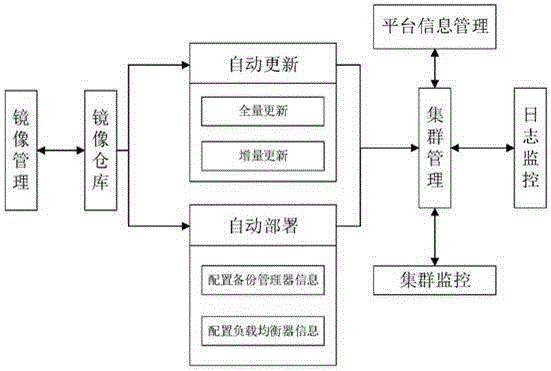
ActiveCN106293820ARealize integrationImplement automatic deploymentSoftware testing/debuggingProgram loading/initiatingApplication softwareMirror image
The invention discloses a development, testing, operation and maintenance integration system, deployment and a full-quantity and incremental updating method. The system comprises an automatic deployment module and an automatic updating module, wherein the automatic deployment module configures corresponding backup controller information and load balancer information according to mirror images in a mirror image warehouse at a developer end, automatically generates an application deployment script, and automatically / manually spreads the application deployment script to a testing deployment end; the testing deployment end automatically deploys an application to the testing, operation and maintenance environment by executing an application deployment script file, the automatic updating module updates an application program according to the mirror images in the mirror image warehouse at the developer end, generates an update pack file in a full-quantity or incremental updating mode and automatically / manually spreads the update pack file to the testing deployment end; the testing deployment end automatically deploys the updated application to the testing, operation and maintenance environment by executing the update pack file. Cooperation obstacles among development, testing, operation and