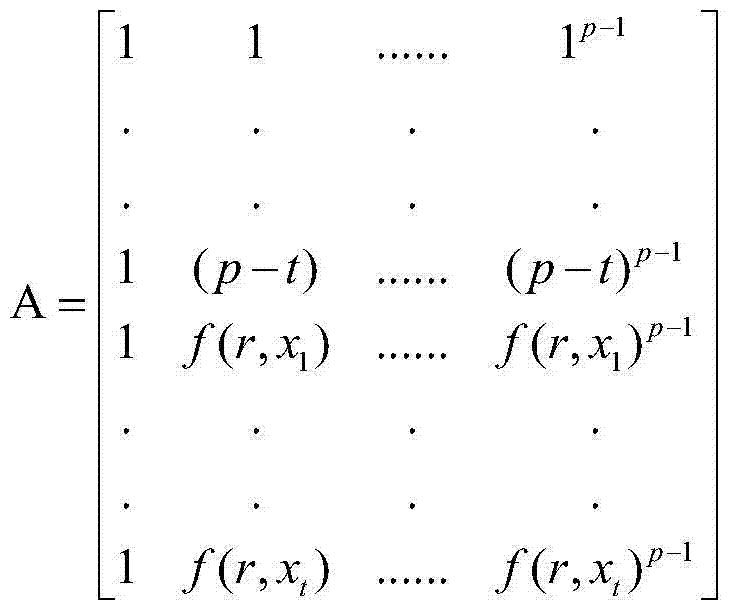Patents
Literature
542results about How to "Not easy to find" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
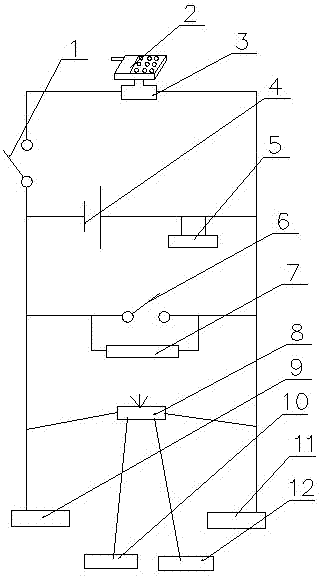
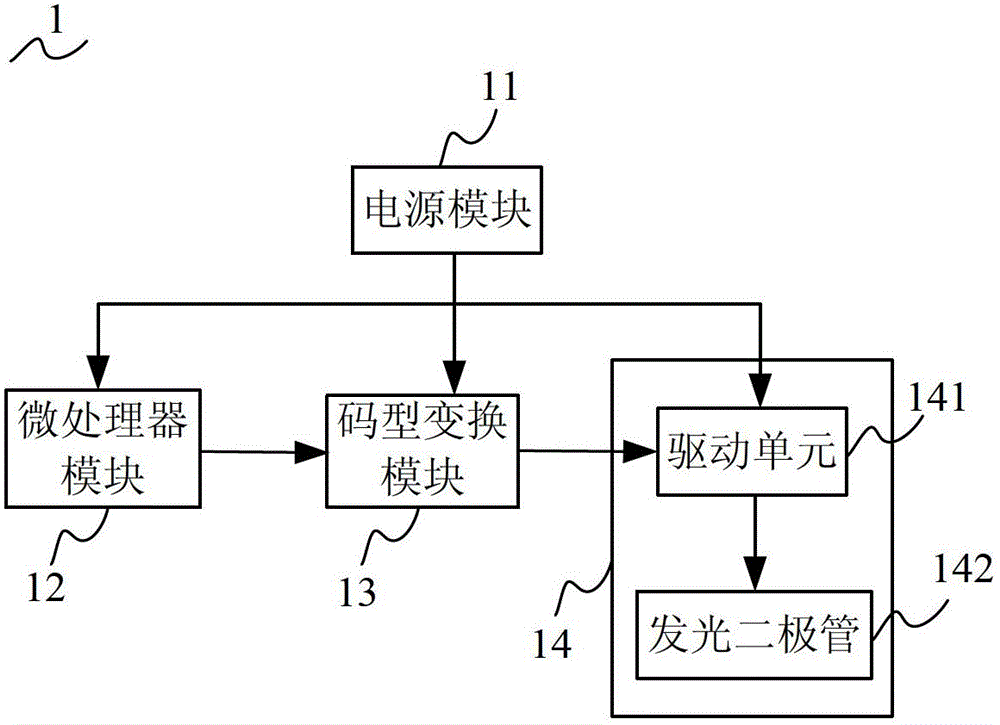
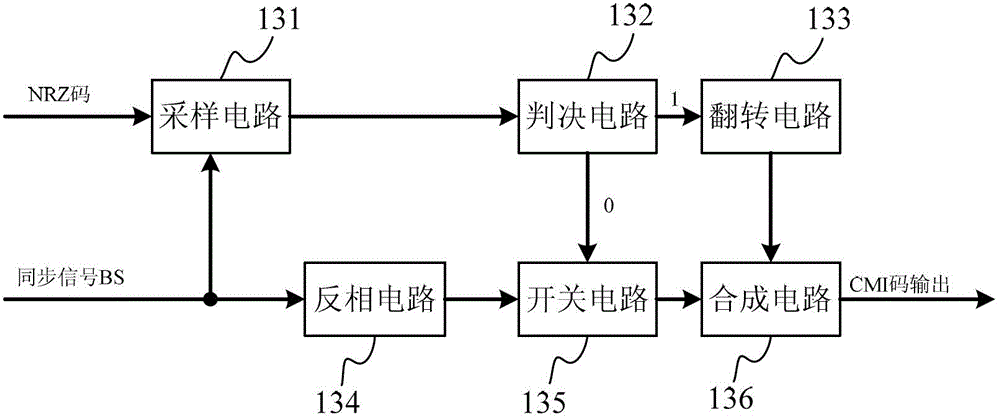
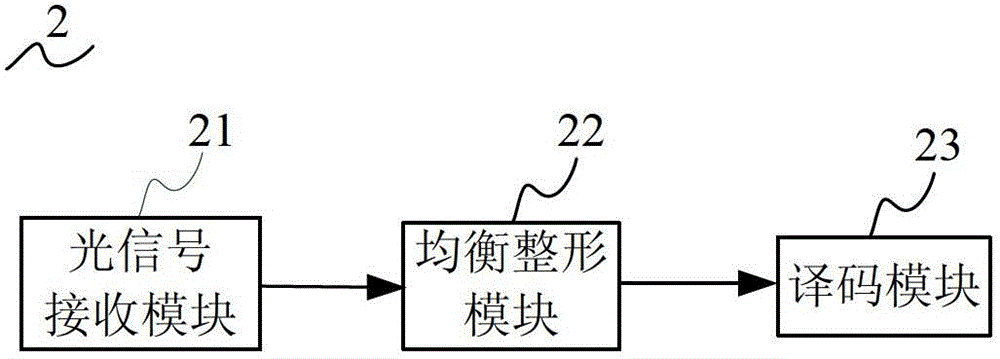
Intelligent monitoring method and relevant equipment
InactiveCN104135642ALess power consumptionReduce the trouble of additional deploymentClosed circuit television systemsBurglar alarmComputer terminalMonitor equipment
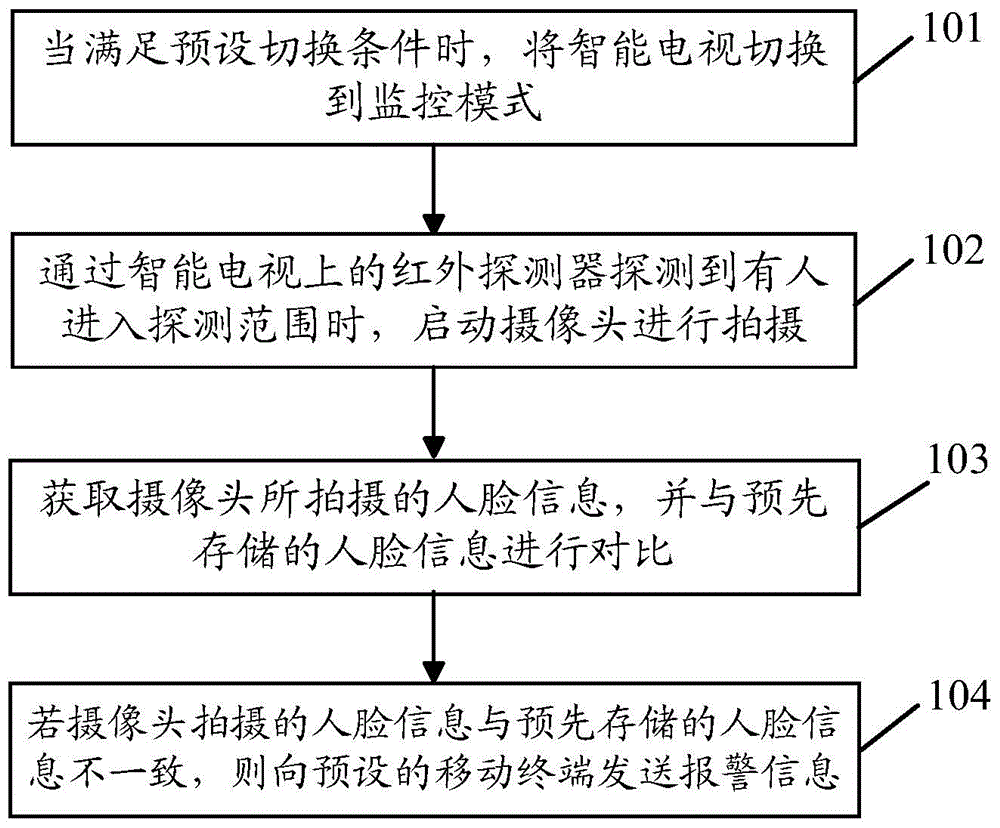
The invention discloses an intelligent monitoring method and relevant equipment. The intelligent monitoring method comprises the following steps: when a preset switching condition is satisfied, switching a smart television to a monitoring mode; when the entrance of a person into a detection range is detected through an infrared detector on the smart television, starting a camera for shooting; acquiring information of a human face shot by the camera, and comparing the human face information with pre-stored human face information; and if the information of the human face shot by the camera is inconsistent with the pre-stored human face information, transmitting alarm information to a preset mobile terminal. Compared with the prior art, a monitoring scheme provided by the embodiment of the invention has the advantages that monitoring equipment does not need to be arranged additionally, cost is saved, the camera is prevented from being found easily, the safety is improved, and the situation of false alarm caused by the entrance of family members is avoided.
Owner:QINGDAO GOERTEK
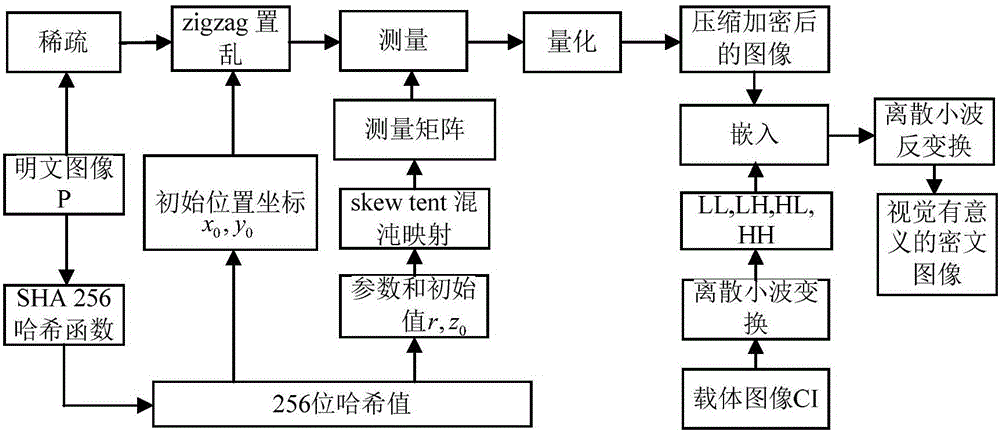
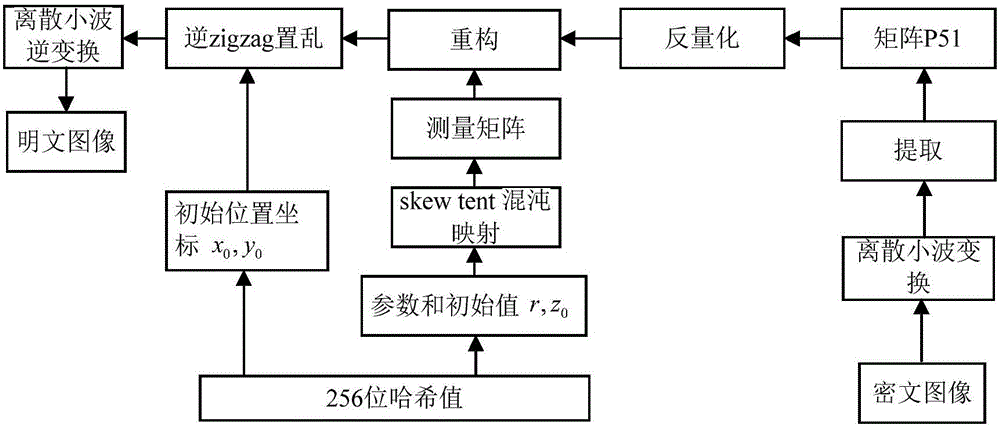
Image encryption method and image decryption method with visual security and data security based on compressed sensing
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
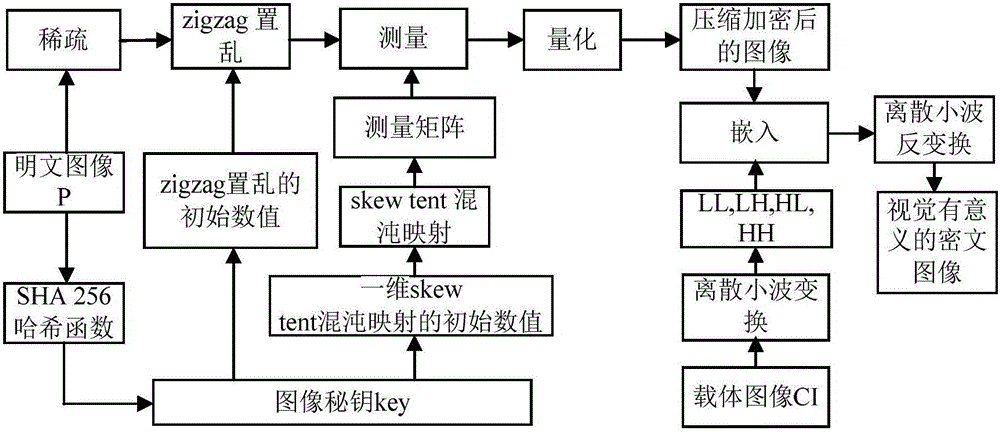
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
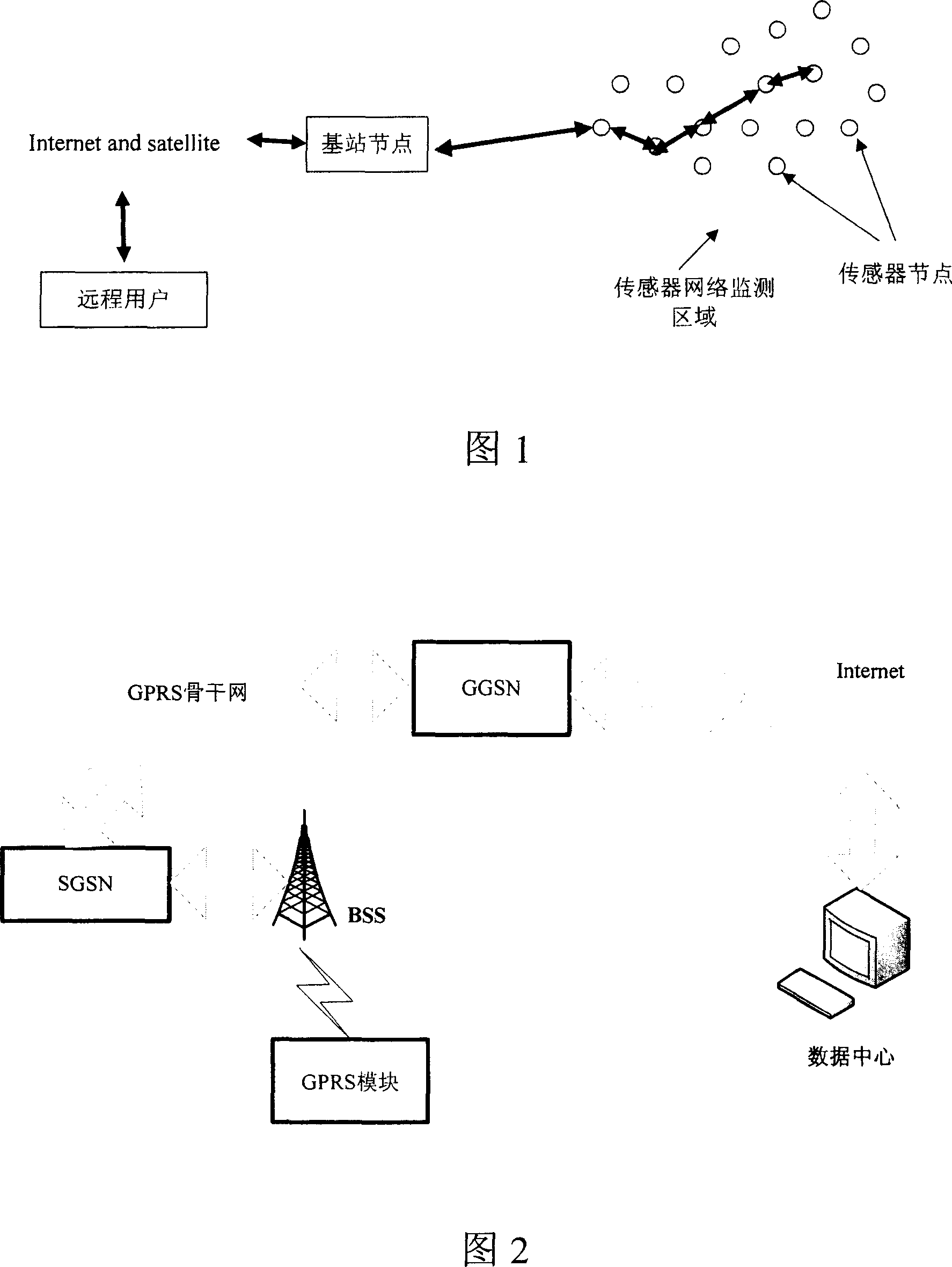
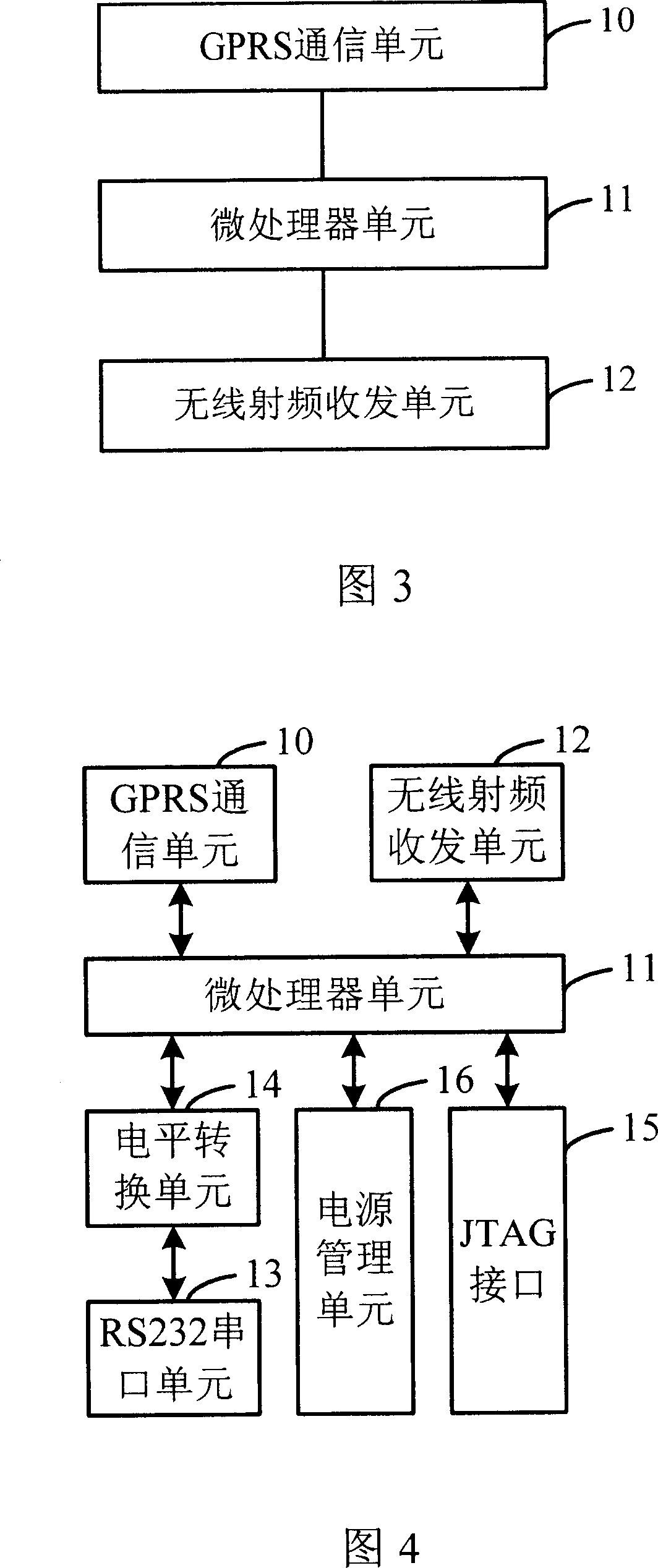
A wireless sensor network gateway device
InactiveCN101009619ALow costReduce power consumptionData switching by path configurationRadio/inductive link selection arrangementsLine sensorTransceiver
The disclosed gateway device for wireless sensor network comprises: a GPRS communication unit to communicate between the gateway and Internet or wireless communication network, a wireless RF transceiver for gateway and wireless sensor network, and a MPU to control the communication of former two units, wherein the MPU uses UART (general asynchronous serial interface) to communicate with the GPRS unit and SPI (synchronous serial interface) to communicate with the RF transceiver. This invention realizes reliable remote connection and bidirectional transmission for request in real application.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
