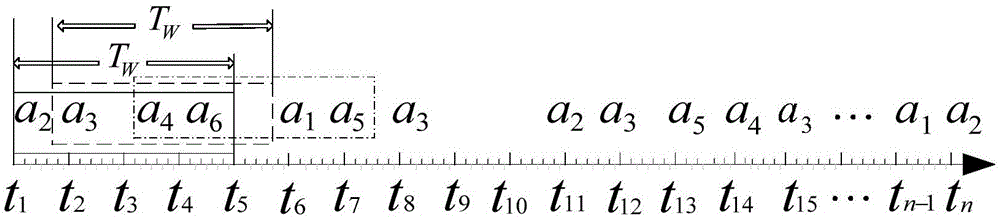Patents
Literature
3945 results about "Correlation analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Correlation analysis is a method of statistical evaluation used to study the strength of a relationship between two, numerically measured, continuous variables (e.g. height and weight). This particular type of analysis is useful when a researcher wants to establish if there are possible connections between variables.
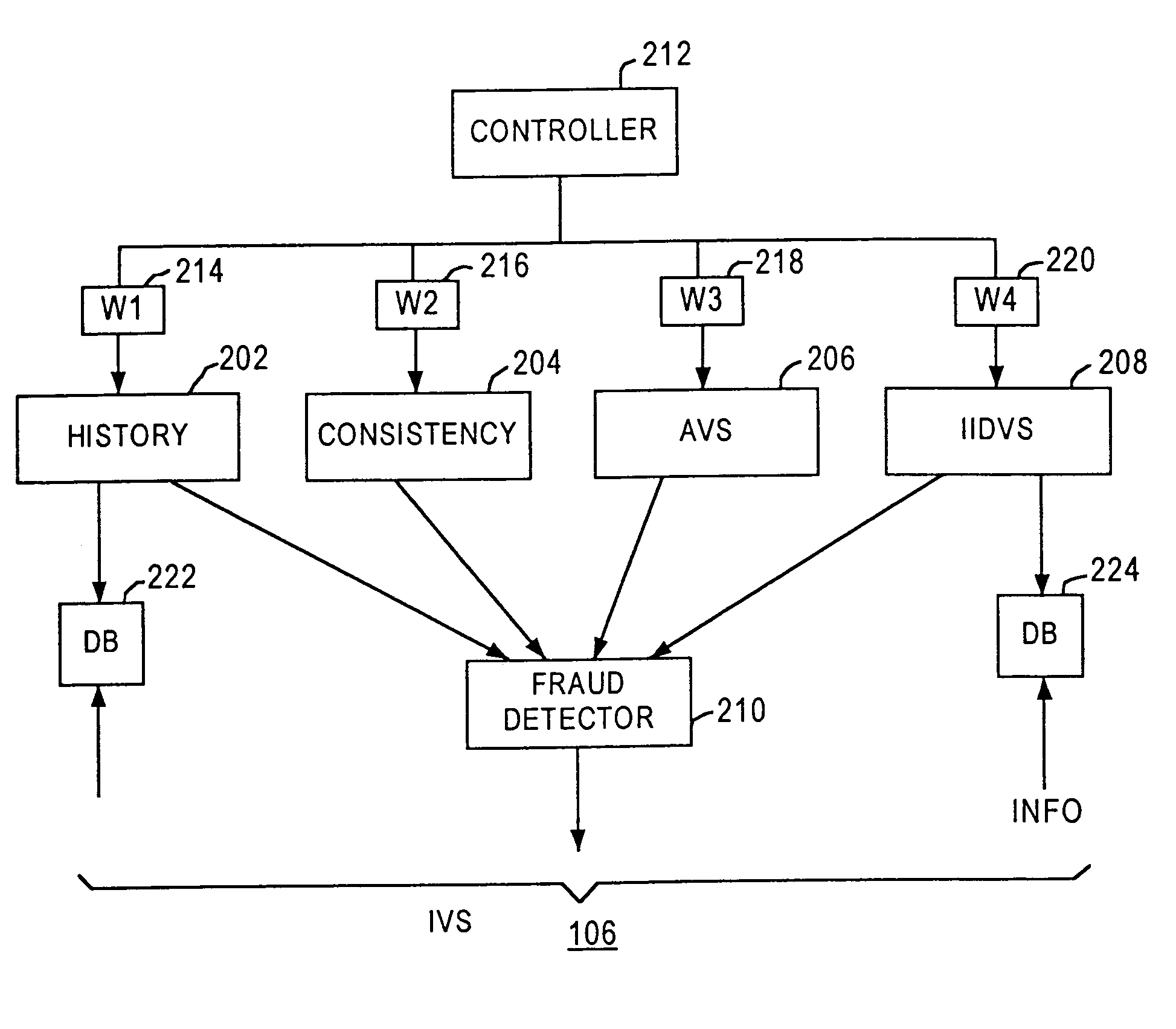
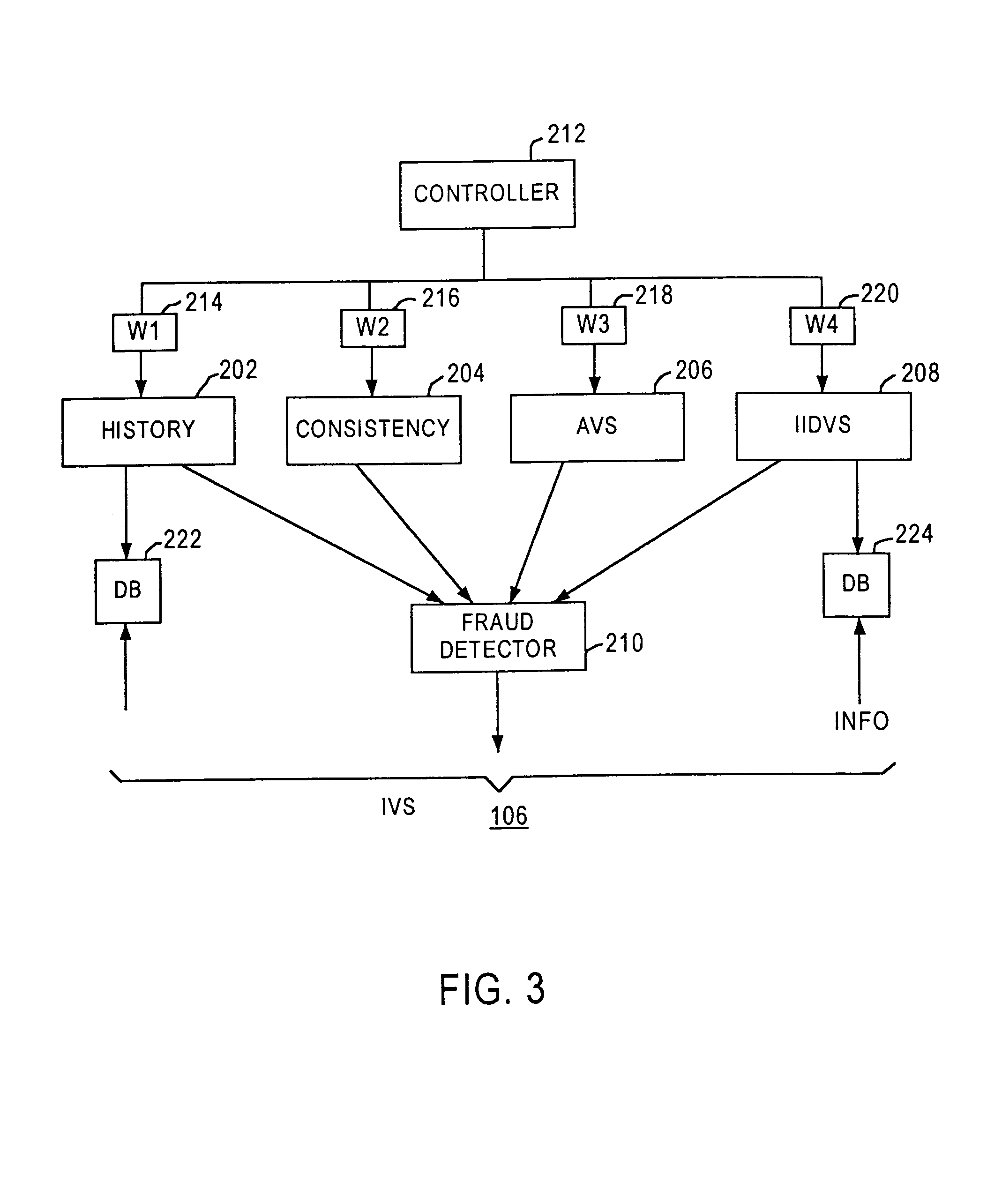
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
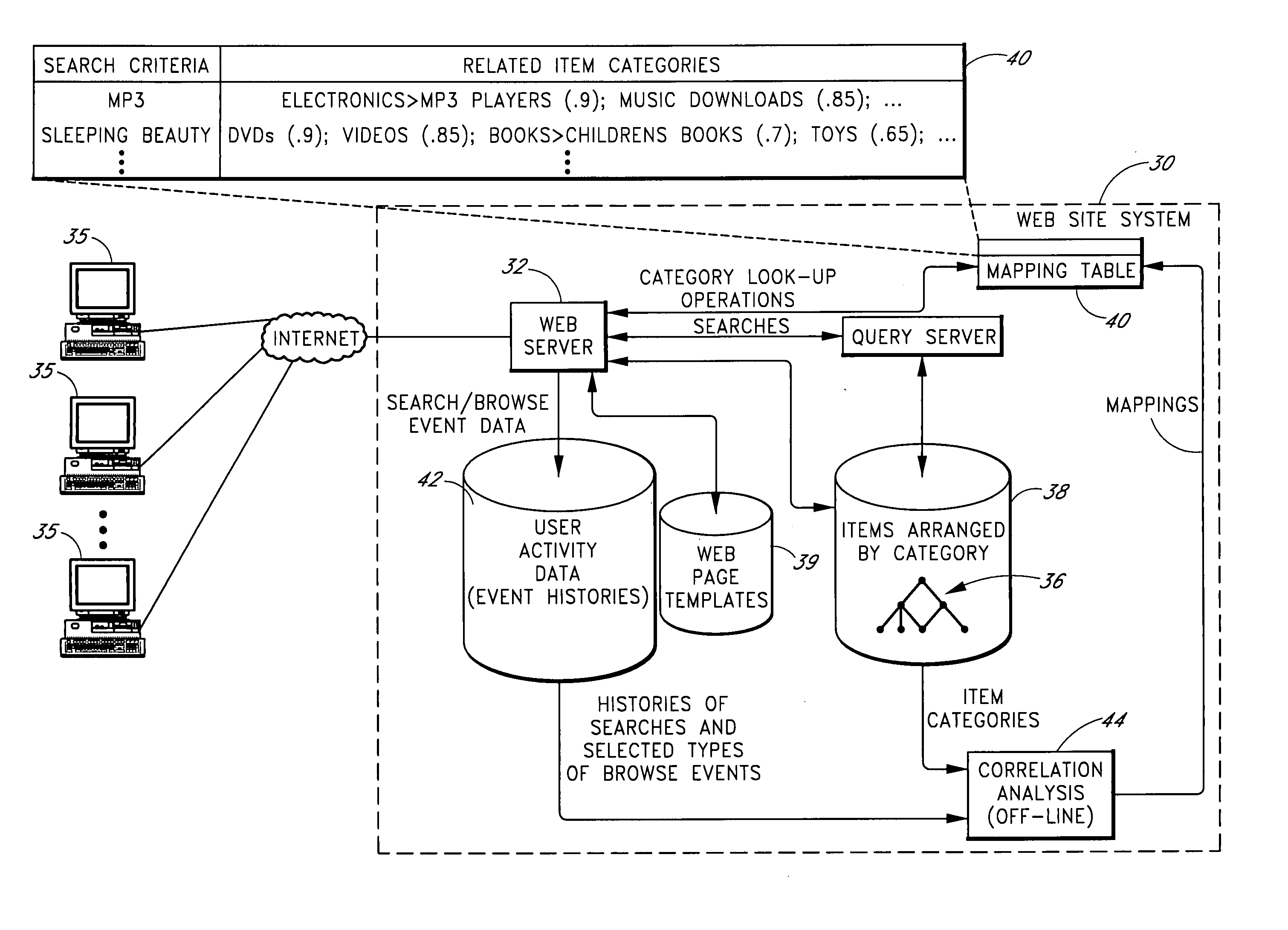
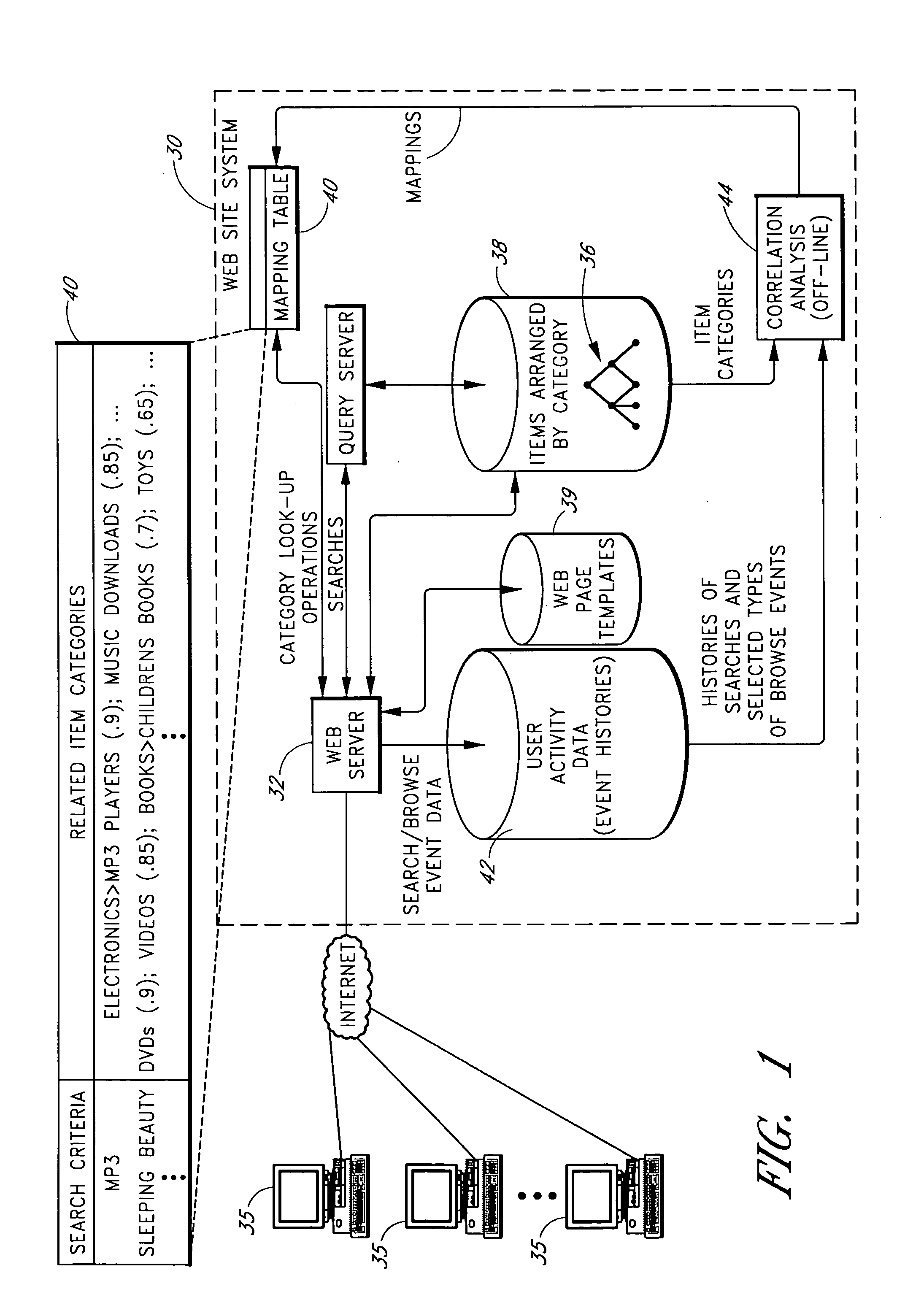
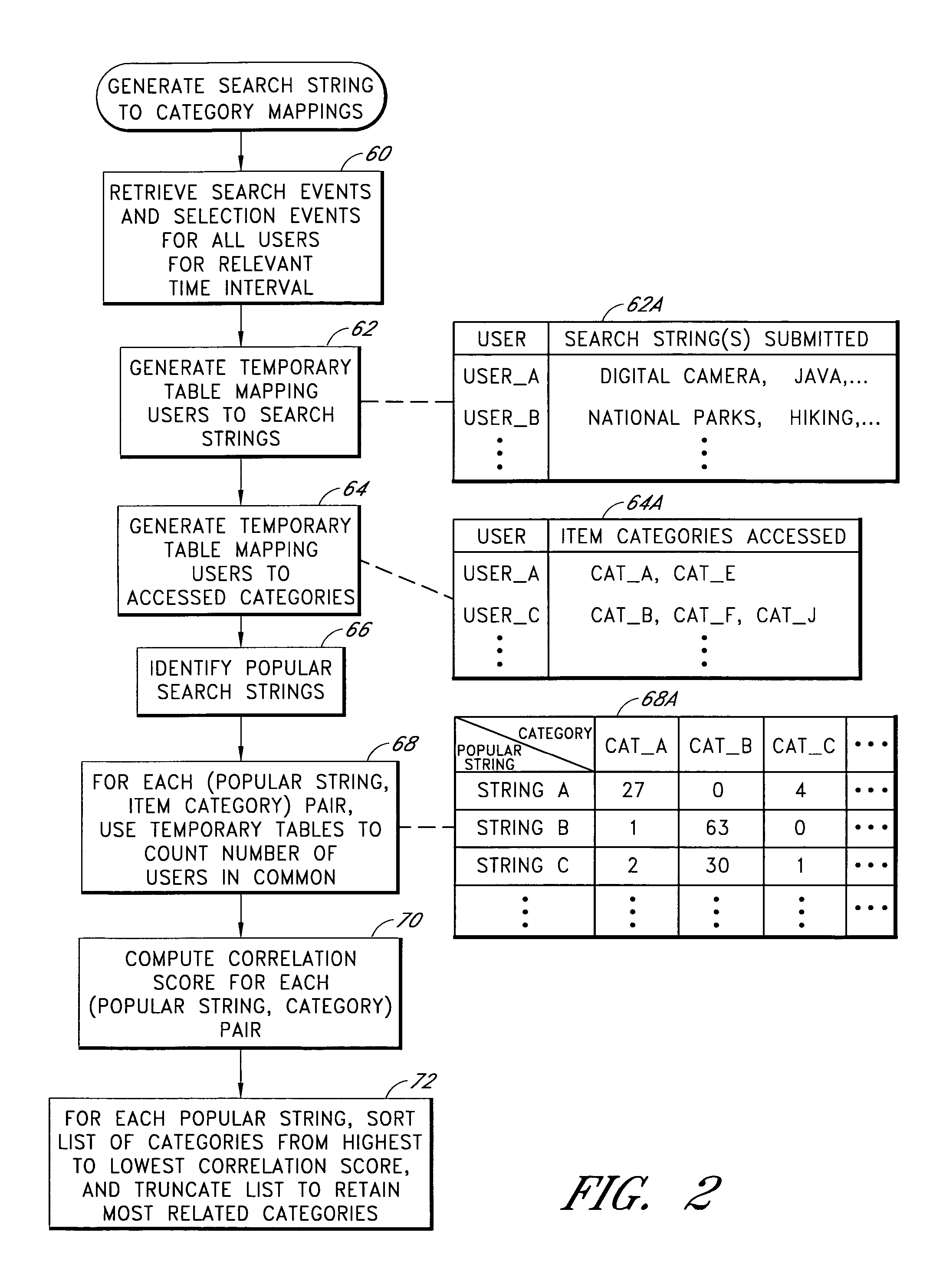
Automated detection of associations between search criteria and item categories based on collective analysis of user activity data
A web site or other database access system provides access to a database in which items are arranged within item categories, such as browse categories of a hierarchical browse tree. Actions of users of the system are monitored and recorded to generate user activity data reflective of searches, item selection actions, and possibly other types of actions. A correlation analysis component collectively analyses the user activity to automatically identify associations between specific search criteria, such as specific search strings, and specific item categories. The results of the analysis are stored in a mapping table that is used to suggest specific item categories on search results pages.
Owner:AMAZON TECH INC
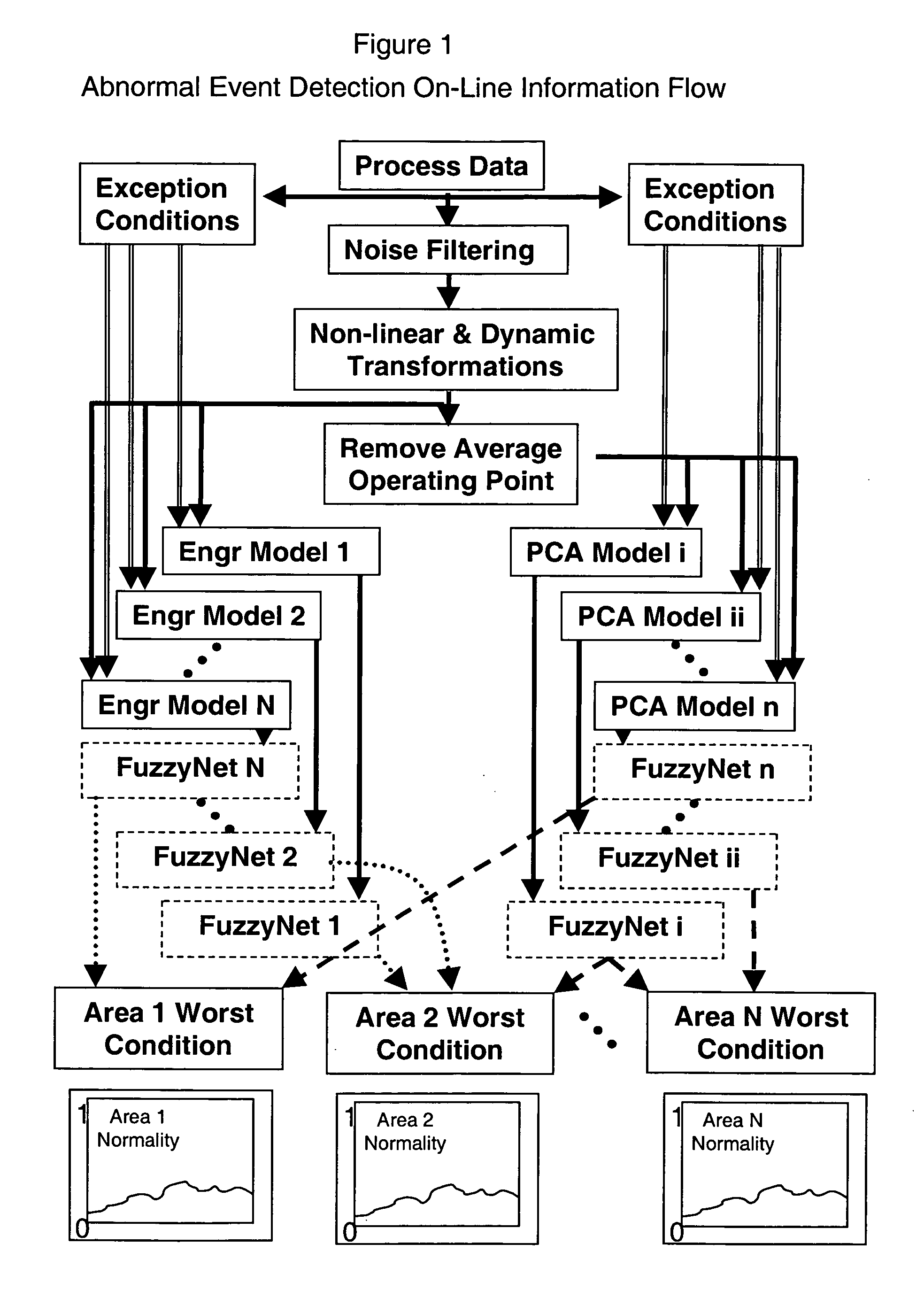
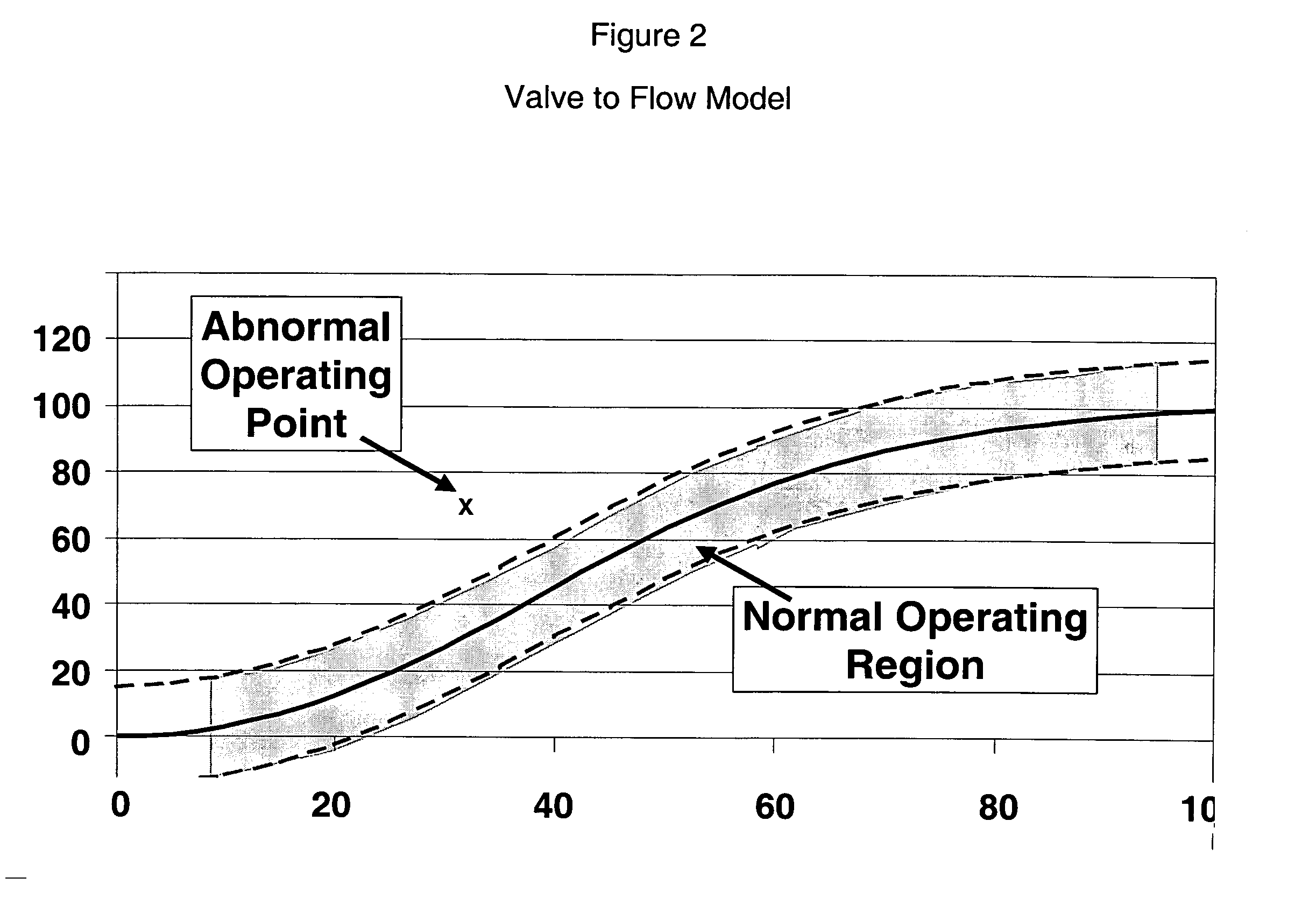
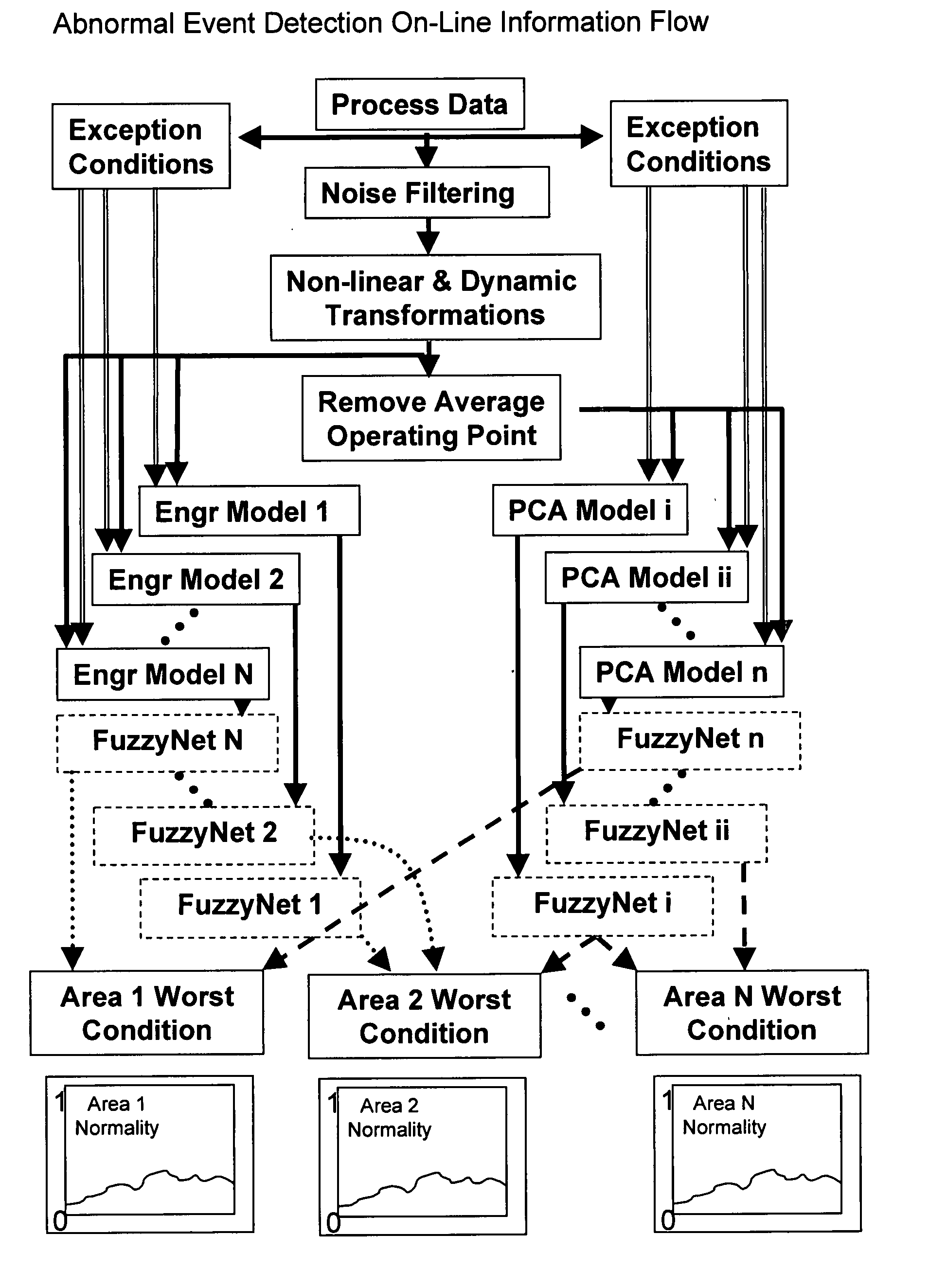
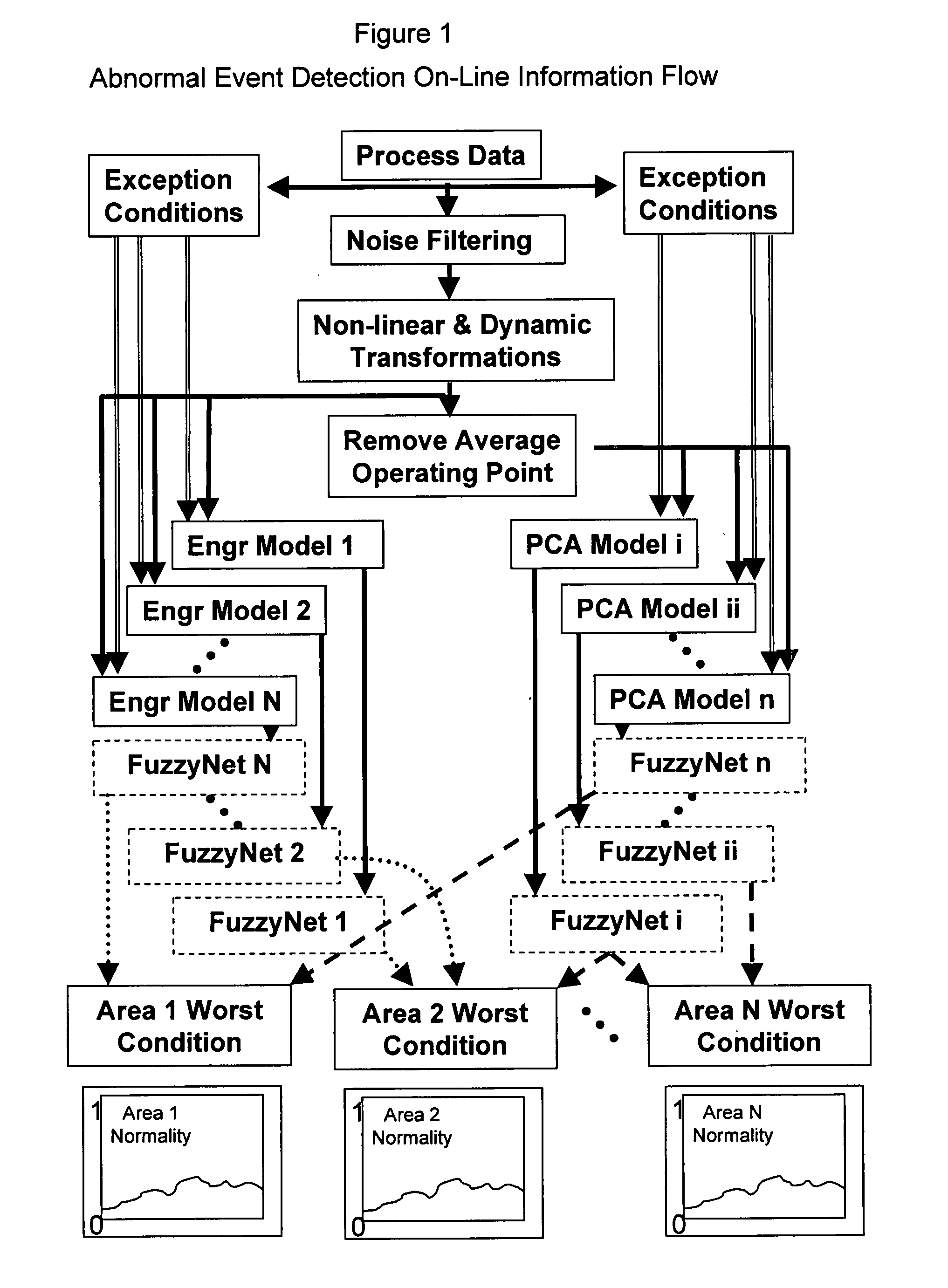
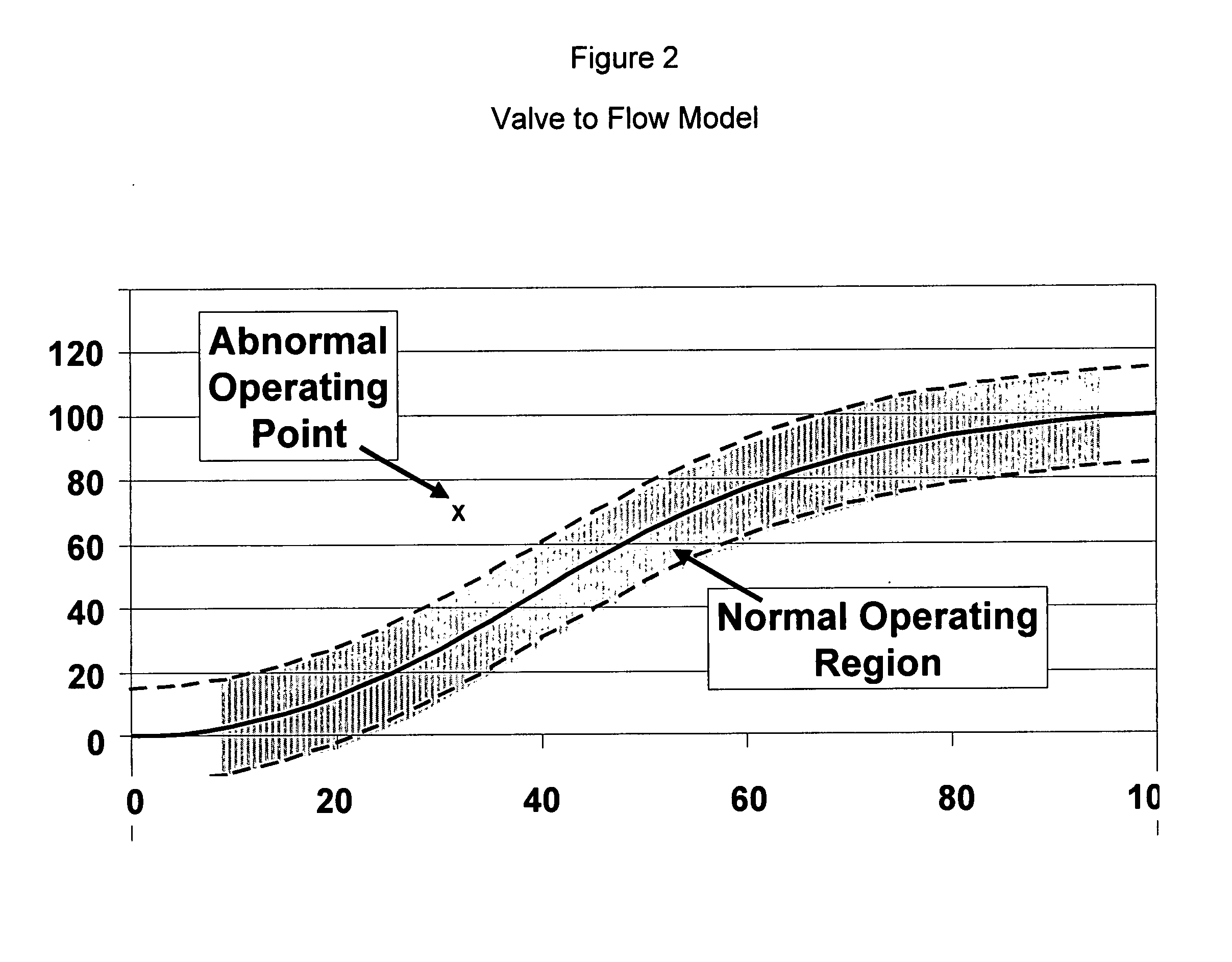
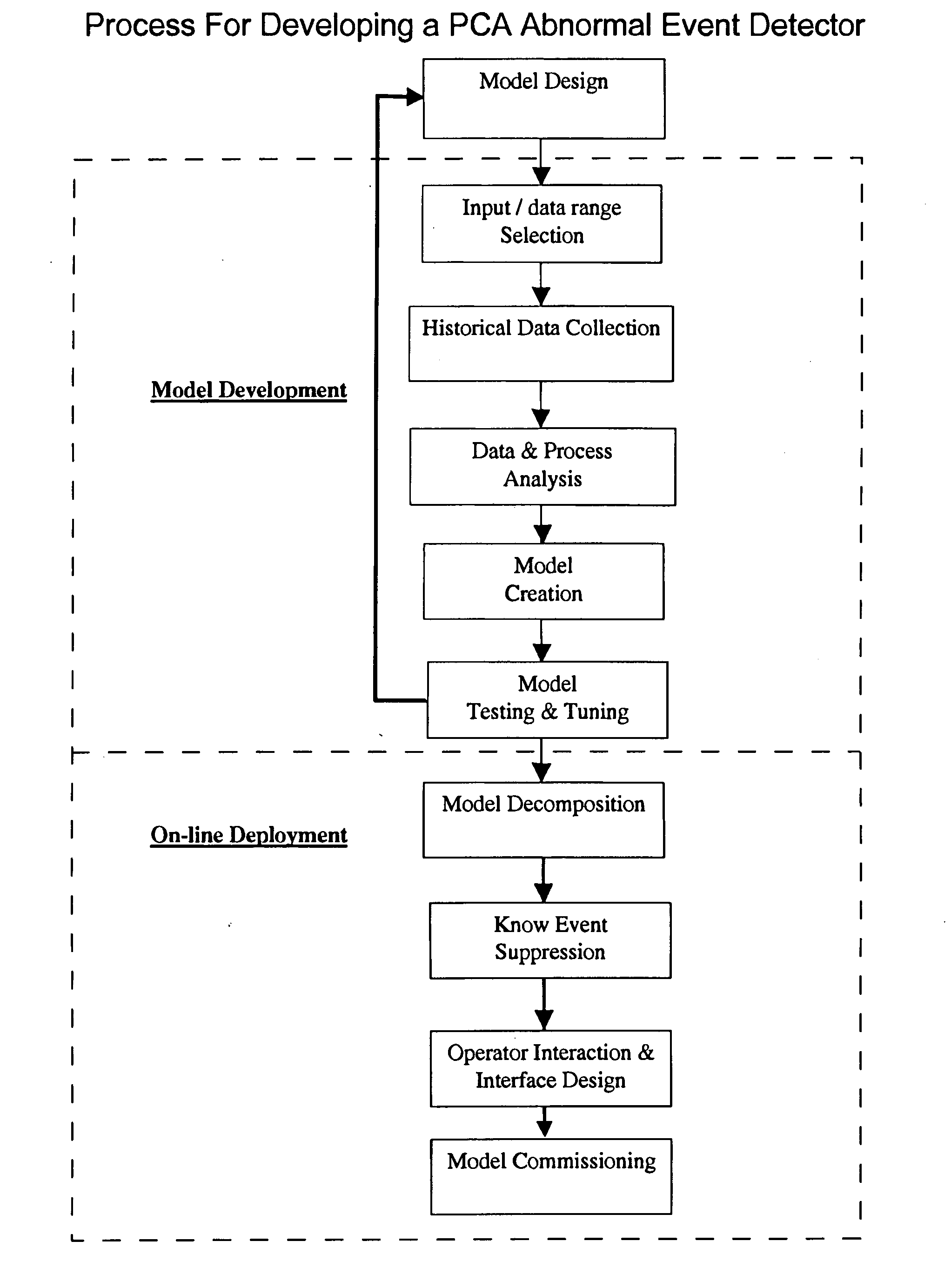
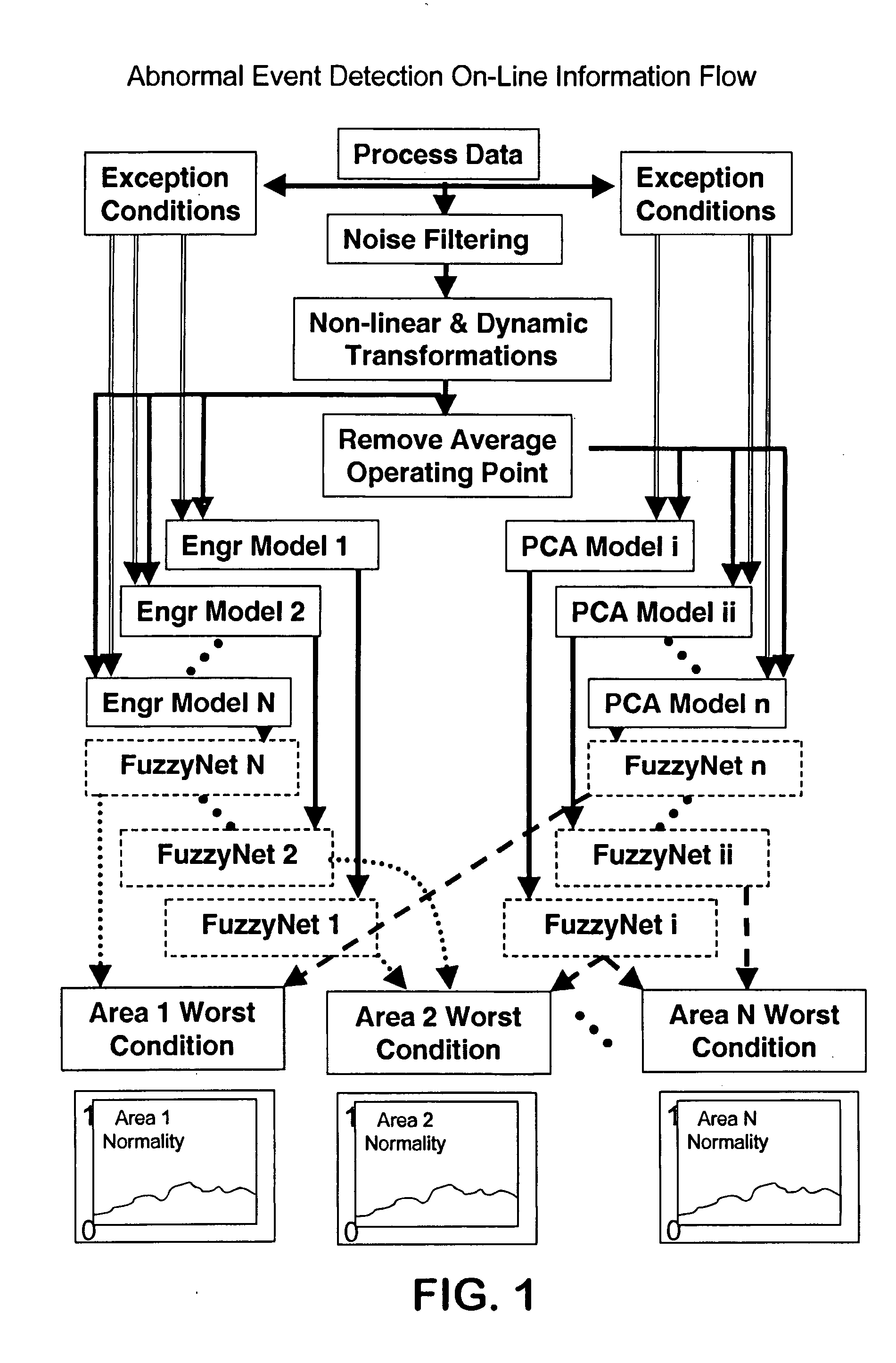
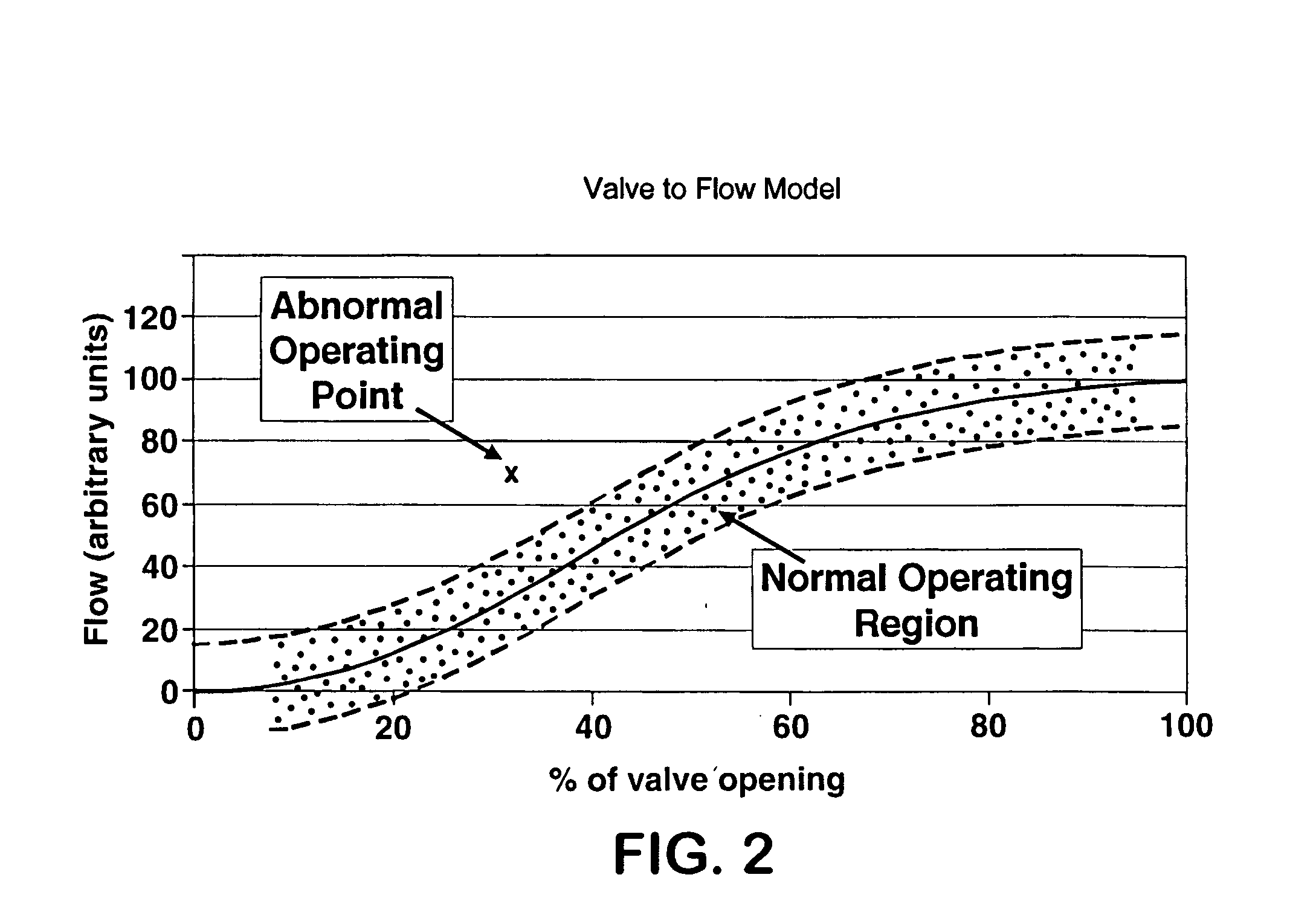
