Asymmetric multi-image encryption method based on Logistic chaotic mapping
An encryption method and chaotic mapping technology, applied in the field of image processing, can solve the problems of insufficient security, small key space, low image encryption efficiency, etc., and achieve the effect of expanding the key space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
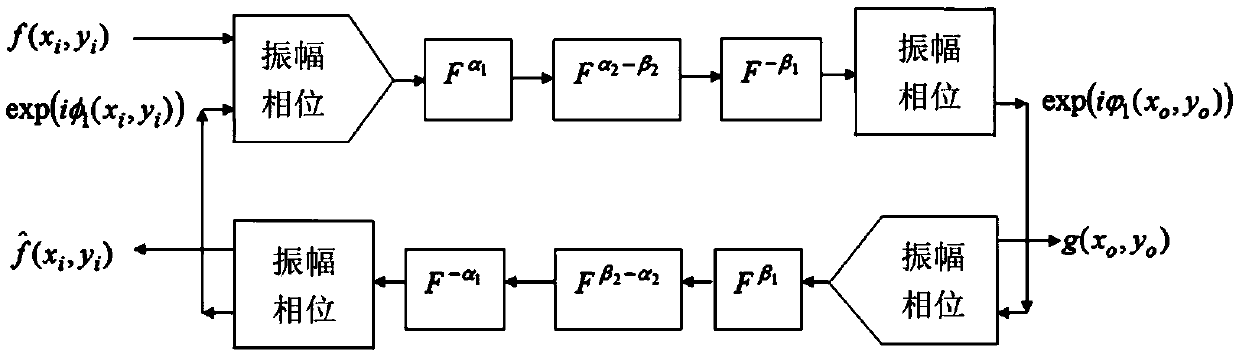
[0078] use Figure 2a-Figure 2i to verify the feasibility of the proposed multi-image encryption cryptosystem. The two sets of fractional orders are set to α 1 = 0.2, α 2 = α 1 +0.4, beta 1 = α 1 +0.3, beta 2 = α 2 +0.1, α3=α1. The value of the initial dual-coupled logistic map is set to x 0 =0.21,y 0 =0.83, K was set to 2000. The Logistic mapping of the system parameters for double coupling was set to p = 3.56995 and ε = 0.471. The threshold for MSE as a convergence criterion is set to 1.0e -9 . Specific steps are as follows:
[0079] Step 1, refer to image 3 , by using two symmetrically coupled identical logistic maps to the image f i Add interference to get the added interference image f' i , Figure 4a It is the "Lena" image after adding interference in the present invention; Figure 4b is the "Zelda" image after the present invention has added interference; the iterative expression of the double Logistic mapping is:
[0080] x n+1 =p×x n ×(1-x n )+ε...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com