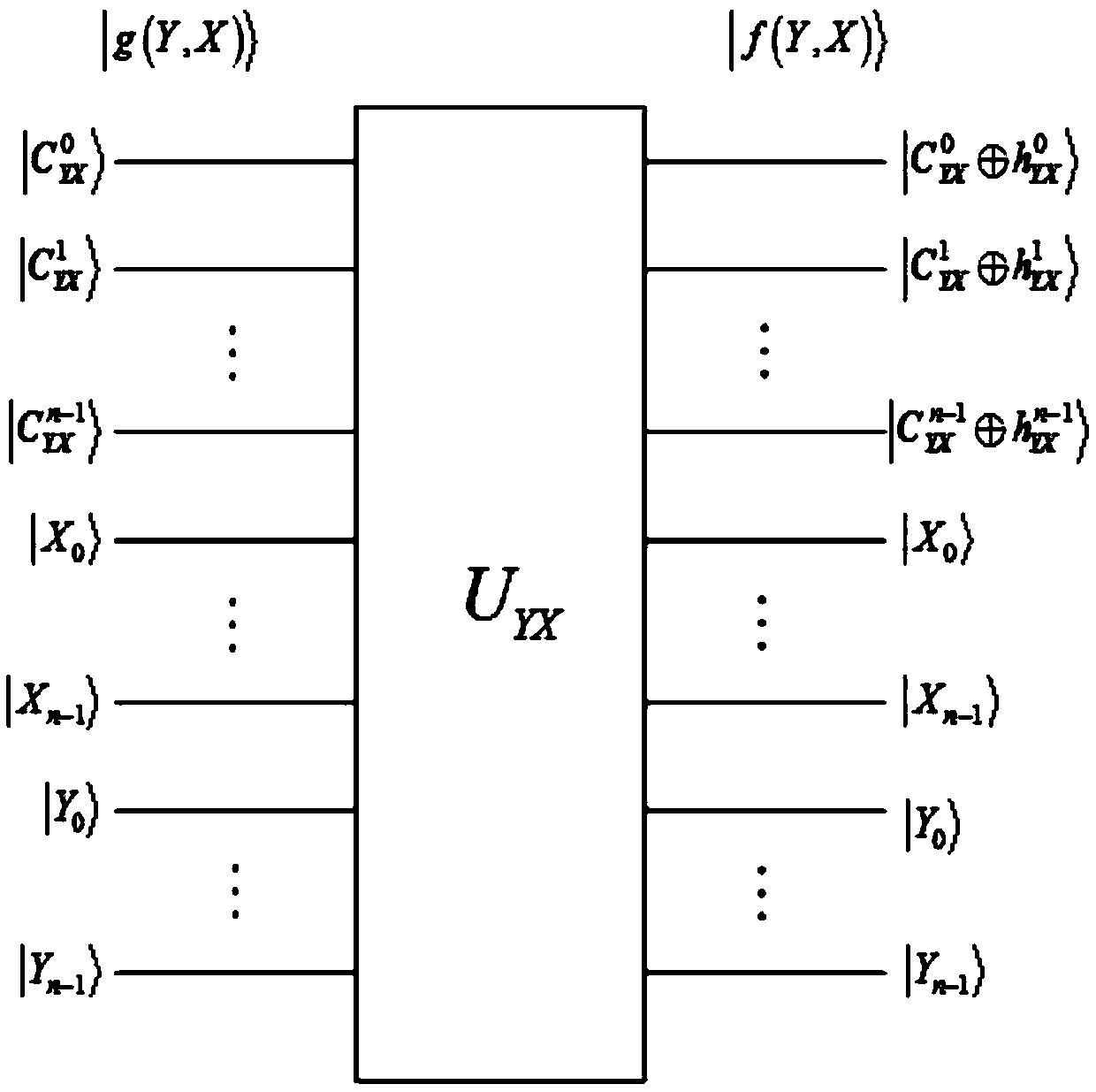
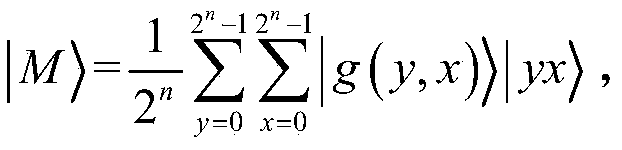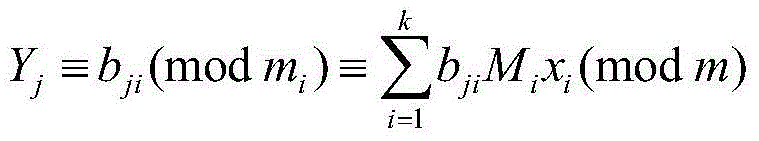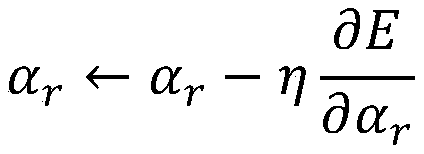Patents
Literature
190 results about "Key space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, an algorithm's key space refers to the set of all possible permutations of a key.
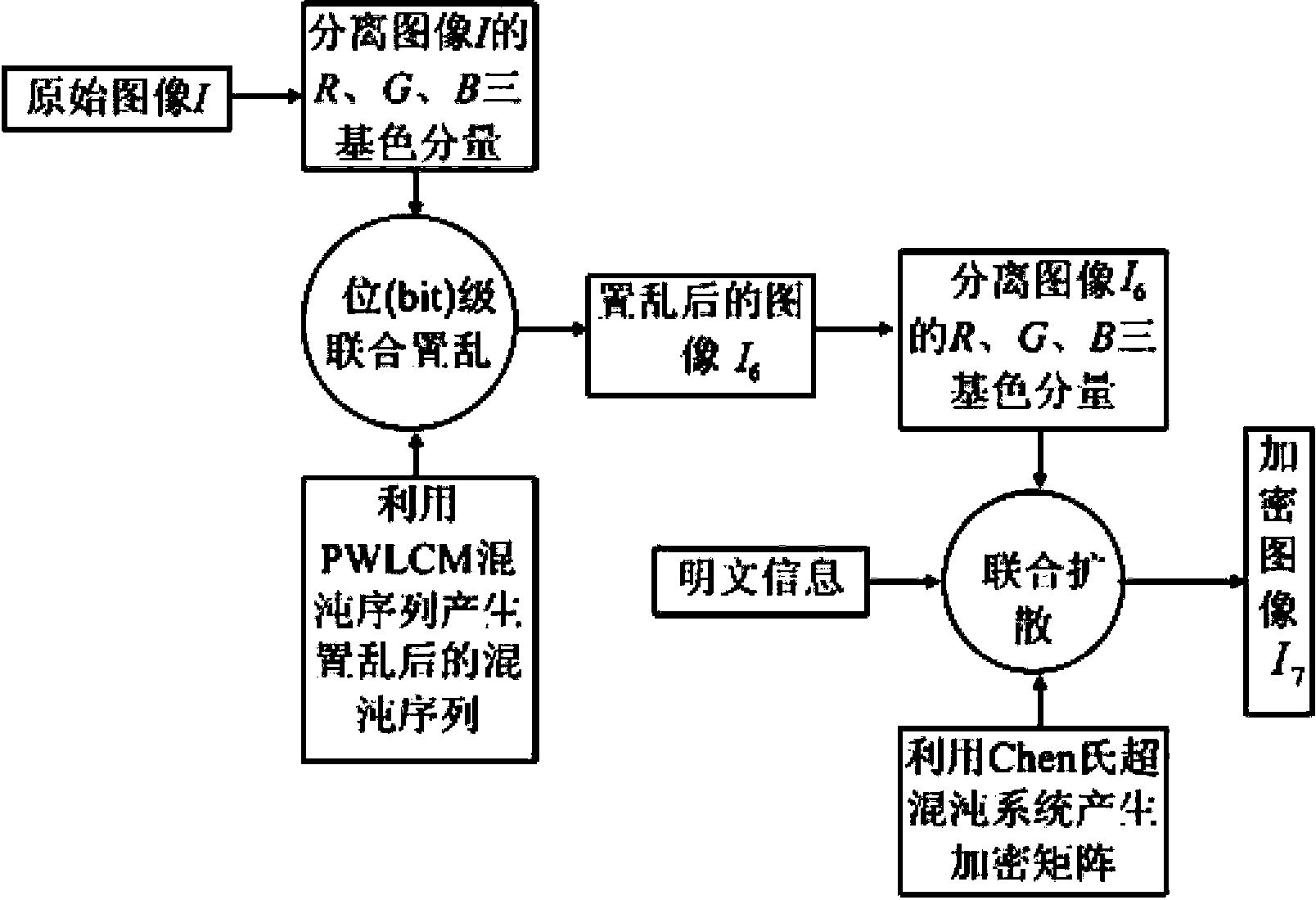
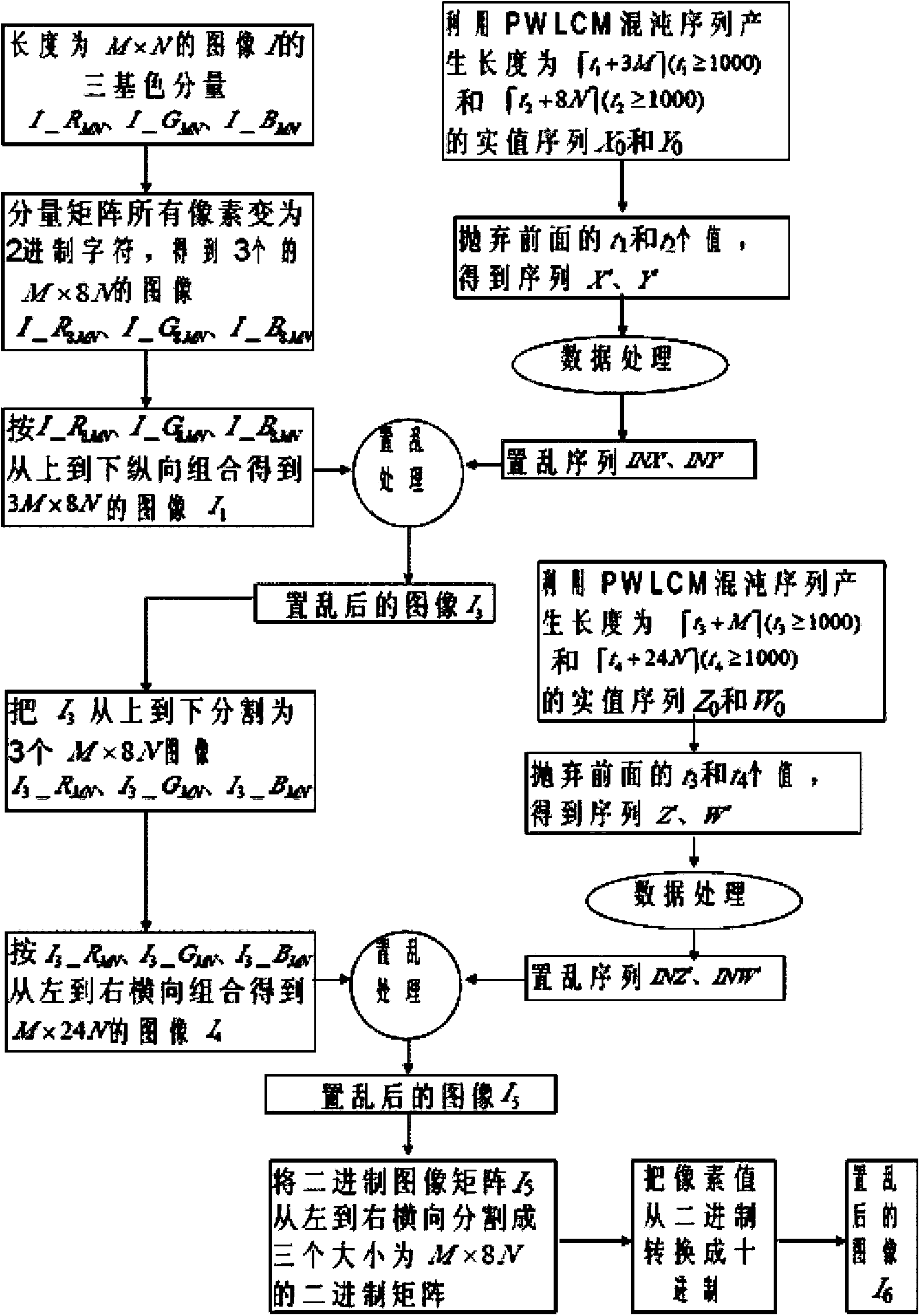
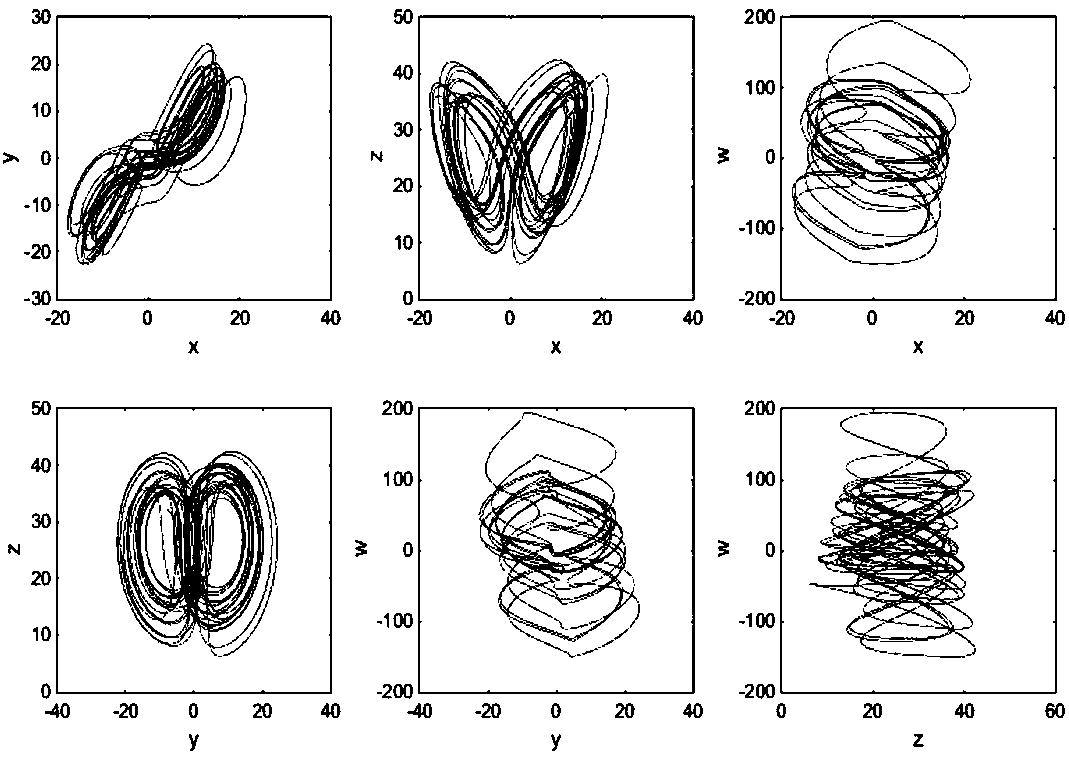
Color image encryption method based on chaos sequence and hyper-chaos system
InactiveCN103489151AImprove securityLarge key spaceImage data processing detailsChaotic systemsDiffusion
The invention relates to a color image encryption method based on a chaos sequence and a hyper-chaos system. The color image encryption method mainly comprises the following steps: an original color image is subjected to bit level united scrambling to obtain a scrambled image; the scrambled image is decomposed into three primary color components, that is R, G and B, and the hyper-chaos system is used for generating an encryption matrix which is used for encrypting the scrambled image; all pixel values of the three primary color components of the scrambled image are changed by utilizing the encryption matrix in combination with plaintext information and information of the three primary color components, united diffusion is conducted to obtain the three primary color components of the image after the united diffusion, and therefore a final encrypted image is obtained. By means of the color image encryption method, a secret key space is greatly enlarged, the safety, the encryption effect and the sensitivity of a secret key are higher, the anti-attack ability is stronger, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
Color image encryption and decryption method based on multiple-fractional-order chaotic systems
ActiveCN102982499ARich Dynamic BehaviorBig Key SensitivityImage data processing detailsKey spaceAlgorithm
The invention discloses a color image encryption and decryption method based on multiple-fractional-order chaotic systems. An encryption algorithm comprises an original image scrambling stage and a scrambling image encryption stage. Firstly, two different fractional-order chaotic systems are utilize to generate three scrambling arrays and respectively process R, G and B three primary color component arrays of an original color image I0 in a scrambling mode to obtain scrambled image I1. Furthermore, another two different fractional-order chaotic systems are utilize to generate three secret key arrays and carries out exclusive OR operation on elements on the secret key arrays and pixel of the scrambled image I1 one by one to change values of all pixel points of the scrambled image I1 to obtain encrypted image I2, and the image decryption is a reversed process of the encryption. The method uses the multiple-fractional-order chaotic systems so as to greatly enhance safety. Furthermore, the algorithm secret keys are large in space, high in secret key sensitiveness and strong in impact resistance.
Owner:HENAN UNIVERSITY
Image two-grade encrypting method based on double-chaos system
InactiveCN102693523ALarge key spaceEnhanced ability to resist known plaintext attacksImage data processing detailsKnown-plaintext attackComputer vision
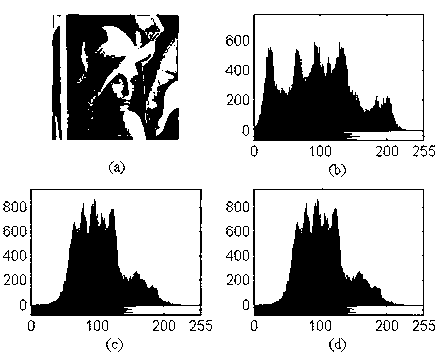
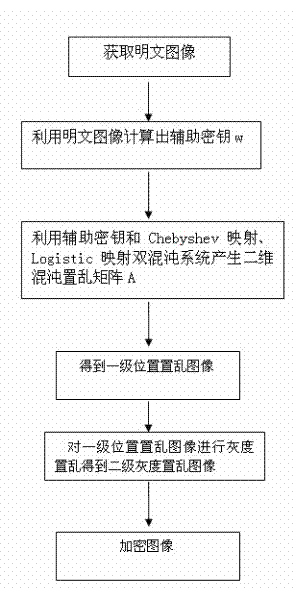
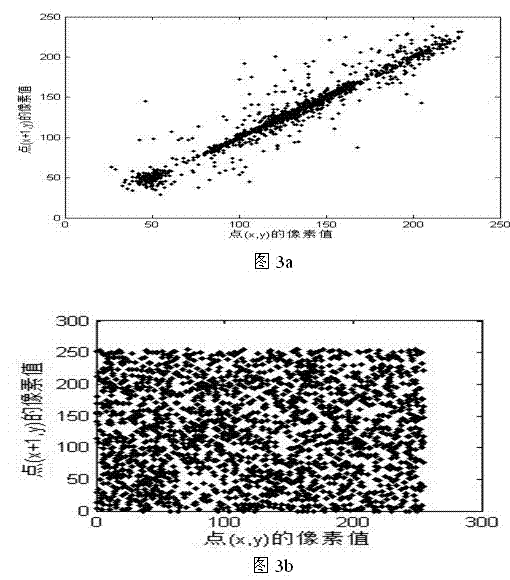
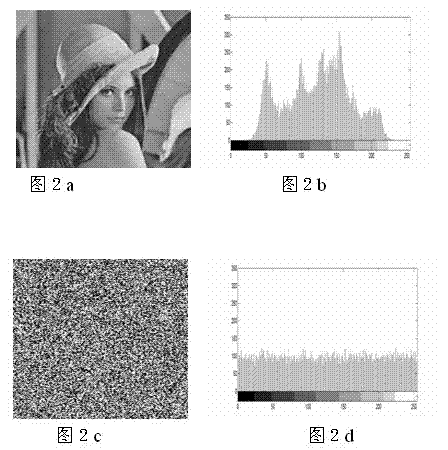
The invention discloses an image two-grade encrypting method based on a double-chaos system, relating to the field of image encrypting systems. The adopted method comprises the steps of creating an auxiliary key by a plaintext image firstly; creating a two-dimension chaos scrambling matrix by the auxiliary key combined with the double-chaos system of the Chebyshev mapping and Logistic mapping to dually scramble the position and grey level of the pixels of plaintext image so as to realize the encryption of images. According to the image two-grade encrypting method, the auxiliary key based on the plaintext image is introduced to expand key space and correlate the key with the plaintext, so that the ability of the image encryption system for resisting attack of the known plaintext is enhanced; and meanwhile, the complicated characteristics of dynamics of the double-chaos system is utilized to dually scramble the position and grey level of the plaintext image, with good encryption effect and high security.