Application of abnormal event detection technology to fluidized catalytic cracking unit
ActiveUS20060073013A1PropellersSpecial data processing applicationsPrincipal component analysisCorrelation analysis
The present invention is a method for detecting an abnormal event for process units of a Fluidized Catalytic Cracking Unit. The method compares the operation of the process units to a statistical and engineering models. The statistical models are developed by principle components analysis of the normal operation for these units. In addition, the engineering models are based on partial least squares analysis and correlation analysis between variables. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
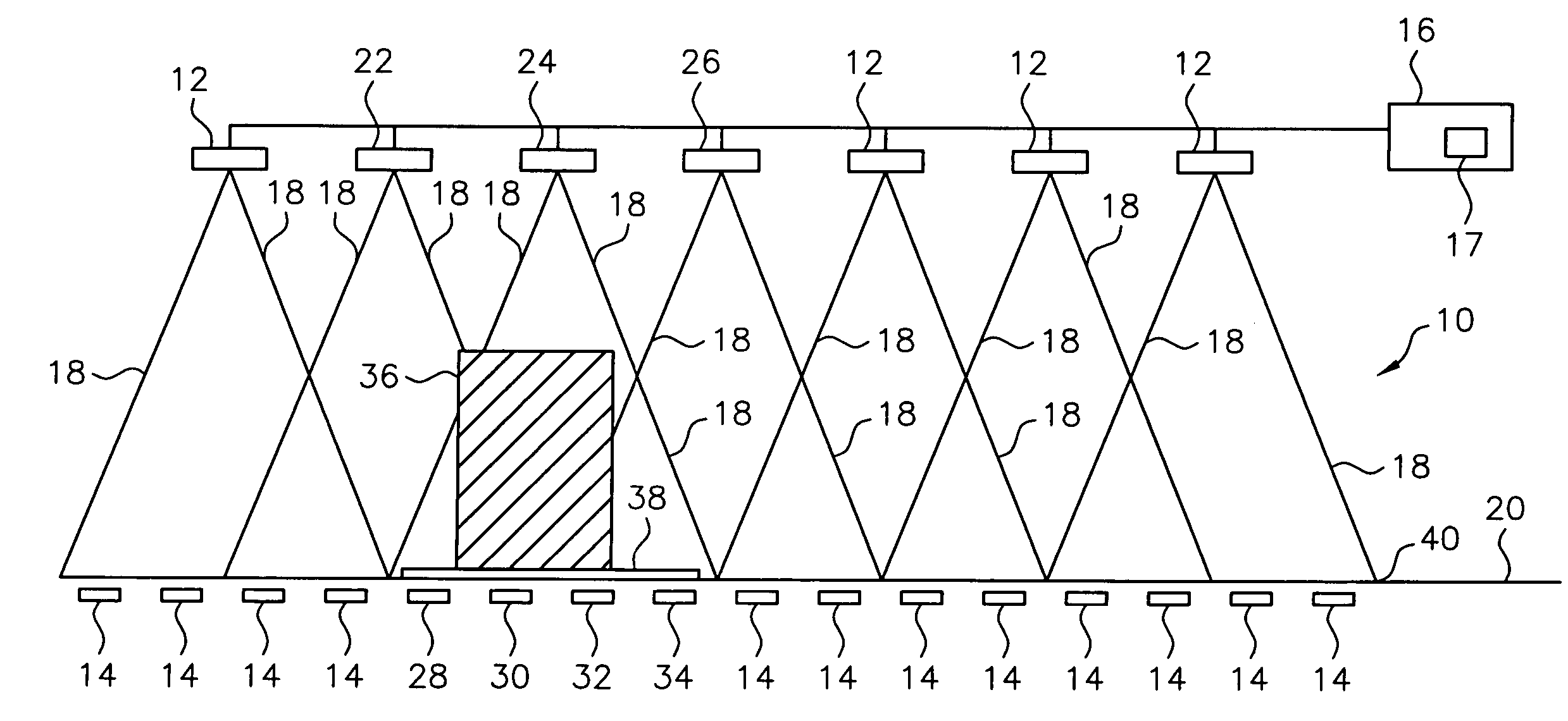
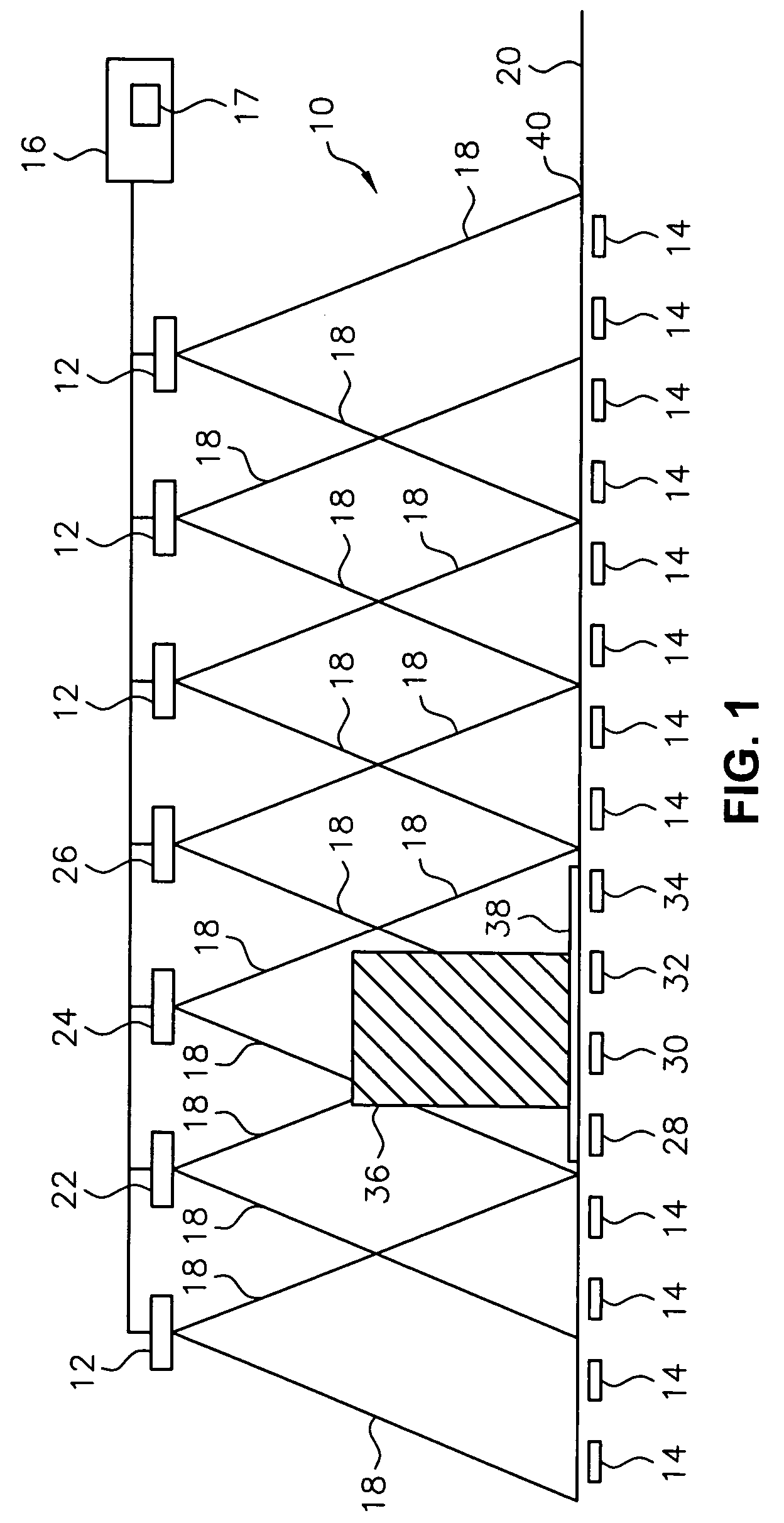
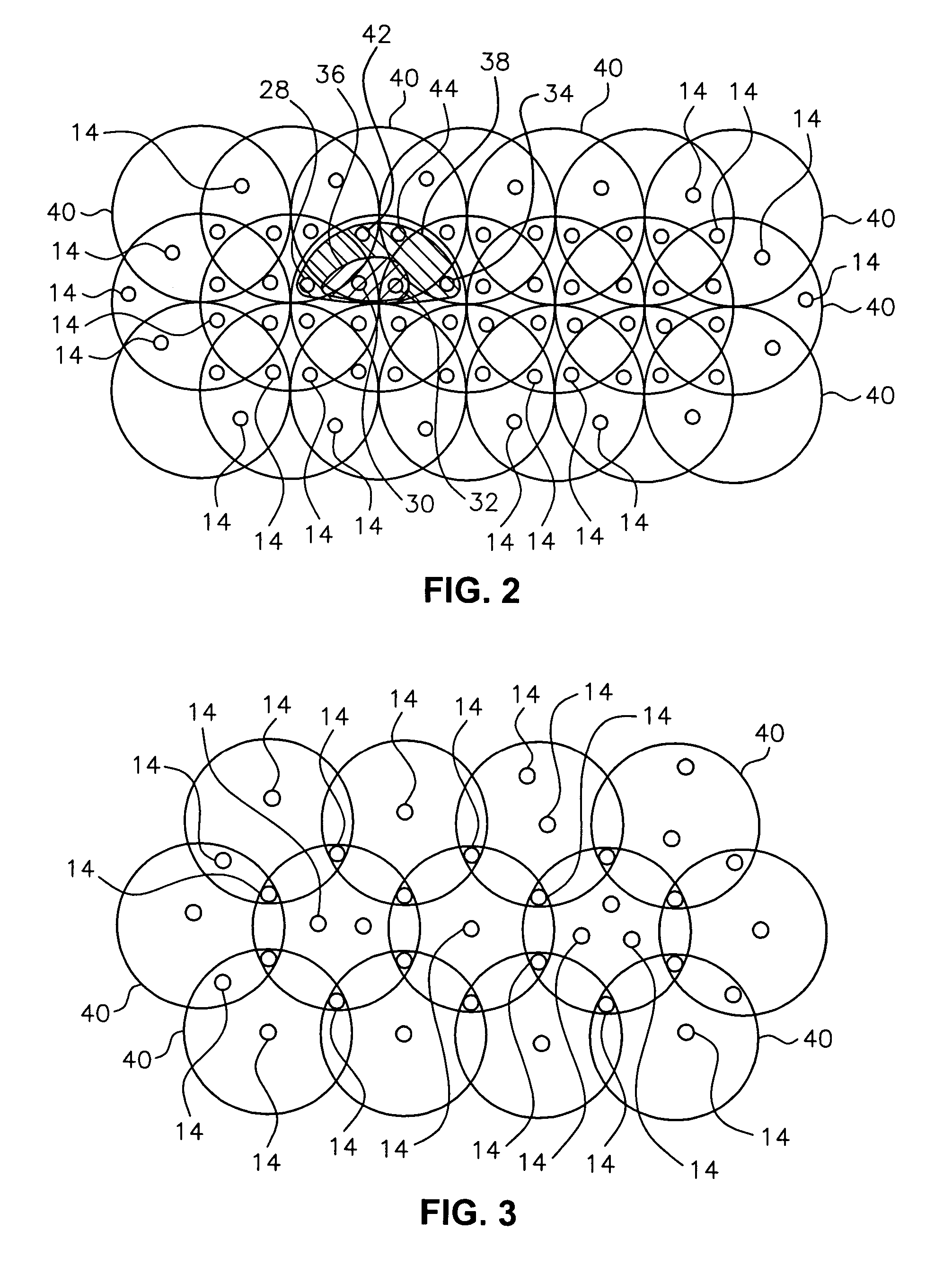
Article identification and tracking using electronic shadows created by RFID tags
InactiveUS20050012613A1Easy to identifyEasy to trackElectric signal transmission systemsMemory record carrier reading problemsElectromagnetic couplingEngineering
A tracking system uses RFID (radio frequency identification) tag technology to facilitate the identification and tracking of items in an environment through a technique known as shadowing. As an object or target moves within a pre-described detection zone with communicating antenna and RFID sensors, the object or target blocks the line of sight between respective antenna and sensors, preventing electromagnetic coupling between the sensor and the antenna and thus casting an electromagnetic shadow along the line of sight. One approach of this invention uses this shadow technique to perform functions such as theft (shrink) deterrence / detection; tracking the motion of objects through an environment by monitoring the shadow; and correlation analysis of people shadows to tagged items (e.g., merchandise, articles) to foster marketing and merchandising effectiveness.
