Method for disposing inbreak detection system
An intrusion detection system and intrusion detection technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of high false alarm rate and false alarm rate, increased cost, and increased security risks, so as to improve the accuracy rate and Efficiency, load reduction, and flexible deployment effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
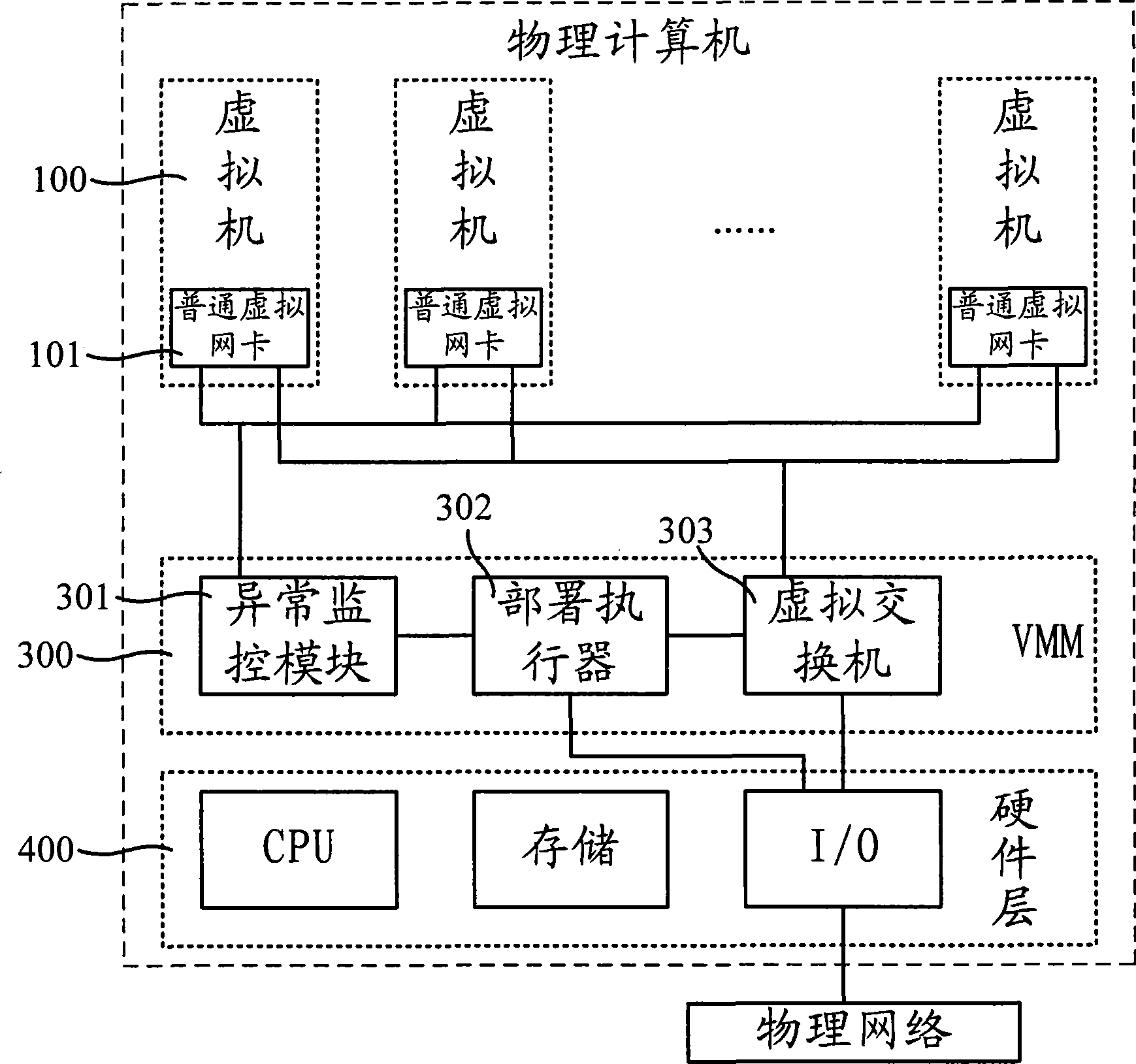
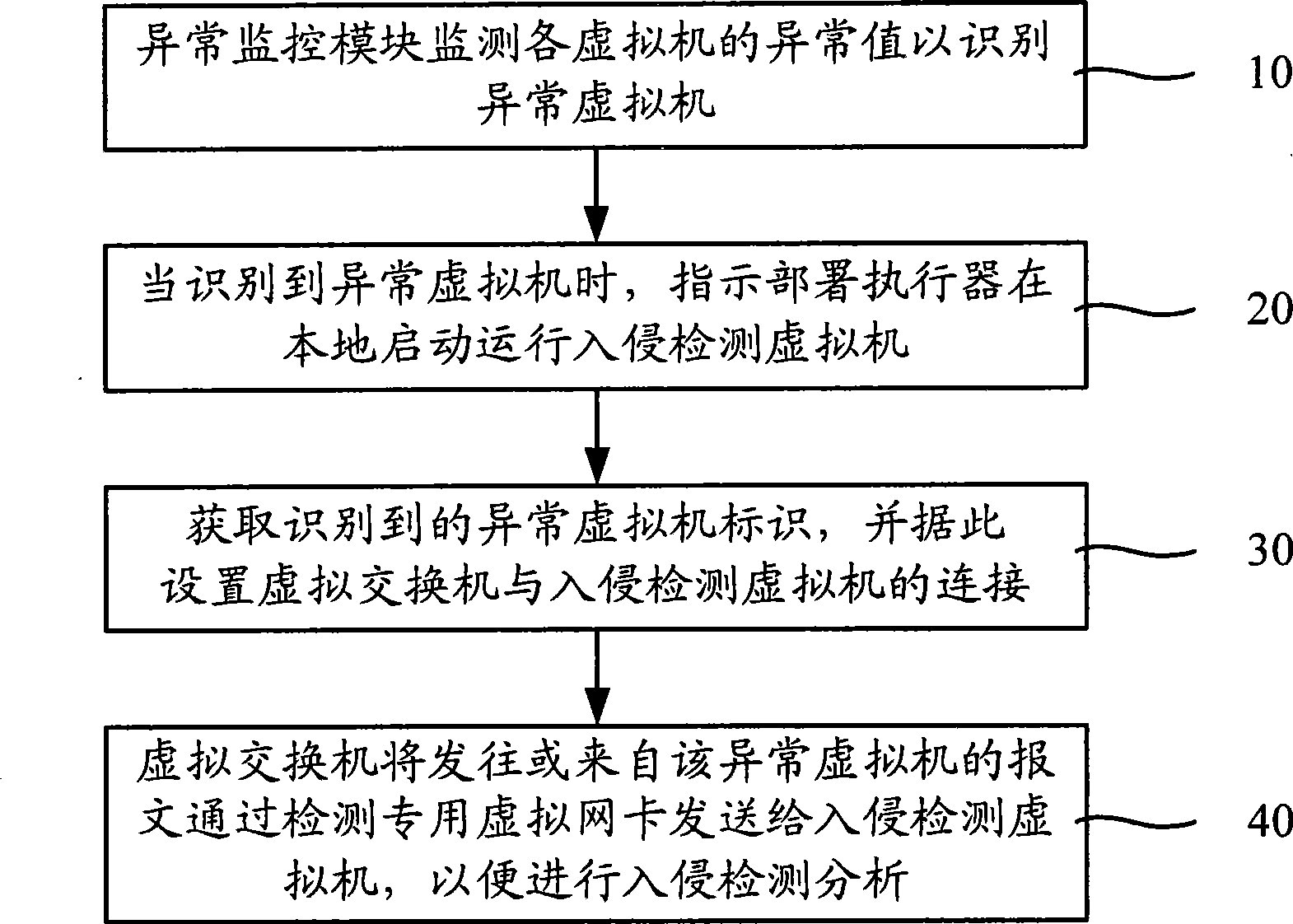
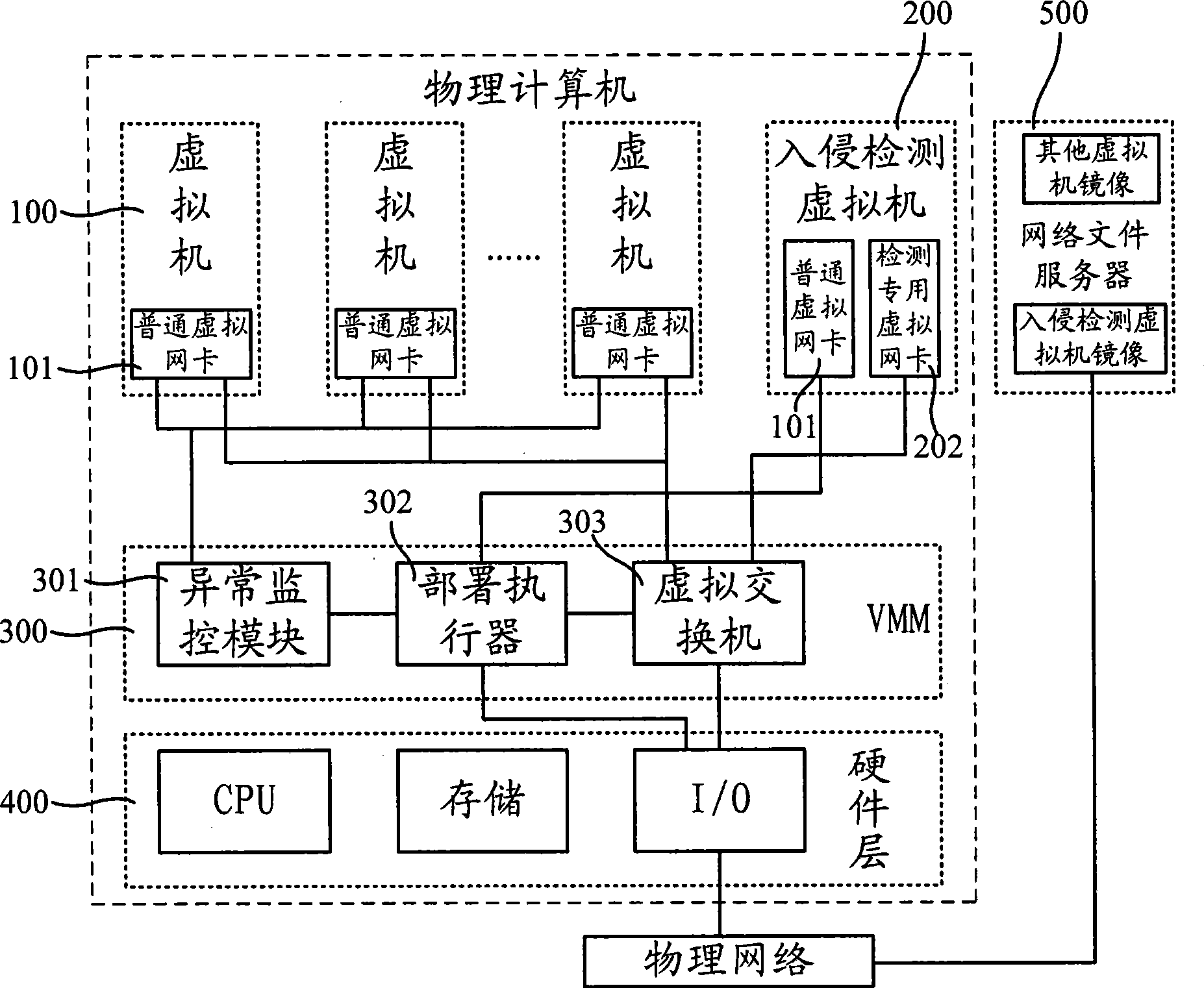
[0034] The deployment method of the intrusion detection system of the present invention is realized based on virtual machine technology, and can be realized by installing virtual machine software, such as "vmware", "xen" and so on, in the computer to be deployed IDS. Virtual machine technology can simulate a computer system with complete hardware system functions through software. Among them, the software specifically refers to the virtual machine monitor (Virtual Machine Monitor; hereinafter referred to as: VMM) software, which can encapsulate, isolate, monitor and manage multiple virtual machine instances, so that the same physical computer can be independently and without conflict. Run many types of operating systems. In addition, virtual machine technology provides a new way for software distribution and deployment. The software is encapsulated in the virtual machine image, and the deployment and migration of the virtual machine are used to flexibly realize the distributi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com