Owner:SOUTH CHINA UNIV OF TECH
Image encryption method based on chaotic mapping and bit-level replacement
ActiveCN112084517ALarge key spaceImprove securityDigital data protectionSecuring communication by chaotic signalsKey spaceAlgorithm
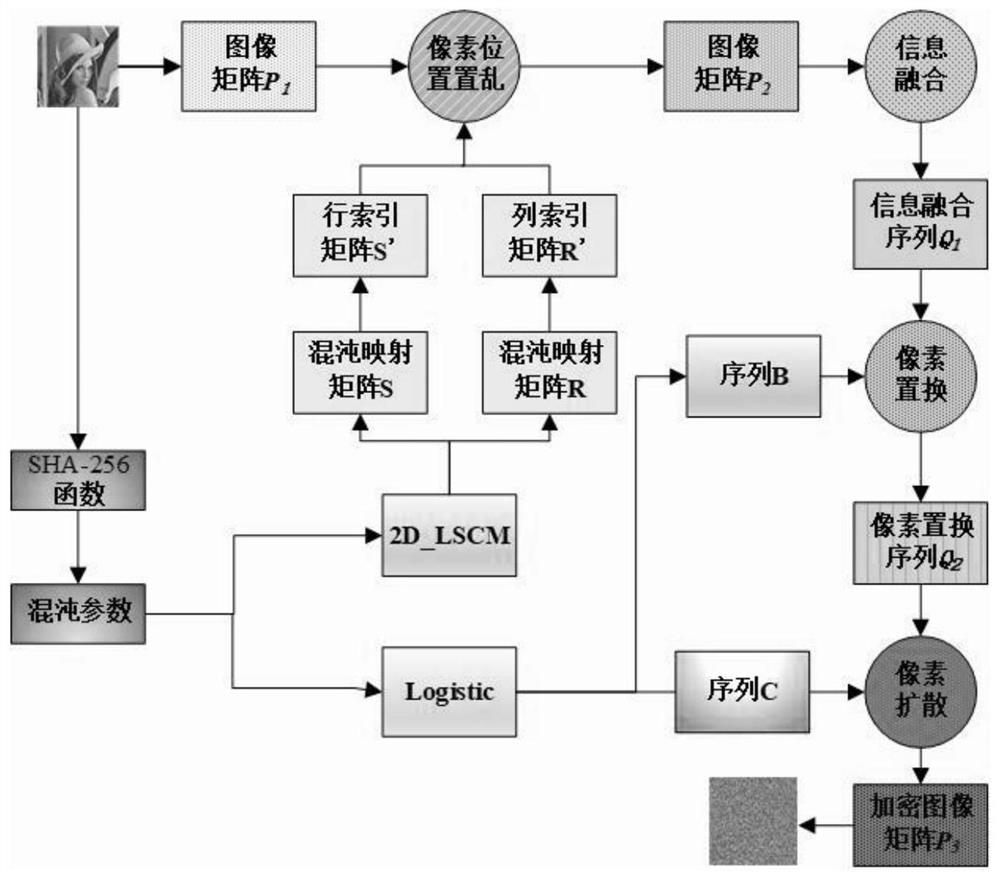
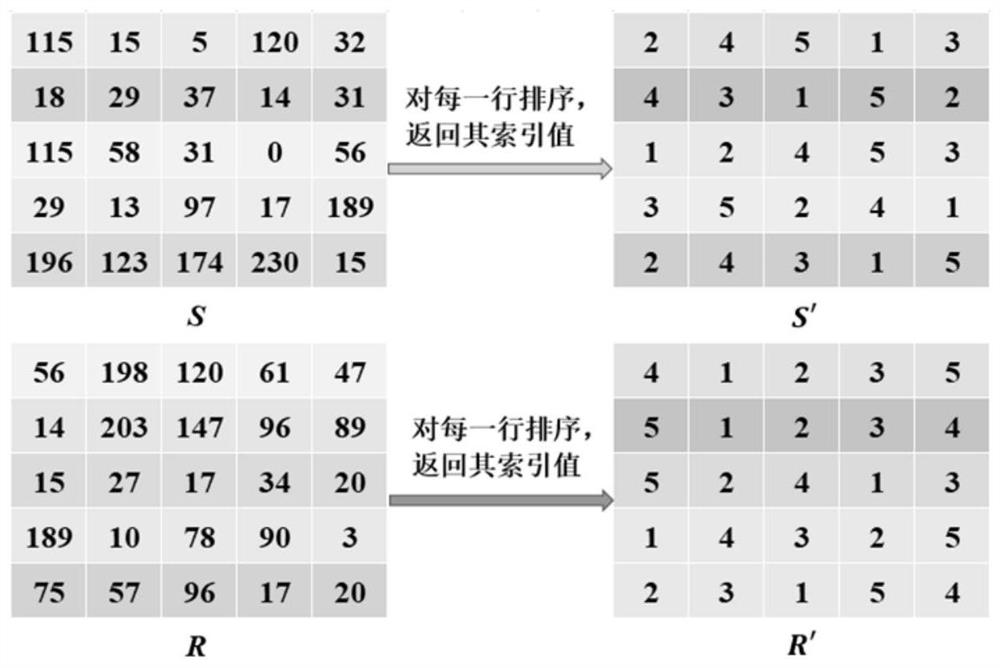
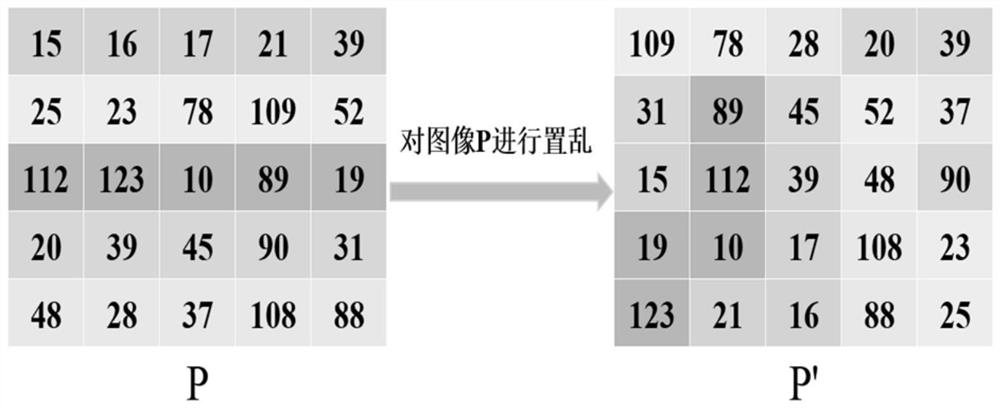
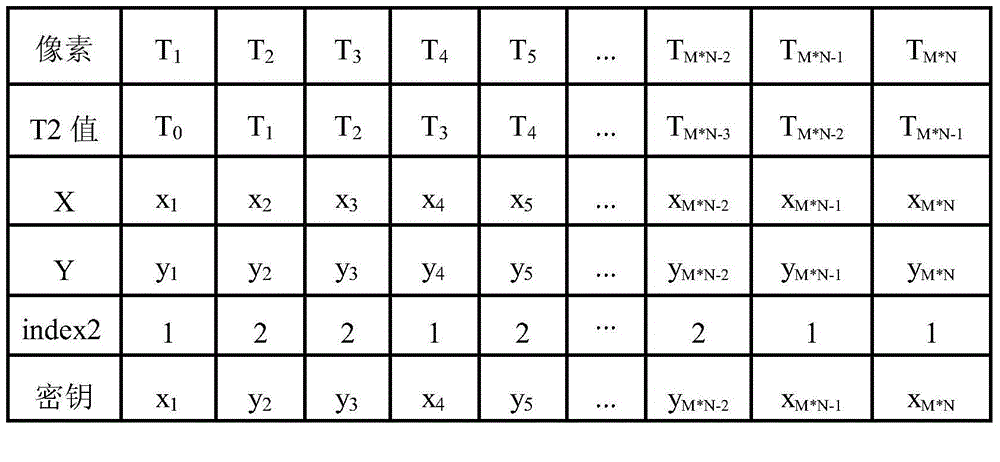
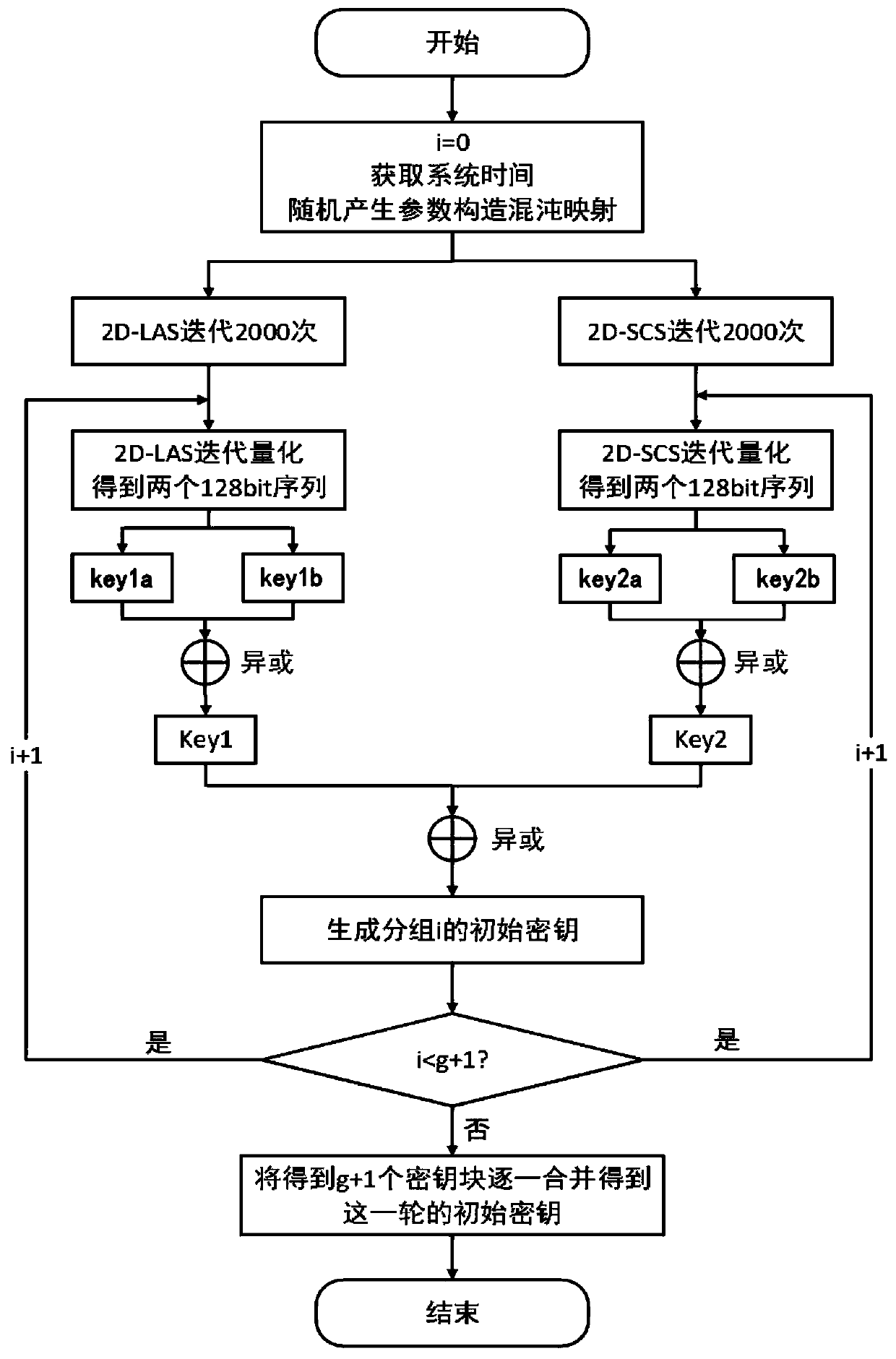
The invention provides an image encryption method based on chaotic mapping and bit-level replacement. The method comprises the following steps: converting a grayscale image into an image matrix; iterating 2D-LSCM mapping to generate a chaotic sequence and mapping the chaotic sequence into a matrix, and returning a position index to perform pixel position exchange on the image matrix after descending sorting of each row; sequentially exchanging the lowest three bits in every two pixel bits to obtain an information fusion sequence of the image; performing iteration on the Logistic mapping to generate a chaotic sequence, and performing operation on the information fusion sequence and the chaotic sequence to obtain a pixel replacement column of the image; and performing pixel diffusion on thepixel replacement sequence of the image by using a chaotic sequence and a ciphertext diffusion technology to obtain an encrypted image. The chaotic mapping and scrambled images are used for replacement operation, the differential attack resistance is enhanced through bit information fusion operation and an image pixel-based diffusion method, the secret key space is large enough, violent attack canbe better resisted, and good safety is achieved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image encryption method based on multidimensional chaotic system and Josephf scrambling
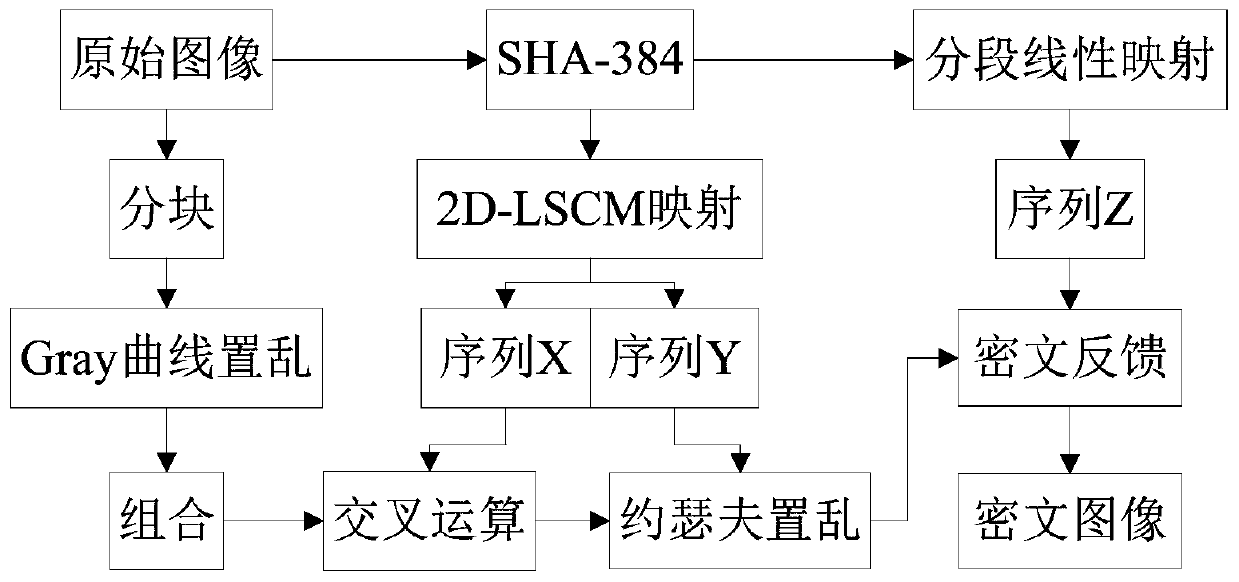
ActiveCN111105339AAchieve diffusionIncreased sensitivityImage data processing detailsKey spaceAlgorithm
The invention provides an image encryption method based on a multi-dimensional chaotic system and Josephf scrambling, and the method comprises the steps: carrying out the initialization of PWLCM mapping and 2D-LSCM mapping, and obtaining a sequence X, a sequence Y and a sequence Z; uniformly dividing the original image into sub-matrixes according to indexes, carrying out Gray curve scrambling on pixels in the sub-matrixes, and carrying out sequential recombination to obtain a recombined image matrix; taking out elements in the sequence X as a crossover operator, and performing bit crossover operation on the recombined image matrix to obtain an image matrix; taking out a pseudo-random value in the sequence Y as the step value of fixed-step Josephh scrambling, and performing Josephh scrambling operation on the image matrix to obtain a matrix; and taking out the pseudo-random value in the sequence Z and the element pixel value in the matrix to carry out XOR ciphertext feedback to obtain afinal encrypted image. The method can effectively encrypt the image, has a large key space, has high sensitivity to the to-be-encrypted image and the initial key, and has good defense capability whenresisting various attack modes.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
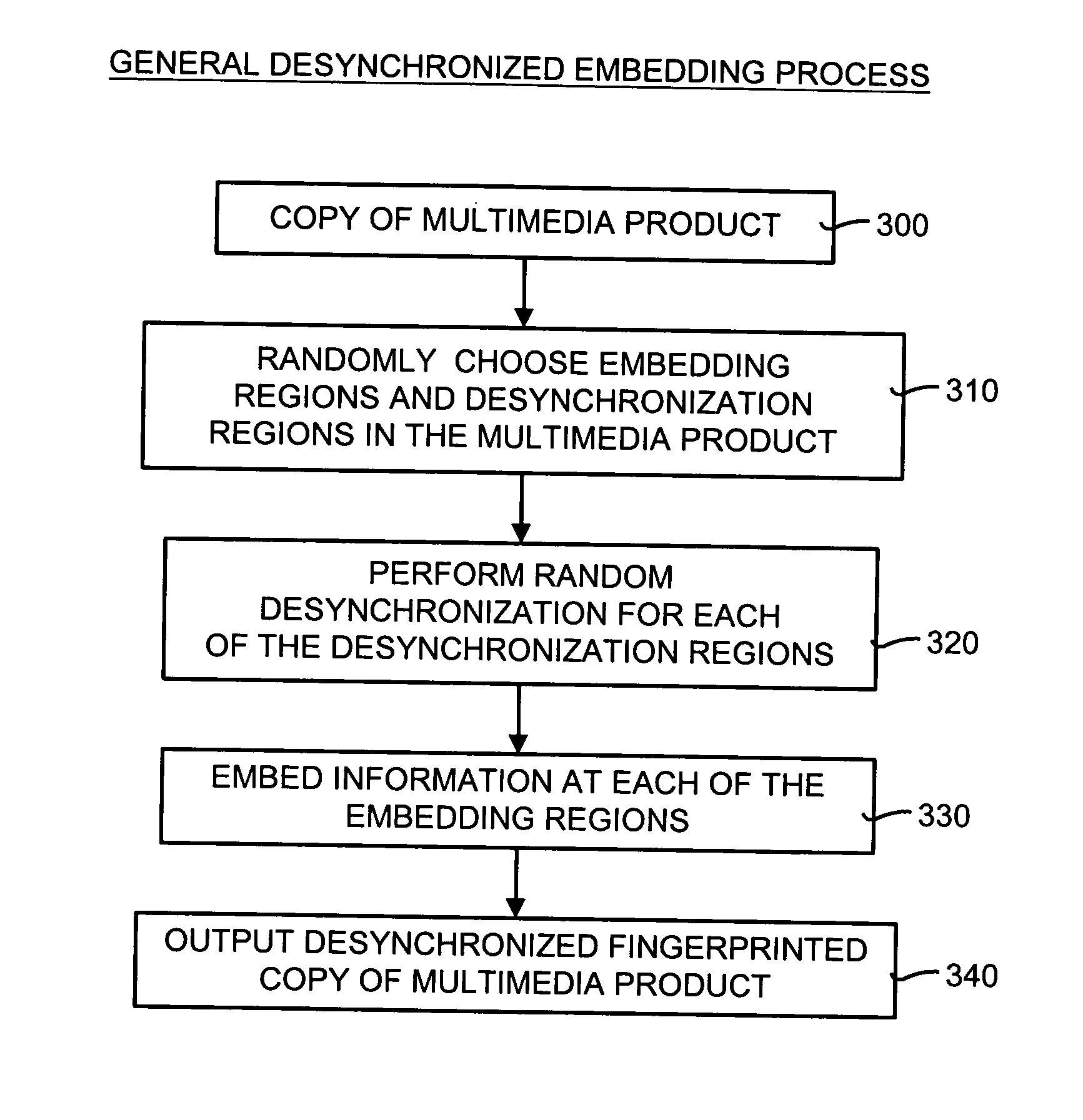
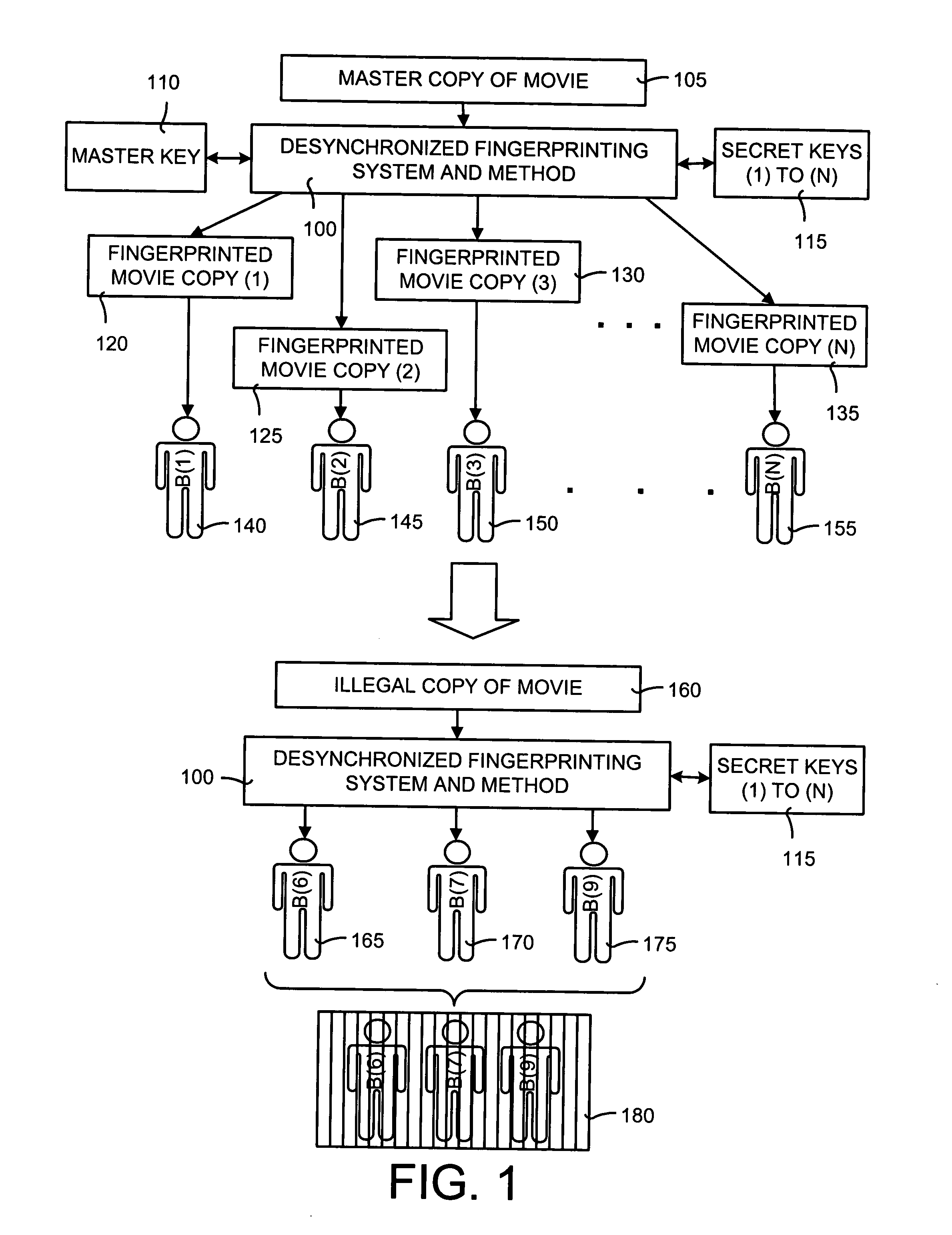
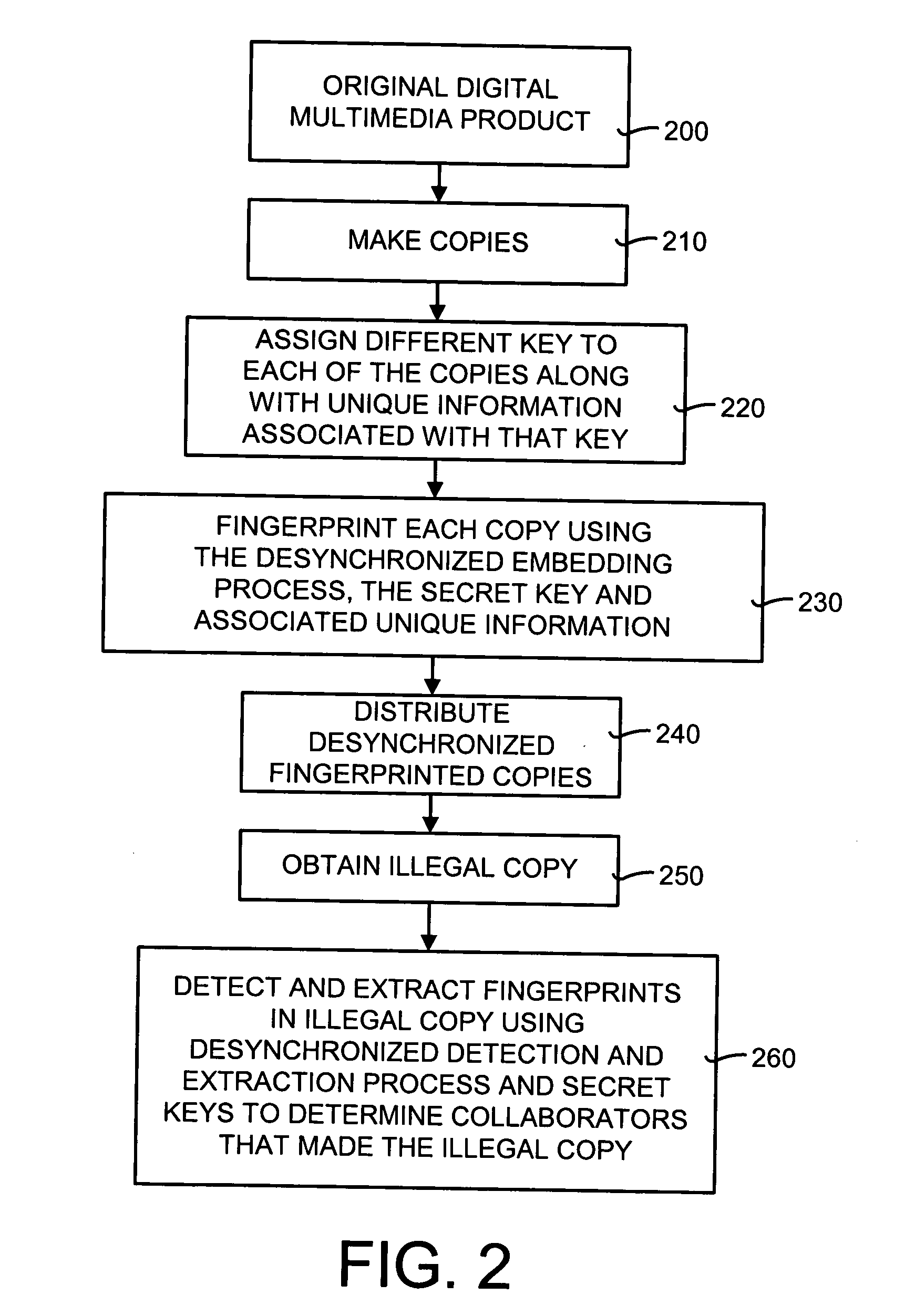
Desynchronized fingerprinting method and system for digital multimedia data
InactiveUS20050175224A1Resist attackIncrease the number ofUser identity/authority verificationCharacter and pattern recognitionDigital dataHash function
A desynchronized fingerprinting method and system for identifying collaborators in the making of illegal copies of digital multimedia products. The desynchronized fingerprinting system and method can be used for both audio and video applications. The method and system include an embedding feature and a detection and extraction feature. A different and unique key is assigned to each buyer of a copy of the digital data. The embedding feature includes applying a pseudo-random transformation to selected embedding regions. The key for the pseudo-random transform is user-specific. These regions are chosen by using a secure multimedia hash function. The detection and extraction feature includes a brute-force search in the key space of the buyers. If one of the keys is likely enough, then it can be said that that user was been involved in the production of an illegal copy.
