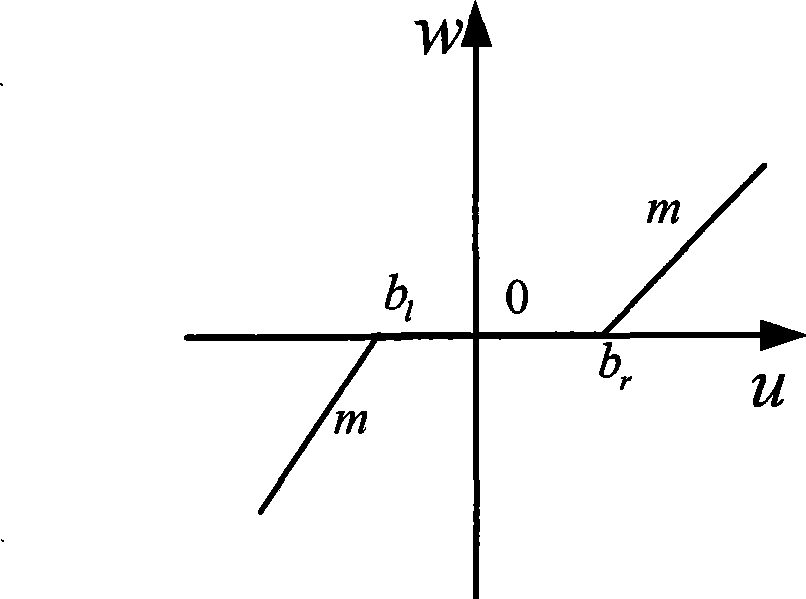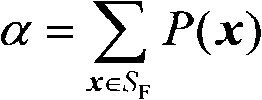Patents
Literature
284 results about "Network size" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The network provides limits. For IP, the minimum size is 20 bytes. The maximum size is 65535, but almost all media limit that further, typically to 1500 bytes.
Method and apparatus for communication network cluster formation and transmission of node link status messages with reduced protocol overhead traffic
InactiveUS6980537B1Facilitate cluster formationQuantity minimizationNetwork traffic/resource managementAssess restrictionNetwork sizeProtocol overhead
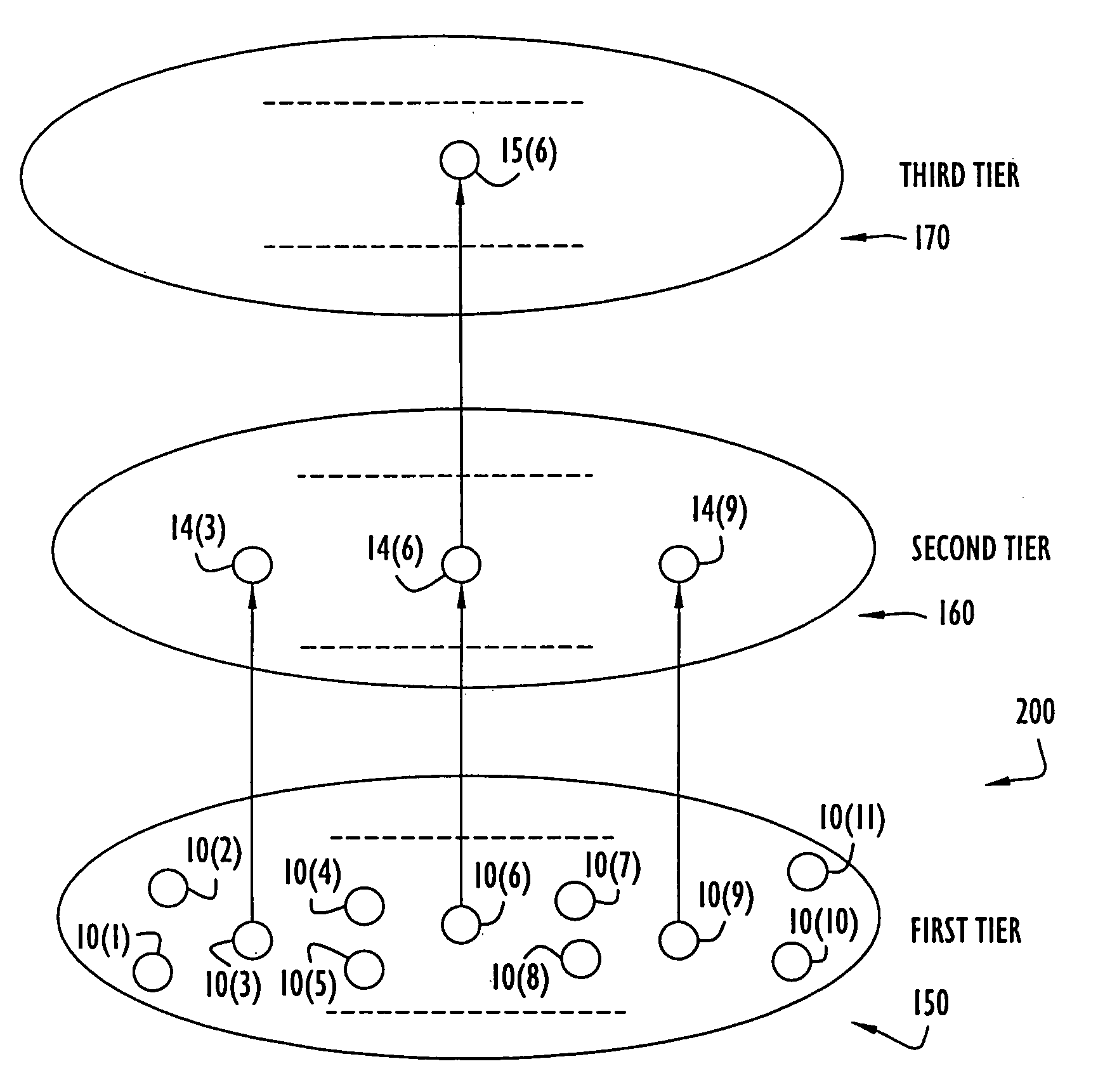
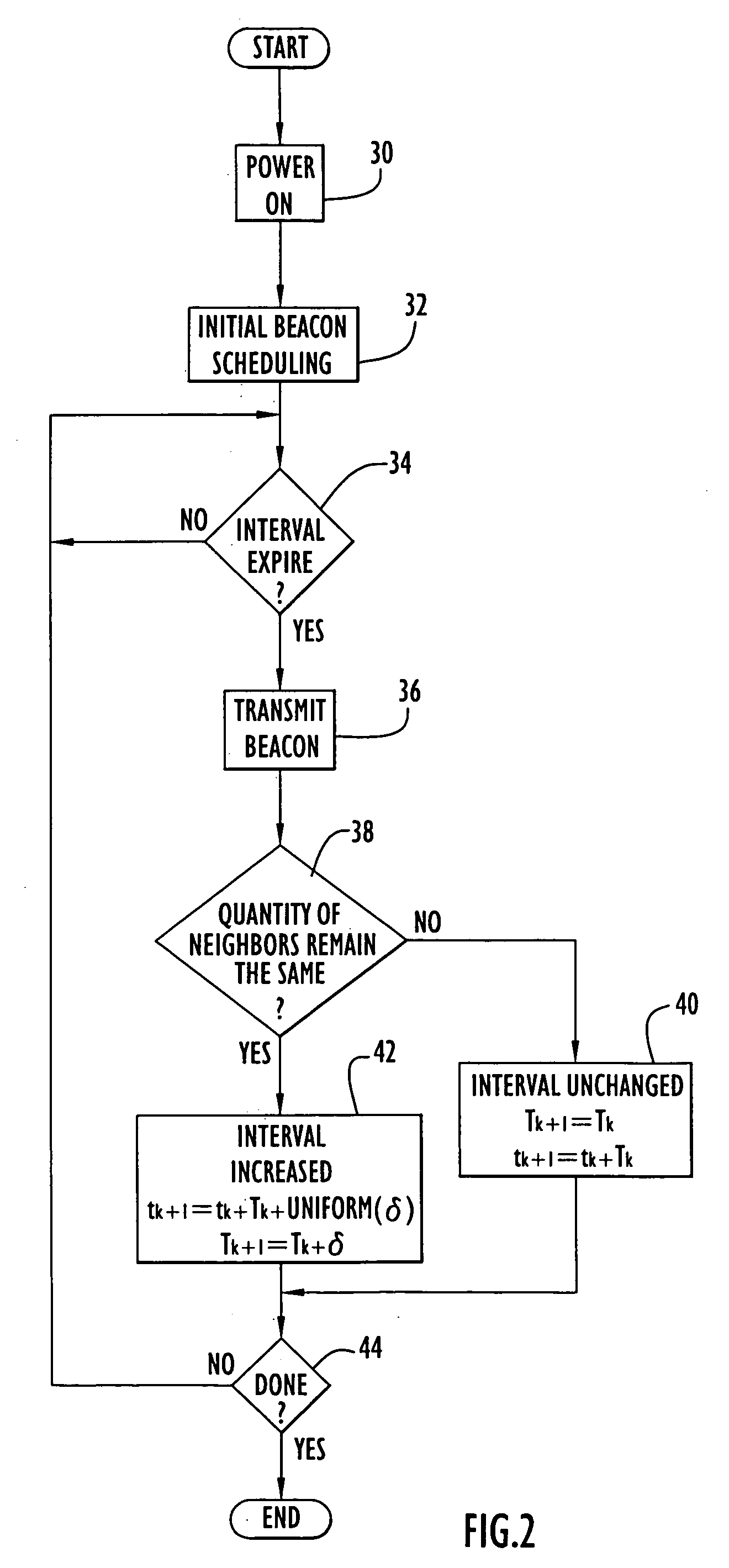
The present invention facilitates cluster formation within a communications network by utilizing network topology information to designate network nodes that are crucial for relaying traffic as cluster head nodes, while remaining network nodes are designated as member nodes. A beacon packet transmission rate of a network node or the interval between successive beacon packet transmissions by that node is adjusted by the present invention to facilitate cluster formation independent of network size and varying initial start times of network nodes. In addition, the present invention utilizes the above described cluster formation technique to form a three tier architecture for transmission or flooding of routing information from head node databases throughout the network. The cluster formation technique is applied to cluster head nodes to form an additional network tier of super nodes that distribute routing information, while cluster head nodes route network data traffic. The databases of cluster head nodes are examined subsequent to flooding of head node database information by super nodes, where data missing from a head node database is requested from a corresponding super node, thereby eliminating transmissions of acknowledgment messages.
Owner:STINGRAY IP SOLUTIONS LLC
Directional two-dimensional router and interconnection network for field programmable gate arrays, and other circuits and applications of the router and network
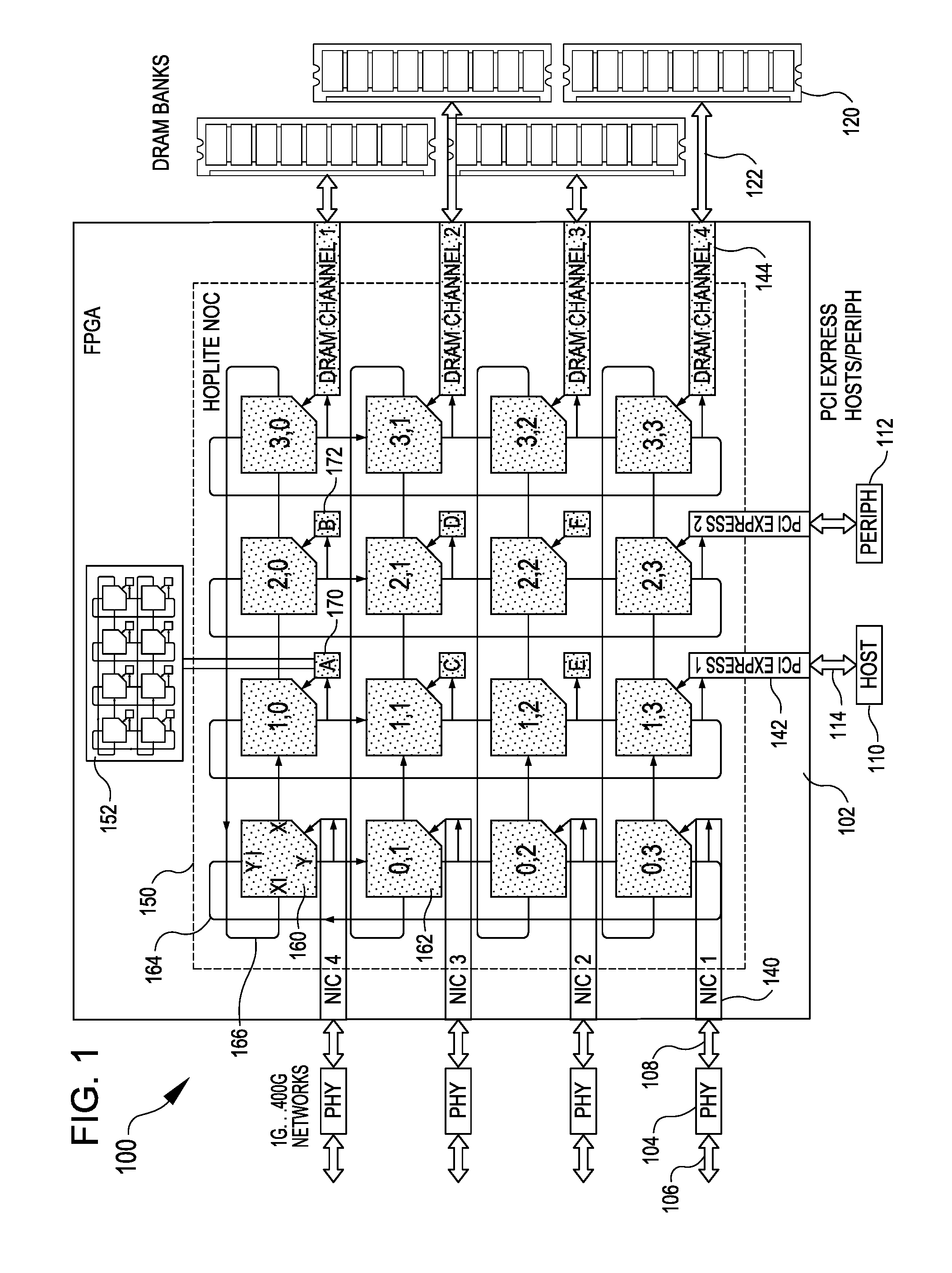
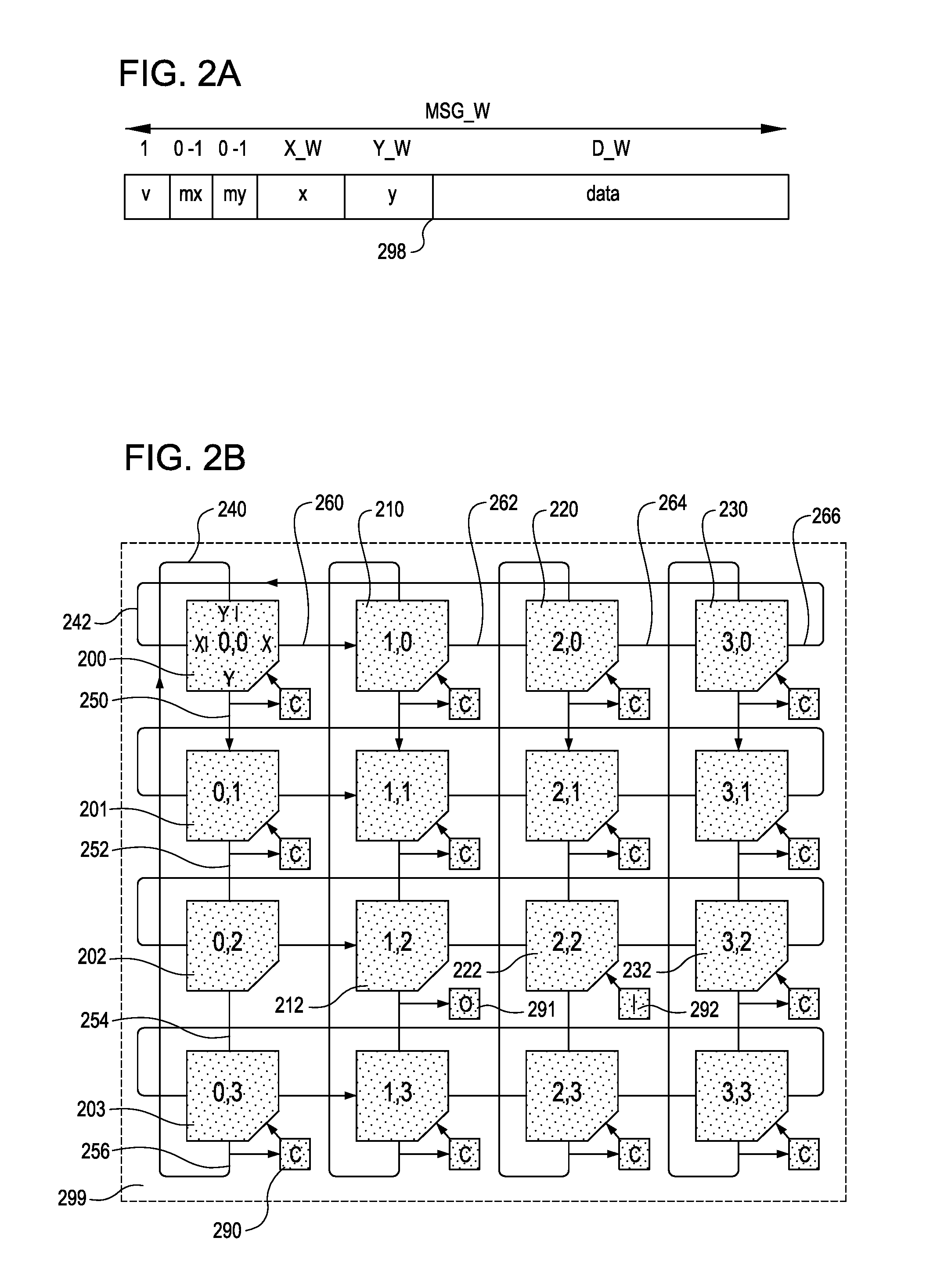
ActiveUS20160344629A1Reduce switching delayLower latencyData switching networksNetwork sizeFpga implementations
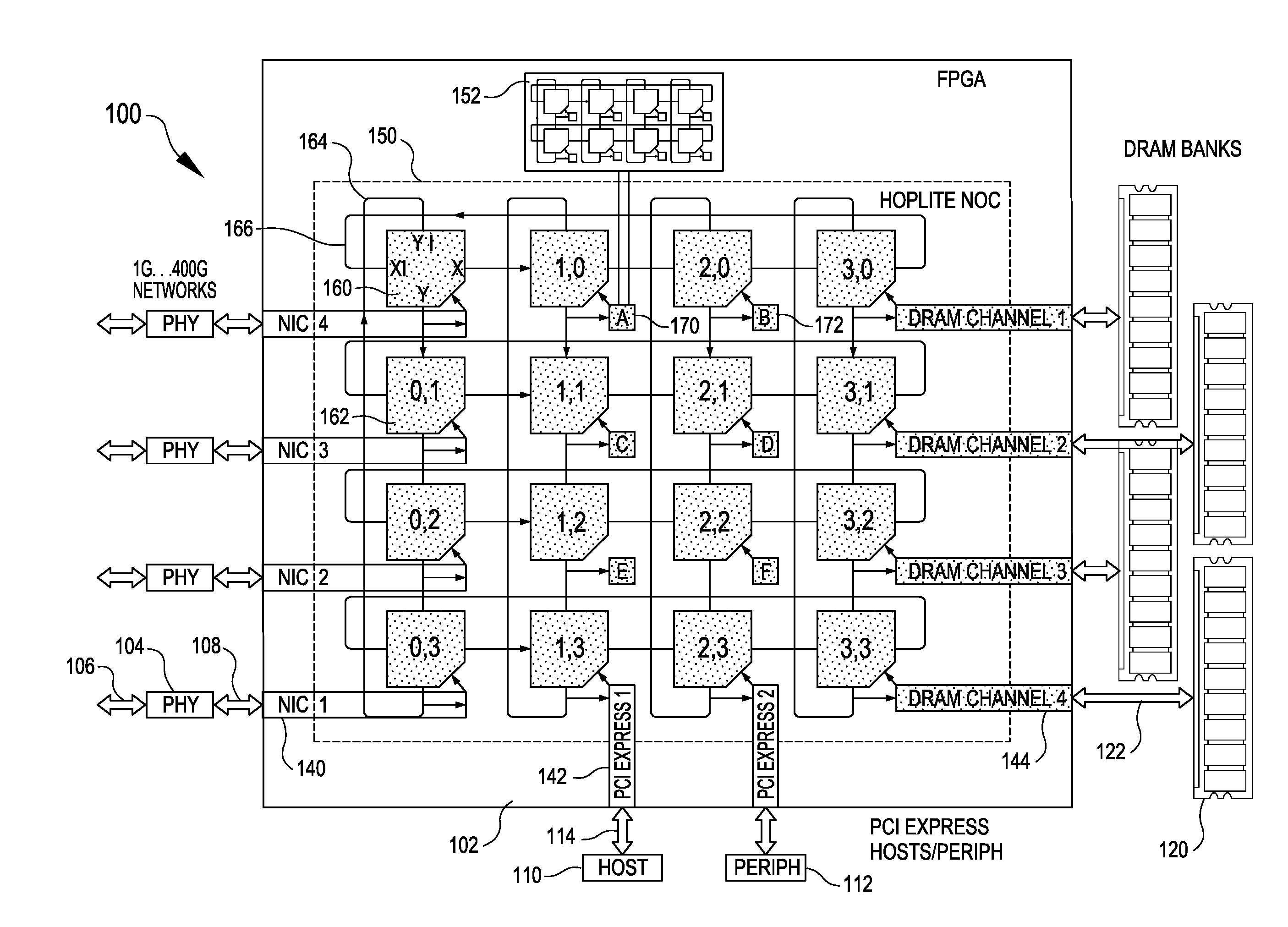
A configurable directional 2D router for Networks on Chips (NOCs) is disclosed. The router, which may be bufferless, is designed for implementation in programmable logic in FPGAs, and achieves theoretical lower bounds on FPGA resource consumption for various applications. The router employs an FPGA router switch design that consumes only one 6-LUT or 8-input ALM logic cell per router per bit of router link width. A NOC comprising a plurality of routers may be configured as a directional 2D torus, or in diverse ways, network sizes and topologies, data widths, routing functions, performance-energy tradeoffs, and other options. System on chip designs may employ a plurality of NOCs with different configuration parameters to customize the system to the application or workload characteristics. A great diversity of NOC client cores, for communication amongst various external interfaces and devices, and on-chip interfaces and resources, may be coupled to a router in order to efficiently communicate with other NOC client cores. The router and NOC enable feasible FPGA implementation of large integrated systems on chips, interconnecting hundreds of client cores over high bandwidth links, including compute and accelerator cores, industry standard IP cores, DRAM / HBM / HMC channels, PCI Express channels, and 10G / 25G / 40G / 100G / 400G networks.