Owner:CHECKPOINT SYST INC
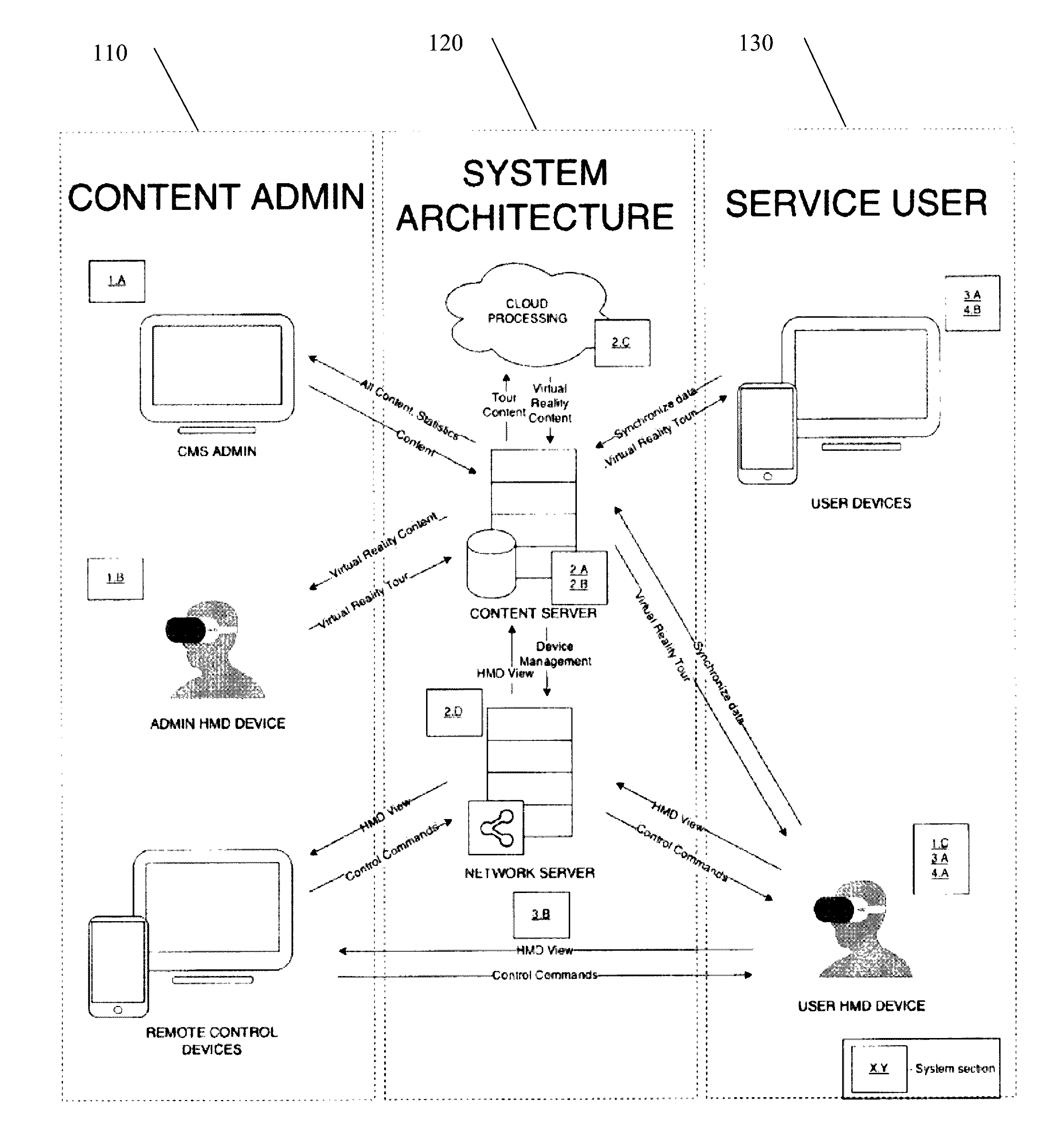
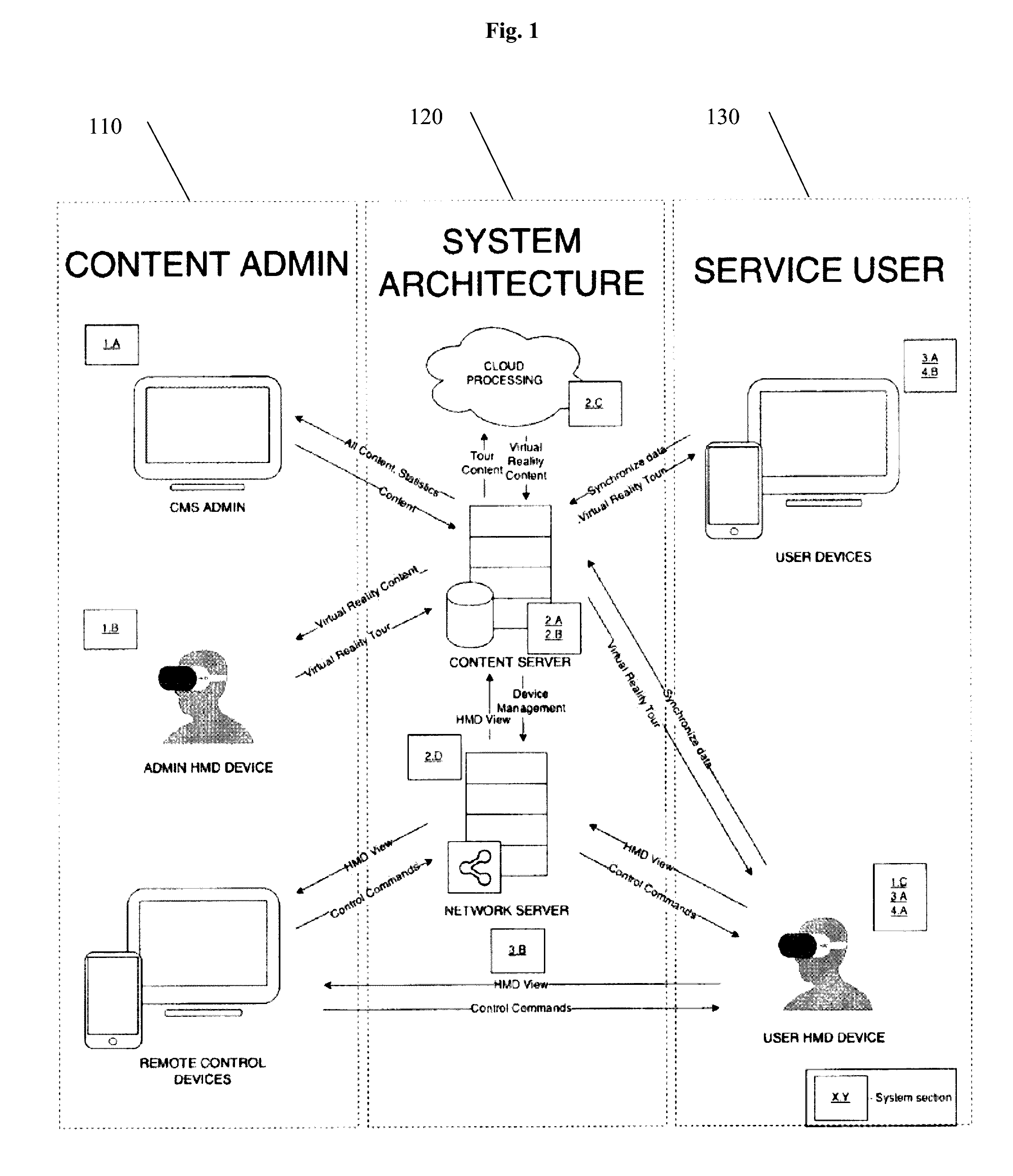
Systems, media, and methods for providing improved virtual reality tours and associated analytics
InactiveUS20160300392A1Improve performanceLower latencyInput/output for user-computer interactionImage enhancementCorrelation analysisMedical treatment
Platforms, systems, media, and methods for providing virtual reality (VR) tour builder and editor applications, multi-modal VR tour applications, and VR tour analytics applications useful in real estate sales and marketing, advertising, entertainment, education, healthcare scenarios.
Owner:VR GLOBAL INC
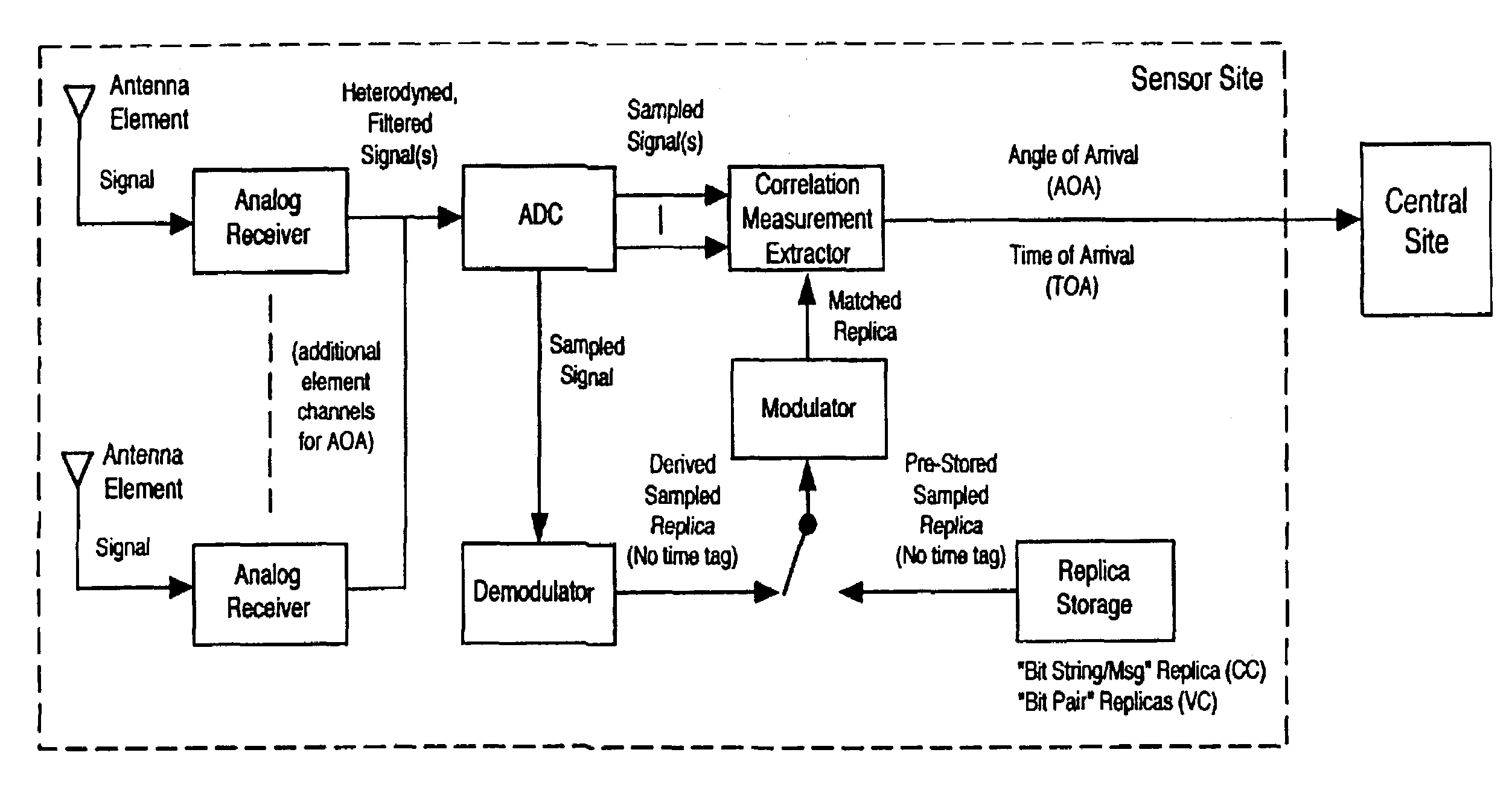
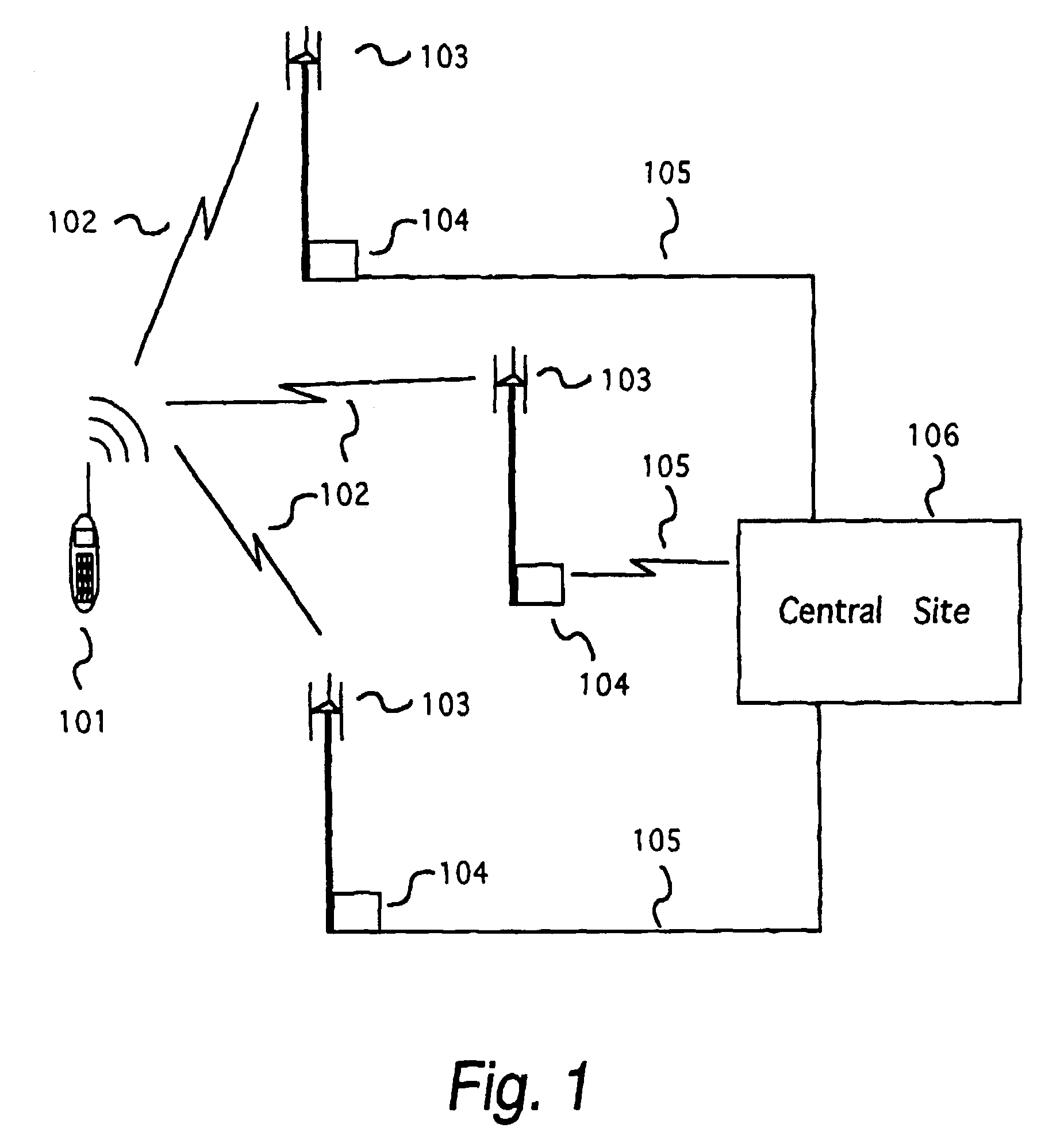
Robust, efficient, localization system
InactiveUS7340259B2Quick responseEasy to measure in real timeDirection finders using radio wavesPosition fixationLocalization systemCode division multiple access
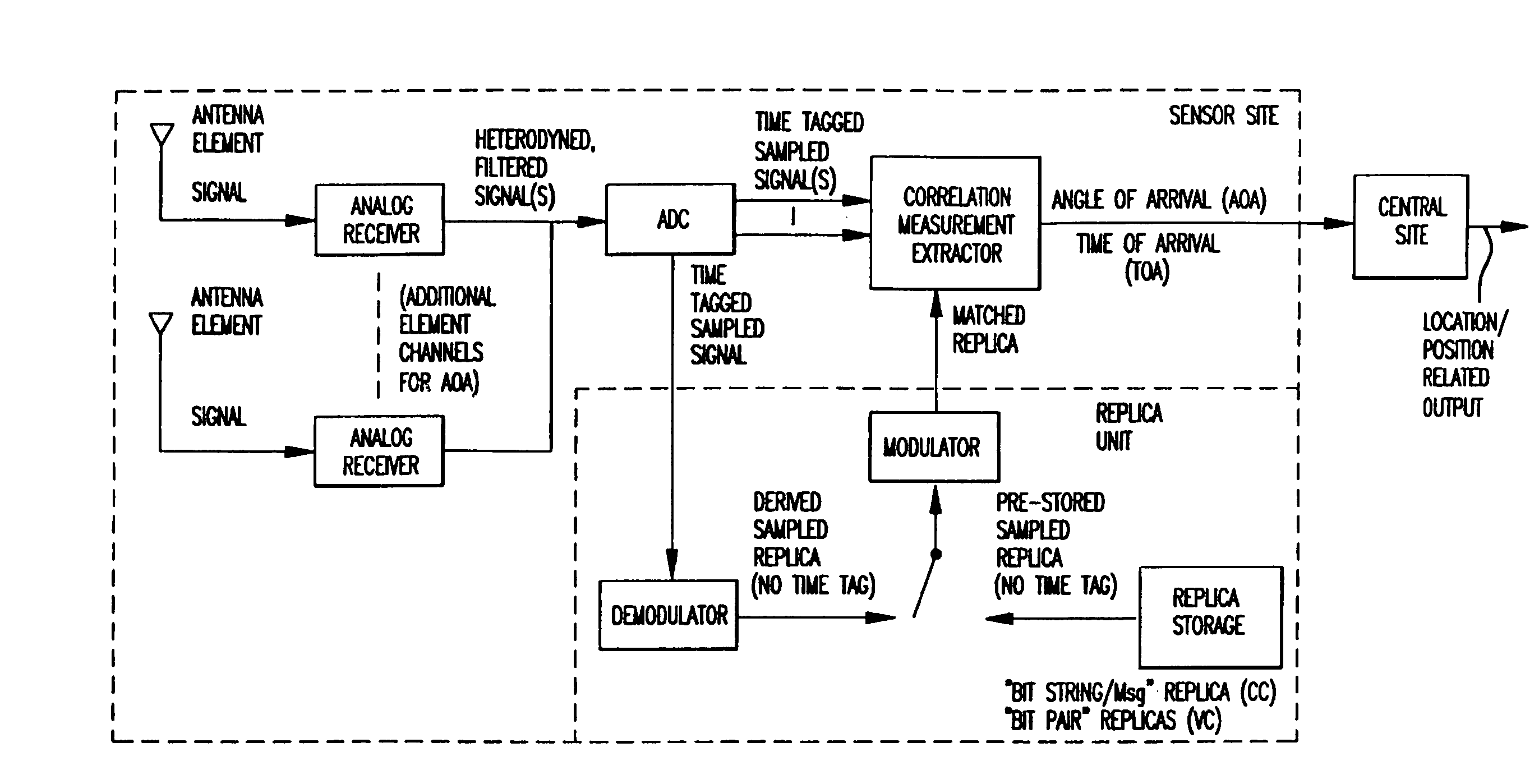
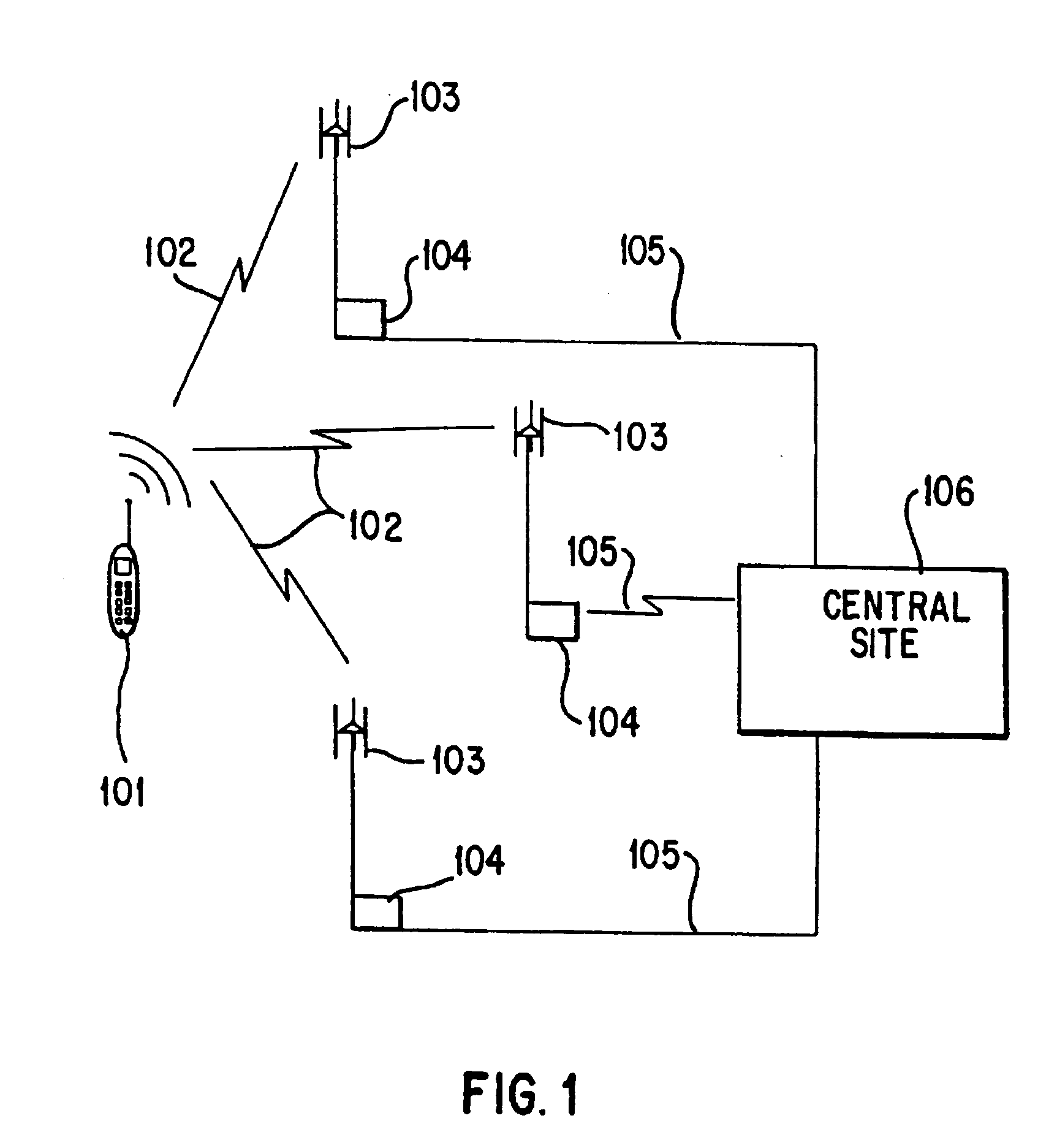
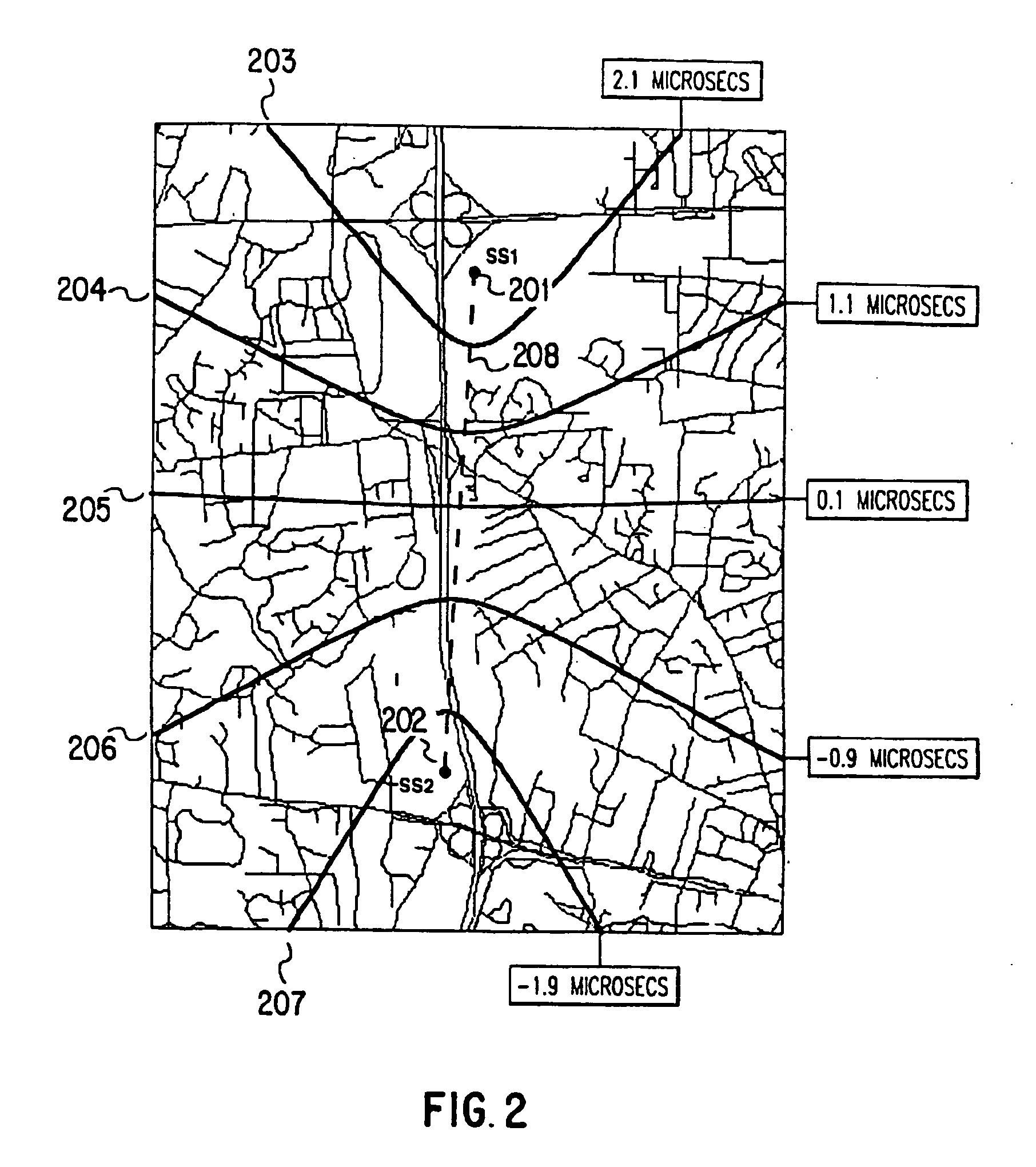
Replica correlation processing, and associated representative signal-data reduction and reconstruction techniques, are used to detect signals of interest and obtain robust measures of received-signal parameters, such as time differences of signal arrival and directional angles of arrival, that can be used to estimate the location of a cellularized-communications signal source. The new use in the present invention of signal-correlation processing for locating communications transmitters. This enables accurate and efficient extraction of parameters for a particular signal even in a frequency band that contains multiple received transmissions, such as occurs with code-division-multiple-access (CDMA) communications. Correlation processing as disclosed herein further enables extended processing integration times to facilitate the effective detection of desired communications-signal effects and replication measurement of their location-related parameters, even for the communications signals modulated to convey voice conversations or those weakened through propagation effects. Using prior, constructed, signal replicas in the correlation processing enables elimination of the inter-site communications of the signal representations that support the correlation analyses. Reduced-data representations of the modulated signals for voiced conversation, or for the variable components of data communications, are used to significantly reduce the inter-site communications that support the correlation analyses.