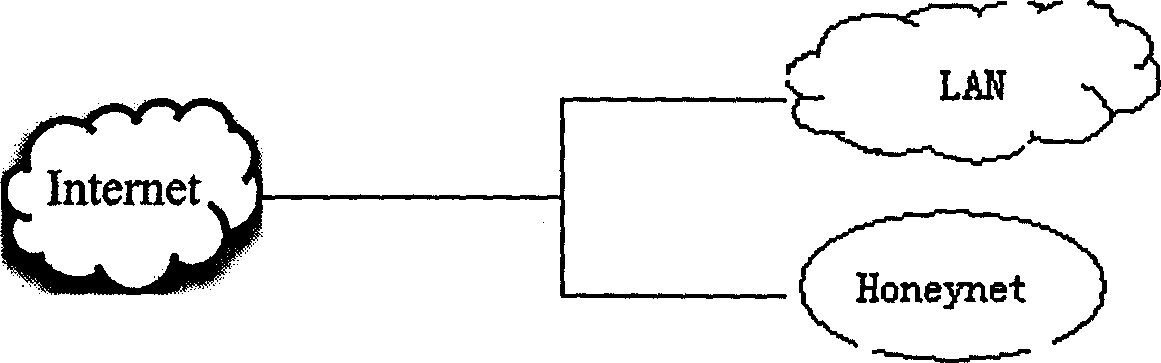
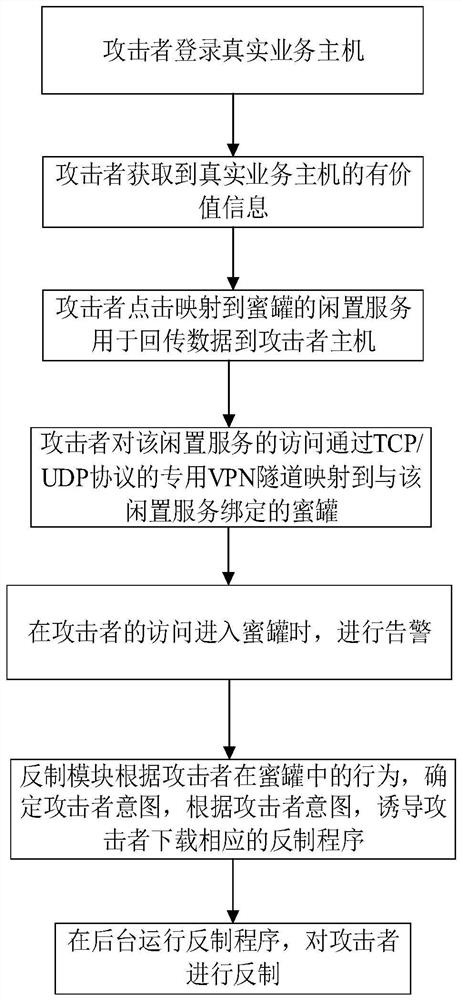
Honeynet protection method and system
ActiveCN107370756AImprove concealmentAchieve consistencyTransmissionAnomaly detectionNetwork overhead
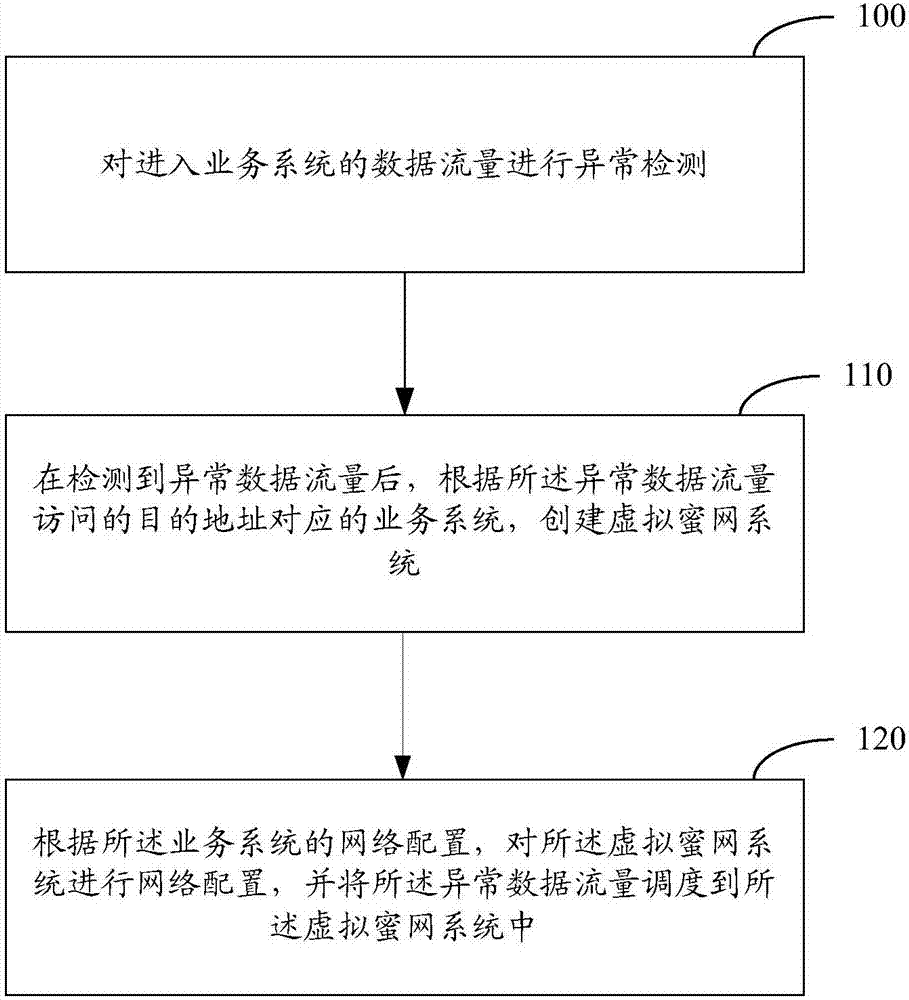
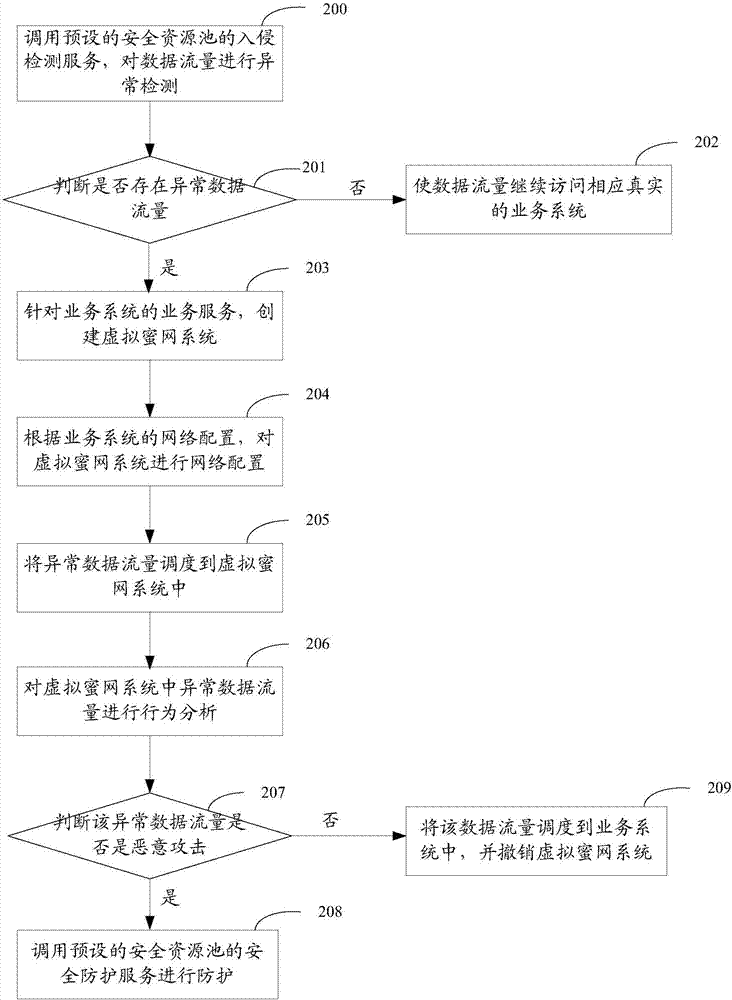
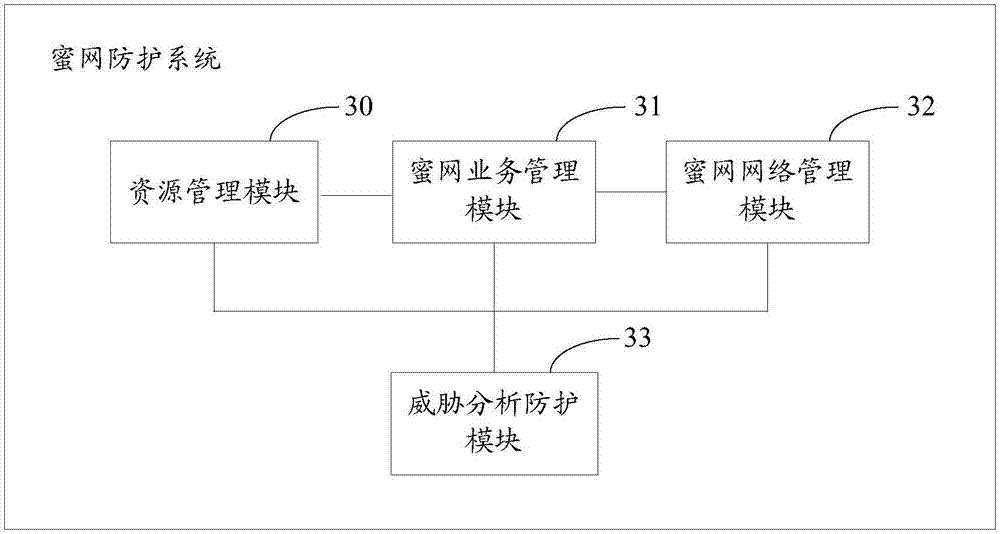
The invention relates to the field of network security, and especially relates to a Honeynet protection method and system. The method includes the following steps: detecting whether the data traffic entering a business system is abnormal; after detecting abnormal data traffic, creating a virtual Honeynet system according to a business system corresponding to a destination address accessed by the abnormal data traffic; and carrying out network configuration on the virtual Honeynet system according to the network configuration of the business system, and scheduling the abnormal data flow to the virtual Honeynet system. The virtual Honeynet system consistent with the business service of the business system is created, and network configuration is carried out on the virtual Honeynet system. The consistency between the virtual Honeynet system and the business system in business logic and network configuration is ensured, the virtual Honeynet system is more concealed, and attack seduction and forensic analysis are more concealed and less detectable to attackers. Moreover, the deployment is relatively simple, and the method and the system can be quickly deployed to an SDN (Software Defined Network) to achieve security protection without increasing the overhead of the business network.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
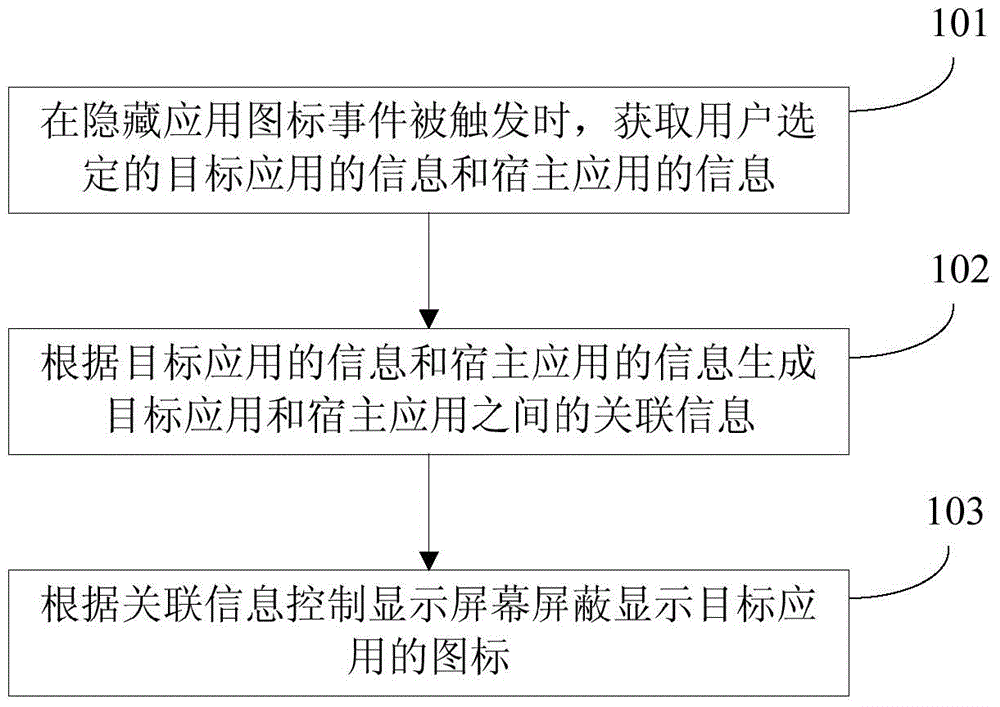
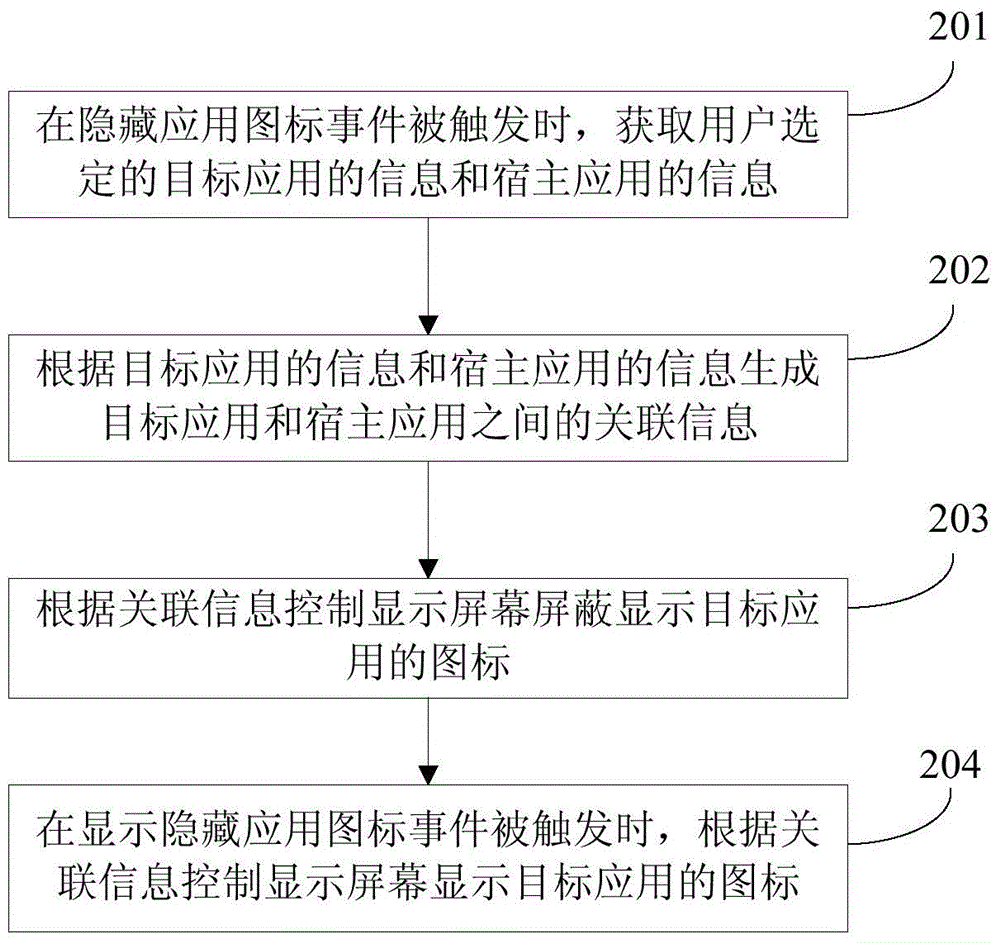
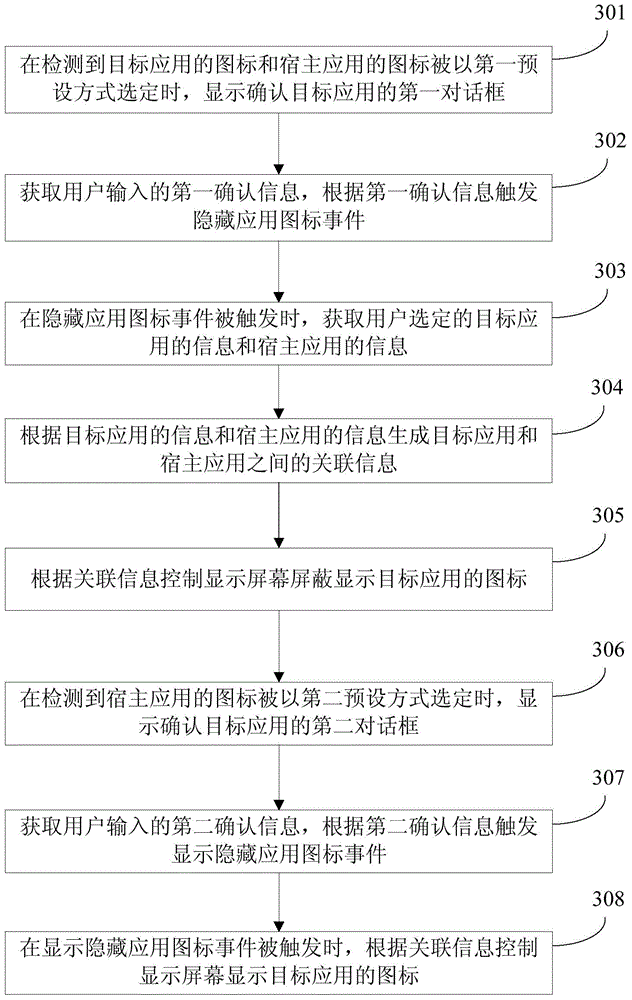
Method and device for hiding application icons
ActiveCN104573552AHide thoroughlySolve the imperfect functionDigital data protectionInput/output processes for data processingMobile deviceInformation control
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method for abstracting graph and text infromation utilizing half-hue image networking hiding
InactiveCN101022499AGuaranteed lossEasy to findPattern printingPictoral communicationHueInformation hiding
A method of utilizing halftone to hide and to pick up alphaphotographic information includes hiding alphaphotographic information effectively in printed manuscript at printing process and simultaneously enabling to use printing film prepared by present invention to easily pick up false proof information hidden in said printed manuscript.