Owner:MICROSOFT TECH LICENSING LLC
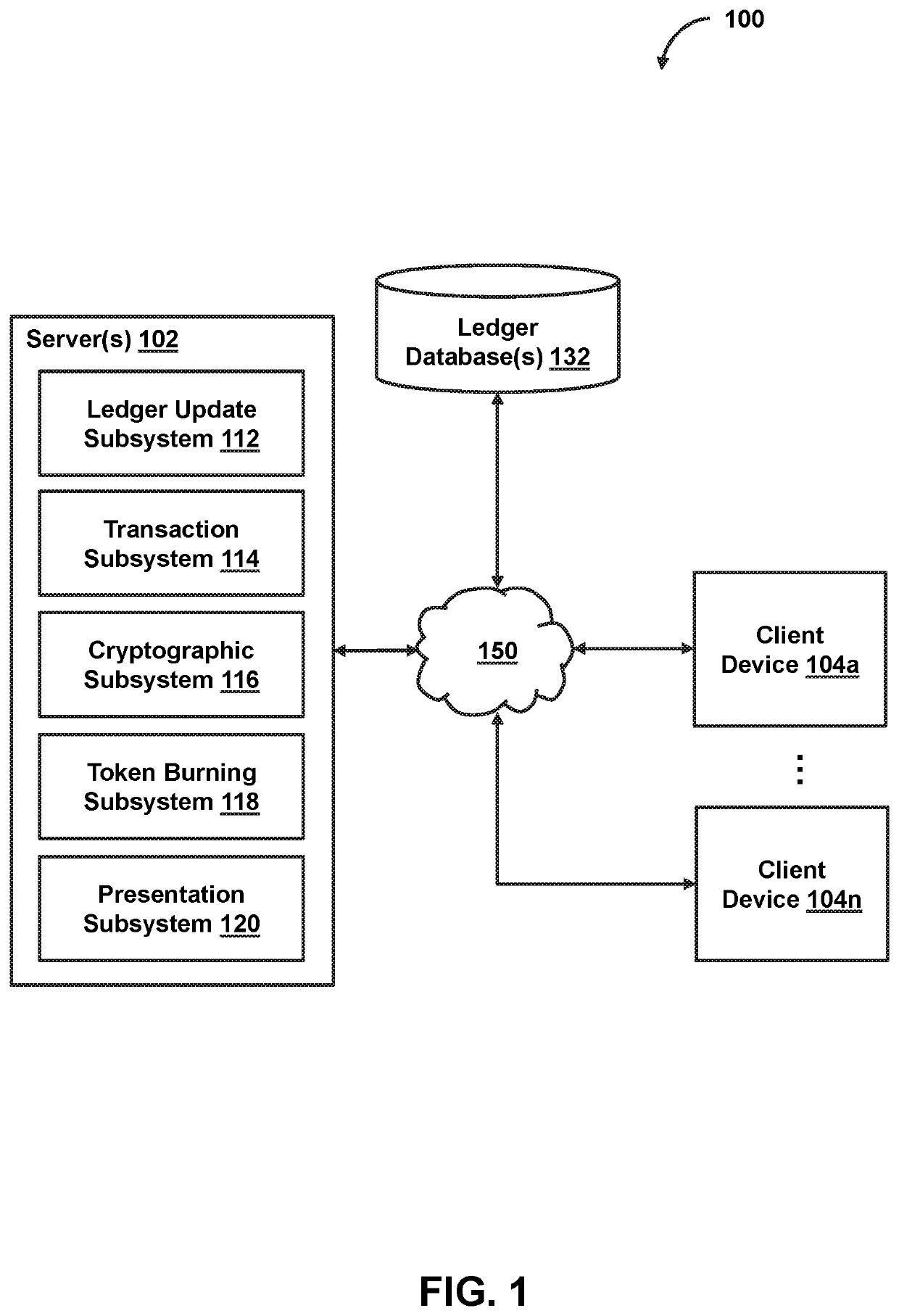
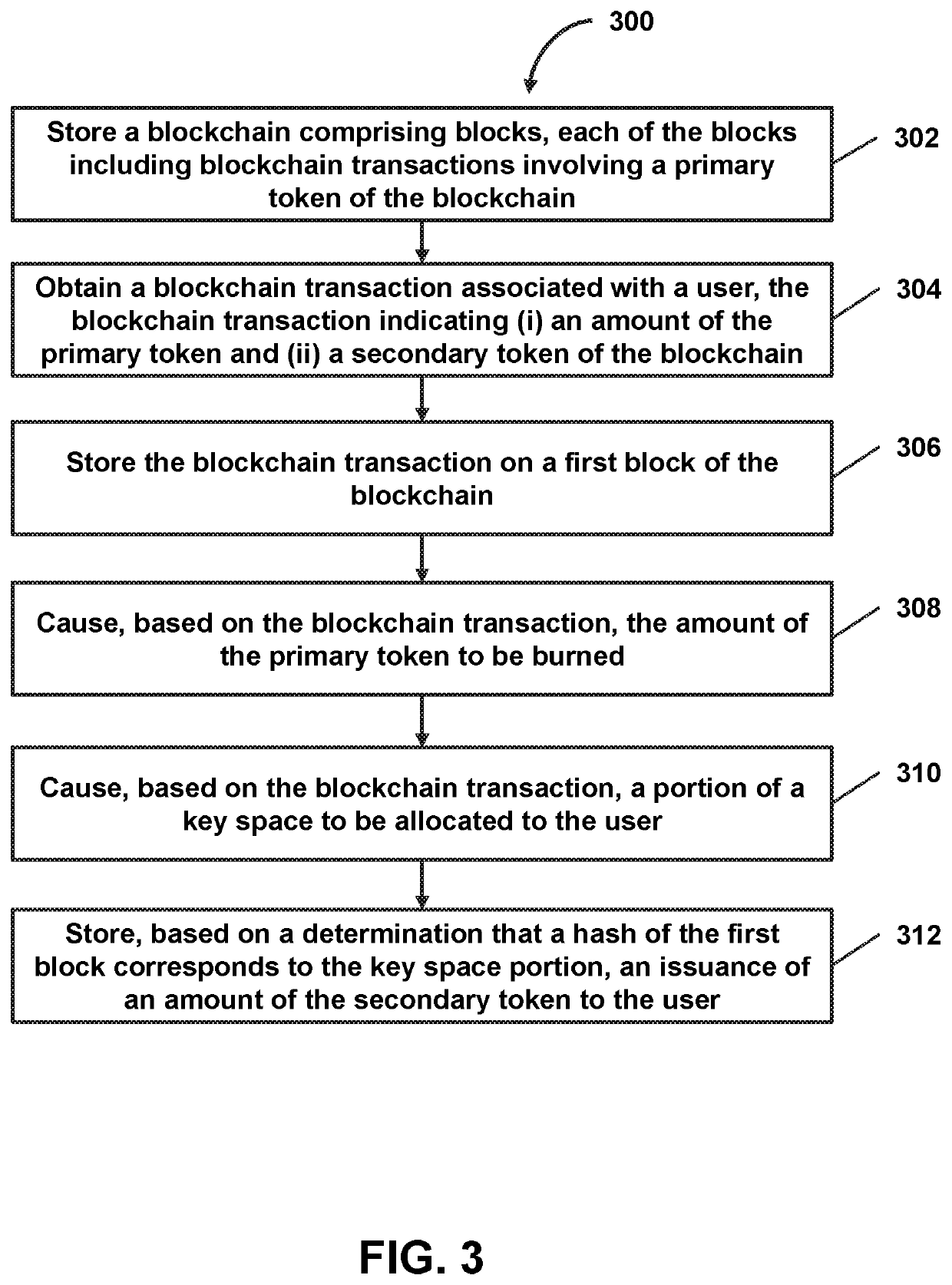
Probabilistic secondary token issuance on a blockchain based on burning of a primary token of the blockchain
ActiveUS10581591B1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesKey spaceComputer network
In certain embodiments, probabilistic secondary token issuance on a blockchain may be facilitated based on a burning of a primary token of the blockchain. In some embodiments, a blockchain transaction associated with a user may be obtained. The blockchain transaction may indicate (i) an amount of a primary token of the blockchain (owned by the user) to be burned and (ii) a secondary token of the blockchain. Based on the blockchain transaction, (i) the amount of the primary token may be burned, and (ii) a portion of a key space may be allocated to the user. Based on a determination that a hash of at least a portion of a first block of the blockchain corresponds to the key space portion allocated to the user, an issuance of an amount of the secondary token to the user may be stored on a second block for the blockchain.
Owner:BRANTON MATTHEW
Method for constructing block encryption algorithm based on random function
ActiveCN102571330AImprove securityHeavy calculationKey distribution for secure communicationPlaintextPassword
The invention belongs to the field of information security and relates to construction of encryption algorithm. The password (encryption) algorithm is uncertain and random by using the random function to construct the block encryption method. The uncertainties are determined by partial data in the secret key and some information of plaintext. The encryption method has the advantage that the indeterminacy of the algorithm ensures that the password analysis becomes very difficult as a result of the lack of the information about the algorithm, so that a great amount of known (selected) plaintext ciphertext pair of the same algorithm and the same secret key cannot be acquired, and the condition for password analysis is destroyed to enhance the security. The existing abundant password analysis aims at determined algorithm, and the password analysis is difficult to perform when the algorithm is random. The uncertainty of the password system is increased through multiple ways. The encryption algorithm of the plaintext is uncertain, and the algorithms of different blocks are different, therefore, the secret key space can be increased so as to enhance the safety.
Owner:桂林碧琪信息科技有限公司
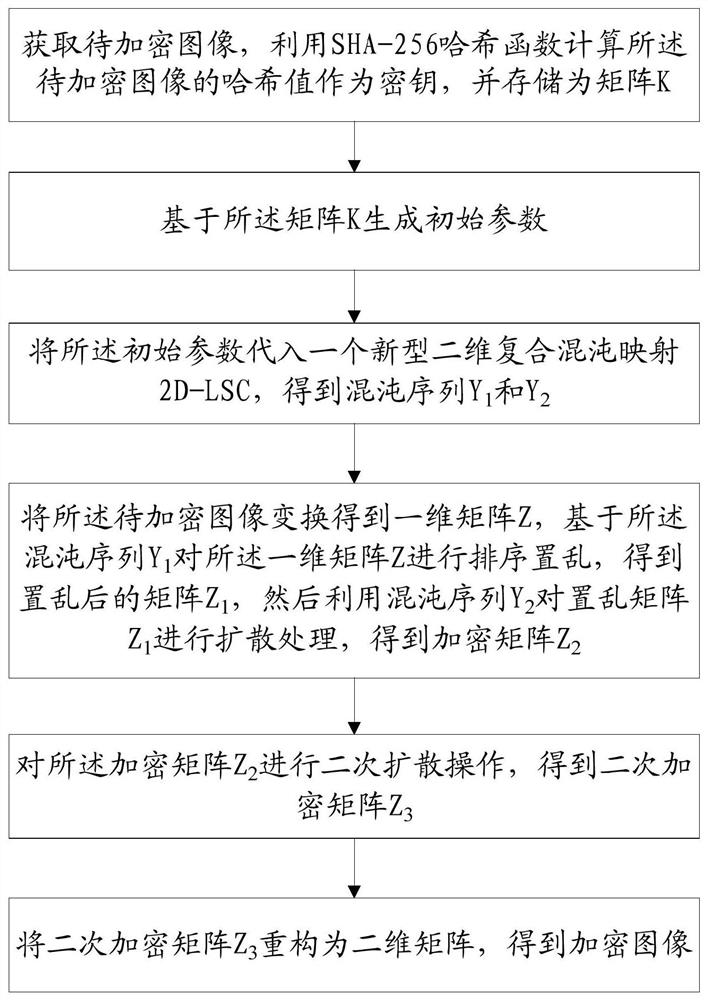
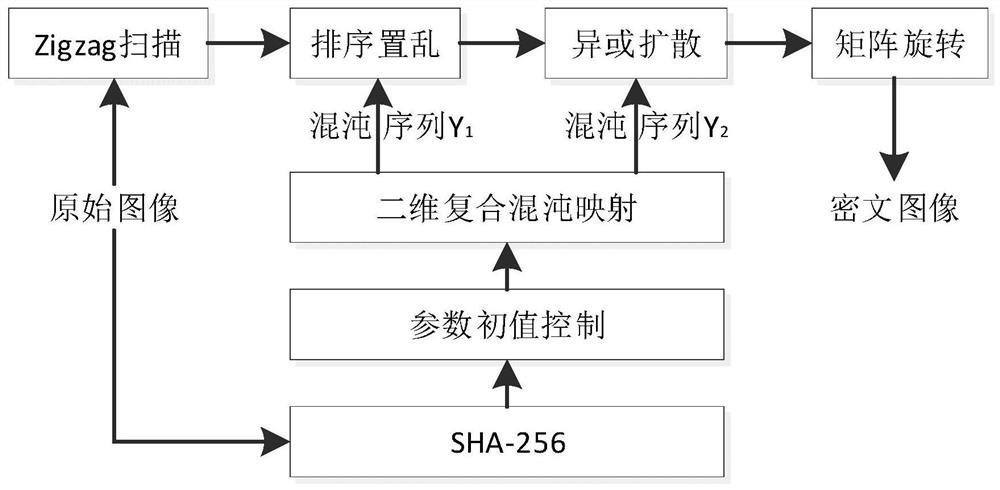
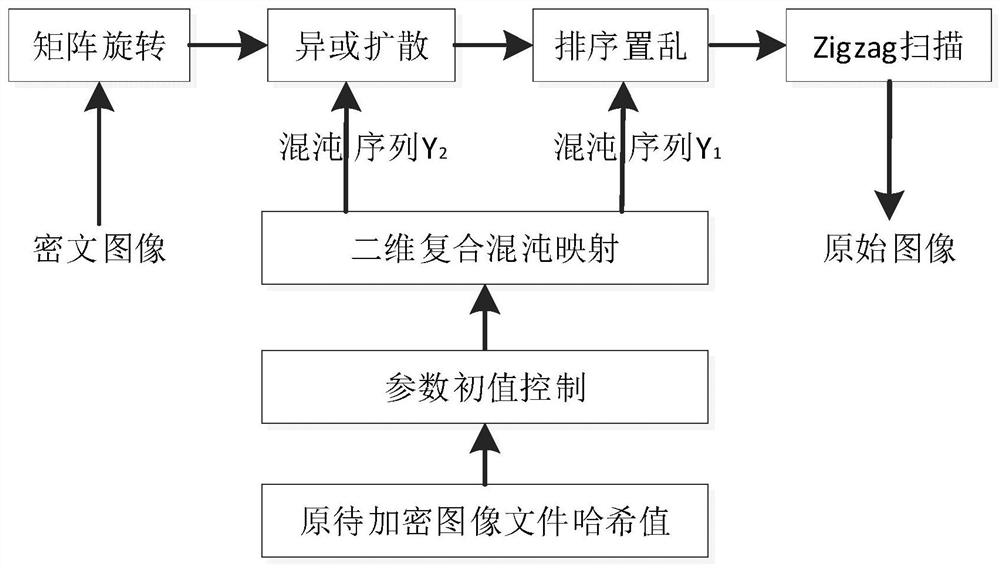
Image encryption method and device based on novel two-dimensional composite chaotic mapping and SHA-256
ActiveCN113538203ALow cost of executionIncreased complexityDigital data protectionImage data processing detailsKey spaceHash function
The invention provides an image encryption method based on novel two-dimensional composite chaotic mapping and SHA-256. The method comprises the following steps: calculating a Hash value of a to-be-encrypted image by using an SHA-256 Hash function, and taking the Hash value as a system input key; linking plaintext image information and the whole image encryption process closely by using the one-way irreversible characteristic of Hash calculation, therefore, the algorithm key space is expanded, and violent attacks of attackers can be effectively resisted; carrying out blocking and operation on the hash value to obtain an iterative initial parameter of the composite chaotic system; substituting into a composite chaotic system for iteration and processing to generate a chaotic sequence; converting the to-be-encrypted image into a one-dimensional matrix; sorting and scrambling the original image based on the chaotic sequence; performing primary diffusion processing on the matrix based on the chaos sequence to obtain an encrypted matrix; performing secondary diffusion processing on the encryption matrix through a parameter generated by a key to obtain a secondary encryption matrix; and finally, reconstructing to obtain an encrypted image. According to the invention, the security of image encryption is improved, and the execution cost is reduced.
