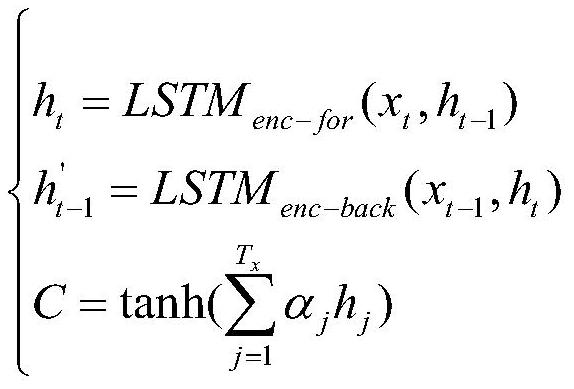Patents
Literature
411 results about "Honeypot" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site, but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, who are then blocked. This is similar to police sting operations, colloquially known as "baiting" a suspect.
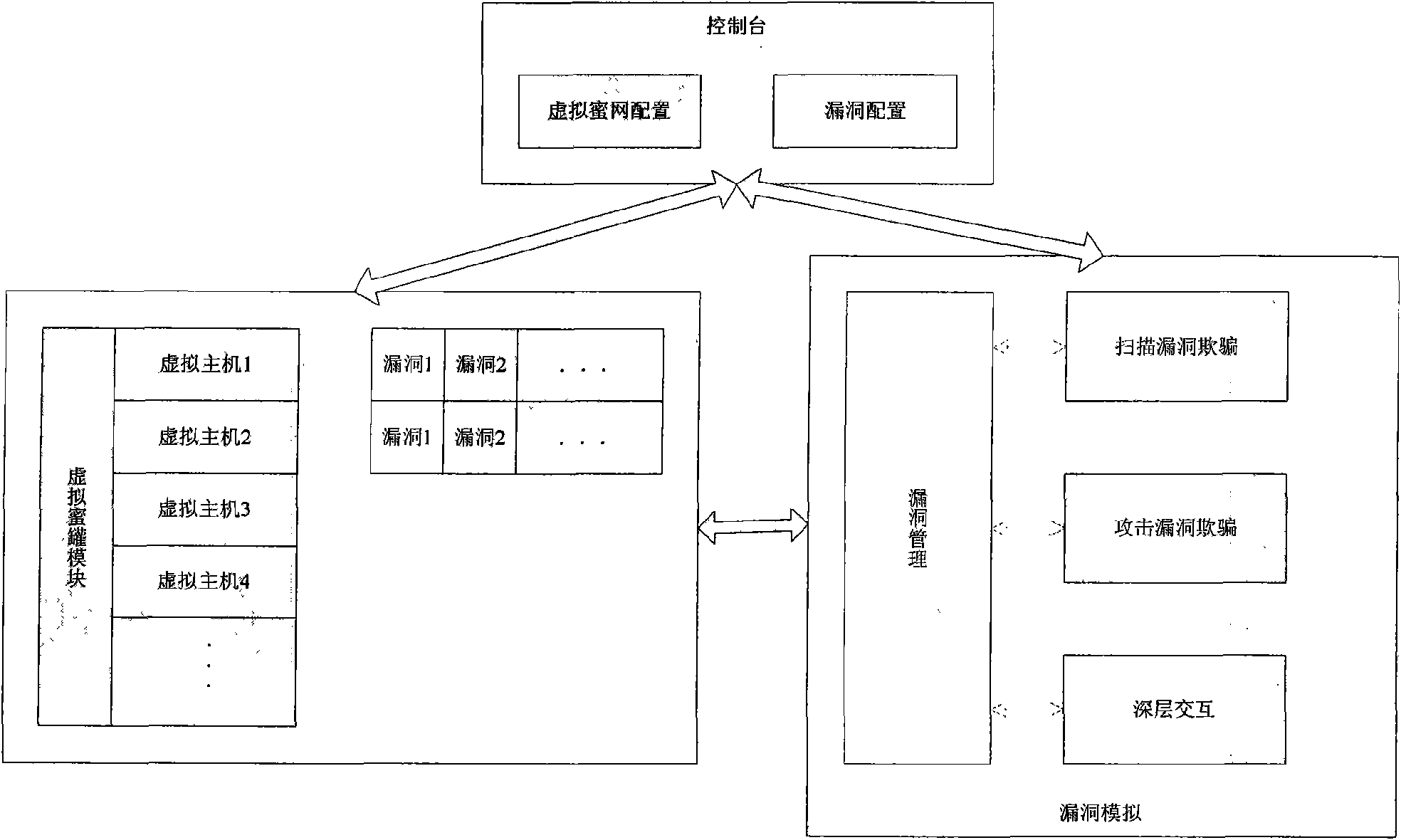
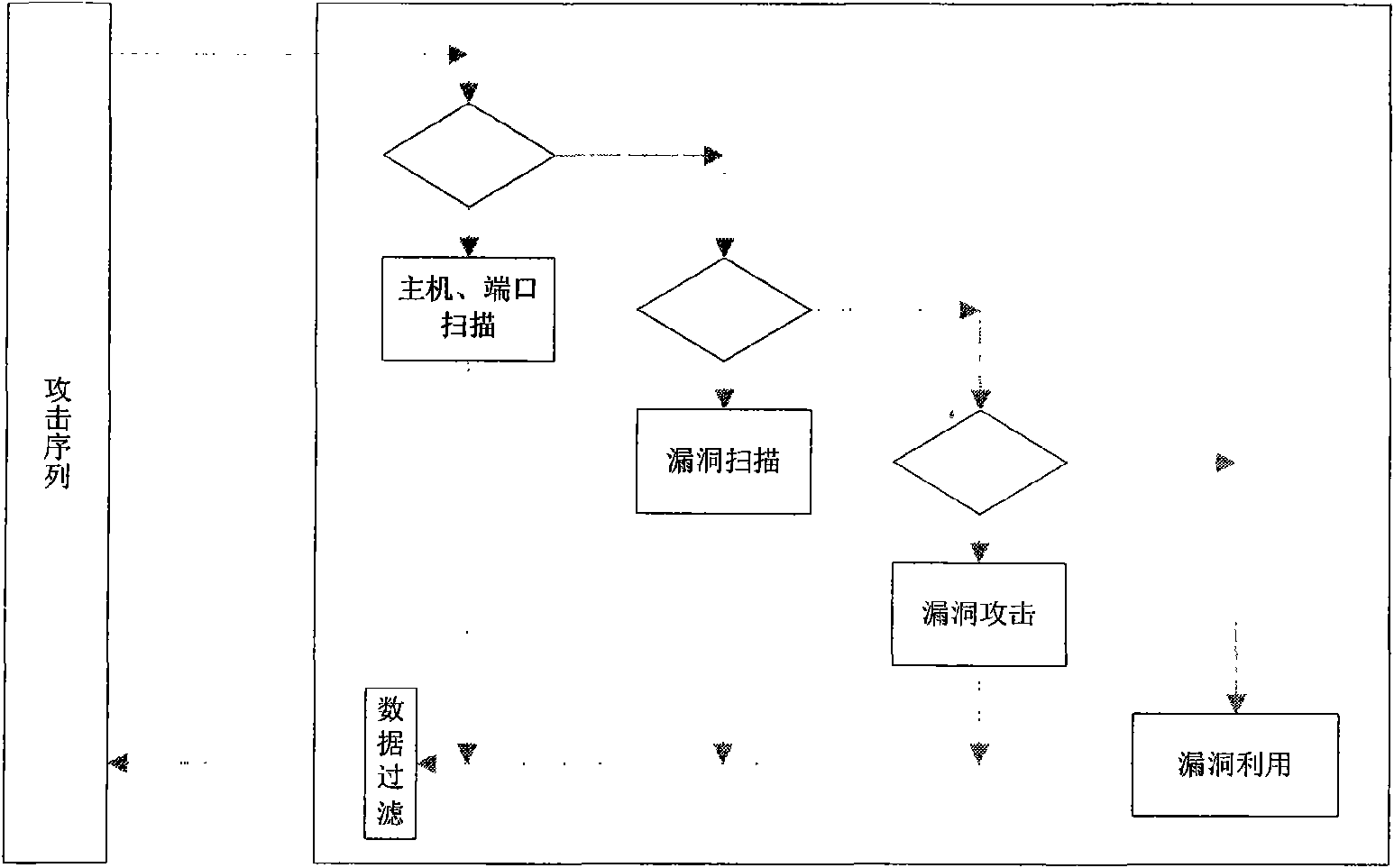
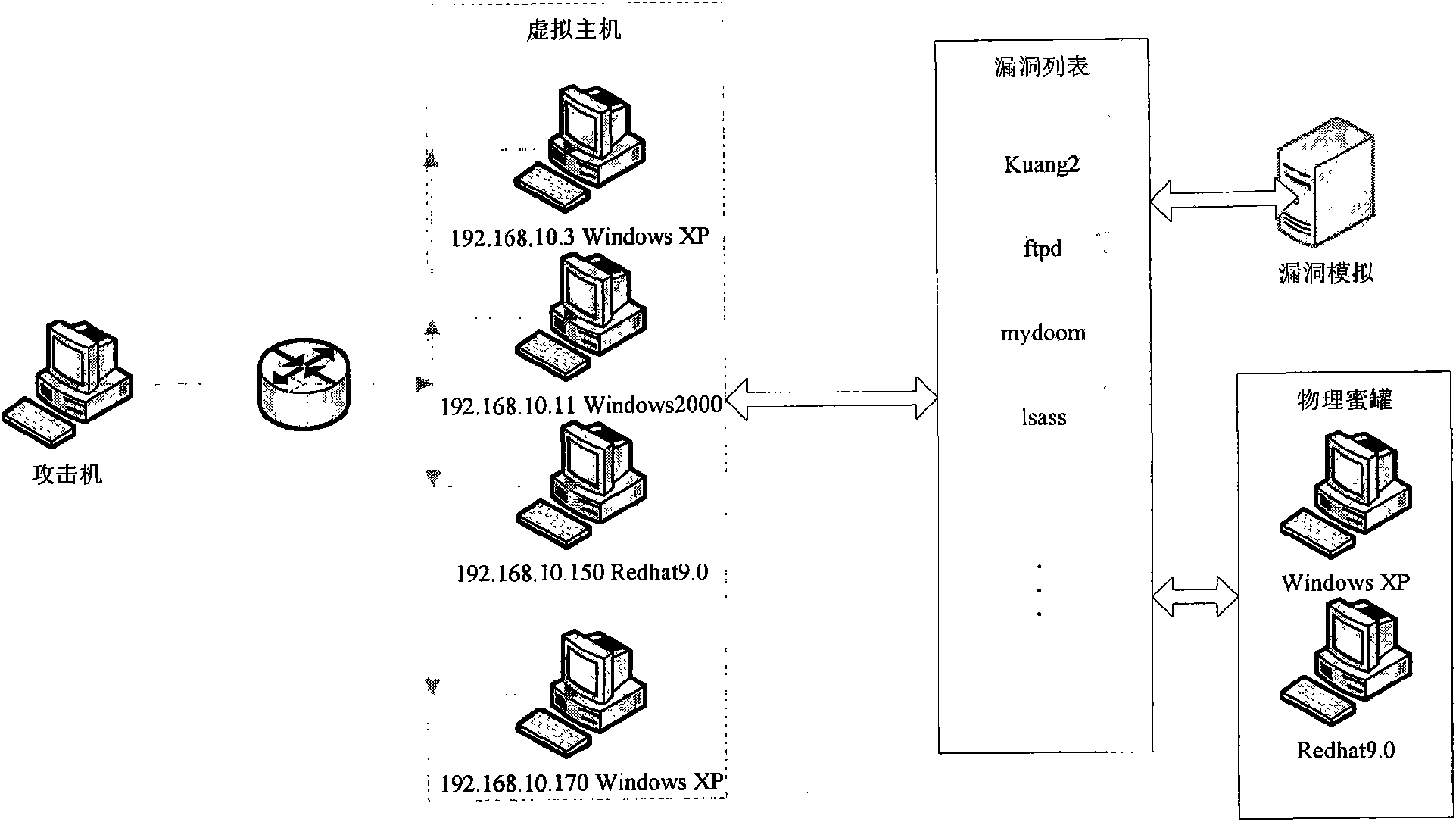
Vulnerability simulation overload honeypot method
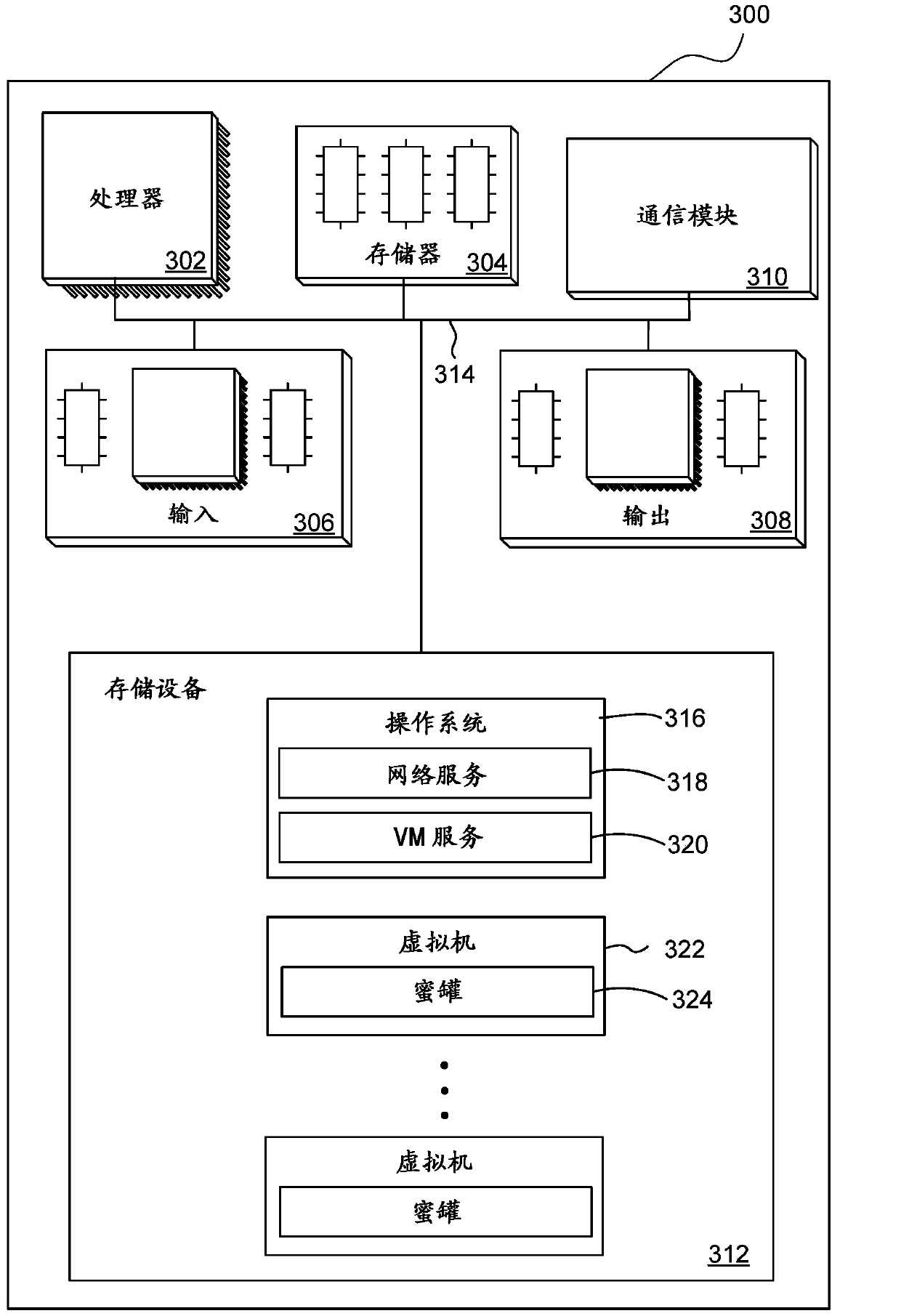
InactiveCN101567887AAdd interactive functionComplete Attack DataData switching networksControl powerOperating system
The present invention discloses a vulnerability simulation overload honeypot method which comprises a host computer, a port scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability attach deception simulating module, a data auditing module and a vulnerability utilizing module. When the attach sequence arrives at the simulated honeypot, a simulated honeypot system is used for processing according to the situation. When an attacker executes vulnerability scanning to the virtual host computer, the simulated honeypot responds and processes according to the vulnerability configuration information. Afterwards, these vulnerabilities are used for further attacking. Hereon, the simulated honeypot system transmits the vulnerability attack data flow to a vulnerability honeypot system. The vulnerability utilization attach of the attacker is processed and responded by a vulnerability attack simulating module. Finally, when the attacker successfully obtains the control power through the vulnerability attack, the attack data hereon is transmitted to a physical honeypot module. All attack processes and related data are recorded by a data auditing module for analyzing comprehensively. The method reduces the number of hardware devices in the honeynet and reduces the cost.
Owner:中国人民解放军总参谋部第五十四研究所 +2
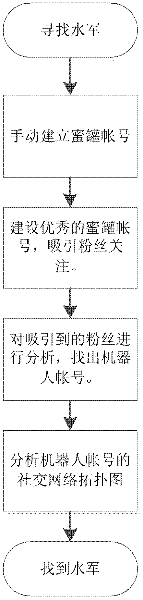
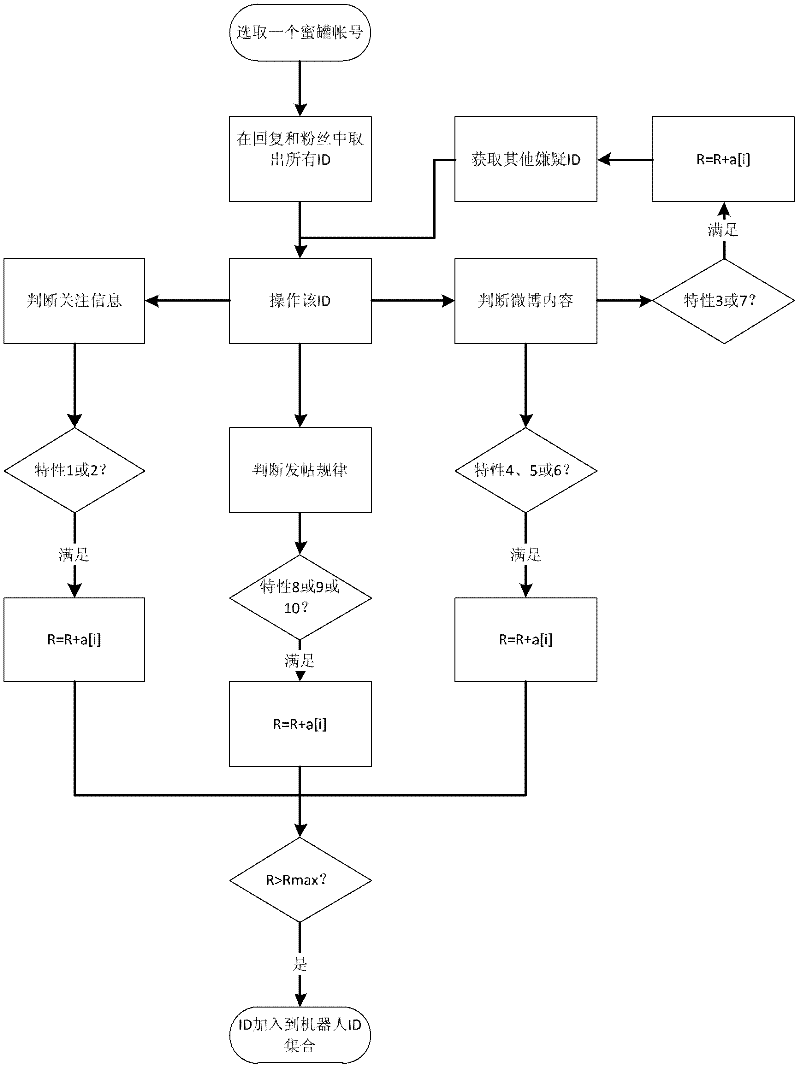
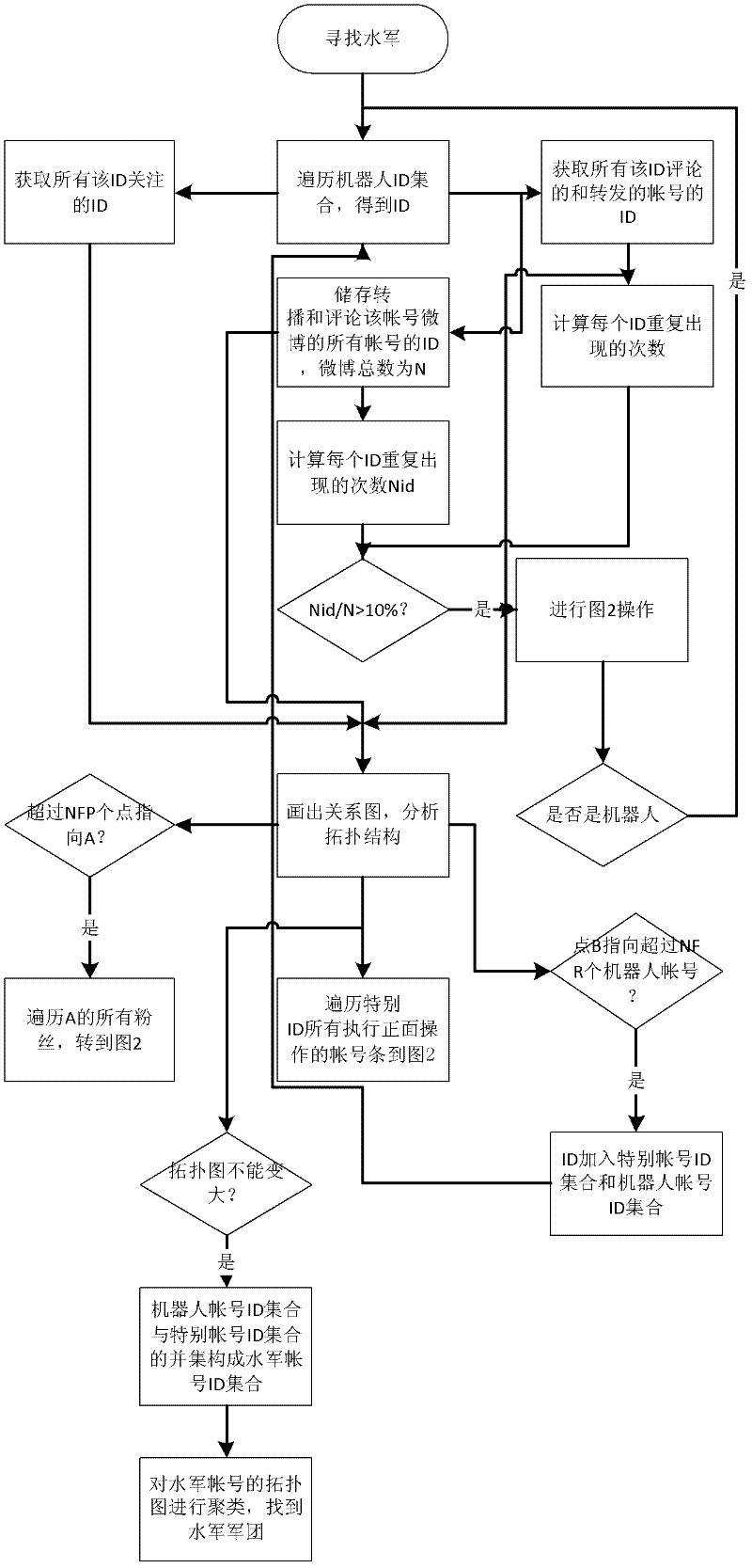
Method for detecting and finding online water army
InactiveCN102571484ADetect and control the spreadMaintain the truthData switching networksFeature vectorData mining
The invention discloses a method for detecting and finding an online water army, which comprises the following steps: firstly, building honeypot accounts; uniformly planning all honeypot accounts by an account management module; determining the posting and attention paying strategy of the honeypot accounts; detecting the account of a robot from collected accounts; describing an account characteristic vector by an account characteristic module, wherein the vector comprises multiple dimensions; detecting the online water army for the collected accounts by the account detection module according to the degree for the account characteristic vector conforming to a robot account characteristic; and finding more robot accounts and water armies by the detected robot accounts. According to the method, more robot accounts or water army accounts can be found from a social network to determine the distribution of the water army group.
