Patents
Literature
73 results about "Multiple attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
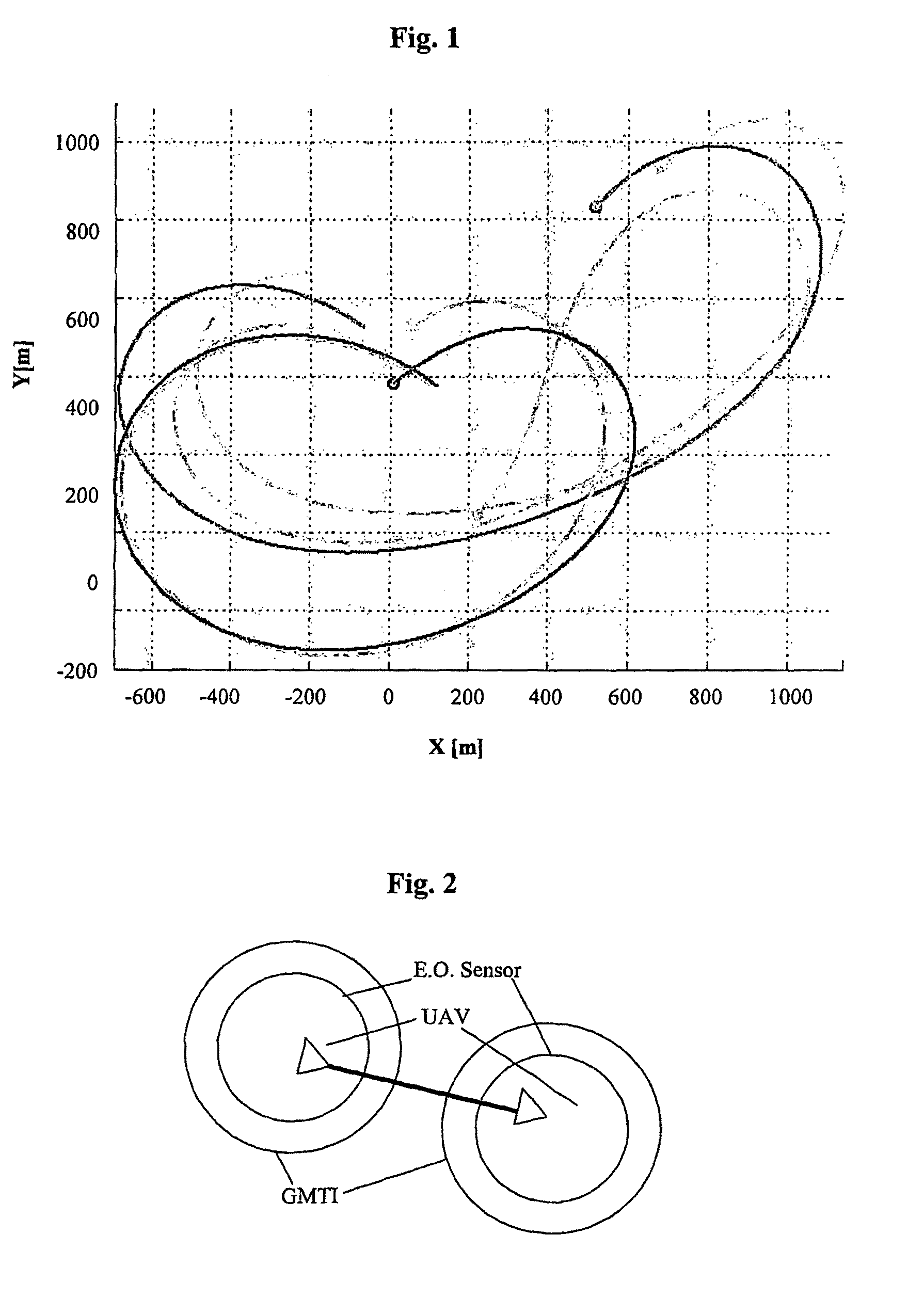
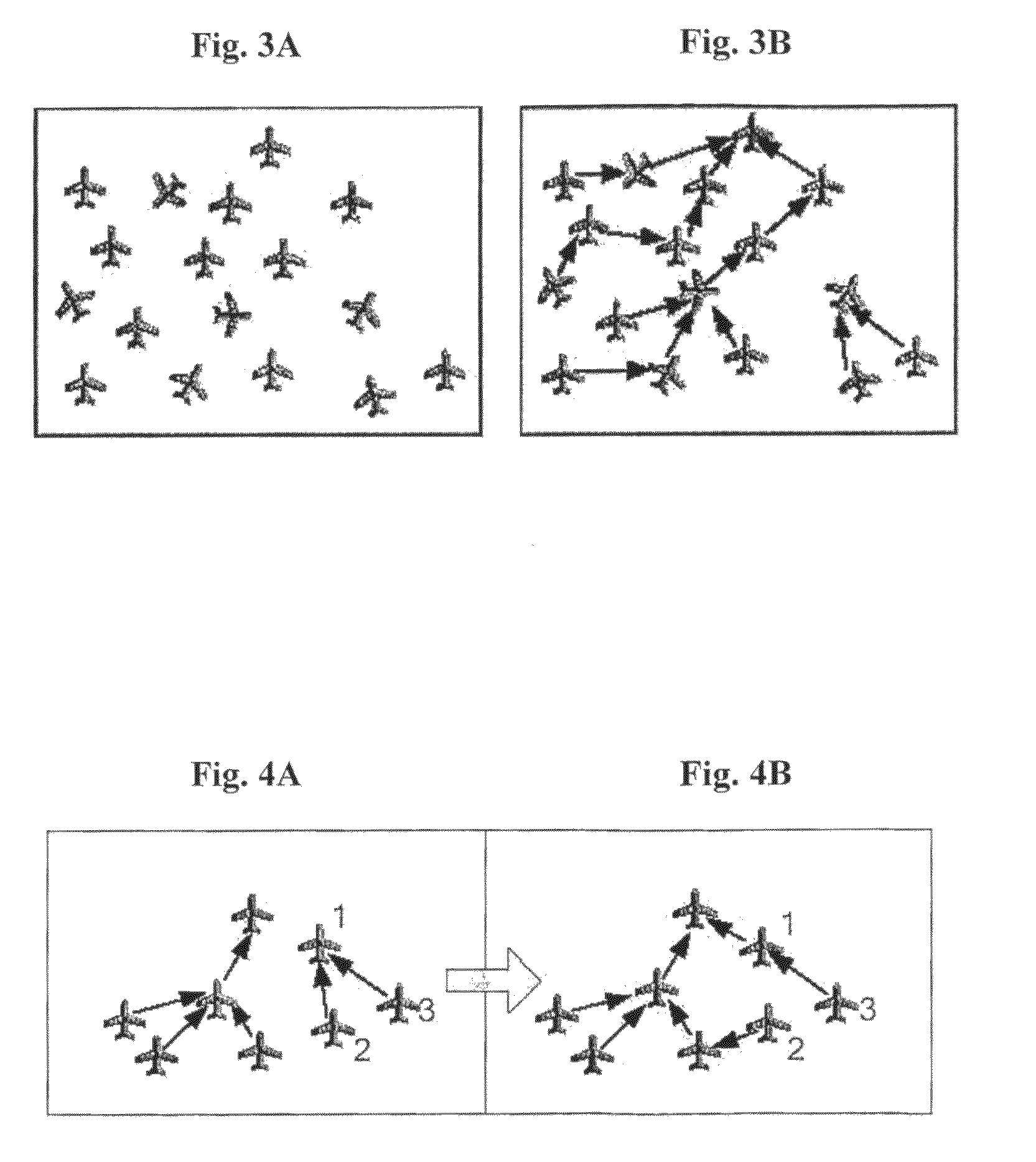
UAV decision and control system
ActiveUS20100163621A1Improve efficiencyAutonomous decision making processSpecial data processing applicationsGraph theoreticControl system
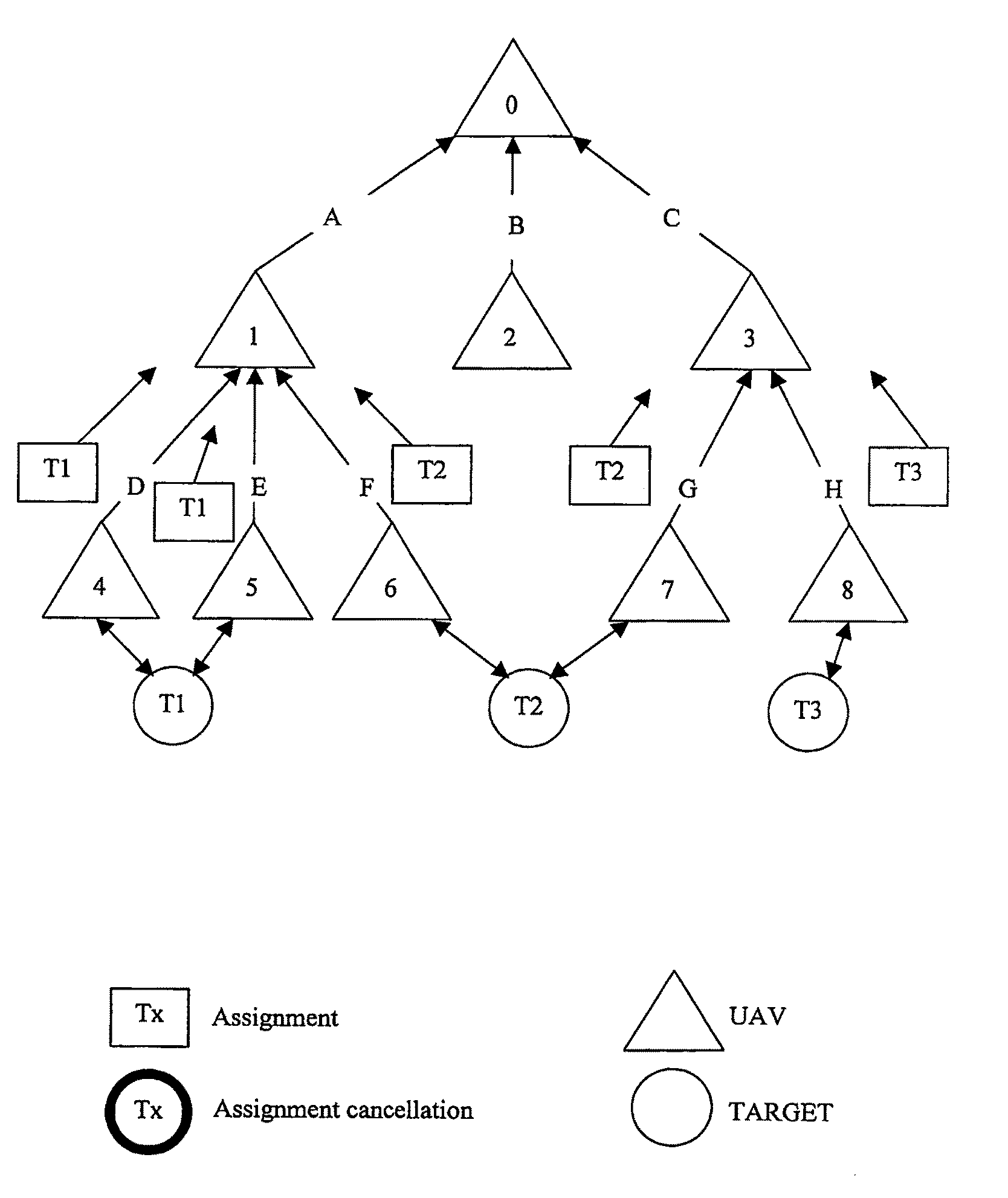
The present invention relates to a hierarchical system and method for task assignment (TA), coordination and communication of multiple Unmanned Aerial Vehicles (UAV's) engaging multiple attack targets and conceives an ad-hoc routing algorithm for synchronization of target lists utilizing a distributed computing topology. Assuming limited communication bandwidth and range, coordination of UAV motion is achieved by implementing a simple behavioral flocking algorithm utilizing a tree topology for target list routing. The TA algorithm is based on a graph-theoretic approach, in which a node locates all the detectable targets, identifies them and computes its distance to each target. The node then produces an attack plan that minimizes the sum of distances of the UAV's in the subtree of a given node to the targets.
Owner:TECHNION RES & DEV FOUND LTD +1