Owner:HUAQIAO UNIVERSITY +1
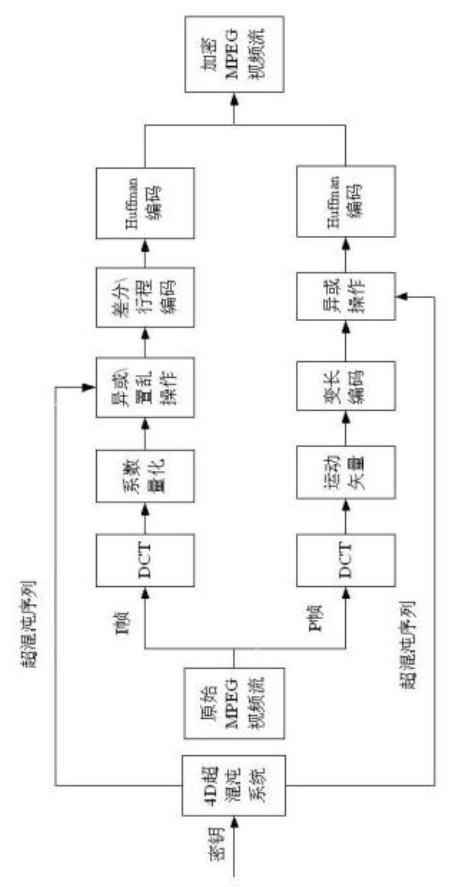
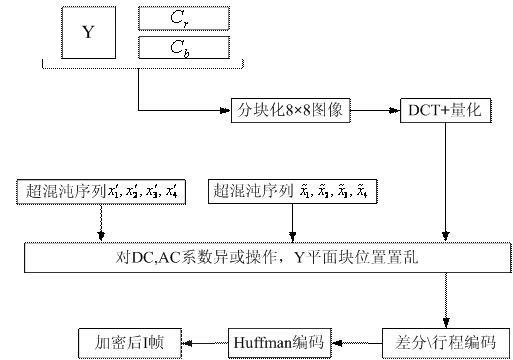
Method for encrypting video streaming information based on hyper-chaotic sequence
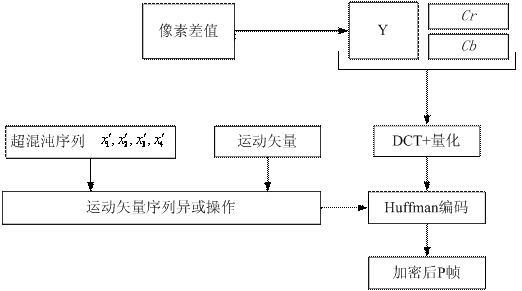
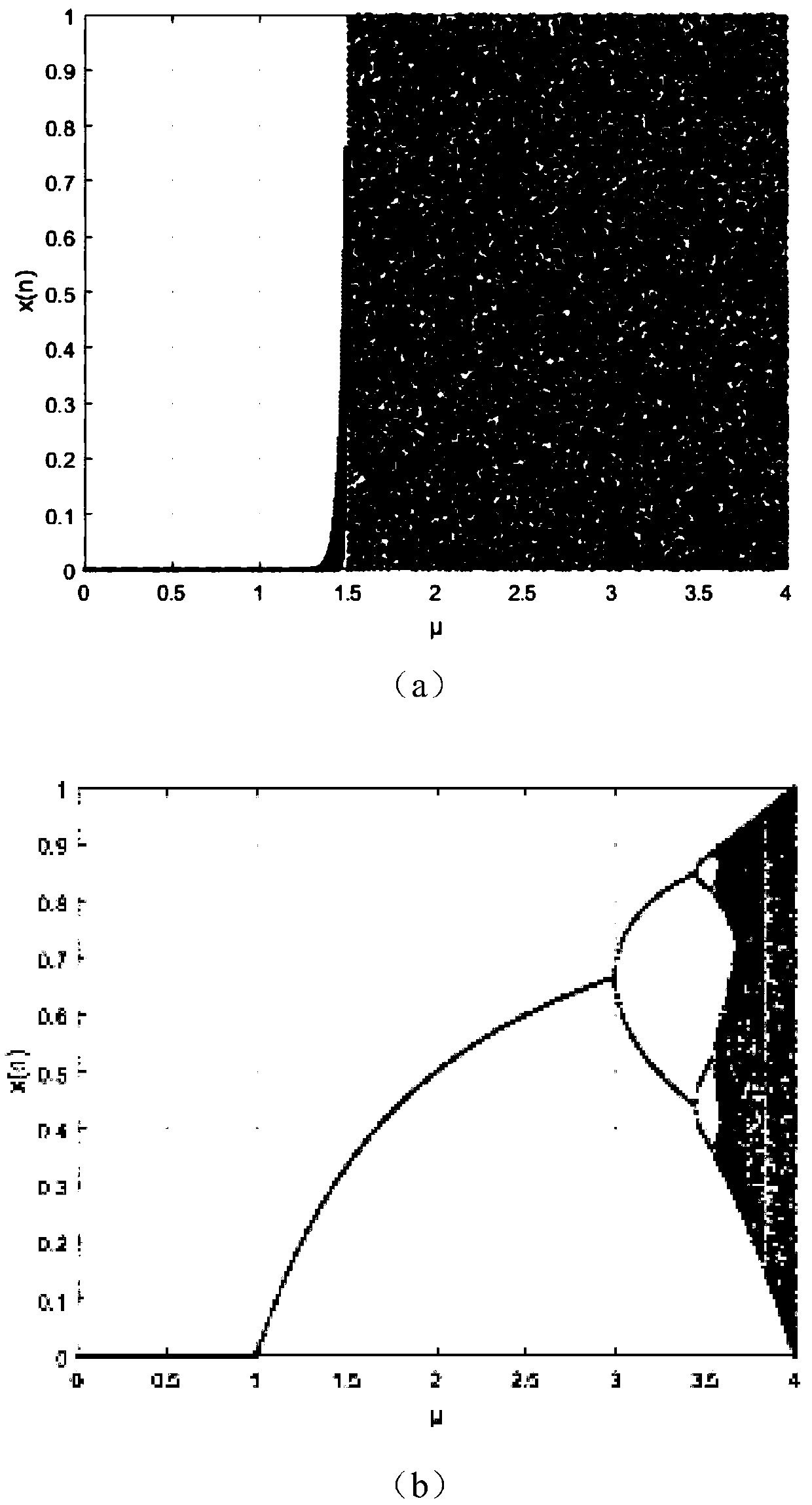
InactiveCN102176759AImprove real-time performanceThe key space is hugeTelevision systemsDigital video signal modificationPlaintextComputer hardware
The invention provides a method for encrypting MPEG (moving picture experts group) video streaming information based on a hyper-chaotic sequence, which is characterized in that a streaming encryption technology is combined with a block encryption technology so as to encrypt I frames and P frames of MPEG video streaming; in an algorithm, an initial value of a four-dimensional hyper-chaotic system is taken as an external secret key, the hyper-chaotic sequence generated by the four-dimensional hyper-chaotic system is utilized, and AC (alternating current) coefficients of video images are utilized to generate an inner secret key; and an XOR operation is carried out on DC (direct current) and AC coefficients of the I frames respectively, position scrambling is carried out on luminance information of the I frames by taking a 8*8 block as a unit, the XOR operation is carried out on motion vectors of F macro blocks in the P frames, and original video information is disturbed sufficiently. In the method, the space of the secret keys is huge, and the capacity to resist brute force attacks is strong; because an encryption process is embedded into an MPEG coding process, the method is good in instantaneity; and due to the introduction of the inner secrete key, the capacity of the encryption algorithm to resist plain text attacks is strengthened.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Image encryption method based on L-F cascade chaos and 3D bit scrambling
InactiveCN110889877AGuaranteed speedExpand the chaotic intervalImage codingDigital data protectionChosen-plaintext attackKey space
The invention discloses an image encryption method based on L-F cascade chaos and 3D bit scrambling. Image encryption is mainly divided into two steps: (1) 3D bit scrambling encryption and (2) diffusion operation. A novel L-F cascade chaos is constructed, the problem that a blank window exists due to uneven distribution of Logistic is solved while the rapidity of the Logistic is guaranteed, the chaos interval and number of parameters are increased, the secret key space is increased, and the exhaustion attack resistance of the system is improved. According to the method, the randomness of scrambled ciphertext is improved by adopting a 3D cyclic shift bit scrambling mode, and the problem that a bit scrambling sequence is insensitive is solved. According to the method, high-order informationcontaining a large amount of plaintext information and low-order information containing a small amount of plaintext information are separately scrambled, so that the noise attack resistance of the system is improved. According to the encryption system, the plaintext SHA-256 is used for carrying out strong association on the chaotic key, so that the plaintext sensitivity and the capability of resisting the attack of the selected plaintext are effectively improved.
Owner:QIQIHAR UNIVERSITY
Method for pre-distributing wireless sensor network cipher key
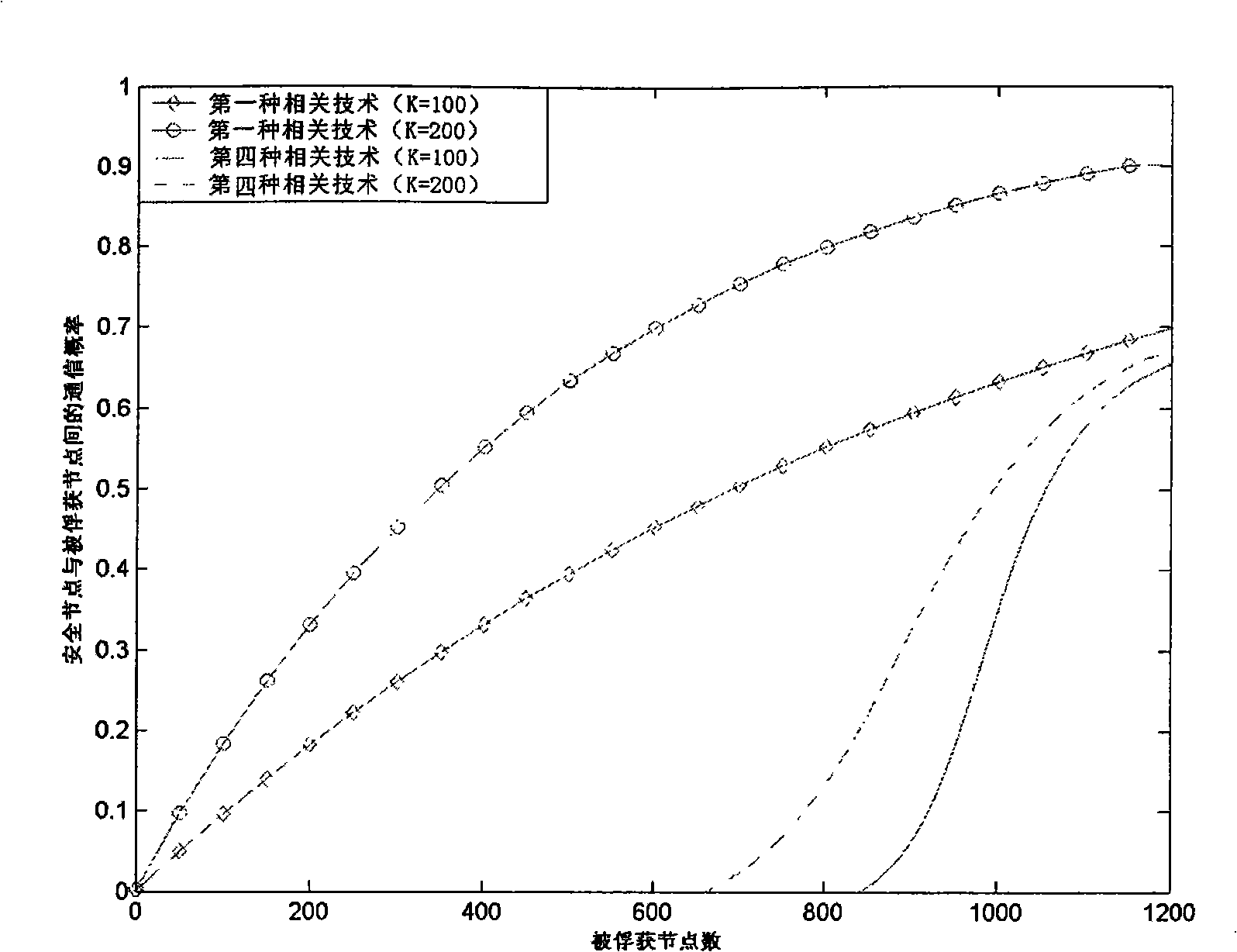
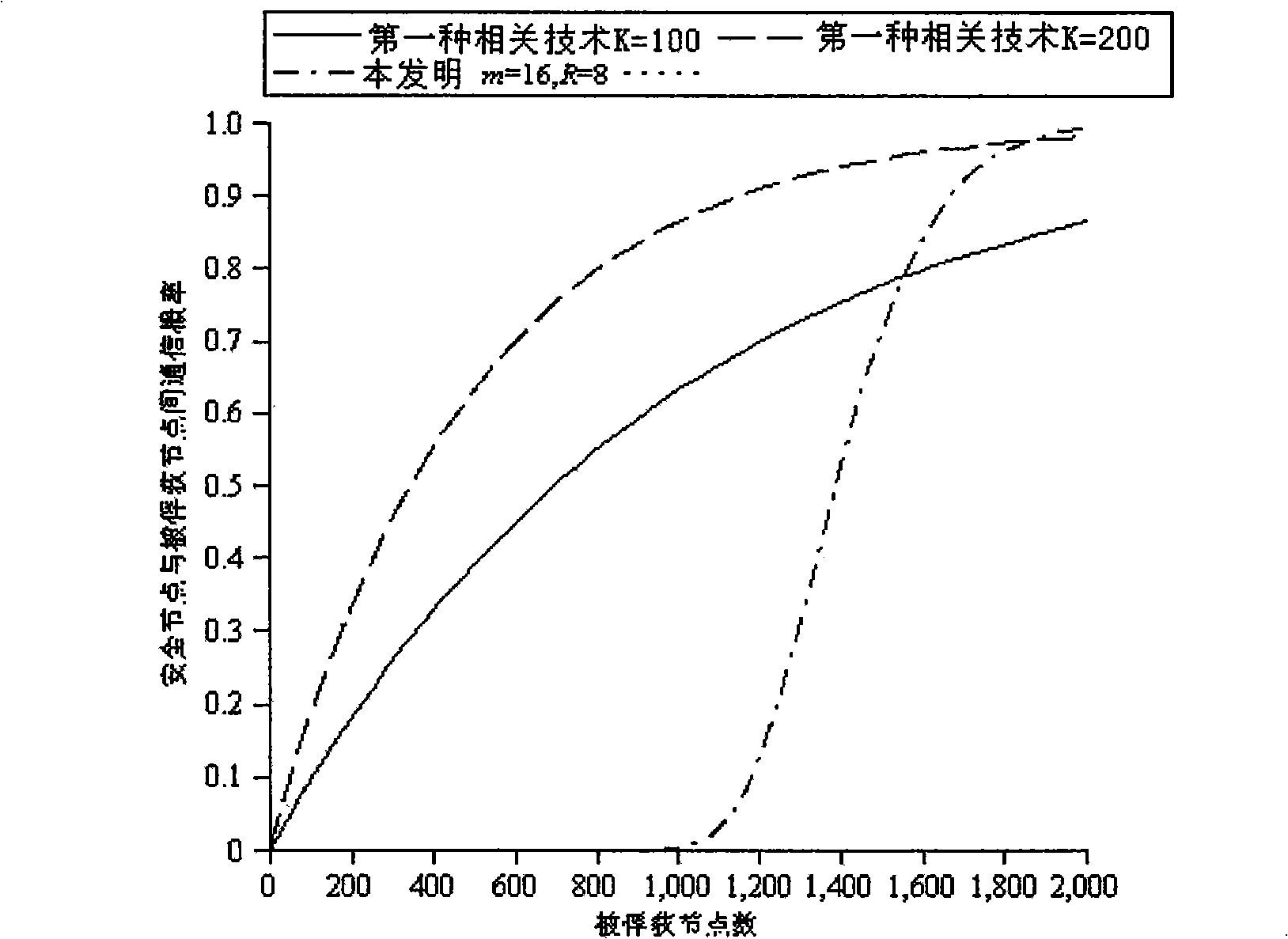
The invention relate to a wireless sensor network key pre-distribution method, which comprises the following steps: step S001: disposition server generating R upper triangular matrixes G and R diagonal matrixes D at random on the finite field GF (q); step S002: generating R groups of real symmetric matrixes K; step S003: saving the ID of every node, row vector seed gir, column vector; step S004: starting base station, and clustering networking; step S005: discovering the shared secret key pair corresponding to secret key space between nodes by pre-distributing secret key; step S006: distributing cluster secret keys with cluster head towards inner-cluster by the constructed shared secret key pair between nodes; step S007: expanding the secret key space dimension. The invention achieves lower node capacity, communication complexity and calculation complexity while ensuring the network completely is communicated; and has higher node anti-capture capability.
Owner:SOUTHEAST UNIV
Multi-image encryption method based on fractional fourier domain phase template multiplexing
InactiveCN103700058AFast convergenceSolve the speed problemImage data processing detailsPictoral communicationMultiplexingMulti-image
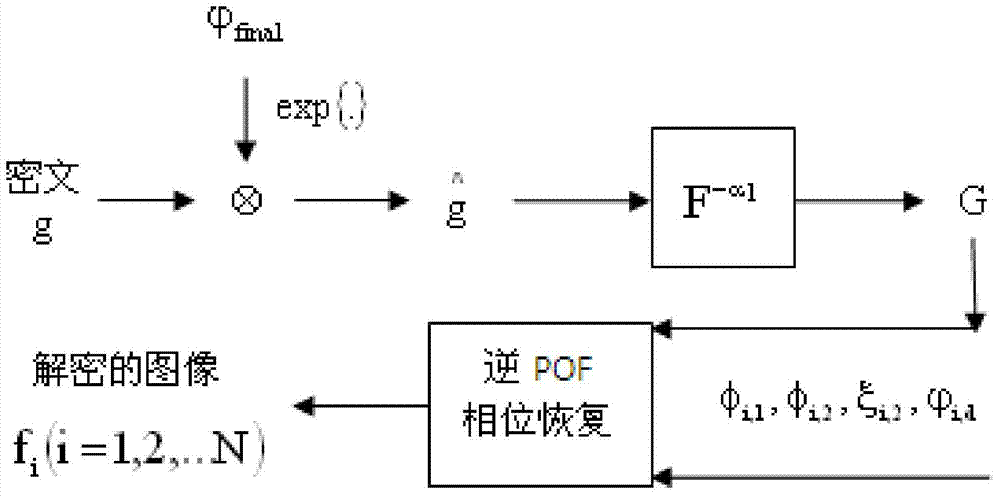
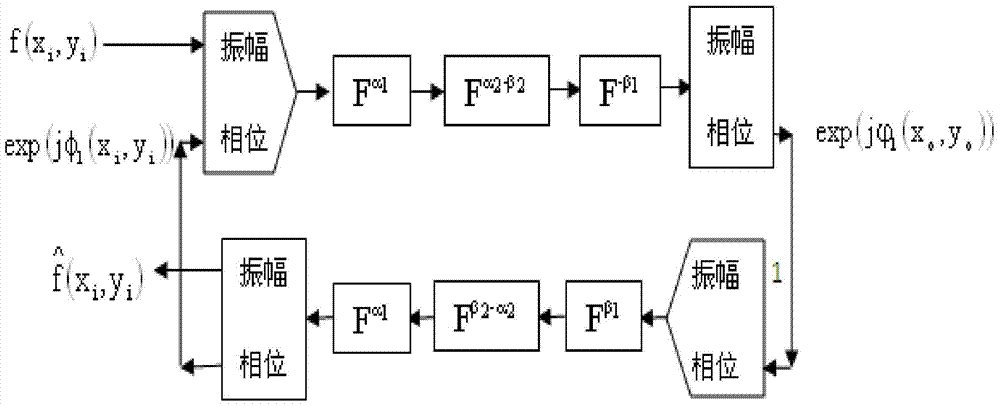
A multi-image encryption method based on fractional fourier domain phase template multiplexing comprises the steps of pure phase extraction, phase modulation and fractional fourier transform. The method applies a fractional fourier domain phase recovery procedure to multi-image encryption, increases a convergence rate of an encryption system, avoids crosstalk noise influence, enlarges a key space, and solves the problems of low convergence rate, crosstalk noise presence and small key space of the existing encryption method, an encryption procedure and a decryption procedure can be realized by an optical method, a system is simple, and the method is convenient to operate.
Owner:XIAN UNIV OF TECH
Image encryption method based on pixel information association of hyperchaotic system
ActiveCN107819580AImprove securityImprove plaintext sensitivityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesComputer visionData information
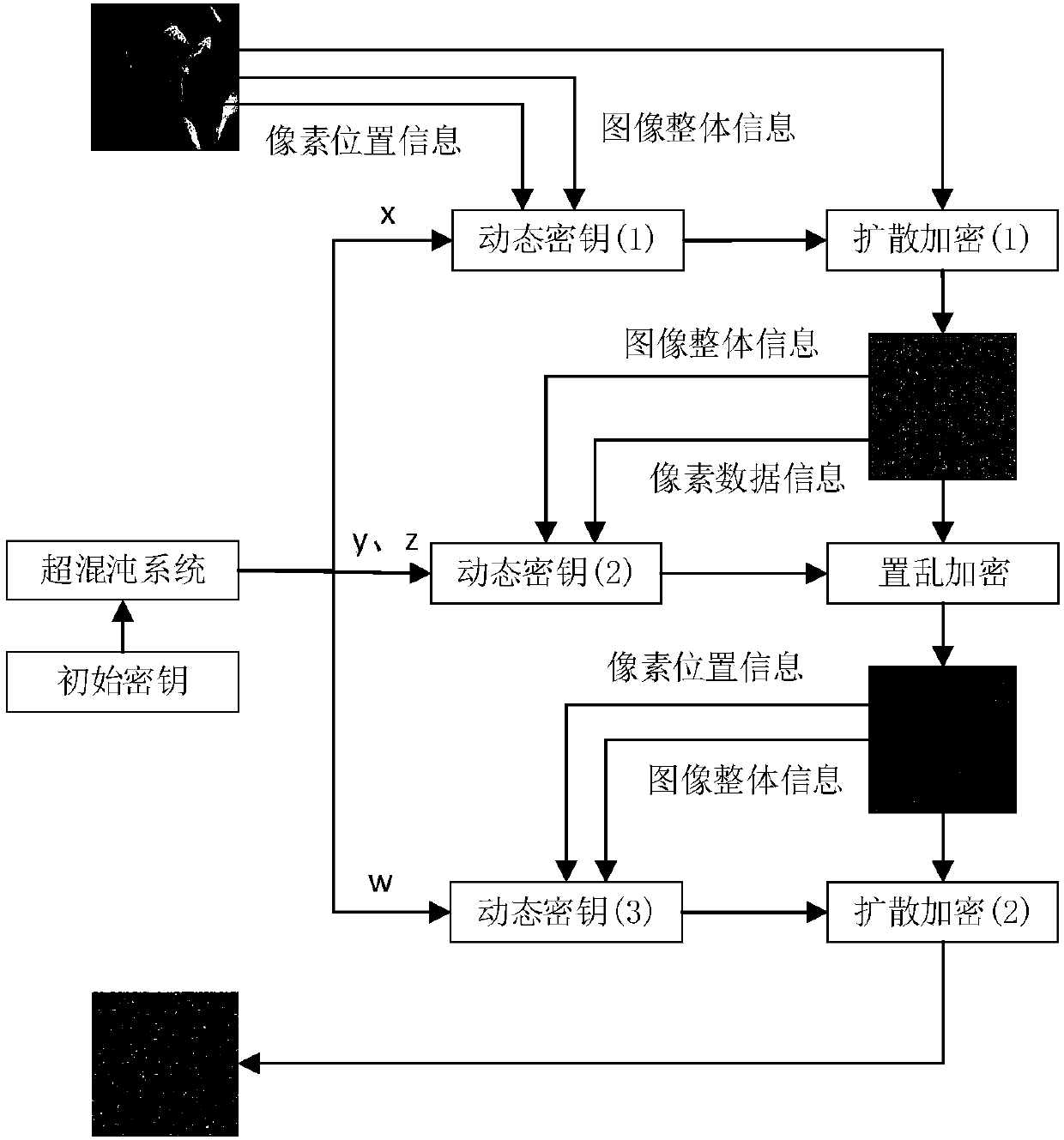
The invention discloses an image encryption method based on pixel information association of a hyperchaotic system. The image encryption method adopts a three-stage encryption structure of image diffusion encryption, image scrambling encryption and image diffusion encryption; each stage of encryption key in the three-stage encryption structure is dynamically generated by different chaos sequencesgenerated by the hyperchaotic system, integral information of an image and information of pixel points; an x chaos sequence generated by the hyperchaotic system and position information of cleartext image pixel points generate a dynamic key for first image diffusion encryption; a key for image scrambling encryption is generated by three parts of y and z chaos sequences generated by the hyperchaotic system. Integral information of a diffusion encrypted ciphertext and data information of the diffusion encrypted ciphertext together; and a chaos sequence w and position information of scrambling encrypted ciphertext pixel points generate a dynamic key for second image diffusion encryption. The image encryption method disclosed by the invention has the characteristics of high cleartext sensitivity, large key space and high ciphertext information entropy.