Owner:SHANGHAI JIAO TONG UNIV
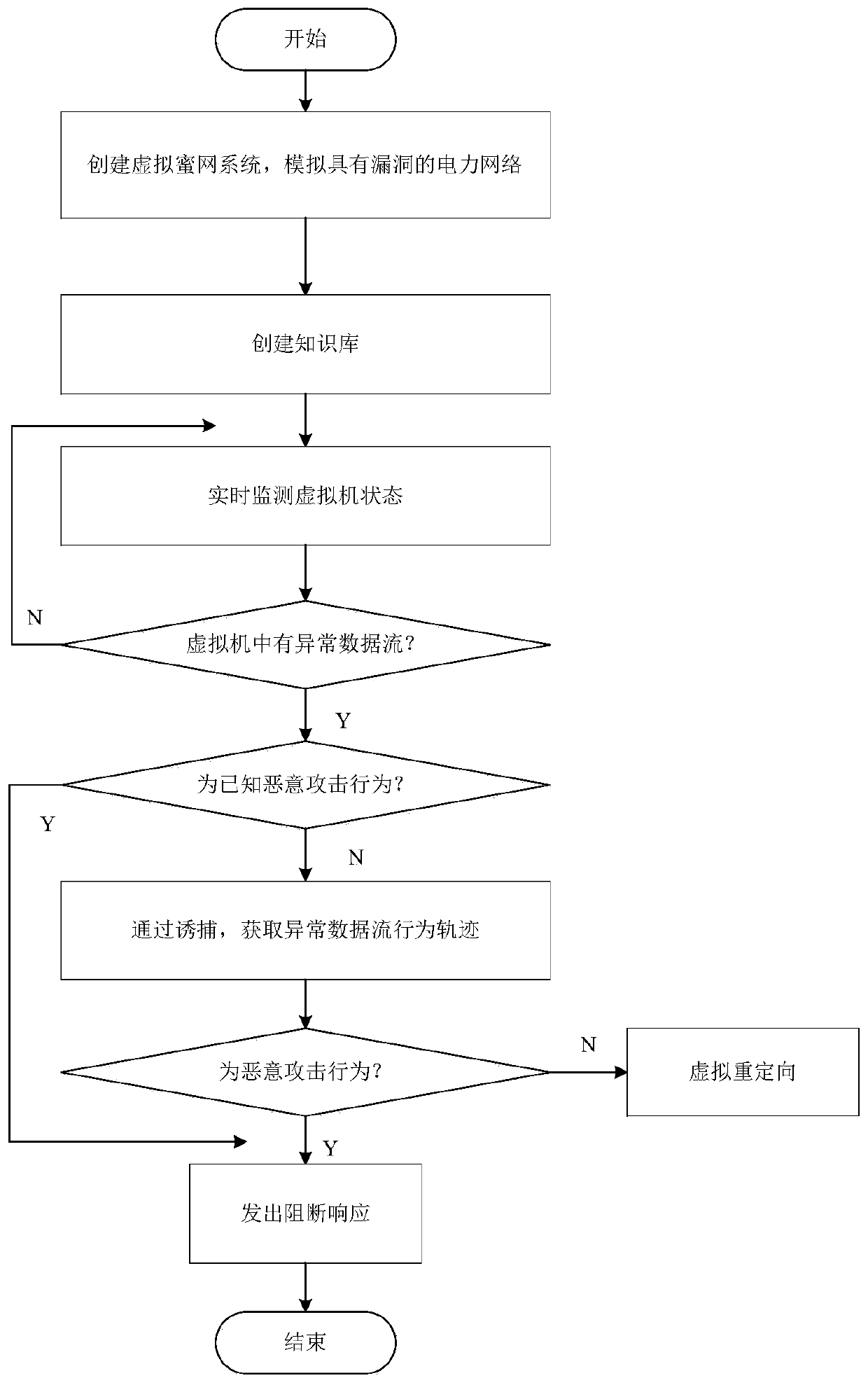
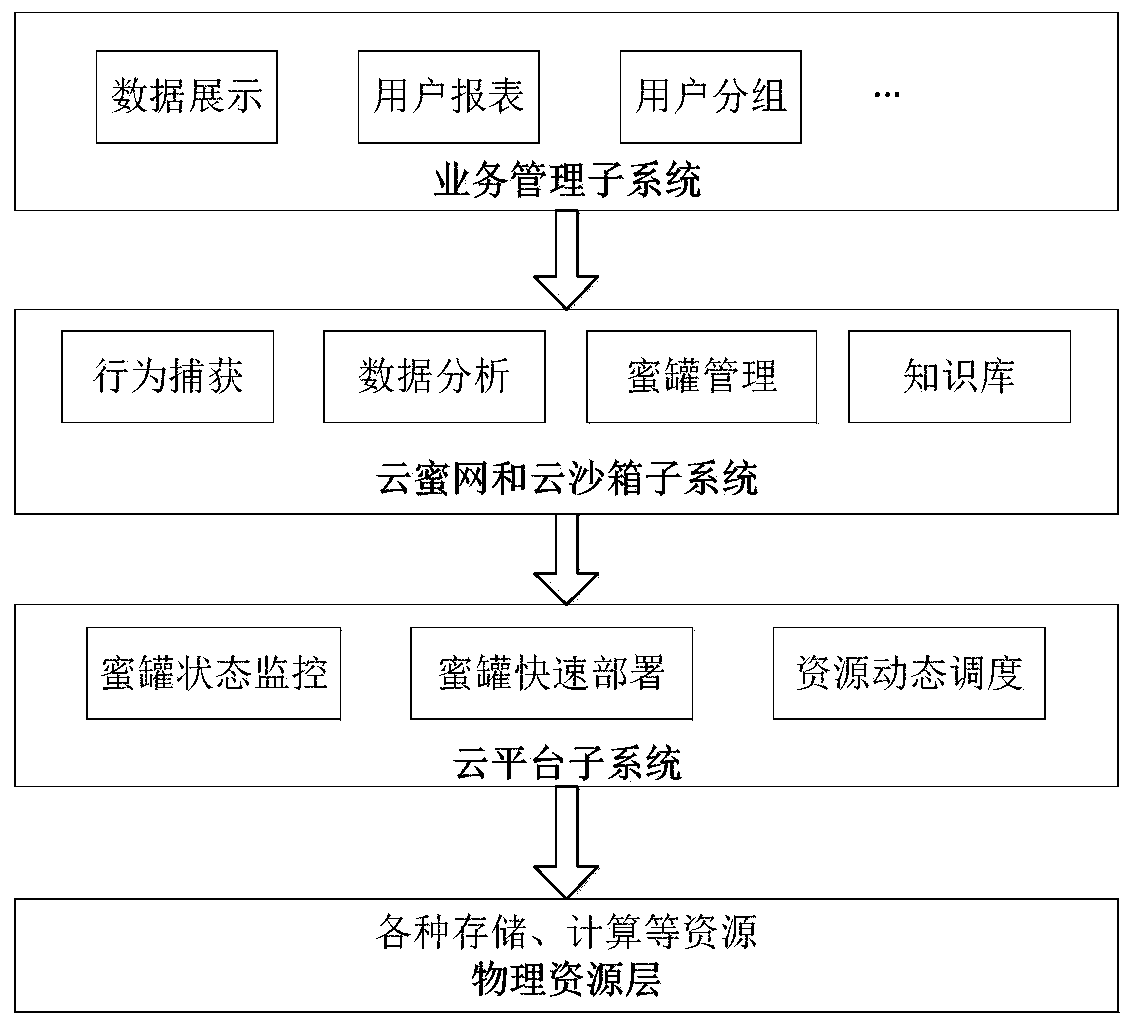
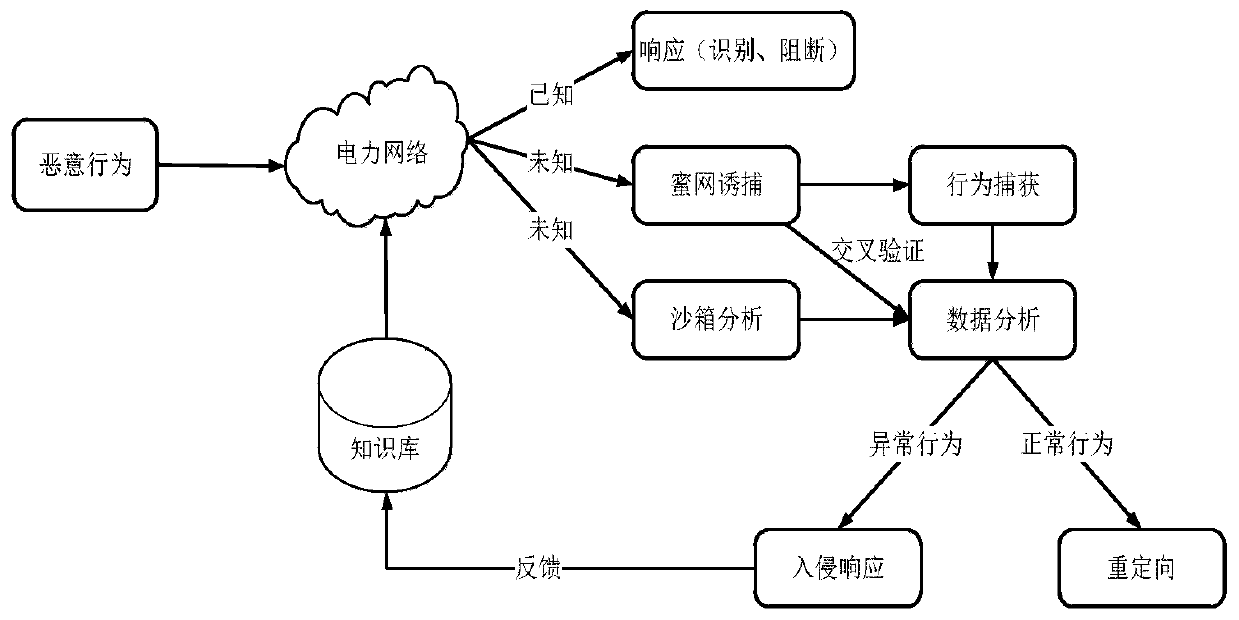
Power monitoring active defense method and system based on virtualization dynamic deployment
InactiveCN110784476AImprove securityReduce the likelihood of being detectedTransmissionVirtualizationData stream
The invention relates to a power monitoring active defense method and system based on virtualization dynamic deployment, and the method comprises the steps: (1), building a virtual honeynet system, and simulating a real business system of a power network; (2) monitoring the state of the virtual machine in real time, and carrying out honeynet trapping to obtain an abnormal behavior track when an abnormal data flow is monitored; and (3) analyzing whether the behavior is a malicious attack behavior or not, and carrying out blocking response. The active defense system adopting the honeypot and sandbox technology can reduce the possibility that a real service network of the power system is detected, increase the attack cost difficulty and timeliness of attackers, and effectively complement passive protection measures existing in the power system.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +2
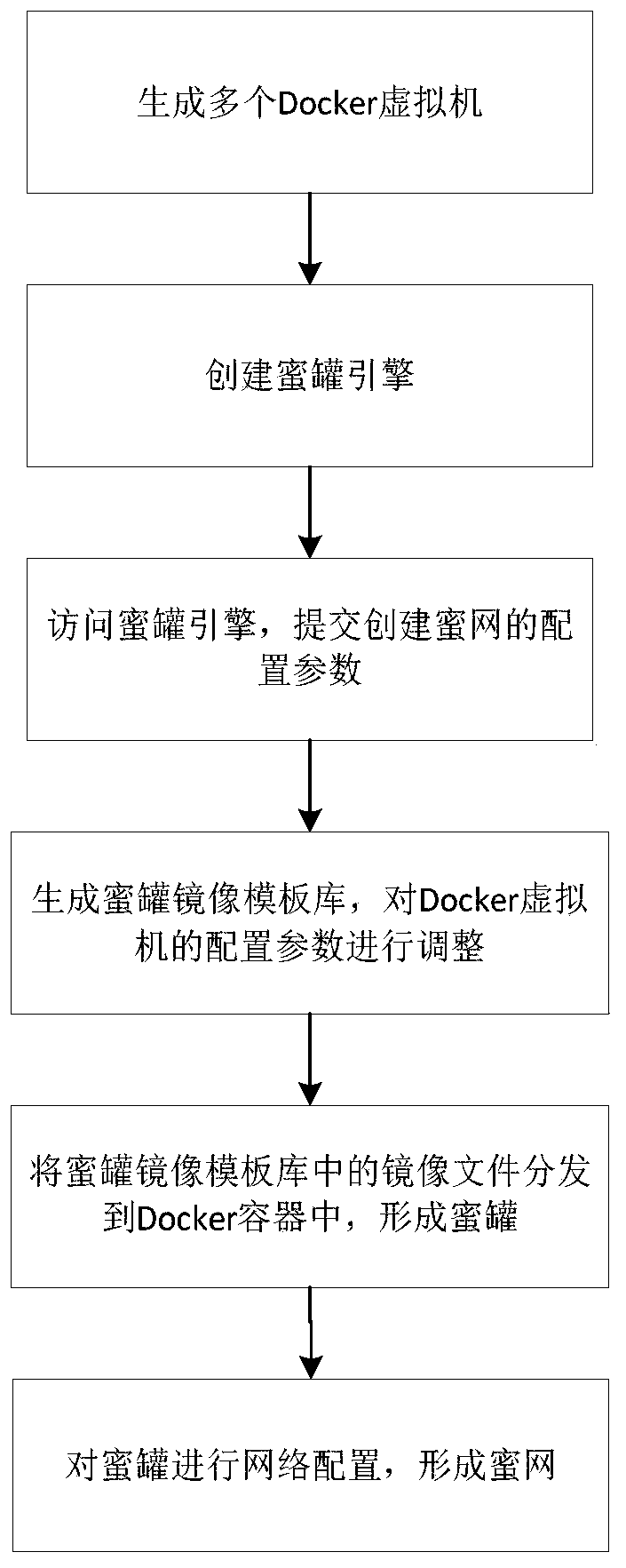
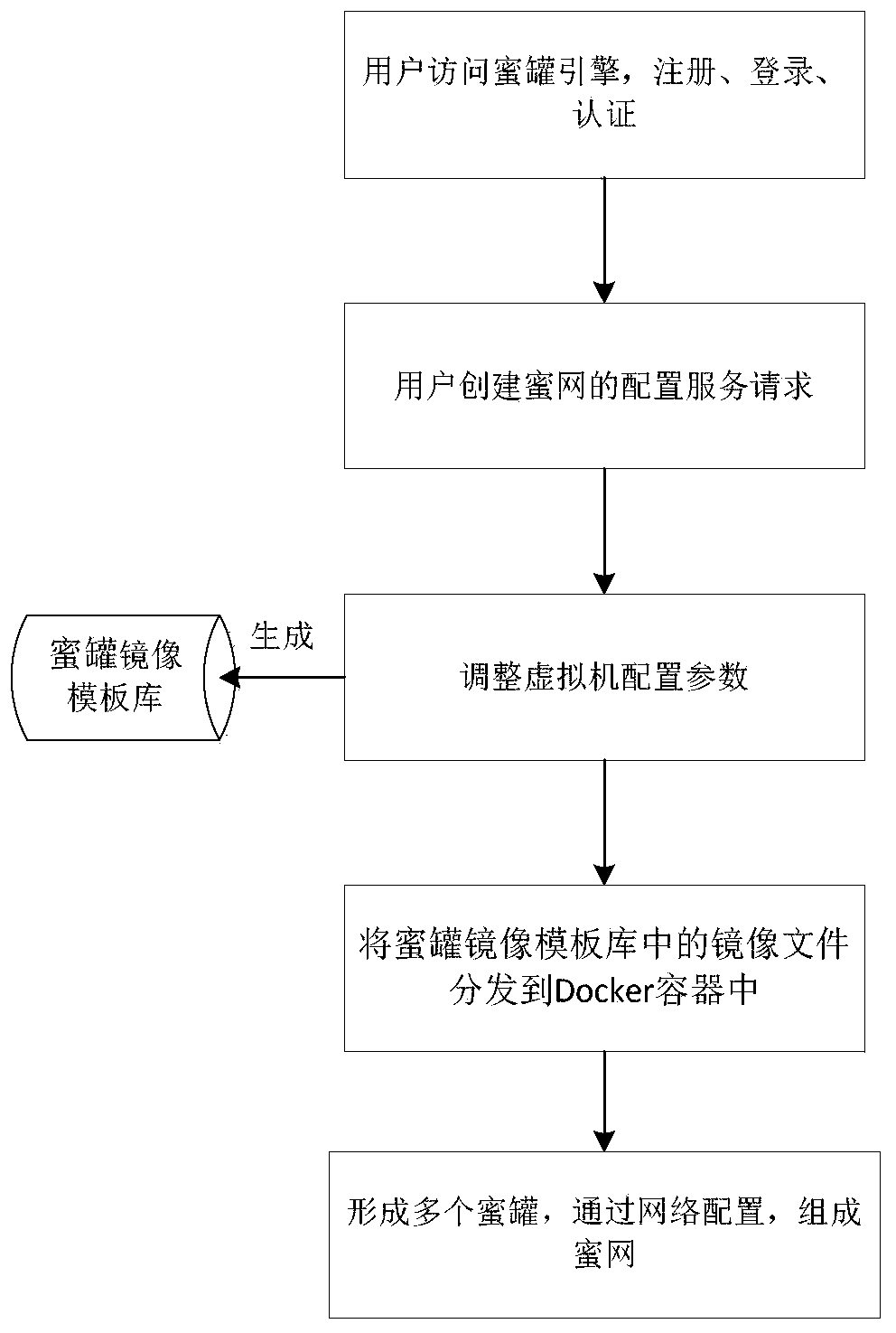
Virtual cloud honeynet deployment method, device and system and computer readable storage medium
InactiveCN110784361ALow costAchieve maximum utilizationData switching networksVirtualizationIndustrial systems
The invention relates to a virtual cloud honeynet deployment method, device and system and a computer readable storage medium. The method comprises the steps of (1) generating a plurality of Docker virtual machines; (2) creating a honeypot engine; (3) submitting configuration parameters for creating the honeynet; (4) generating a honeypot mirror image template library, and adjusting configurationparameters of each Docker virtual machine; (5) distributing the mirror image files in the honeypot mirror image template library to containers of the Docker virtual machines to form a plurality of honeypots; and performing network configuration on the Docker virtual machine corresponding to each honeypot to form a honeynet. The method is simple in configuration and high in starting speed, meanwhile, the cost of honeypot deployment in the aspect of physical host hardware resources in an industrial system is reduced, and the problems that in a traditional virtualization technology, configurationis tedious, the starting speed is low, and the hardware resources are wasted can be solved.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +2
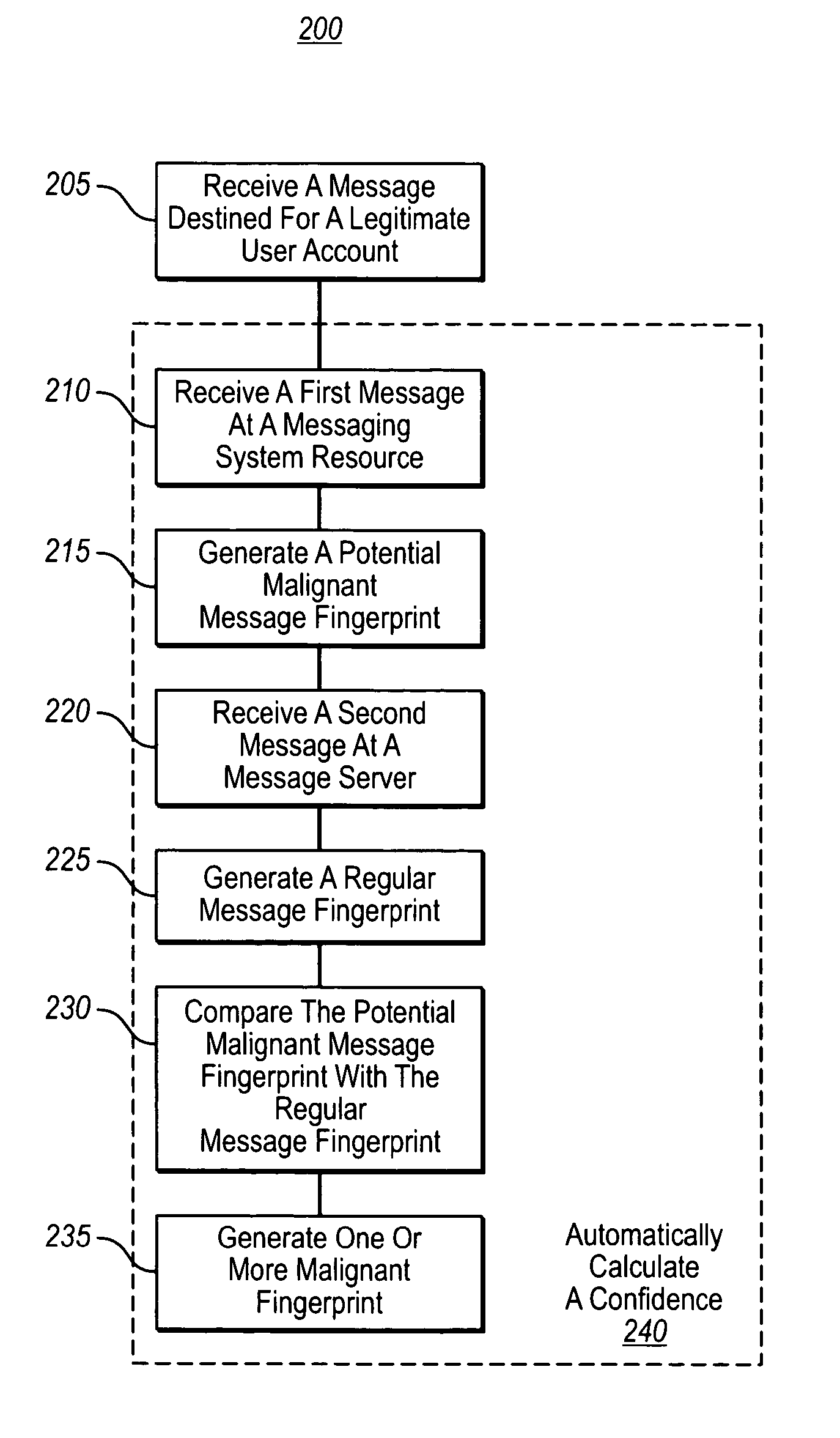
Automatic elimination of viruses and spam
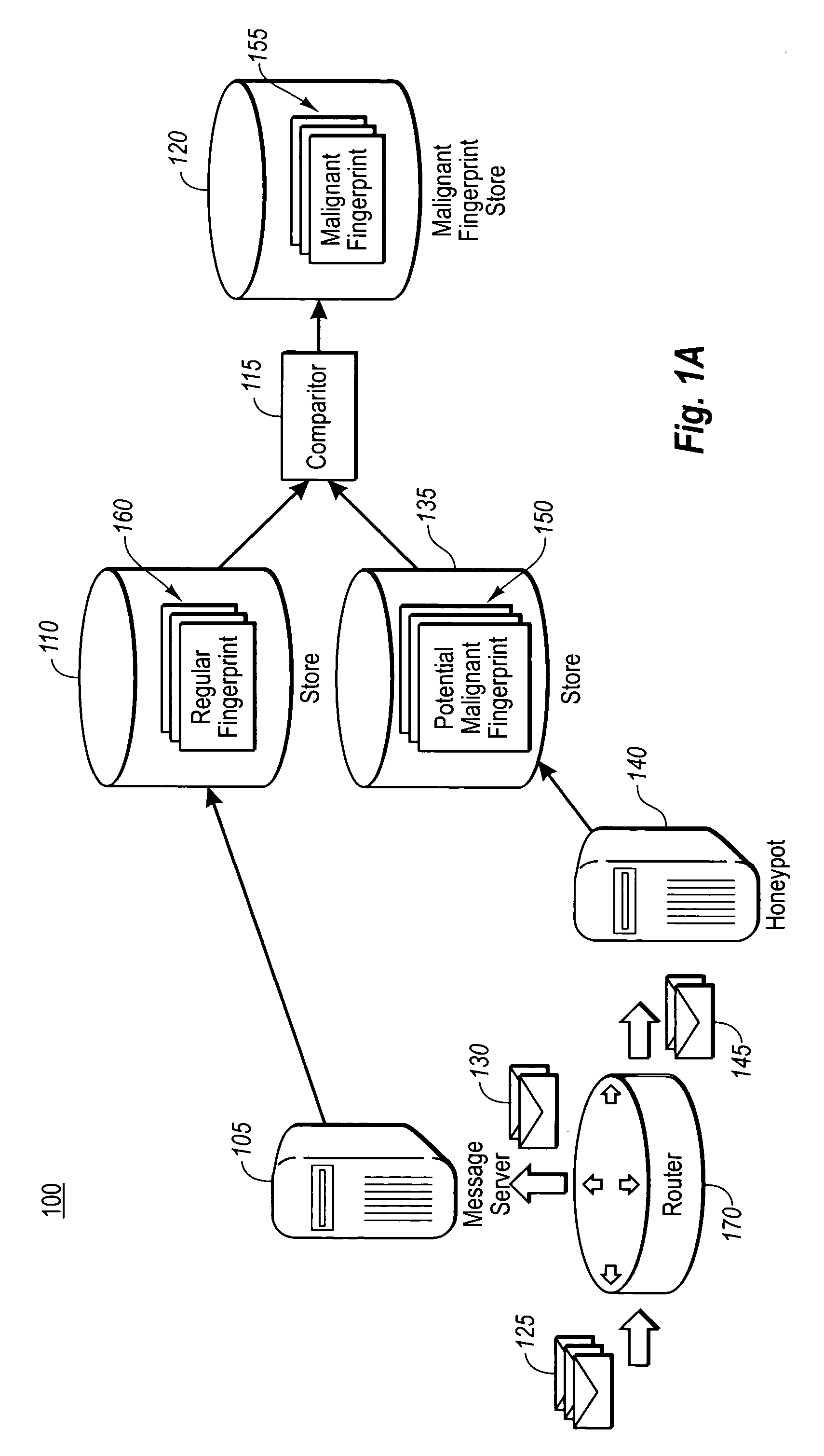
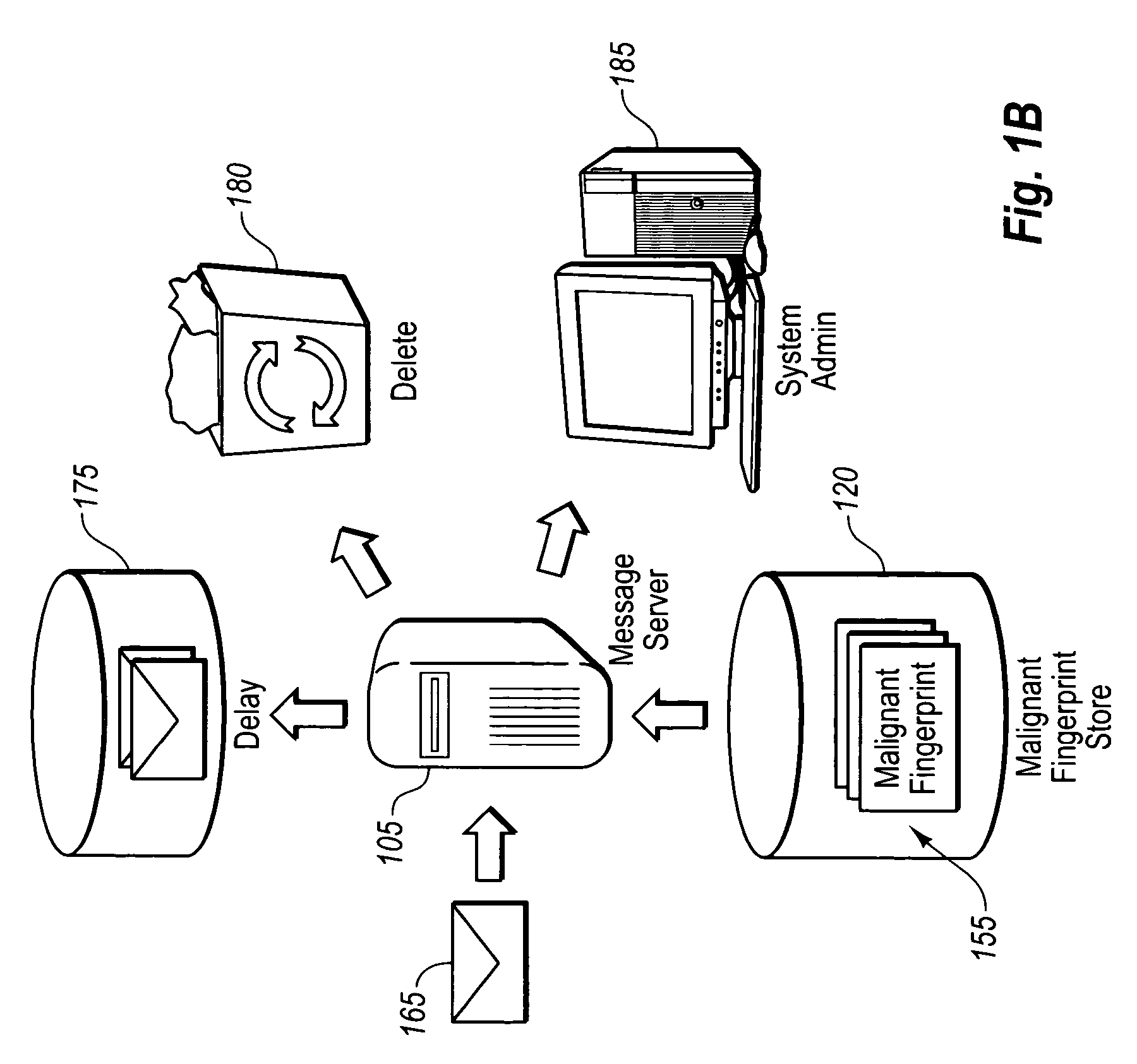
InactiveUS20060075099A1Automatic detectionDigital computer detailsData switching networksVirusWorld Wide Web
The present invention utilizes honeypots, which are messaging system resources set up to attract unauthorized or illicit use thereof, for automatically identifying messages with malignant content. As messages are received at a honeypot, fingerprints of the messages are generated, which correspond to pattern information within the messages. These fingerprints are then used to determine a confidence level that messages received at a legitimate messaging service are malignant. Based on the confidence level, various actions (e.g., deleting the malignant content) may be executed.