Owner:GRAY RES LLC
Method and system for analyzing a network environment and network parameters
InactiveUS20040198234A1Reliable and low solutionEfficient executionReceivers monitoringRadio transmissionNetwork sizeNetwork control
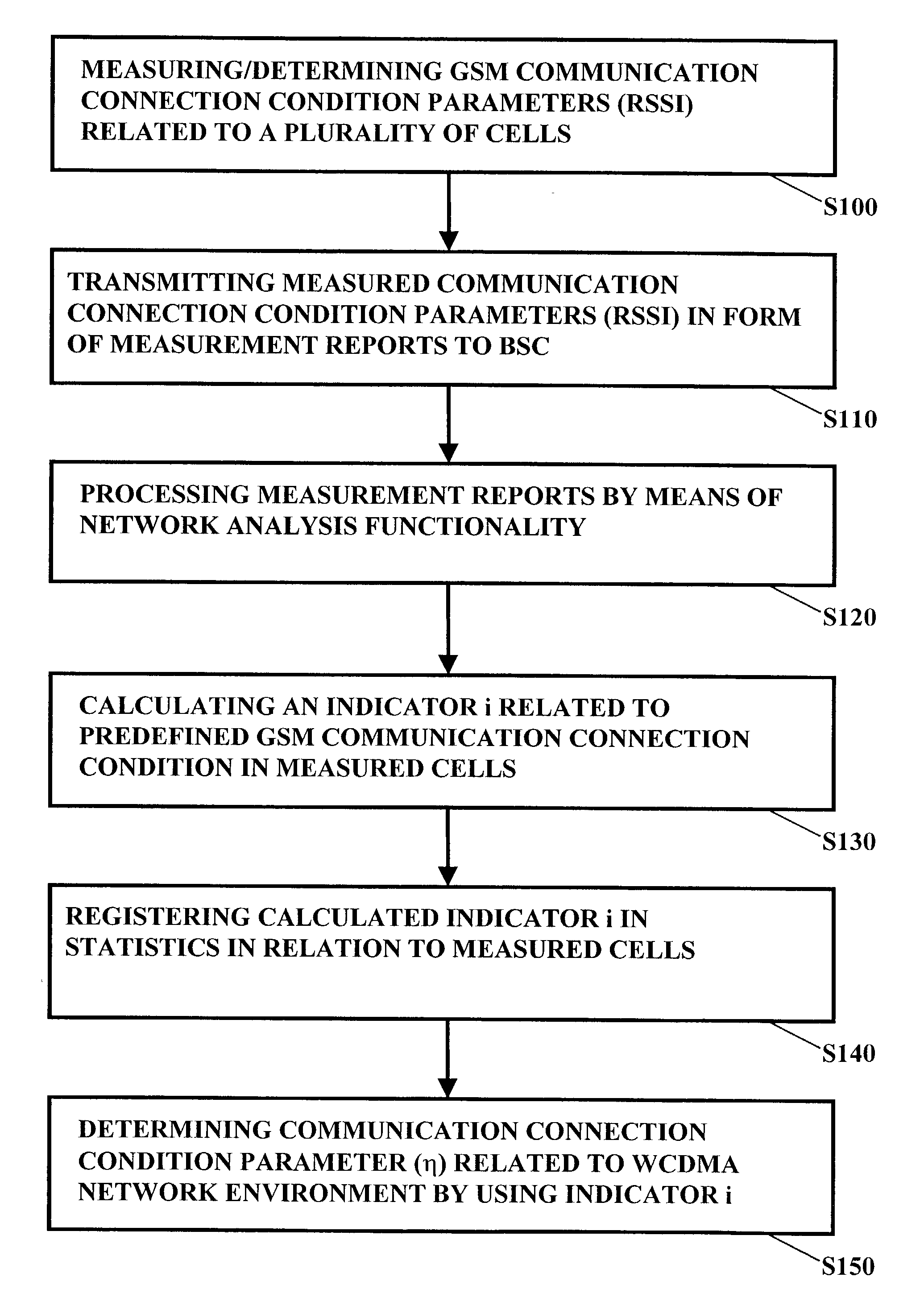
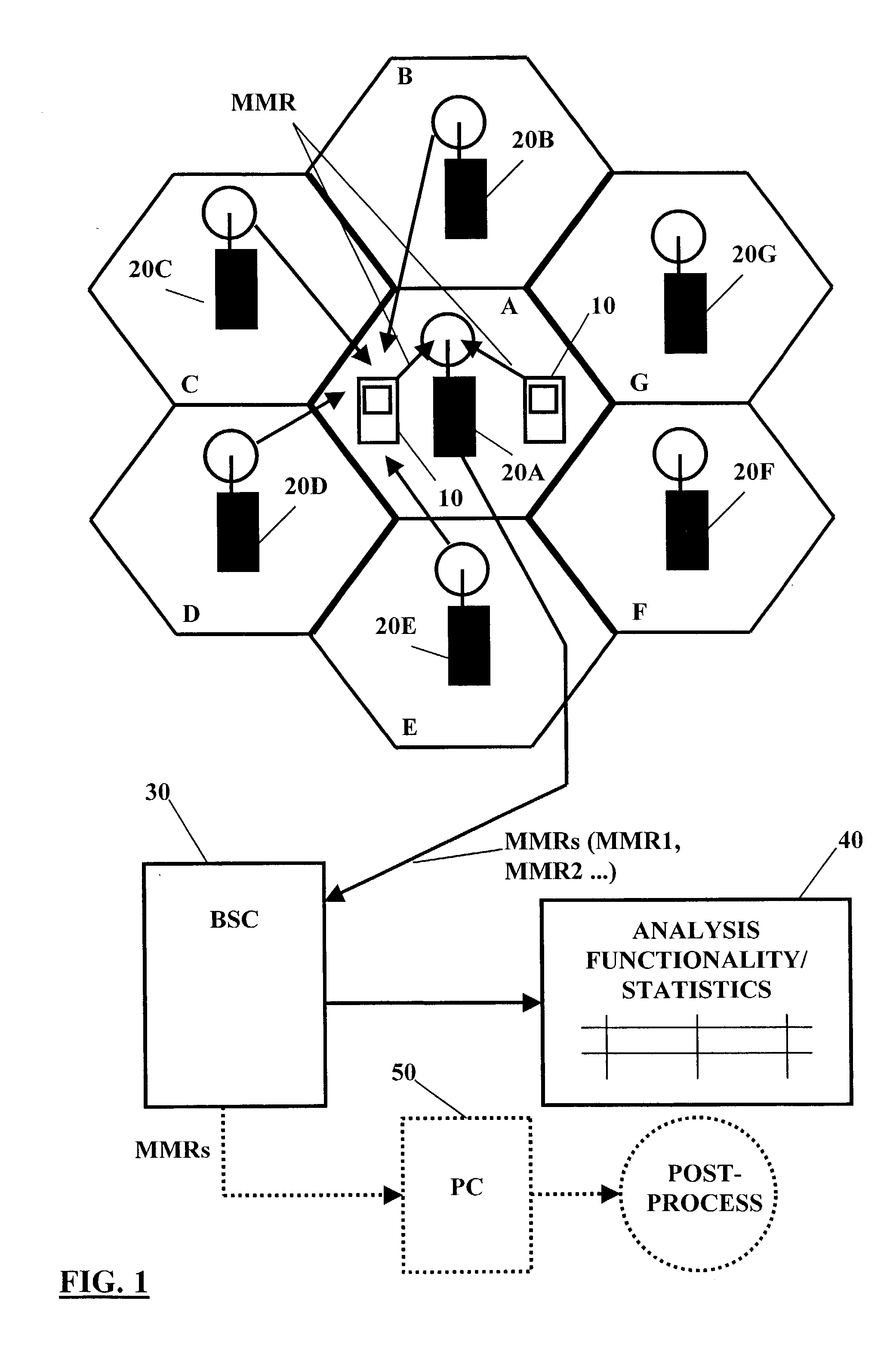
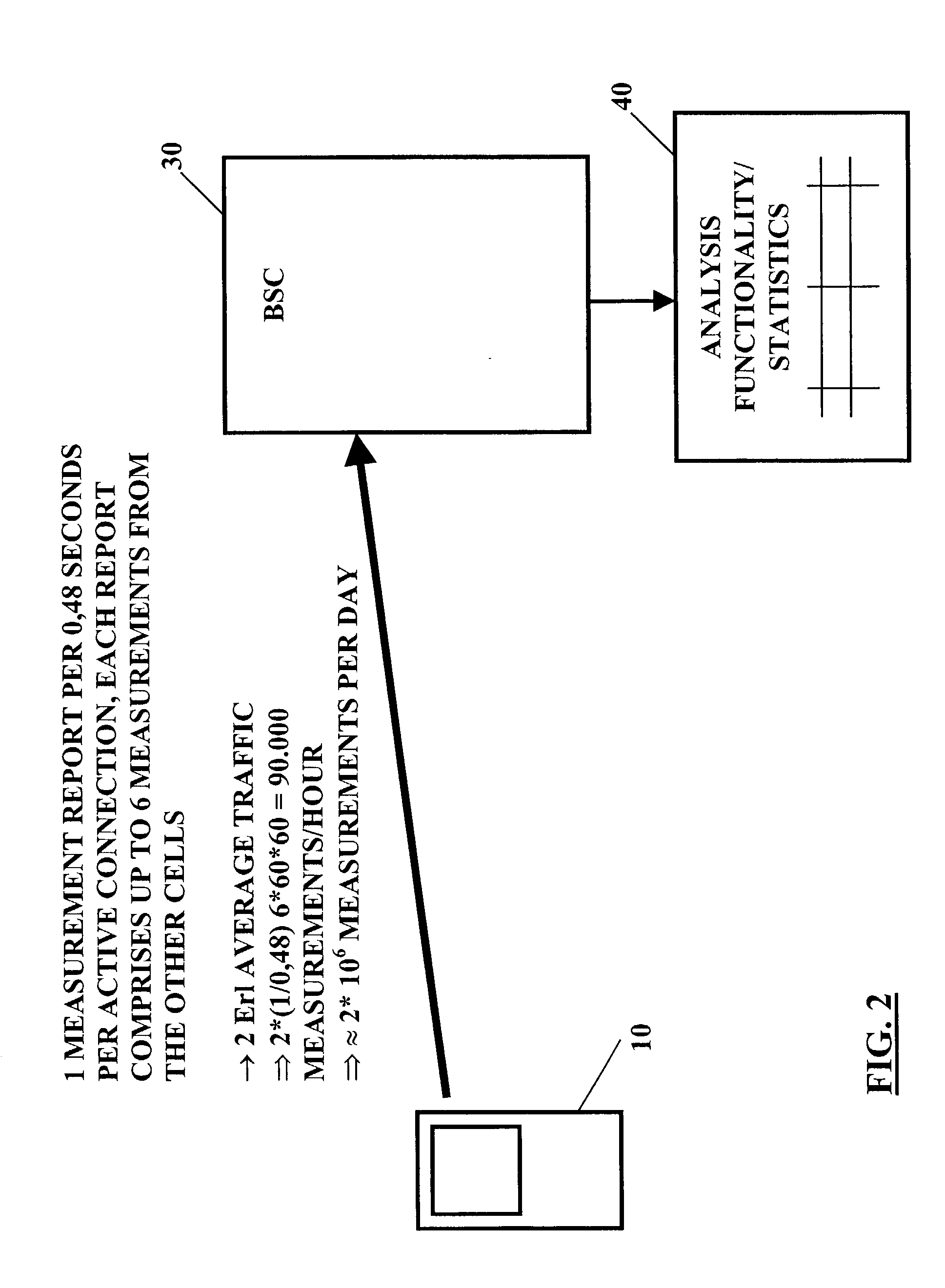
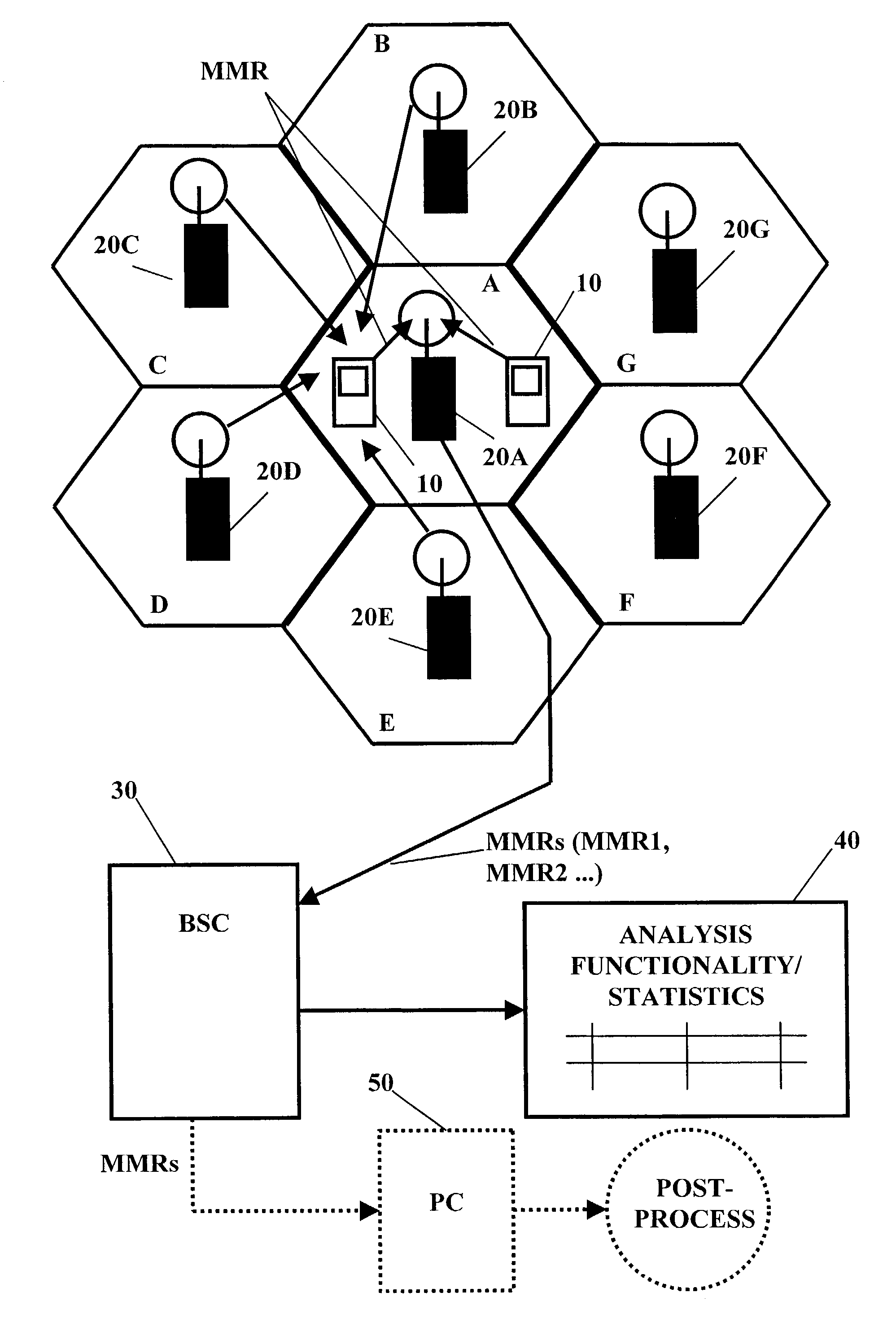
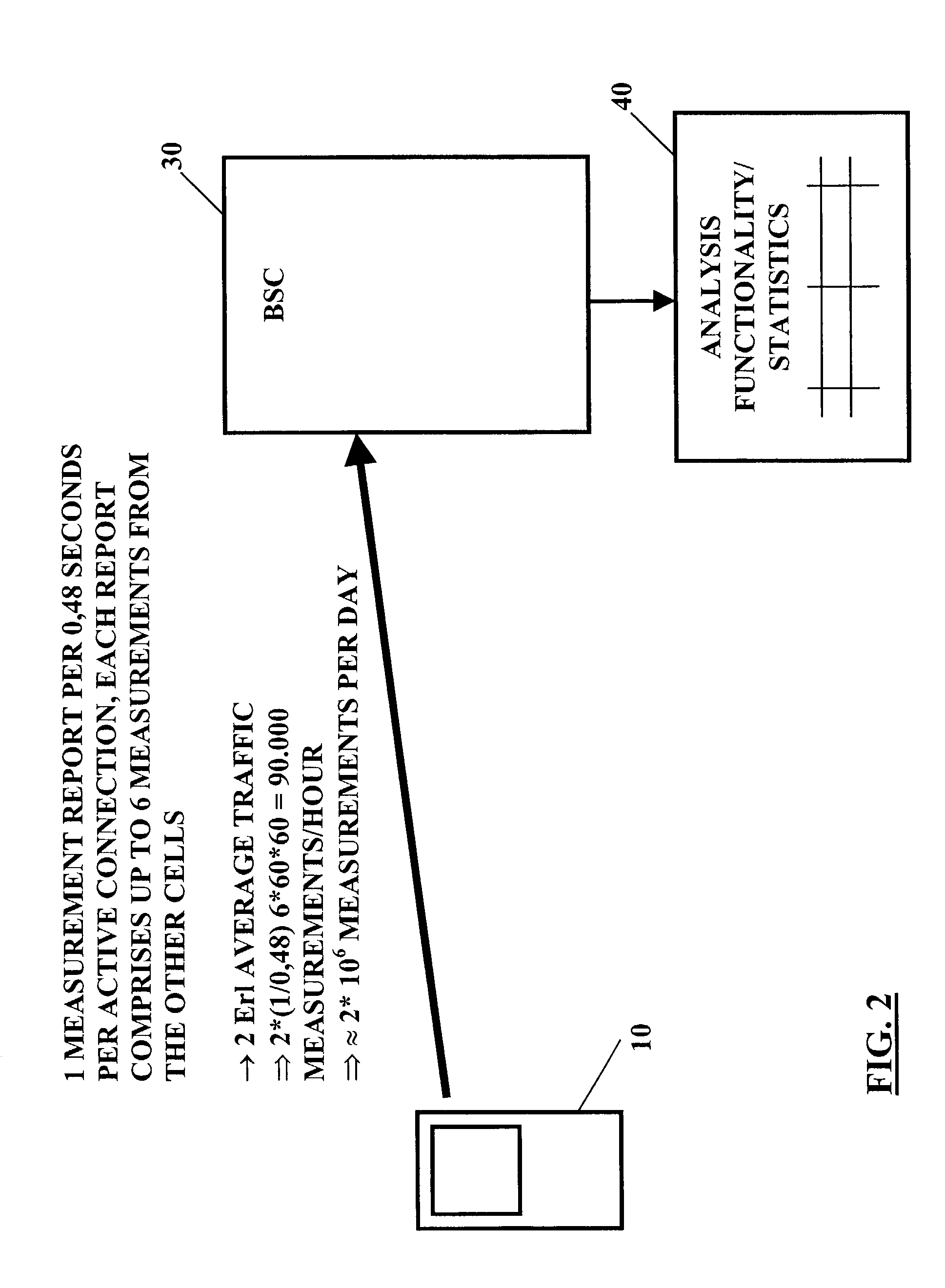
A method, system, device and computer program product are provided for analyzing a cellular wireless communication network of a first type. For analyzing the cellular wireless communication network of the first type, communication connection condition parameters for one cell are measured, which communication connection condition parameters are derived from signals received by a mobile station from the one cell and from a plurality of other cells. The communication connection condition parameters are transmitted to a network control element in the form of mobile measurement reports. A network analysis functionality associated with the network control element processes the mobile measurement reports and evaluates, on the basis of processing results, a potential of the one cell for a usage in a wireless communication network of a second type, and / or estimated network parameters of the wireless communication network of the second type, like network performance or network dimensioning. This is repeated in all other cells in the wireless communication network of the first type.
Owner:WSOU INVESTMENTS LLC
Method and apparatus for interconnecting IPv4 and IPv6 networks
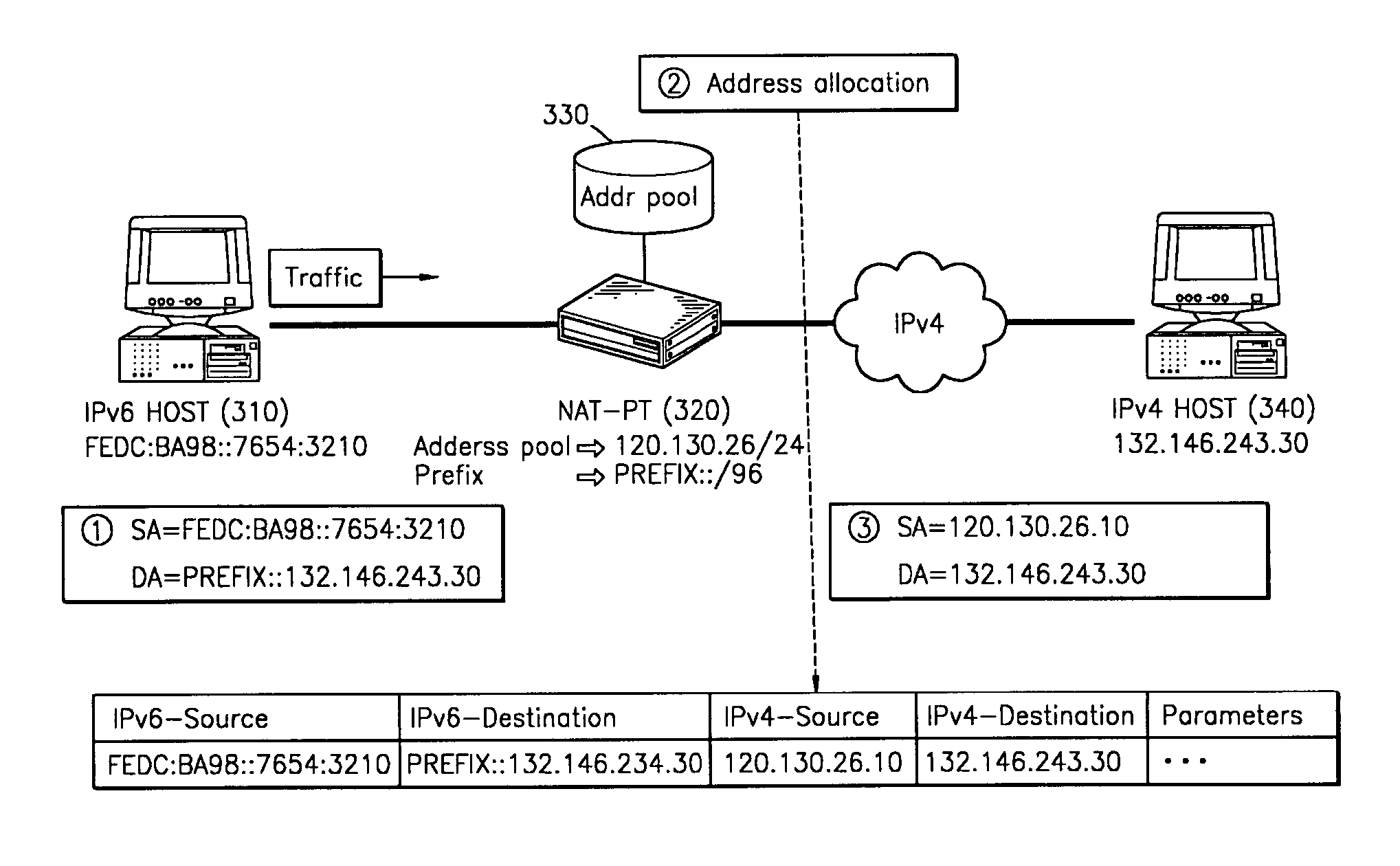
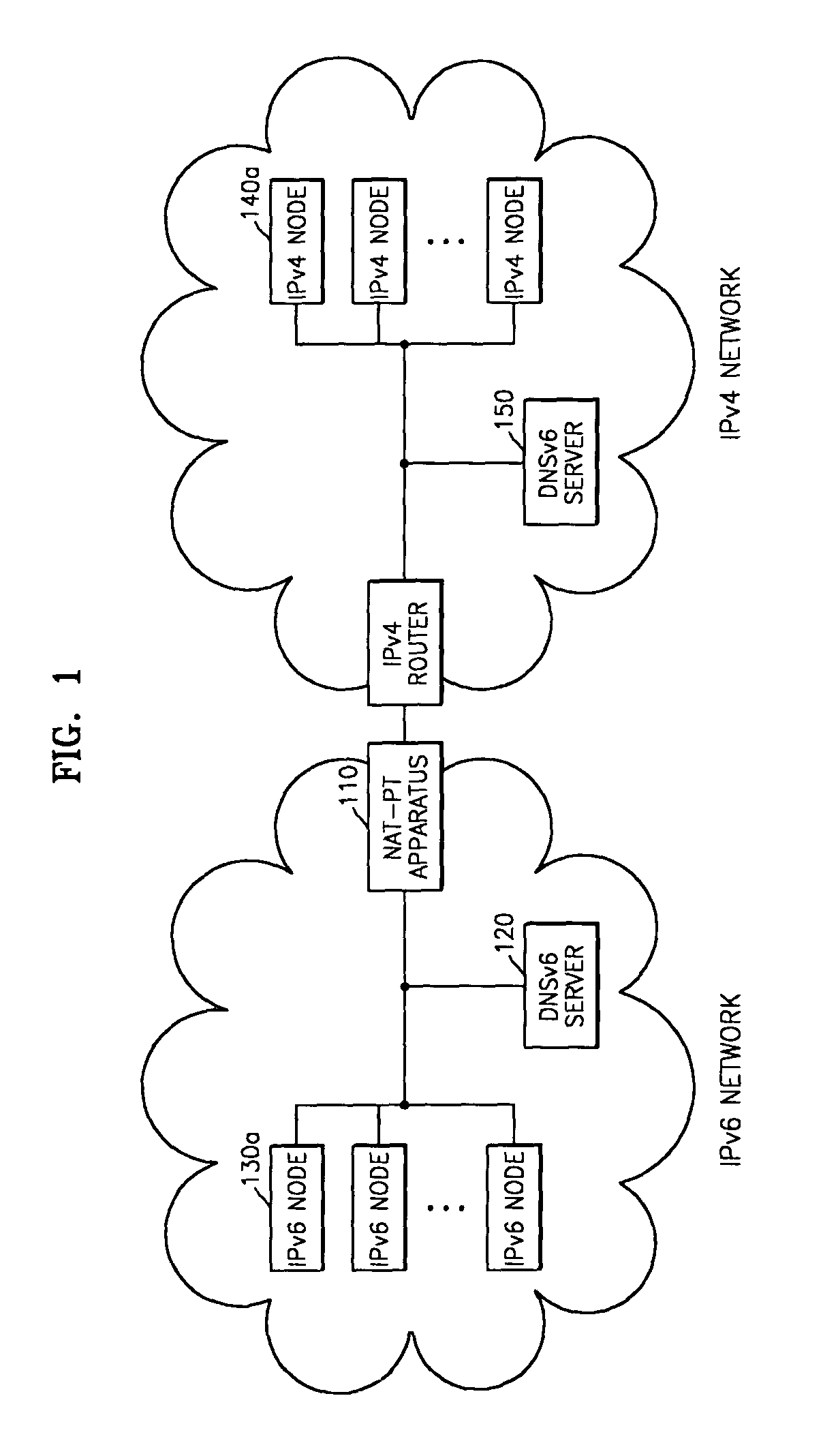
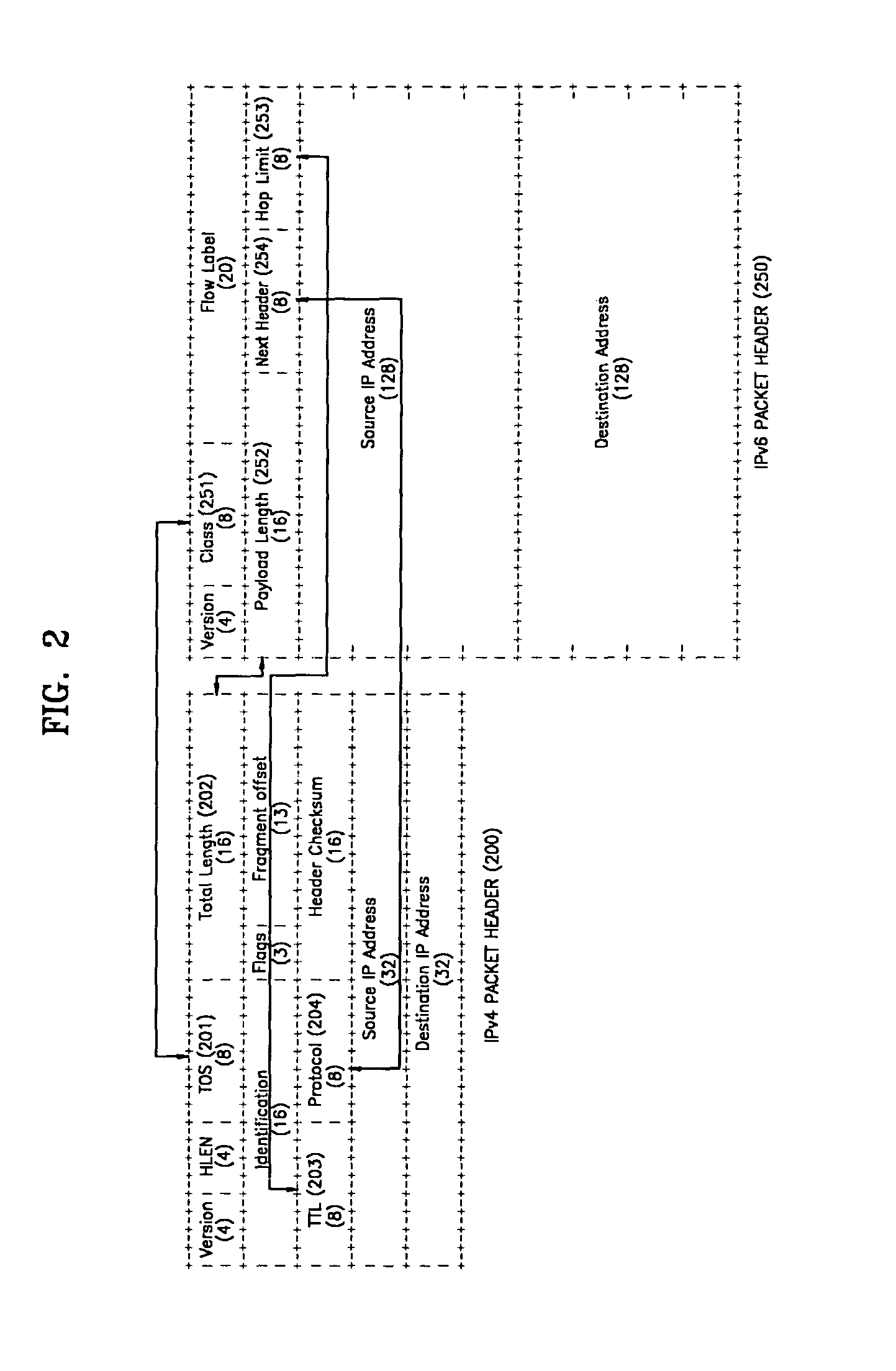
A method and system for interconnecting an Internet protocol version 4 (IPv4) network and an Internet protocol version 6 (IPv6) network are provided. The system for interconnecting an IPv4 network and an IPv6 network includes IPv4 nodes, IPv6 nodes, and apparatuses for transmitting IP packets between the IPv4 nodes and the IPv6 nodes, wherein the apparatuses for transmitting IP packets share processing state information of the IP packets, using a predetermined message, to distribute their load of processing the IP packets. The IPv4-IPv6 interconnection method involves appropriately arranging NAT-PT apparatuses depending on the size of the networks such that packet processing speed and performance are improved over the use of a single NAT-PT apparatus.