Owner:BEIJING UNIV OF TECH
Chaotic encryption method and system based on three-dimensional probability forming
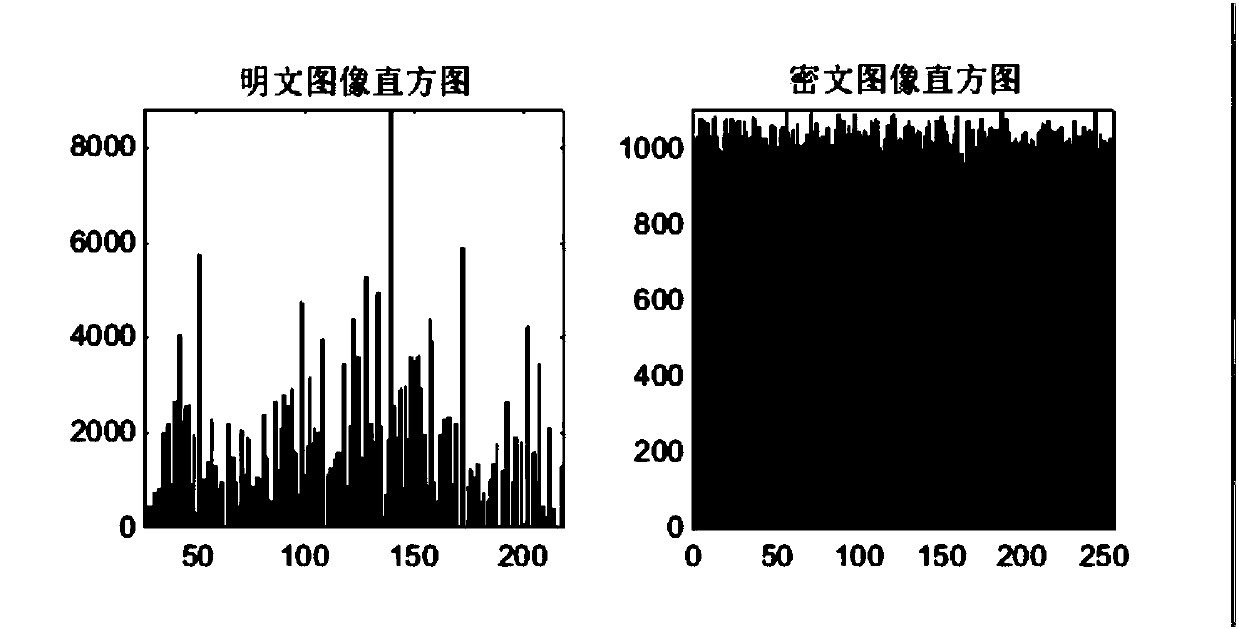
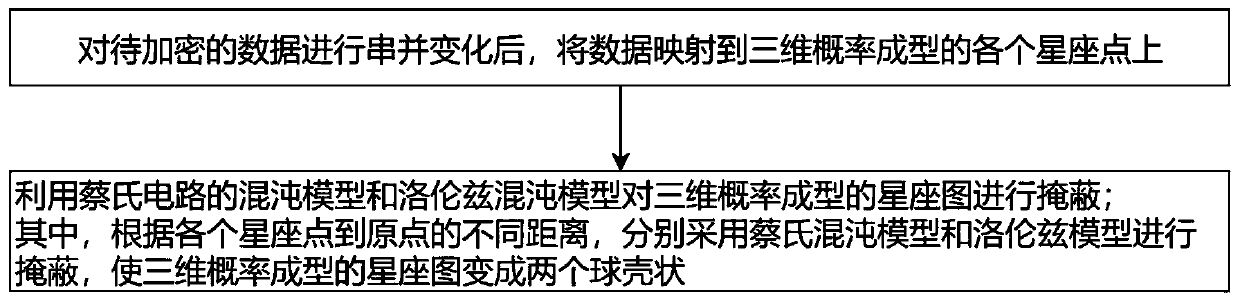
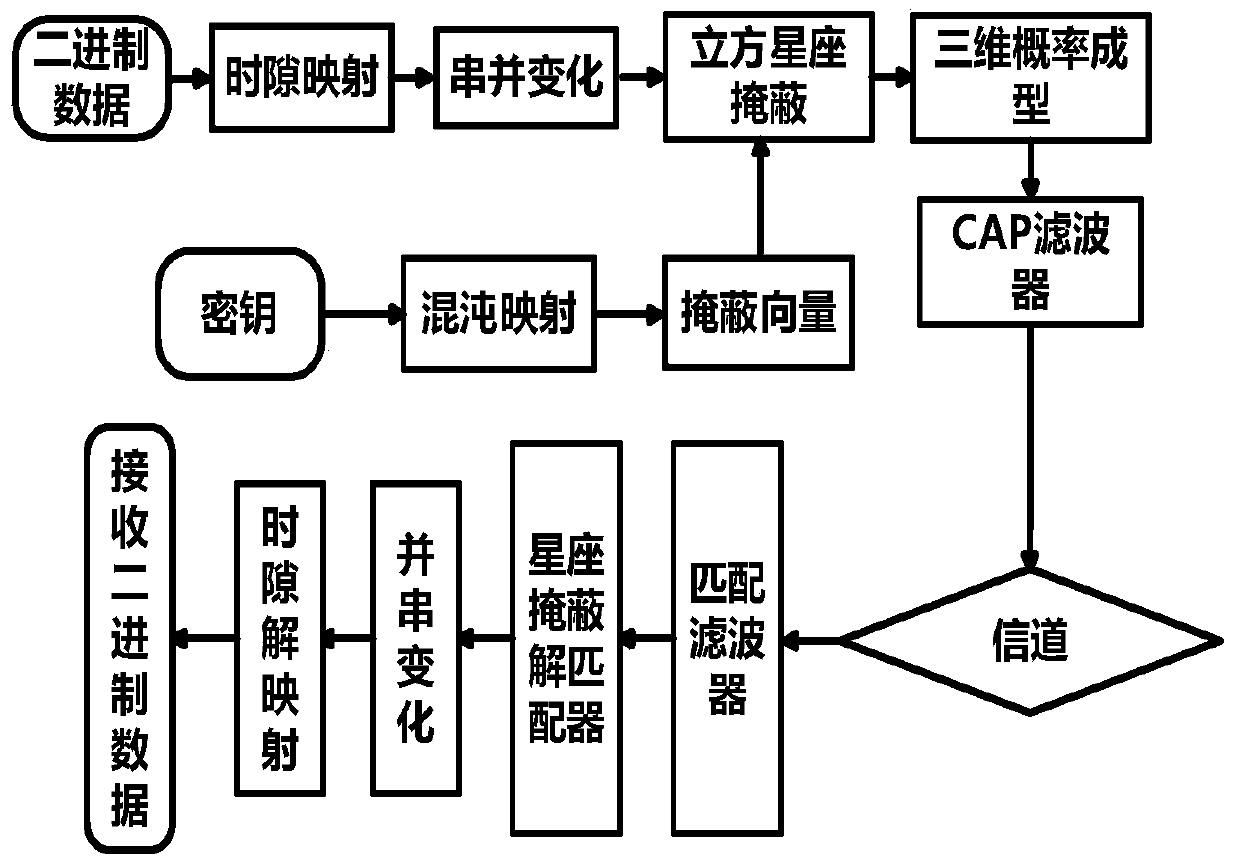
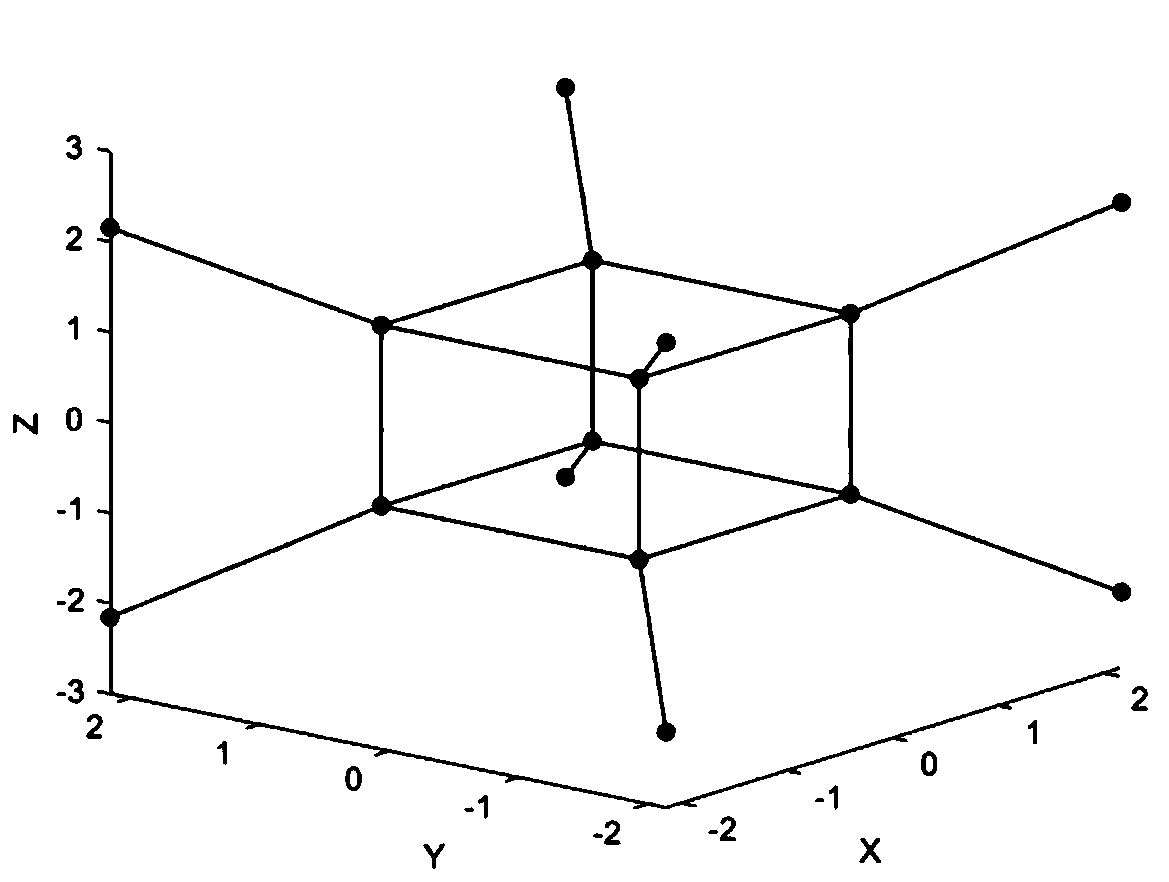
ActiveCN111245596ASuitable for transmissionReduce transmit powerFibre transmissionSecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses a chaotic encryption method based on three-dimensional probability forming, which comprises the following steps: after carrying out serial-parallel change on to-be-encrypted data, mapping the data to each constellation point of three-dimensional probability forming; and masking the constellation diagram of three-dimensional probability forming by utilizing a chaotic model of the Chua's circuit and a Lorentz chaotic model, wherein the Chua's chaotic model and the Lorentz model are respectively adopted for masking according to different distances from each constellation point to an original point, so that the constellation diagram of three-dimensional probability forming is changed into two spherical shells. According to the invention, after spherical three-dimensional probability forming, the transmitting power of the whole system can be greatly reduced, and a new carrier after probability forming has Gaussian energy distribution and is more suitable for transmission of an optical signal in an optical fiber channel; and the Chua's circuit model and the Lorentz model are used for chaotic mapping, compared with a traditional masking mode, the encryption effectis good, and larger key space and higher flexibility are provided.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Method and device for constructing sequential cipher
InactiveCN1694397AImprove security strengthSecuring communicationKey spaceTheoretical computer science
This invention relates to a method for setting up sequence ciphers and a device, the main content is how to generate the cryptographic key sequence including the following steps: appointing a large enough root cryptographic key space to select seeds secretly and appointing steps to determine the current root cryptographic key as the new seed value. A single-way hash transformation is carried out to the current root cryptographic key to get the current frame cryptographic key, the process of generating said key is repeated to get the necessary key sequence and further enhance the randomness of said generated key sequence.
Owner:侯方勇
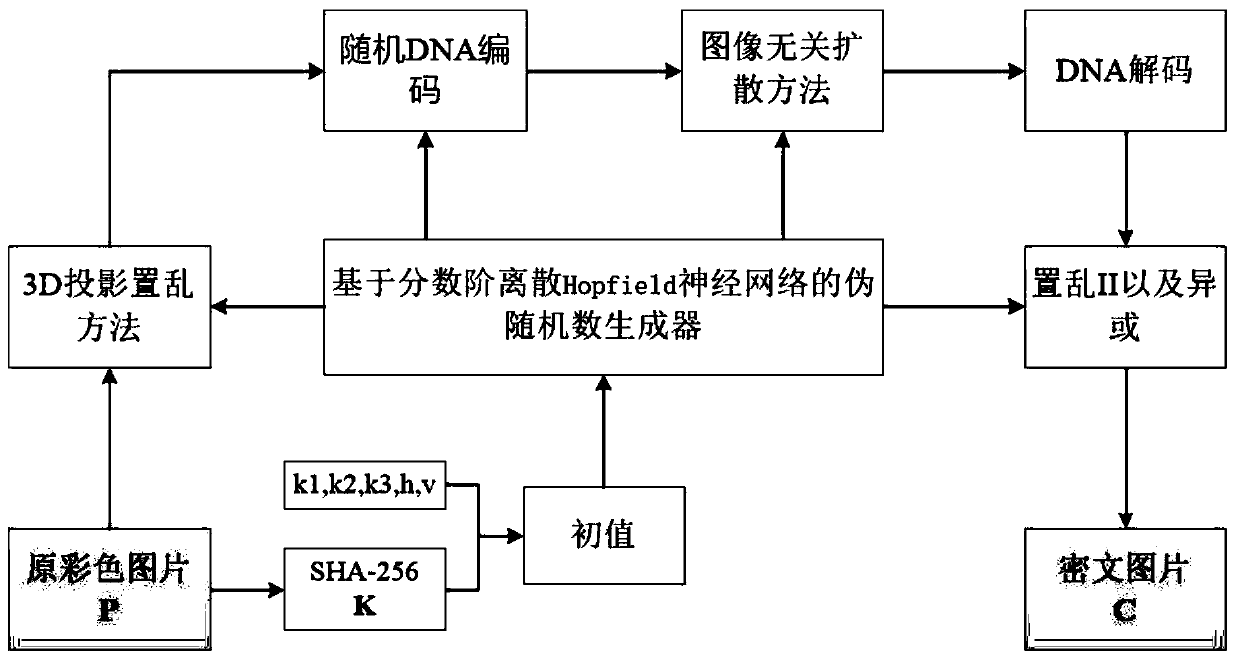
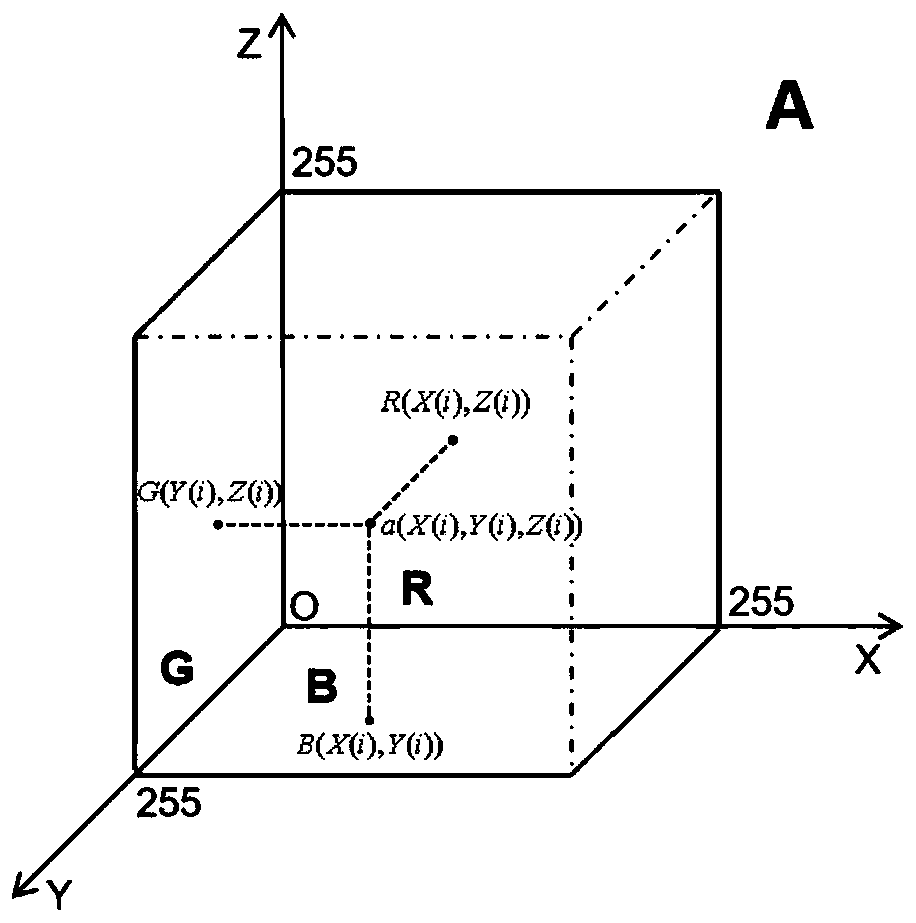
Color image encryption method based on fractional order discrete neural network and DNA operation
ActiveCN110837651AAddress insensitivityDigital data protectionSecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses a color image encryption method based on a fractional order discrete neural network and DNA operation. The method comprises the following steps: S1, establishing an initial value; s2, scrambling pixels among the three color components R, G and B; s3, calculating a DNA code; s4, in order to further improve the encryption security, giving a plaintext-independent DNA diffusionalgorithm based on DNA operation; s5, carrying out secondary scrambling and XOR, wherein secondary scrambling is used for disturbing the positions of elements in the three signal channels. The methodhas the advantages that 1, the problems that the dynamic behavior is not complex enough and the secret key space is small due to the fact that an integer order chaotic system is used in traditional chaotic encryption are solved; 2, the problems of single encryption rule and insensitivity to plaintexts and secret keys of partial DNA encryption algorithms are solved; and 3, the problem that the ciphertext cannot resist noise and information loss attacks in the transmission process is solved; and 4, noise and shear attacks can be dealt with.
