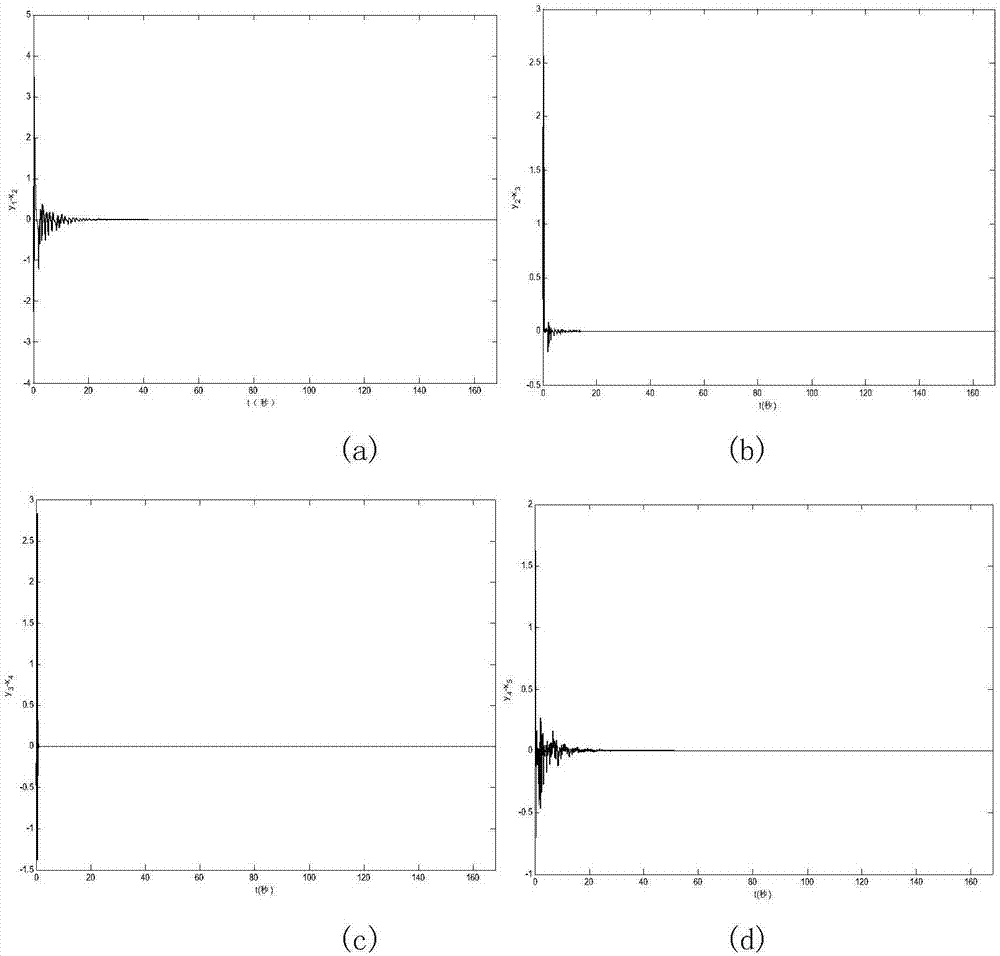
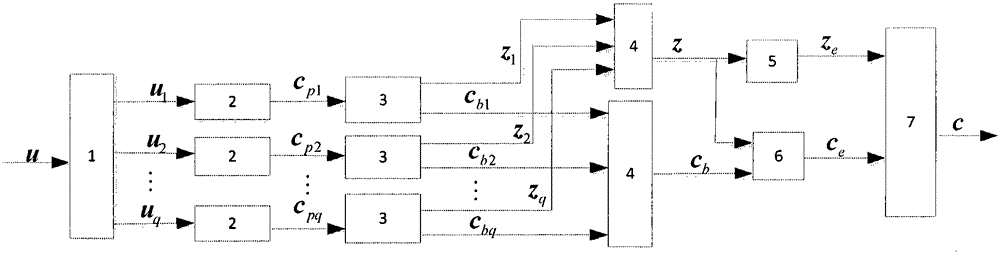
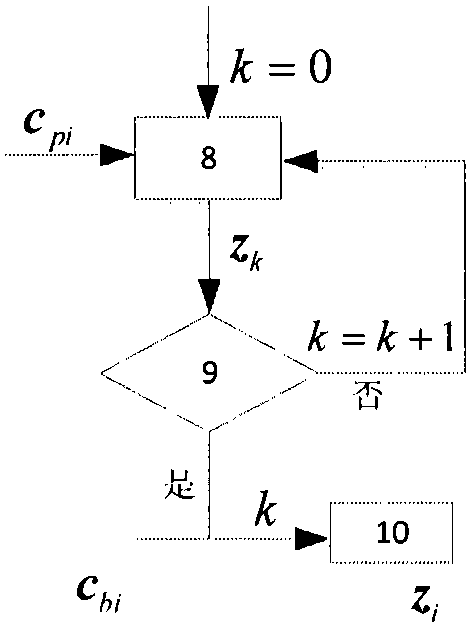
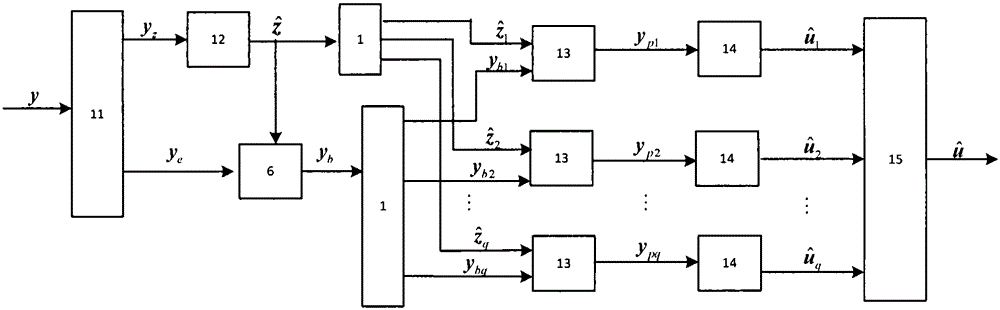
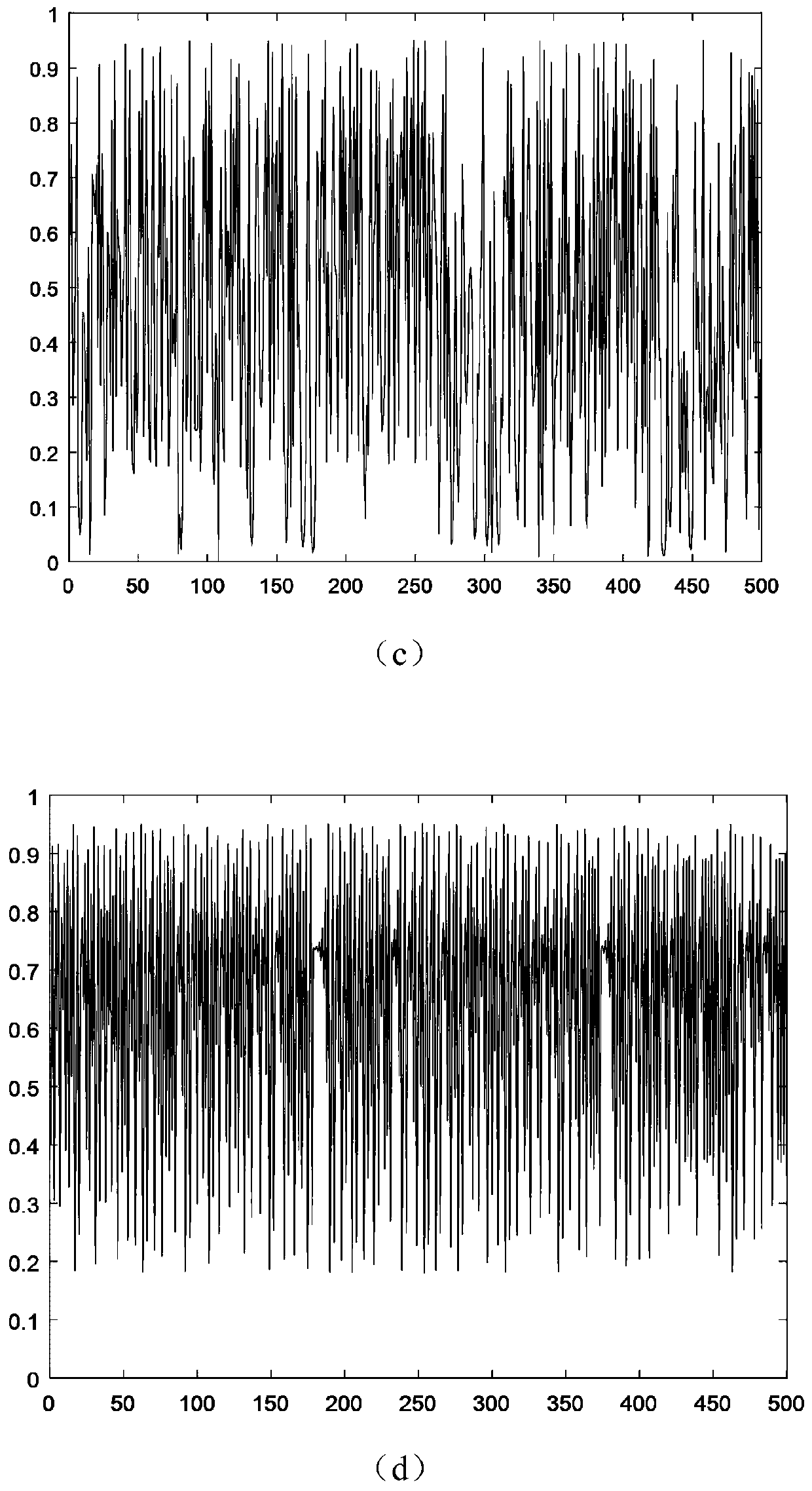
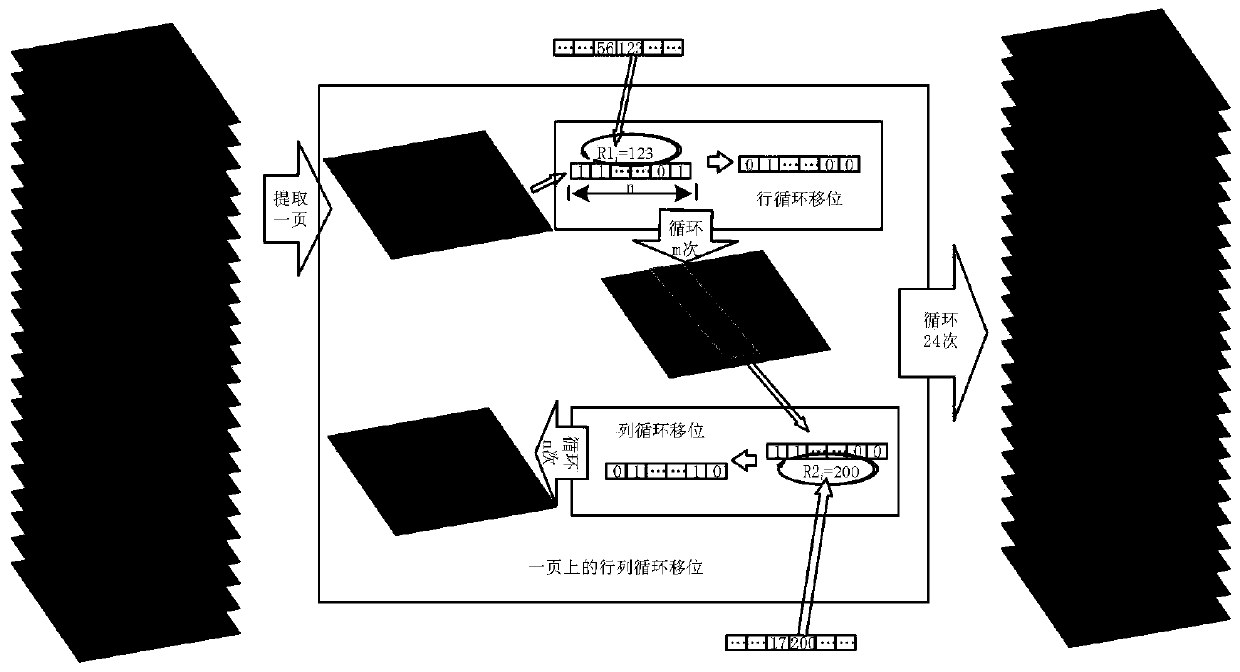
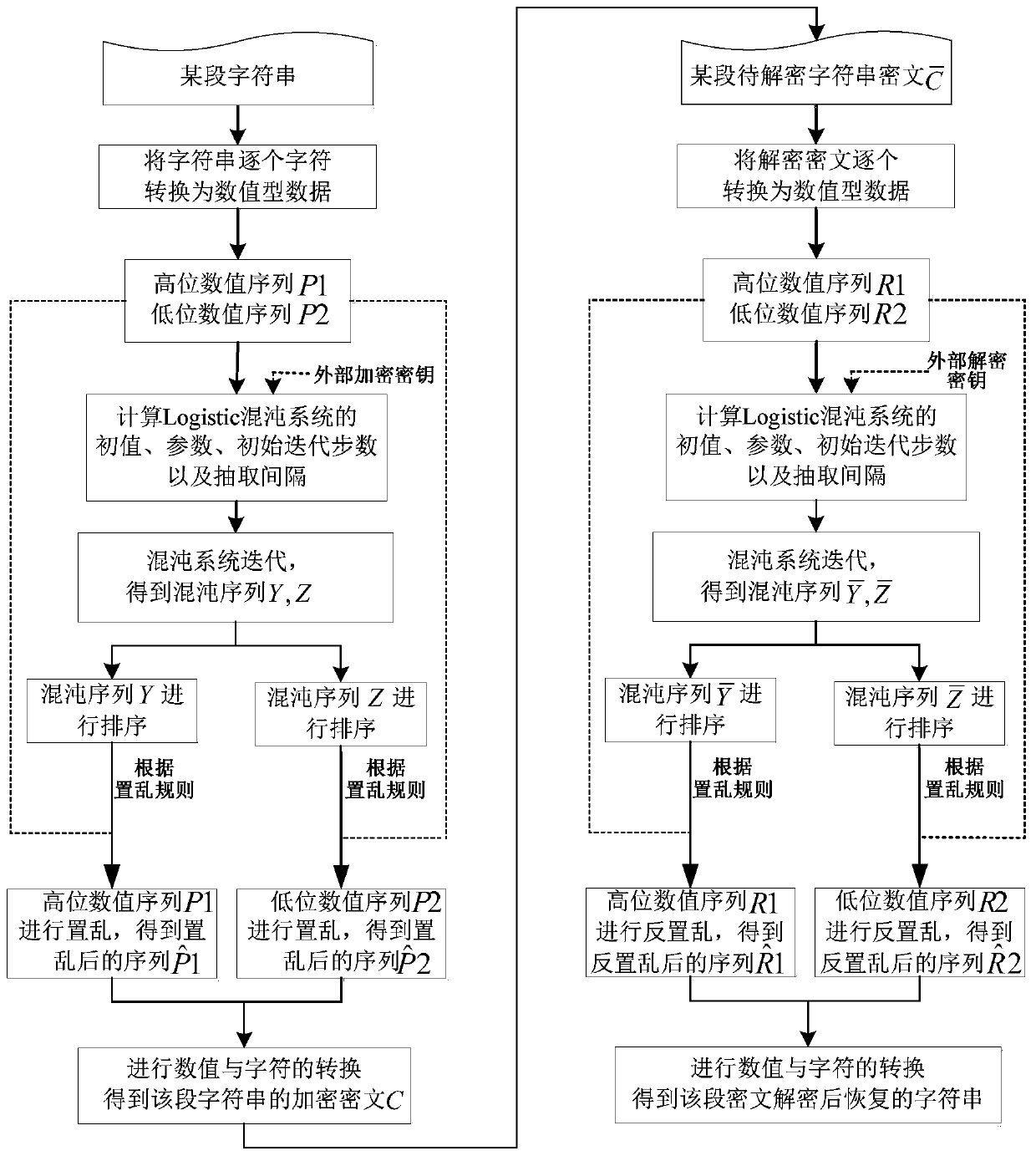
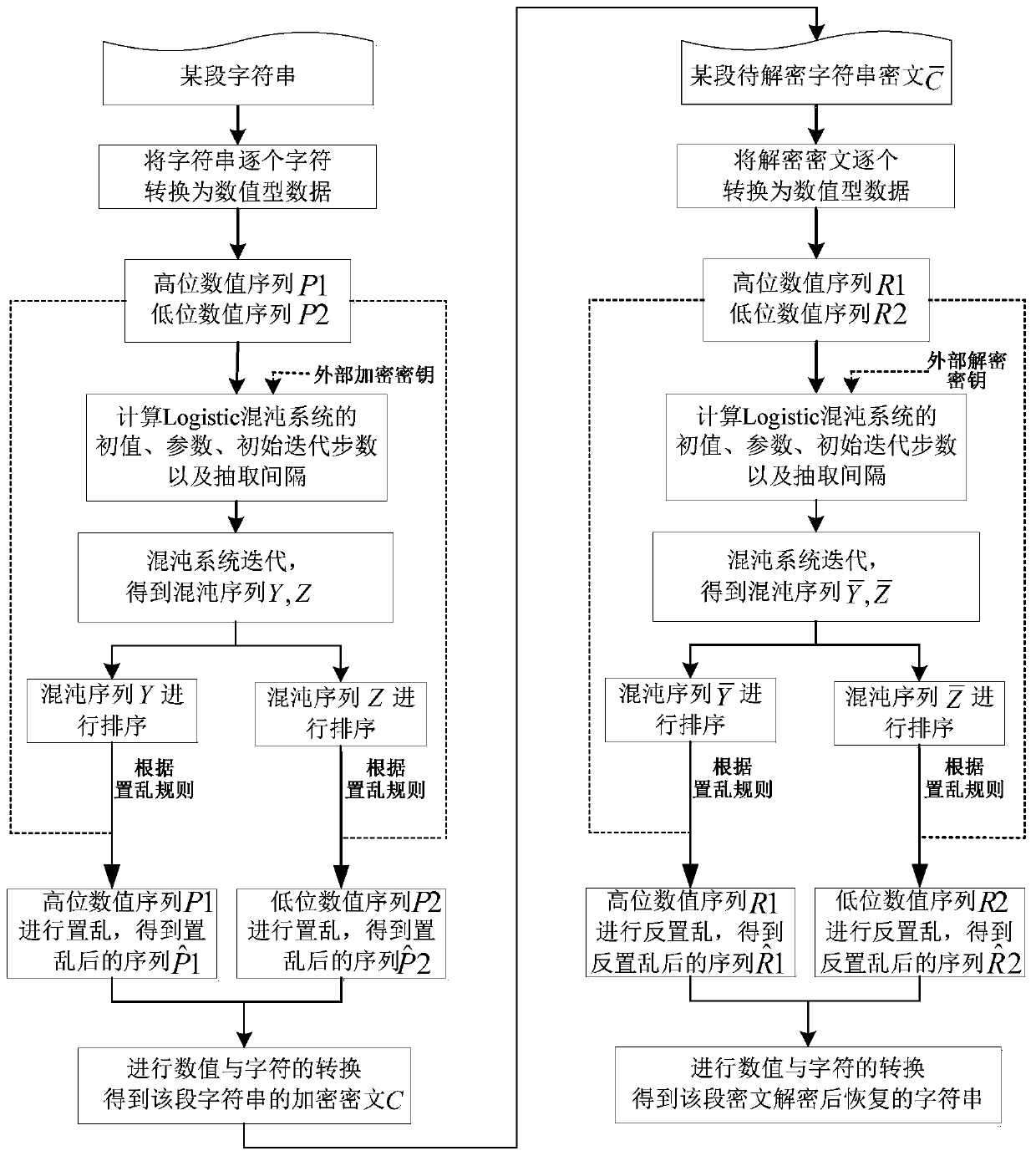
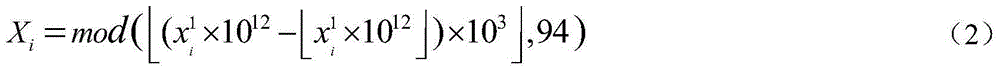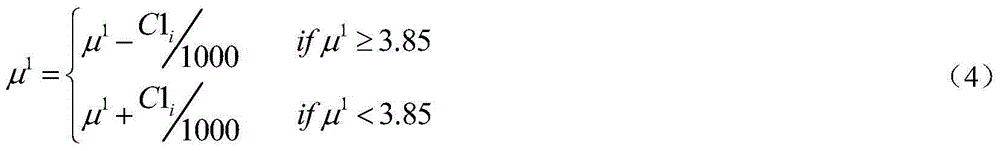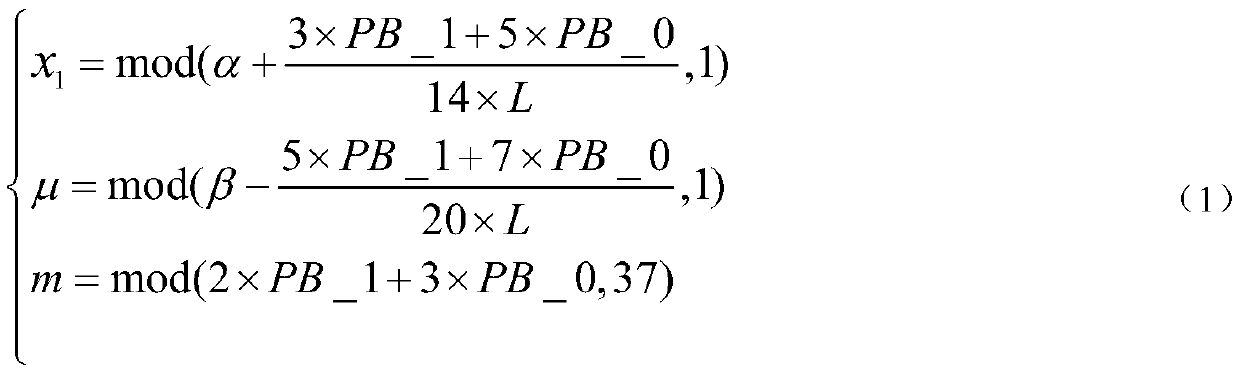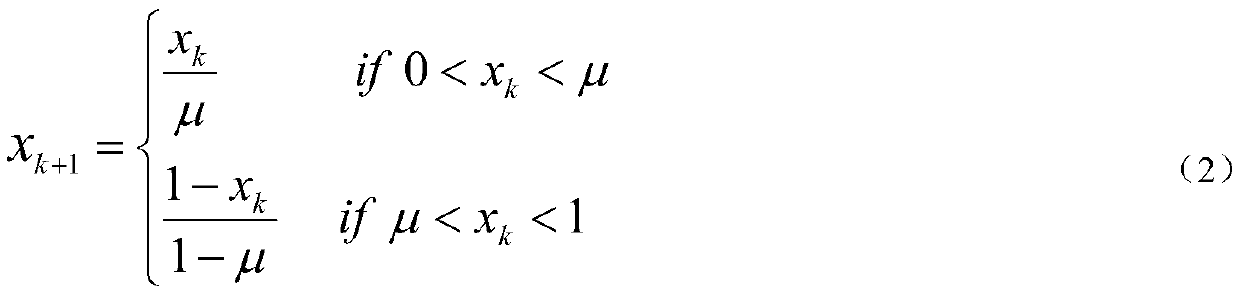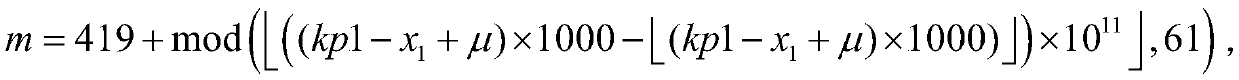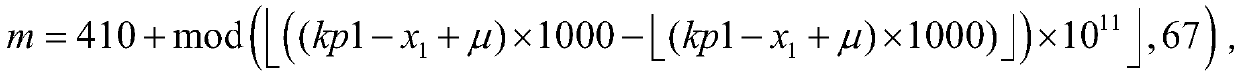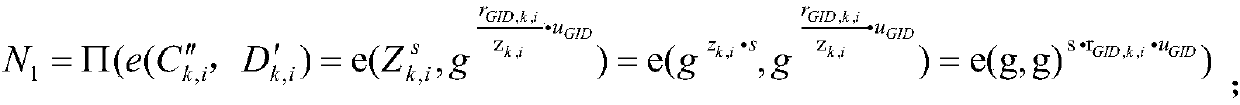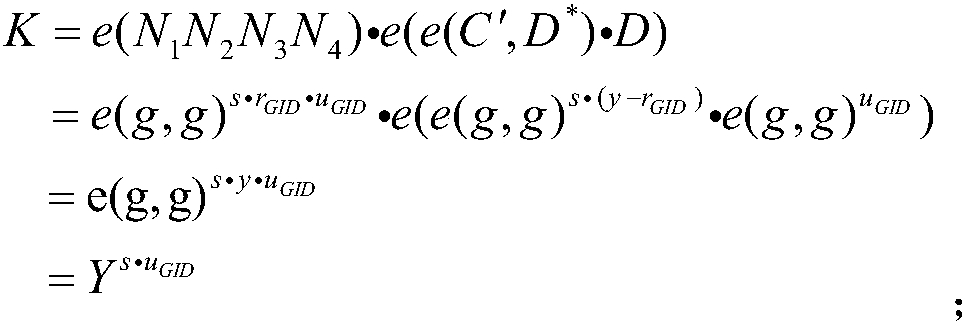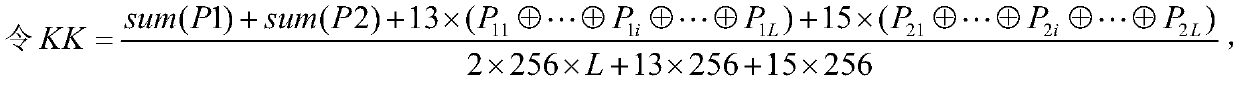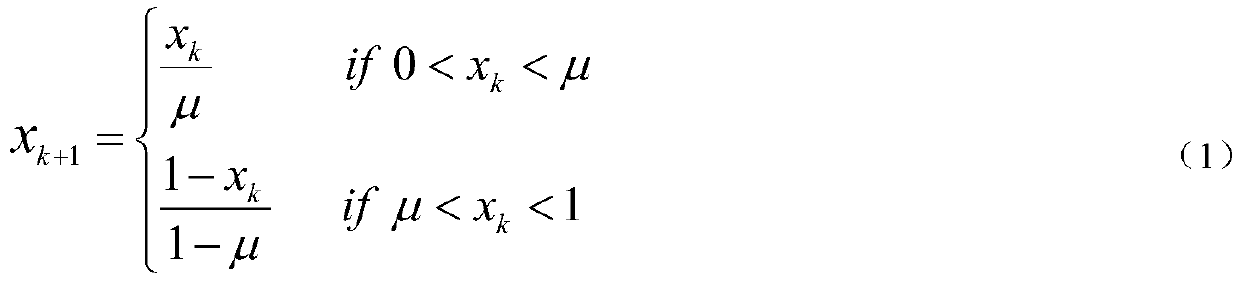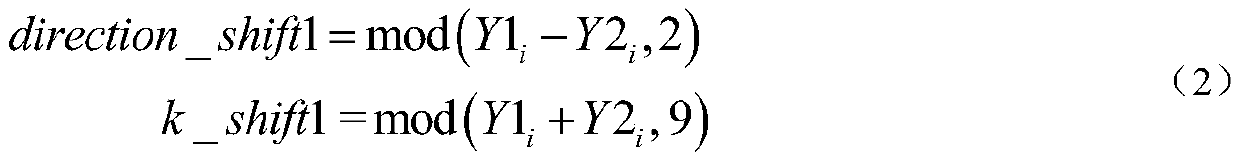Patents
Literature
128 results about "Chosen-plaintext attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts. The goal of the attack is to gain information that reduces the security of the encryption scheme.