maintenance are reduced, the cooperation efficiency is improved, application deployment processes are simplified, a developer pays close attention to business flows, and the requirement for technological levels of operation and maintenance staffs is lowered.
Owner:SHANDONG UNIV
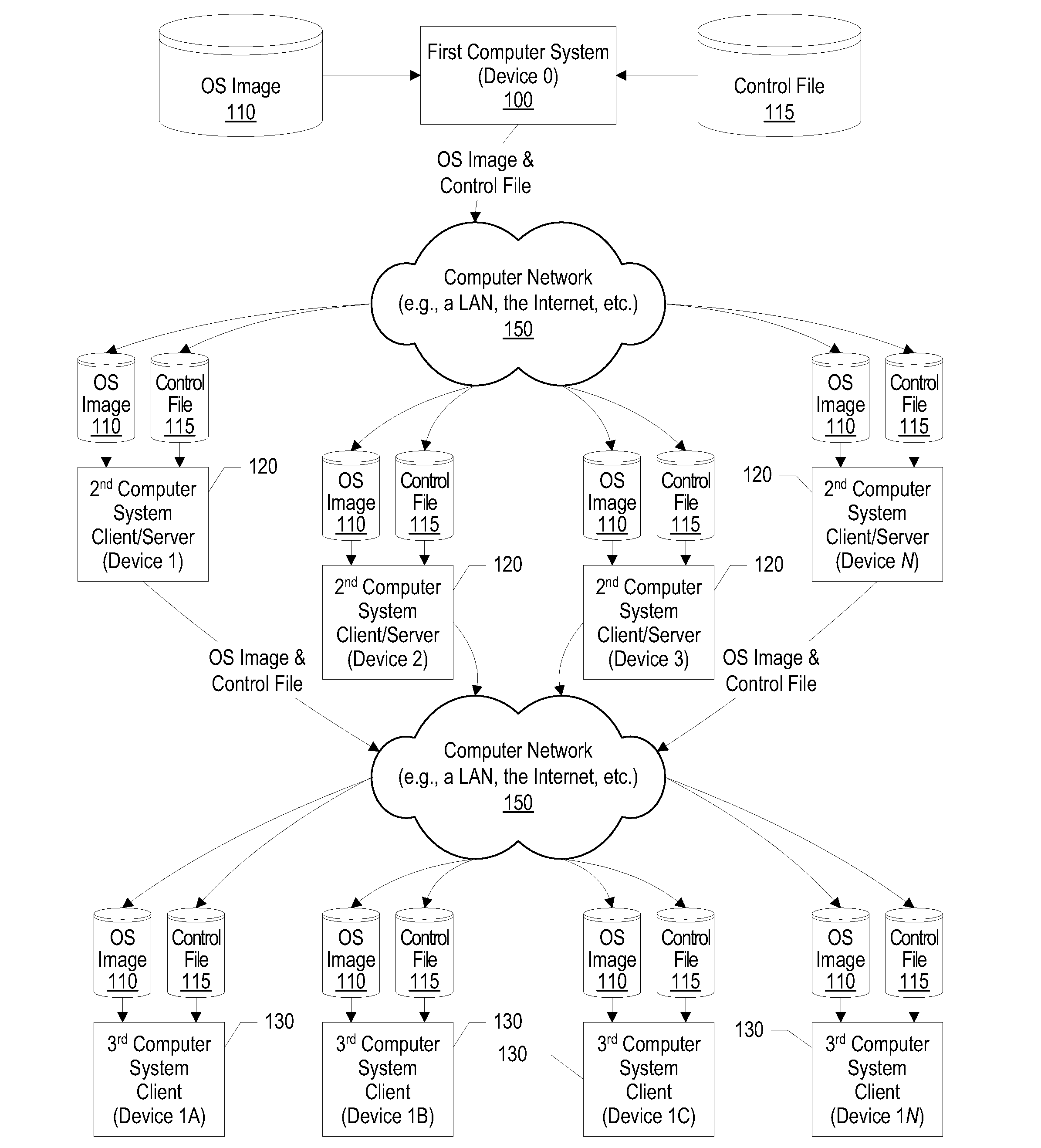
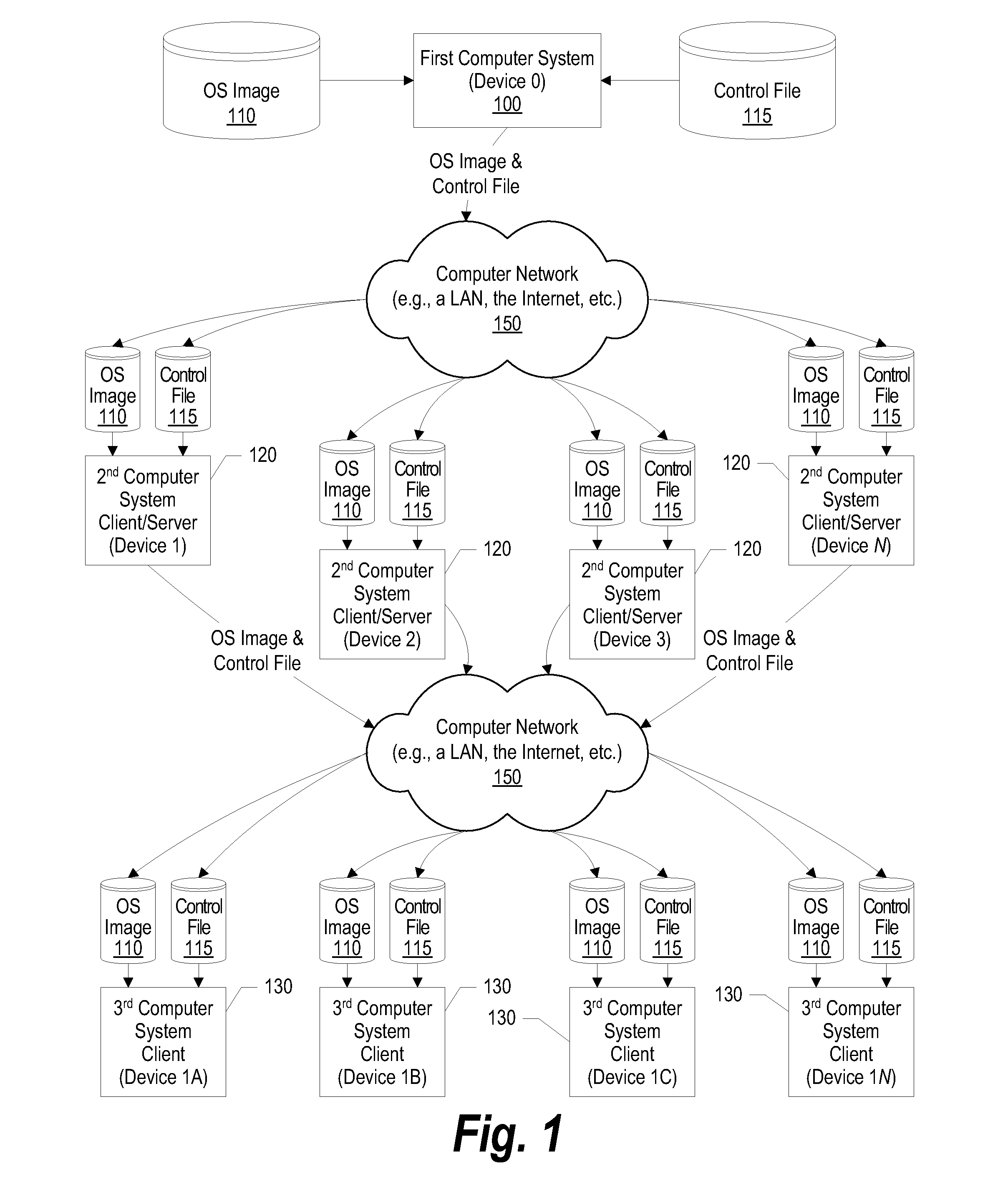
System and method for operating system deployment in a peer-to-peer computing environment
InactiveUS20080141015A1Digital computer detailsProgram loading/initiatingOperational systemPeer to peer computing
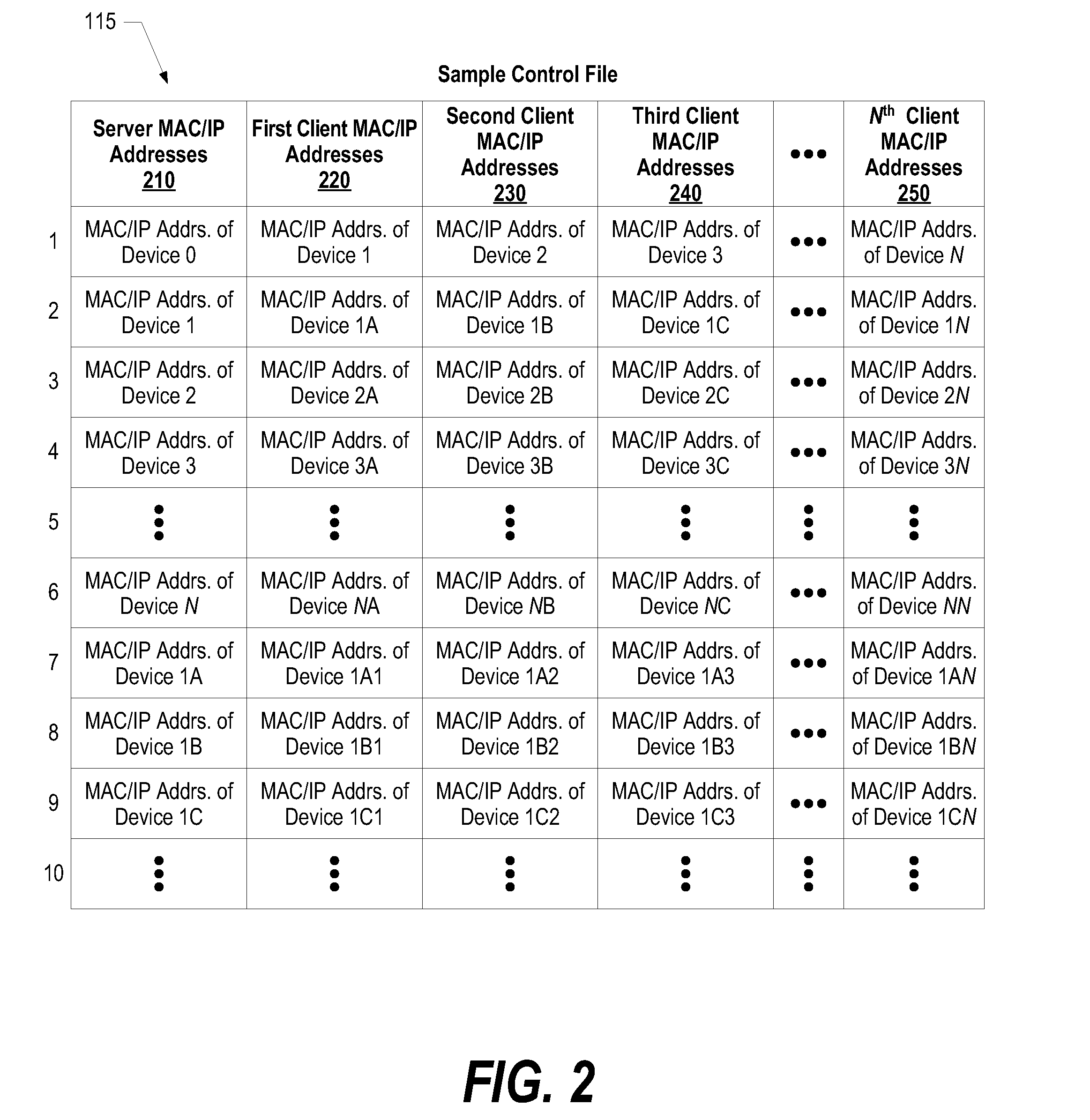
A system, method, and program product is provided that deploys an operating system. The first computer system sends a Wake-on-LAN instruction and boots each of the second computer systems. The second computer system identifies a set of third computer identifiers that corresponds to each of the selected second computer systems. The second computer systems send the Wake-on-LAN instruction to each of the third computer systems, and the third computer systems are booted over the computer network from the second computer systems. A control file lists the first computer system as a “server” of the second computer systems and lists the second computer systems as “servers” of the third computer systems. The control file is transmitted from a server to each of the server's clients. When a client is booted, it checks the control file to determine if the client is also a server to other computer systems.