Owner:HEFEI UNIV OF TECH
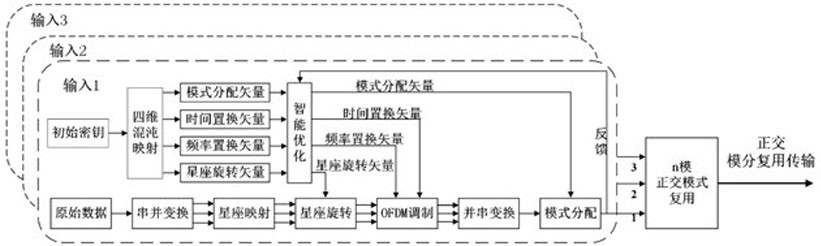
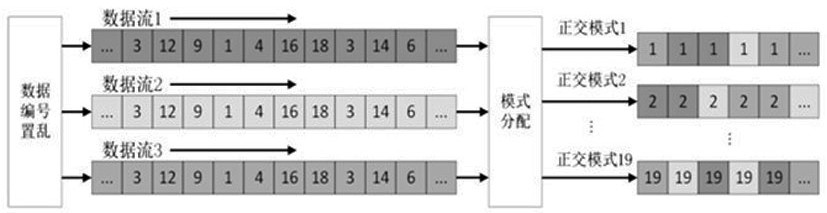
Intelligent optimization four-dimensional chaotic vector encryption orthogonal transmission method
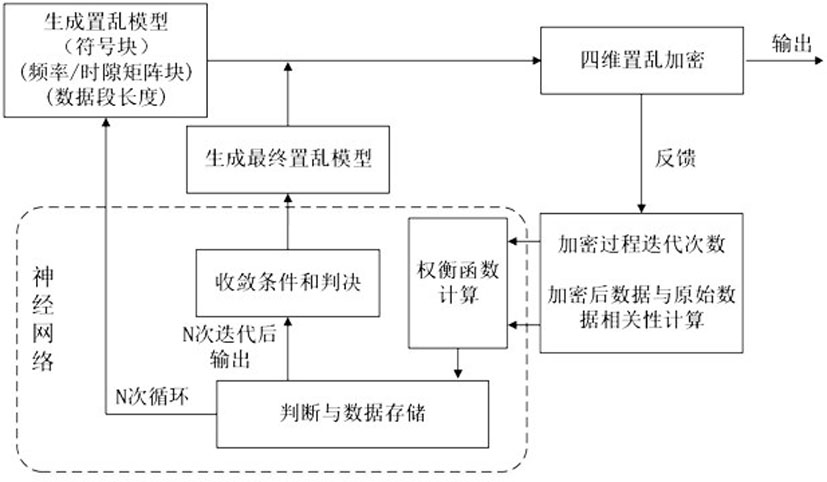
ActiveCN111934848AAchieve coordinated optimizationReduce negative efficiencyOptical mode multiplex systemsFree-space transmissionDigital signal processingCommunications security
The invention discloses an intelligent optimization four-dimensional chaotic vector encryption orthogonal transmission method. The invention belongs to the technical field of information transmission,the method is based on an orthogonal mode division multiplexing transmission system. A communication system is encrypted from four dimensions of communication constellation, OFDM subcarrier frequency, the time and the mode; enough key space can be provided by multi-dimensional hyper-chaotic encryption to provide powerful guarantee for communication security, innovatively utilize machine learningto multi-dimensional encryption optimization, and realize coordination optimization between dimensions, thereby effectively reducing the time of an encryption processing process, and reducing the negative efficiency of the communication system with encryption steps in the digital signal processing module. Compared with a traditional encryption transmission scheme, the scheme provided by the invention has more powerful security guarantee, and the encryption cost is lower.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Key generation method based on deep learning generative adversarial network
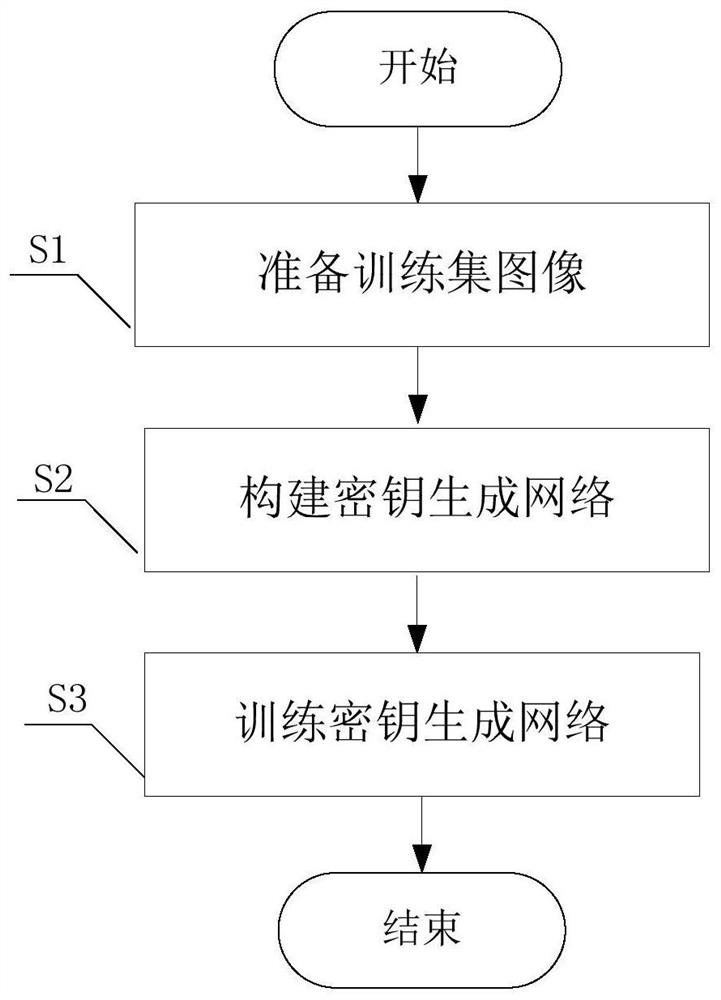
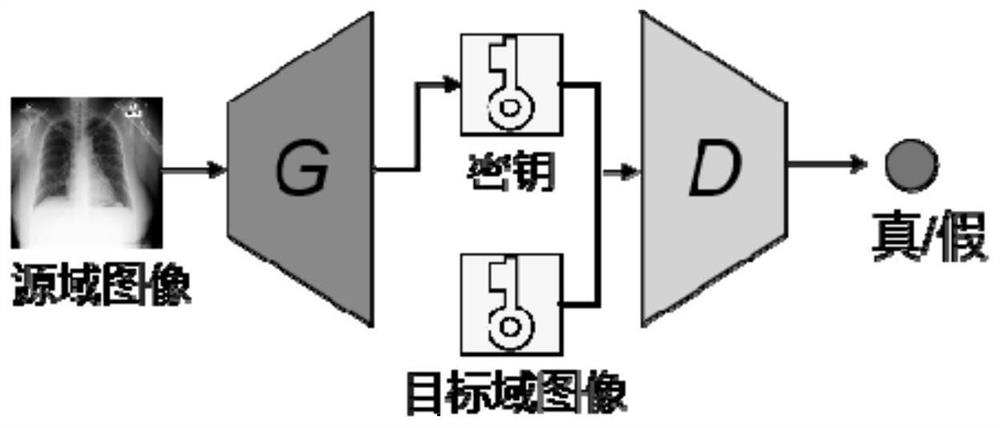
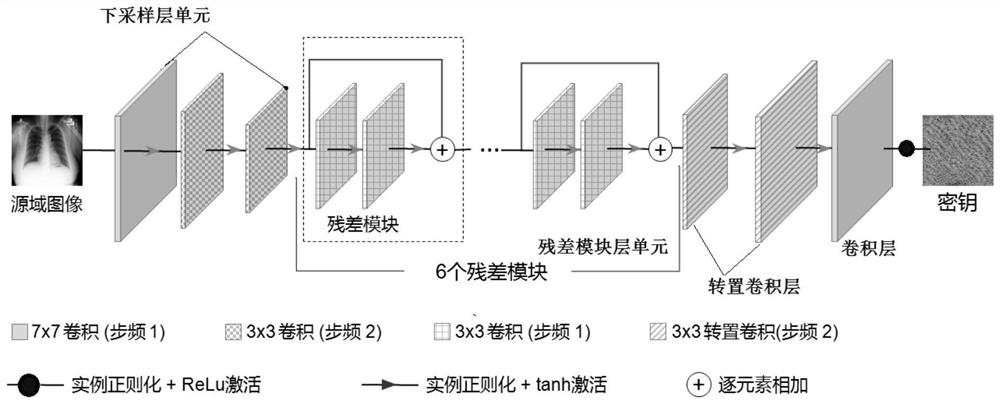
ActiveCN111654368ARealize generationRealize the discrimination functionKey distribution for secure communicationMedical imagesKey spaceGenerative adversarial network
The invention provides a secret key generation method based on a deep learning generative adversarial network, and the method comprises the steps: firstly preparing a training set image; constructinga key generation network: constructing the key generation network according to a generator network and a discriminator network, and inputting the training set image into the key generation network; and training a key generation network: training the key generation network by using a deep learning method to generate a key. The secret key generated by the method has the characteristics of large secret key space, pseudo randomness, one-time pad and sensitivity to an initial value. The method is one of the earliest researches of trying to adopt a deep learning method in the field of key generation, and the generated key is used for encrypting the plaintext medical image, so that relatively high security can be brought.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Color image encryption and decryption method and system based on double-chaos cross diffusion
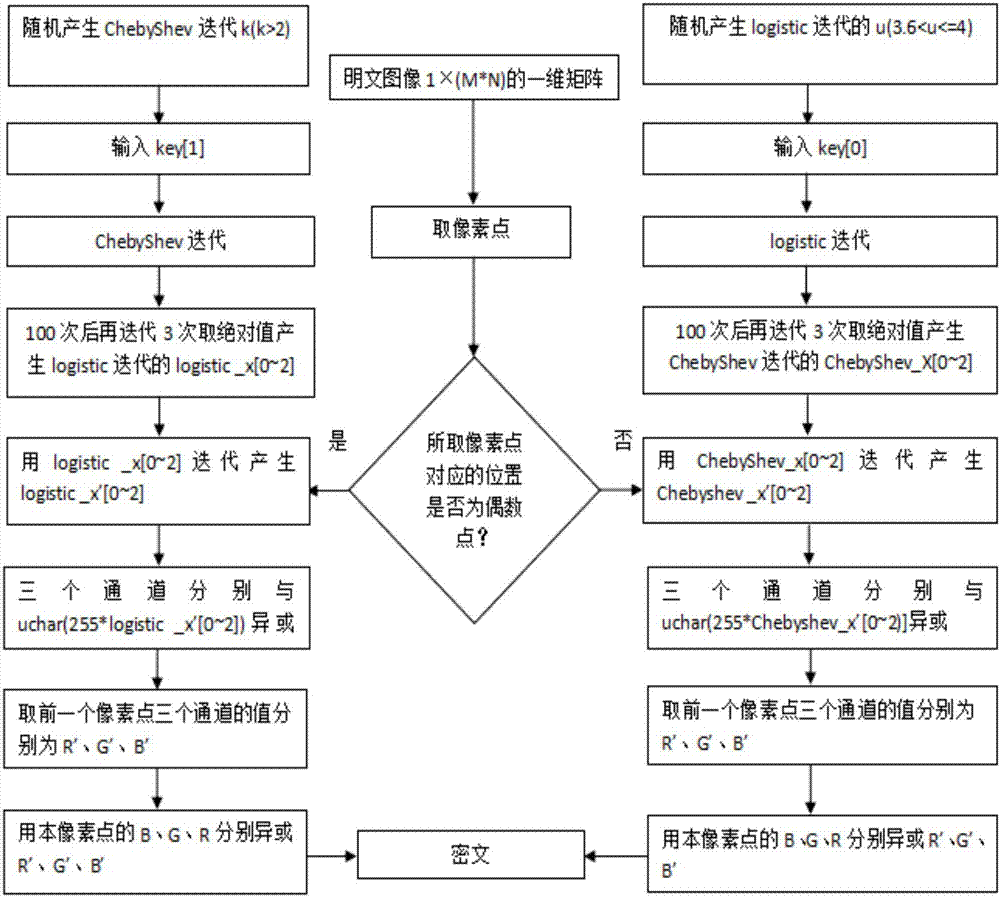
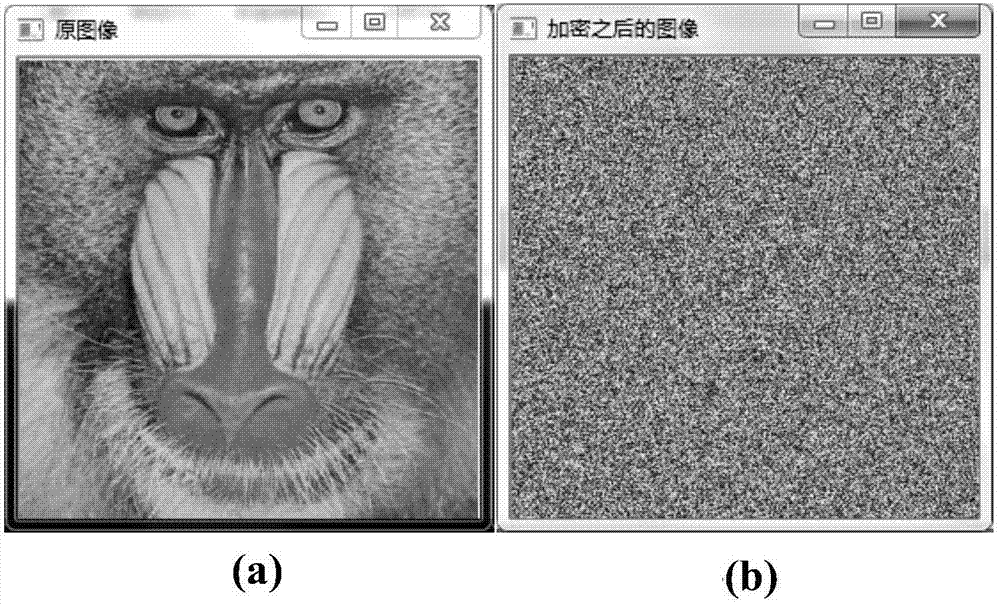
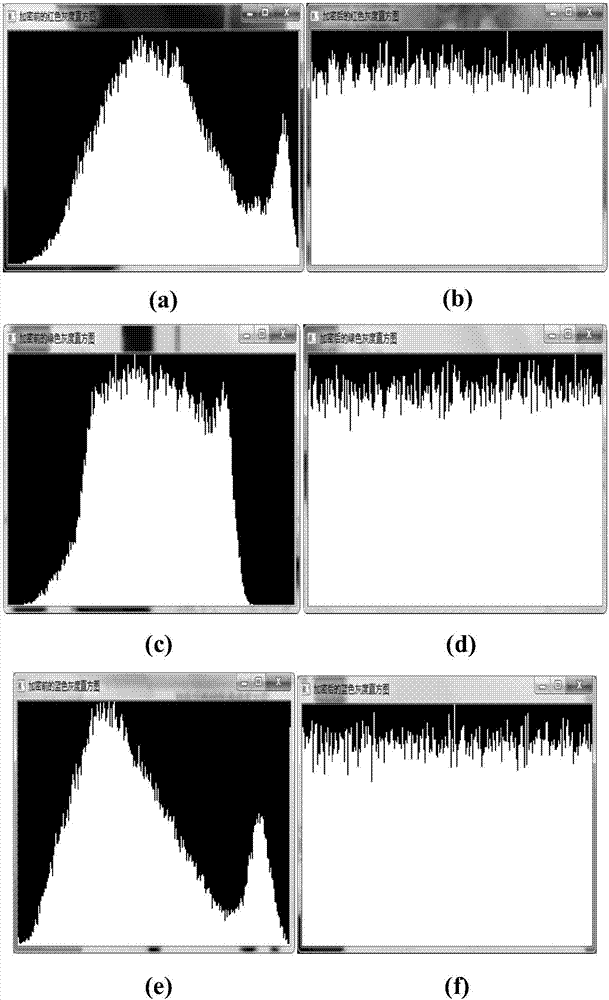
PendingCN107330338AExpand the key spaceDestroy correlationDigital data protectionImage data processing detailsNumeric ValueTablet computer
The invention discloses a color image encryption and decryption method and system based on double-chaos cross diffusion. Firstly, parameters of Logistic and ChebyShev iteration are randomly generated, initial secret keys needed by Logistic and ChebyShev iteration are input, after a transit state is eliminated through multiple times of iteration, Logistic and ChebyShev are used for carrying out iteration three times respectively, iteration results serve as initial secret keys used during encryption respectively, and therefore secret key space is actually increased. Then a pixel point in an image is taken, if the value corresponding to the position of the pixel point is an odd number, an encryption key is obtained through ChebyShev iteration, or else the encryption key is obtained through Logistic iteration, and therefore the dependency between adjacent pixel points is reduced. Then R, G and B channels of the pixel point and R', G' and B' of the former encrypted pixel point are subjected to difference or operation for diffusion. The iteration frequency is reduced on the premise of guaranteeing safety, the encryption time can be shortened, efficiency is improved, and the method and system are especially suitable for image encryption of mobile equipment such as mobile phones and tablet computers with the high real-time performance requirement.
Owner:HENGYANG NORMAL UNIV
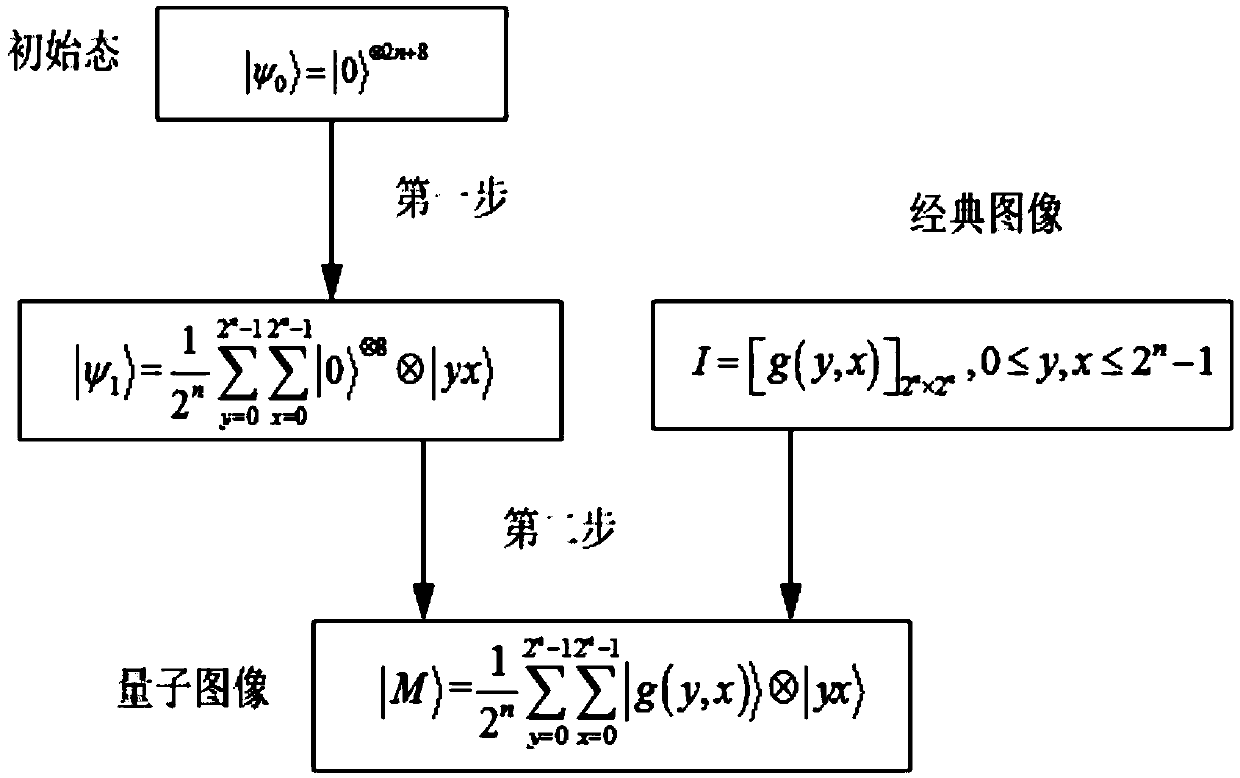
Hyperchaotic system based quantum image encryption method
ActiveCN105373739AImprove resistance to attackImprove securityChaos modelsDigital data protectionComputer hardwareQuantum
The invention discloses a hyperchaotic system based quantum image encryption method. The method comprises: finishing quantum image encryption by utilizing CNOT operation to realize XOR operation of a quantum image, namely, generating a hyperchaotic sequence by a Chen's hyperchaotic system, controlling unit transformation and NOT gate by a processed hyperchaotic sequence to construct CNOT transformation, and then, utilizing the CNOT operation to realize the XOR operation of the quantum image, thereby finishing the quantum image encryption. According to the method, the XOR operation of the quantum image is constructed for the first time and applied to the quantum image encryption, so that the attack resistance and security of an encryption algorithm can be enhanced; an initial condition of the Chen's hyperchaotic system serves as a secret key of the encryption algorithm, so that the effect of expanding secret key space is achieved; and the algorithm can resist strong attack, so that the secret key is easier to allocate, store and memorize.