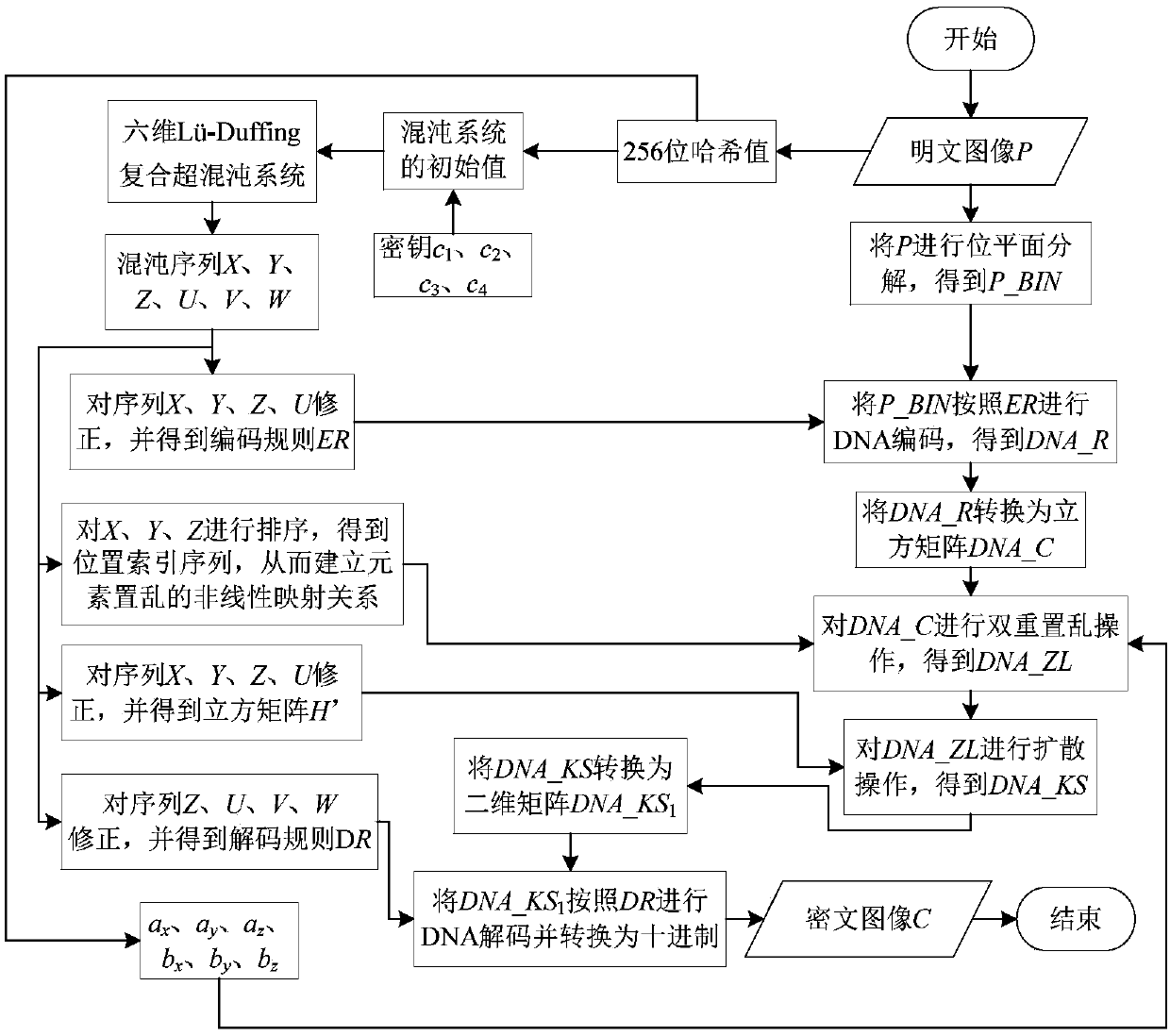
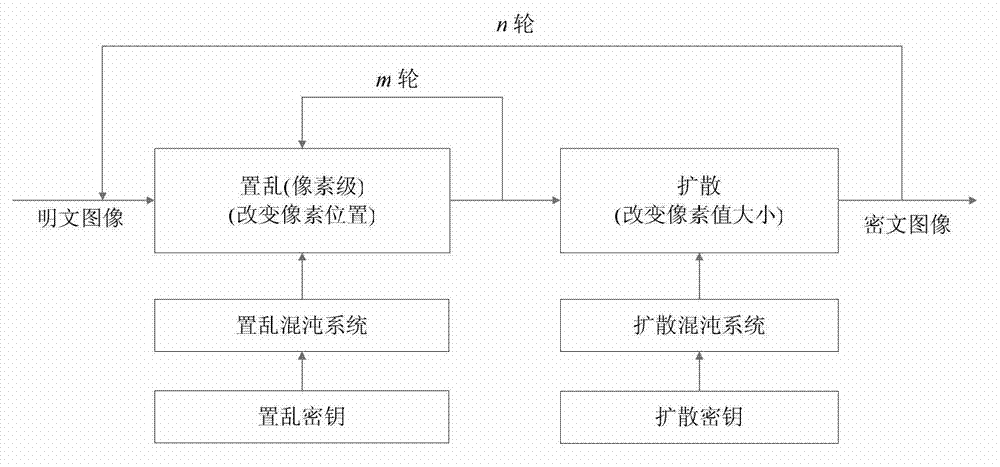
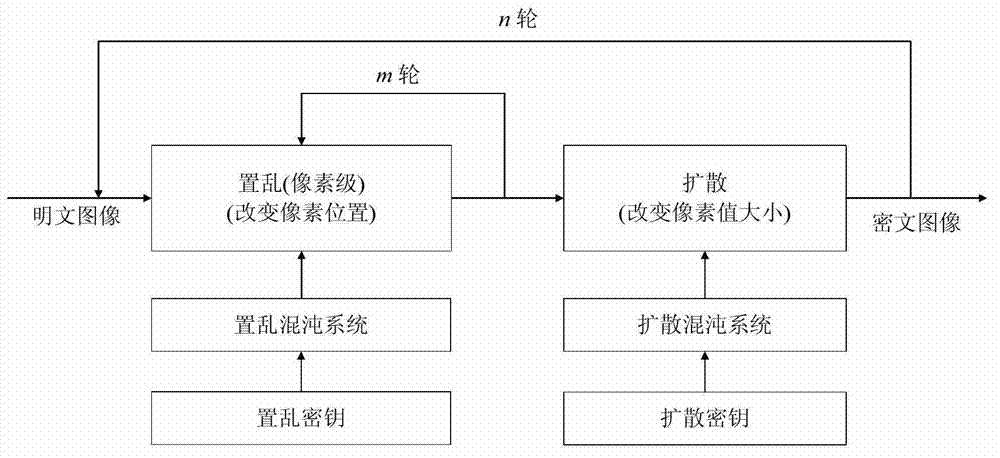
Chaos image encryption method based on dual scrambling and DNA coding
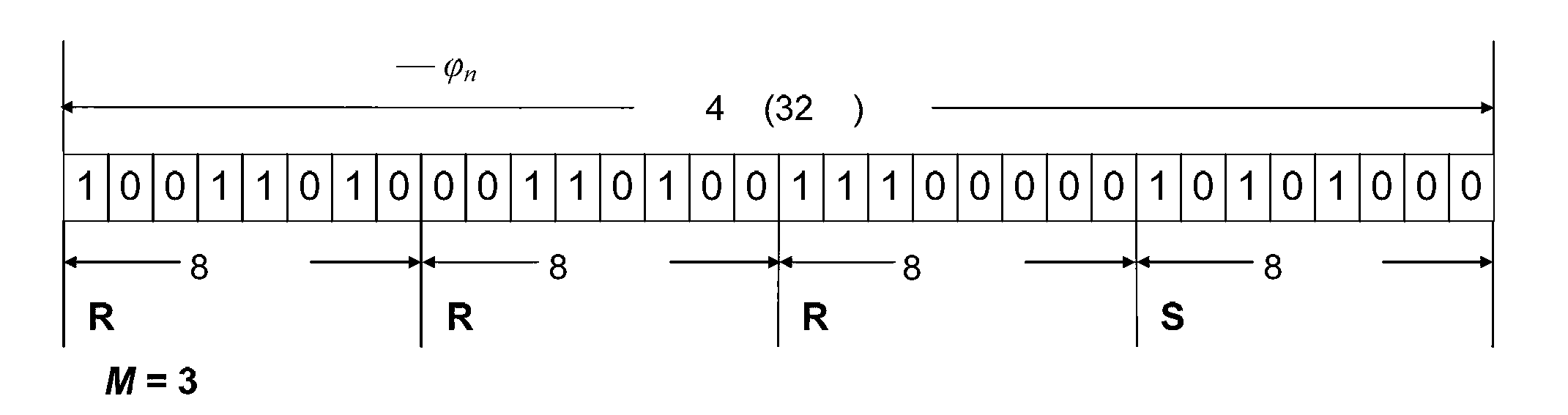
ActiveCN108898025AAvoid multiple iterationsImprove securityDigital data protectionChosen-plaintext attackDiffusion
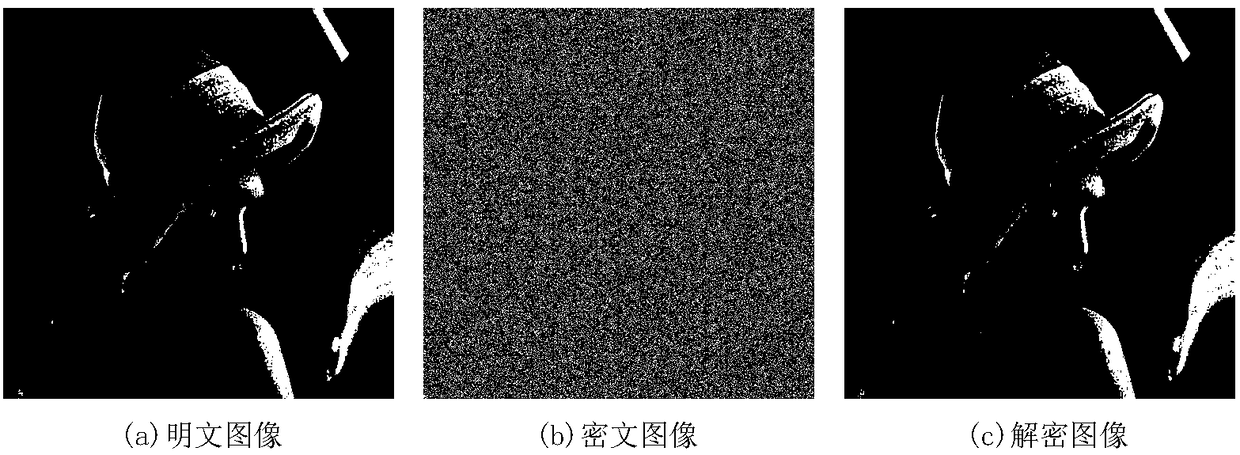
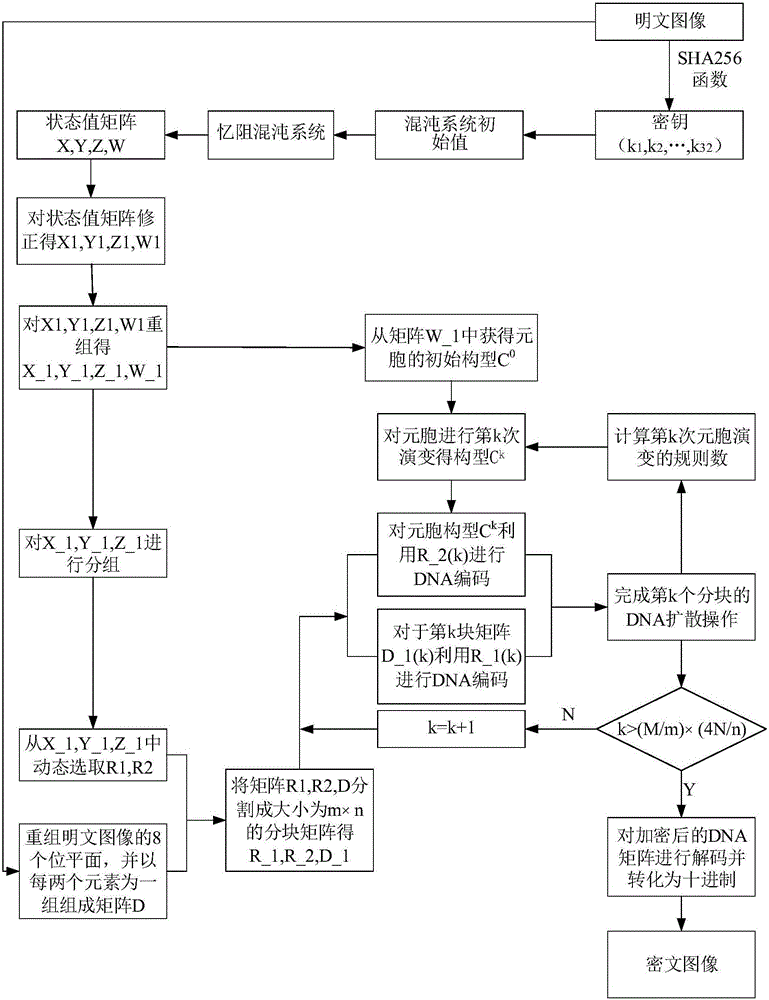
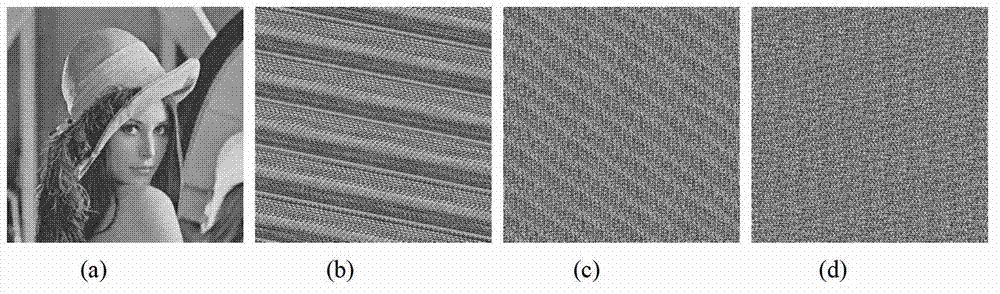
The invention relates to a chaos image encryption method based on dual scrambling and DNA coding, firstly, carrying out bit plane decomposition on a plaintext image and carrying out DNA coding and transformation on the image to turn the image into a three-dimensional DNA matrix; then, scrambling the three-dimensional DNA matrix through the dual scrambling operation, wherein the sequence of the chaotic sequences is scrambled and the DNA sequence is scrambled in a bit level through combining the three-dimensional cat mapping; next, performing diffusion operation on the scrambled three-dimensional DNA matrix, and converting the diffused matrix into a two-dimensional DNA matrix; finally, performing decoding operation on the two-dimensional DNA matrix to obtain a ciphertext image. According tothe invention, the SHA256 hash function of the plaintext image is used to calculate the initial value of the chaotic system, and the parameters of three-dimensional cat mapping are also related to theplaintext image, which enhances the ability of the algorithm to resist the selection of plaintext attack. Experimental results and safety analysis show that the encryption scheme can resist various known attacks, and can effectively protect the security of images and also can improve the security level.