Owner:PEKING UNIV +2
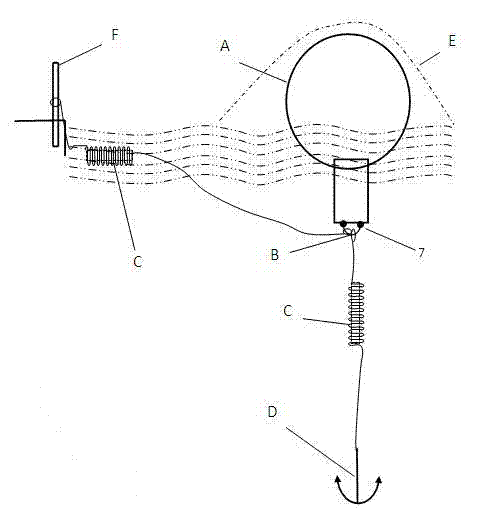
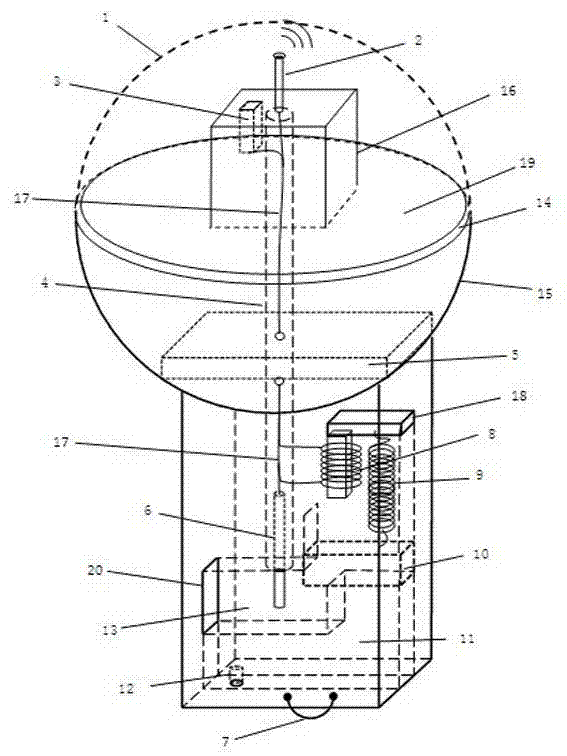
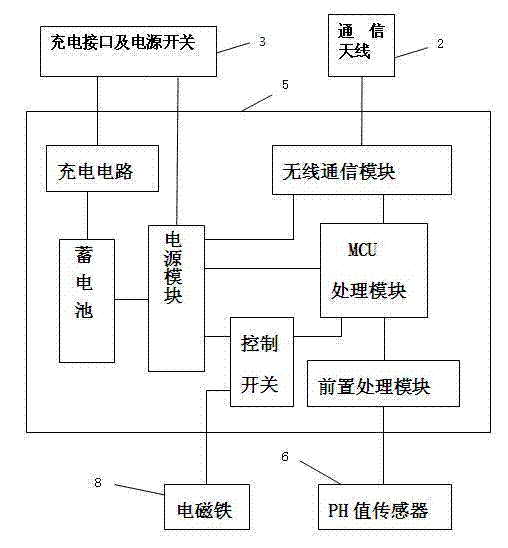
PH value monitoring wireless sensing network (WSN) node device for preventing secrete drainage of sewage and monitoring method
InactiveCN103245766AImprove work efficiencyIntelligentWithdrawing sample devicesTesting waterPower switchingSewage
The invention discloses a PH value monitoring wireless sensing network (WSN) node device for preventing secrete drainage of sewage and a monitoring method. The PH value monitoring WSN node device comprises a floating ball floating in water in a sealed manner and a square shell which is fixedly connected with the bottom of the floating ball and is immersed in the water, wherein an antenna bracket table and a communication antenna are fixedly arranged in an upper half ball cover; a charging interface and a power switch are arranged on the antenna bracket table; a circuit board is fixed at the bottom in a lower half ball cover; a water storehouse is arranged at the bottom in the square shell; a water feeding storehouse is arranged on one side of the upper part of the water storehouse; a magnet valve is arranged between the water feeding storehouse and the water storehouse; the lower end of a PH value sensor extends into and is suspended in the water feeding storehouse; an electromagnet bracket fixed on the inner wall of the square shell is arranged on the upper part in the square shell; an electromagnet is supported on the electromagnet bracket; the upper end of a spring is fixedly connected with the electromagnet bracket, and the lower end of the spring is connected with the magnet valve just under the electromagnet; and when the PH value of a target water domain reaches an abnormal alarm threshold value, the valve can automatically open and collect samples with low water quality.
Owner:JIANGSU UNIV
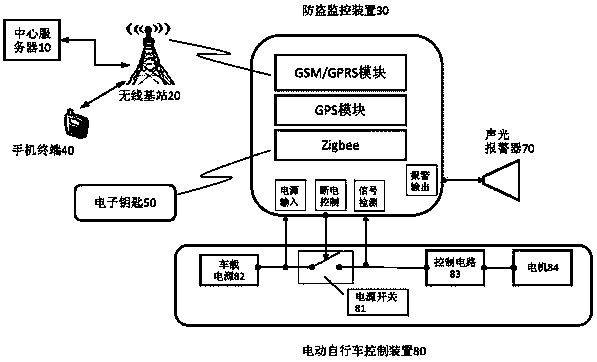
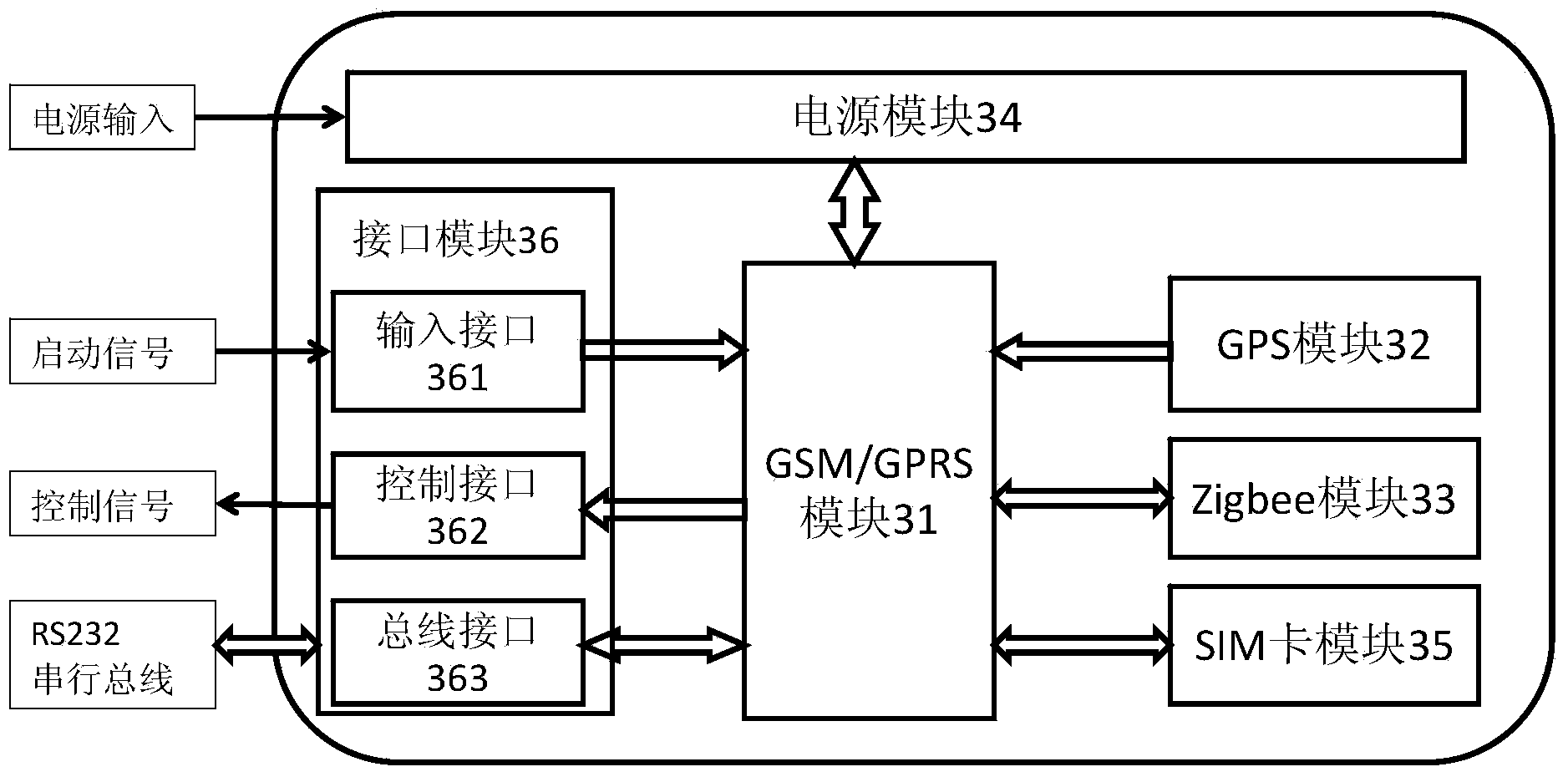
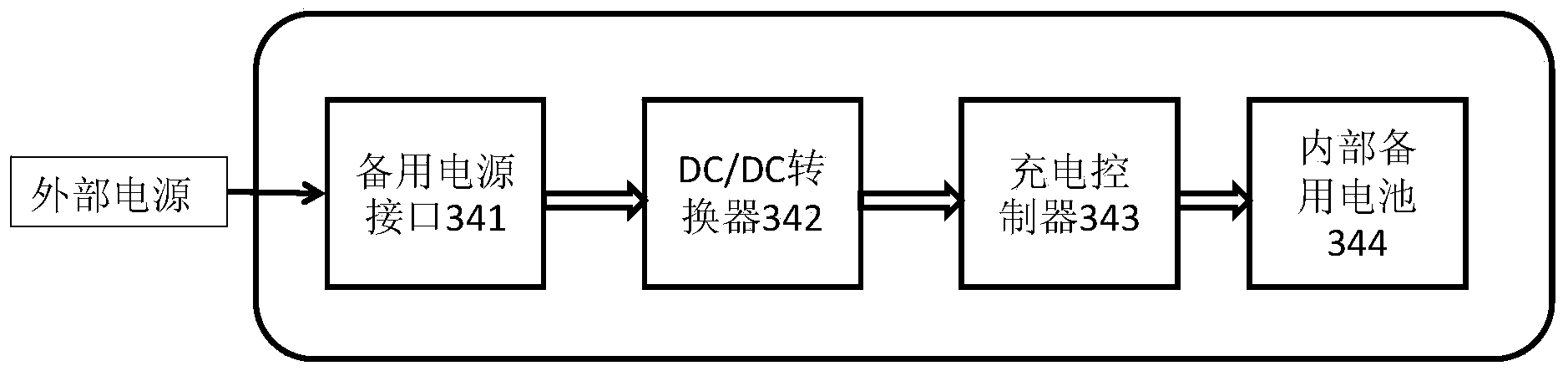
Anti-theft monitoring device and electric bicycle anti-theft tracking system and method
The invention provides an anti-theft monitoring device, and an electric bicycle anti-theft tracking system and method. The anti-theft monitoring device comprises a power module, a GSM / GPRS module, a GPS module, a Zigbee module, an SIM card module and an interface module, wherein the power module supplies electricity, the GSM / GPRS module receives external input, and outputs control signals of an electric bicycle, the GPS module is used for transmitting position information of the electric bicycle to the GSM / GPRS module, the Zigbee module is used for transmitting external instructions to the GSM / GPRS module, user ID information and safety passwords are stored in the SIM card module, the SIM card module is in two-way communication with the GSM / GPRS module, and the interface module comprises an input interface, a control interface and a bus interface. The anti-theft monitoring device and a control circuit of the electric bicycle can be integrally arranged, and therefore the anti-theft monitoring device cannot be easily found by a thief; through the electric bicycle anti-theft tracking system and method, the position of the electric bicycle can be tracked in time, once the electric bicycle is stolen, remote alarm and positioning can be achieved, remote recording control is carried out, and the stolen electric bicycle can be tracked as soon as possible.
Owner:北京玛施德利科技有限公司
Method for realizing chaff network data flow heavy orientation
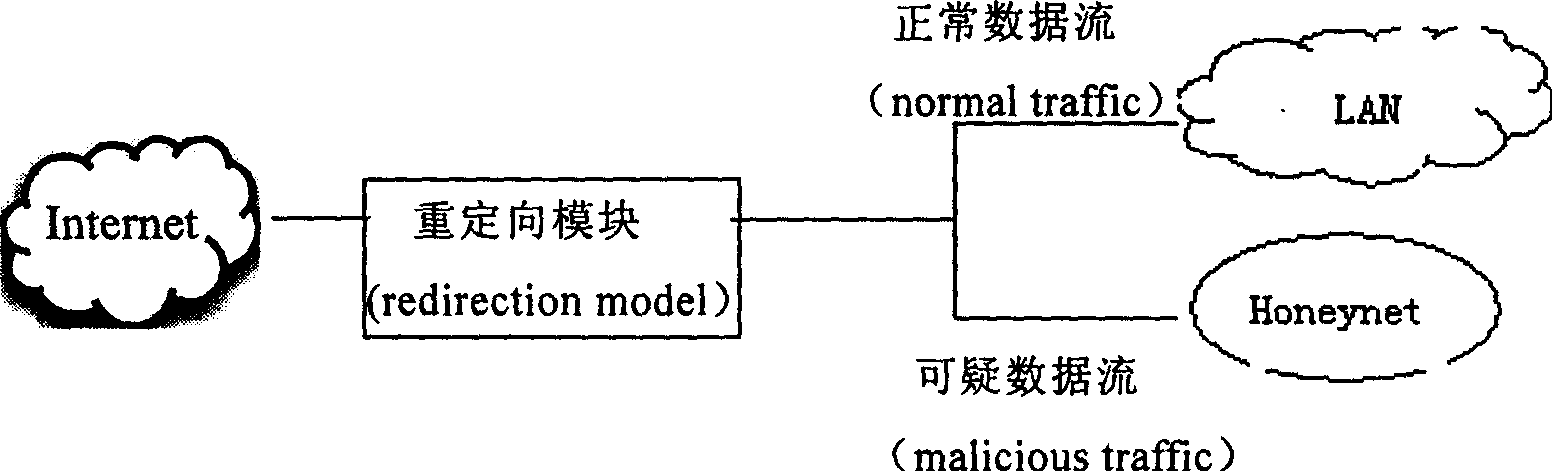
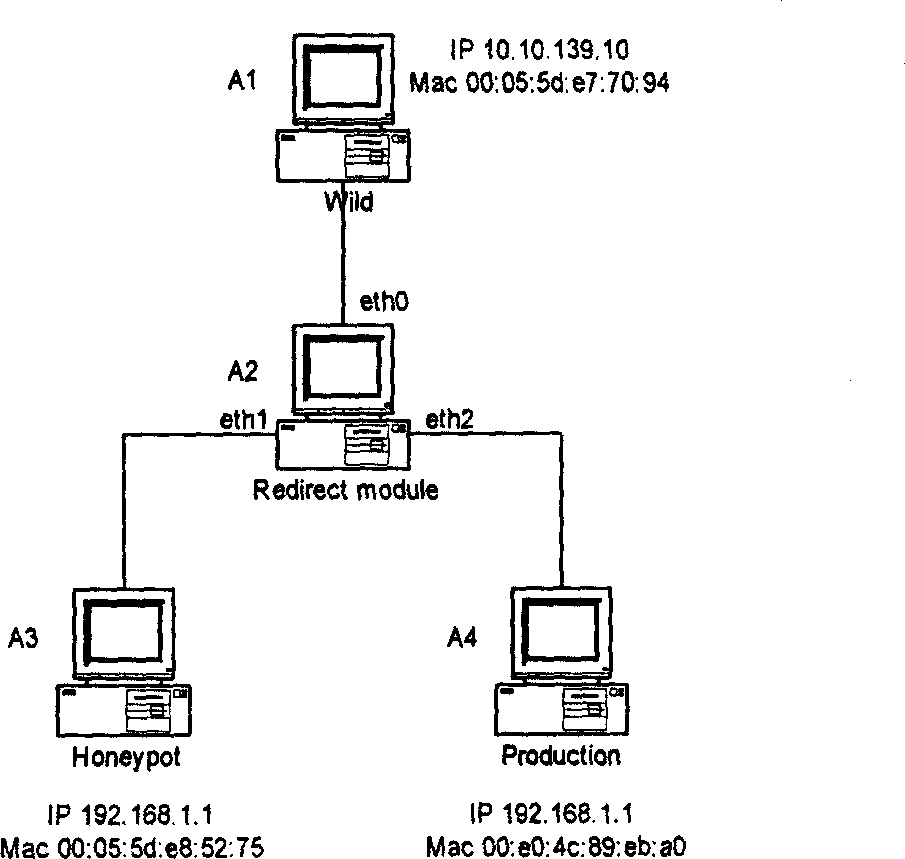
InactiveCN1585346AProcessing speedEasy to findData switching networksSecuring communicationIp addressThe Internet
The method includes following steps: all data accessing into the network are redirected , if the data is from Internet, the source address will be checked to decide if it is in list of questionable IP, if it is in the questionable IP list, its destination MAC address is replaced by the MAC address of the host corresponding to trap network, then transmitting it to trap network; if it is not in the questionable IP address list, it will be checked by using fire wall rule or the rule of instruction detection system, if it doesn't match the detection rules, it means the data is normal, then it will be sent to the protected network, if it matches the detection rules, it means the data is questionable, its destination address will be added into the questionable IP list, then it will be sent to trap network; if all data is from LAN, they will be directly sent out through Internet interface; if the data is from Honeyport, its source MAC address will be replaced by MAC address of corresponding host in LAN, then it will be sent out through Internet interface.