Owner:IBM CORP
Method, system and program product for deploying and allocating an autonomic sensor network ecosystem
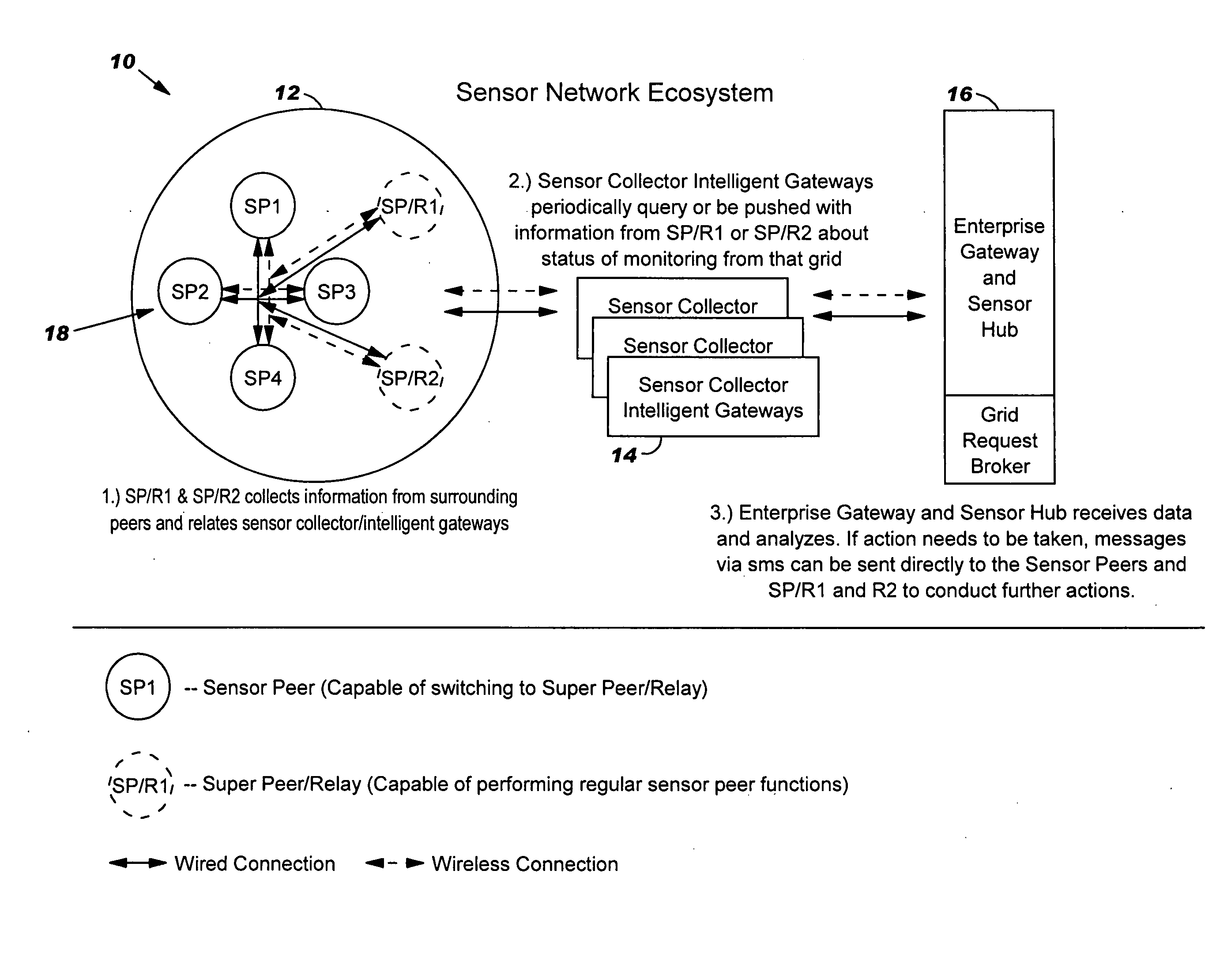
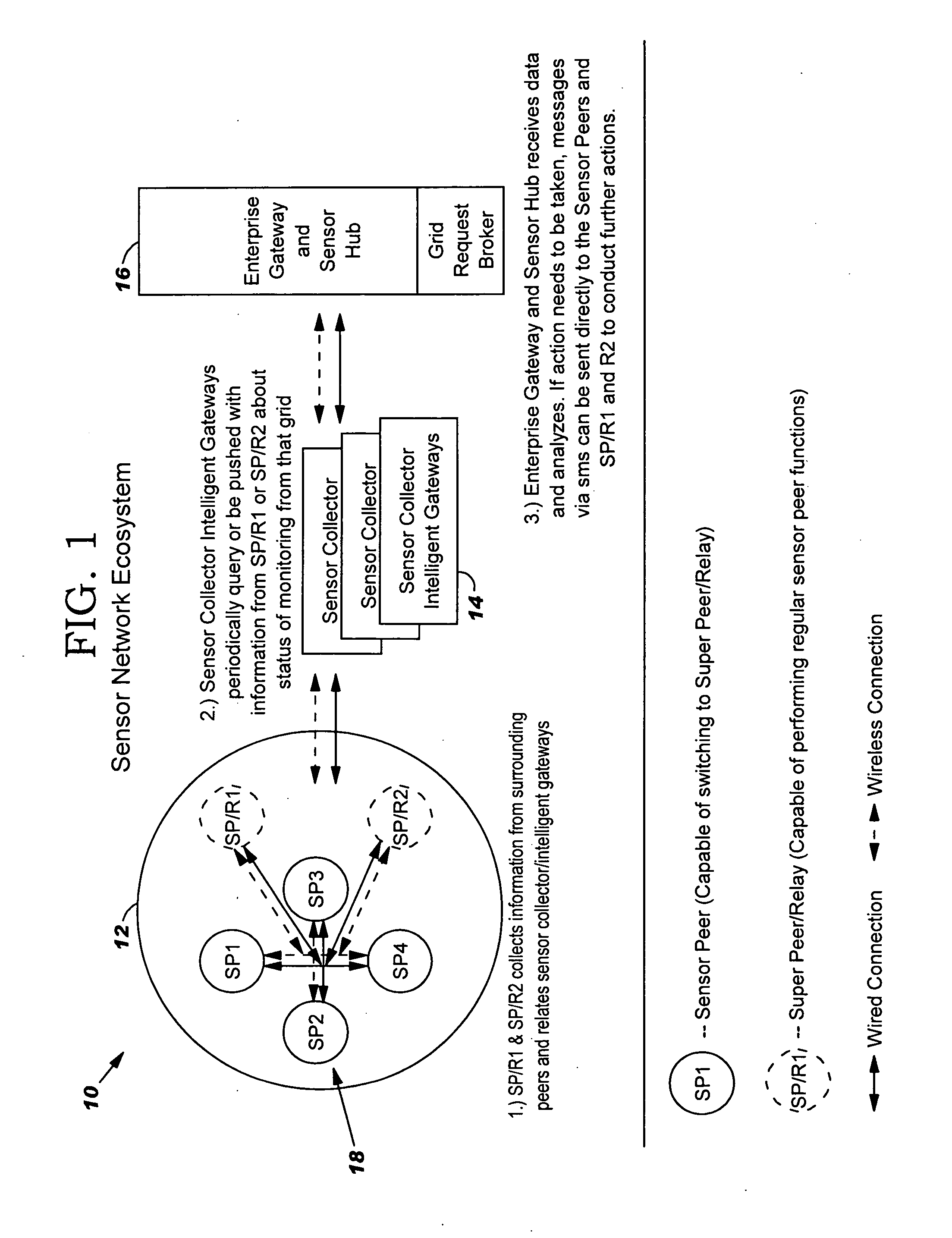
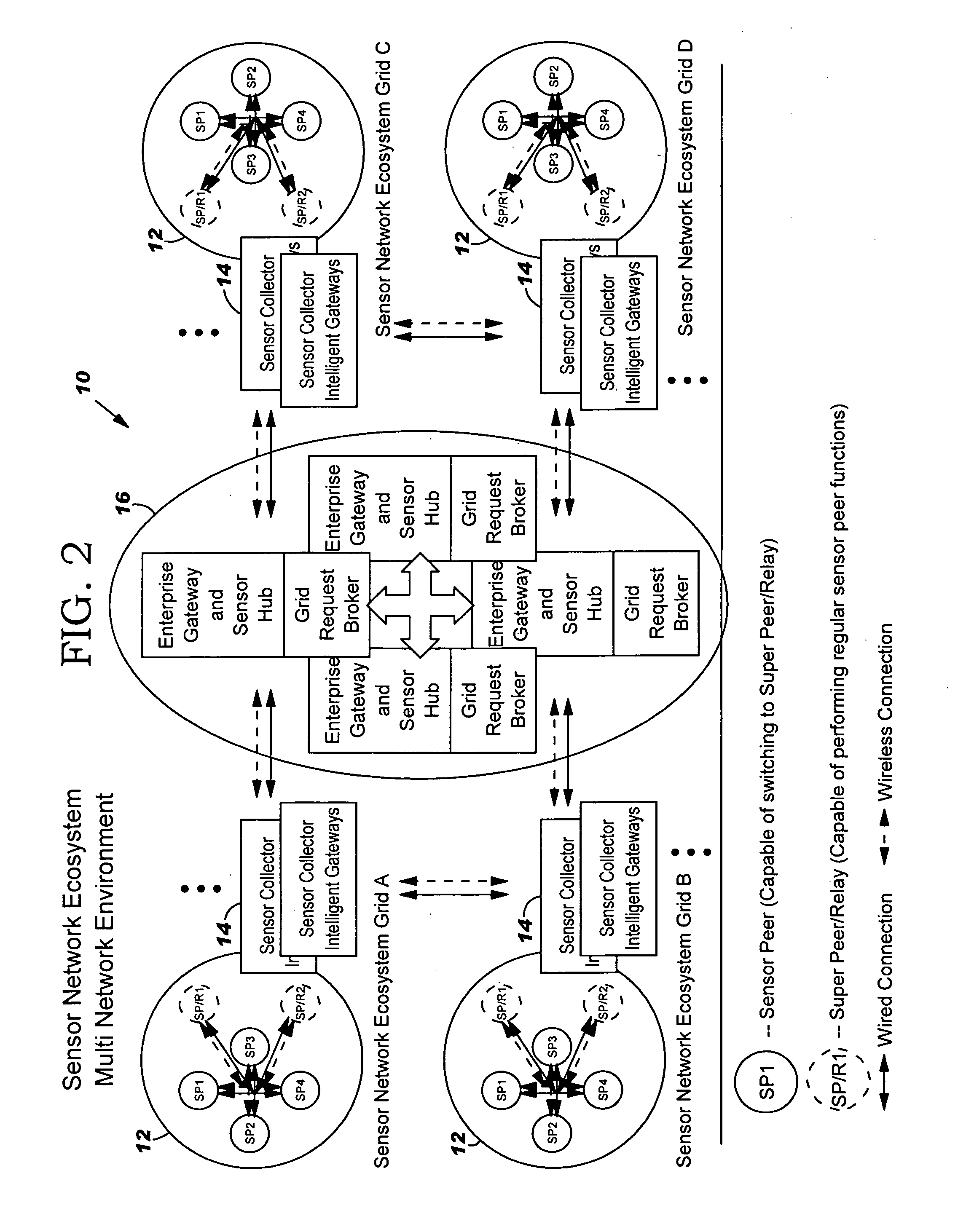
The present invention provides a method, system and program product for deploying, allocating and providing backup for an autonomic sensor network ecosystem. Under the present invention, the autonomic sensor network ecosystem includes: (1) a set (e.g., one or more) of sensor networks for storing data components; (2) a set of sensor collector information gateways in communication with the sensor networks; and (3) a set of enterprise gateways and storage hubs (hereinafter enterprise gateways). Each sensor network includes a set of sensor peers and at least one super peer. The super peer manages the sensor network and communicates with the set of sensor collector information gateways. The autonomic sensor network ecosystem of the present invention is deployed and allocated in such a manner that backup and resiliency is provided.