Owner:SAMSUNG ELECTRONICS CO LTD
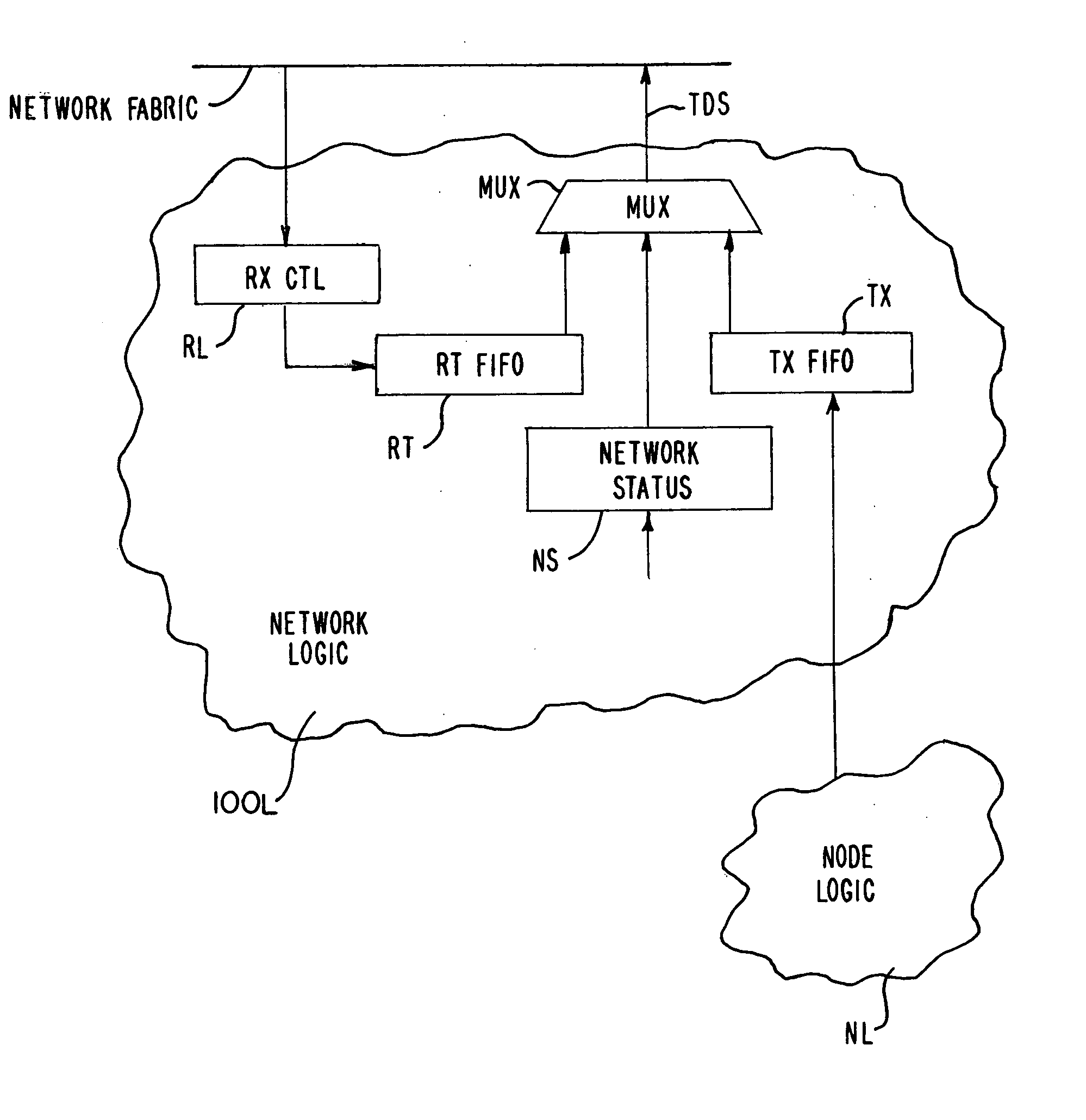
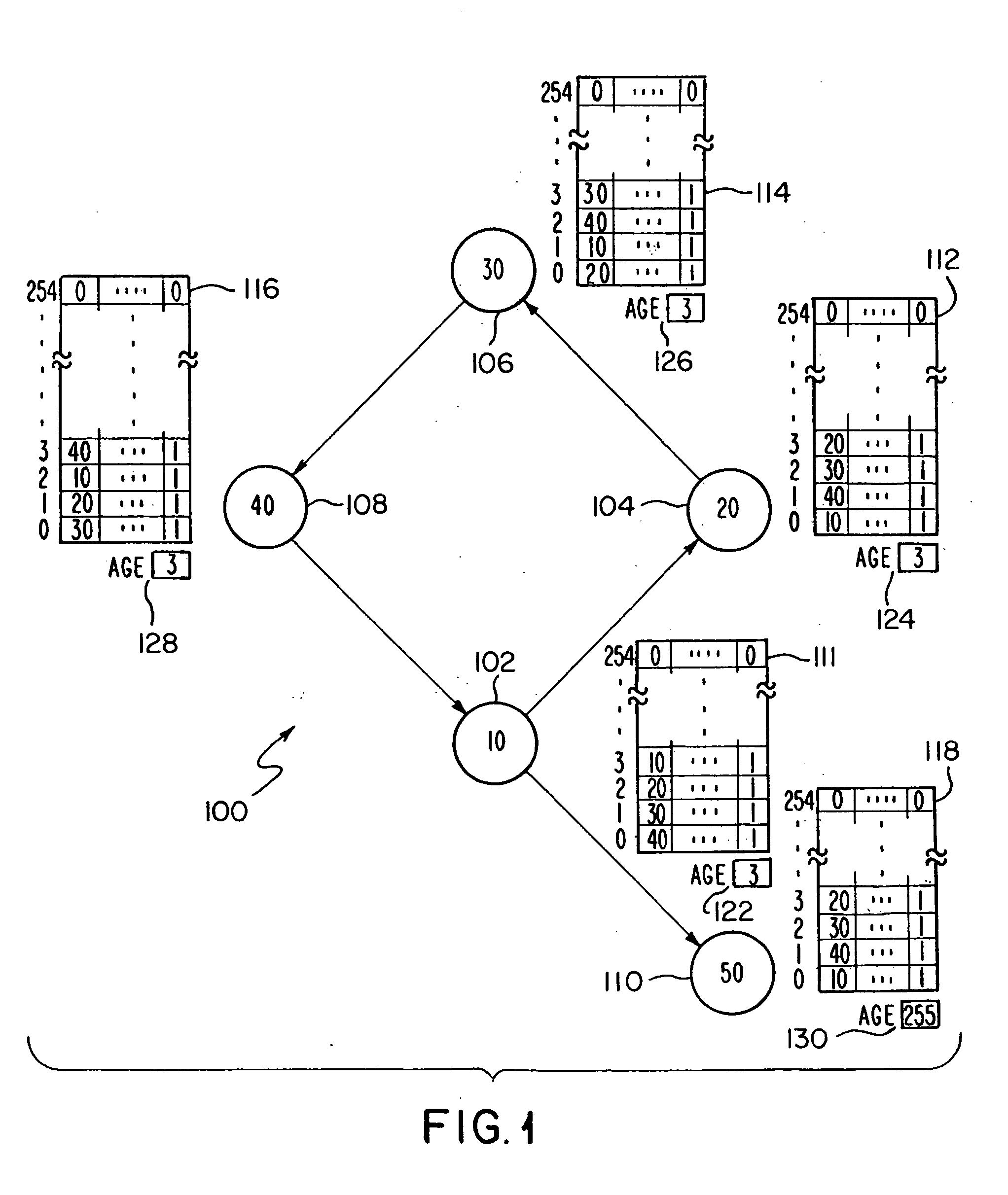
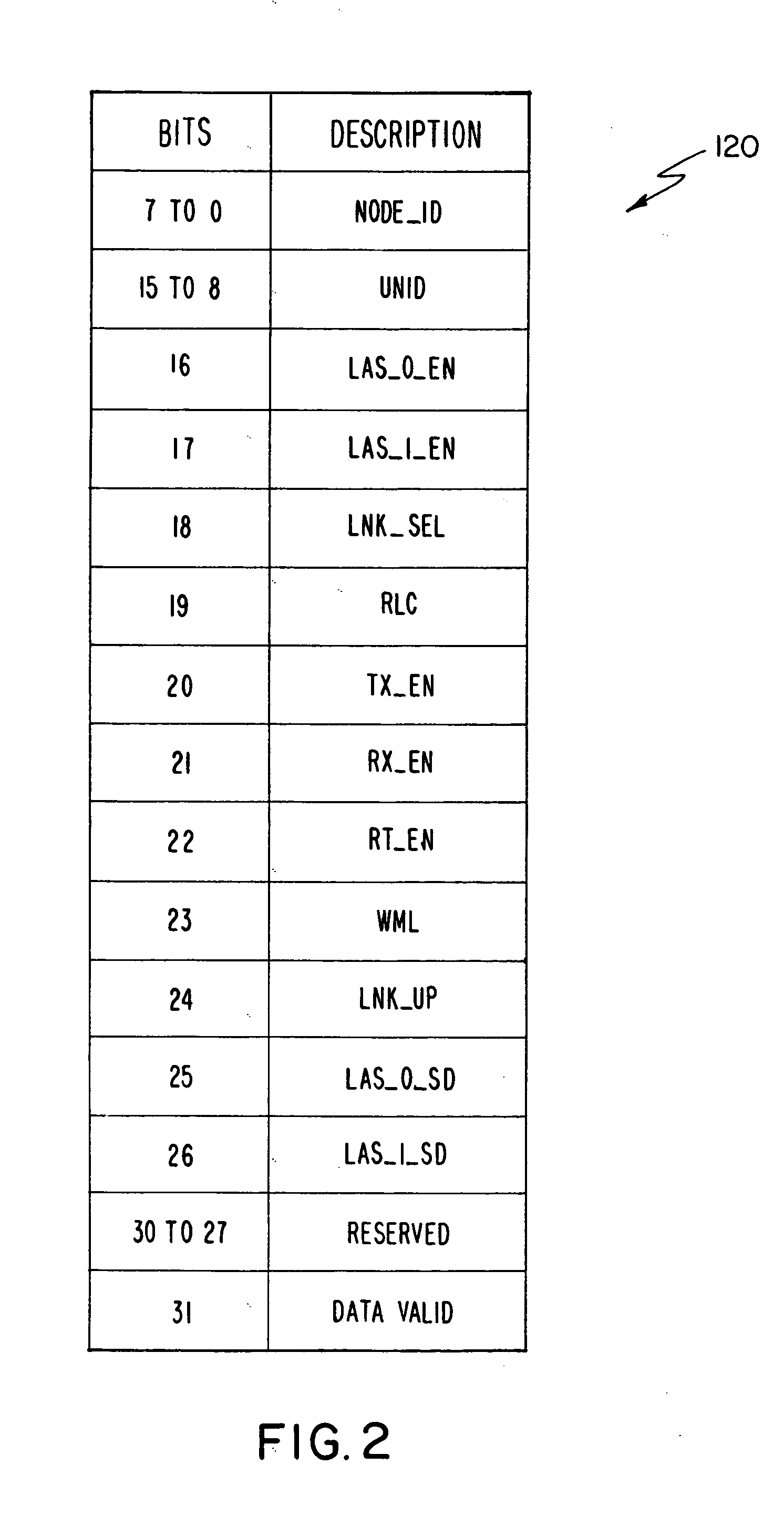
Network status messaging
InactiveUS20050097196A1Digital computer detailsData switching networksNetwork sizeDistributed computing
In a register insertion network having a plurality of nodes, each node generates status messages including at least an identification of the node that generated the status message and a message age. These status messages are periodically transmitted by each node of the network and received at each node of the network. When received, the status messages are aged and retransmitted onto the network unless the receiving node was the source of the status message in which case it is removed from the network. Node statuses, determined from the status messages, are stored at each node and enable the determination of network size, structure or topology and status of the nodes to assist in monitoring and testing of the network.
Owner:SYSTRAN
Block chain adaptive consensus method based on dynamic authorization and network environment perception
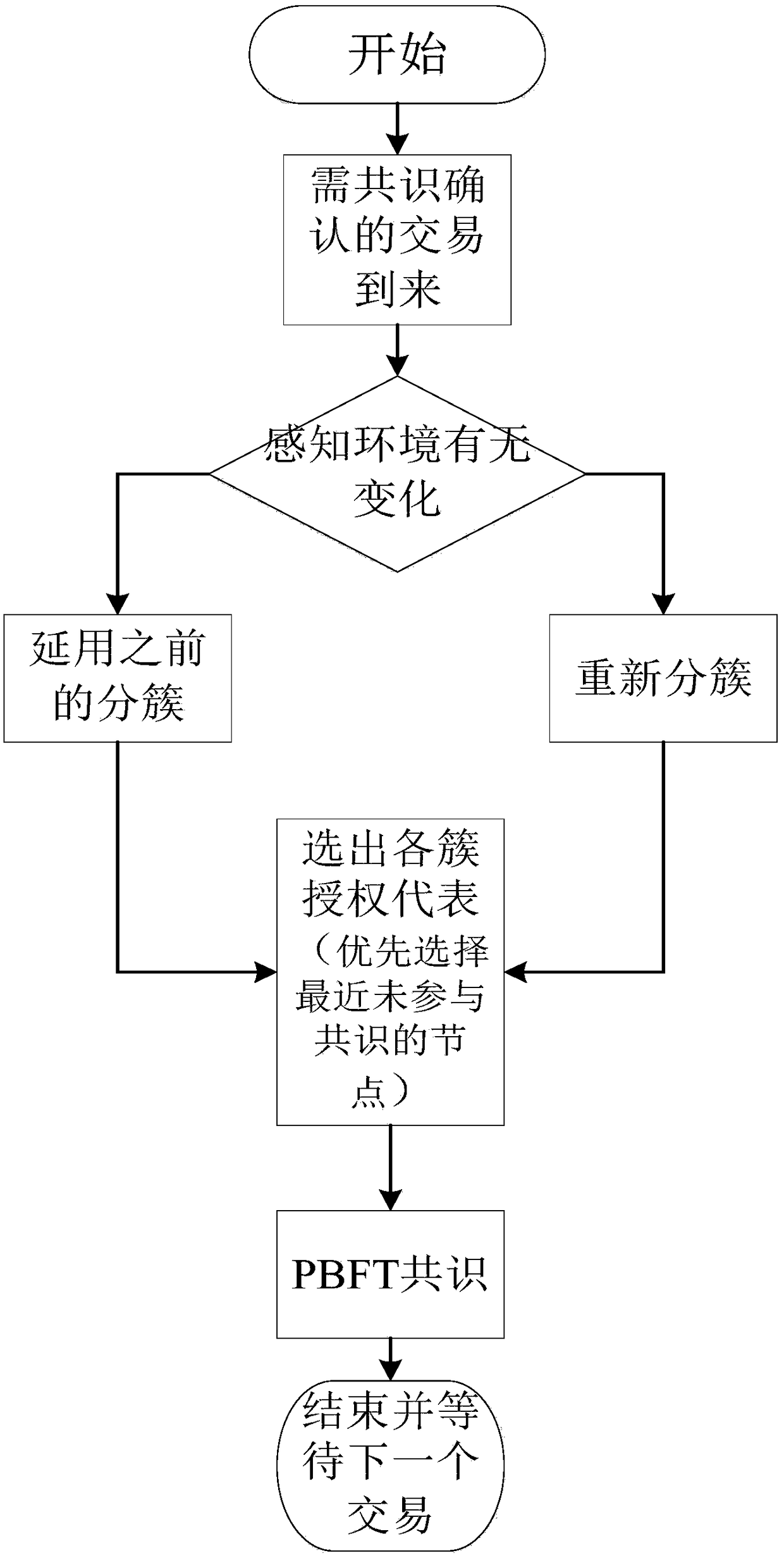
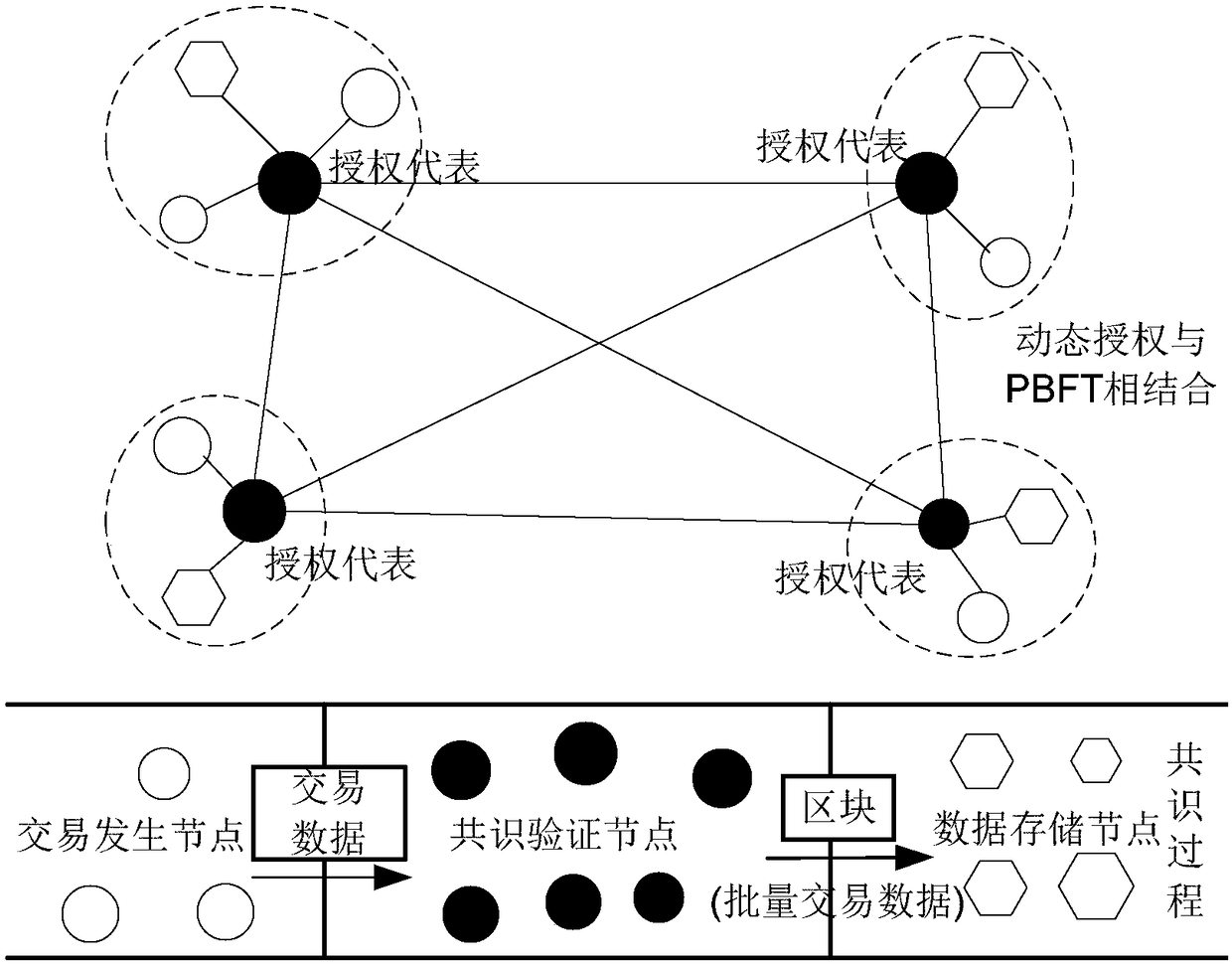
ActiveCN108616596ASolve low throughputSolve the delay problemFinanceDigital data protectionByzantine fault toleranceNODAL
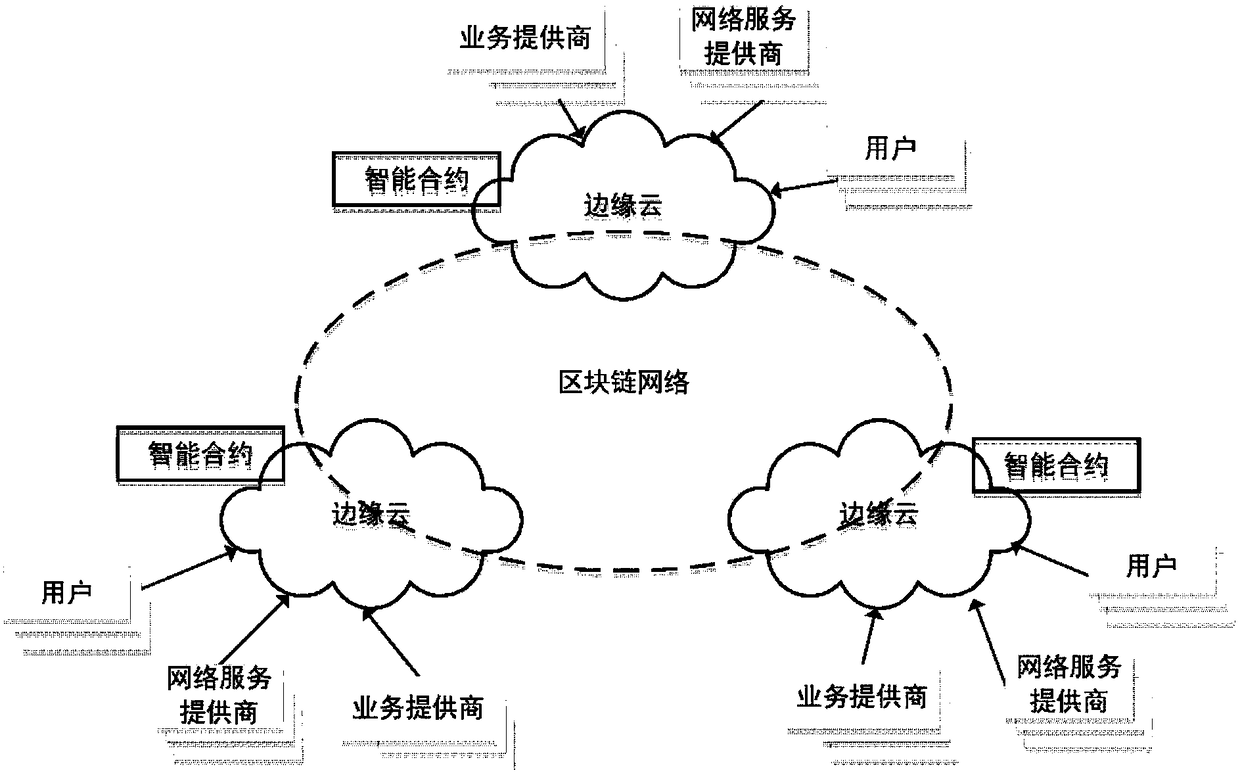
The invention discloses a block chain adaptive consensus method based on dynamic authorization and network environment perception; the method comprises the following steps: 1, clustering block chain network nodes according to geological positions, and selecting one authorization representative from the same cluster; 2, allowing the authorization representatives selected from all clusters to form all consensus nodes that verify this transaction, wherein a Byzantium fault tolerance algorithm is employed among the consensus nodes so as to reach a consensus that whether this transaction is established or not; 3, adjusting or re-clustering according to network scale, topology, resource or business type changes; 4, updating authorization representatives in the next deal after one deal is verified. The advantages are that the method can set up a fast and credit synergy mechanism among distributed edge clouds based on block chain, so edge nodes can fast and effectively reach consensus withoutany trust basis, thus solving the low throughput, high time delay and low efficiency problems of a consensus algorithm that uses workload proves as representatives.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system for analyzing a network environment and network parameters
InactiveUS7136638B2Reliable and low solutionEfficient executionReceivers monitoringRadio/inductive link selection arrangementsNetwork sizeNetwork control
Owner:WSOU INVESTMENTS LLC
RFID devices for verification of correctness, reliability, functionality and security
InactiveUS7712674B1Effective monitoringCost-effective designMultiplex system selection arrangementsSubscribers indirect connectionNetwork sizeTransceiver
The present invention differs from the prior art in that the present invention provides one or a network of passive or active radio frequency identification (RFID) transceivers and antenna elements in different numbers, in various network sizes, in different configurations and on various substrates. The RFID transceiver can be co-located with standard semiconductor devices, for cost-effective circuit design and non-destructive fabrication test and analysis of integrated circuits and printed circuit boards after fabrication, and to locate, track and identify the integrated circuit, printed circuit boards and products in which they are implemented. The RFID transceivers can be coupled to substrates containing matter in gas, liquid, or solid form, such as medical devices like breast implants, for effective monitoring of the substrates to ensure that the substrate is in an unaltered state and the matter is still contained securely within. The RFID transceivers can be coupled to secure tapes of various lengths and widths and mesh bags or sheets of various sizes and they can be applied at the carton-level using them to locate, track and identify the integrated circuit, printed circuit boards and products in which they are implemented and / or the cartons in which they were placed.
Owner:EIGENT TECH
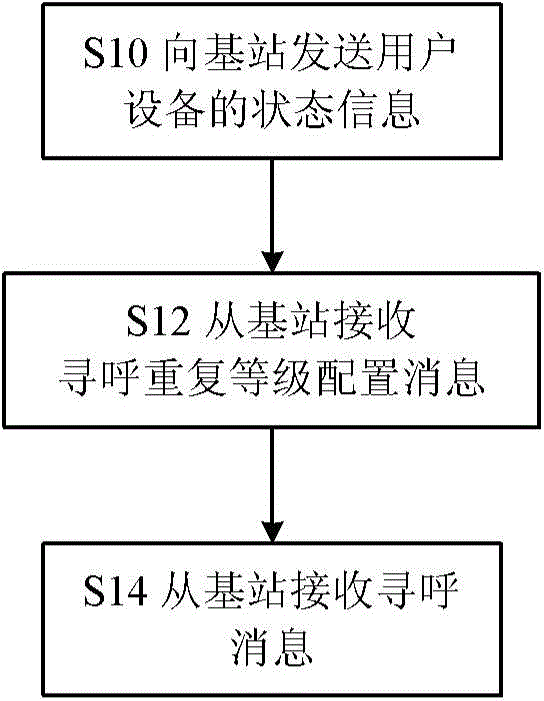
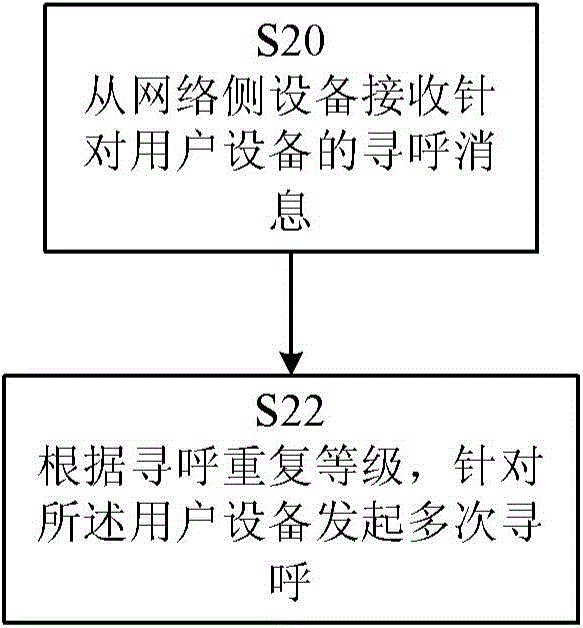
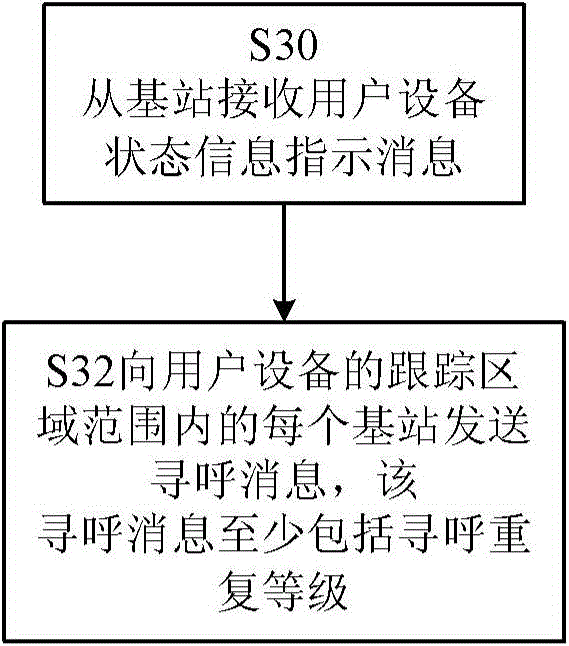
Paging message receiving/sending method and related user equipment, base station and network-size equipment
ActiveCN105101044AImprove resource utilizationImproved Spectrum/Energy EfficiencyWireless commuication servicesHigh level techniquesFrequency spectrumNetwork size
Provided is a paging message reception method executed by a user equipment, comprising: reporting to a base station the status information of the user equipment, the status information comprising coverage enhancement related information of the user equipment and information of the cell in which the user equipment is, the coverage enhancement related information comprising information indicating the coverage enhancement level that the user equipment needs; receiving from the base station a paging repetition level configuration message, the paging repetition level configuration message indicating the paging repetition level of the user equipment; receiving from the base station the paging message transmitted according to the paging repetition level of the user equipment and / or the information of the cell in which the user equipment is. Also provided are a related method executed by the base station and network device, and related device. The technical solution of the present invention enhances the resource utilization rate of LTE that supports MTC user equipment and enhances frequency spectrum / energy efficiency.