Owner:MICROSOFT TECH LICENSING LLC
Honeypot defense method and system based on mimicry defense, equipment and medium
The invention discloses a honeypot defense method and system based on mimicry defense, equipment and a medium, which are applied to the technical field of network security. A virtualization managementsubsystem comprises a mirror image management module, a honeypot management module, a virtual network management module and a control scheduler which are connected in sequence, the mirror image management module constructs a mimicry honeypot mirror image through a KVM virtual machine mirror image technology, a plurality of virtual high-interaction honeypots and a mimicry honeypot system are obtained, and the honeypots are mimicry honeypots; the honeypot management module manages the honeypots and monitors the state of the honeypots; the virtual network management module controls the honeypotsystem to perform data access and network communication; and a control scheduler dynamically switches the mimicry honeypots and the network according to the output judgment result of the mimicry honeypots. According to the invention, mimicry defense is combined with the honeypot system, so that the security and controllability of network space security defense are improved.
Owner:PURPLE MOUNTAIN LAB +1
Network attack information processing method and device, electronic equipment and storage medium
ActiveCN111565199AEnable mass deploymentImprove processing efficiencyTransmissionMultiplexingInformation processing
The invention provides a network attack information processing method. The network attack information processing method comprises the following steps: acquiring attack traffic for attacking a target system; in response to the acquired attack traffic, triggering a port multiplexing process to monitor the attack traffic forwarded by the target port; triggering an attack information classification model, and identifying the category of the attack traffic; triggering a port forwarding process based on an identification result of the attack information classification model, and forwarding the attack traffic. The invention further provides a network attack information processing device, electronic equipment and a storage medium. According to the invention, the attack traffic can be forwarded tothe corresponding honeypot systems of different types, the network attack information processing efficiency of the honeypot systems is improved, the number of deployed servers is reduced, the cost ofa user is saved, and the large-scale deployment of the honeypot systems is realized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Implementation method and device of application-type honeypot
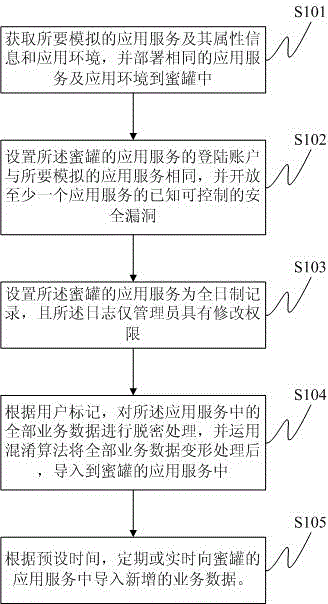
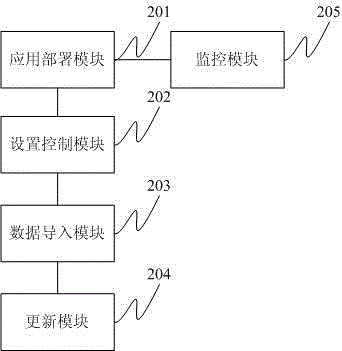
InactiveCN104978519ADetect behavioral intentionDiscovery Analysis ForensicsPlatform integrity maintainanceSoftware engineeringBusiness data
The invention provides an implementation method and device of an application-type honeypot. The implementation method comprises the following steps: obtaining application service to be simulated and the attribute information and the application environment of the application service to be simulated, and deploying the same application service and application environment into the honeypot; setting the corresponding attributes of the honeypot, for example, a login account of the application service of the honeypot is set to be the same with the application service to be simulated, and the known controllable security holes of at least one application service is opened; according to a user flag, carrying out decryption processing on all pieces of business data in the application service, applying a confounding algorithm to carry out deformation processing on all pieces of business data, and then, importing the business data into the application service of the honeypot; and importing newly-added business data into the application service of the honeypot in fixed time or real time. The invention also provides corresponding equipment. The application-type honeypot can be combined with the real business data of the user to confuse an attacker to a maximum degree, and the attacker is enabled to think that the honeypot is the real application service data of the user.
Owner:HARBIN ANTIY TECH
SDN-based virtual honeynet dynamic deployment method and system
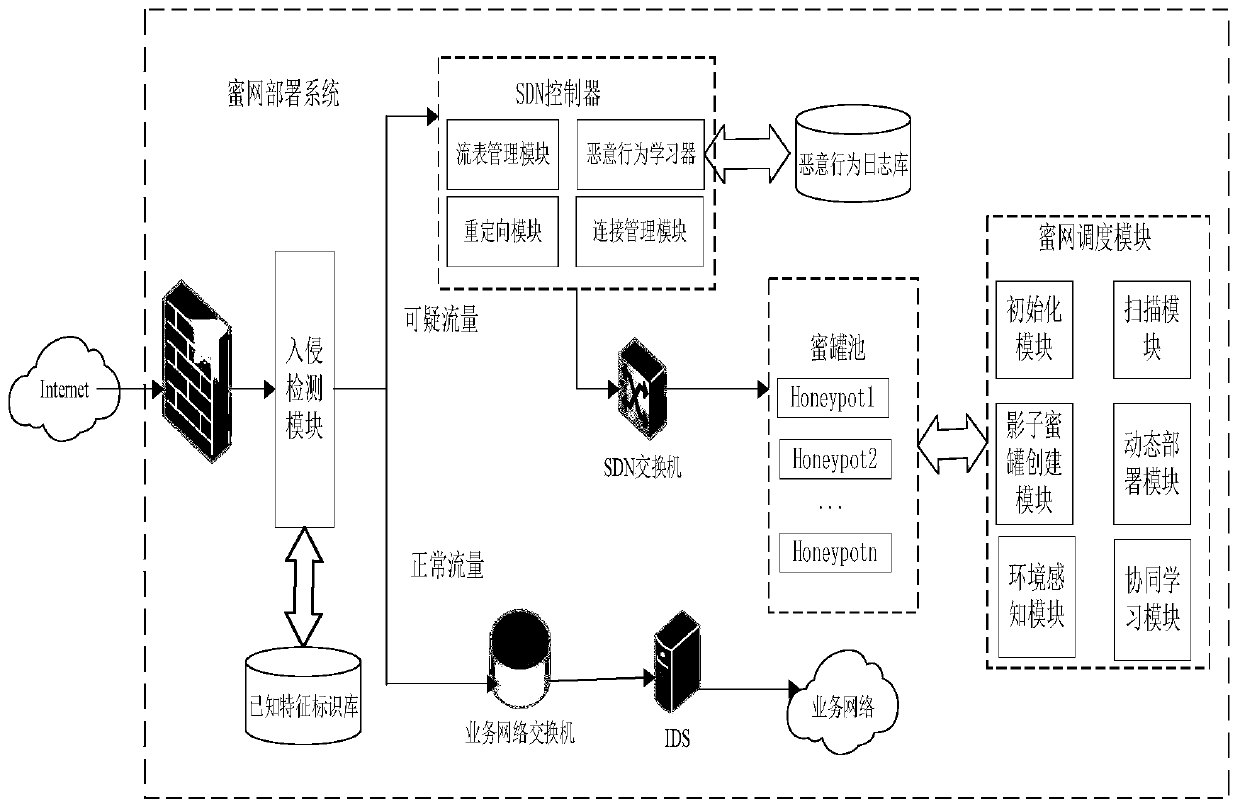
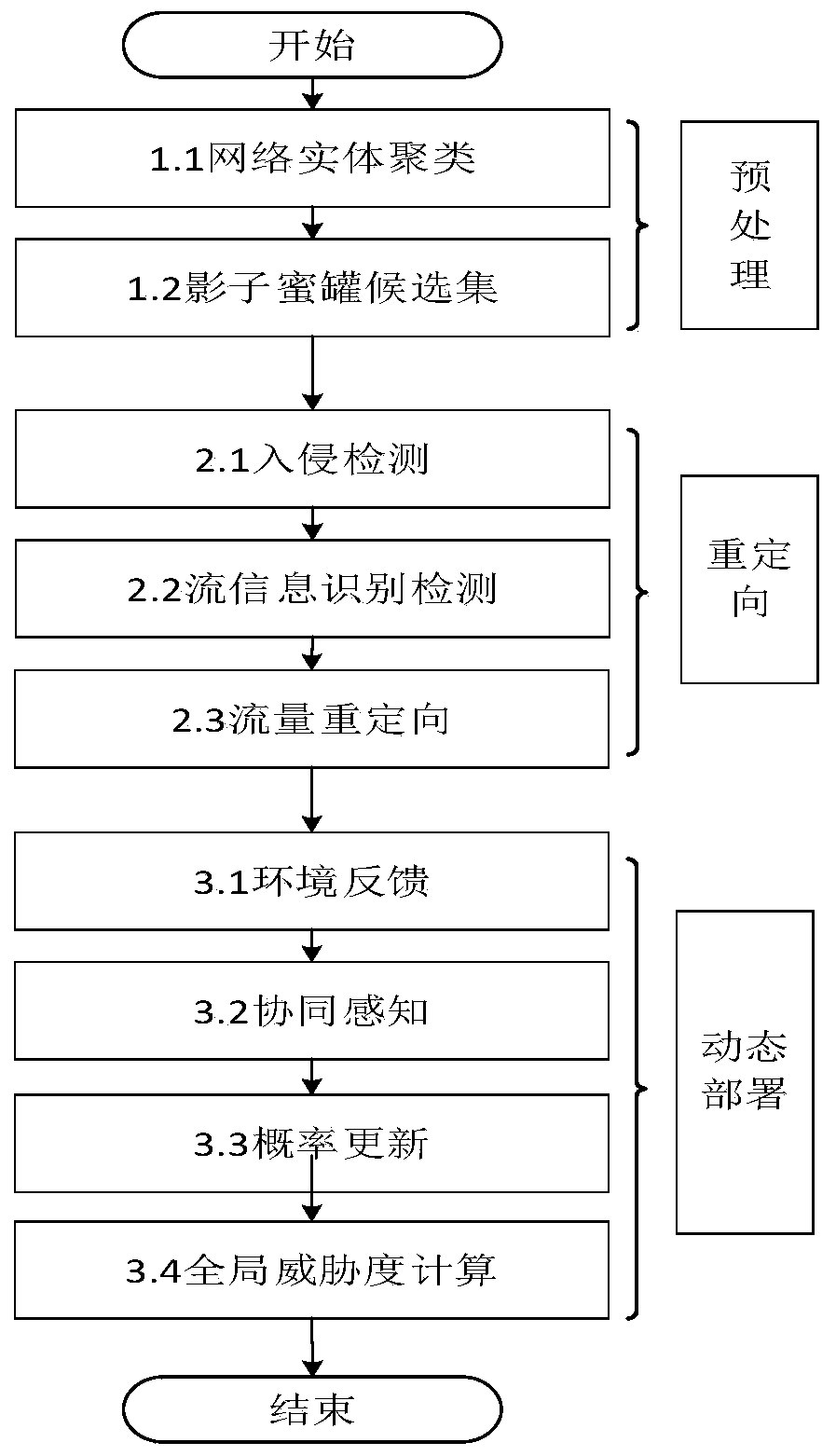
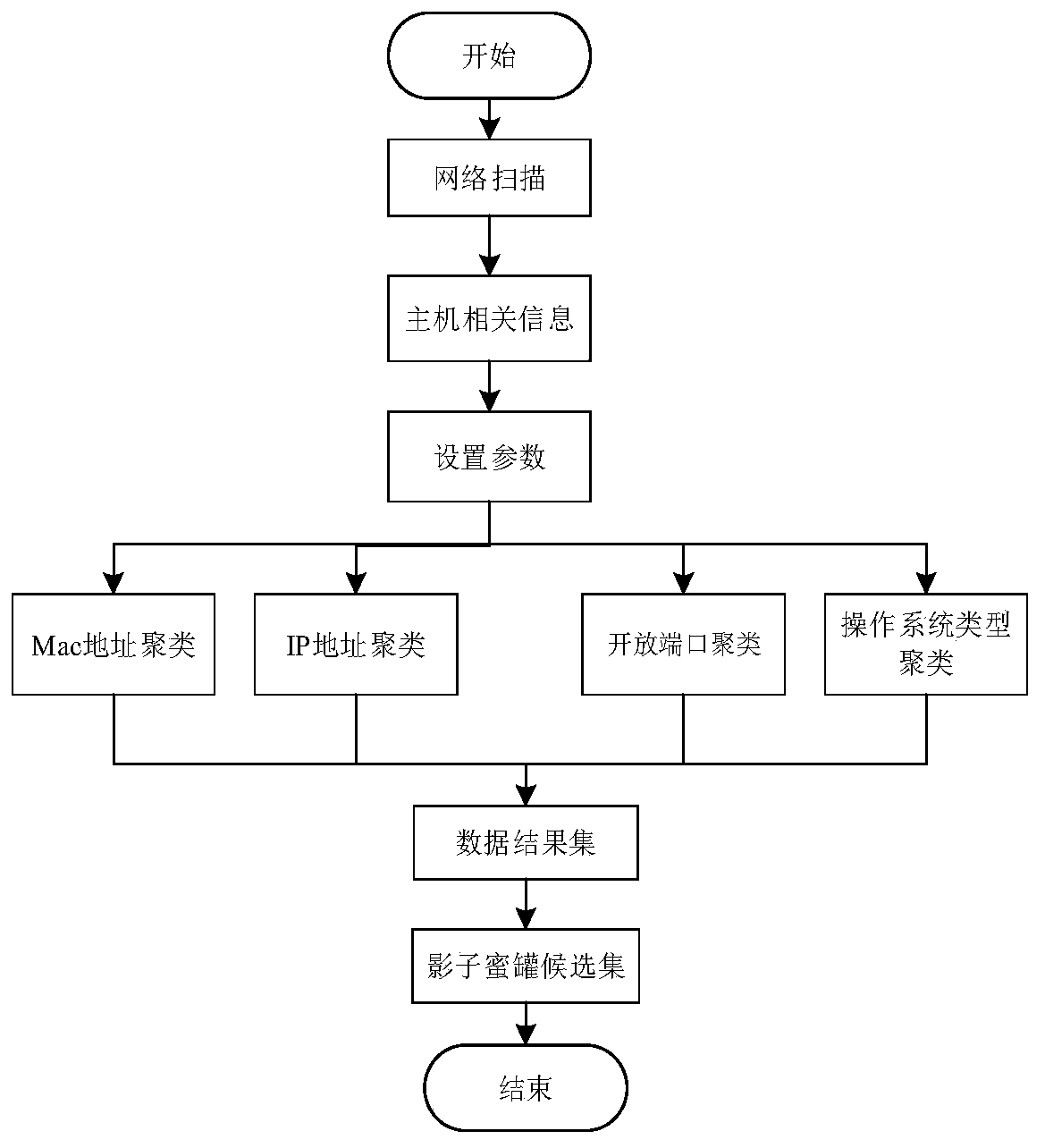
InactiveCN110768987AIncrease deceptionSolve manual configurationArtificial lifeTransmissionHoneypotResult set
The invention relates to the technical field of network security, discloses an SDN-based virtual honeynet dynamic deployment method, and solves the technical problems of difficulty in dynamic construction and active induction, inflexibility in configuration and maintenance, poor expandability and low decoy degree of a honeynet in the prior art. The method comprises the steps of A, scanning a honeynet to obtain a network entity, performing clustering analysis according to attributes of the network entity to obtain a clustering result set, and setting a shadow honeypot candidate set according tothe clustering result set; b, performing intrusion detection on the access traffic, and redirecting suspicious traffic according to a matching rule; and C, performing rewards and punishment operations on behaviors of deployed honeypots based on environmental feedback, updating the behavior probability of a set of deployed honeypots, obtaining the current honeynet deployment quality through calculation of the honeynet global threat degree, and then selecting the honeypots from the shadow honeypot candidate set according to the quality scores for dynamic deployment. In addition, the invention also discloses an SDN-based dynamic deployment system for the virtual honeynet, and the system is suitable for dynamic deployment of the virtual honeynet.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
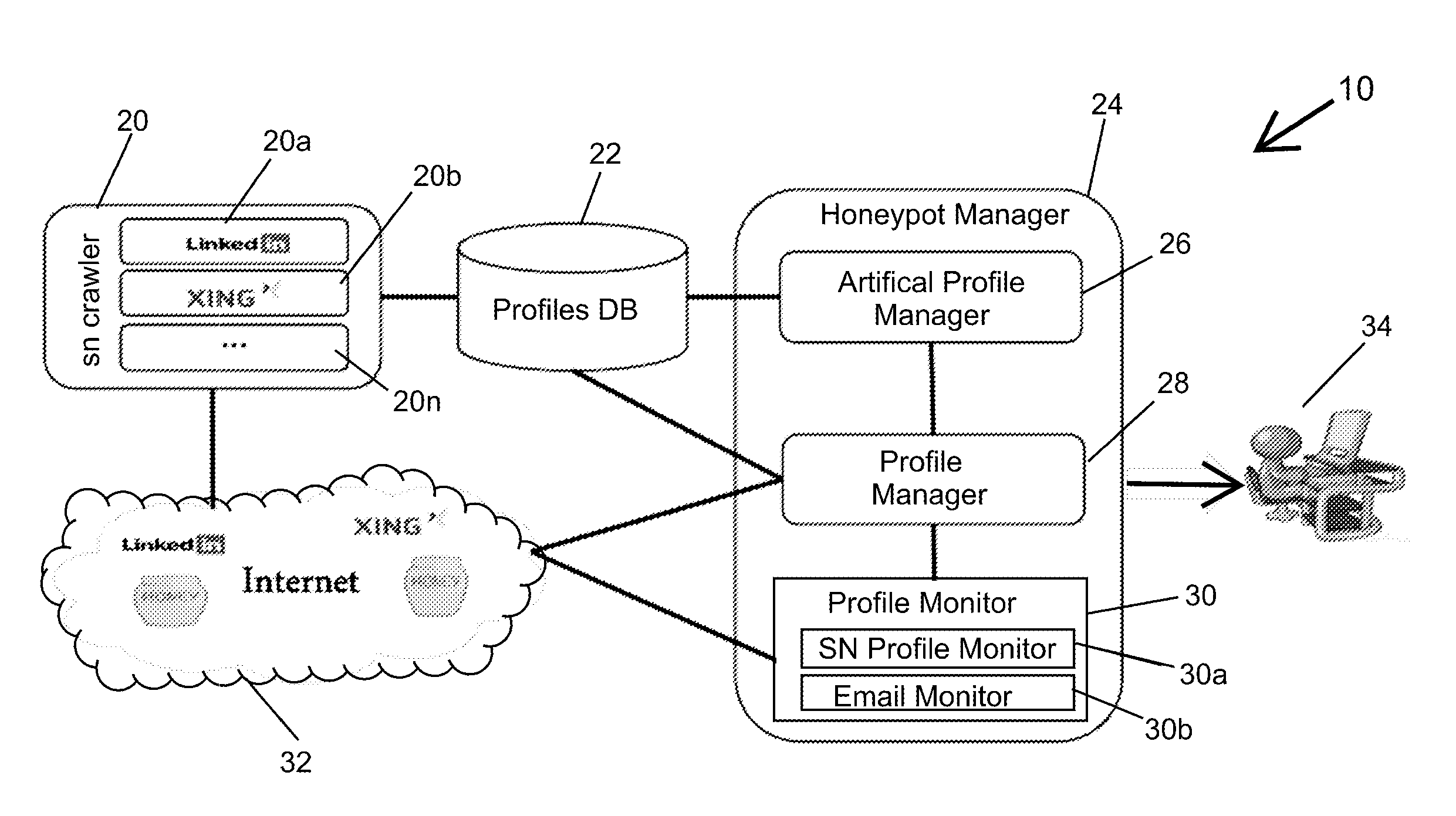
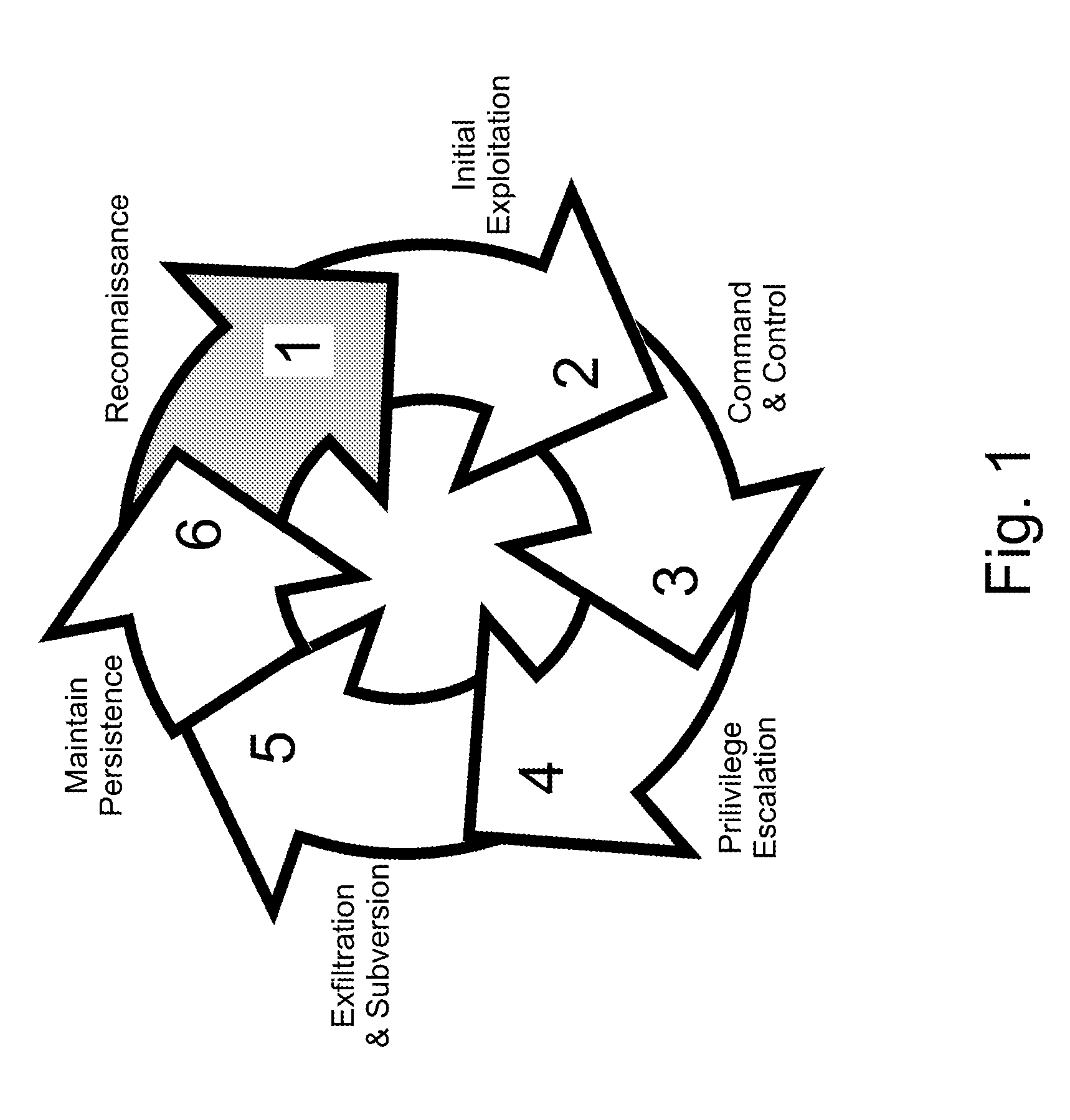
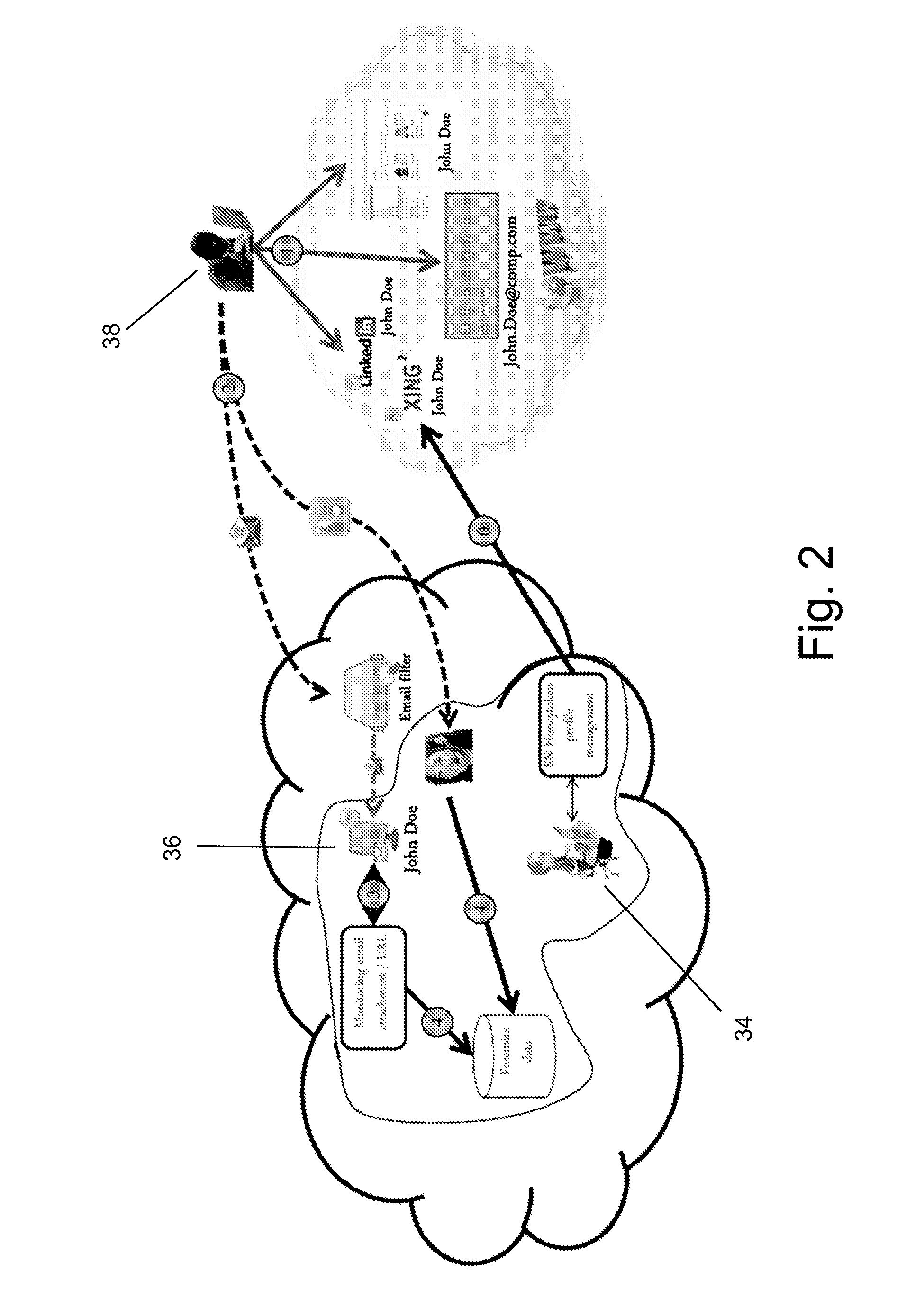
Social network honeypot
The invention is a method and system for detecting attackers that are interested in attacking an organization's infrastructure during the reconnaissance phase of an Advanced Persistent Threat (APT). APTs are very sophisticated attacks and incorporate advanced methods for evading current security mechanisms. Therefore, the present invention uses an innovative social network honeypot.