Owner:KYNDRYL INC
Deployment system for ruggedized illuminating, marking, or signaling device
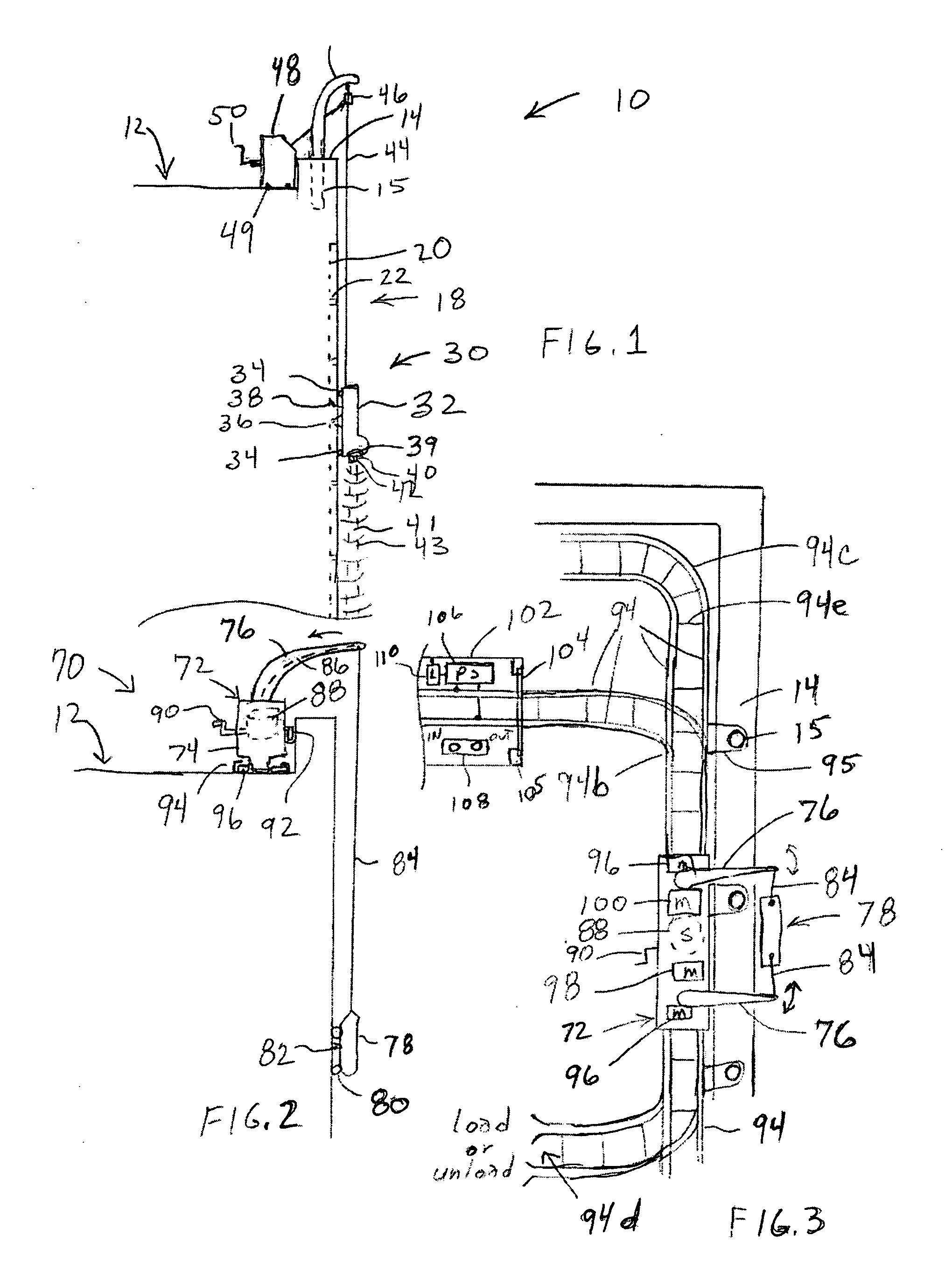
ActiveUS7106179B1Reduce the risk of firePortable emergency signal deviceRoad vehicles traffic controlLight equipmentUtility company
A deployment system for illumination devices, including: a holding mechanism for engaging at least one illumination device; and a deploying mechanism for causing the at least one illumination device to exit the system. In the preferred embodiment, the deploying mechanism is at least one solenoid, where the at least one solenoid extends to cause the illumination device to exit the system. The system allows a user or an automated system to deploy illumination devices without being exposed to dangerous conditions. For example, the system can be mounted internally or externally to a law enforcement, road crew, or utility company vehicle. The user may then deploy the illumination devices to mark the road without being subjected to the dangers of oncoming traffic.
