Mobile terminal as well as tracking method and tracking system thereof
A technology for mobile terminals and receivers, applied in the field of wireless communication, to achieve the effect of avoiding the leakage of private information and enriching information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
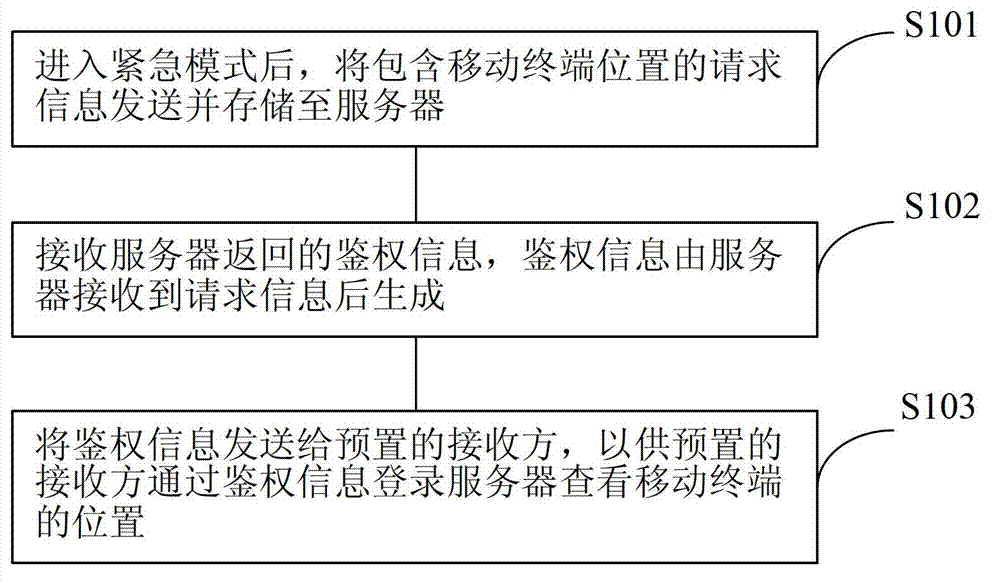
[0047] refer to figure 1 , which shows a flow chart of a method for tracking a mobile terminal in this embodiment, and this embodiment may specifically include the following steps:
[0048] S101. After entering the emergency mode, send and store the request information including the location of the mobile terminal to the server;
[0049] The request information sent by the mobile terminal also includes the device identification number ID that uniquely identifies the mobile terminal. The device identification number ID is an inherent identification information of the mobile terminal device, which is burned into the main board through the hardware device. Only through professional Only hardware devices can be modified.
[0050] It should be noted that before the emergency mode of the mobile terminal is activated in this embodiment, it also includes: setting emergency mode setting items and storing them in the server. The emergency mode setting items include: preset contact info...
Embodiment 2
[0099] refer to Figure 4 , which shows an interactive schematic diagram of a mobile terminal tracking method in this embodiment. This embodiment may specifically include the following steps:
[0100] S401, the mobile terminal sets the emergency mode setting item, and sends the setting information to the server;
[0101] The emergency mode setting items include: the preset receiver's contact information and emergency setting function;
[0102] The contact information of the preset recipients includes: one or more preset recipients, or emergency call numbers.
[0103] In this embodiment, the preset receiver's contact information is the number of two emergency contacts, and two emergency contacts are set: emergency contact 1 and emergency contact 2;
[0104] Set the activation delay time in the emergency setting function to 20 seconds, and the activation is successful through the triple vibration feedback, and the content of the message received by the emergency contact is "Pl...
Embodiment 3
[0119] refer to Figure 5 , which shows a flow chart of a method for tracking a mobile terminal in this embodiment, and this embodiment may specifically include the following steps:
[0120] S501. Receive request information sent after the mobile terminal enters the emergency mode, where the request information includes the location of the mobile terminal;
[0121] S502. After receiving the request information, generate authentication information;
[0122] In this embodiment, after the server generates the authentication information according to the request information, the method of sending the authentication information to the mobile terminal in the first embodiment is no longer used, and the mobile terminal then sends the authentication information to the preset receiver. Sending directly to the preset receiver avoids unnecessary information transmission, saves time, and saves time for rescuers when encountering robbers. Moreover, without sending the authentication inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com