Owner:DEUTSCHE TELEKOM AG
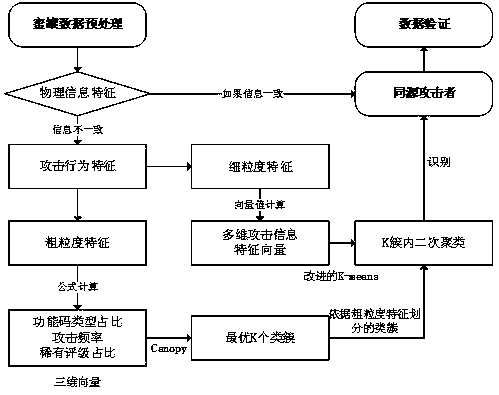
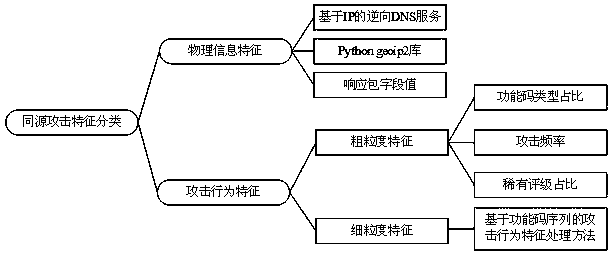
Homologous attack analysis method for industrial control honeypot
The invention discloses a homologous attack analysis method for an industrial control honeypot, and the method comprises the steps: introducing coarse-grained and fine-grained attack behavior featuresthrough the physical position features of an attacker, converting the information of the attacker into a group of multi-dimensional attack behavior feature vectors, finding an optimal K value by using a Canopy method according to the coarse-grained attack information of the attacker, and determining attackers or attack organizations with close Euclidean distances as homologous attacks by using animproved K-means clustering method according to the fine-grained attack information of the attacker. According to the method and the system, the behavior characteristics of the homologous attacker can be modeled into the characteristic vector based on the function code sequence, and the method and the system are suitable for analyzing various industrial control protocol honeypot data with function code characteristics; a verification method is provided for solving the problem that it is difficult to judge and verify the same attack source of honeypot data, for some unknown enterprise scannersor attackers, an open source abuse IP database is used for query, and the traditional attacker information of the other unknown attackers is verified.
Owner:山西星泽汇联科技有限公司
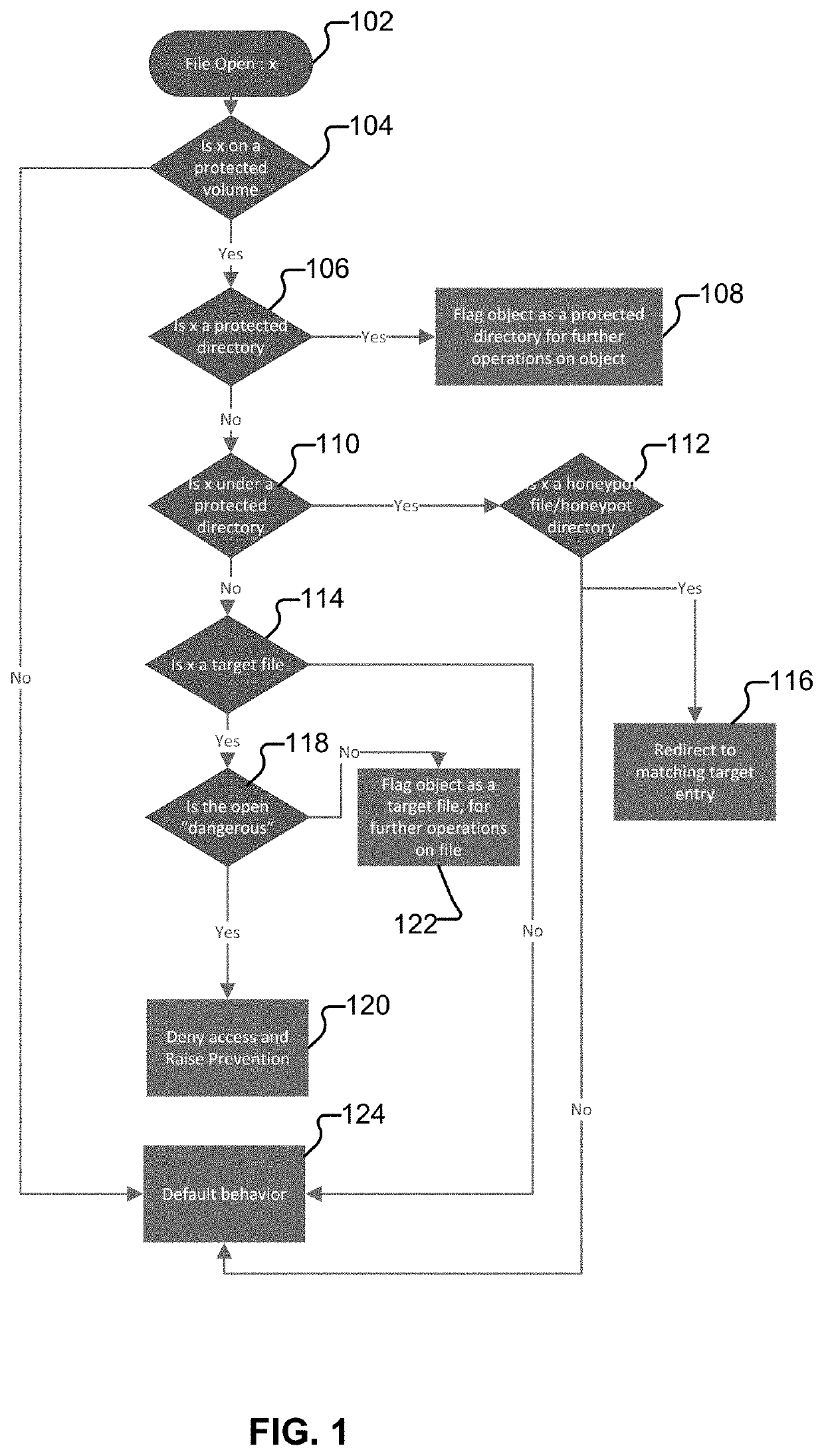
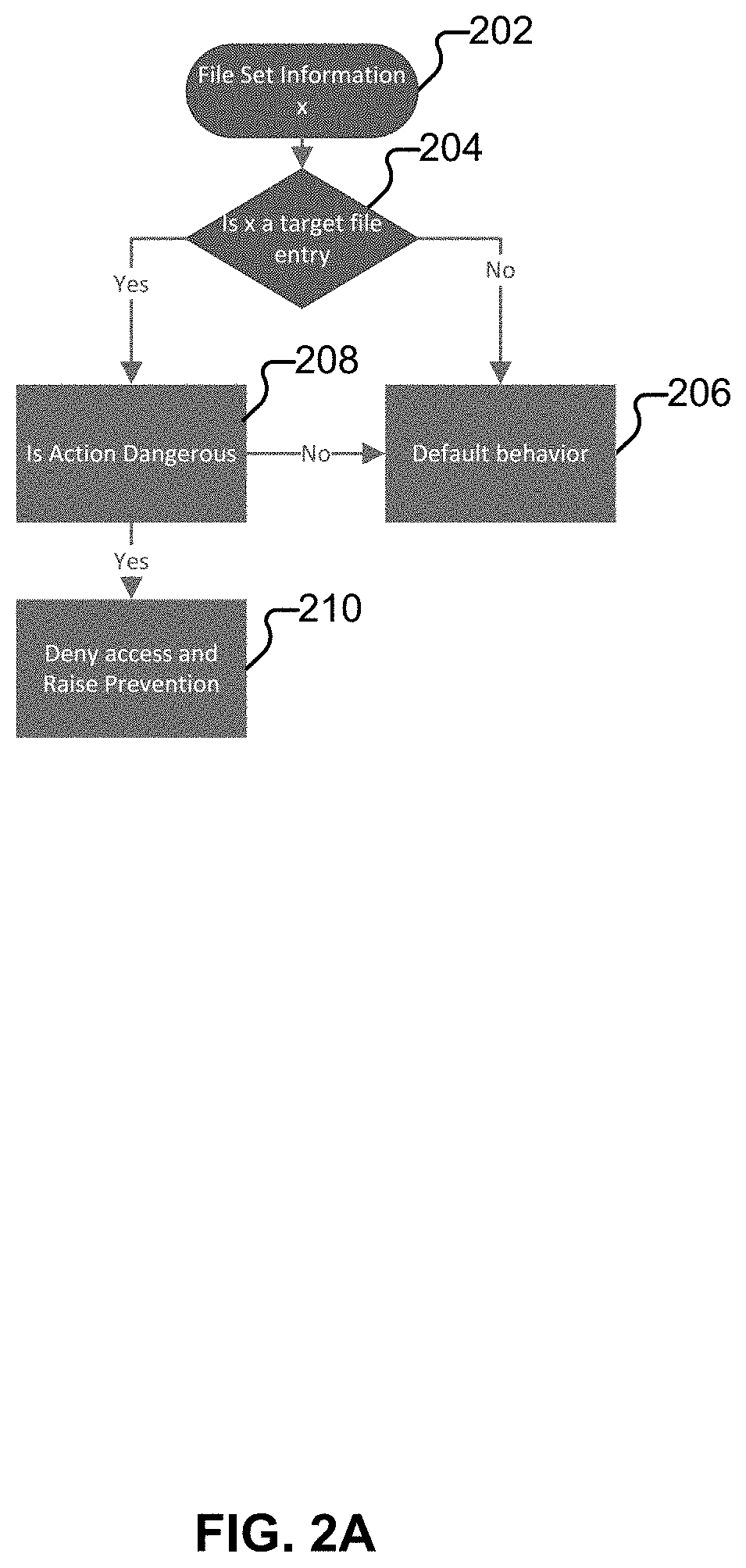
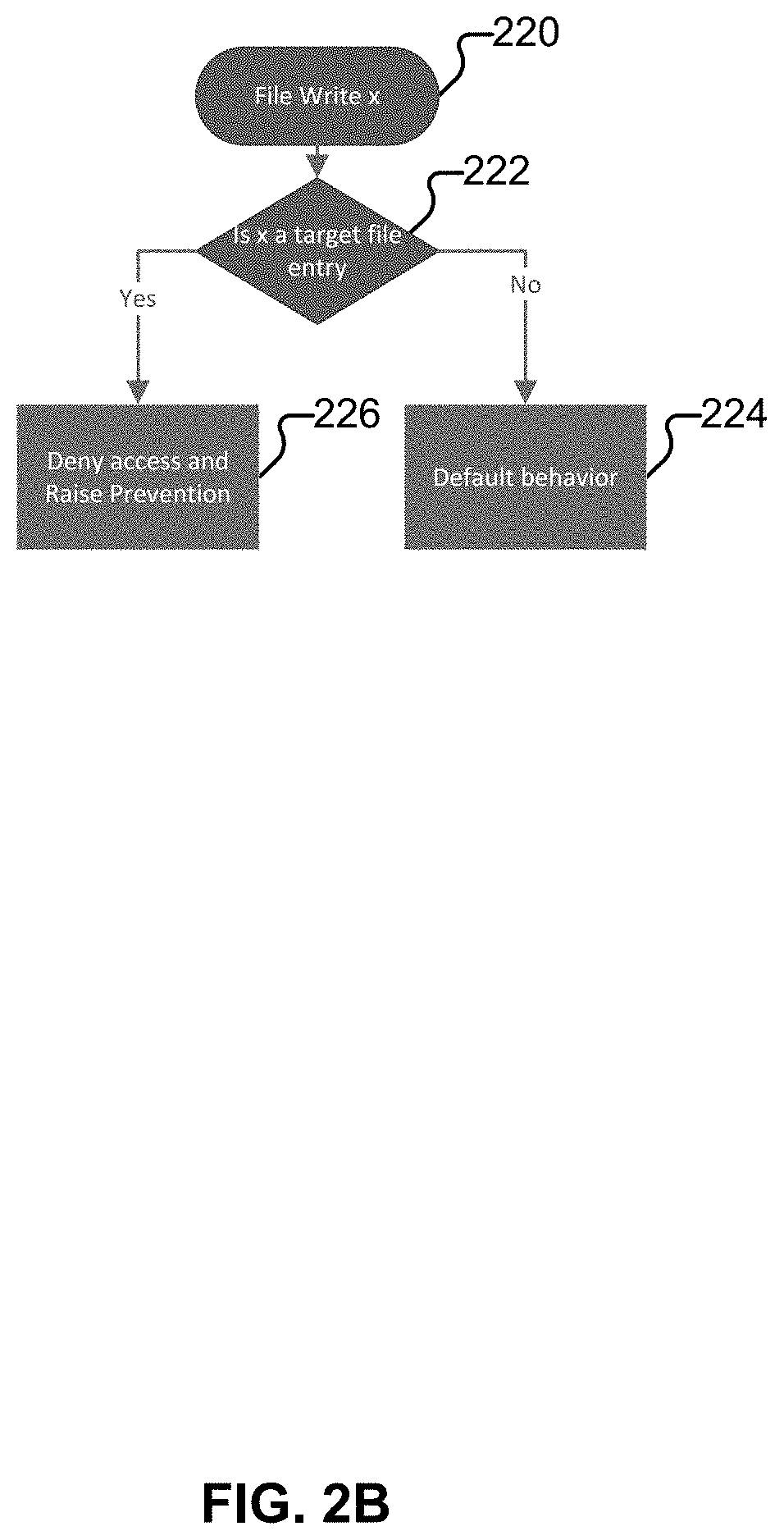
Preventing ransomware from encrypting files on a target machine
Techniques for preventing ransomware from encrypting files on a target machine are disclosed. In some embodiments, a system / process / computer program product for preventing ransomware from encrypting files on a target machine includes monitoring file system activities on a computing device; detecting an unauthorized activity associated with a honeypot file or honeypot folder; and performing an action based on a policy in response to the unauthorized activity associated with the honeypot file or honeypot folder.
Owner:PALO ALTO NETWORKS INC
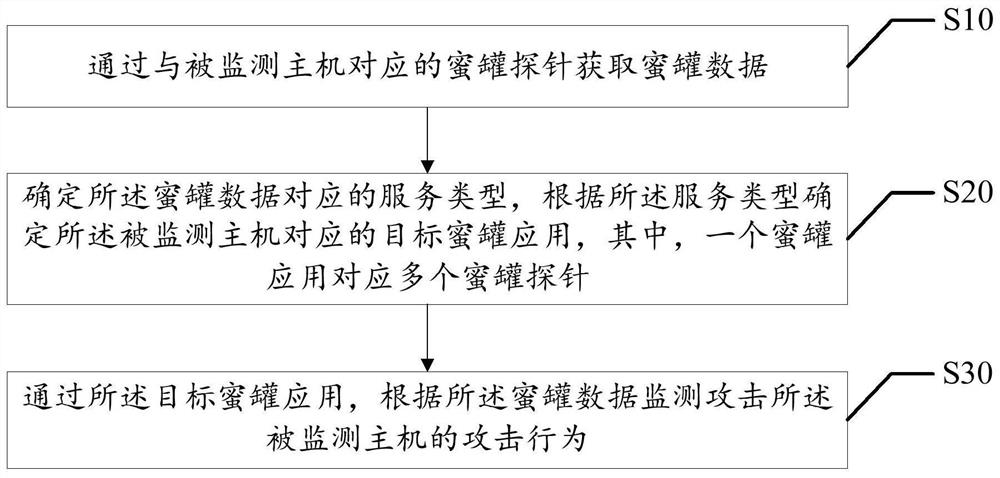
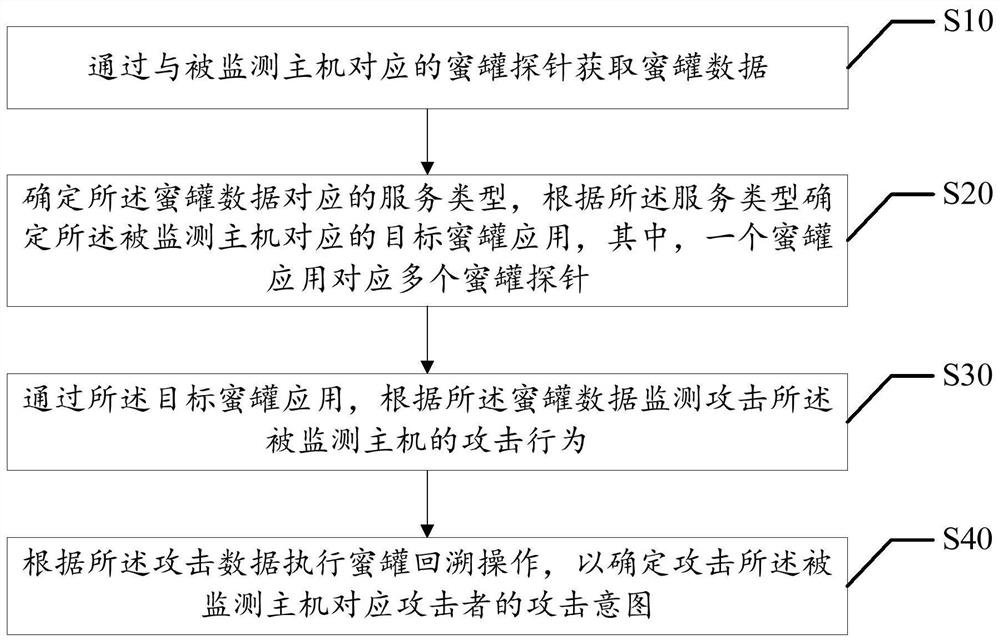
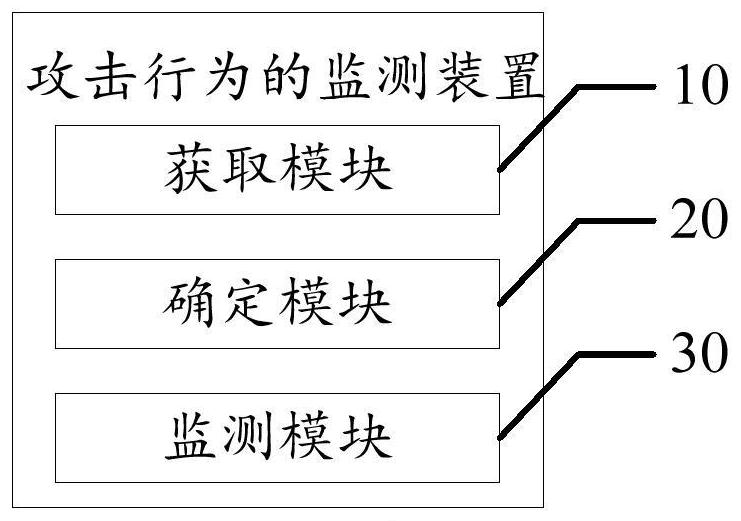
Attack behavior monitoring method, device, equipment and storage medium
The invention discloses an attack behavior monitoring method, a device, equipment and a storage medium, and relates to the field of financial science and technology, and the attack behavior monitoringmethod comprises the following steps: obtaining honeypot data through a honeypot probe corresponding to a monitored host; determining a service type corresponding to the honeypot data, and determining a target honeypot application corresponding to the monitored host according to the service type, one honeypot application corresponding to a plurality of honeypot probes; and through the target honeypot application, monitoring an attack behavior attacking the monitored host according to the honeypot data. According to the method, the lightweight setting of the system architecture between the front-end host and the rear-end honeypot server is realized, and the accuracy of monitoring the attack behavior of an attacker through the honeypot application is improved.