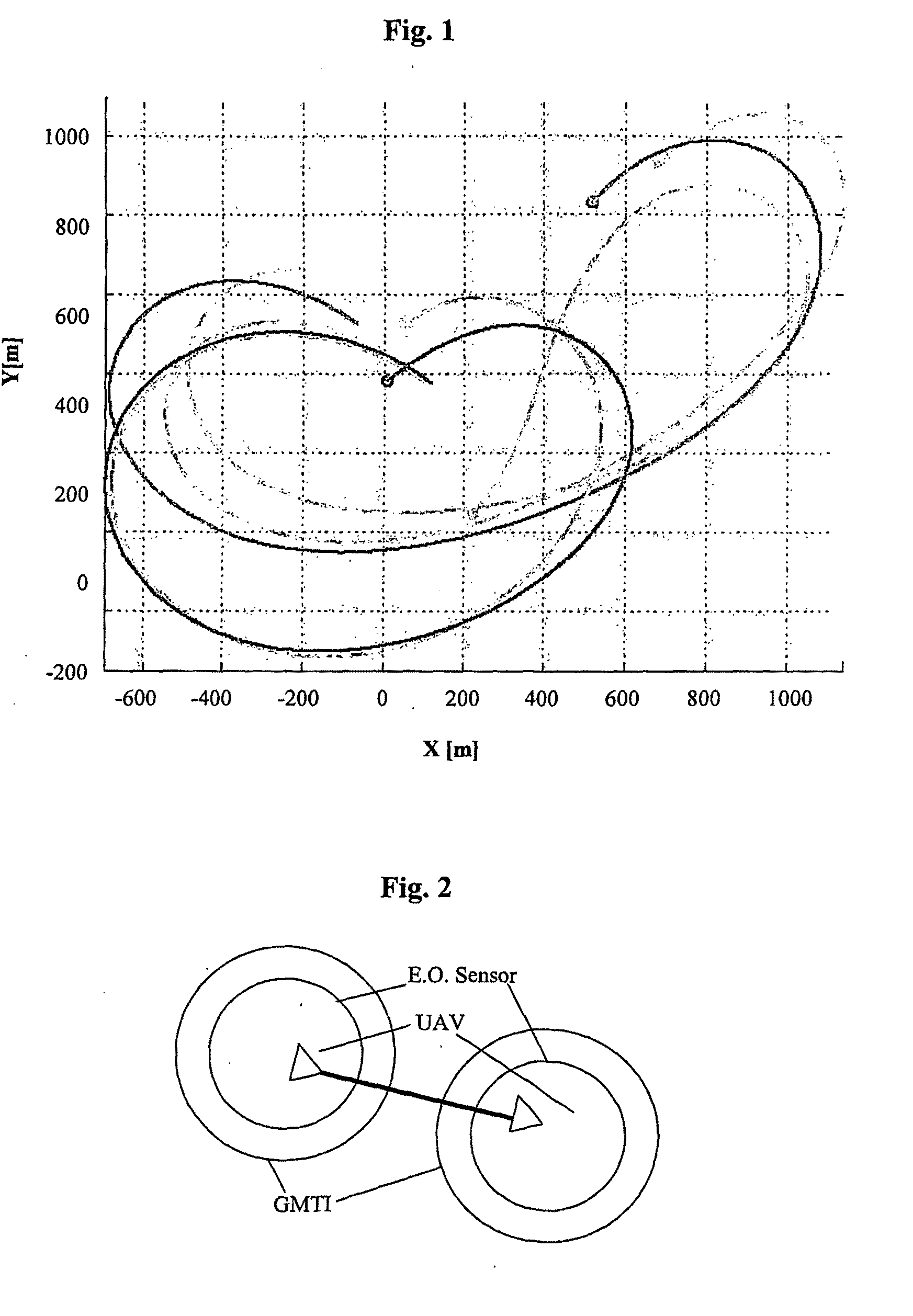
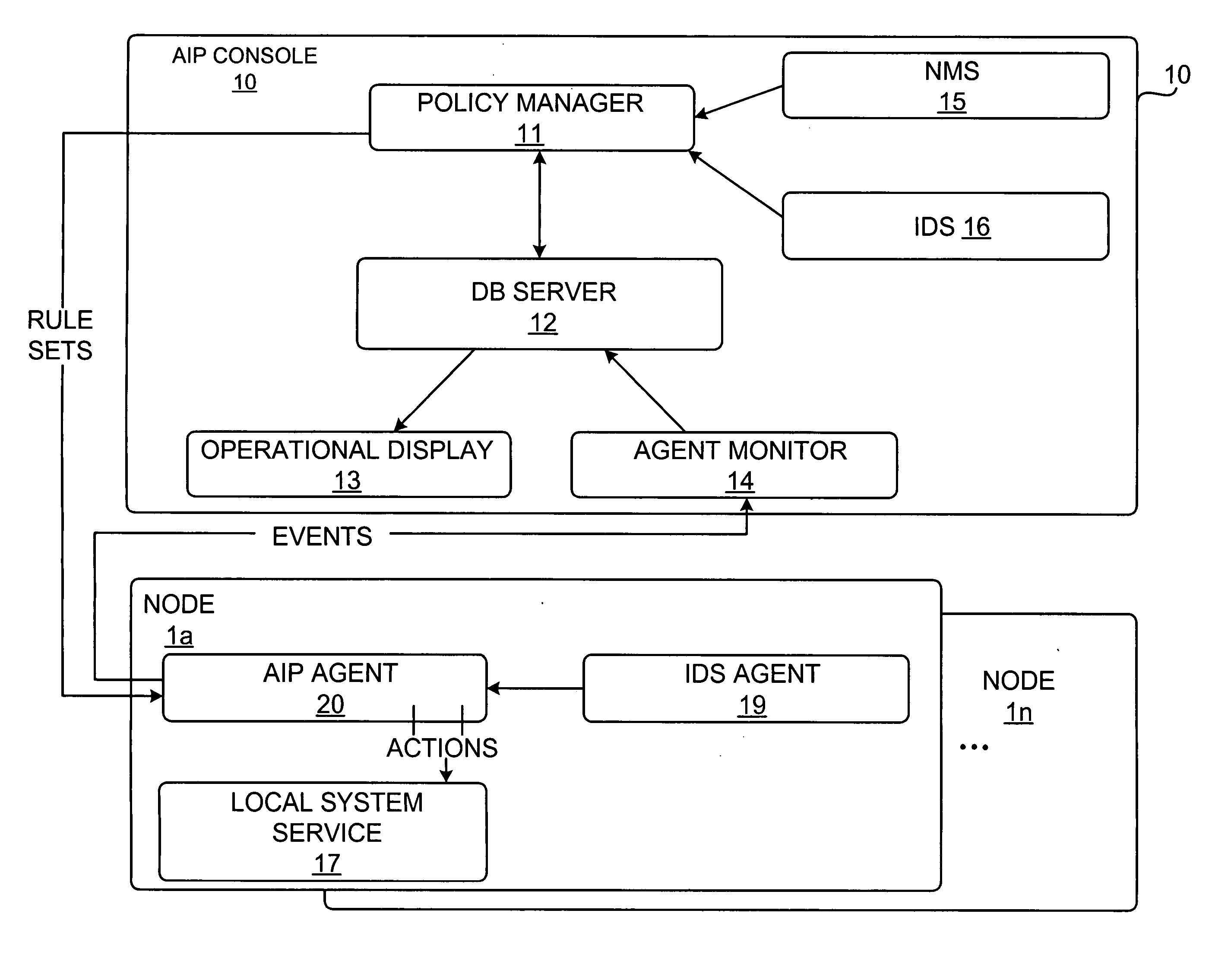
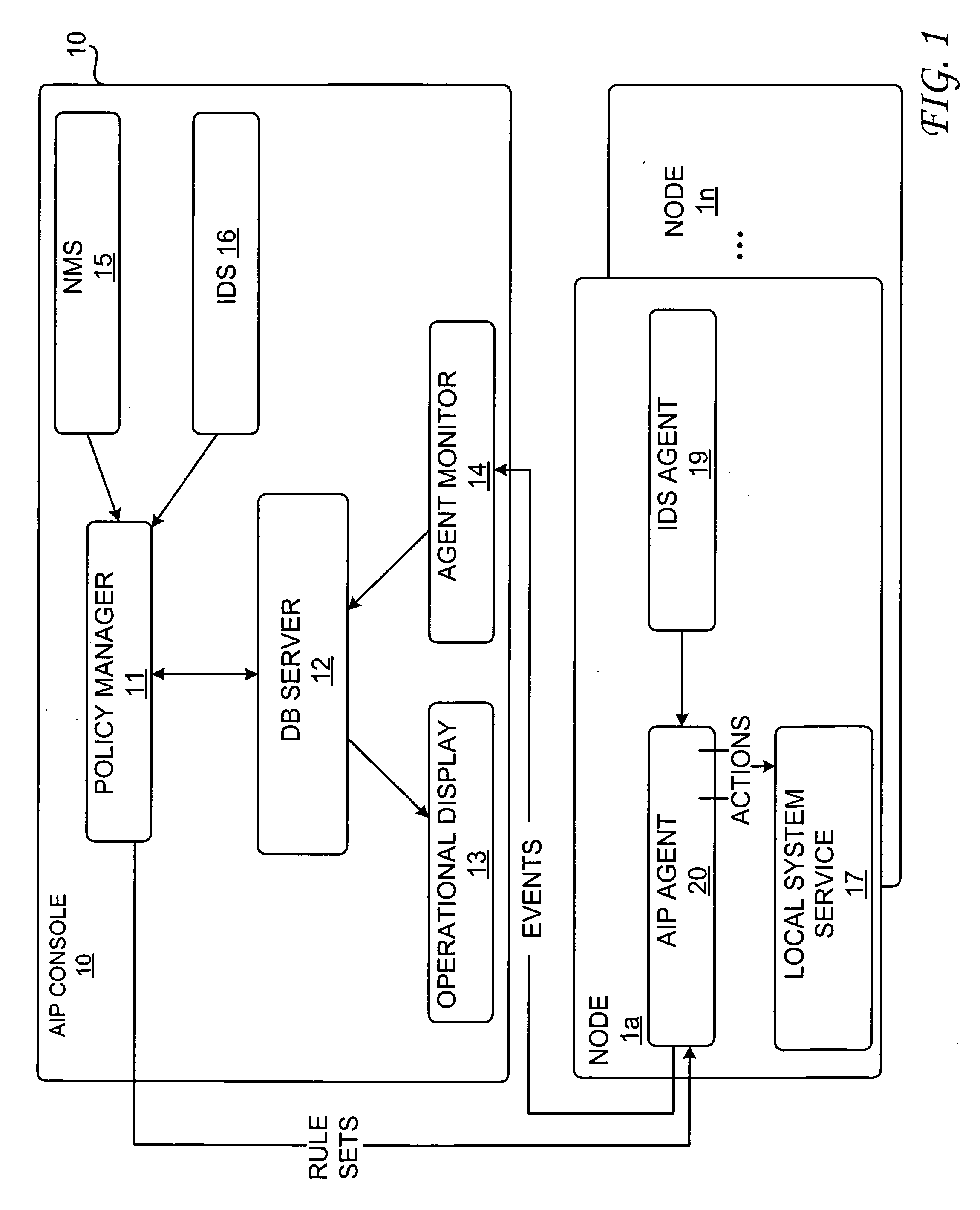
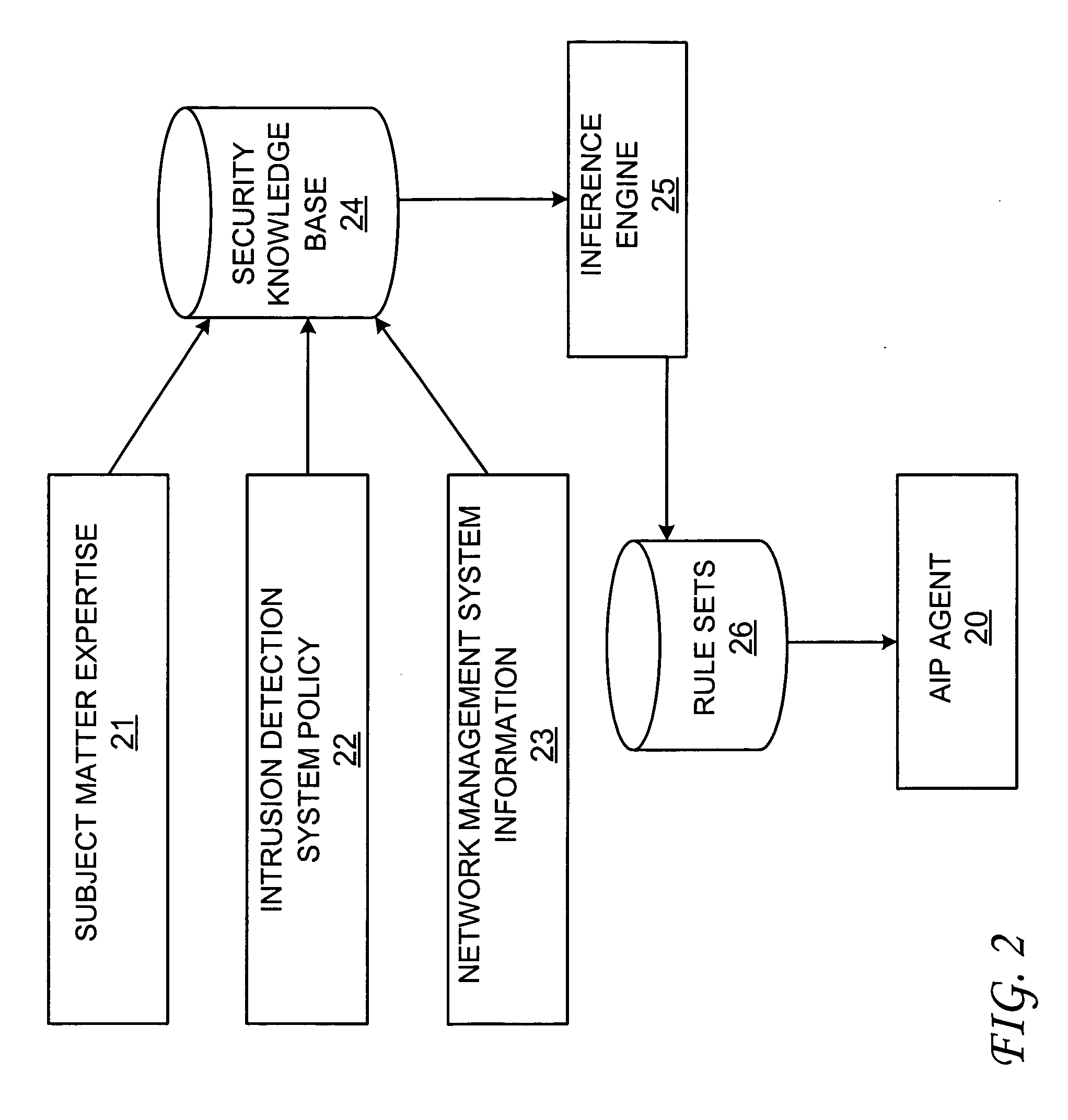
Attack impact prediction system
InactiveUS20060010493A1Memory loss protectionError detection/correctionPrediction systemMultiple attack
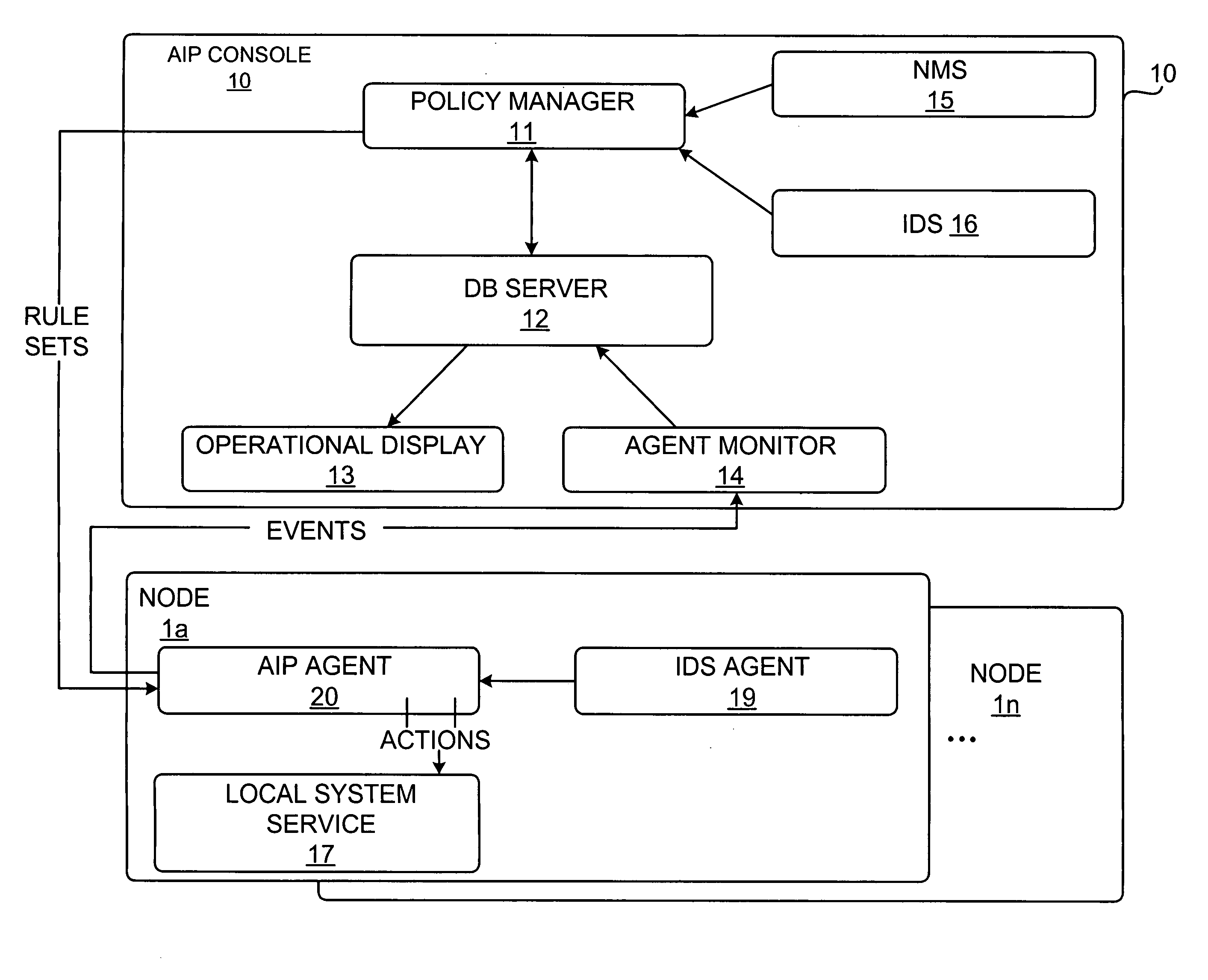
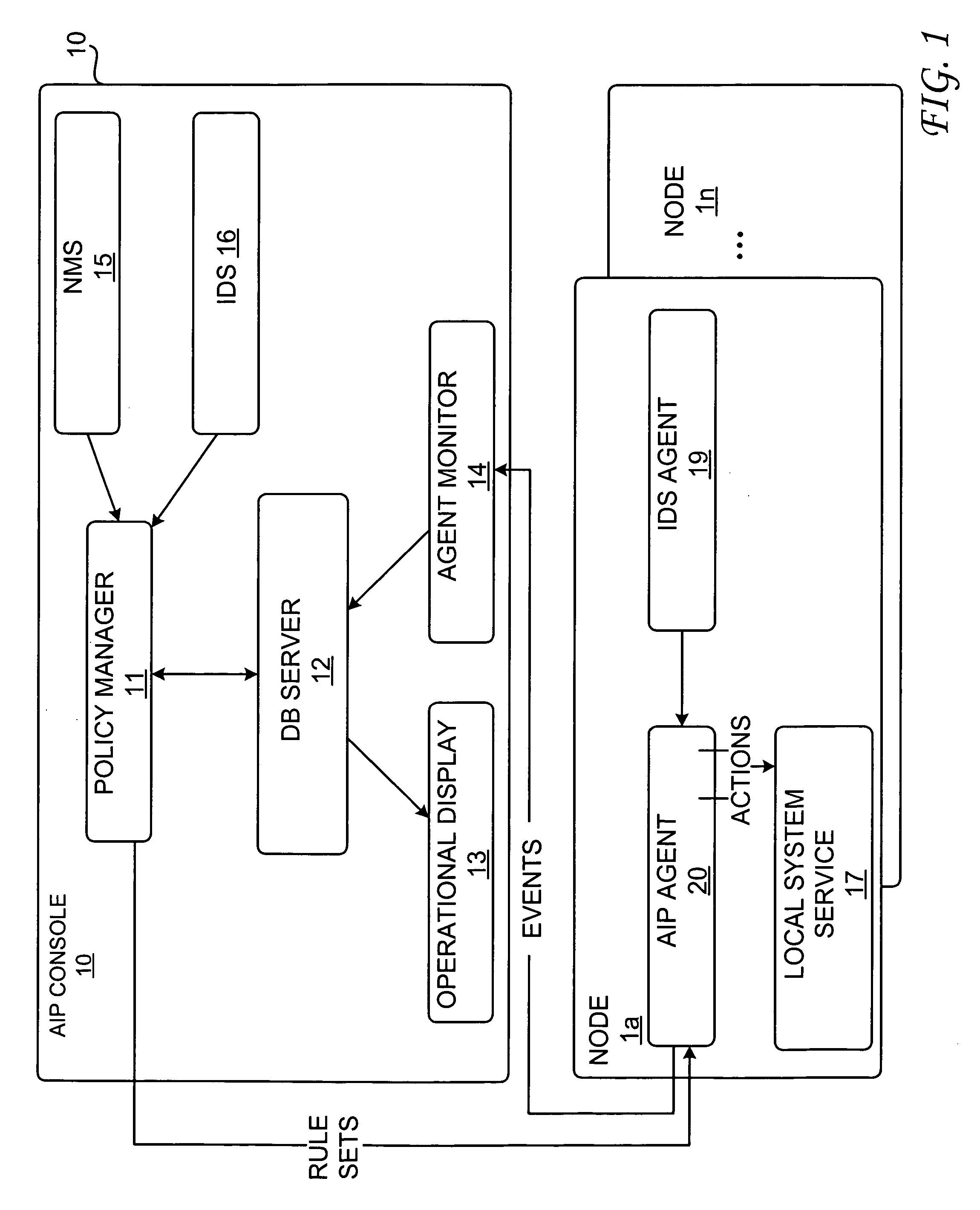
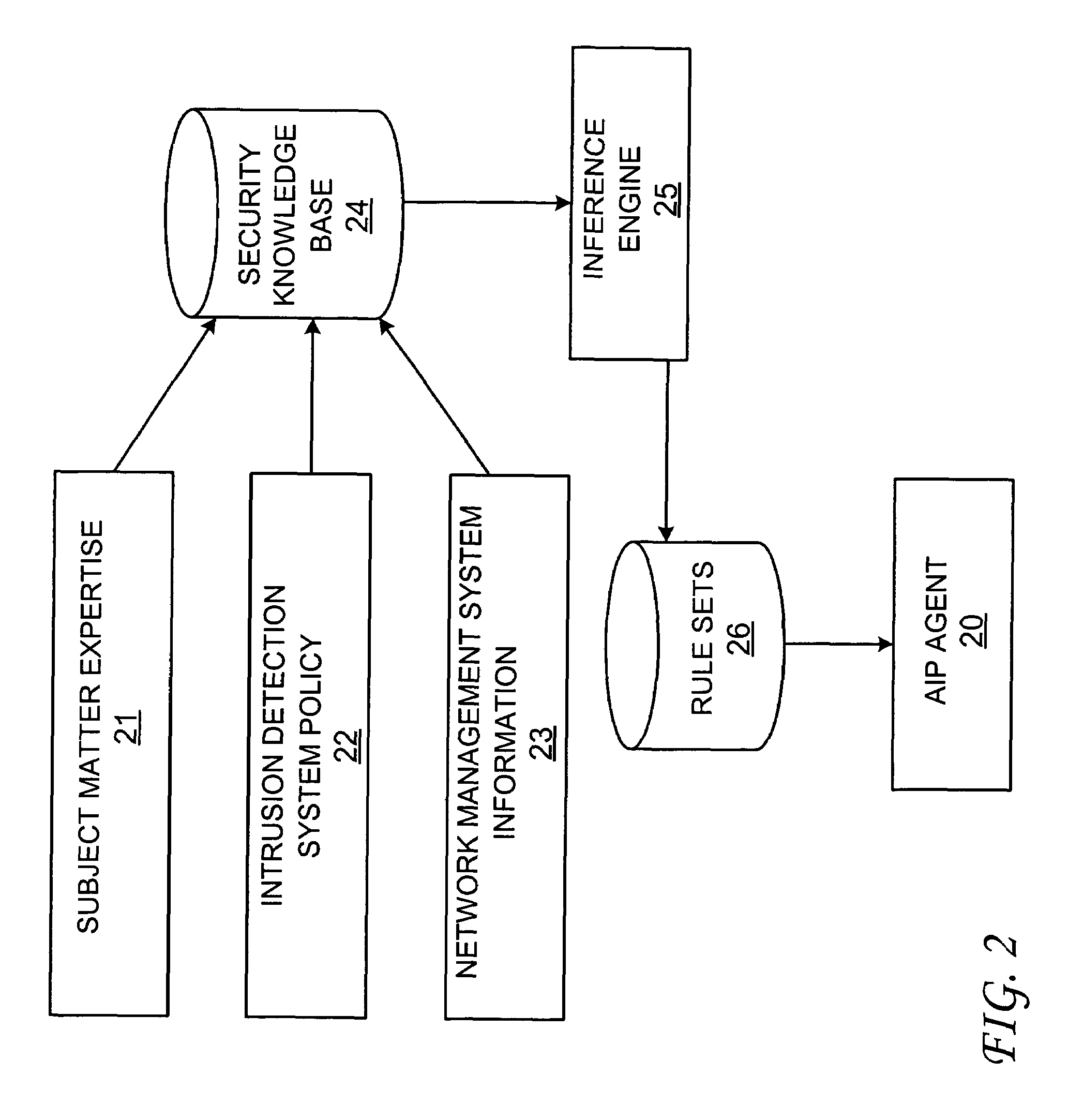
An attack impact prediction system for providing network security for computer networks is disclosed. A computer network includes multiple attack impact prediction (AIP) agents. In response to a detection of an intrusion to a computer network, an AIP agent is notified of the intrusion. In turn, the AIP agent broadcasts the detected intrusion to other AIP agents within the computer network. An impact of the detected intrusion is then determined at each node by its respective AIP agent. In response to a determination that an impact of the detected intrusion on a node exceeds a predetermined severity threshold, then actions need to be taken by each respective AIP agent is ascertained. Finally, the ascertained actions are performed by one or more AIP agents at various points within the computer network.