Owner:TRUE POSITION INC
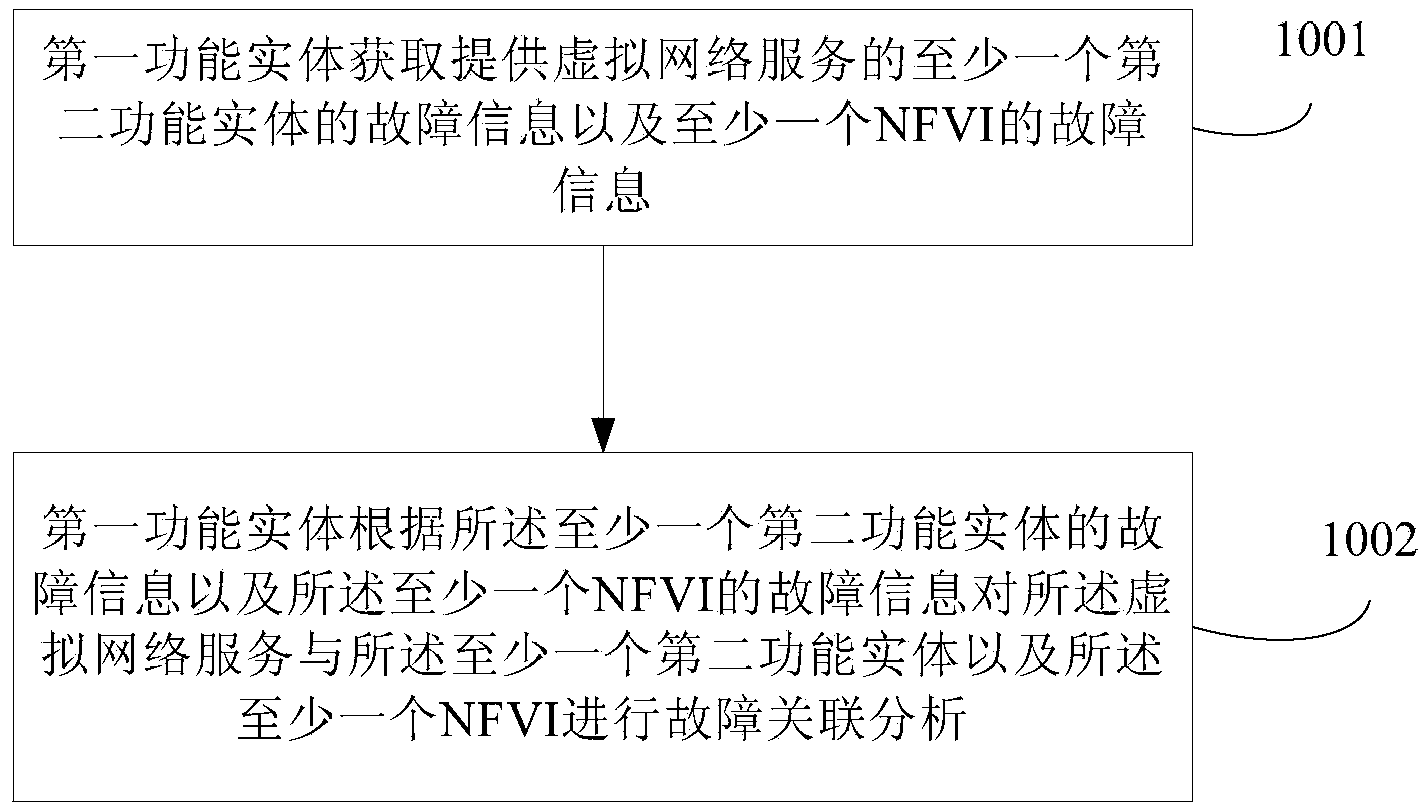
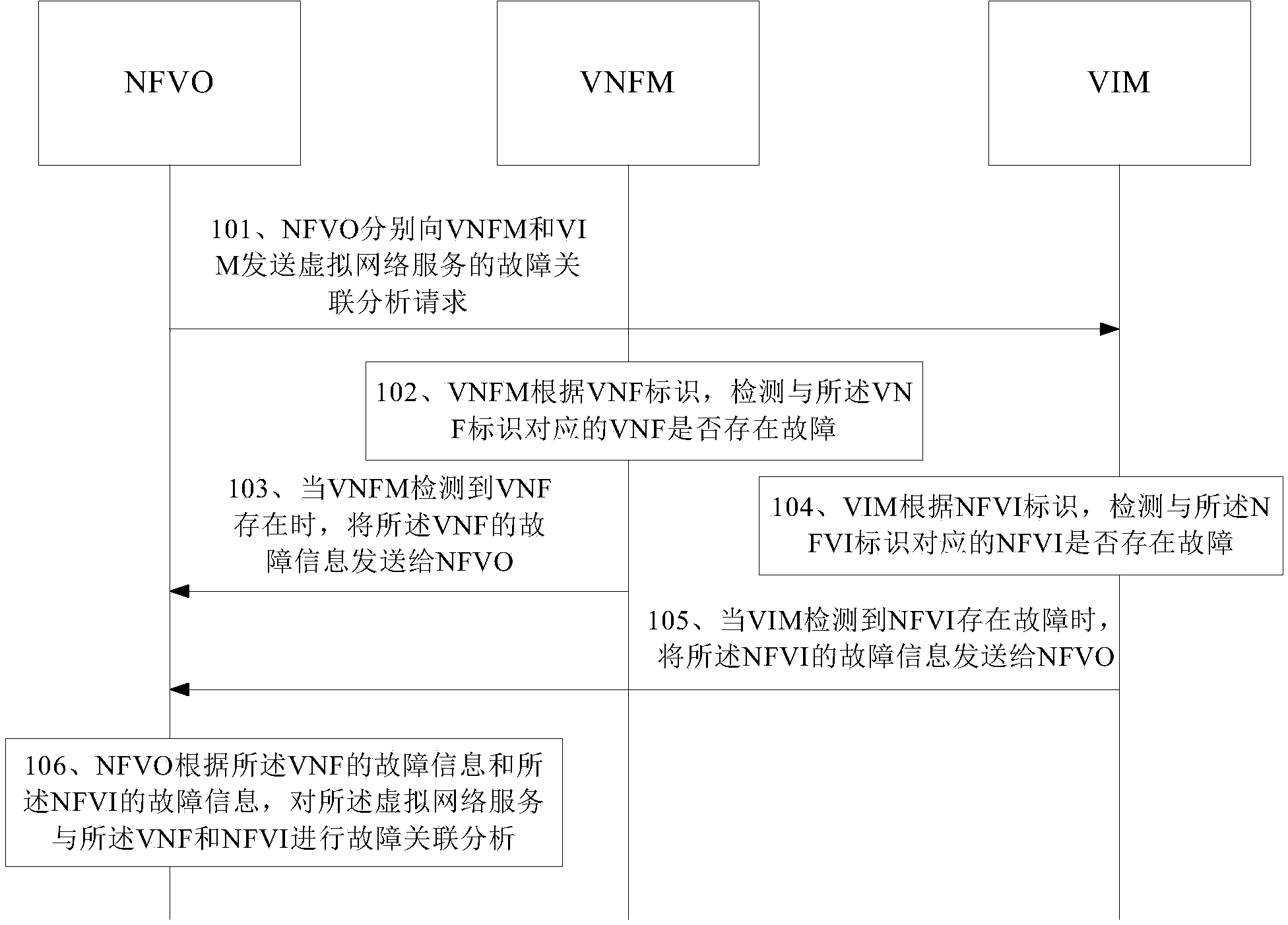
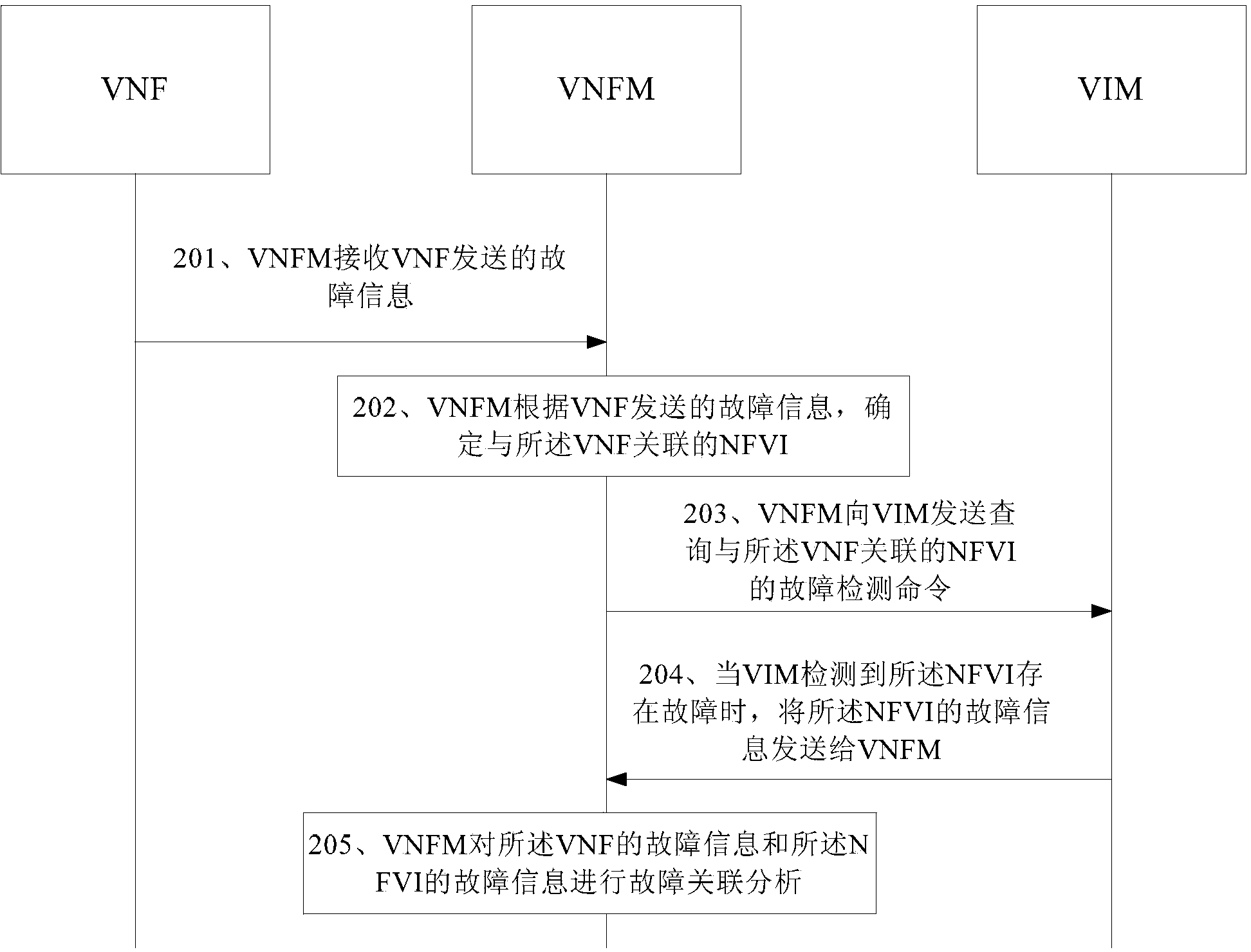
Fault handling method, device and system based on network function virtualization
ActiveCN104170323AReduce fault correlation processing timeReduce business downtimeData switching networksCorrelation analysisNetwork service
Embodiments of the invention disclose a fault handling method, device and system based on network function virtualization. A fault correlation analysis request of virtualized network service is sent to a first functional entity via a second functional entity, so that the first functional entity can send the fault information of a VNF and the fault information of an NFVI to the second functional entity when detecting that faults exist in the VNF and the NFVI corresponding to a VNF identifier according to the VNF identifier and an NFVI identifier included in the fault correlation analysis request. Therefore, the second functional entity can perform fault correlation analysis on the virtualized network service and the VNF and the NFVI according to the fault information of the VNF and the fault information of the NFVI. The handling time for fault correlation between the virtualized network service and the VNF and the NFVI is shortened and the fault handling efficiency is improved.
Owner:HUAWEI TECH CO LTD
Application of abnormal event detection technology to delayed coking unit
ActiveUS20070250292A1Efficiently presentedPlug gaugesMeasurement arrangements for variablePrincipal component analysisCorrelation analysis
The present invention is a method for detecting an abnormal event for process units of a Delayed Coking Unit. The method compares the operation of the process units to statistical and engineering models. The statistical models are developed by principal components analysis of the normal operation for these units. The engineering models are based statistical and correlation analysis between variables. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
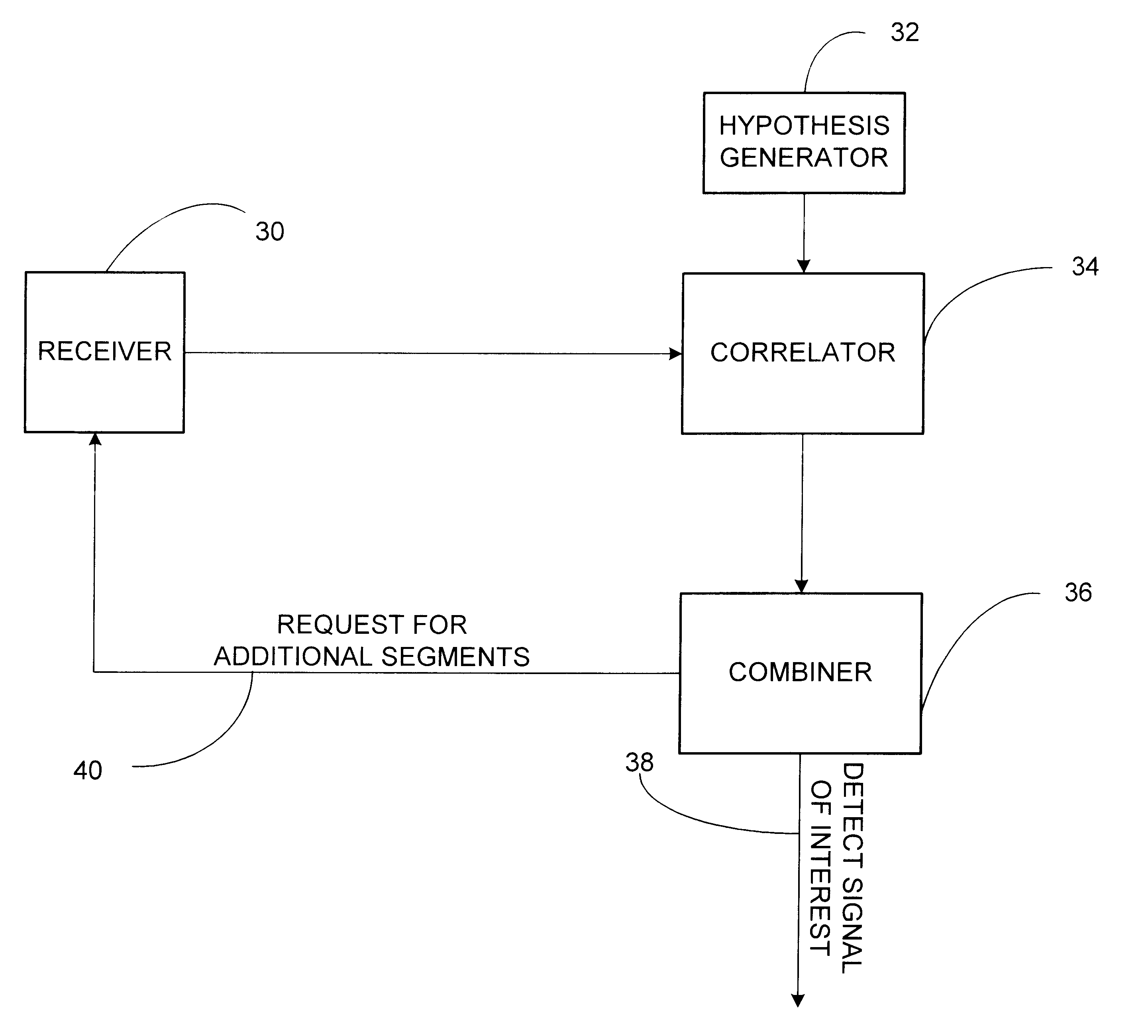
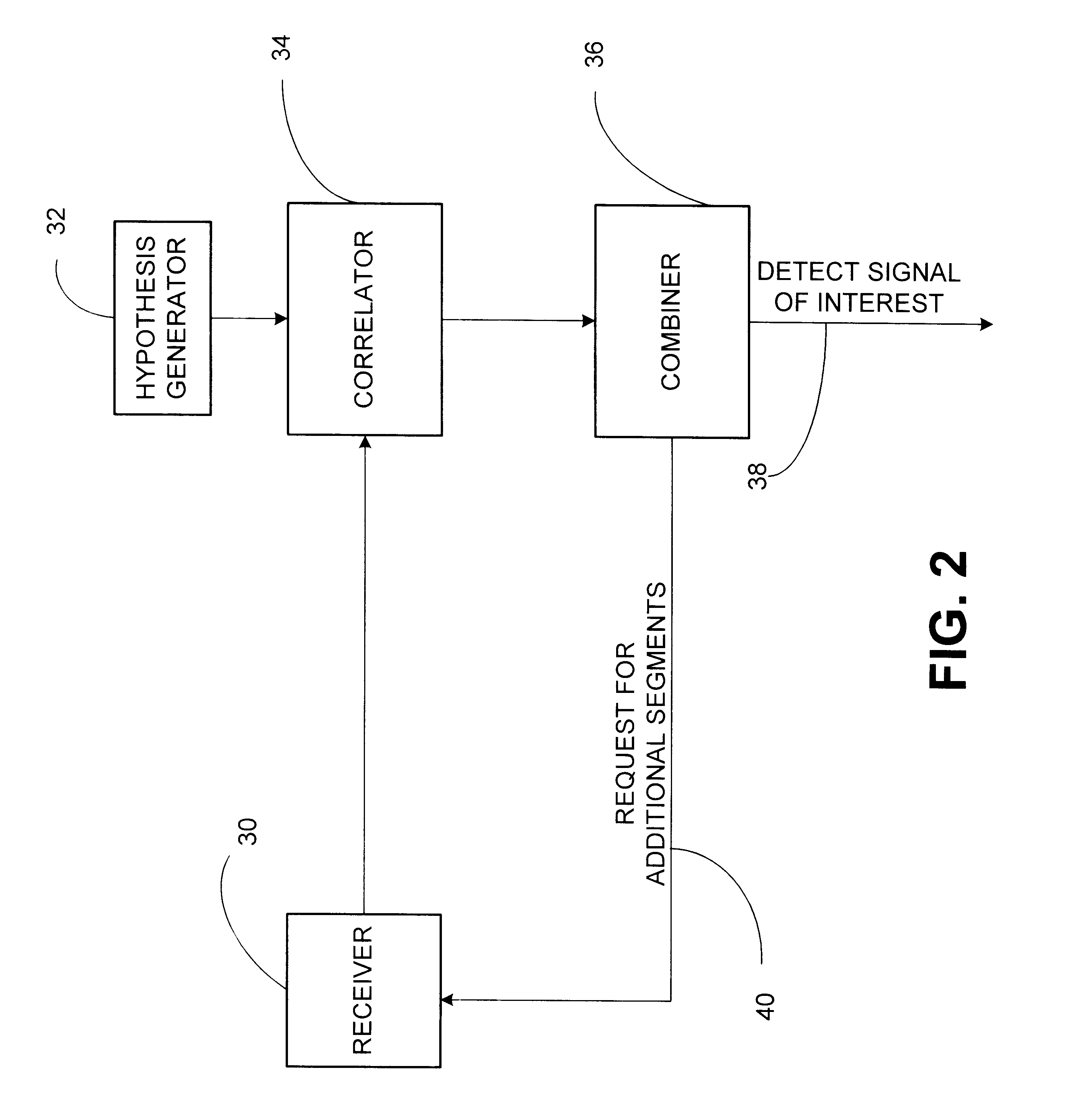
Signal detector employing correlation analysis of non-uniform and disjoint sample segments
InactiveUS6304216B1Cosmetic preparationsRadio wave direction/deviation determination systemsGps receiverCorrelation analysis
A signal detector is provided in which correlation analyses of multiple segments of a received signal from separate and distinct periods of time are combined to improve the detection capability of the signal detector. In one embodiment, the signal detector is part of a GPS receiver.
Owner:CSR TECH INC
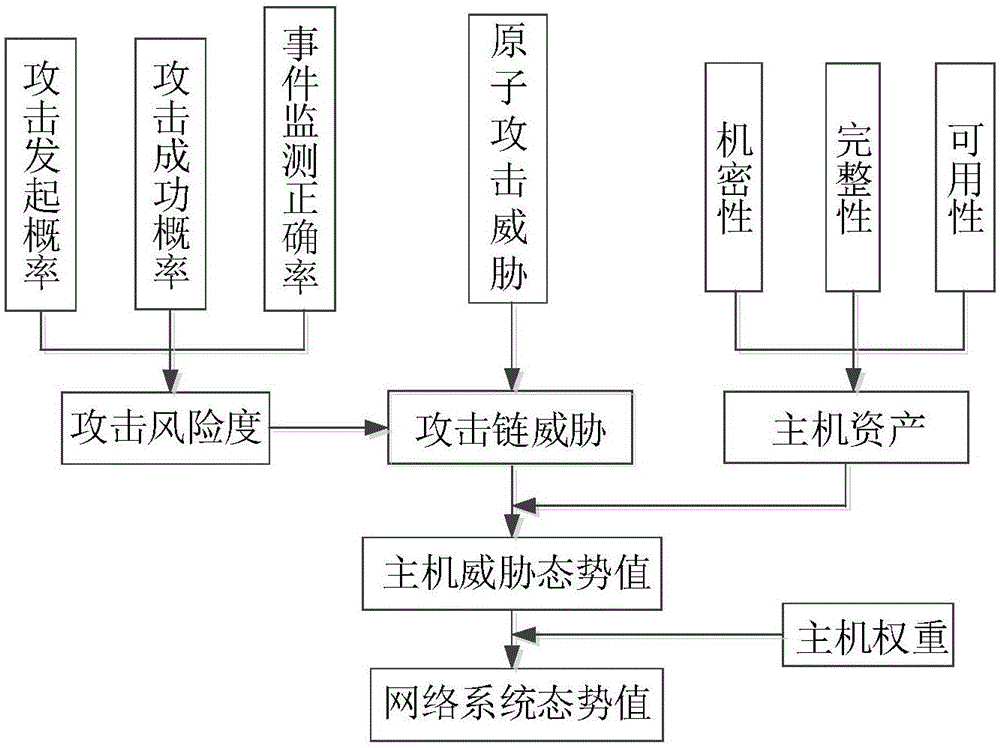
Network safety situation awareness early-warning method and system based big data
InactiveCN105553957AReal-time online detectionAdvanced APT attackTransmissionOriginal dataElectric power system
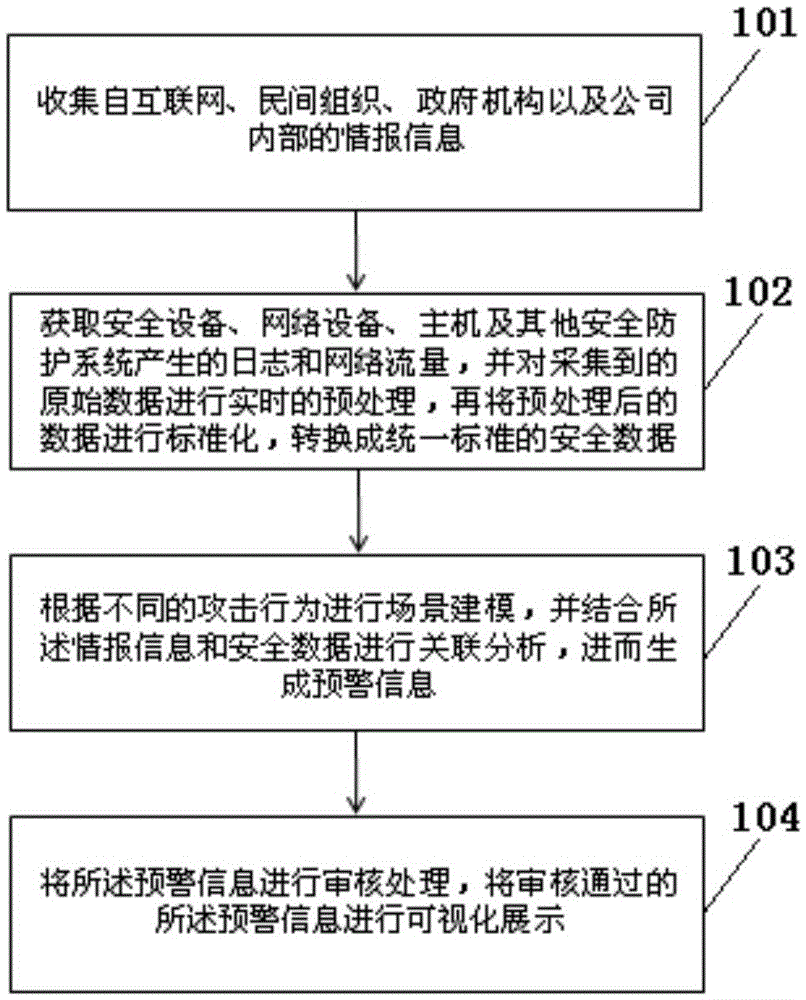
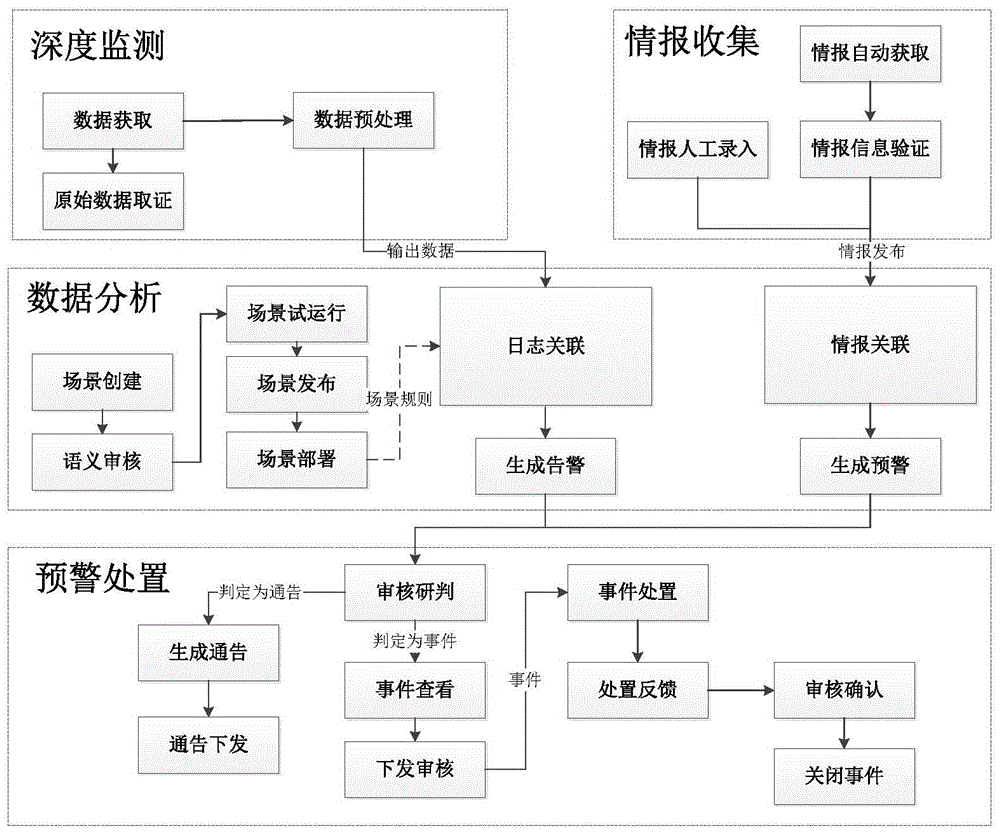
The invention discloses a network safety situation awareness early-warning method and system based big data, and the method comprises the steps: collecting intelligence information from the Internet, non-governmental organizations, governmental agencies and interiors of companies; obtaining log and network flow generated by safety equipment, network equipment, a host and other safety protection systems, carrying out the real-time preprocessing of the collected original data, carrying out the standardization of the data after preprocessing, and converting the data into safety data with the unified standard; carrying out scene modeling according to different attack behaviors, carrying out correlation analysis through combining with the intelligence information and the safety data, and generating early-warning information; carrying out the check processing of the early-warning information, and carrying out the visualized display of the early-warning information after check. The method can achieve the complete sensing of a safety situation, the early warning of safety threats and the capability of timely handling and responding of a safety event, and improves the overall safety protection capability of a power system.