Owner:SHARP KK
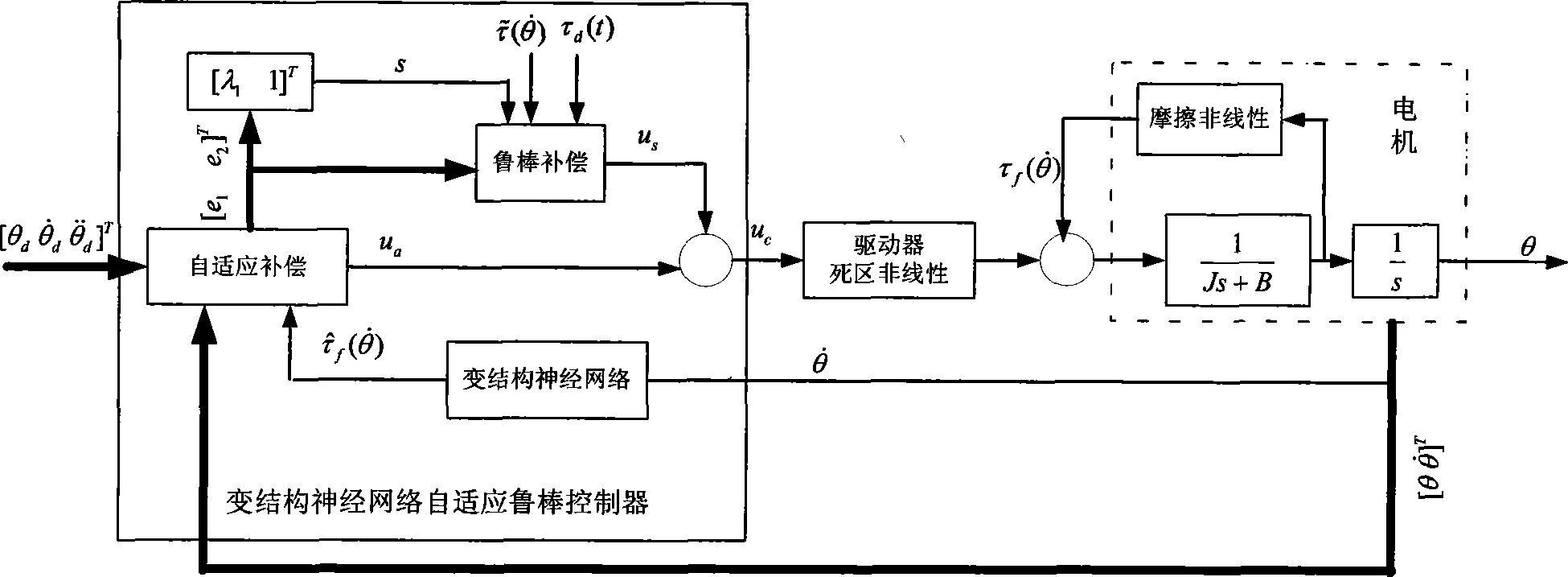
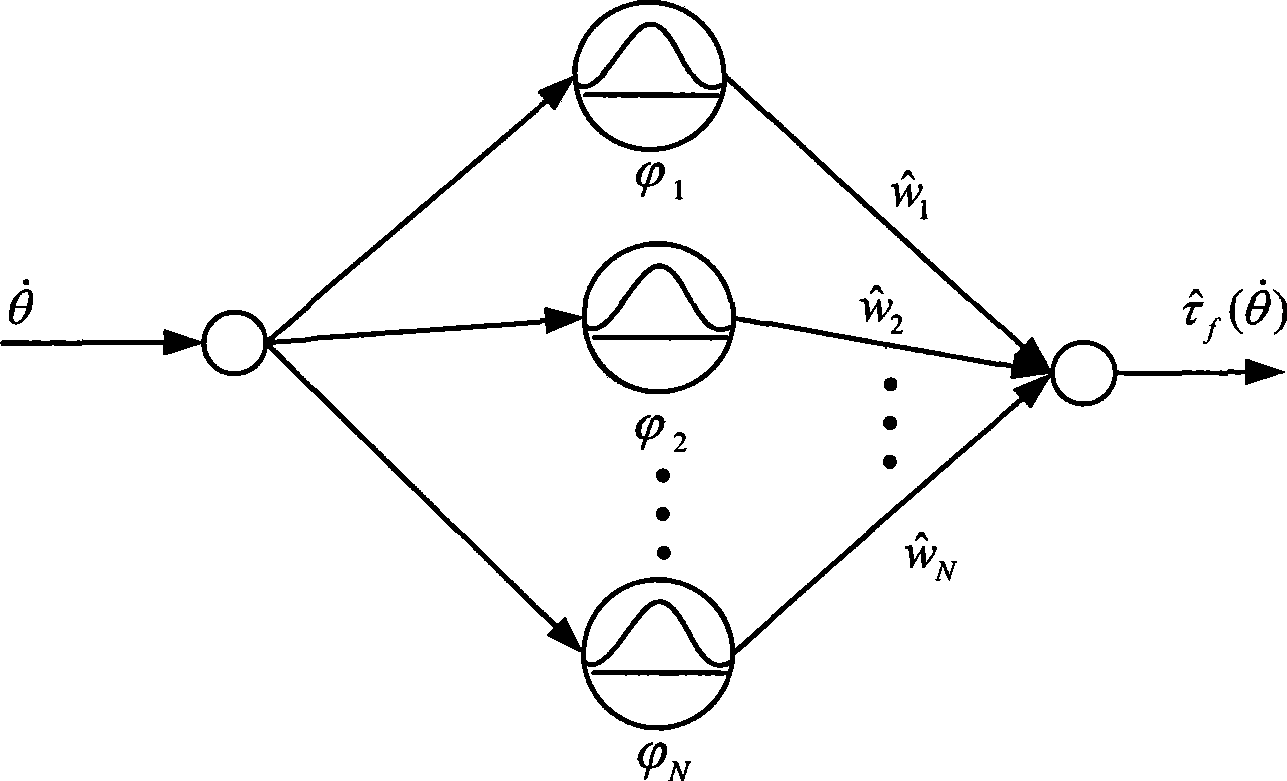
Essentially nonlinear compensation controller of servo system
InactiveCN101488010AImprove practicalityAchieve friction compensationAdaptive controlNetwork sizeDead zone nonlinearity
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
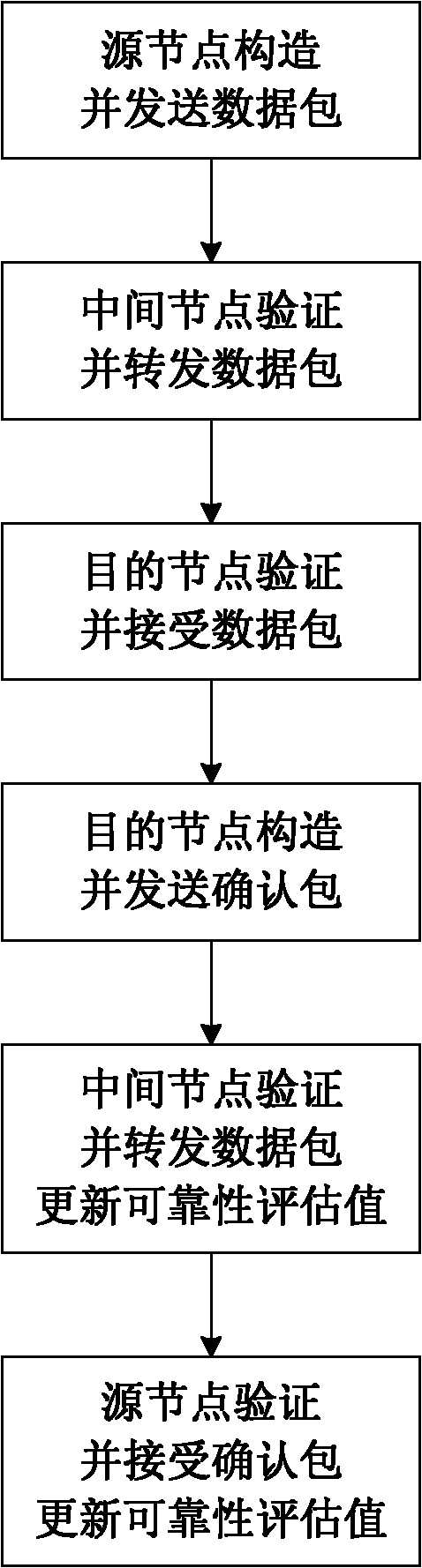
Mobile AD Hoc network self-adapting secure routing method based on reliability
ActiveCN102158864AGuaranteed validityIntegrity guaranteedNetwork topologiesSecurity arrangementRouting decisionNetwork size
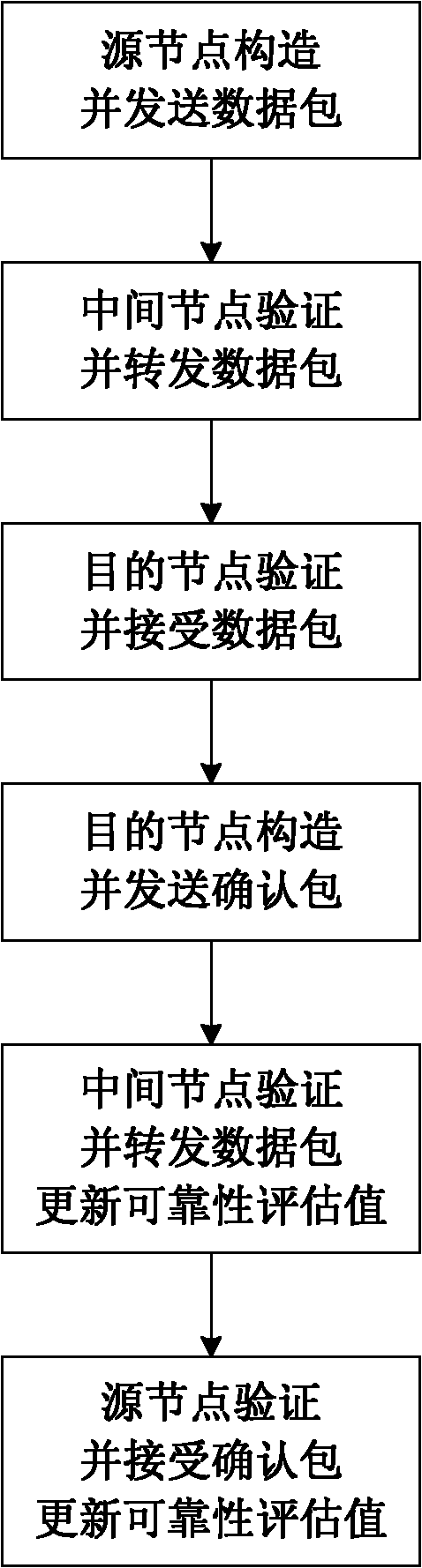
The invention discloses a mobile AD Hoc network self-adapting secure routing method based on reliability. The method comprises the following four major steps: step I, a source node transmits data packets; step II, an intermediate node forwards the data packets; step III, a destination node receives the data packets; and step IV, the data packets are transmitted and confirmed and reliability is updated. The method integrates route discovery and data transmission into a whole process, each node evaluates the reliability of adjacent nodes reaching the destination node through a response feedbackmechanism, and independently makes a route decision according to reliability evaluation level, so that unreliable nodes are avoided and a reliable path is selected from a plurality of alternative paths, the method solves secure and reliable data transmission and symmetrical secret key transmission while solving secure routing discovery problem, and improves the security and the adaptability of the network. Compared with an existing AD Hoc network routing method, the method can resist attack to a greater extent on the basis that higher expense is not needed, still has good restorability when anetwork size is changed, nodes rapidly moves and even attack in a large scope exists and error of nodes exists, and is applicable to large-scale network with rapidly moving nodes. The method has a higher practical value and a wide application prospect in the technical field of mobile AD Hoc network security.
Owner:BEIHANG UNIV
Data center network topology system based on module expansion
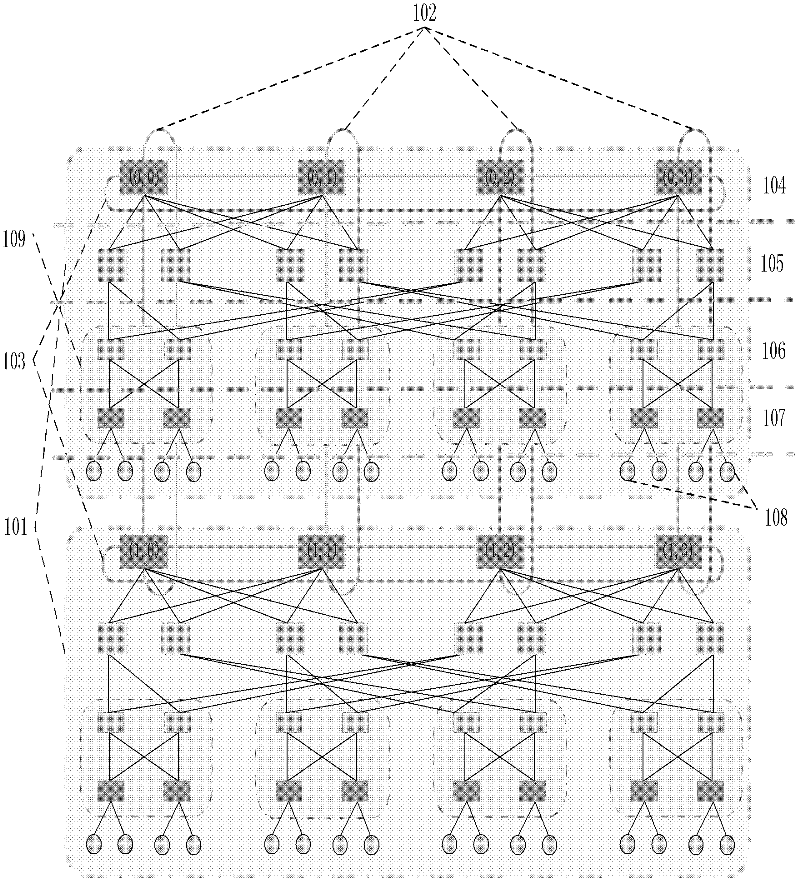
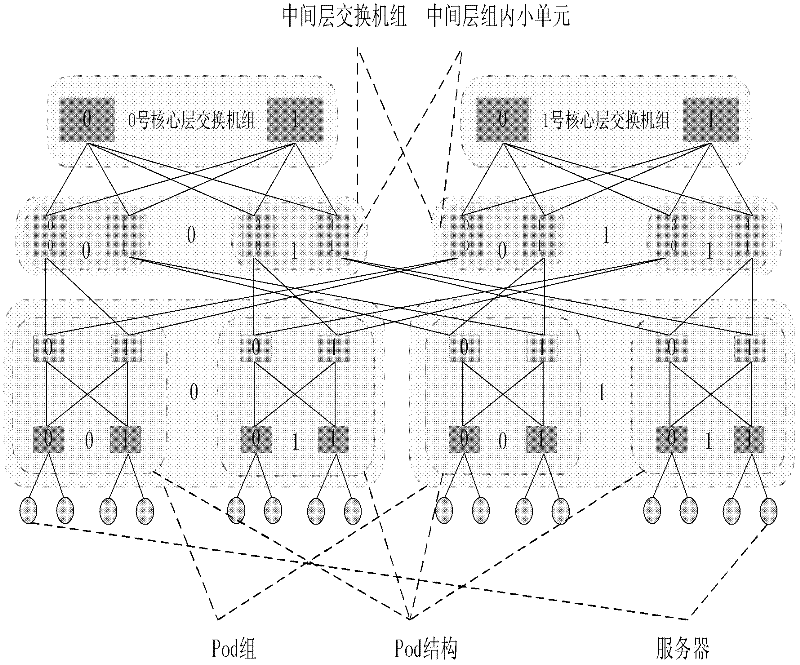
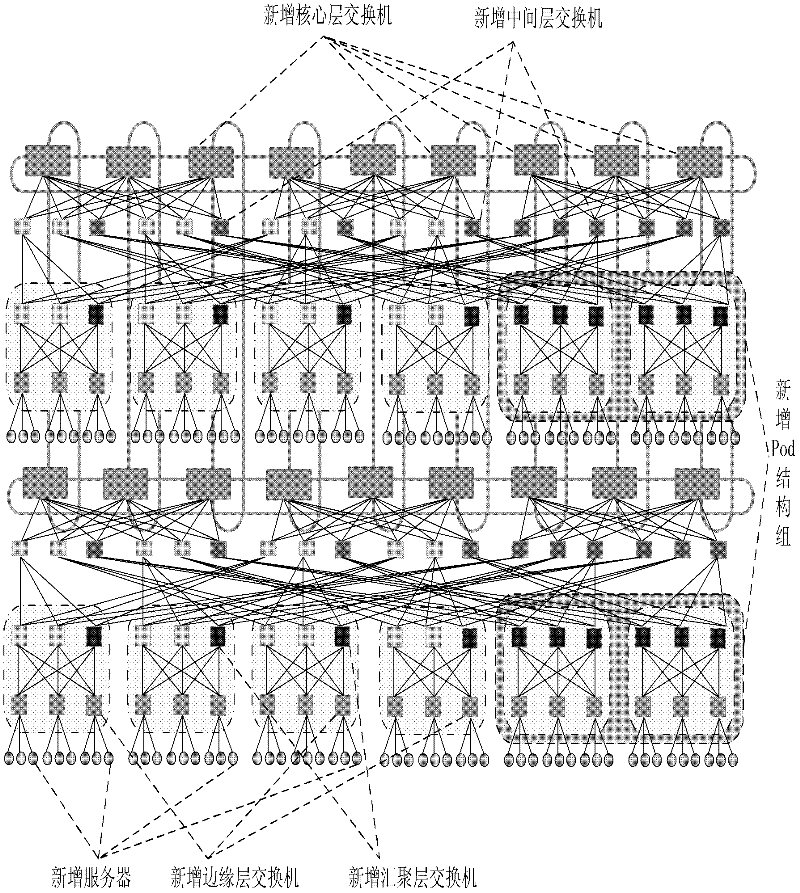
InactiveCN102394782AMeet application development needsAchieving dynamic selectivityData switching networksFault toleranceNetwork size
The invention discloses a data center network topology system based on module expansion. And therefore, a problem that an expansion capability of tree topology of a data center is limited to the number of ports of a switch device and insufficiency of dynamic selectivity of a downlink can be solved. The implementation steps of system are as follows: an intermediate layer is introduced between a core layer and a convergence layer of a fat tree structure; a small network that is formed by connection of switches and servers of each of the layer is recorded as a basic module, so that a plurality of basic modules are constructed; four additional ports of switches of the core layer are utilized to connect all the basic modules to form a large whole network, so that a demand of construction of a data center network can be met and dynamic selection of a down link can be satisfied as well as a high halving bandwidth is provided; and lateral expanding, vertical expanding or mixing expanding is carried out on the network topology system as well as expansion of the network scale is supported flexibly. According to the invention, the system has a high network fault tolerance performance; more server devices can be accommodated; and a demand of application expansion in the future can be met; therefore, the system can be applied to construction of a data center network and high bandwidth data transmission can be provided.
Owner:XIDIAN UNIV
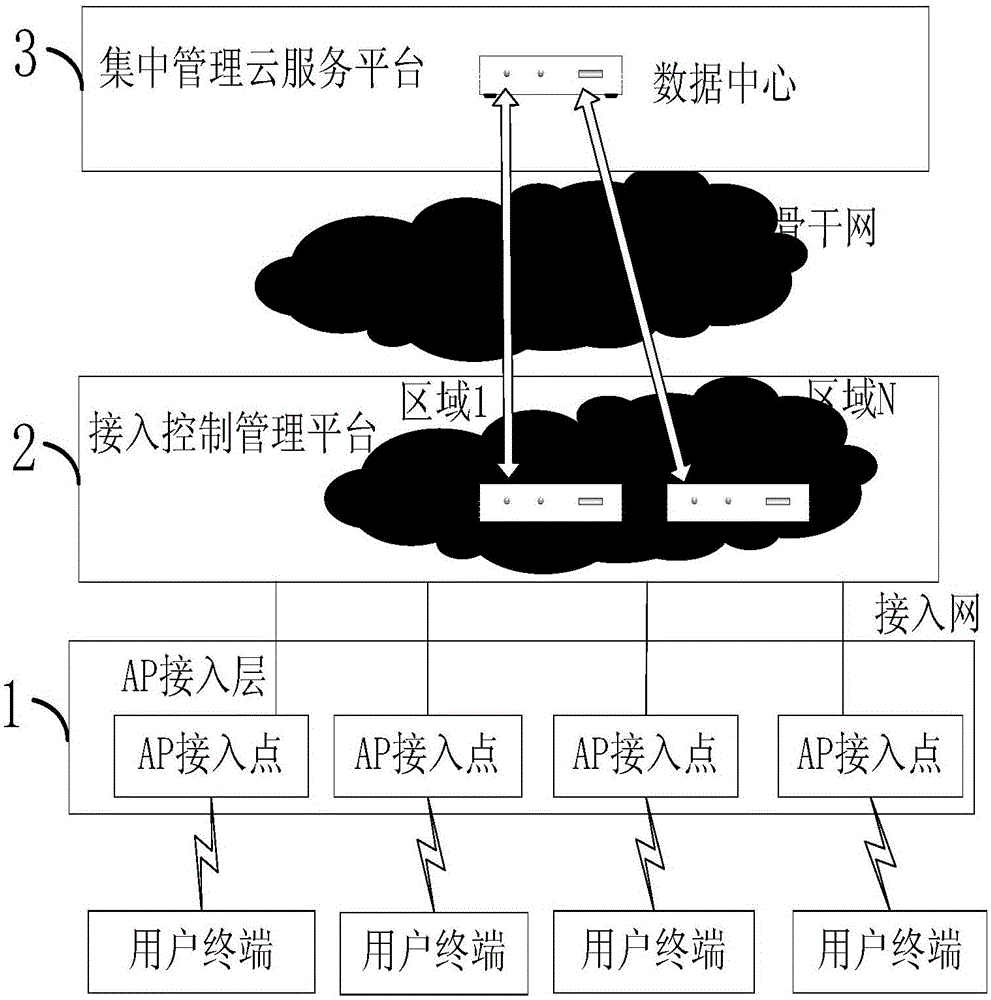
Cloud platform distributed system and method based on Internet and wifi mode
InactiveCN105049457AAchieve the role of advertisingRealize plug and playNetwork topologiesNetworks interconnectionNetwork sizeThe Internet
The invention discloses a cloud platform distributed system and method based on Internet and a wifi (Wireless Fidelity) mode. The system comprises an AP (Access Point) access layer, an access control management platform layer and a centralized management cloud service platform layer from top to bottom in sequence. Through adopting a layered management technology based on the cloud service, a wlan (Wireless Local Area Network) is taken as a wireless access technology and the Internet is taken as a carrier to implement a new cloud management system of the wlan. After a user terminal is connected to an AP access point, the centralized management cloud service platform layer pushes a webpage which is customized by a merchant so as to achieve an advertising effect. According to the distributed three-layer cloud structure, the flexibility of a wlan application is implemented, and plug and play of the AP access point can be implemented, so that the expansion capability and the flexibility of the system can be greatly improved, and the system can accomplish with ease under the modes of public cloud, private cloud and mixed cloud; owing to virtual sharing of a storage of a controller, the system can support a larger network scale as a representative of a latest generation of wireless networking technology.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
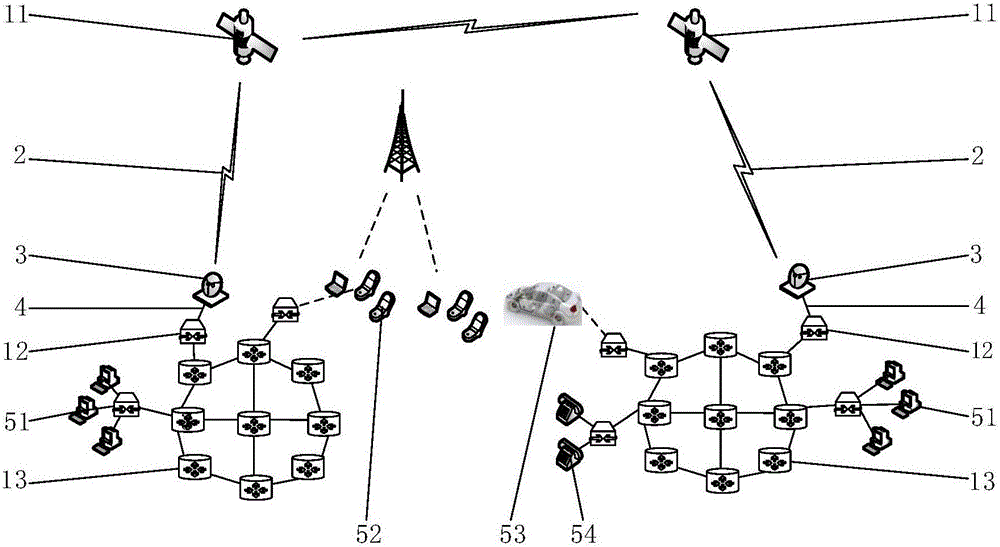
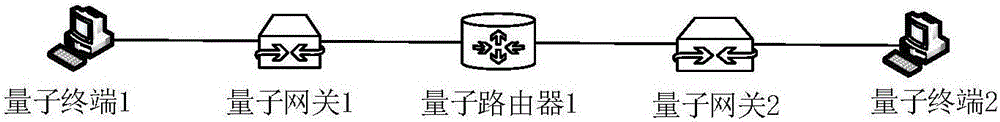
Satellite wide-area quantum communication network system and communication method
InactiveCN107437995AScale upAchieve distributionKey distribution for secure communicationRadio transmissionWide areaNetwork size
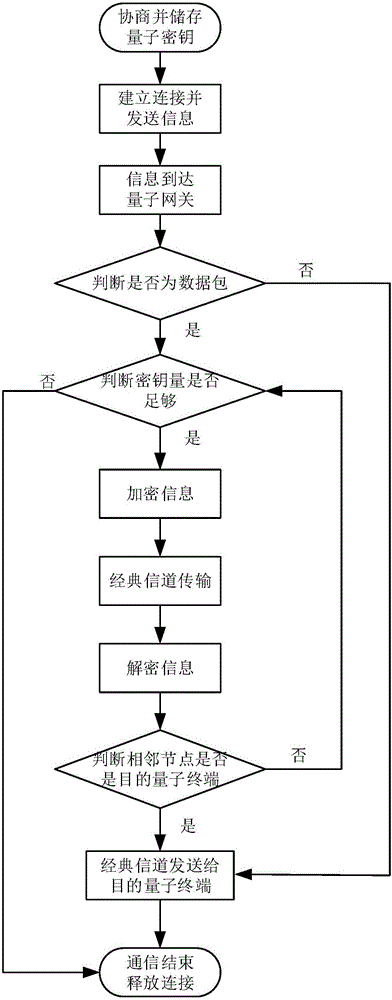
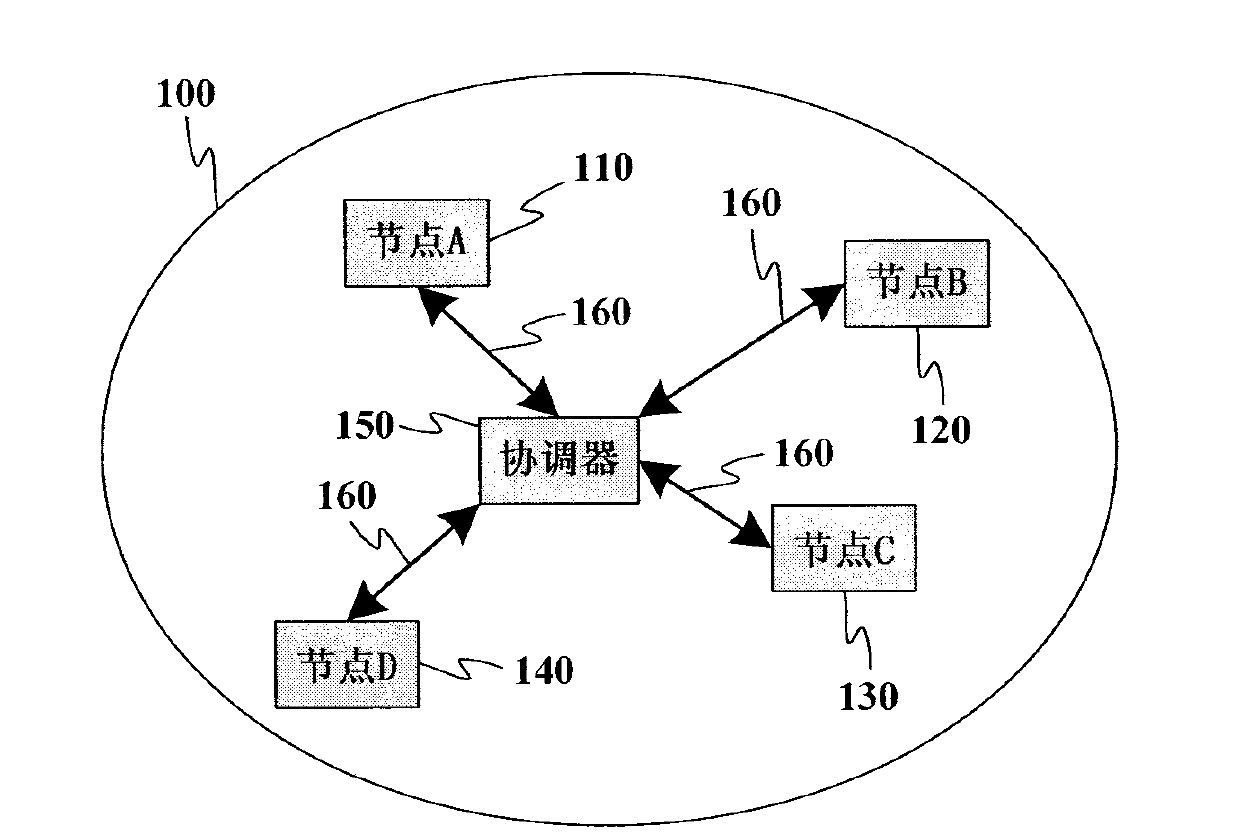
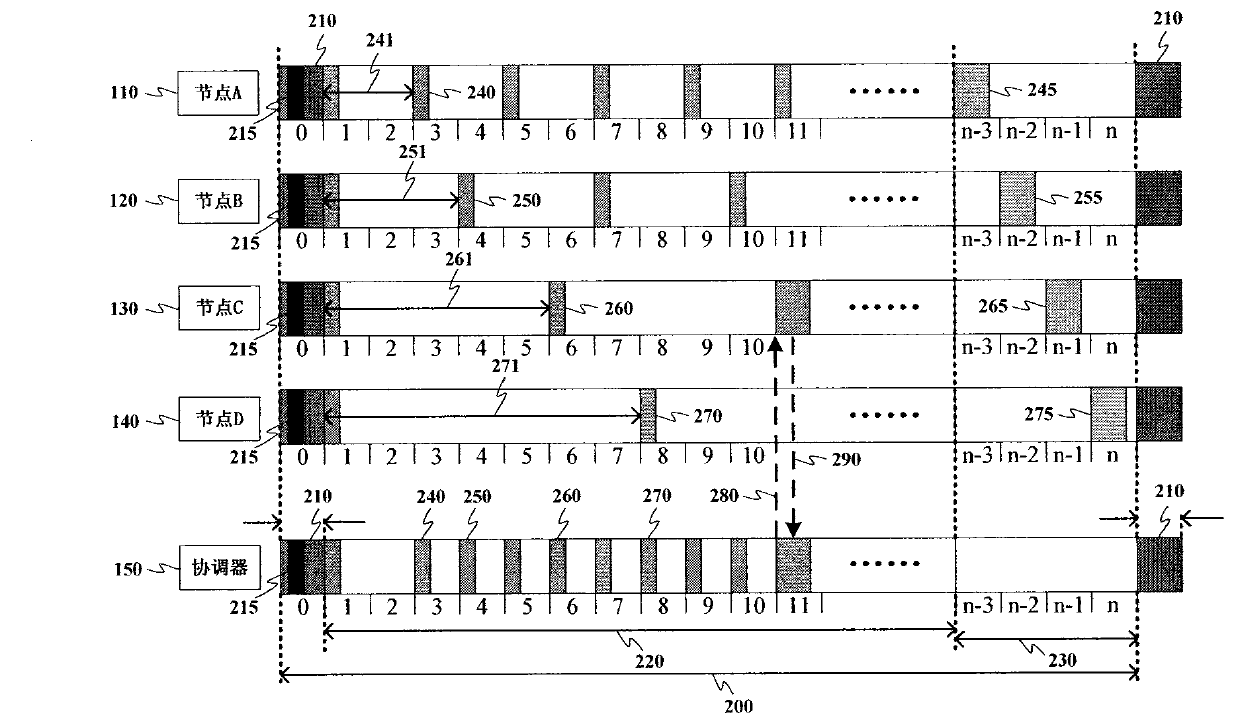
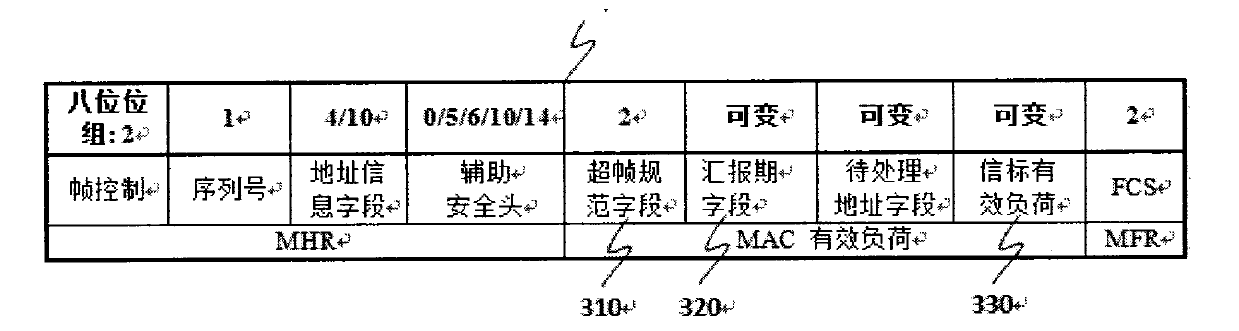
The present invention provides a satellite wide-area quantum communication network system and a communication method. The invention aims to solve the technical problem of small network scales and short communication distances in the prior art. The network system includes a plurality of quantum trusted relays, a plurality of ground stations, a plurality of quantum terminals, a plurality of optical fiber quantum key distribution links and a plurality of free space quantum key distribution links, wherein the quantum trusted relays comprise quantum routers, satellites and quantum gateways, the optical fiber quantum key distribution links are used for realizing connections between the quantum gateways and the quantum routers and connections between the ground stations and the quantum routers, and the free space quantum key distribution links are used for realizing connections between the satellites and the ground stations and connections between the satellites. The communication method includes the following steps that: the quantum trusted relays negotiate with each other to obtain keys and store the keys, and the satellites and the ground stations negotiate with each other to obtain keys and store the keys; and the quantum terminals establish connections between each other and transmit information; a current node judges whether the information needs to be encrypted; the current node encrypts the information and transmits the encrypted information; and the quantum terminals release the connections therebetween.