Owner:LOCKHEED MARTIN CORP
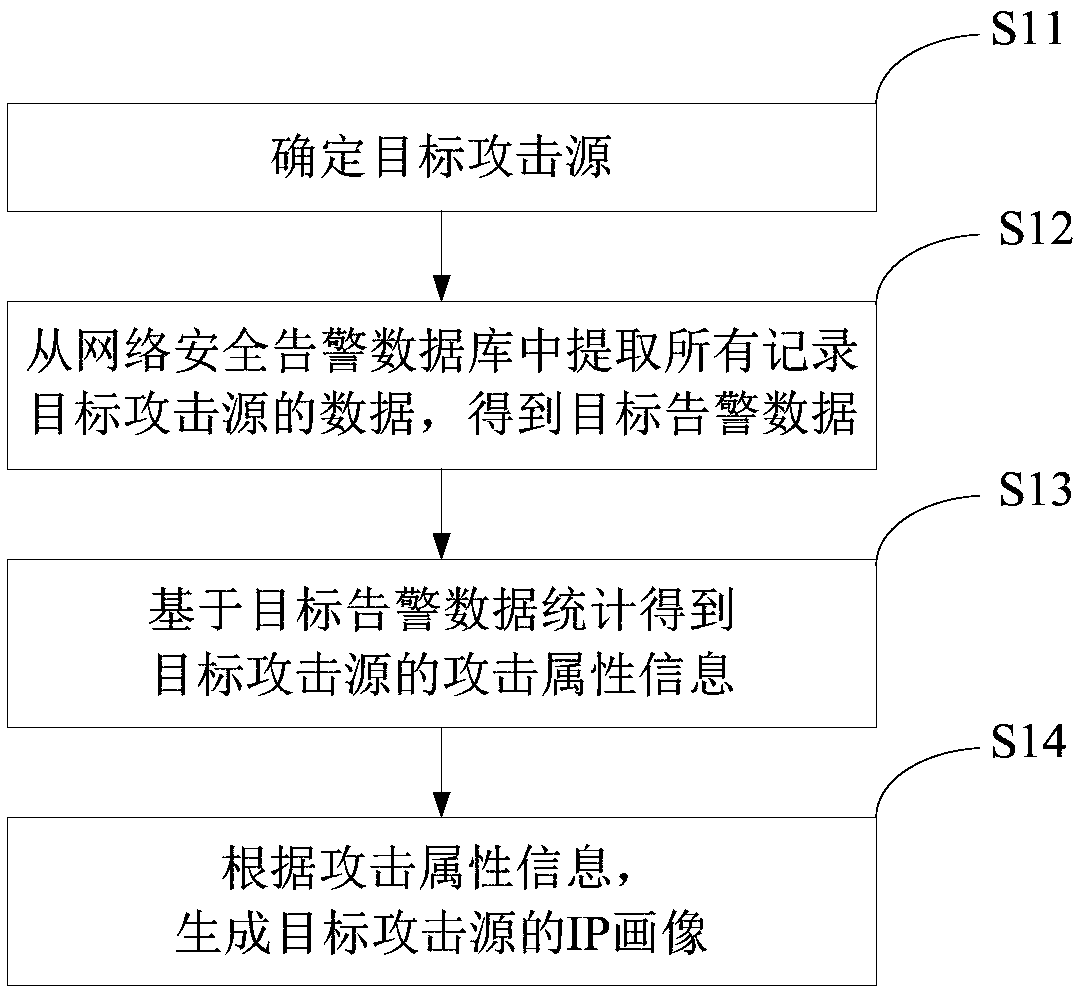
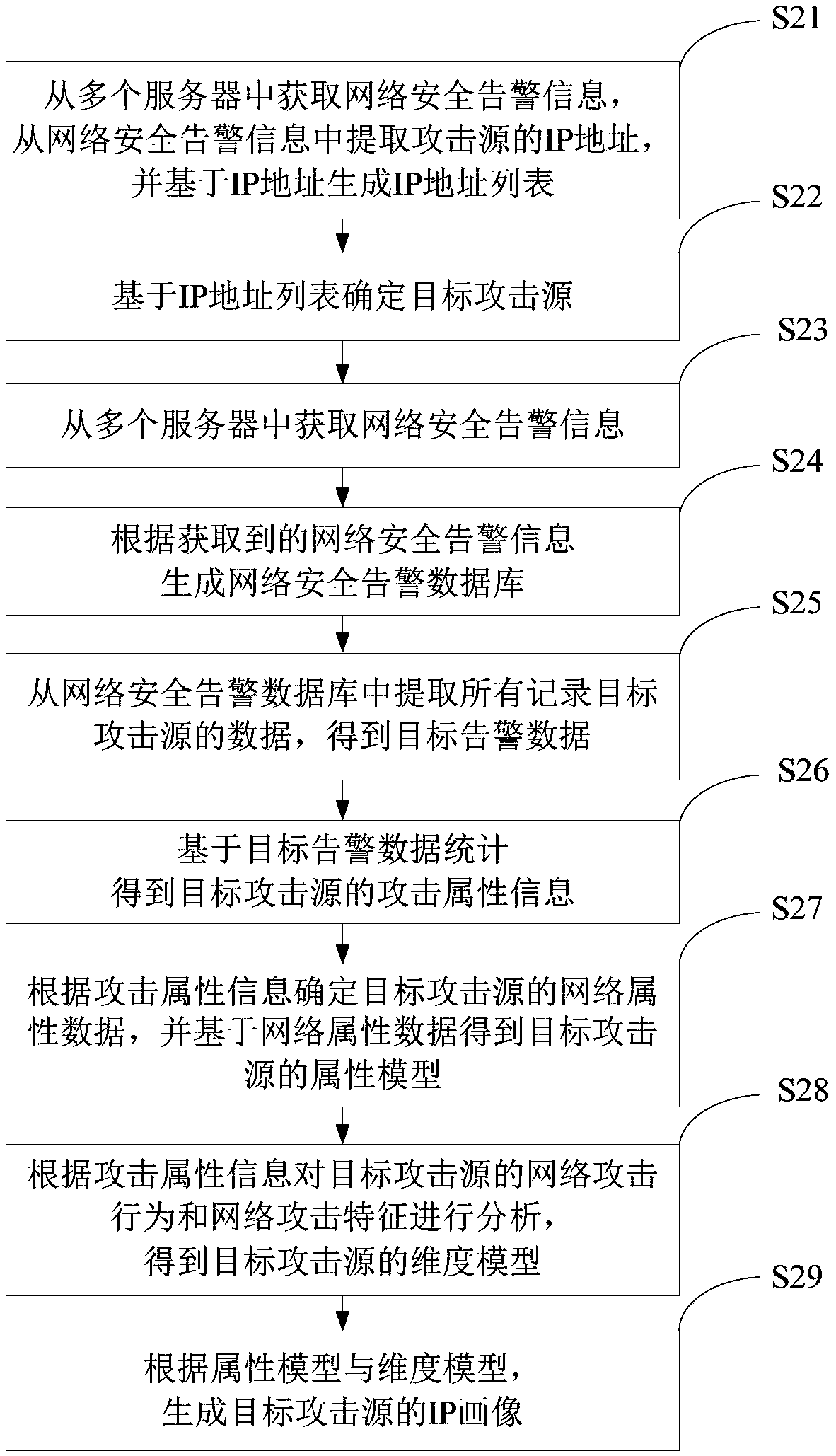
Attack source IP portrait generation method and device based on network attack behavior
The invention provides an attack source IP portrait generation method and device based on a network attack behavior, and relates to the field of network security technology. The attack source IP portrait generation method based on a network attack behavior comprises: determining a target attack source; extracting all data recording the target attack source from a network security alarm database toobtain target alarm data, wherein the network security alarm database comprises alarm data of multiple attack sources; obtaining attack attribute information of the target attack source based on statistics on the target alarm data; generating an IP portrait of the target attack source according to the attack attribute information. The method and the device solve the technical problems that the existing attack source information acquisition method for a network attack behaviors in the prior art is limited and cannot effectively understand the attack source IP of the network attack behavior.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Plaintext or ciphertext selection based side channel power analysis attack method on round function output of SM4 cipher algorithm
InactiveCN104202145APractical applicabilityIncrease flexibilityEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
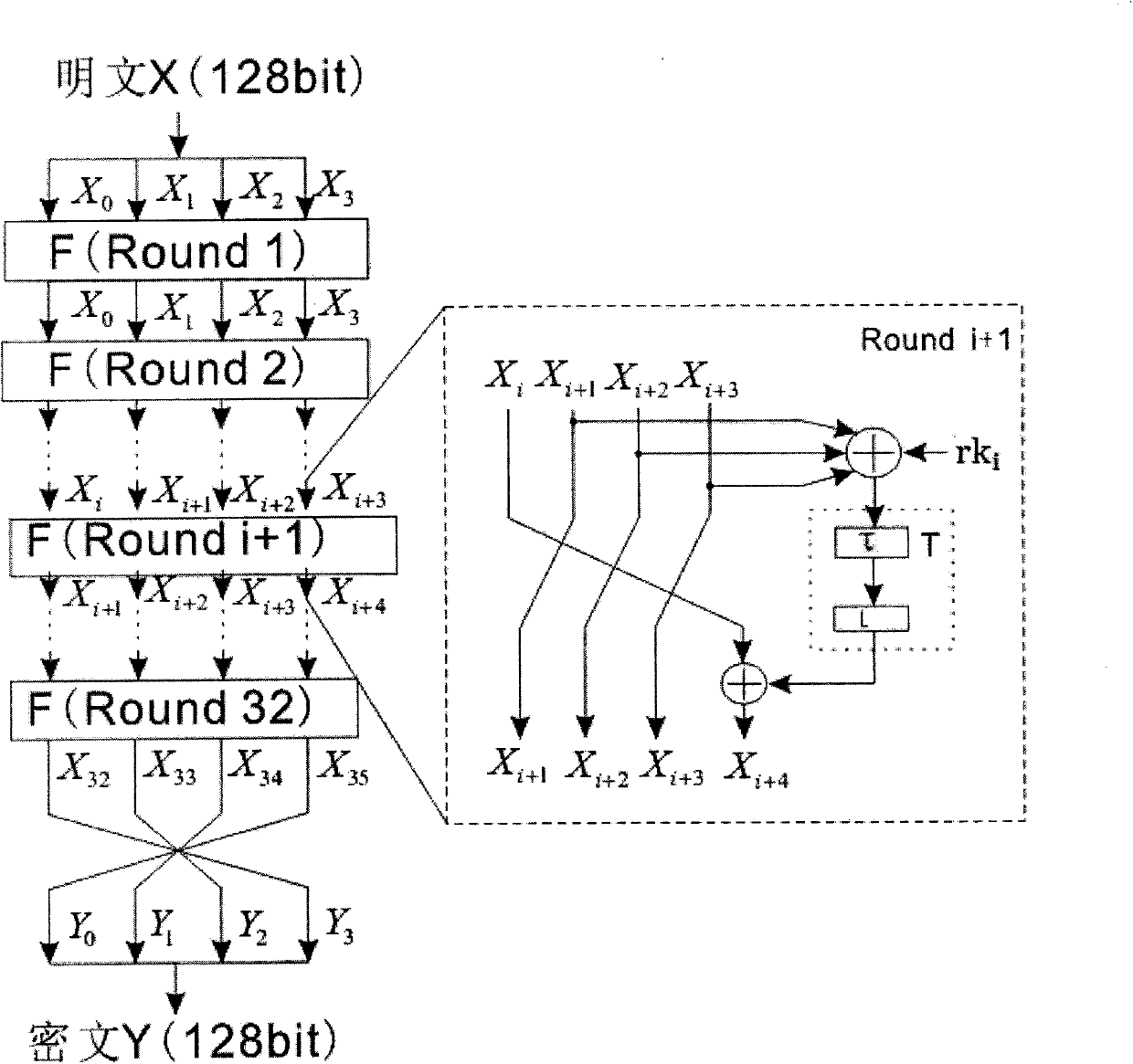
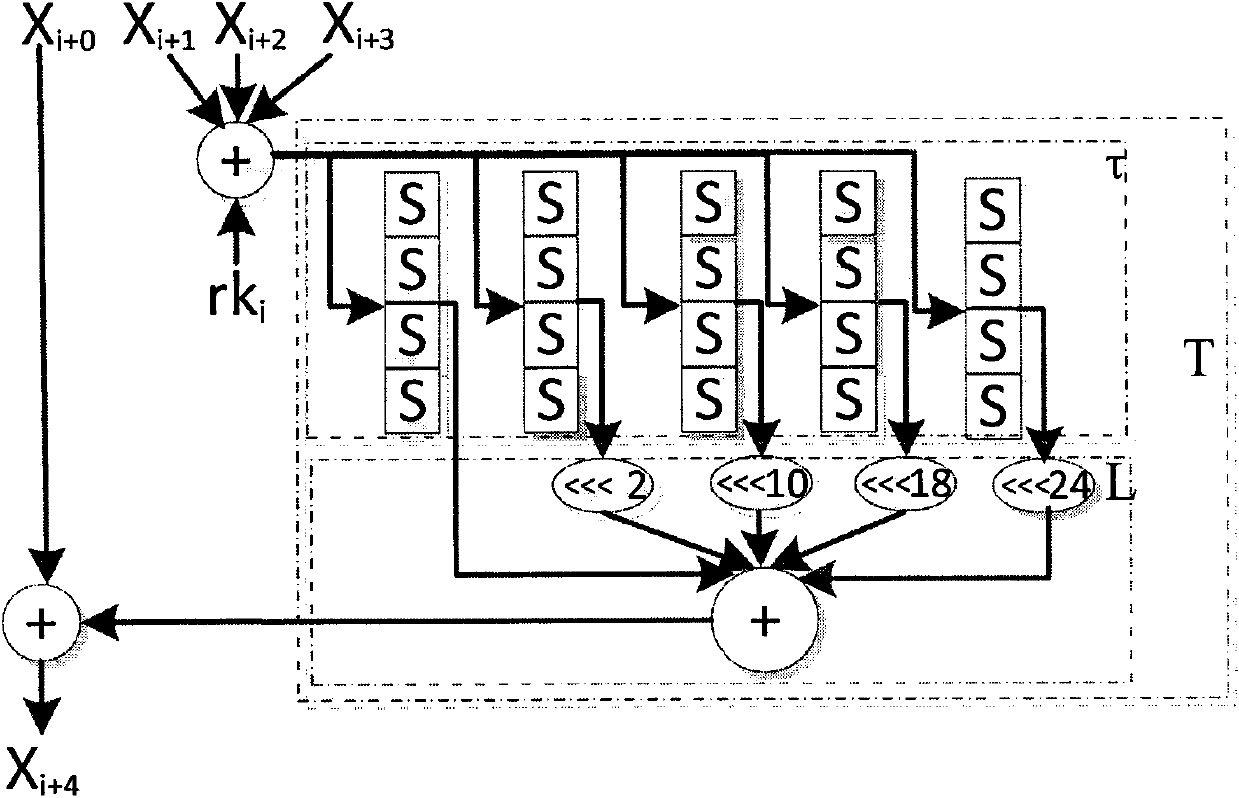
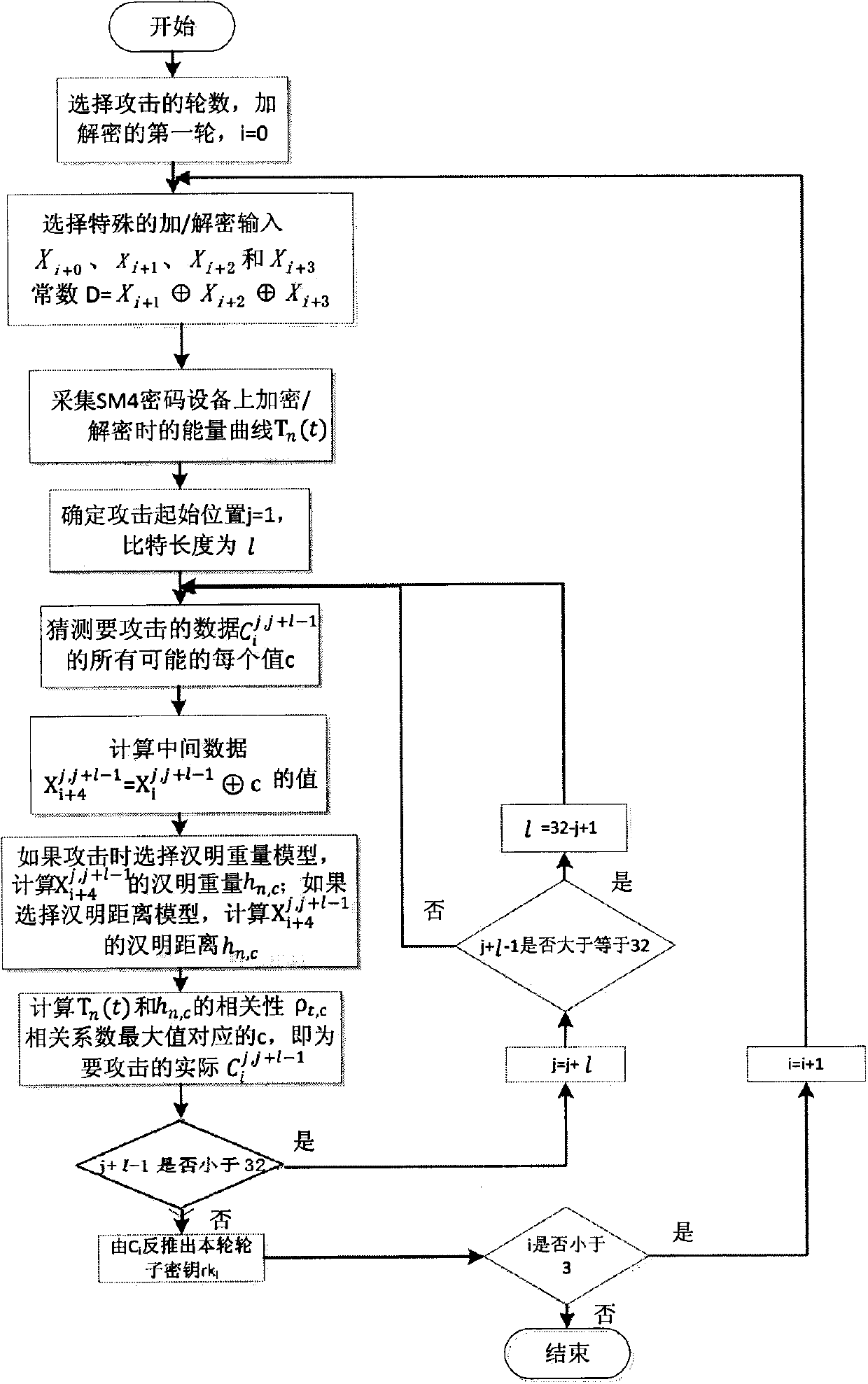
The invention discloses a plaintext or ciphertext selection based side channel power analysis attack method on round function output of the SM4 cipher algorithm. The method includes the steps of S1, selecting plaintext or ciphertext to input X<i+0>, X<i+1>, X<i+2> and X<i+3> on the condition of allowing the exclusive OR result of the X<i+1>, X<i+2> and X<i+3> to be a constant value and guaranteeing randomness of the X<i+0>, utilizing side channel power attack processes to attack the output C of linear transform L of each round of the first four round functions, and deducing inversely to acquire the round key rk of the first four round functions in encryption or decryption according to the output C; S2, according to the round keys rk<0>, rk<1>, rk<2> and rk<3> of the first four found functions, inversely calculating the initial key by a key expansion algorithm. The method can realize power analysis attack by means of multiple attacks and can attack with selection of proper-length bits according to actual computing capacity, thus flexibility, effectiveness and success rate of analysis are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +2
Event detection method
InactiveUS20080010680A1Improve acceleration performanceImprove efficiencyMemory loss protectionError detection/correctionPushdown automatonAlgorithm
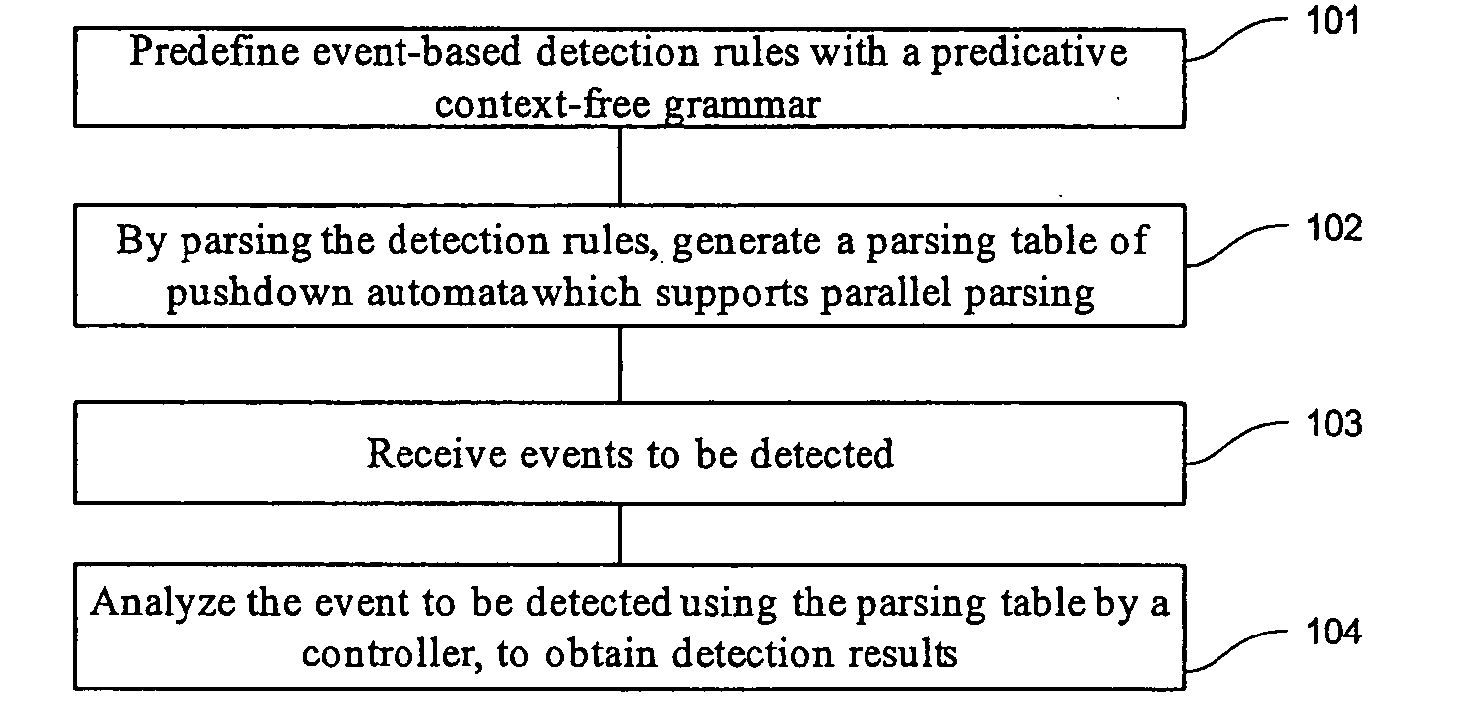
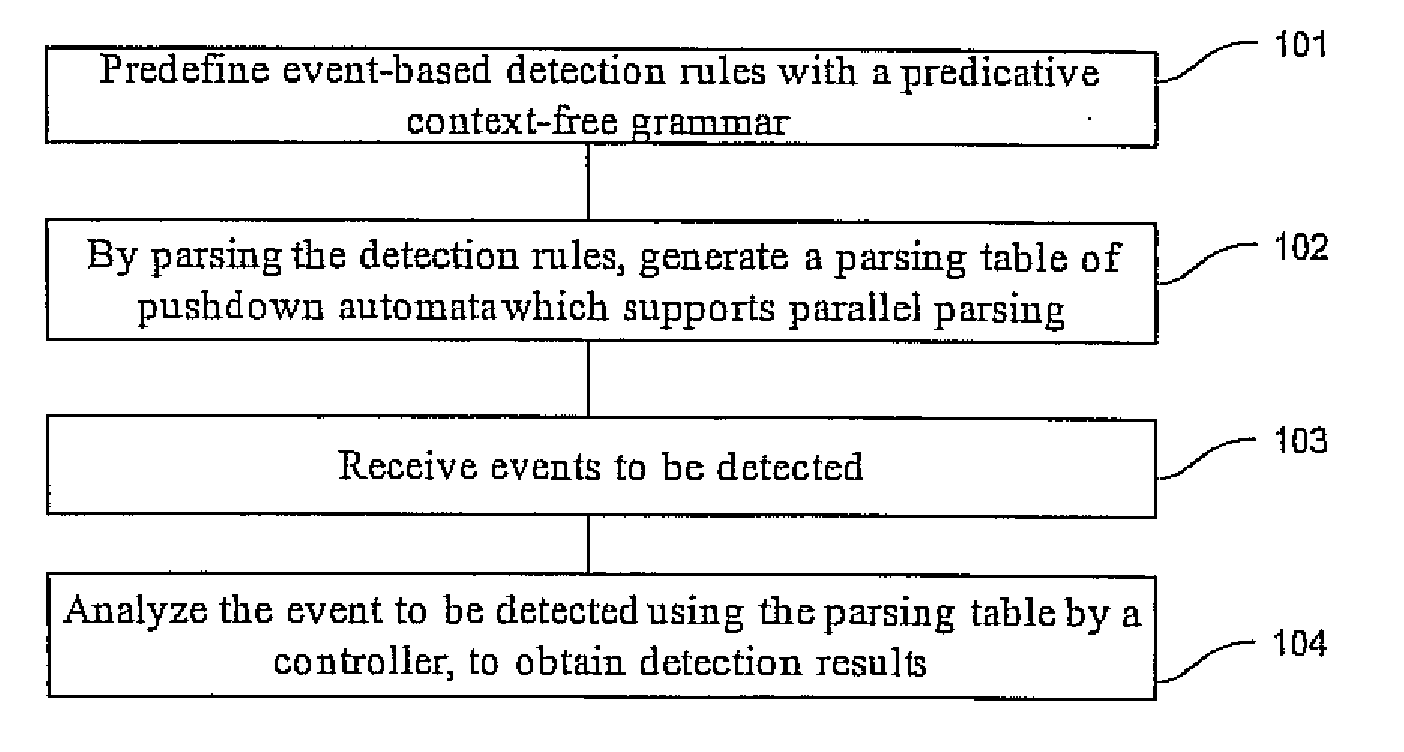
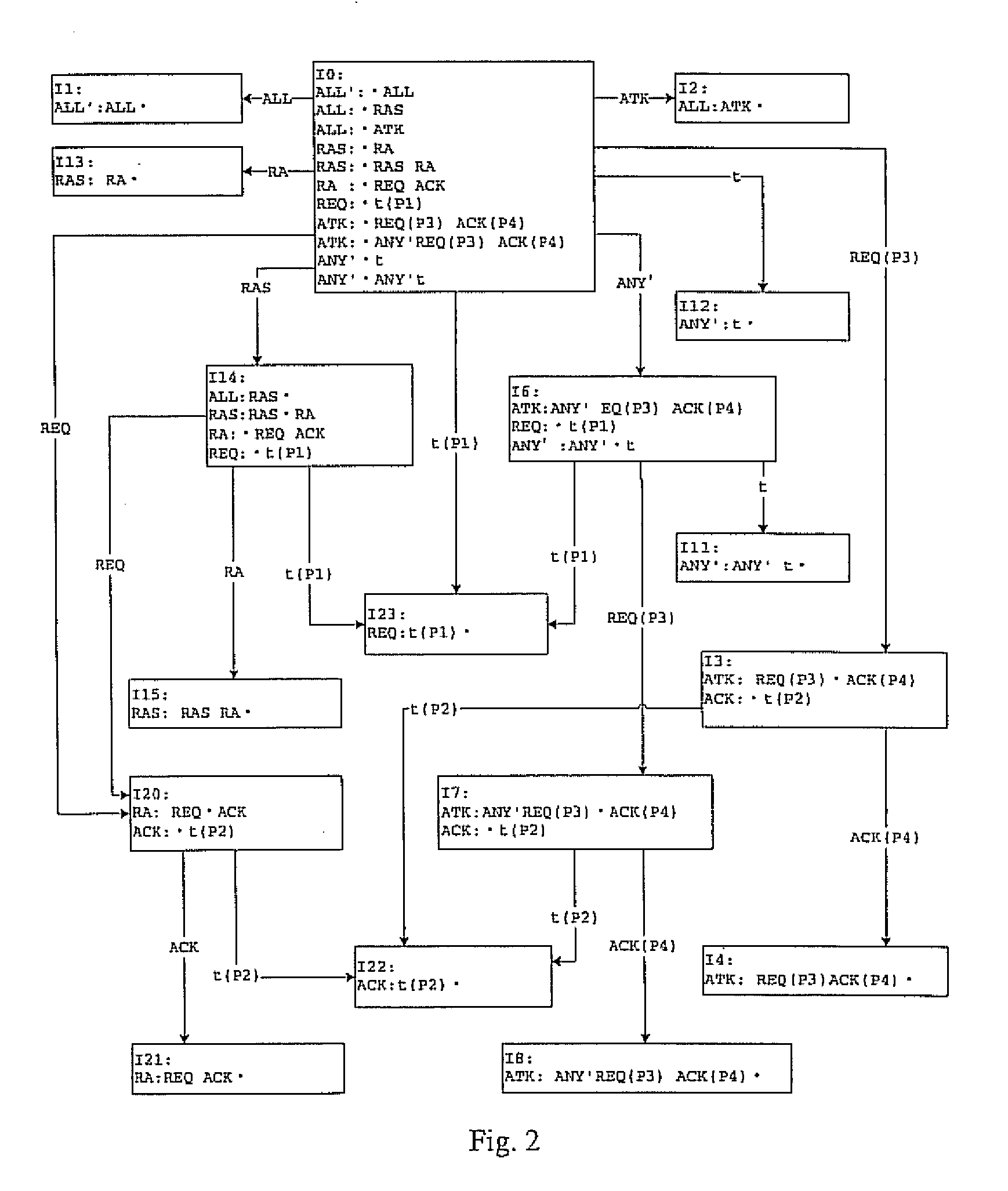