Owner:NANJING UNIV OF POSTS & TELECOMM
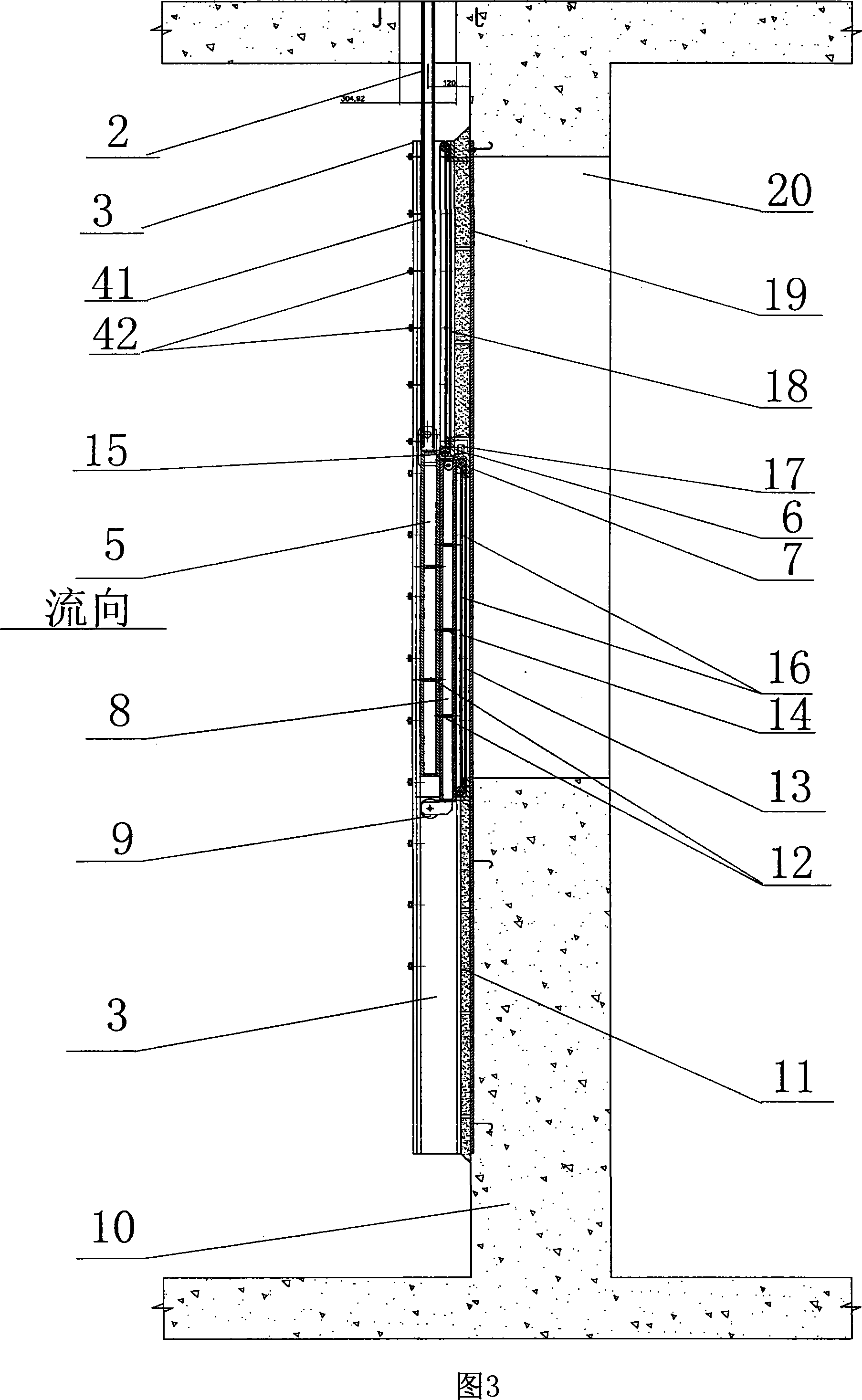
Lower open-type grading gate-plate gate
InactiveCN101182047AGood labor and material saving effectLow costBarrages/weirsWater/sewage treatmentPulleyRaw material
The invention relates to a gate technique which is a grading lower open-type restrictor gate. The lower open-type restrictor gate comprises a brake base, a gate frame at an outlet of the gate, restrictors that are matched with the gate frame, a hoist above the restrictor, a water-stop rubber and a locking apparatus which is used for controlling the efficiency of water sealing. The gate is characterized in that the upper restrictor which descends primarily when the gate is opened and the lower restrictor are arranged in the gate frame; two mounting frames of the water-stop rubber are arranged in the gate frame which faces to the outlet of the gate, wherein, the water-stop rubber is fixed on the four borders of the mounting frame which is contacted with a water-stop surface of the inner wall of the restrictor. A locating pull plate which extrudes from the surface of the restrictor is arranged at the both sides of the upper end of the lower restrictor, wherein, the inner side of the locating pull plate is provided with an upper wheel and the edge of the upper wheel is contacted with the upper restrictor, meanwhile the both sides of the lower end of the lower restrictor are provided with a lower wheel that extends to one side of the upper restrictor. The grading restrictor has reasonable structure, good water-stop efficiency, space conservation due to the grading restrictor, labor and material conservation in construction, light weight of stainless steel which is used as raw material, convenient installation and transportation.
Owner:余姚水利机械有限公司
Emergency communication method and device
InactiveCN104219644AEasy to operateIncrease success rateWireless commuication servicesEmergency/hazardous communication serviceTouchscreenSTI Outpatient
Owner:XIAOMI INC
Embedding and extracting methods for video steganography information
InactiveCN104125467AImprove robustnessImproving Steganographic RobustnessDigital video signal modificationSelective content distributionComputer scienceVisual perception
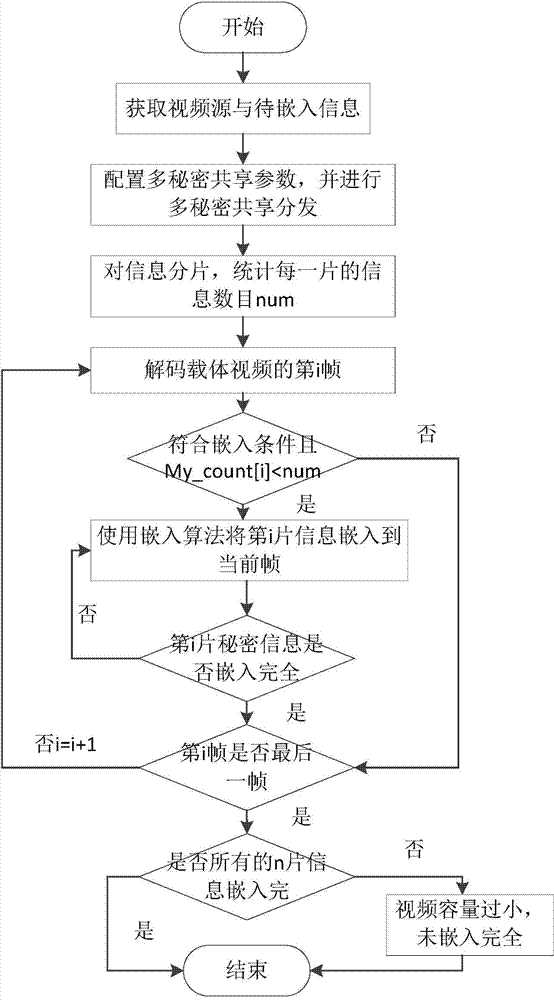
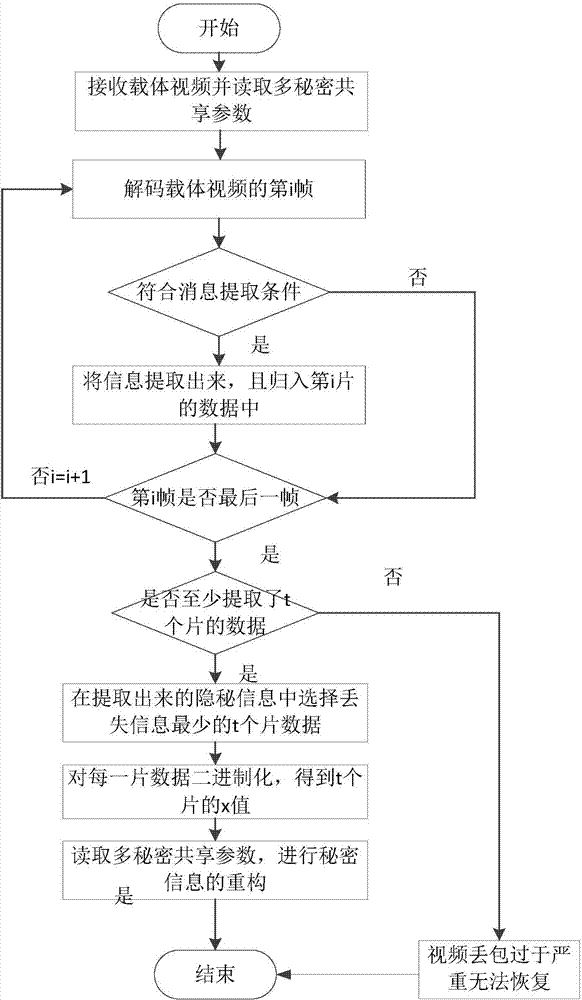
The invention discloses a robust method for video steganography information. The robust method comprises an embedding portion and an extracting portion. An embedding method comprises the following steps: acquiring a network video source taken as a carrier, and receiving secret information needing to be embedded of a user; distributing and processing the secret information by using a multi-secrete sharing technology; decoding a carrier video, and embedding the distributed secrete information till all information is completely embedded into the video. An extracting method comprises the following steps: acquiring a carrier video of which a portion of data tend to be lost after network transmission and the like; decoding the video and extracting the embedded secrete information; restoring the extracted information by using the multi-secrete sharing technology to obtain original secrete information. The robust method has low redundancy and high visual imperceptibility. The method is easy to apply, supports special application in the national fields of military, foreign affairs and essential business, serves for the national network space security strategy, and has a wide application environment. A technical method can be provided for video steganography, and guidance is provided for the construction of a video steganography communication platform.
Owner:ZHENGZHOU NORMAL UNIV
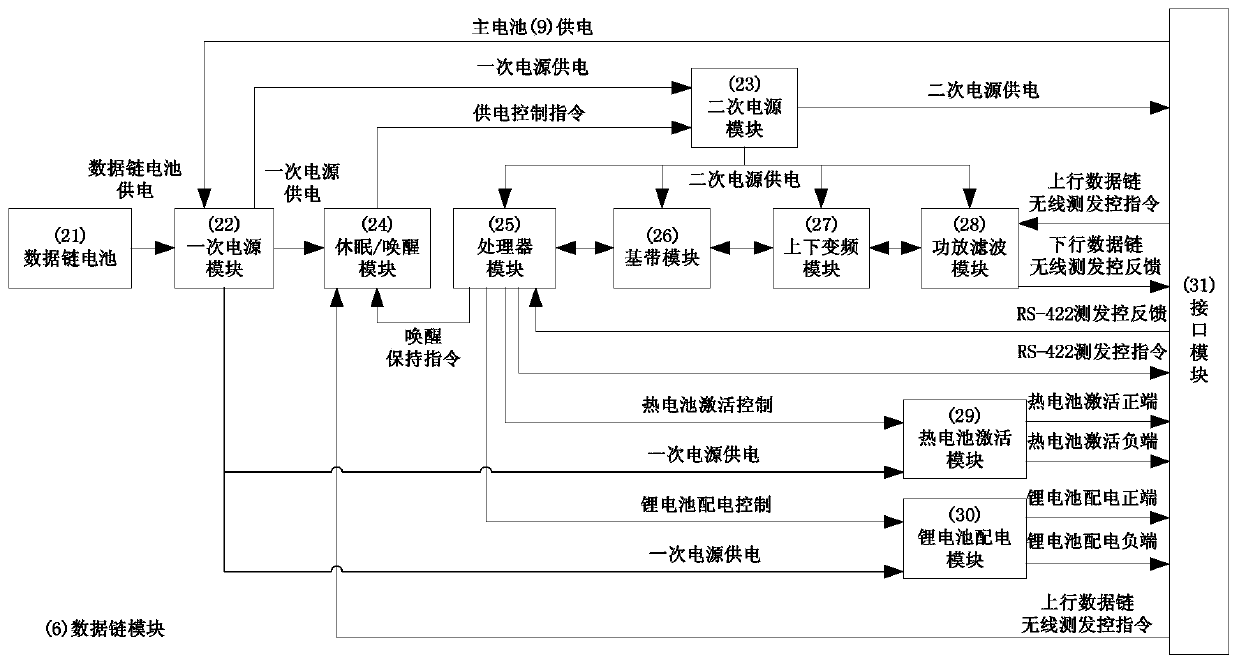
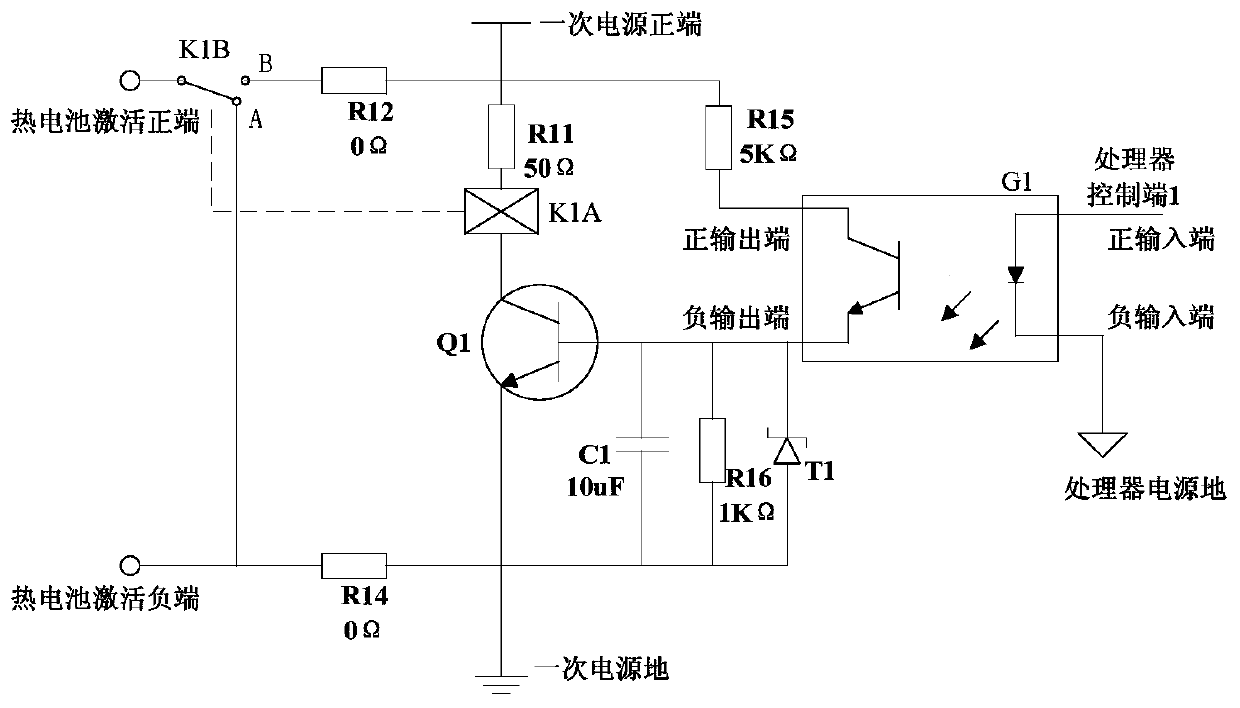
Wireless test launch and control system for aircraft
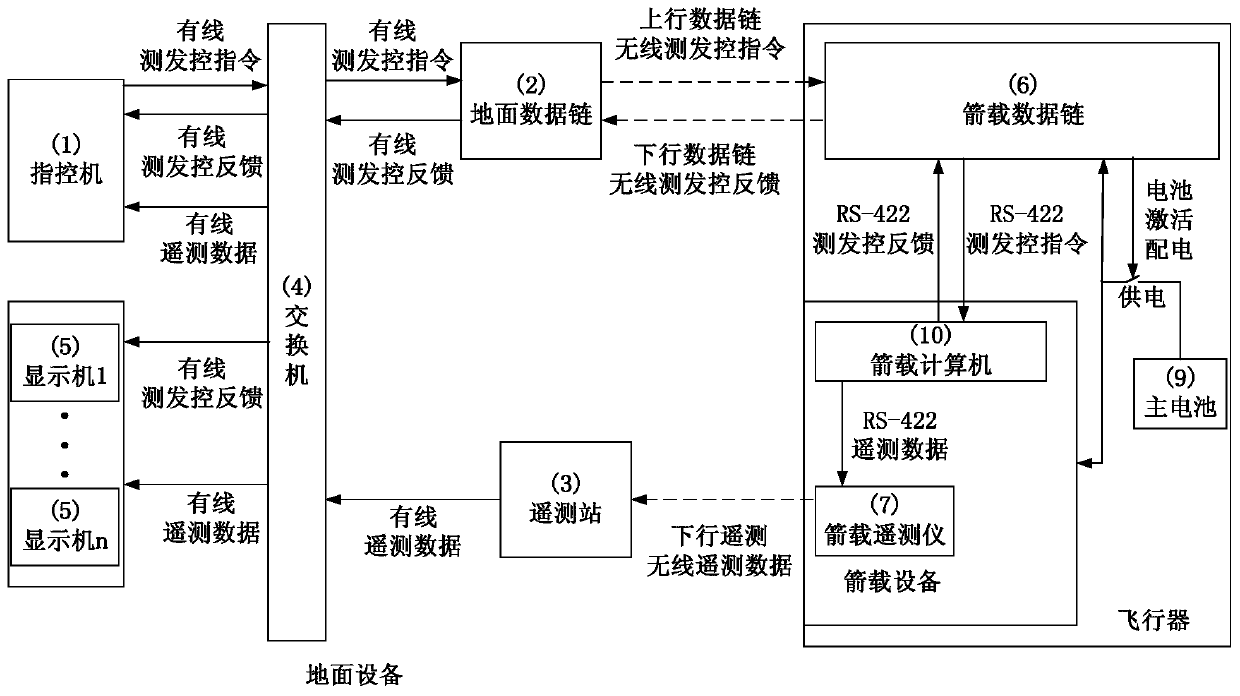
ActiveCN110412910AOptimize layoutEnsure safetyProgramme controlComputer controlTelecommunications linkCommand and control
The invention discloses a wireless test launch and control system for an aircraft. The wireless test launch and control system is composed of ground equipment and rocket-borne equipment, wherein the ground equipment comprises a command and control machine, a ground data link, a telemetering station, a switch and a display machine, and the rocket-borne equipment contains a rocket-borne data link, arocket-borne telemetering instrument and a rocket-borne computer. A wireless communication link contains an upward data link access, a downward data link access and a downward telemetering access andrealizes a test launch and control instruction, test launch and control feedback and telemetering data transmission of the aircraft. The rocket-borne data link has a low-power-consumption sleep function, can wake up a rocket-borne battery of the aircraft and control the rocket-borne battery of the aircraft to be activated as well as power distribution after an upward wireless test launch and control instruction is received and then starts a test launch and control process. The system disclosed by the invention does not need to connect ground test launch and control equipment with the aircraftby virtue of an umbilical cable, so that ablation of the umbilical cable due to flame of an engine of the aircraft is avoided; and ground communication equipment is simple to pave, a target range communication network does not need to be used, and the system disclosed by the invention has a function of receiving telemetering data in a flying process of the aircraft and a command and control function at the same time.