Owner:XIDIAN UNIV
Medium access control (MAC) layer node scheduling method based on beacon frame synchronization and communication asynchronization
InactiveCN102946631AReduce the probability of collisionReduce average communication delayEnergy efficient ICTPower managementNetwork sizeBeacon frame
The embodiment of the invention discloses a listening period dynamic adjustment medium access control (MAC) layer node scheduling method based on the combination of beacon frame synchronization and communication asynchronization and relates to the technical field of wireless communication. According to the method, a coordinator periodically sends beacon frames to nodes and establishes a novel superframe and entire network synchronization, in the novel superframe period, each node is switched between sleeping / listening states in different periods respectively, and the coordinator and the nodes perform data communication and control transceiving of command frames in an asynchronous wake-up mode. The method is applicable to intelligent meter reading and intelligent housing system based on wireless sensor network. By means of the method, when the wireless sensor network is applied to a real-time monitoring scene in which the communication times are few, the data flow is low and the network size is small, the network communication and control energy consumption is reduced, the communication conflict rate is lowered, and the management capability of the network to the nodes is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method of analyzing network attack situation
InactiveUS20050138425A1Accurately detected real timeAccurate detectionDigital data processing detailsMultiple digital computer combinationsNetwork sizeNetwork attack
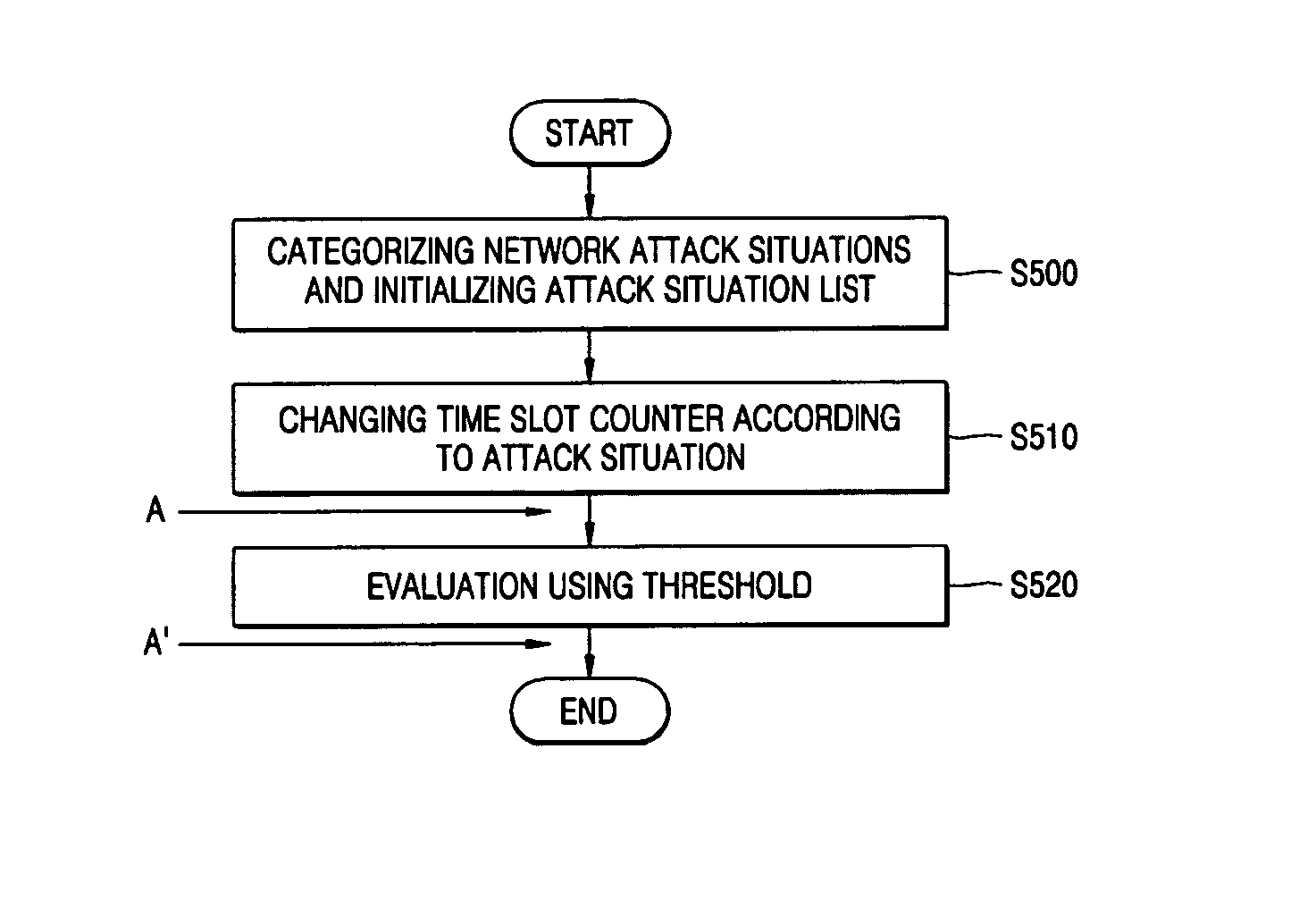
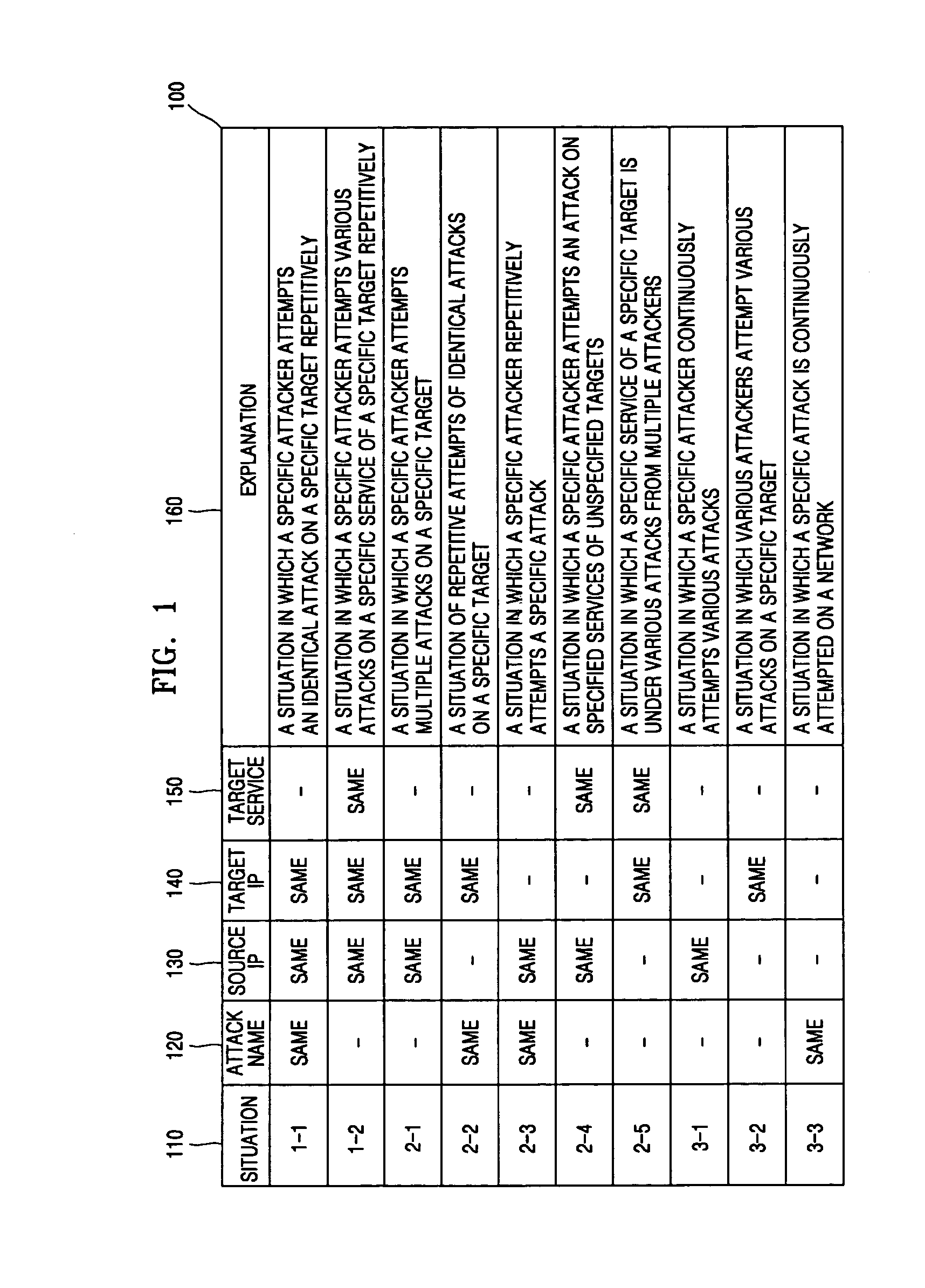
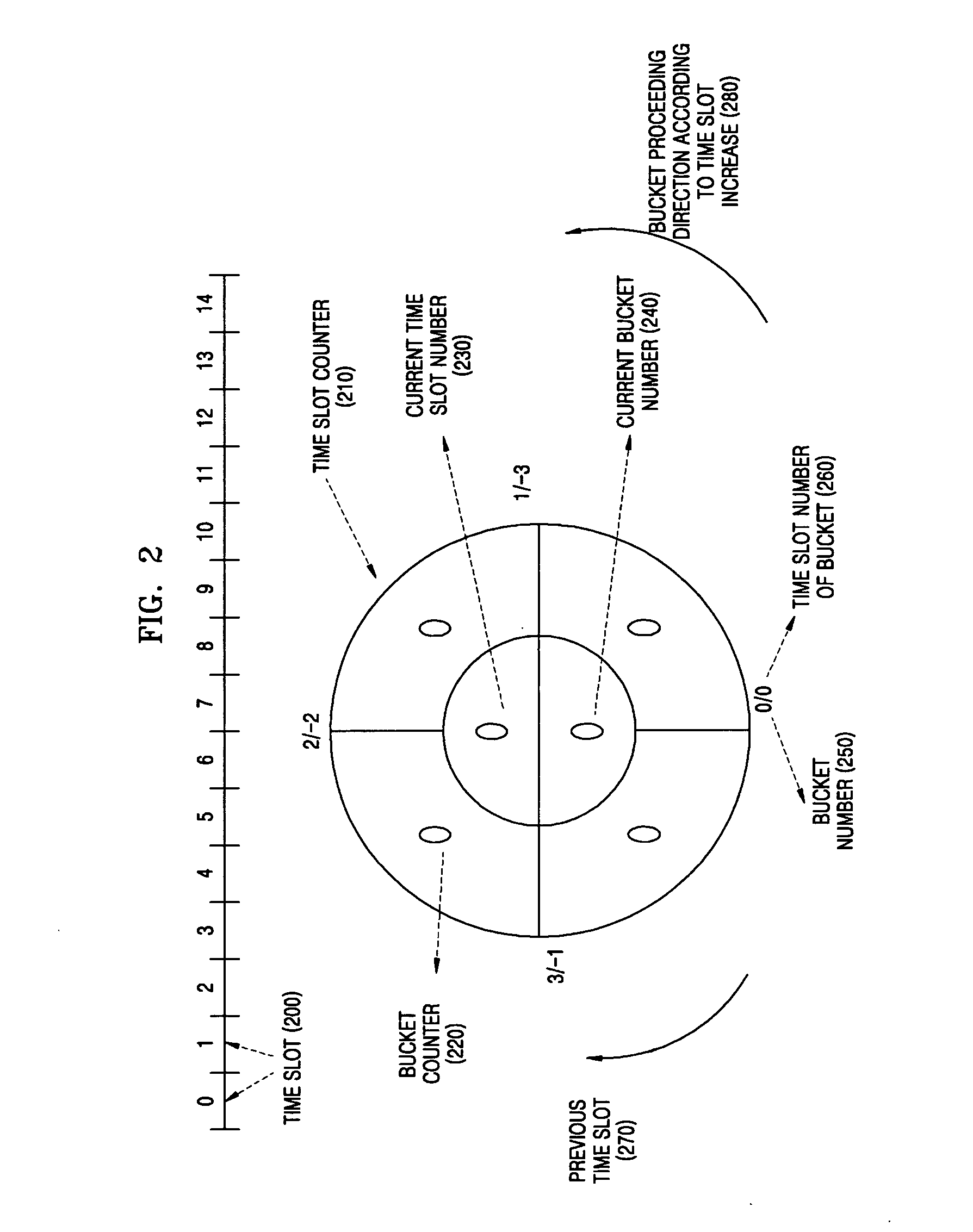
Provided is a method for analyzing a network attack situation. The method categorizes network intrusion detection alerts into network attack situations, counts the frequency of same-featured intrusion alert occurrence for each network attack situation using a counting algorithm based on time slots, and analyzes the network attack situation based on the frequency of same-featured intrusion detection alert occurrence, the rate of same-featured intrusion detection alert occurrence, or an AND / OR combination of them. The network attack situation can be correctly detected in real time without relatively being influenced by the size of the network or amount of the occurrence of the intrusion detection alerts.
Owner:ELECTRONICS & TELECOMM RES INST
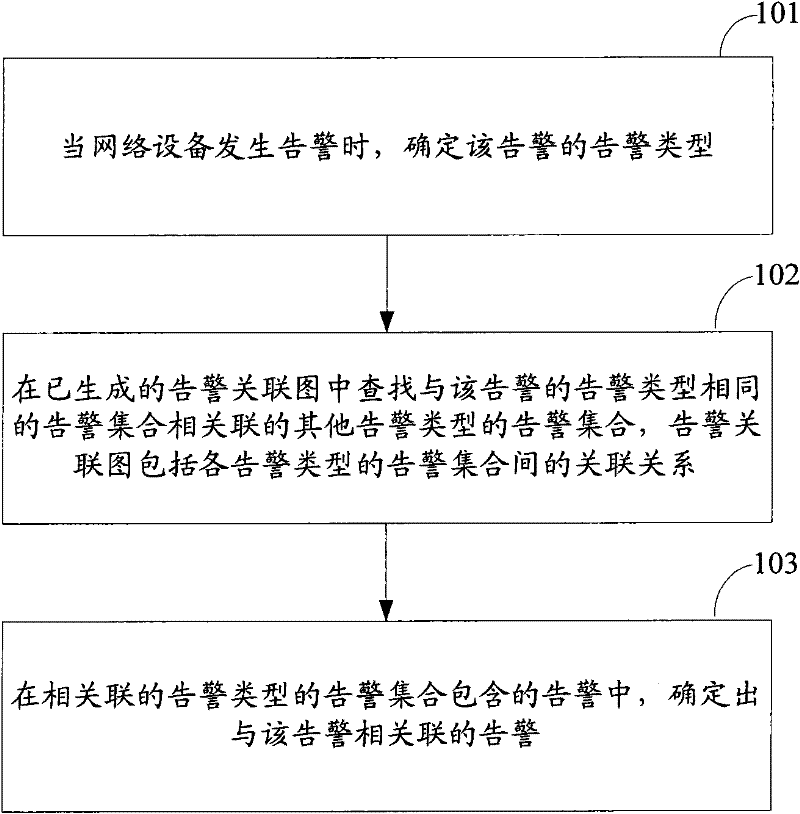
Method and device for generating alarm correlation diagram and method and device for determining related alarm
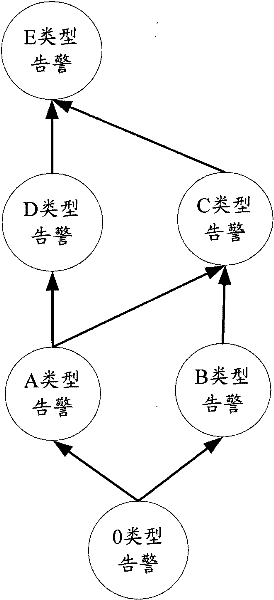
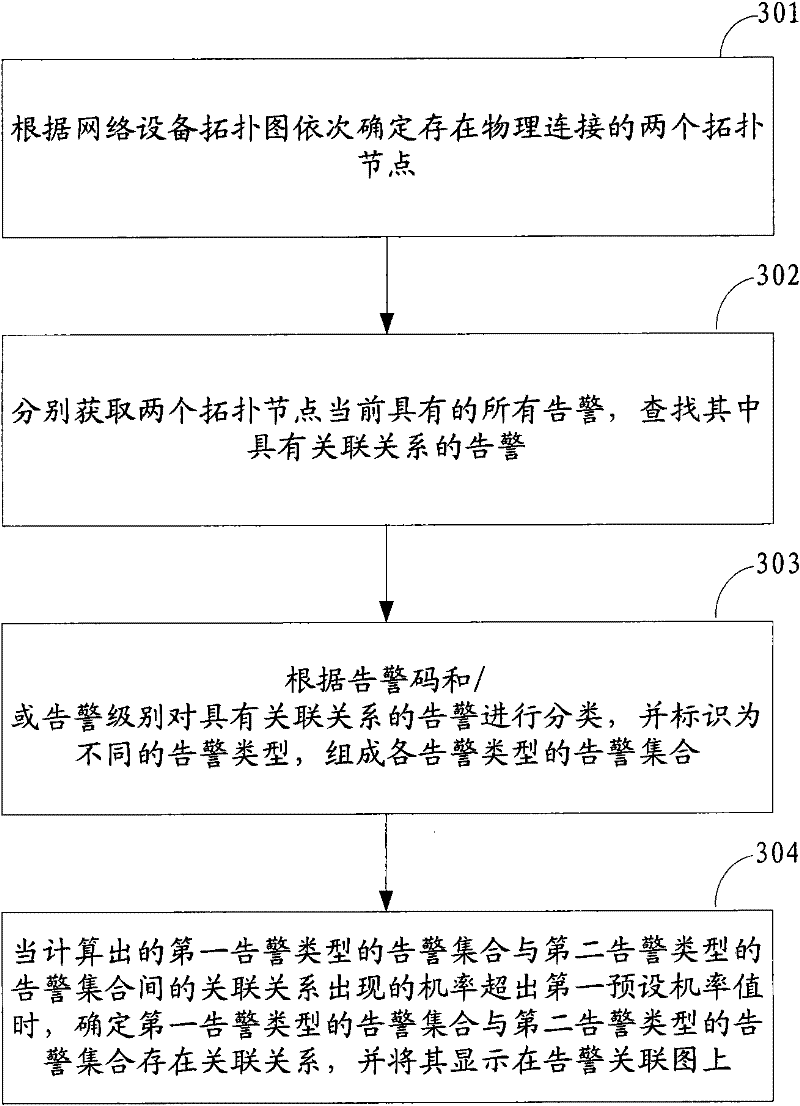
InactiveCN102291247AUnlimited scaleReduce complexityData switching networksNetwork sizeTopological graph
A method and device for generating an alarm association graph, and a method and device for determining association alarms are disclosed. The method for generating an alarm association graph includes the following steps: determining successively two topologic nodes connected physically according to a network equipment topologic graph; acquiring all the alarms currently contained in the two topologic nodes respectively, and searching the alarms therein having association relationships; classifying the alarms having association relationships according to alarm properties, and generating an alarm collection for each alarm type; determining that an association relationship exists between the alarm collection of a first alarm type and the alarm collection of a second alarm type when the calculated probability of the occurrence of the association relationship between the alarm collection of the first alarm type and the alarm collection of the second alarm type, exceeds a first preset probability value,, and displaying the association relationship on the alarm association graph. The method could reflect the association relationships between the alarms simply and directly, and not be restricted to the network size, and be extended easily.