Owner:STATE GRID CORP OF CHINA +1
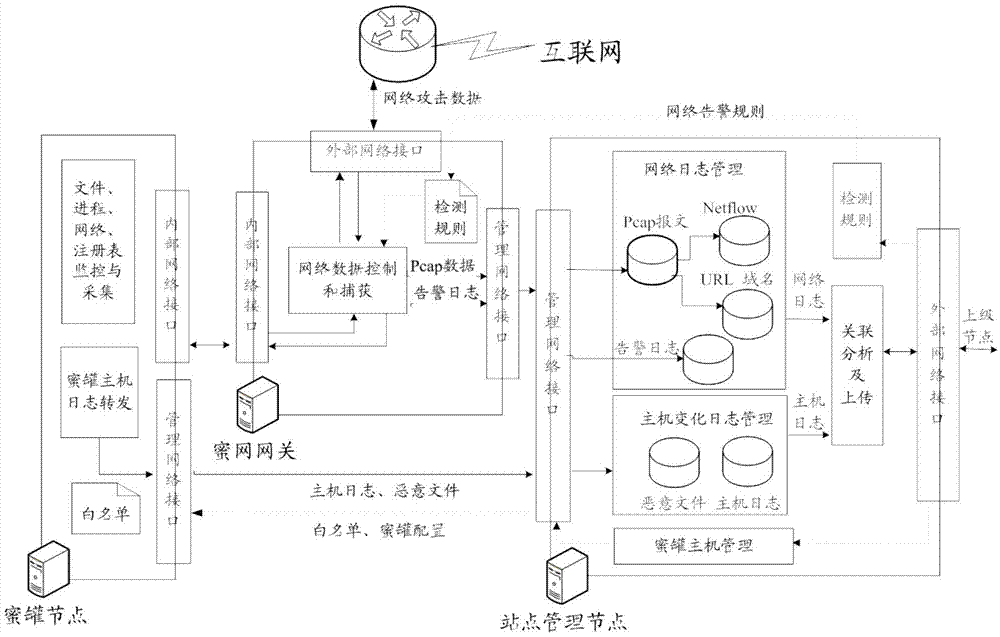
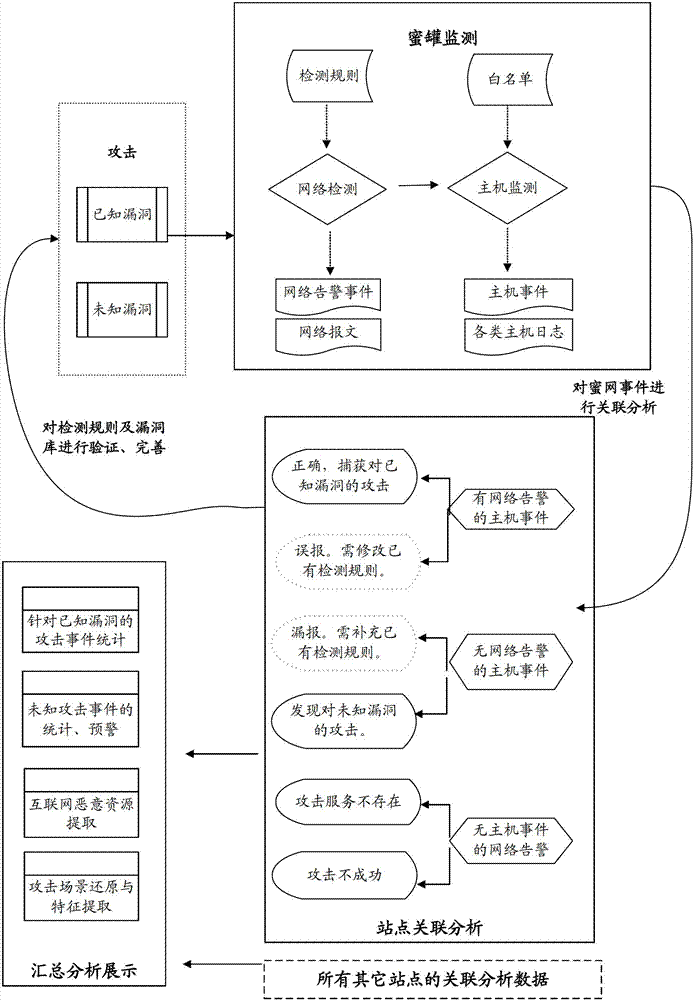
High-interaction honeypot based network security system and implementation method thereof
InactiveCN102739647AImplement auto-discoveryAchieve acquisitionData switching networksResource informationNetwork behavior
The invention discloses a high-interaction honeypot based network security system and an implementation method thereof. The system comprises a honeypot monitoring module, a website correlation analysis module, a summarizing analysis / display module, wherein the honeypot monitoring module is used for carrying out classified acquisition on the attack incidents network behavior logs and host behavior logs; the website correlation analysis module is used for carrying out summarization and automatic correlation analysis on the attack incidents network behavior logs and the host behavior logs, and filtering invalid network alarms, capturing known attack incidents, automatically finding out unknown attack incidents, and extracting concealed Internet malicious resource information according to the automatic correlation analysis results; and the summarizing analysis / display module is used for summarizing and accounting known attack incidents and / or unknown attack incidents captured on all honeypot websites, displaying and reducing selected attack incidents for users, and carrying out automatic detection on concealed Internet malicious resources according to the concealed Internet malicious resource information.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
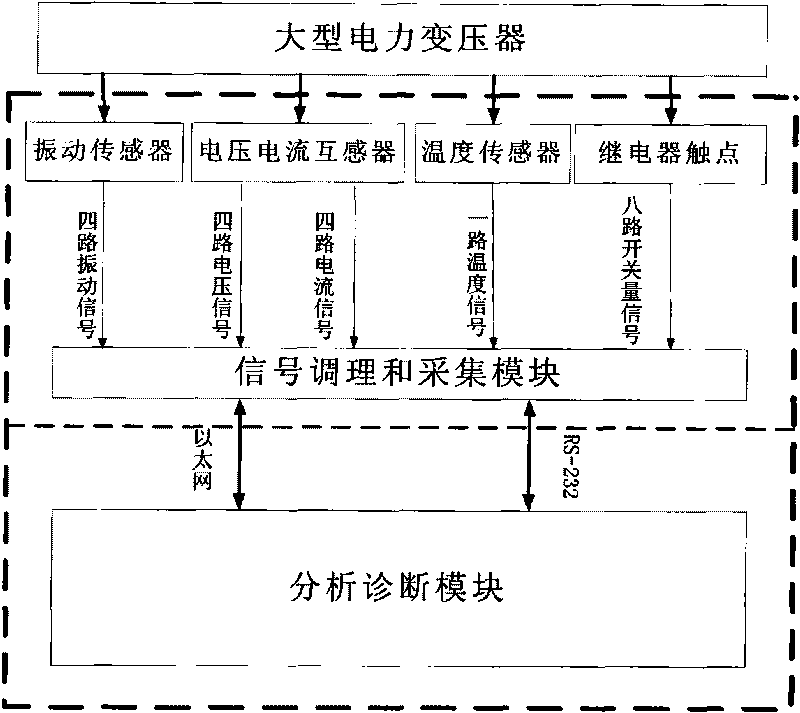
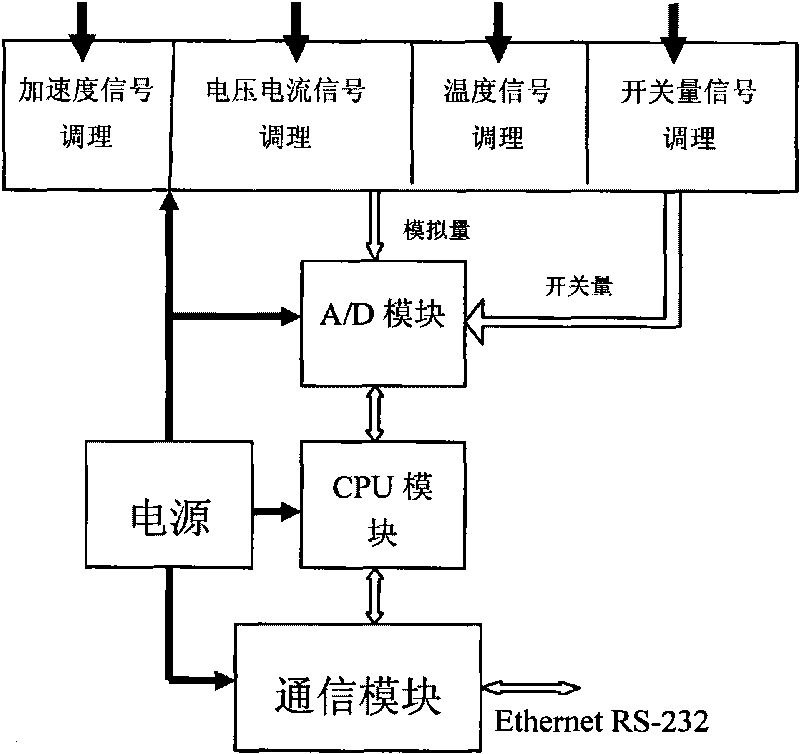
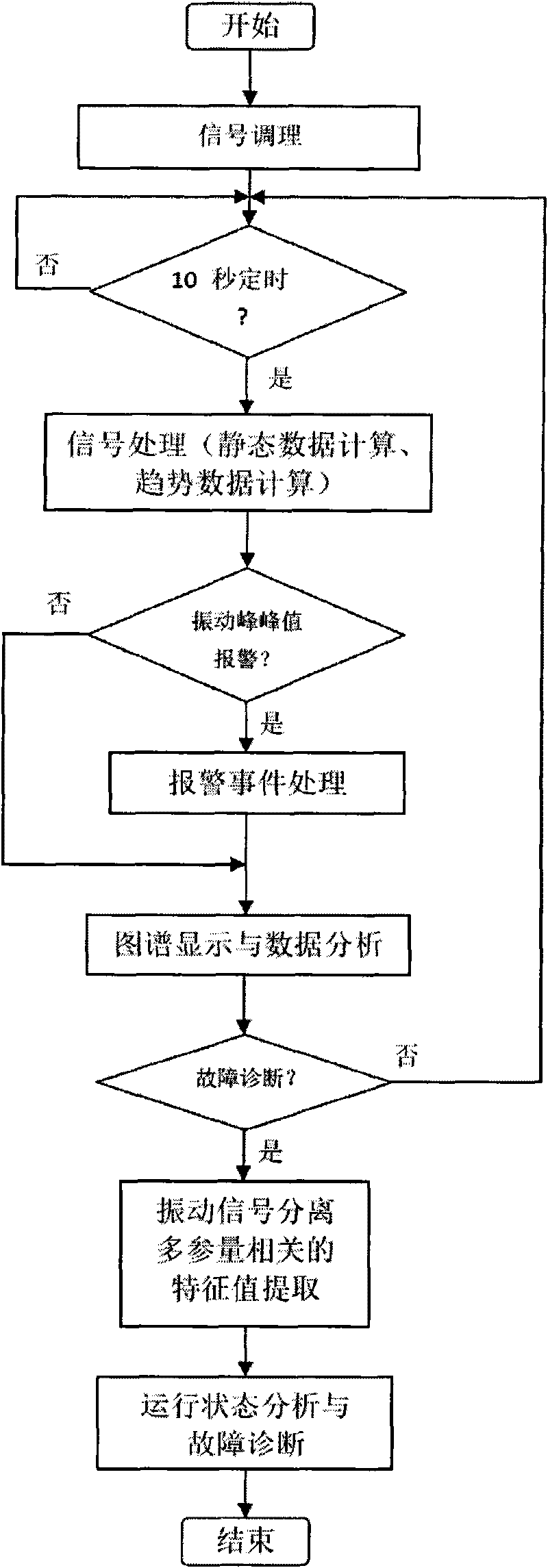
Methods for vibration online monitoring and fault diagnosis of power transformer
InactiveCN101709995ASafe and stable operationImprove accuracyThermometer detailsSubsonic/sonic/ultrasonic wave measurementSignal conditioningEngineering
The invention discloses a method for vibration online monitoring and fault diagnosis of a power transformer. The surface vibration of an oil tank of a transformer, the voltage, the current and the oil temperature of the transformer, and the switching values reflecting the on-states of a vibration source fan and the oil tank of the transformer are taken as basic monitoring parameters to be monitored; after signal conditioning is performed on the monitoring parameters, continuous synchronous waveform data sampling, processing and saving are performed; then the processed waveform data are continuously displayed in real time; signal decomposition, multi-parameter correlation analysis and characteristic vector magnitude extraction are performed on the waveform data; and then various characteristic vector thresholds of a specific transformer are compared to analyze and diagnose the operating state and the fault of the transformer. With the method, the operating state of the power transformer can be monitored in real time, and early warning as well as the analysis and the diagnosis of the fault condition of the transformer are provided, thus guaranteeing the secure and stable operation of the transformer.
Owner:ZHEJIANG UNIV
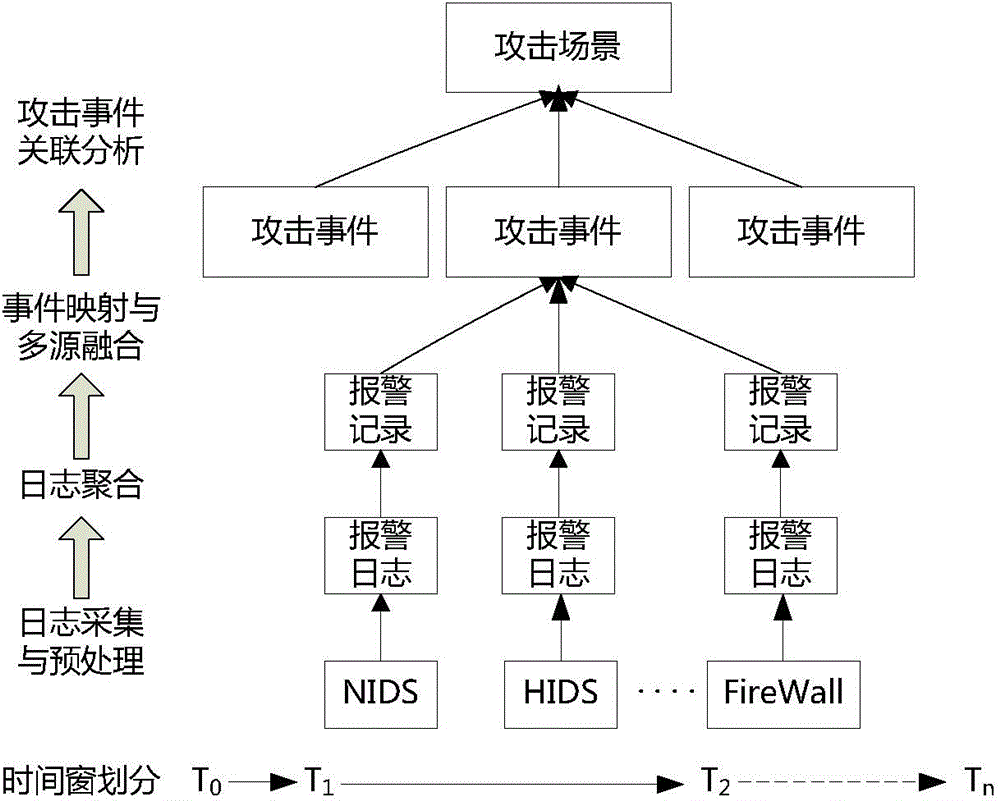
Network attack scene generating method based on multi-source alarm logs
InactiveCN104539626AReflects security threat statusShow intentData switching networksCorrelation analysisNetwork attack
The invention relates to a network attack scene generating method based on multi-source alarm logs. The network attack scene generating method includes the steps that firstly, the alarm logs generated by multiple network security protection devices are collected, effective alarm log data are extracted through preprocessing, and noise, redundancy or ineffective logs are removed; for the effective alarm logs acquired by one device, log format differences of different devices are shielded through single-source log aggregation and mapping, and attack event information is analyzed and extracted; attack events extracted from different sources are fused and analyzed, and network attack events with high credibility are generated; then through correlation analysis of the attack events, a network attack scene graph is generated, and the whole attack process of one attack operation is analyzed. Due to the fact that the multi-source logs are fused, the analyzed attack event information can more completely and more reliably depict attacks to which a network is subject, attack scenes are acquired through correlation analysis of the attack events, the intentions of attackers can be more clearly shown, and the security threat state of the network can be more clearly reflected.
Owner:THE PLA INFORMATION ENG UNIV
Robust, Efficient, Localization System
InactiveUS20080161015A1Faster routingConvenient and effective detectionDirection finders using radio wavesPosition fixationLocalization systemCode division multiple access
Replica correlation processing, and associated representative signal-data reduction and reconstruction techniques, are used to detect signals of interest and obtain robust measures of received-signal parameters, such as time differences of signal arrival and directional angles of arrival, that can be used to estimate the location of a cellularized-communications signal source. The new use in the present invention of signal-correlation processing for locating communications transmitters. This enables accurate and efficient extraction of parameters for a particular signal even in a frequency band that contains multiple received transmissions, such as occurs with code-division-multiple-access (CDMA) communications. Correlation processing as disclosed herein further enables extended processing integration times to facilitate the effective detection of desired communications-signal effects and replication measurement of their location-related parameters, even for the communications signals modulated to convey voice conversations or those weakened through propagation effects. Using prior, constructed, signal replicas in the correlation processing enables elimination of the inter-site communications of the signal representations that support the correlation analyses. Reduced-data representations of the modulated signals for voiced conversation, or for the variable components of data communications, are used to significantly reduce the inter-site communications that support the correlation analyses.
Owner:TRUE POSITION INC
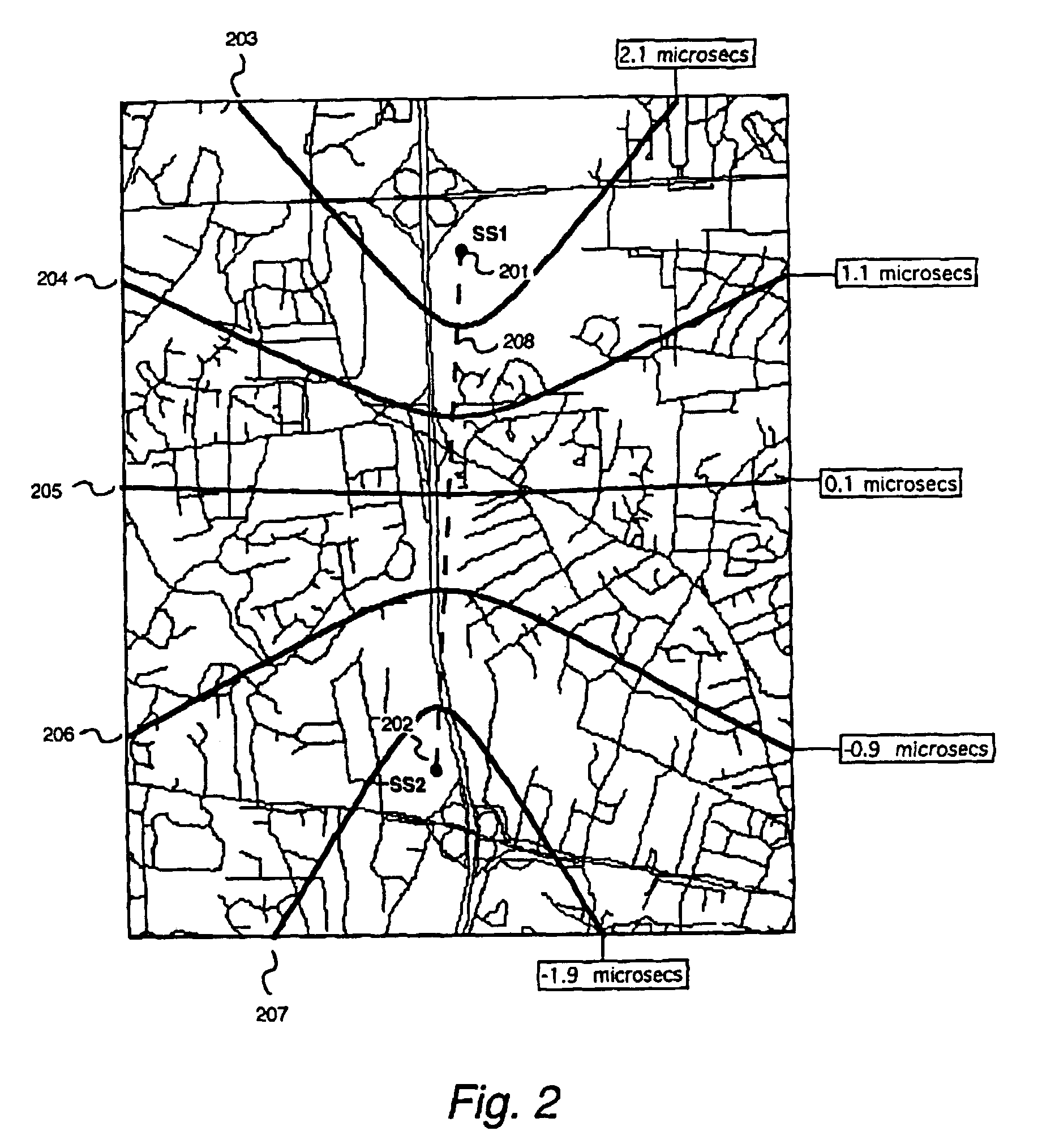
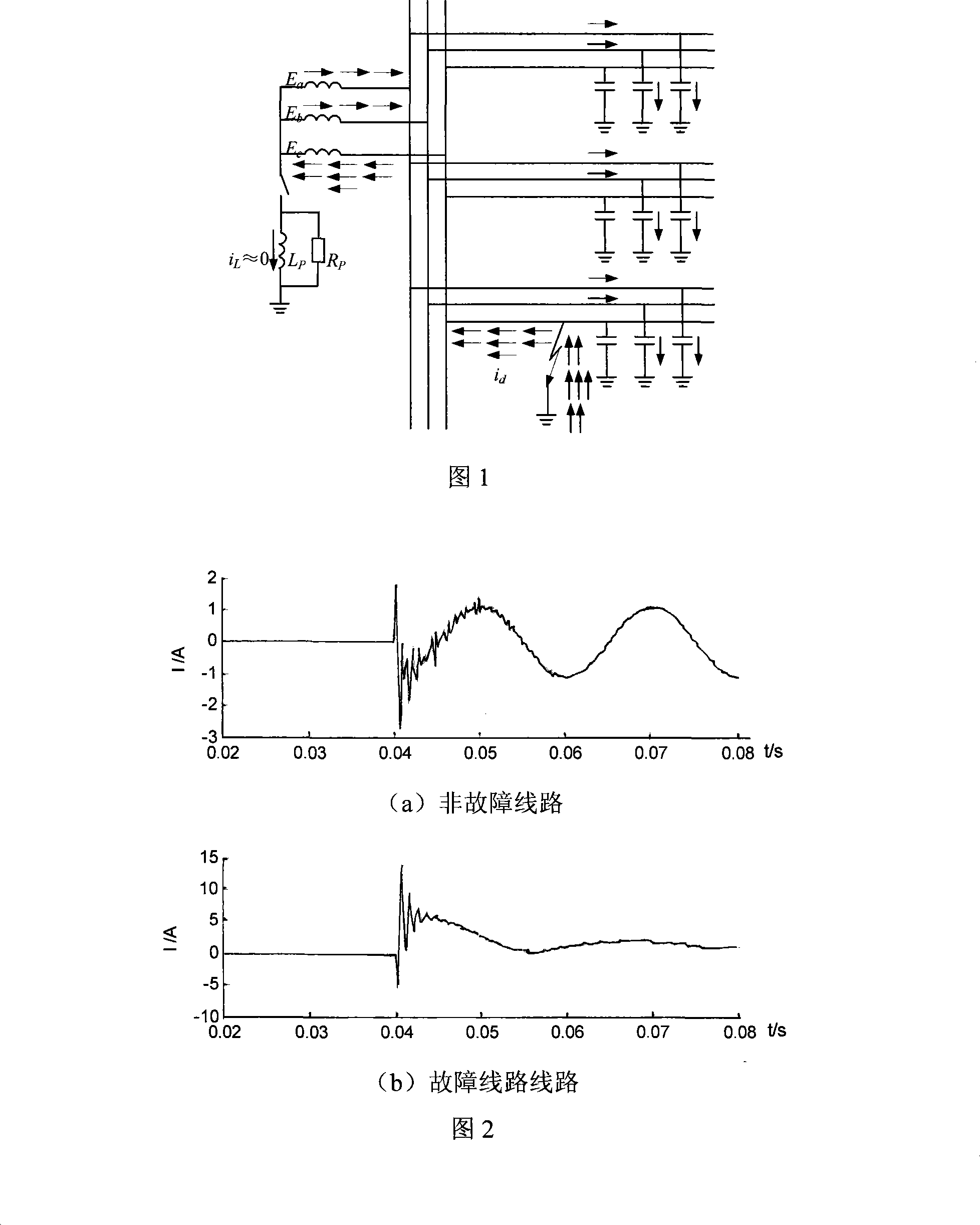
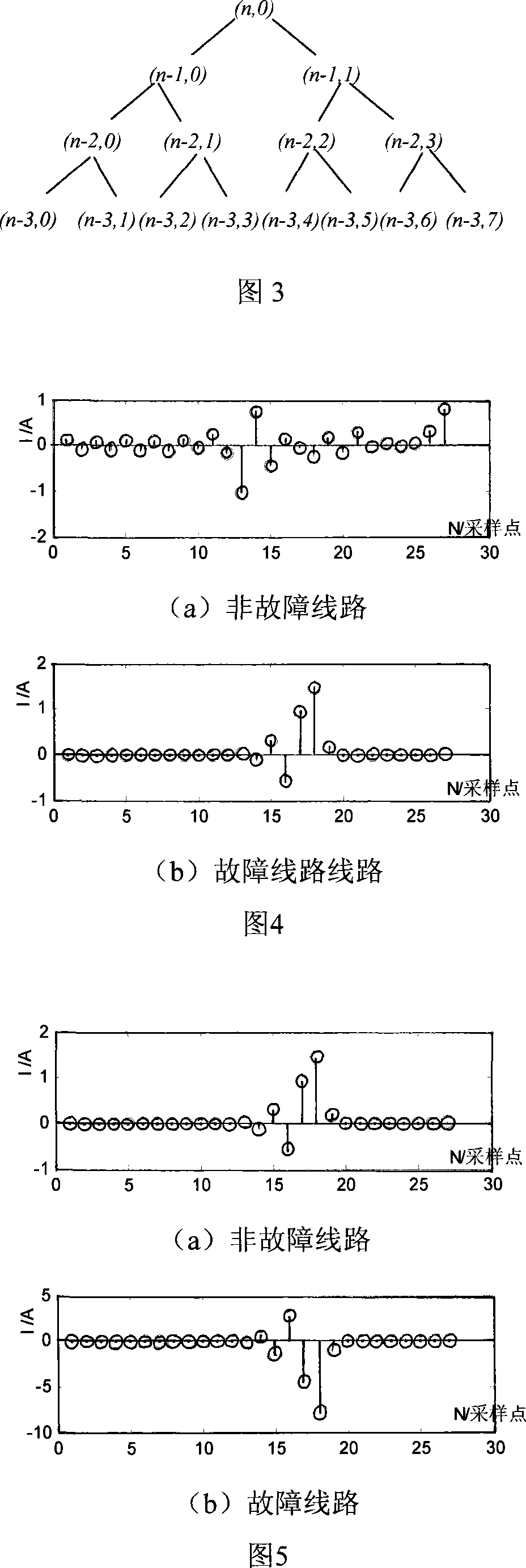
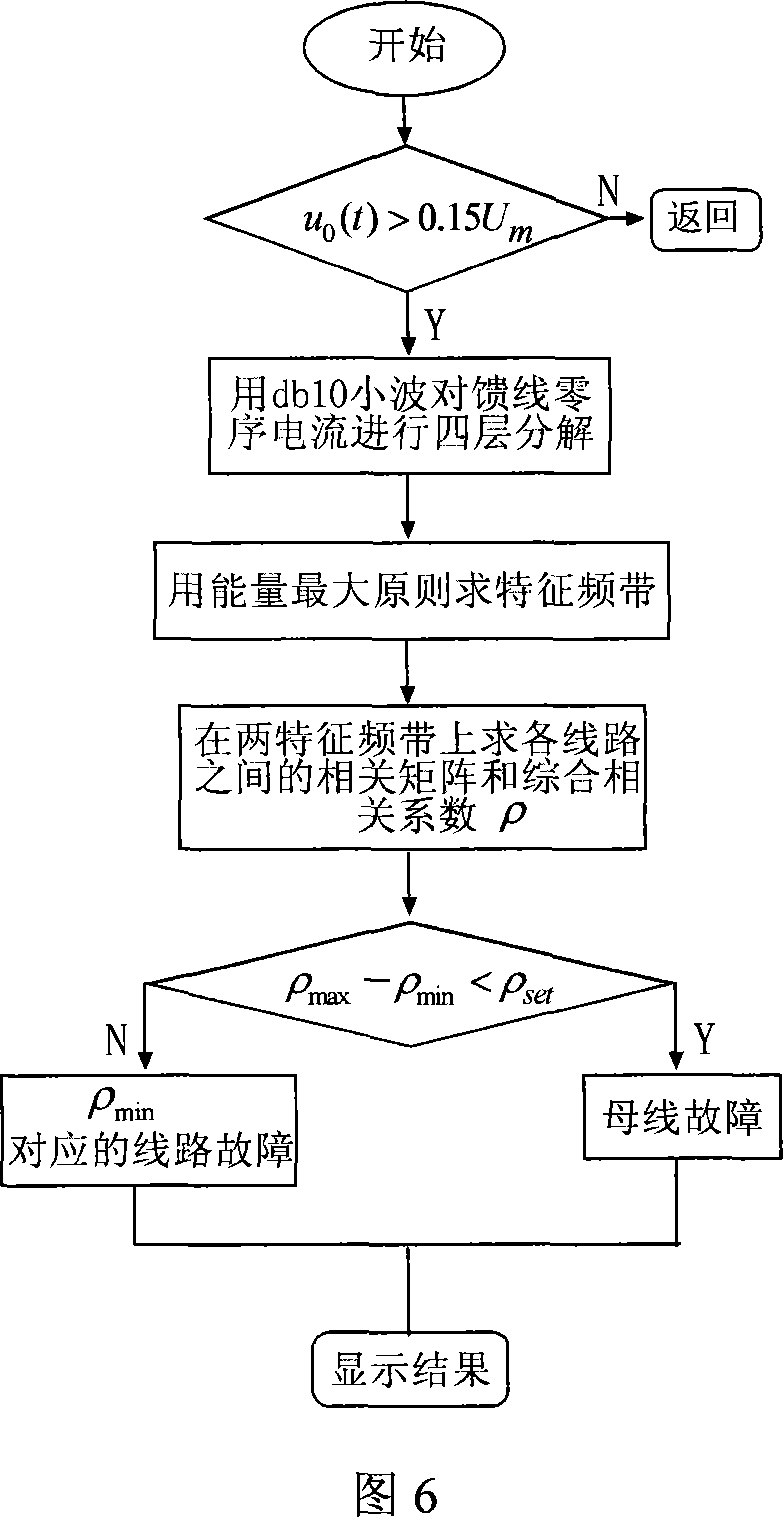
Low current neutral grounding system fault route selecting method by wavelet package decompose and correlation analysis
InactiveCN101162838ARealize correct line selectionStrong anti-arc grounding abilityEmergency protective circuit arrangementsFault locationElectric power systemDecomposition
The present invention relates to a small current grounding system fault line selecting method by wavelet package decomposition and relevant analysis, belonging to the power system relay protection technical field. The method comprises: starting the fault line selecting device and recording wave to acquire transient zero-order current on each of the feeder lines when bus zero-order voltage transient value exceeds limit; calculating energy on each of frequency bands of the transient zero-order current after wavelet package decomposition, summing the energy of transient zero-order current on all the lines according to frequency bands and selecting the frequency bands with the maximum and secondary value of energy and values as the characteristic frequency bands, applying relevant analysis method to line transient zero-order current on the selected characteristic frequency bands in order; and finally determining fault point integrating the relevant analysis results of two frequency bands. The method uses wavelet package decomposition and relevant analysis, thereby effectively using information (amplitude and phase) contained in fault transient process and reflecting differences between fault line and non-fault line to maximum degree. Principle analysis and simulations demonstrate that the method has precise and reliable line selection.
