Novel honeypot networking method and honeypot system
A honeypot and networking technology, applied in the field of network security, can solve the problems of low capture probability, unusable service ports of service hosts, and low attack capture rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
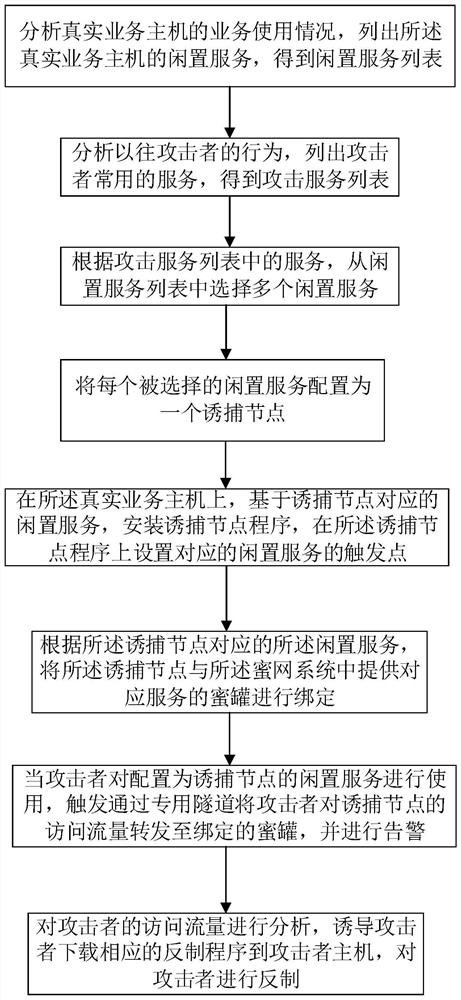
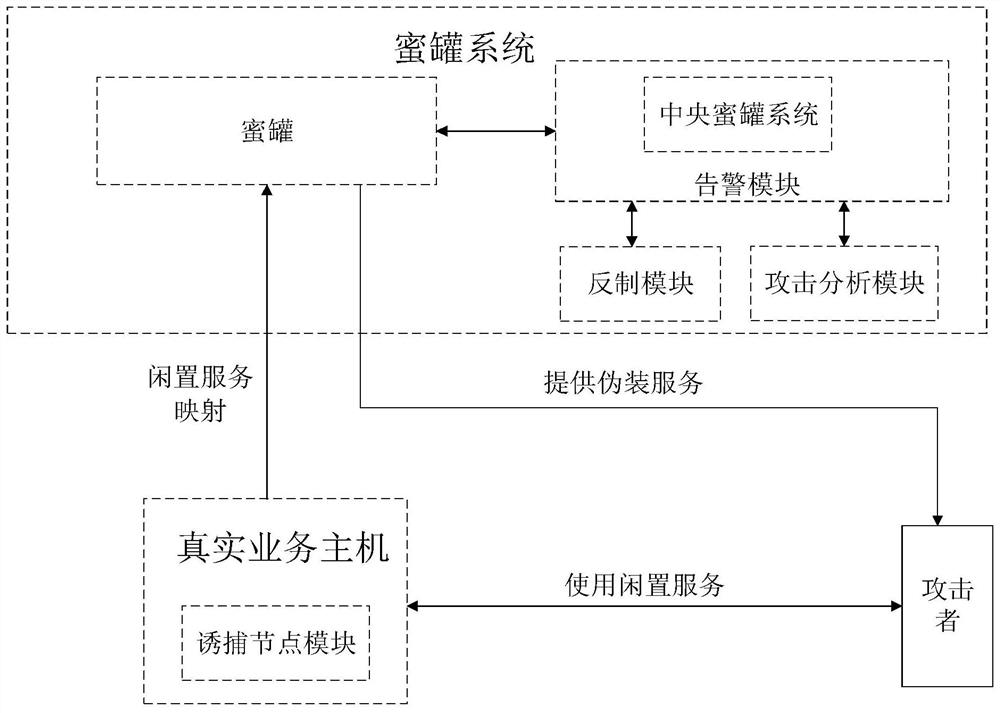
[0142] Refer to attached figure 1 , 2 and 3, according to a specific embodiment of the present invention, the honeypot networking method provided by the present invention is described in detail.
[0143] For example:
[0144] The IP address of the real business host is: 10.1.2.3;
[0145] The idle service list is: ftp service, SSH service, smb service, etc.;
[0146] The list of commonly used services by attackers is: ftp service, SSH service, remote desktop service, etc.;
[0147] The idle services selected from the idle service list are: ftp service and SSH service, and the corresponding port numbers are 21 and 22 respectively;
[0148] The trapping nodes bound to idle service ports are configured as: 10.1.2.3:21 and 10.1.2.3:22;
[0149] The honeypot configurations bound to the trapping nodes are: ftp service honeypot and SSH service honeypot;
[0150] Trapped node 1: IP address is 10.1.2.3, port number is 21;
[0151] Trapped node 2: IP address is 10.1.2.3, port num...
Embodiment 2
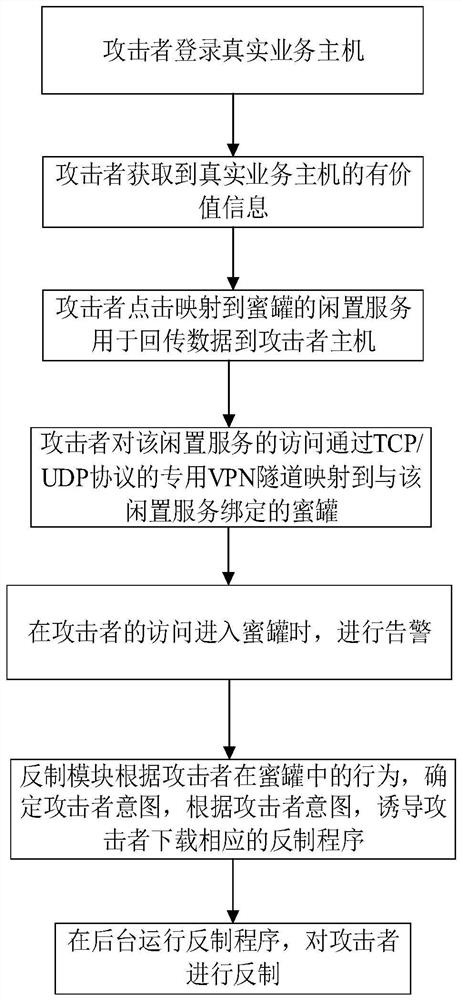
[0188] Refer to attached figure 2 , according to yet another specific embodiment of the present invention, the processing flow of the present invention will be described in detail when the attacker accesses the idle service port where the decoy node is deployed by using the present invention.
[0189] For example:
[0190] The IP address of the real business host is: 192.168.1.5;
[0191] The idle service list is: Remote Desktop Service, etc.;
[0192] The list of commonly used services by attackers is: Remote Desktop Services, etc.
[0193] The idle service selected from the idle service list is: Remote Desktop Service, and the corresponding port number is 3389;
[0194] The trap node configuration bound to the idle service port is: 192.168.1.5:3389;
[0195] The honeypot configurations bound to the decoy nodes are as follows:
[0196] Trapped node 1: IP address is 192.168.1.5, port number is 3389;
[0197] The attacker entered the real host 192.168.1.5. When the attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com