Owner:HENAN UNIVERSITY
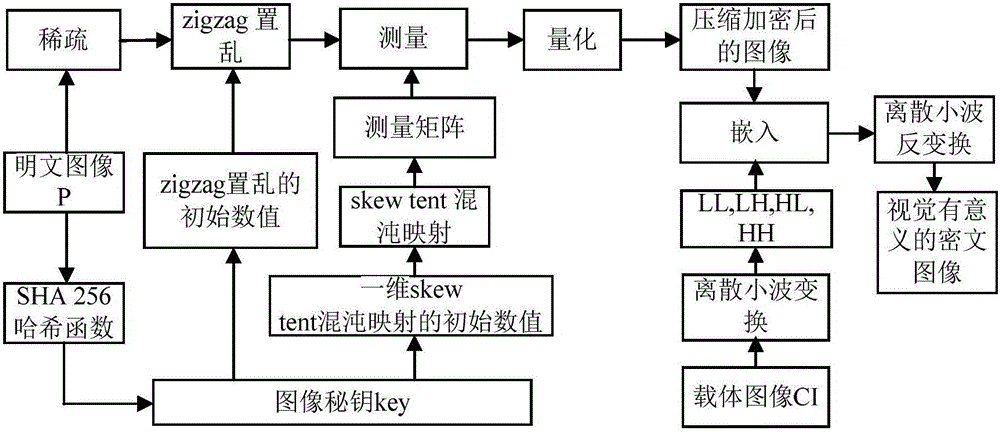
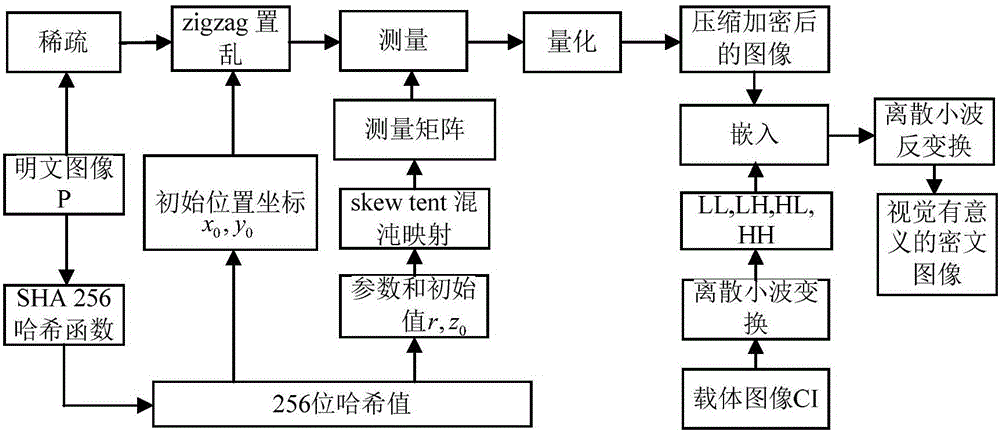
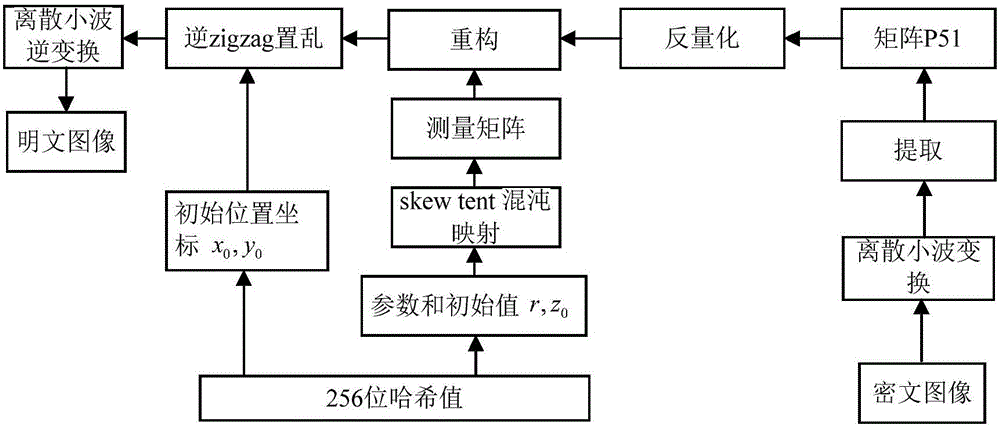
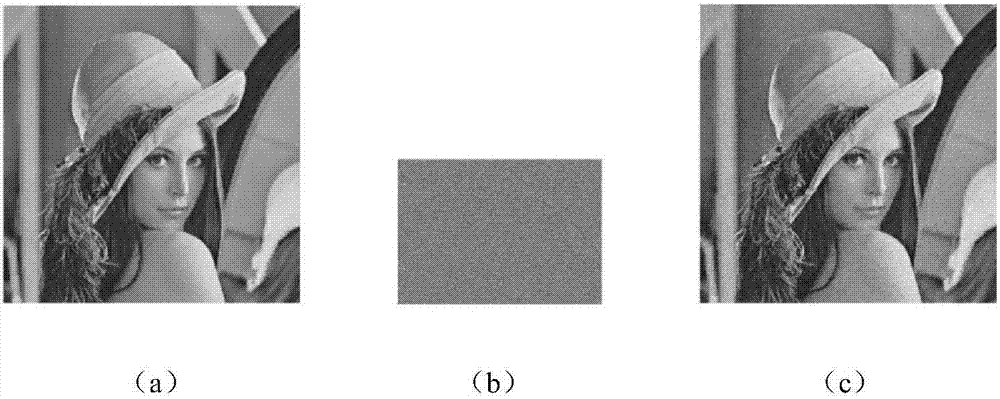
Image encryption method and image decryption method with visual security and data security based on compressed sensing
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
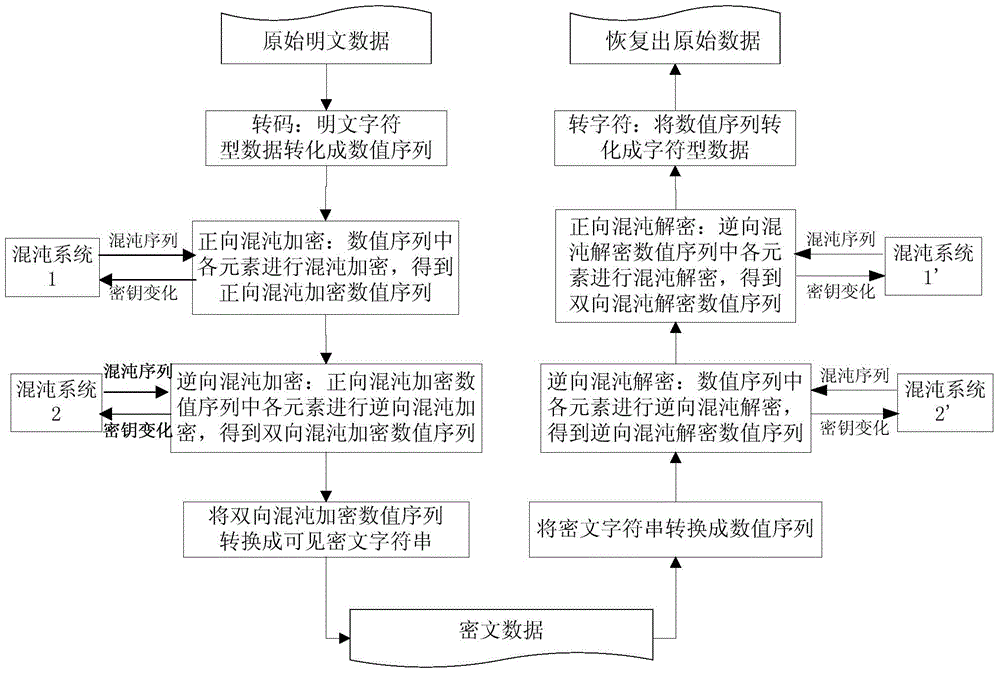
Encryption and decryption method of character data
ActiveCN104486073AEnsure safetyGuaranteed feasibilitySecuring communicationComputer hardwareCiphertext-only attack
The invention discloses an encryption and decryption method of character data. The encryption and decryption method comprises the following steps: converting plaintext character data into a numerical sequence; carrying out bidirectional encryption on all elements in the numerical sequence by utilizing a chaotic signal generated by a variable key chaotic system and obtaining a bidirectional chaotic encryption numerical sequence; self-defining a corresponding relation between numerical data and a visible ciphertext character, converting the bidirectional chaotic encryption numerical sequence into a visible ciphertext character sequence, obtaining a ciphertext string unequal to the plaintext character data in length, and decrypting and restoring a ciphertext into original character data through a similar method. The encryption and decryption method has the benefits that the self-defined corresponding relation is adopted for carrying out bidirectional chaos encryption processing on the character data so as to generate the length-variable ciphertext string, and the ciphertext string has good resistance to known / chosen-plaintext attack, ciphertext-only attack, so that the safety and the feasibility of data encryption and decryption are ensured.
Owner:SHANGHAI TAIYU INFORMATION TECH
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
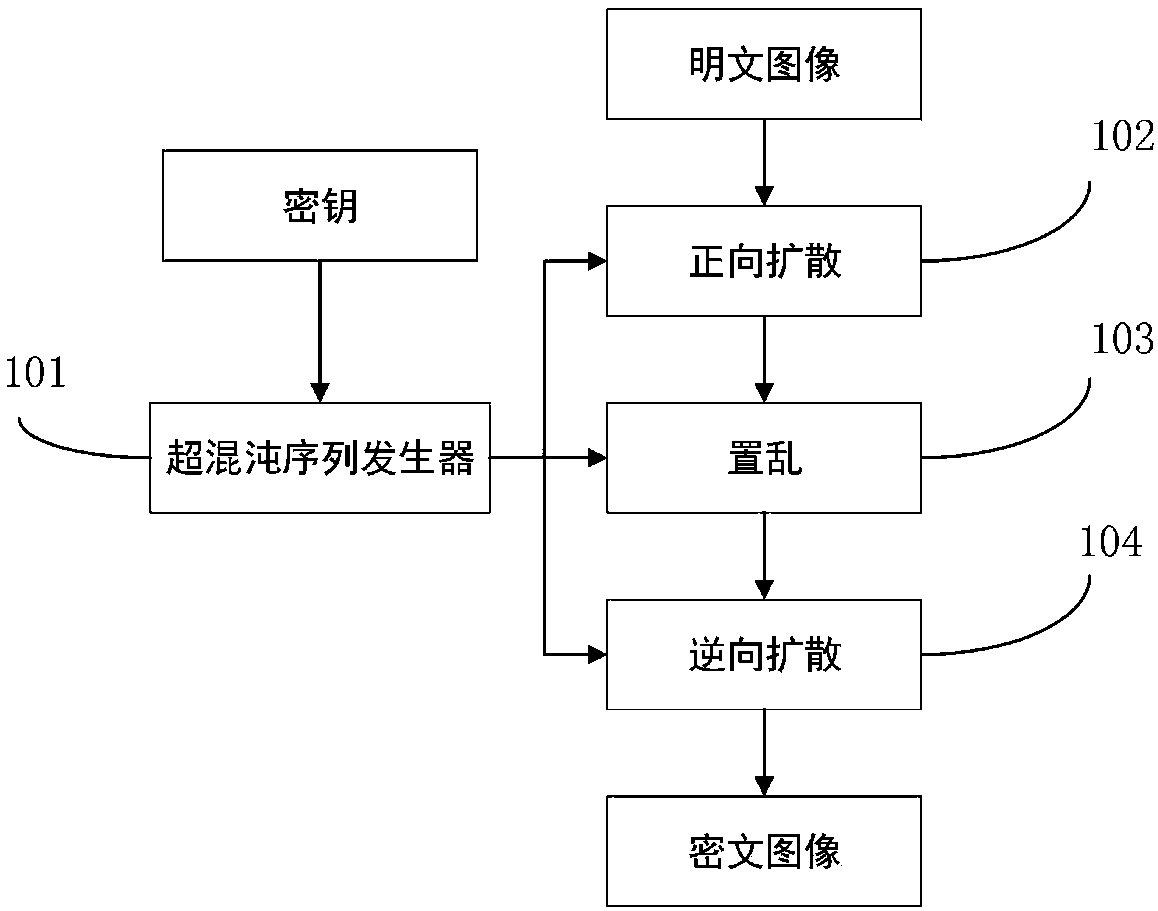
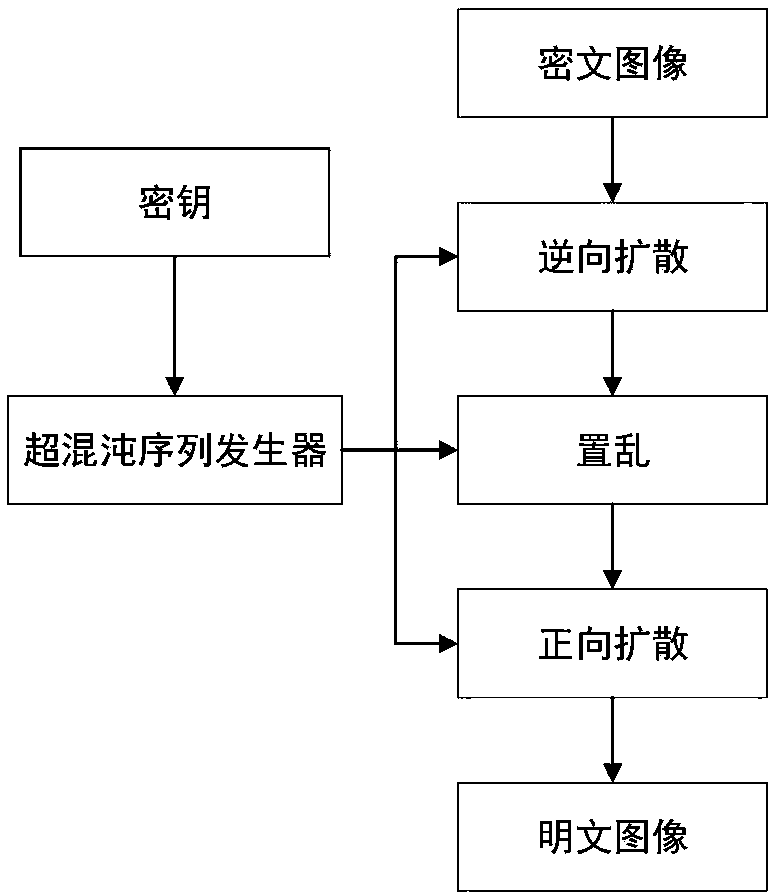
Plaintext associated image encryption algorithm based on hyperchaos Chen system
InactiveCN108234813AReduce the number of iterationsImprove the ability to resist known plaintext attacksKey distribution for secure communicationSecuring communication by chaotic signalsChosen-plaintext attackRelevant information
The invention relates to an image encryption algorithm based on a chaotic system, used for solving security problems that the image encryption algorithm is small in key space and poor in capacity of resisting to plaintext attacks. The algorithm comprises four modules such as a hyperchaos sequence generator, a forward diffusion module, a scrambling module and a reverse diffusion module. Firstly thehyperchaos Chen system is used for generating four chaotic pseudorandom sequences, a chaotic sequence and a plaintext image are used for performing forward diffusion operation to acquire a matrix A,then computation is performed in combination with the pseudorandom sequences and information related to the plaintext image to acquire a scrambled coordinate, the coordinate scrambling is performed onthe matrix A to acquire a matrix B, and at last the chaotic pseudorandom sequences and the matrix B are used for performing reverse diffusion operation to acquire a ciphertext image C. An experimentsimulation result expresses that the algorithm can improve the defect that the image encryption algorithm is small in key space, effectively resist to statistical attacks, differential attacks, and chosen-plaintext attacks, and achieve good encryption effect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Protecting against chosen plaintext attacks in untrusted storage environments that support data deduplication
ActiveUS8281143B1Digital data processing detailsUser identity/authority verificationChosen-plaintext attackData deduplication
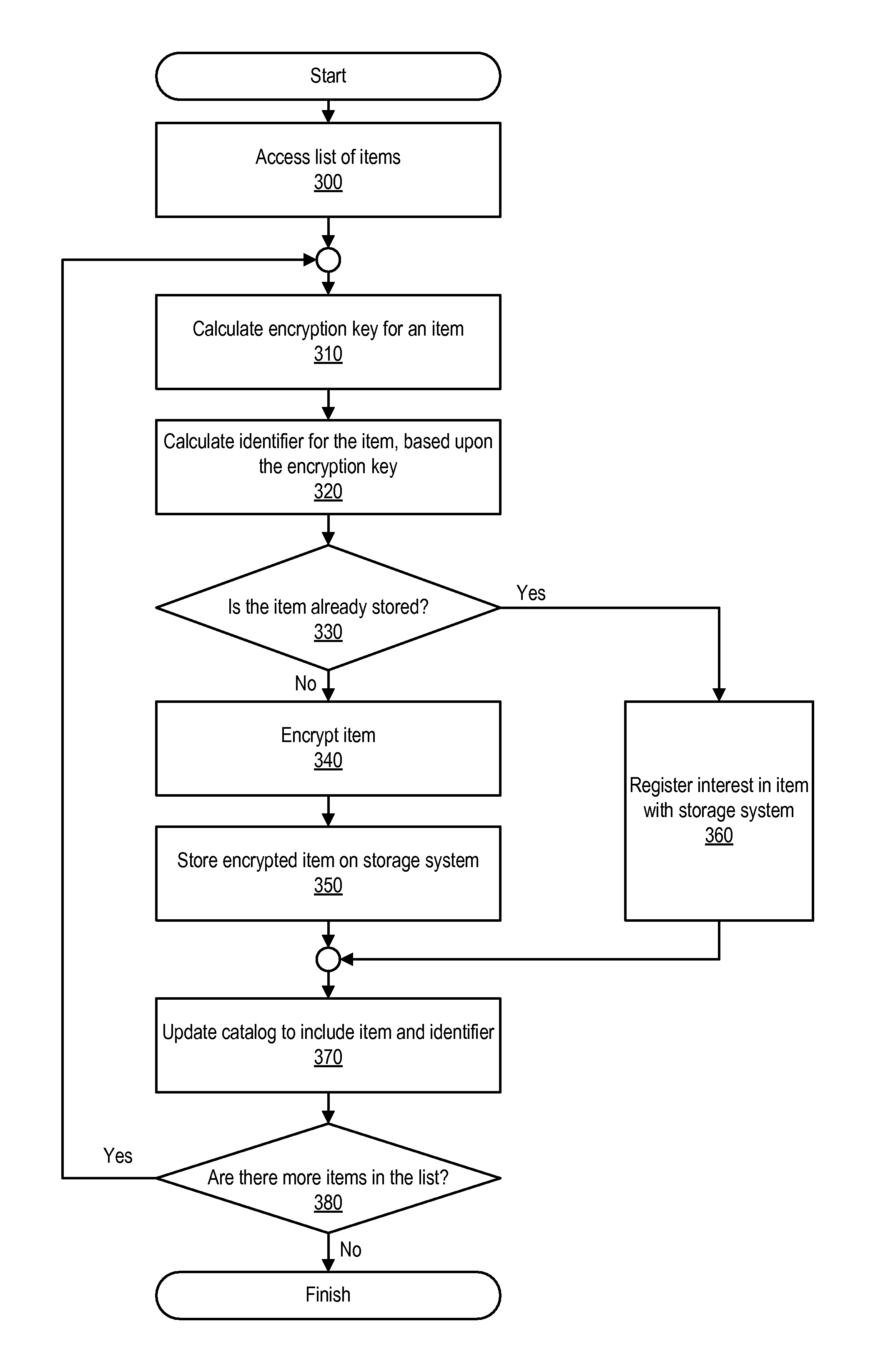
Various methods and systems for protecting against chosen plaintext attacks when encrypting data for storage on an untrusted storage system are disclosed. One method involves generating an encryption key for use in encrypting data and generating an identifier for the data. Generation of the encryption key is based upon a hash of the data to be encrypted. The method also involves detecting whether an encrypted copy of the data is already stored by a storage system, based upon the identifier. The method also modifies the data to be encrypted or the encryption key, based upon a client-specific value, prior to generating the identifier.