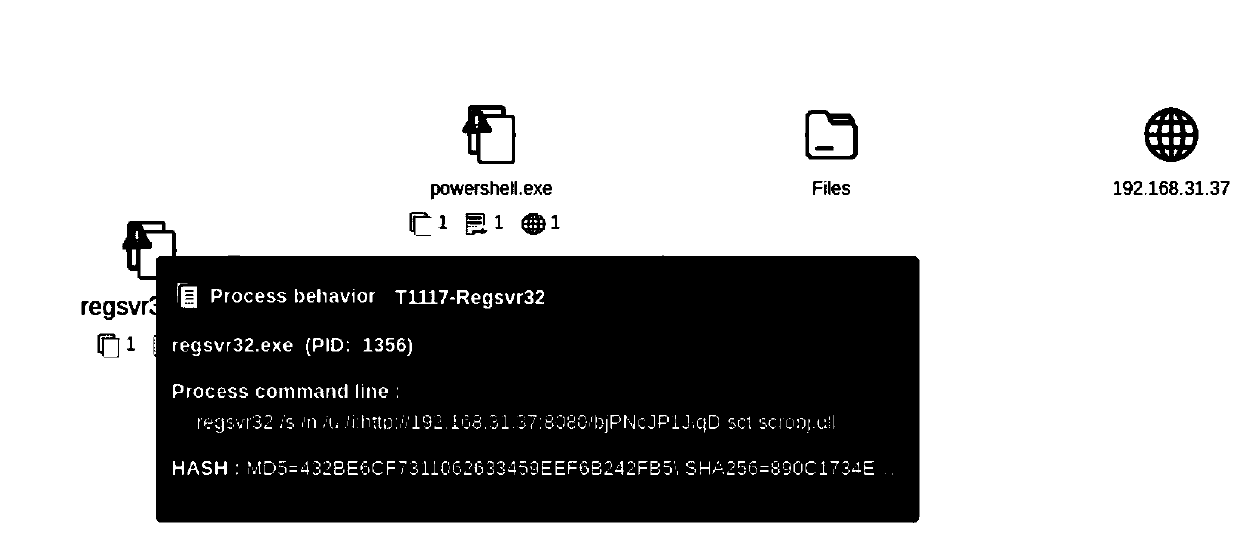
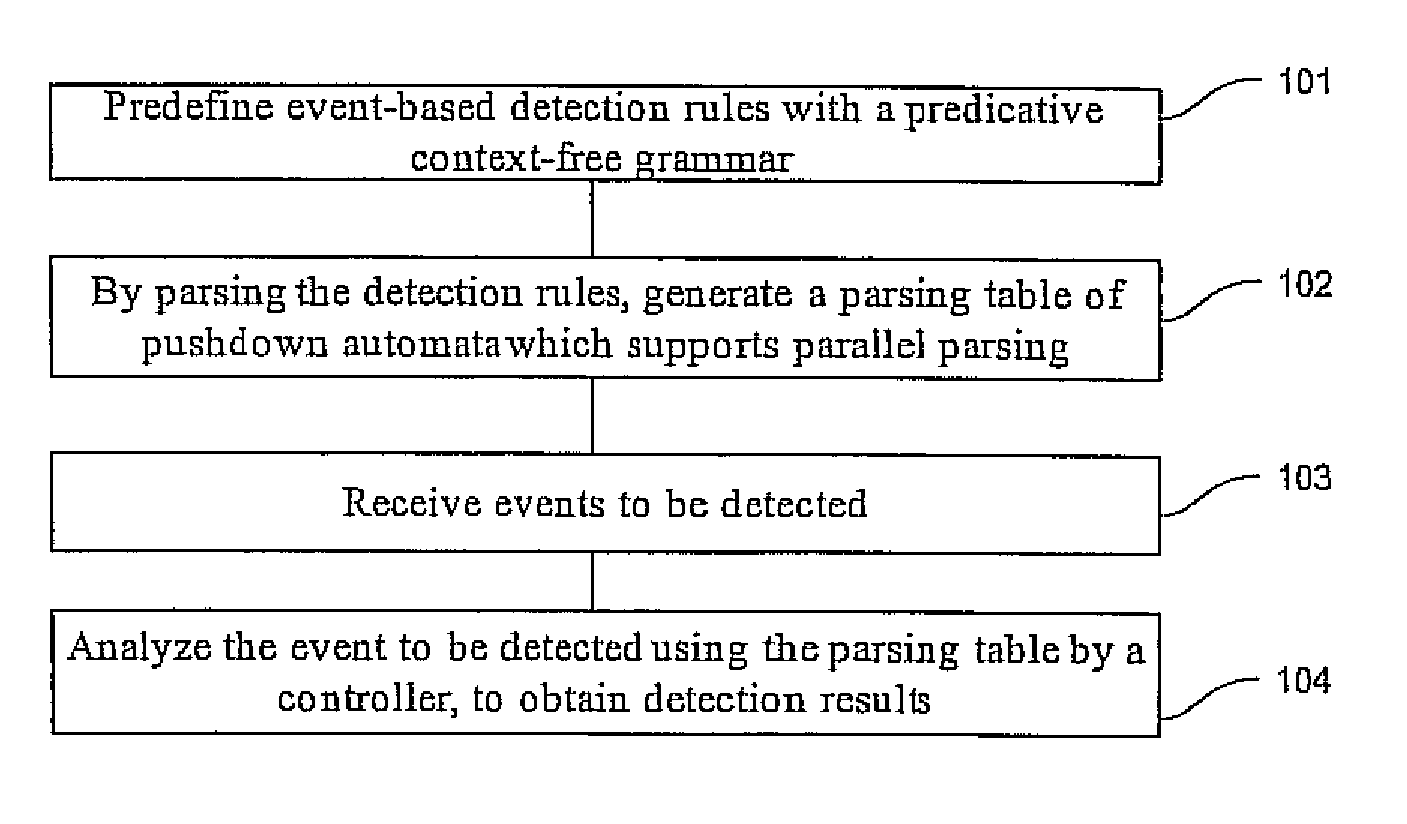
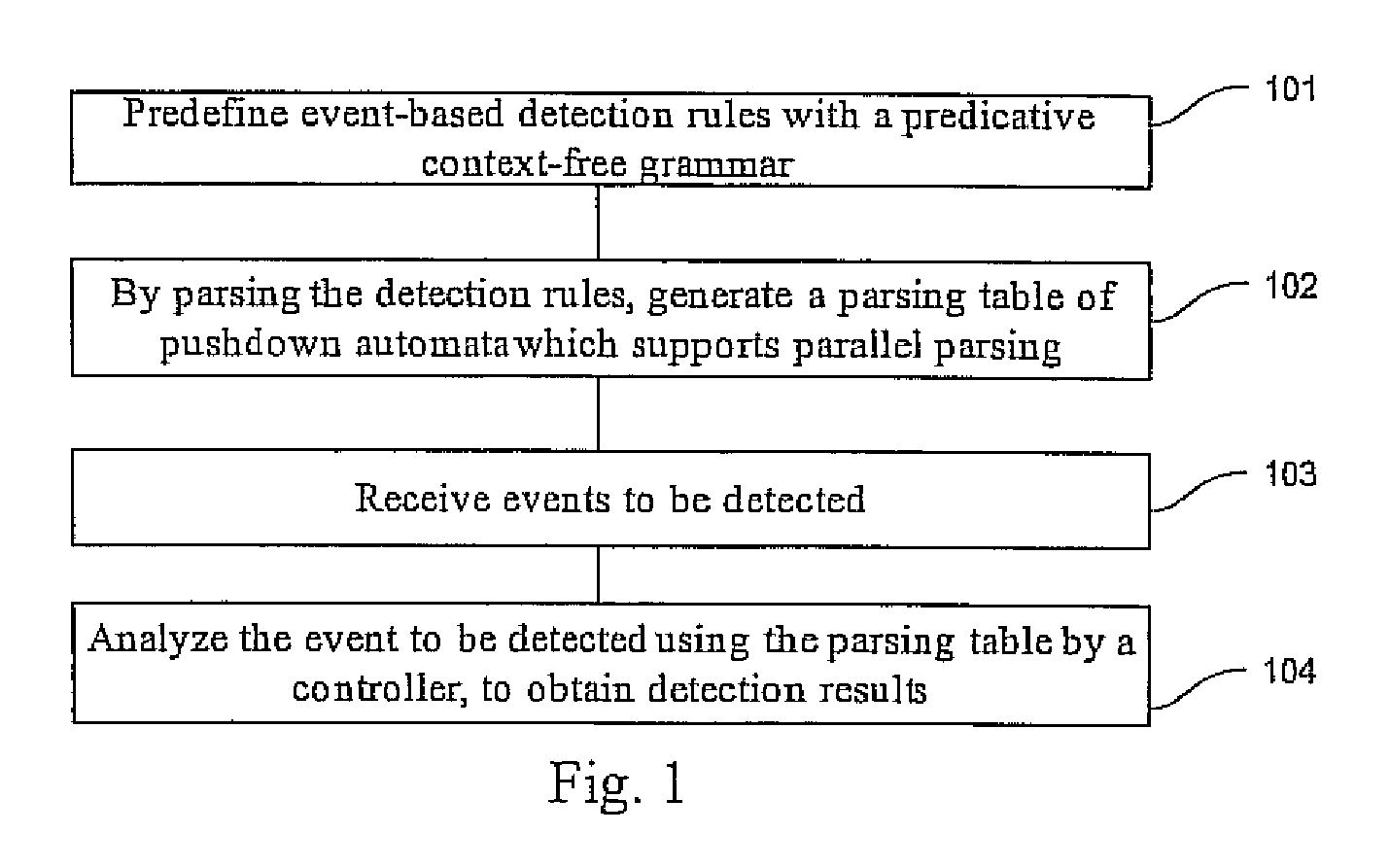
The embodiments of the present invention disclose an event detection method and device. The method includes: predefining event-based detection rules with a predicative context-free grammar; generating by parsing the detection rules a parsing table of pushdown automaton which supports parallel parsing; receiving an event to be detected; and analyzing by a controller the event to be detected according to the parsing table, to obtain a detection result. The present invention is especially applicable to detection of network attack events. The embodiments of the present invention detect the attacks with a predicative context-free grammar on the basis of events, and ensure a close combination of a protocol parsing process and an attack detection process, as well as a close combination of multiple attack detection rules, thus decreasing unnecessary calculations. In addition, with an optimized parallel pushdown automaton, the embodiments of the present invention can efficiently analyze the predicative context-free grammar. Consequently, besides hierarchical processing capability and state description capability, the embodiments of the present invention deliver high efficiency.
Owner:NEUSOFT CORP
UAV decision and control system
ActiveUS8186589B2Improve efficiencyAutonomous decision making processSpecial data processing applicationsControl systemProgram planning
Owner:TECHNION RES & DEV FOUND LTD +1
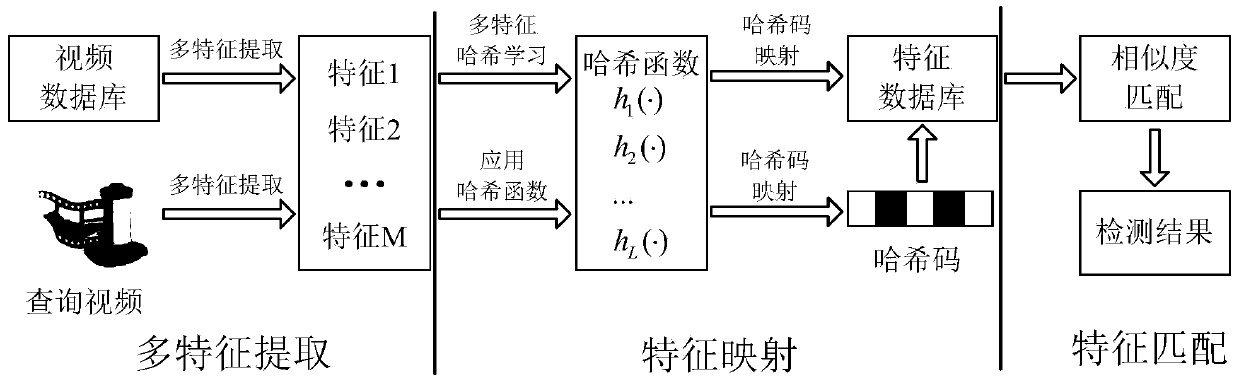
Video copy detection method based on multi-feature Hash
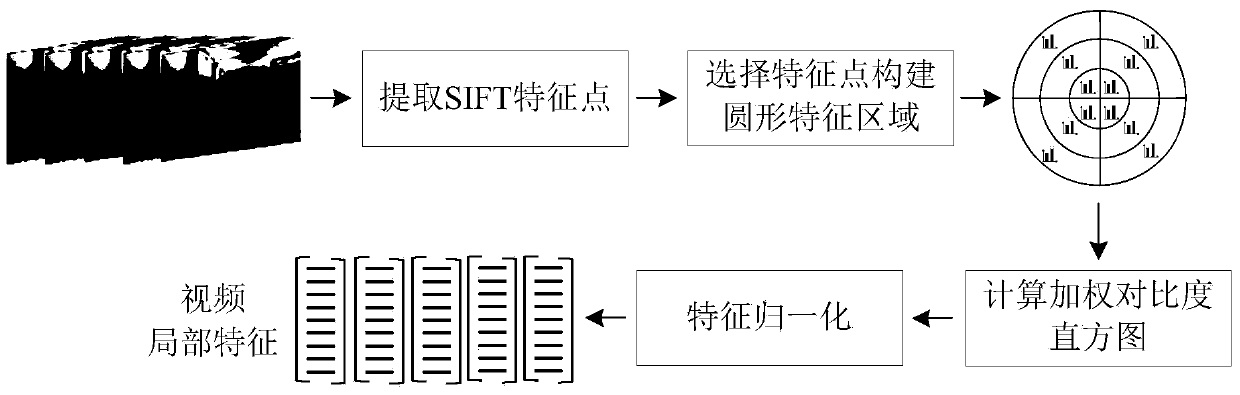
InactiveCN103744973AHigh precisionImprove robustnessCharacter and pattern recognitionSpecial data processing applicationsDigital videoHash function
The invention discloses a video copy detection method based on multi-feature Hash, which mainly solves the problem that detection efficiency and detection accuracy cannot be effectively balanced in the exiting video copy detection algorithm. The video copy detection method based on multi-feature Hash comprises the following realization steps of: (1) extracting the pyramid histogram of oriented gradients (PHOG) of a key frame as the global feature of the key frame; (2) extracting a weighted contrast histogram based on scale invariant feature transform (SIFT) of the key frame as the local feature of the key frame; (3) establishing a target function by a similarity-preserving multi-feature Hash learning SPM2H algorithm, and obtaining L Hash functions by optimization solution; (4) mapping the key frame of a database video and the key frame of an inquired video into an L-dimensional Hash code by virtue of the L Hash functions; (5) judging whether the inquired video is the copied video or not through feature matching. The video copy detection method based on multi-feature Hash disclosed by the invention is good in robustness for multiple attacks, and capable of being used for copyright protection, copy control and data mining for digital videos on the Internet.