Owner:CHINA ACAD OF AEROSPACE AERODYNAMICS +1
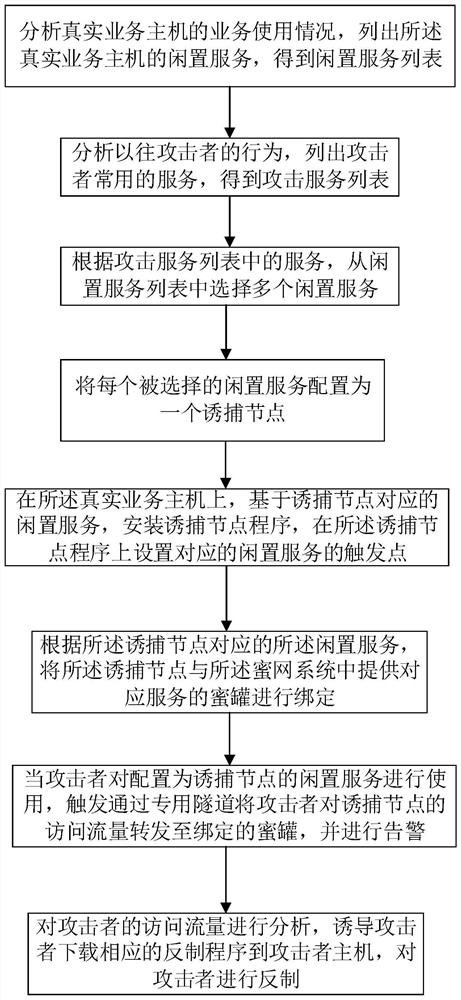
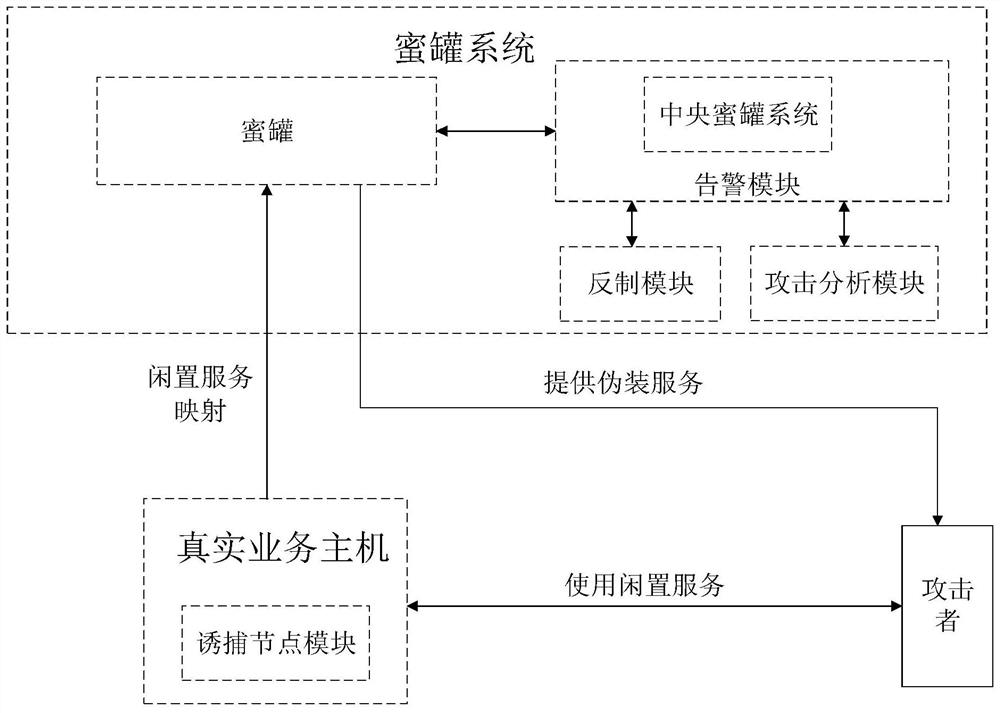
Novel honeypot networking method and honeypot system
The invention provides a novel honeypot networking method and a honeypot system, and belongs to the technical field of network security. The invention provides a honeypot networking method, and the method comprises the following steps: listing idle services of a real business host, listing attacker common services, selecting some idle services from the idle services of the real business host according to the attacker common services, deploying the idle services as trapping nodes, deploying one trapping node for each selected idle service, and deploying one trapping node for each selected trapping node; binding the trapping node with the honeypot; when an attacker accesses an idle service, introducing attacker access flow into the honeypot, enabling the honeypot system to analyze the attacker access flow, automatically downloading a countering program and countering the attacker. According to the method, the trapping nodes are deployed on the idle service of the real service host, so that a large number of special servers or special virtual machines created on the idle servers are saved for deploying the trapping nodes, the capture efficiency is high, and the idle service is utilized.
Owner:广州锦行网络科技有限公司
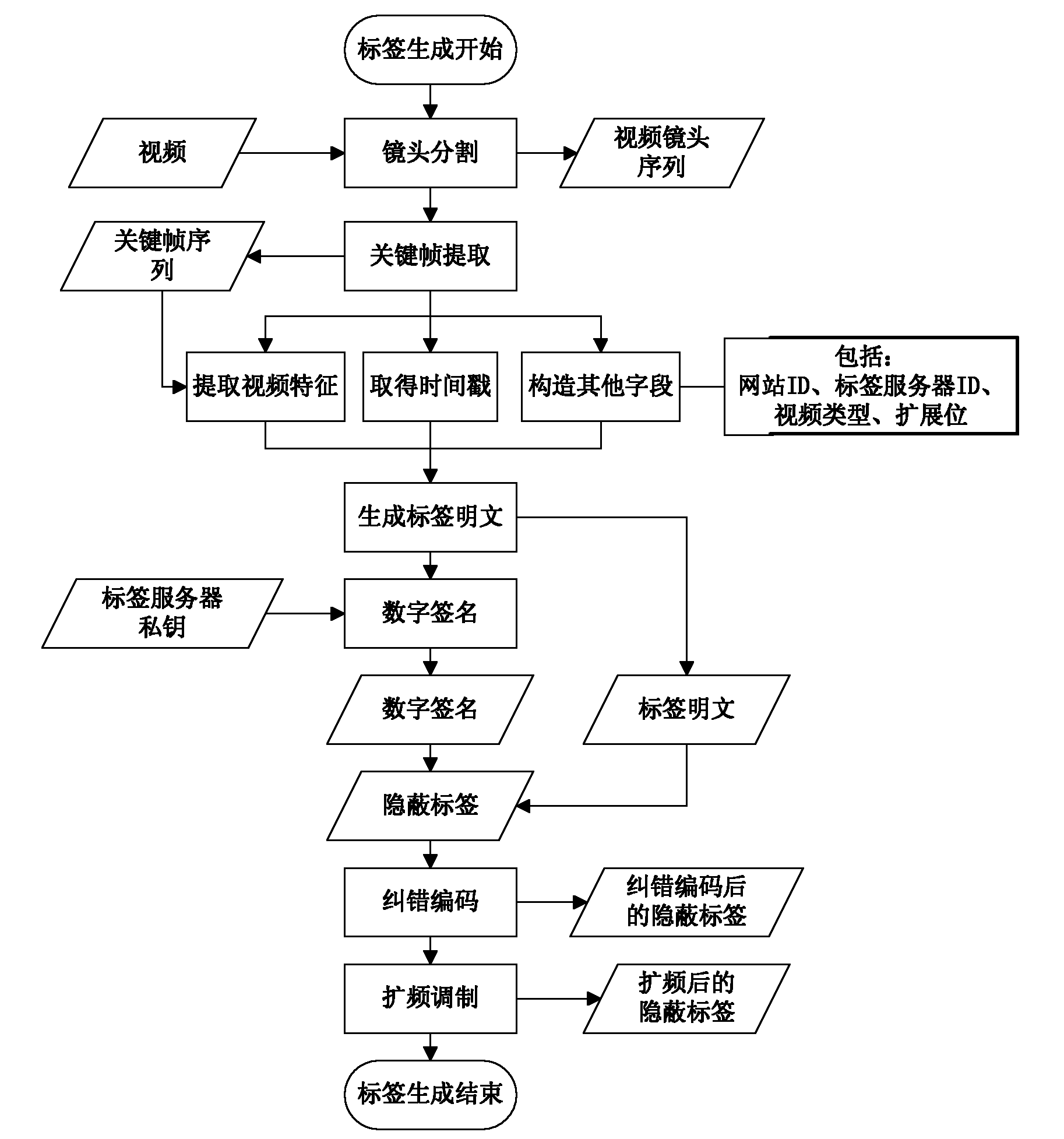
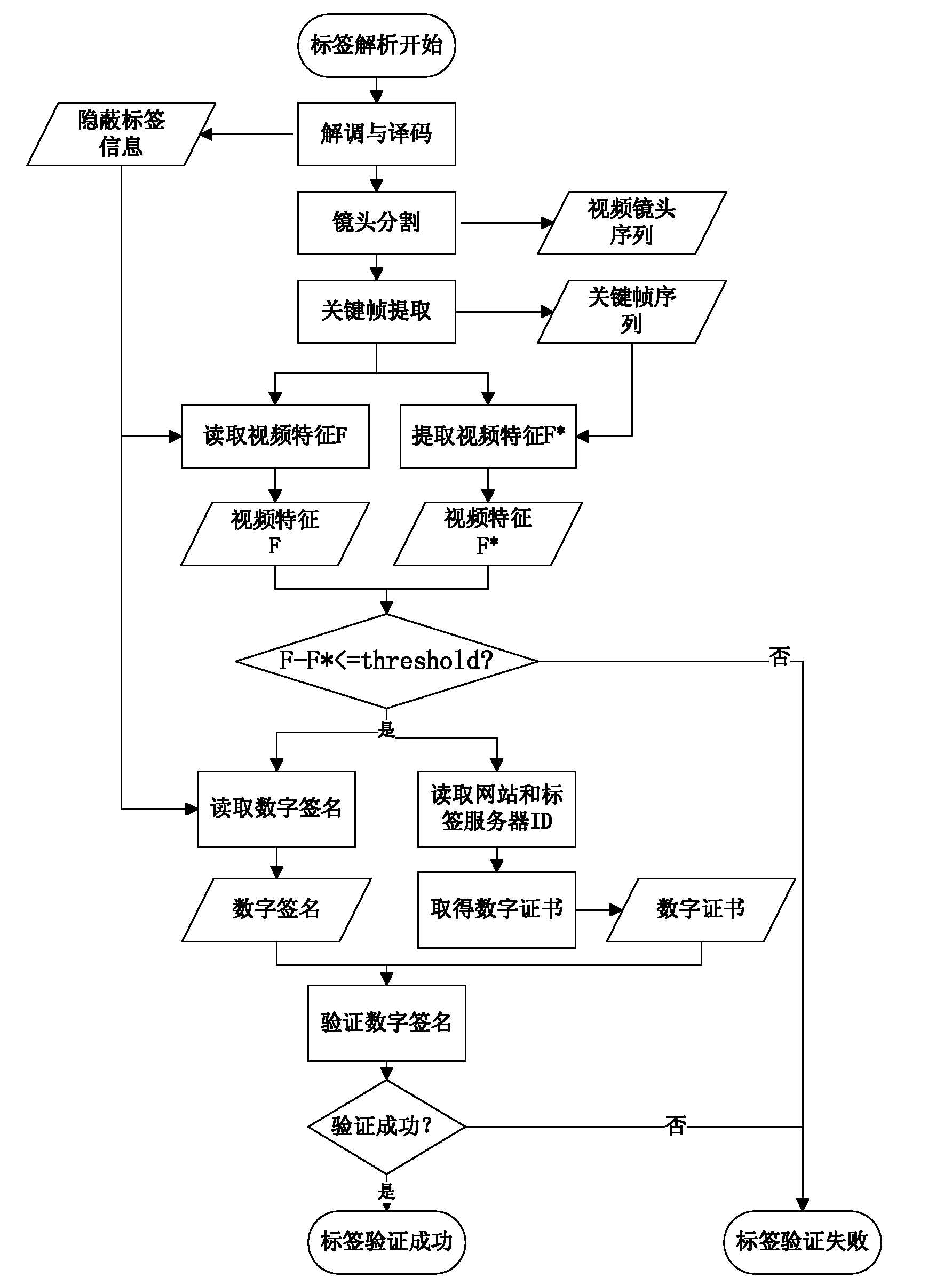
Method for generating and authenticating hidden video tags based on video characteristics and digital signatures
ActiveCN101977319ADefense against replay attacksImplement integrity verificationTelevision systemsTransmissionDigital signatureInformation security
The invention provides a method for generating and authenticating hidden video tags based on video characteristics and digital signatures, belonging to the technical field of information safety. In the method, a way for extracting and optimizing groups based on visual descriptors is used to generate video characteristics serving as one part of the tags, thereby realizing binding of the tags and the video, and effectively resisting conspiracy attack behaviors of attackers to authorized tags. The hidden tags constructed by the method have not only preferably robustness and safety, but also integrity and non-repudiation which are not endowed to the common video watermarks, as well as unique binding of the tags and the video and the like.
Owner:SHANGHAI JIAO TONG UNIV
Electric meter box device with functions of preventing electricity stealing and carrying out monitoring
InactiveCN103487622AAvoid interferenceAccurate measurementTime integral measurementElectricityTime delays
The invention discloses an electric meter box device with the functions of preventing electricity stealing and carrying out monitoring. The electric meter box device comprises a reed tube, a power source, an alarm, a release switch and a time-delay relay. The power source, the alarm and the reed tube form a magnetic field alarm circuit. The time-delay relay, the release switch and the power source form a trigger alarm circuit. A mobile phone with the one-key get-through function is arranged below the time-delay relay. A camera module is arranged in a box body and used for collecting audio-video data and sending the audio-video data to an audio-video decoder, then compressed encoding processing is conducted on the audio-video data, and the audio-video data after the compressed encoding processing is conducted are sent to an M2M module and then are uploaded to a management platform through the M2M module. After the electric meter box device is used, not only is the good effect of preventing electricity stealing achieved, but also criminal offenders are arrested lawfully and unwittingly, arrogance of the criminal offenders is greatly struck, and behaviors of stealing electricity and damaging an electric meter box are eliminated.
Owner:NANYANG POWER SUPPLY COMPANY OF STATE GRID HENAN ELECTRIC POWER
LED lamp intrusion alarm based on visible light communication
ActiveCN102722951ANot easy to be disturbedGood reliabilityElectromagnetic transmissionBurglar alarm short radiation actuationActive detectionVisible light communication
The invention relates to an LED lamp intrusion alarm based on visible light communication. The LED lamp intrusion alarm comprises an LED lamp and a light signal receiver. The LED lamp is an LED decorative lamp, an illuminating lamp or the like and used for transmitting a light signal containing information to the light signal receiver; and the light signal receiver is used for receiving the light signal, converting the light signal into an electric signal and transmitting the electric signal to a monitoring alarm system. As active detection is carried out by means of visible light communication, the LED lamp intrusion alarm based on the visible light communication, provided by the invention, has the advantages of uneasiness for being interfered and better reliability; except for having a common intrusion detecting function, the LED lamp intrusion alarm based on visible light communication, provided by the invention, can be also made into various LED decorative lamps, LED illuminating lamps and the like through the visible light characteristics; therefore, the LED lamp intrusion alarm based on the visible light communication, provided by the invention, has the advantages of uneasiness for being found as well as extremely perfect concealment and safety.
Owner:南通趣易信息技术有限公司
Multi-angle camera adjustment device for security monitoring system
InactiveCN106657877ANot easy to findImprove concealmentTelevision system detailsColor television detailsEngineeringSecurity monitoring
The invention discloses a multi-angle camera adjustment device for a security monitoring system, which comprises a rectangular frame body, a cavity, a lateral driving device, a moving block, limiting blocks, a vertical driving device, a rotating driving device and a camera. Through arranging the rectangular frame body and arranging each driving device and the camera in the cavity of the rectangular frame body, the camera can be hidden and is not likely to be found, the hiding performance is good, and the safety is high; through arranging the lateral driving device, the vertical driving device and the rotating driving device, the camera can perform lateral movement, vertical movement and multi-angle rotation freely, the monitoring range is increased, the monitoring effects are good, and manual operation is not needed; and the device has the advantages of simple structure, convenient operation, and high automatic degree.