Owner:WEBANK (CHINA)
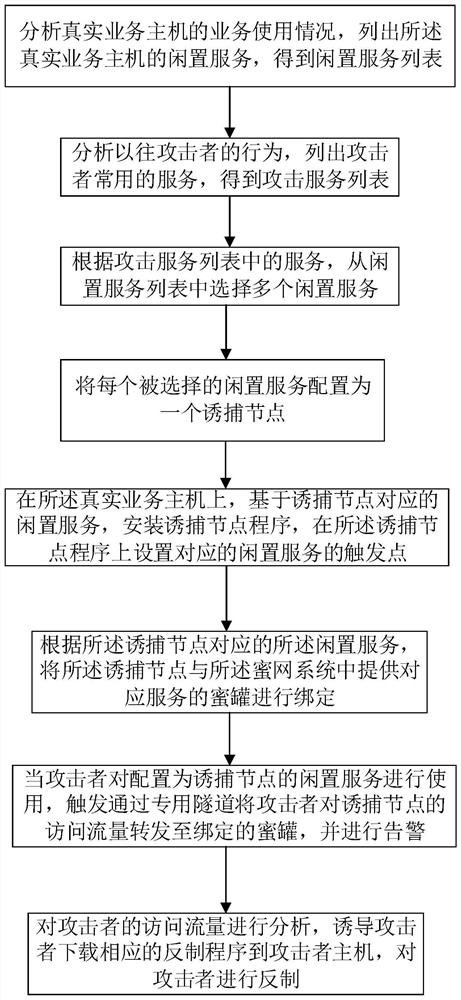
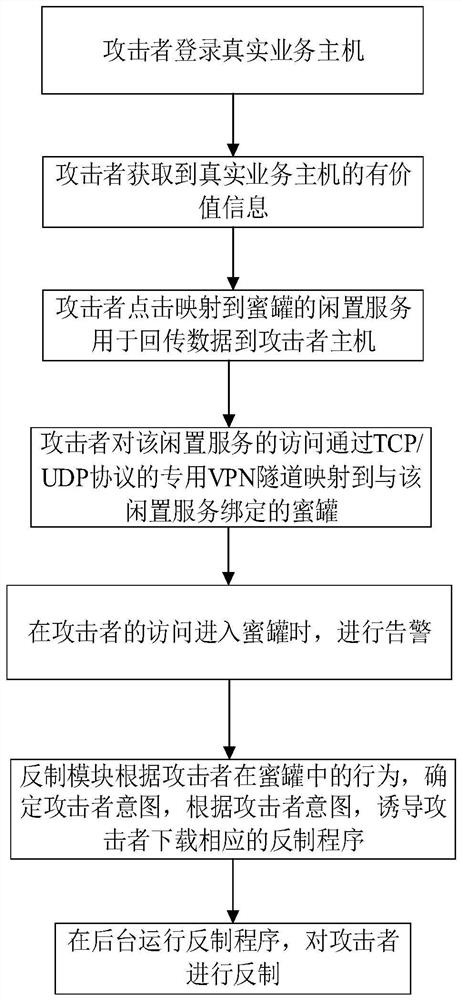
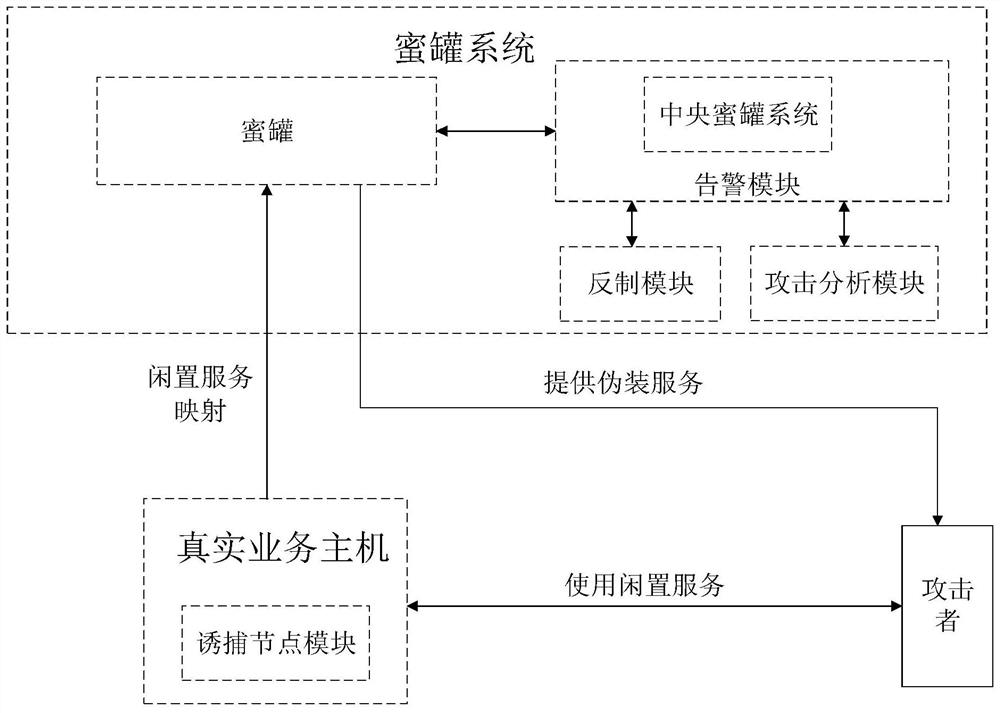
Novel honeypot networking method and honeypot system
The invention provides a novel honeypot networking method and a honeypot system, and belongs to the technical field of network security. The invention provides a honeypot networking method, and the method comprises the following steps: listing idle services of a real business host, listing attacker common services, selecting some idle services from the idle services of the real business host according to the attacker common services, deploying the idle services as trapping nodes, deploying one trapping node for each selected idle service, and deploying one trapping node for each selected trapping node; binding the trapping node with the honeypot; when an attacker accesses an idle service, introducing attacker access flow into the honeypot, enabling the honeypot system to analyze the attacker access flow, automatically downloading a countering program and countering the attacker. According to the method, the trapping nodes are deployed on the idle service of the real service host, so that a large number of special servers or special virtual machines created on the idle servers are saved for deploying the trapping nodes, the capture efficiency is high, and the idle service is utilized.
Owner:广州锦行网络科技有限公司
Method of forwarding attack traffic to honeypot
The invention discloses a method for forwarding attack traffic to a honeypot. A gateway agent mode is adopted; a gateway and a flow forwarding module are simply deployed; request access to a sensitiveport on a real service server is forwarded to a gateway; the gateway carries out flow forwarding module rule configuration, forwards the request of the attacker to the honeypot, the honeypot carriesout attack evidence obtaining and replies the access request of the attacker, forwarding of the data packet is easily achieved through the gateway, and the situation that the whole communication quality is affected by instability generated in the agent disguising process is prevented. Intrusion detection is carried out, deployment is easy and convenient, operability is high, network safety and enterprise service safety and stability are maintained, and convenience is provided for disguise agency deployment of small and medium-sized enterprises.
Owner:江苏天网计算机技术有限公司
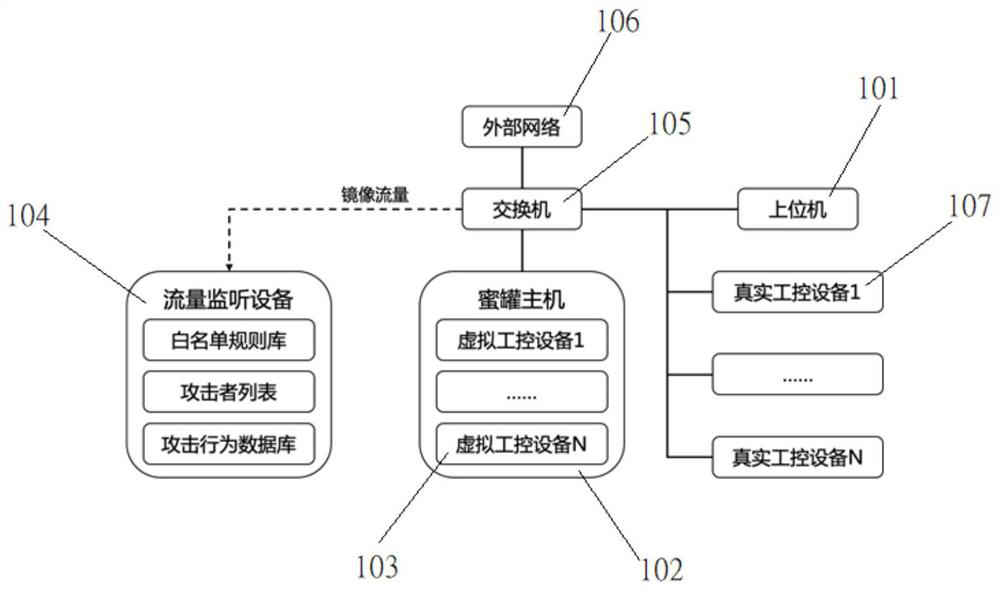
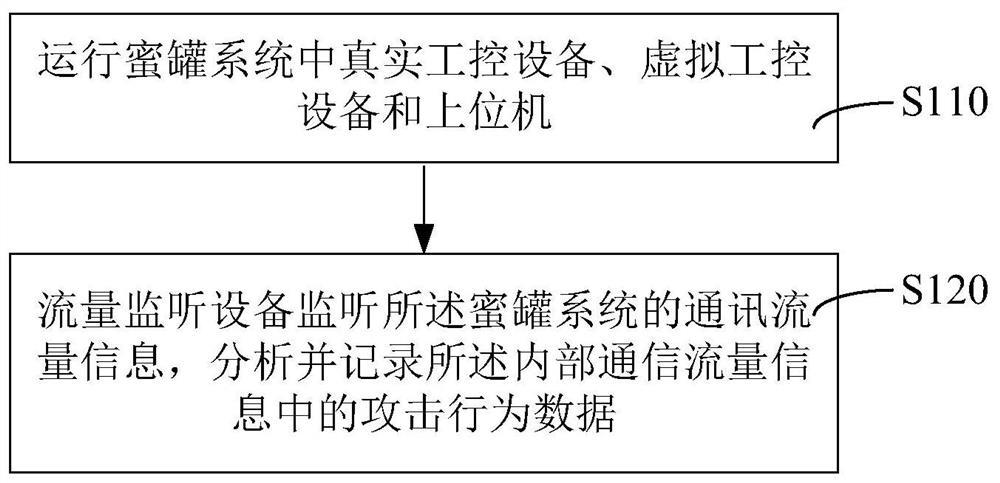
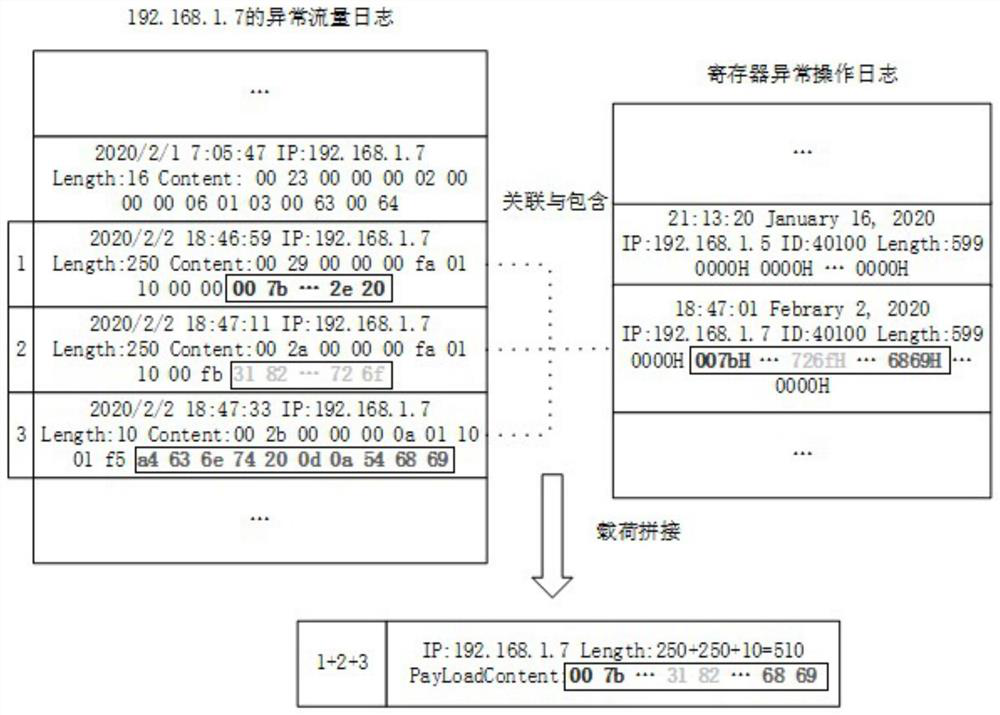
Attack data acquisition method and device of honeypot system
ActiveCN112054996ARich feature informationEasy to identifyTransmissionTotal factory controlAttackHoneypot
The invention relates to an attack data acquisition method and device of a honeypot system. The method comprises the steps that real industrial control equipment, virtual industrial control equipmentand an upper computer in the honeypot system are operated; wherein the upper computer is used for sending a control instruction to the real industrial control equipment and the virtual industrial control equipment and reading state data; and the flow monitoring device monitors the communication flow information of the honeypot system, and analyzes and records attack behavior data in the communication flow information. By adopting the method, the simulation degree of the honeypot system can be improved, and an cracking of an attacker is prevented.
Owner:浙江木链物联网科技有限公司
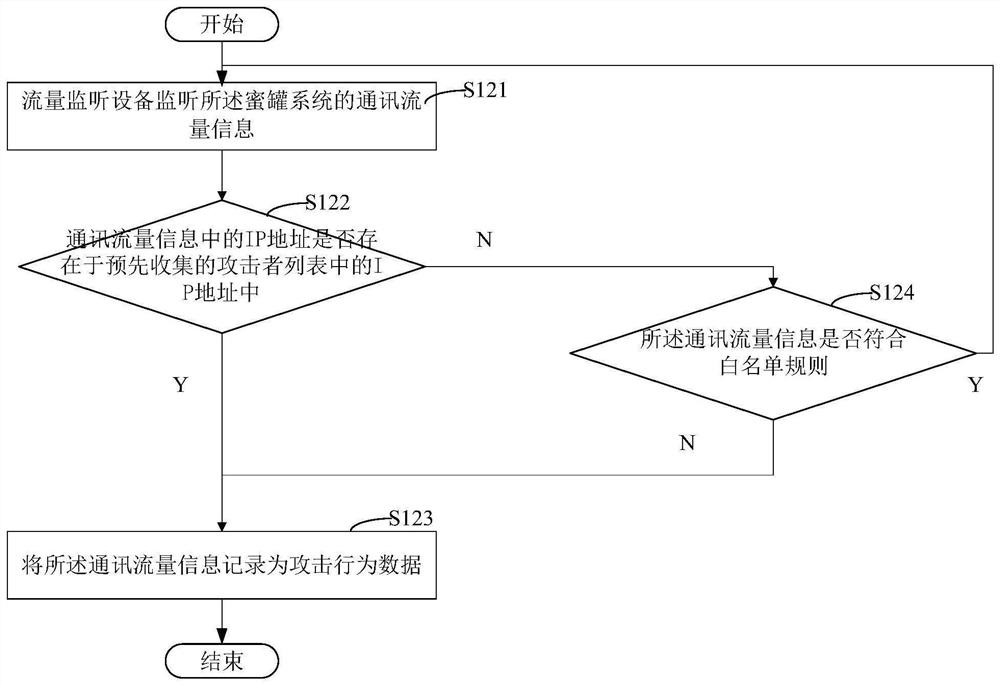
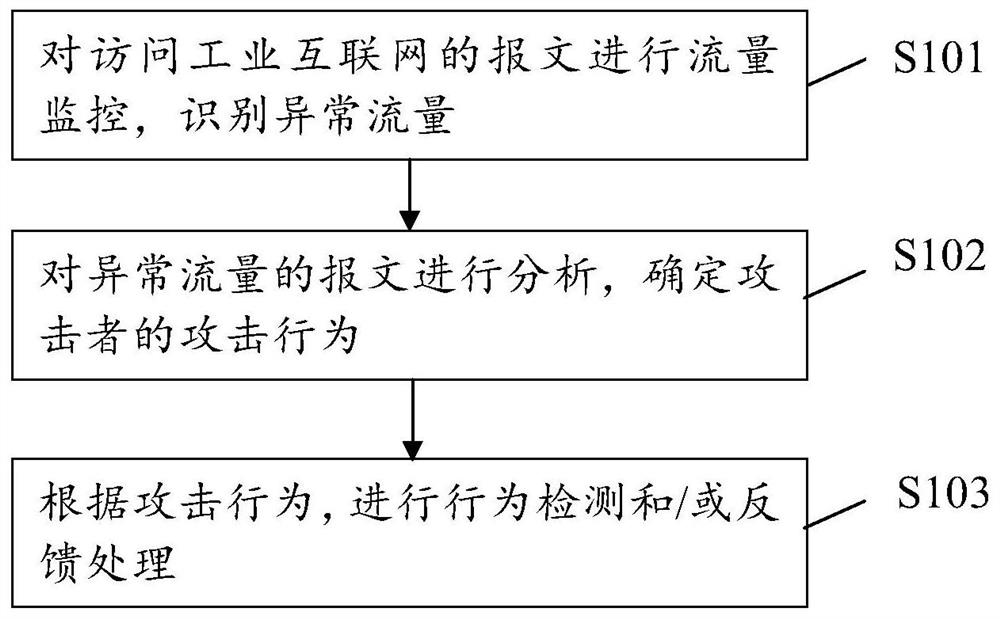
Industrial control honeypot method and device
One or more embodiments of the invention provide an industrial control honeypot method and device, and the method comprises the steps: carrying out the traffic monitoring of a message accessing the industrial Internet, and recognizing the abnormal traffic; analyzing the message of the abnormal traffic, and determining an attack behavior of an attacker; and performing behavior detection and / or feedback processing according to the attack behavior. According to the industrial control honeypot method and device, the concealment of the industrial control honeypot can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
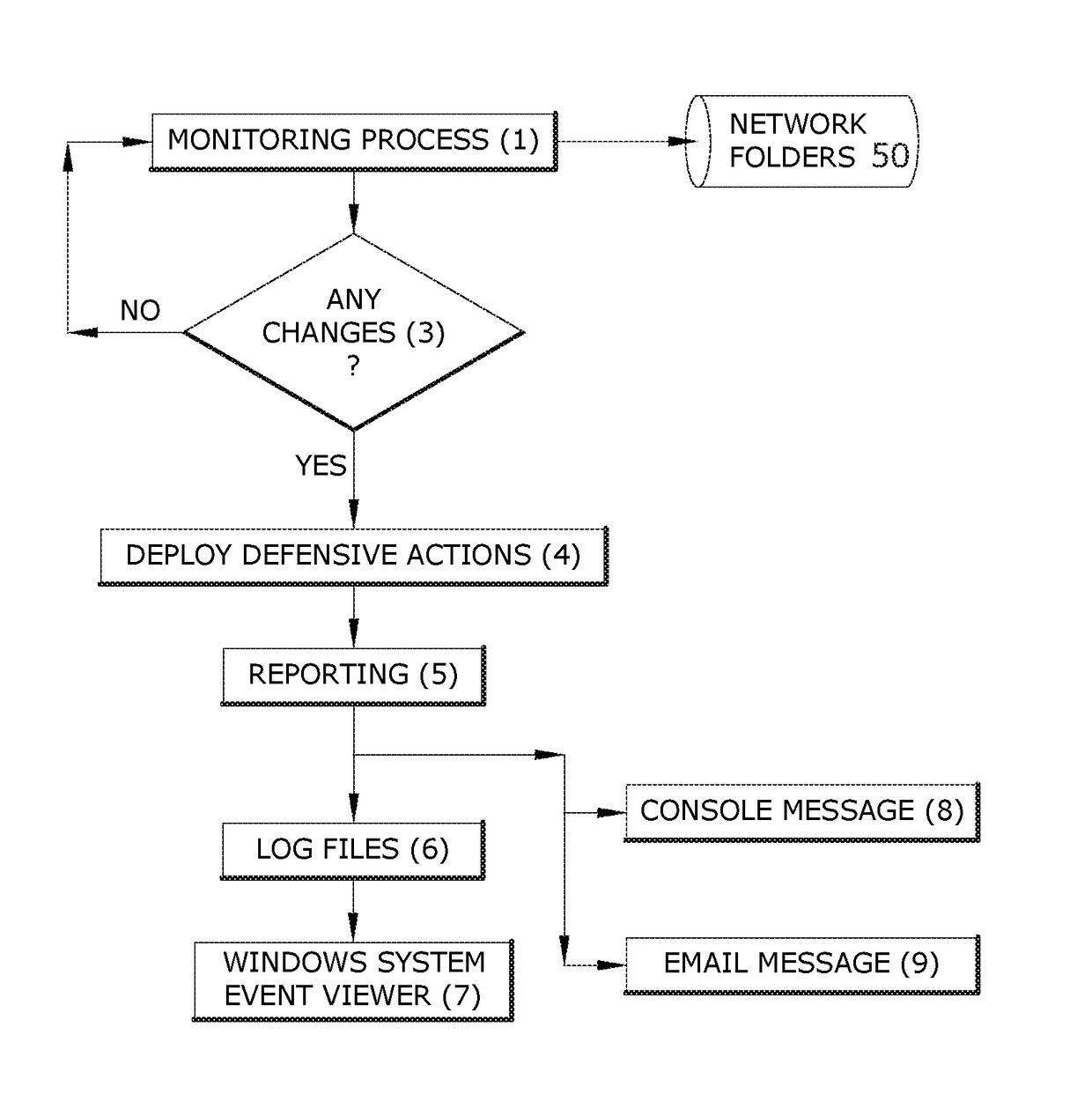
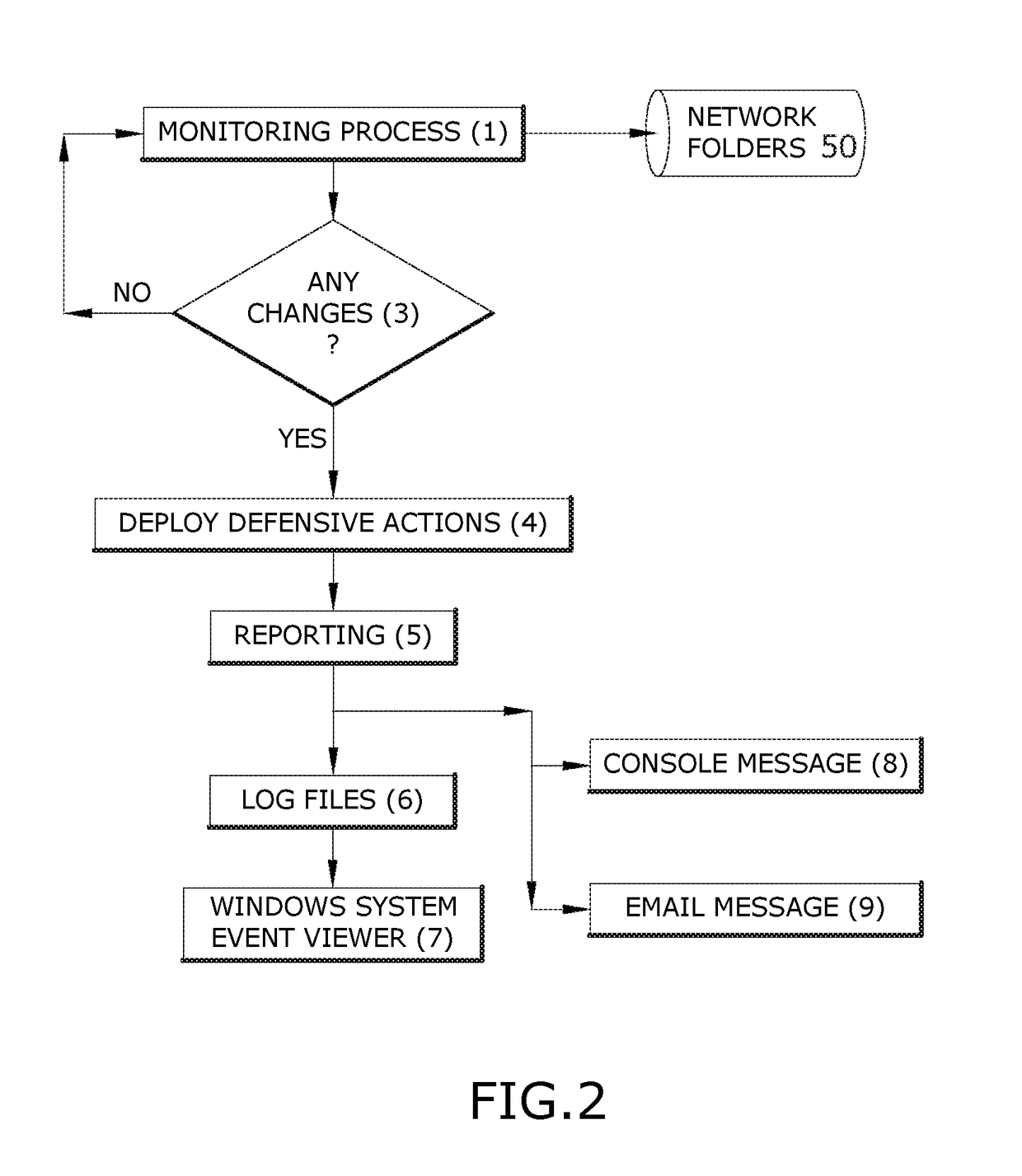
Computer network security system for protecting against malicious software
A computer network security system is provided. The system offers a last line of defense against malicious software through a novel software adapted to detect and deploy defensive action against the presence of malicious activity in a shared file environment. The novel software allows the administrator to create random honeypot files of known parameters that can be stored in vulnerable folders in a user-friendly manner. The novel software constantly monitors those files. If the novel software detects any unwanted action on the monitored honeypot files, through detection of a change in the known parameters, the present invention deploys defensive actions to protect the server including establishing fire walls and cessation of file sharing. Once defensive actions have been taken, the software reports all active sessions and open files as of the time of detection.