Owner:KUNMING UNIV OF SCI & TECH
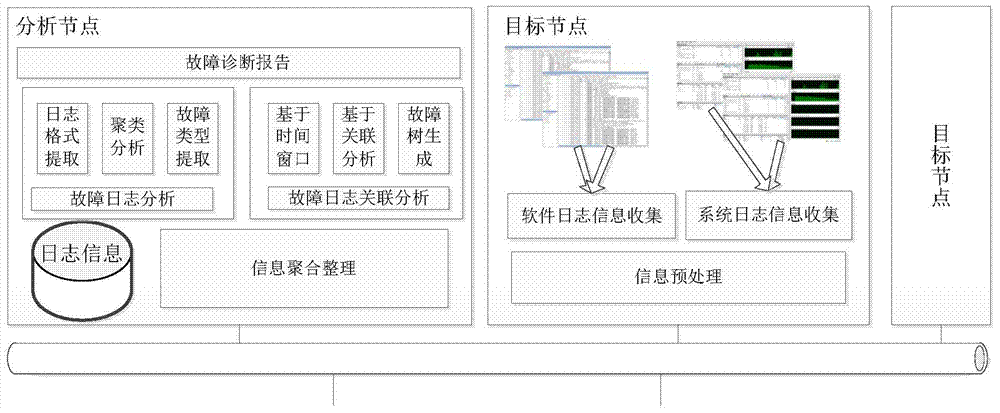
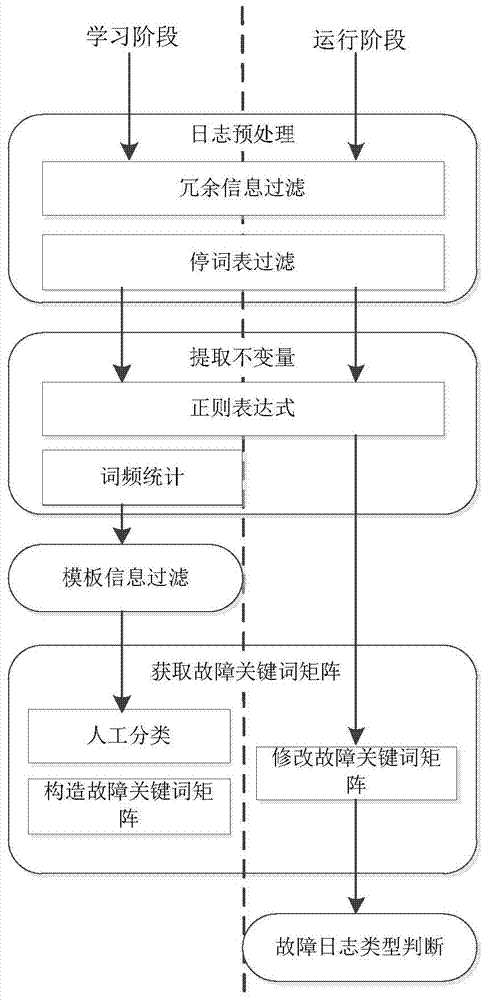
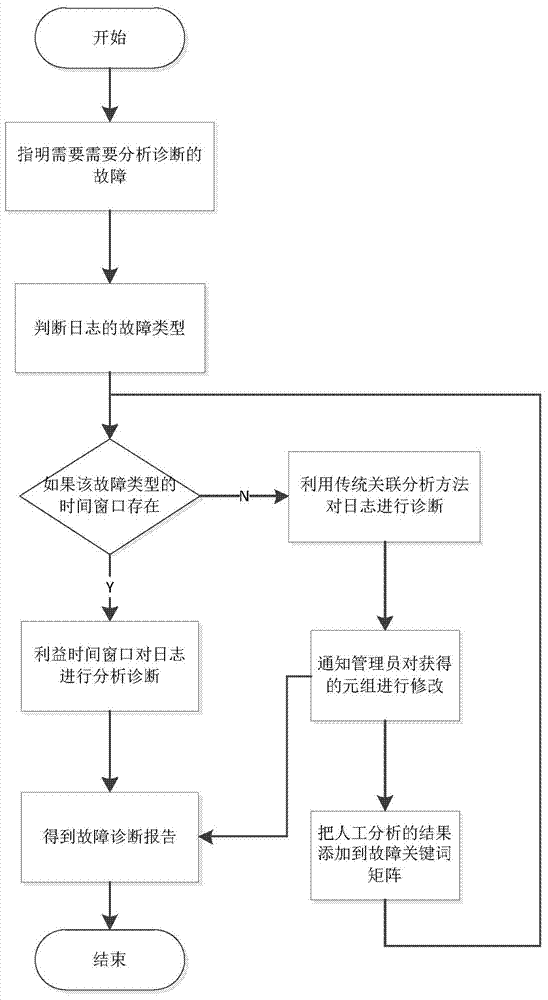
Log based computer system fault diagnosis method and device
InactiveCN103761173AConvenient and rapid fault classificationProcessing speedDetecting faulty computer hardwareHardware monitoringProcess systemsLog management
The invention discloses a log management and fault diagnosis method and device under multiple hosts. The method comprises fault log collection, fault log analysis and fault log correlation analysis. Fault log collection comprises collecting fault logs of all hardware and software in the cluster and storing the logs in a log server uniformly. Fault log analysis comprises filtering the fault logs, extracting log template information and classifying the logs according to log types. Fault log correlation analysis comprises performing fault reason analysis by using log analysis results and combining time windows, clustering the related faults caused by the same fault into a category and trying to find the root of the type of the faults. The method and the device are capable of analyzing the system operation condition effectively, assisting administrators to process system faults and improving the fault type determination accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
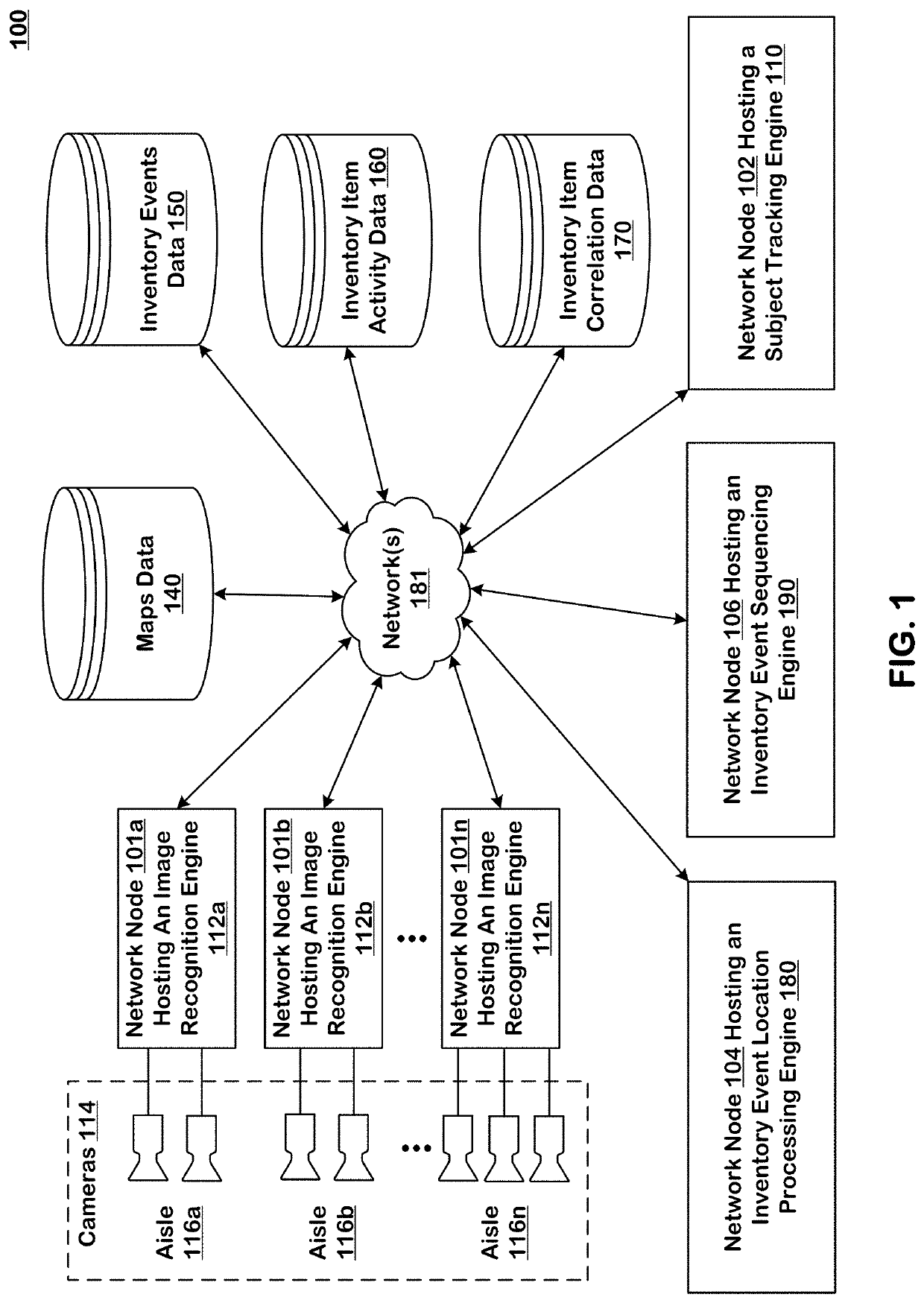
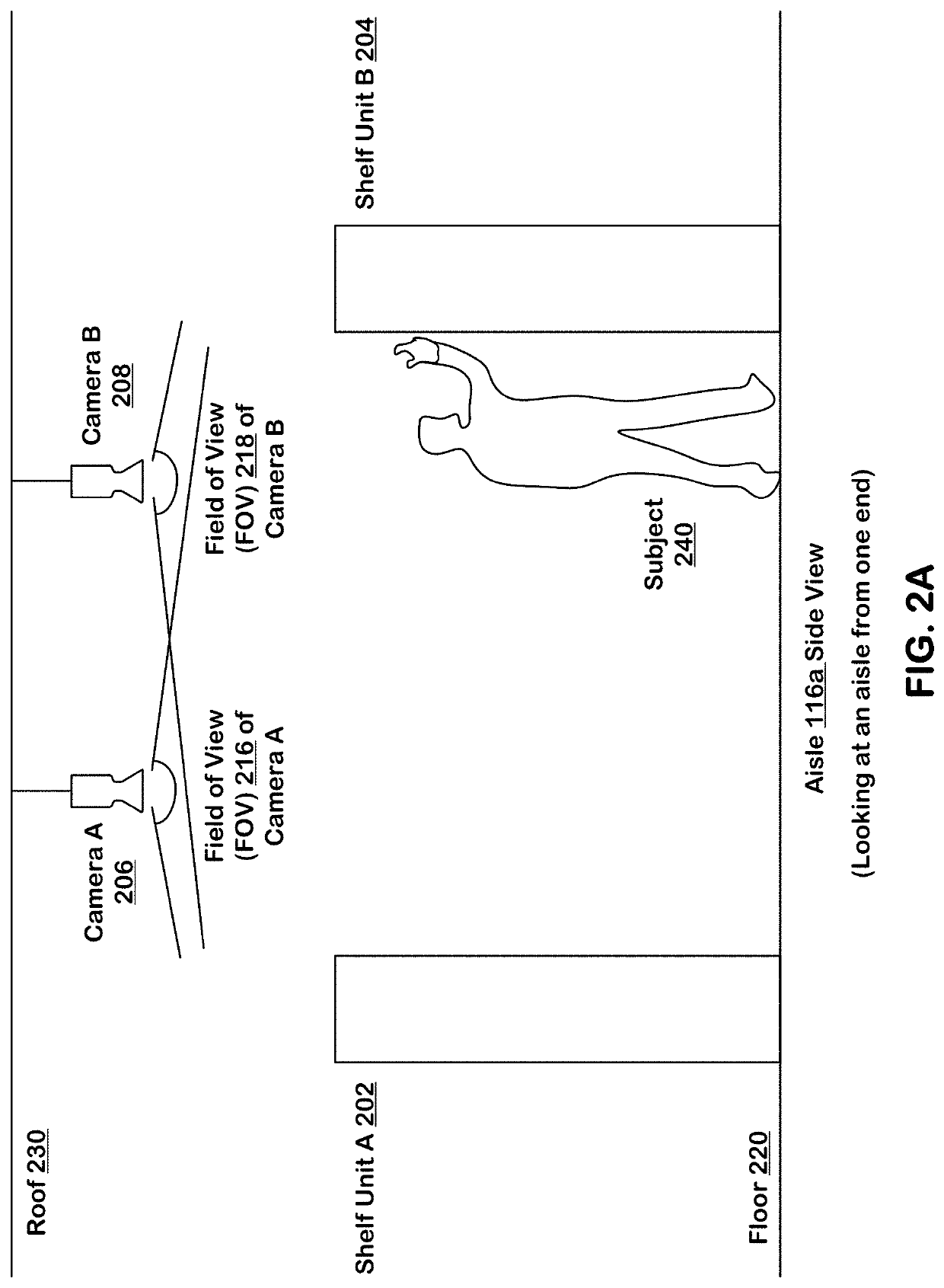
Product correlation analysis using deep learning
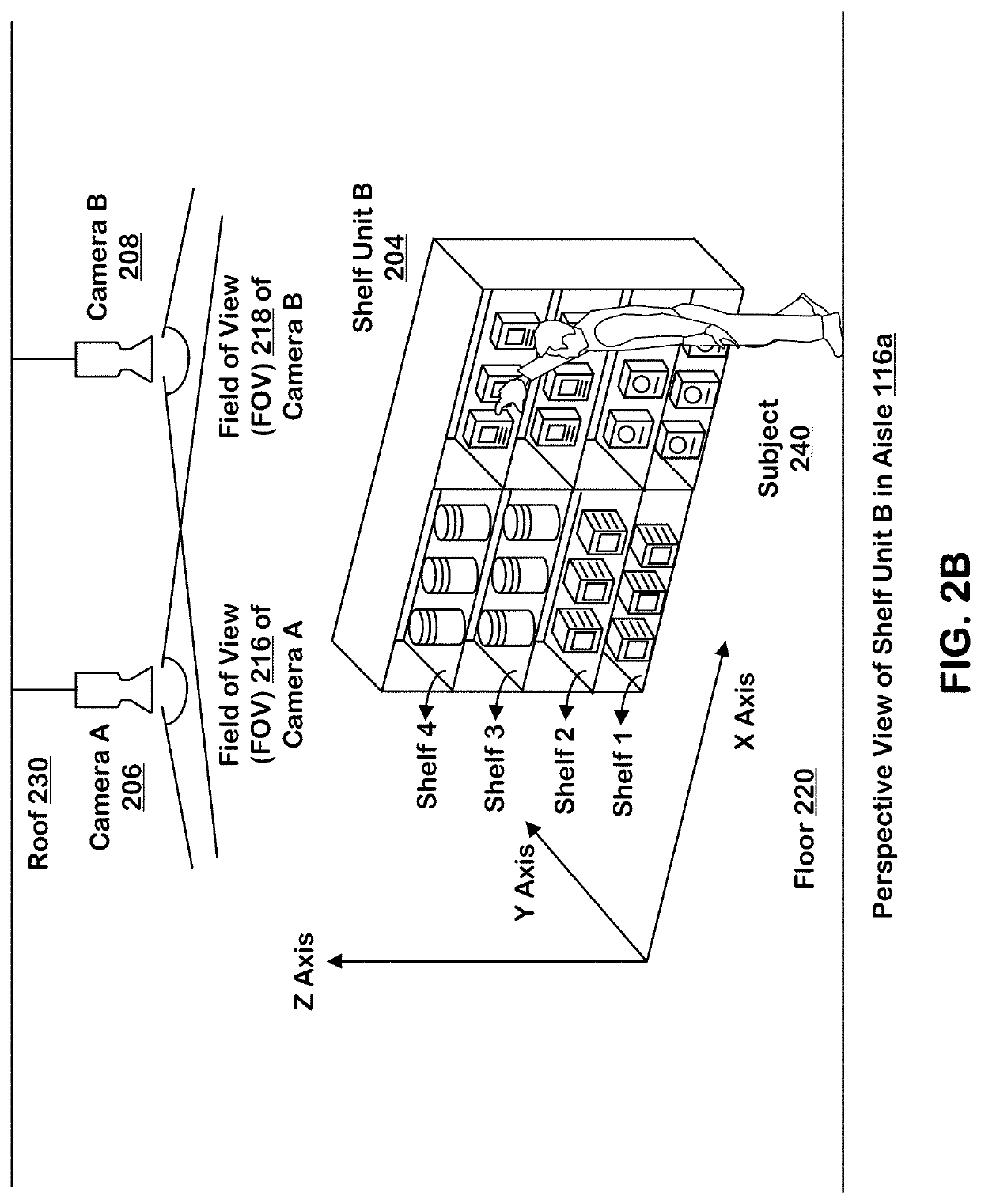
ActiveUS20190347611A1Improve reliabilityImage enhancementTelevision system detailsTimestampCorrelation analysis
Systems and techniques are provided for tracking inventory events in an area of real space. A plurality of sensors produce respective sequences of frames in corresponding fields of view in the real space. The field of view of each sensor overlaps with the field of view of at least one other sensor. The processing system uses the sequences of frames produced by sensors in the plurality of sensors to identify gestures by detected subjects in the area of real space and produce inventory events. The inventory events include a subject identifier identifying a detected subject, a gesture type of the identified gesture by the detected subject, an item identifier identifying an inventory item linked to the gesture by the detected subject, a location of the gesture represented by positions in three dimensions of the area of real space and a timestamp.
Owner:STANDARD COGNITION CORP
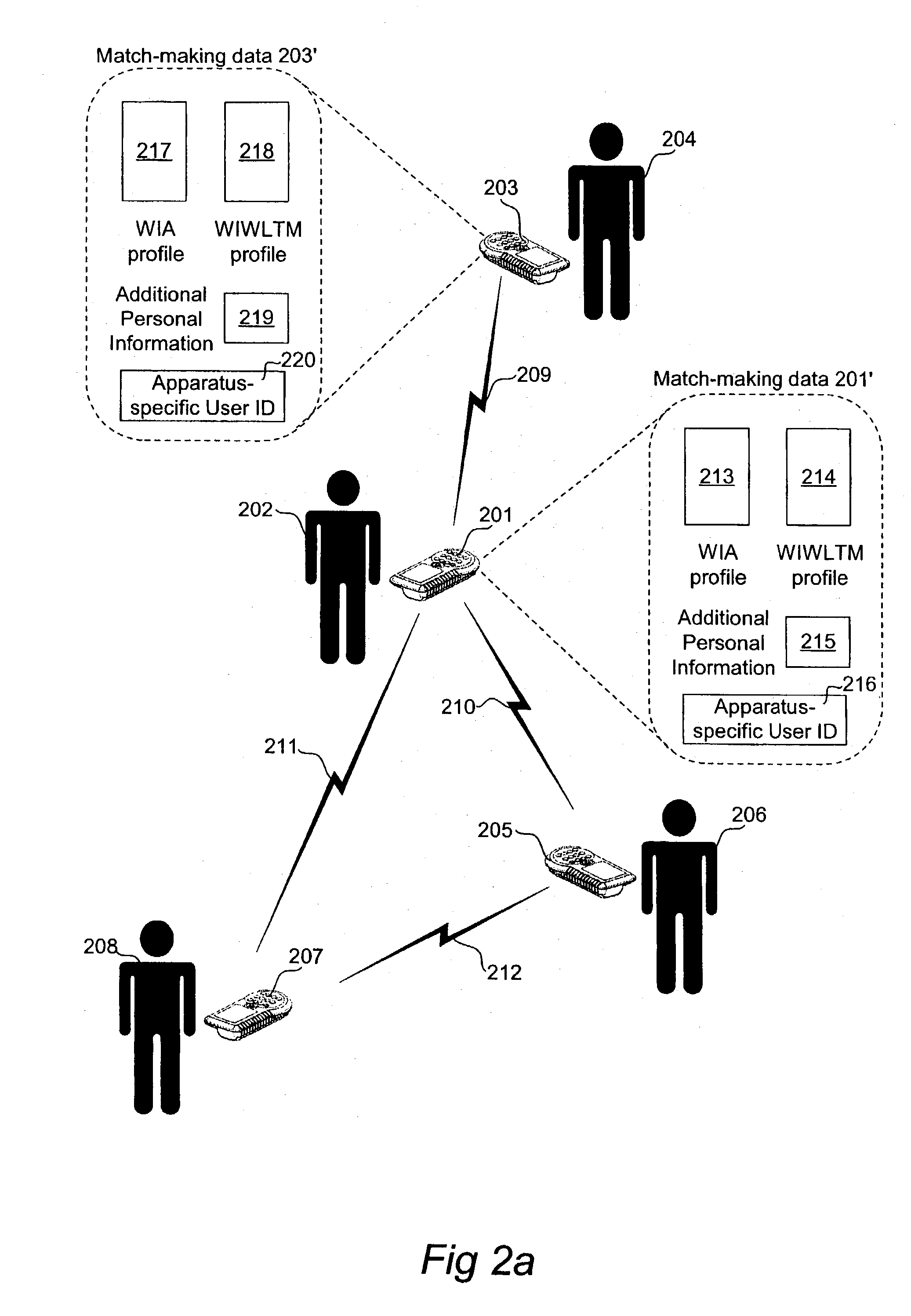
Portable communication apparatus and methods for match-making with distributed memory
A portable communication apparatus for match-making with a plurality of remote communication apparatuses has memory means adapted to store match-making data, including local match-making data associated with the portable communication apparatus. A transceiver is adapted for wireless communication with a first remote communication apparatus, so as to transmit the local match-making data to the first remote communication apparatus, as well as to receive first remote match-making data associated with the first remote communication apparatus. A processing device is adapted to perform a correlation analysis between the local match-making data and the first remote match-making data and-in case a result of the correlation analysis indicates a match between the portable communication apparatus and the first remote communication apparatus-provide an alert to a user of the portable communication apparatus. The memory means is adapted to store the first remote match-making data, and the transceiver is adapted to transmit the first remote match-making data, in addition to the local match-making data, to a second remote communication apparatus.