Owner:SYMANTEC OPERATING CORP
Password encryption method and system, and cryptographic check method and system
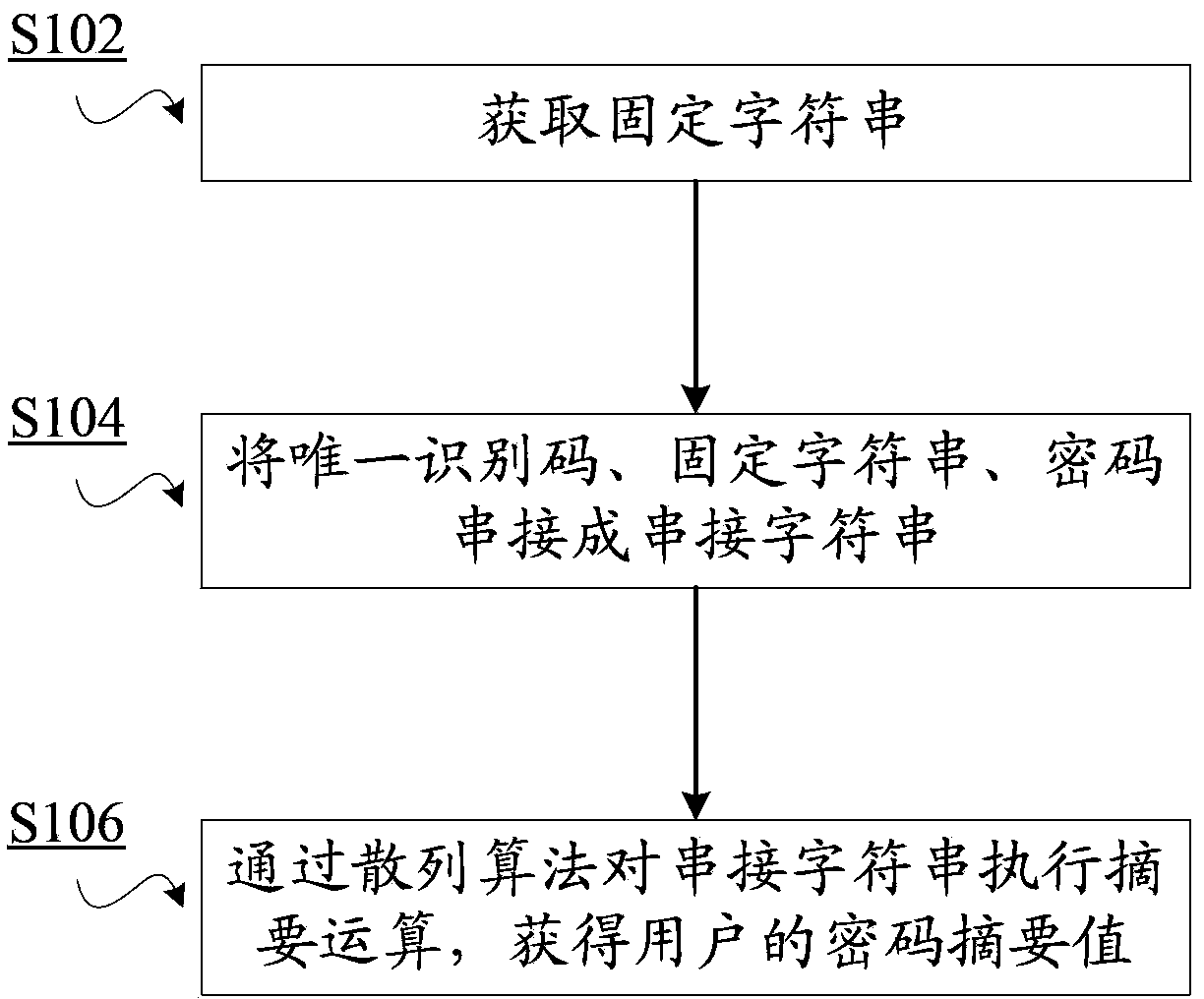
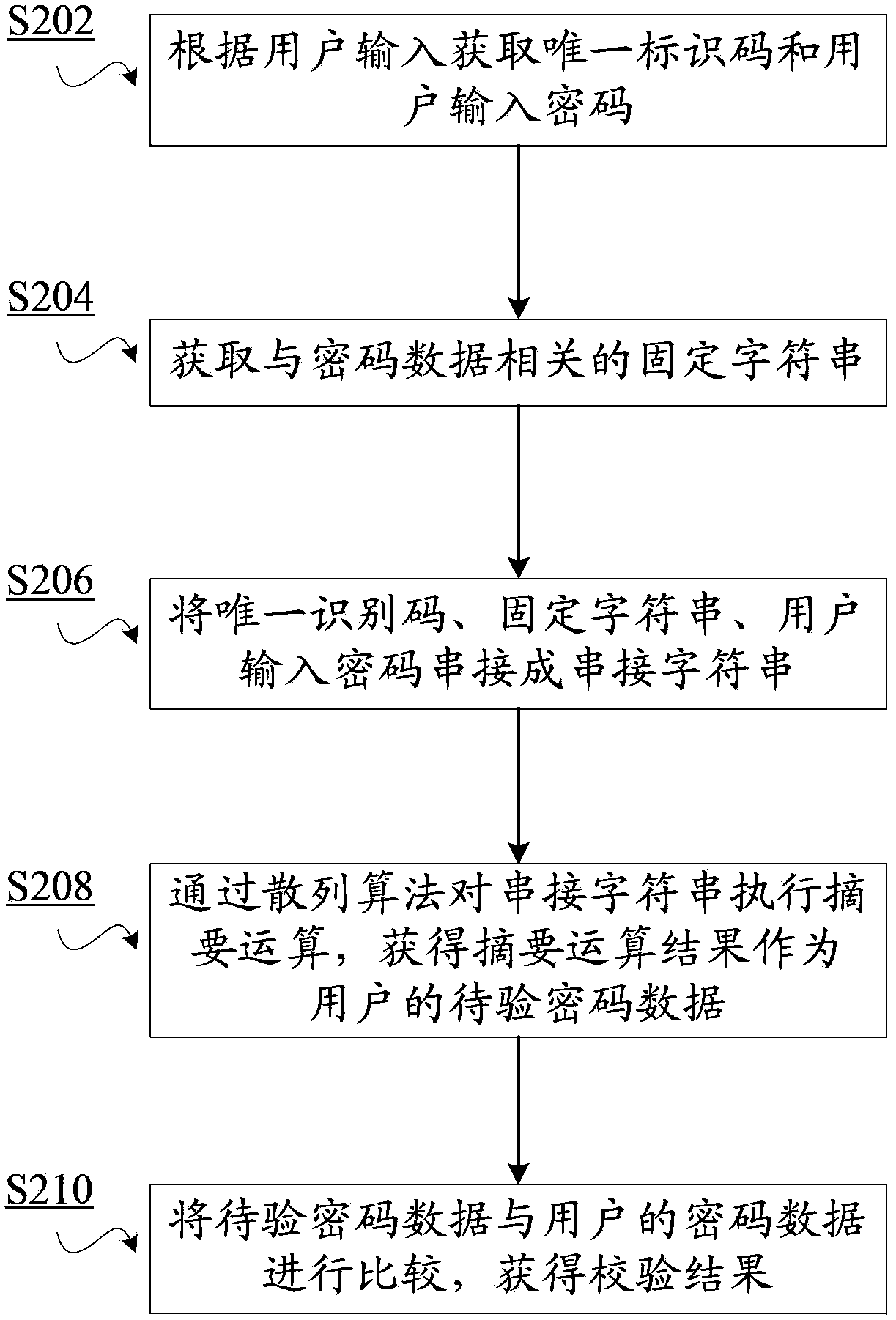
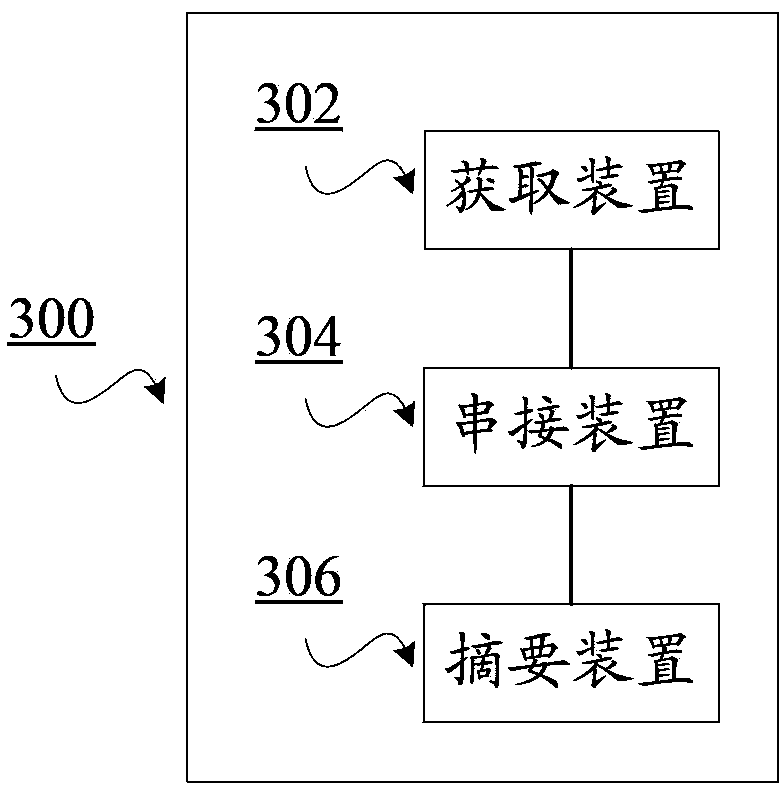
ActiveCN103780379AUniqueness guaranteedAdd unique factor - user unique identification codeUser identity/authority verificationChosen-plaintext attackPassword
The invention discloses a password encryption method used for performing encryption on passwords of users, wherein each user has a unique identification code. The method includes the following steps: acquiring a fixed character string; cascading the unique identification code, the fixed character string and a password into a cascaded character string; and executing a digest operation on the cascaded character string through a hash algorithm and acquiring a password digest value of a user. Through application of the password encryption method and system, and a cryptographic check method and system, the methods and systems are applicable to card-password data protection and user security-problem answer protection and the like. Because in a user password digest operation process, a user unique factor, that is, the user unique identification code is added so that uniqueness of a user password digest value is ensured and thus password database files are endowed with capabilities of resisting chosen-plaintext attacks and beforehand chosen-plaintext attacks.
Owner:ADVANCED NEW TECH CO LTD
Image encryption algorithm based on memoristor hyper-chaotic system, cellular automaton and DNA calculation
ActiveCN106023052AImprove securityEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackCellular automation
The invention relates to an image encryption algorithm based on memoristor hyper-chaotic system, cellular automaton and DNA calculation. First of all, a four-dimensional memoristor hyper-chaotic system based on a Chua circuit is employed, at the same time, a secret key is generated by enabling a plaintext image on an SHA256 function; a pseudo random sequence generated by the chaos system is taken as a basis of DNA dynamic encoding, rules of cellular dynamic evolution are determined according to a DNA matrix after diffusion, and in an encryption process, partitioning processing is performed on the image; and finally, the image is encrypted through a pseudo DNA calculation method, and diffusion operation is carried out while the image is scrambled. According to the invention, on one hand, secret key space is increased and the capability of the algorithm in fending off violent attacks is enhanced; and on the other hand, the secret key is enabled to be generated through close reliance on a plaintext, the capability of the algorithm in fending off plaintext attacks is improved, the capability of fending off exhausive attacks is higher, parallel calculation is facilitated, the operation efficiency is further improved, and the security of the algorithm is improved.
Owner:HENAN UNIVERSITY
Digital image encryption method with rapid key stream generative mechanism
InactiveCN103258312AReduce the number of iterationsHigh speedImage data processing detailsComputer hardwareChosen-plaintext attack
The invention discloses a digital image encryption method with a rapid key stream generative mechanism, and belongs to the field of image encryption. According to a digital image encryption system with the rapid key stream generative mechanism, a plurality of key stream elements are generated every time chaotic system iteration and key stream element quantification are conducted in a diffusion stage, the number of chaotic system iteration is effectively reduced, so that speed of the encryption system is increased significantly. In addition, the number of the key stream elements which are generated in each time of iteration and quantification is relevant to plaintexts, and capacity of the encryption system for resisting attack from known plaintexts and chosen plaintexts is improved. Cryptology analyses and encryption speed tests indicates that the encryption speed of the digital image encryption system with the rapid key stream generative mechanism is one time higher than the encryption speed in a tradition method on the premise that the encryption system is high in safety.
Owner:NORTHEASTERN UNIV
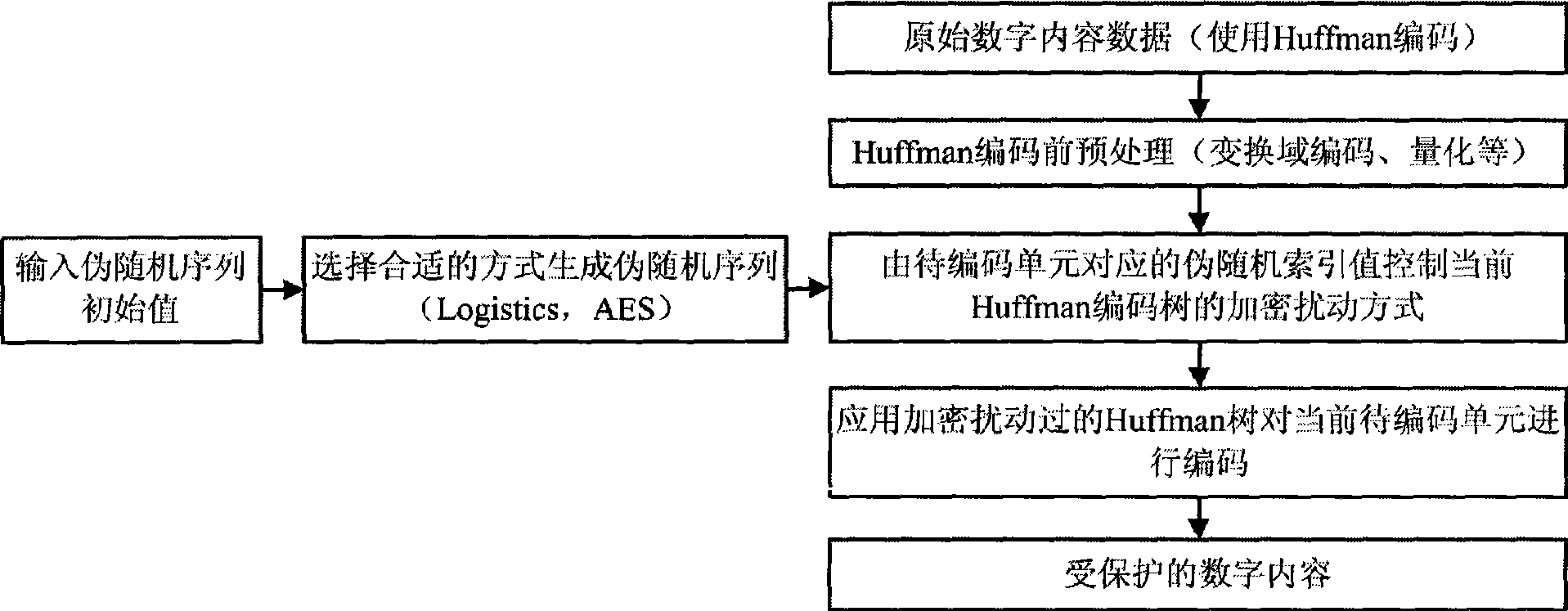
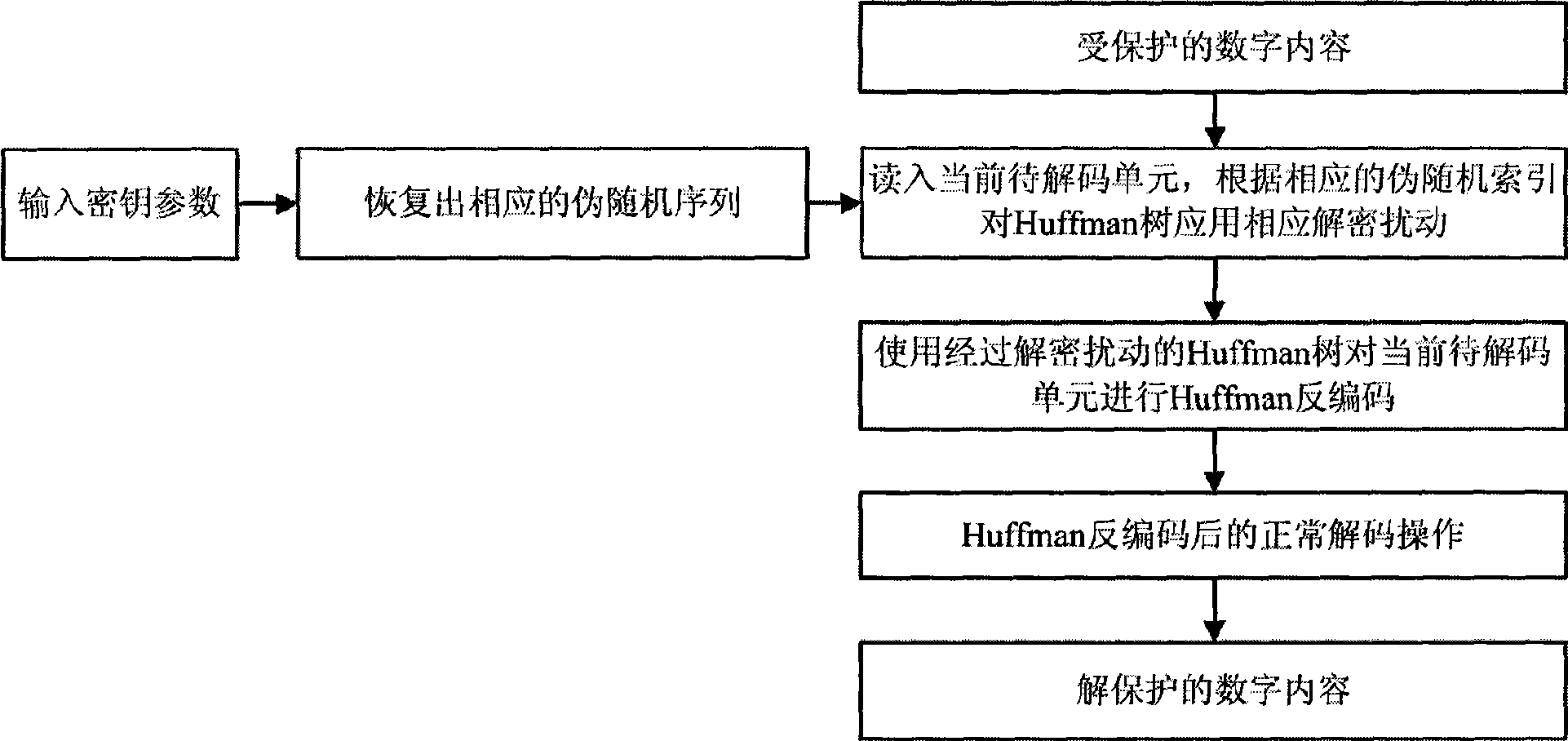
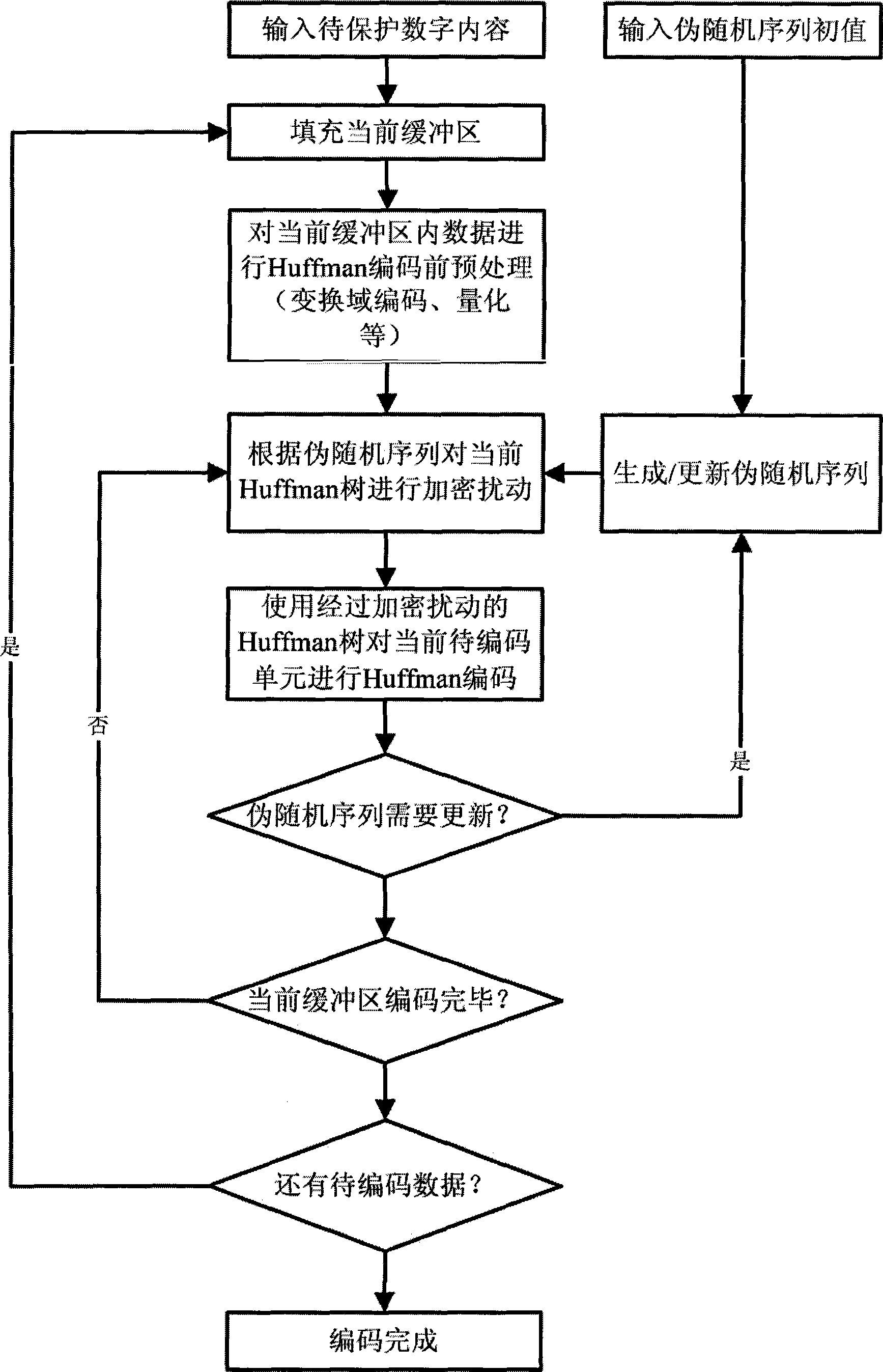
Encrypted Huffman encoding method and decoding method
InactiveCN101465724AHigh protection execution efficiencyImprove performanceDigital data protectionTelevision systemsChosen-plaintext attackComputer architecture
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
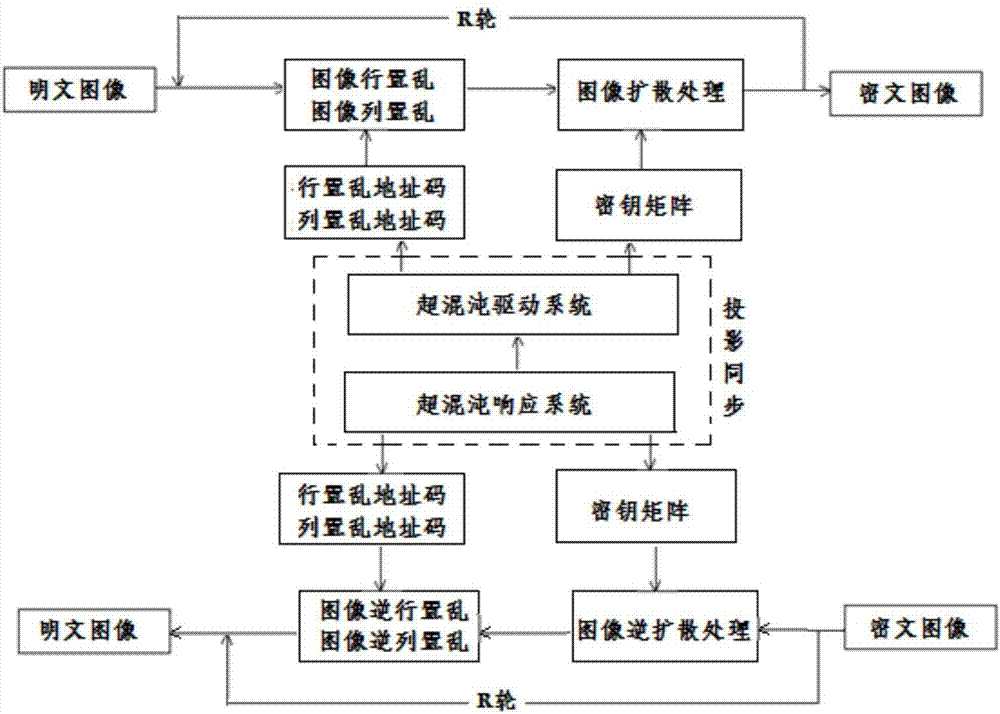
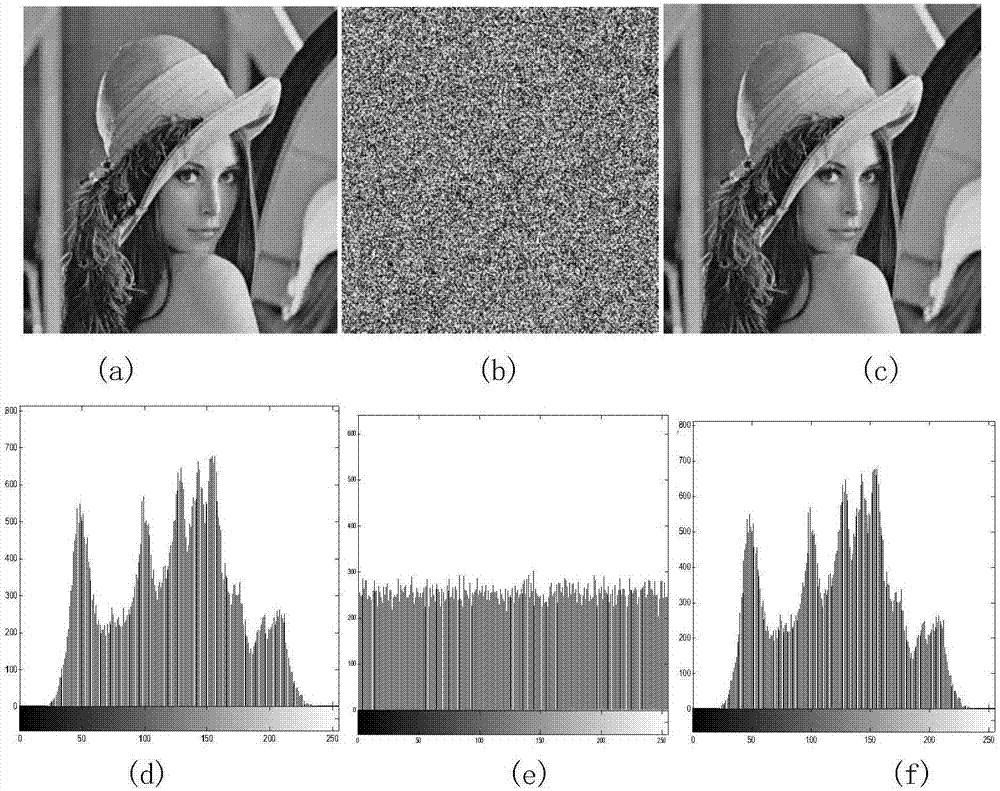
Image encryption method based on projection synchronization of hyperchaotic system
ActiveCN106997606AHas cryptographic propertiesIncreased complexityImage codingSecuring communication by chaotic signalsChosen-plaintext attackChaotic systems
The invention discloses an image encryption method based on the projection synchronization of a hyperchaotic system. The method comprises the steps of plaintext image quantifying and ciphertext image quantifying. The first step comprises generating of a hyperchaotic sequence of a hyperchaotic driving system, image row scrambling, image column scrambling, image diffusing, circulation image row scrambling, image column scrambling, multiple rounds of image diffusing, and a ciphertext image is acquired. The second step comprises ciphertext image quantifying, generating of a hyperchaotic sequence of a hyperchaotic response system, time acquiring, column scrambling index and line scrambling index valuing, image inverse diffusing, image inverse column scrambling, image inverse row scrambling, circulation image inverse diffusing, image inverse column scrambling, multiple rounds of image inverse row scrambling, and a decrypted image is acquired. According to the invention, a feedback mechanism with the current image is introduced; the row (column) scrambling address code and the key matrix are dynamically changed in each round of encryption; experiments show that the method has the advantages of good encryption effect, high security and large key space, can resist selected plaintext attacks, known plaintext attacks and various statistical attacks.
