Power network vulnerability evaluation method based on multiple attack strategies
A power network and vulnerability technology, applied in the field of power network vulnerability assessment based on multiple attack strategies, can solve problems such as power network paralysis and collapse
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to facilitate understanding, the technical solutions in the embodiments of the present invention will be clearly and detailedly described below in conjunction with the accompanying drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
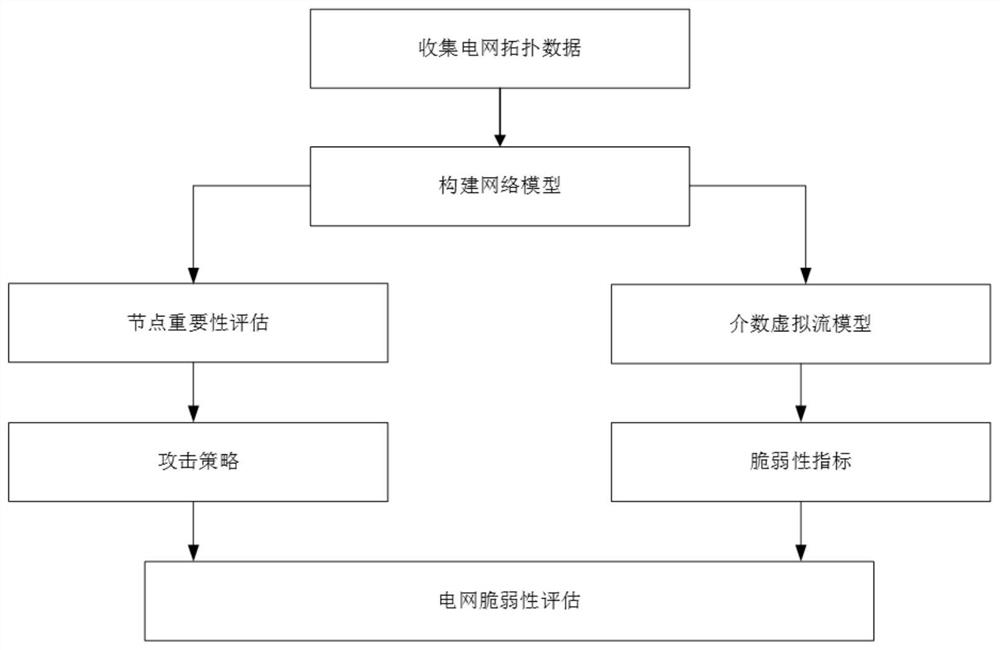
[0035] Such as figure 1 As shown, a power network vulnerability assessment method based on multiple attack strategies mainly includes the following steps:
[0036] S1: Firstly, construct the power grid model according to the topology data of the collected IEEE300 power system.
[0037] The power grid modeling method is a network structure presented in the form of a natural network. The power station in the power network is abstracted as a node, and the power line connecting two power stations is abstracted as an edge. When there is a connection between two power stations, then in the topology There is an edge between these two nodes in the structure, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com