Owner:PRIMM BRAD AUSTIN
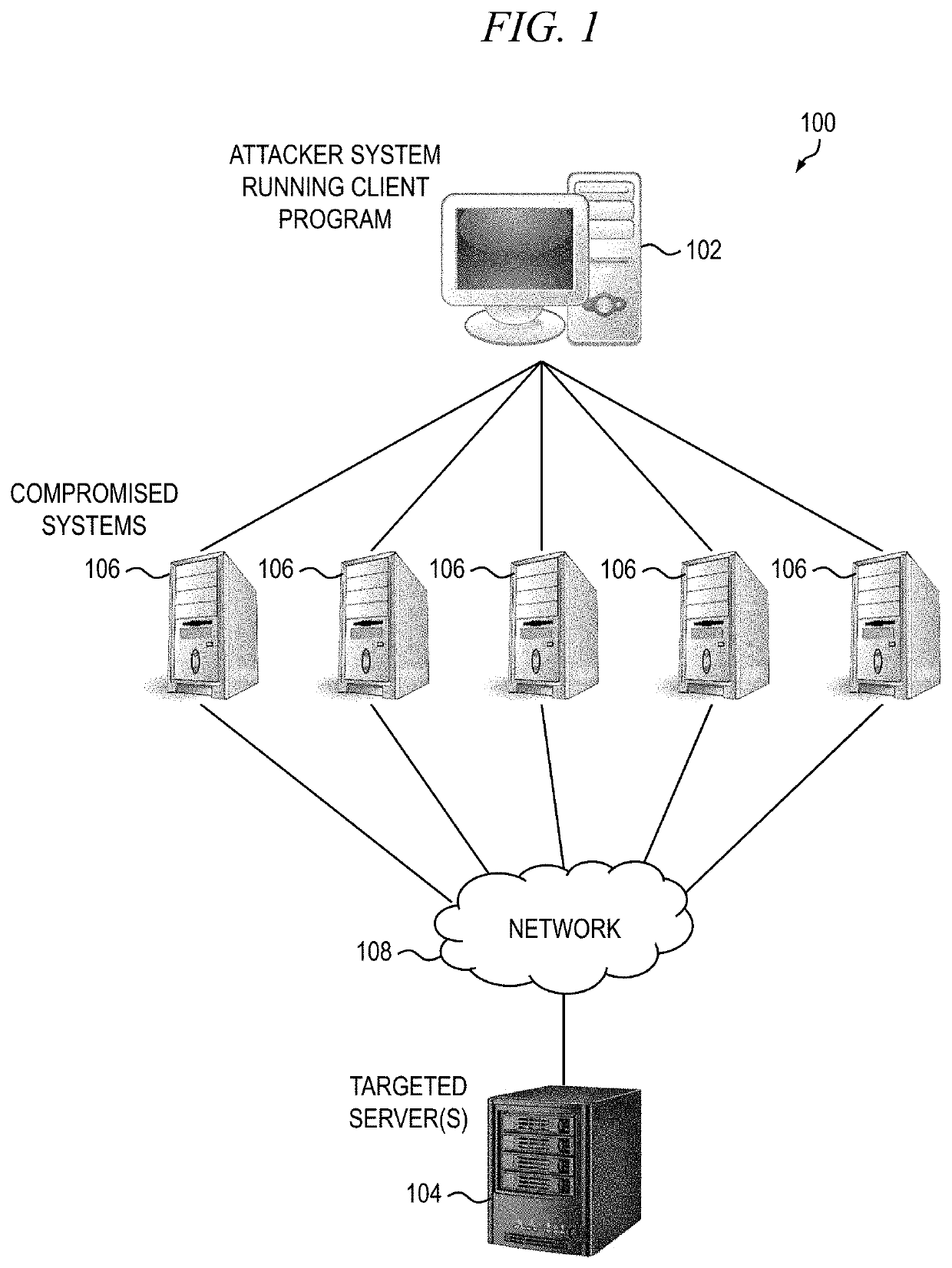
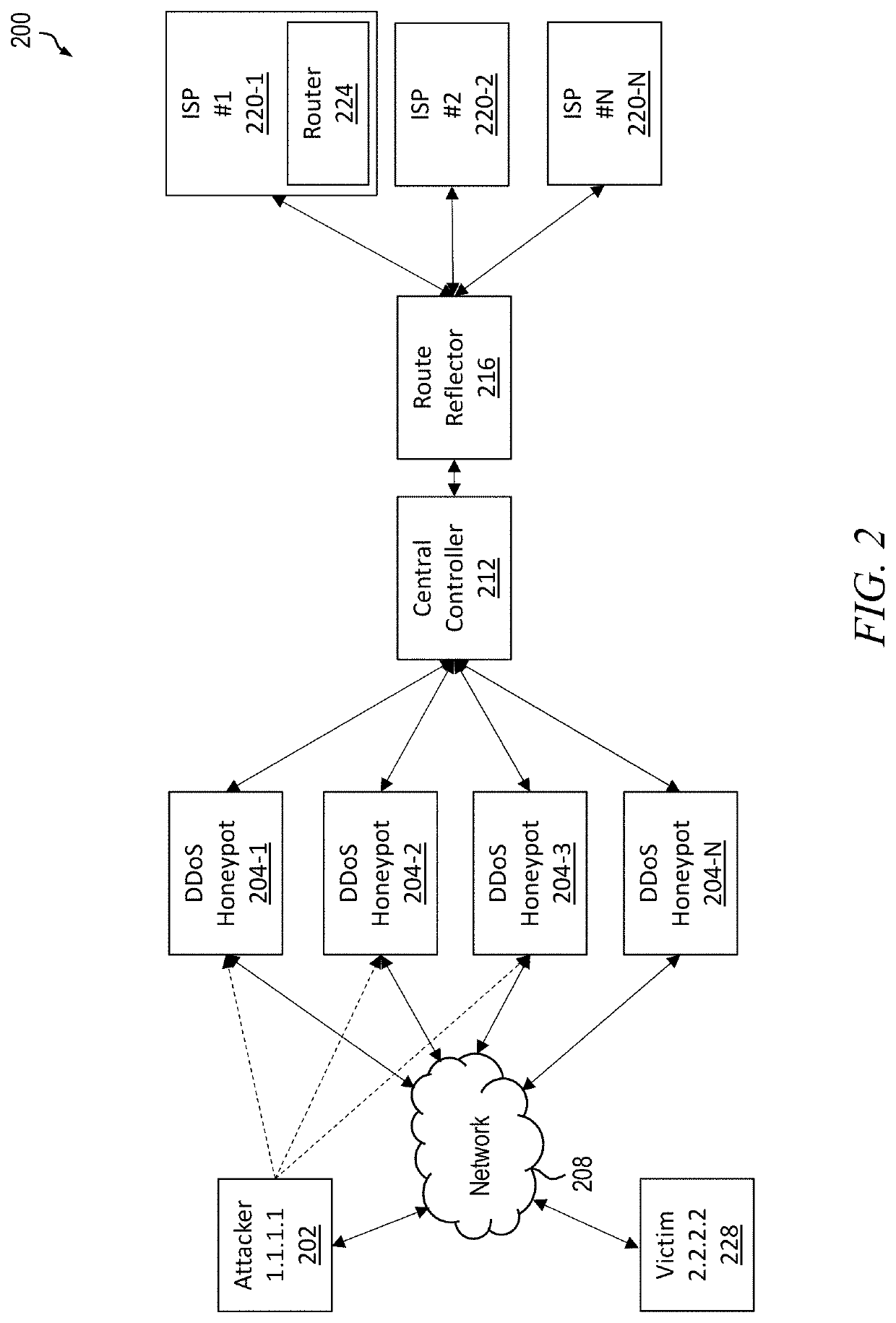
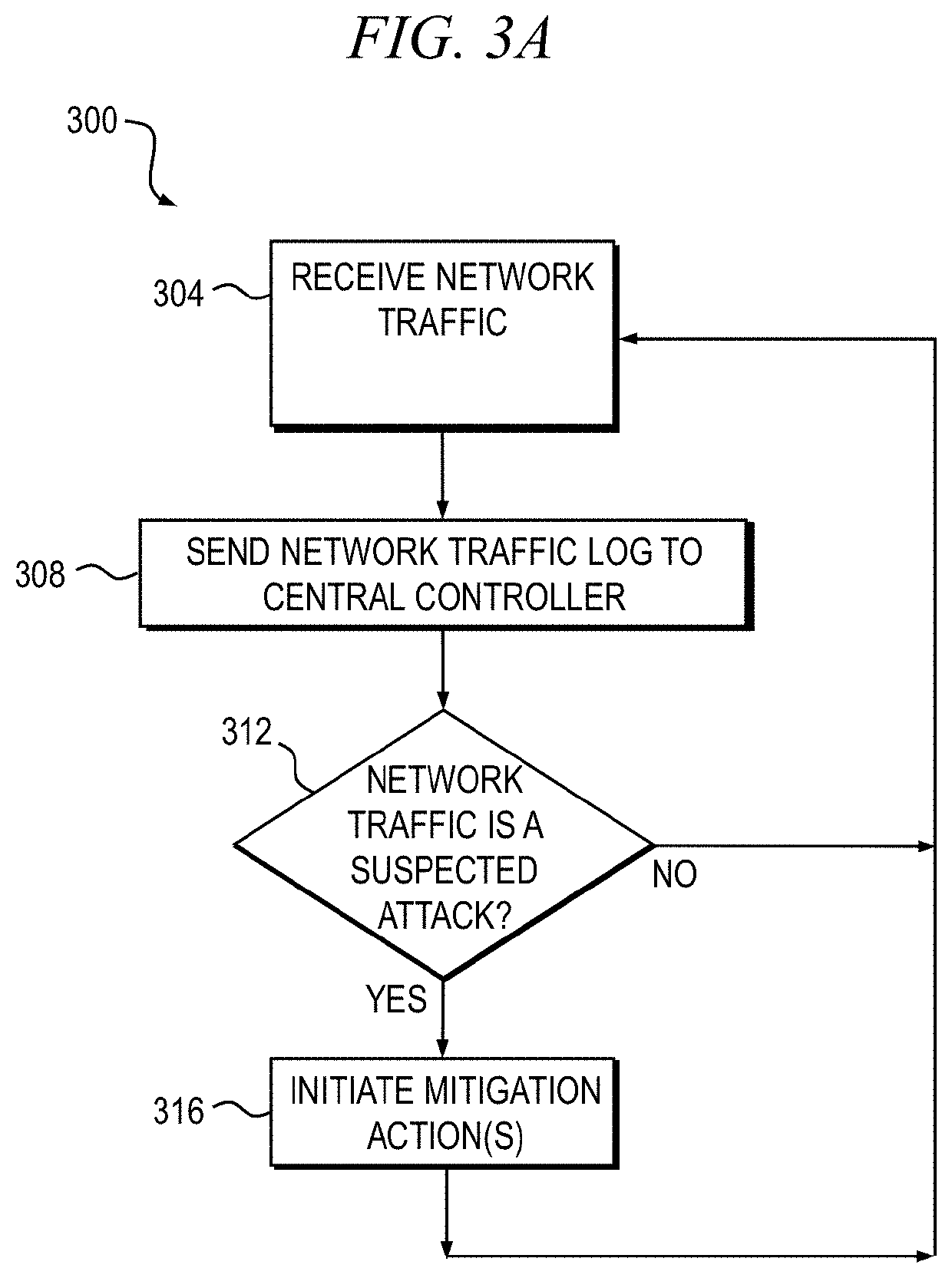
Detection and mitigation solution using honeypots
A system and method for mitigating a distributed denial-of-service (DDoS) attack in a networked computing system. At least one DDoS honeypot in operative communication with a central controller in the networked computing system is configured to receive a data packet from a network, determine a source address of the data packet, and send the source address to the central controller. The central controller is configured to initiate a mitigation action based on the source address and one or more mitigation rules, wherein a determination of whether the received data packet is part of the DDoS attack is based on one or more detection rules.
Owner:CHARTER COMM OPERATING LLC
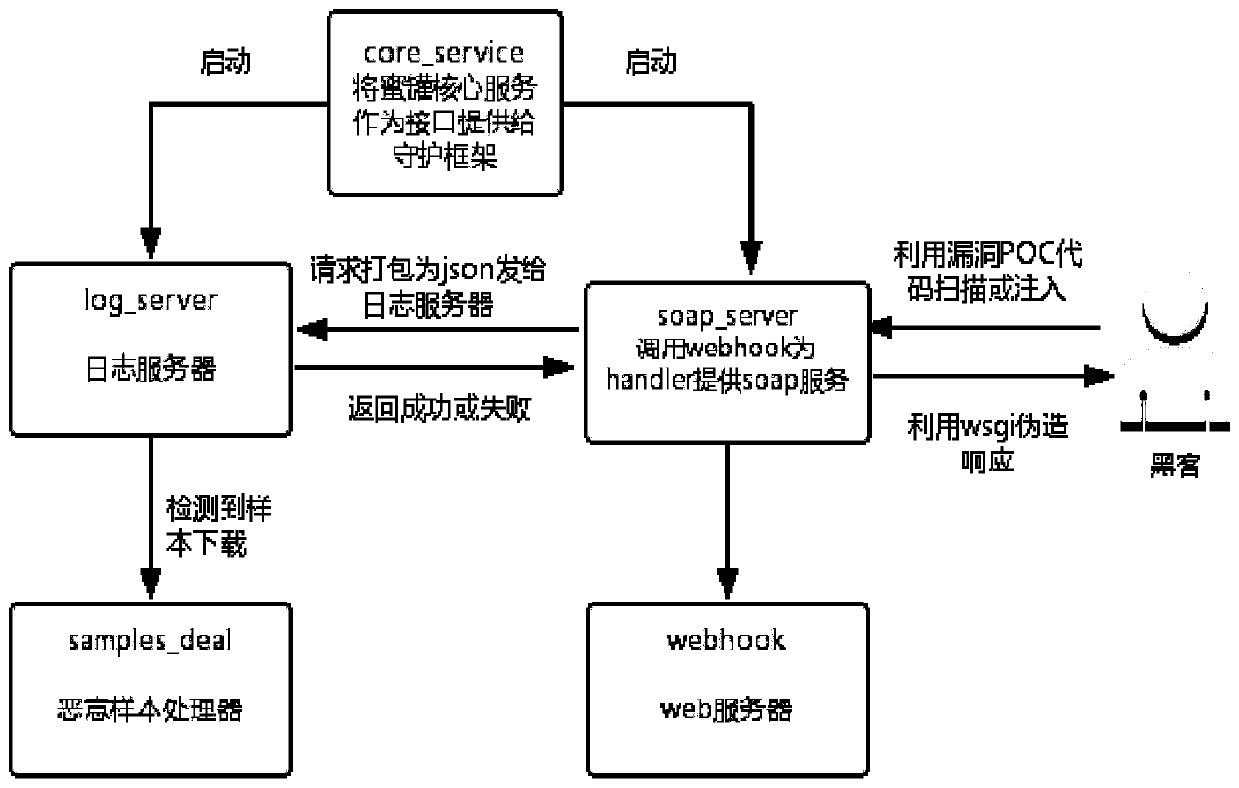
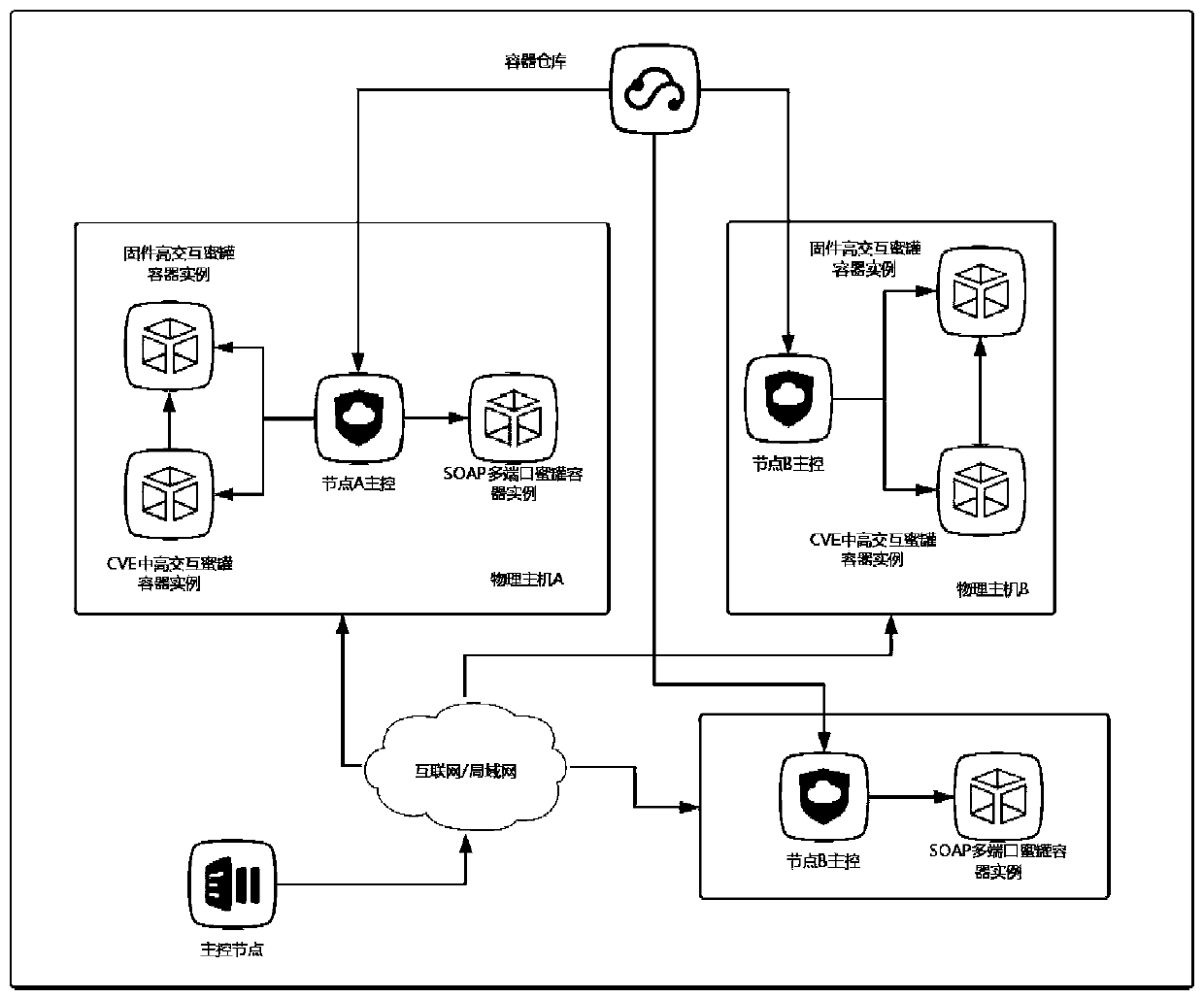
Internet of Things honeynet system based on SOAP service simulation
The invention discloses an Internet of Things honeynet system based on SOAP service simulation, and belongs to the technical field of Internet of Things security. The objective of the invention is tomonitor and collect the security state of the Internet of Things, capture the malicious request of a hacker for the Internet of Things, and collect malicious samples. According to the method, a middle-high interaction honeypot is designed according to a router SOAP service vulnerability CVE-2017-17215;; in order to prevent the situation that a hacker performs injecting service details which are not completed by the simulation serviceand the simulation service honeypot cannot respond and cannot capture subsequent malicious codes and samples, the function of supplementing the simulation servicehoneypot with the honeypot for providing the real SOAP service is realized by using equipment firmware with vulnerabilities; in order to capture more types of SOAP attacks, the SOAP port exposed mostin 2018 is analyzed, and a corresponding multi-port honeypot is manufactured. The honeypots are deployed to a plurality of nodes, a control center is designed at the same time to distribute commands and transmit files, and Docker technology packaging is assisted to achieve rapid deployment. Hackers cannot control the Internet of Things equipment through SOAP service vulnerabilities, so that the security of the Internet of Things is improved.
Owner:HARBIN INST OF TECH
A honeypot host
InactiveCN102216900AEasy to set upMultiple digital computer combinationsTransmissionHoneypotEngineering
Owner:MIMOS BERHAD
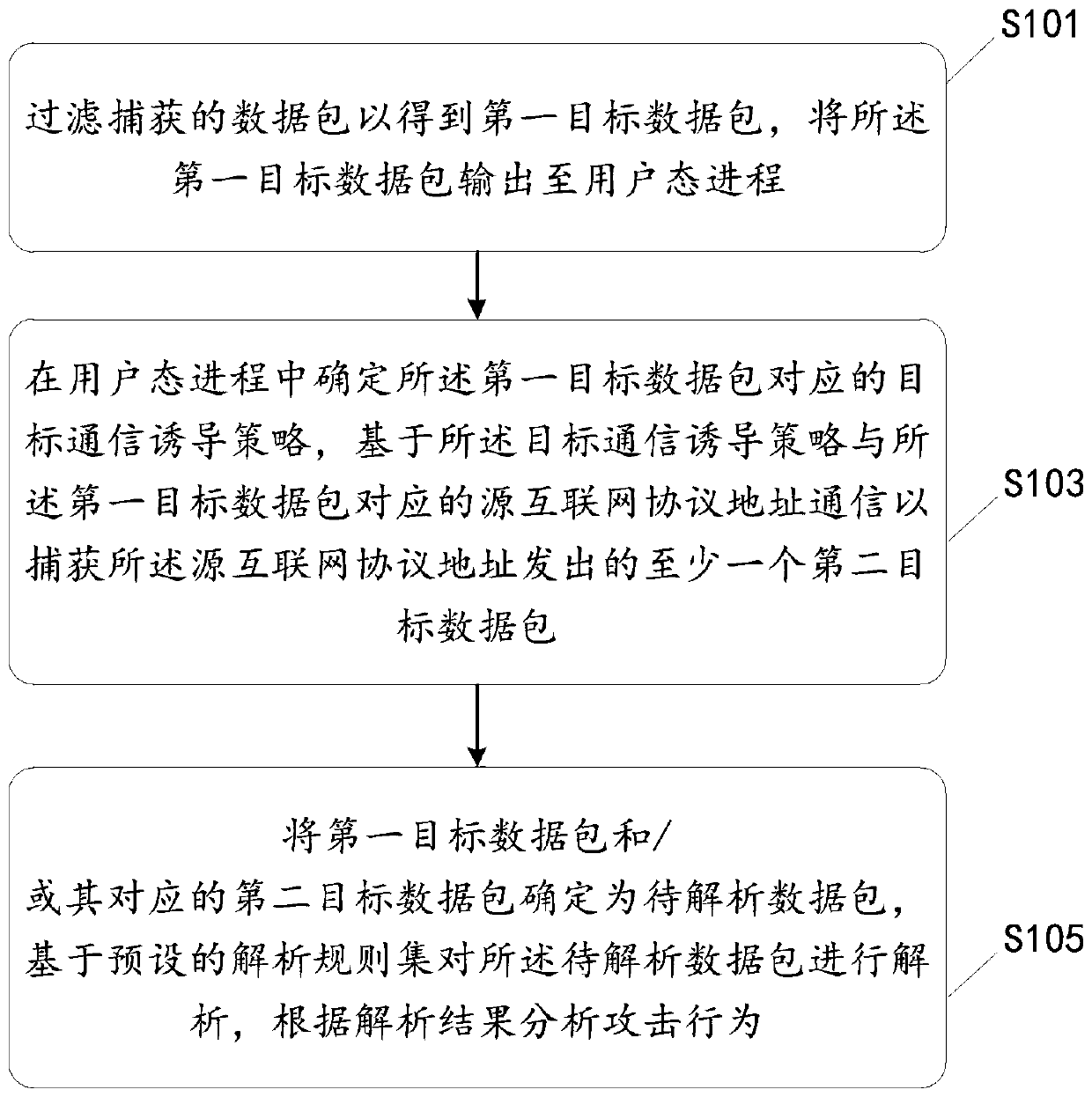
Attack perception method, device and equipment based on honeypot induction and medium
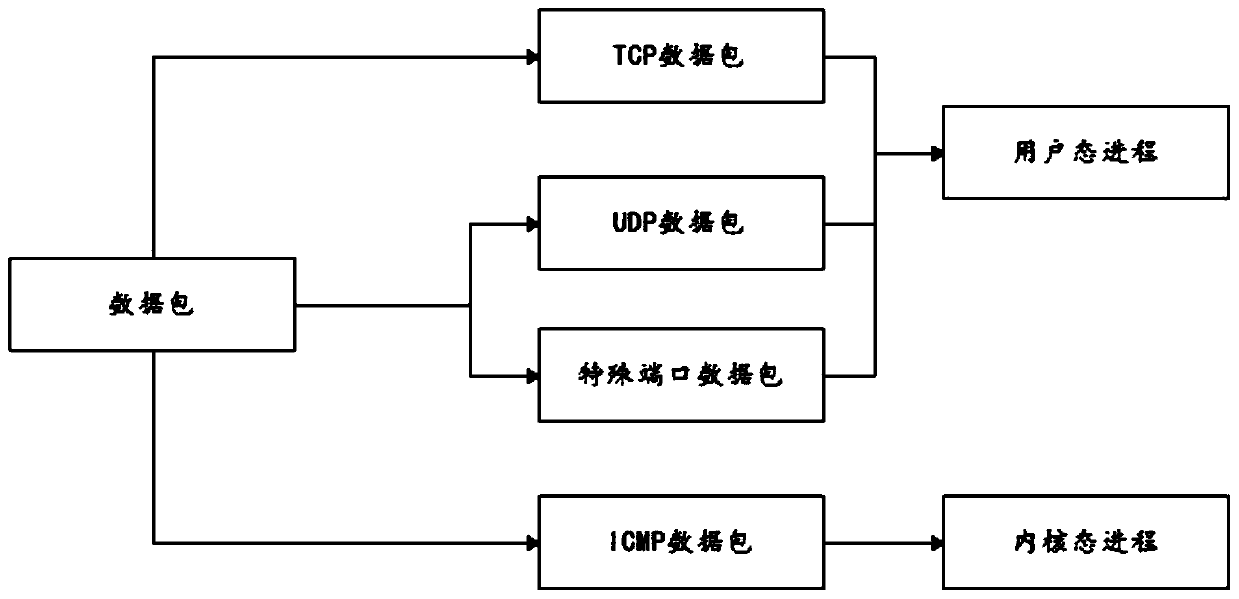
The invention discloses an attack perception method, device and equipment based on honeypot induction and a medium. The method comprises the following steps: filtering a captured data package to obtain a first target data package, and outputting the first target data package to a user mode process; determining a target communication induction strategy corresponding to the first target data packetin a user mode process, and communicating with a source Internet protocol address corresponding to the first target data packet based on the target communication induction strategy to capture at leastone second target data packet sent by the source Internet protocol address; and determining the first target data packet and / or the second target data packet corresponding to the first target data packet as a to-be-analyzed data packet, analyzing the to-be-analyzed data packet based on a preset analysis rule set, and analyzing an attack behavior according to an analysis result. The system has thedual advantages of an intrusion detection system and a honeypot system, attack information can be captured more comprehensively, and the safety of the network is protected.