Owner:SHAANXI NORMAL UNIV
Joint channel security coding method based on balance index and polarization code
InactiveCN106341208AIncrease valueReduce overheadError preventionComputer hardwareChosen-plaintext attack
The invention discloses a joint channel security coding method based on a balance index and a polarization code. The method comprises the steps that after polarization code coding is carried out on all message sequences, the sequences are encoded into balance code words with the same number of 0 and 1; the balance index is used to carry out one-time pad sequence password encryption with small complexity on the balance code words; and private key encryption system encryption is carried out on the balance index based on the polarization code. The code words have dual functions of error correction and encryption, which can reduce the overhead of a system. In the design of the private key encryption system, the redundant information freeze bit of the polarized code is used as one private key which has the tasks of error correction and encryption; a randomly generated error vector ensures that the system is resistant to the existing exhaustive attack and selection plaintext attack; and the decoding complexity is reduced.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
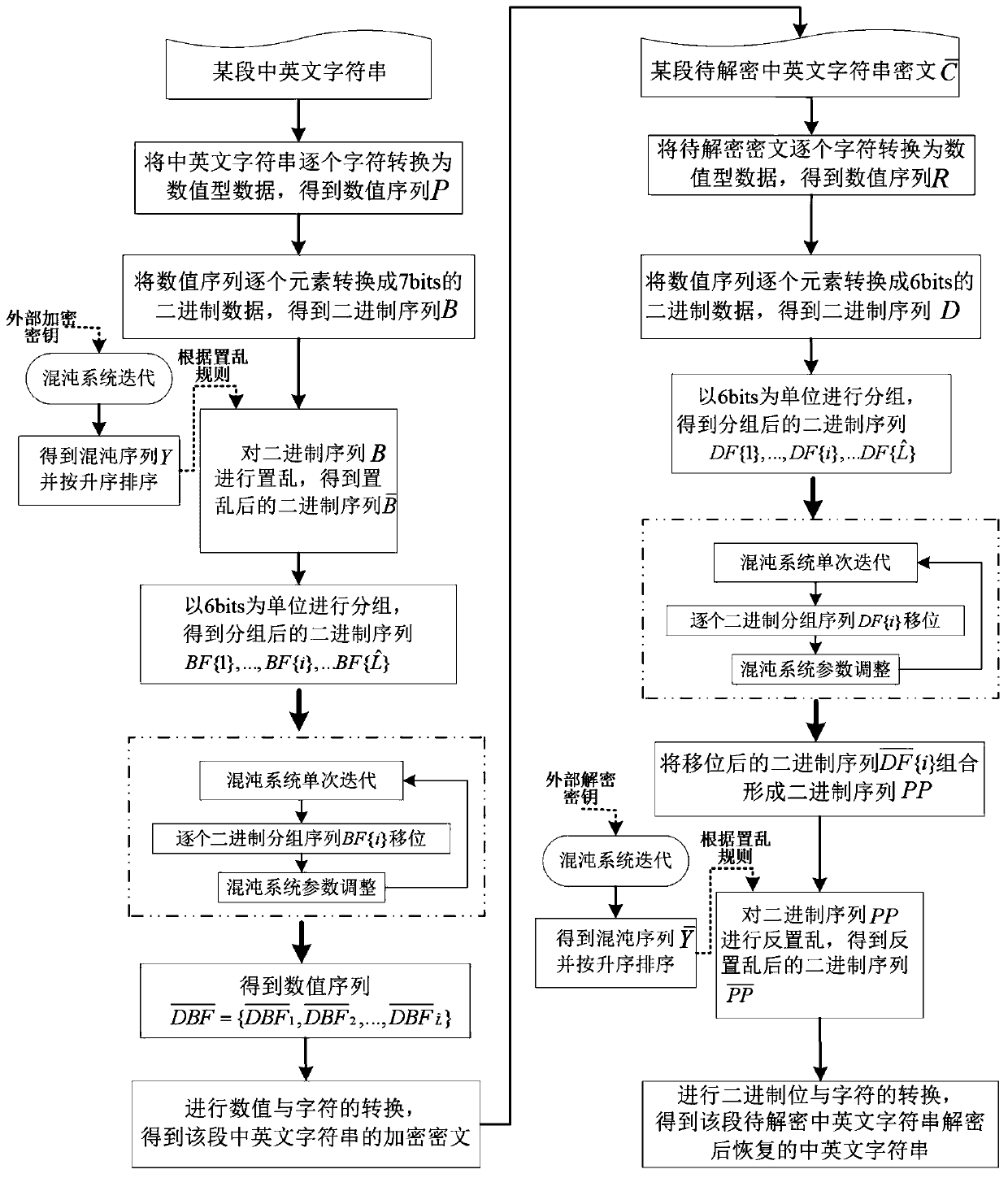
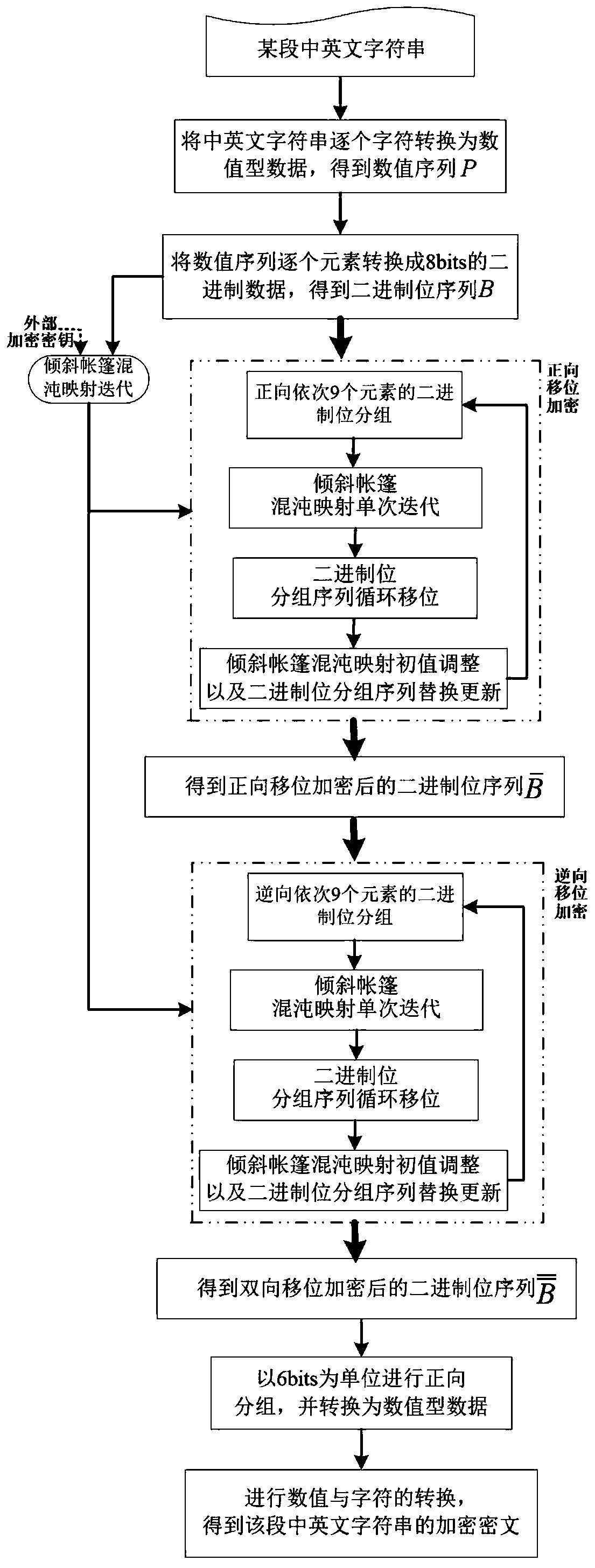
Encryption and decryption method for Chinese and English character strings
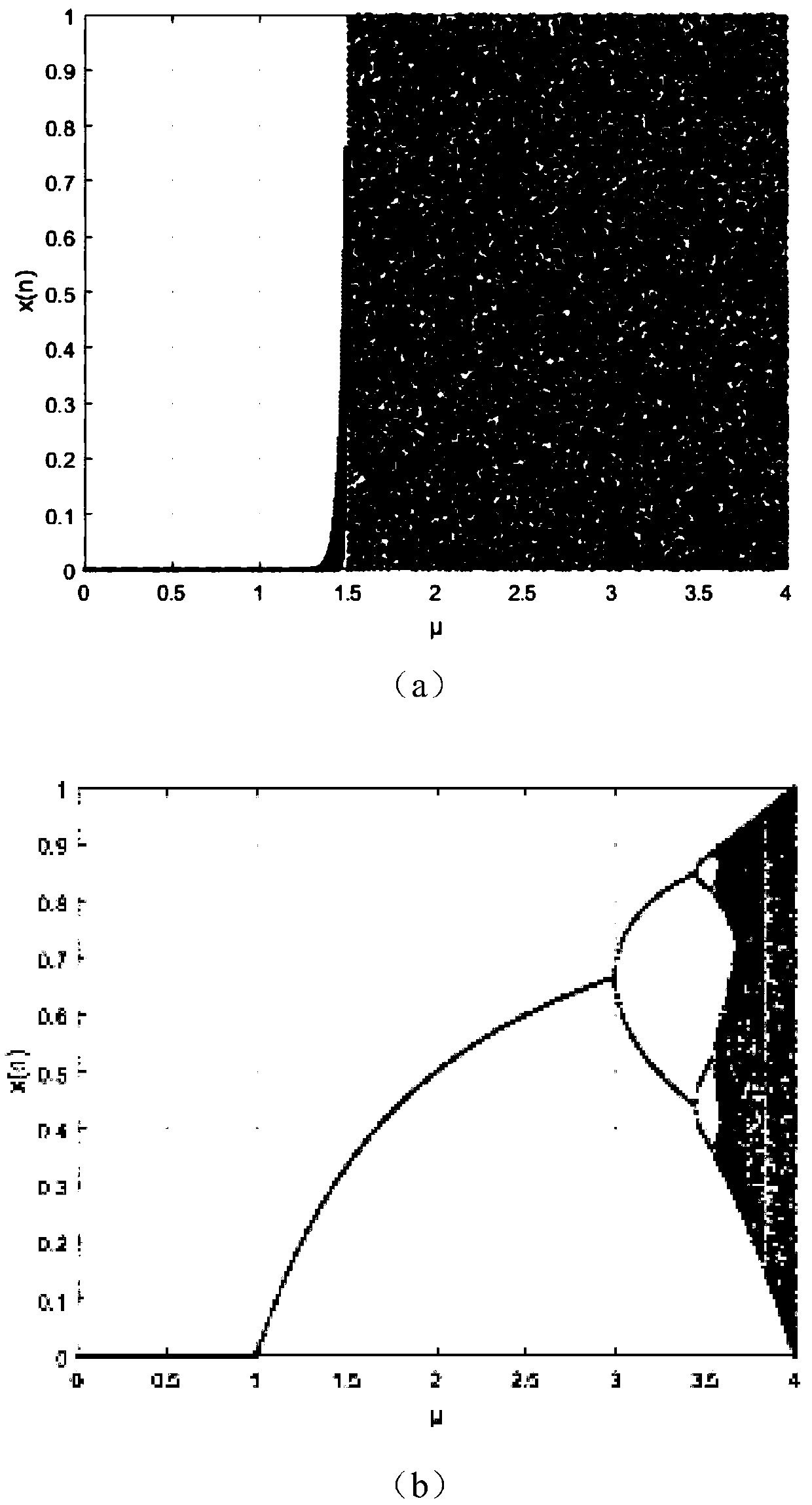
ActiveCN110299989AEnsure safetyGuaranteed feasibilityData stream serial/continuous modificationSecuring communication by chaotic signalsCiphertext-only attackChosen-plaintext attack
The invention discloses an encryption and decryption method for Chinese and English character strings, which comprises the following steps of: converting a certain section of Chinese and English character string into numerical data one by one, and converting the numerical data into 7bits binary data to obtain a binary sequence; secondly, scrambling the binary sequence according to the position change rules before and after the chaotic signals are ranked; through a cyclic operation of single iteration of a chaotic system, shifting of binary grouping sequences one by one and parameter adjustmentof the chaotic system, completing shifting of the scrambled binary sequences; and finally, carrying out numerical value and character conversion to obtain an encrypted ciphertext of the Chinese and English character string, and decrypting the ciphertext through a similar method to restore the original Chinese and English character string. According to the method, the password characteristic of the chaotic signal is utilized to encrypt / decrypt a binary sequence formed by converting Chinese and English character strings through scrambling, grouping, shifting and other operations, known / selectedplaintext attacks and only ciphertext attacks can be resisted, and the encryption and decryption safety of the Chinese and English character strings is ensured.
Owner:NANTONG UNIVERSITY
Image encryption method based on L-F cascade chaos and 3D bit scrambling
InactiveCN110889877AGuaranteed speedExpand the chaotic intervalImage codingDigital data protectionChosen-plaintext attackKey space
The invention discloses an image encryption method based on L-F cascade chaos and 3D bit scrambling. Image encryption is mainly divided into two steps: (1) 3D bit scrambling encryption and (2) diffusion operation. A novel L-F cascade chaos is constructed, the problem that a blank window exists due to uneven distribution of Logistic is solved while the rapidity of the Logistic is guaranteed, the chaos interval and number of parameters are increased, the secret key space is increased, and the exhaustion attack resistance of the system is improved. According to the method, the randomness of scrambled ciphertext is improved by adopting a 3D cyclic shift bit scrambling mode, and the problem that a bit scrambling sequence is insensitive is solved. According to the method, high-order informationcontaining a large amount of plaintext information and low-order information containing a small amount of plaintext information are separately scrambled, so that the noise attack resistance of the system is improved. According to the encryption system, the plaintext SHA-256 is used for carrying out strong association on the chaotic key, so that the plaintext sensitivity and the capability of resisting the attack of the selected plaintext are effectively improved.
Owner:QIQIHAR UNIVERSITY
Method for encrypting and decrypting character string
ActiveCN109995504AEnsure safetyGuaranteed feasibilityData stream serial/continuous modificationSecuring communication by chaotic signalsCiphertext-only attackChosen-plaintext attack
The invention discloses a method for encrypting and decrypting a character string. The method comprises the following steps of converting a certain section of character string into a high-order numerical value sequence and a low-order numerical value sequence; generating a chaotic signal by using a chaotic system according to the external encryption key and data such as an initial value, parameters, an initial iteration step number and an extraction interval of the chaotic system related to the to-be-encrypted character string; according to the position change scrambling rules before and afterchaotic sequence sorting, scrambling the high-order numerical sequence and the low-order numerical sequence respectively, carrying out numerical value and character conversion, obtaining an encrypted ciphertext of the section of character string, and decrypting and restoring the ciphertext to an original section of character string through a similar method. According to the method, a chaotic sequence scrambling rule is adopted to scramble or inversely scramble a numerical sequence formed by character conversion, so that the method has good performance of resisting known / selected plaintext attacks and ciphertext-only attacks, and the security and feasibility of character string encryption and decryption are ensured.