Owner:POWERFLARE CORP
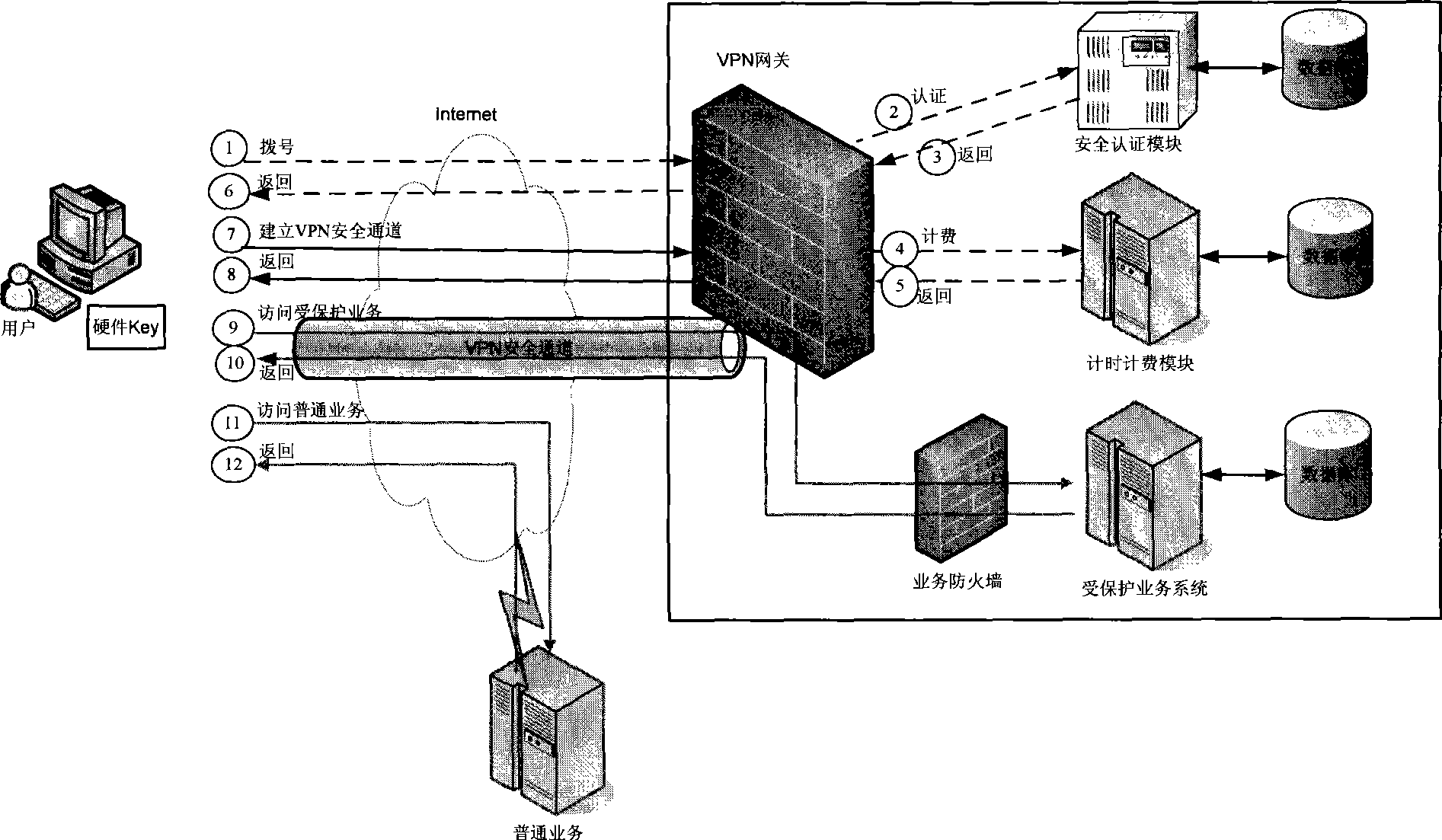
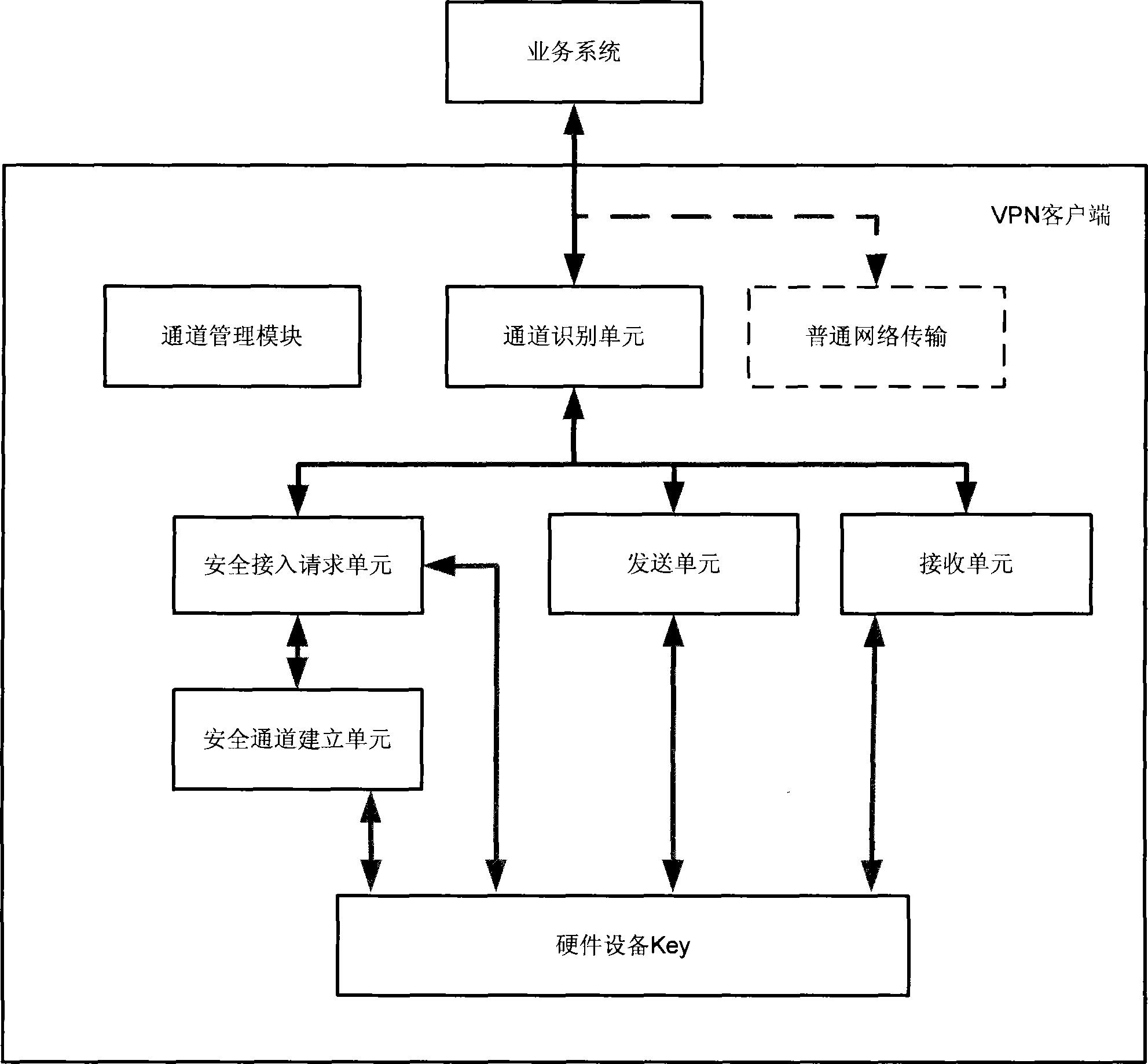
VPN secure access method and system thereof
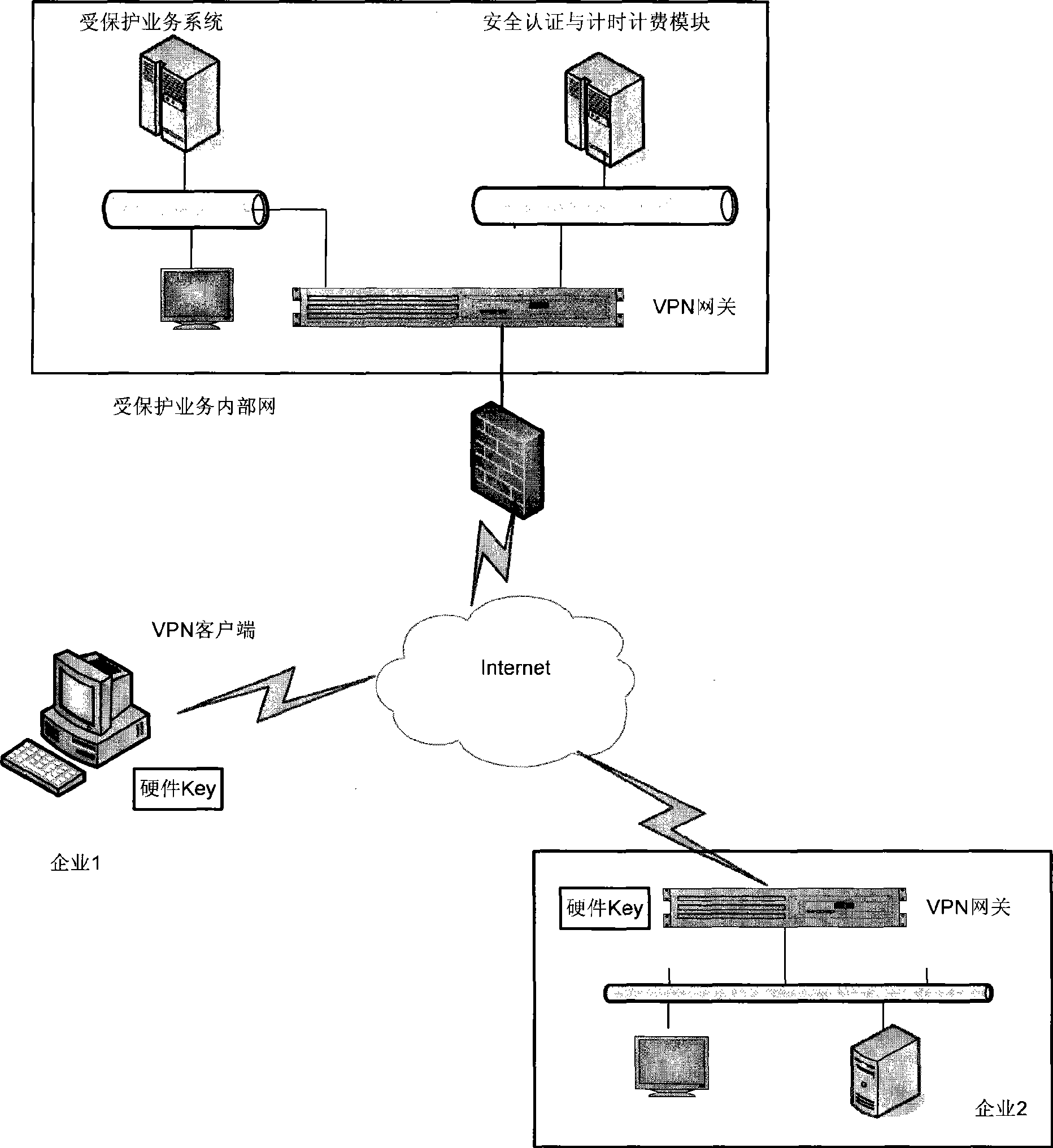
InactiveCN101447907ATo achieve the purpose of secure accessImprove security levelUser identity/authority verificationNetworks interconnectionAccess methodHigh intensity
The invention relates to the technical field of network security and provides a VPN secure access method, a system and a VPN client thereof; wherein, the VPN secure access method comprises the steps as follows: the VPN client, which employs a hardware Key, sends an access request to the network; the access request is signed and encrypted by the hardware Key; the network carries out identity authentication on the VPN client after receiving the access request and establishes a safe passage with the VPN client after the identity authentication is passed; and the VPN client carries out safety service interaction with the network by the hardware Key and the safe passage. The invention integrates secure access, identity