Owner:TENCENT TECH (SHENZHEN) CO LTD
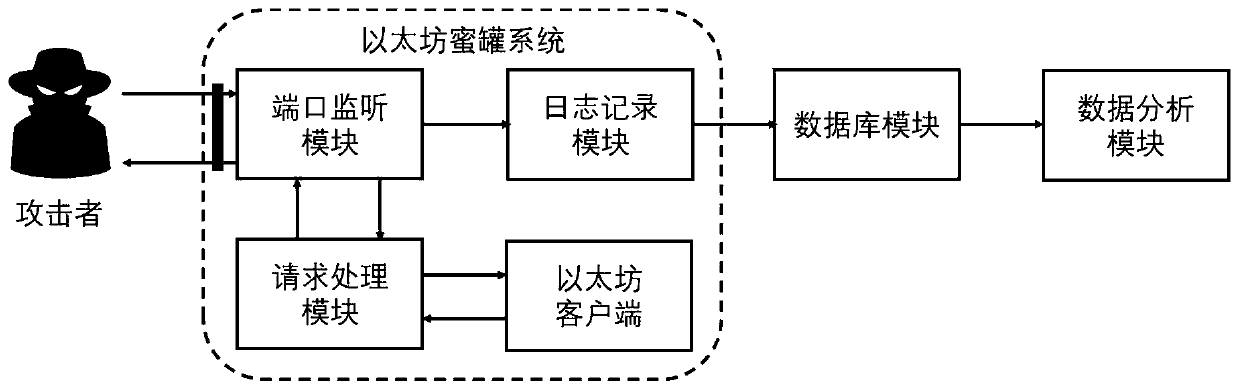
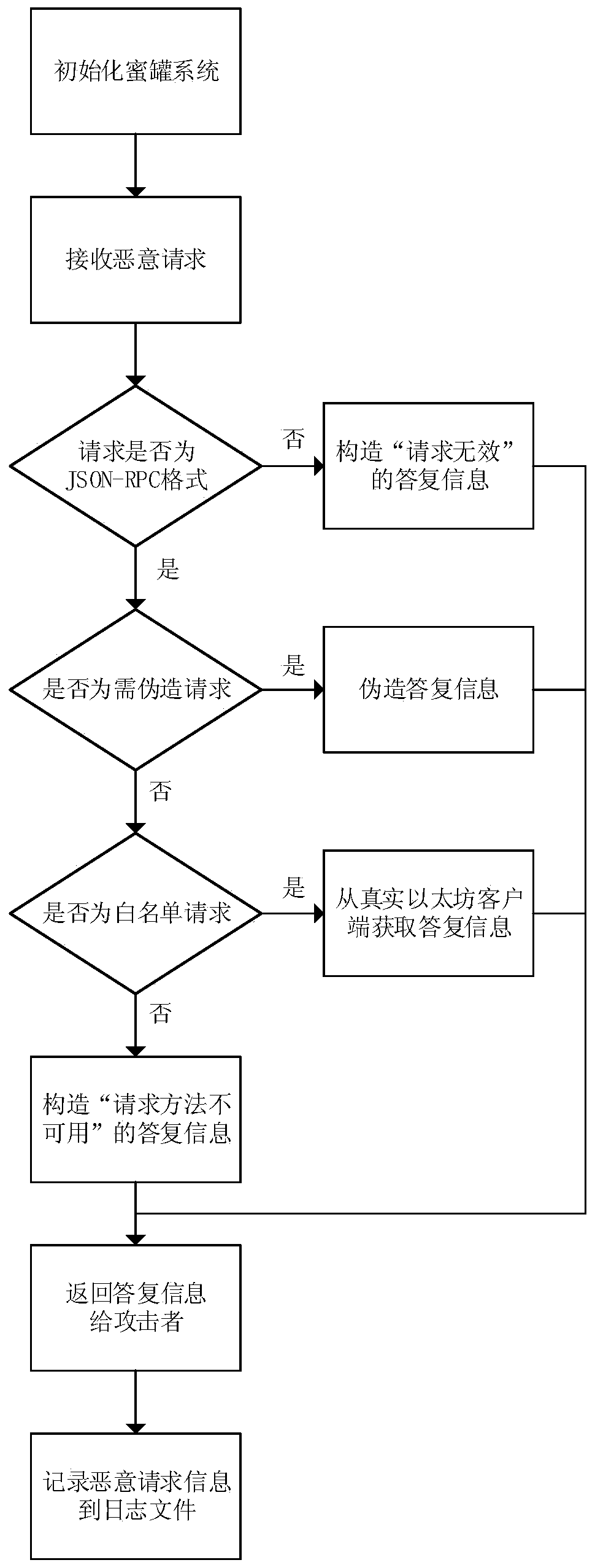
System and method for detecting Ethereum digital currency stealing attacks
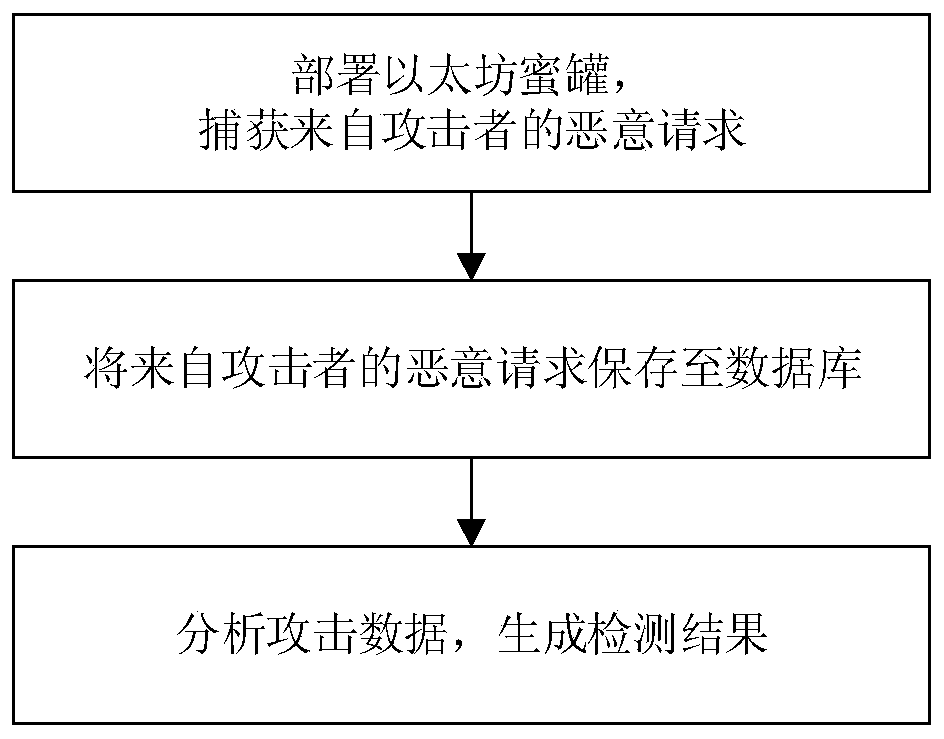
The invention discloses a system and method for detecting Ethereum digital currency stealing attacks. The method comprises the steps: deploying an Ethereum honeypot, inducing a network attacker to quickly find a honeypot host, transmitting a detection request, and capturing a malicious request from the attacker; storing the malicious request from the attacker in a database; and analyzing the attack data, associating the malicious request, detecting an attack behavior, identifying an attack method used by an attacker, tracking the attacker, and generating a detection result. According to the method, the malicious request sent by the attacker is attracted and captured, and the attack technique used by the attacker is further recognized, and weak points of an existing system are effectively found, so that the Ethereum system is better protected.
Owner:XIDIAN UNIV
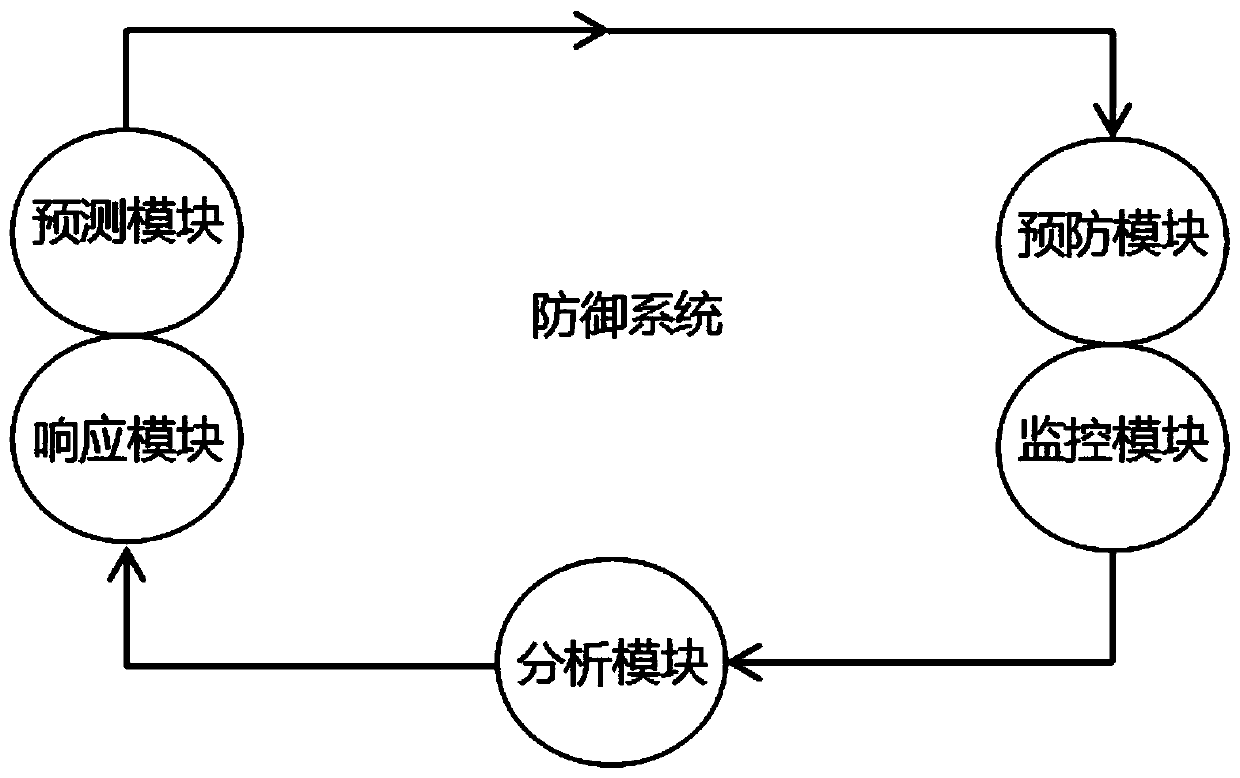
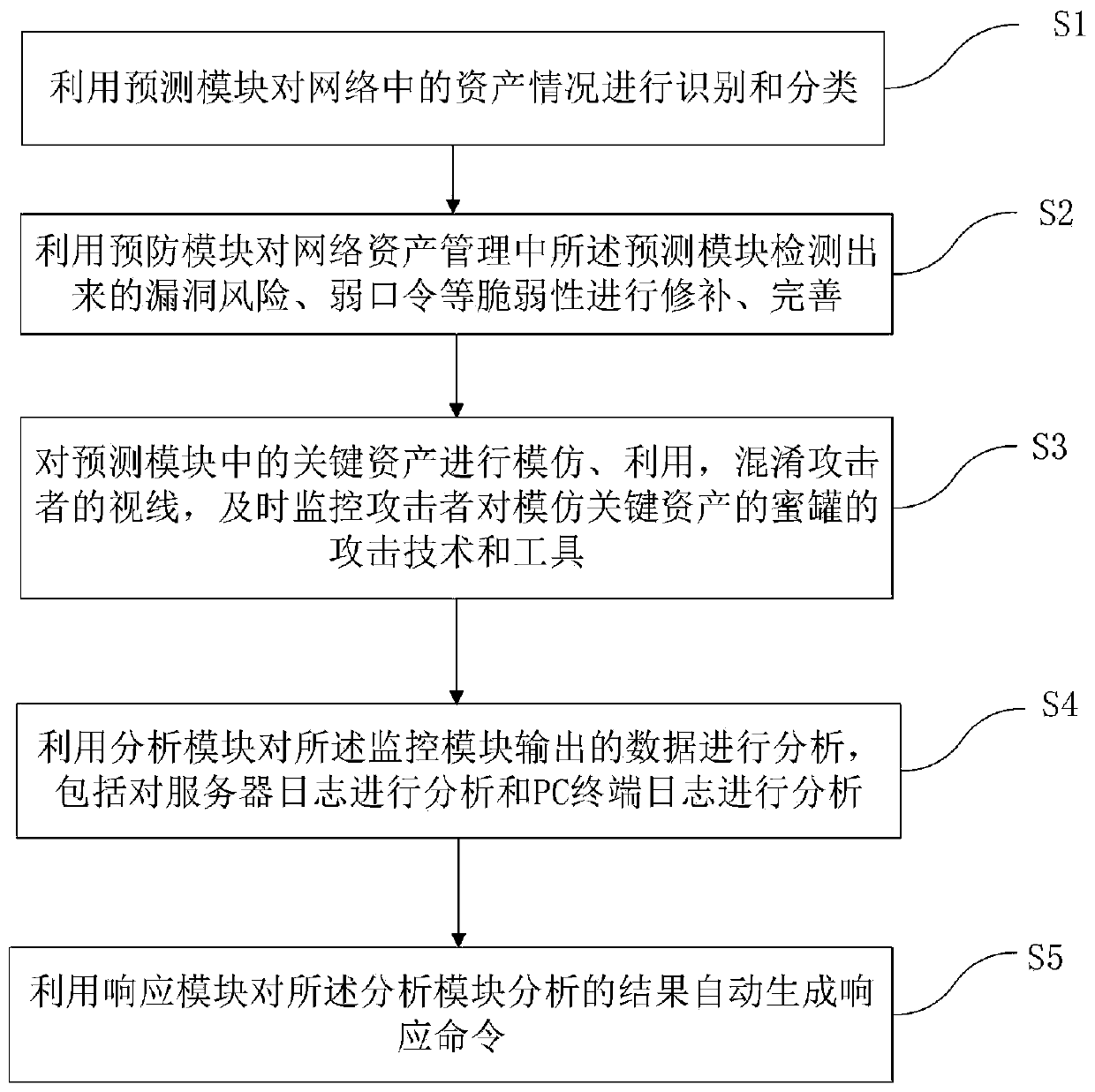
Defense system and method for solving network threats in self-adaptive closed-loop mode
The invention relates to a defense system and method for solving network threats in a self-adaptive closed-loop mode, and the system comprises a prediction module which is used for the recognition andclassification of asset conditions in a network on one hand, and is also used for the vulnerability scanning and weak password scanning of the network on the other hand; a prevention module which isused for repairing and perfecting vulnerability such as vulnerability risks and weak passwords detected by the prediction module in network asset management; a monitoring module which is used for simulating the key assets in the prediction module, utilizing and confusing the sight of an attacker, and monitoring the attack technology and tool of the attacker on honeypots simulating the key assets in time; an analysis module which is used for analyzing the data output by the monitoring module, and a response module which is used for automatically generating a response command for an analysis result of the analysis module. The defense system and method for solving the network threats in the self-adaptive closed-loop manner are specifically adapted to environments with different network resources and can effectively solve the threats in a network.
Owner:南京经纬信安科技有限公司
Honeypots for infrastructure-as-a-service security
Techniques for using honeypots to lure attackers and gather data about attackers and attack patterns on Infrastructure-as-a-Service (IaaS) instances. The gathered data may then be analyzed and used to proactively prevent such attacks.
Owner:ORACLE INT CORP
Honeypot bait distribution method and device, storage medium and electronic equipment
ActiveCN113037777AImprove securityIncrease the probability of falling into a honeypotTransmissionPathPingAttack
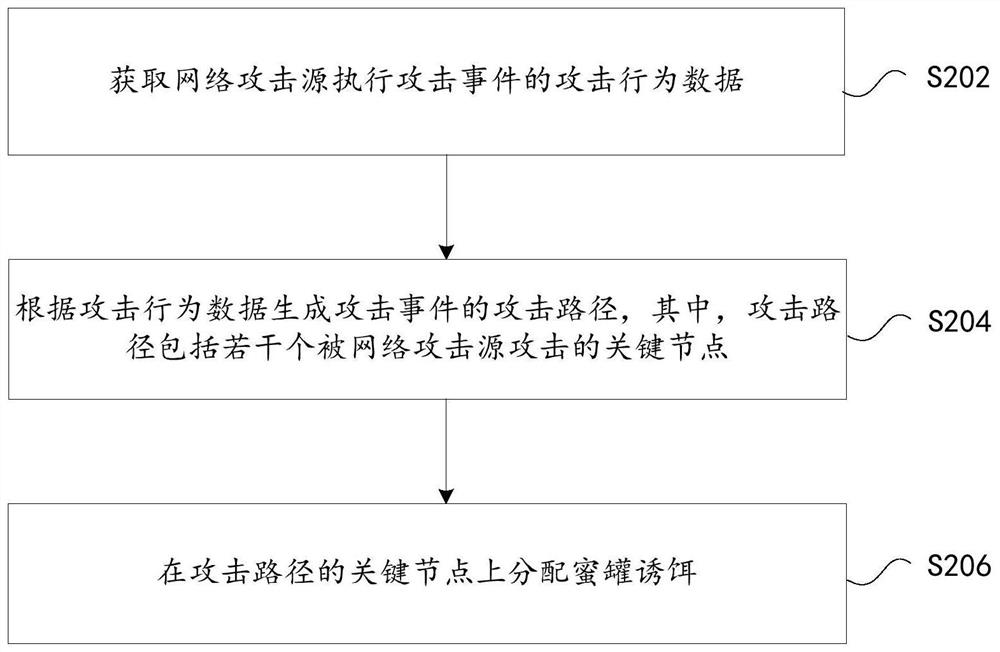
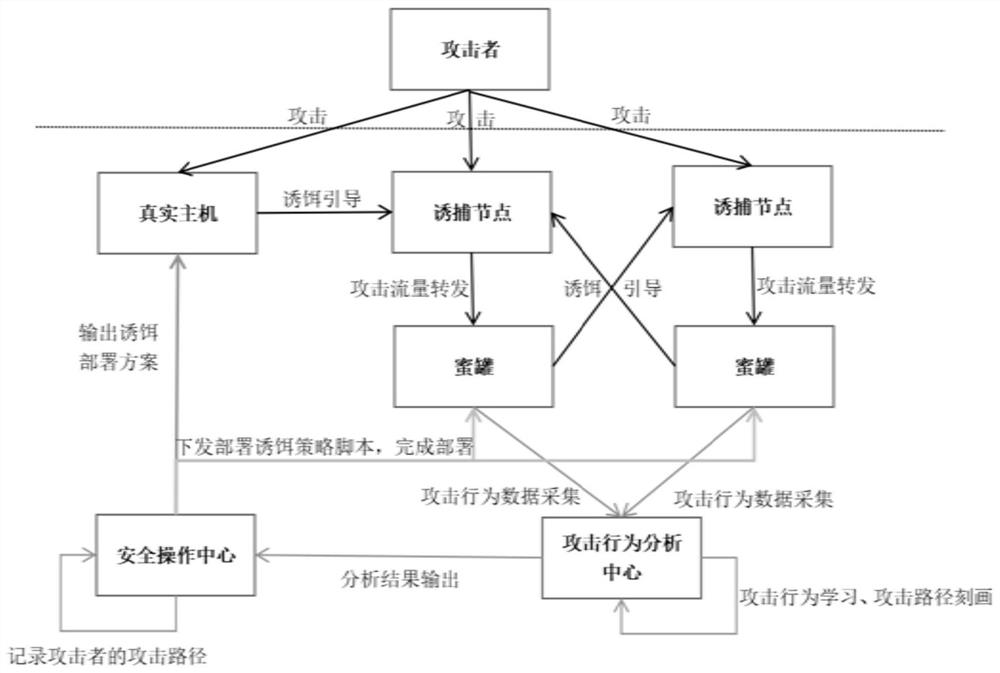
The invention discloses a honeypot bait distribution method and device, a storage medium and electronic equipment, and belongs to the field of network security. The method comprises the following steps: acquiring attack behavior data of a network attack source for executing an attack event; generating an attack path of the attack event according to the attack behavior data, wherein the attack path comprises a plurality of key nodes attacked by the network attack source; and distributing honeypot bait on the key node of the attack path. Through the method and the device, the technical problem that a honeypot in the related technology cannot defend attacks in a targeted manner is solved, and the defense efficiency of a honeypot network is improved.