Owner:XIDIAN UNIV
Attack impact prediction system
An attack impact prediction system for providing network security for computer networks is disclosed. A computer network includes multiple attack impact prediction (AIP) agents. In response to a detection of an intrusion to a computer network, an AIP agent is notified of the intrusion. In turn, the AIP agent broadcasts the detected intrusion to other AIP agents within the computer network. An impact of the detected intrusion is then determined at each node by its respective AIP agent. In response to a determination that an impact of the detected intrusion on a node exceeds a predetermined severity threshold, then actions need to be taken by each respective AIP agent is ascertained. Finally, the ascertained actions are performed by one or more AIP agents at various points within the computer network.
Owner:LOCKHEED MARTIN CORP
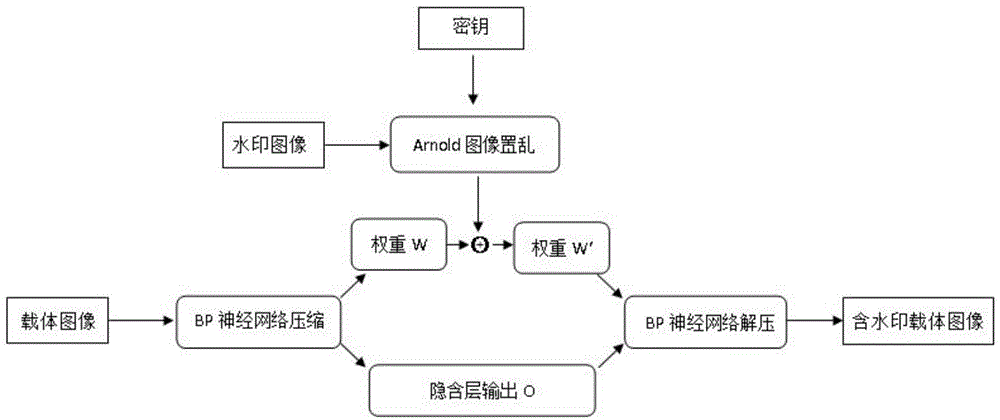
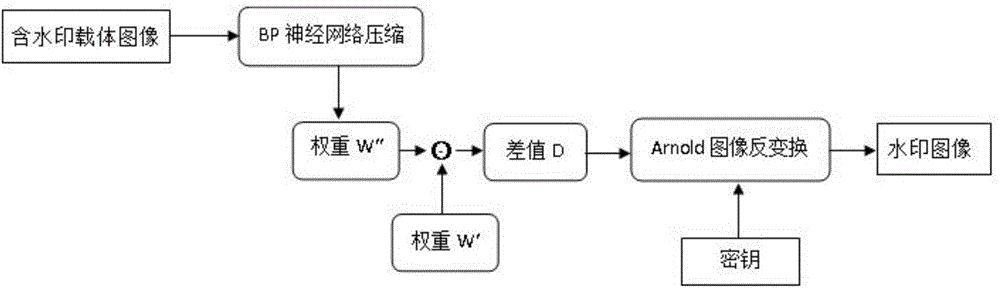
Image watermark embedding and extracting method based on back propagation (BP) neural network compressed domain
InactiveCN104616244AImprove securityAchieve complete imperceptibilityImage data processing detailsNeural learning methodsHidden layerPattern recognition
The invention discloses an image watermark embedding and extracting method based on a back propagation (BP) neural network compressed domain. The image watermark embedding and extraction method is based on Arnold transformation, to support BP neural network image compression processing, and the watermark is embedded into the neural network hidden layer to the output layer weight of the carrier image almost no effect, invisibility is very strong, and more secure. In the compressed domain that BP neural network, the carrier watermarked image even after multiple attack, is still able to remember the local relationship between pixels in order to achieve the correct detection of the watermark signal, making this embedding and extracting methods images of a variety of conventional attack has strong robustness, good balance contradictory and robust image watermarking imperceptibility between, and enables the blind to detect the watermark image.
Owner:HENAN NORMAL UNIV
Method and system for simulating a hacking attack on a network
InactiveCN101682626AComputer security arrangementsTransmissionCommunication linkDistributed computing
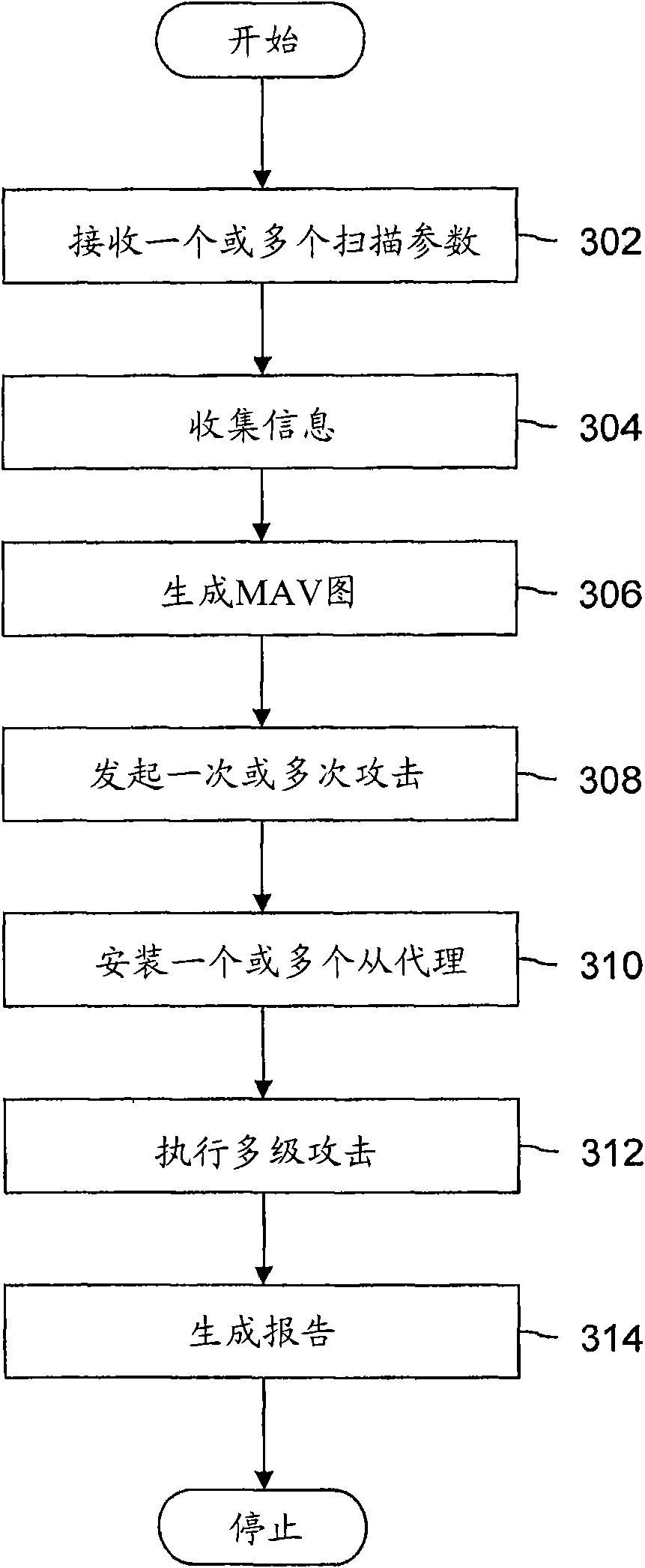
The present invention describes a method for simulating a hacking attack on a Network, wherein the Network comprises at least one of a plurality of data processing units (DPUs), a plurality of users and a plurality of communication links, to assess vulnerabilities of the Network. The method includes receiving one or more scan parameters for the Network. Further, the method includes creating at least one master agent by a system to gather information about the Network, wherein the information pertains to critical and non-critical information about the Network. The method includes creating an Information Model and then incrementally updating the Information Model during the hacking attack. The Information Model is the abstract representation of information collected by the system. Furthermore, the method includes generating a Multiple Attack Vector (MAV) graph based on one or more scan parameters and the Information Model. MAV has the ability to combine plurality of low and medium severity vulnerabilities associated with the data processing units (DPUs), users and communication links, correlate vulnerabilities in combination with Information Model and generate high severity attack paths that can lead to compromise of the Network. Moreover, the method includes launching one or more attacks based on the MAV graph to compromise the Network. The method further includes installing atleast one slave agent on the compromised Network to perform the one or more attacks in a distributed manner. Moreover, the method includes performing a multi stage attack by using the at least one slave agent and the at least one master agent by repeating above steps. Finally, the method includes generating a report by the scan controller, wherein the report contains details about the compromisedNetwork and the vulnerabilities of the Network.
Owner:IVIZ TECHNO SOLUTIONS PVT
Event detection method and device
ActiveUS20080052780A1Improve acceleration performanceImprove efficiencyMemory loss protectionError detection/correctionPushdown automatonAlgorithm
The embodiments of the present invention disclose an event detection method and device. The method includes: predefining event-based detection rules with a predicative context-free grammar; generating by parsing the detection rules a parsing table of pushdown automaton which supports parallel parsing; receiving an event to be detected; and analyzing by a controller the event to be detected according to the parsing table, to obtain a detection result. The present invention is especially applicable to detection of network attack events. The embodiments of the present invention detect the attacks with a predicative context-free grammar on the basis of events, and ensure a close combination of a protocol parsing process and an attack detection process, as well as a close combination of multiple attack detection rules, thus decreasing unnecessary calculations. In addition, with an optimized parallel pushdown automaton, the embodiments of the present invention can efficiently analyze the predicative context-free grammar. Consequently, besides hierarchical processing capability and state description capability, the embodiments of the present invention deliver high efficiency.
Owner:NEUSOFT CORP
Method for protecting integrity of digital vector map
InactiveCN102800041ADoes not affect normal operationImprove storage speedImage data processing detailsComputer graphics (images)Vector map
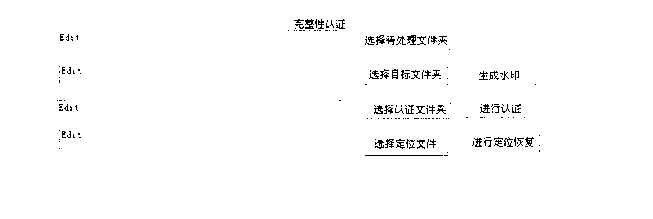
The invention relates to the field of cryptology, information safety, geographic information system and digital image processing, in particular to a method for protecting and authenticating the integrity of a digital vector map which can withstand multiple attacks and improve the data writing speed. The method comprises three parts, namely watermark generating, watermark hiding and integrity authenticating, wherein the watermark generating comprises generating an authenticating watermark, generating a positioning watermark and generating a recovery watermark; the watermark hiding comprises transmitting the watermark information to a drive layer and hiding the watermark information; and the integrity authenticating comprises extracting an authenticating watermark, extracting a positioning watermark, extracting a recovery watermark and finishing falsification recovery. By the method, the storage speed is improved, the storage data volume is reduced, the safety is ensured, and the data writing speed is improved.
Owner:HARBIN ENG UNIV
Device and method for testing structural fatigue of H-shaped vertical shaft wind turbine blade
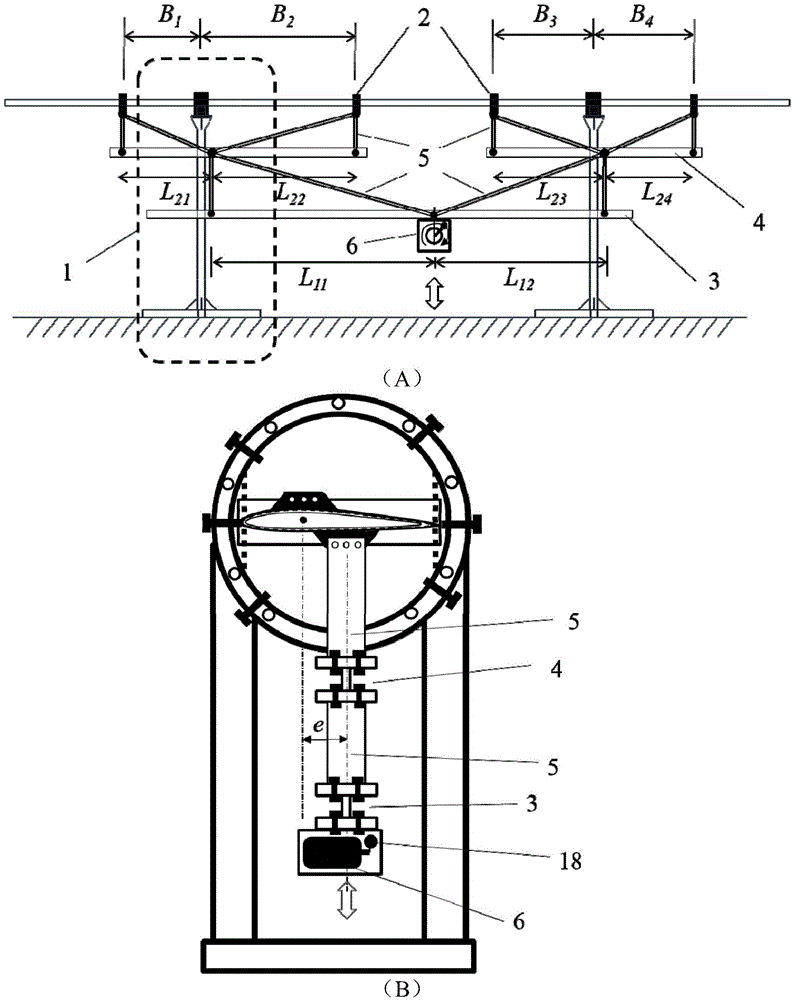
ActiveCN104792516ATo reverse the realizationEvaluate fatigue structural performanceMachine part testingFatigue loadingStructural fatigue
The invention relates to a device and a method for testing the structural fatigue of an H-shaped vertical shaft wind turbine blade. The device comprises a support base component, a distribution beam, a loading hoop, a support connecting rod and an eccentric motor, wherein the distribution beam, the loading hoop and the support connecting rod are connected together by using bolts so as to form a whole load distribution system, so that the fatigue load which acts in an upper and lower reciprocation manner can be effectively conducted. When the device is used for experiment, the fatigue bending moment distribution of the blade under various working conditions can be simulated by adjusting the length L of the distribution beam and the position B of the loading hoop, and the fatigue stress state of the blade in axial torsion and multiple attack angles can be simulated by adjusting the structural modes of the support base component and the loading hoop; the strain distribution of the blade under the fatigue loaded condition can be measured, and furthermore, the fatigue structural property of the blade can be evaluated; by only exerting one external fatigue load to the device, combined fatigue loading modes such as bending, torsion and multiple attack angles of the blade can be achieved, and the device is simple and convenient to operate, accurate and reliable in result and relatively high in universality.
Owner:INST OF ENGINEERING THERMOPHYSICS - CHINESE ACAD OF SCI
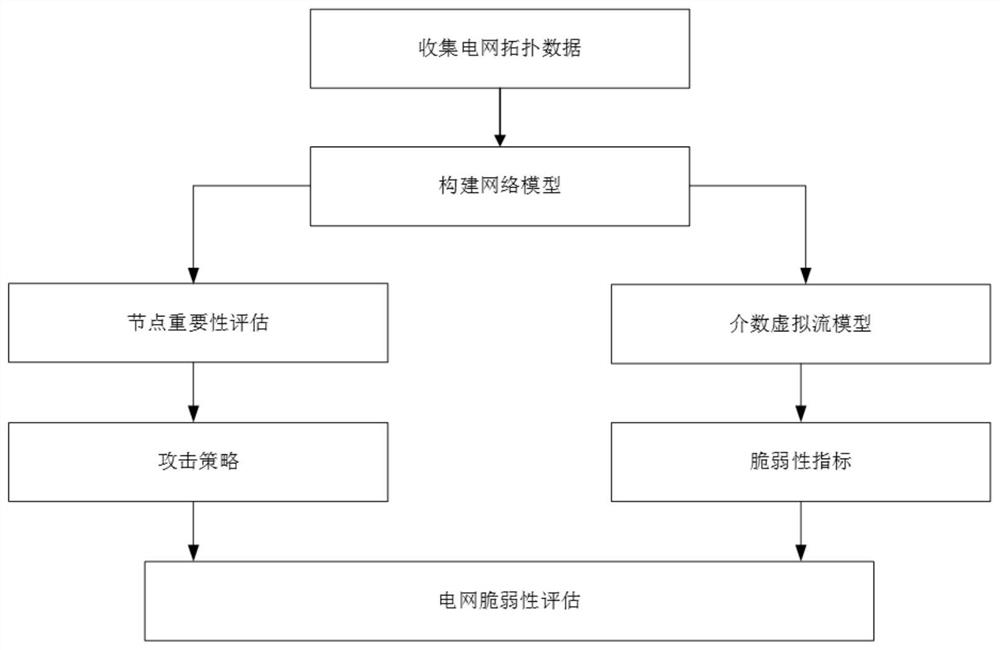
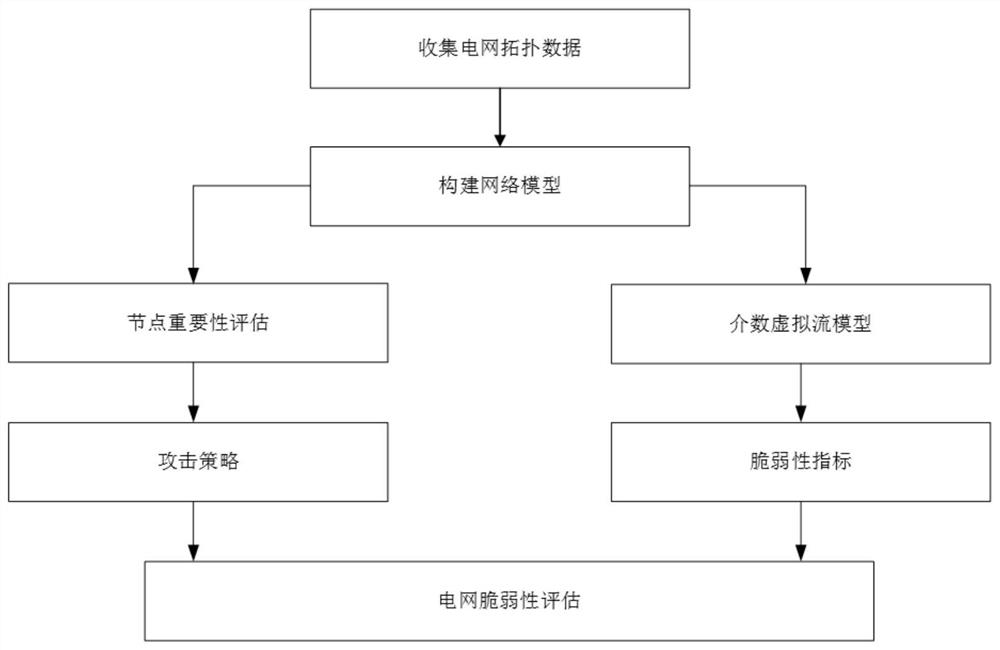
Power network vulnerability evaluation method based on multiple attack strategies
InactiveCN111950153AFacilitate identificationFeatures at the functional levelDesign optimisation/simulationResourcesElectric power systemAttack
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes; 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in a power system; and 4) establishing a vulnerability index based on the betweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change ofthe vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenance work of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
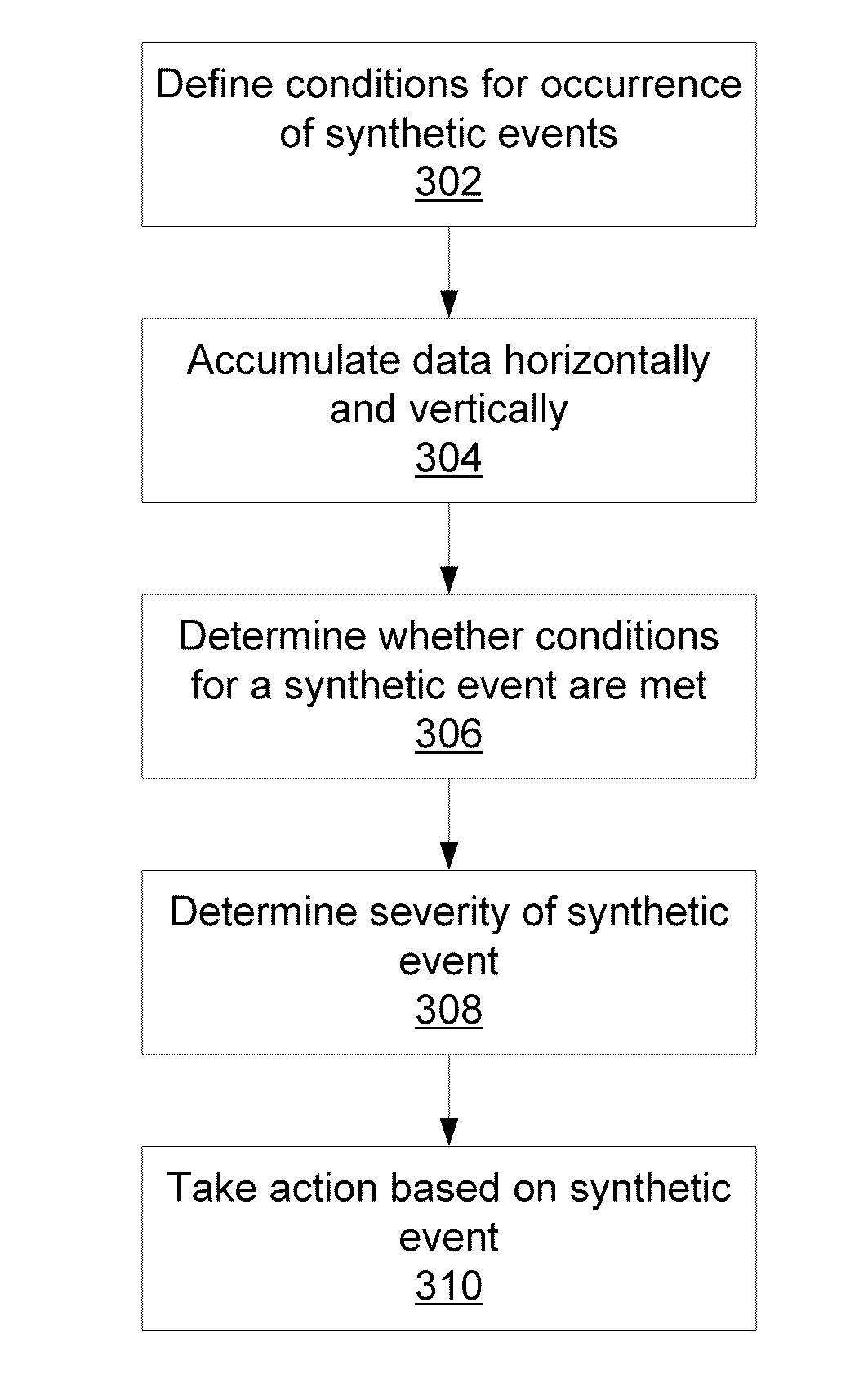
Probabilistically detecting low-intensity, multi-modal threats using synthetic events
Methods and systems for event detection include defining a plurality of conditions that represent one or more synthetic events. Data from a plurality of data sources is aggregated across a period of time, multiple attack surfaces, and geographically distinct locations. The aggregated data is matched to the conditions to determine whether a synthetic event has occurred. A response to the synthetic event is formed to resist an attack.