Owner:DONGGUAN LIANZHOU INTPROP OPERATION MANAGEMENT CO LTD
Method for processing watermarks and tracing data on basis of original data deformation
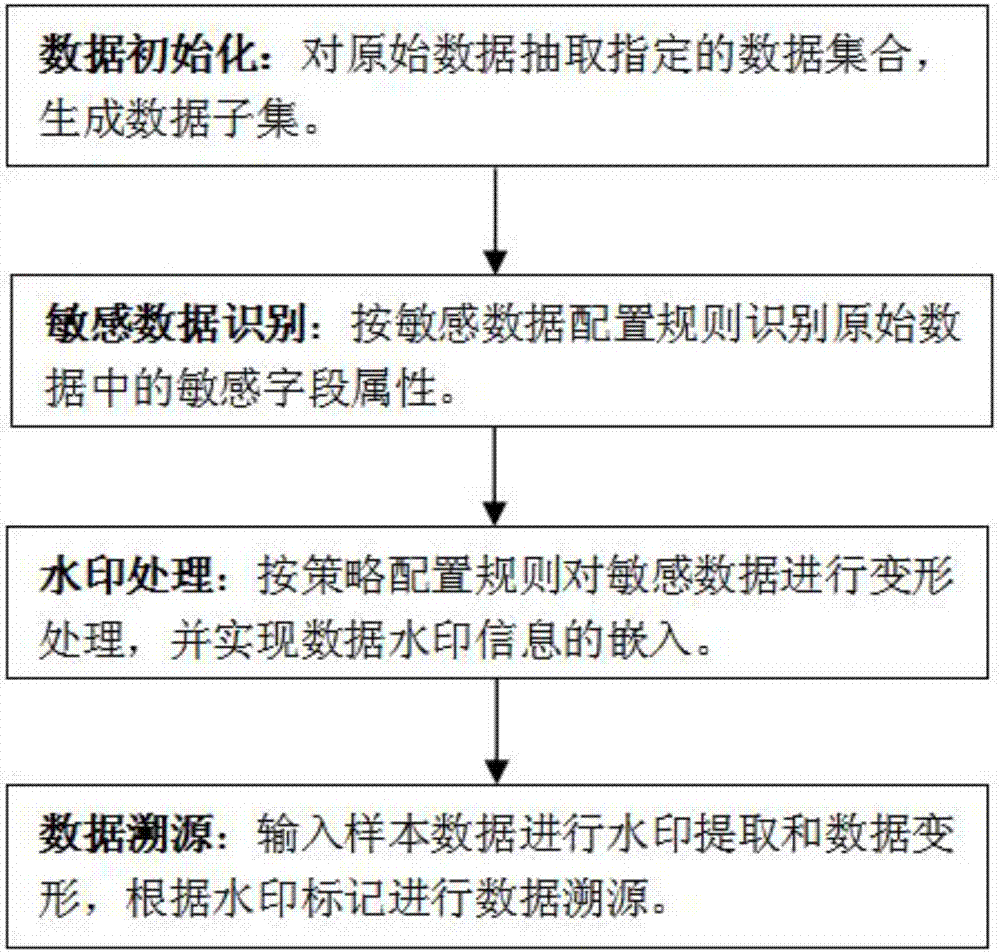
ActiveCN107992727AEasy to useDoes not affect traceabilityImage data processing detailsCommerceData setOriginal data
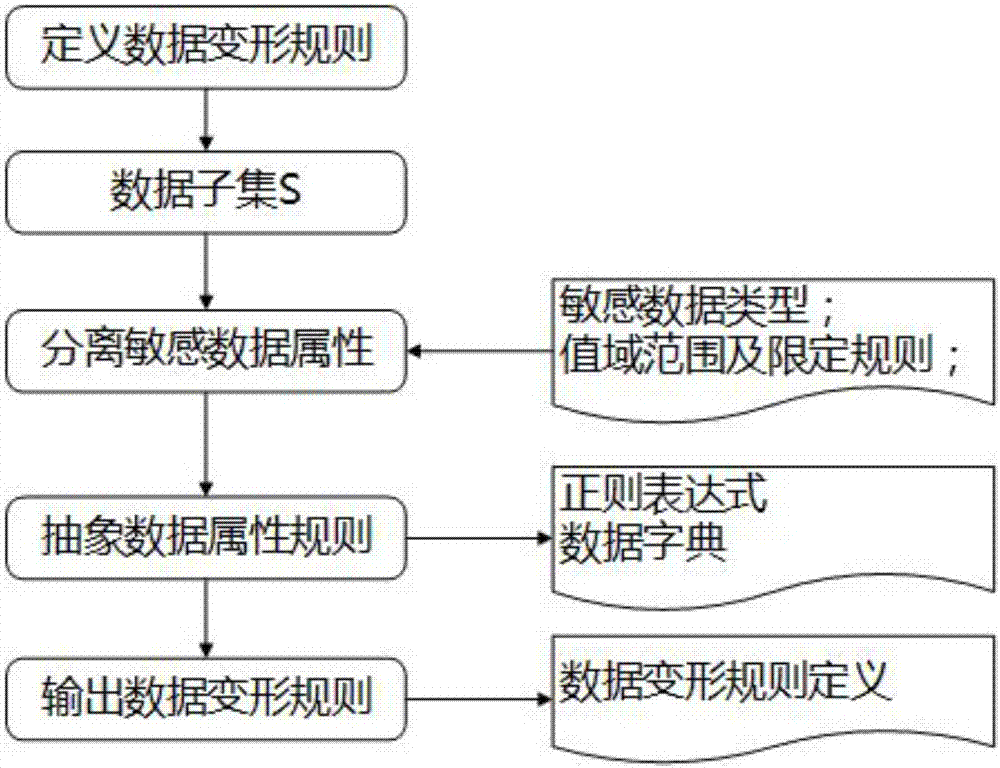
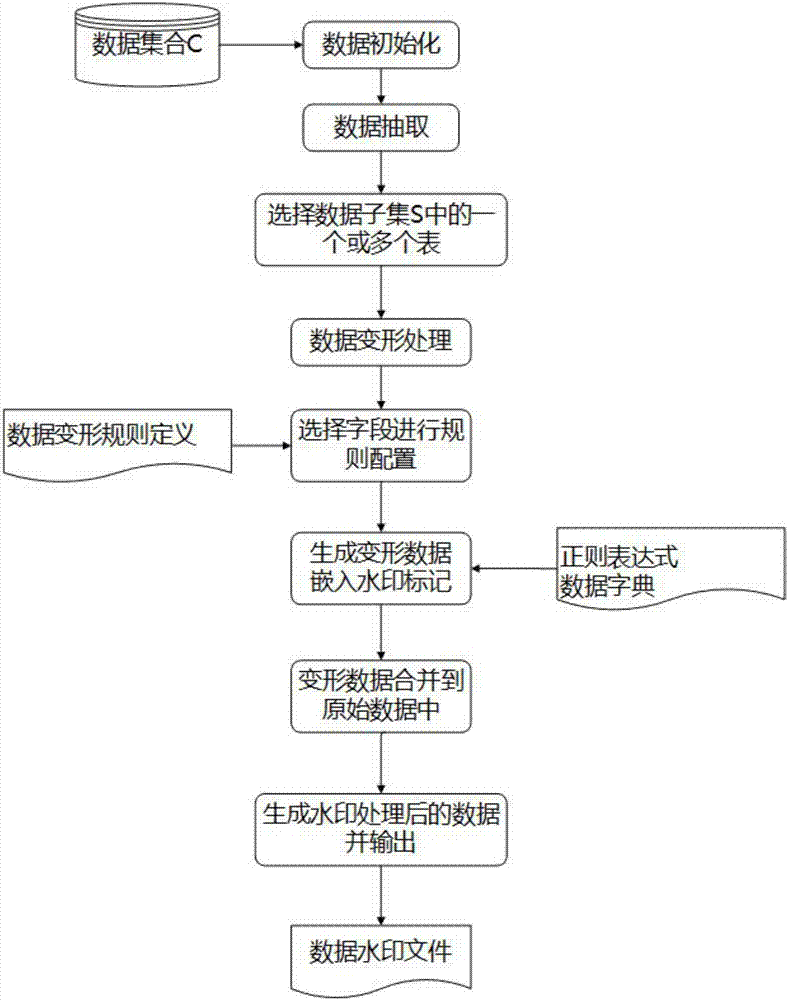
The invention relates to a method for processing watermarks and tracing data on the basis of original data deformation. The method is technically characterized by comprising extracting data from raw data with a plurality of tuples to form data subsets S; identifying sensitive data in the data subsets S to obtain sets C of tables with sensitive attributes; processing the watermarks for the data sets C; inputting sample data, extracting data watermarks and tracing the data according to extracted watermark information. Attributes of tables in the data subsets S contain sensitive information. Themethod has the advantages that the method is reasonable in design, and the safety protection capability in data sharing procedures can be improved; the data watermarks can be embedded on the basis ofthe data deformation, the leaked data can be traced on the basis of the data deformation, and accordingly the method can be used in extensive application scenes.
Owner:BEIJING ANHUA JINHE TECH
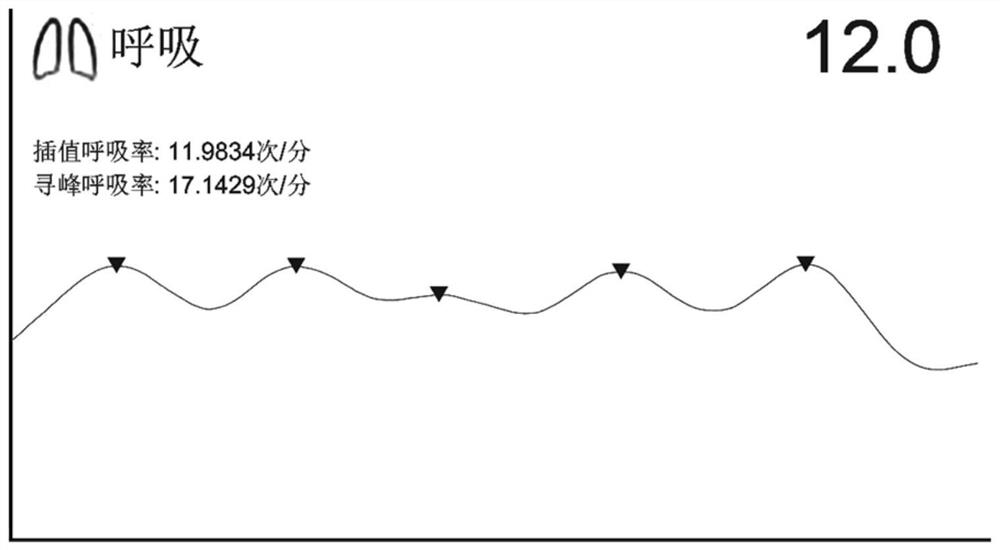
Vital sign detection and identity recognition system and method based on millimeter wave radar
PendingCN112998701ANot easy to forgeNo privacy issuesPerson identificationSensorsIdentity recognitionPrivacy protection
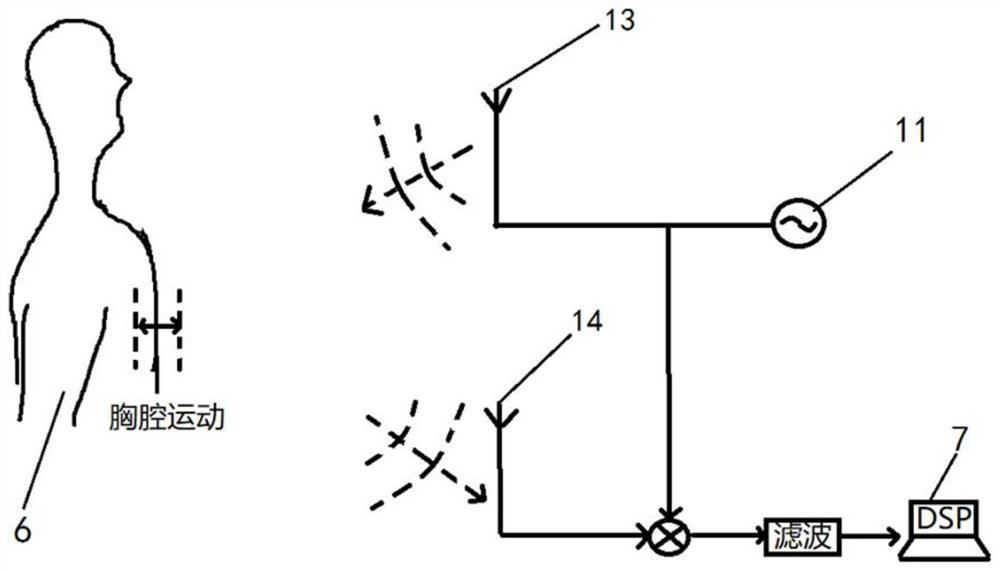
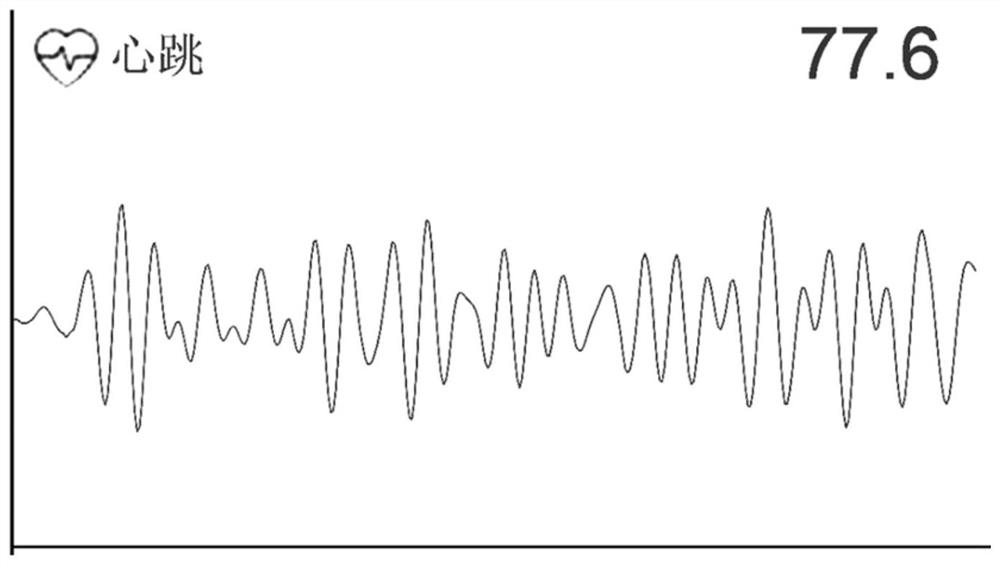
The invention relates to a vital sign detection and identity recognition system based on millimeter-wave radar, which comprises a millimeter-wave radar subsystem, a radar data preprocessing subsystem, a vital sign characteristic database subsystem, an identity recognition subsystem and an intelligent interaction interface subsystem which are in communication connection with one another, the millimeter wave radar subsystem is placed beside an object to be measured, comprises a transmitting antenna and a receiving antenna, and is used for obtaining original radar data; the radar data preprocessing subsystem is used for decomposing a respiration signal and a heartbeat signal in the original radar data and extracting vital sign characteristic information; the vital sign feature database subsystem is used for storing identity information and corresponding vital sign feature information; the identity recognition subsystem learns vital sign feature information, classifies the vital sign feature information and determines corresponding identity information; the intelligent interaction interface subsystem comprises a display screen for displaying vital sign information and identity recognition results, and compared with the prior art, the system has the advantages of being high in practicability, safe in privacy protection and the like.