Owner:NANCHANG UNIV
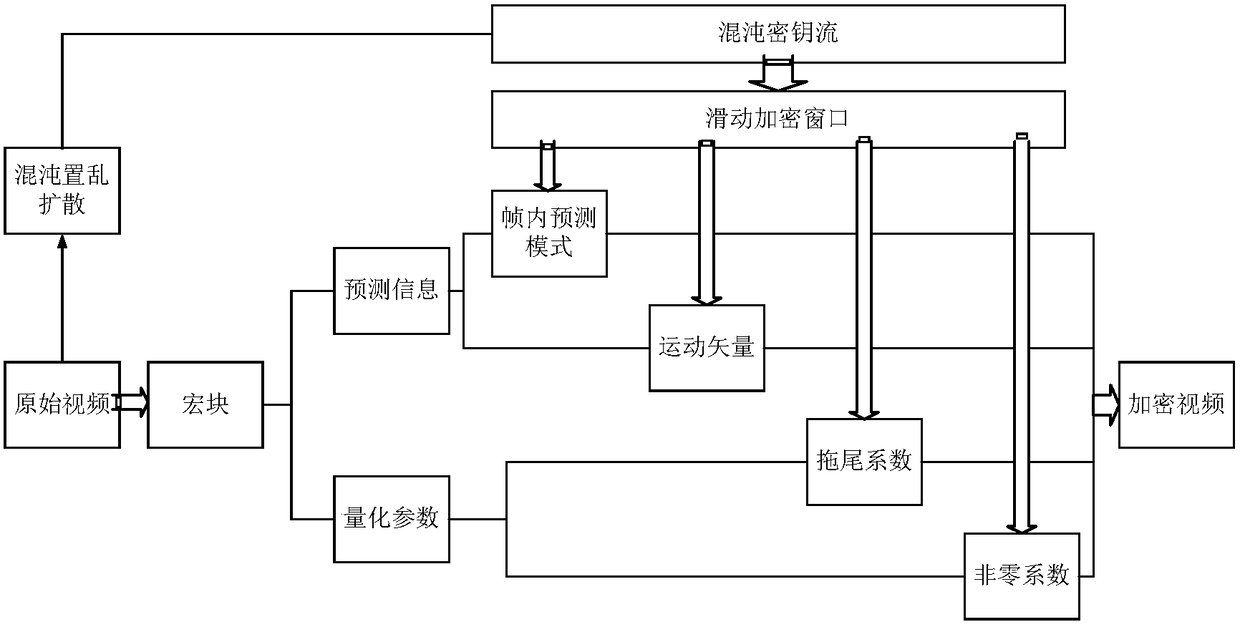
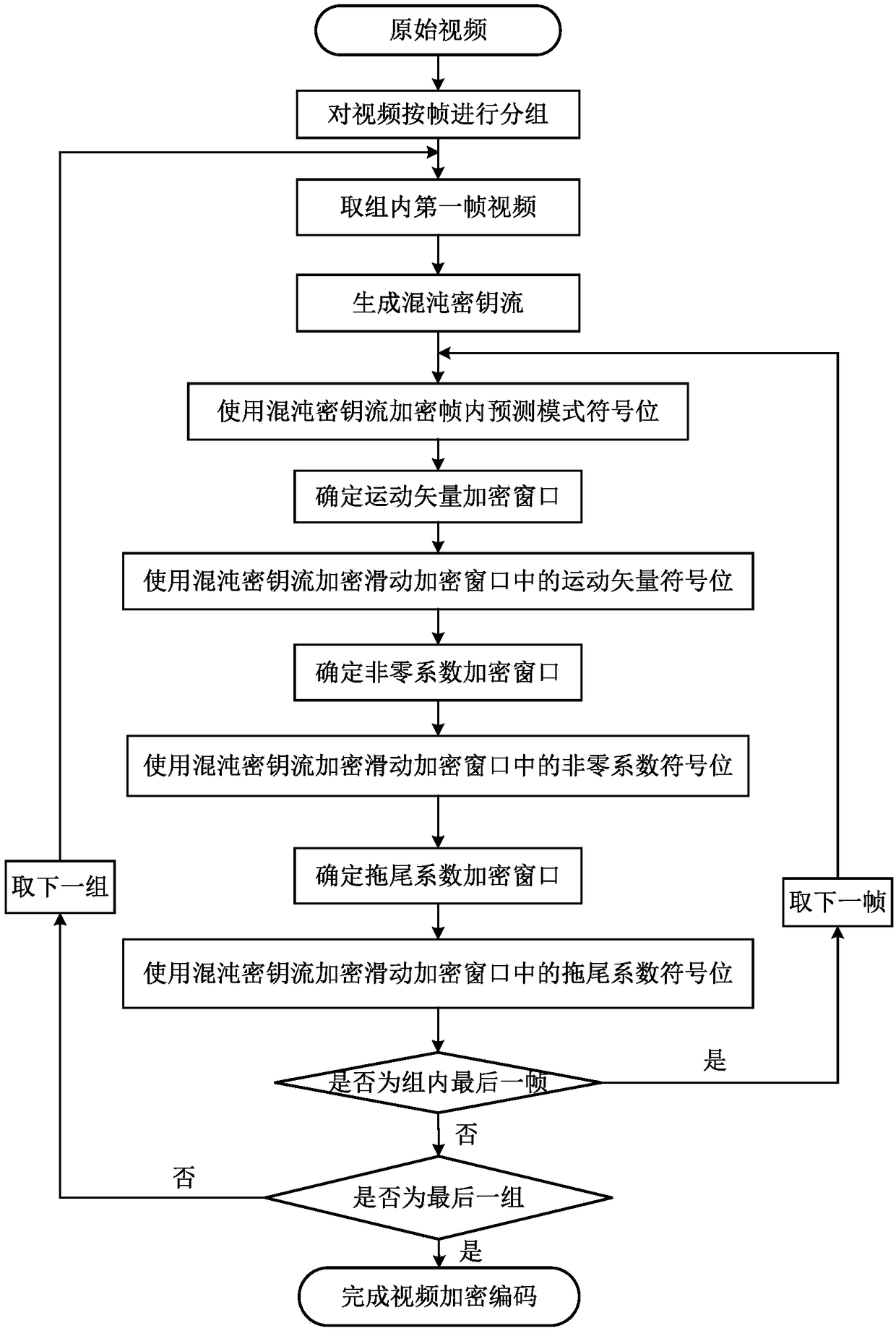
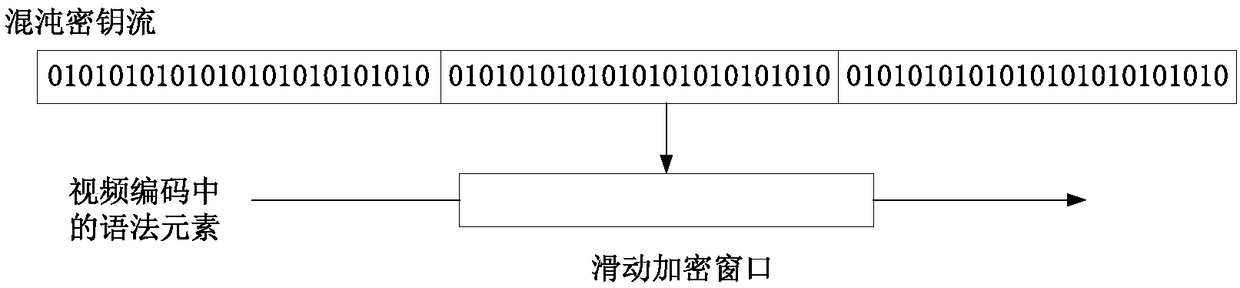
Chaotic video encryption method based on sliding encryption window
ActiveCN108199823AGood pseudorandomnessGood unpredictabilitySecuring communication by chaotic signalsDigital video signal modificationChaotic systemsComputer hardware
The invention relates to the technical field of video encryption, and provides a chaotic video encryption method based on a sliding encryption window, which aims to solve the problems of high encryption computation overhead, contradiction between a high speed and high safety of video encryption and the like of the conventional video encryption method. The method has the advantages that a chaotic system and video encryption are combined, so that an enormous key space and extremely high key sensitiveness are achieved, the anti-attack performance of the encryption method is improved, and complexnon-linear dynamic properties are obtained; while high safety is guaranteed, the sliding encryption window is utilized to select the optimum and the most effective encryption key data, so that the operation speed and the encryption efficiency are high; and compared with a selective video encryption method without the sliding encryption window, the method can reduce the computation overhead by above 86%.
Owner:CHANGCHUN UNIV OF SCI & TECH
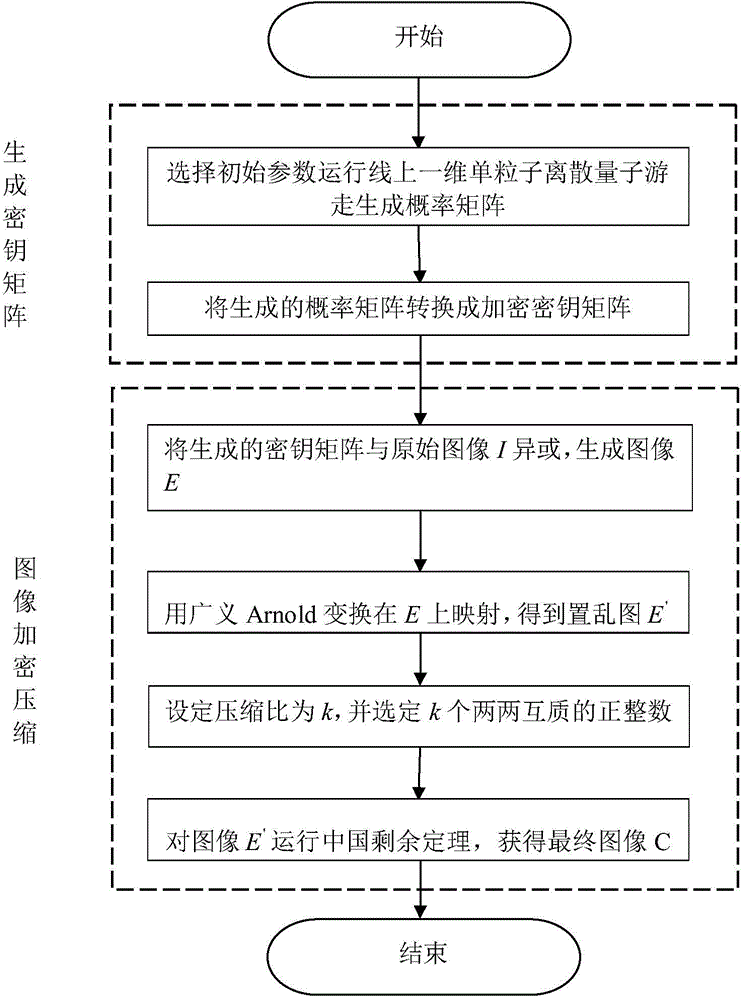
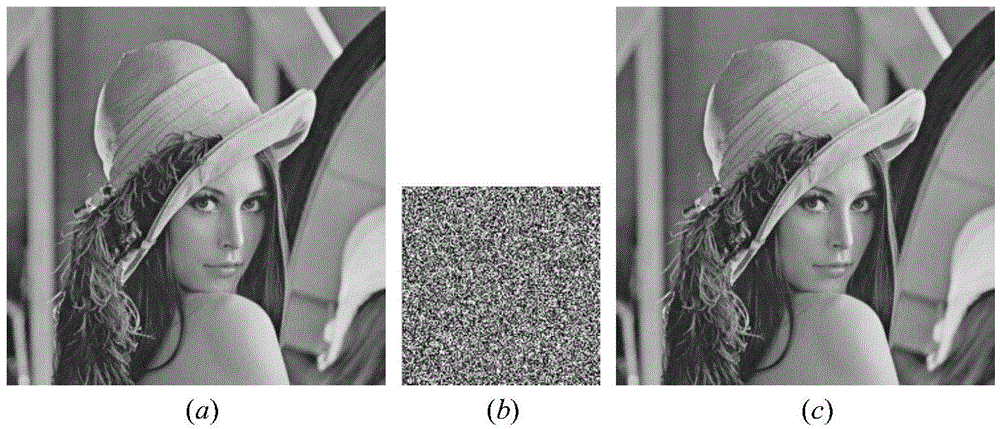
Image encryption compression method based on discrete quantum walk and Chinese remainder theorem
InactiveCN103957418ALarge key spaceCiphertext correlation is lowDigital video signal modificationKey spaceArnold transformation
The invention relates to an image encryption compression method based on a discrete quantum walk and a Chinese remainder theorem. The method comprises two phases: a secret key generation phase, i.e., generating probability distribution by use of a linear single particle one-dimensional discrete quantum random walk (QRW), and converting the probability distribution into a secret key matrix capable of encryption; and an image encryption compression phase, i.e., compressing an image by use of the generated secret key matrix and the Chinese remainder theorem. XOR operation is performed on an obtained encryption secret key and an original image, afterwards, Arnold transformation is performed on an obtained image. Diffusion and compression are carried out on a scrambling image according to a given compression ratio k by use of the Chinese remainder theorem. Compared to an image encryption compression scheme based on chaos and optics, the method provided by the invention has higher safety and better compression performance. The greatest advantage of the algorithm is that a theoretical infinite large secret key space can be generated so as to oppose a violent attack capability. Various performance comparisons indicate that the algorithm is better than prior research and can better satisfy actual demands.
Owner:BEIJING UNIV OF TECH
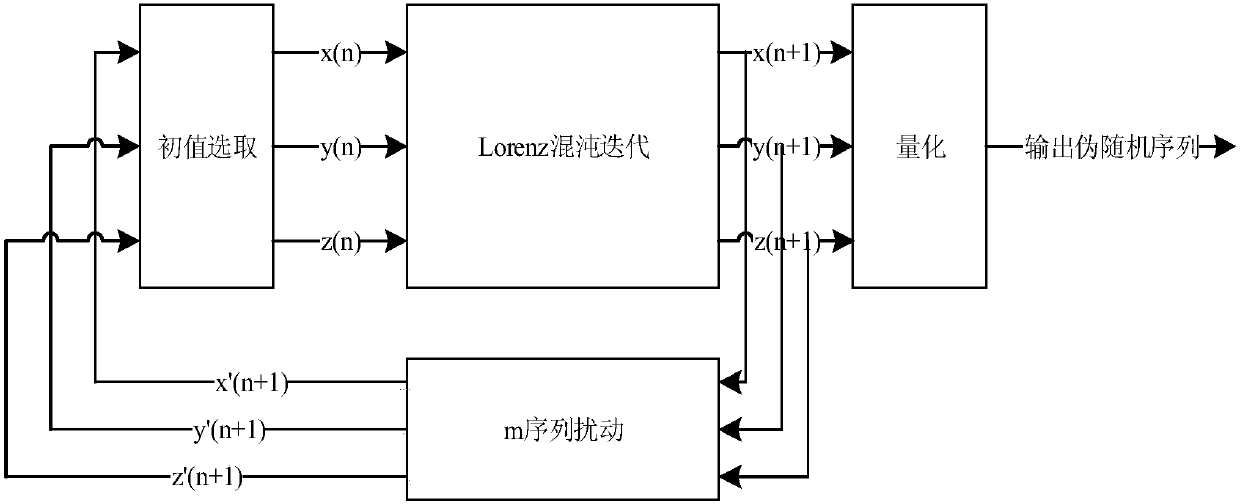
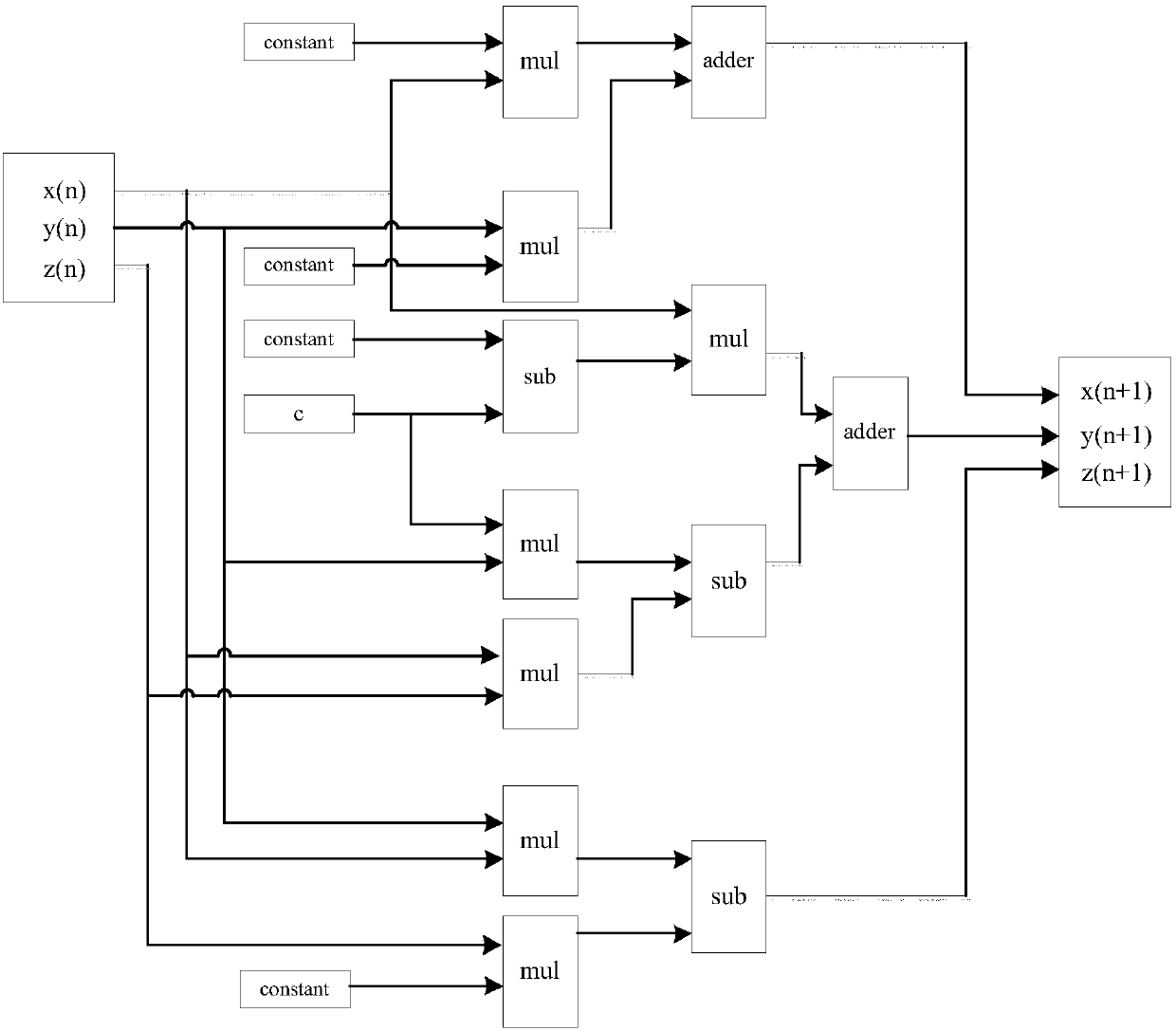
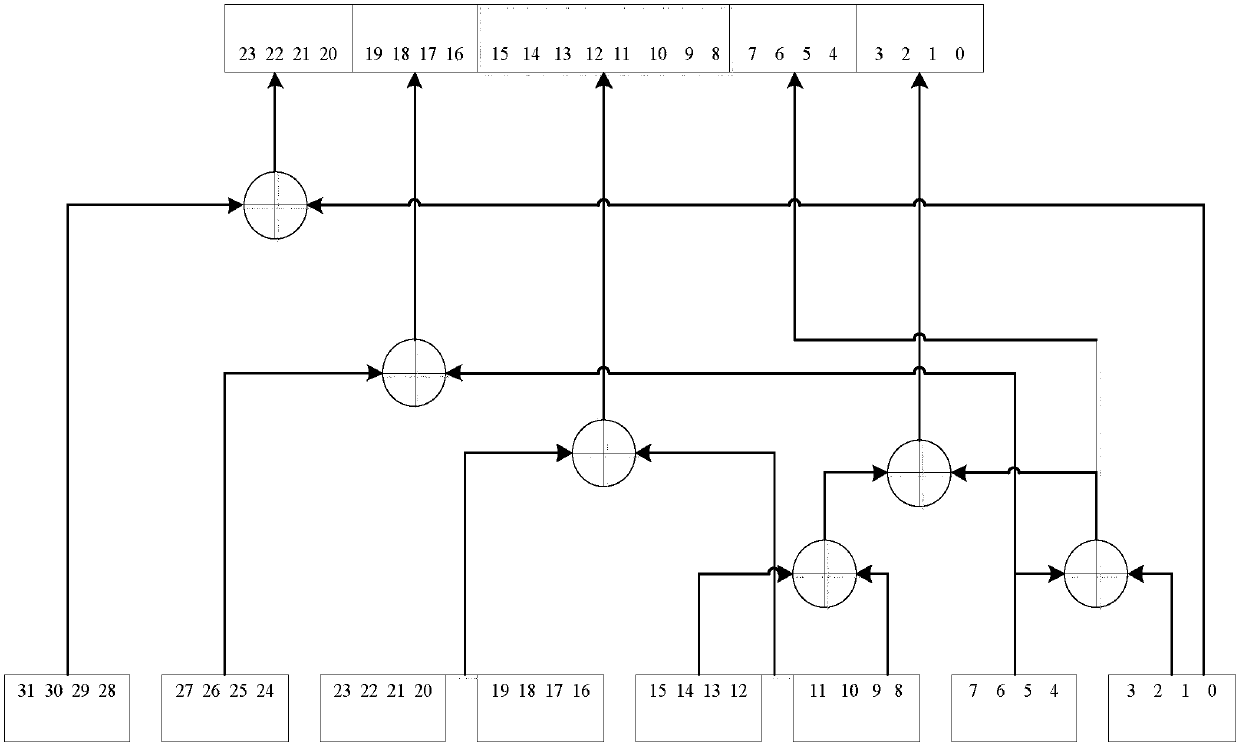
Lorenz chaotic pseudo-random sequence generator based on m sequence
InactiveCN107678729AImprove randomnessIncrease resource consumptionRandom number generatorsChaoticSequence design
Owner:SOUTHEAST UNIV
Image encryption method and device, electronic equipment and readable storage medium
ActiveCN110912674AAvoid the phenomenon of degenerative diffusionLarge key spaceEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsKey spaceEngineering
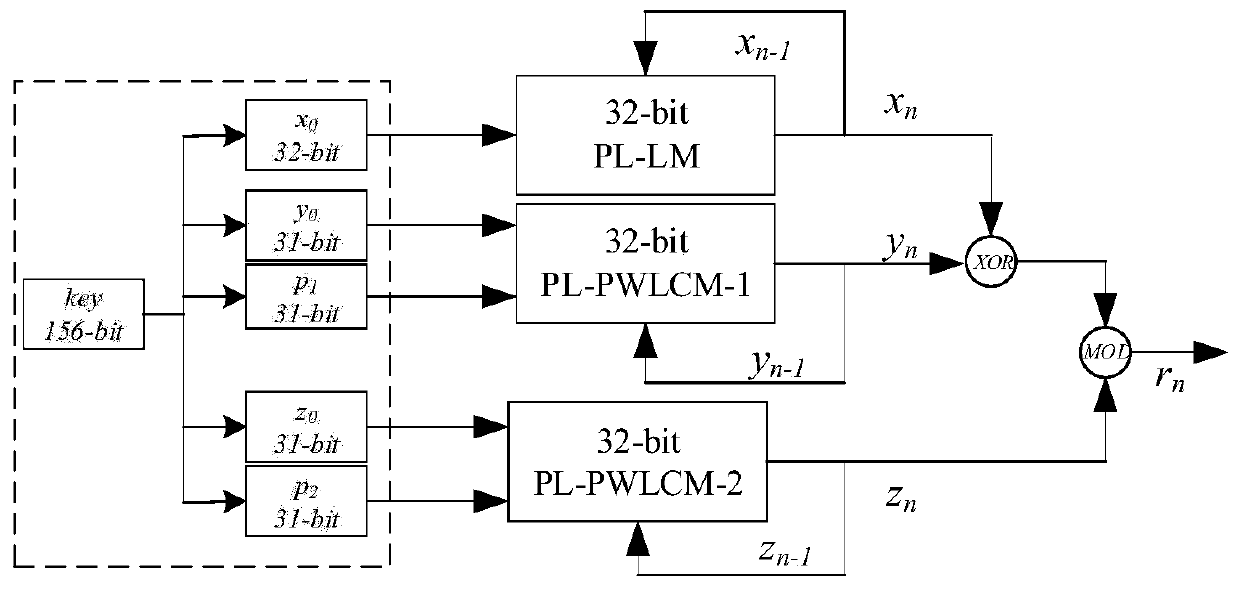
The invention provides an image encryption method and device, electronic equipment and a readable storage medium. The method comprises following steps of acquiring a first pseudo-random sequence and asecond pseudo-random sequence with preset lengths by connecting a hybrid chaotic system in parallel in a precision limited mode; processing the first pseudo-random sequence with the preset length toobtain a first permutation matrix and a first diffusion matrix; according to the first permutation matrix, replacing the to-be-encrypted image by a square formed by four adjacent pixel points as a unit to obtain a first image after replacement; and performing row diffusion and column diffusion on the replaced first image according to a first diffusion matrix to obtain an intermediate result image,and performing a second round of replacement and diffusion on the intermediate result image through the same method to obtain an encrypted image. With the method, the secret key space is increased, the operation speed is increased, higher safety is achieved, and the calculated amount during replacement and diffusion can be reduced.