Owner:ZTE CORP
Method for carrying out data flow analysis and management on network appliance
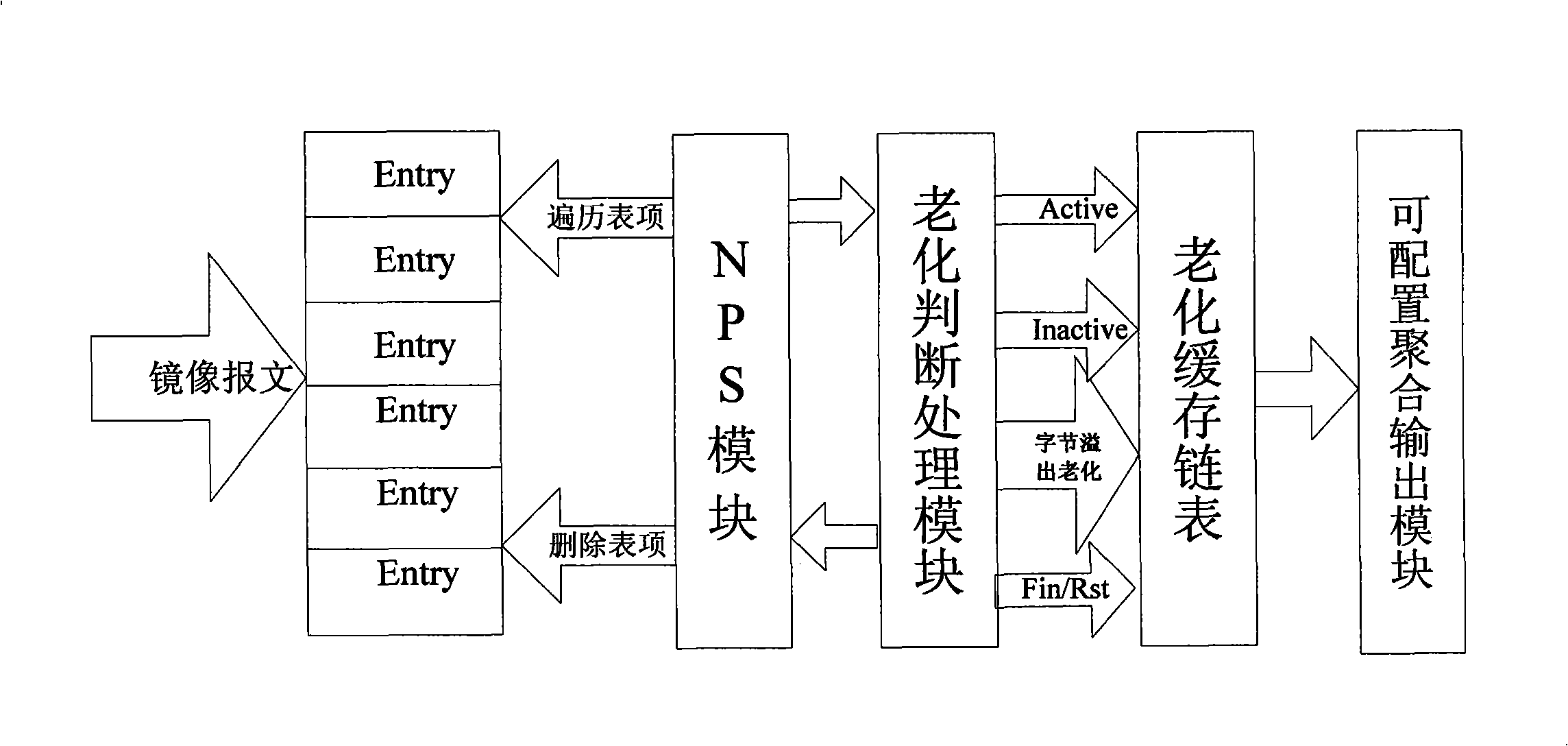
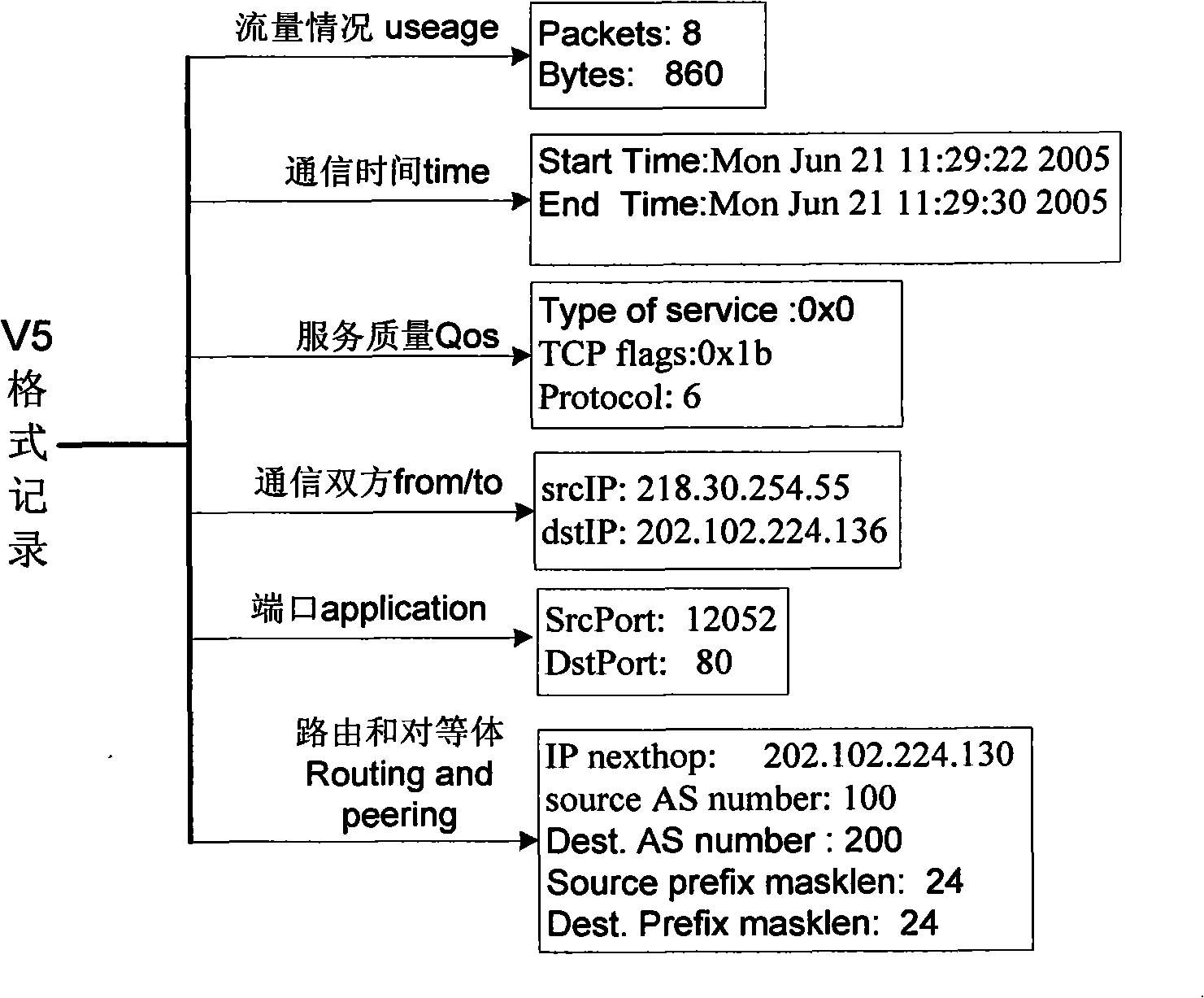
ActiveCN101335686AGuaranteed treatment effectFlexible analysisData switching networksTraffic capacityNetwork size
The invention discloses a method for carrying out data flow analysis management on network equipment. The method overcomes the technical limitations of the current network management system to network flow and flow direction analyzing function, can not only carry out statistics to network bandwidth utilization rate with high efficiency, but also carry out analysis and statistics to the flow and the flow direction of businesses of different types. Therefore, after being adopted, the method of the invention can not only provide a solving proposal for IP charging, but also provide a network security detection tool for enterprises and network administrators; in addition, a plurality of specific convergence manners are allocated in a router or an exchanger terminal, thus greatly reducing flow coarseness sent to the administration server of a network management center and ensuring that the processing capability of a management system can adapt to the increase of network scale in the future.
Owner:SHANGHAI BAUD DATA COMM
Clustering-wireless-sensor-network-orientated two-stage adaptive frequency-hopping method
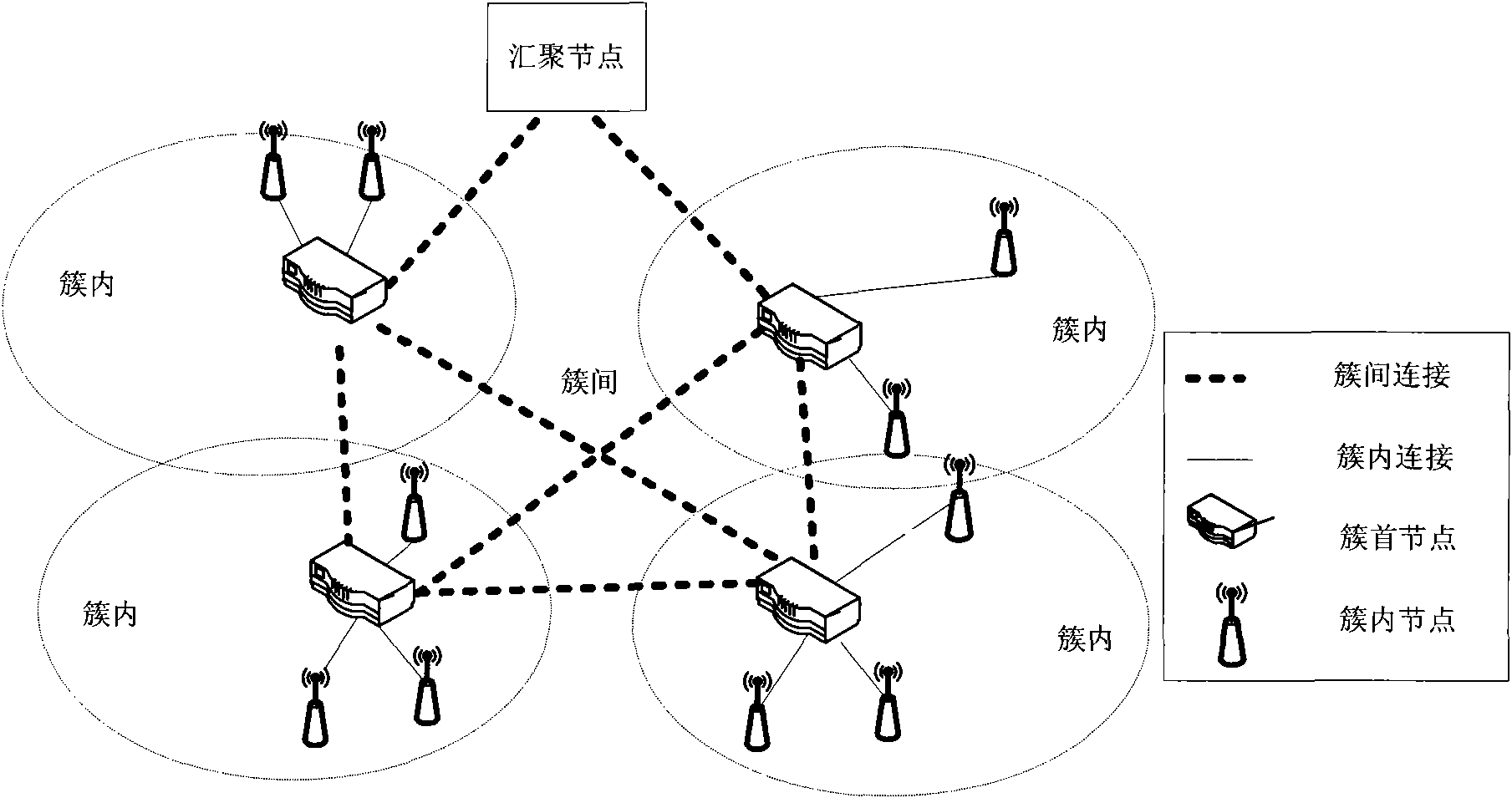
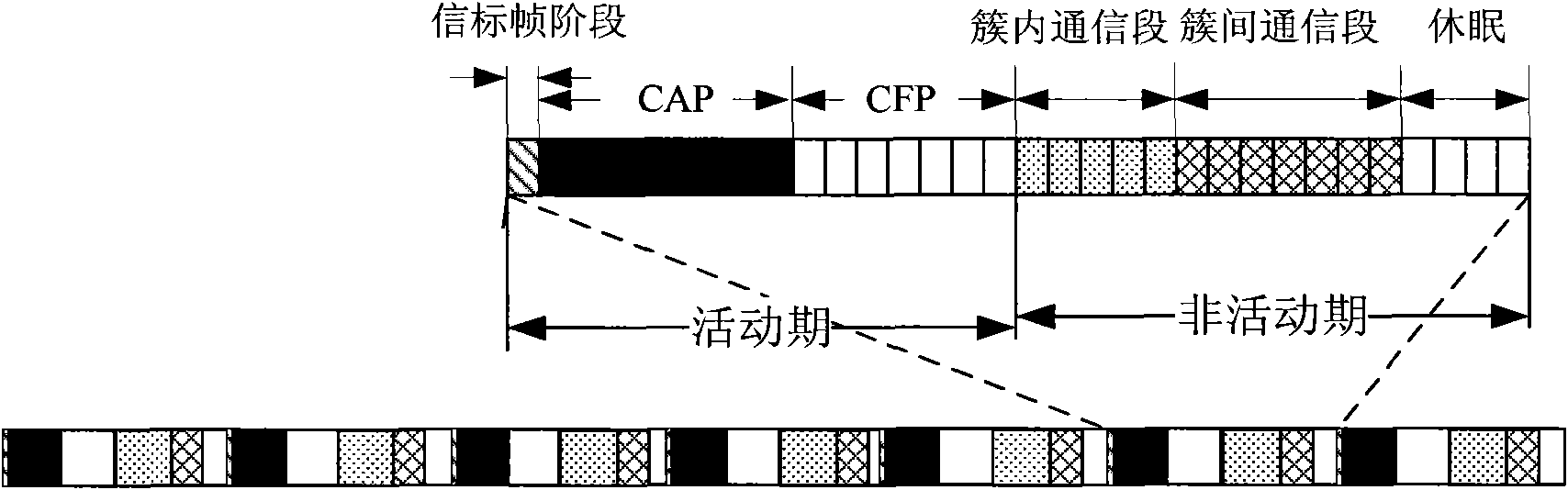
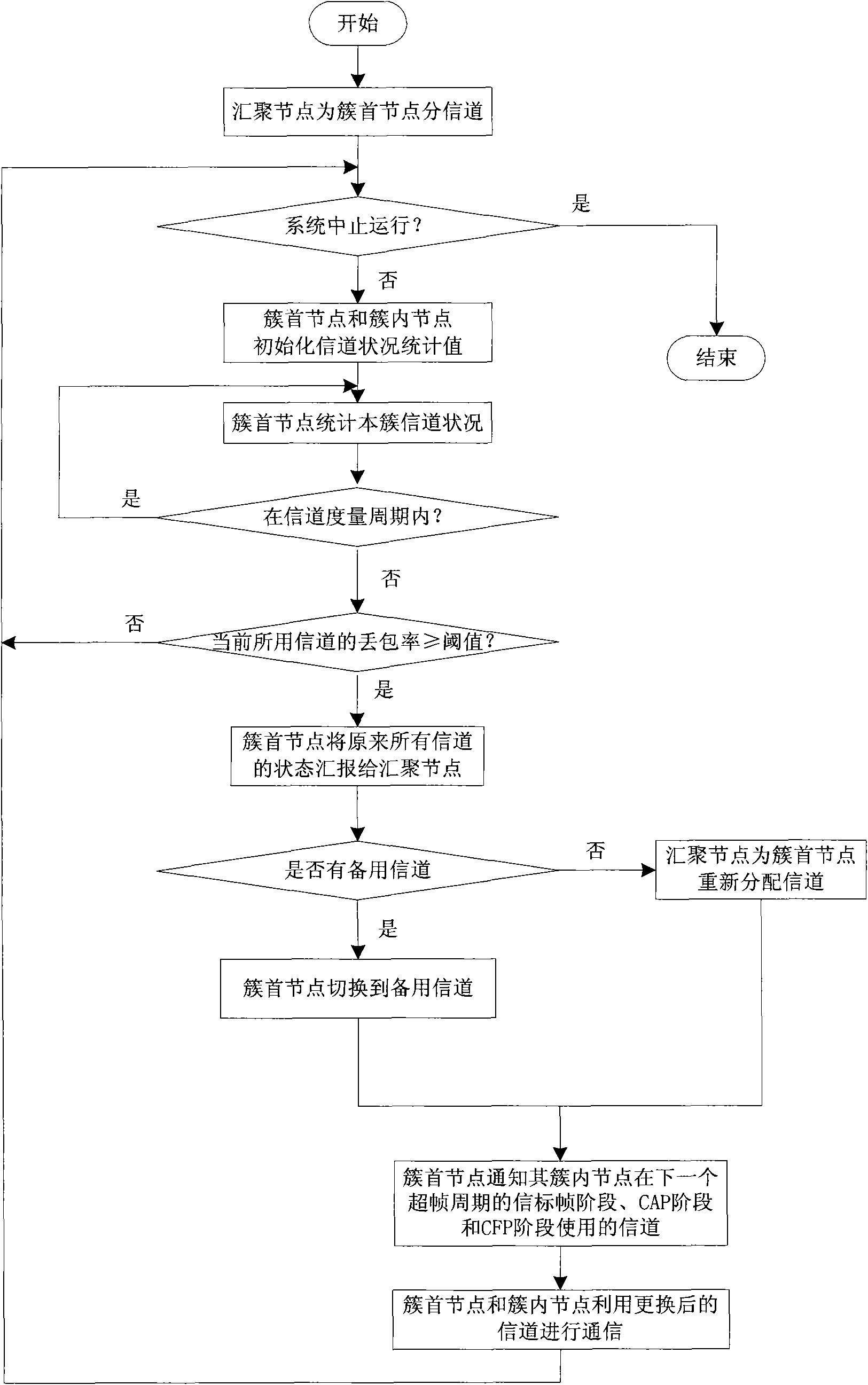
InactiveCN102122973AScale upReduce difficultyAssess restrictionNetwork topologiesBroadcast channelsNetwork size
The invention relates to a clustering-wireless-sensor-network-orientated two-stage adaptive frequency-hopping method. The method comprises the following steps of: constructing the clustering wireless sensor network; defining a super-frame structure based on institute of electrical and electronic engineer (IEEE) 802.15.4 according to the topological structure of the clustering wireless sensor network; accessing a format of a beacon frame of a control layer based on a medium of the original IEEE 802.15.4, and extending a content of a beacon frame load; and accessing the beacon frame of the control layer based on the super-frame structure and the extended medium of the IEEE 802.15.4 so as to realize a two-stage adaptive frequency-hopping process of a node in the network. By the clustering wireless sensor network, the network size is expanded, the difficulty in maintenance and management is lowered, and the system flexibility is improved; as the two-stage frequency-hopping method is designed, the compatibility with the IEEE 802.15.4 and the system reliability are guaranteed; and based on the beacon frame load of the IEEE 802.15.4, no special frame is not needed to be designed for a broadcast channel distribution result during a channel switching process, so that the network design is simplified, the number of the frames for controlling is reduced, and the network throughput is increased.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
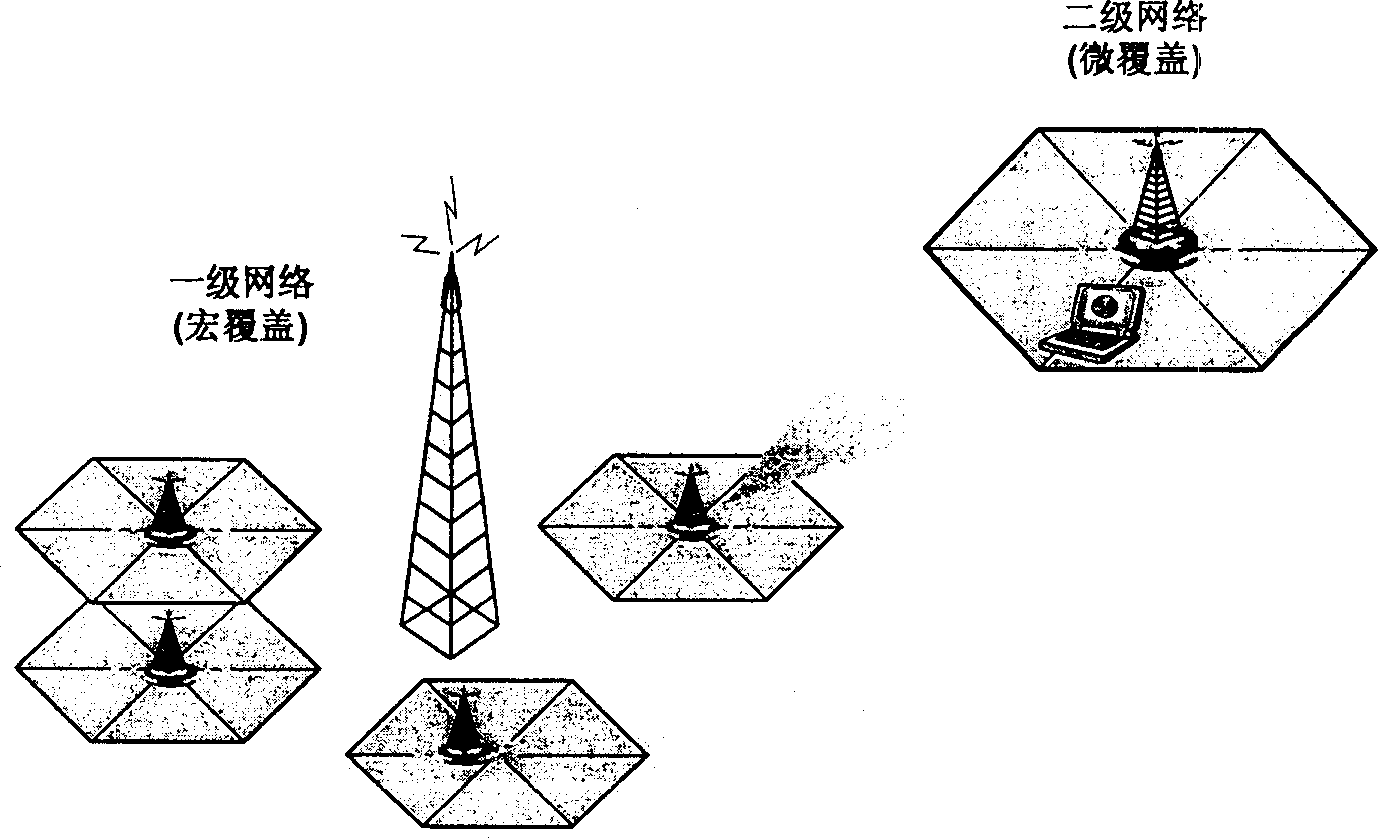
Digital interactive multimedia network system and data transmission method therewith
A data interactive mode multimedia network and data transmission method by utilizing this network, comprises two stages network collaboration. The main feature is that the network includes: a first stage network comprising the macro overlay networks, having high transmission power, used for one-way broadcasting; a second stage network comprising micro overlay networks, formed by cellular, used for broadcasting and two-way communication. This network allows seamless transition from basic broadcasting service to premium grade two-way wide band service; according to needs of traffic application and the difference of network size. The first network can be configured based on multi mode, running on the other one frequency range, according to the feature of cellular and two-way communication service. The second network has the different parametric combination being selected and configured. The broadcasting service of This network expands on the macro overlay networks, the two-way communication service starts to run based on the establishment of cellular network.
Owner:TIMI TECH
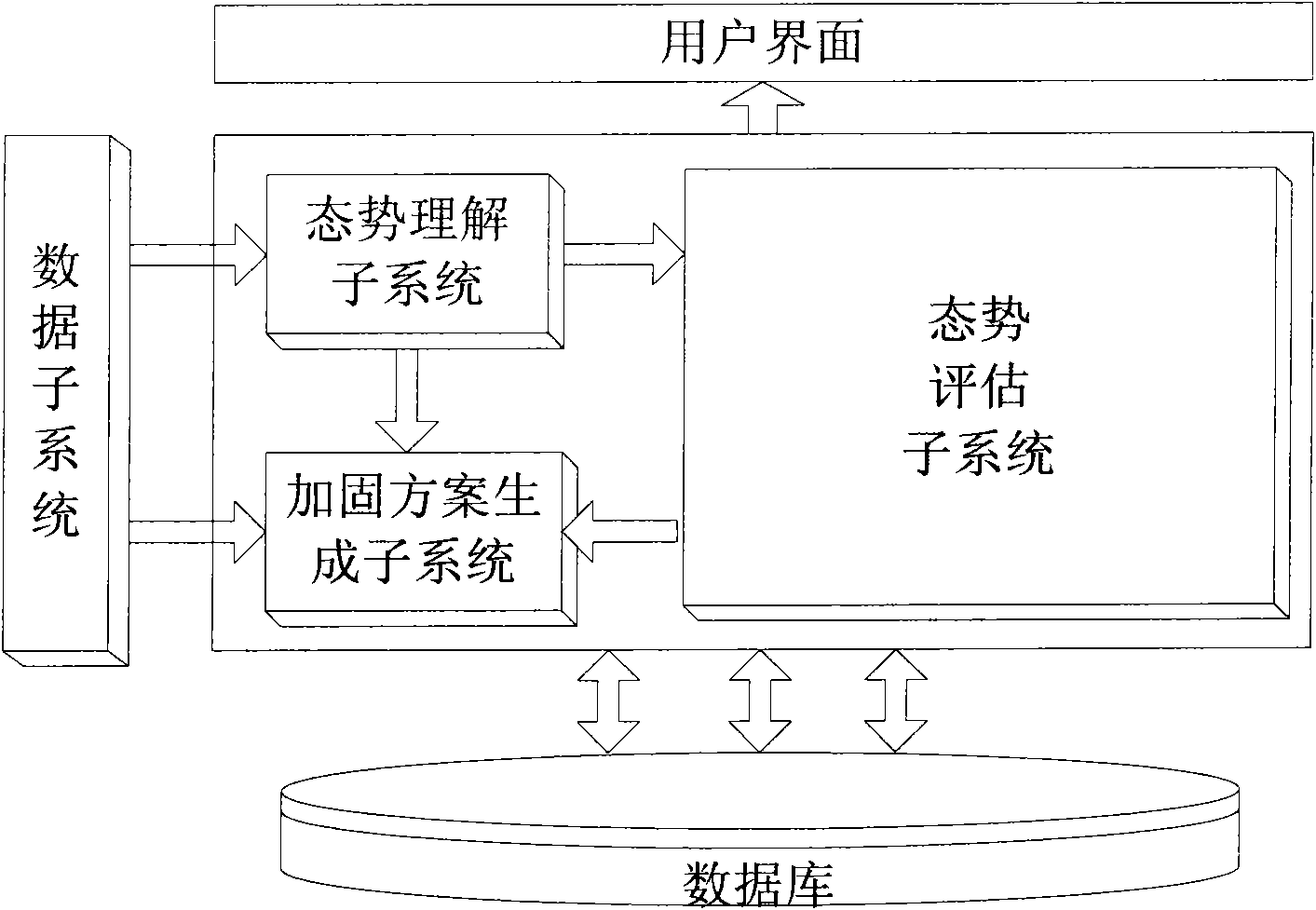
System and method for estimating network security situation based on index logarithm analysis
InactiveCN102148820AIntuitive calculation processEasy to understandData switching networksNetwork sizeConfidentiality
The invention discloses a system and method for estimating network security situation based on index logarithm analysis. The system is characterized by comprising a data acquisition sub-system, a network security situation understanding sub-system, a network security situation estimation sub-system and a security reinforcement scheme sub-system. The method comprises the following steps: A, carrying out statistical data fusion and correlation analysis on data of a network system in the aspects of asset, threat and vulnerability so as to obtain standardized data, wherein the data is acquired by a transducer; and B, carrying out the network security situation estimation on the fused standardized data in the step A based on the index logarithm analysis. The confidentiality, the integrity and the availability of the network security situation are estimated in the aspects of the asset, the threat and the vulnerability, and the estimation result is output. The system and method provided by the invention can be applied to the situation estimation and risk estimation. According to the system and method provided by the invention, the linear increment of the security situation can be avoided with the increment of network size, thus not only highlighting influences on security incidents with high hazard and significant assets, but also considering influences on security incidents with low hazard and nonsignificant assets, thereby complying with practical situations.
Owner:UNIV OF SCI & TECH OF CHINA
Network route convergence processing method and network route convergence processing device
The invention discloses a network route convergence processing method. According to the method, a preset non-pruning multicast distribution tree is utilized as a fast channel, when network topology is changed, after adjacent devices of a topological change source detect the topological change, a layered service provider (LSP) message is generated according to topological change type, and the LSP message is sent out through the fast channel, and then convergence processing modules on the adjacent devices continue to carry out route convergence process to the topological change event. After a device on the fast channel receives the LSP message, the message is transmitted, and at the same time, the message is sent to the convergence processing modules for route convergence process. The invention further provides a corresponding network route convergence processing device. By means of the network route convergence processing method and the network route convergence processing device, convergence of a whole network is enabled basically not to be limited by network size and topological change positions, and the convergence performance of the whole network is close to the convergence performance of a single device.