Owner:STEPHEN J CARLTON
Article identification and tracking using electronic shadows created by RFID tags
InactiveUS7081818B2Facilitate identification and trackingFoster marketing and merchandising effectivenessElectric signal transmission systemsMemory record carrier reading problemsElectromagnetic couplingCorrelation analysis
A tracking system uses RFID (radio frequency identification) tag technology to facilitate the identification and tracking of items in an environment through a technique known as shadowing. As an object or target moves within a pre-described detection zone with communicating antenna and RFID sensors, the object or target blocks the line of sight between respective antenna and sensors, preventing electromagnetic coupling between the sensor and the antenna and thus casting an electromagnetic shadow along the line of sight. One approach of this invention uses this shadow technique to perform functions such as theft (shrink) deterrence / detection; tracking the motion of objects through an environment by monitoring the shadow; and correlation analysis of people shadows to tagged items (e.g., merchandise, articles) to foster marketing and merchandizing effectiveness.
Owner:CHECKPOINT SYST INC
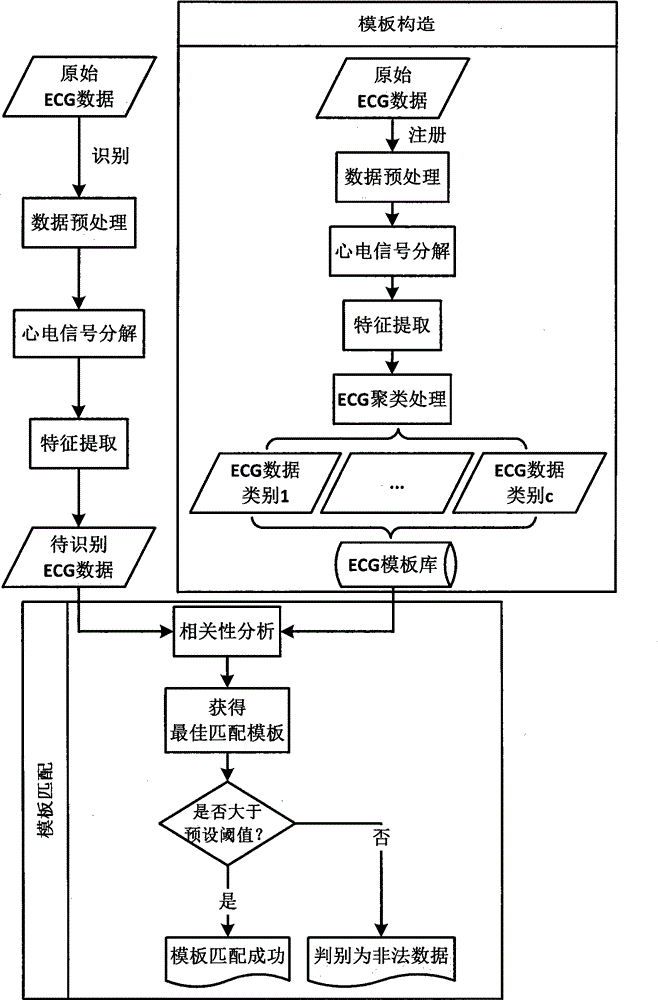
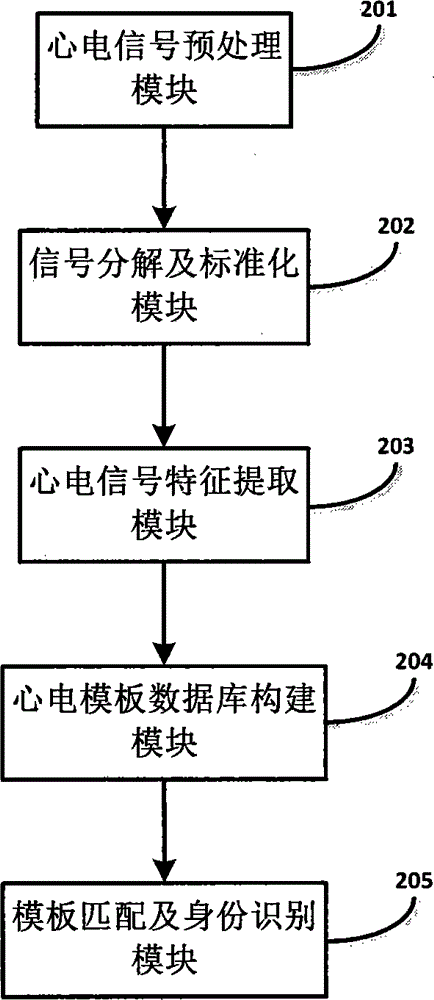
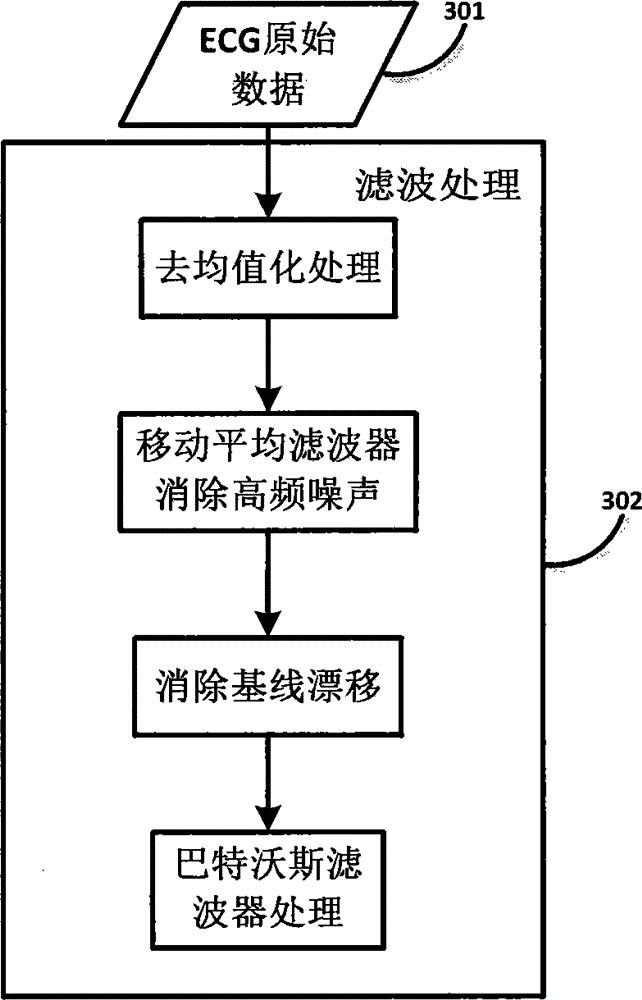
Multiple-template matching identity recognition method based on ECG (Electrocardiogram) under electrocardiogram abnormality state
ActiveCN104102915AEliminate inconsistenciesReduce time complexityCharacter and pattern recognitionDiagnostic recording/measuringEcg signalHuman body
The invention relates to a multiple-template matching identity recognition method based on an ECG (Electrocardiogram) under an electrocardiogram abnormality state, and belongs to the technical field of biological characteristic identity recognition. The ECG data of a user to be recognized is compared with the data of a registered user in a template library to obtain an identity recognition result. The key technology of the method comprises the following steps: carrying out electrocardiosignal preprocessing for eliminating noise interference; carrying out electrocardiosignal decomposition to separate an electrocardiogram waveform of each period; carrying out standardized processing for independently achieving standardization on time and amplitude scales; carrying out characteristic extraction: in the step, characteristics are extracted by wavelet transform, and clustering analysis is carried out by an ISODATA (Iterative Self-organizing Data Analysis Techniques Algorithm) so as to construct an ECC template library; and carrying out correlation analysis: in the step, correlation between ECG test data and each template is calculated, an optimal matching template is selected, and finally, an identity recognition result is obtained. The multiple-template matching identity recognition method provided by the invention utilizes the intrinsic electrocardiosignal of a human body to recognize an identity, and the ECG data under the abnormality state is considered.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
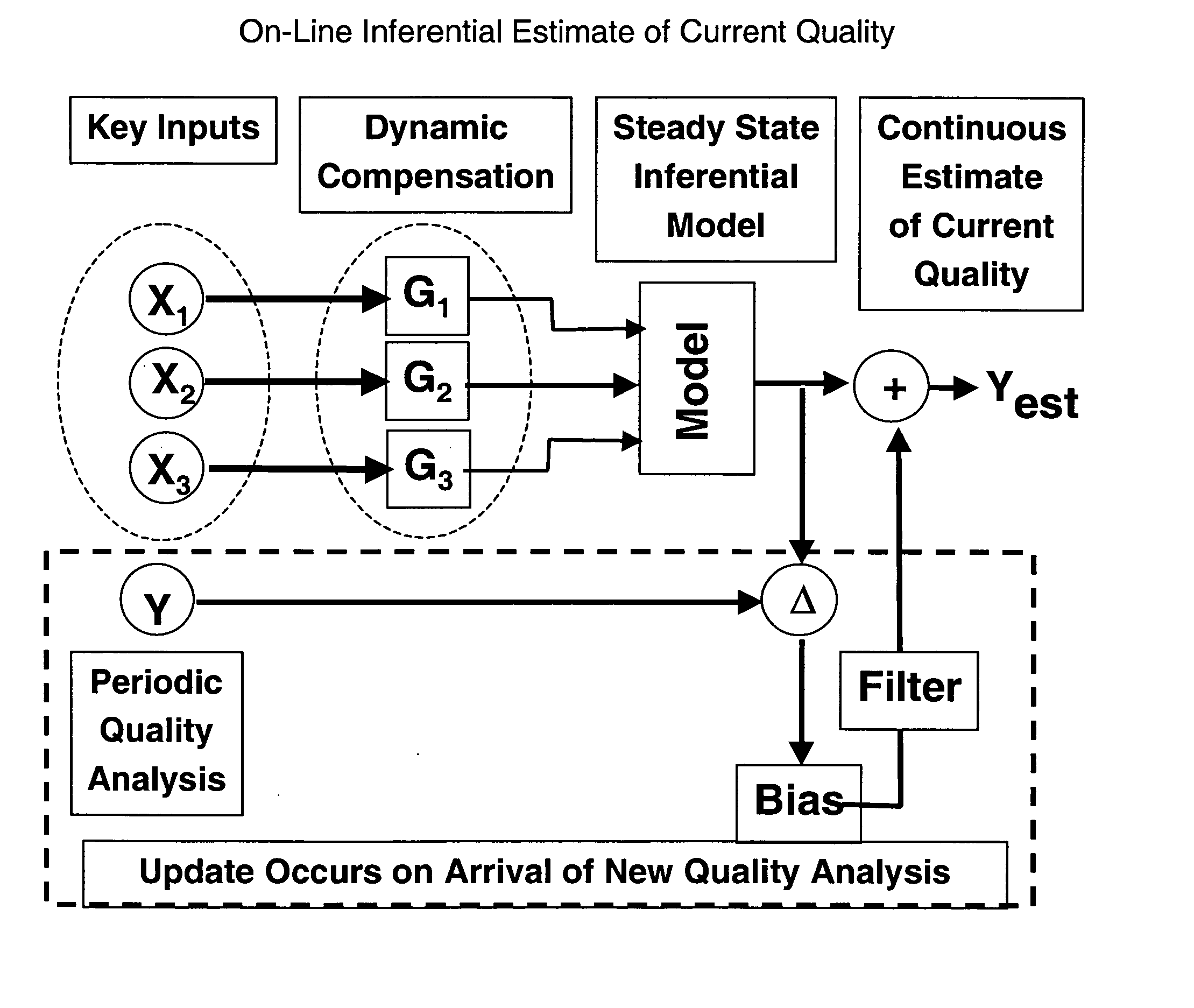
Automated quality control protocols in a multi-analyzer system
ActiveUS20050037502A1Simple interfaceImprove reliabilityWithdrawing sample devicesMaterial analysis by optical meansQuality controlCorrelation analysis
A method for automatically operating a sample handling system and associated analyzers to conduct assays on a number of patient samples by comparing the assays to be conducted with a set of assay defined rules, subdividing the analyzers into analyzers which are in compliance with the assay defined rules and analyzers not in compliance with the set of assay defined rules; thereafter, operating the system to supply patient samples to analyzers in compliance or operating the system so as to bring at least one analyzer into compliance with the assay defined rules and supplying patient samples to such an analyzer.
Owner:SIEMENS HEALTHCARE DIAGNOSTICS INC
Method for scanning, analyzing and handling various kinds of digital information content
InactiveUS20050108227A1Data processing applicationsDigital data information retrievalDigital dataData set
Owner:MICROSOFT TECH LICENSING LLC
Application of abnormal event detection (AED) technology to polymers process
ActiveUS20080097637A1Efficiently presentedSimulator controlTesting/monitoring control systemsPrincipal component analysisCorrelation analysis
The present invention is a method and system for detecting an abnormal event for process units of a Polymers Unit. The method compares the operation of the process units to statistical, engineering or heuristic models. The statistical models are developed by principle components analysis of the normal operation for these units. In addition, the engineering models are based on correlation analysis between variables or simple engineering calculations. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
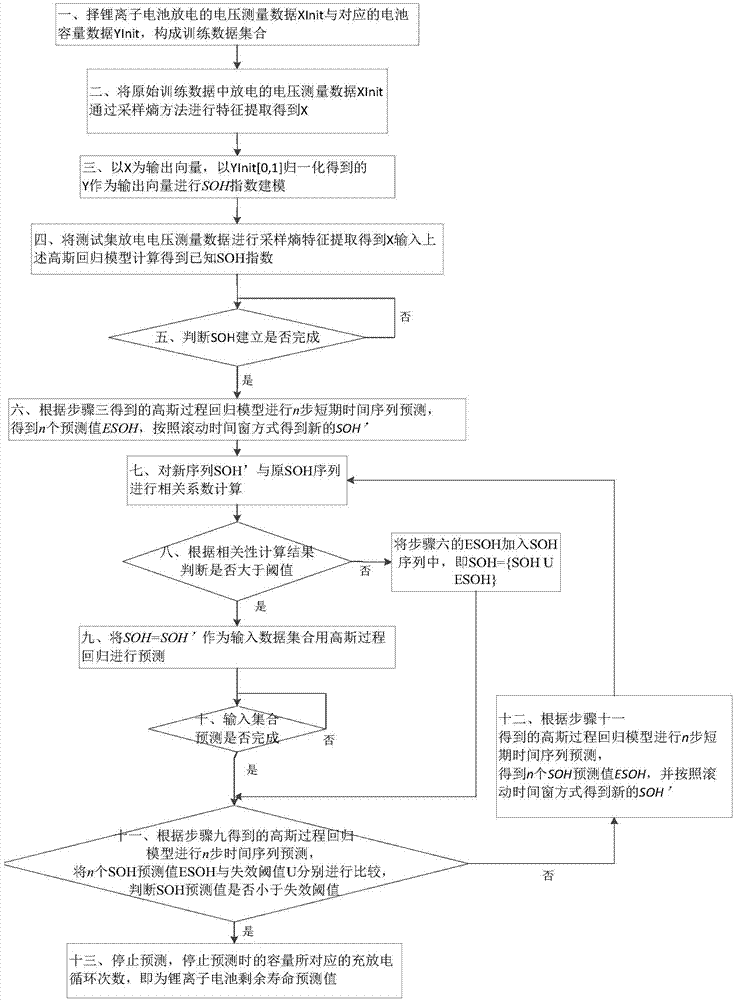
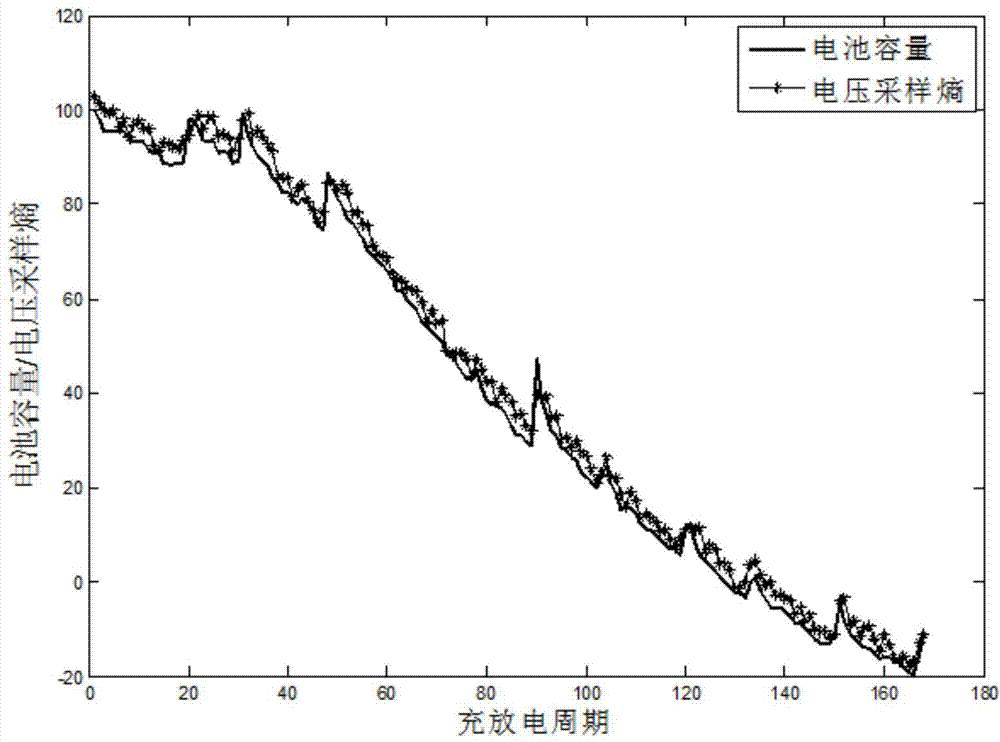
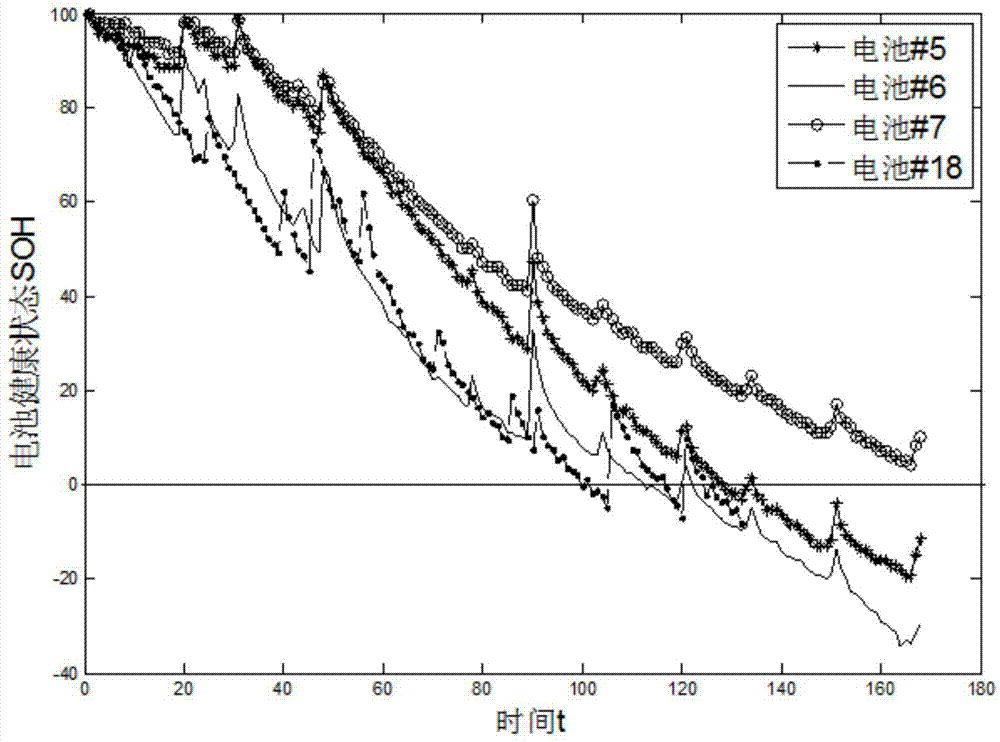
Method for remain useful life prognostic of lithium ion battery with model active updating strategy
InactiveCN103778280AEasy Adaptive AcquisitionFlexible inferenceElectrical testingSpecial data processing applicationsHealth indexEngineering
The invention relates to a method for remain useful life prognostic of a lithium ion battery with a model active updating strategy. According to a time series obtained through a voltage range of a discharge curve, conversion is conducted so that an equivalent discharge difference series obtained by discharge circulation at each time can be obtained, and therefore a health index time series of the ion battery is obtained; according to correspondence of a discharge voltage series and a time series, prognostic is conducted on the health index series to determine the remain useful life of the battery. Sampling entropy characteristic extraction and modeling are conducted on a charge voltage curve so that a relationship between a complete and accurate charge / discharge process and a battery performance index can be provided. On the basis of a performance index model, a short-term time series prognostic result is continuously updated to a known performance index data series and correlation analysis is conducted. According to the difference of the correlation degrees, retraining is conducted in the mode of training set expansion. The method is different from an existing iteration updating draining method, the prognostic model is updated dynamically, and therefore the prognostic precision is improved.
Owner:SHANGHAI JIAO TONG UNIV
IT-service concentrated monitoring and managing system based on Apriori algorithm
InactiveCN106681882AEasy to operateInnovative designHardware monitoringManagement unitMonitoring system
The invention provides an IT-service concentrated monitoring and managing system based on the Apriori algorithm. The IT-service concentrated monitoring and managing system is characterized by comprising an IT-service concentrated monitoring and managing unit and an IT-service-concentrated-monitoring-system core process unit; the IT-service concentrated monitoring and managing unit comprises an IT device state data collecting module, a state alarm trigger module and an operation-and-maintenance-event processing module; an IT-device-state-data concurrent collecting process, a state-alarm-rule diagnosis process and an alarm-correlated-event positioning process are adopted in the IT-service-concentrated-monitoring-system core process unit. The Apriori algorithm calculation is carried out with WEKA software, all kinds of data mining tasks can be borne, and include data pretreating, classifying, returning, clustering and correlation analysis to complete the task such as server-terminal automatic data mining, the operation performance is better optimized, design is novel, and the IT-service concentrated monitoring and managing system based on the Apriori algorithm is a quite-good design scheme.