Owner:IBM CORP
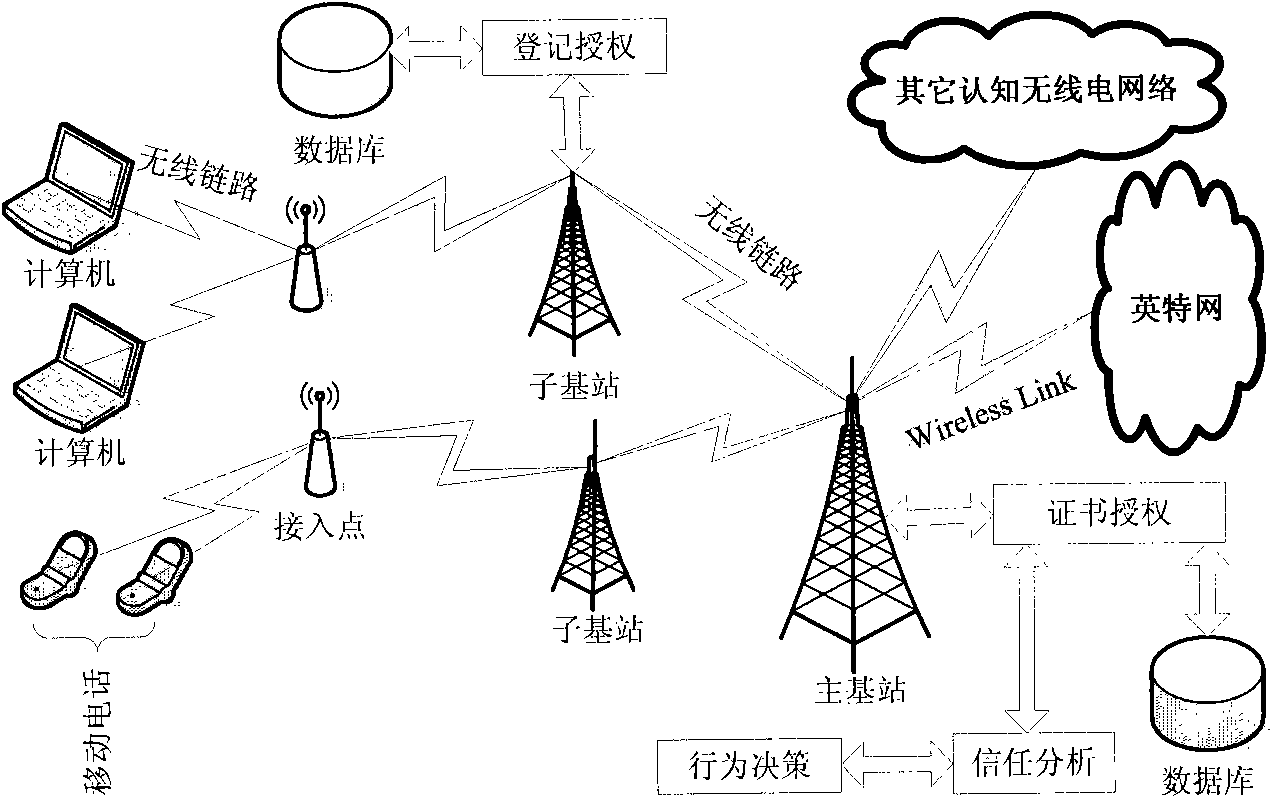
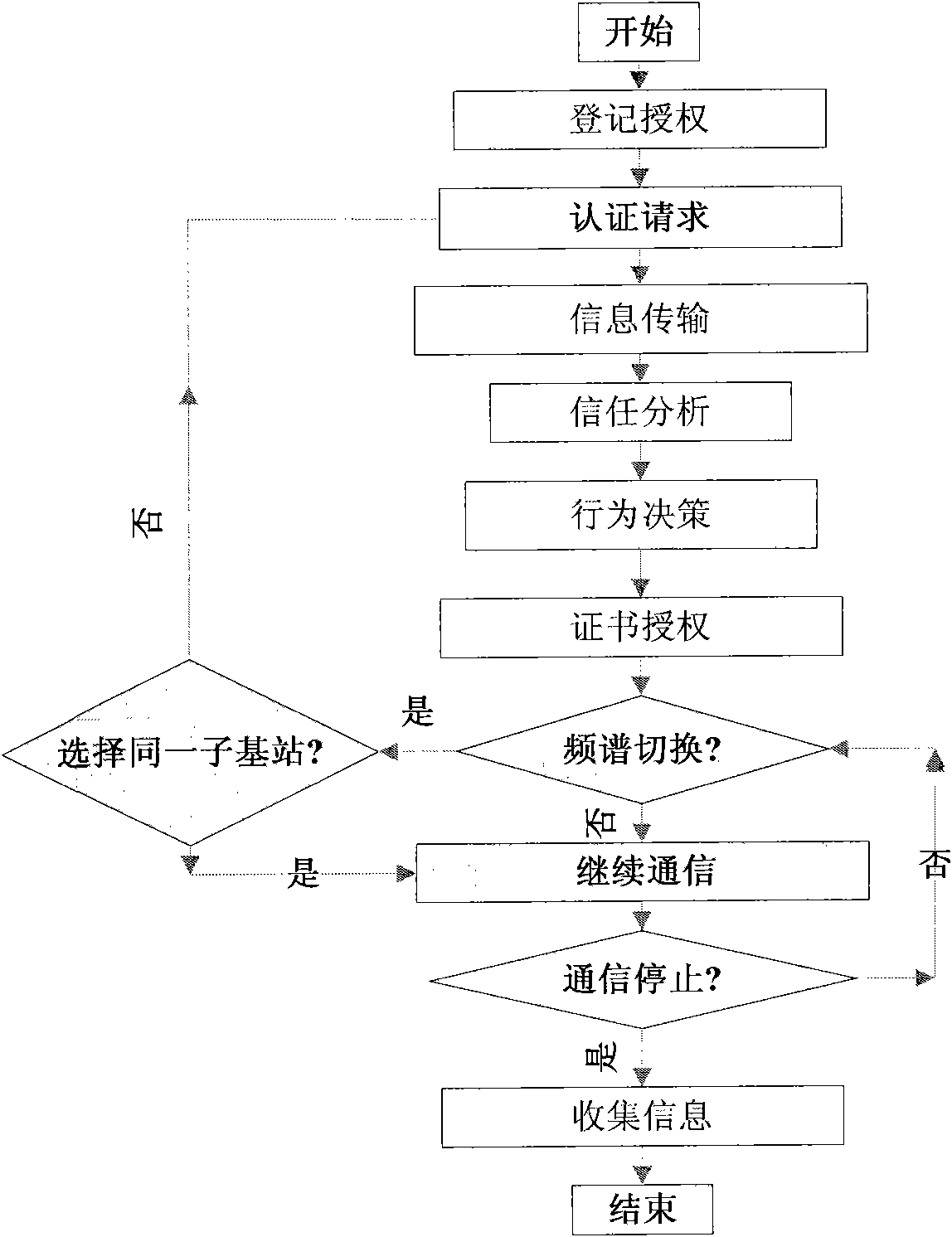
Entity authenticating system and method of cognitive radio network based on hierarchical structure
InactiveCN101860861APrevent impersonation attacksAvoid congestionAssess restrictionSecurity arrangementSecure communicationSecurity question
The invention provides entity authenticating system and method of a cognitive radio network, which relates to the relevant applying field in information safety technology. The entity authenticating system and the method of the cognitive radio network based on a hierarchical structure ensure the safe communication between secondary users by authenticating the identities of the secondary users in the cognitive radio network. In the process of sending the authentication request by the secondary user, the credibility is judged, and the public key verification is allowed to further execute only in the premise that the condition is satisfied. The trusting mechanism can effectively prevent the malignant users from generating multiple attacks in the network. The safety is based on n RSA algorithm, and simultaneously the symmetrical keys and the public key system are combined. In the premise of ensuring that the authenticating safety is not decreased, the authenticating efficiency is greatly enhanced, thereby effectively decreasing the authenticating delay. In addition, the invention has obvious effects on the safety problems of preventing the reproducing attack, controlling network congestion and the like.
Owner:UNIV OF SCI & TECH BEIJING
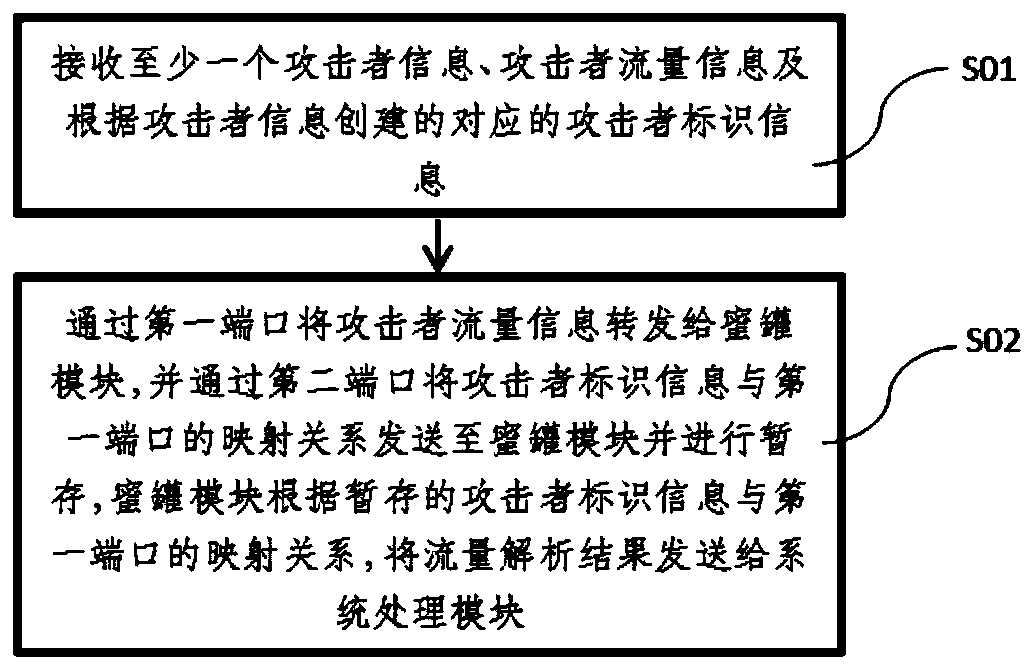
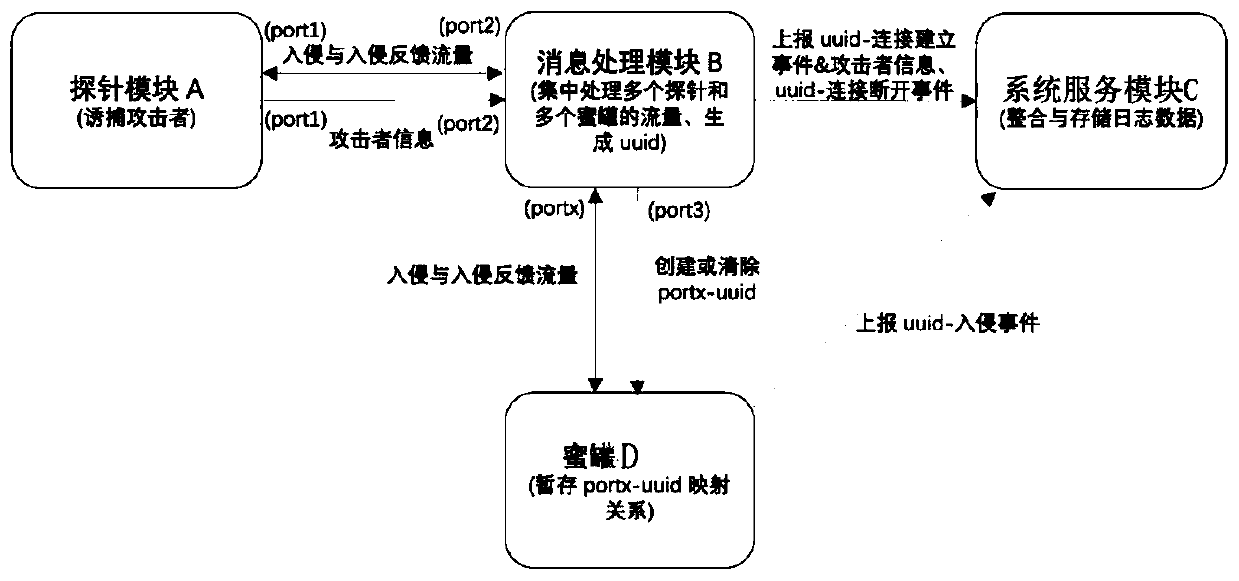
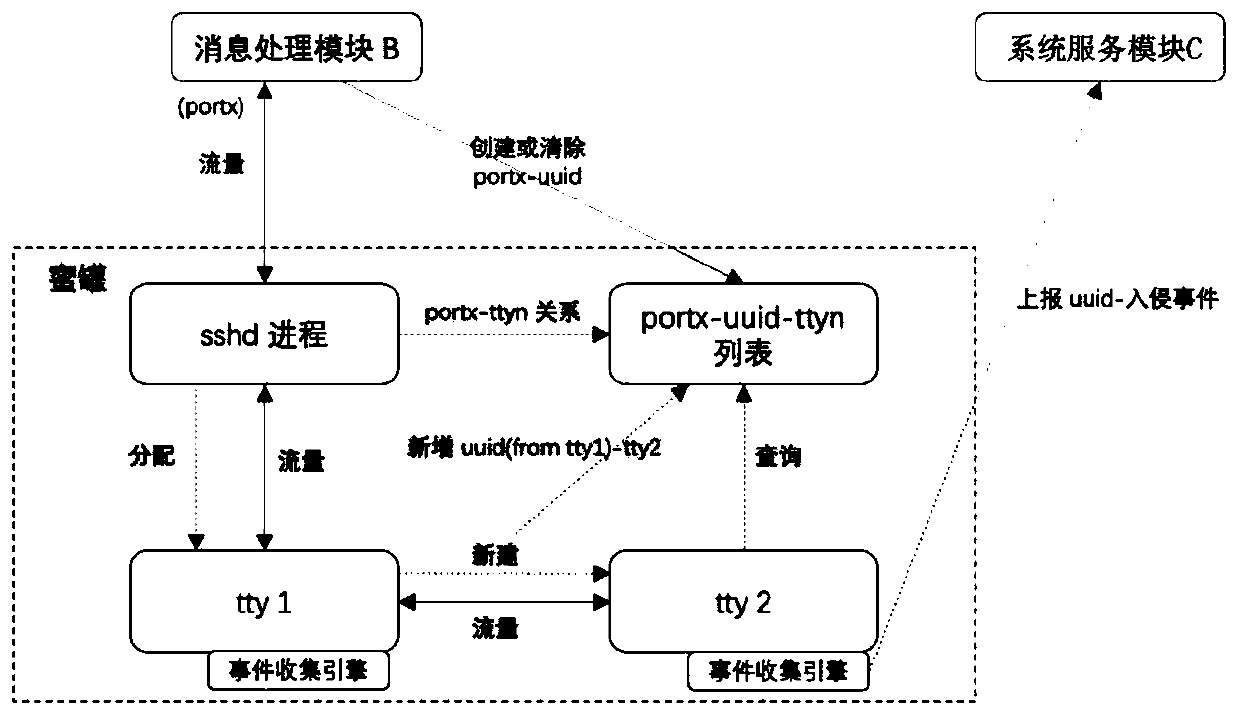
Method, device and system for detecting multiple attack behaviors
The embodiment of the invention discloses a method for acquiring multiple pieces of attack behavior information. The method comprises the following steps: receiving at least one piece of attacker information, attacker flow information and corresponding attacker identification information created according to the attacker information; forwarding the attacker flow information to the honeypot throughthe first port; sending the mapping relationship between the attacker identification information and the first port to the honeypot through the second port and temporarily storing the relationship; and enabling a honeypot to send the flow analysis result to the system service module according to the temporarily stored mapping relationship between the attacker identification information and the first port. According to the technical scheme disclosed by the invention, the effect of completely recording and restoring the attack timeline under the condition of multi-node management can be achieved.
