Image two-grade encrypting method based on double-chaos system
An encryption method and double-chaos technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as difficulty for attackers to identify original images, weak security functions, small key space, etc., and achieve enhanced resistance to known plaintext Attack capability, overcoming the small key space, and expanding the effect of the key space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
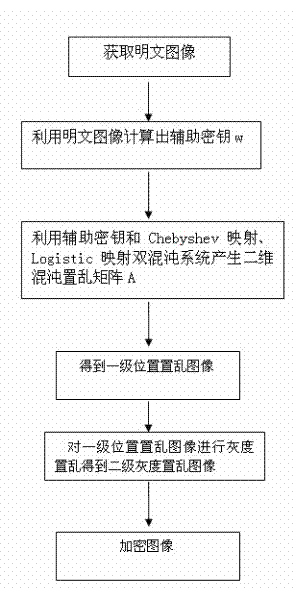
[0052] Such as figure 1 Shown in the present invention is a kind of image secondary encryption method based on double chaotic system, comprising the following steps:
[0053] S1: Obtain the plaintext image, and use the plaintext image to generate an auxiliary key w. The specific method is: set the size of the plaintext image to be encrypted as M×N, sum the gray values of all pixels in the plaintext image, and calculate 20001 Take the remainder to get an auxiliary key w between [0,20000], the formula is as follows:
[0054]
[0055] In the formula, Indicates the gray value of the corresponding pixel in the image, , Indicates the coordinates of the pixel, the M indicates that there are M pixels in the horizontal direction of the plaintext image, and N indicates that there are N pixels in the vertical direction of the plaintext image.
[0056] S2: Using the auxiliary key w combined with Chebyshev mapping and Logistic mapping double chaotic system to generate an M×N ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com