authentication for clients with high intensity and a timing and charging module seamlessly, and provides a whole secure access proposal, thus reducing the difficulty of system distribution and operation maintenance while guaranteeing the network safety, and facilitating the use for clients.
Owner:北京东方中讯联合认证技术有限公司
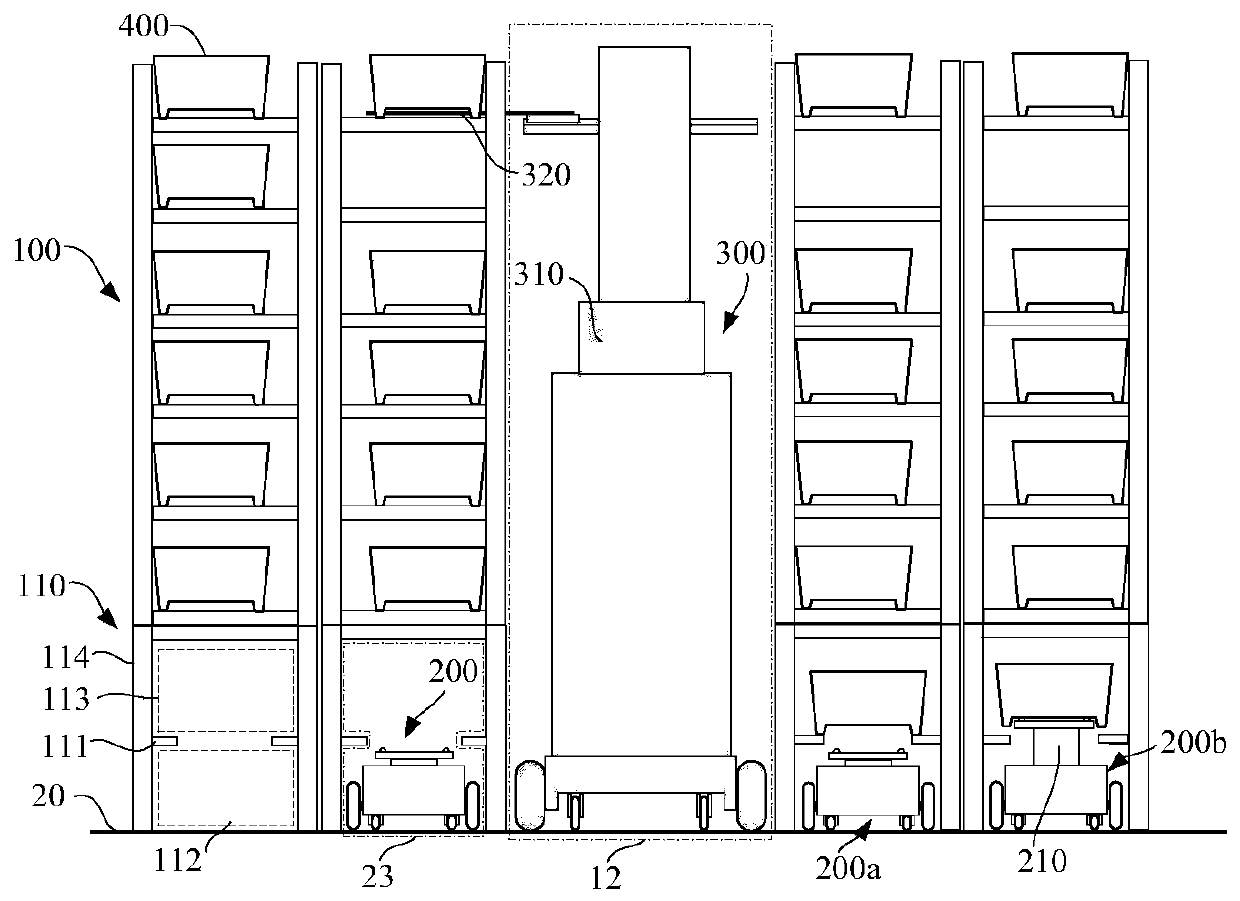
Unmanned storage system and warehouse output and input method
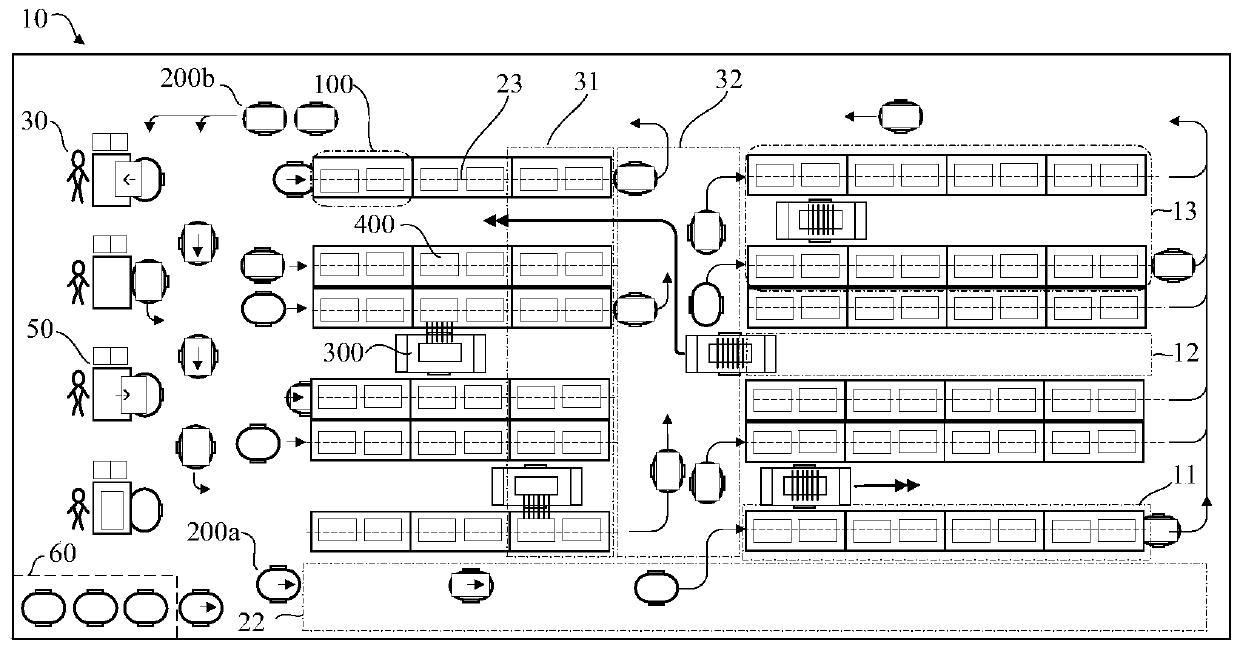
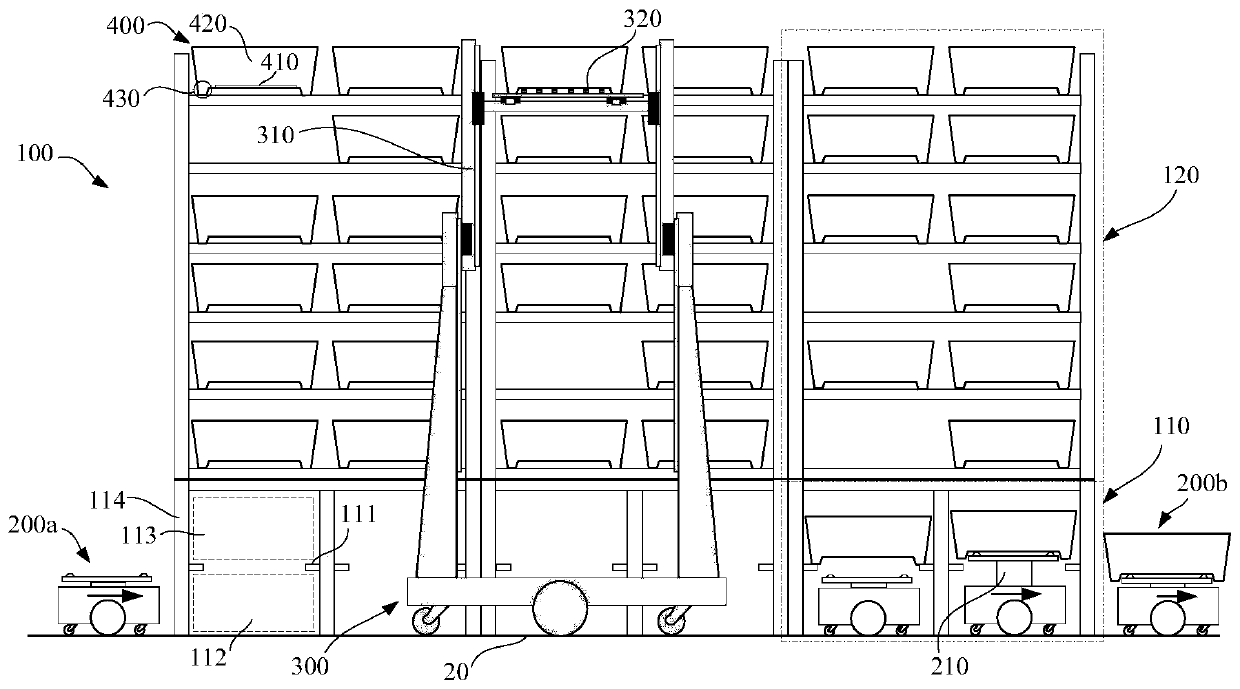
ActiveCN109987366AIncrease flexibilityEfficient transportStorage devicesComputer scienceOverall efficiency
The invention discloses an unmanned storage system and a warehouse output and input method. The problems that an existing system is complex in deployment, inconvenient to maintain, high in cost and the like are solved. In the embodiment of the invention of the system, two-layered channel supporting frames are arranged below storage racks, lower layers are used for allowing automatic guided vehicles to pass, upper layers are used for allowing normalized containers to be temporally cached or pass through, and interlayer supporting plates are through in the length direction or width directions ofthe whole storage racks. During implementation of goods warehouse output, forklift trucks move to the specified storage racks automatically and align the corresponding storage racks, the normalized containers on the storage racks are taken out with a goods collecting mechanism, then the forklift trucks descend to the upper layers of the supporting frames, and the containers are cached on the supporting plates; afterwards, the automatic guided vehicles move to the lower sides of the containers via the lower layers of the supporting frames to jack up the containers and further be disengaged from supporting pieces; and then the vehicles move to sorting sites via channels and roadways, and the warehouse input process is just on the contrary. The system can be deployed easily and is easy to maintain and low in cost, a large quantity of robots can execute concurrent operations through a scheduling system and the overall efficiency is high.