Owner:FUDAN UNIV
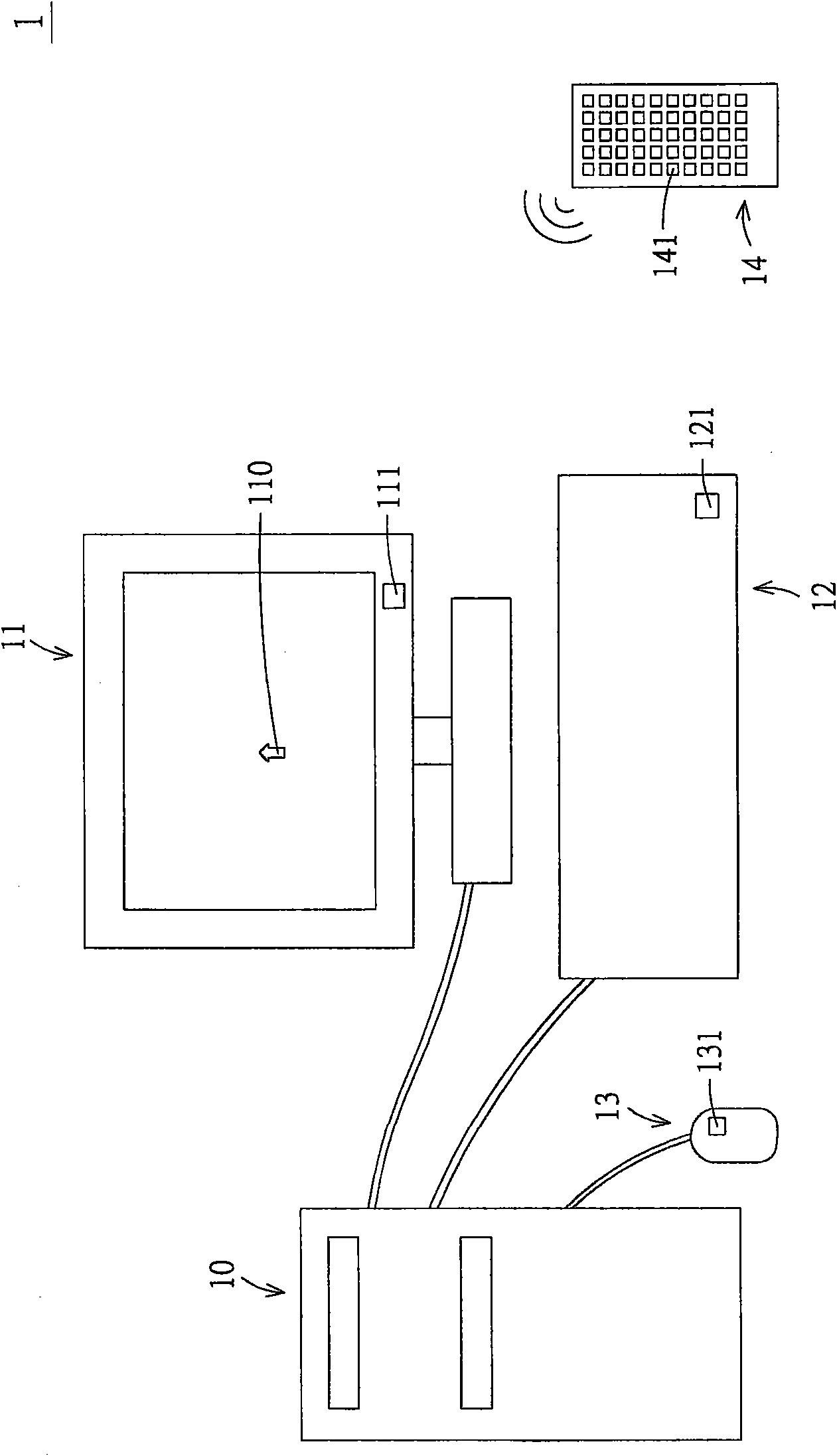
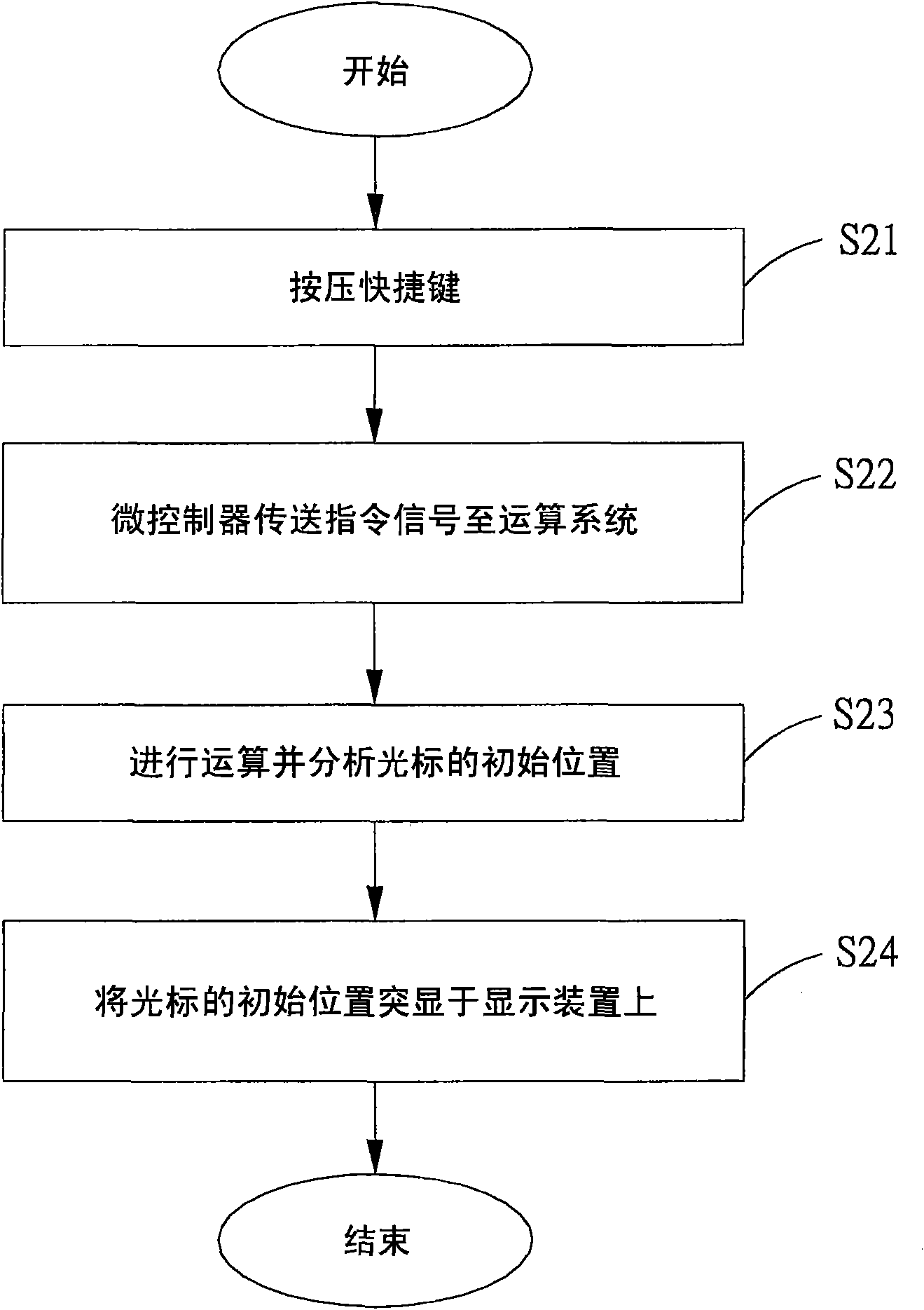
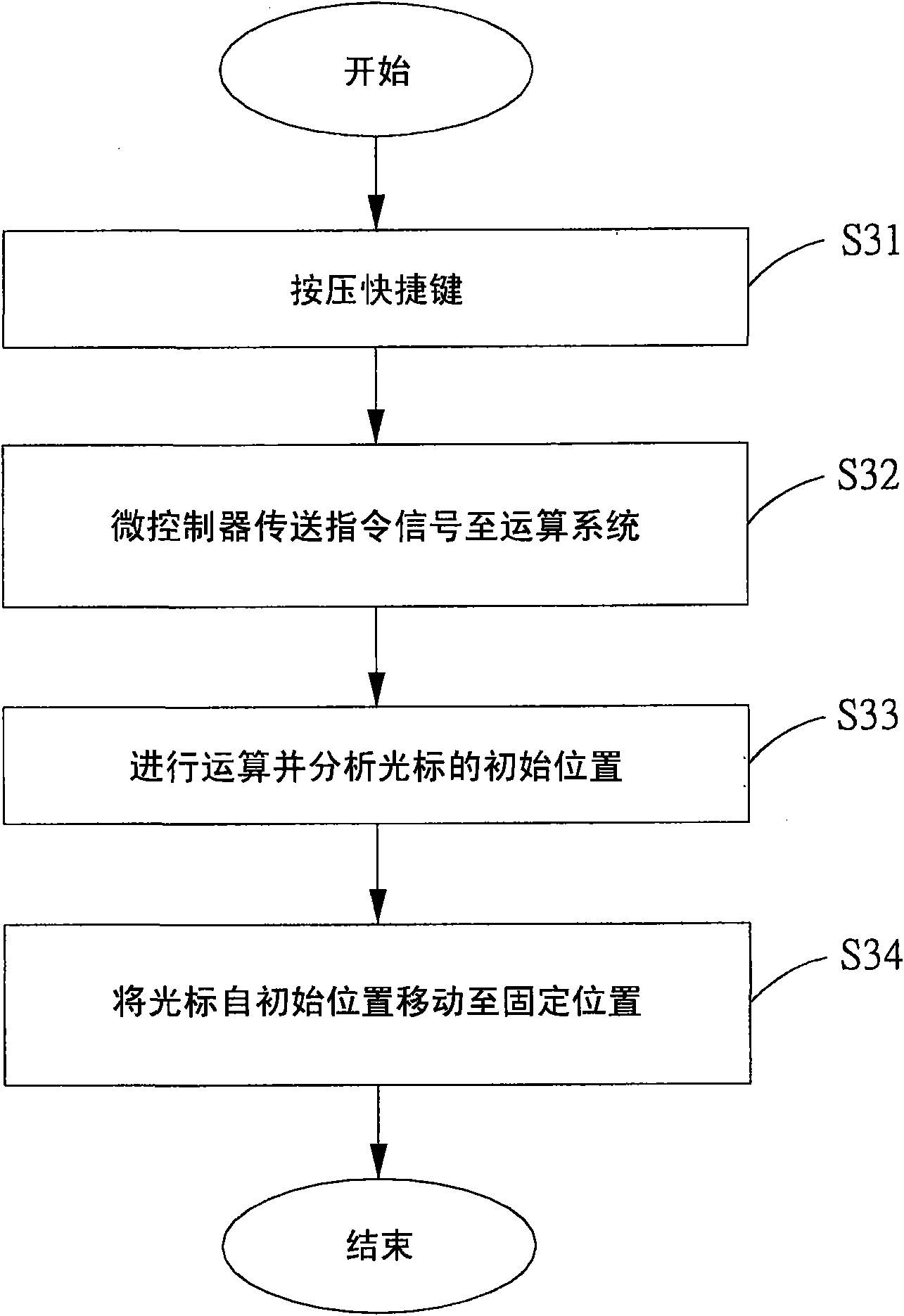
Method and device for locating cursor position
InactiveCN101556532ANot easy to findLarge screen sizeDigital output to display deviceDisplay deviceEmbedded system
The invention relates to a method and a device for locating a cursor position, which are suitable for an electronic device comprising an arithmetic system and a display device. The method at least comprises the following steps: a triggering medium transmits a driving signal to the arithmetic system; the arithmetic system calculates an initial position of a cursor and displays the initial position of the cursor on the display device comprising a processing unit, and the processing unit is used for displaying the initial position passed back by the arithmetic system on the display device.
Owner:ACER INC
Flexible transparent conductive film and manufacturing method thereof and touch panel
ActiveCN102723128AGood resistance stabilityPattern discoveryConductive layers on insulating-supportsCable/conductor manufactureSputteringCapacitance
The invention provides a transparent conductive film and a manufacturing method thereof. The film comprises a flexible base material and a transparent conductive oxide layer, a first hard coating layer, a first ground coating and a second ground coating are sequentially stacked on the surface of the flexible base material from inside to outside, and the transparent conductive oxide layer is arranged on the second ground coating. The invention further provides a touch panel with the flexible transparent conductive film. One side of the flexible base material is sequentially provided with the hard coating layer, the first ground coating, the second ground coating and the transparent conductive oxide layer from inside to outside, so that a patterned portion and a non-patterned portion are basically undifferentiated, patterns are not easy to discover, and the transparent conductive film is good in appearance and can be widely used for electrostatic capacitance combined touch panels. During manufacturing, all layers are formed by sequentially continuously depositing once by means of the intermediate-frequency response magnetron sputtering technology, and the manufacturing method is short in product production process, environment-friendly, high in production efficiency and low in cost.
Owner:深圳豪威科技集团股份有限公司
Multistage separable-type unmanned underwater vehicle
ActiveCN108622342AExtend underwater working timeExpand your searchRotary propellersUnderwater equipmentButt jointLocking mechanism
The invention discloses a multistage separable-type unmanned underwater vehicle. The multistage separable-type unmanned underwater vehicle is characterized in that the multistage separable-type unmanned underwater vehicle comprises a vehicle shell; the vehicle head and the vehicle tail are arranged at the two ends of the vehicle shell correspondingly, and a butt-joint locking mechanism and a flexible butt-joint mechanism are arranged at the vehicle head and the vehicle tail correspondingly; the flexible butt-joint mechanism is used for being in butt joint with the next-stage vehicle head, andthe next-stage vehicle head is locked through the butt-joint locking mechanism; and a non-shaft counter-rotating dual-oar propeller is configured at the tail of the vehicle shell. The multistage separable-type unmanned underwater vehicle has the advantages of being small in noise, small in size, high in flexibility and capable of being freely separated and combined according to instructions to adapt to various underwater tasks.
Owner:WUHAN UNIV OF TECH
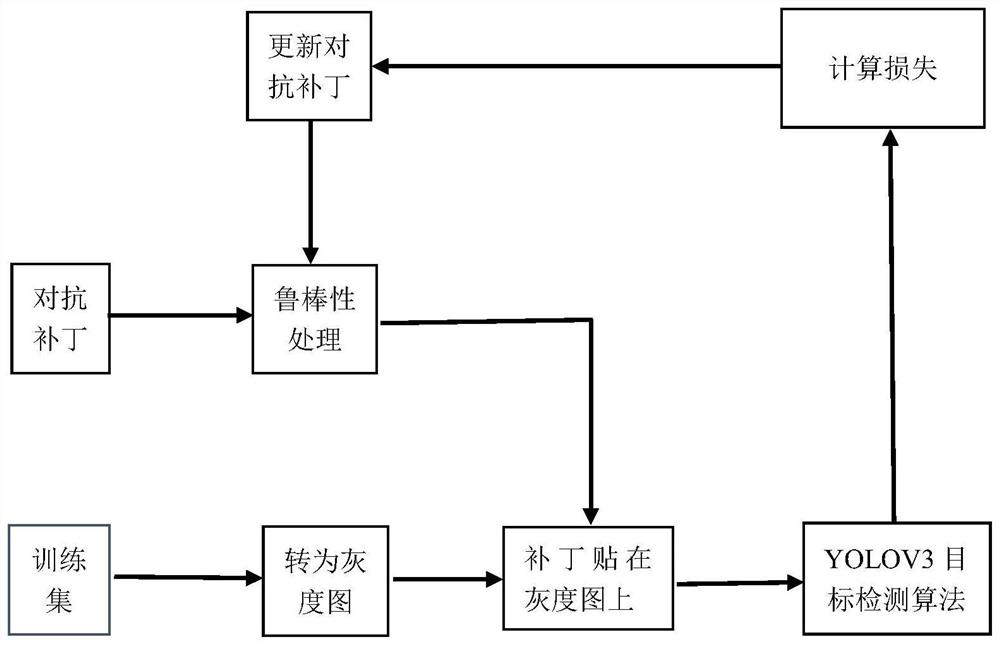
Target detection-oriented physical attack adversarial patch generation method and system
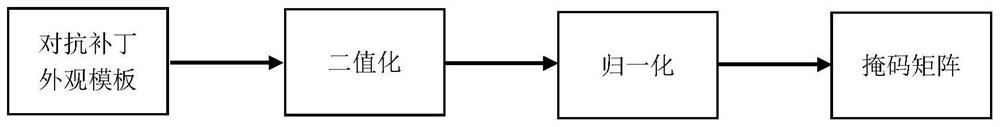
PendingCN113361604AImprove robustnessNot easy to findCharacter and pattern recognitionNeural learning methodsAlgorithmThresholding
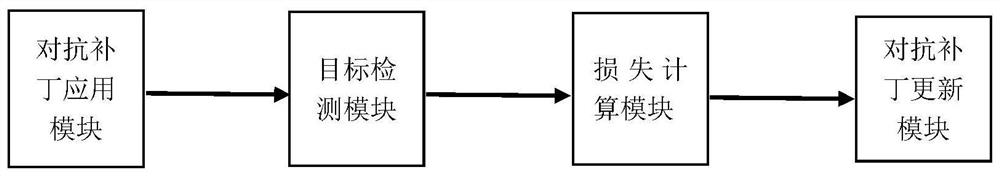
The invention discloses a target detection-oriented physical attack adversarial patch generation method. The method comprises the following steps of: (1) generating a rectangular adversarial patch with random pixel values; (2) carrying out robustness processing on the adversarial patch; (3) initializing a mask matrix; (4) applying the adversarial patch to a training set; (5) extracting real category confidence from a result; (6) designing a loss function and calculating loss; (7) calculating the gradient, then updating the adversarial patch, and circulating the step 2 to the step 7 until the maximum number of iterations is reached or the attack success rate reaches a threshold value; (8) printing the patch, and carrying out physical environment testing. The invention further comprises a target detection-oriented physical attack adversarial patch generation system, which consists of an adversarial patch application module, a target detection module, a loss calculation module and an adversarial patch updating module. According to the invention, the patch shape can be self-defined, the gradient is solved according to a designed loss function, the adversarial patch is updated, and finally a physical environment test is performed.
Owner:ZHEJIANG UNIV OF TECH
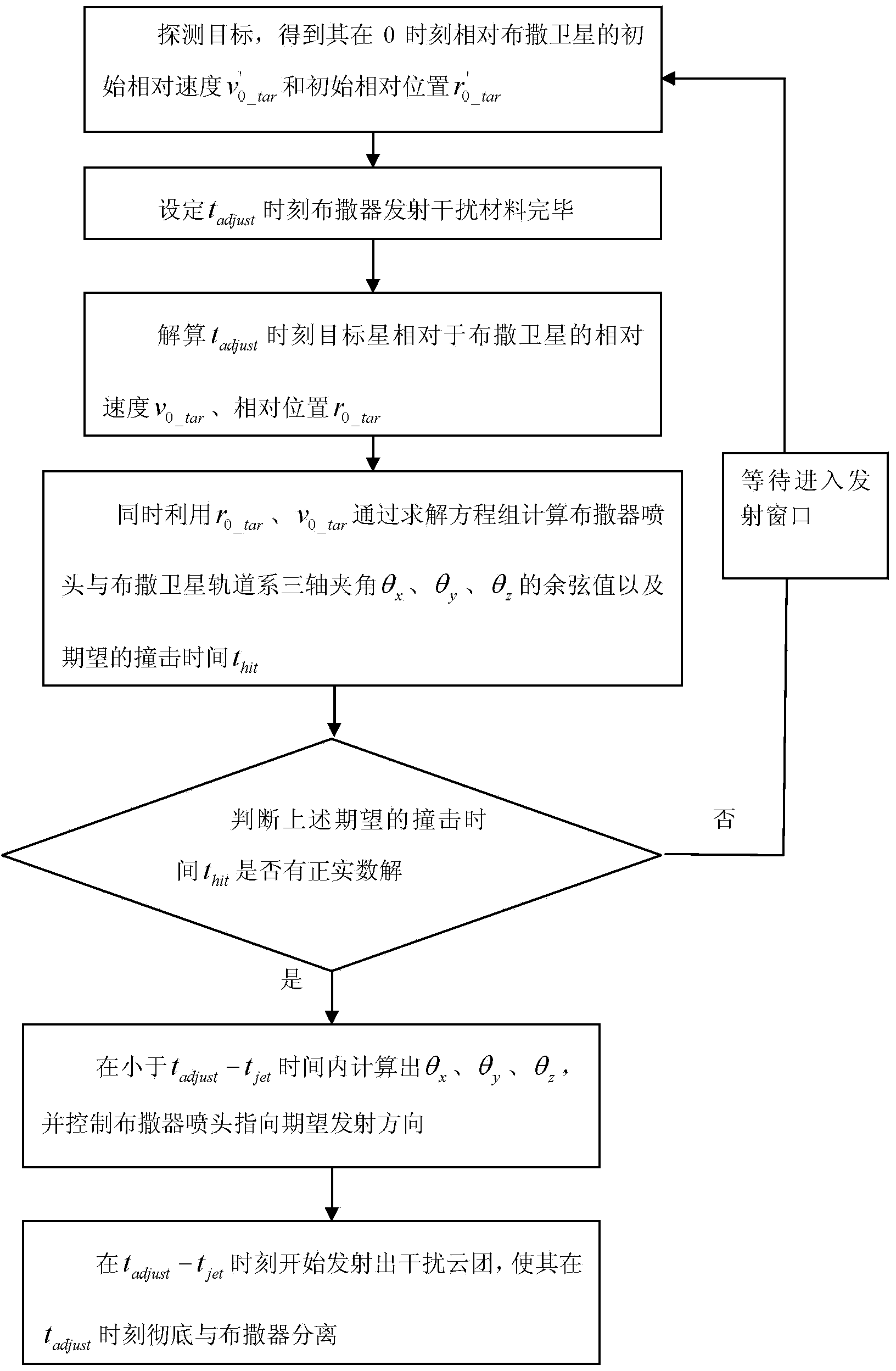
Space-based dispenser different-plane orbit dispersion control method
The invention provides a space-based dispenser different-plane orbit dispersion control method, and relates to the technical field of satellite control. The method aims to accurately control a satellite which is launched to be close to different-plane orbits of a target satellite and provided with a dispenser to spray interference cloud clusters so as to interfere the target satellite so that the target satellite can loss corresponding functions. The tadjust moment when the dispenser completes jetting of interference materials; v0_tar and r0_tar of the target satellite relative to a dispersion satellite at the tadjust moment are solved; cosine values of triaxial included angles of theta x, theta y and theta z of an orbit system of a dispenser spray head and the dispersion satellite and expected hit time thit are calculated by utilizing r0_tar and v0_tar to solve an equation set at the same time; if thit has a proper positive real number solution, the relative state of the two satellites is in a jetting window, and the next step can continue to be conducted; otherwise, the two satellites wait for entering the jetting window; the theta x, theta y and theta z are figured out within time less than tadjust - tjet, and the dispenser spray head is controlled to point to the expected jetting direction; the interference cloud clusters begin to be jetted at the tadjust - tjet moment and are made to separated from the dispenser thoroughly at the tadjust moment. The method is applied to the anti-satellite control process.