Owner:HUAWEI TECH CO LTD
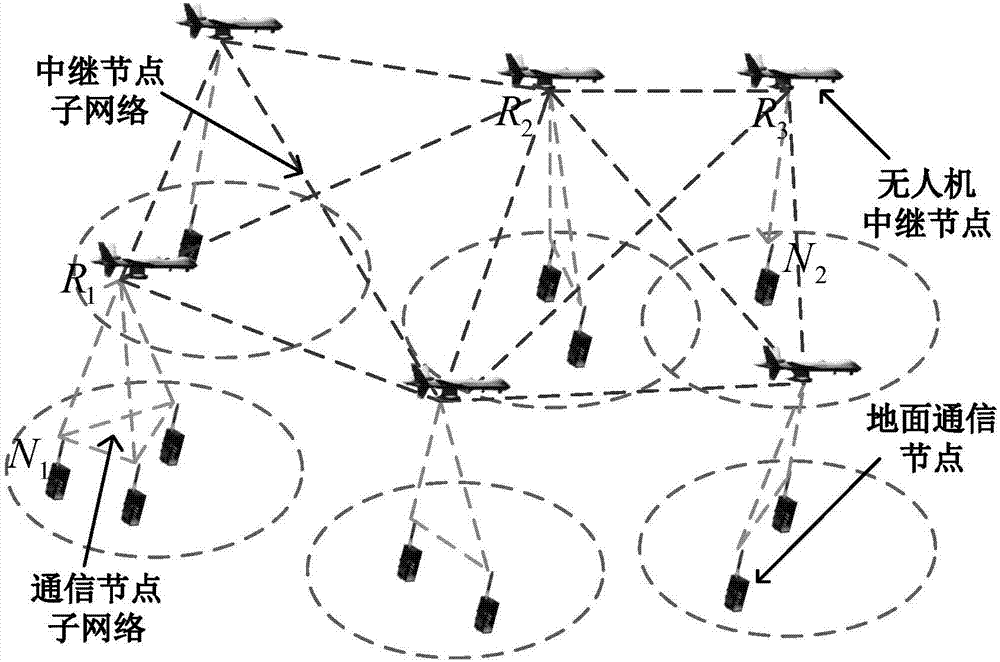
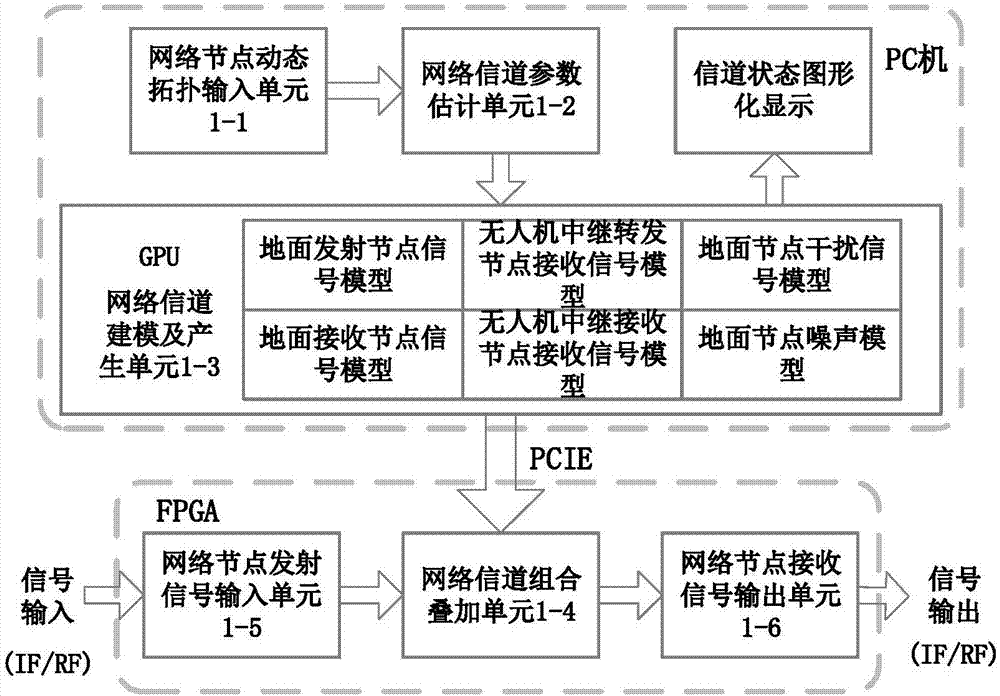
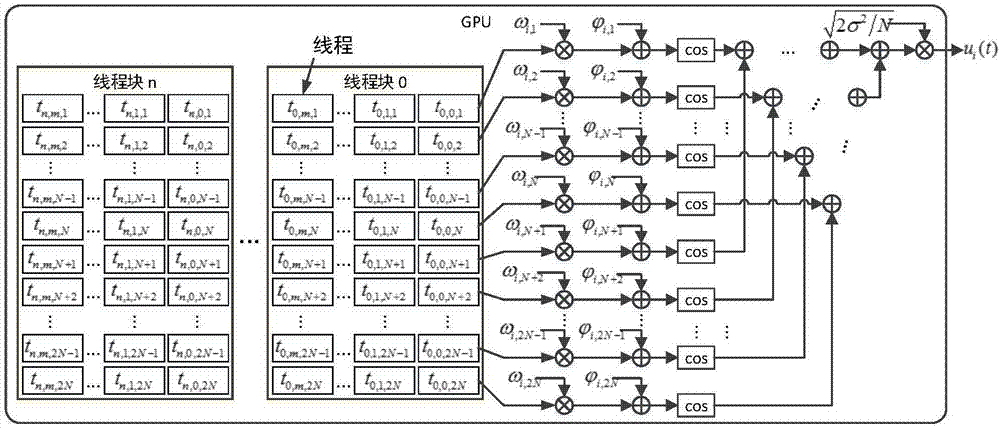
Large-scale UAV relay network channel simulation device and GPU real-time simulation method
ActiveCN107579789ASupport dynamic adjustmentSimplify complexityTransmission monitoringNetwork sizeReal-time simulation
The invention discloses a large-scale UAV relay network channel simulation device and a GPU real-time simulation method. The large-scale UAV relay network channel simulation device includes a networknode dynamic topology parameter input unit, a network channel parameter estimation unit, a network channel modeling and generating unit, a network channel combination superposition unit, a network node transmitting signal input unit and a network node receiving signal output unit. The simulation system is flexible and general, and supports the dynamic adjustment of the network size and topology structure; the signal, interference and noise of each relay link are modeled using the equivalent method, the complexity of system simulation is greatly simplified; and for different communication scenes, different nodes are supported to adopt different channel models and updated in real time, the mutual interference between network nodes are considered.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
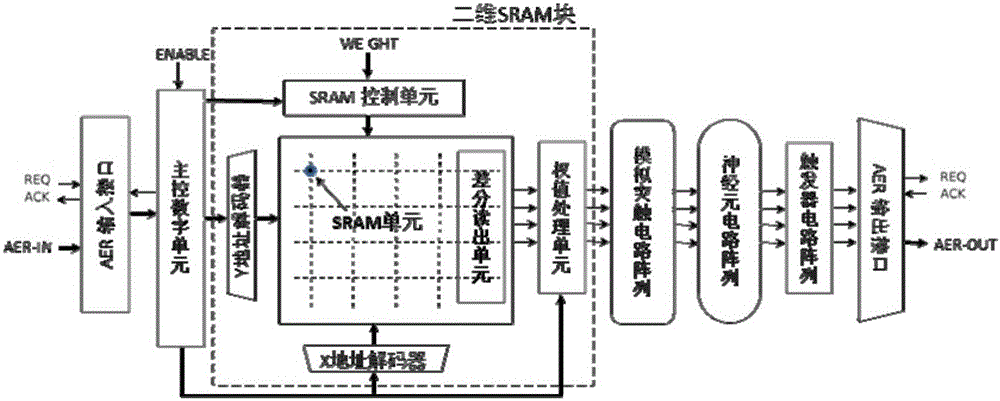
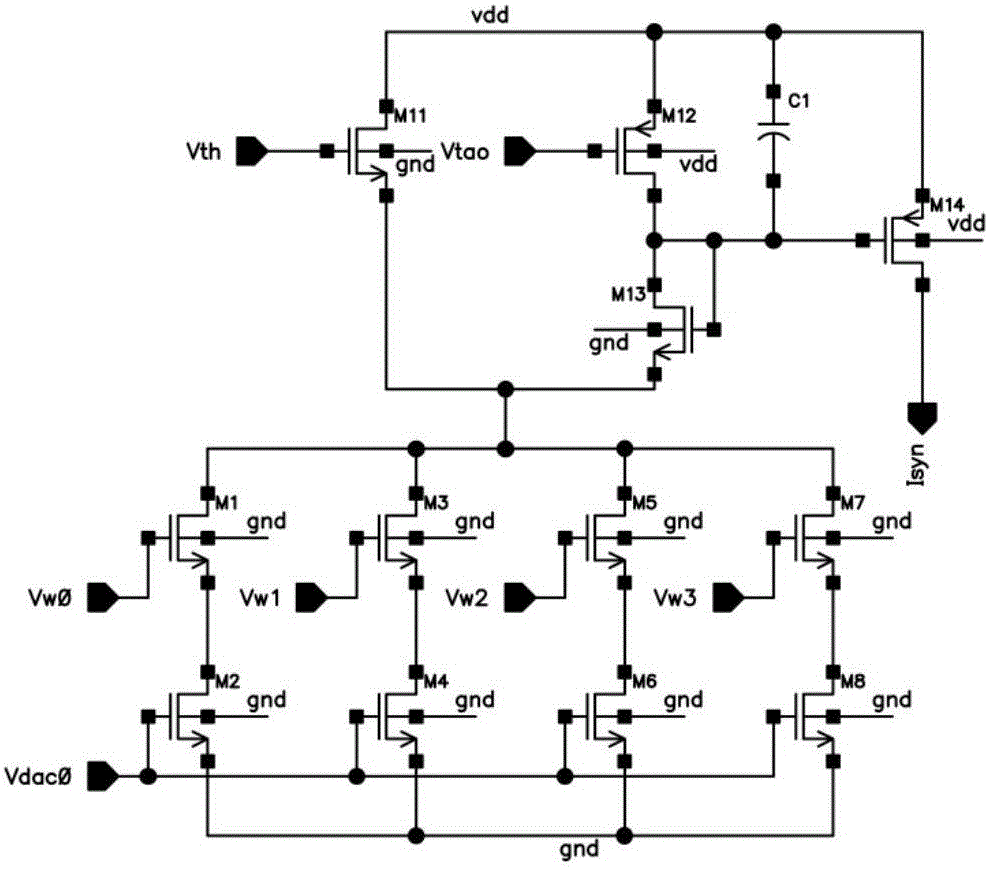
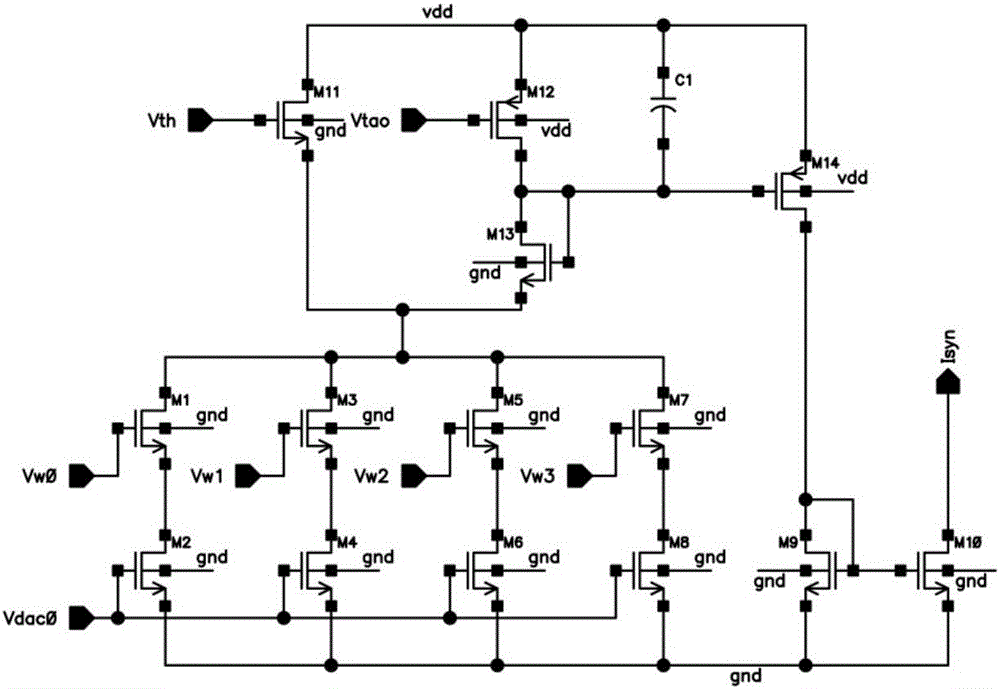
Digital-analog hybrid neural network chip architecture
The invention discloses a digital-analog hybrid neural network chip architecture. The architecture comprises a two-dimensional SRAM module, an analog synaptic circuit, a nerve cell circuit, an AER communication module, and a master control digital unit. The two-dimensional SRAM module is taken as a storage unit of neural network connection relation and a synaptic weight value. The analog synaptic circuit and the nerve cell circuit respectively consist of an MOSFET circuit working in a subthreshold section. The AER communication module serves as the input and output interfaces of a chip, and employs an AER protocol for communication. All control circuits in the architecture are synchronous digital circuits. The architecture is low in power consumption, is high in degree of parallelism, and can achieve a neural network algorithm in a reasonable chip area, wherein the neural network algorithm is more complex in nerve cell functions, is larger in network scale, and is more flexible in connection.
Owner:ZHEJIANG UNIV
Statistical priority multiple access method for a high time-sensitive service
InactiveCN109803294AReduce end-to-end latencyTransmission monitoringWireless communicationNetwork sizeAccess method
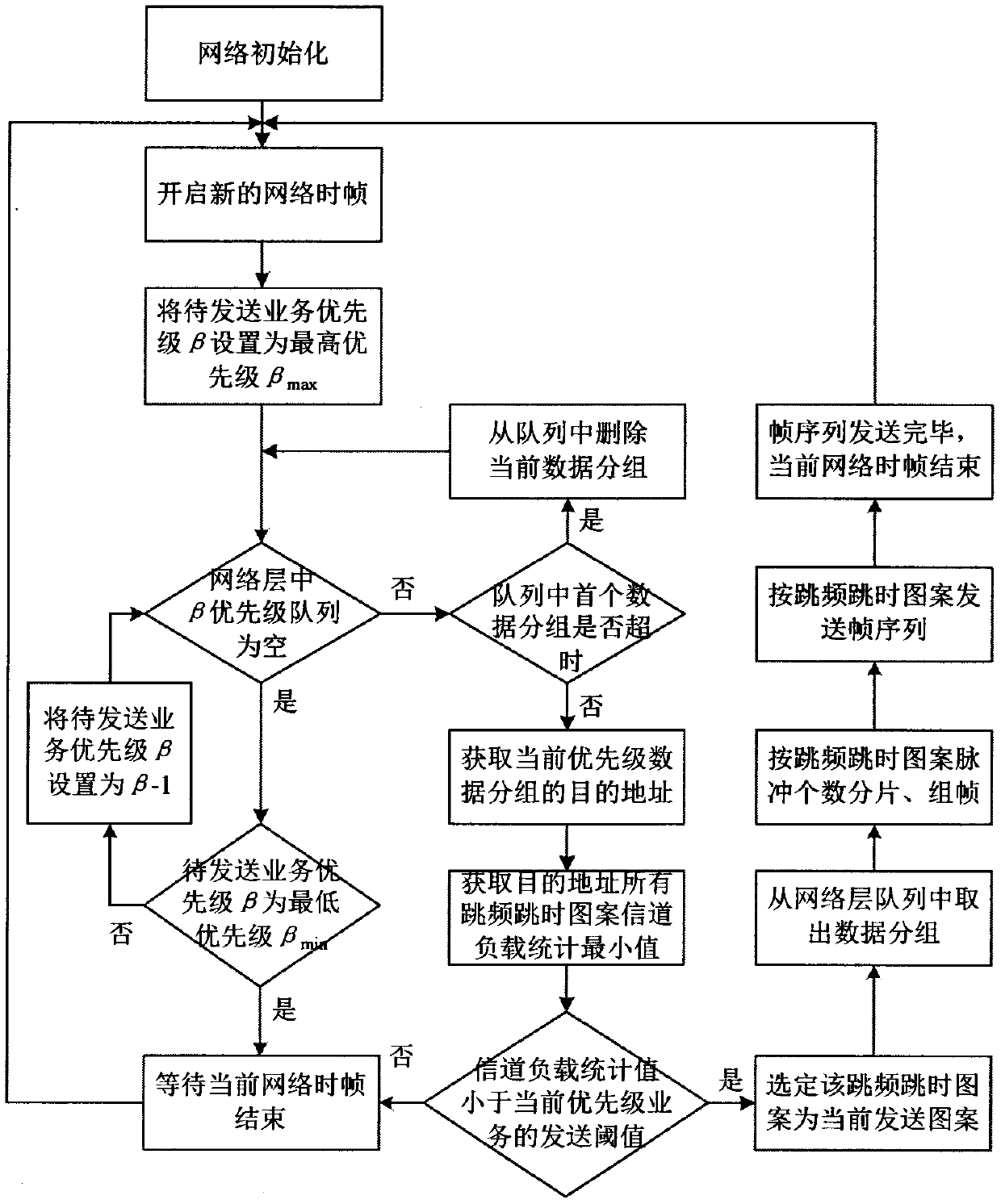
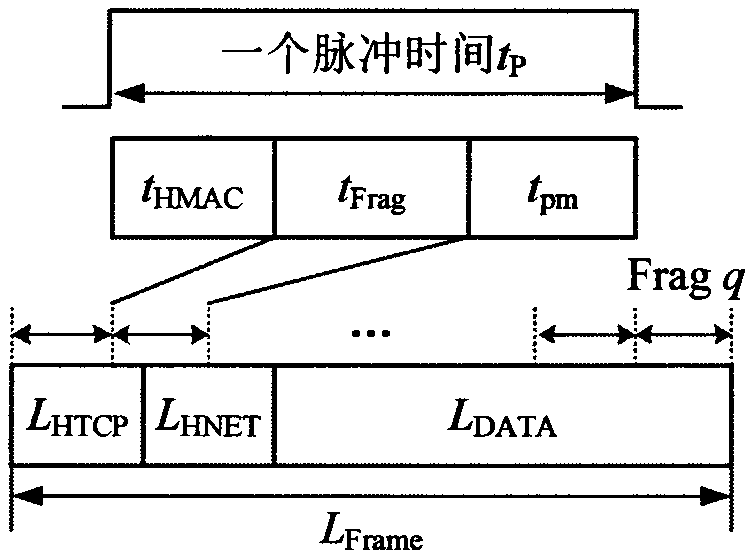
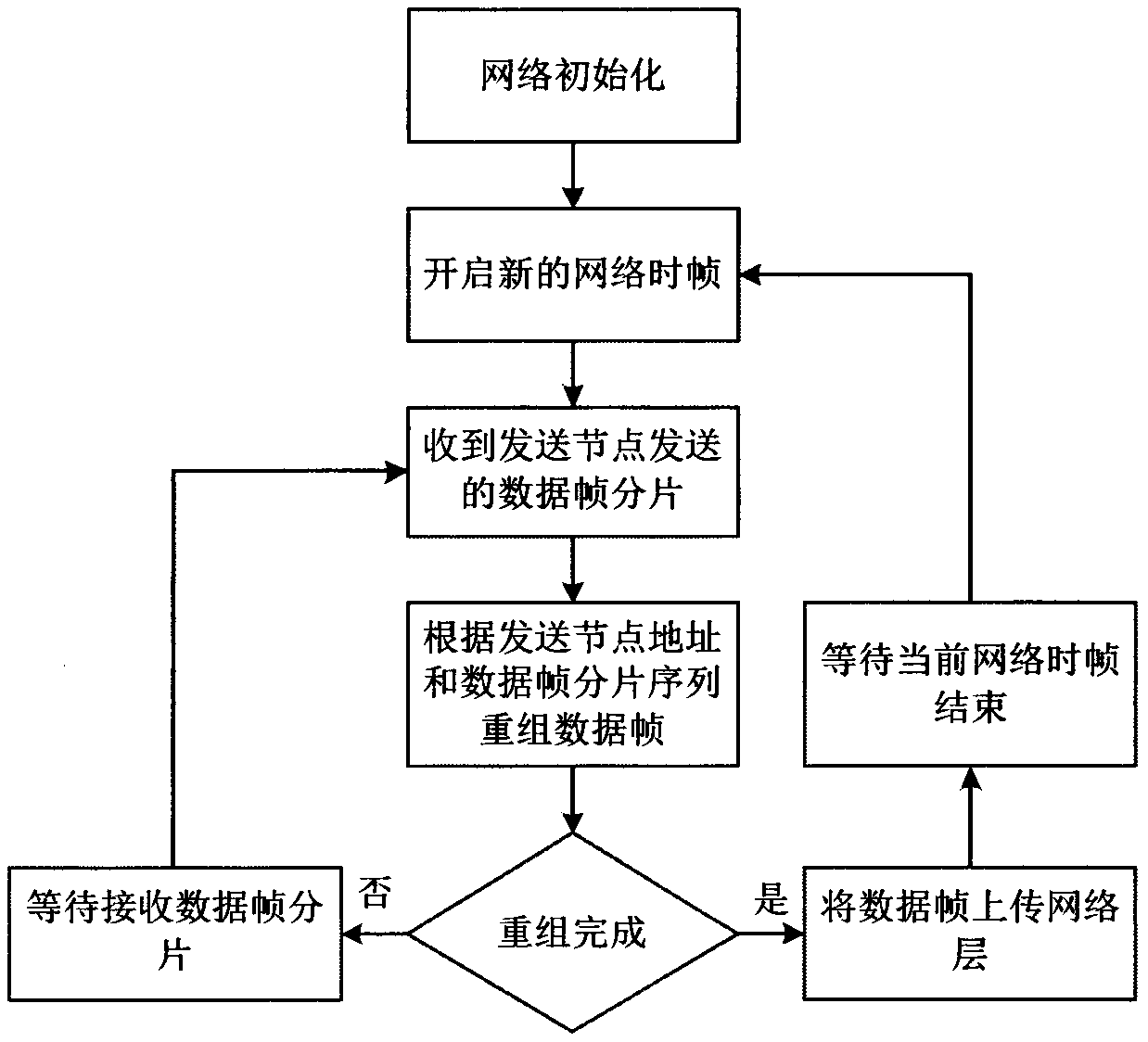
The invention discloses a statistical priority multiple access method for a high time-sensitive service. According to the method, it is assumed that a physical layer adopts frequency hopping and timehopping communication technologies, and frequency hopping and time hopping patterns are distributed to nodes firstly according to the network scale and service transmission requirements; The service load value of the logic channel corresponding to the frequency hopping and time hopping pattern is obtained by detecting the occupation condition of the pulse time slot, and the transmission thresholdvalues of various priority services are calculated by adopting a filling test method. And at the beginning of each network time frame, the sending node sequentially checks whether to-be-sent data packets exist in the network layer queue according to the priority order, and compares the service load values of the frequency hopping and time hopping patterns of the receiving nodes of the data packetswith the sending threshold value of the priority service. And if the service load value is smaller than the sending threshold value, the node can send the data packet with the priority according to the frequency hopping and time hopping pattern of the receiving node. A simulation result in an EXata network simulation environment proves that the method can reliably support transmission of the high-time-sensitivity service.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method for realizing optical group broadcasting in intelligent optical network
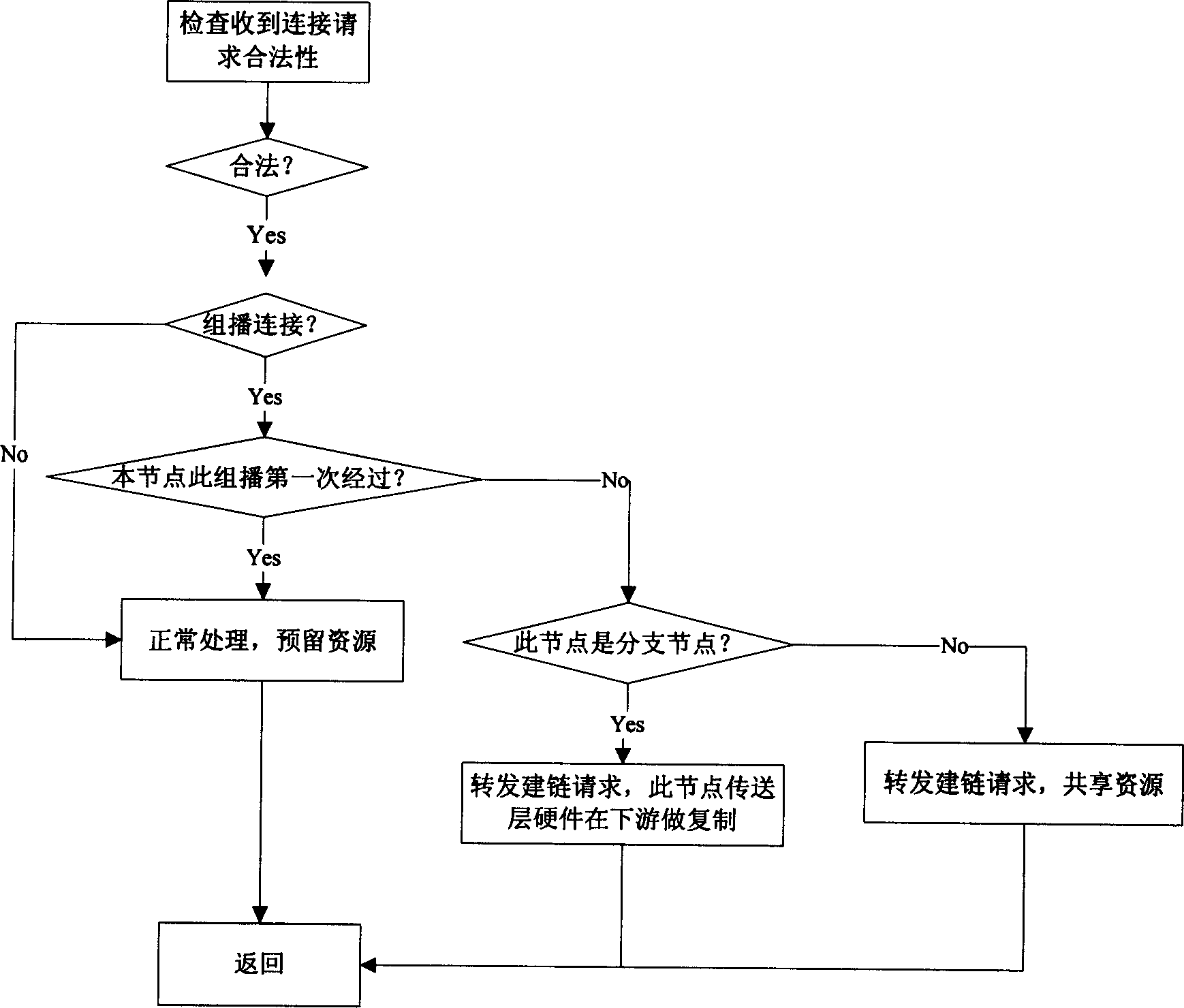
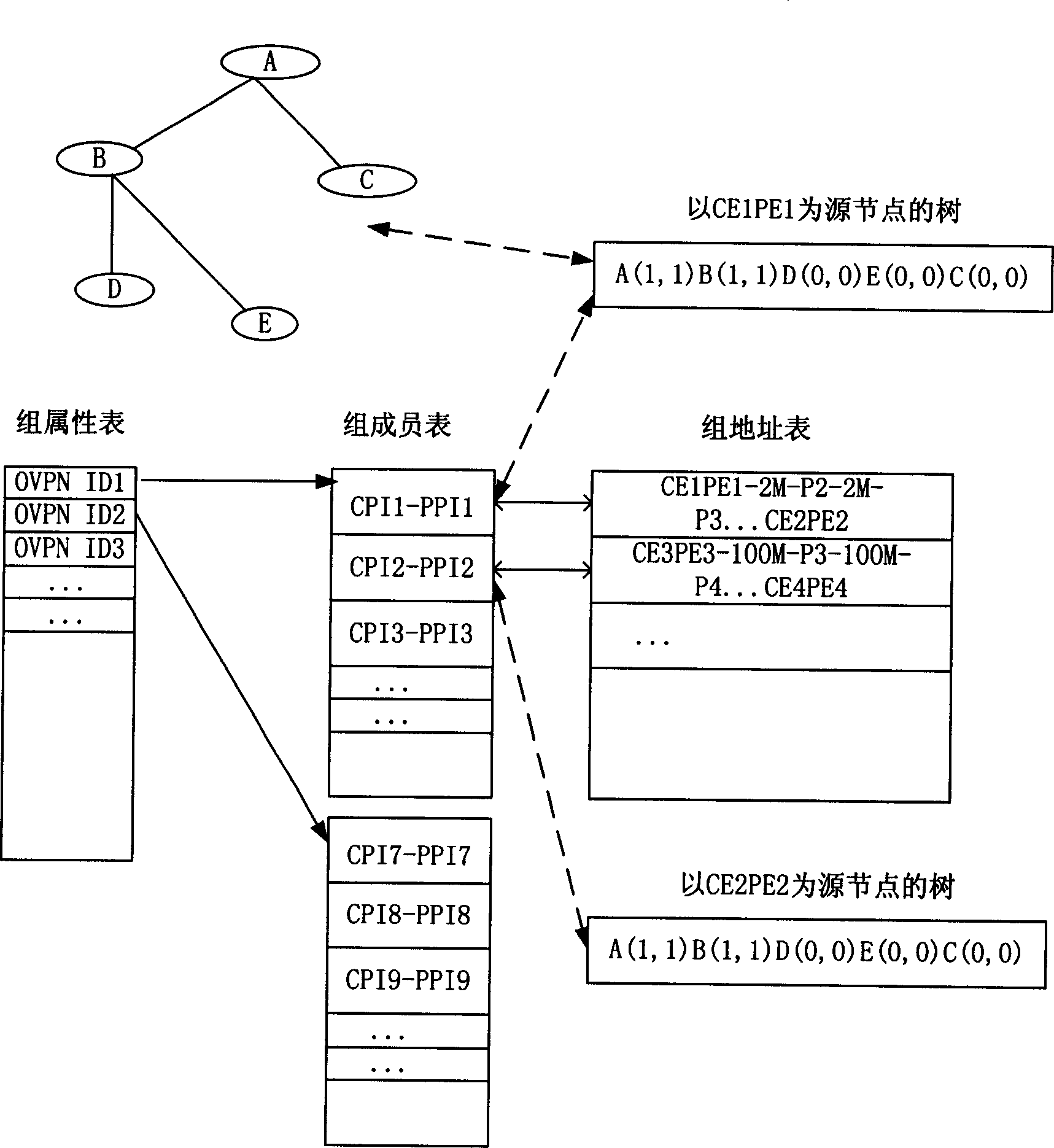
ActiveCN1773947AShort hopsReduce occupancySpecial service provision for substationData switching by path configurationControl layerNetwork size
A method for realizing light multicast in intelligent light network includes forming user group management base by utilizing service management module in management layer; applying light multicast mechanism managed by management layer and control layer and utilizing manner of dynamically setting up multicast route, adding and deleting leaf node, summing ¿C up link and setting up connection one by one to achieve light multicast on large network for saving a lot of routes and bandwidth.