Owner:NANTONG UNIVERSITY
Encryption and decryption method of OFDM-PON system based on cell neural network
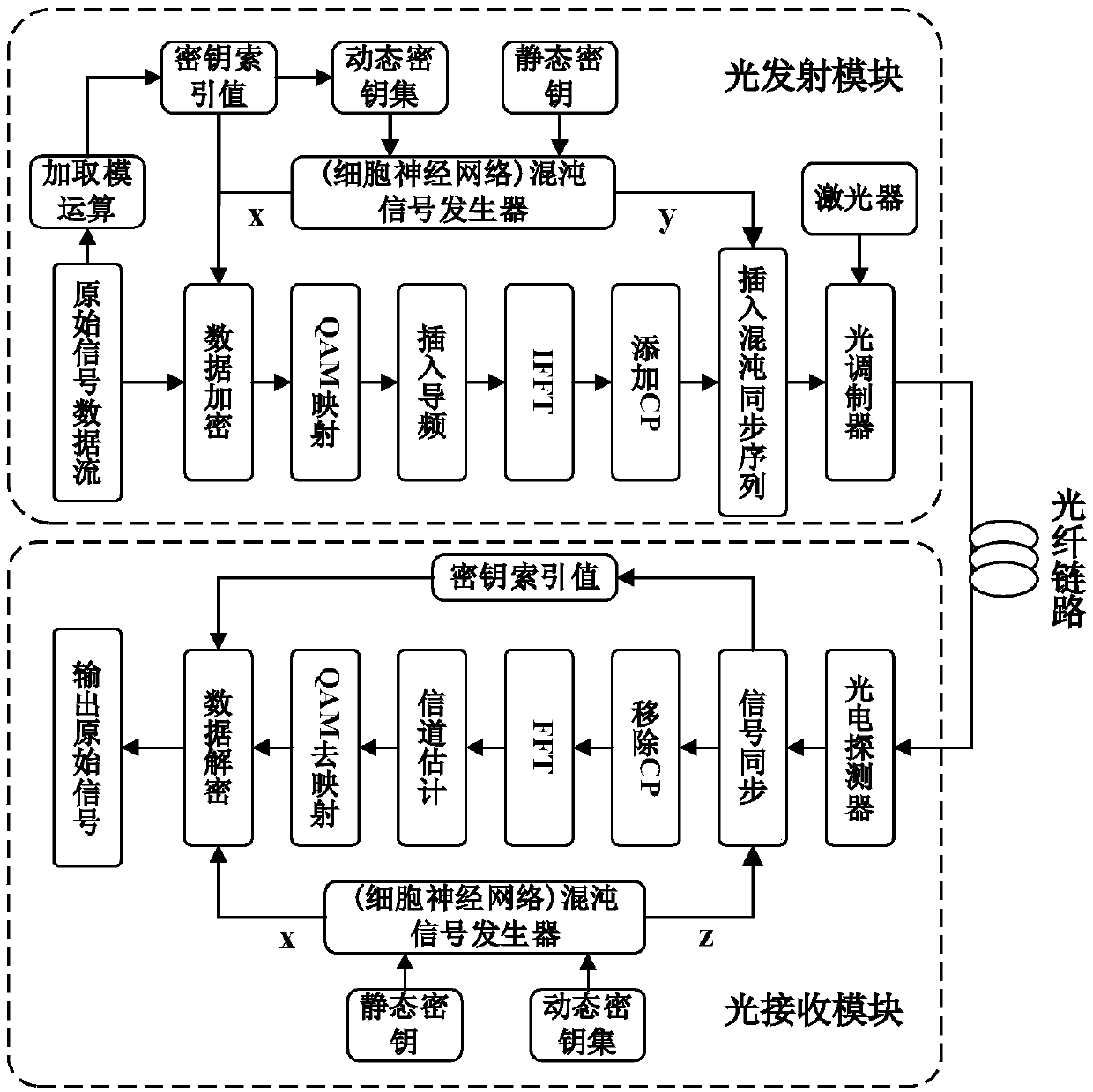
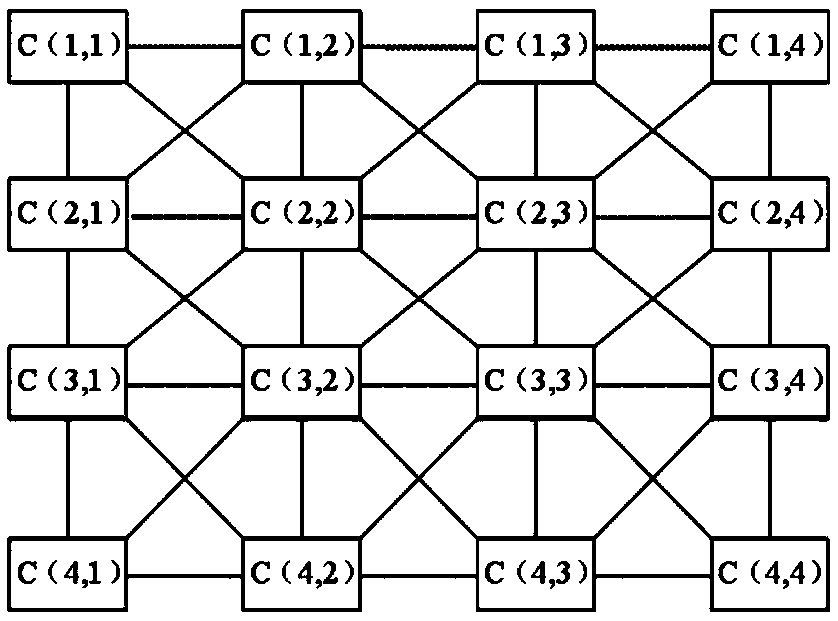
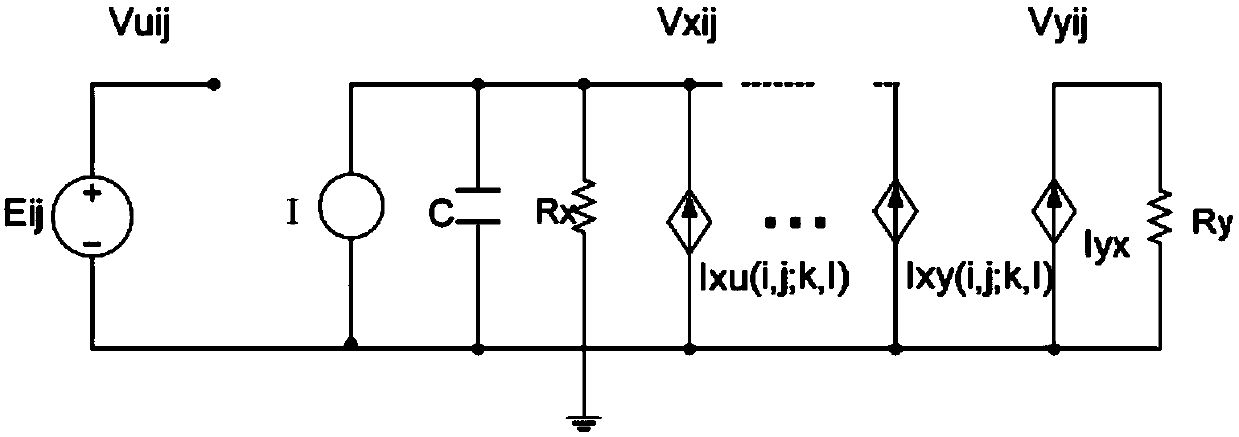
ActiveCN109672517AStrong randomnessHigh degree of hardware implementationElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsChosen-plaintext attackNerve network
The invention belongs to the technical field of the optical communication encryption, and specifically relates to an encryption and decryption method of an OFDM-PON system based on a cell neural network. The encryption method comprises the following steps: constructing a dynamic key set of the cell neural network, performing summation and modulo operation on input digital signals, and taking an obtained value as an index value of the dynamic key set of the cell neural network; determining an initial value of the cell neural network through the index value, thereby generating a corresponding chaotic sequence as a synchronization sequence of the OFDM-PON system; performing plaintext-chosen attack resistant encryption on the original data by utilizing the chaotic sequence generated by the cell neural network and the index value; and entering optical fiber transmission after the OFDM modulation and electro-optical modulation conversion. By utilizing the chaotic characteristic of the cell neural network, multiple initial values are combined as a key set, the key is randomly selected every time to improve the dynamic feature of the key; and a plaintext-chosen attack resistant encryptionscheme is constructed by utilizing the randomness of plaintext sending, and the security is high.
Owner:HANGZHOU DIANZI UNIV
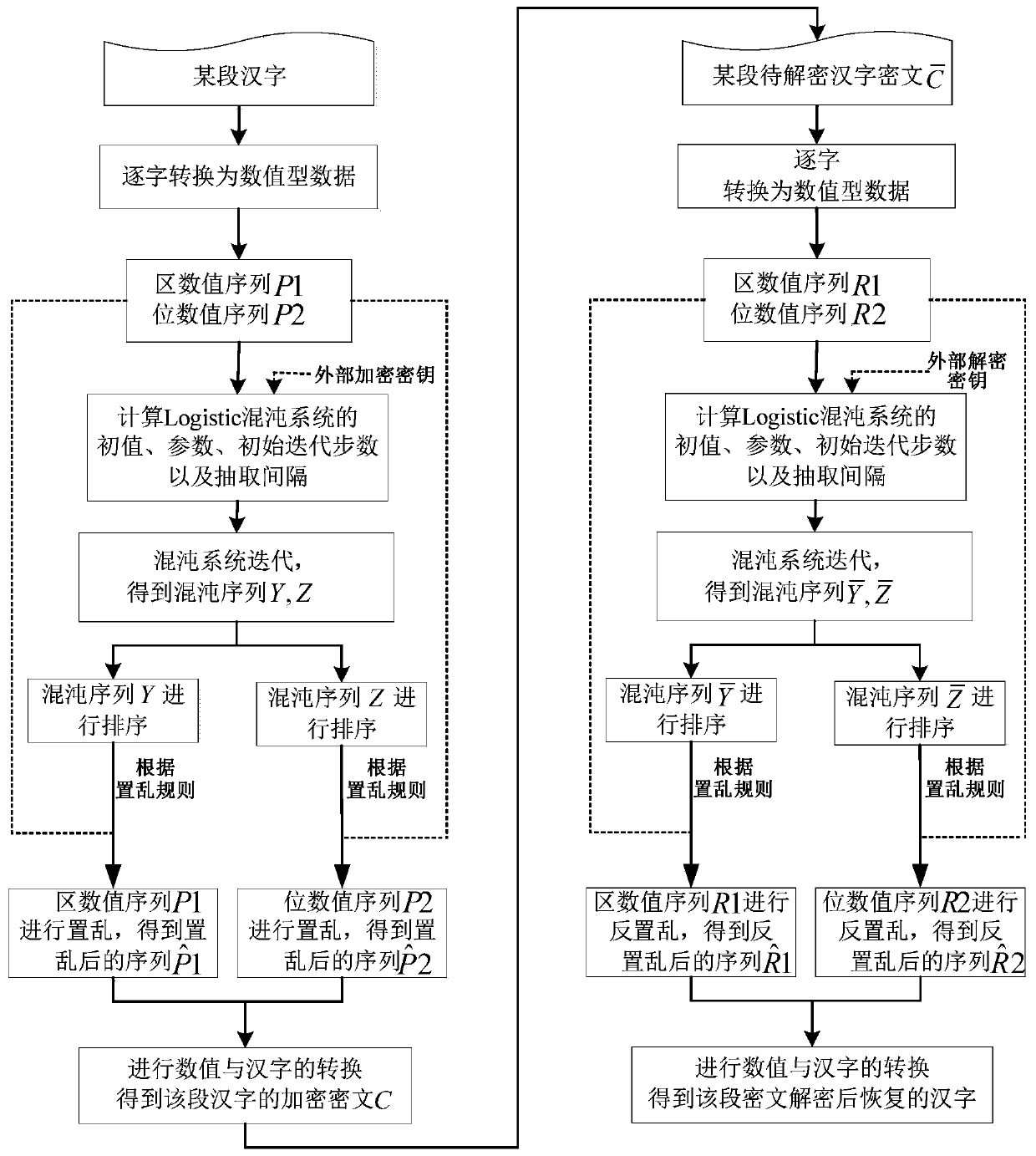
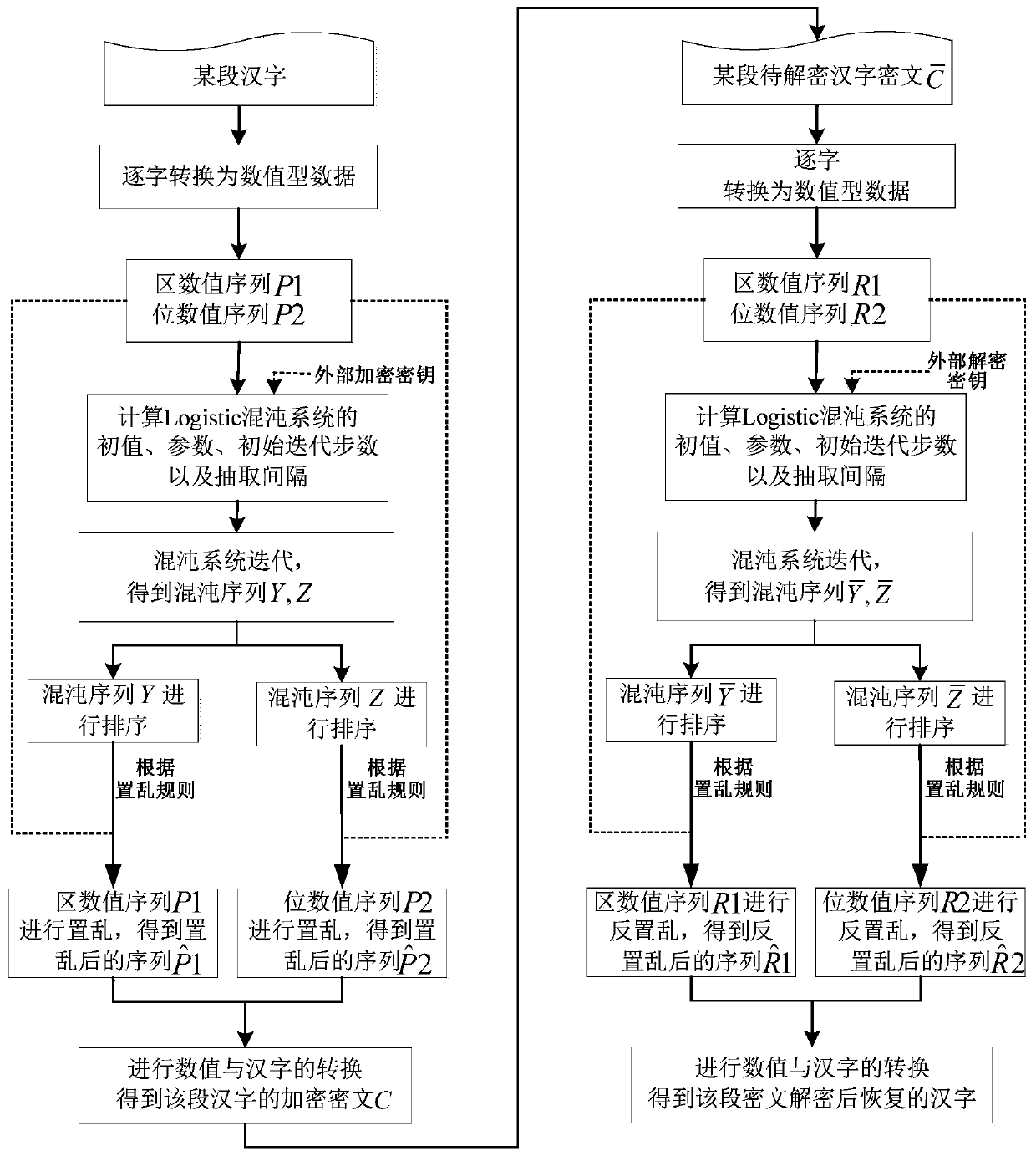
Chinese character encryption and decryption method
ActiveCN110011783AEnsure safetyGuaranteed feasibilitySecuring communication by chaotic signalsCryptographic attack countermeasuresCiphertext-only attackChosen-plaintext attack
The invention discloses a Chinese character encryption and decryption method. The method comprises the following steps of: converting a certain section of Chinese characters into a zone value sequenceand a code value sequence; generating a chaotic signal by using a chaotic system according to the external encryption key and data such as an initial value, parameters, an initial iteration step number and an extraction interval of the chaotic system related to the to-be-encrypted Chinese character; according to the position change scrambling rules before and after the chaos sequences are ranked,respectively scrambling the region value sequence and the code value sequence, then carrying out conversion of values and Chinese characters to obtain an encrypted ciphertext of the section of Chinese characters, so the ciphertext can be decrypted and restored to an original section of Chinese characters through a similar method. The Chinese character encryption and decryption method adopts the scrambling rule of the chaotic sequence to scramble or inversely scramble the numerical sequence formed by converting the Chinese characters, has good performance of resisting known / selected plaintextattacks and ciphertext-only attacks, and ensures the safety and feasibility of Chinese character encryption and decryption.
Owner:NANTONG UNIVERSITY
Chaotic image encryption method with plaintext-related key flow generation mechanism
InactiveCN106910156AImprove operational efficiencyFacilitated DiffusionDigital data protectionImage data processing detailsComputer hardwareChosen-plaintext attack
The invention discloses a chaotic image encryption method with a plaintext-related key flow generation mechanism. The method is implemented based on a 'confusion-diffusion' architecture. A confusion algorithm is based on a pixel point exchange mechanism, and the location of an exchange target is generated by logistic chaotic mapping. A diffusion key flow is generated based on a generalized Lorenz-Like system, and a plaintext-related key flow element quantization mechanism is introduced. The mechanism enhances the ability of an encryption system to resist known plaintext and chosen plaintext attacks, speeds up the diffusion process, and can reduce the number of rounds of diffusion needed to achieve the desired diffusion performance. Compared with the existing key flow and plaintext related technologies, the problem that a chaotic sequence cannot be reused in multiple rounds of encryption is solved, and the computational load is lower. The results of cryptographic analysis show that the encryption method presented by the invention is of high security.
Owner:NORTHEASTERN UNIV
Optical image encryption method based on Gyrator transform and coupled chaos
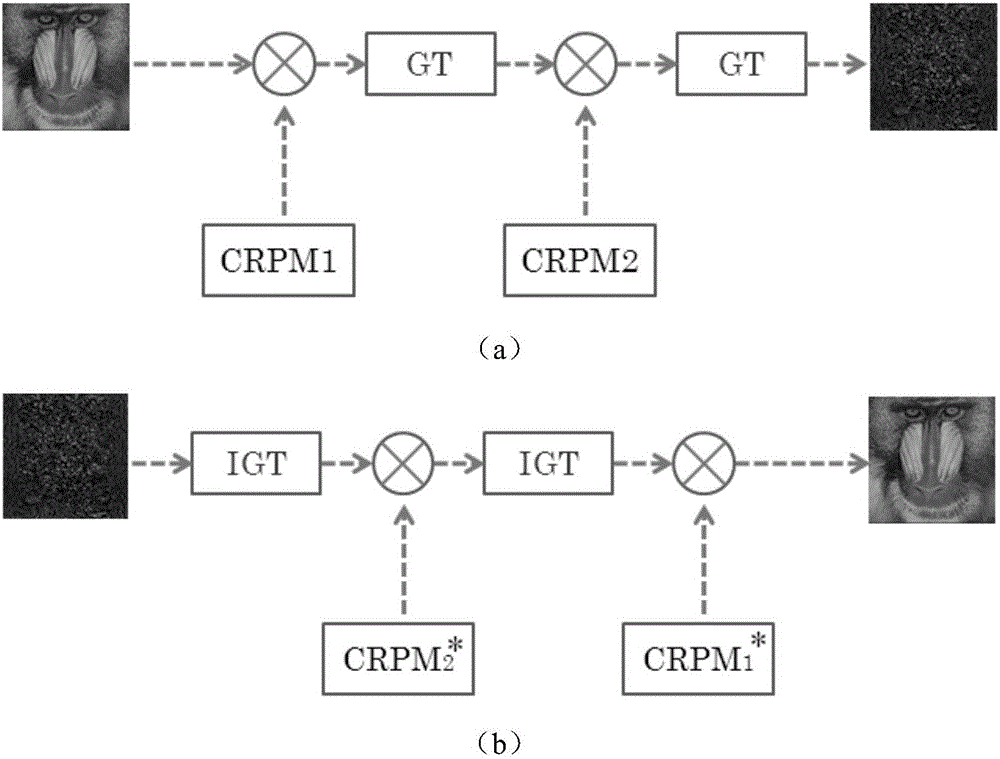
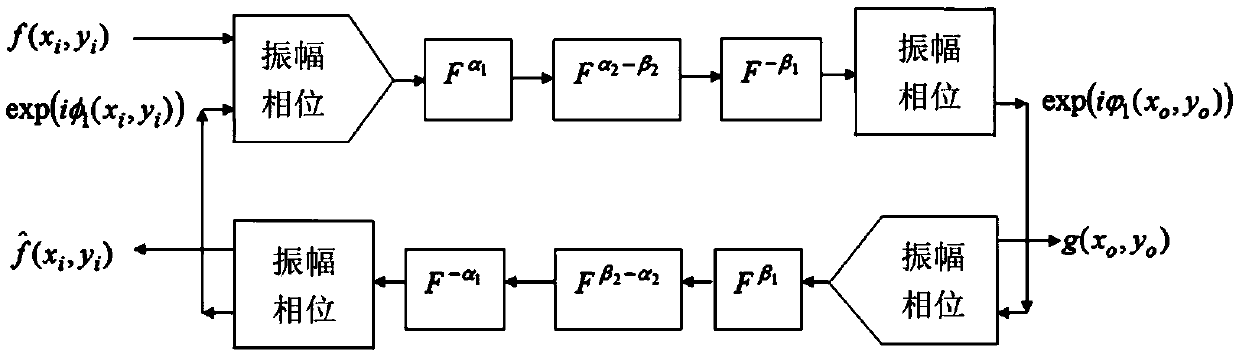
InactiveCN106651736AEnsure safetyEasy to manageImage data processing detailsInformation processingChosen-plaintext attack
The invention relates to the technical field of image information security and optical information processing, and aims to effectively resist known plaintext attack and chosen plaintext attack and make key management and transmission more convenient. The technical scheme adopted in the invention is as follows: an optical image encryption method based on Gyrator transform and coupled chaos comprises the following steps: (1) construction of a coupled Logistic chaos: two one-dimensional Logistic chaos maps are associated together by a coupling parameter; (2) generation of a chaotic key: two random phase masks serving as a master key are generated by coupled Logistic chaos systems controlled by different chaotic parameters; and (3) image encryption and decryption based on Gyrator transform: first, a to-be-encrypted image is modulated by the first chaos random phase mask in the process of encryption, and second, the image is modulated by the complex conjugate of the first chaos random phase mask. The method is mainly applied to an image information security occasion.