Owner:北京长亭未来科技有限公司
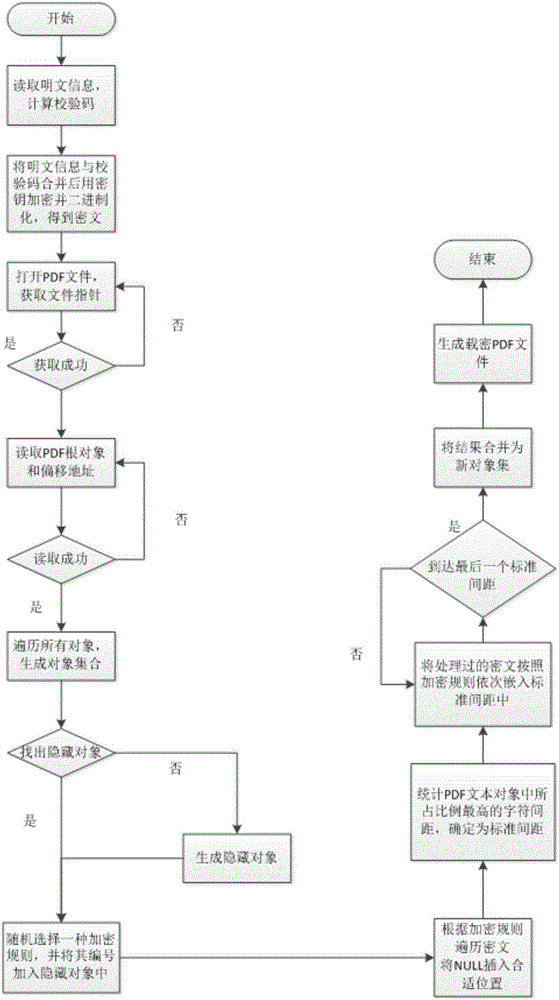
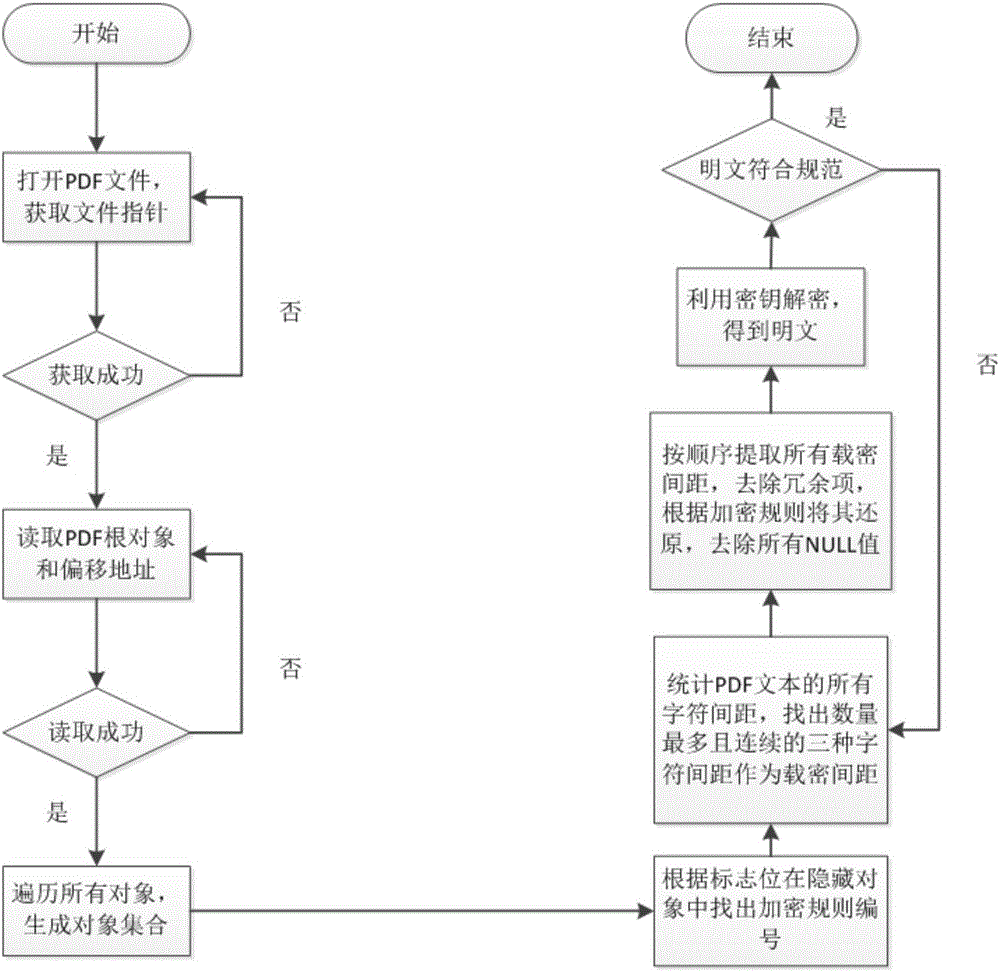
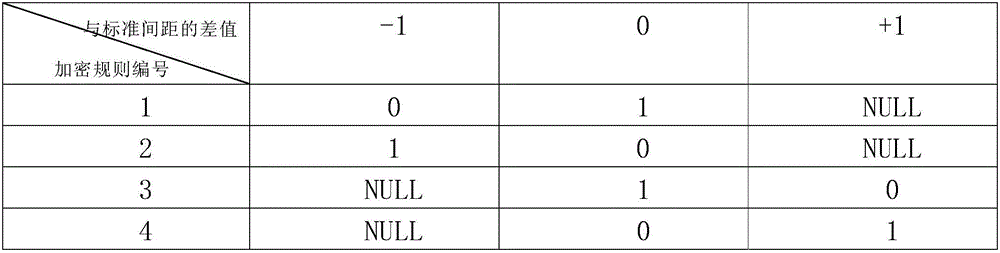
A digital fingerprint-based PDF document copyright protection method
ActiveCN106126982AIncrease redundancyImprove robustnessDigital data protectionProgram/content distribution protectionPlaintextInformation embedding
The invention provides a digital fingerprint-based PDF document copyright protection method. The method comprises the steps of firstly, designing encryption rules; secondly, hiding digital fingerprints through the information embedding algorithm to obtain a cipher-carrying PDF file; thirdly, extracting the digital fingerprints through the information extraction algorithm to convert the cipher-carrying PDF file to a plaintext. The method can track the identity information of a document leaking person and provide a new layer of protection aside from traditional file protection; the method uses a mixed method to hide identity information and increases the redundancy of hidden information through cyclic embedding, thereby improving the robustness of hidden information, being capable of resisting multiple attack modes and guaranteeing high security of hidden information. The method has certain practical value and a certain market promotion prospect, and not only can be used for protecting secret documents of enterprises and offices but also can be widely applied to copyright protection.
Owner:ZHEJIANG STARSINO INFORMATION TECH
Three-dimensional mesh model blind watermarking method based on image discrete cosine transformation
InactiveCN104318505AAccurate extractionLarge capacityImage data processing detailsDiscrete cosine transform3D modeling
The invention relates to a three-dimensional mesh model blind watermarking method based on image discrete cosine transformation. The three-dimensional mesh model watermarking method involves selecting two stable geometrical characteristics to facilitate ordering to obtain a unique three-dimensional vertex sequence and adding watermark data to the texture coordinates of a vertex so that the vertex sequence with a watermark embedded therein can also be correctly obtained even after affine transformation, and the watermark can be correctly extracted accordingly. By using the method provided by the invention, original grids and pretreatment are unnecessary for watermark extraction. Multiple attacks can be resisted, including rotation, zooming, translation, noise and vertex reordering. At the same time, an algorithm also has a quite large watermarking capacity because when a carrier image is taken as the watermark for adding to a three-dimensional mode, the watermark transparency of the carrier image does not have to be considered, and thus the watermarking capacity is greatly improved.
Owner:HANGZHOU DIANZI UNIV
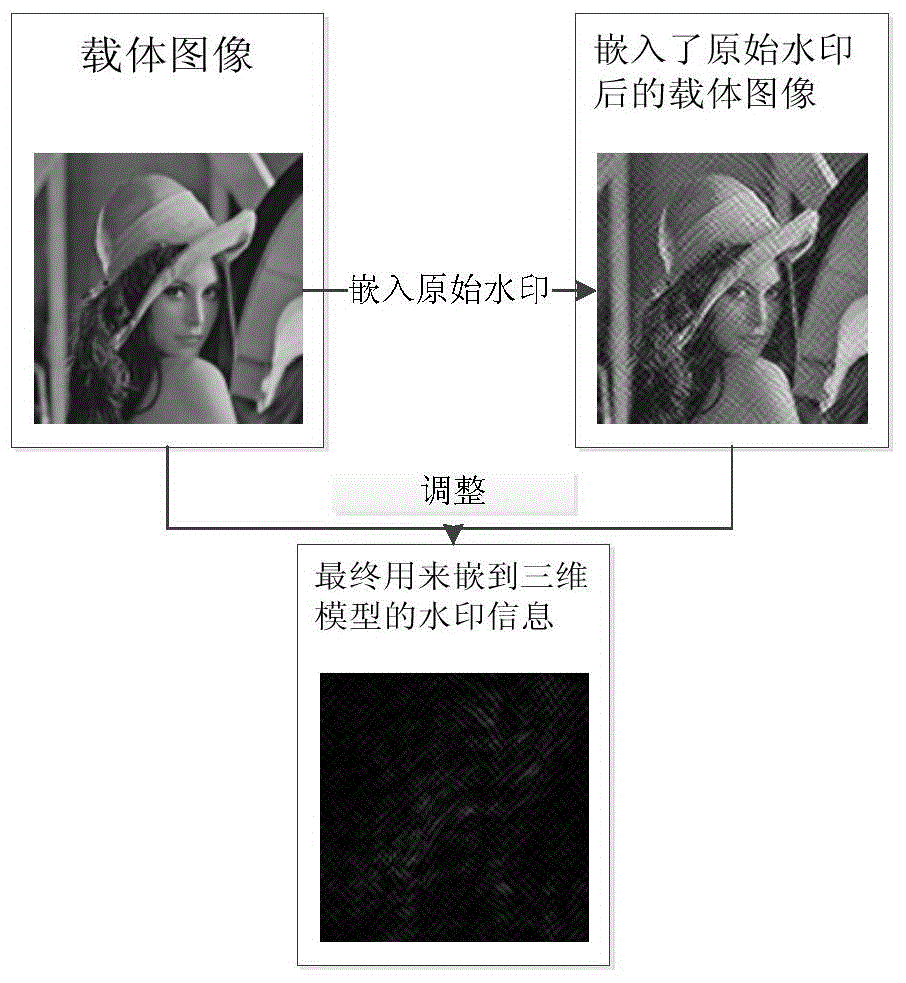
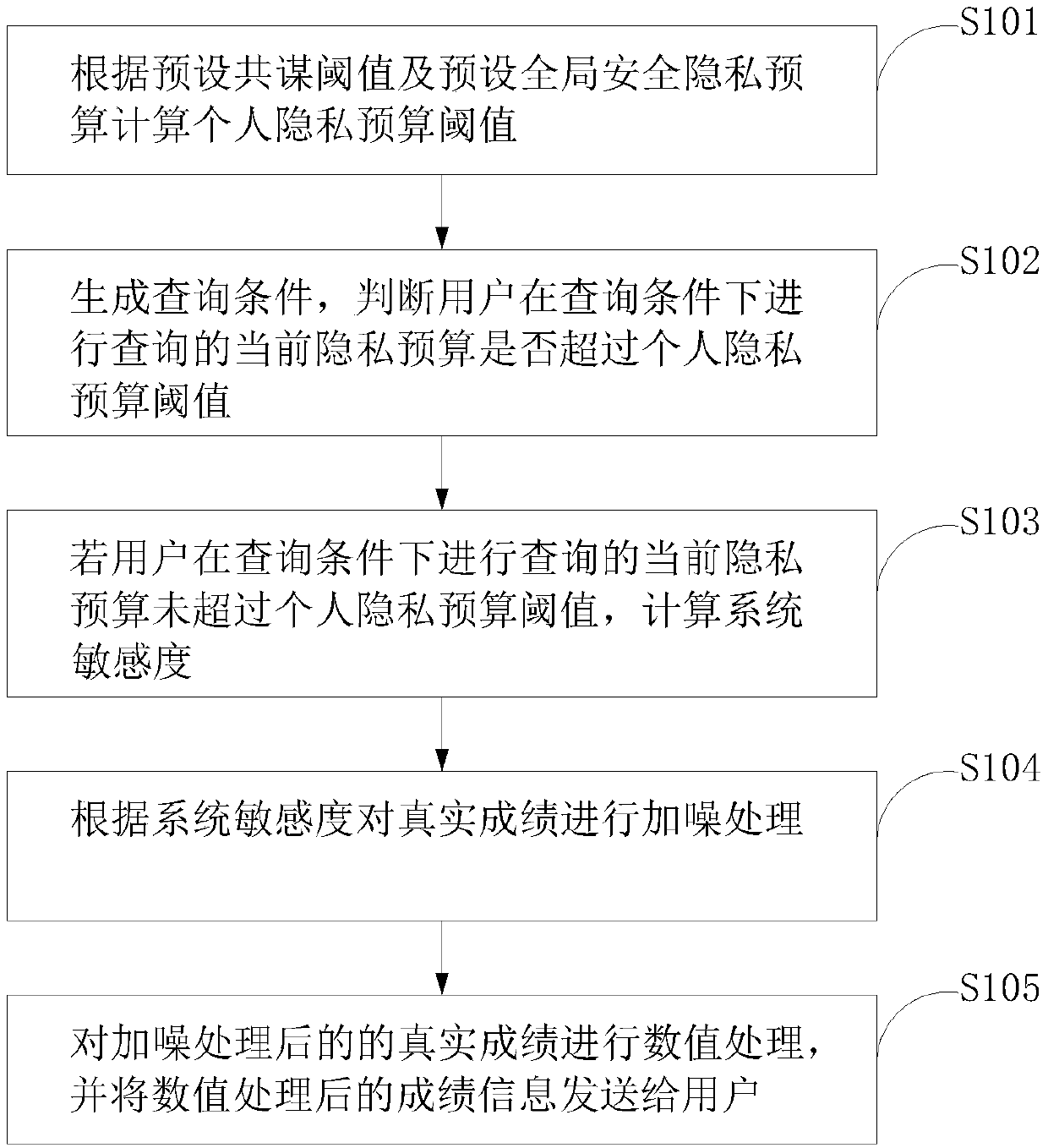
Privacy protection method and device for inquiring average score, computer device, and storage medium
The invention discloses a privacy protection method and device for inquiring an average score, a computer device and a storage medium, wherein the method comprises the following steps: calculating a personal privacy budget threshold; generating query conditions and judging whether the current privacy budget of a user exceeds the personal privacy budget threshold; calculating the sensitivity of thesystem if the privacy budget threshold is not exceeded; according to the sensitivity of the system, conducting noise processing on the real score; conducting numerical processing on the real score after noise processing, and sending the numerically processed score information to the user. The privacy budget threshold is calculated, and when the current privacy budget does not exceed the preset privacy threshold, the sensitivity of the system is calculated, noise processing is performed on the real score, and then the real score is sent to the user after numerical processing, so the security of the score inquiry system is improved in the face of multiple attacks at the same time organized by multiple people.
Owner:ANHUI UNIVERSITY
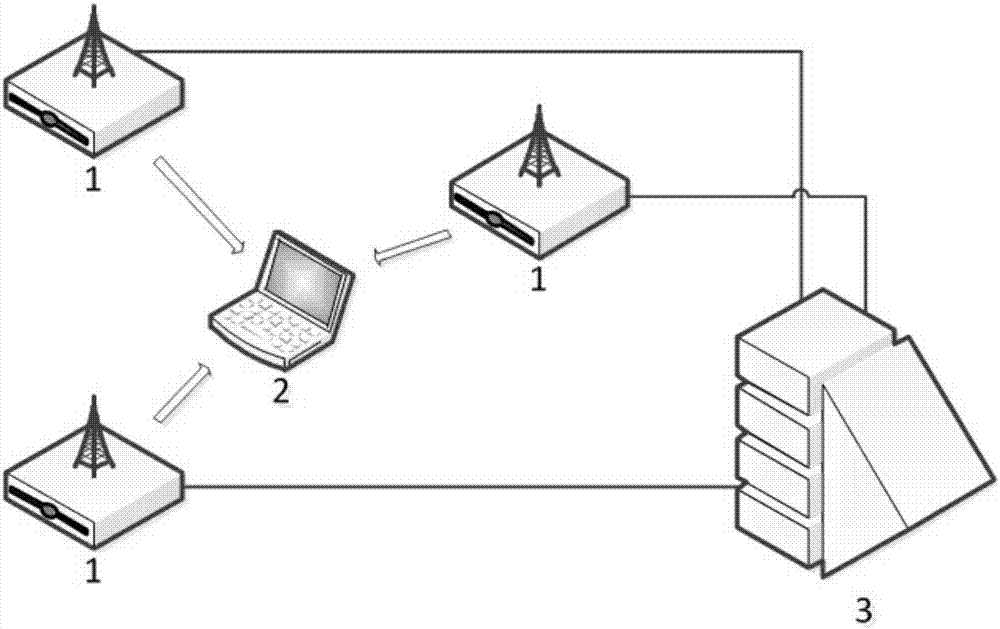
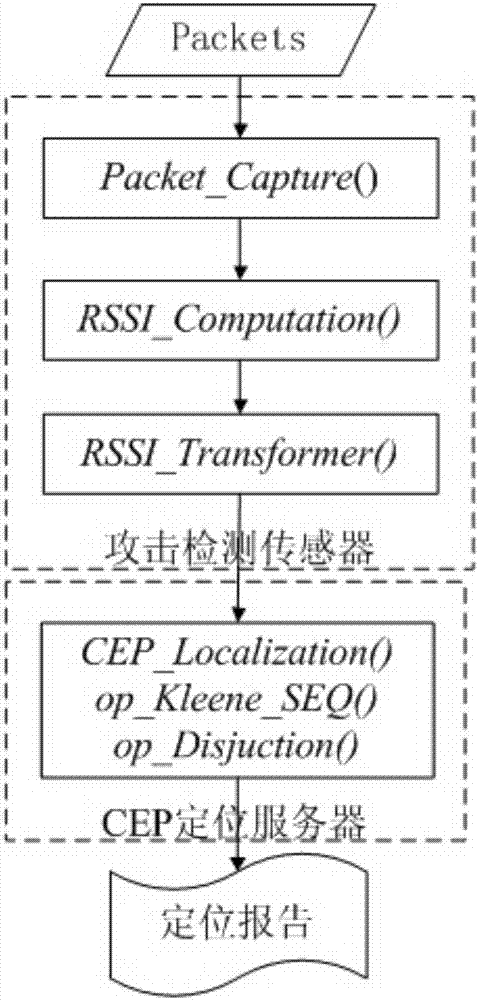
Wireless network attack positioning method
ActiveCN106899978AQuick responseHigh precisionTransmissionSecurity arrangementNetwork packetTime frame
The invention relates to network security, and aims at providing a wireless network attack positioning method. Through the wireless network attack positioning method, at least three attack detection sensors are deployed in a target monitoring region, the attack detection sensors are connected with the same CEP positioning server, and an attacker in a wireless network is positioned in the target monitoring region, wherein the wireless network attack positioning method comprises the specific steps as follows: each attack detection sensor performs attack detection, and the CEP positioning server perform the attack positioning. The positioning method disclosed by the invention is fast in response, tightly combined with the attack detection process, and capable of starting positioning at once after detecting the attack; mass of historic data can be used for positioning without sending mass of data packets after detecting the attack; a positioning result with higher precision is formed by actively associating multiple attack detection sensors and synthesizing a detection result; and a rough trajectory of the attacker can be obtained by synthetically computing historic RSSI information at different time frames.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Power network vulnerability evaluation method based on multiple attack strategies
InactiveCN112507552AEasy to identifyFeatures at the functional levelDesign optimisation/simulationResourcesComputer networkElectric power system
The invention discloses a power system vulnerability evaluation method based on multiple attack strategies. The method comprises the following steps: 1) constructing a power grid model; 2) evaluatingthe importance of nodes in the network from four aspects of node degree, betweenness, local centrality and node fault loss, and completing the formulation of an attack strategy according to the importance of the network nodes. 3) establishing a betweenness virtual flow model to simulate a cascade fault propagation process in the power system. and 4) establishing a vulnerability index based on thebetweenness virtual flow model, simulating a network attack by adopting a plurality of attack strategies, and evaluating the vulnerability of the IEEE300 power system network according to the change of the vulnerability index. Aiming at the vulnerability of the power network under the condition of various attack strategies, the betweenness virtual flow model and the various attack strategies are established to analyze the performance change of the power grid under the cascade failure. The importance of nodes in a power network can be identified, and decision support is provided for maintenancework of power system managers and power system fault prevention of designers.
Owner:XUZHOU NORMAL UNIVERSITY
Preparation method of composite ceramic
The invention provides a preparation method of a composite ceramic. The preparation method of the composite ceramic comprises the following steps that fiber cloth is bonded on the surface of a bulletproof back plate; a plurality of packaged ceramic small blocks are bonded on the surface of the fiber cloth; the fiber cloth is bonded on the surface of the plurality of packaged ceramic small blocks to form a ceramic plate; and the ceramic plate is cured to obtain the composite ceramic. The composite ceramic prepared by the method provided by the invention forms a new integral ceramic plate, and has the shock wave isolation effect, so that the anti-multiple attack ability is remarkably enhanced; the ceramic small blocks are bonded to one another, so that the overall bending strength is remarkably improved, the structural integrity and the bulletproof performance of the ceramic small blocks are not reduced under a long-term static load or dynamic load; and after impact, the damaged ceramicsmall blocks can be removed and replaced with the new ceramic small blocks in order to be used for multiple times and improve the use efficiency of the ceramic plate, and even in an emergency situation, the ceramic plate can be repaired. The invention further provides a composite ceramic.