Owner:杭州大氚智能科技有限公司
Method and device for deploying application system
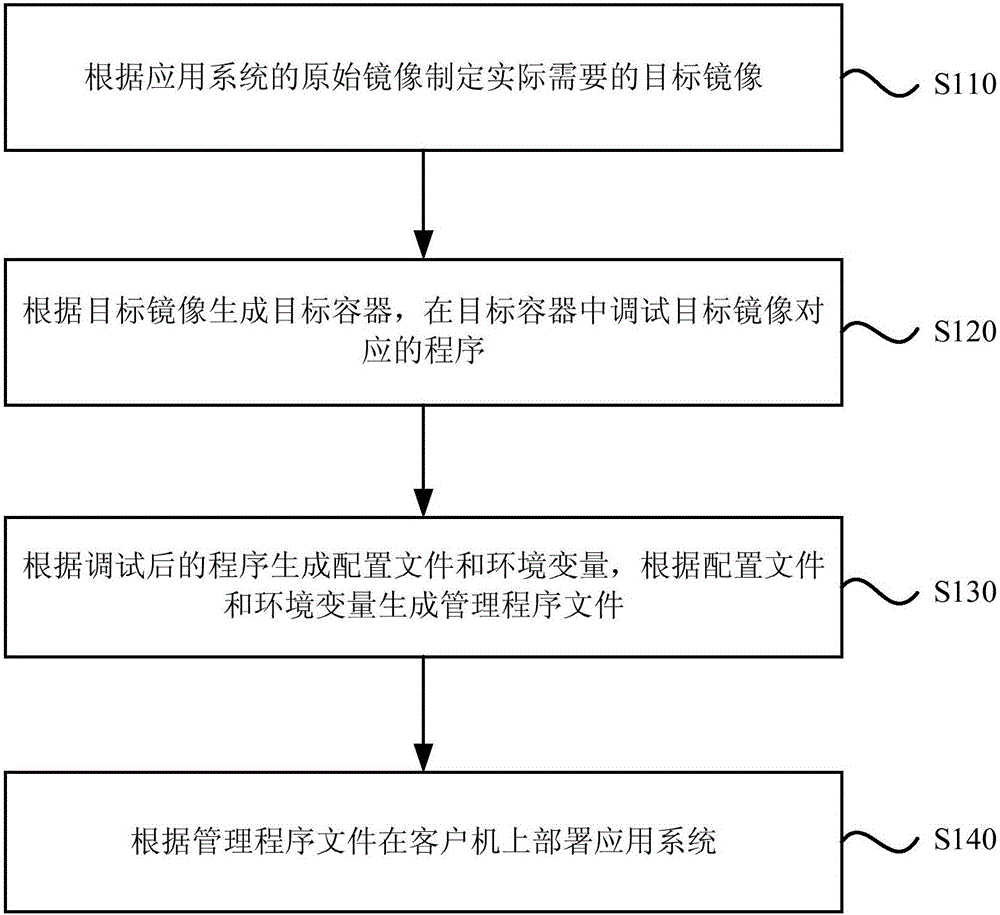
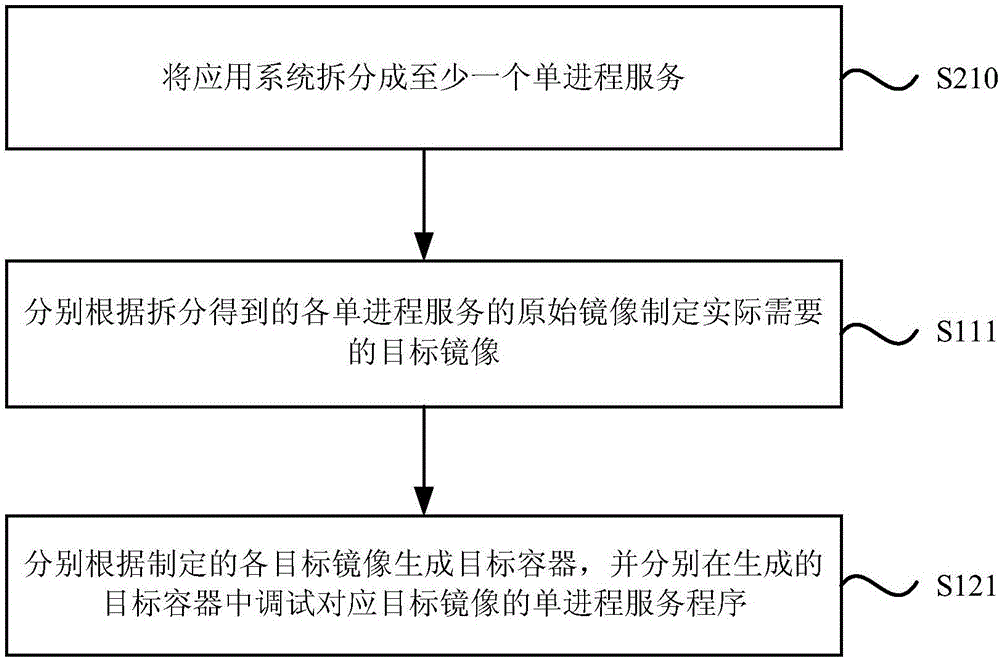
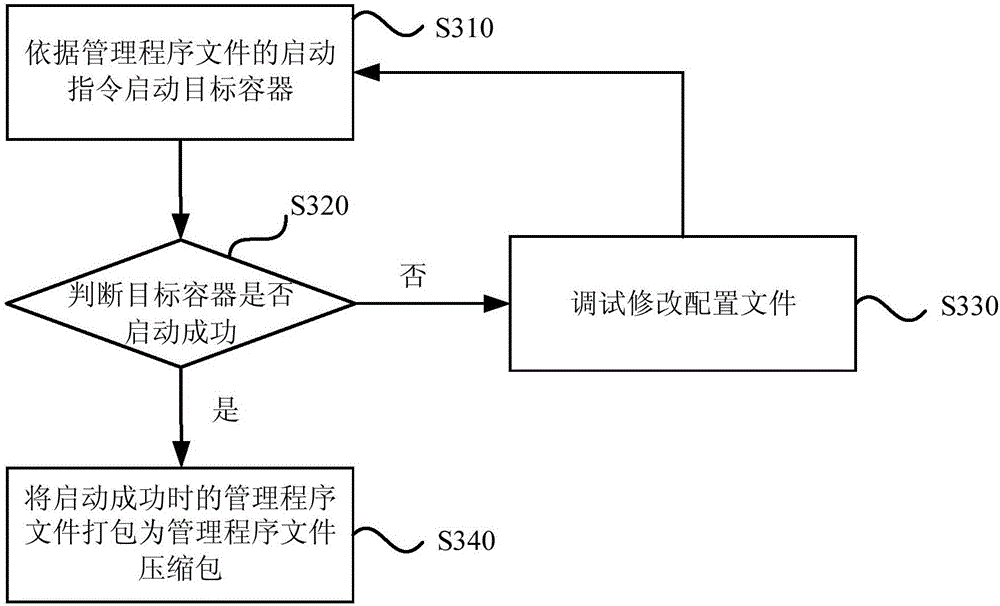
InactiveCN106648741AEasy to deployImprove deployment efficiencyPlatform integrity maintainanceProgram loading/initiatingData sourceMirror image
The embodiment of the invention discloses a method and device for application system deployment. The method for application system deployment includes the following steps: 1, according to an original mirror image of the application system, a target mirror image that is actually needed is drawn, and the original mirror image is pulled from a corresponding data source of a container engine; 2, a target container is generated according to the target mirror image,and a procedure corresponding to the target mirror image is debugged in the target container; 3, a configuration file and environment variables are generated according to the debugged procedure, and according to the configuration file and the environment variables, a supervisor file is generated; 4, according to the supervisor file, the application system is deployed on the client. The method anddevice for application system deployment enable the deployment of the application system without considering environment dependence and conflict problems, improve the deployment efficiency of the application system, and make the deployment of the application system convenient.
Owner:GUANGZHOU SHIRUI ELECTRONICS +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com