Owner:TIANJIN UNIV
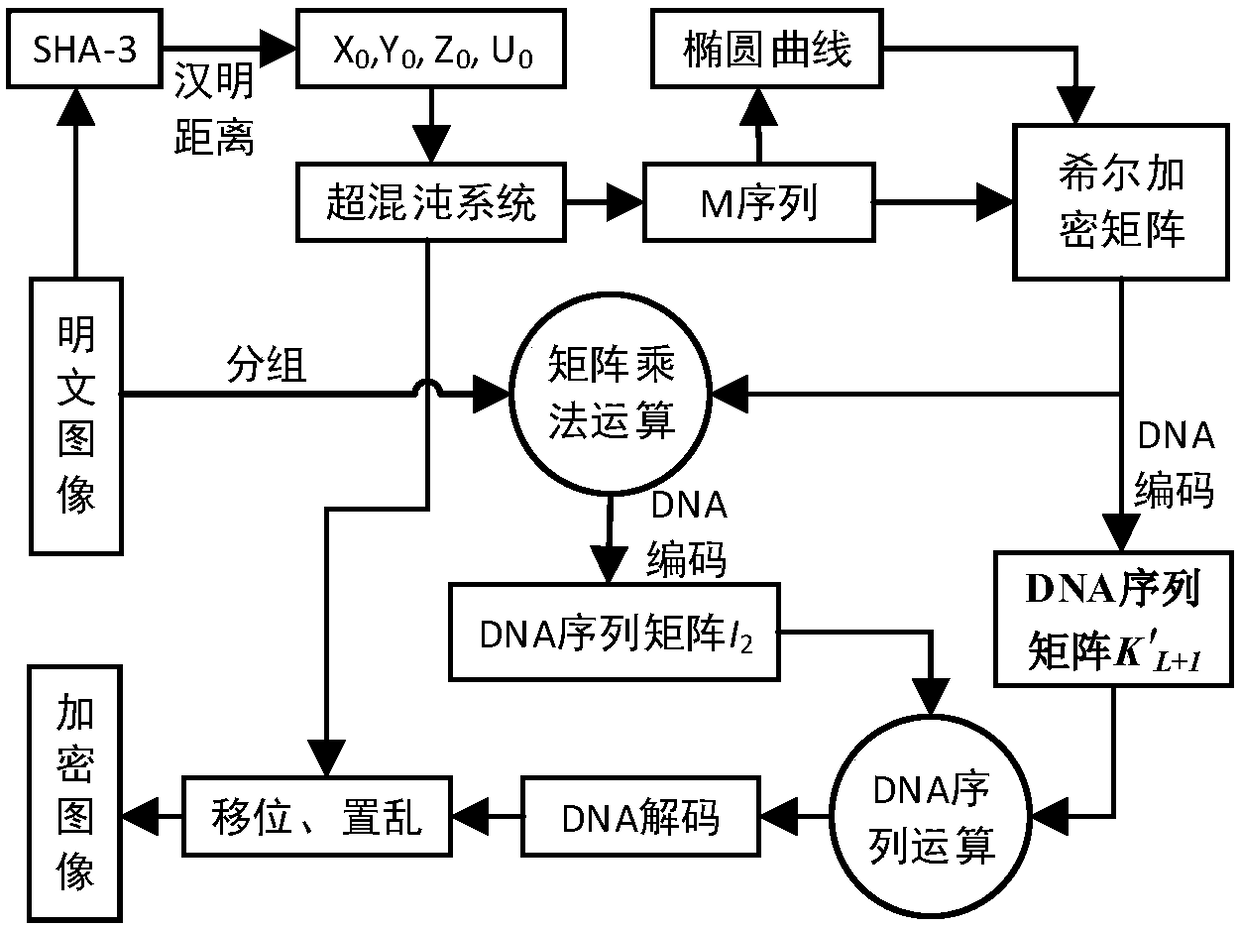
Hill encryption and dynamic DNA coding based image encryption method
ActiveCN108388808AAvoid complexityAvoid impossibilityPublic key for secure communicationDigital data protectionChosen-plaintext attackDna encoding
The invention discloses a hill encryption and dynamic DNA coding based image encryption method which is used for solving the problem that an existing image encryption algorithm is too complex and is liable to crack. The hill encryption and dynamic DNA coding based image encryption method is characterized in that a hill encryption matrix is constructed to perform replacement encryption on an imageby adopting a method combining a hyperchaotic system with an elliptic curve, so that strong dependency among elements is avoided, and complexity and difficulty in realizing of elliptic curve encryption are avoided, and therefore, the encryption algorithm is simple; a dynamic DNA coding rule is combined, and the coding rule is randomly selected according to different positions of pixels for performing DNA coding on the pixels, so that safety of the encryption algorithm is improved, and dependency among secret keys is reduced, therefore, a ciphertext is difficult to crack; and finally, a hyperchaotic sequence is used for scrambling the image. The hill encryption and dynamic DNA coding based image encryption method improves secret key sensibility, safety of transmitted data, further can effectively resist known plaintext and selected plaintext attack, has relatively good ability of resisting exhaustive attack, statistical attacks and differential attacks.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image encryption method based on composite chaotic system and image processing device
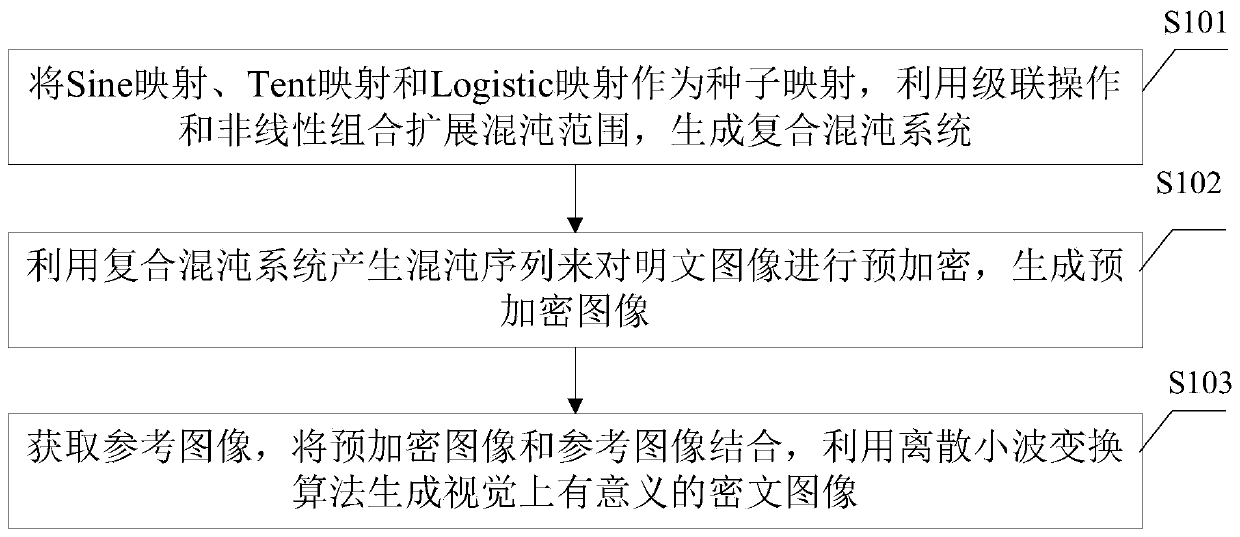
ActiveCN109977686AWide range of chaosComplex chaotic behaviorDigital data protectionImage data processing detailsChosen-plaintext attackImaging processing
The invention is applicable to the field of image encryption, and provides an image encryption method based on a composite chaotic system and an image processing device. The method comprises the following steps of taking Sine mapping, Tent mapping and Logistic mapping as seed mapping, and generating a composite chaotic system by utilizing a cascade operation and a nonlinear combination expansion chaotic range; generating a chaotic sequence by using a composite chaotic system to pre-encrypt the plaintext image, and generating a pre-encrypted image; and obtaining a reference image, combining thepre-encrypted image with the reference image, and generating a visually meaningful ciphertext image by using a discrete wavelet transform (DWT) algorithm. The method provided by the invention has a wider chaotic range and the more complex chaotic behaviors, and the encryption performance is improved. In addition, due to the fact that the visually significant ciphertext image is generated, the attack probability is reduced, the selected plaintext attack and the exhaustion attack can be resisted, and the encryption performance is better.
Owner:GUILIN UNIV OF ELECTRONIC TECH
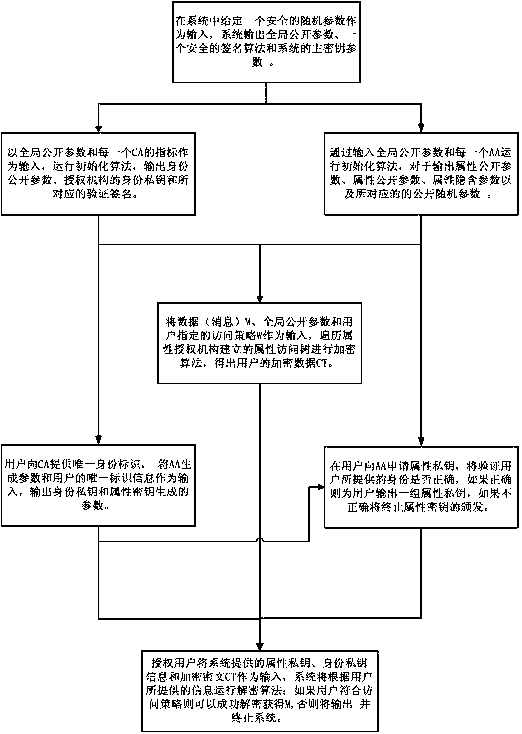
Multi-authorization attribute encryption and decryption method
ActiveCN107276766ASolve UtilizationSafeKey distribution for secure communicationUser identity/authority verificationAccess structureChosen-plaintext attack
The invention provides a multi-authorization attribute encryption and decryption method comprising system initialization, data encryption, key distribution and ciphertext decryption and other steps. The multi-authorization attribute encryption and decryption method has the beneficial effects of solving the problems of large encryption and decryption operation consumption and high storage space occupation rate caused by the sparse access structure in a large-scale attribute encryption system, and compensating the shortcomings of other schemes on the aspect; meanwhile, the problem of computing efficiency and data storage rate are solved by the multi-authorization attribute encryption and decryption method, and the multi-authorization attribute encryption and decryption method also has collusion attack resistance and plaintext attack selection security.
Owner:HENAN UNIV OF SCI & TECH
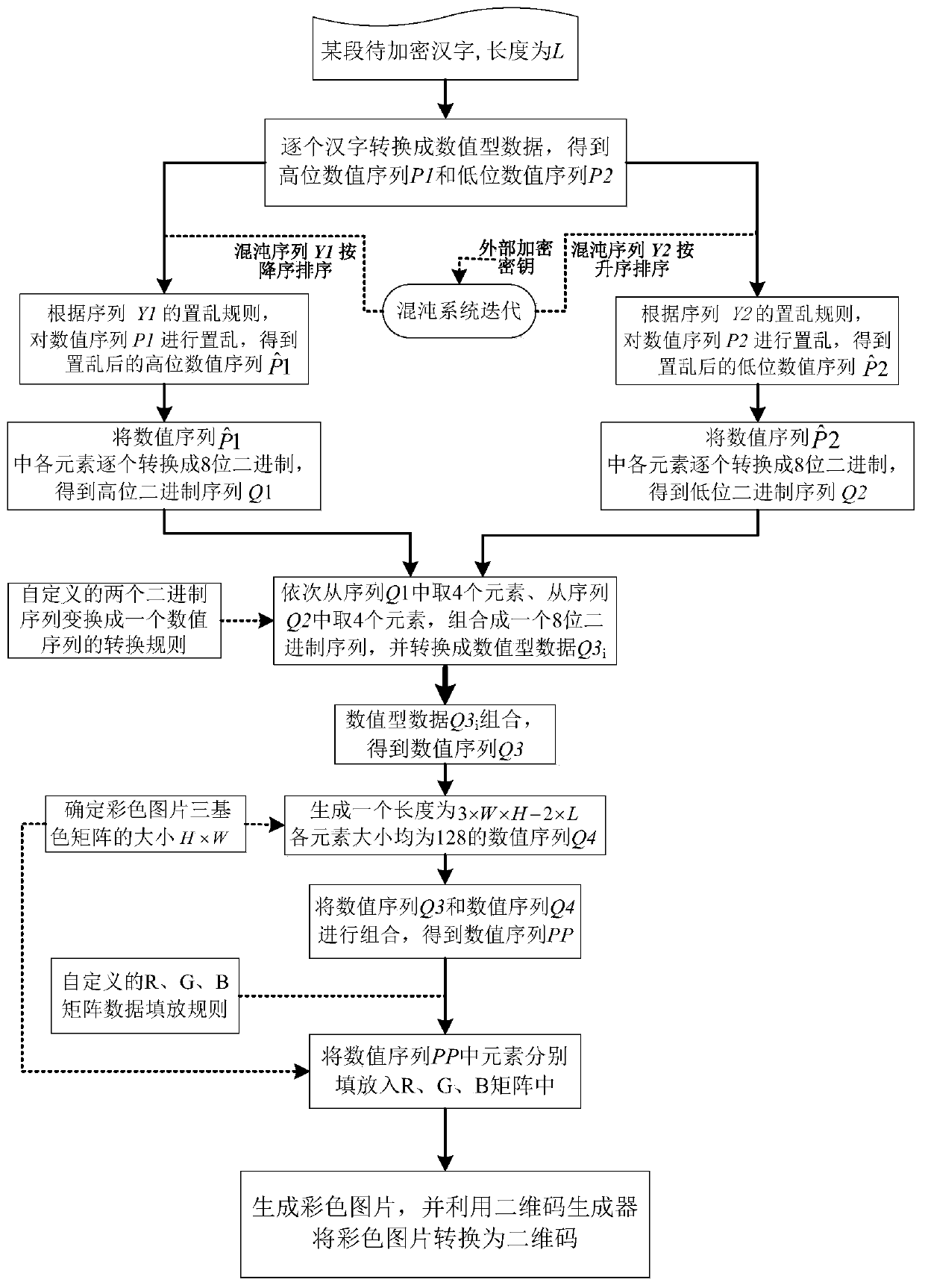
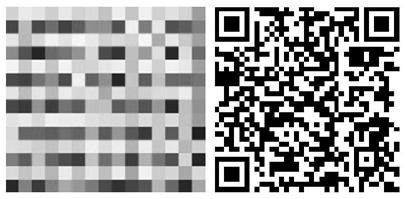
Chinese character-to-picture encryption method
ActiveCN111382452AEnsure safetyGuaranteed feasibilityDigital data protectionNatural language data processingChosen-plaintext attackChinese characters
The invention discloses a Chinese character-to-picture encryption method, which comprises the following steps of: firstly, converting a paragraph of Chinese characters into numeric data one characterby one character to obtain a high-order numeric sequence and a low-order numeric sequence; secondly, generating a chaotic sequence by utilizing a chaotic system according to an external encryption keyand a certain paragraph of to-be-encrypted Chinese characters, and scrambling the high-order numeric sequence and the low-order numeric sequence according to descending and ascending scrambling rulesof the chaotic sequence; respectively converting the scrambled high-order and low-order numeric sequences into binary sequences; and according to a self-defined conversion rule of converting two binary sequences into a numeric sequence and a self-defined R, G and B matrix data filling rule, filling elements in the converted numeric sequence into R, G and B matrixes so as to generate a color picture, and converting the color picture into a two-dimensional code. The Chinese character-to-picture method provided by the invention has good performance of resisting known / selected plaintext attacks,and ensures the security and feasibility of the Chinese character-to-picture conversion encryption method.
Owner:NANTONG UNIVERSITY
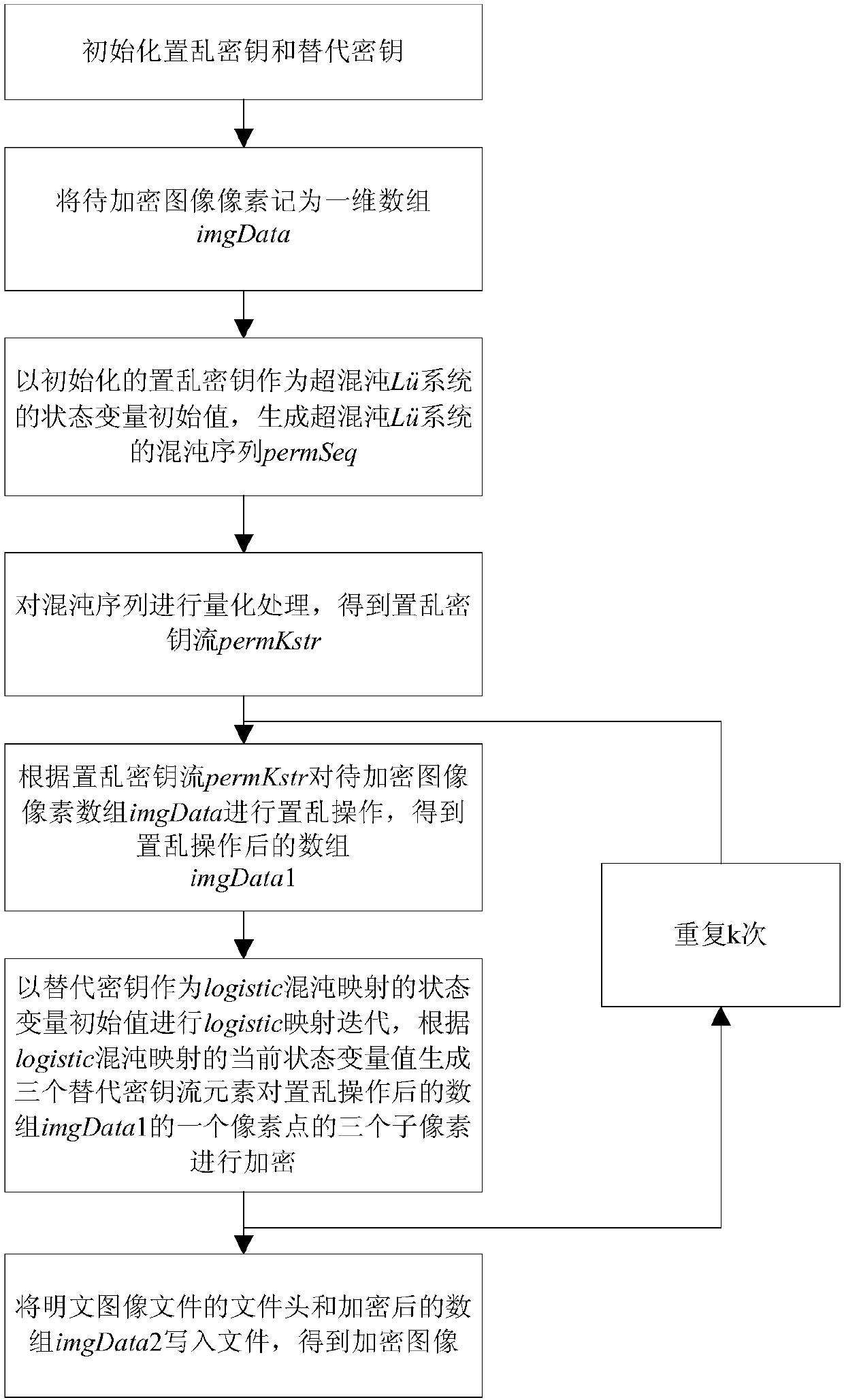
Chaos-based quick color image encryption method
ActiveCN107633175AEnhanced ability to resist chosen plaintext attacksImprove random statsEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareChosen-plaintext attack
The invention provides a chaos-based quick color image encryption method. According to the method, a scrambling key and a substitution key are initialized; to-be-encrypted image pixels are marked as aone-dimensional array; a chaotic sequence of a hyperchaotic Lu system is generated; quantification processing is performed on the chaotic sequence to obtain a scrambling key stream; scrambling operation is performed on the array of the to-be-encrypted image pixels according to the scrambling key stream permKstr; the substitution key is used as a state variable initial value of logistic chaotic mapping for logistic mapping iteration, and three substitution key stream elements are generated according to a current state variable value of logistic chaotic mapping to encrypt three sub-pixels of one pixel point of the array imgDatal after scrambling operation; and the to-be-encrypted image pixels are encrypted multiple turns, and an encrypted array is obtained. In this way, encryption efficiency is remarkably improved; by introducing a plaintext-based chaotic orbit disturbance mechanism, the key stream is relevant to a plaintext, the ability of an encryption system in resisting selection ofa plaintext attack is enhanced, and meanwhile the random statistical characteristic of the chaotic key stream sequence is improved.
Owner:CHINA WATERBORNE TRANSPORT RES INST +1
Asymmetric multi-image encryption method based on Logistic chaotic mapping
InactiveCN108833736ACollect faster thanScramble faster thanSecuring communication by chaotic signalsPictoral communicationPattern recognitionChosen-plaintext attack
The invention discloses an asymmetric multi-image encryption method based on Logistic chaotic mapping. The method comprises the following steps: 1) providing an encrypted plain text image fi by assuming the image amount as P and the size of each image as M*N pixels, performing interference adding on the image fi by using two symmetrically coupled same logistic mappings, thereby obtaining an interference-added image f'I; 2) retrieving POF of each interference-added image f'I by using an iteration process in the FrFT domain,, wherein the POF retrieval process is an iteration process between twogray images; 3) modulating POFs of all interferce-added images as an intermediate stage, namely, modulating all POFSs as a complex matrix G, wherein the size of the complex matrix G is same as each original image; and 4) extending the complex matrix G to the final ciphertext in a chaotic diffusion model. The method disclosed by the invention has high security under chosen-plaintext attack.