Owner:ZTE CORP
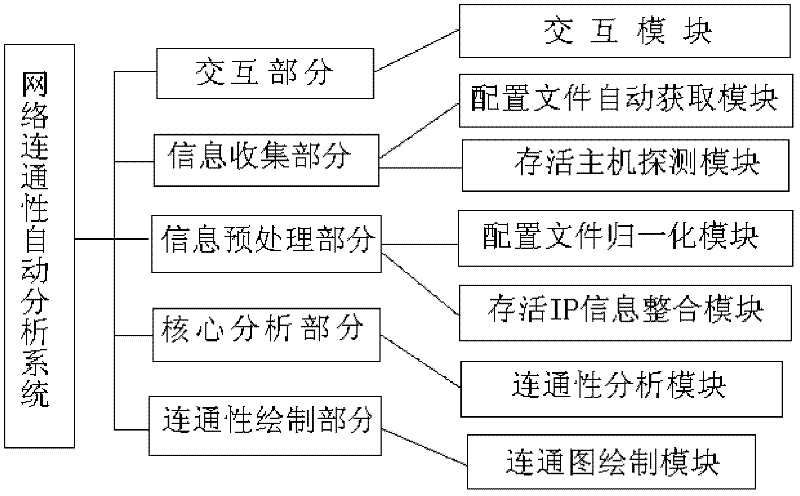
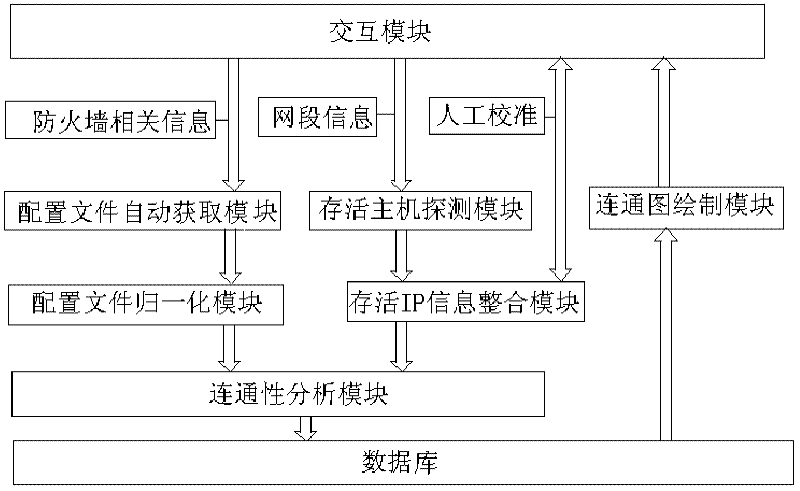
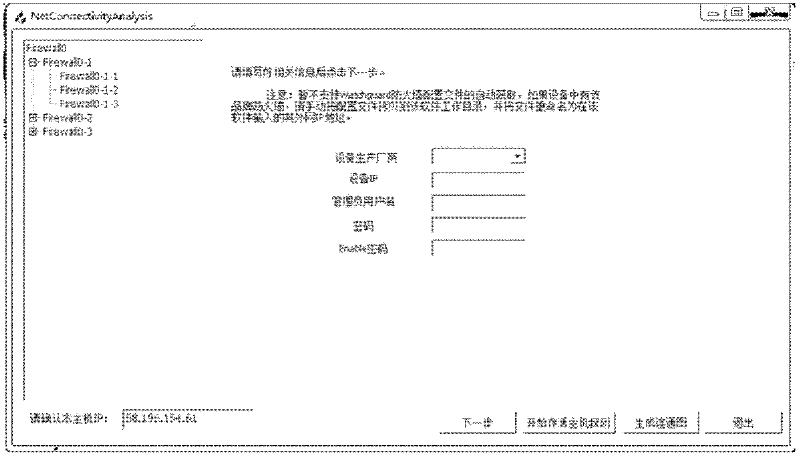
System for automatically analyzing computer network connectivity
The invention discloses a system for automatically analyzing computer network connectivity, wherein the system acquires the connectivity of any two hosts alive in a network by analyzing configuration files of a device (which is mainly a firewall) influencing the connectivity in the network, and comprises a human-machine interaction part, an information acquisition part, an information preprocessing part, a core analysis part and a connected graph drawing part. The human-machine interaction part is used for realizing the interaction between a user and system information; the information acquisition part is used for completing the acquisition of the configuration files of the firewall and the detection of hosts alive in the network; the information preprocessing part is used for preprocessing information acquired by the information acquisition part; the core analysis part is used for analyzing a result generated by the information preprocessing part and acquiring the connectivity information between any two hosts alive; and the connected graph drawing part is used for drawing a network connected graph. The system disclosed by the invention is high in operating speed and basically free from network scale, can be applied to large-scale networks and further has the advantages of high automation degree, wide application range and strong expandability.
Owner:SHANGHAI JIAO TONG UNIV
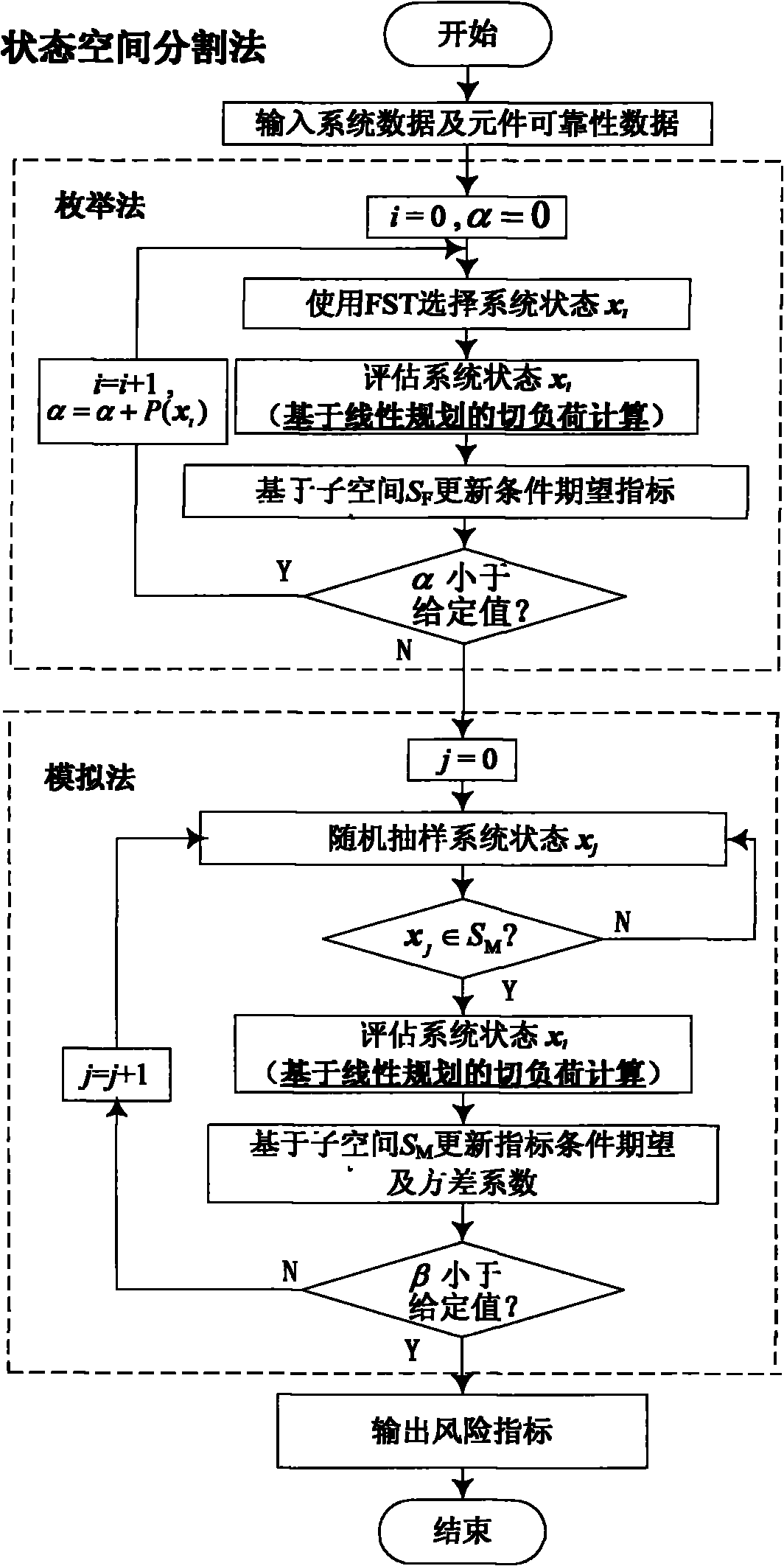
Large-scale interconnected power grid spinning reserve risk assessment method based on state space division method
ActiveCN102055187AAdaptableFast convergenceData processing applicationsPower network operation systems integrationCurse of dimensionalityNetwork size
The invention provides a large-scale interconnected power grid spinning reserve risk assessment method based on a state space division method Along with the appearance of a large-scale interconnected power grid, the quantity of elements of a power grid system is sharply increased, and the network scale is further complicated, thus the traditional reserve risk assessment method cannot meet the development requirements of the large-scale interconnected power grid, has the problems of curse of dimensionality in the aspect of state selection and inability of assessment in the aspect of state analysis, and can be influenced by transmission capacity restraint of area connecting lines. In the invention, the system state is selected by using a state space division method and analyzed by using a load reduction technology based on linear programming, thus the method better solves the problems of huge system scale and transmission capacity restraint of the area connecting lines in the spinning reserve risk assessment, realizes the quick and precise calculation of a spinning reserve risk index of the large-scale interconnected power grid, can provide real-time system spinning reserve information for personnel of a dispatching system, is beneficial for the dispatching personnel to taking effective measures in time, improves the reliability level of the system, and reduces the power-off risk of the system.
Owner:CHINA ELECTRIC POWER RES INST +1
Fault early warning method of gearbox of wind turbine generator set
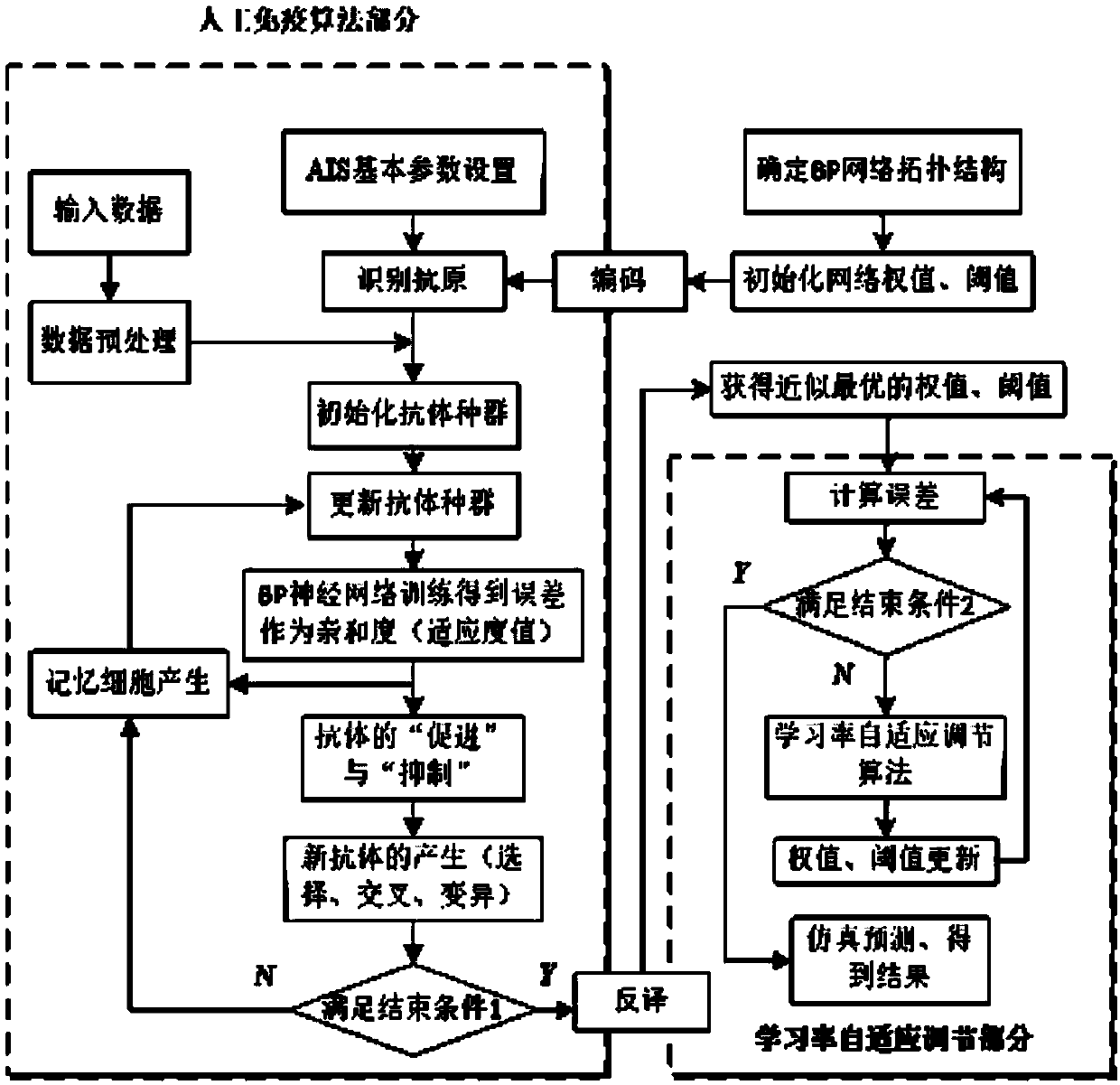
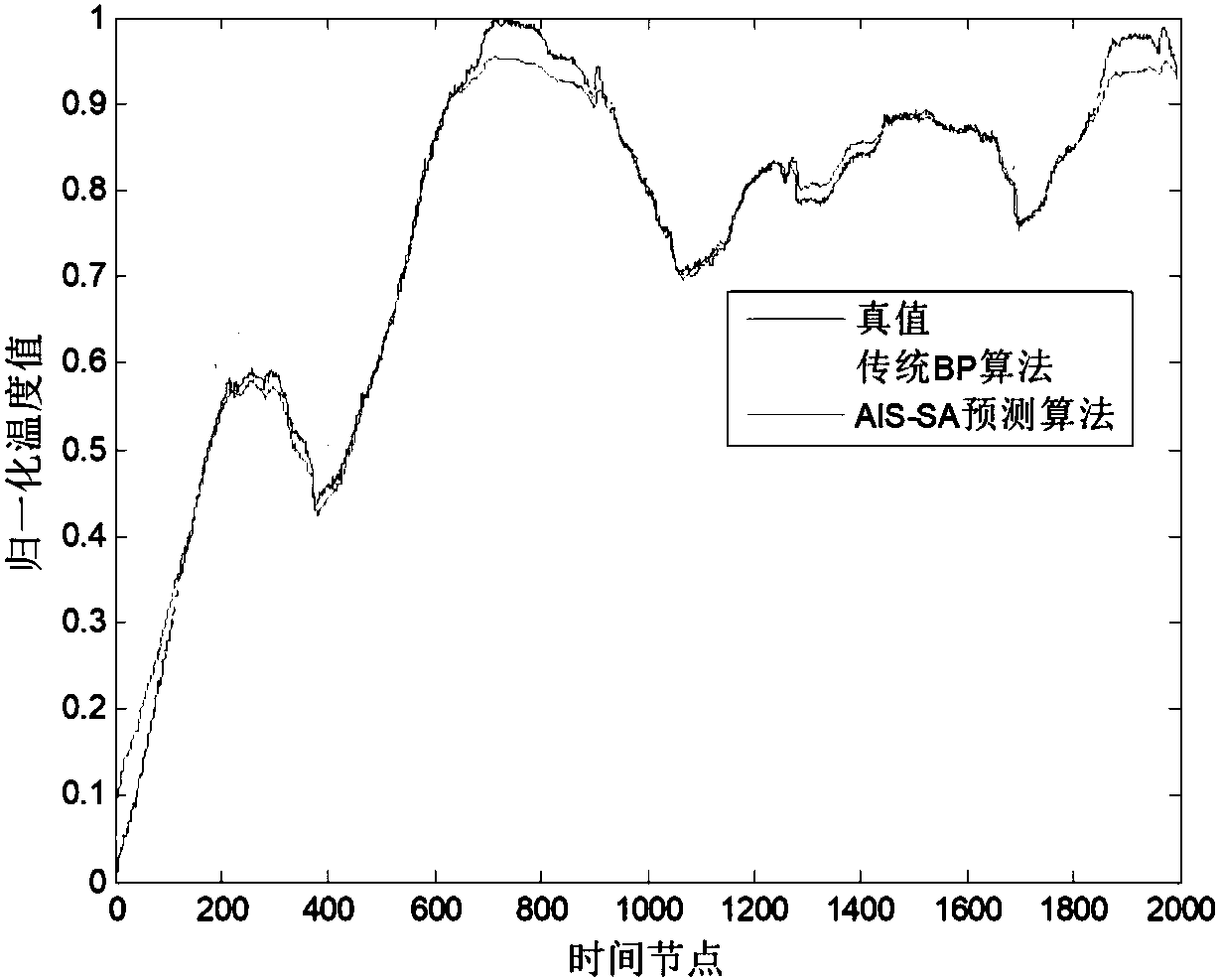
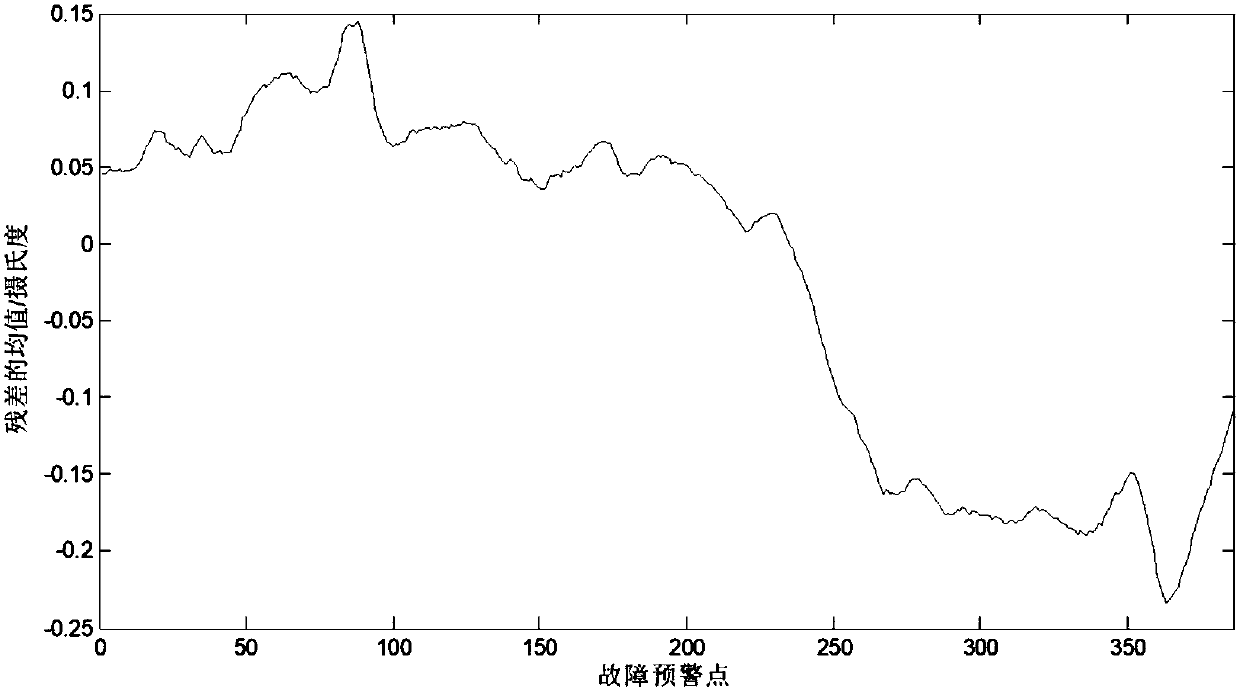
InactiveCN107742008APredicting Future Temperature ChangesImprove reliabilityGeometric CADSpecial data processing applicationsNumerical weather predictionNetwork size
The invention discloses a fault early warning method of a gearbox of a wind turbine generator. The early warning method mainly includes the following steps of data acquisition, wherein a terminal acquires the historical data of wind turbine generator power, environment temperature and wind speed through a hard contact temperature sensor, a soft contact temperature sensor and a temperature acquisition card arranged in the gearbox or calls the historical data of wind turbine generator power, environment temperature and wind speed from wind power plant recorded data, and the time span of the datacovers the whole fault evolution section; data processing, wherein input data is normalized, the integrity of the input data is verified, abnormal data and incomplete data are deleted from the inputdata, a BP neural network including an AIS-SA hybrid network prediction algorithm is established, and then the network size and various initial connection weights and thresholds are determined; earlywarning calculation, wherein the acquired temperature data is predicted through the optimized network, the wind speed is subjected to approximate substitution in combination with numerical weather prediction, a temperature prediction conversion curve in a certain future time is obtained, the residual of predicted temperature and actual temperature is calculated, and with several recording points as an early warning section, the residual mean and standard deviation of the two temperatures in the section are worked out.
Owner:SHANGHAI DIANJI UNIV
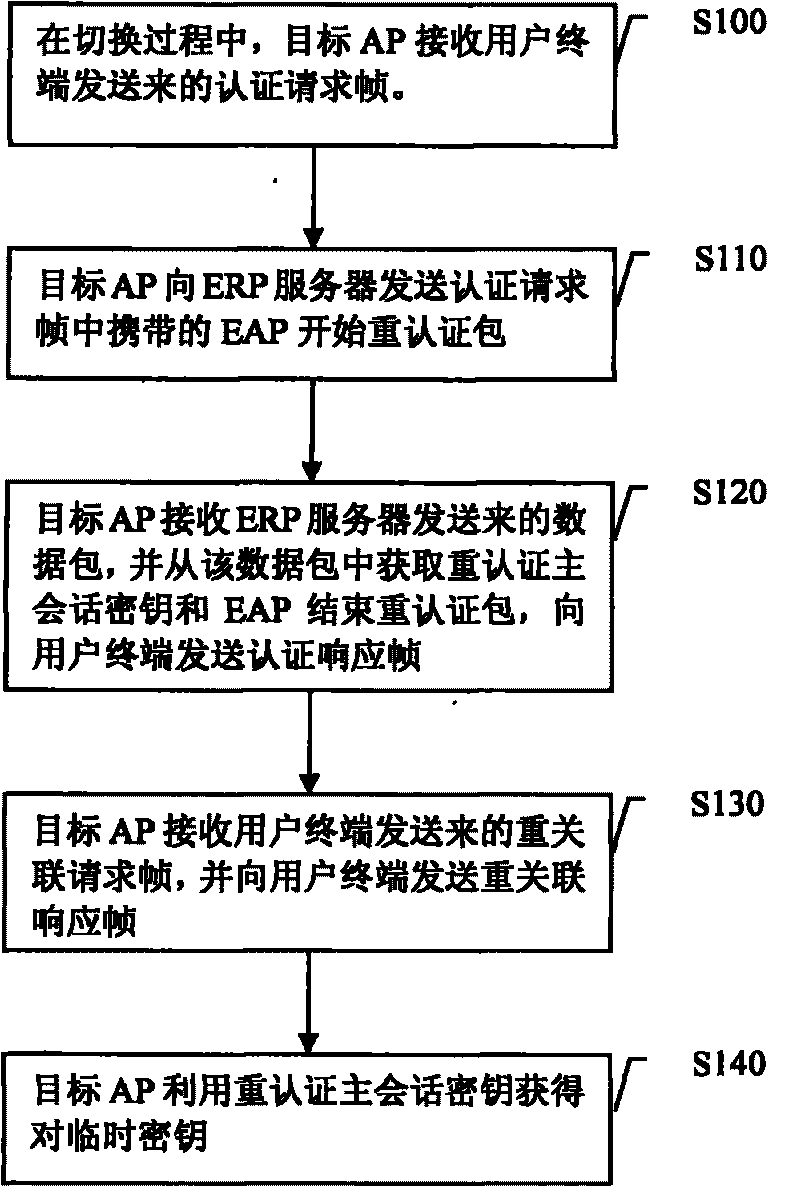
Switching method, device and system
InactiveCN101695165AAvoid scale limitationsReduce administrative overheadSecurity arrangementNetwork sizeSession key
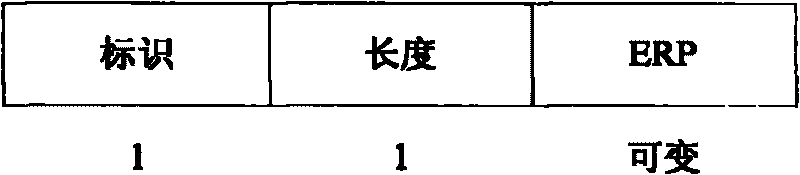
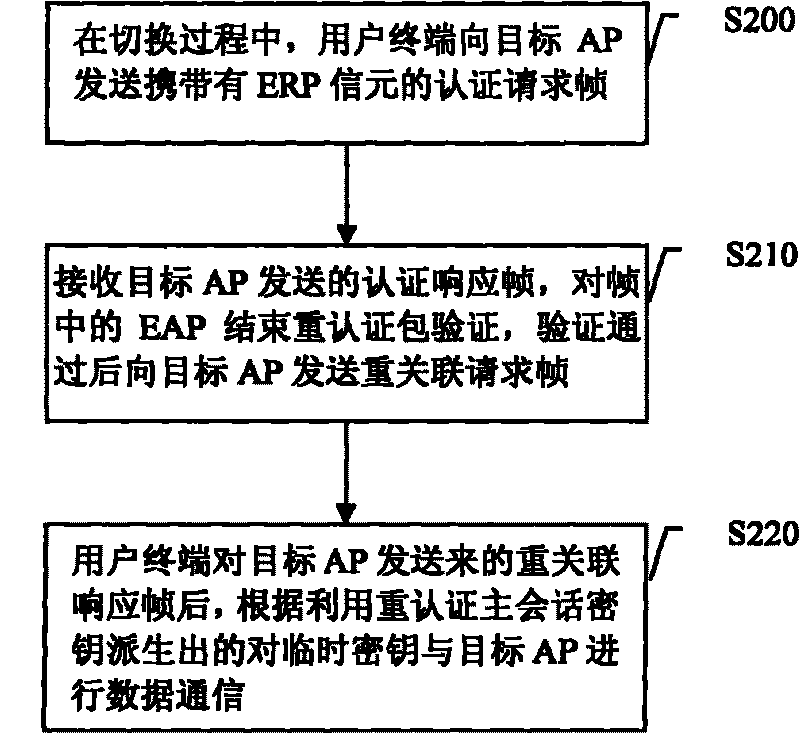
The invention provides switching method, device and system, wherein the switching method comprises the following steps: a target AP receives an authentication request frame sent from a user terminal and carrying an EAP starting reauthentication package and sends the EAP starting reauthentication package carried by the authentication request frame to an ERP server; the target AP acquires a reauthentication main session key and an EAP ending reauthentication package from a data package sent from the ERP server and sends an authentication response frame carrying the EAP ending reauthentication package; the target AP receives a reassociated request frame sent from the user terminal and sends a reassociated response frame to the user terminal; and the target AP uses the reauthentication main session key to derive a key used for realizing data communication with the user terminal after successful switching. The technical scheme of the information not only ensures key safety and less authentication delay, but also reduces the cost on key management and avoids network size limitation and other problems, thereby realizing quick and safe switching.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com