Owner:上海瑞致软件有限公司
Defense method and system rejecting service attack based on data mining technology
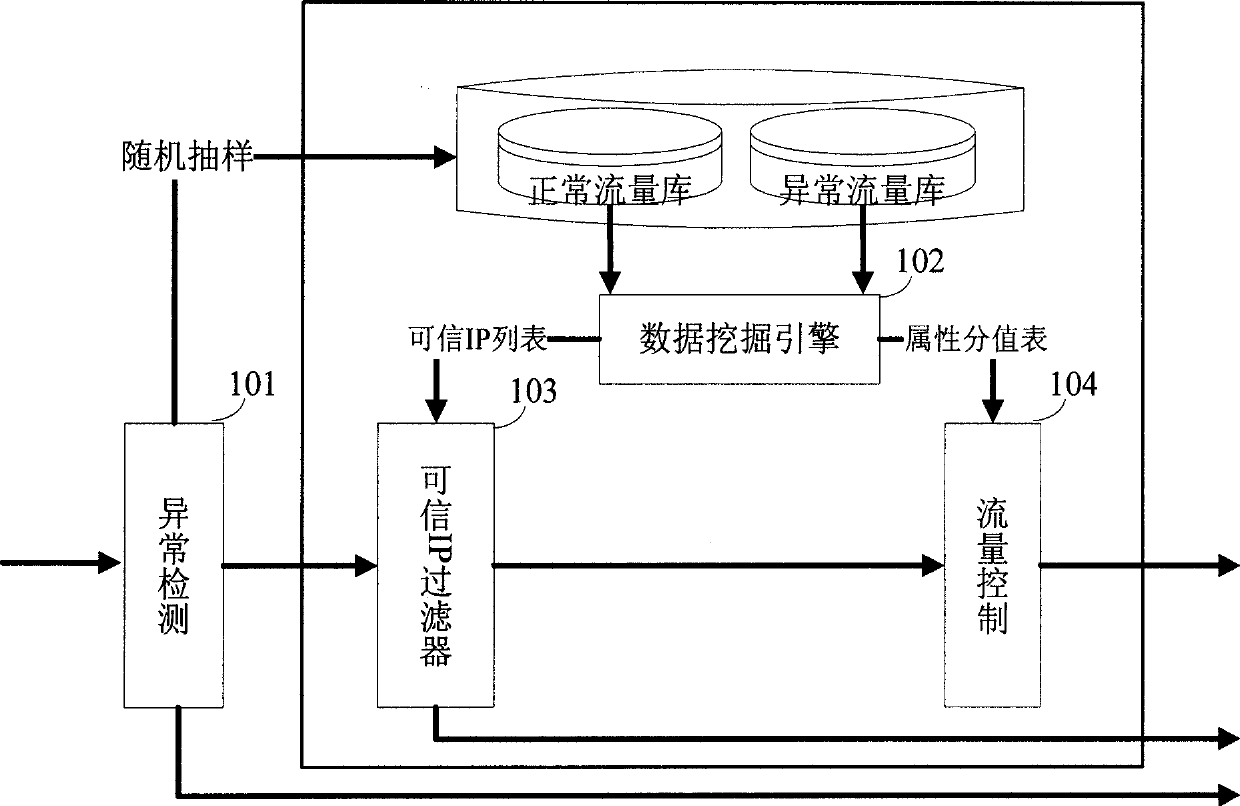
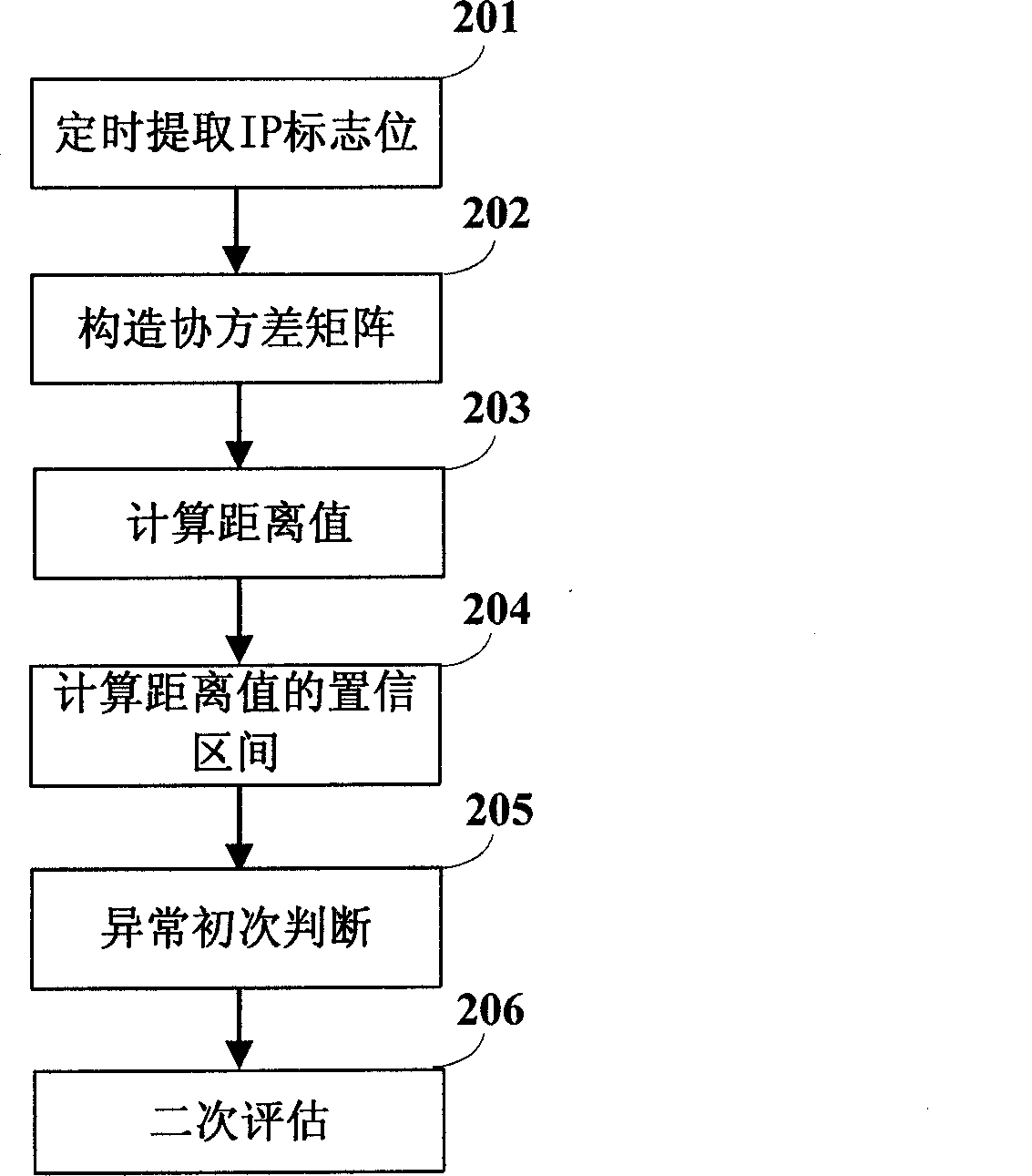
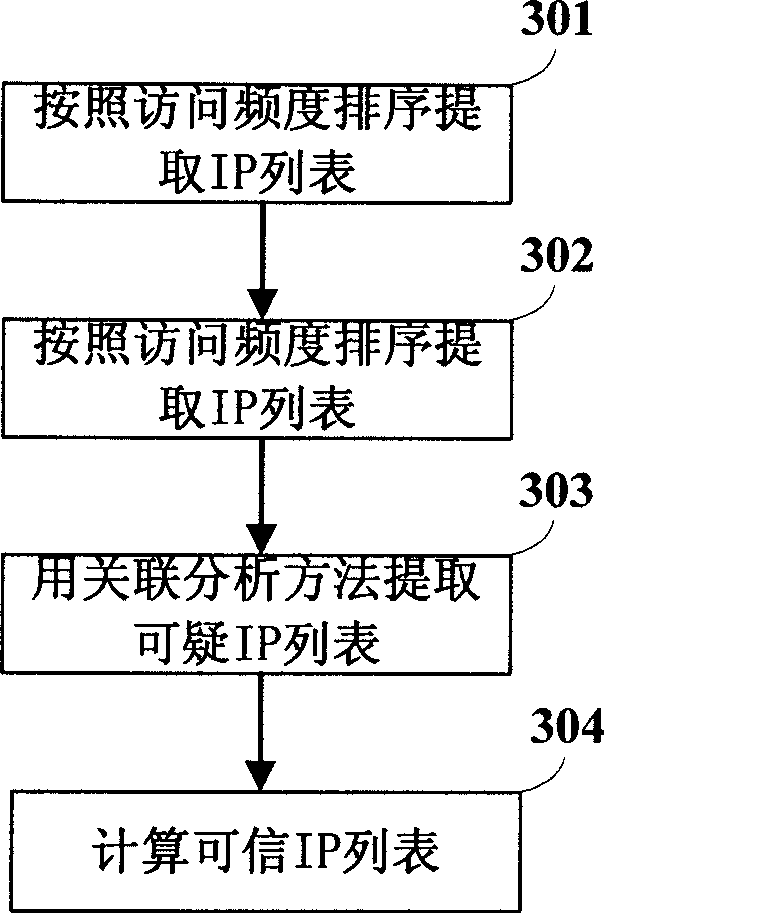
InactiveCN101383694AResolve failureTrusted source IP is realData switching networksSecuring communicationTraffic capacityCovariance method
The invention discloses a dos attacking and defending method based on the data mining technique and a system thereof. The system comprises an anomaly detection module, a data mining engine module, a trust IP list filter module and a flow control module. The anomaly detection module adopts an efficient analysis covariance method to analyze the current network flow so as to judge the current system is abnormal or not, the data mining engine module uses a correlation analysis method to pick up a trust IP list to be used for filtering a data packet. The attacking system overcomes the shortcomings of the traditional system based on the trust IP list filtration, and can effectively differentiate normal flow and abnormal flow when defending the attack. The data mining engine module of the system picks up and transmits the IP trust list and the attribute value list with high efficiency so as to cause the system to defend the dos attack (Dos / DDoS) in real time.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
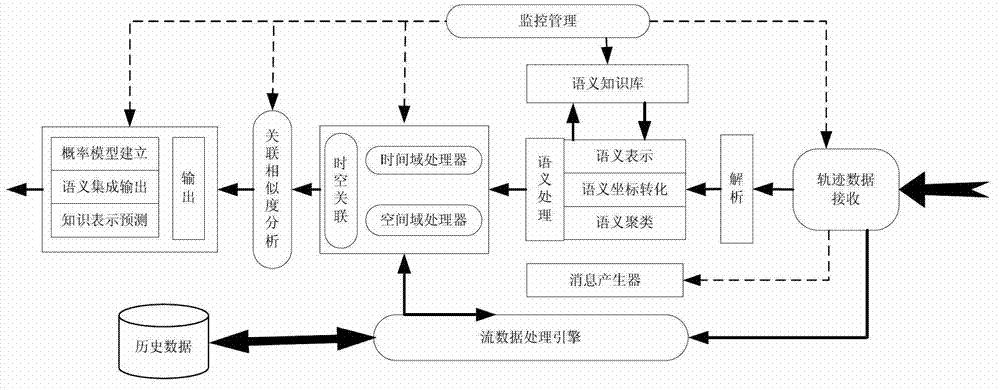
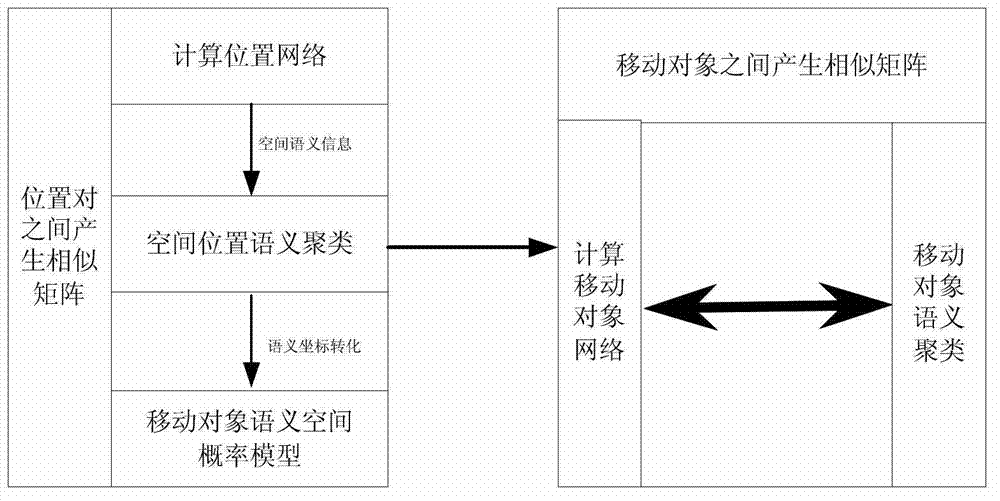
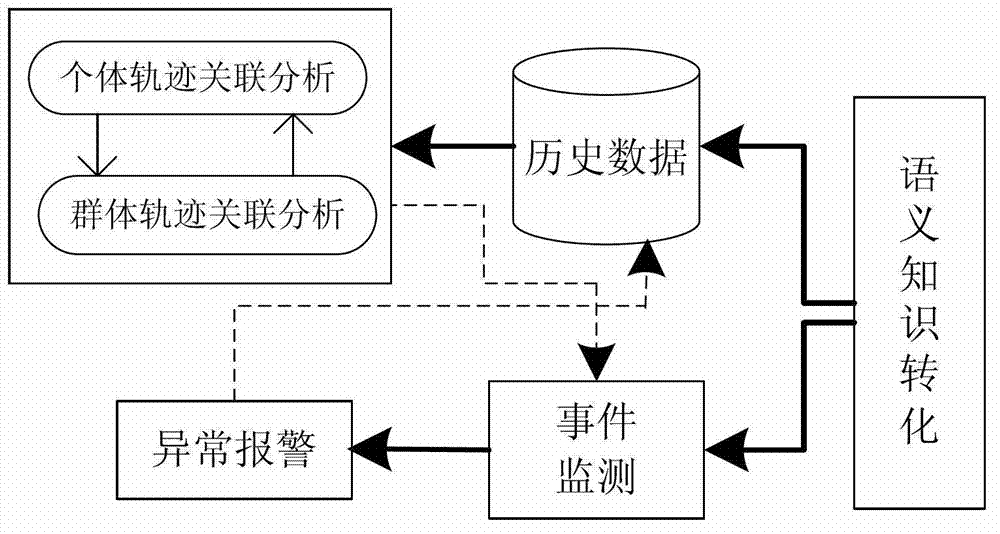
Movement space-time trajectory analysis method in sense network environment
ActiveCN103593361AEasy constructionEasy maintenanceSpecial data processing applicationsReal time analysisCorrelation analysis
The invention relates to the technical field of movement behavioral analysis and prediction in a sense network environment, and specifically to a movement space-time trajectory analysis method in the sense network environment. The movement space-time trajectory analysis method in the sense network environment comprises data reception of receiving trajectory movement position data generated by a positioning device and resolving the data format into a data format applicable to data treatment; semantic treatment of performing clustering operation on the semantic trajectory data; space-time correlation of performing characteristic analysis and statistics on clustered semantic trajectory data in a time domain and a space domain, and performing time-space correlation analysis in combination with the time domain and the space domain; correlation similarity analysis of calculating space-time correlation similarity of the semantic trajectory and performing analysis and calculation on the correlation among different space domains and different movement objects; outputting a result. The movement space-time trajectory analysis method in the sense network environment solves the problem of continuous treatment and mutual correlation of time and space dimensions in a traditional transactional database, and meets the need from a sense network application service to real-time analysis of trajectory movement data.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
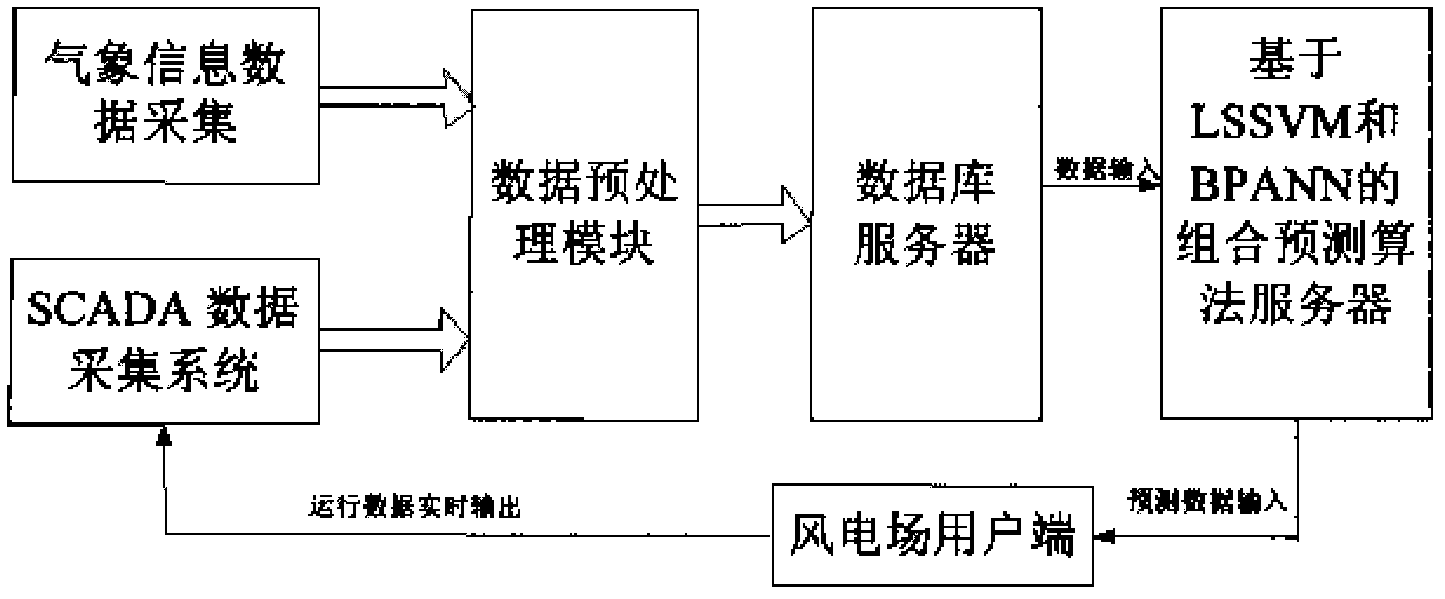
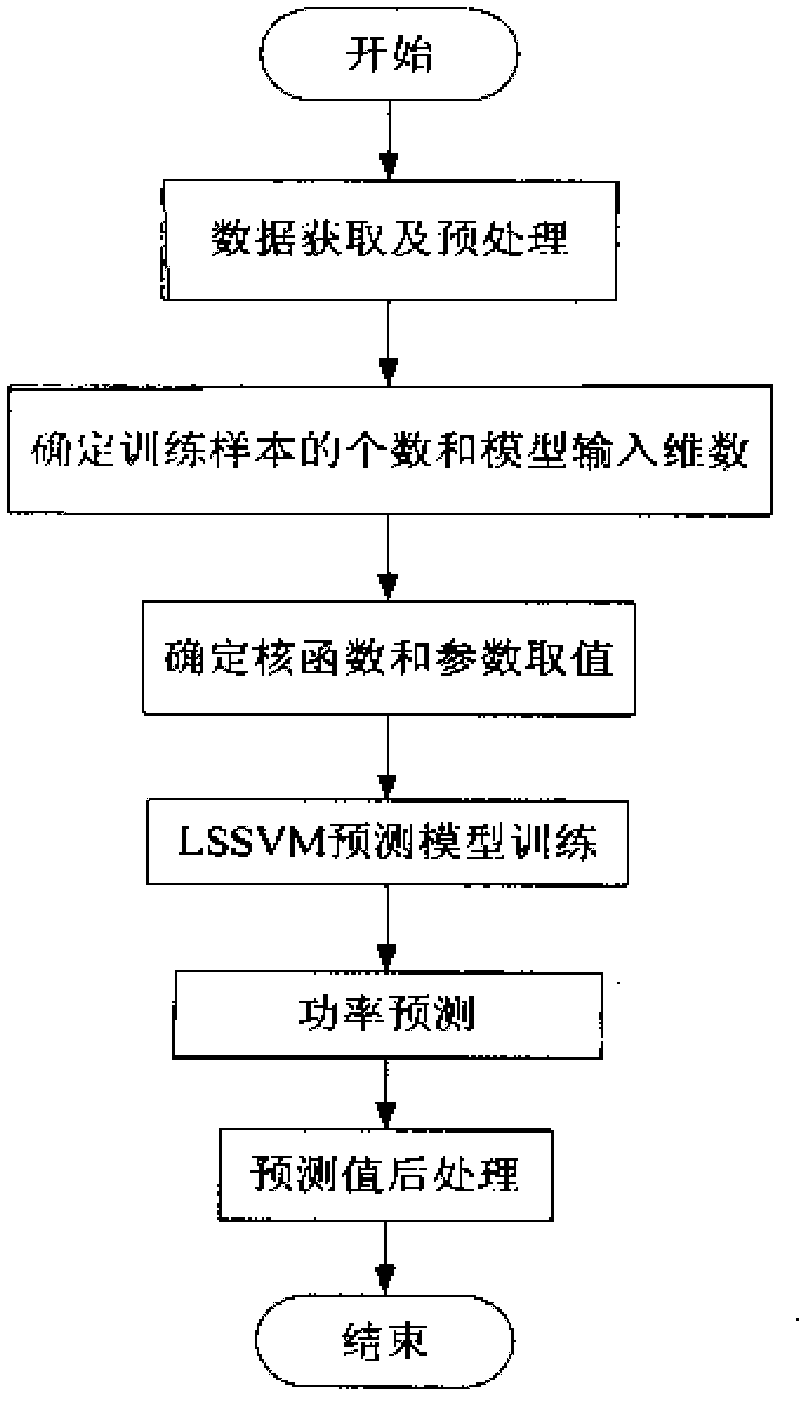
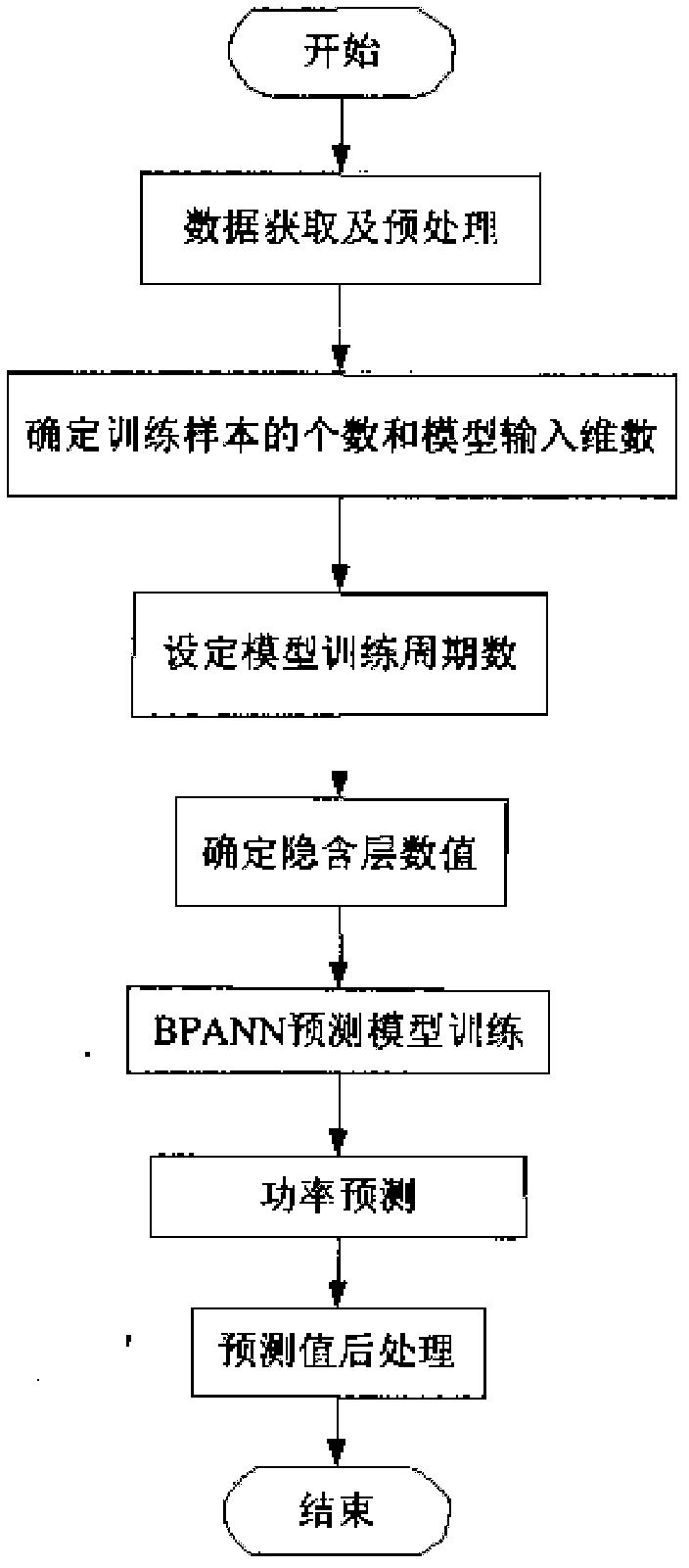
Combination forecast modeling method of wind farm power by using gray correlation analysis
ActiveCN102663513AAvoiding the quadratic programming problemFast solutionForecastingNeural learning methodsPredictive modellingPrediction algorithms
The invention discloses a combination forecast modeling method of wind farm power by using gray correlation analysis, belonging to the technical field of wind power generation modeling. In particular, the invention is related to a weighted combination forecast method of wind power based on a least square support vector machine and an error back propagation neural network. The forecast method comprises that forecasted values of wind speed and wind direction are acquired in advance from meteorological departments while real-time output power is acquired from a wind farm data acquiring system; that the forecasted values of wind speed and wind direction and the real-time output power are inputted into a data processing module for data analyzing extraction and data normalization, and then normalized data is loaded to a database server; processed data in the database server is extracted by a combination forecast algorithm server to carry out model training and power forecast, and the wind farm sends running data to the data processing module in real time to realize rolling forecasting. The method of the invention achieves the goal of combination forecast of wind farm output in a short time. The method not only maximally utilizes advantages of two algorithms but also increases forecast efficiency by saving computing resources and shortening computing time.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
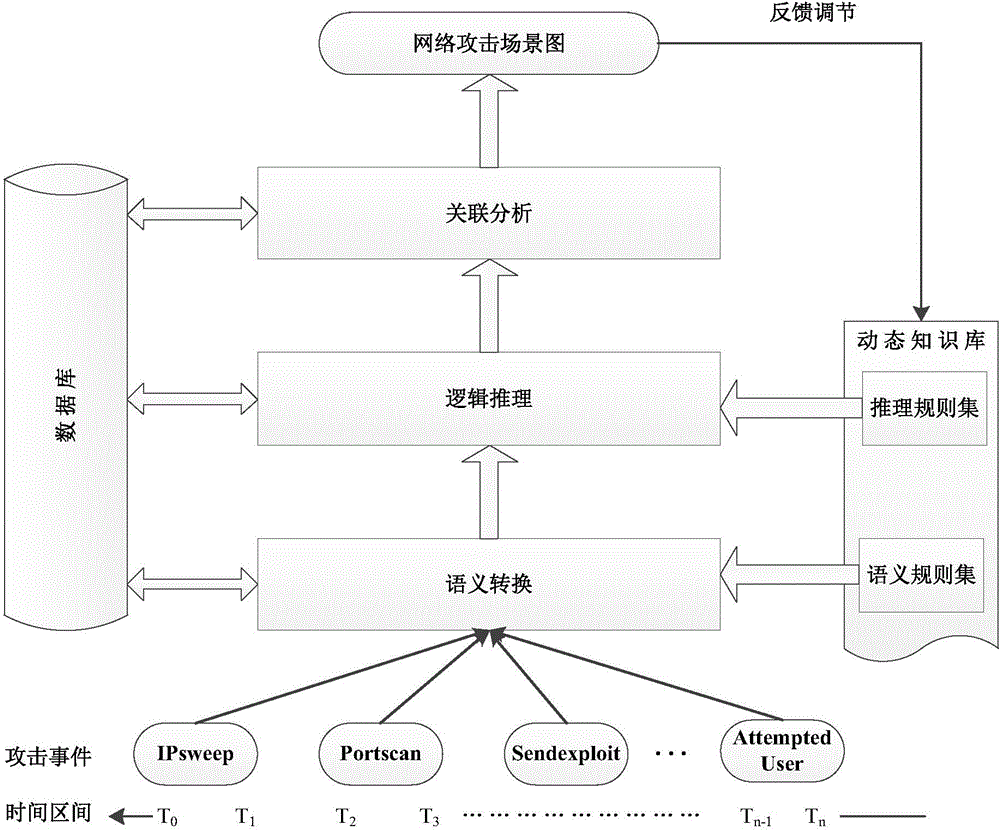
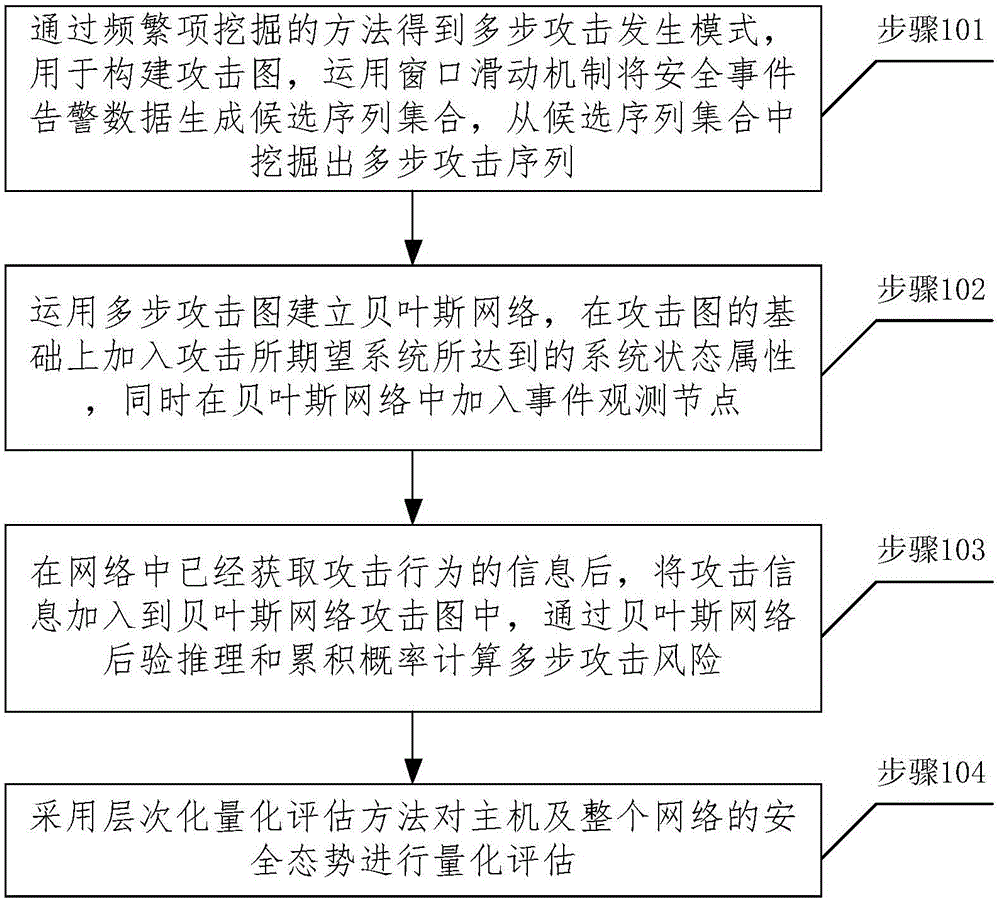
Bayesian network-based multi-step attack security situation assessment method
ActiveCN106341414AReal-time assessmentEffective assessmentPlatform integrity maintainanceTransmissionAttack graphCorrelation analysis
The invention relates to a network security situation assessment method, in particular, a Bayesian network-based multi-step attack security situation assessment method. The method includes the following steps that: multi-step attack generating patterns are mined through association analysis, so that an attack graph can be constructed; a Bayesian network is established according to the multi-step attack graph, attack wills, probability of success of attacks and the accuracy of event monitoring are defined as the probability attributes of the Bayesian network; based on the event monitoring, a multi-step attack risk is calculated according to the posterior reasoning and cumulative probability of the Bayesian network; and the security situations of a host and the whole network are quantitatively assessed according to a hierarchical quantitative assessment method. With the method of the invention adopted, the problem of lack of correlation analysis in a network security situation assessment process can be solved. According to the method of the invention, monitoring events are taken into risk assessment, and a network security situation assessment model is accurately established, and therefore, the effectiveness and real-time performance of the method of the invention can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
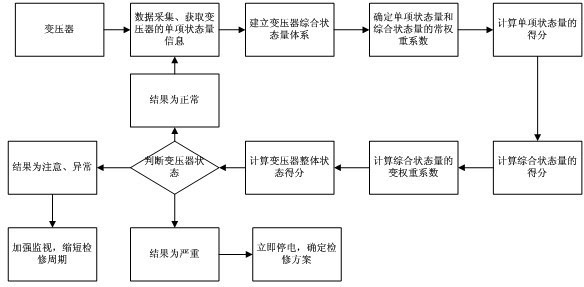
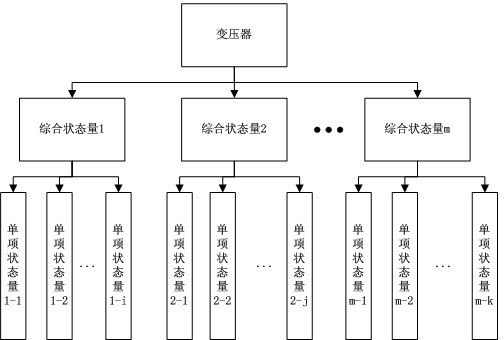
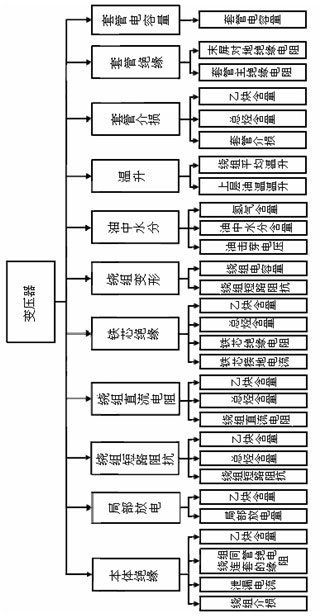
Transformer state evaluation method based on correlation analysis and variable weight coefficients
InactiveCN102621421AQuickly judge the running statusEasy programmingElectrical testingTransformerWeight coefficient
The invention relates to a transformer state evaluation method based on correlation analysis and variable weight coefficients, which includes collecting data of transformer states; classifying and processing the collected data as a basis of the transformer state evaluating; evaluating the transformer states; applying a correlation analysis method to establish a comprehensive state quantity evaluation system of the transformer; utilizing a single state quantity score calculating method and a transformer overall score calculating method to grade the transformer states; extracting constant weight coefficients of each of single state quantities and comprehensive state quantities; calculating constant weight coefficients of each of the comprehensive state quantities; calculating an overall score of the transformer states based on scores of each of the comprehensive state quantities and the constant weight coefficients; and determining a transformer operation state based on the overall score of the transformer states. The transformer state evaluation method has the advantages that evaluation models are simple and easy to program, no abundant state evaluation samples are needed, operation states of transformers can be determined rapidly, and operation states and conditions of transformers are truly reflected.
Owner:GUIYANG POWER SUPPLY BUREAU OF GUIZHOU POWER GRID CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com