Owner:BEIJING TONGYIZHONG NEW MATERIAL TECH CORP
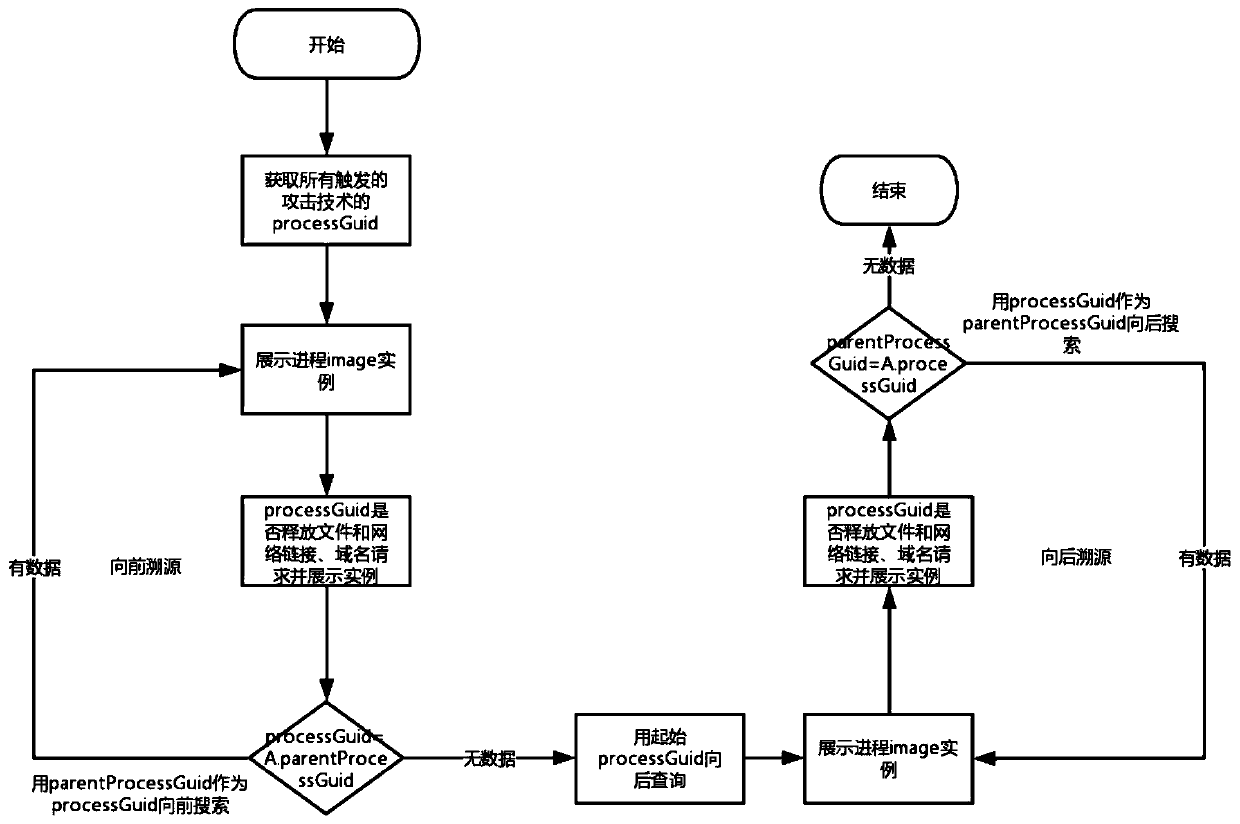
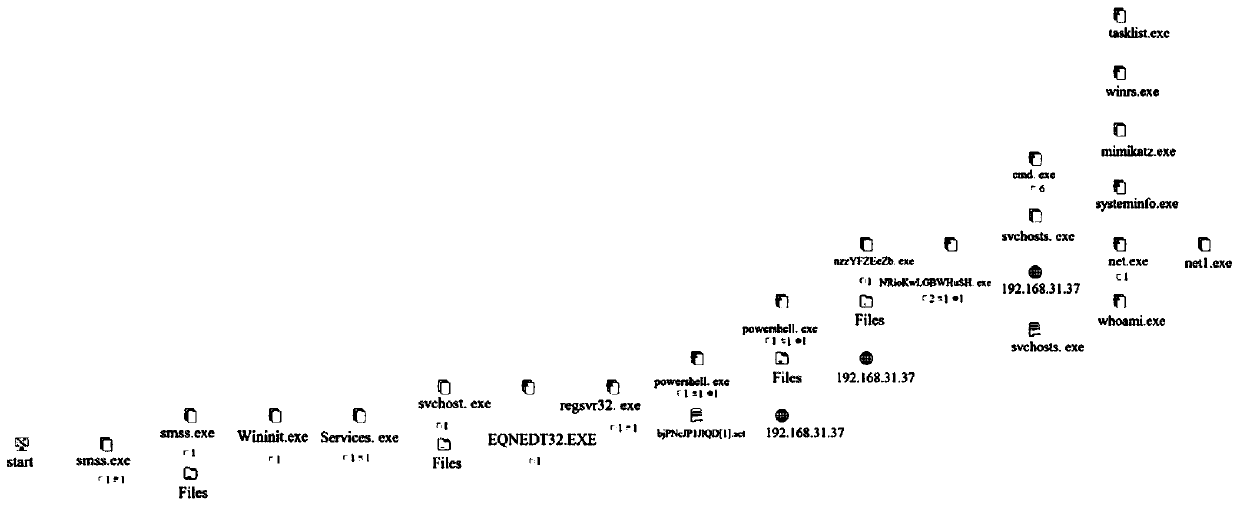
High-risk asset discovery and network attack tracing method based on TTP
The invention provides a high-risk asset discovery and network attack tracing method based on TTP. The method comprises the following steps that process tree tracing is conducted on processes triggering TTP related rules, whether TTP threats are also detected by other processes on a process tree or not is inquired, and then all detected TTP information is displayed on the corresponding processes on the process tree; each attack technology Techniques is detected through an alarm rule model, each technology corresponds to one Techniques number (TTP number) after the technology Techniques is detected, and besides the Techniques number, tactical Tactics numbers are further included; when the attack technology Techniques is detected, the process tree of the attack process is traced; whether a plurality of attack technologies Techniques are covered on the process tree or not is analyzed; it is envisaged that when only one attack technology Techniques is detected on one process tree, it is possible to misreport a detection rule; and if multiple attack technologies Techniques are detected on one process tree, the probability that the equipment sinks and is controlled by an attacker is large, and multiple malicious attack behaviors are carried out.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Event detection method and device
ActiveUS7913304B2Accurately sequenceSolve the low detection efficiencyMemory loss protectionError detection/correctionPushdown automatonAlgorithm
The embodiments of the present invention disclose an event detection method and device. The method includes: predefining event-based detection rules with a predicative context-free grammar; generating by parsing the detection rules a parsing table of pushdown automaton which supports parallel parsing; receiving an event to be detected; and analyzing by a controller the event to be detected according to the parsing table, to obtain a detection result. The present invention is especially applicable to detection of network attack events. The embodiments of the present invention detect the attacks with a predicative context-free grammar on the basis of events, and ensure a close combination of a protocol parsing process and an attack detection process, as well as a close combination of multiple attack detection rules, thus decreasing unnecessary calculations. In addition, with an optimized parallel pushdown automaton, the embodiments of the present invention can efficiently analyze the predicative context-free grammar. Consequently, besides hierarchical processing capability and state description capability, the embodiments of the present invention deliver high efficiency.
Owner:NEUSOFT CORP
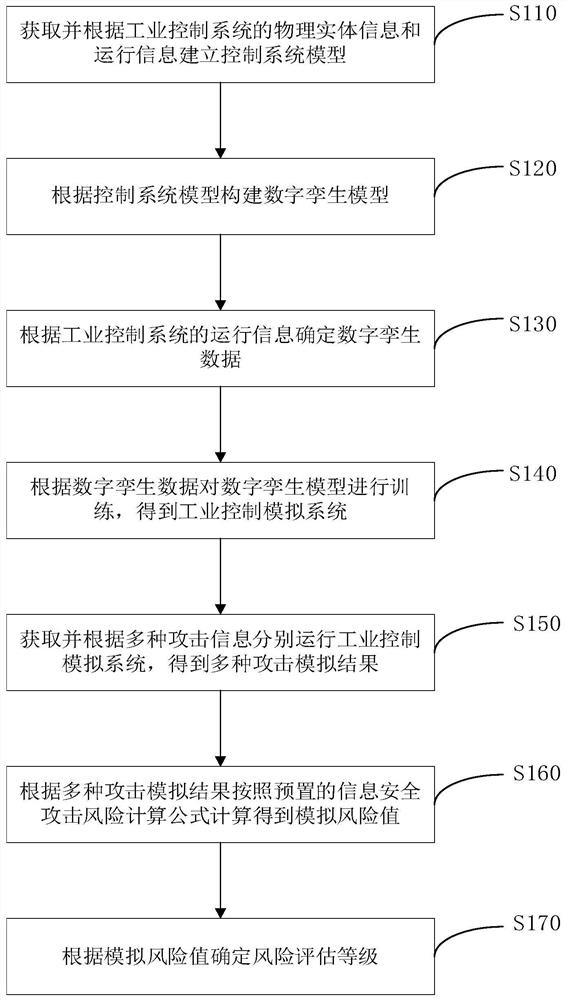
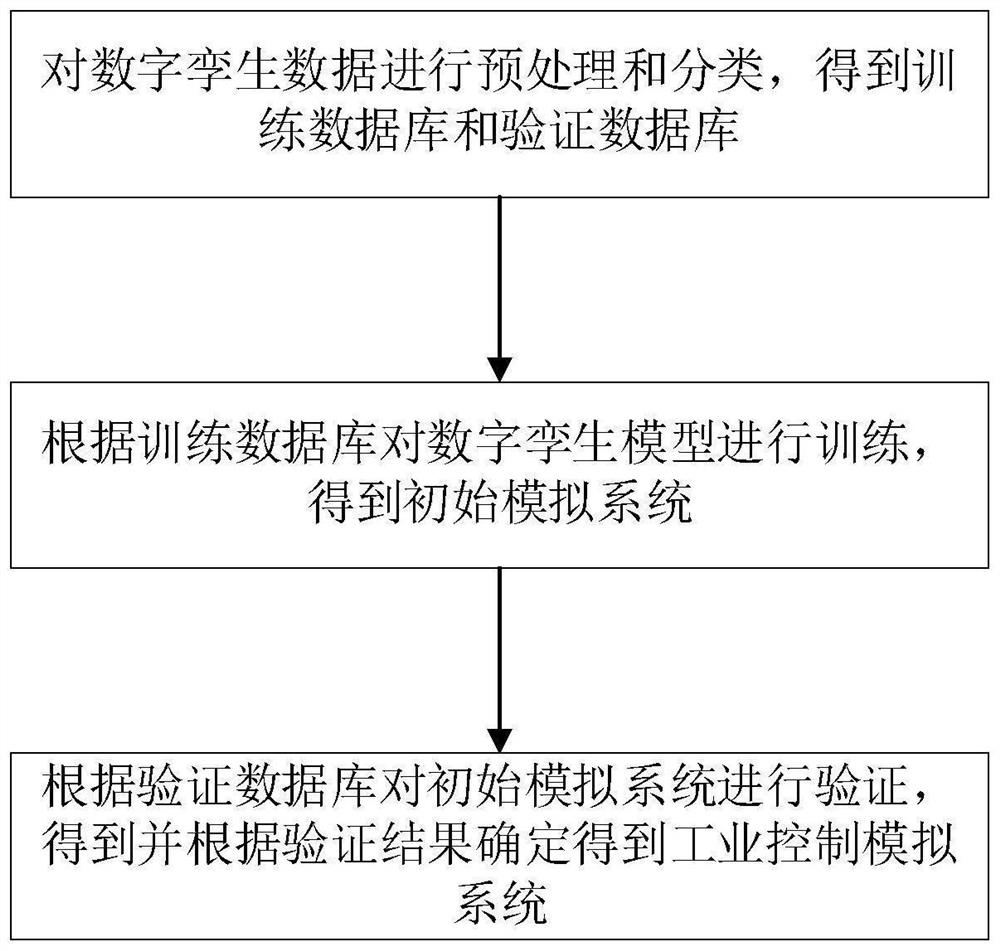
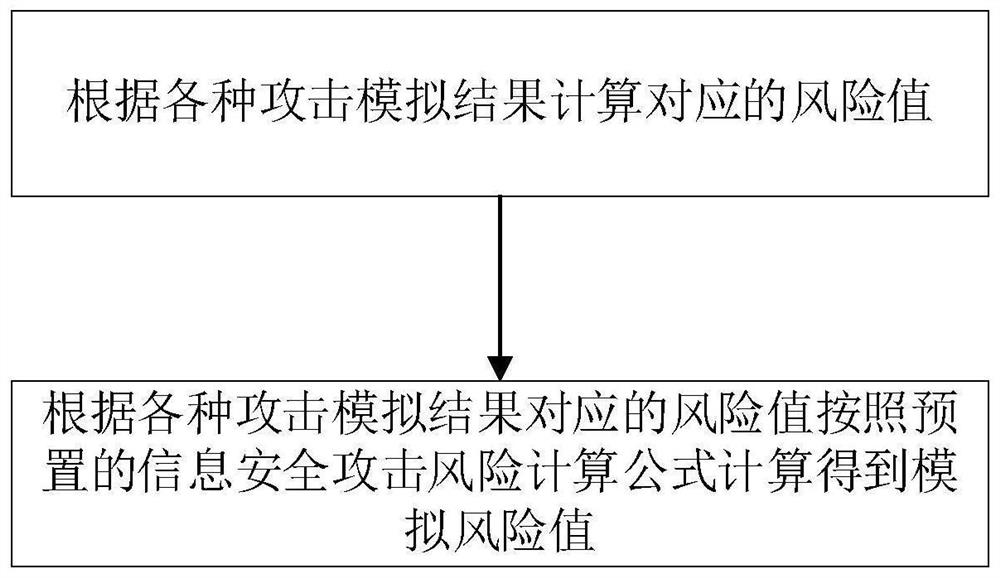
Industrial control system information security attack risk assessment method and system
PendingCN114879613AHigh riskGuaranteed accuracyTotal factory controlProgramme total factory controlAttackInformation security
The invention provides an industrial control system information security attack risk assessment method and system, and relates to the technical field of industrial control system risk assessment. Physical entity information and operation information of an industrial control system are obtained and a control system model is established according to the information; constructing a digital twinborn model according to the control system model; determining digital twin data according to the operation information of the industrial control system; training a digital twinning model according to the digital twinning data to obtain an industrial control simulation system; then acquiring and respectively operating the industrial control simulation system according to various attack information to obtain various attack simulation results; then, according to the multiple attack simulation results, a simulation risk value is obtained through calculation according to a preset information security attack risk calculation formula; and finally determining a risk assessment level according to the simulated risk value. The risk assessment is obtained by integrating various attacks and then performing assessment, so that the accuracy of the risk assessment is improved.
Owner:方圆标志认证集团浙江有限公司
Vector space data digital fingerprint method based on GD-PBIBD coding
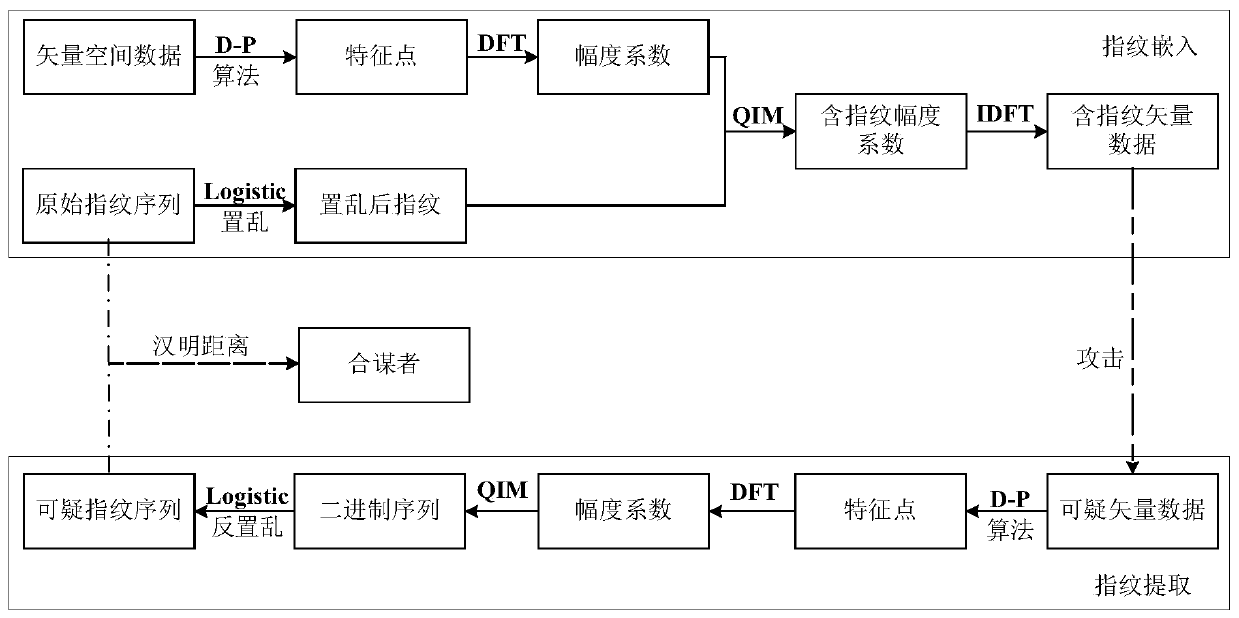
ActiveCN110223213AEfficient extractionImprove robustnessImage watermarkingProgram/content distribution protectionOriginal dataTheoretical computer science
The invention discloses a vector space data digital fingerprint method based on GD-PBIBD coding. The method comprises the following steps: constructing a fingerprint code by using GD-PBIBD with limited conditions, scrambling the fingerprint sequence to be embedded by using Logistic mapping; extracting feature points of vector space data through a D-P algorithm, performing DFT on the feature pointsto obtain a phase coefficient and an amplitude coefficient, then applying a QIM method to embed a fingerprint into the amplitude coefficient of a DFT domain, and finally applying inverse DFT to obtain the vector space data containing the fingerprint. The colluder can be tracked according to the Hamming distance between the suspicious data fingerprint and the original data fingerprint. The methodis simple in coding construction, can accommodate more users compared with a BIBD code under the condition that the code length is fixed, and is high in coding efficiency. Robustness to single-user fingerprint attacks and multiple attacks is good, and the problem of data copyright recognition can be solved. Multi-user minimum value and maximum and minimum value attacks can also be resisted, all traitors can be tracked, and a basis is provided for vector space data traitor tracking.
Owner:LANZHOU JIAOTONG UNIV
Programmable controller for game peripheral
InactiveCN106955490AExperienceResponse speedVideo gamesProgrammable logic controllerInterface protocol
The invention discloses a programmable controller for a game peripheral. The programmable controller is characterized by comprising a micro-processor, a key input interface, a PS2 keyboard interface and a USB keyboard interface, wherein the PS2 keyboard interface and the USB keyboard interface are connected with a PC (personal computer) through an interface protocol, and the micro-processor only recognizes one keyboard interface during working; the key input interface comprises two setting keys, four direction keys, two auxiliary keys, multiple attack keys and one reset key, and the keys except the setting keys and the reset key all correspond to a key value of a universal key of the PC; multiple conventional game key layouts are stored in the micro-processor, and factory default key value parameters are restored by pressing the reset key for a long time. The programmable controller has the advantages that the programmable controller is no longer limited to several unchanged arcade games supported by gamepads and can be widely applied to various online games and single games. The games can be configured in the micro-processor before delivery and can also be automatically downloaded through software configured on the PC.
Owner:张志刚
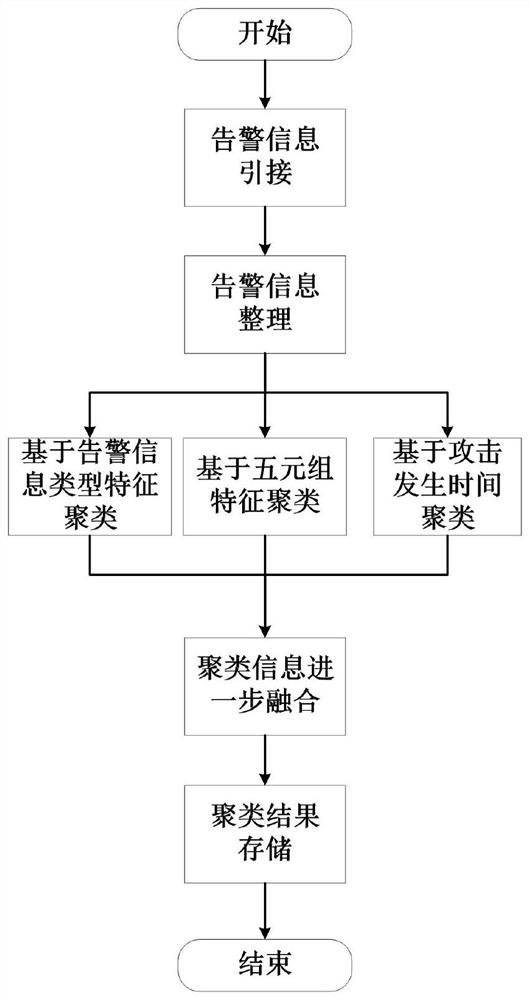
Network alarm information clustering method based on attribute correlation
InactiveCN113569116AReflect the intrinsic attributesTransmissionOther databases clustering/classificationPattern recognitionInformation type
The invention discloses a network alarm information clustering method based on attribute correlation. The method comprises the following specific steps: arranging network alarm information; clustering the network alarm information with the same attack source or the same attack target according to the quintuple features; clustering the network alarm information with the same data characteristics and attack types according to the attack type characteristics of the alarm information to obtain a network alarm information set with the network alarm information type characteristics; clustering network alarm information based on attack occurrence time; and clustering network alarm information and fusing again. The alarm information clustering of the space-time global perspective is realized based on the multi-dimensional attribute feature clustering, which is matched with the situation that an attacker often carries out combined attack on an attacked target by adopting multiple attack technical and tactical methods in an actual attack event, and can cover the full view and important details of the attack event; and better basic conditions are prepared for attack event analysis and attack scene restoration.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP +2
Copyright protection method and system of image data
ActiveCN106097238AGood clipping resistanceImprove translationImage watermarkingProgram/content distribution protectionEncoding algorithmImaging algorithm
The invention provides a copyright protection method of image data. Character information comprising copyright information is encoded to an image sequence formed by combining a limited number of binary image templates, and through combination with image feature points and a wavelet transformation technology, the binary image sequence is embedded into an image. For the purpose of fending off rotation and zoom attacks, preset template linear points are embedded into a circular ring Fourier transformation area of SIFT feature points of the image. During extraction, through analyzing distribution of the template linear points, rotation and zoom deformation parameters applied to the image are estimated, the image is restored by use of the parameters, and then the extraction is performed, through matching watermark binary images obtained through the extraction with preset template images, a watermark character sequence is restored according to an encoding algorithm. The algorithm has quite high robustness and solves the problem of incapability of simultaneously fending off multiple attacks especially cutting and rotation zoom geometric attacks by use of a conventional image algorithm.
Owner:武汉圆周率软件科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com