Owner:XIAN UNIV OF TECH
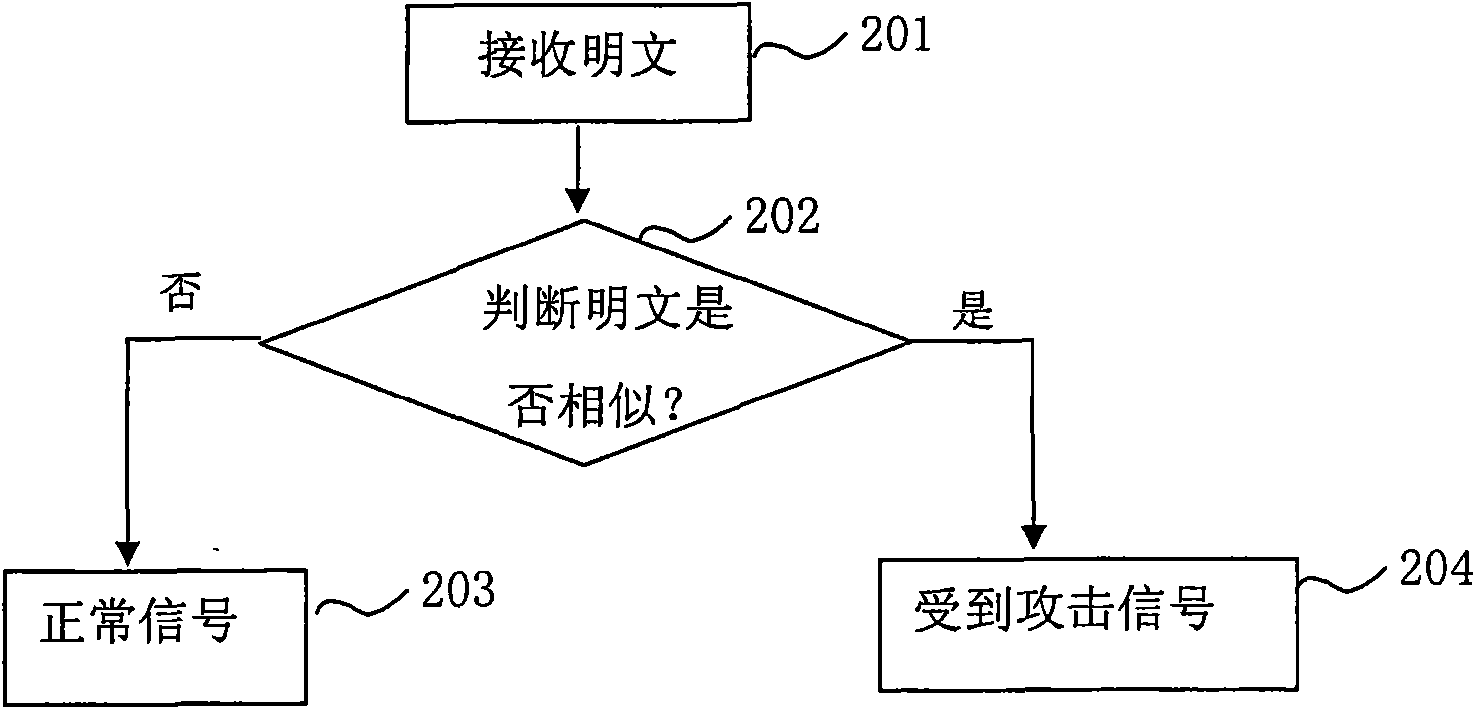
Attack test method and device
InactiveCN101588578AReduce capacity requirementsHigh speedPublic key for secure communicationData switching networksChosen-plaintext attackAttack patterns
The invention provides an attack test method and a device. The invention provides the attack test method aiming to solve chosen-plaintext attack of a key in an encryption algorithm of the prior art. The method comprises the following steps: receiving a plaintext; storing at least one part of the plaintext; judging whether the analogical number of the stored at least one part of the plaintext and other stored at least one part of the plaintext is more than or equal to a first threshold value; outputting a signal with an attack mode in the current plaintext if the analogical number is more than or equal to the first threshold value, otherwise, outputting a normal signal; and repeating the steps before the next plaintext comes. The method and the device have the advantages that the method and the device can test the inputting plaintext with obvious attack mode and avoid the chosen-plaintext attack on the key.
Owner:GIESECKE & DEVRIENT (CHINA) INFORMATION TECH CO LTD
Regular Hartley transform chaotic dual random phase coding optical image encryption method
InactiveCN106548044AEnsure safetyEasy to manageDigital data protectionImage data processing detailsInformation processingChosen-plaintext attack
The present invention relates to the technical field of image information security and optical information processing, and aims to provide an optical image encryption / decryption method, which can effectively resist known plain attack and select plain attack, makes key management and transmission more convenient, further ensures security, and has excellent capabilities of resisting a violence attack, a statistical attack, a noise attack and a cut attack. The technical scheme adopted by the present invention is a regular Hartley transform chaotic dual random phase coding optical image encryption method. The method comprises the following steps: 1) constructing a two-dimensional regular Hartley transform system; 2) generating a chaotic key, wherein two random phase masks that function as a master key are separately generated by a one-dimensional ICMIC chaotic system controlled by different chaotic parameters, an initial value and a control parameter of the ICMIC chaotic system are used as the master key; and 3) encrypting and decrypting an image. The method provided by the present invention is mainly applied to the field of image information security and optical information processing.
Owner:TIANJIN UNIV
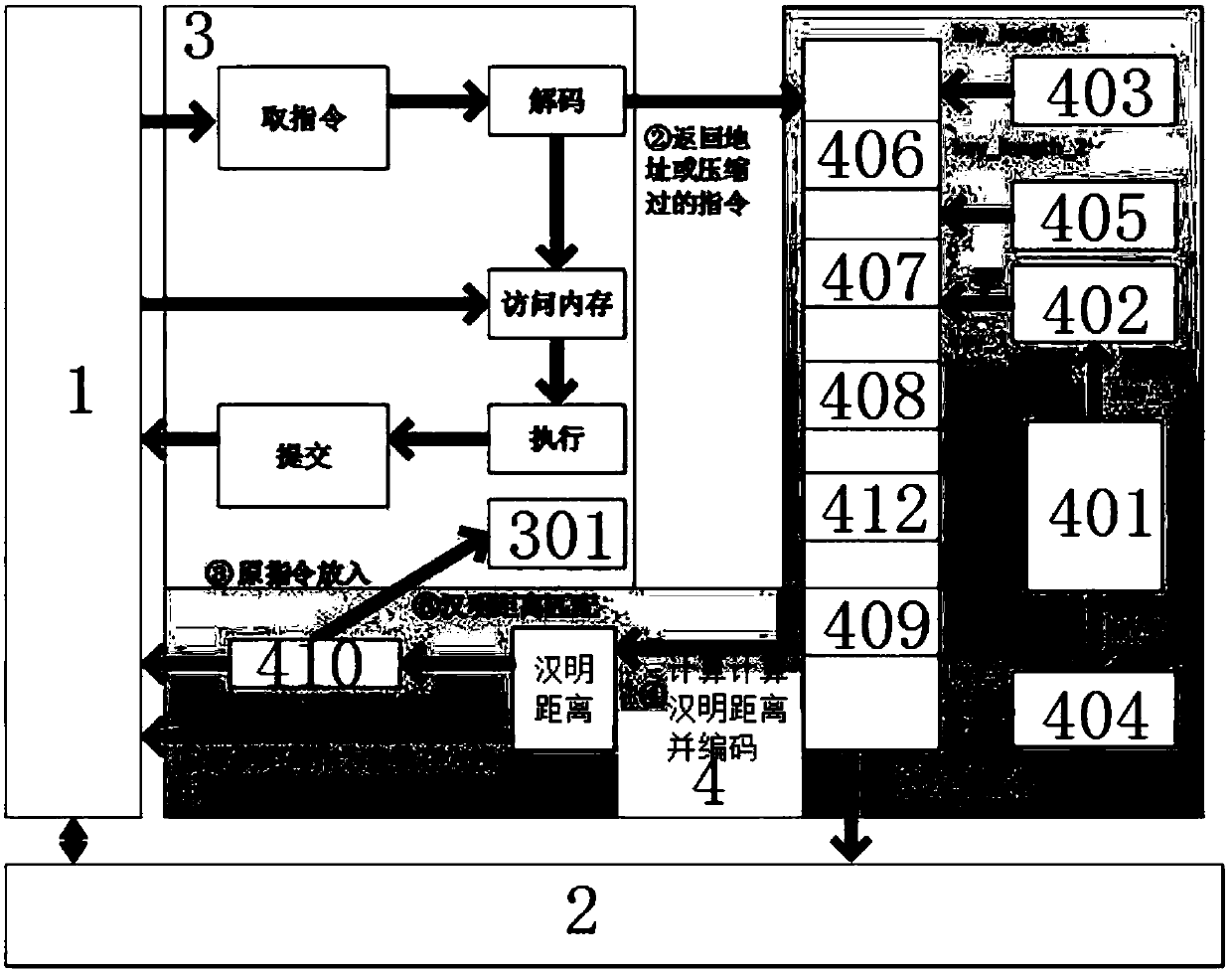
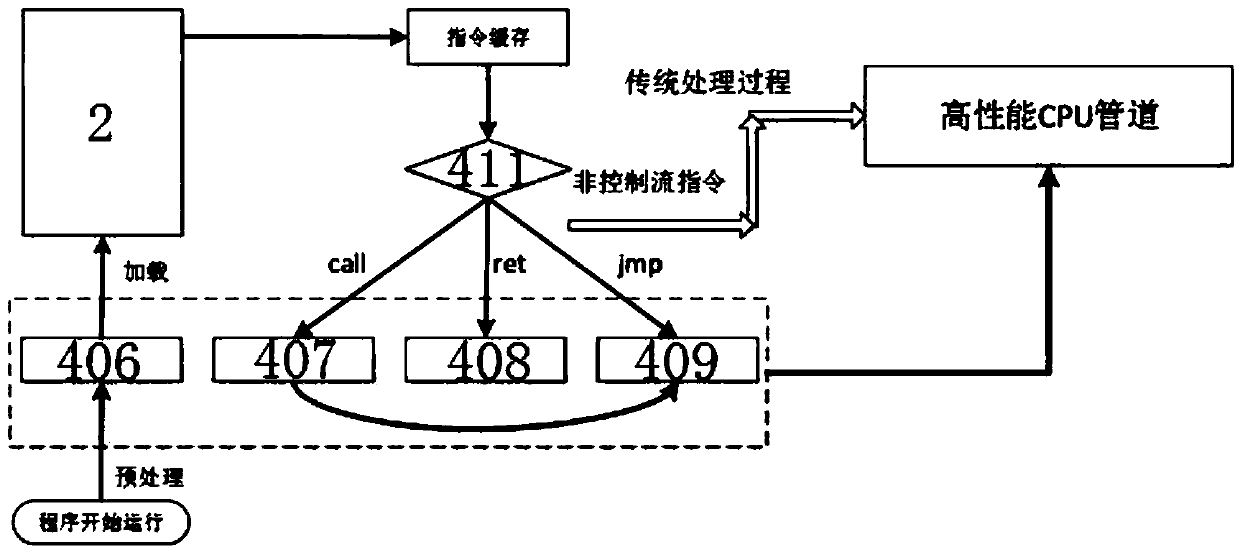
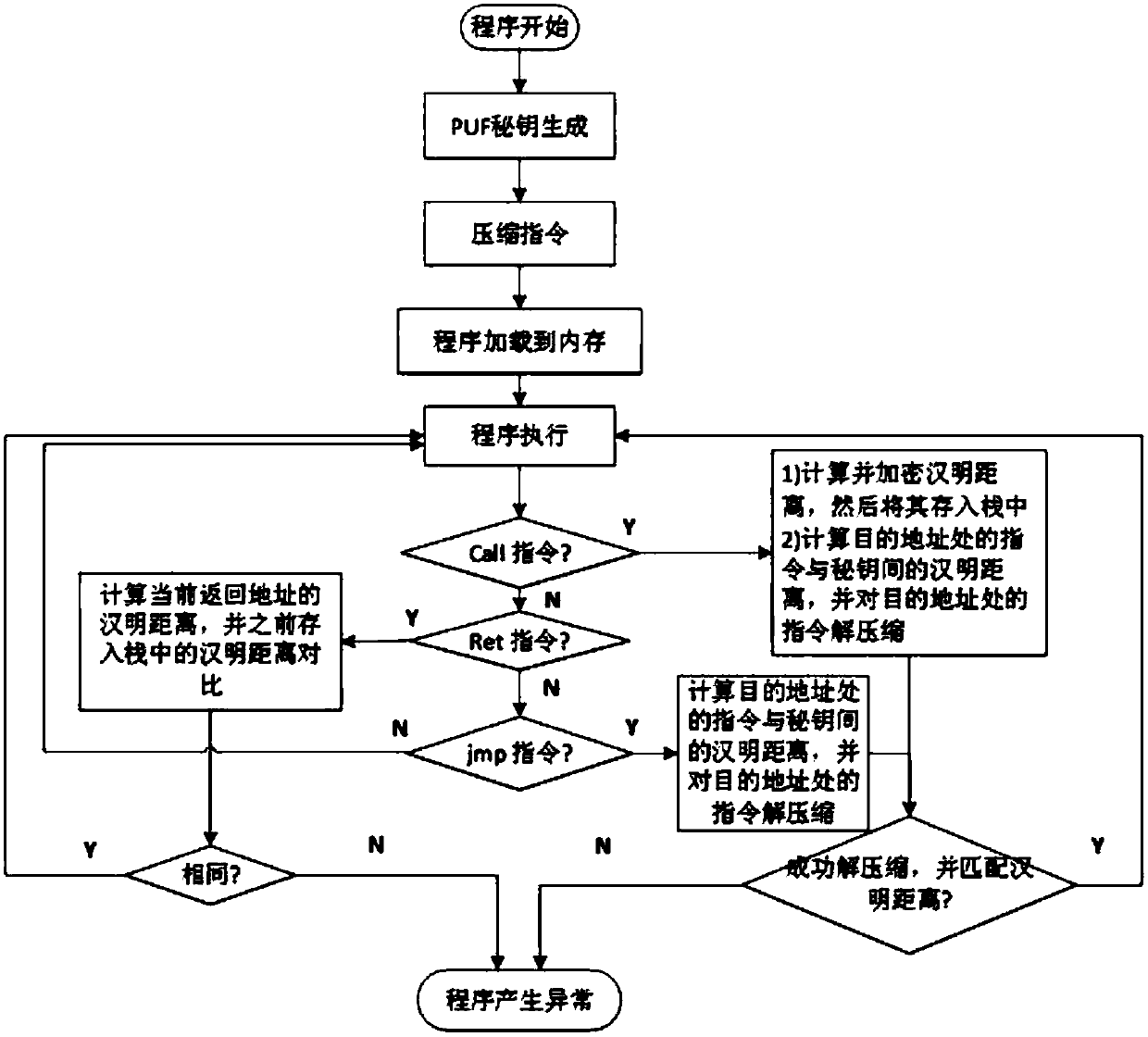
Hardware-assisted code-reuse-attack-resistant defence system and method
ActiveCN107590385AEliminate security concernsImprove securityInternal/peripheral component protectionPlatform integrity maintainanceCode moduleChosen-plaintext attack
The invention discloses a hardware-assisted code-reuse-attack-resistant defence system and method, wherein the defence system comprises a pre-processing module, a cache, a memory, a CPU and an encryption and decryption architecture; and the encryption and decryption architecture comprises a PUF module, a first key register, a first length register, a second key register, a second length register,a PUF encryption module, a Hamming distance coding module, a Hamming distance decoding module, a decompression module and a judgment module. According to the hardware-assisted code-reuse-attack-resistant defence system and method disclosed by the invention, the ROP attack is resisted by utilizing and matching the Hamming distance between the return address of a program and a key; because the Hamming distance is coded, the security problem that an attacker can guess a key generated by the PUF module in a plaintext attack manner in the past work can be eliminated; therefore, the security is high; simultaneously, an instruction-level data hiding technology is applied to JOP attack defence; therefore, the performance cost is low; an instruction set does not need to be changed; the universalityis good; and the security is high.
Owner:HUNAN UNIV
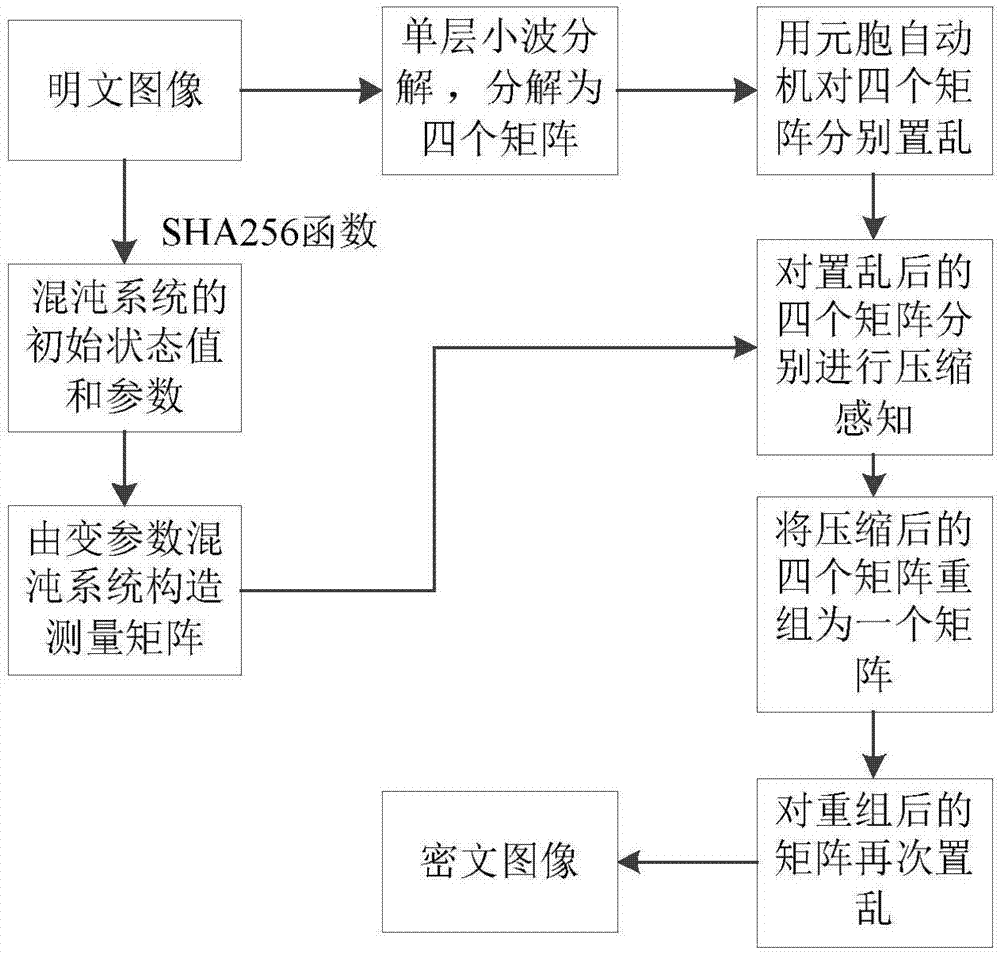
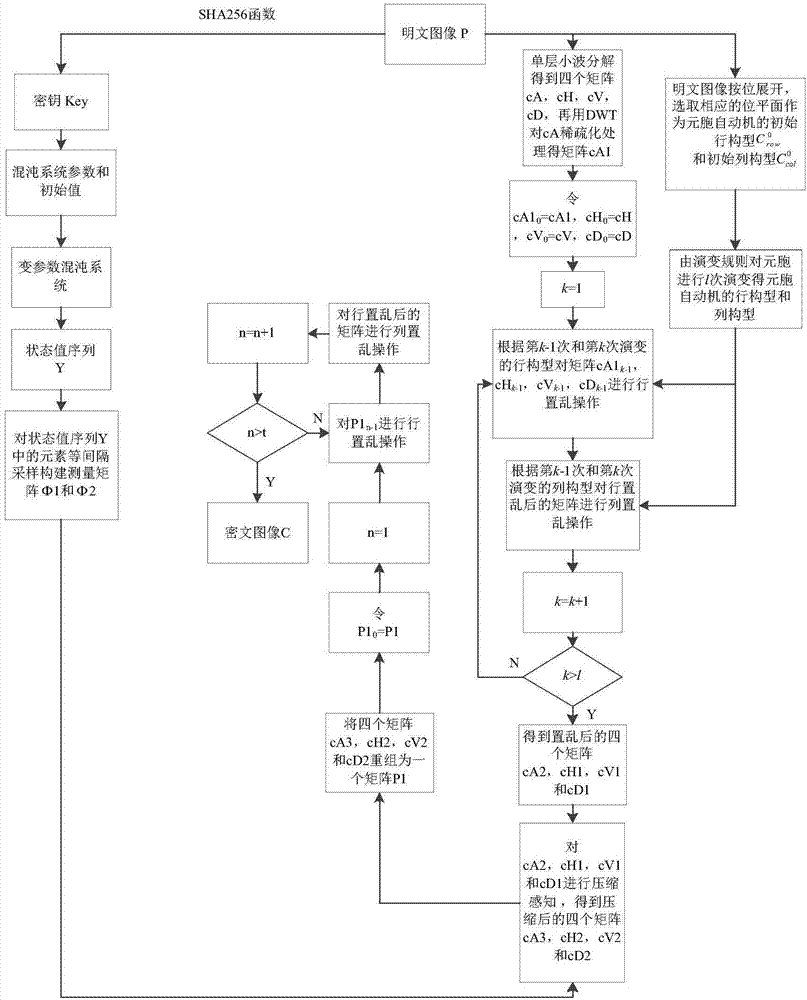
Image encryption method based on cellular automata and partition compression perception
ActiveCN107481180AImprove rebuild speedImprove securityImage codingImage data processing detailsComputer hardwareChosen-plaintext attack
The invention relates to an image encryption method based on a cellular automata and partition compression perception; the method comprises the following steps: using a single layer wavelet decomposition mode to decompose an image into four matrixes containing high frequency and low frequency, and using primary cellular automata to respectively scramble the matrixes; using different compression ratios to carry out compression perception, using a variable element chaotic system to build a measuring matrix, wherein the chaotic system initial value and parameters are formed by a plaintext image SHA256 function; regrouping the compressed four matrixes, scrambling the regrouped matrixes, thus obtaining a cryptograph image. The method uses the primary cellular automata to scramble the image so as to improve the algorithmic security, uses the compression perception to compress and encrypt the image, thus reducing the data bulk; a secret key space is added on one hand, thus increasing the algorithm anti-violence attack capability; on the other hand, the secret key generation is tightly depended on the plaintext, thus improving the algorithm anti-selection plaintext attack capability.
Owner:HENAN UNIVERSITY
Chinese and English character string encryption method
ActiveCN110650005AEnsure safetyGuaranteed feasibilityEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsChosen-plaintext attackTheoretical computer science
The invention discloses a Chinese and English character string encryption method, comprising the following steps: converting a certain section of Chinese and English character string to obtain a binary bit sequence B; carrying out forward shift encryption on the binary bit sequence B and then carrying out reverse shift encryption on the binary bit sequence B; obtaining a binary bit sequence B after bidirectional shift encryption, wherein shift encryption comprises repeated operations of binary bit grouping of nine elements in sequence in the forward / reverse direction, chaotic mapping single iteration, grouping sequence cyclic shift, chaotic mapping initial value adjustment, grouping sequence replacement and updating and the like; and finally, grouping the sequence B by taking six elementsas units in the forward direction, converting the grouped sequence B into numeric data, and converting numerical values and characters to obtain an encrypted ciphertext of the section of Chinese and English character string. According to the Chinese and English character string encryption method, bidirectional shift encryption is carried out on the binary bit sequence converted from the Chinese and English character strings by utilizing the password characteristic of the chaotic signal, so that the Chinese and English character string encryption method has good performance of resisting known / selected plaintext attacks, and can ensure the security and feasibility of Chinese and English character string encryption.
Owner:NANTONG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com