Owner:ZHUHAI DAHENGQIN TECH DEV CO LTD
Hyper-chaotic system-based secret key dynamic selection image encryption algorithm
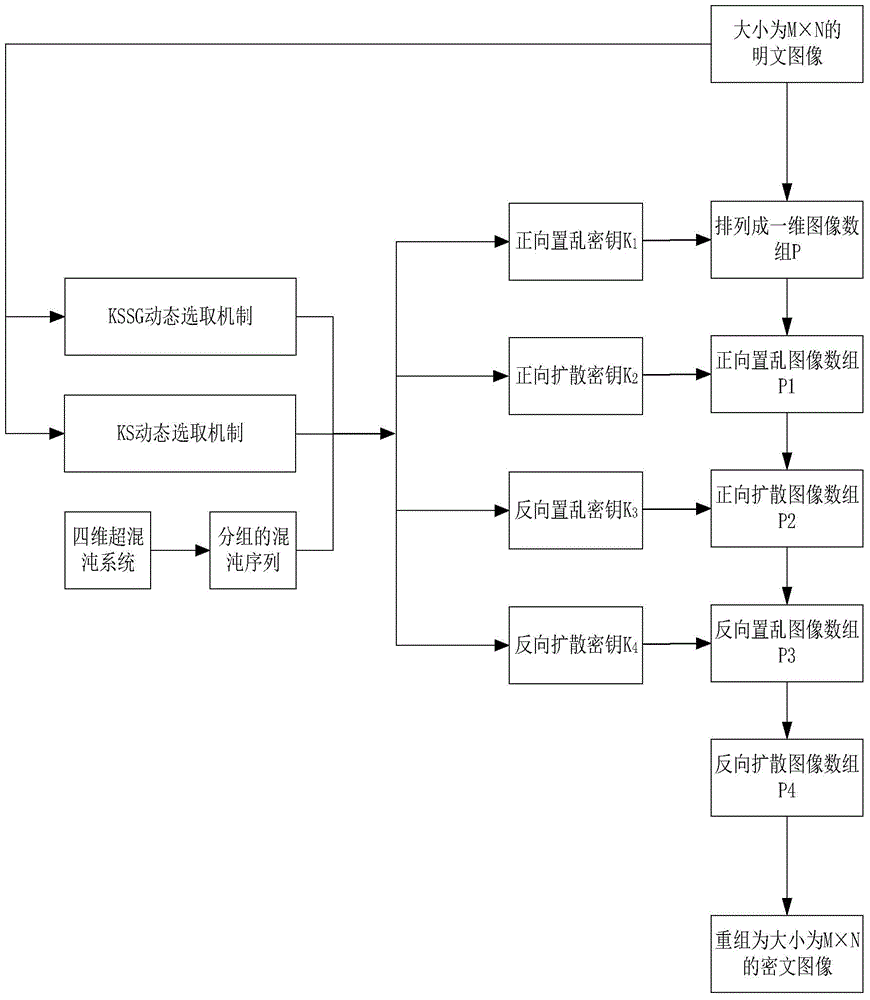
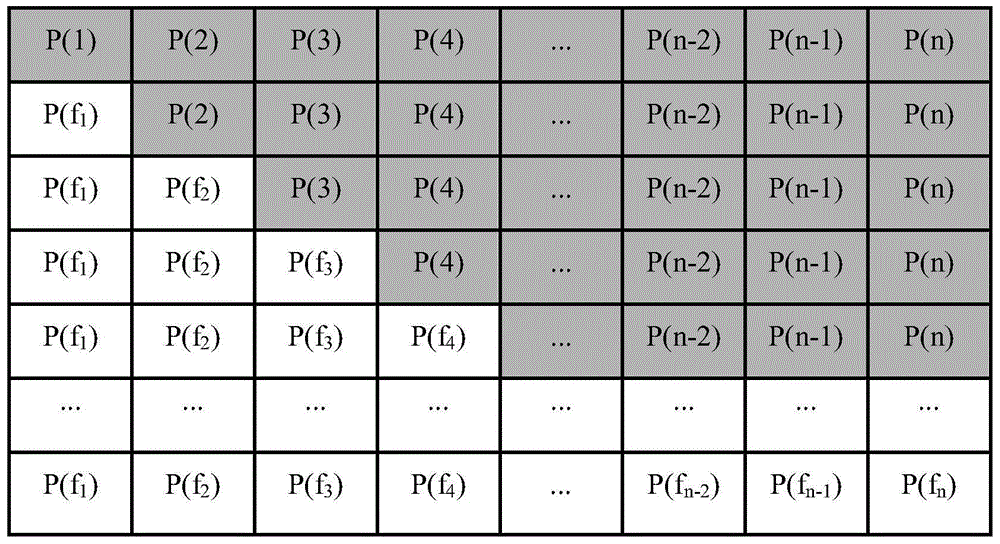
The invention relates to a hyper-chaotic system-based secret key dynamic selection image encryption algorithm. The algorithm mainly comprises the following steps of arranging original plaintext images into an image array P, using a hyper-chaotic system to generate a chaotic sequence, and performing grouping; generating a forward scrambling secret key K1 with the combination of a KSSG and KS dynamic selection mechanism based on a plaintext and performing forward scrambling of the P to obtained P1; generating a forward diffusion secret key K2 with the combination the KSSG and KS dynamic selection mechanism and performing forward diffusion of the P1 to obtain a P2; generating a backward scrambling secret key K3 with the combination of the KSSG and KS dynamic selection mechanism and performing backward scrambling of the P2 to obtain a P3; and generating a backward diffusion secret key K4 with the combination the KSSG and KS dynamic selection mechanism, performing forward diffusion of the P3 to obtain a P4, and performing regrouping of the P4 to obtain a final cryptograph image. The abovementioned method provided by the invention increases the secret key space, enables the security, the encryption effect and the secret key sensitivity to be higher and the anti-attach performance to be stronger, and is easy in hardware implementation.
Owner:HENAN UNIVERSITY
Qi super chaotic video encryption method based on FPGA
InactiveCN107612676AProcessing speedTake up less resourcesSelective content distributionSecuring communicationChaotic systemsVideo streaming
The invention discloses a Qi super chaotic video encryption method based on an FPGA, and belongs to the technical field of real-time video encryption. The method comprises the steps that a 144-bit secret key is input through an upper computer; through a serial port sending module, a Qi super chaotic system receives the secret key, and the Qi super chaotic system is controlled through an encryptionand decryption key to generate a pseudo random sequence; super chaotic encryption and decryption are conducted on video streaming data collected by a camera and an explicit address of a SDRAM; the data is cached by the SDRAM, and a video is displayed by a VGA. According to the method, an FPGA hardware mode is adopted, so that collection, display and super chaotic double encryption of the video are achieved, the video is smoothly displayed, elapsed time is short, few resources are occupied, the encryption effect is good, and secret key space is large; the method is mainly used for real-time video encryption.
Owner:TIANJIN POLYTECHNIC UNIV
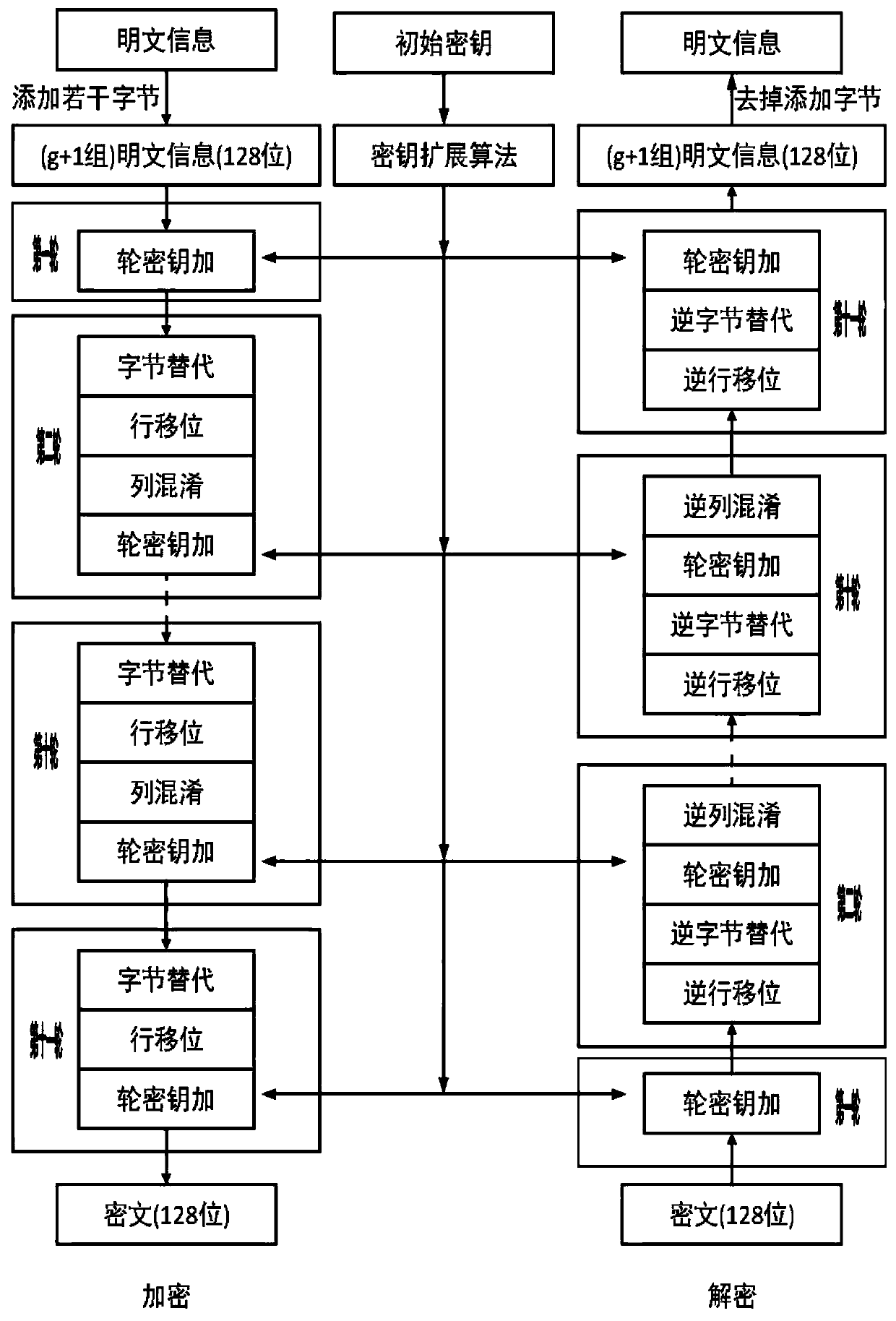
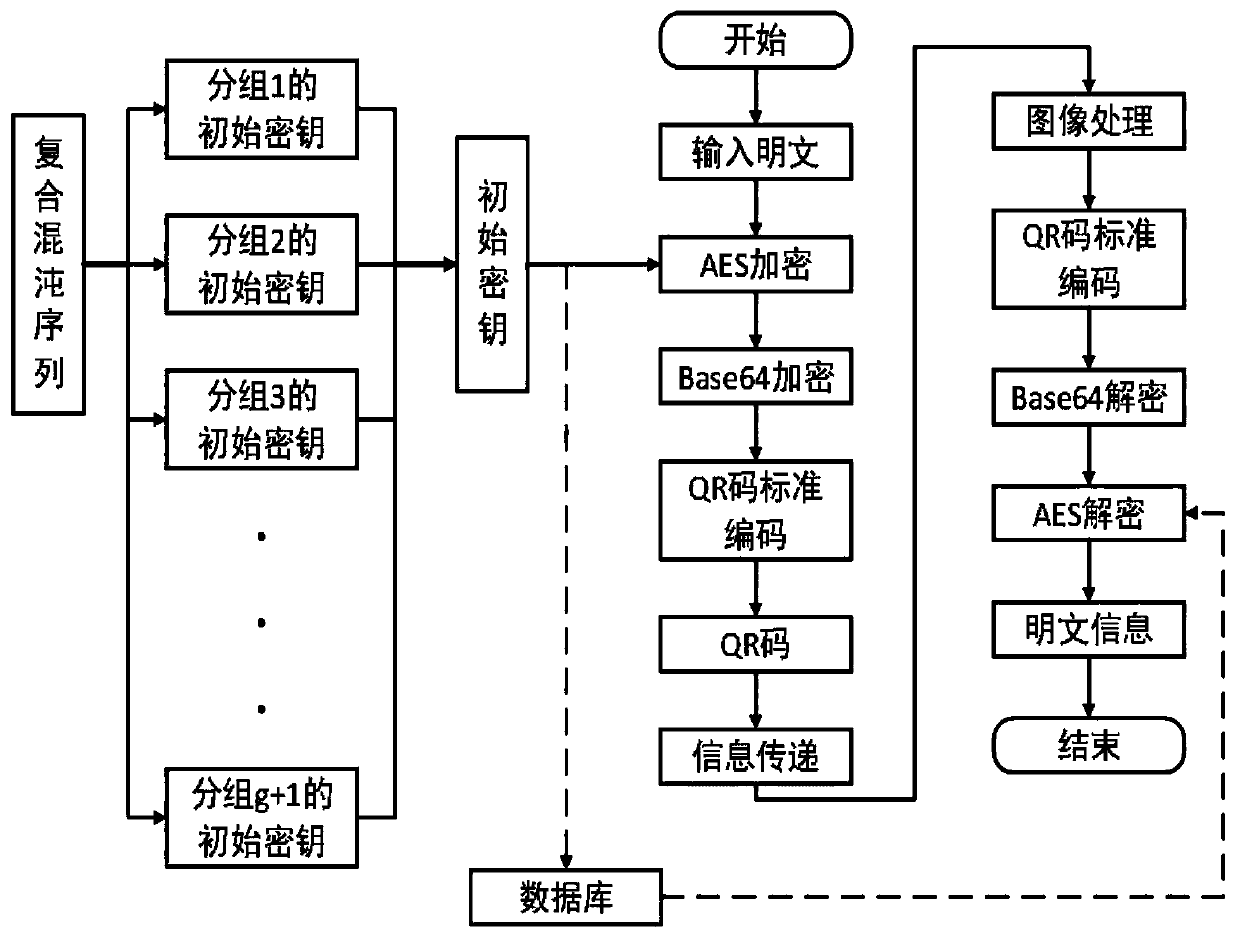
Power battery traceability management code encryption method based on improved AES algorithm
InactiveCN111262684AImprove encryptionGuaranteed symbol structureEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPlaintextKey space
The invention provides a power battery traceability management code encryption method based on an improved AES algorithm. The power battery traceability management code encryption method comprises thefollowing steps: step 1, grouping plaintext information; step 2, generating an initial key by using a two-dimensional composite chaotic sequence, and performing AES algorithm improved encryption; step 3, carrying out Base64 secondary encryption; step 4, carrying out QR coding; step 5, conducting a decryption process. According to the invention, a two-dimensional composite chaotic sequence is combined with a traditional AES encryption algorithm, and an improved AES encryption algorithm is provided. One group initial key correspondingly encrypts one piece of QR code plaintext information, the security problems of fixed initial secret keys, mutual derivation among the secret keys and secret key space determination in a traditional AES encryption algorithm are effectively eliminated, the decryption difficulty is increased, the confidentiality and privacy of the QR code information are greatly improved, the information of a power battery is effectively protected, data sharing among power battery maintenance, fault analysis, equipment accessories and battery storage is achieved, and scientific and refined management is achieved.
Owner:YANSHAN UNIV
Watermark encryption and decryption algorithm based on chaotic neural network
PendingCN110766595ALarge key spaceImprove securityImage data processing detailsNeural architecturesKey spaceAlgorithm
The invention relates to a watermark encryption and decryption algorithm based on a chaotic neural network, and belongs to the technical field of information hiding. The characteristic that Logistic chaotic mapping is extremely sensitive to an initial value and the good approximation effect of the Chebyshev neural network are utilized, and an LCNN network is established to encrypt the watermark, so that the security of the watermark is ensured. The network weights obtained by the LCNN neural network during each operation are different, and the secret keys for watermark encryption are also different, so that the encryption algorithm obtained based on the LCNN has a large secret key space, and the security is high. Besides, when the chaos initial value is slightly changed, the secret key isgreatly changed, the encrypted watermarks obtained after encryption are different from one another, the expected goal of one-time pad can be achieved, and the safety of the algorithm is improved.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
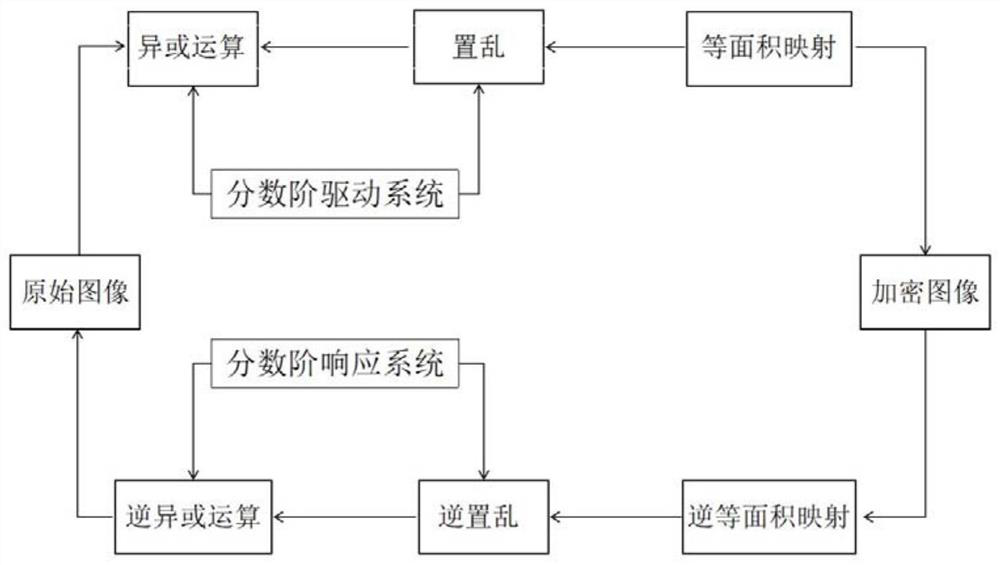
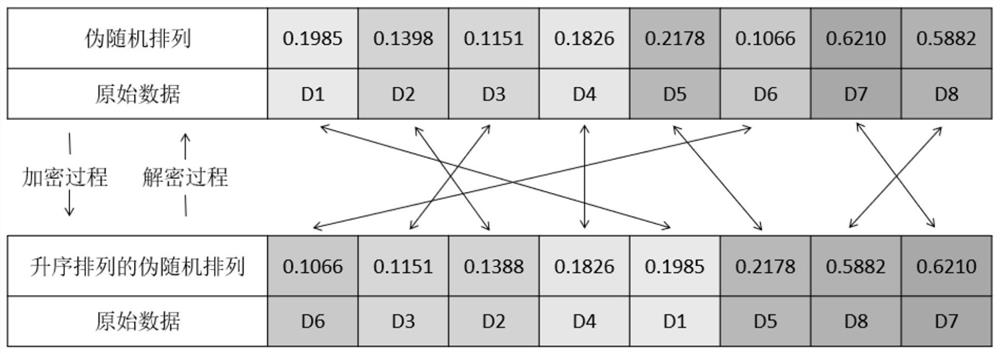
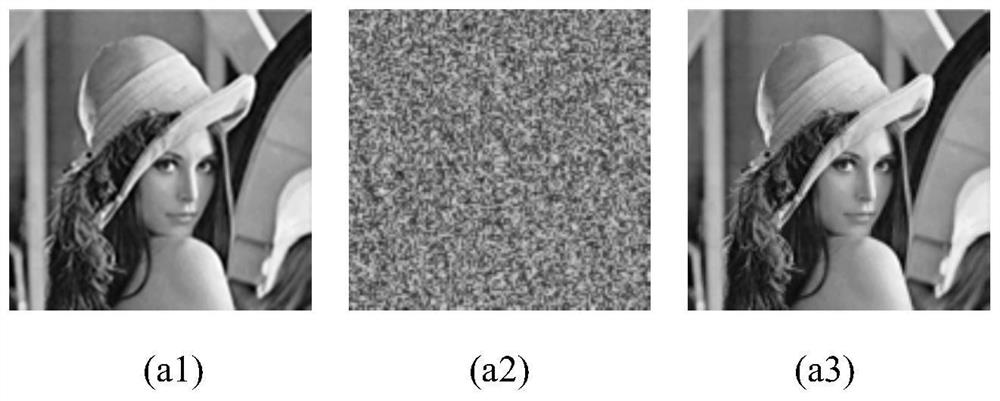
Image encryption method based on finite time synchronization of fractional order driven response system
ActiveCN113556223AEnsure safetyGuaranteed confidentialitySecuring communication by chaotic signalsCryptographic attack countermeasuresColor imageKey space
The invention provides an image encryption method based on finite time synchronization of a fractional order driving response system. The method comprises the steps of reading a three-dimensional color image to obtain a color component matrix; obtaining chaos signals based on a fractional order driving system, and carrying out resampling to obtain a discrete chaos sequence; arranging and recombining the discrete chaotic sequence according to a column mode to obtain a two-dimensional array, and normalizing the two-dimensional array to obtain a pseudo-random matrix; performing binary XOR operation on the color component matrix by using a pseudo-random matrix to obtain a color component matrix encrypted for the first time; performing scrambling operation on the color component matrix encrypted for the first time and a pseudo-random matrix to obtain a color component matrix encrypted for the second time; and performing equal-area mapping scrambling on the color component matrix encrypted for the second time to obtain a final encrypted image color component matrix. The method has the advantages of large key space, high sensitivity and high attack resistance, and can effectively ensure the security and confidentiality of the encrypted image.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com