Owner:HARBIN INST OF TECH
Ceramic base lightweight bulletproof helmet and the production method
The invention discloses a ceramic light-quality bulletproof helmet and preparing method, which is composed of ceramic base layer in the middle of helmet and PE layer on two sides through hot-pressed attaching, wherein the ceramic base layer is split by multiple prismoids, multiple pyramids and multiple bosses. The preparing method comprises the following steps: designing PE layer on the inner side of outer and inner surface of inner mould; splitting a layer of ceramic multiple prismoids, multiple pyramids and multiple bosses on the inner side of PE layer; pressing inner and outer mould through heating.
Owner:马斌 +3
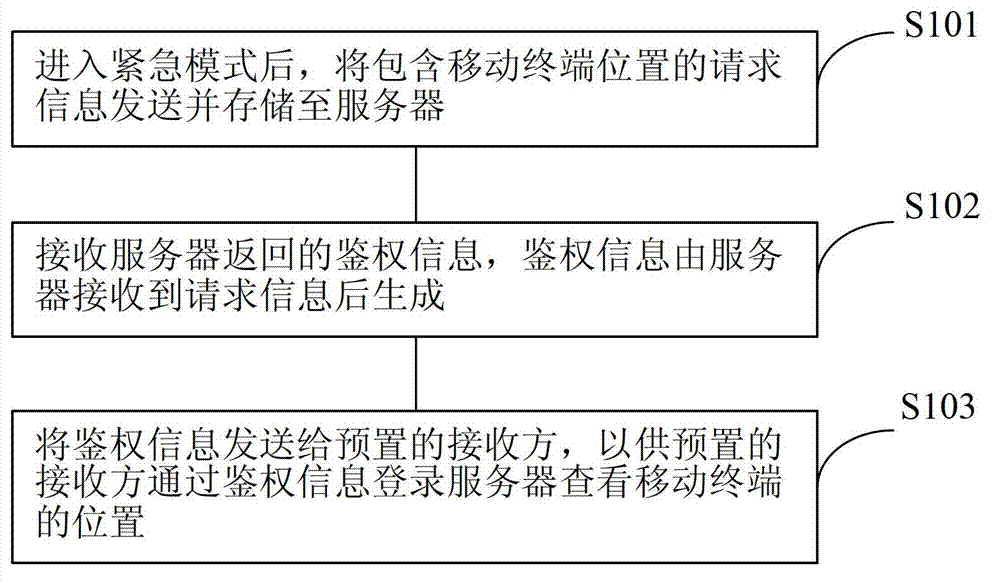
Mobile terminal as well as tracking method and tracking system thereof
InactiveCN102932733AEasy rescueRealize timely trackingMessaging/mailboxes/announcementsTransmissionComputer terminalComputer science
The embodiment of the invention provides a mobile terminal as well as a tracking method and a tracking system thereof and solves the problem of tracking the position of a user. The tracking method comprises the steps of: sending and storing request information containing the position of the mobile terminal into a server after entering an emergency mode; receiving authentication information fed back by the server, wherein the authentication information is generated after the server receives the request information; and sending the authentication information to a pre-set receiving party, so as to enable the pre-set receiving party to log in the server to look up the position of the mobile terminal by the authentication information. The mobile terminal as well as the tracking method and the tracking system of the mobile terminal can be used for realizing the real-time tracking on the position of the user.
Owner:XIAOMI INC
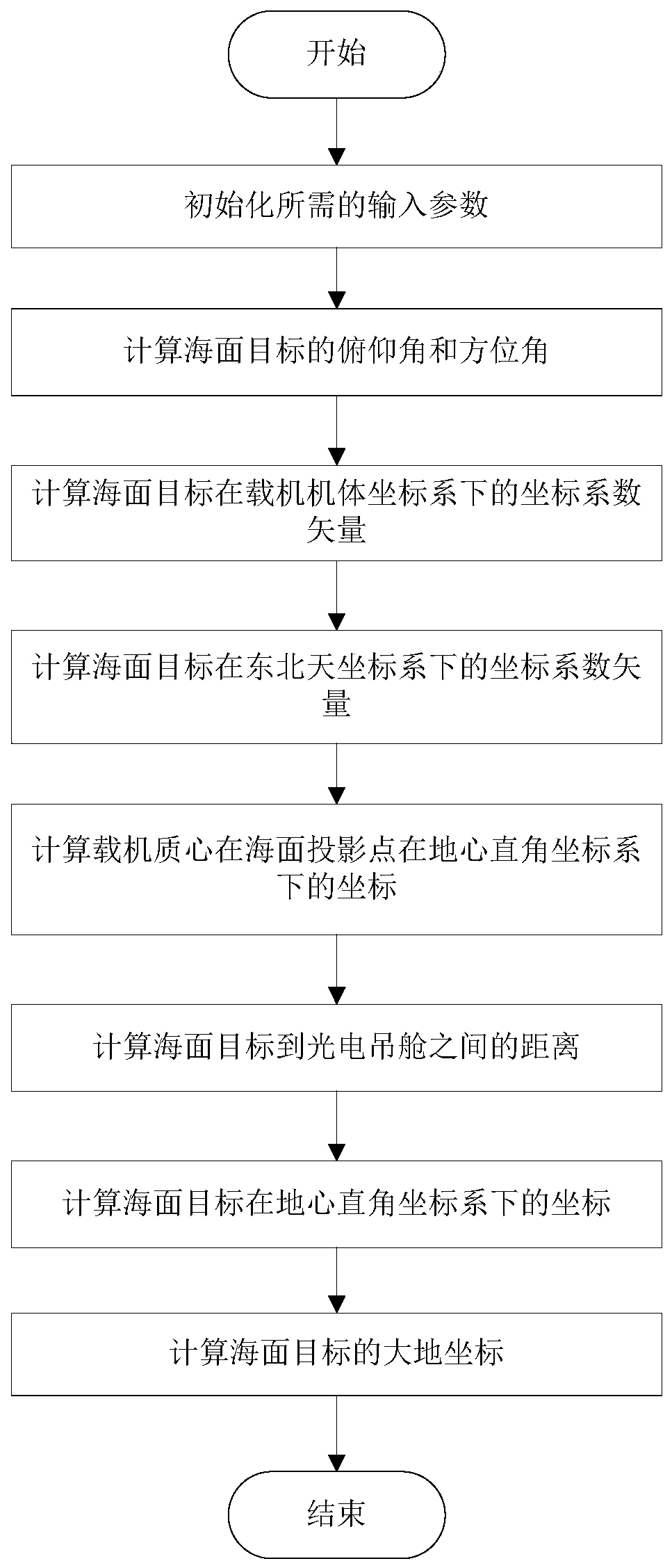
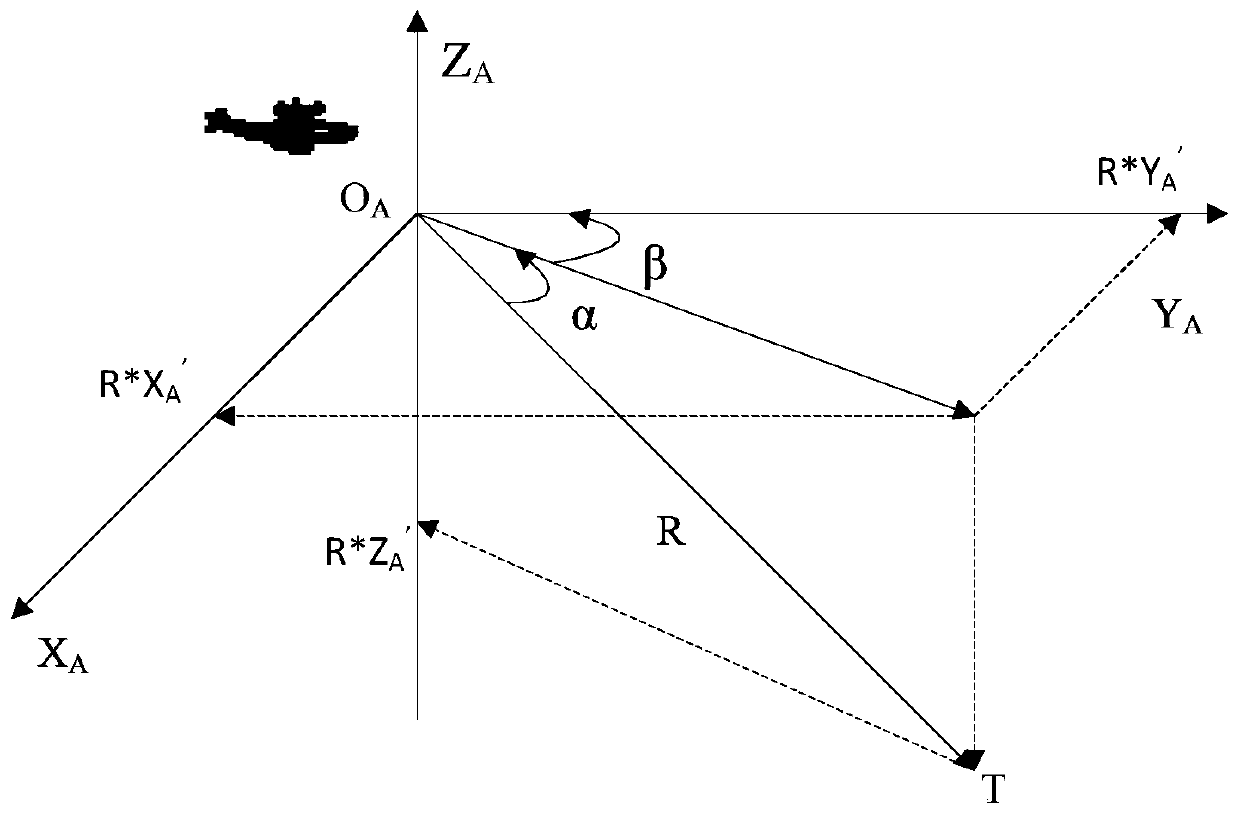
Airborne photoelectric high-precision passive positioning method suitable for sea surface target
PendingCN110487266ASave construction spaceReduce weightNavigation by terrestrial meansNavigation by speed/acceleration measurementsPassive detectionAzimuth
The invention discloses an airborne photoelectric high-precision passive positioning method suitable for a sea surface target and relates to the technical field of airborne photoelectric passive detection and positioning. The method comprises eight steps of: 1, initializing parameters measured by a sensor; 2, calculating a sea surface target azimuth angle and a sea surface target pitch angle; 3, calculating coordinate coefficient vectors (XA ', YA', ZA ') of a sea surface target under an aerial carrier body coordinate system; 4, calculating coordinate coefficient vectors (Cx1, Cy1, Cz1) of thesea surface target under the northeast sky coordinate system; 5, calculating coordinates (XP, YP, ZP) of a projection point of a aerial carrier centroid on the sea surface under a geocentric rectangular coordinate system; 6, calculating a distance between the sea surface target and a photoelectric pod; 7, calculating coordinates (Xd, Yd, Zd) of the sea surface target under the geocentric rectangular coordinate system; and 8, calculating geodetic coordinates of the sea surface target. Through the above eight steps, the high-precision passive positioning technology of airborne photoelectricityto the sea surface target is realized.
Owner:西安应用光学研究所
Anti-counterfeiting material and preparation method thereof
ActiveCN106652767AWide range of incident anti-counterfeiting spectrumReduce repetition rateStampsIdentification meansMicro nanoReflectivity
The invention discloses anti-counterfeiting material and a preparation method thereof. The anti-counterfeiting material comprises anti-counterfeiting micro-nano modules which are mutually discrete in the unbound state. Each anti-counterfeiting micro-nano module comprises first and second micro-nano recognition layers. The first and second micro-nano recognition layers comprise base material layers used for processing anti-counterfeiting recognition feature layers and micro-nano structural layers. Anti-counterfeiting label patterns are arranged in the anti-counterfeiting. The first and second micro-nano recognition layers have different or same absorptivity, light transmittance and reflectivity. In terms of the structure, anti-counterfeiting information and features with complicated internal structures are made from the inside to the outside and processed layer by layer. The appearance of the anti-counterfeiting micro-nano modules are in integrally wrapping states. External anti-counterfeiting incident spectrums are refracted by the first and second micro-nano recognition layers and subjected to mutual comparisons, mapping and mixture between an emitted light source and the anti-counterfeiting label patterns such that a light source of the anti-counterfeiting micro-nano modules reflected to an anti-counterfeiting recognition system comprises optical spectrum coding anti-counterfeiting information with high cost in reverse cracking.
Owner:福州固钛光电科技有限公司
Hidden online monitoring system for marine monitoring equipment
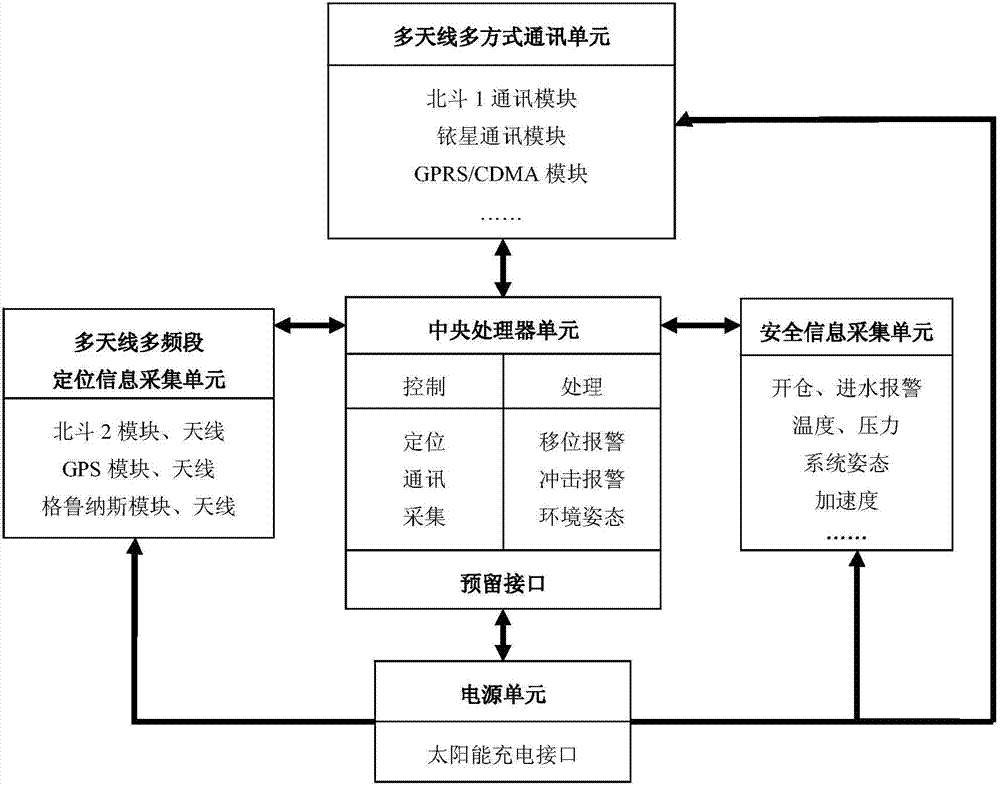
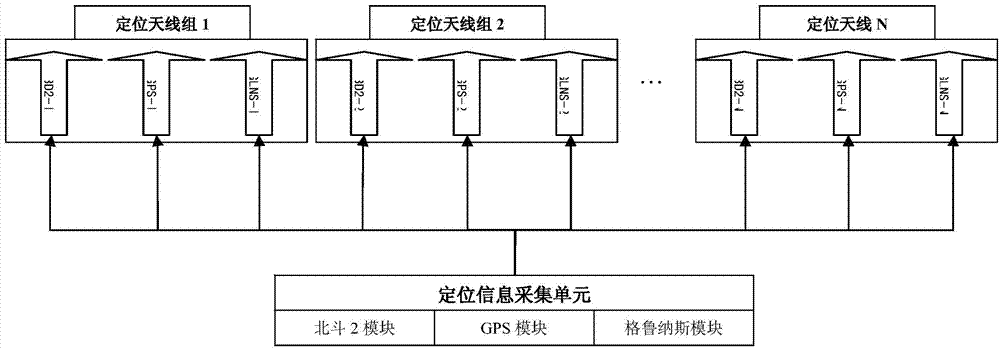
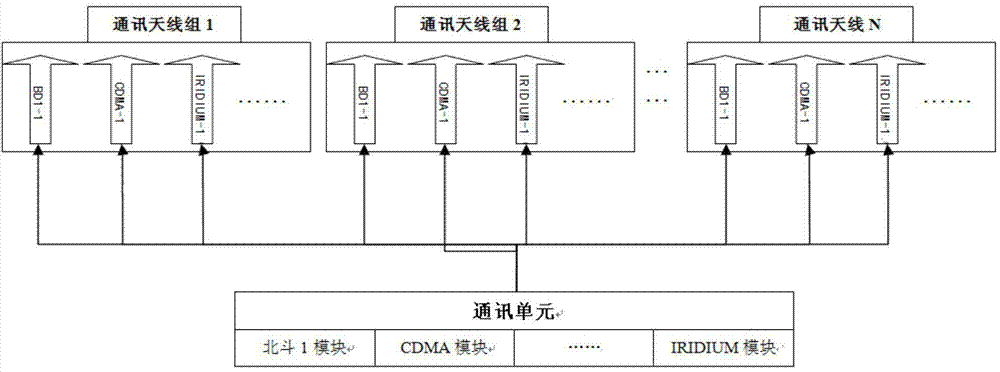
InactiveCN104731070AMonitor the running position in timeMonitor posture in timeTotal factory controlProgramme total factory controlInstrumentationData lines
The invention discloses a hidden online monitoring system for marine monitoring equipment. The hidden online monitoring system comprises a power supply unit, a locating information acquisition unit, a safety information acquisition unit, a communication unit and a central processing unit, wherein the locating information acquisition unit comprises N locating units and N locating antenna groups; the communication unit comprises N communication modules and N communication antenna groups; the power supply unit is electrically connected with the locating information acquisition unit, the safety information acquisition unit, the communication unit and a power supply drive terminal of the central processing unit; an I / O port of the central processing unit is electrically connected with the locating information acquisition unit, the safety information acquisition unit and the communication unit through data lines. By the adoption of the technical scheme, the hidden online monitoring system is suitable for multi-frequency band and multi-antenna locating of different offshore platforms and multi-frequency band and multi-antenna communication and monitors the state of a monitored instrument in real time.
Owner:STATE OCEAN TECH CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com