Owner:广州锦行网络科技有限公司
Virtual honeypot
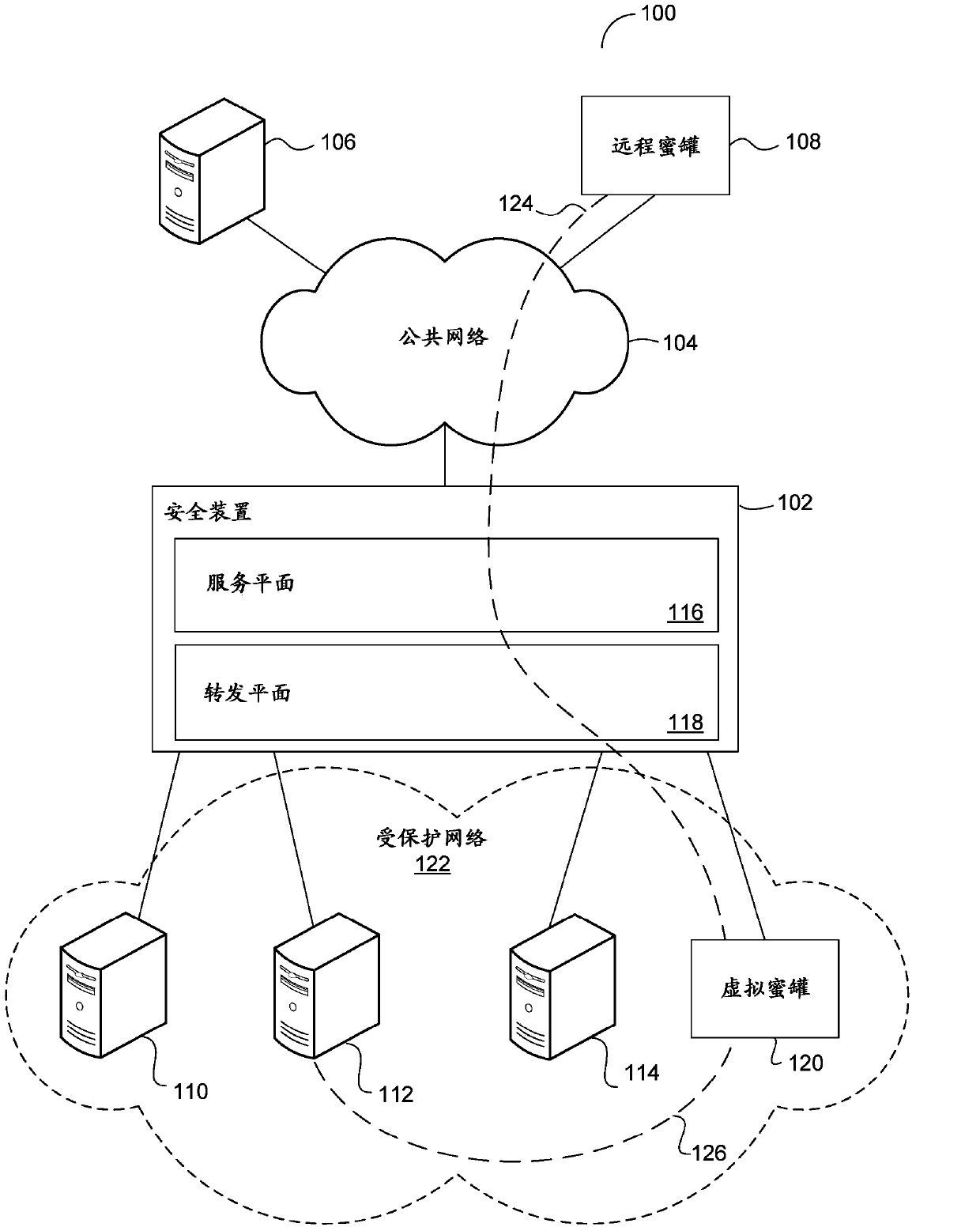
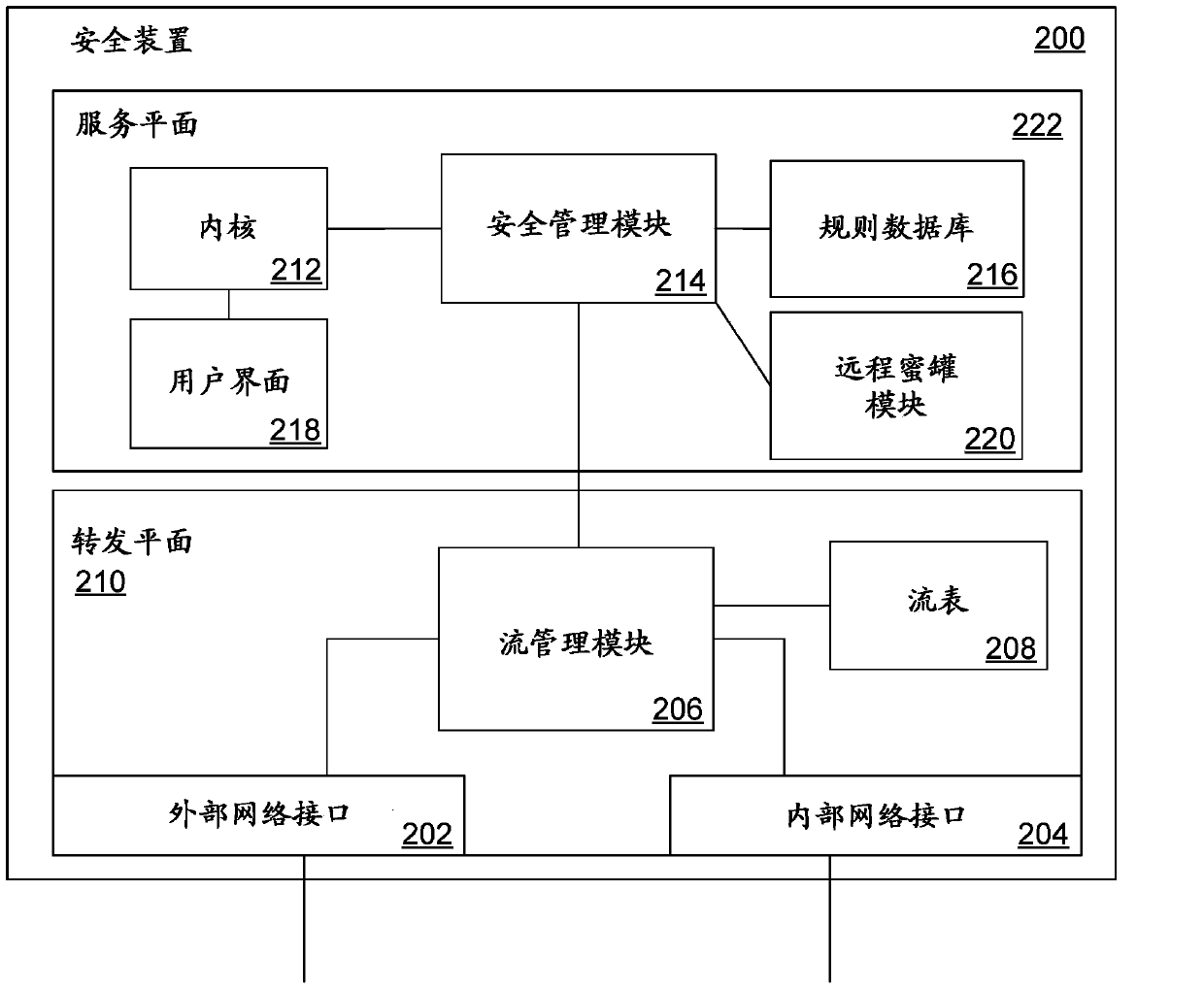
InactiveCN103746956AReduce the burden onReduce operating costsComputer security arrangementsNetworks interconnectionNetwork addressNetwork addressing
A virtual honeypot is configured within a security appliance by configuring one or more network addresses associated with the virtual honeypot. The security appliance receives network traffic destined for the virtual honeypot sent to the one or more network addresses associated with the virtual honeypot, and forwards the traffic to a remote honeypot such that the remote honeypot appears to be connected to a network local to the security appliance.
Owner:JUMIPER NETWORKS INC
Attack defense method, device, equipment, storage medium and system
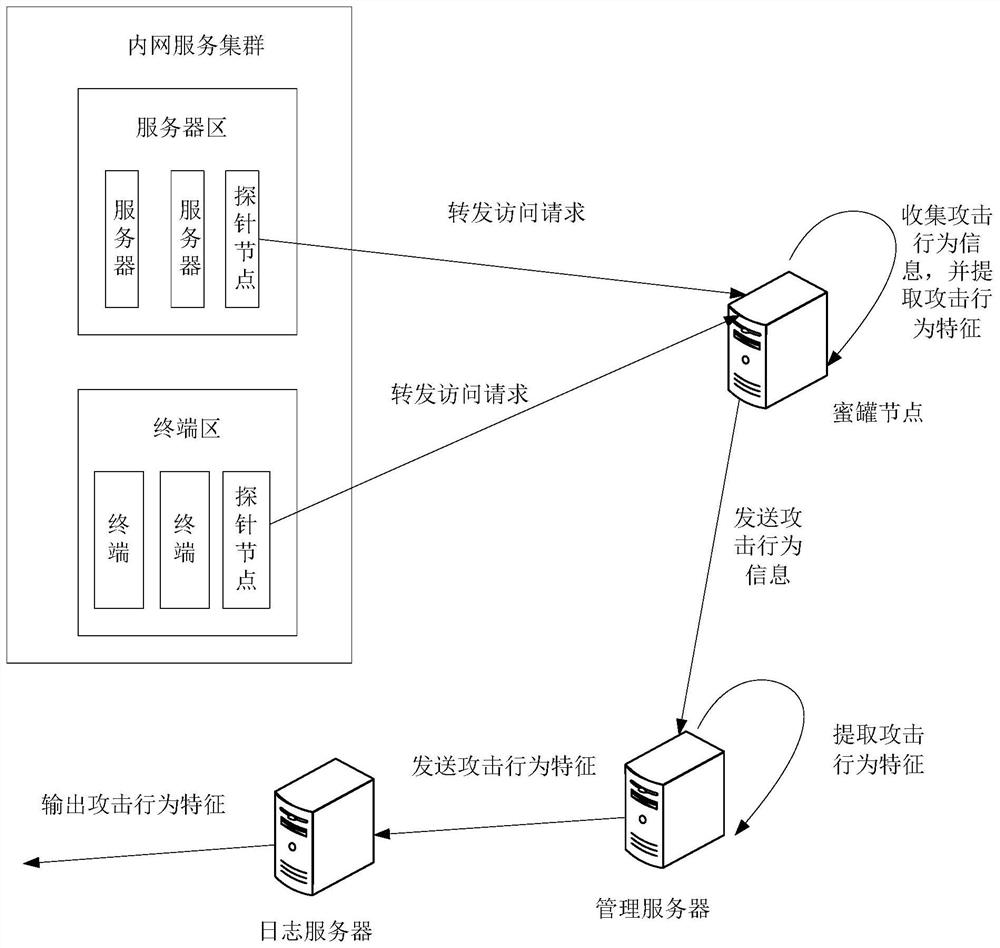
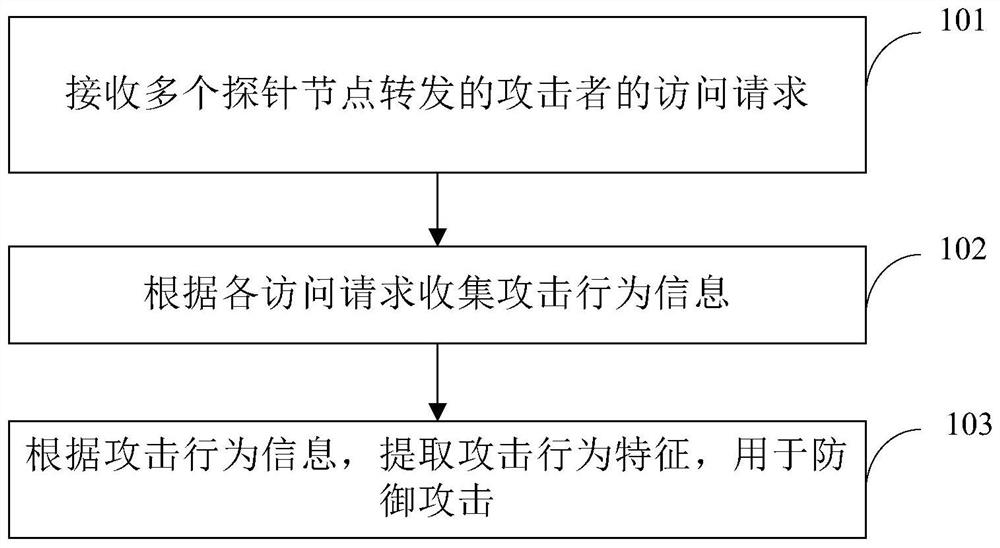
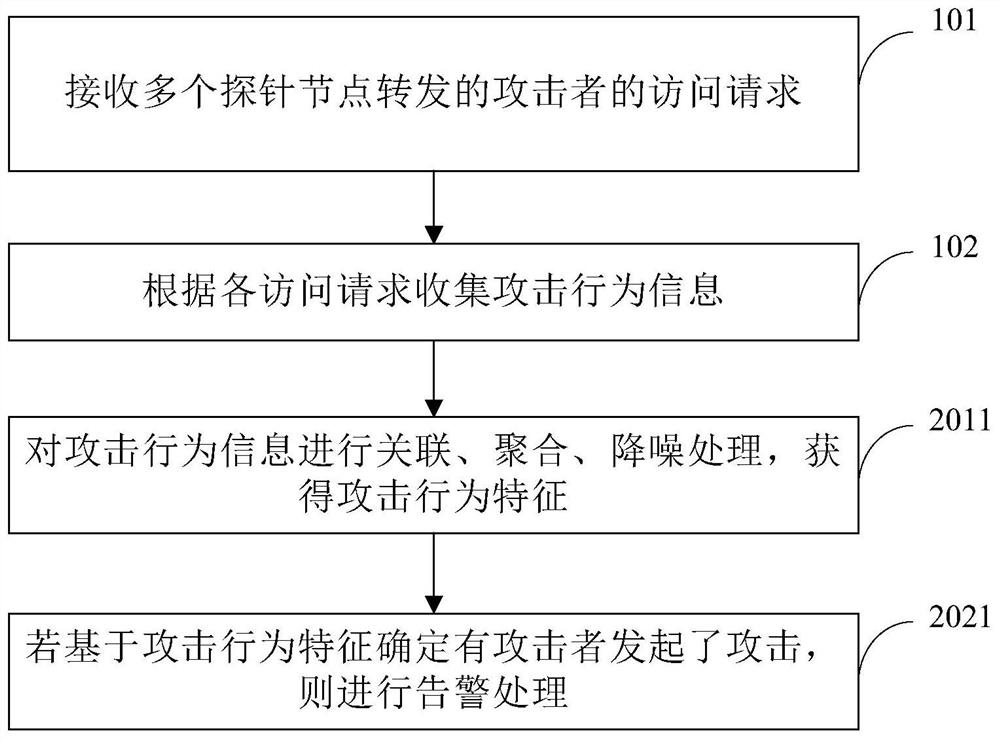
PendingCN112134854ASolve the problem that it is difficult to play the role of honeypot and the protection range is not comprehensive enoughTake up less resourcesTransmissionAttackHoneypot
The invention discloses an attack defense method, device and equipment, a storage medium and a system. The method comprises the following steps: receiving access requests of attackers forwarded by a plurality of probe nodes; collecting attack behavior information according to each access request; according to the attack behavior information, extracting attack behavior characteristics for defendingagainst attacks. According to the invention, the monitoring in a larger range can be realized based on a small amount of high-interaction honeypot, the cost is effectively reduced, the deployment andimplementation are simple, the occupied resources are less, and the problems that a small amount of honeypot nodes are difficult to play a honeypot role and the protection range is not comprehensiveenough in the prior art are solved.
Owner:北京华赛在线科技有限公司
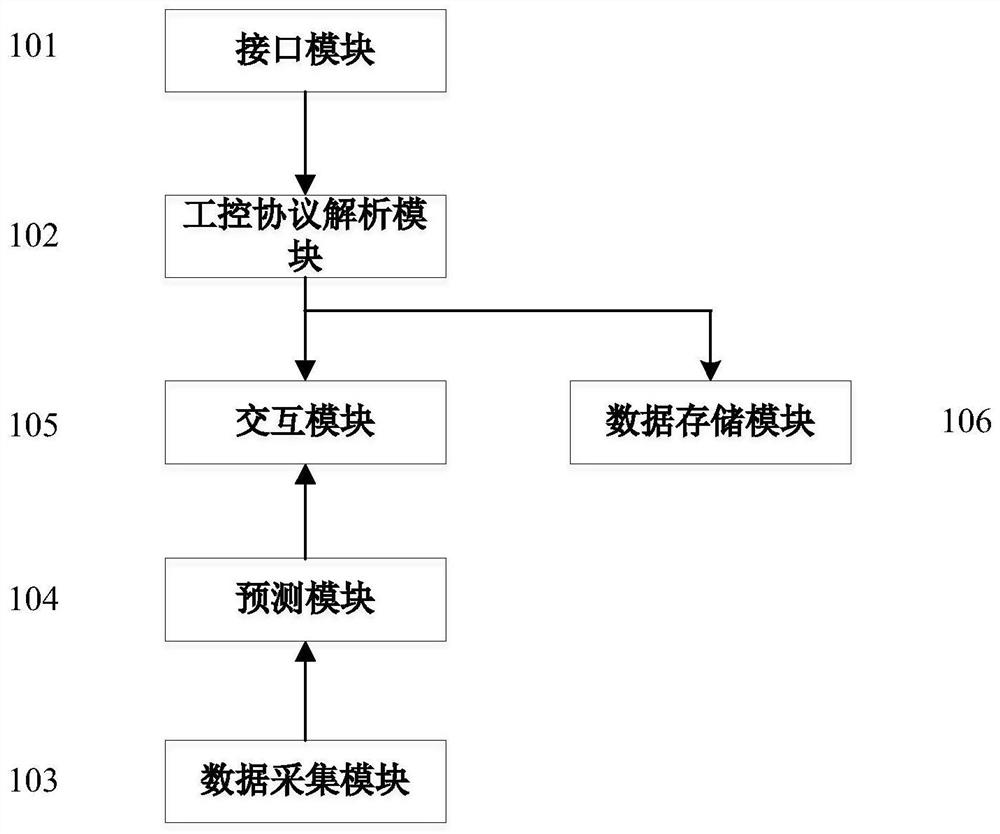
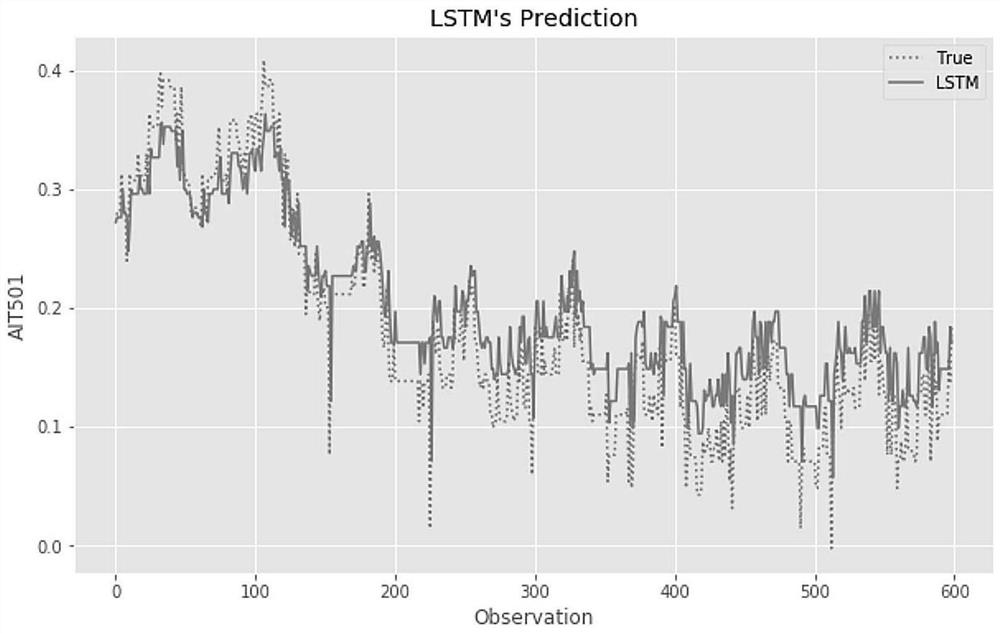
Industrial control honeypot interaction system based on time sequence prediction
PendingCN112182564AEffective Defense StrategyIncrease deceptionPlatform integrity maintainanceNeural architecturesAttackHoneypot
The invention belongs to the technical field of network security, and discloses an industrial control honeypot interaction system based on time sequence prediction. According to the invention, prediction is carried out by using the prediction data, so that the data security is improved. Most industrial control data is periodic and has a certain rule, prediction data is used for prediction, real data is prevented from being input again, and the real-time performance of honeypot interaction is guaranteed. The real equipment state change condition in the industrial control scene is predicted fora long time by using the time sequence prediction method, deep simulation of the industrial control equipment is completed by combining the honeypot technology, instant response information conformingto the industrial control scene is made to an attacker, the fraudulence of honeypots is improved. Attack information can be collected while attackers are lured to attack for multiple times, portraying of the attackers is facilitated, passivity is changed into initiative, and the safety of the industrial control network is better maintained.
Owner:NORTHEASTERN UNIV
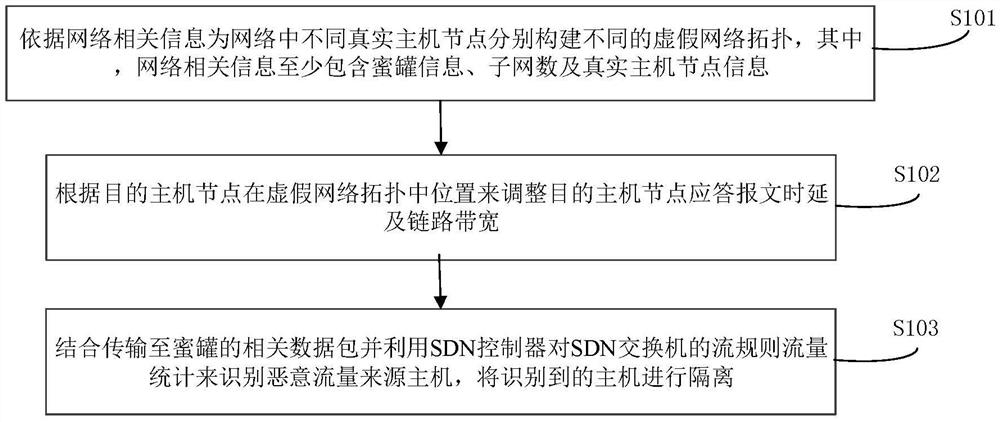
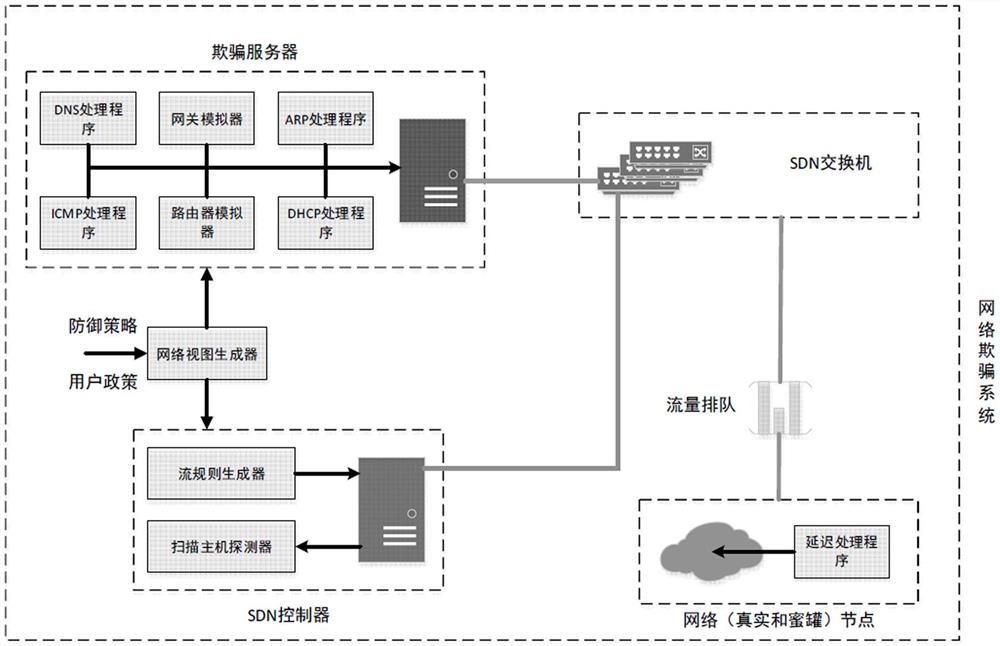
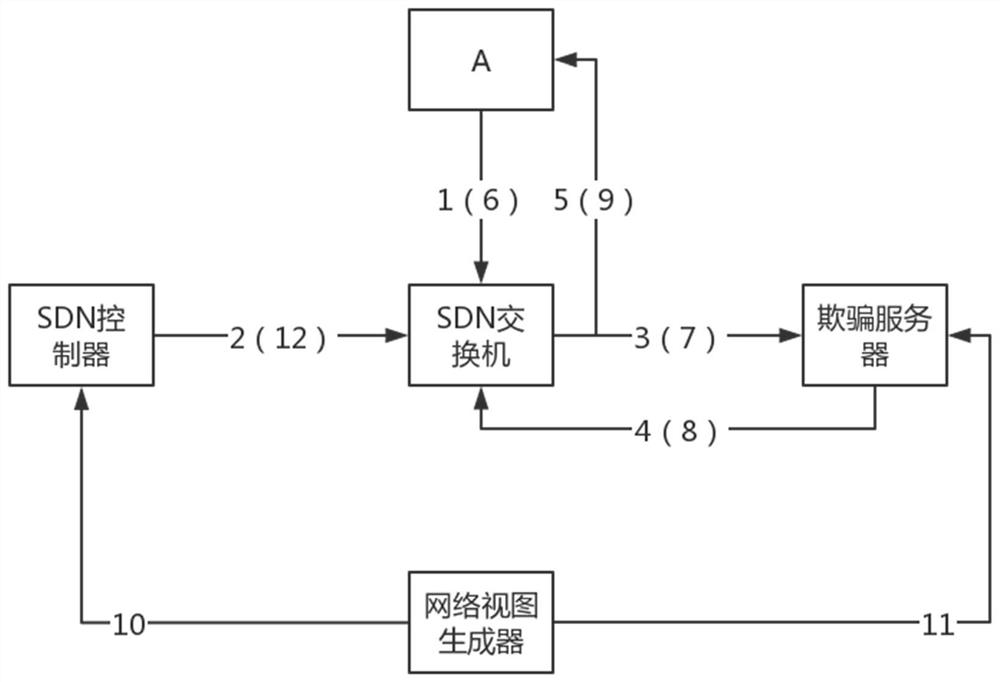
Network protection method and system based on false topology generation and system architecture
PendingCN112769771AExtension of timeAchieve the purpose of deceiving advanced attackersTransmissionData packHoneypot
The invention belongs to the technical field of network security, and particularly relates to a network protection method and system based on false topology generation and a system architecture, and the method comprises the steps: constructing different false network topologies for different real host nodes in a network according to network related information, wherein the network related information at least comprises honeypot information, the number of subnets and real host node information; adjusting the response message delay and link bandwidth of the destination host node according to the position of the destination host node in the false network topology; and identifying the malicious traffic source host by combining the related data packet transmitted to the honeypot and utilizing the SDN controller to carry out flow rule traffic statistics on the SDN switch, and isolating the identified host. In order to solve the problem that real network configuration is easy to obtain by network investigation in the existing static network, the invention uses the idea of mimicry defense to cheat internal attackers by constructing a false network topology so as to protect a benign host in the network and improve the stability and reliability of network operation.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com